
Vulnerebility Articles - H 2020 1 2 3 4 5 6 7 8 9 Vulnerebility List - H 2021 2020 2019 2018 Vulnerebility blog Vulnerebility blog
Number of WordPress Attacks powered by compromised routers is rapidly dropping
3.5.2017 securityaffairs Vulnerebility
Experts from security firm WordFence reported a rapid reduction of WordPress attacks originating from hundreds of ISPs worldwide.
Experts at the security firm Wordfence a few weeks ago reported that tens of thousands of flawed routers from dozens of ISPs worldwide were recruited in a botnet used to power several types of attacks against WordPress websites.
Hackers exploited the CVE-2014-9222 flaw, also known as ‘Misfortune Cookie,‘ to hack thousands of home routers and abuse them for WordPress attacks.
According to a new analysis published by WordFence, the volume of the attacks had started to drop significantly over the weekend, by Monday evening, the 30,000 or 40,000 attack attempts coming every hour from some ISPs had dropped to less than 5,000. and the frequency of the attacks continued to decrease.
According to the researchers, this frequency is continuing to decrease.
“Yesterday morning we noticed that there was a rapid drop-off in attacks from the ISPs we identified 3 weeks ago, that had targeted WordPress websites.” reads the analysis published by WordFence.
“This is what the change in activity looked like from the top 50 ISPs from where these attacks were originating during a 72 hour period ending yesterday (Monday) evening. Click the chart for a larger version.”
“As you can see, starting at around midnight on Sunday night (April 30th) Pacific time, the number of attacks we are seeing from ISPs where we found vulnerable routers have dropped from peaks of 40,000 in some cases to peaks of just above 5,000 attacks per hour. In many cases the attacks drop to much lower levels and continue to decrease.”

The root cause of this drop is still unclear, researchers at WordFence believe the situation will be more clear in the next week.
A possible cause is that the attackers ended their operation for some reason, otherwise law enforcement along security firms have tracked the botnet and took down the command and control (C&C) servers.
A few weeks ago, US authorities announced have dismantled the infamous Kelihos botnet. In the same period, the Interpol located and shut down nearly 9,000 Command and control servers located in Asia and hacked with a WordPress plug-in exploit.
This reduction of WordPress attacks originating from hundreds of ISPs worldwide is a good news. The experts were able to track the WordPress attacks originating from these ISPs and ban IP addresses involved in the botnet.
“The attacks originating from these ISPs were also resulting in their IP addresses being blacklisted by Wordfence and other services like SpamHaus. That resulted in the customers of those ISPs suffering because certain websites and services would block them. By reducing these attacks, this ensures those ISP customers have full internet access again.” concluded WordFence.
Google Patches 6 Critical Android Mediaserver Bugs in May Security Update
3.5.2017 thehackernews Vulnerebility
Google has released its monthly security patches for Android this week, addressing 17 critical vulnerabilities, 6 of which affect Android Mediaserver component that could be used to execute malicious code remotely.
Besides patches for Mediaserver, Google also fixed 4 critical vulnerabilities related to Qualcomm components discovered in Android handsets, including Google's Nexus 6P, Pixel XL, and Nexus 9 devices.
According to the Google security bulletin for Android published Monday, this month's security update is one of the largest security fixes the company ever compiled in a single month.
Google has split Android's monthly security bulletin into security "patch levels":
Partial security patch level (2017-05-01) covers patches for vulnerabilities that are common to all Android devices.
Complete security patch level (2017-05-05) includes additional fixes for hardware drivers as well as kernel components that are present only in some devices.
Critical RCE Flaw in Android Mediaserver
The most severe vulnerability exists in Mediaserver – an Android component that handles the processing of image and video files and has been a source of many issues over the past few years, including the critical Stagefright vulnerabilities.
According to the search engine giant, the Mediaserver vulnerability "could enable remote code execution on an affected device through multiple methods such as email, web browsing, and MMS when processing media files."
In other words, attackers could exploit the Mediaserver vulnerability by tricking users into downloading a specially crafted multimedia file on their devices, or sharing the media file via email or other messaging apps and remotely execute arbitrary code.
Interestingly, this vulnerability could be triggered while you sleep, as it’s not even necessary for you to open the file because as soon as your device receives the media file, the file system will cause Mediaserver to process it.
The vulnerability was discovered in early January and affects Android versions 4.4.4 KitKat through 7.1.2 Nougat.
Kernel-level Vulnerabilities in Qualcomm
Google has also patched four critical vulnerabilities that stemmed from Qualcomm components and could allow an attacker to gain high-level (root) privileges on an Android device.
Two critical vulnerabilities (CVE-2016-10275 and CVE-2016-10276) in Qualcomm bootloader create conditions ripe for an elevation of privilege attacks, enabling "a local malicious application to execute arbitrary code within the context of the kernel," according to the bulletin.
Another critical Qualcomm bug (CVE-2017-0604) in power driver could also allow a local malicious application to execute malicious code on the device within the context of the kernel, which is the most privileged area of the OS.
No Evidence of Flaws Being Exploited in the Wild
Six of the 17 critical patches are addressed with the 2017-05-01 partial security patches, while the remaining 11 critical security flaws affecting various drivers, libraries and bootloaders are patched in the 2017-05-05 complete patch level.
Good news is that Google assured its users that there are no reports of any of the security vulnerabilities being exploited in the wild.
Google says, having two patch levels "provide Android partners with the flexibility to more quickly fix a subset of vulnerabilities that are similar across all Android devices."
So, users are strongly advised to download the most recent Android security update to keep their devices protected against any potential attack.
Nexus and Pixel devices will receive the complete patch in an over-the-air update in the coming days, or the owners can download it directly from Google's developer site.
It's also worth noting that Google revealed last week that the Nexus 6 and Nexus 9, which were released in November 2014, would no longer be "guaranteed" to receive security updates after October 2017.
A similar timeline has been offered for newer Pixel and Pixel XL handsets of October 2019. After that, the tech giant will only push necessary security fixes to those devices.
Netgear Patches RCE Flaws in Routers, Switches
2.5.2017 securityweek Vulnerebility
Netgear recently informed customers that it has released firmware updates for some of its routers and switches to address remote code execution and other types of vulnerabilities.
Netgear announced the launch of a bug bounty program in early January and the company has been regularly publishing security advisories and notifications over the past months. The firm has been offering between $150 and $15,000 for responsibly disclosed vulnerabilities, and it already claims to have rewarded more than 150 bug reports.
In the most recent advisories, Netgear informed users about the existence of CVE-2017-6862, a buffer overflow vulnerability that can be exploited by a remote attacker to bypass authentication and execute arbitrary commands.
The flaw, discovered by Maxime Peterlin of ON-X, affects WNR2000v3, WNR2000v4, WNR2000v5 and R2000 routers. Firmware updates that patch the vulnerability are available for all impacted models.
Netgear said the weakness can only be exploited by an attacker with access to the network hosting the device, or if the router has the remote management feature enabled. This feature is disabled by default.
A different advisory describes a vulnerability affecting some of the company’s smart and managed switches. The flaw allows an unauthenticated attacker to access a debugging URL from where they can execute arbitrary commands, including for resetting and rebooting the switch.
An attack can be launched remotely if the switch is remotely accessible, but Netgear believes most users have firewalls in place that should prevent exploitation.
The security hole affects nearly three dozen switches, including FS, GS, M, S and XS models. Firmware updates that patch the flaw are available for most of the impacted devices.
Another recent advisory warns users of a vulnerability affecting CM700 high speed cable modems. The bug does not pose any risk to data, but it can allow an attacker to disrupt a targeted user’s network connection. No workarounds or patches are available.
Intel Warns of Critical Vulnerability in Processor Firmware
2.5.2017 securityweek Vulnerebility
Nine-Year-Old Critical Vulnerability Affects Intel Active Management Technology
Intel issued a critical alert Monday concerning an escalation of privilege vulnerability affecting Intel Active Management Technology (AMT), Intel Small Business Technology (SBT), and Intel Standard Manageability. Firmware updates are available in all cases -- but that's not the end of the story.
While the Intel alert states, "This vulnerability does not exist on Intel-based consumer PCs," security commentators such as Charlie Demerjian suggest "there is literally no Intel box made in the last 9+ years that isn't at risk. This is somewhere between nightmarish and apocalyptic." The vulnerability affects every Intel system from Nehalem in 2008 to Kaby Lake in 2017.
According to Intel, the vulnerability (CVE-2017-5689) can be accessed in two ways. Where AMT and ISM have been provisioned, an unprivileged network attacker could gain system privileges. Where not provisioned, a local attacker could provision them and gain local system privileges on AMT, ISM and SBT. Intel gives no details on the vulnerability itself.
The three main issues for business are the extent of the damage that could be done through this vulnerability; the difficulty in knowing what systems are vulnerable; and the lack of control over the availability of Intel's firmware updates.
AMT is intended to give IT departments a means to manage client systems. When enabled, packets sent to ports 16992 or 16993 are redirected through Intel's Management Engine (a small, separate processor independent of the main CPU) and passed to AMT. The operating system never sees these packets. AMT can be used to install media, reboot the machine and more, remotely. It requires a password for access; but this vulnerability suggests that the password can be bypassed.
Understanding the extent of the risk could also be difficult. "What about embedded devices that are increasingly PC based?" asks Demerjian. "Digital signage perhaps? Industrial controls. HVAC. Security systems. Flight controls. Air traffic controls. Medical devices. I could go on but all of these are likely PC based and anything infrastructure related is likely networked."
SANS' Richard Porter suggests, "Get a good, complete hardware inventory together, and get a good software inventory -- know what's in your organization and on your network, and know what's running on that gear. This includes elevator controls, industrial presses, MRI machines, point of sale stuff, TVs, DVRs and photocopiers -- all of it! Without knowing what's on your network, the best you'll do is to get a reasonable percentage of affected systems -- you'll never patch the machines you don't know about."
The third issue is patching. While it is Intel's responsibility to develop the patches (which it has done), it is not Intel's responsibility to deliver them. That's down to the device manufacturers and OEMs; and it is generally thought that not all will do so.
Demerjian warns, "If you have a white-box PC or one from a sketchy vendor, chances are they won't bother with a firmware update. Security is a cost center and most OEMs run on margins too thin to bother with security patches even if they cared. Most simply don't care." Put bluntly, many systems will likely never be patched.
This raises two further issues: what should be done when you have little or no control over whether or even if you will receive patches; and secondly, how urgent is this issue? The latter takes us into conjecture. The Intel alert makes no statement over whether the company is aware of any current exploitation of the vulnerability -- the alert neither confirms nor denies it.
Researchers have been warning Intel for years. In 2012, Demerjian wrote, "Intel doesn't understand security, but they are not shy about shouting it from the rooftops. They took a good idea, vPro [which includes AMT], and turned it into a remote exploit and security risk that prevents a compromised machine from being repaired."
Demerjian in particular wonders, 'why now?'; adding "SemiAccurate strongly suspects this vulnerability is being exploited in the wild as we speak." It is conjecture, but it could be true (and all the while we don't know whether Shadow Brokers has any further exploits to announce).
The implication is clear: business cannot wait for a solution to be handed to it; it needs to be proactive and mitigate the vulnerability as soon as possible. Luckily, Intel has published separate documents that should help.
How To Find Intel® vPro™ Technology Based PCs will help to determine whether a system is AMT, SBA or ISM capable. If it is not, then no mitigation is required.
INTEL-SA-00075 Detection Guide steps through the process of using Intel's System Discovery utility to determine the firmware version and whether it is vulnerable.
INTEL-SA-00075 Mitigation Guide provides "instructions on how to implement mitigations on Intel's manageability SKU systems that are vulnerable to a known privilege escalation issue."
All three documents are useful; but business is advised to employ mitigations where necessary as soon as possible. The mitigation document provides details on removing the supporting code in Windows. "What it boils down to," says SANS' Porter, "is you want to stop and disable the LMS Service (Local Management Service), then delete LMS.exe."
A critical RCE flaw in Intel Management Engine affects Intel enterprise PCs dates back 9 years
2.5.2017 securityaffairs Vulnerebility
A critical remote code execution vulnerability tracked as CVE-2017-5689 in Intel Management Engine affects Intel enterprise PCs dates back 9 years.
A critical remote code execution (RCE) vulnerability tracked as CVE-2017-5689 has been discovered in the remote management features implemented on computers shipped with Intel Chipset in past 9 years.
The vulnerability affects the Intel Management Engine (ME) technologies such as Active Management Technology (AMT), Small Business Technology (SBT), and Intel Standard Manageability (ISM) and could be exploited by hackers to remotely take over the vulnerable systems.
The remote management features allow system administrators to remotely manage computers over an enterprise network. Such kind of features are implemented only in enterprise solutions and doesn’t affect chips running on Intel-based consumer PCs.
“There is an escalation of privilege vulnerability in Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology versions firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 that can allow an unprivileged attacker to gain control of the manageability features provided by these products. This vulnerability does not exist on Intel-based consumer PCs. ” reads the advisory published by Intel.
The vulnerability rated by Intel as highly critical, could be exploited in two ways:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel® Active Management Technology (AMT) and Intel® Standard Manageability (ISM).
CVSSv3 9.8 Critical /AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology (SBT).
CVSSv3 8.4 High /AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An attacker can exploit the vulnerability to remotely access the vulnerable machine and perform in a stealth way malicious activities, including to deliver a malware.
The flaw was first reported in March by the security expert Maksim Malyutin of Embedi.
These flawed remote management features have been implemented in many Intel chipsets for nine years, starting from Nehalem Core i7 in 2008. Modern Apple Macs do not ship with the AMT software, so they are not affected.
This kind of flaw is very insidious because any countermeasure implemented at the operating system level is not able to detect malicious operation because AMT has direct access to the computer’s network hardware. Malicious traffic is routed directly to the Management Engine and passed on to AMT, but the local OS never sees it.
According to Intel, the remote code execution vulnerability affects Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel’s AMT, ISM, and SBT platforms. Versions before 6 or after 11.6 are not impacted.
Intel promptly released new firmware versions along with a detection guide to check if a system is vulnerable. The company also shared a mitigation guide that is essential for those organizations that can not immediately install updates.
The chipmaker is recommending vulnerable customers install a firmware patch as soon as possible.
Yahoo awarded $7,000 a bug hunter for Flickr account hijacking vulnerability
2.5.2017 securityaffairs Vulnerebility
Yahoo awarded $7,000 to the bug hunter Michael Reizelman, aka mishre, for Flickr account hijacking vulnerability.
Reizelman was a popular bug hunter that discovered vulnerabilities in many web services, including Badoo, Dropbox, GitHub, Google, Imgur, Slack, Twitter, and Uber.
The expert has discovered three vulnerabilities in the company’s image and video hosting service that could have been chained together to take over Flickr accounts.
Reizelman discovered that every time a user logs in to his Flickr.com account, it is redirected to the login.yahoo.com domain used for the authentication.
Below the URL used to redirect the user:
https://login.yahoo.com/config/login?.src=flickrsignin&.pc=8190&.scrumb=0&.pd=c%3DH6T9XcS72e4mRnW3NpTAiU8ZkA--&.intl=il&.lang=en&mg=1&.done=https%3A%2F%2Flogin.yahoo.com%2Fconfig%2Fvalidate%3F.src%3Dflickrsignin%26.pc%3D8190%26.scrumb%3D0%26.pd%3Dc%253DJvVF95K62e6PzdPu7MBv2V8-%26.intl%3Dil%26.done%3Dhttps%253A%252F%252Fwww.flickr.com%252Fsignin%252Fyahoo%252F%253Fredir%253Dhttps%25253A%25252F%25252Fwww.flickr.com%25252F
The user provides his credentials and if they are valid, he is redirected back to Flickr.com and authenticated with the following URL:
https://www.flickr.com/signin/yahoo/?redir=https%3A%2F%2Fwww.flickr.com%2F&.data={first-token-value}&.ys={second-token-value}
The researcher also observed that the user is redirected in the background to login.yahoo.com if he is already logged in,
The request to login.yahoo.com is used to obtain an access token for the user.
Reizelman discovered that is possible to manipulate a parameter named ‘.done’ that is used to control where the login token is sent.
Yahoo just checks that the token could only be sent to the flickr.com domain.
“The first thing I have noticed is that the second .done parameter can be manipulated. This parameter actually controls where the login tokens are sent. It appears that Yahoo’s servers only verify that it starts with https://www.flickr.com/signin/yahoo/ but we can still append ../ so if we append ../../test to the .done original value the .ys and .data tokens will be sent to https://www.flickr.com/test endpoint.” explained the researcher in a blog post.

Initially, Reizelman searched for an open redirect vulnerability on flickr.com to exploit the vulnerability, but he had no success. Anyway, the expert devised another method to exploit the issue by embedding an image from an attacker-controlled server into a Flickr.com page using the <img> tag.
The expert found a method to bypass Yahoo checks, he was able to embed an external image into comments posted on flickr.com/help/forum/en-us/, which did not have a Content Security Policy (CSP).
Then he pointed the .done parameter to a malicious image embedded into a post on the Flickr help forum, with this mechanism an attacker could send the access tokens to his server.
In the attack scenario, a hacker has to trick the user into clicking on a specially crafted link to obtain his access token and take over the victim’s Flickr account.
The researcher reported the vulnerabilities to Yahoo on April 2, he was awarded a $7,000 bounty. The company operates a bug bounty program through HackerOne.
Below the Timeline of the Flickr Account Hijacking flaw:
Apr 2nd 2017 – Initial Report via Hackerone
Apr 3rd 2017 – Report Triaged
Apr 10th 2017 – Report Resolved
Apr 21st 2017 – 7K$ Bounty Rewarded
Yahoo fixed the problem by only allowing the .done parameter to point to flickr.com/signin/yahoo, adding CSP to the Flickr forum, the experts also neutralized the image embedding bypass method.
Flaws Found in Evoko Meeting Room Management Devices
1.5.2017 securityweek Vulnerebility
Meeting room management devices from Evoko have flaws that can be exploited by malicious actors in attacks aimed at enterprises that use the product, researchers warned.
The Evoko Liso product allows the employees of an organization to book meeting rooms from their calendar or by using the touchscreen interface of the device installed at each meeting room’s door. The system is managed, configured and updated via the Evoko Home software.
The product is used by thousands of organizations worldwide, including the U.S. Senate, Microsoft, Verizon, HP, Atos, Coca Cola, Siemens, DHL, Ernst & Young, Philips and McDonald’s.

Researchers at TrueSec performed a three-day analysis of the solution for a client and discovered that it’s affected by many potentially serious vulnerabilities, including ones that can be exploited to remotely hijack the device.Evoko Liso vulnerabilities
One of the flaws allows an attacker who has physical access to the device to boot a custom Linux system from a USB drive and install a backdoor that remains active even after a firmware update. The flaw can be exploited to access sensitive information, including passwords, and to create a reverse shell on the device.
Researchers determined that the device’s firmware upgrade process is also vulnerable. They discovered that while firmware images are encrypted, the encryption key is derived from a hardcoded password, and the firmware update functionality does not include integrity and authenticity checks. The firmware update process is also vulnerable to man-in-the-middle (MitM) attacks.
Malicious actors could also manipulate firmware metadata and file content to exploit an arbitrary file write vulnerability that allows the execution of arbitrary code with root privileges.
An attacker who has access to the device can also break out of the kiosk mode and launch a Chrome browser that is running with root privileges. Once they have access to the browser, a hacker can access sensitive information and execute arbitrary shell commands with root privileges from a JavaScript loaded in the browser.
Experts said hackers can also execute shell commands as root by abusing the device’s Wi-Fi connection menu.
As for the Evoko Home software, researchers determined that an attacker with network access to the application can exploit various flaws to create new admin accounts, send out emails, cause a denial-of-service (DoS) condition, and read arbitrary files on the system.
Experts also said the DDP remote procedure call used between Liso and Home allows unauthenticated connections, which can be exploited by attackers to obtain sensitive information, trigger firmware updates, and send emails.
TrueSec reported its findings to Evoko in late January. The vendor told researchers that most of the issues they reported have been patched in recent releases of its firmware, and steps have been taken to mitigate remaining issues. TrueSec said it could not confirm these claims as the company no longer has access to the tested Evoko Liso devices.
SecurityWeek has reached out to the vendor for comment last week, but the company has not responded.
“The Evoko Liso device is a typical example of embedded equipment that will be connected to a corporate network. These devices contain a full Linux system, but corporate IT admins have very little control over them (due to their encapsulated design and limited interfaces). This leaves most of the security decisions to the device vendors – for application code, operating system and third party libraries,” TrueSec’s Emil Kvarnhammar said in a blog post. “It is crucial that IoT vendors build secure and robust systems, and that the systems can be updated remotely in a secure fashion when new vulnerabilities are discovered.”
Yahoo Awards $7,000 for Flickr Account Hijacking Flaws
1.5.2017 securityweek Vulnerebility
A bug bounty hunter has earned $7,000 from Yahoo for finding vulnerabilities in the company’s image and video hosting service Flickr.
Michael Reizelman, aka mishre, said he uncovered three minor flaws that could have been chained together to take control of Flickr accounts.
According to the researcher, when users log in to their Flickr.com account, they are redirected to the login.yahoo.com domain, where their credentials are entered and verified. If the credentials are valid, the user is taken back to Flickr.com and authenticated. The redirect to login.yahoo.com also occurs if the user is already logged in, but it takes place in the background.
The request to login.yahoo.com is used to obtain an access token for the user. Reizelman noticed that a parameter named .done, which controls where the login token is sent, could have been manipulated. However, Yahoo made sure that the token could only be sent to the flickr.com domain.
While finding an open redirect vulnerability on flickr.com could have allowed him to exploit the vulnerability, the expert could not find such weaknesses. He did however discover another method that involved embedding an image from an attacker-controlled server into a Flickr.com page using the <img> tag.
Yahoo had been manipulating this type of code to prevent abuse, but the expert discovered a bypass method.
Reizelman noticed that he could embed an external image into comments posted on flickr.com/help/forum/en-us/, which did not have a Content Security Policy (CSP). By pointing the .done parameter to a malicious image embedded into a post on the Flickr help forum, an attacker could have ensured that the access tokens were sent to their server.
An attacker simply needed to trick the targeted user into clicking on a specially crafted link. Once the token was in their possession, they could have easily accessed the victim’s Flickr account.
The researcher reported the vulnerabilities to Yahoo on April 2 via the tech giant’s HackerOne bug bounty program. The vendor addressed the issue roughly one week later and awarded the expert a $7,000 bounty.
Yahoo addressed the security hole by only allowing the .done parameter to point to flickr.com/signin/yahoo, adding CSP to the Flickr forum, and ensuring that the expert’s image embedding bypass method no longer works.
Reizelman has also earned bounties for reporting vulnerabilities to Uber, GitHub, Dropbox, Twitter, Google, Slack, Badoo and Imgur.
Email Security Device "nomx" Has Serious Flaws: Researchers
1.5.2017 securityweek Vulnerebility
Researchers claim to have found some serious vulnerabilities in “nomx,” a product designed for securing email communications. The vendor has disputed the findings and assured customers that its devices cannot be hacked remotely.
Nomx is a protocol and device that allegedly “ensures absolute privacy for personal and commercial email and messaging.”
British researchers Scott Helme and Professor Alan Woodward have been asked by the BBC to analyze the nomx personal email server appliance, which costs between $199 and $399, depending on its storage capacity. Their analysis revealed the existence of several security issues, including flaws that can be exploited remotely to hijack a device.
An inspection of nomx hardware components showed that the device had actually been powered by a Raspberry Pi, which made it easier for the experts to gain root access and analyze the software running on it.Nomx not as secure as vendor claims
In a post published on his personal blog, Helme said he found several pieces of outdated software running on the email security device, including Raspbian and PHP from 2015, OpenSSL and MySQL versions from 2016, a Postfix variant from 2013, and nginx and Dovecot from 2012.

According to Helme, the software running on the device does not do much in terms of securing email communications, and the expert said many major email service providers may actually block messages sent via nomx as they share some characteristics with spam.
An analysis of the nomx web interface revealed the existence of several cross-site scripting (XSS) and cross-site request forgery (CSRF) vulnerabilities. Helme said the CSRF flaws can be exploited to create new administrator accounts (i.e. backdoors) and make configuration changes by getting a user to visit a specially crafted webpage.
The researcher said he also discovered a documented, default account that provides administrator access to the device. The main problem is that the documentation does not encourage users to change the password to this account and there is no mechanisms in place to force a password change after the first login.
Helme also reported that the device he had analyzed had no update mechanism that would allow users to patch the vulnerable software running on the appliance.
Nomx disputes findings and says researchers made false claims
In a statement posted on its website, Nomx disputed the findings and accused the researchers of making false claims. The company said the attack methods detailed by Helme on his blog could not be carried out in a real world scenario.
Nomx pointed out that Helme’s attack involved physical access to the device. However, the researcher said he conducted hardware hacking in order to find out more about how the device works, but this phase of his research is not related to the attacks that can be launched remotely.
Nomx said only earlier versions of its product were based on a Raspberry Pi and claimed the analyzed devices were actually demo units. The firm also provided recommendations on how users can protect themselves against potential CSRF attacks.
“No nomx devices, accounts or data was ever compromised and the blogger could not show any evidence of such actions,” the company stated.
The vendor claims to have challenged Helme and others to hack its device in a real world scenario, but they allegedly failed to complete the task. On the other hand, the researcher denies taking part in this test.
Both the experts and the BBC said they stand by their reports and claimed that the devices they received for testing were described as production units, not early demo units.
Severe vulnerability in GE Multilin SR poses a serious threat to Power Grid
28.4.2017 securityaffairs Vulnerebility
Security experts discovered a critical vulnerability in GE Multilin SR that poses a serious threat to the power grid worldwide.
A team of researchers from New York University has found a serious vulnerability in some of GE Multilin SR protection relays that poses a serious threat to power grid.
The experts will provide further details about the vulnerability at the upcoming Black Hat conference in Las Vegas, below an excerpt from the abstract published on the conference website.
“Essentially, we completely broke the homebrew encryption algorithm used by these protection and management devices to authenticate users and allow privileged operations,” explained the experts in their abstract. “Knowledge of the passcode enables an attacker to completely pwn the device and disconnect sectors of the power grid at will, locking operators out to prolong the attack.”
The experts will propose also a live demo showcasing exploitation of the vulnerability during their talk anticipating that an attack leveraging on the issue would have a significant impact on a nation.
The ICS-CERT published a security advisory on this threat that was tracked as CVE-2017-7095.
An attacker can obtain the password either from the front LCD panel or via Modbus commands and use it to gain unauthorized access to vulnerable products.
“Successful exploitation of this vulnerability may allow a remote attacker to obtain weakly encrypted user passwords, which could be used to gain unauthorized access to affected products.” reads the advisory.
“Cipher text versions of user passwords were created with a non-random initialization vector leaving them susceptible to dictionary attacks. Cipher text of user passwords can be obtained from the front LCD panel of affected products and through issued Modbus commands.”

The following versions of GE Multilin SR relays are affected by the flaw:
750 Feeder Protection Relay, firmware versions prior to Version 7.47,
760 Feeder Protection Relay, firmware versions prior to Version 7.47,
469 Motor Protection Relay, firmware versions prior to Version 5.23,
489 Generator Protection Relay, firmware versions prior to Version 4.06,
745 Transformer Protection Relay, firmware versions prior to Version 5.23, and
369 Motor Protection Relay, all firmware versions.
GE has promptly released firmware updates that fix the vulnerability for most of the above products. The firmware updates for 369 Motor Protection Relays are expected to be released in June.
To mitigate the vulnerability GE recommends that users apply updated firmware versions to affected products, as well as implement the following best practices:
Control access to affected products by keeping devices in a locked and secure environment,
Remove passwords when decommissioning devices,
Monitor and block malicious network activity, and
Implement appropriate network segmentation and place affected devices within the control system network, behind properly configured firewalls. Protection and Control system devices should not be directly connected to the Internet or business networks.
While the recent disruptions to Ukraine’s energy supply have clearly demonstrated that attacks on the power grid are a reality, it’s not uncommon for cybersecurity researchers to exaggerate the impact of their findings. It remains to be seen exactly how easily this flaw can be exploited after more information is made available.
Critical Flaw in GE Protection Relays Exposes Power Grid: Researchers
28.4.2017 securityaffairs Vulnerebility
A critical vulnerability that affects some of GE’s protection relays poses a serious threat to the power grid, researchers have claimed. The vendor has started releasing patches for the security hole.
A team of researchers from New York University said they identified a severe flaw in some of GE’s Multilin SR protection relays, which are widely deployed in the energy sector. The experts will detail and demonstrate an exploit at the upcoming Black Hat conference in Las Vegas, but they have shared some information on their findings.
“Essentially, we completely broke the home brew encryption algorithm used by these protection and management devices to authenticate users and allow privileged operations,” the experts wrote in their abstract for the conference. “Knowledge of the passcode enables an attacker to completely pwn the device and disconnect sectors of the power grid at will, locking operators out to prolong the attack.”
In an advisory published on Thursday, ICS-CERT said the remotely exploitable vulnerability, tracked as CVE-2017-7095, is related to the use of non-random initialization vectors when encrypting passwords, which exposes them to dictionary attacks.
An attacker who can obtain the password — either from the front LCD panel or via Modbus commands — can hijack the affected device.
ICS-CERT reported that the flaw affects the 750 and 760 Feeder Protection Systems, 369 and 469 Motor Protection Relays, 745 Transformer Protection Relays, and 489 Generator Protection Relays.
GE has already released firmware updates that address the vulnerability for most of these devices, except for 369 Motor Protection Relays, for which patches are expected to become available in June.
The vendor has also advised users to follow physical and network security best practices to prevent exploitation of the flaw, including keeping the devices in a secure environment, removing passwords for decommissioned devices, implementing network segmentation, and monitoring the network for malicious activity.
GE has released an advisory, but it’s only available to customers. The company told SecurityWeek that the affected products are “a limited family of legacy GE products that were developed in the 1990s before current industry expectations for security.” GE said it was not aware of any incidents where the security hole had been exploited.
While the recent disruptions to Ukraine’s energy supply have clearly demonstrated that attacks on the power grid are a reality, it’s not uncommon for cybersecurity researchers to exaggerate the impact of their findings. It remains to be seen exactly how easily this flaw can be exploited after more information is made available.
StringBleed SNMP Authentication Bypass affects numerous devices online
28.4.2017 securityaffairs Vulnerebility
Security researchers discovered an SNMP flaw dubbed StringBleed that affects several models of Internet-connected devices.
Simple Network Management Protocol (SNMP) authentication bypass affects several IoT devices, hackers could exploit the issue by simply sending random values in specific requests.
The problem, dubbed StringBleed and tracked as CVE 2017-5135, was reported by the security researchers Ezequiel Fernandez and Bertin Bervis.
The SNMP protocol supports three methods for client authentication and to authenticate requests on remote SNMP devices, two of them are affected by the authentication bypass issue.
The StringBleed issue resides in the way SNMP agent in running on differed IoT devices handles a human-readable string datatype value called “community string” that SNMP version 1 and 2 use.
“we know there are 3 ways to authenticate the client and requests in the remote SNMP device, SNMP version 1 & 2 use a human-readable string datatype value called “community string” (usually public or private) in SNMP version 3 you have the option to use a user, password and authentication methods. ” explained the researchers.
The researchers used a simple python script to build a “snmpget” request that used the sysDescr OID, then they started scanning the Internet for devices that would respond to the request. The experts were searching for sysDescr OID information provided by the devices in response to requests using test strings like ‘admin’, ‘root’, and ‘user.’
The researchers were looking to retrieve the sysDescr OID information successfully when the test string value (‘admin’, ‘root’, ‘user, etc.) was the same as the one stored in the SNMP agent for authentication.
“We wrote a simple python script from scratch using sockets in order to build the “snmpget” request, in the request we used the sysDescr OID , if the string value we are testing (admin,root etc etc) is the same stored in the SNMP agent for authentication , we are going to retrieve the sysDescr OID information successfully, is like a kind of “brute force”. After some days of scanning we noticed something weird, some devices/fingerprints were always responding no matter which value we used, so what’s going here??? researchers added.
As I mentioned before, the SNMP version 1 & 2 authentication should only accept the value stored in the SNMP agent authentication mechanism, but the behavior based in our results is not accurate like the statement explained previously.”
The StringBleed vulnerability is an Incorrect Access Control issue, remote attackers could exploit the issue to execute code on the vulnerable devices and gain “full read/write remote permissions using any string/integer value.”
“In few words, we discovered the following: you can use any value string or integer in order to authenticate the SNMP agent successfully in some specific devices, but the worse thing here is : you have full read/write remote permissions using any string/integer value.” said the researchers.
The results of the Internet Scan were disconcerting, an attacker could use any value string or integer to authenticate the SNMP agent on the flawed devices.
The experts discovered the but by testing the attack on the CISCO DPC3928SL wireless residential gateway, which is now owned by Technicolor.

The company confirmed the presence of the StringBleed bug on the device but clarified that it was only a “control misconfiguration issue” and that it was isolated to a single Internet Service Provider (ISP).
According to the experts, the issue is widespread and hackers could easily target exposed on the Internet.
One of the researchers revealed in a discussion on Reddit that 78 vulnerable models were found vulnerable to date to the StringBleed flaw.
Stay Tuned …. the number of models could rapidly increase.
SNMP Authentication Bypass Plagues Numerous Devices
28.4.2017 securityweek Vulnerebility
The Simple Network Management Protocol (SNMP) embedded in some Internet connected devices allows an attacker to bypass authentication by simply sending random values in specific requests, security researchers have discovered.
SNMP is a popular protocol for network management that features support for three ways to authenticate the client and requests on remote SNMP devices. The first two of these are vulnerable to an authentication bypass if random values are sent in requests, security researchers Ezequiel Fernandez (Argentina) and Bertin Bervis (Costa Rica) argue.
The issue, the researchers say, resides in the manner in which the SNMP agent in different devices (usually cable modems) handles a human-readable string datatype value called “community string” that SNMP version 1 and 2 use.
Called StringBleed and tracked as CVE 2017-5135, the vulnerability is referred to as Incorrect Access Control and could allow an attacker to execute code remotely on the vulnerable device. Successful exploitation would provide them with “full read/write remote permissions using any string/integer value,” the researchers argue.
With the help of a python script meant to build a “snmpget” request that used the sysDescr OID, the researchers started searching the Internet for devices that would respond to the request. The researchers were looking to retrieve the sysDescr OID information successfully when the test string value (admin, root, user, etc) was the same as the one stored in the SNMP agent for authentication.
The script was supposedly going to work as a type of brute force, the researchers say, but the results were surprising, as some of the discovered devices would respond to the request regardless of the used value.
“SNMP version 1 and 2 authentication should only accept the value stored in the SNMP agent authentication mechanism,” the researchers note. However, their testing revealed that an attacker could use any value string or integer to authenticate the SNMP agent successfully on specific device types.
The bug was initially discovered on the CISCO DPC3928SL wireless residential gateway, which is now owned by Technicolor, and which confirmed the bug, but said it was only a “control misconfiguration issue” and that it was isolated to a single Internet Service Provider (ISP).
The researchers, however, claim that the manufacturer is at fault and that the issue is more widespread. According to them, attackers could easily execute code or leak passwords and other sensitive information from vulnerable devices pertaining to several vendors.
In a post on Reddit, one of the researchers revealed that 78 vulnerable models were found to date, and also said that continuous scans might reveal more of them.
Expert Discloses Several Flaws Found in Sugar CRM
26.4.2017 securityweek Vulnerebility
A researcher has discovered several vulnerabilities in SugarCRM’s popular customer relationship management (CRM) product. While most of the flaws appear to have been patched, the expert’s disclosure suggests that the vendor needs to make some improvements in how it communicates with individuals who report security holes.
Sugar is one of the most popular CRM solutions on the market. The product is used by many major organizations, including IBM, Audi, T-Mobile, HTC and Reebok.
Italy-based researcher Egidio Romano has been analyzing Sugar since 2011 and he claims to have identified more than 50 security issues. Many of the weaknesses were discovered during a virtual internship with the company that involved the analysis of SugarCRM Community Edition, which is open source.
While most of the vulnerabilities have been addressed, Romano disclosed over the weekend the details of several flaws that had apparently not been patched. After the researcher published his blog post, SugarCRM clarified that all the issues had in fact been fixed in the commercial version of its product.
The expert’s blog post describes CVE-2012-0694, a serialization-related code execution vulnerability he discovered back in 2012, and how last year he managed to find a way to bypass SugarCRM’s fix by leveraging a PHP flaw tracked as CVE-2016-7124.
During the summer of 2016, Romano also discovered several other vulnerabilities, including stored cross-site scripting (XSS), local file inclusion, SQL injection and authentication bypass vulnerabilities.
Some of the flaws could have been exploited by an unauthenticated attacker to gain access to user information, including names, email addresses, phone numbers, IP addresses, and credentials for services such as FTP, SSH, databases and VPNs.
Romano has also described a vulnerability involving SugarCRM’s updates.sugarcrm.com domain. According to the researcher, an attacker who manages to compromise this server may be able to hack all 2 million Sugar instances.
The expert said many of the flaws remain unpatched in the latest version of Sugar Community Edition.
In a security notice posted in response to Romano’s blog post, SugarCRM claimed all the vulnerabilities reported by the researcher last summer were patched in October with the release of Sugar 7.7.2.0.
SugarCRM has clarified that the company is focusing on its commercial products and the evolution of its open source program ended with the release of Sugar 7.
SugarCRM says it has been working on addressing the PHP-related serialization vulnerabilities and it plans on moving away from the use of this technique due to the risks it poses.
The firm said all of the flaws reported by Romano last summer had been classified as “medium” or “low” severity, and these types of weaknesses are no longer being patched in the Community Edition. Security holes that have a severity of “medium” or lower are not mentioned in release notes for the commercial product.
The vendor’s statement does not mention the communication issues it had in this case with the researcher. The company has however pointed out that it will make some changes to its policy concerning the inclusion of less severe vulnerabilities in its release notes.
Flaws in Hyundai App Allowed Hackers to Steal Cars
26.4.2017 securityweek Vulnerebility
South Korean carmaker Hyundai has released updates for its Blue Link mobile applications to address vulnerabilities that could have been exploited by hackers to locate, unlock and start vehicles.
The Blue Link application, available for both iOS and Android devices, allows users to remotely access and monitor their car. The list of features provided by the app includes remote engine start, cabin temperature control, stolen vehicle recovery, remote locking and unlocking, vehicle health reports, and automatic collision notifications.
Researchers at security firm Rapid7 discovered that the app had two potentially serious flaws related to a log transmission feature introduced in December

Versions 3.9.4 and 3.9.5 of the Blue Link apps upload an encrypted log file to a pre-defined IP address over HTTP. The name of the file includes the user’s email address and the file itself contains various pieces of information, such as username, password, PIN, and historical GPS data.
While the log file is encrypted, the encryption relies on a hardcoded key that cannot be modified. A man-in-the-middle (MitM) attacker — e.g. via a compromised or rogue Wi-Fi network — can intercept HTTP traffic associated with the Blue Link application and access the log file and the data it contains.
The information in this log file can be used by the attacker to locate, unlock and start the targeted vehicle.
Rapid7 has published a blog post detailing the vulnerabilities. ICS-CERT has also released an advisory which rates the MitM issue (CVE-2017-6052) as a medium severity flaw and the hardcoded cryptographic key weakness (CVE-2017-6054) as high severity.
The flaws were discovered by Rapid7 in February and Hyundai patched them in March with the release of Blue Link 3.9.6 for both iOS and Android. The new version removes the log transmission feature and disables the TCP service located at the IP address where the log files were sent. Hyundai has made the app update mandatory for users.
Hyundai said there was no evidence that the vulnerabilities had been exploited for malicious purposes.
While the flaws could have had a serious impact, Rapid7 and Hyundai pointed out that it would have been “difficult to impossible to conduct this attack at scale,” due to the fact that the attacker needed privileged network access in order to exploit the security holes.
The fact that a mobile application provided by a car manufacturer is vulnerable to hacker attacks is not surprising. In the past months, researchers reported finding flaws in many car apps, including from Tesla.
Display Software Flaw Affects Millions of Devices
25.4.2017 securityweek Vulnerebility
A potentially serious vulnerability has been found in third-party software shipped by several major vendors for their displays. The developer has rushed to release a patch for the flaw, which is believed to affect millions of devices worldwide.
The security hole was identified by researchers at SEC Consult in display software developed by Portrait Displays. The impacted product allows users to configure their displays (e.g. rotation, alignment, colors and brightness) via a software application instead of hardware buttons.
Portrait Displays’ products are used by several major vendors, including Sony, HP, Acer, Fujitsu, Philips, Dell, Benq, Lenovo, Sharp and Toshiba. However, SEC Consult could only confirm the vulnerability for Fujitsu’s DisplayView, HP’s Display Assistant and My Display, and Philips’ SmartControl applications. The apps, which are pre-installed on millions of devices, have been classified by the security firm as bloatware.
According to researchers, the vulnerability, tracked as CVE-2017-3210, exists in the Portrait Displays SDK service and it allows any authenticated attacker to execute arbitrary commands and escalate their privileges to SYSTEM.
SEC Consult said a hacker can exploit the flaw -- by changing the service’s binary path -- for various tasks, including to create new users, add users to groups, or change privileges.
Portrait Displays, which has classified the vulnerability as critical, has released a patch and advised users to install it immediately. The company says it’s not aware of any attacks where this flaw may have been exploited, but a “comprehensive review” is being conducted to confirm this.
As an alternative, users can address the problem by removing the vulnerable service’s permissions via the “sc” command in Windows. CERT/CC has also released an advisory for this security hole.
While a patch has been made available, SEC Consult told SecurityWeek that it’s unlikely regular users will install it any time soon, especially since many will not even know they are affected. On the other hand, experts believe affected vendors could push the patch to users via their automatic software installers (e.g. Fujitsu DeskUpdate).
“It is quite juicy to observe that companies selling millions of notebooks, PCs and convertibles simply do not care (enough) about security,” SEC Consult’s Werner Schober said in a blog post. “The affected companies do have a net worth of multiple billions, but they do not have a few thousand euros/dollars/yen to conduct a proper security review on the software and services they are acquiring from 3rd parties. This vulnerability would have been identified immediately in a thorough security review of the application/service if an audit would have been conducted by security experts before shipping devices with this software. Even automated vulnerability scans would detect such weak service permissions.”
Webroot 'mistakenly' flags Windows as Malware and Facebook as Phishing site
25.4.2017 thehackernews Vulnerebility
Popular antivirus service Webroot mistakenly flagged core Windows system files as malicious and even started temporarily removing some of the legit files, trashing user computers around the world.
The havoc caused after the company released a bad update on April 24, which was pulled after approximately 15 minutes. But that still hasn't stopped some PCs from receiving it, causing serious issues for not just individuals, but also companies and organizations relying on the software.
Webroot even Blocked Facebook
According to the reports by many customers on social media and Webroot's forum, hundreds and even thousands of systems were broken down after antivirus software flagged hundreds of benign files needed to run Windows and apps that run on top of the operating system.
The faulty update even caused the antivirus to incorrectly block access to Facebook after flagging the social network service as a phishing website, preventing users from accessing the social network.
"Webroot has not been breached and customers are not at risk," the company said on its online forum. "Legitimate malicious files are being identified and blocked as normal."
What all went Wrong?
The buggy update caused Webroot anti-virus service to detect legitimate Windows files, including those signed by Microsoft, as W32.Trojan.Gen files – generic malware, in other words.
This behavior, eventually, moved critical Windows system files essential to the operating system's effective functioning into quarantine, making them unavailable to Windows and rendering hundreds of thousands of computers unstable.
Even files associated with some of the applications had also been flagged as malicious and quarantined.
Webroot is Working on a Universal Fix
Webroot, which claims to have over 30 million customers last year, has suggested fixes for those using the Home edition and Business edition of its anti-virus software.
The company's technical team also moved quickly and pushed a fix for the Facebook issue last night, according to the post on the company's forum.
However, the company has yet to provide a definitive fix for its entire affected user base. The company confirms that it's "currently working on this universal solution now," but did not say when it would arrive.
What Affected Users should do
Meanwhile, the company has provided workarounds to restore files and prevent its antivirus from re-detecting the same Windows files as W32.Trojan.Gen, though it is only useful for home edition users and not for managed services providers (MSPs).
However, one user on Webroot's forum is reporting that uninstalling Webroot, then restoring quarantined files from a backup drive, and then re-installing Webroot believes in fixing the issue.
Webroot started tagging Windows files, Facebook as malicious after a faulty update
25.4.2017 Securityaffairs Vulnerebility
Webroot home and business products are tagging Windows files and Facebook as malicious after a recent faulty update. Users are going crazy.
The Webroot home and business defense solutions started tagging legitimate Windows and Facebook as malicious after a recent update.

Many organizations claimed hundreds and even thousands of malfunctions to their endpoints, the glitch caused the Webroot product to detect legitimate Windows files, including digitally signed ones, as W32.Trojan.Gen.
Many customers started reporting the embarrassing problem to online, they reported the issue through social media and Webroot’s forum complain serious problems for their businesses.
Files tagged as malicious by Webroot had been quarantined with important problems for the end-users.
Follow
Limbaughnomicon @Limbaughnomicon
@Webroot @WebrootSupport This false positive issue is driving me insane. As an MSP, a true nightmare. No quarantine restores work. HELP!
3:25 AM - 25 Apr 2017
Retweets likes
Follow
Bob Ripley @M5_Driver
@Webroot I seem to have installed a nasty Ransomware app. It's called Webroot. They already have my money, should I contact the FBI?
12:13 AM - 25 Apr 2017
Retweets 7 7 likes
The update is also blocking the Webroot security product to block access to Facebook as reported by many users on Twitter, the antivirus flagged the popular social network as a phishing website.

Keith Sieman @KeithSieman
> Tfw @Webroot gives you a link to their @facebook page on the very same screen that's blocking access to Facebook... 🙃
3:13 AM - 25 Apr 2017
Retweets likes
The company has published an official statement to calm down its customers, it explained that the system of the company wasn’t under attack.
“We are still working to resolve this issue through the night and will keep you updated as soon as more information becomes available.” read the message shared by Webroot on its forum.
“Webroot has not been breached and customers are not at risk. Legitimate malicious files are being identified and blocked as normal. We continue to work on a comprehensive resolution, but a live fix has been released for the Facebook issue and is propagating through to customers now.”
Webroot has provided a workaround solution for small business customers, unfortunately, managed services providers (MSPs) have to wait to fix the problem.
The company also provided a fix for the Facebook problem.
“We understand that this is a consumer and business issue. For our small business customers, the fix below will work.
We understand that MSPs will require a different solution. We are currently working on this universal solution now.” continues the company.
Experts highlighted that this is the second incident involving Webroot products this year, a faulty update issued in February caused many systems to crash.
Are you thinking to change product?
Probably you need to know that similar problems affected products of other IT security giants such as Norton and ESET.
Webroot Tags Windows Files, Facebook as Malicious
25.4.2017 securityweek Vulnerebility
An update released by Webroot has caused the company’s home and business products to flag legitimate files and websites as malicious.
While the faulty update was only available for less than 15 minutes on Monday, many customers took to social media and Webroot’s forum to complain that it had caused serious problems for their organization. Users reported that hundreds and even thousands of their endpoints were affected.
The update caused Webroot to detect legitimate Windows files, including files signed by Microsoft, as W32.Trojan.Gen. Users also reported that files associated with some of their applications had been flagged as malicious and quarantined.
Follow
Limbaughnomicon @Limbaughnomicon
@Webroot @WebrootSupport This false positive issue is driving me insane. As an MSP, a true nightmare. No quarantine restores work. HELP!
3:25 AM - 25 Apr 2017
Retweets likes
The update also caused the antivirus to block access to Facebook after flagging the service as a phishing website.
“Webroot has not been breached and customers are not at risk. Legitimate malicious files are being identified and blocked as normal,” Webroot said on its forum.
The company has provided a workaround for small business customers, but there is still no solution for managed services providers (MSPs). A fix has also been pushed out for the Facebook issue.
“We understand that MSPs will require a different solution,” Webroot said. “We are currently working on this universal solution now.”
This is the second buggy update released by Webroot this year. An update rolled out in February caused many systems to crash.
Webroot is not the only security firm whose products have caused problems for users. Buggy updates were also released in the past by ESET, Panda Security, Norton and other antivirus vendors.
Squirrelmail 1.4.22 is affected by a Remote Code Execution flaw, no fix is available
25.4.2017 securityaffairs Vulnerebility
The popular PHP webmail package SquirrelMail is affected by a remote code execution vulnerability tracked as CVE-2017-7692.
The popular PHP webmail package SquirrelMail is affected by a remote code execution vulnerability tracked as CVE-2017-7692, that could be exploited by hackers to execute arbitrary commands on the target and fully control it.
The recent version, 1.4.22, and prior versions of the package could be affected by the vulnerability.

The issue was discovered by the popular security researcher Dawid Golunski from Legal Hackers, in January the expert reported it to the maintainers of the project.
Follow
Dawid Golunski @dawid_golunski
[Advisory] SquirrelMail <=1.4.22 Auth. Remote Code Exec#exploit #0day #cybersecurity #infosec #vuln #hacking #rcehttps://legalhackers.com/advisories/SquirrelMail-Exploit-Remote-Code-Exec-CVE-2017-7692-Vuln.html …
8:44 PM - 23 Apr 2017
40 40 Retweets 60 60 likes
You remind Golunski as the expert who discovered other RCE flaws in the email libraries PHPMailer and SwiftMailer.
Despite the maintainers have been informed of the issue, it is still unclear if and when the problem will be solved.
The vulnerability stems from insufficient escaping of user-supplied data when the package is configured with Sendmail as its main transport.
“SquirrelMail is affected by a critical Remote Code Execution vulnerability which stems from insufficient escaping of user-supplied data when SquirrelMail has been configured with Sendmail as the main transport.” wrote Golunski in a security advisory.”An authenticated attacker may be able to exploit the vulnerability to execute arbitrary commands on the target and compromise the remote system.”
Sendmail is a popular mail transfer agent that comes configured as default on email environments.
SquirrelMail configured to use Sendmail fails to take into account a character that can be used by hackers to inject additional parameters.
“SquirrelMail allows authenticated users to control envelopefrom (Return-Path) address through the webmail web interface.” continues Golunski.
“As we can see it calls str_replace() to sanitize the user input to prevent injection of additional parameters to the sendmail command.
Unfortunately it does not take into account \t (TAB) character which can be used by attackers to inject additional parameters.”
The advisory includes the proof of concept code to inject specific parameters to a malicious Sendmail config file, which can then be uploaded as an attachment to trigger the RCE flaw.
The PoC code contains payloads for file write and remote code execution,
Golunski decided to publish release the PoC code after that Filippo Cavallarin, CEO at security firm Segment, disclosed the same vulnerability via the Full Disclosure mailing list archives.
Cavallarin also shared the following unofficial patch for the above issue:
BOF
diff -ruN squirrelmail-webmail-1.4.22/class/deliver/Deliver_SendMail.class.php
squirrelmail-webmail-1.4.22-fix-CVE-2017-7692/class/deliver/Deliver_SendMail.class.php
--- squirrelmail-webmail-1.4.22/class/deliver/Deliver_SendMail.class.php 2011-01-06 02:44:03.000000000 +0000
+++ squirrelmail-webmail-1.4.22-fix-CVE-2017-7692/class/deliver/Deliver_SendMail.class.php 2017-04-18
11:42:26.505181944 +0000
@@ -93,9 +93,9 @@
$envelopefrom = trim($from->mailbox.'@'.$from->host);
$envelopefrom = str_replace(array("\0","\n"),array('',''),$envelopefrom);
// save executed command for future reference
- $this->sendmail_command = "$sendmail_path $this->sendmail_args -f$envelopefrom";
+ $this->sendmail_command = escapeshellcmd("$sendmail_path $this->sendmail_args -f") .
escapeshellarg($envelopefrom);
// open process handle for writing
- $stream = popen(escapeshellcmd($this->sendmail_command), "w");
+ $stream = popen($this->sendmail_command, "w");
return $stream;
}
EOF
Golunski suggests SquirrelMail users of switching to a non-Sendmail transport, like SMTP.
Hardcoded Credentials Give Attackers Full Access to Moxa APs
24.4.2017 securityweek Vulnerebility
Taiwan-based industrial networking, computing and automation solutions provider Moxa has released an update for some of its wireless access points (APs) to address a critical vulnerability that can be exploited by hackers to gain complete control of affected devices.
Researchers at Cisco’s Talos intelligence and research group have analyzed Moxa’s AWK-3131A AP/bridge/client product, which is recommended for any type of industrial wireless application, and discovered hardcoded credentials corresponding to an account that cannot be disabled or removed.
Moxa AP
According to researchers, an attacker can leverage the username “94jo3dkru4” and the password “moxaiwroot” to log in to an undocumented account that provides root privileges.
The flaw, tracked as CVE-2016-8717, has been patched by Moxa with a software update. Users who cannot immediately apply the patch have been advised by Cisco to disable remote access services such as SSH and Telnet.
Experts at Cisco have identified a significant number of vulnerabilities as part of their research into Moxa’s AWK-3131A product. The list includes authentication issues that allow dictionary attacks and session hijacking, many cross-site scripting (XSS) vulnerabilities in the web interface, information disclosure bugs, denial-of-service (DoS) flaws, and several command injections.
Learn More at SecurityWeek's 2017 Singapore ICS Cyber Security Conference
Technical details on the other security holes were made public earlier this month after Moxa had released fixes. CVE-2016-8717 was mentioned in Cisco’s initial advisory, but its details were not disclosed to prevent potential attacks.
Cisco said Moxa has been very cooperative and it even gave researchers access to some of its source code.
Flaws Allowed Hackers to Bypass LastPass 2FA
21.4.2017 securityweek Vulnerebility
LastPass vulnerabilities
Design flaws in LastPass’ implementation of two-factor authentication (2FA) could have been exploited by hackers to bypass the protection mechanism and gain access to user accounts.
Martin Vigo, one of the Salesforce researchers who in November 2015 reported finding several vulnerabilities in LastPass, has once again analyzed the popular password manager, particularly its 2FA mechanism.
The temporary 2FA codes are generated based on several variables, including a secret seed which is typically encoded in a QR code that the user scans with a 2FA app such as Google Authenticator.
Vigo’s tests showed that the request made when a QR code image was displayed to the user contained the login hash used by LastPass for authentication. In fact, the 2FA secret seed had been derived from the user’s password, which defeated the entire purpose of 2FA protection as the attacker presumably already possesses the password.
While determining the URL of the QR code was not difficult, a hacker needed to be authenticated for the attack to work. However, exploiting a cross-site request forgery (CSRF) vulnerability could address this problem. Getting a logged-in user to click on a specially crafted link that exploits a CSRF flaw could have allowed an attacker to obtain the QR code image.
According to Vigo, an attacker could have also leveraged cross-site scripting (XSS) vulnerabilities on popular websites to avoid having the victim visit his malicious site, which would be more likely to raise suspicion.
The researcher also found a simple way to disable 2FA using a CSRF vulnerability. As with all CSRF attacks, the hacker needed to get the victim to visit a malicious website.
LastPass was informed about these vulnerabilities on February 7 and immediately started working on patches. The company addressed the CSRF flaws, added a security mechanism for checking the origin of a QR code request, and eliminated the use of password hashes for the secret seed.
In a blog post published on Thursday, LastPass informed users that they don’t need to take any action as all the fixes have been done on the server side. The company also pointed out that exploiting the flaws required a combination of factors that made attacks more difficult.
“To exploit this issue an attacker would have needed to take several steps to bypass Google Authenticator,” LastPass said. “First, the attacker would have had to lure a user to a nefarious website. Second, the user would have to be logged in to LastPass at the time of visiting the malicious site.”
Vigo’s disclosure comes shortly after Google Project Zero researcher Tavis Ormandy reported finding several vulnerabilities in the LastPass browser extensions.
Vulnerabilities in Linksys routers allow attackers to hijack dozens of models
21.4.2017 securityaffairs Vulnerebility
Cyber security experts disclosed the existence of 10 unpatched security flaws in dozens of Linksys routers widely used today.
The IOActive senior security consultant Tao Sauvage and the independent security researcher Antide Petit have reported more than a dozen of unpatched security vulnerabilities affecting 25 different Linksys Smart Wi-Fi Routers models.
The security duo published a blog post on Wednesday providing details of their discoveries.Attackers can exploit the security vulnerabilities to extract sensitive information from the devices, trigger DoS conditions, change settings, and completely take them over.The vulnerabilities effects dozens of Linksys models, including EA3500 Linksys Smart Wi-Fi, WRT and Wireless-AC series.Linksys routers flaws
Out of 10 security vulnerabilities, six issues can be exploited by remote unauthenticated attackers.
All these products are widely by private users and by small businesses, for this reason, the impact of the discovery is huge. It has been estimated that over 7,000 routers that have their web-based administrative interfaces exposed to the Internet are exposed to attacks.
The experts discovered determined that 11 percent of the 7,000 Linksys routers still used default credentials.
“We performed a mass-scan of the ~7,000 devices to identify the affected models. In addition, we tweaked our scan to find how many devices would be vulnerable to the OS command injection that requires the attacker to be authenticated. We leveraged a router API to determine if the router was using default credentials without having to actually authenticate.” reads the blog post published by the two experts.
“We found that 11% of the ~7000 exposed devices were using default credentials and therefore could be rooted by attackers.”
Most of the flawed Linksys routers (~69%) are located in the USA, followed by Canada (~10%), Hong Kong (~1.8%), Chile (~1.5%), and the Netherlands (~1.4%).
If we consider the possibility that a local attacker exploits the issues to target systems over a local area network, the number of devices at risk dramatically increases.
The experts avoided to provided technical details about the flaw in the Linksys routers to avoid mass attacks against the vulnerable devices. The duo confirmed that two of the flaws could be exploited to trigger a denial-of-service condition on flawed routers, making them unusable or reboot by sending specifically crafted requests to a specific API.
Other vulnerabilities affecting the web interfaces of the Linksys routers allow attackers to bypass authentication and access many CGI scripts that can reveal sensitive information about the flawed devices and their configurations. An attacker can exploit the issues to obtain the Wi-Fi Protected Setup (WPS) PIN and to access the wireless network for further lateral movement from within. An attacker can exploit the vulnerability to determine firmware and kernel versions of the vulnerable Linksys routers and obtain a list of running processes, information about computers connected to the routers, a list of USB devices and the configuration settings for the FTP and SMB file-sharing servers.
The most severe flaw discovered by the experts could be exploited by attackers to inject and execute shell commands with root privileges on the affected routers. The flaw could be exploited to set up a backdoor administrative account that wouldn’t be listed in the web interface.
“Finally, authenticated attackers can inject and execute commands on the operating system of the router with root privileges. One possible action for the attacker is to create backdoor accounts and gain persistent access to the router. Backdoor accounts would not be shown on the web admin interface and could not be removed using the Admin account.” states the post.The flaw requires authentication to be exploited, this means the attackers need to have access to an existing account.
“It should be noted that we did not find a way to bypass the authentication protecting the vulnerable API; this authentication is different than the authentication protecting the CGI scripts.”
Linksys confirmed it is currently working on firmware updates to fix the vulnerabilities, meantime, as mitigation measures it suggests users disable the guest Wi-Fi network feature on their routers.
“Linksys was recently notified of some vulnerabilities in our Linksys Smart Wi-Fi series of routers.
As we work towards publishing firmware updates, as a temporary fix, we recommend that customers using Guest Networks on any of the affected products below temporarily disable this feature to avoid any attempts at malicious activity.” states the advisory. “We
will be releasing firmware updates for all affected devices.”
The complete list of vulnerable Linksys routers is reported in the security advisory issued by the company.
Beware! Dozens of Linksys Wi-Fi Router Models Vulnerable to Multiple Flaws
20.4.2017 thehackernews Vulnerebility
Bad news for consumers with Linksys routers: Cybersecurity researchers have disclosed the existence of nearly a dozen of unpatched security flaws in Linksys routers, affecting 25 different Linksys Smart Wi-Fi Routers models widely used today.
IOActive's senior security consultant Tao Sauvage and independent security researcher Antide Petit published a blog post on Wednesday, revealing that they discovered 10 bugs late last year in 25 different Linksys router models.
Out of 10 security issues (ranging from moderate to critical), six can be exploited remotely by unauthenticated attackers.
According to the researchers, when exploited, the flaws could allow an attacker to overload the router, force a reboot by creating DoS conditions, deny legitimate user access, leak sensitive data, change restricted settings and even plant backdoors.
Many of the active Linksys devices exposed on the internet scanned by Shodan were using default credentials, making them susceptible to the takeover.
Researchers found more than 7,000 devices impacted by the security flaws at the time of the scan, though this does not include routers protected by firewalls or other network protections.
"We performed a mass-scan of the ~7,000 devices to identify the affected models," IOActive says. "We found that 11% of the ~7000 exposed devices were using default credentials and therefore could be rooted by attackers."
IOActive made Linksys aware of the issues in January this year and is working "closely and cooperatively" with the company ever since to validate and address the vulnerabilities.
Here's How critical are these Flaws:
The researchers did not reveal more details about the vulnerabilities until the patch is made available to users, although they said two of the flaws could be used for denial-of-service attacks on routers, making them unresponsive or reboot by sending fraudulent requests to a specific API.
Other flaws could allow attackers to bypass CGI scripts to collect sensitive data such as firmware versions, Linux kernel versions, running processes, connected USB devices, Wi-Fi WPS pins, firewall configurations, FTP settings, and SMB server settings.
CGI, or Common Gateway Interface, is a standard protocol which tells the web server how to pass data to and from an application.
Researchers also warned that attackers those have managed to gain authentication on the devices can inject and execute malicious code on the device's operating system with root privileges.
With these capabilities in hands, attackers can create backdoor accounts for persistent access that are even invisible in the router smart management console and so to legitimate administrators.
However, researchers did not find an authentication bypass that can allow an attacker to exploit this flaw.
List of Vulnerable Linksys Router Models:
Here's the list of Linksys router models affected by the flaws:
EA2700, EA2750, EA3500, EA4500v3, EA6100, EA6200, EA6300, EA6350v2, EA6350v3, EA6400, EA6500, EA6700, EA6900, EA7300, EA7400, EA7500, EA8300, EA8500, EA9200, EA9400, EA9500, WRT1200AC, WRT1900AC, WRT1900ACS, and WRT3200ACM.
The majority of the exposed devices (nearly 69%) are located in in the United States, and others are spotted in countries including Canada (almost 10%), Hong Kong (nearly 1.8%), Chile (~1.5%), and the Netherlands (~1.4%).
A small percentage of vulnerable Linksys routers have also been spotted in Argentina, Russia, Sweden, Norway, China, India, UK, and Australia.
Here's How you can Mitigate Attacks originating from these Flaws:
As temporary mitigation, Linksys recommended its customers to disable the Guest Network feature on any of its affected products to avoid any attempts at the malicious activity.
The company also advised customers to change the password in the default account in order to protect themselves until a new firmware update is made available to patch the problems.
Linksys is working to release patches for reported vulnerabilities with next firmware update for all affected devices. So users with Smart Wi-Fi devices should turn ON the automatically update feature to get the latest firmware as soon as the new versions arrive.
Experts Find 10 Flaws in Linksys Smart Wi-Fi Routers
20.4.2017 securityweek Vulnerebility
Researchers at IOActive have analyzed Linksys routers and discovered a total of 10 vulnerabilities. Patches have yet to be released, but the vendor has provided some mitigation advice.
The research has focused on Linksys routers that support the Smart Wi-Fi feature, which enables users to manage and control their home wireless network remotely from a mobile application. According to Linksys, the vulnerabilities found by IOActive affect 25 EA and WRT series routers.
IOActive will not disclose any specific information until Linksys releases firmware updates and users have had a chance to patch their devices. However, experts said the vulnerabilities they have identified can be exploited to cause a denial-of-service (DoS) condition, obtain potentially sensitive data, and even to plant backdoors.Linksys routers vulnerable to attacks
Two of the flaws can be used for DoS attacks. Unauthenticated hackers can cause the router to become unresponsive or reboot by sending specially crafted requests to a specific API. Exploitation of these flaws disrupts network connections and prevents device administrators from accessing the web interface.
Authentication bypass vulnerabilities allow attackers to access certain CGI scripts that provide access to various types of information, including firmware and Linux kernel versions, running processes, connected USB devices, and the WPS PIN. Attackers can also collect data on firewall configurations, FTP settings, and SMB server settings.
IOActive also warned that attackers who do manage to log in to the router can inject and execute commands on the device’s operating system with root privileges. This allows them to create backdoor accounts that are not visible to legitimate administrators.
However, researchers pointed out that they did not manage to find an authentication bypass that can allow an attacker to exploit this vulnerability – the authentication bypass they did find only provides access to some CGI scripts, not the API that enables these more damaging attacks.
A Shodan search conducted by IOActive revealed 7,000 vulnerable devices that can be accessed directly from the Internet. Nearly 70 percent of them were located in the United States, followed by Canada, Hong Kong, Chile, Netherlands, Venezuela, Argentina, Russia, Sweden, Norway, China, India, UK and Australia.
While researchers have not found a way to bypass authentication in order to exploit the command injection vulnerability, they did determine that 11 percent of the 7,000 exposed devices had been using default credentials.
IOActive reported the vulnerabilities to Linksys in mid-January. The vendor is working on releasing firmware updates for affected devices and, in the meantime, it has provided some mitigation advice. The company recommends temporarily disabling the Guest Network feature, and changing the default admin password.
This research was conducted just a few months after IOActive reported finding multiple vulnerabilities in BHU Wi-Fi uRouter, a device manufactured and sold in China.
Cisco Fixes Serious Flaws in Security, Other Products
20.4.2017 securityweek Vulnerebility
Cisco has released software updates for its Firepower, IOS, Adaptive Security Appliance (ASA) and Unified Communications Manager (Unified CM) products to address high severity denial-of-service (DoS) vulnerabilities.
One of the flaws, identified as CVE-2016-6368, can affect several products running Cisco Firepower System Software, including ASA, Advanced Malware Protection (AMP), Firepower, Sourcefire 3D and Industrial Security appliances. An unauthenticated attacker can exploit the vulnerability remotely to cause a DoS condition.
Related: Cisco Launches New Firepower Firewalls
A DoS vulnerability (CVE-2017-3808) that can be exploited by a remote, unauthenticated attacker has also been found in Cisco Unified CM, namely in the session initiation protocol UDP throttling process.
Several high severity DoS flaws have also been discovered in the EnergyWise module of Cisco’s IOS and IOS XE software. EnergyWise is designed for monitoring and managing the power usage of devices in a domain, including networking devices and Power over Ethernet (PoE) endpoints.
Cisco has also published four advisories describing remotely exploitable weaknesses in its ASA software. The security holes affect components such as the IKEv1 XAUTH code, the SSL/TLS code, IPsec code and DNS code.
Two of the vulnerabilities can be exploited by an unauthenticated attacker, while the other two require authentication.
Most of these flaws have been discovered by Cisco itself and there is no evidence that any of them have been exploited for malicious purposes.
Cisco is one of the several tech companies whose products have been targeted by exploits described recently by WikiLeaks as part of a dump called “Vault 7.” The networking giant has discovered a zero-day vulnerability affecting many of its switches.
Patches have yet to be made available for the flaw and Cisco warned customers last week that a researcher has released a proof-of-concept (PoC) exploit.
Drupal Patches Critical Access Bypass Flaw
20.4.2017 securityweek Vulnerebility
Updates released for versions 8.2 and 8.3 of the Drupal content management system (CMS) address a critical access bypass vulnerability.
The flaw, discovered by Drupal developer Samuel Mortenson and tracked as CVE-2017-6919, has been classified as critical by the Drupal security team, but it only affects websites if certain conditions are met.
Websites are vulnerable to attacks exploiting this flaw if they have the RESTful Web Services (RESTWS) module enabled and they allow PATCH requests. The attacker must also be able to register an account on the targeted site.
Nevertheless, the security hole is potentially serious, which is why Drupal developers have released a patch not only for the 8.3 branch, but also for the 8.2 series, which has reached end of life and will not receive other updates.
Drupal has advised 8.2.x users to update to Drupal 8.2.8, but still recommends updating to Drupal 8.3 at a later time. In the case of Drupal 8.3, the vulnerability has been patched with the release of version 8.3.1. Drupal 7 is not affected.
Vulnerabilities involving the RESTWS module have been known to be exploited in the wild. In September 2016, researchers spotted attempts to exploit a RESTWS flaw that had been patched two months earlier.
The latest updates come only one day after Drupal announced the availability of a patch for a critical flaw affecting a popular third-party module.
The References module, used by more than 121,000 websites, had not been updated since 2013 and Drupal flagged it as unsupported. However, Drupal has managed to find a new maintainer for the module and the security hole has been fixed.
Critical vulnerability in Drupal References Module opens 120,000 Sites to hack
19.4.2017 securityaffairs Vulnerebility
A critical vulnerability affects the Drupal References module that is used by hundreds of thousands of websites using the popular CMS.
The Drupal security team has discovered a critical vulnerability in a third-party module named References.
The Drupal team published a Security advisory on April 12 informing its users of the critical flaw.
The flaw has a huge impact on the Drupal community because the affected module is currently used by more than 121,000 websites.
“The module is currently used by over 120 000 individual Drupal installations, but is no longer maintained. The last update was done in February 2013. Unfortunately, a critical security vulnerability in this references module has been reported by the Drupal core security team as SA-CONTRIB-2017-38:
Please note, the security team will not release information on this vulnerability for up to a month, the recommendation is to migrate. Emails asking for details on the vulnerability will not be responded to. If you would like to maintain the module, please follow the directions below.
” states Drupal.
The References module allows users to add references between nodes for more complex information architectures.
The module was initially flagged by the Drupal development team as unsupported, its last update was provided in February 2013.
The good news for References users is that, on April 14, the Drupal security team announced it was assigned to a new maintainer.
“2017-04-14 – A potential new maintainer is working through the process of fixing the References module. When this is complete a new release will be published and this SA will be updated.” reads the advisory.
A few days later, on April 18 the problem has been fixed with the release of references 7.x-2.2.
References module
The Drupal security team did not disclose the technical details about the vulnerability in order to avoid the exploitation of the flaw in the wild. Unfortunately, it will very difficult to upgrade websites heavily using the Reference module.
“With a critical issue in an unsupported module so widely used, it is almost guaranteed that a large number of sites will be subject to attacks using this as a vector.” states Drupal. “Given the tradition of Drupal doing big backward breaks with regards to compatibility, some sites might be difficult to upgrade. Upgrading an enterprise site heavily using References may simply be impossible and hopefully drive the module to be maintained by a corporate entity.”
Drupal will release information on the critical vulnerability in the next few weeks.
Security experts believe threat actors could find the vulnerability by analyzing the source code of the module and could develop and exploit.
Drupal CMS is a privileged target for hackers that try to exploit vulnerabilities in the out-dated plugin.
In June 2016, security experts warned of the Drupalgeddon attacks against Drupal websites, more than 19 months after the public disclosure of the CVE-2014-3704.
Oracle Patches Record Number of Vulnerabilities
19.4.2017 securityweek Vulnerebility
Oracle’s Critical Patch Update (CPU) for April 2017 contains 299 fixes, the highest number compared to previous CPUs.
More than half of the vulnerabilities could be remotely exploitable without authentication. 40 of the issues were rated Critical, and 25 had a CVSS score of 10.
Oracle Financial Services Applications was the most affected product, receiving fixes for 47 vulnerabilities this month, with 19 of them rated critical with a CVSS score of 10. Aditionally, 25 of the 47 vulnerabilities may be remotely exploitable without authentication, Oracle’s advisory reveals.
Oracle CPU April 2017Released this week, Oracle latest CPU addressed vulnerabilities in 25 applications: MySQL and Retail Applications (39 fixes each), Fusion Middleware (31), Sun Systems Products Suite (21), PeopleSoft (16), Virtualization (15), Berkeley DB (14), Support Tools (13), E-Business Suite (11), Communications Applications (11), Java SE (8), Utilities Applications (7), Primavera Products Suite (7), Hospitality Applications (6), Commerce (3), Database Server (2), Enterprise Manager Grid Control (2), and Secure Backup, Hyperion, Supply Chain Products Suite, JD Edwards Products, Siebel CRM, Health Sciences Applications, and Insurance Applications (1 each).
The most important of the addressed issues are related to the Remote Code Execution flaw in Apache Struts 2 that was found last month to be exploited in the wild after someone published a proof-of-concept (PoC) exploit. Cisco and VMWare products were impacted as well.
“Cybercrime has always been a lucrative business. Nowadays, hackers set their eyes on enterprises more than on individuals, as they understood that it is more profitable. Taking into account that Oracle’s products are installed in the largest enterprises, these applications can be the ultimate target. The good news is that the vendor drew its attention to this critical area before a serious data breach happens. The bad news is that Oracle admins will long work on installing numerous patches,” Alexander Polyakov, CTO at ERPScan, says.
Oracle addressed critical bugs in the Solaris component of Oracle Sun Systems Products Suite, MySQL Enterprise Monitor component of Oracle MySQL (Struts 2), Oracle FLEXCUBE Private Banking component of Oracle Financial Services Applications (Struts 2), Oracle Financial Services Asset Liability Management component of Oracle Financial Services Applications (Struts 2), and Oracle Financial Services Data Integration Hub component of Oracle Financial Services Applications (Struts 2).
Over the past several quarters, Oracle has been patching an increasingly higher number of vulnerabilities with each new CPU. With 276 patches, the July 2016 CPU was the first to include over 250 fixes, but the trend continued each quarter since, with 253 flaws addressed in October 2016, and 270 in January 2017.
The trend is expected to continue in the following quarters as well. However, as it usually happens with all software, this doesn’t mean the applications are becoming more vulnerable, but that the researcher community is getting better at finding security issues.
Kaspersky Adds Password Manager to Bug Bounty Program
19.4.2017 securityweek Vulnerebility
Kaspersky Lab has informed researchers that its bug bounty program has been extended. The company has also decided to add a new product to its program and increase the maximum reward.
Kaspersky launched its HackerOne-powered bug bounty program in August 2016. The first phase, which lasted for six months and promised a total of $50,000 in bounties, led to the discovery of more than 20 flaws.
Given the program’s success so far, the security firm has decided to extend it and make some changes. Bug bounty hunters can now earn rewards for finding vulnerabilities in Kaspersky Password Manager 8. Until now, only Kaspersky Internet Security 2017 and Kaspersky Endpoint Security 10 were in scope.
The security firm also announced that the maxim reward for remote code execution vulnerabilities has been increased from $2,000 to $5,000. White hat hackers can earn, on average, $1,000 for local privilege escalation flaws and $2,000 for sensitive information disclosure issues. The minimum reward is $300.
“Since August, it is fair to say that our Bug Bounty Program has been successful in optimising our internal and external mitigation measures to continuously improve the resiliency of our products. That’s why we’ve decided to extend it,” said Nikita Shvetsov, Chief Technology Officer at Kaspersky Lab.
“We appreciate the enthusiastic participation of security researchers worldwide. As a mark of our respect for the work they do in helping us to bolster our solutions, we’ve increased the remuneration on offer in this second phase of the program and extended the scope to include other important Kaspersky Lab products,” Shvetsov added.
Google Project Zero researcher Tavis Ormandy has reported finding several vulnerabilities in Kaspersky products in the past years. The most recent, disclosed in January, was related to how the security firm’s products inspect SSL/TLS connections.
Flaw in Drupal Module Exposes 120,000 Sites to Attacks
19.4.2017 securityweek Vulnerebility
A critical vulnerability has been found in a Drupal module used by many websites. While the flaw has been fixed, Drupal developers initially advised users to migrate as the affected module had not been updated for several years.
The Drupal security team informed users on April 12 that the third-party module named References was affected by a critical security hole. The module, currently used by more than 121,000 websites, allows users to add references between nodes for more complex information architectures.
References was initially flagged by Drupal developers as unsupported due to the fact that it had received its last update in February 2013. However, on April 14, the Drupal security team announced that they may have found a new maintainer for the module.
On Tuesday, Drupal announced that the vulnerability has been fixed with the release of References 7.x-2.2, which also includes new features and bug fixes.
Drupal’s security team has not released any information on the vulnerability to prevent exploitation, but experts are concerned that malicious actors could manage to find the flaw on their own by analyzing the source code. Drupal said it will release information on this weakness in the next few weeks.
While the References module appears to have found a new maintainer, Drupal website owners can also try out Entity Reference, a module that provides similar functionality. A special module is available for migrating from References to Entity Reference.
Hackers have been known to target Drupal websites using vulnerabilities in third-party modules. Last year, researchers started seeing attempts to exploit a RESTWS module flaw two months after it had been patched.
The most well-known Drupal vulnerability is the one dubbed “Drupalgeddon,” which had still been exploited nearly two years after a patch was released.
VMware Patches Critical RCE Flaw in vCenter Server
18.4.2017 securityaffairs Vulnerebility
VMware has released patches for its vCenter Server product to address a critical remote code execution flaw that exists due to the use of a vulnerable third-party component.
Earlier this month, CERT/CC informed users that Markus Wulftange, senior penetration tester at Code White, had identified three potentially serious deserialization-related flaws in several Java implementations of AMF3, the latest version of Adobe’s Action Message Format.
The vulnerabilities can be exploited for denial-of-service (DoS) attacks, remote code execution and to obtain sensitive data. The affected software includes Apache’s Flex BlazeDS, Atlassian’s JIRA, Exadel’s Flamingo, GraniteDS, Spring spring-flex, and WebORB for Java by Midnight Coders.
One of the BlazeDS vulnerabilities, tracked as CVE-2017-5641, has been found to affect VMware vCenter Server, which uses BlazeDS to process AMF3 messages.
“The issue is present in the the Customer Experience Improvement Program (CEIP) functionality. If a customer has opted out of CEIP the vulnerability is still present. Also opting out will not remove the vulnerability,” VMware said in its advisory.
The security hole affects vCenter Server 6.0 and 6.5; version 5.5 or other VMware products are not impacted. VMware has advised users to apply the 6.5c and 6.0U3b patches to address the vulnerability.
According to CERT/CC, the deserialization vulnerabilities identified by Wulftange could also affect products from HPE and SonicWall.
Flaws in the Bosch Drivelog Connector dongle could allow hackers to halt the engine
16.4.2017 securityaffairs Vulnerebility
Security experts discovered vulnerabilities in the Bosch Drivelog Connector dongle that could be exploited by hackers to stop the engine.
Security Researchers at automotive cybersecurity firm Argus discovered vulnerabilities in Bosch Drivelog Connect solution that can be exploited by hackers to inject malicious messages into a vehicle’s CAN bus.
The Bosch Drivelog Connect is the system that provides information about the state of a vehicle, it includes the Drivelog Connector dongle.

