In late September, we noticed an attempt to download a malicious file on one of the machines connected to our Cowrie honeypot:
BotNet Articles - H 2020 1 2 BotNet List - H 2021 2020 2019 2018 BotNet blog BotNet blog
We infiltrated an IRC botnet. Here’s what we found
20.11.20 BotNet Securityaffairs
The CyberNews.com Investigation team carried out an infiltration operation against an IRC botnet and reported it to CERT Vietnam to help take it down.
Original post @ https://cybernews.com/security/we-infiltrated-an-irc-botnet-heres-what-we-found/
In order to gather valuable information about the IRC botnet’s activity, we joined its Command and Control channel where we met the botmaster who was responsible for running the entire network of compromised systems. We also used this infiltration opportunity to learn the botmaster’s motives and the possible purpose of the IRC botnet.
What follows is a story of how we managed to detect an attempt to infect one of our systems, and how our curiosity led us to an unlikely interview with the botmaster of a rare, dying breed of a botnet.
Here’s how it all happened.
About this investigation
To conduct this investigation, a CyberNews researcher infiltrated an IRC botnet that we captured in one of our honeypots. By conversing with the botmaster, the researcher attempted to find out what the IRC botnet is being used for, as well as whether the cybercriminals who were controlling it were involved in other activities.
After interviewing the botmaster, the researcher reported the botnet to CERT, so they could close down the command and control server of the botnet.
How we found the IRC botnet
Infiltrating a cybercriminal operation can provide valuable data about different types of malicious activities, including DDoS attacks, malware distribution, and more. That’s why our researchers use multiple cyberattack detection strategies and are always on the lookout for possible interception and infiltration opportunities.
This September, one such opportunity presented itself to one of our researchers.
Our honeypot setup
In cybersecurity terms, a honeypot is a decoy service or system that poses as a target for malicious actors. When targeted by a threat actor, the honeypot system uses their intrusion attempt to gain valuable information about the attacker.
In order to capture malware and monitor cyberattacks across the internet in real-time, we run multiple honeypot systems that are contained in isolated execution environments, otherwise known as containers. One of the honeypot systems that we run in a container is a Cowrie honeypot, which is designed to detect and log brute force attacks as well as shell interactions (attempts by a threat actor to create a malicious communications tunnel between them and the compromised machine) that are carried out by an attacker or an attacker’s script.
Initial detection: Someone is trying to infect us
In late September, we noticed an attempt to download a malicious file on one of the machines connected to our Cowrie honeypot:
The malicious file contained a Perl script that was designed to infect the host machine and allow the attacker to execute remote commands on the system.
We investigated the file and determined that the malicious program used by the attackers was likely created back in 2012 by the w0rmer Security Team, a now seemingly defunct hacker team that was linked to the infamous hacktivist group Anonymous.
While investigating the script, we learned that this malicious program is used to recruit the host machine into an IRC botnet. This really piqued our interest, because IRC botnets, while relatively widespread in the past, are considered a rarity in 2020. They’re relatively easy to take down and there are far larger botnets powered by newer technologies such as the Internet of Things (IoT).
A vintage botnet, rarely seen in the wild
By further analyzing the code, we observed that the malicious program was able to carry out DDoS attacks over UDP, TCP, HTTP, and other protocols and to execute commands that all pointed towards the program being used for distributed denial of service (DDoS) campaigns:
We could also identify the IP address and port number of the botnet’s Command and Control server, as well as the botmaster’s nicknames and the IRC channel that was used to control the bots.
This led us to believe that we have just encountered an IRC botnet – an old, dying breed of botnets rarely encountered in this age of massive networks of infected IoT devices.
Internet Relay Chat (IRC) networks use simple, low bandwidth communication methods. This makes them suitable for hosting centralized servers that can be used to remotely control massive collections of infected machines (called ‘zombies’ or ‘bots’). These collections of infected bots controlled over IRC channels are called IRC botnets and are still used by cybercriminals to spread malware and carry out small-scale DDoS attacks.
Reconnaissance: Joining the botmaster’s IRC channel
With the acquired information in hand, we jumped at the opportunity to carry out reconnaissance. We wanted to find out as much as we could about this vintage botnet and the cybercriminals behind it. Once we had collected enough data to bring the botnet down, we would report everything we discovered to the appropriate authorities.
Our researcher began reconnaissance by connecting to the IRC server address found in the malicious file to see whether the botnet server was still active.
It was:
Excited by this discovery, the researcher joined the IRC channel that was used for communication between the bots and the botmaster. What they found was a functioning IRC botnet with no less than 137 compromised systems. Most of the zombies were named “lol-XXXX” and were currently connected to the botnet’s Command and Control center, with 241 bots being the maximum number for this particular botnet:
This meant that the IRC botnet was not very significant in scale, and could in all likelihood only be used to carry out minor DDoS attacks or commit other, relatively small-scale malicious acts.
As we continued to observe the botnet over the next several days, the number of bots kept fluctuating. It was, however, decreasing over time.
The interview: Striking a conversation with the botmaster
Before taking action against the IRC botnet, we wanted to ascertain the botmaster’s motives: why were they operating this botnet? Did they run any other criminal operations as well?
Also, we needed to know what exactly the botnet was being used for. To get these answers, our researcher (BLUE) initiated a conversation with the botmaster (RED) on the IRC channel.
After a brief back-and-forth, the botmaster invited the researcher to move to Discord, presumably thinking that the researcher was a fellow cybercriminal.
As soon as the researcher entered the botmaster’s Discord channel, they noticed that it was populated by four users who were previously informed that our researcher had entered the botnet IRC server.
Not only that, but the botmaster also apparently already knew that their malicious activity was captured on a honeypot, since honeypots are widely used to detect such botnets.
Soon after, the botmaster expressed frustration with people (they used a far less charitable term) frequently stumbling upon their IRC server. They went on to state that they usually dealt with such intruders by carrying out DDoS attacks against them.
Testing, backdoors, and money
After a bit of relatively inconsequential chat, the researcher began to gently interrogate the botmaster about the purpose of the IRC botnet. The botmaster provided several answers, claiming to use the network for DDoS attacks, as well as “testing,” “backdoors,” and “money.”
While we can only speculate as to the true purpose of this relatively small and very old-school IRC botnet, the botmaster was likely using it to conduct malware tests or experiment with planting and executing various exploits on compromised systems.
An infamous cybercriminal and an aspiring YouTuber?
As the interview went on, the botmaster’s ego appeared to be growing bigger with each subsequent question. Late into the conversation, they claimed to have operated a botnet that spanned a whopping 100,000 (!) IoT devices, a very large botnet by today’s standards. With a botnet this big, they would be able to carry out large-scale DDoS attacks and launch massive spam campaigns.
And the bragging didn’t stop there. The botmaster then went on to claim to be the criminal mastermind behind the infamous DynDNS attack, the massive cyberattack that brought down countless websites across the US and Europe, including the likes of Twitter, Reddit, Netflix, CNN, and many others back in 2016.
This kind of shameless bravado is particularly common among cybercriminals. Needless to say, the botmaster did not provide any proof for their claim when asked to do so.
When asked about their current activities, the botmaster claimed to be accumulating networks of compromised devices and selling them off for $3000 to other cybercriminals.
This time, the botmaster even provided proof in the form of a promotional video. Upon further investigation, the researcher discovered more videos on the botmaster’s YouTube channel, featuring multiple ads of botnets for sale.
According to the botmaster, these botnets vary from 100 Gbps to 300 Gbps. Gigabits per second (Gbps) is used to measure a botnet’s size and memory or bandwidth capacity – the bigger the bandwidth, the bigger the DDoS attacks the botnet can carry out. The botnets advertised by the cybercriminal would have enough bandwidth to launch medium-scale targeted DDoS attacks that could cripple various online services.
Finally, the botmaster claimed that they had 7,000 compromised IoT devices/bots in their current botnet, and that the IRC botnet found by the researcher was only used for testing.
An abrupt ending
As far as conversations with cybercriminals go, this one was going quite well, and it was then that we decided to try our luck and ask the botmaster for an official interview that we would conduct anonymously. This would allow us to dig deeper into the botmaster’s motives and perhaps gain more valuable insights into their other operations.
Unfortunately, as soon as our researcher revealed his professional identity and made his request, the botmaster promptly declined and went radio silent.
Our only option from that point on was to report the IRC botnet to CERT in Vietnam, where the Command and Control server of the botnet was apparently located. We informed CERT Vietnam about the botnet on October 26, and the country’s computer emergency response team is currently working to shut down the botmaster’s Command and Control server.
Original post available at https://cybernews.com/security/we-infiltrated-an-irc-botnet-heres-what-we-found/
Muhstik botnet adds Oracle WebLogic and Drupal exploits
12.11.20 BotNet Exploit Securityaffairs
Muhstik botnet leverages known web application exploits to compromise IoT devices, now it targeting Oracle WebLogic, Drupal.
Muhstik is a botnet that is known to use web application exploits to compromise IoT devices, it has been around for at least 2018.
Botnet operators monetize their efforts via XMRig, cgmining and with DDoS-for-hire services.
The botnet leverages IRC servers for command-and-control (C2) communications, experts noticed that it has consistently used the same infrastructure since it first appeared in the threat landscape.
The bot propagates by compromising home routers, but experts observed multiple attempted exploits for Linux server propagation. The list of targeted routers include GPON home router, DD-WRT router, and the Tomato router.
According to researchers from cloud security firm Lacework, Muhstik operators added Web application exploits for Drupal and Weblogic to their bot.
The bot includes exploits for Oracle WebLogic Server vulnerabilities CVE-2019-2725 and CVE-2017-10271, and the Drupal RCE flaw tracked as CVE-2018-7600.
Researchers from Lacework have analyzed the attack chain implemented by the Muhstik bot.
In the first stage of the attack, a payload downloads the other components. The payload is named “pty” followed by a number used to map the architecture. Below some download URL examples:
hxxp://159.89.156.190/.y/pty2
hxxp://167.99.39.134/.x/pty3
“Upon successful installation Mushtik will contact the IRC channel to receive commands. (For more details on the Muhstik protocol, refer to the write up by Subexsecure). Usually Muhstik will be instructed to download an XMRmrig miner and a scanning module.” reads the analysis published by the researchers. “The scanning module is used for growing the botnet through targeting other Linux servers and home routers.”
