Vulnerebility 2024 2023 2022 2021 2020
Millions of devices could be hacked exploiting flaws targeted by tools stolen
from FireEye
25.12.2020
Vulnerebility
Securityaffairs
Millions of devices are potential exposed to attacks targeting the
vulnerabilities exploited by the tools stolen from the arsenal of FireEye.
Security experts from Qualys are warning that more than 7.5 million devices are
potentially exposed to cyber attacks targeting the vulnerabilities exploited by
the tools stolen from the arsenal of FireEye.
As a result of the recent SolarWinds supply chain attack, multiple organizations were compromised, including FireEye.
“While the number of vulnerable instances of SolarWinds Orion are in the hundreds, our analysis has identified over 7.54 million vulnerable instances related to FireEye Red Team tools across 5.29 million unique assets, highlighting the scope of the potential attack surface if these tools are misused. Organizations need to move quickly to immediately protect themselves from being exploited by these vulnerabilities.” reads the post published by Qualys.
The experts discovered that the vulnerable instances were associated with nearly 5.3 million unique assets belonging to Qualys’ customers.
About 7.53 million out of 7.54 million vulnerable instances (99.84%) are from the following eight vulnerabilities in Microsoft’s software:
CVE ID Release Date Name CVSS Qualys QID(s)
CVE-2020-1472 08/11/2020
Microsoft Windows Netlogon Elevation of Privilege Vulnerability 10 91668
CVE-2019-0604 02/12/2019 Microsoft Office and Microsoft Office Services and Web
Apps Security Update February 2019 Microsoft SharePoint 9.8 110330
CVE-2019-0708 05/14/2019 Microsoft Windows Remote Desktop Services Remote Code
Execution Vulnerability (Blue. Keep) 9.8 91541, 91534
CVE-2014-1812
05/13/2014 Microsoft Windows Group Policy Preferences Password Elevation of
Privilege Vulnerability (KB2962486) 9 91148, 90951
CVE-2020-0688 02/11/2020
Microsoft Exchange Server Security Update for February 2020 8.8 50098
CVE-2016-0167 04/12/2016 Microsoft Windows Graphics Component Security Update
(MS16-039) 7.8 91204
CVE-2017-11774 10/10/2017 Microsoft Office and Microsoft
Office Services and Web Apps Security Update October 2017 7.8 110306
CVE-2018-8581 11/13/2018 Microsoft Exchange Server Elevation of Privilege
Vulnerability 7.4 53018
The tools that were stolen from the FireEye’s arsenal
also exploit other eight vulnerabilities affecting products from Pulse Secure,
Fortinet, Atlassian, Citrix, Zoho, and Adobe.
The full list of 16 exploitable vulnerabilities and their patch links is available here.
Qualys released free tools and other resources that can help organizations to address the above vulnerabilities, the company is offering a free service for 60 days, to rapidly address this risk.
This week, security experts started analyzing the DGA mechanism used by threat actors behind the SolarWinds hack to control the Sunburst/Solarigate backdoor and published the list of targeted organizations.
The list contains major companies, including Cisco, Deloitte, Intel, Mediatek, and Nvidia.
Google reported that Microsoft failed to fix a Windows zero-day flaw
25.12.2020
Vulnerebility
Securityaffairs
Google’s Project Zero experts publicly disclosed details of an improperly
patched zero-day code execution vulnerability in Windows.
White hat hackers
at Google’s Project Zero team has publicly disclosed details of an improperly
patched zero-day vulnerability in Windows.
The vulnerability tracked as CVE-2020-0986, resides in the Print Spooler API and could be exploited by a threat actor to execute arbitrary code.
Google experts published the details of the vulnerability after Microsoft failed to address the issue within 90 days of responsible disclosure on September 24.
The flaw was reported to Microsoft by an anonymous user working with Trend Micro’s Zero Day Initiative (ZDI) in December 2019.
“The vulnerability is almost exactly the same as CVE-2019-0880 [detailed technical analysis]. Just like CVE-2019-0880, this vulnerability allows the attacker to call memcpy with arbitrary parameters in the splwow64 privileged address space. The arbitrary parameters are sent in an LPC message to splwow64.” reads the security advisory. “In this case, the vulnerable message type is 0x6D, which is the call to DocumentEvent. After DocumentEvent is called from GdiPrinterThunk, a call to memcpy can occur as long as you craft specific fields in your LPC message to the right values. This memcpy call is at gdi32full!GdiPrinterThunk+0x1E85A.”
Splwow64.exe is a Windows core system file that allows 32-bit applications to connect with the 64-bit printer spooler service on x64 Windows builds.
On May 19, 2010, ZDI published an advisory after that threat actors exploited
the flaw in the wild in a campaign tracked as “Operation PowerFall.”
In May
2020, Kaspersky experts spotted an attack on a South Korean company, threat
actors chained two zero-day exploits: a remote code execution exploit for
Internet Explorer and an elevation of privilege exploit for Windows.
“This
vulnerability allows local attackers to escalate privileges on affected
installations of Microsoft Windows. An attacker must first obtain the ability to
execute low-privileged code on the target system in order to exploit this
vulnerability.” reads the ZDI’s advisory.
“The specific flaw exists within the user-mode printer driver host process splwow64.exe. The issue results from the lack of proper validation of a user-supplied value prior to dereferencing it as a pointer. An attacker can leverage this vulnerability to escalate privileges from low integrity and execute code in the context of the current user at medium integrity.”
An attacker could exploit this zero-day to manipulate the memory of the “splwow64.exe” process to achieve execution of arbitrary code in kernel mode. The flaw could allow installing malicious programs, view, change, or delete data, and create new accounts with full user rights.
Microsoft attempted to address the issue with the June Patch Tuesday security updates, but Google Project Zero experts discovered that the issue has not been fully solved.
“CVE-2020-0986, which was exploited in the wild[1] was not fixed. The vulnerability still exists, just the exploitation method had to change.” reads the advisory published by Google Project Zero researcher Maddie Stone.
The issue received a new CVE, CVE-2020-17008, and will be likely fixed by Microsoft in January.
Google experts have also shared a proof-of-concept (PoC) exploit code for CVE-2020-17008.
Google Discloses Poorly-Patched, Now Unpatched, Windows 0-Day Bug
25.12.2020
Vulnerebility
Thehackernews
Google's Project Zero team has made public details of an improperly patched zero-day security vulnerability in Windows print spooler API that could be leveraged by a bad actor to execute arbitrary code.
Details of the unpatched flaw were revealed publicly after Microsoft failed to patch it within 90 days of responsible disclosure on September 24.
Originally tracked as CVE-2020-0986, the flaw concerns an elevation of privilege exploit in the GDI Print / Print Spooler API ("splwow64.exe") that was reported to Microsoft by an anonymous user working with Trend Micro's Zero Day Initiative (ZDI) back in late December 2019.
But with no patch in sight for about six months, ZDI ended up posting a public advisory as a zero-day on May 19 earlier this year, after which it was exploited in the wild in a campaign dubbed "Operation PowerFall" against an unnamed South Korean company.
"splwow64.exe" is a Windows core system binary that allows 32-bit applications
to connect with the 64-bit printer spooler service on 64-bit Windows systems. It
implements a Local Procedure Call (LPC) server that can be used by other
processes to access printing functions.
Successful exploitation of this vulnerability could result in an attacker manipulating the memory of the "splwow64.exe" process to achieve execution of arbitrary code in kernel mode, ultimately using it to install malicious programs; view, change, or delete data; or create new accounts with full user rights.
However, to achieve this, the adversary would first have to log on to the target system in question.
Although Microsoft eventually addressed the shortcoming as part of its June Patch Tuesday update, new findings from Google's security team reveals that the flaw has not been fully remediated.
"The vulnerability still exists, just the exploitation method had to change," Google Project Zero researcher Maddie Stone said in a write-up.
"The original issue was an arbitrary pointer dereference which allowed the attacker to control the src and dest pointers to a memcpy," Stone detailed. "The 'fix' simply changed the pointers to offsets, which still allows control of the args to the memcpy."
The newly reported elevation of privilege flaw, identified as CVE-2020-17008, is expected to be resolved by Microsoft on January 12, 2021, due to "issues identified in testing" after promising an initial fix in November.
Stone has also shared a proof-of-concept (PoC) exploit code for CVE-2020-17008, based off of a POC released by Kaspersky for CVE-2020-0986.
"There have been too many occurrences this year of zero-days known to be actively exploited being fixed incorrectly or incompletely," Stone said. "When [in the wild] zero-days aren't fixed completely, attackers can reuse their knowledge of vulnerabilities and exploit methods to easily develop new 0-days."
Millions of Devices Affected by Vulnerabilities Used in Stolen FireEye Tools
23.12.2020
Vulnerebility
Securityweek
Millions of devices are exposed to potential attacks exploiting the vulnerabilities used in the tools that threat actors recently stole from FireEye, security and compliance solutions provider Qualys reported on Tuesday.
Qualys said it identified more than 7.5 million instances related to vulnerabilities associated with the stolen FireEye tools and compromised versions of the SolarWinds Orion product. The vulnerable instances were discovered across nearly 5.3 million unique assets belonging to Qualys’ more than 15,000 customers.
As FireEye pointed out when it announced that threat actors breached its systems and stole some of its Red Team assessment tools, no zero-day vulnerabilities are exploited by these tools, which means patches and mitigations are available for each of the security holes. Now it’s up to impacted organizations to ensure that the vulnerabilities have been patched.
The stolen FireEye tools exploit 16 known vulnerabilities affecting products from Pulse Secure, Microsoft, Fortinet, Atlassian, Citrix, Zoho, and Adobe.
However, Qualys pointed out that a vast majority of the vulnerable instances (99.84%) are exposed to attacks due to eight critical and high-severity flaws affecting Microsoft products. Patching these issues can significantly reduce the attack surface.
Vulnerability remediation orchestration firm Vulcan Cyber has also shared a brief analysis of the FireEye tool vulnerabilities. Both Qualys and Vulcan Cyber have made available free tools and other resources that can help organizations address the security holes.
FireEye announced on December 8 that a highly sophisticated threat actor, which some believe is linked to Russia, had breached its corporate network and stole some of its Red Team hacking tools.
A few days later, it turned out that the attack on FireEye was related to a major cyber-espionage campaign targeting Texas-based IT management and monitoring solutions provider SolarWinds and its customers. SolarWinds has 300,000 customers worldwide, including many high-profile companies and government organizations.
The company says up to 18,000 may have been impacted as the attackers apparently only targeted customers of the Orion monitoring platform, by delivering trojanized updates for this product.
Several major companies have confirmed being affected, but they claim impact has been limited. It’s possible that U.S. government organizations may have been hit harder.
New Critical Flaws in Treck TCP/IP Stack Affect Millions of IoT Devices
23.12.2020
Vulnerebility
Thehackernews
The US Cybersecurity Infrastructure and Security Agency (CISA) has warned of critical vulnerabilities in a low-level TCP/IP software library developed by Treck that, if weaponized, could allow remote attackers to run arbitrary commands and mount denial-of-service (DoS) attacks.
The four flaws affect Treck TCP/IP stack version 6.0.1.67 and earlier and were reported to the company by Intel. Two of these are rated critical in severity.
Treck's embedded TCP/IP stack is deployed worldwide in manufacturing, information technology, healthcare, and transportation systems.
The most severe of them is a heap-based buffer overflow vulnerability (CVE-2020-25066) in the Treck HTTP Server component that could permit an adversary to crash or reset the target device and even execute remote code. It has a CVSS score of 9.8 out of a maximum of 10.
The second flaw is an out-of-bounds write in the IPv6 component (CVE-2020-27337, CVSS score 9.1) that could be exploited by an unauthenticated user to cause a DoS condition via network access.
Two other vulnerabilities concern an out-of-bounds read in the IPv6 component (CVE-2020-27338, CVSS score 5.9) that could be leveraged by an unauthenticated attacker to cause DoS and an improper input validation in the same module (CVE-2020-27336, CVSS score 3.7) that could result in an out-of-bounds read of up to three bytes via network access.
Treck recommends users to update the stack to version 6.0.1.68 to address the flaws. In cases where the latest patches cannot be applied, it's advised that firewall rules are implemented to filter out packets that contain a negative content-length in the HTTP header.
The disclosure of new flaws in Treck TCP/IP stack comes six months after Israeli cybersecurity company JSOF uncovered 19 vulnerabilities in the software library — dubbed Ripple20 — that could make it possible for attackers to gain complete control over targeted IoT devices without requiring any user interaction.
What's more, earlier this month, Forescout researchers revealed 33 vulnerabilities — collectively called AMNESIA:33 — impacting open-source TCP/IP protocol stacks that could be abused by a bad actor to take over a vulnerable system.
Given the complex IoT supply chain involved, the company has released a new detection tool called "project-memoria-detector" to identify whether a target network device runs a vulnerable TCP/IP stack in a lab setting.
You can access the tool via GitHub here.
Smart Doorbell Disaster: Many Brands Vulnerable to Attack
22.12.2020
Vulnerebility
Threatpost
Investigation reveals device sector is problem plagued when it comes to security bugs.
Smart doorbells, designed to allow homeowners to keep an eye on unwanted and wanted visitors, can often cause more security harm than good compared to their analog door bolt alternatives. Consumer-grade digital doorbells are riddled with potential cybersecurity vulnerabilities ranging from hardcoded credentials, authentication issues and devices shipping with unpatched and longstanding critical bugs.
That fresh assessment comes from NCC Group, which published a report last week outlining “domestic IoT nightmares.” In partnership with the publication Which?, it assessed smart doorbell models made by three vendors Victure, Qihoo and Accfly along with white-box offerings from three additional doorbell makers.
The verdict?
“Overall the issues we have seen during this research have
outlined a poor approach to developing secure IoT devices. There are still
devices being developed, shipped and sold with an array of issues let alone
these issue being cloned into knock-off, copycat devices,” wrote NCC Group’s
co-authors of the report.
2020 Reader Survey: Share Your Feedback to Help Us ImproveThe scope of the problems uncovered included undocumented features that, if known, could be exploited by hackers. Other issues found were tied to the mobile applications used to access the doorbells along with vulnerabilities in the hardware itself.
Noticeably absent from the analysis are the names of market-share leader Ring Video Doorbell and the handful other big players such as Nest, Vivint and Remo. Nevertheless, the study comes as a flood smart doorbells have been introduced into the consumer market feeding a robust appetite for the niche.
Smart doorbells lead the charge when it came to a 33 percent increase in smart home gadgets flooding U.S homes in 2020, according to Hub Entertainment Research. Thirty-nine percent of all U.S homes have a connected device.
Dangerous Doorbells
Specific models examined were Victure’s VD300, Accfly’s
Smart Video Doorbell V5 and Qihoo’s 360 D819 Smart Video Doorbell. Another
doorbell device, identified only as “Smart WiFi Doorbell” and that used hardware
from manufacture YinXx, was also examined. In addition, an unspecified “HD Wi-Fi
Video Doorbell V5” model was tested.
Lastly, a smart doorbell identified only as XF-IP007H, was tested. A number of brands use “XF-IP007H” in their product names, including Extaum, Docooler and Tickas. These doorbells, as with all tested by NCC Group, are each sold at competitive prices and available through Amazon’s ecommerce website, Walmart.com and other popular online retailers.
Researchers said the majority of the devices analyzed were clones of the Victure doorbell, which had a number of preexisting security issues associated with it.
Undocumented Features
One issue identified in the Qihoo device was an
undocumented and fully functional DNS service. “Investigation into this type of
service can sometimes lead down the route of a covert DNS channel for malware
delivery. We did not see anything during testing that could lead us into such a
rabbit hole,” wrote researchers.
With the Victure’s doorbell an undocumented HTTP service was found running on port 80. Researchers noted the port required credentials, however those credentials could easily be extracted from “an unbranded clone of this device for sale online.”
“The firmware was extracted from the cloned device to retrieve the login details by simply performing strings across the firmware. Further analysis of the device firmware revealed the API calls required to interact with the device,” researcher wrote. Next, combing through the output logs researchers found cleartext Wi-Fi name and passwords to be used in an attack against the Victure doorbell.
Mobile App Attack
Digital lock picking via the mobile application used to
control the digital doorbells were a cinch, thanks to unencrypted
communications.
“On a number of devices, HTTPS was not enforced or didn’t even exist as a communication method on a range of mobile applications such as the Victure mobile application which was found to be requesting a root certificate via a HTTP request,” researchers wrote.
A lack of encryption could allow sensitive information, such as username and passwords, to be “seen” in the data communications between mobile device and the digital lock’s backend services.
Another attack vector discussed was the abuse of QR codes, a type of image-based barcode for quickly obtaining additional information. Many of the digital doorbells, in attempts to simplify access, allowed customers to use their phone’s camera to take a picture of a QR code, which configures the user’s app with the correct credentials.
“Some people use their smartphones to take screenshots of different things, while most modern smartphones also automatically backup photos,” researcher said. In this scenario, an adversary with access to a user’s cloud-based camera roll backup would also have access to QR codes. “The attacker can then quickly decode the QR code and extract the plaintext BSSID and password for the Wi-Fi network instead of having to attempt a deauth and/or evil twin attack,” they wrote.
Hardware Horrors
Researchers pointed out that often the physical doorbell
hardware was not securely mounted and could be easily removed – for tampering
purposes.
“The main method for these devices to be secured was using a mounting bracket that was either glued or screwed onto a flat surface and the device sat in the mounting bracket. It would be easy for an attacker to quickly release the doorbell from the bracket and steal the device in under 10 seconds and some of the devices had no method of notifying the user until it was too late that it was turned off, or moved,” they wrote.
Only one digital doorbell used a pressure trigger that if tampered with would start an alarm. Even so, the researchers pointed out a 2.4GHz jammer could thwart any alarm then the attacker could remove the devices batteries or disable the power cable.
By disjoining the hardware, an attacker could siphon video captured by the doorbell and stored to an SD card to determine typical occupant behavior. Also, firmware could be extracted and either be used to identify the Wi-Fi BSSID and plaintext Wi-Fi password for access a network.
“Once the firmware was obtained it was possible to analyse it using a range of binary analysis tools (Binwalk, Ghidra, even Linux tools as simple as Strings) to break down the firmware structure and discover sensitive information contained within the firmware including hardcoded credentials, IP addresses and break down the firmware to understand the firmware and its potential weaknesses,” researchers wrote.
Using this technique, NCC Group researchers determined one of the doorbell devices still had an unpatched Key Reinstallation Attacks (KRACK) vulnerability. The KRACK vulnerability, plugged in 2017, allows attackers to decrypt encrypted traffic, steal data and inject malicious code depending on the network configuration.
Concerns Over Victure Clones
“It can be confirmed conclusively that the
majority of the devices analyzed were clones of the Victure doorbell which
already had a range of security issues associated with it. There was also
evidence to show that the mobile applications that were being used by multiple
cloned doorbells were clones of each other as well,” researchers wrote.
Researchers said that the concerns were widespread and pointed to a lack of a security-by-design ethos by doorbell manufacturers. They added that, sadly digital doorbell makers weren’t alone and that similar issues plagued other devices such as smart plugs.
Critical Vulnerabilities Expose Dell Wyse Thin Client Devices to Attacks
22.12.2020
Vulnerebility
Securityweek
Dell on Monday informed customers that updates released for some of its Wyse Thin Client products patch a couple of critical vulnerabilities that can be exploited remotely without authentication to compromise devices.
The vulnerabilities were discovered by researchers at CyberMDX, a company that specializes in healthcare cybersecurity, and they can be leveraged to access arbitrary files on affected devices and execute malicious code.
Dell Wyse Thin Client is a small form-factor PC series that runs an operating system named ThinOS, which Dell advertises as “the most secure thin client operating system.” According to CyberMDX, there are more than 6,000 organizations using these products, including many healthcare providers, in the U.S. alone.Dell Wyse Thin Client vulnerability
CyberMDX researchers noticed that the local FTP server used by Wyse Thin Client devices to obtain new firmware, packages and configurations is, by default, accessible without credentials, allowing anyone on the network to access it.
An attacker could access an INI file stored on this server that contains configuration data for thin client devices and make modifications to that file.
“The INI files contain a long list of configurable parameters detailed on more than 100 pages by official Dell documentation,” CyberMDX explained in its advisory. “Reading or altering those parameters opens the door to a variety of attack scenarios. Configuring and enabling VNC for full remote control, leaking remote desktop credentials, and manipulating DNS results are some of the scenarios to be aware of.”
Attacks are possible due to two vulnerabilities: CVE-2020-29491, which allows an unauthenticated attacker to access the configuration file, and CVE-2020-29492, which allows them to make changes to the file.
Dell informed customers that the vulnerabilities impact Wyse 3040, 5010, 5040, 5060, 5070, 5470 and 7010 thin client devices running ThinOS 8.6 and prior. The flaws have been patched with the release of version 8.6 MR8 of ThinOS.
Earlier this month, CyberMDX disclosed a critical vulnerability impacting over 100 medical devices made by GE Healthcare. The flaw can be exploited to access or modify health information.
Two Critical Flaws — CVSS Score 10 — Affect Dell Wyse Thin Client Devices
22.12.2020
Vulnerebility
Thehackernews
A team of researchers
today unveils two critical security vulnerabilities it discovered in Dell Wyse
Thin clients that could have potentially allowed attackers to remotely execute
malicious code and access arbitrary files on affected devices.
The flaws, which were uncovered by healthcare cybersecurity provider CyberMDX and reported to Dell in June 2020, affects all devices running ThinOS versions 8.6 and below.
Dell has addressed both the vulnerabilities in an update released today. The flaws also have a CVSS score of 10 out of 10, making them critical in severity.
Thin clients are typically computers that run from resources stored on a central server instead of a localized hard drive. They work by establishing a remote connection to the server, which takes care of launching and running applications and storing relevant data.
Tracked as CVE-2020-29491 and CVE-2020-29492, the security shortcomings in Wyse's thin clients stem from the fact that the FTP sessions used to pull firmware updates and configurations from a local server are unprotected sans any authentication ("anonymous"), thus making it possible for an attacker in the same network to read and alter their configurations.

The first flaw, CVE-2020-29491, enables the user to access the server and read
configurations (.ini files) belonging to other clients.
A second consequence of having no FTP credentials is that anyone on the network can access the FTP server and directly alter the .ini files holding the configuration for other thin client devices (CVE-2020-29492).
Most devastatingly, the configuration may include sensitive data, including potential passwords and account information that could be used to compromise the device.
Given the relative ease of exploitation of these flaws, it's recommended that the patches are applied as soon as possible to remediate the risk.
CyberMDX also recommends updating compatible clients to ThinOS 9, which removes the INI file management feature. In the event an upgrade is not feasible, it's advised to disable the use of FTP for fetching the vulnerable files and instead rely on an HTTPS server or Wyse Management Suite.
"Reading or altering those parameters [in the .ini files] opens the door to a variety of attack scenarios," CyberMDX researchers said. "Configuring and enabling VNC for full remote control, leaking remote desktop credentials, and manipulating DNS results are some of the scenarios to be aware of."
Authentication Bypass Vulnerability Patched in Bouncy Castle Library
19.12.2020
Vulnerebility
Securityweek
A high-severity authentication bypass vulnerability was recently addressed in the Bouncy Castle cryptography library.
Founded in 2000, the project represents a collection of APIs used in cryptography for both Java and C#, with a strong emphasis on standards compliance and adaptability.
Synopsys CyRC security researchers revealed this week that an authentication vulnerability they identified in the OpenBSDBcrypt class of the Java cryptography library could be abused to bypass password checks in applications relying on the library. Tracked as CVE-2020-28052, the bug has a CVSS score of 8.1.
The OpenBSDBcrypt class leverages the Bcrypt algorithm for hashing passwords, and the researchers explain that the bug is the result of a flawed verification routine implemented in the method OpenBSDBcrypt.doCheckPassword.
“The code checks for an index of characters from 0 to 59 inclusive, rather than checking that characters at positions from 0 to 59 match. This means that passwords that result in hashes that, for instance, don’t contain bytes between 0x00 and 0x3B match every other password hash that don’t contain them,” Synopsys CyRC explains.
This means that an attacker can pass the check even if they can’t byte-for-byte match a stored hash value. Successful exploitation of the vulnerability could result in authentication bypass, allowing the attacker to perform operations as a legitimate user, including administrators.
According to the security researchers, an attacker needs to perform brute-force attempts on the passwords until they can trigger the bypass.
“Our experiments show that 20% of tested passwords were successfully bypassed within 1,000 attempts. […] Further, our investigation shows that all password hashes can be bypassed with enough attempts. In rare cases, some password hashes can be bypassed with any input,” the researchers say.
The issue was found to affect Bouncy Castle versions 1.65 and 1.66, but not previous releases. Bouncy Castle 1.67 was released on November 1, 2020, with patches for the vulnerability.
Both vendors and users of software that relies on this library are advised to upgrade to Bouncy Castle Java release 1.67 or later, to ensure they are not exposed.
5M WordPress Sites Running ‘Contact Form 7’ Plugin Open to Attack
18.12.2020 Vulnerebility Threatpost
A critical unrestricted file upload bug in Contact Form 7 allows an unauthenticated visitor to take over a site running the plugin.
A patch for the popular WordPress plugin called Contact Form 7 was released Thursday. It fixes a critical bug that allows an unauthenticated adversary to takeover a website running the plugin or possibly hijack the entire server hosting the site. The patch comes in the form of a 5.3.2 version update to the Contact Form 7 plugin.
The WordPress utility is active on 5 million websites with a majority of those sites (70 percent) running version 5.3.1 or older of the Contact Form 7 plugin.
The critical vulnerability (CVE-2020-35489) is classified as an unrestricted file upload bug, according to Astra Security Research, which found the flaw on Wednesday.
Quick Fix
“The plugin developer (Takayuki Miyoshi) was quick to fix the
vulnerability, realizing its critical nature. We communicated back and forth
trying to release the update as soon as possible to prevent any exploitation. An
update fixing the issue has already been released, in version 5.3.2,” according
to Astra.
The bug hunter credited for identifying the flaw, Jinson Varghese,
wrote that the vulnerability allows an unauthenticated user to bypass any form
file-type restrictions in Contact Form 7 and upload an executable binary to a
site running the plugin version 5.3.1 or earlier.
Next, the adversary can do a number of malicious things, such as deface the website or redirect visitors to a third-party website in attempt to con visitors into handing over financial and personal information.
In addition to taking over the targeted website, an attacker could also commandeer the server hosting the site if there is no containerization used to segregate the website on the server hosting the WordPress instance, according to researchers.
Easy to Exploit
“It is easily exploitable. And the attacker wouldn’t need to
be authenticated and the attack can be done remotely,” said Naman Rastogi,
digital marketer and growth hacker with Astra, in an email interview with
Threatpost.
He said a Contact Form 7 update has now been pushed. “For users who have automatic updates on for WordPress plugin the software will automatically update. For others, they indeed will be required to proactively update,” he told Threatpost.
To keep perspective on the bug, web analytics firm Netcraft estimates there are 455 million websites using the WordPress platform right now. That suggests 1.09 percent of WordPress sites could be vulnerable to attack via this flaw.
5 million WordPress sites potentially impacted by a Contact Form 7 flaw
18.12.2020
Vulnerebility
Securityaffairs
The development team behind the Contact Form 7 WordPress plugin discloses an
unrestricted file upload vulnerability.
Jinson Varghese Behanan from Astra
Security discovered an unrestricted file upload vulnerability in the popular
Contact Form 7 WordPress vulnerability. The WordPress plugin allows users to add
multiple contact forms on their site.
“By exploiting this vulnerability, attackers could simply upload files of any type, bypassing all restrictions placed regarding the allowed upload-able file types on a website.” reads the post published by the Astra Security Research team. “Further, it allows an attacker to inject malicious content such as web shells into the sites that are using the Contact Form 7 plugin version below 5.3.1 and have file upload enabled on the forms.”
The development team already addressed the flaw with the release of the 7 5.3.2 version and urges site admins to upgrade their installs.
Behanan praised the development team that quickly fixed the vulnerability.
The WordPress plugin has over 5 million active installs, attackers can exploit the vulnerability to upload a file that can be executed as a script file on the underlying server.
The issue allows attackers to can bypass the plugin’s filename sanitization.
“Contact Form 7 5.3.2 has been released. This is an urgent security and maintenance release. We strongly encourage you to update to it immediately.” reads the security advisory published by the development team.
“An unrestricted file upload vulnerability has been found in Contact Form 7 5.3.1 and older versions. Utilizing this vulnerability, a form submitter can bypass Contact Form 7’s filename sanitization, and upload a file which can be executed as a script file on the host server.”
Below the disclosure timeline:
December 16, 2020 – Initial discovery of the Unrestricted File Upload
vulnerability
December 16, 2020 – The Astra Security Research reached out to
the plugin developers and receives an acknowledgment
December 17, 2020 – We
send over full vulnerability disclosure details to the Contact Form 7 team
December 17, 2020 – After fixing up the vulnerability the initial insufficient
patch was released
December 17, 2020 – We provided more details about the
vulnerability to the plugin developers
December 17, 2020 – The final
sufficient patch is released in the plugin version 5.3.2
Trend Micro Patches Serious Flaws in Product Used by Companies, Governments
18.12.2020
Vulnerebility
Securityweek
Trend Micro informed customers this week that an update for its InterScan Web Security Virtual Appliance (IWSVA) patches several potentially serious vulnerabilities, including ones that can be exploited to remotely take control of the appliance.
The vulnerabilities were discovered by Wolfgang Ettlinger, a researcher at Austria-based cybersecurity consultancy SEC Consult, and they were reported to Trend Micro in the summer of 2019. However, the vendor only managed to completely patch all of the security holes in late November 2020, with the release of IWSVA 6.5 SP2 CP b1919.
While the validation and patching process took a fairly long time, SEC Consult told SecurityWeek that the Trend Micro PSIRT handled the issue very professionally, “in contrast to other larger companies we have encountered in the past.”
Trend Micro IWSVA is a web gateway that helps enterprises protect their systems against online threats, while also providing real-time visibility and control of employee internet usage.
Ettlinger identified a total of six types of vulnerabilities in the IWSVA product, including CSRF protection bypass, XSS, authorization and authentication bypass, command execution, and command injection issues, a majority of which have been classified as high severity.
SEC Consult told SecurityWeek that it has identified three attack scenarios that can exploit these vulnerabilities. In one of them, an attacker can gain root access to a targeted appliance remotely from the internet by chaining the CSRF and command execution vulnerabilities.
In another scenario, an attacker with access to the HTTP proxy port could exploit the authentication/authorization bypass vulnerabilities and the command execution flaw to take over the appliance as root, without user or admin interaction.
In the third attack scenario described by the company, an attacker with network access to the admin interface could exploit the command injection vulnerability — which affects the login process under certain configurations — to execute arbitrary OS commands on the appliance as a user named “iscan” and possibly elevate privileges.
While it’s unclear exactly how many organizations are using the affected Trend Micro product, SEC Consult told SecurityWeek that it has notified cybersecurity agencies in Germany and Austria, and learned that the product is used by major corporations and even government organizations.
SEC Consult has published an advisory containing technical information for each
of the vulnerabilities, but the company says it’s not releasing the actual PoC
exploits. A video demonstrating an attack has also been made available:
“We are aware of the vulnerabilities found in the IWSVA product and commend SEC Consult for responsibly disclosing them and working closely with us to resolve the issues,” Trend Micro told SecurityWeek in an emailed statement. “We have released a critical patch that resolves these vulnerabilities and the solution is available now. We recommend customers apply the patch and review our bulletin for some additional best practice configuration recommendations.”
HPE discloses critical zero-day in Systems Insight Manager
17.12.2020
Vulnerebility
Securityaffairs
HPE has disclosed a zero-day vulnerability in the latest versions of its HPE
Systems Insight Manager (SIM) software for both Windows and Linux.
Hewlett
Packard Enterprise (HPE) has disclosed a zero-day remote code execution flaw
that affects the latest versions of its HPE Systems Insight Manager (SIM)
software for Windows and Linux.
HPE SIM is a management and remote support automation solution for multiple HPE solutions, including servers, storage, and networking products.
The flaw stems from the lack of proper validation of user-supplied data that can result in the deserialization of untrusted data. The vulnerability could be exploited by attackers with no privileges without user interaction.
“A potential security vulnerability has been identified in HPE Systems Insight Manager (SIM) version 7.6. The vulnerability could be exploited to allow remote code execution.” reads the security advisory.
At the time of this writing, the issue is yes to be fixed, the IT giant only provided mitigations for Windows while it is working to address the issue.
The zero-day flaw, tracked as CVE-2020-7200, was discovered by the researcher Harrison Neal that reported it through the Trend Micro’s Zero Day Initiative.
The vulnerability affects HPE Systems Insight Manager (SIM) 7.6.x., it received a severity score of 9.8/10.
HPE did not reveal if it is aware of attacks in the wild exploiting the zero-day
vulnerability.
To avoid exploitation of the issue, the company recommends
removing the “Federated Search” & “Federated CMS Configuration” feature with
this step-by-step procedure:
Stop HPE SIM Service
Delete <C:\Program Files\HP\Systems Insight
Manager\jboss\server\hpsim\deploy\simsearch.war> file from sim installed path
del /Q /F C:\Program Files\HP\Systems Insight
Manager\jboss\server\hpsim\deploy\simsearch.war
Restart HPE SIM Service
Wait for HPE SIM web page “https://SIM_IP:50000” to be accessible and execute
the following command from command prompt. mxtool -r -f
tools\multi-cms-search.xml 1>nul 2>nul
Millions of Unpatched IoT, OT Devices Threaten Critical Infrastructure
16.12.2020
Vulnerebility
Threatpost
Industrial, factory and
medical gear remain largely unpatched when it comes to the URGENT/11 and CDPwn
groups of vulnerabilities.
Thousands of organizations remain at risk from the URGENT/11 and CDPwn collections of vulnerabilities, which affect operational technology (OT) gear and internet of things (IoT), respectively. Unfortunately, there has been a rampant lack of patching, researchers said.
According to researchers at Armis, a whopping 97 percent of the OT devices impacted by URGENT/11 have not been patched, despite fixes being delivered in 2019. And, 80 percent of those devices affected by CDPwn remain unpatched.
URGENT/11 is a collection of 11 different bugs that can affect any connected device leveraging Wind River’s VxWorks that includes an IPnet stack (CVEs from Wind River available here). VxWorks is a real-time operating system (RTOS) that third-party hardware manufacturers have embedded in more than 2 billion devices across industrial, medical and enterprise environments.
Affected devices, including programmable logic controllers from Schneider Electric and Rockwell Automation, are typically used in production and manufacturing environments to carry out various mission-critical tasks, such as monitoring and control of physical devices that operate various instruments (e.g motors, valves, pumps, etc.).
Most concerningly, URGENT/11 includes six remote code-execution (RCE) vulnerabilities that could give an attacker full control over a targeted device, via unauthenticated network packets.
“URGENT/11 could allow attackers to remotely exploit and take over mission critical devices, bypassing traditional perimeter and device security. Every business with these devices needs to ensure they are protected,” said Yevgeny Dibrov, CEO and co-founder of Armis, when the bugs were discovered. “The vulnerabilities in these unmanaged and IoT devices can be leveraged to manipulate data, disrupt physical world equipment, and put people’s lives at risk.”
CDPwn encompasses five critical vulnerabilities discovered in February in the Cisco Discovery Protocol (CDP), the info-sharing layer that maps all Cisco equipment on a network. The bugs can allow attackers with an existing foothold in the network to break through network-segmentation efforts and remotely take over millions of devices.
CDP is a Cisco proprietary Layer 2 network protocol that is used to discover information about locally attached Cisco equipment. CDP aids in mapping the presence of other Cisco products in the network and is implemented in virtually all Cisco products – including switches, routers, IP phones and IP cameras. Many of these devices cannot work properly without CDP, and do not offer the ability to turn it off, according to Armis.
The lack of patching lays open critical environments to takeover, according to Ben Seri, vice president of research at Armis.
“These devices are not simply used in everyday businesses but are core to our healthcare, manufacturing and energy industries,” he said, in a recent blog post.
The news comes as attackers continue to exploit the bugs. For instance, in October, the NSA identified one of the CDPwn flaws (CVE-2020-3118) as No. 24 on the list of the Top 25 vulnerabilities that are currently being consistently scanned, targeted and exploited by Chinese state-sponsored hacking groups.
Some of the URGENT/11-affected manufacturers did not provide updates, Seri noted, but even for those that did, it is a labor-intensive program to update impacted devices because they tend to be mission-critical and taking them offline to patch is often not an option. Cisco meanwhile did provide patches for CDPwn at the time of disclosure.
Seri note the increasingly common scenario where combining the CDPwn and URGENT/11 vulnerabilities represents a very serious risk to these environments—giving attackers the opportunity to take over Cisco network equipment, move laterally across the network, and gain access to mission-critical devices like infusion pumps and PLCs.
“An attacker can infiltrate a network, lie in wait, and conduct reconnaissance undetected, then execute an attack that could cause significant financial or property damage, impact production or operations, or impact patient delivery and care,” he warned.
To protect themselves, organizations should patch wherever possible, but should also strive for complete visibility of their device footprint, behavioral analysis of the activity of those devices, and a capability to remediate issues or isolate compromised devices, Seri said.
“Most of the IT, internet of medical things (IoMT), OT and IoT devices lack any means of installing cybersecurity software or agents, which means you need to have agentless protection capable of discovering every device in the environment and detecting vulnerable code on devices,” Seri added. “You should also be able to map connections from devices throughout your network and detect anomalies in behavior that indicate suspicious or malicious behavior or communications so you can take the appropriate action.”
Easy WP SMTP Security Bug Can Reveal Admin Credentials
16.12.2020
Vulnerebility
Threatpost
A poorly configured file
opens users up to site takeover.
Easy WP SMTP, a WordPress plugin for email management that has more than 500,000 installations, has a vulnerability that could open the site up to takeover, researchers said.
Easy WP SMTP allows users to configure and send all outgoing emails via a SMTP server, so that they don’t end up in the recipient’s junk/spam folder. Version 1.4.2 and below contains a flaw in the debug file that is exposed because of a fundamental error in how the plugin maintains a folder, according to researchers at GBHackers.
“[The vulnerability] would allow an unauthenticated user to reset the admin password which would enable the hacker to take complete control of the website,” according to a Monday posting.
This optional debug log is where the plugin writes all email messages (headers and body) sent by the website. It is located inside the plugin’s installation folder, “/wp-content/plugins/easy-wp-smtp/,” researchers said.
The log is a simple text file; and the plugin’s folder doesn’t have an index.html file, so that on servers that have directory listing enabled, hackers can find and view the log, paving the way for a username enumeration scan. This can allow attackers to find the admin login.
“Hackers can also perform the same task using the author achieve scans (/?author=1),” the researchers explained. “They access the login page and ask for the reset of the admin password. Then, they access the Easy WP SMTP debug log again in order to copy the reset link sent by WordPress. Once the link is received, they reset the admin password.”
Logging into the admin dashboard gives attackers run of the site, including the ability to install rogue plugins, the researchers said.
Users should update to the current version 1.4.4 to patch the issue.
Problematic Plugins
WordPress plugins continue to provide a convenient avenue
to attack for cybercriminals.
In November, a security vulnerability was found in the Welcart e-Commerce plugin opens up websites to code injection. This can lead to payment skimmers being installed, crashing of the site or information retrieval via SQL injection, researchers said.
In October, two high-severity vulnerabilities were disclosed in Post Grid, a WordPress plugin with more than 60,000 installations, which opened the door to site takeovers. And in September, a high-severity flaw in the Email Subscribers & Newsletters plugin by Icegram was found to affect more than 100,000 WordPress websites.
Earlier, in August, a plugin that is designed to add quizzes and surveys to WordPress websites patched two critical vulnerabilities. The flaws could be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites. Also in August, Newsletter, a WordPress plugin with more than 300,000 installations, was discovered to have a pair of vulnerabilities that could lead to code-execution and even site takeover.
And, researchers in July warned of a critical vulnerability in a WordPress plugin called Comments – wpDiscuz, which is installed on more than 70,000 websites. The flaw gave unauthenticated attackers the ability to upload arbitrary files (including PHP files) and ultimately execute remote code on vulnerable website servers.
Firefox Patches Critical Mystery Bug, Also Impacting Google Chrome
16.12.2020 Vulnerebility Threatpost
Mozilla Foundation releases Firefox 84 browser, fixing several flaws and delivering performance gains and Apple processor support.
A Mozilla Foundation update to the Firefox web browser, released Tuesday, tackles one critical vulnerability and a handful of high-severity bugs. The update, released as Firefox version 84, is also billed by Mozilla as boosting the browser’s performance and adding native support for macOS hardware running on its own Apple processors.
In total, six high-severity flaws were fixed, in addition to the critical bug, tracked as CVE-2020-16042. The specific critical bug in Firefox was also highlighted earlier this month in Google’s Chrome browser security update, where it was rated as a high-severity flaw.
The Firefox and Chrome bug in question (CVE-2020-16042) is still not fully described by either browser maker, and is only listed as a memory bug.
Mystery Bug Also Impacts Google Chrome Web Browser
In the Mozilla security
advisory, CVE-2020-16042 is described as a flaw in the JavaScript component
called BigInt that “could have caused uninitialized memory to be exposed.”
BigInt is a JavaScript component used to represent “arbitrarily large integers” in the context of a JavaScript process within the browser, according to a Mozilla description.
Google describes the same flaw differently. It calls it an “uninitialized-use” bug impacting Chrome’s V8 JavaScript engine. It is also unclear from Google’s bulletin the exact nature of the flaw. But cybersecurity researchers have described these types of uninitialized-use bugs as “largely overlooked” and often “regarded as insignificant memory errors.”
“[These] are actually a critical attack vector that can be reliably exploited by hackers to launch privilege-escalation attacks in the Linux kernel,” according to 2017 research published by the Georgia Institute of Technology.
The CVE was also referenced last week by Microsoft, as part of its December Patch Tuesday list of bugs impacting its Edge browser version 87.0.664.57. Microsoft’s Edge browser, release in January 2020, is based on Google’s open-source software project Chromium. The Chromium source code is used in Google’s Chrome browser and Microsoft’s 2020 Edge browser.
The V8 JavaScript Engine and WebAssembly
The V8 open-source JavaScript
engine was developed by the Chromium Project for Google Chrome and Chromium web
browsers. The V8 JavaScript engine is not supported by Firefox, but the
WebAssembly component, often associated with V8, is.
WebAssembly, or WASM for short, is an open standard that defines a portable binary-code format for executable programs, according to the WebAssembly project. “WebAssembly describes a memory-safe, sandboxed execution environment that may even be implemented inside existing JavaScript virtual machines,” according to the project website.
Mozilla’s Firefox browser is not Chromium based. WASM is supported in Mozilla Firefox and Apple Safari, even though both do not use Google’s V8. Some clues as to the nature of the bug can be derived by the fact the bug impacts both the Firefox and Chrome browser – the common denominator is WASM. In addition, a 2018 analysis of WASM and V8 bugs warned of possible security issues.
In 2018, Google’s Project Zero published research titled “The Problems and Promise of WebAssembly” and identified three vulnerabilities, which were mitigated. One future WASM threats, Google warned, was tied to WebAssembly’s garbage collector (GC) function.
WebAssembly the Culprit?
GC is an important process tied to JavaScript
engines. “Java applications obtain objects in memory as needed. It is the task
of GC in the Java virtual machine (JVM) to automatically determine what memory
is no longer being used by a Java application and to recycle this memory for
other uses,” describes John Worthington in a post on the importance of GC.
As for Google, it warned in 2018:
“WebAssembly GC is another potential feature of WebAssembly that could lead to security problems. Currently, some uses of WebAssembly have performance problems due to the lack of higher-level memory management in WebAssembly. For example, it is difficult to implement a performant Java Virtual Machine in WebAssembly. If WebAssembly GC is implemented, it will increase the number of applications that WebAssembly can be used for, but it will also make it more likely that vulnerabilities related to memory management will occur in both WebAssembly engines and applications written in WebAssembly.”
At both national vulnerability database repositories, MITRE and NIST, the technical specifics of the CVE have yet to be publicly disclosed. In Google’s December Security Bulletin, it noted details tied to CVE-2020-16042 and other bugs were being withheld, “until a majority of users are updated with a fix.” It also noted that when and if bugs exist in third-party code libraries used in other devices or platforms, technical details of the bugs are limited.
Credited for finding the bug is bug hunter André Bargull, who originally reported the bug on November 23, according to Google.
Six High-Severity Firefox Bugs
Memory issues dominated the list of
high-severity bugs patched by Mozilla Tuesday. Two “memory safety bugs”
(CVE-2020-35114 and CVE-2020-35113) were patched. Both CVEs addressed bugs in
Firefox 84 and its large-enterprise Firefox extended support release (ESR) 78.6
browser.
“Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code,” Mozilla wrote of both bugs.
Also tied to browser memory are bugs tracked as CVE-2020-26971, CVE-2020-26972 and CVE-2020-26973, which include a heap-buffer-overflow in WebGL, use-after-free in WebGL and a CSS sanitizer performed incorrect sanitization flaw.
Vast Majority of OT Devices Affected by Urgent/11 Vulnerabilities Still
Unpatched
16.12.2020
Vulnerebility
Securityweek
A vast majority
of operational technology (OT) devices affected by the Urgent/11 vulnerabilities
and many devices impacted by the CDPwn flaws remain unpatched, IoT security firm
Armis reported on Tuesday.
According to the company, 97% of industrial devices affected by the Urgent/11 vulnerabilities have not been patched. As for the CDPwn bugs, 80% of impacted devices are still vulnerable to attacks.
Armis told SecurityWeek that this is based on data from the company’s Device Knowledgebase, a crowd-sourced, cloud-based device behavior knowledgebase that tracks 280 million devices.
“To determine the vulnerable devices, we used Armis' Device Knowledgebase to track the firmware versions installed on a subset of impacted vendors and models,” explained Ben Seri, VP of research at Armis. “For URGENT/11 and the impact on OT, we looked at a large subset of Rockwell and Schneider PLCs. For CDPwn, we looked at Cisco Nexus Switches and Cisco VoIPs (78xx series and 88xx series). Armis has very detailed data on the firmware versions that each device is running, and matching rules for CVEs. So we pulled the data on the number of devices of certain vendors and the models that are running firmwares that aren’t patched, versus those that are.”
For example, Armis found that only 2.38% of Rockwell Automation devices and less than 1% of Schneider Electric devices affected by Urgent/11 have been patched since the disclosure of the vulnerabilities in July 2019.
The 11 vulnerabilities tracked as Urgent/11 affect Wind River’s VxWorks and other real time operating systems (RTOS). The security holes are believed to affect hundreds of millions of devices — including industrial, enterprise and medical devices — and some of them can allow attackers to take control of targeted devices.
The vulnerabilities collectively tracked as CDPwn affect the Cisco Discovery Protocol (CDP) and they are believed to impact tens of millions of Cisco products, including IP phones, routers, switches and cameras. At least one of the CDPwn vulnerabilities has been exploited by Chinese state-sponsored hackers, the NSA reported a few weeks ago.
Armis has published a paper showing how attackers could bypass existing mitigations to exploit the CDPwn vulnerabilities to target IoT devices in enterprise networks. The company has determined that in industries such as retail and aviation, more than 80% of Cisco VoIP devices are vulnerable to CDPwn attacks. As for Cisco Nexus switches, the aviation and OT sectors lag behind, with more than 85% of devices unpatched.
While there haven’t been any reports of the Urgent/11 vulnerabilities being exploited in malicious attacks, Armis researchers have demonstrated how attackers could leverage the flaws to take control of programmable logic controllers (PLCs) from Schneider Electric and Rockwell Automation, without authentication or user interaction.
“In the case of the Rockwell Automation PLC, we were able to take control of the
Ethernet module that manages communication between the PLC and the engineering
workstation and gain unconstrained access over the PLC,” Armis explained in a
blog post. “In the case of the Schneider Electric PLC, the Ethernet module is
built-in within the Modicon PLC, thus by taking it over we had also gained
ring-0 access to the entire PLC.”
Vulnerability in NI Controller Can Allow Hackers to Remotely Disrupt Production
12.12.2020
Vulnerebility
Securityweek
A potentially serious vulnerability affecting CompactRIO controllers made by NI (National Instruments) could allow hackers to remotely disrupt production processes in an organization, according to researchers.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) last week published an ICS-CERT advisory to inform organizations about a high-severity vulnerability affecting NI’s CompactRIO product, a rugged, real-time controller used in industrial environments in sectors such as heavy equipment, industrial manufacturing, transportation, power generation, and oil and gas.CompactRIO controller vulnerability
According to CISA, the vulnerability, identified by researchers at Spain-based industrial cybersecurity company Titanium Industrial Security, is related to “incorrect permissions set by default for an API entry-point of a specific service.” A remote and unauthenticated attacker can leverage the flaw to trigger a function that can cause the device to reboot.
The security hole, tracked as CVE-2020-25191, has been patched by NI and the CISA advisory contains instructions on how to deploy the patch, but it’s worth noting that part of the patching process needs to be repeated for each of the affected CompactRIO controllers.
“We are aware of the issue and have taken immediate action to address the vulnerability in recent versions of NI’s CompactRio driver,” an NI spokesperson said in an emailed statement. “We are not aware of any incidents where this potential vulnerability has been exploited but have provided recommended steps for mitigation as part of the disclosure filed with CISA. Maintaining the safety and security of all NI products remains our top priority.”
Borja Lanseros, CEO of Titanium Industrial Security, told SecurityWeek that the vulnerability was reported to the vendor in May 2019, but it was only patched in September 2020.
Lanseros explained that an attacker could exploit the vulnerability to repeatedly reboot the device, causing a prolonged denial-of-service (DoS) condition and potentially disrupting associated industrial processes.
“[An attack can cause] a sudden stop of the production process for some period of time. This could lead to economic losses for the affected company,” Lanseros said.
The security hole can be exploited remotely from the internet and Titanium Industrial Security said it had identified nearly 150 internet-exposed devices using the Shodan search engine.
Critical Steam Flaws Could Let Gamers Crash Opponents’ Computers
11.12.2020 Vulnerebility Threatpost
Valve fixed critical bugs in its Steam gaming client, which is a platform for popular video games like Counter Strike: Global Offensive, Dota2 and Half Life.
Game developer Valve has fixed critical four bugs in its popular Steam online game platform. If exploited, the flaws could allow a remote attacker to crash an opponent’s game client, take over the computer – and hijack all computers connected to a third-party game server.
Steam is utilized by more than 25 million users, and serves as a platform for a number of wildly popular video games, including Counter Strike: Global Offensive, Dota2 and Half Life. The vulnerabilities, which were disclosed on Thursday, were discovered in the network library of Steam, which is known as Steam Sockets. This library is part of a toolkit for third-party game developers.
“Video games have reached an all-time-high during the coronavirus pandemic,” Eyal Itkin, security researcher at Check Point, said in a Thursday analysis. “With millions of people currently playing online games, even the slightest security issue can be a serious concern for gaming companies and gamer privacy. Through the vulnerabilities we found, an attacker could have taken over hundreds of thousands of gamer computers every day, with the victims being completely blind to it.”
Researchers disclosed the flaws to Valve in September; the vendor rolled out fixes after three weeks to different Steam games. Researchers said that in order to apply the patches, Steam gamers were required to install the update before they could launch a game.
The four flaws (CVE-2020-6016, CVE-2020-6017, CVE-2020-6018 and CVE-2020-6019) exist in Steam Sockets prior to version v1.2.0. The first three CVEs score 9.8 out of 10 on the CVSS scale, making them critical in severity, while the fourth ranks 7.5 out of 10, making it high-severity.
CVE-2020-6016 exists because Steam Sockets improperly handles “unreliable segments” in the function SNP_ReceiveUnreliableSegment(). This can lead to a heap-based buffer underflow, where the input data is (or appears to be) shorter than the reserved space.
The flaw tied to CVE-2020-6017 is due to SNP_ReceiveUnreliableSegment() improperly handling long unreliable segments when configured to support plain-text messages, leading to a heap-based buffer overflow (where the input data is longer than the reserved space).
The bug tied to CVE-2020-6018 meanwhile is due to the improper handling of long encrypted messages in the function AES_GCM_DecryptContext::Decrypt(), leading to a stack-based buffer overflow.
And finally, the flaw relating to CVE-2020-6019 stems from the function CConnectionTransportUDPBase::Received_Data() improperly handling inlined statistic messages.
In order to exploit the flaws, an attacker would need to connect to a target game server. Then, the attacker could launch the exploit by sending bursts of malicious packets to opponent gamers or target servers. No interaction is needed from the target gamer or server.
“From this point, the attacker could deploy the same vulnerability, as both the game clients and game servers are vulnerable, to force the server to take over all connected clients, without any of them noticing,” said researchers.
That could open up various attack scenarios. One such scenario would include sabotaging online games, in which an attacker is able to crash the server at any time they please, forcing the game to stop for all gamers at once.
Researchers suggest that Valve gamers should make sure that they don’t have a notification about a pending update that they should install, though they should already protected through the fix. And, they should check that their games have indeed updated.
“Gamers of third-party games should check that their game clients received an update in recent months,” they said. “If not, they will need to contact the game developers to check when will an update be released.”
Steam has dealt with security issues before. In 2019, a researcher dropped a zero-day vulnerability that affected the Steam game client for Windows, after Valve said it wouldn’t fix it. Valve then published a patch, that the same researcher said can be bypassed and dropped a second zero day.
Zero-Click Wormable RCE Vulnerability in Cisco Jabber Gets Fixed, Again
11.12.2020 Vulnerebility Threatpost
A series of bugs, patched in September, still allow remote code execution by attackers.
Cisco Systems released an updated patch for a critical vulnerability in its video and instant messaging platform Jabber, originally patched in September. The cross-site scripting bug could have allowed an adversary to execute arbitrary code by merely sending a specially-crafted chat message and compromise a target’s system running the Jabber application.
This critical bug “does not require user interaction and is wormable, since the payload is delivered via an instant message,” said the researchers at Watchcom who found the flaw. “This means that it can be used to automatically spread malware without any user interaction,” they told Threatpost on Thursday.
The bug impacts Cisco Jabber for Windows, Jabber for MacOS and the Jabber for mobile platforms. The flaw (CVE-2020-26085) has a CVSS score of 9.9 out of 10, making it critical in severity. Researchers with Watchcom, who discovered the flaw, said at the time of the original discovery the implications of the vulnerability are especially serious given the current pandemic-driven work-from-home trend.
