Charming Kitten Targets Iranian Dissidents with Advanced Cyber Attacks
14.8.23 APT The Hacker News

Germany's Federal Office for the Protection of the Constitution (BfV) has warned of cyber attacks targeting Iranian persons and organizations in the country since the end of 2022.
"The cyber attacks were mainly directed against dissident organizations and individuals – such as lawyers, journalists, or human rights activists – inside and outside Iran," the agency said in an advisory.
The intrusions have been attributed to a threat actor called Charming Kitten, which is also tracked under the names APT35, Mint Sandstorm, TA453 and Yellow Garuda.
While Iranian nation-state actors lag behind their Russian and Chinese counterparts in sophistication, they have demonstrated a continued advancement of tools and techniques, adding an arsenal of custom malware to facilitate information gathering and rapidly exploiting n-day security flaws to obtain initial access.
Cybersecurity
Charming Kitten, in particular, has a long, storied history of leveraging elaborate social engineering and fictitious online identities that are tailor-made to target victims. It also impersonates real journalists and NGO employees in a bid to build rapport and increase the likelihood of success of the attacks.
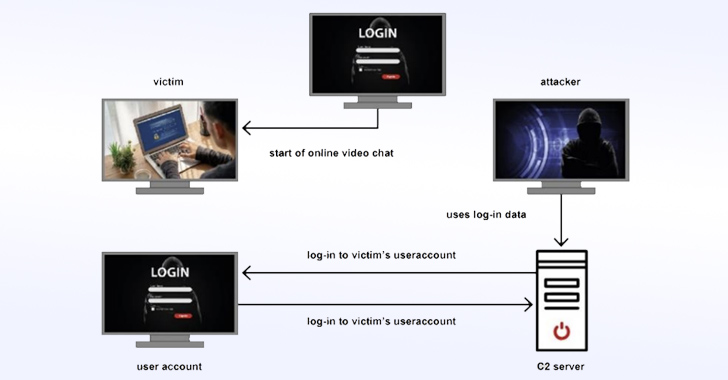
Once a successful contact is made, the hacking crew has been observed sending links to an online video chat that, when clicked, urge victims to enter their login information on a phishing page, effectively resulting in credential theft. The phishing site impersonates a legitimate online service provider such as Google or Microsoft.
"If an online video chat occurs, it serves to conceal the attack," BfV said. "After logging in to the victim's user account from a C2 server6, the attacker is able to download the entire user data, e.g. by means of Google Takeout."
It's worth noting that the Google Threat Analysis Group (TAG), in August 2022, detailed a malware called HYPERSCRAPE used by the threat actor to retrieve user data from Gmail, Yahoo!, and Microsoft Outlook accounts.
Cybersecurity
The attacks also mirror prior findings from Certfa Lab and Human Rights Watch (HRW), which disclosed a credential phishing campaign aimed at human rights activists, journalists, researchers, academics, diplomats, and politicians working in the Middle East around the same time.
The development comes as Sophos revealed a mobile malware campaign targeting customers of four Iranian banks, Bank Mellat, Bank Saderat, Resalat Bank, and Central Bank of Iran, with as many as 40 bogus Android apps designed to steal sensitive information.
"All the apps, which were available for download between December 2022 and May 2023, collect internet banking login credentials and credit card details, and have several other capabilities," security researcher Pankaj Kohli said in a report published late last month.
This includes "hiding their icons to maintain stealth and intercepting incoming SMS messages which some banks use as part of multi-factor authentication schemes." Also present is a feature to search the infected device for several other apps relating to banking, payment, or cryptocurrency.