The main payload and the scanning module of the Muhstik botnet encrypt their configurations using the Mirai source code which employs a single byte XOR of 0x22.
The decoded configuration for the Muhstik scanning module has common settings that are common to multiple Mirai-based botnets.
The analysis of the botnet’s attack infrastructure exposed some interesting correlations. IRC C2 irc.de-zahlung.eu shared an SSL cert with site jaygame.net, which is an amateur site about a game involving an Anime character named ‘Jay’. The site is currently leveraging Google Analytics ID UA-120919167-1, a reverse Google Analytics search exposed the following 3 domains using the same ID:
fflyy.su
kei.su
“The two other domains linked to the analytics ID (ffly.su and kei.su) were also configured as C2s for various other Linux Tsunami malware linked to the same infrastructure. If the infrastructure is administered by a single attacker then we can presume it’s related.” states the analysis. “This related infrastructure has allowed possible attribution to what Lacework has dubbed “Wasp 8220”. This set of activity has been tied to other cryptomining variants and Linux backdoors . These all have links to the same malware upload path belonging to Chinese forensics firm Shen Zhou Wang Yun Information Technology Co., Ltd. “

Lacework researchers linked the Muhstik botnet to the Chinese forensics firm Shen Zhou Wang Yun Information Technology Co., Ltd.
Experts also observed that original malware samples were uploaded to VirusTotal all at once before Muhstik was spreading in the wild.
The samples contained multiple strings mentioning “shenzhouwangyun,” such as in /home/wys/shenzhouwangyun/shell/downloadFile/tomato.deutschland-zahlung.eu_nvr a circumstance that suggests that the malware was developed by Shen Zhou Wang Yun.
Lacework also shared up to date Indicators of Compromise (IOCs) for the recent attacks.
KashmirBlack Botnet Hijacks Thousands of Sites Running On Popular CMS Platforms
29.10.20 BotNet Thehackernews
An active botnet comprising hundreds of thousands of hijacked systems spread across 30 countries is exploiting "dozens of known vulnerabilities" to target widely-used content management systems (CMS).
The "KashmirBlack" campaign, which is believed to have started around November 2019, aims for popular CMS platforms such as WordPress, Joomla!, PrestaShop, Magneto, Drupal, Vbulletin, OsCommerence, OpenCart, and Yeager.
"Its well-designed infrastructure makes it easy to expand and add new exploits or payloads without much effort, and it uses sophisticated methods to camouflage itself, stay undetected, and protect its operation," Imperva researchers said in a two-part analysis.
The cybersecurity firm's six-month-long investigation into the botnet reveals a complex operation managed by one command-and-control (C2) server and more than 60 surrogate servers that communicate with the bots to send new targets, allowing it to expand the size of the botnet via brute force attacks and installation of backdoors.
The primary purpose of KashmirBlack is to abuse resources of compromised systems for Monero cryptocurrency mining and redirect a website's legitimate traffic to spam pages. But it has also been leveraged to carry out defacement attacks.
Regardless of the motive, the exploitation attempts begin with making use of PHPUnit RCE vulnerability (CVE-2017-9841) to infect customers with next-stage malicious payloads that communicate with the C2 server.
Based on the attack signature it found during once such defacements, Imperva researchers said they believed the botnet was the work of a hacker named Exect1337, a member of the Indonesian hacker crew PhantomGhost.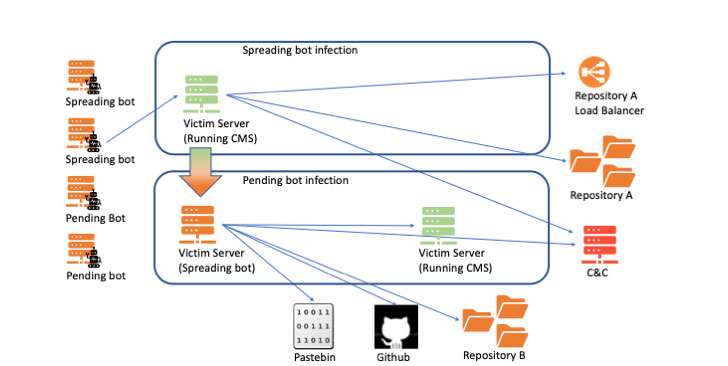
KashmirBlack's infrastructure is complex and comprises a number of moving parts, including two separate repositories — one to host exploits and payloads, and the other to store the malicious script for communication with the C2 server.
The bots themselves are either designated as a 'spreading bot,' a victim server that communicates with the C2 to receive commands to infect new victims, or a 'pending bot,' a newly compromised victim whose purpose in the botnet is yet to be defined.
While CVE-2017-9841 is used to turn a victim into a spreading bot, successful exploitation of 15 different flaws in CMS systems leads to a victim site becoming a new pending bot in the botnet. A separate WebDAV file upload vulnerability has been employed by the KashmirBlack operators to result in defacement.
But just as the botnet grew in size and more bots began fetching payloads from the repositories, the infrastructure was tweaked to make it more scalable by adding a load balancer entity that returns the address of one of the redundant repositories that were newly setup.
The latest evolution of KashmirBlack is perhaps the most insidious one. Last month, the researchers found the botnet using Dropbox as a replacement for its C2 infrastructure, abusing the cloud storage service's API to fetch attack instructions and upload attack reports from the spreading bots.
"Moving to Dropbox allows the botnet to hide illegitimate criminal activity behind legitimate web services," Imperva said. "It is yet another step towards camouflaging the botnet traffic, securing the C&C operation and, most importantly, making it difficult to trace the botnet back to the hacker behind the operation."
TrickBot operators employ Linux variants in attacks after recent takedown
29.10.20 BotNet Securityaffairs
A few days after the TrickBot takedown, Netscout researchers spotted a new TrickBot Linux variant that was used by its operators.
A few days ago, Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joined the forces and announced a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
Microsoft has taken down 120 of the 128 servers that were composing the Trickbot infrastructure.
Microsoft announced to have taken down 62 of the original 69 TrickBot C&C servers, seven servers that could not be brought down last week were Internet of Things (IoT) devices.
Microsoft also revealed that operators tried to resume the operations, The company brought down 58 of the 59 servers the operators attempted to bring online after the recent takedown.
According to a new report published by researchers from security firm Netscout, TrickBot’s operators have started to use a new variant of their malware in an attempt to Linux systems and expand the list of its targets.
TrickBot is a popular banking Trojan that has been around since October 2016, its authors have continuously upgraded it by implementing new features.
At the end of 2019, researchers spotted a new TrickBot backdoor framework dubbed Anchor that was using the DNS protocol for C2 communications.
Stage 2 Security researcher Waylon Grange first spotted the new Linux variant of Anchor_DNS in July and called it “Anchor_Linux.”
“The actors behind Trickbot, a high profile banking trojan, have recently developed a Linux port of their new DNS command and control tool known as Anchor_DNS.” explained Grange.
“Often delivered as part of a zip, this malware is a lightweight Linux backdoor. Upon execution it installs itself as a cron job, determines the public IP [address] for the host and then begins to beacon via DNS queries to its C2 server.”
Researchers from Netscout now published an analysis of the variant detailing the communication flow between the bot and the C2 server.
The client sends “c2_command 0” to the server along with information about the compromised system and the bot ID, the server, in turn, responds with the message “signal /1/” back to the bot.

The infected host responds by sending the same message back to the C2, which in turn sends the command to be executed by the bot. Once executed the command, the bot sends the result of the execution to the C2 server.
“The complexity of Anchor’s C2 communication and the payloads that the bot can execute reflect not only a portion of the Trickbot actors’ considerable capabilities, but also their ability to constantly innovate, as evidenced by their move to Linux.” concludes the report. “It is important to note that Trickbot operators aren’t the only adversaries to realize the value of targeting other operation systems”
TrickBot Linux Variants Active in the Wild Despite Recent Takedown
28.10.20 BotNet Thehackernews
Efforts to disrupt TrickBot may have shut down most of its critical infrastructure, but the operators behind the notorious malware aren't sitting idle.
According to new findings shared by cybersecurity firm Netscout, TrickBot's authors have moved portions of their code to Linux in an attempt to widen the scope of victims that could be targeted.
TrickBot, a financial Trojan first detected in 2016, has been traditionally a Windows-based crimeware solution, employing different modules to perform a wide range of malicious activities on target networks, including credential theft and perpetrate ransomware attacks.
But over the past few weeks, twin efforts led by the US Cyber Command and Microsoft have helped to eliminate 94% of TrickBot's command-and-control (C2) servers that were in use and the new infrastructure the criminals operating TrickBot attempted to bring online to replace the previously disabled servers.
Despite the steps taken to impede TrickBot, Microsoft cautioned that the threat actors behind the botnet would likely make efforts to revive their operations.
TrickBot's Anchor Module
At the end of 2019, a new TrickBot backdoor framework called Anchor was discovered using the DNS protocol to communicate with C2 servers stealthily.
The module "allows the actors — potential TrickBot customers — to leverage this framework against higher-profile victims, said SentinelOne, adding the "ability to seamlessly integrate the APT into a monetization business model is evidence of a quantum shift."
Indeed, IBM X-Force spotted new cyberattacks earlier this April revealing collaboration between FIN6 and TrickBot groups to deploy the Anchor framework against organizations for financial profit.
The variant, dubbed "Anchor_DNS," enables the infected client to utilize DNS tunneling to establish communications with the C2 server, which in turn transmits data with resolved IPs as a response, NTT researchers said in a 2019 report.
But a new sample uncovered by Stage 2 Security researcher Waylon Grange in July found that Anchor_DNS has been ported to a new Linux backdoor version called "Anchor_Linux."
"Often delivered as part of a zip, this malware is a lightweight Linux backdoor," Grange said. "Upon execution it installs itself as a cron job, determines the public IP [address] for the host and then begins to beacon via DNS queries to its C2 server."
