CZ.NIC spouští HaaS: honeypot as a service
20.2.2018 Root.cz Zabezpečení
Přesněji, přivítat jste ho mohli v říjnu loňského roku, kdy jsme spustili jeho beta verzi. Z počátku jsme nechávali volnou registraci a ladili první nedostatky, zátěžovou zkouškou pak bylo přesunutí všech uživatelů routerů Turris.
Veškeré problémy a připomínky jsme vyřešili a nic nebránilo tomu spustit ostrý provoz služby HaaS neboli Honeypot as a Service.
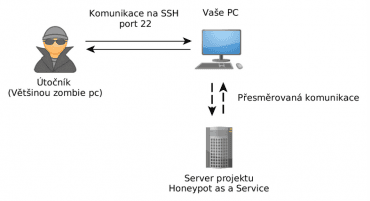
Co to vlastně HaaS je a k čemu slouží? Honeypot je speciální aplikace, která simuluje operační systém a dovoluje potenciálnímu útočníkovi se přihlásit přes SSH do koncového zařízení a provést libovolné příkazy nebo třeba stáhnout malware. Nainstalovat si takovou aplikaci není jednoduché a pokud se v ní objeví chyby, může být i nebezpečná. Proto jsme se rozhodli vzít bezpečnostní riziko na sebe a zpřístupnit honeypot jako veřejnou službu, na kterou mohou uživatelé Internetu přesměrovat útoky vedené na jejich routery.
Moc rádi bychom řekli, že stačí na vašem routeru či serveru povolit port 22 a přesměrovat na naše servery, ale není tomu tak. Snažili jsme se však o co nejjednodušší řešení, co se instalace a vývoje týče. Věřte, že jsme minimálně měsíc strávili pouze výběrem proxy, která musí u uživatelů běžet. K čemu proxy je? Pouze k jednomu malému, ale velmi důležitému detailu. Abychom znali IP adresu útočníka, která slouží k následné analýze chování útočníků s cílem odhalení nových, dosud neznámých útoků.
Dobrá zpráva je, že i přes krátkou dobu provozu a porodní bolesti máme hodně dat. S přírůstkem deset tisíc SSH sessions za hodinu, v takto malém počtu uživatelů (aktuálně 1 600 aktivních uživatelů), budeme brzy řešit zajímavé úlohy, jak všechna data stihnout analyzovat. Uděláme pro to maximum, protože botnety volající rm -rf jako první příkaz nás děsí a je třeba s nimi zatočit.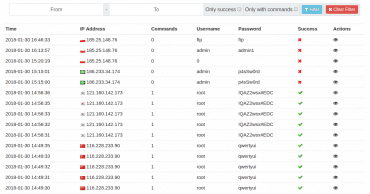
Nasbíraná data využívá Národní bezpečnostní tým CSIRT.CZ pro zkoumání útoků z českých IP adres, o čemž jsou pak majitelé informováni a hlavně vyzváni k nápravě. Největší počet útoků pochází z Číny, proto již spolupracujeme s Taiwanem, aby i u nich mohli zasáhnout. Na spolupráci s dalšími bezpečnostními týmy se pracuje.
NMI18_Materna
Pokud se chcete do projektu zapojit, můžete tak učinit na stránkách haas.nic.cz, kde se zaregistrujete a dle pokynů nainstalujete HaaS proxy (dostupné jako deb a rpm balíček, na PyPI nebo jen tar). V případě zájmu o analýzu dat jsou anonymizovaná data dostupná na stránce s globálními statistiky. Chybí v nich úmyslně použitá hesla, protože jsme zaznamenali nejeden případ, při kterém se uživatel omylem dostal do svého vlastního honeypotu.
Velká část e-mailů putuje internetem nešifrovaně. Kdo to změní?
20.2.2018 Root.cz Zabezpečení
Máme rok 2018 a stále jsme se ještě nevypořádali ani s pořádným šifrováním elektronické pošty. IETF má nyní nová doporučení ohledně šifrování a co možná nejlepší ochrany uživatelů. Jak jsou na tom vaše maily?
Internet Engineering Task Force (IETF) se dlouhodobě snaží o bezpečný a důvěryhodný internet. Nejnovějším příspěvkem na tomto poli je nový standard zavádějící bezpečnější přístup k elektronické poště. Přestože máme rok 2018, stále je v této oblasti co dohánět, protože velká část pošty putuje internetem v otevřené podobě nebo s velmi slabým zabezpečením.
