
Vulnerebility Articles - H 2020 1 2 3 4 5 6 7 8 9 Vulnerebility List - H 2021 2020 2019 2018 Vulnerebility blog Vulnerebility blog
Critical Vulnerabilities Found in Nuke Plant Radiation Monitors
27.7.2017 securityweek Vulnerebility
Critical Vulnerabilities Found in Radiation Monitors Used in Nuclear Power Plants, Seaports and Airports
LAS VEGAS - BLACK HAT USA - Researchers have discovered multiple unpatched vulnerabilities in different radiation monitoring devices that could be leveraged by attackers to reduce personnel safety, delay detection of radiation leaks, or help international smuggling of radioactive material.
In a paper (PDF) delivered by Ruben Santamarta, principal security consultant at Seattle-based IOActive, at Black Hat Wednesday, it was disclosed that radiation monitors supplied by Ludlum, Mirion and Digi contain multiple vulnerabilities.
Patching will be difficult since these are design flaws rather than software bugs; and the vendors' early response to IOActive's discoveries was, in each case, to decline to work on patches. Since then, Digi has told IOActive that it is collaborating with Mirion to patch the critical vulnerabilities.
Vulnerabilities in different radiation monitoring devices Nevertheless, IOActive concludes, "we should acknowledge these issues are not currently patched, so increasing awareness of the possibility of such attacks will help to mitigate the risks." It is likely that the same flaws will be present in other vendors' radiation monitoring devices.
There are many kinds of radiation monitor used in many different environments. IOActive concentrated its research on portal monitors, used at airports and seaports; and area monitors, used at Nuclear Power Plants (NPPs). However, little effort was required for the portal monitors: "the initial analysis revealed a complete lack of security in these devices, so further testing wasn't necessary to identify significant vulnerabilities," notes the report.
In the Ludlum Model 53 personnel portal, IOActive found a backdoor password that granted the highest privilege. With this, malicious personnel could bypass authentication and take control of the device, preventing the triggering of proper alarms.
In the Ludlum Model 4525 gate monitor, IOActive discovered a complete lack of security in the communication between the gate and the controller Windows device. With these vulnerabilities, IOActive warns, "Malicious actors can perform a man-in-the-middle attack that alters the readings when the radioactive material they are interested in trafficking is detected. This would allow them to safely bypass these gate monitors while maintaining the compromised device in a working condition."
In fact, adequately resourced attackers could fine-tune their malware, says IOActive, to deploy "an advanced payload that hides specific isotopes from detectors, while providing the expected readings for others."
For its analysis of area monitors used at NPPs, IOActive concentrated on the Mirion WRM2 protocol used in numerous devices. It found that it could insert false information into the communications. There are two 'worst-case' scenarios.
In the first, under normal working conditions, attackers could simulate a radiation leak by inserting a dataset of falsified readings. Although this on its own is unlikely to cause a reactor shutdown (because of the need for human intervention), it could lead to an evacuation of the site.
In the second, in a real accident situation, the course of the evacuation could be manipulated: "attackers may falsify these readings to trick authorities into giving the wrong directions for the evacuation, thus increasing the damage and/or potential casualties."
"Failed evacuations, concealed persistent attacks and stealth man-in-the-middle attacks are just a few of the risks I flagged in my research," said Santamarta. "Being able to properly and accurately detect radiation levels, is imperative in preventing harm to those at or near nuclear plants and other critical facilities, as well as for ensuring radioactive materials are not smuggled across borders."
Experts found critical flaws in Diebold Opteva ATM that allow to vend notes from the machine
27.7.2017 securityaffairs Vulnerebility
Experts at the US firm IOActive have discovered a critical physical and authentication bypass vulnerability in the Diebold Opteva ATM.
The researchers have found two vulnerabilities in the Diebold Opteva ATM machines with the AFD platform that could be chained to allow an unauthorized user to vend notes from the device.
“IOActive has discovered two vulnerabilities in Opteva ATMs with the AFD platform that, when combined, may allow an unauthorized user to vend notes from the device.” reads the advisory.

The Diebold Opteva line of ATMs with the AFD platform is composed of an upper cabinet for the operating system and a lower cabinet for the safe, each part requests its own authentication requirements.
Chaining the vulnerabilities allows the attacker to bypass both authentication mechanisms and take the control of the Diebold Opteva ATM.
