
Dridex banking Trojan and the FriedEx ransomware were developed by the same group
30.1.2018 securityaffairs Ransomware
Security researchers from ESET have tied another family of ransomware, dubbed FriedEx (aka BitPaymer), to the authors of the Dridex Trojan.
The Dridex banking Trojan that has been around since 2014, it was involved in numerous campaigns against financial institutions over the years and crooks have continuously improved it.
In April 2017, millions of people were targeted by a phishing campaign exploiting a Microsoft Word 0day and aimed to spread the Dridex Banking Trojan, a few days ago security researchers at Forcepoint spotted a new spam campaign that is abusing compromised FTP servers as a repository for malicious documents and infecting users with the Dridex banking Trojan.
Now, security researchers from ESET have tied another strain of ransomware, dubbed FriedEx (aka BitPaymer), to the authors of the Dridex Trojan.
FriedEx was first spotted in July, and in August it was responsible for infections at NHS hospitals in Scotland.
The FriedEx ransomware was involved in attacks against high profile targets, researchers believe it was delivered via Remote Desktop Protocol (RDP) brute force attacks.
The ransomware encrypts each file using a randomly generated RC4 key that is then encrypted with a hardcoded 1024-bit RSA public key.
“Initially dubbed BitPaymer, based on text in its ransom demand web site, this ransomware was discovered in early July 2017 by Michael Gillespie. In August, it returned to the spotlight and made headlines by infecting NHS hospitals in Scotland.” states the analysis published by ESET.
“FriedEx focuses on higher profile targets and companies rather than regular end users and is usually delivered via an RDP brute force attack. The ransomware encrypts each file with a randomly generated RC4 key, which is then encrypted using the hardcoded 1024-bit RSA public key and saved in the corresponding .readme_txt file.”
The analysis of FriedEx code revealed that many similarities with Dridex code.
For example, the Dridex and FriedEx binaries share the same portion of a function used for generating UserID, the experts also noticed that the order of the functions in the binaries is the same in both malware families, a circumstance that suggests the two malware share the same codebase.

“It resolves all system API calls on the fly by searching for them by hash, stores all strings in encrypted form, looks up registry keys and values by hash, etc. The resulting binary is very low profile in terms of static features and it’s very hard to tell what the malware is doing without a deeper analysis.” states ESET.
Both Dridex and FriedEx use the same packer, but experts explained that the same packer is also used by other malware families like QBot, Emotet or Ursnif also use it.
Another similarity discovered by the researchers is related to the PDB (Program Database) paths included in both malware. PDB paths point to a file that contains debug symbols used by vxers to identify crashes, the paths revealed the binaries of both threats are compiled in Visual Studio 2015.
The experts also analyzed the timestamps of the binaries and discovered in many cases they had the same date of compilation, but it is not a coincidence.
“Not only do the compilations with the same date have time differences of several minutes at most (which implies Dridex guys probably compile both projects concurrently), but the randomly generated constants are also identical in these samples. These constants change with each compilation as a form of polymorphism, to make the analysis harder and to help avoid detection.” continues the analysis.
The experts concluded that FriedEx was developed by the Dridex development team, they believe that the criminal gang not only will continue to improve the banking Trojan but it will also follow malware “trends” developing their own strain of ransomware.
Microsoft Disables Spectre Mitigations Due to Instability
30.1.2018 securityweek Vulnerebility
Out-of-band Windows updates released by Microsoft over the weekend disable mitigations for one of the Spectre attack variants as they can cause systems to become unstable.
Both microcode and software updates designed to address the Spectre and Meltdown vulnerabilities have turned out to be buggy, often making systems unbootable or causing them to reboot more frequently. Intel has suspended its patches until the issue is resolved and advised customers to stop deploying the updates.
HP, Dell, Lenovo, VMware, Red Hat and others had paused the patches and now Microsoft has done the same.
The problem appears to be related to CVE-2017-5715, which has been described as a “branch target injection vulnerability.” This is one of the flaws that allows Spectre attacks, specifically Spectre Variant 2 attacks.
Microsoft has confirmed that Intel’s patches cause system instability and can in some cases lead to data loss or corruption. Update KB4078130 released by the company over the weekend for Windows 7, Windows 8.1 and Windows 10 – for both clients and servers – disables the mitigation for CVE-2017-5715.
The company has also provided instructions for advanced users on how to manually enable and disable Spectre Variant 2 mitigations through registry settings.
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” Microsoft said in its advisory.
Microsoft quickly released mitigations for Meltdown and Spectre after the attack methods were disclosed, but the company’s own updates were also buggy. Shortly after it had started rolling them out, Microsoft was forced to suspend patches for devices with AMD processors due to instability issues.
The Spectre and Meltdown vulnerabilities allow malicious applications to bypass memory isolation mechanisms and access sensitive data. The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities. However, Intel does not appear too concerned that the incident will affect its bottom line – the company expects 2018 to be a record year in terms of revenue.
Exercise Tracking App Reveals Details of Military Sites
30.1.2018 securityweek BigBrothers
A map showing paths taken by users of an exercise tracking app reveals potentially sensitive information about American and allied military personnel in places including Afghanistan, Iraq and Syria.
While some bases are well known to groups that want to attack them, the map also shows what appear to be routes taken by forces moving outside of bases -- information that could be used in planning bombings or ambushes.
The map, made by Strava Labs, shows the movements of its app users around the world, indicating the intensity of travel along a given path -- a "direct visualization of Strava's global network of athletes," it says.
Routes are highlighted over large parts of some countries, but in others, specific locations stand out.
The map of Iraq is largely dark, indicating limited use of the Strava app, but a series of well-known military bases where American and allied forces have been deployed as part of their war against the Islamic State (IS) group are highlighted in detail.
These include Taji north of Baghdad, Qayyarah south of Mosul and Al-Asad in Anbar Province. 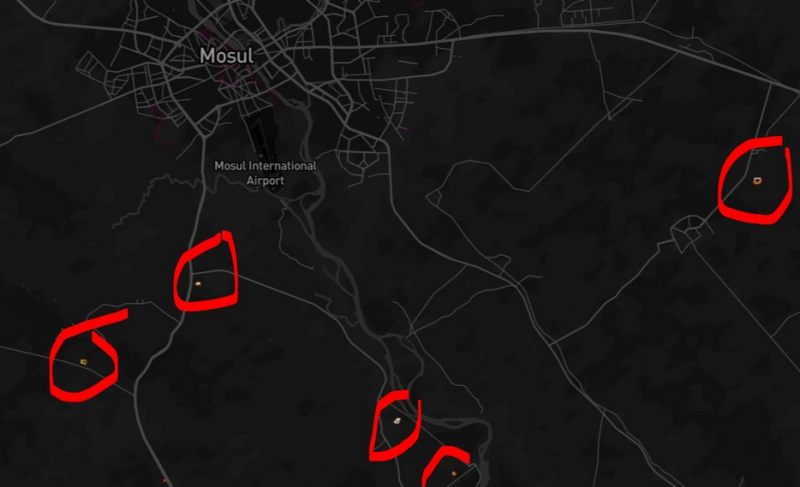
Smaller sites also appear on the map in northern and western Iraq, indicating the presence of other, lesser-known installations.
Stretches of road are also highlighted, indicating that Strava users kept their devices on while traveling, potentially providing details about commonly-taken routes.
In Afghanistan, Bagram Airfield north of Kabul is a hive of activity, as are several locations in the country's south and west.
- Opting out an option -
Tobias Schneider, a security analyst who was among the group of people who highlighted the military bases shown on the map, noted that it shows military sites in Syria and Iraq as well as the Madama base used by French forces in Niger.
