New Hacker Group 'GambleForce' Tageting APAC Firms Using SQL Injection Attacks
CATEGORIE : Hacking |
DATE: 14.12.23 |
| WEB : The Hacker News |
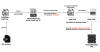
A previously unknown hacker outfit called GambleForce has been attributed to a series of SQL injection attacks against companies primarily in the Asia-Pacific (APAC) region since at least September 2023.
"GambleForce uses a set of basic yet very effective techniques, including SQL injections and the exploitation of vulnerable website content management systems (CMS) to steal sensitive information, such as user credentials," Singapore-headquartered Group-IB said in a report shared with The Hacker News.