In the attack scenario presented IOActive, the researchers physical accessed to the internal computer by inserting a metal rod through a speaker hole on the front of the ATM, lifting a metal locking bar and gaining access to the upper cabinet of the Diebold Opteva ATM that contains the computer. Once accessed to the computer, the researchers removed the USB connection from the Windows host and gained a direct line of communication to the AFD controller for the safe.
At this point, the hackers triggered the second flaw to get to the money.
The experts made a reverse engineering of the AFD’s protocol and firmware, they were able to gain access to the content of the safe without authenticating.
“Using the USB that connects the AFD to the computer in the upper cabinet, the team was able to initiate two-way communication. This would normally require a shared encryption key and a device identifier; however, the team was able to complete the authentication protocol unencrypted and set up communications without properly authenticating. This allowed the team to act as an authenticated user and gain access to the contents of the safe.” continues the analysis. “The protocol does not require any device specific knowledge to carry out the attack. This would imply that an attacker with access to one device could reverse engineer enough of the controller protocol to effectively bypass authentication and vend notes from any other device that uses an AFD as long as the vulnerability remains unpatched.”
IOActive reported the issue to Diebold in February 2016, only one year later, in May 2017 Diebold responds, “[your]..system is very old (2008/2009 vintage) and is unpatched;”
IOActive asked if retesting a recent supported version would be possible, but without receiving a reply.
Finally, on July 26, 2017, IOActive opted for the public disclosure.
Unfortunately, it is still unclear whether the ATMs have been patched, nor whether any newer firmware versions are still vulnerable.
DEF CON Talk Will Expose The Latest SMB Vulnerability SMBLoris
27.7.2017 securityaffairs Vulnerebility
Security researchers at RiskSense have identified a 20-year-old Windows SMB vulnerability they are calling SMBloris, a DEF CON Talk Will Expose it.
Server Message Block (SMB) has been a foundational piece of Microsoft Windows’ networking all the way back to the LAN Manager days, facilitating “shared access to files, printers and serial ports.” It is so common that a free software implementation called Samba was developed long ago to allow UNIX-like systems to share network resources with Windows systems. It is a rare company that doesn’t have SMB packets running on the network.
Over the years SMB has gone through many versions to add features and improve performance. It has also had its share of vulnerabilities on all of the platforms it has been implemented, with many, many patches along the way. No matter how many times it is patched or upgraded, it seems that there is always another vulnerability to be uncovered. Many times a vulnerability that was patched in an earlier version is rediscovered years later. In 2015, security researchers at Cylance discovered a new attack vector for an 18-year-old SMB vulnerability. The new method dubbed Redirect to SMB, “impacted products from Microsoft, Apple, Abode, Symantec, Box, Oracle, and more.” In 2014, the Guardians of Peace used an SMB worm exploit to hack Sony Pictures. And an SMB exploit called ETERNALBLUE was part of the cache of NSA tools released by Shadow Brokers in 2017. This exploit was eventually wrapped up and released on the World as the initial exploit point for WannaCry ransomware. Many of these vulnerabilities existed in the SMB code for many years until they were publicly exploited.
In a seeming case of deja vu, security researchers at RiskSense have identified a 20-year-old Windows SMB vulnerability they are calling SMBloris (a nod to the Slowloris DoS attack.)
SMBLoris Windows RCE vulnerability
The exploit is a Denial of Service (DoS) attack affecting “every version of the SMB protocol and every Windows version dating back to Windows 2000.” Like most DoS attacks, the target system is overwhelmed by multiple service requests rendering it unavailable. Most modern systems require coordination of a massive number of attacking systems to overwhelm the target, referred to as a Distributed Denial of Service (DDoS) attack. However, the flaws discovered in the Windows SMB service are easily exploited by a single, low-powered computer.
According to researcher Sean Dillon, “While working on EternalBlue, we observed a pattern in the way memory allocations were done on the non-paged pool of the Windows kernel. The non-paged pool is memory that has to be reserved in physical RAM; it can’t be swapped out. That’s the most precious pool of memory on the system. We figured out how to exhaust that pool, even on servers that are very beefy, even 128 GB of memory. We can take that down with a Raspberry Pi.”
