BotNet 2024 2023 2022 2021 2020
New Malvertising Campaign Distributing PikaBot Disguised as Popular Software
19.12.23 BotNet The Hacker News
The malware loader known as PikaBot is being distributed as part of a malvertising campaign targeting users searching for legitimate software like AnyDesk.
"PikaBot was previously only distributed via malspam campaigns similarly to QakBot and emerged as one of the preferred payloads for a threat actor known as TA577," Malwarebytes' Jérôme Segura said.
The malware family, which first appeared in early 2023, consists of a loader and a core module that allows it to operate as a backdoor as well as a distributor for other payloads.
This enables the threat actors to gain unauthorized remote access to compromised systems and transmit commands from a command-and-control (C2) server, ranging from arbitrary shellcode, DLLs, or executable files, to other malicious tools such as Cobalt Strike.
One of the threat actors leveraging PikaBot in its attacks is TA577, a prolific cybercrime threat actor that has, in the past, delivered QakBot, IcedID, SystemBC, SmokeLoader, Ursnif, and Cobalt Strike.
Last month, it emerged that PikaBot, along with DarkGate, is being propagated via malspam campaigns mirror that of QakBot. "Pikabot infection led to Cobalt Strike on 207.246.99[.]159:443 using masterunis[.]net as its domain," Palo Alto Networks Unit 42 disclosed recently.
The latest initial infection vector is a malicious Google ad for AnyDesk that, when clicked by a victim from the search results page, redirects to a fake website named anadesky.ovmv[.]net that points to a malicious MSI installer hosted on Dropbox.
It's worth pointing out that the redirection to the bogus website only occurs after fingerprinting the request, and only if it's not originating from a virtual machine.
"The threat actors are bypassing Google's security checks with a tracking URL via a legitimate marketing platform to redirect to their custom domain behind Cloudflare," Segura explained. "At this point, only clean IP addresses are forwarded to the next step."
Interestingly, a second round of fingerprinting takes place when the victim clicks on the download button on the website, likely in an added attempt to ensure that it's not accessible in a virtualized environment.
Malwarebytes said the attacks are reminiscent of previously identified malvertising chains employed to disseminate another loader malware known as FakeBat (aka EugenLoader).
"This is particularly interesting because it points towards a common process used by different threat actors," Segura said. "Perhaps, this is something akin to 'malvertising-as-a-service' where Google ads and decoy pages are provided to malware distributors."
This disclosure comes as the cybersecurity company said it detected a spike in malicious ads through Google searches for popular software like Zoom, Advanced IP Scanner, and WinSCP to deliver a previously never-before-seen loader called HiroshimaNukes as well as FakeBat.
"It uses several techniques to bypass detection from DLL side-loading to very large payloads," Segura said. "Its goal is to drop additional malware, typically a stealer followed by data exfiltration."
The rise in malvertising is indicative of how browser-based attacks act as channels for infiltrating target networks. This also includes a new Google Chrome extension framework codenamed ParaSiteSnatcher, which allows threat actors to "monitor, manipulate, and exfiltrate highly sensitive information from multiple sources."
Specifically designed to compromise users in Latin America, the rogue extension is noteworthy for its use of the Chrome Browser API to intercept and exfiltrate all POST requests containing sensitive account and financial information. It's downloaded through a VBScript downloader hosted on Dropbox and Google Cloud and installed onto an infected system.
"Once installed, the extension manifests with the help of extensive permissions enabled through the Chrome extension, allowing it to manipulate web sessions, web requests, and track user interactions across multiple tabs using the Chrome tabs API," Trend Micro said last month.
"The malware includes various components that facilitate its operation, content scripts that enable malicious code injection into web pages, monitor Chrome tabs, and intercept user input and web browser communication."
New KV-Botnet Targeting Cisco, DrayTek, and Fortinet Devices for Stealthy Attacks
16.12.23 BotNet The Hacker News
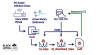
A new botnet consisting of firewalls and routers from Cisco, DrayTek, Fortinet, and NETGEAR is being used as a covert data transfer network for advanced persistent threat actors, including the China-linked threat actor called Volt Typhoon.
Dubbed KV-botnet by the Black Lotus Labs team at Lumen Technologies, the malicious network is an amalgamation of two complementary activity clusters that have been active since at least February 2022.
"The campaign infects devices at the edge of networks, a segment that has emerged as a soft spot in the defensive array of many enterprises, compounded by the shift to remote work in recent years," the company said.
The two clusters – codenamed KY and JDY – are said to be distinct yet working in tandem to facilitate access to high-profile victims as well as establish covert infrastructure. Telemetry data suggests that the botnet is commandeered from IP addresses based in China.
While the bots part of JDY engages in broader scanning using less sophisticated techniques, the KY component, featuring largely outdated and end-of-life products, is assessed to be reserved for manual operations against high-profile targets selected by the former.
It's suspected that Volt Typhoon is at least one user of the KV-botnet and it encompasses a subset of their operational infrastructure, which is evidenced by the noticeable decline in operations in June and early July 2023, coinciding with the public disclosure of the adversarial collective's targeting of critical infrastructure in the U.S.
Microsoft, which first exposed the threat actor's tactics, said it "tries to blend into normal network activity by routing traffic through compromised small office and home office (SOHO) network equipment, including routers, firewalls, and VPN hardware."
The exact initial infection mechanism process used to breach the devices is currently unknown. It's followed by the first-stage malware taking steps to remove security programs and other malware strains so as to ensure that it's the "only presence" on these machines.
