Hacking Articles - H 2020 1 2 3 4 5 6 7 8 9 Hacking List - H 2021 2020 2019 2018 0 1 Hacking blog Hacking blog
Experts reported the hack of several supercomputers across Europe
17.5.2020 Securityaffairs Hacking
Organizations managing supercomputers across Europe reported their systems have been compromised to deploy cryptocurrency miners.
Crooks have compromised supercomputers across Europe to deploy cryptocurrency miners, incidents have been already reported in the UK, Germany, and Switzerland. Rumors are circulating about a similar infection of a supercomputer located in Spain.
The supercomputers have shut down to investigate the security breaches.
On Monday, the German bwHPC organization announced that five of its supercomputers had to be shut down due to a cryptominer infection.
Below the message published by the organization:
“Dear users, due to an IT security incident the state-wide HPC systems
bwUniCluster 2.0,
ForHLR II,
bwForCluster JUSTUS,
bwForCluster BinAC, and
Hawk”
Another system that was reportedly infected early last week, is the ARCHER supercomputer at the University of Edinburgh.
“Due to a security exploitation on the ARCHER login nodes, the decision has been taken to disable access to ARCHER while further investigations take place.” reads the status page for the system.
“As you may be aware, the ARCHER incident is part of a much broader issue involving many other sites in the UK and internationally. We are continuing to work with the National Cyber Security Centre (NCSC) and Cray/HPE and further diagnostic scans are taking place on the system.”
The organization reset SSH passwords in response to the incident.
On Wednesday another supercomputer was compromised the system was located in Barcelona, Spain and the infection was reported by security researcher Felix von Leitner.
“More incidents surfaced the next day, on Thursday. The first one came from the Leibniz Computing Center (LRZ), an institute under the Bavarian Academy of Sciences, which said it was disconnected a computing cluster from the internet following a security breach.” reported ZDNet.
“The LRZ announcement was followed later in the day by another from the Julich Research Center in the town of Julich, Germany. Officials said they had to shut down the JURECA, JUDAC, and JUWELS supercomputers following an “IT security incident.”
Other similar incidents made the headlines, on Saturday a high-performance computing cluster at the Faculty of Physics at the Ludwig-Maximilians University in Munich, Germany was infected with a malware.
The Swiss Center of Scientific Computations (CSCS) in Zurich, Switzerland also reported a cyber incident and it shut down any external access to its infrastructure in response to the security breach.
“CSCS detected malicious activity in relation to these attacks. Due to this situation, the external access to the centre has been closed until having restored a safe environment. The users were informed immediately and are kept up to date. Not affected are the weather forecasts of MeteoSwiss, which are also calculated at CSCS.” reads the security advisory.
“We are currently investigating the illegal access to the centre. Our engineers are actively working on bringing back the systems as soon as possible to reduce the impact on our users to a minimum” says CSCS-Director Thomas Schulthess.”
Today, the Computer Security Incident Response Team (CSIRT) for the European Grid Infrastructure has released technical details of a malware involved in these incidents.
Researchers from security firm Cado Security also released Indicators of Compromise (IoCs).
ZDNet, citing the opinion of a security researcher, speculates that threat actors have exploited the CVE-2019-15666 vulnerability to gain root access to the supercomputers then deploy a Monero (XMR) cryptocurrency miner.
Other experts speculate that the supercomputers were hacked by nation-state actors because they were involved in the research on the COVID-19 outbreak.
Researcher finds 1,236 websites infected with credit card stealers
16.5.2020 Bleepingcomputer Hacking
A security researcher collected in a span of a few weeks over 1,000 domains infected with payment card skimmers, showing that the MageCart continues to be a prevalent threat that preys on insecure webshops.
MageCart was first spotted over a decade ago by cybersecurity company RiskIQ but attacks have grown rampant over the past two years when big-name companies were hit - British Airways, Ticketmaster, OXO, Newegg.
Since then, automated systems tuned specifically to detect this type of threat found hundreds of thousands of websites that on checkout pages malicious JavaScript designed to steal card data from shoppers.
200 alerts sent, no reply
Using freely available tools and some elbow grease, security researcher Max Kersten was able to compile a list of 1,236 domains that were hit by a web skimmer hosted on an external domain.
He started with one domain that hosted a skimmer and the Urlscan.io website scanning service. This allowed searching for a time when the skimmer domain changed in the infection chain.
“Repeating this process results in a list of all the exfiltration domains in the chain until it either breaks or the search is stopped. Additionally, one can recursively query every affected domain to search for other skimmer domains” - Max Kersten
Most of the domains included in the research are already available from other sources, since this one-man effort took some time to reach a conclusion.
Kersten says that his goal is to add to those publicly available resources from companies (RiskIQ, Sansec, Group-IB, Malwarebytes, Trustwave) and other researchers (Willem de Groot, Jérôme Segura, Affable Kraut, Jacob Pimental, and Mikhail Kasimov) on domains hosting JavaScript code for stealing payment card info.
Although the data is about two to three weeks old, the researcher believes the results should be roughly the same at this time. The fact that he received no reply to the 200 notifications he sent to website owners or administrators adds to this speculation.
