Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks

CATEGORIE : APT |
DATE: 29.12.23 |
| WEB : The Hacker News |
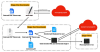
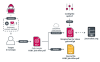
Nation-state actors affiliated to North Korea have been observed using spear-phishing attacks to deliver an assortment of backdoors and tools such as AppleSeed, Meterpreter, and TinyNuke to seize control of compromised machines.
South Korea-based cybersecurity company AhnLab attributed the activity to an advanced persistent threat group known as Kimsuky.