"In Syria, known Coalition (i.e. US) bases light up the night. Some light markers over known Russian positions, no notable coloring for Iranian bases," Schneider wrote on Twitter.
US troops are deployed in support of local forces battling IS in Syria as well as Iraq, while Russian and Iranian units are backing President Bashar al-Assad's Syria government in that country's civil war.
"A lot of people are going to have to sit thru lectures come Monday morning," Schneider wrote, referring to soldiers likely to be taken to task for inadvertently revealing sensitive information while trying to keep in shape.
"Bases are fixed & hard to conceal," he wrote, so the "biggest potential threat is to tracking movement."
The US Department of Defense said it is "reviewing" the situation.
"Recent data releases emphasize the need for situational awareness when members of the military share personal information," Major Audricia Harris, a Pentagon spokeswoman, told AFP.
"DoD takes matters like these very seriously and is reviewing the situation to determine if any additional training or guidance is required, and if any additional policy must be developed to ensure the continued safety of DoD personnel at home and abroad," Harris said.
The Pentagon "recommends limiting public profiles on the internet, including personal social media accounts," she said.
The issue could have been fairly easily avoided. According to Strava, "athletes with the Metro/heatmap opt-out privacy setting have all data excluded" from the mapping project.
Top Dutch Banks, Revenue Service Hit by Cyber Attacks
30.1.2018 securityweek Attack
The top three banks in the Netherlands have been targeted in multiple cyber attacks over the past week, blocking access to websites and internet banking services, they said on Monday.
The Dutch Revenue Service was also briefly targeted on Monday by a similar attack, but services were quickly restored, a spokesman said.
The number one Dutch bank, ING, was hit by a so-called distributed denial of service (DDoS) attack on Sunday evening while the eurozone nation's third largest lender, ABN Amro, suffered three attacks over the weekend in a total of seven over the last week, Dutch media reported.
Rabobank, the country's number two lender, saw its internet banking services go down on Monday morning.
"We have been targeted by a DDoS attack since 9.10 am (0810 GMT) this morning (Monday) and our clients don't have access or very little access to online banking," Rabobank spokeswoman Margo van Wijgerden said. "We are working to resolve the problem as quickly as possible," she told AFP.
Also on Monday, the Dutch Revenue Services saw its website go down for about 10 minutes due to an attack, spokesman Andre Karels said.
"Things are running as normal and we are investigating the incident," Karels told AFP.
ING, which has some eight million private clients, experienced an attack on Sunday evening, it said on its website.
"During the DDoS attack ING's internet site was blasted with data traffic causing our servers to overload and which put pressure on the availability of online banking," ING said, adding services had been restored.
ABN Amro experienced a similar attack but also said services were restored. It will "keep monitoring availability and is extra alert since the weekend's attacks," it said in a statement.
The banks all stressed that clients' banking details were not compromised or leaked.
It is not the first time Dutch banks were targeted in a DDoS attack with central bank chief Klaas Knot telling a TV news programme Sunday there were "thousands of attacks a day" on his own institution.
"I think these (recent) attacks are serious, but our own website is being attacked thousands of times per day," Knot told the Buitenhof talk show. "That is the reality in 2018," he said.
*UPDATED with brief cyber attack on Dutch Revenue services
phpBB Website Served Malicious Packages
30.1.2018 securityweek Virus
The developers of the free and open source forum software phpBB informed users over the weekend that the official website had served malicious files for roughly three hours on Friday.
According to phpBB staff, the download URLs for two packages, namely version 3.2.2 of the full package and the automatic updater package for 3.2.1 to 3.2.2, pointed to a third-party server. Users who downloaded one of these packages between 12:02 PM and 15:03 PM UTC on January 26 likely obtained the malicious version.
phpBB hacked
It’s unclear how the links were replaced, but phpBB noted that the “point of entry was a third-party site” and the attack did not exploit any vulnerabilities in the phpBB software or website.
The modified packages contain malicious code designed to load JavaScript from a remote server. The domain hosting that JavaScript code is now controlled by phpBB, which neutralizes the attack.
“We can additionally say that due to the limited window during which the packages were live, we estimate the total number of affected downloads does not exceed 500,” the phpBB team said in a security alert.
Users who believe they have downloaded the malicious packages have been advised to check the validity of the file by comparing its SHA256 hash to the one listed on the downloads page.
Users who have already installed one of the compromised packages can file an incident report and the phpBB team will help them remove the malicious code.
This is not the first time malicious actors have targeted phpBB. Back in 2009, hackers managed to obtain 400,000 email addresses belonging to phpBB users after exploiting a vulnerability in the email marketing tool phpList.
In 2014, phpBB shut down its network and asked users to change their passwords after hackers breached several of its servers.
Dridex Authors Build New Ransomware
30.1.2018 securityweek Ransomware
The authors of the infamous Dridex banking Trojan have created a sophisticated ransomware family, ESET warns.
Around since 2014, Dridex has been one of the most prolific financial threats over the past several years, and the actors behind it have been constantly adopting new techniques, improving their malware, and changing resources to ensure increased efficiency.
Thus, it did not come too much as a surprise when the Locky ransomware was tied to Dridex two years ago, when ransomware was booming. Locky became a top threat fast, catching a lot of attention from the security community as well, and its developers attempted alternatives such as Bart in 2016 and Jaff in May 2017.
Now, security researchers have tied yet another ransomware family to the Dridex authors, namely FriedEx, which is also known as BitPaymer.
This ransomware was initially discovered in July 2017 and made it to the headlines in August, when it infected NHS hospitals in Scotland.
Mainly focused on high profile targets and companies rather than end users, the malware is typically delivered via Remote Desktop Protocol (RDP) brute force attacks. Once it has managed to infect a system, the malware encrypts each file on it with a randomly generated RC4 key (which it then encrypts using a hardcoded 1024-bit RSA public key and saves it in a .readme_txt file).
While analyzing FriedEx, ESET discovered that it features code resemblance to Dridex. The ransomware also uses the same techniques as the banking Trojan, hiding as much information about its behavior as possible.
The malware “resolves all system API calls on the fly by searching for them by hash, stores all strings in encrypted form, looks up registry keys and values by hash, etc. The resulting binary is very low profile in terms of static features and it’s very hard to tell what the malware is doing without a deeper analysis,” ESET explains.
The researchers discovered that the very same part of a function used for generating UserID that is present across all Dridex binaries can be found in the FriedEx binaries as well. The order of the functions in the binaries is the same in both malware families, which suggests they use the same codebase or static library.
Both Dridex and FriedEx use the same malware packer, but that is not proof that they are connected, since other well-known families like QBot, Emotet or Ursnif also use it.
ESET also discovered that samples of both Dridex and FriedEx include PDB (Program Database) paths, which revealed that their binaries are being built in the same, distinctively named directory. The binaries of both Dridex and FriedEx are compiled in Visual Studio 2015.
Some binaries for both projects revealed the same date of compilation, and the researchers say this isn’t coincidence. The samples have time differences of several minutes at most and feature identical randomly generated constants (these constants change with each compilation to hinder analysis), which suggests they were probably built during the same compilation session.
“With all this evidence, we confidently claim that FriedEx is indeed the work of the Dridex developers. This discovery gives us a better picture of the group’s activities – we can see that the group continues to be active and not only consistently updates their banking Trojan to maintain its webinject support for the latest versions of Chrome and to introduce new features like Atom Bombing, but that it also follows the latest malware “trends”, creating their own ransomware,” ESET says.
UK Warns Critical Industries to Boost Cyber Defense or Face Hefty Fines
30.1.2018 securityweek BigBrothers
The UK government has warned that Britain's most critical industries must boost their cybersecurity or face potentially hefty fines under the EU's Networks and Information Systems Directive (NISD).
