
The analysis of the file system of the vehicle’s Telematics Control Unit (TCU), to which they gained access by obtaining an interactive shell with root privileges, they uncovered passwords and certificates for the backend server.
Hacking Articles - H 2020 1 2 3 4 5 6 7 8 9 Hacking List - H 2021 2020 2019 2018 0 1 Hacking blog Hacking blog
Remotely hack a Mercedes-Benz E-Class is possible, experts demonstrated
9.8.20 Hacking Securityaffairs
Chinese researchers discovered tens of vulnerabilities in a Mercedes-Benz E-Class, including issues that can be exploited to remotely hack it.
A team of Chinese experts from Sky-Go, the Qihoo 360 division focused on car hacking, discovered 19 vulnerabilities in a Mercedes-Benz E-Class, including some issues that can be exploited by attackers to remotely hack a vehicle.
The experts analyzed a Mercedes E-Class model because it is a connected car with a powerful infotainment system with a rich set of functionalities.
The research began in 2018 and in August 2019, the experts reported their findings to Daimler, which owns the Mercedes-Benz. In December 2019, the carmaker announced a partnership with the 360 Group to strengthen car IT security for the industry.
“In 2018, we begin research on Mercedes-Benz, since it is one of the most famous car brands in the world and an industry benchmark in the automotive industry. We analyze the security of Mercedes-Benz cars. There are so many models from Mercedes-Benz, and we finally chose the research target on Mercedes-Benz E-Class, since the E-Class’s in-vehicle infotainment system has the most connectivity functionalities of all.” reads the research paper.
Last week, during the Black Hat cybersecurity conference, representatives of Sky-Go and Daimler disclosed the findings of their research. The experts avoided to publicly disclose technical details of the issues to prevent malicious exploitation in the wild.
The team of experts was able to exploit the flaws to remotely unlock the car’s doors and start the engine of a Mercedes-Benz E-Class. According to the experts, the flaw could have affected 2 million vehicles only in China.
The experts initially collected relevant information from the target devices, such as network topology, pin definitions, chip model, and enable signals in the car. Then disassembled the center panel in the car to analyze the wiring connections between the Electronic Control Units (ECUs).

The analysis of the file system of the vehicle’s Telematics Control Unit (TCU), to which they gained access by obtaining an interactive shell with root privileges, they uncovered passwords and certificates for the backend server.
“If we have to debug the TCU client programs dynamically, we need to tamper the filesystem to get an interactive shell with ROOT privileges.” continues the research.
The researchers were also able to gain access to backend servers by analyzing the vehicle’s embedded SIM (eSIM) card used for the external connectivity.
“Car Backend is the core of Connected Cars. As long as Car Backends’ services can be accessed externally, it means that car backend is at risk of being attacked. The vehicles connecting to this Car Backend are in danger, too. So, our next step is to try to access Car Backend.” continues the research. “For accessing the APN networks of backend, one possibility would be using the e-sim of car-parts since the sim account wouldn’t log out automatically. After tearing down this eSIM, we put it into the 4G router.”
Experts noticed the lack of authentication between the backend servers and the “Mercedes me” mobile app, which allows users to remotely control multiple functions of the car. The researchers explained that once they got access to the backend, they could control any car in China.
The experts said that they did not manage to hack any critical safety functions of the tested vehicles.
“During the research and joint workshop, we see so many security designs in Mercedes-Benz Connected Cars and these designs are protecting the cars from various attacks.” the paper concluded. “The capability of a car company to work jointly with researchers contributes to the overall security of our cars.”
Attackers Horn in on MFA Bypass Options for Account Takeovers
8.8.20 Hacking Threatpost
Legacy applications don’t support modern authentication — and cybercriminals know this.
An uptick in business email compromise attacks is being attributed to successful compromises of multi-factor authentication (MFA) and conditional access controls, according to researchers. While brute-forcing and password spraying techniques are the most common way to mount account takeovers, more methodical cybercriminals are able to gain access to accounts even with more secure MFA protocols in place.
According to Abnormal Security, cybercriminals are zeroing in on email clients that don’t support modern authentication, such as mobile email clients (for example, iOS Mail for iOS 10 and older); and legacy email protocols, including IMAP, SMTP, MAPI and POP. Thus, even if MFA is enabled on the corporate email account, an employee checking email via mobile won’t be subject to that protection.
“While MFA and modern authentication protocols are an important advancement in account security and should be used whenever possible…this means that it is not possible to enforce MFA when a user signs into their account using one of these applications,” said Erin Ludert, writing in a blog post on Friday.
Thus, she noted that a common pattern in account-takeover attacks is that after being blocked by MFA, an adversary will immediately switch to using a legacy application.
“In fact, most credential stuffing campaigns utilize legacy applications such as IMAP4 to ensure they do not encounter difficulties from MFA at any point,” Ludert said, adding, “Many enterprises are under the mistaken impression that they are fully protected by MFA and do not need to worry about account takeovers. This is a dangerous assumption.”
Meanwhile, many Office 365 licenses provide the ability to configure conditional-access policies, which block access by users to certain applications. This can be used to block legacy applications that may be targeted for password-spraying campaigns, for instance. However, according to Abnormal Security, attackers are also focused on ferreting out targets that don’t have this implemented, or, bypassing it.
“First and foremost, conditional access is not included with all licenses, meaning that many enterprises simply have no way to protect themselves from this type of attack,” Ludert said. “Additionally, legacy applications are still in widespread use in most enterprises. Completely blocking all users from legitimate access using these applications will be quite disruptive to the workforce. Also, legacy access is enabled by default on Office 365. In order to effectively block legacy access, it must be disabled on a per-tenant basis – for all users and platforms.”
Additionally, attempting to apply legacy blocking based on the platform (Windows, mobile, etc.) relies on the user agent to do so. The user agent is basically the software agent that is acting on behalf of a user, such as a web browser or email reader – and as such, it’s very easy to falsify, the researcher noted. Thus, even with conditional access in place, cybercriminals are mounting attacks by obscuring the app that they are using.
“In one case, the attacker initially attempted to sign in using a legacy application but was blocked by conditional access,” Ludert said. “The attacker then waited several days before trying again, this time with the app information obscured, and successfully gained access to the account.”
As MFA becomes more widespread, cybercrooks are looking to stay a step ahead. In May, researchers observed a phishing campaign that bypassed MFA on Office 365 to access victims’ data stored on the cloud and use it to extort a Bitcoin ransom; attackers used a malicious SharePoint link to trick users into granting permissions to a rogue application..
The tactic leveraged the OAuth2 framework and OpenID Connect (OIDC) protocol, which are the technical bits behind functions like “Log in with Faceboook” – being signed into a trusted application is used to verify a user on a second application, essentially. When OIDC and OAuth are used to authenticate a user, no credentials are exposed to the application, so MFA isn’t triggered.
Reddit massive hack: hackers defaced channels with pro-Trump messages
8.8.20 Hacking Securityaffairs
Reddit suffered a massive hack, threat actors compromised tens of Reddit channels and defaced them showing messages in support of Donald Trump’s campaign.
Reddit suffered a massive hack, threat actors defaced tens of channel to display messages in support of Donald Trump’s reelection campaign.
At the time of writing, the massive hack is still ongoing and Reddit’s security team is working to restore the operations.
Below a list containing some of the impacted subreddits, some of them having tens of millions of members:
r/NFL
r/CFB (Canadian Football League)
r/TPB (The Pirate Bay’s Reddit channel)
r/BlackMirror (TV show)
/r/Buffy (TV show)
r/Avengers (Movie franchise)
r/Vancouver (city)
r/Dallas (city)
r/Plano (city)
r/Japan
r/Gorillaz (music band)
r/Podcasts
/r/Disneyland
r/49ers (NFL team)
/r/BostonCeltics (NBA team)
r/Leafs (Toronto Mapple Leafs)
/r/EDM (electronic dance music channel)
/r/Food
r/Beer
r/Renting
r/Lockpicking
r/Subaru (car maker)
r/freefolk (Game of Thrones fan channel)
r/Space
r/ISS
r/DestinyTheGame (video game)
r/LawSchool
r/StartledCats
r/TheDailyZeitgeist
r/Supernatural
/r/Naruto
/r/RupaulsDragRace
r/GRE
r/GMAT
r/greatbritishbakeoff
r/11foot8
r/truecrimepodcasts
r/comedyheaven
r/weddingplanning
r/Chadsriseup
r/BertStrips
r/KingkillerChronicle (book series)
r/PoliticalDiscussion
r/MadLads
r/DNDMemes
r/woodpaneled
r/telescopes
r/WeAreTheMusicMakers
r/DeTrashed
r/Samurai8
r/3amjokes
r/ANGEL
r/PhotoshopBattles
r/Animemes
r/comedyheaven/
r/awwducational
r/gamemusic
r/hentaimemes
r/ShitAmericansSay
r/ShitPostCrusaders
r/SweatyPalms
r/Locklot
r/BadHistory
r/CrewsCrew/
r/ListenToThis
r/PokemonGOBattleLeague
r/FacingTheirParenting
r/TwoSentenceHorror
r/BookSuggestions
r/FreezingFuckingCold/
r/woof_irl
r/BurningAsFuck
r/ImagineThisView
r/AnotherClosetAtheist
r/CasualTodayILearned
r/ShowerBeer
r/TookTooMuch
r/DallasProtests/
r/BannedFromClubPenguin
r/creepyPMs
r/RedditDayOf
r/AquaticAsFuck
r/HeavyFuckingWind/
r/BlackPeopleTwitter
r/HuskersRisk
r/Fireteams/
r/LuxuryLifeHabits
r/IRLEasterEggs
r/nononono
r/nonononoyes
r/ThatsInsane
According to Reddit, the hacker compromised several subreddit moderator accounts.
Owners of the channel that are facing security issues could report problems in this Reddit ModSupport thread, meantime they are recommended to enable two-factor authentication (2FA) on their accounts and to change their passwords.
Indicators of compromise for the Reddit moderator accounts are:
• moderator received email notification that the password and/or email address on your account changed but you didn’t request changes
• moderator notice authorized apps on your profile that you don’t recognize
• moderator notice unusual IP history on your account activity page
• moderator see votes, posts, comments, or moderation actions that you don’t remember making, or private messages that you don’t remember sending
One of the moderators who had their account compromised published the details of the actions performed by attackers on his behalf.
“Help! I’ve been hacked by some bizarre pro-trump bot! It wrecked my subreddit’s style sheet, deleted all mods below me, updated the wiki… I’m in way over my head. What can I do? PSA: Change your passwords and enable 2-factor authentication!” reads the title of the discussion.
Once the attacker has taken the control of the mod’s account, he changed his subrreddit’s CSS stylesheet, deleted all mods with fewer permissions than him, and changed the community’s wiki.
Finally, the hacker published the message: “We Stand With Donal Trump #MIGA2020.”
The Twitter account https://twitter.com/advanceHCAjobs claimed responsibility for the massive Reddit hack, but currently, the account was suspended. While the hackers were targeting subreddits, they asking Twitter users to vote on them.
In June, Reddit has banned a channel of President Trump supporters, r/The_Donald, after he received reports of harassment, bullying, and threats of violence.
Chinese Researchers Show How They Remotely Hacked a Mercedes-Benz
8.8.20 Hacking Securityweek
A team of Chinese researchers has described the analysis process that resulted in the discovery of 19 vulnerabilities in a Mercedes-Benz E-Class, including flaws that can be exploited to remotely hack a car.
The research was conducted starting in 2018 by Sky-Go, the vehicle cybersecurity unit of Chinese security solutions provider Qihoo 360. The findings were disclosed to Daimler, which owns the Mercedes-Benz brand, in August last year. The car maker patched the security holes and in December 2019 it announced that it had joined forces with the Sky-Go team in an effort to improve the security of its vehicles.
Representatives of Sky-Go and Daimler disclosed the findings this week at the Black Hat cybersecurity conference and published a research paper detailing the findings. However, some information was not made public to protect Daimler’s intellectual property and to prevent malicious exploitation.
The researchers conducted their analysis on a real Mercedes-Benz E-Class and demonstrated how a hacker could have remotely unlocked the car’s doors and started its engine. The experts estimated that the vulnerabilities could have impacted 2 million vehicles in China.