It's also designed to retrieve the main payload from a remote server, which, in addition to beaconing back to the same server, is also capable of uploading and downloading files, running commands, and executing additional modules.
Over the past month, the botnet's infrastructure has received a facelift, targeting Axis IP cameras, indicating that the operators could be gearing up for a new wave of attacks.
"One of the rather interesting aspects of this campaign is that all the tooling appears to reside completely in-memory," the researchers said. "This makes detection extremely difficult, at the cost of long-term persistence."
"As the malware resides completely in-memory, by simply power-cycling the device the end user can cease the infection. While that removes the imminent threat, re-infection is occurring regularly."
The findings arrive as The Washington Post reported that two dozen critical entities in the U.S. have been infiltrated by Volt Typhoon over the past year, including power and water utilities as well as communications and transportation systems.
"The hackers often sought to mask their tracks by threading their attacks through innocuous devices such as home or office routers before reaching their victims," the report added.
New P2PInfect Botnet MIPS Variant Targeting Routers and IoT Devices
5.12.23 BotNet The Hacker News
Cybersecurity researchers have discovered a new variant of an emerging botnet called P2PInfect that's capable of targeting routers and IoT devices.
The latest version, per Cado Security Labs, is compiled for Microprocessor without Interlocked Pipelined Stages (MIPS) architecture, broadening its capabilities and reach.
"It's highly likely that by targeting MIPS, the P2PInfect developers intend to infect routers and IoT devices with the malware," security researcher Matt Muir said in a report shared with The Hacker News.
P2PInfect, a Rust-based malware, was first disclosed back in July 2023, targeting unpatched Redis instances by exploiting a critical Lua sandbox escape vulnerability (CVE-2022-0543, CVSS score: 10.0) for initial access.
A subsequent analysis from the cloud security firm in September revealed a surge in P2PInfect activity, coinciding with the release of iterative variants of the malware.
The new artifacts, besides attempting to conduct SSH brute-force attacks on devices embedded with 32-bit MIPS processors, pack in updated evasion and anti-analysis techniques to fly under the radar.
The brute-force attempts against SSH servers identified during the scanning phase are carried out using common username and password pairs present within the ELF binary itself.
It's suspected that both SSH and Redis servers are propagation vectors for the MIPS variant owing to the fact that it's possible to run a Redis server on MIPS using an OpenWrt package known as redis-server.
One of the notable evasion methods used is a check to determine if it's being analyzed and, if so, terminate itself, as well as an attempt to disable Linux core dumps, which are files automatically generated by the kernel after a process crashes unexpectedly.
The MIPS variant also includes an embedded 64-bit Windows DLL module for Redis that allows for the execution of shell commands on a compromised system.
"Not only is this an interesting development in that it demonstrates a widening of scope for the developers behind P2PInfect (more supported processor architectures equals more nodes in the botnet itself), but the MIPS32 sample includes some notable defense evasion techniques," Cado said.
"This, combined with the malware's utilization of Rust (aiding cross-platform development) and rapid growth of the botnet itself, reinforces previous suggestions that this campaign is being conducted by a sophisticated threat actor."
GoTitan Botnet Spotted Exploiting Recent Apache ActiveMQ Vulnerability
29.11.23 BotNet The Hacker News
The recently disclosed critical security flaw impacting Apache ActiveMQ is being actively exploited by threat actors to distribute a new Go-based botnet called GoTitan as well as a .NET program known as PrCtrl Rat that's capable of remotely commandeering the infected hosts.
The attacks involve the exploitation of a remote code execution bug (CVE-2023-46604, CVSS score: 10.0) that has been weaponized by various hacking crews, including the Lazarus Group, in recent weeks.
Following a successful breach, the threat actors have been observed to drop next-stage payloads from a remote server, one of which is GoTitan, a botnet designed for orchestrating distributed denial-of-service (DDoS) attacks via protocols such as HTTP, UDP, TCP, and TLS.
"The attacker only provides binaries for x64 architectures, and the malware performs some checks before running," Fortinet Fortiguard Labs researcher Cara Lin said in a Tuesday analysis.
"It also creates a file named 'c.log' that records the execution time and program status. This file seems to be a debug log for the developer, which suggests that GoTitan is still in an early stage of development."

Fortinet said it also observed instances where the susceptible Apache ActiveMQ servers are being targeted to deploy another DDoS botnet called Ddostf, Kinsing malware for cryptojacking, and a command-and-control (C2) framework named Sliver.
Another notable malware delivered is a remote access trojan dubbed PrCtrl Rat that establishes contact with a C2 server to receive additional commands for execution on the system, harvest files, and download and upload files from and to the server.
"As of this writing, we have yet to receive any messages from the server, and the motive behind disseminating this tool remains unclear," Lin said. "However, once it infiltrates a user's environment, the remote server gains control over the system."
Mirai-based Botnet Exploiting Zero-Day Bugs in Routers and NVRs for Massive DDoS Attacks
24.11.23 BotNet The Hacker News
An active malware campaign is leveraging two zero-day vulnerabilities with remote code execution (RCE) functionality to rope routers and video recorders into a Mirai-based distributed denial-of-service (DDoS) botnet.
"The payload targets routers and network video recorder (NVR) devices with default admin credentials and installs Mirai variants when successful," Akamai said in an advisory published this week.