The warning comes less than four months before the deadline for the NISD, adopted by the EU on July 6, 2016, to be transposed into EU member states' national laws (May 9, 2018, which aligns with the date for GDPR enforcement).
NISD is designed to ensure the security of network systems not already covered by the GDPR -- but its primary purpose is to ensure the security of the industries that comprise the critical infrastructure (such as power and water, healthcare and transport). These companies, or covered entities, are defined within the directive as 'operators of essential services' (OES), and 'digital service providers' (DSPs).
Since it is a Directive rather than a Regulation, the NIS Directive has some national flexibility in its implementation. For example, the UK government had earlier proposed that maximum fines under the directive should be between €10 million and €20 million or 2% to 4% of annual global turnover. It has now settled on a maximum fine of €17 million.
The government announcement on Sunday stems from its published response (PDF) to a public consultation it initiated in August 2017.
The UK has made it clear that a breach of an OES will not automatically trigger a fine. This will depend on the judgment of separate industry sector regulators, or competent authorities. The primary factor will be whether the breached OES/DSP has made adequate cyber security provisions -- in practice, this will probably depend upon how well the firm has implemented the 'NIS Directive: Top-level objectives' guidelines published by the National Cyber Security Centre (NCSC, part of GCHQ) Sunday. However, the government also states, "New regulators will be able to assess critical industries to make sure plans are as robust as possible."
The key part of the EU's NIS Directive is Article 14: Security requirements and incident notification. This specifies, "Member States shall ensure that operators of essential services take appropriate and proportionate technical and organizational measures to manage the risks posed to the security of network and information systems."
The NCSC guidelines say this can be implemented through conforming to four top-level objectives comprising 14 security principles. The top-level objectives are: managing security risk; protecting against cyber-attack; detecting cyber security events; and minimizing the impact of cyber security incidents. Each of the objectives is then broken into the series of sector-agnostic security principles. "Each principle," states the NCSC, "describes mandatory security outcomes to be achieved."
Only one of the four objectives takes the traditional view of cyber security: protecting against cyber-attack -- recognizing the difference between commercial and critical organizations. For the former, personal information and profitability are the primary motivations; for the latter, it is continuity (or recovery) of operation that is important. "This legislation clearly signals the move away from pure protection-based cybersecurity thinking," comments Steve Malone, director of security product management at Mimecast. "Robust business continuity strategies have never been more important to ensure organizations can continue to operate during an attack and get back up on their feet quickly afterwards."
The objective that concentrates on protection against a cyber-attack recognizes that technology is not a complete solution. For example, Principle B1 deals with policies and procedures. Principle B6 handles staff awareness and training. This latter is particularly welcomed by Stephen Burke, Founder and CEO at Cyber Risk Aware.
Noting that the critical infrastructure is actively targeted by nation state actors more than cyber criminals, he asks, "But how do nation states get in? The simple answer is through people. For example, the Saudi Aramco breach affected 35,000 machines and the attackers got in because a Saudi Aramco employee clicked on a link in a spear-phishing email and meant 10 percent of the world's supply was at risk.
"This emphasizes the fact that any institutions no matter how big they are and no matter how sophisticated their technical defenses are, they need to help staff and make them become aware of the cyber dangers they face as that’s how actors are going to breach defenses.”
But it isn't just about cyber-attacks and data loss. NISD "will also cover other threats affecting IT such as power outages, hardware failures and environmental hazards," says the government announcement. "Under the new measures recent cyber breaches such as WannaCry and high-profile systems failures would be covered by the Network and Information Systems (NIS) Directive.
"These incidents would have to be reported to the regulator who would assess whether appropriate security measures were in place. The regulator will have the power to issue legally-binding instructions to improve security, and – if appropriate – impose financial penalties."
This raises another issue. Most of the critical industries will have customer databases, and that could make them liable to GDPR as well as NISD, plus any existing sector-specific regulations. "Under this new legislation," warns Andy Miles, CEO of ThinkMarble, "companies could potentially be fined under the GDPR, the Government and by a regulator, so there is a risk of double or even triple jeopardy here."
The government's response document specifies the regulator (or 'competent authority') for the different critical sectors. This is often the government itself; that is, the relevant Secretary of State for that sector -- although it is the Information Commissioner (ICO) who is the competent authority for digital service providers just as with the GDPR. This could lead to confusion and lack of consistency since Secretaries of State change, and different enforcement levels could change rapidly in line with a changing political situation. "I believe that the NCSC, working alongside the ICO, should take the lead in putting these sanctions in place -- and the regulators should feed into them, not the other way around," suggests Miles.
There is a danger that NISD has simply been overshadowed by GDPR. There is concern that many of the covered entities will not be ready for its implementation in May 2018. Miles warns that "27% of respondents [to the governments consultation period] had no plans to implement further security measures, and 31% did not know if they would make any changes. This suggests that there is much still to be done in educating companies about the importance of protecting themselves from cyber-attacks."
Lorena Marciano, EMEAR data protection & privacy officer at Cisco, told SecurityWeek that organizations seen as privacy-immature experience far greater losses than those considered as privacy-mature. The implication, she said, is that NISD provisions, "shouldn’t be adopted for the single purpose of avoiding fines, but that organizations which are willing to go beyond the set compliances will reap the long-term financial benefits as well as protecting customer data.”
This means that the NCSC's guidelines should be considered as the base-line for critical industries, and that they should then go beyond them. The first step would clearly be a gap analysis between existing security controls and the NCSC's guidelines.
"Importantly, meeting those four objectives and 14 principles will demand a degree of cyber maturity that is far removed from prescriptive, compliance-based tick-box exercises," comments Robert Orr, cyber security principal consultant CNI, Context Information Security. "This means that [covered entities] will need to put as much emphasis on NIS as they should be putting on that other EU regulation, GDPR; not least because the level of fine for non-compliance is similarly punitive." That will require OES and DSPs to assess their existing cyber security and resilience, to identify any gaps in meeting the NIS outcomes, and to develop improvement plans to close those gaps -- and then go beyond them.
Phishing Pages Hidden in "well-known" Directory
30.1.2018 securityweek Phishing
UK-based cybercrime disruption services provider Netcraft has spotted thousands of phishing pages placed by cybercriminals in special directories that are present on millions of websites.
In the past month, the company spotted more than 400 new phishing websites hosted in a folder named /.well-known/. This directory serves as a Uniform Resource Identifier (URI) path prefix that allows users and automated processes to obtain policy and other information about the host.
The /.well-known/ directory is commonly used to demonstrate ownership of a domain. The administrators of HTTPS-protected websites that use Automatic Certificate Management Environment (ACME) to manage SSL certificates place a unique token inside the /.well-known/acme-challenge/ or /.well-known/pki-validation/ folders to show the certificate issuer that they control the domain.
“Consequently, most of the phishing attacks that make use of the /.well-known/ directory have been deployed on sites that support HTTPS, using certificates issued by ACME-driven certificate authorities like Let's Encrypt and cPanel,” Netcraft’s Paul Mutton explained.
