
Sreeram discovered a bug in the transmission process of the messages to “feedback.googleusercontent.com.” He explained that an attacker could modify the frame to an arbitrary, external website, to steal Google Docs screenshots.
Hacking 2024 2023 2022 2021 2020
Google Docs bug could have allowed hackers to hijack screenshots
31.12.2020 Hacking Securityaffairs
Google has addressed a bug in its feedback tool incorporated across its services that could have allowed attackers to view users’ private docs.
Google has addressed a flaw in its feedback tool that is part of multiple of its services that could be exploited by attackers to take screenshots of sensitive Google Docs documents by embedding them in a malicious website.
The vulnerability was discovered by the security researcher Sreeram KL, he demonstrated how to exploit it to hijack Google Docs screenshot of any document due to postmessage misconfiguration and browser behavior.
The issue affected the “Send Feedback” function that is included in most Google products. The ‘Send Feedback’ feature was implemented to allow users to submit feedback to Google. The function implements a feature that allows users to add screenshots to the feedback with a brief description of the problem.
The feedback feature is deployed in Google’s main domain (“www.google.com”) and is integrated into other domains by including an iframe element that loads the pop-up’s content from “feedback.googleusercontent.com” via PostMessage.
The Iframe loads the screenshot of the document you were working on. The expert pointed out that the origin of the iframe (www.google.com) is different from the Google docs (docs.google.com) and the cross-origin communication to render the screenshot is possible through PostMessage.
When a screenshot of the Google Docs window is included in the feedback, the rendering of the image is done by transmitting RGB values of every pixel to google.com, which in turn redirects those RGB values to the feedback’s domain, which constructs the image and sends it back in Base64 encoded format.

Sreeram discovered a bug in the transmission process of the messages to “feedback.googleusercontent.com.” He explained that an attacker could modify the frame to an arbitrary, external website, to steal Google Docs screenshots.
for which he was awarded $3133.70 as part of Google’s Vulnerability Reward Program.
The flaw is caused by the lack of X-Frame-Options header in the Google Docs domain.
“After watching the video, I learned a new trick that I didn’t knew before. That is, you can change the location of an iframe which is present in cross origin domain (If it lacks X-Frame-Header). For example, if abc.com have efg.com as iframe and abc.com didn’t have X-Frame header, I could change the efg.com to evil.com cross origin using, frames.location.” wrote the expert.
“The final postmessage on submitting feedback was configured like, windowRef.postmessage(“<Data>”,”*”); as there is no domain check the browser happily sent the data to my domain, which I was able to capture and hijack the screenshot. But wait! I said the parent domain shouldn’t have X-Frame header, how am I going to achieve that? Luckily Google docs didn’t have one.”
Below the video PoC published by Sreeram KL:
An attacker could embed a Google Docs file in an iFrame on a malicious website and hijacking the feedback pop-up frame to redirect the screenshots to a domain under his control.
Researchers shared the lists of victims of SolarWinds hack
23.12.2020 Hacking Securityaffairs
Security experts shared lists of organizations that were infected with the SolarWinds Sunburst backdoor after decoding the DGA mechanism.
Security experts started analyzing the DGA mechanism used by threat actors behind the SolarWinds hack to control the Sunburst/Solarigate backdoor and published the list of targeted organizations.
Researchers from multiple cybersecurity firms published a list that contains major companies, including Cisco, Deloitte, Intel, Mediatek, and Nvidia.
The researchers decoded the DGA algorithm used by the backdoor to assign a subdomain of the C2 (avsvmcloud[.]com) for each of the compromised organizations.
“Prevasio would like to thank Zetalytics for providing us with an updated (larger) list of passive (historic) DNS queries for the domains generated by the malware.” reported the analysis published by Prevasio.
Researchers from several security firms, including TrueSec, Prevasio, QiAnXin RedDrip, and Kaspersky shared the results of their analysis.
Prevasio researchers detailed the decoding process, for example considering the following address:
fivu4vjamve5vfrtn2huov[.]appsync-api.us-west-2[.]avsvmcloud[.]com
“The first part of the domain name (before the first dot) consists of a 16-character random string, appended with an encoded computer’s domain name. This is the domain in which the local computer is registered.” state the researchers.
Other major companies, including FireEye, Microsoft, and VMware also revealed to have been impacted by the SolarWinds supply chain attack.
Truesec researchers speculate that threat actors might have exfiltrated a massive amount of highly confidential information from multiple organizations. It is also highly likely that attackers compromised the software and systems of their victims.
“This list contains the decoded values of internal domain names. We can therefore only assume that they belong to an organization based on the name of the domains and publicly available information,” reads the post published by TrueSec.
“More information will be disclosed during the upcoming months but the full extent of this breach will most likely never be communicated to the public, and instead will be restricted to trusted parts of the intelligence community.”
DECODED INTERNAL NAME ORGANIZATION
(POSSIBLY INACCURATE) RESPONSE ADDRESS FAMILY COMMAND FIRST SEEN
mnh.rg-law.ac.il College of Law and Business,
Israel NetBios HTTP Backdoor 2020-05-26
ad001.mtk.lo Mediatek NetBios HTTP Backdoor 2020-08-26
Aeria NetBios HTTP Backdoor 2020-06-26
Ameri NetBios HTTP Backdoor 2020-08-02
ank.com Ankcom Communications NetBios HTTP Backdoor 2020-06-06
azlcyy NetBios HTTP Backdoor 2020-08-07
banccentral.com BancCentral Financial
Services Corp. NetBios HTTP Backdoor 2020-07-03
barrie.ca City of Barrie NetBios HTTP Backdoor 2020-05-13
BCC.l NetBios HTTP Backdoor 2020-08-22
bhq.lan NetBios HTTP Backdoor 2020-08-18
cds.capilanou. Capilano University NetBios HTTP Backdoor 2020-08-27
Centr NetBios HTTP Backdoor 2020-06-24
chc.dom NetBios HTTP Backdoor 2020-08-04
christieclinic. Christie Clinic Telehealth NetBios HTTP Backdoor 2020-04-22
CIMBM NetBios HTTP Backdoor 2020-09-25
CIRCU NetBios HTTP Backdoor 2020-05-30
CONSO NetBios HTTP Backdoor 2020-06-17
corp.ptci.com Pioneer Telephone
Scholarship Recipients NetBios HTTP Backdoor 2020-06-19
corp.stingraydi Stingray (Media and
entertainment) NetBios HTTP Backdoor 2020-06-10
corp.stratusnet Stratus Networks NetBios HTTP Backdoor 2020-04-28
cosgroves.local Cosgroves (Building services
consulting) NetBios HTTP Backdoor 2020-08-25
COTES Cotes (Humidity Management) NetBios HTTP Backdoor 2020-07-25
csnt.princegeor City of Prince George NetBios HTTP Backdoor 2020-09-18
cys.local CYS Group (Marketing analytics) NetBios HTTP Backdoor 2020-07-10
digitalsense.co Digital Sense (Cloud Services) NetBios HTTP Backdoor 2020-06-24
ehtuh- NetBios HTTP Backdoor 2020-05-01
escap.org NetBios HTTP Backdoor 2020-07-10
f.gnam NetBios HTTP Backdoor 2020-04-04
fhc.local NetBios HTTP Backdoor 2020-07-06
fidelitycomm.lo Fidelity Communications (ISP) NetBios HTTP Backdoor 2020-06-02
fisherbartoninc.com The Fisher Barton Group
(Blade Manufacturer) NetBios HTTP Backdoor 2020-05-15
fmtn.ad City of Farmington NetBios HTTP Backdoor 2020-07-21
FWO.I NetBios HTTP Backdoor 2020-08-05
ggsg-us.cisco Cisco GGSG NetBios HTTP Backdoor 2020-06-24
ghsmain1.ggh.g NetBios HTTP Backdoor 2020-06-09
gxw NetBios HTTP Backdoor 2020-07-07
htwanmgmt.local NetBios HTTP Backdoor 2020-07-22
ieb.go.id NetBios HTTP Backdoor 2020-06-12
int.ncahs.net NetBios HTTP Backdoor 2020-09-23