The Drivelog Connector dongle is connected to the OBD2 diagnostics interface of the vehicle, and a mobile application communicates with it via Bluetooth.
The researchers analyzed the protocol of communication between the mobile app and the dongle and identified two potentially serious vulnerabilities.
“The vulnerabilities allowed us to stop the engine of a moving vehicle using the Drivelog platform. On February 20th, 2017, in accordance with Argus’ responsible disclosure policy, upon uncovering the vulnerabilities we informed Bosch of our findings. On February 21st, 2017, Bosch’s Product Security Incident Response Team (PSIRT) contacted Argus and began addressing the issue.” reads the analysis published by Argus.
“In summary, the following two vulnerabilities were found:
An information leak in the authentication process between the Drivelog Connector Dongle and the Drivelog Connect smartphone application.
Security holes in the message filter in the Drivelog Connector dongle.”
One of the vulnerabilities affects the authentication process between the Drivelog Connector and the Drivelog Connect mobile app. The experts have analyzed the Android version of the mobile app.
The second flaw resides in the message filter in the Drivelog Connector dongle.
According to researchers, diagnostic messages can only be sent to the CAN bus using a valid service ID, but the attacker can use OEM-specific messages that pass the filter in order to have a physical effect on the car.
An attacker with root privileges on the driver’s mobile phone can leverage this message filter bypass to send malicious CAN messages outside of the scope a small subset of diagnostic messages (i.e., OBDII PIDs).
According to Argus, during the tests, its researchers managed to remotely stop the engine of a moving car by triggering the vulnerability.
Car vendors highlight that such kind of attack is very hard to prevent because attackers have taken over the smartphone of the legitimate driver.
Researchers from Argus have gone beyond, they devised a method to launch the attack without compromising the driver’s smartphone.
The experts discovered an information disclosure vulnerability in the authentication process between the app and the dongle that could be exploited by an attacker to connect to a targeted device without compromising the phone first.
Analyzing the authentication process, researchers discovered the dongle sends any connecting Android device various pieces of information that can be used to obtain the user-supplied authorization PIN.
The amount of data is enough to guess the PIN offline through a brute-force attack only limited in the number of possible PINs.
“Since, a Drivelog Dongle’s PIN has eight digits, there are 100 million possible PINs. A single verification requires a SHA256 calculation and a public key encryption operation. The calculations can be trivially parallelized – but the reality is, there’s no need: a modern laptop can run 100 million SHA256 computations and encryptions in roughly 30 minutes (according to independent benchmarks for the Ed25519 public-key signature system) using properly optimized software.” reads the analysis. “The time needed can be further reduced by running several brute-forcing servers in parallel.”
Once the connection has been established, the attacker can send malicious CAN bus messages from their device, instead of having to compromise the driver’s smartphone, the only limitation if that the hacker needs to be in a Bluetooth range of the targeted vehicle.
Bosch fixed the issues by introducing two-step verification in the authentication process.
“The improper authentication vulnerability in the Bluetooth communication has been mitigated by activating a two-step verification for additional users to be registered to a device. This has been implemented on the server, so no action is required by the user. To further increase security in the authentication process an application and dongle firmware update will also be released.” states the advisory published by the Bosch.
The company plans to release a firmware update for the Drivelog Connector dongle to prevent such kind of attacks.
Turns Out Microsoft Has Already Patched Exploits Leaked By Shadow Brokers
15.4.2017 thehackernews Vulnerebility
The latest dump of hacking tools allegedly belonged to the NSA is believed to be the most damaging release by the Shadow Brokers till the date.
But after analyzing the disclosed exploits, Microsoft security team says most of the windows vulnerabilities exploited by these hacking tools, including EternalBlue, EternalChampion, EternalSynergy, EternalRomance and others, are already patched in the last month's Patch Tuesday update.
"Most of the exploits that were disclosed fall into vulnerabilities that are already patched in our supported products. Customers still running prior versions of these products are encouraged to upgrade to a supported offering," Microsoft Security Team said in a blog post published today.
On Good Friday, the Shadow Brokers released a massive trove of Windows hacking tools allegedly stolen from NSA that works against almost all versions of Windows, from Windows 2000 and XP to Windows 7 and 8, and their server-side variants such as Server 2000, 2003, 2008, 2008 R2 and 2012, except Windows 10 and Windows Server 2016.
The hacking exploits could give nearly anyone with technical knowledge the ability to break into millions of Windows computers and servers all over the Internet, but those which are not up-to-date.
"Of the three remaining exploits, “EnglishmanDentist”, “EsteemAudit”, and “ExplodingCan”, none reproduces on supported platforms, which means that customers running Windows 7 and more recent versions of Windows or Exchange 2010 and newer versions of Exchange are not at risk." Microsoft says.
The data dump also includes some top-secret presentations and excel sheets, indicating that the leaked exploits may have been used to hack the SWIFT banking system of several banks across the world.
Even though NSA exploits are patched, the Shadow Brokers leak is still big, which provides info on NSA targeting SWIFT Networks
CLICK TO TWEET
Hacking tool, called Eternalromance, contains an easy-to-use interface and exploits Windows systems over TCP ports 445 and 139.
The most noteworthy exploit in the Friday's dump is Eternalblue — an SMBv1 (Server Message Block 1.0) exploit that could cause older versions of Windows to execute code remotely.
Matthew Hickey, a security expert and co-founder of Hacker House, also published a video demonstration, using this exploit against a computer running Windows Server 2008 R2 SP1 and pulling off the hack in less than 2 minutes with another alleged zero-day FuzzBunch, which is being used to compromise a virtual machine running Windows Server 2008.
But if the company already patched this flaw last month, then how could this exploit works against an updated machine? It seems like the researcher tried this exploit against a Windows PC without installing the latest updates.
"The patches were released in last month's update, I tested on a fully patched Windows 2008 R2 SP1 (x64), so many hosts will be vulnerable - if you apply MS17-010 it should protect hosts against the attacks," Matthew clarifies during a conversation with The Hacker News.
No Acknowledgement for SMB RCE Issue by Microsoft
There's also news floating around the Internet that the "NSA has had, at a minimum, 96 days of warning," knowing that the Shadow Brokers could drop the files at any time, but the agency did not report the flaws to Microsoft.
The Intercept also reported that Microsoft told it that the company had not been contacted by any "individual or organization," in relation to the hacking tools and exploits released by the Shadow Brokers.
The vulnerabilities have already been patched by Microsoft, which acknowledges all security researchers for reporting the issues in its products, but, interesting, there are no acknowledgments for MS17-010 which patched most of the critical flaws from the Shadow Brokers dump.
It’s noteworthy, there’s no acknowledgement for recently patched MS17-10 SMB flaw on Microsoft (used in Eternalblue)
CLICK TO TWEET
This indicates that someone from the agency or linked with defense contractor might have warned the company of the SMB RCE issue.
So, only those who are still using Windows XP, which Microsoft doesn't support for very long, are at risk of getting their machines hacked.
And there is no need to panic if you use updated Windows 7, 8 or 10 (or even Windows Vista, whose support ended just last week and the issue was patched last month).
The simple advice for you is to always keep your Windows machines and servers up-to-date in order to prevent yourself from being hacked.
Watch out, the Riddle vulnerability affects some Oracle MySQL versions. Update them now
15.4.2017 securityaffairs Vulnerebility
A bug dubbed Riddle vulnerability affecting MySQL 5.5 and 5.6 clients exposed user credentials to MiTM attacks. Update to version 5.7.
A coding error dubbed The Riddle has been uncovered in the popular DBMS Oracle MySQL, the issue can be potentially exploited by attacker powering a man-in-the-middle attack to steal usernames and passwords.
“The Riddle is a critical security vulnerability found in Oracle’s MySQL 5.5 and 5.6 client database libraries. The vulnerability allows an attacker to use riddle in the middle for breaking SSL configured connection between MySQL client and server.” states the description of the flaw.“This vulnerability is a very critical security hole because it affects MySQL — a very popular SQL database — and SSL connection which is by its definition secure.”
The flaw, tracked as CVE-2017-3305, potentially exposes login credentials to eavesdropping, an attacker can capture them when a MySQL clients 5.5 and 5.6 send them to servers.
A security update released for the versions 5.5.49 and 5.6.30 failed to completely fix the bug. The experts noticed that the Versions 5.7 and later, as well as MariaDB systems, are not affected by this issue.
According to security researcher Pali Rohár, the Riddle vulnerability results for the failed attempt to patch the BACKRONYM vulnerability affecting the MySQL database. The Backronym vulnerability exposes passwords to attackers who are in a position to run a man-in-the-middle attack, even if the traffic is encrypted.
“Security update for the stable MySQL 5.5.49 and 5.6.30 versions consisted of adding a verification of security parameters after the authentication process was finished.” “Since it is done after the authentication, riddle in the middle attack together with SSL-downgrade attack can be used by the attacker to steal login data for immediate authentication and log into the MySQL server,” wrote Rohár.

“Ridiculous part is that MySQL client doesn’t report any SSL-related error when MySQL server declines to authenticate a user and instead reports unencrypted error message send by the server. Furthermore, the error message is controlled by the attacker, when the riddle in the middle attack is active.”
The expert suggests updating the client software to MySQL 5.7 or MariaDB, because the security updates for these applications correctly work.
The Riddle vulnerability was discovered in February, but today the bug still affect the Oracle MySql software.
“Reporting bugs to Oracle is useless (even those which are security related) if you are not an Oracle customer. They can perfectly ignore any reports and they would be very happy if nobody knew about it so they don’t have to fix the bugs,” explains Rohár.
“It looks like immediate public disclosure is the best responsible solution for the users, as it is the only way to protect them and let them know immediately what should be done if they are affected.”
Cisco warns of two critical issues in IOS and Apache Struts
14.4.2017 securityaffairs Vulnerebility
Cisco issued two “critical” security advisories, one for Cisco IOS and Cisco IOS XE Software, another for a flaw affecting Apache Struts 2.
Today Cisco issued two “critical” security advisories, the first one for Cisco IOS and Cisco IOS XE Software, the second one for the recently discovered flaw affecting Apache Struts 2.
The vulnerability in Cisco IOS affects the Cisco Cluster Management Protocol (CMP) that could be exploited by an unauthenticated, remote attacker to trigger a DoS condition via a reload of the device, or remotely execute code with elevated privileges.
“A vulnerability in the Cisco Cluster Management Protocol (CMP) processing code in Cisco IOS and Cisco IOS XE Software could allow an unauthenticated, remote attacker to cause a reload of an affected device or remotely execute code with elevated privileges.” reads the Cisco Security Advisory.
According to Cisco a wide range of devices is affected by the flaw, including the Cisco Catalyst 2350-48TD-S Switch and the Cisco SM-X Layer 2/3 EtherSwitch Service Module.
“The Cluster Management Protocol utilizes Telnet internally as a signaling and command protocol between cluster members. The vulnerability is due to the combination of two factors: The failure to restrict the use of CMP-specific Telnet options only to internal, local communications between cluster members and instead accept and process such options over any Telnet connection to an affected device, and the incorrect processing of malformed CMP-specific Telnet options.” states Cisco.
The attacker can exploit the vulnerability establishing a Telnet session with vulnerable devices and by sending malformed CMP-specific Telnet options. At the time, I was writing there is no workaround to temporary fix the problem.
“An exploit could allow an attacker to execute arbitrary code and obtain full control of the device or cause a reload of the affected device,” continues the advisory.
As for the flaw in Apache Struts2, Cisco confirmed that some products using the application could be remotely hacked. The remote code execution flaw disclosed by Apache in March, tracked as CVE-2017-5638, affects the Jakarta-based file upload Multipart parser.
The IT giant is still investigating its products to determine affected products, as for now the company confirmed that Cisco SocialMiner, Identity Services Engine (ISE), Prime License Manager and others are affected.
Unpatched Magento Flaw Exposes Online Stores to Attacks
14.4.2017 securityweek Vulnerebility
Magento, the popular e-commerce platform used by more than 250,000 merchants worldwide, is affected by a potentially serious vulnerability that can be exploited to hijack online stores, researchers warned.
The flaw was found by DefenseCode in November and reported to Magento via the company’s Bugcrowd-based bug bounty program. The vendor indicated at the time that it had been aware of the issue, but it still hasn’t addressed it. After its attempts to obtain a status update on the vulnerability failed, DefenseCode decided to make its findings public.
The vulnerability is related to a feature that allows users to add Vimeo video content for an existing product. When a video is added, Magento automatically retrieves a preview image via a POST request.
This request method can be changed from POST to GET, allowing an attacker to launch a cross-site request forgery (CSRF) attack and upload an arbitrary file. While invalid image files are not allowed, the file is still saved on the server before it is validated.
The location of the file can be easily determined, enabling a hacker to upload a malicious PHP script to the server. In order to achieve remote code execution, the attacker also needs to upload a .htaccess file to the same directory.
For the attack to work, a hacker needs to convince a user with access to the shop’s administration panel, regardless of their role and permissions, to access a specially crafted web page that triggers the CSRF attack.
Researchers warned that successful exploitation of the vulnerability can allow an attacker to take complete control of a targeted system, including gain access to sensitive customer information stored in the compromised store’s database.
“Full administrative access is not required to exploit this vulnerability as any Magento administrative panel user regardless of assigned roles and permissions can access the remote image retrieval functionality. Therefore, gaining a low privileged access can enable the attacker to compromise the whole system or at very least, the database (e.g. traversing to /app/etc/env.php to grab the database password),” DefenseCode wrote in its advisory.
The latest security updates were released by Magento developers in February, when they addressed a critical remote code execution vulnerability that allegedly affected only few systems.
Flaws in Bosch Car Dongle Allow Hackers to Stop Engine
14.4.2017 securityweek Vulnerebility
Vulnerabilities found by researchers in Bosch’s Drivelog Connect product can be exploited by hackers to inject malicious messages into a vehicle’s CAN bus. The vendor has implemented some fixes and is working on adding more attack protections.
Bosch’s Drivelog Connect is a service that provides information about the condition of a vehicle, including potential defects, service deadlines, and data on fuel consumption and driving behavior. The product includes a dongle called Drivelog Connector, which is connected to the car’s OBD2 diagnostics interface, and a mobile application that communicates with the dongle via Bluetooth.
Researchers at automotive cybersecurity firm Argus have identified some potentially serious vulnerabilities in the communications between the mobile app and the dongle.Vulnerabilities in Bosch’s Drivelog Connect
One of the security holes is related to the authentication process between the Drivelog Connector and the Drivelog Connect smartphone app. The app is available for both iOS and Android, but experts focused on the Android application. The second flaw affects the dongle’s message filter.
According to researchers, diagnostic messages can only be sent to the CAN bus using a valid service ID. However, this message filter can be bypassed by sending OEM-specific messages that can be obtained through CAN traffic monitoring or by fuzzing CAN bus messages.
An attack leveraging this message filter bypass can be launched by a hacker who has obtained root access to the targeted user’s smartphone. During the tests they conducted, Argus researchers said they managed to remotely stop the engine of a moving car by exploiting the vulnerability. They pointed out that, depending on the make and model of the car, other actions may have been possible.
This attack scenario requires root access to the Android device and a malicious patch to the mobile app. Car manufacturers have often pointed out that it’s difficult to prevent attacks once a smartphone has been compromised.
However, Argus researchers have found a way to launch attacks without this requirement. An information disclosure vulnerability in the authentication process between the app and the dongle allows an attacker to connect to a targeted device without hacking the phone first.
During the authentication process, the dongle sends any connecting Android device various pieces of information that can be used to obtain the user-supplied authorization PIN. The PIN can be brute-forced offline – the attack takes up to 30 minutes on a modern laptop – and it can then be used to connect to the dongle.
Once the connection has been completed, the attacker can send malicious CAN bus messages from their own device, instead of having to hijack the targeted user’s smartphone. This attack is mitigated by the fact that the hacker needs to be in Bluetooth range of the targeted vehicle.
In an advisory it published this week, Bosch said it addressed the authentication vulnerability on the server side by introducing two-step verification when additional users are registered to a device. The company is also working on a firmware update for the dongle to prevent attackers from sending unauthorized CAN messages from a hijacked mobile app.
CVE-2016-10229 Linux remote code execution flaw potentially exposes systems at risk of hack
14.4.2017 securityaffairs Vulnerebility
The Linux remote vulnerability tracked as CVE-2016-10229 poses Linux systems at rick of hack if not patched.
A Linux kernel vulnerability, trackers as CVE-2016-10229, potentially allows attackers to remotely take over a vulnerable system (i.e. Servers, desktops, IoT devices and mobile devices).
“udp.c in the Linux kernel before 4.5 allows remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag.” reads the description of the flaw published by the NDV.
The CVE-2016-10229 flaw expose systems to attacks via UDP traffic, according to the experts. the attackers can potential hack a system running a software receiving data through the system call recv() with the MSG_PEEK flag set on. This means that attackers would send to the target specifically crafted packets that trigger the CVE-2016-10229 flaw by forcing a second checksum operation on the incoming data. In this way, the attacker can execute malicious code within the kernel with root privileges, fortunately the issue is hard to exploit as explained by the popular Google Project Zero hacker Tavis Ormandy.
16h
Dan Rosenberg @djrbliss
I have reviewed the relevant code and I mostly understand it, but I'm missing the security ramifications.
Follow
Tavis Ormandy ✔ @taviso
@djrbliss I'm as confused as you are...
7:18 PM - 13 Apr 2017
4 4 Retweets 17 17 likes
Common software, like the Nginx web server, set the MSG_PEEK flag on some connections, potentially exposing the system to the attack.
The bug can also be potentially exploited by a local attacker to escalate privileges.
The vulnerability was discovered by the expert from Google Eric Dumazet who explained that the issue dates back the end of 2015 when a small fix was applied to the Linux kernel.
Affected versions are the Kernel versions below 4.5, all the way down to 2.6, are likely at risk, major Linux distribution such as Ubuntu and Debian were distributing fixed builds of the kernel by February this year.
According to Red Hat, it Linux distribution were never affected by the CVE-2016-10229 flaw.

Google has already rolled out security patches for Android that also fixed the CVE-2016-10229 in mobile devices.
“So, in short, yes, there is a remote kernel-level code execution vulnerability in Linux, which sounds like the worst of the very worst, but it is pretty much patched by now – and it appears to be tricky to exploit. It was silently addressed in the kernel source over a year ago, and fixed in updates to machines earlier this year, but only now has it come to wider attention.” reported The Register.
Hundreds of thousands Magento e-shops are exploited to hack due to an unpatched flaw
14.4.2017 securityaffairs Vulnerebility
An unpatched vulnerability in Magento platform could be exploited by hackers to compromise fully web servers that host the e-commerce sites.
An unpatched vulnerability in the Magento e-commerce platform could be exploited by attackers to upload and execute malicious PHP scripts on web servers that host online shops.
The vulnerability was reported by experts at the security firm DefenseCode, the issue resides in a feature that was implemented to retrieves preview images for Vimeo videos. The feature was implemented to allow Magento admins to add videos to product listings.
The experts noticed that if the image URL references a different file, such as a PHP script, Magento will download the file to validate it. If the file is not an image, Magento will display the message “Disallowed file type”, leaving it on the server.
An attacker triggering the vulnerability could remotely execute code by first tricking Magento to download an .htaccess configuration file that enables PHP execution inside the download directory and then downloading a malicious PHP script that can work as a backdoor.
At this point it is possible to access the backdoor by accessing it via the browser, the experts explained that the attacker can exploit the script to browse the server directories and read the database password from Magento’s configuration file.
The vulnerability could be exploited only by an authenticated attacker, even if it is a lower-privileged user.
The experts added that if the Magento e-shop doesn’t have the “Add Secret Key to URLs” option turned on, the attacker can launch a cross-site request forgery (CSRF) attack to force a user’s browser to perform an unauthorized request on a website when visiting a different one.
The attacker can hack the Magento shop by tricking the victims into clicking on a link shared by mail or by visiting a specifically crafted web page.
The attack will work against all the users who have active Magento sessions in their browser, exploiting this attack vector hackers might take over users’ accounts.
“By changing the request method from POST to GET, a lack of a form_key parameter which serves as a CSRF token will be ignored and thus enable cross-site request forgery (CSRF) attacks.” reads the advisory published by DefenseCode.
“The attack can be constructed as simple as “
DefenseCode reported these issues to the Magento development team in November, but the flaws are still unpatched and almost all the the Magento CE versions are affected.
Below the disclosure Timeline
11/18/2016 Vendor contacted via BugCrowd platform
11/18/2016 Vendor responded – aware of issue
04/11/2017 Vendor contacted again without response
04/13/2017 Advisory released to the public
In order to mitigate the attack, experts suggest enforcing the use of ‘Add Secret Key to URLs’
CVE-2017-0199 Zero Day exploit used to deliver FINSPY spyware
13.4.2017 securityaffairs Vulnerebility
Security researchers at FireEye discovered that the Microsoft Word CVE-2017-0199 exploit was linked to cyberspying in Ukraine conflict.
The zero-day vulnerability in Microsoft Office that was recently fixed by Microsoft was used to deliver a surveillance malware to Russian-speaking targets.
Security experts from firm FireEye spotted the targeted attacks leveraging specifically crafted Microsoft Word documents that pretend to be a Russian military training manual.

When the victim opened the document, the attacks starts and a the surveillance malware FinSpy is delivered, the malware is developed by a subsidiary of Gamma Group. Officially the software would be offered for sale only to Government agencies and law enforcement bodies, but privacy advocate speculate the spyware of also sold to authoritarian regime.
“FireEye assesses with moderate confidence that CVE-2017-0199 was leveraged by financially motivated and nation-state actors prior to its disclosure.” reads the analysis published by FireEye. “Actors leveraging FINSPY and LATENTBOT used the zero-day as early as January and March, and similarities between their implementations suggest they obtained exploit code from a shared source. Recent DRIDEX activity began following a disclosure on April 7, 2017.”
The experts are still investigating who is the final target of the attacks, however, the decoy document appears to have been published in the Donetsk People’s Republic, a breakaway region in Ukraine that’s received Russian support.
“As early as Jan. 25, 2017, lure documents referencing a Russian Ministry of Defense decree and a manual allegedly published in the “Donetsk People’s Republic” exploited CVE-2017-0199 to deliver FINSPY payloads. Though we have not identified the targets, FINSPY is sold by Gamma Group to multiple nation-state clients, and we assess with moderate confidence that it was being used along with the zero-day to carry out cyber espionage.” continues FireEye.
“The malicious document, СПУТНИК РАЗВЕДЧИКА.doc (MD5: c10dabb05a38edd8a9a0ddda1c9af10e), is a weaponized version of a widely available military training manual (Figure 1). Notably, this version purports to have been published in the “Donetsk People’s Republic,” the name given to territory controlled by anti-Kyiv rebels in Eastern Ukraine.”
The weaponized Russian training manual can download additional payloads along with another fake document claiming to be a Russian decree approving a forest management plan.
FireEye experts suspect a non-state actor may have hacked targets operating like government operators using the FinSpy software.
It is also possible that the zero-day exploit circulated in the cyber criminal underground, in March, a separate attack triggering the same flaw was spotted by the experts.
“As early as March 4, 2017, malicious documents exploiting CVE-2017-0199 were used to deliver the LATENTBOT malware. The malware, which includes credential theft capability, has thus far only been observed by FireEye iSIGHT Intelligence in financially motivated threat activity. Additionally, generic lures used in this most recent campaign are consistent with methods employed by financially motivated actors.” adds FireEye.
Likely different hacking groups may have obtained the zero-day knowledge from the same source.
SAP Patches Critical Code Injection Flaw in TREX
13.4.2017 securityweek Vulnerebility
SAP this week released its April 2017 set of patches. The most important of the 15 security notes resolves a Very High priority (Hot News) vulnerability in TREX / BWA that could allow an attacker to execute commands on the affected system.
Carrying a CVSS score of 9.4, and discovered by ERPScan, the note is the third in a series of patches that SAP has been releasing for NetWeaver Search and Classification (TREX) and NetWeaver Business Warehouse Accelerator (BWA) since December 2015, to prevent remote command execution. The issue was initially addressed with SAP Note 2234226, which was later updated with SAP Note 2273881, and now patched with SAP Note 2419592.
Onapsis, the firm that discovered the original vulnerability in 2015, explains that TREXNet, the internal communication protocol developed for TREX service, does not enforce any kind of authentication, but is required by TREX servers. This means that it exposes systems to malicious actors, who can remotely execute critical system and OS commands.
According to ERPScan, a company that specializes in securing SAP and Oracle products, because TREX is deployed in over a dozen SAP products, including SAP HANA, this vulnerability is considered one of the most widespread and severe SAP server-side issues. What’s more, the advisory with all the details was available on the web for 2 years, thus exposing numerous applications to attacks, ERPScan says.
“I reversed a protocol for HANA and then for the TREX search engine. As they share a common protocol, the exploit has been easily adapted. SAP fixed some features, but not everything affecting the core protocol. It was still possible to get full control on the server even with a patched TREX,” Mathieu Geli, Head of SAP Threat Intelligence at ERPScan and the researcher who discovered the issue, explains.
SAP’s April 2017 advisory reveals that three of the 15 security notes included in this month’s Security Patch Day were updates to previous notes, including one to a Remote Code Execution vulnerability in SAP GUI for Windows. Four of the security notes had a High severity rating, 8 were rated Medium risk, and two were considered Low severity.
ERPScan, on the other hand, says that there were 12 additional security notes included in this set of patches, for a total of 27 notes (17 SAP Security Patch Day Notes and 10 Support Package Notes).
7 of the patches were Missing Authorization Checks, 4 were Cross-Site request forgery, 3 Cross-Site Scripting, 2 Remote Code Execution (RCE), 2 XML external entity, 2 information disclosure, 2 denial of service, 1 open redirect, 1 buffer overflow, 1 directory traversal, and 2 other flaws.
In addition to the RCE flaw in TREX / BWA, SAP addressed three more vulnerabilities found by ERPScan researchers: a Cross-Site Scripting vulnerability in SAP NetWeaver Central Technical Configuration (CVSS Base Score: 6.3), a Cross-Site Scripting vulnerability in SAP NetWeaver Java Archiving Framework (CVSS Base Score: 6.1), and an XML external entity vulnerability in SAP Knowledge Management ICE Service (CVSS Base Score: 4.9).
Other critical issues SAP resolved this month include a Denial of service vulnerability in SAP SAPLPD (CVSS Base Score: 7.5), an XML external entity vulnerability in SAP Web Dynpro Flash Island (CVSS Base Score: 7.5), and a Missing authorization check vulnerability in SAP NetWeaver ADBC Demo Programs (CVSS Base Score: 6.3).
“After a pretty significant March Update, which included the highest critical note of the year (SAP HANA Self Service Vulnerability with CVSS 9.8 and other relevant High Priority notes) this is the second month with remote code injection vulnerabilities present. As a result, SAP Security Note #2419592 should be prioritized among the others as it implies a similar attack as the two others previously mentioned that impact TREX,” Onapsis says.
Juniper Networks Patches Several Flaws With Junos Updates
13.4.2017 securityweek Vulnerebility
Updates released by Juniper Networks for its Junos operating system patch several high and medium severity vulnerabilities. The company has also updated some of the third-party software used by its products.
Juniper Networks informed customers on Tuesday that it has launched an investigation into the new batch of exploits made public last week by the hacker group calling itself Shadow Brokers. The first round of files leaked by the Shadow Brokers in the summer of 2016 was found to contain some exploits targeting devices running Juniper’s ScreenOS.
Until it determines if any of its products are targeted by the newly released exploits, which are believed to have been used by the NSA-linked Equation Group, Juniper Networks has released updates that patch several vulnerabilities in the FreeBSD-based Junos OS.
The most severe of the flaws, based on its CVSS score, is CVE-2016-10142, an issue related to the IPv6 protocol specification, namely ICMP Packet Too Big (PTB) messages. The vulnerability can be exploited for denial-of-service (DoS) attacks.
Another high severity flaw is CVE-2016-1886, a keyboard driver buffer overflow that can be exploited to cause a DoS condition, read parts of the kernel memory, or execute arbitrary code.
It’s worth pointing out that CVE-2016-10142 and CVE-2016-1886 are not specific to Juniper products; the vulnerabilities are in FreeBSD and other Linux distributions.
The third high severity vulnerability is CVE-2017-2313, a DoS issue that affects some Junos systems when BGP is enabled.
The medium severity weaknesses disclosed by the company this week are DoS flaws affecting various configurations. These security holes are tracked as CVE-2017-2313, CVE-2017-2312 and CVE-2017-2340.
Juniper is not aware of any instances where these vulnerabilities have been exploited for malicious purposes.
The vendor also announced patches for vulnerabilities affecting its NorthStar Controller application, and updates for the BIND and NTP components used by the company’s products. The NTP and BIND patches applied by Juniper were first made available several months ago, and other fixes have since been released for both NTP and BIND.
Office 0-Day Abused in Latentbot, WingBird Attacks
13.4.2017 securityweek Vulnerebility
A Microsoft Office 0-day vulnerability that was disclosed just days ago is already being exploited by attackers associated with malware families such as Latentbot and WingBird.
Tracked as CVE-2017-0199, the security bug allows a malicious actor to craft a RTF (Rich Text Format) document that would download and execute a Visual Basic script containing PowerShell commands. Microsoft has already addressed the flaw, but not quick enough to prevent malware such as the Dridex banking Trojan from abusing it in attacks.
The exploit for this vulnerability was found to bypass most mitigations available before a patch was released, and could also render Protected View useless, security researchers discovered. This means that attacks leveraging the vulnerability don’t require user interaction to be successful.
The exploit leverages Office’s Object Linking and Embedding (OLE) functionality to link to an HTA (HTML Application) file hosted on a remote server. When the user opens the RTF document received via spam email, winword.exe issues a HTTP request to retrieve the malicious HTA file, which loads and executes the malicious Visual Basic script. In turn, the script downloads and executes malware.
According to FireEye, the malicious scripts used in these incidents were also observed terminating the winword.exe processes (to hide a prompt from OLE2link) and loading decoy documents.
The security researchers stumbled upon such attacks designed to distribute a newer variant of Latentbot, a highly obfuscated bot that has been active since 2013. The bot has a highly modular plugin architecture and has been also associated with the Pony infostealer.
Latentbot packs different injection mechanisms for Windows XP (x86) and Windows 7 operating systems: it uses Attrib.exe patching and Svchost code Injection on the former, but injects code into svchost.exe directly on the latter.
Another attack abusing this vulnerability consisted of two malicious stages, and distributed a variant of the dropper known as WingBird (which has similar characteristics as FinFisher). Heavily obfuscated, the malware packs several anti-analysis measures, including a custom VM to slow analysis, and was recently associated with the activities of a threat group known as NEODYMIUM.
Netskope Threat Research Labs, on the other hand, say that this Office zero-day vulnerability can also be linked to the Godzilla botnet loader. The researchers observed that the IPs related to the loader were serving payloads associated with exploits for this bug, but say that they “cannot speculate that the spam campaign and zero-day are related,” although the same attack group appears to be behind the attacks.
Office users are advised to apply the newly released patches as soon as possible, to ensure they are protected from these attacks.
Critical bug in SAP TREX affects SAP HANA and other applications
13.4.2017 securityaffairs Vulnerebility
SAP has issued a security patch for the SAP TREX search engine that addresses also a two-years old critical vulnerability.
SAP has issued a security patch for the SAP TREX search engine that addresses multiple vulnerabilities discovered by the experts in a 2015 patch released in December 2015.
The SAP TREX search engine is used by many SAP products, including SAP HANA and itsNetWeaver application and integration platform.
“SAP, the largest enterprise software maker, closed a critical vulnerability affecting SAP’s search engine TREX. The issue stayed exposed almost 2 years.” reads a blog post published by the company ERPScan that discovered the flaw. “The vulnerable component is included in the old SAP NetWeaver platform as well as in the new SAP HANA one, which makes it one of the most widespread and severe SAP server-side issues so far with CVSS score 9.4 out of 10. The vulnerability was identified by specialists at ERPScan,” “If exploited, the vulnerability would allow a remote attacker to get full control over the server without authorization.”
SAP was affected by a critical code injection vulnerability (SAP Security Note 2419592) that he company addressed with the 2015 patch, unfortunately the problem was not completely solved.
Mathieu Geli from ERPScan discovered that the TREXNet communication protocol implemented in the SAP TREX search engine did not implement an authentication mechanism.
“Originally, the vulnerability was discovered in SAP HANA in 2015 and the corresponding SAP Security Note (2234226) was released in December 2015. The issue was dubbed a potential technical information disclosure and fixed by removing some critical functions.” continues the post. “Later on, Mathieu Geli from ERPScan conducted a further research and revealed that the vulnerability was still exploitable. He found out that TREXNet, an internal communication protocol used by TREX, did not provide an authentication procedure. “
The expert made a reverse engineering of a protocol for HANA and then for the SAP TREX search engine. Both share a common protocol, for this reason the exploit could be easily adapted. He highlighted that SAP fixed just some features related to the core protocol.
“I reversed a protocol for HANA and then for the TREX search engine. As they share a common protocol, the exploit has been easily adapted. SAP fixed some features, but not everything affecting the core protocol. It was still possible to get full control on the server even with a patched TREX.” explained the expert.
The vulnerability, tracked as CVE-2017-7691, could be exploited by an attacker to read or create operating system files by sending a crafted request to TREXNet ports.
The flaw was fized along with other bugs in SAP’s April security release.
Not Just Criminals, But Governments Were Also Using MS Word 0-Day Exploit
13.4.2017 thehackernews Vulnerebility
Recently we reported about a critical code execution vulnerability in Microsoft Word that was being exploited in the wild by cyber criminal groups to distribute malware like Dridex banking trojans and Latentbot.
Now, it turns out that the same previously undisclosed vulnerability in Word (CVE-2017-0199) was also actively being exploited by the government-sponsored hackers to spy on Russian targets since at least this January.
The news comes after security firm FireEye, that independently discovered this flaw last month, published a blog post, revealing that FinSpy spyware was installed as early as January using the same vulnerability in Word that was patched on Tuesday by Microsoft.
For those unaware, the vulnerability (CVE-2017-0199) is a code execution flaw in Word that could allow an attacker to take over a fully patched and up to date computer when the victim opens a Word document containing a booby-trapped OLE2link object, which downloads a malicious HTML app from a server, disguised as a document created in Microsoft's RTF (Rich Text Format).
FinSpy or FinFisher is associated with the controversial UK-based firm Gamma Group, which sells so-called "lawful intercept" spyware to governments around the world.
"Though only one Finspy user has been observed leveraging this zero-day exploit, the historical scope of Finspy, a capability used by several nation-states, suggests other customers had access to it," FireEye researchers said.
"Additionally, this incident exposes the global nature of cyber threats and the value of worldwide perspective—a cyber espionage incident targeting Russians can provide an opportunity to learn about and interdict crime against English speakers elsewhere."
Months later in March, the same then-zero-day vulnerability was used to install Latentbot, a bot-like, information-stealing and remote-access malware package used by financially motivated criminals.
Latentbot has several malicious capabilities including credential theft, remote desktop functions, hard drive and data wiping, and the ability to disable antivirus software.
FireEye said criminals used social engineering to trick victims into opening the attachments with generic subject lines like "hire_form.doc", "!!!!URGENT!!!!READ!!!.doc", "PDP.doc", and "document.doc".
However, on Monday, the criminals behind the attack modified their campaign to deliver a different malware package called Terdot, which then installed software that uses the TOR anonymity service to hide the identity of the servers it contacted with.
According to FireEye researchers, the MS Word exploit used to install Finspy on Russian computers by government spies and the one used in March to install Latentbot by criminal hackers was obtained from the same source.
This finding highlights that someone who initially discovered this zero-day vulnerability sold it to many actors, including the commercial companies who deals in buying and selling of zero-day exploits as well as financially motivated online criminals.
Also, just Monday evening, Proofpoint researchers too discovered a massive campaign of spam email targeting millions of users across financial institutions in Australia with the Dridex banking malware, again, by exploiting the same vulnerability in Word.
FireEye researchers are still not sure of the source for the exploit that delivered the Dridex banking trojan, but it is possible that the vulnerability disclosure by McAfee last week provided insight that helped Dridex operators use the flaw, or that someone with access to the Word exploit gave it to them.
Microsoft patched the MS Word vulnerability on Tuesday, which hackers, as well as government spies, had been exploiting it for months. So, users are strongly advised to install updates as soon as possible to protect themselves against the ongoing attacks.
BIND Updates Patch Three Vulnerabilities
13.4.2017 securityweek Vulnerebility
The Internet Systems Consortium (ISC) announced this week that updates released for the DNS software BIND patch several denial-of-service (DoS) vulnerabilities that can be exploited remotely.
BIND versions 9.9.9-P8, 9.10.4-P8 and 9.11.0-P5 address three new security holes that could lead to an assertion failure.
The most serious of the flaws, with a “high” severity rating and a CVSS score of 7.5, is CVE-2017-3137. The vulnerability allows an attacker to cause a DoS condition, and it mainly affects recursive resolvers, but authoritative servers could also be vulnerable if they perform recursion.
“A server which is performing recursion can be forced to exit with an assertion failure if it can be caused to receive a response containing CNAME or DNAME resource records with certain ordering,” ISC said in its advisory.
Another vulnerability patched with the latest BIND updates is CVE-2017-3136, a medium severity issue that affects servers configured to use DNS64 with the "break-dnssec yes;" option.
The third flaw, CVE-2017-3138, can be exploited to cause the BIND name server (named) process to exit by sending it a null command string on its control channel. However, the flaw can only be exploited remotely from hosts that are allowed access to the control channel.
ISC said there was no evidence that any of these vulnerabilities had been exploited in the wild.
BIND vulnerable to new reflection attacks
Earlier this month, Ixia security software engineer Oana Murarasu reported finding a new DDoS attack amplification method. The expert discovered that BIND’s recursive DNS resolver allows reflection attacks through root DNAME query responses.
“This amplification attack generates responses 10 or more times larger than the query sent,” Murarasu explained. “For every 1 megabit of traffic sent, 10 megabits is sent to the victim.”
The issue has been reported to ISC, but the organization determined that these attacks are possible due to a protocol design flaw and not a vulnerability in BIND itself. Ixia said Microsoft’s DNS server is not susceptible to such attacks.
Microsoft Issues Patches for Actively Exploited Critical Vulnerabilities
11.4.2017 thehackernews Vulnerebility
Besides a previously undisclosed code-execution flaw in Microsoft Word, the tech giant patches two more zero-day vulnerabilities that attackers had been exploiting in the wild for months, as part of this month's Patch Tuesday.
In total, Microsoft patches 45 unique vulnerabilities in its nine products, including three previously undisclosed vulnerabilities under active attack.
The first vulnerability (CVE-2017-0199) under attack is a remote-code execution flaw that could allow an attacker to remotely take over a fully patched and up to date computer when the victim opens a Word document containing a booby-trapped OLE2link object.
The attack can bypass most exploit mitigations developed by Microsoft, and according to Ryan Hanson of security firm Optiv, in some cases, exploits can execute malicious code even when Protected View is enabled.
As The Hacker News reported Monday, this code-execution flaw in Microsoft Word was being exploited by hackers to spread a version of infamous Dridex banking trojan.
Also, according to blog posts published Tuesday by security firms FireEye and Netskope, hackers are exploiting the same Word vulnerability to install Latentbot and Godzilla malware respectively.
Microsoft has released a fix for CVE-2017-0199 and credited Hanson with responsible reporting the critical vulnerability to the company.
Patch for Critical IE Flaw Being Exploited in the Wild
The company also pushed out a patch for another critical vulnerability (CVE-2017-0210) under active attack. The flaw is an elevation of privilege vulnerability in Internet Explorer that would allow an attacker to trick a victim into visiting a compromised website.
The vulnerability could allow the attacker to access sensitive information from one domain and inject it into another domain.
"The vulnerability by itself does not allow arbitrary code to be run. However, the vulnerability could be used in conjunction with another vulnerability (for example, a remote code execution vulnerability) that could take advantage of the elevated privileges when running arbitrary code," Microsoft's guidance for the flaw reads.
This IE vulnerability is also being exploited in the wild.
Another Critical Word Vulnerability Yet Unpatched!
The third previously undisclosed flaw (CVE-2017-2605) resides in the Encapsulated PostScript (EPS) filter in Microsoft Office, but Microsoft did not actually release an update for this flaw in Tuesday's update batch.
However, the tech giant issued an update for Microsoft Office that, by default, disable the EPS filter in MS Office as a defense measure. This Word vulnerability is also being exploited in the wild when a target opens a malicious EPS image in Word.
"Microsoft is aware of limited, targeted attacks that could leverage an unpatched vulnerability in the EPS filter and is taking this action to help reduce customer risk until the security update is released," the guidance for the flaw reads.
The company also issued a patch for Windows 10 Creators Update, which was made available on Tuesday, addressing some remote code execution flaws and elevation of privilege bugs.
In total, Microsoft rolled out 15 security updates on Tuesday patching dozens of unique CVEs in its products, including the Windows OS, Exchange Server, Edge and Internet Explorer, Office, Office Services and Office Web Apps, Visual Studio for Mac Silverlight and Adobe Flash.
Users are strongly advised to install updates as soon as possible in order to protect themselves against the active attacks in the wild on three separate Microsoft products.
Adobe Patches Flash, Reader Flaws Exploited at Pwn2Own
12.4.2017 securityweek Vulnerebility
Adobe released security updates for several of its products on Tuesday to address a total of 59 vulnerabilities, including flaws disclosed last month at the Pwn2Own 2017 hacking competition.
A majority of the security holes, 47 to be precise, have been patched in the Windows and Mac versions of Adobe Acrobat and Reader. The vulnerabilities, rated critical with a priority rating of 2 (i.e. no exploits and exploitation not imminent), have been described as memory corruptions that could lead to arbitrary code execution or memory address leaks.
Seven critical vulnerabilities have been patched in Adobe Flash Player. The security holes are use-after-free and memory corruption issues that could lead to code execution.
Many of the flaws patched on Tuesday were reported to Adobe via Trend Micro’s Zero Day Initiative (ZDI), including several Reader and Flash Player vulnerabilities disclosed at ZDI’s Pwn2Own competition.
ZDI has published five advisories detailing the Pwn2Own security holes tracked as CVE-2017-3062, CVE-2017-3063, CVE-2017-3055, CVE-2017-3056 and CVE-2017-3057.
Adobe has also resolved vulnerabilities in Photoshop CC for Mac and Windows, Campaign, and the Creative Cloud Desktop Application for Windows. The company has found no evidence of exploitation in the wild.
Microsoft has also released patches for tens of vulnerabilities this Tuesday, including for zero-day flaws exploited in the wild.
One of the zero-days is CVE-2017-0199, an Office and WordPad vulnerability that has been exploited to deliver malware such as Dridex, WingBird, Latentbot and Godzilla. Another zero-day is CVE-2017-0210, a privilege escalation vulnerability affecting Internet Explorer.
The third zero-day impacts Office and it hasn’t actually been patched, but Microsoft did release a mitigation that should help reduce the risk of exploitation. This flaw has been exploited in limited, targeted attacks.
Microsoft Patches Office, IE Flaws Exploited in Attacks
12.4.2017 securityweek Vulnerebility
Microsoft’s security updates for April 2017 address more than 40 critical, important and moderate severity vulnerabilities, including three zero-day flaws that have been exploited in attacks.
According to Microsoft, the updates resolve flaws affecting Edge, Internet Explorer, Windows, Office, Visual Studio for Mac, .NET Framework, Silverlight and Adobe Flash Player components.
One of the zero-days patched by Microsoft this month is CVE-2017-0199, an Office and WordPad vulnerability that can be exploited for remote code execution. The security hole has been exploited in the wild by malicious actors to deliver various pieces of malware, including Dridex, WingBird, Latentbot and Godzilla.
Another vulnerability that has been actively exploited is CVE-2017-0210, a privilege escalation weakness affecting Internet Explorer. Microsoft said the flaw exists due to the lack of proper enforcement of cross-domain policies, and it can be exploited by tricking the targeted user into accessing a specially crafted web page. However, the company has not shared any information about the attacks it has been exploited in.
The third zero-day, an Office flaw which Microsoft says has been exploited in limited targeted attacks, has not been patched with this month’s updates. However, the company has released a mitigation that should help reduce the risk of exploitation until a patch is made available.
The issue, tracked by Microsoft with the identifier 2017-2605 (no CVE), is related to the Encapsulated PostScript (EPS) Filter in Office. The company’s mitigation turns off the EPS filter by default.
The list of critical flaws addressed on Tuesday also includes 13 bugs affecting Internet Explorer, Edge, .NET, Office and Hyper-V.
Microsoft has been transitioning from security bulletins to a database called Security Update Guide. The transition has now been completed – no security bulletins have been published this month – and while some users welcome the change, others said they liked the old format better.
“[The] Security Update Guide provides a number of nice filtering options, but you lose a bit of the organization,” said Chris Goettl, product manager with Ivanti. “For instance, to look at all CVEs that are resolved for a single update, you must now look at each individually where the bulletin page had them organized into one place. Likely, it will take a while for people to get used to.”
It’s also worth noting that this is the last round of security updates for Windows Vista, which has reached end of support.
Adobe patches tens of flaws across several products
Security updates released on Tuesday by Adobe patch nearly 60 vulnerabilities across several of the company’s products. The Acrobat and Reader updates address 47 flaws, including many that could lead to arbitrary code execution.
The rest of the security holes impact Flash Player, Photoshop CC for Mac and Windows, Campaign, and the Creative Cloud Desktop Application for Windows. Adobe has found no evidence of exploitation in the wild.
Microsoft Patch Tuesday fixes three flaws actively exploited in attacks in the wild
12.4.2017 securityaffairs Vulnerebility
Today Microsoft Patch Tuesday fixed the zero-day Word vulnerability that has been actively exploited in attacks in the wild.
Microsoft today patched the zero-day Word vulnerability that has been exploited in attacks in the wild. Just yesterday I wrote about a phishing campaign leveraging the flaw to deliver the Dridex banking Trojan.
Microsoft published security patches that addressed a total of 45 CVEs in nine products, including Internet Explorer, Microsoft Edge and Windows 10. Most of the updates address problems in Microsoft IE and Edge browsers.
The company confirmed that three of the vulnerabilities among this Tuesday updates are under active attack in the wild.
The first vulnerability actively exploited by attackers is tracked as CVE-2017-0199, it allowed attackers to use a specially-crafted document embedding an OLE2link object to spread malware such as the Dridex banking Trojan.
“While labelled as an Outlook issue, this is actually bug actually stems from an issue within RTF files. According to published reports, the exploit uses an embedded OLE2link object in a specially-crafted document. It should also be noted that these attacks can be thwarted by enabling Office’s Protective View feature. There are updates for both Office and Windows to be applied, and both should be considered necessary for complete protection.” reads the Patch Tuesday analysis by the Zero Day Initiative.
The second flaw exploited in the wild is an Internet Explorer elevation of privilege vulnerability tracked as CVE-2017-0210. The flaw could be exploited by attackers to access information from one domain and inject it into another domain.
“The exploit allows an attacker to access sensitive information from one domain and inject it into another domain, which could allow the attacker to gain elevated privileges. However, direct code execution is not possible through this bug alone. Instead, it would likely be used with a bug that executes code at a low integrity level to elevate the code execution to medium level integrity.” continues ZDI.
Microsoft published an the 2017-2605*: “Defense-in-Depth Update for Microsoft Office”, to address a flaw tracked as CVE-2017-2605. It is a Microsoft Office bug in the Encapsulated PostScript (EPS) filter in Office.
“According to Microsoft, they are aware of “limited targeted attacks” that take advantage of an unpatched vulnerability in the EPS filter. This temporary measure is being pushed out until a true fix is released. Issues like this used to be covered by Security Advisories, so perhaps this indicates Microsoft has chosen to do away with these as well.” states the analysis.
Microsoft did not issue an update to address this flaw, it opted to update Microsoft Office turning off, by default, the EPS filter in Office as a defense-in-depth measure.
Patch Tuesday
Microsoft also issued a fix for Windows 10 (Creators Update) that addresses several remote code execution and elevation of privilege flaws.
Giving a look at the list of the vulnerabilities fixed by this last Microsoft Patch Tuesday we can find:
CVE-2017-0201 IE RCE vulnerability ;
CVE-2017-0093 Edge scripting engine memory corruption vulnerability;
CVE-2017-0162, CVE-2017-0163, CVE-2017-0180 Hyper-V vulnerabilities;
OWASP Proposes New Vulnerabilities for 2017 Top 10
11.4.2017 securityweek Vulnerebility
OWASP Top 10 - 2017 RC1-English.pdf
The Open Web Application Security Project (OWASP) announced on Monday the first release candidate for the 2017 OWASP Top 10, which proposes two new vulnerability categories.
The new categories proposed for OWASP Top 10 - 2017 are “insufficient attack detection and prevention” and “unprotected APIs.”
OWASP wants to make room for the “unprotected APIs” category by dropping “unvalidated redirects and forwards,” the 10th item on the current (2013) list, which was added to the top 10 in 2010.
The new insufficient attack protection category would be added to the 7th position. OWASP wants to make room for it by merging the current 4th and 7th items, namely insecure direct object references with missing function level access control. The organization has proposed the merger of the two old categories into “broken access control”, as it was back in 2004.
OWASP has provided the following description for the insufficient attack protection category: “The majority of applications and APIs lack the basic ability to detect, prevent, and respond to both manual and automated attacks. Attack protection goes far beyond basic input validation and involves automatically detecting, logging, responding, and even blocking exploit attempts. Application owners also need to be able to deploy patches quickly to protect against attacks.”
In a discussion on Reddit, several users said “insufficient attack protection” should not be classified as a flaw. It remains to be seen if enough users agree to make OWASP change its mind about creating a new category for it.
As for the unprotected APIs category, OWASP says, “Modern applications often involve rich client applications and APIs, such as JavaScript in the browser and mobile apps, that connect to an API of some kind (SOAP/XML, REST/JSON, RPC, GWT, etc.). These APIs are often unprotected and contain numerous vulnerabilities.”
Comments on the 2017 Top 10 proposal can be submitted via email until June 30 to OWASP-TopTen(at)lists.owasp.org, or dave.wichers(at)owasp.org (for private comments). The final version will be released in either July or August.
Cisco Finds Many Flaws in Moxa Industrial APs
11.4.2017 securityweek Vulnerebility
Cisco’s Talos intelligence and research group has conducted a two-week analysis of an industrial wireless access point (AP) from Taiwan-based Moxa and discovered more than a dozen vulnerabilities, including ones that can be exploited to take full control of a device.
A blog post published by Talos on Monday describes the vulnerabilities found by researchers during their tests. All of the flaws have been addressed by Moxa, except for one critical weakness, whose details will not be disclosed until a patch becomes available.
Experts focused on Moxa’s AWK-3131A AP, which is recommended for any type of industrial wireless application.Moxa AP vulnerabilties
On the first day of testing, researchers identified the services available on the BusyBox-powered device, including SSH (Dropbear), Telnet, HTTP and HTTPS. Talos said Moxa agreed to share the source code of its BusyBox implementation for proper analysis.