How the C2 Communication Works Using Anchor
Netscout's latest research decodes this flow of communication between the bot and the C2 server. During the initial setup phase, the client sends "c2_command 0" to the server along with information about the compromised system and the bot ID, which then responds with the message "signal /1/" back to the bot.
As an acknowledgment, the bot sends the same message back to the C2, following which the server remotely issues the command to be executed on the client. In the last step, the bot sends back the result of the execution to the C2 server.
"Every part of communication made to the C2 follows a sequence of 3 different DNS queries," Netscout security researcher Suweera De Souza said.
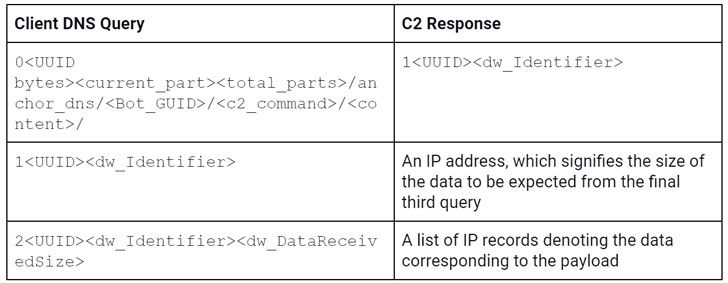
A list of IP records denoting the data corresponding to the payload
The result of the third query is a list of IP addresses that are subsequently parsed by the client to build the executable payload.
The last piece of data sent by the C2 server corresponds to a range of commands (numbered 0-14 in Windows, and 0-4, 10-12, and 100 in Linux) for the bot to execute the payload via cmd.exe or by injecting it into multiple running processes such as Windows File Explorer or Notepad.
"The complexity of Anchor's C2 communication and the payloads that the bot can execute reflect not only a portion of the Trickbot actors' considerable capabilities, but also their ability to constantly innovate, as evidenced by their move to Linux," De Souza said.
KashmirBlack, a new botnet in the threat landscape that rapidly grows
27.10.20 BotNet Securityaffairs
Security experts spotted a new botnet, tracked as KashmirBlack botnet, that likely infected hundreds of thousands of websites since November 2019.
Security experts from Imperva have spotted a new sophisticated botnet, tracked as KashmirBlack is believed to have already infected hundreds of thousands of websites by exploiting vulnerabilities in their content management system (CMS) platforms.
The KashmirBlack botnet has been active at least since November 2019, operators leverages dozens of known vulnerabilities in the target servers.
Experts believe that the botmaster of the KashmirBlack botnet is a hacker that goes online with moniker “Exect1337,” who is a member of the Indonesian hacker crew ‘PhantomGhost’.
The experts observed millions of attacks per day on average, on thousands of victims in more than 30 different countries around the world.
“It has a complex operation managed by one C&C (Command and Control) server and uses more than 60 – mostly innocent surrogate – servers as part of its infrastructure. It handles hundreds of bots, each communicating with the C&C to receive new targets, perform brute force attacks, install backdoors, and expand the size of the botnet.” reads the first part of two reports published by the experts detailing the DevOps implementation behind the botnet.

The primary purpose of the KashmirBlack botnet is to abuse resources of compromised systems for cryptocurrency mining and redirecting a site’s legitimate traffic to spam pages.
Experts observed a continuous growth of the botnet since its discovery along with an increasing level of complexity.
In May experts observed an increase in the command-and-control (C&C) infrastructure and the exploits used by botnet operators.
KashmirBlack scans the internet for sites using vulnerable CMS versions and attempting to exploit known vulnerabilities to them and take over the underlying server.
Below a list of vulnerabilities exploited by the botnet operators to compromise websites running multiple CMS platforms, including WordPress, Joomla!, PrestaShop, Magneto, Drupal, vBulletin, osCommerce, OpenCart, and Yeager:
PHPUnit Remote Code Execution – CVE-2017-9841
jQuery file upload vulnerability – CVE-2018-9206
ELFinder Command Injection – CVE-2019-9194
Joomla! remote file upload vulnerability
Magento Local File Inclusion – CVE-2015-2067
Magento Webforms Upload Vulnerability
CMS Plupload Arbitrary File Upload
Yeager CMS vulnerability – CVE-2015-7571
Multiple vulnerabilities including File Upload & RCE for many plugins in multiple platforms here
WordPress TimThumb RFI Vulnerability – CVE-2011-4106
Uploadify RCE vulnerability
vBulletin Widget RCE – CVE-2019-16759
WordPress install.php RCE
WordPress xmlrpc.php Login Brute-Force attack
WordPress multiple Plugins RCE (see full list here)
WordPress multiple Themes RCE (see full list here)
Webdav file upload vulnerability
“During our research we witnessed its evolution from a medium-volume botnet with basic abilities to a massive infrastructure that is here to stay,” Imperva concludes.
The second part of the report also includes Indicators of Compromise (IoCs) for this botnet.
Microsoft Says Most TrickBot Servers Are Down
22.10.20 BotNet Securityweek
Most of the servers associated with the TrickBot botnet have been taken down following the technical and legal effort announced last week, Microsoft says.
The takedown was meant to disable Trickbot’s infrastructure and prevent its operators from reviving the botnet, but initial reports claimed that the network of infected machines continued operations unhindered.
The TrickBot operators, which some say are the hackers that also use Ryuk and Conti ransomware, appeared largely unaffected by the takedown attempt, with only a relatively small percentage of the bots being isolated.
On Tuesday, threat intelligence company Intel 471 revealed that newly observed TrickBot control servers were unable to respond to bot requests, and Microsoft now says its actions have successfully prevented newly registered servers from becoming operational.
The tech giant explains that it managed to take down 62 of the 69 initial TrickBot servers around the world, as well as 58 of the 59 new servers that the malware operators attempted to add to their infrastructure.
“In sum, from the time we began our operation until October 18, we have taken down 120 of the 128 servers we identified as Trickbot infrastructure around the world,” Tom Burt, Corporate Vice President of Customer Security & Trust at Microsoft, says.
Burt also notes that, due to the botnet’s unique architecture, Microsoft and its partners are taking a “persistent and layered approach to addressing Trickbot’s operations around the world.” Furthermore, he says, the same action will continue throughout election day on November 3.
Microsoft’s partners, he says, are working to clean and remediate compromised Internet of Things (IoT) devices that are being used as non-traditional command and control (C&C) infrastructure.
“These compromised routers pose a unique challenge for the internet service providers (ISPs) as they must simultaneously work to remediate devices while keeping legitimate traffic uninterrupted, and this delicate work is underway. Finally, we’re working with ISPs and others to also clean devices in people’s homes and businesses that might be infected,” Burt notes.
The focus of this effort, he adds, is to disrupt TrickBot during peak election activity, and so far the company feels confident with the progress it has made, as the cybercriminals need to invest a lot into rebuilding their server infrastructure.
“We fully expect that Trickbot’s operators will continue looking for ways to stay operational, and we and our partners will continue to monitor them and take action. We encourage others in the security community who believe in protecting the elections to join the effort and share their intelligence directly with hosting providers and ISPs that can take Trickbot’s infrastructure offline,” Burt concludes.
Microsoft took down 120 of 128 Trickbot servers in recent takedown
21.10.20 BotNet Securityaffairs
Microsoft brought down TrickBot infrastructure last week, but a few days later the botmasters set up a new command and control (C&C) servers.
Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joined the forces and announced last week a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
Even if Microsoft and its partners have brought down the TrickBot infrastructure TrickBot operators attempted to resume the operations by setting up new command and control (C&C) servers online.

Microsoft provided an update on its takedown efforts and announced a new wave of takedown actions against TrickBot.
According to the IT giant, the operation conducted last week has taken down 94% of the servers composing the Trickbot infrastructure. Trickbot enables ransomware attacks which have been identified as one of the biggest threats to the upcoming U.S. elections.
“We initially identified 69 servers around the world that were core to Trickbot’s operations, and we disabled 62 of them. The seven remaining servers are not traditional command-and-control servers but rather internet of things (IoT) devices Trickbot infected and was using as part of its server infrastructure; these are in the process of being disabled. As expected, the criminals operating Trickbot scrambled to replace the infrastructure we initially disabled. We tracked this activity closely and identified 59 new servers they attempted to add to their infrastructure.” said Tom Burt, CVP of Customer Security and Trust at Microsoft. “We’ve now disabled all but one of these new servers. In sum, from the time we began our operation until October 18, we have taken down 120 of the 128 servers we identified as Trickbot infrastructure around the world.”
Microsoft has taken down 120 of the 128 servers that were composing the Trickbot infrastructure.
Microsoft announced to have taken down 62 of the original 69 TrickBot C&C servers, seven servers that could not be brought down last week were Internet of Things (IoT) devices.
Microsoft also revealed that operators tried to resume the operations, The company brought down 58 of the 59 servers the operators attempted to bring online after the recent takedown.
Burt praised the role of Microsoft’s lawyers who quickly requested new court orders to take down the new servers set up by the Trickbot operators in response to the takedown.
“We have identified new Trickbot servers, located their respective hosting provider, determined the proper legal methodology to take action, and completely disabled those servers in less than three hours. Our global coordination has allowed a provider to take quick action as soon as we notify them – in one case, in less than six minutes.” continues the expert. “What we’re seeing suggests Trickbot’s main focus has become setting up new infrastructure, rather than initiating fresh attacks, and it has had to turn elsewhere for operational help.”
Currently, a few Trickbot C2 servers are still active and operators are using them to control the botnet. Researchers from cyber-security firm Intel 471 reported that these servers are based in Brazil, Colombia, Indonesia, and Kyrgyzstan, and that they still are able to respond to Trickbot bot requests.
“This small number of working control servers was not listed in the most recent distributed Trickbot sample.” states Intel 471.
Burt pointed out that TrickBot operators are working to restore their infrastructure instead of conducting new attacks.
