Hacking 2024 2023 2022 2021 2020
Google Blocks Dozens of Malicious Domains Operated by Hack-for-Hire Groups
1.7.22 Hacking Thehackernews
Google's Threat Analysis Group (TAG) on Thursday disclosed it had acted to block as many as 36 malicious domains operated by hack-for-hire groups from India, Russia, and the U.A.E.
In a manner analogous to the surveillanceware ecosystem, hack-for-hire firms equip their clients with capabilities to enable targeted attacks aimed at corporates as well as activists, journalists, politicians, and other high-risk users.
Where the two stand apart is that while customers purchase the spyware from commercial vendors and then deploy it themselves, the operators behind hack-for-hire attacks are known to conduct the intrusions on their clients' behalf in order to obscure their role.
"The hack-for-hire landscape is fluid, both in how the attackers organize themselves and in the wide range of targets they pursue in a single campaign at the behest of disparate clients," Shane Huntley, director of Google TAG, said in a report.
"Some hack-for-hire attackers openly advertise their products and services to anyone willing to pay, while others operate more discreetly selling to a limited audience."
A recent campaign mounted by an Indian hack-for-hire operator is said to have targeted an IT company in Cyprus, an education institution in Nigeria, a fintech company in the Balkans, and a shopping company in Israel, indicating the breadth of victims.
The Indian outfit, which Google TAG said it's been tracking since 2012, has been linked to a string of credential phishing attacks with the goal of harvesting login information associated with government agencies, Amazon Web Services (AWS), and Gmail accounts.
The campaign involves sending spear-phishing emails containing a rogue link that, when clicked, launches an attacker-controlled phishing page designed to siphon credentials entered by unsuspecting users. Targets included government, healthcare, and telecom sectors in Saudi Arabia, the United Arab Emirates, and Bahrain.
Google TAG attributed the Indian hack-for-hire actors to a firm called Rebsec, which, according to its dormant Twitter account, is short for "Rebellion Securities" and is based in the city of Amritsar. The company's website, down for "maintenance" as of writing, also claims to offer corporate espionage services.
A similar set of credential theft attacks targeting journalists, European politicians, and non-profits has been linked to a Russian actor dubbed Void Balaur, a cyber mercenary group first documented by Trend Micro in November 2021.
Over the past five years, the collective is believed to have singled out accounts at major webmail providers like Gmail, Hotmail, and Yahoo! and regional webmail providers like abv.bg, mail.ru, inbox.lv, and UKR.net.
Lastly, TAG also detailed the activities of a group based in the U.A.E. and has connections to the original developers of a remote access trojan called njRAT (aka H-Worm or Houdini).
The phishing attacks, as previously uncovered by Amnesty International in 2018, entail using password reset lures to steal credentials from targets in government, education, and political organizations in the Middle East and North Africa.
Following the account compromise, both the threat actors have a pattern of maintaining persistence by granting an OAuth token to a legitimate email application like Thunderbird, generating an App Password to access the account via IMAP, or linking the victim's Gmail account to an adversary-owned account on a third-party mail provider.
The findings come a week after Google TAG revealed details of an Italian spyware company named RCS Lab, whose "Hermit" hacking tool was used to target Android and iOS users in Italy and Kazakhstan.
Researchers Find Bluetooth Signals Can be Fingerprinted to Track Smartphones
11.6.22 Hacking Thehackernews
A new research undertaken by a group of academics from the University of California San Diego has revealed for the first time that Bluetooth signals can be fingerprinted to track smartphones (and therefore, individuals).
The identification, at its core, hinges on imperfections in the Bluetooth chipset hardware introduced during the manufacturing process, resulting in a "unique physical-layer fingerprint."
"To perform a physical-layer fingerprinting attack, the attacker must be equipped with a Software Defined Radio sniffer: a radio receiver capable of recording raw IQ radio signals," the researchers said in a new paper titled "Evaluating Physical-Layer BLE Location Tracking Attacks on Mobile Devices."
The attack is made possible due to the ubiquitous nature of Bluetooth Low Energy (BLE) beacons that are continuously transmitted by modern devices to enable crucial functions such as contact tracing during public health emergencies.
The hardware defects, on the other hand, stem from the fact that both Wi-Fi and BLE components are often integrated together into a specialized "combo chip," effectively subjecting Bluetooth to the same set of metrics that can be used to uniquely fingerprint Wi-Fi devices: carrier frequency offset and IQ imbalance.
Fingerprinting and tracking a device then entails extracting CFO and I/Q imperfections for each packet by computing the Mahalanobis distance to determine "how close the features of the new packet" are to its previously recorded hardware imperfection fingerprint.
