
Researchers Exploitee.rs conducted a new test session on the device and discovered a way to enable the Telnet service and the local web interface by exploiting a command injection flaw in a collection of scripts that were not removed by the vendor.
Hacking Articles - H 2020 1 2 3 4 5 6 7 8 9 Hacking List - H 2021 2020 2019 2018 0 1 Hacking blog Hacking blog
Ukraine Power Company Confirms Hackers Caused Outage
20.1.2017 Securityweek Hacking
The investigation is ongoing, but Ukraine’s national power company Ukrenergo has confirmed that the recent electricity outage in the Kiev region was caused by a cyberattack.
In a statement emailed to SecurityWeek on Thursday, Ukrenergo said a preliminary analysis showed that the normal operation of workstations and SCADA servers had been disrupted due to “external influences.”
The analysis indicates that the incident, described as a planned and layered intrusion, involved malware that allowed the attackers to remotely control internal systems. Investigators are in the process of establishing a timeline of events and identifying compromised accounts, points of entry, and devices infected with malware that may be lying dormant.
Ukrenergo is confident that the results of this investigation will help the company implement organizational and technological measures that would help prevent cyber threats and reduce the risk of power failure.
The incident took place on the night between December 17 and 18 at the substation in Pivnichna, causing blackouts in the capital city of Kiev and the Kiev region. Power was fully restored after just over an hour.
Ukrenergo officials immediately suspected external interference and brought in cybersecurity experts to conduct an investigation.
One of the experts involved in the probe told the BBC that the 2016 attacks were more sophisticated and better organized compared to the ones launched in December 2015. It also appears that several threat groups had worked together, and they may have tested techniques that could be used in other campaigns as well.
Russia is again the main suspect, the country being blamed for many of the cyberattacks launched recently against Ukraine.
A report published in October by Booz Allen Hamilton showed that the December 2015 attacks on Ukraine’s electric grid were part of a long-running campaign that also targeted the railway, media, mining and government sectors.
In the meantime, researchers continue to monitor KillDisk, one of the pieces of malware involved in the 2015 attack. They recently discovered that the destructive malware had turned into ransomware and started infecting Linux machines as well.
Suspected Russian Hacker Wanted by U.S. Jailed in Spain
20.1.2017 Securityweek Hacking
An alleged Russian hacker wanted for fraud has been detained in Spain and jailed pending extradition to the United States, police and a court spokesman said Thursday.
Stanislav Lisov, a computer programmer, was wanted by US authorities, a spokesman for the Guardia Civil police force said.
"He is accused of conspiracy to commit fraud via electronic media and conspiracy to commit fraud and abuse with computers," a spokesman for Spain's top-level National Court added.
Lisov was detained last week in Barcelona's El Prat airport when he was about to board a flight, police said.
He was jailed on January 13 after being questioned via videoconference by a judge in Madrid's National Court, which investigates suspected crimes that have an international remit.
The judge decided to put him in prison as he does not live in Spain and could escape, and due to the "gravity of the offences."
"Now begins the process of extradition to the United States," the National Court spokesman said, without giving further details.
2016 Christmas Ukraine power outage was caused by hackers
20.1.2017 securityaffairs Hacking
Ukrenergo confirmed that preliminary results of its investigation showed that the Ukraine power outage occurred in December was caused by hackers.
In December 2016, the Government Ukraine energy company Ukrenergo suffered a severe power outage that affected the ”North” substation at Pivnichna. The incident caused blackouts in the city of Kiev and neighboring regions.
The head of the NEC “Ukrenergo” Vsevolod Kovalchuk explained in a message posted on Facebook that experts at the company were able to restore power in 30 minutes with a manual procedure. According to Kovalchuk, the operations were fully restored after just over an hour.
Kovalchuk pointed out that an equipment malfunction or a cyber attack can be the cause of the problem. According to Kovalchuk, an “external interference through the data network” could have caused the power outage.
Ukraine power outage
In a statement sent via email to SecurityWeek on this, Ukrenergo confirmed that preliminary results of its investigation showed that the normal operation of workstations and SCADA systems had been disrupted due to “external influences.”
Once broken in the target network, attackers used a malware to gain a remote control of systems at the power plant. Experts are still investigating to establish a timeline of events and identify the entry point of the hackers. They don’t exclude that the threat could still be inside the target network in a dormant state.
The company is working to secure its system by implementing organizational and technological measures that would make its systems resilient to further attacks.
“The cyber-security company Information Systems Security Partners (ISSP) has linked the incident to a hack and blackout in 2015 that affected 225,000.” reported the BBC. “ISSP, a Ukrainian company investigating the incidents on behalf of Ukrenergo, now appears to be suggesting a firmer link.
It said that both the 2015 and 2016 attacks were connected, along with a series of hacks on other state institutions this December, including the national railway system, several government ministries and a national pension fund.
Oleksii Yasnskiy, head of ISSP labs, said: “The attacks in 2016 and 2015 were not much different – the only distinction was that the attacks of 2016 became more complex and were much better organised.“”
Who is behind the power outage?
Intelligence experts suspect blames the Russia one again.
Hackers Offered Over $1 Million at Pwn2Own 2017
19.1.2017 Securityweek Hacking
For the 10th anniversary of the Pwn2Own hacking contest, Trend Micro and the Zero Day Initiative (ZDI) have introduced new exploit categories and they are prepared to offer more than $1 million worth of prizes.
Pwn2Own 2017 will take place in mid-March alongside the CanSecWest conference in Vancouver, Canada. Organizers have announced five major categories for the event: virtual machine (VM) escapes, web browsers and plugins, local privilege escalation, enterprise applications, and server side.
VM escapes were first introduced at Pwn2Own 2016 with VMware, but none of the contestants demonstrated a successful exploit. Researchers did manage to hack VMware Workstation and earned $150,000 in November at the PwnFest competition in South Korea.
At this year’s Pwn2Own, experts can earn $100,000 if they manage to execute arbitrary code on the host from a non-admin account in the guest operating system. In addition to VMware Workstation, Microsoft Hyper-V has also been added to the list of targets.
In the web browsers category, Mozilla Firefox has been reintroduced this year and hacking it can earn researchers $30,000. Exploits targeting Microsoft Edge and Google Chrome are worth $80,000, while Apple Safari and Adobe Flash Player exploits are worth $50,000.
Bonuses will be awarded for SYSTEM-level code execution on Windows ($30,000) and Mac OS X ($20,000), and VM escapes ($100,000). The bonuses are cumulative so, for example, if a contestant hacks Chrome, elevates privileges to SYSTEM and escapes the VM, they can earn $210,000 in one go.
Considering that local privilege escalation vulnerabilities can be highly useful for a piece of malware, these types of flaws get their own category this year, with prizes of $30,000 for Windows 10, $20,000 for macOS and $15,000 for Ubuntu Desktop.
The “enterprise applications” category includes Adobe Reader and the Microsoft Office apps Word, Excel and PowerPoint. Hackers can earn $50,000 for vulnerabilities affecting these applications.
The most valuable exploits are in the “server side” category. Hackers can earn $200,000 for successful exploits against Apache Web Server running on Ubuntu Server.
Each exploit will also be rewarded with Master of Pwn points. The contestant with the highest number of total points will receive 65,000 ZDI reward points, which are worth roughly $25,000.
Registration for Pwn2Own 2017 closes on March 12 at 5 PM Pacific Time. Additional information and rules are available on ZDI’s website.
Smile! Hackers Can Remotely Access Your Samsung SmartCam Security Cameras
19.1.2017 thehackernews Hacking
It's not necessary to break into your computer or smartphone to spy on you. Today all devices in our home are becoming more connected to networks than ever to make our lives easy.
But what's worrisome is that these connected devices can be turned against us, anytime, due to lack of stringent security measures and insecure encryption mechanisms implemented in these Internet of Things (IoTs) devices.
The most recent victim of this issue is the Samsung's range of SmartCam home security cameras.
Yes, it's hell easy to hijack the popular Samsung SmartCam security cameras, as they contain a critical remote code execution (RCE) vulnerability that could let hackers gain root access and take full control of these devices.
SmartCam is one of the Samsung's SmartThings range of devices, which allows its users to connect, manage, monitor and control "smart" devices in their home using their smartphones or tablets.
Back in 2014, the hacking group Exploiteers, which was previously known as GTVHacker, listed some SmartCam exploits that could have allowed remote attackers to execute arbitrary commands and let them change the camera's administrator password.
But instead of patching the flaw, Samsung decided to rip out the accessible web interface and use an alternate route that forced its users to run their SmartCams through the company's SmartCloud website.
So, it turns out that Exploiteers broke into the Samsung's SmartCam devices again with a different hacking exploit, allowing hackers to view what are supposed to be private video feeds.
What went wrong? Samsung had patched the original flaws but left one set of scripts untouched: Some PHP scripts that provide firmware updates through the SmartCam's "iWatch" webcam monitoring software.
These PHP scripts have a command injection vulnerability which could allow unauthorized users without admin privileges to execute remote shell commands with root privileges.
"The vulnerability occurs because of improper sanitization of the iWatch firmware update filename," a post on Exploiteers website reads. "A specially crafted request allows an attacker the ability to inject his command providing the attacker remote root command execution."
This defect, in turn, allows the web management system to be turned on, which was turned off by the vendor.
Exploiteers has also provided a proof-of-concept video demonstration that shows their exploit successfully working on the SmartCam SNH-1011 model, but security experts believe all Samsung SmartCam devices are affected.
How to Mitigate the Vulnerability?
An official patch from Samsung does not appear to be available yet, but the good news is that the folks at Exploiteers have shared a DIY patch that can be downloaded by SmartCam users.
However, I personally advise users to wait for an official firmware update from the company, rather than running untrusted code on their devices, though there's no indication yet if Samsung has any plan to issue a proper patch in upcoming days.
Another way to mitigate the vulnerability is by keeping your SmartCam behind a network firewall.
Samsung has yet to respond on the issue.
Hackers demonstrate how to hack Samsung SmartCam
17.1.2017 securityaffairs Hacking
Researchers Exploitee.rs discovered a flaw in Samsung SmartCam IP cameras that could be exploited to execute commands and hijack vulnerable devices.
Samsung SmartCam IP cameras are affected by a serious vulnerability that could be exploited by remote attackers to execute commands and hijack vulnerable devices.
Samsung Electronics sold the Samsung Techwin security division to the Hanwha Group in 2014, but Hanwha SmartCam products are still distributed as Samsung.
In 2014 at DEFCON 22, security experts at Exploitee.rs revealed a number of exploits that could have been used to execute arbitrary commands on Samsung SmartCam. An attacker could use the exploits to change device settings, including the administrator password.
A few months ago, the experts from Pen Test Partners also reported security issues in Samsung SmartCam products.
The researcher focused their analysis on the Samsung branded indoor IP camera SNH-6410BN, they noticed for example that the device still has SSH and a web server running on it, potentially open doors for hackers.
Samsung decided to solve the issue by disabling SSH and local access to the web interface. Actually, users can access the Samsung SmartCam via the SmartCloud online service.
Researchers Exploitee.rs conducted a new test session on the device and discovered a way to enable the Telnet service and the local web interface by exploiting a command injection flaw in a collection of scripts that were not removed by the vendor.
“Today we’re re-visiting a device that we’ve hacked in a previous session. At DEFCON 22, we released exploits for the Samsung Smartcam network camera in our “Hack All The things” presentation. These exploits allowed for remote command execution and the ability to arbitrarily change the camera’s administrator password.” states the analysis published Exploitee.rs.
These scripts exploited by the hackers are related to the iWatch webcam monitoring service and are used for firmware update functionality. The researchers discovered an iWatch Install.php root command execution issue.
“The iWatch Install.php vulnerability can be exploited by crafting a special filename which is then stored within a tar command passed to a php system() call,” researchers explained. “Because the web-server runs as root, the filename is user supplied, and the input is used without sanitization, we are able to inject our own commands within to achieve root remote command execution.”
Researchers at Exploitee.rs have also released a proof-of-concept (PoC) code for the vulnerability, and a fix. The exploit works with the SNH-1011 model, but researchers believe all Samsung SmartCam devices are affected.
“The vulnerability can be patched by first logging in to the server after spawning a shell with the POC curl command above, then running the following command.”
sed -i -e 's/" . $file . "/" . escapeshellarg($file) . "/' /mnt/custom/iwatch/web/install.php
Researchers have warned that enabling the web interface reintroduces some of the older vulnerabilities previously discovered.
How To Stop Larry From Hacking Your WiFi in 2017
17.1.2017 thehackernews Hacking
It’s 2017, and we’re not any further along with Wi-Fi security than we were 10 years ago. There are Intrusion Detection Systems and 2nd generation antivirus apps to protect us from some vulnerabilities but the simple fact that some people and businesses still don’t set their network up well in the first place.
Installing WiFi is like running Ethernet to your parking lot. It’s a cliche thing to say, but it is often true.
If I can attack your network sitting in my car from the parking lot, what chance do you have? And 99% of the time I’m successful.
Lots of companies are moving to new offices that have wide open office layouts. Some may not have BYOD policies or wireless security plans in place, and anyone can bring their own device to work that you may not know about.
I’ve even seen some companies installing IoT devices like smart led light bulbs and thermostats. Even some security camera systems which are always running unsecured and default passwords.
So what can you do to protect people like me from exploiting weaknesses in your wireless security networks and PWNing your company?
Follow
Pwnie Express @PwnieExpress
We're sorry, but your new password must contain an upper case letter, a number, a punctuation mark and a gang sign 😳🤔
7:56 PM - 16 Jan 2017
10 10 Retweets 15 15 likes
Be sure WEP does not exist in your infrastructure. WEP is the weakest of the weak for encryption but was a reaction to open networks early on.If enough packets are observed the key can be brute forced easily. Remember doing that like 15 years ago?
WPA/WPA2 PSK can be your friend. It’s mostly secure, but there are still things you need to lock down to be sure.
Create a plan on what to do when an attack happens. Develop and implement a wireless security policy. Be ready when you do detect a rogue device or when someone’s banging on your network from the parking lot.
Want to watch us talk about penetration testing and hear stories from 200 clients I’ve been hired to hack into their network?
We’re running a webinar tomorrow with Pwnie Express and Larry Pesce.
You can sign up here, and I’ll send you the link to watch us as well as a guide for 2017 on how you can lock down wireless networks and keep people like me out of your company's networks.
Russian Channel One alleged hacked and BBC Sherlock Final Leaked
17.1.2017 securityaffairs Hacking
On Monday, Russian State Television Channel One leaked online the BBC Sherlock Final episode, the broadcaster blames hackers.
On Monday, a Russian state television Channel One blamed hackers for the leak online of the final episode of the BBC drama Sherlock a day before its actual planning.
The Russian Channel One was set to transmit the end-of-season episode of the fourth series of Sherlock the detective on Monday just after midnight Moscow time (2100 GMT), simultaneously with the UK.
“The BBC is trying to establish whether an episode of Sherlock was deliberately leaked from within the offices of a Russian state broadcaster, after last night’s hotly-anticipated series finale was circulated on the internet ahead of transmission.” Reported The Telegraph.
“A Russian-language version of the 90-minute episode, entitled The Final Problem, appeared online on Saturday, featuring a three-second continuity announcement identifying it as having originated from Channel One, which holds the rights to air Sherlock in Russia.”
According to the Russian broadcaster, hackers broke into its system and leaked online a full episode professionally dubbed into the Russian language. Of course, copies of the final episode of the BBC drama Sherlock appeared across numerous sites.
“According to preliminary findings, the cause was a hacker attack,” Channel One spokeswoman Larisa Krymova revealed to the AFP.
[the channel] “has been in close contact with the BBC from the moment it learnt of the leak and is carrying out an investigation to identify the source of the material uploaded onto the Internet.”
[Channel One]” will be ready to share full information on the incident with colleagues after the investigation is completed,” explained the Channel One spokeswoman.
The BBC confirmed it had launched an investigation on the case.
“We have brought everything up to beyond gold standard, which is why things like this are so surprising. This is more than an accident.” stated a source at the corporation.
“BBC Worldwide takes breaches of our stringent content security protocols very seriously and we have initiated a full investigation into how this leak has occurred.” said a BBC spokesman.
The show’s producer Sue Vertue invited Sherlock fans to avoid sharing the illegal copy of the final episode.
Follow
sue vertue ✔ @suevertue
Russian version of #Sherlock TFP has been illegally uploaded.Please don't share it. You've done so well keeping it spoiler free.Nearly there
4:54 PM - 14 Jan 2017
1,999 1,999 Retweets 3,934 3,934 likes
Analysts believe that the attack was politically motivated, the attack can be considered a Russia’s retaliation against the BBC.
“There appears to be no profit motive, no benefit to the broadcaster from doing this. What remains is a political motive. The most obvious explanation is that this is punitive.” explained Ben Nimmo, information fellowdefence at the Atlantic Council think tank.
Weak passwords are still the root cause of data breaches
16.1.2017 securityaffairs Hacking
Key findings of a new study conducted by Keeper Security that analyzed 10 million hacked accounts from breached data dumps for the most popular passwords.
Users’ bad habits are still one of the biggest problems for the IT industry, weak passwords and their reuse on multiple websites every day potentially expose a billion users to cyber attacks.
I’m not surprised by the results of a new study conducted by the security firm Keeper Security that analyzed 10 million hacked accounts from breached data dumps for the most popular passwords.
Below the Top 10 Keeper Security’s 2016 most popular password list:
123456
123456789
qwerty
12345678
111111
1234567890
1234567
password
123123
987654321
Most used passwords continue to be 123456 and 123456789 despite the numerous awareness campaigns on a proper security posture, “123456” accounts for 17 per cent of the overall amount of hacked accounts the firm used as data sample.
“Looking at the list of 2016’s most common passwords, we couldn’t stop shaking our heads. Nearly 17 percent of users are safeguarding their accounts with “123456.” What really perplexed us is that so many website operators are not enforcing password security best practices.” states the report published by Keeper Security. “We scoured 10 million passwords that became public through data breaches that happened in 2016.”
The bad news is that the list of most popular passwords hasn’t changed over the years.
“The list of most frequently used passwords has changed little over the past few years. That means that user education has limits.” continues the study.
This aspect highlights the lack of a security policy that contemplates also the use of strong passwords and enforces it. Four of the top 10 passwords on the list are composed of just six characters or shorter, it’s very easy to brute force them it the system is not properly protected.
“today’s brute-force cracking software and hardware can unscramble those passwords in seconds. Website operators that permit such flimsy protection are either reckless or lazy.”
The list also includes passwords like “1q2w3e4r” and “123qwe,” it is likely that some users attempt to use unpredictable patterns to generate strong passwords. Unfortunately dictionary-based password crackers include these variations.
The last point emerged from the report is that email providers don’t correcly monitor the use of their services made by botnet used for spam.
“Security expert Graham Cluley believes that the presence of seemingly random passwords such as “18atcskd2w” and “3rjs1la7qe” on the list indicates that bots use these codes over and over when they set up dummy accounts on public email services for spam and phishing attacks.” states the report.

Explained — What's Up With the WhatsApp 'Backdoor' Story? Feature or Bug!
15.1.2017 thehackernews Hacking
What is a backdoor?
By definition: "Backdoor is a feature or defect of a computer system that allows surreptitious unauthorized access to data, " either the backdoor is in encryption algorithm, a server or in an implementation, and doesn't matter whether it has previously been used or not.
Yesterday, we published a story based on findings reported by security researcher Tobias Boelter that suggests WhatsApp has a backdoor that "could allow" an attacker, and of course the company itself, to intercept your encrypted communication.
The story involving the world's largest secure messaging platform that has over a billion users worldwide went viral in few hours, attracting reactions from security experts, WhatsApp team, and Open Whisper Systems, who partnered with Facebook to implement end-to-end encryption in WhatsApp.
Note: I would request readers to read complete article before reaching out for a conclusion. And also, suggestions and opinions are always invited :)
What's the Issue:
The vulnerability relies on the way WhatsApp behaves when an end user's encryption key changes.
WhatsApp, by default, trusts new encryption key broadcasted by a contact and uses it to re-encrypt undelivered messages and send them without informing the sender of the change.
In my previous article, I have elaborated this vulnerability with an easy example, so you can head on to read that article for better understanding.
Facebook itself admitted to this WhatsApp issue reported by Boelter, saying that "we were previously aware of the issue and might change it in the future, but for now it's not something we're actively working on changing."
What Experts argued:
According to some security experts — "It's not a backdoor, rather it’s a feature to avoid unnecessarily re-verification of encryption keys upon automatic regeneration."
Open Whisper Systems says — "There is no WhatsApp backdoor," "it is how cryptography works," and the MITM attack "is endemic to public key cryptography, not just WhatsApp."
A spokesperson from WhatsApp, acquired by Facebook in 2014 for $16 Billion, says — "The Guardian's story on an alleged backdoor in WhatsApp is false. WhatsApp does not give governments a backdoor into its systems. WhatsApp would fight any government request to create a backdoor."
What's the fact:
Notably, none of the security experts or the company has denied the fact that, if required, WhatsApp, on government request, or state-sponsored hackers can intercept your chats.
What all they have to say is — WhatsApp is designed to be simple, and users should not lose access to messages sent to them when their encryption key is changed.
Open Whisper Systems (OWS) criticized the Guardian reporting in a blog post saying, "Even though we are the creators of the encryption protocol supposedly "backdoored" by WhatsApp, we were not asked for comment."
What? "...encryption protocol supposedly "backdoored" by WhatsApp…" NO!
No one has said it's an "encryption backdoor;" instead this backdoor resides in the way how end-to-end encryption has been implemented by WhatsApp, which eventually allows interception of messages without breaking the encryption.
As I mentioned in my previous story, this backdoor has nothing to do with the security of Signal encryption protocol created by Open Whisper Systems. It's one of the most secure encryption protocols if implemented correctly.
Then Why Signal is more Secure than WhatsApp?
You might be wondering why Signal private messenger is more secure than Whatsapp, while both use the same end-to-end encryption protocol, and even recommended by the same group of security experts who are arguing — "WhatsApp has no backdoor."
It's because there is always room for improvement.
The signal messaging app, by default, allows a sender to verify a new key before using it. Whereas, WhatsApp, by default, automatically trusts the new key of the recipient with no notification to the sender.
And even if the sender has turned on the security notifications, the app notifies the sender of the change only after the message is delivered.
So, here WhatsApp chose usability over security and privacy.
It’s not about 'Do We Trust WhatsApp/Facebook?':
WhatsApp says it does not give governments a "backdoor" into its systems.
No doubt, the company would definitely fight the government if it receives any such court orders and currently, is doing its best to protect the privacy of its one-billion-plus users.
But what about state-sponsored hackers? Because, technically, there is no such 'reserved' backdoor that only the company can access.
Why 'Verifying Keys' Feature Can't Protect You?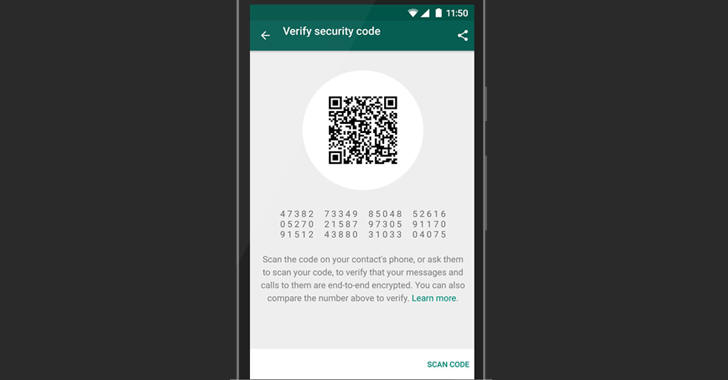
WhatsApp also offers a third security layer using which you can verify the keys of other users with whom you are communicating, either by scanning a QR code or by comparing a 60-digit number.
But here’s the catch:
This feature ensure that no one is intercepting your messages or calls at the time you are verifying the keys, but it does not ensure that no one, in the past had intercepted or in future will intercept your encrypted communication, and there is no way, currently, that would help you identify this.
WhatsApp Prevention against such MITM Attacks are Incomplete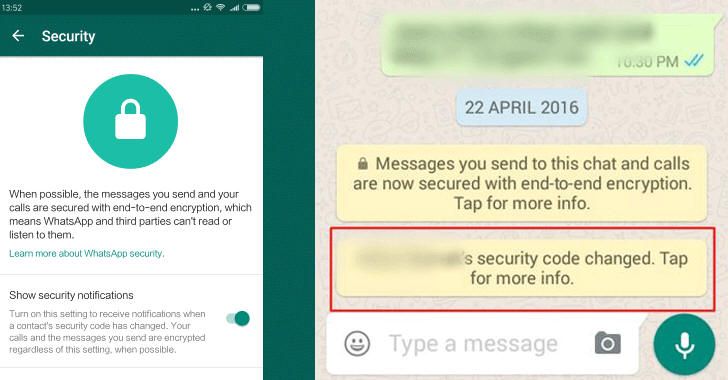
WhatsApp is already offering a "security notifications" feature that notifies users whenever a contact's security code changes, which you need to turn on manually from app settings.
But this feature is not enough to protect your communication without the use of another ultimate tool, which is — Common Sense.
Have you received a notification indicating that your contact's security code has changed?
Instead of offering 'Security by Design,' WhatsApp wants its users to use their common sense not to communicate with the contact whose security key has been changed recently, without verifying the key manually.
The fact that WhatsApp automatically changes your security key so frequently (for some reasons) that one would start ignoring such notifications, making it practically impossible for users to actively looking each time for verifying the authenticity of session keys.
What WhatsApp should do?
Without panicking all one-billion-plus users, WhatsApp can, at least:
Stop regenerating users' encryption keys so frequently (I clearly don't know why the company does so).
Give an option in the settings for privacy-conscious people, which if turned on, would not automatically trust new encryption key and send messages until manually accepted or verified by users.
...because just like others, I also hate using two apps for communicating with my friends and work colleagues i.e. Signal for privacy and WhatsApp because everyone uses it.
Hackers that hit MongoDB installs now switch on exposed Elasticsearch clusters
15.1.2017 securityaffairs Hacking
The hackers that targeted MongoDB installations with ransom attacks now switch on the exposed Elasticsearch clusters with a similar tactic.
A few days ago I reported the news of a string of cyber attacks against MongoDB databases. Hackers broke into unprotected MongoDB databases, stealing their content, and asking for a ransom to return the data.
Now it seems that the same hackers have started targeting Elasticsearch clusters that are unprotected and accessible from the internet.
Elasticsearch is a Java-based search engine based on the free and open-source information retrieval software library Lucene. It is developed in Java and is released as open source, it is used by many organizations worldwide.
Crooks are targeting Elasticsearch cluster with ransom attacks in the same way they have made with MongoDB.
The news was reported on the official support forums this week, a user who was running a test deployment accessible from the internet reported hackers removed all the indices and added a new index “warning” was created there.
The user has found the following text from the raw index data:
“SEND 0.2 BTC TO THIS WALLET: 1DAsGY4Kt1a4LCTPMH5vm5PqX32eZmot4r IF YOU WANT RECOVER YOUR DATABASE! SEND TO THIS EMAIL YOUR SERVER IP AFTER SENDING THE BITCOINS…”
Something quite similar to the recent ransom attacks against MongoDB.
“Late last week, a malicious attack was initiated, in which data from thousands of open source databases was copied, deleted and held for ransom. Although no malware, or “ransomware” was used in these attacks, and they are not related to product vulnerabilities, they nonetheless represent serious security incidents involving a data loss, or even a data breach.” reads the description of the discussion in the official forum. “The good news is that data loss from similar attacks is easily preventable with proper configuration.”