Výsledkem je RFC 8314, ve kterém Chris Newman z Oracle a Keith Moore z Windrock vysvětlují, že v některých případech není komunikace mezi klientem a serverem šifrovaná. Zároveň dokument novelizuje celou řadu předchozích standardů a zavádí přísnější přístup s cílem zajistit uživatelům výrazně vyšší bezpečnost.
Oportunistické šifrování nestačí
Dokument identifikuje hlavní nedostatky v komunikaci mezi e-mailovým klientem (MUA) a servery. Ty mohou být přitom dvojího druhu – pro odesílání pošty (Submission) a příjem pošty (Access). Používají různé protokoly jako Internet Message Access Protocol (IMAP) (RFC3501), Post Office Protocol (POP) (RFC1939) a Simple Mail Transfer Protocol (SMTP) Submission (RFC6409).
Obvykle se při jejich použití používá zabezpečení pomocí Transport Layer Security (TLS) (RFC5246), ale často to není prováděno tím nejlepším způsobem vzhledem k utajení e-mailové komunikaci při přenosu internetem.
Typickým příkladem je takzvané oportunistické (česky příležitostné) šifrování. Předchozí standardy (RFC 2595, 3207 a 3501) totiž doporučovaly používat právě tento způsob. Klient se k serveru připojí běžným otevřeným protokolem bez šifrování a teprve v průběhu komunikace může navrhnout přechod na šifrovanou komunikaci pomocí příkazu STARTTLS.
Konkrétní podoba šifrovaného kanálu pak závisí na dohodnutých schopnostech obou stran. Jinými slovy: pokud o to klient výslovně požádá, může být zahájeno vyjednávání o sestavení nového šifrovaného kanálu pro bezpečnější komunikaci. K němu ovšem vůbec nemusí dojít, pokud se protistrany nedohodnou, přenese se pošta v klidu nešifrovaně. Navíc začátek celé komunikace vždy probíhá v otevřeném prostředí a může tak být odposloucháván nebo manipulován.
Řešení existuje, je jím implicitní šifrování, tedy použití odděleného TCP portu, na kterém se nejprve vždy povinně naváže TLS spojení a teprve v něm probíhá komunikace s poštovním serverem. Čerstvě vydané RFC tedy pro protokoly POP, IMAP, SMTP a další příbuzné doporučuje právě použití této bezpečnější metody.
Klient musí ověřovat certifikáty
Nový dokument zavádí povinnou validaci certifikátů na straně klienta, který se tak musí při navazování spojení řídit RFC 7817. V případě POP3S a IMAPS s tím není problém, protože implicitní TLS je dnes na serverech už velmi rozšířené. Jinak je to ale v případě SMTP, kde je stále ještě častým zvykem používat oportunistické šifrování se STARTTLS. Aby byl přechod pro uživatele pokud možno hladký, měly by servery po přechodné období implementovat jak STARTTLS na portu 587, tak bezpečnější implicitní TLS na portu 465.
TCP port 465 původně vznikl pro TLS variantu SMTP, ale poté se ukázalo, že není možné nijak pomocí MX záznamu signalizovat šifrování (a tedy ani použití jiného portu). Proto se stále pro komunikaci mezi servery používá původní port 25 a vyhrazení nového portu 465 bylo zrušeno. Řada uživatelů ale už mezi tím začala nový port používat pro doručení pošty ze svého klienta s implicitním TLS. Tento postup se nyní formalizuje zavedením nové služby Submissions.
Port 25 není určen pro klienty
Stále rozšířené je použití TCP portu 25 také pro doručení pošty na odesílající server (SMTP Submission), pro které jsou ovšem vyhrazeny už zmíněné porty 587 a 465. Tvůrci nového RFC proto říkají, že by poskytovatelé služeb měli své uživatele co nejdříve přesunout na bezpečnější varianty – ať už oportunistické nebo implicitní. To navíc bez ohledu na to, zda se uživatelé při použití dané služby musejí autentizovat.