Researchers first identified some authentication issues that made it easy for attackers to launch dictionary attacks against the web interface’s login page, and flaws that allowed hackers to hijack user sessions.
On the third day of the investigation, researchers discovered many cross-site scripting (XSS) vulnerabilities in the front-end of the web interface. These flaws can be exploited to hijack user sessions and gain access to the web interface.
Once they are authenticated, attackers can exploit one of the several command injection vulnerabilities in order to gain full control of the targeted AP.
Several of the security holes found by Talos can allow malicious actors to obtain potentially valuable information without any authentication, including passwords, firewall rules and network configuration data.
Experts have also uncovered a denial-of-service (DoS) vulnerability that can be exploited remotely to crash the web application.
On the last day of testing, researchers identified several cryptography-related issues. Specifically, they determined that the Moxa AP used an outdated version of OpenSSL (1.0.0d from 2011) and it had been vulnerable to attacks such as POODLE and DROWN.
“Our research demonstrates how many vulnerabilities can be quickly discovered by analyzing a device,” Talos researchers said. “There is nothing to suggest that this device is more or less vulnerable than any other. Indeed, the vulnerabilities we discovered are exactly the types of vulnerabilities likely to be discovered on any ICS device.”
Unpatched Microsoft Word Flaw is Being Used to Spread Dridex Banking Trojan
11.4.2017 thehackernews Vulnerebility
If you are a regular reader of The Hacker News, you might be aware of an ongoing cyber attack — detected in the wild by McAfee and FireEye — that silently installs malware on fully-patched computers by exploiting an unpatched Microsoft Word vulnerability in all current versions of Microsoft Office.
Now, according to security firm Proofpoint, the operators of the Dridex malware started exploiting the unpatched Microsoft Word vulnerability to spread a version of their infamous Dridex banking trojan.
Dridex is currently one of the most dangerous banking trojans on the Internet that exhibits the typical behavior of monitoring a victim's traffic to bank sites by infiltrating PCs and stealing victim's online banking credentials and financial data.
The Dridex actors usually relied on macro-laden Word files to distribute the malware through spam messages or emails.
However, this is the first time when researchers found the Dridex operators using an unpatched zero-day flaw in Microsoft Word for distributing their banking trojan.
According to a blog post published Monday night by Proofpoint, the latest Dridex spam campaign is delivering Word documents weaponized with this zero-day to millions of recipients across several organizations, including banks primarily located in Australia.
"Emails in this campaign used an attached Microsoft Word RTF (Rich Text Format) document. Messages purported to be from "[device]@[recipient's domain]." [Device] may be "copier", "documents", "noreply", "no-reply", or "scanner"," Proofpoint researchers say.
"The subject line in all cases read "Scan Data" and included attachments named "Scan_123456.doc" or "Scan_123456.pdf", where "123456" was replaced with random digits...the spoofed email domains and the common practice of emailing digitized versions of documents make the lures fairly convincing."
As we reported on Saturday, this zero-day flaw is severe because it gives hackers power to bypass most exploit mitigations developed by Microsoft, and unlike past Word exploits seen in the wild, it doesn't require victims to enable Macros.
Moreover, given the danger of Dridex – also known as Bugat and Cridex – banking trojan, people are strongly advised not to open Word documents attached to an email from anyone, even if you know the sender until Microsoft releases a patch.
Microsoft knew of the flaw very long ago
According to researchers at McAfee and FireEye, Microsoft has known of the remote code flaw since January and could release a patch for the vulnerability today, as part of its regular Patch Tuesday routine.
However, an independent security researcher Ryan Hanson claimed that he discovered this 0-day, along with the two other flaws, in July and reported it to Microsoft in October 2016.
"The initial discovery was in July, which was followed up by additional research and the identification of a protected view bypass vulnerability. Those two bugs and an additional Outlook bug were submitted to MS in October," Hanson told The Hacker News.
"There may very well be additional HTA related vectors in Office, but based on the detail provided by McAfee, the vulnerability they've identified functions exactly like the one I disclosed. The only difference I see is the VBScript payload, since my payload simply executed calc.exe."
If the claims made by Hanson is true and his reported vulnerability is the same being used in the wild to spread Dridex, Microsoft left its customers vulnerable to the attacks even after being known of the critical flaw for quite long.
Enable 'Protected View' in Microsoft Office to Prevent Attack
Since the attack does not work when a malicious document is viewed in Office Protected View, users are advised to enable this feature in order to view any Office documents.
For more technical details about the latest Dridex malware campaign exploiting the unpatched Microsoft Word flaw, you can head on to the blog post published by Proofpoint.
Serious Vulnerabilities Found in Riverbed SteelCentral Portal
10.4.2017 securityweek Vulnerebility
Researchers at vulnerability management services provider Digital Defense have identified four security holes in Riverbed SteelCentral, a popular application and network performance monitoring product.
The flaws affect the SteelCentral Portal application and they can be exploited by unauthenticated attackers for remote command execution and to obtain user information. The vulnerabilities were reported to Riverbed Technology in January and they were later patched by the vendor.
According to Digital Defense, there are two remote command execution vulnerabilities that can be exploited to take full control of the host running the SteelCentral Portal application, and from there hijack all connected data sources using administrator credentials.
One of the flaws, related to the UploadImageServlet function, can be exploited to upload arbitrary files to a directory that is remotely accessible. An attacker can upload a JavaServer Page (JSP) shell that allows execution of arbitrary commands with SYSTEM privileges.
The second RCE weakness is related to the H2 web console, a service that can be accessed remotely without authentication. In its advisory, Digital Defense said the H2 console is designed for access during development, but it’s still present in the default installation of the SteelCentral Portal.
Researchers determined that the console can be used to access the Portal’s PostgreSQL database – this database normally doesn’t allow remote connections, but the H2 console bypasses the restriction by connecting from localhost.
“Once connected to the PostgreSQL database, an attacker can create a new table; insert the file content for a JSP shell into the table, then export the table contents to a file in the root directory of the web application. An attacker can then gain access to a web shell without authentication, and run arbitrary commands with SYSTEM privileges,” Digital Defense said in its advisory.
Experts have also identified two information disclosure flaws that can be exploited by unauthenticated attackers to enumerate usernames. Once the usernames are obtained, a hacker can launch a brute-force attack against the SteelCentral Portal interface.
Researchers managed to exploit the vulnerabilities in versions 1.3.1 and 1.4.0. Riverbed customers can obtain information on the patches through the company’s support portal.
Critical Office Zero-Day Exploited in Attacks
10.4.2017 securityweek Vulnerebility
An unpatched critical vulnerability in Microsoft Office is being exploited by malicious actors to achieve full code execution on target machines, McAfee and FireEye security researchers warn.
The vulnerability resides in the Object Linking and Embedding (OLE) functionality in Office and can be abused to create malicious RTF (Rich Text Format) documents that link to HTA (HTML Application) files hosted on remote servers. These HTA files load and execute a final malicious Visual Basic script.
“Because .hta is executable, the attacker gains full code execution on the victim’s machine,” McAfee explains, adding that the malicious RTF samples they observed were using the .doc extension.
Both McAfee and FireEye explain that this logical bug allows attackers to bypass memory-based mitigations developed by Microsoft, as well as other security products. The malicious documents are used to download and execute malicious payloads pertaining to various well-known malware families.
The HTA files used in the observed attacks were masquerading as normal RTF files to trick users and evade detection. When successful, the exploit closes the original Office document, then opens a new one and displays it to the victim, while the malicious code is being installed in the background.
“In both observed documents the malicious script terminated the winword.exe process, downloaded additional payload(s), and loaded a decoy document for the user to see. The original winword.exe process is terminated in order to hide a user prompt generated by the OLE2link,” FireEye explains.
The vulnerability was initially observed in January, but attacks that leverage it continue to surface, McAfee says. The security company said that all Office versions are affected by this issue, including Office 2016 on Windows 10.
According to FireEye, they too have been aware of the vulnerability for some time, but they have been coordinating with Microsoft for several weeks to release information on the matter only after a patch was available. Microsoft’s next set of security patches is scheduled to roll-out as soon as this Tuesday.
Users are advised to avoid opening Office files that come from unknown sources and to leave Office Protected View enabled to ensure no malicious code runs without their knowledge. Apparently, the vulnerability can’t bypass Protected View.
Researchers warn of a Windows Zero-Day Attack observed in the wild
10.4.2017 securityaffairs Vulnerebility
Security researchers from firms McAfee and FireEye are warning of a Windows zero-day attack in the wild that put Microsoft users at risk of hack.
Security researchers from security firms McAfee and FireEye are warning of hackers exploiting an
Just opening an MS Word document could put you at risk, the exploitation of the flaw could allow an attacker to silently install a malware on a fully patched Windows machine.
The attack vectors are malicious emails that come with a weaponized Word document containing a booby-trapped OLE2link object.
“The attack involves a threat actor emailing a Microsoft Word document to a targeted user with an embedded OLE2link object. When the user opens the document, winword.exe issues a HTTP request to a remote server to retrieve a malicious .hta file, which appears as a fake RTF file. The Microsoft HTA application loads and executes the malicious script.” reads the analysis shared by FireEye. “In both observed documents the malicious script terminated the winword.exe process, downloaded additional payload(s), and loaded a decoy document for the user to see. The original winword.exe process is terminated in order to hide a user prompt generated by the OLE2link. “The vulnerability is bypassing most mitigations”
When the user opens the document, the malicious code is executed, it first connects to a remote server to download a malicious HTML application file (HTA) that’s masquerading as a document created in Microsoft’s RTF (Rich Text Format).
Windows Zero-Day Attack
The HTA file is automatically executed automatically with attackers gaining full code execution on the target machine, downloading additional malicious payloads to fully compromise the machine.
The Windows zero-day attack leverage on .hta content that is disguised as a normal RTF file to evade security solutions, but researchers at McAfee spotted the malicious Visual Basic scripts in a later part of the file.
The exploit displays a decoy Word document for the victims to see before terminating to avoid suspicion.
“The successful exploit closes the bait Word document and pops up a fake one to show the victim. In the background, the malware has already been stealthily installed on the victim’s system.” reads a blog post published by McAfee.
“The root cause of the zero-day vulnerability is related to the Windows Object Linking and Embedding (OLE), an important feature of Office. (Check our Black Hat USA 2015 presentation, in which we examine the attack surface of this feature.)”
This Window zero-day attack is very insidious, it doesn’t require victims interaction, for example, it doesn’t need victims enabling Macros.
The Window zero-day attack works on all Windows OS version, even against Windows 10.
The security firm reported the Windows zero-day attacks to Microsoft back in January 2017, for this reason, McAfee decided to publicly disclose the vulnerability and a day after also FireEye made the same.
This Tuesday Microsoft will release security updates, let’s hope the company will address also the zero-day exploited in the wild.
Below the recommendations to mitigate such kind of Windows zero-day attack:
Do not open any Office files obtained from untrusted locations.
According to our tests, this active attack cannot bypass the Office Protected View, so we suggest everyone ensure that Office Protected View is enabled.
Beware of an Unpatched Microsoft Word 0-Day Flaw being Exploited in the Wild
9.4.2017 thehackernews Vulnerebility
It's 2017, and opening a simple MS Word file could compromise your system.
Security researchers are warning of a new in-the-wild attack that silently installs malware on fully-patched computers by exploiting a serious — and yet unpatched — zero-day vulnerability in all current versions of Microsoft Office on fully-patched PCs.
The Microsoft Office zero-day attack, uncovered by researchers from security firms McAfee and FireEye, starts simply with an email that attaches a malicious Word file containing a booby-trapped OLE2link object.
When opened, the exploit code gets executed and makes a connection to a remote server controlled by the attacker, from where it downloads a malicious HTML application file (HTA) that's disguised as a document created in Microsoft's RTF (Rich Text Format).
The HTA file then gets executed automatically with attackers gaining full code execution on the victim’s machine, downloading additional payloads from "different well-known malware families" to take over the victim's PC, and closing the weaponized Word file.
Zero-Day Attack Works on All Windows OS — Even Windows 10
According to researchers, this zero-day attack is severe as it gives the attackers the power to bypass most exploit mitigations developed by Microsoft, and unlike past Word exploits seen in the wild, it does not require victims to enable Macros.
Due to these capabilities, this newly discovered attack works on all Windows operating systems even against Windows 10, which is believed to be Microsoft's most secure operating system to date.
Besides this, the exploit displays a decoy Word document for the victims to see before terminating in order to hide any sign of the attack.
"The successful exploit closes the bait Word document and pops up a fake one to show the victim," McAfee researchers wrote in a blog post published Friday. "In the background, the malware has already been stealthily installed on the victim's system."
"The root cause of the zero-day vulnerability is related to the Windows Object Linking and Embedding (OLE), an important feature of Office."
Microsoft is aware of the zero-day flaw as the researchers say they responsibly disclosed the issue to the company after detecting active attacks leveraging this unpatched flaw back in January this year.
FireEye disclosed the details of the vulnerability a day after McAfee went public with the flaw.
The next scheduled Microsoft's release of security updates is this Tuesday, so it's highly unlikely the company will be able to deliver a patch before that day.
How to Protect Yourself against this Attack?
Since the attack works on fully patched systems, users are highly advised to follow the below recommendations to mitigate such attacks:
Do not open or download any suspicious Word files that arrive in an e-mail, even if you know the sender until Microsoft releases a patch.
Since the attack does not work when a malicious document is viewed in Office Protected View feature, users are advised to enable this feature to view any Office documents.
Always keep your system and antivirus up-to-date.
Regularly backup your files in an external hard-drive.
Disabling Macros does not offer any protection, but yet users are advised to do so in an attempt to protect themselves against other attacks.
Always beware of phishing emails, spams, and clicking the malicious attachment.
Millions of mobile phones and laptops potentially exposed to attack leveraging baseband zero-days
9.4.2017 securityaffairs Vulnerebility
The researcher Ralf Weinmann revealed that millions of mobile phones and laptops are potentially exposed to attack leveraging baseband zero-days he discovered.
The researcher Ralf-Phillip Weinmann, managing director at security firm Comsecuris, has disclosed a zero-day baseband vulnerability affecting Huawei smartphones, laptop WWAN modules, and IoT components.
Baseband is firmware used on smartphones to connect to cellular networks, to make voice calls, and transmit data.
An attacker can exploit baseband flaws to eavesdrop mobile communications, take over the device making calls and sending SMS messages to premium numbers or to exfiltrate data.
The expert revealed the flaw this week at the Infiltrate Conference, the vulnerability could be exploited by attackers to execute a memory-corruption attack against affected devices over the air.
Fortunately, the attack is quite difficult to conduct.
The baseband vulnerability resides in the HiSilicon Balong integrated 4G LTE modems. The Balong application processor is called Kirin, it is produced by the Hisilicon Technologies, a subsidiary of Huawei Technologies. The affected firmware is present in several Huawei Honor smartphones, including the P10, Huawei Mate 9, Honor 9, 7, 5c and 6.

Weinmann believes that millions of Honor smartphones could be exposed to the to attack.
Weinmann presented multiple baseband vulnerabilities found in the Kirin application processor.
The expert also revealed that many laptops produced by IT vendors leverage the HiSilicon Balong integrated modem, such as a number IoT devices.
“This baseband is much easier to exploit than other basebands. Why? I’m not sure if this was intentional, but the vendor actually published the source code for the baseband which is unusual,” Weinmann said. “Also, the malleability of this baseband implantation doesn’t just make it good for device experimenting, but also network testing.”
Weinmann speculates HiSilicon may have wrong released the Kirin source code as part of a developer tar archive associated with the Huawei H60 Linux kernel data.
Weinmann demonstrated several attack scenarios against mobile phones.
A first attack scenario presented by the researcher involves setting up a bogus base station using open-source software called OpenLTE that is used by an attacker to simulate a network operator. The attacker can send specially crafted packets over the air that trigger a stack buffer overflow in the LTE stack causing the phone crashing. Once the phone rebooted an attacker can gain persistence installing a rootkit.
In a second attack scenario, the attacker with a physical access to the phone and private key pair data would install malicious tools on the firmware.
“It requires key material that is stored both by the carrier and on the SIM card in order to pass the mutual authentication between the phone and the network. Without this key material, a base station cannot pose as a legit network towards the device.”
Weinmann used for its test his own VxWorks build environment using an evaluation version of VxWorks 7.0 that shipped with Intel Galileo several years ago. The expert explained that the existence of a Lua scripting interpreter running in the baseband gives him further offensive options.
Weinmann did not disclose the technical details to avoid threat actors in the wild will abuse his technology.
“I have chosen to only disclose lower-severity findings for now. Higher severity findings are in the pipeline.” Weinmann said.
Critical Vulnerabilities Patched in QNAP Storage Devices
7.4.2017 securityweek Vulnerebility
QNAP recently patched roughly 20 vulnerabilities in its network-attached storage (NAS) products, including weaknesses that can be exploited to take control of affected devices.
According to an advisory published by the vendor last month, the flaws were patched with the release of version 4.2.4 build 20170313 of QTS, the operating system running on QNAP NAS devices.
The update patches privilege escalation, command injection, SQL injection, cross-site scripting (XSS), clickjacking, credentials management, access bypass and various memory corruption vulnerabilities.
Three of the command injection flaws were reported to QNAP by Harry Sintonen of F-Secure, who on Thursday published an advisory detailing his findings. The expert said he informed the vendor of the vulnerabilities in late February.
The security holes discovered by Sintonen, tracked as CVE-2017-6361, CVE-2017-6360 and CVE-2017-6359, can be exploited by authenticated or unauthenticated attackers to execute arbitrary commands on vulnerable devices. Exploitation of the unauthenticated command injection flaws can be automated in attacks aimed at devices that are connected to the Internet.
According to Sintonen, the flaws allow an attacker to gain root access to a device and read or modify all the data stored on it.
Researchers Pasquale Fiorillo and Guido Oricchio also published an advisory detailing a privilege escalation vulnerability (CVE-2017-5227) that was patched with the release of QTS 4.2.4.
The experts discovered that a local user can access a configuration file that contains a poorly encrypted Windows domain administrator password. The password is stored in the configuration file if the NAS device has joined an Active Directory domain, researchers said.
A couple of researchers from Salesforce have also been credited for finding security holes patched in QTS 4.2.4. The flaws found by Fiorillo, Oricchio and Sintonen are the only ones that have been assigned CVE identifiers.
It’s important that users install the update as soon as possible since malware that specifically targets QNAP devices is not unheard of. A few years ago, researchers warned that a worm had been exploiting the ShellShock vulnerability to plant backdoors on NAS devices from QNAP.
Cisco Patches Critical Flaw in Aironet Access Points
6.4.2017 securityweek Vulnerebility
Cisco published an advisory on Wednesday to warn customers that some of the company’s Aironet access points are affected by a critical flaw that could allow an attacker to take complete control of a vulnerable device.
The security hole, tracked as CVE-2017-3834, involves the existence of default credentials that can be used by a remote attacker who has layer 3 connectivity to log in to a device with elevated privileges via SSH.
The vulnerability impacts Cisco Aironet 1830 and 1850 series APs running an 8.2.x version of the Mobility Express software prior to 8.2.111.0. The company pointed out that the weakness can be exploited regardless of whether the device is configured as a master, subordinate or standalone AP.
Cisco has also informed customers of a medium severity shell bypass vulnerability affecting Aironet 1800, 2800 and 3800 series APs. A local attacker with root privileges can exploit the flaw to gain root access to the underlying Linux operating system. This root shell is designed only for advanced troubleshooting and it should not be available to any user, even if they have root privileges.
The networking giant has also published advisories detailing three high severity denial-of-service (DoS) vulnerabilities affecting its Wireless LAN Controller (WLC) software.
These security holes affect the Wireless Multimedia Extensions (WME), IPv6 UDP ingress packet processing, and the web management interface components of the WLC software. Remote or adjacent attackers can exploit the flaws without authentication.
Cisco has released software updates for each of the affected WLC versions. Workarounds are not available.
Most of these vulnerabilities were discovered by Cisco itself and the company said there was no evidence of exploitation in the wild.
Be careful, Cisco Mobility Express is shipped with some Cisco Aironet devices has a hard-coded password. Fix it!
6.4.2017 securityaffairs Vulnerebility
The Mobility Express Software shipped with Cisco Aironet 1830 Series and 1850 Series access points has a hard-coded admin-level SSH password.
Yesterday I wrote about SCADA systems that are currently shipped with an unchangeable hard-coded password, and today I’m here to discuss you a similar problem.
The Mobility Express Software developed by the IT giant CISCO that is shipped with Aironet 1830 Series and 1850 Series access points has a hard-coded admin-level SSH password.

The presence of default credentials could be exploited by attackers to remotely exploit a “layer 3 connectivity to an affected device”.
“A vulnerability in Cisco Aironet 1830 Series and Cisco Aironet 1850 Series Access Points running Cisco Mobility Express Software could allow an unauthenticated, remote attacker to take complete control of an affected device.” reads the security advisory. “The vulnerability is due to the existence of default credentials for an affected device that is running Cisco Mobility Express Software, regardless of whether the device is configured as a master, subordinate, or standalone access point. An attacker who has layer 3 connectivity to an affected device could use Secure Shell (SSH) to log in to the device with elevated privileges. A successful exploit could allow the attacker to take complete control of the device”
To discover which release of Cisco Mobility Express Software is running on your device you can use the Cisco Mobility Express wireless controller web interface or the CLI.
The release number is available in the section under the web interface under Management > Software Update.
The security advisory published by the company is part of a wider set that addresses security issued for the Aironet 1830/1850 series.
The problem affects every access point running the 8.2.x release of Cisco Mobility Express Software prior to Release 8.2.111.0., regardless of whether the device is configured as a master, subordinate, or standalone access point.
CISCO has released free software updates that fixed the flaw described in the advisory. It is important to remind that customers may only install and receive support for software versions for which they have purchased a license.
Other security issues related the Aironet technology are:
An input validation bug in the Cisco Wireless LAN Controller (WLC);
An IPv6 UDP denial-of-service (DoS) vulnerability in the WLC; and
A DoS vulnerability in the WLC’s management GUI.
Cisco has already issued security fixes to patch the above problems.
Researchers Disclose Unpatched Flaws in Schneider Electric PLCs
5.4.2017 secureweek Vulnerebility
Researchers have disclosed the details of two vulnerabilities affecting some of Schneider Electric’s Modicon programmable logic controllers (PLCs) after the vendor failed to provide any status updates or feedback.
A team of experts from Germany-based OpenSource Security discovered the flaws in Schneider’s Modicon M221 PLCs, namely TM221CE16R running firmware version 1.3.3.3.
According to advisories published on Tuesday by the researchers, the vulnerabilities are critical and they can be easily exploited.
One of the flaws is related to the fact that the Project Protection feature, designed to prevent unauthorized access to project files, uses a hardcoded encryption key.
The project’s password is stored in an XML file that is encrypted using the AES algorithm in CBC mode. The problem is that the encryption key is the same for all systems and it cannot be changed, allowing an attacker to decrypt the XML file and obtain the password set by the user.
The password can then be used to access and modify a project via SoMachine Basic, the software designed for programming Modicon controllers.
The second vulnerability is related to the Application Protection feature, which prevents the transfer of an application from a PLC to a SoMachine Basic project. Researchers discovered that sending a simple command via Modbus to the controller on TCP port 502 will return the Application Protection password in clear text.
The password can be used via the SoMachine software to download applications from the controller, modify them and upload them back to the device.
The researchers said they reported their findings to Schneider Electric on December 23, but the only information they got from the vendor was the confirmation that the vulnerability report had been received.
Contacted by SecurityWeek, Schneider Electric admitted making a mistake and promised to share mitigation advice for these flaws as soon as possible on its cybersecurity support portal.
“Schneider Electric acknowledges the security note on its product Modicon TM221CE16R, Firmware 1.3.3.3, disclosed by OpenSource Security,” the company said in an emailed statement.
“Conscious about user Cyber Security concerns, Schneider Electric places a high priority on the evaluation of security research as it becomes available and produces documentation to advise users on mitigations that can be taken if they are required. Because of an issue in our standard process for interactions with cybersecurity advisory & consulting firms, we have missed the opportunity to respond to the researchers from OpenSource Security (Simon Heming, Maik Brüggemann, Hendrik Schwartke, Ralf Spenneberg) and offer mitigation to users, and we do apologize for this. We’re reviewing and updating our processes to make sure such a situation never happens again,” the company added.
Schneider Electric recently notified customers about the availability of patches and mitigations for three vulnerabilities affecting some of its Modicon PLCs.
Flaws in Java AMF Libraries Allow Remote Code Execution
5.4.2017 secureweek Vulnerebility
Deserialization-related vulnerabilities found in several Java implementations of AMF3 can be exploited for unauthenticated remote code execution and XXE attacks, warned CERT/CC.
The security holes were reported to CERT/CC and vendors by Markus Wulftange, senior penetration tester at Code White. Patches have been made available for some of the affected products.
Serialization is the process where an object is converted to a stream of bytes in order to store or transmit that object to memory or a file. The process in which serialized data is extracted is called deserialization and it can lead to significant security flaws if not handled properly.
AMF3, the latest version of Adobe’s Action Message Format, is a compact binary format used to serialize ActionScript object graphs. AMF was first introduced in Flash Player 6 in 2001 and AMF3 has been around since Flash Player 9.
There have been several reports in the past few years about remote code execution vulnerabilities introduced in Java-based applications due to inadequate serialization implementations.
Wulftange has discovered that some Java implementations of AMF3 deserializers introduce potentially serious vulnerabilities, allowing unauthenticated attackers to remotely execute code or cause a denial-of-service (DoS) condition. An XXE flaw reported by the researcher can also lead to disclosure of sensitive data on the server.
CERT/CC’s advisory mentions three vulnerabilities. The first flaw allows an attacker who can spoof or control an RMI (Remote Method Invocation) server to execute code. This security hole is said to affect Atlassian’s JIRA, Exadel’s Flamingo, GraniteDS, Spring spring-flex, and WebORB for Java by Midnight Coders.
The second vulnerability can also be exploited for arbitrary code execution by an attacker who can spoof or control information. This weakness impacts Flamingo, Apache’s Flex BlazeDS and GraniteDS. The XXE flaw has been found to affect the same products along with WebORB.
Some of the vulnerable libraries, such as GraniteDS and Flamingo, have been discontinued. Atlassian and Apache have released patches for the flaws impacting their products.
According to CERT/CC, products from HPE, SonicWall and VMware could also be affected. The organization has advised developers to use versions of JDK that implement serialization blacklisting filters and ensure that their products properly handle deserialized data from untrusted sources.
UEFI Vulnerabilities allow to fully compromise Gigabyte Mini PCs
4.4.2017 securityaffairs Vulnerebility
Experts at Cylance disclosed two UEFI flaws that can be exploited by attackers to install a backdoor on some Gigabyte BRIX mini PCs.
Experts at security firm Cylance have disclosed two UEFI vulnerabilities that can be exploited by attackers to install a backdoor on some Gigabyte BRIX mini PCs.
The experts tested the latest firmware for GB-BSi7H-6500 and GB-BXi7-5775 mini PCs and discovered that lack of some protection feature that could allow an attacker to exploit the flaws to deliver a ransomware payload that prevents the system from booting.
“These new mitigations, based on virtualization technologies in Windows 10, are vulnerable to UEFI-based attacks from System Management Mode (SMM). Because SMM allows direct access to physical memory, it’s possible to bypass the virtualization layer of isolation (Intel VT-x) . This kind of attack is already discussed in detail in ‘Attacking Hypervisors via Firmware and Hardware’. ” reads the analysis published by Cylance.
One of the issues, tracked as CVE-2017-3197, is related to the SMI handler and it could be exploited to execute code in System Management Mode (SMM). The researchers discovered that the American Megatrends (AMI) firmware running on the affected devices has disabled write-protection mechanisms. The security features are normally enabled by Gigabyte seems to have disabled it.
The flaw is very dangerous, an attacker can trigger it by tricking victims into visiting a specifically crafted website or by opening a weaponized document. Once triggered the flaw, the attacker can elevate privileges to achieve kernel-mode code execution. The attacker can exploit the SMI vulnerability to execute code in SMM and make direct changes to the flash memory.
Below the attack described by the experts:
1. User-mode execution (ring 3)
2. Kernel mode execution (ring 0)
3. SMM execution (ring -2)
4. SPI Flash Write
“The attacker gains user-mode execution through an application vulnerability such as a browser exploit or a malicious Word document with an embedded script. From there, the attacker elevates his privileges by exploiting the kernel or a kernel module such as Capcom.sys to execute code in ring 0. A vulnerable SMI handler allows the attacker to execute code in SMM mode (ring -2) where he finally can bypass any write protection mechanisms and install a backdoor into the system’s firmware.”
gigabyte
The second vulnerability tracked as CVE-2017-3198, is caused by the fact that the Gigabyte UEFI does not perform a cryptographic check to ensure the authenticity and integrity of a firmware update. This means that an attacker that exploited the issue is able to provide malicious firmware onto the device.
“The GIGABYTE UEFI firmware does not cryptographically validate images prior to updating the system firmware. Additionally, the firmware updates are served over HTTP without checksums for verifying authenticity.” reads a blog post published by Cylance.
An attacker can use the provided AMI Firmware Update (AFU) utility to write arbitrary code to the firmware.”
“As mentioned in our previous post, successful infection at such a low level has the potential to be disastrous. UEFI rootkits and ransomware, as we demonstrated at both RSA Conference and BlackHat Asia, could provide attackers with a degree of control that is difficult, if not near-impossible, to detect or rectify.” continues a blog post published by Cylance.
The security flaws were discovered just before Christmas and the experts reported it to Gigabyte in mid-January. The company has already developed a firmware update, version vF7, that is currently in testing phase and will be soon released. However, the update will only be available for GB-BSi-7H-6500 as the GB-BXi7-5775 model has reached
Unfortunately, the update will only be available for GB-BSi-7H-6500 because the GB-BXi7-5775 model has reached end of life.
Wi-Fi Flaws Expose iPhone, Nexus Phones to Attacks
5.4.2017 securityweek Vulnerebility
Vulnerabilities in Broadcom’s Wi-Fi system-on-chip (SoC) can be exploited to hijack iPhone, Nexus, Samsung and other smartphones without requiring any user interaction.
Google Project Zero researcher Gal Beniamini has identified several remote code execution, privilege escalation and information disclosure vulnerabilities in Broadcom firmware.
Since Broadcom’s Wi-Fi chips are widely used, the flaws affect many devices, including Google’s Nexus 5, 6 and 6P, all iPhones since iPhone 4, and most of Samsung’s flagship Android smartphones.
Beniamini has published a lengthy blog post describing the Broadcom Wi-Fi chipset and vulnerabilities that can be exploited for remote code execution. The researcher has also promised to publish another blog post that will provide details on the second part of the exploit chain, which involves elevating privileges from the SoC to the operating system’s kernel.
An attacker who is in Wi-Fi range can exploit the security holes found by the Google researcher to take complete control of a vulnerable device without any user interaction.
Beniamini applauded Broadcom’s response, stating that the company was responsive and helpful in fixing the vulnerabilities and making the patches available to affected device manufacturers.
The researcher said Broadcom’s firmware lacks all basic exploit mitigations, but the company claims newer versions do include some security mechanisms and exploit mitigations are being considered for future versions.
Apple released an emergency update this week for iOS to address the remote code execution vulnerability (CVE-2017-6975), but the company did not provide any details.
The Broadcom flaws were also patched in Android with the release of the April security updates.
Samsung has also released maintenance updates this week for its Android devices. The updates include both the Google patches and fixes for vulnerabilities specific to Samsung products.
UEFI Vulnerabilities Found in Gigabyte Mini PCs
3.4.2017 securityweek Vulnerebility
Endpoint security firm Cylance has disclosed the details of two potentially serious UEFI vulnerabilities that can be exploited to install a backdoor on some Gigabyte BRIX mini PCs. The vendor is working on a firmware update that will address the flaws.
Cylance said it had tested the latest firmware for GB-BSi7H-6500 and GB-BXi7-5775 mini PCs and discovered that some important protection mechanisms are missing. The company has described an attack scenario where a malicious actor exploits the vulnerabilities to deliver a ransomware payload that prevents the system from booting.
One of the vulnerabilities found by researchers, tracked as CVE-2017-3197, is related to the SMI handler and it allows an attacker to execute code in System Management Mode (SMM). The American Megatrends (AMI) firmware present on affected devices does normally provide write-protection mechanisms designed to prevent unauthorized changes, but these protections have not been enabled by Gigabyte.
Hackers can exploit this flaw for malicious attacks by first gaining access to the targeted system via a browser or document exploit. The attacker can then elevate privileges to achieve kernel mode code execution. Since write-protection mechanisms are not enabled, the attacker can exploit the SMI vulnerability to execute code in SMM and make changes to the flash memory.
The second vulnerability, identified as CVE-2017-3198, is related to the fact that the Gigabyte UEFI does not perform a cryptographic check to ensure that a firmware update is legitimate. Furthermore, firmware updates are served over HTTP.
An attacker who obtains access to the targeted system can install the legitimate UEFI update utility and use it to push a malicious firmware onto the device.
“Successful infection at such a low level has the potential to be disastrous,” Cylance researchers said in a blog post. “UEFI rootkits and ransomware could provide attackers with a degree of control that is difficult, if not near-impossible, to detect or rectify.”
The vulnerabilities were discovered on December 20 and they were reported to Gigabyte in mid-January. The vendor says it has prepared a firmware update, version vF7, that is in the final phase of testing. However, the update will only be available for GB-BSi-7H-6500 as the GB-BXi7-5775 model has reached end of life.
Splunk Patches Information Theft and XSS Flaws
3.4.2017 securityweek Vulnerebility
Splunk last week released an update for Splunk Enterprise to address an information theft bug and a persistent Cross Site Scripting (XSS) vulnerability.
Discovered last year by security researcher John Page (who goes by the online handle of hyp3rlinx), the information theft issue is tracked as CVE-2017-5607 and has been assessed a CVSS Base Score of 3.5. The vulnerability can be exploited by a remote attacker to siphon information from Splunk Enterprise when the user visits a malicious webpage.
In an advisory, the security researcher notes that an attacker exploiting this vulnerability could access data such as the currently logged in username and if remote user setting is enabled. With the username in hand, the attacker could either phish or brute force the Splunk Enterprise login.
The attacker can use JavaScript to exploit the issue, as the root cause of it is the global Window JS variable assignment of config?autoload=1 '$C', the security researcher notes in his advisory.
“To steal information we simply can define a function to be called when the '$C' JS property is ‘set’ on webpage, for example.
Object.defineProperty( Object.prototype, "$C", { set:function(val){...
The Object prototype is an Object that every other object inherits from in JavaScript, if we create a setter on the name of our target in this case "$C", we can get/steal the value of this data, in this case it is very easy as it is assigned to global Window namespace,” the researcher explains.
Splunk has confirmed that affected Splunk Enterprise versions include 6.5.x before 6.5.3; 6.4.x before 6.4.6; 6.3.x before 6.3.10; 6.2.x before 6.2.13.1; 6.1.x before 6.1.13; 6.0.x before 6.0.14; 5.0.x before 5.0.18; and Splunk Light before 6.5.2.
The security researcher discovered the bug in November 2016 and reported it to Splunk the same month. He received acknowledgement of the bug a couple of days later, but the patch was released only last week. The researcher published not only details pertaining to the vulnerability, but also proof-of-concept JavaScript code and a video to demonstrate the flaw.
The second vulnerability addressed in Splunk Enterprise last week was a persistent Cross Site Scripting in Splunk Web, which was found to allow an attacker to inject and store arbitrary script, but only if they are authenticated in Splunk web before exploiting the bug. Assessed with a CVSS Base Score of 6.6, the flaw impacts Splunk Enterprise versions 6.5.x before 6.5.3; 6.4.x before 6.4.6; 6.3.x before 6.3.10; 6.2.x before 6.2.13; and Splunk Light before 6.5.2.
Attackers can siphon data from Splunk Enterprise if an authenticated user visits a malicious webpage
3.4.2017 thehackernews Vulnerebility
Splunk has fixed the security issue in the JavaScript implementation, tracked as CVE-2017-5607, that can be exploited to siphon data.
Splunk has fixed the security issue in the JavaScript implementation, tracked as CVE-2017-5607, that leaks user information. Splunk provides the leading platform for Operational Intelligence that is used to search, monitor, analyze and visualize machine data. Splunk Enterprise, collects and analyzes high volumes of machine-generated data.

The security issue could be exploited by an attacker tricking an authenticated user into visiting a malicious Web page. The bug leaks the username, and whether that user has enabled remote access, allowing an attacker to target the user with a spear phishing attack to steal the user’s credentials.
“Attackers can siphon information from Splunk Enterprise if an authenticated Splunk user visits a malicious webpage. Some useful data gained is the currently logged in username and if remote user setting is enabled.” reads the advisory published at Full Disclosure. “After, the username can be use to Phish or Brute Force Splunk Enterprise login. Additional information stolen may aid in furthering attacks.
Root cause is the global Window JS variable assignment of config?autoload=1 ‘$C’.”
The problem resides in the way Splunk uses Object prototypes in JavaScript. The Object prototype is an Object that every other object inherits from in JavaScript.
“To steal information we simply can define a function to be called when the ‘$C’ JS property is “set” on webpage, for example. Object.defineProperty( Object.prototype, “$C”, { set:function(val){…” continues the advisory,
Below the proof-of-concept JavaScript code published in the advisory:
<script>
Object.defineProperty( Object.prototype, “$C”, { set:function(val){
//prompt(“Splunk Timed out:\nPlease Login to Splunk\nUsername:
“+val.USERNAME, “Password”)
for(var i in val){
alert(“”+i+” “+val[i]);
}
}
});
</script>
Affected Splunk Enterprise versions are:
6.5.x before 6.5.3
6.4.x before 6.4.6
6.3.x before 6.3.10
6.2.x before 6.2.13.1
6.1.x before 6.1.13
6.0.x before 6.0.14
5.0.x before 5.0.18 and Splunk Light before 6.5.2
Linux Kernel vulnerability CVE-2017-7184 disclosed at Pwn2Own 2017 fixed
3.4.2017 securityaffairs Vulnerebility
The Linux kernel flaw exploited by the hackers at the Zero Day Initiative’s Pwn2Own 2017 competition to hack Ubuntu has been patched.
The Chaitin Security Research Lab (@ChaitinTech) discovered a Linux Kernel flaw, , tracked as CVE-2017-7184, during the last Pwn2Own 2017 competition. The experts hacked Ubuntu Desktop exploiting a Linux kernel heap out-of-bound access and earned $15,000 and 3 Master of Pwn points. It was the first time for an Ubuntu Linux hack at the Pwn2Own.
“This vulnerability allows local attackers to execute arbitrary code on vulnerable installations of the Linux Kernel. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability.” reads the ZDI advisory.
“The specific flaw exists within the handling of xfrm states. The issue results from the lack of proper validation of user-supplied data, which can result in a memory access past the end of an allocated buffer. An attacker can leverage this vulnerability to elevate privileges and execute arbitrary code under the context of the kernel.”
Linux Kernel Flaw CVE-2017-7184 Pwn2Own 2017
The vulnerability can be exploited to cause a denial-of-service (DoS) condition or to execute arbitrary code. It could be exploited by a local attacker to escalate privileges on the system.
Red Hat rated the flaw as “high severity,” anyway its experts confirmed that the flaw cannot be exploited for privilege escalation on default or common configurations of Red Hat Enterprise Linux 5, 6 and 7.
The CVE-2017-718 flaw was quickly fixed in the Linux kernel a few days after the Pwn2Own 2017 competition, and Ubuntu development team has fixed it at the end of March. Other Linux distributions are already working on security patches.
Schneider Electric Patches Flaws in Modicon, Wonderware Products
31.3.2017 securityweek Vulnerebility
Schneider Electric has released software and firmware updates to address several vulnerabilities affecting some of the company’s Wonderware and Modicon products.
According to advisories released by Schneider Electric and ICS-CERT, the Access Anywhere extension of the Wonderware InTouch HMI visualization software is affected by four medium and high severity vulnerabilities.
The list includes a cross-site request forgery (CSRF) on the Gateway component (CVE-2017-5156), an information disclosure flaw that could lead to the exposure of credentials (CVE-2017-5158), and a weakness related to the use of outdated cipher suites and improper verification of SSL certificates (CVE-2017-5160).
The fourth vulnerability, only mentioned in Schneider’s advisory, has been described as a flaw that allows an attacker to escape remote InTouch applications and launch other processes.
The security holes affect Wonderware InTouch Access Anywhere 2014 R2 SP1b (11.5.2) and prior, and they have been addressed with the release of Wonderware InTouch Access Anywhere 2017 (17.0.0). The vendor has also provided recommendations for mitigating the vulnerabilities.
Three medium and high severity vulnerabilities have also been identified in Schneider Electric’s Modicon programmable logic controllers (PLCs).
The flaws are related to the exposure of login credentials during transmission (CVE-2017-6028), predictable authentication cookies (CVE-2017-6026), and insufficiently random TCP initial sequence numbers (CVE-2017-6030). Schneider Electric has published separate advisories for each of the issues.
The security holes affect Modicon M221, M241 and M251 PLCs. The vendor has released firmware updates that address the weaknesses related to insufficiently random values, and provided recommendations for reducing the risk of exploitation for the credentials protection vulnerability.
In early March, Schneider also released an advisory to warn customers of a flaw that can be exploited to execute arbitrary commands on Modicon PLCs.
The company also informed users this month about a high severity denial-of-service (DoS) vulnerability affecting the Flexera FlexNet Publisher component used in the Schneider Electric Floating License Manager. This license manager is used by both the PowerSCADA Expert and PlantStruxure PES products.
Linux Kernel Flaw Disclosed at Pwn2Own Patched
31.3.2017 securityweek Vulnerebility
The Linux kernel vulnerability leveraged at the Zero Day Initiative’s Pwn2Own 2017 competition to hack Ubuntu has been patched.
The flaw was disclosed at the event by researchers at Beijing-based enterprise security firm Chaitin Tech. The exploit, which earned the hackers $15,000, was part of the only attempt to break Ubuntu at this year’s Pwn2Own.
The vulnerability, tracked as CVE-2017-7184, has been described as an out-of-bounds heap access weakness that can be exploited to cause a denial-of-service (DoS) condition or to execute arbitrary code. A local attacker can exploit the flaw to escalate privileges on the system.
“The specific flaw exists within the handling of xfrm states,” ZDI explained in its advisory. “The issue results from the lack of proper validation of user-supplied data, which can result in a memory access past the end of an allocated buffer.”
The vulnerability was addressed in the Linux kernel a few days after Pwn2Own ended. Ubuntu has released fixes and other Linux distributions are working on patches as well.
Red Hat has classified it “high severity,” but pointed out that the flaw cannot be exploited for privilege escalation on default or common configurations of Red Hat Enterprise Linux 5, 6 and 7.
Mozilla and VMware have also patched the Firefox and Workstation vulnerabilities disclosed at Pwn2Own, and ZDI has made its advisories public for these security holes.
Google Patches Dangerous Vulnerabilities in Chrome 57
31.3.2017 securityweek Vulnerebility
Google on Wednesday released an update for its Chrome web browser to address five vulnerabilities in the application: one rated Critical and four High risk.
Chrome 57.0.2987.133 was released for Windows, Mac, and Linux users just weeks after version 57 of the browser graduated to the stable channel. In addition to bringing several functionality improvements, the previous browser release included the availability of CSS Grid Layout, along with patches for 36 vulnerabilities.
The most severe bug resolved in the new update is a Critical Use after free vulnerability in printing. Tracked as CVE-2017-5055, the issue was discovered by Wadih Matar, who was awarded a $9,337 bounty for the finding, according to Google’s advisory.
The first of the four High risk flaws resolved in this release is a Heap buffer overflow in V8 (CVE-2017-5054), discovered by Nicolas Trippar of Zimperium zLabs and awarded a $3000 bounty. Another was a Bad cast in Blink (CVE-2017-5052), found by JeongHoon Shin and awarded $1000.
The other two flaws included a Use after free in Blink (CVE-2017-5056), discovered by a researcher who opted to remain anonymous, and an Out of bounds memory access in V8 (CVE-2017-5053), found by Team Sniper (Keen Lab and PC Mgr) and reported through ZDI (ZDI-CAN-4587). Google didn’t reveal the bounties paid for these two issues.
A new version of Chrome for Android (57.0.2987.132) was also released this week to address a High risk Use after free vulnerability in Blink (CVE-2017-5056).
In late January, Google released Chrome 56 in the stable channel to resolve 51 vulnerabilities in the browser. Roughly two weeks later, the Internet giant announced that Gmail was dropping support for Chrome version 53 and below, hitting Windows XP and Vista users hard (Chrome 49 was the last browser iteration released for these platforms).
Audit Finds Over a Dozen NTP Vulnerabilities
30.3.2017 securityweek Vulnerebility
Researchers at Germany-based security firm Cure53 have conducted a 32-day audit of the Network Time Protocol (NTP) and the NTPsec project and discovered more than a dozen vulnerabilities.
Experts identified a total of 16 security-related issues, including 8 weaknesses that only affect NTP and two that only impact NTPsec, which is meant to be a secure, hardened and improved implementation of NTP. Cure53 has published separate reports focusing on the NTP and NTPsec problems.
The Network Time Foundation addressed the flaws earlier this month with the release of ntp-4.2.8p10.
Cure53 has classified one vulnerability as being critical. CVE-2017-6460, which only affects NTP, has been described as a stack-based buffer overflow that can be triggered by a malicious server when a client requests the restriction list. The flaw can be exploited to cause a crash and possibly to execute arbitrary code.
The security holes rated by Cure53 as high severity are CVE-2017-6463 and CVE-2017-6464, both of which can be exploited for DoS attacks.
It’s worth noting that while some of the vulnerabilities have been classified as critical and high severity by Cure53, NTP developers have only assigned medium, low and informational-level severity ratings to the discovered flaws.
Ntp-4.2.8p10 patches a total of 15 vulnerabilities and also includes just as many non-security fixes and improvements. Of the 15 security holes resolved in the latest version, 14 were discovered by Cure53, which also noticed that a flaw initially patched in December 2014 was reintroduced in November 2016.
One of the vulnerabilities fixed in ntp-4.2.8p10 was reported by researchers at Cisco Talos. Experts identified a DoS vulnerability affecting the origin timestamp check functionality. The company has published a blog post and a technical advisory describing the issue.
This is not the only audit conducted recently by Cure53. In the past months, the company also analyzed the cURL data transfer tool and the Dovecot email server.
Over 8.3 million live websites using IIS 6.0 are affected by a Zero-Day
30.3.2017 securityaffairs Vulnerebility
Millions of websites are affected by a buffer overflow zero-day vulnerability, tracked as CVE-2017-7269, that resides in the IIS 6.0.
The II6 6.0 zero-day flaw was discovered by two researchers with the Information Security Lab & School of Computer Science & Engineering, South China University of Technology Guangzhou, China who published a PoC code exploit on GitHub.
Microsoft has already acknowledged the vulnerability that was exploited in the wild in July or August 2016.
More than 8 million websites could be affected by the flaw that resides in the ScStoragePathFromUrl function of the Web Distributed Authoring and Versioning (WebDAV) service in Windows Server 2003 R2’s IIS 6.0.
The issue is caused by the improper validation of an ‘IF’ header in a PROPFIND request and could allow an attacker to trigger a denial of service condition or to run arbitrary code.
“Microsoft Internet Information Services (IIS) 6.0 is vulnerable to a zero-day Buffer Overflow vulnerability (CVE-2017-7269) due to an improper validation of an ‘IF’ header in a PROPFIND request.” reads the analysis published by Trend Micro.

“A remote attacker could exploit this vulnerability in the IIS WebDAV Component with a crafted request using PROPFIND method. Successful exploitation could result in denial of service condition or arbitrary code execution in the context of the user running the application.”
The Web Distributed Authoring and Versioning (WebDAV) extension of the HTTP protocol allows clients to perform remote Web content authoring operations. It allows to extend the support HTTP methods, including COPY, LOCK, MKCOL, PROPFIND, and UNLOCK.
“This vulnerability is exploited using the PROPFIND method and IF header. The PROPFIND method retrieves properties defined on the resource identified by the Request-URI. All the WebDAV-Compliant resources must support the PROPFIND method.” continues the analysis.
The impact of this vulnerability is wide, according to data provided by the W3Techs, Microsoft’s IIS is currently the third most popular web server solution in the wild (11.4% of all websites). IIS 6.0 accounts for 11.3%, roughly 1.3% of all websites on the Internet.
The vulnerability doesn’t affect newer versions of Microsoft Internet Information Services.
According to BuiltWith, IS 6.0 version is currently used by 2.3% of the entire Internet, over 8.3 million live websites are using IIS 6.0.
In order to mitigate the risk of cyber attacks, it is possible to disable the WebDAV service on IIS 6.0 installations.
“To mitigate the risk, disabling the WebDAV service on the vulnerable IIS 6.0 installation is recommended. Newer versions of Windows Server shipped with newer versions of IIS are not affected by this vulnerability.” concluded Trend Micro.
Millions of Websites Affected by IIS 6.0 Zero-Day
29.3.2017 securityweek Vulnerebility
More than 8 million websites could be exposed to a buffer overflow vulnerability in Internet Information Services (IIS) 6.0 that has been exploited in the wild since July 2016, researchers warn.
The bug was found in the ScStoragePathFromUrl function of the Web Distributed Authoring and Versioning (WebDAV) service in Windows Server 2003 R2’s IIS 6.0. The issue, tracked as CVE-2017-7269, resides in the improper validation of an ‘IF’ header in a PROPFIND request and could allow an attacker to cause denial of service or to run arbitrary code.
Discovered by two researchers with the Information Security Lab & School of Computer Science & Engineering, South China University of Technology Guangzhou, China, the vulnerability was exploited in the wild in July or August 2016. This week, the researchers published a proof-of-concept on GitHub and revealed that Microsoft has already acknowledged the bug.
The WebDAV extension of the HTTP protocol allows clients to perform remote Web content authoring operations, offering support for new HTTP methods, including COPY, LOCK, MKCOL, PROPFIND, and UNLOCK.
The exploit abuses the PROPFIND method and IF header. The former, Trend Micro’s Virendra Bisht explains, “retrieves properties defined on the resource identified by the Request-URI” and is supported by all WebDAV-Compliant resources, while the latter “handles the state token as well as the ETags.”
According to Bisht, “the vulnerability could be exploited with an overly large ‘IF’ header in the ‘PROPFIND’ request with at least two http resource in the IF header.” The researcher also explains that, while successful attacks could lead to remote code execution, unsuccessful attacks could sometimes lead to denial of service conditions.
Data from W3Techs reveals that Microsoft’s IIS is currently the third most popular web server technology out there, powering 11.4% of all websites. While newer versions of Microsoft’s technology are more popular, IIS 6.0 still accounts for 11.3% of the IIS-powered websites, which results in 1.3% of all websites out there being powered by this version.
According to BuiltWith, however, IIS powers 13.8% of all live websites, while the IIS 6.0 version is used by 2.3% of the entire Internet. This means that over 8.3 million live websites are using IIS 6.0, including tens of thousands of the most popular sites out there. However, the number is constantly dropping.
Disabling the WebDAV service on the vulnerable IIS 6.0 installations can mitigate the risk posed by this vulnerability, Trend Micro’s researcher says. The flaw does not affect newer versions of IIS.
Because IIS 6.0 was included with Windows Server 2003, an old operating system version that is no longer supported by Microsoft, it’s unlikely that a patch will be released for this zero-day.
“Nobody should be running IIS 6 in 2017. This is unsupported and unsafe software and must be upgraded ASAP," Craig Young, Prinicpal Security Researcher for Tripwire, told SecurityWeek. "All vulnerabilities in this software are going to be zero-day forever and while there may be mitigations for this attack, it is incredibly risky to run obsolete software on the Internet.”
Siemens RUGGEDCOM Devices Affected by Several Flaws
29.3.2017 securityweek Vulnerebility
Siemens has shared recommendations for mitigating several medium and high severity vulnerabilities affecting some of the company’s RUGGEDCOM products.
Four types of security holes have been identified in RUGGEDCOM appliances running any version of ROX I (Rugged Operating System on Linux). The affected products are industrially hardened security appliances with integrated router, firewall and VPN functionality. They are used worldwide at electric utility substations, traffic control cabinets and in other harsh environments.
A majority of the vulnerabilities were discovered and reported by researcher Maxim Rupp, including cross-site scripting (XSS), path traversal, privilege escalation and cross-site request forgery (CSRF) issues. One XSS flaw was also discovered by Siemens itself.
Rupp has identified roughly 20 parameters that allow hackers to launch XSS attacks and execute arbitrary JavaScript code due to improper input validation (CVE-2017-2687). The expert has also identified a path traversal vulnerability (CVE-2017-2686) that can be exploited to read arbitrary files and possibly access sensitive information.
Another flaw, described as a privilege escalation (CVE-2017-2689), can be exploited to bypass access restrictions and obtain privileged file system access or change configuration settings.
The security hole exists due to several issues related to improper access control mechanisms, missing checks for unrestricted file uploads, and server misconfigurations.
Rupp has also identified a CSRF vulnerability (CVE-2017-2688) that can be exploited to perform various actions on behalf of a logged-in user who is tricked into clicking on a malicious link. The researcher said an attacker can combine the CSRF with the privilege escalation flaw to access files on the host without access to the device’s web interface.
The vulnerabilities affect the web interface on port 10000/TCP and they either require the targeted user to click on a link, or the attacker needs to have network access and valid credentials in order to exploit them.
Advisories have been made available by ICS-CERT, Siemens and Rupp. While it hasn’t released any updates, Siemens has advised users to obtain a mitigation tool that can be used to disable the web interface and guest/operator accounts on the affected ROX I devices. The vendor also recommends limiting access to trusted admins, and using VPNs.
“As a general security measure Siemens strongly recommends to protect network access to the web interface at 10000/TCP of ROX I-based devices with appropriate mechanisms. It is advised to configure the environment according to our operational guidelines in order to run the devices in a protected IT environment,” Siemens said.
VMware Patches Flaws Disclosed at Pwn2Own
29.3.2017 securityweek Vulnerebility
VMware has released updates and patches for its ESXi, Workstation and Fusion products to address critical and moderate severity vulnerabilities disclosed at the Pwn2Own 2017 competition.
Pwn2Own participants earned more than $200,000 this year for exploits involving VMware virtual machine escapes. Researchers at Qihoo 360 earned $105,000 for an Edge exploit that achieved a VM escape, and Tencent Security’s Team Sniper received $100,000 for a Workstation exploit that leveraged two vulnerabilities.
According to VMware, the Qihoo 360 team leveraged a heap buffer overflow (CVE-2017-4902) and an uninitialized stack memory usage in SVGA (CVE-2017-4903) that allow an attacker in the guest operating system to execute code on the host.
One of the security holes exploited by Team Sniper is an uninitialized memory usage issue (CVE-2017-4904) in the XHCI controller that can be exploited to execute code on the host from the guest OS.
The second flaw disclosed by Team Sniper at Pwn2Own, rated “moderate severity,” is an information leak weakness also caused by uninitialized memory usage (CVE-2017-4905).
The flaws affect ESXi 6.0 and 6.5, Workstation 12.x on all operating systems, and Fusion 8.x on OS X. CVE-2017-4904 and CVE-2017-4905 also affect ESXi 5.5, but the former can only be exploited for denial-of-service (DoS) attacks and not code execution.
Mozilla has also patched a Firefox vulnerability disclosed at Pwn2Own. However, the organization addressed the security bug within a day after it was presented at the hacking competition.
This was not the first time VMware patched flaws disclosed at such an event. Last year, it resolved a Workstation and Fusion vulnerability demonstrated at PwnFest, a hacking competition that took place in South Korea at the Power Of Community (POC) conference.
VMware has also released patches for the recently disclosed Apache Struts2 vulnerability, which the company has classified as “catastrophic.”
Google Researcher Finds New Flaw in LastPass
28.3.2017 Securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy has identified yet another serious vulnerability in the LastPass browser extension. The developers of the password manager are aware of the flaw and are working on a patch.
Since the vulnerability has not been fixed, only few details have been made public by Ormandy and LastPass. The researcher said the security hole affects the latest version of the app, and the exploit he developed should work on all web browsers.
Similar to a previously found weakness, this vulnerability can be exploited to steal a user’s passwords and, if the LastPass binary component is enabled, execute arbitrary code.
“This attack is unique and highly sophisticated,” LastPass said in a blog post. “We don’t want to disclose anything specific about the vulnerability or our fix that could reveal anything to less sophisticated but nefarious parties. So you can expect a more detailed post mortem once this work is complete.”
Since these vulnerabilities can typically be exploited by getting the targeted user to access a specially crafted web page, LastPass has advised customers to protect themselves against potential attacks by using the LastPass Vault to access websites in order to ensure that the site they visit is legitimate. Users have also been advised to enable two-factor authentication when possible and beware of phishing attempts.
In recent weeks, Ormandy has identified several serious LastPass vulnerabilities that can be exploited to steal user passwords or execute arbitrary code. LastPass has released patches within days after learning of their existence. The fixes are pushed out automatically and users don’t have to take any action.
There is no evidence of exploitation in the wild and LastPass told users that there is no need to change any passwords.
One of the vulnerabilities found by the Google researcher affected the 3.3.2 version of the Firefox extension. LastPass addressed the vulnerability, but the company pointed out that it plans to retire this branch in the near future.
QNAP QTS Domain Privilege Escalation Vulnerability
24.3.2017 securityaffairs Vulnerebility
The vulnerability allows any local user, such as “httpdusr” used to run web application, to escalate to Domain Administrator if the NAS is a domain member.
Pasquale ‘sid’ Fiorillo from ISGroup (www.isgroup.biz), an Italian
Security Company, and Guido ‘go’ Oricchio of PCego (www.pcego.com), a System Integrator, have just released a critical security advisory for any version of QNAP NAS prior to 4.2.4 Build 20170313 (https://www.qnap.com/en/support/con_show.php?cid=113).