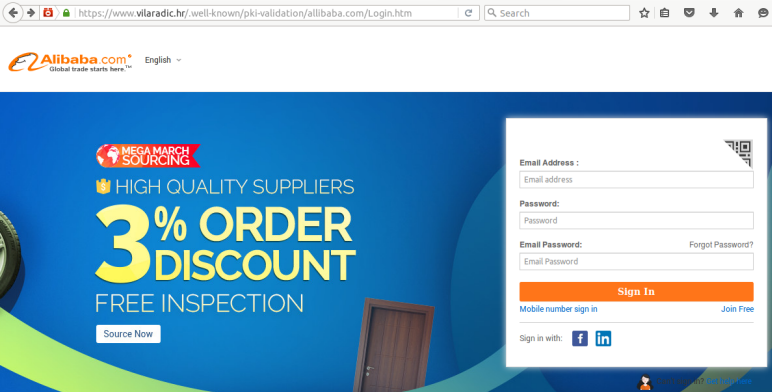
The /.well-known/ location can be a great place to hide a phishing page due to the fact that while the folder is present on millions of websites – mainly due to the success of ACME and Let’s Encrypt – many administrators are not aware of its presence.
Mutton noted that since there is a dot in front of the directory’s name, listing files using the ls command will not display it as files and folders that start with “.” are hidden. In an effort to make their phishing pages even more difficult to find, cybercriminals have placed them in subdirectories of /acme-challenge/ and /pki-validation/.
“Shared hosting platforms are particularly vulnerable to misuse if the file system permissions on the /.well-known/ directories are overly permissive, allowing one website to place content on another customer's website,” Mutton warned. “Some of the individual servers involved in these attacks were hosting ‘well-known’ phishing sites for multiple hostnames, which lends weight to this hypothesis.”
The expert pointed out that while /acme-challenge/ and /pki-validation/ are not the only well-known URIs, these are the only ones that have been used to host phishing sites.
Netcraft said it was not clear how malicious actors had hijacked the websites found to be hosting these phishing pages.
Researchers Connect Lizard Squad to Mirai Botnet
30.1.2018 securityweek BotNet
Lizard Squad and Mirai, which are responsible for a series of notorious distributed denial of service (DDoS) attacks, are connected to one another, a recent ZingBox report reveals.
Lizard Squad is a hacking group known for some of the most highly publicized DDoS attacks in history, including the disruption of Sony PlayStation and Xbox Live networks. Over the past several years, multiple individuals suspected to have used Lizard Squad’s LizardStresser DDoS service have been arrested.
While the hacking group has been operating for several years, Mirai has been around for only one year and a half, making headlines in late 2016 following massive DDoS attacks against Brian Krebs’ blog and Dyn’s DNS infrastructure. The malware’s source code was made public within weeks of these attacks and numerous variants have emerged since.
Now, ZingBox researchers claim to have discovered evidence that links the Lizard Squad hackers and Mirai, including the common use of the same Ukraine hosting provider Blazingfast.
The Mirai source code, the researchers point out, was released nine days after Lizard Squad founder Zachary Buchta was arrested. According to them, the DDoS attack on Brian Krebs’ blog in late 2016 appears the result of the journalist’s criticism against Lizard Squad, and there are also references to Mirai on a Lizard Squad website.
Analysis of a domain associated with a Mirai-based malware campaign in late 2017 led the researchers to bigbotPein, a group linked to Lizard Squad. The analyzed domain was registered by an individual associated with Lizard Squad, a ZingBox report (PDF ) claims.
bigbotPein, a group that emerged in support to Buchta following his arrest, adopted Mirai as part of their Internet of Things arsenal and is currently targeting multiple architectures, including x86, x64, ARM, MIPS, SuperH, SPARC and ARC.
What’s more, the group has also added Ethereum and Monero miners to their malware portfolio, while also adopting increased sophistication, the security researchers say.
A Mirai-based campaign observed in October 2017 was pointing to the domain bigbotpein[.]com. The website’s Start of Authority (SOA) points to blazingfast[.]io, the Ukraine hosting provider that is also used by Mirai authors for the botnet control server, ZingBox says.
The security researchers claim they were also able to link the group to multiple Mirai variants out there, including Satori and Masuta. According to them, the Satori campaign was initially called Okiru and was using the control[.]almahosting[.]ru and network[.]bigbotpein[.]com domains.
Starting with mid-January 2018, all the domains related to Lizard Squad and bigbotPein switched to US-base ISPs (Rackspace and Search Guide), which suggests a clear connection between the two groups.
Two other Mirai variants observed last year include Masuta and Memes. The former, detailed only this month, targeted x86, ARM and MIPS architectures. The latter appears to be the work of the same author and might be an evolution of Masuta.
The malware code, ZingBox claims, includes a “structure previously identified in July 2017 related to Lizard Squad.” This code allows the malware to hide and decode second stage payload in memory. Both an Ethereum dropper variant linked to Lizard Squad and Masuta/Memes use this same code structure.
Other evidence linking Lizard Squad and Mirai include the dropping of a file from bigbotPein domain control[.]almahosting[.]ru as part of a Satori campaign in November 2017, leading to the Monero Stratum miner.
A Satori variant observed in early January 2018 was employing an extra level of obfuscation, along with the s[.]sunnyjuly[.]gq domain, and pointing to the use of an Etherum miner for Windows, although the initial attack vector, however, targeted the MIPS architecture.
“During this research, we witnessed firsthand the evolving complexity of the different variants of Lizard Squad and bigbotPein group’s malware within a span of one year […]. The Lizard Squad and bigbotPein groups used to be very active creating most of the well-known variants of Mirai,” ZingBox’ report reads.
“Despite the courageous efforts of our law enforcement agencies to identify and tear down various hacking groups, the collaboration between groups makes it extremely difficult to completely shut down their efforts for good. Arrests of high-profile members and founders of such groups certainly slows down their momentum, but organizations can’t take their foot off the gas when it comes to being vigilant about the security of their network,” Xu Zou, CEO and co-founder, ZingBox, said.
Lenovo Addresses Hardcoded Password in Fingerprint Manager
30.1.2018 securityweek Vulnerebility
Computer maker Lenovo has updated Fingerprint Manager Pro for Windows 7, 8, and 8.1 to address several insecure credential storage issues in the software, including the presence of a hardcoded password.
Rated High severity and tracked as CVE-2017-3762, the vulnerability was discovered by Jackson Thuraisamy from Security Compass. An attacker attempting to exploit the issue could escalate their privileges on the local system.
The flaw only impacts Lenovo Fingerprint Manager Pro, a utility for Windows 7, 8, and 8.1 that has been designed to help users log into their PCs or authenticate to configured websites by means of fingerprint recognition.
The bug resides in the use of a weak algorithm when encrypting sensitive data stored by Fingerprint Manager Pro, such as users’ Windows logon credentials and fingerprint data, the company said in an advisory.
What’s more, the application was found to contain a hardcoded password and to be accessible to all users with local non-administrative access to the computer it is installed on.
According to Lenovo, the application may be installed on a large number of device models, including ThinkPad L560, P40 Yoga, P50s, T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560, W540, W541, W550s, X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT), X240, X240s, X250, X260, Yoga 14 (20FY), and Yoga 460; ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, and M93z; and ThinkStation E32, P300, P500, P700, P900.
The vulnerability has been addressed in Lenovo Fingerprint Manager Pro version 8.01.87. Owners of the aforementioned models should update to the new software release.
U.S. Floats Idea Nationalizing High-Speed Networks, Drawing Rebukes
30.1.2018 securityweek BigBrothers
US officials have launched a debate on a proposal to nationalize the newest generation of high-speed wireless internet networks in the name of national security, provoking sharp criticism from across the political spectrum.
One official familiar with the proposal but not authorized to speak publicly told AFP the idea "has been discussed over the past couple of weeks" at the request of US national security officials.
The proposal was first reported by the news website Axios, citing a memo proposing government control of the newest and fastest part of the nation's mobile network -- the fifth generation, or 5G -- to guard against China's growing online capabilities.
Axios cited a memo by a senior official as contending that the US need to quickly deploy 5G because China is in a top position with the technology and "is the dominant malicious actor" online.