Dillon and his research partner Zach Harding followed a responsible disclosure process and privately notified the SMBloris flaw to Microsoft of the vulnerability in early June. Mid June Microsoft replied with their assessment that the vulnerability presented only a “moderate risk”, and would not be moved into the security branch which means it is unlikely to ever be fixed.
Speaking to Threatpost, a Microsoft spokesperson did suggest, “For enterprise customers who may be concerned, we recommend they consider blocking access from the Internet to SMBv1.”
Given the long history of vulnerabilities in SMB, I hope that everyone is already blocking SMB at their firewalls! Given rumors that a single, low-powered computer is able to exploit the SMB vulnerability for a successful DoS attack, it is not unreasonable to anticipate an attack launched against internal servers from internal clients. Perhaps a properly crafted email attachment that is executed on a desktop?
Dillon and Harding are expected to release full details of the vulnerability at a DEF CON talk on Saturday. With more details, you will be able to assess for yourself whether the risk is “moderate” or something you need to encourage Microsoft to address.
Code Execution Vulnerabilities Patched in FreeRDP
27.7.2017 securityweek Vulnerebility
Researchers at Cisco’s Talos security intelligence and research group have discovered several potentially serious vulnerabilities in FreeRDP. The tool’s developers patched the flaws on Monday with the release of an update.
FreeRDP is an open-source implementation of Microsoft’s Remote Desktop Protocol (RDP). The software, which allows users to remotely connect to other devices, is included in several Linux distributions and is available for both Windows and Mac systems. The FreeRDP library is also used by many commercial applications.
While FreeRDP is typically used for legitimate purposes, it has also been leveraged by cybercriminals, including the notorious group known as Carbanak and Anunak.
Talos researchers discovered that FreeRDP 2.0.0-beta1 on Windows, Linux and Mac OS X is affected by six vulnerabilities that can be exploited for remote code execution and denial-of-service (DoS) attacks.
The RCE flaws, both tracked as CVE-2017-2834 and assigned a severity rating of “high,” exist due to the use of untrusted data in handling the license authentication and reception of an RDP packet from the server.
“The license message sent by the server contains a length field, which is not correctly verified by FreeRDP. For internal purposes, the library decreases this value by 4, if the server is sent a value inferior to 3, this will result in a negative value and the writing of packet contents outside of the allocated buffer in memory. This vulnerability can allow the execution of arbitrary code on the FreeRDP client side,” Talos said in its advisory.
The DoS vulnerabilities, which allow an attacker to crash the client, exist due to the way the client handles proprietary server certificates, security data, and license challenge packets.
The security holes can be exploited by sending specially crafted packets, either via a man-in-the-middle (MitM) attack or by compromising the server.
Talos has made available technical details and developed proof-of-concept (PoC) exploits for the vulnerabilities.
The flaws were patched with the release of FreeRDP 2.0.0-rc0 on Monday. FreeRDP developers have also published an advisory pinpointing the changes made to the code.
Critical Vulnerability Found in Diebold ATM Machine
27.7.2017 securityweek Vulnerebility
Seattle-based IOActive has issued a critical security advisory detailing a physical and authentication bypass in the Diebold Opteva ATM.
"IOActive has discovered two vulnerabilities in Opteva ATMs with the AFD platform that, when combined," warns the advisory "may allow an unauthorized user to vend notes from the device."
The combined use of the vulnerabilities is necessary because of ATMs' practice of separating the safe from the operating system. Diebold's Opteva line of ATMs with the AFD platform contain an upper cabinet for the operating system and a lower cabinet for the safe, each with its own authentication requirements.
Opteva ATMThe researchers first gained physical access to the internal computer by inserting a metal rod through a speaker hole in the ATM, lifting a metal locking bar and gaining access to the upper cabinet of the ATM containing the computer. With access to the computer, they were able to get a direct line to the AFD controller for the safe. But they still needed a second vulnerability to get to the money.
For this, IOActive reverse engineered the AFD's protocol and firmware. From here, the team was able to complete the authentication protocol unencrypted and set up communications without properly authenticating. In short, the two vulnerabilities allowed the team to act as an unauthenticated user and gain access to the content of the safe.
Since the process does not require any device specific knowledge, IOActive concludes that "an attacker with access to one device could reverse engineer enough of the controller protocol to effectively bypass authentication and vend notes from any other device that uses an AFD as long as the vulnerability remains unpatched."