QNAP Systems, founded in 2004, provides network attached storage (NAS) and network video recorder (NVR) solutions for home and business use to
the global market. QNAP also delivers a cloud service, called myQNAPcloud, that allows
users to access and manage devices from anywhere. QTS is a QNAP device proprietary firmware based on Linux.
The issue involves all the QNAP NAS (all models and all versions) that are members of a Microsoft Active Directory and allows a local QTS admin user, or other low privileged user (such as “httpdusr” used to run web application) to access configuration file that includes a bad crypted Microsoft Domain Administrator password.
The affected component is the “uLinux.conf” configuration file, created with a world-readable permission used to store a Domain Administrator password.
This password is stored in the file obfuscated by a simple XOR cypher and base64 encoded.
“The vulnerability allows a local QTS admin user, or other low privileged user, to access configuration file that includes a bad crypted Microsoft Domain Administrator password if the NAS was joined to a Microsoft Active Directory domain.” reads the advisory. “The affected component is the “uLinux.conf” configuration file, created with a world-readable permission used to store a Domain Administrator password. Admin user can access the file using ssh that is enabled by default. Other users are not allowed to login, so they have to exploit a component, such as a web application, to run arbitrary command or arbitrary file read. Anyone is able to read uLinux.conf file, world readable by default, can escalate to Domain Administrator if a NAS is a domain member.”
Users are strongly advised to update their systems to the latest version released by the vendor
(https://www.qnap.com/en/support/con_show.php?cid=113).
The Official advisory is available at: http://www.ush.it/team/ush/hack-qnap/qnap.txt
Cisco Finds Critical Flaw in Industrial Routers
23.3.2017 securityweek Vulnerebility
Cisco informed customers on Wednesday that some of its industrial routers are exposed to attacks due to a critical remote code execution vulnerability in the IOx application environment.
The flaw, identified as CVE-2017-3853, affects the Data-in-Motion (DMo) process of IOx and is caused by the lack of proper bounds checking. A remote, unauthenticated attacker can exploit the vulnerability to trigger a stack overflow by sending specially crafted packets that are forwarded to the DMo process for evaluation.Cisco industrial router vulnerability
Successful exploitation of the security hole can allow the attacker to execute arbitrary code with root privileges in the virtual instance running on the vulnerable device. However, Cisco pointed out that the router itself is not impacted.
The vulnerability affects Cisco IR809 and IR829 industrial integrated services routers running IOx versions 1.0.0.0 and 1.1.0.0. Users can determine what version is running on their devices through the IOx Local Manager interface.
The flaw has been patched with the release of IOx 1.2.4.2 and Cisco says it’s not aware of any attacks exploiting this vulnerability.
Learn More at the 2017 Singapore ICS Cyber Security Conference
On Wednesday, Cisco also published seven other advisories describing high severity vulnerabilities affecting IOS software, and the application-hosting framework (CAF) component of IOx.
The CAF weaknesses, described as arbitrary file creation and path traversal issues, affect not only 800 series industrial routers, but also 4000 series integrated services routers (ISR4K) and ASR 1000 series aggregation services routers (ASR1K).
A majority of the IOS and IOS XE problems allow remote attackers to cause devices to reload and enter a denial-of-service (DoS) condition, and one can be exploited to inject arbitrary commands with root privileges. Only the command injection exploit requires authentication.
These flaws were discovered by Cisco and there is no evidence of exploitation. All the security bugs have been patched.
Code Execution Vulnerability Found in LabVIEW
23.3.2017 securityweek Vulnerebility
Researchers at Cisco Talos have reported finding a high severity code execution vulnerability in the LabVIEW system design software from National Instruments.
According to Talos, LabVIEW 2016 version 16.0 is affected by a heap-based buffer overflow vulnerability which can be triggered with a specially crafted VI file (a LabVIEW specific format) that causes a user-controlled value to be used as a loop terminator.
By getting a targeted user to open a malicious VI file, a remote attacker can execute arbitrary code. Cisco has published an advisory containing technical details about the flaw, which is tracked as CVE-2017-2775.
The security hole was reported to National Instruments on January 13 and it was disclosed on March 22, but it’s unclear if a patch is available. An update released recently by the vendor does address a memory corruption issue that fits the description.
SecurityWeek has reached out to both Cisco and National Instruments for clarifications and will update this article if they respond.
LabVIEW is often used for data acquisition, instrument control and industrial automation, and this vulnerability could allow a threat actor to compromise a device responsible for controlling a physical system.
Learn More at the 2017 Singapore ICS Cyber Security Conference
“Organizations using this and similar software to control physical systems need to bear in mind the possibility of attackers exploiting vulnerabilities in control software to gain access to physical systems,” Talos said in a blog post.
“Equally, organizations should remember that proprietary file formats do not protect against software vulnerabilities. Even in the absence of a published file format specification vulnerabilities triggered by malicious files may still be discovered,” it added.
High Severity Flaws Patched in Rockwell Automation Tools
22.3.2017 securityweek Vulnerebility
High severity vulnerabilities have been patched by Rockwell Automation in the company’s Connected Components Workbench and FactoryTalk Activation tools, ICS-CERT said on Wednesday.
One of the flaws, discovered by researcher Ivan Sanchez and tracked as CVE-2017-5176, affects Connected Components Workbench (CCW), a design and configuration application for Rockwell devices. The product is used worldwide in various industries.
According to ICS-CERT, CCW is affected by a DLL hijacking vulnerability that allows a skilled attacker with access to the targeted system to inject malicious code into processes or cause a denial-of-service (DoS) condition.
The flaw affects CCW Developer and Free Standard editions, versions 9.01.00 and earlier. A patch is included in versions 10.00 and 10.01.
Learn More at the 2017 Singapore ICS Cyber Security Conference
The second high severity vulnerability was identified by Rockwell Automation in FactoryTalk Activation, a tool used for activating and managing Rockwell software and activation files. The tool is used by several products, including FactoryTalk, Arena, Emonitor, RSFieldBus, RSLinx, RSLogix, RSNetWorx, RSView32, SoftLogix and Studio 5000.
The security hole, CVE-2017-6015, is related to the improper handling of search paths and it can be exploited by a local user with limited rights to execute arbitrary code with elevated privileges.
The vulnerability affects FactoryTalk Activation 4.00.02 and prior, and it has been addressed with the release of version 4.01.
Rockwell customers that cannot immediately update their software have been provided mitigation instructions for both the CCW and FactoryTalk Activation flaws.
Vulnerabilities in LastPass allowed attackers to steal passwords
22.3.2017 securityaffairs Vulnerebility
The notorious Google Project Zero hacker Tavis Ormandy discovered numerous vulnerabilities in the Chrome and Firefox extensions of the LastPass password manager.
The Security expert at Google Project Zero Tavis Ormandy discovered several vulnerabilities in Chrome and Firefox extensions of the LastPass password manager that can be exploited to steal passwords.
The expert also wrote PoC exploit for the flaw and highlighted that only one of them appears to have been patched by LastPass.
Ormandy first discovered a flaw in the Firefox version of the LastPass extension (version 3.3.2), he avoided to publicly disclose the details for obvious reasons. According to the Google disclosure policy, LastPass has 90 days to solve the issue before Project Zero experts will disclose the details.
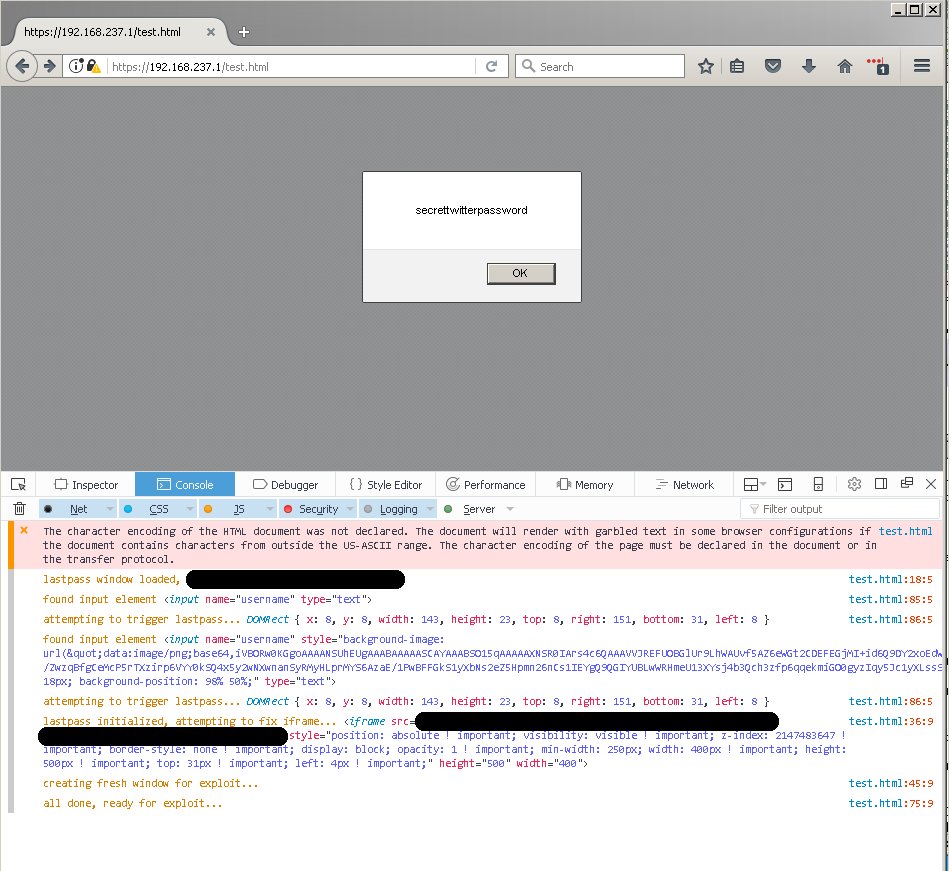
Follow
Tavis Ormandy @taviso
Wrote a quick exploit for another LastPass vulnerability. Only affects version on http://addons.mozilla.org (3.3.2), report on way. ¯\_(ツ)_/¯
3:45 AM - 16 Mar 2017
546 546 Retweets 681 681 likes
LastPass confirmed that the security team is already working to fix the bug.
Follow
LastPass ✔ @LastPass
We are aware of reports of a Firefox add-on vulnerability. Our security is investigating and working on issuing a fix.
1:17 AM - 22 Mar 2017
61 61 Retweets 93 93 likes
Yesterday, Ormandy reported another flaw that affected both the Chrome and Firefox versions of LastPass. The researcher explained that the vulnerability allowed attackers to steal a user’s passwords and, if the binary component was enabled, execute arbitrary code via remote procedure call (RPC) commands.
In order to exploit the flaw, the attacker has to trick victims into visiting a specially crafted web page.
In this case, LastPass promptly issued a temporary fix and immediately after announced it has fully patched the vulnerability on the server side.
Follow
LastPass ✔ @LastPass
The issue reported by Tavis Ormandy has been resolved. We will provide additional details on our blog soon.
2:17 PM - 21 Mar 2017
70 70 Retweets 108 108 likes
Ormandy publicly disclosed the details of the flaw including a proof-of-concept (PoC) code. The flaw existed due to the websiteConnector.js content script proxying unauthenticated messages to the extension. An attacker can exploit it to gain access to internal LastPass RPC commands.
“Therefore, this allows complete access to internal privileged LastPass RPC commands. There are hundreds of internal LastPass RPCs, but the obviously bad ones are things copying and filling in passwords (copypass, fillform, etc).” wrote the expert. “If you install the binary component (https://lastpass.com/support.php?cmd=showfaq&id=5576), you can also use “openattach” to run arbitrary code.”
Ormandy also spotted another vulnerability that can be exploited to steal passwords for any domain.
Follow
Tavis Ormandy @taviso
I found another bug in LastPass 4.1.35 (unpatched), allows stealing passwords for any domain. Full report will be on the way shortly.
Vulnerabilities Found in Popular Solar Park Monitoring System
22.3.2017 securityweek Vulnerebility
Vulnerabilities in solar park monitoring devices
Researchers at IT security services company SEC Consult have discovered several potentially serious vulnerabilities in solar park monitoring systems from Solar-Log. The vendor has released a firmware update to patch the flaws.
Solare Datensysteme’s Solar-Log was recently named the largest vendor for residential and commercial photovoltaic (PV) monitoring. The company says its products have been used to monitor more than 260,000 solar plants worldwide.
An advisory published on Wednesday by SEC Consult shows that the firm has identified a total of seven vulnerabilities. The security holes have been discovered after testing Solar-Log 1200 devices running firmware version 3.5.2-85 and Solar-Log 800e with firmware version 2.8.4-56. Other models are likely also affected considering that they use the same firmware.
SEC Consult told SecurityWeek it has identified tens of thousands of potentially vulnerable devices that can be reached directly from the Internet.
The security holes include an information disclosure flaw that allows an unauthenticated attacker to download a configuration file containing login credentials, and a cross-site request forgery (CSRF) that can be leveraged to modify or remove a device’s password by getting a logged-in user to click on a malicious link.
Another flaw allows an unauthenticated attacker to upload arbitrary files to the Solar-Log system using specially crafted POST requests.
Other vulnerabilities are related to the Beck IPC@CHIP embedded controller used by the Solar-Log monitoring devices. One of these flaws, known since 2001 (CVE-2001-1341), allows an attacker to obtain potentially sensitive information on the network configuration.
Other IPC@CHIP-related bugs can be exploited to change network configurations, cause a denial-of-service (DoS) condition, and reprogram the device’s flash memory. While some of the flaws may exist due to outdated IPC@CHIP software/firmware, SEC Consult pointed out that some attacks are possible because Solar-Log has failed to implement password protection functionality made available by Beck.
The information disclosure, CSRF and arbitrary file upload vulnerabilities can be exploited over the Internet is most cases, while the other weaknesses can be exploited by an attacker with network access to the devices, SEC Consult told SecurityWeek.
The vendor said it addressed the vulnerabilities with the release of firmware version 3.5.3-86, but SEC Consult could not confirm that the flaws have been patched properly.
Multiple Vulnerabilities Uncovered in Google Nest Cam
22.3.2017 securityweek Vulnerebility
A security researcher took it to GitHub to disclose information on multiple vulnerabilities allegedly affecting Nest Cam and Dropcam Pro devices after receiving no response from Google for several months.
The issues were discovered by security researcher Jason Doyle and affect the devices’ Bluetooth connectivity, allowing an attacker to access the affected device remotely or knock it offline for 60 to 90 seconds. Basically, a burglar capable of shutting the camera down could slip past it unnoticed.
Doyle revealed that three vulnerabilities impact the Bluetooth (BLE) connectivity of Dropcam, Dropcam Pro, Nest Cam Indoor/Outdoor models running firmware version 5.2.1. The researcher reveals that Google, which bought Nest several years ago, was notified on the issue on October 26, 2016. The company even acknowledged the bugs, but hasn’t released a fix to date.
The first bug is a buffer overflow condition that can be triggered when setting the SSID parameter on the camera. According to the researcher, an attacker exploiting the issue would have to be within Bluetooth range at any time during the camera’s powered on state. This is possible, however, because Bluetooth on the device is never disabled, not even after initial setup.
Another buffer overflow condition can be triggered when setting the encrypted password parameter on the camera. Similarly, the attacker must be in Bluetooth range of the device. The attack results in the camera to crash and reboot back to operational state.
The third issue, the researcher reveals, could allow an attacker to temporarily disconnect the camera from its Wi-Fi connection by supplying it with a new SSID to connect to. Because the affected cameras don’t come with support for local storage of video footage, the surveillance capabilities of the targeted device are temporarily disabled.
This attack can be leveraged to knock the camera offline while it attempts association with the newly set SSID. The device goes offline for around 60-90 seconds before re-connecting to the original Wi-Fi network and resuming normal operation.
The security researcher published all of the details pertaining to the three vulnerabilities, complete with example exploits.
Unpatchable 'DoubleAgent' Attack Can Hijack All Windows Versions — Even Your Antivirus!
22.3.2017 thehackernews Vulnerebility
A team of security researchers from Cybellum, an Israeli zero-day prevention firm, has discovered a new Windows vulnerability that could allow hackers to take full control of your computer.
Dubbed DoubleAgent, the new injecting code technique works on all versions of Microsoft Windows operating systems, starting from Windows XP to the latest release of Windows 10.
What's worse? DoubleAgent exploits a 15-years-old undocumented legitimate feature of Windows called "Application Verifier," which cannot be patched.
Application Verifier is a runtime verification tool that loads DLLs (dynamic link library) into processes for testing purpose, allowing developers quickly detect and fix programming errors in their applications.
Unpatchable Microsoft Application Verifier Exploit
The vulnerability resides in how this Application Verifier tool handles DLLs. According to the researchers, as part of the process, DLLs are bound to the target processes in a Windows Registry entry, but attackers can replace the real DLL with a malicious one.
Simply by creating a Windows Registry key with the name same as application he wants to hijack, an attacker can provide his own custom verifier DLL he would like to inject into a legitimate process of any application.
Once the custom DLL has been injected, the attacker can take full control of the system and perform malicious actions, such as installing backdoors and persistent malware, hijacking the permissions of any existing trusted process, or even hijacking other users’ sessions.
Here's how the Cybellum researchers say this attack can work:
"DoubleAgent gives the attacker the ability to inject any DLL into any process. The code injection occurs extremely early during the victim’s process boot, giving the attacker full control over the process and no way for the process to protect itself."
Using DoubleAgent Attack to Take Full Control of Anti-Virus
In order to demonstrate the DoubleAgent attack, the team hijacked anti-virus applications -- which is the main defense on systems to prevent any malware from running -- using their technique and turn them into malware.
The team was able to corrupt the anti-virus app using the DoubleAgent attack and get the security software to act as disk-encrypting ransomware.
The attack works on every version of Windows OS from Windows XP to Windows 10 and is hard to block because the malicious code can be re-injected into the targeted legitimate process after the system reboots – Thanks to the persistent registry key.
The researchers said most of the today's security products on the market are susceptible to the DoubleAgent attacks. Here's the list of affected security products:
Avast (CVE-2017-5567)
AVG (CVE-2017-5566)
Avira (CVE-2017-6417)
Bitdefender (CVE-2017-6186)
Trend Micro (CVE-2017-5565)
Comodo
ESET
F-Secure
Kaspersky
Malwarebytes
McAfee
Panda
Quick Heal
Norton
After hijacking the anti-virus software, attackers can also use the DoubleAgent attack to disable the security product, making it blind to malware and cyber attacks, using the security product as a proxy to launch attacks on the local computer or network, elevating the user privilege level of all malicious code, hiding malicious traffic or exfiltrate data, or damaging the OS or causing a denial of service.
Note: Cybellum researchers only focused on anti-virus programs, though the DoubleAgent attack could work with any application, even Windows operating system itself.
Many Antiviruses Still Unpatched Even After 90 Days Of Responsible Disclosure
Cybellum said the company had reported the DoubleAgent attack to all affected anti-virus vendors more than 90 days ago.
Cybellum researchers have been working with some anti-virus companies to patch the issue, but so far, only Malwarebytes and AVG have released a patch, while Trend-Micro has planned to release one soon, as well.
So, if you use any of the three apps mentioned above, you are strongly advised to update it as soon as possible.
As a mitigation, the researchers note that the simplest fix for antivirus vendors is to switch from Application Verifier to a newer architecture called Protected Processes.
Protected processes mechanism protects anti-malware services against such attacks by not allowing other apps from injecting unsigned code, but this mechanism has so far been implemented only in Windows Defender, which was introduced by Microsoft in Windows 8.1.
Cybellum has also provided a video demonstration of the DoubleAgent attack, showing how they turned an antivirus app into a ransomware that encrypts files until you pay up.
The company also posted proof-of-concept (PoC) code on GitHub, and two blog posts detailing the DoubleAgent attack.
Metaspoit's New RFTransceiver Finds Security Flaws in IoT Radio Communications
21.3.2017 securityweek Vulnerebility
The Internet of Things is pervasive, rapidly growing, and largely insecure. Researchers have discovered security flaws in products ranging from baby alarms and dolls, to motor vehicles and medical equipment -- and the likelihood is that there are many more simply not yet discovered.
Metasploit has now released a new hardware bridge extension to help researchers and pentesters -- and IoT user organizations -- discover security flaws in IoT radio communications. While many of the known flaws are found in consumer devices, IoT devices are increasingly making their way into and onto business premises; and it is very difficult for security teams to control them.
"Wireless systems often control alarm systems, surveillance monitoring, door access, server room HVAC controls, and many other areas," writes Craig Smith, Transportation Research Lead at Rapid7 in a blog announcement today. These same devices can often contain flaws that can be used by attackers, but are unknown to the user.
With Metasploit's new RFTransceiver radio frequency testing extension, companies will be able to better understand their true security posture. They will, suggests Smith, "be able to test physical security controls and better understand when foreign IoT and other devices are brought onto the premises."
In October 2016, Rapid7 reported a vulnerability in a medical insulin pump. The pump was remotely controlled, but communication was sent between the controller and the device in cleartext rather than encrypted. This could allow a hacker to spoof the controller and trigger unauthorized insulin injections. The problem for security teams is that there is no easy way to know what communication happens between a device and its control server.
"We strongly believe," writes Smith, "that RF testing is an incredibly important -- though currently often overlooked -- component of vulnerability testing. We believe that failing to test the usage of radio frequency in products puts people and organizations at risk. We also believe the importance of RF testing will continue to escalate as the IoT ecosystem further expands."
His "often overlooked" comment is valid and serious. Freelance security consultant and researcher Robin Wood (aka DigiNinja pentester) told SecurityWeek, "Being able to easily test RF that isn't the standard 802.11 wifi is going to be really useful for physical tests where clients are really switched on and want to know exactly what is going on in their environments.
"Unfortunately, at the moment I find this type of client is few and far between but, as the technology to do the testing gets cheaper and easier to use, hopefully more testers will start using it and offering it as a service which will then start drawing more clients in; in turn increasing the exposure of RF based devices and so creating a feedback loop."
Wood believes that the Metasploit capability will "make it easier for people to do research in this area which again will start to increase awareness and hopefully the overall security."
The danger, of course, is that criminal elements could also use Metasploit to find flaws suitable for exploiting. It is a criticism that has always been leveled against Metasploit, and one that Smith mentions. "The most common criticism of any technology created for the purpose of security testing is that bad guys could use it to do bad things." But he adds that the bad guys are already doing bad things, and the best defense is to know what they can do. "Sunlight is the best disinfectant," he adds.
F-Secure is at least one security firm that agrees. "RF has traditionally been a fruitful attack vector," a spokesperson told SecurityWeek, "so maybe the availability of more tools in the field will improve that situation. When a widely-used tool like Metasploit starts offering a module that allows this sort of work, it lowers the entry barrier considerably. We may see more device manufacturers starting to pay attention to the RF attack vectors against their devices, but we are also almost certain to see more attacks from this angle as well."
At the same time, F-Secure is aware of the dangers. "This sort of technology is very much 'dual use' in the sense that while it is essential to security researchers and red teams, it can also be used as an attack tool by malicious parties."
Senior security consultant Taneli Kaivola added, "Now that the door has been opened for the wider public, we can expect to see the scope and capability of this tool expanding. I fully expect to see SDRs (software defined radios, adding additional frequencies) supported in the framework popping up like mushrooms in the rain."
Chester Wisniewski, principal research scientist at Sophos told SecurityWeek, primarily sees the dangerous side. "Rapid7 is correct that RF testing can be a critical component in many areas of security research, but it is very different from traditional pentesting tools. To me this is a concerning development. Take average hacker-types with no knowledge of RF and the regulatory frameworks designed to allow our devices to work and provide them a tool that can send and receive signals with almost no knowledge.
"What could possibly go wrong?" he asks. "Other than breaking just about anything that operates over RF in a difficult to detect manner... I just don't think making it a toolkit anyone can use is a good idea. Software-defined radios have already breached this wall, but I suspect simplifying their use will end in tears."
Cisco Patches Serious DoS Flaws in IOS
21.3.2017 securityweek Vulnerebility
Cisco has released updates for its IOS and IOS XE software to address a couple of high severity flaws that can be exploited to cause a denial-of-service (DoS) condition on vulnerable devices.
The security holes were disclosed on Monday by Omar Eissa, a researcher at Germany-based security firm ERNW, at the TROOPERS conference in a talk focusing on Cisco’s Autonomic Networking Infrastructure (ANI). The ANI vulnerabilities found by Eissa allow unauthenticated attackers to cause affected devices to reload.
One of the flaws, identified as CVE-2017-3850, can be exploited by a remote attacker simply by knowing the targeted Cisco device’s IPv6 address. The weakness can be exploited by sending a specially crafted IPv6 packet to an appliance, but the attack only works if the device runs a version of IOS that supports ANI and its IPv6 interface is reachable.
The second vulnerability, CVE-2017-3849, can be exploited if the targeted device is running an IOS release that supports ANI, it’s configured as an autonomic registrar, and it has a whitelist configured.
If these conditions are met, an adjacent attacker can cause a DoS condition by sending the appliance a specially crafted autonomic network channel discovery packet.
Cisco has published indicators of compromise (IoC) and the company’s IOS Software Checker can be used by customers to determine if their IOS and IOS XE software is vulnerable to such attacks. The networking giant has found no evidence of exploitation in the wild.
These are not the only serious IOS vulnerabilities disclosed recently by Cisco. Last week, the company informed customers that an analysis of the Vault 7 files made public this month by WikiLeaks revealed the existence of a critical remote code execution flaw affecting more than 300 of the company’s switches and modules.
In the Vault 7 files, which allegedly describe the CIA’s hacking capabilities, Cisco also identified a piece of malware that can hijack its devices and abuse them for various purposes, including data theft and manipulating web traffic.
Serious Flaws Found in Moodle Learning Platform
20.3.2017 securityweek Vulnerebility
Researchers have discovered serious vulnerabilities in Moodle, a popular open-source learning platform used by many top universities in the United States, the United Kingdom and other countries around the world.
Moodle updates released last week address a total of four vulnerabilities, including two that have a “serious” severity/risk rating and two classified as “minor.”
One of the serious flaws, tracked as CVE-2017-2641, can be exploited by an attacker to execute arbitrary PHP code on a vulnerable Moodle server. While the security hole is tracked as a single issue, Netanel Rubin, the expert who discovered the problem, says an attack is possible due to several smaller weaknesses affecting the platform.
The flaw can be exploited by an authenticated attacker to conduct an SQL injection attack via user preferences and add a new administrator user to the system. Once the attacker has an admin account on the system, they can execute arbitrary code by uploading a new plugin or a template to the server, Rubin said.
This vulnerability affects Moodle 3.2 to 3.2.1, 3.1 to 3.1.4, 3.0 to 3.0.8, 2.7.0 to 2.7.18 and older versions, and it has been fixed with the release of versions 3.2.2, 3.1.5, 3.0.9 and 2.7.19.
Moodle developers noted that the flaw can only be exploited in Moodle versions prior to 3.2 by users with manager or admin rights. In version 3.2, the attack works with any type of user account, including teacher and student accounts.
Rubin, who recently warned that vulnerabilities in smart electricity meters expose consumers and electric utilities to cyberattacks, has published a lengthy blog post detailing his findings.
The second serious flaw patched by Moodle last week has been described as a cross-site scripting (XSS) flaw in the functionality that allows users to attach files for evidence of prior learning.
“Serving files attached to evidence of prior learning did not force download. When viewed by other users they would be opened in current moodle sessions,” Moodle wrote in its advisory.
The flaw, reported by a researcher who uses the online moniker “wez3” and tracked as CVE-2017-2645, only affects versions 3.2 to 3.2.1 and 3.1 to 3.1.4.
Jaymark Pestaño discovered a less severe XSS vulnerability in the evidence of prior learning section, and Nadav Kavalerchik identified an issue related to usernames being displayed in global search for unauthenticated users. Both issues are considered minor.
Mozilla Patches Firefox Flaw Disclosed at Pwn2Own
20.3.2017 securityweek Vulnerebility
Mozilla has already patched a Firefox vulnerability disclosed last week at the Pwn2Own 2017 competition by a team of researchers from Beijing-based enterprise security firm Chaitin Tech.
The Chaitin Security Research Lab team hacked Firefox with a SYSTEM-level escalation and earned $30,000. The experts used an integer overflow to break Firefox and an uninitialized buffer flaw in the Windows kernel to escalate privileges.
The integer overflow vulnerability, rated critical and tracked as CVE-2017-5428, was patched on Friday with the release of Firefox 52.0.1. No other security fixes or improvements are included in this release.
“An integer overflow in createImageBitmap() was reported through the Pwn2Own contest,” Mozilla wrote in its advisory. “The fix for this vulnerability disables the experimental extensions to the createImageBitmap API. This function runs in the content sandbox, requiring a second vulnerability to compromise a user's computer.”
Chaitin Security Research Labs hacks Firefox and runs notepad.exe as SYSTEM
Moritz Jodeit of Blue Frost Security also targeted Firefox at the Pwn2Own competition, but he failed to demonstrate his exploit chain in the allocated timeframe.
In addition to Firefox, the Chaitin Security Research Lab targeted Safari, macOS and Ubuntu, and earned a total of $90,000 for its exploits.
The white hat hackers who took part in Pwn2Own 2017 received a total of $833,000 for finding 51 vulnerabilities in Windows, macOS, Ubuntu, Firefox, Edge, Safari, Flash Player, Adobe Reader and VMware Workstation.
No Chrome flaws have been disclosed at this year’s event and only one was reported at Pwn2Own 2016. It has become increasingly difficult to find critical security holes in Google’s web browser, which is why the company recently decided to increase rewards for remote code execution vulnerabilities to $31,337.
CIA Vault7 Leak – Cisco IOS and IOS XE Software Cluster Management Protocol Remote Code Execution flaw
20.3.2017 securityaffairs Vulnerebility
After the leak of the CIA Vault7 archive, experts from CISCO warn of Cisco IOS and IOS XE Software Cluster Management Protocol Remote Code Execution flaw.
Recently Wikileaks announced it is planning to share with IT firms details about vulnerabilities in a number of their products, the flaw are exploited by the hacking tools and techniques included in the CIA Vault7 data leak.
Assange sent an email to tech firms including “a series of conditions” that they need to fulfill before gaining access to details included in the Vault7.
But it seems that some IT Giants will not accept the conditions, one of them is CISCO that started its analysis of the documents included in the Vault7 documents. The company has already identified an IOS / IOS XE bug that affects more than 300 of its switch models.
Vault7
The flaw in the Cisco Cluster Management Protocol (CMP) processing code in Cisco IOS and Cisco IOS XE Software could be exploited by a remote, unauthenticated attacker to remotely execute code with elevated privileges and also to cause a reload of the affected device.
The hack could allow attackers to obtain full control of the vulnerale device.
The Cluster Management Protocol leverages on Telnet internally as a signaling and command protocol between members of the cluster.
“The vulnerability is due to the combination of two factors:
The failure to restrict the use of CMP-specific Telnet options only to internal, local communications between cluster members and instead accept and process such options over any Telnet connection to an affected device, and
The incorrect processing of malformed CMP-specific Telnet options.”
An attacker could trigger the vulnerability by sending malformed CMP-specific Telnet options while establishing a Telnet session with an affected Cisco device configured to accept Telnet connections.
The vulnerability affects the default configuration of the flawed devices even when the user doesn’t have switch clusters configured, and can be exploited over either IPv4 or IPv6.
“An attacker could exploit this vulnerability by sending malformed CMP-specific Telnet options while establishing a Telnet session with an affected Cisco device configured to accept Telnet connections. An exploit could allow an attacker to execute arbitrary code and obtain full control of the device or cause a reload of the affected device”, Cisco’s advisory states.
CISCO advisory confirms that the vulnerability affects 264 Catalyst switches, 51 industrial Ethernet switches, and three other CISCO devices. Of course, the vulnerable devices are all running IOS and configured to accept Telnet connections.
As mitigation measures, experts from CISCO suggest to disabled Telnet connections, SSH remains the best option to remotely access the devices.
At the time I was writing it is not clear if the flaw was exploited in the wild.
Disable TELNET! Cisco finds 0-Day in CIA Dump affecting over 300 Network Switch Models
20.3.2017 thehackernews Vulnerebility
Cisco is warning of a new critical zero-day IOS / IOS XE vulnerability that affects more than 300 of its switch models.
The company identified this highest level of vulnerability in its product while analyzing "Vault 7" — a roughly 8,761 documents and files leaked by Wikileaks last week, claiming to detail hacking tools and tactics of the Central Intelligence Agency (CIA).
The vulnerability resides in the Cluster Management Protocol (CMP) processing code in Cisco IOS and Cisco IOS XE Software.
If exploited, the flaw (CVE-2017-3881) could allow an unauthenticated, remote attacker to cause a reboot of an affected device or remotely execute malicious code on the device with elevated privileges to take full control of the device, Cisco says in its advisory.
The CMP protocol has been designed to pass around information about switch clusters between cluster members using Telnet or SSH.
The vulnerability is in the default configuration of affected Cisco devices, even if the user doesn't configure any cluster configuration commands. The flaw can be exploited during Telnet session negotiation over either IPv4 or IPv6.
According to the Cisco researchers, this bug occurs in Telnet connections within the CMP, due to two factors:
The protocol doesn't restrict the use of CMP-specific Telnet options only to internal, local communications between cluster members; instead, it accepts and processes commands over any Telnet connection to an affected device.
The incorrect processing of malformed CMP-specific Telnet options.
So, in order to exploit this vulnerability, an attacker can send "malformed CMP-specific Telnet options while establishing a Telnet session with an affected Cisco device configured to accept Telnet connections," researchers say.
This exploitation could allow the attacker to remotely execute malicious code and obtain full control of the affected device or cause a reload of the affected device.
Disable Telnet On Vulnerable Models — Patch is not Available Yet!
The vulnerability affects 264 Catalyst switches, 51 industrial Ethernet switches, and 3 other devices, which includes Catalyst switches, Embedded Service 2020 switches, Enhanced Layer 2/3 EtherSwitch Service Module, Enhanced Layer 2 EtherSwitch Service Module, ME 4924-10GE switch, IE Industrial Ethernet switches, RF Gateway 10, SM-X Layer 2/3 EtherSwitch Service Module, and Gigabit Ethernet Switch Module (CGESM) for HP. (check complete list here)
Currently, this vulnerability is unpatched, and until patches are available, Cisco recommends its users to disable the Telnet connection to the switch devices in favor of SSH.
The company's advisory doesn't talk about any working exploit using this flaw, but if there's one, tens of thousands, if not hundreds of thousands, of devices installed around the world look to have been at great risk for an unknown period — Thanks to the CIA for holding the flaw.
Cisco will update its IOS Software Checker tool immediately as soon as the patches come out.
Researcher leveraged App Paths to bypass User Account Control in Windows 10
20.3.2017 securityaffairs Vulnerebility
The security expert Matt Nelson has devised a new method that leverages App Paths to bypass the User Account Control (UAC) only on Windows 10.
The researcher detailed a bypass technique that is quite differed to the previous ones he devices, the new method “doesn’t rely on the IFileOperation/DLL hijacking approach”.
“I’ve previously blogged about two different bypass techniques, and this post will highlight an alternative method that also doesn’t rely on the IFileOperation/DLL hijacking approach.” reads a blog post published by Nelson. “This technique works on Windows 10 build 15031, where the vast majority of public bypasses have been patched.”
The expert explained that there are several signed binaries in Microsoft OS that auto-elevate due to their manifest. Nelson analyzed them and focused its investigation on sdclt.exe, which is the process associated with the Backup and Restore tool in Windows.
He discovered that sdclt.exe auto-elevates due to its manifest only in Windows 10.
The sdclt.exe starts control.exe to open up a Control Panel item in high-integrity context, the process obtains the path to control.exe by querying the App Path key for it within the HKEY_CURRENT_USER hive.
“Looking again at the execution flow, sdclt.exe queries the App Path key for control.exe within the HKEY_CURRENT_USER hive.” explained Nelson.
“Calls to HKEY_CURRENT_USER (or HKCU) from a high integrity process are particularly interesting. This often means that an elevated process is interacting with a registry location that a medium integrity process can tamper with,”
An attacker can modify the key that is retrieved by the sdclt.exe query, the expert managed to have cmd.exe returned to the query.

The method doesn’t allow for using parameters, in order to exploit it the attacker has to place the malicious payload to the disk.
“If you try to give the binary any parameters (e.g, C:\Windows\System32\cmd.exe /c calc.exe), it will interpret the entire string as the lpFile value to the ShellExecuteInfo structure, which is then passed over to ShellExecuteEx. Since that value doesn’t exist, it will not execute.” continues Nelson.
The expert published a PoC script to demonstrate the method, he explained that attack can be prevented by setting the UAC level to “Always Notify” or by removing the current user from the Local Administrators group.
App Paths Used to Bypass User Account Control in Windows 10
19.3.2017 securityaffairs Vulnerebility
A new technique that leverages App Paths to bypass the User Account Control (UAC) in Windows 10 has been detailed by security researcher Matt Nelson.
Over the past several months, Nelson detailed other UAC bypass methods as well, namely one abusing Event Viewer and another leveraging the Disk Cleanup utility. The former has been used in live attacks by Remcos RAT and Erebus ransomware operators, as well as by a threat actor targeting military and aerospace organizations in Russia and Belarus.
Now, the researcher uncovered yet another bypass that “doesn’t rely on the IFileOperation/DLL hijacking approach,” but which works only on Windows 10. According to Nelson, Microsoft has focused on resolving the issues leading to previously disclosed bypasses, but the new technique works on Windows 10 build 15031, “where the vast majority of public bypasses have been patched.”
Because there are Microsoft signed binaries that auto-elevate due to their manifest, the researcher decided to have a closer look, and discovered an issue associated with sdclt.exe, which is the process associated with the Backup and Restore tool in Windows. As it turns out, sdclt.exe auto-elevates due to its manifest, but only in Windows 10 (its manifest in Windows 7 prevents auto-elevation when started from medium integrity).
The execution flow of sdclt.exe reveals that the binary starts control.exe to open up a Control Panel item in high-integrity context, and the researcher discovered that the process obtains the path to control.exe by querying the App Path key for it within the HKEY_CURRENT_USER hive.
“Calls to HKEY_CURRENT_USER (or HKCU) from a high integrity process are particularly interesting. This often means that an elevated process is interacting with a registry location that a medium integrity process can tamper with,” Nelson says.
If the search for the full path of control.exe doesn’t return the key from the HKCU hive, sdclt.exe continues the typical Windows search order. However, since the key can be modified and the process searchers for it first, an attacker can use this to have sdclt.exe query a modified App Paths key. The researcher managed to have cmd.exe returned to the query, a process that is high integrity.
One thing that this technique doesn’t allow for, however, is parameters, meaning that the attacker has to place the payload to the disk. When parameters are added, the string is interpreted as the lpFile value to the ShellExecuteInfo structure, which is passed over to ShellExecuteEx, but won’t execute, given that the value doesn’t exist.
The researcher also published a script to GitHub to demonstrate the attack. “The script takes a full path to your payload. C:\Windows\System32\cmd.exe is a good one to validate. It will automatically add the keys, start sdclt.exe and then cleanup,” Nelson explains.
The attack can be prevented by setting the UAC level to “Always Notify” or by removing the current user from the Local Administrators group, the researcher explains. Further monitoring for this attack could be achieved by utilizing methods/signatures to look for and alert on new registry entries in HKCU\Microsoft\Windows\CurrentVersion\App Paths\Control.exe.
Hackers Earn Big Bounties for GitHub Enterprise Flaws
17.3.2017 securityweek Vulnerebility
White hat hackers have earned tens of thousands of dollars in bounties after finding serious vulnerabilities in GitHub Enterprise.
GitHub Enterprise is the on-premises version of GitHub.com, for which organizations pay an annual fee of $2,500 for every 10 users. The product promises enterprise-grade security, 24/7 technical support, hosting options, and several administration features not available for GitHub.com.
GitHub Enterprise versions 2.8.5, 2.8.6 and 2.8.7, released in January, patch several flaws rated critical and high severity, including ones that can be exploited to bypass authentication and remotely execute arbitrary code.
The researchers who discovered the vulnerabilities have started making their findings public, and information from GitHub and the experts themselves shows that they earned significant rewards.
GitHub included the Enterprise product in its bug bounty program at the beginning of the year, when it announced that the most severe bugs reported in January and February would also receive bonus rewards.
Two of the vulnerabilities rated critical were identified by Greece-based researcher Ioannis Kakavas. The expert discovered a couple of flaws in the Security Assertion Markup Language (SAML) implementation of GitHub Enterprise, and received a research grant to conduct a full assessment of SAML in GitHub.
Kakavas, who is currently the second best hacker in GitHub’s bug bounty program, earned a total of $27,000 for the flaws he uncovered. He recently published a blog post containing technical details and proof-of-concept (PoC) code.
Another critical flaw was discovered by German bug bounty hunter Markus Fenske. The expert found a weakness in the management console that could have been exploited to execute arbitrary commands on the GitHub Enterprise appliance.
Fenske has received a total of $18,000 for his findings, which includes a $10,000 bounty, the maximum reward offered by GitHub, and an $8,000 bonus.
Researcher Orange Tsai, who last year managed to hack a Facebook server, received $5,000 and a $5,000 bonus for responsibly disclosing a high severity SQL injection vulnerability related to the pre-receive hook APIs used by GitHub Enterprise.
GitHub said there was no evidence that the vulnerabilities identified by Fenske and Kakavas had been exploited in the wild.
Critical Flaw Exposes Many Ubiquiti Devices to Attacks
17.3.2017 securityweek Vulnerebility
Dozens of products from Ubiquiti Networks are affected by a critical flaw that can be exploited to hijack devices. The security hole was reported to the vendor in November, but patches have yet to be released for most of the impacted versions.
The vulnerability, discovered by researchers at SEC Consult, has been described as a command injection in the administration interface of Ubiquiti devices. The weakness affects the pingtest_action.cgi component and it’s partly caused by the use of a very old version of PHP, namely PHP 2.0.1 from 1997.
The flaw can be exploited by authenticated attackers from a low privileged read-only account, or remotely by unauthenticated hackers if they can trick a user into clicking on a specially crafted link. The remote attack works due to the lack of cross-site request forgery (CSRF) protection, SEC Consult said in its advisory.
An attacker can exploit the vulnerability to open a reverse root shell and take over the device. Depending on what the device is used for, it may also be possible for an attacker to hijack other machines on the network.
According to SEC Consult, the flaw affects roughly 40 Ubiquiti access points, including Rocket Prism, PowerBeam, NanoBeam, LiteBeam, airGateway and airFiber products.
The security firm reported the vulnerability to Ubiquiti Networks on November 22 via the vendor’s HackerOne page. The company was initially responsive, but it stopped providing status updates in early February, which led to SEC Consult’s decision to make its findings public.
SEC Consult has published a video demonstrating its findings, but only limited technical details have been made available to prevent abuse:
After SEC Consult published its advisory, an Ubiquiti employee responded to users on Reddit, claiming that the company stopped responding to the researchers due to a communications issue with the HackerOne platform.
The company said the vulnerability was fixed in version 8.0.1 of AirOS, the operating system running on affected products. It has also promised to release updates soon for versions 5.x, 6.x ad 7.x.
“Agree this looks very bad, but I can assure you the optics of this aren't an accurate reflection of how security issue reports are handled,” said the Ubiquiti employee. “We did drop the ball in communication here, but it wasn't due to the issue being ignored.”
CVE-2017-2636 Linux kernel flaw was spotted after seven years and quickly fixed
17.3.2017 securityaffairs Vulnerebility
A flaw recently fixed in the Linux kernel tracked as CVE-2017-2636 might have been exploited to gain privilege escalation or cause a DoS condition.
The security expert Alexander Popov from Positive Technologies has discovered a race condition in the n_hdlc driver that might be exploited by attackers for privilege escalation in the operating system.
Linux kernel CVE-2017-2636 flaw
The vulnerability tracked as CVE-2017-2636, received a CVSS v3 score of 7.8., it went uncovered for seven years but it is not possible to say if hackers have exploited it in the wild.
“This is an announcement of CVE-2017-2636, which is a race condition in the n_hdlc Linux kernel driver (drivers/tty/n_hdlc.c). It can be exploited to gain a local privilege escalation.” reads the security advisory published on SecList. “This driver provides HDLC serial line discipline and comes as a kernel module in many Linux distributions, which have CONFIG_N_HDLC=m in the kernel config. Exploiting the flaw in the vulnerable module n_hdlc does not require Microgate or SyncLink hardware. The module is automatically loaded if an unprivileged user opens a pseudoterminal and calls TIOCSETD ioctl for it setting N_HDLC line discipline.”
Tha attackers can automatically load the flawed module with just unprivileged user rights and without using any special hardware.
The CVE-2017-2636 vulnerability affects the majority of popular Linux distributions including Ubuntu, RHEL 6/7, Fedora, SUSE, and Debian.
Linux users can install latest security updates or manually disable the vulnerable module.
Popov explained that the vulnerability is widespread on Linux systems due to its age.
According to the expert, the vulnerability was introduced on June 22, 2009. It was spotted years later during system calls testing with the syzkaller fuzzer and it was reported to kernel.org along with a patch to solve it and a PoC exploit code.
The flaw was publicly disclosed on March 7, and development team behind the major distributions quickly released security updates.
Another Old Flaw Patched in Linux Kernel
16.3.2017 securityweek Vulnerebility
A researcher has identified another potentially serious Linux kernel vulnerability that has been around for several years. The flaw was addressed in the kernel more than one week ago, but some of the affected Linux distributions have yet to release patches.
The security hole was discovered using the syzkaller fuzzer by Positive Technologies expert Alexander Popov, who reported it to Linux kernel developers on February 28. The researcher said the vulnerability was introduced in June 2009.
The flaw, tracked as CVE-2017-2636, is a race condition in the n_hdlc driver that can lead to a double-free error. A local attacker with limited privileges can exploit the weakness to cause a denial-of-service (DoS) condition or escalate privileges.
"The vulnerability is old, so it is widespread across Linux workstations and servers,” explained Popov. “To automatically load the flawed module, an attacker needs only unprivileged user rights. Additionally, the exploit doesn't require any special hardware.”
The security hole affects Red Hat, Ubuntu, Debian, SUSE and other distributions, but patches have not been made available for all affected versions. The bug was patched in the Linux kernel on March 7.
Until fixes become available, users can mitigate the vulnerability by manually blocking the affected module from loading. Popov says he plans on releasing a proof-of-concept (PoC) exploit once users have had the chance to update their installations.
Several of the Linux kernel flaws identified in the past months had been introduced years prior to their discovery, including CVE-2016-0728 and CVE-2016-5696, both introduced in 2012 and both affecting Linux and Android devices. An even older vulnerability, CVE-2017-6074, which came to light last month, was introduced in 2005.
Researcher Kees Cook recently analyzed the Linux kernel vulnerabilities discovered since 2011 in an effort to determine for how long they had gone unnoticed. The expert determined that the average lifespan of a security hole is roughly 5 years, with critical issues being discovered after 3.3 years and high severity bugs found after more than 6 years.
Linux Kernel Gets Patch For Years-Old Serious Vulnerability
16.3.2017 thehackernews Vulnerebility
Another dangerous vulnerability has been discovered in Linux kernel that dates back to 2009 and affects a large number of Linux distros, including Red Hat, Debian, Fedora, OpenSUSE, and Ubuntu.
The latest Linux kernel flaw (CVE-2017-2636), which existed in the Linux kernel for the past seven years, allows a local unprivileged user to gain root privileges on affected systems or cause a denial of service (system crash).
Positive Technologies researcher Alexander Popov discovered a race condition issue in the N_HLDC Linux kernel driver – which is responsible for dealing with High-Level Data Link Control (HDLC) data – that leads to double-free vulnerability.
“Double Free” is one of the most common memory corruption bug that occurs when the application releases same memory location twice by calling the free() function on the same allocated memory.
An unauthenticated attacker may leverage this vulnerability to inject and execute arbitrary code in the security context of currently logged in user.
The vulnerability affects the majority of popular Linux distributions including Red Hat Enterprise Linux 6, 7, Fedora, SUSE, Debian, and Ubuntu.
Since the flaw dates back to June 2009, Linux enterprise servers and devices have been vulnerable for a long time, but according to Positive Technologies, it is hard to say whether this vulnerability has actively been exploited in the wild or not.
"The vulnerability is old, so it is widespread across Linux workstations and servers," says Popov. "To automatically load the flawed module, an attacker needs only unprivileged user rights. Additionally, the exploit doesn't require any special hardware."
The researcher detected the vulnerability during system calls testing with the syzkaller fuzzer, which is a security code auditing software developed by Google.
Popov then reported the flaw to kernel.org on February 28, 2017, along with the exploit prototype, as well as provided the patch to fix the issue.
The vulnerability has already been patched in the Linux kernel, and the security updates along with the vulnerability details were published on March 7.
So, users are encouraged to install the latest security updates as soon as possible, but if unable to apply the patch, the researcher advised blocking the flawed module (n_hdlc) manually to safeguard enterprise as well as home use of the operating system.
Intel Offers Up to $30,000 for Hardware Vulnerabilities
16.3.2017 securityweek Vulnerebility
Intel has launched its first bug bounty program and the tech giant is prepared to offer up to $30,000 for vulnerabilities found in its products.
The bug bounty program, hosted on the HackerOne platform, covers Intel’s software, firmware and hardware. It does not cover Intel Security (McAfee) products, the company’s web infrastructure, or acquisitions completed less than six months ago. Third-party and open source applications are also not in scope of the program.
Researchers who find critical hardware vulnerabilities can earn a maximum of $30,000. Critical flaws in Intel software and firmware are worth up to $7,500 and $10,000, respectively.
The severity of a vulnerability is determined based on its CVSS 3.0 base score, and adjusted depending on the affected product’s threat model and security objectives.
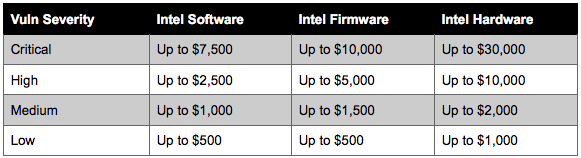
“We want to encourage researchers to identify issues and bring them to us directly so that we can take prompt steps to evaluate and correct them, and we want to recognize researchers for the work that they put in when researching a vulnerability,” Intel said.
Following the recent Vault 7 leak by WikiLeaks, which describes the CIA’s alleged hacking capabilities, Intel announced the availability of a CHIPSEC framework module that can be used to verify the integrity of EFI firmware executables.
Microsoft launches new Office bug bounty program
Microsoft also made a bug bounty announcement on Wednesday. The company has launched a new program for Office Insider Builds on Windows.
This new bug bounty program, which runs between March 15 and June 15, promises payouts ranging from $6,000 to $15,000 for various types of vulnerabilities. Researchers can earn rewards if they find privilege escalation vulnerabilities via Office Protected View, flaws that allow macro execution by bypassing security policies, and code execution through a bypass of automatic attachment blocking policies in Outlook.
The announcement comes shortly after Microsoft decided to temporarily double bug bounty payouts for vulnerabilities found in core applications of the Office 365 suite.
Several Vulnerabilities Patched in Drupal 8
16.3.2017 securityweek Vulnerebility
Several vulnerabilities have been patched in the Drupal content management system (CMS) with the release of version 8.2.7, including access bypass, cross-site request forgery (CSRF) and remote code execution flaws.
The most serious of them, rated critical and tracked as CVE-2017-6377, is an access bypass weakness affecting the editor module.
“When adding a private file via a configured text editor (like CKEditor), the editor will not correctly check access for the file being attached, resulting in an access bypass,” Drupal said in its security advisory.
The CSRF flaw, identified as CVE-2017-6379 and rated moderately critical, can be exploited to disable some blocks on a website, but the attacker needs to know the targeted block’s ID. The security hole is caused by the lack of CSRF protection on some administrative paths.
The remote code execution vulnerability, CVE-2017-6381, which has also been rated moderately critical, affects a third-party development library. The flaw, related to development dependencies, is mitigated by the fact that Composer dependencies are typically not installed, and by the default PHP execution protection in .htaccess.
Drupal 8.2.7 includes a security update for phpunit development dependencies. This version ensures that Drupal core requires the most secure version of phpunit available. Using development dependencies in production is not recommended.
Drupal also announced this week that it has found a way to make it easier for users to update the CMS, including from one major version to the next (e.g. from Drupal 8 to the future Drupal 9).
While Drupal is not as targeted as WordPress or Joomla, security firms have seen attacks aimed at websites powered by this CMS. In its latest hacked website report, Sucuri said many of the Drupal websites compromised last year had been running outdated versions.
In September, the SANS Institute’s Internet Storm Center reported seeing attempts to exploit a highly critical vulnerability that had been patched two months earlier.
Drupal version 8.2.7 address multiple vulnerabilities in the current version of the popular CMS
16.3.2017 securityaffairs Vulnerebility
Drupal development team has issued a new release of the popular content management system (CMS), Drupal version 8.2.7, that fixes multiple vulnerabilities.
The Drupal development team has released the Drupal version 8.2.7 that addressed a number of vulnerabilities in the popular CMS. The list of flaws includes an access bypass issue, a cross-site request forgery (CSRF) vulnerability, and a remote code execution flaw.
An access bypass flaw, tracked as CVE-2017-6377, affecting the editor module is considered the most severe vulnerability
“When adding a private file via a configured text editor (like CKEditor), the editor will not correctly check access for the file being attached, resulting in an access bypass,” reads the description provided in the security advisory by Drupal.
Another moderately critical vulnerability is a CSRF flaw tracked as CVE-2017-6379, it is related to the lack of CSRF protection for some administrative paths. An attacker can exploit the issue to disable some blocks of a website by knowing their block ID.
Going on in the list, we find also a remote code execution vulnerability, CVE-2017-6381, which has also been rated moderately critical. The RCE flaw CVE-2017-6381 affects a third-party development library and is related to development dependencies.
The good news is that Drupal Composer dependencies are typically not installed, and by the default PHP execution protection in .htaccess.
In order to improve the security of the Drupal installs, the last release Drupal 8.2.7 includes a security update for phpunit development dependencies. Basically, the Drupal core in the new release requires the most secure version of phpunit available.
It is essential to update the Drupal version, CMS are privileged targets of hackers that try to exploit known vulnerabilities using exploit codes available online.
Outdated versions expose websites that its users to the risk of cyber attacks.
In September, the researchers at the SANS Institute’s Internet Storm Center reported seeing attempts to exploit a highly critical vulnerability in a third-party Drupal module, the RESTful Web Services (RESTWS) module.
WhatsApp, Telegram Patch Account Hijacking Vulnerability
15.3.2017 securityweek Vulnerebility
A vulnerability found in the web versions of WhatsApp and Telegram could have been exploited to hijack accounts by sending the targeted user a malicious HTML file disguised as an image or a video.
The flaw was discovered by researchers at Check Point earlier this month and it was quickly patched by both Telegram and WhatsApp on the server side.
According to experts, an attacker could have leveraged the vulnerability to take complete control of a user’s account, including personal and group conversations, photos, videos and contact list. The hacker could have not only stolen information, but also interact with the victim’s contacts (e.g. send spam, hijack their accounts using the same method).
Telegram and WhatsApp allow users to send various types of files to their contacts, including documents, audio files, videos and images. Users are normally blocked from sending unauthorized file types, but researchers have found a way to bypass restrictions and upload a malicious HTML file by manipulating its MIME type and making it appear as an authorized file.
Once the user opens the fake image or the fake video in a new browser tab, local storage data associated with the instant messaging applications is sent to the attacker, allowing them to take control of the account.
“In order to do that, the attacker creates a JavaScript function that will check every 2 seconds if there is new data in the backend, and replace local storage with the victim’s local storage,” researchers explained.
In the case of WhatsApp, the victim is normally alerted if there is more than one active session. However, the attacker’s malicious code could have caused the victim’s browser window to get stuck. The hacker could have maintained access to the victim’s account until they logged out – simply closing the browser did not lock the attacker out.
Telegram allows multiple active sessions, which means the victim is not alerted if an unauthorized user logs in to their account at the same time.
WordPress Content Injection Flaw Makes XSS Bug More Severe
15.3.2017 securityweek Vulnerebility
Sucuri has shared details about one of the cross-site scripting (XSS) vulnerabilities patched last week in WordPress. The flaw can be highly useful to attackers if combined with a content injection bug that has been exploited in the wild.
WordPress 4.7.3, released on March 6, patches six vulnerabilities, including three XSS issues. One of them, a stored XSS tracked as CVE-2017-6817, was identified and reported by Sucuri researcher Marc Montpas.
The flaw allows an authenticated attacker to inject arbitrary JavaScript code into posts, and it can be exploited via YouTube URLs and shortcodes. An attacker with contributor privileges can leverage the flaw to create a backdoor on the targeted website.
Since exploitation requires at least contributor privileges, the vulnerability is considered low risk. However, the risk is higher on WordPress versions prior to 4.7.2, which addresses a critical content injection and privilege escalation flaw.
The content injection vulnerability, also discovered by researchers at Sucuri, has been exploited in the wild for remote code execution and to deface a large number of web pages. Combining the content injection flaw with the stored XSS allows a remote attacker to inject malicious JavaScript code into posts on a WordPress site.
“Combined with the recent content injection vulnerability we found, it’s possible for a remote attacker to deface a random post on the site and store malicious Javascript code in it,” explained Montpas. “This code would be executed when visitors view the post and when anyone edits the post from the WordPress dashboard. As a result, an administrator tries to fix the defaced post, they would unknowingly trigger the malicious script, which could then be used to put a backdoor on the site and create new admin users.”
The stored XSS has been around for some time, even before version 4.7, while the content injection flaw affects versions 4.7 and 4.7.1. Version 4.7.x is running on roughly half of WordPress websites, and judging by the large number of sites affected by the content injection attacks, many of them are not updated automatically.
Microsoft Finally Releases Security Patches For Publicly-Disclosed Critical Flaws
15.3.2017 thehackernews Vulnerebility
After last month's postponement, Microsoft's Patch Tuesday is back with a massive release of fixes that includes patches for security vulnerabilities in Windows and associated software disclosed and exploited since January's patch release.
Meanwhile, Adobe has also pushed out security updates for its products, releasing patches for at least seven security vulnerabilities in its Flash Player software.
Microsoft patched a total of 140 separate security vulnerabilities across 18 security bulletins, nine of them critical as they allow remote code execution on the affected computer.
Microsoft Finally Patches Publicly Disclosed Windows Flaws
Among the "critical" security updates include a flaw in the SMB (server message block) network file sharing protocol, which had publicly disclosed exploit code since last month. The original patch released last year for this flaw was incomplete.
The flaw is a memory corruption issue that could allow remote code execution (RCE) of a malicious code if an attacker sends specially crafted messages to a Microsoft SMBv1 server.
All versions of Microsoft Windows are affected by this issue that could allow a remote, unauthenticated attacker to crash systems with denial of service attack.
Microsoft admitted: "Remote code execution vulnerabilities exist in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerabilities could gain the ability to execute code on the target server. To exploit the vulnerability, in most situations, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv1 server."
Microsoft patched the vulnerability but did not credit Laurent Gaffié, who found the flaw last year and released the exploit code in February.
Microsoft Also Patches Flaws Uncovered By Google
Another critical patch (MS17-013) contains a dozen of serious flaws in Windows' Graphics Component GDI Library used in Office, Skype, Lync, and Silverlight.
The flaws reside in the way Windows handles certain image files. Hackers can exploit the weaknesses to achieve remote code execution on your system by making you visit a booby-trapped website or open a malware-ridden document. No further user interaction is needed.
Google's Project Zero also disclosed this flaw with proof-of-concept exploit late last month before Microsoft had fixed it.
All supported releases of Microsoft Windows back to Windows Vista are vulnerable to this flaw. The tech giant originally patched this issue in June last year, but the patch was incomplete.
Microsoft also patched seven other critical flaws, including two cumulative updates for Internet Explorer and its Edge browser, and nine important ones.
In late last month, Google's Project Zero research team publicly disclosed details and proof-of-concept exploit for a code execution flaw in Microsoft's Internet Explorer and Edge browsers that could allow attackers to cause a crash of the browsers.
Meanwhile, Adobe also released patches for its Flash Player software for Windows, Macintosh, Linux and Chrome OS.
Users are advised to apply Windows as well as Adobe patches to keep away hackers and cybercriminals from taking control over your computer.
Security updates fix critical vulnerabilities in Flash player and Shockwave player
15.3.2017 securityaffairs Vulnerebility
Adobe patches vulnerabilities in Flash Player and Shockwave for Windows, Mac, Linux and Chrome OS.
Adobe issued security updates for Flash Player and Shockwave Player products. The security updates released by the company on Tuesday address seven vulnerabilities in Flash Player and one flaw in Shockwave Player.
The Flash Player 25.0.0.127 version fixes critical security vulnerabilities that affect version 24.0.0.221 and earlier on Windows, Mac, Linux and Chrome OS.
The flaws could be exploited by an attacker to gain control over the vulnerable system.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system. ” reads the security advisory published by Adobe.
The list of vulnerabilities addressed by the security updates includes a buffer overflow CVE-2017-2997 flaw, two memory corruption issues (CVE-2017-2998, CVE-2017-2999), a random number generator flaw (CVE-2017-3000), and three use-after-free vulnerabilities (CVE-2017-3001, CVE-2017-3002, CVE-2017-3003).
Adobe thanked the following researchers for reporting the flaws:
Tao Yan (@Ga1ois) of Palo Alto Networks (CVE-2017-2997, CVE-2017-2998, CVE-2017-2999)
Wang Chenyu and Wu Hongjun of Nanyang Technological University (CVE-2017-3000)
Yuki Chen of Qihoo 360 Vulcan Team working with Chromium Vulnerability Rewards Program and Anonymous working with Trend Micro’s Zero Day Initiative (CVE-2017-3001)
Yuki Chen of Qihoo 360 Vulcan Team working with Chromium Vulnerability Rewards Program (CVE-2017-3002, CVE-2017-3003)
Flash Player Shockwave updates
The security updates also fixed an important privilege escalation flaw in Shockwave Player (CVE-2017-2983) related to the directory search path used to find resources.
The flaw discovered by Nitesh Shilpkar.
According to Adobe, there is no evidence that vulnerabilities fixed by the security updates have been exploited by threat actors in the wild.
Microsoft Patches Many Exploited, Disclosed Flaws
15.3.2017 securityweek Vulnerebility
Microsoft has released a total of 18 security bulletins to address tens of vulnerabilities, including more than a dozen that have already been publicly disclosed or exploited in attacks.
The March 2017 updates also include the patches that should have been released last month. Microsoft postponed most of the February security updates – except the updates that fixed Flash Player flaws – due to an unspecified “last minute issue.”
The latest security updates patch critical and important vulnerabilities in Windows, Edge, Internet Explorer, Office, Skype, Lync and Silverlight.
The advisories published by Microsoft show that 12 of the vulnerabilities have been publicly disclosed, including an SMB-related denial-of-service (DoS) flaw in Windows (CVE-2017-0016), a Windows kernel privilege escalation (CVE-2017-0050), a remote code execution bug in a graphics component (CVE-2017-0014), a DoS issue in Office (CVE-2017-0029), and a Hyper-V DoS vulnerability (CVE-2017-0097).
The list of flaws whose details have been made public also includes information disclosure vulnerabilities in Edge (CVE-2017-0065) and Internet Explorer (CVE-2017-0008), several spoofing flaws in the two web browsers (CVE-2017-0012, CVE-2017-0033, CVE-2017-0069), and memory corruption and privilege escalation issues in Internet Explorer (CVE-2017-0037, CVE-2017-0154).
In February, Google Project Zero disclosed the details of a medium-severity information disclosure flaw affecting the Windows Graphics Device Interface (GDI). The security hole, tracked as CVE-2017-0038, has been addressed, but Microsoft’s advisory erroneously shows that it has not been disclosed.
There are three vulnerabilities that, according to Microsoft, have been exploited in attacks before patches were made available.
One of them is CVE-2017-0149, a memory corruption vulnerability affecting Internet Explorer. The weakness allows an attacker to execute arbitrary code in the context of the current user by getting the target to access a specially crafted website or open a malicious email attachment.
Another zero-day is CVE-2017-0005, a privilege escalation vulnerability caused due to the way the Windows GDI component handles objects in memory. The flaw allows an authenticated attacker to run arbitrary code in kernel mode, Microsoft said.
The third zero-day has been described as an XML Core Services information disclosure vulnerability (CVE-2017-0022), which allows an attacker to test for the presence of files on the disk.
Microsoft has not shared any information on the attacks involving these zero-days, but security firms could provide more details in the upcoming days.
Adobe released security updates on Tuesday to address a total of eight vulnerabilities in Flash Player and Shockwave Player. One of the bulletins released by Microsoft addresses the Flash Player flaws in the libraries used by Internet Explorer and Edge.
Microsoft intends to stop publishing security bulletins and instead provide security update information on the new Security Update Guide website. However, in an effort to make the transition easier for customers, the company has published security bulletins as well this month.
SAP Patches Five Vulnerabilities in HANA Database Platform
14.3.2017 securityweek Vulnerebility
SAP this week released another set of monthly security updates to address various issues in its products, including five vulnerabilities in SAP HANA, one of which was rated Hot News.
The March 2017 SAP Security Patch Day includes 25 security notes, SAP announced. Additionally, there were two updates to previously released security notes, for a total of 27 SAP Security Notes released this month. One Security Note has a Very High priority rating, while other 7 were rated High severity.
According to ERPScan, a company that specializes in securing SAP and Oracle applications, the patch update includes 35 SAP Notes (28 SAP Security Patch Day Notes and 7 Support Package Notes), with 4 of the Notes released after the second Tuesday of the previous month, and 7 Notes being updates to previously released Security Notes.
The most important of the issues addressed this month was a Missing Authorization Check vulnerability in the SAP HANA User Self-Service. With a CVSS score of 9.8 (Very High), this critical bug could allow an attacker to take control of the affected system, SAP’s Holger Mack reveals.
The Self Service tool for SAP HANA provides the option to activate features such as password change, forgotten password reset, or user self-registration. The Hot News vulnerability could allow an unauthenticated attacker to impersonate other users, even those of high privileged accounts, security technology firm Onapsis explains. The attacker could take full control of the SAP HANA platform remotely.
According to SAP, however, the issue only affects customers who enabled the optional User Self Service component (it is disabled by default) and exposed it to an untrusted network. “The security note contains instructions on how to check if the User Self Service tool is enabled and how to protect the system by either updating or deactivating the affected service (if not needed anymore or as temporary measure),” Mack says.
With a CVSS score of 8.8 (High risk), the second most important flaw addressed this month (also discovered by Onapsis) was affecting SAP HANA as well: a session fixation vulnerability in SAP HANA extended application services, classic model. By exploiting it, an authenticated attacker could predict valid session IDs for concurrent users that are logged on to the system.
The remaining three vulnerabilities in SAP HANA were also found by Onapsis: two SQL Injection vulnerabilities with a CVSSv3 Base Score of 2.7, and an information disclosure in SAP HANA Cockpit for offline administration, with a CVSSv3 Base Score of 4.9.
“The risk of these SAP HANA vulnerabilities is critical indeed. However, the likelihood of mass-exploitation is low as SAP HANA User Self-Service is enabled only on 13% internet-exposed SAP systems (according to a custom scan). There are numerous other services in SAP HANA, which are not enabled by default and susceptible to critical issues. For example, last month we helped SAP to close vulnerability with the same risk of remote authentication bypass but in other web service dubbed Sinopia,” Alexander Polyakov, CTO at ERPScan, says.
In addition to the aforementioned bug in SAP HANA, the High risk flaws patched this month include a Remote Code Execution (RCE) vulnerability in SAP GUI for Windows, Denial of service (DOS) in Visual Composer, Denial of service (DOS) in SAP Netweaver Dynpro Engine, Improved security for HTTP URL outgoing connections in SAP Netweaver, and an update to a previous Security Note.
The RCE (CVSS Base Score: 8.0) and two DOS flaws (CVSS Base Score: 7.5 each) were found by ERPScan, along with a Cross-Site Scripting (XSS) vulnerability in SAP Enterprise Portal (CVSS Base Score: 6.1) and a Denial of service vulnerability in SAP Java Script Engine (CVSS Base Score: 2.7).
A total of 11 XSS flaws were addressed this month, along with 7 missing authorization checks, 5 DOS issues, 4 SQL Injection vulnerabilities, 3 Information disclosure bugs, 2 Implementation flaws, 1 RCE, 1 XML external entity, and 1 session fixation.
Adobe Patches Vulnerabilities in Flash, Shockwave
14.3.2017 securityweek Vulnerebility
Security updates released by Adobe on Tuesday patch seven vulnerabilities in Flash Player and one vulnerability in Shockwave Player.
Flash Player 25.0.0.127 fixes critical security holes that affect version 24.0.0.221 and earlier on Windows, Mac, Linux and Chrome OS. Adobe has found no evidence of exploitation in the wild.
The vulnerabilities include buffer overflow, use-after-free and other memory corruption issues that can lead to arbitrary code execution. The latest version also addresses an information disclosure problem related to a random number generator.
The weaknesses were reported to Adobe by researchers at Qihoo 360, Palo Alto Networks, the Nanyang Technological University in Singapore, and an expert who wanted to remain anonymous.
In the case of Shockwave Player, version 12.2.8.198 for Windows patches an important privilege escalation flaw (CVE-2017-2983) related to the directory search path used to find resources.
The flaw was disclosed responsibly by Nitesh Shilpkar and there is no evidence that it has been exploited for malicious purposes.
Last month, Adobe patched more than a dozen code execution vulnerabilities in Flash Player, and several other bugs in Digital Editions and the Campaigns marketing tool.
VMware Preparing Patches for "Catastrophic" Struts Flaw
14.3.2017 securityweek Vulnerebility
VMware informed customers on Monday that the recently disclosed Apache Struts2 vulnerability, which has been exploited in the wild over the past week, affects several of its products.
The remote code execution vulnerability, tracked as CVE-2017-5638, has been described by VMware as “catastrophic.” The issue impacts versions 6.x and 7.x of the VMware Horizon Desktop-as-a-Service (DaaS) platform, vCenter Server 6.0 and 6.5, vRealize Operations Manager (vROps) 6.x, and vRealize Hyperic Server 5.x.
vCenter 5.5 is not affected. Until fixes become available for vCenter 6.0 and 6.5, users can disable the performance charts service to prevent potential attacks. However, VMware noted that applying the workaround will cause Overview Performance Charts to become unavailable in vSphere Web Client.
Cisco has also launched an investigation to determine which of its products are affected. The networking giant initially identified three products, but the number has now reached 10 and there are still several devices and services under investigation.
Attacks in the wild
This Apache Struts2 vulnerability exists in the Jakarta Multipart parser and is caused by the improper handling of Content-Type header values. A remote, unauthenticated attacker can exploit the flaw to execute arbitrary commands by sending a specially crafted HTTP request.
The security hole was patched on March 6 with the release of versions 2.3.32 and 2.5.10.1, and the first attacks were observed one day later, after a proof-of-concept (PoC) exploit was made public.
Imperva reported seeing thousands of attack attempts in the days following March 7. The attacks were traced to more than 1,300 IP addresses across 40 countries, including China and the United States, which accounted for 67 percent and 17 percent of the attempts, respectively.
According to data from Imperva, 90 percent of attackers focused their efforts on less than 10 applications, while the rest targeted as many as 181 apps.
A majority of the attacks observed by the security firm were attempts to determine if the targeted web application had been vulnerable, but researchers also noticed attempts to create files.
In some cases, the hackers had tried to download and execute files from a remote server. A control panel found on one of these servers showed that some of the files had been downloaded hundreds of times.
The Canada Revenue Agency (CRA) shut down its website for roughly 48 hours last week after learning of the Struts vulnerability. The organization said its site had been taken offline as a precaution, not as a result of a successful breach.
Hackers did manage to breach Statistics Canada's website by exploiting the flaw, but officials said no sensitive data was compromised, CBC reported.
Vulnerabilities Found in Double Telepresence Robots
13.3.2017 securityweek Vulnerebility
Researchers at Rapid7 discovered several vulnerabilities in Double telepresence robots from Double Robotics. The vendor has addressed the more serious issues with server-side fixes.
Double is a robot that allows people to have a physical presence at their workplace or school without actually being there in person. The product, often described as an iPad on a stick, has been used by many companies and universities.
Rapid7 researchers discovered that the Double telepresence robot had been affected by at least three vulnerabilities, including ones that could have been, or can be, exploited to take control of the machine.Double robot
One of the flaws found by experts allowed an unauthenticated attacker to gain access to device information, including GPS coordinates, device serial numbers, current and historical driver and robot session data, a device installation keys. The security hole could have been exploited simply by incrementing the value of a parameter in a specified URL.
The second vulnerability is related to the access token (driver_token) created when an account is assigned to a robot. The problem, according to researchers, was that the token never changed or expired, allowing an attacker who possessed the token to remotely take control of a robot.
The access token could have been obtained via a SSL man-in-the-middle (MitM) attack or from the robot’s iPad.
The third weakness is related to the fact that an attacker does not need to know the challenge PIN when pairing the mobile application (i.e. the iPad) to the drive unit via Bluetooth, enabling them to take control of the drive unit.
However, there are some mitigations against potential attacks. The attacker needs to be in Bluetooth range – the distance can be up to one mile if a high-gain antenna is used – and only one mobile device can be paired with the drive unit at one time.
The vulnerabilities were reported to Double Robotics in December, and the unauthenticated data access and session management flaws were addressed in mid-January on the server side.
The vendor believes the Bluetooth pairing issue is not a serious vulnerability and it does not plan on fixing it. Nevertheless, Rapid7 believes users should be aware of the flaw.
“Rapid7's thorough penetration tests ensure all of our products run as securely as possible, so we can continue delivering the best experience in telepresence,” said Double Robotics co-founder and CEO David Cann. “Before the patches were implemented, no calls were compromised and no sensitive customer data was exposed. In addition, Double uses end-to-end encryption with WebRTC for low latency, secure video calls.”
Rapid7 also reported the vulnerabilities to CERT/CC. The organizations agreed not to assign CVE identifiers considering that only one instance of the software was affected and users were not required to take any action to apply the patches.
Rapid7’s security advisory comes just days after IOActive warned that many robots are affected by serious vulnerabilities.
The CVE-2017-5638 Apache Struts 2 command execution flaw affects Cisco products
13.3.2017 securityaffairs Vulnerebility
On Friday, Cisco confirmed that at least some of its products are affected by an Apache Struts 2 command execution vulnerability tracked as CVE-2017-5638.
The CVE-2017-5638 remote code execution zero-day has been exploiting by attackers in the wild, it affects Struts 2.3.5 through 2.3.31 and Struts 2.5 through 2.5.10.
According to the experts from Cisco Talos, the flaw affects the Jakarta-based file upload Multipart parser under Apache Struts 2.
Tinfoil Security has published an online tool that allows website owners to check if they are vulnerable to CVE-2017-5638 attacks.
The issue was first spotted by the Chinese developer Nike Zheng, the attack sends an invalid Content-Type value to the uploader throwing an exception creating the condition for the remote code execution.
The issue is documented at Rapid7’s Metasploit Framework GitHub site and attackers in the wild are exploiting a publicly available PoC code that triggers the vulnerability.
“Talos has observed a new Apache vulnerability that is being actively exploited in the wild. The vulnerability (CVE-2017-5638) is a remote code execution bug that affects the Jakarta Multipart parser in Apache Struts, referenced in this security advisory.” reads the security advisory published by the Talos group. “Talos began investigating for exploitation attempts and found a high number of exploitation events.”
Now Cisco confirmed that the vulnerability affects the Cisco Identity Services Engine (ISE), the Prime Service Catalog Virtual Appliance, and the Unified SIP Proxy Software.