"Also, since BLE devices have temporarily stable identifiers in their packets [i.e., MAC address], we can identify a device based on the average over multiple packets, increasing identification accuracy," the researchers said.
That said, there are several challenges to pulling off such an attack in an adversarial setting, chief among them being that the ability to uniquely identify a device depends on the BLE chipset used as well as the chipsets of other devices that are in close physical proximity to the target.
Other critical factors that could affect the readings include device temperature, differences in BLE transmit power between iPhone and Android devices, and the quality of the sniffer radio used by the malicious actor to execute the fingerprinting attacks.
"By evaluating the practicality of this attack in the field, particularly in busy settings such as coffee shops, we found that certain devices have unique fingerprints, and therefore are particularly vulnerable to tracking attacks, others have common fingerprints, they will often be misidentified," the researchers concluded.
"BLE does present a location tracking threat for mobile devices. However an attacker's ability to track a particular target is essentially a matter of luck."
Experts Warn of Rise in ChromeLoader Malware Hijacking Users' Browsers
28.5.22 Hacking Thehackernews
A malvertising threat is witnessing a new surge in activity since its emergence earlier this year.
Dubbed ChromeLoader, the malware is a "pervasive and persistent browser hijacker that modifies its victims' browser settings and redirects user traffic to advertisement websites," Aedan Russell of Red Canary said in a new report.
ChromeLoader is a rogue Chrome browser extension and is typically distributed in the form of ISO files via pay-per-install sites and baited social media posts that advertise QR codes to cracked video games and pirated movies.
While it primarily functions by hijacking user search queries to Google, Yahoo, and Bing and redirecting traffic to an advertising site, it's also notable for its use of PowerShell to inject itself into the browser and get the extension added.

The malware, also known as Choziosi Loader, was first documented by G DATA earlier this February.
"For now the only purpose is getting revenue via unsolicited advertisements and search engine hijacking," G DATA's Karsten Hahn said. "But loaders often do not stick to one payload in the long run and malware authors improve their projects over time."
Another trick up ChromeLoader's sleeve is its ability to redirect victims away from the Chrome extensions page ("chrome://extensions") should they attempt to remove the add-on.

Furthermore, researchers have detected a macOS version of the malware that works against both Chrome and Safari browsers, effectively turning ChromeLoader into a cross-platform threat.
"If applied to a higher-impact threat — such as a credential harvester or spyware — this PowerShell behavior could help malware gain an initial foothold and go undetected before performing more overtly malicious activity, like exfiltrating data from a user's browser sessions," Russell noted.
Hackers Increasingly Using Browser Automation Frameworks for Malicious Activities
28.5.22 Hacking Thehackernews
Cybersecurity researchers are calling attention to a free-to-use browser automation framework that's being increasingly used by threat actors as part of their attack campaigns.
"The framework contains numerous features which we assess may be utilized in the enablement of malicious activities," researchers from Team Cymru said in a new report published Wednesday.
"The technical entry bar for the framework is purposefully kept low, which has served to create an active community of content developers and contributors, with actors in the underground economy advertising their time for the creation of bespoke tooling."
The U.S. cybersecurity company said it observed command-and-control (C2) IP addresses associated with malware such as Bumblebee, BlackGuard, and RedLine Stealer establishing connections to the downloads subdomain of Bablosoft ("downloads.bablosoft[.]com"), the maker of the Browser Automation Studio (BAS).
Bablosoft was previously documented by cloud security and application delivery firm F5 in February 2021, pointing to the framework's ability to automate tasks in Google's Chrome browser in a manner similar to legitimate developer tools like Puppeteer and Selenium.

Threat telemetry for the subdomain's IP address — 46.101.13[.]144 — shows that a vast majority of activity is originating from locations in Russia and Ukraine, with open source intelligence indicating that Bablosoft's owner is allegedly based in the Ukrainian capital city of Kyiv.
It's being suspected that the operators of the malware campaigns connected to the Bablosoft subdomain for purposes of downloading additional tools for use as part of post-exploitation activities.
Also identified are several hosts associated with cryptojacking malware like XMRig and Tofsee communicating with a second subdomain named "fingerprints.bablosoft[.]com" to use a service that helps the mining malware conceal its behavior.
"Based on the number of actors already utilizing tools offered on the Bablosoft website, we can only expect to see BAS becoming a more common element of the threat actor's toolkit," the researchers said.
Learn How Hackers Can Hijack Your Online Accounts Even Before You Create Them
26.5.22 Hacking Thehackernews
Malicious actors can gain unauthorized access to users' online accounts via a new technique called "account pre-hijacking," new research has found.