internal.jtl.c NetBios HTTP Backdoor 2020-05-19
ironform.com Ironform (metal fabrication) NetBios HTTP Backdoor 2020-06-19
isi NetBios HTTP Backdoor 2020-07-06
itps.uk.net Infection Prevention Society (IPS) NetBios HTTP Backdoor 2020-08-11
jxxyx. NetBios HTTP Backdoor 2020-06-26
kcpl.com Kansas City Power and
Light Company NetBios HTTP Backdoor 2020-07-07
keyano.local Keyano College NetBios HTTP Backdoor 2020-06-03
khi0kl NetBios HTTP Backdoor 2020-08-26
lhc_2f NetBios HTTP Backdoor 2020-04-18
lufkintexas.net Lufkin (City in Texas) NetBios HTTP Backdoor 2020-07-07
magnoliaisd.loc Magnolia Independent
School District NetBios HTTP Backdoor 2020-06-01
MOC.l NetBios HTTP Backdoor 2020-04-30
moncton.loc City of Moncton NetBios HTTP Backdoor 2020-08-25
mountsinai.hosp Mount Sinai Hospital NetBios HTTP Backdoor 2020-07-02
netdecisions.lo Netdecisions (IT services) NetBios HTTP Backdoor 2020-10-04
newdirections.k NetBios HTTP Backdoor 2020-04-21
nswhealth.net NSW Health NetBios HTTP Backdoor 2020-06-12
nzi_9p NetBios HTTP Backdoor 2020-08-04
city.kingston.on.ca City of Kingston,
Ontario, Canada NetBios HTTP Backdoor 2020-06-15
dufferincounty.on.ca Dufferin County,
Ontario, Canada NetBios HTTP Backdoor 2020-07-17
osb.local NetBios HTTP Backdoor 2020-04-28
oslerhc.org William Osler Health System NetBios HTTP Backdoor 2020-07-11
pageaz.gov City of Page NetBios HTTP Backdoor 2020-04-19
pcsco.com Professional Computer Systems NetBios HTTP Backdoor 2020-07-23
pkgix_ NetBios HTTP Backdoor 2020-07-15
pqcorp.com PQ Corporation NetBios HTTP Backdoor 2020-07-02
prod.hamilton. Hamilton Company NetBios HTTP Backdoor 2020-08-19
resprod.com Res Group (Renewable
energy company) NetBios HTTP Backdoor 2020-05-06
RPM.l NetBios HTTP Backdoor 2020-05-28
sdch.local South Davis
Community Hospital NetBios HTTP Backdoor 2020-05-18
servitia.intern NetBios HTTP Backdoor 2020-06-16
sfsi.stearnsban Stearns Bank NetBios HTTP Backdoor 2020-08-02
signaturebank.l Signature Bank NetBios HTTP Backdoor 2020-06-25
sm-group.local SM Group (Distribution) NetBios HTTP Backdoor 2020-07-07
te.nz TE Connectivity (Sensor
manufacturer) NetBios HTTP Backdoor 2020-05-13
thx8xb NetBios HTTP Backdoor 2020-06-16
tx.org NetBios HTTP Backdoor 2020-07-15
usd373.org Newton Public Schools NetBios HTTP Backdoor 2020-08-01
uzq NetBios HTTP Backdoor 2020-10-02
ville.terrebonn Ville de Terrebonne NetBios HTTP Backdoor 2020-08-02
wrbaustralia.ad W. R. Berkley Insurance Australia NetBios HTTP Backdoor 2020-07-11
ykz NetBios HTTP Backdoor 2020-07-11
2iqzth ImpLink Enum processes 2020-06-17
3if.2l 3IF (Industrial Internet) ImpLink Enum processes 2020-08-20
airquality.org Sacramento Metropolitan
Air Quality Management District ImpLink Enum processes 2020-08-09
ansc.gob.pe GOB (Digital Platform of
the Peruvian State) ImpLink Enum processes 2020-07-25
bcofsa.com.ar Banco de Formosa ImpLink Enum processes 2020-07-13
bi.corp ImpLink Enum processes 2020-12-14
bop.com.pk The Bank of Punjab ImpLink Enum processes 2020-09-18
camcity.local ImpLink Enum processes 2020-08-07
cow.local ImpLink Enum processes 2020-06-13
deniz.denizbank DenizBank ImpLink Enum processes 2020-11-14
ies.com IES Communications
(Communications technology) ImpLink Enum processes 2020-06-11
insead.org INSEAD Business School ImpLink Enum processes 2020-11-07
KS.LO ImpLink Enum processes 2020-07-10
mixonhill.com Mixon Hill (intelligent
transportation systems) ImpLink Enum processes 2020-04-29
ni.corp.natins ImpLink Enum processes 2020-10-24
phabahamas.org Public Hospitals Authority,
Caribbean ImpLink Enum processes 2020-11-05
rbe.sk.ca Regina Public Schools ImpLink Enum processes 2020-08-20
spsd.sk.ca Saskatoon Public Schools ImpLink Enum processes 2020-06-12
yorkton.cofy Community Options for
Families & Youth ImpLink Enum processes 2020-05-08
.sutmf Ipx Update config 2020-06-25
atg.local No Match Unknown 2020-05-11
bisco.int Bisco International
(Adhesives and tapes) No Match Unknown 2020-04-30
ccscurriculum.c No Match Unknown 2020-04-18
e-idsolutions. IDSolutions (video conferencing) No Match Unknown 2020-07-16
ETC1. No Match Unknown 2020-08-01
gk5 No Match Unknown 2020-07-09
grupobazar.loca No Match Unknown 2020-06-07
internal.hws.o No Match Unknown 2020-05-23
n2k No Match Unknown 2020-07-12
publiser.it No Match Unknown 2020-07-05
us.deloitte.co Deloitte No Match Unknown 2020-07-08
ush.com No Match Unknown 2020-06-15
xijtt- No Match Unknown 2020-07-21
xnet.kz X NET (IT provider in Kazakhstan) No Match Unknown 2020-06-09
zu0 No Match Unknown 2020-08-13
staff.technion.ac.il N/A N/A N/A
digitalreachinc.com N/A N/A N/A
orient-express.com N/A N/A N/A
tr.technion.ac.il N/A N/A N/A
lasers.state.la.us N/A N/A N/A
ABLE. N/A N/A N/A
abmuh_ N/A N/A N/A
acmedctr.ad N/A N/A N/A
ad.azarthritis.com N/A N/A N/A
ad.library.ucla.edu N/A N/A N/A
ad.optimizely. N/A N/A N/A
admin.callidusc N/A N/A N/A
aerioncorp.com N/A N/A N/A
agloan.ads N/A N/A N/A
ah.org N/A N/A N/A
AHCCC N/A N/A N/A
allegronet.co. N/A N/A N/A
alm.brand.dk N/A N/A N/A
amalfi.local N/A N/A N/A
americas.phoeni N/A N/A N/A
amr.corp.intel N/A N/A N/A
apu.mn N/A N/A N/A
ARYZT N/A N/A N/A
b9f9hq N/A N/A N/A
BE.AJ N/A N/A N/A
belkin.com N/A N/A N/A
bk.local N/A N/A N/A
bmrn.com N/A N/A N/A
bok.com N/A N/A N/A
btb.az N/A N/A N/A
c4e-internal.c N/A N/A N/A
calsb.org N/A N/A N/A
casino.prv N/A N/A N/A
cda.corp N/A N/A N/A
central.pima.g N/A N/A N/A
cfsi.local N/A N/A N/A
ch.local N/A N/A N/A
ci.dublin.ca. N/A N/A N/A
cisco.com N/A N/A N/A
corp.dvd.com N/A N/A N/A
corp.sana.com N/A N/A N/A
Count N/A N/A N/A
COWI. N/A N/A N/A
coxnet.cox.com N/A N/A N/A
CRIHB N/A N/A N/A
cs.haystax.loc N/A N/A N/A
csa.local N/A N/A N/A
csci-va.com N/A N/A N/A
csqsxh N/A N/A N/A
DCCAT N/A N/A N/A
deltads.ent N/A N/A N/A
detmir-group.r N/A N/A N/A
dhhs- N/A N/A N/A
dmv.state.nv. N/A N/A N/A
dotcomm.org N/A N/A N/A
DPCIT N/A N/A N/A
dskb2x N/A N/A N/A
e9.2pz N/A N/A N/A
ebe.co.roanoke.va.us N/A N/A N/A
ecobank.group N/A N/A N/A
ecocorp.local N/A N/A N/A
epl.com N/A N/A N/A
fremont.lamrc. N/A N/A N/A
FSAR. N/A N/A N/A
ftfcu.corp N/A N/A N/A
gksm.local N/A N/A N/A
gloucesterva.ne N/A N/A N/A
glu.com N/A N/A N/A
gnb.local N/A N/A N/A
gncu.local N/A N/A N/A
gsf.cc N/A N/A N/A
gyldendal.local N/A N/A N/A
helixwater.org N/A N/A N/A
hgvc.com N/A N/A N/A
ia.com N/A N/A N/A
inf.dc.net N/A N/A N/A
ingo.kg N/A N/A N/A
innout.corp N/A N/A N/A
int.lukoil-international.uz N/A N/A N/A
intensive.int N/A N/A N/A
ions.com N/A N/A N/A
its.iastate.ed N/A N/A N/A
jarvis.lab N/A N/A N/A
-jlowd N/A N/A N/A
jn05n8 N/A N/A N/A
jxb3eh N/A N/A N/A
k.com N/A N/A N/A
LABEL N/A N/A N/A
milledgeville.l N/A N/A N/A
nacr.com N/A N/A N/A
ncpa.loc N/A N/A N/A
neophotonics.co N/A N/A N/A
net.vestfor.dk N/A N/A N/A
nih.if N/A N/A N/A
nvidia.com N/A N/A N/A
on-pot N/A N/A N/A
ou0yoy N/A N/A N/A
paloverde.local N/A N/A N/A
pl8uw0 N/A N/A N/A
q9owtt N/A N/A N/A
rai.com N/A N/A N/A
rccf.ru N/A N/A N/A
repsrv.com N/A N/A N/A
ripta.com N/A N/A N/A
roymerlin.com N/A N/A N/A
rs.local N/A N/A N/A
rst.atlantis-pak.ru N/A N/A N/A
sbywx3 N/A N/A N/A
sc.pima.gov N/A N/A N/A
scif.com N/A N/A N/A
SCMRI N/A N/A N/A
scroot.com N/A N/A N/A
seattle.interna N/A N/A N/A
securview.local N/A N/A N/A
SFBAL N/A N/A N/A
SF-Li N/A N/A N/A
siskiyous.edu N/A N/A N/A
sjhsagov.org N/A N/A N/A
Smart N/A N/A N/A
smes.org N/A N/A N/A
sos-ad.state.nv.us N/A N/A N/A
sro.vestfor.dk N/A N/A N/A
superior.local N/A N/A N/A
swd.local N/A N/A N/A
ta.org N/A N/A N/A
taylorfarms.com N/A N/A N/A
thajxq N/A N/A N/A
thoughtspot.int N/A N/A N/A
tsyahr N/A N/A N/A
tv2.local N/A N/A N/A
uis.kent.edu N/A N/A N/A
uncity.dk N/A N/A N/A
uont.com N/A N/A N/A
viam-invenient N/A N/A N/A
vms.ad.varian.com N/A N/A N/A
vsp.com N/A N/A N/A
WASHO N/A N/A N/A
weioffice.com N/A N/A N/A
wfhf1.hewlett. N/A N/A N/A
woodruff-sawyer N/A N/A N/A
HQ.RE-wwgi2xnl N/A N/A N/A
xdxinc.net N/A N/A N/A
y9k.in N/A N/A N/A
zeb.i8 N/A N/A N/A
zippertubing.co N/A N/A N/A
VMware and Cisco also impacted by the SolarWinds hack
23.12.2020 Hacking Securityaffairs
The IT giants VMware and Cisco revealed they were impacted by the recently disclosed SolarWinds supply chain attack.
