
The Comcast remote. Credit: Guardicore
Hacking Articles - H 2020 1 2 3 4 5 6 7 8 9 Hacking List - H 2021 2020 2019 2018 0 1 Hacking blog Hacking blog
Hackers Target Puerto Rico Firefighting Department Servers
16.10.20 Hacking Securityweek
Puerto Rico’s firefighting department said Wednesday that its database was hacked by unknown people demanding $600,000 in an act of alleged extortion.
The department’s director, Alberto Cruz, said in a statement the situation has not affected its ability to respond to emergencies.
Police said the department received an email notifying it that hackers had encrypted its servers and wouldn’t release them until they got paid.
The department contacted police and have not paid the money, officials said. The investigation is ongoing.
Comcast TV Remote Hack Opens Homes to Snooping
8.10.20 Hacking Threatpost
Researchers disclosed the ‘WarezTheRemote’ attack, affecting Comcast’s XR11 voice remote control.
A security flaw allowing attackers to remotely snoop in on victims’ private conversations was found to stem from an unexpected device – their TV remotes.
The flaw stems from Comcast’s XR11, a popular voice-activated remote control for cable TV, which has more than 18 million units deployed across the U.S. The remote enables users to say the channel or content they want to watch rather than keying in the channel number or typing to search.
However, researchers found a serious vulnerability in the remote, allowing attackers to take it over (details below). Worse, the ensuing attack, dubbed WarezTheRemote, does not require any interaction from the victim — it’s extremely cheap to carry out (a hacker merely needs a low-priced RF transceiver and antenna), and can be launched remotely (from up to 65 feet away).
Threatpost Webinar Promo Retail Security
Click to Register!
Researchers worked with Comcast’s security team after finding the flaw and fixes have been released that remediate the issues that make the attack possible – however, in a disclosure post on Wednesday, they stressed that the incident is an important reminder of the inherent security and privacy issues plaguing even the least-suspected internet of things (IoT) devices.
“Few people think of their television remote controls as ‘connected devices,’ fewer still would guess that they can be vulnerable to attackers, and almost no one would imagine that they can jeopardize their privacy,” said researchers with Guardicore, in a Wednesday post. “In this case, the recent development of RF-based communication and voice control makes this threat real. Even more so in these strange times: With so many of us working from home, a home-recording device is a credible means to snoop on trade secrets and confidential information.”
The Flaw
By extensively reverse-engineering both the remote’s firmware and the software it communicates with on the set-top box, researchers found an error in the way the remote handles incoming RF packets.

The Comcast remote. Credit: Guardicore
To understand the flaw, it’s first important to look at how XR11 voice remotes work. The remote communicates with the television set-top box over the RF4CE (Radio Frequency for Consumer Electronics) protocol. RF4CE, which is a subset of the Zigbee family of power-saving RF protocols, has a feature called, straightforwardly, “security” — which should encrypt the contents of RF4CE packets to bar attackers from injecting malicious packets into the connection.
However, in the XR11’s implementation, the RF4CE “security” feature is set on a packet-by-packet basis. Each packet has a “flags” byte, and when one of its bits is set to 1, its contents will be encrypted – and if the bit isn’t set, the packet will be sent in plaintext.
The vulnerability lies in the fact that the original XR11 firmware didn’t verify that responses to encrypted requests are encrypted as well, said researchers. That means an attacker within RF range (about 65 feet away) could view requests from the remote in plaintext – allowing them to easily formulate a malicious response to that request.
“WarezTheRemote used a man-in-the-middle attack to exploit remote’s RF communication with the set-top box and over-the-air firmware upgrades – by pushing a malicious firmware image back the remote, attackers could have used the remote to continuously record audio without user interaction,” they said.
The Attack
Researchers say that the remote’s firmware queries the box it is paired with – be default – for a new firmware once every 24 hours. That means in a real-life attack, a bad actor would need to wait for the a firmware upgrade query to occur.
“The request packet is encrypted, so an attacker can’t actually read its contents, but there is a non-encrypted byte in the packet’s header that indicates that this request is firmware-related, which allows the attack to guess its contents without actually decrypting it,” they said.
Following this initial exchange, the remote then sends out a series of requests asking for the contents of the firmware image, chunk by chunk. The order these chunk requests are sent in is entirely predictable – meaning attackers can easily guess which chunk of the firmware the remote is asking for.
“By carefully timing our responses, we were able to send exactly the right firmware chunk to the remote each time,” they said. “Furthermore, we found a way to temporarily crash the software running on the cable box using a malformed RF4CE packet. This simple DoS prevented the box from interfering over the course of the attack.”
Researchers said an attacker would only need a basic RF transceiver, which is cheap – a Texas Instruments CC2531 costs only a few dollars for a whole development kit – as well as a cheap 2 dBi antenna (researchers used a 16dBi antenna for better results).
“We didn’t push this to the limit, but we were easily able to push firmware to the remote around 65 feet away from outside the apartment it was in,” they said. “This is the alarming part – it conjures up the famous ‘van parked outside’ scene in every espionage film in recent memory.”
Researchers disclosed the vulnerability to Comcast April 21, and Comcast began to release a patch on July 24. On Sept. 24, Comcast confirmed that all devices were patched.
“Nothing is more important than keeping our customers safe and secure, and we appreciate Guardicore for bringing this issue to our attention,” said Comcast in a press statement. “As detailed in this report, we fixed this issue for all affected Xfinity X1 voice remotes, which means the issue described here has been addressed and the attack exploiting it is not possible.”
Smoke and Mirrors – Hack-for-Hire Group Builds Fake Online Empire
8.10.20 Hacking Securityweek
Hack-for-hire group BAHAMUT managed to build a fake online empire to leverage in cyber-espionage operations targeting the Middle East and other regions around the world, BlackBerry reports.
Dubbed BAHAMUT, but also tracked as EHDEVEL, WINDSHIFT, URPAGE, and THE WHITE COMPANY, the cyber-espionage group was initially detailed in 2017, but its activity spans a much longer period of time.
In fact, the threat actor’s activities appear to have been described in several other reports that lack attribution, including a 2016 Kaspersky report on attacks exploiting InPage word processor vulnerabilities.
“BlackBerry assesses that the InPage zero-day exploit first identified by Kaspersky in 2016 and given CVE-2017-12824 but never attributed, was in fact used by BAHAMUT. We also assess that it was first developed by a Chinese threat group in 2009 for use in targeting a group in diaspora perceived to be a potential threat to the power of the Chinese Communist Party,” BlackBerry notes in a new report.
The threat actor was able to fly under the radar through the use of a large number of fake identities, including social media personas, websites, and applications, some of which had original content and were meant to distort reality, but did not immediately show a malicious purpose.
In fact, the use of original websites, applications, and personas across a wide array of industries and regions is what sets this group apart from similar threats. Its fake empire suggests legitimacy and is able to distort consumers’ perception of reality.
Furthermore, the adversary strives to ensure campaigns, network infrastructure, and phishing tools are kept separate, it builds anti-analysis tools directly into backdoors and exploit shellcode, and immediately changes tactics when exposed. The group is also believed to be re-using tools from other groups and to mimic their tradecraft, to hinder attribution.
BAHAMUT, BlackBerry says, has a diverse and long list of targets, including government officials, politicians, human rights activists and organizations, human rights NGOs, financial services and technology companies, Egypt-focused media and foreign press, military organizations, aerospace entities, and scholars.
The group mainly focuses on South Asia (particularly India and Pakistan) and the Middle East (UAE and Qatar in particular), but victims were also identified in China and Northern and Eastern Europe. The hackers appear to be avoiding targets located in the United States.
“BAHAMUT’s targeting is all over the map, which makes it difficult to concoct a single victimology. BAHAMUT appears to be not only well-funded and well-resourced, but also well-versed in security research and the cognitive biases analysts often possess. Taken together, these aspects present a considerable attribution challenge,” BlackBerry notes.
The group is also believed to have access to at least one zero-day developer and to be operating over a dozen malicious apps for Android and iOS. Some of these apps were previously mentioned by Trend Micro in a report on Urpage.
New applications were also identified, all accompanied by well-designed websites, privacy policies, and terms of service, thus increasing the sense of legitimacy. They were able to bypass Google’s static code safeguards and five of them were still in Google Play as of July 2020 (they appeared designed specifically for targets in UAE).
Several other websites were employed for the distribution of additional applications, including seven of which were being distributed in recent campaigns. These included VPN and compass applications, but also apps that catered to the Sikh separatist movement.
“A variety of modifications were made to the APKs we found, and most had limited to no detection in a commonly used malware repository. In most cases the APK files were comprised of completely legitimate code and well-known Android libraries which helped cloak the underlying activity from common static detection methods,” BlackBerry says.