Two additional flaws, also patched in September, were also patched Thursday. Researchers at Watchcom, that originally found three of the bugs patched by Cisco, said they identified new ways to exploit the same flaws. Cisco also released additional patches, on Thursday, for high-severity bugs opening up Jabber to remote attackers to execute arbitrary commands on a targeted systems.
Watchcom and Cisco both said they were not aware of any active exploitation of any of the bugs in the wild.
Patch, Update, Patch and Repeat
The Cisco Jabber vulnerabilities that are
still open to exploitation are a cross-site scripting bug leading to RCE
(CVE-2020-26085), with a 9.9 CVSS rating. The second is a password hash stealing
information disclosure flaw (CVE-2020-27132), with a CVSS 6.5 severity rating.
Cisco has also patched a custom protocol handler command injection vulnerability
(CVE-2020-27133), rated high-severity with an CVSS rating of 8.8. An information
disclosure vulnerability (CVE-2020-27132), with a CVSS rating of medium, was
also patched. Lastly, there is the protocol handler command injection
vulnerability (CVE-2020-27127), with a CVSS severity-rating of 4.3.
Updated patches are available via Cisco’s Security Advisories support site.
“Cisco released a patch that fixed the injection points we reported, but the underlying problem has not been fixed,” wrote Watchcom researchers about the three vulnerabilities it identified (CVE-2020-26085, CVE-2020-27132, CVE-2020-27127) in September and re-identified as vulnerable to attack.
“We were able to find new injection points that could be used to exploit the vulnerabilities. All currently supported versions of the Cisco Jabber client (12.1 – 12.9) are affected. The three vulnerabilities have been assigned new CVE numbers to distinguish them from the vulnerabilities disclosed in September,” researchers wrote.
Both the original discovery of the vulnerabilities and the ‘re-discovery’ were made during security audits for a client, researchers said.
Nightmare Attack Scenario
In order to exploit these vulnerabilities, all a
hacker needs to be able to send a Jabber chat message to the victim, Watchcom
describes.
“This could happen if the targeted company allows adding contacts outside of the organization or if the attacker gains access to an employee’s Jabber username and password,” researchers wrote. “Once the attacker is able to send chat messages, he can take full control over the computers of everyone in the organization. The person receiving the message does not have to do anything, the attackers malicious code will run automatically once the message is received.”
To exploit the two Jabber message handling vulnerabilities (CVE-2020-26085, CVE-2020-27132) an attacker would need to send an Extensible Messaging and Presence Protocol (XMPP) message to a system running the Cisco Jabber client. “Attackers may require access to the same XMPP domain or another method of access to be able to send messages to clients,” Cisco noted.
Next, an attacker can cause the Jabber application to “run an arbitrary executable that already exists within the local file path of the application,” researchers said. The executable would run on the end-user system with the privileges of the user who initiated the Cisco Jabber client application, Watchcom wrote. Systems using Cisco Jabber in phone-only mode without XMPP messaging services enabled are not vulnerable to exploitation.
Breaking Down the Bugs
The most serious of the bugs (CVE-2020-26085), a
cross-site scripting flaw, impacts Cisco Jabber for Windows and Cisco Jabber for
MacOS. The flaw allow an authenticated, remote attacker to execute programs on a
targeted system.
“The vulnerability is due to improper validation of message contents. An attacker could exploit this vulnerability by sending specially crafted XMPP messages to the affected software. A successful exploit could allow the attacker to cause the application to execute arbitrary programs on the targeted system with the privileges of the user account that is running the Cisco Jabber client software, possibly resulting in arbitrary code execution,” Cisco wrote.
Watchcom said that flaw can be exploited to achieve RCE by escaping the client’s Chromium-based sandbox. Worse, is the fact the attack vector would be zero-click, wormable via an instant message and can be used to automatically spread malware without any user interaction.
The high-severity bug, tracked as CVE-2020-27134 by Cisco, is a message handling script injection vulnerability. Vulnerable is the Cisco Jabber for Windows, MacOS, and mobile platforms. The bug allows an authenticated, remote attacker to inject arbitrary script and potentially execute arbitrary commands on some platforms, Cisco said.
“The vulnerability is due to improper validation of message contents. An attacker could exploit this vulnerability by sending specially crafted XMPP messages to the affected software. By convincing a targeted user to interact with a message, an attacker could inject arbitrary script code within the Jabber message window interface,” according to the Cisco bulletinCisco explained the vulnerabilities are not dependent on one another. “Exploitation of one of the vulnerabilities is not required to exploit another vulnerability. In addition, a software release that is affected by one of the vulnerabilities may not be affected by the other vulnerabilities,” it wrote in its Cisco Security Advisory Thursday.
A second high-severity bug (CVE-2020-27133), effecting Cisco Jabber for Windows, is tied to improper handling of input to the application protocol handlers. According to Cisco, this could allow an unauthenticated, remote attacker to execute arbitrary commands.
“An attacker could exploit this vulnerability by convincing a user to click a link within a message sent by email or other messaging platform. A successful exploit could allow the attacker to execute arbitrary commands on a targeted system with the privileges of the user account that is running the Cisco Jabber client software,” Cisco said.
Discover, Disclosure Timeline
Watchcom said the timeline for the
vulnerabilities (CVE-2020-26085, CVE-2020-27132, CVE-2020-27127) it originally
found and then rediscovered is:
2nd September 2020: Original vulnerabilities publicly disclosed. Patches
released by Cisco.
25th September 2020: New vulnerabilities discovered and
reported to Cisco PSIRT. Case number assigned by Cisco. Issue forwarded to the
Cisco Jabber engineering team.
12th October 2020: Vulnerabilities confirmed
by Cisco.
12th October 2020 – 10th December 2020: Patches developed.
10th
December 2020: Patches released. Vulnerabilities publicly disclosed.
Cisco addresses critical RCE vulnerability in Jabber
11.12.2020
Vulnerebility
Securityaffairs
Cisco addressed a new critical RCE vulnerability that affects several versions
of Cisco Jabber for Windows, macOS, and mobile platforms.
Cisco has released
security updates to address a critical remote code execution (RCE) flaw
affecting several versions of Cisco Jabber for Windows, macOS, and mobile
platforms.
Cisco Jabber is an instant messaging and web conferencing desktop app that delivers messages between users using the Extensible Messaging and Presence Protocol (XMPP). The application is built on the Chromium Embedded Framework (CEF) and uses web technologies like HTML, CSS and JavaScript for its UI.
In September Cisco released security updates to address another critical RCE security flaw (CVE-2020-3495) stemming from a Cross-Site Scripting (XSS) issue in Cisco Jabber.
After Cisco mitigated the above issue, researchers at Watchcom discovered a new wormable RCE flaw and reported it to the IT giant. Watchcom explained that three flaws, including an RCE issue, have not been properly mitigated by the vendor.
The expert discovered new flaws that affect all currently supported Cisco Jabber versions, from 12.1 up to 12.9.
The RCE vulnerability discovered by the researchers is an XSS bug tracked as CVE-2020-26085. The flaw could be exploited by an attacker to execute arbitrary code remotely by escaping Cisco Jabber’s CEF sandbox.
“The vulnerability is due to improper validation of message contents. An attacker could exploit this vulnerability by sending specially crafted XMPP messages to the affected software.” reads the advisory published by Cisco. “A successful exploit could allow the attacker to cause the application to execute arbitrary programs on the targeted system with the privileges of the user account that is running the Cisco Jabber client software, possibly resulting in arbitrary code execution.”
The vulnerability could be exploited without user interaction and is wormable.
The experts published a video PoC f that attack that exploits the Cisco Jabber vulnerabilities fixed in September 2020.
Cybersecurity Agencies Warn of High-Severity OpenSSL Vulnerability
11.12.2020 Vulnerebility Securityweek
Computer emergency response teams (CERTs) and other cybersecurity agencies around the world have released alerts and advisories for a recently disclosed denial-of-service (DoS) vulnerability affecting OpenSSL, and vendors have started assessing the impact of the flaw on their products.
The OpenSSL Project announced this week that OpenSSL 1.1.1i fixes a high-severity vulnerability that can be exploited for remote DoS attacks. The security hole, tracked as CVE-2020-1971 and described as a NULL pointer dereference issue, was reported by Google’s David Benjamin and it impacts all 1.1.1 and 1.0.2 versions.
“The X.509 GeneralName type is a generic type for representing different types of names. One of those name types is known as EDIPartyName. OpenSSL provides a function GENERAL_NAME_cmp which compares different instances of a GENERAL_NAME to see if they are equal or not. This function behaves incorrectly when both GENERAL_NAMEs contain an EDIPARTYNAME. A NULL pointer dereference and a crash may occur leading to a possible denial of service attack,” the OpenSSL Project said in its advisory.
After the patch was made available, several organizations issued advisories and alerts to inform users about the risk posed by the vulnerability.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has advised admins and users to review the OpenSSL advisory and take action as needed.
The list of national cybersecurity agencies that have released advisories and alerts for CVE-2020-1971 includes Japan’s JPCERT, France’s CERT-FR, India’s National Critical Information Infrastructure Protection Center (NCIIPC), and Australia’s AusCERT. The European Union’s CERT-EU has shared links to news articles and advisories covering CVE-2020-1971.
Linux distributions have also released advisories, including Red Hat, Debian, Ubuntu and CloudLinux, which is a distribution designed for hosting providers and data centers.
In an advisory released on Wednesday, the CERT at Chinese cybersecurity firm Qihoo 360 said it spotted millions of impacted servers, with the highest numbers in the United States (1.2 million) and China (900,000).
Palo Alto Networks published an advisory on Wednesday to inform customers that the OpenSSL vulnerability does not impact its PAN-OS, GlobalProtect App, or Cortex XSOAR products. “The scenarios required for successful exploitation do not exist on these products,” the company said.
IBM published several security bulletins for OpenSSL vulnerabilities this week, but none of them references CVE-2020-1971 — they address OpenSSL flaws patched last year.
Cisco, F5 Networks and other major companies whose products use OpenSSL could also release advisories in the coming days.
Cisco Reissues Patches for Critical Bugs in Jabber Video Conferencing Software
11.12.2020
Vulnerebility
Thehackernews
Cisco has once again
fixed four previously disclosed critical bugs in its Jabber video conferencing
and messaging app that were inadequately addressed, leaving its users
susceptible to remote attacks.
The vulnerabilities, if successfully exploited, could allow an authenticated, remote attacker to execute arbitrary code on target systems by sending specially-crafted chat messages in group conversations or specific individuals.
They were reported to the networking equipment maker on September 25 by Watchcom, three weeks after the Norwegian cybersecurity firm publicly disclosed multiple security shortcomings in Jabber that were found during a penetration test for a client in June.
The new flaws, which were uncovered after one of its clients requested a verification audit of the patch, affects all currently supported versions of the Cisco Jabber client (12.1 - 12.9).
"Three of the four vulnerabilities Watchcom disclosed in September have not been sufficiently mitigated," Watchcom said in a report published today. "Cisco released a patch that fixed the injection points we reported, but the underlying problem has not been fixed. As such, we were able to 7ind new injection points that could be used to exploit the vulnerabilities."
Most critical among the flaws is CVE-2020-26085 (similar to CVE-2020-3495),
which has a severity rating of 9.9 out of 10, a zero-click cross-site scripting
(XSS) vulnerability that can be used to achieve remote code execution by
escaping the CEF sandbox.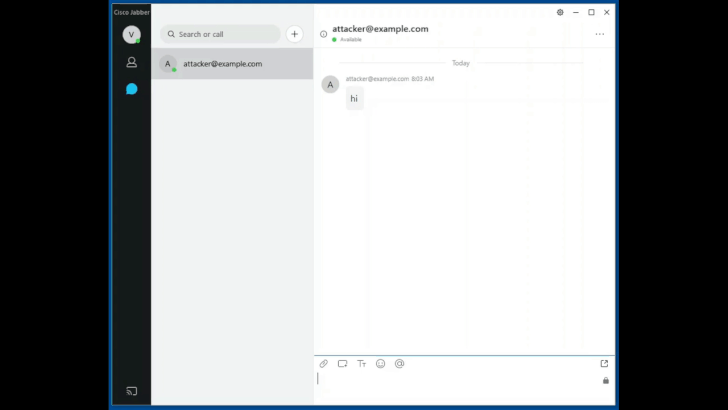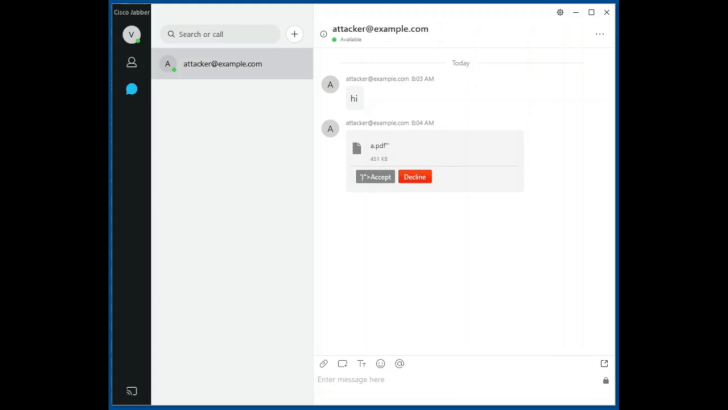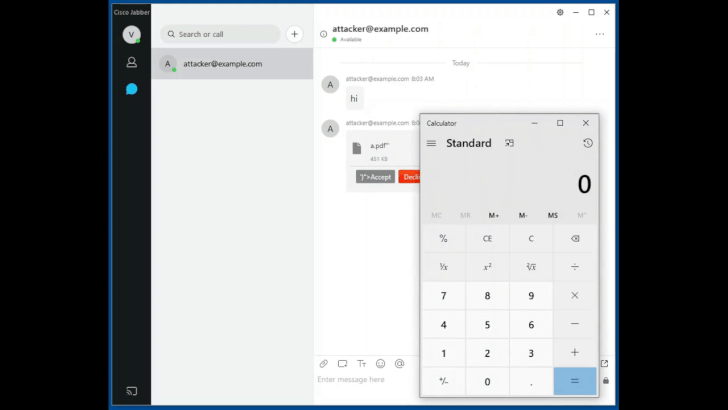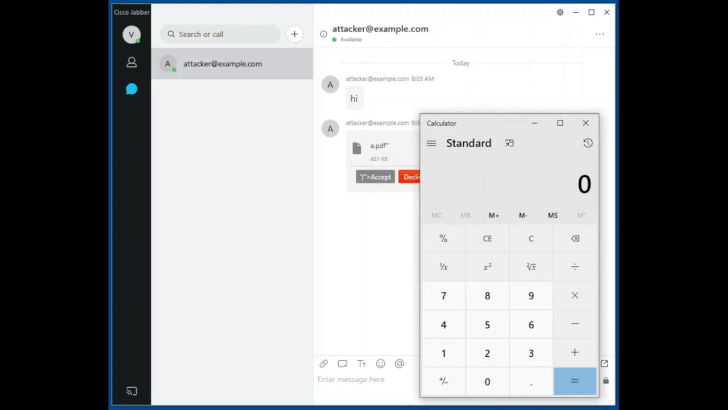
CEF or Chromium Embedded Framework is an open-source framework that's used to embed a Chromium-based web browser within other apps.
While the embedded browser is sandboxed to prevent unauthorized access to files, the researchers found a way to bypass the protections by abusing the window.CallCppFunction, which is designed to open files sent by other Cisco Jabber users.
All an adversary has to do is initiate a file transfer containing a malicious ".exe" file and force the victim to accept it using an XSS attack, then trigger a call to the aforementioned function, causing the executable to be run on the victim's machine.
Worse, this vulnerability doesn't require user interaction and is wormable, meaning it can be used to automatically spread the malware to other systems by disguising the payload in a chat message.
A second flaw, CVE-2020-27132, stems from the way it parses HTML tags in XMPP messages, an XML-based communications protocol used for facilitating instant messaging between any two or more network entities.
Due to the lack of proper sanitization of these tags, a harmless file transfer message can be manipulated by injecting, say, an image HTML tag pointing to a malicious URL or even execute malicious JavaScript code.
"No additional security measures had been put in place and it was therefore possible to both gain remote code execution and steal NTLM password hashes using this new injection point," the researchers said.
The third and final vulnerability (CVE-2020-27127) is a command injection flaw concerning protocol handlers, which are used to inform the operating system to open specific URLs (e.g., XMPP://, IM://, and TEL://) in Jabber, making it possible for an attacker to insert arbitrary command-line flags by simply including a space the URL.
Given the self-replicating nature of the attacks, it's advised that Jabber users update to the latest version of the software to mitigate the risk.
Watchcom also recommends that organizations consider disabling communication with external entities through Cisco Jabber until all employees have installed the update.
Valve's Steam Server Bugs Could've Let Hackers Hijack Online Games
11.12.2020
Vulnerebility
Thehackernews
Critical flaws in a core networking library powering Valve's online gaming functionality could have allowed malicious actors to remotely crash games and even take control over affected third-party game servers.
"An attacker could remotely crash an opponent's game client to force a win or even perform a 'nuclear rage quit' and crash the Valve game server to end the game completely," Check Point Research's Eyal Itkin noted in an analysis published today. "Potentially even more damaging, attackers could remotely take over third-party developer game servers to execute arbitrary code."
Valve is a popular US-based video game developer and publisher behind the game software distribution platform Steam and several titles such as Half-Life, Counter-Strike, Portal, Day of Defeat, Team Fortress, Left 4 Dead, and Dota.
The four flaws (CVE-2020-6016 through CVE-2020-6019) were uncovered in Valve's Game Networking Sockets (GNS) or Steam Sockets library, an open-sourced networking library that provides a "basic transport layer for games," enabling a mix of UDP and TCP features with support for encryption, greater reliability, and peer-to-peer (P2P) communications.
Steam Sockets is also offered as part of the Steamworks SDK for third-party game developers, with the vulnerabilities found on both Steam servers and on its clients installed on gamers' systems.
The attack hinges on a specific flaw in the packet reassembly mechanism (CVE-2020-6016) and a quirk in C++'s implementation of iterators to send a bunch of malicious packets to a target game server and trigger a heap-based buffer underflow, ultimately causing the server to abort or crash.
Following responsible disclosure to Valve on September 2, 2020, the binary updates containing the fixes were shipped to Valve's game clients and servers on September 17.
But according to Check Point, certain third-party game developers are yet to patch their clients as of December 2.
"Video games have reached an all-time-high during the coronavirus pandemic," Itkin said. "With millions of people currently playing online games, even the slightest security issue can be a serious concern for gaming companies and gamers' privacy. Through the vulnerabilities we found, an attacker could have taken over hundreds of thousands of gamer computers every day, with the victims being completely blind to it."
"Popular online platforms are good harvesting grounds for attackers. Whenever you have millions of users logging into the same place, the power of a strong and reliable exploit raises exponentially."
Check Point said that gamers playing Valve's games through Steam are already protected by the fix, although gamers of third-party games should ensure their game clients received an update in recent months to mitigate the risk associated with the flaw.
D-Link Routers at Risk for Remote Takeover from Zero-Day Flaws
10.12.2020 Vulnerebility Threatpost
Critical vulnerabilities discovered by Digital Defense can allow attackers to gain root access and take over devices running same firmware.
Buggy firmware opens a number of D-Link VPN router models to zero-day attacks. The flaws, which lack a complete vendor fix, allow adversaries to launch root command injection attacks that can be executed remotely and allow for device takeover.
Impacted are D-Link router models DSR-150, DSR-250, DSR-500 and DSR-1000AC VPN running firmware version 3.14 and 3.17, according to a report published Tuesday by Digital Defense. The attacks are dependent on three chained bugs identified by researchers as an unauthenticated remote LAN/WAN root command injection flaw, authenticated root command injection vulnerability and an authenticated crontab injection.
The flaws (CVE-2020-25757, CVE-2020-25759, CVE-2020-25758) were confirmed by D-Link. However, the company says beta firmware patches and hot-patch mitigations available for its DSR-150, DSR-250 and DSR-500 models significantly reduce the ability for an adversary to target a vulnerable router.
Threatpost Webinar Promo Bug Bounty
Click to register.
“The two vulnerabilities were confirmed, and patches are under development. One of the reported vulnerabilities is how the device functionally works, and D-Link will not correct it on this generation of products,” D-Link wrote in response to the research.
Some of the impacted router models were first introduced in 2012 and appear to lack the same type of patching cadence as more modern D-Link router models. For example, D-Link’s DSR-150, was released over seven-years ago.
Absent from the D-Link support page is information or fixes for more recent router models DSR-500 and DSR-1000AC VPN. Both were identified by Digital Defense as vulnerable to remotely exploitable root command injection flaws.
Work-from-Home Reality Increase Router Risks
The routers are common home
networking devices sold at numerous retail outlets, which means that people
working remotely due to the COVID-19 pandemic likely are exposing not only their
own environments but also corporate networks to risk, Digital Defense
researchers noted.
The key vulnerability can be exploited over the internet without authentication using both WAN and LAN interfaces, giving a a remote, unauthenticated attacker with access to the router’s web interface the ability to execute arbitrary commands as root, “effectively gaining complete control of the router,” according to the Digital Defense report.
“With this access, an attacker could intercept and/or modify traffic, cause denial of service conditions and launch further attacks on other assets,” researchers said, adding that D-Link routers can connect up to 15 other devices simultaneously.
D-Link Offers Technical Insights
D-Link provided some technical detail about
the bug in its report, noting that “the following Lua CGI actions, which are
accessible without authentication, execute a Lua library function which passes
user-supplied data to a call to os.popen() as part of a command intended to
calculate a hash: /platform.cgi?action=duaAuth, /platform.cgi?action=duaLogout.”
In addition to the unauthenticated command injection vulnerability, Digital Defense also reported two others to D-Link that can be exploited by attackers to take control of the routers, the company said.
The second flaw is similar to the firm but requires an authenticated user with access to the “Unified Services Router” web interface to inject arbitrary commands that will be executed with root privileges, according to D-Link.
“The Lua CGI, which handles requests from the ‘Package Management’ form in the ‘Unified Services Router’ web interface, has no server-side filtering for the multi-part POST parameters payload, which are passed to os. execute () functions intended to move the uploaded file to another directory,” according to D-Link.
The third issue is an authentication crontab injection vulnerability that allows authenticated users with access to the “Unified Services Router” web interface, either on LAN or WAN, to inject arbitrary CRON entries, according to D-Link. These will be executed as root by modifying a downloaded router configuration file, updating the CRC, and reuploading the resulting crafted configuration file, the company said.
“The configuration file’s mechanism is authenticated upon upload is trivially bypassed by a malicious user creating a crafted configuration file that adds new cron entries to execute arbitrary commands as root,” according to D-Link.
Beta Patches and Partial Fixes
Final patches for the first two flaws are
currently under development and will be released by mid-December, according to
D-Link.
“D-Link has made a patch in the form of a hotfix for the affected firmware versions and models. Reference the information provided in D-Link’s support announcement. The official firmware release is anticipated in mid-December. Users are advised to verify their hardware model and firmware to identify vulnerable devices and apply provided hotfix and any other updates until the official firmware is available,” Digital Defense wrote.
Home networks and the devices that run them have risen among security concerns since March when COVID-19 pandemic restrictions first forced those who could to work from home, a situation for which many organizations were largely unprepared. As the pandemic persists, so also do those concerns with the safety of corporate networks when connected to home networks, which are inherently less secure and present a host of new threats.
Indeed, a report released earlier this year found that most home routers contain a number of known vulnerabilities—sometimes hundreds of them—that remained largely unpatched, meaning that many of those currently working from home are likely at risk.
Amnesia:33 — Critical TCP/IP Flaws Affect Millions of IoT Devices
10.12.2020
Vulnerebility
Thehackernews
Cybersecurity researchers disclosed a dozen new flaws in multiple widely-used embedded TCP/IP stacks impacting millions of devices ranging from networking equipment and medical devices to industrial control systems that could be exploited by an attacker to take control of a vulnerable system.
Collectively called "AMNESIA:33" by Forescout researchers, it is a set of 33 vulnerabilities that impact four open-source TCP/IP protocol stacks — uIP, FNET, picoTCP, and Nut/Net — that are commonly used in Internet-of-Things (IoT) and embedded devices.
As a consequence of improper memory management, successful exploitation of these flaws could cause memory corruption, allowing attackers to compromise devices, execute malicious code, performing denial-of-service (DoS) attacks, steal sensitive information, and even poison DNS cache.
In the real world, these attacks could play out in various ways: disrupting the functioning of a power station to result in a blackout or taking smoke alarm and temperature monitor systems offline by using any of the DoS vulnerabilities.
The flaws, which will be detailed today at the Black Hat Europe Security
Conference, were discovered as part of Forescout's Project Memoria initiative to
study the security of TCP/IP stacks.
The development has prompted the CISA ICS-CERT to issue a security advisory in an attempt to provide early notice of the reported vulnerabilities and identify baseline preventive measures for mitigating risks associated with the flaws.
Millions of devices from an estimated 158 vendors are vulnerable to AMNESIA:33, with the possibility of remote code execution allowing an adversary to take complete control of a device, and using it as an entry point on a network of IoT devices to laterally move, establish persistence, and co-opt the compromised systems into botnets without their knowledge.
"AMNESIA:33 affects multiple open source TCP/IP stacks that are not owned by a single company," the researchers said. "This means that a single vulnerability tends to spread easily and silently across multiple codebases, development teams, companies and products, which presents significant challenges to patch management."
Because these vulnerabilities span across a complex IoT supply chain, Forescout cautioned it's as challenging it is to determine which devices are affected as they are hard to eradicate.
Like the Urgent/11 and Ripple20 flaws that were disclosed in recent times, AMNESIA:33 stems from out-of-bounds writes, overflow flaws, or a lack of input validation, leading to memory corruption and enabling an attacker to put devices into infinite loops, poison DNS caches, and extract arbitrary data.
Three of the most severe issues reside in uIP (CVE-2020-24336), picoTCP (CVE-2020-24338), and Nut/Net (CVE-2020-25111), all of which are remote code execution (RCE) flaws and have a CVSS score of 9.8 out of a maximum of 10.
CVE-2020-24336 - The code for parsing DNS records in DNS response packets sent
over NAT64 does not validate the length field of the response records, allowing
attackers to corrupt memory.
CVE-2020-24338 - The function that parses domain
names lacks bounds checks, allowing attackers to corrupt memory with crafted DNS
packets.
CVE-2020-25111 - A heap buffer overflow occurring during the
processing of the name field of a DNS response resource record, allowing an
attacker to corrupt adjacent memory by writing an arbitrary number of bytes to
an allocated buffer.
As of writing, vendors such as Microchip Technology and
Siemens that have been affected by the reported vulnerabilities have also
released security advisories.
"Embedded systems, such as IoT and [operational technology] devices, tend to have long vulnerability lifespans resulting from a combination of patching issues, long support lifecycles and vulnerabilities 'trickling down' highly complex and opaque supply chains," Forescout said.
"As a result, vulnerabilities in embedded TCP/IP stacks have the potential to affect millions – even billions – of devices across verticals and tend to remain a problem for a very long time."
Besides urging organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures, CISA has recommended minimizing network exposure, isolating control system networks and remote devices behind firewalls, and using Virtual Private Networks (VPNs) for secure remote access.
Microsoft Wraps Up a Lighter Patch Tuesday for the Holidays
9.12.2020
Vulnerebility
Threatpost
Nine critical bugs and
58 overall fixes mark the last scheduled security advisory of 2020.
Microsoft has addressed 58 CVEs (nine of them critical) for its December 2020 Patch Tuesday update. This brings the computing giant’s patch tally to 1,250 for the year – well beyond 2019’s 840.
This month’s security bugs affect Microsoft Windows, Edge (EdgeHTML-based), ChakraCore, Microsoft Office and Office Services and Web Apps, Exchange Server, Azure DevOps, Microsoft Dynamics, Visual Studio, Azure SDK and Azure Sphere, according to the update. None are listed as publicly known or under active attack. Also, no vulnerability was assigned a CVSSv3 severity score of 9.0 or higher.
Critical Bug Breakdown
Three of the critical flaws are found in Microsoft
Exchange (CVE-2020-17117, CVE-2020-17132 and CVE-2020-17142), all allowing
remote code execution (RCE). One of these occurs due to improper validation of
cmdlet arguments, according to Microsoft, which doesn’t provide an attack
scenario but does note that the attacker needs be authenticated with privileges.
“This indicates that if you take over someone’s mailbox, you can take over the entire Exchange server,” according to Dustin Childs at Trend Micro’s Zero Day Initiative (ZDI), writing in a Tuesday analysis. “With all of the other Exchange bugs, definitely prioritize your Exchange test and deployment.”
Also on the Exchange front, CVE-2020-17132 addresses a patch bypass for CVE-2020-16875, which was reported and patched in September’s Patch Tuesday release. While not critical, it’s of note, Childs said.
Childs also flagged CVE-2020-17121, one of two critical RCE bugs in Microsoft SharePoint (the other is CVE-2020-17118). Originally reported through ZDI program, the bug could allow an authenticated user to execute arbitrary .NET code on an affected server in the context of the SharePoint Web Application service account.
“In its default configuration, authenticated SharePoint users are able to create sites that provide all of the necessary permissions that are prerequisites for launching an attack,” Childs explained. “Similar bugs patched earlier this year received quite a bit of attention. We suspect this one will, too.”
In fact, the Sharepoint CVEs should take patching priority, Immersive Labs’ Kevin Breen, director of cyberthreat research, said via email. “Both are rated as critical as they have RCE, and Sharepoint can be used like a watering hole inside large organizations by an attacker,” he said. “All it takes is for a few weaponized documents to be placed for malicious code to spread across an organization.”
Another critical bug of note is tracked as CVE-2020-17095, a Hyper-V RCE vulnerability that allows an attacker to escalate privileges from code execution in a Hyper-V guest to code execution on the Hyper-V host by passing invalid vSMB packet data. The flaw carries the highest CVSS score in the update, coming in at 8.5, since no special permissions are needed to exploit it.
“To exploit this vulnerability, an adversary could run a custom application on a Hyper-V guest that would cause the Hyper-V host operating system to allow arbitrary code execution when it fails to properly validate vSMB packet data,” explained Automox researcher Jay Goodman, via email. “The vulnerability is present on most builds of Windows 10 and Windows Server 2004 and forward.”
Two post-authentication RCE flaws in Microsoft Dynamics 365 for Finance and Operations (on-premises) (CVE-2020-17158 and CVE-2020-17152) round out the critical patches, along with a memory-corruption issue in the Chakra Scripting Engine, which impacts the Edge browser (CVE-2020-17131).
“Only one [of the critical-rated updates] (surprisingly) impacts the browser,” Childs said. “That patch corrects a bug within the JIT compiler. By performing actions in JavaScript, an attacker can trigger a memory-corruption condition, which leads to code execution. The lack of browser updates could also be a conscious decision by Microsoft to ensure a bad patch for a browser does not disrupt online shopping during the holiday season.”
Though it’s a lighter than usual month for the volume of patches, the steady flow of critical RCE bugs present a great deal of risk, said Justin Knapp, researcher at Automox, via email.
“Instead of having to manipulate a user to click a malicious link or attachment, bad actors merely have to target an unpatched system to gain initial access, at which point a number of methods can be employed to increase access to valuable assets,” he said, referring to this month’s critical RCE problems. “It goes without saying that the speed at which an organization can deploy these fixes will dictate the level of risk they take on.”
Other Bugs, Patching
In addition to the critical bugs, a full 46 of the bugs
are rated as important, and three are rated moderate in severity. The important
bugs include 10 Office issues bugs impacting Outlook, PowerPoint and Excel — for
these, Office 2019 versions for Mac do not have patches yet.
“This is a book-end to a year that began with Microsoft addressing 49 CVEs in January of 2020, followed by eight consecutive months with over 90 CVEs addressed. In 2020, Microsoft released patches for over 1,200 CVEs,” Satnam Narang, principal research engineer, Tenable, told Threatpost.
Patching may be more difficult than ever going forward. “One of the things that stands out is that Microsoft has removed a lot of the detail they usually share with such advisories,” Breen said. “For me, this could lead to some issues. Patching is not as easy as just clicking an update button and security teams like to gain a deeper understanding of what they are doing. Instead, however, they are expected to operate with less information.”
Elsewhere, Adobe issued patches for flaws tied to one important-rated and three critical-severity CVEs, during its regularly scheduled December security updates.
“While lighter than usual, the most severe allow for arbitrary code execution including three critical severity CVEs and one less severe (important-rated) flaw identified,” Nick Colyer, researcher from Automox said. “The holidays present unique challenges to security teams’ upcoming out-of-office time and the severity of the vulnerabilities Adobe has addressed are non-trivial against those challenges. It is important to prioritize any major vulnerabilities during holidays to reduce the threat surface exposed to would-be attackers.”
Critical, Unpatched Bugs Open GE Radiological Devices to Remote Code Execution
9.12.2020
Vulnerebility
Threatpost
A CISA alert is flagging a critical default credentials issue that affects 100+ types of devices found in hospitals, from MRI machines to surgical imaging.
A pair of critical vulnerabilities have been discovered in dozens of GE Healthcare radiological devices popular in hospitals, which could allow an attacker to gain access to sensitive personal health information (PHI), alter data and even shut the machine’s availability down.
The flaws affect 100 different kinds of CT scanners, PET machines, molecular imaging devices, MRI machines, mammography devices, X-Ray machines and ultrasound devices. The U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) disclosed the bugs on Tuesday, which were found by researchers at CyberMDX back in May. They carry a CVSS severity score of 9.8, making them critical, and patches are forthcoming, according to the alert.
“Successfully exploiting the vulnerability may expose sensitive data – such as PHI – or could allow the attacker to run arbitrary code, which might impact the availability of the system and allow manipulation of PHI,” CyberMDX noted.
Healthcare Security in the COVID-19 Era
The bugs arise because of default credentials used with GE’s proprietary management software, which controls the devices’ integrated PC that runs a Unix-based operating system. The software manages the device as well as its maintenance and update procedures, which are carried out by GE over the internet.
The issue is that the update and maintenance software authenticates connections by using credentials that are publicly exposed and can be found online. The first bug (CVE-2020-25175) allows specific credentials to be exposed during transport over the network., while the second CVE-2020-25179 allows exposed/default credentials to be utilized to access or modify sensitive information.
The firm first discovered the bugs after noticing similar patterns of unsecured communications between the medical devices and the corresponding vendor’s servers, across several different health database organizations (HDOs).
HDOs are regional health care databases that hold medical records, imaging files and more, to facilitate electronic medical record efforts for physicians and patients.
Further research showed that these communications were stemming from the aforementioned multiple recurring maintenance processes, which GE’s server automatically triggers at certain intervals, researchers said, in a Tuesday posting.
All of this means that a remote attacker can connect to a device with no user interaction or escalated privileges needed – and from there can access the unsecured communications flowing between the devices and the HDOs. The exploitation complexity level extremely low, researchers said.
“The maintenance protocols rely on the machine having certain services available/ports open and using specific globally used credentials,” according to CyberMDX. “These global credentials provide hackers with easy access to crucial medical devices. They also enable them to run arbitrary code on impacted machines and provide access to any data from the machine.”
The affected product lines include: Brivo; Definium; Discovery; Innova; Optima; Odyssey; PetTrace; Precision; Seno; Revolution; Ventri; and Xeleris.
GE has confirmed the vulnerability, which impacts the radiological devices as well as certain workstations and imaging devices used in surgery, according to the CyberMDX alert. GE Healthcare plans to provide patches, it confirmed – but no timeline has been mapped out.
In the meantime, administrators should contact GE Healthcare and request a credentials change on all affected devices in a facility. Unfortunately, the change can only be performed by the GE Healthcare Support team.
This is the second group of unpatched issues for GE Healthcare devices this year. In January, CyberMDX disclosed a collection of six cybersecurity vulnerabilities in a range of GE Healthcare devices for hospitals. Dubbed “MDhex,” the bugs would allow attackers to disable the devices, harvest PHI change alarm settings and alter device functionality.
“Over the past few months we’ve seen a steady rise in the targeting of medical devices and networks, and the medical industry is unfortunately learning the hard way the consequences of previous oversights,” said Elad Luz, head of research at CyberMDX. “Protecting medical devices so that hospitals can ensure quality care is of utmost importance. We must continue to eliminate easy access points for hackers and ensure the highest level of patient safety is upheld across all medical facilities.”
Possible Code Execution Flaw in Apache Struts
9.12.2020
Vulnerebility
Securityweek
The Apache
Software Foundation has released a security update for Struts 2, to address what
is described as a “possible remote code execution” flaw related to the OGNL
technology.
The open-source model-view-controller (MVC) web application framework, which allows developers to build Java apps, is known to have been impacted by critical vulnerabilities, many of them related to the OGNL technology that Struts 2 employs.
Tracked as CVE-2020-17530, the newly addressed bug resides in “forced OGNL evaluation, when evaluated on raw user input in tag attributes,” according to an Apache advisory.
Specifically, when forced OGNL evaluation is applied using the %{...} syntax, tag's attributes could perform double evaluation, the company says. Furthermore, remote code execution could be achieved when forced OGNL evaluation is used on untrusted input.
A similar vulnerability (tracked as CVE-2019-0230) was addressed in August 2020, with the release of Struts 2.5.22.
Double evaluation was included in Struts 2 by design, meant to be applied when referencing validated values in the given expression. When untrusted user input is referenced, however, malicious code could be injected.
The workaround solution proposed by Apache is simple: developers should make sure that forced OGNL evaluation is not used on untrusted input.
The vulnerability was found to affect Struts 2.0.0 to Struts 2.5.25 and was addressed in Struts 2.5.26, where checks are performed to ensure that expression evaluation won't result in double evaluation.
The Cybersecurity and Infrastructure Security Agency (CISA) today published an advisory to inform on the availability of patches for CVE-2020-17530, warning that the flaw could allow an attacker to take over vulnerable systems and encouraging users and administrators to apply the available patch.
Microsoft Patches Critical SharePoint, Exchange Security Holes
9.12.2020
Vulnerebility
Securityweek
Microsoft’s
final batch of security patches for 2020 shipped today with fixes for at least
58 documented vulnerabilities affecting a wide range of OS and software
products.
The December security updates include fixes for code execution vulnerabilities in the company’s flagship Windows operating system and serious problems in Microsoft Sharepoint, Microsoft Exchange, HyperV, and a Kerberos security feature bypass.
Microsoft slapped a “critical” severity rating on nine of the 58 bulletins, while 46 are rated “important.” None of the documented bugs are under active attack and Microsoft said it was unaware of the availability of public exploit code.
According to Dustin Childs, a researcher who closely tracks security patches for Zero Day Initiative, Windows users should pay special attention to the following bulletins:
CVE-2020-17132 — Microsoft Exchange Remote Code Execution Vulnerability — This
is one of several Exchange code execution bugs, and it is credited to three
different researchers. This implies the bug was somewhat easy to find, and other
researchers are likely to find the root cause, too. Microsoft doesn’t provide an
attack scenario here but does note that the attacker needs to be authenticated.
This indicates that if you take over someone’s mailbox, you can take over the
entire Exchange server. With all of the other Exchange bugs, definitely
prioritize your Exchange test and deployment.
CVE-2020-17121 — Microsoft
SharePoint Remote Code Execution Vulnerability — Originally reported through the
ZDI program, this patch corrects a bug that could allow an authenticated user to
execute arbitrary .NET code on an affected server in the context of the
SharePoint Web Application service account. In its default configuration,
authenticated SharePoint users are able to create sites that provide all of the
necessary permissions that are prerequisites for launching an attack.
CVE-2020-17095 — Hyper-V Remote Code Execution Vulnerability — This patch
corrects a bug that could allow an attacker to escalate privileges from code
execution in a Hyper-V guest to code execution on the Hyper-V host by passing
invalid vSMB packet data. It appears that no special permissions are needed on
the guest OS to exploit this vulnerability. This bug also has the highest CVSS
score (8.5) for the release.
CVE-2020-16996 — Kerberos Security Feature
Bypass Vulnerability — This patch corrects a security feature bypass (SFB) bug
in Kerberos, but thanks to Microsoft’s decision to remove executive summaries
and only provide a CVSS score, we don’t know what specific features are being
bypassed.
Security researchers are urging enterprise admins to pay special
attention to CVE-2020-17096, a remote code execution vulnerability in Windows
NTFS, the primary file system for Windows.
“A remote attacker with SMBv2 access to a vulnerable system could send specially crafted requests over a network to exploit this vulnerability and execute code on the target system,” Microsoft warned in its advisory.
Microsoft has also released an advisory to address a spoofing vulnerability affecting the Windows DNS Resolver. The company has made available a workaround that involves making changes in the registry.
In the second half of 2020, Microsoft’s Patch Tuesday updates — excepting October and December — fixed more than 110 vulnerabilities every month. In total, Microsoft patched over 1,200 vulnerabilities this year, far more than the 851 fixed in 2019.
Adobe Patches Code Execution Flaws in Prelude, Experience Manager, Lightroom
9.12.2020
Vulnerebility
Securityweek
Adobe on
Tuesday announced that security updates for its Prelude, Experience Manager and
Lightroom products patch critical arbitrary code execution vulnerabilities.
In the Windows and macOS versions of the Prelude video logging and ingest tool, Adobe fixed a critical uncontrolled search path issue that can lead to arbitrary code execution in the context of the targeted user.
Uncontrolled search path issues are typically DLL hijacking vulnerabilities whose exploitation requires the attacker to have elevated privileges on the targeted system in order to plant a malicious DLL file that would get executed by a legitimate application.
The flaw was reported to Adobe by Hou JingYi of Chinese cybersecurity firm Qihoo 360. The same researcher also informed Adobe of a similar uncontrolled search path flaw affecting the Windows and macOS versions of the photo editing and organizing software Lightroom.
In its Experience Manager marketing product, Adobe fixed two vulnerabilities: an important-severity blind server-side request forgery (SSRF) bug that can lead to the disclosure of sensitive data, and a critical stored cross-site scripting (XSS) issue that can lead to JavaScript code execution in the browser.
The software giant has also informed customers that it has updated over a dozen Experience Manager dependencies to patch various types of vulnerabilities, including resource consumption, SSRF, XXE injection, improper authorization, code execution, and directory traversal issues.
Adobe said it was not aware of any attacks exploiting these vulnerabilities and, based on the priority ratings assigned to the flaws, the company does not expect them to be targeted by threat actors.
It would not be surprising if these are not the last security updates released by Adobe this year, considering that the company often releases another round of patches after Patch Tuesday.
OpenSSL Ships ‘High Severity’ Security Patch
9.12.2020
Vulnerebility
Securityweek
The OpenSSL
Project today warned that the widely deployed TLS/SSL toolkit is vulnerable to a
serious security flaw that exposes users to denial-of-service attacks.
The vulnerability, discovered and reported by Google’s David Benjamin, carries a “high severity” rating. It is described as a null pointer dereference and a crash that may trigger disruptive denial-of-service attacks.
According to an alert from the open-source group, the problem is caused by a specific function that “behaves incorrectly” if an attacker successfully triggers certain conditions.
Details from the advisory:
The X.509 GeneralName type is a generic type for representing different types of names. One of those name types is known as EDIPartyName. OpenSSL provides a function GENERAL_NAME_cmp which compares different instances of a GENERAL_NAME to see if they are equal or not. This function behaves incorrectly when both GENERAL_NAMEs contain an EDIPARTYNAME. A NULL pointer dereference and a crash may occur leading to a possible denial of service attack.
OpenSSL itself uses the GENERAL_NAME_cmp function for two purposes:
1) Comparing CRL distribution point names between an available CRL and a CRL distribution point embedded in an X509 certificate
2) When verifying that a timestamp response token signer matches the timestamp authority name (exposed via the API functions TS_RESP_verify_response and TS_RESP_verify_token)
If an attacker can control both items being compared then that attacker could trigger a crash. For example if the attacker can trick a client or server into checking a malicious certificate against a malicious CRL then this may occur.
All OpenSSL 1.1.1 and 1.0.2 versions are affected by this issue, the group said, urging all users to upgrade to OpenSSL 1.1.1i.
Unauthenticated Command Injection Flaw Exposes D-Link VPN Routers to Attacks
9.12.2020
Vulnerebility
Securityweek
D-Link is working on releasing firmware updates to address two command injection vulnerabilities that affect multiple VPN router models.
Security researchers at Digital Defense identified a total of three vulnerabilities that affect several D-Link VPN routers, including authenticated and unauthenticated command injection flaws, and an authenticated crontab injection issue.
Initially discovered in DSR-250 routers running firmware version 3.17, the vulnerabilities were confirmed to affect other devices as well, namely D-Link DSR-150, DSR-250, DSR-500, and DSR-1000AC VPN routers running firmware versions 3.17 and earlier.
The most important of these bugs could allow an unauthenticated attacker able to access the "Unified Services Router" web interface over LAN or WAN to inject arbitrary commands that are executed with root privileges. The attacker would need to send specially crafted requests to trigger the flaw.
“The following lua cgi actions, which are accessible without authentication, execute a lua library function which passes user-supplied data to a call to os.popen() as part of a command intended to calculate a hash: /platform.cgi?action=duaAuth, /platform.cgi?action=duaLogout,” D-Link explains in an advisory.
According to Digital Defense, exploitation of this vulnerability could essentially allow an unauthenticated attacker to gain complete control of the router. Thus, they could intercept and modify traffic, cause a denial of service (DoS) condition, or set up for further attacks, targeting additional assets.
Similarly, the second vulnerability could allow an attacker to inject commands that would be executed with root privileges. Unlike the first bug, however, this one requires authentication.
“The Lua CGI, which handles requests from the ‘Package Management’ form in the ‘Unified Services Router’ web interface, has no server-side filtering for the multi-part POST parameters payload, which are passed to os. execute () functions intended to move the uploaded file to another directory,” D-Link says.
The third bug could allow an authenticated user to inject arbitrary CRON entries that will then be executed as root.
According to D-Link, a fix won’t be released for this vulnerability, for this generation of products. The company explains that an attacker looking to exploit this bug would first need to find a way to access the device and upload a configuration file.
Thus, D-Link considers that, once the firmware release that patches the first two issues is available, the third vulnerability is low-impact and does not require addressing.
The company plans on making the patched firmware available for its users in mid-December. Until then, however, users can download the available hotfixes, which are considered beta firmware releases.
Microsoft Releases Windows Update (Dec 2020) to Fix 58 Security Flaws
9.12.2020
Vulnerebility
Thehackernews
Microsoft on Tuesday
released fixes for 58 newly discovered security flaws spanning as many as 11
products and services as part of its final Patch Tuesday of 2020, effectively
bringing their CVE total to 1,250 for the year.
Of these 58 patches, nine are rated as Critical, 46 are rated as Important, and three are rated Moderate in severity.
The December security release addresses issues in Microsoft Windows, Edge browser, ChakraCore, Microsoft Office, Exchange Server, Azure DevOps, Microsoft Dynamics, Visual Studio, Azure SDK, and Azure Sphere.
Fortunately, none of these flaws this month have been reported as publicly known or being actively exploited in the wild.
The fixes for December concern a number of remote code execution (RCE) flaws in Microsoft Exchange (CVE-2020-17132), SharePoint (CVE-2020-17118 and CVE-2020-17121), Excel (CVE-2020-17123), and Hyper-V virtualization software (CVE-2020-17095), as well as a patch for a security feature bypass in Kerberos (CVE-2020-16996), and a number of privilege escalation flaws in Windows Backup Engine and Windows Cloud Files Mini Filter Driver.
CVE-2020-17095 also carries the highest CVSS score of 8.5 among all vulnerabilities addressed in this month's release.
"To exploit this vulnerability, an attacker could run a specially crafted application on a Hyper-V guest that could cause the Hyper-V host operating system to execute arbitrary code when it fails to properly validate vSMB packet data," Microsoft noted.
Additionally included as part of this month's release is an advisory for a DNS cache poisoning vulnerability (CVE-2020-25705) discovered by security researchers from Tsinghua University and the University of California last month.
Dubbed a Side-channel AttackeD DNS attack (or SAD DNS attack), the flaw could enable an attacker to spoof the DNS packet, which can be cached by the DNS Forwarder or the DNS Resolver, thereby re-enabling DNS cache poisoning attacks.
To mitigate the risk, Microsoft recommends a Registry workaround that involves changing the maximum UDP packet size to 1,221 bytes (4C5 Hexadecimal).
"For responses larger than 4C5 or 1221, the DNS resolver would now switch to TCP," the Windows maker stated in its advisory.
Since the attack relies on sending spoofed UDP (User Datagram Protocol) messages to defeat source port randomization for DNS requests, implementing the tweak will cause larger DNS queries to switch to TCP, thus mitigating the flaw.
It's highly advised that Windows users and system administrators apply the latest security patches to resolve the threats associated with these issues.
To install the latest security updates, Windows users can head to Start > Settings > Update & Security > Windows Update, or by selecting Check for Windows updates.
Critical remote code execution fixed in PlayStation Now
8.12.2020
Vulnerebility
Securityaffairs
Security flaws in the PlayStation Now cloud gaming Windows application allowed
hackers to execute arbitrary code on Windows systems.
Bug bounty hunter
Parsia Hakimian discovered multiple security flaws in the PlayStation Now (PS
Now) cloud gaming Windows application that allowed hackers to execute arbitrary
code on Windows devices running vulnerable app versions.
The bugs affected PS Now version 11.0.2 and earlier on systems running Windows 7
SP1 or later.
Since the its launch in 2014, PlayStation Now reached more than
2.2 million subscribers [PDF] at the end of April 2020.
Hakimian reported the bugs to Sony on May 13, 2020, through PlayStation’s official bug bounty program operated via bug bounty platform HackerOne. PlayStation addressed the issues on June 25th, 2020 and rewarded the experts with a $15,000 bounty.
Chaining the vulnerabilities found by Hakimian, an unauthenticated attacker could achieve remote code execution (RCE) by exploiting a code injection vulnerability.
“The PlayStation Now application version 11.0.2 is vulnerable to remote code execution (RCE).” explained Hakimian. “Any website loaded in any browser on the same machine can run arbitrary code on the machine through a vulnerable websocket connection.”
The attackers can run malicious code on a PS NOW user’s computer via a local
WebSocket server started by the psnowlauncher.exe on port 1235 using the AGL
Electron application it spawns after launch.
“The local websocket server at
localhost:1235 does not check the origin of incoming requests.
This allows websites loaded in browsers on the same machine to send requests to
the websocket server.” continues the Hakimian.
Websockets are not bound by
the Same-Origin Policy so the websocket server has to do this manually.”
“JavaScript loaded by AGL will be able to spawn processes on the machine. This
can lead to arbitrary code execution. The AGL application performs no checks on
what URLs it loads.”
This issue stems from WebSocket server that started on the target’s device without performing any Origin header or request origin checks.
An attacker could exploit the flaw by triking PS NOW users into opening a specially crafted site using a malicious link provided via phishing emails, forums, Discord channels, etc.
Upon opening the link in the victim’s browser, malicious scripts on the website will connect to the local WebSocket server and ask AGL to load malicious Node code from another site and run it on the target’s machine.
The PlayStation bug bounty program via HackerOne has been launched by Sony in June 2020, it covers vulnerabilities in the PlayStation Network, in Sony gaming consoles PlayStation 4 and 5, operating systems, and accessories.
White hat hackers could receive bounty payouts ranging from $100 up to $50,000 for a PlayStation 4 critical vulnerability.
QNAP fixed eight flaws that could allow NAS devices takeover
8.12.2020
Vulnerebility
Securityaffairs
Network-attached storage (NAS) vendor QNAP addressed vulnerabilities that could
enable attackers to take over unpatched NAS devices.
The Taiwanese vendor
QNAP has released security updates to fix eight vulnerabilities that could be
exploited by attackers to over unpatched NAS devices.
The list of vulnerabilities addressed by QNAP is available here, it includes XSS and command injection issues. The flaws fixed by the vendor are rated as medium and high severity security.
The high-severity vulnerabilities tracked as CVE-2020-2495, CVE-2020-2496, CVE-2020-2497, and CVE-2020-2498 are cross-side-scripting flaws that could allow remote attackers to inject malicious code in File Station, to inject malicious code in System Connection Logs, and to inject malicious code in certificate configuration.
Other high severity issues fixed by the vendor are:
CVE-2020-2493 –
Cross-site Scripting Vulnerability in Multimedia Console
CVE-2020-2491 –
Cross-site Scripting Vulnerability in Photo Station
The Taiwanese vendor
released security updates for QNAP QuTS hero high-performance ZFS-based
operating system and the QTS NAS OS.
Customers have to apply the security updates as soon as possible to prevent their devices from being compromised.

In October, the vendor published an advisory to warn customers that certain
versions of its NAS OS (QTS) are affected by the Zerologon vulnerability.
In October, QNAP also addressed two critical security vulnerabilities in the
Helpdesk app that can potentially allow threat actors to take over the
vulnerable QNAP network-attached storage (NAS) devices.
In September, while
the AgeLocker ransomware was continuing to target QNAP NAS systems, the
Taiwanese vendor urged customers to update the firmware and apps.
In early August, the Taiwanese company urged its users to update the Malware
Remover app to prevent NAS devices from being infected by the QSnatch malware.
In June the company also warned of eCh0raix ransomware attacks that targeted its
NAS devices.
Expert discloses zero-click, wormable flaw in Microsoft Teams
8.12.2020
Vulnerebility
Securityaffairs
Security expert disclosed technical details about a wormable, cross-platform
flaw in Microsoft Teams that could allow stealth attacks.
Security researcher
Oskars Vegeris from Evolution Gaming has published technical details on a
wormable, cross-platform vulnerability in the business communication platform
Microsoft Teams.
The flaw is a cross-site scripting (XSS) issue that impacts the ‘teams.microsoft.com’ domain, it could be exploited by an attacker to achieve remote code execution in the MS Teams desktop application.
An attacker could exploit the flaw by sending a specially crafted message to any Microsoft Teams user or channel.
“A Remote Code Execution vulnerability has been identified in MS Teams desktop which can be triggered by a novel XSS (Cross-Site Scripting) injection in teams.microsoft.com. A specifically crafted chat message can be sent to any Microsoft Teams member or channel which will execute arbitrary code on victim PC’s with NO USER INTERACTION.” reads the advisory published by Vegeris.
“Remote Code Execution has been achieved in desktop applications across all supported platforms (Windows, macOS, Linux). Code execution gives attackers full access to victim devices and company internal networks via those devices,”
Even without gaining arbitrary code execution, the attacker could exploit the XSS flaw to obtain SSO authorization tokens for MS Teams or other services of the IT giant (e.g. Skype, Outlook, Office365). The issue could also allow attackers to access confidential conversations and files from the communications service.