Cisco published a list of dozens of products that are not affected, but the experts are conducting further analysis to assess all the potentially impacted products.
“Cisco is investigating its product line to determine which products may be affected by this vulnerability and the impact on each affected product. Please refer to the Vulnerable Products andProducts Confirmed Not Vulnerable sections of this advisory for information about whether a product is affected.” reads the security advisory published by CISCO.
“The Vulnerable Products section includes Cisco bug IDs for each affected product. The bugs are accessible through the Cisco Bug Search Tool and contain additional platform-specific information, including workarounds (if available) and fixed software releases.”
At the time the advisory was published, Cisco has not found any evidence of attacks targeting its products, but the company has warned users that a PoC exploit is publicly available.
The experts also observed malicious attacks which turn off firewall processes on the target servers and then drop malicious payloads such as IRC bouncers and DDoS bots.
According to the security Rapid7, the majority of malicious traffic comes from two machines located in Zhengzhou and Shanghai, China.
“Based on the traffic we are seeing at this time it would appear that the bulk of the non-targeted malicious traffic appears to be limited attacks from a couple of sources. This could change significantly tomorrow if attackers determine that there is value in exploiting this vulnerability.” reads the blog post published by Rapid 7.
Security vendors have started releasing firewall rules that could be used by administrators to protect their systems and block the attacks.
Zero-day Conundrum: Keep or Disclose Vulnerability Stockpiles?
11.3.2017 securityweek Vulnerebility
Zero-Day Stockpiles
Business Should Move to an Incident Response Security Posture and Accept that Governments Will Maintain Stockpiles of Zero-days
With surprising concurrency, the RAND Corporation has published a lengthy study into zero-day exploits stockpiled by government just two days after WikiLeaks released its batch of documents on CIA hacking tools. While many have been surprised and even appalled that the government should maintain a stockpile of zero-day vulnerabilities and exploits, RAND seems to accept it as a matter of fact that all governments do so.
For the purpose of its research, "RAND obtained rare access to a dataset of information about zero-day software vulnerabilities and exploits." This dataset spans 14 years from 2002 to 2016, and contains information on more than 200 exploits and their vulnerabilities. More than half of these were still zero-days on March 1, 2017.
RAND describes itself as "a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous." In this study, it analyzes the life-span of a zero-day exploit with the intention of helping government policy on whether to stockpile or disclose.
"There is an ongoing policy debate," says the report (PDF), "of whether the U.S. government -- or any government -- should retain so-called zero-day software vulnerabilities or disclose them so they can be patched." The implication is that RAND's statistical analysis of the lifespan of the zero-day exploit will help government to decide whether to keep or disclose, because "many worry that keeping these vulnerabilities secret can expose people who use the vulnerable software to malware attacks and other attempts to collect their private information."
This is not a major concern of the study. The research is not about when government should disclose to keep the user safe, but when government should disclose because adversary governments also know about the vulnerability.
Responsible Vulnerability Disclosure
"If both sides have the same stockpiles, then some argue that there is little point to keeping them private -- whereas a smaller overlap might justify retention. But without information on the overlap, or concrete metrics based on actual data, it is challenging to make a well-informed decision about stockpiling," the report reads.
These challenges are also problematic for RAND's research. A zero-day exploit is zero-day until it is patched by the vendor. But there is no limit to the number of actors who could be in possession of the exploit -- it remains zero-day until it is patched. This means that a government, many adversary governments, and any number of criminal actors may be in possession of the same vulnerability knowledge and it still remain zero-day.
RAND acknowledges that refusal to disclose a vulnerability could be problematic for the user if it is also known to bad actors. It claims that its research "shows that that the collision rates for zero-day vulnerabilities are nonzero." By this it simply means that not all zero-days in its sample were known only to its supplier. Most people will assume that the supplier is the US government; but it makes no difference to the argument.
"Some may argue that, if there is any probability that someone else (especially an adversary) will find the same zero-day vulnerability, then the potentially severe consequences of keeping the zero-day private and leaving a population vulnerable warrant immediate vulnerability disclosure and patch. In this line of thought, the best decision may be to stockpile only if one is confident that no one else will find the zero-day; disclose otherwise."
The difficulty here is the impossibility of knowing absolutely whether an adversary or criminal bad actor has that vulnerability until or unless it is used and discovered; by which time disclosure will be too late to benefit the victim. The implication is that governments knowingly accept that in stockpiling vulnerabilities there may be collateral damage among the user population that could have been prevented had the vulnerabilities been disclosed rather than kept.
"RAND talks about stockpiling 'either for defensive purposes (e.g., penetration testing) or offensive operations'," comments ESET senior research fellow David Harley. "Noticeably absent from that sentence is any suggestion of disclosure for the benefit of potential victims... Leaving aside the issue of internal testing, which in times of economic stringency is probably honored more in the breach than the observance, I'd guess that the main potential conflict is between direct danger to the IT-using population as a whole, and disclosure as a perceived threat to national security (for instance, by endangering the effectiveness of a planned or ongoing offensive operation). Complicated, perhaps, by factors such as the urgency of the issue, the number and grouping of people potentially affected, and so on."
This question of national security versus public benefit was also noticed by Eric O’Neill, national security strategist at Carbon Black; but he suggests the onus is on government to be able to make a reasonable judgment. "The key thing to consider here is that software vulnerabilities are weapons and should be treated as such," he explained. "When issues of national security are concerned, governments should be protecting these weapons and preventing them from getting in the wrong hands at all costs. When national security is not involved, the government should conduct a transparent dialogue with concerned parties to ensure that these weapons are known about, patches are created and then widely deployed."
The point, he added, is that government cannot excuse itself from all liability to business. "If there is a high probability that zero-days will get into the wrong hands, and these zero-days do not directly conflict with national security interests, the government should act responsibly and disclose appropriately on an agreeable timeline," he added.
"This disclosure should include detailed notification about the vulnerability, recommendations for patching and a proposed timeline for patch deployment. This level of transparency keeps the interests of all parties in mind. Simply mass stock-pilling all vulnerabilities or disclosing all vulnerabilities on a macro level leaves too many potential gaps. Vulnerabilities need to be handled like weapons and how communication about these weapons occurs is critical to security."
RAND's conclusions on the implications of its study 'for defense and offense' are no more reassuring for business. It makes no comment on whether government should automatically disclose the vulnerabilities it finds, but instead says business should improve its general defensive posture. "Defenders likely need better options to both find zero-day vulnerabilities and detect when a system or software package is being exploited. In addition, rather than focusing only on finding zero-day vulnerabilities, defenders may be able to shift the balance in their favor by starting from the assumption of compromise, investigating ways to improve system architecture design to contain the impact of compromise, and adopting different techniques to identify vulnerabilities."
In other words, RAND's advice is standard contemporary advice: business should move to an incident response security posture; and simply accept that government will have and maintain its own stockpile of zero-days.
It may also be worth noting that the WikiLeaks disclosures probably come nowhere near the CIA's actual stockpile. If we assume that RAND got its dataset from the US government, then RAND says that as of March 1, 2017, the majority of the vulnerabilities were unknown. Industry response to the WikiLeaks disclosures, however, suggests that the majority of the vulnerabilities are old and already patched. The two datasets appear at this stage to be completely different.
Critical Vulnerabilities Found in Popular DNA Sequencing Software
10.3.2017 securityweek Vulnerebility
dnaLIMS DNA Sequencing Software Vulnerabilities
Multiple Vulnerabilities in dnaLIMS Disclosed After Vendor Failed to Engage with Security Researchers
Multiple vulnerabilities exist in dnaLIMS, a web based laboratory information management system that provides scientists and researches with tools for processing and managing DNA sequencing requests. dnaLIMS, developed and sold by dnaTools, is used by academia, business and government; and is found in many US universities. The vulnerabilities are described as critical.
They were discovered in Q4 2016 by boutique security firm Shorebreak Security, and were reported to the vendor on Nov. 6. Shorebreak had been commissioned by a hospital user of dnaLIMS to perform a blackbox penetration test of the product. Users of dnaLIMS should note that at the time of writing this, the vulnerabilities have not been patched and are publicly known. For now, users should restrict access to authorized hosts only and make sure that the product cannot be accessed from the public internet; although in university environments that will still leave potential access to many thousands of students and academic researchers.
Shorebreak attempted to follow 'responsible disclosure' guidelines and reported seven serious vulnerabilities privately to the vendor. After four months of trying to engage with the vendor, it publicly disclosed the vulnerabilities in an advisory published this week. "Researchers cannot keep quiet about vulnerabilities indefinitely," Shorebreak CEO Mark Wolfgang told SecurityWeek. "If we can find these problems, so can hackers -- and dnaLIMS users need to be aware of the issues."
The vulnerabilities include an improperly protected web shell, unauthenticated directory traversal, insecure password storage, session hijacking, multiple cross-site scripting, and improperly protected content.
"An unauthenticated attacker," warns the advisory, "has the ability to execute system commands in the context of the web server process, hijack active user sessions, retrieve system files (including the plaintext password file), and inject untrusted html or JavaScript into the dnaLIMS application. An attacker could use these vulnerabilities together in order to gain control of the application as well as the operating system hosting the dnaLIMS software. If this software is being hosted publicly or in a DMZ this could act as a pivot point to launch further attacks or move laterally into trusted network(s)."
Wolfgang described his frustrations in trying to engage with the vendor. When he asked dnaTools for a PGP key to deliver the details securely, he was told to print them out and send hard copy through the post. "I got the feeling," Wolfgang told SecurityWeek, "they thought or hoped we wouldn't bother." But he did. He did so on Nov. 16, 2016, using USPS Certified Mail. But it wasn't until Dec. 8 that dnaTools acknowledged receipt and suggested that users place the application behind a firewall.
When he asked the vendor if it had a plan to address the vulnerabilities, he received the reply, "Yes, we have a plan. Please gather a DNA sequence, PO Number, or Fund Number and go to your local grocery store and see what it will buy you." The vendor clearly believes that the vulnerabilities cannot lead to meaningful data loss.
SecurityWeek emailed dnaTools requesting its point of view, but received no reply.
Earlier this week, Zenofex of exploiteers disclosed a series of vulnerabilities in Western Digital's My Cloud range of storage devices. Zenofex went straight to full public disclosure because, he told SecurityWeek, he had no confidence "in regards to [the] manufacturer's ability to properly triage and fix vulnerabilities in their code."
With dnaTools, Shorebreak Security attempted to follow responsible disclosure guidelines -- indeed, it exceeded those guidelines by giving the vendor four months to fix the product. But in the end, the result was the same in both cases: full public disclosure with no immediate fix from the vendor.
Chrome 57 Patches 35 Vulnerabilities
10.3.2017 securityweek Vulnerebility
Google announced on Thursday that the stable channel of its Chrome web browser has been updated to version 57 on Windows, Mac and Linux.
The latest version brings several new features, including the availability of CSS Grid Layout, and various functionality improvements. Chrome 57 also patches 35 vulnerabilities, more than half of which were reported by external researchers who earned a total of $38,000 for their work.
The most serious of the flaws, based on the bounty amount, is a memory corruption bug (CVE-2017-5030) in the V8 JavaScript engine. Brendon Tiszka received $7,500 for this find.
Researcher Looben Yang earned $5,000 for a use-after-free vulnerability (CVE-2017-5031) in the Almost Native Graphics Layer Engine (ANGLE).
Other high severity vulnerabilities, which earned experts between $500 and $3,000, have been described as an out-of-bounds write in PDFium, an integer overflow in libxslt, three use-after-free weaknesses in PDFium, incorrect security UI in Omnibox, and multiple out-of-bounds writes in ChunkDemuxer.
The medium severity flaws patched in Chrome 57 have been described as an address spoofing issue in Omnibox, bypass of the content security policy in Blink, incorrect handling of cookies in Cast, a heap overflow in Skia, a couple of use-after-free bugs in GuestView, and information disclosures in V8, XSS Auditor and Blink.
The list of researchers credited for finding the security holes patched with the release of Chrome 57 includes Ashfaq Ansari of Project Srishti, Holger Fuhrmannek, Ke Liu of Tencent, Enzo Aguado, Yongke Wang of Tencent, Choongwoo Han, jinmo123, Jordi Chancel, Nicolai Grødum, Mike Ruddy, Kushal Arvind Shah of Fortinet, Dhaval Kapil and Masato Kinugawa. Some of the individuals who reported vulnerabilities wanted to remain anonymous.
Google has paid out more than $9 million since the launch of its bug bounty program in 2010, including more than $3 million last year. As vulnerabilities become more difficult to find, the tech giant has decided to offer more money for critical issues. Last week, the company informed researchers that the reward for remote code execution vulnerabilities has increased to $31,337.
Researchers discovered severe flaws in the Confide which is also used by White House staffers
9.3.2017 securityaffairs Vulnerebility
Confide App, the secure messaging app used by staffers in the White House and on Capitol Hill is not as secure as the company claims.
Confide is the secure messaging app used by President Donald Trump’s staffers for their secret communication. The official website of the application defines the encryption implemented by the mobile application with this statement:
“Confide uses military-grade end-to-end encryption to keep your messages safe and to ensure they can only be read by the intended recipients.” states the website.
The app allows users to send encrypted messages that self-destruct implementing end-to-end encryption.
News of the day is that two separate studies revealed that Confide app is not secure as previously thought.
The experts at the security firm IOActive discovered multiple critical flaws in the Confide app while auditing the version 1.4.2 for Windows, Mac OS X, and Android. The researchers ethically reported them to the Confide development team that quickly resolved the issue.
“During the evaluation, multiple security vulnerabilities of varying severities were identified, with corresponding attacker exploitation risks ranging from account impersonation and message tampering, to exposing user contact details and hijacking accounts.” reads the analysis published by IOActive.
According to IOActive, the confide flaws could be exploited for the following purposes:
Hijack an account session or guess a password to impersonate contacts. The Confide app failed to prevent brute-force attacks on account passwords.
Spy on contact details of Confide users (i.e. real names, email addresses, and phone numbers).
Intercept a conversation and decrypt messages. The researchers discovered that it is possible to launch MiTM attacks because the app’s notification system didn’t require any valid SSL server certificate to communicate. An attacker can capture messages in transit.
Modify the contents of a message or attachment in transit without first decrypting it.
Send malformed messages that can crash or slow the Confide application.
According to the research paper published by IOActive, the researchers gained access to more than 7,000 account records created between February 22 and 24, out of a database containing between 800,000 and 1 Million records.
During their 2-day test, the team was able to find a Donald Trump associate and several employees from the Department of Homeland Security (DHS) who downloaded the Confide app.
Below the Timeline disclosed by IOActive:
Timeline February 2017: IOActive conducts testing on the Confide application.
February 25, 2017: Confide begins fixing issues uncovered by the detection of anomalous behavior during the testing window.
February 27, 2017: IOActive contacts Confide via several public email addresses to establish a line of communication.
February 28, 2017: IOActive discloses issues to Confide. Confide communicates that some mitigations are already in progress and plans are being made to address all issues.
March 2, 2017: Confide releases an updated Windows client (1.4.3), which includes fixes that address some of IOActive’s findings.
March 3, 2017: Confide informs IOActive that remediation of critical issues is complete.
March 8, 2017: Findings are published.
As anticipated, a separate team of experts from Quarkslab also reviewed the code of the iOS app and demonstrated Confide exploits.
According to the experts, a series of design vulnerabilities in the Confide for iOS app could allow the company to read user messages, adding that the app didn’t notify users when encryption keys were changed.
“Confide server can read your messages by performing a man-in-the-middle attack” “The end-to-end encryption used in Confide is far from reaching the state of the art. Building a secure instant messaging is not easy, but when claiming it, some strong mechanisms should really be enforced since the beginning.” reads the analysis of Quarkslab.
“The confidentiality of the exchanged messages depends on the robustness of TLS. Confide can technically read all the messages that pass through its servers. End-to-end encryption, as it is implemented, solely relies on the server through which the messages pass.”
Confide is not just an encrypted messenger. It provides other interesting security features:
Screenshot prevention: Received messages can theoretically not be copied by a user. As the astute reader may have noticed, the previous paragraphs present screenshots of the application.
Message deletion: Once a user reads a message, it is deleted from the client and from the server. Is it possible to prevent message deletion?
Secrets protection: Confide handle secrets, like private keys required to decrypt messages. Are these keys correctly protected?“
The Quarkslab researchers explained that Confide server could generate its own key pair and transmit the public key to a client when requesting the public key of a recipient.
“This client then unknowingly encrypts a message that can be decrypted by the server,” the researchers added. “Finally, when the server sends the message to the recipient, it is able to re-encrypt the message with its own key for the actual recipient.”
Which is reply of the company?
In response to the analysis conducted by Quarkslab, Confide co-founder and president Jon Brod explained that the researchers have intentionally undermined the security of their own system to bypass several layers of Confide’s protection.
“The researchers intentionally undermined the security of their own system to bypass several layers of Confide’s protection, including application signatures, code obfuscation, and certificate pinning. The attack that they claim to be demonstrating does not apply to legitimate users of Confide, who are benefiting from multiple security protections that we have put in place. Undermining your own security or taking complete control of a device makes the entire device vulnerable, not just the Confide app.” said Brod.
Confide has released a version that fixes the critical vulnerabilities discovered by the researchers. According to the company, there is no evidence for their exploitation by attackers in the wild.
Several Flaws Found in Navetti Pricing Product
9.3.2017 securityweek Vulnerebility
Researchers at SEC Consult have discovered several potentially serious vulnerabilities in a popular pricing solution from Sweden-based company Navetti. The vendor has released a software update that patches the flaws.
Navetti PricePoint is a piece of software designed for controlling, managing and measuring all aspects of an organization’s pricing. According to the company, its product is used by several major organizations, including ABB, Husqvarna, Scania and Electrolux.
SEC Consult has conducted a quick security check of the Navetti PricePoint product and identified four types of vulnerabilities, including SQL injection, stored and reflected cross-site scripting (XSS), and cross-site request forgery (CSRF).
The security firm told SecurityWeek that the software is often accessible from the Internet, allowing attackers to remotely exploit all the vulnerabilities.
The SQL injection flaw affects search functionality, and it allows a low-privileged attacker to inject arbitrary SQL commands and gain access to the content of the application database.
The stored XSS vulnerabilities allow low-privileged users to inject malicious JavaScript payloads persistently into the application. The security holes can also be exploited to gain elevated privileges to the application by creating a new superuser account or adding the attacker’s account to the superuser group.
Both the SQL injection and stored XSS vulnerabilities require authentication, but SEC Consult said even the lowest access rights are sufficient.
The CSRF vulnerability, caused by the lack of CSRF tokens or nonces, can be exploited by getting the targeted user to access a specially crafted web page. An attacker can leverage the flaw to perform various actions on behalf of the victim, including to add or delete users, change user privileges, and modify application settings.
The reflected XSS bugs affect the filename fields of file upload dialog boxes and the code used to generate error messages within the PricePoint application. These flaws can be exploited by getting the targeted user to click on a malicious link.
The vulnerabilities were reported to Navetti in late July 2016 and they were patched on October 1 with the release of PricePoint 4.7.0.0. The vendor told SEC Consult that this version also brings other security improvements to its product.
Apache Struts Vulnerability Exploited in the Wild
9.3.2017 securityweek Vulnerebility
A high severity remote code execution (RCE) vulnerability affecting the Apache Struts 2 framework has been exploited in the wild, warns Cisco’s Talos intelligence and research group.
The vulnerability, tracked as CVE-2017-5638, can be triggered when performing file uploads with the Jakarta Multipart parser. The security hole, caused due to improper handling of the Content-Type header, allows a remote, unauthenticated attacker to execute OS commands on the targeted system.
The flaw affects Struts 2.3.5 through 2.3.31 and Struts 2.5 through 2.5.10, and it was addressed on March 6 with the release of versions 2.3.32 and 2.5.10.1.
Cisco Talos spotted the first exploitation attempts on March 7, shortly after someone published a proof-of-concept (PoC) exploit. According to researchers, a majority of the exploitation attempts leverage the publicly available PoC code.
Some of the attacks involve the execution of a simple Linux command, likely in an effort to determine if the targeted system is vulnerable. Researchers have observed the use of commands such as “whoami” and “ifconfig,” which allow attackers to see what user is running the service and gather information on the network configuration.
In more sophisticated attacks, threat actors stopped the Linux firewall, downloaded a malicious payload from a web server, and executed that payload. Cisco said the payloads included IRC bouncers, DoS bots, and the BillGates malware.
In other attacks, hackers also attempted to make the malware persistent by copying it to a benign folder from where it would get executed on system boot. These attacks also involved disabling the firewall service on boot.
“It is likely that the exploitation will continue in a wide scale since it is relatively trivial to exploit and there are clearly systems that are potentially vulnerable,” said Cisco’s Nick Biasini.
Biasini said many of the compromised websites have already taken steps to clean the infection. Users are advised to update their Apache Struts installations as soon as possible.
Qualys has also published a blog post and a security advisory for this vulnerability.
Dahua Video Recorders and Cameras affected by a serious flaw. Is it a backdoor?
8.3.2017 securityaffairs Vulnerebility
The manufacture Dahua Technology has started releasing firmware updates fix a serious flaw in some models of its video recorders and IP cameras.
Security experts believe the flaw is a true backdoor that could be used to remotely access the user database containing usernames and hashed passwords.
The backdoor was discovered by a researcher that is known online as “bashis.”
Once the attacker gains the administrator credentials stored in the database, he can be used to log in to the device. Representatives at the company Dahua admitted the issue and classified it as a ‘coding issue’ that was not done intentionally.
Of course, the researcher who discovered the flaw expresses skepticism of the error claim.
According to an analysis shared by IPVM, the password hashes can be used directly to log in, in fact, there is no need to crack them.
Bashis did not report the issue to Dahua, initially, he also released a proof-of-concept (PoC) exploit code that was later removed by the researchers due to a request of the manufacturer.
On April 5, the researchers made against available online the PoC.
Dahua replied with a security bulletin that admits the presence of the error in the code of its devices.
“We were recently made aware of a cybersecurity vulnerability that affects certain Dahua recorders and IP cameras. It’s important to note that the vulnerability is not the result of a malicious attack on any specific installation where our products are deployed; it was discovered by Bashis conducting independent testing of various suppliers’ surveillance products.” reads the security bulletin.
The company published a list of vulnerable devices, users are invited to download and updated the firmware of their devices.
Model Number Where to Update Firmware
DH-IPC-HDW23A0RN-ZS
DH-IPC-HDBW23A0RN-ZS
Download Link
DH-IPC-HDBW13A0SN
DH-IPC-HDW13A0SN
DH-IPC-HFW13A0SN-W
Download Link
DH-IPC-HDBW13A0SN
DH-IPC-HDW13A0SN
DH-IPC-HFW13A0SN-W
Download Link
DHI-HCVR51A04HE-S3 Download Link
DHI-HCVR51A08HE-S3 Download Link
DHI-HCVR58A32S-S2 Download Link
Dahua is still investigating the issues, it is likely that other devices may be affected by the same issue.
The security of IoT devices is crucial, recently I reported in exclusive the news of a large-scale attack launched by a criminal gang leveraging the SSH TCP direct forward attack technique through a thingbot.
According to a report published by FlashPoint, the recent attacks on the Mirai botnet involved a huge number of Dahua devices.
The researchers explained that the botnet was mainly composed of video surveillance devices manufactured by Dahua Technology.
“While investigating the recent large-scale distributed denial-of-service (DDoS) attacks, Flashpoint identified the primary manufacturer of the devices that utilize the default username and password combination known as root and xc3511.” reads a report published by Flashpoint. “The Dahua devices were identified early because of their distinctive interface and recent use in other botnets. Utilizing the “botnets. Utilizing the “Low Impact Identification Tool” or LIFT, Flashpoint was able to identify a large number of these devices in the attack data provided.” states the report.
Backdoor Found in Dahua Video Recorders, Cameras
8.3.2017 securityweek Vulnerebility
Video surveillance company Dahua Technology has started releasing firmware updates to address a serious vulnerability in some of its video recorders and IP cameras.
The flaw was discovered by a researcher with the online moniker “bashis.” The expert, who has classified the issue as a backdoor, noticed that he could remotely download a device’s complete user database, including usernames and password hashes.
The administrator credentials stored in the database can be used to log in to the device. IPVM reported that the password hashes can be used directly to log in, without the need to crack them (i.e. pass the hash attack).
Bashis did not notify Dahua before making his findings public, but he did remove the proof-of-concept (PoC) code he had released at the vendor’s request. The PoC will be made public again on April 5.
In the meantime, Dahua has published a security bulletin to warn customers of the vulnerability. The company said the flaw had been caused by a “small piece of code.”
“It’s important to note that the vulnerability is not the result of a malicious attack on any specific installation where our products are deployed; it was discovered by Bashis conducting independent testing of various suppliers' surveillance products,” the company said.
Dahua has so far identified 11 affected IP cameras and video recorders, and released firmware updates for them. The company’s investigation is ongoing and other impacted devices could be discovered in the upcoming days.
It’s important that users update the firmware on their devices as Dahua products are often targeted by Internet of Things (IoT) botnets. Researchers reported last year that many of the devices hijacked by the BASHLITE and Mirai botnets had been surveillance products from Dahua.
Google Patches 35 Critical Android Vulnerabilities
8.3.2017 securityweek Vulnerebility
Google this week released a new set of monthly security patches for Android to address over 100 vulnerabilities in the platform, 35 of which carry a Critical severity rating.
In a newly published Security Bulletin, Google reveals that two partial security patch level strings are rolling out this month: the 2017-03-01 security patch level to resolve 36 vulnerabilities (11 Critical, 15 High, 9 Moderate, 1 Low), and the 2017-03-05 security patch level to address 71 flaws (24 Critical, 32 High, 14 Moderate, 1 Low).
The 11 Critical flaws resolved with the 2017-03-01 security patch level include nine Remote Code Execution (RCE) issues in Mediaserver; one RCE in OpenSSL & BoringSSL; and an Elevation of privilege (EoP) vulnerability in recovery verifier.
The 15 vulnerabilities rated High included three RCE bugs in AOSP Messaging, libgdx, and Framesequence library; two EoP issues in Audioserver; one EoP in NFC; and nine Denial of Service (DoS) vulnerabilities in Mediaserver.
The Medium risk flaws include EoP issues in Location Manager, Wi-Fi, Package Manager, and System UI; Information disclosure vulnerabilities in AOSP Messaging and Mediaserver; and DoS bugs in Setup Wizard and Mediaserver. The Low severity issue addressed in 2017-03-01 security patch level is a DoS vulnerability in Audioserver.
The 24 Critical risk issue resolved in 2017-03-05 security patch level include 19 EoP vulnerabilities (seven in MediaTek components, five in NVIDIA GPU driver, two in kernel ION subsystem, one in Broadcom Wi-Fi driver, one in kernel FIQ debugger, one in Qualcomm GPU driver, and two in kernel networking subsystem) and 5 various vulnerabilities in Qualcomm components.
Elevation of privilege issues clearly dominated the patch level, given that 25 rated High severity were addressed as well. They affected kernel networking subsystem, Qualcomm input hardware driver, MediaTek Hardware Sensor Driver, Qualcomm ADSPRPC driver, Qualcomm fingerprint sensor driver, Qualcomm crypto engine driver, Qualcomm camera driver, MediaTek APK, Qualcomm Wi-Fi driver, Synaptics touchscreen driver, Qualcomm IPA driver, HTC Sensor Hub Driver, NVIDIA GPU driver, Qualcomm networking driver, kernel security subsystem, and Qualcomm SPCom driver.
Six of the remaining High risk issues addressed in 2017-03-05 security patch level are Information disclosure vulnerabilities (affecting kernel networking subsystem, MediaTek driver, Qualcomm bootloader, Qualcomm power driver, NVIDIA GPU driver), while the last one is a Denial of service vulnerability in kernel cryptographic subsystem.
The Moderate risk flaws addressed in this patch level include an EoP in Qualcomm camera driver (device specific), and 13 Information disclosure bugs (in Qualcomm Wi-Fi driver, MediaTek video codec driver, Qualcomm video driver, Qualcomm camera driver, HTC sound codec driver, Synaptics touchscreen driver, and kernel USB gadget driver). The Low severity bug was an Information disclosure vulnerability in Qualcomm camera driver.
All of the above issues should be addressed by security patch levels of 2017-03-05 or later, Google notes on its advisory. The company already started pushing an over-the-air update to Google Devices (Android One, Nexus, and Pixel devices) with the March 05, 2017 security patch level.
Serious flaws in Western Digital My Cloud NAS devices allow attackers to fully control them
8.3.2017 securityaffairs Vulnerebility
Researchers discovered serious issues in Western Digital My Cloud NAS that can be exploited by attackers to gain root control of the affected devices.
Western Digital Corporation network-attached storage owners were warned of Critical flaws in Western Digital NAS boxes of the My Cloud NAS line could be exploited by remote attackers to gain remote control of the affected devices.
The attackers can combine the flaws to steal sensitive data or to exploit flawed devices in lateral movements.
“By combining the vulnerabilities documented in this advisory an attacker can fully compromise a WD My Cloud device. In the worst case one could steal sensitive data stored on the device or use it as a jump host for further internal attacks.”
“SEC Consult recommends not to attach WD My Cloud to the network until a thorough security review has been performed by security professionals and all identified issues have been resolved.” reads the advisory published by SCVL.
The affected products belong to Western Digital MyCloud NAS devices, including DL4100, EX4, EX2 Ultra and PR2100. The full list of flawed devices is available online.
The attackers can trigger the flaw to bypass logins, insert commands, upload files without permission, and gain control of boxes.
“This is a serious vulnerability, as the chances for the device to be fully compromised is very high,” explained the SEC Consult Vulnerability Lab (SCVL).
The flaws have been reported by SCVL experts to Western Digital on Jan. 18, 2016 and publicly disclosed the flaw March 7, 2017. Another group of experts from the security firm Exploitee.rs have discovered the vulnerabilities and publicly disclosed them.
The flaws discovered by the experts include a command injection vulnerabilities, a stack-based buffer overflow bug, and a cross-site request forgery flaw. As anticipated, by combining the exploitation of the cross-site request forgery issue with a command injection vulnerability the attacker can gain root access of the affected device and fully compromise it.
“The (cross-site request forgery flaw) can be combined with a command injection vulnerability to gain complete control (root access) of the affected device,” explained the advisory issued by the SCVL.
As of this writing, Western Digital has not provided any information regarding the vulnerabilities or supplied software updates to fix the reported bugs.

According to the researchers at Exploitee.rs, in December, the expert Steve Campbell discovered two command injection flaws in Western Digital MyCloud NAS (CVE-2016-10107 & CVE-2016-10108) that were patched by the company in the same month, but according to Exploitee.rs the patches did not fix the problems and introduced a new Login Bypass vulnerability.
The Exploitee.rs researcher Zenofex who analyzed the Login Bypass issue discovered a wrong implementation of the user authentication mechanism when the Secure Shell (SSH) access was enabled. The login check leverage on cookies that can be crafted by an attacker to bypass the login process.
“The above code contains a function called “login_check”, this function is used by all of the backend PHP scripts and is used to verify pre-authenticated users. The above code has two paths, one which involves checking the session values for “username” and “isAdmin” and another (if the prior fails) attempts to complete the same process but with cookies.” explained Zenofex.
“Because cookies are supplied by the user, the requirements that the scripts are looking for can be met by the attacker. The above process for sessions and cookies is summed up as follows.
“username” variable is set and is not empty – User is logged in as a normal privileged user.
“isAdmin” variable is set to 1 – User is logged in as an administrator.
This means that any time there is a login check within the PHP scripts, an attacker is able to bypass the check by supplying 2 specially crafted cookie values.”
The experts at Exploitee.rs have found 85 security issues tied to Western Digital My Cloud NAS devices
My Cloud users can contact the Customer Service for any question and to receive support. It is important that My Cloud NAS devices are configured to enable automatic firmware updates.
Bug Allowed Free Uber Rides
7.3.2017 securityweek Vulnerebility
A bug in Uber could have been used by users to ride for free anywhere where the service is available, a researcher has discovered.
Discovered by Anand Prakash from Bangalore, India, the issue could have been abused by attackers to take unlimited free rides from their Uber account. In fact, the researcher took free rides in both the United States and India to demonstrate the vulnerability, but only after the Uber team agreed to this, he says.
The issue was found to be related to the payment method that users are required to specify when creating an account on Uber.com. Such an account is required to be able to use the service, and users can either pay with cash when the ride is completed, or can have the cost automatically charged to their credit/debit card.
The researcher discovered that if an invalid payment method is specified, one could ride Uber for free. The bug, he explains, resides in a POST request to dial.uber.com. To reproduce the vulnerability, one would simply need to input an invalid value for “payment_method_id” in said request:
{"start_latitude":12.925151699999999,"start_longitude":77.6657536,
"product_id":"db6779d6-d8da-479f-8ac7-8068f4dade6f","payment_method_id":"xyz"}
Prakash reported the vulnerability to Uber via the company’s bug bounty program on HackerOne, which offers rewards between $100 and $10,000 for bugs in several dozen Uber properties. The issue was apparently discovered in August 2016, and Uber was able to fix it the same day the researcher disclosed it. The company awarded the researcher $5,000 for this finding.
In addition to making information about the issue public, the researcher also published a video that shows how the vulnerability can be abused.
A member of the HackerOne community since 2013, Prakash is actively hunting bugs in other services as well, including Twitter, Souq.com, Yahoo!, and Slack. The researcher is ranked 29 on HackerOne, but ranks 14 in Uber’s bug bounty program (and is placed third in Twitter’s).
WordPress 4.7.3 is out to fix 6 security issues, but CSRF flaw remains unpatched
7.3.2017 securityaffairs Vulnerebility
WordPress 4.7.3 release is out to fix six security issues, but a CSRF vulnerability discovered in July 2016 remains unpatched.
WordPress has issued a new security release, the WordPress 4.7.3 release, that addresses six security flaws, including three cross-site scripting (XSS) vulnerabilities. The flaws were discovered by the security experts Chris Andrè Dale, Yorick Koster, Simon P. Briggs, Marc Montpas and a user that goes online with the moniker “Delta.”
The XSS vulnerabilities can be exploited via media file metadata, video URLs in YouTube embeds, and taxonomy term names.
WordPress 4.7.3
Below the list of vulnerabilities addressed by the WordPress 4.7.3 release:
Cross-site scripting (XSS) via media file metadata. Reported by Chris Andrè Dale, Yorick Koster, and Simon P. Briggs.
Control characters can trick redirect URL validation. Reported by Daniel Chatfield.
Unintended files can be deleted by administrators using the plugin deletion functionality. Reported by xuliang.
Cross-site scripting (XSS) via video URL in YouTube embeds. Reported by Marc Montpas.
Cross-site scripting (XSS) via taxonomy term names. Reported by Delta.
Cross-site request forgery (CSRF) in Press This leading to excessive use of server resources. Reported by Sipke Mellema.
It is interesting to note that both CSRF and XSS flaws were discovered in July 2016 during the Summer of Pwnage competition organized by the security firm Securify. The researchers released proof-of-concept (PoC) code to exploit both issues.
According to Koster, who spotted the vulnerabilities in the playlist functionality, the attacker needs to convince an editor or administrator into uploading an MP3 file containing specially crafted metadata. Using this trick the attacker’s malicious code attacker’s code will be executed when the metadata is processed by the renderTracks() or wp_playlist_shortcode() functions.
However, there is a CSRF vulnerability in WordPress that still has not been patched, the flaw was discovered in July 2016 and the details for the exploitation were not disclosed.
The flaw could be exploited by an attacker to steal FTP and SSH login credentials.
The security expert Cengiz Han Sahin explained this vulnerability may have a high impact, but the probability of exploitation is low.
Six Flaws Patched With Release of WordPress 4.7.3
7.3.2017 securityweek Vulnerebility
WordPress developers announced on Monday the availability of version 4.7.3, a security release that includes patches for six vulnerabilities and 39 maintenance fixes.
WordPress 4.7.3 addresses three cross-site scripting (XSS) flaws that can be exploited via media file metadata, video URLs in YouTube embeds, and taxonomy term names. Chris Andrè Dale, Yorick Koster, Simon P. Briggs, Sucuri researcher Marc Montpas, and a user with the moniker “Delta” have been credited for finding these security holes.
The latest WordPress update also fixes a vulnerability that allows control characters to trick redirect URL validation (reported by Daniel Chatfield), and a bug that can lead to administrators deleting unintended files via the plugin deletion functionality (reported by xuliang).
Another vulnerability patched on Monday, identified by Sipke Mellema, is a cross-site request forgery (CSRF) in the “Press This” function. Exploitation of this flaw can lead to excessive use of server resources and a denial-of-service (DoS) condition.
Mellema and Koster identified the CSRF and XSS vulnerabilities in July 2016 as part of the Summer of Pwnage competition organized by Dutch security firm Securify. The details of the security holes and proof-of-concept (PoC) code have been made public on the Summer of Pwnage website.
According to Koster, he identified two XSS flaws in WordPress’ playlist functionality. An attacker needs to convince an editor or administrator into uploading an MP3 file containing specially crafted metadata. The attacker’s code will get executed when the metadata is processed by the renderTracks() or wp_playlist_shortcode() methods.
Over 100 vulnerabilities have been found in the WordPress core and plugins as part of the Summer of Pwnage project, and most of the issues have been disclosed on March 1, regardless of whether or not they have been fixed.
One WordPress core vulnerability that still has not been patched is a CSRF found by Koster in July 2016. The details of the flaw have not been disclosed, but Cengiz Han Sahin, co-founder of Securify, told SecurityWeek that the unpatched flaw could, in theory, allow an attacker to steal FTP and SSH login credentials. The expert said the vulnerability can have a high impact, but the probability of exploitation is low.
While the developers of the content management system (CMS) claim WordPress 4.7.3 patches six vulnerabilities, there could be other issues they have not disclosed in an effort to protect users. When WordPress 4.7.2 was released on January 26, it appeared to patch only three vulnerabilities, but in reality it also resolved a critical privilege escalation and content injection issue that was disclosed only one week later.
This critical flaw has been exploited in defacements carried out by script kiddies and attacks whose goal was to gain full control of a website.
Multiple Zero-days Disclosed in Western Digital NAS Storage Devices
6.3.2017 securityweek Vulnerebility
The Western Digital My Cloud range of storage devices, ranging from consumer products with up to 16TB storage (My Cloud Mirror) to business devices with up to 32TB storage (My Cloud Pro and My Cloud Expert) contain multiple firmware vulnerabilities that can be exploited remotely.
Bugs reported by Zenofex of Exploiteers comprise of a login bypass, an arbitrary file write, 13 unauthenticated command execution bugs, and 70 authentication required bugs. The authentication required bugs can be reached via the login bypass bug.
In a blog posted on Saturday, Zenofex explains that he was analyzing a bug that had separately been found and reported (with others) to Western Digital by ESET researcher Kacper Szurek. In January, Szurek reported that on 1 January 2017, Western Digital told him the issue had been fixed.
Meanwhile, Securify also issued an advisory on the same authentication bypass bug. The timeline is very similar to Szurek's but quotes a different firmware release to fix the bug -- and laments that it had not been informed by Western Digital that the bug had been fixed.
Zenofex does not quote firmware release numbers. He merely wrote on Saturday that in patching the old bug, Western Digital had introduced a new one with the very same consequences into its latest firmware. Western Digital 'fixed' the old cookie-based vulnerability by adding a new "wto_check()" function. The problem here, says Zenofex, "is the incorrect use of the PHP method "escapeshellcmd()" which, in its intended usage, handles an entire command string, and not just an argument... Because of this," he adds, "instead of actually checking if the user is logged in, we can add new arguments and log the user in ourselves."
Once the attacker has logged on, he can exploit any one of many unsanitized CGI scripts. Instead of being properly sanitized, they appear to rely on only being accessible to an authenticated user -- which cannot be guaranteed because of the authentication bypass vulnerability. "This basic pattern resulting in a command injection vulnerability is used multiple times within the many scripts used by the web interface," comments Zenofex. "Also, it is important to note that all commands executed through the web interface are done so as the user the web-server is running as, which, in this case is root."
Users of My Cloud products should note that these are effectively zero-day vulnerabilities with published exploits. Zenofex explained that he has little confidence in Western Digital's willingness to patch the faults rapidly. He pointed out that Szurek mentioned a second bug -- a remote root execution vulnerability as well as the authentication bypass. "Although the reported authentication bypass vulnerability was 'patched'," Zenofex told SecurityWeek, "the fact that the more dangerous of the two bugs has been left unfixed does not give us confidence in the manufacturer."
To this he adds Western Digital's Pwnie award for the Lamest Vendor Response at last summer's Vegas BlackHat. This followed the 2015 discovery that Western Digital's 32-bit encryption key was actually a 4-bit key repeated eight times -- making it very weak. A Western Digital spokesperson said at the time, "We continue to evaluate the observations."
This, Zenofex told SecurityWeek, "eliminates the confidence we have in regards to a manufacturer's ability to properly triage and fix vulnerabilities in their code. It's also important to note that in all our previous research on consumer devices, until researching the My Cloud, we hadn't come across an administrator interface with as many severe security vulnerabilities as that found through our research in this product. To us this signifies a code base that had not properly been audited prior to its use within a retail product as well as programmers who are unaware of safe programming practices."
This is not the first time that exploiteers have found bugs in patched code. Patches to Samsung SmartCams were revealed in January to be incomplete.
Exploiteers started life in 2011 as GTVHacker, with, explained Zenofex, "the intention to help unlock devices within the GoogleTV platform. These GoogleTV devices were being created by manufacturers and came locked to a specific configuration. The devices would then be abandoned shortly after their launch causing the consumer to buy a new device, sending the old one to the landfill. Our goal was to give the consumers the ability to unlock their devices and repurpose them, preventing the need to purchase another. A few years after our conception, the GoogleTV platform died and we renamed ourselves 'Exploitee.rs'. This fits our new mission statement: hacking everything and therefore creating a better state for online devices."
Western Digital has been invited to respond to Zenofex's exploits and criticisms, and has promised to do so later today. We will update this article as soon as any response is received.
Temporary Fix Available for Windows GDI Vulnerability
6.3.2017 securityweek Vulnerebility
A temporary fix is available for the Windows Graphics Device Interface (Windows GDI) vulnerability that was disclosed a couple of weeks ago.
The flaw was initially discovered by Mateusz Jurczyk, an engineer with Google's Project Zero team, in March 2016, along with other issues in the user-mode Windows GDI library (gdi32.dll). Microsoft attempted to resolve the bug with its June 2016 patches but failed to do so, and the researcher filed another report in November 2016.
As per Google’s Project Zero’s policy, vendors have 90 days to resolve the disclosed vulnerabilities before they are made public, and this policy applied to the Windows GDI flaw as well. However, because Microsoft didn’t release a monthly set of security updates in February, but pushed the patches to March, the vulnerability wasn’t resolved within the 90 days window.
Tracked as CVE-2017-0038, the vulnerability is related to the handling of DIBs (Device Independent Bitmaps) embedded in EMF records. The security researcher who discovered it was able to reproduce the vulnerability both locally (in Internet Explorer) and remotely (in Office Online, using a DOCX file containing a specially crafted EMF file).
Although Microsoft hasn’t released a fix for the issue yet, Luka Treiber with the 0patch Team devised a temporary fix for the issue. For that, the researcher worked with the proof of concept that Google’s Jurczyk published, and says that the issue was visible each time the specially crafted EMF file was loaded in Internet Explorer 11.
“CVE-2017-0038 is a bug in EMF image format parsing logic that does not adequately check image dimensions specified in the image file being parsed against the amount of pixels provided by that file. If image dimensions are large enough the parser is tricked into reading memory contents beyond the memory-mapped EMF file being parsed,” Treiber explains.
By leveraging this vulnerability, an attacker could steal sensitive data that an application holds in memory, but could also abuse it in other attacks, where they need to defeat Address space layout randomization (ASLR).
The fix for the flaw, the security researcher explains, needs to include a check that cbBitsSrc (the size of source bitmap bits) is smaller than cxSrc * cySrc * 4 (width of the source rectangle, in logical units * height of the source rectangle, in logical units * number of bytes representing each pixel). The researcher notes that he first focused on finding the right location for the patch, before writing it, so that he could write as little code as possible.
The temporary fix for the zero-day Windows GDI issue should be already available on machines with 0patch Agent installed, because they already have patches ZP-258 through ZP-264, the researcher says. Moreover, he notes that Microsoft’s patch for this will replace this fix.
“Note that when Microsoft’s update fixes this issue, it will replace the vulnerable gdi32.dll and our patch will automatically stop getting applied as it is strictly tied to the vulnerable version of the DLL. We have deployed this patch for the following platforms: Wind ows 10 64bit, Windows 8.1 64bit, Windows 7 64bit and Windows 7 32bit,” the researcher says.
It should also be noted that security vendors have already updated their products to keep them safe from potential attacks attempting to abuse this vulnerability.
Hackers who breached Barts NHS Trust exploited a zero-day vulnerability
5.3.2017 securityaffairs Vulnerebility
In January, a cyber attack breached some systems at Barts NHS Trust and forced them offline. Hackers exploited a zero-day vulnerability.
In January, a cyber attack breached some systems at Barts NHS Trust and forced them offline.
Barts Health Trust runs the Royal London, St Bartholomew’s, Whipps Cross, Mile End and Newham hospitals.
The hackers used a malicious code to bypass security measured and compromise internal systems.
Shortly after the attack, Barts NHS Trust issued an initial report that confirmed its systems had been infected by ransomware, but further investigation allowed experts to discover that attackers exploited a zero-day vulnerability.
Barts NHS Trust took offline some systems as a precautionary measure and reported that patient data had not been affected by the attack.
Law enforcement and experts are still investigating the case, but the minutes related to a recent board meeting disclosed some new information.
The malware infected all the sites run by the Barts Health Trust except Whipps Cross. The incident response worked correctly and the malware was promptly contained. The malware infected pathology systems, internal personnel switched in manual mode its operations.
“An IT virus had affected the Trust’s networks during January 2017. It was confirmed that this had affected all sites, except Whipps Cross but that the response had been effective and the Trust had swiftly returned to business as usual.” reads the minutes.”The virus had affected pathology systems (requiring the temporary use of manual systems), but no other IT systems used to deliver clinical care. A serious incident investigation was under way and further details would be shared once this had concluded.”
According to Deputy chief executive Tim Peachey, the malware that hit the systems wasn’t a ransomware, and no patient information systems had been compromised. He confirmed that the malware was able to bypass antivirus software because it had not been seen before and leveraged a zero-day exploit.
The software supplier for the infected application patched the flaw and issued a security patch within 8 hours.
Unfortunately, the number of cyber attacks on hospitals continues to increase and ransomware is among the most dangerous threats to this critical infrastructure.
In November 2016, a malware compromised the National Health Service (NHS) network, hundreds of scheduled operations, appointments, and diagnostic procedures have been canceled.
The hospitals hit by the malware-based attack are all located in the Lincolnshire, in England. In response to the incident, the IT staff shut down all the systems within its shared IT network aiming to “isolate and destroy” the malware.
Some patients, including major trauma patients, were diverted to the neighboring hospitals. The hospitals affected by the incident were the Diana Princess of Wales in Grimsby, Scunthorpe general and Goole and District.
Who will be the next?
Rockstar Games Launches Public Bug Bounty Program
4.3.2017 securityweek Vulnerebility
Rockstar Games this week launched a public bug bounty program through HackerOne, after running it in private mode for more than nine months.
On the program’s page, the company reveals that the minimum bounty for successful vulnerability submissions is $150, but that researchers can get higher rewards, depending on the severity and complexity of the identified potential vulnerability. However, the company notes that higher bounties may be paid out at its own discretion.
For the time being, researchers are required to look for vulnerabilities only in a specific set of domains operated by the company.
“No authorization is given to test any other web applications, video game titles or mobile applications. No bounties will be given for any disclosures relating to any applications outside the scope of this program,” the company specifies.
At the same time, researchers are encouraged to hunt for bugs in support.rockstargames.com, because the portal is run on top of the Zendesk platform, and because Zendesk also participates in the HackerOne bounty program.
Interested researchers should head to the bug bounty program’s page and go through all of the recommendations and guidelines that the company published there, as submissions that don’t follow those requirements may not qualify for a bounty.
Valid submissions, Rockstar Games says, should include details on the type of issue being reported, the kind of attack, whether it fits a CWE (Common Weakness Enumeration) number, details on the steps necessary to reproduce the issue (issues that can’t be reliably reproduced can’t be fixed, the company notes), info on potential impact of the bug, and details on how a malicious user could potentially benefit from the issue.
“The privacy, security and experience of our users are of the utmost importance. Under no circumstances may any testing target or negatively affect our users. You must use only accounts you own and/or created specifically for testing purposes,” the company also notes.
To ensure their submissions qualify for a bounty, the researchers should be the first to submit a vulnerability and avoid publicly disclosing or discussing the vulnerability before or after submitting it. The company also published a list of bugs that are excluded from the program, yet it didn’t say what type of flaws are accepted, most probably because all other types of security issues are.
Rockstar’s bug bounty program has been running in private mode for the past nine months, which allowed the company to resolve “readily identifiable types of vulnerabilities found across their network,” HackerOne says. With over 150 vulnerabilities identified and closed and more than $85,000 in bounties paid, the program is considered a “huge success.”
Vulnerable Services Emulator Released for Metasploit
4.3.2017 securityweek Vulnerebility
A new tool that can emulate vulnerable services and help researchers get more from the Metasploit penetration testing platform is now available in open source.
Designed to help security researchers understand security from the attacker’s perspective, Metasploit’s main issue was that it was rather difficult to use without vulnerable services at hand. Vulnerable OS images (Metasploitable2 and Metasploitable3) have previously been available, but they weren’t enough, as only a “small subset of the thousands of Metasploit modules available for users” was included in them.
Available on GitHub, the Vulnerable Services Emulator, however, comes to solve that problem, Jin Qian notes in a blog post. It has been designed as a framework to allow researchers easily emulate the vulnerable services for penetration testing purposes.
“Right now, it emulates over 100 vulnerable services, covering things like compromising credentials, getting a shell from the victim, and more. After going through module exercises, users can learn details about security vulnerabilities and how to test them, and are encouraged to continue to learn and play with Metasploit’s capabilities,” Qian explains.
The tool, he says, is very easy to install and use, as all that it requires is a working Perl installation for Windows, Mac or Linux. Moreover, the emulator was designed to be language independent, with the service emulation in JSON format. Thus, anyone can quickly add, remove, or edit a service in JSON.
One thing that users should keep in mind when running the emulator, however, is that “the commands typed on the shell session spawned are actually executed on the target.” Anyone using the emulator should run it in a safe environment to avoid any issues.
The Vulnerable Services Emulator was meant to help IT professionals and engineers easily test Metasploit modules, as well as to get training on Metasploit. At the moment, the tool includes support for over 100 emulated vulnerable services, but work is being done to add “as many of the 1000+ modules in Metasploit as possible.”
“At the core of the project, we implemented a framework (an interpreter) to execute the JSON based service description file. The current implementation is in Perl, but you can implement the framework in other programming languages of your choice,” Qian notes. Additional technical details on the tool are available on the project’s page on GitHub.
Google Offers $31,337 for RCE Vulnerabilities
3.3.2017 securityweek Vulnerebility
Google informed bug bounty hunters on Thursday that it has made some changes to its Vulnerability Rewards Program (VRP), including offering more money for certain types of flaws.
Until now, the tech giant had offered $20,000 for remote code execution (RCE) vulnerabilities and $10,000 for unrestricted file system or database access issues. The rewards have now increased to $31,337 and $13,337, respectively.
Researchers can earn $31,337 if they find command injections, sandbox escapes and deserialization bugs in highly sensitive applications, such as Google Search, Accounts, Wallet, Inbox, Code Hosting, Chrome Web Store, App Engine, Google Play, and Chromium Bug Tracker. If the flaws affect non-integrated acquisitions or apps that have a lower priority, the maximum reward is $5,000.
The unrestricted file system or database access category includes unsandboxed XXE and SQL injection vulnerabilities. These types of flaws can earn bounty hunters up to $13,337 if they affect highly sensitive services.
Google also announced that rewards attributed to vulnerability reports from its internal web security scanner will be donated; $8,000 have been donated this year to rescue.org.
The company reported in late January that it has paid out more than $9 million since the launch of its bug bounty program in 2010, including $3 million awarded last year. More than $400,000 of the total amount paid out in 2016 represented rewards that exceeded $20,000, including a single reward of $100,000.
A survey conducted by Google among its top researchers showed that, in 2016, 57 percent of them looked for vulnerabilities a few times a month, nearly 24 percent looked rarely or never, and 19 percent put their skills to work almost every day. Half of the respondents said they sometimes found flaws, while 16.7 percent said they almost always found flaws. One-third of respondents said they very rarely or never discovered bugs.
The highest numbers of researchers paid in 2016 were based in China, the United States and India.
Highest paid researchers
High severity bug discovered in CISCO NETFLOW GENERATION APPLIANCE
3.3.2017 securityaffairs Vulnerebility
A flaw in Cisco NetFlow Generation Appliance tracked as CVE-2017-3826, could be exploited by an unauthenticated, remote attacker to cause a DoS condition.
“A vulnerability in the Stream Control Transmission Protocol (SCTP) decoder of the Cisco NetFlow Generation Appliance (NGA) could allow an unauthenticated, remote attacker to cause the device to hang or unexpectedly reload, causing a denial of service (DoS) condition.” reads the Cisco Security Advisory.
NetFlow Generation Appliances are used in enterprise data centers to monitor Gigabit Ethernet high-throughput networks.
According to Cisco, the vulnerability resides in the hardware’s Stream Control Transmission Protocol (SCTP) used by the appliance.
The flaw is due to incomplete validation of SCTP packets being monitored on the Cisco NetFlow Generation Appliance data ports. The attackers can trigger the flaw by sending malformed SCTP packets on a network that is monitored by an NGA data port.
“SCTP packets addressed to the IP address of the NGA itself will not trigger this vulnerability. An exploit could allow the attacker to cause the appliance to become unresponsive or reload, causing a DoS condition. User interaction could be needed to recover the device using the reboot command from the CLI.” continues the advisory.
The bug impacts Cisco NetFlow Generation Appliances NGA 3140, NGA 3240 and NGA 3340.

Cisco this week has released a security patch for its devices and the IT giant confirmed that there are no workarounds to fix the issue. Users need to apply the security update (Cisco NetFlow Generation Appliance Software release 1.1 (1a)) that fixes the bug as soon as possible.
The security patch is not available for the model NGA 3140 because it was dismissed on January 11, 2014.
Robots Vulnerable to Cyberattacks: Researchers
2.3.2017 securityweek Vulnerebility
The software and firmware that bring robots to life are affected by potentially serious vulnerabilities that can allow hackers to remotely take control of the machines, according to an analysis conducted by security firm IOActive.
Robots are increasingly common in homes, businesses, industrial environments, the military and law enforcement, and healthcare organizations. International Data Corporation (IDC) estimated in January that worldwide spending on robotics and related services will reach $188 billion in 2020.
There have been many cases in the past years where people were injured or killed in accidents involving robots, but experts warn that robots could pose a serious threat if they are vulnerable to remote hacker attacks.
IOActive researchers have analyzed home, industrial and business robots from six different vendors: SoftBank Robotics (NAO and Pepper robots), UBTECH Robotics (Alpha 1S and Alpha 2), ROBOTIS (ROBOTIS OP2 and THORMANG3), Universal Robots (UR3, UR5 and UR10), Rethink Robotics (Baxter and Sawyer), and Asratec Corp (V-Sido robot control system).
The researchers have not acquired the actual robots and instead conducted tests on their mobile applications, software and firmware.
IOActive said it identified nearly 50 vulnerabilities in the tested components, but the security firm noted that it did not conduct an in-depth analysis, which suggests that the actual number of weaknesses is likely much higher.
The company has only published a paper providing a non-technical description of the vulnerabilities. Technical details will be made available after vendors have had a chance to address the flaws.
IOActive told SecurityWeek that it has notified all affected vendors, but only four of them have responded so far: SoftBank Robotics, UBTECH Robotics, Universal Robots and Rethink Robotics.
“Just one, SoftBank Robotics, said they were going to fix the issues but without any further details on when and how they are going to do it and what issues they were going to fix,” said Cesar Cerrudo, IOActive’s CTO and one of the paper’s authors. “Then Universal Robots said that our findings were interesting and that they should do something about it without giving any details. The rest haven’t mentioned if they are going to fix the issues or not.”
Robot vulnerabilities and impact
According to IOActive, the robots it has analyzed are affected by various types of vulnerabilities, including problems related to communications, authentication, authorization mechanisms, cryptography, privacy, default configurations, and open source components.
The flaws allow attackers to intercept communications between the robot and the application controlling it, remotely access critical services without a username and password, install malicious software, and extract sensitive information that is not encrypted properly.
Researchers said the vulnerabilities they identified can be exploited for spying via the robot’s camera and microphone, steal personal or business data, and even take control of the machine and cause physical damage or harm.
“Vendors need to start focusing more on security when speeding the latest innovative robot technologies to market or the issue of malfunctioning robots will certainly be exasperated when malicious actors begin exploiting common security vulnerabilities to add intent to malfunction,” Cerrudo said.
Aruba Patches Vulnerabilities in AirWave Product
2.3.2017 securityweek Vulnerebility
HPE-owned network access solutions provider Aruba has patched XML external entity (XXE) and cross-site scripting (XSS) vulnerabilities in its AirWave network management platform.
The vulnerabilities were reported to Aruba by Pichaya Morimoto of SEC Consult and independently by two other researchers. Both weaknesses affect AirWave’s VisualRF component.
The XXE flaw, tracked as CVE-2016-8526, allows a low-privileged user to read files on the system, including ones that could include passwords, which could lead to privilege escalation.
According to Aruba, this security hole is considered low risk on AirWave systems with a single administrator, but the risk increases in environments with users that have different privilege levels.
“The vulnerability can be exploited by a low privileged read-only user to read sensitive information / files with malicious XML code,” SEC Consult said in its advisory. “Note that as Aruba's passwords are encrypted with a shared static key, privilege escalation to admin role is also possible!”
The reflected XSS flaw, identified as CVE-2016-8527, can allow an attacker to obtain sensitive information, such as passwords and session cookies, but they need to trick an AirWave administrator into clicking on a specially crafted link.
The vulnerabilities were reported by SEC Consult in late November 2016 and they were fixed on February 21 with the release of AirWave 8.2.3.1. SEC Consult has classified the flaws as “high impact,” but Aruba has assigned them a “medium” severity rating.
Last year, Google security engineer Sven Blumenstein reported finding more than two dozen vulnerabilities in Aruba products, including ArubaOS, AirWave and Aruba Instant.
This is also not the first time SEC Consult has analyzed Aruba products. As part of its research into the reuse of cryptographic keys, the security firm discovered that Aruba had been using the same certificate for tens of thousands of devices.
Aruba has been running a private bug bounty program on BugCrowd with rewards of up to $1,500 per vulnerability.
Flaws Patched in Siemens RUGGEDCOM NMS Product
2.3.2017 securityweek Vulnerebility
An update released by Siemens for its RUGGEDCOM network management system (NMS) patches a couple of cross-site request forgery (CSRF) and cross-site scripting (XSS) vulnerabilities.
Used in various sectors worldwide, the RUGGEDCOM NMS allows organizations to monitor, configure and maintain their RUGGEDCOM mission-critical networks.
According to advisories published by Siemens and ICS-CERT, the product is affected by flaws that may allow a remote attacker to perform administrative operations.
The CSRF vulnerability, tracked as CVE-2017-2682 and assigned a CVSS score of 8.8, affects the product’s web interface and it can be exploited to get an authenticated user to execute various commands on behalf of the attacker. The attacker needs to trick the targeted user into clicking on a specially crafted link.
The XSS flaw, identified as CVE-2017-2683 and assigned a CVSS score of 6.3, could allow a non-privileged attacker to obtain administrative permissions by getting a user to click on a malicious link.
2017 Singapore ICS Cyber Security Conference Call for Papers is Open
The vulnerabilities affect all versions of the RUGGEDCOM NMS, for both Windows and Linux, prior to 2.1.0. Siemens has advised customers to update their installations to the latest version and configure their environments as specified in the company’s operational guidelines for industrial security.
ICS-CERT said there was no evidence that the flaws had been exploited for malicious purposes.
In recent months, Siemens has also released security updates for SIPROTEC, SCALANCE, Desigo PX, SIMATIC and various other products.
Slack Quickly Patches Account Hijacking Flaw
2.3.2017 securityweek Vulnerebility
It only took the developers of the Slack team collaboration tool five hours to patch a critical vulnerability that could have been exploited to steal a user’s private token and gain access to their account.
The security hole was identified by Detectify researcher Frans Rosén, who discovered that an attacker can steal a user’s token by getting them to access a specially crafted webpage.
The attack method targeted the xoxs token, which provides complete access to a user’s Slack account. A malicious hacker could have obtained this token by creating a page that reconnected the victim’s Slack WebSocket to their own WebSocket.
The vulnerability was reported by Rosén on February 17 and it was patched by Slack developers within five hours. The researcher, who currently has the second highest number of reputation points in Slack’s HackerOne bug bounty program, has been awarded $3,000 for his work.
Slack said it performed a thorough investigation to ensure that the vulnerability was never exploited for malicious purposes. Rosén has made available detailed technical information and a video demonstrating the attack.
Last year, Detectify warned that many developers had unknowingly leaked their Slack tokens on GitHub, exposing business-critical and other sensitive information. Experts identified more than 1,500 tokens at the time.
Slack has so far paid out more than $200,000 through its bug bounty program, including $9,000 to researcher David Vieira-Kurz for a couple of serious vulnerabilities that could have been leveraged to obtain sensitive information and take over user accounts.
Google Employees Help Thousands Of Open Source Projects Patch Critical ‘Mad Gadget Bug’
2.3.2017 thehackernews Vulnerebility
google-mad-gadget-vulnerability-operation-rosehub-open-source-projects
Last year Google employees took an initiative to help thousands of Open Source Projects patch a critical remote code execution vulnerability in a widely used Apache Commons Collections (ACC) library.
Dubbed Operation Rosehub, the initiative was volunteered by some 50 Google employees, who utilized 20 percent of their work time to patch thousands of open source projects on Github, those were vulnerable to "Mad Gadget vulnerability."
Mad Gadget vulnerability (CVE-2015-6420) is a remote code execution bug in the Java deserialization used by the Apache Commons Collections (ACC) library that could allow an unauthenticated, remote attacker to execute arbitrary code on a system.
The ACC Library is widely deployed by many Java applications to decode data passed between computers. To exploit this flaw, all an unauthorized attacker need to do is submit maliciously crafted input to an application on a targeted system that uses the ACC library.
Once the vulnerable ACC library on the affected system deserializes the content, the attacker could remotely execute arbitrary code on the compromised system, which could then be used to conduct further attacks.
Remember ransomware attack on Muni Metro System? Late last year, an anonymous hacker managed to infect and take over more than 2,000 computers using this same Mad Gadget flaw in the software used to operate San Francisco's public transport system.
Following the public disclosure of the Mad Gadget flaw, almost every commercial enterprise including Oracle, Cisco, Red Hat, VMWare, IBM, Intel, Adobe, HP, Jenkins, and SolarWinds formally disclosed that they had been impacted by this vulnerability and patched it in their software.
However, few months after all big businesses patched the flaw, one of the Google employees noticed that several prominent open source libraries were still depending on the vulnerable versions of ACC library.
"We recognized that the industry best practices had failed. An action was needed to keep the open source community safe. So rather than simply posting a security advisory asking everyone to address the vulnerability, we formed a task force to update their code for them. That initiative was called Operation Rosehub," Justine Tunney, Software Engineer on TensorFlow, wrote on Google Open Source Blog.
Under Operation Rosehub, patches were sent to many open source projects, although the Google employees were only able to patch open source projects on GitHub that directly referenced vulnerable versions of ACC library.
According to the Open Source Blog, if the San Francisco Municipal Transportation Agency's software systems had been open source, Google engineers would also have been able to deliver patches for Mad Gadget to them, and their systems would have never been compromised.
WordPress Plugin With 1 Million Installs Has Critical Flaw
1.2.2017 securityweek Vulnerebility
Researchers discovered that NextGEN Gallery, a WordPress image gallery plugin that has more than 1 million active installs, is affected by a critical SQL injection vulnerability.
The flaw, identified by experts at web security firm Sucuri, allows a remote attacker to easily gain access to the targeted website’s database, including sensitive data such as passwords and secret keys.
The SQL injection vulnerability exists because the plugin’s developers have not properly sanitized user input. The issue was addressed last week with the release of version 2.1.79, but there is no mention of it in the changelog.
“This is quite a critical issue,” warned Sucuri vulnerability researcher Slavco Mihajloski. “If you’re using a vulnerable version of this plugin, update as soon as possible!”
According to Mihajloski, there are two different attack scenarios: one where the targeted site uses a NextGEN Basic TagCloud Gallery, and one where users are allowed to submit posts for review.
In the first attack scenario, the attacker can execute SQL queries by modifying the URL of the gallery. In the second scenario, an authenticated attacker can execute malicious code via shortcodes.
There are no reports about the vulnerability being exploited in the wild, but attacks could be launched in the upcoming period considering the large number of potentially vulnerable installations.
This is not the first time researchers have found a serious vulnerability in the NextGEN Gallery plugin. Last year, experts uncovered a remote code execution flaw.
A study conducted last year by RIPS Technologies showed that 8,800 plugins available in the official WordPress plugins directory had been affected by at least one vulnerability. Nearly 2,800 apps had high severity and 41 had critical flaws.
WordPress continues to be the most targeted content management system (CMS) and attackers have plenty of vulnerabilities to choose from when targeting WordPress websites.
A critical vulnerability patched in WordPress in January has been exploited against a large number of websites, including for defacements and remote code execution, despite WordPress developers not immediately disclosing its existence in an effort to give users enough time to patch their installations.
XSS flaws in Zscaler Cloud management software allow logged attackers to hack coworkers
1.3.2017 securityaffairs Vulnerebility
Zscaler has fixed persistent XSS vulnerabilities affecting Zscaler Cloud management software that allow logged attackers to hack coworkers.
Serious cross-site scripting (XSS) flaws in the Zscaler Cloud management software could be exploited by attackers to inject malicious HTML and JavaScript into the browsers of other users who visit the portal.
In order to exploit the flaws, the attacker needs to be logged into the website, then he can take over the accounts of other users and act on their behalf.
Zscaler highlighted that the flaws would only expose the hack users within the same organization, this means that an attacker can only inject code into the webpages of coworkers while they were accessing the Zscaler’s admin portal.
“Zscaler has addressed persistent XSS vulnerabilities identified in admin.zscaler[X].net and mobile.zscaler[X].net portals. The post-auth vulnerabilities would have allowed authenticated admin users to inject client-side content into certain admin UI pages which could impact other admin users of the same company.” reads the security advisory shared by Zscaler. “Zscaler would like to thank Alex Haynes for responsibly reporting the issues and working with Zscaler to ensure that they were properly remediated.”
Cross-site scripting flaws are wrongly considered minor issues, but they are very insidious and easy to spot also with XSS scanners.
XSS attacks occur when an attacker uses a web application to send malicious code (i.e. browser side script) to a different end user. For further information, I suggest you visit the OWASP website.
Amazon S3 outage. Increased error rates. Amazon AWS is down
1.3.2017 securityaffairs Vulnerebility
An Amazon AWS S3 outage is causing serious problems for a huge number of websites, applications, and Internet of Things devices.
The Amazon S3 web-based storage service is experiencing serious widespread issues. Web services and mobile apps leveraging on Amazon S3 suffered a significant outage.
According to the company, the Amazon S3 outage was caused by “high error rates with S3 in US-EAST-1.”
Follow
Amazon Web Services ✔ @awscloud
We continue to experience high error rates with S3 in US-East-1, which is impacting some other AWS services.
8:56 PM - 28 Feb 2017
458 458 Retweets 284 284 likes
“We have now repaired the ability to update the service health dashboard. The service updates are below. We continue to experience high error rates with S3 in US-EAST-1, which is impacting various AWS services. We are working hard at repairing S3, believe we understand rootcause , and are working on implementing what we believe will remediate the issue.” reads the statement published on the AWS service health dashboard.
Many websites were affected by the Amazon S3 outage, including Quora, Imgur, Medium, Business Insider, filesharing in Slack, and many others.
Amazon S3 service is used by a large number of service to store data online, including Runkeeper, Yahoo webmail and Trello.
Amazon S3 outage also affected IoT devices backed by the Amazon service, such as connected thermostats and lightbulbs, users were not able to control their devices.
According to data tracked by SimilarTech, Amazon S3 is used by more than 148,000 websites and 120,oo0 unique domains, mostly in the US. 0.8 percent of the top 1 million websites leverage on the Amazon service.
Amazon S3 outage
The users are angry, AWS still continue to downplay the issue classifying it as a case of “increased error rates.”
The status dashboard for AWS shows all green ticks at time of writing, but users are still facing the Amazon S3 outage.
“We’ve identified the issue as high error rates with S3 in US-EAST-1, which is also impacting applications and services dependent on S3. We are actively working on remediating the issue,” states AWS.
SQLi flaw in the NextGEN Gallery plugin exposes at risk of hack more than 1 Million WordPress Installs
1.3.2017 securityaffairs Vulnerebility
More than 1 million WordPress website are at risk due to a critical SQL injection vulnerability in the NextGEN Gallery plugin. Update it asap.
Security experts at Sucuri firm have identified a SQL injection flaw in the WordPress image gallery NextGEN Gallery that could be exploited by a remote to gain access to the targeted website’s backend, including sensitive data such as passwords and secret keys.
Hackers can trigger the flaw to access the database and steal sensitive data, including passwords and secret keys.
“While working on the WordPress plugin NextGEN Gallery, we discovered a severe SQL Injection vulnerability. This vulnerability allows an unauthenticated user to grab data from the victim’s website database, including sensitive user information.” reads the analysis published by Sucuri.
The WordPress plugin NextGEN doesn’t validate the user input, for this reason, the development team has fixed the bug releasing the version 2.1.79.
“From the source code, we notice the $container_ids string is created from tag input and its values are not properly sanitized. They are safe from SQL injection but wouldn’t prevent arbitrary format string directives/input from being inserted, which may cause issues with the WordPress database abstraction prepare() method.” noticed the experts.
According to the analysis published by the security firm, there are two different attack scenarios for the exploitation of the flaw:
The website administrator uses a NextGEN Basic TagCloud Gallery on the website. In this scenario, the attacker can execute SQL queries by modifying the URL of the gallery.
The website administrator allows users to submit posts to be reviewed (contributors). In this case, an authenticated attacker can execute malicious code via shortcodes.
NextGEN Gallery plugin flaw
An unauthenticated attacker could add extra sprintf/printf directives to the SQL query and exploit the $wpdb->prepare’s behavior to add its code to the executed query.
The researchers also shared some examples of the final attack payloads that would look like the following ones:
http://target.url/2017/01/17/new-one/nggallery/tags/test%251%24%25s))%20or%201=1%23
http://target.url/2017/01/17/new-one/nggallery/tags/test%251%24%25s))%20or%201=2%23
The good news is that the flaw in the NextGEN Gallery hasn’t been exploited in the wild, but it is easy to predict a spike in the number of attacks leveraging the flawed plugin.
The flaw in the NextGEN Gallery is very serious due to the huge number of websites that use it, the popular WordPress image gallery plugin has more than 1 million active installations.
WordPress continues to be a privileged target for hackers, a critical flaw patched in WordPress in January has been exploited against a large number of websites.
Once again … Never trust the input!
Robots Vulnerable to Cyberattacks: Researchers
1.3.2017 securityweek Vulnerebility
Robots vulnerable to cyberattacks
The software and firmware that bring robots to life are affected by potentially serious vulnerabilities that can allow hackers to remotely take control of the machines, according to an analysis conducted by security firm IOActive.
Robots are increasingly common in homes, businesses, industrial environments, the military and law enforcement, and healthcare organizations. International Data Corporation (IDC) estimated in January that worldwide spending on robotics and related services will reach $188 billion in 2020.
There have been many cases in the past years where people were injured or killed in accidents involving robots, but experts warn that robots could pose a serious threat if they are vulnerable to remote hacker attacks.
IOActive researchers have analyzed home, industrial and business robots from six different vendors: SoftBank Robotics (NAO and Pepper robots), UBTECH Robotics (Alpha 1S and Alpha 2), ROBOTIS (ROBOTIS OP2 and THORMANG3), Universal Robots (UR3, UR5 and UR10), Rethink Robotics (Baxter and Sawyer), and Asratec Corp (V-Sido robot control system).
The researchers have not acquired the actual robots and instead conducted tests on their mobile applications, software and firmware.
IOActive said it identified nearly 50 vulnerabilities in the tested components, but the security firm noted that it did not conduct an in-depth analysis, which suggests that the actual number of weaknesses is likely much higher.
The company has only published a paper providing a non-technical description of the vulnerabilities. Technical details will be made available after vendors have had a chance to address the flaws.
IOActive told SecurityWeek that it has notified all affected vendors, but only four of them have responded so far: SoftBank Robotics, UBTECH Robotics, Universal Robots and Rethink Robotics.
“Just one, SoftBank Robotics, said they were going to fix the issues but without any further details on when and how they are going to do it and what issues they were going to fix,” said Cesar Cerrudo, IOActive’s CTO and one of the paper’s authors. “Then Universal Robots said that our findings were interesting and that they should do something about it without giving any details. The rest haven’t mentioned if they are going to fix the issues or not.”
Robot vulnerabilities and impact
According to IOActive, the robots it has analyzed are affected by various types of vulnerabilities, including problems related to communications, authentication, authorization mechanisms, cryptography, privacy, default configurations, and open source components.
The flaws allow attackers to intercept communications between the robot and the application controlling it, remotely access critical services without a username and password, install malicious software, and extract sensitive information that is not encrypted properly.
Researchers said the vulnerabilities they identified can be exploited for spying via the robot’s camera and microphone, steal personal or business data, and even take control of the machine and cause physical damage or harm.
“Vendors need to start focusing more on security when speeding the latest innovative robot technologies to market or the issue of malfunctioning robots will certainly be exasperated when malicious actors begin exploiting common security vulnerabilities to add intent to malfunction,” Cerrudo said.
Critical Flaw in ESET Antivirus Exposes Mac Users to Remote Hacking
28.2.2017 thehackernews Vulnerebility
What could be more exciting for hackers than exploiting a vulnerability in a widely used software without having to struggle too much?
One such easy-to-exploit, but critical vulnerability has been discovered in ESET's antivirus software that could allow any unauthenticated attackers to remotely execute arbitrary code with root privileges on a Mac system.
The critical security flaw, tracked as CVE-2016-9892, in ESET Endpoint Antivirus 6 for macOS was discovered by Google Security Team's researchers Jason Geffner and Jan Bee at the beginning of November 2016.
As detailed in the full disclosure, all a hacker needs to get root-level remote code execution on a Mac computer is to intercept the ESET antivirus package's connection to its backend servers using a self-signed HTTPS certificate, put himself in as a man-in-the-middle (MITM) attacker, and exploit an XML library flaw.
The actual issue was related to a service named esets_daemon, which runs as root. The service is statically linked with an outdated version of the POCO XML parser library, version 1.4.6p1 released in March 2013.
This POCO version is based on a version of the Expat XML parser library version 2.0.1 from 2007, which is affected by a publicly known XML parsing vulnerability (CVE-2016-0718) that could allow an attacker to execute arbitrary code via malicious XML content.
Now, when esets_daemon sent a request to https://edf.eset.com/edf during activation of the ESET Endpoint Antivirus product, an MITM attacker can intercept the request to deliver a malformed XML document using a self-signed HTTPS certificate.
This event triggers the CVE-2016-0718 flaw that executes the malicious code with root privileges when esets_daemon parsed the XML content.
This attack was possible because the ESET antivirus did not validate the web server's certificate.
Here's what the duo explain:
"Vulnerable versions of ESET Endpoint Antivirus 6 are statically linked with an outdated XML parsing library and do not perform proper server authentication, allowing for remote unauthenticated attackers to perform arbitrary code execution as root on vulnerable clients."
Now since the hacker controls the connection, they can send malicious content to the Mac computer in order to hijack the XML parser and execute code as root.
The Google researchers have also released the proof-of-concept (PoC) exploit code, which only shows how the ESET antivirus app can be used to cause a crash.
ESET addressed this vulnerability on February 21 by upgrading the POCO parsing library and by configuring its product to verify SSL certificates.
The patch is made available in the release of version 6.4.168.0 of ESET Endpoint Antivirus for macOS. So, make sure your antivirus package is patched up to date.
A flaw in ESET Endpoint Antivirus allows to hack Apple Macs, patch it now
28.2.2017 securityaffairs Vulnerebility
A flaw in ESET Endpoint Antivirus is exploitable to get remote root execution on Apple Mac systems via Man-In-The-Middle (MiTM) attacks.
According to the security advisory published by Google Security Team’s Jason Geffner and Jan Bee on Seclists, it is possible to get remote root execution on Apple Mac systems via Man-In-The-Middle (MiTM) attacks. The attackers can get root-level remote code execution on a Mac by intercepting the ESET antivirus package’s connection to company backend servers. The attack is possible due to the presence of a buffer overflow vulnerability in the XML library tracked as CVE-2016-0718.
“Vulnerable versions of ESET Endpoint Antivirus 6 are statically linked with an outdated XML parsing library and do not perform proper server authentication, allowing for remote unauthenticated attackers to perform arbitrary code execution as root on vulnerable clients.” reads the advisory.
According to the experts, the attack is possible because the esets_daemon uses an old version of POCO’s XML parser library that is affected by the buffer overflow vulnerability.