Details of the flaws are currently under wraps to allow the two vendors to publish patches and prevent other threat actors from abusing them. The fixes for one of the vulnerabilities are expected to be shipped next month.
The attacks were first discovered by the web infrastructure and security company against its honeypots in late October 2023. The perpetrators of the attacks have not been identified as yet.
The botnet, which has been codenamed InfectedSlurs due to the use of racial and offensive language in the command-and-control (C2) servers and hard-coded strings, is a JenX Mirai malware variant that came to light in January 2018.
Akamai said it also identified additional malware samples that appeared to be linked to the hailBot Mirai variant, the latter of which emerged in September 2023, according to a recent analysis from NSFOCUS.
"The hailBot is developed based on Mirai source code, and its name is derived from the string information 'hail china mainland' output after running," the Beijing-headquartered cybersecurity firm noted, detailing its ability to propagate via vulnerability exploitation and weak passwords.
The development comes as Akamai detailed a web shell called wso-ng, an "advanced iteration" of WSO (short for "web shell by oRb") that integrates with legitimate tools like VirusTotal and SecurityTrails while stealthily concealing its login interface behind a 404 error page upon attempting to access it.
One of the notable reconnaissance capabilities of the web shell involves retrieving AWS metadata for subsequent lateral movement as well as searching for potential Redis database connections so as to obtain unauthorized access to sensitive application data.
"Web shells allow attackers to run commands on servers to steal data or use the server as a launch pad for other activities like credential theft, lateral movement, deployment of additional payloads, or hands-on-keyboard activity, while allowing attackers to persist in an affected organization," Microsoft said back in 2021.
The use of off-the-shelf web shells is also seen as an attempt by threat actors to challenge attribution efforts and fly under the radar, a key hallmark of cyber espionage groups that specialize in intelligence gathering.
Another common tactic adopted by attackers is the use of compromised-but-legitimate domains for C2 purposes and malware distribution.
In August 2023, Infoblox disclosed a widespread attack involving compromised WordPress websites that conditionally redirect visitors to intermediary C2 and dictionary domain generation algorithm (DDGA) domains. The activity has been attributed to a threat actor named VexTrio.
Alert: OracleIV DDoS Botnet Targets Public Docker Engine APIs to Hijack Containers
14.11.23 BotNet The Hacker News
Publicly-accessible Docker Engine API instances are being targeted by threat actors as part of a campaign designed to co-opt the machines into a distributed denial-of-service (DDoS) botnet dubbed OracleIV.
"Attackers are exploiting this misconfiguration to deliver a malicious Docker container, built from an image named 'oracleiv_latest' and containing Python malware compiled as an ELF executable," Cado researchers Nate Bill and Matt Muir said.
The malicious activity starts with attackers using an HTTP POST request to Docker's API to retrieve a malicious image from Docker Hub, which, in turn, runs a command to retrieve a shell script (oracle.sh) from a command-and-control (C&C) server.
Oracleiv_latest purports to be a MySQL image for docker and has been pulled 3,500 times to date. In a perhaps not-so-surprising twist, the image also includes additional instructions to fetch an XMRig miner and its configuration from the same server.
That said, the cloud security firm said it did not observe any evidence of cryptocurrency mining performed by the counterfeit container. The shell script, on the other hand, is concise and incorporates functions to conduct DDoS attacks such as slowloris, SYN floods, and UDP floods.
Exposed Docker instances have become a lucrative attack target in recent years, often used as conduits for cryptojacking campaigns.
"Once a valid endpoint is discovered, it's trivial to pull a malicious image and launch a container from it to carry out any conceivable objective," the researchers said. "Hosting the malicious container in Docker Hub, Docker's container image library, streamlines this process even further."
It's not just Docker, as vulnerable MySQL servers have emerged as the target of another DDoS botnet malware known as Ddostf, according to the AhnLab Security Emergency Response Center (ASEC).
"Although most of the commands supported by Ddostf are similar to those from typical DDoS bots, a distinctive feature of Ddostf is its ability to connect to a newly received address from the C&C server and execute commands there for a certain period," ASEC said.
"Only DDoS commands can be performed on the new C&C server. This implies that the Ddostf threat actor can infect numerous systems and then sell DDoS attacks as a service."
Compounding matters further is the emergence of several new DDoS botnets, such as hailBot, kiraiBot, and catDDoS that are based on Mirai, whose source code leaked in 2016.
"These newly developed Trojan horses either introduce new encryption algorithms to hide critical information or better hide themselves by modifying the go-live process and designing more covert communication methods," cybersecurity company NSFOCUS revealed last month.
Another DDoS malware that has resurfaced this year is XorDdos, which infects Linux devices and "transforms them into zombies" for follow-on DDoS attacks against targets of interest.
Palo Alto Networks Unit 42 said the campaign began in late July 2023, before peaking around August 12, 2023.
"Before malware successfully infiltrated a device, the attackers initiated a scanning process, employing HTTP requests to identify potential vulnerabilities in their targets," the company noted. "To evade detection, the threat turns its process into a background service that runs independently of the current user session."
AVRecon Botnet Leveraging Compromised Routers to Fuel Illegal Proxy Service
31.7.23 BotNet The Hacker News

More details have emerged about a botnet called AVRecon, which has been observed making use of compromised small office/home office (SOHO) routers as part of a multi-year campaign active since at least May 2021.
AVRecon was first disclosed by Lumen Black Lotus Labs earlier this month as malware capable of executing additional commands and stealing victim's bandwidth for what appears to be an illegal proxy service made available for other actors. It has also surpassed QakBot in terms of scale, having infiltrated over 41,000 nodes located across 20 countries worldwide.