Port 25 by tak měl být vyhrazen pro komunikaci mezi servery a klienti by přes něj neměli vůbec poštu na svůj odesílací server předávat. Bohužel je historicky na použití tohoto portu řada uživatelů zvyklá, takže i někteří poskytovatelé poštovních služeb nabízejí přijetí pošty přes tento port. Zároveň ale poskytovatelé připojení často použití portu 25 blokují kvůli boji s odchozím spamem, takže jsou uživatelé chtě něchtě tlačeni do použití správných rozhraní.
Změny na obou stranách
Výše uvedené změny se týkají e-mailových klientů (Thunderbird, Outlook, Apple Mail a dalších), ale také serverů. Ty podle RFC musí implementovat TLS na zmíněných komunikačních protokolech a měly by tak učinit i na jakýchkoliv dalších. Povinně musí TLS umožnit na těch protokolech, kde se uživatel přihlašuje pomocí jména a hesla.
NMI18_Sedivy
Poskytovatelé poštovních služeb by co nejdříve měli ukončit podporu nešifrovaných protokolů, čemuž by měla předcházet postupná migrace uživatelů na šifrované kanály. Za bezpečné se při tom považuje TLS verze 1.1 a vyšší. Server by měl buďto spojení se starší verzí úplně odmítnout nebo přijmout, ale poté zamítnout přihlášení uživatele. Druhá varianta umožňuje navázat komunikaci a poté předat zprávu o důvodu selhání, přináší ale riziko vyzrazení přihlašovacích údajů uživatele. Po nových uživatelích by tak mělo být od začátku požadováno použití TLS alespoň verze 1.1.
RFC 8314 zavádí řadu nových MUST a SHOULD pro obě strany komunikace: klienta i server. Cílem je opustit zastaralé oportunistické šifrování a přinést i do přenosu elektronické pošty podobné standardy, na jaké jsme zvyklí například u HTTPS. Bohužel svět webu a svět elektronické pošty dělí dvě dekády (alespoň po formalizační stránce) a starší protokoly se novým trendům obecně přizpůsobují pomaleji.
Russian Cyberspies Shift Focus From NATO Countries to Asia
20.2.2018 securityweek BigBrothers
The Russia-linked cyber espionage group known as Sofacy, APT28, Fancy Bear, Pawn Storm, Sednit and Strontium has shifted its focus from NATO member countries and Ukraine to Central Asia and even further east, Kaspersky Lab reported on Tuesday.
Sofacy, which is believed to be behind attacks targeting the 2016 presidential election in the United States, has been known to target Ukraine and NATO countries. NATO was heavily targeted in early 2017, including with zero-day exploits, but Kaspersky said the group later started to shift its focus towards the Middle East and Central Asia, which had been less targeted in the first half of the year.
According to the security firm, by mid-2017, detections of a Sofacy backdoor tracked as SPLM, CHOPSTICK and X-Agent showed that the hackers had been increasingly targeting former Soviet countries in Central Asia, including telecoms firms and defense-related organizations. The attacks were aimed at countries such as Turkey, Kazakhstan, Armenia, Kyrgyzstan, Jordan and Uzbekistan.
Attacks involving SPLM and a tool tracked as Zebrocy were increasingly spotted between the second and fourth quarters of 2017 further east. The list of countries where these pieces of malware were detected by Kaspersky includes China, Mongolia, South Korea and Malaysia.
Zebrocy, which allows attackers to collect data from victims, has been used to target various types of organizations, including accounting firms, science and engineering centers, industrial organizations, ministries, embassies and consulates, national security and intelligence agencies, press and translation services, and NGOs.
As for the infrastructure used in these attacks, researchers pointed out that Sofacy has been fairly consistent throughout the years and many of its techniques and patterns have been publicly disclosed. As a result, Kaspersky expects to see some changes this year.
“Sofacy is one of the most active threat actors we monitor, and it continues to spear-phish its way into targets, often on a remarkable global scale,” explained Kurt Baumgartner, principal security researcher at Kaspersky Lab. “Our data and detections show that in 2017, the threat actor further developed its toolset as it moved from high volume NATO spear-phish targeting towards the Middle East and Central Asia, before finally shifting its focus further East. Mass campaigns appear to have given way to subsets of activity and malware involving such tools as Zebrocy and SPLM.”