VMware and Cisco confirmed to have been both impacted by the recent SolarWinds hack.
A recent advisory published by the NSA is warning that Russian state-sponsored hackers are exploiting the recently patched CVE-2020-4006 VMware flaw to steal sensitive information from their targets.
The CVE-2020-4006 flaw affects Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector.
The popular investigator Brian Krebs learned from sources that the threat actors behind the SolarWinds hack also exploited the VMware flaw.
Last week, VMware published a statement to confirm that it is not aware of attacks exploiting the CVE 2020-4006 flaw “in conjunction with the SolarWinds supply chain compromise.”
The company also added that it has not found any evidence of exploitation in its network.
“To date, VMware has received no notification that the CVE 2020-4006 was used in conjunction with the SolarWinds supply chain compromise.” reads the security advisory.
“In addition, while we have identified limited instances of the vulnerable Orion software in our own internal environment, our own internal investigation has not revealed any indication of exploitation. This has also been confirmed by SolarWinds own investigations to date.”
Cisco also confirmed to have found instances of the Solarwinds backdoor in a small number of lab environments and a limited number of employee endpoints.
“While Cisco does not use SolarWinds for its enterprise network management or monitoring, we have identified and mitigated affected software in a small number of lab environments and a limited number of employee endpoints.” reads the Cisco’s advisory. “we have identified and mitigated affected software in a small number of lab environments and a limited number of employee endpoints.”
Last week, Microsoft has confirmed that it was one of the companies breached in the recent SolarWinds supply chain attack, but the IT giant denied that the nation-state actors compromised its software supply-chain to infect its customers.
Unfortunately, the list of impacted organizations is long, SolarWinds revealed at least 18,000 of its customers may be impacted.
If you want to receive the weekly Security Affairs Newsletter for free subscribe here.
Air-Gap Attack Turns Memory Modules into Wi-Fi Radios
18.12.2020 Hacking Threatpost
Attack turns SDRAM buses into a Wi-Fi radio to leak data from air-gapped computers.
Super-secure air-gapped computers are vulnerable to a new type of attack that can turn a PC’s memory module into a modified Wi-Fi radio, which can then transmit sensitive data at 100 bits-per-second wirelessly to nearly six feet away.
Noted air-gap researcher Mordechai Guri created the proof-of-concept (PoC) attack and described it in a research paper released earlier this month under the auspices of Ben-Gurion University of the Negev, Israel’s cybersecurity research center.
“Malware in a compromised air-gapped computer can generate signals in the Wi-Fi frequency bands. The signals are generated through the memory buses — no special hardware is required,” Guri wrote (PDF).
A memory bus is made up of a set of wires and conductors that connect and transfer data from a computer’s main memory to a system’s central processing unit or a memory controller.
Wireless Wonder Hack
In his proof-of-concept attack, Guri showed how an adversary could manipulate the electrical current on a system’s DDR SDRAM bus in order to generate electromagnetic waves and transmit a weak Wi-Fi signal (2,400 GHz). It’s not a quick attack though: At a top speed of 100 bps, it would take 22 hours and 13 minutes to send 1MB of data to a receiving device no more than 69 inches away.
“Since the clock speed of memory modules is typically around the frequency of 2.4 GHz or its harmonics, the memory operations generate electromagnetic emissions around the IEEE 802.11b/g/n Wi-Fi frequency bands,” Guri wrote.
The hack requires perfectly timed read-write operations, which would be driven by malware installed on the targeted computer. The principle behind this type of attack is, electronic components generate electromagnetic waves. Similarly, radio frequency transmitters, such as routers, are also based on a type of electromagnetic radiation. Ergo what Guri calls his AIR-FI hack, based on electromagnetic manipulation.
Initial Infection
This air-gap attack vector skips one important detail – how to sneak the malicious code onto the targeted system to begin and how to collect the data once pried from the target.
Air-Gap Attack Memory Modules: Proof of Concept Guri explains planting malware could be done by a nation-state adversary at the time of manufacturing, during the shipping of equipment or simply via an infected USB drive plugged into the targeted computer. As for collecting the data, researchers say a nearby Wi-Fi capable device such as a smartphone, laptop or internet-of-things (IoT) device could work.
An attacker could “intercept these signals, decode them and send them to the attacker over the internet,” he wrote. In previous research, Guri showed how a wide range of IoT devices, such as smart bulbs and smart locks, could be used as part of the export chain of data.
Speeds and Feeds
Wireless transmission error rates, speeds and proximity varied widely based on systems used in the PoC attacks. For example, specially crafted malware running on a relatively robust air-gapped PC with a ASRock ATX motherboard, Intel Core i7 3.2Ghz CPU sporting 4GB of Crucial 2.4GHz DDR4 SRAM on the Ubuntu operating system delivered the best results.
“We transmitted the data at a bit rate of 100 bps and maintained a bit error rate (BER) of 8.75 percent for a distance up to 180 cm from the transmitter. Note that due to the local ramifications and interference, the signal quality may vary with the distance and location of the receiver,” he wrote.
Researchers said they were able to manipulate the ambient electromagnetic signals of the memory modules by using a feature introduced by chipmaker Intel designed to allow gamers to overclock their systems for better performance. The feature, Extreme Memory Profile (XMP), allows anyone to manipulate the latency of the read command delivered between the processor and the DDR SDRAM hardware.
“The memory buses generate electromagnetic radiation at a frequency correlated to its clock frequency and harmonics. For example, DDR4-2400 emits electromagnetic radiation at around 2400 MHz,” researchers wrote.
Guri said there are many ways to protect against such attacks, such banning network-connected phones, laptops or IoT gear near air-gapped hardware. Wi-Fi jamming would also thwart a potential attack of this nature.
Further air-gap research authored by the Guri can be found at his Air-Gap Research Page.
RAM-Generated Wi-Fi Signals Allow Data Exfiltration From Air-Gapped Systems
17.12.2020 Hacking Securityweek
Covert Wi-Fi signals generated by DDR SDRAM hardware can be leveraged to exfiltrate data from air-gapped computers, a researcher claims.
In a newly published paper, Mordechai Guri from the Ben-Gurion University of the Negev in Israel details AIR-FI, a new data exfiltration technique in which malware installed on a compromised air-gapped system can generate Wi-Fi signals that a nearby device intercepts and sends to the attacker, over the Internet.
The technique leverages memory buses for the generation of covert signals, thus eliminating the need of Wi-Fi hardware. For the interception of these signals, Wi-Fi capable devices such as smartphones, IoT devices, and laptops are used.
Disconnected form the internet, air-gapped networks and computers are used for storing sensitive data or applications, but motivated cyber-attackers are constantly searching for new ways to breach these isolated systems, either through targeting the supply chain, using malicious insiders, or tricking unsuspecting insiders into carrying out nefarious actions.
Over the past years, numerous new data exfiltration techniques aimed at air-gapped computers have been disclosed, and threat actors were observed increasingly targeting air-gapped systems in their attacks.
The newly detailed method assumes that the adversary was able to compromise the air-gapped system and has already collected data of interest, including biometric information, credentials, documents, and files. Wi-Fi frequency bands are used as a channel for data exfiltration.
The AIR-FI attack relies on DDR SDRAM buses for emitting electromagnetic signals on the 2.4 GHz Wi-Fi band and for encoding data on top of these signals. A nearby Wi-Fi-capable device that has been infected with malware is used to intercept these signals, decode them, and then transmit them to the attacker, over the Internet.
According to the researcher, the attack works on virtual machines (VMs) too, does not require a Wi-Fi transmitter or special privileges, and can leverage a broad range of devices as receivers. The low-level physical layer information exposed by Wi-Fi chips to the application layers is used for signal extraction.
Proposed countermeasures include the zone separation that U.S. and NATO telecommunication security standards propose as protection against TEMPEST (Telecommunications Electronics Materials Protected from Emanating Spurious Transmissions) threats; runtime detection; jamming the Wi-Fi frequency bands; interfering with the execution of the malicious process; and Faraday shielding (which blocks or limits electromagnetic fields).
“Our results show that the covert channel can be effective at distances up to several meters from air-gapped computers. We achieved effective bit rates ranging from 1 to 100 bit/sec, depending on the type and mode of receiver used,” the researcher concludes.
Exfiltrating Data from Air-Gapped Computers via Wi-Fi Signals (Without Wi-Fi Hardware)
15.12.2020 Hacking Thehackernews
A security researcher has demonstrated that sensitive data could be exfiltrated from air-gapped computers via a novel technique that leverages Wi-Fi signals as a covert channel—surprisingly, without requiring the presence of Wi-Fi hardware on the targeted systems.
Dubbed "AIR-FI," the attack hinges on deploying a specially designed malware in a compromised system that exploits "DDR SDRAM buses to generate electromagnetic emissions in the 2.4 GHz Wi-Fi bands" and transmitting information atop these frequencies that can then be intercepted and decoded by nearby Wi-Fi capable devices such as smartphones, laptops, and IoT devices before sending the data to remote servers controlled by an attacker.
The findings were published today in a paper titled "AIR-FI: Generating Covert Wi-Fi Signals from Air-Gapped Computers" by Dr. Mordechai Guri, the head of R&D at Ben-Gurion University of the Negev's Cyber-Security Research Center, Israel.
"The AIR-FI attack [...] does not require Wi-Fi related hardware in the air-gapped computers," Dr. Guri outlined.