In the list he provides, the latest detection date for some domains is from 2018. This could mean that they are no longer infected or were no longer checked through URLio.
The endeavor to email all 1,236 companies was stopped by Google’s spam detection since Kersten’s messages were exactly the same, save for the affected domain name and the skimmer detection timestamp.
Main suspect: MageCart Group 12
The methodology used for this research is in no way tracking all MageCart infections but shows that independent work can uncover a pretty large number of affected online stores.
Kersten found affected domains by using a scanner he made to parse and store results from Urlscan.io’s API and several rules that detected the malicious JavaScript. He then removed incorrect and double entries and subdomains that would have affected the final set of unique domains.
For the most part, the results from this effort track partial activity from MageCart Group 12, which is considered a more advanced threat actor in the web skimming business.
Kersten told BleepingComputer that the confidence level in attributing infections to this group increases proportionally to the freshness of the detection date.
In a report published on his blog, the researcher says that 70% of the online stores compromised in a MageCart attack could be pinged when he checked if they were reachable.
This only indicates that they’re no longer feeding cybercriminals with credit card info but shoppers were affected at one point.
Also, some of them were still under development, as indicated by the generic Lorem Ipsum placeholder text in “about” pages. Despite this, they did engage in commercial activity.
“Note that not all infections within the data set loaded the actual skimmer, as the skimmer domain could have been either unreachable or taken down. This is favourable for the shopping customer, but the infection on the web shop was still present, as the request was recorded“ - Max Kersten
Most affected shops are in the U.S.
As for the categories of products sold on compromised websites and geographical regions, the researcher spent five evenings to check them manually.
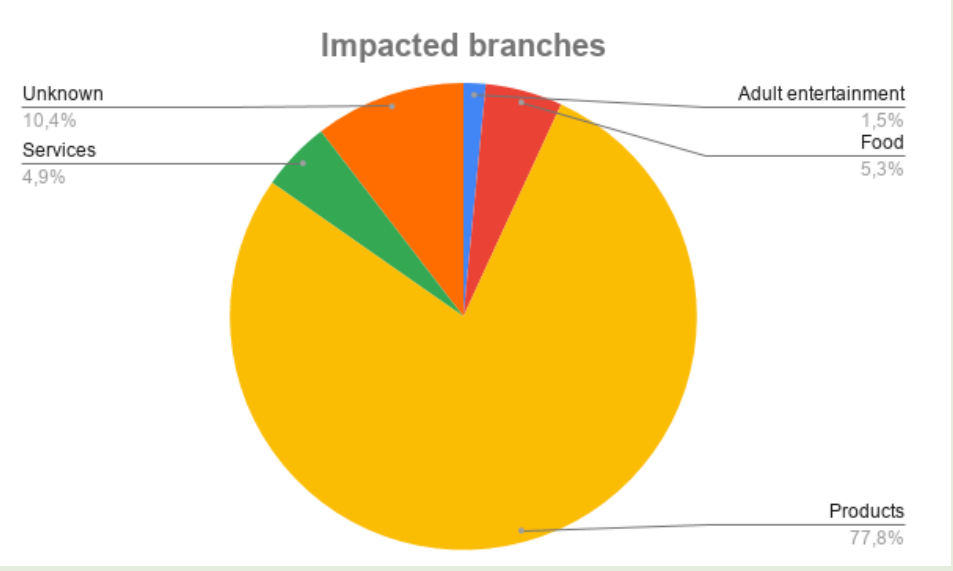
Food-related shops, services, adult items, and miscellaneous products are the main categories, along with an “unknown” segment that stands for shops that were not accessible or found in other sources.
Based on Kersten’s research, the country with the most shops impacted by MageCart is the U.S., while individual countries in Europe seem to be the least affected, as the U.K. is in the lead with just 68 shops:
US (303)
Unknown (280)
IN (79)
UK (68)
DE (50)
AU (47)
BR (46)
FR (34)
IT (31)
NL (28)
CA (23)
ES (19)
The researcher provides in his post the full list of domains where a credit card skimmer was detected. Payment info of those that shopped on those sites between the provided time interval is likely compromised. If the card has not expired, it would be a good idea to check for account balance inconsistencies and ask the issuing bank for a new one.
WordPress plugin bugs can let hackers take over almost 1M sites
15.5.2020 Hacking
Two high severity vulnerabilities found in the Page Builder WordPress plugin installed on more than 1,000,000 sites can let hackers create new admin accounts, plant backdoors, and ultimately take over the compromised websites.
The vulnerabilities are a Cross-Site Request Forgery (CSRF) leading to Reflected Cross-Site Scripting (XSS) attacks and they affect all Page Builder versions up to and including 2.10.15.
Attackers can exploit these security flaws by tricking WordPress site administrator into clicking specially crafted links or attachments and execute malicious code in their browsers, as well as forge requests on their behalf.
Page Builder is a popular plugin developed by SiteOrigin to help users easily build responsive grid page content using a widget-based page creating editor. 