The problem here, and one of the most disturbing aspects of the advisory, is that IOActive doesn't know whether it has been patched. It first reported the issue to Diebold in February 2016; but it did not get a secure transit from Diebold to allow it to disclose the issue until January 2017.
In February 2017, one year after the first notification to Diebold, Diebold requested and received tracelogs from IOActive. IOActive tried to follow-up, and eventually was told, "[your]... system is very old (2008/2009 vintage) and is unpatched." Its offer to retest current firmware was ignored, as were further attempts to follow-up with Diebold.
Finally, on July 26, 2017, more than 18 months after initially contacting the vendor, IOActive decided to go public. At this stage, it is unknown whether the devices have been patched, nor whether any newer versions of the firmware are still vulnerable.
The advisory from IOActive is available here.
New Debian 9.1 release includes 26 security fixes for 55 packages
24.7.2017 securityaffairs Vulnerebility
The Debian Project announced the Debian 9.1 GNU/Linux, a version that brings numerous updates and addresses many security issues.
The Debian Project announced the new Debian 9.1 release that includes 26 security fixes. The list of fixed problems includes the Heimdal Kerberos man-in-the-middle vulnerability, a 20 years-old vulnerability in Kerberos that was parched this week for both Microsoft and Linux distros.
“The Debian project is pleased to announce the first update of its stable distribution Debian 9 (codename stretch). This point release mainly adds corrections for security issues, along with a few adjustments for serious problems. Security advisories have already been published separately and are referenced where available.” states the announcement.
“Please note that the point release does not constitute a new version of Debian 9 but only updates some of the packages included. There is no need to throw away old stretch media. After installation, packages can be upgraded to the current versions using an up-to-date Debian mirror.”
Debian 9.1 isn’t a new Debian version or bring new features, it only updates the existing packages with a special focus on cyber security.
Debian 9.1 also addresses security issues in Apache, and includes a number of Linux updates and patches for OpenVPN flaws (including recently fixed CVE-2017-7508, CVE-2017-7520, CVE-2017-7520).
The new release fixes the CVE-2017-1000381 in the c-ares function “ares_parse_naptr_reply()“, it also addresses several issues in thedwarfutils link shortener and in libquicktime.
“The c-ares function `ares_parse_naptr_reply()`, which is used for parsing NAPTR responses, could be triggered to read memory outside of the given input buffer if the passed in DNS response packet was crafted in a particular way.” states the description for the CVE-2017-1000381 flaw.

For updating all packages run the following command:
apt-get update && apt-get upgrade
For downloading Debian 9.1 images, refer one of the mirrors at the following URL:
https://www.debian.org/mirror/list
Hundreds of Java Flaws Patched by Schneider in Trio TView Software
22.7.2017 securityweek Vulnerebility
Energy management and automation solutions giant Schneider Electric was informed by a researcher that its Trio TView software uses a version of Java that was released in 2011 and is affected by hundreds of vulnerabilities.
Researcher Karn Ganeshen informed Schneider that the version of Java Runtime Environment (JRE) used in Trio TView, a management and diagnostics software for industrial radio systems, is outdated and contains numerous vulnerabilities.
JRE 1.6.0 update 27, released in August 2011, is plagued by more than 360 flaws, including security holes that over the past years have been exploited in attacks by both cybercriminals and state-sponsored threat actors. The list includes CVE-2015-4902, CVE-2015-2590 and CVE-2012-4681, all of which were zero-day vulnerabilities at some point.
The outdated version of Java is present in TView 3.27.0 and earlier. With the release of TView 3.29.0, Schneider updated the Java component to version 1.8.0 update 131, which Oracle released in mid-April 2017.
Ganeshen previously notified Schneider of several vulnerabilities, including ones affecting some of the company’s power meters.
Vulnerabilities in Schneider Electric PowerSCADA Anywhere and Citect Anywhere
Schneider has informed ICS-CERT that it has released patches for several medium and high severity vulnerabilities impacting its PowerSCADA Anywhere and Citect Anywhere.
The vulnerable applications are extensions of Citect SCADA, a high performance SCADA software for industrial process customers.
Versions 1.0 of PowerSCADA Anywhere and Citect Anywhere are affected by a high severity cross-site request forgery (CSRF) flaw that can be exploited to initiate “state-changing requests” by getting the targeted user to click on a specially crafted link.