Apple Fixes Indian Character Crash Bug in iOS, macOS
20.2.2018 securityweek Apple
Updates released by Apple on Monday for iOS, macOS, tvOS and watchOS patch a flaw that causes applications to crash when rendering specific strings of Indian characters.
Someone noticed recently that displaying a string written in India’s Telugu language (జ్ఞా) caused many apps on iOS and macOS to crash. The list of impacted apps includes Twitter, Firefox, Chrome, Safari, WhatsApp, Mail, Thunderbird, Instagram, Slack and others.
Apple became aware of the issue after news of the bug started to spread on social media networks and trolls and pranksters started exploiting it. One individual apparently showed how he could crash the Uber app on drivers’ phones by setting his name to the problematic string and requesting a ride.
SecurityWeek can confirm that conducting a search for the string in any web browser on macOS causes the applications to immediately crash. Attempting to send or receive an email using Mail or Thunderbird has the same effect.
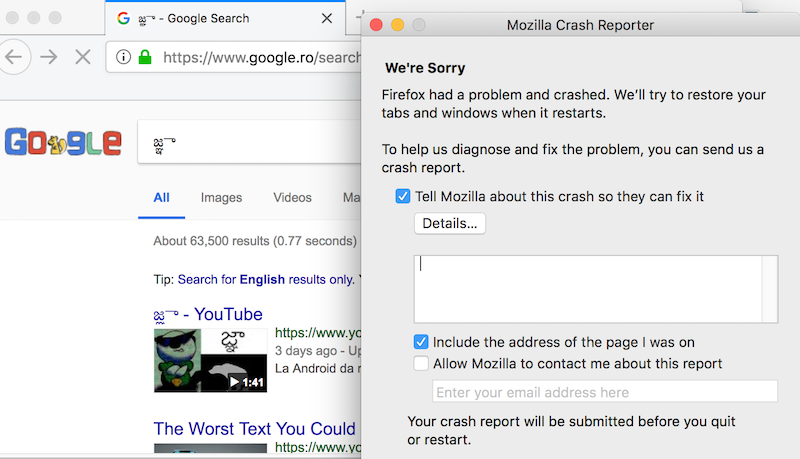
While initially only a certain Telugu string appeared to work, some later noticed that a specific string using characters of India’s Bengali language also caused apps on iOS and macOS to crash. There are several theories on what may be causing the crash, including from Mozilla research engineer Manish Goregaokar and Philippe Verdy of the Unicode Consortium.
Apple tracks the vulnerability as CVE-2018-4124 and describes it as a heap corruption triggered when processing a maliciously crafted string. “A memory corruption issue was addressed through improved input validation,” Apple said.
The company patched the flaw on Monday with the release of macOS High Sierra 10.13.3 Supplemental Update, iOS 11.2.6, watchOS 4.2.3 and tvOS 11.2.6. watchOS and tvOS are affected due to the fact that they are based on iOS. The latest operating system updates don’t fix any other vulnerabilities.
3 Million New Android Malware Samples Discovered in 2017
20.2.2018 securityweek Android
More than 3 million new malware samples targeting the Android operating system were discovered in 2017, marking a slight decrease from the previous year, G Data reports.
The security firm counted 3,002,482 new Android malware samples during 2017, at an average of 8,225 per day, or 343 new malware samples every hour. Although the number is slightly lower when compared to 2016 (when 3,246,284 samples were discovered), the decrease isn’t significant.
In late January, Google revealed that it took down over 700,000 bad apps from Google Play during 2017, a 70% increase compared to the previous year. Many of these programs were copycats – they were either apps packing unacceptable content or malware posing as legitimate apps.
With Android being the most popular mobile operating system out there, it’s no wonder cybercriminals are focused on bypassing Google’s protection mechanisms in their attempt to push malware into the official app store.
This also shows that users should not rely solely on Google’s security features to protect their devices and data. A third-party security program should also be installed and maintained, to detect applications with malicious functions in due time.
Despite the large number of new Android malware samples and that of malicious programs slipping through Google’s protections, the overall security of the operating system appears to be improving, especially with the Internet giant stepping up the platform update process.
Previously, the update process involved multiple steps: the Android team published the open source code, processor providers adapted it to their specific hardware, smartphone providers worked on customizations for the software, network operators also added their own modifications, and only then could an update finally be released.