"Instead, an attacker can exploit the DDR SDRAM buses to generate electromagnetic emissions in the 2.4 GHz Wi-Fi bands and encode binary data on top of it."
Guri, earlier this May, also demonstrated POWER-SUPPLaY, a separate mechanism that allows the malware to exploit a computer's power supply unit (PSU) to play sounds and use it as an out-of-band, secondary speaker to leak data.
Air-gapped computers — machines with no network interfaces — are considered a necessity in environments where sensitive data is involved in an attempt to reduce the risk of data leakage.
Thus in order to carry out attacks against such systems, it is often essential that the transmitting and receiving machines be located in close physical proximity to one another and that they are infected with the appropriate malware to establish the communication link.
Be AIR-FI is unique in that the method neither relies on a Wi-Fi transmitter to generate signals nor requires kernel drivers, special privileges such as root, or access to hardware resources to transmit the data.
What's more, the covert channel works even from within an isolated virtual machine and has an endless list of Wi-Fi enabled devices that can be hacked by an attacker to act as a potential receiver.
The kill chain in itself consists of an air-gapped computer onto which the malware is deployed via social engineering lures, self-propagating worms such as Agent.BTZ, tampered USB flash drives, or even with the help of malicious insiders.
It also requires infecting Wi-Fi capable devices co-located in the air-gapped network by compromising the firmware of the Wi-Fi chips to install malware capable of detecting and decoding the AIR-FI transmission and exfiltrating the data over the Internet.
With this setup in place, the malware on the target system collects the relevant data (e.g., confidential documents, credentials, encryption keys), which is then encoded and transmitted in the Wi-Fi band at 2.4 GHz frequency using the electromagnetic emissions generated from the DDR SDRAM buses used to exchange data between the CPU and the memory, thus defeating air-gap isolation.
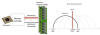
To generate the Wi-Fi signals, the attack makes use of the data bus (or memory bus) to emit electromagnetic radiation at a frequency correlated to the DDR memory module and the memory read/write operations executed by processes currently running in the system.
AIR-FI was evaluated using four types of workstations with different RAM and hardware configurations as well as using software-defined radio (SDR) and a USB Wi-Fi network adapter as receivers, finding that the covert channel can be effectively maintained at distances up to several meters from air-gapped computers and achieving bit rates ranging from 1 to 100 bit/sec, depending on the type and mode of receiver used.
If anything, the new research is yet another reminder that electromagnetic, acoustic, thermal, and optical components continue to be lucrative vectors to mount sophisticated exfiltration attacks against air-gapped facilities.
As a countermeasure, Dr. Guri proposes zone protections to safeguard against electromagnetic attacks, enabling intrusion detection systems to monitor and inspect for processes that perform intensive memory transfer operations, jamming the signals, and using Faraday shields to block the covert channel.
The AIR-FI malware shows "how attackers can exfiltrate data from air-gapped computers to a nearby Wi-Fi receiver via Wi-Fi signals," he added.
"Modern IT environments are equipped with many types of Wi-Fi capable devices: smartphones, laptops, IoT devices, sensors, embedded systems, and smart watches, and other wearables devices. The attacker can potentially hack such equipment to receive the AIR-FI transmissions from air-gapped computers."
Watch Out! Adrozek Malware Hijacking Chrome, Firefox, Edge, Yandex Browsers
12.12.2020 Hacking Thehackernews
Microsoft on Thursday took the wraps off an ongoing campaign impacting popular web browsers that stealthily injects malware-infested ads into search results to earn money via affiliate advertising.
"Adrozek," as it's called by the Microsoft 365 Defender Research Team, employs an "expansive, dynamic attacker infrastructure" consisting of 159 unique domains, each of which hosts an average of 17,300 unique URLs, which in turn host more than 15,300 unique malware samples.
The campaign — which impacts Microsoft Edge, Google Chrome, Yandex Browser, and Mozilla Firefox browsers on Windows — aims to insert additional, unauthorized ads on top of legitimate ads displayed on search engine results pages, leading users to click on these ads inadvertently.
Microsoft said the persistent browser modifier malware has been observed since May this year, with over 30,000 devices affected every day at its peak in August.
"Cybercriminals abusing affiliate programs is not new—browser modifiers are some of the oldest types of threats," the Windows maker said. "However, the fact that this campaign utilizes a piece of malware that affects multiple browsers is an indication of how this threat type continues to be increasingly sophisticated. In addition, the malware maintains persistence and exfiltrates website credentials, exposing affected devices to additional risks."
Once dropped and installed on target systems via drive-by downloads, Adrozek proceeds to make multiple changes to browser settings and security controls so as to install malicious add-ons that masquerade as genuine by repurposing the IDs of legitimate extensions.
Although modern browsers have integrity checks to prevent tampering, the malware cleverly disables the feature, thus allowing the attackers to circumvent security defenses and exploit the extensions to fetch extra scripts from remote servers to inject bogus advertisements and gain revenue by driving traffic to these fraudulent ad pages.
What's more, Adrozek goes one step further on Mozilla Firefox to carry out credential theft and exfiltrate the data to attacker-controlled servers.
"Adrozek shows that even threats that are not thought of as urgent or critical are increasingly becoming more complex," the researchers said.
"And while the malware's main goal is to inject ads and refer traffic to certain websites, the attack chain involves sophisticated behavior that allows attackers to gain a strong foothold on a device. The addition of credential theft behavior shows that attackers can expand their objectives to take advantage of the access they're able to gain.
New Injection Technique Exposes Data in PDFs
11.12.2020 Hacking Securityweek
Security researchers on Thursday documented and described a new injection technique capable of extracting sensitive data from PDF files.
“One simple link can compromise the entire contents of an unknown PDF,” researcher Gareth Heyes warned during a presentation at the Black Hat Europe security conference.
The new code-injection technique essentially allows hackers to inject code to launch dangerous XSS (cross-site scripting) attacks within the bounds of a PDF document.
PDF, short for Portable Document Format, is the de-facto standard for document sharing among businesses. The format is widely used with airline tickets, boarding passes and other documents that typically contain passport numbers, home addresses, bank account details and other valuable private data.
Heyes, a researcher at web application security testing firm PortSwigger, warned that malicious hackers are capable of injecting PDF code to “escape objects, hijack links, and even execute arbitrary JavaScript” inside PDF files.
He explained that the problem is caused because vulnerable PDF libraries do not properly parse code -- specifically parentheses and backslashes, exposing PDF files to danger.
Heyes tested the technique on several popular PDF libraries and confirmed two popular libraries were vulnerable to the exploitation technique -- PDF-Lib (52,000 weekly downloads) and jsPDF (250,000 downloads).
“You'll learn how to create the "alert(1)" of PDF injection and how to improve it to inject JavaScript that can steal the contents of a PDF on [multiple] readers,” he said in a blog post.
Heyes found that he could exfiltrate the contents from PDFs to a remote server using a rigged URL. “Even PDFs loaded from the filesystem in Acrobat, which have more rigorous protection, can still be made to make external requests,” he warned, demonstrating how he successfully crafted an injection that can perform an SSRF attack on a PDF rendered server-side.
“I've also managed to read the contents of files from the same domain, even when the Acrobat user agent is blocked by a WAF,” he said, noting that the attack also allows malicious hackers to steal the contents of a PDF without user interaction.
Vaccine Documents Hacked as West Grapples With Virus Surge
11.12.2020 Hacking Securityweek
Documents related to the Pfizer coronavirus vaccine were illegally accessed during a cyberattack at the EU regulator, the company said Wednesday, as Germany and other northern hemisphere countries grappled with a winter surge in the pandemic.
The Amsterdam-based European Medicines Agency (EMA) reported the cyberattack as European countries eagerly await a vaccine, including Germany where Chancellor Angela Merkel is pushing for tougher action against a second wave of Covid-19 that is proving deadlier than the first there.
While the EMA did not give details on the attack, Pfizer and BioNTech said documents relating to their vaccine candidate had been accessed, but that "no systems have been breached in connection with this incident."
The EMA has promised to reach a decision on conditional approval for Pfizer/BioNTech's vaccine by December 29, with a ruling on Moderna's version to follow by January 12.
Canada on Wednesday became the latest nation to approve the Pfizer-BioNTech vaccine, a day after Britain gave out the first approved vaccine jabs in the Western world.
The United States is expected to follow suit within days, after a Food and Drug Administration advisory panel meets on the issue Thursday.
But a top government scientist said the FDA would probably ask people with a known history of severe allergies not to take it -- after two health care workers in Britain needed treatment for allergic reactions.
The cyberattack comes after Britain accused Kremlin-linked hackers in July of targeting labs researching coronavirus vaccines and after a US newspaper reported that cybercriminals had tried to attack several pharmaceutical firms developing vaccines.
They included Johnson & Johnson, Novavax, AstraZeneca and South Korean laboratories.
Both Russia and China have already begun inoculation campaigns with domestically produced vaccines
The Russian space agency said on Wednesday it planned to offer the Sputnik coronavirus vaccine to cosmonauts but insisted it would be on a voluntary basis.
Israel accepted its first shipment of the Pfizer vaccine on Wednesday, Prime Minister Benjamin Netanyahu promising to be the first to be injected -- although the vaccine has yet to pass regulatory hurdles there.
"What is important to me is that Israeli citizens get vaccinated," he said. "I want to serve as an example to them."
AU Commission chairman Moussa Faki Mahamat meanwhile said Wednesday that Africa must be among the first beneficiaries of the vaccines, adding that "those who have the (financial) means must not monopolize the vaccines."
The virus has now killed more than 1.5 million worldwide since it emerged in China late last year.
- Change 'for the better' -
In Germany, where the daily death toll hit a new high of 590 on Wednesday, Merkel urged regions to take more drastic action to curb the virus spread, after state leaders agreed to ease what are already comparatively modest social restrictions for the Christmas holidays.
