14.12.23 Hacking The Hacker News
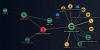
A previously unknown hacker outfit called GambleForce has been attributed to a series of SQL injection attacks against companies primarily in the Asia-Pacific (APAC) region since at least September 2023.
Hacking 2024 2023 2022 2021 2020
New Hacker Group 'GambleForce' Tageting APAC Firms Using SQL Injection Attacks
14.12.23 Hacking The Hacker News
A previously unknown hacker outfit called GambleForce has been attributed to a series of SQL injection attacks against companies primarily in the Asia-Pacific (APAC) region since at least September 2023.
"GambleForce uses a set of basic yet very effective techniques, including SQL injections and the exploitation of vulnerable website content management systems (CMS) to steal sensitive information, such as user credentials," Singapore-headquartered Group-IB said in a report shared with The Hacker News.
The group is estimated to have targeted 24 organizations in the gambling, government, retail, and travel sectors across Australia, Brazil, China, India, Indonesia, the Philippines, South Korea, and Thailand. Six of these attacks were successful.
The modus operandi of GambleForce is its exclusive reliance on open-source tools like dirsearch, sqlmap, tinyproxy, and redis-rogue-getshell at different stages of the attacks with the ultimate goal of exfiltrating sensitive information from compromised networks.
Also used by the threat actor is the legitimate post-exploitation framework known as Cobalt Strike. Interestingly, the version of the tool discovered on its attack infrastructure used commands in Chinese, although the group's origins are far from clear.
The attack chains entail the abuse of victims' public-facing applications of victims by exploiting SQL injections as well as the exploitation of CVE-2023-23752, a medium-severity flaw in Joomla CMS, to gain unauthorized access to a Brazilian company.
It's currently not known how GambleForce leverages the stolen information. The cybersecurity firm said it also took down the adversary's command-and-control (C2) server and notified the identified victims.
"Web injections are among the oldest and most popular attack vectors," Nikita Rostovcev, senior threat analyst at Group-IB, said.
"And the reason being is that sometimes developers overlook the importance of input security and data validation. Insecure coding practices, incorrect database settings, and outdated software create a fertile environment for SQL injection attacks on web applications."
New PoolParty Process Injection Techniques Outsmart Top EDR Solutions
11.12.23 Hacking The Hacker News
A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while evading endpoint detection and response (EDR) systems.
SafeBreach researcher Alon Leviev said the methods are "capable of working across all processes without any limitations, making them more flexible than existing process injection techniques."
The findings were first presented at the Black Hat Europe 2023 conference last week.
Process injection refers to an evasion technique used to run arbitrary code in a target process. A wide range of process injection techniques exists, such as dynamic link library (DLL) injection, portable executable injection, thread execution hijacking, process hollowing, and process doppelgänging.
PoolParty is so named because it's rooted in a component called Windows user-mode thread pool, leveraging it to insert any type of work item into a target process on the system.
It works by targeting worker factories – which refer to Windows objects that are responsible for managing thread pool worker threads – and overwriting the start routine with malicious shellcode for subsequent execution by the worker threads.

"Other than the queues, the worker factory that serves as the worker threads manager may be used to take over the worker threads," Leviev noted.
SafeBreach said it was able to devise seven other process injection techniques using the task queue (regular work items), I/O completion queue (asynchronous work items), and the timer queue (timer work items) based on the supported work items.
PoolParty has been found to achieve 100% success rate against popular EDR solutions, including those from CrowdStrike, Cybereason, Microsoft, Palo Alto Networks, and SentinelOne.
The disclosure arrives nearly six months after Security Joes disclosed another process injection technique dubbed Mockingjay could be exploited by threat actors to bypass security solutions to execute malicious code on compromised systems.
"Though modern EDRs have evolved to detect known process injection techniques, our research has proven that it is still possible to develop novel techniques that are undetectable and have the potential to make a devastating impact," Leviev concluded.
"Sophisticated threat actors will continue to explore new and innovative methods for process injection, and security tool vendors and practitioners must be proactive in their defense against them."
Microsoft Warns of COLDRIVER's Evolving Evasion and Credential-Stealing Tactics
8.12.23 Hacking The Hacker News
The threat actor known as COLDRIVER has continued to engage in credential theft activities against entities that are of strategic interests to Russia while simultaneously improving its detection evasion capabilities.
The Microsoft Threat Intelligence team is tracking under the cluster as Star Blizzard (formerly SEABORGIUM). It's also called Blue Callisto, BlueCharlie (or TAG-53), Calisto (alternately spelled Callisto), and TA446.
The adversary "continues to prolifically target individuals and organizations involved in international affairs, defense, and logistics support to Ukraine, as well as academia, information security companies, and other entities aligning with Russian state interests," Redmond said.
Star Blizzard, linked to Russia's Federal Security Service (FSB), has a track record of setting up lookalike domains that impersonate the login pages of targeted companies. It's known to be active since at least 2017.
In August 2023, Recorded Future revealed 94 new domains that are part of the threat actor's attack infrastructure, most of which feature keywords related to information technology and cryptocurrency.
Microsoft said it observed the adversary leveraging server-side scripts to prevent automated scanning of the actor-controlled infrastructure starting April 2023, moving away from hCaptcha to determine targets of interest and redirecting the browsing session to the Evilginx server.
The server-side JavaScript code is designed to check if the browser has any plugins installed, if the page is being accessed by an automation tool like Selenium or PhantomJS, and transmit the results to the server in the form of a HTTP POST request.
"Following the POST request, the redirector server assesses the data collected from the browser and decides whether to allow continued browser redirection," Microsoft said.
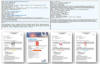
"When a good verdict is reached, the browser receives a response from the redirection server, redirecting to the next stage of the chain, which is either an hCaptcha for the user to solve, or direct to the Evilginx server."
Also newly used by Star Blizzard are email marketing services like HubSpot and MailerLite to craft campaigns that serve as the starting point of the redirection chain that culminates at the Evilginx server hosting the credential harvesting page.
In addition, the threat actor has been observed using a domain name service (DNS) provider to resolve actor-registered domain infrastructure, sending password-protected PDF lures embedding the links to evade email security processes as well as host the files on Proton Drive.
That's not all. In a sign that the threat actor is actively keeping tabs on public reporting into its tactics and techniques, it has now upgraded its domain generation algorithm (DGA) to include a more randomized list of words when naming them.
Despite these changes, "Star Blizzard activities remain focused on email credential theft, predominantly targeting cloud-based email providers that host organizational and/or personal email accounts," Microsoft said.
"Star Blizzard remains constant in their use of pairs of dedicated VPSs to host actor-controlled infrastructure (redirector + Evilginx servers) used for spear-phishing activities, where each server usually hosts a separate actor registered domain."
U.K. and U.S. Sanction Two Members of Star Blizzard#
The development comes as the U.K. called out Star Blizzard for "sustained unsuccessful attempts to interfere in U.K. political processes" by targeting high-profile individuals and entities through cyber operations.
Besides linking Star Blizzard to Centre 18, a subordinate element within FSB, the U.K. government sanctioned two members of the hacking crew – Ruslan Aleksandrovich Peretyatko and Andrey Stanislavovich Korinets (aka Alexey Doguzhiev) – for their involvement in the spear-phishing campaigns.