Page Builder plugin (SiteOrigin)
Malicious code injection
The two Page Builder security vulnerabilities are rated as high severity by Wordfence's Threat Intelligence team who discovered them and reported the issues to the plugin's developers on May 4.
The development team released a patch to fix both security issues the next day, on May 5, by adding nonce checks to both the Live Editor feature and the builder_content action were the two bugs were found.
As the researchers explain, exploiting the two bugs can "be used to redirect a site’s administrator, create a new administrative user account, or, as seen in the recent attack campaign targeting XSS vulnerabilities, be used to inject a backdoor on a site."
Attackers who know what they're doing can also fully take over compromised WordPress websites once they create rogue admin accounts and plant backdoors for maintaining access.
Millions of WordPress sites waiting for patches
Page Builder's development team updated the plugin to 2.10.16 almost a week ago to fix the two security flaws and users are urged to patch their installations to avoid attacks.
However, just over 220,000 of all 1 million users have updated their Page Builder installation to the last, patched version since its release last week.
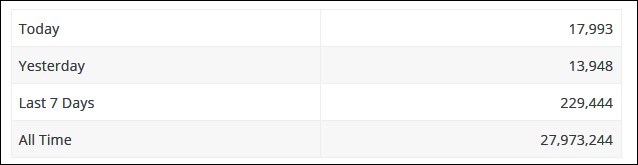
Page Builder update history
Starting with May 6, Hackers are exploiting two other vulnerabilities in the Elementor Pro and Ultimate Addons for Elementor WordPress plugins to remotely execute arbitrary code and fully compromising unpatched targets.
Another series of attacks against over 900,000 WordPress sites started on April 28 with the attackers attempting to redirect visitors to malvertising sites or plant backdoors if their admins are logged in.
The threat actor behind these attacks was observed while using at least 24,000 IP addresses to deliver malicious requests to over 900,000 sites, with over 20 million attacks having been launched against more than half a million sites on May 3rd alone.
To mitigate these attacks, WordPress admins should immediately update their plugins to patch the vulnerabilities threat actors could exploit to compromise their sites.
UK Electricity Market Administrator Elexon Targeted by Hackers
15.5.20 Securityweek Hacking
Elexon, a company involved in the management of the electricity market in the United Kingdom, has been hit by a cyberattack that impacted its internal IT systems.
Elexon manages the Balancing and Settlement Code (BSC) on behalf of the electricity sector in the UK. The BSC defines the rules and governance for the balancing mechanism and imbalance settlement processes of electricity in Britain.
“We compare how much electricity generators and suppliers said they would produce or consume with how much electricity they actually generated and supplied. After calculating these volumes, we work out a price for the imbalances and charge organisations accordingly. This involves taking 1.2 million meter readings every day and handling over £1.5 billion of our customers’ funds each year,” Elexon says on its website.Elexon suffers data breach
Elexon initially revealed that its internal IT systems, including its ability to send and receive email, were affected by a cyberattack, but noted that the BSC central systems and EMR (Electricity Market Reform) systems were not affected.
In a later update, the company said it identified the root cause and it had started restoring impacted systems.
While Elexon says only its internal systems are impacted, the UK’s National Grid electricity system operator (ESO) said on Twitter that it’s investigating any potential impact on its own networks, but pointed out that electricity supply was not affected by the incident.
“We have robust cybersecurity measures across our IT and operational infrastructure to protect against cyber threats,” National Grid ESO said.
It’s not uncommon for organizations in the electricity sector to be targeted in cyberattacks. Earlier this year, the European Network of Transmission System Operators for Electricity (ENTSO-E) admitted that hackers breached its corporate network, and an electric utility in Massachusetts reported being hit by ransomware.
Industrial cybersecurity firm Dragos reported in January that an increasing number of threat groups had been targeting electric utilities in North America.
Hacker group floods dark web with data stolen from 11 companies
10.5.2020 Bleepingcomputer Hacking
A hacking group has started to flood a dark web hacking marketplace with databases containing a combined total of 73.2 million user records over 11 different companies.
For the past week, a hacking group known as Shiny Hunters has been busy selling a steady stream of user databases from alleged data breaches.
It started last weekend with Tokopedia, Indonesia's largest online store, where a database of over 90 million user records was being sold.
Soon after, Shiny Hunters began selling a database of 22 million user records for Unacademy, one of India's largest online learning platforms. After being contacted by BleepingComputer, the company released a statement that their company was breached.
On Wednesday, Shiny Hunters continued their rampage by claiming to hack into Microsoft's GitHub account earlier this year and leaking files from the company's private source code repositories.
Microsoft GitHub account breach
While Microsoft has not officially admitted that their GitHub account was breached, sources have told BleepingComputer that the shared data was indeed private repositories only accessible to Microsoft employees.
Now selling user records from 11 data breaches
Earlier this week, BleepingComputer was told by cyber intelligence firm ZeroFox that Shiny Hunters had begun selling databases for the meal kit delivery service HomeChef, photo print service ChatBooks, and Chronicle.com, a news source for higher education.