According to the security researcher Niall Merrigan, more than 600 Elasticsearch clusters have been targeted by the hackers.
Unfortunately, the number of internet-accessible Elasticsearch installs are much greater, roughly 35,000. The experts believe that the number of wiped Elasticsearch installs would rapidly increase, has it has happened for the MongoDB databases.
View image on Twitter
View image on Twitter
Follow
Niall Merrigan @nmerrigan
The #Elastic ransomware is speading .. now 600+ hosts
8:48 AM - 13 Jan 2017
10 10 Retweets 3 3 likes
It is important to protect Elasticsearch clusters exposed on the Internet as soon as possible, there is no reason to expose them.
Researchers from the company Itamar Syn-Hershko have published a blog post that includes recommendations for securing Elasticsearch installations.
“Have a Single Page Application that needs to query Elastic and get jsons for display? Pass it through a software facade that can do request filtering, audit-logging and most importantly, password-protect your data,” states the blog post. “Without that, (a) you are for sure binding to a public IP and you shouldn’t, (b) you are risking unwanted changes to your data, (c) and the worst – you can’t control who accesses what and all your data is visible for all to see. Just what’s happening now with those Elasticsearch clusters.”
The experts suggest disabling the features that users don’t need such as dynamic scripting with non-sandboxed languages (mvel, groovy) used in old versions.
As usual, let me suggest you to avoid paying, but report the incident to law enforcement.
@Kapustkiy is back and hacked the Government of Venezuela
14.1.2017 securityaffairs Hacking
The popular hacker Kapustkiy hacked a website belonging to the Government of Venezuela in protest against the dictatorship of Nicolas Maduro.
The White hat hacker Kapustkiy has hacked the Government of Venezuela and leaked data on Pastebin http://pastebin.com/ud0pewGL.
Kapustkiy hacked the website www.gdc.gob.ve by exploiting a Local File Inclusion (LFI) vulnerability in:
http://www.gdc.gob.ve/2.0/gui_resources/css/?f=../../../../../../../../../../etc/passwd
“I have found a LFI in the Capital website of the Government of Venezuela. And I hacked other two websites by exploiting a SQLi. I found around 800 users in the second website and the third website had 52 accounts.” said Kapustkiy. “I hacked them in protest against the dictatorship of Nicolas Maduro.”
The hacker hacked in protest against the President of Venezuela explaining that he is destroying the life of innocent people.
“Hacked By Kapustkiy from New World Hackers. I am against the dictatorship of Nicolas Maduro on Venezuela. I am tired of seeing, Nicolas Maduro is still running as president. It is time to leave, you motherfucker.” states the manifesto published on PasteBin.
Kapustkiy is currently working as white hat hacker reporting the flaws, but this time he made an exception for a political motivation.
In December 2016, Kapustkiy hacked the Russian Visa Center in the USA and accessed information of around 3000 individuals.
In the same month, the young hacker hacked the website of the Costa Rica Embassy in China and the breached the Slovak Chamber of Commerce (www.scci.sk) affecting more than 4,000 user records.
In 2016, Kapustkiy targeted several organizations, including the Consular Department of the Embassy of the Russian Federation, the Argentinian Ministry of Industry, the National Assembly of Ecuador, the Venezuela Army, the High Commission of Ghana & Fiji in India, the India Regional Council as well as organizations and embassies across the world.
He also broke into the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
Thousands of unpatched Magento shops hacked in the last two years
12.1.2017 securityaffairs Hacking
According to the BSI more than 6,000 online stores running eBay’s Magento platform have been hacked across the last two years.
According to the Germany’s Federal Office for Information Security, more than 6,000 online stores running eBay’s Magento platform have been hacked across the last two years. Crooks targeted the e-commerce platform in order to steal credit card data, they used to inject carding malware on unpatched Magento e-shops.
The Germany’s Federal Office for Information Security confirmed that roughly 1,000 online stores are in Germany, it did not provide info regarding the overall number of stolen data.
“The Federal Office for Information Security (BSI) has received information according to which currently at least 1,000 German online -Shops of online skimming affected. Here use Cyber -Kriminelle vulnerabilities in outdated versions of Shop software to inject malicious code. This then peaks the customer’s payment information during the ordering process and sends it to the perpetrators. Affected are online -Shops that on the widely used software based Magento.” reads the translation of the advisory issued by BSI. “The infected code and the associated data flow is usually not visible to users. The BSI is currently not aware of the extent of the payment data already passed through these attacks.”
The Federal Office reported the attacks to the victim, but many of them failed in fixing the issue. The security expert Willem de Groot first reported carding attacks against unpatched Magento shops in October. The Dutch expert analyzed a cyber attack against the website belonging to the National Republican Senatorial Committee allowed people to make donations. According to de Groot, who analyzed the traffic on the platform, hackers roughly accessed data related to 3,500 transactions per month between March 16 and October 5, 2016.
Card data was sent back to Russian IP addresses, the expert suspected that some 21,000 credit cards were stolen at the time.
de Groot believes that the attacks against Magento shops at the time that had compromised some 6,000 sites spanning 18 months.The experts also published a free vulnerability scanning service that could be used by operators of Magento shops to check their websites.
It is not clear if there are the same threat actors behind the attacks against the unpatched Magento shops
The German Federal office now tried again to warn operators of Magento shops that were compromised by hackers. Unfortunately, once again operators failed to complain necessary security measure to protect the e-commerce platform.
“Unfortunately, there are still indicators that many operators have been negligent in securing their online stores,” said the BSI president Arne Schönbohm.
“A variety of shops are running outdated software versions which contain several known vulnerabilities. Operators must fulfill their customer responsibilities and ensure their services are fixed quickly and consistently.”
“The BSI has at this point out that the obligation to secure systems not only for companies but also for all other businesslike operators of websites apply. This includes, for example, websites from private individuals or associations, if their operation is to generate revenues permanently. This is already assumed when banners placed on websites are placed in the form of banners.” states the BSI. “Customers and operators of online -Shops based on Magento can use the free service MageReportcheck whether your shop system has known vulnerabilities and is affected by the current attacks.”
Browser AutoFill Feature Can Leak Your Personal Information to Hackers
11.1.2017 thehackernews Hacking
Hackers Can Steal Your Personal Information, Thanks to Browser AutoFill Feature
Just like most of you, I too really hate filling out web forms, especially on mobile devices.
To help make this whole process faster, Google Chrome and other major browsers offer "Autofill" feature that automatically fills out web form based on data you have previously entered in similar fields.
However, it turns out that an attacker can use this autofill feature against you and trick you into spilling your private information to hackers or malicious third parties.
Finnish web developer and whitehat hacker Viljami Kuosmanen published a demo on GitHub that shows how an attacker could take advantage of the autofill feature provided by most browsers, plugins, and tools such as Password Managers.
The proof-of-concept demo website consists of a simple online web form with just two fields: Name and Email. But what's not visible are many hidden (out of sight) fields, including the phone number, organization, address, postal code, city, and country.
Giving away all your Personal Information Unknowingly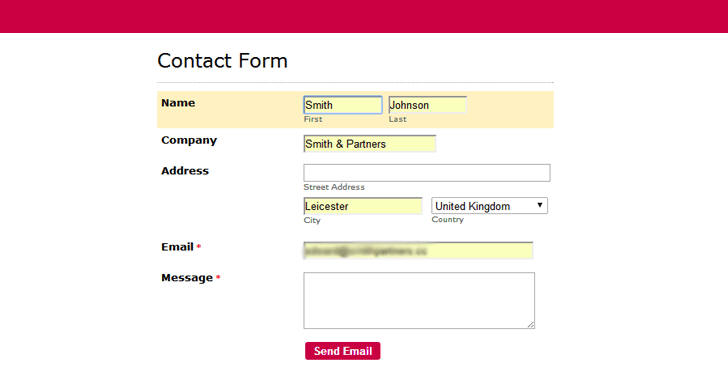
So, if users with an autofill profile configured in their browsers fill out this simple form and click on submit button, they'll send all the fields unaware of the fact that the six fields that are hidden to them but present on the page also get filled out and sent to unscrupulous phishers.
You can also test your browser and extension autofill feature using Kuosmanen's PoC site.
Kuosmanen can make this attack even worse by adding more personal fields out of user's sight, including the user's address, credit card number, expiration date, and CVV, although auto-filling financial data forms will trigger warnings on Chrome when sites do not offer HTTPS.
Kuosmanen attack works against a variety of major browsers and autofill tools, including Google Chrome, Apple Safari, Opera, and even the popular cloud security vault LastPass.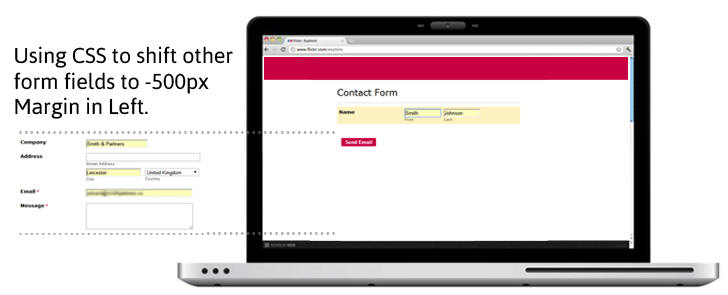
Mozilla's Firefox users do not need to worry about this particular attack as the browser currently, does not have a multi-box autofill system and forces users to select pre-fill data for each box manually.
Therefore, the Firefox browser can't be tricked into filling text boxes by programmatic means, Mozilla principal security engineer Daniel Veditz says.
Here's How to Turn Autofill Feature Off
The simplest way to protect yourself against such phishing attacks is to disable form autofill feature in your browser, password manager or extension settings.
Autofill feature is turned on by default. Here's how to turn this feature off in Chrome:
Go to Settings → Show Advanced Settings at the bottom, and under the Passwords and Forms section uncheck Enable Autofill box to fill out web forms with a single click.
In Opera, go to Settings → Autofill and turn it off.
In Safari, go to Preferences and click on AutoFill to turn it off.
Debugging mechanism in Intel CPUs allows seizing control via USB port
10.1.2017 SC Magazine UK Hacking
Researchers are warning that an Intel chip debugger leaves the chip open to hacking and because it sits below the software layer isn't easily detected.
Are attacks on the physical layer on the rise?
Researchers from Positive Technologies have revealed that some new Intel CPUs contain a debugging interface, accessible via USB 3.0 ports, that can be used to obtain full control over a system and perform attacks that are undetectable by current security tools.
An attacker could use this to bypass all security systems for the embedding of code over a certain period of time, reading all possible data and even making the machine inoperative, for instance by re-writing its BIOS.
A talk on the mechanisms needed for such attacks, and ways to protect against them, was given by Maxim Goryachy and Mark Ermolov at the 33rd Chaos Communication Congress in Hamburg, Germany.
The duo noted: “These manufacturer-created hardware mechanisms have legitimate purposes, such as special debugging features for hardware configuration and other beneficial uses. But now these mechanisms are available to attackers as well. Performing such attacks does not require nation-state resources or even special equipment.”
The duo analysed and demonstrated one of these mechanisms in their presentation. The JTAG (Joint Test Action Group) debugging interface, now accessible via USB, has the potential to enable dangerous and virtually undetectable attacks. JTAG works below the software layer for the purpose of hardware debugging of the OS kernel, hypervisors and drivers. At the same time, though, this CPU access can be abused for malicious purposes.
On older Intel CPUs, accessing JTAG required connecting a special device to a debugging port on the motherboard (ITP-XDP). JTAG was difficult to access for both troubleshooters and potential attackers.
However, starting with the Skylake processor family in 2015, Intel introduced the Direct Connect Interface (DCI) which provides access to the JTAG debugging interface via common USB 3.0 ports.
No software or hardware manipulations are required to make target computers vulnerable — merely having the DCI interface enabled is sufficient. As the researchers found, this can be accomplished in several ways, and on many computers, DCI is enabled out-of-the-box and not blocked by default.
SC Media UK spoke with Maxim Goryachy, and asked how would someone go about tricking someone into enabling the DCI interface?
Goryachy said: “There are several ways someone could do this. An attacker could change the BIOS configuration (for example, with a use of a Flash programmator) when they have physical access to the equipment during manufacturing, storage or usage. Some BIOSs do not block the DCI configuration which is why there is the possibility of turning on the DCI.”
Goryachy and Ermolov speculated that this mechanism in Intel CPUs could lead to a whole new class of Bad USB-like attacks, but at a deeper and even more dangerous level than their predecessor.
In their concluding remarks, the researchers proposed a number of protective measures based on use of Intel's BootGuard feature and forbidding activation of the debugging interface.
SC asked Goryachy if he would compare this vulnerability to Stuxnet, to which he said: “This mechanism can be used on a hacked system regardless of the OS installed. Stuxnet was infecting only Windows machines, meanwhile the DCI can be used on any system with Intel U-series processor. This series is used on laptops and NUC. As of today, no publicly available security system will detect it.”
Goryachy told SC, “We have reported this case to Intel. As of today, this mechanism can be exploited only on Intel U-series processors.”
Netgear launches Bug Bounty Program for Hacker; Offering up to $15,000 in Rewards
6.1.2017 thehackernews Hacking
It might be the easiest bug bounty program ever.
Netgear launched on Thursday a bug bounty program to offer up to $15,000 in rewards to hackers who will find security flaws in its products.
Since criminals have taken aim at a rapidly growing threat surface created by millions of new Internet of things (IoT) devices, it has become crucial to protect routers that contain the keys to the kingdom that connects the outside world to the IP networks that run these connected devices.
To combat this issue, Netgear, one of the biggest networking equipment providers in the world, has launched a bug bounty program focusing on its products, particularly routers, wireless security cameras and mesh Wi-Fi systems.
Bug bounty programs are cash rewards given by companies or organizations to white hat hackers and researchers who hunt for serious security vulnerabilities in their website or products and then responsibly disclose for the patch release.
Also Read: How Hackers Hack Bank Accounts with Router Vulnerabilities
Bug bounties are designed to encourage security researchers, hackers and enthusiasts to responsibly report the vulnerabilities they discovered, rather than selling or exploiting it.
On Thursday, Netgear announced that the company has partnered up with Bugcrowd to launch Netgear Responsible Disclosure Program that can earn researchers cash rewards ranging from $150 to $15,000 for finding and responsibly reporting security vulnerabilities in its hardware, APIs, and the mobile apps.
Meanwhile, on the same day, The Federal Trade Commission (FTC) filed a lawsuit against D-Link, another large networking equipment providers, arguing that the company failed to implement necessary security protection in its routers and Internet-connected security cameras that left "thousands of consumers at risk" to hacking attacks.
If you are a bug bounty hunter, you should read all terms and conditions before shooting your exploits against Netgear products or website.
One of them explicitly mentioned, "You may only exploit, investigate, or target security bugs against your own accounts and/or your own devices. Testing must not violate any law, or disrupt or compromise any data or access data that is not yours; intentional access of customer data other than your own is prohibited."
The company is paying out up to $15,000 for each vulnerability. The highest bounty will be given for the flaws that would allow access to the cloud storage video files or live video feeds of all its customers, and bugs that allow remote access to routers from the Internet, as shown in the chart above.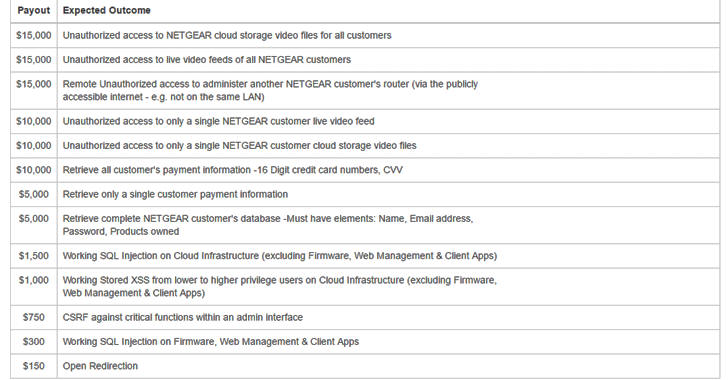
However, the Netgear will also pay $10,000 for video feed and cloud storage access bugs that cannot be exploited in mass attacks. The same payout will also be given for security issues that provide access to the payment card data of all Netgear customers.
Also Read: Someone Just Hacked 10,000 Routers to Make them More Secure.
Others vulnerabilities that qualify the bounty program include:
SQL injection bug
Information disclosure flaw
Stored cross-site scripting (XSS) vulnerability
Cross-site request forgery (CSRF) bug
Open redirect issues
Here's the Bingo! Bug bounty hunters will be rewarded with a triple prize if they will successfully exploit at least three flaws in a chain.
So, what are you waiting for? Go and Grab 'em all!
FBI Hacked, Again! Hacker Leaks Data After Agency Failed to Patch Its Site
5.1.2017 thehackernews Hacking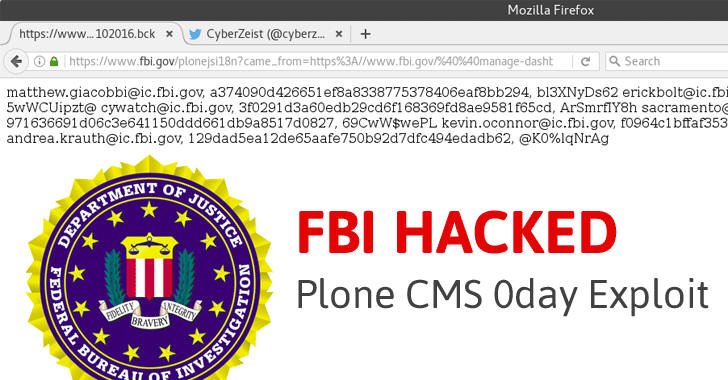
It seems like the FBI has been hacked, once again!
A hacker, using Twitter handle CyberZeist, has claimed to have hacked the FBI's website (fbi.gov) and leaked personal account information of several FBI agents publically.
CyberZeist had initially exposed the flaw on 22 December, giving the FBI time to patch the vulnerability in its website's code before making the data public.
The hacker exploited a zero-day vulnerability in the Plone CMS, an Open Source Content Management software used by FBI to host its website, and leaked personal data of 155 FBI officials to Pastebin, including their names, passwords, and email accounts.
CyberZeist tweeted multiple screenshots as proof of his claims, showing his unauthorized access to server and database files using a zero-day local file inclusion type vulnerability affecting its python plugins.
Hacker also found that the FBI's website is hosted on a virtual machine running a customized older version of the open-source FreeBSD operating system.
According to another tweet, the Plone CMS zero-day exploit is up for sale on an unnamed dark web marketplace.
The Plone CMS is considered to be one of the most secure CMSes available today and is used by many major websites like Google, and major United States agencies including the FBI and the CIA.
CyberZeist also warned other agencies, including the European Union Agency for Network and Information Security, Intellectual Property Rights Coordination Center, and Amnesty International, which are currently using the Plone CMS that they too are vulnerable to a similar attack.
The FBI authorities have yet to respond to the claims.
Update — Official Statement from Plone Security Team:
Meanwhile, Plone Security team has released a security advisory saying that it will release a security update on 17th January to its customers to "patch various vulnerabilities."
For now Advisory doesn't include much technical information about the vulnerabilities, but all supported Plone versions (4.x, 5.x). Previous versions could be affected.
"The advisory information we give in those pre-announcements is standard. In fact, the upcoming patch is to fix a minor issue with Zope which is neither a RCE or LFI inclusion problem."
Notably, Plone Security team has also mentioned that "there is no evidence that the issues fixed here are being actively exploited."
"The issue we are fixing in no way resembles CyberZeist's claims, neither do the issues we fixed last month." Matthew Wilkes, Plone security team, told The Hacker News.
"The aim of releasing information from such a hack is to convince people that you've indeed hacked the target. Claims of hacks that only give information that is publicly available (such as open-source code) or impossible to verify (such as hashed passwords) are common signs of a hoax," Matthew said.
“It is extremely easy to fake a hack like this; it takes rudimentary Photoshop skills or use of Chrome javascript developer console.“ - Nathan van Gheem, Plone security team, told THN.
Also, Mr. Alexandru Ghica, Eau de Web, the maintainer of an EU website which hacker also claimed to have hacked says, "I can say for sure that at least some of the data posted as proof is 100% fake. The hoax was a bit elaborate indeed, but that's it."
This is not the first time CyberZeist claimed to have hacked the FBI website. In 2011, the hacker breached the FBI website as a member of the infamous hacker collective known as "Anonymous.
FBI website hacked by CyberZeist and data leaked online
5.1.2017 securityaffairs Hacking
The notorious black hat hacker CyberZeist (@cyberzeist2) has broken into the FBI website FBI.gov and leaked data on Pastebin.
The hacker leaked the FBI.GOV accounts that he found in several backup files (acc_102016.bck, acc_112016.bck, old_acc16.bck, etc).
Leaked records contain accounts data, including names, SHA1 Encrypted Passwords, SHA1 salts, and emails.
The intrusion occurred on December 22, 2016, the hacker revealed to have exploited a zero-day vulnerability in the Plone Content Management System
“Going back to 22nd December 2016, I tweeted about a 0day vulnerability in Plone CMS which is considered as the most secure CMS till date. This CMS is used by many top
agencies including FBI”

CyberZeist explained that he did not find the zero-day in CMS he exploited, he was just tasked to test it against the websites of the FBI and Amnesty. Other websites are potentially exposed to the same zero-day attack, including Intellectual Property Rights Coordination Center and EU Agency for Network Information and Security.
The vulnerability resides in some python modules of the CMS.
Other Vulnerable websites include EU Agency for Network Information and Security along with Intellectual Property Rights Coordination Center.

The hacker also Tweeted an image of the FBI website that was down just after the hack.

CyberZeist tested the 0-day because the vendor was too afraid to use it aginst the FBI website. The hacker noticed that while media from Germany and Russia published the news about the hack, but US based publishers ignored it.
According to CyberZeist, the FBI contacted him to pass on the leaks.
“I was contacted by various sources to pass on the leaks to them that I obtained after hacking FBI.GOV but I denied all of them. Why? just because I was waiting for FBI to
react on time. They didn’t directly react and I don’t know yet what are they up to, but at the time I was extracting my finds after hacking FBI.GOV,” he wrote.
The expert added further info on the attack, while experts at the FBI were working to fix the issue, he noticed that the Plone 0day exploit was still working against the CMS backend.
“I couldn’t gain a root access (obviously!), but I was able to recon that they were running FreeBSD ver 6.2-RELEASE that dates back to 2007 with their own custom configurations. Their last reboot time was 15th December 2016 at 6:32 PM in the evening.” he added.
It seems that administrators of the websites made some regrettable errors, for example teh exposed the backup files on the same server, it was a joke for the hacker to access them even if he decided don’t publish them immediatelly.
“While exploiting FBI.GOV, it was clearly evident that their webmaster had a very lazy attitude as he/she had kept the backup files (.bck extension) on that same folder
where the site root was placed (Thank you Webmaster!), but still I didn’t leak out the whole contents of the backup files, instead I tweeted out my findings and thought to
wait for FBI’s response”

Now let’s sit and wait for the FBI’s response.I obviously cannot publish the 0day attack vector myself as
The hacker confirmed that the 0-day is offered for sale on Tor by a hacker that goes by the moniker “lo4fer.” Once this 0day is no longer being sold, I will tweet out the Plone CMS 0day attack vector myself.
“Once this 0day is no longer being sold, I will tweet out the Plone CMS 0day attack vector myself.” CyberZeist added.
This isn’t the first time CyberZeist hacked the website of the Federal Bureau of Investigation, in 2011 when he was one of the members of the Anonymous collective he broke into the database of the law enforcement agency.
Let’s close with a curiosity … CyberZeist is asking you to chose the next target.
https://www.poll-maker.com/poll885856x749D3f82-36.
The hacker is very popular, among his victims, there are Barclays, Tesco Bank and the MI5.
To remain in touch with CyberZeist visit his page on Pastebin
http://pastebin.com/u/CyberZeist2
Did someone hack the Brazilian google.com.br?
5.1.2017 securityaffairs Hacking
Many users speculated about a possible compromise of the address of www.google.com.br. Did someone hack it? Let’s see what has happened.
Two days ago, we followed many news and comments regarding the compromise of the address www.google.com.br. At the beginning, many (me included) discredited the news, however, big online portals quickly started to propagate the event. People close to me also reported being accessing the invalid content and ask me for help.
G1 Portal (http://g1.globo.com/tecnologia/noticia/google-nega-ter-sido-alvo-de-hackers-no-brasil-entenda.ghtml) brought some up-to-date information about the fact, including the official answer by Google:
“Some internet users in Brazil faced problems accessing google.com.br due to compromised DNS servers: that means, the malicious change of the routing configuration of those DNS servers, taking the user to a different website than the desired one”, informs Google in its note to G1.
“Google is not responsible by the affected DNS servers, whence notified the administrators, which fixed the problem in 30 minutes. The affected users may also switch their network DNS server, as the Google system was not affected”, Google assures.
This notification is split into two parts. At the first part, we analyze the technique used in the incident by digging up public information from DNS servers cache which retained the swapped “google.com.br” domain content while it was compromised. At the second part, based on the technical analysis, we make our deductions and conclusions about the case and provide a few preventive security recommendations.
Situation Analysis
For this analysis, we used an environment whose users were still seeing the incorrect content while accessing www.google.com.br. Following, the technical details of the performed procedures.
1.1. Address Resolution www.google.com.br
While resolving “www.google.com.br”, we obtained the IP address 91.148.168.111 as a response, as seen in Picture 1.

Picture 1 – Invalid address returned by www.google.com.br
Using “whois”, we saw that the address IP 91.148.168.111 does not belong to Google, but to a Bulgarian entity, as can be seen in Picture 2.

Picture 2 – Entity responsible for the IP address 91.148.168.111
The same query to the address “www.google.com.br” from an environment which shows the legitimate Google page returns the IP address 216.58.202.3 (Picture 3).

Picture 3 – Result is the legitimate Google IP address
As seen in the analysis, it was possible to validate that the invalid content was not hosted on an address from Google, that is, the content of the Google website was not altered. There is yet to explain why the users were being taken to the wrong address. We continue our analysis.
1.2. DNS Cache Analysis
We begin now our search of a DNS server whose cache is pointing to the invalid IP address for “www.google.com.br”, alas, 91.148.168.111. The goal is to find out which DNS server is returning the invalid IP. After finding one such server, we fetch its cache with the PowerShell command Show-DnsServerCache.
Below, the cache address entries for the “*google.com.br” addresses:

Table 1 – Cache from a DNS server during the incident with the domain google.com.br
Notice that the SOA (Start of Authority) entry, the registry that identifies the DNS server responsible for “google.com.br” zone points to the address “ns1-leader.vivawebhost.com”. The address resolves to IP 91.148.168.6, whose responsible is the same entity of IP 91.148.168.111.
Just to be sure, we did a DNS consult using the address www.google.com.br pointing to the DNS server ns1-leader.vivawebhost.com. The first attempt returned a timeout error – likely because the server was being strangled by the number of requests. In our second try, the address 91.148.168.111 was resolved. Exactly the same IP users were being directed, as seen in Picture 4.

Picture 4 – The consult result to the address www.google.com.br on the DNS server used for the attack
To be sure of the cache information, we did consult the SOA registry pointing to the address ns1-leader.vivawebhost.com.

Picture 5 – Result for the SOA query with google.com.br at the DNS server used during the attack
The results for the same query for a legitimate Google environment should return the following:

Picture 6 – Result for the legitimate domain
We did then query the domain “google.com.br” at registro.br, the entity responsible for “.br” domains. The result shows that the moment this report was being written, the DNS servers responsible for the domain are ns1.google.com, ns2.google.com, ns3.google.com e ns4.google.com. As expected, there are no records pointing to the invalid address ns1-leader.vivawebhost.com.

Picture 7 – Querying the domain “google.com.br” at Jan. 03, 2017 after the incident was resolved
A identified point of attention is the date of the last domain update at registro.br: Jan. 03, 2017, the day of the incident.
2. Conclusion
These analysis results make us believe the attacked managed, some way, to access the “google.com.br” domains configuration at registro.br and change it to point to ns1-leader.vivawebhost.com and ns2-leader.vivawebhost.com. This type of attack is known as “domain kidnapping”.
While the values of the DNS servers were adulterated, users trying to access www.google.com.br were taken to the incorrect address. As the response to the identified incident, the administrators responsible for the “google.com.br” domain with registro.br quickly reverted the configuration to the original values.
As the attackers used the TTL (time to live) value of 86400 seconds (24 hours), the DNS servers which refreshed their Google address at the time window will be kept handing over the invalid information for a long period. To speed things up, in case this problem is affecting your organization, I suggest you clean your DNS server cache. An easy way to do this is by resetting your DNS service.
The problem could have been worse. An attack of this kind has great damage potential for the organization which owns the Internet domain as well as for users that access the address. We list a few example below (none happened this time, though):
The address for which the users are redirected to could infect them with malicious code. This is usually done by advertising a fake software update.
The attacker could have redirected the user’s e-mails for the kidnapped domain to a server under its control and access the content.
By simulating an SMTP/IMAP/IMAPs server, the attackers could have stolen domain user credentials during the authentication attempt.
In case you delegate the task of administering your Internet domains to a third party organization, we recommend you to be sure that they follow access management good security practices for Domain Registry entities, like having the second authentication factor enabled.
For more information regarding domain kidnapping, access the article written by me at the end of the last year, describing a case study through this link.
Someone Hijacking Unsecured MongoDB Databases for Ransom
4.1.2017 thehackernews Hacking
Nearly two years back, we warned users about publicly accessible MongoDB instances – almost 600 Terabytes (TB) – over the Internet which require no authentication, potentially leaving websites and servers at risk of hacking.
These MongoDB instances weren't exposed due to any flaw in its software, but due to a misconfiguration (bad security practice) that let any remote attacker access MongoDB databases without using any special hacking tool.
MongoDB later resolved the issue in the next version of its software by setting unrestricted remote access by default in the configuration, thousands of site administrators have not updated their servers yet.
But trust me, they'll now regret this!
A Hacker is now hijacking and wiping out unsecured MongoDB databases, but keeping a copy of those databases for asking administrators a ransom of 0.2 Bitcoins (nearly US$211) to return the lost data. So, admins without backups are left in a bind.
In fact, the rising price of Bitcoin even hints at some of its troubles. At the time od writing, 1 Bitcoin = USD1063.93.
Security researcher and co-founder of the GDI Foundation Victor Gevers (@0xDUDE) discovered the attacks and notified exposed non-password-protected MongoDB installations to owners via Twitter.
Gevers identified nearly 200 instances of a MongoDB installation that's been erased and held for ransom, while this number reached approximately 2,000 databases as of 4:00 p.m, as reported by John Matherly, the Founder of Shodan, where many exposed MongoDB databases can be found.
These attacks have been going on for over a week, targeting servers all over the world. It is believed that instead of encrypting the data, the attacker who goes by the name "harak1r1," ran a script that replaced the content of the database with the attacker's ransom note.
While accessing one of the open servers, Gevers found that in place of the database content, there is only one table, named "WARNING," which reads:
"SEND 0.2 BTC TO THIS ADDRESS 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq AND CONTACT THIS EMAIL WITH YOUR IP OF YOUR SERVER TO RECOVER YOUR DATABASE !"
16 Victims Already Paid the Ransom
It appears that around 16 organizations so far have paid the ransom to the attacker.
Matherly has been warning of the dangers of exposed MongoDB installations since 2015, allowing an attacker to remotely access the databases over the Internet without the need of any form of authentication.
Matherly said the majority of publicly exposed 30,000 MongoDB instances run on cloud servers such as Amazon, Digital Ocean, Linode, and Internet service and hosting provider OVH and do so without authentication, making cloud services buggier than datacenter hosting.
How to Know if You've Been Hacked?
Check the MongoDB accounts to see if no one added a secret (admin) user.
Check the GridFS to look if someone stored any files there.
Check the log files to see who accessed the MongoDB.
How to Protect Yourself?
Enable authentication that provides you 'Defense in depth' if your network is compromised. Edit your MongoDB configuration file — auth = true.
Use firewalls — Disable remote access to the MongoDB, if possible. Admins are advised to use firewalls to protect the MongoDB installations by blocking access to port no. 27017.
Configure Bind_ip — Limit access to the server by binding local IP addresses.
Upgrade — Administrators are strongly recommended to upgrade their software to the latest release.
MongoDB is the most popular, open-source NoSQL database used by companies of all sizes, from eBay and Sourceforge to The New York Times and LinkedIn. Administrators are encouraged to follow a security checklist provided by the company.
#33C3- Changing travelers flight bookings is really too easy for hackers
2.1.2017 securityaffairs Hacking
Changing travelers flight bookings is too easy. Absolutely astounding the Karsten Nohl research on the insecurity of traveler flight information.
The current travel booking systems is deeply insecure, it lacks of cyber security by design and the notorious hackers Karsten Nohl and Nemanja Nikodijevic have demonstrated it at the 33rd Chaos Communications Congress held in Hamburg last week (“Where in the World Is Carmen Sandiego?”).
The experts explained that it is quite easy to modify any passenger’s reservation, cancel their flight bookings, and even use the refunds to book tickets for themselves.
The security duo has conducted for several months a research on security employed by the Global Distribution Systems (GDSs) that are used by various actors in the travel industry, including airlines, travel agencies, hotels and car rental companies.
Below the video of the presentation held during the 33rd Chaos Communications Congress.
GDSs are enormous archives containing all information about travel bookings, they include so-called Passenger Name Records (PNRs), records include information such as traveler’s name, itinerary, travel dates, ticket details, phone number, email, passport information, credit card numbers, seat numbers and baggage information. Travel data is precious for scammers and phishers that could use them to launch targeted attacks and organize complex frauds.
As explained by the experts the most important GDS operators in the world are Sabre, Travelport, and Amadeus. The disconcerting discovery made by the researcher is that it is possible to add or modify any travel data by accessing the system with a last name and a six-character booking code.
We have to think GDSs as systems accessible from everywhere, access points could be airline websites, travel agencies, and also third-party websites like CheckMyTrip. Every time a travel includes flights with different airlines the booking can be modified through the websites of any of the airlines that operate the trip.
Attackers could cancel a flight, and if the booking allows the change crooks could use the credit given by the airline to book a new ticket.
Unfortunately, the level of protection for the PNR is very poor, the booking code is easy to obtain, it is printed on luggage tags and is also embedded in the QR codes printed on the tickets.
Passengers use to throw away old Boarding Pass even when the overall travel isn’t yet completed, or even worse, they post on social networks the pictures of the tickets.
We explained in the past that Boarding Pass contains personal information that could be exploited by hackers.
The popular investigator Brian Krebs published an interesting post on the topic explaining that a Boarding Pass Barcode contains a lot of data.

Experts highlighted that there is no logging implemented in the GDSs, this means that is impossible to discriminate the accesses.
“In the short term, at the very least we should expect websites that give access to travelers’ personal information to have the bare minimum of web security, and this includes at the very least some rate limiting,” the researcher said. “And until passwords and other security measures become common, I think we have a right to know who accesses our records and there must be some accountability, especially knowing how insecure these systems are today.” explained Nohl.
Karsten Nohl and Nemanja Nikodijevic explained that many airline and trip checking websites don’t limit the number of bad codes users can enter before they’re blocked, opening the door to brute force code-guessing attacks.
The duo demonstrated that it is a question of minutes to find matching booking codes for popular last names by using automated methods. Working with GDSs brute force code-guessing attacks are very easy because the systems use only uppercase letters. The researchers explained that one of GDS analyzed doesn’t use 1 and 0 to avoid confusion with the letters I and O, two other GDSs increase the codes sequentially making easier for an attacker to guess the code withing a sequence.
“The travel agencies have their own master logins into the GDSs and these accounts have very weak passwords. In one case the password was WS, which stands for web service, followed by the date when the login was created in DDMMYY format. This can easily be brute-forced and unfortunately it was one of the most complex travel agency passwords the researchers observed.” reported CSOonline.
The lack of security could be exploited by crooks to add their frequent flier number to other passengers’ long-haul flights in order gain the reward miles for themselves.
As demonstrated by the experts, hackers can do much more than change flight bookings,
Trump will soon reveal the truth about the alleged Russian hacking
2.1.2017 securityaffairs Hacking
President Donald J. Trump is expressing skepticism about intelligence assessments of the Russian hacking and will provide more information very soon.
The executive order issued by President Obama in retaliation of the alleged Russian interference on Presidential Election is raising a heated debate on the on the measures adopted by the US Government and its ability to provide evidence of Russian malicious cyber activities.
The US ejected 35 Russian intelligence operatives from the United States and imposed sanctions on nine entities and individuals.The US Government sanctioned the Russian intelligence services, the GRU (Russian Main Intelligence Directorate) and the FSB (Federal Security Service), four GRU officers, and three other organizations.
The report published by the US Government doesn’t provide any new info, all the information it includes were already reported in the analysis conducted by security firms such as Crowdstrike.
In June, the security research firm CrowdStrike reported on a cyber breach of the Democratic National Committee (DNS). CrowdStrike’s incident response time discovered not one, but two hacking groups that it considers “some of the best adversaries out of the all the numerous nation-state” groups the company encounters daily – COZY BEAR and FANCY BEAR.
This is exactly the same info that we have found in the JAR report published by the US Government that linked the cyber activity to a Russian threat actor designated as GRIZZLY STEPPE.
Security experts at the security firm Wordfence published an interesting report in which they analyzed the PHP malware sample and the IP addresses that the US government has provided as proof the involvement of Russian hackers in the attacks against the Presidential Election.
“We used the PHP malware indicator of compromise (IOC) that DHS provided to analyze the attack data that we aggregate to try to find the full malware sample. We discovered that attackers use it to try to infect WordPress websites. We found it in the attacks that we block.”
Experts from Wordfence traced the malware code to a tool available online, dubbed P.A.S., that claims to be “made in Ukraine.”
“One might reasonably expect Russian intelligence operatives to develop their own tools or at least use current malicious tools from outside sources,” the report says.
The report published by WordFence includes the list of IP addresses that “don’t appear to provide any association with Russia” and “are probably used by a wide range of other malicious actors.”
“The malware sample is old, widely used and appears to be Ukrainian. It has no apparent relationship with Russian intelligence and it would be an indicator of compromise for any website.” reads the report from WordFence.
The IT security industry is aware of the Russian interference, but clearly, the analysis provided by the US Government is really poor of interesting elements.
Which is the position of President-elect Donald J. Trump on the Russian hacking?
We all know that alleged Russian interference aimed to disrupt Clinton’s campaign due to the relationship between Puting and Trump.
President Donald J. Trump is expressing skepticism about intelligence assessments of the Russian hacking and the Kremlin’s interference in the election.
Trump Russian Hacking
According to the NYT, speaking to reporters outside his Palm Beach, Fla., club, Mar-a-Lago on Saturday evening, he revealed to know of “things that other people don’t know” about the alleged hacking campaigns that targeted Presidential Election. Trump announced that he will share the information “on Tuesday or Wednesday.”
“I just want them to be sure because it’s a pretty serious charge,” said Mr. Trump.“If you look at the weapons of mass destruction, that was a disaster, and they were wrong,” he added, referring to intelligence cited by the George W. Bush administration to support its march to war in 2003. “So I want them to be sure,” the president-elect said. “I think it’s unfair if they don’t know.”
“If you look at the weapons of mass destruction, that was a disaster, and they were wrong,” he added, referring to intelligence reports that were provided the George W. Bush administration in 2003. “So I want them to be sure,” “I think it’s unfair if they don’t know.”
“And I know a lot about hacking. And hacking is a very hard thing to prove. So it could be somebody else. And I also know things that other people don’t know, and so they cannot be sure of the situation.”
The Trump’s approach to technology is anachronistic, he advised people to avoid computers when dealing with a delicate material.
“It’s very important, if you have something really important, write it out and have it delivered by courier, the old-fashioned way, because I’ll tell you what, no computer is safe,” Mr. Trump said.
“I don’t care what they say, no computer is safe,” he added. “I have a boy who’s 10 years old; he can do anything with a computer. You want something to really go without detection, write it out and have it sent by courier.”
The only sensible answer to date is that of Russian President Putin who avoided responding Obama executive order.
Hacked Sony Music Entertainment account tweeted about Britney Spears’s Death
27.12.2016 securityaffairs Hacking
Hackers compromised the Sony Music Entertainment Twitter account and posted the messages on Britney Spears’s Death. Experts blame OurMine crew.
Sony Music Entertainment’s Twitter account was compromised and hackers posted the news of the Britney Spears’s death.
“RIP @britneyspears #RIPBritney 1981-2016” and “Britney spears is dead by accident! We will tell you more soon #RIPBritney.” states the messages posted by the hackers.