A total of nine malicious iOS applications attributed to BAHAMUT were identified in the Apple App Store, all of which were still available as of August 2020. The apps had generic themes with universal appeal: messaging, VOIP, prayer, file management, and password saver applications.
According to BlackBerry, the threat actor also masters the art of phishing, at a level superior to other groups, with targeted spear-phishing operations lasting anywhere between a few hours to months. Additionally, the adversary has the ability to learn from its mistakes and constantly improves its tradecraft.
The security firm, which claims to have “a solid grasp of BAHAMUT’s existing infrastructure,” assesses that BAHAMUT is a hack-for-hire group, just as independent security researchers Collin Anderson and Claudi Guarnieri suggested before.
“For a group that historically set themselves apart by employing above-average operational security and extremely skilled technical capabilities, BAHAMUT operators are, at the end of the day, still human. While their mistakes have been few, they have also proven devastating. BlackBerry found that the idiom “old habits die hard” applies to even the most advanced of threat groups,” BlackBerry concludes.
Fullz House hacked the website of Boom! Mobile provider to steal credit cards
6.10.20 Hacking Securityaffairs
The credit card skimming group Fullz House has compromised the website of US mobile virtual network operator (MVNO) Boom! Mobile.
The credit card skimming group Fullz House has compromised the website of US mobile virtual network operator (MVNO) Boom! Mobile in a classic MageCart attack.
Boom! Mobile offers postpaid and prepaid no-contract wireless service plans to its customers that allow them to use the lines of the nation’s largest cellular networks including AT&T, T-Mobile, and Verizon.
The Fullz House hackers injected an e-skimmer into the website and unfortunately, the malicious software has yet to be removed.
The e-skimmer was first spotted by researchers at Malwarebytes’ Threat Intelligence Team, the researchers noticed a single line of code that is used to load an external JavaScript library from paypal-debit[.]com/cdn/ga.js.
“Our crawlers recently detected that their website, boom[.]us, had been injected with a one-liner that contains a Base64 encoded URL loading an external JavaScript library.” reads the analysis published by Malwarebytes. “Once decoded, the URL loads a fake Google Analytics script from paypal-debit[.]com/cdn/ga.js. We quickly recognize this code as a credit card skimmer that checks for input fields and then exfiltrates the data to the criminals.”
The malicious software collects payment card information provided by the users, then exfiltrates the harvested data as a Base64 encoded GET request.
Researchers believe that the Fullz House Magecart group has compromised the Boom’s website by exploiting a vulnerability in the PHP version 5.6.40 used by the company, which is no more supported since January 2019.
The experts attempted to report the compromise to Boom! Mobile without success.
The Fullz House group was first spotted by security experts at RiskIQ in November 2019, when it was using phishing and web skimming for its attacks. Since August-September of 2019, the group started using a hybrid technique that leverages on MiTM and phishing attacks to target sites using external payment processors.
Hacker groups under the Magecart umbrella continue to target to steal payment card data with so-called software skimmers. Security firms have monitored the activities of a dozen groups at least since 2010.
According to a joint report published by RiskIQ and FlashPoint in 2019, some groups are more advanced than others, in particular, the gang tracked as Group 4 appears to be very sophisticated.
MalwareBytes researchers also shared Indicators of Compromise for this attack in its analysis.
Hackers stole a six-figure amount from Swiss universities
6.10.20 Hacking Securityaffairs
Threat actors have hacked at least three Swiss universities, including the University of Basel and managed to drain employee salary transfers.
Threat actors have managed to steal employee salary payments at several Swiss universities, including the University of Basel.
“According to our information, several universities in Switzerland have been affected,” explained Martina Weiss, Secretary General of the Rectors’ Conference of the Swiss Universities.
The hackers carried out spear-phishing attacks against the Swiss universities in an attempt of tricking its employees into providing their access data.
According to the SonntagsZeitung, the Basel public prosecutor’s office confirmed that hackers compromised the systems at the universities, then the threat actors hijacked the employee salary transfers by changing the beneficiaries’ accounts.
The SonntagsZeitung also added that hackers attempted to breach the University of Zurich, but the employees at the university recognised the phishing attempts and neutralized them.
It seems that the hackers stolen a six-figure amount and immediately moved the funds abroad.
“The cybercriminals embezzled a six-figure amount, the office said. It added that part of the misappropriated funds was now in foreign accounts.” reads the site SwissInfo.
“Umbrella organisation swissuniversities has sent a warning email to keep universities on their guard.”
Hackers Steal Swiss University Salaries
6.10.20 Hacking Securityweek
As yet unidentifed hackers have managed to steal employee salary payments at several Swiss universities, officials said Sunday.
"According to our information, several top schools in Switzerland have been affected," Martina Weiss, director general of the rectors group of Switzerland's public universities, told AFP.
The hackers used information obtained by phishing -- tricking a person into passing on their personal details -- for their attacks on at least three universities, including the University of Basel.
According to the SonntagsZeitung newspaper, they accessed the universities' payment systems and changed the instructions on salary transfers, stealing a six-figure sum.
The University of Zurich managed to fend off the hackers after employees recognised their modus operandi, SonntagsZeitung reported.
Hacked Hospital Chain Says All 250 US Facilities Affected
2.10.20 Hacking Securityweek
The hospital chain Universal Health Services said Thursday that computer services at all 250 of its U.S. facilities were hobbled in last weekend’s malware attack and efforts to restore hospital networks were continuing.
Doctors and nurses at affected hospitals and clinics, many already burdened with coronavirus care, have had to rely on manual record-keeping, with lab work slowed. Employees have described chaotic conditions impeding patient care.
The chain has not commented on reports it was hit by ransomware, though its description of the attack in a statement Thursday was consistent with malware variety that encrypts data into gibberish that can only be restored with software keys after ransoms are paid.
King of Prussia, Pennsylvania-based UHS said its “systems were quickly disconnected and the network was shut down in order to prevent further propagation.”
The company, with 90,000 employees, said electronic medical records systems were not impacted by the attack and it was making steady progress restoring and reconnecting systems. Company spokeswoman Jane Crawford said via email that all 250 U.S. facilities were affected.
UHS workers reached by The Associated Press at company facilities in Texas and Washington, D.C., earlier in the week described mad scrambles after the outage began to render care, including longer emergency room waits and anxiety over determining which patients might be infected with the virus that causes COVID-19.
BleepingComputer, an online cybersecurity news site, spoke to UHS employees who described ransomware with the characteristics of Ryuk, which has been widely linked to Russian cybercriminals and used against large enterprises.
UHS operates hospitals and clinics, many treating behavioral health and addiction problem. Its acute care hospitals are concentrated in states including California, Texas, Nevada and Florida.
NFL, NBA Players Hacked in Would-Be Cyber-Slam-Dunk
2.10.20 Hacking Threatpost
Federal prosecutors charged two men with crimes that carry up to 20 years in prison.
NFL and NBA athletes whose social-media accounts were taken over have been thrown the ball of justice.
Multiple professional and semi-pro athletes were victimized by two men who infiltrated their personal accounts, according to testimony in federal court on Wednesday. Trevontae Washington of Thibodaux, La., and Ronnie Magrehbi, of Orlando, Fla., faced separate judges in the Eastern District of Louisiana and the Middle District of Florida, respectively, and were charged with one count of conspiracy to commit wire fraud, and one count of conspiracy to commit computer fraud and abuse.
Federal prosecutors alleged that between December 2017 and April 2019, Washington and Magrehbi actively took part in illegal schemes to gain access to social media and other personal online accounts of the players.
Washington allegedly specialized in NBA and NFL players, and phished for their credentials by taking advantage of public platforms like Instagram. He would send them messages with embedded links to what appeared to be legitimate social media log-in sites, prosecutors said, but these were actually phishing pages used to steal the athletes’ user names and passwords. Once the athletes entered their credentials, they would be sent to Washington, who, along with others allegedly locked the athletes out of their accounts. They also used the credentials against other accounts, banking on password reuse. Prosecutors claimed that Washington then sold access to the compromised accounts to others for amounts ranging from $500 to $1,000.
Magrehbi, meanwhile, is alleged to have obtained access to accounts belonging to one professional football player, including an Instagram account and personal email account. Magrehbi took a ransomware-like tack, prosecutors said, and extorted the player. He demanded payment in return for restoring access to the accounts – and was paid, according to Department of Justice documents. However, even though the player sent funds on at least one occasion, portions of which were transferred to a personal bank account controlled by Magrehbi – he was double-crossed and the athlete never regained access, prosecutors said.
The DoJ has not released the names of the affected players.
“Instagram is built as a mobile-first experience, which means that these attackers knew they could build a mobile-specific phishing campaign to increase the likelihood of success,” Hank Schless, senior manager of security solutions at Lookout, told Threatpost. “Since we carry our mobile devices with us all the time, we trust them to be inherently secure. Threat actors know this and socially engineer targets through SMS, social media and third-party messaging apps and convince them to click a malicious link.”