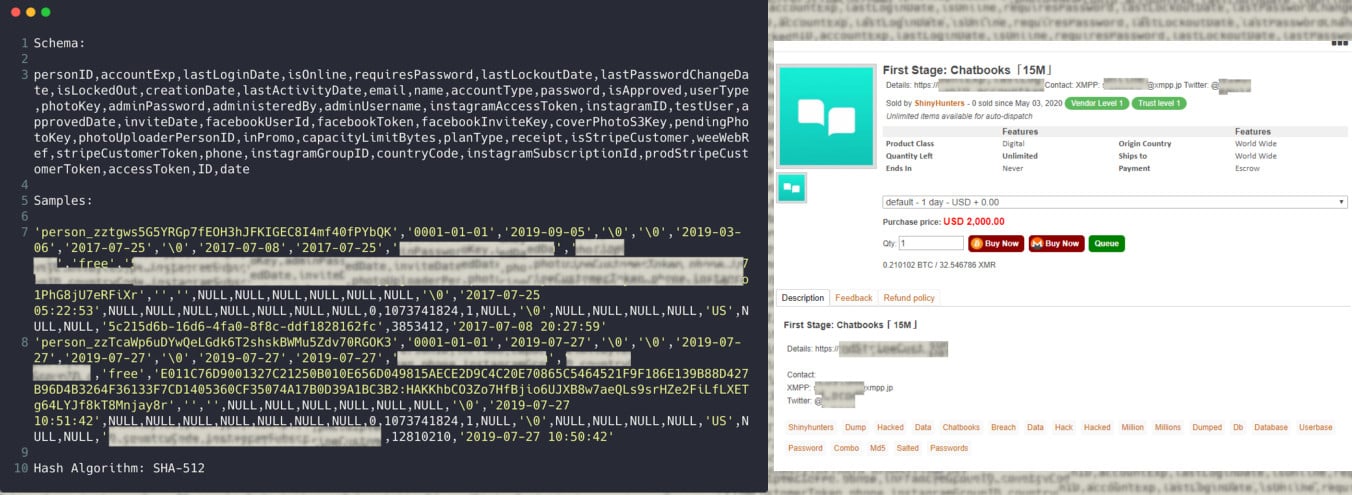
With the three databases combined, there are a total of 26 million accounts being sold with prices for each database ranging between $1,500 and $2,500.
Soon after reporting on these breaches, ChatBooks started sending data breach notifications to their users.
Last night, cyber intelligence firm Cyble told BleepingComputer that Shiny Hunters had started to "flood the market" with new data breaches from other companies, bringing the total amount of user databases being sold to 11.
Company User Records Price
Tokopedia 91 million $5,000
Homechef 8 million $2,500
Bhinneka 1.2 million $1,200
Minted 5 million $2,500
Styleshare 6 million $2,700
Ggumim 2 million $1,300
Mindful 2 million $1,300
StarTribune 1 million $1,100
ChatBooks 15 million $3,500
The Chronicle Of Higher Education 3 million $1,500
Zoosk 30 million $500
From samples of user records seen by BleepingComputer, the data breaches look legitimate, but they have not been 100% confirmed.
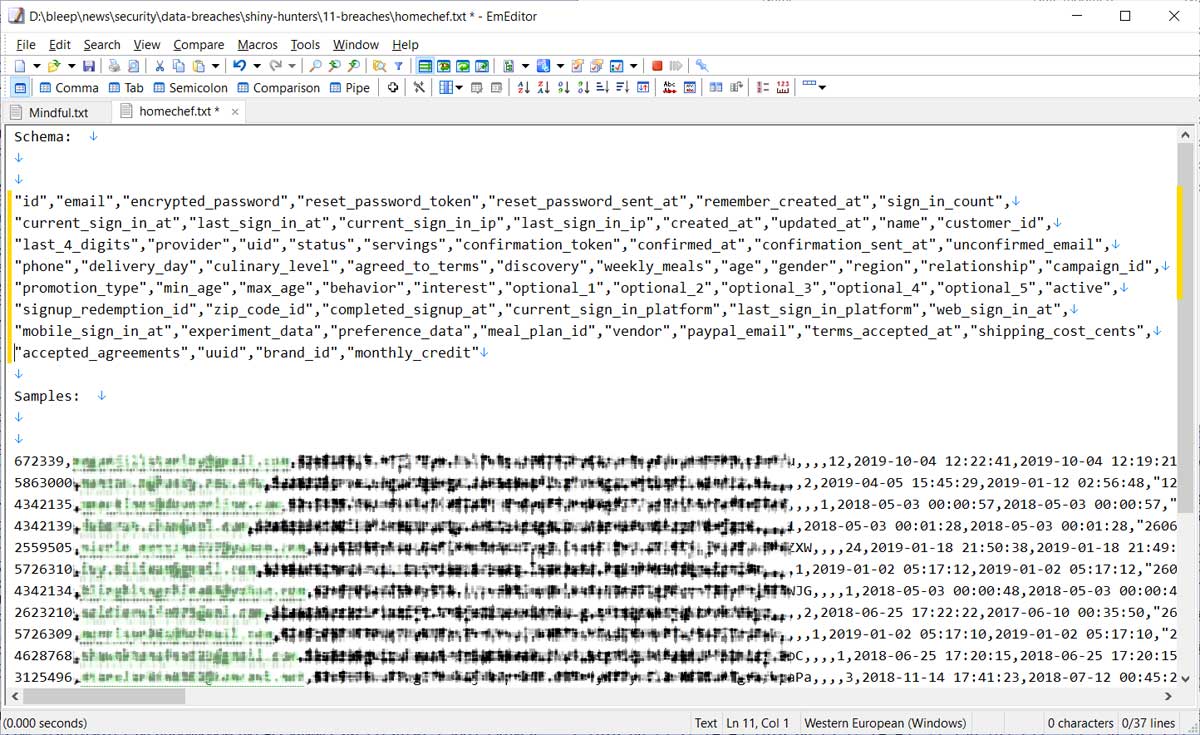
Sample user database being sold
After being told about the new databases being sold, BleepingComputer had contacted the affected companies but has not heard back yet.