Sony Music Entertainment quickly deleted the messages and confirmed the hack of its account.
“Sony Music Entertainment’s Twitter account was compromised. This has been rectified,” it said.
“Sony Music apologizes to Britney Spears and her fans for any confusion.”
Separately, the official Twitter account for Bob Dylan featured a tweet that read:
“Rest in peace @britneyspears,” but the message was later deleted.
Adam Leber, a spokesman for the pop star told CNN the news was fake.
“I assume their account has been hacked,” said Spears’ manager, Adam Leber.”I haven’t spoken to anyone… as of yet but I am certain their account was hacked. Britney is fine and well. There have been a few Internet clowns over the years who have made similar claims about her death, but never from the official Sony Music Twitter account.” said the spokesman.
Who is behind the hack?
Security experts suspect the account was hacked by the notorious hacker group OurMine, the same that recently hacked the NetFlix account and the accounts belonging to many Very Important People.
OurMine is a very popular hacker group that hacked multiple high-profile accounts including Mark Zuckerberg, Twitter co-founder Evan Williams, David Guetta Daniel Ek, former Twitter CEO Dick Costolo, the CEO and founder of Spotify, Google CEO Sundar Pichai, and many others.
The group uses to hack the accounts to demonstrate the poor security, then it offers its consultancy to prevent future attacks.
Two Tweets posted by the hacked Sony Music Entertainment’s Twitter account suggest the involvement of the OurMine Team:
“We detected unusual activity on the account and we checked the account if it’s hacked or not”, states one Tweet, followed by, “we saw a new IP logged in to the account a few minutes ago and the tweet is posted by a new IP so @britneyspears is still alive #OurMine”.

Hacked Sony Music Entertainment account
This isn’t the first time hackers target Sony, in November 2014 the hacking group known as GOP broke into the company systems and stole sensitive information, including employees data.
The FBI blamed the North Korea for the cyber attack.
Cryptolulz666 hacked the Dutch Chamber of Commerce in HK
26.12.2016 securityaffairs Hacking
@Cryptolulz666 and his colleague Kapustkiy broke into the systems of another website belonging to a HK corporation, the Dutch Chamber of Commerce.
The hacker @Cryptolulz666, with a little help from the colleague Kapustkiy, has broken into the website of the Dutch Chamber of Commerce in Hong Kong (http://www.dutchchamber.hk/).
The hacker accessed data belonging to around 200 users, but he decided to leak only half of them as proof of the hack.
Cryptolulz666 told me he exploited a SQL injection vulnerability affecting the website.
A few days ago, he hacked “The Standard Hong Kong” newspaper, he confirmed me that his choice is not casual, he wants to target organizations in Hong kong.
“Yes … As you seen in the previous hack I chose a big corporation in Hong kong and I succeded… this time also chose Hong Kong because I want to make an impact on this country.” he told me. ” no country is safe”
He highlighted the fact that a silly flaw like a SQL Injection could have serious consequences if admins ignore the pillars of security.
Data leaked on Pastebin includes data related to companies working with the Dutch Chamber of Commerce.
Cryptolulz ( @Cryptolulz666) is a former member of the Powerful Greek Army, who hacked several government websites, including the one of the Russian embassy of Armenia (www.embassyru.am).
He also launched DDoS attacks against the website http://italiastartupvisa.mise.gov.it/ belonging to the Italian Government and the website of the Russian Federal Drug Control Service liquidation commission.
Merry Xmas, @Kapustkiy hacked Russian Visa center in USA
25.12.2016 securityaffairs Hacking
The notorious white hat hacker Kapustkiy hacked the Russian Visa Center in the USA and accessed information of around 3000 individuals.
The Russian Visa Center is an organization that helps Americans to obtain Russian Visa, this morning the white hat hacker Kapustkiy informed me that he broke into the database its website and accessed data of around 3000 individuals.
Kapustkiy told me to have exploited a SQL Injection in the website, he hacked the website on Friday.
“I used SQL Injection to gain access” said Kapustkiy.
He shared with me the records as proof of the hack, the leaked information include data about individuals that obtained the Russian Visa.

The Russian Visa Center is part of Invisa Logistic Services, it has five offices in the US where people can receive assistance in getting a Russian visa.
The records include their full names, emails, phone numbers, birthday and other information. The archive also includes data of the staff, such as full names, usernames, encrypted passwords, permissions and other information.
Kapustkiy will not make public the accessed data because the database contains sensitive information,
The young hacker contacted the Russian Visa Center but hasn’t received any response, he also reported the issue to the US-CERT.
The young hacker is very active, a few days ago he announced the hack of website of the Costa Rica Embassy in China and the data breach of the Slovak Chamber of Commerce (www.scci.sk) that affected more than 4,000 user records.
Recently Kapustkiy targeted several organizations, including the Consular Department of the Embassy of the Russian Federation, the Argentinian Ministry of Industry, the National Assembly of Ecuador, the Venezuela Army, the High Commission of Ghana & Fiji in India, the India Regional Council as well as organizations and embassies across the world.
He also broke into the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
Phantom Squad and PoodleCorp tango down against Steam and Origin Servers
24.12.2016 securityaffairs Hacking
The servers of the Steam gaming platform and Origin are down. Phantom Squad and PoodleCorp are claiming responsibility for the attacks.
It’s holiday time and hackers can transform this period in a nightmare for gamers. Two years ago Lizard Squad hackers took down the networks of Sony PSN and Microsoft XBox Live.
Now the notorious Phantom Squad group has claimed responsibility for conducting a series of massive DDoS attacks against the online gaming platform Steam and Origin servers.
According to HackRead, Phantom Squad and one of the members of the PoodleCorp hacker crew, @cripthepoodle, are targeting Steam and Origin accounts.
One year ago, Phantom Squad launched several cyber attacks against Electronic Arts and Steam last year. PoodleCorp hacker group became famous due to a long string of attacks against gaming communities, including Blizzard, EA, GTA, PlayStation, PokemonGo, and League of Legends.
At the time I was writing, both companies haven’t confirmed the attacks against their systems. Some users are reporting problems to both via Twitter.
Below one of the numerous tweets from affected users:
22 Dic
Steam ✔ @steam_games
Steam Winter Sale On Now! Plus, Vote For The Steam Awards! #SteamSale #SteamAwards http://zpr.io/PGkCe pic.twitter.com/T3iqTvsPgI
Segui
René | 2 Days ^-^ @DafuqRene
@steam_games Nice Sale, I love it! #SteamSale pic.twitter.com/RshEFsBBDk
20:14 - 22 Dic 2016
13 13 Retweet 80 80 Mi piace
The Down Detector service that provides information about the status of services confirmed that both EA and Steam platforms were down at the time I was writing.
The hackers started the DDoS attack on Steam servers causing serious problems to the gaming servers across the world. Steam operates about 17 regional servers, all its activities including the Steam community and the Steam Store are down, this means that users are not able to buy Steam games for Christmas.

Stay Tuned …
Update
Steam services are back up now
Hackers threaten to take down Xbox Live and PSN on Christmas Day
24.12.2016 thehackernews Hacking
It's once again the time when most of you will get new PlayStations and XBoxes that continue to be among the most popular gifts for Christmas, but possibilities are you'll not be able to log into the online gaming console, just like what happens on every Christmas holidays.
On 2014 Christmas holidays, the notorious hacker group Lizard Squad knocked the PlayStation Network and Xbox Live offline for many gamers by launching massive DDoS attacks against the gaming networks.
This time a new hacking group, who managed to take down Tumblr this week for almost two hours, has warned gamers of launching another large-scale distributed denial-of-service (DDoS) attack against XBox Live and PlayStation networks.
Calling itself R.I.U. Star Patrol, the hacking group, posted a video on YouTube, announcing that they’re planning to take down Sony’s PSN and Microsoft’s Xbox Live on Christmas Day by launching coordinated DDoS attacks.
"We do it because we can," the group said. "We have not been paid a single dollar for what we do."
On Wednesday, when R.I.U. Star Patrol took down Tumblr, the group contacted Mashable and explained its reason for attacking: "There is no sinister motive. It’s all for light hearted fun."
Neither Sony nor Microsoft has yet responded to the hackers' warning.
However, both Sony and Microsoft previously promised to enhance the protection of their systems to block any attack disrupting their networks, but downtime and short outages happened almost every Christmas time.
Knowing the current abilities of hackers to launch DDoS attack that can reach 1 Tbps, it goes without saying that both the companies should be prepared to see DDoS attacks targeting its servers on this Christmas that can go beyond their expectations.
We saw coordinated DDoS attacks against DNS hosting provider Dyn last fall that broke large portions of the Internet, causing a significant outage to a ton of websites and services, including Twitter, GitHub, PayPal, Amazon, Reddit, Netflix, and Spotify.
The massive DDoS attack was launched just by a botnet of an estimated 100,000 so-called Internet of Things (IoT) – everyday devices and appliances that are connected to the web – that closed down the Internet for millions of users.
So, it remains to be seen if gamers would be able to enjoy this Christmas or not.
Hackers breached the “The Standard Hong Kong” newspaper
24.12.2016 securityaffairs Hacking
The hacker @Cryptolulz666 and his colleague @EvoIsGod have broken into the website of the Hong Kong English newspaper “The Standard Hong Kong” (www.thestandard.com.hk)
The hackers breached the database of the website and uploaded data to Pastebin.
I reached the hackers who confirmed to have hacked the website by exploiting a SQL Injection flaw in their CMS.

The hackers posted only a small portion of around 12000 users contained in the database.
“Most of the info is not dumped due to legal stuffs. It had around 12000 users but I dumped only quarter” wrote the hackers on Pastebin.
The hackers leaked the tables of the Customers and Employees.
According to @Cryptolulz666, most of the information in the database is quite confidential and should not be leaked for privacy reason.
When I asked them about the motivation of the attack they told me that their goal is to spread awareness of cyber security.
“Our objective is to embarrass the institutions… by exploiting their silly flaws…” they told me. “As I said we exploited a SQL injection vulnerability on their main website.”
Cryptolulz ( @Cryptolulz666) is a former member of the Powerful Greek Army, who hacked several government websites, including the one of the Russian embassy of Armenia (www.embassyru.am).
He also launched DDoS attacks against the website http://italiastartupvisa.mise.gov.it/ belonging to the Italian Government and the website of the Russian Federal Drug Control Service liquidation commission.
Hackers want to take down Xbox Live and PSN on Christmas Day
24.12.2016 securityaffairs Hacking
Christmas time is a critical period for the gaming industry that is threatened by hackers that want to paralyze their services with massive attacks.
Yesterday I reported the DDoS attacks launched by Phantom Squad and PoodleCorp against Steam and Origin Servers, and unfortunately they are not alone.
Hackers threaten to take down Xbox Live and PSN on Christmas Day, and we know that someone already done is in the same period two years ago when Lizard Squad hackers took down the networks of Sony PSN and Microsoft XBox Live.
Which are the risks for gamers?
People that will buy or will receive new PlayStation and XBoxe consoles will not be able to log into the online gaming console, it will be not possible to download and buy online games, neither play online with other gamers.
Now a hacker group that called itself R.I.U. Star Patrol (StarPatrolling) posted a video on YouTube, announcing that they will take down Xbox Live and PSN on Christmas Day with a massive DDoS attack.
The threat is considered credible, the same group managed to take down Tumblr this week for two hours.
“We do it because we can,” the group said. “We have not been paid a single dollar for what we do.”
Segui
R.I.U. Star Patrol @StarPatrolling
@mashable We are claiming responsibility for the Tumblr outage #StarPatrol
23:14 - 21 Dic 2016
1 1 Retweet 2 2 Mi piace
Just after the attack, the hackers released an interview with Mashable and motivated the attack with the following statement.
“There is no sinister motive,” they replied when asked for the cause of the attacks.”It’s all for light hearted fun.”
Via DM, the group told Mashable the DDoS attack wasn’t meant to harm anyone.
Xbox Live and PSN networks were both target in the past by hacker so they worked to improve their defense anyway recent attacks powered by the Mirai botnet demonstrated that it could be quite simple for hackers to take down major web services.
Signal implements ‘domain fronting’ technique to bypass censorship
23.12.2016 securityaffairs Hacking
The latest update of Signal introduces the ‘domain fronting’ technique that has been implemented to circumvent censorship.
Signal is considered the most secure instant messaging app, searching for it on the Internet it is possible to read the Edward Snowden’ testimony:
“Use anything by Open Whisper Systems” Snowden says.
The Cryptographer and Professor at Johns Hopkins University Matt Green and the popular security expert Bruce Schneier are other two admirers of the Signal app.
The latest update of Signal has just been developed to implement mechanisms to circumvent censorship and restrictions applied by governments that want to avoid its use.
Some states are already blocking the application with the support of ISPs. The Government of Egypt and the United Arab Emirates applied measures to block Signal, for this reason, the Open Whisper Systems who develop the app has revised the Android version introducing a technique called domain fronting.
“With today’s release, domain fronting is enabled for Signal users who have a phone number with a country code from Egypt or the UAE,” said company founder Moxie Marlinspike in a blog post. “When those users send a Signal message, it will look like a normal HTTPS request to www.google.com. To block Signal messages, these countries would also have to block all of google.com.”
The domain fronting is a technique that relies on the use of different domain names at different application layers to evade censorship.
The domain fronting techniques “hides the remote endpoint of a communication. Domain fronting works at the application layer, using HTTPS, to communicate with a forbidden host while appearing to communicate with some other host, permitted by the censor,” as described in a paper published by researchers from the University of California, Berkeley, Psiphon, and Brave New Software.
“The key idea is the use of different domain names at different layers of communication. One domain appears on the “outside” of an HTTPS request—in the DNS request and TLS Server Name Indication—while another domain appears on the “inside”—in the HTTP Host header, invisible to the censor under HTTPS encryption.” continues the paper.”A censor, unable to distinguish fronted and nonfronted traffic to a domain, must choose between allowing circumvention traffic and blocking the domain entirely, which results in expensive collateral damage”
The Domain fronting technique is easy to deploy and use and doesn’t require special activities by network intermediaries.
If the front domain is a popular website like ‘google.com, if the censor will block it would have a serious impact on the users.
Domain fronting has a cost.
Domain fronting leverages a CDN that have to receive the request and forward it to the domain in the HTTP host header, or a service that provides similar functionality, like Google’s App Engine.
Such services typically have a cost that according to the paper ranges from $0.10–0.25 per GB using a service like Google App Engine, Amazon CloudFront, Microsoft Azure, Fastly, and CloudFlare. This may explain why Signal isn’t making domain fronting a default everywhere.
Due to this cost, Signal isn’t providing domain fronting by default.
What about domain fronting for the iOS version of Signal?
Marlinspike confirmed that an iOS version of Signal that supports domain fronting is expected soon, meantime it is available a beta version.
Kapustkiy hacked the website of the Costa Rica Embassy in China
22.12.2016 securityaffairs Hacking
The popular hacker Kapustkiy continues to target websites of embassies across the world, the last victim is the Costa Rica Embassy in China.
The hacker Kapustkiy continues its string of hack, today he announced a news data breach, the victim is the Costa Rica Embassy in China.
Kapustkiy accessed a database containing 280 login credentials, but just published online 50 of them as a proof of the attack. Just after the attack, the Costa Rica Embassy in China, costaricaembassycn.com, was not reachable.

The website has 280 user entries, it was running on a WordPress platform and after a few tests, the hacker discovered that it was affected by several SQL Injection flaws.
“The first thing I did was to start the exploitation of a SQL vulnerability I have discovered.” said Kapustkiy. “Then I tried brute force and I got a huge list of users”
“I have published around 50 users, the rest is private”
The hacker, who discovered 4 databases in the hack, leaked data belonging to Costa Rica Embassy in China at the following URL:
http://pastebin.com/hEWsuaq2
Leaked records include IDs, emails, and encrypted passwords. Kapustkiy confirmed me that he has reported the vulnerability to the CNCERT/CC and to the website administrator.
The young hacker is very active, a few days ago he announced the data breach of the Slovak Chamber of Commerce (www.scci.sk) that affected more than 4,000 user records.
Recently Kapustkiy targeted several organizations, including the Consular Department of the Embassy of the Russian Federation, the Argentinian Ministry of Industry, the National Assembly of Ecuador, the Venezuela Army, the High Commission of Ghana & Fiji in India, the India Regional Council as well as organizations and embassies across the world.
He also broke into the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
A curiosity, in the manifesto published on PasteBin the hacker wrote
“A SQL Weapon is the most dangerous weapon on the Internet”
and the facts seem to confirm it.
Hackers Suspected of Causing Second Power Outage in Ukraine
21.12.2016 thehackernews Hacking
The same group of hackers that caused the power outage across several regions in Ukraine last Christmas holidays might have once again shut down power supply in northern Ukraine during the weekend.
According to Ukrainian energy provider Ukrenergo, a cyber attack on Kyiv's power grid may have caused the power outages in the country on Saturday, December 17, near midnight.
The blackout affected the northern part of Kiev, the country's capital, and surrounding areas, Ukrenergo Director Vsevolod Kovalchuk explained in a post on Facebook.
Shortly after the incident, Ukrenergo engineers switched to manual mode and started restoring power in approximately 30 minutes in an effort to deal with the cyber attack. Power was fully restored after just an hour and fifteen minutes of the blackout.
According to Kovalchuk, the one responsible for the weekend outage could be an "external interference through data network," however, the company's cybersecurity experts are investigating the incident and will provide more information soon.
Although the reason for the outage is not yet confirmed, authorities believe that the unexpected power outage could be the latest in the series of cyber attacks that managed to strike the Ukrainian electric grid and financial infrastructure in December 2015.
The 2015 energy blackouts were caused with the help of a malware attack, known as BlackEnergy, which was distributed through boobytrapped Word documents and tricked recipients into enabling macros to activate the malicious payload.
Last year, the Ukraine's state security service SBU blamed Russia for causing outages by planting malware on the networks of several regional energy companies.
Also, the United States Cyber firm iSight Partners identified the perpetrator as a Russian group of hackers known as "Sandworm."
While security experts have found no hard evidence that links these attacks on Ukrainian energy grid to Russia, they believe that the attackers appear to be a nation state with significant resources.
SCADA system has always been an attractive target for cybercrooks, given the success of Stuxnet malware that was developed by the US and Israeli together to sabotage the Iranian nuclear facilities a few years ago, and "Havex" that previously targeted organizations in the energy sector.
How to hack Panasonic In-Flight Entertainment IFE Systems
21.12.2016 securityaffairs Hacking
A researcher at IOActive disclosed several vulnerabilities found in Panasonic Avionics in-flight entertainment, aka IFE systems.
The in-flight entertainment (IFE) and communications systems manufactured by Panasonic Avionics are among the most common components in the aviation industry.
According to data provided by the company, it has delivered more than 8,000 in-flight entertainment and communications systems and 1,300 in-flight connectivity solutions to major airlines.
Older models of Panasonic IFE systems (e.g. 3000/3000i) rely on Linux, but the newer ones belonging to the X Series products run on Android OS.
The security of IFE systems is crucial, the Panasonic Avionics recently launched a private bug bounty program offering rewards ranging between $100 and $10,000 to the participants.
Main components of the IFE systems are:
The seat display unit (SDU) that an embedded device that allows passengers to watch movies and connect to the Internet via a touchscreen. Sometimes the SDU is also equipped with a personal control unit (PCU).
The cabin crew panel that controls lights and other features of the aircraft.
The system control unit (SCU) is the server that provides flight information, and other features such as on-board shopping capabilities.
IFE systems
Ruben Santamarta, a security researcher from IOActive decided to participate the bug bounty program. He analyzed the latest firmware updates for the IFE systems used by major airlines, including Emirates, Air France, United, American, KLM, Scandinavian, Aerolineas Argentinas, Virgin, Iberia, Singapore, FinnAir, Qatar, and Etihad.
Santamarta found several flaws in the firmware updates, including a SQL Injection flaw and a bug that allows bypassing credit card checks.
Below the video PoCs published by the researcher that demonstrate how to bypass credit card checks, to trigger arbitrary file access issues and a SQL injection flaw. In the video the hacker interacted with the IFE systems using the touchscreen and PCU.
According to Santamarta, the hack of the IFE system could allow the attacker to interfere with flight operations and to steal sensitive information. It is important to highlight that if the IFE system is physically separated from aircraft control system, such kind of attacks will have no impact on the flight safety.
“On the IT side, compromising the IFE means an attacker can control how passengers are informed aboard the plane. For example, an attacker might spoof flight information values such as altitude or speed, and show a bogus route on the interactive map. An attacker might compromise the CrewApp unit, controlling the PA, lighting, or actuators for upper classes. If all of these attacks are chained, a malicious actor may create a baffling and disconcerting situation for passengers.” reads the analysis published by IOActive.
“The capture of personal information, including credit card details, while not in scope of this research, would also be technically possible if backends that sometimes provide access to specific airlines’ frequent-flyer/VIP membership data were not configured properly.”
Unfortunately, in some cases, the lack of a physical separation between IFE systems and control systems could allow an attacker to threaten the flight safety.
“In some scenarios such an attack would be physically impossible due to the isolation of these systems, while in other an attack remains theoretically feasible. The ability to cross the ‘red line’ between the passenger entertainment and owned devices domain and the aircraft control domain relies heavily on the specific devices, software and configuration deployed on the target aircraft,” Santamarta added.
IOActive reported these findings to Panasonic Avionics in March 2015, but there is no information about their fix.
Hacker Demonstrates How Easy In-flight Entertainment System Can Be Hacked
21.12.2016 thehackernews Hacking
Next time when you hear an announcement in the flight, “Ladies and gentlemen, this is your captain speaking…," the chances are that the announcement is coming from a hacker controlling your flight.
Dangerous vulnerabilities in an in-flight entertainment system used by the leading airlines, including Emirates, United, American Airlines, Virgin, and Qatar, could let hackers hijack several flight systems and even take control of the plane.
According to security researchers from IOActive, the security vulnerabilities resides in the Panasonic Avionics In-Flight Entertainment (IFE) system used in planes run by 13 major airlines, providing a gateway for hackers which is absolutely terrifying.
The security holes could be exploited by hackers that could allow them to spoof flight information like map routes, speed statistics, and altitude values, and steal credit card information.
IOActive's Ruben Santamarta managed to "hijack" in-flight displays to change information like altitude and location, control the cabin lighting, as well as hack into the announcements system.
"Chained together this could be an unsettling experience for passengers," said Santamarta. "I don't believe these systems can resist solid attacks from skilled malicious actors. This only depends on the attacker's determination and intentions, from a technical perspective it's totally feasible."
Besides these critical issues, the researcher said in some instances; hackers could access credit card details of passengers stored in the automatic payment system and use their frequent flyer membership details to capture personal data.
The vulnerabilities affect 13 different airlines that use Panasonic Avionics system, which include American Airlines, United, Virgin, Emirates, Etihad, Qatar, FinnAir, KLM, Iberia, Scandinavian, Air France, Singapore, and Aerolineas Argentinas.
The vulnerabilities were reported to Panasonic in March last year, and the researcher waited more than a year and a half to go public, so the company had "enough time to produce and deploy patches, at least for the most prominent vulnerabilities."
Emirates is working with Panasonic to resolve these issues and regularly update its systems. "The safety of our passengers and crew on board is a priority and will not be compromised," Emirates said, reported the Telegraph.
Santamarta is the same researcher who warned of security issues in systems used by different aircraft in the past.
Back in 2014, he discovered that it was possible to reverse engineer a bug, which let him connect to the Wi-Fi signal or the in-flight entertainment system to connect to airplanes’ equipment, including the navigation system.
For in-depth technical details about the new vulnerabilities discovered by Santamarta, you can head on to IOActive's official blog post published today.
A new Ukraine power outage may have been caused by hackers
20.12.2016 securityaffairs Hacking
A cyber attack against the Government Ukraine energy company Ukrenergo may be the root cause of power outage that occurred in Ukraine late on Saturday.
A new cyber attack may be the root cause of power outage that occurred in Ukraine late on Saturday.
According to the Ukraine energy company Ukrenergo, the power outage occurred at the midnight between Saturday and Sunday, the problems affected the”North” substation at Petrivtsi.
The incident caused blackouts in the city of Kiev and neighboring regions.
The company published an official statement to announce the power outage, unfortunately at the time I was writing the website of the Government Ukraine energy company Ukrenergo is down.
The head of the NEC “Ukrenergo” Vsevolod Kovalchuk explained in a message posted on Facebook that experts at the company were able to restore power in 30 minutes with a manual procedure. According to Kovalchuk, the operations were fully restored after just over an hour.
“Our experts quickly switched the equipment into the manual mode and already after 30 minutes began restoring power. In one hour and fifteen minutes power was fully restored,” he wrote.
“For the time being, the main version is the external interference through the data network. Our experts in cybersecurity promise to provide a report in the near future,” he added.
Kovalchuk pointed out that an equipment malfunction or a cyber attack can be the cause of the problem. According to Kovalchuk, an “external interference through the data network” could have caused the power outage.
The experts at Ukrenergo are investigating the power outage.
Of course, the incident brought to mind the power outage that occurred in December 2015 in Ukraine. The Ukrainian security service SBU and several security experts accused Russia of causing outages.
According to a report published by Booz Allen Hamilton, the attacks that caused the power outage in Ukraine were part of a huge hacking campaign that targeted across the years the critical infrastructure of the country.
Experts at eiSight Partners speculated that the Russian Sandworm APT group was responsible for the Ukrainian power outage.
Alleged Russian state-sponsored hackers have used the BlackEnergy malware alongside with a DDoS attack to compromise the power plants in Ukraine and delay restore operations.
In 2015 power outage, Ukrainian experts were able to restore service within 3-6 hours with manual operations.
Kapustkiy hacked the Slovak Chamber of Commerce
19.12.2016 securityaffairs Hacking
Kapustkiy announced the data breach of the Slovak Chamber of Commerce (www.scci.sk), more than 4,000 users record were accessed.
New Week, new hack! This is Kapustkiy ‘s motto that announced the breach of the Slovak Chamber of Commerce (www.scci.sk). The popular hacker accessed data belonging to more than 4,000 users and published it on Pastebin.
The hacker exploited an SQLInjection vulnerability, the archive contains users’ data including real names, email addresses, phone numbers and encrypted passwords.
Kapustkiy told me that there is no specific reason for the choice of this specific target, he was just searching for a government website while scanning the Internet.
“I breached this target because it is related to the Government its funny to see how bad their security is.” he told me.
He added to have hacked the website to make awareness and push admis to adopt a better security posture to protect their users.
“My motivation is to let admins see the consequence of a data breach.” said Kapustkiy. “And understand the danger.”

The hacker tried to report the issue to the admins two days ago, but he received no response.
Kapustkiy also told me that he joined the New World Hackers team.
“I work as Researcher and Pentester there” he told me.
Recently Kapustkiy targeted several organizations, the last in order of time is the Consular Department of the Embassy of the Russian Federation.
Kapustkiy also has breached the Argentinian Ministry of Industry, the National Assembly of Ecuador, the Venezuela Army, the High Commission of Ghana & Fiji in India, the India Regional Council as well as organizations and embassies across the world.
He also broke into the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
Russian hacker Rasputin allegedly stole logins from the US election agency EAC
19.12.2016 securityaffairs Hacking
The Russian-speaking hacker Rasputing was attempting to sell the allegedly stolen login credentials from the US Election Assistance Commission (EAC).
According to the security firm Record Future, a Russian-speaking hacker was offering for sale stolen login credentials for a U.S. agency that tests and certifies voting equipment, the U.S. Election Assistance Commission (EAC).
The EAC Agency was formed in 2002, it is tasked of certifying voting systems and developing best practices for administering elections.
More than 100 allegedly compromised U.S. Election Assistance Commission login credentials were offered for sale by a hacker that uses the Rasputin online moniker.
“On December 1, 2016, Recorded Future threat intelligence technology identified chatter related to a suspected breach of the U.S. Election Assistance Commission (EAC).” Record Future said in a Thursday blog post.
“Further research identified a Russian hacker (Recorded Future refers to this actor as Rasputin) soliciting a buyer for EAC database access credentials.”
Researchers discovered that some of these credentials included the highest administrative privileges that could be used by an attacker to steal sensitive information from the U.S. Election Assistance Commission or deploy an Exploit kit to compromise targeted individuals in a watering hole attack.
Recorded Future shared multiple screenshots that demonstrate the hacker had access to the system at the U.S. Election Assistance Commission.

Election and software systems test reports (image provided by Rasputin).
The Rasputin hacker claimed to have broken in the system via an unpatched SQL injection (SQLi) vulnerability.
The U.S. Election Assistance Commission (EAC) investigated the incident with authorities and has terminated access to the vulnerable application.
“The U.S. Election Assistance Commission (EAC) has become aware of a potential intrusion into an EAC web-facing application. The EAC is currently working with Federal law enforcement agencies to investigate the potential breach and its effects.” reads a statement issued by the Agency.
The Election Assistance Commission clarified that it does not administer elections.
“The EAC does not maintain voter databases. The EAC does not tabulate or store vote totals,” added the commission.
The discovery of this new data breach raises the debate around possible interference with 2016 Presidential. The US Government blamed the Russia for attempted to influence the U.S. election through several high-profile cyber attacks.
Who is the Rasputin hacker?
Record Future has been following Rasputin since 2015, according to the security firm he may also have tried to sell details about the SQL injection to a broker working on behalf of a Middle Eastern government.
Based on Rasputin’s historical criminal forum activity, the experts exclude he is sponsored by a foreign government.
Now the important question is how long the flaw remained unpatched and who exploited it too.
Indian Institute of Technology Kharagpur hacked by Cryptolulz666
19.12.2016 securityaffairs Hacking
Cryptolulz666 announced another data breach, he hacked the database of the Indian Institute of Technology Kharagpur, the second of the country.
Just after 24 hours of the hack of the Indian Institute of Technology – IIT Bombay, Cryptolulz666 notified me another data breach, he hacked the database of the Indian Institute of Technology Kharagpur, the second of the country.
Cryptolulz666 broke into the database of the Indian Institute of Technology Kharagpur and accessed users data, including emails, passwords, phone numbers, and security questions.
The hacker told me to have accessed data belonging to 12000 plus users, but as proof of the hack, he leaked only a small portion of them on Pastebin.

When I asked more details about the data breach he told be that he found a SQL injection flaw in the website.
“In this hack, I triggered an error based SQL injection… and I leaked the data on Pastebin” the hacker told me.
The database contains had around 12555 users but I just leaked even less than a quarter of it as the institution might get sued on this info disclosure.
Once again the hacker highlights the lack of security of the organizations. His intent is creating awareness amongst the authorities.
“If you make a website to you definitely have to protect it on every aspect.” he added.
Cryptolulz666 explained that many hackers would love to get their hands on such kind of data so it is important to address these flaws before them.
Last week Cryptolulz666 broke into the database of the website of Russian embassy of Armenia (www.embassyru.am) and leaked data. The hacker also launched DDoS attacks against a Russian and Italian Government websites.
Hacking1
Cryptolulz666 hacked the Indian Institute of Technology – IIT Bombay
18.12.2016 securityaffairs Hacking
Cryptolulz666 is once again in the headlines, this time he hacked the Indian Institute of Technology – IIT Bombay, one of the best Indian colleges.
Cryptolulz666 is back, now he hacked the Indian Institute of Technology – IIT Bombay, one of the best Indian colleges, that has a current world rank of 200.
The hacker broke into the database of the college and leaked on Pastebin its database containing 54 tables.
The hacker told me to have used Blind SQL Injection attack, he sent an email to the admins, but he did not receive any response yet.
The motivation of the hack is the intent of creating awareness of cyber security. It is curious that one of the Top 200 colleges of the world has a so low level of security.