It’s more difficult to spot phishing targets on mobile, he added.
“Smaller screens, a simplified user experience and shortened URLs make it difficult to tell if a site is legitimate or not,” he said. “It’s also much easier to create a legitimate-looking account or phone number that could convince a target that the communication is real. Lookout discovered a mobile-specific phishing campaign earlier this year that intended to phish individual mobile banking login credentials through SMS.”
The wire fraud conspiracy charges carry a statutory maximum of 20 years in prison and a fine of up to $250,000. The computer fraud conspiracy charges carry a statutory maximum of five years in prison and a fine of up to $250,000.
To avoid being a victim of a mobile phishing scam, “first and foremost, be aware,” Shahrokh Shahidzadeh, CEO at Acceptto, told Threatpost. “Do not click on texts or respond to texts if you are not sure who they’re coming from. Even if it does come from a reputable source, but still seems off, consider checking in with them to make sure it was meant to be sent to you before clicking. Companies and end-users that are relying solely on binary authentication tactics, such as two-factor authentication (2FA) or multifactor authentication (MFA) via SMS, need to understand that these items are static and stored somewhere, waiting to be compromised time and time again. The best way to avoid these scams is to assume all credentials, even those yet to be created have been compromised.”
Meanwhile, account takeovers of high-profile accounts have been in the news lately, after hackers “mislead certain employees” to gain access to internal tools at Twitter to take over celebrity and company handles and push out a Bitcoin scam.
In that case, the attackers targeted 130 Twitter accounts, ultimately tweeting from 45, accessing the direct messages of 36 and downloading the Twitter Data of seven. Accounts for Joe Biden, Bill Gates, Elon Musk, Apple and Uber were all hijacked in the scheme.
Red Team — Automation or Simulation?
28.9.20 Hacking Thehackernews
What is the difference between a penetration test and a red team exercise? The common understanding is that a red team exercise is a pen-test on steroids, but what does that mean?
While both programs are performed by ethical hackers, whether they are in-house residents or contracted externally, the difference runs deeper.
In a nutshell, a pen-test is performed to discover exploitable vulnerabilities and misconfigurations that would potentially serve unethical hackers. They primarily test the effectiveness of security controls and employee security awareness.
The purpose of a red team exercise, in addition to discovering exploitable vulnerabilities, is to exercise the operational effectiveness of the security team, the blue team. A red team exercise challenges the blue team's capabilities and supporting technology to detect, respond, and recover from a breach. The objective is to improve their incident management and response procedures.
The challenge with pen-testing and red team exercises is that they are relatively high-resource intensive. A pen test can run for 1 to 3 weeks and a red team exercise for 4 to 8 weeks and are typically performed annually, if at all.
Today's cyber environment is one of rapid and constant change. It is driven by evolving threats and adversarial tactics and techniques, and by the accelerated rate of change in IT and adaptations to the security stack. This has created a need for frequent security testing and demand for automated and continuous security validation or breach and attack simulation (BAS).
These solutions discover and help remediate exploitable vulnerabilities and misconfigurations, and they can be performed safely in the production environment. They enable security teams to measure and improve the operational effectiveness of their security controls more frequently than pen-testing. But can they be used in a red team exercise?
There are two approaches that need to be considered. The first, red team automation, has the obvious advantage of increasing the operational efficiency of a red team. It enables them to automate repetitive and investigative actions, identify exploitable weaknesses and vulnerabilities, and it provides them a good picture of what they are up against, fast.
In principle, this is not too far from what BAS provides today by supporting a broad set of attack simulations and providing a rich library of atomic executions codified to the MITRE ATT&CK framework. They even provide red teams the capability to craft their own executions. Red team automation can support red team activities, but the value is limited, and most red teams have their own set of homegrown tools developed for the same purpose.
A new approach, red team simulation, takes these capabilities a step further. It enables a red team to create complex attack scenarios that execute across the full kill chain, basically creating custom APT flows. Instead of executing a bank of commands to find a weakness, it performs a multi-path, sequenced flow of executions.
The primary advantage of this approach is that it incorporates logic into the flow. As the simulation progresses, it leverages the findings of previous executions in addition to external data sources and tools. It will even download tools on a target machine, based on the dependencies of an execution.
For example, a sample flow could include Mimikatz providing credential input to a PSexec based technique and drop to disk PSexec on the target machine if it's missing. A red team simulation can include all the stages of an attack from initial access to impact and even reconnaissance performed in the pre-attack stage.
The benefits of red team simulation extend beyond operational efficiency for both in-house red teams and companies that provide red team services. Scenarios can be replayed to validate lessons learned from previous exercises. Red teams that operate in global companies can cover more geographies.
Even with red team simulation, the human factor remains key in assessing the result of an exercise and providing guidance to improve incident management and response procedures, but it makes red team exercises accessible and achievable to a larger market, where cost is a limiting factor.
Fortinet VPN with Default Settings Leave 200,000 Businesses Open to Hackers
25.9.20 Hacking Thehackernews
As the pandemic continues to accelerate the shift towards working from home, a slew of digital threats have capitalized on the health concern to exploit weaknesses in the remote work infrastructure and carry out malicious attacks.
Now according to network security platform provider SAM Seamless Network, over 200,000 businesses that have deployed the Fortigate VPN solution to enable employees to connect remotely are vulnerable to man-in-the-middle (MitM) attacks that could allow an attacker to present a valid SSL certificate and fraudulently take over a connection.
"We quickly found that under default configuration the SSL VPN is not as protected as it should be, and is vulnerable to MITM attacks quite easily," SAM IoT Security Lab's Niv Hertz and Lior Tashimov said.
"The Fortigate SSL-VPN client only verifies that the CA was issued by Fortigate (or another trusted CA), therefore an attacker can easily present a certificate issued to a different Fortigate router without raising any flags, and implement a man-in-the-middle attack."
To achieve this, the researchers set up a compromised IoT device that's used to trigger a MitM attack soon after the Fortinet VPN client initiates a connection, which then steals the credentials before passing it to the server and spoofs the authentication process..jpg)
SSL certificate validation, which helps vouch for the authenticity of a website or a domain, typically works by verifying its validity period, digital signature, if it was issued by a certificate authority (CA) that it can trust, and if the subject in the certificate matches with the server the client is connecting to.
The problem, according to the researchers, lies in the use of default self-signed SSL certificates by companies.
Given that every Fortigate router comes with a default SSL certificate that is signed by Fortinet, that very certificate can be spoofed by a third-party as long as it's valid and issued either by Fortinet or any other trusted CA, thus allowing the attacker to re-route traffic to a server their control and decrypt the contents.
The main reason for this is that the bundled default SSL certificate uses the router's serial number as the server name for the certificate. While Fortinet can use the router's serial number to check if the server names match, the client appears to not verify the server name at all, resulting in fraudulent authentication.
In one scenario, the researchers exploited this quirk to decrypt the traffic of the Fortinet SSL-VPN client and extract the user's password and OTP.
"An attacker can actually use this to inject his own traffic, and essentially communicate with any internal device in the business, including point of sales, sensitive data centers, etc," the firm said. "This is a major security breach that can lead to severe data exposure."
For its part, Fortinet said it has no plans to address the issue, suggesting that users can manually replace the default certificate and ensure the connections are safe from MitM attacks. 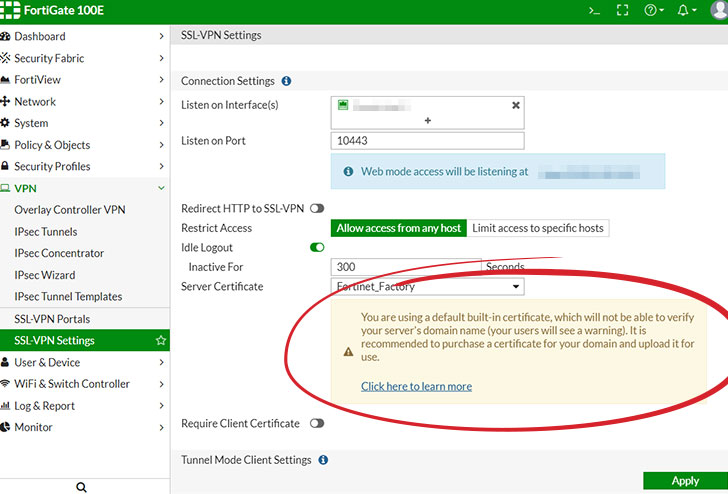
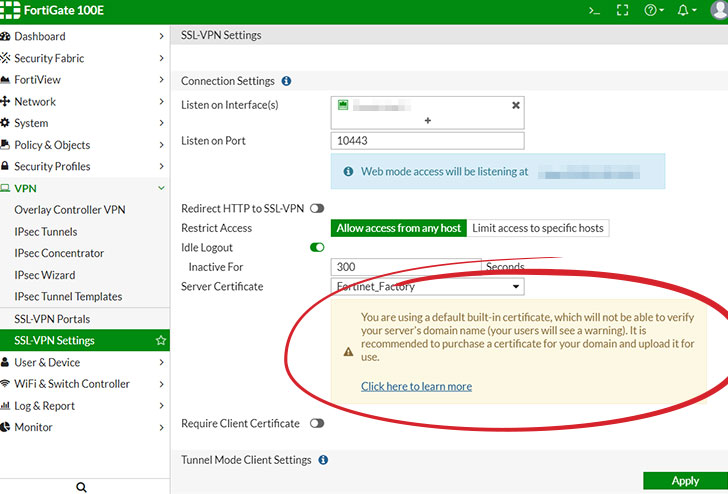
Currently, Fortinet provides a warning when using the default certificate: "You are using a default built-in certificate, which will not be able to verify your server's domain name (your users will see a warning). It is recommended to purchase a certificate for your domain and upload it for use."