Sky-Go said it targeted the E-Class, which Mercedes describes as the most intelligent business saloon, for its infotainment system, which has the most connectivity functionalities.
The researchers disassembled the center panel and analyzed the car’s head unit, telematics control unit (TCU), and the backend.
In the file system of the vehicle’s TCU, to which they gained access by obtaining an interactive shell with root privileges, they uncovered passwords and certificates for the backend server.
“The car backend is the core of connected cars,” the researchers explained. “As long as the car backend’s services can be accessed externally, it means that the car backend is at risk of being attacked. The vehicles connecting to this car backend are in danger, too.”
They ultimately gained some access to backend servers after analyzing the vehicle’s embedded SIM (eSIM) card, which is typically used to provide connectivity, identify a car, and encrypt communications.
The problem was that backend servers did not authenticate requests from the “Mercedes me” mobile app, which allows users to remotely manage the vehicle and control various functions. Once they got access to the backend, they could control any car in China, the researchers claimed.
A hacker could have exploited this vulnerability to remotely lock and unlock the doors, open and close the roof, activate the horn and lights, and in some cases even start the engine. The researchers said they did not manage to hack any critical safety functions.
A majority of the 19 vulnerabilities discovered by the Sky-Go team affected the TCU and the backend, with a handful found in the head unit and other components. Some of the TCU flaws have been assigned CVE identifiers.
‘Hack-For-Hire’ Firms Spoof WHO To Target Google Credentials
30.5.2020 threatpost Hacking
Google TAG report reveals that “hack for hire” firms are tapping into the coronavirus pandemic via WHO phishing lures.
“Hack-for-hire” organizations are the latest group of cybercriminals to take advantage of the ongoing coronavirus pandemic, using COVID-19 as a lure in phishing emails bent on stealing victims’ Google credentials.
Researchers with Google’s Threat Analysis Group (TAG) warned that they’ve spotted a spike in activity from several India-based firms that have been creating Gmail accounts that spoof the World Health Organization (WHO) to send coronavirus-themed phishing emails.
“The lures themselves encourage individuals to sign up for direct notifications from the WHO to stay informed of COVID-19 related announcements, and link to attacker-hosted websites that bear a strong resemblance to the official WHO website,” according to Shane Huntley, in Google’s TAG bulletin for the first quarter of 2020.
These websites purport to be fake login pages, that then convince victims to hand over their Google account credentials and personal identifiable information (PII), like their phone numbers.

The accounts have largely targeted business leaders in financial services, consulting and healthcare corporations within numerous countries, including the U.S., — as well as Bahrain, Canada, Cyprus, India, Slovenia and the U.K.
Over the last months, Google said they sent 1,755 warnings to users whose accounts were targets of government-backed attackers in coronavirus-related campaigns. These included attacks from advanced persistent threat (APT) group Charming Kitten on medical and healthcare professionals, including WHO employees. The WHO in particular has attracted the notice of cybercriminals as the worldwide COVID-19 pandemic continues to play out, with a doubling of attacks recently, according to officials there. That includes recent reports that the DarkHotel APT group has tried to infiltrate its networks to steal information.
“Generally, 2020 has been dominated by COVID-19. The pandemic has taken center stage in people’s everyday lives, in the international news media, and in the world of government-backed hacking,” said Huntley.
YouTube-Based Campaigns
Another top trend that researchers highlighted as part of their Q1 2020 TAG bulletin is a spike in influence campaigns launched via YouTube, Google AdSense, Google Play and advertising accounts.

This includes a coordinated influence operation that was disbanded in February, leading to the termination of 82 YouTube channels and one advertising account. The campaign was linked to Egypt, sharing political content in Arabic supportive of Bahrain, Egypt, Saudi Arabia and the UAE, and and critical of Iran and Qatar. Another March influence campaign, linked to India, led to the termination of three advertising accounts, one AdSense account, and 11 YouTube channels. The campaign was sharing messages in English supportive of Qatar, according to Google.
Huntley said that since March, Google has removed more than a thousand YouTube channels that are believed to be part of a large campaign and that were behaving in a coordinated manner.
“These channels were mostly uploading spammy, non-political content, but a small subset posted primarily Chinese-language political content similar to the findings of a recent Graphika report,” said Huntley.
Exclusive – Any Mitron (Viral TikTok Clone) Profile Can Be Hacked in Seconds
30.5.2020 Thehackernews Hacking
Mitron (means "friends" in Hindi), you have been fooled again!
Mitron is not really a 'Made in India' product, and the viral app contains a highly critical, unpatched vulnerability that could allow anyone to hack into any user account without requiring interaction from the targeted users or their passwords.
I am sure many of you already know what TikTok is, and those still unaware, it's a highly popular video social platform where people upload short videos of themselves doing things like lip-syncing and dancing.
The wrath faced by Chinese-owned TikTok from all directions—mostly due to data security and ethnopolitical reasons—gave birth to new alternatives in the market, one of which is the Mitron app for Android.
Mitron video social platform recently caught headlines when the Android app crazily gained over 5 million installations and 250,000 5-star ratings in just 48 days after being released on the Google Play Store.
Popped out of nowhere, Mitron is not owned by any big company, but the app went viral overnight, capitalizing on its name that is popular in India as a commonly used greeting by Prime Minister Narendra Modi.
Besides this, PM Modi's latest 'vocal for local' initiative to make India self-reliant has indirectly set up a narrative in the country to boycott Chinese services and products, and of course, #tiktokban and #IndiansAgainstTikTok hashtags trending due to TikTok vs. YouTube battle and CarryMinati roast video also rapidly increased the popularity of Mitron.
Any Mitron Users Account Can Be Hacked in Seconds
The insecurity that TikTok is a Chinese app and might have allegedly been abusing its users' data for surveillance, unfortunately, turned millions into signing up for less trusted and insecure alternative blindly.
The Hacker News learned that the Mitron app contains a critical and easy-to-exploit software vulnerability that could let anyone bypass account authorization for any Mitron user within seconds.
The security issue discovered by Indian vulnerability researcher Rahul Kankrale resides in the way app implemented 'Login with Google' feature, which asks users' permission to access their profile information via Google account while signing up but, ironically, doesn't use it or create any secret tokens for authentication.
In other words, one can log into any targeted Mitron user profile just by knowing his or her unique user ID, which is a piece of public information available in the page source, and without entering any password—as shown in a video demonstration Rahul shared with The Hacker News.
Mitron App Was Not Developed; Instead Bought For Just $34
Promoted as a homegrown competitor to TikTok, in separate news, it turns out that the Mitron app has not been developed from scratch; instead, someone purchased a ready-made app from the Internet, and simply rebranded it.
While reviewing the app's code for vulnerabilities, Rahul found that Mitron is actually a re-packaged version of the TicTic app created by a Pakistani software development company Qboxus who is selling it as a ready-to-launch clone for TikTok, musical.ly or Dubsmash like services.
In an interview with the media, Irfan Sheikh, CEO of Qboxus, said his company sells the source code, which the buyers are expected to customize.
"There is no problem with what the developer has done. He paid for the script and used it, which is okay. But, the problem is with people referring to it as an Indian-made app, which is not true, especially because they have not made any changes," Irfan said.
Besides Mitron's owner, more than 250 other developers have also purchased the TicTic app code since last year, potentially running a service that can be hacked using the same vulnerability.
Who is Behind the Mitron App? An Indian or a Pakistani?
Though the code has been developed by the Pakistani company, real identity of the person behind the Mitron app—TicTic at heart TikTok by face—has yet not been confirmed; however, some reports suggest it's owned by a former student of the Indian Institute of Technology (IIT Roorkee).
Rahul told The Hacker News that he tried responsibly reporting the flaw to the app owner but failed as the email address mentioned on the Google Play Store, the only point of available contact, is non-operational.
Besides this, the homepage for the web server (shopkiller.in), where the backend infrastructure of the app is hosted, is also blank.
Considering that the flaw actually resides in the TicTic app code and affects any other similar cloned service running out there, The Hacker News has reached out to Qboxus and disclosed details of the flaw before publishing this story.
We will update this article when we receive a response.
Is Mitron App Safe to Use?
In short, since:
the vulnerability has not yet been patched,
the owner of the app is unknown,
the privacy policy of the service doesn't exist, and
there are no terms of use,
... it's highly recommended to simply do not install or use the untrusted application.
If you're among those 5 million who have already created a profile with the Mitron app and granted it access to your Google profile, revoke it immediately.
Unfortunately, there's no way you can delete your Mitron account yourself, but the hacking of Mitron user profile would not severely impact unless you have at least a few thousand followers on the platform.
However, keeping an untrusted app installed on your smartphone is not a good idea and could put your data from other apps and sensitive information stored on it at risk, so users are advised to uninstall the app for good.
Researchers Unmask Brazilian Hacker Who Attacked Thousands of Websites
29.5.2020 Securityweek Hacking
Researchers at cybersecurity company Check Point said on Thursday that they have found the real identity of VandaTheGod, a Brazilian hacker involved in both hacktivist operations and financially-motivated cybercrimes.
Check Point told SecurityWeek that it informed law enforcement about its findings in October 2019, but the hacker continued to be active up until May 2020.
VandaTheGod, who is also known online as Vanda de Assis and SH1N1NG4M3, appears to have been active since 2013 and claims to be associated with the Brazilian Cyber Army, which describes itself as an “ethical hacking group.” VandaTheGod also claimed to be a member of the hacking group UGNazi, whose members were arrested in 2012.
The hacker’s account on Zone-H, a popular website defacement archive, shows that VandaTheGod defaced more than 4,800 domains between July 2019 and February 2020, including ones belonging to government organizations and corporations across 40 countries.
While his defacements were apparently part of hacktivism campaigns fighting against government corruption, VandaTheGod also leaked and offered to sell stolen corporate and payment card information. At one point, he offered to sell the medical records of 1 million patients from New Zealand for $200.
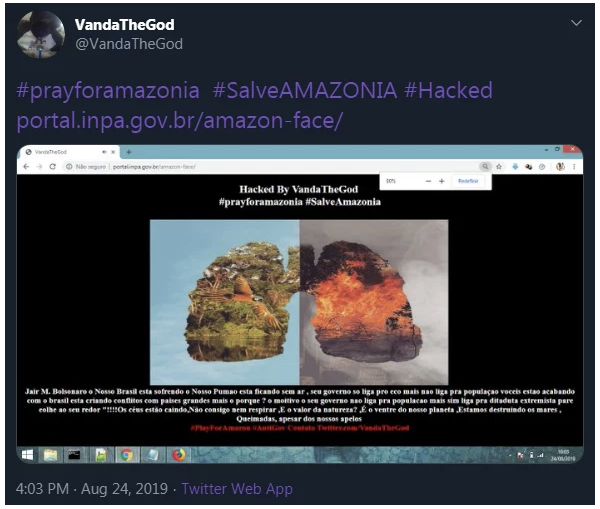
Check Point researchers investigated VandaTheGod’s online presence and noticed that the hacker’s website had been registered from Uberlândia, a city in Brazil.
One of the screenshots posted by the hacker on Twitter showed a browser tab open to a Facebook account for “Vanda De Assis (VandaTheGod).” A different screenshot included a tab with the initials M.R. and a search for individuals with these initials in Uberlândia led researchers to the Facebook profile of a man who endorsed the Brazilian Cyber Army.
Further analysis revealed that one picture of a man holding a bottle of whisky had been posted on both the Vanda de Assis Facebook profile and the profile of the individual with the initials M.R. Moreover, the furniture and setup in a picture posted on Facebook by M.R. while he was playing on his PlayStation was exactly the same as in a picture posted by VandaTheGod on Twitter.
Check Point has not made the alleged hacker’s name public, but reported its findings to law enforcement.
“VandaTheGod succeeded in carrying out many hacking attacks, but ultimately failed from the OPSEC perspective, as he left many trails that led to his true identity, especially at the start of his hacking career,” Check Point said in a blog post. “Ultimately, we were able to connect the VandaTheGod identity with high certainty to a specific Brazilian individual from the city of Uberlândia, and relay our findings to law enforcement to enable them to take further action.”