"The malware has been used to create residential proxy services to shroud malicious activity such as password spraying, web-traffic proxying, and ad fraud," the researchers said in the report.
This has been corroborated by new findings from KrebsOnSecurity and Spur.us, which last week revealed that "AVrecon is the malware engine behind a 12-year-old service called SocksEscort, which rents hacked residential and small business devices to cybercriminals looking to hide their true location online."
The basis for the connection stems from direct correlations between SocksEscort and AVRecon's command-and-control (C2) servers. SocksEscort is also said to share overlaps with a Moldovan company named Server Management LLC that offers a mobile VPN solution on the Apple Store called HideIPVPN.
Black Lotus Labs told The Hacker News that the new infrastructure it identified in connection with the malware exhibited the same characteristics as the old AVrecon C2s.
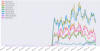
The new SocksEscort nodes, which shifted during the second week of July (Source: Lumen Black Lotus Labs)
"We assess that the threat actors were reacting to our publication and null-routing of infrastructure, and attempting to maintain control over the botnet," the company said. "This suggests the actors wish to further monetize the botnet by maintaining some access and continue enrolling users in the SocksEscort 'proxy as a service.'"
Routers and other edge appliances have become lucrative attack vectors in recent years owing to the fact that such devices are infrequently patched against security issues, may not support endpoint detection and response (EDR) solutions, and are designed to handle higher bandwidths.
AVRecon also poses a heightened threat for its ability to spawn a shell on a compromised machine, potentially enabling threat actors to obfuscate their own malicious traffic or retrieve further malware for post-exploitation.
"While these bots are primarily being added to the SocksEscort proxy service, there was embedded functionality within the file to spawn a remote shell," the researchers said.
"This could allow the threat actor the ability to deploy additional modules, so we suggest that managed security providers attempt to investigate these devices in their networks, while home users should power-cycle their devices."
DDoS Botnets Hijacking Zyxel Devices to Launch Devastating Attacks
21.7.23 BotNet The Hacker News
Several distributed denial-of-service (DDoS) botnets have been observed exploiting a critical flaw in Zyxel devices that came to light in April 2023 to gain remote control of vulnerable systems.
"Through the capture of exploit traffic, the attacker's IP address was identified, and it was determined that the attacks were occurring in multiple regions, including Central America, North America, East Asia, and South Asia," Fortinet FortiGuard Labs researcher Cara Lin said.
The flaw, tracked as CVE-2023-28771 (CVSS score: 9.8), is a command injection bug affecting multiple firewall models that could potentially allow an unauthorized actor to execute arbitrary code by sending a specifically crafted packet to the targeted appliance.
Last month, the Shadowserver Foundation warned that the flaw was being "actively exploited to build a Mirai-like botnet" at least since May 26, 2023, an indication of how abuse of servers running unpatched software is on the rise.
The latest findings from Fortinet suggest that the shortcoming is being opportunistically leveraged by multiple actors to breach susceptible hosts and corral them into a botnet capable of launching DDoS attacks against other targets.
This comprises Mirai botnet variants such as Dark.IoT and another botnet that has been dubbed Katana by its author, which comes with capabilities to mount DDoS attacks using TCP and UDP protocols.
"It appears that this campaign utilized multiple servers to launch attacks and updated itself within a few days to maximize the compromise of Zyxel devices," Lin said.
The disclosure comes as Cloudflare reported an "alarming escalation in the sophistication of DDoS attacks" in the second quarter of 2023, with threat actors devising novel ways to evade detection by "adeptly imitating browser behavior" and keeping their attack rates-per-second relatively low.

Adding to the complexity is the use of DNS laundering attacks to conceal malicious traffic via reputable recursive DNS resolvers and virtual machine botnets to orchestrate hyper-volumetric DDoS attacks.
"In a DNS Laundering attack, the threat actor will query subdomains of a domain that is managed by the victim's DNS server," Cloudflare explained. "The prefix that defines the subdomain is randomized and is never used more than once or twice in such an attack."
"Due to the randomization element, recursive DNS servers will never have a cached response and will need to forward the query to the victim's authoritative DNS server. The authoritative DNS server is then bombarded by so many queries until it cannot serve legitimate queries or even crashes all together."
Another noteworthy factor contributing to the increase in DDoS offensives is the emergence of pro-Russian hacktivist groups such as KillNet, REvil, and Anonymous Sudan (aka Storm-1359) that have overwhelmingly focused on targets in the U.S. and Europe. There is no evidence to connect REvil to the widely known ransomware group.
KillNet's "regular creation and absorption of new groups is at least partially an attempt to continue to garner attention from Western media and to enhance the influence component of its operations," Mandiant said in a new analysis, adding the group's targeting has "consistently aligned with established and emerging Russian geopolitical priorities."
"KillNet's structure, leadership, and capabilities have undergone several observable shifts over the course of the last 18 months, progressing toward a model that includes new, higher profile affiliate groups intended to garner attention for their individual brands in addition to the broader KillNet brand," it further added.
New SOHO Router Botnet AVrecon Spreads to 70,000 Devices Across 20 Countries
14.7.23 BotNet The Hacker News
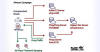
A new malware strain has been found covertly targeting small office/home office (SOHO) routers for more than two years, infiltrating over 70,000 devices and creating a botnet with 40,000 nodes spanning 20 countries.