Merkel has been in no mood for celebration, repeatedly urging regional leaders who have responsibility for health policies to clamp down more strongly.
"If we have too many contacts before Christmas and it ends up being the last Christmas with the grandparents, then we'd really have failed," she said.
Two weeks ago, Germany's states agreed rules limiting social mixing to five people but agreed to double the limit to 10 for the holiday season -- something Merkel argued against.
- Divisions laid bare -
The United States is also mired in political rows over an epidemic that has killed more than 280,000 -- the world's heaviest toll.
President Donald Trump signed an executive order on Tuesday that sought to guarantee access to vaccines for all Americans, but critics immediately queried what legal force it could have given drug firms have already signed contracts with other countries.
Joe Biden, who will take over from Trump in January and unveiled a plan for 100 million jabs in his first 100 days, has urged Congress to come up with funding to prevent vaccine distribution from stalling.
As America's politicians grappled over resources to fight Covid-19, a new study showed that the country's 651 billionaires have seen their wealth rise by more than $1 trillion since the start of the pandemic, according to the Institute for Policy Studies and Americans for Tax Fairness.
At the other end of the spectrum, experts are warning that hunger in the Philippines has reached new levels thanks in part to restrictions that have crippled the economy and left many without livelihoods.
Crooks hide software skimmer inside CSS files
10.12.2020 Hacking Securityaffairs
Security researchers have uncovered a new technique to inject a software skimmer onto websites, the malware hides in CSS files.
Security researchers have uncovered a new technique used by threat actors to inject a software skimmer onto websites, the attackers hide the malware in CSS files.
Security experts have analyzed multiple Magecart attack techniques over the past months, threat actors compromised websites by hiding malicious code in multiple components of the sites, including live chat windows, images, and favicons.
Now researchers from security firm Sansec have spotted Magecart attacks that hide the software skimmer cascading style sheets (CSS) files.
Cascading Style Sheets (CSS) is a style sheet language used for describing the presentation of a document written in a markup language such as HTML. CSS is designed to enable the separation of presentation and content, including layout, colors, and fonts.
One of the most recent features supported by CSS language allows it to load and run JavaScript code from within a CSS rule. Unfortunately, this new feature is now being abused by threat actors to compromise websites.
The code used by the attackers is a common keystroke logger, since the company disclosed its discovery the code has been taken offline.
“We found a handful of victim stores with this injection method,” SanSec founder Willem de Groot told ZDNet.
“However, the infrastructure has been in place since September and was previously used for several dozen more traditional attacks. This CSS disguise looks like a recent experiment.”
Researchers recommend shoppers to use virtual cards designed for one-time payments to avoid being victims of these attacks.
Virtual debit cards allow to securely complete a transaction, even if the attackers are able to steal payment card details, the card data is useless once the transaction is completed or the card is expired.
‘Free’ Cyberpunk 2077 Downloads Lead to Data Harvesting
8.12.2020 Hacking Threatpost
The hotly anticipated game — featuring a digital Keanu Reeves as a major character — is being used as a lure for cyberattacks.
The hotly anticipated videogame title Cyberpunk 2077 comes out on Dec. 10, inspiring breathless countdowns from gaming publications and enthusiasts across the globe. As with all things zeitgeisty, cybercriminals are looking to cash in on the excitement, with scams that offer “free copies” while stealing personal information.
Cyberpunk 2077, an open-world game that lets players create a character called “V” who lives in Night City and is looking to become a top-tier criminal, will be available for PC, PlayStation 4, Xbox One and Stadia, with compatibility with PS5 and Xbox Series X. It will cost $60 – a steep price tag for many.
According to researchers at Kaspersky, a series of websites have gone live in a range of languages, all with URLs containing keywords like “PC”, “games” and “download.” And they all offer free purported downloads for the game.
“If the visitor clicks the [download] button, the site downloads an executable file that appears to be an installer to the computer,” researchers noted in a Monday posting. “Opening it, the user sees a menu with some inactive buttons, creating the illusion that, once installed, the app can be used to run and configure the game.”
This menu offers three options: Install, Support and Exit. Clicking Install opens a window that pretends to be installing the game – and it eventually asks for a license key. Obviously the target won’t have said key, so the process offers a convenient “Get License Key” button.
Clicking this button directs users to a website that offers the user a chance to take a survey or enter a giveaway to get the key.
“The next prompt is a set of unrelated questions, as well as requests for a phone number and email address,” according to Kaspersky. “That contact information is the likely target of the attack; contact information is useful for spamming.”
Once victims complete the survey, they receive a supposed “key” which, when entered into the fake installer, appears to start loading the game, researchers said. The fake progress is then impaired though, with a splash screen that says users are missing a dynamic link library (DLL) required to run the game. Another download link is presented, which again redirects to a survey page – and that’s where the gambit ends.
This particular hoax is just one flavor of Cyberpunk 2077 scams, according to the firm.
“Downloading a nongame, wasting time on pointless surveys, and landing in yet another spam database is bad, although not fatal,” Kaspersky researchers said. “But similar schemes can be more dangerous.”
For example, cybercriminals could ask for money in exchange for the key. Or they could use the same routine to install malware.
“This year, we already registered several thousand infection attempts through fake Cyberpunk 2077 downloads,” researchers noted. “Ultimately, no matter how much you’re itching to plunge into the long-awaited game with a digitized Keanu Reeves, you’ll have to wait for the official release.”
Imprisoned Hacker Ordered to Be Released, Promptly Deported
5.12.2020 Hacking Securityweek
A computer hacker serving 20 years for giving the Islamic State group the personal data of more than 1,300 U.S. government and military personnel has been granted compassionate release because of the coronavirus pandemic and will be placed in ICE custody for prompt deportation, a federal judge ordered Thursday.
U.S. District Judge Leonie M. Brinkema in Alexandria signed the order reducing the sentence of Ardit Ferizi to time served. Brinkema also ordered the Bureau of Prisons to immediately place Ferizi in a 14-day quarantine to ensure he’s not infected with the coronavirus. At the end of the quarantine, Ferizi will be released into the custody of Immigration and Customs Enforcement so he can be deported to Kosovo, the judge ordered.
Ferizi, 24, will remain on supervised release for 10 years as imposed when he was sentenced in September 2016, Brinkema wrote.
In a handwritten motion from prison, Ferizi said earlier this fall that his asthma and obesity placed him at greater risk for COVID-19. He also said special restrictions at the prison require him to check in with staff every two hours, increasing his contact with guards and his risk of contracting the coronavirus.
Brinkema initially rejected Ferizi’s request at a hearing in October, citing concerns that he might resume hacking if released, among other issues. Prosecutors had opposed Ferizi’s release.
Hackers hide software skimmer in social media sharing icons
4.12.2020 Hacking Securityaffairs
Security researchers have uncovered a new technique to inject a software skimmer onto checkout pages, the malware hides in social media buttons.
Security experts at Sansec have detailed a new technique used by crooks to inject a software skimmer into checkout pages. E-skimming took place when hackers compromise an e-commerce site and plant a malicious code designed to siphon payment card data or personally identifiable information (PII).
E-skimming attacks were initially observed in the wild in 2016, their number rapidly increased since then. In the last years, numerous attacks involving software skimmers were carried out by threat actors under the Magecart umbrella.
The attacks used various techniques across the time to carry out an e-skimming attack, such as exploiting flaws in the e-commerce platform (i.e. Magento, OpenCart). In other attacks, hackers have compromised plugins used by e-commerce platforms in a classic supply chain attack. Threat actors also injected software skimmers inside a company’s cloud hosting account that was poorly protected.
Another attack scenario sees hackers targeting the administrators of the platform with social engineering attacks in an attempt to obtain his credentials and use them to plant the malicious code in the e-store.
Hacker groups under the Magecart umbrella focus in the theft of payment card data with software skimmers.
Sansec researchers were the first that discovered the new malware. The malicious code has two components, a concealed payload and a decoder used to decode the software skimmer and executes the concealed code.
The malicious payload is concealed as social media buttons that mimic social sharing icons such as Facebook, Twitter, and Instagram. This is the first time that payload has been constructed as a perfectly valid image that is not detectable by security scanners that only performs syntax checks.
Attackers concealed the software skimmer in a social sharing icon loaded as an HTML ‘svg’ element with a ‘path’ element as a container and named using social media platform names (e.g., google_full, facebook_full, twitter_full, instagram_full, youtube_full, pinterest_full).
![]()
Attackers make these attacks hard to detect also by separating the decoder from the concealed payload.
“It is worth noting that the decoder does not have to be injected in the same location as the payload. This adds to it’s concealment, as finding only one of the parts, one might not deduce the true purpose of a slightly strangely formatted svg.” reads the analysis published by the Sansec experts.
“An attacker can of course conceal any payload with this technique. Samples taken by Sansec revealed payment skimming as the true purpose of the malware injections.”
In June, experts detected a similar malware using this innovative loading technique. The malicious code was not as sophisticated, experts detected it only on 9 sites on a single day. Some of the software skimmers were only working partially, likely because the attackers deployed them as test runs.
“Of these 9 infected sites, only 1 had functional malware. The 8 remaining sites all missed one of the two components, rendering the malware useless.” concludes the experts.
“After the discovery of this new and more sophisticated malware, the question arises if the June injections could have been the creator running a test to see how well their new creation would fare. This new malware was first found on live sites in mid-September.”
Spotify Wrapped 2020 Rollout Marred by Pop Star Hacks
3.12.2020 Hacking Threatpost
Spotify pages for Dua Lipa, Lana Del Rey, Future and others were defaced by an attacker pledging his love for Taylor Swift and Trump.
In the midst of its popular Spotify Wrapped 2020 playlist rollout of the year’s most popular songs, the streaming service is grappling with a security breach, which affected the pages of some of its biggest stars, including Lana Del Rey, Dua Lipa, Future, Pop Smoke and others.