But the proposal -- which would run counter to the longstanding US policy of relying on private telecom networks -- drew immediate rebukes from the industry and even from US regulatory officials.
The official familiar with the proposal noted that "it's not hard to find people who think it's a dumb idea."
Industry leaders pointed out that the private sector is already in the process of building and deploying 5G systems, which will be important for a range of connected devices from appliances to self-driving cars.
The federal government stepping in would "slam the brakes" on momentum to deploy 5G, argued Jonathan Spalter, chief of USTelecom trade association.
"The best way to future-proof the nation's communications networks is to continue to encourage and incentivize America's broadband companies... in partnership with government, to continue do what we do best: invest, innovate, and lead," Spalter said in a statement.
Meredith Attwell Baker, president of the wireless industry group CTIA, added that while 5G is important, "the government should pursue the free market policies that enabled the US wireless industry to win the race to 4G."
Federal Communications Commission chairman Ajit Pai, whose agency regulates the telecom sector, also voiced strong opposition.
"Any federal effort to construct a nationalized 5G network would be a costly and counterproductive distraction from the policies we need to help the United States win the 5G future," Pai, a Republican, said.
Pai's Democratic colleague on the FCC, Mignon Clyburn, agreed, saying a network built by the federal government "does not leverage the best approach needed for our nation to win the 5G race."
Conservative advocacy group FreedomWorks also came out against the idea, arguing that the move would put the US on the same level as China in controlling online access.
FreedomWorks president Adam Brandon said, "We're not beating the Chinese if we sacrifice what makes our government so different from theirs."
Military personnel improperly used Fitness Strava Tracker exposed their bases
30.1.2018 securityaffairs BigBrothers
Military worldwide have publicly shared online their exercise routes recorded through the fitness tracker Strava revealing the fitness sessions conducted inside or near military bases
We discussed many times privacy risks related to IoT devices, here we are to discuss an alarming case, fitness tracker Strava revealed details of Military Bases.
American and allied military worldwide have publicly shared their exercise routes online revealing the fitness sessions conducted inside or near military bases, including Afghanistan, Iraq, and Syria.
This leak of information has happened because military personnel turned on their fitness Strava tracker while making exercises at the bases.
A map showing exercise routes recorded by users of a tracking app reveals sensitive information about military personnel in locations around the world, including Afghanistan, Iraq, and Syria.
Such kind of information could be used by enemies and terrorists to plan an attack.
Obviously while in some regions of the globe it is impossible to distinguish the activity of the military personnel, in other locations the routes immediately stand out.
For example, examining the map of Iraq you can notice that the entire region is dark, except for a series of well-known military bases used by the American military and its allies.
The list of the bases easy to locate thank to the map associated to the fitness tracker Strava includes Taji north of Baghdad, Qayyarah south of Mosul, Speicher near Tikrit and Al-Asad in Anbar Province and a number of minor sites highlighted in northern and western Iraq.
Searching for bases in Afghanistan, it is easy to locate the Bagram Air Field in the north of Kabul along with other smaller sites south of the country.
![]()
The movements of soldiers within Bagram air base – the largest US military facility in Afghanistan – Source BBC
Similarly, in Syria it is Qamishli in the northwest, a stronghold of US-allied Kurdish forces, is clearly visible.
Tobias Schneider, one of the security experts that discovered the map, shared details about the bases on Twitter, including the French Madama base in Niger.
27 Jan
Tobias Schneider
✔
@tobiaschneider
Replying to @tobiaschneider
Worth browsing a bit. Three positions around the US outpost at Tanf: pic.twitter.com/jS7S4LR2QS
Tobias Schneider
✔
@tobiaschneider
My focus is on Syria, but obviously works all over. French military base Madama in Niger: pic.twitter.com/1e9SRR73xS
7:57 PM - Jan 27, 2018
View image on Twitter
7 7 Replies 174 174 Retweets 331 331 likes
Twitter Ads info and privacy
27 Jan
Tobias Schneider
✔
@tobiaschneider
Replying to @tobiaschneider
A lot of people are going to have to sit thru lectures come Monday morning.
Tobias Schneider
✔
@tobiaschneider
So much cool stuff to be done. Outposts around Mosul (or locals who enjoy running in close circles around their houses): pic.twitter.com/wHItJwYUUI
8:37 PM - Jan 27, 2018
View image on Twitter
10 10 Replies 187 187 Retweets 469 469 likes
Twitter Ads info and privacy
The researchers Nathan Ruser spotted also activities of Russians in Khmeimim.
27 Jan
Nathan Ruser
@Nrg8000
Replying to @Nrg8000
Not just US bases. Here is a Turkish patrol N of Manbij pic.twitter.com/1aiJVHSMZp
Nathan Ruser
@Nrg8000
You can see the Russian operating area in Khmeimim, but also the guard patrol to the NE. pic.twitter.com/iWiX5Kozc1
7:28 PM - Jan 27, 2018
View image on Twitter
3 3 Replies 77 77 Retweets 114 114 likes
Twitter Ads info and privacy
The good news is this issue could be easily fixed, Strava confirmed that “athletes with the Metro/heatmap opt-out privacy setting have all data excluded.”
The app allows users to set up “privacy zones,” that are areas where the Strava tracker doesn’t collect GPS info. These areas can be designed around the user’s home or work, but evidently, the military personnel ignored it.
A new report from MALWAREBYTES reveals a rise of 90% on ransomware detection in business
30.1.2018 securityaffairs Vulnerebility
A new report from MALWAREBYTES titled “Malwarebytes Annual State of Malware Report” reveals a rise of 90% on ransomware detection in business.
The report brings to light new trends on hackers activities and threats especially the rise of ransomware as a tool of choice.
Researchers from MALWAREBYTES had gathered an enormous amount of data from the telemetry of their products, intel teams, and data science from January to November 2016 and to January to November 2017 to consolidate the evolution of the threat landscape of malware.
It is taken into account the tactics of infection, attack methods, development and distribution techniques used by hackers to target and compromise business and customers alike. There was a surge of 90% in ransomware detection for business customers in such way that it had become the fifth most detected threat. Regarding its modus operandi, the researchers found out a change in the distribution of malicious payloads, which includes banker Trojans and cryptocurrency miners.
Ransomware was on the rise, but it was not the only method employed by hackers. The report reveals that hackers had used banking trojans, spyware and hijackers to steal data, login credentials, contact lists, credit card data and spy on the user as an alternative way to compromise system security. The report discovered that hijackers detection grew 40% and spyware detection grew 30%. The report lists the Top 10 business threat detections with the five most significant threats being: Hijacker, Adware, Riskware Tool, Backdoor, and Ransomware respectively.
While the report covers a variety of threats, it emphasizes how malware outbreak had evolved. A game changer to the ransomware outbreak like WannaCry was the government exploit tool EternalBlue that was leaked and has been employed to compromise update processes and increased geo-targeting attacks. According to the report these tactics had been adopted to bypass traditional methods of detection.
The report highlights the delivery techniques utilized by ransomware due to the EternalBlue exploit tool leaked from NSA. The usage of this exploit tool was a ground break landmark to the development of WannaCry and NotPetya ransomware. The EternalBlue (CVE-2017-0144) is a vulnerability in Server Message Block (SMB) handling present in many Windows operating systems. WannaCry was able to widespread globally due to operating systems that were not properly updated.
The report dedicates a special attention to NotPetya ransomware, as it was influenced by ransomware Petya and WannaCry. This ransomware has used two Server Message Block (SMB) vulnerabilities: EternalBlue (CVE2017-0144) and EternalRomance (CVE-2017-0145) and was also able to encrypt the MFT (Master File Table) and the MBR (Master Boot Record) on affected systems. Other malware analyzed in the report, that used the leaked exploit tools from the NSA was: Adylkuzz, CoinMiner, and Retefe.