"The Fortigate issue is only an example of the current issues with security for the small-medium businesses, especially during the epidemic work-from-home routine," Hertz and Tashimov noted.
"These types of businesses require near enterprise grade security these days, but do not have the resources and expertise to maintain enterprise security systems. Smaller businesses require leaner, seamless, easy-to-use security products that may be less flexible, but provide much better basic security."
Microsoft Says Hackers Actively Targeting Zerologon Vulnerability
24.9.20 Hacking Securityweek
Microsoft says it has observed threat actors actively targeting the Zerologon vulnerability affecting Windows Server.
Tracked as CVE-2020-1472, the security flaw is related to the Netlogon remote protocol (MS-NRPC) and it could result in an unauthenticated attacker gaining domain administrator access through leveraging a specially crafted application that runs on a device on the network.
The attacker could abuse the flaw when establishing “a vulnerable Netlogon secure channel connection to a domain controller,” Microsoft said in an advisory. The tech giant released patches to address the flaw on August 2020 Patch Tuesday.
Last week, the United States Department of Homeland Security (DHS) issued an Emergency Directive requiring all federal agencies to apply the available patches for the Zerologon vulnerability within days.
“This vulnerability poses an unacceptable risk to the Federal Civilian Executive Branch and requires an immediate and emergency action,” the DHS’s Cybersecurity and Infrastructure Security Agency (CISA) said.
Also last week, Samba announced patches for the Zerologon flaw, explaining that Samba implements the Netlogon protocol and that it’s vulnerable when used as domain controller only.
Several exploits have been released for the flaw, and Microsoft revealed on Wednesday that it had already observed hackers leveraging some of these exploits to actively target vulnerable systems.
“Microsoft is actively tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon. We have observed attacks where public exploits have been incorporated into attacker playbooks,” the company said.
The company also released indicators of compromise (IoC) for these exploits and encourages customers to apply the available fixes as soon as possible.
“We strongly recommend customers to immediately apply security updates for CVE-2020-1472. Microsoft 365 customers can use threat & vulnerability management data to see patching status,” Microsoft said.
The tech giant also promised to share additional information on these attacks as the situation evolves.
Gamer Credentials Now a Booming, Juicy Target for Hackers
24.9.20 Hacking Threatpost
Credential abuse drives illicit market for in-game rare skins, special weapons and unique tools.
Credential theft targeting hardcore gamers has hit an all-time high as scams, illicit markets and account takeovers have become a booming business.
The driving force behind the uptick in gaming-related crime is a sudden spike in usage of online games, spurred by the coronavirus pandemic and social-distancing lockdowns, according to researchers.
A recent survey found that 55 percent of frequent online game players said their accounts had been compromised at some point, according to a study by Akamai and DreamHack.
“Criminals are launching relentless waves of attacks against games and players alike in order to compromise accounts, steal and profit from personal information and in-game assets, and gain competitive advantages,” said Steve Ragan, Akamai security researcher who authored the State of the Internet / Security report, released Wednesday.
According to the report, companies experienced 10.6 billion web application attacks between July 2018 and June 2020, more than 152 million of which were directed toward the gaming industry.
Impacted are not just console platform leaders such as Microsoft Xbox Live and Sony PlayStation Network, but also PC gaming platforms like Valve’s Steam, and mobile games from firms like Epic Games and its wildly popular Fortnite.
Stolen credentials are used by criminals to perpetrate a number of crimes. One popular cottage industry, easily discovered via a search for “boosting and ranking” services, illustrates how widespread the problem is, Ragan pointed out.
He said these services often use dozens of hijacked accounts that can be programmed to repeatedly lose against one opponent, who is paying a third-party service to have their game ranking artificially jacked up to elite status.
More common, Akamai said, is attackers using stolen credentials to log in to a game account and simply steal a user’s profile information, financial data and whatever valuable virtual merchandise and currency they can find. Or, criminals might use a victim’s virtual currency to buy in-game merchandise and upgrades such as rare skins, special weapons and unique tools — and then steal them.
Gaming the Gamers
Sixty-seven percent of gamers surveyed said they have experienced in-game phishing attempts. Half said they had come across hacked accounts and in-game assets being sold or traded online. Yet, 50 percent of respondents said they were not worried about their accounts being hijacked.

“Gamers are highly targeted, because they have several qualities that criminals look for. They’re engaged and active in social communities. For the most part, they have disposable income, and they tend to spend it on their gaming accounts and gaming experiences. When these factors are combined, criminals see the gaming industry as a target-rich environment,” wrote Ragan.
Akamai recorded 100 billion credential-stuffing attacks from July 2018 to June 2020. Nearly 10 billion of those attacks targeted the lucrative gaming industry, worth $159 billion in 2019, according to data cited in the report and attributed to NewZoo.
Game Strategy: Methods and Tactics
For this report, Ragan looked at several criminal marketplace specializing in the game industry. One, he notes, included a collection of gaming databases dating back to 2019 for sale that included the credentials of users for the popular game titles Battlefield, Minecraft, Counter-Strike: Global Offensive and Witcher.
“No platform is off limits,” he told Threatpost in a phone interview. That includes mobile gaming platforms and companies like Unity Technologies and Epic Games, and their popular game titles War Robots and Fortnite.
“Criminals obtain the usernames and passwords needed for credential-stuffing from a number of places… Criminals will conduct [Structured Query Language injection (SQLi)] attacks to harvest login details,” he said.
In a related study published in July 2019, researchers at Enzoic noted that gaming communities built on DIY platforms such as vBulletin, IPBoard, MyBB, PHPBB and PunBB are often ripe for SQL injection attacks. The sites are often running outdated software and are poorly maintained by game fans.
Hardest hit by credential-stuffing abuse is the United States, Akamai reported, followed by China and Russia.
Credential-stuffing is accomplished by hackers who take advantage of users who often reuse the same passwords across multiple online accounts. The cyberattackers use stolen passwords and user names from previous data breaches to brute-force accounts on a wide scale, and when a match is found, they can take over the victim’s account.
But phishing attacks are the preferred way that criminals target gamers directly. A typical ploy involves a criminal creating a legitimate-looking website related to a game or gaming platform, with the goal of tricking gamers into revealing their login credentials, the report states.
One common ploy uses a phishing kit displayed via a random message with a call to action, such as “Add Friend,” or an attempt to entice the recipient to buy or trade a rare game-related item on the platform. Messages prompt the target to share their credentials – which are then stolen.
The Gaming Industry’s Response?
The response to the uptick in attacks on gaming platforms is to introduce a host of security features ranging from promoting the use of password managers, introducing the option of two-factor authentication (2FA) for sign-ins and making third-party authentication apps, Akamai said.
“Microsoft, Blizzard and Steam have their own authenticator apps, but others, including Ubisoft and Nintendo, will allow you to use third-party authenticator apps like Google Authenticator. When an authenticator isn’t an option, most gaming companies, like Sony, will use two-step verification, delivering a one-time passcode to the phone via SMS,” according to the report.
The report’s author, Ragan, pointed out that the scourge of credential abuse isn’t just about protecting gaming accounts. “Some victims were targeted long before their gaming profiles were compromised. Criminals will target everything, including email and social media, and use those trusted networks and expected safe spaces as a launching pad toward other targets and new attacks,” he said.
Rogue employees at Shopify accessed customer info without authorization
24.9.20 Hacking Securityaffairs
E-commerce platform provider Shopify revealed that two members of its support staff accessed customer information without authorization.
E-commerce platform provider Shopify on Tuesday confirmed that two employees of its support staff were accessing customer information without authorization.
“Recently, Shopify became aware of an incident involving the data of less than 200 merchants. We immediately launched an investigation to identify the issue–and impact–so we could take action and notify the affected merchants.” reads the Shopify announcement.