Researchers Uncover Brazilian Hacktivist's Identity Who Defaced Over 4800 Sites
28.5.2020 Thehackernews Hacking
It's one thing for hackers to target websites and proudly announce it on social media platforms for all to see. It's, however, an entirely different thing to leave a digital trail that leads cybersecurity researchers right to their doorsteps.
That's exactly what happened in the case of a hacktivist under the name of VandaTheGod, who has been attributed to a series of attacks on government websites since July 2019.
In a report shared with The Hacker News, researchers from Check Point said they were able to map VandaTheGod's activity over the years, and eventually zero down the attacker's real identity to a Brazilian individual from the city of Uberlândia.
The cybersecurity firm said it notified concerned law enforcement of its findings for further action, adding the social media activities on profiles associated with VandaTheGod came to a halt towards the end of 2019.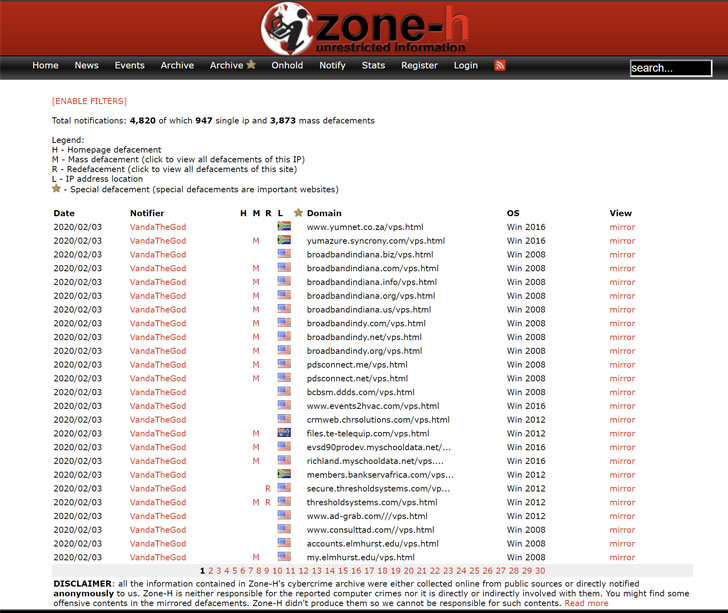
VandaTheGod has a long history of going after government websites, universities, and healthcare providers. Notably, the attacker claimed to have breached the database of New Zealand's Tū Ora Compass Health and offered medical details of one million patients for sale on Twitter last October.
The hacker in question, allegedly part of the "Brazilian Cyber Army" (BCA), has also vandalized dozens of websites to spread anti-government messages, in addition to displaying BCA's logo in screenshots of compromised accounts and websites.
"Many of the messages left on the defaced websites implied that the attacks were motivated by anti-government sentiment, and were carried out to combat social injustices that the hacker believed were a direct result of government corruption," the researchers said.
website hacker
What's more, a timeline of VandaTheGod's tweets shows that the person enjoyed the attention from media reports mentioning the hacking endeavors, even going to the extent of stating that "I will stop hacking websites" once the total reaches 5,000.
"VandaTheGod didn't just go after government websites, but also launched attacks against public figures, universities, and even hospitals. In one case, the attacker claimed to have access to the medical records of 1 million patients from New Zealand, which were offered for sale for $200," the researchers said.
According to Zone-H records, a security portal that holds an archive of all web intrusions, there are currently 4,820 entries of hacked websites linked to VandaTheGod, most of which belongs to individuals and entities in the United States, Australia, Netherlands, Italy, South Africa, Canada, UK, and Germany.
Check Point said they worked by tracking down the WHOIS information for the domain "VandaTheGod.com," which led them to an email address ("fathernazi@gmail.com") that was used to register other websites, such as "braziliancyberarmy.com."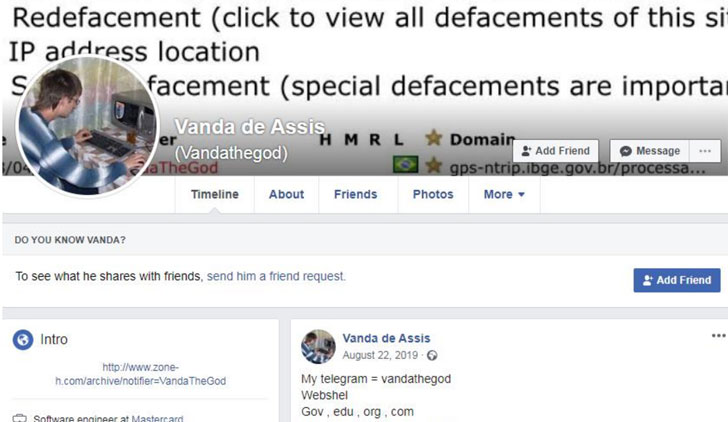
But what ultimately gave away VandaTheGod's real identity were a couple of screenshots that were uploaded to Twitter, from which the researchers identified a Facebook profile belonging to the attacker ("Vanda De Assis") as well as the person's real name — identified only by the initials M. R.
Consequently, the researchers said they were able to identify a number of cross-posts between the Facebook profile tied to M. R. and that of Vanda De Assis, including photos of the individual's living room, proving that both the M.R. and VandaTheGod accounts were controlled by the same individual.
"VandaTheGod succeeded in carrying out many hacking attacks, but ultimately failed from the OPSEC perspective, as he left many trails that led to his true identity, especially at the start of his hacking career," Check Point researchers concluded.
"Ultimately, we were able to connect the VandaTheGod identity with high certainty to a specific Brazilian individual from the city of Uberlândia, and relay our findings to law enforcement to enable them to take further action."
Tools Used in GhostDNS Router Hijack Campaigns Dissected
22.5.2020 Securityweek Hacking
The source code of the GhostDNS exploit kit (EK) has been obtained and analyzed by researchers. GhostDNS is used to compromise a wide range of routers to facilitate phishing -- perhaps more accurately, pharming -- for banking credentials. Target routers are mostly, but not solely, located in Latin America.
The source code used in a GhostDNS campaign was obtained by Avast researchers. Avast Antivirus includes a Web Shield to protect users from malicious web content. One of its users was up to no good, and attempted to upload a RAR archive with malicious content. He forgot to disable Web Shield and password protect the RAR. Web Shield detected it as malicious, automatically analyzed the content, and flagged it as an exploit kit.
"We downloaded the linked file and found the complete source code of the GhostDNS exploit kit," reports the Avast Threat Intelligence Team. The RAR archive is named KL DNS.rar, indicating its purpose -- a DNS hijack redirecting users to a phishing/pharming page where a keylogger is used to extract the user's credentials or bank card details.
The archive contained everything necessary for a DNS hijack campaign, both from inside the network, or externally from the internet. Internal attacks are often via malvertising. Malvertising allows the EK to directly attack the router from a computer that uses the router. External attacks from the internet require scanning for and locating vulnerable routers before they can be attacked. Everything necessary for both forms of attack were contained in the RAR archive.
Most GhostDNS campaigns target routers in Latin America, and Brazil in particular. According to telemetry obtained from Avast's antivirus product, 76% of routers in Brazil have weak or default credentials, making the region a lucrative target.
For attacks from the internet, the archive included BRUT, a free internet scanner that locates and attacks routers with a public IP address and an open HTTP port. Avast has found two versions of BRUT. One targets a lower number of devices and ports but with a long list of default and common passwords that could be used, while the other targets a higher number of devices with a smaller number of possible credentials. The latter appears to be the more recent version.
The researchers postulate that this "may be because most users never change the default credentials in their SOHO routers, and therefore using a smaller number of credentials for the attack may be effective enough." Fewer credentials against more router models may be more effective than many credentials against a limited number of different routers. Interestingly, both sets of credentials include the password 'deadcorp2017’, which is used by GhostDNS as a new password in infected routers -- which means that new campaigns can gain access to routers already infected even if the original password is not included in the current campaign.
The basic attack methodology is to use cross site request forgery (CSRF) requests to change the DNS settings on the router. The process establishes a rogue DNS server that is specified by the attacker for each GhostDNS campaign. There were three different malicious DNS setting in the code found by Avast -- none of which are currently operational.
Once the DNS settings have been changed, users can be silently redirected to pre-made pharming pages. The RAR file obtained by Avast included source code for several such pages. These included the biggest banks in Brazil -- such as Banco Bradesco, Itau, Santander and CrediCard -- and Netflix. The source code indicated that other domains were prepared to work, but that the phishing web pages had not been implemented.
The internal attack associated with a malvertising campaign operates differently. The EK searches for routers with an open port (either 80 or 8080). It produces a BASE64 encoded iframe representing a simple webpage with a function that changes HTTP requests to WebSocket requests. These requests change the DNS settings to the predefined malicious IP addresses. Only eight username/password pairs are found in this attack, but they include the most-used default router logins used in Brazil.
Once the victim has been successfully redirected to a malicious pharming page, a keylogger steals login details and bank card details and emails them to the attacker.
Hackers Target Oil Producers During COVID-19 Slump
19.5.2020 Securityaffairs Hacking
Recent research shows that the oil industry — already experiencing difficulties due to COVID-19 — must remain abreast of threats to stay safe from hackers.
Spear-phishing is a rapidly emerging threat. It’s more specific than generic phishing attempts and often targets a single person or company. Recent research shows that the oil industry — already experiencing difficulties due to COVID-19 — must remain abreast of threats to stay safe from hackers.
Cybercriminals Capitalizing on the Chaos
The coronavirus is forcing companies in most industries to operate substantially differently. Many may find it takes time to adjust to the changes. Others do not immediately have the resources for a major shift, such as having all employees work remotely.
A related concern is that COVID-19 is both a new and anxiety-inducing issue. People want to learn as much as they can about it, and their haste may result in them clicking on links without thinking. Cybercriminals view these conditions as ideal for orchestrating their attacks. Data from Barracuda cybersecurity researchers identified a 667% increase in spear-phishing attacks between the end of February and the following month.
Real-Life Examples of Spear-Phishing Attacks in the Energy Production Sector
The threat of spear-phishing for energy companies is, unfortunately, not a theoretical one. Coverage published in late April by Bitdefender illuminated a carefully executed attack. The research team found evidence of a campaign occurring March 31, whereby hackers impersonated a well-known engineering company with experience in on- and off-shore energy projects.
The messages — which did not include many of the telltale signs of phishing like spelling and grammatical errors — asked recipients to submit equipment and materials bids for the Rosetta Sharing Facilities Project. Participants would do so on behalf of Burullus, a gas joint venture partially owned by another Egyptian state oil brand.
The emails also contained two attachments, which were supposedly bid-related forms. Downloading them infected a user’s system with a type of trojan spyware not previously seen in other utilities industry cyberattacks. The effort targeted oil companies all over the world, from Malaysia to South Africa, in a single day.
Bitdefender’s research team also uncovered a more geographically specific spear-phishing attempt to target the gas sector on April 12. It centered on a relatively small number of shipping companies based in the Philippines. The emails asked them to send details associated with an oil tanker vessel and contained industry-specific language. This spear-phishing campaign occurred over two days.
The cybersecurity experts that studied these attacks stressed that, since the messages contained accurate details about real-life companies and events associated with the oil industry, the attackers took the time to research to craft maximally convincing content.
Hackers Love Causing Severe Disruptions
Why are cyberattacks in the energy industry suddenly on the rise? One reason may stem from the way hackers often deploy tactics to cause tremendous harm to necessary services. The oil industry operates on a vast scale. For example, a company specializing in oil and gas exploration planned as much as 300,000 feet of total footage for drilling in one region during 2018.
The ability to get such impressive outcomes undoubtedly helps oil companies. The increased scale also may make it more necessary to safeguard against cyberattacks, especially as criminals look for ways to cause the most damage. Another recent incident, announced in a United States government alert on February 18, shut down a natural gas compression facility. Operations stopped for two days, causing losses in productivity and revenue.
Although the publication did not name the energy company, it mentioned that the hackers depended on spear-phishing to get the credentials necessary for entering the businesses’ information technology (IT) network. It then used that access to wreak havoc on the enterprise’s operational technology infrastructure.