Cryptolulz666 also told me that the site of the IIT Bombay is also affected by a cross-site scripting flaw.
Cryptolulz666 told me that this attack has a special meaning for him.
“I am an Indian guy passionate about cyber security. This hack is very important for me because I spent my entire life in dreaming to be accepted at the IIT Bombay.
I’m so young, but I was enough skilled to broke into one of the most prestigious college in India and all over the world.” Cryptolulz666 told me.
This week Cryptolulz666 broke into the database of the website of Russian embassy of Armenia (www.embassyru.am) and leaked data. The hacker also launched DDoS attacks against a Russian and Italian Government websites.
Cryptolulz666 continues targeting Government websites with DDoS
16.12.2016 securityaffairs Hacking
Cryptolulz666 is back targeting government websites to demonstrate that it is very simple for hackers to bring down them with DDoS attacks.
A few days ago a reported the attack conducted by the black hat hacker Cryptolulz ( @Cryptolulz666), a former member of the Powerful Greek Army, who hacked the website of Russian embassy of Armenia (www.embassyru.am). He hacked the website of Russian embassy of Armenia to create awareness amongst the authorities, the hacker confirmed me that he used a blind SQL Injection vulnerability.
Now Cryptolulz is back, he wanted to demonstrate that it is very simple for hackers, even small groups, to launch a massive DDoS attack against any target.
Yesterday he first launched a DDoS attack against the website http://italiastartupvisa.mise.gov.it/ belonging to the Italian Government.
It was just testing his own botnet, then later he targeted the website of the Russian Federal Drug Control Service liquidation commission.
The Russian website was down for several hours.
When I asked a comment he told me:
“from my perspective…. this is just low security, and for a government, it’s quite bad” said Cryptolulz666
He confirmed me to be a youngster with a great passion for cyber security that aims to spread awareness on the risks.
He launched a DDoS attack leveraging on the NetBIOS amplification technique. NetBIOS is a protocol used in computer software to allow applications to talk to each other via LAN networks.
“A NetBIOS NBSTAT query will obtain the status from a NetBIOS-speaking endpoint, which will include any names that the endpoint is known to respond to as well as the device’s MAC address for that endpoint. A NBSTAT response is roughly 3x the size of the request, and because NetBIOS utilizes UDP, this can be used to conduct traffic amplification attacks against other assets, typically in the form of distributed reflected denial of service (DRDoS) attacks.” states Rapid7.
The hacker scanned roughly 10 % of the Internet searching for potential bots to use in the attack and he found 2 million bots.
“which is pretty perfect for amp vectors..” he told me.
He confirmed me to have shut down the site of the Russian government with a single shot and maintained it down for hours.
In this specific attack he other two spoofing server in order to guarantee a stable malicious traffic against the target, and he made this with python scripts.
“I used another two spoofing servers to launch dos attacks with my self-coded python scripts.” he added.I did it to create awareness among the authorities and users of the website.
I did it to create awareness among the authorities and users of the website.
He confirmed me that he will target other government websites in next attacks, always for the same reason.
“you see the government don’t care about security so we gonna exploit it hard.” added Cryptolulz666
Cryptolulz hacked the website of the Russian embassy of Armenia
15.12.2016 securityaffairs Hacking
The black hat hacker Cryptolulz broke into the database of the website of Russian embassy of Armenia (www.embassyru.am) and leaked data.
The black hat hacker Cryptolulz, a former member of the Powerful Greek Army, hacked the website of Russian embassy of Armenia (www.embassyru.am).
“I would like to tell you that I have successfully penetrated the site” Cryptolulz told me via Twitter. “I have taken over its database”

He exploited a blind SQL Injection vulnerability, he hacked the website of Russian embassy of Armenia to create awareness amongst the authorities.
“because I don’t think they care much about security … lol”
The hacker tried to contact the admins of the website some time ago, but he hasn’t received any response.
“I left them an email but no reply so I decided to leak a short amount of their database…” he added.
He broke into the database a0014414_embassy that contains 36 tables, but the hacker leaked only the “user” table which contains the credentials for the admin, the editor and other people in the stuff. He avoided disclosing the members’ records because they may include classified information.
Data was published on Pastebin, leaked records include id, name, type, email, login, password, last visit IP address, last visit date, profile creation date.
Cryptolulz was involved in several data leaks of government websites, including the Mexican telecommunication website and several DDoS attacks against government website and banks. He defined its motivation as “politically driven hacking.”
My reason for targeting this website was to create awareness amongst the people and higher authorities… because I don’t think they
Cryptolulz now joined a new hacking team called Fallensec.
Expedia Hacked By Its Own Employee, a case study
14.12.2016 securityaffairs Hacking
The Expedia employee, John Ly, is accused of hacking into executives computers to access corporate confidential information.
Its no secret, cyber criminals are constantly looking towards greener pastures – money green that is. The most sought pastures…. insider trading and market manipulation. It’s a perfect storm scenario with almost everyone losing but the hacker. Luckily regulators are very well aware, dedicating massive resources to detect and deter such fraud. A recent case pursued by the SEC paints a small picture of how these frauds are evolving. It also demonstrates their determination in pursuing these cases.
Last week the SEC published the results of its investigation against one of Expedia IT specialists. The employee, John Ly, is accused of hacking into executives computers to access corporate confidential information.
Over a 3 year span from 2013 to 2016, Ly was able to exploit his managerial role, access privileges and credentials to hack executives’ computers which contained unreleased financial reports that included earnings and market reaction opinions. All cyber criminals wear cloaks, usually multiple cloaks – when those criminals are employees their concealment can be misleading.
In this particular case, the Expedia employee attempted to mask himself by using stolen credentials and passwords belonging to other employees. The earnings reports that were obtained were then used to trade on, prior to their release. In all, Ly was able to execute a total of 9 trades, most under 50k, and the largest at almost 120k, netting him an approximate profit of 350k. A nice pay day for 3 years of work, but pretty minuscule in the grand scheme of things. When the scheme was eventually discovered (by Expedia), they immediately reported it to the FBI. After
All cyber criminals wear cloaks, usually multiple cloaks – when those criminals are employees their concealment can be misleading. In this particular case, Ly attempted to mask himself by using stolen credentials and passwords belonging to other employees. The earnings reports that were obtained were then used to trade on, prior to their release. In all, Ly was able to execute a total of 9 trades, most under 50k, and the largest at almost 120k, netting him an approximate profit of 350k. A nice pay day for 3 years of work, but pretty minuscule in the grand scheme of things. When the scheme was eventually discovered (by Expedia), they immediately reported it to the FBI. After an SEC investigation, Ly was ultimately charged with violating rule 10-b and 17-a of the SEC Act.
This is not the first case of cyber-related insider trading/market manipulation. The largest case of its kind was a large scale breach committed by FIN4 which saw a team of foreign hackers accessed corporate nonpublic information from sites like PRNewswire.
Those reports were then traded on through a systematic network, prior to release, for an estimated profit 100 Mill. In a separate attack, hackers were able to employ a targeted spear phishing campaign to access (and weaponize) information on upcoming mergers. This case does, however, contain some unique characteristics. It is one of the first reported cases of an IT director committing an inside hack with the intent of insider trading, effectively demonstrating that insider trading is not limited to fraud perpetrated by outside actors.
This really applies to cyber crime in general. Organizations can all too easily get overly caught up with implementing digital cyber security controls to shield their networks from outside intrusions while overlooking the human element and cyber/crime risks sitting next to them. Accordingly, companies should be employing training and controls to identify suspicious internal/employee behavior. Lastly, this case also demonstrates that the SEC is paying close attention, aggressively investigating and pursuing even seemingly smaller cases.
Expedia
In reviewing the sequence of events, it is important to note the degree to which internal control failures may have contributed. For one, the IT professional was able to utilize passwords of employees with seemingly, a certain level of ease. Controls that require employees to change their passwords after working with any IT professionals or flag suspicious behavior could have helped minimize or eliminate such unauthorized usage. Secondly, the employee was able to continue this fraud even after being let go, via a secretly kept company laptop. Something such as a kill switch to cut off remote access from the company issued, mobile devices, also could have helped minimize the damage. Sure, this is all easy to say in retrospect and we don’t mean to sound like a Monday morning quarterback, but rather we address these concerns simply to raise awareness for organizations looking to build more robust controls. Lastly, the fact that this scheme was perpetrated over a period of 3 years, with a total of 9 trades, is an important detail in order to highlight just how long intrusions remain undetected. In this particular
Lastly, the fact that this scheme was perpetrated over a period of 3 years, with a total of 9 trades, is an important detail in order to highlight just how long intrusions remain undetected. In this particular case, the damage surmounted to 350k, and in large part, that alone may be a key reason for having gone undetected as long as it did…however, it should go without saying that the damage could have be considerably more severe. The fact the hacker was also an employee in this case, undoubtedly contributed to the long duration-to-discovery.
These types of insider trading security events can inflict significant damage. To start, the costs to comply with a prolonged regulatory investigation can be severe – from e-forensics to document production to defense costs. More frightening however is the potential for following shareholder/investor litigation following a stock drop. These claims will often assert negligence and/or failure to implement adequate security controls to prevent such an event. The fact that this fraud was perpetrated over a 3-year span is troubling. It can often be easy for companies to relate all cyber losses back to a cyber insurance policy, however, there is often a bigger picture that needs to be addressed. We briefly address insurance, because when intrusions such as these occur, the initial reaction (understandably so) is to look to the underlying insurance carrier for indemnification. Companies instinctively looking to their cyber insurance carrier would mostly be looking in the wrong direction. Cyber policies regularly contain broad “securities” exclusions which eliminate any coverage. The fact that the fraud was committed by an employee creates an additional barrier to coverage since most cyber policies are worded to provide coverage for intrusions by “outside” actors. Much of these damages, however, can be insured against through a well-structured Directors and officers insurance policy which extends coverage for CISOs, and CTOs that also might be named in a lawsuit. This is particularly true for public companies for whom D&O insurance is an absolute must to protect against these exact claims. Whole there are many lessons to be learned here, this is just one case, of likely many to come, demonstrating how security failures can result in “securities” fraud.
About the Author Evan bundschuh
Evan bundschuh is vice president and commercial lines head at GB&A, an independent insurance brokerage located in New York focused on insurance programs and risk management solutions for tech companies, financial & professional services, manufacturers and product-based businesses. As an RPLU with 15 years of industry experience, Evan assists clients with insurance program coordination and client-side advising on Directors & Officers (D&O), Professional Liability (E&O) and Cyber Insurance, and is a contributor on the topics of cyber risk.
Kapustkiy hacked the Consular Department of the Embassy of the Russian Federation
13.12.2016 securityaffairs Hacking
Kapustkiy breached website for the Consular Department of the Embassy of the Russian Federation in the Netherlands and accessed passport numbers and PPI.
The white hat hacker Kapustkiy breached the website for the Consular Department of the Embassy of the Russian Federation in the Netherlands (ambru.nl). The hacker broke into the database and accessed personal information of approximately 30,000 users, as proof of the attack he leaked only 129 records in order to give the opportunity to administrators to fix the issue. Exposed records include emails, phone numbers, passport numbers, and IP addresses.
Embassy of the Russian Federation
“So this could happend? And we give zero fucks about this? You should be a shame ambru.nl When are you guys going to fucking listen to me. A lot people have emailed you guys. SO TELL ME WHY YOU IGNORE ME FFS?” states the hacker’s manifesto published on PasteBin.
When asked about the hacking vulnerability exploited and the attack technique used, Kapustkiy told me that he has exploited a blind SQL Injection.
He hacked the website to push website administrators to boost the security of their platform and patch vulnerabilities that would expose personal details of the users.
Why the Consular Department of the Embassy of the Russian Federation?
Segui
Kapustkiy @Kapustkiy
Going to breach a database that is related to the Russian Government. Tuesday!
21:50 - 11 Dic 2016
9 9 Retweet 17 17 Mi piace
There is no political motivation, the hacker was searching for the embassy websites like the Indian ones he breached weeks ago.
IT staff at the Consular Department of the Embassy of the Russian Federation contacted Kapustkiy and told him that they are working to solve the problem.
Kapustkiy reported the data breach to the Russian authorities, but he didn’t receive a response.
Recently Kapustkiy has breached the Argentinian Ministry of Industry and the National Assembly of Ecuador and leaked the data via PasteBin. A few days ago the hacker breached the Venezuela Army and many other websites.
He also hacked the website at the High Commission of Ghana & Fiji in India and the India Regional Council as well as organizations and embassies across the world.
Recently he hacked the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
President Obama Orders 'Full Review' of Possible Russian hacking in US Election
10.12.2016 thehackernews Hacking
In his final month in office, President Barack Obama has ordered U.S. intelligence agencies to conduct a "full review" of pre-election cyber attacks against Democratic Party organizations that many believe affected the outcome of the 2016 presidential election.
The United States intelligence agencies have attributed those series of cyber-attacks to Russia that shook the US election season.
"The President earlier this week instructed the intelligence community to conduct a full review of the pattern of malicious cyber activity related to our presidential election cycle," White House spokesman Eric Schultz told reporters.
At an event hosted by the Christian Science Monitor, White House's counterterrorism adviser Lisa Monaco announced that the president had "directed the Intelligence Community to conduct a full review of what happened during the 2016 election process."
President is expecting a full report before the end of his term, and President-elect Donald Trump takes office in January of 2017, as Monaco said that the results of the pre-election hacking's investigation would be released to Congress before President Obama left office.
At a Heritage Foundation event on Wednesday, Chairman of House Homeland Security Michael McCaul, also called for "consequences" for Russia's interference in the 2016 election. "If we don’t respond and show them that there are consequences," McCaul said, "the bad behavior will continue… our democracy itself is being targeted."
The announcement comes after Democrats in Congress forced the White House office to reveal details of Russian hacking and disinformation in the presidential election.
"We may be crossed into a new threshold, and it is incumbent upon us to take stock of that, to review, to conduct some after-action, to understand what this means, what has happened and to impart those lessons learned," Obama told reporters.
Monaco said the new administration would inherit a rapidly growing national security threat that comes from the Internet across all dimensions.
Meanwhile, Trump has said he was not convinced Russia was behind the pre-election cyber attacks.
"I don't believe they interfered," Trump told in an interview with Time magazine this week. "That became a laughing point – not a talking point, a laughing point. Anytime I do something, they say, 'Oh, Russia interfered.'"
In October, the DHS and the US intelligence agency officially blamed Russia of hacking the Democratic National Committee (DNC) and other political organizations "intended to interfere with the US election process." Though Russia has denied all accusations.
Russian hackers also allegedly stole private emails from a Clinton associate that were later published by WikiLeaks just weeks before election day.
With that, the full report by Obama administration on pre-election hacking might face serious challenges in the next government.
Hackers targeted the heavy industry ThyssenKrupp and stole industrial secrets
9.12.2016 securityaffairs Hacking
Alleged Asian hackers have targeted the German heavy industry giant ThyssenKrupp to steal company secrets.
Hackers from Southeast Asia targeted the German heavy industry giant ThyssenKrupp in the attempt of obtaining “technological know-how and research results.”
The news was announced on Thursday by a company spokesman that confirmed a report in the Wirschaftswoche weekly and added that the company as successfully repelled the attack.
The cyber attack was discovered by the IT security office, which spotted the hacking activities while they were ongoing and blocked them.
“The attack is over and had been repelled,” said the company spokesman.
The investigators speculate the attack was carried out by a group of professional hacked from Southeast Asia that is interested in the technological know-how and research activities of the company.
At the time I was writing there are no further details on the cyber attack neither the exact nature of the attackers (i.e. nation-state actors, cybercriminals).
The hackers launched a “massive cyber attack” against the divisions dealing with orders planning of industrial plants, the conglomerate’s Industrial Solutions, and Steel Europe business divisions.
Critical IT systems at the ThyssenKrupp such as the Marine Systems business unit and blast furnaces and power plants in Duisburg, were not affected
The ThyssenKrupp Marine should be a privileged target for hackers because it is the division that builds warships, including submarines for the German and Israeli navies.
The company excluded any sabotage or manipulation of data or applications, but it was unable to estimate if a limited portion of data, “data fragments,” had been stolen by the hackers.
“Experts say that in the complex IT landscapes of large companies, it is currently virtually impossible to provide viable protection against organized, highly professional hacking attacks,” the company added.
Israeli TV broadcast hacked, attackers played Muslim call to prayer
9.12.2016 securityaffairs Hacking
On Tuesday night, a group of unknown hackers took control of the Israeli TV broadcast Channel 2 and played Muslim call to prayer.
On Tuesday night, a group of hackers took control of an Israeli news Channel 2 and played Muslim call to prayer. The hackers want to protest a controversial bill that limits the volume of the call to prayer from mosques.
The hackers broke into the Israeli TV broadcast and disrupted the transmissions after gained access to TV satellites.
According to Israeli media, the hacker appeared to be from Saudi Arabia

Source teztv.com
Segui
חדשות 2 ✔ @Channel2News
האקרים השתלטו על שידורי מהדורת חדשות 2, ובמקום - שידרו קריאת מואזין
20:41 - 29 Nov 2016
24 24 Retweet 50 50 Mi piace
In November, the representatives of the Knesset have given their approval to the “muezzin bill” that bans religious leaders from using loudspeakers that call the worshippers for prayers.
The Israeli Government’s bill aims to protect its citizens from noise.
“While the bill is primarily targeted at curbing noise pollution, critics have noted the proposed law contains a clause which says that “freedom of religion should not be harmful to quality of life nor used to convey religious or nationalist messages, and sometimes even words of incitement”, which they say is targeted at Muslims.” states the Independent.
The hackers are protesting of a the bill, they spread messages written in the Hebrew language warning of “punishment from God” and said that “the fire burned hearts”.
“The fire burned hearts” and “To for big great God [is] war from God (the fire burns you).” states the other messages.
“Residents in northern Israel viewing Channel 2 via satellite TV reported that during the evening broadcast someone took over central control of the broadcast and played the voice of the muezzin,” reported the Tribune.
The Arab politicians Ahmad Tibi and Taleb Abu Arar staged a Muslim call to prayer, the ‘Azan,’ in the parliament in protest against the bill.
The bill has received the Israeli Prime Minister Benjamin Netanyahu’s support.
“I cannot count the times – they are simply too numerous – that citizens have turned to me from all parts of Israeli society, from all religions, with complaints about the noise and suffering caused them by the excessive noise coming to them from the public address systems of houses of prayer,” Mr Netanyahu told a cabinet meeting.
Turkish Hackers Are Giving Away Prizes For Participating In DDoS Attacks
8.12.2016 thehackernews Hacking
DDoS has become a game now that could knock any service offline.
A Turkish hacking group is encouraging individuals to join its DDoS-for-Points platform that features points and prizes for carrying out distributed denial-of-service (DDoS) attacks against a list of predetermined targets.
The points earned can later be redeemed for various online click-fraud and hacking tools.
Dubbed Sath-ı Müdafaa, translated as Surface Defense in English, this DDoS-for-Points platform is advertised via local Turkish hacking forums, including Turkhackteam and Root Developer.
Surface Defense prompts other hackers in Turkey to sign up and asks them to attack political websites using a DDoS tool known as Balyoz, translated as Sledgehammer.
According to Forcepoint security researchers, who discovered this program, Balyoz works via Tor and requires a username and password to log in. The tool then uses a DoS technique to flood targets with traffic.
Here's How the Balyoz Tool Works
Once a user downloads the Surface Defense collaboration software from hacking forums and registers, the program then runs locally on a computer, prompting the user to download DDoS attack tool in order to assault the limited list of target sites.
The DDoS traffic is then routed through Tor to disrupt online services. For every 10 minutes the tool attack a website with fraudulent traffic, the participant receives a point.
The points can then be used to obtain rewards including a more powerful version of the Balyoz DDoS attacking tool, "click-fraud" bots that automatically clicks on ads for pay-to-click (PTC) services like Ojooo and Neobux PTC to generate revenue, and a program that has ability to infect PCs and scare the victim with images and sounds.
The DDoS Tool Contains Hidden Backdoor
The DDoS platform software also contains a hidden backdoor that allows the Surface Defense operator to "hack the hackers," raising concerns over the operator's actual motives.
"The backdoor is a very small Trojan and its sole purpose is to download, extract and execute another .NET assembly from within a bitmap image," Forcepoint researchers said.
"It also downloads a secondary 'guard' component which it installs as a service. This 'guard' component ensures that if the backdoor is deleted then it will be re-downloaded and also installed as a service."
The list of predefined targets includes Kurdish websites of the Kurdistan Workers Party (PKK), its military wing the People's Defense Force (HPG), an organization by NATO members, Kurdish radio and TV stations, Kurdish hacking crews, and more.
Other politically-motivated targets include the Armenian Genocide website, the German Christian Democratic Party -- which is led by Angela Merkel -- and many Israeli websites.
"Users can also suggest new websites to add to the list of targets," Forcepoint researchers said. "There is a live scoreboard for participants to see how they compare to other participants."
The researchers have managed to track down the IP address of the Surface Defense software, despite running on the Dark Web through Tor.
This development helped researchers gathered some information on the hacker's identity, like the operator might act under the handle "Mehmet," runs two YouTube channels advertising the Balyoz DDoS tool, and the operator is possibly based in the Turkish city of Eskisehir.
For more technical details on the Surface Defense platform, you can head on to the Forcepoint's 30-page research paper [PDF] titled, "Sledgehammer - Gamification of DDoS attacks (for ideology, profit & mischief)."
Hacker who stole Celebrity Emails, Sex Tapes, Movie Scripts Gets 5 Years in Prison
7.12.2016 thehackernews Hacking
Hacker who stole Celebrity Emails, Sex Tapes, Movie Scripts Gets 5 Years in Prison
A hacker who was arrested last year for hacking into celebrities' email accounts to steal the unreleased movie and television scripts, their private messages, and sex tapes to sell them has finally been sentenced five years in prison.
Alonzo Knowles, a 24-year-old Bahamian man, was convicted by U.S. District Judge Paul A. Engelmayer in Manhattan on Tuesday.
Knowles, who maintained a list of emails and phone numbers of 130 celebrities, pleaded guilty in May to charges of identity theft and criminal copyright infringement.
The sentence is twice longer than the amount of years the federal sentencing guidelines suggested, as the judge felt that Knowles "would be a clear and present danger to commit the very same crime again," the New York Times reports.
The hacker expressed remorse in court and had already handed over unreleased scripts, songs, and $1,900 in cash.
The authorities arrested Knowles late December and seized his laptop that was later destroyed by investigators. The authorities found folders containing stolen data that includes:
Social Security numbers for actors and professional athletes
Private, explicit images
Scripts for unreleased TV shows and movies and even contract documents
Emails and phone numbers of at least 130 celebrities
Sex tapes of celebrities
The hacker was arrested after flying to New York from the Bahamas to sell 15 movie and TV shows scripts and the Social Security Numbers (SSNs) of a movie actress and two athletes to an undercover U.S. Department of Homeland Security agent for $80,000.
According to prosecutors, Knowles appeared anxious to continue exploiting celebrities once released even after pleading guilty.
The judge cited the book the hacker claimed he would someday write to "shake up Hollywood," with plans to sell them at $35 per copy, in which Knowles said: "When I get out, I'm going to shake up Hollywood."
The book, Knowles claimed, will contain information that can "jeopardize their careers, their security, and their personal relationships."
The affected celebrities were not identified, though the judge acknowledged that the court received a statement from 20th Century Fox. However, Knowles apologized for his conduct on Tuesday, saying he regretted "the stupid things I did and said."
An individual hacked back the San Francisco Muni hacker
7.12.2016 securityaffairs Hacking
In November, an unknown attacker hacked the computer systems of the San Francisco’s Municipal, now an individual hacked back the San Francisco Muni hacker.
A couple of weeks ago, an unknown attacker hacked the computer systems of the San Francisco’s Municipal railway giving riders a free ride all day on Saturday. Now the same hacker seems to have been hacked. According to the popular investigator Brian Krebs, an individual took over the email account of one of the San Francisco’s Municipal hackers that was reported in the ransom note provided in the attack.
The ransom demanded in the specific case to the FMTA was 100 BTC, or $73,184 USD with current exchange rates.
The hackers that targeted the San Francisco’s Municipal railway left the following message on the compromised machines in the Muni stations:
“Contact for key (cryptom27@yandex.com)”

Infected machine at the SF Muni station (Source: Brian Krebs)
The individual who hacked backed the Muni hacker broke into the email account by guessing the security question protecting it, then he reset the password and locked down the account and secondary address cryptom2016@yandex.com.
“On Monday, KrebsOnSecurity was contacted by a security researcher who said he hacked this very same cryptom27@yandex.com inbox after reading a news article about the SFMTA incident. The researcher, who has asked to remain anonymous, said he compromised the extortionist’s inbox by guessing the answer to his secret question, which then allowed him to reset the attacker’s email password.” wrote Krebs. “A screen shot of the user profile page for cryptom27@yandex.com shows that it was tied to a backup email address, cryptom2016@yandex.com, which also was protected by the same secret question and answer.”
The analysis of the Bitcoin wallets used by the Muni hacker revealed that he earned $140,000 in the last three months, a circumstance that confirms that he is a cyber criminal. In this period he used to continuously switch Bitcoin wallets randomly every few days or weeks in order to make harder the investigation. Most of the attampts of extortion targeted US-based construction and manufacturing companies, and in many cases, the victims appear to have complied with the demands.
“On Nov. 20, hacked emails show that he successfully extorted 63 bitcoins (~$45,000) from a U.S.-based manufacturing firm.” added Krebs. ““Emails from the attacker’s inbox indicate some victims managed to negotiate a lesser ransom. China Construction of America Inc., for example, paid 24 Bitcoins (~$17,500) on Sunday, Nov. 27 to decrypt some 60 servers infected with the same ransomware — after successfully haggling the attacker down from his original demand of 40 Bitcoins. Other construction firms apparently infected by ransomware attacks from this criminal include King of Prussia, Pa. based Irwin & Leighton; CDM Smith Inc. in Boston; Indianapolis-based Skillman; and the Rudolph Libbe Group, a construction consulting firm based in Walbridge, Ohio.””
The analysis of the account revealed a number of messages sent to the attacker’s cryptom2016@yandex.com account. These messages show a financial relationship with at least two different hosting providers. The hacked inbox also included emails containing credentials needed to manage one of those servers, then Krebs shared them with some experts such as Alex Holden, chief information security officer at Hold Security Inc.
The expets discovered that the server was used to hack into systems worldwide, it was hosting several open-source hacking tools.
“It appears our attacker has been using a number of tools which enabled the scanning of large portions of the Internet and several specific targets for vulnerabilities,” Holden said. “The most common vulnerability used ‘weblogic unserialize exploit’ and especially targeted Oracle Corp. server products, including Primavera project portfolio management software.”
The experts discovered that the Muni hacker used internet addresses based in Iran, they found also some notes which were translated into Farsi.
“That server kept detailed logs about the date, time and Internet address of each login. A review of the more than 300 Internet addresses used to administer the server revealed that it has been controlled almost exclusively from Internet addresses in Iran. Another hosting account tied to this attacker says his contact number is +78234512271, which maps back to a mobile phone provider based in Russia.” continues Krebs. “But other details from the attack server indicate that the Russian phone number may be a red herring.”
It is bad time also for crooks!
Argentinian Ministry of Industry hacked by Kapustkiy
7.12.2016 securityaffairs Hacking
The young hacker Kapustkiy and his colleague Kasimierz have broken into another website, the Argentinian Ministry of Industry (Ministerio de Produccion).
The data breach exposed personal information, contact details (i.e. names, addresses, emails, phone numbers, Facebook and Twitter accounts), and private documents of a large number of individuals.
The hackers breached the Argentinian Ministry of Industry website produccion.gob.ar by gaining access to an administrator account. The hackers confirmed that the login credentials used to protect the website are very weak demonstrating the poor level of security at the Argentinian Ministry.
Kapustkiy shared evidence of the data breach and provided the credentials for the admin panel that allowed the hackers accessing to personal information of employees and documents belonging to the ministry.
“When I was in the admin panel. I managed to download all the files that they got.”Kapustkiy told me.
Argentinian Ministry of Industry hacked by Kapustkiy
According to Kapustkiy, the overall archive includes approximately 18,000 accounts, he confirmed that he will not leak the stolen data to protect the users of the Argentinian Ministry of Industry website.
Kapustkiy reported the data breach to the Argentinian Ministry of Industry that still hasn’t replied.
When asked about the hacking technique used, Kapustkiy told me that they didn’t use a SQL injection, but he avoided to provide me further details.
Recently Kapustkiy has breached the National Assembly of Ecuador and leaked the data via PasteBin. Once again he exploited a SQL injection.
A few days ago the hacker announced to have hacked the Venezuela Army, but the list of victims is long.
He also hacked the website at the High Commission of Ghana & Fiji in India and the India Regional Council as well as organizations and embassies across the world.
Recently he hacked the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
Hacking Millions with Just an Image — Recipe: Pixels, Ads & Exploit Kit
7.12.2016 THEHACKERNEWS Hacking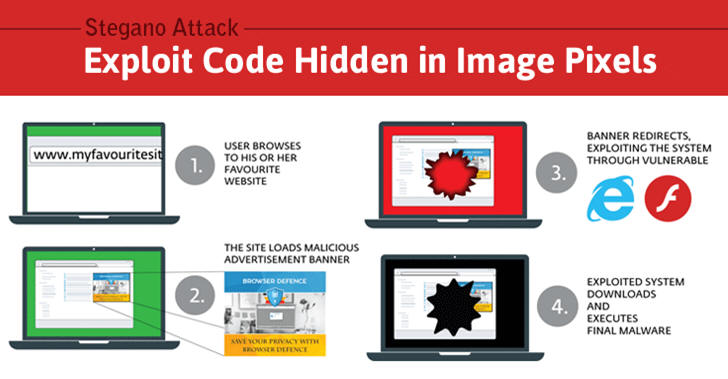
If you have visited any popular mainstream website over the past two months, your computer may have been infected — Thanks to a new exploit kit discovered by security researchers.
Researchers from antivirus provider ESET released a report on Tuesday stating that they have discovered an exploit kit, dubbed Stegano, hiding malicious code in the pixels of banner advertisements that are currently in rotation on several high profile news websites.
Stegano originally dates back to 2014, but since early October this year, cyber crooks had managed to get the malicious ads displayed on a variety of unnamed reputable news websites, each with Millions of daily visitors.
Stegano derived from the word Steganography, which is a technique of hiding messages and content inside a digital graphic image, making the content impossible to spot with the naked eye.
In this particular malvertising campaign, operators hide malicious code inside transparent PNG image's Alpha Channel, which defines the transparency of each pixel, by altering the transparency value of several pixels.
The malvertising campaign operators then packed the altered image as an advertisement and managed to display those malicious ads on several high-profile websites.
According to the researchers, the malicious ads promote applications called "Browser Defense" and "Broxu," and the methodology makes it tough for ad networks to detect.
Here's How the Stegano Attack Works:
Once a user visits a site hosting malicious advertisement, the malicious script embedded in the ad reports information about the victim's computer to the attacker's remote server without any user interaction.
The malicious code then uses the CVE-2016-0162 vulnerability in Microsoft's Internet Explorer (IE) browser in order to scan the target computer to see if it is running on a malware analyst's machine.
After verifying the targeted browser, the malicious script redirects the browser to a website that hosts Flash Player exploits for three now-patched Adobe Flash vulnerabilities: CVE-2015-8651, CVE-2016-1019, and CVE-2016-4117.
"Upon successful exploitation, the executed shell code collects information on installed security products and performs – as paranoid as the cybercriminals behind this attack – yet another check to verify that it is not being monitored," ESET researchers wrote in a blog post. "If results are favorable, it will attempt to download the encrypted payload from the same server again, disguised as a gif image."
When downloaded to the victim's computer, the encrypted payload is then decrypted and launched via regsvr32.exe or rundll32.exe in Microsoft Windows.
Just Visit a Site, and You'll be Hacked in Just 2-3 Sec
Below is an ESET infographic that explains the working of Stegano's exploit attack: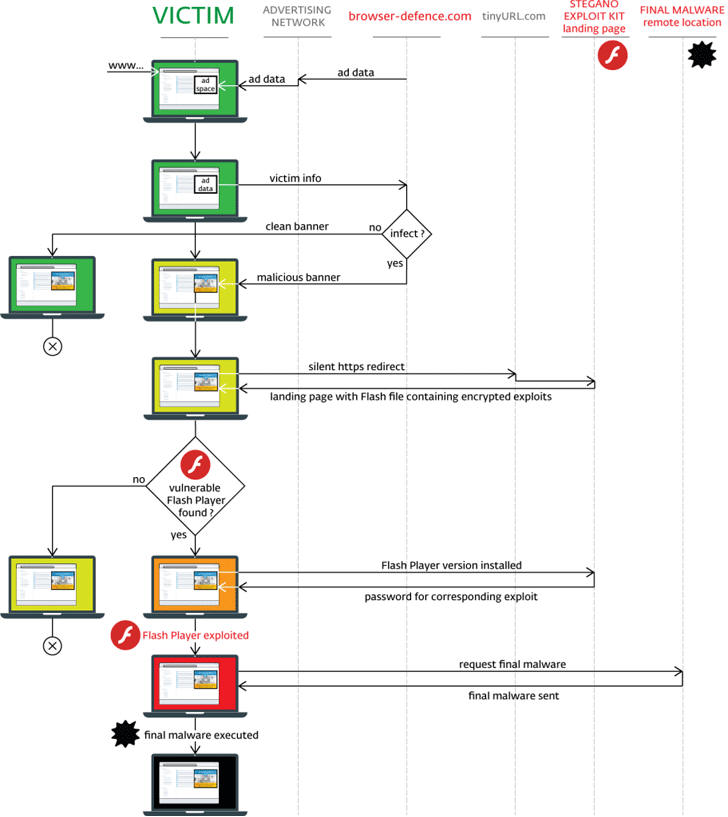
All the above operations execute automatically without any user interactions and takes place in the span of just 2-3 seconds.
So far, the Stegano exploit kit has pushed various trojan downloaders, the Ursnif and Ramnit banking trojans, backdoors, spyware, and file stealers.
The Stegano exploit kit was initially used in 2014 to target people in the Netherlands, and then in 2015, moved on to residents in the Czech Republic. The latest attack campaign is targeting people in Canada, the UK, Australia, Spain, and Italy.
The best way to protect yourself against any malvertising campaign is always to make sure you are running updated software and apps. Also use reputed antivirus software that can detect such threats before they infect your system.
North Korea's Linux-based Red Star OS can be Hacked Remotely with just a Link
6.12.2016 thehackernews Hacking
North Korea's own homegrown computer operating system, that's supposed to be fully hacker proof and more secure than foreign OS, like Microsoft's Windows, can easily be hacked remotely.
A group of hackers managed to break into Red Star OS — North Korea's government sanctioned Linux-based OS — using just a link.
Red Star OS is North Korea's own homegrown OS that looks remarkably just like Apple's OS X and gives North Korean authorities more control over the computers, providing not only security but also spying tools that help track files in a way that if the government wants, every bit of user's data can be traced easily.
According to the information security company Hacker House, Red Star OS contains a critical vulnerability that makes it possible for hackers to gain remote access to any PC running North Korea's OS just by tricking victims into opening a hyperlink.
The latest version of Red Star OS ships with a Firefox-based web browser called Naenara, and according to researchers, the "trivial remote exploit attack vectors" contained in the web browser allows attackers to hack into the system.
Here's how the exploit work:
The Hacker House hackers exploited a particular Red Star application that handles Uniform Request Identifiers (URI) – a string of characters used to identify resources in a network.
Hackers noted that the "mailto" URI request used for email could be exploited by hackers to remotely "execute arbitrary commands."
Since this particular URI does not remove requests from the application's command line, hackers could "trivially obtain code execution" just by injecting malicious links into the command line.
"Whilst probing for vulnerabilities it was noticed that registered URL handlers were passed to a command line utility '/usr/bin/nnrurlshow.' This application (aside from having null ptr de-refs and other cute bugs) takes URI arguments for registered URI handlers when handling application requests such as 'mailto' and 'cal,' the Hacker House hackers explains.
"Naenara doesn't sanitize the command line when handling these URI argument requests and as such you can trivially obtain code execution by passing malformed links to the nnrurlshow binary."
In short, this security flaw can be used easily to install malware or exploit PCs running the Red Star operating system.
Rival South Korea has long blamed North Korea for mounting various cyber attacks against its government, military, and other organizations.
Just recently, the South Korean military blamed North Korea for breaching its military cyber command. A spokesman for the military cyber command told BBC that classified information was thought to have been stolen, although it's not clear exactly what data was accessed.
[Video] How to Hack a Credit Card in 6 Seconds, Experts Reveal
6.12.2016 thehackernews Hacking
As India attempts an upgrade to a cashless society, cyber security experts have raised serious concerns and revealed how to find credit card information – including expiration dates and CVV numbers – in just 6 Seconds.
And what's more interesting? The hack uses nothing more than guesswork by querying multiple e-commerce sites.
In a new research paper entitled "Does The Online Card Payment Landscape Unwittingly Facilitate Fraud?" published in the academic journal IEEE Security & Privacy, researchers from the University of Newcastle explains how online payments remain a weak spot in the credit card security which makes it easy for fraudsters to retrieve sensitive card information.
The technique, dubbed Distributed Guessing Attack, can circumvent all the security features put in place to protect online payments from fraud. The similar technique is believed to be responsible for the hack of thousands of Tesco customers in the U.K last month.
The issue relies on the Visa payment system, where an attacker can guess and attempt all possible permutations and combinations of expiration dates and CVV numbers on hundreds of websites.
Researchers discovered two weaknesses in the way online transactions are verified using the Visa payment system. They are as follows:
Online payment systems do not detect multiple incorrect payment requests if they're performed across multiple sites. They also allow a maximum of 20 attempts per card on each site.
Web sites do not run checks regularly, varying the card information requested.
Newcastle University PhD candidate Mohammed Ali says neither weakness is alone too severe, but when used together and exploited properly, a cyber criminal can recover a credit card's security information in just 6 seconds, presenting "a serious risk to the whole payment system."
The attack is nothing but a very clever brute force attack that works against some of the most popular e-commerce sites.
So, instead of brute-forcing just one retailer's website that could trigger a fraud detection system due to incorrect guesses or lock the card, the researchers spread out guesses for the card's CVC number across multiple sites with each attempt narrowing the possible combinations until a valid expiration dates and CVV numbers are determined.
The video demonstration shows that it only takes 6 seconds for a specially designed tool to reveal a card's secure code.
First, an attacker needs a card's 16-digit number, which can be obtained either from black-market websites for less than $1, or from a smartphone equipped with a near-field communication (NFC) reader to skim them.
Once a valid 16-digit number is obtained, the hacker use web bots to brute force three-digit card verification value (or CVV) and expiration date to hundreds of retailers at once. The CVV takes a maximum of 1,000 guesses to crack it and the expiry date takes no more than 60 attempts.
The bots then work to obtain the billing address, if required. The paper suggests the whole attack can be carried out in just 6 seconds.
"These experiments have also shown that it is possible to run multiple bots at the same time on hundreds of payment sites without triggering any alarms in the payment system," researchers explain in the paper.
"Combining that knowledge with the fact that an online payment request typically gets authorized within two seconds makes the attack viable and scalable in real time. As an illustration, with the website bot configured cleverly to run on 30 sites, an attacker can obtain the correct information within four seconds."
The attack works against Visa card customers, as the company does not detect multiple attempts to use a card across its network, while MasterCard detects the brute force attack after fewer than 10 attempts, even when the guesses are spread across multiple websites.
How to Protect yourself?
The team investigated the Alexa top-400 online merchants’ payment websites and found that the current payment platform facilitates the distributed guessing attack.
The researchers contacted the 36 biggest websites against which they ran their distributed card number-guessing attack and notified them of their findings. As a result of the disclosure, eight sites have already changed their security systems to thwart the attacks.
However, the other 28 websites made no changes despite the disclosure.
For Visa, the best way to thwart the distributed card number-guessing attack is to adopt a similar approach to MasterCard and lock a card when someone tries to guess card details multiple times, even tried across multiple websites.
For customers, avoid using Visa credit or debit cards for making online payments, always keep an eye on your statements, and keep spending limit on your Visa card as low as possible.
Kapustkiy hacked the National Assembly of Ecuador website
5.12.2016 securityaffairs Hacking
Kapustkiy’s has breached the National Assembly of Ecuador and leaked the data via PasteBin. Once again he exploited a SQL injection.
Here we go again with a Kapustkiy’s hack, this time the young hacker has breached the National Assembly of Ecuador and leaked the data via PasteBin.
The hacker broke into the backend of the www.asambleanacional.gob.ec website accessing a total of 930 records. As proof of concept of the hack the hacker leaked roughly 550-600 records.
According to Wikipedia the National Assembly (Spanish: Asamblea Nacional) is the legislative branch of the government of Ecuador that replaced the National Congress in 2009, under the 2008 Constitution.