“Our investigation determined that two rogue members of our support team were engaged in a scheme to obtain customer transactional records of certain merchants. We immediately terminated these individuals’ access to our Shopify network and referred the incident to law enforcement.”
The duo abused their permissions to access data related to transactions a number of merchants that are estimated to be less of 200.
The company already notified all the impacted merchants and fired the two employees.
Data accessed by the two rogue employees without authorization included name, email address, physical address, and order details (e.g. products and services purchased). The company confirmed that financial information were not impacted.
Law enforcement is currently investigating into the incident.
“We are currently working with the FBI and other international agencies in their investigation of these criminal acts. While we do not have evidence of the data being utilized, we are in the early stages of the investigation and will be updating affected merchants as relevant,” continues the company.

The company is not aware of the illegal use of the accessed data, it pointed out that the incident was not the result of a security vulnerability in its platform.
“Our teams have been in close communication with affected merchants to help them navigate this issue and address any of their concerns. We don’t take these events lightly at Shopify.”the company concludes. “We have zero tolerance for platform abuse and will take action to preserve the confidence of our community and the integrity of our product,”
This incident confirms that insider threats are hard to discover and the effects of their operations could be serious for the organization.
Airbnb Accounts Exposed to Hijacking Due to Phone Number Recycling
23.9.20 Hacking Securityweek
A cybersecurity enthusiast learned recently that Airbnb accounts can be easily hijacked by creating a new account on the home-rental service with a phone number that in the past belonged to another Airbnb customer.
The security risk posed by recycled phone numbers has been known for years, and the services of several major companies were found to be impacted in the past.
It seems that Airbnb is affected as well, but the company says only a very small number of users are impacted.
A SecurityWeek reader named Maya contacted us recently after her husband was accidentally signed into another user’s account when trying to create an Airbnb account.
After entering his phone number during the account registration process, Maya’s husband received a 4-digit code via SMS that, when entered, resulted in him being logged into the account of the previous owner of his phone number.
The account they accidentally accessed belonged to a woman from North Carolina and it included her photo, email address, phone number, and other personal information. The account still had a valid payment card attached, making it possible to make a booking on her behalf, using her card.
Maya said she confirmed the issue related to recycled phone numbers by conducting tests with the phone numbers of some of their friends (with their consent). She noted that Airbnb did not inform the new owner of the phone number that the number they were using to sign up for an account was already taken, and it also did not notify the legitimate owner of the account of a potentially suspicious login.
Maya says she works in the tech industry and while she has analyzed the security of her company’s own products, she says she would not describe herself as a security researcher.
Airbnb runs a bug bounty program on HackerOne with rewards of up to $15,000. The company claims to have paid out more than $1 million through its bug bounty program to date, and HackerOne named it one of its top 10 bug bounty programs earlier this year.
Since she is not a professional bug bounty hunter, Maya was not aware of Airbnb’s bug bounty program and she attempted to report her findings through Airbnb’s support channel — she said her only goal was to convince Airbnb to patch the flaw. However, after several attempts to get Airbnb to acknowledge the severity of her findings, she says the issue still hasn’t been addressed — Maya said she last checked on September 22.
Airbnb support staff told Maya to register an account using a different phone number, and claimed that the company ensures every account is secured and can only be accessed by the legitimate account holder. This statement does not seem true given that recycled phone numbers apparently provide a means to repeatedly access other users’ accounts.
“Airbnb support kept telling us the same thing over and over: use a different phone number,” Maya explained. “Without realizing the security issue we raised (although, we've been clear with them, and explained ourselves to several people along the way). After all, we did login to another user's account by accident, and it seems to me they don't find this as alarming as we do.”
She believes Airbnb should change their login security mechanisms, or at least notify users of suspicious logins in their account.
Airbnb, on the other hand, claimed last week that it had taken action to fix the problem, but it refused to elaborate on the changes it made.
“We’ve developed a resolution for the reported issue involving recycled phone numbers and new account sign ups, which fortunately only affected a very small number of our users. We are constantly evaluating and improving our protections and are committed to strengthening the security controls of our platform,” an Airbnb spokesperson told SecurityWeek.
The handling of the issue by Airbnb suggests that the company’s support staff is not well trained when it comes to handling reports describing security issues. While a majority of security-related issues are typically reported to vendors by professional bug bounty hunters, regular users identifying serious vulnerabilities is not unheard of, and these regular users are more likely to attempt to report their findings through a support channel rather than an official vulnerability disclosure program.
One example is the case of CVE-2019-6223, a FaceTime spying vulnerability uncovered last year by a 14-year-old. The teen found the flaw by accident and his attempts to report it to Apple were ignored before details of the issue were made public.
Mozilla Discontinues Firefox Feature Abused in Malware, Phishing Attacks
21.9.20 Hacking Securityweek
Mozilla is decommissioning Firefox Send and Firefox Notes, two legacy services that emerged out of the Firefox Test Pilot program.
Firefox Send, the browser maker reveals, is being discontinued because it has been abused for delivering malware and phishing attacks.
The feature was designed for encrypted file sharing and became popular among a loyal set of users, Mozilla says. However, the company also admits that the functionality started being abused to send malware and conduct spear-phishing attacks.
After taking Firefox Send offline to mitigate these attacks, Mozilla reassessed its portfolio and decided against bringing the service back to life.
“Because the service is already offline, no major changes in status are expected,” the browser maker notes.
All files that users sent in the past using Firefox Send have been securely wiped from Mozilla’s servers. Files shared from any device will still be available on that device but, as of September 17, 2020, with Firefox Send discontinued, users are no longer able to upload or receive files, Mozilla points out.
Firefox Notes is also getting the boot, but that won’t happen until November 1, 2020.
Initially meant as an experiment for new ways to sync encrypted data, Firefox Notes became a utility tool for both desktop and Android users. In November, however, the Android Notes app will be decommissioned, as well as the syncing service, Mozilla announced.
“The Firefox Notes desktop browser extension will remain available for existing installs and we will include an option to export all notes, however it will no longer be maintained by Mozilla and will no longer be installable,” the company reveals.
Those who have Firefox Notes installed will be able to use its functionality as long as they do not remove it from Firefox, as it won’t be available for new installs. Users are provided with the option to export all of their Notes, as well as specific ones.
A Bug Could Let Attackers Hijack Firefox for Android via Wi-Fi Network
20.9.20 Hacking Thehackernews
Dear Android users, if you use the Firefox web browser on your smartphones, make sure it has been updated to version 80 or the latest available version on the Google Play Store.
ESET security researcher Lukas Stefanko yesterday tweeted an alert demonstrating the exploitation of a recently disclosed high-risk remote command execution vulnerability affecting the Firefox app for Android.
Discovered originally by Australian security researcher Chris Moberly, the vulnerability resides in the SSDP engine of the browser that can be exploited by an attacker to target Android smartphones connected to the same Wi-Fi network as the attacker, with Firefox app installed.
SSDP, stands for Simple Service Discovery Protocol, is a UDP based protocol that is a part of UPnP for finding other devices on a network. In Android, Firefox periodically sends out SSDP discovery messages to other devices connected to the same network, looking for second-screen devices to cast.
Any device on the local network can respond to these broadcasts and provide a location to obtain detailed information on a UPnP device, after which, Firefox attempts to access that location, expecting to find an XML file conforming to the UPnP specifications.
According to the vulnerability report Moberly submitted to the Firefox team, the SSDP engine of the victims' Firefox browsers can be tricked into triggering an Android intent by simply replacing location of the XML file in the response packets with a specially crafted message pointing to an Android intent URI.
For this, an attacker connected to a targeted Wi-Fi network can run a malicious SSDP server on his/her device and trigger intent-based commands on nearby Android devices through Firefox—without requiring any interaction from the victims.
Activities allowed by the intent also includes automatically launching the browser and open any defined URL, which, according to the researchers, is sufficient to trick victims into providing their credentials, install malicious apps, and other malicious activities based on the surrounding scenarios.
"The target simply has to have the Firefox application running on their phone. They do not need to access any malicious websites or click any malicious links. No attacker-in-the-middle or malicious app installation is required. They can simply be sipping coffee while on a cafe's Wi-Fi, and their device will start launching application URIs under the attacker's control," Moberly said.
"it could have been used in a way similar to phishing attacks where a malicious site is forced onto the target without their knowledge in the hopes they would enter some sensitive info or agree to install a malicious application."
Moberly reported this vulnerability to the Firefox team a few weeks back, which the browser maker has now patched in the Firefox for Android versions 80 and later.
Moberly has also released a proof-of-concept exploit to the public that Stefanko used to demonstrate the issue in the above video against three devices connected to the same network.