The researchers discovered that the flawed library also handles license activation with a request to the following static address:
https://edf.eset.com/edf.
When the ESET Endpoint Antivirus tries to activate the license, the esets_daemon sends a request to the above address, but it doesn’t validate the web server’s certificate opening the door to a man-in-the-middle attack.
An attacker can intercept the request and send to the ESET Endpoint Antivirus a self-signed HTTPS certificate, then the esets_daemon service
parses the response as an XML document.
In this phase, the attacker can pass a specifically XML document that can trigger the CVE-2016-0718 to achieve arbitrary code execution
as root.
“When ESET Endpoint Antivirus tries to activate its license, esets_daemon sends a request to https://edf.eset.com/edf. The esets_daemon service does not validate the web server’s certificate, so a man-in-the-middle can intercept the request and respond using a self-signed HTTPS certificate.” reads the security advisory. “The esets_daemon service parses the response as an XML document, thereby allowing the attacker to supply malformed content and exploit CVE-2016-0718 to achieve arbitrary code execution as root.”
The security duo has also published the Proof of Concept code to exploit the attack.
ESET has promptly fixed the issue in ESET Endpoint Antivirus version 6.4.168.0.
Update your system as soon as possible.
TLS Bug in Blue Coat Proxy Breaks Chromebooks, PCs
28.2.2017 securityweek Vulnerebility
Products from Symantec-owned Blue Coat and likely other vendors can cause serious problems for devices running the Chrome web browser or Chrome OS due to poor implementation of the TLS 1.3 protocol.
Google warned last week that the use of Blue Coat proxies causes connection problems when Chrome 56 or Chrome OS 56 attempt to connect via TLS 1.3. The tech giant believes the issue affects products running version 6.5 of the Blue Coat SGOS operating system.
An employee of Montgomery County Public Schools in Maryland reported that thousands of the organization’s Chromebooks and PCs had broken down due to the bug. The affected devices had automatically updated to Chrome OS 56, respectively Chrome 56, which introduce support for TLS 1.3.
The employee said the organization’s Chromebooks are “stuck in a state of flickering between a login screen and a ‘Network not available’ screen. Occasionally, you can see a SSL_HANDSHAKE_ERROR briefly at the login screen before switching back to the ‘Network not available’ screen.”
Other major education organizations are affected as well, likely because SSL/TLS inspection is common in this sector, Google said.
The company has provided some workarounds and released a Chrome update that disables TLS 1.3. A future version of the web browser will re-enabled TLS 1.3; hopefully, firewall and proxy vendors will address the issue until then.
According to Google, Blue Coat was informed of TLS 1.3 several months ago, but the company failed to properly test its software. SecurityWeek has reached out to Symantec for comment and will update this article if the company responds.
A study conducted recently by researchers from Mozilla, Google, CloudFlare and various universities showed that many antiviruses and network appliances that intercept TLS connections for visibility into encrypted traffic weaken security and introduce vulnerabilities.
The study found that only Blue Coat’s ProxySG product maintained an optimal TLS connection, but those tests were conducted on TLS 1.2.
TLS 1.3 is still under development, but a final version is expected soon. The new version of the protocol improves speed and eliminates some of the features that have been leveraged in the TLS attacks disclosed over the past years.
CVE-2017-0037 – Google Project Zero discloses another unpatched Microsoft Edge and IE Vulnerability
27.2.2017 securityaffairs Vulnerebility
The researchers at Google’s Project Zero have revealed another flaw, tracked as CVE-2017-0037, that affects Microsoft Edge and IE.
It has happened again, the researchers at Google’s Project Zero have revealed another flaw, tracked as CVE-2017-0037, in Microsoft products.
The flaw affects Microsoft’s Internet Explorer and Edge browsers, it was first reported on November 25 by the Google researcher Ivan Fratric, and Google publicly released the details of the vulnerability as Microsoft did not fix it within its 90-day disclosure deadline.
The CVE-2017-0037 vulnerability, so-called “type confusion flaw,” resides in a module in Microsoft Edge and Internet Explorer that let attackers execute arbitrary code on the target machine when the victim visits a malicious website.
The flaw affects all Windows 7, Windows 8.1, and Windows 10 users.
The researcher has also published a proof-of-concept exploit that can crash Edge and IE, allowing an attacker to execute code and gain administrator privileges on the affected systems.
In the note included in the exploit code, Fratric confirmed that the attack works on the 64-bit version of IE on Windows Server 2012 R2. The flaw affects both 32-bit IE 11, as well as Microsoft Edge.
Giving a look at the technical details of the CVE-2017-0037 vulnerability it is possible to note that it works by attacking a type confusion in
HandleColumnBreak
OnColumnSpanningElement.
The 17-line proof-of-concept code crashes this process working with the two variables rcx and rax.
“However, an attacker can affect rax by modifying table properties such as border-spacing and the width of the firs th element. Let’s see what happens if an attacker can point rax to the memory he/she controls.” reads the analysis shared by Project Zero Team.
“Assuming an attacker can pass a check on line 00007ffe`8f330a59, MSHTML!Layout::Patchable<Layout::PatchableArrayData<Layout::MultiColumnBox::SMultiColumnBoxItem> >::Readable is called again with the same arguments. After that, through a series of dereferences starting from rax, a function pointer is obtained and stored in rdi. A CFG”
Earlier this month, Microsoft delayed February’s Patch Tuesday, the experts at Project Zero publicly disclosed the flaw in Windows’ Graphics Device Interface (GDI) library because Microsoft failed to patch it within the 90-day window given by the Google.
On Tuesday Microsoft issued the security updates KB 4010250 that address flaws in Adobe Flash Player, but two already disclosed flaws remain unpatched.
The first flaw is a Windows SMB (Server Message Block) vulnerability that affects Windows 8, Windows 10 and Windows Server. It is a memory corruption vulnerability in the SMBprotocol that can be exploited by a remote attacker, the proof-of-concept exploit code of the flaw was recently publicly released.
The second flaw doesn’t address by the last security updates is the one recently disclosed by the Google Project Zero team that affects Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10.
Google Discloses Unpatched Flaw in Edge, Internet Explorer
27.2.2017 securityweek Vulnerebility
Google Project Zero has disclosed a potentially serious vulnerability in Microsoft’s Edge and Internet Explorer web browsers before the tech giant could release patches.
The details of the flaw and proof-of-concept (PoC) code were made public last week by Google Project Zero researcher Ivan Fratric after Microsoft failed to meet the 90-day disclosure deadline.
The security hole, tracked as CVE-2017-0037, has been described as a high severity type confusion. The vulnerability can be exploited to cause the web browsers to crash, but arbitrary code execution could also be possible.
This is the second unpatched vulnerability in a Microsoft product disclosed by Google Project Zero this month. Earlier, Mateusz Jurczyk released the details of a medium severity information disclosure flaw tracked as CVE-2017-0038.
In addition, there is an unpatched denial-of-service (DoS) flaw in Windows caused by how SMB traffic is handled.
Microsoft only released patches for Adobe Flash Player this month after postponing its February 2017 updates to March 14 due to an unspecified “last minute issue.” It’s possible that the three vulnerabilities affecting Windows and the browsers were supposed to be fixed by the delayed security updates.
Microsoft claimed last month that the security mechanisms in Windows 10 can block the exploitation of zero-day vulnerabilities even before patches are made available. As an example the company provided two flaws exploited in sophisticated attacks against organizations in South Korea and the United States before fixes could be released.
D-Link Patches Serious Flaws in DGS-1510 Switches
25.2.2017 securityweek Vulnerebility
D-Link has released firmware updates for the company’s DGS-1510 stackable managed switches to address serious vulnerabilities that can be exploited remotely to hijack the devices.
Security researchers Aditya K Sood and Varang Amin discovered that the D-Link DGS-1510 switches, which are recommended for small and medium-sized enterprises, have an insecure authentication design.
According to the experts, a remote attacker can exploit the authentication bypass vulnerabilities to execute commands on the switch, and extract configuration and other data.
A proof-of-concept (PoC) shared by the researchers with SecurityWeek shows how an unauthenticated attacker can harvest user information from a device, including username and password, and add a new user with administrator privileges. The PoC will be made publicly available at a later date.
Sood and Amin said they identified dozens of systems on the Internet, but they did not attempt to determine exactly how many devices can be exploited remotely from the Web.
In its own advisory, D-Link described the vulnerabilities as unauthenticated command bypass and unauthenticated information disclosure issues. The flaws affect DGS-1510-28XMP, DGS-1510-28X, DGS-1510-52X, DGS-1510-52, DGS-1510-28P, DGS-1510-28 and DGS-1510-20 models running any firmware version prior to 1.31.B003.
The firmware update that addresses the security holes is currently in beta and it will be made generally available once it passes long-term quality assurance testing, D-Link said.
The problems were reported to D-Link in January and the patch, tested by the researchers, was released on February 21.
Serious vulnerabilities were found in many D-Link products last year, including cameras, access points, modems, routers, storage solutions and connected home products.
In early January, the U.S. Federal Trade Commission (FTC) filed a lawsuit against the Taiwan-based networking equipment provider, accusing the company of making deceptive claims about the security of its products. D-Link is determined to fight the “unwarranted and baseless” charges.
Google Does It Again: Discloses Unpatched Microsoft Edge and IE Vulnerability
25.2.2017 thehackernews Vulnerebility
Google Does It Again: Discloses Microsoft Edge and IE Vulnerability In Public
This month has yet been kind of interesting for cyber security researchers, with Google successfully cracked SHA1 and the discovery of Cloudbleed bug in Cloudflare that caused the leakage of sensitive information across sites hosted behind Cloudflare.
Besides this, Google last week disclosed an unpatched vulnerability in Windows Graphics Device Interface (GDI) library, which affects Microsoft's Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10.
While the Windows vulnerability has yet to be patched by the company, Google today released the details of another unpatched Windows security flaw in its browser, as Microsoft did not act within its 90-day disclosure deadline.
The vulnerability (CVE-2017-0037), discovered and disclosed by Google Project Zero team's researcher Ivan Fratric, is a so-called "type confusion flaw" in a module in Microsoft Edge and Internet Explorer that potentially leads to arbitrary code execution.
Proof-of-Concept Code Released!
This time, with the details of this arbitrary code execution bug, the researcher has also published a proof-of-concept exploit that can crash Edge and IE, opening the door for potential hackers to execute code and gain administrator privileges on the affected systems.
Fratric says he successfully ran his PoC code on the 64-bit version of IE on Windows Server 2012 R2, but both 32-bit IE 11, as well as Microsoft Edge, is affected by the same vulnerability.
In short, the vulnerability affects all Windows 7, Windows 8.1, and Windows 10 users.
You can know more details about the recently disclosed flaw on Google's bug report blog, along with proof-of-concept code that causes a crash of the browsers, though sophisticated hackers can build more dangerous exploits as well.
This vulnerability was reported to Microsoft on November 25, and it went public on February 25, after Google Project Zero's 90-day disclosure policy.
Three Unpatched, but Already Disclosed Windows Flaws
While Microsoft has delayed this month's Patch Tuesday and already has to patch two already disclosed, but unpatched vulnerabilities, it is hard to say if the company actually included a patch for this vulnerability discovered by Google in its next roll out of patches.
Yes, Microsoft has to patch two other severe security flaws as well, which have already been publicly disclosed with working exploit code but remain still unpatched, giving hackers enough time to target Windows users.
First one is a Windows SMB flaw that affects Windows 8, Windows 10 and Windows Server. The PoC exploit code of this flaw was released almost two weeks ago.
The other one is the vulnerability disclosed by Google last week that affects Microsoft's Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10.
Meanwhile, just to remain on the safer side, Windows users are advised to replace their Internet Explorer and Edge browsers with a different one if possible and avoid clicking on suspicious links and websites they do not trust.
D-Link Patches Serious Flaws in DGS-1510 Switches
24.2.2017 securityweek Vulnerebility
D-Link has released firmware updates for the company’s DGS-1510 stackable managed switches to address serious vulnerabilities that can be exploited remotely to hijack the devices.
Security researchers Aditya K Sood and Varang Amin discovered that the D-Link DGS-1510 switches, which are recommended for small and medium-sized enterprises, have an insecure authentication design.
According to the experts, a remote attacker can exploit the authentication bypass vulnerabilities to execute commands on the switch, and extract configuration and other data.
A proof-of-concept (PoC) shared by the researchers with SecurityWeek shows how an unauthenticated attacker can harvest user information from a device, including username and password, and add a new user with administrator privileges. The PoC will be made publicly available at a later date.
Sood and Amin said they identified dozens of systems on the Internet, but they did not attempt to determine exactly how many devices can be exploited remotely from the Web.
In its own advisory, D-Link described the vulnerabilities as unauthenticated command bypass and unauthenticated information disclosure issues. The flaws affect DGS-1510-28XMP, DGS-1510-28X, DGS-1510-52X, DGS-1510-52, DGS-1510-28P, DGS-1510-28 and DGS-1510-20 models running any firmware version prior to 1.31.B003.
The firmware update that addresses the security holes is currently in beta and it will be made generally available once it passes long-term quality assurance testing, D-Link said.
The problems were reported to D-Link in January and the patch, tested by the researchers, was released on February 21.
Serious vulnerabilities were found in many D-Link products last year, including cameras, access points, modems, routers, storage solutions and connected home products.
In early January, the U.S. Federal Trade Commission (FTC) filed a lawsuit against the Taiwan-based networking equipment provider, accusing the company of making deceptive claims about the security of its products. D-Link is determined to fight the “unwarranted and baseless” charges.
Serious Bug Exposes Sensitive Data From Millions Sites Sitting Behind CloudFlare
24.2.2017 thehackernews Vulnerebility
A severe security vulnerability has been discovered in the CloudFlare content delivery network that has caused big-name websites to expose private session keys and other sensitive data.
CloudFlare, a content delivery network (CDN) and web security provider that helps optimize safety and performance of over 5.5 Million websites on the Internet, is warning its customers of the critical bug that could have exposed a range of sensitive information, including passwords, and cookies and tokens used to authenticate users.
Dubbed Cloudbleed, the nasty flaw is named after the Heartbleed bug that was discovered in 2014, but believed to be worse than Heartbleed.
The vulnerability is so severe that it not only affects websites on the CloudFlare network but affects mobile apps as well.
What exactly is "Cloudbleed," how it works, how are you affected by this bug, and how you can protect yourself? Let's figure it out.
What is Cloudbleed?
Discovered by Google Project Zero security researcher Tavis Ormandy over a week ago, Cloudbleed is a major flaw in the Cloudflare Internet infrastructure service that causes the leakage of private session keys and other sensitive information across websites hosted behind Cloudflare.
CloudFlare acts as a proxy between the user and web server, which caches content for websites that sits behind its global network and lowers the number of requests to the original host server by parsing content through Cloudflare’s edge servers for optimization and security.
Almost a week ago, Ormandy discovered a buffer overflow issue with Cloudflare's edge servers that were running past the end of a buffer and were returning memory containing private data like HTTP cookies, authentication tokens, and HTTP POST bodies, with some of the leaked data already cached by search engines.
Here's How Serious is Cloudbleed:
"I'm finding private messages from major dating sites, full messages from a well-known chat service, online password manager data, frames from adult video sites, hotel bookings," Ormandy wrote in a blog post that was also published Thursday. "We're talking full HTTPS requests, client IP addresses, full responses, cookies, passwords, keys, data, everything."
According to Ormandy, Cloudflare had code in its "ScrapeShield" feature that did something similar to this:
int Length = ObfuscateEmailAddressesInHtml(&OutputBuffer, CachedPage);
write(fd, OutputBuffer, Length);
But the company was not checking if the obfuscation parsers returned a negative value because of malicious HTML.
The Cloudflare's "ScrapeShield" feature parses and obfuscates HTML, but since reverse proxies are shared among customers, it would affect all CloudFlare customers.
Ormandy contacted Cloudflare and reported it about his findings. The company identified the cause of the issue, and immediately disabled 3 minor Cloudflare features — Email obfuscation, Server-side Excludes, as well as Automatic HTTPS Rewrites — that were using the same HTML parser chain, which was causing the leakage.
Ormandy observed encryption keys, passwords, cookies, chunks of POST data, and HTTPS requests for the other leading Cloudflare-hosted websites from other users and immediately contacted Cloudflare.
Since CloudFlare patched the issue but did not notify customers by Wednesday of the data leak issue, Ormandy made public his findings on Thursday, following Project Zero's seven-day policy for actively exploited attacks.
Following Ormandy's public disclosure of the vulnerability on Thursday, CloudFlare confirmed the flaw, ensuring its customers that their SSL private keys were not leaked.
"Cloudflare has always terminated SSL connections through an isolated instance of NGINX that was not affected by this bug," Cloudflare CTO John Graham-Cumming wrote in a blog post. "The bug was serious because the leaked memory could contain private information and because it had been cached by search engines."
"We are disclosing this problem now as we are satisfied that search engine caches have now been cleared of sensitive information," he added. "We have also not discovered any evidence of malicious exploits of the bug or other reports of its existence."
The Root Cause of Cloudbleed:
The root cause of the Cloudbleed vulnerability was that "reaching the end of a buffer was checked using the equality operator and a pointer was able to step past the end of the buffer."
"Had the check been done using >= instead of == jumping over the buffer end would have been caught," said Cumming.
Cloudflare has also confirmed that the greatest period of impact was between February 13 and February 18 with almost one in every 3,300,000 HTTP requests via Cloudflare potentially resulting in memory leakage, which is about 0.00003% of requests.
However, the researcher argued that the DNS provider was double-dealing, claiming that the Cloudbleed vulnerability had existed for months, based on Google's cached data.
How Does Cloudbleed Affect You?
There are a large number of Cloudflare's services and websites that use parsing HTML pages and modify them through the Cloudflare's edge servers.
Even if you do not use CloudFlare directly, that does not mean that you are spared. There is always a chance that websites you visit and web services you use may have been affected, leaking your data as well.
Of course, if you are using Cloudflare services in front of your site, the flaw could impact you, exposing sensitive information that flowed between your servers and end-users through CloudFlare's proxies.
While CloudFlare's service was rapidly patched the bug and has said the actual impact is relatively minor, data was leaking constantly before this — for months.
Some of this leaked data were publicly cached in search engines such as Google, Bing, Yahoo, who now removed it, but some engines like DuckDuckGo still host those data.
Also, other leaked data might exist in other services and caches throughout the Web, which is impossible to delete across all of these locations.
Cloudbleed Also Affects Mobile Apps
Cloudbleed also affects mobile apps, because, in many cases, the apps are designed to make use of the same backends as browsers for content delivery and HTTPS (SSL/TLS) termination.
Users on YCombinator have confirmed the presence of HTTP header data for apps like Discord, FitBit, and Uber by searching through DuckDuckGo caches with targeted search terms.
In an analysis conducted by NowSecure, the researchers have discovered some 200 iOS apps that identified as using Cloudflare services from a sampling of some 3,500 of the most popular apps on the app store.
There is always a possibility of someone discovering this vulnerability before Tavis, and may have been actively exploiting it, although there is no evidence to support this theory.
Some of the Cloudflare's major customers affected by the vulnerability included Uber, 1Password, FitBit, and OKCupid. However, in a blog post published by 1Password, the company assured its users that no sensitive data was exposed because the service was encrypted in transit.
However, a list of websites that have potentially been impacted by this bug has been published by a user, who go by the name of 'pirate,' on GitHub, which also included CoinBase, 4Chan, BitPay, DigitalOcean, Medium, ProductHunt, Transferwise, The Pirate Bay, Extra Torrent, BitDefender, Pastebin, Zoho, Feedly, Ashley Madison, Bleeping Computer, The Register, and many more.
Since CloudFlare does not yet provide the list of affected services, bear in mind that this is not a comprehensive list.
What should You do about the Cloudbleed bug?
Online users are strongly recommended to reset their passwords for all accounts in case you have reused the same passwords on every site, as well as monitor account activity closely as cleanup is underway.
Moreover, customers who are using Cloudflare for their websites are advised to force a password change for all of their users.
Update: Uber representative reached out to me via an email and said their investigation revealed that the CloudBleed bug exposed no passwords of their customers. Here's the statement provided by Uber:
"Very little Uber traffic actually goes through Cloudflare, so only a handful of tokens were involved and have since been changed. Passwords were not exposed."
CVE-2017-6074 – a new 11-year old Linux Kernel flaw discovered
23.2.2017 securityaffairs Vulnerebility
Security expert discovered a new 11-year old privilege escalation vulnerability, tracked as CVE-2017-6074, in the Linux kernel.
A new privilege escalation vulnerability, tracked as CVE-2017-6074, has been discovered in the Linux kernel and the astonishing new is that it is an 11-year old flaw.
The local privilege-escalation vulnerability, discovered by security researcher Andrey Konovalov, affects all the major Linux distro, including Debian, OpenSUSE, Redhat, and Ubuntu.
The flaw discovered by Konovalov resides in the DCCP (Datagram Congestion Control Protocol) implementation using Syzkaller that is a kernel fuzzing tool released by Google.
The Datagram Congestion Control Protocol (DCCP) is a message-oriented transport layer protocol that implements reliable connection setup, maintenance, and teardown, of an unreliable packet flow, and the congestion control of that packet flow.
The flaw is a use-after-free vulnerability in the way the Linux kernel’s “DCCP protocol implementation freed SKB (socket buffer) resources for a DCCP_PKT_REQUEST packet when the IPV6_RECVPKTINFO option is set on the socket.”
“In the current DCCP implementation an skb for a DCCP_PKT_REQUEST
packet is forcibly freed via __kfree_skb in dccp_rcv_state_process if
dccp_v6_conn_request successfully returns [3].” reads the description of the flaw published on the full disclosure mailing list.
“However, if IPV6_RECVPKTINFO is set on a socket, the address of the
skb is saved to ireq->pktopts and the ref count for skb is incremented
in dccp_v6_conn_request [4], so skb is still in use. Nevertheless, it
still gets freed in dccp_rcv_state_process.”
CVE-2017-6074
An attacker can control an object and overwrite its content with a pointer to a execute arbitrary code in the Kernel.
“An attacker can control what object that would be and overwrite its content with arbitrary data by using some of the kernel heap spraying techniques. If the overwritten object has any triggerable function pointers, an attacker gets to execute arbitrary code within the kernel,” full disclosure mailing list about the vulnerability reads.
It is important to highlight that the CVE-2017-6074 flaw is a local issue that could not be exploited by a remote attacker. In order to exploit the flaw, an attacker needs to have a local account access on the system.
The CVE-2017-6074 vulnerability has already been patched in the mainline kernel, users can apply the patch and rebuild the kernel of their OS or they can wait for the next kernel update from their Linux distro provider.
In December 2016, security experts discovered another privilege-escalation vulnerability in Linux kernel, tracked as CVE-2016-8655, that dated back to 2011.
The flaw was discovered by the security expert Phil Oester who dubbed it ‘Dirty COW.‘ The flaw could be exploited by a local attacker to escalate privileges.
The name “Dirty COW” is due to the fact that it’s triggered by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
Code Execution Flaw Affected Linux Kernel Since 2005
23.2.2017 securityweek Vulnerebility
A researcher has discovered a serious locally exploitable vulnerability that appears to have been around in the Linux kernel for more than 11 years. The flaw has been addressed in the kernel and Linux distributions are working on releasing patches.
The weakness, a double-free vulnerability tracked as CVE-2017-6074, was discovered by Google software engineering intern Andrey Konovalov using syzkaller, an open source Linux fuzzer developed by the tech giant.
The flaw affects the Datagram Congestion Control Protocol (DCCP) implementation for Linux since the release of version 2.6.14 in October 2005. In fact, this was the first kernel version to include support for DCCP.
According to the researcher, the vulnerability allows an unprivileged process to execute arbitrary code within the kernel. Affected Linux distributions said the flaw can be exploited for privilege escalation or denial-of-service (DoS) attacks.
“A flaw was found in the Linux kernel’s implementation of the DCCP protocol in which a local user could create influence timing in which a [socket buffer] could be used after it had been freed by the kernel,” explained Gentoo developer Thomas Deutschmann. “An attacker who is able to craft structures allocated in this free memory will be able to create memory corruption, privilege escalation or crash the system.”
The vulnerability was reported to Linux kernel developers on February 15 and a fix was released within two days. Linux distributions were informed about the flaw on February 18 and they are working on patches.
Fixes have already been released for Ubuntu, and Red Hat has informed users that the exploit can be mitigated using recent versions of SELinux.
Konovalov says he will make a proof-of-concept (PoC) exploit available after users have had a chance to update their installations.
11-Year Old Linux Kernel Local Privilege Escalation Flaw Discovered
22.2.2017 thehackernews Vulnerebility
Another privilege-escalation vulnerability has been discovered in Linux kernel that dates back to 2005 and affects major distro of the Linux operating system, including Redhat, Debian, OpenSUSE, and Ubuntu.
Over a decade old Linux Kernel bug (CVE-2017-6074) has been discovered by security researcher Andrey Konovalov in the DCCP (Datagram Congestion Control Protocol) implementation using Syzkaller, a kernel fuzzing tool released by Google.
The vulnerability is a use-after-free flaw in the way the Linux kernel's "DCCP protocol implementation freed SKB (socket buffer) resources for a DCCP_PKT_REQUEST packet when the IPV6_RECVPKTINFO option is set on the socket."
The DCCP double-free vulnerability could allow a local unprivileged user to alter the Linux kernel memory, enabling them to cause a denial of service (system crash) or escalate privileges to gain administrative access on a system.
"An attacker can control what object that would be and overwrite its content with arbitrary data by using some of the kernel heap spraying techniques. If the overwritten object has any triggerable function pointers, an attacker gets to execute arbitrary code within the kernel," full disclosure mailing list about the vulnerability reads.
DCCP is a message-oriented transport layer protocol that minimizes the overhead of packet header size or end-node processing as much as possible and provides the establishment, maintenance and teardown of an unreliable packet flow, and the congestion control of that packet flow.
This vulnerability does not provide any way for an outsider to break into your system in the first place, as it is not a remote code execution (RCE) flaw and require an attacker to have a local account access on the system to exploit the flaw.
Almost two months ago, a similar privilege-escalation vulnerability (CVE-2016-8655) was uncovered in Linux kernel that dated back to 2011 and allowed an unprivileged local user to gain root privileges by exploiting a race condition in the af_packet implementation in the Linux kernel.
The vulnerability has already been patched in the mainline kernel. So, if you are an advanced Linux user, apply the patch and rebuild kernel yourself.
OR, you can wait for the next kernel update from your distro provider and apply it as soon as possible.
Microsoft Flaws Mitigated by Removing Admin Rights: Avecto
22.2.2017 securityweek Vulnerebility
Microsoft patched a total of 530 vulnerabilities in 2016 and many of them were mitigated by the removal of administrator rights, according to a report published this week by endpoint security firm Avecto.
Avecto’s Microsoft Vulnerabilities Report for 2016 shows that 189 of the flaws fixed by the tech giant last year were classified as critical, and 94 percent of the Windows issues can be mitigated by removing admin rights. This mitigation works for all critical vulnerabilities affecting Internet Explorer and Edge, and 99 percent of Office flaws.
Roughly two-thirds of all the vulnerabilities affecting Microsoft products can be mitigated using this method. The percentage increased in 2016, but it has been at a fairly steady level over the past years.
According to Avecto, the number of security holes reported to Microsoft has increased by more than 60 percent in the past years, from 333 in 2013 to 530 in 2016. However, judging by the first round of updates for 2017, the number could drop significantly this year.
While Windows 10 has been advertised as the most secure version of the operating system, experts pointed out that it had the highest proportion of vulnerabilities compared to other versions. The number of flaws affecting Windows 10 was nearly 50 percent higher than in Windows 8 and 8.1. Removal of admin rights mitigated 93 percent of Windows 10 vulnerabilities.
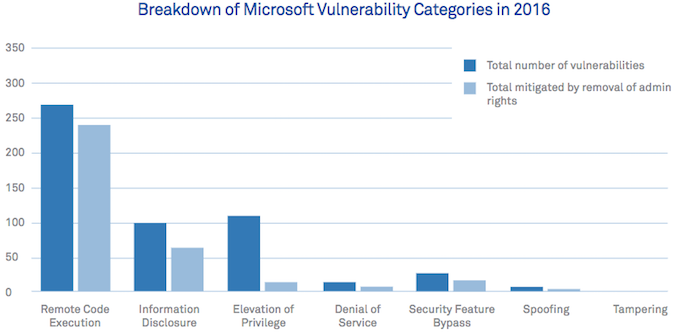
“Privilege management and application control should be the cornerstone of your endpoint security strategy, building up from there to create ever stronger, multiple layers of defense. These measures can have a dramatic impact on your ability to mitigate today's attacks,” explained Mark Austin, co-founder and co-CEO of Avecto. “Times have changed; removing admin rights and controlling applications is no longer difficult to achieve.”
Microsoft releases security updates for Flash Player, but two disclosed flaws remain unpatched
22.2.2017 securityaffairs Vulnerebility
On Tuesday Microsoft issued the security updates KB 4010250 that address flaws in Adobe Flash Player, but two already disclosed flaws remain unpatched.
On Tuesday Microsoft issued the security updates KB 4010250 that address flaws in Adobe Flash Player. The updates fix the vulnerabilities in Internet Explorer on Windows 8.1 and later, as well as Edge for Windows 10, but two already disclosed flaws remain unpatched.
The bad news is that two already disclosed flaws still remain uncovered by the security updates and could be exploited by attackers in the wild.
A few days ago, Microsoft announced that the February patches would be delayed until March due to a last minute issue, in response Google Project Zero experts published the details of the Remote Code Execution vulnerability in Windows.
Microsoft alerted its customers anticipating the incoming patches on Monday and urged them to update their systems as soon as possible.
Now Microsoft released the security patches and the company confirmed that “No other security updates are scheduled for release until the next scheduled monthly update release on March 14, 2017.”
The Bulletin MS17-005 for Adobe Flash Player addresses critical remote code execution (RCE) affecting Windows systems.
“Security Update for Adobe Flash Player (4010250) This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016.” reads the security bulletin.
SMB zero-day flaw
As anticipated, the two flaws will remain unpatched until 14th March, giving attackers the opportunity to target Windows systems.
The first flaw is a Windows SMB (Server Message Block) vulnerability that affects Windows 8, Windows 10 and Windows Server. It is a memory corruption vulnerability in the SMBprotocol that can be exploited by a remote attacker, the proof-of-concept exploit code of the flaw was recently publicly released.
The second flaw doesn’t address by the last security updates is the one recently disclosed by the Google Project Zero team that affects Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10.
Don’t waste time check for updates on your Windows PC and patch your system immediately to avoid the exploitation of the Flash Player software in your browser.
FTP Injection flaws in Java and Python allows firewall bypass
22.2.2017 securityaffairs Vulnerebility
The two programming languages, Java and Python, are affected by serious FTP Injection flaws that can be exploited by hackers to bypass any firewall.
Attackers can trick Java and Python applications to execute rogue FTP commands that would open ports in firewalls
The unpatched flaws reside in the way the two programming languages handle File Transfer Protocol (FTP) links, both don’t validate the syntax of the username parameter allowing attackers to trigger a so-called “protocol injection flaw.”Let’s see in details the two flaws:
Java/Python FTP Injection allows attackers to send unauthorized SMTP Emails
The security researcher Alexander Klink published the analysis of the FTP protocol injection vulnerability in Java’s XML eXternal Entity (XXE). The expert explained how to trigger the flaw to inject non-FTP malicious commands inside an FTP connection request.
It is important to highlight that the attack works even if the FTP connection fails, as FTP servers do support authentication, but doesn’t check for the present of carriage returns (CR) or line feeds (LF) in usernames.
“This attack is particularly interesting in a scenario where you can reach an (unrestricted, maybe not even spam- or malware-filtering) internal mail server from the machine doing the XML parsing.” states the blog post published by Alexander Klink. “It even allows for sending attachments, since the URL length seems to be unrestricted and only limited by available RAM (parsing a 400MB long URL did take more than 32 GBs of RAM for some reason, though ;-)).”

Java/Python FTP Injection allows attackers to Bypass Firewall
The security researcher Timothy Morgan from Blindspot Security devised a new attack technique leveraging on Java/Python FTP Injection to bypass firewalls.
The FTP protocol injection flaw could be exploited to trick the target firewall into accepting TCP connections from the web to the vulnerable host’s system on its “high” ports (from 1024 to 65535).”
FTP protocol injection attack is caused by an old and well-known security issue in FTP protocol called classic mode FTP that is still supported by default by many firewall vendors.
When a classic mode FTP connection is initiated, the firewall temporarily opens a port (typically included in the range 1024 and 65535) specified in the PORT command.
Using the FTP protocol injection issue in Java and Python, the attacker just needs to know the targeted host’s internal IP address while classic mode FTP connection is started.
In order to open a port in the targeted firewall the attackers need to make the following requests:
Determining Internal IP – Identify the victim’s internal IP address, in order to do it, the attackers “send an URL, see how the client behaves, then try another until the attack is successful.”
Packet Alignment – Determine packet alignment and ensure that the PORT command is injected at the right moment, making the attack work.
Exploit the vulnerability.
Once identified the process to bypass the firewall, all an attacker needs to do to launch the attack is to trick victims into accessing a malicious Java or Python applications running on a server to bypass the network defense.
“If a desktop user could be convinced to visit a malicious website while Java is installed, even if Java applets are disabled, they could still trigger Java Web Start to parse a JNLP (Java Network Launch Protocol) file,” Morgan said. “These files could contain malicious FTP URLs which trigger this bug.” reads the analysis.
“Also note, that since Java parses JNLP files before presenting the user with any security warnings, the attack can be entirely successful without any indication to the user (unless the browser itself warns the user about Java Web Start being launched).”
A similar flaw resides in Python’s urllib2 and urllib libraries, although “this injection appears to be limited to attacks via directory names specified in the URL.”
Both flaws were already reported to the companies, the FTP protocol injection flaw was reported to the Python team in January 2016 and Oracle in November 2016, but they are still unpatched.
Morgan has also developed a proof-of-concept (PoC) exploit code that he will release only after both Oracle and Python will relaese the necessary security updates.
According to Morgan his exploit code has successfully been tested against Palo Alto Networks and Cisco ASA firewalls, the list of vulnerable network security devices could include many other systems.
Below Morgan’s recommendations:
Consider uninstalling Java from all desktop systems. If this is not possible due to legacy application requirements, disable the Java browser plugin from all browsers and disassociate the .jnlp file extension from the Java Web Start binary.
Consider requesting an update to fix these issues from Oracle and the Python Software Foundation. Be sure to apply security updates to all versions of Java and Python, including those running on application servers and appliances.
Disable classic mode FTP in all firewalls, allowing only passive mode.
Microsoft releases update for Flash Player, but leaves two disclosed Flaws Unpatched
22.2.2017 thehackernews Vulnerebility
Microsoft on Tuesday released security update (KB 4010250) to patch flaws in Adobe Flash Player for its customers using Internet Explorer on Windows 8.1 and later, as well as Edge for Windows 10, but two already disclosed flaws remain unpatched.
Just last week, Microsoft announced that its February patches would be delayed until March due to a last minute issue, a move that led to Google publishing details of an unpatched Windows bug.
However, the software giant emailed a handful of big business to alert them to the incoming patches on Monday, advising them to update their systems as soon as possible.
The security patches are now available to all Windows customers over Windows Update, and "No other security updates are scheduled for release until the next scheduled monthly update release on March 14, 2017," Microsoft says.
Bulletin MS17-005 for Adobe Flash Player addresses remote code execution (RCE) vulnerabilities for some currently supported Windows systems.
The flaws are rated "Critical" for Windows client operating systems to Windows 8.1 and Windows Server 2016, but "Moderate" for Windows Server 2012.
But Microsoft Won't Patch Two Disclosed Flaws Until 14th March
However, two security vulnerabilities, which have already been publicly disclosed with working exploit code, remain still unpatched, giving attackers enough time to target Windows users.
First one is a Windows SMB vulnerability that affects Windows 8, Windows 10 and Windows Server. The proof-of-concept exploit code of this flaw was released just over a week ago.
The other one is the flaw disclosed by Google earlier this week that affects Microsoft's Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10 that had yet to be patched.
Google disclosed the vulnerability, which resides in Windows' Graphics Device Interface (GDI) library, with POC exploit, meaning attackers can exploit the vulnerability before Microsoft issue a patch.
The latest security patches come a week after Microsoft's usual Patch Tuesday.
Since details of the security updates released by Microsoft on Tuesday remain sketchy, what these patches resolve is not currently known.
So if you check for updates on your Windows PC and find one waiting for you, don't be surprised and patch your software immediately to make sure your Flash Player software is secure, though you’ll still be waiting until March 14 for the complete Patch Tuesday fix.
Microsoft Releases Security Update for Flash Player Libraries
22.2.2017 securityweek Vulnerebility
While most of this month’s security updates have been postponed to March 14, Microsoft has decided to release one bulletin to address the Flash Player vulnerabilities fixed by Adobe on Patch Tuesday.
The critical bulletin, MS17-005, resolves 13 vulnerabilities in the Flash Player libraries used by Internet Explorer 10, Internet Explorer 11 and Edge.
The patches, obtainable via Windows Update and the Microsoft Update Catalog, are available for Windows 8, Windows RT 8.1, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016, and Windows 10.
The Flash Player flaws patched by Adobe this month are memory corruption issues that can be exploited for arbitrary code execution. They were reported to the vendor by researchers at Google Project Zero, Microsoft, Palo Alto Networks, Fortinet’s FortiGuard Labs and CloverSec Labs.
There had been no evidence of exploits in the wild, but apparently Microsoft decided that the flaws are serious enough to warrant the release of an out-of-band update.
There are at least two Windows zero-day vulnerabilities that Microsoft is expected to address next month. One of them is a denial-of-service (DoS) flaw caused by how SMB traffic is handled.
The second one is a medium severity information disclosure issue discovered by Google Project Zero researchers. Google made the details of the security hole public after Microsoft failed to release a patch within 90 days.
Microsoft still hasn’t shared any information on why it had to delay the February patches, only saying that it was a last minute issue. Some have speculated that it could have something to do with cumulative updates or an infrastructure problem.
Unpatched Python and Java Flaws Let Hackers Bypass Firewall Using FTP Injection
21.2.2017 thehackernews Vulnerebility
This newly discovered bugs in Java and Python is a big deal today.
The two popular programming languages, Java and Python, contain similar security flaws that can be exploited to send unauthorized emails and bypass any firewall defenses.
And since both the flaws remain unpatched, hackers can take advantage to design potential cyber attack operations against critical networks and infrastructures.
The unpatched flaws actually reside in the way Java and Python programming languages handle File Transfer Protocol (FTP) links, where they don't syntax-check the username parameter, which leads to, what researchers call, protocol injection flaw.
Java/Python FTP Injection to Send Unauthorized SMTP Emails
In a blog post published over the past week, security researcher Alexander Klink detailed the FTP protocol injection vulnerability in Java's XML eXternal Entity (XXE) that allows attackers to inject non-FTP malicious commands inside an FTP connection request.
To demonstrate the attack, Alexander showed how to send an unauthorized email via SMTP (Simple Mail Transfer Protocol) in an FTP connection attempt, even though the FTP connection failed, as FTP servers does support authentication, but doesn't check for the present of carriage returns (CR) or line feeds (LF) in usernames.
"This attack is particularly interesting in a scenario where you can reach an (unrestricted, maybe not even spam- or malware-filtering) internal mail server from the machine doing the XML parsing," Alexander concluded.
Java/Python FTP Injections Allow to Bypass Firewall
However, two days later in a separate security advisory, security researcher Timothy Morgan from Blindspot Security came forward with his findings, showing more threatening exploitation scenario where the FTP URL handlers in both Java and Python can be used to bypass firewalls.
Morgan said such FTP protocol injection flaw could be used to trick a victim's firewall into accepting TCP connections from the web to the vulnerable host's system on its "high" ports (from 1024 to 65535).
Besides the FTP protocol injection attack, there's reside a decade old security issue in FTP protocol called classic mode FTP – an insecure mechanism of client-server FTP interactions, but many firewall vendors still support it by default.
When a classic mode FTP connection is initiated, the firewall temporarily opens a port – typically between 1024 and 65535 – specified in the PORT command, which introduces security risks.
Using the FTP protocol injection issue in Java and Python, an attacker who knows the targeted host’s internal IP address can start a classic mode FTP connection, which attackers can use for nefarious purposes.
Morgan has determined that an attacker can open up one port in the targeted firewall with only three requests:
Identify the victim's internal IP address – this requires an attacker to "send an URL, see how the client behaves, then try another until the attack is successful."
Determine packet alignment and ensure that the PORT command is injected at the right moment, making the attack work.
Exploit the vulnerability.
Each additional request can be used to open up another TCP port.
Easily Exploitable Protocol Injection Flaw
However, the researcher warned that his exploit could be used for man-in-the-middle (MitM) attacks, server-side request forgery (SSRF), an XEE attack and more – and once bypassed the firewall, desktop hosts can be attacked even if they do not have Java installed.
All an attacker need is to convince victims into accessing a malicious Java or Python applications installed on a server to bypass the entire firewall.
"If a desktop user could be convinced to visit a malicious website while Java is installed, even if Java applets are disabled, they could still trigger Java Web Start to parse a JNLP (Java Network Launch Protocol) file," Morgan said. "These files could contain malicious FTP URLs which trigger this bug."
"Also note, that since Java parses JNLP files before presenting the user with any security warnings, the attack can be entirely successful without any indication to the user (unless the browser itself warns the user about Java Web Start being launched)."
According to Morgan, a nearly identical flaw also exists in Python's urllib2 and urllib libraries, although "this injection appears to be limited to attacks via directory names specified in the URL."
Protocol Injection Flaw Is Still Unpatched
Morgan said the FTP protocol injection flaw was reported to the Python team in January 2016 and Oracle in November 2016 by his company, but neither of the two has issued any update to address the issue.
Morgan has developed a proof-of-concept (PoC) exploit but is currently holding back publication of his exploit until Oracle and Python respond to the disclosure and release patches.
The Morgan's exploit has successfully been tested against Palo Alto Networks and Cisco ASA firewalls, though researchers believe many commercial firewalls are also vulnerable to FTP stream injection attacks.
So until patches become available, Morgan suggests users uninstall Java on their desktops and in browsers, as well as disable support for "classic mode" FTP on all firewalls.
Unpatched Flaws in Python, Java Allow Firewall Bypass
21.2.2017 securityweek Vulnerebility
Unpatched vulnerabilities related to how Java and Python handle file transfer protocol (FTP) URLs can be exploited for various purposes, including for sending unauthorized emails and bypassing firewalls, researchers warned.
In a blog post published over the weekend, Alexander Klink showed how XML external entity (XXE) and server-side request forgery (SSRF) vulnerabilities can be exploited to send emails via SMTP (Simple Mail Transfer Protocol) commands using specially crafted FTP URLs.
Klink’s attack method relies on Java XML parsers and the expert believes it can be particularly useful for scenarios where the attacker has access to an internal mail server from the system that does the XML parsing. The researcher showed how a specially crafted FTP URL can be used to send emails, including ones with attachments.
However, according to Blindspot Security’s Timothy Morgan, the attack method can be used for more than just sending emails. Furthermore, in addition to Java’s FTP URL handling code, a similar vulnerability affects Python’s urllib and urllib2 libraries.
After seeing Klink’s blog post, Morgan also published an advisory describing his findings. He pointed out that such FTP injections can be used to trick a firewall into accepting TCP connections from the Web to the vulnerable system on a specified port.
When a classic mode FTP connection is initiated, the firewall needs to temporarily open a port – typically between 1024 and 65535 – specified in the PORT command. This has been known to introduce security risks for well over a decade, but many firewall vendors still support classic mode FTP by default.
Using the vulnerability, an attacker who knows the targeted host’s internal IP address can inject a malicious PORT command into the stream and open an arbitrary port. The challenge is to determine the victim’s IP address and ensure that the PORT command is sent at the beginning of a packet.
Morgan has determined that an attacker can open up one port in the targeted firewall with only three requests: one to identify the victim’s internal IP, one to determine packet alignment and ensure that the PORT command is injected at the right moment, and one to actually exploit the vulnerability. Each additional request can be used to open up another TCP port.
There are several methods that can be used to exploit the flaw, including via man-in-the-middle (MitM), SSRF and XXE attacks. The most “startling” attack scenario, according to Morgan, involves JNLP (Java Network Launch Protocol) files.
“If a desktop user could be convinced to visit a malicious website while Java is installed, even if Java applets are disabled, they could still trigger Java Web Start to parse a JNLP file. These files could contain malicious FTP URLs which trigger this bug,” Morgan explained. “Also note, that since Java parses JNLP files before presenting the user with any security warnings, the attack can be fully successful without any indication to the user (unless the browser itself warns the user about Java Web Start being launched).”
Python developers were notified about the issue more than one year ago, and Oracle was provided the details of the attack method in November. However, the issue still hasn’t been addressed in either Java or Python.
Morgan has developed a proof-of-concept (PoC) exploit, but it will only be made public after Oracle and Python release patches.
The method has been tested against Palo Alto Networks and Cisco ASA firewalls, but experts believe many commercial firewalls are vulnerable to FTP stream injection attacks.
Until patches become available, attacks can be prevented by uninstalling Java and by disabling classic mode FTP in firewalls.
Siklu fixed a serious RCE vulnerability in the Siklu EtherHaul Radios
21.2.2017 securityaffairs Vulnerebility
The security researcher Ian Ling discovered a serious remote command execution (RCE) flaw in the Siklu EtherHaul Radios devices.
Security expert Ian Ling has discovered a severe remote command execution (RCE) vulnerability in the Siklu’s EtherHaul wireless point-to-point radios.
The flaw could be exploited by remote unauthenticated attackers to execute commands and retrieve sensitive information, including usernames and plaintext passwords from the device.
The Israeli firm Siklu has already released a patch to address the vulnerability in the vast majority of its products that have been sold to mobile operators, service providers, wireless security network operators, governments, and enterprises.
The security expert discovered the flaw while testing a feature in the web interface that could be used by operators to configure one radio from another that has a wireless connection to it.
“Siklu EtherHaul devices (wireless point-to-point radios) have a feature in the web interface that allows you to configure both radios in a pair from either side.” reads the post published by the experts.

Ling noticed that the EtherHaul radios have three ports open, the 22 and 443 for management purposes, and the 555 (its use was not clear).
Further analysis of the port 555 allowed the researchers to discover that the service it exposes requires only a username for the authentication process. This means that a remote attacker can send specially crafted requests that look like sent from another Siklu EtherHaul device in order to execute arbitrary commands on the radio.
“Using another vulnerability I found on the EtherHauls, I was able to log in as root and access a Linux shell. The EtherHauls have a tcpdump binary on them, which allowed me to record a packet capture of all traffic involving port 555 and see exactly what data was being sent between the devices.” continues the analysis.
“Prior to the “mo-info rf” command being sent, the device making the request first “authenticates” by sending the username of whoever is logged in, surrounded by a lot of null bytes:”
The researcher discovered that using specific commands it was possible to retrieve login credentials of the EtherHauls and set a new administrator password.
Ling has published the following proof-of-concept (PoC) code exploits:
Show username and password in plaintext: https://gist.github.com/ianling/c06636fba1b294393f0d3b7df082aa91
Set password to “Abc123123″: https://gist.github.com/ianling/6f4b8c76aa369618e3ae7dd494958762
The vulnerability was reported to Siklu on December 22 and the company issued security updates on February 13.
Last year, Ling has spotted another serious vulnerability in the Siklu EtherHaul radios, a hidden root account that had the same unchangeable password on all devices.
Severe Vulnerability Patched in Siklu Radios
21.2.2017 securityweek Vulnerebility
Researcher Ian Ling has discovered a serious remote command execution (RCE) vulnerability in Siklu’s EtherHaul wireless point-to-point radios. Updates that patch the flaw have been released for a majority of the affected products.
Siklu is a Tel-Aviv, Israel-based company that specializes in millimeter wave wireless connectivity radios. The firm says it has a 30% market share and it has sold thousands of radios worldwide to mobile operators, service providers, wireless security network operators, governments and enterprises.
Ling discovered the vulnerability while analyzing a feature in the web interface that allows users to configure one radio from another that has a wireless connection to it. An analysis showed that EtherHaul radios have three ports open, including TCP port 555, which devices connect to during this process.
An analysis of the traffic on port 555 led the researcher to discover that the service running on this port requires only a username for authentication. This allows an attacker to send specially crafted requests that appear to come from another EtherHaul device and execute arbitrary commands on the radio.
One of the commands can be used to retrieve the device’s username and password in plain text. Another command can be leveraged to set a new administrator password. Ling has published proof-of-concept (PoC) code for both these exploits.
According to the expert, the service running on port 555 can be accessed by anyone over the Internet as it is not protected by a firewall or an access control list (ACL).
The vulnerability was reported to Siklu on December 22 and patches were released on February 13. Updates have been made available for all EtherHaul radios, except for models that have reached end of life.
This is not the first time Ling has identified a serious vulnerability in Siklu EtherHaul radios. Roughly one year ago, he reported finding a hidden root account that had the same unchangeable password on all devices. The account, accessible via the device’s interface and SSH, granted access to the underlying Linux operating system, giving an attacker full control.
Bug Allowed Theft of Over $400,000 in Zcoins
20.2.2017 securityweek Vulnerebility
An implementation bug has allowed someone to make a profit of more than $400,000 after creating roughly 370,000 units of the Zcoin cryptocurrency, users were told on Friday.
Zcoin (XZC), worth approximately $2 per unit, is an implementation of the Zerocoin protocol, which aims to provide fully anonymous currency transactions. Zerocoin has also been used to create a new protocol called Zerocash and the ZCash digital currency.
A typo in the code allowed an attacker to fraudulently obtain Zcoins. They managed to create roughly 370,000 coins and sold a majority of it for a profit of approximately 410 bitcoins ($435,000).Zcoin
Zcoin representatives pointed out that the exploit was possible due to a bug in the code and not a cryptographic weakness, and that the anonymity provided by Zerocoin has not been compromised. Zcoin said the damage was “mostly absorbed by the markets.”
“From what we can see, the attacker (or attackers) is very sophisticated and from our investigations, he (or she) did many things to camouflage his tracks through the generation of lots of exchange accounts and carefully spread out deposits and withdrawals over several weeks,” said Zcoin’s Reuben Yap.
Ian Miers, one of the founders of ZCash, has provided a likely explanation for what went wrong. Miers believes it was probably a bug that resulted from copying and pasting code.
The bug was addressed over the weekend and pools and exchanges have been instructed to update their code. Zcoin said no coins will be forfeited or blacklisted, despite the severity of the hack.
Incidents involving cryptocurrencies are not uncommon. In June 2016, the value of the Ethereum digital currency plummeted after someone exploited a vulnerability in the DAO.
Google Discloses Unpatched Windows GDI Vulnerability
20.2.2017 securityweek Vulnerebility
An unpatched vulnerability affecting the Windows Graphics Device Interface (Windows GDI) was publicly disclosed last week after Microsoft failed to address it within 90 days after being notified.
The issue was disclosed by Mateusz Jurczyk, an engineer with Google's Project Zero team, who initially discovered it along with other bugs in the user-mode Windows GDI library (gdi32.dll) in March 2016. Microsoft attempted to address these issues with the June 2016 set of monthly patches (security bulletin MS16-074), but apparently failed to do so.
While taking a look at the patched gdi32.dll, the Google security researcher discovered that some of the bugs were indeed resolved, but that others were still presenting security risks. In November 2016, the researcher filed another report to inform Microsoft on his findings.
As per Google’s Project Zero’s policy, vendors are provided with 90 days to resolve the reported vulnerabilities before they become public knowledge. As soon as the 90 days passed, the report went public, along with a proof-of-concept published by Jurczyk.
This public disclosure, however, appears to have been timed with the publishing of Microsoft’s February 2017 security update, which was expected to happen on February 14, but was delayed for one month “due to a last minute issue that could impact some customers.” The patches were expected to resolve a previously revealed high risk SMB 0-day as well.
Tracked as CVE-2017-0038, the newly disclosed vulnerability is related to the handling of DIBs (Device Independent Bitmaps) embedded in EMF records. Last year, Google’s Jurczyk found missing checks “in at least 10 different records,” and says that Microsoft was able to nail only some of them with MS16-074, but that some of them are still posing security risks.
Jurczyk notes that a careful audit of all EMF record handlers that are responsible for dealing with DIBs is required, as it would ensure that all of them can correctly enforce all four conditions. If not all conditions are enforced, invalid memory access (and subsequent memory disclosure) while processing the bitmaps is possible.
The security researcher managed to reproduce the vulnerability locally in Internet Explorer and remotely in Office Online, via a .docx document containing the specially crafted EMF file. The flaw is considered Medium severity.
In November last year, Google went public with information related to a 0-day vulnerability in Windows only 10 days after informing Microsoft on the matter, although a patch hadn’t been released yet. That disclosure too fell within the search giant’s policy, which gives vendors a 7-day deadline to resolve issues actively exploited by malicious actors.
A couple of years ago, Google made changes to its vulnerability disclosure policy after being criticized for enforcing it too strictly.
Microsoft failed to patch a flaw in GDI library, Google released a PoC exploit
19.2.2017 Securityaffairs Vulnerebility
Security experts at the Google Project Zero group have publicly disclosed a vulnerability affecting Microsoft’s Windows OS.
It has happened again, the hackers at Google Project Zero have publicly disclosed a vulnerability affecting Microsoft’s Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10, that had yet to be patched by the IT giant.
The experts also published a proof-of-concept exploit code.
In October, the experts at the Google Project Zero publicly disclosed a critical Windows zero-day vulnerability ten days after reporting it to Microsoft.
According to Google, the reason for going public without waiting for a patch is that its experts have observed exploits for the flaw in the wild.
According to Google disclosure timeline for vulnerability, when a flaw is exploited in the wild Google public disclosed the flaw after seven days.
Back to the present, the experts at Project Zero publicly disclosed the flaw in Windows OS because Microsoft failed to patch it within the 90-day window given by the Google.
The flaw affected the Windows’ Graphics Device Interface (GDI) library, the Google’s Project Zero member Mateusz Jurczyk reported it to the Microsoft Security Team on the 9th of June last year.
The impact of the vulnerability is serious, it affects any application that uses this GDI library. An attacker can exploit the vulnerability to steal sensitive data from the memory of the vulnerable system.
As explained before, Microsoft failed to address the flaw in the GDI library with a patch released on 15th June. The security updates did not solve all the issues in the Windows library, for this reason, the Project Zero experts report it to Microsoft with a proof-of-concept on 16th of November.
“As a result, it is possible to disclose uninitialized or out-of-bounds heap bytes via pixel colors, in Internet Explorer and other GDI clients which allow the extraction of displayed image data back to the attacker,” states Jurczyk in the second report.
Three months have passed, but Microsoft failed to solve the vulnerability so Google security experts released the details of the flaw to the public.
This implies that threat actors in the wild now can exploit the flaw in targeted attacks.
The good news, in this case, is that an attacker needs a physical access to the target machine to exploit the vulnerability.
Recently Microsoft delayed this month’s Patch Tuesday by a month due to “a last-minute issue that could impact some customers and was not resolved in time for [Microsoft’s] planned updates” on 14th February.
Experts believe that the flaw in the GDI library will remain unsolved for almost a month, this means that attackers in the wild may exploit it.
Google Discloses Windows Vulnerability That Microsoft Fails To Patch, Again!
18.2.2017 thehackernews Vulnerebility
Google Discloses Windows Vulnerability That Microsoft Fails To Patch, Again!
Microsoft is once again facing embarrassment for not patching a vulnerability on time.
Yes, Google's Project Zero team has once again publicly disclosed a vulnerability (with POC exploit) affecting Microsoft's Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10 that had yet to be patched.
A few months back, the search engine giant disclosed a critical Windows vulnerability to the public just ten days after revealing the flaw to Microsoft.
However, this time Google revealed the vulnerability in Windows to the public after Microsoft failed to patch it within the 90-day window given by the company.
Google's Project Zero member Mateusz Jurczyk responsibly reported a vulnerability in Windows' Graphics Device Interface (GDI) library to Microsoft Security Team on the 9th of June last year.
The vulnerability affects any program that uses this library, and if exploited, could potentially allow hackers to steal information from memory.
While Microsoft released a patch for the vulnerability on 15th June, the company did not fix all the issues in the GDI library, forcing the Project Zero researcher to once again report it to Microsoft with a proof-of-concept on 16th of November.
"As a result, it is possible to disclose uninitialized or out-of-bounds heap bytes via pixel colors, in Internet Explorer and other GDI clients which allow the extraction of displayed image data back to the attacker," Jurczyk notes in the new report.
Now, after giving the three-month grace period to the company, Google released the details of the vulnerability to the public, including hackers and malicious actors.
Google Project Zero team routinely finds security holes in different software and calls on the affected software vendors to publicly disclose and patch bugs within 90 days of discovering them. If not, the company automatically makes the flaw along with its details public.
Although Windows users need not panic, as hackers will require physical access to the host machine to exploit the vulnerability, the Redmond giant will have to release an emergency patch before sophisticated exploits are developed.
Microsoft recently delayed its this month's Patch Tuesday by a month due to "a last-minute issue that could impact some customers and was not resolved in time for [Microsoft's] planned updates" on 14th February.
So, if there is no expected emergency patch this month, this newly disclosed vulnerability will be left open for hackers for almost a month to exploit — just like we saw last time when Russian hackers actively exploited then-unpatched Windows kernel bug in the wild — which could put Windows users at potential risk.
Apple Patches Code Execution Flaw in GarageBand
16.2.2017 securityweek Vulnerebility
An update released this week by Apple for the music creation app GarageBand addresses a high severity vulnerability that can be exploited for arbitrary code execution.
The vulnerability, discovered by researchers at Cisco Talos and reported to Apple in mid-December, is an out-of-bounds write issue caused due to the way saved files are parsed. An attacker can exploit the flaw by getting the targeted user to open a specially crafted GarageBand project file (.band).
“The format is broken into chunks with a specific length field for each,” explained Tyler Bohan, the Cisco Talos researcher who found the bug. “This length is controlled by the user and can be leveraged to expose an exploitable condition.”
Apple first attempted to patch the vulnerability, which it describes as a memory corruption issue, on January 18 with the release of GarageBand 10.1.5 for OS X and macOS.
However, researchers determined that the fix had been incomplete so Apple released GarageBand 10.1.6 on Monday in an effort to properly address the flaw.
The vulnerability also affects Apple’s Logic Pro X audio production suite. Apple claimed to have addressed the flaw in mid-January with the release of version 10.3.
The CVE identifiers assigned to this security hole are CVE-2017-2374 and CVE-2017-2372. Technical details are available in advisories published by Cisco Talos.
This is not the first time Talos researchers have found vulnerabilities in Apple software. In July 2016, they reported discovering several remote code execution vulnerabilities in iOS and OS X that could be exploited using specially crafted image files.
High Severity Flaw Patched in OpenSSL 1.1.0
16.2.2017 securityweek Vulnerebility
A high severity denial-of-service (DoS) vulnerability was patched on Thursday in OpenSSL with the release of version 1.1.0e.
The flaw, tracked as CVE-2017-3733, has been described as an “Encrypt-Then-Mac renegotiation crash.” The security hole, reported by Joe Orton of Red Hat on January 31, does not affect OpenSSL 1.0.2.
“During a renegotiation handshake if the Encrypt-Then-Mac extension is negotiated where it was not in the original handshake (or vice-versa) then this can cause OpenSSL to crash (dependent on ciphersuite). Both clients and servers are affected,” the OpenSSL Project said in its advisory.
The OpenSSL Project has once again reminded users that versions 1.0.1, 1.0.0 and 0.9.8 are not supported and they no longer receive security updates. Version 1.0.2 has a long term support (LTS) date of December 31, 2019, and there are no plans for a 1.0.3 release.
This is the second security update released this year. The first, released in late January, patched four low and moderate severity vulnerabilities.
Microsoft Postpones February Security Updates to March 14
16.2.2017 securityweek Vulnerebility
Microsoft has informed customers that the February security updates, which the company delayed due to unspecified issues, will only be released next month as part of the planned Update Tuesday.
The February 2017 security updates should have been released on Tuesday, but the company told users that the patches had to be delayed “due to a last minute issue that could impact some customers.”
Microsoft shared an update on Wednesday, saying that the February patches will be merged with the ones scheduled for release on March 14.
Johannes B. Ullrich, dean of research at the SANS Technology Institute, believes this is “probably overall the least disruptive solution at this point.”
Since Microsoft decided to postpone the release of the security fixes by a full month, it is likely that none of the vulnerabilities they were supposed to address are critical, although many are concerned about an unpatched denial-of-service (DoS) flaw in Windows caused by how SMB traffic is handled.
It’s still unclear what the last minute issue is, but many believe it could have something to do with cumulative updates. Although, some experts speculated that there may have been a different problem.
“Before the cumulative update model, a single patch could be pulled from the release without impacting the entire Patch Tuesday release. Now, speculation as to if this was an issue with one of the cumulative updates that caused this delay is not entirely unfounded, but thinking about this, if it were one update that was broken Microsoft could release everything else,” said Chris Goettl, product manager with Ivanti. “The fact is Microsoft didn¹t release anything, which sounds more like an infrastructure issue.”
In addition to the SMB-related vulnerability, the next security updates could patch a medium-severity information disclosure flaw discovered by Google Project Zero researchers. The weakness, tracked as CVE-2017-0038, was reported to Microsoft on November 16 and its details were disclosed on Wednesday after the 90 day deadline.
Microsoft will no longer publish security bulletins, replacing them with an online database called Security Updates Guide.
Adobe just fixed thirteen code execution flaws in Flash Player
15.2.2017 securityaffairs Vulnerebility
Adobe addressed thirteen highest severity code execution vulnerabilities in Flash Player for Windows, MAC OS, and Chrome.
Adobe released security updates that address two dozen vulnerabilities in Flash Player, Digital Editions, and the Campaigns marketing tool.
Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. The updates address critical vulnerabilities that could be exploited by an attacker to take control of the vulnerable system.
Flash Player 24.0.0.221 addressed 13 critical code execution flaws, including type confusion, integer overflow, use-after-free, heap buffer overflow and other memory corruption issues.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system.” reads the Adobe Security Advisory for the Flash product.
The flaws were discovered by researchers at Google Project Zero, Microsoft, Palo Alto Networks, Fortinet’s FortiGuard Labs and CloverSec Labs who reported the security issued to Adobe.
Nine flaws affecting the Digital Editions ebook reader were also fixed by Adobe with the release of version 4.5.4 for Windows, Mac, and Android.
Adobe fixed several kinds of vulnerabilities including a critical heap-based buffer overflow that can be exploited for arbitrary code execution and several important buffer overflows that could lead to a memory leak.
The flaws were discovered by the researcher Steven Seeley of Source Incite and Ke Liu of Tencent’s Xuanwu LAB.
“Adobe has released a security update for Adobe Digital Editions for Windows, Macintosh and Android. This update resolves a critical heap buffer overflow vulnerability that could lead to code execution and important buffer overflow vulnerabilities that could lead to a memory leak.” reads the Adobe Security Advisory for the Digital Editions product.
Adobe Flash Player flaws
The last set of flaws was affecting the Adobe Campaign product for Windows and Linux, the release of Adobe Campaign 6.11 addresses a moderate severity security bypass flaw affecting the client console. The flaws could be exploited by an authenticated attacker to upload and execute a malicious file, which could result in read/write access to the system.
The experts also fixed another flaw in the latest version of Campaign, it is a moderate severity input validation issue that can be exploited for cross-site scripting (XSS) attacks. The flaws were reported to Adobe by researcher Léa Nuel.
“Adobe has released a security update for Adobe Campaign v6.11 for Windows and Linux. This update resolves a moderate security bypass affecting the Adobe Campaign client console. An authenticated user with access to the client console could upload and execute a malicious file, potentially resulting in read and write access to the system (CVE-2017-2968). This update also resolves a moderate input validation issue that could be used in cross-site scripting attacks (CVE-2017-2969).” reads the Adobe Security Advisory for the Adobe Campaign product.
SAP Patches 22 Vulnerabilities With February 2017 Security Updates
14.2.2017 securityweek Vulnerebility
SAP on Tuesday announced the release of its February 2017 security updates, which includes 15 Patch Day Security Notes and 3 updates to previously released Patch Day Security Notes.
Only High risk and Medium severity vulnerabilities were addressed this month, with the highest CVSS score of the vulnerabilities being 8.5. Multiple patches were released for SAP's HANA database management system.
According to ERPScan, a company specialized in securing SAP and Oracle products, SAP’s February 2017 Security Patch Day also saw the release of 7 Support Package Notes, for a total of 22 patches across products. 7 of the patches were rated High risk, while the remaining 15 were assessed as Medium severity.
The most common vulnerability type addressed this month is Missing Authorization check (5 patches), followed by Cross-Site Scripting (4 patches), denial of service (3 patches), and XML external entity (2 patches). The remaining 8 flaws include: directory transversal, implementation flaw, privilege escalation, buffer overflow, ABAP code injection, cross-site request forgery, clickjacking, and multiple issues.
The most important issues addressed this month include a Missing Authorization Check vulnerability (CVSS Base Score: 8.5) in SAP Netweaver Data Orchestration (which could allow an attacker to access the service without authorization and use service functionality that has restricted access), along with an Implementation flaw vulnerability (CVSS Base Score: 8.2) in SAP GRC Access Control EAM (which can cause unpredictable behavior of a system, troubles with stability and safety).
Additionally, SAP patched a Memory Corruption vulnerability (CVSS Base Score: 8) in SAP 3D Visual Enterprise Author, Generator and Viewer, which could allow an attacker to inject a specially crafted code into a working memory which will be executed by the vulnerable application (the executed commands run with the same privileges as the service that executed the command).
Three of the issues were disclosed by ERPScan researchers, including multiple vulnerabilities in SAP HANA (CVSS Base Score: 8.3) – namely a denial of service that could allow an attacker to crush a process of a vulnerable component, and an Implementation Flaw (insecure default user creation policy) in third-party repository server Sinopia –, and an XML external entity vulnerability in SAP Visual Composer VC70RUNTIME (CVSS Base Score: 6.5).
The vulnerabilities in SAP HANA can be exploited together, ERPScan says: “The first vulnerability allows an attacker to create a new user over the Internet without authentication. After that, an adversary can create a new repository. If a package name contains special characters, the server will crash. As a result of the attack, the project would be unavailable meaning a stoppage of developing processes. Moreover, the vendor’s advisory states that other SAP HANA XS components also could be potentially impacted.”
In related news, Microsoft announced on Tuesday that a last minute issue forced the company to delay the release of its security updates for February 2017. It’s unclear when the patches will be made available.
Over a Dozen Code Execution Flaws Patched in Flash Player
14.2.2017 securityweek Vulnerebility
Adobe on Tuesday released security updates that address two dozen vulnerabilities in Flash Player, Digital Editions and the Campaigns marketing tool, but none of the flaws have been exploited in the wild.
Flash Player 24.0.0.221 patches 13 critical vulnerabilities that can be exploited for arbitrary code execution, including type confusion, integer overflow, use-after-free, heap buffer overflow and other memory corruption issues.
The security holes were reported to Adobe by researchers at Google Project Zero, Microsoft, Palo Alto Networks, Fortinet’s FortiGuard Labs and CloverSec Labs.
In the Digital Editions ebook reader Adobe fixed nine flaws with the release of version 4.5.4 for Windows, Mac and Android. The patched vulnerabilities include a critical heap-based buffer overflow that can be exploited for arbitrary code execution and several important buffer overflows that could lead to a memory leak.
A majority of the flaws were reported to Adobe by Steven Seeley of Source Incite, but the critical issue was identified by Ke Liu of Tencent's Xuanwu LAB.
With the release of Adobe Campaign 6.11 for Windows and Linux, the vendor patched a moderate severity security bypass flaw affecting the client console. The weakness allows an authenticated attacker to upload and execute a malicious file, which could result in read/write access to the system.
A second flaw addressed in the latest version of Campaign is a moderate severity input validation bug that can be exploited for cross-site scripting (XSS) attacks. The vulnerabilities were reported to Adobe by researcher Léa Nuel.
Last Minute Issue Delays Microsoft Security Updates
14.2.2017 securityweek Vulnerebility
Microsoft has apologized to customers “for any inconvenience” after a last minute issue forced the company to delay the release of its security updates for February 2017. It’s unclear when the patches will be made available.
“Our top priority is to provide the best possible experience for customers in maintaining and protecting their systems. This month, we discovered a last minute issue that could impact some customers and was not resolved in time for our planned updates today,” Microsoft said. “After considering all options, we made the decision to delay this month’s updates.”
The security updates released by the company for January 2017 consisted of only four bulletins, including one for Flash Player fixes. It is unclear how many flaws will be patched this month, but many hope Microsoft will address the recently disclosed denial-of-service (DoS) flaw in Windows caused by how SMB traffic is handled.
Starting with this month, Microsoft will no longer publish security bulletins, replacing them with an online database called Security Updates Guide. For January, the company published both security bulletins and some release notes in the Security Updates Guide.
Microsoft has recently introduced a new patch process that includes a Monthly Rollup, which contains both security and non-security fixes, a preview of the Monthly Rollup, and security-only updates.
In order to reduce the size of the security-only update, starting with this month, Internet Explorer patches will be made available as a separate update. The Monthly Rollup will include all patches, including the ones for IE.
The decision to separate the browser updates was made after users asked Microsoft to provide increased flexibility by allowing them to independently deploy Windows and Internet Explorer patches.
Johannes B. Ullrich, dean of research at the SANS Technology Institute, speculated that this change in process may have caused this month’s delay.
Potentially Serious DoS Flaw Patched in BIND
11.2.2017 securityweek Vulnerebility
A potentially serious denial-of-service (DoS) vulnerability was patched this week by the Internet Systems Consortium (ISC) in the BIND DNS software.
The flaw, tracked as CVE-2017-3135, affects BIND 9.8.8, all 9.9 releases since 9.9.3, all 9.10 releases, and all 9.11 releases.
In the case of servers with specific configurations, the vulnerability is remotely exploitable and rated as “high severity” with a CVSS score of 7.5.
“Under some conditions when using both DNS64 and RPZ [Response Policy Zones] to rewrite query responses, query processing can resume in an inconsistent state leading to either an INSIST assertion failure or an attempt to read through a NULL pointer,” ISC said in its advisory.
“Servers utilizing both DNS64 and RPZ are potentially susceptible to encountering this condition. When this condition occurs, it will result in either an INSIST assertion failure (and subsequent abort) or an attempt to read through a NULL pointer. On most platforms a NULL pointer read leads to a segmentation fault (SEGFAULT), which causes the process to be terminated,” ISC added.
Servers that don’t use RPZ and DNS64 at the same time are not affected by the security hole.
The vulnerability, reported by Ramesh Damodaran and Aliaksandr Shubnik of Infoblox, has been patched with the release of versions 9.9.9-P6, 9.10.4-P6 and 9.11.0-P3. Users have been advised to update their installations, but removing DNS64 or RPZ from the configuration or restricting the contents of the policy zone are considered a workaround.
The flaw was disclosed on Wednesday, but advance notifications were sent out on February 1. Linux distributions, most of which have classified this as a medium severity issue, are working on releasing patches.
Valve is going to fix a serious vulnerability in Steam online gaming platform
8.2.2017 securityeek Vulnerebility
The online game platform Steam is fixing a serious bug that could be exploited to redirect users to malicious websites and take over their profile.
The popular online game platform Steam is going to fix a serious vulnerability that could be exploited by hackers to redirect users to malicious websites, use their market funds, and also change their profile.
It seems that the XSS exploit on Steam Profiles has been only partially fixed, it seems that the flaw had been fixed only the initial activity feed pages, but it is still present on subsequent pages.
The attackers can exploit the flaw by inserting JavaScript and other malicious code into their profiles, then the code is executed without any warning on the computers of anyone who visits the booby-trapped page.
The vulnerability was first reported in a Reddit thread this week, and experts observed that in a few hours after its disclosure many people were creating profiles that contained the code to trigger the vulnerability.
According to Ars, most of the exploit pages just redirect visitors to a site with PHP code that prompts them to download an unknown file.
“Such redirections, however, are possibly only a small sample of what the underlying exploit makes possible. One Reddit participant said here and here that viewing malicious profiles could force people to make purchases using their Steam market funds.” reported the Ars.
Clearly, the flaw in the Steam platform could be also exploited to steal authentication cookies used and control the user accounts of the visitors.
It is expected that the number of infected profiles would rapidly grow because it is enough that users visit an existing malicious profile.
Steam
The Steam platform was already exploited by hackers in the past to launch cyber attacks. In October 2016, the malware researcher Lawrence Abrams discovered a Reddit user which is warning of the existence of hacked Steam accounts used to spread a Remote Access Trojan (RAT).
In March 2016, the security expert at Kaspersky Lab, Santiago Pontiroli, and Bart P, an independent security researcher, published an interesting analysis of malware targeting the Steam gaming platform and evolution of threats through the last few years,
Valve estimated that nearly 77,000 accounts are hijacked and pillaged each month.
Back to the present, Steam users who think they may have visited a malicious profile urge to check their settings and should change their passwords. I always suggest also to enable two-factor authentication to avoid ugly surprises.
Windows SMB 0-Day Risk Downplayed
7.2.2017 securityweek Vulnerebility
A 0-day vulnerability (CVE-2017-0016) affecting Windows’ SMBv3 (Server Message Block) protocol that was revealed last week is no longer considered a Critical issue, but High-risk.
The issue resides in the manner in which Windows handles SMB traffic and allows an unauthenticated attacker to remotely exploit and cause a denial of service. The issue is triggered when a vulnerable Windows client system connects to a malicious SMB server.
SMB is an application-layer network protocol that allows computers to access files, printers, serial ports, and miscellaneous communications between nodes on a local network. It also offers an authenticated inter-process communication mechanism.
The flaw was publicly revealed after the security researcher who discovered it published a proof-of-concept exploit on GitHub. The CERT Coordination Center (CERT/CC) at Carnegie Mellon University assessed the issue as critical and even suggested that it would have a severity score of 10, because of a possible exploitation for arbitrary code execution.
In the meantime, however, CERT revised the initial advisory and removed all mentions of arbitrary code execution, while also downgrading the severity score. With a CVSS (Common Vulnerability Scoring System) score of 7.8, the bug is rated High risk in the updated advisory.
“To be vulnerable, a client needs to support SMBv3, which was introduced in Windows 8 for clients and Windows 2012 on servers,” Johannes B. Ullrich, Ph.D., Dean of Research for the SANS Technology Institute, notes.
Initially mentioning only Windows 10 and Windows 8.1 as confirmed vulnerable platforms, the advisory has been modified to refer to their server counterparts as well: “We have confirmed the crash with fully-patched Windows 10 and Windows 8.1 client systems, as well as the server equivalents of these platforms, Windows Server 2016 and Windows Server 2012 R2,” CERT notes.
As before, the advisory points out that no practical solution to the issue is yet known, but that a workaround would involve blocking outbound SMB connections (TCP ports 139 and 445 along with UDP ports 137 and 138) from the local network to the WAN.
Given that this is no longer considered a Critical flaw, Microsoft is unlikely to patch it via an out-of-band update, but rather via the monthly set of security patches, which are expected to arrive next week. SecurityWeek contacted Microsoft for specifics on this but hasn’t heard back yet.
WordPress content injection flaw abused in defacement campaigns
7.2.2017 securityaffairs Vulnerebility
According to experts at the security firm Sucuri, a critical content injection flaw in WordPress recently disclosed has already been exploited to deface thousands of websites.
Recently a critical vulnerability has been discovered in the WordPress CMS, it is a zero-day content injection flaw that affects the WordPress REST API.