Lumen Black Lotus Labs has dubbed the malware AVrecon, making it the third such strain to focus on SOHO routers after ZuoRAT and HiatusRAT over the past year.
"This makes AVrecon one of the largest SOHO router-targeting botnets ever seen," the company said. "The purpose of the campaign appears to be the creation of a covert network to quietly enable a range of criminal activities from password spraying to digital advertising fraud."
A majority of the infections are located in the U.K. and the U.S., followed by Argentina, Nigeria, Brazil, Italy, Bangladesh, Vietnam, India, Russia, and South Africa, among others.
AVrecon was first highlighted by Kaspersky senior security researcher Ye (Seth) Jin in May 2021, indicating that the malware has managed to avoid detection until now.
In the attack chain detailed by Lumen, a successful infection is followed by enumerating the victim's SOHO router and exfiltrating that information back to an embedded command-and-control (C2) server.
It also checks if other instances of malware are already running on the host by searching for existing processes on port 48102 and opening a listener on that port. A process bound to that port is terminated.
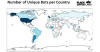
The next stage involves the compromised system establishing contact with a separate server, called the secondary C2 server, to await further commands. Lumen said it identified 15 such unique servers that have been active since at least October 2021.
It's worth noting that tiered C2 infrastructure is prevalent among notorious botnets like Emotet and QakBot.
AVrecon is written in the C programming language, making it easy to port the malware for different architectures. What's more, a crucial reason why such attacks work is because they leverage infrastructure living on the edge that typically lacks support for security solutions.
Evidence gathered so far points to the botnet being used for clicking on various Facebook and Google ads, and to interact with Microsoft Outlook. This likely indicates a two-pronged effort to conduct advertising fraud and data exfiltration.
"The manner of attack seems to focus predominantly on stealing bandwidth – without impacting end-users – in order to create a residential proxy service to help launder malicious activity and avoid attracting the same level of attention from Tor-hidden services or commercially available VPN services," the researchers said.
TeamTNT's Silentbob Botnet Infecting 196 Hosts in Cloud Attack Campaign
14.7.23 BotNet The Hacker News
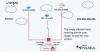
As many as 196 hosts have been infected as part of an aggressive cloud campaign mounted by the TeamTNT group called Silentbob.
"The botnet run by TeamTNT has set its sights on Docker and Kubernetes environments, Redis servers, Postgres databases, Hadoop clusters, Tomcat and Nginx servers, Weave Scope, SSH, and Jupyter applications," Aqua security researchers Ofek Itach and Assaf Morag said in a report shared with The Hacker News.
"The focus this time seems to be more on infecting systems and testing the botnet, rather than deploying cryptominers for profit."
The development arrives a week after the cloud security company detailed an intrusion set linked to the TeamTNT group that targets exposed JupyterLab and Docker APIs to deploy the Tsunami malware and hijack system resources to run a cryptocurrency miner.
The latest findings suggest a broader campaign and the use of a larger attack infrastructure than previously thought, including various shell scripts to steal credentials, deploy SSH backdoors, download additional payloads, and drop legitimate tools like kubectl, Pacu, and Peirates to conduct reconnaissance of the cloud environment.
The attack chains are realized through the deployment of rogue container images hosted on Docker Hub, which are designed to scan the internet for misconfigured instances and infect the newly identified victims with Tsunami and a worm script to co-opt more machines into a botnet.
"This botnet is notably aggressive, rapidly proliferating across the cloud and targeting a wide array of services and applications within the Software Development Life Cycle (SDLC)," the researchers said. "It operates at an impressive speed, demonstrating remarkable scanning capability."
Tsunami uses the Internet Relay Chat (IRC) protocol to connect to the command-and-control (C2) server, which then issues commands to all the infected hosts under its control, thereby allowing the threat actor to maintain backdoor access.
What's more, the cryptomining execution is hidden using a rootkit called prochider to prevent it from being detected when a ps command is run on the hacked system to retrieve the list of active processes.
"TeamTNT is scanning for credentials across multiple cloud environments, including AWS, Azure, and GCP," the researchers said, noting it's the latest evidence that the threat actors are upgrading their tradecraft.
"They are not only looking for general credentials but also specific applications such as Grafana, Kubernetes, Docker Compose, Git access, and NPM. Additionally, they are searching for databases and storage systems such as Postgres, AWS S3, Filezilla, and SQLite."
SCARLETEEL Tied to TeamTNT#
The development comes days after Sysdig disclosed a new attack mounted by SCARLETEEL to compromise AWS infrastructure with the goal of conducting data theft and distributing cryptocurrency miners on compromised systems.

While there were circumstantial links connecting SCARLETEEL to TeamTNT, Aqua told The Hacker News that the intrusion set is in fact linked to the threat actor.
"This is another campaign by TeamTNT," Morag, lead data analyst at Aqua Nautilus research team, said. "The SCARLETEEL IP address, 45.9.148[.]221, was used just days ago in TeamTNT's IRC channel C2 server. The scripts are very similar and the TTPs are the same. It looks like TeamTNT never stopped attacking. If they ever retired, it was only for a brief moment."
Alarming Surge in TrueBot Activity Revealed with New Delivery Vectors
5.6.23 BotNet The Hacker News
A surge in TrueBot activity was observed in May 2023, cybersecurity researchers disclosed.
"TrueBot is a downloader trojan botnet that uses command and control servers to collect information on compromised systems and uses that compromised system as a launching point for further attacks," VMware's Fae Carlisle said.