To be safe, if you have an account at any of the sites listed above, it is strongly suggested that you change your password to a strong and unique one used only at that site.
If the same password has been used at other sites, change your password to a unique one there as well.
Microsoft's GitHub account hacked, private repositories stolen
10.5.2020 Bleepingcomputer Hacking
A hacker claims to have stolen over 500GB of data from Microsoft's private GitHub repositories, BleepingComputer has learned.
This evening, a hacker going by the name Shiny Hunters contacted BleepingComputer to tell us they had hacked into the Microsoft GitHub account, gaining full access to the software giant's 'Private' repositories.

Actor's proof of access to Microsoft's private GitHub repos
The individual told us that they then downloaded 500GB of private projects and initially planned on selling it, but has now decided to leak it for free
Based on the file stamps in full directory listing of the leaked files, the breach may have occurred on March 28th, 2020.
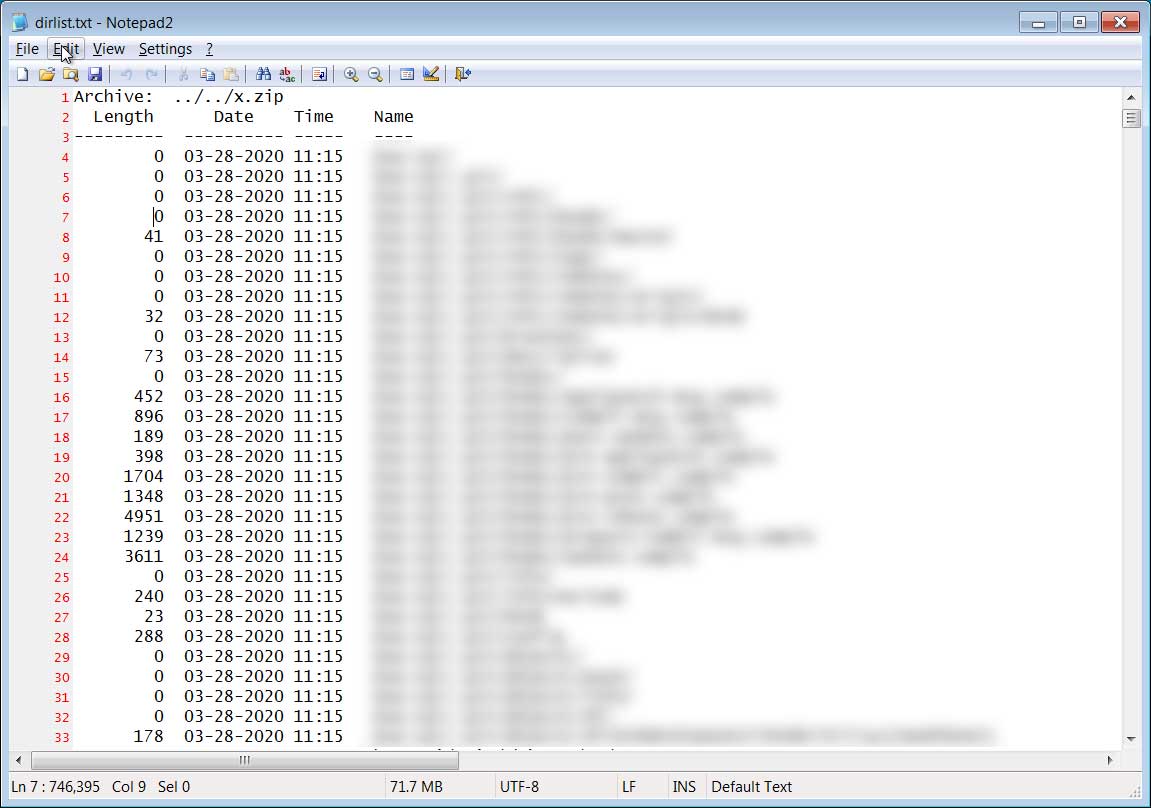
Leaked data listing showing the breach date
Shiny Hunters told BleepingComputer that they no longer have access to Microsofts GitHub account.