Not a New Concern
Utilities industry cyberattacks have long worried cybersecurity analysts. If concentrated efforts from hackers shut down the electric grid, the effects could be long-lasting and hit virtually every industry and consumer in the affected areas. The risks to the energy sector began before the coronavirus pandemic, too.
In November 2019, cybersecurity publications discussed a ransomware attack on Petróleos Mexicanos, Mexico’s largest oil and gas company. The perpetrators asked for 562 bitcoins to restore the data. The affected enterprise did not comply, and it had important data backed up.
Toll Group, an Australian transportation and logistics company with oil and gas companies as clients, suffered a ransomware attack this spring. It was the second such issue in four months, with the first happening in February.
The Energy Industry Must Remain Vigilant
The challenges posed by COVID-19 and its effect on oil prices may make the respective parties feel the impacts of cyberattacks in the energy industry more acutely. An ideal aim is to prevent those events rather than dealing with the damage afterward. Paying attention to cybersecurity vulnerabilities can help companies make meaningful gains and stay protected.
Over 70% of ICS Vulnerabilities Disclosed in First Half of 2020 Remotely Exploitable
20.8.20 ICS Securityweek
Over 70% of the industrial control system (ICS) vulnerabilities disclosed in the first half of 2020 were remotely exploitable through a network attack vector, industrial cybersecurity company Claroty reported on Wednesday.
Claroty has analyzed the 365 ICS flaws added to the National Vulnerability Database (NVD) and 385 vulnerabilities covered in advisories published by ICS-CERT (CISA). The security holes affect products from a total of 53 vendors and nearly three quarters of them were identified by security researchers.
Claroty told SecurityWeek that it has decided to analyze both vulnerabilities covered in ICS-CERT advisories and the NVD to “get the most comprehensive data about the state of security of ICS products.” While many of the advisories overlap, there are some discrepancies.
“Based on our research we have seen cases that some ICS-related CVEs are not covered 100% by the ICS-CERT advisories but are shown in the NVD, and vice versa,” explained Amir Preminger, VP of Research at Claroty. “In future reports we are planning to expand our covered sources since we have found that more information can be collected from different CERTs and vendor advisories.”
Learn more about ICS vulnerabilities at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
The number of vulnerabilities added to the NVD in the first half of 2020 is roughly 10% higher compared to the number of flaws disclosed in the same period of 2019. ICS-CERT published 139 advisories, compared to 105 in the first half of the previous year.
“While it may seem logical to assume that this and similar increases were caused by an increase in adversary activity and/or a decrease in ICS vendors’ security posture, the primary factors are likely heightened awareness of the risks posed by ICS vulnerabilities and increased focus from researchers and vendors on identifying and remediating such vulnerabilities as effectively and efficiently as possible,” Claroty explained in its report.
According to the company, the fact that over 70% of the vulnerabilities covered in the NVD can be exploited remotely shows that fully air-gapped industrial networks that are better protected against cyber threats have become “vastly uncommon.”
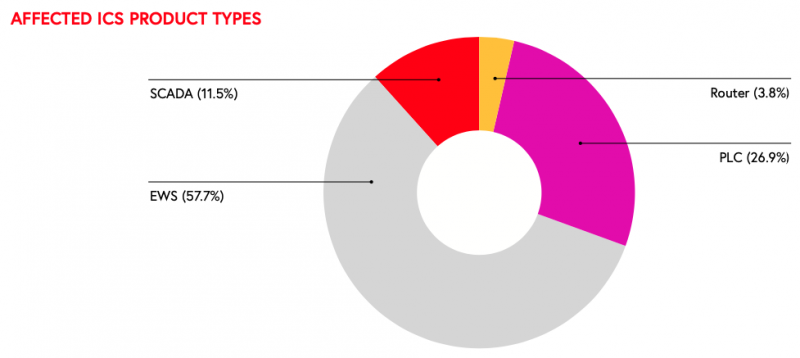
Nearly half of the identified vulnerabilities can be exploited for remote code execution, 41% of them can allow an attacker to read application data, 39% can be exploited for DoS attacks, and 37% to bypass security mechanisms.
In the case of the advisories published by ICS-CERT, more than 81% impact products used worldwide, and 7% of the advisories are for products used exclusively in the U.S.
The sectors most impacted by these vulnerabilities are energy (236 vulnerabilities), critical manufacturing (197), and water and wastewater (171). These were also the top three sectors last year, but the number of flaws affecting them is now much higher.
Vulnerabilities in Protocol Gateways Can Facilitate Attacks on Industrial Systems
5.8.20 ICS Securityweek
Vulnerabilities found in protocol gateway devices can facilitate stealthy attacks on industrial systems, enabling threat actors to obtain valuable information and sabotage critical processes.
Protocol gateways are small devices designed to ensure that various types of IT and OT devices can communicate with each other even if they use different protocols. For instance, they can translate traffic sent on the same protocol but on two different physical layers (e.g. TCP to RTU), translate traffic on the same physical layer but different protocols (e.g. Modbus RTU to Profibus), or translate traffic on different physical layers and protocols (e.g. Modbus TCP to Profibus).
There are two types of protocol gateways: ones that translate traffic in real-time, and data stations, which store the translated traffic and provide it on request.
Threat actors could target protocol gateways for several reasons. For instance, they can cause serious disruption if the device fails to properly translate traffic. Secondly, protocol gateways are less likely to be monitored by security products, making it less likely that the attack will be detected. And since translation issues are not easy to diagnose, an attack can be very stealthy.
Researchers at Trend Micro have analyzed the Nexcom NIO50, Schneider Electric Link 150, Digi One IA, Red Lion DA10D, and Moxa MGate 5105-MB-EIP protocol gateways, which are used in many organizations. The research focused on the translation of the Modbus communications protocol, which is one of the most widely used OT protocols.Protocol gateway vulnerabilities
The researchers first tested how well these devices can handle heavy or malformed traffic, such as the one that would be sent by an attacker.
In the case of real-time gateways, the researchers used a fuzzer to generate thousands of invalid Modbus TCP and Modbus RTU packets that were fed to the Schneider, Digi One and Nexcom products to test their firewalling capabilities. Both the Schneider and the Digi One devices filtered out most of the invalid TCP packets, but the one from Nexcom completely failed this test.
Trend Micro researchers showed that the Nexcom device’s failure to handle the malformed packets — the packets should have been dropped or fixed before being translated — can be exploited by an attacker to bypass firewalls and send malicious requests to the devices connected to the protocol gateway. The experts showed how an attacker can send malicious requests to a PLC in an effort to manipulate the processes it controls. For example, the attacker can turn on a motor and deactivate critical safety sensors, leaving operators in the dark.
Trend Micro reported this vulnerability to Nexcom, which said it would not be releasing a patch due to the product reaching end of life. The cybersecurity firm says it has not tested the affected product’s successor.
In the case of data stations, Trend Micro tested the Moxa and Red Lion products. Data stations need to be configured before deployment to assign functions and commands to switches, sensors or other devices. This configuration is stored in what is called an I/O mapping table, which is stored in a SQLite3 database.
I/O mapping tables can contain a lot of information that can be useful to a malicious actor when planning an attack, and making unauthorized changes to the table can result in disruption to PLCs, HMIs and other devices connected to the targeted data station.
The researchers have found vulnerabilities in the Moxa device that an attacker could exploit to gain access to the I/O mapping table, manipulate processes, and cause disruption. In the case of the Red Lion device, they identified memory leakage and DoS issues.
“By themselves, protocol gateways are likely not directly involved in the product or the output of a facility. However, they are a crucial link in the flow of information between different sensors, interfaces, devices, and machinery within a facility,” Trend Micro said.
It added, “Operators need to be able to see and trust the data of the facility and take action to prevent accidents or potential production issues. Vulnerable or exposed protocol gateways can allow threat actors to compromise the integrity of the reported data, the operators’ ability to view data, or prevent operators from taking action.”
Steganography Anchors Pinpoint Attacks on Industrial Targets
30.5.2020 threatpost Attack ICS
Ongoing spear-phishing attacks aim at stolen Windows credentials for ICS suppliers worldwide.
A targeted series of attacks on suppliers of equipment and software for industrial enterprises is playing out globally, researchers said, hinging on phishing and a steganography tactic to hide malware on public, legitimate image resources.
According to Kaspersky ICS CERT, the attacks seem bent on stealing Windows credentials in order to lay the groundwork for lateral movement inside a target network and follow-on activity. They have so far been seen being mounted on systems in Germany, Italy, Japan and the U.K. The kill chain starts with phishing emails, which are tailored and customized to the specific language for each victim.
“For example, in the case of an attack on a company from Japan, the text of a phishing email and a Microsoft Office document containing a malicious macro were written in Japanese,” researchers explained, in an analysis on Thursday. “Also, to successfully decrypt the malware module, the operating system must have had a Japanese localization as well.”
The emails contain an “urgent request” to open an attached document. It’s an Excel spreadsheet with a malicious macro; users are requested to enable active content, which triggers the malicious PowerShell script.
“The script is executed in spite of the configured policy, in a hidden window and without loading the user configuration,” according to Kaspersky.
It goes on to randomly select one of the URL addresses included in the coding – which leads to the legitimate public image hosting services called imgur.com and imgbox.com. The script then downloads an image and starts a data-extraction procedure.
Steganography Tactic
The data is hidden in the downloaded image, and is parsed out by the malware from pixels as defined by an algorithm in the script. Hiding malware in an image file, known as steganography, is a well-known though not that common way to circumvent detection – many filters and gateways let image file formats pass without too much scrutiny.
In this case, the data is encoded with several encryption layers (using the Base64 and RSA algorithms), which, when decrypted and decoded, is assembled into a secondary PowerShell script, which Kaspersky flagged as an advanced technique.
“The malicious module is encoded in an image using steganographic techniques and the image is hosted on legitimate web resources,” according to the research. “This makes it virtually impossible to detect such malware using network traffic monitoring and control tools while it is being downloaded. From the standpoint of technical solutions, this activity is indistinguishable from sending ordinary requests to legitimate image hosting services.”
Here too, the geolocation aspect of the campaign is evident.
“Curiously, the script has an error in its code, included on purpose, with the exception message used as the decryption key,” said the researchers. “Notably, the text in the exception message depends on the language pack installed in the operating system. Apparently, the attackers prepare the malicious script specifically for victims from a particular country.”
The use of the exception message as the decryption key for the malicious payload is notable, the researchers said – and it also can help the malware evade detection in sandboxes. Also, it “makes analyzing the functionality of the malware significantly more difficult for researchers if they do not know what language pack was used on the victim’s computer,” they said.
Meanwhile, the second PowerShell script in turn unpacks itself into a third PowerShell script, which turns out to be an obfuscated sample of the Mimikatz utility, used to steal Windows account credentials from a compromised system.
“Criminals can use this information to gain access to other systems on the enterprise network and move laterally,” according to the analysis. “It is a particularly dangerous situation if attackers obtain the credentials for accounts with domain administrator privileges.”
The ultimate goal of the criminals remains unknown, researchers said.
“The use of [steganography], combined with the pinpoint nature of the infections, indicates that these were targeted attacks,” the researchers concluded. “It is a matter of concern that attack victims include contractors of industrial enterprises. If the attackers are able to harvest the credentials of a contractor organization’s employees, this can lead to a range of negative consequences, from the theft of sensitive data to attacks on industrial enterprises via remote administration tools used by the contractor.”
Steganography in targeted attacks on industrial enterprises in Japan and Europe
29.5.2020 Securityaffairs ICS
Threat actors targeted industrial suppliers in Japan and several European countries in sophisticated attacks, Kaspersky reported.
Researchers from Kaspersky’s ICS CERT unit reported that threat actors targeted industrial suppliers in Japan and several European countries in sophisticated attacks.
The experts first observed the attacks in early 2020, while in early May, threat actors targeted organizations in Japan, Italy, Germany and the UK.
Hackers targeted suppliers of equipment and software for industrial enterprises with spear-phishing messages using malicious Microsoft Office documents. Attackers used PowerShell scripts, as well as various techniques to evade the detection and avoid the analysis of the malware.