The expert pointed out that the attack is stealth, it doesn’t require any user interaction and there are no indicators of compromise for this attack.
The flaw is also ‘wormable,’ this means that it is possible to automatically repost the exploit payload to other companies, channels, users without interaction
Successful exploitation could cause complete loss of confidentiality and integrity for end-users, attackers could access sensitive info into private chats, files, internal network, along with private keys and personal data outside MS Teams
The flaw could also open to phishing attacks by redirecting the victims to attackers’ site or requesting SSO credential input.
Affected products include:
MS Teams (teams.microsoft.com) – Cross-Site
Scripting
MS Teams macOS v 1.3.00.23764 (latest as of 2020-08-31)
MS Teams
Windows v 1.3.00.21759 (latest as of 2020-08-31)
MS Teams Linux v
1.3.00.16851 (latest as of 2020-08-31)
Vegeris also published a demo on how
to exploit the vulnerability, he is disappointed by the Microsoft’choice to rate
the issues “Important, Spoofing,” which is one of the lowest in-scope ratings
possible.

He added that the IT giant wouldn’t issue a CVE number for the vulnerability,
because issues in Microsoft Teams are fixed via automatic updates.
Microsoft has addressed the flaw with an update released in October.
Researcher Awarded $15,000 for Code Execution Flaw in PlayStation Now App
8.12.2020
Vulnerebility
Securityweek
A critical vulnerability addressed earlier this year in the PlayStation Now application for Windows could have been exploited by malicious websites to execute arbitrary code.
The PlayStation Now application allows users to access an on-demand game collection directly from their Windows PCs. To enjoy the games, users also need a PlayStation Network account and a compatible controller.
As part of Sony’s bug bounty program on HackerOne, a security researcher that goes by the handle of “parsiya” reported a critical flaw in the PlayStation Now application that could have been abused by any website to execute code on vulnerable systems.
The report for this issue was submitted on May 13, more than one month before Sony launched a public PlayStation bug bounty program on HackerOne.
What the researcher discovered was that, because of a vulnerable websocket connection to the application, websites opened in any browser on the machine could send requests to the application, and have it load malicious URLs that could then execute code on the system.
The issue, parsiya explained, was that the application created a local websocket server that failed to check the origin of incoming requests, which made it possible for websites loaded in the browser to send requests to PlayStation Now.
Furthermore, the Electron application AGL that PlayStation Now launches could have been instructed to load specific websites, using commands sent to the websocket server. AGL can also be used to run a local application.
The security researcher also discovered that the AGL Electron application allowed for the JavaScript on loaded web pages to spawn new processes, essentially enabling code execution.
Parsiya, who provided full technical details on this vulnerability in his HackerOne report, noted that the issue could be resolved by ensuring that the local websocket server always validates the origin of incoming requests against a set list.
The flaw was assigned a severity score of 9.6 (critical). Sony awarded the researcher a $15,000 bounty for his report and addressed the issue within weeks. However, the vulnerability was disclosed publicly only now.
WARNING — Critical Remote Hacking Flaws Affect D-Link VPN Routers
8.12.2020
Vulnerebility
Thehackernews
Some widely sold
D-Link VPN router models have been found vulnerable to three new high-risk
security vulnerabilities, leaving millions of home and business networks open to
cyberattacks—even if they are secured with a strong password.
Discovered by researchers at Digital Defense, the three security shortcomings were responsibly disclosed to D-Link on August 11, which, if exploited, could allow remote attackers to execute arbitrary commands on vulnerable networking devices via specially-crafted requests and even launch denial-of-service attacks.
D-Link DSR-150, DSR-250, DSR-500, and DSR-1000AC and other VPN router models in the DSR Family running firmware version 3.14 and 3.17 are vulnerable to the remotely exploitable root command injection flaw.
The Taiwanese networking equipment maker confirmed the issues in an advisory on December 1, adding that the patches were under development for two of three flaws, which have now been released to the public at the time of writing.
"From both WAN and LAN interfaces, this vulnerability could be exploited over the Internet," Digital Defense said in a report published today and shared with The Hacker News.
"Consequently, a remote, unauthenticated attacker with access to the router's web interface could execute arbitrary commands as root, effectively gaining complete control of the router."
The flaws stem from the fact that the vulnerable component, the "Lua CGI," is
accessible without authentication and lacks server-side filtering, thus making
it possible for an attacker — authenticated or otherwise — to inject malicious
commands that will be executed with root privileges.
A separate vulnerability reported by Digital Defense concerns the modification of the router configuration file to inject rogue CRON entries and execute arbitrary commands as the root user.
However, D-Link said it will not correct this flaw "on this generation of products," stating this is the intended function.
"The device uses a plain text config, which is the design to directly edit and upload the config to the same DSR devices accordingly," the company said.
"If D-Link mitigates issue #1 and #2, as well as other, recently reported issues, the malicious user would need to engineer a way of gaining access to the device to upload a configuration file, so we understand the report but classify the report as low-threat once the patched firmware is available."
With the unprecedented rise in work from home as a result of the COVID-19 pandemic, more employees may be connecting to corporate networks using one of the affected devices, Digital Defense cautioned.
As organizations have scrambled to adapt to remote work and offer secure remote access to enterprise systems, the change has created new attack surfaces, with flaws in VPNs becoming popular targets for attackers to gain entry into internal corporate networks.
It's recommended that businesses using the affected products apply the relevant updates as and when they are available.
QNAP High-Severity Flaws Plague NAS Systems
8.12.2020 Vulnerebility Threatpost
The high-severity cross-site scripting flaws could allow remote-code injection on QNAP NAS systems.
QNAP Systems is warning of high-severity flaws that plague its top-selling network attached storage (NAS) devices. If exploited, the most severe of the flaws could allow attackers to remotely take over NAS devices.
NAS devices are systems that consist of one or more hard drives that are constantly connected to the internet – acting as a backup “hub” or storage unit that stores all important files and media such as photos, videos and music. Overall, QNAP on Monday issued patches for cross-site scripting (XSS) flaws tied to six CVEs.
Four of these vulnerabilities stem from an XSS issue that affects earlier versions of QTS and QuTS hero. QTS is the operating system for NAS systems, while the QuTS Hero is an operating system that combines the app-based QTS with a 128-bit ZFS file system to provide more storage management.
Two of these XSS flaws (CVE-2020-2495 and CVE-2020-2496) could allow remote attackers to inject malicious code into File Station. File Station is a built-in QTS app that allows users to manage files stored on their QNAP NAS systems.
Another flaw (CVE-2020-2497) can enable remote attackers to inject malicious code in System Connection Logs; while the fourth flaw (CVE-2020-2498) allows attackers to remotely inject malicious code into the certificate configuration.
QNAP said “we strongly recommend updating your system to the latest version” of QTS and QuTS hero: QuTS hero h4.5.1.1472 build 20201031 and later, QTS 4.5.1.1456 build 20201015 and later, QTS 4.4.3.1354 build 20200702 and later, QTS 4.3.6.1333 build 20200608 and later, QTS 4.3.4.1368 build 20200703 and later, QTS 4.3.3.1315 build 20200611 and later; and QTS 4.2.6 build 20200611 and later.
Users can do so by logging onto the QTS or QuTS hero as an administrator, going to Control Panel > System > Firmware Update and clicking Check for Updating under “Live Update.”
Another high-severity XSS vulnerability (CVE-2020-2491) exists in the Photo Station feature of QNAP NAS systems, which enables remote photo management. The flaw allows attackers to remotely inject malicious code.
According to QNAP, it has been fixed in the following versions of the QTS operating system: QTS 4.5.1 (Photo Station 6.0.12 and later); QTS 4.4.3 (Photo Station 6.0.12 and later); QTS 4.3.6 (Photo Station 5.7.12 and later); QTS 4.3.4 (Photo Station 5.7.13 and later); QTS 4.3.3 (Photo Station 5.4.10 and later) and QTS 4.2.6 (Photo Station 5.2.11 and later).
The final XSS flaw (CVE-2020-2493) exists in the Multimedia Console of QNAP NAS systems, and allows remote attackers to inject malicious code. The Multimedia Console feature enables indexing, transcoding, thumbnail generation and content management so users can manage multimedia apps and services more efficiently.
“We have already fixed this vulnerability in Multimedia Console 1.1.5 and later,” said QNAP in its advisory.
QNAP Systems hardware are no strangers to being attack targets. Last year, attackers crafted malware specifically designed to target NAS devices. Also in July 2019, researchers highlighted an unusual Linux ransomware, called QNAPCrypt, which targeted QNAP NAS servers. Researchers have also previously found multiple bugs in QNAP’s Q’Center Web Console; while in 2014, a worm exploiting the Bash vulnerability in QNAP network attached storage devices was also discovered.
Wormable, Zero-Click Vulnerability in Microsoft Teams
8.12.2020
Vulnerebility
Securityweek
Security researcher Oskars Vegeris has published documentation on a wormable, cross-platform vulnerability in Microsoft Teams that could allow invisible malicious hacker attacks.
Vegeris, a security engineer at Evolution Gaming, warned that a novel cross-site scripting (XSS) vulnerability at the ‘teams.microsoft.com’ domain could be abused to trigger a remote code execution flaw in the Microsoft Teams desktop application.
Microsoft Teams, which competes in the enterprise space with the likes of Slack and Zoom, counts about 115 million daily active users and is widely deployed as part of Microsoft’s Office 365 family of products. Teams is a proprietary business communication platform that provides users with workspace chat, file storage and sharing, app integration, and videoconferencing capabilities.
According to an advisory published by Vegeris, an attacker simply needs to send a specially crafted message to any Teams user or channel to launch a successful exploit that runs silently in the background, without the user noticing anything.
“Remote Code Execution has been achieved in desktop applications across all supported platforms (Windows, macOS, Linux). Code execution gives attackers full access to victim devices and company internal networks via those devices,” Vegeris warned.
He said an attacker could abuse the XSS flaw to obtain SSO authorization tokens for Teams or other Microsoft services, or to access confidential conversations and files from the communications service.
On top of that, the vulnerability is wormable, allowing a successful attacker to automatically send the exploit payload to other users/channels, also without interaction.
The successful exploitation of the bug could potentially give access to private keys and personal data outside Teams, possibly leaking internal network information and allowing adversaries to set up for phishing attacks.
Remote code execution, Vegeris explains, can be achieved only if the XSS in teams.microsoft.com (in user 'mentions' functionality) is chained with the novel cross-platform exploit for the Teams desktop clients.
The security researcher, who provides technical details on the flaw and a demonstration on how it can be exploited, claims Microsoft has downplayed the severity of the vulnerability, assigning an "important" rating with a "spoofing" risk.
He said Microsoft took the Teams desktop clients “out of scope” and told the researcher it wouldn’t issue a CVE number for the flaw, because vulnerabilities in Microsoft Teams are fixed via automatic updates.
Affected products include Microsoft Teams for macOS v 1.3.00.23764, Windows v 1.3.00.21759, and Linux v 1.3.00.16851. The company has already addressed the vulnerability.
“We mitigated the issue with an update in October, which has automatically deployed and protected customers,” a Microsoft spokesperson said, responding to a SecurityWeek inquiry.
Zero-Click Wormable RCE Vulnerability Reported in Microsoft Teams
8.12.2020
Vulnerebility
Thehackernews
A zero-click remote code execution (RCE) bug in Microsoft Teams desktop apps could have allowed an adversary to execute arbitrary code by merely sending a specially-crafted chat message and compromise a target's system.
The issues were reported to the Windows maker by Oskars Vegeris, a security engineer from Evolution Gaming, on August 31, 2020, before they were addressed at the end of October.
"No user interaction is required, exploit executes upon seeing the chat message," Vegeris explained in a technical write-up.
The result is a "complete loss of confidentiality and integrity for end users — access to private chats, files, internal network, private keys and personal data outside MS Teams," the researcher added.
Worse, the RCE is cross-platform — affecting Microsoft Teams for Windows (v1.3.00.21759), Linux (v1.3.00.16851), macOS (v1.3.00.23764), and the web (teams.microsoft.com) — and could be made wormable, meaning it could be propagated by automatically reposting the malicious payload to other channels.
This also means the exploit can be passed on from one account to a whole group of users, thereby compromising an entire channel.
To achieve this, the exploit chain strings together a cross-site scripting (XSS) flaw present in the Teams '@mentions' functionality and a JavaScript-based RCE payload to post a harmless-looking chat message containing a user mention either in the form of a direct message or to a channel.
Simply visiting the chat at the recipient's end leads to the execution of the payload, allowing it to be exploited to log users' SSO tokens to local storage for exfiltration and execute any command of the attacker's choice.
This is not the first time such RCE flaws were observed in Teams and other enterprise-focused messaging apps.
Chief among them is a separate RCE vulnerability in Microsoft Teams (CVE-2020-17091) that the company patched as part of its November 2020 Patch Tuesday last month.
Earlier this August, Vegeris also disclosed a critical "wormable" flaw in Slack's desktop version that could have allowed an attacker to take over the system by simply sending a malicious file to another Slack user.
Then in September, networking equipment maker Cisco patched a similar flaw in its Jabber video conferencing and messaging app for Windows that, if exploited, could allow an authenticated, remote attacker to execute arbitrary code.
Google Launches XS-Leaks Vulnerability Knowledge Base
7.12.2020
Vulnerebility
Securityweek
Google this week announced the launch of a knowledge base with information on a class of vulnerabilities referred to as cross-site leaks, or XS-Leaks.
These vulnerabilities, Google explains, are rooted in the modern web applications’ misuse of long-standing web platform behaviors, thus resulting in websites leaking information on the user or the information the user has entered in other web applications.
XS-Leaks, the search giant says, are challenging for both security engineers and web browser developers, as they open the door for a broad range of attacks and the deployment of comprehensive defenses is rather complex.
The newly launched XS-Leaks wiki is meant to help the security community better understand these issues and improve defenses. In fact, Google invites security researchers to help expand the wiki and to share details on new attacks and defenses.
The XS-Leaks wiki is available at xsleaks.dev, providing information on the principles leading to cross-site leaks. It includes small articles detailing each cross-site leak, its implications, and mitigation techniques, along with proof-of-concept code to demonstrate it.
The wiki is also meant to help web developers understand how the defense mechanisms within browsers can keep their applications protected from cross-site leaks.
“Each attack described in the wiki is accompanied by an overview of security features which can thwart or mitigate it; the wiki aims to provide actionable guidance to assist developers in the adoption of new browser security features such as Fetch Metadata Request Headers, Cross-Origin Opener Policy, Cross-Origin Resource Policy, and SameSite cookies,” Google explains.
The Internet search company encourages the security community to help expand the XS-Leaks wiki with details on both offensive and defensive techniques, noting that its resource might fuel research into mitigating a major class of web security threats.
Recently disclosed CVE-2020-4006 VMware zero-day was reported by NSA
5.12.2020
Vulnerebility
Securityaffairs
VMware addressed CVE-2020-4006 zero-day flaw in VMware Workspace One Access,
Access Connector, Identity Manager, and Identity Manager Connector.
VMware
has finally released security updates to fix the CVE-2020-4006 zero-day flaw in
VMware Workspace One Access, Access Connector, Identity Manager, and Identity
Manager Connector.
At the end of November, VMware only has released a workaround to address the critical zero-day vulnerability that affects multiple VMware Workspace One components. VMware Workspace ONE allows to simply and securely deliver and manage any app on any device. The flaw is a command injection bug that could be exploited by attackers to execute commands on the host Linux and Windows operating systems using escalated privileges.
“VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector contain a Command Injection Vulnerability in the administrative configurator. VMware has evaluated the this issue to be of Critical severity with a maximum CVSSv3 base score of 9.1.” reads the security advisory published by the virtualization giant.
Affected versions are:
VMware Workspace One Access 20.10 (Linux)
VMware Workspace One Access 20.01
(Linux)
VMware Identity Manager 3.3.1 up to 3.3.3 (Linux)
VMware Identity
Manager Connector 3.3.2, 3.3.1 (Linux)
VMware Identity Manager Connector
3.3.3, 3.3.2, 3.3.1 (Windows)
The Cybersecurity and Infrastructure Security
Agency (CISA) also published a security advisory on the CVE-2020-4006 zero-day
flaw.
“VMware has released workarounds to address a vulnerability—CVE-2020-4006—in VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector. An attacker could exploit this vulnerability to take control of an affected system.” reads the CISA’s advisory.
At the time of the public disclosure of the flaw, VMware did not reveal the identity of the organization or researcher who reported the vulnerability. Now the virtualization giant confirmed that the zero-day vulnerability was reported by the US intelligence agency NSA.
VMware downplayed the severity of the bug to 7.2/10 score rating the issue from ‘Critical’ to ‘Important.’
“A malicious actor with network access to the administrative configurator on port 8443 and a valid password for the configurator admin account can execute commands with unrestricted privileges on the underlying operating system,” the advisory explains.
“This account is internal to the impacted products and a password is set at the time of deployment. A malicious actor must possess this password to attempt to exploit CVE-2020-4006.”
Below the list of updates for CVE-2020-4006 provided by the company.
Affected product Patch
VMware Workspace ONE Access 20.10
VMware Workspace
ONE Access 20.01
VMware Identity Manager 19.03
VMware Identity Manager
19.03.0.1
VMware Identity Manager 3.3.3
VMware Identity Manager 3.3.2
VMware Identity Manager 3.3.1
DHS-CISA published an alert to encourage admins
and users to install the security updates released by VMware to prevent
CVE-2020-4006 exploitation.
“The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review VMware Security Advisory VMSA-2020-0027.2 and apply the necessary updates.” states the advisory published by CISA.
GitHub Says Vulnerabilities in Some Ecosystems Take Years to Fix
4.12.2020
APT
Vulnerebility
Developers often need years to
address some of the vulnerabilities introduced in their software, a new GitHub
report reveals.
The report, which is based on the analysis of more than 45,000 active repositories, shows that it typically takes 7 years to address vulnerabilities in Ruby, while those in npm are usually patched in five years. This is due to the fact that they often remain undetected or unnoticed.
Repositories taken into consideration for the report use one of six supported package ecosystems (Composer, Maven, npm, NuGet, PyPI, or RubyGems) and have dependency graph enabled, the Microsoft-owned platform explains.
According to the report, open source dependencies in JavaScript (94%), Ruby (90%), and .NET (90%) are used the most. Over the past 12 months, Ruby (81%) and JavaScript (73%) repositories had the highest chance to receive a security alert from GitHub’s Dependabot.
“Security vulnerabilities often go undetected for more than four years before being disclosed. Once they are identified, the package maintainer and security community typically create and release a fix in just over four weeks,” GitHub notes.
The software hosting platform also notes that most of the vulnerabilities identified in software are the result of coding mistakes, and do not represent malicious attacks. However, the analysis of 521 advisories revealed that 17% of advisories were related to malicious behavior.
“Security vulnerabilities can impact software directly or through its dependencies—any code referenced and bundled to make a software package work. That is, code may be vulnerable either because it contains vulnerabilities, or because it relies on dependencies that contain vulnerabilities,” the report reads.
When direct dependencies are taken into consideration, JavaScript was found to have the highest number of median dependencies, at ten, with Ruby and PHP next in line at nine, Java at eight, and .NET and Python at six.
The report also notes that the vulnerability that could be considered the most-impactful bug of the year is CVE-2020-8203 (Prototype Pollution in lodash, one of the most widely used npm packages), as it triggered more than five million Dependabot alerts.
A scan of 4 Million Docker images reveals 51% have critical flaws
3.12.2020
Vulnerebility
Securityaffairs
Security experts analyzed 4 million public Docker container images hosted on
Docker Hub and found half of them was having critical flaws.
Container
security firm Prevasio has analyzed 4 million public Docker container images
hosted on Docker Hub and discovered that the majority of them had critical
vulnerabilities.
The cybersecurity firm used its Prevasio Analyzer service that ran for one month on 800 machines.
51% of the 4 million images were including packages or app dependencies with at least one critical flaw and 13% had high-severity vulnerabilities.
“The dynamic analysis also revealed 6,432 malicious or potentially harmful
container images, representing 0.16% of all publicly available images at Docker
Hub.” reads the analysis published by Prevasio. “This report explains the work
that we’ve done, our findings, the types of malware found and several typical
examples of container images found to contain malicious or potentially harmful
software.”
Researchers who focused on Linux container images only, revealed
that nearly 1% of all images were excluded from the analysis because are built
for Windows only and/or have no Linux-specific builds.
The researchers also discovered that 6,432 images included potentially malicious software, such as cryptocurrency miners (44%, 2,842 images and Pull count: 129.5M), hacking tools (20%, 1,269 images and Pull count: 70M), the malicious npm package flatmap-stream (23%, 1,482 images, Pull count: 95M), and tainted applications (trojanized WordPress plugins, Apache Tomcat, and Jenkins).

The total pull count of the malicious or potentially harmful images is over 300
million.
Some of the images contained dynamic payloads that at runtime were downloading the source code of a cryptocurrency miner and execute it.
Experts pointed out that currently, most of the malware found in the images targets Windows.
“The investigation conducted by Prevasio illustrates that Linux OS, and Linux containers in particular are not immune to security risks” concludes the report. “Our research shows that the primary security risk is enabled by critical vulnerabilities. More than half of all container images hosted by Docker Hub, contain one or more critical vulnerability, and are, therefore, potentially exploitable.Another risk is in the fact that out of 4 million publicly available images, 6,432 are found to contain malicious or potentially harmful code.”
Analysis of 4 Million Docker Images Shows Half Have Critical Vulnerabilities
2.12.2020
Vulnerebility
Securityweek
Container security company Prevasio has analyzed 4 million public Docker container images hosted on Docker Hub and found that over half of them had critical vulnerabilities and thousands of images included malicious or potentially harmful elements.
The cybersecurity firm used its Prevasio Analyzer service to analyze all the container images on Docker Hub, the largest library and community for container images. In order to analyze the large amount of images, the Prevasio service ran non-stop for one month on 800 machines.
The analysis found that 51% of the 4 million images included packages or app dependencies with at least one critical vulnerability and 13% had high-severity flaws.
Roughly 6,400 containers, representing 0.16% of the total, were classified as malicious or potentially harmful due to the presence of malware, cryptocurrency miners, hacking tools, a malicious npm package (flatmap-stream), and trojanized applications.
According to Prevasio, these malicious or potentially harmful Docker images have been downloaded more than 300 million times.
Crypto-miners were detected in 44% of the 6,400 containers and while in many cases developers clearly state that their container images contain these miners, the miners are often hidden.
“Regardless of the original intention, if an employee pulls from Docker Hub and then runs a coinmining container image at work, there is a very high chance that the company’s resources are not used as originally intended. A system administrator might find such container images undesirable for a corporate environment or even potentially harmful,” Prevasio wrote in a report detailing its findings.
The research also uncovered images with dynamic payloads, where the original image does not appear to include anything malicious, but they are scripted to — at runtime — download the source code of a miner, compile it, and execute it.
As for trojanized applications, the analysis uncovered trojanized WordPress plugins, Apache Tomcat, and Jenkins. While much of the malware currently found in the images targets Windows, malware could pose a bigger issue in the future with the rise of cross-platform threats.
“If a company’s developer takes a shortcut by fetching a pre-built image, instead of composing a new image from scratch, there is a viable risk that such pre-built image might come pre-trojanised. If such an image ends up in production, the attackers may potentially be able to access such containerized applications remotely via a backdoor,” Prevasio warned.
Electronic Medical Records Cracked Open by OpenClinic Bugs
2.12.2020
Vulnerebility
Threatpost
Four security
vulnerabilities in an open-source medical records management platform allow
remote code execution, patient data theft and more.
Four vulnerabilities have been discovered in the OpenClinic application for sharing electronic medical records. The most concerning of them would allow a remote, unauthenticated attacker to read patients’ personal health information (PHI) from the application.
OpenClinic is an open-source health records management software; its latest version is 0.8.2, released in 2016, so the flaws remain unpatched, researchers at Bishop Fox said. The project did not immediately return Threatpost’s request for comment.
According to researchers, the four bugs involve missing authentication; insecure file upload; cross-site scripting (XSS); and path-traversal. The most high-severity bug (CVE-2020-28937) stems from a missing authentication check on requests for medical test information.
Authenticated healthcare users of the application can upload medical test documents for patients, which are then stored in the ‘/tests/’ directory. Unfortunately, there’s no requirement for patients to sign in in order to view the test results.
“Anyone with the full path to a valid medical test file could access this information, which could lead to loss of PHI for any medical records stored in the application,” according to the firm, writing in a Tuesday posting.
A mitigating factor is the fact that an attacker would need to know or guess the names of files stored in the “/tests/” directory in order to exploit the vulnerability.
“However, medical test filenames can be predictable, and valid filenames could also be obtained through log files on the server or other networking infrastructure,” researchers wrote.
Medical records are a hot commodity on the cybercriminal underground — fraudsters bent on identity theft or phishing efforts can use the store of personal information to craft convincing campaigns.
Other Bugs
Another vulnerability found by Bishop Fox allows an authenticated
attacker to obtain remote code execution on the application server. This
insecure file-upload bug (CVE-2020-28939) allows the Administrative and
Administrator user roles to upload malicious files, such as PHP web shells,
which can lead to arbitrary code execution on the application server.
“Administrative users with the ability to enter medical tests for patients were able to upload files to the application using the ‘/openclinic/medical/test_new.php endpoint,'” according to Bishop Fox. “This endpoint did not restrict the types of files that could be uploaded to the application. As a result, it was possible to upload a file containing a simple PHP web shell.”
Malicious users of the application could use this vulnerability to obtain access to sensitive information, escalate privileges, install malicious programs on the application server, or use the server as a pivot point to gain access to the internal network.
A third vulnerability, a medium-severity stored XSS vulnerability (CVE-2020-28938), allows an unauthenticated attacker to embed a payload that, if clicked by an admin user, would escalate privileges on the attacker’s account.
“While the application code contained measures to prevent XSS, it was found that these measures could be bypassed,” according to Bishop Fox. “HTML tags that could be included with user input were limited to [a] whitelist specified in /lib/Check.php.”
That means that in a real attack scenario, attackers could send a malicious link to victims – which when clicked would allow them to force actions on behalf of another user, according to Bishop Fox.
“To demonstrate impact, an XSS payload was embedded into a patient’s medical record with the lower-privileged Administrative user role,” researchers explained. “When clicked by an administrator, this payload created a new admin account under the attacker’s control, thereby allowing them to escalate privileges.”
The last vulnerability is a low-impact path traversal issue (no CVE was assigned) that could allow an authenticated attacker to store files outside of designated directories on the application server.
“Admin users could upload new themes to the application through the ‘/admin/theme_new.php’ endpoint,” according to researchers. “This caused new files to be created under the css folder in the directory where OpenClinic was installed. It was possible to navigate out of the css folder and store the files elsewhere on the filesystem.”
Bishop Fox first found the bugs in late August, and made several attempts to contact the OpenClinic development team through email, with no response.
“There is no version of OpenClinic available that does not suffer from the identified vulnerabilities, and the recommendation is to switch to a different medical records management software,” researchers said.
WebKit Vulnerabilities Allow Remote Code Execution via Malicious Websites
1.12.2020
Vulnerebility
Securityweek
The WebKit browser engine is affected by several vulnerabilities, including ones that can be exploited for remote code execution by convincing the targeted user to visit a malicious website.
WebKit is an open source engine that has been used by Safari and other Apple products, as well as many other apps for macOS, iOS and Linux.
Cisco’s Talos threat intelligence and research group revealed on Monday that one of its researchers identified several high-severity use-after-free vulnerabilities that can be exploited for remote code execution by getting the targeted user to access a specially crafted web page with a browser that uses WebKit.
The vulnerabilities are related to WebKit’s WebSocket, AudioSourceProviderGStreamer and ImageDecoderGStreamer functionality.
According to Talos, the flaws were reported this fall and they were patched earlier this month. The CVE identifiers CVE-2020-13584, CVE-2020-13558 and CVE-2020-13543 have been assigned.
An advisory published last week by the developers of WebKitGTK, a full-featured port of WebKit, and WPE, the WebKit implementation for embedded and low-consumption devices, mentions two code execution vulnerabilities found by Talos — one disclosed now and one disclosed in September — as well as several flaws reported by other researchers.
Talos has published detailed technical advisories for each of the vulnerabilities and the company has made available SNORT rules to help customers detect exploitation attempts.
Apple will likely patch the latest WebKit vulnerabilities with upcoming software updates
SD-WAN Product Vulnerabilities Allow Hackers to Steer Traffic, Shut Down
Networks
30.11.20
Vulnerebility
Securityweek
Researchers at cybersecurity consulting firm Realmode Labs have identified vulnerabilities in SD-WAN products from Silver Peak, Cisco, Citrix and VMware, including potentially serious flaws that can be exploited to steer traffic or completely shut down an organization’s network.
Realmode Labs has published four blog posts this month describing the vulnerabilities found by Ariel Tempelhof and Yaar Hahn in SD-WAN solutions from VMware, Cisco, Citrix and Silver Peak, which HP acquired earlier this year. Tempelhof told SecurityWeek that the details of the vulnerabilities were disclosed after each of the impacted vendors released patches within 90 days.
In Silver Peak’s Unity Orchestrator, the researchers discovered a total of three vulnerabilities, including an authentication bypass issue and two flaws that can be chained for remote code execution.
In Citrix’s SD-WAN Center, they identified two authentication bypass bugs — one of them impacted the CakePHP web framework — and two shell injections, which also could have been exploited for remote code execution.
In Cisco’s SD-WAN (Viptela) vManage network management system they found four vulnerabilities, including two directory traversal issues that resulted in SSH key extraction, as well as a shell injection vulnerability and a privilege escalation bug, which also led to remote code execution.
The security holes found in VMware’s SD-WAN (VeloCloud) Orchestrator product can also allow remote code execution. The list includes a backdoor, path traversal, SQL injection, and file inclusion weaknesses.
“For each vendor we studied the central management unit of their SD-WAN topology,” Tempelhof explained. “Gaining unrestricted access to this allows the attacker to set the way traffic is being routed in the international network of the company. This may lead to traffic steering or even complete shutdown of the company's network.”
He pointed out that all of the analyzed products were developed by relatively small companies — ones that were not security-focused — that have been acquired by major organizations.
“Big software companies bought those startups and put their stamp on it,” Tempelhof said. “We're wondering what was the security assessment due diligence during this transition (if any) and what should they've done better in the process.”
Drupal emergency updates fix critical arbitrary PHP code execution
28.11.20
Vulnerebility
Securityaffairs
Drupal has released emergency security updates to fix a critical flaw with known
exploits that could allow for arbitrary PHP code execution.
Drupal has
released emergency security updates to address a critical vulnerability with
known exploits that could be exploited to achieve arbitrary PHP code execution
on some CMS versions.
The Drupal project uses the PEAR Archive_Tar library that was recently updated to address the CVE-2020-28948 and CVE-2020-28949.
As a consequence, multiple vulnerabilities impact Drupal installs when they are configured to allow .tar, .tar.gz, .bz2, or .tlz file uploads and processes them.
“Drupal has released security updates to address vulnerabilities in Drupal 7, 8.8 and earlier, 8.9, and 9.0. An attacker could exploit this vulnerability to take control of an affected system.” reads the advisory published by CISA.
“The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review Drupal Advisory SA-CORE-2020-013 and apply the necessary updates.”
“According to the regular security release window schedule, November 25th would not typically be a core security window,” reads the security advisory published by Drupal.
“However, this release is necessary because there are known exploits for one of core’s dependencies and some configurations of Drupal are vulnerable.”
Drupal released the following updates to address the issues:
Drupal 9.0 users should update to Drupal 9.0.9
Drupal 8.9 users should update
to Drupal 8.9.10
Drupal 8.8 or earlier users should update to Drupal 8.8.12
Drupal 7 users should update to Drupal 7.75
“Versions of Drupal 8 prior to
8.8.x are end-of-life and do not receive security coverage,” Drupal’s security
team added.
Drupal also recommends to mitigate this issue by preventing untrusted users from uploading .tar, .tar.gz, .bz2, or .tlz files.
The number of vulnerable Drupal installs is approximatively over 940,000 out of a total of 1,120,94.
Last week, the Drupal development team has released security updates to fix a remote code execution vulnerability related caused by the failure to properly sanitize the names of uploaded files.
The vulnerability, tracked as CVE-2020-13671, has been classified as critical according to the NIST Common Misuse Scoring System.
The flaw could be exploited by an attacker by uploading files with certain types of extensions (phar, php, pl, py, cgi, html, htm, phtml, js, and asp) to the server to achieve remote code execution.
Unofficial Patch Released for Windows 7 Zero-Day Vulnerability
27.11.20
Vulnerebility
Securityweek
An unofficial patch is now available through ACROS Security’s 0patch service for a zero-day vulnerability identified earlier this month in Windows 7 and Windows Server 2008 R2.
The privilege escalation flaw, detailed by security researcher Clément Labro on November 12, exists because all users have write permissions for HKLM\SYSTEM\CurrentControlSet\Services\Dnscache and HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper, two keys that could be used for code execution.
Specifically, the researcher discovered that a local non-admin user could target any of the two keys to create a Performance subkey, then trigger performance monitoring to load an attacker DLL through the Local System WmiPrvSE.exe process, and execute code from it.
The Performance subkey specifies the name of the driver’s performance DLL and that of specific functions in that DLL. Because a user could add value entries to the subkey, a local user could abuse the issue to execute code with SYSTEM privileges.
The researcher, who has created proof-of-concept code targeting the bug, says the impact of this flaw is low, given the required local access, not to mention the fact that only older, no longer supported versions of Windows are affected.
Both Windows 7 and Windows Server 2008 R2 reached end of support on January 2020 and are currently in the Extended Security Updates (ESU) period, but will no longer receive security fixes past January 2023.
ACROS Security, however, has promised fixes for these platform iterations even after Microsoft stops providing support for them, and even for systems that are not enrolled in the ESU program.
As part of its 0patch service, the Slovenia-based company has now released an unofficial, free micropatch for the newly disclosed zero-day, to eliminate the use of this specific Performance key, thus preventing its abuse.
“This obviously breaks performance monitoring for the affected services but that's a trade-off we believe is beneficial to our users. In case performance monitoring is needed for these services, the micropatch can always be temporarily disabled (again, no restart of the service, much less of the computer, is needed for that),” the company explains.
The micropatch, which can be viewed in action in this video, targets Windows 7 and Server 2008 R2 computers with and without ESU, which have the November 2020 or January 2020 updates, respectively.
A zero-day in Windows 7 and Windows Server 2008 has yet to be fixed
27.11.20
Vulnerebility
Securityaffairs
Researcher discovers a zero-day vulnerability in Windows 7 and Windows Server
2008 while he was working on a Windows security tool.
The French security
researcher Clément Labro discovered a zero-day vulnerability was discovered
while the security researcher was working on an update Windows security tool.
The researcher was developing his own Windows privilege escalation enumeration script, named PrivescCheck, which is a sort of updated and extended version of the famous PowerUp.
“If you have ever run this script on Windows 7 or Windows Server 2008 R2, you probably noticed a weird recurring result and perhaps thought that it was a false positive just as I did. Or perhaps you’re reading this and you have no idea what I am talking about.” wrote the expert. “Anyway, the only thing you should know is that this script actually did spot a Windows 0-day privilege escalation vulnerability. Here is the story behind this finding…”
The expert confirmed that the flaw impacts the Windows 7 and Windows Server 2008 R2 operating systems.
The vulnerability impacts two misconfigured registry keys for the RPC Endpoint Mapper and DNSCache services.
HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper
HKLM\SYSTEM\CurrentControlSet\Services\Dnscache
An attack with access to
vulnerable systems can modify these registry keys to activate a sub-key with the
name of the user’s service usually employed by the Windows Performance
Monitoring mechanism.
The researchers was looking for some sort of tree
structure detailing all the subkeys and values defining a service’s
configuration when he found some interesting info on using “Performance” and
“DLL” keywords.
A performance key specifies information for optional
performance monitoring. It is possible to specify the name of the driver’s
performance DLL and the names of certain exported functions in that DLL by
setting the values under this key using AddReg entries in the driver’s INF file.
This implies that it is theoretically possible to register a DLL in a driver
service in order to monitor its performances using the Performance subkey.
This mechanism is still available in Windows 7 and Windows Server 2008 and
allows developers to load their own DLL files to monitor performance using their
own tools.
At the time of writing it is impossible to know if Microsoft will address the vulnerability disocvered by Labro.
Although both Windows OSs have reached the end of support in January 2020 this year, they will be covered by the Extended Security Updates (ESU) until January 2023, which means that even fully ESU-updated machines are currently affected by this issue.
Researchers at 0patch, have developed their own micropatch for the zero-day in Windows 7 and Server 2008 R2.
“As an alternative to ESU, we at 0patch have “security adopted” Windows 7 and Windows Server 2008 R2 and are providing critical security patches for these platforms. Consequently, vulnerabilities like this one get our attention – and, usually, micropatches.” reported 0patch.
Source code of the micropatch developed by 0patch
Critical MobileIron RCE Flaw Under Active Attack
26.11.20
Vulnerebility
Securityaffairs
Attackers are
targeting the critical remote code-execution flaw to compromise systems in the
healthcare, local government, logistics and legal sectors, among others.
Advanced persistent threat (APT) groups are actively exploiting a vulnerability in mobile device management security solutions from MobileIron, a new advisory warns.
The issue in question (CVE-2020-15505) is a remote code-execution flaw. It ranks 9.8 out of 10 on the CVSS severity scale, making it critical. The flaw was patched back in June, however, a proof of concept (PoC) exploit became available in September. Since then, both hostile state actors and cybercriminals have attempted to exploit the flaw in the U.K., according to a new advisory by the National Cyber Security Centre (NCSC).
“These actors typically scan victim networks to identify vulnerabilities, including CVE-2020-15505, to be used during targeting,” said the NCSC in an advisory this week. “In some cases, when the latest updates are not installed, they have successfully compromised systems.”
The NCSC said that the healthcare, local government, logistics and legal sectors have all been targeted – but others could also be affected.
Separately, the Cybersecurity and Infrastructure Security Agency (CISA) in October warned that APT groups are exploiting the MobileIron flaw in combination with the severe Microsoft Windows Netlogon/Zerologon vulnerability (CVE-2020-1472).
The Flaw
The flaw, first reported to MobileIron by Orange Tsai from DEVCORE,
could allow an attacker to execute remote exploits without authentication.
MobileIron provides a platform that allows enterprises to manage the end-user mobile devices across their company. The flaw exists across various components of this platform: In MobileIron Core, a component of the MobileIron platform that serves as the administrative console; and in MobileIron Connector, a component that adds real-time connectivity to the backend. Also impacted is Sentry, an in-line gateway that manages, encrypts and secures traffic between the mobile-device and back-end enterprise systems; and Monitor and Reporting Database, which provides comprehensive performance management functionality.
The bug affects Core and Connector versions 10.3.0.3 and earlier, 10.4.0.0, 10.4.0.1, 10.4.0.2, 10.4.0.3, 10.5.1.0, 10.5.2.0 and 10.6.0.0; and Sentry versions 9.7.2 and earlier, and 9.8.0; and Monitor and Reporting Database (RDB) version 2.0.0.1 and earlier that allows remote attackers to execute arbitrary code via unspecified vectors.
Patches
MobileIron, for its part, said in an update this week that it has
been engaging in “proactive outreach to help customers secure their systems,”
and estimates that 90 to 95 percent of all devices are now managed on
patched/updated versions of software.
While the company said it will continue to follow up with the remaining customers where we can determine that they have not yet patched affected products, it strongly urges companies to make sure they are updated.
“MobileIron strongly recommends that customers apply these patches and any security updates as soon as possible,” said the company in its security update.
Threatpost has reached out to MobileIron for further comment.
2-Factor Authentication Bypass Flaw Reported in cPanel and WHM Software
25.11.20
Vulnerebility
Thehackernews
cPanel, a provider of popular administrative tools to manage web hosting, has patched a security vulnerability that could have allowed remote attackers with access to valid credentials to bypass two-factor authentication (2FA) protection on an account.
The issue, tracked as "SEC-575" and discovered by researchers from Digital Defense, has been remedied by the company in versions 11.92.0.2, 11.90.0.17, and 11.86.0.32 of the software.
cPanel and WHM (Web Host Manager) offers a Linux-based control panel for users to handle website and server management, including tasks such as adding sub-domains and performing system and control panel maintenance. To date, over 70 million domains have been launched on servers using cPanel's software suite.
The issue stemmed from a lack of rate-limiting during 2FA during logins, thus making it possible for a malicious party to repeatedly submit 2FA codes using a brute-force approach and circumvent the authentication check.
Digital Defense researchers said an attack of this kind could be accomplished in minutes.
"The two-factor authentication cPanel Security Policy did not prevent an attacker from repeatedly submitting two-factor authentication codes," cPanel said in its advisory. "This allowed an attacker to bypass the two-factor authentication check using brute-force techniques."
The company has now addressed the flaw by adding a rate limit check to its cPHulk brute-force protection service, causing a failed validation of the 2FA code to be treated as a failed login.
This is not the first time the absence of rate-limiting has posed a serious security concern.
Back in July, video conferencing app Zoom fixed a security loophole that could have allowed potential attackers to crack the numeric passcode used to secure private meetings on the platform and snoop on participants.
It's recommended that cPanel customers apply the patches to mitigate the risk associated with the flaw.
Critical Unpatched VMware Flaw Affects Multiple Corporates Products
24.11.20
Vulnerebility
Thehackernews
VMware has released
temporary workarounds to address a critical vulnerability in its products that
could be exploited by an attacker to take control of an affected system.
"A malicious actor with network access to the administrative configurator on port 8443 and a valid password for the configurator admin account can execute commands with unrestricted privileges on the underlying operating system," the virtualization software and services firm noted in its advisory.
Tracked as CVE-2020-4006, the command injection vulnerability has a CVSS score of 9.1 out of 10 and impacts VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector.
While the company said patches for the flaw are "forthcoming," it didn't specify an exact date by when it's expected to be released. It's unclear if the vulnerability is under active attack.
The complete list of products affected are as follows:
VMware Workspace One Access (versions 20.01 and 20.10 for Linux and Windows)
VMware Workspace One Access Connector (versions 20.10, 20.01.0.0, and 20.01.0.1
for Windows)
VMware Identity Manager (versions 3.3.1, 3.3.2, and 3.3.3 for
Linux and Windows)
VMware Identity Manager Connector (versions 3.3.1, 3.3.2
for Linux and 3.3.1, 3.3.2, 3.3.3 for Windows)
VMware Cloud Foundation
(versions 4.x for Linux and Windows)
vRealize Suite Lifecycle Manager
(versions 8.x for Linux and Windows)
VMware said the workaround applies only
to the administrative configurator service hosted on port 8443.
"Configurator-managed setting changes will not be possible while the workaround is in place," the company said. "If changes are required please revert the workaround following the instructions below, make the required changes and disable again until patches are available."
The advisory comes days after VMware addressed a critical flaw in ESXi, Workstation, and Fusion hypervisors that could be exploited by a malicious actor with local administrative privileges on a virtual machine to execute code and escalate their privileges on the affected system (CVE-2020-4004 and CVE-2020-4005).
The vulnerability was discovered by Qihoo 360 Vulcan Team at the 2020 Tianfu Cup Pwn Contest held earlier this month in China.
VMware fixed SD-WAN flaws that could allow hackers to target enterprise networks
24.11.20
Vulnerebility
Securityaffairs
VMware addressed six vulnerabilities in its SD-WAN Orchestrator product that can
potentially expose enterprise networks to hack.
VMware last week addressed
six vulnerabilities (CVE-2020-3984, CVE-2020-3985, CVE-2020-4000, CVE-2020-4001,
CVE-2020-4002, CVE-2020-4003) in its SD-WAN Orchestrator product, including some
issues that can be chained by an attacker to hijack traffic or shut down an
enterprise network.
The following vulnerabilities have been reported by Ariel Tempelhof of Realmode Labs, they can be chained by remote unauthenticated attackers to achieve remote code execution.
The SQL injection vulnerability in SD-WAN Orchestrator, tracked as
CVE-2020-3984, is caused by improper input validation. The flaw can be exploited
by an authenticated SD-WAN Orchestrator user via a vulnerable API call using
specially crafted SQL queries which may lead to unauthorized data access.
A
Directory traversal file execution in SD-WAN Orchestrator, tracked as
CVE-2020-4000, allows for executing files through directory traversal.
A
default passwords Pass-the-Hash Attack, tracked as CVE-2020-4001, could allow
attackers to carry out a Pass-the-Hash Attack.
“SD-WAN Orchestrator ships
with default passwords for predefined accounts which may lead to to a
Pass-the-Hash attack.” reads the security advisory published by VMware. “The
same salt is used in conjunction with the default password of predefined
accounts on freshly installed systems allowing for for Pass-the-Hash-Attacks.
That same system could be accessed by an attacker using the default password for
the predefined account.”
The remaining flaws are:
An API endpoint privilege escalation, tracked as CVE-2020-3985, can be exploited
by a user to elevate their privileges by calling a vulnerable API.
An unsafe
handling of system parameters, tracked as CVE-2020-4002, which can be triggered
by an authenticated SD-WAN Orchestrator user with high privileges to execute
arbitrary code on the underlying operating system.
A SQL injection
Information Disclosure, tracked as CVE-2020-4003, that can be exploited by an
authenticated SD-WAN Orchestrator user to inject code into SQL queries which may
lead to information disclosure.
German COVID-19 Contact-Tracing Vulnerability Allowed RCE
20.11.20
Vulnerebility
Threatpost
Bug hunters at GitHub Security Labs help shore up German contact tracing app security, crediting open source collaboration.
A security vulnerability in the infrastructure underlying Germany’s official COVID-19 contact-tracing app, called the Corona-Warn-App (CWA), would have allowed pre-authenticated remote code execution (RCE).
Researcher Alvaro Muñoz wrote in a report this week that he and his team at GitHub Security Labs were chasing down RCE vulnerabilities on the platform and found one in the infrastructure supporting CWA for Android and OS. The team said it worked with SAP to mitigate the issue, adding as a server-side issue, the mobile apps themselves were not impacted, and that no data was collected beyond a device’s IP address.
“There appeared to be a pre-authentication RCE vulnerability in Corona-Warn-App Server, which drives Germany’s COVID-19 contact-tracing application infrastructure,” according to Muñoz. “This vulnerability had the potential to affect the integrity of Germany’s COVID-19 response and as such warranted an immediate response from our team.”
The Bug
The vulnerable code was located in the Submission Service, which is a
micro service developed on top of the Spring Boot framework responsible for
validating the information that CWA users submit.
This uses a function called the SubmissionController, which verifies various aspects of the user-supplied information, such as making sure all mandatory fields are filled out. The data isvalidated by the “ValidSubmissionPayload” validator.
“As explained in our previous research on Java Bean Validation vulnerabilities, if any validated bean properties flow into a custom constraint violation template, [an] attacker-controlled property will be evaluated as an Expressional Language (EL) expression, which allows for the evaluation of arbitrary Java code,” the researcher explained.
This turns out to be the case for two of the validation checks on the user supplied submissions: One checks to make sure that the “visited countries” information is valid, and the other checks to make sure the origin country is valid.
The upshot, the researcher said, is that any POST requests sent to the Submission endpoint are allowed by default and require no further authorization or authentication. And the Submission endpoint itself is publicly exposed, allowing remote contact.
CWA was commissioned by the German government and built by SAP and Deutsche Telekom using the GitHub development platform. It functions by exchanging anonymous tokens through the exposure notification API from Apple and Google, over Bluetooth Low Energy. The log is saved for 14 days. If the user tests positive, the anonymous log is submitted to the CWA server, which keeps track of exposure and can then, in turn, alert people to isolate after a set amount of exposure.
“The app informs us if we have had contact with a person diagnosed with COVID-19,” according to the CWA site. “It protects us and others around us, as well as our privacy.”
The app was released in June after only 50 days in development, according to SAP. The timeline was supercharged by making the open-source project available to the public on GitHub.
“More than 109,000 visitors viewed the code and approximately 7,250 community and project members participated,” SAP said in a statement in June about the app’s release. “The Corona-Warning-App is the largest open-source project ever implemented in Germany on behalf of the German government.”
For their part, GitHub is touting the finding of the bug as a success for both open source and the fight against COVID-19.
“This research is yet another example of open source saving the day – without involving the broader development community, GitHub Security Lab would not have been able to discover and help fix this vulnerability, risking a mission critical piece of infrastructure in the global fight against COVID-19,” Jamie Cool, vice president of product management, security at GitHub told Threatpost.
Contact-Tracing and Privacy
Privacy concerns have been a barrier to adoption
of contact-tracing apps, which require widespread use to be valuable. People are
leery about handing over their location data to government entities.
In Sept., the nonprofit Electronic Frontier Foundation warned about the possible implications of contact tracing apps to be used to stifle free speech protections, specifically calling out California’s lack of privacy considerations in developing a tracing app for the state.
“Privacy protections are necessary to public health programs, particularly when a program needs high levels of participation to be effective,” EFF’s Hayley Tsukayama wrote in a blog post in Sept. “People will not use applications they can’t trust. That’s why EFF and other privacy groups have called on Governor Newsom to place basic privacy guardrails on any contact-tracing program run by or with the state.”
Also, Utah’s “Healthy Together” app was slammed last May for throwing out the Google and Apple API which assigns an anonymous identifier beacon to protect privacy and instead using a system developed for a social-networking site which critics said collected gobs of user location data.
Muñoz said building these applications on open source not only offers transparency to users about what data is being collected and where its going, but it also allows others to help spot security holes, which in turn builds critical public trust.
Cisco fixed flaws in WebEx that allow ghost participants in meetings
18.11.20
Vulnerebility
Securityaffairs
Cisco has addressed three flaws in Webex Meetings that would have allowed
unauthenticated remote attackers to join ongoing meetings as ghost participants.
Cisco has addressed three vulnerabilities in Webex Meetings (CVE-2020-3441,
CVE-2020-3471, and CVE-2020-3419) that would have allowed unauthenticated remote
attackers to join ongoing meetings as ghost participants.
“A vulnerability in Cisco Webex Meetings and Cisco Webex Meetings Server could allow an unauthenticated, remote attacker to join a Webex session without appearing on the participant list.” reads the security advisory published by Cisco.
The vulnerabilities were discovered earlier this year by security by IBM researchers as part of an assessment of the tools used by its personnel for remote working during the COVID-19 pandemic.
Ghost participants to a meeting could be seen in the user list, but they can access any media within the meeting, even if they were not invited.
The flaws also allowed attackers to remain in the Webex meeting as ghost audio
users after admins would remove them, they also allowed them to access Webex
users’ information, including full names, email addresses, and IP addresses.
The bugs affect Cisco Webex Meetings and Cisco Webex Meetings Server, they
reside in the “handshake” process that allows establishing a new Webex meeting.
“Malicious actors could abuse these flaws to become a ‘ghost’ joining a meeting without being detected.” reads the report published by IBM. “The now-patched flaws, discovered by IBM researchers, would have allowed an attacker to:
Join a Webex meeting as a ghost without being seen on the participant list with
full access to audio, video, chat and screen-sharing capabilities.
Stay in a
Webex meeting as a ghost after being expelled from it, maintaining audio
connection.
Gain access to information on meeting attendees — including full
names, email addresses and IP addresses — from the meeting room lobby, even
without being admitted to the call.”
The experts were able to exploit the
flaws on MacOS, Windows, and the iOS version of Meetings applications and Webex
Room Kit appliance.
IBM experts also published a video PoC of the attack.
“Once a host starts or unlocks a meeting, a ghost could slip in and join the meeting using the handshake manipulation, without ever showing up on any participant list, including the host’s participant list. The ghost could see and hear other participants, as well as view shared screens and chat without revealing their presence.” continues the report.
“With this technique, the only indication the participants would have that they
may not be alone is the beep of a new audio connection. For especially large
meetings, the host might disable the entry and exit tone, allowing the ghost to
enter perfectly stealthily. In other instances, the ghost’s entry tone would
play, but may go unnoticed by the host or other participants who aren’t counting
and associating each tone with a specific participant.”
Cisco has patched
cloud-based Cisco Webex Meetings sites and released security updates for
on-premises software to address the flaws.
Researchers Warn of Critical Flaws Affecting Industrial Automation Systems
18.11.20
Vulnerebility
Thehackernews
A critical
vulnerability uncovered in Real-Time Automation's (RTA) 499ES EtherNet/IP (ENIP)
stack could open up the industrial control systems to remote attacks by
adversaries.
RTA's ENIP stack is one of the widely used industrial automation devices and is billed as the "standard for factory floor I/O applications in North America."
"Successful exploitation of this vulnerability could cause a denial-of-service condition, and a buffer overflow may allow remote code execution," the US cybersecurity and infrastructure agency (CISA) said in an advisory.
As of yet, no known public exploits have been found to target this vulnerability. However, "according to public search engines for Internet-connected devices (e.g. shodan.io) there are more than 8,000 ENIP-compatible internet-facing devices."
Tracked as CVE-2020-25159, the flaw is rated 9.8 out of 10 in severity by the industry-standard Common Vulnerability Scoring System (CVSS) and impacts all versions of EtherNet/IP Adapter Source Code Stack prior to 2.28, which was released on November 21, 2012.
The stack overflow vulnerability was disclosed to CISA last month by Sharon Brizinov, a security researcher for operational technology security company Claroty.

Although it appears that RTA removed the attackable code from its software as
early as 2012, it's suspected that many vendors may have bought vulnerable
versions of this stack before the 2012 update and integrated it into their own
firmware, thereby putting multiple devices at risk.
"Eleven devices were found to be running RTA's ENIP stack in products from six unique vendors," the researchers said.
The flaw in itself concerns an improper check in the path parsing mechanism employed in Common Industrial Protocol (CIP) — a communication protocol used for organizing and sharing data in industrial devices — allowing an attacker to open a CIP request with a large connection path size (greater than 32) and cause the parser to write to a memory address outside the fixed-length buffer, thus leading to the potential execution of arbitrary code.
"The older code in the RTA device attempted to reduce RAM usage by limiting the size of a particular buffer used in an EtherNet/IP Forward Open request," RTA said in its disclosure. "By limiting the RAM, it made it possible for an attacker to attempt to overrun the buffer and use that to try to get control of the device."
Claroty researchers scanned 290 different ENIP-compatible modules, of which 11 devices from six different vendors were found to be using RTA's ENIP stack. There are currently more than 8,000 ENIP-compatible internet-facing devices, according to a search on Shodan.