Spotify is the most popular music streaming service in the world with 320 million users, according to the company.
The target of the attack, according to the BBC, was a Spotify site specifically for musicians and their labels, called Spotify for Artists. The site is password-protected to allow only artists and their teams to make changes to the pages. The attacker seemingly bypassed those protections.
The malicious actor called himself “Daniel” and used the pop stars’ pages to ask people to follow him on Snapchat, adding “Trump 2020,” to the message. Daniel also used the stunt to pledge his love to one pop star in particular: “Best of all shout out to my queen Taylor Swift,” he wrote.
Users shared images of the hijacked pages on Twitter, including this one for Lana Del Rey where Daniel swapped out Lana’s photo for Taylor’s.
Future’s Spotify page featured what is presumably a pic of Daniel listening to Pop Smoke’s page. Images of both takeovers were posted to Twitter by users who generally thought the scam was more funny than dangerous.
The pages appear to have been restored, but Spotify has not responded to requests for comment to confirm that the breach is contained.
Tim Mackey, who is a principal strategist with Synopsys, warned users to take breaches like these seriously — even if their mastermind is a teen punk motivated by a crush on Taylor Swift.
“While the details of what weaknesses in Spotify’s security practices remain unknown, the attack highlights an important aspect of all cyberattacks – the attackers define the rules of their attack,” Mackey said. “In this case, vandalism is an obvious component, but it could also be but one aspect of their ultimate goal.”
Mackey said that due to the lack of information from Spotify about the breach, users should review their passwords and security protections for the app.
Reports of the breach came on the same day the streaming service announced its popular 2020 Wrapped list of the most popular songs and podcasts streamed this year, meaning that one of it’s most high-profile annual promotions will have to compete with headlines about the security lapse. The news also comes hard on the heels of account-takeover reports last week. It is a situation Mackey said should serve as a teachable moment for businesses in any sector.
“Businesses seeking to learn from this incident should ask themselves how quickly they would be able to identify if they had fallen victim to a similar defacement effort,” Mackey advises. “If the answer isn’t affirming, then a review of audit and monitoring practices is in order, along with a review of incident-response planning.”
Laser-Based Hacking from Afar Goes Beyond Amazon Alexa
26.11.20 Hacking Securityaffairs
The team that hacked Amazon Echo and other smart speakers using a laser pointer continue to investigate why MEMS microphones respond to sound.
Imagine someone hacking into an Amazon Alexa device using a laser beam and then doing some online shopping using that person account. This is a scenario presented by a group of researchers who are exploring why digital home assistants and other sensing systems that use sound commands to perform functions can be hacked by light.
The same team that last year mounted a signal-injection attack against a range of smart speakers merely by using a laser pointer are still unraveling the mystery of why the microelectro-mechanical systems (MEMS) microphones in the products turn the light signals into sound.
Researchers at the time said that they were able to launch inaudible commands by shining lasers – from as far as 360 feet – at the microphones on various popular voice assistants, including Amazon Alexa, Apple Siri, Facebook Portal, and Google Assistant.
“[B]y modulating an electrical signal in the intensity of a light beam, attackers can trick microphones into producing electrical signals as if they are receiving genuine audio,” said researchers at the time.
Now, the team– Sara Rampazzi, an assistant professor at the University of Florida; and Benjamin Cyr and Daniel Genkin, a PhD student and an assistant professor, respectively, at the University of Michigan — has expanded these light-based attacks beyond the digital assistants into other aspects of the connected home.

Demonstration of Light Commands vulnerability and exploitation on MEMS microphones.
They broadened their research to show how light can be used to manipulate a wider range of digital assistants—including Amazon Echo 3 — but also sensing systems found in medical devices, autonomous vehicles, industrial systems and even space systems.
The researchers also delved into how the ecosystem of devices connected to voice-activated assistants — such as smart-locks, home switches and even cars — also fail under common security vulnerabilities that can make these attacks even more dangerous. The paper shows how using a digital assistant as the gateway can allow attackers to take control of other devices in the home: Once an attacker takes control of a digital assistant, he or she can have the run of any device connected to it that also responds to voice commands. Indeed, these attacks can get even more interesting if these devices are connected to other aspects of the smart home, such as smart door locks, garage doors, computers and even people’s cars, they said.
“User authentication on these devices is often lacking, allowing the attacker to use light-injected voice commands to unlock the target’s smartlock-protected front doors, open garage doors, shop on e-commerce websites at the target’s expense, or even unlock and start various vehicles connected to the target’s Google account (e.g., Tesla and Ford),” researchers wrote in their paper.
The team plans to present the evolution of their research at Black Hat Europe on Dec. 10, though they acknowledge they still aren’t entirely sure why the light-based attack works, Cyr said in a report published on Dark Reading.
“There’s still some mystery around the physical causality on how it’s working,” he told the publication. “We’re investigating that more in-depth.”
The attack that researchers outlined last year leveraged the design of of smart assistants’ microphones — the last generation of Amazon Echo, Apple Siri, Facebook Portal and Google Home — and was dubbed “light commands.”
Researchers focused on the MEMs microphones, which work by converting sound (voice commands) into electrical signals. However, the team said that they were able to launch inaudible commands by shining lasers — from as far as 110 meters, or 360 feet — at the microphones.
The team does offer some mitigations for these attacks from both software and hardware perspectives. On the software side, users can add an extra layer of authentication on devices to “somewhat” prevent attacks, although usability can suffer, researchers said.
In terms of hardware, reducing the amount of light that reaches the microphones by using a barrier or diffracting film to physically block straight light beams — allowing soundwaves to detour around the obstacle — could help mitigate attacks, they said.
Researchers show how to steal a Tesla Model X in a few minutes
24.11.20 Hacking Securityaffairs
Boffins have demonstrated how to steal a Tesla Model X in a few minutes by exploiting vulnerabilities in the car’s keyless entry system.
A team of researchers from the Computer Security and Industrial Cryptography (COSIC) group at the KU Leuven University in Belgium has demonstrated how to steal a Tesla Model X in minutes by exploiting vulnerabilities in the car’s keyless entry system.
The COSIC researchers reported the vulnerabilities to Tesla in August and the carmaker addressed them with an over-the-air update (version 2020.48) that is currently being rolled out to vehicles.
The key fob used in Tesla Model X communicates with the vehicle with Bluetooth Low Energy (BLE). The experts discovered that the updating mechanism for the software running on the Bluetooth chip of the key fob is not secure.
The experts modified a Model X electronic control unit (ECU) and used it to force the victim’s key fob to advertise itself as a connectable Bluetooth device. Then, they exploited the insecure update mechanism to deliver a tainted firmware to the fob. The malicious code was designed to extract a piece of radio code that would allow the researchers to unlock the Tesla.
“Lennert Wouters, a security researcher at Belgian university KU Leuven, today revealed a collection of security vulnerabilities he found in both Tesla Model X cars and their keyless entry fobs.” Lennert Wouters explained to Wired. “He discovered that those combined vulnerabilities could be exploited by any car thief who manages to read a car’s vehicle identification number—usually visible on a car’s dashboard through the windshield—and also come within roughly 15 feet of the victim’s key fob.”
Upon unlocking the vehicle, the researchers exploited a second vulnerability to pair their own key fob with the victim’s vehicle after a minute’s work and drive the car away.
“Basically a combination of two vulnerabilities allows a hacker to steal a Model X in a few minutes time,” added Wouters, who plans to present his findings at the Real World Crypto conference in January. “When you combine them, you get a much more powerful attack.”
Using this process the researchers achieved permanent access to the Tesla Model X.
The researchers used cheap components for their hack, just $300 worth of equipment that includes the ECU, a Raspberry Pi, a secondhand Model X BCM, a key fob, a power converter, and a battery.

The researchers also published the following video PoC for the attack:
Back in 2018 time, the COSIC research team demonstrated a similar attack against the key fob of a Tesla Model S.
Hacker Closing Out Prison Sentence in Chicago Halfway House
20.11.20 Hacking Securityweek
Computer hacker Jeremy Hammond, who is serving a 10-year prison sentence for breaking into computer systems of security firms and law-enforcement agencies, will serve out the remainder of his term in a Chicago halfway house, a U.S. Bureau of Prison spokesman said Wednesday.
Hammond, who has gained mythic status among his supporters, was released Tuesday from the Memphis Federal Correctional Institution in Tennessee to community confinement, said Bureau of Prisons spokesman Emery Nelson. Citing privacy and security reasons, Nelson refused to release information on the conditions of Hammond’s confinement. He is scheduled for release in March.
The FBI arrested Hammond, who prosecutors called a hacking “recidivist,” during a 2012 raid on his Chicago home after getting the cooperation of Hector Xavier Monsegur, a hacker who helped law enforcement infiltrate the hacking movement ”Anonymous,” which led to the conviction of eight hackers.
The raid came after Hammond penetrated the Texas-based security think tank Strategic Forecasting Inc., known as Stratfor. The company’s clients include the U.S. Department of Homeland Security and the Defense Department. He was also accused of hacking the FBI’s Virtual Academy, the Arizona Department of Public Safety, the Boston Police Patrolmen’s Association, and the Jefferson County, Alabama, Sheriff’s Office.
He’d been working with a subgroup of “Anonymous” to disrupt the networks of Sony Pictures, the Public Broadcasting Service, the Arizona Department of Public Safety and others when a member of the group enlisted him to help break into Stratfor’s systems.
The hackers posted emails between Stratfor employees and clients on the WikiLeaks website, along with credit card data from a client list that included Northrop Grumman, the Marine Corps and Time Warner Cable. They used some of the credit card numbers to donate money to the Red Cross, according to court records.
Federal prosecutors alleged the Stratfor hack resulted in more than a million dollars in losses to individuals and threatened public safety.
Hammond argued during his sentencing the hacks were civil disobedience to expose the pervasiveness of government and private surveillance.