“Phishing emails, used as the initial attack vector, were tailored and customized under the specific language for each specific victim. The malware used in this attack performed destructive activity only if the operating system had a localization that matched the language used in the phishing email.” reads the report published by Kaspersky. “For example, in the case of an attack on a company from Japan, the text of a phishing email and a Microsoft Office document containing a malicious macro were written in Japanese. “
The phishing messages are crafted to trick victims into opening the attached document and enable the macros. The emails are written in the target’s language, and the malware only starts if the operating system language on the machine matches the language in the phishing email.
Hackers used the Mimikatz tool to steal the authentication data of Windows accounts stored on a compromised system. At the time, the final goal of the threat actors is still unknown.
Kaspersky experts only observed malicious activity on IT systems, OT networks were not impacted in the attacks.
Upon executing the macro script contained in the bait document, a PowerShell script is decrypted and executed. This script downloads an image from image hosting services such as Imgur or imgbox, experts noticed that the URL of the image is randomly selected from a list.
The image contains data that is extracted by the malware to create another PowerShell script, which in turn creates another PowerShell script that is an obfuscated version of Mimikatz post-exploitation tool.
“The data is hidden in the image using steganographic techniques and is extracted by the malware from pixels defined by the algorithm. Using steganography enables the attackers to evade some security tools, including network traffic scanners.” continues the analysis.
“The data extracted from the image is consecutively encoded using the Base64 algorithm, encrypted with the RSA algorithm and encoded using Base64 again. Curiously, the script has an error in its code, included on purpose, with the exception message used as the decryption key.”
Attackers also used an exception message as the decryption key for a malicious payload, also in this case the technique aims at evade the detection.
Kaspersky confirmed that its solutions have blocked all the attacks it has detected.
“This attack has caught the attention of researchers because the attackers use several unconventional technical solutions.” concludes Kaspersky.
“The use of the above techniques, combined with the pinpoint nature of the infections, indicates that these were targeted attacks. It is a matter of concern that attack victims include contractors of industrial enterprises. If the attackers are able to harvest the credentials of a contractor organization’s employees, this can lead to a range of negative consequences, from the theft of sensitive data to attacks on industrial enterprises via remote administration tools used by the contractor.”
Industrial Suppliers in Japan, Europe Targeted in Sophisticated Attacks
29.5.2020 Securityweek ICS
Threat actors have targeted industrial suppliers in Japan and several European countries in sophisticated attacks that employed various techniques to make malware detection and analysis more difficult, Kaspersky’s ICS CERT unit reported on Thursday.
The first attacks were spotted in early 2020 and, as of early May, Kaspersky has seen targeted organizations in Japan, Italy, Germany and the UK. The cybersecurity firm says the targets supply equipment and software for industrial organizations, particularly for the energy sector.
Kaspersky said its products blocked the malware in each of the attacks it observed, and the company currently does not know what the hackers’ goals are.
“We may only guess that focus on the power and energy organization suppliers may suggest the attackers are seeking an entry point into power and energy enterprises,” Evgeny Goncharov, Head of Kaspersky ICS CERT, told SecurityWeek.
Goncharov said they detected malicious activity on IT systems, but not in OT networks. The attackers have apparently been trying to steal authentication credentials.
According to Kaspersky, the attacks start with a phishing email sent to the targeted organization. These emails are customized and written in the target’s language, and the malware only starts conducting its activities after ensuring that the operating system language on the compromised machine matches the language in the phishing email.
The phishing emails carry a Microsoft Office document containing a malicious macro script which, when triggered by the victim, decrypts and executes a PowerShell script. This script is designed to download an image from image hosting services such as Imgur or imgbox — the URL of the image is randomly selected from a list.
The image contains data that is extracted by the malware to generate another PowerShell script, which in turn creates yet another PowerShell script that is an obfuscated version of Mimikatz, the popular password-stealing tool.
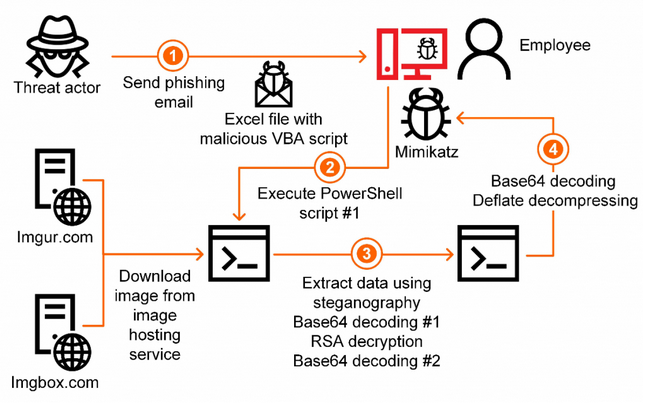
Kaspersky has pointed out that the use of steganography to hide malicious code in an image and the use of legitimate services to host that image “makes it virtually impossible to detect such malware using network traffic monitoring and control tools while it is being downloaded.”
Another interesting technique observed in these attacks involves the use of an exception message as the decryption key for a malicious payload.
“This technique can help the malware evade detection in automatic analysis systems of the sandbox class and makes analyzing the functionality of the malware significantly more difficult for researchers if they do not know what language pack was used on the victim’s computer,” Kaspersky said.
“The use of the above techniques, combined with the pinpoint nature of the infections, indicates that these were targeted attacks. It is a matter of concern that attack victims include contractors of industrial enterprises. If the attackers are able to harvest the credentials of a contractor organization’s employees, this can lead to a range of negative consequences, from the theft of sensitive data to attacks on industrial enterprises via remote administration tools used by the contractor,” the company added.
Vulnerabilities Found in Emerson SCADA Product Made for Oil and Gas Industry
27.5.2020 Securityweek ICS
A researcher from Kaspersky has identified several vulnerabilities in Emerson OpenEnterprise, a supervisory control and data acquisition (SCADA) solution designed for the oil and gas industry.
Roman Lozko, a researcher at Kaspersky’s ICS CERT unit, discovered four vulnerabilities in Emerson OpenEnterprise. The security flaws were reported to the vendor in December 2019 and patches were released a few months later.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and Kaspersky published advisories for three of the vulnerabilities last week. The remaining vulnerability was described by Kaspersky in an earlier advisory.
According to Emerson, OpenEnterprise is specifically designed to address the requirements of organizations focusing on oil and gas production, transmission and distribution.
The security holes found by Lozko have been described as heap-based buffer overflow, missing authentication, improper ownership management, and weak encryption issues.
The first two are the most serious. Tracked as CVE-2020-6970 and CVE-2020-10640 and both rated critical, they can allow an attacker to remotely execute arbitrary code with elevated privileges on devices running OpenEnterprise.
“The most critical vulnerabilities allow remote attackers to execute any command on a computer with OpenEnterprise on it with system privileges, so this might lead to any possible consequences,” Vladimir Dashchenko, security expert at Kaspersky, told SecurityWeek.
Dashchenko says an attacker could exploit these vulnerabilities either from the network or directly from the internet. However, there do not appear to be any instances of the affected product exposed to the internet.
“Based on Shodan statistics, currently there are no directly exposed OpenEnterprise SCADA systems available,” Dashchenko explained. “It means that asset owners with installed OpenEnterprise are definitely following the basic security principles for industrial control systems.”
The remaining vulnerabilities can be exploited to escalate privileges and to obtain passwords for OpenEnterprise user accounts, but exploitation in both cases requires local access to the targeted system.
Siemens Says Power Meters Affected by Urgent/11 Vulnerabilities
13.5.2020 Securityweek ICS
Siemens informed customers on Tuesday that some of its low and high voltage power meters are affected by the Wind River VxWorks vulnerabilities dubbed Urgent/11.
According to Siemens, its Power Meter 9410 and 9810 series products are affected by ten of the eleven Urgent/11 flaws. The German industrial giant says 9410 series devices are only affected if they run a firmware version prior to 2.1.1, which patches the vulnerabilities. In the case of 9810 devices, a patch has yet to be released and Siemens recommends some workarounds and mitigations until a firmware update becomes available.Siemens working to patch Urgent/11 vulnerabilities in power meters
“The [vulnerabilities] could allow an attacker to execute a variety of exploits for the purpose of Denial-of-Service (DoS), data extraction, RCE, etc. targeting both availability and confidentiality of the devices and data,” Siemens said in its advisory.
Siemens is just one of the many industrial and automation solutions providers whose products are affected by the Urgent/11 vulnerabilities. The company previously published advisories to warn customers that the flaws impact its RUGGEDCOM WIN products and SIPROTEC 5 Ethernet plug-in communication modules and devices.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s 2020 ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
Schneider Electric also updated its initial advisory on the Urgent/11 flaws on Tuesday to inform customers about more patches for affected products. The company has been gradually releasing patches since the disclosure of the vulnerabilities in July 2019.
Urgent/11 is the name given to a series of vulnerabilities found by researchers at IoT security firm Armis in the Wind River VxWorks real time operating system (RTOS). VxWorks is used by a wide range of companies in their products, including in the aerospace, motor, industrial and medical industries. Armis estimated that hundreds of millions of devices were affected by the vulnerabilities at the time of disclosure.
Exploitation of some Urgent/11 flaws can allow a remote attacker to take complete control of an affected device without any user interaction.
Advanced attack scenarios and sabotage of smart manufacturing environments
12.5.2020 Net-security Attack ICS
Advanced hackers could leverage unconventional, new attack vectors to sabotage smart manufacturing environments, according to Trend Micro.

Industry 4.0 Lab, the system that Trend Micro analyzed during this research
“Past manufacturing cyber attacks have used traditional malware that can be stopped by regular network and endpoint protection. However, advanced attackers are likely to develop Operational Technology (OT) specific attacks designed to fly under the radar,” said Bill Malik, vice president of infrastructure strategies for Trend Micro.
“As our research shows, there are multiple vectors now exposed to such threats, which could result in major financial and reputational damage for Industry 4.0 businesses. The answer is IIoT-specific security designed to root out sophisticated, targeted threats.”
Smart manufacturing equipment relying on proprietary systems
Critical smart manufacturing equipment relies primarily on proprietary systems, however these machines have the computing power of traditional IT systems. They are capable of much more than the purpose for which they are deployed, and attackers are able to exploit this power.
The computers primarily use proprietary languages to communicate, but just like with IT threats, the languages can be used to input malicious code, traverse through the network, or steal confidential information without being detected.
Though smart manufacturing systems are designed and deployed to be isolated, this seclusion is eroding as IT and OT converge. Due to the intended separation, there is a significant amount of trust built into the systems and therefore very few integrity checks to keep malicious activity out.
The systems and machines that could be taken advantage of include the manufacturing execution system (MES), human machine interfaces (HMIs), and customizable IIoT devices. These are potential weak links in the security chain and could be exploited in such a way to damage produced goods, cause malfunctions, or alter workflows to manufacture defective products.
Defense and mitigation measures
Deep packet inspection that supports OT protocols to identify anomalous payloads at the network level
Integrity checks run regularly on endpoints to identify any altered software components
Code-signing on IIoT devices to include dependencies such as third-party libraries
Risk analysis to extend beyond physical safety to automation software
Full chain of trust for data and software in smart manufacturing environments
Detection tools to recognize vulnerable/malicious logic for complex manufacturing machines
Sandboxing and privilege separation for software on industrial machines
New Actors Attack Industrial Control Systems, Old Ones Mature
23.2.2020 Bleepingcomputer ICS
Industrial control systems (ICS) across the world have become a larger target in 2019 as researchers discovered new threat actors attacking this sector while old ones have evolved and expanded their operations.
ICS security firm Dragos identified three new adversaries last year and an overall increase in the number of threats and their sophistication.
Frequent targets are oil and gas, electric power, and water suppliers, and the nature of the attacks is mainly disruptive or destructive. This requires significant resources, thus indicating a well-funded attacker.
New names in the game
The first new name in the ICS threatscape is Hexane (a.k.a. Lyceum) - focusing on oil and gas companies in the Middle East and also attacking telecommunication providers that could provide a stepping stone to reach the primary target.