The other vulnerabilities have been described as information exposure issues, use of outdated cipher suites, and a weakness that can be exploited to escape the application and launch other processes.
Patches for these security holes are included in version 1.1 of the affected products. Schneider has also provided a series of recommendations for hardening systems running PowerSCADA Anywhere and Citect Anywhere.
Apple Patches Vulnerabilities Across All Platforms
20.7.2017 securityweek Vulnerebility Apple
Apple this week released security patches for all four of its operating systems to resolve tens of security bugs in each of them.
The tech giant addressed 37 vulnerabilities with the release of macOS Sierra 10.12.6 (and Security Update 2017-003 El Capitan and Security Update 2017-003 Yosemite). The vast majority of the issues could result in arbitrary code execution. Impacted components include audio, Bluetooth, contacts, Intel graphics driver, kernel, libarchive, and libxml2, Apple reveals.
The release of iOS 10.3.3 adressed 47 vulnerabilities, many allowing for arbitrary code execution and some for unexpected application termination or information disclosure. WebKit was the most affected component, with over 20 bugs squashed in it. Kernel, Safari, messages, contacts, libarchive, and libxml2 were also among the affected components.
Tracked as CVE-2017-9417 and affecting Broadcom's BCM4354, 4358, and 4359 chips, one of the vulnerabilities could allow an attacker within range to execute arbitrary code on the Wi-Fi chip. Because said chips are used in various smartphones, including devices from HTC, LG, and Samsung, Google too addressed the issue with its latest Android patches.
Apple addressed 16 security flaws with the release of watchOS 3.2.3, including CVE-2017-9417. Kernel was affected the most, with 9 bugs resolved in it. Contacts, IOUSBFamily, libarchive, libxml2, libxpc, messages, and Wi-Fi were also impacted. These vulnerabilities could result in arbitrary code execution, unexpected application termination, information disclosure, or an app’s ability to read restricted memory.
Apple's tvOS 10.2.2 resolves 38 bugs, most of which affect WebKit and Kernel (they were addressed in iOS and watchOS as well). Most of these issues could lead to arbitrary code execution, in some cases with elevated privileges (kernel or system), Apple notes in its advisory.
Apple also released Safari 10.1.2 this week, addressing a bug in Safari Printing and 24 issues in WebKit or related to it. iTunes 12.6.2 for Windows patches 23 security issues (one in iTunes, another in libxml2, and 21 in WebKit), while iCloud for Windows 6.2.2 resolves 22 vulnerabilities (one in libxml2 and 21 in WebKit).
Critical Code Injection Flaw In Gnome File Manager Leaves Linux Users Open to Hacking
20.7.2017 thehackernews Vulnerebility
A security researcher has discovered a code injection vulnerability in the thumbnail handler component of GNOME Files file manager that could allow hackers to execute malicious code on targeted Linux machines.
Dubbed Bad Taste, the vulnerability (CVE-2017-11421) was discovered by German researcher Nils Dagsson Moskopp, who also released proof-of-concept code on his blog to demonstrate the vulnerability.
The code injection vulnerability resides in "gnome-exe-thumbnailer" — a tool to generate thumbnails from Windows executable files (.exe/.msi/.dll/.lnk) for GNOME, which requires users to have Wine application installed on their systems to open it.
Those who are unaware, Wine is a free and open-source software that allows Windows applications to run on the Linux operating system.
Moskopp discovered that while navigating to a directory containing the .msi file, GNOME Files takes the filename as an executable input and run it in order to create an image thumbnail.
For successful exploitation of the vulnerability, an attacker can send a crafted Windows installer (MSI) file with malicious VBScript code in its filename, which if downloaded on a vulnerable system would compromise the machine without further user interaction.
"Instead of parsing an MSI file to get its version number, this code creates a script containing the filename for which a thumbnail should be shown and executes that using Wine," Moskopp explains while demonstrating his PoC.
"The script is constructed using a template, which makes it possible to embed VBScript in a filename and trigger its execution."
The flaw can be exploited by potential hackers using other attack vectors as well, for example, by directly inserting a USB-drive with a malicious file stored on it, or delivering the malicious file via drive-by-downloads.
How to Protect Yourself from Bad Taste
Moskopp reported the vulnerability to the GNOME Project and the Debian Project. Both of them patched the vulnerability in the gnome-exe-thumbnailer file.