I reached Kapustkiy to receive more info about the data breach and he confirmed me that once again he exploited an SQLinjection flaw.
“I used an simple SQLi to gain acces and I have reported it. I did not leak real names etc..” Kapustkiy told me.
A few days ago the hacker announced to have hacked the Venezuela Army.
He also hacked the website at the High Commission of Ghana & Fiji in India and the India Regional Council as well as organizations and embassies across the world.
Recently he hacked the ‘Dipartimento della Funzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya. Kapustkiy.
Russian Central bank loses $31 million in cyber heist
3.12.2016 securityaffairs Hacking
It’s official, hackers have stolen 2 billion rubles, roughly 31 million US dollars, from accounts at the Russian central bank.
While I was reporting the news that the FSB unnamed foreign hackers are planning to undermine Russian Banks, the Russian Central Bank confirmed hackers have stolen 2 billion rubles (roughly $31M) in cyber attacks
Central bank official Artyom Sychyov confirmed the incident and added that the hackers had attempted to steal much more, about 5 billion rubles.
“We were lucky to return some of money,” said a Russian central bank spokesperson.

Sychyov was commenting on a central bank report released yesterday by the FSB. The hackers broke into bank accounts by faking a client’s credentials. The bank provided few other details in its lengthy report.
“Hackers stole more than 2 billion rubles ($31 million) from correspondent accounts at the Russian central bank, the bank said on Friday, the latest example of an escalation of cyber attacks on financial institutions around the globe.” reported the Reuters.
At the time I was writing there are no details about the attack.
The recent string of attacks against the SWIFT system urged financial regulators around the world to force banks to beef up cyber security.
In September the SWIFT disclosed more attacks against banks worldwide, pressures banks on security and urged member banks to implement the new SWIFT software by November 19.
In the last months, a worrisome string of cyber attacks against banks worldwide through the SWIFT system has alarmed the banking industry. The so-called “SWIFT hackers” have conducted multiple cyber attacks against financial institutions. We reported the successful cyber heists on the Bangladesh bank, against a Ukrainian bank, and the Ecuadorian bank, meanwhile, a Vietnam bank reported to have blocked an ongoing cyber heist.
In May, a fourth Bank in the Philippines was a victim of the SWIFT hackers and the experts at Symantec confirmed the malware used by the crooks shares code with tools used by the notorious Lazarus group linked to the North Korean Government.
According to the Reuters agency, the SWIFT issued a new warning urging member banks to implement the new SWIFT software by 19 November.
The latest version of SWIFT’s software implements new security features specifically designed to defeat such kind of attacks. The authentication processes have been improved such as the implementation of mechanisms to early detect fraudulent activities.
FSB accuses foreign hackers of plotting to undermine the Russian banks
3.12.2016 securityaffairs Hacking
According to the FSB unnamed foreign hackers are planning to undermine Russian Banks with cyber attacks and PSYOPS via social media.
The Kremlin is accusing unnamed foreign hackers of plotting to undermine the Russian banks in the country.
The Russian Government believes that foreign powers plan to conduct a PSYOps to destabilize the banks. Hackers could combine the diffusion of fake documents about the status of Russian banks with massive cyber attacks.
The news was spread by the Russia’s intelligence service, the FSB. According to the Russian intelligence, a group of servers in the Netherlands and leased to the Ukrainian web hosting firm BlazingFast were ready to launch an assault next Monday.
“Russia’s domestic intelligence agency, the Federal Security Service (FSB), said that the servers to be used in the alleged cyber attack were located in the Netherlands and registered to a Ukrainian web hosting company called BlazingFast.” reported the Reuters.
“The attack, which was to target major national and provincial banks in several Russian cities, was meant to start on Dec. 5, the FSB said in a statement.”
russian banks
Servers physically located in the Netherlands and leased to BlazingFast, a Ukrainian web-hosting firm, were primed to launch an assault next Monday.
“It was planned that the cyber attack would be accompanied by a mass send-out of SMS messages and publications in social media of a provocative nature regarding a crisis in the Russian banking system, bankruptcies and license withdrawals.” reads a statement issued by the FSB.
“The FSB is carrying out the necessary measures to neutralise threats to Russia’s economic and information security.”
The Russia’s central bank confirmed to the Reuters agency that it was aware of the imminent threat, for this reason, it is working with the security services.
“The situation is under control. Banks have been given necessary guidance,” the central bank said. “Banks have been given necessary guidance.”
Anton Onoprichuk, the director of the firm BlazingFast, told Reuters that he was not aware of the alleged plan of attack, neither the FSB nor any other intelligence agency had been in touch with him.
Recently Russian banks were targeted by a series of massive DDoS attacks powered by the Mirai IoT botnet.
Kapustkiy hacked a website belonging to the Venezuela Army
2.12.2016 securityaffairs Hacking
The hacker Kapustkiy has breached the Venezuela Army and leaked 3000 user records containing personal information such as names, emails, and phones.
We left the young hacker Kapustkiy after his hack at the High Commission of Ghana & Fiji in India when he also confirmed to have joined the Powerful Greek Army hacked crew.
The hacker breached the India Regional Council as well as organizations and embassies across the world. Recently he hacked the ‘Dipartimento della Funzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya. Kapustkiy.
Now the hacker is back announcing that he left the Powerful Greek Army and that he hacked the Venezuela Army.
Segui
Kapustkiy @Kapustkiy
Venezuela Army #Leaked http://pastebin.com/8iXAFJj8 3000 Users Exposed CC: @fbajak @jammastergirish @RCTVenlinea @Noticias24
09:59 - 2 Dic 2016
1 1 Retweet 9 9 Mi piace
Kapustkiy has hacked the Venezuela Army and leaked 3000 user records on Pastebin containing personal information such as names, emails, and phones.

The hacker breached the CATROPAEJ (“Caja de Ahorros de la Tropa Profesional del Ejercito Bolivariano Venezolano”) database, he also discovered some logins for the Army’s webmail system, but he did use them.
I reached Kapustkiy that confirmed me the exploitation of an SQLi vulnerability in the target application.
He triggered an Error-Based SQL Injection, this means that he tried to trigger errors in the database by passing unsanitized input in the URL.
Kapustkiy reported the problem to Venezuela Army more than a week ago, but he received no reply.
He told me that he is focusing on South America Governments and Asian organizations.
Hacking – German politicians fear Russian interference in the next election
30.11.2016 securityaffairs Hacking
German politicians fear Russian interference in the next election after the cyber attack that hit at least 900,000 routers.
During the weekend an improved version of the Mirai Botnet caused serious connectivity problems to at least 900,000 routers of the Deutsche Telekom.
Just after the attack, some experts speculated the involvement of Russian hackers behind the botnet that powered it.
The Government of Berlin fears possible interference of Russian nation-state hackers with the 2017 German election.
The attack demonstrated once again how much vulnerable it modern society to cyber threats, which then can also interfere with a political election. German politicians fear the Kremlin’s cyber capabilities. The alleged Russian interference in the US Presidential election is unleashing a domino effect and insinuating the fear in governments.
“I don’t have any concrete information about the origin of the attacks on the Telekom network,” Chancellor Angela Merkel said on Tuesday in Berlin. “Let me just say that such cyberattacks, or ‘hybrid attacks’ as they’re known in Russian doctrine, are part of everyday life today, and we need to learn to deal with them.”
Russian Interference Bundestag
State-sponsored hackers or non-nation state actor?
Even if the attack was launched by Russian hackers its attribution still remains the biggest problem to solve. Governments need to properly manage such kind of situation through the definition of norms of state behavior that can deal with cyber attacks launched by both categories of threat actors.
The Germany’s Interior Minister Thomas de Mazière expressed a great concern for explicitly blaming Moscow.
“It’s possible that we can’t clearly distinguish between criminal activities launched from a certain country and state activities,” Maizière declared at a conference of federal state interior ministers in Saarbrücken, when asked if Moscow was responsible for the attacks against the German routers.
The new president of German intelligence service (BND), Bruno Kahl, confirmed that foreign hackers can try to launch cyber attacks in the attempt to “delegitimize the democratic process” in the country.
“In an interview with the Süddeutsche Zeitung newspaper, Bruno Kahl – the new president of German intelligence service, the BND – complained about hackers trying to “delegitimize the democratic process as such” and said he had “indications” that the hacks “came from certain quarters,” namely Russia. And the Telekom hack is by no means the only attack of its kind in Germany.” reported DW.com.
In the past German infrastructure were targeted several times by foreign hackers. In June 2015, the German Government announced that hackers who breached the Bundestagsystems in May have also stolen data from targeted network. A spokeswoman for the Bundestag confirmed that unknown hackers stole data during the cyber attack, the investigators have uncovered several data leaks.
The daily Der Spiegel speculated that the Russian Government was involved in the attack occurred in May 2015. The news agency reported the opinion government representatives close to the Bundestag’s tech department.
“Behind the Cyber attack on the data network of the German Bundestag experts suspect Russian professional hackers. The SPIEGEL ONLINE learned from multiple sources familiar with the case. Thus, the German security authorities are now available clear indications that an authorship Russian cyber spies – point – perhaps a secret.” states the Der Spiegel website.
The attackers, likely Russian state-sponsored hackers, used a sophisticated strain of malware to violate the Bundestag network and syphon sensitive data. The experts that analyzed the malicious have found it similar to the malware used in a previous attack against on a German Government network occurred in 2014.
German intelligence is aware of cyber espionage campaigns against its political leaders.
“We have indications that hacker groups from Russia are active in this area, but we also know what foreign intelligence services are capable of,” Social Democratic Bundestag deputy Lars Klingbeil told Deutsche Welle. “For me this shows that we really need to protect ourselves structurally. Looking ahead to the national elections next year, this could become a major issue.”
More than 900k routers of Deutsche Telekom German users went offline
29.11.2016 securityaffairs Hacking
Deutsche Telekom confirmed that more than 900,000 routers began to have serious problems connectivity problems due to a cyber attack.
More than 900,000 routers belonging to Deutsche Telekom users in Germany were not able to connect to the Internet due to an alleged cyber-attack.
The affected routers were used by the Deutsche Telekom customers also for fixed telephony and TV services.
The problems lasted at least two days, the outage began on Sunday, November 27, at around 17:00, local time.
Deutsche Telekom users all over the country were not able to connect online using the users provided by the company.
Below a graphic representation of the outage provided by the Allestoerungen.de.

The outage lasted a couple of hours on Sunday, then the problems continued on Monday morning from 08:00.
The company notified via Facebook its 20 million customers to have solved the problems at around 12:00, local time, but users continued to face connectivity issues.
What has happened?
According to the company, hackers targeted the routers exploiting a security issue. Deutsche Telekom and router vendors are working together to develop a firmware fix and roll out the software patch.
Deutsche Telekom is currently rolling out firmware updates.
“The massive interference from connections of Deutsche Telekom, according to findings from the Federal Office for Security in Information Technology (BSI), follow a worldwide attack.” reads the abendblatt.de.
“According to BSI, the attacks were also noticeable in the government-protected government network, but could be repelled with effective protection measures. “
Deutsche Telekom customer case recommended that users unplug their devices, wait for 30 seconds and restart their router. In case this procedure is not able to restore the connectivity it is suggested to permanently disconnect the router from the Deutsche Telekom network.
“German Telekom is now offering a firmware update for the affected routers. Details (in German) are here: https://www.telekom.de/hilfe/geraete–zubehoer/router/speedport-w-921v/firmware-zum-speedport-w-921v. Affected user are advised to power off their router and power it on again after 30 seconds. During bootup the router should retrieve the new firmware from the Telekom servers.” reported the SANS Institute.
Deutsche Telekom is offering free mobile Internet until the technical problem is resolved.
Deutsche Telekom didn’t provide further technical details about the alleged cyber attack either the affected router models.
It is not clear which is the threat that compromised the Deutsche Telekom routers, experts speculated the involvement of a malware that could have prevented equipment from connecting to the company’s network.
Security experts from ISC Sans published an interesting report that revealed a significant increase in scans and exploitation attempts for a SOAP Remote Code Execution (RCE) vulnerability via port 7547 against Speedport routers.
This specific model of routers is widely used by Deutsche Telekom for German users.
“For the last couple days, attack against port 7547 have increased substantially. These scans appear to exploit a vulnerability in popular DSL routers. This issue may already have caused severe issues for German ISP Deutsche Telekom and may affect others as well (given that the US is just “waking up” from a long weekend). For Deutsche Telekom, Speedport routers appeared to be the main issue.” added the ICS SANS.
“According to Shodan, about 41 Million devices have port 7547 open. The code appears to be derived from Mirai with the additional scan for the SOAP vulnerability. Currently, honeypots see about one request every 5-10 minutes for each target IP.”
According to the ICS SANS report, it seems that attackers tried to exploit a common vulnerability in the TR-069 configuration protocol. Experts highlighted the availability of a Metasploit module implementing the exploit for this vulnerability.
An unconfirmed List of vulnerable routers includes the Eir D1000 Wireless Router (rebranded Zyxel Modem used by Irish ISP Eir) and the Speedport Router (Deutsche Telekom).
Of course. when dealing with IoT devices and cyber threats, the most dreaded malware is the Mirai bot that was recently involved in several massive DDoS attacks.
According to BadCyber, the responsible is the Mirai botnet that was designed to exploit Eir D100 (Zyxel Modems) via port 7547.
“TR-064 protocol is based on HTTP and SOAP and its default port is TCP 7547. Commands are sent as POST requests to this port.” states the BadCyber.
!The malware itself is really friendly as it closes the vulnerability once the router is infected. It performs the following command:
busybox iptables -A INPUT -p tcp –destination-port 7547 -j DROP
busybox killall -9 telnetd
which should make the device “secure”, unless until next reboot. The first one closes port 7547 and the second one kills the telnet service, making it really hard for the ISP to update the device remotely.”
Hacker who exposed Steubenville Rape Faces longer Prison term than Rapists
28.11.2016 thehackernews Hacking
Remember Steubenville High School Rape Case?
In 2012, Steubenville (Ohio) high school's football team players gang-raped an unconscious teenage girl from West Virginia and took photographs of the sexual assault.
In December 2012, a member of the hacker collective Anonymous hacked into the Steubenville High School football fan website Roll Red Roll and leaked some evidence of the rape, including a video taken and shared by the crime's perpetrators in which they joked about the sexual assault.
The hack exposed information about the gang rape by two football team players — Trent Mays and Ma’lik Richmond, both 16 at the time of the crime — who were eventually convicted and sentenced in 2013 to 2 and one years behind bars, respectively, but have since been released.
In 2013, the FBI raided the home of Deric Lostutter — Anonymous member, also known online as "KYAnonymous" — and seized two laptops, flash drives, CD's, an external hard-drive, cell phones and an XBox, and arrested him.
Lostutter, a 29-year-old man from Winchester, pleaded guilty in federal court in Kentucky on Wednesday to one count of conspiring to illegally break into the computers to draw attention to the Steubenville rape case without authorization and one count of lying to an FBI agent.
What's weird? The hacker is facing a longer prison term than the rapists.
Lostutter said he hacked into the site with just an intention to expose information about the gang rape. He said in court Wednesday, "We wanted to stand up for a girl who had no voice, and we went about it the wrong way," according to WTVQ.
However, prosecutors alleged that Lostutter participated in an online campaign against the school in late 2012 under the banner of Anonymous. They also said Lostutter used the online alias KYAnonymous to conspire online with other hacktivists in December 2012.
According to prosecutors, the goal was to intimidate and harass an individual who ran Roll Red Roll, the website dedicated to the football team. Lostutter gained unauthorized access to the target's website and leaked its owner's personal emails online.
There's no doubt that the operation against the school website helped bring the Steubenville rape case into the national spotlight. But Lostutter was questioned over his participation after the campaign got off the ground.
"Lostutter filmed a video wearing a mask and wrote a manifesto, which was both posted on the website to harass and intimidate people, and to gain publicity for Lostutter and [Noah] McHugh's online identities," said the protectors.
"Specifically, the messages threatened to reveal personal identifying information of Steubenville High School students, and made false claims that the administrator of the fan website was involved in child pornography and directed a 'rape crew.'"
Lostutter faces a maximum sentence of 10 years in prison and $250,000 in fines. He is scheduled to appear before the judge for sentencing on March 8, 2017. His defense did not comment on the plea agreement.
Noah McHugh, co-conspirator of Lostutter, was pleaded guilty in September to hacking the Steubenville website. He is slated to be sentenced in December.
Hackers crashed San Francisco’s Municipal railway systems
28.11.2016 securityaffairs Hacking
Last week, unknown attackers hacked the computer systems of the San Francisco’s Municipal railway giving riders a free ride all day on Saturday.
Last week, hackers crashed the computer system of the San Francisco’s Municipal railway, unknown attackers took offline the ticket kiosks offline and gave riders a free ride all day on Saturday, until Sunday morning.
Computers at the San Francisco Muni station computers displayed the message “You Hacked” on Saturday.
According to a spokesperson, the San Francisco’s Muni rail system “opened the fare gates as a precaution to minimize customer impact.”
According to San Francisco’s CBS affiliate, the system had been hacked for days.
Hackers also breached the Muni’s email system and rumors say employees weren’t sure if they would get paid this week.
“Meanwhile, riders will continue to find the metro gates open, and the system is not reading their payment cards. The fare gates were still wide open Saturday at 6 p.m. at the Embarcadero Station.” reported the San Francisco’s CBS affiliate.
“Ticket kiosks were also out of service.”

The San Francisco Municipal Transportation Agency, SFMTA, confirmed the cyber attack, but it confirmed that the incident has not affected any service.
A spokesperson with the transit agency tells KPIX 5 it is an ongoing investigation.
“There’s no impact to the transit service, but we have opened the fare gates as a precaution to minimize customer impact,” said Muni spokesperson Paul Rose. “Because this is an ongoing investigation it would not be appropriate to provide additional details at this point.”
“I think it is terrifying,” said one rider. “I really do I think if they can start doing this you know here, we’re not safe anywhere.”
“I was like, is this part of Black Friday deal, or something?” added another.
Sources confirmed the investigation is ongoing, but at the time I was writing the experts at the transit agency have no idea who is responsible for the cyber attack.
Hacker found issues in Uber UberCENTRAL Tool that exposed user data
26.11.2016 securityaffairs Hacking
Bounty hunter Kevin Roh has discovered several security vulnerabilities in the Uber UberCENTRAL Tool that exposed user data.
Security expert and bounty hunter Kevin Roh has discovered several security vulnerabilities in Uber’s UberCENTRAL Tool that exposed user data.
The UberCENTRAL service was launched in July, according to the company it is a dashboard that enables any business to request, manage, and pay for multiple Uber rides on behalf of their customers.
The UberCENTRAL console could be used by operators (i.e. employees) who can request rides for their customers. Administrators can easily add operators using only their email address.
Roh described in a blog post the flaws he discovered during his tests.
The first flaw allows enumerating userUUID via emails, an attacker can send requests with possible email addresses and if the address is associated with an account the server will include the user’s UUID in the response.
If the email address is not valid, the response sent by the server will contain an error.
Below an example of request sent to the server:
POST /admin/api/organizations/[organizationUUID]/operators HTTP/1.1 Host: central.uber.com Connection: close Content-Length: 40 Accept: application/json Origin: https://central.uber.com x-csrf-token: XXXX x-uber-origin: web-central-admin User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36 Content-Type: application/json Referer: https://central.uber.com/admin/locations Accept-Encoding: gzip, deflate, br Accept-Language: en-US,en;q=0.8 Cookie: _ua=XXXX {"operatorEmail":"r****@unlv.nevada.edu"}
The attacker could write a simple script that tries all possible values for the ‘operationEmail‘ parameter and analyze all the responses received by the server for each of them.

The second flaw is similar to the first one, it allows enumerating userUUID via GET request instead email addresses.
Roh found a third flaw that could have been exploited to obtain much more data, including full name, phone numbers, emails and userUUID.
The vulnerabilities were reported to the company between September and October, and the company promptly patched them in October.
Uber awarded the expert Roh under the company bounty program. The hacker received hundreds of dollars for each of the vulnerabilities, the exact amounts have not been revealed.
Kapustkiy joins the Powerful Greek Army and hacked High Commission of Ghana & Fiji in India
26.11.2016 securityaffairs Hacking
Kapustkiy hacked the High Commission of Ghana & Finland in India, he also confirmed to have joined the Powerful Greek Army hacked crew.
Last week, the hacker Kapustkiy, one of the most active hackers at this moment, hacked the India Regional Council, today he sent me a message to announce to have hacked the High Commission of Ghana & Finland in India.
The hacked archives are:
www.ghana-mission.co.in, Database: jadon_ghana
www.indianhighcommissionfiji.org, Database: jadon_hcfiji
The hacker has found other SQLi flaws in the above websites and the way to exploit them to access their databases. The database contains users’ personal information, including real names, phone numbers and email.
Among the first hacks of Kapustkiy there is are the data breach of Indian embassies across the worlds, a few weeks later the young hacker decided to verify if the flaws were fixed after his disclosure.
“I was curious about the Indian Embassy if they had fix everything that they promised to me. So I’ve found two sites that were related to the Indian Embassy” ha told me.
Kapustkjy published a small portion of the compromised databases on Pastebin. The hackers announced that he is now a member of the Powerful Greek Army hacker group.
Below the manifesto published by the hacker:
“DISCLAIMER: Don’t leak this somewhere else and don’t claim that it is your work
And don’t abuse this information. This is only to let adminstrators to see the danger of a weak website with no security and what the consequence are. I have reported the vulnerable.
YOU AGREE THAT YOU DON’T ABUSE THIS INFORMATION
YOU AGREE THAT YOU ARE NOT SHARING IT ON OTHER WEBSITES
YOU AGREE THAT THIS IS DONE BY KAPUSTKIY FROM POWERFUL GREEK ARMY
YOU AGREE THAT THIS WILL BE DELETED WHEN ADMINSTRATORS ARE GOING TO FIX IT
Contact them about the vulnerability please: Yatin.Patel10@mea.gov.in & jsegit@mea.gov.in”
Kapustkiy is a seventeen years old pentester that is targeting organizations and embassies across the world. Recently he breached the ‘Dipartimento della Funzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and a few days ago the hacker and his friend Kasimierz (@Kasimierz_) hacked the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya. Kapustkiy and his friend Kasimierz (@Kasimierz_).
He also targeted Universities, including two subdomains of Virginia University & Sub domain of University of http://pastebin.com/i1wmM5D1Wisconsin ( ) and another embassy, the Indian Embassy in New York (http://pastebin.com/Akm9x4dD )
The Indian authorities have issued a public statement to thank the young hacker for exposing the vulnerabilities in their websites.
“Thank you for your advice,” said Sanjay Kumar Verma, Joint Secretary, eGovernance and Information Technology. “We are fixing codes one by one. Your help in probing websites of various Indian embassies is a great help.”
The administrators of the Italian website also thanked him,
Crooks steal millions from European ATMs with jackpotting attacks
25.11.2016 securityaffairs Hacking
Criminal gangs like the Cobalt gang are now focusing their efforts on the banks to steal cash directly from the ATMs with jackpotting attacks.
Security experts are assisting a change of tactics for the criminal organizations who target the ATMs and online banking credentials. Crooks are now focusing their efforts on the banks in the attempt to steal cash directly from the ATMs.
In the last months, cyber criminals targeted ATM machines in Taiwan and Thailand, in both cases, crooks used a malware to infect the machine and have instructed them on spitting out cash on demand. The principal ATM manufacturers, Diebold Nixdorf and NCR Corp., confirmed to be aware of the ATM attacks and had already been working with their customers to mitigate the threat.
“We have been working actively with customers, including those who have been impacted, as well as developing proactive security solutions and strategies to help prevent and minimize the impact of these attacks,” said Owen Wild, NCR’s global marketing director for enterprise fraud and security.
This technique is known as ATM jackpotting, the FBI has warned U.S. banks of the potential attacks.
The FBI confirmed in a bulletin earlier this month that it is “monitoring emerging reports indicating that well-resourced and organized malicious cyber actors have intentions to target the U.S. financial sector.”
According to law enforcement, the malware used in the attack could be a product of the Buhtrap ATM gang, which stole 1.8 Billion rubles ($28 Million) from Russian banks between August 2015 and January 2016.
The cyber security firm Group-IB who investigated the string of ATM jackpotting attack confirmed that cyber criminals have remotely infected ATMs with malware in more than dozen countries across Europe this year. The name of targeted banks was not disclosed, but the researchers confirmed the victims were located in Armenia, Bulgaria, Estonia, Georgia, Belarus, Kyrgyzstan, Moldova, Spain, Poland, the Netherlands, Romania, the United Kingdom, Russia, and Malaysia.
According to Group-IB, crooks have been targeting ATMs for at least five years, but the recent wave of attacks mostly targeted small numbers of ATMs because criminals have to physical access to the machines.
“To perform a logical attack, hackers access a bank’s local network, which is further used to gain total control over ATMs in their system. Cash machines are then remotely triggered to dispense money, allowing criminals to steal large amounts with relative ease. With full control over ATMs, criminals can choose the exact attack time to loot newly filled ATMs.” states the report from Group-IB. “This results in millions of dollars lost, as in the case of the First Bank. That said, such attacks do not require developing expensive advanced software – a significant amount of tools used by the hackers is widely available from public sources, as will be further covered later in this report. ”
Group-IB attributed the attacks against the ATMs across Europe to a single criminal group, dubbed Cobalt.
The group launched spear phishing attacks with a malicious attachment in order to infect systems in the target banks. The emails purport to come from the European Central Bank, the ATM maker Wincor Nixdorf, or other banks.
“Criminals send emails with attachments containing exploits and password-protected archives with executable files. In the attacks, phishing emails were sent from virtual servers, which had installed an anonymous mailing script “yaPosylalka v.2.0” (another name of the service is “alexusMailer v2.0”) developed by Russian-speaking cyber-criminals.” continues Group-IB.
The criminal gang use Cobalt Strike, a legitimate program designed to perform penetration testing and the Mimikatz tool to compromise domain and local accounts.

The researchers from Group-IB believe that Cobalt gang is linked to Buhtrap,
“Group-IB specialists believe that just after the arrest of the Buhtrap group in May their botnet was sold to other criminals who are continuing its use to steal money from corporate accounts. That said, according to our analysis of Cobalt attacks on ATMs of Russian and European banks, the methods used by criminals to deliver phishing emails and obtain control over a domain controller are identical to those used by the Buhtrap group. Purportedly, at least a part of the Buhtrap group became Cobalt members, or more likely Buhtrap core members shifted their focus to attacks on ATMs. ” explains Group-IB.
I suggest the reading of the Group-IB report on the Cobalt gang, it is full of details that are very useful to prevent such kind of attacks.
How to steal a Tesla car by hacking the mobile app
25.11.2016 securityaffairs Hacking
A group of researchers from the security firm Promon has demonstrated how cyber criminals could take control of the Tesla Car and steal it.
A group of security experts from security firm Promon has demonstrated how to exploit the Tesla app (for both Android and iOS) to locate, unlock and steal a Tesla Model S. The hackers used a laptop to remotely control the vehicle as demonstrated in the following video PoC.
“Our researchers have demonstrated that because of lack of security in the Tesla smartphone app, cyber criminals could take control of the company’s vehicles, to the point where they can track and locate the car in real-time, and unlock and drive the car away unhindered.” reada a blog post published by the Promon firm.