The attack takes aim at the account creation process that's ubiquitous in websites and other online platforms, enabling an adversary to perform a set of actions before an unsuspecting victim creates an account in a target service.
The study was led by independent security researcher Avinash Sudhodanan in collaboration with Andrew Paverd of the Microsoft Security Response Center (MSRC).
Pre-hijacking banks on the prerequisite that an attacker is already in possession of a unique identifier associated with a victim, such as an email address or phone number, information which can be obtained either from scraping the target's social media accounts or credential dumps circulating on the web as a result of countless data breaches.
The attacks can then play out in five different ways, including the use of the same email address during account creation by both the adversary and the victim, potentially granting the two parties concurrent access to the account.
A consequence of pre-hijacking attacks is the same as that of account hijacking in that they could permit the adversary to stealthily access the victim's confidential information without their knowledge or even impersonate the individual depending on the nature of the service.
"If the attacker can create an account at a target service using the victim's email address before the victim creates an account, the attacker could then use various techniques to put the account into a pre-hijacked state," the researchers said.

"After the victim has recovered access and started using the account, the attacker could regain access and take over the account." The five types of pre-hijacking attacks are below -
Classic-Federated Merge Attack, in which two accounts created using classic and federated identity routes with the same email address allow the victim and the attacker to access to the same account.
Unexpired Session Identifier Attack, in which the attacker creates an account using the victim's email address and maintains a long-running active session. When the user recovers the account using the same email address, the attacker continues to maintain access because the password reset did not terminate the attacker's session.
Trojan Identifier Attack, in which the attacker creates an account using the victim's email address and then adds a trojan identifier, say, a secondary email address or a phone number under their control. Thus when the actual user recovers access following a password reset, the attacker can use the trojan identifier to regain access to the account.
Unexpired Email Change Attack, in which the attacker creates an account using the victim's email address and proceeds to change the email address to one under their control. When the service sends a verification URL to the new email address, the attacker waits for the victim to recover and start using the account before completing the change-of-email process to seize control of the account.
Non-Verifying Identity Provider (IdP) Attack, in which the attacker creates an account with the target service using a non-verifying IdP. If the victim creates an account using the classic registration method with the same email address, it enables the attacker to gain access to the account.
In an empirical evaluation of 75 of the most popular websites from Alexa, 56 pre-hijacking vulnerabilities were identified on 35 services. This includes 13 Classic-Federated Merge, 19 Unexpired Session Identifier, 12 Trojan Identifier, 11 Unexpired Email Change, and one Non-Verifying IdP attacks spanning several notable platforms -
Dropbox - Unexpired Email Change Attack
Instagram - Trojan Identifier Attack
LinkedIn - Unexpired Session and Trojan Identifier Attacks
Wordpress.com - Unexpired Session and Unexpired Email Change Attacks, and
Zoom - Classic-Federated Merge and Non-verifying IdP Attacks
"The root cause of all of the attacks [...] is a failure to verify ownership of the claimed identifier," the researchers said.
"Although many services do perform this type of verification, they often do so asynchronously, allowing the user to use certain features of the account before the identifier has been verified. Although this might improve usability (reduces user friction during sign up), it leaves the user vulnerable to pre-hijacking attacks."

While implementing strict identifier verification in services is crucial to mitigating pre-hijacking attacks, it's recommended that users secure their accounts with multi-factor authentication (MFA).
"Correctly implemented MFA will prevent the attacker from authenticating to a pre-hijacked account after the victim starts using this account," the researchers noted. "The service must also invalidate any sessions created prior to the activation of MFA to prevent the Unexpired Session attack."
On top of that, online services are also advised to periodically delete unverified accounts, enforce a low window to confirm a change of email address, and invalidate sessions during password resets for a defense in-depth approach to account management.
"When a service merges an account created via the classic route with one created via the federated route (or vice-versa), the service must ensure that the user currently controls both accounts," Sudhodanan and Paverd said.
New Bluetooth Hack Could Let Attackers Remotely Unlock Smart Locks and Cars
20.5.22 Hacking Thehackernews
A novel Bluetooth relay attack can let cybercriminals more easily than ever remotely unlock and operate cars, break open residential smart locks, and breach secure areas.
The vulnerability has to do with weaknesses in the current implementation of Bluetooth Low Energy (BLE), a wireless technology used for authenticating Bluetooth devices that are physically located within a close range.