The vulnerability affects gnome-exe-thumbnailer before 0.9.5 version. So, if you run a Linux OS with the GNOME desktop, check for updates immediately before you become affected by this critical vulnerability.
Meanwhile, Moskopp also advised users to:
Delete all files in /usr/share/thumbnailers.
Do not use GNOME Files.
Uninstall any software that facilitates automatically execution of filenames as code.
Moskopp also advised developers to not use "bug-ridden ad-hoc parsers" to parse files, to "fully recognise inputs before processing them," and to use unparsers, instead of templates.
Organizations Slow to Patch Critical Memcached Flaws
19.7.2017 securityweek Vulnerebility
Tens of Thousands of Internet-Exposed Memcached Servers Are Vulnerable to Attacks
Tens of thousands of servers running Memcached are exposed to the Internet and affected by several critical vulnerabilities disclosed last year by Cisco’s Talos intelligence and research group.
In late October 2016, Talos published an advisory describing three serious flaws affecting Memcached, an open source, high performance distributed memory caching system used to speed up dynamic web apps by reducing the database load.
The vulnerabilities, tracked as CVE-2016-8704, CVE-2016-8705 and CVE-2016-8706, allow a remote attacker to execute arbitrary code on vulnerable systems by sending specially crafted Memcached commands. The flaws can also be leveraged to obtain sensitive data that could allow an attacker to bypass exploit mitigations.
The security holes were patched by Memcached developers before Talos disclosed its findings. A few months later, in late February and early March 2017, researchers conducted Internet scans to find out how many organizations had patched their installations.
The scans uncovered a total of more than 107,000 servers accessible over the Internet and nearly 80 percent of them, or roughly 85,000 servers, were still vulnerable. Furthermore, only approximately 22 percent of the servers, or roughly 24,000, required authentication.
Nearly 30,000 of the vulnerable servers were located in the United States, followed by China (17,000), the United Kingdom (4,700), France (3,200), Germany (3,000), Japan (3,000), the Netherlands (2,600), India (2,500) and Russia (2,300).
After completing the scans, Cisco obtained contact email addresses for all the IP addresses associated with the vulnerable servers and attempted to notify affected organizations.
Six months later, researchers conducted another scan, but the situation improved only slightly, with roughly 10 percent of systems patched since the previous analysis. However, the number of servers requiring authentication dropped to 18,000, or 17 percent of the total.
Interestingly, researchers noticed that more than 28,000 of the previously discovered servers were no longer online. However, since the total number of Internet-facing installations remained the same, experts determined that some servers either changed their IPs or organizations had been deploying new systems with vulnerable versions of Memcached.
Talos warned that these vulnerable Memcached installations could be targeted in ransom attacks similar to the ones that hit MongoDB databases in early 2017. While Memcached is not a database, it can still contain sensitive information and disrupting it could have a negative impact on other dependent services.
“The severity of these types of vulnerabilities cannot be understated,” experts warned. “These vulnerabilities potentially affect a platform that is deployed across the internet by small and large enterprises alike. With the recent spate of worm attacks leveraging vulnerabilities this should be a red flag for administrators around the world. If left unaddressed the vulnerabilities could be leveraged to impact organizations globally and impact business severely.”
The number of Memcached instances accessible from the Internet has remained fairly constant over the past years. An analysis conducted in August 2015 uncovered 118,000 Memcached instances exposing 11 terabytes of data.
Millions of IoT Devices Possibly Affected by 'Devil's Ivy' Flaw
19.7.2017 securityweek Vulnerebility
A vulnerability dubbed by researchers “Devil’s Ivy,” which exists in an open source library present in the products of many companies, could affect millions of security cameras and other Internet of Things (IoT) devices.
The flaw, a stack-based buffer overflow, was discovered by IoT security startup Senrio in a camera from Axis Communications, one of the world’s largest security camera manufacturers.
The weakness, tracked as CVE-2017-9765, can be exploited to cause a denial-of-service (DoS) condition and to execute arbitrary code. Senrio has published a technical advisory and a video showing how an attacker could exploit the flaw to hijack a security camera and gain access to its video feed.