“We fully expect that Trickbot’s operators will continue looking for ways to stay operational, and we and our partners will continue to monitor them and take action.” Microsoft concludes. “We encourage others in the security community who believe in protecting the elections to join the effort and share their intelligence directly with hosting providers and ISPs that can take Trickbot’s infrastructure offline.”
New TrickBot Control Servers Unable to Respond to Bot Requests
21.10.20 BotNet Securityweek
Control servers included in the configuration file of new TrickBot samples fail to respond to bot requests, according to researchers at threat intelligence company Intel 471.
Released in 2016 by the Dyre gang, TrickBot has evolved into one of the most prevalent malware families out there, having ensnared in excess of one million systems to date and being employed by both nation-state and cybercrime actors for malicious operations.
Last week, Microsoft announced that, together with industry partners, it was able to legally take over and disrupt infrastructure used by TrickBot, as well as to block efforts from the its operators to register new infrastructure and revive the botnet.
Days after the announcement, however, Intel 471’s researchers revealed that TrickBot resumed operations, and that Emotet was observed serving TrickBot payloads to infected machines.
CrowdStrike too confirmed that TrickBot was still operational, saying that only approximately 10,000 bots were seen becoming unreachable after being served a non-standard configuration file.
On Tuesday, Intel 471 revealed that, starting Monday, October 19, Emotet has distributed TrickBot samples that include new control servers in their configuration, but that these servers were not able to respond to bot requests.
Most of these controllers, the security firm reveals, are located in the United States and Germany, with some of them based in Bosnia and Herzegovina, Romania, the Netherlands, and Turkmenistan.
“On Oct. 19, 2020, when this latest Trickbot sample was distributed, none of the above listed control servers were able to respond to Trickbot bot requests, a state that continued at the time of this report. Intel 471 believes disruption operations against Trickbot are currently global in nature and have had success against Trickbot infrastructure,” Intel 471 says.
The researchers also note that there are other controllers that do work, and these are located in Brazil, Colombia, Indonesia, and Kyrgyzstan. These control servers, however, were not listed in the most recently distributed TrickBot samples.
TrickBot Botnet Survives Takedown Attempt
16.10.20 BotNet Securityweek
The TrickBot botnet appears to have resumed normal operations days after Microsoft announced that it managed to take it down using legal means.
On October 12, Microsoft and several partners announced that they were able to disrupt the TrickBot infrastructure by legally disabling IP addresses, making servers inaccessible and suspending services employed by the botnet. The effort was also aimed at preventing operators from registering new infrastructure.
Only three days after the announcement, however, security researchers with Intel 471 revealed that the botnet has resumed operations, despite Microsoft’s takedown attempt and efforts from the U.S. Cyber Command to hack TrickBot’s servers.
On October 14, the Emotet botnet began distributing malicious Word documents meant to download and execute a copy of Emotet. The Emotet bots, the researchers say, received commands to fetch and run Trickbot on victim machines.
Intel 471 also notes that the Trickbot plugin server configuration file has received an update which added fifteen server addresses and retained two old servers, along with the server’s .onion address.
The change, the researchers believe, was likely performed as a fix that would ensure that the botnet’s infrastructure remains operational.
“The fact that Trickbot has resumed normal operations despite the best efforts of U.S. Cyber Command and Microsoft shows how resilient of an operation Trickbot is and how much more effort is needed to fully take the botnet offline for good,” Intel 471 said.
The researchers, who have been tracking the botnet’s activity for months, assess that TrickBot’s operators have IT support that any legitimate enterprise takes advantage of, including automated deployment, backups, continuity planning, and a dedicated team behind, which allows them to react to disruptions fast.
“About 10 years ago it was much easier to completely take over or significantly disrupt a botnet, but cybercriminals are students of takedowns and have learned to make their operations more resilient to takedown efforts. That’s why every takedown attempt has some potential of giving ground to the adversary. You’re teaching them where the weaknesses in their armor are and they have a team of developers ready to act on that information. So unless you strike a killing blow, you’re not going to impact them long term,” Intel 471 COO Jason Passwaters said.
To fully disrupt TrickBot, the researchers say, a multi-prolonged effort is needed. Multinational law enforcement support with focus on arresting operators, an aim at the botnet’s main infrastructure, and tight collaboration between governments and the private sector for de-infection are required for a successful takedown.
TrickBot Takedown Disrupts Major Crimeware Apparatus
14.10.20 BotNet Threatpost
Microsoft and partners went after the botnet using a copyright infringement tactic and hunting down C2 servers.
The TrickBot trojan has been dealt a serious blow thanks to a coordinated action led by Microsoft that disrupted the botnet that spreads it. However, researchers warn that the operators will quickly try to revive their operations.
TrickBot is known for spreading other malware, especially ransomware. Microsoft said this week that the United States District Court for the Eastern District of Virginia granted a request for a court order to halt TrickBot’s operations, which it carried out in concert with other firms, including ESET, Lumen’s Black Lotus Labs, NTT Ltd., Symantec and others.
“We disrupted TrickBot through a court order we obtained, as well as technical action we executed in partnership with telecommunications providers around the world,” wrote Tom Burt, corporate vice president, Customer Security & Trust, at Microsoft, in a Monday posting. “We have now cut off key infrastructure so those operating TrickBot will no longer be able to initiate new infections or activate ransomware already dropped into computer systems.”
Threatpost Webinar Promo Retail Security
Click to Register!
TrickBot is a well-known and sophisticated trojan first developed in 2016 as a banking malware – it has a history of transforming itself and adding new features to evade detection. Moving far beyond its banking roots, it has developed over the years into a full-fledged, module-based crimeware solution typically aimed at attacking corporations and public infrastructure.
Users infected with the TrickBot Trojan will see their device become part of a botnet that can allow attackers to gain complete control of the device. Typical consequences of TrickBot infections are bank account takeover, high-value wire fraud and ransomware attacks. It’s often seen working in concert with Emotet, another concerning and widespread trojan that’s known for its modular design.
“What makes [TrickBot] so dangerous is that it has modular capabilities that constantly evolve, infecting victims for the operators’ purposes through a ‘malware-as-a-service’ model,” Burt said. “Its operators could provide their customers access to infected machines and offer them a delivery mechanism for many forms of malware, including ransomware. Beyond infecting end user computers, TrickBot has also infected a number of Internet of Things devices, such as routers, which has extended TrickBot’s reach into households and organizations.”
TrickBot has infected more than 1 million computing devices around the world since late 2016, according to Microsoft.
The Takedown
Microsoft and partners were able to thwart TrickBot’s mechanisms to evade detection and uncover its command-and-control (C2) infrastructure, including the location of its servers.
ESET for example said that it analyzed more than 125,000 malicious samples and downloaded and decrypted more than 40,000 configuration files used by the different Trickbot modules, which gave the team a window into the C2 setup.
TrickBot accounts for infections globally. Source: ESET.
According to ESET, one of the keys to the investigation was the fact that TrickBot’s modular architecture uses a variety of plugins to perform its vast array of malicious actions.
“One of the oldest plugins developed for the platform allows TrickBot to use web injects, a technique allowing the malware to dynamically change what the user of a compromised system sees when visiting specific websites,” according to the post. “To operate, this plugin relies on configuration files downloaded by the main module. These contain information about which websites should be modified and how.”
These decrypted configuration files contain targeted URLs and the malicious C2 URLs the bot should contact when a victim accesses a targeted site.
“As we observed the infected computers connect to and receive instructions from command-and-control servers, we were able to identify the precise IP addresses of those servers,” Microsoft’s Burt explained. “With this evidence, the court granted approval for Microsoft and our partners to disable the IP addresses, render the content stored on the command-and-control servers inaccessible, suspend all services to the botnet operators, and block any effort by the TrickBot operators to purchase or lease additional servers.”
This is a different approach than the takedown of the Necurs peer-to-peer botnet, which Microsoft led in March. The firm worked with technical and legal partners in 35 countries to disrupt that malware.
“By analyzing the algorithm Necurs used to systematically generate new domains, Microsoft was able to accurately predict the 6+ million unique domains that would be created within the next 25 months,” said Nozomi Networks co-founder Andrea Carcano, via email. “Microsoft reported these domains to their respective registries worldwide, allowing the websites to be blocked and preventing them from becoming part of the Necurs infrastructure.”
Copyright Claim
Interestingly, Microsoft’s request for legal approval hinges on a copyright claim against TrickBot’s malicious use of its software code. It’s the first time the computing giant has used this approach, Burt said, adding that the tactic “allowed us to take civil action to protect customers in the large number of countries around the world that have these laws in place.”
He added that because TrickBot retains its focus on online banking websites, and stealing funds from people and financial institutions, the Financial Services Information Sharing and Analysis Center (FS-ISAC) was a co-plaintiff in the legal action.
“While botnet operators are using every trick in the book to expand their malicious activity, defenders for obvious reasons have to comply with the law when implementing the countermeasures,” said Carcano. “But as Microsoft’s actions show, this doesn’t mean that you cannot be creative with the technical and non-technical tools available. The beauty of this latest approach is that while defenders have to suffer the asymmetry of attackers operating behind the limits of the law, by taking the case to court, Microsoft gained a legal advantage to regain control.”

TrickBot may be disrupted for now, but researchers pointed out that the operators have other projects going on.
“One of these projects is the so-called Anchor project, a platform mostly geared towards espionage rather than crimeware,” according to ESET. “They are also likely involved in the development of the Bazar malware — a loader and backdoor used to deploy malware, such as ransomware, and to steal sensitive data from compromised systems.”
“Prior to the disruption, we had already observed some actors that were previously distributing TrickBot switch to BazaLoader, which has been linked by code similarity to TrickBot,” said Sherrod DeGrippo, senior director of threat research at Proofpoint, via email.
TrickBot itself will likely re-emerge, according to Burt.
“We fully anticipate TrickBot’s operators will make efforts to revive their operations, and we will work with our partners to monitor their activities and take additional legal and technical steps to stop them,” he said.
DeGrippo went further and noted that the takedown’s efficacy remains to be seen.