The Tesla app implements numerous functionalities, it allows to check the battery level, locate the car, set the climate control and flash the lights.
The app performs the operations by sending an HTTP request to the Tesla server, these requests leverage an OAuth token for the authentication. The token is obtained by the users once he completed the authentication through username and password.
The experts noticed that the first time the user logs into the Tesla app, the mobile device receives a token that is stored in cleartext in a file in the app’s sandbox folder. Every time the app is restarted, the token is read and used for subsequent requests.
Attackers can steal it to impersonate the victim and access to the vehicle.
“In our tests, this token was valid for 90 days, meaning that the user has to re-enter his username and password once in a while. Stealing this token enables an attacker to locate the car and open its doors. In order to enable keyless driving, the password is required as well. Because of that, the hack focused on obtaining the username and password.” continues the analysis.
There are several methods to steal the login credentials, the hackers in their test used a modified Tesla app that includes the code to steal the username and password and send to an attacker.
In order to replace the Tesla app and manipulate the token, the attackers used a privilege escalation attack.
When the Tesla car owner connects to the bogus Wi-Fi hotspot and visits a web page, he is redirected to a captive portal that displays an advertisement targeting Tesla owners.
“In this example, an app was advertised that offers the Tesla owner a free meal at the nearby restaurant. When the Tesla owner then clicks on the advertisement, he is redirected to the Google Play store where the malicious app is displayed.” states the experts.
Once the Tesla owner has installed and started the malicious app, it will then gain root permissions and replace the legitimate Tesla app. When the user starts the app the next time, he will be prompted to provide his login credentials that the Tesla app will send back to the attacker.
The attackers have to trick the Tesla owner into installing this malicious app, for example through a phishing attack.
In a first step, the hackers have to convince the owner to download a malicious app onto their Smartphone. The hackers set up a free and open Wi-Fi hotspot in a proximity of a Tesla charging station, which offers a free burger to Tesla owners who download a special app. Of course, the attackers could use various incentives to trick users into downloading the malicious app.
“At this point the target knows nothing about the free burger app’s true intentions, but now the hackers have access to the Tesla app, they can track the car. Once parked up for the night, they can track down the car, instruct it to unlock (a feature of the app), then enable ‘keyless driving’ mode. Created by Tesla, this feature lets Tesla owners remotely unlock and start their cars by entering a password; this can come in handy when asking a neighbour to move the car to a different parking space while you are on holiday, for example.”
It is important to highlight that the hack isn’t a related to a flaw in Tesla car, a Tesla spokesperson told IBTimes UK that the report does not demonstrate any Tesla-specific vulnerabilities.
“Mobile-focused criminals are more skilled than ever before, and are using a lack of security in mobile apps as an increasingly lucrative source of revenue.” said Tom Lysemose Hansen, founder and chief technology officer of Promon.
“Remotely controlling and stealing Tesla cars is a particularly dangerous example of just what can be done, but in theory any app without the necessary protection in place could be affected.”
Microsoft Shares Telemetry Data Collected from Windows 10 Users with 3rd-Party
24.11.2016 thehackernews Hacking
Cyber security is a major challenge in today's world, as cyber attacks have become more automated and difficult to detect, where traditional cyber security practices and systems are no longer sufficient to protect businesses, governments, and other organizations.
In past few years, Artificial Intelligence and Machine Learning had made a name for itself in the field of cyber security, helping IT and security professionals more efficiently and quickly identify risks and anticipate problems before they occur.
The good news is that if you are a Windows 10 user, Microsoft will now offer you a machine learning based threat intelligence feature via its inbuilt Windows security service, which will improve the security capabilities available on Windows 10 devices.
But, the bad news is that it is not free.
The company is offering this "differentiated intelligence" feature on its newly added service to Windows 10, dubbed Windows Defender Advanced Threat Protection (WDATP), which helps enterprises detect, investigate, and respond to advanced attacks on their networks.
This becomes possible after Microsoft recently signed a deal with FireEye that integrates the security vendor's iSIGHT Threat Intelligence into Windows Defender Advanced Threat Protection.
As part of the partnership, Microsoft will give FireEye access to all the telemetry data from every device running Windows 10, Australian website ARN reports.
"FireEye has invested in nation-state grade threat intelligence, and we are strategically partnering with industry leaders to operationalize this high-quality intel," Ken Gonzalez, FireEye's Vice President of Corporate Development, said in the official press release.
"By working with Microsoft, we’re able to offer differentiated threat intelligence within WDATP and together help make organizations more secure."
It's no secret that Windows 10 collects all sorts of usage information on users and sends them back to Microsoft, which then uses this telemetry data to help identify security issues, fix problems and improve the quality of its operating system.
This telemetry data includes information on the device running Windows 10, a list of installed apps, crash dumps, and other statistics from devices powered by its latest operating system.
However, this Microsoft's data mining capability also raised some privacy concerns among Windows users.
This newly-signed deal with FireEye is the first time that Microsoft has publicly agreed to share telemetry data of Windows 10 users with a third-party, which is definitely worrying for many users.
At this moment, the official press release says nothing about Microsoft providing FireEye with access to data collected from Windows 10 users.
Microsoft has yet to comment on this matter.
Your Headphones Can Spy On You — Even If You Have Disabled Microphone
24.11.2016 thehackernews Hacking
Have you considered the possibility that someone could be watching you through your webcam? Or Listening to all your conversations through your laptop’s microphone?
Even a bit of thought about this probability could make you feel incredibly creepy.
But most people think that they have a solution to these major issues i.e. simply covering their laptop’s webcam and microphone with tape, just like Facebook CEO Mark Zuckerberg and FBI Director James Comey.
But it's 2016, and a piece of tape won't help you, as a new experiment has proved that how easily hackers can turn your headphones into a microphone to spy on all your conversations in the background without your knowledge.
A group of Israeli security researchers at Ben Gurion University have created a proof-of-concept code (malware) that converts typical headphones into microphones and then use them to record all your conversations in the room just like a fully-featured spying device.
Speake(a)r Malware Weaponizes Headphones and Speakers
Using headphones as microphones is a decade-old technique. There are many videos available on YouTube, which show that earbuds can function as microphones in a pinch.
But what the researchers managed to do is switching an output channel of the audio card on your laptop — running either Windows or Mac OS — to an input signal and then recording the sound without any dedicated microphone channel from as far as 20 feet away.
Dubbed "Speake(a)r," the malicious code (malware) is disturbingly able to hijack a computer to record audio even when its microphone is disabled or completely disconnected from the computer.
"People don’t think about this privacy vulnerability," says lead researcher Mordechai Guri told Wired. "Even if you remove your computer’s microphone, if you use headphones you can be recorded."
Speake(a)r actually utilizes the existing headphones to capture vibrations in the air, converts them to electromagnetic signals, alters the internal functions of audio jacks, and then flips input jacks (used by microphones) to output jacks (used for speakers and headphones).
This allows a hacker to record audio, though at a lower quality, from computers with disabled or no microphone or from computers of a paranoid user, who has intentionally removed any existing audio components.
But What made this Hack Possible?
Thanks to a little-known feature of Realtek audio codec chips that actually "retask" the computer's output channel as an input channel silently.
This makes it possible for the researchers' malware to record audio even when the earbuds is connected into an output-only jack and do not even have a microphone channel on their plug.
What's even worse? Since RealTek chips are being used on the majority of systems these days, the Speake(a)r attack works on practically any computer, running Windows or MacOS, and most laptops, as well, leaving most computers vulnerable to such attacks.
"This is the real vulnerability," said Guri. "It’s what makes almost every computer today vulnerable to this type of attack."
The feature of RealTek audio codec chips is truly dangerous, as it can not be easily fixed. The only way to deal with this issue is to redesign and replace the chip in current as well as future computers, which is impractical.
Security researchers also published a YouTube video which shows the Speake(a)r eavesdropping attack in work.
For more detailed and technical explanation of the Speake(a)r attack, you can head on to the research paper [PDF] titled "Speake(a)r: Turn Speakers to Microphones for Fun and Profit."
Registral Function of the State Mexico (FREM) hacked. Shad0wS3C is back
23.11.2016 securityaffairs Hacking
The hacker group Shad0wS3C is back and hacked the Institute of the Registral Function of the State Mexico (FREM), it leaked the database.
Shad0wS3C is Back and hacked the Institute of the Registral Function of the State Mexico (FREM) and leaked a dump of its database.
The hacker leaked the database at the following URL
https://t.co/6XgwSf4uWW

The archive includes three files containing personal information of the users, including passport info and other sensitive details.
In the past, Shad0wS3C was an hacktivist group, it seems to have changed its mission and started hacking without any specific political motivation.
Its member Gh0s7, told me that the FREM data breach is just an anticipation of future attacks.
“This leak is just a simple demonstration for our future attacks. We will be leaking more gov and private corps.” Gh0s7 told me.
The group launched a targeted attack, the first of a new wave that aims to hit government servers and corporations worldwide.
The hackers have a list of targets composed of gov and private servers to hack.
This is their “black list.”
Hackers did not reveal details of the data breach, they simply told me to have used a “private exploit.”
The last time hack in order of time made by Shad0wS3C is the Paraguay’s Secretary of National Emergency (SNE) data breach occurred in August. The hackers leaked online a dump from a PostgreSQL database also in this case.
Armed Forces recruitment website hacked, visitors redirected to China
23.11.2016 securityaffairs Hacking
Canada Armed Forces recruitment website was taken down after it was hacked and would-be recruits are redirected to a Chinese government page.
The Canadian Armed Forces recruitment website was hacked last week, visitors have been redirected to the Chinese government’s main page instead of the legitimate website.
According to CTV television, anyone trying to sign up for Canada’s Armed Forces on the forces.ca/en/home page was redirected to the www.gov.cn site instead. The armed forces quickly took down the page.
“The recruiting web page for the Canadian Armed Forces appears to have been hacked Thursday, redirecting users to an official Chinese state page.” reported CBC News.
“Users visiting forces.ca, which is the main landing page for would-be recruits, were instead getting a page full of information and statements about Chinese government ministers, and their activities, in that country. The site now shows an error message instead”
The Canadia Armed Force promptly took the recruiting page off-line.

Two government sources told CBC News that the recruiting website was hosted externally by a private-sector provider.
One of the officials who has spoken with the media outlet revealed that servers at the Department of National Defence were not compromised in the attack.
“This is a serious matter,” Public Safety Minister Ralph Goodale told reporters Thursday after question period. “We don’t want to jump to conclusions, but when something of this nature happens … we treat it with real gravity, and we’ll investigate it. That process is underway right now.”
The news of the hack was confirmed by the Defense ministry spokeswoman Ashley Lemire, who added that there is no information regarding the responsible.
Canadian authorities have long complained about incursions of foreign hackers into government computer networks.
“In 2014, Canada’s then Conservative government took the unusual step of singling out Chinese-based hackers for attacking a key computer network and lodged a protest with Beijing.” reported the Reuters.
Michigan State University Data Breach, 400,000 Records Exposed
22.11.2016 securityaffairs Hacking
Hackers attempted to extort Michigan State University after they have breached into its database containing 400,000 records of students and employees.
Crooks hacked the Michigan State University breaching into a database containing 400,000 student and employee records, then tried to monetize the efforts attempted to extort the organization.
Michigan State University reported the data breach occurred on November 13 when an unauthorized party accessed into a server of the organization.
“Michigan State University has confirmed that on Nov. 13 an unauthorized party gained access to a university server containing certain sensitive data.
The database, which contained about 400,000 records, included names, social security numbers and MSU identification numbers of some current and former students and employees. It did not contain passwords or financial, academic, contact or health information.” reported the Michigan State University.
Of those records, 449 were confirmed to be accessed by the unauthorized party. The affected database was taken offline within 24 hours of the unauthorized access.”
The records accessed by the hackers contain personal information of current and former students and employees, including names, social security numbers, MSU identification numbers, and dates of birth.
The MSU Police Department confirmed that is investigating the case with federal law enforcement authorities.
The database includes information as far back as 1970, the Michigan State University highlighted that passwords, financial information, and contact details were not included in the archive.
The university said it took the affected database offline within 24 hours after discovering the breach and it determined that only 449 of the records have been accessed by the hackers.
“At Michigan State University, we are committed to data and privacy protection. Regrettably, we were recently the target of a criminal act in which unauthorized users gained access to our computer and data systems. Information security is a top priority of our university, and we know the frustration this is causing members of our community.” said President Lou Anna K. Simon. “Only 449 records were confirmed to be accessed within the larger database to which unauthorized individuals gained access. However, as a precaution, we will provide credit monitoring and ID theft services for any member of our community who may have been impacted by this criminal act. We also will continue to work diligently in our efforts to protect the integrity of our data systems and improve the security of information that is entrusted to us.”
Representatives from the University told Fox47News that the hackers attempted to extort the organization after breached in their database.
This is the second time that the Michigan State University was hacked this year.
In October, the hacker Mys7erioN told me to have hacked into the Michigan State University.
As proof of the hack, Mys7erioN published on Pastebin the records of the table containing user data, including ‘user,’ including names, logins, phone numbers, emails published and encrypted passwords.

Mys7erioN was scanning some websites when discovered an SQL injection vulnerability.
In 2012, a hacker leaked 1,500 records from the University and in 2013, the University confirmed that hackers modified employee banking information using stolen credentials.
Hackers Steal Millions From European ATMs Using Malware That Spit Out Cash
22.11.2016 thehackernews Hacking
ATM hackers who long relied on tactics of stealing payment card numbers and online banking credentials to steal millions are now targeting the bank itself to steal cash directly from the machines.
Earlier this year, a gang of cyber criminals infected several ATMs with malware in Taiwan and Thailand that caused the machines to spit out millions in cash, and the gang members then stood in front of the infected ATMs at the appointed hour and collected the money.
Now, the FBI has warned U.S. banks of the potential for similar ATM jackpotting attacks, saying that the agency is "monitoring emerging reports indicating that well-resourced and organized malicious cyber actors have intentions to target the U.S. financial sector."
ATM jackpotting is a technique used to force automated teller machines to spit out cash.
According to Russian cyber security firm Group-IB, cyber crooks have remotely infected ATMs with malware in more than dozen countries across Europe this year, which forces machines to spit out cash.
The world's two largest ATM manufacturers, Diebold Nixdorf and NCR Corp., said they were aware of the ATM attacks and had already been working with their customers to mitigate the threat.
The cyber criminals have been targeting ATMs for at least five years, but the latest hacking campaigns mostly involved small numbers of ATMs due to the fact that hackers required physical access to the machines to collect cash.
Group-IB did not name the banks targeted in the campaign but said the victims were located in Armenia, Bulgaria, Estonia, Georgia, Belarus, Kyrgyzstan, Moldova, Spain, Poland, the Netherlands, Romania, the United Kingdom, Russia, and Malaysia.
Both Diebold Nixdorf and NCR said they had already provided banks with information on how to thwart the attack, Reuters reported.
"We have been working actively with customers, including those who have been impacted, as well as developing proactive security solutions and strategies to help prevent and minimize the impact of these attacks," said Owen Wild, NCR's global marketing director for enterprise fraud and security.
The disclosure of the new campaign comes months after two large ATM hacks, wherein hackers stole $2.5 Million from Taiwan's First Bank and $350,000 from Thailand's state-owned Government Savings Bank.
While Group-IB believes the attacks across Europe were conducted by a single criminal group, dubbed Cobalt, the FBI believes the malicious software used in the attack could be linked to the Russian ATM gang known as Buhtrap, the Wall Street Journal reported.
However, citing the tools and techniques used by both groups, Group-IB believes that Cobalt is linked to Buhtrap, which stole 1.8 Billion rubles ($28 Million) from Russian banks between August 2015 and January 2016.
Eastern India Regional Council hacked by Kapustkiy
21.11.2016 securityaffairs Hacking
Kapustkiy, one of the most prolific hackers at this moment announced a new data breach, the victim is the India Regional Council.
Last week, I was contacted by a young hacker that breached Indian embassies across the worlds, he goes online with the moniker Kapustkiy.
Kapustkiy is a seventeen years old pentester that is targeting organizations and embassies across the world. Recently he breached the ‘Dipartimento della Funzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and a few days ago the hacker and his friend Kasimierz (@Kasimierz_) hacked the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya. Kapustkiy and his friend Kasimierz (@Kasimierz_).
He also targeted Universities, including two subdomains of Virginia University & Sub domain of University of Wisconsin (http://pastebin.com/i1wmM5D1 ) and another embassy, the Indian Embassy in New York (http://pastebin.com/Akm9x4dD )
The Indian authorities have issued a public statement to thank the young hacker for exposing the vulnerabilities in their websites.
“Thank you for your advice,” said Sanjay Kumar Verma, Joint Secretary, eGovernance and Information Technology. “We are fixing codes one by one. Your help in probing websites of various Indian embassies is a great help.”
This time the young hacker breached the database at the Eastern India Regional Council and leaked online a small portion of the archive composed of 17,000 users. Kapustkiy leaked an excel file containing more than 2000 user records as proof of the breach.

The records in the database of Eastern India Regional Council contain many attributes, including membership numbers, usernames, passwords, email addresses, registration numbers.
Kapustkiy used some web scanners to find several vulnerabilities in the target website and a simple SQL Injection tool to exploit the flaw he discovered. The hacker tried to contact the organization but they seem to ignore emails.
Once again Kapustkiy is inviting website administrators to pay attention to the security of their infrastructure.
Kapustkiy breached an Italian Government website, exposing 9,000 of 45,000 records
19.11.2016 securityaffairs Hacking
Hacker Kapustkiy breached into an Italian Government website (Dipartimento della Funzione Pubblica) exposing 9,000 users of 45,000.
A few days ago I was contacted by a young hacker that breached Indian embassies across the worlds, he goes online with the moniker Kapustkiy.
Kapustkiy is a pentester that is targeting organizations and embassies across the world. Recently he breached the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), while a few days ago the hacker and his friend Kasimierz (@Kasimierz_) hacked the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya. Kapustkiy and his friend Kasimierz (@Kasimierz_).
Indian authorities have issued a public statement to thank the young hacker for exposing the vulnerabilities in their websites.
“Thank you for your advice,” said Sanjay Kumar Verma, Joint Secretary, eGovernance and Information Technology. “We are fixing codes one by one. Your help in probing websites of various Indian embassies is a great help.”
Other victims are two subdomains of Virginia University & Sub domain of University of Wisconsin (http://pastebin.com/i1wmM5D1 ) and another embassy, the Indian Embassy in New York (http://pastebin.com/Akm9x4dD )
Yesterday he contacted me because he hacked a website belonging to the Italian Government. The database accessed by the hacker contains roughly 45,000 users, including login credentials.
Kapustkiy told me he has exploited an SQLi flaw in the ‘Dipartimento della Funzione Pubblica’ website to gain access to the database. He shared a Pastebin link containing the reference to an excel file containing the user records in the database.
The excel includes email addresses of the users, used as username, and encrypted passwords.
The link points to an excel file containing only 9,000 records, the young hacker published only a small portion of overall data in order to give Italian experts time to solve the problem.
Kapustkiy first contacted the site’s administrators to report the issue but without reply, only after the news went public someone has put the site in maintenance mode.

“I did not get any response from the administrators. I hope they will improve their security,” he told me.
At the time I was writing the excel file is still online.
OurMine hackers hacked Mark Zuckerberg’s online accounts for the second time
18.11.2016 securityaffairs Hacking
For the second time this year, the hacker group OurMine breached one of the online accounts of the Facebook CEO Mark Zuckerberg.
For the second time, this year hackers seems to have breached the Facebook CEO Mark Zuckerberg. The notorious hacking group known as OurMine has claimed credit for hacking Mark Zuckerberg’s online accounts.
The news was reported by Zack Whittaker from Zero Day who was contacted by the notorious group of hackers. OurMine told Whittaker they had hacked the Zuckerberg’s Pinterest account, the hacker changed the tagline and published the group’s web address. At the time I was writing the situation has been restored to the normal.
“Don’t worry, we are just testing your security.” displayed the defaced Zuckerberg’s Pinterest account.
The group did not provide further information about the attack, they only clarified to haven’t used data from leaked databases.
The group admitted having exploited a flaw in Pinterest but avoided to reveal it.
“When pressed, the group said that it has “a exploit on Pinterest” but didn’t say how. The last time it said that it had exploited a platform, it turned out to be a fake.” wrote Whittaker.
The OurMine hacker group targeted many other high-profile users, the list of victims is very long and include names like Mark Zuckerberg, Twitter co-founder Evan Williams, David Guetta Daniel Ek, former Twitter CEO Dick Costolo, the CEO and founder of Spotify, Google CEO Sundar Pichai, and many others.
Which is the motivation?
It seems that the OurMine group is linked to a Security Firm that is trying to obtain notoriety from the attacks and is offering its services to the targets, that evidently need them to avoid further incidents.

One of the messages posted by the group states:
“We are just testing people security (sic), we never change their passwords, we did it because there is other hackers can hack them and change everything.”
Whittaker revealed that hackers also emailed his Zuckerberg’s username, and his password for his Twitter account. The OurMine group confirmed that Zuckerberg had enabled two-factor authentication after they hacked it for the first time.
The hackers disclosed more information, for example, they said the phone number associated with the account ended in “86”, while the current Twitter password was Zuckerberg’s former personal Gmail password, which was changed six months ago.
The hacker Kapustkiy continues to target embassies and universities
18.11.2016 securityaffairs Hacking
The hacker Kapustkiy is back and breached another embassy and two universities. He leaked data on Pastebin.
The security pentester who goes online with the moniker Kapustkiy continues to target organizations and embassies across the world.
Recently he breached the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), while a few days ago the hacker and his friend Kasimierz (@Kasimierz_) hacked the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya. Kapustkiy and his friend Kasimierz (@Kasimierz_).
The last victims of the hacker are two subdomains of Virginia University & Sub domain of University of Wisconsin (http://pastebin.com/i1wmM5D1 ) and another embassy, the Indian Embassy in New York (http://pastebin.com/Akm9x4dD )
Segui
Kapustkiy @Kapustkiy
Virginia & Wisconsin Sub Domain #Hacked #Leaked http://pastebin.com/i1wmM5D1
17:52 - 12 Nov 2016
1 1 Retweet 2 2 Mi piace
He contacted me via Twitter to report the data breaches, in the case of the Indian Embassy in New York he explained to have leaked only a small portion of stolen data that doesn’t include US personnel.
“Hi, Its me Kaputski, A few weeks ago I breached several websites that were related to the Indian ShitEmbassy. So I thought they will fix all the vulnerables in there domains and also look at there other domains that maybe could have a simple ”SQLi” vulnerable. So guess what? they did not look at all and only fixed some of there domains SMH……….” wrote Kapustkiy.
“I’m tired to report all the errors that I find in there website that I decided to breach them, NOW FIX YOUR SECURITY FUCKING ADMINS! NOTE: There was also a table named ”Newyork_contact” which had 7000 entries. I didn’t leak that out of privacy of people. Also the table ”Newyork_registration” had also information like Address,City,zipcode,phone number” I only leaked this but it could be more.”.
The databases related to universities include users personal information such as names, login, passwords, phone and many other information of students and staff.
As you can see in same cases the passwords are stored in plain text.

Records belonging to the hacked embassy include also phone numbers, let me highlight once again that such kind of information is a precious commodity for nation-state hackers that intend to launch a spear phishing campaign against diplomats.
Kapustkiy explained to have leaked the data because the administrators of the targeted entities ignore his warning via email.
It is likely Kapustkiy exploited SQli injection flaws in the last string of data breaches.
Who is the next one?
SWIFT Hack: Bangladesh Bank Recovers $15 Million from a Philippines Casino
10.11.2016 thehackernews Hacking
Part of the $81 Million stolen from Bangladesh bank's New York Federal Reserve account earlier this year in the wake of the major malware attack on the SWIFT interbank transfer network has been tracked down to a casino in the Philippines.
SWIFT, or Society for Worldwide Interbank Telecommunication, is a global financial messaging system that thousands of banks and organizations around the world use to transfer billions of dollars every day.
In February, hackers dropped a piece of malware on a SWIFT terminal employed by Bangladesh's central bank, obtained credentials needed for payment transfers from the New York Federal Reserve Bank, and then transferred large amount to fraudulent accounts based in the Philippines and Sri Lanka.
In March, the investigation revealed that the stolen money was then sold to a black market foreign exchange broker and later transferred to at least 3 local casinos in the Philippines.
In September, Philippine court ordered the return of $15 Million surrendered by a junket operator at Solaire Resort & Casino to Bangladesh Bank, reports Reuters.
On Monday, a team of Bangladesh central bank arrived in Manila to take back its $15 Million of the $81 Million stolen funds surrendered by Chinese-born Kim Sin Wong, casino's junket operator of Eastern Hawaii Leisure Company.
bangladesh-swift-hack-casino
Wong, who returned $4.63 Million and 488.28 Million pesos (around $10.05 Million) to Philippine authorities, said the stolen money came from two Chinese high-rollers, Gao Shu Hua from Beijing and Ding Zhi Ze from Macau.
However, Wong denied any role in one of the world's biggest bank heists.
The recovered $15 Million amount is now secure in the vaults of the Philippine central bank, said Bangladesh's Ambassador to the Philippines John Gomes, adding that there's more to come.
"The writ of execution that the money be handed back to Bangladesh has already been done by the court," Gomes told Reuters. "The good thing is now that the process on this $15 Million is more or less completed, we will go for the rest."
Bangladesh was not the first bank which became the victim of SWIFT malware. This year, some unknown hackers targeted banks across the world by gaining access to SWIFT that is being used to transfer Billions of dollars every day.
Investigators also revealed that the malware used in the Bangladesh cyber heist was almost identical to one used to infiltrate banks in Ecuador, Vietnam, and the Philippines.
19-Year-Old Teenage Hacker Behind DDoS-for-Hire Service Pleads Guilty
3.11.2016 thehackernews Hacking
Due to the worldwide promotion of Mirai botnet that knocked down half of the Internet last Friday, hackers and even script kiddies have started creating their own botnet networks by hacking millions of IoT devices and selling them as DDoS-for-hire service to overwhelm targets with data.
A 19-year-old student from Hertford has pled guilty to running one such DDoS-for-hire service that shortly became one of the most popular DDoS booter tools in the market to conduct distributed denial of service (DDoS) attacks.
Dubbed Titanium Stresser, the tool was used to conduct coordinated DDoS attacks around the world and brought Adam Mudd an income of more than US$385,000 (£315,000 A$505,000), according to the Eastern Region Special Operations Unit (ERSOU).
On 28 October at the Old Bailey, Mudd pleaded guilty to two counts of the Computer Misuse Act and one count of money laundering offense and will be sentenced in December.
Mudd, who was arrested at his home in 2015, admitted to committing unauthorized acts of creating the DDoS service, using it himself, and then renting it to other cyber criminals through the service's website.
Titanium-Stresser-ddos-tool
Prosecutor Jonathan Polnay says the teenager allegedly launched 592 DDoS attacks against 181 IP addresses between December 2013 and March last year.
"Titanium Stresser is a computer program created by the defendant, and it is not an unimpressive piece of software in terms of design," Polnay told the court. "It carried out DDoS attacks, and it takes down computer networks and websites."
Moreover, from the detailed logs authorities discovered in his home, investigators were able to determine that other criminals had used Titanium Stresser to launch a whopping 1.7 Million DDoS attacks on targets worldwide.
It has also been believed that the infamous Lizard Squad gang used the source code of Titanium Stresser as a base for its Lizard Stresser -- another DDoS-for-hire service most famously used to take down the PlayStation and Xbox Live networks in 2014.
Mudd is scheduled to be sentenced in December 2016.
Stealth Cell Tower, how to spy on workers with a harmless printer
2.11.2016 securityaffairs Hacking
Stealth Cell Tower, it is an antagonistic GSM base station concealed in an office printer that could be used for surveillance purposes.
Are you angry with your boss or your colleagues? Do you want to spy on them? The engineer Julian Oliver has demonstrated how to do it with a tiny cellphone base station concealed in an apparently innocuous office printer.
Oliver dubbed his project Stealth Cell Tower, it is an antagonistic GSM base station concealed in an office printer.
The expert explained that the Stealth Cell Tower is part of an ongoing research on the practice of disguising cell towers as other things (i.e. like trees or church spires), in 2014 he wrote an interesting article titled “Stealth Infrastructure.”
Here, Stealth Cell Tower situates this same outdoor practice indoors, where an HP printer is perhaps the most innocuous of flora.
“Stealth Cell Tower is an antagonistic GSM base station in the form of an innocuous office printer. It brings the covert design practice of disguising cellular infrastructure as other things – like trees and lamp-posts – indoors, while mimicking technology used by police and intelligence agencies to surveil mobile phone users.” reads a blog post on the project.
Oliver used a common HP Laserjet 1320 because it has a helpful free space inside the casing, then assembled inside the device a RaspberryPi 3 with a couple of antennas, the BladeRF SDR board and some cabling to power these components.
The complete list of the hardware used by the expert includes:
A Hewlett Packard Laserjet 1320 printer modified to contain and power components
BladeRF x40
Raspberry Pi 3
2x short GSM omnidirectional antennae with magnetic base
2x SMA cable
Cigarette-lighter-to-USB-charger circuit (converting 12-24v to 5v)
1x USB Micro cable (cut and soldered to output of USB charger)
1x USB A cable (cut and soldered to printer mainboard)
Oliver explained that the Raspberry Pi 3 was chosen after failed attempts to achieve stable YateBTS performance on the Intel Edison, Beaglebone Black and I-MX6 Marsboard, that were first choices due to their small footprint.
“The Raspberry Pi 3 was chosen after failed attempts to achieve stable YateBTS performance on the Intel Edison (tiny – would’ve saved space!), Beaglebone Black and even an I-MX6 Marsboard,” he wrote. “Unlike the antiquated OpenBTS, YateBTS really seems to need those extra cores, otherwise ignoring accelerators like NEON on the Cortex A8/9 platforms.”
The core of the experiment is the code written by Oliver and running on the tiny PC, it operates as a bogus cellphone tower that detects nearby phones and sends them SMS messages.
“Masquerading as a regular cellular service provider, Stealth Cell Tower surreptitiously catches phones and sends them SMSs written to appear they are from someone that knows the recipient. It does this without needing to know any phone numbers.”

The Stealth Cell Tower is able to print for each response to the above messages a transcript that includes various information such as the captured message sent, the victim’s unique IMSI number and other identifying data. The printer also randomly calls victim’s phones in the environment and on answering, Stevie Wonder’s 1984 classic hit I Just Called To Say I Love You is heard.
It is clear that a similar configuration could be used in a real attack scenario, for example by sending out phishing SMS messages or to perform man-in-the-middle attacks against workers.
In short, it could become a very powerful surveillance device, the next time you mount a printer in the office, look inside.
You can download the full code used by the expert here (sha256sum eaabeb72eb5bf3e62cbfedb43dbc623437b40728b25555d88c9e8f06ca31d090).
Philip Hammond invokes an active defence of UK hacking back the attackers
2.11.2016 securityaffairs Hacking
The British Government announces an active defence posture in response to nation-state cyber attacks, Chancellor warns UK will retaliate against attacks.
Hacking back, or “active defence” as security experts prefer to call it, is becoming a high debated argument.
While the number of cyber attacks continues to increase and attackers are using even more sophisticated techniques, many Governments are planning to hack back crooks and nation-state hackers that threaten their infrastructure.
Recently a china’s cybersecurity draft law plans to hit back foreign hackers that power.
The British government fears that “old legacy IT systems used by many organizations in the UK” are increasingly targeted by hackers who have no problem to compromise them.
Britain will strike back against nation-state actors that will launch cyber attacks on the national critical infrastructure.
Chancellor Philip Hammond promised retaliatory countermeasures in response to state-sponsored attacks, he also unveiled a £1.9bn package designed to boost Government defenses against cyber threats as part of a five-year national cyber security strategy.
The strategy of the UK Government has a five-year plan and aims to “work to reduce the impact of cyber attacks and to drive up security standards across public and private sectors.”
Philip Hammond he reiterated that the measures are a question of national security.
UK active defence chancellor-philip-hammond
Source The telegraph
The most interesting part of the measures announced by Hammond, is the intention of the UK Government to adopt an active defence model which includes possible offensives against attackers. Hammond explained that hack back is the unique alternative to a conflict.
“Speaking before the launch, Hammond said Britain must “keep up with the scale and pace of the threats we face” and insisted that the new funding will “allow us to take even greater steps to defend ourselves in cyberspace and to strike back when we are attacked”.” reported The Guardian
“The money – which almost doubles the amount set out for a similar strategy in 2011 – will be used to improve automated defences to safeguard citizens and businesses, support the cybersecurity industry and deter attacks from criminals and “hostile actors”.”
Hammond announced a new posture of the UK against the cyber threats, with a specific focus on the protection of the nation’s critical national infrastructure and business.
“We will deter those who seek to steal from us, or harm our interests,” Hammond told at the Microsoft’s Future Decoded conference in London on Tuesday. “We will strengthen law enforcement to raise cost and reduce rewards,” he said of criminal attackers.
This is just first step ahead in cyber security matter, he promised the UK would “continue to invest in cyber defense capabilities,” in particular in the technology that could allow the British cyber army to trace and hack back the state-sponsored hackers.
“If we don’t have the ability to respond in cyberspace to attack that takes down power networks or air traffic control systems we would be left with the impossible choice of turning the other cheek or resorting to a military response – that’s a choice we don’t want to face.”
“No doubt the precursor to any state-on-state conflict would be a campaign of escalating cyber attack. We will not only defend ourselves in cyberspace but will strike back in kind when attacked.”
In the same day, Hammond, who chairs the Cabinet’s cross-department cyber-security committee, had listed high-profile cyber attacks against British critical infrastructure.
The active defence model implemented by the UK Government includes a new generation software to detect and repel cyber attacks and also the creation of dedicated cyber units.
Hammond pointed to the recent deployment of an application that was able to zero incidence of 50,000 fraudulent emails from crooks that pretend to be sent from Government offices.
Hammond also referenced the TalkTalk data breach that exposed details of 156,959 customers and that lead the Information Commissioner to fine the company £400,000.
“CEOs and boards must recognise they have responsibility to manage cybersecurity,” Hammond said.
Hammond stressed the adoption of a proper security posture also for private businesses that are a privileged target of hackers.
“Similarly, technology companies must take responsibility for incorporating the best possible security measures into the technology of their products. Getting this right will be crucial to keeping Britain at the forefront of digital security technology.”
No doubts, the active defence is the new approach of many governments in response to the growing cyber threats.
Domain Hijacking – An Invisible and Destructive Threat We Should Watch For
26.10.2016 securityaffairs Hacking
The Morphus Labs warns about another major threat, the domain hijacking incident, a threat that can completely subvert your information security strategy.
The Morphus Labs warns this week about another major threat. Renato Marinho and Victor Pasknel treated a domain hijacking incident, a threat that can completely subvert your information security strategy. They give details in this article how the incident was handled and how we can prevent similar scenarios.
Introduction
It’s Saturday morning and you, the CSO of a huge company, start to receive messages from various sources, including press, informing that all of your organization Internet addresses are getting visitors to fake websites offering malicious content in form of fake security modules and/or updates.
What appeared to be a website defacement attack, turned out to be something much worse. In examining more closely, you realize that cybercriminals did, in fact, the kidnapping of the entire organization domain and directed all addresses to fake websites aiming to steal information from your customers and spreading malicious code. The worst thing is that there was no action that depended exclusively on you to solve the problem immediately.
In this article, we describe the incident response to the scenario described above and how this threat, being capable to subvert your entire strategy and security investment, can be mitigated with very simple actions.
Domain Name System (DNS) basics
To better understanding what happened, it’s important to understand some basic DNS concepts. If you are familiar with this subject, just jump to section 3.
DNS stands for Domain Name System and works as a foundation for the Internet . All addresses names we use daily to reach Websites and other Internet services have to be translated to IP (Internet Protocol); the translation or resolution process between an internet address name and IP address is the main role of DNS Servers.
DNS Servers work as a hierarchy of sorts, where the resolution requests are passed through it to the right server that is in charge of resolving the names for a certain domain, is reached. The root of this hierarchy, that is the invisible domain dot (“.”) in the end of any Internet address, is controlled by a group of DNS Servers distributed in different places around the world. Those root DNS Servers have to know the IP address of the DNS Servers that are in charge of all Top Level Domains (TLD), like the “.com”. The “.com” DNS servers in turn, have to know the IP address of the DNS Servers that are in charge of your company’s domain name, like “yourdomain.com” and so on.
For example, when someone asks for “www.yourdomain.com.”, the request reaches the root servers (“.”) that in turn, reaches the “.com” servers, that in turn, reach your company’s DNS servers, that finally resolves the address “www” and return the correct IP address.
The TLDs are controlled and managed by registry operators, also called Network Information Center (NIC). The registry operators manage the registration of domain names within the domains for which they are responsible. So, the “.com” registry operator is the organization that will hold the configuration of the DNS Servers IP addresses that are in charge of resolving the IP address of a domain like “yourcompany.com”.