Former Cisco employee pleads guilty to hacking, damaging company systems
29.8.20 Hacking Securityaffairs
A former Cisco employee has pleaded guilty to hacking charges and intentionally causing damage to the systems of his company.
The former Cisco employee Sudhish Kasaba Ramesh (30) pleaded guilty in federal court in San Jose today to intentionally accessing a protected computer of his company without authorization and causing damage.
The news was announced by United States Attorney David L. Anderson and Federal Bureau of Investigation Special Agent in Charge John L. Bennett.
Sudhish Kasaba Ramesh worked for Cisco until April 2018, a few months after he resigned from the tech giant, he accessed without authorization to Cisco’s AWS cloud infrastructure and deployed code from his Google Cloud Project account that deleted over 450 virtual machines associated with the Cisco Webex Teams application.
“During his unauthorized access, Ramesh admitted that he deployed a code from his Google Cloud Project account that resulted in the deletion of 456 virtual machines for Cisco’s WebEx Teams application, which provided video meetings, video messaging, file sharing, and other collaboration tools.” reads the press release published by the DoJ. “He further admitted that he acted recklessly in deploying the code, and consciously disregarded the substantial risk that his conduct could harm to Cisco.”
The Ramesh’s sabotage caused the shut down of over 16,000 WebEx Teams accounts for up to two weeks. Cisco spent roughly $1,400,000 in employee time to restore the damage to the application and refunded over $1,000,000 to the impacted customers. The good news is that customer data was compromised as a result of Ramesh’s conduct.
At the time it is not clear which is the motivation of the defendant’s conduct.
Ramesh is currently released on bond, the bail was set at $50,000, his sentencing hearing is scheduled for December 9, 2020,
Ramesh is an Indian nation and is in the United States on an H1-B work visa. If condemned, he could be deported as a result of his actions.
According to court documents, Ramesh’s current employer, the online personal styling service Stitch Fix, “is willing to work with him regarding the possibility of his remaining in the country and continuing to work for the company.”
Former Employee Admits Hacking, Damaging Cisco Systems
28.8.20 Hacking Securityweek
A former Cisco employee has pleaded guilty to hacking charges related to him accessing the networking giant’s systems and causing damage.
According to the U.S. Justice Department, 30-year-old Sudhish Kasaba Ramesh worked for Cisco until April 2018. A few months after he resigned from the company, he gained unauthorized access to Cisco’s AWS cloud infrastructure and deployed code that caused over 450 virtual machines associated with the Cisco Webex Teams application to be deleted.
Deleting the VMs resulted in more than 16,000 Webex Teams accounts being shut down for up to two weeks. Cisco spent roughly $1.4 million in employee time to respond to the incident and it had to refund over $1 million to impacted customers, authorities said.
There was no indication that customer data was compromised as a result of the incident. No information has been shared about the man’s motives.
At the time of the incident, many Webex users complained about the outage, but Cisco did not provide any information on its cause and there was no indication that it was the result of external activity.
Ramesh was charged with one count of intentionally accessing a protected computer without authorization and recklessly causing damage. He has pleaded guilty and is set to be sentenced in December. He has been released on a $50,000 bond.
Ramesh is based in San Jose, California, but court documents show the man is from India and he is in the United States on an H1-B work visa. He could be deported as a result of his actions, but court documents claim his current employer, online personal styling service Stitch Fix, “is willing to work with him regarding the possibility of his remaining in the country and continuing to work for the company.”
Experts hacked 28,000 unsecured printers to raise awareness of printer security issues
28.8.20 Hacking Securityaffairs
Cybersecurity experts at CyberNews hijacked close to 28,000 unsecured printers worldwide and forced them to print out a guide on printer security
Original post: https://cybernews.com/security/we-hacked-28000-unsecured-printers-to-raise-awareness-of-printer-security-issues/
Most of us already know the importance of using antivirus, anti-malware, and VPNs to secure our computers, phones, and other devices against potential attacks. Printers? Not so much. We at CyberNews wanted to show users the importance of protecting printers from becoming easy prey for cybercriminals, so we decided to bring the message home.
In order to help as many people as possible secure their devices against potential cyberattacks, the CyberNews security team accessed 27,944 printers around the world and forced the hijacked devices to print out a short 5-step guide on how to secure a printer, with a link to a more detailed version of the guide on our website.
About this experiment
To perform the experiment, we used Internet of Things (IoT) search engines to search for open devices that utilized common printer ports and protocols. After filtering out most of the false positives, we were left with more than 800,000 printers that had network printing features enabled and were accessible over the internet.
While this does not mean that all 800,000 of these printers were necessarily vulnerable to cyberattacks, our estimates have shown that we could successfully target approximately 500,000 of these devices.
After selecting a sample of 50,000 open printers and creating a custom printing script, we managed to print out PDF documents on 27,944 unprotected devices.
How we did it
Before performing the attacks, our initial step was to gather the total number of available targets. To find out how many printers were on the menu for our experiment, we searched for IP addresses with open ports on specialized IoT search engines, such as Shodan and Censys. While performing the search, we made sure that the open devices we found were actual printers, as opposed to unrelated services that simply used those ports for other purposes.
Out of 800,000+ available printers, we selected a sample of 50,000 devices that we would try to access and force to print our guide on printer security.
Our selection was based on:
Device location (to cover the entire globe)
Device manufacturer
Protocols used to access the printers
We then created our own custom script that was specifically designed to only target the printing process, without gaining access to any other features or data stored on the printers.

As soon as we launched the script, it began hijacking the printing processes in unsecured devices and forced them to print out the printer security guide.

The results
In the end, we managed to hijack 27,944 printers out of the 50,000 devices that we targeted, which amounts to a 56% success rate. Taking this percentage into account, we can presume that out of 800,000 internet-connected printers across the world, at least 447,000 are unsecured.
These numbers speak volumes about the general lack of protection of networked devices worldwide.
Example of available open printers on a single IoT search engine (Shodan.io):

As we can see, many users and organizations still use internet-connected devices without thinking about security, installing firmware updates, or taking into account the implications of leaving their devices publicly accessible. Which means that the humble printer remains one of the weakest links in the security of both organizational and home networks.
While security experts have been aware of printer vulnerabilities for quite a while, even previous large-scale attacks on printers like the Stackoverflowin hack in 2017 and the PewDiePie hack in 2018 did not seem to shock the public into securing their networked devices.
Even though securing each and every printer in the world might seem like a pipe dream, this does not mean that institutions and security experts should stop raising awareness about printer security and implementing stricter cybersecurity policies across organizations. Otherwise, the world might be just one massive cyberattack away from potential disaster.
Why printer security is important
While we were deliberately careful to only target the printing processes of the unsecured printers during the experiment, IoT hijacking attacks – when performed by bad actors without ethical limitations – can cause serious damage to organizations and individuals who neglect printer security.
From legal firms to banks to government departments, office printers are used by organizations of all types and sizes to print sensitive, confidential, and classified data. Not only that, these printers can also store copies of that data in their memory. Needless to say, attackers can easily exfiltrate this data by accessing unsecured office printers and use it for blackmail or corporate espionage, or simply sell it on the black markets of the dark web.
Bad actors can also take over unsecured printers and incorporate them into botnets in order to perform DDoS attacks, send spam, and more. What’s more, cybercriminals can use internet-connected printers to gain an initial foothold into the local or corporate networks and find more ways to cause more damage to the unsuspecting victims. Or they can simply use these printers to mine cryptocurrency, ramping up their victims’ electricity bills in the process.
Securing your printer
Our experiment has shown that printer security remains a serious concern for individuals and organizations across the world. With that said, most of the printers we managed to hijack could have been easily secured by following common security best practices and a few simple steps.
To quote the security guide we printed on tens of thousands of unsecured printers, “here’s how”:
1. Secure your printing ports and limit your printer’s wireless connections to your router. Configure your network settings so that your printer only answers commands that come via specified ports on your network router. The standard protocol for secure printing on new printers is IPPS protocol via SSL port 443.
2. Use a firewall. This will protect unused protocols that can allow cybercriminals to remotely access your printer from outside the network.
3. Update your printer firmware to the latest version. Printer manufacturers regularly fix known vulnerabilities in the firmware for the devices they produce, so make sure your printer always stays up-to-date security-wise.
4. Change the default password. Most printers have default administrator usernames and passwords. Change it to a strong, unique password in the utility settings of your printer and make sure print functions require log on credentials.
For more detailed information on printer security, read our guide on securing your printer against cyberattacks here.
Researchers Hijack 28,000 Printers to Show How Easily They Can Be Hacked
28.8.20 Hacking Securityweek
Researchers have once again demonstrated that many printers can be hacked remotely, by hijacking 28,000 devices and instructing them to print out a printer security guide.
The research was conducted by security experts at CyberNews, who claim to have identified more than 800,000 printers that were accessible over the internet and had network printing features enabled.