The activity "resulted in unauthorized access and exfiltration of sensitive data, which was intended to undermine UK organizations and more broadly, the UK government," it said.
The Five Eyes intelligence alliance comprising Australia, Canada, New Zealand, the U.K., and the U.S. further highlighted the threat actor's pattern of impersonating known contacts' email accounts to appear trustworthy, creating fabricated social media profiles, and creating malicious domains that resemble legitimate organizations.
The spear-phishing attacks are preceded by a research and preparatory phase to conduct reconnaissance of their targets, before approaching them via their personal email addresses in a likely attempt to bypass security controls on corporate networks and build rapport in hopes of ultimately delivering links that mimic the sign-in page for a legitimate service.
"The sender address could be from any free email provider, but special attention should be paid to emails received from Proton account senders (@proton.me, @protonmail.com) as they are frequently used by Star Blizzard," Microsoft said.
The credentials entered by the targets on these pages are then captured and used to access the victims' emails and attachments, not to mention their contacts list, which are subsequently used for follow-on phishing activity via the compromised accounts.
In a newly unsealed indictment against Peretyatko and Korinets, the U.S. Department of Justice (DoJ) said the defendants used spoofed email accounts to send messages that purported to come from email providers suggesting the recipients had violated terms of service, but, in actuality, were engineered to trick them into providing their email account credentials to false login prompts.
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) implicated the FSB in long-running hack-and-leak operations with the goal of shaping narratives in targeted countries and advancing Russia's strategic interests.
It also accused Korinets of setting up at least 39 bogus credential harvesting domains for phishing campaigns between 2016 and 2020. Peretyatko is alleged to have used a fraudulent email account in 2017 to send phishing emails that redirected victims to a malicious domain created by Korinets.
"Peretyatko and other FSB officers responsible for the spear phishing campaigns have researched new tools that would support their malicious cyber activities," the Treasury Department said.
"One of the tools included malware that allows for the evasion of two-factor authentication, another permits for the control of a device with limited risk of detection, and a third that allows access to webmail inboxes."
The sanctions notwithstanding, the U.S. Department of State has also announced a $10 million reward for any information leading to the identification of Star Blizzard's members and their activities as part of its Rewards for Justice (RFJ) program.
Responding to the sanctions blockade, the Russian Embassy in the U.K. characterized it as a "futile move" and "yet another act of poorly staged drama," with President Vladimir Putin stating "Western elites use sanctions, provoking conflicts in whole macro-regions in an attempt to maintain their slipping domination."S
Alert: Threat Actors Can Leverage AWS STS to Infiltrate Cloud Accounts
7.12.23 Hacking The Hacker News
Threat actors can take advantage of Amazon Web Services Security Token Service (AWS STS) as a way to infiltrate cloud accounts and conduct follow-on attacks.
The service enables threat actors to impersonate user identities and roles in cloud environments, Red Canary researchers Thomas Gardner and Cody Betsworth said in a Tuesday analysis.
AWS STS is a web service that enables users to request temporary, limited-privilege credentials for users to access AWS resources without needing to create an AWS identity. These STS tokens can be valid anywhere from 15 minutes to 36 hours.
Threat actors can steal long-term IAM tokens through a variety of methods like malware infections, publicly exposed credentials, and phishing emails, subsequently using them to determine roles and privileges associated with those tokens via API calls.
"Depending on the token's permission level, adversaries may also be able to use it to create additional IAM users with long-term AKIA tokens to ensure persistence in the event that their initial AKIA token and all of the ASIA short term tokens it generated are discovered and revoked," the researcher said.
In the next stage, an MFA-authenticated STS token is used to create multiple new short-term tokens, followed by conducting post-exploitation actions such as data exfiltration.
To mitigate such AWS token abuse, it's recommended to log CloudTrail event data, detect role-chaining events and MFA abuse, and rotate long-term IAM user access keys.
"AWS STS is a critical security control for limiting the use of static credentials and the duration of access for users across their cloud infrastructure," the researchers said.
"However, under certain IAM configurations that are common across many organizations, adversaries can also create and abuse these STS tokens to access cloud resources and perform malicious actions."
North Korean Hackers Distribute Trojanized CyberLink Software in Supply Chain Attack
23.11.23 Hacking The Hacker News
A North Korean state-sponsored threat actor tracked as Diamond Sleet is distributing a trojanized version of a legitimate application developed by a Taiwanese multimedia software developer called CyberLink to target downstream customers via a supply chain attack.
"This malicious file is a legitimate CyberLink application installer that has been modified to include malicious code that downloads, decrypts, and loads a second-stage payload," the Microsoft Threat Intelligence team said in an analysis on Wednesday.
The poisoned file, the tech giant said, is hosted on the updated infrastructure owned by the company while also including checks to limit the time window for execution and bypass detection by security products.
The campaign is estimated to have impacted over 100 devices across Japan, Taiwan, Canada, and the U.S. Suspicious activity associated with the modified CyberLink installer file was observed as early as October 20, 2023.
The links to North Korea stem from the fact that the second-stage payload establishes connections with command-and-control (C2) servers previously compromised by the threat actor.
Microsoft further said it has observed the attackers utilizing trojanized open-source and proprietary software to target organizations in information technology, defense, and media sectors.
Diamond Sleet, which dovetails with clusters dubbed TEMP.Hermit and Labyrinth Chollima, is the moniker assigned to an umbrella group originating from North Korea that's also called Lazarus Group. It's known to be active since at least 2013.
"Their operations since that time are representative of Pyongyang's efforts to collect strategic intelligence to benefit North Korean interests," Google-owned Mandiant noted last month. "This actor targets government, defense, telecommunications, and financial institutions worldwide."
Interestingly, Microsoft said it did not detect any hands-on-keyboard activity on target environments following the distribution of the tampered installer, which has been codenamed LambLoad.
The weaponized downloader and loader inspect the target system for the presence of security software from CrowdStrike, FireEye, and Tanium, and if not present, fetch another payload from a remote server that masquerades as a PNG file.
"The PNG file contains an embedded payload inside a fake outer PNG header that is, carved, decrypted, and launched in memory," Microsoft said. Upon execution, the malware further attempts to contact a legitimate-but-compromised domain for the retrieval of additional payloads.
The disclosures come a day after Palo Alto Networks Unit 42 revealed twin campaigns architected by North Korean threat actors to distribute malware as part of fictitious job interviews and obtain unauthorized employment with organizations based in the U.S. and other parts of the world.
Last month, Microsoft also implicated Diamond Sleet in the exploitation of a critical security flaw in JetBrains TeamCity (CVE-2023-42793, CVSS score: 9.8) to opportunistically breach vulnerable servers and deploy a backdoor known as ForestTiger.
North Korean Hackers Pose as Job Recruiters and Seekers in Malware Campaigns
23.11.23 Hacking The Hacker News
North Korean threat actors have been linked to two campaigns in which they masquerade as both job recruiters and seekers to distribute malware and obtain unauthorized employment with organizations based in the U.S. and other parts of the world.
The activity clusters have been codenamed Contagious Interview and Wagemole, respectively, by Palo Alto Networks Unit 42.
While the first set of attacks aims to "infect software developers with malware through a fictitious job interview," the latter is designed for financial gain and espionage.