The researchers also unveil a new attack vector employed by hackers: Geo Targeting attacks. In this type of attack, groups of hackers or rogue nations employ a variety of techniques to disrupt, destabilize, or compromise data in specific countries. The Magniber malicious code targeted South Korea specifically and the BadRabbit had targeted Ukraine. Although NotPetya emerged in Ukraine its action was not limited within its borders.
Finally, the report brings forth to light trends based on data collected. Cyptocurrency miners already become a new threat with the recent news of a steal of bitcoins from Japan. Other trends to watch out this year in the report is the attacks on the supply chain, the increase of malware in MAC systems and leaks in government and in companies that will lead to new zero-day vulnerabilities
On Saturday Malwarebytes delivered a buggy update that caused excessive memory usage and crashes.
30.1.2018 securityaffairs Vulnerebility
On Saturday Malwarebytes issued a buggy update to its home and enterprise products that caused serious problems for the users, including excessive memory usage, connectivity issues, and in some cases system crashes.
A buggy update rolled out over the weekend by Malwarebytes to its home and enterprise products caused serious problem for the users, including excessive memory usage, connectivity issues, and in some cases system crashes.
Malwarebytes issued the buggy update on Saturday morning (PST) and according to the security firm the software was only available only for 16 minutes before it removed it.
“On the morning of Saturday, January 27th, 2018 protection update v1.0.3798 was released for all versions of Malwarebytes for Windows. As endpoints updated to this release, customers noticed their machines were reporting many Internet block notifications, and a sudden large increase in RAM usage” reads the Root Cause Analysis published by Malwarebytes.
“There are detection syntax controls in place to prevent such events as the one experienced in this incident. Recently we have been improving our products so that we can show the reason for a block, i.e. the detection “category” for the web protection blocks. In order to support this new feature, we added enhanced detection syntaxes to include the block category in the definitions. The unfortunate oversight was that one of the syntax controls was not implemented in the new detection syntax, which cause the malformed detection to be pushed into production.”

Some users reported problems to their connections that were blocked by the security software after the installation of the buggy update. Another displeasing problems reported by the users is the abnormal memory usage, the process associated with the application had used up more than 10 Gb of the (RAM), in some cases were also observed system crashes.

Malwarebytes confirmed that the broken detection was present in the update version v1.0.3798 thru v1.0.3802. (v2018.01.27.03 – v2018.01.27.11
for MBES customers).
The buggy update was issued to all software versions for Windows, below the list of affected versions:
Malwarebytes for Windows Premium
Malwarebytes for Windows Premium Trial
Malwarebytes Endpoint Security (MBES)
Malwarebytes Endpoint Protection (Cloud Console)
The problem was addressed with the v1.0.3803 (v2018.01.27.12 for MBES customers).
Affected users can follow the recovery solutions published by the company to remove the buggy update and install the correct one.
The company remarked that it pushes tens of thousands updates routinely testing each one before it is distributed.
“We have pushed upwards of 20,000 of these protection updates routinely. We test every single one before it goes out. We pride ourselves on the safety and accuracy of our detection engines and will work to ensure that this does not happen again,” Malwarebytes stated following the incident.
Over the weekend Microsoft rolled out out-of-band updates to disable mitigations for Spectre v2 attacks
30.1.2018 securityaffairs Vulnerebility
Over the weekend, Microsoft rolled out out-of-band updates to disable mitigations for one of the Spectre attack variants because they can cause systems to become unstable.
The situation is becoming embarrassing! Just after the release of the Meltdown and Spectre security updates Intel excluded any problems for their deployments citing testing activities of conducted by other tech giants.
At the same time, some companies were claiming severe issued, including performance degradation and in some cases crashes.
Last week, Intel changed its position on the security patches, it first published the results of the test conducted on the Meltdown and Spectre patches and confirmed that the impact on performance could be serious, then it recommended to stop deploying the current versions of Spectre/Meltdown patches.
Over the weekend, Microsoft rolled out out-of-band updates to disable mitigations for one of the Spectre attack variants because they can cause systems to become unstable.
“Our own experience is that system instability can in some circumstances cause data loss or corruption.” states the security advisory published by Microsoft.
“While Intel tests, updates and deploys new microcode, we are making available an out of band update today, KB4078130, that specifically disables only the mitigation against CVE-2017-5715 – “Branch target injection vulnerability.” In our testing this update has been found to prevent the behavior described.”
Microsoft was among the first companies that provided security updates for Meltdown and Spectre vulnerabilities, anyway, the patches caused severe issues to AMD architectures.
The decision follows the similar actions adopted by other tech giants like Red Hat, HP, Dell, Lenovo, VMware.
Microsoft and the companies above observed problems after the installation of the Spectre vulnerability (Variant 2, aka CVE-2017-5715, that is a branch target injection vulnerability) for this reason opted to revert previous patches.
While the Meltdown and Variant 1 of the Spectre attacks can be mitigated efficiently with software updates, the Spectre Variant 2 requires microcode updates to be fully addressed.
Intel published a technical note about the mitigation of the Spectre flaw, it addressed the issue with an opt-in flag dubbed IBRS_ALL bit (IBRS states for Indirect Branch Restricted Speculation).
The famous Linus Torvalds expressed in an email to the Linux Kernel mailing list his disappointment, he defined the Linux Spectre Patches “UTTER GARBAGE”
Microsoft confirmed that the patches issued by Intel cause system instability and can in some cases lead to data loss or corruption, for this reason, the company distributed over the weekend the Update KB4078130 for Windows 7, Windows 8.1 and Windows 10 that disables the mitigation for CVE-2017-5715.
The company has also provided detailed instructions for manually enable and disable Spectre Variant 2 mitigations through registry settings.
Microsoft said it is not aware of any attack in the wild that exploited the Spectre variant 2 (CVE 2017-5715 ).
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” continues the advisory.
Malwarebytes Delivers Buggy Update to Home, Enterprise Users
29.1.2018 securityweek Vulnerebility
A protection update pushed out over the weekend by Malwarebytes to its home and enterprise users caused serious problems, including Web connection issues, excessive memory usage, and even system crashes.
The problematic update was released on Saturday morning, Pacific Standard Time (PST), and it was only available for 16 minutes before Malwarebytes took action to stop it from being distributed. However, it was enough for the update to reach a significant number of devices protected by the security firm’s products.
“There are detection syntax controls in place to prevent such events as the one experienced in this incident. Recently we have been improving our products so that we can show the reason for a block, i.e. the detection ‘category’ for the web protection blocks,” Malwarebytes explained. “In order to support this new feature, we added enhanced detection syntaxes to include the block category in the definitions. The unfortunate oversight was that one of the syntax controls was not implemented in the new detection syntax, which caused the malformed detection to be pushed into production.”
Some users reported that their Web connections had been blocked and the process associated with the Malwarebytes application had used up more than 10 Gb of their random access memory (RAM), causing their systems to become very slow and even crash.
The buggy protection update, namely v1.0.3798, was sent out to all versions of Malwarebytes for Windows. The affected applications include Malwarebytes for Windows Premium, including the trial version, Malwarebytes Endpoint Security (MBES), and Malwarebytes Endpoint Protection (Cloud Console). The Mac, Android, and other apps were not impacted.
Malwarebytes has provided detailed instructions for both home and enterprise users on how to recover from this incident and install the correct update on their systems. Users who had their devices turned off when the buggy update was delivered should not be affected.