Parisite is another newcomer to the game. It was discovered in October 2019 to attack several industrial sectors that count aerospace, oil and gas, and multiple water, electricity, and gas suppliers.
The targets are spread across the globe (U.S., the Middle East, Europe, Australia) and the compromise relies on known VPN vulnerabilities that are exploited to run reconnaissance activity.
Dragos' assessment for the moment is that this group "does not appear to have an ICS-specific disruptive or destructive capability" and that it sets the scene for another group, Magnallium.
Discovered last year, the Wassonite threat actor has been active since at least 2018 and is responsible for the attack on the Kudankulam Nuclear Power Plant in India noticed on September 4.
According to Dragos' observations, Wassonite focuses on multiple industrial control systems involved in electric generation, nuclear energy,
manufacturing, and organizations implicated in space-centric research.
India seems to be the region of interest for this group, although the security company does not exclude entities in Japan and South Korea as possible targets.
For the moment, Wassonite carries out first-stage attack activities - initial access operations, reconnaissance, collecting data, and does not appear to have disruptive or destructive capabilities.
"WASSONITE operations rely on deploying DTrack malware for remote access to victim machines, capturing credentials via Mimikatz and publicly available tools, and utilizing system tools to transfer files and move laterally within the enterprise system" - Dragos
Older actors threatening ICS environments
In total, the company tracks 11 groups. Two of them, Covellite and Electrum, are no longer on the radar due to inactivity. This is likely because the actors switched to different tactics and changed the targeting focus.
Other actors whose activity Dragos keeps an eye on are:
Raspite - active since at least 2017, targets the utility sector (political and strategic targets in the Middle East)
Chrysene (OilRig, APT34, Greenbug) - in the game since at least mid-2017, focuses on electric utilities, oil and gas companies in Europe, North America, and the Middle East; likely involved in the development of ZeroCleare data-wiping malware
Allanite - carries ICS intrusion and reconnaissance operations against victims in the U.S. and the U.K.
Dymalloy - active since at least 2015, typically focuses on energy companies and advanced industry organizations in Europe, Turkey, and North America. In 2019 the group targeted entities in Ukraine; relies on commodity malware Goodor, DorShel, and Karagany
Xenotime - carries out disruptive attacks, considered the most dangerous of the bunch tracked by Dragos; deployed the Triton/Trisis malware in an oil and gas facility in 2017
Magnallium - initially focused on oil and gas targets in the Middle East, expanded to the North America region to attack companies electric utilities, government, and financial institutions; in 2019 it gained the capability to disrupt and destroy via malware that Dragos named Killgrave, likely developed in collaboration with Parisite
In a report published today, Dragos underlines that most of the changes exhibited by these adversaries represent a broadening of their focus and ICS entities have not been removed from the target list.
The assessment of the threat activity observed in 2019 is that common enterprise tactics are still effective but threat actors have started to adapt to the context and use ICS-specific capabilities more often.
Remotely hack a Mercedes-Benz E-Class is possible, experts demonstrated
9.8.20 Hacking Securityaffairs
Chinese researchers discovered tens of vulnerabilities in a Mercedes-Benz E-Class, including issues that can be exploited to remotely hack it.
A team of Chinese experts from Sky-Go, the Qihoo 360 division focused on car hacking, discovered 19 vulnerabilities in a Mercedes-Benz E-Class, including some issues that can be exploited by attackers to remotely hack a vehicle.
The experts analyzed a Mercedes E-Class model because it is a connected car with a powerful infotainment system with a rich set of functionalities.
The research began in 2018 and in August 2019, the experts reported their findings to Daimler, which owns the Mercedes-Benz. In December 2019, the carmaker announced a partnership with the 360 Group to strengthen car IT security for the industry.
“In 2018, we begin research on Mercedes-Benz, since it is one of the most famous car brands in the world and an industry benchmark in the automotive industry. We analyze the security of Mercedes-Benz cars. There are so many models from Mercedes-Benz, and we finally chose the research target on Mercedes-Benz E-Class, since the E-Class’s in-vehicle infotainment system has the most connectivity functionalities of all.” reads the research paper.
Last week, during the Black Hat cybersecurity conference, representatives of Sky-Go and Daimler disclosed the findings of their research. The experts avoided to publicly disclose technical details of the issues to prevent malicious exploitation in the wild.
The team of experts was able to exploit the flaws to remotely unlock the car’s doors and start the engine of a Mercedes-Benz E-Class. According to the experts, the flaw could have affected 2 million vehicles only in China.
The experts initially collected relevant information from the target devices, such as network topology, pin definitions, chip model, and enable signals in the car. Then disassembled the center panel in the car to analyze the wiring connections between the Electronic Control Units (ECUs).

The analysis of the file system of the vehicle’s Telematics Control Unit (TCU), to which they gained access by obtaining an interactive shell with root privileges, they uncovered passwords and certificates for the backend server.
“If we have to debug the TCU client programs dynamically, we need to tamper the filesystem to get an interactive shell with ROOT privileges.” continues the research.
The researchers were also able to gain access to backend servers by analyzing the vehicle’s embedded SIM (eSIM) card used for the external connectivity.
“Car Backend is the core of Connected Cars. As long as Car Backends’ services can be accessed externally, it means that car backend is at risk of being attacked. The vehicles connecting to this Car Backend are in danger, too. So, our next step is to try to access Car Backend.” continues the research. “For accessing the APN networks of backend, one possibility would be using the e-sim of car-parts since the sim account wouldn’t log out automatically. After tearing down this eSIM, we put it into the 4G router.”
Experts noticed the lack of authentication between the backend servers and the “Mercedes me” mobile app, which allows users to remotely control multiple functions of the car. The researchers explained that once they got access to the backend, they could control any car in China.
The experts said that they did not manage to hack any critical safety functions of the tested vehicles.
“During the research and joint workshop, we see so many security designs in Mercedes-Benz Connected Cars and these designs are protecting the cars from various attacks.” the paper concluded. “The capability of a car company to work jointly with researchers contributes to the overall security of our cars.”
Attackers Horn in on MFA Bypass Options for Account Takeovers
8.8.20 Hacking Threatpost
Legacy applications don’t support modern authentication — and cybercriminals know this.
An uptick in business email compromise attacks is being attributed to successful compromises of multi-factor authentication (MFA) and conditional access controls, according to researchers. While brute-forcing and password spraying techniques are the most common way to mount account takeovers, more methodical cybercriminals are able to gain access to accounts even with more secure MFA protocols in place.
According to Abnormal Security, cybercriminals are zeroing in on email clients that don’t support modern authentication, such as mobile email clients (for example, iOS Mail for iOS 10 and older); and legacy email protocols, including IMAP, SMTP, MAPI and POP. Thus, even if MFA is enabled on the corporate email account, an employee checking email via mobile won’t be subject to that protection.
“While MFA and modern authentication protocols are an important advancement in account security and should be used whenever possible…this means that it is not possible to enforce MFA when a user signs into their account using one of these applications,” said Erin Ludert, writing in a blog post on Friday.
Thus, she noted that a common pattern in account-takeover attacks is that after being blocked by MFA, an adversary will immediately switch to using a legacy application.
“In fact, most credential stuffing campaigns utilize legacy applications such as IMAP4 to ensure they do not encounter difficulties from MFA at any point,” Ludert said, adding, “Many enterprises are under the mistaken impression that they are fully protected by MFA and do not need to worry about account takeovers. This is a dangerous assumption.”
Meanwhile, many Office 365 licenses provide the ability to configure conditional-access policies, which block access by users to certain applications. This can be used to block legacy applications that may be targeted for password-spraying campaigns, for instance. However, according to Abnormal Security, attackers are also focused on ferreting out targets that don’t have this implemented, or, bypassing it.
“First and foremost, conditional access is not included with all licenses, meaning that many enterprises simply have no way to protect themselves from this type of attack,” Ludert said. “Additionally, legacy applications are still in widespread use in most enterprises. Completely blocking all users from legitimate access using these applications will be quite disruptive to the workforce. Also, legacy access is enabled by default on Office 365. In order to effectively block legacy access, it must be disabled on a per-tenant basis – for all users and platforms.”
Additionally, attempting to apply legacy blocking based on the platform (Windows, mobile, etc.) relies on the user agent to do so. The user agent is basically the software agent that is acting on behalf of a user, such as a web browser or email reader – and as such, it’s very easy to falsify, the researcher noted. Thus, even with conditional access in place, cybercriminals are mounting attacks by obscuring the app that they are using.
“In one case, the attacker initially attempted to sign in using a legacy application but was blocked by conditional access,” Ludert said. “The attacker then waited several days before trying again, this time with the app information obscured, and successfully gained access to the account.”
As MFA becomes more widespread, cybercrooks are looking to stay a step ahead. In May, researchers observed a phishing campaign that bypassed MFA on Office 365 to access victims’ data stored on the cloud and use it to extort a Bitcoin ransom; attackers used a malicious SharePoint link to trick users into granting permissions to a rogue application..
The tactic leveraged the OAuth2 framework and OpenID Connect (OIDC) protocol, which are the technical bits behind functions like “Log in with Faceboook” – being signed into a trusted application is used to verify a user on a second application, essentially. When OIDC and OAuth are used to authenticate a user, no credentials are exposed to the application, so MFA isn’t triggered.
Reddit massive hack: hackers defaced channels with pro-Trump messages
8.8.20 Hacking Securityaffairs
Reddit suffered a massive hack, threat actors compromised tens of Reddit channels and defaced them showing messages in support of Donald Trump’s campaign.
Reddit suffered a massive hack, threat actors defaced tens of channel to display messages in support of Donald Trump’s reelection campaign.
At the time of writing, the massive hack is still ongoing and Reddit’s security team is working to restore the operations.
Below a list containing some of the impacted subreddits, some of them having tens of millions of members:
r/NFL
r/CFB (Canadian Football League)
r/TPB (The Pirate Bay’s Reddit channel)
r/BlackMirror (TV show)
/r/Buffy (TV show)
r/Avengers (Movie franchise)
r/Vancouver (city)
r/Dallas (city)
r/Plano (city)
r/Japan
r/Gorillaz (music band)
r/Podcasts
/r/Disneyland
r/49ers (NFL team)
/r/BostonCeltics (NBA team)
r/Leafs (Toronto Mapple Leafs)
/r/EDM (electronic dance music channel)
/r/Food
r/Beer
r/Renting
r/Lockpicking
r/Subaru (car maker)
r/freefolk (Game of Thrones fan channel)
r/Space
r/ISS
r/DestinyTheGame (video game)
r/LawSchool
r/StartledCats
r/TheDailyZeitgeist
r/Supernatural
/r/Naruto
/r/RupaulsDragRace
r/GRE
r/GMAT
r/greatbritishbakeoff
r/11foot8
r/truecrimepodcasts
r/comedyheaven
r/weddingplanning
r/Chadsriseup
r/BertStrips
r/KingkillerChronicle (book series)
r/PoliticalDiscussion
r/MadLads
r/DNDMemes
r/woodpaneled
r/telescopes
r/WeAreTheMusicMakers
r/DeTrashed
r/Samurai8
r/3amjokes
r/ANGEL
r/PhotoshopBattles
r/Animemes
r/comedyheaven/
r/awwducational
r/gamemusic
r/hentaimemes
r/ShitAmericansSay
r/ShitPostCrusaders
r/SweatyPalms
r/Locklot
r/BadHistory
r/CrewsCrew/
r/ListenToThis
r/PokemonGOBattleLeague
r/FacingTheirParenting
r/TwoSentenceHorror
r/BookSuggestions
r/FreezingFuckingCold/
r/woof_irl
r/BurningAsFuck
r/ImagineThisView
r/AnotherClosetAtheist
r/CasualTodayILearned
r/ShowerBeer
r/TookTooMuch
r/DallasProtests/
r/BannedFromClubPenguin
r/creepyPMs
r/RedditDayOf
r/AquaticAsFuck
r/HeavyFuckingWind/
r/BlackPeopleTwitter
r/HuskersRisk
r/Fireteams/
r/LuxuryLifeHabits
r/IRLEasterEggs
r/nononono
r/nonononoyes
r/ThatsInsane
According to Reddit, the hacker compromised several subreddit moderator accounts.