The vulnerability was discovered by a security researcher at firm Sucuri who explained that the flaw could be exploited by an unauthenticated attacker to inject malicious content as well as for privilege escalation.
The attacker could exploit the zero-day content injection flaw to modify posts, pages, as well any other content.
“This privilege escalation vulnerability affects the WordPress REST API that was recently put into widespread use across WordPress sites with the introduction of official API endpoints in version 4.7.” states a blog post published by Sucuri. “One of these endpoints allows access (via the API) to view, edit, delete and create posts. Within this particular endpoint, a subtle bug allows visitors to edit any post on the site.
The REST API is enabled by default on all sites using WordPress 4.7 or 4.7.1. If your website is on these versions of WordPress then it is currently vulnerable to this bug.”
The impact of the flaw is severe, at least 18 million websites run the popular WordPress CMS, roughly 26% of the top 10,000 websites are running WordPress.
Experts from Sucuri have worked with the WordPress development team that fixed the zero-day content injection vulnerability in the last release 4.7.2 issued on January 26.
The bad news is that many WordPress websites still haven’t been updated leaving the installation open to the attacks.
Experts from Sucuri reported first attacks leveraging the above vulnerability less than 48 hours after its disclosure.
“In less than 48 hours after the vulnerability was disclosed, we saw multiple public exploits being shared and posted online. With that information easily available, the internet-wide probing and exploit attempts began.” states a report published by Sucuri.
The experts observed several massive defacement campaigns targeting WordPress across the world, in one of these campaigns, the hackers replaced the content of more than 60,000 web pages with “Hacked by” statements.

The other three operations, two of which seem to share a single IP address, have each targeted roughly 500 pages.
Sucuri monitored other three operations, two of which are linked to the same IP address as a source and have each targeted roughly 500 pages.
The risk when dealing with such kind of massive defacement is that crooks will leverage the vulnerability in WordPress to conduct Black SEO campaigns.
“What we expect to see is a lot more SEO spam (Search Engine Poisoning) attempts moving forward. There’s already a few exploit attempts that try to add spam images and content to a post. Due to the monetization possibilities, this will likely be the #1 route to abuse this vulnerability.” states Sucuri.
Search engine poisoning is a profitable activity for the cyber crime ecosystem.
Sucuri WAF network has observed a significant increase of the number of exploit attempts, in the last week, as reported in the following graph.

A recent report published by Sucuri states that more than half of the WordPress websites hijacked in 2016 were running an outdated version. By default, WordPress installations are updated automatically, so it is strongly suggested to website administrators to avoid disabling this feature.
Windows SMB Zero-Day Exploit Released in the Wild after Microsoft delayed the Patch
6.2.2017 thehackernews Vulnerebility
Last weekend a security researcher publically disclosed a zero-day vulnerability in Windows 10, Windows 8.1 and Server editions after Microsoft failed to patch it in the past three months.
The zero-day memory corruption flaw resides in the implementation of the SMB (server message block) network file sharing protocol that could allow a remote, unauthenticated attacker to crash systems with denial of service attack, which would then open them to more possible attacks.
According to US-CERT, the vulnerability could also be exploited to execute arbitrary code with Windows kernel privileges on vulnerable systems, but this has not been confirmed right now by Microsoft.
Without revealing the actual scope of the vulnerability and the kind of threat the exploit poses, Microsoft has just downplayed the severity of the issue, saying:
"Windows is the only platform with a customer commitment to investigate reported security issues, and proactively update impacted devices as soon as possible. We recommend customers use Windows 10 and the Microsoft Edge browser for the best protection."
However, the proof-of-concept exploit code, Win10.py, has already been released publicly for Windows 10 by security researcher Laurent Gaffie and does not require targets to use a browser.
The memory corruption flaw resides in the manner in which Windows handles SMB traffic that could be exploited by attackers; all they need is tricking victims to connect to a malicious SMB server, which could be easily done using clever social engineering tricks.
"In particular, Windows fails to properly handle a server response that contains too many bytes following the structure defined in the SMB2 TREE_CONNECT Response structure," CERT said in the advisory.
"By connecting to a malicious SMB server, a vulnerable Windows client system may crash (BSOD) in mrxsmb20.sys."
Since the exploit code is now publicly available to everyone and there is no official patch from Microsoft, all Windows users are left open to potential attacks at this time.
Until Microsoft patches the memory corruption flaw (most probably in the upcoming Windows update or out-of-band patch), Windows users can temporarily fix the issue by blocking outbound SMB connections (TCP ports 139 and 445 and UDP ports 137 and 138) from the local network to the WAN.
The vulnerability has been given Common Vulnerability Scoring System (CVSS) score of 7.8. Proof-of-concept code has been published on GitHub.
Windows SMB 0-Day Exposes Systems to Attacks
3.2.2017 securityweek Vulnerebility
A 0-day memory corruption vulnerability discovered in the SMB (Server Message Block) protocol can be exploited to cause denial of service or potentially execute arbitrary code on a vulnerable system.
According to the United States Computer Emergency Readiness Team (US-CERT), which has already published an advisory on the matter, the bug resides in the manner in which Windows handles SMB traffic and can be exploited by remote, unauthenticated attackers for nefarious purposes.
SMB (one of its versions was also known as Common Internet File System, or CIFS), operates as an application-layer network protocol designed to allow machines to access files, printers, serial ports, and miscellaneous communications between nodes on a local network, while also offering an authenticated inter-process communication mechanism.
According to US-CERT, the Windows platform fails to properly handle a server response containing too many bytes following the structure defined in the SMB2 TREE_CONNECT Response structure. Thus, when a vulnerable Windows client system connects to a malicious SMB server, it can crash (Black Screen of Death or BSOD) in mrxsmb20.sys.
The advisory also notes that the vulnerability has been already confirmed as being exploitable in denial of service attacks, but that it’s not clear whether it could be exploited further. By exploiting the vulnerability, an attacker might also be able to execute arbitrary code with Windows kernel privileges, US-CERT warns.
“We have confirmed the crash with fully-patched Windows 10 and Windows 8.1 client systems. Note that there are a number of techniques that can be used to trigger a Windows system to connect to an SMB share. Some may require little to no user interaction,” the advisory also notes.
With exploit code for the vulnerability already publicly available but no practical solution to this problem known at this time, suggested workarounds include blocking outbound SMB connections (TCP ports 139 and 445 along with UDP ports 137 and 138) from the local network to the WAN.
The vulnerability has a base Common Vulnerability Scoring System (CVSS) score of 10.0. It has been publicly reported by @PythonResponder, who says that Windows Server 2012 and 2016 versions are also affected. Proof-of-concept code has been published on GitHub.
Several Flaws Patched in Honeywell Controllers
3.2.2017 securityweek Vulnerebility
Honeywell has released updates for its XL Web II controllers to address several critical and high severity vulnerabilities that can be exploited remotely from the Internet.
XL Web II or Excel Web II controllers, which are also sold under the Falcon brand, are web-based SCADA (supervisory control and data acquisition) systems designed for building management applications.
Security researcher Maxim Rupp discovered last summer that the product is affected by flaws that allow a remote attacker to obtain sensitive information and use the affected system as an entry point into the targeted organization’s network.
Rupp told SecurityWeek that, using the Shodan search engine, he has identified more than 600 vulnerable devices accessible from the Internet.Vulnerabilities in Honeywell Excel Web controllers
ICS-CERT has published an advisory describing the vulnerabilities, but the researcher says there are some inaccuracies. According to the expert’s own report, the flaws affect XL20xxBxx controllers running firmware version XLWeb2_vUBC_3-04-04-07 and prior, and CLEA20xxBxx devices running firmware version Eagle_vUBC_3-04-04-07 and prior.
The most serious of the flaws, rated critical based on their CVSS score, are related to exposed credentials. The expert discovered that the application stores passwords in easily accessible JavaScript files for client-side verification (CVE-2017-5140). These passwords are stored in clear text (CVE-2017-5139) and an attacker can access them without authentication.
2017 Singapore ICS Cyber Security Conference Call for Papers is Open!
Another vulnerability rated critical is an improper privilege management issue (CVE-2017-5142) that allows a user with limited privileges to access certain functions simply by navigating to a specific URL. These functions are normally accessible only to users with higher privileges.
Rupp has also discovered a high severity path traversal flaw (CVE-2017-5143) that allows an unauthenticated attacker to gain access to files that can contain sensitive information.
ICS-CERT’s advisory also mentions a medium severity session fixation flaw that could allow an attacker to gain access to a targeted user’s account (CVE-2017-5141). Rupp said this vulnerability was not included in his report and that it likely refers to a combination of weaknesses.
According to the researcher and ICS-CERT, Honeywell addressed the vulnerabilities with the release of version 3.04.05.05. Users can obtain the patches by contacting their vendor. There is no evidence that the flaws have been exploited in the wild.
Authentication Bypass Vulnerability found in Cisco Prime Home product
3.2.2017 securityaffeirs Vulnerebility
The experts at Cisco have discovered a critical authentication bypass vulnerability in the Cisco Prime Home during an internal security testing.
Cisco has released a security update for CISCO Prime Home remote management and provisioning solution to fix a flaw that could be exploited to authentication bypass. The experts at Cisco have discovered the critical authentication bypass flaw during an internal security testing.
The Cisco Prime Home is a product used by Internet service providers (ISPs) to view customers’ home networks, it allows to make configuration changes and software upgrades, and could be used for the remote diagnostics.
The flaw, tracked as CVE-2017-3791, resides in the web-based user interface of the Cisco Prime Home, it can be remotely exploited by an unauthenticated attacker to bypass authentication and execute any action with administrator privileges.
“The vulnerability is due to a processing error in the role-based access control (RBAC) of URLs. An attacker could exploit this vulnerability by sending API commands via HTTP to a particular URL without prior authentication.” states the Cisco advisory. “An exploit could allow the attacker to perform any actions in Cisco Prime Home with administrator privileges.”

The flaw affects Cisco Prime Home versions 6.3, 6.4 and 6.5, versions 5.2 and earlier are not impacted. Cisco fixed the issue with the version 6.5.0.1, It is important to highlight the absence of a workaround.
The experts at the Cisco Product Security Incident Response Team (PSIRT) are not aware of any public announcements or exploitation of the flaw.
Critical McAfee ePO Flaw Ideal For Reconnaissance
3.2.2017 securityweek Vulnerebility
Intel Security has fixed a critical vulnerability in its McAfee ePolicy Orchestrator (ePO) centralized security management product. Researchers warn that the flaw is ideal for profiling the users and infrastructure of an organization.
The flaw, tracked as CVE-2016-8027 and assigned a CVSS score of 10.0, is a blind SQL injection discovered by a member of the Cisco Talos Vulnerability Development Team. The security hole can be triggered using specially crafted HTTP POST requests and it allows an unauthenticated attacker to obtain information from the application database.
McAfee ePO allows organizations to manage their security policies from a central console. The solution requires the deployment of agents on each endpoint, and these agents communicate over a proprietary protocol known as SPIPE.
The vulnerable component is in the application server and it can be reached directly via the administration console or over SPIPE. Researchers warned that exploitation of the flaw can also allow attackers to impersonate an agent, which can reveal information related to that agent.
“Vulnerabilities like this can allow deep insight into the organisation without an attacker requiring any privileged access to centralised platforms such as Active Directory, with this access an attacker can profile users and the infrastructure passively,” Talos researchers said in a blog post.
The security hole affects McAfee ePO version 5.1.3 and earlier, and 5.3.2 and earlier. Intel Security has released hotfixes to address the vulnerability. While the vendor says there are no mitigations or workarounds, Talos believes attacks can be prevented by limiting access to port 8443.
Cisco has published technical details on the vulnerability and Intel Security has released an advisory with information on affected versions and patches.
It’s not uncommon for researchers to find vulnerabilities in enterprise security products. Serious flaws have also been identified in solutions from Symantec, FireEye, Kaspersky, Sophos and several other vendors.
Critical Cisco Prime Home Flaw Allows Authentication Bypass
2.2.2017 securityweeks Vulnerebility
Cisco has released a software update for its Prime Home remote management and provisioning solution to address a critical authentication bypass vulnerability discovered by the company during internal security testing.
Cisco Prime Home is designed to give Internet service providers (ISPs) visibility into their customers’ home networks, allowing them to easily make configuration changes and software upgrades, and remotely diagnose and troubleshoot problems.
The networking giant discovered that the product’s web-based user interface is affected by a vulnerability that can be remotely exploited by an unauthenticated attacker to bypass authentication and execute any action with administrator privileges.
The flaw, tracked as CVE-2017-3791, is caused by a processing error in the role-based access control (RBAC) of URLs. The security hole can be exploited by sending specially crafted API commands to a particular URL.
The vulnerability affects versions 6.3, 6.4 and 6.5 and it has been addressed with the release of version 6.5.0.1. Workarounds are not available.
Versions 5.2 and earlier are not impacted. However, it’s worth pointing out that, in November 2016, the company informed users about a similar critical authentication bypass vulnerability affecting Cisco Prime versions 5.1.1.6 and earlier and 5.2.2.2 and earlier.
Cisco is only aware of three security holes affecting Cisco Prime Home. The third one, disclosed in September 2016, is a medium severity XML External Entity (XXE) flaw that allows a remote attacker to access information stored on the affected system.
Another critical vulnerability patched recently by Cisco affects the WebEx browser extensions for Chrome, Internet Explorer and Firefox. The vendor has released several updates until it managed to create a proper patch.
WordPress Delayed Disclosure of Critical Vulnerability
2.2.2017 securityweek Vulnerebility
WordPress has disclosed a critical privilege escalation vulnerability patched on January 26 with the release of version 4.7.2. The developers of the content management system (CMS) said they wanted to make sure users were protected against potential attacks before making the details public.
When it announced the release of version 4.7.2, WordPress said the latest version patched three vulnerabilities, including SQL injection, cross-site scripting (XSS) and access control issues.
However, it turns out that WordPress 4.7.2 also addresses a severe privilege escalation flaw that can be exploited to hijack websites. Fortunately, there is no evidence that the weakness has been exploited in the wild.
The security hole, discovered by researchers at Sucuri, has been described by WordPress developers as an unauthenticated privilege escalation vulnerability in a REST API endpoint. The flaw affects WordPress websites running versions 4.7.0 and 4.7.1.
By sending a specially crafted request, an unauthenticated attacker can change the content of any post on the targeted website. Next, they can add plugin-specific shortcodes and exploit other flaws that would normally be restricted to users with elevated privileges. An attacker can also abuse the compromised website for SEO spam, to inject ads, and even execute PHP code, depending on which plugins are enabled.
In a blog post published on Wednesday, WordPress Core Contributor Aaron D. Campbell explained that the disclosure of the vulnerability was delayed by one week to give websites time to update their installations.
Sucuri’s Marc-Alexandre Montpas reported the vulnerability to WordPress on January 20 and a fix was created shortly after. While the patch was being tested by developers, Sucuri configured its Web Application Firewall (WAF) to block exploitation attempts and WordPress reached out to companies such as SiteLock, Incapsula and CloudFlare so that they could protect their customers as well. WordPress hosts were also notified and provided instructions on how to protect users.
“Data from all four WAFs and WordPress hosts showed no indication that the vulnerability had been exploited in the wild,” Campbell said. “As a result, we made the decision to delay disclosure of this particular issue to give time for automatic updates to run and ensure as many users as possible were protected before the issue was made public.”
Cisco Patches WebEx Flaw in Firefox, IE Plugins
2.2.2017 securityweek Vulnerebility
Cisco has shared additional information on the recently disclosed vulnerability affecting WebEx, and informed customers that patches have also been made available for the Internet Explorer and Firefox plugins.
The vulnerability, identified as CVE-2017-3823, allows an unauthenticated attacker to remotely execute arbitrary code with the privileges of the web browser by getting the targeted user to access a specially crafted web page.
The flaw was discovered by Google Project Zero researcher Tavis Ormandy in the WebEx extension for Chrome and disclosed after it was apparently patched by Cisco. Further investigation by Ormandy and Cisco revealed that the initial fix was incomplete and that the security hole also affected the plugins for Firefox and Internet Explorer.
Cisco has determined that the vulnerability also impacts WebEx Meetings Server and WebEx Centers (Meeting Center, Event Center, Training Center, and Support Center) on Windows.
According to the networking giant, the flaw has been patched in Chrome with the release of version 1.0.7 of the WebEx extension, and in Firefox with the release of version 106 of the ActiveTouch General Plugin Container.
In Internet Explorer, version 10031.6.2017.0126 and version 2.1.0.10 of the GpcContainer Class ActiveX and Download Manager ActiveX control plugins, respectively, address the issue.
The patches for Internet Explorer and Firefox were released on January 28. Both Google and Mozilla have restored the WebEx extension after temporarily removing it from their web stores.
Cisco pointed out that the security hole does not affect Microsoft’s Edge browser or other operating systems.
Users have been advised to ensure that they have the latest version installed, although browsers typically check for updates at regular intervals and install them automatically. Some customers of WebEx Meetings Server and WebEx Meeting Centers may need to request the patches from their service providers or download them from Cisco’s website.
While the details of the vulnerability have been publicly available for more than a week, Cisco says it has not found any evidence of exploits in the wild.
Zimperium Throws $1.5 Million at Mobile N-day Exploits
2.2.2017 securityweek Vulnerebility
Zimperium Launches Exploit Acquisition Program for Android and iOS N-Days, But No Interest in 0-Days
Bug bounty programs exist to encourage researchers to find and report zero-day vulnerabilities. The theory is that the vulnerability is patched and the threat goes away. In reality, however, the zero-day vulnerability simply becomes an N-day exploit; where 'n' is the number of days between the patch and its deployment. During this period, an N-day exploit is as dangerous as a 0-day exploit.
This is a particular problem in the mobile world, where millions of users remain at risk for extended periods due to poor deployment processes that never reach the majority of mobile devices. Now Zimperium, which raised $12 million in Series B funding in February 2015, is attempting to upset the status quo with the announcement of a zLabs $1.5 million N-day exploit acquisition program.
Mobile N-Days and Zero-Days
"Unfortunately, the security patching process for mobile devices' operating systems is extremely slow, which leaves companies and individuals highly vulnerable to dozens of security threats," explains Zuk Avraham, CTO and founder at Zimperium. "Through zLab's new Exploit Acquisition Program, our customers, partners, and the rest of the cybersecurity community will be notified of these vulnerabilities so that they will be able to provide the highest level of protection possible."
There are several actual and hoped-for effects. The first is that once an N-day exploit is known, it will apply pressure to the mobile ecosystem to rethink and improve the security process update. The second is that it will encourage and reward those researchers that develop exploits that immediately become worthless, in bug bounty terms, as soon as the vulnerability is known to the vendor.
The third is that it will simply make for a more secure mobile market. With the researcher's approval, the exploit will be released to members of the Zimperium Handset Alliance (ZHA). This includes Samsung, Softbank, Telstra, Blackberry and more than 30 members of well-known handset vendors and mobile carriers around the world. Zimperium will publicly release the exploit crediting the researcher after between one and three months.
The fourth is Zimperium's own reward. It will use the exploits and the techniques used in the exploit to enhance its own machine learning z9 threat detection engine. This will give customers protection against the exploit even before the patch is released and deployed.
The reporting process is relatively simple for researchers who produce relevant N-day exploits. They should simply email ninja_exploits at nothuman.ninja, describe the exploit, quote the CVE number, explain how the exploit chain works, and state whether they wish to release the code publicly, and receive credit for it.
The exploit is then evaluated by a zLabs committee, and a researcher compensation offer raised. "As a rule," Avraham told SecurityWeek, "critical flaws -- such as a full, remote exploit chain -- will receive more compensation than local exploits. Once we are able to trigger a vulnerability on an older device/OS, we will provide a quote."
"It's simple," he wrote in a blog post today. "We'll buy remote or local exploits targeting any version other than the latest version of iOS and Android."
It could be argued that by encouraging the development of N-day exploits and incorporating their solution into the z9 detection engine, Zimperium is increasing the threat level for any user not using Zimperium. Avraham refutes this suggestion. "While individual device owners won't see the benefits of this program immediately," he told SecurityWeek, "we're doing everything we can to enhance the way that users receive security updates.
"Sophisticated attackers," he continued, "didn't wait for this program to research the monthly security bulletins. These vulnerabilities already exist and are explored by sophisticated actors. Making these vulnerabilities available to the Zimperium Handset Alliance (ZHA) and then the security community, decreases the chances that they will be used in targeted attacks, increases the chances of the carriers to stop these attacks, increases the chances of the vendors allocating resources to provide an update, and helps the entire ecosystem."
In reality, the scheme formalizes and increases what Zimperium has already done. In September 2015 it published an exploit for a critical Android Stagefright vulnerability. The vulnerability had already been patched by Google, but the existence of a published exploit applied pressure on Android suppliers to deliver the patch.
It is certainly true that anything done to decrease the duration of an N-day exploit must be beneficial. But what happens if the $1.5 million runs out? "That will be a great problem to have," said Avraham. "Depending on the success of the program we may allocate more."
Zero-day Content Injection Vulnerability found in WordPress
2.2.2017 securityaffeirs Vulnerebility
A new dangerous Zero-day Content Injection vulnerability has been discovered in the WordPress CMS, it affects the WordPress REST API.
A new dangerous vulnerability has been discovered in the WordPress CMS, it is a zero-day content injection flaw in the WordPress REST API.
The vulnerability discovered by a security researcher at firm Sucuri could be exploited by an unauthenticated attacker to inject malicious content as well as for privilege escalation.
The attacker could exploit the zero-day content injection vulnerability to modify posts, pages, as well any other content.
“This privilege escalation vulnerability affects the WordPress REST API that was recently put into widespread use across WordPress sites with the introduction of official API endpoints in version 4.7.” states a blog post published by Sucuri. “One of these endpoints allows access (via the API) to view, edit, delete and create posts. Within this particular endpoint, a subtle bug allows visitors to edit any post on the site.
The REST API is enabled by default on all sites using WordPress 4.7 or 4.7.1. If your website is on these versions of WordPress then it is currently vulnerable to this bug.”
The impact of the flaw is severe, at least 18 million websites run the popular WordPress CMS, roughly 26% of the top 10,000 websites are running WordPress.
Experts from Sucuri have worked with the WordPress development team that fixed the zero-day content injection vulnerability in the last release 4.7.2.
Experts at Sucuri did not provide technical details about the flaw to prevent that crooks can exploit the vulnerability in attacks in the wild.
“This is a serious vulnerability that can be misused in different ways to compromise a vulnerable site. We are hiding some technical details to make it harder for the bad guys, but depending on the plugins installed on a site, it can lead to a RCE (remote command execution). Also, even though the content is passed through wp_kses, there are ways to inject Javascript and HTML through it. Update now!” continues the post.
Administrators that have not enabled automatic updates on their website need to update it as soon as possible.
Critical Flaws Patched in MailStore Server
1.2.2017 securityweek Vulnerebility
An update released earlier this month for MailStore Server patches a couple of cross-site scripting (XSS) and open redirect vulnerabilities found by a researcher from Germany-based security firm Secuvera.
MailStore Server is one of the most widely used solutions for email archiving, management and compliance. According to MailStore, the product is used by thousands of organizations around the world, including private companies and government agencies.
The security holes, classified by MailStore as “critical,” affect Web Access, the component that allows users to access their mail archive through a web browser.
Secuvera’s Tobias Glemser discovered that MailStore Server’s Web Access component did not properly filter user input, allowing malicious actors to launch both XSS and open redirect attacks.
The reflected XSS flaw, which affects the search function in Web Access, can allow an attacker to gain access to an organization’s email archive by getting an authenticated user to click on a specially crafted link.
The open redirect vulnerability, which affects the dereferrer component, can be exploited by an attacker to lure users to a potentially malicious website by tricking them into clicking on a specially crafted link that appears to point to a trusted domain. The user does not need to be authenticated for the attack to work.
The XSS vulnerability affects MailStore Server 9.2 and newer, while the open redirect issue affects version 9.0 and newer. The flaws were reported to the vendor on January 9 and they were patched on January 18 with the release of version 10.0.2. MailStore has advised users to update their installations as soon as possible.
Only a few MailStore Server vulnerabilities have been disclosed in the past years, including one in 2016 and two in 2014.
VMware Patches Vulnerabilities in AirWatch Android Apps
31.1.2017 securityweek Vulnerebility
VMware has released updates for some of its AirWatch Android applications to address a couple of important vulnerabilities related to local data encryption and rooted device detection.
In the first security advisory released in 2017, VMware informed customers that Finn Steglich from SySS GmbH discovered flaws in several components of the company’s AirWatch enterprise mobility management solution.
One of the security holes, tracked as CVE-2017-4895, affects AirWatch Agent for Android, which allows users to authenticate and enroll their devices in the system. During the enrollment process, the application checks if the smartphone has been rooted – AirWatch classifies rooted and jailbroken devices as “compromised.”
The AirWatch Agent vulnerability found by Steglich allows a device to bypass root detection during enrollment, which, according to VMware, could lead to the device having unrestricted access over local AirWatch security controls and data. The flaw was patched earlier this month with the release of version 7.0.
The second vulnerability patched by VMware affects the secure email client AirWatch Inbox and AirWatch Console on Android. This weakness allows a rooted device to decrypt the local data used by the app, which could result in disclosure of sensitive information.
Patches and workarounds have been made available to address the security hole tracked as CVE-2017-4896. VMware pointed out that Pin-Based Encryption (PBE), a feature introduced in AirWatch Console 9.0 FP1 and AirWatch Inbox 2.12, must be enabled in order to resolve the vulnerability.
VMware has only published one other security advisory for AirWatch products since it acquired AirWatch in early 2014. In December 2014, the company informed users of an AirWatch update that addressed information disclosure vulnerabilities which exposed sensitive IT-related organizational information.
Other flaws, including a root detection bypass issue, were discovered before VMware acquired AirWatch.
Check If Your Netgear Router is also Vulnerable to this Password Bypass Flaw
31.1.2017 thehackernews Vulnerebility
Again bad news for consumers with Netgear routers: Netgear routers hit by another serious security vulnerability, but this time more than two dozens router models are affected.
Security researchers from Trustwave are warning of a new authentication vulnerability in at least 31 models of Netgear models that potentially affects over one million Netgear customers.
The new vulnerability, discovered by Trustwave's SpiderLabs researcher Simon Kenin, can allow remote hackers to obtain the admin password for the Netgear router through a flaw in the password recovery process.
Kenin discovered the flaw (CVE-2017-5521) when he was trying to access the management page of his Netgear router but had forgotten its password.
Exploiting the Bug to Take Full Access on Affected Routers
So, the researcher started looking for ways to hack his own router and found a couple of exploits from 2014 that he leveraged to discover this flaw which allowed him to query routers and retrieve their login credentials easily, giving him full access to the device.
But Kenin said the newly discovered flaw could be remotely exploited only if the router's remote management option is enabled.
While the router vendor claims the remote management option is turned off on its routers by default, according to the researcher, there are "hundreds of thousands, if not over a million" routers left remotely accessible.
"The vulnerability can be used by a remote attacker if remote administration is set to be internet facing. By default this is not turned on," Kenin said. "However, anyone with physical access to a network with a vulnerable router can exploit it locally. This would include public Wi-Fi spaces like cafés and libraries using the vulnerable equipment."
If exploited by bad actors, the vulnerability that completely bypasses any password on a Netgear router could give hackers complete control of the affected router, including the ability to change its configuration, turn it into botnets or even upload entirely new firmware.
After trying out his flaw on a range of Netgear routers, Kenin was surprised to know that more than ten thousand vulnerable devices used the flawed firmware and can be accessed remotely.
He has also released an exploit code for testing purpose, written in Python.
List of Vulnerable NETGEAR Router Models
The SpiderLabs researcher stressed that the vulnerability is very serious as it affects a large number of Netgear router models. Here's a list of affected Netgear routers:
R8500
R8300
R7000
R6400
R7300DST
R7100LG
R6300v2
WNDR3400v3
WNR3500Lv2
R6250
R6700
R6900
R8000
R7900
WNDR4500v2
R6200v2
WNDR3400v2
D6220
D6400
C6300 (firmware released to ISPs)
Update the Firmware of your NETGEAR Router Now!
Kenin notified Netgear of the flaw, and the company confirmed the issue affects a large number of its products.
Netgear has released firmware updates for all of its affected routers, and users are strongly advised to upgrade their devices.
This is the second time in around two months when researchers have discovered flaws in Netgear routers. Just last month, the US-CERT advised users to stop using Netgear's R7000 and R6400 routers due to a serious bug that permitted command injection.
However, in an effort to make its product safe, Netgear recently partnered up with Bugcrowd to launch a bug bounty program that can earn researchers cash rewards of up to $15,000 for finding and responsibly reporting flaws in its hardware, APIs, and the mobile apps.
Hundreds of thousands, if not over a million Netgear routers open to hack
31.1.2017 securityaffeirs Vulnerebility
Hundreds of thousands of Netgear routers are vulnerable to password bypass, the company issued updates only for a number models.
An impressive number of Netgear routers is affected by two flaws that can lead to password disclosure.
It has been estimated that hundreds of thousand devices, potentially more than one million Netgear routers, could be hacked, by both a local or a remote attacker.
Simon Kenin, a security researcher at Trustwave, discovered the flaw and confirmed the vulnerabilities can be remotely exploited when the remote management option of the Netgear routers is enabled.
While Netgear claims remote management is turned off on routers by default,
Kenin explained that despite Netgear claims remote management is turned off on routers by default, there are “hundreds of thousands, if not over a million” Netgear routers with the feature turned on.
Hacking the Netgear routers by exploiting this password bypass it is quite simple, attackers just need to send a simple request to the web management server running on the device.
In this way the expert is able to determine a number that corresponds to a password recovery token, then he could use it to call the passwordrecovered.cgi script.
Kenin discovered by the password bypass by leveraging two exploits disclosed in 2014 on some Netgear routers.
“After few trials and errors trying to reproduce the issue, I found that the very first call to passwordrecovered.cgi will give out the credentials no matter what the parameter you send. This is totally new bug that I haven’t seen anywhere else. When I tested both bugs on different NETGEAR models, I found that my second bug works on a much wider range of models.” Kenin wrote in a blog post.
“A full description of both of these findings as well as the python script used for testing can be found here. The vulnerabilities have been assigned CVE-2017-5521 and TWSL2017-003.”
Trustwave reported the vulnerability to Netgear in April 2016, but Netgear only in in July provided firmware updates for a fraction of the affected router models.
This week Netgear published detailed instructions on the affected models and the way to download and install firmware updates. According to the security advisory, there are 31 vulnerable models, but only 18 of them have been patched.
The owners of the unpatched devices have to manually enable password recovery and disable remote management on their Netgear routers in order to avoid problems.
“The potential for password exposure remains if you do not complete both steps. NETGEAR is not responsible for any consequences that could have been avoided by following the recommendations in this notification,” the company writes.
Kenin points out the dangers caused by malware like the Mirai bot that once obtained a login credential for the routers could cause serious problems.
“With malware such as the Mirai botnet being out there, it is also possible that some of the vulnerable routers could be infected and ultimately used as bots as well. If running a bot is not possible, the DNS can be easily changed to a rogue one, as described by Proofpoint, to further infect machines on the network,” Kenin added.
Printer Vulnerabilities Expose Organizations to Attacks
30.1.2017 securityweek Vulnerebility
A team of researchers from Ruhr-Universität Bochum in Germany has analyzed 20 printers and multifunction printers (MFPs) from several vendors and discovered that each of them is affected by at least one vulnerability, including flaws that can be exploited to crash the device or obtain sensitive information that provides access to the organization’s network.
The experts conducted their tests on printers from HP, Brother, Lexmark, Dell, Samsung, Konica, OKI and Kyocera using a Python-based piece of software they named PRinter Exploitation Toolkit (PRET). The analysis revealed the existence of both old and new vulnerabilities and attack vectors that can be exploited locally or remotely.
Some of the attack methods detailed by the researchers involve what they call PostScript malware. PostScript, created more than 30 years ago by Adobe, is a computer language used to describe the appearance of text and graphics on a page. The language is supported by all major printer manufacturers.
According to researchers, an attacker can abuse PostScript to manipulate documents, such as in the attack where thousands of printers were hijacked and made to print anti-Semitic flyers, or to capture the content of documents that are printed.
Such attacks can be launched through USB, remotely over the local network, or from the Internet via a malicious website using cross-site printing (XSP) and cross-origin resource sharing (CORS) spoofing.
Experts also showed how PostScript and Printer Job Language (PJL) can be leveraged to access the entire file system on some printers, including passwords for the embedded web server. This vulnerability has been known for several years, but experts say it still hasn’t been completely fixed.
“OKI MC342dn allows an attacker to execute one level of path traversal, where a directory called ‘hidden/’ is located which contains stored fax numbers, email contacts and local users’ PINs as well as the SNMP community string,” researchers said in their paper. “More interesting, however, is the fact that this MFP can be integrated into a network using features like Email-to-Print or Scan-to-FTP. An attacker could find passwords for LDAP, POP3, SMTP, outbound HTTP proxy, FTP, SMB, and Webdav as well as the IPsec pre-shared keys. This is a good example how an attacker can escalate her way into a company’s network, using the printer device as a starting point.”
They also discovered that buffer overflow vulnerabilities in the Line Printer Daemon (LPD) and the PJL interpreter can be exploited for denial-of-service (DoS) attacks and possibly even arbitrary code execution. PJL commands can also be used to cause physical damage to the device’s non-volatile memory (NVRAM) and gain access to sensitive information stored in the NVRAM, such as web server passwords.
These security holes can also be exploited locally, or remotely using XSP and CORS spoofing.
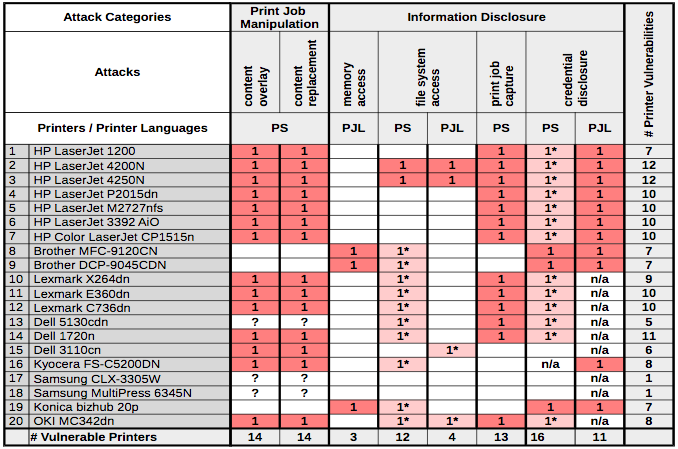
The experts have also analyzed Google Cloud Print, a service that allows users to print from anywhere, including their mobile device, to any printer. They showed that the Google service was also affected by some security issues, for which they earned a $3,133.7 reward from the search giant.
The researchers have also notified other affected vendors of their findings. However, they pointed out that the old vulnerabilities they had identified affected the latest versions of the firmware. In some cases, the vulnerabilities have been known for more than a decade, which they believe suggests that printer manufacturers don’t take security seriously, or they lack the proper security analysis tools.
Many NETGEAR Routers Leak Admin Passwords
30.1.2017 securityweek Vulnerebility
NETGEAR has released firmware updates for many of its routers after an expert discovered that they are affected by serious vulnerabilities that can be exploited to obtain the administrator password for the user interface.
Trustwave researcher Simon Kenin started analyzing NETGEAR routers nearly one year ago, when he was too lazy to get out of bed to perform a cold reboot of his router, and instead attempted to reboot it from its web interface. Since he had forgotten the password, he started looking for ways to remotely hack the device.
The researcher discovered a couple of exploits from 2014 that could be used to obtain a NETGEAR router’s login password via the unauth.cgi and passwordrecovered.cgi script files. Experts had previously demonstrated that a numeric password recovery token provided by unauth.cgi can be used in a request to passwordrecovered.cgi to obtain the device’s username and password in clear text.
Passwordrecovered.cgi is related to a password recovery feature present in NETGEAR routers. If the password recovery feature is disabled, which is the default setting, the current password can be obtained by sending a request to passwordrecovered.cgi with the correct recovery token.
Kenin noticed that the old exploits still worked, but he also discovered a new variant of this authentication bypass flaw. He determined that the token is not checked properly on the very first request after a reboot of the device, allowing an attacker to obtain the password by passing any data to passwordrecovered.cgi, not necessarily a correct token.
The vulnerabilities, tracked as CVE-2017-5521, can be exploited by an attacker with access to the local network or from the Internet if the remote administration feature, which is disabled by default, is enabled on the device.
NETGEAR was informed about the vulnerabilities in April 2016. The vendor released an initial advisory in June, but only workarounds were made available at the time.
The latest version of the advisory shows that NETGEAR has released security updates for 20 affected routers, but there are still a dozen models and firmware versions that remain unpatched. For devices that don’t have a firmware fix available, the manufacturer recommends manually enabling the password recovery feature – the exploits do not work if this feature is enabled – and disabling remote management.
Trustwave has identified more than 10,000 vulnerable devices that are remotely accessible. However, considering that NETGEAR is one of the top router manufacturers and has a significant market share, experts believe hundreds of thousands and possibly even more than one million routers could be affected.
“As many people reuse their password, having the admin password of the router gives us an initial foothold on the network. We can see all the devices connected to the network and try to access them with that same admin password,” Kenin said in a blog post. “With malware such as the Mirai botnet being out there, it is also possible that some of the vulnerable routers could be infected and ultimately used as bots as well.”
NETGEAR recently announced the launch of a bug bounty program, with rewards of up to $15,000 per vulnerability. The decision to launch the program came after several researchers complained about how the company handled vulnerability disclosures.
IBM Patches XSS Flaws in InfoSphere BigInsights
30.1.0217 securityweek Vulnerebility
IBM has released patches for two cross-site scripting (XSS) vulnerabilities affecting the company’s InfoSphere BigInsights analytics platform.
Fortinet researcher Honggang Ren has identified a couple of stored XSS flaws in the web console of InfoSphere BigInsights, a software platform that allows organizations to discover, analyze and visualize data from disparate sources.
One of the flaws, tracked as CVE-2016-2924, affects the “name” field in the “Add Alert Type” window of the “User-Defined Alerts” feature in the InfoSphere BigInsights user interface. The second vulnerability, identified as CVE-2016-2992, affects the “SQL Editor” feature.
The vulnerabilities allow an attacker to use a guest account to inject malicious JavaScript code into the system. The code is executed when an administrator performs various operations on the pages containing the code. An attacker could leverage the flaws to obtain authentication data from the targeted admin.
“IBM Infosphere BigInsights is vulnerable to cross-site scripting, caused by improper validation of user-supplied input. A remote attacker could exploit this vulnerability using a specially-crafted URL to execute script in a victim's Web browser within the security context of the hosting Web site, once the URL is clicked,” IBM and Fortinet said in their advisories.
The flaws affect IBM BigInsights 4.1 and 4.2. The vendor has classified them as “medium severity,” but their exploitability is “high.”
This was not the first time Ren identified XSS vulnerabilities in IBM products. In October, the expert reported finding a similar security hole in IBM Rational Collaborative Lifecycle Management (CLM).
IBM also informed customers last week of vulnerabilities introduced by various third-party components. For instance, cURL, NTP and Python flaws affect PowerKVM, and a vulnerability in GnuPG impacts IBM Security Network Protection.
Uber pays $9,000 bug bounty payoff for partner firm’s vulnerability
30.1.2017 securityaffairs Vulnerebility
A security expert discovered a flaw in a ransomware protection service that opened Uber service, and many others, to cyber attacks.
The Russian penetration tester Vladimir Ivanov from the security firm Positive Technologies has discovered a vulnerability in anti-ransomware backup service Code42. The flaw could be exploited by attackers to steal data from the organizations using the services, including Uber, Adobe, and Lockheed Martin.

Ivanov discovered the XML external entity vulnerability while it was searching for flaws in the Uber service that was covered by the bug bounty program of the company.
Ivanov reported the flaw to Uber that agreed to pay him US$9,000 considering that Code42 doesn’t have a bug bounty program.
“The only option to break the service and get a bounty for pwning the [Code42] application was to find a zero day,” Ivanov says.
“[The vulnerability] could give access to backups of all users in a given company. Uber security guys were excited with this vulnerability: they contacted vendor and confirmed that this vulnerability was a zero day.”
An XML External Entity issue occurs everytime an XML input containing a reference to an external entity is processed by a not properly configured XML parser, as a result, it can cause the disclosure of confidential data, denial of service conditions and trigger server-side request forgery attacks.
Ivanov reported the issue to Uber in May through its HackerOne bug bounty, then the company informed Code42 of the flaw that promptly fixed it.
“As a proof-of-concept for Uber, I retrieved the contents of /home/ directory of the server, which was a nice impact illustration to my report at Hackerone,” wrote Ivanov.
“I like to show impact of a given vulnerability, so you don’t have to ask me twice. Given permission to show further exploitation, I quickly found the folder, where backup logs were stored. ”

Code42 asked Ivanov to wait all customers had applied the security updates to fix the flaw before publicly disclose it.
CVE-2017-3792 – Cisco TelePresence MCU affected by a Remote Code Execution issue
29.1.2017 securityAffeirs Vulnerebility
A critical flaw tracked as CVE-2017-3792 affects three different models of the CISCO TelePresence MCU platform, MCU 5300 Series, MSE 8510
and MCU 4500.
A critical vulnerability tracked as CVE-2017-3792 affects three different models of the CISCO TelePresence MCU platform.
Cisco TelePresence MCU platform is a high-definition multimedia conferencing bridge that is widely adopted due to its ability to work with endpoint systems of the many vendors.
The flaw could be exploited by attackers to remotely execute code on the affected systems or to trigger a denial-of-service (DoS) condition. The flaw was discovered during the resolution of a support case.
The vulnerability affects a proprietary device driver in the kernel of the Cisco TelePresence Multipoint Control Unit (MCU) Software running on platform models 4500, MSE 8510 and 5300 Series.
An attacker could exploit the flaw to trigger a buffer overflow and execute an arbitrary code or cause a DoS condition on the vulnerable system.
“A vulnerability in a proprietary device driver in the kernel of Cisco TelePresence Multipoint Control Unit (MCU) Software could allow an unauthenticated, remote attacker to execute arbitrary code or cause a denial of service (DoS) condition.” reads the Cisco security bulletin.
“The vulnerability is due to improper size validation when reassembling fragmented IPv4 or IPv6 packets. An attacker could exploit this vulnerability by sending crafted IPv4 or IPv6 fragments to a port receiving content in Passthrough content mode. An exploit could allow the attacker to overflow a buffer. If successful, the attacker could execute arbitrary code or cause a DoS condition on the affected system.”
Systems running software version 4.3(1.68) or later configured for “Passthrough” content mode are affected by the flaw.
Cisco issued two security updates for MSE 8510 and 5300 Series users, the Cisco TelePresence MCU 4500 platform will not be fixed because it has reached the end-of-software on July 9, 2016.
Cisco confirmed that there are no workarounds to fix the flaw. In order to prevent exploitation of this vulnerability, the company suggests configuring the CISCO TelePresence MCU Software to use Transcoded content mode instead of Passthrough content mode.
WordPress 4.7.2 release addresses XSS, SQL Injection vulnerabilities
29.1.2017 securityAffeirs Vulnerebility
According to the release notes the latest version of WordPress 4.7.2 addresses three security, including XSS, SQL Injection flaws.
The WordPress development team has pushed the WordPress 4.7.2 version that fixed three security issues, including a cross-site scripting and a SQL injection vulnerability.
The new update comes just two weeks after WordPress released its previous version. Two weeks ago WordPress released the WordPress 4.7.1, a security release for all previous versions that according to the release notes addressed eight security flaws and other 62 bugs.
“WordPress 4.7.2 is now available. This is a security release for all previous versions and we strongly encourage you to update your sites immediately.” reads the official announcement published on the WordPress’ blog.

The SQL injection affected the WordPress’ WP_Query class that is used to access variables, checks, and functions coded into the WordPress core. The expert Mohammad Jangda discovered the class is vulnerable when passing unsafe data. The flaw didn’t affect the core of the WordPress CMS, but there was the risk that plugins and themes would cause further vulnerabilities.
“WP_Query is vulnerable to a SQL injection (SQLi) when passing unsafe data. WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from accidentally causing a vulnerability. Reported by Mo Jangda (batmoo).” states the announcement published by WordPress.
The cross-site scripting vulnerability fixed with this last update affected the class that manages the posts list table. The flaw was discovered by the member of WordPress’ Security Team Ian Dunn.
The third flaw resided the Press This function that allows WordPress users to publish blog posts with a web browser bookmarklet.
“The user interface for assigning taxonomy terms in Press This is shown to users who do not have permissions to use it. Reported by David Herrera of Alley Interactive.” states WordPress advisory.
According to the WordPress team, the previous WordPress 4.7 release has been downloaded over 10 million times since its release on December 6, 2016.
Cisco Starts Patching Critical WebEx Flaw
27.1.2017 SecurityWeek Vulnerebility
Cisco has released a proper fix for the critical remote code execution vulnerability affecting the WebEx browser extension, but the patch is currently only available for the Chrome version.
Google Project Zero researcher Tavis Ormandy reported a few days ago that Cisco’s WebEx extension for Chrome, which has roughly 20 million active installs, was affected by a serious flaw that could have been exploited to execute arbitrary code simply by getting a user to access a specially crafted website.
The expert disclosed the details of the flaw after Cisco claimed to have patched it, but it later turned out that the initial fix was incomplete. Ormandy warned that the security hole could still be exploited without any user interaction if an attacker could find a cross-site scripting (XSS) vulnerability on *.webex.com domains – which he did find.
Cisco on Thursday released version 1.0.7 of the WebEx extension for Chrome and Ormandy said he had not found a way to defeat the new patch.
According to Cisco, the vulnerability also affects Firefox and Internet Explorer on Windows, but patches have yet to be released for these web browsers.
Google has restored the WebEx extension in its Chrome Web Store, but Mozilla is still blocking it in Firefox. The networking giant said Mac OS X and Linux systems are not impacted.
The vulnerability, tracked as CVE-2017-3823, can be exploited through a “magic string” used to activate the WebEx extension inside the browser. In an advisory describing the security hole, Cisco said the flaw is caused by a design defect in an API response parser.
In addition to the patch for the Chrome extension, Cisco released Snort rules to help organizations detect potential attacks. Other security vendors have also provided information on how their products can block exploitation attempts. For the time being, there is no evidence that the vulnerability has been exploited in the wild.
WordPress 4.7.2 Patches Three Vulnerabilities
27.1.2017 SecurityWeek Vulnerebility
The developers of WordPress have released version 4.7.2 on Thursday to address three vulnerabilities affecting earlier versions of the content management system (CMS).
One of the flaws addressed by this security release is a SQL injection in WP_Query, a class that handles the intricacies of a post’s requests to a WordPress blog.
The vulnerability, reported by developer Mohammad Jangda, affects WP_Query when passing unsafe data. While the WordPress core is not affected, some improvements have been made to prevent themes and plugins from accidentally introducing a flaw.
Another weakness patched in WordPress 4.7.2 is a cross-site scripting (XSS) vulnerability found by Ian Dunn of the WordPress security team in the posts list table.
David Herrera of Alley Interactive discovered an access control issue. He found that the user interface for assigning taxonomy terms in “Press This” is shown to users who don’t have the necessary permissions.
While none of these vulnerabilities seem critical from the description provided by WordPress developers, an advisory published by US-CERT says a “remote attacker could exploit some of these vulnerabilities to take control of an affected website.”
WordPress 4.7.2 was released less than two weeks after version 4.7.1, which addressed 62 bugs and eight security holes, including remote code execution, information disclosure, cross-site request forgery (CSRF), XSS and crypto-related issues.
WordPress is still the most targeted CMS. According to web security firm Sucuri, of all the hacked websites monitored by the company last year, a majority ran WordPress.
A recent study conducted by RIPS Technologies has showed that over 8,800 of the plugins available in the official WordPress plugins directory are affected by at least one vulnerability.
Hacker discovered security flaws in Amazon, Apple and Google epub services
27.1.2017 SecurityAffeirs Vulnerebility
A hacker discovered a XXE flaw in the EpubCheck library that affects major epub services causing information disclosure and denial of service conditions.
The security expert and bug hunter Craig Arendt (@craig_arendt) has discovered flaws in major eBook readers including the ones commercialized by Amazon, Apple, and Google.
The expert discovered different XML external entity (XXE) vulnerabilities in the online epub ebook services that use leverages the ‘EpubCheck’ library. The library is used for the operations of format conversions into the universal Epub book format.
“Applying a familiar XXE pattern to exploit services & readers that consume the ePUB format. Exploiting vulnerabilities in EpubCheck <= 4.0.1 (ePub Validation Java Library & tool), Adobe Digital Editions <= 4.5.2 (book reader), Amazon KDP (Kindle Publishing Online Service), Apple Transporter, and Google Play Book uploads, etc.”
“ePub is a standard format for open books maintained by IDPF (International Digital Publishing Forum). IDPF is a trade and standards association for the digital publishing industry, set up to establish a standard for ebook publishing. Their membership list: http://idpf.org/membership/members” reads a blog post published by Arendt.
The researcher focused its tests the tool/Java library called EpubCheck (provided by IDPF) used to validate books in the ePub format. Publishers perform a validation step using the library to verify that the format is valid and Arendt discovered the XML external entity (XXE) issue.
“The validator tool (EpubCheck) was vulnerable to XXE, so any application that relies on a vulnerable version to check the validity of a book would be susceptible to this type of attack.” continues the analysis.
epub services
Arendt explained that in the case of Amazon, the KDP Kindle file upload service used to help publishers upload their books was affected by an XXE flaw that could be exploited by attackers to steal books and data.
A similar flaw affected the Apple Transporter service that ships books to the App Store.
“Parsing maliciously crafted EPUB may lead to disclosure of user information
Description: An information disclosure issue existed in the parsing of EPUB. This issue was addressed through improved parsing. CVE-2016-7666: Craig Arendt of Stratum Security” state the advisory published by Apple.
Arendt confirmed that during the test he accidentally grabbed the shadow password file for one of the epub services using the vulnerable EpubCheck library.
The Google Play Books service was not affected by the XXE flaw, but the expert discovered the possibility to trigger an XML Entity expansion flaw that could be exploited to cause denial of service through an explosive growth of parsed data.
“The software uses XML documents and allows their structure to be defined with a Document Type Definition (DTD), but it does not properly control the number of recursive definitions of entities.” states the advisory published by the Mitre.org.
“If the DTD contains a large number of nested or recursive entities, this can lead to explosive growth of data when parsed, causing a denial of service.”
Similar problems affect other services that permit Java and Flash, Arendt will disclose further attacks once the vendors have fixed the vulnerabilities he reported.
All the vendors above have already applied the necessary security patches to the vulnerable epub services.
Chrome 56 Patches 51 Vulnerabilities
27.1.2017 Securityweek Vulnerebility
Google this week released Chrome 56 in the stable channel, patching no less than 51 vulnerabilities in the popular browser.
Available for download for Windows, Mac and Linux as Chrome 56.0.2924.76, the new browser iteration patches 21 vulnerabilities reported by external researchers, 7 of which were assessed with a High severity rating, 8 as Medium risk, and 6 as Low severity. Google paid a total of more than $54,000 in bug bounties for these flaws.
Four of the High severity flaws, all Universal XSS issues in Blink (CVE-2017-5006, CVE-2017-5007, CVE-2017-5008, and CVE-2017-5010), were found by Mariusz Mlynski, who earned $32.337 in bug bounties for his discoveries.
The remaining flaws included an Unauthorised file access in Devtools (CVE-2017-5011), found by Khalil Zhani ($3000), an Out of bounds memory access in WebRTC (CVE-2017-5009), found by Sean Stanek and Chip Bradford ($3000), and a Heap overflow in V8 (CVE-2017-5012), found by Gergely Nagy ($5500).
The Medium severity flaws included two Address spoofing in Omnibox, discovered by Haosheng Wang and Armin Razmdjou, respectively ($2000 each), a Heap overflow in Skia, found by sweetchip ($2000), a Use after free in Renderer, credited to Wadih Matar ($2000), a UI spoofing in Blink, found by Haosheng Wang ($1000), an Uninitialised memory access in webm video, discovered by danberm ($500), and two Universal XSS issues in chrome://apps and chrome://downloads, both discovered by Rob Wu.
The Low severity vulnerabilities included a Use after free in Extensions, a Bypass of Content Security Policy in Blink, a Type confusion in metrics, two Heap overflows in FFmpeg, and an UI spoofing. Google has yet to detail the bounties paid for these flaws.
Last month, Google released Chrome 55 to resolve 36 vulnerabilities affecting the application, but also to turn off Flash in the browser. By blocking Flash content by default, Google was pushing for a safer browsing experience when using Chrome, given that Adobe’s plugin has been long considered one of the most vulnerable programs. Microsoft Edge and Mozilla’s Firefox also started blocking Flash content recently.
OpenSSL Patches Four Vulnerabilities
26.1.2017 Securityweek Vulnerebility
The OpenSSL Project announced on Thursday the availability of OpenSSL versions 1.1.0d and 1.0.2k, which address a total of four low and moderate severity vulnerabilities.
One of the flaws, tracked as CVE-2017-3731, allows an attacker to trigger an out-of-bounds read using a truncated packet and crash an SSL/TLS server or client running on a 32-bit host.
The weakness, reported in mid-November by Google security researcher Robert Swiecki, affects both the 1.1.0 and 1.0.2 branches when certain ciphers are used, specifically the ChaCha20-Poly1305 for version 1.1.0 and RC4-MD5 for 1.0.2.
Both OpenSSL branches are also affected by a carry propagation bug in the x86_64 Montgomery squaring procedure (CVE-2017-3732). A successful attack relying on a carry propagation bug can allow an attacker to recover encryption keys.
However, in this case, the OpenSSL Project said elliptic curve (EC) algorithms are not affected and attacks against RSA and DSA are difficult to carry out.
“Attacks against DH are considered just feasible (although very difficult) because most of the work necessary to deduce information about a private key may be performed offline,” the OpenSSL Project said in its advisory. “The amount of resources required for such an attack would be very significant and likely only accessible to a limited number of attackers. An attacker would additionally need online access to an unpatched system using the target private key in a scenario with persistent DH parameters and a private key that is shared between multiple clients.”
The flaw, reported earlier this month by Google’s OSS-Fuzz project, is very similar to CVE-2015-3193, which OpenSSL patched in December 2015.
The third vulnerability, identified as CVE-2017-3730, affects the 1.1.0 branch and it can be exploited in a denial-of-service (DoS) attack. A malicious server that supplies bad parameters for a DHE or ECDHE key exchange can cause the client to crash.
The flaw, reported recently by Guido Vranken, was fixed by OpenSSL developers before knowing that it had security implications.
OpenSSL 1.0.2k also addresses a low severity vulnerability that was patched in the 1.1.0 branch in November.
Currently, the only supported versions of OpenSSL are 1.0.2 and 1.1.0. Version 1.0.1 no longer receives security updates since January 1.
Cisco Patches Serious Flaws in Collaboration Products
26.1.2017 Securityweek Vulnerebility
Cisco has released software updates that patch critical and high severity vulnerabilities in its TelePresence and Expressway collaboration products.
The most severe of them is a critical remote code execution vulnerability affecting the device driver in the kernel of Cisco TelePresence Multipoint Control Unit (MCU). The flaw can be exploited by a remote, unauthenticated attacker to trigger a buffer overflow and execute arbitrary code or cause a denial-of-service (DoS) condition.
The security hole, tracked as CVE-2017-3792, affects TelePresence MCU 5300 Series, MCU MSE 8510 and MCU 4500 when running version 4.3(1.68) or later of the software – versions prior to 4.3(1.68) are not impacted. Affected users have been advised to update to version 4.5(1.89).
Cisco TelePresence, specifically the Video Communications Server (VCS) software, is also affected by a DoS vulnerability that can be exploited remotely without authentication. The same issue also affects the Expressway Series collaboration gateway.
The flaw exists in all versions of the Cisco Expressway Series and TelePresence VCS software prior to X8.8.2.
A separate advisory published by Cisco this week describes a high severity DoS vulnerability affecting the ASA CX Context-Aware Security module. An attacker can exploit the flaw to cause the module to no longer process traffic. Patches have yet to be released and there are no workarounds, but Cisco has provided some recommendations for limiting exposure.
These weaknesses have been found during the resolution of support cases and Cisco is not aware of any exploits in the wild.
Still no complete patch for critical WebEx flaw
A few days ago, Google Project Zero researcher Tavis Ormandy disclosed a critical remote code execution vulnerability affecting the Cisco WebEx browser extensions for Chrome, Firefox and Internet Explorer. The expert made the details of the flaw public after the networking giant informed him that the issue had been patched, but it later turned out that the fix was incomplete.
Cisco has confirmed that version 1.0.5 of the add-on does not fully address the problem found by Ormandy. The company is currently working on a proper patch.
The vulnerability allows an attacker to execute arbitrary code on WebEx users’ systems simply by getting them to access a specially crafted website. According to Cisco, the flaw is caused by a “design defect in an application programing interface (API) response parser within the plugin.”
Western Digital Patches Vulnerabilities in "My Cloud" Products
25.1.2017 Securityweek Vulnerebility
The latest firmware update released by Western Digital for the My Cloud Mirror personal cloud storage product patches serious remote command execution and authentication bypass vulnerabilities.
ESET researcher Kacper Szurek recently discovered that WD My Cloud Mirror devices running firmware version 2.11.153, which had been the most recent version, were affected by several vulnerabilities caused by the lack of proper user input escaping.
The most serious of the flaws affects the index page of the product’s web interface and it allows an attacker to execute arbitrary commands via the “username” parameter. Commands can be executed using the following line as “username”: a" || your_command_to_execute || "
Szurek also discovered that an attacker can bypass authentication to the WD My Cloud Mirror interface. The problem, according to the expert, is that the function designed to check if the user has logged in can be easily bypassed as it only checks if the “username” and “isAdmin” cookies exist.
An attacker can bypass authentication by setting the values “username=1” and “isAdmin=1,” and then accessing one of the webpages (e.g. php/users.php).
The vulnerabilities were reported to WD in mid-November and they were patched on December 20 with the release of version 2.11.157 of the firmware. The vendor’s release notes describe these issues as a “security vulnerability related to remote access.”
Earlier this month, researcher Steven Campbell also reported finding a couple of flaws in WD’s My Cloud devices, including a command injection issue. The vendor patched the command injection vulnerability (CVE-2016-10108) in December with the release of firmware version 2.21.126. The second bug, tracked as CVE-2016-10107 and described as “variable checking for PHP pages for authenticated users,” will be addressed with an upcoming update.
This was not the first time researchers found security holes in WD’s personal cloud storage products. VerSprite identified a remote command injection vulnerability in My Cloud in September 2015.
A flaw in the Cisco WebEx Extension allows Remote Code Execution
24.1.2017 securityaffairs Vulnerebility
Tavis Ormandy, a security expert at Google Project Zero, has discovered a critical remote code execution vulnerability in the Cisco WebEx browser extension.
Google Project Zero researcher Tavis Ormandy has discovered a critical remote code execution vulnerability in the Cisco WebEx browser extension. Cisco’s initial fix does not appear to be complete, which has led to Google and Mozilla temporarily removing the add-on from their stores.
Follow
Tavis Ormandy @taviso
There was a secret URL in WebEx that allowed any website to run arbitrary code. ¯\_(ツ)_/¯ https://bugs.chromium.org/p/project-zero/issues/detail?id=1096 …
10:23 PM - 23 Jan 2017
1,289 1,289 Retweets 937 937 likes
The popular Google Project Zero researcher Tavis Ormandy has discovered a critical code execution vulnerability in the Cisco WebEx browser extension. The flaw has a significant impact considering that the WebEx extension for Google Chrome has roughly 20 million active users.
The expert discovered that an attacker can trigger the vulnerability by using any URL that contains a “magic” pattern. The flaw could be exploited to remotely execute arbitrary code on the targeted WebEx user’s system by tricking victims into visiting a specially crafted website.
Cisco tried to fix the issue limiting the magic URL to https://*.webex.com and https://*.webex.com.cn domains but the Google researcher highlighted the it could still be exploited due to a potential cross-site scripting (XSS) flaw on webex.com.
“The extension works on any URL that contains the magic pattern “cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html”, which can be extracted from the extensions manifest. Note that the pattern can occur in an iframe, so there is not necessarily any user-visible indication of what is happening, visiting any website would be enough.” states the advisory published by Ormandy.
“The extension uses nativeMessaging, so this magic string is enough for any website to execute arbitrary code (!!).”
The expert discovered that even without the XSS an attacker can remotely execute arbitrary code on the target system if the victims click “OK” when they are prompted to allow a WebEx meeting to launch on the rogue website.
Ormandy published and PoC exploit and published a demo here for testing. A successful execution of the demo needs a working WebEx installation on the victim machine. Below the link to the PoC exploit:
https://lock.cmpxchg8b.com/ieXohz9t/