“Typically, these types of actions don’t result in a direct reduction of threat activity,” the researcher noted. “Threat actors will often replace the lost infrastructure quickly and easily out of a different country so we will need to wait and see what the direct impact will be…We believe it’s unlikely we’ll see any immediate significant changes in Trickbot email delivery volumes…The most recent Trickbot campaigns are already using new command-and-control channels, which shows the threat actors are actively adapting their campaigns.”
Microsoft partnered with other security firms to takedown TrickBot botnet
13.10.20 BotNet Securityaffairs
A joint operation conducted by FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, Symantec, and Microsoft aimed at takedown the TrickBot botnet.
Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joint the forces and announced today a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
The experts that participated in the takedown have supported the investigation into TrickBot’s backend infrastructure for several months.
“Through our monitoring of Trickbot campaigns, we collected tens of thousands of different configuration files, allowing us to know which websites were targeted by Trickbot’s operators. The targeted URLs mostly belong to financial institutions,” Jean-Ian Boutin, Head of Threat Research at ESET.
“Trying to disrupt this elusive threat is very challenging as it has various fallback mechanisms, and its interconnection with other highly active cybercriminal actors in the underground makes the overall operation extremely complex.”
The security firms have collected more than 125,000 TrickBot malware samples and mapped the command and control infrastructure. The TrickBot botnet was considered by security experts one of the biggest botnets.

Internet service providers (ISPs) and computer emergency readiness teams (CERTs) around the world also supported the operation by notifying all infected users.
The information gathered by the security firm was used by Microsoft to receive a warrant to takedown the TrickBot servers.
“We took today’s action after the United States District Court for the Eastern District of Virginia granted our request for a court order to halt Trickbot’s operations.” reads the post published by Microsoft.
“With this evidence, the court granted approval for Microsoft and our partners to disable the IP addresses, render the content stored on the command and control servers inaccessible, suspend all services to the botnet operators, and block any effort by the TrickBot operators to purchase or lease additional servers,”
This is the second-ever major botnet takedown operation this year, after Necurs one in March.
Microsoft pointed out that this takedown represents a new legal approach that its DCU used for the first time, it includes copyright claims against Trickbot’s operators that have illegally used the software code of the IT giant. Microsoft has chosen this approach to take civil action against botnet operators and protect its customers across the world.
According to the security firms that took part in the operation, the TrickBot botnet had infected more than one million devices at the time of its takedown.
Trickbot has been active since 2016, at the time the authors of the author designed it to steal banking credentials. Over the years, the threat evolved and its operators implemented a modular structure that allowed them to offer the threat as malware-as-a-service. The Trickbot infrastructure was used by crooks to compromise systems and carry out human-operated campaigns, notably its use for the deployment of the Ryuk ransomware.
The malware first started out in 2016 as a banking trojan before shifting into a multi-purpose malware downloader that infected systems and provided access to other criminal groups using a business model known as MaaS (Malware-as-a-Service).
The TrickBot operators also deployed banking trojans and info-stealer trojans and were providing access to corporate networks for crooks focused on scams and cyber espionage.
“The action against Trickbot is one of the ways in which Microsoft provide real-world protection against threats. This action will result in protection for a wide range of organizations, including financial services institutions, government, healthcare, and other verticals from malware and human-operated campaigns delivered via the Trickbot infrastructure.” concludes Microsoft.
Microsoft and Other Tech Companies Take Down TrickBot Botnet
13.10.20 BotNet Thehackernews
Days after the US Government took steps to disrupt the notorious TrickBot botnet, a group of cybersecurity and tech companies has detailed a separate coordinated effort to take down the malware's back-end infrastructure.
The joint collaboration, which involved Microsoft's Digital Crimes Unit, Lumen's Black Lotus Labs, ESET, Financial Services Information Sharing and Analysis Center (FS-ISAC), NTT, and Broadcom's Symantec, was undertaken after their request to halt TrickBot's operations were granted by the US District Court for the Eastern District of Virginia.
The development comes after the US Cyber Command mounted a campaign to thwart TrickBot's spread over concerns of ransomware attacks targeting voting systems ahead of the presidential elections next month. Attempts aimed at impeding the botnet were first reported by KrebsOnSecurity early this month.
Microsoft and its partners analyzed over 186,000 TrickBot samples, using it to track down the malware's command-and-control (C2) infrastructure employed to communicate with the victim machines and identify the IP addresses of the C2 servers and other TTPs applied to evade detection.
"With this evidence, the court granted approval for Microsoft and our partners to disable the IP addresses, render the content stored on the command and control servers inaccessible, suspend all services to the botnet operators, and block any effort by the TrickBot operators to purchase or lease additional servers," Microsoft said.
Since its origin as a banking Trojan in late 2016, TrickBot has evolved into a Swiss Army knife capable of pilfering sensitive information, and even dropping ransomware and post-exploitation toolkits on compromised devices, in addition to recruiting them into a family of bots.
"Over the years, TrickBot's operators were able to build a massive botnet, and the malware evolved into a modular malware available for malware-as-a-service," Microsoft said.
"The TrickBot infrastructure was made available to cybercriminals who used the botnet as an entry point for human-operated campaigns, including attacks that steal credentials, exfiltrate data, and deploy additional payloads, most notably Ryuk ransomware, in target networks."
Typically delivered via phishing campaigns that leverage current events or financial lures to entice users into open malicious file attachments or click links to websites hosting the malware, TrickBot has also been deployed as a second-stage payload of another nefarious botnet called Emotet.
The cybercrime operation has infected over a million computers to date.
Microsoft, however, cautioned that it did not expect the latest action to permanently disrupt TrickBot, adding that the cybercriminals behind the botnet will likely make efforts to revive their operations.
According to Swiss-based Feodo Tracker, eight TrickBot control servers, some of which were first seen last week, are still online after the takedown.
Tech Companies Take Down TrickBot Botnet Infrastructure
12.10.20 BotNet Securityweek
Microsoft on Monday revealed that it worked together with industry partners to shut down the infrastructure used by TrickBot operators and block efforts to revive the botnet.
The Washington Post reported last week that the U.S. Cyber Command too attempted to hack TrickBot's C&C servers, in an attempt to take the botnet down to prevent attacks seeking to disrupt the U.S. presidential elections. This is said to have been a separate operation that was not coordinated with Microsoft.
TrickBot emerged in 2016 as a banking Trojan, supposedly from the same group that operated the Dyre Trojan, and has become one of the most prevalent threats out there, with more than one million infected machines all around the world.
Over time, TrickBot has received updates that expanded its capabilities, evolved into a modular threat that ensnared computers into a botnet being offered under a malware-as-a-service model. Both nation-states and criminal networks are believed to have employed it for nefarious purposes.
The network of infected machines has been leveraged in malicious campaigns aimed at stealing credentials and data, and delivering additional malware, such as the Ryuk ransomware.
TrickBot has been distributed in email campaigns that leveraged current events as lures, with malicious documents attached. The attacks targeted a wide range of verticals in numerous regions, Microsoft says. Other distribution methods included lateral movement via Server Message Block (SMB), or deployment via other malware, such as Emotet.
“Over the years we’ve tracked it, Trickbot compromises have been reported in a steady manner, making it one of the largest and longest-lived botnets out there. Trickbot is one of the most prevalent banking malware families, and this malware strain represents a threat for internet users globally,” Jean-Ian Boutin, Head of Threat Research at ESET, explains.
As part of one TrickBot attack, once the victim was enticed to open the malicious attachment, a script was executed to gather system information, perform queries to the affected organization’s domain controller, and gather data about the Active Directory.
Additional payloads were executed to eventually gain control over the affected system, gather information on potentially high-value devices on the network, and move laterally. TrickBot was used to steal credentials from the Windows Vault and Credentials Manager, so that security mechanisms could be evaded. The attackers added the initial script to Startup for persistence.
Microsoft says that its investigation into TrickBot involved the analysis of roughly 61,000 malware samples, which revealed constantly evolving modular capabilities, and support for infecting Internet of Things (IoT) devices.
Various TrickBot modules are meant for banking credentials theft, reconnaissance, data theft, password grabbing, cookies theft, information stealing, point-of-sale reconnaissance, remote control, SMB spreading, Outlook theft, lateral movement, and RDP brute-force.
Microsoft notes that it managed to disrupt TrickBot’s infrastructure “after United States District Court for the Eastern District of Virginia granted our request for a court order to halt Trickbot’s operations.”
The company worked together with industry partners to take action against TrickBot, and received help from the Financial Services Information Sharing and Analysis Center (FS-ISAC), ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom-owned Symantec. Internet service providers (ISPs) and computer emergency readiness teams (CERTs) around the world were also contacted, to help with remediation efforts.
“The court granted approval for Microsoft and our partners to disable the IP addresses, render the content stored on the command and control servers inaccessible, suspend all services to the botnet operators, and block any effort by the Trickbot operators to purchase or lease additional servers,” Microsoft says.
The company expects that TrickBot’s operators will attempt to revive their operation, but says that it will work with its partners to monitor such activities and take further action when necessary. The malware has various fallback mechanisms and its operators are connected to other highly active cybercriminal actors, which made the disruption difficult, ESET notes.
As Symantec explains, the takedown “relied upon intellectual-property laws to effectively evict the botnet operators from the command-and-control servers they need to maintain access to victim machines.”
C&C Panels of 10 IoT Botnets Compromised by Researchers
9.10.20 BotNet Securityweek
At the Virus Bulletin Conference last week, two security researchers explained how they were able to compromise the command and control (C&C) panels of 10 Internet of Things (IoT) botnets.
The researchers, Aditya K. Sood of F5 Networks and Rohit Bansal of SecNiche Security Labs, revealed at the online conference that they were able to access the C&C panels of the Mana, Vivid, Kawaii, Verizon, Goon, 911-Net, Purge Net, Direct, 0xSec, and Dark botnets.
According to Sood and Bansal, possible approaches to such compromise would first involve mapping the remote servers that are distributing binaries, or extracting the binaries dropped onto compromised IoT devices, and then extracting the hardcoded IP addresses from these files, to learn where those panels are located.
However, it is also possible to extract artefacts from network traffic, including IP addresses, or even extract C&C information from malicious processes running on the compromised devices (effective if the address is generated on the fly).