Owners of the channel that are facing security issues could report problems in this Reddit ModSupport thread, meantime they are recommended to enable two-factor authentication (2FA) on their accounts and to change their passwords.
Indicators of compromise for the Reddit moderator accounts are:
• moderator received email notification that the password and/or email address on your account changed but you didn’t request changes
• moderator notice authorized apps on your profile that you don’t recognize
• moderator notice unusual IP history on your account activity page
• moderator see votes, posts, comments, or moderation actions that you don’t remember making, or private messages that you don’t remember sending
One of the moderators who had their account compromised published the details of the actions performed by attackers on his behalf.
“Help! I’ve been hacked by some bizarre pro-trump bot! It wrecked my subreddit’s style sheet, deleted all mods below me, updated the wiki… I’m in way over my head. What can I do? PSA: Change your passwords and enable 2-factor authentication!” reads the title of the discussion.
Once the attacker has taken the control of the mod’s account, he changed his subrreddit’s CSS stylesheet, deleted all mods with fewer permissions than him, and changed the community’s wiki.
Finally, the hacker published the message: “We Stand With Donal Trump #MIGA2020.”
The Twitter account https://twitter.com/advanceHCAjobs claimed responsibility for the massive Reddit hack, but currently, the account was suspended. While the hackers were targeting subreddits, they asking Twitter users to vote on them.
In June, Reddit has banned a channel of President Trump supporters, r/The_Donald, after he received reports of harassment, bullying, and threats of violence.
Chinese Researchers Show How They Remotely Hacked a Mercedes-Benz
8.8.20 Hacking Securityweek
A team of Chinese researchers has described the analysis process that resulted in the discovery of 19 vulnerabilities in a Mercedes-Benz E-Class, including flaws that can be exploited to remotely hack a car.
The research was conducted starting in 2018 by Sky-Go, the vehicle cybersecurity unit of Chinese security solutions provider Qihoo 360. The findings were disclosed to Daimler, which owns the Mercedes-Benz brand, in August last year. The car maker patched the security holes and in December 2019 it announced that it had joined forces with the Sky-Go team in an effort to improve the security of its vehicles.
Representatives of Sky-Go and Daimler disclosed the findings this week at the Black Hat cybersecurity conference and published a research paper detailing the findings. However, some information was not made public to protect Daimler’s intellectual property and to prevent malicious exploitation.
The researchers conducted their analysis on a real Mercedes-Benz E-Class and demonstrated how a hacker could have remotely unlocked the car’s doors and started its engine. The experts estimated that the vulnerabilities could have impacted 2 million vehicles in China.
Sky-Go said it targeted the E-Class, which Mercedes describes as the most intelligent business saloon, for its infotainment system, which has the most connectivity functionalities.
The researchers disassembled the center panel and analyzed the car’s head unit, telematics control unit (TCU), and the backend.
In the file system of the vehicle’s TCU, to which they gained access by obtaining an interactive shell with root privileges, they uncovered passwords and certificates for the backend server.
“The car backend is the core of connected cars,” the researchers explained. “As long as the car backend’s services can be accessed externally, it means that the car backend is at risk of being attacked. The vehicles connecting to this car backend are in danger, too.”
They ultimately gained some access to backend servers after analyzing the vehicle’s embedded SIM (eSIM) card, which is typically used to provide connectivity, identify a car, and encrypt communications.
The problem was that backend servers did not authenticate requests from the “Mercedes me” mobile app, which allows users to remotely manage the vehicle and control various functions. Once they got access to the backend, they could control any car in China, the researchers claimed.
A hacker could have exploited this vulnerability to remotely lock and unlock the doors, open and close the roof, activate the horn and lights, and in some cases even start the engine. The researchers said they did not manage to hack any critical safety functions.
A majority of the 19 vulnerabilities discovered by the Sky-Go team affected the TCU and the backend, with a handful found in the head unit and other components. Some of the TCU flaws have been assigned CVE identifiers.
‘Hack-For-Hire’ Firms Spoof WHO To Target Google Credentials
30.5.2020 threatpost Hacking
Google TAG report reveals that “hack for hire” firms are tapping into the coronavirus pandemic via WHO phishing lures.
“Hack-for-hire” organizations are the latest group of cybercriminals to take advantage of the ongoing coronavirus pandemic, using COVID-19 as a lure in phishing emails bent on stealing victims’ Google credentials.
Researchers with Google’s Threat Analysis Group (TAG) warned that they’ve spotted a spike in activity from several India-based firms that have been creating Gmail accounts that spoof the World Health Organization (WHO) to send coronavirus-themed phishing emails.
“The lures themselves encourage individuals to sign up for direct notifications from the WHO to stay informed of COVID-19 related announcements, and link to attacker-hosted websites that bear a strong resemblance to the official WHO website,” according to Shane Huntley, in Google’s TAG bulletin for the first quarter of 2020.
These websites purport to be fake login pages, that then convince victims to hand over their Google account credentials and personal identifiable information (PII), like their phone numbers.

The accounts have largely targeted business leaders in financial services, consulting and healthcare corporations within numerous countries, including the U.S., — as well as Bahrain, Canada, Cyprus, India, Slovenia and the U.K.
Over the last months, Google said they sent 1,755 warnings to users whose accounts were targets of government-backed attackers in coronavirus-related campaigns. These included attacks from advanced persistent threat (APT) group Charming Kitten on medical and healthcare professionals, including WHO employees. The WHO in particular has attracted the notice of cybercriminals as the worldwide COVID-19 pandemic continues to play out, with a doubling of attacks recently, according to officials there. That includes recent reports that the DarkHotel APT group has tried to infiltrate its networks to steal information.
“Generally, 2020 has been dominated by COVID-19. The pandemic has taken center stage in people’s everyday lives, in the international news media, and in the world of government-backed hacking,” said Huntley.
YouTube-Based Campaigns
Another top trend that researchers highlighted as part of their Q1 2020 TAG bulletin is a spike in influence campaigns launched via YouTube, Google AdSense, Google Play and advertising accounts.

This includes a coordinated influence operation that was disbanded in February, leading to the termination of 82 YouTube channels and one advertising account. The campaign was linked to Egypt, sharing political content in Arabic supportive of Bahrain, Egypt, Saudi Arabia and the UAE, and and critical of Iran and Qatar. Another March influence campaign, linked to India, led to the termination of three advertising accounts, one AdSense account, and 11 YouTube channels. The campaign was sharing messages in English supportive of Qatar, according to Google.
Huntley said that since March, Google has removed more than a thousand YouTube channels that are believed to be part of a large campaign and that were behaving in a coordinated manner.
“These channels were mostly uploading spammy, non-political content, but a small subset posted primarily Chinese-language political content similar to the findings of a recent Graphika report,” said Huntley.
Exclusive – Any Mitron (Viral TikTok Clone) Profile Can Be Hacked in Seconds
30.5.2020 Thehackernews Hacking
Mitron (means "friends" in Hindi), you have been fooled again!
Mitron is not really a 'Made in India' product, and the viral app contains a highly critical, unpatched vulnerability that could allow anyone to hack into any user account without requiring interaction from the targeted users or their passwords.
I am sure many of you already know what TikTok is, and those still unaware, it's a highly popular video social platform where people upload short videos of themselves doing things like lip-syncing and dancing.
The wrath faced by Chinese-owned TikTok from all directions—mostly due to data security and ethnopolitical reasons—gave birth to new alternatives in the market, one of which is the Mitron app for Android.
Mitron video social platform recently caught headlines when the Android app crazily gained over 5 million installations and 250,000 5-star ratings in just 48 days after being released on the Google Play Store.
Popped out of nowhere, Mitron is not owned by any big company, but the app went viral overnight, capitalizing on its name that is popular in India as a commonly used greeting by Prime Minister Narendra Modi.
Besides this, PM Modi's latest 'vocal for local' initiative to make India self-reliant has indirectly set up a narrative in the country to boycott Chinese services and products, and of course, #tiktokban and #IndiansAgainstTikTok hashtags trending due to TikTok vs. YouTube battle and CarryMinati roast video also rapidly increased the popularity of Mitron.
Any Mitron Users Account Can Be Hacked in Seconds
The insecurity that TikTok is a Chinese app and might have allegedly been abusing its users' data for surveillance, unfortunately, turned millions into signing up for less trusted and insecure alternative blindly.
The Hacker News learned that the Mitron app contains a critical and easy-to-exploit software vulnerability that could let anyone bypass account authorization for any Mitron user within seconds.
The security issue discovered by Indian vulnerability researcher Rahul Kankrale resides in the way app implemented 'Login with Google' feature, which asks users' permission to access their profile information via Google account while signing up but, ironically, doesn't use it or create any secret tokens for authentication.
In other words, one can log into any targeted Mitron user profile just by knowing his or her unique user ID, which is a piece of public information available in the page source, and without entering any password—as shown in a video demonstration Rahul shared with The Hacker News.
Mitron App Was Not Developed; Instead Bought For Just $34
Promoted as a homegrown competitor to TikTok, in separate news, it turns out that the Mitron app has not been developed from scratch; instead, someone purchased a ready-made app from the Internet, and simply rebranded it.
While reviewing the app's code for vulnerabilities, Rahul found that Mitron is actually a re-packaged version of the TicTic app created by a Pakistani software development company Qboxus who is selling it as a ready-to-launch clone for TikTok, musical.ly or Dubsmash like services.
In an interview with the media, Irfan Sheikh, CEO of Qboxus, said his company sells the source code, which the buyers are expected to customize.
"There is no problem with what the developer has done. He paid for the script and used it, which is okay. But, the problem is with people referring to it as an Indian-made app, which is not true, especially because they have not made any changes," Irfan said.
Besides Mitron's owner, more than 250 other developers have also purchased the TicTic app code since last year, potentially running a service that can be hacked using the same vulnerability.
Who is Behind the Mitron App? An Indian or a Pakistani?
Though the code has been developed by the Pakistani company, real identity of the person behind the Mitron app—TicTic at heart TikTok by face—has yet not been confirmed; however, some reports suggest it's owned by a former student of the Indian Institute of Technology (IIT Roorkee).
Rahul told The Hacker News that he tried responsibly reporting the flaw to the app owner but failed as the email address mentioned on the Google Play Store, the only point of available contact, is non-operational.
Besides this, the homepage for the web server (shopkiller.in), where the backend infrastructure of the app is hosted, is also blank.
Considering that the flaw actually resides in the TicTic app code and affects any other similar cloned service running out there, The Hacker News has reached out to Qboxus and disclosed details of the flaw before publishing this story.
We will update this article when we receive a response.
Is Mitron App Safe to Use?
In short, since:
the vulnerability has not yet been patched,
the owner of the app is unknown,
the privacy policy of the service doesn't exist, and
there are no terms of use,
... it's highly recommended to simply do not install or use the untrusted application.
If you're among those 5 million who have already created a profile with the Mitron app and granted it access to your Google profile, revoke it immediately.
Unfortunately, there's no way you can delete your Mitron account yourself, but the hacking of Mitron user profile would not severely impact unless you have at least a few thousand followers on the platform.
However, keeping an untrusted app installed on your smartphone is not a good idea and could put your data from other apps and sensitive information stored on it at risk, so users are advised to uninstall the app for good.
Researchers Unmask Brazilian Hacker Who Attacked Thousands of Websites
29.5.2020 Securityweek Hacking
Researchers at cybersecurity company Check Point said on Thursday that they have found the real identity of VandaTheGod, a Brazilian hacker involved in both hacktivist operations and financially-motivated cybercrimes.
Check Point told SecurityWeek that it informed law enforcement about its findings in October 2019, but the hacker continued to be active up until May 2020.
VandaTheGod, who is also known online as Vanda de Assis and SH1N1NG4M3, appears to have been active since 2013 and claims to be associated with the Brazilian Cyber Army, which describes itself as an “ethical hacking group.” VandaTheGod also claimed to be a member of the hacking group UGNazi, whose members were arrested in 2012.
The hacker’s account on Zone-H, a popular website defacement archive, shows that VandaTheGod defaced more than 4,800 domains between July 2019 and February 2020, including ones belonging to government organizations and corporations across 40 countries.