Private repositories leaked
As a teaser, the hacker offered 1GB of files on a hacker forum for registered members to use site 'credits' to gain access to the leaked data.
As some of the leaked files contain Chinese text or references to latelee.org, other threat actors on the forum do not feel that the data is real.
Based on the full directory listing of the stolen data and and source code from private repositories that was sent to BleepingComputer by the hacker, the stolen files appear to be mostly code samples, test projects, an eBook, and other generic items.
Some private repositories look a bit more interesting such as ones named some 'wssd cloud agent', a The Rust/WinRT language projection', and a 'PowerSweep' PowerShell project.
Overall, from what was shared, there does not appear to be anything significant for Microsoft to worry about, as it did not contain more sensitive code for software like Windows or Office.
Cyber intelligence firm Under the Breach, who also saw the leak on the hacker forum, shares BleepingComputer's opinion that there is not much to worry about.
They did express concern that private API keys or passwords could have accidentally been left behind in some of the private repositories like other developers have done in the past.
Since publishing this story, a Microsoft employee who wished to remain anonymous has told BleepingComputer that the stolen data is legitimate.
Other employees who had previously denounced the leak as fake, have since deleted their tweets.
Microsoft has told BleepingComputer that they are "aware of these claims and are investigating."
Update 5/8/20: Updated to include info that the breach was confirmed as legitimate by MS employee and statement from Microsoft.
WordPress plugin bug lets hackers create rogue admin accounts
2.5.2020 Bleepingcomputer Hacking
WordPress owners are advised to secure their websites by updating the Real-Time Find and Replace plugin to prevent attackers from injecting malicious code into their sites and creating rogue admin accounts by exploiting a Cross-Site Request Forgery flaw.
The security vulnerability is a Cross-Site Request Forgery (CSRF) that leads to Stored Cross-Site Scripting (Stored XSS) attacks and it impacts all Real-Time Find and Replace versions up to 3.9.
It can be abused to trick WordPress admins into injecting malicious JavaScript into their own websites' pages after clicking a malicious link within a comment or email.
The Real-Time Find and Replace WordPress plugin is installed on over 100,000 sites and it allows users to temporarily replace text and code content on their sites in real-time without having to actually go into the sites' source code and make permanent changes.
Trickery and malicious code injections
An attacker can take advantage of the plugin's functionality to replace any content on a targeted site with malicious code, as detailed in a report published today by Wordfence threat analyst Chloe Chamberland.
This JavaScript code would get automatically executed "anytime a user navigated to a page that contained the original content," according to Chamberland.
For instance, attackers could abuse the vulnerability to replace an HTML tag like <head> with their malicious code, which would lead to almost all pages on the attacked WordPress site being converted into a malicious tool and leading to a high impact attack following successful exploitation.
The malicious code could then "be used to inject a new administrative user account, steal session cookies, or redirect users to a malicious site, allowing attackers the ability to obtain administrative access or to infect innocent visitors browsing a compromised site," per Chamberland's report.
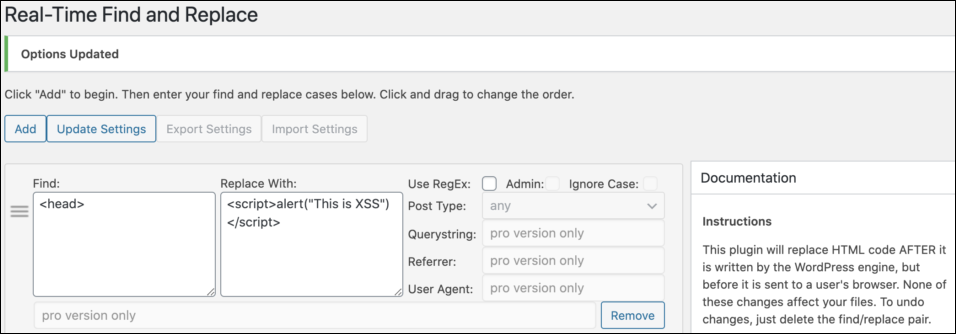
Injecting malicious code (Wordfence)
To replace content before the website data is sent to a site visitor's browser, "the plugin registers a sub-menu page tied to the function far_options_page with a capability requirement to activate_plugins," Chamberland explains.
"The far_options_page function contains the core of the plugin’s functionality for adding new find and replace rules," she added.
"Unfortunately, that function failed to use nonce verification, so the integrity of a request’s source was not verified during rule update, resulting in a Cross-Site Request Forgery vulnerability."
Patched within hours, over 70K sites still vulnerable
The vulnerability was discovered and reported on April 22 and Real-Time Find and Replace's developer responded with a full patch within a few hours after the initial disclosure report.
Wordfence has rated this security flaw with a CVSS score of 8.8 which makes it a high severity issue, a fact that should prompt all users to immediately update to version 4.0.2, the plugin release that fully patches the bug.