"An attacker can falsely indicate the proximity of Bluetooth LE (BLE) devices to one another through the use of a relay attack," U.K.-based cybersecurity company NCC Group said. "This may enable unauthorized access to devices in BLE-based proximity authentication systems."
Relay attacks, also called two-thief attacks, are a variation of person-in-the-middle attacks in which an adversary intercepts communication between two parties, one of whom is also an attacker, and then relays it to the target device without any manipulation.
While various mitigations have been implemented to prevent relay attacks, including imposing response time limits during data exchange between any two devices communicating over BLE and triangulation-based localization techniques, the new relay attack can bypass these measures.
"This approach can circumvent the existing relay attack mitigations of latency bounding or link layer encryption, and bypass localization defenses commonly used against relay attacks that use signal amplification," the company said.
To mitigate such link layer relay attacks, the researchers recommend requiring additional checks beyond just inferred proximity to authenticate key fobs and other items.
This could range from modifying apps to force user interaction on a mobile device to authorize unlocks and disabling the feature when a user's device has been stationary for over a minute based on accelerometer readings.
After being alerted to the findings on April 4, 2022, the Bluetooth Special Interest Group (SIG) acknowledged that relay attacks are a known risk and that the standards body is currently working on "more accurate ranging mechanisms."
Web Trackers Caught Intercepting Online Forms Even Before Users Hit Submit
19.5.22 Hacking Thehackernews
A new research published by academics from KU Leuven, Radboud University, and the University of Lausanne has revealed that users' email addresses are exfiltrated to tracking, marketing, and analytics domains before such is submitted and without prior consent.
The study involved crawling 2.8 million pages from the top 100 websites, and found that as many as 1,844 websites allowed trackers to capture email addresses before form submission in the European Union, a number that jumped to 2,950 when the same set of websites were visited from the U.S.
"Emails (or their hashes) were sent to 174 distinct domains (eTLD+1) in the U.S. crawl, and 157 distinct domains in the EU crawl," the researchers said. Furthermore, 52 websites were determined to be collecting passwords in the same manner, an issue that has since been addressed following responsible disclosure.
LiveRamp, Taboola, Adobe, Verizon, Yandex, Meta Platforms, TikTok, Salesforce, Listrak, and Oracle accounted for some of the top third-party tracker domains to which email addresses have been transmitted to, while Yandex, Mixpanel, and LogRocket lead the list in the password-grabbing category.
"Certain third parties send email addresses character-by-character, as the user types in their address," the researchers said. "This behavior appears to be due to session replay scripts that collect users' interactions with the page including key presses and mouse movements."
fashion/beauty, online shopping, and general news emerging as the top categories ->
fashion/beauty, online shopping, general news, software/hardware, and business emerging as the top categories
Email addresses pose a number of advantages. Not only are they unique, enabling third-parties to track users across devices, it can also be employed to match their online and offline activities, say, in scenarios where they make an in-store purchase that requires them to share their email address or sign up for a loyalty card.
The idea behind harvesting email addresses entered in online forms, even in cases where the users do not submit any form, has also been fueled by ongoing attempts by browser vendors to drop support for third-party cookies, forcing marketers to look for alternative static identifiers to track users.
This is not the first time such a concern has been raised. In June 2017, Gizmodo discovered that a third party called NaviStone was collecting personal information from mortgage calculator forms prior to their submission, with very few websites explicitly disclosing this practice in their privacy policy.
Fast forward five years later, not much has changed, the researchers said, what with websites related to fashion/beauty, online shopping, and general news emerging as the top categories with the most "leaky forms."
"Despite filling email fields on hundreds of websites categorized as pornography, we have not a single email leak," the findings show, noting how it lines up with previous studies that have shown that adult websites have relatively fewer third-party trackers when compared to general sites with comparable popularity.
What's more, such a practice may be in violation of at least three different General Data Protection Regulation (GDPR) requirements in the E.U., contravening principles of transparency, purpose limitation, and user consent.
In recent years, browser makers with the notable exception of Google Chrome have introduced new mechanisms to curtail cross-site cookies, but both Apple Safari and Mozilla Firefox have been found to do nothing to protect against scripts that export email addresses for tracking purposes.
One countermeasure against this tracking method is to install browser extensions such as uBlock Origin or switch to browsers that come with built-in ad blocking functionality, regardless of the type of device used.
"Users should assume that the personal information they enter into web forms may be collected by trackers—even if the form is never submitted," the researchers concluded, calling on a further investigation from browser vendors, privacy tool developers, and data protection agencies.
Hackers Gain Fileless Persistence on Targeted SQL Servers Using a Built-in Utility
19.5.22 Hacking Thehackernews
Microsoft on Tuesday warned that it recently spotted a malicious campaign targeting SQL Servers that leverages a built-in PowerShell binary to achieve persistence on compromised systems.