“We have pushed upwards of 20,000 of these protection updates routinely. We test every single one before it goes out. We pride ourselves on the safety and accuracy of our detection engines and will work to ensure that this does not happen again,” Malwarebytes stated following the incident.
This was not the first time a security solutions provider released an update that caused headaches for home users and system administrators. Other companies involved in similar incidents in recent years include Panda Security, ESET, and Webroot.
Microsoft Disables Spectre Mitigations Due to Instability
29.1.2018 securityweek Vulnerebility
Out-of-band Windows updates released by Microsoft over the weekend disable mitigations for one of the Spectre attack variants as they can cause systems to become unstable.
Both microcode and software updates designed to address the Spectre and Meltdown vulnerabilities have turned out to be buggy, often making systems unbootable or causing them to reboot more frequently. Intel has temporarily suspended its patches until the issue is resolved and advised customers to stop deploying the updates.
HP, Dell, Lenovo, VMware, Red Hat and others had paused the patches and now Microsoft has done the same.
The problem appears to be related to CVE-2017-5715, which has been described as a “branch target injection vulnerability.” This is one of the flaws that allows Spectre attacks, specifically Spectre Variant 2 attacks.
Microsoft has confirmed that Intel’s patches cause system instability and can in some cases lead to data loss or corruption. Update KB4078130 released by the company over the weekend for Windows 7, Windows 8.1 and Windows 10 – for both clients and servers – disables the mitigation for CVE-2017-5715.
The company has also provided instructions for advanced users on how to manually enable and disable Spectre Variant 2 mitigations through registry settings.
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” Microsoft said in its advisory.
Microsoft quickly released mitigations for Meltdown and Spectre after the attack methods were disclosed, but the company’s own updates were also buggy. Shortly after it had started rolling them out, Microsoft was forced to suspend patches for devices with AMD processors due to instability issues.
The Spectre and Meltdown vulnerabilities allow malicious applications to bypass memory isolation mechanisms and access sensitive data. The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities. However, Intel does not appear too concerned that the incident will affect its bottom line – the company expects 2018 to be a record year in terms of revenue.
Japan-based digital exchange Coincheck to refund to customers after cyberheist
29.1.2018 securityaffairs Incindent
Coincheck announced it will refund about $400 million to 260,000 customers after the hack, the company will use its own funds.
On Friday the news of the hack of the Japan-based digital exchange Coincheck caused the drop in the value of the major cryptocurrencies, the incident had a significant impact on the NEM value that dropped more than 16 percent in 24 hours.
The company suspended the operations of deposits and withdrawals for all the virtual currencies except Bitcoin, the exchange announced it was investigating an “unauthorised access” to the exchange.
According to the company, the hackers stole worth half a billion US dollars of NEM, the 10th biggest cryptocurrency by market capitalization.
The hackers stole 58 billion yen ($530 million), an amount of money that is greater than the value of bitcoins which disappeared from MtGox in 2014.
Coincheck was founded in 2012, it is one of the most important cryptocurrency exchange in Asia.
The company announced it will refund about $400 million to customers after the hack.
Coincheck will use its own funds to reimburse about 46.3 billion yen to its 260,000 customers who were impacted by the cyberheist.
“At 3 am (1800 GMT) today, 523 million NEMs were sent from the NEM address of Coincheck. It’s worth 58 billion yen based on the calculation at the rate when detected,” said Coincheck COO Yusuke Otsuka.
“We’re still examining how many of our customers are affected,”
Experts believe that the Financial Services Agency will to take disciplinary measures against Coincheck.
It has been estimated that as many as 10,000 businesses in Japan accept bitcoin and bitFlyer, nearly one-third of global Bitcoin transactions in December were denominated in yen.The Cryptocurrencies, and in particular Bitcoin, are very popular in Japan, in April, the Bitcoin was proclaimed by the local authorities as legal tender.
According to Japanese bitcoin monitoring site Jpbitcoin.com, in November, yen-denominated bitcoin trades reached a record 4.51 million bitcoins, or nearly half of the world’s major exchanges of 9.29 million bitcoin.
Japanese media criticized the company blaming the management to have underestimated the importance of security of its investor, they said Coincheck “expanded business by putting safety second”.
Politicians and experts that participated in the World Economic Forum in Davos issued warnings about the dangers of cryptocurrencies, it is expected that government will adopt further measures to avoid abuse and illegal uses of cryptocrurrencies.
Neutopte se v bezpečnostních datech
29.1.2018 SecurityWorld Bezpečnost
Mnoho firem si myslí, že vědí, co jsou klíče k jejich království a kde se nacházejí příslušné brány. Bohužel často zjišťují, že nejzávažnější narušení jejich výsostného území se často stane úplně někde jinde. Threat intelligence jim umožní mít bezpečnostní rizika i bezpečnostní programy pod kontrolou.
Organizace mohou například sledovat aktivity v bankomatech a uniknou jim jemné varovné signály procházející přes jejich centrální počítač, říká Sharon Vardi, marketingový šéf v Securonix. „Aniž si to uvědomují, nechávají firmy své korunovační klenoty napospas.“
Chceme-li vědět, co je nutné hlídat, je potřeba sbírat data k analýze a nechat někoho takovou analýzu vykonávat. Firmy však neuspějí, pokud neshromažďují a neanalyzují úplný datový proud – úspěch vyžaduje více než jen snímek z omezeného časového intervalu. Data se musejí shromažďovat předtím, během a poté, co dojde k záškodnické aktivitě.
„Podniky také musejí zahrnout data z celé sítě, z každého jednotlivého koncového bodu a potenciálně dokonce z externích a veřejných zdrojů umístěných vně sítě,“ vysvětluje Alan Hall, ředitel strategie ve firmě Blue Coat Systems. „V opačném případě budou reakce přinejlepším limitované.“
Nutný kontext
Schopnost reakce na incidenty je místo, kde mohou vznikat problémy. To vyžaduje získat kontext – informace nad rámec toho, co se nachází v nezpracované podobě. Kontext lze použít k identifikaci pokročilého či jinak skrytého útoku nebo kompromitace a poskytuje prostředky ke zjištění nejvhodnějšího způsobu reakce.
„K řádné správě bezpečnostních incidentů potřebují firmy nejen sběr dat, ale také jejich analýzu v reálném čase a ukládání těchto dat, aby je bylo možné použít později k nalezení souvislostí s novými daty proudícími v reálném čase,“ vysvětluje Travis Smith, výzkumník ve společnosti Tripwire. „Problémem je, že ukládání dat stojí peníze a správa a využití těchto dat mohou být také skutečným problémem.“
Realitou je, že bezpečnostní týmy, jež chtějí analyzovat protokoly, jsou vydané na milost vývojářům, kteří rozhodují o tom, co protokolovat a z jakých systémů. Tyto podrobnosti se často vestavějí do systémů (nebo přesněji řečeno se opomíjejí) už při jejich vývoji.
Bezpečnostní protokoly jsou však i tak jen špičkou ledovce. Skutečná podstata spočívá v zachytávání paketů v rámci celé sítě. Překonání této bariéry tvořené jen protokoly a přechod na zachytávání síťového provozu sice přinášejí firmám velké množství bezpečnostních dat, ale také další problém: „Data zabezpečení nejsou totéž co big data,“ vysvětluje Smith. „Jsou to morbidně obézní data.“
Normální osvědčené postupy pro ukládání dat počítají se 30 dny provozu, ačkoli některé oborové zásady vyžadují více a některá vládní nařízení dokonce ještě více. „Je to téměř nedbalost, když bezpečnostní tým funguje jen v režimu pohotovosti a nedokáže analyzovat kontext,“ dodává Hall.