Domain Hijacking
For you to register or manage a domain in any registry operator, you have to previously create an account (basically, username and password) on their web portal. This account will be used to manage the IP addresses of the DNS Servers that will point to the IP addresses of your website or e-mail servers.
Note that the access credentials to the portal operator are extremely sensitive information. Someone malicious in possession of such information would be able to change any configuration of your domains, including IP addresses of the DNS servers. In short, could hijack the Internet Domain of your company and target websites and emails to any address he wanted.
In the incident we treated at Morphus Labs, that’s exactly what happened. The bad actors stole the registry operator’s credentials and changed the primary and secondary DNS servers configuration pointing them to the criminals’ ones. After that, all the company’s customers were directed to a fake company website to download malicious content they were suggested by the fake content. We can imagine what the criminals’ strategy was had they had success spreading their malware.
Needless to say, the crooks changed the password after gaining access to the portal. In other words, they hijacked the domain and made the recovery dependable of the registry operator. “Manual” account recover is usually not easy nor fast.
The Incident Response
Unlike the majority of cyber incidents, you have almost nothing to do in your infrastructure itself to revert the situation, like recovering backup or configurations. Like what happened in this incident, all servers were intact.
Read the full article: https://www.linkedin.com/pulse/domain-hijacking-invisible-destructive-threat-we-should-marinho
And works as the foundation of the internet “ou” and works as a foundation for the internet.
Please, revise if the meaning was kept.
Bad actors? Is this expression clear to the reader?
Ukrainian hackers Cyber Hunta leaked emails of Putin’s Advisor
29.10.2016 securityaffairs Hacking
Hackers of the Cyber Hunta collective leaked thousands of emails allegedly stolen from the account of Vladislav Yuryevich Surkov.
Last week a Russian government website was hacked by the Jester hacker who defaced the website of the Russian Ministry of Foreign Affairs, MID.ru in retaliation for the recent attacks against US targets.
This week a Ukrainian hacker collective called “Cyber Hunta” released a cache of emails linked to the Kremlin’s Vladislav Surkov, also known as the grey cardinal.
Cyber Hunta is a group of hacktivists operates against threat actors from the outside and “internal enemies.”
The group claims to have access breached the internal networks of the Russian presidential administration and the Parliament.
Experts from the Atlantic Council’s Digital Forensic Research Lab who analyzed the Surkov leaks confirmed that email account hacked by the attackers, prm_surkova@gov.ru, was apparently managed by Surkov’s assistants.
“The hacked inbox was for prm_surkova@gov.ru, which was handled by his secretaries or assistants, including a “Masha” (Mariya) and “Yevgenia” (last names unclear). The majority of the emails are briefings from Surkov’s assistants, such as Aleksandr Pavlov. ” states the Atlantic Council’s Digital Forensic Research Lab.
On the other side, the Russian Government denied that the leaked emails belong to Surkov as he did not use email.
According to the Ukrainian security service, the SBU, the leaked emails are genuine, the Associated Press who analyzed the leaked email share the same opinion.
The Ukranian hacker leaked a 1 Gb Outlook data file (.pst) containing 2,337 messages. Some messages contain information about the current internal political developments in the Republic of Abkhazia, Republic of South Ossetia, Ukraine, and the Republic of Moldova.

The precious archive includes email messages related to the war in Donbass, including government expense data and a list of casualties. The messages also show connections between the pro-Russia separatists in eastern Ukraine and Russian government and pro-Russia separatists that operated in the area to destabilize the Ukrainian government.
Who is behind the Cyber Hunta? In the group linked to some governments that is opposite to the Kremlin? Which one?
Perhaps in time we will have some answers.
Michigan State University hacked, personal information leaked online
29.10.2016 securityaffairs Hacking
The young hacker Mys7erioN announced to have hacked into the database of a US organization, the Michigan State University. Data leaked online.
Today I was contacted via Twitter by Mys7erioN who revealed me to have hacked into the database of a US organization, the Michigan State University.
As proof of the hack, Mys7erioN published on Pastebin the records of the table containing user data, including ‘user,’ including names, logins, phone numbers, emails published and encrypted passwords.

Mys7erioN is a young hacker, he told me that he is 17 years old from the Netherlands that is studying IT security at the school.
He was scanning some websites when discovered an SQL injection vulnerability in the systems of the Michigan State University.
In the following image is reported the list of tables included in the hacked database.

One of the tables, “gelstaff_mp2016” seems to be an updated list of users. The hacker also published it on Pastebin, a total of roughly 500 personal information and 222 logins.
This isn’t the first time the Michigan State University is hacked, in 2012 the hacker DARWINARE published approximately 1,500 names, e-mail addresses, encrypted passwords, user IDs and mailing addresses stolen from the University.
You Can Hijack Nearly Any Drone Mid-flight Using This Tiny Gadget
28.10.2016 thehackernews Hacking
Now you can hijack nearly any drone mid-flight just by using a tiny gadget.
Security researcher Jonathan Andersson has devised a small hardware, dubbed Icarus, that can hijack a variety of popular drones mid-flight, allowing attackers to lock the owner out and give them complete control over the device.
Andersson, who is the manager of Trend Micro's TippingPoint DVLab division, demonstrated this new hack at this year's PacSec security conference in Tokyo, Japan on Wednesday.
Besides Drones, the new gadget has the capability of fully hijacking a wide variety of radio-controlled devices, including helicopters, cars, boats and other remote control gears that run over the most popular wireless transmission control protocol called DSMx.
DSMx is a protocol used to facilitate communication between radio controllers and devices, including drones, helicopters, and cars.
This is not the first hardware that can hijack drones mid-flight. There are jamming devices available in the market that block controlling radio signals and render a drone useless. However, these devices do not give you control like Icarus does.
Icarus works by exploiting DMSx protocol, granting attackers complete control over target drones that allows attackers to steer, accelerate, brake and even crash them.
The loophole relies on the fact that DSMx protocol does not encrypt the 'secret' key that pairs a controller and hobbyist device. So, it is possible for an attacker to steal this secret key by launching several brute-force attacks, Andersson explained in his presentation.
Once the drone hijacker, Icarus box, grabs the key, an attacker can send malicious packets to restrict the original owner of the drone from sending legitimate control commands. Instead, the drone will accept commands from the attacker.
You can also watch the demonstration video to learn more about Icarus box.
There's little to be done to mitigate this issue, and affected manufacturers are releasing patches and updated hardware, and securing the industry-wide encryption protocol in future drones.
"My guess is that it will not be easy to completely remedy the situation. The manufacturers and partners in the ecosystem sell standalone radio transmitters, models of all kinds, transmitters that come with models and standalone receivers," Andersson told Ars Technica.
"Only a certain set of standalone transmitters have a firmware upgrade capability, though the fix is needed on the model/receiver side."
Icarus has not been made available for sale, but this kind of gadget could benefit law enforcement as well as people who are worried about their safety and privacy. However, same could also be used for nefarious purposes.
So, next time if any annoying drone fly your overhead? Just hijack it and land it safely, rather than shooting it down.
The Icarus box is able to hijack nearly any drone mid-flight
28.10.2016 thehackernews Hacking
A security researcher presented a small hardware named Icarus box that is able to hijack a variety of popular drones mid-flight.
It could be very easy to hijack nearly any drone mid-flight by using the hardware presented by the Trend Micro researcher Jonathan Andersson at the PacSec hacking conference in Japan this week. Andersson, who leads the Trend Micro’s TippingPoint DVLab division, presented a small hardware named Icarus that is able to hijack a variety of popular drones mid-flight, the attacker is able to gain full control of the vehicle by locking the owner out.
According to Andersson, the Icarus box is able to hack into and radio controlled vehicles that run the SMx radio platform. Unfortunately, the SMx radio platform is very popular for drones, it present in vehicles manufactured by many vendors, including Walkera, NineEagles and AirTronics.
icarus box -drones-hacking
“It’s not a jamming system so i am not competing for control via RF power,” Andersson explained to Vulture South.
“Full flight control is achieved with the target experiencing a complete loss of control — it’s a clean switch-over.
“The range of my proof of concept implementation is equal to a standard DSMx radio transmitter, though standard 2.4GHz ISM band amplification can be applied to extend the range.”
The principle behind the Icarus box is simple, the hardware is able to determine the unique shared secret key within the DSMx binding process by monitoring the activity of the component and running a brute force attack. Once the Icarus box grabs the key, the attacker can send malicious packets to lock the legitimate controller out and send his commands.
Below a video PoC of the attack
“It works against all DSMx based radio systems, which would include drones, airplanes, cars, boats, and so on,” Andersson added.
The only way to protect the drone against such kind of attack is by updating receivers’ firmware protocols, an operation that is not always possible on many drones.
“My guess is that it will not be easy to completely remedy the situation. The manufacturers and partners in the ecosystem sell standalone radio transmitters, models of all kinds, transmitters that come with models and standalone receivers,” Andersson told Ars Technica.
“Only a certain set of standalone transmitters have a firmware upgrade capability, though the fix is needed on the model/receiver side.”
Below the slides prepared by Andersson.
American hacker The Jester defaced a Russian Government website
23.10.2016 securityaffairs Hacking
The popular American hacker The Jester defaced a Russian Government website in retaliation for the recent attacks against US targets.
We are in the middle of a battle in the cyberspace, with the advent of Presidential elections experts observed an intensification of the hacking attacks.
While hackers target parties and personnel involved in the Presidential campaigns, the US Government threatens Russia is blaming its cyber army for the attacks.
There aren’t only nation state actors involved in the battle, there are also hacktivists and patriotic hackers that could power cyber attacks against the adversary.
This week, hackers from NewWorldHackers crew and Anonymous targeted the Dyn DNS service to launch a message to Russia, and in the same hours, the notorious American cyber vigilante The Jester has defaced the website of the Russian Ministry of Foreign Affairs, MID.ru.
The hack was not so complicated for the expert hacker that has found a flaw in the website and exploited it to hack the Russian Government portal.
The Jester targeted the website of the Russian Government in retaliation for attacks against the American entities.
The popular hacker gained access to the Russian government ministry’s website and posted the following message:
“Stop attacking Americans.”
“Comrades! We interrupt regular scheduled Russian Foreign Affairs Website programming to bring you the following important message,” he wrote. “Knock it off. You may be able to push around nations around you, but this is America. Nobody is impressed.”
“His hacking of the website included this gag: Visitors are subjected to the ear-piercing sound of an American civil alert message — that shrieking dial tone that accompanies emergency weather broadcasts.” reported the CNNmoney.

The Jester sent a message to President Putin to blame him for lying about the involvement of Russian hackers in the recent attacks against the American organizations.
“Let’s get real, I know it’s you, even if by-proxy, and you know it’s you,” he wrote. “Now, get to your room. Before I lose my temper.”
Segui
JΞSTΞR ✪ ΔCTUAL³³º¹ @th3j35t3r
#ICYMI MSG 'From Russia with Love' - I'm Jester & I approve this message via the Russian Foreign Affairs Website >> http://bit.ly/2egvpiM
20:32 - 22 Ott 2016
81 81 Retweet 151 151 Mi piace
In the past, The Jester vigilante has conducted several operations against jihadist communities online. The popular hacker said the CNNMoney journalists he chose to attack the Russian Government Website in response to the massive DDoS against the Dyn DNS service that cut off a large portion of US netizens from the Internet.
“I wanted to poke them in the eye and stop feeling like US is just taking it on the chin. Again,” he said. “I’m not gonna sit around watching these f—-rs laughing at us.”
“It’s 4 a.m. in Moscow right now and a weekend. I’m hoping they can’t fix the hole til Monday,” he said.
“Think of this as a professional courtesy,” his public warning states. “Or if you prefer message from ‘USA with love.'”
An Army of Million Hacked IoT Devices Almost Broke the Internet Today
22.10.2016 thehackernews Hacking
A massive Distributed Denial of Service (DDoS) attack against Dyn, a major domain name system (DNS) provider, broke large portions of the Internet on Friday, causing a significant outage to a ton of websites and services, including Twitter, GitHub, PayPal, Amazon, Reddit, Netflix, and Spotify.
But how the attack happened? What's the cause behind the attack?
Exact details of the attack remain vague, but Dyn reported a huge army of hijacked internet-connected devices could be responsible for the massive attack.
Yes, the same method recently employed by hackers to carry out record-breaking DDoS attack of over 1 Tbps against France-based hosting provider OVH.
According to security intelligence firm Flashpoint, Mirai bots were detected driving much, but not necessarily all, of the traffic in the DDoS attacks against DynDNS.
Mirai is a piece of malware that targets Internet of Things (IoT) devices such as routers, and security cameras, DVRs, and enslaves vast numbers of these compromised devices into a botnet, which is then used to conduct DDoS attacks.
Since the source code of Mirai Botnet has already made available to the public, anyone can wield DDoS attacks against targets.
This time hackers did not target an individual site, rather they attacked Dyn that many sites and services are using as their upstream DNS provider for turning internet protocol (IP) addresses into human-readable websites.
The result we all know: Major sites and services including Twitter, GitHub, Reddit, PayPal, Amazon, AirBnb, Netflix, Pinterest, and so on, were among hundreds of services rendered inaccessible to Millions of people worldwide for several hours on Friday.
"Flashpoint has confirmed that at least some of the devices used in the Dyn DNS attacks are DVRs, further matching the technical indicators and tactics, techniques, and procedures associated with previous known Mirai botnet attacks," Flashpoint says in a blog post.
This type of attack is notable and concerning because it largely consists of unsecured IoT devices, which are growing exponentially with time. These devices are implemented in a way that they cannot easily be updated and thus are nearly impossible to secure.
Manufacturers majorly focus on performance and usability of IoT devices but ignore security measures and encryption mechanisms, which is why they are routinely being hacked and widely becoming part of DDoS botnets used as weapons in cyber attacks.
An online tracker of the Mirai botnet suggests there are more than 1.2 Million Mirai-infected devices on the Internet, with over 166,000 devices active right now.
In short, IoT botnets like Mirai are growing rapidly, and there is no easy way to stop them.
According to officials speaking to Reuters, the US Department of Homeland Security (DHS) and the FBI are both investigating the massive DDoS attacks hitting DynDNS, but none of the agencies yet speculated on who might be behind them.
Chinese hackers targeted officials visiting the USS Ronald Reagan vessel
22.10.2016 securityaffairs Hacking
Experts from the cyber security firm FireEye discovered a spear phishing campaign launched against visitors to the Ronald Reagan vessel in South China Sea.
Chinese hackers targeted foreign government personnel who visited a US aircraft carrier the day before a contentious international court ruling on the South China Sea,
According to the FireEye cyber security firm, Chinese hackers targeted US aircraft carrier. The hackers launched an attack against visitors to a US vessel the day before (July 11, 2016) a contentious international court ruling on the South China Sea.
According to the experts at the FireEye’s iSight unit, the Chinese hackers powered a spear phishing attack that leveraged on messages with a malicious document as an attachment. The document impersonating an official message addressed to officials visiting the USS Ronald Reagan, a nuclear-powered aircraft carrier which conducted patrols of the South China Sea in July.

The document appears as an official message that was sent to officials visiting the nuclear-powered aircraft carrier USS Ronald Reagan. The Ronald Reagan aircraft carrier was used by the US Government to patrol the South China Sea in July.
The document allowed the attacker to infect victims with the Enfal malware, which can be used by attackers as a spyware or to download further malicious payloads on the machine.
According to FireEye, the same hackers are responsible for other attacks against US and Vietnamese national defence computer networks.
The Financial Times that reported the discovery made by FireEye, confirmed the absence of direct evidence to link the attack to a Chinese nation-state actor.The researcher discovered that the command and control server used by the attacker was already used in the past by the China-based group.
“Many governments and militaries in Southeast Asia lack cyber security controls that can effectively match these elevated threats,” said Bryce Boland, FirEye’s Asia-Pacific chief technology officer.
“For example, personal webmail and unmanaged devices aren’t unusual, and many organisations lack the technology to detect unique attacks which haven’t been seen before.”
At the time I was writing it is still unclear if hackers have compromised classified information, nor that the hackers have interfered with the vessel’s operations in the South China Sea.
“The official said unclassified information about logistics was often shared with contractors and foreign governments to support port visits for ships.” reported the FT.
Over 43 Million Weebly Accounts Hacked; Foursquare Also Hit By Data Breach
21.10.2016 thehackernews Hacking
2016 is the year of data breaches that has made almost every major companies victims to the cyber attacks, resulting in compromise of over billion of online users accounts.
Weebly and Foursquare are the latest victims of the massive data breach, joining the list of "Mega-Breaches" revealed in recent months, including LinkedIn, MySpace, VK.com, Tumblr, Dropbox, and the biggest one -- Yahoo.
Details for over 43 Million users have been stolen from the San Francisco-based website building service Weebly, according to breach notification site LeakedSource, who had already indexed a copy of the stolen data that it received from an anonymous source.
In addition, LeakedSource posted details of the cyber attack in its blog post on Thursday explaining what happened. The attack believed to have been carried out in February 2016.
"Unlike nearly every other hack, the Co-founder and CTO of Weebly Chris Fanini fortunately did not have his head buried deeply in the sand and actually responded to our communication requests," LeakedSource says.
"We have been working with them to ensure the security of their users meaning password resets as well as notification emails are now being sent out."
The stolen data contains personal data of 43,430,316 Weebly customers, which includes usernames, email addresses, passwords, and IP addresses.
Stolen passwords were stored using the strong hashing function "BCrypt," making it difficult for hackers to obtain user's actual password.
These password hashes also believed to have used a Salt – a random string added to the hashing process to further strengthen passwords in order to make it more difficult for hackers to crack them.
Weebly confirmed the data breach, saying the company has started notifying affected customers and already initiated password reset process and new password requirements.
"Weebly recently became aware that an unauthorized party obtained email addresses and/or usernames, IP addresses and encrypted (bcrypt hashed) passwords for a large number of customers," the company said.
"At this point, we do not have evidence of any customer website being improperly accessed. We do not store any full credit card numbers on Weebly servers, and at this time we’re not aware that any credit card information that can be used for fraudulent charges was part of this incident."
LeakedSource has also published details of a data breach affecting more than 22.5 million customers of location-based check-in service Foursquare, though the company denied the claims.
The Takeaway:
Even if stolen passwords are much difficult to crack, it's still a good idea to change the password for your Weebly account, just to be safe.
Also change passwords for other online accounts immediately, especially if you use the same password for multiple websites.
You can also use a good password manager to create and remember complex passwords for different sites. We have listed some best password managers that would help you understand the importance of password manager and choose one according to your requirement.
Massive ATM Hack Hits 3.2 Million Indian Debit Cards — Change Your PIN Now!
20.10.2016 thehackernews Hacking
India is undergoing the biggest data breaches to date with as many as 3.2 Million debit card details reportedly stolen from multiple banks and financial platforms.
The massive financial breach has hit India's biggest banks including State Bank of India (SBI), HDFC Bank, Yes Bank, ICICI Bank and Axis, and customers are advised to change their ATM PIN immediately.
Hackers allegedly used malware to compromise the Hitachi Payment Services platform — which is used to power country's ATM, point-of-sale (PoS) machines and other financial transactions — and stole details of 3.2 Million debit cards, reports The Economic Times.
Of 3.2 Million debit cards, 2.6 Million are powered by Visa or Mastercard and rest 600,000 work on top of India’s own RuPay platform.
Hacked Debit Cards Reportedly Used in China
It is not yet clear who is behind the cyber attack, but the report adds that a number of affected customers have observed unauthorized transactions made by their cards in various locations in China.
Some banks, including the country's biggest lender SBI, have announced that they'll replace compromised debit cards, while others banks, including HDFC Bank, have urged their customers to change their ATM PINs and avoid using ATMs of other banks.
The extent of damage due to breach also depends on the type of cards customers are using.
Cards which use Magnetic Stripe transmit your account number and secret PIN to merchants in a way that it could make easy for fraudsters to hack them, making these cards easier to clone.
Whereas, banks who are using EMV (Europay, MasterCard, and Visa) chip-equipped cards (better known as Chip-and-Pin cards) store your data in encrypted form and only transmit a unique code (one-time-use Token) for every transaction, making these cards more secure and lot harder to clone.
SBI Blocks and will Re-Issue 600,000 Debit Cards
SBI has blocked affected debit cards and will re-issue over 600,000 cards. Here's what SBI CTO Shiv Kumar Bhasin told the publication:
"It's a security breach, but not in our bank's systems. Many other banks also have this breach—right now and since a long time. A few ATMs have been affected by malware. When people use their card on infected switches or ATMs, there is a high probability that their data will be compromised."
Mastercard also denied that its systems were breached, issuing the following statement:
"We're aware of the data compromise event. To be clear, Mastercard's own systems have not been breached. At Mastercard, safety and security of payments are a top priority for us and we're working on the investigations with the regulators, issuers, acquirers, global and local law enforcement agencies and third party payment networks to assess the current situation."
Meanwhile, the Payments Council of India has ordered a forensic audit on the Indian bank servers to measure the damage and investigate the origin of the cyber attack. Bengaluru-based payment and security specialist SISA will conduct the forensic audit.
Bitcoin Wallet Blockchain.info went down due to a DNS Hijacking
13.10.2016 securityaffairs Hacking
Blockchain.info, the world’s most popular Bitcoin wallet and Block Explorer service went down this week due to a DNS Hijacking attack.
Crypto-currencies continue to be a privileged target of cyber criminals, Bitcoin wallets and services provided by many companies operating in the industries have been targeted by criminal organizations as never before.
Blockchain.info, the world’s most popular Bitcoin wallet and Block Explorer service, suffered a mysterious outage this week and experts speculated that a cyber attack has disrupted the platform.
“Looks like our site is down. We’re working on it and should be back up soon.” reads the message displayed to the visitors during the downtime.
BlockChain informed its users about a possible DNS issue via Twitter.
Segui
Blockchain ✔ @blockchain
We're researching a DNS issue and looking into it. We apologize for the inconvenience. Stay tuned.
12:26 - 12 Ott 2016
67 67 Retweet 60 60 Mi piace
“We’re making progress resolving the issue, but it may take upwards of several hours until services are fully restored,” states a second Tweet from the company while users were not able to access their online accounts.
At the same time, someone on Reddit reported the changes in the DNS records.
It looks like blockchain.info has just had their domain name hijacked. The whois and DNS records suddenly jumped from CloudFlare to a cheap web host. From the cache, the names used to be
Name Server: BETH.NS.CLOUDFLARE.COM
Name Server: JAY.NS.CLOUDFLARE.COM
and were then changed to
Name Server: DED88057-1.HOSTWINDSDNS.COM
Name Server: DED88057-2.HOSTWINDSDNS.COM
when queried these are returning
;; ANSWER SECTION:
blockchain.info. 11360 IN A 192.236.200.26
or
;; ANSWER SECTION:
blockchain.info. 14400 IN A 198.44.48.226″

What happened?
The DNS server records for blockchain.info and blockchain.com were hijacked. Usually, this practice allows crooks to conduct phishing attacks in order to steal bitcoin wallet credentials.
Experts from OpenDns early detected the change in nameservers:
Segui
dnsstream @dnsstream
critical: blockchain(.)info now has completely new nameservers (ded91868-1(.)hostwindsdns(.)com,ded91868-2(.)hostwindsdns(.)com)
12:34 - 12 Ott 2016
2 2 Retweet 3 3 Mi piace
Experts at OpenDns investigates on the IP changes:

OpenDNS blocked the above IPs to prevent their customers using Bitcoins to fall victim of the scammer.
Fortunately, nothing happened to the Blockchain users, but DNS hijacking are very dangerous because unaware users could be redirected to rogue websites that mimic the legitimate ones in the attempt of stealing credentials.
Below the official statement issued by the company about the incident:
“Earlier today, we discovered our DNS registrar had been compromised. We took immediate action to resolve the issue. To be abundantly cautious, we’re waiting for the DNS to propagate universally across the web before bringing our services back. Once DNS has propagated, we expect to restore services ASAP. Our sincerest apologies for any inconvenience.”
At the time I was writing there is no news regarding potential breaches of the users’ bitcoin wallets.
BlockChain.info Domain Hijacked; Site Goes Down; 8 Million Bitcoin Wallets Inaccessible
13.10.2016 thehackernews Hacking
UPDATE: The site is back and working. Blockchain team released a statement via Twitter, which has been added at the end of this article.
If you are fascinated with the idea of digital currency, then you might have heard about BlockChain.Info.
It’s Down!
Yes, Blockchain.info, the world's most popular Bitcoin wallet and Block Explorer service, has been down from last few hours, and it's believed that a possible cyber attack has disrupted the site.
The site is down at the time of writing, and the web server reports a bad gateway error, with a message on the website that reads:
"Looks like our site is down. We're working on it and should be back up soon."
With more than 8 million Digital Wallet customers, BlockChain is users' favorite destination to see recent transactions, stats on mined blocks and bitcoin economy charts.
blockchain-bitcoin-website
A few hours ago, BlockChain team tweeted about the sudden breakdown of the site, saying: "We're researching a DNS issue and looking into it. We apologize for the inconvenience. Stay tuned."
"We're making progress resolving the issue, but it may take upwards of several hours until services are fully restored," another tweet reads.
However, a Reddit user has noted that "The whois and DNS records suddenly jumped from CloudFlare to a cheap web host."
It seems that their domain name has been hijacked, which was later confirmed by the BlockChain team on Reddit, saying:
"Hey everyone, our DNS provider was targeted. It's going to be several hours before our services are fully restored. The CloudFlare DNS is propagating now."
Until resolved, which may take next few hours, Blockchain.info digital wallet users would not be able to access their online accounts. In response to this incident, Blockchain users are in hopes that their online wallet has not been hacked or funds stolen.
Since its DNS server has been hijacked, it could be possible that an attacker can host a fake web page on the same domain in an effort to steal your bitcoin wallet credentials.
So, Blockchain users are strongly recommended not to log in to the site until the Blockchain team releases an official statement via its Twitter account.
Official Statement From BlockChain:
"Earlier today, we discovered our DNS registrar had been compromised. We took immediate action to resolve the issue. To be abundantly cautious, we’re waiting for the DNS to propagate universally across the web before bringing our services back. Once DNS has propagated, we expect to restore services ASAP. Our sincerest apologies for any inconvenience."
However, there is no statement from the Blockchain.info team that suggests any hacking or compromise of its users bitcoin wallets.
ACSC Report – Australian Bureau of Meteorology hacked by foreign spies
12.10.2016 securityaffairs Hacking
A report published by the Australian Cyber Security Centre confirmed the Australian Bureau of Meteorology hack was powered by foreign cyber spies.
In December 2015 the Australian Broadcasting Corporation (ABC) revealed that a supercomputer operated by Australialian Bureau of Meteorology (BoM) was hit by a cyber attack. The Bureau of Meteorology is Australia’s national weather, climate, and water agency, it is the analog of the USA’s National Weather Service.
The supercomputer of the Australian Bureau of Meteorology targeted by the hackers is also used to provide weather data to defence agencies, its disclosure could give a significant advantage to a persistent attacker for numerous reasons.
Initial media reports blamed China for the cyber attack, in 2013 Chinese hackers were accused by authorities of stealing the top-secret documents and projects of Australia’s new intelligence agency headquarters.
“China is being blamed for a major cyber attack on the computers at the Bureau of Meteorology, which has compromised sensitive systems across the Federal Government.” states the ABC. “The bureau owns one of Australia’s largest supercomputers and provides critical information to a host of agencies. Its systems straddle the nation, including one link into the Department of Defence at Russell Offices in Canberra.”
The systems at the Bureau of Meteorology elaborate a huge quantity of information and weather data that are provided to various industries, including the military one.
The consequence of a cyber attack on such kind of systems could represent a menace to the homeland security.
Now new information was disclosed by the government’s Australian Cyber Security Centre that Wednesday published a report on the incident. The experts at Australian Cyber Security Centre attributed “the primary compromise to a foreign intelligence service,” they did not provide any information of the culprit.
“We don’t narrow it down to specific countries, and we do that deliberately,” said the minister for cybersecurity, Dan Tehan. “But what we have indicated is that cyber espionage is alive and well,” he told ABC News 24. “We have to make sure that we’re taking all the steps necessary to keep us safe, because the threat is there. The threat is real. Cybersecurity is something that we, as a nation, have to take very seriously.”

The report confirms the presence of a malware in the system of the Australian Bureau of Meteorology. The national cyber security agency, Australian Signals Directorate (ASD), detected a Remote Access Tool (RAT) malware “popular with state-sponsored cyber adversaries,” and confirmed that the same malicious code was used to compromise other Australian government networks in the past.
“ASD identified evidence of the adversary searching for and copying an unknown quantity of documents from the Bureau’s network. This information is likely to have been stolen by the adversary.” reads the report.
Another interesting aspect of the report is the opinion of the experts of the terrorist cyber threat, they explained that cyber capabilities of terrorists remain rudimentary.
“Apart from demonstrating a savvy understanding of social media and exploiting the internet for propaganda purposes, terrorist cyber capabilities generally remain rudimentary and show few signs of improving significantly in the near future,” states the report.
Animas OneTouch Ping Insulin Pumps could be remotely hacked
8.10.2016 securityaffairs Hacking
Hackers could use Insulin Pumps as weapons, this is not a sci-fi movie, but a disconcerting reality.
The OneTouch Ping insulin pumps manufactured by Animas, a company owned by Johnson & Johnson, are affected by multiple several vulnerabilities that can be exploited by remote hackers to harm the diabetic patients who use them. While the security holes are serious, the risk is considered relatively low and the
The bad news it that the vendor does not plan on releasing a fix for the flaws despite they are serious because they flaws are difficult to exploit.
The researcher Jay Radcliffe from Rapid7 analyzed OneTouch Ping insulin pumps manufactured by Animas. The medical devices are composed of two main components, the actual insulin pump and a component of the remote control.

Radcliffe detailed four major vulnerabilities in a Rapid7 blog post and reported them to the Department of Homeland Security’s CERT Coordination Center that published a specific security advisory.
“The Animas OneTouch Ping insulin pump contains multiple vulnerabilities that may allow an unauthenticated remote attacker to obtain patient treatment or device data, or execute commands on the device. The attacker cannot obtain personally identifiable information.” reads the advisory published by the US-CERT.
It is important to highlight that the OneTouch Ping insulin pumps are not connected to the Internet, this means that the exploitation of the flaws discovered by the experts could not be exploited from remote distances.
The experts explained that using a special radio transmission equipment could allow attacks to be conducted from a distance even up to one mile.
One of the most disconcerting discoveries made by the researcher is that the remote control and the pump communicate over an unencrypted channel. An attacker can exploit this flaw tracked as CVE-2016-5084 to launch a man-in-the-middle (MitM) attack to intercept patient treatment and device data. The only consolation is that data exposed do not include any personally identifiable information.
“Packet captures demonstrate that the communications between the remote and the pump are transmitted in the clear. During the normal course of operation, de-identified blood glucose results and insulin dosage data is being leaked out for eavesdroppers to remotely receive.” states the blog post published by Rapid7.
A second flaw, tracked as CVE-2016-5085, is related to the pump pairing with the remote control, an operation necessary to authenticate the controller with medical devices in order to prevent it from accidentally accepting commands from other remote controllers. In this case, the OneTouch Ping insulin pumps use a key to exchange information with the controllers that are composed of serial numbers and some header information, unfortunately, it is transmitted in clear text. An attacker can exploit the flaw to spoof the remote control and issue commands to arbitrarily dispense insulin, which dramatic consequences.
The researcher also reported also other two serious issues affecting the OneTouch Ping insulin pumps, CVE-2016-5086 and CVE-2016-5686, that could be exploited to spoof the devices by capturing packets and used them at a later time.
Radcliffe confirmed the relatively low risk of exposure to the vulnerabilities, anyway such kind of study raises awareness of the threats and potential damages caused by a cyber attack.
“Removing an insulin pump from a diabetic over this risk is similar to never taking an airplane because it might crash,” the expert noted.
Summarizing the three major flaws reported by Radcliffe during his analysis are:
R7-2016-07.1: Communications transmitted in cleartext (CVE-2016-5084)
R7-2016-07.2: Weak pairing between remote and pump (CVE-2016-5085)
R7-2016-07.3: Lack of replay attack prevention or transmission assurance (CVE-2016-5086)
Johnson & Johnson notified patients and healthcare professionals of Rapid7’s findings via mail, it also explained how to mitigate the threat by features available in the OneTouch Ping insulin pumps.
Give a look at the report, it also includes a video PoC of the attack
Authorities arrested 2 teenagers suspected to be members of Lizard Squad
8.10.2016 securityaffairs Hacking
A joint operation of international law enforcement agencies allowed the arrest of suspected Lizard Squad Hackers in the US and Netherlands.
Law enforcement in the US and in the Netherlands have arrested last month two teenagers suspected of being members of the dreaded hacking groups Lizard Squad and PoodleCorp.
Both hacking teams are known for powerful DDoS DDoS attacks that shut down services of many companies in the gaming industry. The hacker successfully targeted the PlayStation Network, Xbox Live, EA and Blizzard.
Zachary Buchta (19), of Fallston, Maryland, and Bradley Jan Willem van Rooy (19), of Leiden, the Netherlands, have been charged with conspiracy to have hacked and damage protected computers.
“ZACHARY BUCHTA, 19, of Fallston, Md., and BRADLEY JAN WILLEM VAN ROOY, 19, of Leiden, the Netherlands, are charged with conspiring to cause damage to protected computers. The charges are the result of an international investigation into the computer hacking groups “Lizard Squad” and “PoodleCorp,” according to a criminal complaint and affidavit filed in U.S. District Court in Chicago.” reads the announcement issued by the US Department of Justice “Buchta and van Rooy allegedly conspired with others to launch destructive cyber attacks around the world, and trafficked payment accounts that had been stolen from unsuspecting victims in Illinois and elsewhere.”
In addition to the charges, the authorities seized the domains associated with the alleged conspiracy that are shenron.lizardsquad.org, lizardsquad.org, stresser.poodlecorp.org, and poodlecorp.org.