One other approach involves mass scanning the Internet for potentially suspicious IoT devices, finding exposed administrative interfaces and attempting to compromise them to extract information on C&C servers. Scanning for remote servers based on known indicators is also possible.
The next step after identifying the attacker’s server is accessing the C&C panel, which can be done through the frontend admin interface by brute-forcing credentials. Access can also be obtained by compromising a backend database to gain access to administrative credentials, finding and exploiting vulnerabilities in the C&C panel, or using cracked credentials, the researchers said.
In the event that the C&C interface cannot be breached, one could also attempt to crash the server, or kill it. By analyzing the source code of botnet malware, such as that for Mirai, which is available online, one could identify the buffer allocation for various functions, discover vulnerable ones to trigger overflows, craft a buffer and then send it to the target to see if the crash happens.
At the VB 2020 conference, the two researchers revealed that they used these approaches to access the C&C panels of the aforementioned IoT botnets, which then allowed them to learn more about the capabilities of these threats and the manner in which they are operated.
They obtained information on the commands supported by the botnets, the various options available for administrators, including those employed for launching distributed denial of service (DDoS) or similar attacks, as well as the similarities and differences between the different panels.
The two researchers also detailed specific techniques which, they say, could be used to create additional attack scenarios, not only to hack back at IoT botnets, but also to build defensive measures against them.
In fact, they argue, compromising these C&C panels is highly important for gathering threat intelligence and building defenses against IoT botnets, pointing out that otherwise it would be difficult to understand how exactly the botnets operate.
HEH P2P Botnet Sports Dangerous Wiper Function
9.10.20 BotNet Threatpost
The P2P malware is infecting any and all types of endpoints via brute-forcing, with 10 versions targeting desktops, laptops, mobile and IoT devices.
A freshly discovered botnet dubbed HEH by researchers is casting a wide net, looking to infect any and all devices that use Telnet on ports 23/2323. It’s particularly destructive: It contains code that wipes all data from infected systems.
Perhaps ironically, its operators also have a penchant for civil advocacy – a loading of the Universal Declaration of Human Rights, visible to researchers during analysis, accompanies each infection.
Threatpost Webinar Promo Retail Security
Click to Register!
According to a 360Netlab analysis, samples of the bot are being found on a wide range of CPU architectures, including x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III) and PPC – meaning it’s infecting desktops, laptops, mobile and internet-of-things (IoT) devices. It’s looking to brute-force Telnet credentials, and once in, it infects the target with a Go language binary that communicates with other bot nodes using a proprietary peer-to-peer protocol, researchers said.
Craig Young, computer security researcher for Tripwire’s vulnerability and exposure research team (VERT), noted that the use of Golang is an ongoing trend in malware development.
“Golang has been steadily rising in popularity including among IoT malware authors,” he said via email. “Go offers a strong feature set with the ability to easily produce self-contained executables across most popular architectures. This marks a shift from IoT malware like Mirai which uses C to produce very compact binaries compared to a Go executable.”
From a technical perspective, the botnet, which gets its name from phrasing inside the code samples, contains three functional modules, according to 360Netlab: A propagation module, a local HTTP service module and the P2P module.
Infection Routine
Once a device has been successfully brute-forced (its dictionary includes 171 usernames and 504 passwords), a malicious shell script named wpqnbw.txt is executed on the host, according to the analysis. This propagation module is an initial loader, which goes on to download and execute multiple versions of the second-stage binaries – one for each possible device type.
The malicious scripts and binary programs are fetched from a legitimate pomf.cat site, which has been compromised, researchers explained.
“[There are downloads for] every single one of the malicious programs, for all different CPU architectures, there is no environment checking or things like that, [it] just run[s] all the programs in turn,” explained 360Netlab researchers, in a posting this week.
After the correct version of the code for the CPU architecture is determined, the sample is started. It first starts an HTTP server on the local port :80, researchers said – which is where the human-rights angle comes in.
“The initial state of this HTTP server will be set :80/0 to :80/9 a total of 10 URIs,” according to the post. “Correspondingly, the Universal Declaration of Human Rights in eight languages – and two empty contents – are displayed. For example, the :80/0 returns the Chinese version of the Universal Declaration of Human Rights.”
After this, the sample pulls data for the P2P module over the port, which overwrites the declaration. This is where the botnet gets down to business.
P2P Module
In a P2P botnet, each node (a.k.a. “peer”) has the capability to talk to other peers by what’s known as a ping-pong mechanism. Through this, peers share the own command-and-control functions in a distributed way; maintain their own lists of other peers; and can spread other payloads or components to each other.
In the case of HEH, the P2P module itself includes three components, starting with one that pings for all other nodes (peers) in the botnet at 0.1-second intervals (via a UDP service port) and waits for a pong back; and one that updates the node with the latest peer addresses.
On the latter front, this peer update component receives commands every 10 seconds containing new peer addresses; the node will check whether its peer list already contains the peer address information, and if not, adds it to its peer list.
The third component, a UDP service component, does most of the work, researchers explained: It monitors data or instructions sent by other peers, analyzes the instructions and performs corresponding operations.
“This component has two key functions: UDP service port number generation and command parsing,” according to 360Netlab.
For the former, “the UDP service port of HEH botnet is not fixed, nor is it randomly generated, but is calculated based on [the] peer’s own public network IP,” explained the firm. “Each time HEH bot receives a new peer’s IP address, it will calculate the peer’s UDP port according to the algorithm, and pack this information into its peer list.”
Meanwhile, the instructions that the HEH bot can parse come from a command-and-control server (C2), meaning that the botnet isn’t a true P2P architecture – yet.
“The P2P implementation still has flaws,” the researchers said. “The bot does maintain a peer list internally, and there is ongoing Ping<–>Pong communication between peers, but the entire botnet still is considered centralized, as currently the bot node cannot send control commands.”
Commands and Self-Destruction
The commands that peers can parse are divided into two categories: P2P protocol-related functional instructions, which essentially keep the node updated and continuously connected to other peers; and a module responsible for control instructions (“Bot Cmd”).
The Bot Cmd list supported by HEH bot includes commands for restarting or exiting; executing shell commands; updating the peer list; updating the malware itself; and, crucially, something called “SelfDestruct,” which is the wiper function.
SelfDestruct, which is command No. 8, will tell the bot to wipe out everything on all the disks on the host. Wipers like this are usually seen targeting critical infrastructure and nation-state types of targets, which makes this aspect of HEH stand out.
Two other commands, “launch attacks” and “Misc,” are listed but not implemented in the samples analyzed by 360Netlab – potentially meaning that the botnet is still in the development stages. That’s not to say it doesn’t pose a threat.
“The operating mechanism of this botnet is not yet mature,” researchers noted. “With that being said, the new and developing P2P structure, the multiple CPU architecture support, the embedded self-destruction feature, all make this botnet potentially dangerous.”
It’s unclear how many devices make up the botnet, or if the operators have hit the self-destruct button on any of them yet. Threatpost has reached out to 360Netlab for more information.
Users can protect themselves by making sure Telnet ports 23/2323 aren’t open to the public internet, and by ensuring strong passwords on devices.
P2P Botnets on the Rise
P2P architectures are attractive for botnets because they introduce redundancy and decentralization, making them difficult to dismantle. Also, a single communication to a single node is all it takes to propagate a new command or feature, allowing operators more opportunities for stealth when it comes to their control infrastructure.
As such, P2P botnets have been on the rise. For instance, the coin-mining botnet known as DDG for instance adopted a proprietary peer-to-peer (P2P) mechanism in April that has turned the DDG into a highly sophisticated, “seemingly unstoppable” threat, according to researchers.
Meanwhile, in September, news came that the Mozi botnet, a P2P malware known previously for taking over Netgear, D-Link and Huawei routers, has swollen in size to account for 90 percent of observed traffic flowing to and from all IoT devices, according to researchers.
And in October, a new variant of the InterPlanetary Storm P2P botnet emerged, which comes with fresh detection-evasion tactics and now targets Mac and Android devices (in addition to Windows and Linux, which were targeted by previous variants of the malware).
ALERT! Hackers targeting IoT devices with a new P2P botnet malware
8.10.20 BotNet IoT Thehackernews
Cybersecurity researchers have taken the wraps off a new botnet hijacking Internet-connected smart devices in the wild to perform nefarious tasks, mostly DDoS attacks, and illicit cryptocurrency coin mining.
Discovered by Qihoo 360's Netlab security team, the HEH Botnet — written in Go language and armed with a proprietary peer-to-peer (P2P) protocol, spreads via a brute-force attack of the Telnet service on ports 23/2323 and can execute arbitrary shell commands.
The researchers said the HEH botnet samples discovered so far support a wide variety of CPU architectures, including x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III), and PowerPC (PPC).
The botnet, despite being in its early stages of development, comes with three functional modules: a propagation module, a local HTTP service module, and a P2P module.
Initially downloaded and executed by a malicious Shell script named "wpqnbw.txt," the HEH sample then uses the Shell script to download rogue programs for all different CPU architectures from a website ("pomf.cat"), before eventually terminating a number of service processes based on their port numbers.

The second phase commences with the HEH sample starting an HTTP server that displays the Universal Declaration of Human Rights in eight different languages and subsequently initializing a P2P module that keeps track of the infected peers and allows the attacker to run arbitrary shell commands, including the ability to wipe all data from the compromised device by triggering a self-destruct command.
Other commands make it possible to restart a bot, update the list of peers, and exit the current running bot, although an "Attack" command is yet to be implemented by the botnet authors.
"After the Bot runs the P2P module, it will execute the brute-force task against the Telnet service for the two ports 23 and 2323 in a parallel manner, and then complete its own propagation," the researchers said.
In other words, if the Telnet service is opened on port 23 or 2323, it attempts a brute-force attack using a password dictionary consisting of 171 usernames and 504 passwords. On a successful break-in, the newly infected victim is added to the botnet, thereby amplifying it.
"The operating mechanism of this botnet is not yet mature, [and] some important functions such as the attack module have not yet been implemented," the researchers concluded.