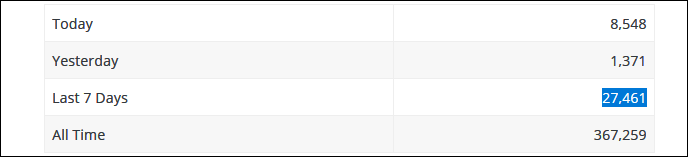
Updates during the last 7 days
Unfortunately, despite the developer's prompt response and the security fix's availability for the past five days, just over 27,000 of all users have updated their Real-Time Find and Replace installations to 4.0.2 — the last, bug-free version.
Revive ad servers being hacked to distribute malicious ads
25.4.2020 Bleepingcomputer Hacking
The Tag Barnakle malvertising group is hacking into Revive ad servers to inject and deliver malicious advertisements on unwary visitors.
Most online publishers use hosted ad server platforms such as Google Ad Manager to deliver their ads, but some still prefer to use self-hosted ad serving platforms to have greater control and flexibility on how they display their ads.
One open-source self-hosted platform that has been around for the past ten years is called the Revive ad server.
Just like any application, Revive has had its share of vulnerabilities that can be used to inject malicious advertisements into web sites that utilize the ad server.
HackerOne bug bounty program for Revive
In a new report by advertising security firm Confiant, we can see how one malvertiser known as Tag Barnakle is mass-compromising Revive ad servers to inject their own code into a publisher's existing advertising campaigns.
"In recent months, we have seen a wave of malvertisements that are attached to Revive creatives spanning dozens of instances of ad servers, including those owned and operated by publishers and ad networks," Confiant security researcher Eliya Stein explained in a report.
When compromising servers, Tag Barnakle will modify existing advertising creatives used by the publisher and append their own malicious JavaScript code to them.
This malicious code will detect when Firebug or a browser's developer console is open, and if not, perform a redirect to malicious sites that are promoting fake Adobe Flash updates.
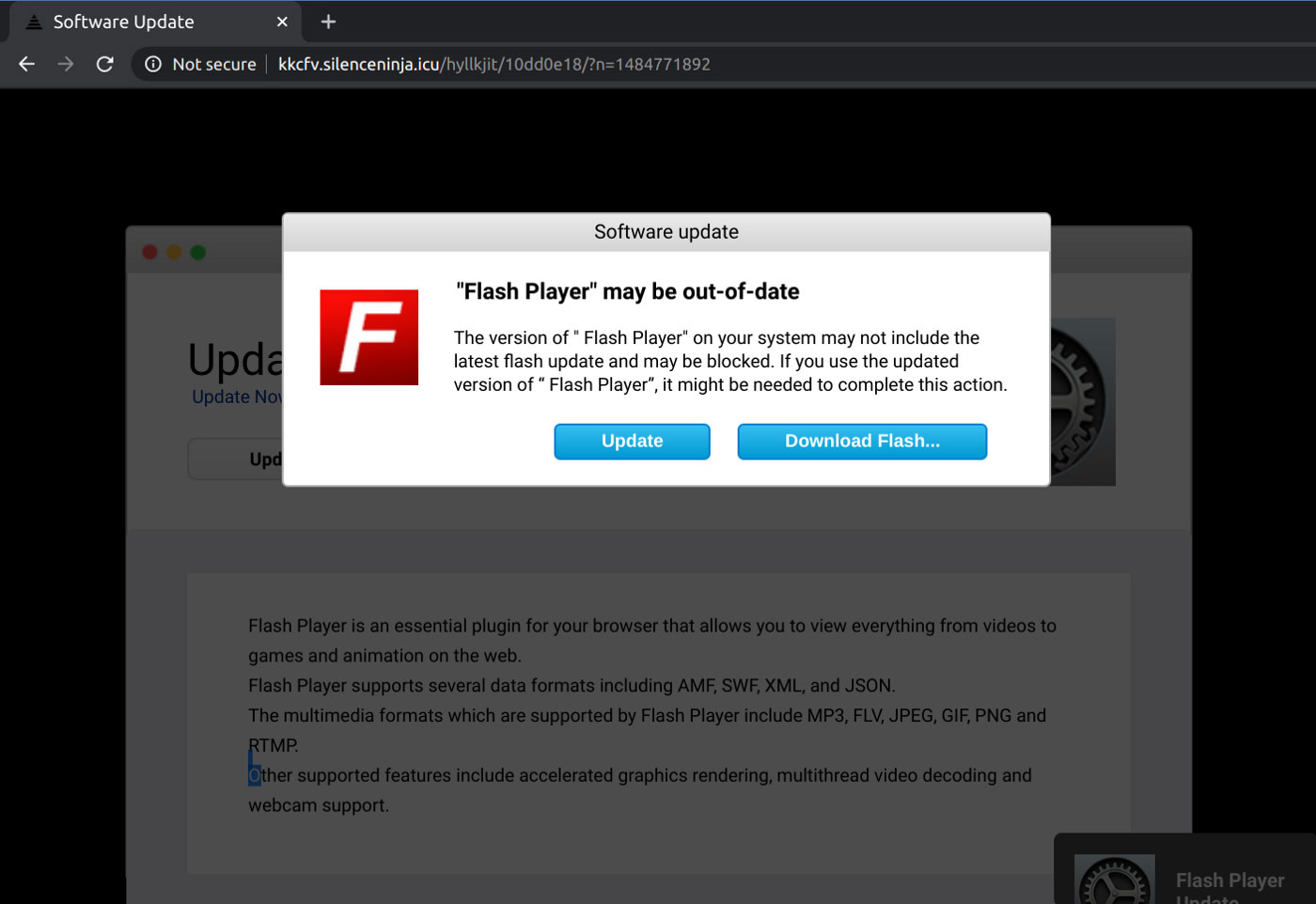
Fake Adobe Flash update
Stein told BleepingComputer that these fake Adobe Flash player updates install the Shalyer Trojan or other botnet bundlers onto macOS systems.