Active since at least 2017, TrueBot is linked to a group known as Silence that's believed to share overlaps with the notorious Russian cybercrime actor known as Evil Corp.
Recent TrueBot infections have leveraged a critical flaw in Netwrix auditor (CVE-2022-31199, CVSS score: 9.8) as well as Raspberry Robin as delivery vectors.

The attack chain documented by VMware, on the other hand, starts off with a drive-by-download of an executable named "update.exe" from Google Chrome, suggesting that users are lured into downloading the malware under the pretext of a software update.
Once run, update.exe establishes connections with a known TrueBot IP address located in Russia to retrieve a second-stage executable ("3ujwy2rz7v.exe") that's subsequently launched using Windows Command Prompt.
The executable, for its part, connects to a command-and-control (C2) domain and exfiltrates sensitive information from the host. It's also capable of process and system enumeration.
"TrueBot can be a particularly nasty infection for any network," Carlisle said. "When an organization is infected with this malware, it can quickly escalate to become a bigger infection, similar to how ransomware spreads throughout a network."
The findings come as SonicWall detailed a new variant of another downloader malware known as GuLoader (aka CloudEyE) that's used to deliver a wide range of malware such as Agent Tesla, Azorult, and Remcos.
"In the latest variant of GuLoader, it introduces new ways to raise exceptions that hamper complete analysis process and its execution under controlled environment," SonicWall said.
New Botnet Malware 'Horabot' Targets Spanish-Speaking Users in Latin America
2.6.23 BotNet The Hacker News
Spanish-speaking users in Latin America have been at the receiving end of a new botnet malware dubbed Horabot since at least November 2020.
"Horabot enables the threat actor to control the victim's Outlook mailbox, exfiltrate contacts' email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim's mailbox," Cisco Talos researcher Chetan Raghuprasad said.
The botnet program also delivers a Windows-based financial trojan and a spam tool to harvest online banking credentials as well as compromise Gmail, Outlook, and Yahoo! webmail accounts to blast spam emails.
The cybersecurity firm said a majority of the infections are located in Mexico, with limited victims identified in Uruguay, Brazil, Venezuela, Argentina, Guatemala, and Panama. The threat actor behind the campaign is believed to be in Brazil.
Targeted users of the ongoing campaign primarily span accounting, construction and engineering, wholesale distribution, and investment verticals, although it's suspected that other sectors in the region may also be affected.
The attacks start with phishing emails bearing tax-themed lures that entice the recipients into opening an HTML attachment, which, in turn, embeds a link containing a RAR archive.
Opening the contents of the file results in the execution of a PowerShell downloader script that's responsible for retrieving a ZIP file containing the main payloads from a remote server and rebooting the machine.
The system restart also serves as a launchpad for the banking trojan and the spam tool, allowing the threat actor to steal data, log keystrokes, capture screenshots, and disseminate additional phishing emails to the victim's contacts.
"This campaign involves a multi-stage attack chain that begins with a phishing email and leads to payload delivery through the execution of a PowerShell downloader script and sideloading to legitimate executables," Raghuprasad said.
The banking trojan is a 32-bit Windows DLL written in the Delphi programming language, and shares overlaps with other Brazilian malware families like Mekotio and Casbaneiro.
Horabot, for its part, is an Outlook phishing botnet program written in PowerShell that's capable of sending phishing emails to all email addresses in the victim's mailbox to propagate the infection. It's also a deliberate attempt to minimize the threat actor's phishing infrastructure from being exposed.
The disclosure arrives a week after SentinelOne attributed an unknown Brazilian threat actor to a long-running campaign targeting more than 30 Portuguese financial institutions with information-stealing malware since 2021.
It also follows the discovery of a new Android banking trojan dubbed PixBankBot that abuses the operating system's accessibility services to conduct fraudulent money transfers over the Brazilian PIX payments platform.
PixBankBot is also the latest example of malware that specifically focuses on Brazilian banks, featuring capabilities similar to BrasDex, PixPirate, and GoatRAT that have been spotted in recent months.
If anything, the developments represent yet another iteration of a broader group of financially motivated hacking efforts emanating from Brazil, making it crucial that users remain vigilant to avoid falling prey to such threats.
Active Mirai Botnet Variant Exploiting Zyxel Devices for DDoS Attacks
1.6.23 BotNet The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a recently patched critical security flaw in Zyxel gear to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
Tracked as CVE-2023-28771 (CVSS score: 9.8), the issue relates to a command injection flaw impacting different firewall models that could enable an unauthenticated attacker to execute arbitrary code by sending a specially crafted packet to the device.
Zyxel addressed the security defect as part of updates released on April 25, 2023. The list of impacted devices is below -
ATP (versions ZLD V4.60 to V5.35, patched in ZLD V5.36)
USG FLEX (versions ZLD V4.60 to V5.35, patched in ZLD V5.36)
VPN (versions ZLD V4.60 to V5.35, patched in ZLD V5.36), and
ZyWALL/USG (versions ZLD V4.60 to V4.73, patched in ZLD V4.73 Patch 1)
The Shadowserver Foundation, in a recent tweet, said the flaw is "being actively exploited to build a Mirai-like botnet" since May 26, 2023. Cybersecurity firm Rapid7 has also warned of "widespread" in-the-wild abuse of CVE-2023-28771.
In light of this development, it's imperative that users move quickly to apply the patches to mitigate potential risks. Federal agencies in the U.S. are mandated to update their devices by June 21, 2023.