"With that being said, the new and developing P2P structure, the multiple CPU architecture support, the embedded self-destruction feature, all make this botnet potentially dangerous."
Tenda Router Zero-Days Emerge in Spyware Botnet Campaign
6.10.20 BotNet Threatpost
A variant of the Mirai botnet, called Ttint, has added espionage capabilities to complement its denial-of-service functions.
Two former Tenda router zero-days are anchoring the spread of a Mirai-based botnet called Ttint. In addition to denial-of-service (DoS) attacks, this variant also has remote-access trojan (RAT) and spyware capabilities.
According to 360Netlab, the botnet is unusual in a few ways. For one, on the RAT front, researchers said that it implements 12 remote access functions, that combine with custom command-and-control (C2) server commands to carry out tasks like setting up a Socket5 proxy for router devices, tampering with router DNS, setting iptables and executing custom system commands.
In addition, Ttint also uses encrypted channels to communicate with the C2 – specifically, using the WebSocket over TLS (WSS) protocol. Researchers said that this allows the traffic to avoid detection while providing additional security.
And finally, the infrastructure seems to migrate. 360Netlab first observed the attackers using a Google cloud service IP, before switching to a hosting provider in Hong Kong.
Zero-Days
Tenda routers are available at big-box stores and are used in homes and small offices. The first vulnerability used to spread Ttint samples (CVE-2018-14558) has been exploited since at least November of last year; but it wasn’t disclosed until July. There’s now a firmware update available to address it.
The bug is a critical command-injection vulnerability, rated 9.8 out of 10 on the CvSS vulnerability-severity scale. It allows attackers to execute arbitrary OS commands via a crafted goform/setUsbUnload request. It arises because the “formsetUsbUnload” function executes a dosystemCmd function with untrusted input.
In late August, a second critical Tenda router vulnerability (CVE-2020-10987) emerged in the campaign. It’s also rated 9.8 out of 10 and was initially disclosed in July by Independent Security Evaluators, after it had tried since January to get a patch from Tenda. It was able to exploit the bug in order to cause a DoS condition.
The bug exists because the goform/setUsbUnload endpoint of Tenda AC15 AC1900 version 15.03.05.19 allows remote attackers to execute arbitrary system commands via the deviceName POST parameter, according to the CVE description.
360Netlab also tried to warn Tenda about issues with the bug, this time for use in botnet infections.
“On August 28, 2020, we reported the details of the second 0-day vulnerability and the PoC [proof of concept] to the router manufacturer Tenda via email, but the manufacturer has not yet responded,” researchers said.
Threatpost has reached out to the manufacturer for more information.
Ttint RAT
Ttint as a malware can carry out 10 typical Mirai DDoS attack instructions (including multiple attack vectors), along with 12 RAT instructions and 22 custom C2 commands that work together.
“Generally speaking, at the host level, Ttint’s behavior is relatively simple,” according to the researchers. “When running, it deletes its own files, manipulates the watchdog and prevents the device from restarting, it runs as a single instance by binding the port; then modifies the process name to confuse the user…it finally establishes a connection with the decrypted C2, reporting device information, waiting for C2 to issue instructions, and executing corresponding attacks or custom functions.”
Researchers said, among the most notable of the RAT functions is the command to bind a specific port issued by C2 to enable Socket5 proxy service. This allows attackers to remotely access the router’s intranet, and roam across the network.
“Generally speaking, Ttint will combine multiple custom functions to achieve specific attack goals,” the researchers explained. “Take the two adjacent commands we captured, the first command is iptables -I INPUT -p tcp –dport 51599 -j ACCEPT, to allow access to port 51599 of the affected device. The next command is to enable the Socket5 proxy function on port 51599 of the affected device. The combination of the two commands enabled and allowed the attacker to use the Socket5 proxy.”
Another command tells the malware to tamper with the router DNS by modifying the resolv.conf file, allowing it to hijack the network access of any of the router’s users. This in turn allows attackers to monitor or steal sensitive information.
Meanwhile, by setting iptables up, the operators can achieve traffic forwarding and target address conversion, which could expose internal network services and lead to information disclosure. And, by implementing a reverse shell through socket, the author of Ttint can operate the shell of the affected routing device as a local shell.
And finally, the custom commands also allow the malware to self-update and self-destruct.
The C2 information of the Ttint Bot sample is encrypted and stored in the configuration information table in the Mirai format, protected with a XOR key, researchers said.
“When the bot is running, it decrypts to obtain the C2 address,…and then communicates with C2 securely through the WebSocket over TLS protocol,” according to the researchers. “When Ttint C2 replies to the bot with a response code of 101, it means that the protocol handshake is completed, and then the bot can communicate using the WebSocket protocol.”
There has of late been a resurgence of Mirai-based malware capable of building large botnets through the exploitation of poorly secured IoT devices. This has contributed to a significant uptick in the number of distributed denial-of-service (DDoS) attacks in the first half of the year, compared to the same period last year. The addition of the RAT and concerning C2 commands marks a change for the Mirai world, however.
“Two zero-days, 12 remote-access functions for the router, encrypted traffic protocol and infrastructure IP that that moves around,” the firm wrote in a recent blog. “This botnet does not seem to be a very typical player.”
Ttint Botnet Targets Zero-Day Vulnerabilities in Tenda Routers
6.10.20 BotNet Securityweek
A new Mirai-based botnet is targeting zero-day vulnerabilities in Tenda routers, according to researchers at 360 Netlab, a unit of Chinese cybersecurity company Qihoo 360.
Dubbed Ttint, the Remote Access Trojan (RAT) contains distributed denial of service capabilities, just as any Mirai offspring does, but also implements 12 remote access functions, including a Socket5 proxy, modifying router DNS and iptables, and running system commands.
In order to circumvent detection of typical traffic generated by Mirai botnets, Ttint uses the WSS (WebSocket over TLS) protocol for communication with the command and control (C&C) server, and also uses encryption.
The botnet’s activity was initially detected in November 2019, when the attackers started abusing the first zero-day vulnerability in Tenda routers (CVE-2020-10987). The second bug started being exploited in August 2020, but 360 Netlab says the vendor has not responded to its emails reporting the flaw.
“We analyzed and compared Ttint samples in the two periods and found that their C2 instructions were exactly the same, but they had some differences in the 0-day vulnerability, XOR Key, and C2 protocol used,” 360 Netlab says.
Ttint, the researchers say, has a relatively simple behavior, where it deletes its own files when running, modifies its process name, manipulates the watchdog, and can prevent device restarts. After establishing a connection to the C&C, it sends device information and starts waiting for instructions.
The malware has many of the features previously observed in Mirai, such as a random process name, encryption of configuration information, support for multiple DDoS attack vectors, or the fact that only a single malware instance is running at a time. However, unlike Mirai, it uses the websocket protocol.
Functions implemented in Ttint allow attackers to remotely access the router's intranet, hijack network access to possibly steal sensitive information, set traffic forwarding rules, and leverage a reverse shell as a local shell. The malware can also update itself or kill its own process, and can execute commands issued by the C&C.
The threat supports a total of 22 commands, including many for launching DDoS attacks.
Tenda router users are advised to check the firmware on their devices and make sure that available updates are installed if necessary. They should also monitor and block the related IoCs shared by 360 Netlab.
New Ttint IoT botnet exploits two zero-days in Tenda routers
5.10.20 BotNet IoT Securityaffairs
Security researchers provided technical details about an IoT botnet dubbed Ttint that has been exploiting two zero-days in Tenda routers
Security researchers at Netlab, the network security division Qihoo 360, have published a report that details an IoT botnet dubbed Ttint.
The experts are monitoring the Mirai-based botnet since November 2019 and observed it exploiting two Tenda router 0-day vulnerabilities to spread a Remote Access Trojan (RAT).

Unlike other IoT DDoS botnets, Ttint implements 12 remote access functions such as Socket5 proxy for router devices, tampering with router firewall and DNS settings, executing remote custom system commands.
The botnet uses the WSS (WebSocket over TLS) protocol for C2 communication to circumvent the typical Mirai traffic detection and provide secure encrypted communication for command and control.
“About the infrastructure, the attacker first used a Google cloud service IP, and then switched to a hosting provider in Hong Kong” reads the analysis published by Netlab.
“Two zero days, 12 remote access functions for the router, encrypted traffic protocol, and infrastructure IP that that moves around. This botnet does not seem to be a very typical player.”
When the botnet was first detected in 2019, experts noticed it was exploiting the Tenda zero-day flaw tracked as CVE-2020-10987.
The vulnerability was detailed in July 2020 by the security researchers Sanjana Sarda.
On August 21, Netlab researchers observed the Ttint botnet exploiting a second zero-day flaw in the family of Tenda routers.
On August 28, 2020, Netlab reported the details of this second 0-day flaw and the PoC to Tenda, but the vendor has not yet responded.
According to the experts, Tenda routers running a firmware version between AC9 to AC18 are vulnerable to the attack.
The report published by Netlab includes Indicators of Compromise (IoCs).
“We recommend that Tenda router users check their firmware and make necessary update.” concludes the report. “We also recommend that our readers monitor and block related IoCs.”
IPStorm botnet evolves to infect Android, Linux, and Mac devices
3.10.20 BotNet Securityaffairs
Researchers from Intezer reported that the IPStorm botnet has evolved to infect other operating systems, including Android, Linux, and Mac devices.
The IPStorm botnet was first uncovered in May 2019 while targeting Windows systems, not experts from Intezer reported that the bot evolved to infect other platforms, including Android, Linux, and Mac devices.
IPStorm botnet continues to infect systems across the world, its size passed from around 3,000 infected systems in May 2019 to more than 13,500 devices this month.
The name IPStorm is the abbreviation of InterPlanetary Storm that came from the InterPlanetary File System (IPFS), which is a peer-to-peer protocol used by the bot for communications with the intent to obscure the malicious traffic.
The bot was written in the Go programming language, it was initially designed to compromise Windows systems only. In June security firms Bitdefender and Barracuda discovered new IPStorm versions that are able to target also Android, Linux, and Mac.