The intrusions, which leverage brute-force attacks as an initial compromise vector, stand out for their use of the utility "sqlps.exe," the tech giant said in a series of tweets.
The ultimate goals of the campaign are unknown, as is the identity of the threat actor staging it. Microsoft is tracking the malware under the name "SuspSQLUsage."
The sqlps.exe utility, which comes by default with all versions of SQL Servers, enables an SQL Agent — a Windows service to run scheduled tasks — to run jobs using the PowerShell subsystem.
"The attackers achieve fileless persistence by spawning the sqlps.exe utility, a PowerShell wrapper for running SQL-built cmdlets, to run recon commands and change the start mode of the SQL service to LocalSystem," Microsoft noted.

Additionally, the attackers have also been observed using the same module to create a new account with sysadmin role, effectively making it possible to seize control over the SQL Server.
This is not the first time threat actors have weaponized legitimate binaries already present in an environment, a technique called living-off-the-land (LotL), to achieve their nefarious goals.
An advantage offered by such attacks is that they tend to be fileless because they do not leave any artifacts behind and the activities are less likely to be flagged by antivirus software owing to them using trusted software.
The idea is to allow the attacker to blend in with regular network activity and normal administrative tasks, while remaining hidden for extended periods of time.
"The use of this uncommon living-off-the-land binary (LOLBin) highlights the importance of gaining full visibility into the runtime behavior of scripts in order to expose malicious code," Microsoft said.
Hackers Deploy IceApple Exploitation Framework on Hacked MS Exchange Servers
12.5.22 Hacking Thehackernews
Researchers have detailed a previously undocumented .NET-based post-exploitation framework called IceApple that has been deployed on Microsoft Exchange server instances to facilitate reconnaissance and data exfiltration.
"Suspected to be the work of a state-nexus adversary, IceApple remains under active development, with 18 modules observed in use across a number of enterprise environments, as of May 2022," CrowdStrike said in a Wednesday report.
The cybersecurity firm, which discovered the sophisticated malware in late 2021, noted its presence in multiple victim networks and in geographically distinct locations. Targeted victims span a wide range of sectors, including technology, academic, and government entities.
A post-exploitation toolset, as the name implies, is not used to provide initial access, but is rather employed to carry out follow-on attacks after having already compromised the hosts in question.
IceApple is notable for the fact that it's an in-memory framework, indicating an attempt on the part of the threat actor to maintain a low forensic footprint and evade detection, which, in turn, bears all hallmarks of a long-term intelligence-gathering mission.
While intrusions observed so far have involved the malware being loaded on Microsoft Exchange Servers, IceApple is capable of running under any Internet Information Services (IIS) web application, making it a potent threat.
The different modules that come with the framework equip the malware to list and delete files and directories, write data, steal credentials, query Active Directory, and export sensitive data. Build timestamps on these components date back to May 2021.
"At its core, IceApple is a post-exploitation framework focused on increasing an adversary's visibility of a target through acquisition of credentials and exfiltration of data," the researchers concluded.
"IceApple has been developed by an adversary with detailed knowledge of the inner workings of IIS. Ensuring all web applications are regularly and fully patched is critical to preventing IceApple from ending up in your environment."
U.S. Proposes $1 Million Fine on Colonial Pipeline for Safety Violations After Cyberattack
11.5.22 Hacking Thehackernews
The U.S. Department of Transportation's Pipeline and Hazardous Materials Safety Administration (PHMSA) has proposed a penalty of nearly $1 million to Colonial Pipeline for violating federal safety regulations, worsening the impact of the ransomware attack last year.
The $986,400 penalty is the result of an inspection conducted by the regulator of the pipeline operator's control room management (CRM) procedures from January through November 2020.
The PHMSA said that "a probable failure to adequately plan and prepare for manual shutdown and restart of its pipeline system [...] contributed to the national impacts when the pipeline remained out of service after the May 2021 cyberattack."
Colonial Pipeline, operator of the largest U.S. fuel pipeline, was forced to temporarily take its systems offline in the wake of a DarkSide ransomware attack in early May 2021, disrupting gas supply and prompting a regional emergency declaration across 17 states.
The incident also saw the company shelling out $4.4 million in ransom to the cybercrime syndicate to regain access to its computer network, although the U.S. government managed to recover a significant chunk of the digital funds paid.
"The pipeline shutdown impacted numerous refineries' ability to move refined product, and supply shortages created wide-spread societal impacts long after the restart," PHMSA said in a Notice of Probable Violation and Proposed Compliance Order.