The disclosure also comes as Palo Alto Networks Unit 42 detailed a new wave of attacks mounted by an active Mirai botnet variant dubbed IZ1H9 since early April 2023.
The intrusions have been found to leverage multiple remote code execution flaws in internet-exposed IoT devices, including Zyxel, to ensnare them into a network for orchestrating distributed denial-of-service (DDoS) attacks.
It's worth noting that Mirai has spawned a number of clones ever since its source code was leaked in October 2016. The botnet, named after the 2011 TV anime series Mirai Nikki, was the handiwork of Paras Jha, Josiah White, and Dalton Norman.
"IoT devices have always been a lucrative target for threat actors, and remote code execution attacks continue to be the most common and most concerning threats affecting IoT devices and linux servers," Unit 42 said.
"The vulnerabilities used by this threat are less complex, but this does not decrease their impact, since they could still lead to remote code execution."
Dark Frost Botnet Launches Devastating DDoS Attacks on Gaming Industry
25.5.23 BotNet The Hacker News
A new botnet called Dark Frost has been observed launching distributed denial-of-service (DDoS) attacks against the gaming industry.
"The Dark Frost botnet, modeled after Gafgyt, QBot, Mirai, and other malware strains, has expanded to encompass hundreds of compromised devices," Akamai security researcher Allen West said in a new technical analysis shared with The Hacker News.
Targets include gaming companies, game server hosting
providers, online streamers, and even other gaming community members with whom the threat actor has interacted directly.
As of February 2023, the botnet comprises 414 machines running various instruction set architectures such as ARMv4, x86, MIPSEL, MIPS, and ARM7.
Botnets are usually made up of a vast network of compromised devices around the world. The operators tend to use the enslaved hosts to mine cryptocurrency, steal sensitive data, or harness the collective internet bandwidth from these bots to knock down other websites and internet servers by flooding the targets with junk traffic.
Dark Frost represents the latest iteration of a botnet that appears to have been stitched together by stealing source code from various botnet malware strains such as Mirai, Gafgyt, and QBot.
Akamai, which reverse-engineered the botnet after flagging it on February 28, 2023, pegged its attack potential at approximately 629.28 Gbps through a UDP flood attack. The threat actor is believed to be active since at least May 2022.
"What makes this particular case interesting is that the actor behind these attacks has published live recordings of their attacks for all to see," the web infrastructure company said.
"The actor was observed boasting about their achievements on social media, utilizing the botnet for petty online disputes, and even leaving digital signatures on their binary file."
The adversary has further set up a Discord channel to facilitate attacks in exchange for money, indicating their financial motivations and plans to flesh it out as a DDoS-for-hire service.
Dark Frost constitutes a modern example of how easy it is for novice cybercriminals with rudimentary coding skills to spring into action using already available malware to inflict significant damage on enterprises.
"The reach that these threat actors can have is staggering despite the lack of novelty in their techniques," West said. "Although not the most advanced or mind-bending adversary, the Dark Frost botnet has still managed to accumulate hundreds of compromised devices to do its bidding."
Andoryu Botnet Exploits Critical Ruckus Wireless Flaw for Widespread Attack
12.5.23 BotNet The Hacker News
A nascent botnet called Andoryu has been found to exploit a now-patched critical security flaw in the Ruckus Wireless Admin panel to break into vulnerable devices.
The flaw, tracked as CVE-2023-25717 (CVSS score: 9.8), stems from improper handling of HTTP requests, leading to unauthenticated remote code execution and a complete compromise of wireless Access Point (AP) equipment.
Andoryu was first documented by Chinese cybersecurity firm QiAnXin earlier this February, detailing its ability to communicate with command-and-control (C2) servers using the SOCKS5 protocol.
While the malware is known to weaponize remote code execution flaws in GitLab (CVE-2021-22205) and Lilin DVR for propagation, the addition of CVE-2023-25717 shows that Andoryu is actively expanding its exploit arsenal to ensnare more devices into the botnet.
"It contains DDoS attack modules for different protocols and communicates with its command-and-control server using SOCKS5 proxies," Fortinet FortiGuard Labs researcher Cara Lin said, adding the latest campaign commenced in late April 2023.
Further analysis of the attack chain has revealed that once the Ruckus flaw is used to gain access to a device, a script from a remote server is dropped onto the infected device for proliferation.

The malware, for its part, also establishes contact with a C2 server and awaits further instructions to launch a DDoS attack against targets of interest using protocols like ICMP, TCP, and UDP.
The cost associated with mounting such attacks is advertised via a listing on the seller's Telegram channel, with monthly plans ranging from $90 to $115 depending on the duration.
RapperBot Botnet Adds Crypto Mining to its List of Capabilities #
The alert follows the discovery of new versions of the RapperBot DDoS botnet that incorporate cryptojacking functionality to profit off compromised Intel x64 systems by dropping a Monero crypto miner.
RapperBot campaigns have primarily focused on brute-forcing IoT devices with weak or default SSH or Telnet credentials to expand the botnet's footprint for launching DDoS attacks.
Fortinet said it detected the latest iteration of the RapperBot miner activity in January 2023, with the attacks delivering a Bash shell script that, in turn, is capable of downloading and executing separate XMRig crypto miners and RapperBot binaries.
Subsequent updates to the malware have merged the two disparate functions into a single bot client with mining capabilities, while also taking steps to terminate competing miner processes.