"Similarly to previous disclosures, such as Ripple20 or Urgent/11, this is another case of a vulnerable third-party core library putting products from [Industrial Control System] vendors at risk," Brizinov noted in an analysis.
It's recommended that operators update to current versions of the ENIP stack to mitigate the flaw. CISA also advised users to minimize network exposure for all control system devices and ensure that they are not accessible from the Internet.
"Locate control system networks and remote devices behind firewalls, and isolate them from the business network," CISA said in its alert. "When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available."
Cisco Patches Critical Flaw After PoC Exploit Code Release
18.11.20
Vulnerebility
Threatpost
A critical path-traversal flaw (CVE-2020-27130) exists in Cisco Security Manager that lays bare sensitive information to remote, unauthenticated attackers.
A day after proof-of-concept (PoC) exploit code was published for a critical flaw in Cisco Security Manager, Cisco has hurried out a patch.
Cisco Security Manager is an end-to-end security management application for enterprise administrators, which gives them the ability to enforce various security policies, troubleshoot security events and manage a wide range of devices. The application has a vulnerability that could allow remote, unauthenticated attackers to access sensitive data on affected systems. The flaw (CVE-2020-27130) has a CVSS score of 9.1 out of 10, making it critical.
“An attacker could exploit this vulnerability by sending a crafted request to the affected device,” according to Cisco, in a Tuesday analysis. “A successful exploit could allow the attacker to download arbitrary files from the affected device.”
According to Cisco, the flaw stems from the improper validation of directory traversal character sequences within requests to an affected device. A path-traversal attack aims to access files and directories that are stored outside the web root folder. If an attacker manipulates variables referencing files (with “dot-dot-slash (../)” sequences), it is possible to access arbitrary files and directories stored on file system, such as application source code, or configuration and critical system files.
PoC exploits for the flaw – as well as 11 other issues in Cisco Security Manager – were published online Monday by security researcher Florian Hauser. Hauser said in a Monday tweet that he had previously reported the flaws 120 days ago – however, Cisco “became unresponsive and the published release 4.22 still doesn’t mention any of the vulnerabilities.”
In a follow-up tweet on Tuesday, Hauser said: “Just had a good call with Cisco! The missing vulnerability fixes were indeed implemented as well but need some further testing. SP1 will be released in the next few weeks. We found a good mode of collaboration now.”
The flaw affects Cisco Security Manager releases 4.21 and earlier; the issue is fixed in Cisco Security Manager Release 4.22.
Other Security Manager Bugs
Cisco on Tuesday also disclosed two high-severity
vulnerabilities in Cisco Security Manager. One of these (CVE-2020-27125) stems
from insufficient protection of static credentials in the affected software.
This flaw could allow a remote, unauthenticated attacker to access sensitive
information on an affected system, according to Cisco.
“An attacker could exploit this vulnerability by viewing source code,” according to Cisco. “A successful exploit could allow the attacker to view static credentials, which the attacker could use to carry out further attacks.”
The other flaw exists in the Java deserialization function that is used by Cisco Security Manager, and could allow an unauthenticated, remote attacker to execute arbitrary commands on an affected device.
That flaw (CVE-2020-27131) stems from insecure deserialization of user-supplied content by the affected software, according to Cisco.
“An attacker could exploit these vulnerabilities by sending a malicious serialized Java object to a specific listener on an affected system,” said Cisco’s advisory. “A successful exploit could allow the attacker to execute arbitrary commands on the device with the privileges of NT AUTHORITY\SYSTEM on the Windows target host.”
Cisco has recently dealt with various flaws across its product line. Last week, the networking giant warned of a high-severity flaw in Cisco’s IOS XR software that could allow unauthenticated, remote attackers to cripple Cisco Aggregation Services Routers (ASR). Cisco also recently disclosed a zero-day vulnerability in the Windows, macOS and Linux versions of its AnyConnect Secure Mobility Client Software.
Multiple Industrial Control System Vendors Warn of Critical Bugs
18.11.20 Vulnerebility Threatpost
Four industrial control system vendors each announced vulnerabilities that ranged from critical to high-severity.
Industrial control system firms Real Time Automation and Paradox both warned of critical vulnerabilities Tuesday that opened systems up to remote attacks by adversaries.
Flaws are rated 9.8 out of 10 in severity by the industry standard Common Vulnerability Scoring System. The Real Time Automation bug is traced back to a component made by Claroty.
“A stack overflow vulnerability was discovered in RTA’s 499ES ENIP stack, all versions prior to 2.28, one of the most widely used OT protocols,” wrote Claroty, which publicly disclosed the bug Tuesday. Third-party code used in the proprietary Real Time Automation (RTA) component, 499ES EtherNet/IP (ENIP), can be triggered to cause a conditions ripe for a denial-of-service attack.
Claroty researchers said it had identified 11 devices using RTA’s ENIP stack from six different vendors, which are likely to be vulnerable to attack. It did not identify those other vendors. Tracked as CVE-2020-25159, Sharon Brizinov of Claroty reported this vulnerability to CISA last month.
RTA, which describes itself as providing industrial control systems for manufacturing and building automation, posted information regarding the vulnerability on Oct. 27.
John Rinaldi, chief strategist, business development manager and CEO of RTA said in October that, “Older code in the RTA device attempted to reduce RAM usage by limiting the size of a particular buffer used in an EtherNet/IP Forward Open request. By limiting the RAM, it made it possible for an attacker to attempt to overrun the buffer and use that to try to get control of the device. That line of code was changed a number of revision levels ago and is not an issue in current EtherNet/IP software revision levels.”
ICS Security System Paradox
Security device maker Paradox also announced a
critical bug (CVE-2020-25189) impacting its IP150 Internet Module that created
conditions ripe for a stack-based buffer overflow attack.
“Successful exploitation of these vulnerabilities could allow an attacker to remotely execute arbitrary code, which may result in the termination of the physical security system,” wrote the Cybersecurity Infrastructure Security Agency (CISA) in a bulletin posted on Tuesday.
According to Paradox, the impacted IP150 Internet Module is a “LAN based communication module that enables you to control and monitor your Paradox security system over a LAN or the internet through any web browser.”
A second high-severity bug, tracked as CVE-2020-25185 with a CVSS rating of 8.8, opens the IP150 Internet Module to “five post-authentication buffer overflows, which may allow a logged in user to remotely execute arbitrary code.”
While Paradox indicated that there are no known public exploits targeting the vulnerabilities, the company also did not offer any specific patches for either bug.
Inquiries to Paradox were not returned.
In lieu of patches Paradox offered a number of mitigation recommendations including ensuring the least-privilege user principle is adhered to and “minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the internet.”
Busy Day for ICS Patches
In addition to the RTA and Paradox bugs,
high-severity flaws were made public by Sensormatic Electronics, a subsidiary of
Johnson Controls, and ICS behemoth Schneider Electric.
Schneider reported nine high-severity bugs in its Interactive Graphical SCADA System. Vulnerabilities include: improper restriction of operations within the bounds of a memory buffer, an out-of-bounds write and an out-of-bounds read flaws.
The Sensormatic bug (CVE-2020-9049) impact equipment: American Dynamics victor Web Client and Software House C•CURE Web Client.
“Successful exploitation of this vulnerability could allow an unauthenticated attacker on the network to create and sign their own JSON web token and use it to execute an HTTP API method without the need for valid authentication/authorization. Under certain circumstances, this could be used by an attacker to impact system availability by conducting a denial-of-service attack,” warned CISA in its security bulletin posted Tuesday.
Large-scale campaign targets vulnerable Epsilon Framework WordPress themes
18.11.20
Vulnerebility
Securityaffairs
Hackers are scanning the Internet for WordPress websites with Epsilon Framework
themes installed to launch Function Injection attacks.
Experts at the
Wordfence Threat Intelligence team uncovered a large-scale wave of attacks
targeting reported Function Injection vulnerabilities in themes using the
Epsilon Framework.
Below a list of themes and related versions that are vulnerable to the above attacks:
Shapely <=1.2.7
NewsMag <=2.4.1
Activello <=1.4.0
Illdy <=2.1.4
Allegiant <=1.2.2
Newspaper X <=1.3.1
Pixova Lite <=2.0.5
Brilliance
<=1.2.7
MedZone Lite <=1.2.4
Regina Lite <=2.0.4
Transcend <=1.1.8
Affluent <1.1.0
Bonkers <=1.0.4
Antreas <=1.0.2
NatureMag Lite <=1.0.5
According to the experts, the vulnerable themes are installed on over 150,000
sites.
“On November 17, 2020, our Threat Intelligence team noticed a
large-scale wave of attacks against recently reported Function Injection
vulnerabilities in themes using the Epsilon Framework, which we estimate are
installed on over 150,000 sites.” reads the analysis published by WordFence. “So
far today, we have seen a surge of more than 7.5 million attacks against more
than 1.5 million sites targeting these vulnerabilities, coming from over 18,000
IP addresses. While we occasionally see attacks targeting a large number of
sites, most of them target older vulnerabilities.”
The vulnerabilities targeted by the threat actors could allow them to takeover
WordPress installs through an exploit chain ending in remote code execution
(RCE). The researcher did not provide technical details on the attacks because
the exploit does not yet appear to be in a mature state.
The researchers
pointed out the vast majority of these attacks appear to be probing attacks
aimed at determining whether a site is running a vulnerable theme.
“These attacks use POST requests to admin-ajax.php and as such do not leave distinct log entries, though they will be visible in Wordfence Live Traffic.” continues the report.
Admins of websites running vulnerable versions of the themes are recommended to update them. If no security patch is available for the installed theme, admins should switch to another theme.
Researcher Discloses Critical RCE Flaws In Cisco Security Manager
17.11.20
Vulnerebility
Thehackernews
Cisco has published
multiple security advisories concerning critical flaws in Cisco Security Manager
(CSM) a week after the networking equipment maker quietly released patches with
version 4.22 of the platform.
The development comes after Code White researcher Florian Hauser (frycos) yesterday publicly disclosed proof-of-concept (PoC) code for as many as 12 security vulnerabilities affecting the web interface of CSM that makes it possible for an unauthenticated attacker to achieve remote code execution (RCE) attacks.
The flaws were responsibly reported to Cisco's Product Security Incident Response Team (PSIRT) three months ago, on July 13.
"Since Cisco PSIRT became unresponsive and the published release 4.22 still doesn't mention any of the vulnerabilities," claimed frycos in a tweet, citing the reasons for going public with the PoCs yesterday.
Cisco Security Manager is an end-to-end enterprise solution that allows organizations to enforce access policies and manage and configure firewalls and intrusion prevention systems in a network.

The company released the 4.22 version of CSM on November 9 with a number of
security enhancements, including support for AnyConnect Web Security WSO along
with deprecating MD5 hash algorithm and DES and 3DES encryption algorithms.
The vulnerabilities allow an attacker to craft malicious requests as well as upload and download arbitrary files in the context of the highest-privilege user account "NT AUTHORITY\SYSTEM," giving the adversary access to all files in a specific directory.
"The vulnerability is due to improper validation of directory traversal character sequences within requests to an affected device," Cisco said in its advisory. "An attacker could exploit this vulnerability by sending a crafted request to the affected device. A successful exploit could allow the attacker to download arbitrary files from the affected device."
The flaw has a CVSS score of 9.1 out of 10, making it critical in severity.
A separate flaw (CVSS score: 8.1) due to an insecure Java deserialization function used by CSM could have allowed an unauthenticated, remote attacker with system privileges to execute arbitrary commands on an affected device.
However, Cisco is yet to address the flaw, with a planned fix set to be included in Cisco Security Manager Release 4.23.
The company also said it's aware of public announcements about the vulnerabilities and that it hasn't so far found any evidence that the flaws were exploited in the wild.
Nvidia Warns Windows Gamers of GeForce NOW Flaw
12.11.20
Vulnerebility
Threatpost
Both Nvidia and Intel
faced severe security issues this week – including a high-severity bug in
Nvidia’s GeForce NOW.
Nvidia is red-flagging a high-severity flaw in its GeForce NOW application software for Windows. An attacker on a local network can exploit the flaw in order to execute code or gain escalated privileges on affected devices.
GeForce NOW is the brand used by Nvidia for its cloud-based gaming service, which enables real-time gameplay on desktops, laptops, Macs and Android devices. With an estimated user base of 4 million, the service is wildly popular in the gaming community.
In a Tuesday security advisory, Nvidia revealed a flaw in the popular service (CVE‑2020‑5992) that has a CVSS score of 7.3.
The bug stems from an “open-source software dependency” having to do with the OpenSSL library, which is a software library for applications that secure communications over computer networks against eavesdropping or which need to identify the party at the other end.
In this situation, OpenSSL library is vulnerable to binary planting attacks, according to Nvidia in its security advisory. Binary planting is a type of attack where the attacker “plants” a binary file that contains malicious code inside a (in this case local) file system, in order for a vulnerable application to load and execute it.
All versions prior to 2.0.25.119 are affected; users are urged to update to version 2.0.25.119.
“To protect your system, open the GeForce NOW application to automatically download the update and follow the instructions for applying it,” according to Nvidia.
Nvidia has recently faced various security issues in its gaming-friendly products. That includes two recent flaws in the Windows version of its GeForce Experience software. The most severe flaw of the two (CVE-2020-5977) can lead to a slew of malicious attacks on affected systems – including code execution, denial of service, escalation of privileges and information disclosure.
In October, Nvidia also released a patch for a critical bug in its high-performance line of DGX servers that could open the door for a remote attacker to take control of and access sensitive data on systems typically operated by governments and Fortune-100 companies.
Other Processor Security Issues
Chip manufacturers have deployed a slew of
security updates this past week. A massive Intel security update on Tuesday, for
instance, addressed flaws across a myriad of products – most notably, critical
bugs that can be exploited by unauthenticated cybercriminals in order to gain
escalated privileges. These critical flaws exist in products related to Wireless
Bluetooth – including various Intel Wi-Fi modules and wireless network adapters
– as well as in its remote out-of-band management tool, Active Management
Technology (AMT).
Also this week, researchers unveiled a new way to steal cryptographic keys from Intel chips through a new side-channel attack, which they call PLATYPUS.
The attack stems from the ability to exploit the Intel Running Average Power Limit (RAPL) interface. RAPL allows monitoring and controlling the power consumption of the CPU and DRAM in software. By launching a side-channel attack against RAPL, researchers were able to not only distinguish different keys, but also reconstruct entire cryptographic keys.
Intel for its part said that the flaws (CVE-2020-8694 and CVE-2020-8695) are medium-severity. That’s in part due to the fact that in order to launch an attack, a bad actor would need to have local access to a device, and would need to be authenticated or privileged.
The chip-maker recommended that users of affected Intel CPUs update to the latest firmware version provided by the system manufacturer (a full list of affected Intel chips and updates can be found here).
“Intel recommends that users of affected Intel Processors install the updates provided by their software vendors,” according to Intel’s advisory. “In Linux, for the change to be effective it will require a reboot. If a reboot is not possible, Intel recommends changing the permissions of the affected sysfs attributes so that only privileged users can access them.”
Cisco Zero-Day in AnyConnect Secure Mobility Client Remains Unpatched
12.11.20
Vulnerebility
Threatpost
Cisco also disclosed high-severity vulnerabilities in its Webex and SD-WAN products.
Cisco has disclosed a zero-day vulnerability – for which there is not yet a patch – in the Windows, macOS and Linux versions of its AnyConnect Secure Mobility Client Software.
While Cisco said it is not aware of any exploits in the wild for the vulnerability, it said Proof-of-Concept (PoC) exploit code has been released, opening up risks of cybercriminals potentially leveraging the flaw. The flaw (CVE-2020-3556) is an arbitrary code execution vulnerability with a CVSS score of 7.3 out of 10, making it high severity.
“Cisco has not released software updates that address this vulnerability,” according to Cisco’s Wednesday advisory. “Cisco plans to fix this vulnerability in a future release of Cisco AnyConnect Secure Mobility Client Software.”
AnyConnect Secure Mobility Client, a modular endpoint software product, provides a wide range of security services (such as remote access, web security features, and roaming protection) for endpoints.
The flaw could allow an attacker to cause a targeted AnyConnect user to execute a malicious script – however, in order to launch an attack a cybercriminal would need to be authenticated and on the local network.
“In order to successfully exploit this vulnerability, there must be an ongoing AnyConnect session by the targeted user at the time of the attack,” according to Cisco. “To exploit this vulnerability, the attacker would also need valid user credentials on the system upon which the AnyConnect client is being run.”
According to Cisco, the vulnerability exists in the interprocess communication (IPC) channel. IPC is a set of programming interfaces that allows a program to handle many user requests at the same time. Specifically in this case, the IPC listener has a lack of authentication.
“An attacker could exploit this vulnerability by sending crafted IPC messages to the AnyConnect client IPC listener,” according to Cisco. “A successful exploit could allow an attacker to cause the targeted AnyConnect user to execute a script. This script would execute with the privileges of the targeted AnyConnect user.”
While there are no workarounds that address this vulnerability, one mitigation is to disable the Auto Update and Enable Scripting features. That’s because a vulnerable configuration requires both the Auto Update setting and Enable Scripting setting to be enabled. Auto Update is enabled by default, and Enable Scripting is disabled by default, said Cisco.
Gerbert Roitburd from Secure Mobile Networking Lab (TU Darmstadt) was credited with reporting the vulnerability.
Cisco on Wednesday issued updates for 13 other high-severity CVEs across multiple products. That includes an arbitrary code execution flaw (CVE-2020-3588) in Cisco’s Webex Meetings Desktop collaboration app, as well as three arbitrary code execution glitches (CVE-2020-3573, CVE-2020-3603, CVE-2020-3604) in its Webex Network Recording Player and Webex Player.
Flaws tied to seven CVEs were also discovered in Cisco SD-WAN, including a file creation bug (CVE-2020-26071), privilege escalation flaw (CVE-2020-26074) and denial-of-service (DoS) flaw (CVE-2020-3574).
Silver Peak SD-WAN Bugs Allow for Network Takeover
12.11.20 Vulnerebility Threatpost
Three security vulnerabilities can be chained to enable unauthenticated remote code execution.
Silver Peak’s Unity Orchestrator, a software-defined WAN (SD-WAN) management platform, suffers from three remote code-execution security bugs that can be chained together to allow network takeover by unauthenticated attackers.
SD-WAN is a cloud-based networking approach used by enterprises and multilocation businesses of all sizes. It allows locations and cloud instances to be connected to each other and to company resources over any type of connectivity. And, it applies software control to managing that process, including the orchestration of resources and nodes. This orchestration is usually centralized via single-view platform – in this case, the Unity Orchestrator, which Silver Peak said has about 2,000 deployments.
According to researchers from Realmode Labs, the three bugs are an authentication bypass, file delete path traversal and an arbitrary SQL query execution, which can be combined in order to execute arbitrary code.
Attackers would first bypass authentication to log onto the platform, then look for a file being run by the web server, the firm noted. Then, they can delete it using the file delete path traversal issue, replacing it with one of their choice using SQL-query execution. Then all that’s needed is to execute the file to run any code or malware that they would like.
“In the best-case scenario, an attacker can use these vulnerabilities to intercept or steer traffic,” said Ariel Tempelhof, co-founder and CEO of Realmode, in a Medium post this week. “However, if an attacker desires, they can instead shutdown a company’s entire international network.”
Bug Details
The issues are present In Silver Peak Unity Orchestrator versions
prior to 8.9.11+, 8.10.11+, or 9.0.1+. Orchestrator instances that are hosted by
customers – on-premise or in a public cloud provider – are affected, Silver Peak
said. Patches are available.
As far as technical specifics, the authentication bypass (CVE-2020–12145) exists in the way Unity handles API calls.
“[Affected platforms use] HTTP headers to authenticate REST API calls from localhost,” according to Silver Peak’s security advisory. “This makes it possible to log in to Orchestrator by introducing an HTTP HOST header set to 127.0.0.1 or localhost.
Essentially this means that no meaningful authentication is performed when the calls originate from localhost, according to Tempelhof.
“The localhost check is being performed [like this]: request.getBaseUri().getHost().equals(“localhost”),” he explained. “Any requests with ‘localhost’ as their HTTP Host header will satisfy this check. This can be easily forged in remote requests of course.”
The path traversal issue (CVE-2020–12146) meanwhile exists because when a locally hosted file is deleted, no path-traversal check is made.
“An authenticated user can access, modify and delete restricted files on the Orchestrator server using the/debugFiles REST API,” according to Silver Peak.
Tempelhof elaborated: “Some of the API endpoints, which are now accessible thanks to the authentication bypass, allow the ability to upload debug logs to an S3 bucket to be examined by Silver Peak. This mechanism prepares the logs, uploads them and then deletes the locally hosted file. The /gms/rest/debugFiles/delete endpoint performing the deletion does not check for path traversal, creating the ability to delete any file on the system (if permissions allow).”
And the final issue, the SQL-query execution bug (CVE-2020–12147), allows an authenticated user to make unauthorized MySQL queries against the Orchestrator database, using the /sqlExecution REST API, according to Silver Peak. These arbitrary SQL queries are possible thanks to a special API endpoint which had been used for internal testing.
“The /gms/rest/sqlExecution endpoint can be leveraged to an arbitrary file write by utilizing an INTO DUMPFILE clause,” Tempelhof explained, adding that while INTO DUMPFILE does not allow overwriting a file directly, attackers can use the path-traversal bug to first delete the file and then rewrite it.
Realmode reported the vulnerabilities on Aug. 9, and Silver Peak issued patches on Oct. 30. No CVSS severity scores have yet been assigned.
Tempelhof said that his team found similar flaws in three other SD-WAN companies (all now patched), which will be disclosed soon.
“We researched the top four SD-WAN products on the market and found major remote code-execution vulnerabilities,” he wrote. “The vulnerabilities require no authentication whatsoever to exploit.”
Top SD-WAN vendors have had issues in the past. For instance, in March, Cisco Systems fixed three high-severity vulnerabilities that could enable local, authenticated attackers to execute commands with root privileges. A similar bug was found a month later in Cisco’s IOS XE, a Linux-based version of Cisco’s Internetworking Operating System (IOS) used in SD-WAN deployments.
And last December, a critical zero-day bug was found in various versions of its Citrix Application Delivery Controller (ADC) and Citrix Gateway products that allowed appliance takeover and RCE, used in SD-WAN implementations. In-the-wild attacks and public exploits quickly piled up after it was announced.
High-Severity Cisco DoS Flaw Can Immobilize ASR Routers
12.11.20
Vulnerebility
Threatpost
The flaw stems from an issue with the ingress packet processing function of Cisco IOS XR software.
A high-severity flaw in Cisco’s IOS XR software could allow unauthenticated, remote attackers to cripple Cisco Aggregation Services Routers (ASR).
The flaw stems from Cisco IOS XR, a train of Cisco Systems’ widely deployed Internetworking Operating System (IOS). The OS powers the Cisco ASR 9000 series, which are fully distributed routers engineered to address massive surges in video traffic.
“A successful exploit could cause the affected device to run out of buffer resources, which could make the device unable to process or forward traffic, resulting in a DoS [denial-of-service] condition,” according to a Tuesday security advisory by Cisco.
The flaw (CVE-2020-26070), which ranks 8.6 out of 10 on the CVSS scale, stems from an issue with the ingress packet processing function of Cisco IOS XR software. Ingress packet processing is a technique used to sort through incoming packets from different networks.
The vulnerability is due to improper resource allocation when an affected device processes network traffic. An attacker could exploit the flaw by sending specific streams of Layer 2 or Layer 3 protocol data units (PDUs) to an affected device, ultimately exhausting its buffer resources and crashing the device.
When a device is experiencing buffer resources exhaustion, the following message may be seen in the system logs: “%PKT_INFRA-spp-4-PKT_ALLOC_FAIL : Failed to allocate n packets for sending”
“This error message indicates that the device is not able to allocate buffer resources and forward network traffic in software switching mode,” said Cisco. “Customers are advised to contact their support organization to review the error messages and determine whether the device has been compromised by an exploitation of this vulnerability.”
The device would need to be restarted to regain functionality, said Cisco. This vulnerability affects Cisco ASR 9000 series routers if they are running a Cisco IOS XR Software release earlier than releases 6.7.2 or 7.1.2. Cisco fixed this vulnerability in Cisco IOS XR Software releases 6.7.2 and later and releases 7.1.2 and later.

Updated Cisco IOS XR versions. Credit: Cisco
Of note, IOS Software, IOS XE Software, IOS XRv 9000 Router and NX-OS Software are not affected.
“The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory,” according to Cisco.
Cisco has recently dealt with various vulnerabilities across its product lines. Last week, Cisco disclosed a zero-day vulnerability in the Windows, macOS and Linux versions of its AnyConnect Secure Mobility Client Software. A few weeks ago, Cisco stomped out a severe flaw that can be exploited by an unauthenticated, remote attacker to launch a passel of malicious attacks — from denial of service (DoS) to cross-site request forgery (CSRF).
Cisco also recently sent out an advisory warning that a flaw (CVE-2020-3118) the Cisco Discovery Protocol implementation for Cisco IOS XR Software was being actively exploited by attackers. The bug, which could be exploited by unauthenticated, adjacent attackers, could allow them to execute arbitrary code or cause a reload on an affected device.
Google addresses two new Chrome zero-day flaws
12.11.20
Vulnerebility
Securityaffairs
Google has released Chrome version 86.0.4240.198 that addresses two additional
zero-day vulnerabilities that were exploited in the wild.
Google has
addressed two zero-day vulnerabilities, actively exploited in the wild, with the
release of Chrome version 86.0.4240.198.
The IT giant has fixed a total of five Chrome zero-day vulnerabilities in only three weeks.
Both zero-day flaws, tracked as CVE-2020-16013 and CVE-2020-16017, were reported by anonymous sources. Google experts did not disclose the way the flaws have been exploited in the attacks, for example, it is not clear if they were chained by threat actors.
“Google is aware of reports that exploits for CVE-2020-16013 and CVE-2020-16017 exist in the wild.” reads the Chrome 86.0.4240.198 changelog.
“We would also like to thank all security researchers that worked with us during the development cycle to prevent security bugs from ever reaching the stable channel.”
The CVE-2020-16013 flaw is an inappropriate implementation in V8 Chrome
component, it was reported by anonymous on November 9, 2020.
The
CVE-2020-16017 flaw is a use after free memory corruption bug in Site Isolation,
it was reported by anonymous on November 7, 2020.
It is interesting to note that one of the vulnerabilities was reported to Google the same day the company released the new version of the popular browser.
The other three zero-days patched by Google in the last weeks were:
CVE-2020-15999 – The flaw is a memory corruption bug that resides in the
FreeType font rendering library, which is included in standard Chrome releases.
CVE-2020-16009 – is a Heap buffer overflow in Freetype in Google Chrome.
CVE-2020-16010 – affects the browser’s user interface (UI) component in Chrome
for Android.
“Many of our security bugs are detected using AddressSanitizer,
MemorySanitizer, UndefinedBehaviorSanitizer, Control Flow Integrity, libFuzzer,
or AFL.” concludes the Chrome changelog for the version 86.0.4240.198.
SAP Patches Several Critical Vulnerabilities With November 2020 Security Updates
12.11.20
Vulnerebility
Securityweek
SAP’s security updates for November 2020 patch several critical vulnerabilities affecting the company’s Solution Manager (SolMan), Data Services, ABAP, S4/HANA, and NetWeaver products.
Since the previous Patch Day, SAP released a total of 19 new and updated security notes. Six of the notes have been assigned a hot news (critical) priority rating, including four new notes and two previously released patches that were updated.
One of the hot news patches resolves a total of four vulnerabilities related to missing authentication checks in SolMan, which provides a central management interface for SAP and non-SAP systems. An unauthenticated attacker could exploit these flaws — they are tracked as CVE-2020-26821, CVE-2020-26822, CVE-2020-26823 and CVE-2020-26824 — to compromise the targeted system.
SAP has also updated a previous hot news security note that addressed a missing authentication check in SolMan.
“We have once more seen that Solution Manager will keep security administrators busy, because of its central role in the system landscape and the criticality of the newly detected vulnerabilities,” said Onapsis, a company that specializes in securing business-critical applications.
Onapsis has published a blog post describing this month’s patches, some of which fix vulnerabilities found by the company’s own researchers.
Another hot news patch addresses two vulnerabilities in SAP Data Services. These flaws were disclosed last year and they impact Apache Struts. Exploitation can lead to remote code execution and a denial-of-service (DoS) condition, respectively.
A code injection vulnerability affecting SAP AS ABAP and S/4 HANA (CVE-2020-26808) and a privilege escalation issue in SAP NetWeaver Application Server for Java (CVE-2020-26820) have also been rated hot news.
Three of the new patches address high-severity vulnerabilities, including server-side request forgery (SSRF) and reflected cross-site scripting (XSS) issues in SAP Fiori Launchpad, an information disclosure issue in SAP Commerce Cloud, and DoS and SSRF bugs in Commerce Cloud.
Medium-severity flaws have been resolved in NetWeaver, Bank Analyzer, S/4 HANA Financial Products, SAP Process Integration, ERP Client for E-Bilanz, and Visual Enterprise Viewer.
Microsoft Patch Tuesday fixes CVE-2020-17087 currently under active exploitation
11.11.20
Vulnerebility
Securityaffairs
Microsoft Patch Tuesday updates for November 2020 address 112 flaws, including a
Windows bug that was chained with Chrome issues in attacks.
Microsoft Patch
Tuesday updates for November 2020 address 112 vulnerabilities in multiple
products, including Microsoft Windows, Office and Office Services and Web Apps,
Internet Explorer (IE), Edge (EdgeHTML-based and Chromium-based), ChakraCore,
Exchange Server, Microsoft Dynamics, Azure Sphere, Windows Defender, Microsoft
Teams, and Visual Studio. The IT giant also addressed the CVE-2020-17087 Windows
flaw that was chained with the CVE-2020-15999 Chrome bug in attacks in the wild.
At the end of October, security researchers from Google have disclosed the zero-day vulnerability in the Windows operating system, tracked as CVE-2020-17087, that is currently under active exploitation.
The CVE-2020-17087 flaw is a Windows Kernel local elevation of privilege
vulnerability.
Ben Hawkes, team lead for Google Project Zero team, revealed
on Twitter that the vulnerability was chained with another Chrome zero-day flaw,
tracked as CVE-2020-15999, that Google recently disclosed.
The Director of Google’s Threat Analysis Group, Shane Huntley (@ShaneHuntley), confirmed that the vulnerability was exploited in targeted attacks that are not related to the forthcoming US election.
On October 20, 2020, Google has released Chrome version 86.0.4240.111 that addresses several issues, including the actively exploited CVE-2020-15999 zero-day flaw. The CVE-2020-15999 flaw is a memory corruption bug that resides in the FreeType font rendering library, which is included in standard Chrome releases.
The flaw can be exploited by attackers for arbitrary code execution by getting the targeted user to access a website hosting a specially crafted font file.
Chaining the Windows and Chrome vulnerabilities, the attackers can escape the Chrome sandbox and execute malicious code on the targeted system.
Microsoft Patch Tuesday updates for November 2020 addressed a total of 17 critical vulnerabilities, most of them are RCE. Some of the critical vulnerabilities fixed by Microsoft affect extensions available in the Microsoft Store.
“Of these 112 patches, 17 are rated as Critical, 93 are rated as Important, and two are rated Low in severity. A total of six of these bugs came through the ZDI program. Only one bug is listed as publicly known and under active attack.” states the analysis published by ZDI.
This week, Microsoft announced to have changed the format used for its security advisories. The new advisories provide information through the Common Vulnerability Scoring System (CVSS) and don’t include the description of the flaw and how it can be exploited.
The complete list of flaws addressed by Microsoft is available on the official Security Update Guide portal.
Vulnerabilities Exploited at Chinese Hacking Contest Patched in Firefox, Chrome
11.11.20
Vulnerebility
Securityweek
Mozilla and Google have already patched the critical Firefox and Chrome vulnerabilities exploited recently by white hat hackers at a competition in China.
The Firefox vulnerability, tracked as CVE-2020-26950, has been described as an issue related to write side effects in MCallGetProperty opcode not being accounted for.
“In certain circumstances, the MCallGetProperty opcode can be emitted with unmet assumptions resulting in an exploitable use-after-free condition,” Mozilla said in an advisory published on Monday.
The flaw was fixed with the release of Firefox 82.0.3, Firefox ESR 78.4.1 and Thunderbird 78.4.2 just a couple of days after it was disclosed at the 2020 Tianfu Cup International PWN Contest, which took place over the past weekend in China.
As for the Chrome vulnerability disclosed at the Tianfu Cup, it’s tracked as CVE-2020-16016 and it has been described by Google as an inappropriate implementation issue in the base component. Google fixed it with an update released for Chrome 86 on Monday.
CVE-2020-26950 and CVE-2020-16016 were demonstrated by a team from Chinese cybersecurity firm Qihoo 360. This team earned over $740,000 of the total of $1.2 million awarded to participants at Tianfu Cup. For the Firefox vulnerability they earned $40,000, while for the Chrome flaw, which allowed them to achieve remote code execution with a sandbox escape, they received $100,000.
The same Qihoo 360 researchers earned $20,000 from Google earlier this year for a sandbox escape vulnerability affecting Chrome.
Microsoft Releases Windows Security Updates For Critical Flaws
11.11.20
Vulnerebility
Thehackernews
Microsoft formally
released fixes for 112 newly discovered security vulnerabilities as part of its
November 2020 Patch Tuesday, including an actively exploited zero-day flaw
disclosed by Google's security team last week.
The rollout addresses flaws, 17 of which are rated as Critical, 93 are rated as Important, and two are rated Low in severity, once again bringing the patch count over 110 after a drop last month.
The security updates encompass a range of software, including Microsoft Windows, Office and Office Services and Web Apps, Internet Explorer, Edge, ChakraCore, Exchange Server, Microsoft Dynamics, Windows Codecs Library, Azure Sphere, Windows Defender, Microsoft Teams, and Visual Studio.
Chief among those fixed is CVE-2020-17087 (CVSS score 7.8), a buffer overflow flaw in Windows Kernel Cryptography Driver ("cng.sys") that was disclosed on October 30 by the Google Project Zero team as being used in conjunction with a Chrome zero-day to compromise Windows 7 and Windows 10 users.
For its part, Google released an update for its Chrome browser to address the zero-day (CVE-2020-15999) last month.
Microsoft's advisory about the flaw doesn't go into any details beyond the fact that it was a "Windows Kernel Local Elevation of Privilege Vulnerability" in part to restructure security advisories in line with the Common Vulnerability Scoring System (CVSS) format starting this month.
Outside of the zero-day, the update fixes a number of remote code execution (RCE) vulnerabilities impacting Exchange Server (CVE-2020-17084), Network File System (CVE-2020-17051), and Microsoft Teams (CVE-2020-17091), as well as a security bypass flaw in Windows Hyper-V virtualization software (CVE-2020-17040).
CVE-2020-17051 is rated 9.8 out of a maximum 10 on the CVSS score, making it a critical vulnerability. Microsoft, however, noted that the attack complexity of the flaw — the conditions beyond the attacker's control that must exist in order to exploit the vulnerability — is low.
As with the zero-day, the advisories associated with these security shortcomings are light on descriptions, with little to no information on how these RCE flaws are abused or which security feature in Hyper-V is being bypassed.
Other critical flaws fixed by Microsoft this month include memory corruption vulnerabilities in Microsoft Scripting Engine (CVE-2020-17052) and Internet Explorer (CVE-2020-17053), and multiple RCE flaws in HEVC Video Extensions Codecs library.
It's highly recommended that Windows users and system administrators apply the latest security patches to resolve the threats associated with these issues.
To install the latest security updates, Windows users can head to Start > Settings > Update & Security > Windows Update, or by selecting Check for Windows updates.
Colossal Intel Update Anchored by Critical Privilege-Escalation Bugs
11.11.20 Vulnerebility Threatpost
Intel released 40 security advisories in total, addressing critical- and high-severity flaws across its Active Management Technology, Wireless Bluetooth and NUC products.
A massive Intel security update this month addresses flaws across a myriad of products – most notably, critical bugs that can be exploited by unauthenticated cybercriminals in order to gain escalated privileges.
These critical flaws exist in products related to Wireless Bluetooth – including various Intel Wi-Fi modules and wireless network adapters – as well as in its remote out-of-band management tool, Active Management Technology (AMT).
Overall, Intel released 40 security advisories on Tuesday, each addressing critical-, high- and medium-severity vulnerabilities across various products. That by far trumps October’s Intel security update, which resolved one high-severity flaw in BlueZ, the Linux Bluetooth protocol stack that provides support for core Bluetooth layers and protocols to Linux-based internet-of-things (IoT) devices.
Critical Flaws
One critical-severity vulnerability exists in Intel AMT and
Intel Standard Manageability (ISM). AMT, which is used for remote out-of-band
management of PCs, is part of the Intel vPro platform (Intel’s umbrella
marketing term for its collection of computer hardware technologies) and is
primarily used by enterprise IT shops for remote management of corporate
systems. ISM has a similar function as AMT.
The flaw (CVE-2020-8752) which ranks 9.4 out of 10 on the CvSS vulnerability-severity scale, stems from an out-of-bounds write error in IPv6 subsystem for Intel AMT and Intel ISM. If exploited, the flaw could allow an unauthenticated user to gain escalated privileges (via network access).
Versions before 11.8.80, 11.12.80, 11.22.80, 12.0.70 and 14.0.45 are affected; users are urged to “update to the latest version provided by the system manufacturer that addresses these issues.”
Another critical-severity flaw (CVE-2020-12321) exists in some Intel Wireless Bluetooth products before version 21.110. That bug, which scores 9.6 out of 10 on the CvSS scale, could allow an unauthenticated user to potentially enable escalation of privilege via adjacent access. This means an attacker is required to have access to a shared physical network with the victim.
Affected products include Intel Wi-Fi 6 AX200 and AX201, Intel Wireless-AC 9560, 9462, 9461 and 9260, Intel Dual Band Wireless-AC 8265, 8260 and 3168, Intel Wireless 7265 (Rev D) family and Intel Dual Band Wireless-AC 3165. Users of these products are recommended to update to version 21.110 or later.
High-Severity Flaws
Intel also fixed multiple high-severity vulnerabilities,
including a path traversal in its Endpoint Management Assistant (CVE-2020-12315)
— which provides tools to monitor and upgrade devices. This flaw could give an
unauthenticated user escalated privileges via network access.
Four high-severity flaws exist in Intel PROSet/Wireless Wi-Fi products before version 21.110. Intel PROSet/Wireless Wi-Fi software is used to set up, edit and manage Wi-Fi network profiles to connect to Wi-Fi networks.
These vulnerabilities stem from insufficient control-flow management (CVE-2020-12313), improper input validation (CVE-2020-12314), protection-mechanism failure (CVE-2020-12318) and improper buffer restriction (CVE-2020-12317). They can enable denial-of-service (DoS) attacks or privilege escalation.
Another high-severity flaw in Intel solid-state drive (SSD) products could allow an unauthenticated user to potentially enable information disclosure – if they have physical access to the device. The flaw (CVE-2020-12309) stems from insufficiently protected credentials in the client SSD subsystems. A range of SSDs – including the Pro 6000p series, Pro 5450s and E 5100s series – are affected and can be found here.
Intel’s Next Unit Computing (NUC) mini PC also had two high-severity flaws; including an insecure default variable initialization issue in the firmware (CVE-2020-12336), that could allow authenticated users (with local access) to escalate their privileges. The other is an improper buffer restriction in the firmware (CVE-2020-12337) enabling privileged users to escalate privileges (via local access).
Other high-severity flaws include an improper buffer restriction (CVE-2020-12325) in Intel Thunderbolt DCH drivers for Windows; an improper access-control hole (CVE-2020-12350) in Intel’s Extreme Tuning Utility and an improper input-validation flaw (CVE-2020-12347) in the Intel Data Center Manager Console.
Microsoft Patches Windows Vulnerability Chained in Attacks With Chrome Bug
11.11.20
Vulnerebility
Securityweek
Microsoft’s Patch Tuesday updates for November 2020 address more than 110 vulnerabilities, including a Windows flaw that was recently disclosed by Google after it was observed being exploited in attacks.
The actively exploited Windows vulnerability is tracked as CVE-2020-17087 and it has been described as a local privilege escalation issue related to the Windows Kernel Cryptography Driver.
Google Project Zero disclosed details of the flaw in late October, several days after its researchers discovered the vulnerability being exploited in attacks alongside a Chrome flaw.
The Chrome vulnerability, identified as CVE-2020-15999, was fixed by Google on October 20 with a Chrome 86 update. It can be exploited for arbitrary code execution by getting the targeted user to access a website hosting a specially crafted font file.
The Windows and Chrome vulnerabilities can be chained to break out of the Chrome sandbox and execute malicious code on the targeted system.
When Google disclosed the Windows bug last month, Microsoft said it had started working on a patch, but noted that its goal is to “help ensure maximum customer protection with minimal customer disruption.”
Microsoft this month patched a total of 17 critical vulnerabilities, most of which can be exploited for remote code execution. Many of the critical flaws impact extensions available in the Microsoft Store.
The vulnerabilities rated important impact Azure Sphere, Windows, browsers, Dynamics 365, Office, SharePoint, Visual Studio and various other products, and they can be exploited for spoofing attacks, DoS attacks, privilege escalation, bypassing security features, and for obtaining information.
Microsoft announced this week that it has changed the format of its security advisories. The new advisories don’t include the section describing the vulnerability and how it can be exploited and instead aims to provide the information through the Common Vulnerability Scoring System (CVSS).
Adobe's Patch Tuesday updates patch vulnerabilities in the company's Connect and Reader Mobile products.
Mandiant Details Recently Patched Oracle Solaris Zero-Day
5.11.20
Vulnerebility
Securityweek
FireEye Mandiant has published detailed information on an Oracle Solaris vulnerability that has been exploited in attacks by a sophisticated threat actor.
Tracked as CVE-2020-14871, the vulnerability was identified in June, but a patch for it was only released as part of Oracle’s October 2020 Critical Patch Update. The threat actor abusing the bug, which is tracked as UNC1945, has been actively targeting Solaris systems for at least a couple of years.
The zero-day vulnerability was discovered in the Pluggable Authentication Modules (PAM) library, which enables user authentication in Solaris applications, while providing admins with the option to configure authentication parameters.
CVE-2020-14871, Mandiant explains, is a stack-based buffer overflow that resides in the parse_user_name function of PAM and is triggered when a username longer than PAM_MAX_RESP_SIZE (which is 512 bytes) is passed to the function. The flaw allows an unauthenticated attacker to compromise Oracle Solaris systems.
“The vulnerability has likely existed for decades, and one possible reason is that it is only exploitable if an application does not already limit usernames to a smaller length before passing them to PAM. One situation where network-facing software does not always limit the username length arises in the SSH server, and this is the exploit vector used by the [EVILSUN] tool that we discovered,” Mandiant notes.
Courtesy of this bug, an attacker could target the SSH Keyboard-Interactive authentication, where SSH is leveraged to relay prompts and responses between the client and the PAM libraries on the server. It supports two-factor and other authentication forms.
“By manipulating SSH client settings to force Keyboard-Interactive authentication to prompt for the username rather than sending it through normal means, an attacker can also pass unlimited input to the PAM parse_user_name function,” Mandiant’s security researchers explain.
The researchers came up with a proof-of-concept exploit designed to trigger the bug and crash the SSH server. On vulnerable servers, the SSH client delivers an “Authentication failed” message, while a non-vulnerable one would repeatedly prompt for a username when receiving one that is too long.
Vulnerable operating systems, Madiant says, include some releases of Solaris 9, all releases of Solaris 10, Solaris 11.0, and Illumos (OpenIndiana 2020.04). Oracle has released patches for Solaris 10 and 11, but not for Solaris 9, which is no longer supported.
On unpatched Solaris 11.1 and later systems, the parse_user_name function remains vulnerable, but some changes to the PAM library result in the username being truncated before being delivered to the vulnerable function, thus preventing exploitation via SSH.
“If the parse_user_name function were reachable in another context, then the vulnerability could become exploitable,” Madiant explains.
For Solaris 9 systems, as well as for the Solaris 10 or 11 servers where patching is inconvenient, modifying the /etc/ssh/sshd_config file by adding the lines ChallengeResponseAuthentication no and KbdInteractiveAuthentication no and restarting the SSH server can be used as a workaround.
However, this does not remove the vulnerability and exploitation might still be possible if an attacker manages to reach the parse_user_name function in any way. Thus, installing the fixes included in the October 2020 Critical Patch Update is the recommended path of action.
Cisco Working on Patch for Code Execution Vulnerability in VPN Product
5.11.20
Vulnerebility
Securityweek
Cisco informed customers on Wednesday that it’s working on a patch for a code execution vulnerability affecting its AnyConnect product. The company says a proof-of-concept (PoC) exploit is available.
The Cisco AnyConnect Secure Mobility Client is designed to provide secure VPN access for remote workers.
According to the networking giant, the product is affected by a flaw, tracked as CVE-2020-3556, that can be exploited by a local, authenticated attacker to cause an AnyConnect user to execute a malicious script.
The vulnerability is related to the lack of authentication for the interprocess communication (IPC) listener. The Linux, Windows and macOS versions of the AnyConnect Secure Mobility Client are affected if both the Auto Update and Enable Scripting settings are enabled. The latter is disabled by default.
“An attacker could exploit this vulnerability by sending crafted IPC messages to the AnyConnect client IPC listener. A successful exploit could allow an attacker to cause the targeted AnyConnect user to execute a script. This script would execute with the privileges of the targeted AnyConnect user,” Cisco said in its advisory.
“In order to successfully exploit this vulnerability, there must be an ongoing AnyConnect session by the targeted user at the time of the attack. To exploit this vulnerability, the attacker would also need valid user credentials on the system upon which the AnyConnect client is being run,” it added.
There are no workarounds for the vulnerability, but concerned users can disable the Auto Update or Enable Scripting settings to prevent exploitation. The company has decided to disclose it as it has become aware of the availability of a PoC exploit, but says it’s not aware of any attacks exploiting the flaw.
Gerbert Roitburd from the Secure Mobile Networking Lab at the TU Darmstadt university has been credited for reporting the flaw. It’s unclear if the PoC exploit was created by Roitburd or someone else.
Cisco also informed customers on Wednesday that it has patched over a dozen high-severity vulnerabilities across its Webex, SD-WAN, IP Phone and IOS XR products.
The IOS XR flaw can allow a remote, unauthenticated attacker to execute unsigned code during the Preboot eXecution Environment (PXE) boot process on an impacted device. However, the attacker needs to compromise or impersonate a PXE boot server in order to exploit the weakness.
A directory traversal vulnerability affecting the SD-WAN vManage software can also be exploited remotely and without authentication, to access sensitive information.
Cisco has warned Webex customers that an attacker can execute arbitrary code on their systems by tricking them into opening malicious ARF or WRF files with Webex Network Recording Player for Windows or Cisco Webex Player for Windows.
The remaining high-severity flaws patched this week by Cisco require authentication and/or local access for exploitation. They can be leveraged for DoS attacks, privilege escalation, arbitrary file creation (which also leads to DoS), and arbitrary code execution.
Zero-day in Cisco AnyConnect Secure Mobility Client yet to be fixed
5.11.20
Vulnerebility
Securityaffairs
Cisco disclosed a zero-day vulnerability in the Cisco AnyConnect Secure Mobility
Client software and the availability of PoC exploit code.
Cisco has disclosed
a zero-day vulnerability, tracked as CVE-2020-3556, in the Cisco AnyConnect
Secure Mobility Client software with the public availability of a
proof-of-concept exploit code.
The CVE-2020-3556 flaw resided in the interprocess communication (IPC) channel
of Cisco AnyConnect Client, it can be exploited by authenticated and local
attackers to execute malicious scripts via a targeted user.
“A vulnerability
in the interprocess communication (IPC) channel of Cisco AnyConnect Secure
Mobility Client Software could allow an authenticated, local attacker to cause a
targeted AnyConnect user to execute a malicious script.” reads the advisory
published by the company.
“The vulnerability is due to a lack of authentication to the IPC listener. An attacker could exploit this vulnerability by sending crafted IPC messages to the AnyConnect client IPC listener. A successful exploit could allow an attacker to cause the targeted AnyConnect user to execute a script. This script would execute with the privileges of the targeted AnyConnect user.”
It affects all AnyConnect client versions for Windows, Linux, and macOS with vulnerable configurations. The IT giant confirmed that iOS and Android clients are not impacted by this flaw.
“In order to successfully exploit this vulnerability, there must be an ongoing AnyConnect session by the targeted user at the time of the attack. To exploit this vulnerability, the attacker would also need valid user credentials on the system upon which the AnyConnect client is being run.” continues the advisory.
“A vulnerable configuration requires both the Auto Update setting and Enable Scripting setting to be enabled, Auto Update is enabled by default, and Enable Scripting is disabled by default.”
The issue could be exploited in presence of active AnyConnect sessions and valid credentials on the targeted device.
Unfortunately, Cisco has yet to address the arbitrary code execution flaw, a fix is expected to be included in a future AnyConnect client release.
Cisco recommends disabling the Auto Update feature to mitigate the CVE-2020-3556 flaw, no workarounds is available to address it.
Cisco Product Security Incident Response Team (PSIRT) is not aware of attacks in the wild that have exploited the vulnerability.
The attack surface can also be drastically decreased by toggling off the Enable Scripting configuration setting on devices where it’s enabled.
The vulnerability was reported to Cisco by Gerbert Roitburd from Secure Mobile Networking Lab (TU Darmstadt).
Cisco also addressed 11 other high severity and 23 medium severity security vulnerabilities in multiple products that could be exploited to trigger a denial of service condition or to execute arbitrary code on vulnerable devices.
Trend Micro Patches Vulnerabilities in InterScan Messaging Security Product
5.11.20 Vulnerebility Securityweek
Trend Micro has patched several vulnerabilities in its InterScan Messaging Security product, including flaws that could have a serious impact.
InterScan Messaging Security is an email and collaboration security product designed to provide protection against spam, phishing and sophisticated attacks. The product has a hybrid SaaS deployment option that combines a gateway virtual appliance with a prefilter to block spam and threats.
Researchers at cybersecurity consultancy SEC Consult discovered that the InterScan Messaging Security Virtual Appliance (IMSVA) is affected by eight types of security issues.
The list includes cross-site request forgery (CSRF), XML external entity (XXE), over-privileged users and services, server-side request forgery (SSRF), local file disclosure, information disclosure, weak password storage, and outdated software components.
One of the most serious vulnerabilities is CVE-2020-27016, a high-severity CSRF issue that can be exploited to modify the product’s policy rules, which, according to SEC Consult, can allow an attacker to bypass malware checks or forward emails to a host they control.
However, in order to exploit this flaw, an attacker needs to convince an authenticated administrator to access a malicious webpage.
SEC Consult also discovered a high-severity XXE vulnerability, tracked as CVE-2020-27017, that can be exploited to read arbitrary local files. While exploitation requires admin privileges, an attacker could achieve this by combining it with the CSRF flaw.
The remaining security holes have been rated medium or low severity. One of them can allow an attacker to access files that should only be accessible to users with high privileges. This weakness can be combined with the XXE flaw to access files that are normally only accessible to the root user, such as /etc/shadow, which contains user account information. The other less severe issues could expose sensitive information.
“Some vulnerabilities need administrative access rights or an administrator actively being logged in (such as for CSRF). A standard user account is sufficient in order to exploit the SSRF/file disclosure vulnerability. The information disclosure vulnerability can be exploited without prior authentication and potentially sensitive data such as key material can be obtained,” SEC Consult told SecurityWeek.
SEC Consult said it informed Trend Micro about the vulnerabilities in late April and patches were released on October 9. However, Trend Micro only issued a security bulletin on November 4.
“We are aware of the vulnerabilities found in the IMSVA product and commend SEC Consult for responsibly disclosing them and working closely with us. We have released a critical patch that resolves these vulnerabilities and encourage customers to ensure that their products have been updated to the latest build,” Trend Micro told SecurityWeek in an emailed statement.
Patch for Critical VMware ESXi Vulnerability Incomplete
5.11.20
Vulnerebility
Securityweek
VMware on Wednesday informed customers that it has released new patches for ESXi after learning that a fix made available last month for a critical vulnerability was incomplete.
The vulnerability, tracked as CVE-2020-3992, was described as a use-after-free bug that affects the OpenSLP service in ESXi. A remote, unauthenticated attacker can exploit the flaw to execute arbitrary code.
However, VMware said the attacker needs to be on the management network and have access to port 427 on an ESXi machine in order to exploit the flaw.
VMware learned about the security hole in July from Lucas Leong of Trend Micro's Zero Day Initiative (ZDI). An advisory was also published in October by ZDI.
“The specific flaw exists within the processing of SLP messages. The issue results from the lack of validating the existence of an object prior to performing operations on the object. An attacker can leverage this vulnerability to execute code in the context of the SLP daemon,” ZDI said.
VMware updated its initial advisory on Wednesday to inform customers that the patches had been incomplete. New fixes have now been released for ESXi 6.5, 6.7 and 7.0, but patches are still pending for VMware Cloud Foundation, the hybrid cloud platform for managing virtual machines and orchestrating containers.
VMware failing to patch a vulnerability on the first try is not unheard of. Earlier this year, the company made several attempts to patch a privilege escalation flaw affecting the macOS version of Fusion.
Games in Microsoft Store Can Be Abused for Privilege Escalation on Windows
5.11.20
Vulnerebility
Securityweek
A researcher at cybersecurity services provider IOActive has identified a privilege escalation vulnerability in Windows that can be exploited by abusing games in the Microsoft Store.
The flaw, tracked as CVE-2020-16877 and rated high severity, affects Windows 10 and Windows Server. It was patched by Microsoft with its Patch Tuesday updates for October 2020.
Donato Ferrante, principal security consultant at IOActive and the researcher credited for reporting the vulnerability to Microsoft, this week published a blog post detailing CVE-2020-16877 and some theoretical attack scenarios. He showed how an attacker with a standard user account could exploit the flaw to escalate privileges to SYSTEM on Windows 10.
Ferrante discovered the vulnerability after Microsoft announced that it started allowing mods for some games in the Microsoft Store. Mods allow users to make unofficial modifications to a game to change how it behaves or looks.
The researcher downloaded a game that supports mods and analyzed its installation process, which he found to run with elevated permissions. He determined that an attacker could abuse this process to escalate privileges by overwriting or deleting arbitrary files on the system.
In order to achieve this, an attacker would have to use symbolic links (symlinks). Symlinks are shortcut files, but it’s well known that they can be abused to write, modify or delete files, which can be leveraged to escalate privileges.