"The first campaign's objective is likely cryptocurrency theft and using compromised targets as a staging environment for additional attacks," the cybersecurity company said.
The fraudulent job-seeking activity, on the other hand, involves the use of a GitHub repository to host resumes with forged identities that impersonate individuals of various nationalities.
The Contagious Interview attacks pave the way for two hitherto undocumented cross-platform malware named BeaverTail and InvisibleFerret that can run on Windows, Linux, and macOS systems.
It's worth noting that the intrusion set shares tactical overlaps with previously reported North Korean threat activity dubbed Operation Dream Job, which involves approaching employees with potential job offers and tricking them into downloading malicious tools – a rogue npm package hosted on GitHub, in this case – as part of an online interview.
"The threat actor likely presents the package to the victim as software to review or analyze, but it actually contains malicious JavaScript designed to infect the victim's host with backdoor malware," Unit 42 said.
BeaverTail, the JavaScript implant, is a stealer and a loader that comes with capabilities to steal sensitive information from web browsers and crypto wallets, and deliver additional payloads, including InvisibleFerret, a Python-based backdoor with fingerprinting, remote control, keylogging, and data exfiltration features.
InvisibleFerret is also designed to download the AnyDesk client from an actor-controlled server for remote access.
Earlier this month, Microsoft warned that the infamous Lazarus Group sub-cluster referred to as Sapphire Sleet (aka BlueNoroff) has established new infrastructure that impersonates skills assessment portals as part of its social engineering campaigns.

This is not the first time North Korean threat actors have abused bogus modules in npm and PyPI. In late June and July 2023, Phylum and GitHub detailed a social engineering campaign that targeted the personal GitHub accounts of employees working in technology firms to disseminate a counterfeit npm package under the guise of collaborating on an open-source project.
The attacks have been attributed to another cluster known as Jade Sleet, which is also called TraderTraitor and UNC4899, and has since been implicated in the JumpCloud hack that took place around the same time.
The discovery of Wagehole echoes a recent advisory from the U.S. government, which disclosed North Korea's subterfuge to beat sanctions by dispatching an army of highly-skilled IT workers who obtain employment in several companies globally and funnel back their wages to fund the country's weapons programs.
"Some resumes include links to a LinkedIn profile and links to GitHub content," the cybersecurity company said.
"These GitHub accounts appear well maintained and have a lengthy activity history. These accounts indicate frequent code updates and socialization with other developers. As a result, these GitHub accounts are nearly indistinguishable from legitimate accounts."
"We would create 20 to 50 fake profiles a year until we were hired," a North Korean IT worker who recently defected was quoted as saying to Reuters, which also shared details of the Wagemole campaign.
The development comes as North Korea claimed that it has successfully put a military spy satellite into space, after two unsuccessful attempts in May and August of this year.
It also follows a new attack campaign orchestrated by the North Korea-linked Andariel group – another subordinate element within Lazarus – to deliver Black RAT, Lilith RAT, NukeSped, and TigerRAT by infiltrating vulnerable MS-SQL servers as well as via supply chain attacks using a South Korean asset management software.
"Software developers are often the weakest link for supply chain attacks, and fraudulent job offers are an ongoing concern, so we expect continued activity from Contagious Interview," Unit 42 said. "Furthermore, Wagemole represents an opportunity to embed insiders in targeted companies."
Owner of BreachForums Pleads Guilty to Cybercrime and Child Pornography Charges
18.7.23 Hacking The Hacker News
Conor Brian Fitzpatrick, the owner of the now-defunct BreachForums website, has pleaded guilty to charges related to his operation of the cybercrime forum as well as having child pornography images.
The development, first reported by DataBreaches.net last week, comes nearly four months after Fitzpatrick (aka pompompurin) was formally charged in the U.S. with conspiracy to commit access device fraud and possession of child pornography.
BreachForums, launched in March 2022, operated as an illegal marketplace that allowed its members to trade hacked or stolen databases, enabling other criminal actors to gain unauthorized access to target systems. It was shut down in March 2023 shortly after Fitzpatrick's arrest in New York.
As many as 888 databases consisting of 14 billion individual records are estimated to have been found in total. The forum had over 333,000 members prior to its takedown.
"The purpose of BreachForums, and Fitzpatrick's intent in operating the forum, was to commit and aid and abet the trafficking of stolen or hacked databases containing, among other things, access devices, and the posting of solicitations to offer databases containing access devices," according to court documents.
The 20-year-old faces a maximum jail term of up to 40 years, with fines totaling $750,000. He is scheduled to be sentenced on November 17, 2023.
News of Fitzpatrick's plea agreement comes as the Spanish National Police apprehended a Ukrainian national wanted internationally for his involvement in a fraudulent scareware operation spanning from 2006 to 2011 and eluded capture for over a decade.
It also follows the sentencing of Ashley Liles, a 28-year-old former IT security analyst, to three years and seven months in prison for attempting to extort his employer during a ransomware attack in 2018.
Liles, from Hertfordshire, is said to have altered the original ransom email and changed the payment address provided by the original attacker in an attempt to divert any ransom payments to himself. He had previously pleaded guilty in April 2023.
"Liles, along with other colleagues, worked with police to investigate the incident," the South East Regional Organised Crime Unit (SEROCU) said in a press release.
"Using the information he learned from this, Liles commenced a secondary attack on the company. He accessed senior board members' emails over 300 times and altered the attackers original email address to an almost identical one."
Hackers Exploiting Unpatched WordPress Plugin Flaw to Create Secret Admin Accounts
1.7.23 Hacking The Hacker News
As many as 200,000 WordPress websites are at risk of ongoing attacks exploiting a critical unpatched security vulnerability in the Ultimate Member plugin.
The flaw, tracked as CVE-2023-3460 (CVSS score: 9.8), impacts all versions of the Ultimate Member plugin, including the latest version (2.6.6) that was released on June 29, 2023.
Ultimate Member is a popular plugin that facilitates the creation of user-profiles and communities on WordPress sites. It also provides account management features.
"This is a very serious issue: unauthenticated attackers may exploit this vulnerability to create new user accounts with administrative privileges, giving them the power to take complete control of affected sites," WordPress security firm WPScan said in an alert.
Although details about the flaw have been withheld due to active abuse, it stems from an inadequate blocklist logic put in place to alter the wp_capabilities user meta value of a new user to that of an administrator and gain full access to the site.
"While the plugin has a preset defined list of banned keys, that a user should not be able to update, there are trivial ways to bypass filters put in place such as utilizing various cases, slashes, and character encoding in a supplied meta key value in vulnerable versions of the plugin," Wordfence researcher Chloe Chamberland said.
The issue came to light after reports emerged of rogue administrator accounts being added to the affected sites, prompting the plugin maintainers to issue partial fixes in versions 2.6.4, 2.6.5, and 2.6.6. A new update is expected to be released in the coming days.
"A privilege escalation vulnerability used through UM Forms," Ultimate Member said in its release notes. "Known in the wild that vulnerability allowed strangers to create administrator-level WordPress users."
WPScan, however, pointed out that the patches are incomplete and that it found numerous methods to circumvent them, meaning the issue is still actively exploitable.