For Windows users, the sample shared with BleepingComputer installs an adware bundle such as InstallCore that is known to infect victims with ransomware, information-stealing Trojans, unwanted browser extensions, and other malware.
Adware bundle
Compromised ad servers have a long reach
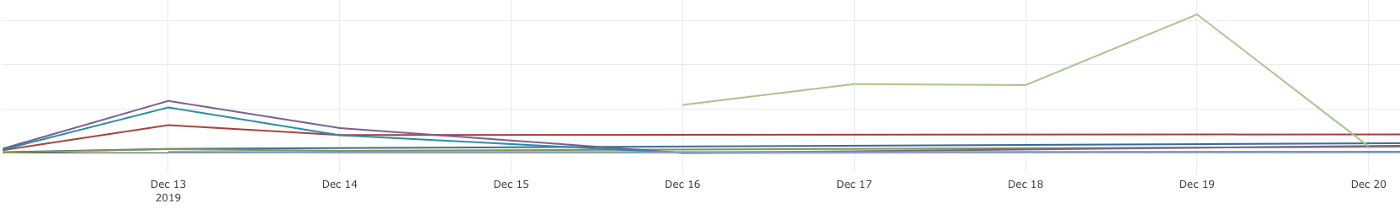
Confiant has seen Tag Barnakle activity on over 360 web sites, but their reach is far larger due to the software being used by smaller real-time bidding ad serving providers.
In one compromised RTB ad provider, Confiant saw up to 1.25MM malicious ad impressions being pushed out in a single day.
"If we take a look at the volumes behind just one of the compromised RTB ad servers — we see spikes of up to 1.25MM affected ad impressions in a single day. For context, Tag Barnakle has compromised ~60 ad servers in total," Confiant stated in their report.
RTB volume
While it may be tempting to utilize your own ad servers, it also opens a publisher to the risk of potential hacks that allow attackers to inject malicious ads.
Therefore, only use an open-source ad server if you have the time and workforce to stay on top of security updates and be able to install them quickly as they are released.
If you are a small company with limited staff, it may be wiser to stick with a hosted solution to avoid these headaches and the risks involved.
Microsoft buys corp.com to prevent Windows account hijacking
12.4.2020 Bleepingcomputer Hacking
Microsoft has purchased the Corp.com domain to prevent it from being used by malicious actors to steal Windows credentials, monitor customer traffic, or serve malicious files.
Internet domain name investor Mike O’Connor has been the owner of Corp.com for the past 26 years but has always been hesitant to sell it as it could be used by malicious actors.
This is because Microsoft in the past would recommend that companies utilize "CORP" as the name of their Activity Directory domain when configuring a new Windows network.
As the DNS and the Internet started to get more tightly integrated into Windows domains, the Windows domains utilizing CORP would begin to have DNS name collision issues with the real corp.com Internet domain.
This would cause Windows to sometimes try and connect to the corp.com Internet domain rather than the Windows domain when accessing resources such as network shares, logins, and printers.
If the corp.com Internet domain was utilized by malicious actors, it could allow them to serve up malicious files or even steal Windows user credentials as user accounts and hashed passwords are sent to the server when trying to access network shares.
Once a threat actors gain access to the hashed password, they can utilize programs like HashCat to crack passwords fairly quickly.
To prevent these types of DNS name collisions, Microsoft recommends that you own any domain that you use for your Active Directory Services on a Windows network.
Microsoft purchases corp.com
According to Brian Krebs, when O'Conner put the corp.com up for sale for $1.7 million, he was hoping that Microsoft would purchase the domain to protect its customers rather than cybercriminals or state-sponsored hacking groups who would use it for malicious purposes.
In a new blog post, Krebs states that Microsoft has agreed to purchase the domain from O'Conner at an undisclosed price to protect their customers.
"To help in keeping systems protected we encourage customers to practice safe security habits when planning for internal domain and network names," Microsoft said in a statement. "We released a security advisory in June of 2009 and a security update that helps keep customers safe. In our ongoing commitment to customer security, we also acquired the Corp.com domain."
While Microsoft now owns the domain, it should be noted that these DNS name collisions can still occur if Microsoft ever decides to put the domain name in use on the Internet.
Therefore, if possible, Windows domains should migrate to domain names that they own to avoid these types of DNS name collision risks from affecting them in the future.