Ferrante created symlinks between the ModifiableWindowsApps folder, which Microsoft created for storing games that can be moded, and a folder placed on a different drive that he could access. This allowed him to hijack the installation process and gain elevated privileges on the system, both by overwriting files and by deleting files.
However, the attack requires the attacker to change Windows storage settings so that new apps are saved to the drive they have access to, and they also need to install a game from the Microsoft Store.
The researcher demonstrated the potential impact of the vulnerability by spawning a shell running with SYSTEM privileges, starting from a standard user account.

The attack scenario described by Ferrante involves steps that would be visible on the screen, such as installing a game from the Microsoft Store and changing storage settings, which would increase the chances of the victim discovering the attack. The researcher told SecurityWeek that it might be possible to conceal some of these activities, but he did not investigate further.
Microsoft said it does not expect to see the vulnerability being exploited in the wild.
Companies paid $4.2M bug bounties for XSS flaws in 2020
1.11.20
Vulnerebility
Securityaffairs
Cross-Site Scripting (XSS) issues are the most common vulnerabilities that
received the highest amount of rewards on the HackerOne vulnerability reporting
platform.
Cross-Site Scripting (XSS) is the most common vulnerability type
and received the highest amount of rewards on the HackerOne vulnerability
reporting platform.
XSS vulnerabilities accounted for 18% of all flaws reported by bug hunters, these issues received a total of $4.2 million in bounties paid by companies (+26% from last year).
The Cross Site Vulnerabilites received an average of just $501 per issue.
XSS vulnerabilities can be exploited by threat actors for multiple malicious
activities, including account takeover and data theft.
“XSS vulnerabilities
are extremely common and hard to eliminate, even for organizations with the most
mature application security. XSS vulnerabilities 2are often embedded in code
that can impact your production pipeline.” reads The 4th Hacker-Powered Security
Report.
“These bugs account for 18% of all reported vulnerabilities, but the average bounty award is just US$501. That means organizations are mitigating this common, potentially painful bug on the cheap.”
Improper Access Control follows XSS in the list of most awarded vulnerability type in 2020, experts observed an increase of 134% in occurrence compared to 2019. Companies paid a total of $4 million in bug bounty rewards through the HackerOne platform.
Information Disclosure accounts for 63% from last year. Companies paid $3
million for reports related to these vulnerabilities.
“Awards for Improper
Access Control increased 134% year over year to just over US$4 million.
Information Disclosure was not far behind, increasing 63% year over year.”
continues the report.
“Both methods expose potentially sensitive data like personally identifiable information. While they range widely in criticality, they can be disastrous if sensitive customer or internal information is leaked by misconfigured permissions.”
Both flaws are very dangerous because they’re nearly impossible to detect using automated tools.
In the third place there are SSRF (Server Side Request Forgery) flaws, experts pointed out that the advent of cloud architecture and unprotected metadata endpoints has rendered these vulnerabilities increasingly critical.
Organizations paid about USD$3 million in SSRF mitigations last year.
Most of the bounties were paid by organizations in the United States with $39.1
million / €33.4 million / ¥273.7 million, accounting for 87% of the total. It is
interesting to note that Latin America increased bounty awards by 371%, while
all other regions increased awards by at least 68%.
“That growth is even more impressive considering the scale, as those three
countries combined paid out more than $380,000 / €324,000 / ¥2,660,000
in
bounties in the past year.” states the report.
In the last year, organizations paid $23.5 million via HackerOne to bug hunters who submitted valid reports for vulnerabilities in the systems of organizations worldwide.
To date, the popular platform already paid $107 million in bug bounties with more than $44.75 million paid within a 12-month.
Google Discloses Actively Targeted Windows Vulnerability
31.10.20
Vulnerebility
Securityweek
Google Project Zero security researchers have identified another Windows vulnerability that has been actively exploited in attacks.
The security bug is an integer overflow with roots in one of the IOCTLs that the Windows Kernel Cryptography Driver (cng.sys) supports, and it could lead to privilege escalation, including a sandbox escape.
Discovered by Google Project Zero researchers Mateusz Jurczyk and Sergei Glazunov and assigned CVE number CVE-2020-17087, the zero-day was discovered in IOCTL 0x390400, in the cng!CfgAdtpFormatPropertyBlock function.
“The Windows Kernel Cryptography Driver (cng.sys) exposes a \Device\CNG device to user-mode programs and supports a variety of IOCTLs with non-trivial input structures. It constitutes a locally accessible attack surface that can be exploited for privilege escalation,” Jurczyk explains.
Details on the vulnerability were submitted to the Google Project Zero discussion board on October 22. Because the flaw was already being exploited in attacks, the information was made public seven days later, as per Google’s policy (for bugs that are not targeted, vendors are given 90 days to patch).
The security researchers have published the source code of a proof-of-concept exploit for the vulnerability, which was tested on “an up-to-date build of Windows 10 1903 (64-bit).”
However, they note that the issue was likely introduced in Windows 7.
“A crash is easiest to reproduce with Special Pools enabled for cng.sys, but even in the default configuration the corruption of 64kB of kernel data will almost surely crash the system shortly after running the exploit,” Jurczyk says.
The vulnerability appears to have been exploited in targeted attacks, but not in incidents related to the U.S. elections.
"Microsoft has a customer commitment to investigate reported security issues and update impacted devices to protect customers. While we work to meet all researchers' deadlines for disclosures, including short-term deadlines like in this scenario, developing a security update is a balance between timeliness and quality, and our ultimate goal is to help ensure maximum customer protection with minimal customer disruption," a Microsoft spokesperson said, replying to a SecurityWeek inquiry.
Microsoft Says Hackers Continue to Target Zerologon Vulnerability
30.10.20
Vulnerebility
Securityweek
Microsoft this week revealed that it continues to receive reports from customers of attacks targeting the Zerologon vulnerability.
Patched on August 11, the security flaw was identified in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC). Tracked as CVE-2020-1472, the issue can be exploited to compromise Active Directory domain controllers and gain domain administrator privileges.
The vulnerability came into the spotlight after the DHS ordered federal agencies to immediately apply available patches, with both Microsoft and CISA publishing information on attackers actively exploiting the bug.
At the end of September, Microsoft published a guide to provide organizations with all the necessary details for addressing the issue within their Active Directory deployments, but it appears that some customers continue to be vulnerable.
“If the original guidance is not applied, the vulnerability could allow an attacker to spoof a domain controller account that could be used to steal domain credentials and take over the domain,” Microsoft now says.
The tech giant also reiterates that the first step into addressing the vulnerability is installing the available patches on every domain controller.
“Once fully deployed, Active Directory domain controller and trust accounts will be protected alongside Windows domain-joined machine accounts. We strongly encourage anyone who has not applied the update to take this step now,” the company notes.
To ensure they are fully protected, customers should apply the update and follow Microsoft’s previously published guidance. The company has already updated the FAQs in that guidance, for further clarity.
Following the update, customers are advised to identify any devices that might still be vulnerable, address them, and then enable enforcement mode, to ensure that CVE-2020-1472 is indeed addressed in their environment.
On Thursday, CISA published an alert to warn of the continuous exploitation of Zerologon and to urge administrators to apply the available patches as soon as possible.
Critical OpenEMR Vulnerabilities Give Hackers Remote Access to Health Records
30.10.20
Vulnerebility
Securityweek
Several vulnerabilities found by researchers in the OpenEMR software can be exploited by remote hackers to obtain medical records and compromise healthcare infrastructure.
OpenEMR is an open source management software designed for healthcare organizations. The free application is highly popular and it provides a wide range of features for managing health records and medical practices.
Researchers at Swiss-based code quality and security solutions provider SonarSource discovered earlier this year that OpenEMR is affected by four types of vulnerabilities that impact servers using the Patient Portal component.
The list of vulnerabilities includes command injection, persistent cross-site scripting (XSS), insecure API permissions, and SQL injection.
The Patient Portal enables healthcare organizations to allow their patients to perform various tasks online, such as communicating with doctors, filling out new patient registration forms, making appointments, making payments, and requesting prescription refills.
However, SonarSource researchers determined that if the Patient Portal is enabled and accessible from the internet, an attacker could take complete control of the OpenEMR server by chaining the vulnerabilities they’ve found.
According to SonarSource, the Patient Portal has its own API interface, which can be used to control all portal actions. Using this API requires authentication, but the researchers found a way to bypass it, allowing them to access and make changes to patient data, or to change information associated with backend users, such as administrators.
An attacker who is able to change administrator account data can exploit the persistent XSS vulnerability to inject malicious code that would get executed when the targeted admin logs in to their account.
The JavaScript code triggered through the XSS vulnerability can then exploit the command injection vulnerability found by the researchers. The ability to execute arbitrary OS commands enables the attacker to take complete control of the OpenEMR server.
Alternatively, if the attacker targets a user with lower privileges rather than an administrator, they can exploit the SQL injection vulnerability to gain access to the patient database and steal potentially valuable data.
Exploitation of the XSS and command injection flaws requires admin privileges, but the SQL injection bug can be exploited with regular user privileges.
SonarSource discovered the vulnerabilities in OpenEMR 5.0.2.1 and they were patched with the release of version 5.0.2.2 in August. Details of the flaws were only made public now to give users enough time to install the update.
NVIDIA Patches Critical Bug in High-Performance Servers
30.10.20
Vulnerebility
Threatpost
NVIDIA said a high-severity information-disclosure bug impacting its DGX A100 server line wouldn’t be patched until early 2021.
NVIDIA released a patch for a critical bug in its high-performance line of DGX servers that could open the door for a remote attacker to take control of and access sensitive data on systems typically operated by governments and Fortune-100 companies.
In all, NVIDIA issued nine patches, each fixing flaws in firmware used by DGX high-performance computing (HPC) systems, which are used for processor-intensive artificial intelligence (AI) tasks, machine learning and data modeling. All of the flaws are tied to its own firmware that runs on its DGX AMI baseboard management controller (BMC), the brains behind a remote monitoring service servers.
“Attacks can be remote (in case of internet connectivity), or if bad guys can root one of the boxes and get access to the BMC they can use the out of band management network to PWN the entire datacenter,” wrote researcher Sergey Gordeychik who is credited for finding the bugs. “If you have access to OOB, it is game is over for the target.”
Given the high-stake computing jobs typically running on the HPC systems, the researcher noted an adversary exploiting the flaw could “poison data and force models to make incorrect predictions or infect an AI model.”
No Patch Until 2021 for One Bug
NVIDIA said a patch fixing one high-severity
bug (CVE‑2020‑11487), specifically impacting its DGX A100 server line, would not
be available until the second quarter of 2021. The vulnerability is tied to a
hard-coded RSA 1024 key with weak ciphers that could lead to information
disclosure. A fix for the same bug (CVE‑2020‑11487), impacting other DGX systems
(DGX-1, DGX-2) is available.
“To mitigate the security concerns,” NVIDIA wrote, “limit connectivity to the BMC, including the web user interface, to trusted management networks.”
Bugs Highlight Weaknesses in AI and ML Infrastructure
“We found a number of
vulnerable servers online, which triggered our research,” the researcher told
Threatpost. The bugs were disclosed Wednesday and presented as part of a
presentation “Vulnerabilities of Machine Learning Infrastructure” at CodeBlue
2020, a security conference in Tokyo, Japan.
During the session Gordeychik demonstrated how NVIDIA DGX GPU servers used in machine learning frameworks (Pytorch, Keras and Tensorflow), data processing pipelines and applications such as medical imaging and face recognition powered CCTV – could be tampered with by an adversary.
The researcher noted, other vendors are also likely impacted. “Interesting thing here is the supply chain,” he said. “NVIDIA uses a BMC board by Quanta Computers, which is based on AMI software. So to fix issues [NVIDIA] had to push several vendors to get a fix.”
Those vendors include:
IBM (BMC Advanced System Management)
Lenovo (ThinkServer Management Module)
Hewlett-Packard Enterprise Megarac
Mikrobits (Mikrotik)
Netapp
ASRockRack IPMI
ASUS ASMB9-iKVM
DEPO Computers
TYAN Motherboard
Gigabyte IPMI Motherboards
Gooxi BMC
Nine CVEs
As for the actual
patches issued by NVIDIA on Wednesday, the most serious is tracked as
CVE‑2020‑11483 and is rated critical. “NVIDIA DGX servers contain a
vulnerability in the AMI BMC firmware in which the firmware includes hard-coded
credentials, which may lead to elevation of privileges or information
disclosure,” according to the security bulletin.
Vulnerable NVIDIA DGX server models impacted include DGX-1, DGX-2 and DGX A100.
Four of the NVIDIA bugs were rated high-severity (CVE‑2020‑11484, CVE‑2020‑11487, CVE‑2020‑11485, CVE‑2020‑11486) with the most serious of the four tracked as CVE‑2020‑11484. “NVIDIA DGX servers contain a vulnerability in the AMI BMC firmware in which an attacker with administrative privileges can obtain the hash of the BMC/IPMI user password, which may lead to information disclosure,” the chipmaker wrote.
Three of the other patched vulnerabilities were rated medium severity and one low.
“Hackers are well aware of AI and ML infrastructure issues and use ML infrastructure in attacks,” Gordeychik said.
Microsoft Introduces Device Vulnerability Report in Defender for Endpoint
30.10.20
Vulnerebility
Securityweek
Microsoft this week announced the availability of a new vulnerability management report in Microsoft Defender, to provide information on vulnerable devices.
The new built-in report complements existing Microsoft Defender for Endpoint (previously known as Microsoft Defender Advanced Threat Protection) threat and vulnerability management capabilities and is catered for those looking to gain insights on devices that pose potential risks due to unpatched vulnerabilities. The feature is currently in preview version.
“The Vulnerable devices report provides extensive insights into your organization’s vulnerable devices with summaries of the current status and customizable trends over time,” Microsoft explains.
Within the report, organizations can access information on the vulnerability security levels of devices, availability of exploits for devices with vulnerabilities, and the age of unpatched security flaws, as well as a list of vulnerable devices, organized by operating system or by Windows 10 version.
Both graphs and bar charts are available in the report, to deliver information on device trends (allows selection of multiple time ranges) and current statistics (only information for the current day).
Data can be filtered based on vulnerability severity or age, availability of exploits, device group, or platform. Additional information can be accessed through selecting a specific bar chart.
According to Microsoft, in each specific graph, devices are only counted once.
The new report is available in the Microsoft Defender Security Center and can be accessed from Reports > Vulnerable devices, but only for those organizations that have the public preview feature enabled.
“This preview version is provided without a service level agreement, and it's not recommended for production workloads. Certain features might not be supported or might have constrained capabilities,” Microsoft notes.
Oracle WebLogic Vulnerability Targeted One Week After Patching
30.10.20
APT Vulnerebility
A vulnerability patched one week ago by Oracle in its WebLogic Server product has already been targeted for exploitation.
The security hole, tracked as CVE-2020-14882 and classified as critical, was patched by Oracle with its October 2020 Critical Patch Update (CPU). The vulnerability can be exploited remotely and without authentication, allowing an attacker to execute arbitrary code.
The issue was reported to Oracle by a researcher at China-based Chaitin Security
Research Lab. On Wednesday, a Vietnamese researcher named Jang published a blog
post detailing CVE-2020-14882 (written in Vietnamese) and he showed how easily
it can be exploited by sending a specially crafted request to the targeted
server.
The SANS Technology Institute reported on Thursday that its honeypots have recorded attempts to exploit this WebLogic vulnerability. Johannes B. Ullrich, dean of research at SANS, said the exploitation attempts appeared to be based on the PoC made public by the Vietnamese researcher.
Ullrich said the attacks that hit SANS honeypots only checked if the system was vulnerable, but others reported seeing exploitation attempts that involved downloading an executable file from a remote server and running it.
The attacks seen by SANS came from four IP addresses assigned to organizations in China, the US and Moldova.
“At this point, we are seeing the scans slow down a bit. But they have reached ‘saturation’ meaning that all IPv4 addresses have been scanned for this vulnerability,” Ullrich said. “If you find a vulnerable server in your network: Assume it has been compromised.”
Oracle WebLogic Server vulnerabilities are often targeted by threat actors, including profit-driven cybercriminals and state-sponsored groups. Many of these vulnerabilities are exploited after they are patched, but hackers exploiting zero-days is not unheard of.
Shortly after the April 2020 CPU was released, Oracle warned customers that a critical WebLogic vulnerability, one that was disclosed to the vendor by multiple researchers, including Jang, had been exploited in the wild.
NVIDIA Patches AMI BMC Vulnerabilities Impacting Several Major Vendors
30.10.20
APT Vulnerebility
NVIDIA on Wednesday released patches to address a total of nine vulnerabilities impacting NVIDIA DGX servers.
NVIDIA’s DGX systems are designed for enterprise AI applications. All of the bugs were found in the AMI Baseboard Management Controller (BMC) firmware running on the affected devices. This means the vulnerabilities are not specific to NVIDIA and they impact the products of several other vendors as well.
The vulnerabilities were reported to NVIDIA by members of the SCADA StrangeLove project, which focuses on ICS/SCADA security, as part of their research into machine learning infrastructure vulnerabilities.NVIDIA DGX vulnerabilities
One of the security flaws has been rated critical, five of them are high severity, two are considered medium severity, and one of them is low severity.
The most important of the bugs is related to the inclusion of hardcoded credentials in the AMI BMC firmware of NVIDIA DGX servers. Tracked as CVE‑2020‑11483, the issue has a CVSS score of 9.8 and exploitation could result in elevation of privileges or information leakage.
Next in line is CVE‑2020‑11484, a vulnerability that could allow an attacker that has administrative privileges to obtain the hash of the BMC/IPMI user password. Featuring a CVSS score of 8.4, the security bug could be exploited to access otherwise restricted information.
The third flaw could lead to information disclosure too. Tracked as CVE‑2020‑11487 (CVSS score 8.2), it exists due to the use of a hardcoded RSA 1024 key with weak ciphers.
With a CVSS score of 8.1, the next two vulnerabilities could lead to remote code execution.
The first of them, CVE‑2020‑11485, is a Cross-Site Request Forgery (CSRF) bug that exists because the web application “does not sufficiently verify whether a well-formed, valid, consistent request was intentionally provided by the user who submitted the request,” and which could also lead to information disclosure.
The second, CVE‑2020‑11486, could be abused by attackers “to upload or transfer files that can be automatically processed within the product's environment,” NVIDIA notes in its advisory.
Another high-risk bug that NVIDIA addressed this week is CVE‑2020‑11615 (CVSS score 7.5), where a hardcoded RC4 cipher key used within the firmware could lead to information disclosure.
The medium-severity flaws that NVIDIA patched could lead to information disclosure. The first of them, CVE‑2020‑11488, resides in the RSA 1024 public key used for firmware signature verification not being validated, while the second, CVE‑2020‑11489, exists due to the use of default SNMP community strings.
Last on the list is CVE‑2020‑11616, a low-severity flaw that exists because “the Pseudo-Random Number Generator (PRNG) algorithm used in the JSOL package that implements the IPMI protocol is not cryptographically strong.” Exploitation of the flaw could lead to information disclosure.
NVIDIA says exploitation of these vulnerabilities requires network access to the BMC of the DGX server.
These security holes were found to affect NVIDIA DGX-1, DGX-2, and DGX A100 servers. However, while DGX-1 servers are impacted by all bugs, only some of them affect DGX-2 products and DGX A100 is impacted by a single flaw.
BMC firmware 3.38.30 addresses the issues for DGX-1 servers and BMC firmware 1.06.06 patches the bugs in DGX-2 servers. An update for DGX A100 servers will become available in the second quarter of 2021.
Since the vulnerabilities were found in AMI BMC firmware, SCADA StrangeLove says other vendors appear to be impacted as well, including ASRock Rack, ASUS, DEPO Computers, Gigabyte, Gooxi, Hewlett Packard Enterprise, IBM, Lenovo, Mikrobits (Mikrotik), NetApp, Quanta Computer, and TYAN Computer.
Contacted by SecurityWeek, AMI said it has a close working relationship with NVIDIA, as well as all the other major silicon vendors in the US and abroad. The company said it contracted a third-party security firm to audit its firmware and these vulnerabilities were discovered before NVIDIA brought them to AMI’s attention. Patches have been developed and distributed to customers.
“From our perspective, this incident shows the complexity of the security paradigm in our industry, which requires the industry to work closely together to collaborate, so that we can address these security issues collectively. Over the years, AMI has come up with what we believe to be a robust security framework, which allows us to keep tabs on the security vulnerabilities that are relevant to AMI products, so we can take immediate action. We work together with industry partners on fixes which AMI then distributes to our customers; keeping in close coordination with our partners also makes it easy for AMI customers to apply the fixes that we have developed,” AMI said in an emailed statement.
It added, “In fact, AMI has been working on various mechanisms to simplify this entire process of creating and applying security fixes and patches to vulnerabilities. From our perspective, we don’t see the threat of security issues going away in the future, so we see ourselves as a partner to all silicon manufacturers in many technical and strategic initiatives over the course of many years and we will continue to do so, also to address security vulnerabilities in a timely, coordinated and effective manner.”
Flaws in Winston Privacy Devices Can Expose Networks to Remote Attacks
27.10.20
Vulnerebility
Securityweek
Researchers say they’ve uncovered a series of potentially serious vulnerabilities in devices made by online privacy firm Winston Privacy. The vendor has released patches that are automatically being sent to devices.
Winston Privacy provides a hardware-based service designed to boost online privacy and security. The company says it can block online surveillance, accelerate browsing, and block ads and trackers, and it also advertises its services as an alternative to traditional VPNs.Vulnerabilities found in Winston Privacy devices
A consultant at offensive security testing company Bishop Fox and an independent researcher discovered a total of 9 vulnerabilities in the device provided by Winston Privacy to customers. Many of the flaws have been assigned a severity rating of critical or high.
The types of security holes identified in the device include command injection, cross-site request forgery (CSRF), improper access control, insecure cross-origin resource sharing (CORS), default credentials, insufficient authorization controls, and undocumented SSH services.
They can be exploited for arbitrary code execution, privilege escalation, changing device settings and launching DoS attacks.
Chris Davis, the Bishop Fox researcher credited for finding the vulnerabilities, told SecurityWeek that an attacker could exploit some of these weaknesses to hack a Winston Privacy device remotely from the internet by convincing the targeted user to access a malicious webpage.
“Alternatively, if an attacker was on the local area network, an unauthenticated API request would also compromise the device,” Davis explained.
Justin Paglierani, the independent researcher credited for finding the vulnerabilities, explained that successful exploitation of the flaws can give an attacker root access to a device.
“In some configurations, this would allow an unauthenticated attacker direct access to your internal network, bypassing NAT, firewalls, etc,” Paglierani said via email. “In other configurations, it would allow an attacker to intercept any unencrypted traffic passing through the device.”
The vulnerabilities were reported to Winston Privacy in July and the vendor told SecurityWeek that it released a critcal hotfix within 24 hours. Patches were then gradually rolled out through last week, when version 1.5.8 was released to patch a remaining minor issue. Firmware updates containing the patches are automatically sent to devices and users do not need to take any action.
“The cost and effort required to mitigate these vulnerabilities was substantial, especially for a small startup,” Richard Stokes, CEO of Winston Privacy, said in an emailed statement. “As a result of these disclosures, we proactively conducted a thorough internal audit of the device and decided that rebuilding and updating the kernel to incorporate leading edge security patches was the best course of action for our users. This led to significant hardening of the device. This underscores the importance of ongoing investment in security which vendors must accept as part of their responsibility to their users. We are proud of the responsiveness we have demonstrated in addressing these issues.”
Bishop Fox has published an advisory with technical details for each of the identified vulnerabilities.
Containerd Bug Exposes Cloud Account Credentials
27.10.20 Vulnerebility Threatpost
The flaw (CVE-2020-15157) is located in the container image-pulling process.
A security vulnerability can be exploited to coerce the containerd cloud platform into exposing the host’s registry or users’ cloud-account credentials.
Containerd bills itself as a runtime tool that “manages the complete container lifecycle of its host system, from image transfer and storage to container execution and supervision to low-level storage to network attachments and beyond.” As such, it offers deep visibility into a user’s cloud environment, across multiple vendors.
The bug (CVE-2020-15157) is located in the container image-pulling process, according to Gal Singer, researcher at Aqua. Adversaries can exploit this vulnerability by building dedicated container images designed to steal the host’s token, then using the token to take over a cloud project, he explained.
“A container image is a combination of a manifest file and some individual layer files,” he wrote in a recent post. “The manifest file [in Image V2 Schema 2 format]…can contain a ‘foreign layer’ which is pulled from a remote registry. When using containerd, if the remote registry responds with an HTTP 401 status code, along with specific HTTP headers, the host will send an authentication token that can be stolen.”
He added, “the manifest supports an optional field for an external URL from which content may be fetched, and it can be any registry or domain.”
The attackers can thus exploit the problem by crafting a malicious image in a remote registry, and then convincing the user to access it through containerd (this can be done through email and other social-engineering avenues), according to the National Vulnerability Database writeup.
“If an attacker publishes a public image with a manifest that directs one of the layers to be fetched from a web server they control, and they trick a user or system into pulling the image, they can obtain the credentials used for pulling that image,” according to the bug advisory. “In some cases, this may be the user’s username and password for the registry. In other cases, this may be the credentials attached to the cloud virtual instance which can grant access to other cloud resources in the account.”
Non-Trivial Exploitation
Researcher Brad Geesaman at Darkbit, who did
original research into the vulnerability (which he calls “ContainerDrip”), put
together a proof-of-concept (PoC) exploit for a related attack vector.
One of the hurdles for exploitation is the fact that containerd clients that pull images may be configured to authenticate to a remote registry in order to fetch private images, which would prevent it from accessing the malicious content. Instead, an attacker would need to place the tainted image into a remote registry that the user already authenticates to.
“The question became: ‘How do I get them to send their credentials to me [for remote-registry authentication]?'” he said in a posting earlier this month. “As it turns out, all you have to do is ask the right question.”
The Google Kubernetes Engine (GKE) is a managed environment for running containerized applications, which can be integrated with containerd. When GKE clusters running COS_CONTAINERD and GKE 1.16 or below are given a deployment to run, a Basic Auth header shows up, which when base64 decoded, turns out to be the authentication token for the underlying Google Compute Engine, used to create virtual machines. This token is attached to the GKE cluster/nodepool.
“By default in GKE, the [Google Cloud Platform] service account attached to the nodepool is the default compute service account and it is granted Project Editor,” explained Geesaman.
That said, also by default, a function called GKE OAuth Scopes “scopes down” the available permissions of that token. Geesaman also found a workaround for that.
“If the defaults were modified when creating the cluster to grant the [“any”] scope to the nodepool, this token would have no OAuth scope restrictions and would grant the full set of Project Editor IAM permissions in that GCP project,” he explained.
And from there, attackers can escalate privileges to “Project Owner” using a known attack vector demonstrated at DEF CON 2020.
He added that the GKE path is one of many possible.
containerd patched the bug, which is listed as medium in severity, in version 1.2.4; containerd 1.3.x is not vulnerable.
Cloud security continues to be a challenge for organizations. Researchers earlier in October disclosed two flaws in Microsoft’s Azure web hosting application service, App Services, which if exploited could enable an attacker to take over administrative servers. Over the summer, malware like the Doki backdoor was found to be infesting Docker containers.
In April, a simple Docker container honeypot was used in a lab test to see just how quickly cybercriminals will move to compromise vulnerable cloud infrastructure. It was quickly attacked by four different criminal campaigns over the span of 24 hours.
NVIDIA Patches Code Execution Flaws in GeForce Experience
27.10.20
Vulnerebility
Securityweek
Patches released by NVIDIA last week for the GeForce Experience software address two arbitrary code execution bugs assessed with a severity rating of high.
The GeForce Experience software is a companion application that is being installed alongside NVIDIA’s GeForce drivers. Functioning as a GPU management tool, it allows users to record and share videos and screenshots, update drivers, and ensure game settings are always optimized.
Tracked as CVE‑2020‑5977 and with a CVSS score of 8.2, the first of the newly addressed issues was identified in the NVIDIA Web Helper NodeJS Web Server and exists because an uncontrolled search path is used to load a node module.
An attacker able to exploit the flaw could execute code in the context of the vulnerable software, could cause denial of service, escalate privileges, or access restricted information, NVIDIA notes in an advisory.
The second vulnerability has the identifier CVE‑2020‑5990 and a CVSS score of 7.3. According to NVIDIA, the flaw was identified in the ShadowPlay component and may lead to code execution, local privilege escalation, denial of service, or information disclosure.
A third vulnerability patched with the new release is CVE‑2020‑5978 (CVSS score of 3.2), identified in the GeForce Experience services. The bug exists because “a folder is created by nvcontainer.exe under normal user login with LOCAL_SYSTEM privileges,” NVIDIA explains.
The flaw could be exploited to achieve denial of service or to escalate privileges.
All three vulnerabilities, NVIDIA explains, impact GeForce Experience versions prior to 3.20.5.70. To keep their systems protected, users are advised to update to version 3.20.5.70 or newer of the software.
HPE addresses critical auth bypass issue in SSMC console
26.10.20
Vulnerebility
Securityaffairs
HPE fixed a remote authentication bypass vulnerability in HPE StoreServ
Management Console (SSMC) data center storage management solution.
Hewlett
Packard Enterprise (HPE) has addressed a maximum severity (rated 10/10) remote
authentication bypass vulnerability, tracked as CVE-2020-7197, affecting the HPE
StoreServ Management Console (SSMC) data center storage management solution.
HPE SSMC is a management and reporting console for HPE Primera (data storage for mission-critical apps) and HPE 3PAR StoreServ systems (AI-powered storage cloud service providers) data center arrays.
The CVE-2020-7197 flaw is a remote authentication bypass vulnerability that affects HPE 3PAR StoreServ Management and Core Software Media prior to 3.7.0.0.
“HPE StoreServ Management Console 3.7.0.0 is an off node multiarray manager web application and remains isolated from data on the managed arrays. SSMC is vulnerable to remote authentication bypass.” reads the advisory.
The flaw can be exploited by threat actors with no privileges and doesn’t require user interaction.
HPE has addressed the issue with the release of the HPE 3PAR StoreServ Management Console 3.7.1.1.
“This SSMC release includes important security and quality improvement defect fixes that strengthen the security posture of SSMC appliances,” reads the changelog.
Hewlett Packard Enterprise acknowledged the researchers Elwood Buck from MindPoint Group for reporting the flaw.
Nvidia Warns Gamers of Severe GeForce Experience Flaws
24.10.20
Vulnerebility
Threatpost
Versions of Nvidia GeForce Experience for Windows prior to 3.20.5.70 are affected by a high-severity bug that could enable code execution, denial of service and more.
Nvidia, which makes gaming-friendly graphics processing units (GPUs), has issued fixes for two high-severity flaws in the Windows version of its GeForce Experience software.
GeForce Experience is a supplemental application to the GeForce GTX graphics card — it keeps users’ drivers up-to-date, automatically optimizes their game settings and more. GeForce Experience is installed by default on systems running NVIDIA GeForce products, Nvidia’s brand of GPUs.
The most severe flaw of the two (CVE-2020-5977) can lead to a slew of malicious attacks on affected systems – including code execution, denial of service, escalation of privileges and information disclosure. It ranks 8.2 out of 10 on the CVSS scale, making it high severity.
In a Thursday security advisory, the graphics giant said users can “download the updates from the GeForce Experience Downloads page or open the client to automatically apply the security update.”
The flaw specifically stems from the Nvidia Web Helper NodeJS Web Server. When users install GeForce Experience, Node.js runs on startup and provides a webserver connection with Nvidia. The issue here is that an uncontrolled search path is used to load a node module, which occurs when an application uses fixed search paths to find resources – but one or more locations of the path are under control of malicious user. Attackers can leverage tactics like DLL preloading, binary planting and insecure library loading in order to exploit this vulnerability.
While further details regarding this specific flaw are not available from Nvidia, the company did say that attackers can leverage the flaw to execute code, launch a DoS attack, escalate their privileges or view sensitive data. Xavier DANEST with Decathlon was credited with discovering the flaw.
Nvidia on Thursday also issued patches for another high-severity flaw in the ShadowPlay component of GeForce Experience (CVE‑2020‑5990), which may lead to local privilege escalation, code execution, DoS or information disclosure. Hashim Jawad of ACTIVELabs was credited with discovering the flaw.
Versions of Nvidia GeForce Experience for Windows prior to 3.20.5.70 are affected; users are urged to update to version 3.20.5.70.
Nvidia has previously warned of security issues affecting its GeForce brand, including an issue affecting GeForce Experience in 2019 that could lead to code execution or denial of service of products if exploited.
In June, Nvidia fixed two high-severity flaws that affected drivers for Windows and Linux users, including ones that use Nvidia’s GeForce, Quadro and Tesla software. And in March, Nvidia issued patches for high-severity bugs in its graphics driver, which can be exploited by a local attacker to launch DoS or code-execution attacks, and also affected display drivers used in GeForce (as well as Quadro and Tesla-branded) GPUs for Windows.
Cisco Patches 17 High-Severity Vulnerabilities in Security Appliances
22.10.20
Vulnerebility
Securityweek
Cisco on Wednesday announced the release of patches for 17 high-severity vulnerabilities in its security appliances as part of its Security Advisory Bundled Publication for October 2020.
The vulnerabilities have been found to impact Adaptive Security Appliance (ASA), Firepower Threat Defense (FTD), and Firepower Management Center (FMC).
A majority of the flaws can be exploited remotely without authentication, including to alter data between FMC and FTD devices via an MitM attack, conduct actions on behalf of a user via a CSRF attack, and bypass FMC authentication.
However, most of the vulnerabilities that can be exploited remotely without authentication allow an attacker to cause a denial-of-service (DoS) condition. In some cases, recovering from this DoS condition requires a manual reboot of the device.
The flaws whose exploitation requires local access or authentication can be exploited to read or write files on a device, cause a DoS condition, bypass the secure boot mechanism, and escape containers and execute commands with root privileges.
A majority of these security holes were found internally and Cisco says it has found no evidence that any of them has been exploited in attacks.
The company did, however, warn customers this week that a Discovery Protocol vulnerability disclosed earlier this year has been exploited in attacks. The U.S. National Security Agency included the flaw, tracked as CVE-2020-3118, in a list of vulnerabilities exploited by Chinese state-sponsored hackers.
Last month, the networking giant released a patch bundle that fixed 34 high-severity vulnerabilities in its IOS and IOS XE software.
QNAP Issues Advisory on Zerologon Vulnerability
22.10.20
Vulnerebility
Securityweek
Storage solutions provider QNAP this week published an advisory to warn customers that certain versions of QTS, the operating system for its network-attached storage (NAS) devices, are affected by the Zerologon vulnerability.
Residing in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC) and addressed on August 2020 Patch Tuesday, the flaw started gaining attention after CISA on September 18 issued an Emergency Directive requiring federal agencies to install the available patches within three days.
Soon after, Microsoft and CISA revealed that threat actors were already targeting the vulnerability in their attacks, urging organizations to patch all domain controllers to ensure their environments are protected.
To date, both Iranian and Russian adversaries were observed abusing Zerologon, and CISA issued an alert to warn of attacks chaining exploits for this flaw with those targeting bugs in Fortinet FortiOS VPN and MobileIron MDM solutions.
This week, QNAP revealed that it too released patches for Zerologon, to ensure that its devices can’t be abused to take over entire networks.
NAS devices can be used as Windows domain controllers to allow administrators to leverage them for operations such as authentication and user account management.
“If exploited, this elevation of privilege vulnerability allows remote attackers to bypass security measures via a compromised QTS device on the network. The NAS may be exposed to this vulnerability if users have configured the device as a domain controller in Control Panel > Network & File Services > Win/Mac/NFS > Microsoft Networking,” the company explains.
QTS 4.5.1.1456 build 20201015 and later, QTS 4.4.3.1439 build 20200925 and later, QTS 4.3.6.1446 build 20200929 and later, QTS 4.3.4.1463 build 20201006 and later, and QTS 4.3.3.1432 build 20201006 and later contain fixes for the vulnerability. QTS 2.x and QES, QNAP notes, are not impacted.
Users are advised to update QTS to the latest available version and to ensure that all other applications on their devices are up to date. Users can check for new updates for their NAS model on the product support status page.
QNAP’s advisory also includes details on how users can apply the newly released QTS updates, as well as on how to update all of the installed applications.
Oracle's October 2020 CPU Contains 402 New Security Patches
22.10.20
Vulnerebility
Securityweek
Oracle on Tuesday released its Critical Patch Update (CPU) for October 2020, which includes 402 new security patches released across the company’s product portfolio.
The advisory for the latest CPU includes information on the patches released after the previous CPU, but the patches are typically cumulative, Oracle notes. Thus, customers are advised to review information on previously released patches, to ensure their systems are protected.
This month, Oracle released two versions of the advisory: a new one where details on patches for security flaws in third-party components that are not exploitable as implemented in Oracle products are listed beneath the product's risk matrix, and the traditional advisory (which mentions a total of 421 patches).
More than half of the 402 new security patches included in this month’s CPU can be exploited remotely without authentication.
More than 80 of the patches address critical-severity bugs, most of them with CVSS scores of 9.8. Two of them, namely CVE-2020-1953, impacting Healthcare Foundation, and CVE-2020-14871, affecting Solaris, have CVSS scores of 10.
Oracle products that saw the highest number of new security patches are Financial Services Applications: 53 patches – 49 of the vulnerabilities can be exploited by remote, unauthenticated attackers; MySQL: 53 fixes – 4 bugs remotely exploitable without the need of credentials; Communications: 52 patches – 41 remotely exploitable flaws; and Fusion Middleware: 46 patches – 36 vulnerabilities exploitable remotely without authentication.
Next in line are Retail Applications (28 patches – 25 flaws exploitable remotely without credentials), E-Business Suite (27 fixes – 25 remotely exploitable bugs), Database Server (18 – 4), PeopleSoft (15 – 12), Enterprise Manager (11 – 10), Communications Applications (9 – 8), Construction and Engineering (9 – 7), Hyperion (9 – 1), Java SE (8 – 8), Systems (8 – 3), Virtualization (7 – 0), Insurance Applications (6 – 6), Policy Automation (6 – 6), and Hospitality Applications (6 – 3).
Products that saw less than five new patches this month include Utilities Applications (5 – 3 vulnerabilities exploitable by remote, unauthenticated attackers), REST Data Services (5 – 2), Health Sciences Applications (4 – 4), TimesTen In-Memory Database (4 – 4), Food and Beverage Applications (4 – 3), Supply Chain (4 – 3), Siebel CRM (3 – 3), Big Data Graph (1 – 1), and GraalVM (1 – 1).
Many of the fixes Oracle lists in each of the products’ risk matrix address various other vulnerabilities, some even tens of issues. For instance, the patch for CVE-2020-14734, a high-severity flaw in the Text component of Database Server, also includes fixes for 38 additional CVEs.
Oracle encourages customers to apply the available patches to ensure their systems remain protected. The company also notes that it continues to receive reports of active targeting of previously addressed issues, underscoring the need for timely patching.
“Due to the threat posed by a successful attack, Oracle strongly recommends that customers apply Critical Patch Update security patches as soon as possible. Until you apply the Critical Patch Update patches, it may be possible to reduce the risk of successful attack by blocking network protocols required by an attack,” Oracle notes.
Google Patches Actively-Exploited Zero-Day Bug in Chrome Browser
21.10.20 Vulnerebility Threatpost
The memory-corruption vulnerability exists in the browser’s FreeType font rendering library.
Google released an update to its Chrome browser that patches a zero-day vulnerability in the software’s FreeType font rendering library that was actively being exploited in the wild.
Security researcher Sergei Glazunov of Google Project Zero discovered the bug which is classified as a type of memory-corruption flaw called a heap buffer overflow in FreeType. Glazunov informed Google of the vulnerability on Monday. Project Zero is an internal security team at the company aimed at finding zero-day vulnerabilities.
By Tuesday, Google already had released a stable channel update, Chrome version 86.0.4240.111, that deploys five security fixes for Windows, Mac & Linux–among them a fix for the zero-day, which is being tracked as CVE-2020-15999 and is rated as high risk.
“Google is aware of reports that an exploit for CVE-2020-15999 exists in the wild,” Prudhvikumar Bommana of the Google Chrome team wrote in a blog post announcing the update Tuesday. Google did not reveal further details of the active attacks that researchers observed.
Andrew R. Whalley, a member of the Chrome security team, gave his team kudos on Twitter for the “super-fast” response to the zero-day.
Still, Ben Hawkes, technical lead for the Project Zero team, warned that while Google researchers only observed the Chrome exploit, it’s possible that other implementations of FreeType might be vulnerable as well since Google was so quick in its response to the bug. He referred users to a fix by Glazunov posted on the FreeType Project page and urged them to update other potentially vulnerable software.
“The fix is also in today’s stable release of FreeType 2.10.4,” Hawkes tweeted.
Meanwhile, security researchers took to Twitter to encourage people to update their Chrome browsers immediately to avoid falling victim to attackers aiming to exploit the flaw.
“Make sure you update your Chrome today! (restart it!),” tweeted London-based application security consultant Sam Stepanyan.
In addition to the FreeType zero day, Google patched four other bugs—three of high risk and one of medium risk–in the Chrome update released this week.
The high-risk vulnerabilities are: CVE-2020-16000, described as “inappropriate implementation in Blink;” CVE-2020-16001, described as “use after free in media;” and CVE-2020-16002, described as “use after free in PDFium,” according to the blog post. The medium-risk bug is being tracked as CVE-2020-16003, described as “use after free in printing,” Bommana wrote.
So far in the last 12 months Google has patched three zero-day vulnerabilities in its Chrome browser. Prior to this week’s FreeType disclosure, the first was a critical remote code execution vulnerability patched last Halloween night and tracked as CVE-2019-13720, and the second was a type of memory confusion bug tracked as CVE-2020-6418 that was fixed in February.
Hackers are targeting CVE-2020-3118 flaw in Cisco devices
21.10.20
Vulnerebility
Securityaffairs
Cisco warns of attacks attempting to exploit the CVE-2020-3118 vulnerability
that affects multiple carrier-grade routers running Cisco IOS XR Software.
Cisco is warning of attacks targeting the CVE-2020-3118 high severity
vulnerability that affects multiple carrier-grade routers running the Cisco IOS
XR Software.
The flaw resides in the Cisco Discovery Protocol implementation for Cisco IOS XR Software and could allow an unauthenticated, adjacent attacker to execute arbitrary code or cause a reload an affected device.
“The vulnerability is due to improper validation of string input from certain fields in Cisco Discovery Protocol messages. An attacker could exploit this vulnerability by sending a malicious Cisco Discovery Protocol packet to an affected device.” reads the advisory. “A successful exploit could allow the attacker to cause a stack overflow, which could allow the attacker to execute arbitrary code with administrative privileges on an affected device.”
Cisco experts pointed out that the flaw can be exploited by unauthenticated adjacent attackers (Layer 2 adjacent) in the same broadcast domain as the vulnerable devices.
It is listed in top 25 vulnerabilities, shared by the NSA, exploited by Chinese state-sponsored hacking groups in attacks in the wild.
The IOS XR Network OS runs on several Cisco router families including NCS 540 & 560, NCS 5500, 8000, and ASR 9000 series routers.
The vulnerability also impacts third-party white box routers and Cisco products that have the Cisco Discovery Protocol enabled both on at least one interface and globally. Below the list of impacted devices:
ASR 9000 Series Aggregation Services Routers
Carrier Routing System (CRS)
IOS XRv 9000 Router
Network Convergence System (NCS) 540 Series Routers
Network Convergence System (NCS) 560 Series Routers
Network Convergence
System (NCS) 1000 Series Routers
Network Convergence System (NCS) 5000 Series
Routers
Network Convergence System (NCS) 5500 Series Routers
Network
Convergence System (NCS) 6000 Series Routers
Cisco addressed the
CVE-2020-3118 flaw in February 2020, along with four other severe issues
collectively tracked as CDPwn.
“In October 2020, the Cisco Product Security Incident Response Team (PSIRT) received reports of attempted exploitation of this vulnerability in the wild,” states the updated advisory.
“Cisco recommends that customers upgrade to a fixed Cisco IOS XR Software release to remediate this vulnerability.”
The following table reports the fixed release for this flaw:
CISCO IOS XR SOFTWARE RELEASE FIRST FIXED RELEASE FOR THIS VULNERABILITY
Earlier than 6.6 Appropriate SMU
6.61 6.6.3 or appropriate SMU
7.0 7.0.2
(Mar 2020) or appropriate SMU
7.1 Not vulnerable
The advisory includes
mitigation to address the flaw, the company suggests disabling Cisco Discovery
Protocol Globally and on an Interface for customers who can immediately apply
the security updates.
CISA Warns of Remote Code Execution Bugs in Visual Studio, Windows Codecs
Library
20.10.20
Virus Vulnerebility
The Cybersecurity and Infrastructure Security Agency (CISA) on Friday informed users about the availability of patches for two remote code execution vulnerabilities that affect Windows Codecs Library and Visual Studio Code.
Fixes for both of the bugs were released days after Microsoft’s October 2020 Patch Tuesday updates, and CISA published its alert to encourage users and administrators alike to install the available patches.
Tracked as CVE-2020-17022, the first of the issues exists in the manner in which the Codecs Library in Microsoft Windows handles objects in memory.
The bug can be triggered during the processing of a specially crafted image file and could allow an attacker to successfully execute arbitrary code on a vulnerable machine.
Residing in Visual Studio Code and tracked as CVE-2020-17023, the second vulnerability can be triggered when the user opens a malicious 'package.json' file. An attacker can trick the victim into cloning a repository and then opening it using Visual Studio Code, which would result in the attacker’s code being executed on the victim’s device.
“An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the current user. If the current user is logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” Microsoft explains.
Microsoft says there are no mitigations or workarounds for either of the two vulnerabilities. Both issues have been assigned a CVSS score of 7.8 and neither appears to have been exploited in the wild.
The vulnerability in Visual Studio was identified by Justin Steven, who in early October revealed on Twitter that Microsoft last month released a botched fix for CVE-2020-16881, a remote code execution bug in Visual Studio Code that could be triggered in a similar manner, through malicious 'package.json' files.
“Microsoft Visual Studio Code seems to have botched the fix for CVE-2020-16881, a ‘remote code execution’ vulnerability regarding ‘malicious package.json files’. The patch can be trivially bypassed,” Steven said, complaining that Microsoft isn’t forthcoming about the bug’s details.
Users who have automatic updates enabled on their computers will receive the patches for CVE-2020-17022 and CVE-2020-17023 without having to take additional steps.
Microsoft released out-of-band Windows fixes for 2 RCE issues
19.10.20
Vulnerebility
Securityaffairs
Microsoft released two out-of-band security updates to address remote code
execution (RCE) bugs in the Microsoft Windows Codecs Library and Visual Studio
Code.
Microsoft has released two out-of-band security updates to address two
remote code execution (RCE) vulnerabilities that affect the Microsoft Windows
Codecs Library and Visual Studio Code.
The two vulnerabilities, tracked as CVE-2020-17022 and CVE-2020-17023, have been rated as important severity.
The CVE-2020-17022 is a remote code execution vulnerability that exists in the way that Microsoft Windows Codecs Library handles objects in memory. An attacker can exploit the vulnerability to execute arbitrary code.
“Exploitation of the vulnerability requires that a program process a specially crafted image file.” reads the advisory. “The update addresses the vulnerability by correcting how Microsoft Windows Codecs Library handles objects in memory.”
The CVE-2020-17022 vulnerability affects all devices running Windows 10, version 1709 or later, and a vulnerable library version.
Windows 10 devices are not affected in their default configuration and that “only customers who have installed the optional HEVC or ‘HEVC from Device Manufacturer’ media codecs from Microsoft Store may be vulnerable.”
The CVE-2020-17022 flaw was reported to Microsoft by Dhanesh Kizhakkinan from
FireEye.
The CVE-2020-17023 vulnerability is a remote code execution
vulnerability that exists in Visual Studio Code. An attacker can trigger the
flaw by tricking a user into opening a malicious ‘package.json’ file, then he
could run arbitrary code in the context of the current user.
“If the current user is logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” reads the advisory.
“To exploit this vulnerability, an attacker would need to convince a target to clone a repository and open it in Visual Studio Code. Attacker-specified code would execute when the target opens the malicious ‘package.json’ file. The update address the vulnerability by modifying the way Visual Studio Code handles JSON files.”
The CVE-2020-17023 vulnerability was reported by Justin Steven.
The IT giant did not provide any mitigating measures or workarounds for the two vulnerabilities.
According to Microsoft, both vulnerabilities are not being exploited in the wild.
Critical Magento Holes Open Online Shops to Code Execution
17.10.20 Vulnerebility Threatpost
Adobe says the two critical flaws (CVE-2020-24407 and CVE-2020-24400) could allow arbitrary code execution as well as read or write access to the database.
Two critical flaws in Magento – Adobe’s e-commerce platform that is commonly targeted by attackers like the Magecart threat group – could enable arbitrary code execution on affected systems.
Retail is set to boom in the coming months – between this week’s Amazon Prime Day and November’s Black Friday – which puts pressure on Adobe to rapidly patch up any holes in the popular Magento open-source platform, which powers many online shops.
The company on Thursday disclosed two critical flaws, six important-rated errors and one moderate-severity vulnerability plaguing both Magento Commerce (which is aimed at enterprises that need premium support levels, and has a license fee starting at $24,000 annually) and Magento Open Source (its free alternative).17.10.20
The most severe of these include a vulnerability that allows for arbitrary code execution. The issue stems from the application not validating full filenames when using an “allow list” method to check the file extensions. This could enable an attacker to bypass the validation and upload a malicious file. In order to exploit this flaw (CVE-2020-24407), attackers would not need pre-authentication (meaning the flaw is exploitable without credentials) – however, they would need administrative privileges.
The other critical flaw is an SQL injection vulnerability. This is a type of web security flaw that allows an attacker to interfere with the queries that an application makes to its database. An attacker without authentication – but also with administrative privileges – could exploit this bug in order to gain arbitrary read or write access to a database.
Adobe also issued patches for various important improper-authorization vulnerabilities, which occur when an application does not properly check that a user is authorized to access functionality — which could ultimately expose data. These include a flaw that could allow unauthorized modification of Magento content management system (CMS) pages (CVE-2020-24404), one that could enable the unauthorized modification of an e-commerce business customer list (CVE-2020-24402) and two that could allow for unauthorized access to restricted resources (CVE-2020-24405 and CVE-2020-24403).
Another important vulnerability stems from an insufficient validation of a User Session, which could give an attacker unauthorized access to restricted resources (CVE-2020-24401).
For all of the flaws above, an attacker would need to have administrative privileges, but wouldn’t need pre-authentication to exploit the flaw, according to Adobe.
Finally, an important-severity cross-site scripting flaw (CVE-2020-24408) was also addressed, which could allow for arbitrary JavaScript execution in the browser. To exploit this, an attacker wouldn’t need administrative privileges, but they would need credentials.
Specifically affected are Magento Commerce, versions 2.3.5-p1 and earlier and 2.4.0 and earlier; as well as Magento Open Source, versions 2.3.5-p1 and earlier and 2.4.0 and earlier. Adobe has issued patches (below) in Magento Commerce and Magento Open Source versions 2.4.1 and 2.3.6, and “recommends users update their installation to the newest version.”
The update for all vulnerabilities is a priority 2, meaning they exist in a product that has historically been at elevated risk – but for which there are currently no known exploits.
“Based on previous experience, we do not anticipate exploits are imminent. As a best practice, Adobe recommends administrators install the update soon (for example, within 30 days),” according to the firm.
Indeed, Magento has had its share of security flaws over the past year. In July, Adobe fixed two critical vulnerabilities and two important-severity flaws that could have enabled code execution and a signature-verification bypass. And in April, Adobe patched several critical flaws in Magento, which if exploited could lead to arbitrary code execution or information disclosure.
The issue also comes after Magento 1 reached end-of-life (EOL) in June, with Adobe making a last-ditch effort to urge the 100,000 online stores still running the outdated version to migrate to Magento 2. E-commerce merchants must migrate to Magento 2, which was released five years ago.
Microsoft Fixes RCE Flaws in Out-of-Band Windows Update
17.10.20
Vulnerebility
Threatpost
The two important-severity flaws in Microsoft Windows Codecs Library and Visual Studio Code could enable remote code execution.
Microsoft has issued out-of-band patches for two “important” severity vulnerabilities, which if exploited could allow for remote code execution.
One flaw (CVE-2020-17023) exists in Microsoft’s Visual Studio Code is a free source-code editor made by Microsoft for Windows, Linux and macOS. The other (CVE-2020-17022) is in the Microsoft Windows Codecs Library; the codecs module provides stream and file interfaces for transcoding data in Windows programs.
“Microsoft has released security updates to address remote code execution vulnerabilities affecting Windows Codecs Library and Visual Studio Code,” according to a Friday CISA alert on the patches. “An attacker could exploit these vulnerabilities to take control of an affected system.”17.10.20
According to Microsoft, one “important” severity flaw (CVE-2020-17022) stems from the way that Microsoft Windows Codecs Library handles objects in memory. This vulnerability has a CVSS score of 7.8 out of 10.
An attacker who successfully exploited the vulnerability could execute arbitrary code, according to Microsoft. While an attacker could be remote to launch the attack, exploitation requires that a program process a specially crafted image file.
Only customers who have installed the optional HEVC or “HEVC from Device Manufacturer” media codecs from Microsoft Store may be vulnerable. The secure Microsoft installed packed versions are 1.0.32762.0, 1.0.32763.0, and later.
“The update addresses the vulnerability by correcting how Microsoft Windows Codecs Library handles objects in memory,” according to Microsoft.
The other “important” severity flaw (which also has a CVSS score of 7.8 out of 10) exists in Visual Studio Code, when a user is tricked into opening a malicious ‘package.json’ file.
According to Microsoft, an attacker who successfully exploited this flaw (CVE-2020-17023) could run arbitrary code in the context of the current user. An attacker would first need to convince a target to clone a repository and open it in Visual Studio Code (via social engineering or otherwise). The attacker’s malicious code would execute when the target opens the malicious ‘package.json’ file.
“If the current user is logged on with administrative user rights, an attacker could take control of the affected system,” said Microsoft. “An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
Microsoft’s update addresses the vulnerability by modifying the way Visual Studio Code handles JSON files.
In a Twitter thread, Justin Steven, who reported the flaw, said that the issue stems from a bypass of a previously deployed patch for an RCE flaw in Visual Studio Code (CVE-2020-16881).