"Colonial Pipeline's ad-hoc approach toward consideration of a 'manual restart' created the potential for increased risks to the pipeline's integrity as well as additional delays in restart, exacerbating the supply issues and societal impacts."
Update: "This notice is the first step in a multi-step regulatory process and we look forward to engaging with PHMSA to resolve these matters," a spokesperson for Colonial Pipeline told The Hacker News, adding that its "incident command structure facilitates a deliberate approach when responding to events."
"As the 2021 cybersecurity incident demonstrated, Colonial's approach to operating manually gives us the flexibility and structure necessary to ensure continued safe operations as we adapt to unplanned events."
"Our coordination with government stakeholders was timely, efficient and effective as evidenced by our ability to quickly restart the pipeline in a safe manner five days after we were attacked — which followed localized manual operations conducted before the official restart."
New Hacker Group Pursuing Corporate Employees Focused on Mergers and Acquisitions
3.5.22 Hacking Thehackernews
A newly discovered suspected espionage threat actor has been targeting employees focusing on mergers and acquisitions as well as large corporate transactions to facilitate bulk email collection from victim environments.
Mandiant is tracking the activity cluster under the uncategorized moniker UNC3524, citing a lack of evidence linking it to an existing group. However, some of the intrusions are said to mirror techniques used by different Russia-based hacking crews like APT28 and APT29.
"The high level of operational security, low malware footprint, adept evasive skills, and a large Internet of Things (IoT) device botnet set this group apart and emphasize the 'advanced' in Advanced Persistent Threat," the threat intelligence firm said in a Monday report.
The initial access route is unknown but upon gaining a foothold, attack chains involving UNC3524 culminate in the deployment of a novel backdoor called QUIETEXIT for persistent remote access for as long as 18 months without getting detected in some cases.
What's more, the command-and-control domains — a botnet of internet-exposed IP camera devices, likely with default credentials — are designed to blend in with legitimate traffic originating from the infected endpoints, suggesting attempts on the part of the threat actor to stay under the radar.
"UNC3524 also takes persistence seriously," Mandiant researchers pointed out. "Each time a victim environment removed their access, the group wasted no time re-compromising the environment with a variety of mechanisms, immediately restarting their data theft campaign."
Also installed by the threat actor is a secondary implant, a web shell, as a means of alternate access should QUIETEXIT stop functioning and for propagating the primary backdoor on another system in the network.
The information-gathering mission, in its final stage, entails obtaining privileged credentials to the victim's mail environment, using it to target the mailboxes of executive teams that work in corporate development.
"UNC3524 targets opaque network appliances because they are often the most unsecure and unmonitored systems in a victim environment," Mandiant said. "Organizations should take steps to inventory their devices that are on the network and do not support monitoring tools."
GitHub Says Recent Attack Involving Stolen OAuth Tokens Was "Highly Targeted"
3.5.22 Hacking Thehackernews
Cloud-based code hosting platform GitHub described the recent attack campaign involving the abuse of OAuth access tokens issued to Heroku and Travis-CI as "highly targeted" in nature.
"This pattern of behavior suggests the attacker was only listing organizations in order to identify accounts to selectively target for listing and downloading private repositories," GitHub's Mike Hanley said in an updated post.
The security incident, which it discovered on April 12, related to an unidentified attacker leveraging stolen OAuth user tokens issued to two third-party OAuth integrators, Heroku and Travis-CI, to download data from dozens of organizations, including NPM.
The Microsoft-owned company said last week that it's in the process of sending a final set of notifications to GitHub customers who had either the Heroku or Travis CI OAuth app integrations authorized in their accounts.
According to a detailed step-by-step analysis carried out by GitHub, the adversary is said to have employed the stolen app tokens to authenticate to the GitHub API, using it to list all the organizations of affected users.
This was then succeeded by selectively choosing targets based on the listed organizations, following it up by listing the private repositories of valuable users accounts, before ultimately moving to clone some of those private repositories.
The company also reiterated that the tokens were not obtained via a compromise of GitHub or its systems, and that the tokens are not stored in their "original, usable formats," which could be misused by an attacker.
"Customers should also continue to monitor Heroku and Travis CI for updates on their own investigations into the affected OAuth applications," GitHub noted.
Brokenwire Hack Could Let Remote Attackers Disrupt Charging for Electric Vehicles
5.4.22 Hacking Thehackernews
A group of academics from the University of Oxford and Armasuisse S+T has disclosed details of a new attack technique against the popular Combined Charging System (CCS) that could potentially disrupt the ability to charge electric vehicles at scale.