Mozilla representatives also remarked that webex.com does not use HTTP Strict Transport Security (HSTS) and Content Security Policy (CSP).
“If I’m an adversary and I can find a single XSS on that domain, all I need to do at any point in the future is intercept an outgoing HTTP request from Chrome, insert a 302 redirect, and I have an instant RCE on who knows how many machines?” said April King, information security engineer at Mozilla.
Both Google and Mozilla have decided to remove the WebEx extension from their stores until Cisco releases will solve the issue.
Cisco WebEx Extension Flaw Allows Code Execution
24.1.2017 Securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy has discovered a critical remote code execution vulnerability in the Cisco WebEx browser extension. Cisco’s initial fix does not appear to be complete, which has led to Google and Mozilla temporarily removing the add-on from their stores.
While analyzing the WebEx extension for Chrome, which has roughly 20 million active users, Ormandy noticed that it works on any URL that contains a “magic” pattern. This allows an attacker to execute arbitrary code on the targeted WebEx user’s system by getting them to access a specially crafted website.
Cisco has attempted to patch the security hole by limiting the magic URL to https://*.webex.com and https://*.webex.com.cn domains. Ormandy said the fix was acceptable, but pointed out that the vulnerability could still be exploited silently through a potential cross-site scripting (XSS) flaw on webex.com.
Furthermore, even without the XSS, an attacker can still execute arbitrary code as long as the victim clicks “OK” when they are prompted to allow a WebEx meeting to launch on the malicious website.
Mozilla representatives said they were unhappy with Cisco’s fix and pointed out that webex.com does not use HTTP Strict Transport Security (HSTS) and Content Security Policy (CSP).
“If I'm an adversary and I can find a single XSS on that domain, all I need to do at any point in the future is intercept an outgoing HTTP request from Chrome, insert a 302 redirect, and I have an instant RCE on who knows how many machines?” noted April King, information security engineer at Mozilla.
Others said they could still get Ormandy’s proof-of-concept (PoC) exploit to work even on the updated version.
As a result, both Google and Mozilla have decided to remove the WebEx extension from their stores until Cisco releases a proper fix.
“This is exactly the kind of ‘just visit this random website and now you have malware’ scenarios that we haven't seen in a while (on a large scale), and that we don't want to go back to,” said Filippo Valsorda, a researcher at CloudFlare.
Valsorda has published a blog post with advice on how to prevent these types of attacks in Chrome using browser profiles.
Heartbleed Still Affects 200,000 Devices: Shodan
23.1.2017 Securityweek Vulnerebility
While the number of services affected by the OpenSSL flaw known as Heartbleed has decreased, the Shodan search engine has still found nearly 200,000 vulnerable devices.
Heartbleed, tracked as CVE-2014-0160, is a critical vulnerability that allows attackers to steal information protected by SSL/TLS encryption. Some researchers believe the flaw was used in an attack where hackers managed to steal 4.5 million healthcare records.
A search for vulnerable devices conducted by Shodan in November 2015 returned 238,000 results and the number dropped by roughly 1,000 by late March 2016. A new search carried out on Sunday showed that 199,594 services are still vulnerable to Heartbleed attacks.
Many of the affected devices are located in the United States (42,000), followed by South Korea (15,000), China (14,000), Germany (14,000), France, (8,700), Russia (6,600), UK (6,500), India (5,800), Brazil (5,500) and Italy (4,800). HTTPS accounts for a large majority of impacted services.
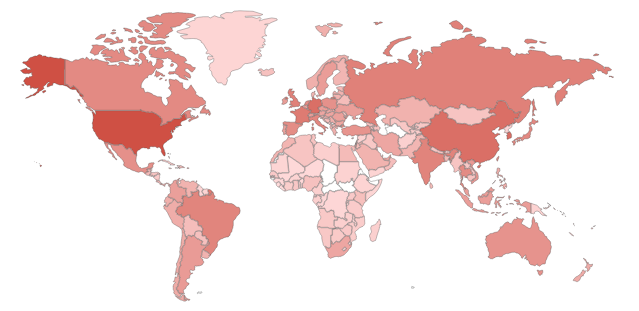
South Korea occupied only the 8th place after previous scans, but it has now become the second most affected country, apparently due to devices operated by SK Broadband, Boranet and KT Corporation (formerly Korea Telecom).
The list of top affected organizations also includes Amazon, Verizon Wireless, German ISP Strato, OVH in France, German hosting firm 1&1 Internet, Comcast, and Taiwan-based HiNet.
Apache HTTP Server (httpd) is by far the most affected product, particularly versions 2.2.22 and 2.2.15, while the top operating system is Linux 3.x. Shodan also found that more than 70,000 of the affected services have expired SSL certificates.
Over 199,500 Websites Are Still Vulnerable to Heartbleed OpenSSL Bug
23.1.2017 thehackernews Vulnerebility
It's more than two and half years since the discovery of the critical OpenSSL Heartbleed vulnerability, but the flaw is still alive as it appears that many organizations did not remediate properly to the serious security glitch.
It was one of the biggest flaws in the Internet's history that affected the core security of as many as two-thirds of the world's servers i.e. half a million servers at the time of its discovery in April 2014.
However, the critical bug still affects more than 199,500 systems even after 2 years and 9 months have already passed, according to a new report published today on Shodan, a search engine that scans for vulnerable devices.
Over 199,500 Systems Still Vulnerable to Heartbleed
Heartbleed (CVE-2014-0160) was a serious bug in the OpenSSL's implementation of the TLS/DTLS heartbeat extension that allowed attackers to read portions of the affected server’s memory, potentially revealing users data that the server isn't intended to reveal.
According to Shodan CEO John Matherly, about 199,500 services remain exploitable by the Heartbleed vulnerability due to unpatched OpenSSL instances.
The countries most affected by Heartbleed still remain the United States, followed by Korea, China, Germany, France, Russian Federation, United Kingdom, India Brazil and Italy.
Matherly discovered 42,032 heartbleed-exploitable services in the United States, 15,380 in Korea, 14,116 in China, and 14,072 services in Germany.
With top organizations vulnerable to the OpenSSL bug is SK Broadband and Amazon.com, and about 75,000 of the vulnerable services use expired SSL certificates and run Linux 3.x.
Heartbleed is one of many flaws that often exist unpatched in the wild, and now that the bug has been more than two and half years old and known to everybody, anyone can simply use it to carry out attacks against the still affected systems.
Around 200,000 is really a troubling number, and one can imagine the danger and damages caused by the bug if exploited.
Software bugs may come and go, but this flaw is more critical and probably the biggest Internet flaw in recent history as it left the contents of a server's memory, where the most sensitive data is stored, exposed to the attackers.
What are the Steps to Protect your Systems against Heartbleed?
It takes roughly three steps to remediate the Heartbleed bug.
Patching: Update your software to the latest versions of OpenSSL; thankfully almost all organization have accomplished this step.
Creation of New Private Keys: Creating new private keys will prevent an attacker, who already exploited the flaw before patching, from being able to spy on your encrypted.
Reissuance of Security Certificates: This step will eliminate the ability of any attacker to spoof organizations and fool or phish their customers.
Oracle Will Stop Trusting MD5-Signed JAR Files in April
20.1.2017 Securityweek Vulnerebility
Oracle has decided to give Java developers more time to ensure that their JAR files are not signed with the MD5 algorithm. Java Runtime Environment (JRE) will no longer trust these types of files starting with April 2017.
The company announced in October plans to stop trusting JAR files signed with the MD5 algorithm, which has been known to have collision vulnerabilities for more than a decade. Oracle stopped using MD5 as the default JAR signing option in 2006 and the company now wants to take things even further.
Starting with Java SE 8u131, scheduled for release with the April 2017 Critical Patch Update (CPU), JAR files signed with MD5 will be treated as unsigned files and will not be trusted. Oracle had initially planned to stop trusting MD5-signed files in January 2017, but some developers have requested additional time to prepare for this change.
Developers have been advised to check if their JAR files have been signed using MD5 and re-sign them with a stronger algorithm or key size. The following command can be used in the Zip utility to remove existing MD5 signatures:
zip -d test.jar 'META-INF/*.SF' 'META-INF/*.RSA' 'META-INF/*.DSA'
“If you are using JARS you did not sign or build yourself, you need to contact your vendor for more information,” explained Oracle’s Erik Costlow in October. “If it can no longer be established if a JAR you are using has been signed with MD5, the recommended practice is to re-sign affected JAR files using a more modern algorithm.”
Other cryptography-related changes planned by Oracle this year for JRE and JDK include disabling SHA-1 in certificate chains anchored by roots included by default in JDK, and increasing the minimum key length for SSL and TLS to 1024 bits.
Oracle’s latest CPU patches a total of 270 vulnerabilities across its products, including 158 weaknesses that can be exploited remotely by an unauthenticated attacker. A significant number of flaws have been found in Oracle’s E-Business Suite, which seems to have attracted the attention of researchers recently.
Docker Patches Escape Container Vulnerability
20.1.2017 Securityweek Vulnerebility
Docker recently resolved a runc privilege escalation vulnerability that could be exploited by a malicious program to escape container and access the host.
Tracked as CVE-2016-9962, the security issue is created because runc passes a file descriptor from the host's filesystem to the "runc init" bootstrap process when joining a container. This means that a malicious process inside the container can gain access to the host filesystem with its current privilege set.
Discovered by Alexander Bergmann, the vulnerability is rather difficult to exploit, because the race window between join-and-execve is quite small. According to Docker’s CVE database, the privilege escalation issue is the result of insecure opening of file-descriptor. Docker 1.12.6 resolves the bug.
Because the issue resides in the runc code, other containers might also be affected, Aqua Security’s Sagie Dulce says. The vulnerability is triggered when exec-ing an application in an already running container, the security researcher explains.
The use of an inherited file descriptor inside the container allows a malicious process to access the file descriptor of a directory that resides on the host and then the rest of the host's filesystem. Because the bug can be leveraged for directory traversal to the host's file system, it results in an effective container escape, Dulce notes.
Apparently, exec-ing commands inside a running container is actually a bigger issue that the problem of an open file descriptor is part of. However, the window of opportunity where the container has access to the runc init process on the host is very small before the runc init process execs the command inside the container.
“This is because runc enters the namespace of the container before it execs the final command. This window could enable a container, for example, to list file descriptors on the host process, which can then lead it to the host’s file system. Because many containers run as root, this indeed has serious implications,” the researcher notes.
The issue can be exploited in containers that lack the CAP_SYS_PTRACE capability, although it is much easier to access the file descriptors if the capability exists. A correctly timed exploit can leverage the vulnerability without having control of the runc init process. “One can escape a container […] by simply patching runc to sleep before calling exec,” Dulce says.
According to Red Hat’s Dan Walsh, SELinux mitigates the vulnerability. “SELinux is the only thing that protects the host file system from attacks from inside of the container. If the processes inside of the container get access to a host file and attempt to read and write the content SELinux will check the access,” he explains.
The released patch for this issue ensures that there are no host file descriptors present in the runc init process. Moreover, the fix sets the runc init process as non-dumpable, before setns into the container, which apparently protects it from processes inside the container.
Security Bug Lurked in Nexus 9 Kernel for Two Years
19.1.2017 Securityweek Vulnerebility
A security vulnerability that allowed a privileged attacker to arbitrary write values within kernel space lurked in Nexus 9’s kernel for two years before being patched, IBM security researchers reveal.
Tracked as CVE-2016-3873, the vulnerability was found in the Tegra kernel branch and was assigned a high severity rating. It was found to plague Nexus 9 ever since its inception in November 2014, and was fixed in the security patch level of 2016-09-05, after being discovered in June 2016.
In its Sept. 2016 Security Bulletin, Google noted that this was an elevation of privilege vulnerability in the NVIDIA kernel and that local malicious applications could leverage it to execute arbitrary code within the context of the kernel. The bug first requires compromising a privileged process, thus was assigned a High severity rating.
IBM X-Force Application Security Research Team’s Sagi Kedmi, the researcher who discovered the bug, explains that a similar issue (CVE-2016-2443) was discovered by security researcher Marco Grassi in spring 2013. Found in the Qualcomm MDP Driver, this bug was patched in Google’s May 2016 Android Security Bulletin.
“Kernel arbitrary write primitives can be used to achieve kernel code execution, which completely compromises the security of the device, not including TrustZone. It increases the TrustZone attack surface and allows attackers to access application data and override the Security-Enhanced Linux (SELinux) policy,” Kedmi explains.
The vulnerable code in Nexus 9 begins with the registers debugfs file node, which is initialized with a specific file operation where, on write system call, the cl_register_write() function securely copies a user space buffer and parses its contents as two numeric values, val and offs. Next, the cl_dvfs_writel() function is fed the two values, and __raw_writel() is used to write value val at offs+, which results in an arbitrary kernel write.
The researcher analyzed the Discretionary Access Control (DAC) and Mandatory Access Control (MAC; SELinux on Android) to determine what active processes can trigger the vulnerability. When it comes to DAC, the attacker needs to execute the code under root within the debugfs SELinux context, so the researcher then looked at the contexts that could write to a debugfs file.
Looking into Nexus 9’s sepolicy (MOB30M), Kedmi found that SELinux-wise, all domains can open, write and append to any file with the debugfs context, and discovered that code execution within the zygote process, several system processes and some other processes can trigger and exploit the Android vulnerability.
“To exploit the vulnerability from an untrusted application security context, start by escalating privileges from an untrusted app to one of the contexts of the aforementioned processes. The commit that fixed the vulnerability indicates that Google simply removed the registers file from the debug file system. Clearly, the registers file node was not needed on production builds,” the researcher concludes.
XSS Found in Silently Installed Acrobat Chrome Extension
19.1.2017 Securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy discovered that a Chrome extension installed silently by Adobe last week had been affected by a cross-site scripting (XSS) vulnerability. Adobe quickly patched the flaw after learning of its existence.
The updates released by Adobe on January 10 for Acrobat and Reader addressed 29 vulnerabilities. However, some users were displeased that the updates also automatically installed an Adobe Acrobat Chrome extension designed for converting web pages into PDF files.
The Windows-only extension requires permission to access data on the websites visited by the user, manage downloads, and communicate with cooperating native apps. The tool also collects some information from the system, but Adobe claims no personal information is involved and the “anonymous data will not be meaningful to anyone outside of Adobe.”
After analyzing the extension, which has roughly 30 million installs, Ormandy identified a DOM-based XSS vulnerability that allowed privileged JavaScript code execution. The expert classified the security hole as “critical severity.”
“I think CSP [Content Security Policy] might make it impossible to jump straight to script execution, but you can iframe non web_accessible_resources, and easily pivot that to code execution, or change privacy options via options.html, etc,” the Google researcher explained in an advisory.
The issue was reported to Adobe on January 12 and it was patched a few days later. It is not surprising that the vulnerability was fixed quickly considering that many of the flaws found in Adobe products are reported by Google Project Zero researchers or through the Chromium Vulnerability Rewards Program.
This was not the first time Ormandy identified a vulnerability in a Chrome extension. Roughly one year ago, the expert revealed that an extension automatically installed by AVG AntiVirus exposed users’ browsing history and other personal data.
US-CERT – Warning, Shadow Brokers Hackers are offering an SMB Zero-Day exploit
19.1.2017 securityaffairs Vulnerebility
The US-CERT has issued a warning after the Shadow Brokers hackers have offered to sell what it claims to be an SMB Zero-Day exploit.
The United States Computer Emergency Readiness Team (US-CERT) has issued a warning after the Shadow Brokers hacker group has offered to sell what it claims to be an SMB Zero-Day exploit.
The Shadow Brokers is the hacker crew that leaked a portion of the arsenal of the NSA-Linked Equation Group, a database containing hacking tools and exploits.
A few days ago the notorious hacker group Shadow Brokers announced the sale of an archive of Windows exploits and hacking tools stolen from the Equation group.
The mysterious hacking group has apparently decided to put an end to their failed attempts to sell exploits and hacking tools they claimed to have stolen from the NSA-linked Equation Group.
While the group claims to have decided to retire, the stolen exploits are still up for sale for the price of 10,000 bitcoins (roughly $8.7 million at the current exchange).
The precious archive seems to include also a zero-day exploit targeting the Server Message Block (SMB) network file sharing protocol.
“In response to public reporting of a potential Server Message Block (SMB) vulnerability, US-CERT is providing known best practices related to SMB. This service is universally available for Windows systems, and legacy versions of SMB protocols could allow a remote attacker to obtain sensitive information from affected systems,” US-CERT said.
Giving a close look at the list published by Shadow Brokers team it is possible to note a tool that claims to be an SMB Zero-Day exploit that goes for 250 bitcoins. The hackers describe the exploit as a remote code execution zero-day targeting SMB. The group is offering it under the name “SMB cloaked backdoor” for 50 bitcoins, but the complete package includes IIS, RDP RPC and SMB exploits for 250 bitcoins.

The US-CERT has advised users and administrators to consider disabling SMB v1, and block all versions of SMB at the network boundary. SMB typically uses port 445 (TCP/UDP), ports 137 and 138 (UDP), and port 139 (TCP).
The US-CERT provided the following recommendations to users and administrators:
disabling SMB v1 and
blocking all versions of SMB at the network boundary by blocking TCP port 445 with related protocols on UDP ports 137-138 and TCP port 139, for all boundary devices.
Anyway, it is important to consider that disabling or blocking SMB may create problems by obstructing access to shared files, data, or devices.
“The benefits of mitigation should be weighed against potential disruptions to users. For more information on SMB, please review Microsoft Security Advisories 2696547(link is external) and 204279(link is external).” continues the advisory.
The US-CERT has already issued in the past an alert following a Shadow Brokers initiative, in September it warned organizations after the hacker crew leaked exploitation tools flaws affecting Cisco ASA solutions.
“In August 2016, a group known as “Shadow Brokers” publicly released a large number of files, including exploitation tools for both old and newly exposed vulnerabilities. Cisco ASA devices were found to be vulnerable to the released exploit code. In response, Cisco released an update to address a newly disclosed Cisco ASA Simple Network Management Protocol (SNMP) remote code execution vulnerability (CVE-2016-6366).”
Thai TrueOnline ZyXEL and Billion routers still unpatched since July
18.1.2017 securityaffairs Vulnerebility
The security researcher Pedro Ribeiro disclosed several vulnerabilities in the ZyXEL customized routers that could be easily exploited by hackers.
Details on serious vulnerabilities in a number of routers freely distributed by the TrueOnline Thai ISP were published on Monday after private disclosures made to the vendors in July went unanswered.
The security researcher Pedro Ribeiro from Agile Information Security disclosed multiple flaws in a number of routers distributed by the Thai ISP TrueOnline.
The Thai ISP distributes several rebranded ZyXEL and Billion routers to its customers.
The models ZyXEL P660HN-T v1, ZyXEL P660HN-T v2 and Billion 5200W-T contain a number of default administrative accounts and their web interfaces are affected by command injection vulnerabilities. On Monday Ribeiro published a proof of concept exploit, he released Metasploit modules for the exploitation of the vulnerabilities in the routers.

All the routers are still in widespread use in Thailand, with the Billion 5200W-T router currently being distributed to new customers.
“TrueOnline is a major Internet Service Provider in Thailand which distributes various rebranded ZyXEL and Billion routers to its customers. Three router models – ZyXEL P660HN-T v1, ZyXEL P660HN-T v2 and Billion 5200W-T – contain a number of default administrative accounts, as well as authenticated and unauthenticated command injection vulnerabilities in their web interfaces, mostly in the syslog remote forwarding function.” reads the advisory. “All the routers are still in widespread use in Thailand, with the Billion 5200W-T router currently being distributed to new customers.”
Ribeiro reported the vulnerabilities via the SecuriTeam Secure Disclosure Program, which notified them to the vendors in July.
The network devices are based on the TC3162U SoC system-on-a-chip manufactured by TrendChip, in particular, flawed routers have two firmware variants called “ras” and “tclinux.”
Riberio discovered security vulnerabilities in the ‘tclinux’ variant, several ASP files in the web interface are affected by command injection attack issues.
“It should be noted that tclinux contains files and configuration settings in other languages (for example in Turkish). Therefore it is likely that these firmware versions are not specific to TrueOnline, and other ISP customised routers in other countries might also be vulnerable,” added Ribeiro. “It is also possible that other brands and router models that use the tclinux variant are also affected by the command injection vulnerabilities (the default accounts are likely to be TrueOnline specific).”
The researcher explained that the majority of the vulnerabilities can be exploited remotely, by both authenticated and unauthenticated attackers.
The ZyXel P660HN-T v1 router is affected by an unauthenticated command injection issue that can be remotely exploited by attackers.
“This router has a command injection vulnerability in the Maintenance > Logs > System Log > Remote System Log forwarding function. The vulnerability is in the ViewLog.asp page, which is accessible unauthenticated. The following request will cause the router to issue 3 ping requests to 10.0.99.102:
POST /cgi-bin/ViewLog.asp HTTP/1.1
remote_submit_Flag=1&remote_syslog_Flag=1&RemoteSyslogSupported=1&LogFlag=0&remote_host=%3bping+-c+3+10.0.99.102%3b%23&remoteSubmit=Save”
The ZyXel P660HN-T V2 router in affected by the same issue, but it can be remotely exploited only by authenticated attackers.
“Unlike in the P660HN-Tv1, the injection is authenticated and in the logSet.asp page. However, this router contains a hardcoded supervisor password (see below) that can be used to exploit this vulnerability. The injection is in the logSet.asp page that sets up remote forwarding of syslog logs, and the parameter vulnerable to injection is the serverIP parameter” states the advisory.
The third router distributed by the Thai ISP is the Billion 5200W-T model, this model is affected by unauthenticated and authenticated command injection issues. According to the researcher a flaw resides in the its adv_remotelog.asp page.
“The Billion 5200W-T router also has several other command injections in its interface, depending on the firmware version, such as an authenticated command injection in tools_time.asp (uiViewSNTPServer parameter),” Ribeiro said. “It should be noted that this router contains several hardcoded administrative accounts that can be used to exploit this vulnerability.”
All the versions use default and weak admin credentials that were remotely accessible.
Talos Team discovered serious issues in Aerospike Database Server
15.1.17 securityaffairs Vulnerebility
Security experts from Cisco Talos discovered several flaws in the Aerospike Database Server, a high-performance, and open source NoSQL database.
Security experts from Cisco Talos have discovered several vulnerabilities in the Aerospike Database Server, a high-performance, and open source NoSQL database.
It is used by several major brands for high-performance applications, including Kayak, AppNexus, Adform, adMarketplace and BlueKai.
The Cisco Talos team discovered that Aerospace Database Server 3.10.0.3, and likely earlier versions, is affected by three flaws that have been rated as critical and high severity, including remote code execution and information disclosure issues.
Talos has published technical details of the vulnerabilities in the advisories that also include proof-of-concept (PoC) code for them.
“Talos is disclosing multiple vulnerabilities discovered in the Aerospike Database Server. These vulnerabilities range from memory disclosure to potential remote code execution. This software is used by various companies that require a high performance NoSQL database. Aerospike fixed these issues in version 3.11.” reads the advisory published by the Talos Team.
TALOS-2016-0264 (CVE-2016-9050) – Aerospike Database Server Client Message Memory Disclosure Vulnerability
TALOS-2016-0266 (CVE-2016-9052) – Aerospike Database Server Index Name Code Execution Vulnerability
TALOS-2016-0268 (CVE-2016-9054) – Aerospike Database Server Set Name Code Execution Vulnerability.
The first security vulnerability, tracked as CVE-2016-9050, is an out-of-bounds read issue that affects the client message-parsing functionality. An attacker can exploit it by sending a specially crafted packet to the listening port which can result in memory disclosure or a denial-of-service (DoS) condition.
A second vulnerability, tracked as CVE-2016-9052, is an arbitrary code execution that affects a different function, namely “as_sindex__simatch_by_iname.”
The third one tracked as CVE-2016-9054, is a stack-based buffer overflow that resides in the querying functionality, specifically the “as_sindex__simatch_list_set_binid” function. It is quite simple to exploit, an attacker has to connect to the listening port to remotely execute arbitrary code via a specially crafted packet that triggers the vulnerability.
The flaws were reported to the Aerospike development team on December 23 and they addresses them on January 5 in version 3.11.0.
Talos has published advisories containing technical details and proof-of-concept (PoC) code for each of the vulnerabilities.
WordPress 4.7.1 released, patches eight vulnerabilities and 62 bugs
14.1.2017 securityaffairs Vulnerebility
According to the release notes the latest version of WordPress 4.7.1 addresses eight security vulnerabilities and other 62 bugs.
Wednesday the latest version of WordPress 4.7.1 was released by the WordPress Team, it is classified as a security release for all previous versions. According to the release notes, the new version addresses eight security flaws and other 62 bugs.
According to the WordPress team, the previous WordPress 4.7 release has been downloaded over 10 million times since its release on December 6, 2016.
The PHPMailer library was updated to patch a remote code execution (RCE) vulnerability, tracked as CVE-2016-10033. Aaron D. Campbell, WordPress Core developer, says that “No specific issue appears to affect WordPress or any of the major plugins we investigated but, out of an abundance of caution, we updated PHPMailer in this release”.
The experts, Brian Krogsgard and Chris Jean, discovered that the REST API “exposed data on all users who had authored a post of a public post type.”

The new version addresses two Cross-site scripting(XSS) vulnerabilities in the WordPress plugins.
“Cross-site scripting (XSS) via the plugin name or version header on update-core.php. Reported by Dominik Schilling of the WordPress Security Team.” reads the advisory.
The second XSS resides in the “theme name fallback” and was reported by Mehmet Ince.
Among the issues fixed by the WordPress Team, there are also two Cross-site request forgery (CSRF) vulnerabilities.
The CSRF bypass via uploading a Flash file was reported by Abdullah Hussam, while Ronnie Skansing reported a CSRF in the accessibility mode of widget editing.
The researchers explained that one of theme identified by Abdullah Hussam can be exploited via a specially crafted Flash file, while the other affects the accessibility mode of widget editing, reported by Ronnie Skansing.
The new release also fixes a weak cryptographic security related to multisite activation key discovered by Jack, the expert described it in a blog post.
Another issue was discovered by John Blackbourn of the WordPress Security Team, it is a post via email checks mail.example.com if default settings aren’t changed.
“Download WordPress 4.7.1 or venture over to Dashboard → Updates and simply click “Update Now.” Sites that support automatic background updates are already beginning to update to WordPress 4.7.1” states the advisory.
A report recently issued by the security firm Sucuri claims that WordPress continues to be the most hacked CMS.
As explained in this article published weeks ago by Pierluigi Paganini, more than 8,800 WordPress Plugins out of 44,705 are flawed
“Security firm RIPS Technologies has analyzed 44,705 in the official WordPress plugins directory and discovered that more than 8,800 of them are flawed.” states the post.
WhatsApp Backdoor allows Hackers to Intercept and Read Your Encrypted Messages
13.1.2017 thehackernews Vulnerebility
Most people believe that end-to-end encryption is the ultimate way to protect your secret communication from snooping, and it does, but it can be intercepted if not implemented correctly.
After introducing "end-to-end encryption by default" last year, WhatsApp has become the world's largest secure messaging platform with over a billion users worldwide.
But if you think your conversations are completely secure in a way that no one, not even Facebook, the company that owned WhatsApp, can intercept your messages then you are highly mistaken, just like most of us and it's not a new concept.
Here's the kick: End-to-end encrypted messaging service, such as WhatsApp and Telegram, contain a backdoor that can be used, if necessary, by the company and of course hackers, or the intelligence agencies to intercept and read your end-to-end encrypted messages, and that’s all without breaking the encryption.
And that backdoor is — TRUST.
No doubt most of the encrypted messaging services generate and store private encryption key offline on your device and only broadcast the public key to other users through the company's server.
Like, In the case of WhatsApp, we have to trust the company that it will not alter public key exchange mechanism between the sender and receiver to perform man-in-the-middle attack for snooping on your encrypted private communication.
Tobias Boelter, security researcher from the University of California, has reported that WhatsApp's end-to-end encryption, based on Signal protocol, has been implemented in a way that if WhatsApp or any hacker intercepts your chats by exploiting trust-based key exchange mechanism, you will never come to know if any change in encryption key has occurred in the background. YES, that's possible.
Note that this backdoor has nothing to do with the Signal encryption protocol, created by Open Whisper Systems. It's one of the most secure encryption protocols if implemented correctly.
“WhatsApp has implemented a backdoor into the Signal protocol, giving itself the ability to force the generation of new encryption keys for offline users and to make the sender re-encrypt messages with new keys and send them again for any messages that have not been marked as delivered. The recipient is not made aware of this change in encryption.” The Guardian reports.
However, users can receive notifications when security codes change, only if "security notifications" option has been turned ON manually from the app settings.
Meanwhile, Fredric Jacobs, who was iOS developer at Open Whisper Systems, also reacted on twitter and admitted that "if you don't verify keys Signal/WhatsApp/... can man-in-the-middle your communications," however he also added, "It's ridiculous that this is presented as a backdoor. If you don't verify keys, authenticity of keys is not guaranteed. Well known fact."
Facebook Haven't Fixed It Since June, 2016
Boelter told the Guardian that he reported the backdoor to Facebook in April 2016 -- the time when WhatsApp implemented end-to-end encryption by default in its messaging app.
However, the researcher was told in reply that Facebook was already aware of the issue and justified it as an "expected behavior."
"WhatsApp says that it implemented the backdoor to aid usability. If the backdoor is not in place, messages sent to an offline user, who then changes their smartphone or has to re-install WhatsApp and in doing so generates new security keys for themselves, would remain undelivered once the user comes back online." The Guardian says.
"In many parts of the world, people frequently change devices and Sim cards. In these situations, we want to make sure people’s messages are delivered, not lost in transit." a WhatsApp spokesperson told the Guardian.
And Yeah, the backdoor still exists in WhatsApp.
How to Protect Yourself from Spying?
To prevent the possibility of MITM attacks, WhatsApp also offers a third security layer in its app using which you can verify the keys of other users with whom you are communicating, either by scanning a QR code (drawback: physical presence required) or by comparing a 60-digit number by another way of communication.
"Security codes are just visible versions of the special key shared between you - and don't worry, it's not the actual key itself, that's always kept secret."
However, this option is useful only when you are actively looking to verify the authenticity of session keys and, we know, only one privacy-conscious paranoid user in thousands would do that.
Secure Alternative to Whatsapp
Oh! You must be thinking — Which secure messaging service then offers protection against such broken trust and interception?
There are several alternatives, such as "Signal Private Messenger", itself, developed by Open Whisper Systems and it's most recommended secure message app.
Donald Trump appoints a CyberSecurity Advisor Whose Own Site is Damn Vulnerable
13.1.2017 thehackernews Vulnerebility
Former New York City Mayor Rudolph W. Giuliani has been appointed as a cyber security advisor for the President-elect Donald Trump, but it appears that he never actually checked the security defenses of his own company's website.
Giuliani is going to head a new Cybersecurity Working group for the President-elect, and "will be sharing his expertise and insight as a trusted friend concerning private sector cyber security problems and emerging solutions developing in the private sector," the Trump's Transition Team announced Thursday.
Trump administration has appointed Giuliani after citing his 16 years of experience "providing security solutions in the private sector," but the news met online criticism with many users on Twitter asking:
'What does the former New York mayor know about cyber security?'
As the news broke, online users started scanning his website "www.giulianisecurity.com" and found that the site for Giuliani Security & Safety is simply a disaster.
The site runs on an old version of Joomla! — a free, open-source content management system (CMS) — which is vulnerable to more than a dozen flaws.
The website also uses an outdated version of the script language PHP, uses an expired SSL certificate, runs over a 10-year-old version of FreeBSD OS server and even fails to follow other basic security practices.
According to Robert Graham of Errata Security, Giuliani did not build the site himself; instead he "contracted with some generic web designer to put up a simple page with just some basic content."
"There's nothing on Giuliani's server worth hacking. The drama over his security, while an amazing joke, is actually meaningless," Graham said in a blog post. "All this tells us is that Verio/NTT.net is a crappy hosting provider, not that Giuliani has done anything wrong."
Although it really doesn't matter who has created the website, if you are in cyber security business to "help the government plan to make us more secure," such ignorance hardly inspires confidence in the expertise of that person.
Giuliani is the CEO of his own private-sector cybersecurity venture, Giuliani Partners, which is an international cyber security consulting firm that claims to offer "a comprehensive range of security and crisis management services."
What Giuliani Partners actually does is not known, because the company promotes its crime reduction successes in countries, but not its cybersecurity work.
The venture recently struck a deal with BlackBerry to provide companies and governments cyber security support by assessing infrastructures, identifying potential cyber security vulnerabilities, addressing gaps and securing endpoints "with the goal of offering another channel to bring customers to a new standard of security."
This clearly suggests that the company is doing something right.
Much details about Giuliani's role in the Trump administration were not immediately available. We'll update the story with new developments.
The ISC issued updates for 4 High severity DoS flaws in BIND
13.1.2017 securityaffairs Vulnerebility
The Internet Systems Consortium (ISC) has issued security updates to address four high severity flaws in the DNS software BIND.
The Internet Systems Consortium (ISC) has issued updates to solve four high severity flaws in the DNS software BIND. The flaw could be exploited by a remote attacker to cause a DoS condition.
An attacker can exploit the vulnerabilities to cause the BIND name server process to encounter an assertion failure and stop executing. The Internet Systems Consortium confirmed that it is not aware of active exploits for the flaws.

Below the list of flaws provided by the ISC:
CVE-2016-9778: An error in handling certain queries can cause an assertion failure when a server is using the nxdomain-redirect feature to cover a zone for which it is also providing authoritative service. A vulnerable server could be intentionally stopped by an attacker if it was using a configuration that met the criteria for the vulnerability and if the attacker could cause it to accept a query that possessed the required attributes.
CVE-2016-9147: Depending on the type of query and the EDNS options in the query they receive, DNSSEC-enabled authoritative servers are expected to include RRSIG and other RRsets in their responses to recursive servers. DNSSEC-validating servers will also make specific queries for DS and other RRsets. Whether DNSSEC-validating or not, an error in processing malformed query responses that contain DNSSEC-related RRsets that are inconsistent with other RRsets in the same query response can trigger an assertion failure. Although the combination of properties which triggers the assertion should not occur in normal traffic, it is potentially possible for the assertion to be triggered deliberately by an attacker sending a specially-constructed answer.
CVE-2016-9131: A malformed query response received by a recursive server in response to a query of RTYPE ANY could trigger an assertion failure while named is attempting to add the RRs in the query response to the cache. While the combination of properties which triggers the assertion should not occur in normal traffic, it is potentially possible for the assertion to be triggered deliberately by an attacker sending a specially-constructed answer having the required properties, after having engineered a scenario whereby an ANY query is sent to the recursive server for the target QNAME. A recursive server will itself only send a query of type ANY if it receives a client query of type ANY for a QNAME for which it has no RRsets at all in cache, otherwise it will respond to the client with the the RRsets that it has available.
CVE-2016-9444: An unusually-formed answer containing a DS resource record could trigger an assertion failure. While the combination of properties which triggers the assertion should not occur in normal traffic, it is potentially possible for the assertion to be triggered deliberately by an attacker sending a specially-constructed answer having the required properties.
The CVE-2016-9778 flaw affects only a subset of servers which are performing NXDOMAIN redirection using the “nxdomain-redirect” function.
The CVE-2016-9131, the CVE-2016-9147, and the CVE-2016-9444 flaws occur during the processing of an answer packet received in response to a query.
“As a result, recursive servers are at the greatest risk; authoritative servers are at risk only to the extent that they perform a limited set of queries (for example, in order to do zone service” state the advisories for the flaws.
The BIND versions 9.9.9-P5, 9.10.4-P5, 9.11.0-P2 and 9.9.9-S7 address the above vulnerabilities.
Microsoft Releases 4 Security Updates — Smallest Patch Tuesday Ever!
11.1.2017 thehackernews Vulnerebility
microsoft-windows-security-update-patch-tuesday
IN BRIEF
Microsoft has issued its first Patch Tuesday for 2017, and it's one of the smallest ever monthly patch releases for the company, with only four security updates to address vulnerabilities in its Windows operating system as well as Adobe Flash Player.
Meanwhile, Adobe has also released patches for more than three dozen security vulnerabilities in its Flash Player and Acrobat/Reader for Windows, MacOS, and Linux desktops.
According to the Microsoft Advisory, only one security bulletin is rated critical, while other three are important. The bulletins address security vulnerabilities in Microsoft's Windows, Windows Server, Office, Edge and Flash Player.
The only security bulletin rated as critical is the one dedicated to Adobe Flash Player, for which Microsoft distributed security patches through Windows Update. Other security bulletins that addresses flaws in Microsoft products are as follows:
Bulletin 1 — MS17-001
This security update resolves just one vulnerability in the Microsoft Edge browser. Microsoft rates this bulletin as important.
The vulnerability (CVE-2017-0002) could let an attacker gain elevated access privileges by tricking users to view a specially crafted web page using Microsoft Edge.
This elevation of privilege flaw exists in Microsoft Edge's cross-domain policies, which could allow "an attacker to access information from one domain and inject it into another domain," Microsoft says.
The update will be rolled out to Windows 10 and Server 2016.
Bulletin 2 — MS17-002
This security bulletin is the one that also patches a single vulnerability in Microsoft Office.
The vulnerability, designated CVE-2017-0003, is a memory corruption issue that allows an attacker to perform remote code execution (RCE) in Microsoft Office 2016 and SharePoint Enterprise Server 2016.
The flaw lets a specially crafted Word file to take control of the target machine with the current user's access privileges.
Users who are logged in with fewer user rights on the system are less impacted than users who operate with administrative user rights, such as some home accounts and server users.
Bulletin 3 — MS17-003
This security bulletin is rated as Critical and resolves 12 security vulnerabilities in Adobe Flash Player for all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016.
The security patch will be automatically rolled out to Windows users running Microsoft Edge or Internet Explorer 11.
Bulletin 4 — MS17-004
This security update, also rated as important, addresses just one denial of service (DoS) vulnerability in Local Security Authority Subsystem Service (LSASS) for Windows Vista, Windows 7, Windows Server 2008, and Windows Server 2008 R2.
The flaw (CVE-2017-0004) resides in the LSASS that handles authentication requests, which could be exploited to reboot the system by sending a specially crafted authentication request to the targeted system or server.
Adobe Security Patch Update
A total of 13 vulnerabilities has been addressed in the Flash Player, while none of the flaws have actively been exploited in the wild.
The Flash Player updates for both Windows and macOS systems have been rated critical, as successful exploitation of the vulnerability could let an attacker perform remote code execution on the target system. However, Linux users are at lower risk for attack.
The update for Adobe Acrobat and Reader addresses some 29 flaws, including some remote code execution (RCE) vulnerabilities in both Windows and macOS.
Users and IT administrators are strongly recommended to apply Windows and Adobe patches as soon as possible in order to keep away hackers and cybercriminals from taking control over your computer.
A system reboot is necessary for installing updates, so users are advised to save work on PCs where the whole package of patches is deployed before initiating the process.
Juniper SRX firewalls open a root-level account due to a flaw
11.1.2017 securityaffairs Vulnerebility
Experts at Juniper have discovered that an update for its Juniper SRX firewalls opens a root-level account on the network device.
The company started warning its users, every user who issued the “request system software” command with the “partition” option is affected by the issue. The failure of the system update leaves it in a state where root CLI login is allowed without a password. The problem affects any system upgraded from Junos OS prior to 12.1X46-D65. When the system upgrade fails, the system goes into a “safe mode” designed to allow a sysadmin to access it and solve the problem.
This implies that a root login without a password is available.
“Using the ‘
request system software
‘ command with the ‘
partition
‘ option on an SRX Series device upgrading from Junos OS releases prior to 12.1X46-D65 can leave the system in a state where root CLI login is allowed without a password due to the system reverting to a “safe mode” authentication triggered by the failed upgrade. Additionally, valid authentication credentials fail to work due to the same issue. Only root with no password will work.” reads a security advisory published by Juniper.
According to the security advisory published by Juniper, no other platform or version of Junos OS is affected by the vulnerability. It also confirmed that no other Juniper Networks products or platforms are affected.
The experts highlighted that any other previously-valid authentication credential is wiped from the system.
In order to definitively solve the problem, it is possible to upgrade the Juniper SRX Series device from an affected release to a fixed release.
Juniper SIRT confirmed that it is not aware of any malicious exploitation of this vulnerability.
“Avoid using the ‘
partition
‘ option when upgrading an SRX Series device to Junos OS 12.1X46 prior to 12.1X46-D65.” continues the advisory. “Note that the symptoms are immediately obvious after an affected upgrade and may be remediated by rebooting the device post-upgrade.”
This means that just rebooting the system the problem will be solved.
The issue is tracked as CVE-2016-1278.
CVE-2016-7200 & CVE-2016-7201 Edge flaws added to the Sundown Exploit Kit
10.1.2017 securityaffairs Vulnerebility
The operators behind the Sundown exploit kit have started using two Microsoft Edge flaws just a few days after researchers published a PoC exploit.
The Sundown exploit kit is becoming one of the most popular crimeware kits in the hacking underground. The last time we saw it was at the end of 2016 when malware researchers spotted a new variant of the Sundown exploit kit leverages on steganography to hide exploit code in harmless-looking image files.
Recently cyber criminals added to the Sundown exploit kit two Edge vulnerabilities tracked as CVE-2016-7200 and CVE-2016-7201.
Both flaws were addressed by Microsoft with a security bulletin (MS16-129) issued in November 2016. The flaws reside in the way the Chakra JavaScript scripting engine handles objects and can trigger memory corruption.
A remote attacker can exploit the vulnerabilities to execute arbitrary code in the context of the current user by tricking victims into visiting a specially crafted website.
On January 4, security experts at the firm Theori confirmed the availability of a PoC exploit for CVE-2016-7200 and CVE-2016-7201, just a few days and the code was included in the Sundown exploit kit.
Segui
Theori @theori_io
Proof-of-Concept exploit for Edge bugs (CVE-2016-7200 & CVE-2016-7201) —https://github.com/theori-io/chakra-2016-11 …
00:52 - 5 Gen 2017
Photo published for theori-io/chakra-2016-11
theori-io/chakra-2016-11
chakra-2016-11 - Proof-of-Concept exploit for Edge bugs (CVE-2016-7200 & CVE-2016-7201)
github.com
210 210 Retweet 196 196 Mi piace
The popular security researcher Kafeine confirmed the exploits being integrated by the Sundown exploit kit.

“The exploits are spotted first in Sundown, but integration in RIG/Empire/Neutrino/Magnitude/Kaixin should be a matter of hours/days.” explained Kafeine.
Crooks leveraged Sundown exploit kit to deliver mostly ZLoader, it was also used to deliver other malicious payloads, including Zeus Panda, Dreambot, Chthonic, Andromeda, Neutrino Bot, Betabot, Smokebot, Remcos, Kronos and a bitcoin miner.
According to Malwarebytes Labs, a variant of the Sundown exploit kit was recently seen distributing a cryptocurrency Monero mining application.
“We recently encountered an atypical case of Sundown EK in the wild – usually the landing page is obfuscated, but in this case there was plain JavaScript. The exploit was dropping some malicious payloads” reads a blog post published by Malwarebytes Labs.
Kafeine highlighted the fact that this is the first true innovation in the exploit kit landscape since 6 months, he also added that the criminal ecosystem lost its locomotive the “Angler EK.”
“After not far from 6 months without new exploit integrated in an EK ecosystem which has lost its innovation locomotive (Angler) , the drive-by landscape is struggling to stay in shape. Low infection rate means more difficulties to properly convert bought traffic.” added Kafeine.
Last time malware researchers observed the introduction of a fresh exploit code in an Exploit Kit was this summer when malware authors added the PoC for CVE-2016-0189 to the Neutrino exploit kit.
FTC filed a lawsuit against D-Link over failure to secure its IoT devices
8.1.2017 securityaffairs Vulnerebility
FTC charges the Taiwanese IT giant D-Link putting consumers’ privacy at risk due to the failure of Implementing secure adequate measures for IoT devices.
The U.S. Federal Trade Commission (FTC) has filed a lawsuit against the Taiwanese firm D-Link, over failure to secure its IoT products, including IP cameras and routers.
The company has produced promotional materials ensuring “Advanced Network Security” for its products, but the reality is different because according to the authorities it has failed to fix flaws exposing consumers to risk.
“A lawsuit the FTC filed against D-Link, a global manufacturer of computer networking equipment and other connected devices, alleges that the company made deceptive claims about the security of its products and engaged in unfair practices that put consumers’ privacy at risk.” reads the announcement from FTC.
The lawsuit includes examples of the D-Link’ choices that put consumers’ privacy at risk:
D-Link allegedly hard-coded login credentials into D-Link camera software that could allow unauthorized access to cameras’ live feed.
D-Link allegedly left users’ login credentials for its mobile app unsecured in clear, readable text on consumers’ devices.
D-Link allegedly mishandled its own private key code used to sign into D-Link software and as a result, it was publicly available online for six months.
D-Link allegedly failed to take reasonable steps to prevent command injection, a known vulnerability that lets attackers take control of people’s routers and send them unauthorized commands.
Usually, hackers that find the flaws report them to the company giving it the necessary time to solve the problems before publicly disclose the vulnerability. Over the past year, some hackers decided to disclose unpatched flaws due to the company’s failure to release necessary security updates that will fix the vulnerabilities.
The Tech giant has been accused of failing to take reasonable steps to secure the software for its IoT devices and for conducting practices that are “likely to cause, substantial injury to consumers in the United States.”
This isn’t the first time that IoT manufacturers tell customers that their products are totally secure while they lack to adopt the necessary security measures.
Earlier 2016, the FTC filed a lawsuit against Asus claiming that the company has put hundreds of thousands of consumers at risk through a series of critical flaws discovered in its products.
“Hackers are increasingly targeting consumer routers and IP cameras — and the consequences for consumers can include device compromise and exposure of their sensitive personal information,” said Jessica Rich, director of the FTC’s Bureau of Consumer Protection. “When manufacturers tell consumers that their equipment is secure, it’s critical that they take the necessary steps to make sure that’s true.”
FTC Sues D-Link Over Failure to Secure Its Routers and IP Cameras from Hackers
6.1.2017 thehackernews Vulnerebility
Image Source: Book - Protect Your Windows Network from Perimeter to Data
The United States' trade watchdog has sued Taiwan-based D-link, alleging that the lax security left its products vulnerable to hackers.
The Federal Trade Commission (FTC) filed a lawsuit (pdf) against D-Link on Thursday, arguing that the company failed to implement necessary security protection in its routers and Internet-connected security cameras that left "thousands of consumers at risk" to hacking attacks.
The move comes as cyber criminals have been hijacking poorly secured internet-connected devices to launch massive DDoS attacks that can force major websites offline.
Over two months back, a nasty IoT botnet, known as Mirai, been found infecting routers, webcams, and DVRs built with weak default passwords and then using them to DDoS major internet services.
The popular Dyn DNS provider was one of the victims of Mirai-based attack that knocked down the whole internet for many users.
To combat this issue, on the one hand, the popular networking equipment provider Netgear has launched a bug bounty program, inviting researchers and hackers to find and responsibly report security flaws in its hardware, mobile apps, and APIs for cash rewards ranging from $150 to $15,000.
But on the other hand, D-Link has been accused of several FTC Act violations, including:
Falsification about security in its router and IP camera user interfaces and promotional materials.
Falsely claiming that reasonable measures have been taken to protect its devices against well-known and easily preventable security flaws, like "hard-coded" user credentials and command injection flaws, which would allow any remote attacker to gain unauthorized access to its devices.
Failure to secure its software.
According to the complaint filed in San Francisco federal court, D-Link's insecure products allowed hackers to "monitor a consumer’s whereabouts to target them for theft or other crimes."
Several security researchers and hackers found serious flaws in D-Link products over the past year, and while some were satisfied with the company addressing the issue, others disclosed unpatched flaws due to its failure to release firmware updates in time.
In response to the complaint, D-Link released a statement saying that the charges brought against it are "unwarranted and baseless" and that the company will "vigorously defend itself."
The FTC "fails to allege, as it must, that actual consumers suffered or are likely to suffer actual substantial injuries," D-Link added.
Due to rise in the IoT threat, the Commission is taking desired steps to protect the Internet-of-Things devices.
The FTC introduced guidelines back in 2015 to (or "intending to") securing IoT devices, and recently it also launched a "prize competition" for public with the aim to find some technical solution for securing IoT devices. The winner of the contest will get $25,000 prize money.
Vulnerebility1
Kaspersky fixing a serious problem with inspection digital certificates
5.1.2017 securityaffairs Vulnerebility
Google hacker Tavis Ormandy discovered a serious flaw that affects the Kaspersky antivirus software and the way it manages inspection digital certificates.
Experts from Kaspersky are solving a problem that disabled certificate validation for 400 million users. The problem was spotted by the notorious Google hacker Tavis Ormandy, the vulnerability affects the Kaspersky antivirus software and the way it used certificates to analyze encrypted traffic.
The security firm is a trusted CA, the Kaspersky Anti-Virus Personal Root, and uses its digital certificate for the traffic inspection, in this way it is able to decrypt it and analyze scanning for malicious patterns.
“In order to inspect encrypted data streams using SSL/TLS, Kasperky installs a WFP driver to intercept all outgoing HTTPS connections. They effectively proxy SSL connections, inserting their own certificate as a trusted authority in the system store and then replace all leaf certificates on-the-fly. This is why if you examine a certificate when using Kaspersky Antivirus, the issuer appears to be “Kaspersky Anti-Virus Personal Root”.” Ormandy wrote in a security advisory.
The process implemented by Kaspersky for certificate interception has previously resulted in serious vulnerabilities. Now the experts discovered other issues such as the way leaf certificates are cached that leverages on an extremely naive fingerprinting technique.
“Kaspersky cache recently generated certificates in memory in case the user agent initiates another connection. In order to do this, Kaspersky fetches the certificate chain and then checks if it’s already generated a matching leaf certificate in the cache. If it has, it just grabs the existing certificate and private key and then reuses it for the new connection.” explained the expert.
“The cache is a binary tree, and as new leaf certificates and keys are generated, they’re inserted using the first 32 bits of MD5(serialNumber||issuer) as the key. If a match is found for a key, they just pull the previously generated certificate and key out of the binary tree and start using it to relay data to the user-agent.”
It is easy to understand that a 32bit key open to brute-forcing attacks to generate a collision in a few seconds. An attacker can produce a collision with other certificates.
Ormandy also provided a description of the attack:
Mallory wants to intercept mail.google.com traffic, for which the 32bit key is 0xdeadbeef.
Mallory sends you the real leaf certificate for mail.google.com, which Kaspersky validates and then generates its own certificate and key for.
On the next connection, Mallory sends you a colliding valid certificate with key 0xdeadbeef, for any commonName (let’s say attacker.com)
Now Mallory redirects DNS for mail.google.com to attacker.com, Kaspersky starts using their cached certificate and the attacker has complete control of mail.google.com.
Ormandy also provided a proof of the bug forcing a collision between Hacker News and manchesterct.gov website.
“You can reproduce this bug, by visiting https://autodiscover.manchesterct.gov, then https://news.ycombinator.com and observing that the content is signed by the wrong certificate.” he added. “So if you use Kaspersky Antivirus in Manchester, Connecticut and were wondering why Hacker News didn’t work sometimes, it’s because of a critical vulnerability that has effectively disabled SSL certificate validation for all 400 million Kaspersky users.”
The expert also provided the C source code that it is possible to use to generate a colliding certificate for testing.
Kaspersky fixing a serious problem with inspection digital certificates
4.1.2017 securityaffairs Vulnerebility
Google hacker Tavis Ormandy discovered a serious flaw that affects the Kaspersky antivirus software and the way it manages inspection digital certificates.
Experts from Kaspersky are solving a problem that disabled certificate validation for 400 million users. The problem was spotted by the notorious Google hacker Tavis Ormandy, the vulnerability affects the Kaspersky antivirus software and the way it used certificates to analyze encrypted traffic.
The security firm is a trusted CA, the Kaspersky Anti-Virus Personal Root, and uses its digital certificate for the traffic inspection, in this way it is able to decrypt it and analyze scanning for malicious patterns.
“In order to inspect encrypted data streams using SSL/TLS, Kasperky installs a WFP driver to intercept all outgoing HTTPS connections. They effectively proxy SSL connections, inserting their own certificate as a trusted authority in the system store and then replace all leaf certificates on-the-fly. This is why if you examine a certificate when using Kaspersky Antivirus, the issuer appears to be “Kaspersky Anti-Virus Personal Root”.” Ormandy wrote in a security advisory.
The process implemented by Kaspersky for certificate interception has previously resulted in serious vulnerabilities. Now the experts discovered other issues such as the way leaf certificates are cached that leverages on an extremely naive fingerprinting technique.
“Kaspersky cache recently generated certificates in memory in case the user agent initiates another connection. In order to do this, Kaspersky fetches the certificate chain and then checks if it’s already generated a matching leaf certificate in the cache. If it has, it just grabs the existing certificate and private key and then reuses it for the new connection.” explained the expert.
“The cache is a binary tree, and as new leaf certificates and keys are generated, they’re inserted using the first 32 bits of MD5(serialNumber||issuer) as the key. If a match is found for a key, they just pull the previously generated certificate and key out of the binary tree and start using it to relay data to the user-agent.”
It is easy to understand that a 32bit key open to brute-forcing attacks to generate a collision in a few seconds. An attacker can produce a collision with other certificates.
Ormandy also provided a description of the attack:
Mallory wants to intercept mail.google.com traffic, for which the 32bit key is 0xdeadbeef.
Mallory sends you the real leaf certificate for mail.google.com, which Kaspersky validates and then generates its own certificate and key for.
On the next connection, Mallory sends you a colliding valid certificate with key 0xdeadbeef, for any commonName (let’s say attacker.com)
Now Mallory redirects DNS for mail.google.com to attacker.com, Kaspersky starts using their cached certificate and the attacker has complete control of mail.google.com.
Ormandy also provided a proof of the bug forcing a collision between Hacker News and manchesterct.gov website.
“You can reproduce this bug, by visiting https://autodiscover.manchesterct.gov, then https://news.ycombinator.com and observing that the content is signed by the wrong certificate.” he added. “So if you use Kaspersky Antivirus in Manchester, Connecticut and were wondering why Hacker News didn’t work sometimes, it’s because of a critical vulnerability that has effectively disabled SSL certificate validation for all 400 million Kaspersky users.”
The expert also provided the C source code that it is possible to use to generate a colliding certificate for testing.
Critical Updates — RCE Flaws Found in SwiftMailer, PhpMailer and ZendMail
3.1.2017 thehackernews Vulnerebility
phpmailer-swiftmailer-zendmail
A security researcher recently reported a critical vulnerability in one of the most popular open source PHP libraries used to send emails that allowed a remote attacker to execute arbitrary code in the context of the web server and compromise a web application.
Disclosed by Polish security researcher Dawid Golunski of Legal Hackers, the issue (CVE-2016-10033) in PHPMailer used by more than 9 Million users worldwide was thought to be fixed with the release of version 5.2.18.
However, Golunski managed to bypass the patched version of PHPMailer that was given a new CVE (CVE-2016-10045), which once again put millions of websites and popular open source web apps, including WordPress, Drupal, 1CRM, SugarCRM, Yii, and Joomla, at risk of remote code execution attack.
PHPMailer eventually fixed the issue with an update, version 5.2.20. All versions of PHPMailer before this critical release are affected, so web administrators and developers are strongly recommended to update to the new version.
In addition to this bug, Golunski also reported a similar vulnerability in two other mailing libraries for PHP, SwiftMailer, and ZendMail, that could have also led to remote code execution attack.
RCE Flaw in SwiftMailer
SwiftMailer is also a popular PHP library used by many major open-source projects, including top PHP programming frameworks like Yii2, Laravel, Symfony for sending emails over SMTP.
The vulnerability (CVE-2016-10074) in SwiftMailer can be exploited in the same manner as the PHPMailer vulnerability by targeting web site components that use SwiftMailer class, such as contact/registration forms, password email reset forms, and so forth.
Attackers can execute arbitrary code remotely in the context of the web server, which could further be exploited to access a web server hosting a web application that used a vulnerable version of the library.
The SwiftMailer vulnerability affects all versions of the library, including the then-current release, version 5.4.5-DEV.
Golunski disclosed the vulnerability to SwiftMailer team, and developers acted fast to fix the issue, rolling out patched version 5.4.5 within a day.
"The mail transport (Swift_Transport_MailTransport) was vulnerable to passing arbitrary shell arguments if the "From," "ReturnPath" or "Sender" header came from a non-trusted source, potentially allowing Remote Code Execution," reads the changelog for SwiftMailer on GitHub.
RCE Flaw in ZendMail
ZendMail is a component of a very popular PHP programming framework Zend Framework with more than 95 Million installations.
The critical vulnerability (CVE-2016-10034) in ZendMail can also be exploited in the same manner as one discovered in PHPMailer and SwiftMailer by targeting web site components that use ZendMail, like contact/registration forms, password email reset forms, and so on.
Attackers could achieve remote code execution in the context of the web server and could remotely compromise the target web application that used the vulnerable version of the ZendMail.
The researcher reported the issue to ZendMail, and the developers fixed the vulnerability and rolled out the patched version.
"When using the zend-mail component to send email via the Zend\Mail\Transport\Sendmail transport, a malicious user may be able to inject arbitrary parameters to the system sendmail program," ZendMail wrote in a blog post.
"The attack is performed by providing additional quote characters within an address; when unsanitized, they can be interpreted as additional command line arguments, leading to the vulnerability."
Golunski has released a proof-of-concept video demonstration that will show all the three attacks in action.
Golunski has also released a dedicated website, nicknamed PwnScriptum, with a logo that contains all the information about the vulnerabilities in PHPMailer, SwiftMailer, and ZendMail in one place.
The researcher will soon be revealing a security white-paper with previously unknown exploitation vectors and techniques that can be used to exploit all the 3 vulnerabilities.
Researcher found a severe flaw in the MONyog monitoring tool
30.12.2016 securityaffairs Vulnerebility
A security expert discovered a vulnerability in the MONyog tool that could be exploited by a normal user to elevate his privilege access.
The security researcher and penetration tester Mutail Mohamed (@muleyl) discovered a vulnerability in the MONyog, the most secure and scalable MySQL monitoring tool of the server monitoring tool.
The application URL is https://www.webyog.com/product/monyog and the affected version is MONyog Ultimate 6.63.
The flaw resides in the session management on Monyog application, it could be exploited by a normal user to elevate his privilege access by altering the session.

The exploitation of the flaw is very simple, the user just has to change the perimeters in the cookie store at that session.
The value associated with a normal user is 0, attackers can change it to 1 to gain admin privileges.
The researcher demonstrated that is to elevate privileges by manipulating the value of the following Cookie parameters;
HasServerEdit
IsAdmin
The hack will allow the user to create roles, view the passwords stored in the setup and change other settings via the admin section.
Below a video PoC of the exploitation of the flaw.
I reached the researcher for a comment:
“Since this is a commercial application and organizations pay for this, they At least need something secure and worth that price. ” explained Mutail.
“The organization could have a huge impact on this, because if let’s say a normal user goes rogue, he could get admin level access to organizations network. Since this application does use LDAP authentication. “
CheckPoint experts spotted Three Critical 0-Day in PHP 7
30.12.2016 securityaffairs Vulnerebility
Researchers at the security firm CheckPoint have discovered three fresh critical zero day vulnerability in the last PHP 7.
Security researchers at the firm CheckPoint have discovered three fresh critical 0-day vulnerabilities in last PHP 7.
These vulnerabilities allow an attacker to take full control over 80 percent of websites which run on the latest release of the popular web programming language. The bad news is that one of the vulnerabilities remains unpatched again.
Security researchers at Check Point’s have analyzed in the last months PHP 7 and focused their efforts into “the unserialized mechanism” which is one of the most well-known vulnerable areas of PHP.
This is the same mechanism that was strongly exploited in PHP 5 and allowed attackers to compromise popular platforms, including Magento, vBulletin, Drupal, Joomla!, Pornhub’s website and other affected web servers in past, by sending maliciously crafted data in client cookies or to expose API calls.
The vulnerabilities are tracked as:
CVE-2016-7479 User After Free(UAF) Code Execution
CVE-2016-7480 Use of Uninitialized Value Code Execution
CVE-2016-7478 Remote Denial of Service
The exploitation of the first two vulnerabilities could allow an attacker to take complete control over affected servers, this means that it is possible to exploit them to spread malware as well as to steal data they store.
The last vulnerability triggers a remote Denial of Service attack/threat which basically hangs the website, exhausts its memory consumption, and a possible site down.

“The first vulnerability allows a remote attacker to unserialize a pathological exception object which refers to itself as the previous exception.” states the report. “When invoking the __toString method of this exception, the code iterates over the chain of exceptions. As the chain of exceptions consists of just that one object that points to itself, the iteration never terminates. “
For more technical details about the vulnerabilities give a look at the report.
“We have reported the three vulnerabilities to the PHP security team on the 15th of September and 6th of August. The PHP security team issued fixes for two of the vulnerabilities on the 13th of October and 1st of December.”
To ensure your webserver’s security, we recommend you should upgrade to latest version of PHP and stay tuned on PHP’s official site for news and updates.
Below the list of vulnerable PHP versions:
CVE-2016-7479 Version <= 7.0.13
CVE-2016-7480 Version < 7.0.12
CVE-2016-7478 Version <= 7.0.13 and 5.6.26
3 Critical Zero-Day Flaws Found in PHP 7 — One Remains Unpatched!
29.12.2016 thehackernews Vulnerebility
3 Critical Zero-Day Flaws Found in PHP 7
Three critical zero-day vulnerabilities have been discovered in PHP 7 that could allow an attacker to take complete control over 80 percent of websites which run on the latest version of the popular web programming language.
The critical vulnerabilities reside in the unserialized mechanism in PHP 7 – the same mechanism that was found to be vulnerable in PHP 5 as well, allowing hackers to compromise Drupal, Joomla, Magento, vBulletin and PornHub websites and other web servers in the past years by sending maliciously crafted data in client cookies.
Security researchers at Check Point's exploit research team spent several months examining the unserialized mechanism in PHP 7 and discovered "three fresh and previously unknown vulnerabilities" in the mechanism.
While researchers discovered flaws in the same mechanism, the vulnerabilities in PHP 7 are different from what was found in PHP 5.
Tracked as CVE-2016-7479, CVE-2016-7480, and CVE-2016-7478, the zero-day flaws can be exploited in a similar manner as a separate vulnerability (CVE-2015-6832) detailed in Check Point's August report.
CVE-2016-7479—Use-After-Free Code Execution
CVE-2016-7480—Use of Uninitialized Value Code Execution
CVE-2016-7478—Remote Denial of Service
The first two vulnerabilities, if exploited, would allow a hacker to take full control over the target server, enabling the attacker to do anything from spreading malware to steal customer data or to defacing it.
The third vulnerability could be exploited to generate a Denial of Service (DoS) attack, allowing a hacker to hang the website, exhaust its memory consumption and eventually shut down the target system, researchers explain in their report [PDF].
According to Yannay Livneh of Check Point's exploit research team, none of the above vulnerabilities were found exploited in the wild by hackers.
The check Point researchers reported all the three zero-day vulnerabilities to the PHP security team on September 15 and August 6.
Patches for two of the three flaws were issued by the PHP security team on 13th October and 1st December, but one of them remains unpatched.
Besides patches, Check Point also released IPS signatures for the three vulnerabilities on the 18th and 31st of October to protect users against any attack that exploits these vulnerabilities.
In order to ensure the webserver’s security, users are strongly recommended to upgrade their servers to the latest version of PHP.
ZyXEL Customized Routers plagues by multiple vulnerabilities
29.12.2016 securityaffairs Vulnerebility
According to the firm SecuriTeam, several ZyXEL customized routers are affected by many vulnerabilities that could be easily exploited by hackers.
According to the firm SecuriTeam, multiple ZyXEL customized routers are affected by many vulnerabilities. The devices are distributed by the Thai IPS TrueOnline. The ZyXEL customized routers are offered for free to the customers with default settings, including default accounts and passwords, a gift for hackers.
The models are widespread, ZyXEL P660HN-T v1, ZyXEL P660HN-T v2, and Billion 5200W-T, the first of which since 2013.
“Several models are distributed by TrueOnline, three in particular are widespread:
ZyXEL P660HN-T v1 (distributed up to 2013)
ZyXEL P660HN-T v2
Billion 5200W-T (currently being distributed to new clients)
These are customized versions of existing ZyXEL and Billion routers. They are MIPS systems and they all run BOA web server.” reads the security advisory published by SecuriTeam.

The vulnerabilities have been discovered by an independent security researcher, they include an unauthenticated remote command execution vulnerability in P660HN-T v1, an unauthenticated remote command execution and authenticated remote command execution flaws in Billion 5200W-T, and an unauthenticated remote command execution vulnerability in P660HN-T v2.
The P660HN-T v1 device is affected by a command injection vulnerability in Maintenance > Logs > System Log > Remote System Log, the issue resides in the remote_host parameter on the ViewLog.asp page, which is accessible by an unauthenticated attacker.
The network device comes with the following default credentials:
username: admin; password: password
username: true; password: true
An unauthenticated command injection is present in the adv_remotelog.asp file of the Billion 5200W-T router. An attacker can trigger the vulnerability in the syslogServerAddr parameter by entering a valid IP address followed by “;<COMMAND>;”.
The same device is affected by an authenticated command injections in the interface tools_time.asp with the uiViewSNTPServer parameter. Also in this case, the expert discovered the device includes the following default accounts:
username: admin; password: password
username: true; password: true
username: user3; password: 12345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678
The third device, the P660HN-T v2 router is affected by a remote command injection vulnerability that results from an authenticated command injection chained with a hardcoded supervisor password. The flaw resides in the logSet.asp file, while the hardcoded supervisor credentials are username: supervisor; password: zyad1234.
“The actual command that can be injected has a length limitation of 28 characters.” states the advisory. “
Default accounts – P660HN-T v2 router
username: admin; password: password
username: true; password: true
username: supervisor; password: zyad1234″
The sad aspect of the story is that the researchers reported the vulnerabilities to ZyXEL in July, but the company still hasn’t issued any patched neither workaround.
Vulnerabilities in IoT devices, including home routers and SOHO devices, are particularly critic, because attackers can exploit them to compromise the equipment and recruit them in powerful “thingbot “such as the Mirai botnet.
Critical PHPMailer Flaw leaves Millions of Websites Vulnerable to Remote Exploit
26.12.2016 thehackernews Vulnerebility
A critical vulnerability has been discovered in PHPMailer, which is one of the most popular open source PHP libraries to send emails used by more than 9 Million users worldwide.
Millions of PHP websites and popular open source web applications, including WordPress, Drupal, 1CRM, SugarCRM, Yii, and Joomla comes with PHPMailer library for sending emails using a variety of methods, including SMTP to their users.
Discovered by Polish security researcher Dawid Golunski of Legal Hackers, the critical vulnerability (CVE-2016-10033) allows an attacker to remotely execute arbitrary code in the context of the web server and compromise the target web application.
"To exploit the vulnerability an attacker could target common website components such as contact/feedback forms, registration forms, password email resets and others that send out emails with the help of a vulnerable version of the PHPMailer class," Golunski writes in the advisory published today.
Golunski responsibly reported the vulnerability to the developers, who have patched the vulnerability in their new release, All versions of PHPMailer before the critical release of PHPMailer 5.2.18 are affected, so web administrators and developers are strongly recommended to update to the patched release.
Since The Hacker News is making the first public disclosure of the vulnerability in the news following Golunski advisory and millions of websites remain unpatched, the researcher has put on hold more technical details about the flaw.
However, Golunski has promised to release more technical details about the vulnerability in coming days, including a proof-of-concept exploit code and video demonstration that will show the attack in action.
We will update this article with additional information on the PHPMailer vulnerability, exploit code and video demonstration, once the researcher makes it public.