In the observed attacks, the flaw is being used to register new accounts under the names apadmins, se_brutal, segs_brutal, wpadmins, wpengine_backup, and wpenginer to upload malicious plugins and themes through the site's administration panel.
Users of Ultimate Member are advised to disable the plugin until a proper patch that completely plugs the security hole is made available. It's also recommended to audit all administrator-level users on the websites to determine if any unauthorized accounts have been added.
New Mockingjay Process Injection Technique Could Let Malware Evade Detection
28.6.23 Hacking The Hacker News
A new process injection technique dubbed Mockingjay could be exploited by threat actors to bypass security solutions to execute malicious code on compromised systems.
"The injection is executed without space allocation, setting permissions or even starting a thread," Security Joes researchers Thiago Peixoto, Felipe Duarte, and Ido Naor said in a report shared with The Hacker News. "The uniqueness of this technique is that it requires a vulnerable DLL and copying code to the right section."
Process injection is an attack method that allows adversaries to inject code into processes in order to evade process-based defenses and elevate privileges. In doing so, it could allow for the execution of arbitrary code in the memory space of a separate live process.
Some of the well-known process injection techniques include dynamic link library (DLL) injection, portable executable injection, thread execution hijacking, process hollowing, and process doppelgänging, among others.
It's worth pointing out that each of these methods requires a combination of specific system calls and Windows APIs to carry out the injection, thereby allowing defenders to craft appropriate detection and mitigation procedures.
What sets Mockingjay stands apart is that it subverts these security layers by eliminating the need to execute Windows APIs usually monitored by security solutions by leveraging pre-existing Windows portable executable files that contain a default memory block protected with Read-Write-Execute (RWX) permissions.
This, in turn, is accomplished using msys-2.0.dll, which comes with a "generous 16 KB of available RWX space," making it an ideal candidate to load malicious code and fly under the radar. However, it's worth noting that there could be other such susceptible DLLs with similar characteristics.
The Israeli company said it explored two different methods -- self injection and remote process injection -- to achieve code injection in a manner that not only improves the attack efficiency, but also circumvents detection.
In the first approach, a custom application is utilized to directly load the vulnerable DLL into its address space and ultimately execute the desired code using the RWX section. Remote process injection, on the other hand, entails using the RWX section in the vulnerable DLL to perform process injection in a remote process such as ssh.exe.
"The uniqueness of this technique lies in the fact that there is no need to allocate memory, set permissions or create a new thread within the target process to initiate the execution of our injected code," the researchers said.
"This differentiation sets this strategy apart from other existing techniques and makes it challenging for Endpoint Detection and Response (EDR) systems to detect this method."
The findings come weeks after cybersecurity firm SpecterOps detailed a new method that exploits a legitimate Visual Studio deployment technology called ClickOnce to achieve arbitrary code execution and obtain initial access.
Researchers Find Way to Recover Cryptographic Keys by Analyzing LED Flickers
27.6.23 Hacking The Hacker News
In what's an ingenious side-channel attack, a group of academics has found that it's possible to recover secret keys from a device by analyzing video footage of its power LED.
"Cryptographic computations performed by the CPU change the power consumption of the device which affects the brightness of the device's power LED," researchers from the Ben-Gurion University of the Negev and Cornell University said in a study.
By taking advantage of this observation, it's possible for threat actors to leverage video camera devices such as an iPhone 13 or an internet-connected surveillance camera to extract the cryptographic keys from a smart card reader.
Specifically, video-based cryptanalysis is accomplished by obtaining video footage of rapid changes in an LED's brightness and exploiting the video camera's rolling shutter effect to capture the physical emanations.
"This is caused by the fact that the power LED is connected directly to the power line of the electrical circuit which lacks effective means (e.g., filters, voltage stabilizers) of decoupling the correlation with the power consumption," the researchers said.
In a simulated test, it was found that the method allowed for the recovery of a 256-bit ECDSA key from a smart card by analyzing video footage of the power LED flickers via a hijacked internet-connected security camera.
A second experiment allowed for the extraction of a 378-bit SIKE key from a Samsung Galaxy S8 handset by training the camera of an iPhone 13 on the power LED of Logitech Z120 speakers connected to a USB hub that's also used to charge the phone.
What makes the attack notable is that the modus operandi is non-intrusive, either banking on physical proximity or over the internet, to steal the cryptographic keys.
That said, there are a few limitations to reliably pull off the scheme. It requires the camera to be placed 16 meters away from the smart card reader and in a manner such that it has a direct line of sight view of the power LED. Then there's the condition that the signatures are recorded for a duration of 65 minutes.
Cybersecurity
It also presupposes that there exists a side-channel based on power consumption that leaks sensitive information which could be used for cryptanalysis, making such attacks an exception rather than a norm.
To counter such attacks, it's recommended that LED manufacturers integrate a capacitor to reduce fluctuations in power consumption or, alternatively, cover the power LED with black tape on the consumer side to prevent leakage.
Ben Nassi, the lead researcher behind the attack technique, has previously devised similar approaches in the past – Lamphone and Glowworm – that employ overhead hanging bulbs and a device's power indicator LED to eavesdrop on conversations.
Then last year, the researchers demonstrated what's called the "little seal bug" attack that utilizes an optical side-channel associated with lightweight reflective objects to recover the content of a conversation.
Adversary-in-the-Middle Attack Campaign Hits Dozens of Global Organizations
14.6.23 Hacking The Hacker News
"Dozens" of organizations across the world have been targeted as part of a broad business email compromise (BEC) campaign that involved the use of adversary-in-the-middle (AitM) techniques to carry out the attacks.
"Following a successful phishing attempt, the threat actor gained initial access to one of the victim employee's account and executed an 'adversary-in-the-middle' attack to bypass Office365 authentication and gain persistence access to that account," Sygnia researchers said in a report shared with The Hacker News.
"Once gaining persistence, the threat actor exfiltrated data from the compromised account and used his access to spread the phishing attacks against other victim's employees along with several external targeted organizations."
The findings come less than a week after Microsoft detailed a similar combination of an AitM phishing and a BEC attack aimed at banking and financial services organizations.
BEC scams typically entail tricking a target over email into sending money or divulging confidential company information. Besides personalizing the emails to the intended victim, the attacker can also impersonate a trusted figure to achieve their goals.
This, in turn, can be achieved by seizing control of the account through an elaborate social engineering scheme, following which the scammer emails the company's clients or suppliers fake invoices that request payment to a fraudulent bank account.
In the attack chain documented by Sygnia, the attacker was observed sending a phishing email containing a link to a purported "shared document" that ultimately redirected the victim to an AitM phishing page designed to harvest the entered credentials and one-time passwords.
What's more, the threat actors are said to have abused the temporary access to the compromised account to register a new multi-factor authentication (MFA) device in order to gain a persistent remote foothold from a different IP address located in Australia.
"In addition to exfiltration of sensitive data from the victim's account, the threat actor used this access to send new phishing emails containing the new malicious link to dozens of the client's employees as well as additional targeted organizations," Sygnia researchers said.
The Israeli cybersecurity company further said the phishing mails spread in a "worm-like fashion" from one targeted firm to the other and among employees within the same company. The exact scale of the campaign is currently unknown.
The development comes as Bolster disclosed a widespread brand impersonation scam campaign that leverages over 3,000 copycat domains to entice users into providing email, password, and credit card details.