“Frequently, these concatenated processes take a very long time, so users do not receive the updates until months after they were released by the Android team,” G Data notes.
Lately, Google has been trying to have updates available for all users faster, and initiatives like Project Treble helps in this direction. Through it, a so-called vendor interface is provided, bridging the Android OS framework and the provider’s modifications and making relevant hardware-specific information readily available. Thus, manufacturers can deliver Android updates quickly.
Last year, developers and researchers discovered a total of 841 vulnerabilities among the various versions of Android, making the platform a clear forerunner when it comes to security issues. As a recent Risk Based Security report revealed, the Android-based Pixel/Nexus devices had the most (354) vulnerabilities featuring CSSv2 Scores 9.0 - 10.0 last year.
This leading position could be explained by Android’s open source nature, which provides more people with the opportunity of researching it.
“However, the problem is not only vulnerabilities in the software, but specifically holes in the hardware. Meltdown and Spectre, the serious security holes in processors, which are also present in mobile devices, have again demonstrated how important a speedy security process is so that users receive new updates quickly,” G Data points out.
North Korean Hacking Group APT37 Expands Targets
20.2.2018 securityweek APT
A lesser known hacker group believed to be working on behalf of the North Korean government has been expanding the scope and sophistication of its campaigns, according to a report published on Tuesday by FireEye.
The threat actor is tracked by FireEye as APT37 and Reaper, and by other security firms as Group123 (Cisco) and ScarCruft (Kaspersky). APT37 has been active since at least 2012, but it has not been analyzed as much as the North Korea-linked Lazarus group, which is said to be responsible for high-profile attacks targeting Sony and financial organizations worldwide.
Cisco published a report in January detailing some of the campaigns launched by the threat actor in 2017, but APT37 only started making headlines in early February when researchers revealed that it had been using a zero-day vulnerability in Adobe Flash Player to deliver malware to South Korean users.
APT37, whose goals appear to align with North Korea’s military, political and economic interests, has mainly focused on targeting public and private entities in South Korea, including government, defense, military and media organizations.
However, according to FireEye, the group expanded its attacks to Japan, Vietnam and even the Middle East last year. The list of targets includes organizations in the chemicals, manufacturing, electronics, aerospace, healthcare, and automotive sectors.
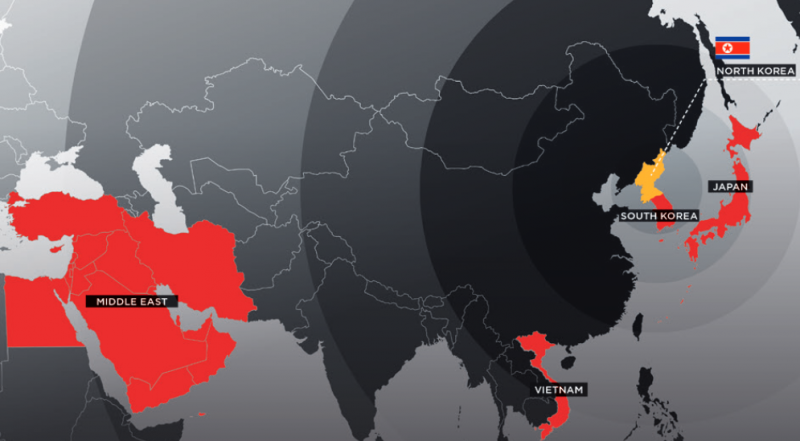
One of the targets in the Middle East was a telecommunications services provider that had entered an agreement with the North Korean government. The deal fell through, which is when APT37 started hacking the Middle Eastern company, likely in an effort to collect information, FireEye said.
APT37 has exploited several Flash Player and Hangul Word Processor vulnerabilities to deliver various types of malware, including the RUHAPPY wiper, the CORALDECK exfiltration tool, the GELCAPSULE and HAPPYWORK downloaders, the MILKDROP and SLOWDRIFT launchers, the ZUMKONG infostealer, the audio-capturing tool SOUNDWAVE, and backdoors tracked by FireEye as DOGCALL, KARAE, POORAIM, WINERACK and SHUTTERSPEED.
This malware has been delivered using social engineering tactics, watering holes, and even torrent sites for wide-scale distribution.
