New Malvertising Campaign Distributing PikaBot Disguised as Popular Software

CATEGORIE : BotNet |
DATE: 19.12.23 |
| WEB : The Hacker News |
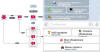
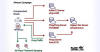
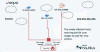
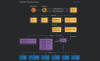
The malware loader known as PikaBot is being distributed as part of a malvertising campaign targeting users searching for legitimate software like AnyDesk.
"PikaBot was previously only distributed via malspam campaigns similarly to QakBot and emerged as one of the preferred payloads for a threat actor known as TA577," Malwarebytes' Jérôme Segura said.