Password Reset Hack Exposed in Honda's E-Commerce Platform, Dealers Data at Risk
12.6.23 Hacking The Hacker News
Security vulnerabilities discovered in Honda's e-commerce platform could have been exploited to gain unrestricted access to sensitive dealer information.
"Broken/missing access controls made it possible to access all data on the platform, even when logged in as a test account," security researcher Eaton Zveare said in a report published last week.
The platform is designed for the sale of power equipment, marine, lawn and garden businesses. It does not impact the Japanese company's automobile division.
The hack, in a nutshell, exploits a password reset mechanism on one of Honda's sites, Power Equipment Tech Express (PETE), to reset the password associated with any account and obtain full admin-level access.
This is made possible due to the fact that the API allows any user to send a password reset request simply by just knowing the username or email address and without having to enter a password tied to that account.
Armed with this capability, a malicious actor could sign in and takeover another account, and subsequently take advantage of the sequential nature of the dealer site URLs (i.e., "admin.pedealer.honda[.]com/dealersite/<ID>/dashboard) to gain unauthorized access to a different dealer's admin dashboard.
Honda E-commerce
"Just by incrementing that ID, I could gain access to every dealers' data," Zveare explained. "The underlying JavaScript code takes that ID and uses it in API calls to fetch data and display it on the page. Thankfully, this discovery rendered the need to reset any more passwords moot."
To make matters worse, the design flaw could have been used to access a dealer's customers, edit their website and products, and worse, elevate privileges to the administrator of the entire platform – a feature restricted to Honda employees – by means of a specially crafted request to view details of the dealer network.
In all, the weaknesses allowed for illegitimate access to 21,393 customer orders across all dealers from August 2016 to March 2023 1,570 dealer websites (of which 1,091 are active), 3,588 dealer accounts, 1,090 dealer emails, and 11,034 customer emails.
Threat actors could also leverage access to these dealer websites by planting skimmer or cryptocurrency mining code, thereby allowing them to reap illicit profits.
The vulnerabilities, following responsible disclosure on March 16, 2023, have been addressed by Honda as of April 3, 2023.
The disclosure comes months after Zveare detailed security issues in Toyota's Global Supplier Preparation Information Management System (GSPIMS) and C360 CRM that could have been leveraged to access a wealth of corporate and customer data.
Magento, WooCommerce, WordPress, and Shopify Exploited in Web Skimmer Attack
5.6.23 Hacking The Hacker News
Cybersecurity researchers have unearthed a new ongoing Magecart-style web skimmer campaign that's designed to steal personally identifiable information (PII) and credit card data from e-commerce websites.
A noteworthy aspect that sets it apart from other Magecart campaigns is that the hijacked sites further serve as "makeshift" command-and-control (C2) servers, using the cover to facilitate the distribution of malicious code without the knowledge of the victim sites.
Web security company Akamai said it identified victims of varying sizes in North America, Latin America, and Europe, potentially putting the personal data of thousands of site visitors at risk of being harvested and sold for illicit profits.
"Attackers employ a number of evasion techniques during the campaign, including obfuscating [using] Base64 and masking the attack to resemble popular third-party services, such as Google Analytics or Google Tag Manager," Akamai security researcher Roman Lvovsky said.
The idea, in a nutshell, is to breach vulnerable legitimate sites and use them to host web skimmer code, thereby leveraging the good reputation of the genuine domains to their advantage. In some cases, the attacks have been underway for nearly a month.
"Rather than using the attackers' own C2 server to host malicious code, which may be flagged as a malicious domain, attackers hack into (using vulnerabilities or any other means at their disposal) a vulnerable, legitimate site, such as a small or medium-sized retail website, and stash their code within it," Akamai noted.
The result of the attacks are two kinds of victims: legitimate sites that have been compromised to act as a "distribution center" for malware and vulnerable e-commerce websites that are the target of the skimmers.

In some cases, websites have not only been subjected to data theft, but also unwittingly served as a vehicle for spreading the malware to other susceptible websites.
"This attack included the exploitation of Magento, WooCommerce, WordPress, and Shopify, demonstrating the growing variety of vulnerabilities and abusable digital commerce platforms," Lvovsky said.
By taking advantage of the established trust the websites have garnered over time, the technique creates a "smokescreen" that makes it challenging to identify and respond to such attacks.
The campaign also adopts other methods to avoid detection. This includes camouflaging the skimmer code as third-party services like Google Tag Manager or Facebook Pixel to conceal its true intentions.
Another trick employed is the JavaScript code snippets function as loaders to fetch the full attack code from the host victim website, thereby minimizing the footprint and likelihood of detection.
The obfuscated skimmer code, which comes in two different variants, is equipped to intercept and exfiltrate PII and credit card details as an encoded string over an HTTP request to an actor-controlled server.
"Exfiltration will only happen once for each user going through checkout," Lvovsky noted. "Once a user's information is stolen, the script will flag the browser to ensure it doesn't steal the information twice (to reduce suspicious network traffic). This further increases the evasiveness of this Magecart-style attack.
Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking
28.5.23 Hacking The Hacker News
A critical security vulnerability has been disclosed in the Open Authorization (OAuth) implementation of the application development framework Expo.io.
The shortcoming, assigned the CVE identifier CVE-2023-28131, has a severity rating of 9.6 on the CVSS scoring system. API security firm Salt Labs said the issue rendered services using the framework susceptible to credential leakage, which could then be used to hijack accounts and siphon sensitive data.
Under certain circumstances, a threat actor could have taken advantage of the flaw to perform arbitrary actions on behalf of a compromised user on various platforms such as Facebook, Google, or Twitter.
Expo, similar to Electron, is an open source platform for developing universal native apps that run on Android, iOS, and the web.
It's worth noting that for the attack to be successful, sites and applications using Expo should have configured the AuthSession Proxy setting for single sign-on (SSO) using a third-party provider such as Google and Facebook.
Put differently, the vulnerability could be leveraged to send the secret token associated with a sign-in provider (e.g., Facebook) to an actor-controlled domain and use it to seize control of the victim's account.
This, in turn, is accomplished by tricking the targeted user into clicking on a specially crafted link that could be sent via traditional social engineering vectors like email, SMS messages, or a dubious website.
Expo, in an advisory, said it deployed a hotfix within hours of responsible disclosure on February 18, 2023. It's also recommended that users migrate from using AuthSession API proxies to directly registering deep link URL schemes with third-party authentication providers to enable SSO features.
"The vulnerability would have allowed a potential attacker to trick a user into visiting a malicious link, logging in to a third-party auth provider, and inadvertently revealing their third-party auth credentials," Expo's James Ide said.
"This was because auth.expo.io used to store an app's callback URL before the user explicitly confirmed they trust the callback URL."
The disclosure follows the discovery of similar OAuth issues in Booking.com (and its sister site Kayak.com) that could have been leveraged to take control of a user's account, gain full visibility into their personal or payment-card data, and perform actions on the victim's behalf.
The findings also come weeks after Swiss cybersecurity company Sonar detailed a path traversal and an SQL injection flaw in the Pimcore enterprise content management system (CVE-2023-28438) that an adversary can abuse to run arbitrary PHP code on the server with the permissions of the webserver.