During a 2014 interview with The Associated Press, Hammond laughed at the idea that some consider such attacks as threatening to national security as terrorism.
“I mean, I didn’t kill anybody,” he said.
Hammond last year was summoned to testify to a federal grand jury in Virginia. He was found guilty of civil contempt after he refused to testify.
Raised in the Chicago suburb of Glendale Heights, Hammond described himself as a :nonconformist, anti-authority” kid who at 8, tried to design video games. A few years later, he started hacking.
He started the University of Illinois at Chicago with a full scholarship, but was kicked out after hacking into the university’s computer science department website and telling administrators about the vulnerability.
Over the years, his supporters have elevated him to near-mythical status on the internet and have sold buttons, t-shirts and other merchandise bearing his name and picture. In a Tuesday tweet, the Jeremy Hammond Support Committee expressed joy that Hammond had been released from prison.
Hacked Websites, Hate Speech Hit Suburban Chicago Schools
16.11.20 Hacking Securityweek
Students at two suburban Chicago school districts were exposed to hate speech and lewd material this week after hackers apparently infiltrated both districts’ websites, school officials said.
Police were investigating Wednesday’s incidents that targeted the Maine Township High School District 207 and Niles Township High School District 219 — both of which have ethnically and racially diverse student populations, the Pioneer Press suburban newspaper group reported.
District 219, which has two schools in Skokie, said in a statement to parents that emails were sent through a district email account Wednesday night to all district students containing “lewd, racist, anti-Semitic and patently offensive content.”
The district said its information technology team is working with the Skokie Police Department to investigate the incident, which prompted school officials to cancel Thursday’s first-period remote learning classes and temporarily suspend student access to district email accounts.
“As a district we condemn these actions and messages,” the district said in its statement.
District 207, which has two schools in Park Ridge and one in Des Plaines, told parents in its statement that “hate speech, images of hate and other inappropriate images” were posted to each of its three school websites and district homepage by an unknown hacker Wednesday night.
Park Ridge Police Department Executive Officer Tom Gadomski confirmed that the department is investigating the incident but declined further comment.
“We are dedicated to investigating this matter and if they are discovered, to prosecute the perpetrators to the fullest extent of the law,” District 207 said in its statement.
ShinyHunters hacked Pluto TV service, 3.2M accounts exposed
16.11.20 Hacking Securityaffairs
A hacker has shared 3.2 million Pluto TV user accounts on a hacking forum for free, he claims they were stolen by ShinyHunters threat actor.
Pluto TV is an American internet television service, it is an advertiser-supported video on demand (AVOD) service that primarily offers a selection of programming content through digital linear channels designed to emulate the experience of traditional broadcast programming.
The service has over 28 million members.
The data breach appears to be the work of a well-known threat actor named ShinyHunters, who is behind many other security breaches, including the hacks of Microsoft’s private GitHub repository, the popular digital banking app Dave.com, and Animal Jam.
This week, a threat actor shared a database containing 3.2 million Pluto TV user records, he also added that the service was hacked by ShinyHunters.

Source Bleeping Computer
The dump includes PLUTO TV’s display name, email address, bcrypt hashed password, birthday, device platform, and IP address.
Bleeping Computer, which has validated the authenticity of the archive, reported that the latest record in the database was created on October 12th, 2018.
Pluto TV users are urged to immediately change their passwords, in case they share the same password at other sites, it is recommended that they change them too.
Premium-Rate Phone Fraudsters Hack VoIP Servers of 1200 Companies
5.11.20 Hacking Thehackernews 
Cybersecurity researchers today took the wraps off an on-going cyber fraud operation led by hackers in Gaza, West Bank, and Egypt to compromise VoIP servers of more than 1,200 organizations across 60 countries over the past 12 months.
According to findings published by Check Point Research, the threat actors — believed to be located in the Palestinian Gaza Strip — have targeted Sangoma PBX, an open-sourced user interface that's used to manage and control Asterisk VoIP phone systems, particularly the Session Initiation Protocol (SIP) servers.
"Hacking SIP servers and gaining control allows hackers to abuse them in several ways," the cybersecurity firm noted in its analysis. "One of the more complex and interesting ways is abusing the servers to make outgoing phone calls, which are also used to generate profits. Making calls is a legitimate feature, therefore it's hard to detect when a server has been exploited."
By selling phone numbers, call plans, and live access to compromised VoIP services from targeted businesses to the highest bidders, the operators of the campaign have generated hundreds of thousands of dollars in profit, alongside equipping them with capabilities to eavesdrop on legitimate calls.
Exploiting a Remote Admin Authentication Bypass Flaw
PBX, short for private branch exchange, is a switching system that's used to establish and control telephone calls between telecommunication endpoints, such as customary telephone sets, destinations on the public switched telephone network (PSTN), and devices or services on voice over Internet Protocol (VoIP) networks.
Check Point's research found that the attack exploits CVE-2019-19006 (CVSS score 9.8), a critical vulnerability impacting the administrator web interface of FreePBX and PBXact, potentially allowing unauthorized users to gain admin access to the system by sending specially crafted packets to the affected server.
The remote admin authentication bypass flaw affects FreePBX versions 15.0.16.26 and below, 14.0.13.11 and below, and 13.0.197.13 and below and was patched by Sangoma in November 2019.
"The attack begins with SIPVicious, a popular tool suite for auditing SIP-based VoIP systems," the researchers noted. "The attacker uses the 'svmapmodule' to scan the internet for SIP systems running vulnerable FreePBX versions. Once found, the attacker exploits CVE-2019-19006, gaining admin access to the system."
In one attack flow, it was discovered that an initial PHP web shell was used to get hold of the FreePBX system's database and passwords for different SIP extensions, granting the attackers unrestricted access to the entire system and the ability to make calls out of every extension.
In the second version of the attack, the initial web shell was utilized to download a base64-encoded PHP file, which is then decoded to launch a web panel that lets the adversary place calls using the compromised system with both FreePBX and Elastix support, as well as run arbitrary and hard-coded commands.
The campaign's reliance on Pastebin to download password-protected web shells has tied the attack to an uploader by the name of "INJ3CTOR3," whose name is linked to an old SIP Remote Code Execution vulnerability (CVE-2014-7235) in addition to a number of private Facebook groups that are used to share SIP server exploits.
A Case of International Revenue Share Fraud
Check Point researchers posited that the hacked VoIP servers could be employed by the attackers to make calls to International Premium Rate Numbers (IPRN) under their control. IPRNs are specialized numbers used by businesses to offer phone-based purchases and other services — like putting callers on hold — for a higher fee.
This fee is typically passed on to customers who make the calls to these premium numbers, making it a system ripe for abuse. Thus, the more calls the owner of an IPRN receives and the longer clients wait in the line to complete the transaction, the more money it can charge telecom providers and customers.
"Using IPRN programs not only allows the hacker to make calls but also abuse the SIP servers to generate profits," the researchers said. "The more servers exploited, the more calls to the IPRN can be made."
This is not the first time switching systems have been exploited for International Revenue Share Fraud (IRSF) — the practice of illegally gaining access to an operator's network in order to inflate traffic to phone numbers obtained from an IPRN provider.
Back in September, ESET researchers uncovered Linux malware dubbed "CDRThief" that targets VoIP softswitches in an attempt to steal phone call metadata and carry out IRSF schemes.
"Our research reveals how hackers in Gaza and the West Bank are making their money, given the dire socio-economic conditions in the Palestinian territories," said Adi Ikan, head of network cybersecurity research at Check Point.
"Their cyber fraud operation is a quick way to make large sums of money, fast. More broadly, we're seeing a widespread phenomenon of hackers using social media to scale the hacking and monetization of VoIP systems this year."
"The attack on Asterisk servers is also unusual in that the threat actors' goal is to not only sell access to compromised systems, but also use the systems' infrastructure to generate profit. The concept of IPRN allows a direct link between making phone calls and making money."
Compromised CMS Credentials Likely Used to Hack Trump Campaign Website
28.10.20 Hacking Securityweek
Security researchers believe that compromised credentials were used by hackers to access the content management system behind Donald Trump’s campaign website.
On Tuesday, hackers managed to break into the website and change content on it. For a short period of time, the message “This site was seized” was displayed on donaldjtrump.com.
The incident has been confirmed by Trump campaign spokesman Tim Murtaugh, who also revealed that law enforcement had been called in to investigate. He also said that no sensitive information had been compromised.
In the message posted on the website, the hackers claimed they managed to compromise sensitive information on President Trump. They also included two cryptocurrency wallet IDs, saying they would release the information if visitors sent money to them.
The message also contained a Pretty Good Privacy (PGP) public key, which can be used to verify future messages supposedly coming from the hackers.
According to WordPress security solutions provider Defiant, which develops the Wordfence product, the hackers most likely used compromised credentials for access, supposedly targeting the underlying Expression Engine content management system (CMS), which is an alternative to WordPress.
While the site content was quickly restored, the “Privacy Policy” and “Terms & Conditions” pages were still delivering a “404 page not found” error hours after the incident was resolved.
“This indicates that something changed on the content management system itself, rather than on the Cloudflare configuration. So we believe that the CMS being compromised is therefore a higher probability than Cloudflare being compromised,” Defiant notes.
The site uses Cloudflare as a content delivery network (CDN), and Defiant says that this could have been used as a point of access only if the attackers knew the IP of the server hosting the site, which is hidden. Thus, this attack vector is less likely to have been used.
If the attackers had access to the campaign’s Cloudflare account and were able to point the domain to their own IP address, the entire website would have been restored by simply pointing it to the right IP address.
However, the issues with the “Privacy Policy” and the “Terms & Conditions” pages suggest this was not the attack vector.
Of even lower probability would be the use of compromised credentials to access the account where the domain donaldjtrump.com was registered; a possible access via FTP or SSH (would require not only FTP or SSH credentials, but also knowledge of the site’s origin IP address); or the use of a zero-day flaw in Expression Engine, which has had few known vulnerabilities, Defiant says.