Interestingly, none of the new RapperBot samples with the integrated XMRig miner incorporate self-propagation capabilities, raising the possibility of an alternate distribution mechanism.
"This suggests the possible availability of an external loader operated by the threat actor that abuses the credentials collected by other RapperBot samples with brute forcing capabilities and infects only x64 machines with the combined bot/miner," Fortinet theorized.
RapperBot's expansion to cryptojacking is yet another indication that financially motivated threat operators leave no stone unturned to "extract the maximum value from machines infected by their botnets."
The twin developments also come as the U.S. Justice Department announced the seizure of 13 internet domains associated with DDoS-for-hire services.
Google Gets Court Order to Take Down CryptBot That Infected Over 670,000 Computers
28.4.23 BotNet The Hacker News
Google on Wednesday said it obtained a temporary court order in the U.S. to disrupt the distribution of a Windows-based information-stealing malware called CryptBot and "decelerate" its growth.
The tech giant's Mike Trinh and Pierre-Marc Bureau said the efforts are part of steps it takes to "not only hold criminal operators of malware accountable, but also those who profit from its distribution."
CryptBot is estimated to have infected over 670,000 computers in 2022 with the goal of stealing sensitive data such as authentication credentials, social media account logins, and cryptocurrency wallets from users of Google Chrome.
The harvested data is then exfiltrated to the threat actors, who then sell the data to other attackers for use in data breach campaigns. CryptBot was first discovered in the wild in December 2019.
The malware has been traditionally delivered via maliciously modified versions of legitimate and popular software packages such as Google Earth Pro and Google Chrome that are hosted on fake websites.
What's more, a CryptBot campaign unearthed by Red Canary in December 2021 entailed the use of KMSPico, an unofficial tool that's used to illegally activate Microsoft Office and Windows without a license key, as a delivery vector.
Then in March 2022, BlackBerry disclosed details of a new and improved version of the malicious infostealer that was distributed via compromised pirate sites that purport to offer "cracked" versions of various software and video games.
The major distributors of CryptBot, per Google, are suspected to be operating a "worldwide criminal enterprise" based out of Pakistan.
Google said it intends to use the court order, granted by a federal judge in the Southern District of New York, to "take down current and future domains that are tied to the distribution of CryptBot," thereby kneecapping the spread of new infections.
To mitigate risks posed by such threats, it's advised to only download software from well-known and trusted sources, scrutinize reviews, and ensure that the device's operating system and software are kept up-to-date.
The disclosure comes weeks after Microsoft, Fortra, and Health Information Sharing and Analysis Center (Health-ISAC) legally joined hands to dismantle servers hosting illegal, legacy copies of Cobalt Strike to prevent the tool's abuse by threat actors.
It also follows Google's endeavors to shut down the command-and-control infrastructure associated with a botnet dubbed Glupteba in December 2021. The malware, however, staged a return six months later as part of an "upscaled" campaign.
Separately, ESET and Microsoft-owned GitHub announced the temporary disruption of a commodity information stealer malware named RedLine Stealer after finding that its command-and-control panels leveraged four different GitHub repositories as dead drop resolvers.
"The removal of these repositories should break authentication for panels currently in use," the Slovak cybersecurity company said. "While this doesn't affect the actual back-end servers, it will force the RedLine operators to distribute new panels to their customers."
New Zaraza Bot Credential-Stealer Sold on Telegram Targeting 38 Web Browsers
17.4.23 BotNet The Hacker News
A novel credential-stealing malware called Zaraza bot is being offered for sale on Telegram while also using the popular messaging service as a command-and-control (C2).
"Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors," cybersecurity company Uptycs said in a report published last week.
"Once the malware infects a victim's computer, it retrieves sensitive data and sends it to a Telegram server where the attackers can access it immediately."
A 64-bit binary file compiled using C#, Zaraza bot is designed to target as many as 38 different web browsers, including Google Chrome, Microsoft Edge, Opera, AVG Browser, Brave, Vivaldi, and Yandex. It's also equipped to capture screenshots of the active window.
It's the latest example of malware that's capable of capturing login credentials associated with online bank accounts, cryptocurrency wallets, email accounts, and other websites deemed of value to the operators.
Stolen credentials pose a serious risk as they not only allow threat actors to gain unauthorized access to victims' accounts, but also conduct identity theft and financial fraud.
Zaraza Bot
Evidence gathered by Uptycs points to Zaraza bot being offered as a commercial tool for other cybercriminals for a subscription. It's currently not clear how the malware is propagated, but information stealers have typically leveraged several methods such as malvertising and social engineering in the past.
Zaraza Bot
The findings come as eSentire's Threat Response Unit (TRU) disclosed a GuLoader (aka CloudEyE) campaign targeting the financial sector via phishing emails by employing tax-themed lures to deliver information stealers and remote access trojans (RATs) like Remcos RAT.
The development also follows a spike in malvertising and search engine poisoning techniques to distribute a growing number of malware families by enticing users searching for legitimate applications into downloading fake installers containing stealer payloads.
Russian cybersecurity firm Kaspersky, in a new analysis, revealed the use of trojanized cracked software downloaded from BitTorrent or OneDrive to deploy CueMiner, a .NET-based downloader that acts as a conduit to installer a cryptocurrency miner known as SilentCryptoMiner.
To mitigate risks stemming from stealer malware, it's recommended that users enable two-factor authentication (2FA) and apply software and operating systems updates as and when they become available.

