Dubbed "Brokenwire," the method interferes with the control communications that transpire between the vehicle and charger to wirelessly abort the charging sessions from a distance of as far as 47m (151ft).
"While it may only be an inconvenience for individuals, interrupting the charging process of critical vehicles, such as electric ambulances, can have life-threatening consequences," the researchers explained.
"Brokenwire has immediate implications for many of the 12 million battery EVs estimated to be on the roads worldwide — and profound effects on the new wave of electrification for vehicle fleets, both for private enterprise and for crucial public services."
Additional details of the attack's modus operandi have been kept under wraps so as to prevent active exploitation in the wild while concerned stakeholders work towards arriving at appropriate countermeasures.
Combined Charging System refers to a type of connector used for rapid-charging electric vehicles. Brokenwire takes aim at this technology by transmitting a malicious electromagnetic signal, causing the charging process to be unexpectedly stopped.
The researchers pointed out that the attack can be mounted with an assorted mix of off-the-shelf components such as software-defined radio, power amplifiers, and a dipole antenna, not to mention be executed in person from a nearby location or by deploying a device at a target site and control it remotely.
"The use of PLC [power-line communications] for charging communication is a serious design flaw that leaves millions of vehicles, some of which belong to critical infrastructure, vulnerable," the researchers said.
Researchers Uncover Hacker Group Behind Organized Financial-Theft Operation
5.1.2022 Hacking Thehackernews
Cybersecurity researchers have taken the wraps of an organized financial-theft operation undertaken by a discreet actor to target transaction processing systems and siphon funds from entities primarily located in Latin America for at least four years.
The malicious hacking group has been codenamed Elephant Beetle by Israeli incident response firm Sygnia, with the intrusions aimed at banks and retail companies by injecting fraudulent transactions among benign activity to slip under the radar after an extensive study of the targets' financial structures.
"The attack is relentless in its ingenious simplicity serving as an ideal tactic to hide in plain sight, without any need to develop exploits," the researchers said in a report shared with The Hacker News, calling out the group's overlaps with another tracked by Mandiant as FIN13, an "industrious" threat actor linked to data theft and ransomware attacks in Mexico stretching back as early as 2016.
Elephant Beetle is said to leverage an arsenal of no fewer than 80 unique tools and scripts to execute its attacks, while simultaneously taking steps to blend in with the victim's environment over long periods to achieve its objectives.
"The unique modus operandi associated with the Elephant Beetle is their deep research and knowledge of victim's financial systems and operations and their persistent search for vulnerable methods to technically inject financial transactions, ultimately leading to major financial theft," Arie Zilberstein, vice president of incident response at Sygnia, told The Hacker News. "Given the long period of persistence this group has in victim's networks, they often change and adapt their techniques and tooling to continue to be relevant."

Zilberstein attributed the success of the campaign to the vast attack surface provided by legacy systems that are present in financial institutions' networks and can serve as entry points, thereby enabling attackers to gain a permanent foothold into target networks.
The adversary's modus operandi follows a low-profile pattern that begins with planting backdoors to study the victim's environment, specifically with an aim to understand the various processes used to facilitate financial transactions, followed by inserting rogue transactions of its own into the network that steal incremental amounts of money from the target to avoid setting off alarm.
But in the event the actor's fraudulent actions come to light, they temporarily cease their operations only to return a few months later. The initial access is brokered by taking advantage of unpatched flaws in external-facing Java-based web servers such as WebSphere and WebLogic, ultimately leading to the deployment of web shells that enable remote code execution and lateral movement —
CVE-2017-1000486 (CVSS score: 9.8) - Primefaces Application Expression Language Injection
CVE-2015-7450 (CVSS score: 9.8) - WebSphere Application Server SOAP Deserialization Exploit
CVE-2010-5326 (CVSS score: 10.0) - SAP NetWeaver Invoker Servlet Exploit
EDB-ID-24963 - SAP NetWeaver ConfigServlet Remote Code Execution
"This attack emphasizes once again that sophisticated attackers are sometimes lurking in networks for [a] long time," Zilberstein said. "While a lot of emphasis is given today to avoiding and preventing the imminent risk of ransomware, some other threat actors are still operating to stealthily proliferate themselves in networks to get a long term and steady financial gain."
"Organizations need to pay extra attention to these systems, particularly those which are externally facing, and perform patching and continuous hunting to prevent and detect attacks of similar nature," Zilberstein added.