According to the US Department of Justice, Buchta used various online monikers, including “@fbiarelosers,” “pein,” “xotehpoodle” and “lizard,” while van Rooy was also known as “Uchiha,”“@UchihaLS,” “dragon” and “fox.”
They have been accused to have operated a platform offered for rent to users that used them to launch distributed denial-of-service (DDoS) attacks.
The authorities also suspected the duo were selling stolen payment card data on the black market.
The two teenagers face a sentence of up to 10 years.
The complaint also refers two other individuals, alleged members of the Lizard Squad and PoodleCorp crews, known with the online monikers “Chippyshell” and “AppleJ4ck.”
According to the complaint, Buchta used the @fbiarelosers account, which exchanged private message with other members of LizardSquad via Twitter discussing DDoS attacks.
Records from Comcast demonstrated that the suspect’s IP connected to an overseas VPN service that had been used to access the @fbiarelosers account and the websites managed by the both Lizard Squad and PoodleCorp groups.
The other suspect, Van Rooy, did not use any precaution to hide his IP while accessing his Twitter accounts that were also used by Lizard Squad.
Magecart campaign – Hackers target eCommerce sites with web-based keylogger injection attacks
8.10.2016 securityaffairs Hacking
Researchers have been monitoring a campaign dubbed Magecart that compromised many ecommerce websites to steal payment card and other sensitive data.
Researchers have been monitoring a campaign in which cybercriminals compromised many e-commerce websites in an effort to steal payment card and other sensitive information provided by their customers.
Security experts from cloud-based security solutions provider RiskIQ have been monitoring a hacking campaign, dubbed Magecart, in which crooks hacked many e-commerce websites in an effort to steal payment card and other sensitive customer data.
The peculiarity of the Magecart campaign is that threat actors were injecting a keylogger directly into the target website.
As explained in the analysis, web-based keylogger injection attacks are still little-known, even though they’ve been occurring for a long time.
“Most methods used by attackers to target consumers are commonplace, such as phishing and the use of malware to target payment cards. Others, such as POS (point of sale) malware, tend to be rarer and isolated to certain industries. However, some methods are downright obscure—Magecart, a recently observed instance of threat actors injecting a keylogger directly into a website, is one of these.” reads the analysis published by RiskIQ.
The Magecart campaign was first spotted in March 2016, but it is likely it was started before and it is still active today.
Researchers observed a peak in the Magecart campaign in June, in conjunction with the adoption of an Eastern European bulletproof hosting service.
The attackers targeted several e-commerce platforms including Magento, Powerfront CMS and OpenCart. The researcher documented attacks against several payment processing services, including Braintree and VeriSign.

Experts at RiskIQ have identified more than 100 online shops compromised as part of the Magecart campaign, including e-commerce platforms of popular book publishers, fashion companies, and sporting equipment manufacturers. The cybercrooks even attacked the gift shop of a UK-based cancer research organization.
The attackers inject a JavaScript code directly in the websites to capture data entered by users, the researchers highlighted also the ability of the malicious code to add bogus form fields to the compromised website in an effort to collect more information from the victims.
“Formgrabber/credit card stealer content is hosted on remote attacker-operated sites, served over HTTPS. Stolen data is also exfiltrated to these sites using HTTPS.” states the analysis.
Once data is captured by the web-keylogger it is sent to the C&C server over HTTPS.
The web-keylogger is loaded from an external source instead of injecting it directly into the compromised website, simplifying the malware maintenance.
The researchers observed a continuous improvement of the threat over time as detailed by RiskIQ:
Testing and capabilities development
Increased scope of targeting payment platforms
Development and testing of enhancements
Addition of obfuscation to hinder analysis and identification
Attempts to hide behind brands of commonplace web technologies to blend in on compromised sites
For further information of the Magecart campaign give a look at the datailed report.
OilRig campaign, Iran-Linked Hackers Target US Government & Energy Grid
8.10.2016 securityaffairs Hacking
OilRig campaign – An Iran-linked hacker group which previously targeted organizations in Saudi Arabia has now set its sights on other countries.
Iranian hackers which previously targeted organizations in Saudi Arabia are now targeting organizations in other countries, including the US, as part of a campaign identified as OilRig campaign.
In addition to expanding its reach, the group has been enhancing its malware tools.
Researchers at Palo Alto Networks have been monitoring the group for some time and have
reported observing attacks launched by a threat actor against financial institutions and technology
companies in Saudi Arabia and on the Saudi defense industry. This campaign referred to as “OilRig,” by Palo Alto Networks, entails weaponized Microsoft Excel spreadsheets tracked as
“Clayslide” and a backdoor called “Helminth.”
Bank attacks by the Iran-linked group were analyzed and documented by FireEye in May. Security
Week reports that Palo Alto Networks, “discovered that it has also targeted a company in Qatar
and government organizations in the United States, Israel and Turkey.”
Helminth is delivered, by the threat actors behind OilRig, by way of spear-phishing emails and
malicious macro-enabled Excel documents. For instance, in the caseof a Turkish government organization, the Excel file was designed to replicate a login portal for an airline. 
There are four variants of the Helminth malware and the threat, capable of communicating with its
command and control (C&C) server over both HTTP and DNS, can gain information on the
infected device and download additional files via a remote server. One type of Helminth malware
relies on VBScript and PowerShell scripts. Another is deployed as an executable file. Delivered by
a Trojan nicknamed “HerHer,” the executable version is able to log keystrokes.
“The Zip archive is encrypted with an unknown password, but we know it contains two files named joboffer.chm and thumb.db. The thumb.db file in the archive has the same name and file size (368128 bytes) as a dropper Trojan we track as ‘HerHer’ (SHA256: fb424443ad3e27ef535574cf7e67fbf9054949c48ec19be0b9ddfbfc733f9b07) that installs a known Helminth executable sample. ” reads the report published by PaloAlto Networks.
Regarding the origins of the threat actors, researchers have pieced together several clues that
point to an Iran-based individual–although they admit that the data can be easily forged.
Palo Alto Networks has been monitoring the activities of several hacker groups believed to be
operating out of Iran. One of these groups utilizes malware which has been dubbed Infy. Over the
summer, the security firm reported that it had disrupted a cyberespionage campaign involving Infy.
And, in August it was discovered that Iranian hackers had compromised messaging app
Telegram, allowing them to access the accounts of almost 15 million Iranian users. The accounts
breached were primarily those of activists, journalists and other high-profile individuals in Iran. The attack reportedly targeted Telegram’s one-time SMS activation and not its end-to-end encryption.
Telegram sends a verification code via an SMS when users want to log in to the app from a new
device. But, the SMS can be intercepted by phone companies and sold to hackers, who are then
able to access the user’s contact list and archived messages.
Of late, the concern regarding malicious hackers is the risk of the energy sector being targeted.
According to RegBlog:
“…cybersecurity threats are an all-too-real risk for many buildings and electric grids
connected to the Internet. According to a U.S. Department of Homeland Security report,
although ‘the energy sector only represents 5-6 percent of U.S. GDP, the energy industry
is subject to roughly 32 percent of all cyberattacks.’
Recent events have highlighted vulnerabilities in the power supply system, paving the way
for the bill’s cyber measures. One headline-grabbing incident occurred in March when the
Southern District of New York indicted a group of Iranian hackers for repeatedly hacking
into a small dam in New York in 2013, targeting numerous major financial companies and
gaining control over water levels. That episode ultimately caused little damage, aside from
inconveniencing customers, but it demonstrated the potential threat nonetheless.”
And, as an example of the type of activity this bill would address:
“One headline-grabbing incident occurred in March, when the Southern District of New
York indicted a group of Iranian hackers for repeatedly hacking into a small dam in New
York in 2013, targeting numerous major financial companies and gaining control over
water levels. That episode ultimately caused little damage, aside from inconveniencing
customers, but it demonstrated the potential threat nonetheless.”
So, Iranian threat actors have gradually begun to move from targeting banks to attacking energy
grids. Incidentally, the fact that hackers are able to gain entry into any of our critical systems is
unsettling.
Grid hacks have the potential for severe and widespread impact.
Peace_of_Mind hacked the hacking forum w0rm_ws and doxed its alleged owner
4.10.2016 securityaffairs Hacking
The notorious hacker Peace_of_Mind has hacked and defaced the official hacking and trading forum w0rm.ws and doxed its alleged owners.
‘Peace_of_Mind‘ (PoM) is a very active actor in The Real Deal Market and The Hell black markets, he offered for sale the dumps from clamorous data breaches, including Yahoo, LinkedIn and MySpace
The w0rm.ws a famous hacking platform, it is an ‘invite only’ hacking and a trading forum where it is possible to sell and buy exploits and stolen data.
Peace_of_Mind has defaced the website and leaked on its homepage the personal information of the alleges mastermind behind the hacking service, Sarpovu Nikolai.
The home page w0rm.ws was displaying Nikolai’s personal details, including date of birth, father’s name, mother’s name, nationality, and residence permit.

The hacker published the following message on the defaced homepage:
“Hacked by Peace of Mind for fucking with Hell Forum”
a circumstance that suggests a dispute between the underground hacking forums The Hell and wOrm.ws.
Also The Hell was hacked in the past, last year unknown crooks breached it and leaked its data, the hacking forum appeared back on the underground earlier this year.
Back to the w0rm.ws case, the colleagues at the Hackread.com published an interesting analysis made by Hacked-DB data mining company on the leaked data.
The main folder of the wOrm.ws, w0rmws.tar.gz, forum reveals that the hacking forum was running on an outdated and vulnerable version of the vBulletin CMS (version 3.8.7). The analysis of the content of the folder allowed the experts to find an email contact and a secret key for the Google captcha.
“Based on the leaked information it seems that the forum was hacked due to the old version of VBulletin with known exploits. The data basically uncover registered user accounts along with their PMs and IPs which can provide the lead if an authority will try to pursuit them. In addition, there are privately traded databases which may be only accessible to the forum users.” reported Hacked-DB.
The researchers at Hacked-DB have discovered that the administrator of the forum was using the Hunter exploit kit, the same used by The Hell and revealed after the data breach. On of the file included in the folder contains server login and timestamps details, it is not clear if they belong to the administrator of the platform.
The experts also found data related to 323 users of the forum, the records include username, encrypted password and personal messages sent by users to the forum admin.
The data dump included users’ activities and transactions successfully completed by the administrator of the forum since its launch:
South Korea ‘s military cyber command was hacked last month
4.10.2016 securityaffairs Hacking
According to the Government of the South Korea, the county military cyber command was hacked last month in the attempt to infect the vaccine routing server.
The Government of Seoul revealed that its cyber command center was hacked last month. The South Korean experts have found evidence of the malware in the systems at the cyber command center, but it is still a mystery the attack vectors used to deliver it.
According to the South Korean Government, the malicious code was spread in the attempt to infect a ”vaccine routing server” used by country’s military cyber command.
The vaccine routing server is a specific component of the south Korean Infrastructure, it was used to implement an extra level of security to protect military networks exposed on the Internet.
“South Korea’s cyber command established to counter external hacking attempts on the country’s military was found to have been hacked last month, a lawmaker said Saturday, raising speculation that North Korea might be behind the latest cyber attack.” reported the Yonhap News.
“Rep. Kim Jin-pyo, a lawmaker of the main opposition Minjoo Party of Korea, told Yonhap News Agency in a telephone interview that the hacking targeted the “vaccine routing server” installed at the cyber command.”
Kim is one of the members of the South Korean parliament’s national defense committee.
“A malicious code has been identified and it seems to have taken advantage of the vulnerability of the routing server,” he said. “In a cautious measure, the server has been separated from the network.” Kim told the news Agency.
Kim speculates that attackers haven’t exfiltrated any sensitive data from the military intranet because it was not directly connected to the targeted server.
According to the Korean Authorities, currently the military Internet system remains up and running.
South Korea vs -north-korea
Who is behind the attack?
As usual, rumors says the South Korea is blaming its first enemy, North Korea and in particular its dreaded North Korea’s Bureau 121, despite the Government of Seoul is still investigating the incident and will not comment it mission and will not officially blame anyone until investigations are completed.
This is the last cyber attack in order of time suffered by the South Korea. In May, Seoul blamed North Korea for hacking a South Korean defense contractor, in June the Government of Seoul reported that North Korean hackers stole defense-related documents and photos from two South Korean companies, and in July authorities in South Korea blamed hackers from North for a massive data breach affecting 10 million Interpark online shoppers.
Last year, Seoul blamed Pyongyang for two attacks respectively on a Nuclear plant and a subway system.
Download: 68 Million Hacked Dropbox Accounts are Just a Click Away!
4.10.2016 thehackernews Hacking
Over a month ago, The Hacker News reported about the Dropbox Hack, where hackers had managed to steal more than 68 Million Dropbox accounts in a data breach that was initially disclosed by the online cloud storage platform in 2012.
Although the initial announcement failed to reveal the true scale of the data breach, it was in late August when the breach notification service LeakBase obtained files containing details on over 68 million accounts, which contains email addresses and hashed passwords for Dropbox users.
Last month, a hacker was selling this Dropbox data dump on a Dark Web marketplace known as TheRealDeal for around $1200.
However, Motherboard recently discovered that a researcher has just uploaded the full dump of hacked Dropbox database online.
Download DropBox Data Dump Here:
Thomas White, known online as The Cthulhu, uploaded Monday the full Dropbox data dump onto his website in a move, as he claims, to help security researchers examine the data breach.
So, anyone can now download the leaked database of 68,680,741 Dropbox accounts, containing email addresses and hashed passwords, totally for FREE.
"The ... dump was allegedly taken from Dropbox sometime in 2012 following a breach," White writes on his website. "I have assisted [in keeping] this breach public for those who are struggling to find a reliable source for research."
White is the same person who previously dumped accounts from massive data breaches in large enterprises, including extramarital affairs site Ashley Madison, social networking site Myspace, and more.
The good news is that out of 68 Million, around 32 Million passwords are secured using strong hashing function BCrypt, which makes it difficult for hackers to obtain many of users' actual passwords.
The rest of the account passwords are hashed with the SHA-1 hashing algorithm and also believed to have used a Salt – a random string added to the hashing process to further strengthen passwords to make it harder for hackers to crack them.
Moreover, the company previously ensured its affected customers that there is no evidence of any malicious access of their accounts, saying "Based on our threat monitoring and the way we secure passwords, we do not believe that any accounts have been improperly accessed."
Dropbox is one of many "Mega-Breaches" revealed this summer, when hundreds of millions of account credentials from years-old data breaches on famous social network sites, including LinkedIn, MySpace, VK.com and Tumblr, were exposed online.
The best way to protect yourself is to change your passwords for Dropbox and other online accounts, especially if you are using the same password for multiple websites, as well as use a good password manager to create and manage complex passwords for different sites.
Beware! You Can Get Hacked Just by Opening a 'JPEG 2000' Image
4.10.2016 thehackernews Hacking
Researchers have disclosed a critical zero-day vulnerability in the JPEG 2000 image file format parser implemented in OpenJPEG library, which could allow an attacker to remotely execute arbitrary code on the affected systems.
Discovered by security researchers at Cisco Talos group, the zero-day flaw, assigned as TALOS-2016-0193/CVE-2016-8332, could allow an out-of-bound heap write to occur that triggers the heap corruption and leads to arbitrary code execution.
OpenJPEG is an open-source JPEG 2000 codec. Written in C language, the software was developed for coding and encoding JPEG2000 images, a format that is often used for tasks like embedding image files within PDF documents through popular software including PdFium, Poppler, and MuPDF.
Hackers can exploit the security vulnerability by tricking the victim into opening a specially crafted, malicious JPEG2000 image or a PDF document containing that malicious file in an email.
The hacker could even upload the malicious JPEG2000 image file to a file hosting service, like Dropbox or Google Drive, and then send that link to the victim.
Once downloaded to the system, it would create a way for hackers to remotely execute malicious code on the affected system.
The flaw was caused "due to an error while parsing mcc records in the jpeg2000 file,...resulting in an erroneous read and write of adjacent heap area memory," Cisco explained in its advisory.
"Careful manipulation of heap layout and can lead to further heap metadata process memory corruption ultimately leading to code execution under attacker control."
The researchers successfully tested the JPEG 2000 image exploit on the OpenJPEG openjp2 version 2.1.1. The flaw was discovered by Aleksandar Nikolic from the Cisco Talos Security team.
The team reported the zero-day flaw to OpenJPEG developers in late July, and the company patched the flaw last week with the release of version 2.1.2.
The vulnerability has been assigned a CVSS score of 7.5, categorizing it as a high-severity bug.
Watch out, hacked Steam accounts used as an attack vector
2.10.2016 securityaffairs Hacking
Malware researcher discovered a Reddit user which is warning of the existence of hacked Steam accounts used to spread a Remote Access Trojan (RAT).
This week the popular malware researcher Lawrence Abrams from Bleepingcomputer.com has found a worrisome message on Reddit. The Reddit user with the moniker Haydaddict was warning of the existence of compromised Steam accounts spreading a Remote Access Trojan (RAT).
“Quinn Lobdell hacked on Steam. Please be aware if others try to send you sketchy links. Scrub Killa and Jessie affected as well.” reads the post.
The accounts were used to send chat messages containing links to videomeo.pw to watch a video.

“When the target went to the page, they would be greeted with a message stating that they needed to update Flash Player in order to watch the video.” explained Lawrence Abrams in a blog post.

The trick is quite simple and leverages on the user’s curiosity when it downloads and executes the Flash Player installer apparently nothing happens, but in reality the victim has opened its machine to the attacker.
The Flash Player installer executes a PowerShell script (zaga.ps1) that downloads a 7-zip archive, 7-zip extractor, and a CMD script from a remote server (http://zahr[.]pw).
The PowerShell then launches the CMD file, which extracts the sharchivedmngr to the %AppData%\lappclimtfldr folder and configures Windows to automatically start an instance of the NetSupport Manager Remote Control Software, renamed as mcrtvclient.exe, when the victim logs in.
When the victims will log in the infected machine, the NetSupport Manager will connect to the NetSupport gateway at leyv.pw:11678 and await commands, at this point the attacker has complete control over the victim’s machine.
“For those who are concerned they are infected with this Steam Trojan, I suggest they check the %AppData% folder for the specified folders.” suggests Lawrence Abrams in order to check if the system is compromised.
Every time you visit a link be careful, and make sure to have installed up to date defense solutions.
37-Year-Old 'Syrian Electronic Army' Hacker Pleads Guilty in US court
30.9.2016 thehackernews Hacking
One of the FBI's Most Wanted Hackers who was arrested in Germany earlier this year has pleaded guilty to federal charges for his role in a scheme that hacked computers and targeted the US government, foreign governments, and multiple US media outlets.
Peter Romar, 37, pleaded guilty Wednesday in a federal court in Alexandria to felony charges of conspiring to receive extortion proceeds and to illegally access computers in his role as a member of the infamous hacking group calling itself the Syrian Electronic Army (SEA), the Department of Justice (DoJ) announced.
Romar was previously extradited from Germany on request of the United States.
"Cybercriminals cannot hide from justice," said U.S. Attorney Dana J. Boente for the Eastern District of Virginia. "No matter where they are in the world, the United States will vigorously pursue those who commit crimes against U.S. citizens and hold them accountable for their actions."
In March, the US charged three men it believed were involved in cyber-attacks carried out the Syrian Electronic Army. Romar was already arrested while the other two - Ahmad Umar Agha (aka The Pro), 22 and Firas Dardar (aka The Shadow), 27 - were believed to be in Syria.
The FBI has also offered a reward of $100,000 for any information that leads to the arrest of Agha and Dardar, who were allegedly involved in hacking Associated Press Twitter account in April 2013 and spreading a false rumor claiming that the White House had been bombed, injuring President Obama, which caused a temporary stock market dip.
All three SEA hackers were allegedly engaged in a long-running cyber-propaganda campaign in support of the Syrian President Bashar al‑Assad.
The group used "spear-phishing" tactics to target computer systems of the US government, foreign organizations, media outlets and other private-sector entities that the SEA deemed as having been antagonistic toward the Syrian Government.
Between 2011 and 2013, SEA targeted multiple entities including the Associated Press, Microsoft, Reuters, CNN, Time, The Daily Dot, The Washington Post, Vice, Human Rights Watch, E! Online, Harvard University, NASA, US Marine, and The Onion, among others.
Dardar and Romar are accused of hacking into the computer systems of businesses for their personal profit. They hacked into victims' computers and then threaten them to damage computers, and delete/sell the data unless they were paid a ransom.
"If a victim could not make extortion payments to the conspiracy's Syrian bank accounts due to sanctions targeting Syria, Romar acted as an intermediary in Germany to evade those sanctions," the DoJ said.
Romar faces up to 5 years in prison and is scheduled to be sentenced on 21st October, while co-defendant Dardar still remains at large and is believed to be in Syria.
Russian hackers spy on Citizen Journalists investigating on Flight MH17 Crash
29.9.2016 securityaffairs Hacking
Researchers at the Bellingcat agency have been hit with spear phishing attacks and account takeover attempts while investigating flight MH17 crash.
Once again cyber security experts warn of a new hacking campaign that this time is targeting Citizen Journalists reporting the crash of the flight MH17 of the Malaysian Airlines. According to the intelligence firm ThreatConnect, reporters from the Bellingcat agency have been targeted by spear phishing messages and suffered account takeover attempts for over a year.
The Bellingcat agency is known for its uncomfortable investigations on strong powers of Governments and organizations worldwide.
Yesterday the Reuters reported the news that the Malaysian flight MH17 was downed by Russian-made missile launched by pro-Russian rebels.
“Malaysia Airlines flight MH17 was shot down by a missile fired from a launcher brought into Ukraine from Russia and located in a village held by pro-Russian rebels, international prosecutors said on Wednesday.” states the post published by the Reuters. “The conclusions were based on thousands of wiretaps, photographs, witness statements and forensic tests during more than two years of inquiries into an incident which led to a sharp rise in tensions between Russia and the West.”
ThreatConnect who investigated the attacks speculates that threat actors have strong ties to the Russian Government, they have targeted a group of citizen journalists for publishing articles critical of Government of Moscow.
Data shared by the Bellingcat’s founder Eliot Higgins indicates the involvement of at least two Russian nation-state groups.
Experts from ThreatConnect claim the involvement of the dreaded Fancy Bear APT group who in the headlines for the attacks against the systems and people involved in the US Presidential election.
“Following our post on DCLeaks as a Russian influence operation, Bellingcat founder Eliot Higgins reached out to us. Bellingcat, a group of citizen investigative journalists, has published articles critical of Russia and has been a key contributor to the international investigation of the shootdown of Malaysian Airlines Flight 17 (MH17) over Ukraine in 2014.” states the report published by ThreatConnect.
“Higgins shared data with ThreatConnect that indicates Bellingcat has come under sustained targeting by Russian threat actors, which allowed us to identify a 2015 spearphishing campaign that is consistent with FANCY BEAR’s tactics, techniques, and procedures.”
According to the experts, the Bellingcat’s agency became a target of the Russian Fancy Bear APT after its reporters investigated the shooting down of the Malaysian Airlines Flight 17 (MH17) occurred in 2014.
The second group behind the attacks is the CyberBerkut, a collective of Ukrainian hackers that are pro-Russia.
The state-sponsored hackers targeted three Bellingcat researchers with a spear phishing campaign between February 2015 and July 2016 for intelligence purposes.

The attackers used messages themed as Gmail security notices in the attempt to trick victims into clicking on the embedded links, but according to ThreatConnect the attacks failed.
“These spearphishing attempts consist of a variety of spoofed Gmail security notices alerting the target that suspicious activity was detected on their account. The target is prompted to click a URL resembling a legitimate Gmail security link to review the details of this suspicious activity.” continues the post.

The report also analyzes activities conducted by the CyberBerkut that defaced the Bellingcat’s website earlier this year and compromised the email account of the government opposition blogger, Ruslan Leviev.
ThreatConnect speculates that Leviev’s email account hosted by the Russian service provider Yandex was compromised with the support of an employee of the company or by the Russian intelligence. In that case the attackers exploited a zero-day in the Yandex service.
“Leviev published a compelling piece of citizen journalism on May 22, 2015 exploring the fate of Russian Spetsnaz soldiers believed to have been killed in combat operations within Ukraine earlier that month. According to Bellingcat founder Higgins, Leviev’s contributor account was compromised and used to post the CyberBerkut message. In an email interview, Leviev makes the following statement regarding the events that led to the compromise of his credentials and the defacement.” continues the analysis.
“In my case, my old email account, which was located on Yandex servers, was hacked. The email account had a long, difficult password, not a word, from various letters, numbers, and special symbols. Plus there was a telephone number bound to the account for second factor authentication.
Exactly how it was hacked — I don’t know.
Either they as employees, or with their active assistance, intercepted the SMS authentication code.
Or they, again, as an officer from the authorities or with their active assistance, gained direct access to the Yandex Mail servers where they seized the email from my old inbox.
Or they know about a vulnerability in Yandex email that nearly nobody else knows about.“
At the time I was writing it is still unclear the relationship between the Fancy Bear and CyberBerkut.
This isn’t the first time that Russian hackers operated to gather sensitive information on the Flight MH17 Crash, in October 2015, according to Trend Micro, the Pawn Storm APT group (aka Fancy Bear) has targeted the Dutch Safety Board to gather information regarding the status of the investigation.
The Dutch Safety Board (known as Onderzoeksraad) became a target of the cyber-espionage group before and after the safety board published their detailed report on the MH17 incident on October 13, 2015. We believe that a coordinated attack from several sides was launched to get unauthorized access to sensitive material of the investigation conducted by Dutch, Malaysian, Australian, Belgian, and Ukrainian authorities.” reported TrendMicro.
Ardit Ferizi, the hacker who helped ISIS to share a Kill List of US Military Personnel has been sentenced to 20 years in prison
25.9.2016 securityaffairs Hacking
The hacker Ardit Ferizi, aka Th3Dir3ctorY, who helped ISIS to share a Kill List of US Military Personnel has been sentenced to 20 years in a US prison
Months ago, I reported you the story of Ardit Ferizi, aka Th3Dir3ctorY, who is the hacker that supported the ISIS organization by handing over data for 1,351 US government and military personnel.
Ferizi is the first man charged with cyber terrorism that was extradited to the US early this year.
He was charged with hacking crimes and providing support to a terrorist organization. The 20-year-old man was accused of supporting the ISIS terrorist organization, he was the subject of extradition from the Malaysian government, where he lived. The man of Kosovar origin was studying computer science in Malaysia.
He was arrested in Malaysia in September 2015 and transferred to the US to face trial.
Now Ardit Ferizi has been sentenced to 20 years in a U.S. prison. According to the US investigators, he provided the data to the popular IS militant Junaid Hussain, which disclosed it on the web. The collaboration between the IS hackers Hussain and Ferizi started in April 2015, according to the US authorities.
The details of the Ferizi’s case are described in the court filings [PDF].
Leaked data included names, e-mail addresses, passwords, locations and phone numbers of 1,351 U.S. military and other government personnel.

Ardit Ferizi cyber terrorism ISIS invites to Kill US military personnel
The stolen data included names, physical addresses, phone numbers, email addresses, and passwords.
Ardit Ferizi, aka Th3Dir3ctorY, from Kosovo was sentenced in federal court in Alexandria, for “providing material support to the Islamic State of Iraq and the Levant (ISIL) and accessing a protected computer without authorization and obtaining information in order to provide material support to ISIL,” the Department of Justice announced on Friday.
The 21-year-old ISIS-linked hacker obtained the data by hacking into the US web hosting company’s servers on June 13, 2015.
The US authorities suspected that Ferizi is a member of a Kosovan hacking team known as KHS, he used the pseudonym of “Th3Dir3ctorY”. The KHS breached a database of a US retailer was able to identify the records belonging to military and government personnel.
The Kosova Hacker’s Security (KHS) hit numerous organizations across the world, including Serbian Government websites, Israeli websites under the #OpIsrael campaign, The Interpol, IBM Research, Hotmail, US National Weather Service Website and numerous targets in Ukraine.

I wrote about Ferizi in October 2015, when the man was arrested by Malaysian authorities because for the first time ever the US Justice Department has charged a suspect for terrorism and hacking (cyber terrorism).
Ferizi was pleaded guilty on June 15, 2016, the faced a sentence of up to 35 years in prison, but the sentence was reduced to a maximum of 25 years in jail after agreeing to plead guilty.
However, the Ferizi’s defense lawyers sustained that his client had no real intention of put militaries in danger, then he asked for a six-year sentence.
Hacker Who Helped ISIS to Build 'Hit List' Of US Military Personnel Jailed for 20 Years
24.9.2016 thehackernews Hacking
A computer hacker who allegedly helped the terrorist organization ISIS by handing over data for 1,351 US government and military personnel has been sentenced to 20 years in a U.S. prison.
Ardit Ferizi, aka Th3Dir3ctorY, from Kosovo was sentenced in federal court in Alexandria, for "providing material support to the Islamic State of Iraq and the Levant (ISIL) and accessing a protected computer without authorization and obtaining information in order to provide material support to ISIL," the Department of Justice announced on Friday.
The 21-year-old ISIS-linked hacker obtained the data by hacking into the US web hosting company's servers on June 13, 2015.
Ferizi then filtered out over 1,300 US military and government employees' information from the stolen data and then handed them over to Junaid Hussain, according to court filings [PDF].
The stolen data contains personally identifiable information (PII), which includes names, email addresses, passwords, locations and phone numbers of US military service members and government workers.
Junaid Hussain, who was a British jihadi and believed to be the then leader and creator of a group of ISIS hackers called the Islamic State Hacking Division (ISHD), posted the names and personal data of 100 US service member's families online.
The Hussain's statements included:
"We are in your emails and computer systems, watching and recording your every move, we have your names and addresses, we are in your emails and social media accounts, we are extracting confidential data and passing on your personal information to the soldiers of the Khilafah, who soon with the permission of Allah will strike at your necks in your own lands!"
Hussain, who was also known as Abu Hussain Al-Britani and used the moniker TriCk, was later killed in a US drone strike in Syria in August last year.
The US authorities also tracked down Ferizi to Malaysia, where he was arrested by the local authorities on October 6, 2015, while trying to catch a flight back to Kosovo.
Before helping ISIS, Ferizi had served as an alleged leader of the Kosova Hacker's Security (KHS) hacking group and hacked into a number of government sites belonging to the Presidency of Macedonia, the Greek Ministry of Education, the Greek Decentralized Administration of Macedonia and Thrace (DAMT), Lifelong Learning and Religion. He also stole data from IBM and Greek mobile telecoms firm OTE.
Ferizi was pleaded guilty on June 15, 2016, and faced a sentence of up to 35 years in prison, but the sentence was reduced to a maximum of 25 years after agreeing to plead guilty. However, defense lawyers said he meant no real harm and asked for a six-year sentence.
Hacker Who Helped ISIS to Build 'Hit List' Of US Military Personnel Jailed for 20 Years
24.9.2016 thehackernews Hacking
A computer hacker who allegedly helped the terrorist organization ISIS by handing over data for 1,351 US government and military personnel has been sentenced to 20 years in a U.S. prison.
Ardit Ferizi, aka Th3Dir3ctorY, from Kosovo was sentenced in federal court in Alexandria, for "providing material support to the Islamic State of Iraq and the Levant (ISIL) and accessing a protected computer without authorization and obtaining information in order to provide material support to ISIL," the Department of Justice announced on Friday.
The 21-year-old ISIS-linked hacker obtained the data by hacking into the US web hosting company's servers on June 13, 2015.
Ferizi then filtered out over 1,300 US military and government employees' information from the stolen data and then handed them over to Junaid Hussain, according to court filings [PDF].
The stolen data contains personally identifiable information (PII), which includes names, email addresses, passwords, locations and phone numbers of US military service members and government workers.
Junaid Hussain, who was a British jihadi and believed to be the then leader and creator of a group of ISIS hackers called the Islamic State Hacking Division (ISHD), posted the names and personal data of 100 US service member's families online.
The Hussain's statements included:
"We are in your emails and computer systems, watching and recording your every move, we have your names and addresses, we are in your emails and social media accounts, we are extracting confidential data and passing on your personal information to the soldiers of the Khilafah, who soon with the permission of Allah will strike at your necks in your own lands!"
Hussain, who was also known as Abu Hussain Al-Britani and used the moniker TriCk, was later killed in a US drone strike in Syria in August last year.
The US authorities also tracked down Ferizi to Malaysia, where he was arrested by the local authorities on October 6, 2015, while trying to catch a flight back to Kosovo.
Before helping ISIS, Ferizi had served as an alleged leader of the Kosova Hacker's Security (KHS) hacking group and hacked into a number of government sites belonging to the Presidency of Macedonia, the Greek Ministry of Education, the Greek Decentralized Administration of Macedonia and Thrace (DAMT), Lifelong Learning and Religion. He also stole data from IBM and Greek mobile telecoms firm OTE.
Ferizi was pleaded guilty on June 15, 2016, and faced a sentence of up to 35 years in prison, but the sentence was reduced to a maximum of 25 years after agreeing to plead guilty. However, defense lawyers said he meant no real harm and asked for a six-year sentence.