FireEye is highly confident that APT37 is linked to the North Korean government based on several pieces of evidence, including the use of a North Korean IP, malware compilation timestamps consistent with a typical workday in North Korea, and objectives that align with Pyongyang’s interests.
“North Korea has repeatedly demonstrated a willingness to leverage its cyber capabilities for a variety of purposes, undeterred by notional redlines and international norms,” FireEye said in its report. “Though they have primarily tapped other tracked suspected North Korean teams to carry out the most aggressive actions, APT37 is an additional tool available to the regime, perhaps even desirable for its relative obscurity. We anticipate APT37 will be leveraged more and more in previously unfamiliar roles and regions, especially as pressure mounts on their sponsor.”
Neither Kaspersky nor Cisco have explicitly attributed the APT37 attacks to North Korea.
Google to Acquire IoT Management Platform Xively
20.2.2018 securityweek IoT
Google is stepping up its Internet of Things (IoT) game as it has entered into an agreement to acquire Xively, a division of LogMeIn, Inc.
The Xively IoT platform can “help companies in any industry profit from the IoT” and claims to provide “everything needed to build and launch a connected product in months, not years.” It also provides one-click integrations with business tools such as Salesforce.
Formerly known as Cosm and Pachube, LogMeIn acquired Xively in 2011 for approximately $11 million, and will be selling it to Google in a $50 million deal.
Built on LogMeIn’s foundation of security, Xively’s IoT platform is enterprise-ready and is expected to help Google accelerate its customers’ production time when building IoT connected businesses.
“By 2020, it’s estimated that about 20 billion connected things will come online, and analytics and data storage in the cloud are now the cornerstone of any successful IoT solution,” Google says.
The Internet giant is already working on providing a fully managed IoT service via Google Cloud, and the acquisition, which is subject to closing conditions, is expected to complement that.
The resulting product, Google says, would easily and securely connect, manage, and ingest “data from globally dispersed devices.” The platform will pair with the security and scale of Google Cloud, which already provides data analytics and machine learning capabilities to customers.
“Through this acquisition, Cloud IoT Core will gain deep IoT technology and engineering expertise, including Xively’s advanced device management, messaging, and dashboard capabilities. Our customers will benefit from Xively’s extensive feature set and flexible device management platform,” Google says.
While they will continue to invest in their Support-of-Things initiatives, by selling Xively, LogMeIn is exiting the IoT connectivity platform space.
“We believe that Google Cloud, now armed with Xively’s team and great technology – and backed by their platform and developer heritage and reach – are a far better fit for the future of platform leadership,” Bill Wagner, President and CEO, LogMeIn, notes in a blog post.
NIST Proposes Metadata Schema for Evaluating Federated Attributes
20.2.2018 securityweek BigBrothers
NIST's Attribute Metadata Schema Could Help Privacy Compliance in Multi-Domain Transactions
Verifying identities (entities) is one problem. Managing the authorized transactions available to that verified entity is a separate problem. As industry and government increasingly move online, both the complexity and criticality of different possible cross-domain transactions increase. A single verified entity may be authorized for some transactions, but not others.
The decision to authorize or decline access to a protected resource depends upon different attributes (metadata) associated with each entity. In a federated identity and access management (IAM) process, different metadata is obtained from different authoritative providers. The National Institute of Standards and Technology (NIST) recently published 'Attribute Metadata: a Proposed Schema for Evaluating Federated Attributes' (PDF) in order to provide the basis for the evolution of a standardized approach to entity attributes.
This is an internal report (NISTIR 8112) that will not be imposed upon federal agencies, but can be used by both public and private organizations. Its purpose is to allow a system (RP, the relying party) that uses federated IAM to better understand and trust different attributes; to apply more granular and effective access authorizations; and to promote the federation of attributes.
"NIST envisions that the core set of metadata proposed here can serve as a library or menu from which both commercial and federal implementers can draw common semantics, syntaxes, and values to support their specific needs," notes the report. "This will serve as a starting point for the development of a metadata standard that can enable greater federation across markets and sectors."
NIST believes that it could become the foundation for a future attribute confidence scoring structure to help align attribute-based authorizations with an organization's risk environment. Furthermore, it adds, "the ideal metadata schema could be used in both commercial and public-sector implementations, thus serving as a foundation to enable greater federation across markets and sectors."