“Almost every possible scenario includes reused credentials being exploited to gain access to the donaldjtrump.com site. In almost every case, having 2-Factor Authentication enabled would have prevented such a scenario from occurring. It’s also a reminder that it is important to enable 2-Factor Authentication not only on your website’s administrative panel, but on every service that offers it, including services you might not think of as being vulnerable,” Defiant concludes.
The attack comes shortly after a Dutch security researcher claimed that he gained access to Donald Trump’s Twitter account by guessing its password, which he said was “maga2020!”. The White House and Twitter have denied the claims and the researcher has yet to provide any definitive proof.
Finland Shocked by Therapy Center Hacking, Client Blackmail
26.10.20 Hacking Securityweek
Finland’s interior minister summoned key Cabinet members into an emergency meeting Sunday after hundreds — and possibly thousands — of patient records at a private Finnish psychotherapy center were accessed by a hacker or hackers now demanding ransoms.
Finnish Interior Minister Maria Ohisalo tweeted that authorities would “provide speedy crisis help to victims” of the security breach at the Vastaamo psychotherapy center, an incident she called “shocking and very serious.”
Vastaamo, which has branches throughout the Nordic country of 5.5 million and operates as a sub-contractor for Finland’s public health system, said its client register with intimate patient information was likely stolen during two attacks that started almost two years ago.
The first incursion probably took place in November 2018 and “it is likely that our (data) systems were penetrated also between the end of November 2018 and March 2019,” Vastaamo said in a statement late Saturday.
The center said the unknown perpetrator or perpetrators had published at least 300 patient records containing names and contact information using the anonymous Tor communication software. “The blackmailer has started to approach victims of the security breach directly with extortion letters,” it said.
The National Bureau of Investigation said Sunday up to “tens of thousands” of Vastaamo clients may have had their personal data compromised. Police were looking for the possible culprits both in Finland and abroad.
It was not immediately clear if the stolen information included diagnoses, notes from therapy sessions or other potentially damaging information. Also, it wasn’t clear why the information was surfacing only now.
“What makes this case exceptional is the contents of the stolen material,” Marko Leponen, the National Bureau of Investigation’s chief investigator assigned to the case, told reporters.
Vastaamo urged clients who receive demands to pay money in exchange for keeping their information private — allegedly dozens already — to immediately contact Finnish police.
Finnish media reported that cyber-criminals have demanded ransoms of 200 euros ($240) paid in Bitcoin, with the amount increased to 500 euros unless paid within 24 hours. The psychotherapy center also reportedly received a ransom demand for 450,000 euros ($534,000) in Bitcoin.
Citizens reacted to the news with disbelief. It also prompted comments from Finland’s leaders. President Sauli Niinisto called the blackmailing “cruel” and “repulsive.” Prime Minister Sanna Marin said the hacking of such sensitive information was ”shocking in many ways.”
The chief research officer of Finnish data security company F-Secure, Mikko Hypponen, told Finnish public broadcaster YLE that the case was exceptional even on an international level.
“I’m not aware of any such case anywhere in the world with such gross misuse of patient records,” said Hypponen, one of Finland’s leading data security experts and an internationally known lecturer on cyber-threats.
Hypponen also tweeted that he knew of “only one other patient blackmail case that would be even remotely similar: the Center for Facial Restoration incident in Florida in 2019. This was a different medical area and had a smaller number of victims, but the basic idea was the same.”
Various Finnish organizations have rapidly mobilized ways to help the victims of the breach, including direct dial-in numbers with churches and therapy services.
Game Titles Watch Dogs: Legion, Albion Both Targeted by Hackers
20.10.20 Hacking Threatpost
In both cases, cybercriminals claim to have reams of information for the popular gaming titles.
A ransomware gang that just emerged this month dubbed Egregor claims to have hacked the source code to the upcoming gaming release, Watch Dogs: Legion.
And in separate gaming news, a popular fantasy title called Albion — a massive multiplayer online role-playing game (MMORPG) — has been hacked. Cybercriminals are offering what they claim are game databases in underground forums.
Source Code Leaked
Watch Dogs: Legion is due to be released a couple of weeks from now, on Oct. 29 – a highly anticipated release thanks to its 4K visuals, “ray tracing” capabilities and a planned Assassin’s Creed crossover.
The Egregor gang claims to have lifted both the code and some proprietary files from the game’s publisher, Ubisoft. Release of the source code would allow fans to develop game hacks and perform all kinds of “modding” (i.e., development of custom features) and jailbreaks.
The group also said that it has files Crytek relating to gaming titles like Arena of Fate and Warface.
According to a look at Egregor’s leak site portal by ZDNet, partial leaks for the hacks appear to have been posted. The operators emailed the outlet as well, noting that they only hacked Ubisoft and didn’t deploy its ransomware. Crytek, meanwhile, “has been encrypted fully.” In both cases, the companies haven’t responded to the incidents, according to the email.
“In case Ubisoft will not contact us we will begin posting the source code of upcoming Watch Dogs and their engine,” the hackers told ZDNet.
The data posted is somewhat inconclusive – the code in the portal could be from an older Watch Dogs version, for instance. In all, the data totals 20 MB from Ubisoft, and 300 MB from Crytek.
Egregor was first spotted in the wild in early October and late September, using a tactic of siphoning off corporate information and threatening a “mass-media” release of it before encrypting all files.
Egregor is an occult term meant to signify the collective energy or force of a group of individuals, especially when the individuals are united toward a common purpose — apropos for a ransomware gang. According to a recent analysis from Appgate, the code seems to be a spinoff of the Sekhmet ransomware (itself named for the Egyptian goddess of healing).
Neither company has acknowledged an attack. Threatpost has reached out for more information.
There is some precedent for hacking claims like these to be bogus. In September, reports surfaced that 500,000 Activision accounts may have been hacked, impacting online Call of Duty (CoD) players. The alleged breach was first flagged by the #oRemyy account on Twitter, and was quickly amplified by others, who claimed that accounts were being taken over and credentials changed, so that the legitimate users couldn’t recover them. The claims were picked up by gaming news outlet Dexterto.com and many others.
The gaming giant categorically disputed the claim as a widespread hoax.
Data Breach for Albion
Meanwhile, the Albion has disclosed a data breach resulting from an outside hack of its forum’s user database.
Albion is a fantasy-themed sandbox game in which players can go to battle, farm, forge alliances, defend territory, take on dragons and other monsters, and even invest in real estate. According to one tracker site, around 225,000 people play per day globally, and it has a total player base of 2.4 million active users.
According to game-owner Sandbox Interactive, the intruder was able to access forum-user profiles, including email addresses, encrypted (hashed and salted) passwords. No payment information was accessed, but the email addresses could be used in brute-force attacks on accounts.
Source: Albion Online
“If you have a forum account, you should, as a precaution, change the password to your Albion Online account,” the company noted. “Should you have also used the same password on other webpages or services, we strongly encourage you to change it there as well, and use unique passwords going forward.”
However, a hacker taking responsibility for the incident claims to have accessed much more than just emails and encrypted passwords. On an underground forum, someone is offering what they claim to be databases for payments, the main game and the forum; and source code for the Albion website and the forum.
For its part, Albion said that has closed off hacker access and is now “running additional checks to ensure the integrity of our systems. Because the safety of your data is a top priority for us, we will also be executing a full security review of all our systems to ensure your information remains absolutely safe.”
Threatpost has reached out to Ubisoft, Crytek and Albion/Sandbox Interactive for more details on all of these incidents.
The forum of the popular Albion Online game was hacked
20.10.20 Hacking Securityaffairs
Albion Online game maker discloses a data breach, hackers gained access to the company forum database by exploiting a known vulnerability.
Albion Online (AO) is a free medieval fantasy MMORPG developed by Sandbox Interactive, a studio based in Berlin, Germany
A threat actor has breached the forum of Albion Online and stole usernames and password hashes from its database.
According to Sandbox Interactive, the intrusion took place on Friday, October 16, and the hacker exploited a vulnerability in its forum platform, known as WoltLab Suite.
“Unfortunately, we have become aware of a data breach in one of our systems, in which a malicious actor gained access to parts of our forum’s user database.” reads the message published on the forum.
“The intruder was able to access forum user profiles, which include the e-mail addresses connected to those forum accounts. On top of that, the attacker gained access to encrypted passwords (in technical terms: hashed and salted passwords).”

The moderator of the forum pointed out that the intruder did not access to payment information.
According to Sandbox Interactive, the passwords were hashed with the Bcrypt hashing function and then salted with random data, which makes it hard to crack if the password is not weak.
“However, there is a small possibility they could be used to identify accounts with particularly weak passwords.” continues the German game maker.
In response to the data breach, the game maker notified the forum members about the intrusion and asked them to reset passwords.
The company notified the authorities, but did not reveal the number of impacted users. The game maker announced to have addressed the flaw exploited in the attack.
“So far we have prioritized fixing vulnerabilities and informing players about this incident,” Sandbox Interactive said.
The game is believed to have more than 2.5 million players, while the number of registered members of the forum was 293,602 at the time of the attack.
Crooks hit Puerto Rico Firefighting Department Servers
16.10.20 Hacking Securityaffairs
Puerto Rico’s firefighting department discloses a security breach, hackers breached its database and demanded $600,000.
Puerto Rico’s firefighting department discloses a security breach, hackers breached its database and demanded a $600,000 ransom.
According to the department’s director, Alberto Cruz, the ability of the department to respond to emergencies was not impacted by the attack.
The department received an email from the threat actors that notifies it that they had encrypted its servers and demanded the payment of a ransom to release them.
Local police launched an investigation into the incident, while the department decided to don’t pay the ransom.
“The department contacted police and have not paid the money, officials said. The investigation is ongoing.” reported the Associated Press.