While his defacements were apparently part of hacktivism campaigns fighting against government corruption, VandaTheGod also leaked and offered to sell stolen corporate and payment card information. At one point, he offered to sell the medical records of 1 million patients from New Zealand for $200.

Check Point researchers investigated VandaTheGod’s online presence and noticed that the hacker’s website had been registered from Uberlândia, a city in Brazil.
One of the screenshots posted by the hacker on Twitter showed a browser tab open to a Facebook account for “Vanda De Assis (VandaTheGod).” A different screenshot included a tab with the initials M.R. and a search for individuals with these initials in Uberlândia led researchers to the Facebook profile of a man who endorsed the Brazilian Cyber Army.
Further analysis revealed that one picture of a man holding a bottle of whisky had been posted on both the Vanda de Assis Facebook profile and the profile of the individual with the initials M.R. Moreover, the furniture and setup in a picture posted on Facebook by M.R. while he was playing on his PlayStation was exactly the same as in a picture posted by VandaTheGod on Twitter.
Check Point has not made the alleged hacker’s name public, but reported its findings to law enforcement.
“VandaTheGod succeeded in carrying out many hacking attacks, but ultimately failed from the OPSEC perspective, as he left many trails that led to his true identity, especially at the start of his hacking career,” Check Point said in a blog post. “Ultimately, we were able to connect the VandaTheGod identity with high certainty to a specific Brazilian individual from the city of Uberlândia, and relay our findings to law enforcement to enable them to take further action.”
Researchers Uncover Brazilian Hacktivist's Identity Who Defaced Over 4800 Sites
28.5.2020 Thehackernews Hacking
It's one thing for hackers to target websites and proudly announce it on social media platforms for all to see. It's, however, an entirely different thing to leave a digital trail that leads cybersecurity researchers right to their doorsteps.
That's exactly what happened in the case of a hacktivist under the name of VandaTheGod, who has been attributed to a series of attacks on government websites since July 2019.
In a report shared with The Hacker News, researchers from Check Point said they were able to map VandaTheGod's activity over the years, and eventually zero down the attacker's real identity to a Brazilian individual from the city of Uberlândia.
The cybersecurity firm said it notified concerned law enforcement of its findings for further action, adding the social media activities on profiles associated with VandaTheGod came to a halt towards the end of 2019.
VandaTheGod has a long history of going after government websites, universities, and healthcare providers. Notably, the attacker claimed to have breached the database of New Zealand's Tū Ora Compass Health and offered medical details of one million patients for sale on Twitter last October.
The hacker in question, allegedly part of the "Brazilian Cyber Army" (BCA), has also vandalized dozens of websites to spread anti-government messages, in addition to displaying BCA's logo in screenshots of compromised accounts and websites.
"Many of the messages left on the defaced websites implied that the attacks were motivated by anti-government sentiment, and were carried out to combat social injustices that the hacker believed were a direct result of government corruption," the researchers said.
website hacker
What's more, a timeline of VandaTheGod's tweets shows that the person enjoyed the attention from media reports mentioning the hacking endeavors, even going to the extent of stating that "I will stop hacking websites" once the total reaches 5,000.
"VandaTheGod didn't just go after government websites, but also launched attacks against public figures, universities, and even hospitals. In one case, the attacker claimed to have access to the medical records of 1 million patients from New Zealand, which were offered for sale for $200," the researchers said.
According to Zone-H records, a security portal that holds an archive of all web intrusions, there are currently 4,820 entries of hacked websites linked to VandaTheGod, most of which belongs to individuals and entities in the United States, Australia, Netherlands, Italy, South Africa, Canada, UK, and Germany.
Check Point said they worked by tracking down the WHOIS information for the domain "VandaTheGod.com," which led them to an email address ("fathernazi@gmail.com") that was used to register other websites, such as "braziliancyberarmy.com."
But what ultimately gave away VandaTheGod's real identity were a couple of screenshots that were uploaded to Twitter, from which the researchers identified a Facebook profile belonging to the attacker ("Vanda De Assis") as well as the person's real name — identified only by the initials M. R.
Consequently, the researchers said they were able to identify a number of cross-posts between the Facebook profile tied to M. R. and that of Vanda De Assis, including photos of the individual's living room, proving that both the M.R. and VandaTheGod accounts were controlled by the same individual.
"VandaTheGod succeeded in carrying out many hacking attacks, but ultimately failed from the OPSEC perspective, as he left many trails that led to his true identity, especially at the start of his hacking career," Check Point researchers concluded.
"Ultimately, we were able to connect the VandaTheGod identity with high certainty to a specific Brazilian individual from the city of Uberlândia, and relay our findings to law enforcement to enable them to take further action."
Tools Used in GhostDNS Router Hijack Campaigns Dissected
22.5.2020 Securityweek Hacking
The source code of the GhostDNS exploit kit (EK) has been obtained and analyzed by researchers. GhostDNS is used to compromise a wide range of routers to facilitate phishing -- perhaps more accurately, pharming -- for banking credentials. Target routers are mostly, but not solely, located in Latin America.
The source code used in a GhostDNS campaign was obtained by Avast researchers. Avast Antivirus includes a Web Shield to protect users from malicious web content. One of its users was up to no good, and attempted to upload a RAR archive with malicious content. He forgot to disable Web Shield and password protect the RAR. Web Shield detected it as malicious, automatically analyzed the content, and flagged it as an exploit kit.
"We downloaded the linked file and found the complete source code of the GhostDNS exploit kit," reports the Avast Threat Intelligence Team. The RAR archive is named KL DNS.rar, indicating its purpose -- a DNS hijack redirecting users to a phishing/pharming page where a keylogger is used to extract the user's credentials or bank card details.
The archive contained everything necessary for a DNS hijack campaign, both from inside the network, or externally from the internet. Internal attacks are often via malvertising. Malvertising allows the EK to directly attack the router from a computer that uses the router. External attacks from the internet require scanning for and locating vulnerable routers before they can be attacked. Everything necessary for both forms of attack were contained in the RAR archive.
Most GhostDNS campaigns target routers in Latin America, and Brazil in particular. According to telemetry obtained from Avast's antivirus product, 76% of routers in Brazil have weak or default credentials, making the region a lucrative target.
For attacks from the internet, the archive included BRUT, a free internet scanner that locates and attacks routers with a public IP address and an open HTTP port. Avast has found two versions of BRUT. One targets a lower number of devices and ports but with a long list of default and common passwords that could be used, while the other targets a higher number of devices with a smaller number of possible credentials. The latter appears to be the more recent version.
The researchers postulate that this "may be because most users never change the default credentials in their SOHO routers, and therefore using a smaller number of credentials for the attack may be effective enough." Fewer credentials against more router models may be more effective than many credentials against a limited number of different routers. Interestingly, both sets of credentials include the password 'deadcorp2017’, which is used by GhostDNS as a new password in infected routers -- which means that new campaigns can gain access to routers already infected even if the original password is not included in the current campaign.
The basic attack methodology is to use cross site request forgery (CSRF) requests to change the DNS settings on the router. The process establishes a rogue DNS server that is specified by the attacker for each GhostDNS campaign. There were three different malicious DNS setting in the code found by Avast -- none of which are currently operational.
Once the DNS settings have been changed, users can be silently redirected to pre-made pharming pages. The RAR file obtained by Avast included source code for several such pages. These included the biggest banks in Brazil -- such as Banco Bradesco, Itau, Santander and CrediCard -- and Netflix. The source code indicated that other domains were prepared to work, but that the phishing web pages had not been implemented.
The internal attack associated with a malvertising campaign operates differently. The EK searches for routers with an open port (either 80 or 8080). It produces a BASE64 encoded iframe representing a simple webpage with a function that changes HTTP requests to WebSocket requests. These requests change the DNS settings to the predefined malicious IP addresses. Only eight username/password pairs are found in this attack, but they include the most-used default router logins used in Brazil.
Once the victim has been successfully redirected to a malicious pharming page, a keylogger steals login details and bank card details and emails them to the attacker.
Hackers Target Oil Producers During COVID-19 Slump
19.5.2020 Securityaffairs Hacking
Recent research shows that the oil industry — already experiencing difficulties due to COVID-19 — must remain abreast of threats to stay safe from hackers.
Spear-phishing is a rapidly emerging threat. It’s more specific than generic phishing attempts and often targets a single person or company. Recent research shows that the oil industry — already experiencing difficulties due to COVID-19 — must remain abreast of threats to stay safe from hackers.
Cybercriminals Capitalizing on the Chaos
The coronavirus is forcing companies in most industries to operate substantially differently. Many may find it takes time to adjust to the changes. Others do not immediately have the resources for a major shift, such as having all employees work remotely.
A related concern is that COVID-19 is both a new and anxiety-inducing issue. People want to learn as much as they can about it, and their haste may result in them clicking on links without thinking. Cybercriminals view these conditions as ideal for orchestrating their attacks. Data from Barracuda cybersecurity researchers identified a 667% increase in spear-phishing attacks between the end of February and the following month.
Real-Life Examples of Spear-Phishing Attacks in the Energy Production Sector
The threat of spear-phishing for energy companies is, unfortunately, not a theoretical one. Coverage published in late April by Bitdefender illuminated a carefully executed attack. The research team found evidence of a campaign occurring March 31, whereby hackers impersonated a well-known engineering company with experience in on- and off-shore energy projects.
The messages — which did not include many of the telltale signs of phishing like spelling and grammatical errors — asked recipients to submit equipment and materials bids for the Rosetta Sharing Facilities Project. Participants would do so on behalf of Burullus, a gas joint venture partially owned by another Egyptian state oil brand.
The emails also contained two attachments, which were supposedly bid-related forms. Downloading them infected a user’s system with a type of trojan spyware not previously seen in other utilities industry cyberattacks. The effort targeted oil companies all over the world, from Malaysia to South Africa, in a single day.
Bitdefender’s research team also uncovered a more geographically specific spear-phishing attempt to target the gas sector on April 12. It centered on a relatively small number of shipping companies based in the Philippines. The emails asked them to send details associated with an oil tanker vessel and contained industry-specific language. This spear-phishing campaign occurred over two days.
The cybersecurity experts that studied these attacks stressed that, since the messages contained accurate details about real-life companies and events associated with the oil industry, the attackers took the time to research to craft maximally convincing content.
Hackers Love Causing Severe Disruptions
Why are cyberattacks in the energy industry suddenly on the rise? One reason may stem from the way hackers often deploy tactics to cause tremendous harm to necessary services. The oil industry operates on a vast scale. For example, a company specializing in oil and gas exploration planned as much as 300,000 feet of total footage for drilling in one region during 2018.
The ability to get such impressive outcomes undoubtedly helps oil companies. The increased scale also may make it more necessary to safeguard against cyberattacks, especially as criminals look for ways to cause the most damage. Another recent incident, announced in a United States government alert on February 18, shut down a natural gas compression facility. Operations stopped for two days, causing losses in productivity and revenue.
Although the publication did not name the energy company, it mentioned that the hackers depended on spear-phishing to get the credentials necessary for entering the businesses’ information technology (IT) network. It then used that access to wreak havoc on the enterprise’s operational technology infrastructure.
Not a New Concern
Utilities industry cyberattacks have long worried cybersecurity analysts. If concentrated efforts from hackers shut down the electric grid, the effects could be long-lasting and hit virtually every industry and consumer in the affected areas. The risks to the energy sector began before the coronavirus pandemic, too.
In November 2019, cybersecurity publications discussed a ransomware attack on Petróleos Mexicanos, Mexico’s largest oil and gas company. The perpetrators asked for 562 bitcoins to restore the data. The affected enterprise did not comply, and it had important data backed up.
Toll Group, an Australian transportation and logistics company with oil and gas companies as clients, suffered a ransomware attack this spring. It was the second such issue in four months, with the first happening in February.
The Energy Industry Must Remain Vigilant
The challenges posed by COVID-19 and its effect on oil prices may make the respective parties feel the impacts of cyberattacks in the energy industry more acutely. An ideal aim is to prevent those events rather than dealing with the damage afterward. Paying attention to cybersecurity vulnerabilities can help companies make meaningful gains and stay protected.