Sonar, back in March 2023, also revealed an unauthenticated, stored cross-site scripting vulnerability impacting LibreNMS versions 22.10.0 and prior that could be exploited to gain remote code execution when Simple Network Management Protocol (SNMP) is enabled.
Alert: Brazilian Hackers Targeting Users of Over 30 Portuguese Banks
25.5.23 Hacking The Hacker News
A Brazilian threat actor is targeting more than 30 Portuguese financial institutions with information-stealing malware as part of a long-running campaign that commenced in 2021.
"The attackers can steal credentials and exfiltrate users' data and personal information, which can be leveraged for malicious activities beyond financial gain," SentinelOne researchers Aleksandar Milenkoski and Tom Hegel said in a new report shared with The Hacker News.
The cybersecurity firm, which began tracking "Operation Magalenha" earlier this year, said the intrusions culminate in the deployment of two variants of a backdoor called PeepingTitle so as to "maximize attack potency."
The links to Brazil stem from the use of the Brazilian-Portuguese language within the detected artifacts as well as source code overlaps with another banking trojan known as Maxtrilha, which was first disclosed in September 2021.
PeepingTitle, like Maxtrilha, is written in the Delphi programming language and is equipped to grant the attacker full control over the compromised hosts as well as capture screenshots and drop additional payloads.
The attack chains begin with phishing emails and rogue websites hosting fake installers for popular software that are engineered to launch a Visual Basic Script responsible for executing a malware loader. The loader subsequently downloads and executes the PeepingTitle backdoors.
PeepingTitle monitors users' web browsing activity, and if a browser tab matching one of the target financial institutions is opened, it exfiltrates screen captures and stages further malware executables from a remote server.
This is achieved by comparing the window title to a predefined set of strings related to targeted organizations, but not before transforming it into lowercase string san any whitespace characters.
"With the first PeepingTitle variant capturing the entire screen, and the second capturing each window a user interacts with, this malware duo provides the threat actor with a detailed insight into user activity," the researchers explained.
An important aspect of Magalenha is the shift from DigitalOcean and Dropbox in 2022 to Timeweb Cloud, a Russian cloud service provider that has a more lenient approach towards infrastructure abuse, for malware hosting and command-and-control.
The sophisticated hacking effort represents the latest iteration in a long line of financially motivated malware campaigns originating from Latin America. Earlier this March, Metabase Q uncovered a Mispadu attack wave targeting Bolivia, Chile, Mexico, Peru, and Portugal.
"Operation Magalenha indicates the persistent nature of the Brazilian threat actors," the researchers said. "These groups represent an evolving threat to organizations and individuals in their target countries and have demonstrated a consistent capacity to update their malware arsenal and tactics, allowing them to remain effective in their campaigns."
"Their capacity to orchestrate attacks in Portuguese- and Spanish-speaking countries in Europe, Central, and Latin America suggests an understanding of the local financial landscape and a willingness to invest time and resources in developing targeted campaigns."
Operation ChattyGoblin: Hackers Targeting Gambling Firms via Chat Apps
10.5.23 Hacking The Hacker News
A gambling company in the Philippines was the target of a China-aligned threat actor as part of a campaign that has been ongoing since October 2021.
Slovak cybersecurity firm ESET is tracking the series of attacks against Southeast Asian gambling companies under the name Operation ChattyGoblin.
"These attacks use a specific tactic: targeting the victim companies' support agents via chat applications – in particular, the Comm100 and LiveHelp100 apps," ESET said in a report shared with The Hacker News.
The use of a trojanized Comm100 installer to deliver malware was first documented by CrowdStrike in October 2022. The company attributed the supply chain compromise to a threat actor likely with associations to China.
The attack chains leverage the aforementioned chat apps to distribute a C# dropper that, in turn, deploys another C# executable, which ultimately serves as a conduit to drop a Cobalt Strike beacon on hacked workstations.
Also highlighted in ESET's APT Activity Report Q4 2022–Q1 2023 are attacks mounted by India-linked threat actors Donot Team and SideWinder against government institutions in South Asia.
Another set of limited attacks has been tied to another Indian APT group called Confucius that's been active since at least 2013 and is believed to share ties with the Patchwork group. The threat actor has in the past used Pegasus-themed lures and other decoy documents to target Pakistan government agencies.
The latest intrusion, per ESET, involved the use of a remote access trojan dubbed Ragnatela that's an upgraded variant of the BADNEWS RAT.
Elsewhere, the cybersecurity company said it detected the Iranian threat actor referred to as OilRig (aka Hazel Sandstorm) deploying a custom implant labeled Mango to an Israeli healthcare company.
It's worth noting that Microsoft recently attributed Storm-0133, an emerging threat cluster affiliated to Iran's Ministry of Intelligence and Security (MOIS), to attacks exclusively targeting Israeli local government agencies and companies serving the defense, lodging, and healthcare sectors.
"The MOIS group used the legitimate yet compromised Israeli website for command-and-control (C2), demonstrating an improvement in operational security, as the technique complicates defenders' efforts, which often leverage geolocation data to identify anomalous network activity," Microsoft noted, further pointing out Storm-0133's reliance on the Mango malware in these intrusions.
ESET also said an unnamed Indian data management services provider was at the receiving end of an attack mounted by the North Korea-backed Lazarus Group in January 2023 using an Accenture-themed social engineering lure.
"The goal of the attackers was to monetize their presence in the company's network, most likely through business email compromise," the company said, calling it a shift from its traditional victimology patterns.
The Lazarus Group, in February 2023, is also said to have breached a defense contractor in Poland via fake job offers to initiate an attack chain that weaponizes a modified version of SumatraPDF to deploy a RAT called ScoringMathTea and a sophisticated downloaded codenamed ImprudentCook.
Rounding off the list is a spear-phishing activity from Russia-aligned APT groups such as Gamaredon, Sandworm, Sednit, The Dukes, and SaintBear, the last of which has been detected employing an updated version of its Elephant malware framework and a novel Go-based backdoor known as ElephantLauncher.
Other notable APT activity spotted during the time period comprises that of Winter Vivern and YoroTrooper, which ESET said strongly overlaps with a group that it has been tracking under the name SturgeonPhisher since the start of 2022.
Evidence gathered so far points to YoroTrooper being active since at least 2021, with attacks singling out government, energy, and international organizations across Central Asia and Europe.
Public disclosure of its tactics in March 2023 is suspected to have led to a "big drop in activity," raising the possibility that the group is currently retooling its arsenal and altering its modus operandi.
ESET's findings follow Kaspersky's own APT trends report for Q1 2023, which unearthed a previously unknown threat actor christened Trila targeting Lebanese government entities using "homebrewed malware that enables them to remotely execute Windows system commands on infected machines."
The Russian cybersecurity company also called attention to the discovery of a new Lua-based malware strain referred to as DreamLand targeting a government entity in Pakistan, marking one of the rare instances where an APT actor has used the programming language in active attacks.
"The malware is modular and utilizes the Lua scripting language in conjunction with its Just-in-Time (JIT) compiler to execute malicious code that is difficult to detect," Kaspersky researchers said.
"It also features various anti-debugging capabilities and employs Windows APIs through Lua FFI, which utilizes C language bindings to carry out its activities."