Neither flaw has been observed being exploited in the wild according to Microsoft. Microsoft also did not offer mitigations or workarounds for other flaws – but updates will be automatically installed for users.
“Affected customers will be automatically updated by Microsoft Store,” according to Microsoft. “Customers do not need to take any action to receive the update.”
The fixes come days after Microsoft’s October Patch Tuesday updates, during which it released fixes for 87 security vulnerabilities, 11 of them critical – and one potentially wormable.
In the case of these bugs, “servicing for store apps/components does not follow the monthly ‘Update Tuesday’ cadence, but are offered whenever necessary,” according to Microsoft.
Juniper fixes tens of flaws affecting the Junos OS
17.10.20
Vulnerebility
Securityaffairs
Juniper Networks has addressed tens of vulnerabilities, including serious flaws
that can be exploited to take over vulnerable systems.
Juniper Networks has
addressed tens of vulnerabilities, including serious issues that can be
exploited to take control of vulnerable systems.
The vendor has published 40 security advisories related to security vulnerabilities in the Junos OS operating system that runs on Juniper’s firewalls and other third-party components.
The vendor addressed multiple critical flaws in the Juniper Networks Mist Cloud UI. The vulnerabilities affect the Security Assertion Markup Language (SAML) authentication, they could be exploited by a remote attacker to bypass SAML authentication.
“Juniper Networks Mist Cloud UI, when SAML authentication is enabled, may incorrectly handle SAML responses, allowing a remote attacker to bypass SAML authentication security controls.” reads the security advisory published by Juniper.
“If SAML authentication is not enabled, the product is not affected. These vulnerabilities can be exploited alone or in combination. The CVSS score below represents the worst case chaining of these vulnerabilities.”
Multiple vulnerabilities in Juniper Networks Junos OS have been fixed by
updating third party software included with Junos OS devices.
Juniper fixed a
critical remote code execution vulnerability in Telnet server tracked as
CVE-2020-10188.
“A vulnerability in the telnetd Telnet server allows remote
attackers to execute arbitrary code via short writes or urgent data, because of
a buffer overflow involving the netclear and nextitem functions.” reads the
advisory.
“This issue only affects systems with inbound Telnet service enabled. SSH service is unaffected by this vulnerability.”
The company also addressed high-severity denial-of-service (DoS) and arbitrary code execution issues.
The good news is that Juniper is not aware of attacks in the wild exploiting the vulnerabilities.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also urges organizations to apply the security updates released by the vendor.
“Juniper Networks has released security updates to address vulnerabilities affecting multiple products. An attacker could exploit some of these vulnerabilities to take control of an affected system.” reads alert issued by CISA.
“The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review the Juniper Networks security advisories page and apply the necessary updates.”
UK NCSC recommends organizations to fix CVE-2020-16952 SharePoint RCE flaw asap
17.10.20
Vulnerebility
Securityaffairs
The U.K. National Cyber Security Centre (NCSC) issued an alert to urge
organizations to patch CVE-2020-16952 RCE vulnerability in MS SharePoint Server.
The U.K. National Cyber Security Centre (NCSC) issued an alert to warn of the
risks of the exploitation for the CVE-2020-16952 remote code execution (RCE)
vulnerability in Microsoft SharePoint Server and urges organizations to address
the flaw.
Attackers could exploit this vulnerability to run arbitrary code and execute operations in the context of the local administrator on vulnerable SharePoint servers.
The issue is caused by the improper validation in user-supplied data and can be exploited when a user uploads a specially crafted SharePoint application package to a vulnerable version of SharePoint.
The vulnerability affects Microsoft SharePoint Foundation 2013 Service Pack 1,
Microsoft SharePoint Enterprise Server 2016, and Microsoft SharePoint Server
2019, while SharePoint Online as part of Office 365 is not impacted.
“The
NCSC strongly advises that organizations refer to the Microsoft guidance
referenced in this alert and ensure the necessary updates are installed in
affected SharePoint products,” reads the alert. “The NCSC generally recommends
following vendor best practice advice in the mitigation of vulnerabilities. In
the case of this SharePoint vulnerability, it is important to install the latest
updates as soon as practicable.”
The server-side include (SSI) vulnerability CVE-2020-16952 was reported by the researcher Steven Seeley from Qihoo 360 Vulcan Team, who also provided a proof-of-concept exploit for the RCE flaw.
An exploit module for the open-source Metasploit penetration testing framework was also available, it works on SharePoint 2019 on Windows Server 2016.
Security experts recommend applying the October 2020 SharePoint security updates
([1],[2],[3]).
Experts pointed out that SharePoint servers are used in
enterprise environments, for this reason, such kind of vulnerabilities is very
dangerous.
The UK NCSC confirms that both CVE-2020-16952 and CVE-2015-1641 flaws are included in the list of most exploited vulnerabilities since 2016 published in a joint advisory by the US Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI).
Juniper Networks Patches Tens of Vulnerabilities
17.10.20
Vulnerebility
Securityweek
Juniper Networks informed customers this week that it has patched tens of vulnerabilities, including serious issues that can be exploited to take control of affected systems.
Juniper Networks has published 40 security advisories describing vulnerabilities in its Junos OS operating system, which powers the company’s firewalls, and various third-party components.
Several vulnerabilities that have collectively been assigned a critical severity rating have been found in the Juniper Networks Mist Cloud UI. The bugs, related to Security Assertion Markup Language (SAML) authentication, allow a remote attacker to bypass SAML authentication.
Juniper has also informed customers of a critical remote code execution vulnerability affecting the Telnet server used by Junos OS.
The other flaws rated critical affect third-party components, including SQLite and the PyYAML YAML parser.
The company has released over a dozen advisories for high-severity vulnerabilities. Many of these weaknesses can be exploited for denial-of-service (DoS) attacks, but some could allow arbitrary code execution, including by sending specially crafted messages or via cross-site scripting (XSS).
Updates have also been released to address crypto-related issues, including in OpenSSL, and vulnerabilities such as SACK Panic (in Linux kernel) and ZombieLoad variant 2 (in Intel processors).
While Juniper says that it has found no evidence of malicious exploitation, the advisories for some of the flaws do inform users about the public availability of exploits.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has advised organizations to review the Juniper advisories and apply the updates.
Almost 800,000 SonicWall VPN appliances online are vulnerable to CVE-2020-5135
16.10.20
Vulnerebility
Securityaffairs
The Tripwire VERT security team spotted almost 800,000 SonicWall VPN appliances
exposed online that are vulnerable to the CVE-2020-5135 RCE flaw.
Security
experts from the Tripwire VERT security team have discovered 795,357 SonicWall
VPN appliances that were exposed online that are vulnerable to the CVE-2020-5135
RCE flaw.
“A buffer overflow vulnerability in SonicOS allows a remote attacker to cause Denial of Service (DoS) and potentially execute arbitrary code by sending a malicious request to the firewall. This vulnerability affected SonicOS Gen 6 version 6.5.4.7, 6.5.1.12, 6.0.5.3, SonicOSv 6.5.4.v and Gen 7 version 7.0.0.0.” reads the advisory published by SonicWall.
The CVE-2020-5135 is a stack-based buffer overflow that affects the SonicWall Network Security Appliance (NSA). The vulnerability can be exploited by an unauthenticated HTTP request involving a custom protocol handler.
The flaw resides in the HTTP/HTTPS service used for product management as well as SSL VPN remote access.
“An unskilled attacker can use this flaw to cause a persistent denial of service condition. Tripwire VERT has also confirmed the ability to divert execution flow through stack corruption indicating that a code execution exploit is likely feasible.” reads the analysis published by Tripwire. “This flaw exists pre-authentication and within a component (SSLVPN) which is typically exposed to the public Internet.”
This vulnerability is very dangerous, especially during the COVID-19 pandemic
because SonicWall NSA devices are used as firewalls and SSL VPN portals allow
employees to access corporate networks.
The vulnerability affects the
following versions:
SonicOS 6.5.4.7-79n and earlier
SonicOS 6.5.1.11-4n and earlier
SonicOS
6.0.5.3-93o and earlier
SonicOSv 6.5.4.4-44v-21-794 and earlier
SonicOS
7.0.0.0-1
Security experts from Tenable have published a post detailing the
flaw, they also shared Shodan dorks for searching SonicWall VPNs.
“Our own
Shodan search for vulnerable SonicWall devices led us to two specific search
queries:
product:”SonicWALL firewall http config”
product:”SonicWALL SSL-VPN http
proxy”
The combined results from Shodan using these search queries led to a
total of 795,674 hosts. In the VERT advisory, they specified that 795,357 hosts
were vulnerable.” wrote Tenable.
At the time of this post, the first search query provides 448,400 results, the second one 24,149, most of the vulnerable devices are in the United States.
SonicWall has already released updates to address the flaw, the company also recommends to disconnect SSL VPN portals from the Internet as temporary mitigation before installing one of the following versions:
SonicOS 6.5.4.7-83n
SonicOS 6.5.1.12-1n
SonicOS 6.0.5.3-94o
SonicOS
6.5.4.v-21s-987
Gen 7 7.0.0.0-2 and onwards
The CVE-2020-5135 is a
critical vulnerability rated as 9.4 out of 10, it could be easily exploited by
unauthenticated attackers.
At the time this post was published, no PoC exploit code was available for the CVE-2020-5135 flaw.
Google Warns of Zero-Click Bluetooth Flaws in Linux-based Devices
16.10.20
Vulnerebility
Thehackernews
Google security researchers are warning of a new set of zero-click vulnerabilities in the Linux Bluetooth software stack that can allow a nearby unauthenticated, remote attacker to execute arbitrary code with kernel privileges on vulnerable devices.
According to security engineer Andy Nguyen, the three flaws — collectively called BleedingTooth — reside in the open-source BlueZ protocol stack that offers support for many of the core Bluetooth layers and protocols for Linux-based systems such as laptops and IoT devices.
The first and the most severe is a heap-based type confusion (CVE-2020-12351, CVSS score 8.3) affecting Linux kernel 4.8 and higher and is present in the Logical Link Control and Adaptation Protocol (L2CAP) of the Bluetooth standard, which provides multiplexing of data between different higher layer protocols.
"A remote attacker in short distance knowing the victim's [Bluetooth device] address can send a malicious l2cap packet and cause denial of service or possibly arbitrary code execution with kernel privileges," Google noted in its advisory. "Malicious Bluetooth chips can trigger the vulnerability as well."
The vulnerability, which is yet to be addressed, appears to have been introduced
in a change to the "l2cap_core.c" module made in 2016.
Intel, which has significantly invested in the BlueZ project, has also issued an alert characterizing CVE-2020-12351 as a privilege escalation flaw.
The second unpatched vulnerability (CVE-2020-12352) concerns a stack-based information disclosure flaw affecting Linux kernel 3.6 and higher.
A consequence of a 2012 change made to the core Alternate MAC-PHY Manager Protocol (A2MP) — a high-speed transport link used in Bluetooth HS (High Speed) to enable the transfer of larger amounts of data — the issue permits a remote attacker in short distance to retrieve kernel stack information, using it to predict the memory layout and defeat address space layout randomization (KASLR)
Lastly, a third flaw (CVE-2020-24490) discovered in HCI (Host Controller Interface), a standardized Bluetooth interface used for sending commands, receiving events, and for transmitting data, is a heap-based buffer overflow impacting Linux kernel 4.19 and higher, causing a nearby remote attacker to "cause denial of service or possibly arbitrary code execution with kernel privileges on victim machines if they are equipped with Bluetooth 5 chips and are in scanning mode."
The vulnerability, which has been accessible since 2018, has been patched in versions 4.19.137 and 5.7.13.
For its part, Intel has recommended installing the kernel fixes to mitigate the risk associated with these issues.
"Potential security vulnerabilities in BlueZ may allow escalation of privilege or information disclosure," Intel said of the flaws. "BlueZ is releasing Linux kernel fixes to address these potential vulnerabilities."
Critical Vulnerability Allows Hackers to Disrupt SonicWall Firewalls
16.10.20
Vulnerebility
Securityweek
A significant number of SonicWall firewalls may be affected by a critical vulnerability that can be exploited for denial-of-service (DoS) attacks and possibly arbitrary code execution.
The vulnerability, identified as CVE-2020-5135, impacts various versions of SonicOS, the operating system powering SonicWall firewalls. The vendor has credited researchers at Tripwire and Positive Technologies for finding the security bug.
Tripwire discovered the flaw, which it described as a stack-based buffer overflow, in the SonicWall Network Security appliance (NSa), a firewall solution designed for medium size networks. The product also includes VPN capabilities that can be used by organizations to ensure secure remote access for employees.
Tripwire explained in a blog post that the vulnerability exists in the HTTP/HTTPS service that is used for device management and VPN access. An unauthenticated attacker can exploit it by sending specially crafted HTTP requests with a custom protocol handler.
While the security hole can definitely be exploited for DoS attacks, Tripwire says arbitrary code execution is “likely feasible” as the company has “confirmed the ability to divert execution flow through stack corruption.”
Even for DoS attacks, the vulnerability can pose a serious threat to organizations as an attacker can leverage it to force a targeted firewall to reboot.
“An attacker can keep the system rebooting by continuously sending the malicious request,” Tripwire’s Craig Young told SecurityWeek. “You could imagine an extortion scheme where someone threatens to keep your VPN workforce offline until you pay them to stop attacking. Particularly during COVID, it could be difficult for the organization to patch a device while under attack as it may require physical device access and prolonged downtime.”
Nikita Abramov, application analysis specialist at Positive Technologies, explained that a DoS attack leads to the “collapse” of the main firewall application, which he says is responsible for all the logic work, including the web interface, command-line interface and other services.
Tripwire said it identified nearly 800,000 exposed SonicWall systems on Shodan, but Young clarified that this list likely also includes devices that are not vulnerable.
Positive Technologies, on the other hand, told SecurityWeek that it identified roughly 460,000 vulnerable devices.
SonicWall has released an advisory that provides information on affected SonicOS versions as well as the availability of updates that should patch CVE-2020-5135.
Positive Technologies has also been credited by SonicWall this week for finding a dozen other vulnerabilities in SonicOS, including several high-severity DoS flaws that can be exploited remotely without authentication to crash a firewall, and less severe DoS, XSS, brute forcing, and admin username enumeration issues.
15.10.20 Vulnerebility Threatpost
The CVE-2020-5135 stack-based buffer overflow security vulnerability is trivial to exploit, without logging in.
A critical security bug in the SonicWall VPN portal can be used to crash the device and prevent users from connecting to corporate resources. It could also open the door to remote code execution (RCE), researchers said.
The flaw (CVE-2020-5135) is a stack-based buffer overflow in the SonicWall Network Security Appliance (NSA). According to the researchers at Tripwire who discovered it, the flaw exists within the HTTP/HTTPS service used for product management and SSL VPN remote access.
An unskilled attacker could trigger a persistent denial-of-service condition using an unauthenticated HTTP request involving a custom protocol handler, wrote Craig Young, a computer security researcher with Tripwire’s Vulnerability and Exposures Research Team (VERT), in a Tuesday analysis. But the damage could go further.
“VPN bugs are tremendously dangerous for a bunch of reasons,” he told Threatpost. “These systems expose entry points into sensitive networks and there is very little in the way of security introspection tools for system admins to recognize when a breach has occurred. Attackers can breach a VPN and then spend months mapping out a target network before deploying ransomware or making extortion demands.”
Adding insult to injury, this particular flaw exists in a pre-authentication routine, and within a component (SSL VPN) which is typically exposed to the public internet.
“The most notable aspect of this vulnerability is that the VPN portal can be exploited without knowing a username or password,” Young told Threatpost. “It is trivial to force a system to reboot…An attacker can simply send crafted requests to the SonicWALL HTTP(S) service and trigger memory corruption.”
However, he added that a code-execution attack does require a bit more work.
“Tripwire VERT has also confirmed the ability to divert execution flow through stack corruption, indicating that a code-execution exploit is likely feasible,” he wrote, adding in an interview that an attacker would need to also leverage an information leak and a bit of analysis to pull it off.
That said, “If someone takes the time to prepare RCE payloads, they could likely create a sizeable botnet through a worm,” he said.
There’s no sign of exploitation so far, Young said, but a Shodan search for the affected HTTP server banner indicated 795,357 vulnerable hosts as of Tuesday.
SonicWall has issued a patch; SSL VPN portals may be disconnected from the internet as a temporary mitigation before the patch is applied.
The following versions are vulnerable: SonicOS 6.5.4.7-79n and earlier; SonicOS 6.5.1.11-4n and earlier; SonicOS 6.0.5.3-93o and earlier; SonicOSv 6.5.4.4-44v-21-794 and earlier; and SonicOS 7.0.0.0-1.
“Organizations exposing VPN portals to the web should not consider these systems as impenetrable fortresses,” Young told Threatpost. “If the last 18 months has shown anything, it is that enterprise VPN firewalls can be just as insecure as a cheap home router. It is crucial to employ a tiered security model to recognize and respond to unauthorized activity.”
Google researcher found BleedingTooth flaws in Linux Bluetooth
15.10.20
Vulnerebility
Securityaffairs
Google security researcher discovered Bluetooth vulnerabilities (BleedingTooth)
in the Linux kernel that could allow zero-click attacks.
Andy Nguyen, a
Google security researcher, has found Bluetooth vulnerabilities, referred to as
BleedingTooth, in the Linux kernel that could be exploited by attackers to run
arbitrary code or access sensitive information.
The BleedingTooth flaws are tracked as CVE-2020-12351, CVE-2020-12352, and CVE-2020-24490.
The most severe of the vulnerabilities is a heap-based type confusion flaw (CVE-2020-12351) that has been rated as high severity and received a CVSS score of 8.3 out of 10.
A remote attacker within the Bluetooth range of the victim can exploit the flaw by knowing the bd address of the target device. The attacker can trigger the vulnerability by sending a malicious l2cap packet, which can lead to denial of service or even execution of arbitrary code, with kernel privileges.
According to the Google security researcher, the issue is a zero-click flaw that means that it does not require user interaction to be exploited.
Nguyen released a Proof-of-concept code for this vulnerability an exploit along with a video PoC demonstrating the issue.
The second issue found by the expert is a stack-based information leak that is tracked as CVE-2020-12352. The flaw impacts Linux kernel 3.6 and higher, it is classified as medium severity and received a CVSS score of 5.3.
“A remote attacker in short distance knowing the victim’s bd address can retrieve kernel stack information containing various pointers that can be used to predict the memory layout and to defeat KASLR. The leak may contain other valuable information such as the encryption keys,” reads the security advisory published by Google.
The third vulnerability tracked as CVE-2020-24490, is a heap-based buffer overflow that resides in net/bluetooth/hci_event.c. and affects Linux kernel 4.19 and higher.
The vulnerability is classified as medium risk and received a CVSS score of 5.3.
“A remote attacker in short distance can broadcast extended advertising data and
cause denial of service or possibly arbitrary code execution with kernel
privileges on victim machines if they are equipped with Bluetooth 5 chips and
are in scanning mode. Malicious or vulnerable Bluetooth chips (e.g. compromised
by BLEEDINGBIT or similar) can trigger the vulnerability as well.” reads the
security advisory.
The researchers published the PoC code for both issue on GitHub.
BleedingTooth: Vulnerabilities in Linux Bluetooth Allow Zero-Click Attacks
15.10.20
Vulnerebility
Securityweek
Bluetooth vulnerabilities that a Google security researcher has identified in the Linux kernel could be exploited to run arbitrary code or access sensitive information.
Referred to as BleedingTooth, the issues were identified by Andy Nguyen, a security engineer from Google, and are tracked as CVE-2020-12351, CVE-2020-12352, and CVE-2020-24490. They were introduced in 2016, 2012, and 2018, respectively.
The most severe of these flaws is CVE-2020-12351, a heap-based type confusion that affects Linux kernel 4.8 and higher. The issue features a high severity rating (CVSS score of 8.3).
The bug can be exploited by a remote attacker within Bluetooth range of the victim and which knows the bd address of the target device. To trigger the flaw, the attacker would have to send a malicious l2cap packet, which can lead to denial of service or even execution of arbitrary code, with kernel privileges.
An attacker looking to trigger the vulnerability can also use a malicious Bluetooth chip for that. Proof-of-concept code for an exploit can be found on GitHub.
The bug, Nguyen explains, does not require user interaction to be exploited (it is a zero-click vulnerability). A video demonstrating the issue is embedded below.
The second issue, CVE-2020-12352, is a stack-based information leak that impacts Linux kernel 3.6 and higher. The bug is considered medium severity (CVSS score of 5.3).
“A remote attacker in short distance knowing the victim's bd address can retrieve kernel stack information containing various pointers that can be used to predict the memory layout and to defeat KASLR. The leak may contain other valuable information such as the encryption keys,” Google’s researchers explain.
Tracked as CVE-2020-24490 and considered medium risk (CVSS score of 5.3), the third vulnerability is a heap-based buffer overflow that affects Linux kernel 4.19 and higher.
A remote attacker within short range of a vulnerable device can trigger the flaw through broadcasting extended advertising data. This could lead to denial of service or even arbitrary code execution with kernel privileges.
Only devices that feature Bluetooth 5 chips and which are in scanning mode are vulnerable to this flaw, but an attacker could also use malicious chips to trigger the vulnerability, Google’s researchers note.
PoC code for both medium-severity flaws has been published on GitHub.
BlueZ, the official Linux Bluetooth protocol stack, has announced Linux kernel fixes that patch all three of these security issues, Intel reveals. The company notes that the vulnerabilities affect “all Linux kernel versions before 5.9 that support BlueZ.”
The tech giant recommends updating Linux kernel to version 5.9 or later. Provided that an update is not possible, several kernel fixes are available to address the issues.
Microsoft October 2020 Patch Tuesday fixes 87 flaws, including 21 RCEs
14.10.20
Vulnerebility
Securityaffairs
Microsoft October
2020 Patch Tuesday security updates address 87 vulnerabilities, including 21
remote code execution (RCE) issues.
The remote code execution (RCE) flaws fixed by Microsoft affects multiple products, including Excel, Outlook, the Windows Graphics component, and the Windows TCP/IP stack.
The most severe vulnerability is an RCE issue tracked as CVE-2020-16898. that
resides in the Windows TCP/IP stack. The vulnerability can be exploited by the
attackers to take over Windows systems by sending malicious ICMPv6 Router
Advertisement packets to an unpatched system via a network connection.
“A
remote code execution vulnerability exists when the Windows TCP/IP stack
improperly handles ICMPv6 Router Advertisement packets. An attacker who
successfully exploited this vulnerability could gain the ability to execute code
on the target server or client.” reads the security advisory published by
Microsoft.
“To exploit this vulnerability, an attacker would have to send specially crafted ICMPv6 Router Advertisement packets to a remote Windows computer.”
The vulnerability received a score of 9.8 out of a maximum of 10, it affects Windows 10 and Windows Server 2019.
Microsoft also provided some workarounds such as disabling ICMPv6 RDNSS support.
Another severe RCE flaw, tracked as CVE-2020-16947, affects MS Outlook and can be exploited by attackers by tricking a user to open a specially crafted file with a vulnerable version of Outlook.
“A remote code execution vulnerability exists in Microsoft Outlook software when the software fails to properly handle objects in memory. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the System user. If the current user is logged on with administrative user rights, an attacker could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.” reads the advisory.
“Exploitation of the vulnerability requires that a user open a specially crafted
file with an affected version of Microsoft Outlook software.”
The list of the
vulnerabilities addressed with the release of the October 2020 Patch Tuesday
updates is available on the Security Update Guide portal.
Microsoft Patches Several Publicly Disclosed Windows Vulnerabilities
14.10.20
Vulnerebility
Securityweek
Microsoft has fixed nearly 90 vulnerabilities with its October 2020 Patch Tuesday updates and while none of them has been exploited in attacks, several of the flaws were publicly disclosed before the patches were released.
The publicly disclosed vulnerabilities have been classified as important severity and their exploitation can lead to information disclosure or privilege escalation. A majority impact Windows and one affects the .NET framework.
The .NET vulnerability allows an authenticated attacker to access the targeted system’s memory, specifically memory layout. Exploitation requires executing a specially crafted application.
Another disclosed flaw impacts the Windows Error Reporting (WER) component and it can be leveraged for privilege escalation. While this particular weakness does not appear to have been exploited, Malwarebytes reported earlier this month that it had spotted an attack in which the payload was injected into the WER service to evade defenses.
Two of the disclosed vulnerabilities affect the Windows kernel. An authenticated attacker could exploit them to obtain information that can be useful to further compromise impacted systems.
One of the flaws whose details have been made public impacts Windows 10 Setup and it can only be exploited for privilege escalation by a local attacker while the computer is upgrading to a newer version of Windows.
The last disclosed issue impacts the Windows Storage VSP Driver and it can allow an authenticated attacker to escalate privileges.
Nearly a dozen of the vulnerabilities patched by Microsoft this month have been rated critical. They impact Windows, Outlook, the Base3D rendering engine, and SharePoint. They can all lead to remote code execution.
One interesting security bug that has been rated critical is CVE-2020-16947, which affects Outlook and allows an attacker to execute arbitrary code by sending a specially crafted email to the targeted user.
“The Preview Pane is an attack vector here, so you don’t even need to open the mail to be impacted,” explained the Zero Day Initiative’s Dustin Childs. “The specific flaw exists within the parsing of HTML content in an email. The issue results from the lack of proper validation of the length of user-supplied data before copying it to a fixed-length heap-based buffer. Although Microsoft gives this an XI rating of 2, we have a working proof-of-concept. Patch this one quickly.”
Another noteworthy vulnerability that was patched this month is CVE-2020-16898, which is related to how the Windows TCP/IP stack handles ICMPv6 Router Advertisement packets. An attacker can exploit the flaw for code execution on a server or client by sending specially crafted packets to the targeted device.
Bharat Jogi, senior manager of vulnerability and threat research at Qualys, warned that this flaw could be wormable.
“An attacker can exploit this vulnerability without any authentication, and it is potentially wormable,” Jogi said in an emailed comment. “We expect a PoC for this exploit would be dropped soon, and we highly encourage everyone to fix this vulnerability as soon as possible. Microsoft has also provided a workaround for this vulnerability and strongly recommends installing updates for this vulnerability quickly.”
It’s worth noting that the number of vulnerabilities fixed this Patch Tuesday is slightly smaller compared to the previous months. Between March and September, the number of patched vulnerabilities never dropped below 110.
Todd Schell, senior product manager for security at Ivanti, pointed out that there do not appear to be any Edge or Internet Explorer patches this month. “Not sure I remember the last time that has happened,” he told SecurityWeek.
Adobe’s October 2020 Patch Tuesday updates only address one critical code execution vulnerability in Flash Player.
Researchers Get Big Bounties From Apple For Critical Vulnerabilities
11.10.20
Vulnerebility
Securityweek
A team of researchers has received hundreds of thousands of dollars in bug bounties from Apple for reporting 55 vulnerabilities, including ones that exposed source code, employee and customer apps, warehouse software, and iCloud accounts.
Researchers Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes decided in early July to take part in Apple’s bug bounty program and attempt to find as many vulnerabilities as possible in the tech giant’s systems and services.
Between July 6 and October 6, they discovered and reported a total of 55 issues, including 11 rated critical and 29 rated high severity. To date, Apple made 32 payments to the researchers totaling $288,500, but they expect to receive more for their findings in the coming months.
The researchers said in a blog published this week that a vast majority of the vulnerabilities they reported to Apple have been patched. The company fixed some of the more serious issues within a few hours.
With Apple’s permission, the white hat hackers disclosed the details of a dozen interesting vulnerabilities they found during the three-month project.
For example, they found a way to bypass authentication and authorization on the Apple Distinguished Educators website, which ultimately could have allowed an attacker to execute arbitrary commands on an Apple web server, access an internal user account management service, and access “the majority of Apple’s internal network.”
They also analyzed a third-party warehouse management solution used by Apple and discovered vulnerabilities that could have been exploited to obtain highly sensitive information or cause significant disruption.
In addition, they found stored cross-site scripting (XSS) flaws in the iCloud
platform, which could have been exploited to execute arbitrary code in a user’s
browser or create an email-based worm that could silently modify or steal
information from iCloud accounts, including photos and videos.
Also related to iCloud, there was a server-side request forgery (SSRF) bug that could have been exploited to gain access to some Apple source code and breach Apple’s internal network.
Actually, there were several vulnerabilities that could have been exploited to gain access to Apple’s internal network and execute arbitrary commands on some of the company’s web servers.
The researchers also reported finding secret keys that could have allowed an attacker to obtain data from Apple’s internal AWS environment, IDOR flaws that could have been leveraged to obtain or modify data, and XSS vulnerabilities that may have provided access to sensitive user data.
“Overall, Apple was very responsive to our reports. The turn around for our more critical reports was only four hours between time of submission and time of remediation,” Curry explained.
“Since no-one really knew much about their bug bounty program, we were pretty much going into unchartered territory with such a large time investment. Apple has had an interesting history working with security researchers, but it appears that their vulnerability disclosure program is a massive step in the right direction to working with hackers in securing assets and allowing those interested to find and report vulnerabilities,” he added.
Cisco addresses three high-severity issues in Webex, IP Cameras and ISE
10.10.20
Vulnerebility
Securityaffairs
Cisco fixed three high-severity flaws in Webex video conferencing system, Video
Surveillance 8000 Series IP Cameras and Identity Services Engine.
Cisco has
addressed three high-severity flaws and eleven medium-severity vulnerabilities
in its Webex video conferencing system, Video Surveillance 8000 Series IP
Cameras and Identity Services Engine.
The most severe of these vulnerabilities is a Remote Code Execution and Denial of Service issue in Cisco’s Video Surveillance 8000 Series IP Cameras.
The vulnerabilty, tracked as Remote Code Execution and Denial of Service Vulnerability. received a CVSS score of 8.8 out of 10.
“A vulnerability in the Cisco Discovery Protocol implementation for Cisco Video Surveillance 8000 Series IP Cameras could allow an unauthenticated, adjacent attacker to execute arbitrary code on an affected device or cause the device to reload.” reads the Cisco’s security advisory.
“This vulnerability is due to missing checks when an IP camera processes a Cisco Discovery Protocol packet.”
An attacker could exploit this vulnerability by sending a malicious Cisco Discovery Protocol packet to a vulnerable device. The flaw could allow an attacker to execute code on the affected IP camera or triggering a DoS condition by forcing the device to reload unexpectedly, resulting in a denial of service (DoS) condition.
Cisco also addressed a high-severity flaw, tracked as CVE-2020-3535, in its Webex platform that is caused by the incorrect handling of directory paths at run time.
An authenticated, local attacker could exploit the flaw to load a malicious library, experts pointed out that to exploit this vulnerability, the attacker needs valid credentials on the Windows system.
“The vulnerability is due to incorrect handling of directory paths at run time. An attacker could exploit this vulnerability by placing a malicious DLL file in a specific location on the targeted system. This file will execute when the vulnerable application launches.” reads the advisory published by Cisco. “A successful exploit could allow the attacker to execute arbitrary code on the targeted system with the privileges of another user’s account.”
The vulnerability affects Cisco Webex Teams for Windows releases 3.0.13464.0 through 3.0.16040.0, the IT giant confirmed that the issue does not affect Webex Teams for Android, Mac or iPhone and iPad.
The third high-severity flaw, tracked as CVE-2020-3467, resides in the web-based management interface of Cisco Identity Services Engine (ISE).
The ISE is a tool that enables the creation and enforcement of security and access policies for endpoint devices connected to the company’s network devices. The vulnerability allows an authenticated, remote attackers to modify parts of the configuration on an affected device.
“The vulnerability is due to improper enforcement of role-based access control (RBAC) within the web-based management interface. An attacker could exploit this vulnerability by sending a crafted HTTP request to an affected device. A successful exploit could allow the attacker to modify parts of the configuration. The modified configuration could either allow unauthorized devices onto the network or prevent authorized devices from accessing the network.” according to reads the Cisco’s advisory “To exploit this vulnerability, an attacker would need valid Read-Only Administrator credentials.”
The good news is that the Cisco Product Security Incident Response Team (PSIRT) is not aware attacks exploiting the above flaws in the wild.
Cisco Fixes High-Severity Webex, Security Camera Flaws
9.10.20
Vulnerebility
Threatpost
Three high-severity flaws exist in Cisco’s Webex video conferencing system, Cisco’s Video Surveillance 8000 Series IP Cameras and Identity Services Engine.
Cisco has issued patches for high-severity vulnerabilities plaguing its popular Webex video-conferencing system, its video surveillance IP cameras and its Identity Services Engine network administration product.
Overall, Cisco on Wednesday issued the three high-severity flaws along with 11 medium-severity vulnerabilities.
The most severe of these is a flaw (CVE-2020-3544) in Cisco’s Video Surveillance 8000 Series IP Cameras, which ranks 8.8 out of 10 on the CVSS scale.
Threatpost Webinar Promo Retail Security
Click to Register!
“A vulnerability in the Cisco Discovery Protocol [CDP] implementation for Cisco Video Surveillance 8000 Series IP Cameras could allow an unauthenticated, adjacent attacker to execute arbitrary code on an affected device or cause the device to reload,” according to Cisco’s security advisory.
The CDP is a network-discovery tool that helps network administrators identify neighboring Cisco devices. The vulnerability is due to missing checks when an IP camera processes a CDP packet.
To exploit the flaw, an attacker does not need to be authenticated. However, the person must be in the same broadcast domain as the affected device — because CDP is a Layer 2 protocol, attackers must be Layer 2-adjacent.
“An attacker could exploit this vulnerability by sending a malicious [CDP] packet to an affected device,” according to Cisco. “A successful exploit could allow the attacker to execute code on the affected IP camera or cause it to reload unexpectedly, resulting in a denial of service (DoS) condition.”
The vulnerability affects cameras running a firmware release earlier than Release 1.0.9-5 that have the CDP enabled, said Cisco. Of note, Cisco Video Surveillance 8000 Series IP Cameras are no longer being sold as of July 24; however, vulnerability and security support does not end until July 24, 2023.
Webex Bug
Cisco also patched a high-severity flaw affecting its Webex
platform. This issue is severe given the troves of workforces turning to video
conferencing systems during the pandemic – however, it is significantly complex
to exploit, as an attacker would need to be both authenticated (needing valid
credentials on the Windows system) and local.
The vulnerability stems from the incorrect handling of directory paths at run time. An attacker could exploit this vulnerability by placing a malicious DLL file in a specific location on the targeted system, which would then execute when the vulnerable application launches.
“A successful exploit could allow the attacker to execute arbitrary code on the targeted system with the privileges of another user’s account,” according to Cisco.
The flaw (CVE-2020-3535) affects Cisco Webex Teams for Windows releases 3.0.13464.0 through 3.0.16040.0; it does not affect Webex Teams for Android, Mac or iPhone and iPad.
Identity Services Flaw
A final high-severity flaw (CVE-2020-3467) exists in
the web-based management interface of Cisco Identity Services Engine (ISE), a
tool that enables the creation and enforcement of security and access policies
for endpoint devices connected to the company’s routers and switches. The flaw
enables authenticated (with valid Read-Only Administrator credentials), remote
attackers to modify parts of the configuration on an affected device.
The bug stems from an improper enforcement of role-based access control (RBAC) within the web-based management interface.
“An attacker could exploit this vulnerability by sending a crafted HTTP request to an affected device,” according to Cisco. “A successful exploit could allow the attacker to modify parts of the configuration. The modified configuration could either allow unauthorized devices onto the network or prevent authorized devices from accessing the network.”
Cisco said it is not aware of any public exploits for any of the three bugs
Microsoft Azure Flaws Open Admin Servers to Takeover
9.10.20 Vulnerebility Threatpost
Two flaws in Microsoft’s cloud-based Azure App Services could have allowed server-side forgery request (SSFR) and remote code-execution attacks.
Researchers have disclosed two flaws in Microsoft’s Azure web hosting application service, App Services, which if exploited could enable an attacker to take over administrative servers.
Azure App Services is an HTTP-based service for hosting web applications, and is available in both Microsoft Azure Cloud and on-premise installations. Researchers found two vulnerabilities in the cloud service that specifically affect Linux servers.
“The two vulnerabilities we found allow us to combine them and enable any attacker with the ability to forge post requests (SSRF) or [remote] code execution on an Azure App Service to take over the Azure App Service administration server,” said Paul Litvak, researcher with Intezer, in a Thursday post.
Threatpost Webinar Promo Retail Security
Click to Register!
Both flaws were discovered three months ago and reported to Microsoft. Microsoft has since issued a fix. The vulnerabilities do not have CVE assignments.
KuduLite Bugs
The first flaw stems from an open-source project called
KuduLite within Azure App Services. This Linux project manages the
administration page that’s used to register admins into the App Service Plan (to
start using App Services a user must first create an App Service Plan).
After discovering that the KuduLite instance’s SSH service uses hardcoded credentials “root:Docker!” to access the application node, researchers were able to log in as root.
“As a reminder, the developers of the App Service KuduLite made sure admins were only able to log into it as a low privileged user, so we knew this was unintended.”
After taking control of the KuduLite instance, researchers could then gain control over the Software Configuration Management (SCM) web server, which systematically manages and controls changes in the documents and codes during the Software Development Life Cycle. This allowed them to then listen to a user’s HTTP requests to the SCM web page, add their own pages and inject malicious Javascript into the user’s web page.
“The user may also choose to let App Services manage the git server, in which case the server will be managed by KuduLite,” said researchers. “The attacker could then add malicious code to the repository to achieve persistence and spread to other instances using the same git server.”
The second flaw exists in the KuduLite API. The issue here stems from the application node being able to send requests to the KuduLite API sans access validation – an error that is especially problematic when considering a web app with an SSRF vulnerability, researchers said.
“An attacker who manages to forge a GET request may access the application node’s file system via the KuduLite VFS API,” said researchers. “This would enable an attacker to easily steal source code and other assets on the application node.”
An attacker who manages to forge a POST request, meanwhile, may achieve remote code execution on the application node via the command API, they said. And, in Windows (where Kudu is used), packets sent from the application node to the manager node are dropped.
These two vulnerabilities can be chained together, since once an attacker
achieves code execution with the second vulnerability, they can then exploit the
first one. One potential attack vector here is for an attacker to use this flaw
to implant a phishing page in what’s supposed to be the SCM web page (as seen in
the video below).
Researchers stressed that cloud security is still relatively new, making it essential to research and document new attack surfaces that arise when using these services.
“As a general best practice, runtime cloud security is an important last line of defense and one of the first actions you can to reduce risk, since it can detect malicious code injections and other in-memory threats that take place after a vulnerability has been exploited by an attacker,” they said.
QNAP addresses 2 critical flaws that can allow hackers to take over NASs
8.10.20
Vulnerebility
Securityaffairs
QNAP has addressed two critical security vulnerabilities in the Helpdesk app
that could enable potential attackers to take over NAS devices.
QNAP has
addressed two critical security vulnerabilities in the Helpdesk app that can
potential allow threat actors to take over vulnerable QNAP network-attached
storage (NAS) devices.
Helpdesk is a built-in app that allows owners of QNAP
NAS to directly submit help requests to the vendor from their NAS, to do this,
the app has specific permission.
According to a security advisory published by the company, both flaws, tracked as CVE-2020-2506 and CVE-2020-2507, are improper access control vulnerabilities.
The Taiwanese vendor confirmed that if exploited, the two improper access control vulnerabilities could allow attackers to obtain control of a QNAP device.
QNAP has addressed these issues with the release of Helpdesk 3.0.3 and later versions, below the step by step instructions to update the helpdesk:
Log on to QTS as administrator.
Open the App Center, and then click .
A
search box appears.
Type “Helpdesk”, and then press ENTER.
The Helpdesk
application appears in the search results.
Click Update.
A confirmation
message appears.
Note: The Update button is not available if you are using
the latest version.
Click OK.
The application is updated.
Recently QNAP
published a security advisory urging its customers to update the firmware and
apps installed on their network-attached storage (NAS) devices to prevent
AgeLocker ransomware infections.
The name AgeLocker comes from the use of the Actually Good Encryption (AGE) algorithm to encrypt files, experts warn that encrypted files can’t be recovered without paying the ransom to the ransomware operators.
Security experts are observing the new strain of ransomware that is targeting QNAP devices since June.
In early August, the Taiwanese company urged its users to update the Malware Remover app to prevent NAS devices from being infected by the QSnatch malware.
At the time, the United States Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) also issued a joint advisory about a massive ongoing campaign spreading the QSnatch data-stealing malware.
Earlier this year, the company issued another alert to warn its users of a wave of attacks spreading a ransomware strain tracked as eCh0raix.
Researchers Find Vulnerabilities in Microsoft Azure Cloud Service
8.10.20
Vulnerebility
Thehackernews
As businesses are increasingly migrating to the cloud, securing the infrastructure has never been more important.
Now according to the latest research, two security flaws in Microsoft's Azure App Services could have enabled a bad actor to carry out server-side request forgery (SSRF) attacks or execute arbitrary code and take over the administration server.
"This enables an attacker to quietly take over the App Service's git server, or implant malicious phishing pages accessible through Azure Portal to target system administrators," cybersecurity firm Intezer said in a report published today and shared with The Hacker News.
Discovered by Paul Litvak of Intezer Labs, the flaws were reported to Microsoft in June, after which the company subsequently addressed them.
Azure App Service is a cloud computing-based platform that's used as a hosting web service for building web apps and mobile backends.
When an App Service is created via Azure, a new Docker environment is created
with two container nodes — a manager node and the application node — along with
registering two domains that point to the app's HTTP web server and the app
service's administration page, which in turn leverages Kudu for continuous
deployment of the app from source control providers such as GitHub or Bitbucket.
Likewise, Azure deployments on Linux environments are managed by a service called KuduLite, which offers diagnostic information about the system and consists of a web interface to SSH into the application node (called "webssh").
The first vulnerability is a privilege escalation flaw that allows for a takeover of KuduLite via hard-coded credentials ("root:Docker!") that makes it possible to SSH into the instance and log in as root, thereby allowing an attacker complete control over the SCM (aka Software Configuration Management) webserver.

According to the researchers, this could enable an adversary to "listen to a
user's HTTP requests to the SCM web page, add our own pages, and inject
malicious Javascript into the user's web page."
The second security vulnerability concerns the way the application node sends requests to the KuduLite API, potentially permitting a web app with an SSRF vulnerability to access the node's file system and steal source code and other sensitive assets.
"An attacker who manages to forge a POST request may achieve remote code execution on the application node via the command API," the researchers said.
What's more, successful exploitation of the second vulnerability implies the attacker can chain the two issues to leverage the SSRF flaw and elevate their privileges to take over the KuduLite web server instance.
For its part, Microsoft has been steadily working to improve security in the cloud and the internet of things (IoT) space. After making available its security-focused IoT platform Azure Sphere earlier this year, it has also opened it up for researchers to break into the service with an aim to "identify high impact vulnerabilities before hackers."
"The cloud enables developers to build and deploy their applications at great speed and flexibility, however, often the infrastructure is susceptible to vulnerabilities out of their control," Intezer said. "In the case of App Services, applications are co-hosted with an additional administration container, and [...] additional components can bring additional threats."
"As a general best practice, runtime cloud security is an important last line of defense and one of the first actions you can to reduce risk, since it can detect malicious code injections and other in-memory threats that take place after a vulnerability has been exploited by an attacker."
'Smart' Male Chastity Device Vulnerable to Locking by Hackers: Researchers
8.10.20
Vulnerebility
Securityweek
A security flaw in an internet-connected male chastity device could allow hackers to remotely lock it -- leaving users trapped, researchers have warned.
The Cellmate, produced by Chinese firm Qiui, is a cover that clamps on the base of the male genitals with a hardened steel ring, and does not have a physical key or manual override.
The locking mechanism is controlled with a smartphone app via Bluetooth -- marketed as both an anti-cheating and a submission sex play device -- but security researchers have found multiple flaws that leave it vulnerable to hacking.
"We discovered that remote attackers could prevent the Bluetooth lock from being opened, permanently locking the user in the device. There is no physical unlock," British security firm Pen Test Partners said Tuesday.
"An angle grinder or other suitable heavy tool would be required to cut the wearer free."
The firm also found other security flaws in the Cellmate -- listed for $189 on Qiui's website -- that could expose sensitive user information such as names, phone numbers, birthdays and location data.
"It wouldn't take an attacker more than a couple of days to exfiltrate the entire user database and use it for blackmail or phishing," PTP's Alex Lomas wrote in their report on the device.
"A number of countries have oppressive laws that may expose users of these types of devices to unwarranted interest from law enforcement and bigots."
Qiui did not immediately respond to AFP's request for comment.
PTP said it reached out to Qiui in April this year, identifying the flaws.
Qiui fixed most of the issues by updating the software, but left the older version active and its users still vulnerable, PTP added, saying other researchers had found similar issues.
Such smart sex toys and devices are among the wave of new "internet of things" products and appliances introduced in recent years that are online and capable of being operated remotely.
Their connectivity has also made them vulnerable to security breaches and privacy violations.
In 2017, the Canadian maker of a smart vibrator agreed to a multi-million-dollar settlement after it was sued for collecting sensitive user information, though it did not admit any wrongdoing.
Next year, cybersecurity firm SEC Consult reported multiple vulnerabilities that hackers could exploit to hijack and control a smartphone-controlled vibrator called Vibratissimo. Sensitive user data was also left exposed.
New Flaws in Top Antivirus Software Could Make Computers More Vulnerable
6.10.20
Vulnerebility
Thehackernews
Cybersecurity
researchers today disclosed details of security vulnerabilities found in popular
antivirus solutions that could enable attackers to elevate their privileges,
thereby helping malware sustain its foothold on the compromised systems.
According to a report published by CyberArk Labs today and shared with The
Hacker News, the high privileges often associated with anti-malware products
render them more vulnerable to exploitation via file manipulation attacks,
resulting in a scenario where malware gains elevated permissions on the system.
The bugs impact a wide range of antivirus solutions, including those from Kaspersky, McAfee, Symantec, Fortinet, Check Point, Trend Micro, Avira, and Microsoft Defender, each of which has been fixed by the respective vendor.
Chief among the flaws is the ability to delete files from arbitrary locations, allowing the attacker to delete any file in the system, as well as a file corruption vulnerability that permits a bad actor to eliminate the content of any file in the system.
Per CyberArk, the bugs result from default DACLs (short for Discretionary Access Control Lists) for the "C:\ProgramData" folder of Windows, which are by applications to store data for standard users without requiring additional permissions.
Given that every user has both write and delete permission on the base level of the directory, it raises the likelihood of a privilege escalation when a non-privileged process creates a new folder in "ProgramData" that could be later accessed by a privileged process.
Antivirus
Vulnerability
Kaspersky Security Center CVE-2020-25043, CVE-2020-25044, CVE-2020-25045
McAfee Endpoint Security and McAfee Total Protection CVE-2020-7250,
CVE-2020-7310
Symantec Norton Power Eraser CVE-2019-1954
Fortinet
FortiClient CVE-2020-9290
Check Point ZoneAlarm and Check Point Endpoint
Security CVE-2019-8452
Trend Micro HouseCall for Home Networks
CVE-2019-19688, CVE-2019-19689, and three more unassigned flaws
Avira
CVE-2020-13903
Microsoft Defender CVE-2019-1161
In one case, it was
observed that two different processes — one privileged and the other run as an
authenticated local user — shared the same log file, potentially allowing an
attacker to exploit the privileged process to delete the file and create a
symbolic link that would point to any desired arbitrary file with malicious
content.
Subsequently, CyberArk researchers also explored the possibility of creating a new folder in "C:\ProgramData" before a privileged process is executed.
In doing so, they found that when McAfee antivirus installer is run after creating the "McAfee" folder, the standard user has full control over the directory, allowing the local user to gain elevated permissions by performing a symlink attack.
To top it all, a DLL hijacking flaw in Trend Micro, Fortinet, and other antivirus solutions could have been exploited by an attacker to place a malicious DLL file into the application directory and elevate privileges.
Urging that access control lists must be restrictive to prevent arbitrary delete vulnerabilities, CyberArk stressed the need to update the installation frameworks to mitigate DLL Hijacking attacks.
While these issues may have been addressed, the report serves as a reminder that weaknesses in software, including those that aim to offer antivirus protection, can be a conduit for malware.
"The implications of these bugs are often full privilege escalation of the local system," CyberArk researchers said. Due to the high privilege level of security products, an error in them could help malware to sustain its foothold and cause more damage to the organization."
HP Offering Big Rewards for Cartridge Vulnerabilities
1.10.20
Vulnerebility
Securityweek
HP announced on Thursday that it has expanded its bug bounty program, inviting several white hat hackers to find vulnerabilities in its office-class ink and toner cartridges.
The printer giant says it’s working with Bugcrowd to run this program for three months. The program is private and only four researchers have been invited to find vulnerabilities in original HP cartridges.
HP says it has invested roughly $200,000 into this initiative and it’s prepared to award an extra $10,000 for each vulnerability, in addition to the researchers’ base fee.HP adds cartridge vulnerabilities to its bug bounty program
HP has been running a bug bounty program for its printers since 2018 — the company claimed at the time that this was the industry’s first printer bug bounty program. The company says there has been an increase in attacks on embedded systems, and printer firmware may also be targeted.
The company has warned that, in addition to poor printing results and the financial damage they cause to the industry, imitation and fake cartridges can introduce unknown and untrusted electrical hardware into an organization’s network.
“While the industry has become sophisticated at spotting and blocking software-based intrusions, the same can’t be said for hardware. In fact, it is well understood in the IT industry that counterfeit hardware can become the source of hardware-based exploitation,” said Shivaun Albright, chief technologist for print security at HP.
HP says it has taken steps to prevent cartridge chips from being replaced or altered in the supply chain.
“Only Original HP cartridges contain a chip with HP proprietary firmware that is designed to be secure and resistant to tampering. Non-HP supplies include chips of unknown origin that may employ untrusted firmware,” Albright explained. “Given that there is a data interface from the chip to the printer, an attacker with the right skills and resources may be able to uncover and exploit a vulnerability, taking advantage of this interface to inject malicious code.”
Zerologon Patches Roll Out Beyond Microsoft
24.9.20
Vulnerebility
Threatpost
A Samba patch and a micropatch for end-of-life servers have debuted in the face of the critical vulnerability.
The “perfect” Windows vulnerability known as the Zerologon bug is getting a patch assist from two non-Microsoft sources, as they strive to fill in the gaps that the official fix doesn’t address.
Both Samba and 0patch have issued fixes for CVE-2020-1472, which, as previously reported, stems from the Netlogon Remote Protocol, available on Windows domain controllers, which is used for various tasks related to user- and machine-authentication.
Exploiting the bug allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services, according to Microsoft. A proof-of-concept exploit was just released for the issue, which is a critical flaw rating 10 out of 10 on the CvSS severity scale.
“This attack has a huge impact: It basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain,” said researchers with Secura, in a whitepaper published earlier this month.
Microsoft did issue a patch for the flaw in August, during its regularly scheduled Patch Tuesday updates. However, not all systems are compatible with the fix, according to Mitja Kolsec, CEO and co-founder at 0patch, which issued a “micropatch” of its own for the bug.
“Our micropatch was made for Windows Server 2008 R2, which reached end-of-support this January and stopped receiving Windows updates,” Kolsec told Threatpost. “Many organizations are still using this server and the only way for it to get extended security updates from Microsoft was to move it to Azure (cloud) — which is an unacceptable option for most organizations.”
The micropatch is logically identical to Microsoft’s fix, he explained in a recent blog post: “We injected it in function NetrServerAuthenticate3 in roughly the same place where Microsoft added the call to NlIsChallengeCredentialPairVulnerable, but since the latter doesn’t exist in old versions of netlogon.dll, we had to implement its logic in our patch.”
0patch is also porting the micropatch to various still-supported Windows Servers for customers who for various reasons can’t apply the Microsoft patch, he added.
Meanwhile, it turns out that Samba, a file-sharing utility for swapping materials between Linux and Windows systems, also relies on the Netlogon protocol, and thus suffers from the vulnerability.
The bug exists when Samba is used as domain controller only (most seriously the Active Directory DC, but also the classic/NT4-style DC), it said in an advisory this week. It added, “installations running Samba as a file server only are not directly affected by this flaw, though they may need configuration changes to continue to talk to domain controllers.”
The company noted that versions 4.8 and above of Samba are not vulnerable unless they have the smb.conf lines ‘server schannel = no’ or ‘server schannel = auto’. Samba versions 4.7 and below are vulnerable unless they have ‘server schannel = yes’ in the smb.conf.
Last Friday, the U.S. Cybersecurity and Infrastructure Security Agency issued an emergency directive for federal agencies to patch against the bug. Federal agencies that haven’t patched their Windows Servers against the Zerologon vulnerability by Monday Sept. 21 at 11:59 pm EDT are in violation.
Samba addresses the CVE-2020-1472 Zerologon Vulnerability
24.9.20
Vulnerebility
Securityaffairs
Samba team has released a security patch to address the Zerologon issue in the
Microsoft Windows Netlogon Remote Protocol (MS-NRPC).
Samba team has released
a security patch to address the Zerologon (CVE-2020-1472) issue in the Microsoft
Windows Netlogon Remote Protocol (MS-NRPC).
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
“An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network.” reads the advisory published by Microsoft.
“To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access.”
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the
Netlogon authentication process and change a computer’s password on the domain
controller’s Active Directory.
Microsoft addressed the vulnerability with the
release of August 2020 Patch Tuesday, last week the Department of Homeland
Security’s CISA issued an emergency directive to order government agencies to
address the Zerologon vulnerability (CVE-2020-1472) by this Monday.
Experts pointed out that the vulnerability also impacted Samba that relies on
Netlogon for file sharing between Linux and Windows systems.
Samba is also
vulnerable to the NetLogon flaw only when used as domain controller, according
to the advisory Active Directory DC installations are the most affected. Default
installations running Samba as a file server only are not directly impacted.
“Since version 4.8 (released in March 2018), the default behaviour of Samba has been to insist on a secure netlogon channel, which is a sufficient fix against the known exploits. This default is equivalent to having ‘server schannel = yes’ in the smb.conf.” reads the advisory. “Therefore versions 4.8 and above are not vulnerable unless they have the smb.conf lines ‘server schannel = no’ or ‘server schannel = auto’,”
Samba versions 4.7 and below are impacted by the vulnerability unless they have ‘server schannel = yes’ in the smb.conf.
“The ‘server schannel = yes’ smb.conf line is equivalent to Microsoft’s ‘FullSecureChannelProtection=1’ registry key, the introduction of which we understand forms the core of Microsoft’s fix. ” continues the advisory.