Někdy je to více než jen otázka jak moc – mohla by to být také otázka jak: zákazníci se snaží od svých programů pro správu zabezpečení dostat to, co chtějí. „Bezpečnostní týmy buď nedostávají žádné výstrahy či příliš málo výstrah ... Nebo trpí vážnou přemírou výstrah a následným vyčerpáním,“ říká John Humphreys, viceprezident společnosti Proficio.
„Rozhodně zachytávejte svá data protokolů, ale směřujte svou pozornost nad rámec protokolů a využívejte také informace z interní sítě. Měli byste také provázat relace dohromady, zachytávat řetězce paketů a nakonec využívat plné zachytávání paketů,“ doporučuje Smith z Tripwiru.
Podle Vardiho by podniky měly uvážit také využití externích zdrojů dat, které se tradičně nepovažují za bezpečnostní údaje. To zahrnuje například aktivity na Facebooku, vyhledávače zaměstnání a další dostupné datové zdroje.
„Za těchto okolností je férové využívat data společnosti za pomoci zpravodajských kanálů z otevřených zdrojů,“ dodává Vardi. Tyto zdroje dat nemusejí vypadat jako bezpečnostní data, ale mohou dramaticky změnit kontext bezpečnostních dat a poskytnout firmám nový způsob, jak se dívat na svůj rizikový profil.
Samozřejmě je pro užitečnost threat intelligence nutné, aby byly zpravodajské kanály věrohodné a založené na spolehlivých zdrojích, jež zahrnují i ty vlastní interní. Existuje velké množství aplikací, které generují spoustu zdánlivě neškodných interních přenosů, z nichž většina je navržena pro sdílení dat, aby mohly firemní týmy dělat svou práci. Přesto není možné zahrnutí těchto zdrojů dat a kvalitu těchto dat opomíjet.
Výhradně interní síťové přenosy se totiž často ignorují nebo nedochází k jejich detekci, pokud se sledují jen systémové protokoly pro vniknutí a úniky dat. To je obvykle způsobené tím, že takové přenosy probíhají horizontálně uvnitř sítě a nikdy neprocházejí přes systémy, které nativně monitorují vniknutí, a ani při své cestě neputují přes hraniční firewall.
„Vniknutí a úniky nastávají jen tehdy, když přenosy zařízení vstupují do podnikové sítě nebo ji opouštějí,“ vysvětluje Carmine Clementelli, manažer divize PFU Systems ve společnosti Fujitsu. „Podobně také řídicí komunikace probíhá mimo síť pomocí externích dočasných webových stránek. Ve většině případů platí, že pokud najdete problém na této vrstvě, je už příliš pozdě.“
Jaký kontext hledat?
Když přijde otázka na určení kontextu, který se použije pro vyhledání hrozeb, jimž společnost čelí, a probíhajících útoků, je nutné vybrat jednu z následujících tří možností:
Nechat systém automaticky definovat kontext a doufat, že jeho dodavatelé definovali konfigurace a pravidla, tak „aby to fungovalo dobře“.
Použít svůj vlastní naučený kontext, který jste během času získali, a doufat, že své prostředí znáte dostatečně nebo alespoň tak dobře jako útočníci.
Definovat kontext za běhu způsobem ad hoc a pokoušet se k tomu použít data o hrozbách a podpůrné informace a pak se doslova modlit, abyste měli stále náskok a nestali se obětí únavy z nadmíry varování.
Anebo lze využít výhody bezpečnostní komunity a využívat oborové sady a oborové profily definované ostatními pro výběr a následné úpravy kontextu. „Bezpečnostní týmy potřebují pozorovat svůj IT život v realitě pomocí zkušeností jiných firem,“ tvrdí Humphreys a dodává, že právě to je dobrý způsob, jak pochopit skutečný kontext.
Co se týká lidí zevnitř, kteří by mohli krást data a posílat je konkurenci, spočívá kontext ve sledování toho, zda nějací zaměstnanci či smluvní dodavatelé nepřistupují k datům mimo obvyklý rámec, například častěji. Můžete také zachytit provoz, který ukazuje, že zaměstnanci sdílejí citlivé údaje mimo organizaci, například pomocí osobního e-mailového účtu nebo vyměnitelného USB disku.
Zaměstnance, který nedávno dostal nějaké špatné hodnocení, lze označit za ještě větší riziko. A pokud se například dodavatel (třetí strana) snaží několikrát přihlásit a přistupovat k systémům firmy mimo obvyklý rámec, může to být příznak, že se buď chová zle on sám, nebo že se stal obětí phishingového útoku.
Ale nejsou to jen lidé a systémy, co poskytují kontext. „Entitou může být také dokument,“ vysvětluje Vardi. „Chování dokumentu je stejně tak důležité sledovat. Kde se nachází? Kdo k němu přistupuje? Z jaké IP adresy se k němu přistupuje? Kam se přenáší?“
Každý z těchto aspektů – při sledování společně s dalšími událostmi a varováními – může přinést dodatečný kontext k jinak nezjištěné škodlivé aktivitě. Pokud se například zaměstnanec, partner nebo zákazník obvykle přihlašují z počítače se systémem Windows a používají Firefox a najednou dochází ke stahování dokumentů z počítače Mac pomocí prohlížeče Safari, potom by to mohl být příznak probíhajícího problému.
Bankomatový podvod je dalším příkladem z reálného světa, který v současné době významně roste. Představte si klienty banky, kteří jsou jejími zákazníky 20 let a většinu této doby s bankou komunikují určitým způsobem. Můžete hledat anomálie v jejich aktivitách: výše jejich výběrů, místa výběrů, použitou kartu. Dokonce i počet použití karty během dne na různých místech.
A stejný princip můžete použít pro monitorování přístupu k podnikovým zdrojům a dalších aktivit uživatelů a systémů v síti. Zde je několik příkladů:
Koncový bod přidělený jednomu uživateli se přihlašuje do sítě několikrát pomocí více uživatelských identit. Pokud toto vidíte, existuje reálná možnost, že došlo ke kompromitaci systému.
Nešifrované přenosy typu sever-jih se souvislostí s interními přenosy východ-západ – mějte se na pozoru před síťovými aktivitami, které přijdou zvenčí a pohybují se laterálně. Takto související přenosy mohou být příznakem neautorizovaného uživatele či zařízení v síti.
Využívání metod detekce založených na chování – sledování odchozích přenosů a přenosů peer-to-peer pro zjišťování, kam přenosy směřují a jak často danou cestou putují. Zaměření na vstup by ale nemělo být jediným přístupem – musíte totiž také předpokládat, že malware je už uvnitř, a sledovat proto i výstupy.
Využijte výhodu detekce řízení a identifikace existujících útoků, které pravděpodobně odesílají data. Uvědomte si přitom, že odesílání dat často neprobíhá jako jeden přenos a může proběhnout jako řada malých akcí za dlouhou dobu. Ve středu, který představuje dlouhé období aktivity, dochází k bočním pohybům. Identifikace je v tomto případě možná na základě chování, nikoliv pouhou analýzou paketů. Uvažte, že web schválený oddělením IT nebo oddělením zabezpečení, který je však unesený a využívaný útočníkem jako úložná služba, nebudou vaše systémy pro reputaci a filtrování vůbec detekovat.
Při analýze používaných funkcí aplikací jděte nad rámec monitorování aplikací na nejvyšší úrovni. Facebook jako celek se může v případě některých zaměstnanců ještě akceptovat, ale jak a kdy se využívají řešení jako chat Facebooku nebo sledování a odesílání videa v rámci této sociální sítě? Jaká a kolik dat se přenáší při využití uvedených funkcí?