The NIST proposal comprises two core concepts: Attribute Schema Metadata (ASM, or the attribute's own metadata -- a definition of the attribute); and Attribute Value Metadata (AVM, or the value contained in the metadata). The ASM for an attribute includes its description, allowed values, its format, its verification frequency, and a description of the basis for processing attributes and attribute values.
The AVM defines 15 separate metadata elements around the value contained in an attribute. There are five categories: provenance (3), accuracy (2), currency (3), privacy (5) and classification (2). The provenance category includes three elements: 'origin', which is the name of the entity that issues the attribute; 'provider', which is the name of the entity providing the attribute and might be different to the origin; and 'pedigree', which is the relationship of the attribute value to an authoritative source, such as 'authoritative', 'derived' or 'self-asserted'.
The Classification (security level) metadata comprises two elements: classification and releasability. The classification metadata element could be any one of six values: unclassified, controlled unclassified, confidential, secret, top secret, and company confidential. The releasability element has seven possible values: NATO, NOFORN (no-one foreign), FVEY (only members of the Five Eye allies), public release, for business purposes, do not release, and none.
However, the remaining eight metadata elements have no defined values nor restrictions on what could be included. The five 'privacy' elements are particularly interesting because they can be used both to provide compliance with privacy regulations -- including aspects of the EU's General Data Protection Regulation -- and demonstrate compliance to auditors. The elements are date of consent, type of consent, acceptable uses, cache time limit, and date for data deletion.
Consent is an essential part of user data collection and user data processing. Having the date consent was given, separate data processors have greater legal status in processing user data. The type of consent is equally important. Values could include 'opt-in', 'opt-out' or parental-delegated consent, among others. Since different jurisdictions can demand 'opt-in' consent, or allow 'opt-out' consent, knowing which attribute applies to the data is important for privacy compliance.
The acceptable uses element can be used to specify the use conditions for the entities that receive attributes. Again, since under GDPR and other regulations, user data can only be used for the purposes for which it was collected, it is an aid to ensuring and demonstrating compliance. The NIST document suggests, "organizations or trust frameworks might also maintain their own categories of acceptable uses based on their policies."
The cache time limit reflects the sensitivity of different data, and can be used to specify the maximum time that data may reside in cache memory, perhaps for re-use in other transactions. "In some cases," says NIST, "the time to live may be dictated by regulation or law, and this information needs to be relayed to RP systems so data are handled accordingly. The more sensitive an attribute value, the shorter time it will likely be enabled to live in temporary memory."
The data deletion data attribute simply ensures that a best practice privacy principle can be applied. "Some attribute values may produce little to no privacy risk for individuals," writes NIST. "Other values may add new privacy risks or increase existing privacy risks. A deletion date ensures that sensitive information does not remain in systems indefinitely."
"This NISTIR," says the report, "defines a set of optional elements of an attribute metadata schema to support cross-organization decision making, such as two executive branch agencies, in attribute assertions. It also provides the semantics and syntax required to support interoperability. NIST does not intend to make any of this schema required in federal systems and attribute-based information sharing. Rather, this schema represents a compendium of possible metadata elements to assist in risk-based decision making by an RP. This schema is focused on subjects (individual users); objects and data tagging, while related, are out of scope."
A new multi-stage attack deploys a password stealer without using macros
20.2.2018 securityaffairs Vulnerebility Attack
Security researchers at Trustwave spotted a new malicious campaign that uses a multi-stage attack to deploy a password stealer.
Researchers at Trustwave have spotted a new malware-based campaign that uses a multi-stage infection to deploy a password stealer malware.
Hackers leverage the infamous Necurs botnet to distribute spam emails delivering Microsoft Office documents that embedded malicious macros.
DOCX attachments used by the attackers contain an embedded OLE object that has external references, the external access is provided to remote OLE objects to be referenced in the document.xml.rels.
“Anyone can easily manipulate data in a Word 2007 file programmatically or manually. As shown below, the DOCX attachment contains an embedded OLE object that has external references. This ‘feature’ allows external access to remote OLE objects to be referenced in the document.xml.rels.” states the analysis published by trustwave.
“When user opens the DOCX file, it causes a remote document file to be accessed from the URL: hxxp://gamestoredownload[.]download/WS-word2017pa[.]doc. This is actually a RTF file that is downloaded and executed.”