An attacker can exploit this vulnerability to completely domain takeover (on Active Directory DC domains), or disclosure of session keys or denial of service (on NT4-like domains).
Vendors supporting Samba 4.7 and below have to patch their installations and packages installing the available patches as soon as possible.
Google Patches Privilege Escalation Vulnerability in Cloud Service
24.9.20
Vulnerebility
Securityweek
Google recently patched a privilege escalation vulnerability in OS Config, a Google Cloud Platform service for Compute Engine that is designed for managing operating systems running on virtual machine instances.
Security researcher Imre Rad analyzed the service, which he says is still in beta. He noticed that the agent process associated with the service, google_osconfig_agent, is running by default, with root privileges.
Google says the OS Config service API and agent allow users to perform various tasks across a group of VM instances, including applying patches, collecting and reviewing OS information, and installing, removing and updating software packages.
According to Rad, tasks executed via OS Config are called recipes, and one type of recipe that is supported executes a shell script. When the agent processed this type of recipe, it temporarily saved files in /tmp/osconfig_software_recipes before executing them. This enabled a low-privileged attacker with access to this folder to replace the files stored in this location with their own, malicious files, leading to those files getting executed with root privileges.
Exploitation of the vulnerability required access to the targeted system: either having a low-privileged shell on the affected VM or control over a compromised network service. However, one additional condition needed to be met for the attack to work: the hacker needed to have control over the folder storing recipes, which, Rad said, was only possible if no recipes were processed in the current session. This requirement made exploitation more difficult.
“A practical privilege escalation exploit is something you just execute and it elevates your privileges in a few seconds,” Rad told SecurityWeek via email. “This one depends on some external events — a new recipe to be deployed via osconfig — via a service that is not yet promoted to be production yet. I think it would be rare to see exploitable systems in the real world.”
Nevertheless, Google thought this was an interesting finding and while the likelihood of exploitation was low, the tech giant apparently agreed that using a predictable location to store recipes was not a good security practice.
Google was informed about the vulnerability, which the company described as a “nice catch,” on August 7 and a patch was rolled out on September 5. The issue was addressed by using a random temporary directory instead of a predictable one. Rad pointed out that users will need to upgrade their OS package in order to prevent potential attacks exploiting this vulnerability.
Rad has made available technical details on how the vulnerability could have been exploited and a proof-of-concept (PoC) exploit. The researcher does not want to disclose the exact bug bounty he has received from Google for his findings, but he told SecurityWeek that it’s in the thousands of dollars range.
Rad noted that Microsoft is offering a much higher reward for similar elevation of privilege vulnerabilities, although it does not have a research grant program, like Google does.
Detecting and Preventing Critical ZeroLogon Windows Server Vulnerability
24.9.20
Vulnerebility
Thehackernews
If you're
administrating Windows Server, make sure it's up to date with all recent patches
issued by Microsoft, especially the one that fixes a recently patched critical
vulnerability that could allow unauthenticated attackers to compromise the
domain controller.
Dubbed 'Zerologon' (CVE-2020-1472) and discovered by Tom
Tervoort of Secura, the privilege escalation vulnerability exists due to the
insecure usage of AES-CFB8 encryption for Netlogon sessions, allowing remote
attackers to establish a connection to the targeted domain controller over
Netlogon Remote Protocol (MS-NRPC).
"The attack utilizes flaws in an authentication protocol that validates the authenticity and identity of a domain-joined computer to the Domain Controller. Due to the incorrect use of an AES mode of operation, it is possible to spoof the identity of any computer account (including that of the DC itself) and set an empty password for that account in the domain," researchers at cybersecurity firm Cynet explain in a blog post.
Though the vulnerability, with a CVSS score of 10.0, was first disclosed to the public when Microsoft released a patch for it in August, it became a matter of sudden concern after researchers published technical details and proof-of-concept of the flaw last week.
Along with Indian and Australian Government agencies, the United States Cybersecurity and Infrastructure Security Agency (CISA) also issued an emergency directive instructing federal agencies to patch Zerologon flaws on Windows Servers immediately.
"By sending a number of Netlogon messages in which various fields are filled with zeroes, an unauthenticated attacker could change the computer password of the domain controller that is stored in the AD. This can then be used to obtain domain admin credentials and then restore the original DC password," the advisories say.
According to Secura, the said flaw can be exploited in the following sequence:
Spoofing the client credential
Disabling RPC Signing and Sealing
Spoofing
a call
Changing Computer's AD Password
Changing Domain Admin Password
"CISA has determined that this vulnerability poses an unacceptable risk to the
Federal Civilian Executive Branch and requires an immediate and emergency
action."
"If affected domain controllers cannot be updated, ensure they are removed from the network," CISA advised.
Moreover, Samba—an implementation of SMB networking protocol for Linux systems—versions 4.7 and below are also vulnerable to the Zerologon flaw. Now, a patch update for this software has also been issued.
Besides explaining the root cause of the issue, Cynet also released details for some critical artifacts that can be used to detect active exploitation of the vulnerability, including a specific memory pattern in lsass.exe memory and an abnormal spike in traffic between lsass.exe.
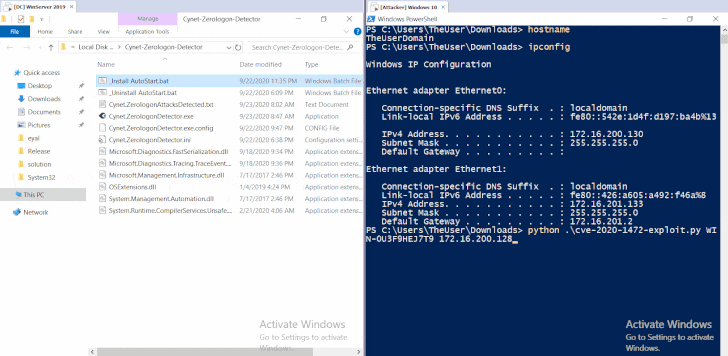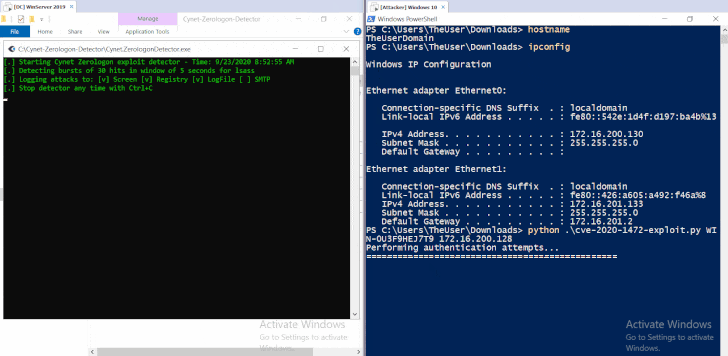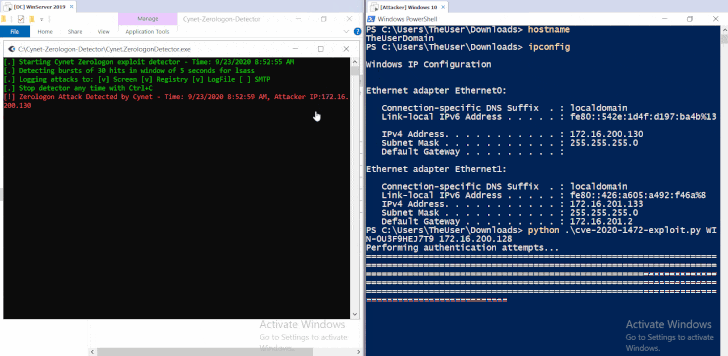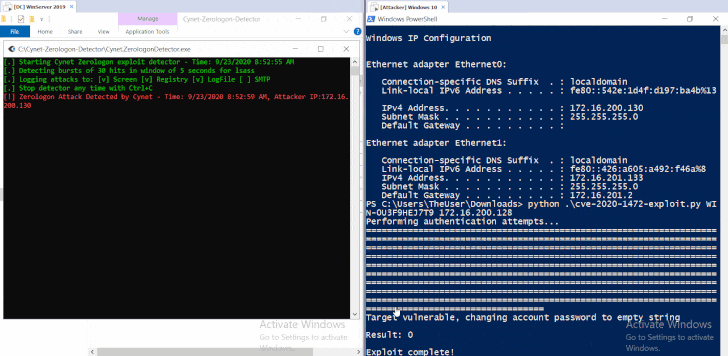
"The most documented artifact is Windows Event ID 4742 'A computer account was
changed', often combined with Windows Event ID 4672 'Special privileges assigned
to new logon'."
To let Windows Server users quickly detect related attacks, experts also released the YARA rule that can detect attacks that occurred prior to its deployment, whereas for realtime monitoring is a simple tool is also available for download.
However, to completely patch the issue, users still recommend installing the latest software update from Microsoft as soon as possible.
Microsoft Explains How It Processes Vulnerability Reports
22.9.20
Vulnerebility
Securityweek
Microsoft has detailed the steps involved in the processing of vulnerability reports, so that reporting researchers know what to expect when submitting information on a bug.
The first thing researches need to do, the company says, is to ensure that the issue they have identified indeed qualifies as a security vulnerability, and only then to head over to Microsoft’s Researcher Portal to submit a report.
The portal, the tech company notes, delivers a secure and guided way for security researchers to share all of the necessary details required to reproduce a reported vulnerability and identify a fix for it. Each vulnerability should have its own report.
“The portal will also guide you in working out what additional information you will need to write a high-quality report. High-quality reports will help your researcher reputation score, and if your report qualifies for one of our bounty program rewards, you also may receive a higher reward amount too,” Microsoft notes.
Once a report has been submitted, Microsoft’s employees will triage it, assessing whether it indeed details a security flaw and assigning it to the relevant product engineering team. Only security vulnerabilities that meet Microsoft’s servicing criteria will be provided a case number.
The company next evaluates the severity and impact of vulnerabilities that can be reproduced, and then the information is sent to product engineers for further action. While a report is marked as ‘New’ in the Researcher Portal during triage and case assignment, its state is changed to ‘Review/Repro’ at the next step, and the reporter is informed via email, Microsoft notes.
“This process can take some time, depending on the complexity of the issue and the completeness of your submission. You will receive an email when your case moves to the development stage, and this can take up to one or two weeks, sometimes less and occasionally more. If you do not hear back from us within two weeks, please check your junk folder before reaching out to us,” the tech company says.
Microsoft also explains that, for vulnerabilities that its employees determine should be addressed through immediate servicing, a fix will be developed and made available in coordination with the release teams. The report’s status in the Researcher Portal in this case is changed to ‘Develop’.
At this stage, the bounty team reviews the submission to determine if it is eligible for an award. The reporter is informed via email if the report qualifies for a bug bounty payout. Researchers are required to have an account with one of the payment providers for the Microsoft Bounty Programs, to receive their reward.
If a fix is being prepared for release, the report’s status changes to ‘Release’. The patch is usually included in the Update Tuesday release, or other service updates. After a fix has been rolled out, the report’s status changes to ‘Complete’, Microsoft says.
IBM Spectrum Protect Plus Security Open to RCE
16.9.20 Vulnerebility Threatpost
Two bugs (CVE-2020-4703 and CVE-2020-4711) in IBM’s Spectrum Protect Plus data-storage protection solution could enable remote code execution.
IBM has issued fixes for vulnerabilities in Spectrum Protect Plus, Big Blue’s security tool found under the umbrella of its Spectrum data storage software branding. The flaws can be exploited by remote attackers to execute code on vulnerable systems.
IBM Spectrum Protect Plus is a data-protection solution that provides near-instant recovery, replication, reuse and self-service for virtual machines. The vulnerabilities (CVE-2020-4703 and CVE-2020-4711) affect versions 10.1.0 through 10.1.6 of IBM Spectrum Protect Plus.
Threatpost Webinar Promo Bug Bounty
Click to Register
The more serious of the two flaws (CVE-2020-4703) exists in IBM Spectrum Protect Plus’ Administrative Console and could allow an authenticated attacker to upload arbitrary files – which could then be used to execute arbitrary code on the vulnerable server, according to researchers with Tenable, who discovered the flaws, in a Monday advisory. The bug ranks 8 out of 10 on the CVSS scale, making it high-severity.
This vulnerability is due to an incomplete fix for CVE-2020-4470, a high-severity flaw that was previously disclosed in June. An exploit for CVE-2020-4470 involves two operations, Tenable researchers said: “The first operation is to upload a malicious RPM package to a directory writable by the administrator account by sending an HTTP POST message to URL endpoint https://<spp_host>:8090/api/plugin,” they said. “The second operation is to install the malicious RPM by sending an HTTP POST message to URL endpoint http://<spp_host>:8090/emi/api/hotfix.”
But IBM’s ensuing fix for CVE-2020-4470 only addressed the second operation by enforcing authentication for the /emi/api/hotfix endpoint. Researchers found, it was still possible to upload unauthenticated arbitrary files to a directory writable by the administrator account, under which the endpoint handlers run – paving the way for code execution on vulnerable systems.
“The attacker can put malicious content (i.e., scriptlets) in the RPM and and issue a ‘sudo /bin/rpm -ivh /tmp/<uploaded_malicious_rpm>’ command to the webshell, achieving unauthenticated RCE as root,” said researchers.
The second flaw, CVE-2020-4711, exists in a script (/opt/ECX/tools/scripts/restore_wrapper.sh) within Spectrum Protect Plus. A directory path check within this function can be bypassed via path traversal. An unauthenticated, remote attacker can exploit this issue by sending a specially crafted HTTP request to a specially-crafted URL endpoint (https://<spp_host>:8090/catalogmanager/api/catalog), Tenable researchers said.
That endpoint doesn’t require any authentication (when the cmode parameter is the restorefromjob method). When the request has been sent, the endpoint handler instead calls a method (com.catalogic.ecx.catalogmanager.domain.CatalogManagerServiceImpl.restoreFromJob) without checking for user credentials. The restoreFromJob method then executes the /opt/ECX/tools/scripts/restore_wrapper.sh script as root – allowing the attacker to view arbitrary files on the system.
Tenable researchers discovered the flaws on July 31 and reported them to IBM on Aug. 18. IBM released the patches and an advisory disclosing the flaws on Monday. Threatpost has reached out to IBM for further comment.
In recent months, various IBM products have been found to have security vulnerabilities. In August, a shared-memory flaw was discovered in IBM’s next-gen data-management software that researchers said could lead to other threats — as demonstrated by a new proof-of-concept exploit for the bug.
And in April, four serious security vulnerabilities in the IBM Data Risk Manager (IDRM) were identified that can lead to unauthenticated remote code execution (RCE) as root in vulnerable versions, according to analysis – and a proof-of-concept exploit is available.
University Project Tracks Ransomware Attacks on Critical Infrastructure
13.9.20
Vulnerebility
Securityweek
A team at Temple University in Philadelphia has been tracking worldwide ransomware attacks on critical infrastructure, and anyone can request access to the data.
Work on this project, described as a repository of critical infrastructure ransomware attacks (CIRWA), started in September 2019. As of August 2020, the database includes over 680 records of ransomware attacks documented since November 2013.
The repository, offered for free as a Microsoft Excel file, stores information on incidents described by the media and cybersecurity companies.
The information includes the name of the targeted organization, the year the attack was launched, the date when the attack started, location of the targeted organization, the targeted sector, duration of the attack, the ransomware family that was used, the ransom amount, the payment method, whether the amount was paid, how much was paid, the source of the information, and related incidents. Based on the type of ransomware that was used, there are also links to the MITRE ATT&CK framework.
An analysis of the data currently shows that government facilities were the most targeted type of critical infrastructure — followed at a distance by education and healthcare — and Maze was the most common ransomware strain. It’s worth noting that the project tracks incidents affecting critical infrastructure as defined by the U.S. Department of Homeland Security.
The most commonly observed duration of a ransomware attack is one week or less, and the most commonly demanded ransom amount is $50,000 or less, but there are 13 known incidents where the attackers demanded more than $5 million.
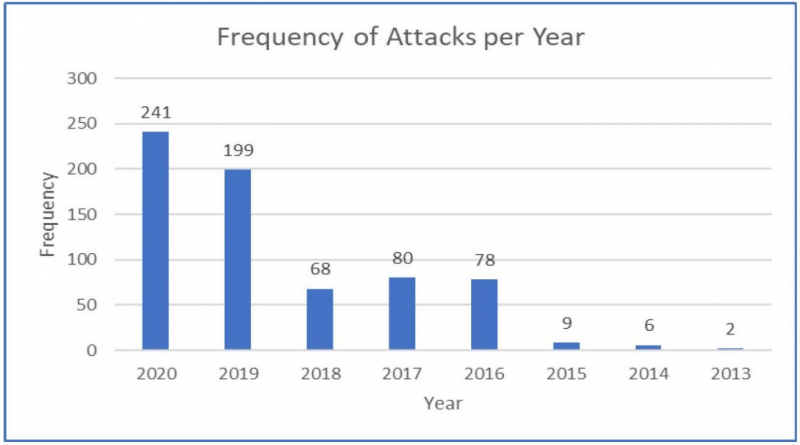
Ransomware attacks on critical infrastructure - click on the image for the full summary
Aunshul Rege, associate professor in the Department of Criminal Justice at Temple University, leads the project, which is funded by her National Science Foundation (NSF) CAREER award. One of the main contributors to the project is her graduate student, Rachel Bleiman, a PhD student in the university’s Criminal Justice program.
“We started with the goal of just providing a dataset based on open-source information on disclosed CIRW incidents,” Rege told SecurityWeek. “My team and I struggled to find datasets that are free/no strings attached in the [critical infrastructure] space, which could be used by researchers/educators (like myself) and also by students.”
She added, “This dataset was driven by the need to contribute to the education/academic space to help educators and students. My team and I were collecting data for my NSF CAREER grant anyway, so we decided to rehash it in a structured way to share with the academic community. We started the CIRW dataset in Sep 2019 with 162 incidents. Today we have 687 incidents!”
According to Rege, a lot of people have found the data useful. She says it has so far been requested by educators in higher education for class projects, research and publications; undergrad students for course projects; grad students for dissertation literature review; government representatives for ICS training classes, raising awareness, and assessing internal responses to critical infrastructure ransomware attacks; researchers for trends and patterns in TTPs across ransomware strains, comparing the data to their own internal datasets, and threat modeling and intelligence; and representatives of the private sector for training, threat intelligence, risk and statistical analysis, raising awareness, and overviewing current trends.
Anyone can request the data for free and Rege says they have approved nearly all the requests they’ve received to date.
“We do get some [requests] that are from personal email addresses (gmail, protonmail, etc), which we follow up on. Two other reasons why we want to keep track of who is using the dataset is so that we can (i) get feedback and (ii) potentially develop collaborative research projects,” Rege explained.
The maintainers of the project have been making improvements based on the feedback they have received from the community, such as mapping attacks to the MITRE ATT&CK framework.
It’s No ‘Giggle’: Managing Expectations for Vulnerability Disclosure
12.9.20
Vulnerebility
Threatpost
Vulnerability-disclosure
policies (VDPs), if done right, can help provide clarity and clear guidelines to
both bug-hunters and vendors when it comes to going public with security flaws.
Sometimes vulnerability disclosure goes well — and sometimes it doesn’t. Security researchers still face legal action for “hacking” when reporting the bugs they find — as is the case with a flaw recently reported to the Giggle social network. However — while the vendor-researcher relationship is still fraught with pitfalls, the good news is that things are slowly starting to get better, say experts.
Notably, the Giggle news (detailed below) comes as releases of vulnerability-disclosure policies (VDPs) have snowballed, with names like Facebook and the U.S. government embracing transparent guidelines for ethical bug-hunting.
In a blog post on Thursday, Saskia Coplans, a founder at a majority-female security firm called Digital Interruption (DI), described a disclosure effort in which the company reached out to Giggle about a privacy flaw. Giggle, which bills itself as a social network “for girls,” offers various female-specific topic areas and communities, including those for victims of abuse and for sex workers. The down side is, according to its privacy policy, Giggle collects all kinds of information about users, including geolocation, personal preferences, demographic data and answers to surveys.
That’s a problem given that the bug that DI found would allow unverified attackers to trivially access this personal information on the platform from anywhere. To boot, the researchers found that the information was still accessible/stored even after a user deleted an account. DI researchers understandably felt it was important to report the issue to prevent exploitation by abusers and others.
The public tweet that started the furor.
So they did just that, first reaching out via Twitter in a direct message to the company. When there was no response after two days, DI published a public tweet directing the company and its founder, Australian screenwriter Sall Grover, to the DM. The researchers also mentioned the company’s perceived anti-trans stance — Giggle uses facial recognition and AI to determine if a user is female or not, which is a “test” many trans women can’t pass — and that’s when the problems began.
“Our public tweet had no engagement at all until Sall, the Giggle founder, decided to share a screenshot of it with her followers. We have since been subject to a tirade of abuse,” according to the blog. “Our three-year incorporated company has been accused of being a creepy bloke who runs private WhatsApp groups full of naked women, a front for the alt-left, making up the vuln to discredit Sall and her company, and hypocrites for wanting to protect the data of users despite the app’s founder having views that counter our own.”
Coplans added that none of the responses mentioned the actual security issue itself.
DI went on to attempt contact nonetheless, but was blocked at every attempt — the firm also asked Troy Hunt of HaveIBeenPwned the to plead its case to the company. Eventually, someone at Giggle did fix the bug.
“No one reached out,” Jahmel Harris, a DI founder and security researcher, told Threatpost. “Even though we sent Sall/Giggle some details right at the start of this, we don’t know if these weren’t passed to the [development team] as Sall (the owner) didn’t seem to understand what I was saying. Based on a recent email with the dev, it sounds like he figured it out based on some of the Twitter noise. We were only able to send full details and a proof of concept after Troy Hunt had asked Sall on our behalf if she would allow us to email her, but by this point it sounded like it had been fixed.”
Giggle has also threatened DI with legal action –though it’s unclear what the allegations will be.
“They’ve claimed they’ve sent all communications to a lawyer and I believe it’s because we published a blog post, not for finding the vulnerability,” Harris said. “I should note that we only published after the issue was fixed.”
Threatpost has contacted Giggle and asked for comment, but as of press time,
there has been no response.
Noted vulnerability-disclosure expert and CEO at Luta Security, Katie
Moussouris, weighed in on Twitter, calling the disclosure experience the “worst
of the year.”
VDPs to the Fore
As the Giggle debacle demonstrates, researchers are still
being sued on occasion. Yet at the same time, this level of difficulty is a
rarity, according to DI’s Harris.
“Honestly…it’s becoming easier to report vulnerabilities to companies now that we have Katie Moussouris and companies like HackerOne and Bugcrowd putting in a lot of effort to protect security researchers,” he told Threatpost. “We’re always going to see companies act like this, but changes in the law can go a long way helping report issues and vulnerability-coordination and bug-bounty platforms will often act as a mediator. This is the first time we’ve had an experience as intense as this. Mostly companies that don’t have much experience with this will at least be thankful we’re disclosing privately. It’s easy to understand this can be a fairly scary experience for a company, but if there is a defined way to respond to security researchers or vuln hunters, it’s often a case of fixing the vuln, thanking them and moving on.”
To that end, Facebook, the State of Ohio, a top voting-machine vendor and the U.S. federal government have all embraced VDPs in recent days — showing that the ethical hacking landscape is indeed improving.
Threatpost Webinar Promo Bug Bounty
Click to Register
By way of definition, VDPs are the latest step for many in the evolution of the vendor-researcher relationship. The industry has seen the rise of bug-bounty programs that pay researchers for their work; and there have also been more safe-harbor policies put into place to protect researchers from legal action. And, responsible disclosure policies have rolled out at many organizations, meant to protect vendors and avoid the disclosure of flaws before there are patches available. A VDP collects all of these factors and more into a centralized, written policy on dealing with disclosures.
Illustrating this, last week, Facebook rolled out a VDP that clarifies how Facebook bug-hunters will deal with flaws that they find in third-party software and open-source projects. Specifically, the tech giant said that it will implement a 90-day policy between a bug being reported and going public. At the same time, Facebook-owned WhatsApp debuted a security disclosure page that will act as a central repository for any bugs found in that platform.
“Facebook’s VDP addresses vulnerabilities of third parties, which helps to normalize vulnerability disclosure,” security researcher and bug-hunter Mike Takahashi told Threatpost. “If those contacted are responsive, it should only benefit them to receive these reports. Inevitably there will be examples where organizations are not responsive or aren’t taking reasonable steps to fix the vulnerabilities. When this happens there will be growing pains from the ensuing chaos of publicly disclosed vulnerabilities without a fix in place. This will open the door for black-hat hackers to exploit a vulnerability which they may not have known about otherwise, but also gives organizations an opportunity to be proactive with their own mitigations before an official fix is released.”
There have also been recent moves around election infrastructure; in August, Ohio’s secretary of state issued a VDP to cover the state’s election-related websites, the first such move by a state; and, Election Systems & Software, the biggest vendor of U.S. voting equipment, issued a VDP last month covering ES&S’s corporate systems and public-facing websites (though not voting machines and other equipment that’s already deployed in the field).
“It’s becoming more mainstream and more tech companies are starting to understand this is just part of the ecosystem,” DI’s Harris said.
Meanwhile, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has mandated that federal agencies must implement VDPs by next March, which would give ethical hackers clear guidelines for submitting bugs found in government systems – and hopefully encourage more bug-hunting overall.
CISA’s announcement also drew praise from the bug-bounty community.
“The government is leaping ahead of much of corporate America…We will look back on this moment years from now to recognize it as a turning point in America’s fight for trustworthy technology.” Alex Rice, CTO and co-founder HackerOne, told Threatpost via email. “HackerOne believes that CISA’s Binding Operational Directive is a pivotal milestone in the mission to restore trust in digital democracy and protect the integrity of federal information systems. Every organization, especially those protecting sensitive information, should have a public-facing way to report potential security gaps. Collaboration with the hacker community provides a crucial advantage: having someone on your team who thinks like an attacker.”
Casey Ellis, CTO at ethical hacking platform Bugcrowd, added: “Those who have both the skills and altruistic interest to identify cyber-risk and improve the safety and security of the internet have been waiting patiently for the better part of 30 years [for acceptance], and our efforts to help have been met with varying responses.” In an August filing with CISA, he noted, “Up until five or six years years ago many of them were fearful, hostile and negative. The evolution of the information attack surface and the capabilities of our adversaries have caused a huge shift: The internet realized that all “hackers” aren’t burglars, many of them are actually locksmiths.”
VDPs in Context
While the VDP moves are net positives for cybersecurity, the
juxtaposition of VDP rollouts with Giggle issue shows that VDPs aren’t simply a
blanket golden ticket to a harmonious vendor-researcher relationship,
researchers noted. There are many things that can go wrong if the policy doesn’t
provide enough transparency and clarity.
For instance, less scrupulous researchers may publish details on a zero-day bug or even proof-of-concept exploits for unpatched issues without coordinating with a vendor, even if the vendor has a VDP and bounty program in place. Such was the case with SandBoxEscaper, who published a spate of zero-day exploits for Microsoft bugs in 2018 and 2019.
On the flip side, vendors may not respond to a report, leaving researchers in a tough situation. Some providers and vendors, like Giggle, don’t want to deal with the issue at all; but others may not provide full patches in a timely fashion. For instance, recently researchers disclosed bugs in Grandstream products for small- and medium-sized businesses even though the issues weren’t fully patched, after the firm’s 90-day disclosure window expired.
The Facebook VDP allows for a raft of exceptions to its 90-day window, including reserving the right to disclose a bug if a vendor doesn’t respond within 21 days of a report being filed.
“An issue that could be improved is vulnerability remediation speed; the industry standard is often 90 days from disclosure to being made public,” Charles Ragland, security engineer at Digital Shadows, told Threatpost. “There are many high-profile instances where patches either weren’t released or were barely released within this 90-day window. That’s a long time for an exploitable vulnerability to be exposed, and it’s likely that if one person figured it out, someone else will, too.”
Different researchers also may have different policies on the latter scenario, potentially leading to confusion as vendors juggle multiple reports from multiple parties with different timelines.
“Whether or not you have an official VDP, it can be a challenge is keeping up with outside reports,” Takahashi said. “This includes being responsive in communication with white-hat hackers and fixing any vulnerabilities. In the two years we’ve seen a huge increase in security issues in the news stemming from mismanagement of vulnerability disclosure. If vulnerability disclosures aren’t taken seriously, they can end up being very costly when they’re publicly disclosed.”
Vendors also need to balance many factors in developing and testing patches, according to Brian Gorenc, senior director of vulnerability research for Trend Micro and head of Zero Day Initiative (ZDI).
“Severity is one of those factors, and researcher may judge severity differently than the vendor,” he told Threatpost in an email interview. “Alternatively, there are times when vendors want to ignore or downplay certain reports and focus on developing new products. There needs to be more understanding on the process on both sides to prevent confusion – and that confusion leads to distrust and hard feelings.”
DI’s Harris also noted the true downsides if companies don’t embrace VDPs and other ethical-hacking measures.
“We understand people have great ideas and want to create applications to meet that need, but it can be very dangerous to move ahead with some of those ideas without getting proper security advice and support,” he told Threatpost. “If [Giggle] had been built with security in mind from the start, they could have still achieved what they wanted to do without putting vulnerable women in danger. Sall disregarded our report, putting the users of the application at risk and denied that a vulnerability was present without investigating. In our opinion, this is a breach of trust. By making it into a ‘fight’ between them and us, they actually encouraged others to look for the vulnerability. We wouldn’t be surprised if, unfortunately, it was exploited before it was fixed because of the way Sall and Giggle responded.”
Best Practices
Transparency with both the researcher and the public is a
crucial factor to minimizing distrust and making VDPs effective, and Gorenc
noted that there are industry best practices that should also be followed. These
are laid out in the ISO 29147 standard, which includes guidance for both filing
reports and receiving them. For instance: Providing clear boundaries for
security researchers in terms of ethical hacking; offering clarity on what is in
scope and what’s not; and specifying how long a researcher must wait before
disclosing publicly, even if there is no patch available.
“Having a well-defined vulnerability disclosure policy is definitely something every agency receiving bug reports should have,” Gorenc said, referring to the just-announced government mandate to implement VDPs at all agencies. “Let’s hope [CISA] follows the guidelines set out in ISO 29147 and establishes a robust program rather than just checking boxes to be in compliance.”
Getting companies interested in developing bug-bounty programs or even simply paying attention to independent researchers reaching out in good faith can still be difficult, Ragland noted, adding that “making the process difficult and obtuse burns people out and leads to more ignored vulnerabilities.”
Thus, independent bug-bounty programs – like those run by HackerOne, Bugcrowd or ZDI – can help vendors by providing them access to an established VDP and bounty program.
“Vendor-agnostic bug-bounty programs can serve as intermediaries and provide an honest broker for researcher and vendor alike,” Gorenc said. “For example, with our program, researchers know their report won’t be ignored. At the same time, vendors know a report from us won’t go public unless our 120-day timeline is disregarded.”
Overall, expectations need to improve – both for researchers and vendors – and appropriately structured VDPs can be a big key to that, he said.
“There are still too many ‘surprises’ in vulnerability disclosure,” Gorenc noted. “Researchers are surprised by a vendor’s response (or lack thereof), and vendors are surprised by a researcher’s disclosure. We as an industry have been doing disclosure long enough that there should be no surprises.”
WordPress Plugin Flaw Allows Attackers to Forge Emails
12.9.20
Vulnerebility
Threatpost
The high-severity flaw in the Email Subscribers & Newsletters plugin by Icegram affects more than 100,000 WordPress websites.
More than 100,000 WordPress websites are affected by a high-severity flaw in a plugin that assists websites in sending out emails and newsletters to subscribers.
The vulnerability exists in the Email Subscribers & Newsletters plugin by Icegram, which enables users to collect leads, send automated new blog post notification emails. A remote, unauthenticated attacker can exploit the flaw to send forged emails to all recipients from the available lists of contacts or subscribers – with complete control over the content and subject of the email.
To fix the flaw, users must “upgrade to WordPress Email Subscribers & Newsletters plugin by Icegram version 4.5.6 or higher,” according to researchers at Tenable, who discovered the flaw, in an advisory on Thursday.
Threatpost Webinar Promo Bug Bounty
Click to Register
The flaw (CVE-2020-5780 ) ranks 7.5 out of 10 on the CVSS scale, making it high severity. It affects versions 4.5.6 and earlier of the WordPress Email Subscribers & Newsletters plugin.
The issue stems from an email forgery/spoofing vulnerability in the class-es-newsletters.php class.
“Unauthenticated users are able to send an ajax request to the admin_init hook,” Alex Peña, research engineer at Tenable, told Threatpost. “This triggers a call to the process_broadcast_submission function.”
By manipulating the request parameters, Peña said an attacker could then schedule a new broadcast to an entire list of contacts, due to a lack of an authentication mechanism in place.
“An unauthenticated user should not be capable of creating a broadcast message,” he told Threatpost.
In a real-life attack scenario, an unauthenticated, remote attacker could first send a specially crafted request to a vulnerable WordPress server. The request would then schedule a new newsletter to be sent to an entire list of contacts, where the scheduled time, contact list, subject and content of the email being broadcast can be arbitrarily set by the attacker.
“This could be used to perform a phishing attack or scam, similar to the attack experienced by Twitter recently, where individuals of a particular organization’s mailing list are targeted,” Peña told Threatpost. “As the email would come from a trusted source, recipients are more likely to trust the communication and be convinced by its content.”
Researchers notified the plugin of the issue on Aug. 26; a patch was issued earlier this week, on Tuesday. Threatpost has reached out to Icegram for further comment.
Peña told Threatpost, researchers are not aware of the flaw being exploited in the wild to date.
WordPress plugins have been found to be riddled with flaws over the past month. Earlier in August, a plugin that is designed to add quizzes and surveys to WordPress websites patched two critical vulnerabilities. The flaws could be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites. Also in August, Newsletter, a WordPress plugin with more than 300,000 installations, was discovered to have a pair of vulnerabilities that could lead to code-execution and even site takeover.
And, researchers in July warned of a critical vulnerability in a WordPress plugin called Comments – wpDiscuz, which is installed on more than 70,000 websites. The flaw gave unauthenticated attackers the ability to upload arbitrary files (including PHP files) and ultimately execute remote code on vulnerable website servers.
Threat actors target WordPress sites using vulnerable File Manager install
12.9.20
Vulnerebility
Securityaffairs
Experts reported threat actors are increasingly targeting a recently addressed
vulnerability in the WordPress plugin File Manager.
Researchers from
WordPress security company Defiant observed a surge in the number of attacks
targeting a recently addressed vulnerability in the WordPress plugin File
Manager.
In early September, experts reported that hackers were actively exploiting a critical remote code execution vulnerability in the File Manager WordPress plugin that could be exploited by unauthenticated attackers to upload scripts and execute arbitrary code on WordPress sites running vulnerable versions of the plugin.
The File Manager plugin allows users to easily manage files directly from WordPress, it is currently installed on more than 700,000 WordPress sites.
The vulnerability was first discovered by Gonzalo Cruz from Arsys, the researcher also confirmed that threat actors are already exploiting the flaw to upload malicious PHP files onto vulnerable sites.
The vulnerability impacts all versions between 6.0 and 6.8 of the popular plugin.
The developers of the plugin have quickly patched the vulnerability with the release of versions 6.9.
Cruz shared his findings with WordPress security firm Wordfence and provided it a working proof of concept exploit for the flaw. The security firm confirmed the ongoing attack, its Web Application Firewall blocked over 450,000 exploit attempts during the last several days.
“The Wordfence firewall has blocked over 450,000 exploit attempts targeting this vulnerability over the past several days. We are seeing attackers attempting to inject random files, all of which appear to begin with the word “hard” or “x.”” Wordfence said.
“From our firewall attack data, it appears that attackers may be probing for the vulnerability with empty files and if successful, may attempt to inject a malicious file. Here is a list of some of the files we are seeing uploaded:
hardfork.php
hardfind.php
x.php”
Wordfence experts revealed that threat
actors were trying to upload PHP files with webshells hidden within images to
the wp-content/plugins/wp-file-manager/lib/files/ folder.
Now Wordfence researchers reveal that a few days after the vulnerability was
addressed with the release of a patch multiple threat actors started targeting
unpatched installs.
Over 1.7 million sites were targeted by hackers in a few
days, and the number of attacks reached 2.6 million as of September 10.
“We’ve seen evidence of multiple threat actors taking part in these attacks, including minor efforts by the threat actor previously responsible for attacking millions of sites, but two attackers have been the most successful in exploiting vulnerable sites, and at this time, both attackers are password protecting vulnerable copies of the connector.minimal.php file,” reads the analysis published by Wordfence.
According to the experts, the first threat actor observed targeting the vulnerability at scale is Moroccan attacker that goes online with the moniker “bajatax.” The threat actors modifies the vulnerable connector.minimal.php file to prevent further attacks, he was observed adding code to exfiltrate user credentials using the Telegram messenger’s API. The attackers added the malicious code to the WordPress core user.php file and, if WooCommerce is installed, two more files are modified to steal user credentials.
Experts also observed a second threat actor targeting vulnerable websites and protecting the connector.minimal.php file with a password to prevent other infections. This threat actor is using a consistent password across infections.
The attacker inserted two copies of the backdoor, with randomized filenames ending in _index.php, into the infected website, one in the webroot and the other in a randomized writable folder of the website. The attacker uses the backdoors to modify core WordPress files to add cryptominers and SEO spam to the vulnerable websites.
Experts monitored attacks originating from more than 370,000 separate IP addresses, with almost no overlaps between the IPs addresses involved in the attacks associated with the two most active attackers.
“If you or anyone you know has had a vulnerable version of the File Manager plugin installed, we urge you to scan your site for malware using a security solution such as Wordfence.” concludes the post. “If your site has been compromised by the “bajatax” threat actor, it is critical that you completely clean your site before contacting all of your users and advising them that their credentials may have been compromised, especially if you are running an e-commerce site.”
New Unpatched Bluetooth Flaw Lets Hackers Easily Target Nearby Devices
11.9.20
Vulnerebility
Thehackernews
Bluetooth SIG—an
organization that oversees the development of Bluetooth standards—today issued a
statement informing users and vendors of a newly reported unpatched
vulnerability that potentially affects hundreds of millions of devices
worldwide.
Discovered independently by two separate teams of academic
researchers, the flaw resides in the Cross-Transport Key Derivation (CTKD) of
devices supporting both — Basic Rate/Enhanced Data Rate (BR/EDR) and Bluetooth
Low Energy (BLE) standard.
Cross-Transport Key Derivation (CTKD) is a
Bluetooth component responsible for negotiating the authenticate keys when
pairing two Bluetooth devices together, also known as "dual-mode" devices.
Dubbed 'BLURtooth' and tracked as CVE-2020-15802, the flaw exposes devices
powered with Bluetooth 4.0 or 5.0 technology, allowing attackers to
unauthorizedly connect to a targeted nearby device by overwriting the
authenticated key or reducing the encryption key strength.
"Dual-mode devices
using CTKD to generate a Long Term Keys (LTK)or Link Key (LK) are able to
overwrite the original LTK or LK in cases where that transport was enforcing a
higher level of security," the researchers explain.
"Vulnerable devices must
permit a pairing or bonding to proceed transparently with no authentication, or
a weak key strength, on at least one of the BR/EDR or LE transports in order to
be susceptible to attack."
In other words, the flaw leverage ability under
specific implementations of the pairing process that could allow devices to
overwrite authorization keys when the transport enforces a higher level of
security.
According to an advisory published by Carnegie Mellon CERT
Coordination Center, the flaw can lead to several potential attacks, grouped as
'BLUR attacks,' including man-in-the-middle attack.
"If a device spoofing
another device's identity becomes paired or bonded on a transport and CTKD is
used to derive a key which then overwrites a pre-existing key of greater
strength or that was created using authentication, then access to authenticated
services may occur," Bluetooth SIG warned of the same.
"This may permit a Man
In The Middle (MITM) attack between devices previously bonded using
authenticated pairing when those peer devices are both vulnerable."
Besides
recommending to introduce restrictions on CTKD mandated in Bluetooth Core
Specification versions 5.1 and later as primary mitigation, Bluetooth SIG has
also started coordinates with affected device manufacturers to help them release
necessary patches rapidly.
"The Bluetooth SIG further recommends that devices
restrict when they are pairable on either transport to times when user
interaction places the device into a pairable mode or when the device has no
bonds or existing connections to a paired device," the researchers said.
Microsoft Announces Public Preview of Automatic VM Guest Patching in Azure
10.9.20
Vulnerebility
Securityweek
Microsoft this week announced the public preview of new functionality to automatically deliver security patches to Windows virtual machines in Azure.
Called automatic VM guest patching, the feature is meant to improve the update management of Windows VMs to ensure security compliance through the automatic delivery of necessary patches.
Should the new feature be enabled, periodic assessment of the VM is performed, to determine if any applicable security updates are available, and all those patches that are classified as critical or security are automatically downloaded and installed, the company explains.
The patching process is automatically performed monthly, when Microsoft releases new security fixes through the Windows Update mechanism. The updates are fetched and applied during off-peak hours, based on the VM's time zone, but only on VMs that are running.
According to Microsoft, patch orchestration is managed by Azure. Furthermore, the tech company says, all patches are delivered based on availability-first principles, within 30 days of the monthly release.
“Patch assessment and installation are automatic, and the process includes rebooting the VM as required,” the tech company says.
Automatic VM guest patching is compatible with all VM sizes and the health of the virtual machine is monitored to identify any patching failures.
“An opt-in procedure is needed to use the public preview functionality. This preview version is provided without a service level agreement, and is not recommended for production workloads. Certain features might not be supported or might have constrained capabilities,” Microsoft notes.
Only virtual machines with the Azure VM Agent installed are supported by the new feature. Furthermore, the Windows Update service must be running on the VM, which needs to be able to access Windows Update endpoints.
Specific details on how the patch installation process is orchestrated, on available patch orchestration modes, and on what OS images are supported can be found on this documentation page.
Intel Releases Firmware Updates to Patch Critical Vulnerability in AMT, ISM
10.9.20 Vulnerebility Securityweek
Intel this week released security patches to address a critical vulnerability in Active Management Technology (AMT) and Intel Standard Manageability (ISM).
The bug, which Intel calls improper buffer restrictions in network subsystems, could be abused by unauthorized users to escalate privileges via network access in provisioned AMT and ISM versions before 11.8.79, 11.12.79, 11.22.79, 12.0.68 and 14.0.39.
On un-provisioned systems, Intel reveals, an authenticated user may abuse the vulnerability to enable privilege escalation via local access.
Tracked as CVE-2020-8758, the security bug features a CVSS score of 9.8 for provisioned systems and a CVSS score of 7.8 on un-provisioned systems.
Intel also notes that firmware versions of AMT 3.x through 10.x are no longer supported and that they will not receive security updates to address the issue.
“Intel recommends that users of Intel AMT and Intel ISM update to the latest version provided by the system manufacturer that addresses these issues,” the chip maker says.
The company also announced the availability of patches for a potential security bug in the BIOS firmware for 8th, 9th and 10th generation Intel Core processors, which could lead to privilege escalation, denial of service, and/or information disclosure, provided that the attacker has physical access to an affected system.
Tracked as CVE-2020-0570, the flaw has a CVSS score of 7.6. The advisory for this issue also addresses a medium-severity information disclosure flaw in BIOS firmware for 8th Gen Intel Core processors and Intel Pentium Silver chips (CVE-2020-0571).
Security patches were released for three other medium-risk bugs in the BIOS firmware for 8th, 9th, and 10th Gen Core and Celeron 4000/5000 series processors, which could lead to elevation of privilege or denial of service (CVE-2020-8672 and CVE-2019-14557), or information disclosure (CVE-2020-8671).
Two low-severity flaws (CVE-2019-14558 and CVE-2019-14556) described in the same advisory could lead to denial of service.
Intel also announced a fix for a medium-severity flaw (CVE-2020-12302) in Intel Driver & Support Assistant before version 20.7.26.7, which could lead to privilege escalation via local access. Version 20.7.26.7 or later of Intel Driver & Support Assistant fix the vulnerability.
Microsoft Releases September 2020 Security Patches For 129 Flaws
9.9.20 Vulnerebility Thehackernews
As part of this month's Patch Tuesday, Microsoft today released a fresh batch of
security updates to fix a total of 129 newly discovered security vulnerabilities
affecting various versions of its Windows operating systems and related
software.
Of the 129 bugs spanning its various products — Microsoft Windows,
Edge browser, Internet Explorer, ChakraCore, SQL Server, Exchange Server,
Office, ASP.NET, OneDrive, Azure DevOps, Visual Studio, and Microsoft Dynamics —
that received new patches, 23 are listed as critical, 105 are important, and one
is moderate in severity.
Unlike the past few months, none of the security
vulnerabilities the tech giant patched in September are listed as being publicly
known or under active attack at the time of release or at least not in knowledge
of Microsoft.
A memory corruption vulnerability (CVE-2020-16875) in Microsoft
Exchange software is worth highlighting all the critical flaws. The exploitation
of this flaw could allow an attacker to run arbitrary code at the SYSTEM level
by sending a specially crafted email to a vulnerable Exchange Server.
"A
remote code execution vulnerability exists in Microsoft Exchange software when
the software fails to properly handle objects in memory," Microsoft explains.
"An attacker could then install programs; view, change, or delete data; or
create new accounts."
Microsoft also patched two critical remote code
execution flaws in Windows Codecs Library; both exist in the way that Microsoft
Windows Codecs Library handles objects in memory, but while one (CVE-2020-1129)
could be exploited to obtain information to compromise the user's system
further, the other (CVE-2020-1319) could be used to take control of the affected
system.
Besides these, two remote code execution flaws affect the on-premises
implementation of Microsoft Dynamics 365, but both require the attacker to be
authenticated.
Microsoft also patched six critical remote code execution
vulnerabilities in SharePoint and one in SharePoint Server. While exploiting the
vulnerability in SharePoint Server requires authentication, other flaws in
SharePoint do not.
Other critical flaws the tech giant patched this month
reside in Windows, Windows Media Audio Decoder, Windows Text Service Module,
Windows Camera Codec Pack, Visual Studio, Scripting Engine, Microsoft COM for
Windows, Microsoft Browser, and Graphics Device Interface.
Vulnerabilities
marked as important reside in Windows, Active Directory, Active Directory
Federation Services (ADFS), Internet Explorer Browser Helper, Jet Database
Engine, ASP.NET Core, Dynamics 365, Excel, Graphics Component, Office, Office
SharePoint, SharePoint Server, SharePoint, Word, OneDrive for Windows, Scripting
Engine, Visual Studio, Win32k, Windows Defender Application Control, Windows
DNS, and more.
Most of these vulnerabilities allow information disclosure,
the elevation of privilege, and cross-Site Scripting. Some also lead to remote
code execution attacks. In contrast, others allow security feature bypass,
spoofing, tampering, and denial of service attacks.
Windows users and system
administrators are highly advised to apply the latest security patches as soon
as possible to keep cybercriminals and hackers away from taking control of their
computers.
For installing security updates, head on to Settings → Update &
security → Windows Update → Check for updates or install the updates manually.
Expert found multiple critical issues in MoFi routers
8.9.20
Vulnerebility
Securityaffairs
Researchers found multiple vulnerabilities in MoFi Network routers, including
critical flaws that can be exploited to remotely hack a device.
The
researchers Rich Mirch from CRITICALSTART discovered ten vulnerabilities
MOFI4500 MoFi Network routers. The expert reported the issues to the vendor in
May but some of the flaws have yet to be patched.
Most of the flaws affect the web management interface, some of the vulnerabilities can be exploited by an unauthenticated, remote attacker with access to the web interface to take over the targeted router.
Some of the issues are related to the presence of hardcoded credentials or the use of weak credentials. Probably the most interesting vulnerability is an undocumented backdoor, tracked as CVE-2020-15835, that can be exploited by attackers to gain root access to a router.
“The authentication function contains undocumented code which provides the ability to authenticate as root without having to know the actual root password. An adversary with the private key can remotely authenticate to the management interface as root.” reads the advisory published by the expert. “Technical details are not included at this time because the vendor has not released a patch and disclosing this would provide enough details for the unpatched CVE-2020-15836 Unauthenticated Command Injection.”
The researcher also discovered another undocumented backdoor that resides in the poof.cgi script which can be exploited by an attacker with the private key to reboot the device. An adversary with the private key can remotely reboot the device without having to know the root password.
The vendor has addressed multiple critical vulnerabilities, but in some cases, the proposed fixes introduced other security issues.
“Multiple critical vulnerabilities have been discovered in the MoFi4500 router, an OpenWRT based wireless router that provides Internet access via LTE. The initial vulnerabilities were reported to the vendor and patches were made available however new critical vulnerabilities were subsequently introduced as a result.” continues the report. “Several firmware versions have been released, but some of the vulnerabilities have not been fully patched.”
The vendor has released roughly 10 firmware updates since the vulnerabilities have been reported.
On June 25, Mirch found 14,382 MoFi routers that were exposing their management interface online using the Shodan search engine.
At the time of writing, the number of exposed devices dropped to roughly 6,610.
New PIN Verification Bypass Flaw Affects Visa Contactless Payments
8.9.20
Vulnerebility
Thehackernews
Even as Visa issued a
warning about a new JavaScript web skimmer known as Baka, cybersecurity
researchers have uncovered an authentication flaw in the company's EMV enabled
payment cards that permits cybercriminals to obtain funds and defraud
cardholders as well as merchants illicitly.
The research, published by a
group of academics from the ETH Zurich, is a PIN bypass attack that allows the
adversaries to leverage a victim's stolen or lost credit card for making
high-value purchases without knowledge of the card's PIN, and even trick a point
of sale (PoS) terminal into accepting an unauthentic offline card transaction.
All modern contactless cards that make use of the Visa protocol, including Visa
Credit, Visa Debit, Visa Electron, and V Pay cards, are affected by the security
flaw, but the researchers posited it could apply to EMV protocols implemented by
Discover and UnionPay as well. The loophole, however, doesn't impact Mastercard,
American Express, and JCB.
The findings will be presented at the 42nd IEEE
Symposium on Security and Privacy to be held in San Francisco next May.
Modifying Card Transaction Qualifiers Via MitM Attack
EMV (short for Europay,
Mastercard, and Visa), the widely used international protocol standard for
smartcard payment, necessitates that larger amounts can only be debited from
credit cards with a PIN code.
But the setup devised by ETH researchers exploits a critical flaw in the
protocol to mount a man-in-the-middle (MitM) attack via an Android app that
"instructs the terminal that PIN verification is not required because the
cardholder verification was performed on the consumer's device."
The issue
stems from the fact the Cardholder verification method (CVM), which is used to
verify whether an individual attempting a transaction with a credit or debit
card is the legitimate cardholder, is not cryptographically protected from
modification.
As a result, the Card Transaction Qualifiers (CTQ) used to determine what CVM
check, if any, is required for the transaction can be modified to inform the PoS
terminal to override the PIN verification and that the verification was carried
out using the cardholder's device such as a smartwatch or smartphone (called
Consumer Device Cardholder Verification Method or CDCVM).
Exploiting Offline
Transactions Without Being Charged
Furthermore, the researchers uncovered a
second vulnerability, which involves offline contactless transactions carried
out by either a Visa or an old Mastercard card, allowing the attacker to alter a
specific piece of data called "Application Cryptogram" (AC) before it is
delivered to the terminal.
Offline cards are typically used to directly pay
for goods and services from a cardholder's bank account without requiring a PIN
number. But since these transactions are not connected to an online system,
there is a delay of 24 to 72 hours before the bank confirms the transaction's
legitimacy using the cryptogram, and the amount of the purchase is debited from
the account.
A criminal can leverage this delayed processing mechanism to use
their card to complete a low-value and offline transaction without being
charged, in addition to making away with purchases by the time the issuing bank
declines the transaction due to the wrong cryptogram.
"This constitutes a
'free lunch' attack in that the criminal can purchase low-value goods or
services without actually being charged at all," the researchers said, adding
the low-value nature of these transactions is unlikely to be an "attractive
business model for criminals."
Mitigating PIN bypass and offline attacks
Aside from notifying Visa of the flaws, the researchers have also proposed three
software fixes to the protocol to prevent PIN bypass and offline attacks,
including using Dynamic Data Authentication (DDA) to secure high-value online
transactions and requiring the use of online cryptogram in all PoS terminals,
which causes offline transactions to be processed online.
"Our attack
show[ed] that the PIN is useless for Visa contactless transactions [and]
revealed surprising differences between the security of the contactless payment
protocols of Mastercard and Visa, showing that Mastercard is more secure than
Visa," the researchers concluded. "These flaws violate fundamental security
properties such as authentication and other guarantees about accepted
transactions."
Operation PowerFall: CVE-2020-0986 and variants
3.9.20
Vulnerebility
Securityaffairs
In August 2020, we
published a blog post about Operation PowerFall. This targeted attack consisted
of two zero-day exploits: a remote code execution exploit for Internet Explorer
11 and an elevation of privilege exploit targeting the latest builds of Windows
10. While we already described the exploit for Internet Explorer in the original
blog post, we also promised to share more details about the elevation of
privilege exploit in a follow-up post. Let’s take a look at vulnerability
CVE-2020-0986, how it was exploited by attackers, how it was fixed and what
additional mitigations were implemented to complicate exploitation of many other
similar vulnerabilities.
CVE-2020-0986
CVE-2020-0986 is an arbitrary pointer dereference vulnerability
in GDI Print/Print Spooler API. By using this vulnerability it is possible to
manipulate the memory of the splwow64.exe process to achieve execution of
arbitrary code in the process and escape the Internet Explorer 11 sandbox
because splwow64.exe is running with medium integrity level. “Print driver host
for applications,” as Microsoft describes splwow64.exe, is a relatively small
binary that hosts 64-bit user-mode printer drivers and implements the Local
Procedure Call (LPC) server that can be used by other processes to access
printing functions. This allows the use of 64-bit printer drivers from 32-bit
processes. Below I provide the code that can be used to spawn splwow64.exe and
connect to splwow64.exe’s LPC server.
When the LPC message is received, it is processed by the function
TLPCMgr::ProcessRequest(PROXY_MSG *). This function takes LpcRequest as a
parameter and verifies it. After that it allocates a buffer for the printer
command and copies it there from shared memory. The printer command function
INDEX, which is used to identify different driver functions, is stored as a
double word at offset 4 in the printer command structure. Almost a complete list
of different function INDEX values can be found in the header file winddi.h.
This header file includes different INDEX values from INDEX_DrvEnablePDEV (0) up
to INDEX_LAST (103), but the full list of INDEX values does not end there.