They then selected a sample of 50,000 exposed printers and sent them a script that instructed the devices to print the security guide. The researchers said the document was printed by nearly 28,000 of those devices, which suggests that 56% of exposed printers can be hijacked. This translates to roughly 447,000 printers of the total number of 800,000 exposed devices.

“To find out how many printers were on the menu for our experiment, we searched for IP addresses with open ports on specialized IoT search engines, such as Shodan and Censys. While performing the search, we made sure that the open devices we found were actual printers, as opposed to unrelated services that simply used those ports for other purposes,” they explained.
CyberNews told SecurityWeek that the experiment did not involve exploitation of any known or unknown vulnerabilities; the researchers abused the fact that the devices were not configured with security in mind.
Researchers have been finding potentially serious printer vulnerabilities that can be exploited for various purposes, including to crash devices and obtain sensitive information. However, experts demonstrated in the past that many printers can be hacked and abused due to insecure configurations.
And this is not the first time someone has demonstrated that printers can be remotely instructed to print arbitrary content. Back in 2016, a researcher hijacked thousands of printers and caused them to print anti-Semitic flyers. This is just one of several examples.
Google Location-Tracking Tactics Troubled Its Own Engineers
27.8.20 Hacking Securityweek
Google’s own engineers were troubled by the way the company secretly tracked the movements of people who didn’t want to be followed until a 2018 Associated Press investigation uncovered the shadowy surveillance, according to unsealed documents in a consumer fraud case.
The behind-the-scenes peek stems from a three-month-old lawsuit against Google filed by Arizona’s attorney general. The files, unsealed late last week, reveal that Google knew it had a massive problem on its hands after an AP article published in August 2018 explained how the company continued to track users’ whereabouts even after they had disabled the feature Google called “location history.”
The released documents include internal Google emails and a fresh version of the state’s civil complaint with fewer redactions than the original.
The same day the AP story was published, the company held what one unidentified email correspondent called an “Oh S—-” meeting to discuss its location tracking tools, according to the unsealed records in Arizona’s Maricopa County Superior Court. Google also began monitoring public reaction to the AP story, including how it was trending across Facebook, Twitter and other influential online services, the documents show.
Some of Google’s own engineers scolded the company for misleading people about how its location tracking settings worked. “I agree with the article,” one engineer wrote in a particularly blunt assessment after the AP story was published. “Location off should mean location off, not except for this case or that case.”
Another Google engineer wrote, “Indeed we aren’t very good at explaining this to users.” Another concurred that what the company was doing was “definitely confusing from a user point of view.”
The release of the emails is embarrassing for a company that tries to build trust with billions of users of free services such as maps and online search, which in turn provide the personal information Google can use to target ads. Those ads generated more than $130 billion in revenue last year alone.
Google is still fighting to keep many of the exhibits and key passages in the lawsuit redacted on the grounds that the contents contain confidential information.
After the AP article on location tracking came out two years ago, Google made changes to its privacy settings to make it easier for users to conceal their movements.
But the revisions didn’t deter Arizona Attorney General Mark Brnovich from opening an investigation that culminated in his suing Google three months ago. The complaint accuses Google of engaging in deceptive business practices that duped Arizona consumers, and could potentially result in billions of dollars of penalties if Brnovich prevails.
“The recently unsealed documents reveal statements from Google’s own engineers that are in conflict with what the company has been representing to the public,” Brnovich said in a Wednesday statement.
Google is seeking to dismiss the lawsuit, arguing that the Arizona law only applies to goods and services that charge consumers. That would exclude free services that draw upon the tracking tools that are at the heart of the lawsuit.
The company also contends that Brnovich, a Republican, may have been prodded to pursue the investigation by Oracle, which has been involved in a long-running legal battle over the rights to some of the software code used in Google’s Android software for smartphones and other mobile devices.
“Privacy controls have long been built into our services and our teams work continuously to discuss and improve them,” Google spokesperson Jose Castaneda said Wednesday. “In the case of location information, we’ve heard feedback, and have worked hard to improve our privacy controls.”
Thousands of WordPress WooCommerce stores potentially exposed to hack
22.8.20 Hacking Securityaffairs
Hackers are attempting to exploit multiple vulnerabilities in the Discount Rules for WooCommerce WordPress plugin, which has 30,000+ installations.
Researchers from security firm WebArx reported that Hackers are actively attempting to exploit numerous flaws in the Discount Rules for WooCommerce WordPress plugin.
The list of vulnerabilities includes SQL injection, authorization flaws, and unauthenticated stored cross-site scripting (XSS) security vulnerabilities.
Discount Rules for WooCommerce is a WordPress plugin that allows users to manage product pricing and discount campaigns on WooCommerce online stores. The plugin has more than 30,000 installations
“The Discount Rules for WooCommerce plugin (versions 2.0.2 and below) suffers from multiple vulnerabilities such as SQL injection, authorization issues and unauthenticated stored cross-site scripting.” reads the post published by security experts.
“In this scenario, the unauthenticated stored cross-site scripting issue could potentially lead to remote code execution.”
Experts observed a wave of attacks attempting to exploit this vulnerability, most of them from the IP address 45[.]140.167.17 which attempts to inject the script poponclick[dot]info/click.js into the woocommerce_before_main_content template hook.
The attackers are attempting to target WooCommerce based sites running outdated versions of the popular plugin.
Experts warn that the vulnerabilities can be exploited by remote attackers to potentially execute arbitrary code on the vulnerable sites and potentially takeover compromised sites.
WebARX reported the flaws to the development team of the Discount Rules plugin on August 7 and on August 13, they released version 2.1.0 to address the vulnerabilities.
The flaws are caused by a lack of nonce token and authorization checks, their exploitation can allow unauthenticated attackers to retrieve a list of all users and coupon codes, inject into any display location, such as the header, footer or any admin page, and trigger remote code execution exploits.
At the time of writing, the plugin has been downloaded over 12,000 times in the last 7 days, this means that more that 17,000 WooCommerce online stores using the Discount Rules plugin are exposed to
Carnival Corp. Hacked; Guest and Worker Information Accessed
19.8.20 Hacking Securityweek
Carnival Corp. says it was the victim of a ransomware attack that likely got some personal information about the cruise company’s guests and employees.
The attack was first detected Saturday. The attack accessed an encrypted portion of technology systems for one of the cruise line’s brands and certain data files were downloaded, the company said in a filing with the U.S. Securities and Exchange Commission.
Carnival operates Carnival Cruise Line, Princess Cruises, Holland America Line and other lines, but the company didn’t say in the filing which cruise line was affected.
The SEC filing also didn’t say how many people’s personal information may have been accessed, and spokesman Roger Frizzell said in an email that the company wasn’t releasing any information other than what was in the securities filing.
Carnival says it has launched an investigation into the ransomware attack and notified law enforcement. The Miami-based company also has reinforced the security of its information systems, Carnival said.
Threat actors managed to control 23% of Tor Exit nodes
13.8.20 Hacking Securityaffairs
A security researcher has discovered that a threat actor controlled roughly 23% of the Tor network’s exit nodes.
A security researcher named Nusenu revealed that in May a malicious controlled roughly 23% of the entire Tor network’s exit nodes. Experts warn that this was the first time that a single actor controlled such a large number of Tor exit nodes.
A Tor exit relay is the final relay that Tor traffic passes through before it reaches the intended destination. The Tor traffic exits through these relays, this means that the IP address of the exit relay is interpreted as the source of the traffic. Tor Exit relays advertise their presence to the entire Tor network, so they can be used by any Tor users.
Controlling these relays it is possible to see which website the user connects to and, if an unsecure connection is used, it is also possible to manipulate traffic.
In May, a malicious actor managed to control over 380 Tor exit nodes, with a peak on May 22, when he controlled the 23.95% of Tor exit relay.
“Figure 1 shows what accumulated fraction of the Tor network’s exit capacity was controlled by the malicious actor and how many confirmed malicious relays were concurrently running (peak at over 380 relays).” reads the analysis published by the expert. “Figure 1 also tells us that we opened up Tor Browser at the peak of the attack on 2020–05–22 you had a 23.95% chance to end up choosing an attacker controlled Tor exit relay. Since Tor clients usually use many Tor exit relays over time the chance to use a malicious exit relay increases over time.”
They were removed, but the threat actors restored them as Tor relays after declaring them as a group using the so-called “MyFamily” setting.
In May, most of the nodes were removed, but they were able to grow from 4% exit capability to over 22% in a few weeks.
“The 3 sharp drops in figure 1 (marked with 1, 2, 3) depict the events when some of these malicious Tor exits got detected, reported and removed from the network by the Tor directory authorities. This also shows us how fast the malicious entity recovered from a single removal event and that we didn’t detect all of them at the same time.” continues the report. “It took them less than 30 days to recover after a removal and reach 22% exit probability again (starting at 4%).”