Packagist Repository Hacked: Over a Dozen PHP Packages with 500 Million Compromised
5.5.23 Hacking The Hacker News
PHP software package repository Packagist revealed that an "attacker" gained access to four inactive accounts on the platform to hijack over a dozen packages with over 500 million installs to date.
"The attacker forked each of the packages and replaced the package description in composer.json with their own message but did not otherwise make any malicious changes," Packagist's Nils Adermann said. "The package URLs were then changed to point to the forked repositories."
The four user accounts are said to have had access to a total of 14 packages, including multiple Doctrine packages. The incident took place on May 1, 2023. The complete list of impacted packages is as follows -
acmephp/acmephp
acmephp/core
acmephp/ssl
doctrine/doctrine-cache-bundle
doctrine/doctrine-module
doctrine/doctrine-mongo-odm-module
doctrine/doctrine-orm-module
doctrine/instantiator
growthbook/growthbook
jdorn/file-system-cache
jdorn/sql-formatter
khanamiryan/qrcode-detector-decoder
object-calisthenics/phpcs-calisthenics-rules
tga/simhash-php
Security researcher Ax Sharma, writing for Bleeping Computer, revealed that the changes were made by an anonymous penetration tester with the pseudonym "neskafe3v1" in an attempt to land a job.
The attack chain, in a nutshell, made it possible to modify the Packagist page for each of these packages to a namesake GitHub repository, effectively altering the installation workflow used within Composer environments.
Successful exploitation meant that developers downloading the packages would get the forked version as opposed to the actual contents.
Packagist said that no additional malicious changes were distributed, and that all the accounts were disabled and their packages restored on May 2, 2023. It's also urging users to enable two-factor authentication (2FA) to secure their accounts.
"All four accounts appear to have been using shared passwords leaked in previous incidents on other platforms," Adermann noted. "Please, do not reuse passwords."
The development comes as cloud security firm Aqua identified thousands of exposed cloud software registries and repositories containing more than 250 million artifacts and over 65,000 container images.
The misconfigurations stem from mistakenly connecting registries to the internet, allowing anonymous access by design, using default passwords, and granting upload privileges to users that could be abused to poison the registry with malicious code.
"In some of these cases, anonymous user access allowed a potential attacker to gain sensitive information, such as secrets, keys, and passwords, which could lead to a severe software supply chain attack and poisoning of the software development life cycle (SDLC)," researchers Mor Weinberger and Assaf Morag disclosed late last month.
Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access
18.4.23 Hacking The Hacker News
The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote administration tools to commandeer targeted systems.
While the nation-state group has previously employed ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has revealed the adversary's use of the SimpleHelp remote support software in June 2022.
MuddyWater, active since at least 2017, is assessed to be a subordinate element within Iran's Ministry of Intelligence and Security (MOIS). Some of the top targets include Turkey, Pakistan, the U.A.E., Iraq, Israel, Saudi Arabia, Jordan, the U.S., Azerbaijan, and Afghanistan.
"MuddyWater uses SimpleHelp, a legitimate remote device control and management tool, to ensure persistence on victim devices," Nikita Rostovtsev, senior threat analyst at Group-IB, said.
"SimpleHelp is not compromised and is used as intended. The threat actors found a way to download the tool from the official website and use it in their attacks."
The exact distribution method used to drop the SimpleHelp samples is currently unclear, although the group is known to send spear-phishing messages bearing malicious links from already compromised corporate mailboxes.
Group-IB's findings were corroborated by Slovak cybersecurity firm ESET earlier this January, detailing MuddyWater's attacks in Egypt and Saudi Arabia that entailed the use of SimpleHelp to deploy its Ligolo reverse tunneling tool and a credential harvester dubbed MKL64.
The Singapore-headquartered company further said it was able to identify hitherto unknown infrastructure operated by the group as well as a PowerShell script that's capable of receiving commands from a remote server, the results of which are sent back to the server.
The disclosure comes weeks after Microsoft detailed the group's modus operandi of carrying out destructive attacks on hybrid environments under the guise of a ransomware operation.
New Python-Based "Legion" Hacking Tool Emerges on Telegram
14.4.23 Hacking The Hacker News
An emerging Python-based credential harvester and a hacking tool named Legion is being marketed via Telegram as a way for threat actors to break into various online services for further exploitation.
Legion, according to Cado Labs, includes modules to enumerate vulnerable SMTP servers, conduct remote code execution (RCE) attacks, exploit unpatched versions of Apache, and brute-force cPanel and WebHost Manager (WHM) accounts.
The malware is said to bear similarities to another malware family called AndroxGh0st that was first documented by cloud security services provider Lacework in December 2022.
Cybersecurity firm SentinelOne, in an analysis published late last month, revealed that AndroxGh0st is part of a comprehensive toolset called AlienFox that's offered to threat actors to steal API keys and secrets from cloud services.
"Legion appears to be part of an emerging generation of cloud-focused credential harvester/spam utilities," security researcher Matt Muir told The Hacker News. "Developers of these tools often steal each other's code, making attribution to a particular group difficult."
Besides using Telegram as a data exfiltration point, Legion is designed to exploit web servers running content management systems (CMS), PHP, or PHP-based frameworks like Laravel.
"It can retrieve credentials for a wide range of web services, such as email providers, cloud service providers, server management systems, databases, and payment platforms like Stripe and PayPal," Cado Labs said.
Some of the other targeted services include SendGrid, Twilio, Nexmo, AWS, Mailgun, Plivo, ClickSend, Mandrill, Mailjet, MessageBird, Vonage, Exotel, OneSignal, Clickatell, and TokBox.
The primary goal of the malware is to enable threat actors to hijack the services and weaponize the infrastructure for follow-on attacks, including mounting mass spam and opportunistic phishing campaigns.
The cybersecurity firm said it also discovered a YouTube channel containing tutorial videos on how to use Legion, suggesting that the "tool is widely distributed and is likely paid malware." The YouTube channel, which was created on June 15, 2021, remains active as of writing.
Furthermore, Legion retrieves AWS credentials from insecure or misconfigured web servers and deliver SMS spam messages to users of U.S. mobile networks such as AT&T, Sprint, T-Mobile, Verizon, and Virgin.
"To do this, the malware retrieves the area code for a U.S. state of the user's choosing from the website www.randomphonenumbers.com," Muir said. "A rudimentary number generator function is then used to build up a list of phone numbers to target."
Furthermore, Legion can retrieve AWS credentials from insecure or misconfigured web servers and deliver SMS spam messages to users of U.S. mobile networks such as AT&T, Sprint, T-Mobile, Verizon, and Virgin by leveraging the stolen SMTP credentials.
"To do this, the malware retrieves the area code for a U.S. state of the user's choosing from the website www.randomphonenumbers[.]com," Muir said. "A rudimentary number generator function is then used to build up a list of phone numbers to target."
Another notable aspect of Legion is its ability to exploit well-known PHP vulnerabilities to register a web shell for persistent remote access or execute malicious code.
The origins of the threat actor behind the tool, who goes by the alias "forzatools" on Telegram, remain unknown, although the presence of Indonesian-language comments in the source code indicates that the developer may be Indonesian or based in the country.
SentinelOne security researcher Alex Delamotte told The Hacker News the latest discovery "highlights some new functionality" that was not previously observed in AlienFox samples and that the two pieces of malware are two distinct toolsets.