Once the victim opened the file, it will attempt to trigger the CVE-2017-11882 memory-corruption flaw that was used by many threat actors in the wild, including the Cobalt hacking group. Microsoft fixed the vulnerability in November, the CVE-2017-11882 flaw was discovered by the security researchers at Embedi, it affects the MS Office component EQNEDT32.EXE that is responsible for insertion and editing of equations (OLE objects) in documents.
The component fails to properly handle objects in the memory, a bug that could be exploited by the attacker to execute malicious code in the context of the logged-in user.
Back to the macro-based Multi-Stage attack discovered by Trustwave, the RTF file accessed after the victim opens the DOCX files executes an MSHTA command line to download and execute a remote HTA file.
The HTA file contains VBScript with obfuscated code that decodes to a PowerShell Script designed to eventually downloads and executes a remote binary file that is a Password Stealer Malware.
“The malware steals credentials from email, ftp, and browser programs by concatenating available strings in the memory and usage of the APIs RegOpenKeyExW and PathFileExistsW to check if registry or paths of various programs exist.” continues the analysis.

The password stealer will send data to the command and control server (C&C) via an HTTP POST.
The most interesting aspect of this attack is the use of multiple stages to deliver the final payload, an approach that Trustwave calls unusual.
Malware researchers at Trustwave highlighted that a so long infection chain is more likely to fail compared to other technique implemented in other attacks.
“It’s pretty unusual to find so many stages and vectors being used to download malware. Indeed, this approach can be very risky for the malware author. If any one stage fails, it will have a domino effect on the whole process. Another noticeable point is that the attack uses file types (DOCX, RTF and HTA), that are not often blocked by email or network gateways unlike the more obvious scripting languages like VBS, JScript or WSF.” concludes Trustwave.
The analysis published by Trustwave includes the Indicators of Compromise (IoCs).
Cyberattacks cost the United States between $57 billion and $109 billion in 2016
20.2.2018 securityaffairs BigBrothers
The report published by the White House Council of Economic Advisers examines the cyberattacks cost that malicious cyber activities cause to the U.S. economy.
How much cost cyber attacks to the US? According to a report published by the White House Council of Economic Advisers last week, the cyberattacks cost between $57 billion and $109 billion in 2016, and things can go worse in the future.
“This report examines the substantial economic costs that malicious cyber activity imposes on the U.S. economy. Cyber threats are ever-evolving and may come from sophisticated adversaries. Due to common vulnerabilities, instances of security breaches occur across firms and in patterns that are difficult to anticipate.” states the report.
“Firms in critical infrastructure sectors may generate especially large negative spillover effects into the wider economy.”
The report analyzed the impact of malicious cyber activities on public and private entities, including DoS attacks, sabotage, business disruption, and theft of proprietary data, intellectual property, and sensitive financial and strategic information.
Damages and losses caused by a cyber attack may spill over from the initial target to economically linked organizations. More exposed are critical infrastructure sectors, at attack against companies and organization in this industry could have a severe impact on the US economy.
The document warns of nation-state actors such as Russia, China, Iran, and North Korea, that are well funded and often conduct sophisticated targeted attacks for both sabotage and cyber espionage.
“Finally, and perhaps most important, if a firm owns a critical infrastructure asset, an attack against this firm could cause major disruption throughout the economy.” reads the report.
“Insufficient cybersecurity investment in these sectors exacerbates the risks of cyberattacks and data breaches. The economic implications of attacks against critical infrastructure assets are described in more detail later in the paper. “

The reports also warn of devastating cyberattacks that would target sectors that are internally interconnected and interdependent with other sectors.
The report offered little in the way of new recommendations on improving cybersecurity, but noted that the situation is hurt by “insufficient data” as well as “underinvestment” in defensive systems by the private sector.
“Cyber connectivity is an important driver of productivity, innovation, and growth for the U.S. economy, but it comes at a cost. Companies, individuals, and the government are vulnerable to malicious cyber activity.” concludes the report. “Effective public and private-sector efforts to combat this malicious activity would contribute to domestic GDP growth. However, the ever-evolving nature and scope of cyber threats suggest that additional and continued efforts are critical, and the cooperation between public and private sectors is key.”