The threat actor continued to use the MyFamily settings to announce the availability of relays groups but avoided to link all of them together. The experts revealed that the attacker used various email addresses to register nodes (i.e. Hotmail, ProtonMail, and Gmail).
The infrastructure used by the threat actors was based hosted on OVH, attackers also leveraged on ISPs such as Frantech, ServerAstra, Trabia, Nice IT Services Group.
The experts observed that attackers removed HTTP-to-HTTPS redirects, in the attempt to manipulate the traffic flowing through their relays.
The expert noticed that the attack was not specific to Tor Browser and in the attempt to make the detection harder, the attackers entity did not attack all websites equally.
“It appears that they are primarily after cryptocurrency related websites — namely multiple bitcoin mixer services. They replaced bitcoin addresses in HTTP traffic to redirect transactions to their wallets instead of the user provided bitcoin address. Bitcoin address rewriting attacks are not new, but the scale of their operations is. It is not possible to determine if they engage in other types of attacks,” Nusenu says.
The situation is still dangerous, according to the expert as of August 8, the threat actor was still in control of over 10% of Tor’s exit capacity.
Microsoft Reveals New Innocent Ways Windows Users Can Get Hacked
12.8.20 Hacking Thehackernews
Microsoft earlier today released its August 2020 batch of software security updates for all supported versions of its Windows operating systems and other products.
This month's Patch Tuesday updates address a total of 120 newly discovered software vulnerabilities, of which 17 are critical, and the rest are important in severity.
In a nutshell, your Windows computer can be hacked if you:
Play a video file — thanks to flaws in Microsoft Media Foundation and Windows Codecs
Listen to audio — thanks to bugs affecting Windows Media Audio Codec
Browser a website — thanks to 'all time buggy' Internet Explorer
Edit an HTML page — thanks to an MSHTML Engine flaw
Read a PDF — thanks to a loophole in Microsoft Edge PDF Reader
Receive an email message — thanks to yet another bug in Microsoft Outlook
But don't worry, you don't need to stop using your computer or without Windows OS on it. All you need to do is click on the Start Menu → open Settings → click Security and Update, and install if any new update is available.
Install Updates! Two Zero-Days Under Active Attacks
Another reason why you should not ignore this advice is that two of the security flaws have reportedly been exploited by hackers in the wild and one publicly known at the time of release.
According to Microsoft, one of the zero-day vulnerabilities under active attack is a remote code execution bug that resides in the scripting engine's library jscript9.dll, which is used by default by all versions of Internet Explorer since IE9.
The vulnerability, tracked as CVE-2020-1380, was spotted by Kaspersky Labs and has been rated critical because Internet Explorer remains an important component of Windows as it still comes installed by default in the latest Windows.
Kaspersky researchers explain that the flaw is a use-after-free vulnerability in JScript that corrupts the dynamic memory in Internet Explorer in such a way that an attacker could execute arbitrary code in the context of the current user. So, if the current user is logged in with administrative privileges, the attacker could control the affected system.
"An attacker could also embed an ActiveX control marked "safe for initialization" in an application or Microsoft Office document that hosts the IE rendering engine. The attacker could also take advantage of compromised websites and websites that accept or host user-provided content or advertisements," Microsoft says in its advisory.
Exploited by unknown threat actors as part of 'Operation PowerFall' attacks, a proof-of-concept exploit code, and technical details for the zero-day vulnerability have been published by Kaspersky.
The second zero-day vulnerability—tracked as CVE-2020-1464 and under active exploitation—is a Windows spoofing bug that exists when Windows incorrectly validates file signatures.
This zero-day bug affects all supported versions of Windows and allows attackers to load improperly signed files by bypassing security features intended to prevent incorrectly signed files from being loaded.
Besides these, notably, the batch also includes a critical patch for an elevation of privilege flaw affecting NetLogon for Windows Server editions, where this RPC service serves as a domain controller.
Tracked as 'CVE-2020-1472,' the vulnerability can be exploited by unauthenticated attackers to use Netlogon Remote Protocol (MS-NRPC) to connect to a Domain Controller (DC) and obtain administrative access to run malicious applications on a device on the network.
Home users and server administrators are strongly recommended to apply the latest security patches as soon as possible to prevent malware or miscreants from exploiting and gain complete remote control over their vulnerable computers.
Google Chrome Bug Could Let Hackers Bypass CSP Protection; Update Web Browsers
12.8.20 Hacking Thehackernews
If you haven't recently updated your Chrome, Opera, or Edge web browser to the latest available version, it would be an excellent idea to do so as quickly as possible.
Cybersecurity researchers on Monday disclosed details about a zero-day flaw in Chromium-based web browsers for Windows, Mac and Android that could have allowed attackers to entirely bypass Content Security Policy (CSP) rules since Chrome 73.
Tracked as CVE-2020-6519 (rated 6.5 on the CVSS scale), the issue stems from a CSP bypass that results in arbitrary execution of malicious code on target websites.
According to PerimeterX, some of the most popular websites, including Facebook, Wells Fargo, Zoom, Gmail, WhatsApp, Investopedia, ESPN, Roblox, Indeed, TikTok, Instagram, Blogger, and Quora, were susceptible to the CSP bypass.
Interestingly, it appears that the same flaw was also highlighted by Tencent Security Xuanwu Lab more than a year ago, just a month after the release of Chrome 73 in March 2019, but was never addressed until PerimeterX reported the issue earlier this March.
After the findings were disclosed to Google, the Chrome team issued a fix for the vulnerability in Chrome 84 update (version 84.0.4147.89) that began rolling out on July 14 last month.
CSP is an extra layer of security that helps detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection attacks. With CSP rules, a website can mandate the victim's browser to perform certain client-side checks with an aim to block specific scripts that are designed to exploit the browser's trust of the content received from the server.
Given that CSP is the primary method used by website owners to enforce data security policies and prevent the execution of malicious scripts, a CSP bypass can effectively put user data at risk.
This is achieved by specifying the domains that the browser should consider to be valid sources of executable scripts, so that a CSP-compatible browser only executes scripts loaded in source files received from those allow-listed domains, ignoring all others.
The flaw discovered by Tencent and PerimeterX circumvents the configured CSP for a website by merely passing a malicious JavaScript code in the "src" property of an HTML iframe element.
It's worth noting that websites like Twitter, Github, LinkedIn, Google Play Store, Yahoo's Login Page, PayPal, and Yandex were not found vulnerable since the CSP policies were implemented using a nonce or hash to allow the execution of inline scripts.
"Having a vulnerability in Chrome's CSP enforcement mechanism doesn't directly mean that sites are breached, as the attackers also need to manage to get the malicious script called from the site (which is why the vulnerability was classified as medium severity)," PerimeterX's Gal Weizman noted.
While the implications of the vulnerability remain unknown, users must update their browsers to the latest version to protect against such code execution. Website owners, for their part, are recommended to use nonce and hash capabilities of CSP for added security.
Besides this, the latest Chrome update 84.0.4147.125 for Windows, Mac, and Linux systems also patches 15 other security vulnerabilities, 12 of which are rated 'high' and two 'low' in severity.
Accounts of Reddit Moderators Hijacked in Pro-Trump Hack
10.8.20 Hacking Securityweek
Multiple Reddit moderator accounts have been compromised and abused to post pro-Trump messages on a variety of subreddits.
The hackers appear to have targeted moderator accounts that did not have two-factor authentication (2FA) enabled, and leveraged their rights to modify subreddits or even remove moderator accounts that had fewer rights.
“There is an ongoing incident with moderator accounts being compromised and used to vandalize subreddits. We’re working on locking down the bad actors and reverting the changes,” a Reddit administrator revealed.
The online platform worked over the weekend on addressing the issue and restoring moderator access, but shared little technical details on the incident, except for the fact that none of the hacked accounts had 2FA enabled.
“We have officially confirmed that none of the accounts that were compromised had 2fa enabled at the time of the compromise. 2fa is not a guarantee of account safety in general, but it’s still an important step to take to keep your account more secure,” the Reddit admin said.
The online platform has already started providing affected users with access to their accounts, as well as notifying the impacted communities of the issue. Further details on the security incident will be provided in a future post, Reddit said.
At least one of the impacted moderators has shared information on the actions the attackers performed during the incident, revealing that automation was used to modify subreddits en-masse.
“Even one of the subs I'm just an in-active mod, it changed all their stuff and deleted those below me in the mod list,” the moderator reveals.
The attackers posted messages that contained Chinese characters and which encouraged users to vote for Trump in the 2020 presidential elections in the United States.
While resolving the security incident, Reddit urged moderators to adopt 2FA to prevent similar attacks from happening. One administrator even noted that 2FA might become a requirement for moderator accounts.