SAILFISH System to Find State-Inconsistency Bugs in Smart Contracts
5.1.2022 Hacking Thehackernews
A group of academics from the University of California, Santa Barbara, has demonstrated what it calls a "scalable technique" to vet smart contracts and mitigate state-inconsistency bugs, discovering 47 zero-day vulnerabilities on the Ethereum blockchain in the process.
Smart contracts are programs stored on the blockchain that are automatically executed when predetermined conditions are met based on the encoded terms of the agreement. They allow trusted transactions and agreements to be carried out between anonymous parties without the need for a central authority.
In other words, the code itself is meant to be the final arbiter of "the deal" it represents, with the program controlling all aspects of the execution, and providing an immutable evidentiary audit trail of transactions that are both trackable and irreversible.
This also means that vulnerabilities in the code could result in hefty losses, as evidenced by hacks aimed at the DAO and more recently, MonoX, where adversaries exploited loopholes to illicitly siphon funds, a scenario that could have catastrophic consequences given the burgeoning adoption of smart contracts over the past few years.
"Since smart contracts are not easily upgradable, auditing the contract's source pre-deployment, and deploying a bug-free contract is even more important than in the case of traditional software," the researchers detailed in a paper.
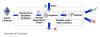
Enter Sailfish, which aims to catch state inconsistency vulnerabilities in smart contracts that allow an attacker to tamper with the execution order of the transactions or take over the control flow within a single transaction (i.e., reentrancy).
The tool works as follows. Given a smart contract, Sailfish converts the contract into a dependency graph, which captures the control and data flow relations between the storage variables and the state-changing instructions of a smart contract, using it identify potential flaws by defining hazardous access, which are implemented as graph queries to determine whether two different execution paths, at least one being a write operation, operate on the same storage variable.
The researchers evaluated Sailfish on 89,853 contracts obtained from Etherscan, identifying 47 zero-day flaws that could be leveraged to drain Ether and even corrupt application-specific metadata. This also includes a vulnerable contract implementing a housing tracker that could be abused in a manner such that a house owner can have more than one active listing.
The findings of the study will be shared at the IEEE Symposium on Security and Privacy (S&P) to be held in May 2022.
This is not the first time problematic smart contracts have attracted attention from academia. In September 2020, Chinese researchers designed a framework for categorizing known weaknesses in smart contracts with the goal of providing a detection criterion for each of the bugs.
Experts Detail Logging Tool of DanderSpritz Framework Used by Equation Group Hackers
1.1.2022 Hacking Thehackernews
Cybersecurity researchers have offered a detailed glimpse into a system called DoubleFeature that's dedicated to logging the different stages of post-exploitation stemming from the deployment of DanderSpritz, a full-featured malware framework used by the Equation Group.
DanderSpritz came to light on April 14, 2017, when a hacking group known as the Shadow Brokers leaked the exploit tool, among others, under a dispatch titled "Lost in Translation." Also included in the leaks was EternalBlue, a cyberattack exploit developed by the U.S. National Security Agency (NSA) that enabled threat actors to carry out the NotPetya ransomware attack on unpatched Windows computers.
The tool is a modular, stealthy, and fully functional framework that relies on dozens of plugins for post-exploitation activities on Windows and Linux hosts. DoubleFeature is one among them, which functions as a "diagnostic tool for victim machines carrying DanderSpritz," researchers from Check Point said in a new report published Monday.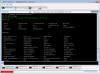
"DoubleFeature could be used as a sort of Rosetta Stone for better understanding DanderSpritz modules, and systems compromised by them," the Israeli cybersecurity firm added. "It's an incident response team's pipe dream."
Designed to maintain a log of the types of tools that could be deployed on a target machine, DoubleFeature is a Python-based dashboard that also doubles up as a reporting utility to exfiltrate the logging information from the infected machine to an attacker-controlled server. The output is interpreted using a specialized executable named "DoubleFeatureReader.exe."
Some of the plugins monitored by DoubleFeature include remote access tools called UnitedRake (aka EquationDrug) and PeddleCheap, a stealthy data exfiltration backdoor dubbed StraitBizarre, an espionage platform called KillSuit (aka GrayFish), a persistence toolset named DiveBar, a covert network access driver called FlewAvenue, and a validator implant named MistyVeal that verifies if the compromised system is indeed an authentic victim machine and not a research environment.
"Sometimes, the world of high-tier APT tools and the world of ordinary malware can seem like two parallel universes," the researchers said. "Nation-state actors tend to [maintain] clandestine, gigantic codebases, sporting a huge gamut of features that have been cultivated over decades due to practical need. It turns out we too are still slowly chewing on the 4-year-old leak that revealed DanderSpritz to us, and gaining new insights."