The experts from both security firms reported that IPStorm was infecting Android systems with ADB (Android Debug Bridge) port exposed online.
The bot was also targeting Linux and Mac devices performs dictionary attacks against SSH services to guess their username and passwords.
Once a connection is established, the malware will check the presence of a honeypot by comparing the hostname of the attacked server to the string “svr04”, which is the default hostname of Cowrie SSH honeypot.
“The Linux variant has additional features over the documented Windows version, such as using SSH brute-force as a means to spread to additional victims and fraudulent network activity abusing Steam gaming and advertising platforms.” reads the Intezer’s report. “The Linux variant has adjusted some features in order to account for the fundamental differences that exist between this operating system and Windows.”
The IPStorm bot also kills a list of processes that could potentially interfere with its operations.
Experts noticed that IPStorm versions for both Linux and Windows systems implement a reverse shell mechanism.
“The Windows variant has a package called powershell which contains functions for achieving reverse shell. The same package is present in the Linux variant but it contains only one function: storm_powershell__ptr_Backend_StartProcess. The function is used to get a reverse shell on the infected system.” continues the analysis.

Curiously, until now, the researchers have not seen the IPStorm operators doing malicious activities, such as performing DDoS attacks or relaying malicious traffic.
“Platforms that are compromised by IPStorm are not only exposed to a backdoor to their services but are also added to the IPStorm Botnet which attempts to spread to other victims.” concludes Intezer. “The attackers behind IPStorm are very active evidenced by the frequent release of updated versions with new features and improvements, as well as the expansion to several different platforms and architectures.”
InterPlanetary Storm Botnet Infects 13K Mac, Android Devices
2.10.20 BotNet Threatpost
In addition to Windows and Linux machines, a new variant of the malware now targets Mac and Android devices.
A new variant of the InterPlanetary Storm malware has been discovered, which comes with fresh detection-evasion tactics and now targets Mac and Android devices (in addition to Windows and Linux, which were targeted by previous variants of the malware).
Researchers say, the malware is building a botnet with a current estimated 13,500 infected machines across 84 countries worldwide – and that number continues to grow. Half of the infected machines are in Hong Kong, South Korea and Taiwan. Other infected systems are in Russia, Brazil, the U.S., Sweden and China.
“While the botnet that this malware is building does not have clear functionality yet, it gives the campaign operators a backdoor into the infected devices so they can later be used for cryptomining, DDoS, or other large-scale attacks,” said researchers with Barracuda in a Thursday analysis.
The first variant of InterPlanetary Storm was discovered in May 2019 and targeted Windows machines. In June, a variant targeting Linux machines was also reported targeting IoT devices, such as TVs that run on Android operating systems, and Linux-based machines, such as routers with ill-configured SSH service.
The botnet, which is written in Go, uses the Go implementation of libp2p, which is a network framework that allows users to write decentralized peer-to-peer (P2P) applications. This framework was originally the networking protocol of InterPlanetary File System (IPFS), on which researchers based the malware’s name.
“The malware is called InterPlanetary Storm because it uses the InterPlanetary File System (IPFS) p2p network and its underlying libp2p implementation,” said researchers. “This allows infected nodes to communicate with each other directly or through other nodes (i.e. relays).”
The malware spreads via brute force attacks on devices with Secure Shell (SSH), a cryptographic network protocol for operating network services securely over an unsecured network. Researchers noted this is similar to FritzFrog, another P2P malware. Another method of infection is by accessing open Apple Desktop Bus (ADB) ports, which connect low-speed devices to computers.
“The malware detects the CPU architecture and running OS of its victims, and it can run on ARM-based machines, an architecture that is quite common with routers and other IoT devices,” said researchers.

Machines infected worldwide by Interplanetary botnet. Credit: Barracuda
The newest variant of the malware has various big changes, most notably extending its targeting to include Mac and Android devices. However, the new variant can also auto-update to the latest available malware version and kill other processes on the machine that present a threat, like debuggers or competing malware (by looking at strings such as “rig,” “xig” and “debug”).
And, it now can detect honeypots by looking for the string “svr04” in the default shell prompt, for instance.
Once infected, devices communicate with the command-and-control (C2) server to inform that they are part of the botnet. Researchers said, the IDs of each infected machine are generated during initial infection and will be reused if the machine restarts or the malware updates. Once downloaded, it also serves malware files to other nodes in the network. The malware also enables reverse shell and can run bash shell, said researchers.
“Libp2p applications handle incoming connection (streams) based on a logical address (i.e. unknown to the transport layer) called protocol ID,” said researchers. “By convention, protocol ids have a path-like structure, with a version number as the final component.”
Botnets – particularly P2P botnets like Mozi, Roboto and DDG – continue to appear in the threat landscape. To avoid infection, researchers suggest end users properly configure SSH access on all devices and use a cloud security posture management tool to monitor SSH access control, eliminating any potential configuration mistakes.
“When password login is enabled and the service itself is accessible, the malware can exploit the ill-configured attack surface,” they said. “This is an issue common with routers and IoT devices, so they make easy targets for this malware.”
Spammers Smuggle LokiBot Via URL Obfuscation Tactic
2.10.20 BotNet Threatpost
Researchers say that the campaign sidesteps end user detection and security solutions.
Spammers have started using a tricky URL obfuscation technique that sidesteps detection – and ultimately infects victims with the LokiBot trojan.
The tactic was uncovered in recent spear-phishing emails with PowerPoint attachments, which contain a malicious macro. When the PowerPoint file is opened, the document attempts to access a URL via a Windows binary (mshta.exe), and this leads to various malware being installed onto the system.
This process is not unusual for macro downloaders. However, because the domains associated with the campaign are already known to host malicious files and data, the attackers used a unique semantic attack on the campaign’s URLs to trick the email recipient and avoid being flagged by email and AV scanners. A semantic URL attack is when a client manually adjusts the parameters of its request by maintaining the URL’s syntax – but altering its semantic meaning. More on that, below.
“We found it interesting that the attackers were using URIs in this way, which essentially is an attack on the user’s preconceived notion of what a URI should look like,” said researchers with Trustwave in a Thursday report. “It may also defeat security solutions, which may be expecting URIs in a certain format.”
The malicious email that was observed by researchers is titled: “URGENT: REQUEST FOR OFFER (University of Auckland)” and the attached PowerPoint is titled “Request For Offer.” The University of Auckland is a public research university in Auckland, New Zealand. Threatpost has reached out to Trustwave for further details on the targeting and lure of this attack.
Obfuscation Tactic
It’s important to distinguish between a URL versus URI here. A URI is an identifier of a specific resource, such as a page, book or a document. A URL, meanwhile, is the most common type of URI that also tells users how to access it (such as HTTPs or FTP).
A URI is made up of a scheme, host and path. The scheme identifies the protocol to be used to access the resource on the internet, while the host identifies the host that holds the resource, and the path identifies the specific resource in the host that the web client wants to access.

The spear phishing email lure. Credit: Trustwave
The spammers behind this attack have horned in on one component of the URI scheme called an Authority component, which holds an optional user-information part. If the “userinfo” subcomponent is present, it is preceded by two slashes and followed by an “@” character. An example of this Authority structure is as follows: authority = [userinfo@]host[:port].
Because “userinfo” is not commonly used, it is sometimes ignored by servers, researchers said. In this specific campaign, attackers took advantage of this fact, utilizing what researchers called a “dummy” userinfo in order to hide their true intent.
The end result is that at face value, end users who click on the link may believe they are being led to one domain, but the URL is actually for another.
In this specific campaign, the URL used (j[.]mp/kassaasdskdd) actually utilizes a URL shortening service offered by Bit.ly and leads to Pastebin, which is a website that allows users to share plain text through public posts called “pastes.” Both the use of URL shortening services and Pastebin are commonly leveraged by cybercriminals; so to avoid being characterized as a short URL and to evade detection signatures, the attackers repeatedly use a randomized, short string (“%909123id”) in the userinfo portion of their URL (see picture below).
Because userinfo is not required to gain access to any resources, the userinfo data will be ignored when the URL is accessed – meaning that at face value, it’s unclear that the URL is shortened, and will redirect the users to Pastebin despite security gates.
“The bad guys are attempting to make the domains unnoticeable yet still conforming with the generic URI syntax,” said researchers.
The PowerPoint attachment and its macro code where the initial malicious URL is formulated. Credit: Trustwave
Researchers conducted a deeper analysis of four URLs associated in the campaign. The first URL, accessed by the PowerPoint attachment, redirects to an obfuscated VBScript hosted on Pastebin. A second URL contains VBScript, which is a dropper that writes a PowerShell downloader into the registry and sets up persistence, said researchers. This PowerShell then downloads and processes the raw data on two more Pastebin URLs, and then executes the output binaries, they said.
The content at the third URL meanwhile contains an obfuscated PowerShell code, which then executes two DotNet compiled Dynamic Link Libraries (DLLs). These DLLs bypass the Windows Anti-Malware Scan Interface (AMSI) on the machine, which is an interface standard allowing user applications and services to integrate with any anti-malware product on a machine.
They then load a DLL injector into the memory. Finally, the last URL contains an obfuscated malware LokiBot sample, which is injected into a legitimate process (notedpad.exe) by the aforementioned DLL injector.
LokiBot Malware
LokiBot is a prolific trojan that’s infamous for being simple and effective with its capabilities to covertly steal information from compromised endpoints. It’s currently being distributed in various forms that can hitch a ride inside other file formats—as is the case in the current campaign. Various versions of LokiBot also in the past were sold on underground markets for as little as $300.
The new tactic comes just a week after The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that LokiBot is seeing a surge across the enterprise landscape. The uptick started in July, according to the agency, and activity has remained “persistent” ever since.
“LokiBot has stolen credentials from multiple applications and data sources, including Windows operating system credentials, email clients, File Transfer Protocol and Secure File Transfer Protocol clients,” according to the alert, issued Tuesday. “LokiBot has [also] demonstrated the ability to steal credentials from…Safari and Chromium and Mozilla Firefox-based web browsers.”