Analysis of gdi32full.dll reveals that that are a number of special INDEX values
and some of them are provided in the table below (to find them in binary, look
for calls to PROXYPORT::SendRequest).
GdiPrinterThunk itself is a very large
function that processes more than 60 different function INDEX values, and the
handler for one of them – namely INDEX_DocumentEvent – contains vulnerability
CVE-2020-0986. The handler for INDEX_DocumentEvent will use information provided
in the printer command (fully controllable from the LPC client) to check that
the command is intended for a printer with a valid handle. After the check it
will use the function DecodePointer to decode the pointer of the function stored
at the fpDocumentEvent global variable (located in .data segment), then use the
decoded pointer to execute the function, and finally perform a call to memcpy()
where source, destination and size arguments are obtained from the printer
command and are fully controllable by the attacker.
Exploitation
In Windows OS the base addresses of system DLL libraries are
randomized with each boot, aiding exploitation of this vulnerability. The
exploit loads the libraries gdi32full.dll and winspool.drv, and then obtains the
offset of the fpDocumentEvent pointer from gdi32full.dll and the address of the
DocumentEvent function from winspool.drv. After that the exploit performs a
number of LPC requests with specially crafted INDEX_DocumentEvent commands to
leak the value of the fpDocumentEvent pointer. The value of the raw pointer is
protected using EncodePointer protection, but the function pointed to by this
raw pointer is executed each time the INDEX_DocumentEvent command is sent and
the arguments of this function are fully controllable. All this makes the
fpDocumentEvent pointer the best candidate for an overwrite. A necessary step
for exploitation is to encode our own pointer in such a manner that it will be
properly decoded by the function DecodePointer. Since we have the value of the
encoded pointer and the value of the decoded pointer (address of the
DocumentEvent function from winspool.drv), we are able to calculate the secret
constant used for pointer encoding and then use it to encode our own pointer.
The necessary calculations are provided below.
At this stage, in order to
achieve code execution from the splwow64.exe process, it’s sufficient to
overwrite the fpDocumentEvent pointer with the encoded pointer of function
LoadLibraryA and provide the name of a library to load in the next LPC request
with the INDEX_DocumentEvent command.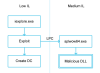
Overview of attack
CVE-2019-0880
Analysis of CVE-2020-0986 reveals that this vulnerability is
the twin brother of the previously discovered CVE-2019-0880. The write-up for
CVE-2019-0880 is available here. It’s another vulnerability that was exploited
as an in-the-wild zero-day. CVE-2019-0880 is just another fully controllable
call to memcpy() in the same GdiPrinterThunk function, just a few lines of code
away in a handler of function INDEX 118. It seems hard to believe that the
developers didn’t notice the existence of a variant for this vulnerability, so
why was CVE-2020-0986 not patched back then and why did it take so long to fix
it? It may not be obvious on first glance, but GdiPrinterThunk is totally
broken. Even fixing a couple of calls to memcpy doesn’t really help.
Arbitrary pointer dereference host for applications
The problem lies in the
fact that almost every function INDEX in GdiPrinterThunk is susceptible to a
potential arbitrary pointer dereference vulnerability. Let’s take a look again
at the format of the LPC request message.
InputBuf and OutputBuf are both
pointers that should point to a shared memory region. InputBuf points to a
location where the printer command is prepared, and when this command is
processed by GdiPrinterThunk the result might be written back to the LPC client
using the pointer that was provided as OutputBuf. Many handlers for different
INDEX values provide data to the LPC client, but the problem is that the
pointers InputBuf and OutputBuf are fully controllable from the LPC client and
manipulation of the OutputBuf pointer can lead to an overwrite of splwow64.exe’s
process memory.
How it was mitigated
Microsoft fixed CVE-2020-0986, but also implemented a
mitigation aimed to make exploitation of OutputBuf vulnerabilities as hard as
possible. Before the patch the function FindPrinterHandle() blindly trusted the
data provided through the printer command in an LPC request and it was easy to
bypass a valid handle check. After the patch the format of the printer command
was changed so it no longer contains the address of the handle table, but
instead contains a valid driver ID (quad word at offset 0x18). Now the linked
list of handle tables is stored inside the splwow64.exe process and the new
function FindDriverForCookie() uses the provided driver ID to get a handle table
securely. For a printer command to be processed it should contain a valid
printer handle (quad word at offset 0x20). The printer handle consists of
process ID and the address of the buffer allocated for the printer driver. It is
possible to guess some bytes of the printer handle, but a successful real-world
brute-force attack on this implementation seems to be unlikely. So, it’s safe to
assume that this bug class was properly mitigated. However, there are still a
couple of places in the code where it is possible to write a 0 for the address
provided as OutputBuf without a handle check, but exploitation in such a
scenario doesn’t appear to be feasible.
MAGMI Magento plugin flaw allows remote code execution on a vulnerable site
3.9.20
Vulnerebility
Securityaffairs
Researchers discovered multiple vulnerabilities in the MAGMI Magento plugin that
could lead to remote code execution on a vulnerable Magento site.
Tenable
published a research advisory for two vulnerabilities impacting the Magento Mass
Import (MAGMI) plugin. The flaws were discovered by Enguerran Gillier of the
Tenable Web Application Security Team.
MAGMI is a Magento database client written in PHP, which allows to perform raw bulk operations on the models of an online store.

In May, the FBI publicly issued a flash alert to warn of attacks in the wild
exploiting a cross-site scripting vulnerability in MAGMI Magento plugin, tracked
as CVE-2017-7391, to target vulnerable Magento sites.
Tenable researchers
investigated the issues and discovered that the developers of the plugin have
yet to address a cross-site request forgery (CSRF) vulnerability present in the
Magmi plugin. The developers only addressed one of the vulnerabilities recently.
An attacker can exploit the vulnerability to execute arbitrary code on servers running a website using the Magmi Magento plugin, he could trigger the flaw by tricking authenticated administrators into clicking a malicious link.
“CVE-2020-5776 is a cross-site request forgery (CSRF) vulnerability in MAGMI for Magento. This flaw exists because the GET and POST endpoints for MAGMI don’t implement CSRF protection, such as random CSRF tokens. An attacker could exploit this vulnerability to perform a CSRF attack by tricking a Magento Administrator into clicking on a link while they are authenticated to MAGMI.” reads the advisory published by Tenable. “The attacker could hijack the administrator’s sessions, allowing them to execute arbitrary code on the server where MAGMI is hosted.”
Tenable released a proof-of-concept code for the vulnerability on its official GitHub repository.
The Magmi Magento plugin is also affected by an authentication bypass that could
be exploited by attackers to use default credentials when the connection to the
Magento database fails.
This second flaw, tracked as CVE-2020-5777, can be
exploited by forcing a denial-of-service (DoS) condition to the Magento database
connection.
“CVE-2020-5777 is an authentication bypass vulnerability in MAGMI for Magento version 0.7.23 and below due to the presence of a fallback mechanism using default credentials.” continues the advisory. “MAGMI uses HTTP Basic authentication and checks the username and password against the Magento database’s admin_user table. If the connection to the Magento database fails, MAGMI will accept default credentials, which are magmi:magmi. As a consequence, an attacker could force the database connection to fail due to a database denial of service (DB- DoS) attack, then authenticate to MAGMI using the default credentials.”
Experts were able to trigger a DoS condition when the maximum number of MySQL connections was larger than the maximum number of concurrent HTTP connections accepted by the server.
“By sending a large number of concurrent connection requests that exceed the MySQL connections limit, but not the maximum Apache HTTP connection limit, attackers could temporarily block access to the Magento database and simultaneously make an authenticated request to MAGMI using the default credentials” – Enguerran Gillier
Experts released a PoC exploit code for this vulnerability, too.
Tenable
reported the flaws to the Magmi development team on June 3, they acknowledged
the issues on July 6 and released a new version of the plugin on August 30.
Unfortunately, the new release only addressed the authentication bypass flaw.
Cisco addresses critical code execution flaw in Cisco Jabber for Windows
3.9.20
Vulnerebility
Securityaffairs
Cisco addressed a critical remote code execution vulnerability affecting
multiple versions of its Cisco Jabber for Windows operating system.
Cisco has
addressed a critical severity remote code execution flaw, tracked as
CVE-2020-3495, that affects multiple versions of Cisco Jabber for Windows.
Cisco Jabber for Windows is a desktop collaboration client that integrates users with presence, audion, video and web conferencing, instant messaging (IM), cloud messaging, and desktop sharing.
The vulnerability was discovered by the security researchers Olav Sortland Thoresen from Watchcom.
The CVE-2020-3495 flaw is caused by the improper input validation of incoming messages’ contents, it could be exploited by an authenticated, remote attacker to execute arbitrary code with the privileges of the user account that is running the Cisco Jabber client software.
“The vulnerability is due to improper validation of message contents. An attacker could exploit this vulnerability by sending specially crafted Extensible Messaging and Presence Protocol (XMPP) messages to the affected software.” reads the security advisory published by Cisco. “A successful exploit could allow the attacker to cause the application to execute arbitrary programs on the targeted system with the privileges of the user account that is running the Cisco Jabber client software, possibly resulting in arbitrary code execution.”
An authenticated, remote attacker can exploit the flaw by sending specially-crafted Extensible Messaging and Presence Protocol (XMPP) messages to vulnerable devices.
The CVE-2020-3495 flaw can be also exploited when the Jabber for Windows client is running in the background, in any case no user interaction is required to trigger the issue.
“To exploit this vulnerability, an attacker must be able to send XMPP messages
to end-user systems running Cisco Jabber for Windows. Attackers may require
access to the same XMPP domain or another method of access to be able to send
messages to clients.” continues the advisory.
“As a result of exploitation,
an attacker could cause the application to run an arbitrary executable that
already exists within the local file path of the application.” “The executable
would run on the end-user system with the privileges of the user who initiated
the Cisco Jabber client application.”
According to the advisory, systems using Cisco Jabber in phone-only mode without XMPP messaging services enabled are not vulnerable to attacks exploiting this issue. Cisco also added that the vulnerability is not exploitable when Cisco Jabber is configured to use messaging services other than XMPP messaging.
The vulnerability affects all currently supported versions of the Windows Cisco Jabber client (12.1 to 12.9).
The Cisco Product Security Incident Response Team (PSIRT) confirmed that it is not aware of attacks in the wild exploiting the vulnerability.
According to Thoresen the vulnerability is warmable and its exploitation could be automated.
“The most severe vulnerability is also wormable, meaning that it can be used to automatically spread malware without any user interaction.” reads the analysis published by the expert.
“Since Cisco Jabber supports file transfers, an attacker can initiate a file transfer containing a malicious .exe file and force the victim to accept it using an XSS attack. The attacker can then trigger a call to window.CallCppFunction, causing the malicious file to be executed on the victim´s machine.”
Cisco Says Hackers Targeting Zero-Days in Carrier-Grade Routers
2.9.20 Vulnerebility Securityweek
Cisco has warned that hackers are targeting not one, but two unpatched vulnerabilities in the DVMRP feature of IOS XR software that runs on many carrier-grade routers.
Over the weekend, the company published an advisory to warn of active attacks targeting a security flaw (CVE-2020-3566) in the Distance Vector Multicast Routing Protocol (DVMRP) feature of IOS XR to cause memory exhaustion denial of service (DoS).
On Monday, the tech giant has updated the advisory to add another CVE to it, namely CVE-2020-3569, which impacts the very same feature and has similar consequences.
Both issues, the company reveals, can be exploited remotely, by an unauthenticated attacker, by sending crafted IGMP traffic to a vulnerable device.
The bugs exist because there is insufficient queue management for Internet Group Management Protocol (IGMP) packets.
According to the company, all Cisco devices that are running any release of IOS XR software are affected, provided that an active interface is configured under multicast routing. Impacted devices include: ASR 9000, NCS 5500, 8000, as well as NCS 540 & 560 series routers.
Cisco has shared information on mitigation steps organizations can take to limit exposure, but has yet to release software updates to address these vulnerabilities.
No workarounds to address the two issues have been detailed yet, but Cisco has published indicators of compromise to help administrators determine whether attackers are exploiting the vulnerabilities in their devices.
Attackers Actively Targeting Cisco IOS XR Vulnerability
1.9.20 Attack Vulnerebility Securityweek
Cisco over the weekend published information on a vulnerability (CVE-2020-3566) in the IOS XR software that could be exploited to cause a denial of service condition.
Cisco has warned that attackers are already attempting to exploit the vulnerability.
The issue resides in the Distance Vector Multicast Routing Protocol (DVMRP) feature of IOS XR. Remote exploitation is possible without authentication, and could result in exhausted process memory and instability of other processes, including those of interior and exterior routing protocols.
According to Cisco, the vulnerability exists due to insufficient queue management for Internet Group Management Protocol (IGMP) packets. As a result, an attacker could send crafted IGMP traffic to a vulnerable device to exploit the flaw.
“This vulnerability affects any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing,” the company says.
Cisco explains that administrators can use the show igmp interface command to determine whether multicast routing is enabled, and the show igmp traffic command to determine whether the device is receiving DVMRP traffic.
“This vulnerability results in memory exhaustion, which can impact other processes on the device. It is possible to recover the memory consumed by the IGMP process by restarting the IGMP process with the process restart igmp command,” the company notes.
There are no workarounds to address the issue, but Cisco has published information on various mitigations that customers can apply to remain protected.
Mitigation steps for the vulnerabilities include implementing a rate limiter for the IGMP traffic, which increases the time needed for a successful exploitation, along with implementing an access control entry (ACE) to an existing interface access control list (ACL).
Tracked as CVE-2020-3566, the flaw has a CVSS score of 8.6. Cisco reveals that attackers are already attempting to exploit the vulnerability.
Multiple iterations of ASR 9000 series aggregation services routers and IOS XR are affected. Cisco will release a software update to patch the bug but did not provide a timeframe for when that might happen.
Microsoft fixes code execution, privilege escalation in Microsoft Azure Sphere
27.8.20
Vulnerebility
Securityaffairs
Microsoft addressed vulnerabilities in Microsoft Azure Sphere that could lead to
the execution of arbitrary code or to the elevation of privileges.
Microsoft
has recently addressed some vulnerabilities impacting Microsoft Azure Sphere
that could be exploited by attackers to execute arbitrary code or to elevate
privileges.
Azure Sphere OS adds layers of protection and ongoing security updates to create
a trustworthy platform for new IoT experiences.
The cloud-based system on a
chip (SoC) leverages a hardware platform composed of several ARM cores, Azure
Sphere OS (custom, Linux-based OS), and the Azure Sphere Security Service.
Researchers from Cisco Talos reported four vulnerabilities in Azure Sphere, two of which could lead to the execution of unsigned code, and two leading to privilege escalation.
The two code execution vulnerabilities exist in the normal world’s signed code execution functionality of Azure Sphere 20.07.
“A code execution vulnerability exists in the normal world’s signed code
execution functionality of Microsoft Azure Sphere 20.07. A specially crafted
shellcode can cause a process’ heap to become executable after having been
writable. An attacker can execute a shellcode that sets the READ_IMPLIES_EXEC
personality to trigger this vulnerability.” reads the advisory published by
Talos.
The first of two issues reside in the Normal World application
READ_IMPLIES_EXEC personality that can be exploited through specially crafted
shellcode that would cause a process’ heap to become executable. The
vulnerability affects version 20.07 of Azure Sphere.
The second issue of them was found in /proc/thread-self/mem and can be exploited via specially crafted shellcode designed to cause a process’ non-writable memory to be written to. An attacker could supply shellcode specifically designed to modify the program and trigger the vulnerability.
The third issue is a privilege escalation flaw that resides in the Capability access control functionality of Microsoft Azure Sphere 20.06. An attacker can write a shellcode that includes a set of specially crafted ptrace syscalls to trigger the issue and elevate privileges.
The second elevation of privilege issue resides in the uid_map functionality of Azure Sphere 20.06 and can be exploited using a specially crafted uid_map file.
“A privilege escalation vulnerability exists in the uid_map functionality of Microsoft Azure Sphere 20.06. A specially crafted uid_map file can cause multiple applications to get the same UID assigned, thus broadening the attack surface. An attacker can modify the uid_map file to trigger this vulnerability.” states the advisory.
These vulnerabilities were discovered in version 20.06.
Microsoft has published a blog post detailing Azure Sphere 20.08 Security Updates, which includes the fixes for the above issues.
Vulnerabilities Expose Popular DVB-T2 Set-Top Boxes to Botnets: Researchers
27.8.20
BotNet Vulnerebility
Securityweek
Avast security researchers have identified vulnerabilities in DVB-T2 devices that could allow attackers to ensnare them in botnets.
An extension of the DVB consortium standard for the broadcast transmission of digital terrestrial television, DVB-T2 (Digital Video Broadcasting — Second Generation Terrestrial) can transmit compressed digital audio, video, and other data.
There is a push for the adoption of DVB-T2, following the European Union’s decision to auction the 700 MHz band to telecommunications operators, but, given that not all TVs support the new standard, set-top boxes that support it are required.
Many such set-top boxes are primitive, consisting of a TV tuner and an output device, some packing Internet support, and many are highly insecure, Avast’s security researchers reveal.
Analysis of two popular devices, namely Thomson THT741FTA and Philips DTR3502BFTA, revealed a series of vulnerabilities that could be exploited to inject malware and create botnets of set-top boxes.
One of the first discoveries the security researchers made was the lack of Telnet protections, with the device allowing them to connect without prompting for a login. Furthermore, the devices allowed for the transmission of data over FTP, courtesy of ftpput and ftpget.
The boxes were found to use the MIPS architecture and run Linux kernel 3.10.23, which stopped receiving support in November 2017.
The researchers also discovered that they could tamper with the content displayed to the user through weather and RSS feed applications on the device, due to the use of unencrypted communication. Both MiTM and DNS hijack attacks can be used for that, they say.
“Consequently, intruders could show a user a ransomware message telling them their TV has been hijacked and demanding a ransom to free the device,” Avast notes.
Furthermore, the researchers discovered that it was possible to move the DNS hijack attack to the device, and that persistent storage on the device was also available, which could essentially allow an attacker to store malware payloads or other tools, thus persisting through reboots and resets.
“And as a bonus, when we added something to /config and performed a factory-reset, the files remained. So even if a user performed a factory reset, the files added to this directory would be left untouched,” Avast explains.
On top of that, the security researchers discovered that the firmware has a wget utility built-in, which allows for the fetching of data from HTTP servers, meaning that adversaries could easily download malicious binaries within the telnet session.
The researchers successfully downloaded a Mirai version onto the set-top box, which, they discovered, closed the telnet daemon, thus preventing other malware from infecting the same device, and started scanning the Internet for additional devices to infect.
“Do not use your set-top box’s network functionality unless it’s absolutely necessary. You are probably better off checking the weather forecast or news on your phone,” Avast notes.
Users are advised to scan their devices for open ports, in the event they do want to connect the device to the network, disable Universal Plug and Play (UPnP) if it is enabled, and check port forwarding configuration and disable it unless absolutely necessary.
Two CVE identifiers were issued for the discovered vulnerabilities, namely CVE-2020-11617, which impacts the RSS application on Thomson THT741FTA 2.2.1 and Philips DTR3502BFTA DVB-T2 2.2.1 set-top boxes, and CVE-2020-116180, for the telnet services hardcoded to start on boot, on both devices.
The researchers contacted the affected vendors, but the issues remain unpatched. While Philips did respond, it said that the subcontractor it uses for new set-top boxes won’t fix the vulnerabilities, and Thomson never replied, the researchers say.
“It is unfortunate that companies continue to push products to the market with no intention of releasing firmware updates and no way for the average customer to secure their box, which in this case is simply disabling Telnet and updating the RSS/Weather apps to use TLS. This negligence affects customers who either cannot afford a new TV or see no need to replace a TV that’s in perfect working order,” Avast concludes.
Cisco Patches ‘High-Severity’ Bugs Impacting Switches, Fibre Storage
27.8.20 Vulnerebility Threatpost
Nine bugs were patched, eight of which are rated ‘high’ severity.
Cisco Systems disclosed eight high-severity bugs impacting a range of its networking gear, including its switches and fiber storage solutions. Cisco’s NX-OS was hardest hit, with six security alerts tied to the network operating system that underpins the networking giant’s Nexus-series Ethernet switches and MDS-series Fibre Channel storage area network switches.
Patches are available for all vulnerabilities, according to a Cisco Security Advisory posted on Wednesday. In addition to the eight patched high-severity bugs, Cisco also fixed a flaw (CVE-2020-3504) listed as medium severity that impacts the Cisco Unified Computing System management software.
High-severity vulnerabilities impacting Cisco’s NX-OS software include CVEs
tracked as CVE-2020-3397, CVE-2020-3398, CVE-2020-3338, CVE-2020-3415,
CVE-2020-3517 and CVE-2020-3454.
Two bugs (CVE-2020-3397 and CVE-2020-3398)
are “Cisco NX-OS software Border Gateway Protocol Multicast VPN denial of
service vulnerabilities,” according to the security bulletin. Both
vulnerabilities allow an attacker to launch either a partial or prolonged DoS
attack via session resets and device reloading.
“The vulnerability is due to incomplete input validation of a specific type of BGP MVPN update message. An attacker could exploit this vulnerability by sending this specific, valid BGP MVPN update message to a targeted device,” wrote Cisco regarding CVE-2020-3397. The other VPN bug is due to incorrect parsing of a specific type of BGP MVPN update message.
Cisco also reported a bug (CVE-2020-3338) in the context of its NX-OS software underlying its IPv6 Protocol Independent Multicast (PIM). “PIMs are used between switches so that they can track which multicast packets to forward to each other and to their directly connected LANs,” according to Cisco.
The vulnerability allows an unauthenticated, remote attacker to cause a denial-of-service (DoS) condition on an affected device, Cisco said. Vulnerable are Nexus 3000 Series Switches (CSCvr91853), Nexus 7000 Series Switches (CSCvr97684) and Nexus 9000 Series Switches in standalone NX-OS mode (CSCvr91853).
One of the more interesting of the patched bugs is the NX-OS software Call Home command injection bug could allow an authenticated, remote attacker to inject arbitrary commands that could be executed with root privileges on the underlying operating system.
“The vulnerability is due to insufficient input validation of specific Call Home configuration parameters when the software is configured for transport method HTTP. An attacker could exploit this vulnerability by modifying parameters within the Call Home configuration on an affected device,” Cisco warned.
Impacted are nine Cisco switches ranging from MDS 9000 Series Multilayer Switches to the Nexus 9500 R-Series Switching Platform.
Microsoft Patches Code Execution, Privilege Escalation Flaws in Azure Sphere
26.8.20
Vulnerebility
Securityweek
Recently addressed Microsoft Azure Sphere vulnerabilities could lead to the execution of arbitrary code or to elevation of privileges, Cisco Talos’ researchers warn.
The cloud-based system on a chip (SoC) platform was designed for Internet of Things (IoT) security, and is comprised of a hardware platform (several ARM cores, each with a different role), Azure Sphere OS (custom, Linux-based OS), and the Azure Sphere Security Service (for continuous security).
Talos’ security researchers discovered a total of four vulnerabilities in Azure Sphere, two of which could lead to the execution of unsigned code, and two leading to privilege escalation. All bugs were addressed, although no CVEs were issued.
According to Talos, both of the code execution flaws affect “the normal world’s signed code execution functionality of Microsoft Azure Sphere.”
The first of them resides in the Normal World application READ_IMPLIES_EXEC personality and can be triggered through specially crafted shellcode that would cause a process’ writable heap to become executable.
The second of them was found in /proc/thread-self/mem and can be exploited via specially crafted shellcode designed to cause a process' non-writable memory to be written to. Thus, the attacker could supply shellcode designed to modify the program and trigger the bug.
Cisco Talos’ security researchers discovered a privilege escalation issue in the Capability access control functionality and reveal that an attacker could leverage shellcode to target the vulnerability and gain elevated privileges via specially crafted ptrace syscalls.
As for the second elevation of privilege bug, it was discovered in the uid_map functionality of Microsoft Azure Sphere 20.06 and can be abused through a specially crafted uid_map file.
By causing multiple applications to have the same UID, an attacker could ensure that a user application is executed with a system application’s UID.
The first of the vulnerabilities was found in version 20.07 of Azure Sphere, while the other three were discovered in version 20.06. Microsoft has published a blog post detailing the improvements and fixes included in Azure Sphere 20.08, which patches the vulnerabilities.
Google Researcher Reported 3 Flaws in Apache Web Server Software
24.8.20
Vulnerebility
Thehackernews
If your web-server
runs on Apache, you should immediately install the latest available version of
the server application to prevent hackers from taking unauthorized control over
it.
Apache recently fixed multiple vulnerabilities in its web server software
that could have potentially led to the execution of arbitrary code and, in
specific scenarios, even could allow attackers to cause a crash and denial of
service.
The flaws, tracked as CVE-2020-9490, CVE-2020-11984, CVE-2020-11993,
were uncovered by Felix Wilhelm of Google Project Zero, and have since been
addressed by the Apache Foundation in the latest version of the software
(2.4.46).
The first of the three issues involve a possible remote code
execution vulnerability due to a buffer overflow with the "mod_uwsgi" module
(CVE-2020-11984), potentially allowing an adversary to view, change, or delete
sensitive data depending on the privileges associated with an application
running on the server.
"[A] Malicious request may result in information
disclosure or [remote code execution] of an existing file on the server running
under a malicious process environment," Apache noted.
A second flaw concerns
a vulnerability that's triggered when debugging is enabled in the "mod_http2"
module (CVE-2020-11993), causing logging statements to be made on the wrong
connection and therefore resulting in memory corruption due to the concurrent
log pool usage.
CVE-2020-9490, the most severe of the three, also resides in
the HTTP/2 module and uses a specially crafted 'Cache-Digest' header to cause a
memory corruption to lead to a crash and denial of service.
Cache Digest is
part of a now-abandoned web optimization feature that aims to address an issue
with server pushes — which allows a server to preemptively send responses to a
client ahead of time — by allowing the clients to inform the server of their
freshly cached contents so that bandwidth is not wasted in sending resources
that are already in the client's cache.
Thus when a specially crafted value
is injected into the 'Cache-Digest' header in an HTTP/2 request, it would cause
a crash when the server sends a PUSH packet using the header. On unpatched
servers, this issue can be resolved by turning the HTTP/2 server push feature
off.
Although there are currently no reports of these vulnerabilities being
exploited in the wild, it's essential that the patches are applied to vulnerable
systems immediately after appropriate testing as well as ensure that the
application has been configured with only the required permissions so as to
mitigate the impact.
ATM vendors Diebold and NCR fixed deposit forgery bugs
24.8.20
Vulnerebility
Securityaffairs
The ATM manufacturer giants, Diebold Nixdorf and NCR, have released software
updates to fix a flaw that could have been exploited for ‘deposit forgery’
attacks
The ATM manufacturers Diebold Nixdorf and NCR have addressed a bug
that could have been exploited for ‘deposit forgery’ attacks
The flaws that
could have allowed crooks to modify the amount of money they deposited on their
card, so-called Deposit forgery, and make fraudulent cash withdrawals abusing of
the new account balance
Once modified the account balance, the cybercriminals quickly attempt to make cash withdrawals, before the bank will detect the anomalous increase of the account balance.
The two bugs, tracked as CVE-2020-9062 and CVE-2020-10124 affect respectively Diebold Nixdorf ProCash 2100xe USB ATMs running Wincor Probase software and NCR SelfServ ATMs running APTRA XFS software.
“Diebold Nixdorf 2100xe USB automated teller machines (ATMs) are vulnerable to physical attacks on the communication channel between the cash and check deposit module (CCDM) and the host computer. An attacker with physical access to internal ATM components may be able to exploit this vulnerability to commit deposit forgery.” reads the advisory for the CVE-2020-9062.
“NCR SelfServ automated teller machines (ATMs) running APTRA XFS 04.02.01 and 05.01.00 are vulnerable to physical attacks on the communications bus between the host computer and the bunch note accepter (BNA).” reads the advisory for the CVE-2020-10124.
As reported in the advisories published by the CERT Coordination Center at Carnegie Mellon University, both flaws request physical access to the vulnerable ATMs.
The problems are related to the lack of encrypting and authentication of the messages sent between the ATM cash deposit boxes and the host computer.
An attacker with physical access to the device can connect to the ATM to tamper with the messages when cash is deposited and change the amount of money deposited during an operation.
“A deposit forgery attack requires two separate transactions. The attacker must first deposit actual currency and manipulate the message from the BNA to the host computer to indicate a greater amount or value than was actually deposited. Then the attacker must make a withdrawal for an artificially increased amount or value of currency. This second transaction may need to occur at an ATM operated by a different financial institution (i.e., a not-on-us or OFF-US transaction).” continues the advisory.
Both Diebold and NCR have released software updates that protect communications between the cash deposit module and the host computer.
The vulnerabilities have been reported by security firm Embedi, a Russian security firm that was sanctioned by the US Treasury Department in June 2018 for allegedly working with the Russian intelligence agency Federal Security Service (FSB).
For this reason, the CERT/CC requested a special permit from the Office of Foreign Assets Control (OFAC) at the US Treasury Department to disclose the issues discovered by the Russian firm.
CERT/CC Warns of Vulnerabilities in Diebold Nixdorf, NCR ATMs
20.8.20
Vulnerebility
Securityweek
The CERT Coordination Center (CERT/CC) at Carnegie Mellon University has published alerts on several vulnerabilities that impact Diebold Nixdorf ProCash and NCR SelfServ automated teller machines (ATMs).
A vulnerability in the Diebold Nixdorf ProCash 2100xe USB ATMs running Wincor Probase version 1.1.30, CERT/CC reveals, could be abused by an attacker with physical access to internal machine components to commit deposit forgery.
The issue exists because the vulnerable devices do not encrypt, authenticate, or verify the integrity of messages transmitted between the cash and check deposit module (CCDM) and the host computer.
“An attacker with physical access to internal ATM components can intercept and modify messages, such as the amount and value of currency being deposited, and send modified messages to the host computer,” the CERT/CC alert reads.
To commit deposit forgery, an attacker would need to perform two separate transactions. First, they would need to deposit actual currency and modify the transmitted messages to indicate that a larger amount was deposited, after which they would need to withdraw an artificially increased amount.
Diebold Nixdorf has issued an update to secure the communication between the CCDM and the host computer, and also published a document detailing procedures for addressing the vulnerability.
Physical attacks are possible against NCR SelfServ ATMs running APTRA XFS 04.02.01 and 05.01.00 as well, CERT/CC reveals in two separate alerts.
The first issue (CVE-2020-10124) impacts the communications bus between the host computer and the bunch note accepter (BNA), and exists because the machine does not encrypt, authenticate, or verify the integrity of messages between the two components.
The ATMs also use 512-bit RSA certificates to validate BNA software updates (CVE-2020-10125), which can be broken by an attacker fast enough to allow them sign arbitrary files, bypass application whitelisting, and execute arbitrary code on the machine.
Because the device doesn’t properly validate software updates for the BNA (CVE-2020-10126), an attacker with physical access could execute arbitrary code with SYSTEM privileges by restarting the machine to initiate the update process.
Devices running APTRA XFS 06.08 are no longer impacted by these vulnerabilities. The update increases the strength of the RSA keys and addresses the bypass of the digital signature check.
Two other vulnerabilities affect the communications bus between the currency dispenser component and the host computer of NCR SelfServ ATMs running APTRA XFS 05.01.00 or older.
The USB HID communications between the two are not authenticated and their identity is not protected (CVE-2020-9063), thus allowing a physical attacker cause a buffer overflow to inject a malicious payload, and run arbitrary code with SYSTEM privileges.
Furthermore, because the currency dispenser component fails to authenticate session key generation requests (CVE-2020-10123), the attacker could generate a new session key and issue commands to dispense currency.
With APTRA XFS 05.01 reaching the end of life in 2015, machines running unsupported software and hardware should be upgraded as soon as possible. APTRA XFS Dispenser Security Update 01.00.00 has been issued for both S1 and S2 dispensers.
All of these vulnerabilities were identified and reported by security researchers associated with Embedi, which in June 2018 was sanctioned by the U.S. Department of Treasury because Digital Security, which, as of May 2017, owned or controlled Embedi, has provided “material and technological support” to Russia’s Federal Security Service (FSB).
CVE-2020-3446 default credentials bug exposes Cisco ENCS, CSP Appliances to hack
20.8.20 Vulnerebility Securityaffairs
Cisco addressed a critical default credentials vulnerability (CVE-2020-3446)
affecting some configurations of its ENCS 5400-W series and CSP 5000-W series
appliances.
Cisco fixed a critical default credentials vulnerability
impacting some configurations of its ENCS 5400-W series and CSP 5000-W series
appliances.
Cisco Wide Area Application Services (WAAS) is technology developed by Cisco Systems that optimizes the performance of any TCP-based application operating in a wide area network (WAN) environment while preserving and strengthening branch security. WAAS combines WAN optimization, acceleration of TCP-based applications, and Cisco’s Wide Area File Services (WAFS) in a single appliance or blade.
The Cisco Cloud Services Platform for WAAS (CSP-W) is a Cisco open x86 hardware platform for deployment of Cisco datacenter network functions virtualization (VNFs).
The Cisco Enterprise Network Compute System (ENCS) is a hybrid platform for branch deployment and for hosting WAAS applications.
Cisco experts revealed that the virtual WAAS (vWAAS) with Enterprise NFV Infrastructure Software (NFVIS)-bundled images for ENCS 5400-W series and 5000-W series appliances includes a default, static password.
The vulnerability, tracked as CVE-2020-3446, could be exploited by a remote, unauthenticated attacker using the the default with static password to log into the NFVIS command line interface (CLI) with administrator privileges.
“A vulnerability in Cisco Virtual Wide Area Application Services (vWAAS) with Cisco Enterprise NFV Infrastructure Software (NFVIS)-bundled images for Cisco ENCS 5400-W Series and CSP 5000-W Series appliances could allow an unauthenticated, remote attacker to log into the NFVIS CLI of an affected device by using accounts that have a default, static password.” reads the security advisory published by Cisco. “The vulnerability exists because the affected software has user accounts with default, static passwords. An attacker with access to the NFVIS CLI of an affected device could exploit this vulnerability by logging into the CLI. A successful exploit could allow the attacker to access the NFVIS CLI with administrator privileges.”
The vulnerability, rated as critical, has received a CVSS Score of 9.8. The issue can be exploited by an attacker who can connect to the targeted device’s NFVIS CLI.
According to Cisco, an attacker could connect to the device’s NFVIS CLI through:
The Ethernet management port for the CPU on an affected ENCS 5400-W Series
appliance. This interface might be remotely accessible if a routed IP is
configured.
The first port on the four-port I350 PCIe Ethernet Adapter card
on an affected CSP 5000-W Series appliance. This interface might be remotely
accessible if a routed IP is configured.
A connection to the vWAAS software
CLI and a valid user credential to authenticate on the vWAAS CLI first.
A
connection to the Cisco Integrated Management Controller (CIMC) interface of the
ENCS 5400-W Series or CSP 5000-W Series appliance and a valid user credential to
authenticate to the CIMC first.
Cisco confirmed that the flaw does not impact
standalone NFVIS running on Cisco ENCS 5000 Series and Cisco CSP 5000 Series
devices, and it does not affect standalone vWAAS software or WAAS software
running on Cisco Wide Area Virtualization Engine (WAVE) appliances.
The IT giant is not aware of any attacks in the wild exploiting the CVE-2020-3446 flaw.
Google fixed email spoofing flaw 7 hours after public disclosure
20.8.20 Vulnerebility Securityaffairs
Google addressed an email spoofing vulnerability affecting Gmail and G Suite a
few hours after it was publicly disclosed.
Google addressed an email spoofing
vulnerability affecting its Gmail and G Suite products a few hours after it was
publicly disclosed, but the IT giant was ware of the flaw since April.
On Wednesday, the researcher Allison Husain published technical details of the email spoofing vulnerability in a blog post, which also includes a proof-of-concept (PoC) code.
The vulnerability is caused by missing verifications when configuring mail routes. The issue could have been exploited by an attacker to send an email that appears as sent by another Gmail or G Suite user, the message is able to bypass protection mechanisms such as Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting and Conformance (DMARC).
“Due to missing verification when configuring mail routes, both Gmail’s and any G Suite customer’s strict DMARC/SPF policy may be subverted by using G Suite’s mail routing rules to relay and grant authenticity to fraudulent messages.” states the post. “This issue is a bug unique to Google which allows an attacker to send mail as any other user or G Suite customer while still passing even the most restrictive SPF and DMARC rules.”
According to Husain, unlike the classic mail spoofing in which the From header is given an arbitrary value, this technique could not be blocked by mail servers using SPF and DMARC.
The researcher used her personal G Suite domain to send an email apparently coming from an @google.com address to a G Suite email account associated with a domain she did not control.
“I am using my personal G Suite domain (mail-relay@ezh.es) to send a seemingly legitimate email from a google.com address to my university’s G Suite email on a domain which I do not control (test@berkeley.edu).” continues the expert. “I chose to send to another G Suite account to demonstrate that Google’s strong mail filtering and anti-spam techniques do not block or detect this attack. Additionally, I chose to impersonate google.com because their DMARC policy is set to p=reject and so any violations of SPF (regardless of the SPF policy) should result in the message simply being dropped with prejudice.”
The attack exploits a bug related to G Suite’s mail routing rules, which an attacker could have subverted to relay and grant authenticity to fraudulent messages.
Husain reported the flaw to Google on April 3, the company acknowledge the issue on April 16 and marked the issue as duplicate on April 21st, 2020.
On August 1, Husain notified Google her intent to publicly disclose the flaw and set disclosure deadline for August 17th (16 days later).
On August 14, Google told her that it would be releasing a patch on September 17, but Husain publicly disclosed the flaw on August 19.
The good news is that Google fixed the issue seven hours after its details were made public.
Google Patches Email Spoofing Vulnerability After Public Disclosure
20.8.20
Vulnerebility
Securityweek
Google released a patch for an email spoofing vulnerability affecting Gmail and G Suite seven hours after it was publicly disclosed, but the tech giant knew about the flaw since April.
The vulnerability was disclosed on Wednesday by researcher Allison Husain, who described her findings in a blog post and shared proof-of-concept (PoC) code. The issue, related to missing verifications when configuring mail routes, could have been exploited by an attacker to send an email as another Gmail or G Suite user while bypassing protection mechanisms such as DMARC and SPF.
Husain demonstrated her findings by using her personal G Suite domain to send an email apparently coming from an @google.com address to a G Suite email account on a domain she did not control.
“I chose to send to another G Suite account to demonstrate that Google’s strong mail filtering and anti-spam techniques do not block or detect this attack,” the researcher explained. “Additionally, I chose to impersonate google.com because their DMARC policy is set to p=reject and so any violations of SPF (regardless of the SPF policy) should result in the message simply being dropped with prejudice.”
The attack leveraged a weakness related to mail routing rules, which an attacker could have abused to “relay and grant authenticity to fraudulent messages.”
The security hole was reported to Google on April 3 and the company confirmed it on April 16, when it assigned priority and severity ratings of “2.” Google later marked the flaw as a duplicate, but it still did not roll out a patch. On August 1, Husain informed the company that she would be making her findings public on August 17.
Google told her that it would be releasing a patch on September 17, but it actually addressed the issue seven hours after its details were made public, 137 days after it learned of its existence.
Vulnerability in IBM Db2 Leads to Information Disclosure, Denial of Service
20.8.20 Vulnerebility Securityweek
A shared memory vulnerability that IBM addressed in its Db2 data management products could allow malicious local users to access sensitive data.
Trustwave, which identified the vulnerability and reported it to IBM, says that the issue exists because the developers forgot to include explicit memory protections for the shared memory that the Db2 trace facility uses.
A malicious local user could gain read and write access to that memory area, allowing them to access critically sensitive data or to modify the functionality of the trace subsystem, thus leading to a denial of service condition in the database.
An unprivileged local user can abuse the vulnerability to write incorrect data over the affected memory section, thus causing denial of service, Trustwave explains in a blog post shared with SecurityWeek.
The vulnerability, which is tracked as CVE-2020-4414, was found to affect IBM Db2 for Linux, UNIX and Windows (including Db2 Connect Server), versions 9.7, 10.1, 10.5, 11.1, and 11.5.
IBM, which released a patch for the bug on June 30, explains that an attacker could send specially crafted requests to exploit the flaw.
According to Martin Rakhmanov, security research manager at Trustwave, organizations should consider applying patches as soon as possible, given that five IBM Db2 editions across all platforms are impacted.
“Although fixable through a patch, the vulnerability could have wider security implications on organizations. For example, a low-privileged processes running on the same computer as the Db2 database, can alter Db2 trace and capture sensitive data and then use that data for subsequent attacks further down the line,” Rakhmanov said in an emailed comment.
“While it may be hard to tell if this has already been exploited by some malicious actors, our recommendation for all businesses is to ensure immediately that they have the latest database version installed and apply any patches that may have been missed,” he continued.
Earlier this year, Rakhmanov identified a shared memory vulnerability (CVE-2020-3347) in the Cisco Webex Meetings desktop app for Windows, but says that this type of security bugs might not be as widespread.
“Through recent research we’ve seen the emergence of shared memory vulnerabilities becoming a more common issue,” Rakhmanov said. “Some database products have this particular issue but I’d not say this is something 'growing' [industry-wide].”
Experts Reported Security Bug in IBM's Db2 Data Management Software
20.8.20
Vulnerebility
Thehackernews
Cybersecurity
researchers today disclosed details of a memory vulnerability in IBM's Db2
family of data management products that could potentially allow a local attacker
to access sensitive data and even cause a denial of service attacks.
The flaw
(CVE-2020-4414), which impacts IBM Db2 V9.7, V10.1, V10.5, V11.1, and V11.5
editions on all platforms, is caused by improper usage shared memory, thereby
granting a bad actor to perform unauthorized actions on the system.
By
sending a specially crafted request, an attacker could exploit this
vulnerability to obtain sensitive information or cause a denial of service,
according to Trustwave SpiderLabs security and research team, which discovered
the issue.
"Developers forgot to put explicit memory protections around the
shared memory used by the Db2 trace facility," SpiderLabs's Martin Rakhmanov
said. "This allows any local users read and write access to that memory area. In
turn, this allows accessing critically sensitive data as well as the ability to
change how the trace subsystem functions, resulting in a denial of service
condition in the database."
IBM released a patch on June 30 to remediate the
vulnerability.
CVE-2020-4414 is caused by the unsafe usage of shared memory the Db2 trace
utility employs to exchange information with the underlying OS on the system.
The Db2 trace utility is used to record Db2 data and events, including reporting
Db2 system information, collecting data required for performance analysis and
tuning, and capture data access audit trail for security purposes.
Given that
the shared memory stores sensitive information, an attacker with access to the
system could create a malicious application to overwrite the memory with rogue
data dedicated to tracing data.
"This means that an unprivileged local user
can abuse this to cause a denial of service condition simply by writing
incorrect data over that memory section," Rakhmanov said.
Even more
concerning, a low-privileged process running on the same computer as the Db2
database could alter Db2 trace and capture sensitive data and use the
information to carry out other attacks.
If the flaw sounds familiar, that's
because it's the same type of memory leakage vulnerability that impacted Cisco's
WebEx video conferencing service (CVE-2020-3347) that could local authenticated
attackers to get hold of usernames, authentication tokens, and meeting
information.
It's recommended that Db2 users update their software to the
latest version to mitigate the risk.
Vulnerability Allowing Full Server Takeover Found in Concrete5 CMS
19.8.20
Vulnerebility
Securityweek
A remote code
execution (RCE) vulnerability addressed recently in Concrete5 exposed numerous
websites to attacks, Edgescan reports.
A point and click, open-source content management system, Concrete5 allows users create websites at ease and is used by many high-profile entities worldwide, including BASF, GlobalSign, REC, the U.S. Army, and more.
The CMS has been designed with ease-of-use in mind, and allows users to edit content directly from the page, without requiring advanced technical skills.
What Edgescan discovered was an RCE flaw in Concrete5 that could have allowed an attacker to inject a reverse shell into vulnerable web servers, thus taking full control of them.
The issue was identified in Concrete5 version 8.5.2, which essentially allowed an attacker to modify site configuration and upload a PHP file onto the server, thus gaining arbitrary command execution capabilities.
Although PHP, HTML and other dangerous file extensions are not typically allowed, the issue could have been exploited “to include PHP extension in the legal file list and then upload the file,” Edgescan says.
To mount an attack, an adversary would need administrative permissions to access the 'Allow File types' feature and include the PHP file type in the list of allowed extensions.
Once that has been achieved, however, the attacker can upload potentially malicious code onto the server and then execute arbitrary commands. Information on how to reproduce the attack has been disclosed on HackerOne.
By exploiting the vulnerability, Edgescan says, an attacker “would be able to take full control over the web server (system). By executing arbitrary commands on the server, an attacker could compromise the integrity, availability and confidentiality. And pivot onto other servers on the internal network.”
The issue was reported via the HackerOne platform in early January 2020, but a fix wasn’t released for six months. Users running the latest stable release (Concrete5 version 8.5.4) are protected from the vulnerability.
“Crucially important to keep your installed scripts and CMS platforms up to date. Create a regular schedule to update or patch your CMS, and all installed plugins and themes. Ensure all components are up-to-date,” Edgescan points out.
Actively Exploited Windows Spoofing Flaw Patched Two Years After Disclosure
18.8.20 Exploit Vulnerebility Securityaffairs
The actively exploited Windows spoofing vulnerability patched last week by Microsoft has been known for more than two years, researchers pointed out.
Microsoft’s August 2020 Patch Tuesday updates addressed 120 vulnerabilities, including an Internet Explorer zero-day that has been chained with a Windows flaw in attacks linked to the threat actor named DarkHotel, and a Windows spoofing issue tracked as CVE-2020-1464.
The tech giant describes CVE-2020-1464 as a spoofing flaw related to Windows incorrectly validating file signatures. An attacker can exploit the vulnerability to bypass security features and load improperly signed files, Microsoft says in its advisory.
Researchers analyzed CVE-2020-1464 after Microsoft released its patch and noticed that it’s likely a vulnerability that has been known for years and which Microsoft has been refusing to fix.
In a blog post published over the weekend, researcher Tal Be'ery explained that the vulnerability, which has been named GlueBall, has been known since August 2018, when a file sample exploiting it was uploaded to VirusTotal.
Microsoft was informed about the issue at the time and details were disclosed on the VirusTotal blog in January 2019, but the vendor decided not to fix it.
“Microsoft Windows keeps the Authenticode signature valid after appending any content to the end of Windows Installer (.MSI) files signed by any software developer. This behaviour can be exploited by attackers to bypass some security solutions that rely on Microsoft Windows code signing to decide if files are trusted. The scenario is especially dangerous when the appended code is a malicious JAR because the resulting file has a valid signature according to Microsoft Windows and the malware can be directly executed by Java,” Bernardo Quintero, founder of VirusTotal, explained in the January 2019 blog post.
Shortly after the blog post was published, several others analyzed the issue and made their findings public. In June 2020, researchers noticed that someone had been exploiting GlueBall to deliver malware, and in August it was finally patched by Microsoft.
“[The] way Microsoft had handled the vulnerability report seems rather strange,” Be’ery noted. “It was very clear to everyone involved, Microsoft included, that GlueBall is indeed a valid vulnerability exploited in the wild. Therefore, it is not clear why it was only patched now and not two years ago.”
SecurityWeek has reached out to Microsoft, but the company has not provided any clarifications regarding its decision not to patch CVE-2020-1464 sooner.
“A security update was released in August. Customers who apply the update, or have automatic updates enabled, will be protected. We continue to encourage customers to turn on automatic updates to help ensure they are protected,” said a Microsoft spokesperson.
Amazon Alexa Vulnerabilities Could Have Exposed User Data
15.8.20 Vulnerebility Securityweek
Check Point security researchers have identified a series of vulnerabilities that potentially opened the gate for a variety of attacks targeting Alexa, Amazon’s virtual assistant.
The attacks involved a Cross-Origin Resource Sharing (CORS) misconfiguration and Cross Site Scripting (XSS) bugs identified on Amazon and Alexa subdomains, which eventually allowed the researchers to perform various actions on behalf of legitimate users.
Successful exploitation of these vulnerabilities could allow an attacker to retrieve the personal information of an Alexa user, as well as their voice history with their Alexa, but also to install applications (skills) on the user’s behalf, list installed skills, or remove them.
“Successful exploitation would have required just one click on an Amazon link
that has been specially crafted by the attacker,” Check Point’s security
researchers, who published a video demonstrating the flaws, explain.
To carry out an attack, an adversary would need to create a malicious link that directs the user to amazon.com, send it to the victim, and trick them into clicking it. The attacker would need code-injection capability on the destination page.
Next, the attacker sends an Ajax request with the user’s cookies to amazon.com/app/secure/your-skills-page, which allows them to retrieve a list of skills installed on the victim’s Alexa account.
The response, Check Point says, also contains the CSRF token, which the attacker can use to remove one common skill from the list. Then, the attacker can use the same invocation phrase to install a skill, which results in the user triggering the attacker skill instead of the original one.
The security researchers note that, while Amazon does not record banking login credentials, the attacker can access users’ interaction with the banking skill and grab their data history. Moreover, usernames and phone numbers can also be retrieved, based on the installed skills.
Amazon was alerted on the discovered vulnerabilities in June 2020 and has already addressed them. The company has security mechanisms in place to prevent malicious skills from being published to its store.
"The security of our devices is a top priority, and we appreciate the work of independent researchers like Check Point who bring potential issues to us. We fixed this issue soon after it was brought to our attention, and we continue to further strengthen our systems. We are not aware of any cases of this vulnerability being used against our customers or of any customer information being exposed, " an Amazon spokesperson told SecurityWeek in an emailed comment.
Check Point concluded, “Virtual assistants are used in Smart Homes to control everyday IoT devices […]. They grew in popularity in the past decade to play a role in our daily lives, and it seems as technology evolves, they will become more pervasive. This makes virtual assistants an attractive target for attackers looking to steal private and sensitive information, or to disrupt an individual’s smart home environment.”
This attack, which relies on social engineering to trick the victim into accessing a link, can be avoided through security training, Javvad Malik, Security Awareness Advocate, KnowBe4, pointed out.
“From a technological perspective, as the connected ecosystem of devices grows, it becomes increasingly important for manufacturers to ensure all code and access is assessed not just for technical security flaws, but also where processes can be bypassed by criminals to reveal sensitive information, corrupt data, or make them unavailable,” Malik said.
“Security in IoT devices such as the Amazon Echo and associated Alexa voice assistant service is an important issue,” Matt Aldridge, Principal Solutions Architect, Webroot, said in an emailed comment.
“The growing demand for these devices requires that manufacturers focus on their security and privacy. IoT manufacturers need to work more closely with cybersecurity professionals to ensure that device security is considered and understood at the design stage – not implemented as an afterthought,” Aldridge added.
Microsoft failed to fix LSASS elevation of privilege flaw
14.8.20 Vulnerebility Securityaffairs
Microsoft did not properly address an elevation of privilege flaw
(CVE-2020-1509) in the Windows Local Security Authority Subsystem Service
(LSASS).
Google Project Zero researcher who discovered the elevation of
privilege flaw (CVE-2020-1509) in the Windows Local Security Authority Subsystem
Service (LSASS) warn that Microsoft did not properly address it.
“An
elevation of privilege vulnerability exists in the Local Security Authority
Subsystem Service (LSASS) when an authenticated attacker sends a specially
crafted authentication request. A remote attacker who successfully exploited
this vulnerability could cause an elevation of privilege on the target system’s
LSASS service.” reads the Microsoft’s advisory.
“The security update addresses the vulnerability by changing the way that LSASS handles specially crafted authentication requests.”
An attacker, who has obtained Windows credentials for the local network, could trigger the flaw by sending specially crafted authentication requests.
“LSASS doesn’t correctly enforce the Enterprise Authentication Capability which allows any AppContainer to perform network authentication with the user’s credentials,” Project Zero security researcher James Forshaw explained in a post published in May.
The Google researcher discovered that the issue is related to the original legacy AppContainer capabilities that grants access to Enterprise Authentication
At the time, the researcher explained that the issue is related to a legacy AppContainer capability providing access to the Security Support Provider, and consequently to the SSPI functions. The SSPI interface makes it simple to install line of business (LOB) applications within enterprise environments.
When the target specified in the call is a proxy the authentication should be allowed, anyway Forshaw discovered that the authentication would be allowed even if the network name doesn’t match a registered proxy.
“If the target is a proxy then the authentication process is allowed, even if
the Enterprise Auth Cap is not specified. The issue is, even if
LsapIsTargetProxy returns false the authentication is still allowed to proceed
but an additional flag is set to indicate this state. I couldn’t find any code
which checked this flag, although it’s a bit unclear as it comes from a TLS
block so tracking down usage is awkward.” continues the expert.
“What this
means is that an AppContainer can perform Network Authentication as long as it
specifies a valid target name to InitializeSecurityContext, it doesn’t matter if
the network address is a registered proxy or not.”
An attacker could exploit the issue to authenticate to resources exposed on the network without restrictions, bypassing SPN checking and SMB signing.
Upon exploiting the flaw, the attacker could also access to the localhost services, albeit with some limitations.
Forshaw also published proof-of-concept (POC) code to achieve elevated privileges through Enterprise Authentication bypass, it will connect to the local SMB server and list the network shares which shouldn’t be something the AC can do.
Microsoft addressed the vulnerability with the release of August 2020 Patch Tuesday, but a few hours late Forshaw discovered that the updates failed to fix the issue.
One day after the fix was released, however, Forshaw revealed that the patch failed to correctly address the vulnerability.
According to Forshaw, the POC he released is still working in case the attacker has added a proxy server in the settings, he also pointed out that the code should be executed with specific arguments.
“After review it seems that this hasn’t been completely fixed. In line with our policy outlined at https://googleprojectzero.blogspot.com/2020/01/policy-and-disclosure-2020-edition.html any incomplete fix is added to the issue tracker as additional information and is not granted an additional time to fix.” reads the update published by the researcher.
“To verify with the original PoC.
1) Run the CheckNetIsolation.exe command as admin to add Calculator to loopback
exemption.
2) Add a proxy server manually in the settings. For example set a
manual proxy to 192.168.0.10 port 1234.
3) Run the PoC specifying the
arguments 127.0.0.1 CIFS/localhost/192.168.0.10.
This will connect to the local SMB server and print the shares. This will work even if SPN verification is enabled as the SMB server ignores the Service Name component of the SPN.”