"There are many feature overlaps, yet the tools are developed independently and implementation varies," Delamotte explained. "I believe the actors are practicing their own form of business intelligence, watching the features developed by other toolsets and implementing similar features in their own tools."
"Since this malware relies heavily on misconfigurations in web server technologies and frameworks such as Laravel, it's recommended that users of these technologies review their existing security processes and ensure that secrets are appropriately stored," Muir said.
Lazarus Hacker Group Evolves Tactics, Tools, and Targets in DeathNote Campaign
14.4.23 Hacking The Hacker News
The North Korean threat actor known as the Lazarus Group has been observed shifting its focus and rapidly evolving its tools and tactics as part of a long-running campaign called DeathNote.
While the nation-state adversary is known for persistently singling out the cryptocurrency sector, recent attacks have also targeted automotive, academic, and defense sectors in Eastern Europe and other parts of the world, in what's perceived as a "significant" pivot.
"At this point, the actor switched all the decoy documents to job descriptions related to defense contractors and diplomatic services," Kaspersky researcher Seongsu Park said in an analysis published Wednesday.
The deviation in targeting, along with the use of updated infection vectors, is said to have occurred in April 2020. It's worth noting that the DeathNote cluster is also tracked under the monikers Operation Dream Job or NukeSped. Google-owned Mandiant has also tied a subset of the activity to a group it calls UNC2970.
The phishing attacks directed against crypto businesses typically entail using bitcoin mining-themed lures in email messages to entice potential targets into opening macro-laced documents in order to drop the Manuscrypt (aka NukeSped) backdoor on the compromised machine.
The targeting of the automotive and academic verticals is tied to Lazarus Group's broader attacks against the defense industry, as documented by the Russian cybersecurity firm in October 2021, leading to the deployment of BLINDINGCAN (aka AIRDRY or ZetaNile) and COPPERHEDGE implants.

In an alternative attack chain, the threat actor employed a trojanzied version of a legitimate PDF reader application called SumatraPDF Reader to initiate its malicious routine. The Lazarus Group's use of rogue PDF reader apps was previously revealed by Microsoft.
The targets of these attacks included an IT asset monitoring solution vendor based in Latvia and a think tank located in South Korea, the latter of which entailed the abuse of legitimate security software that's widely used in the country to execute the payloads.
The twin attacks "point to Lazarus building supply chain attack capabilities," Kaspersky noted at the time. The adversarial crew has since been blamed for the supply chain attack aimed at enterprise VoIP service provider 3CX that came to light last month.
Kaspersky said it discovered another attack in March 2022 that targeted several victims in South Korea by exploiting the same security software to deliver downloader malware capable of distributing a backdoor as well as an information stealer for harvesting keystroke and clipboard data.
"The newly implanted backdoor is capable of executing a retrieved payload with named-pipe communication," Park said, adding it's also "responsible for collecting and reporting the victim's information."
Around the same time, the same backdoor is said to have been utilized to compromise a defense contractor in Latin America using DLL side-loading techniques upon opening a specially-crafted PDF file using a trojanized PDF reader.
The Lazarus Group has also been linked to a successful breach of another defense contractor in Africa last July in which a "suspicious PDF application" was sent over Skype to ultimately drop a variant of a backdoor dubbed ThreatNeedle and another implant known as ForestTiger to exfiltrate data.
"The Lazarus group is a notorious and highly skilled threat actor," Park said. "As the Lazarus group continues to refine its approaches, it is crucial for organizations to maintain vigilance and take proactive measures to defend against its malicious activities."
Fake ChatGPT Chrome Browser Extension Caught Hijacking Facebook Accounts
24.3.23 Hacking The Hacker News
Google has stepped in to remove a bogus Chrome browser extension from the official Web Store that masqueraded as OpenAI's ChatGPT service to harvest Facebook session cookies and hijack the accounts.
The "ChatGPT For Google" extension, a trojanized version of a legitimate open source browser add-on, attracted over 9,000 installations since March 14, 2023, prior to its removal. It was originally uploaded to the Chrome Web Store on February 14, 2023.
According to Guardio Labs researcher Nati Tal, the extension was propagated through malicious sponsored Google search results that were designed to redirect unsuspecting users searching for "Chat GPT-4" to fraudulent landing pages that point to the fake add-on.
Installing the extension adds the promised functionality – i.e., enhancing search engines with ChatGPT – but it also stealthily activates the ability to capture Facebook-related cookies and exfiltrate it to a remote server in an encrypted manner.
Once in possession of the victim's cookies, the threat actor moves to seize control of the Facebook account, change the password, alter the profile name and picture, and even use it to disseminate extremist propaganda.

The development makes it the second fake ChatGPT Chrome browser extension to be discovered in the wild. The other extension, which also functioned as a Facebook account stealer, was distributed via sponsored posts on the social media platform.
If anything, the findings are yet another proof that cybercriminals are capable of swiftly adapting their campaigns to cash in on the popularity of ChatGPT to distribute malware and stage opportunistic attacks.
"For threat actors, the possibilities are endless — using your profile as a bot for comments, likes, and other promotional activities, or creating pages and advertisement accounts using your reputation and identity while promoting services that are both legitimate and probably mostly not," Tal said.
Fake ChatGPT Chrome Extension Hijacking Facebook Accounts for Malicious Advertising
13.3.23 Hacking The Hacker News 
A fake ChatGPT-branded Chrome browser extension has been found to come with capabilities to hijack Facebook accounts and create rogue admin accounts, highlighting one of the different methods cyber criminals are using to distribute malware.
"By hijacking high-profile Facebook business accounts, the threat actor creates an elite army of Facebook bots and a malicious paid media apparatus," Guardio Labs researcher Nati Tal said in a technical report.
"This allows it to push Facebook paid ads at the expense of its victims in a self-propagating worm-like manner."
The "Quick access to Chat GPT" extension, which is said to have attracted 2,000 installations per day since March 3, 2023, has since been pulled by Google from the Chrome Web Store as of March 9, 2023.
The browser add-on is promoted through Facebook-sponsored posts, and while it offers the ability to connect to the ChatGPT service, it's also engineered to surreptitiously harvest cookies and Facebook account data using an already active, authenticated session.
This is achieved by making use of two bogus Facebook applications – portal and msg_kig – to maintain backdoor access and obtain full control of the target profiles. The process of adding the apps to the Facebook accounts is fully automated.
The hijacked Facebook business accounts are then used to advertise the malware, thereby effectively expanding its army of Facebook bots.

The development comes as threat actors are capitalizing on the massive popularity of OpenAI's ChatGPT since its release late last year to create fake versions of the artificial intelligence chatbot and trick unsuspecting users into installing them.
Last month, Cyble revealed a social engineering campaign that relied on an unofficial ChatGPT social media page to direct users to malicious domains that download information stealers, such as RedLine, Lumma, and Aurora.
Also spotted are fake ChatGPT apps distributed via the Google Play Store and other third-party Android app stores to push SpyNote malware onto people's devices.
"Unfortunately, the success of the viral AI tool has also attracted the attention of fraudsters who use the technology to conduct highly sophisticated investment scams against unwary internet users," Bitdefender disclosed last week.