“When exploited, [the vulnerability] allows an attacker to remotely access a video feed or deny the owner access to the feed,” Senrio said in a blog post. “Since these cameras are meant to secure something, like a bank lobby, this could lead to collection of sensitive information or prevent a crime from being observed or recorded.”
Devil's Ivy Exploit in Axis Security Camera from Senrio Labs on Vimeo.
Axis has determined that the vulnerability impacts nearly 250 of its camera models and it has started releasing firmware updates that patch the bug. The company has notified its customers and partners of Devil’s Ivy.
An investigation revealed that the security hole was actually in gSOAP, a development toolkit that simplifies the use of XML in server and client web applications. gSOAP is used by most of the top Fortune 500 companies and its developer, Genivia, claims it has been downloaded more than one million times.
The library is also used by some members of the ONVIF Forum, an organization that focuses on standardizing IP connectivity for cameras and other physical security products. ONVIF was established by Axis, Bosch and Sony in 2008 and its current members also include Canon, Cisco, D-Link, Honeywell, Huawei, Netgear, Panasonic, Siemens and Toshiba.
Senrio believes the Devil’s Ivy vulnerability could affect tens of millions of systems to some degree. A Shodan search conducted by the company on July 1 uncovered nearly 15,000 Axis dome cameras accessible from the Internet.
However, Genivia, which provided patches and mitigations, believes the vulnerability is not easy to exploit for arbitrary code execution.
Axis also pointed out in its advisory that exploitation of the flaw for code execution requires a skilled and determined attacker. The hacker needs to have access to the network housing the vulnerable device, but products exposed to the Internet are at much higher risk.
Both Axis and Senrio have advised users to place their cameras and other IoT devices behind a firewall to reduce the risk of exploitation.
Oracle Patches Record-Breaking 308 Vulnerabilities in July Update
19.7.2017 securityweek Vulnerebility
Oracle on Tuesday released its July 2017 Critical Patch Update (CPU) to address a total of 308 vulnerabilities, the highest number of security fixes ever released in a quarter by the enterprise software giant.
This month’s CPU resolves security issues in 22 different Oracle products, including Oracle Database Server, Oracle Enterprise Manager, Oracle Fusion Middleware, Oracle Hyperion, Oracle E-Business Suite, Oracle Industry Applications (Communications, Retail, and Hospitality), Oracle Primavera, Oracle Sun Products, Oracle Java SE, and Oracle MySQL.
Of the total 308 vulnerabilities addressed, 27 were assessed as critical issues, with a CVSS base score between 9.0 and 10.0 (only one bug was rated 10). Over half of the vulnerabilities addressed this month can be exploited remotely without authentication.
Oracle Hospitality Applications received the largest number of security fixes, at 48 – 11 of these may be remotely exploitable without authentication. Oracle Fusion Middleware received 44 fixes (31 remotely exploitable without authentication), including one that addressed a critical vulnerability (CVE-2017-10137 – CVSS score 10.0) in Oracle WebLogic Server.
Oracle also resolved large numbers of vulnerabilities in Oracle Java SE (32 – 28 remotely exploitable without authentication), Oracle PeopleSoft Products (30 – 20 remotely exploitable), Oracle MySQL (30 – 9 remotely exploitable), Oracle E-Business Suite (22 – 18 remotely exploitable), and Oracle Financial Services Applications (20 – 4 remotely exploitable).
The record-breaking number of 30 flaws addressed in PeopleSoft is worrying, especially since 20 of the bugs can be exploited over the network without user credentials, ERPScan, a firm that specializes in security SAP and Oracle software, notes.
“Oracle PeopleSoft combines Supplier Relationship Management, Human Capital Management, Supply Chain Management, and other applications. The software has 6000+ enterprise customers and serves 20 million end users worldwide including more than 800 universities. Over 1000 PeopleSoft systems are available on the Internet putting organizations at risk. According to the latest survey from Crowd Research partners, 89% of responders agreed that the number cyber-attacks on ERP will significantly grow in the near future. SAP Attacks may cost up to $50 million, PeopleSoft is definitely the same weight category,” Alexander Polyakov, CTO at ERPScan, told SecurityWeek in an emailed statement.
82 of the vulnerabilities addressed in this quarter’s CPU affect a scope of crucial business applications from Oracle, such as Oracle PeopleSoft, E-Business Suite, Siebel CRM, Oracle Financial Services, and Oracle Primavera Products Suite. Around 53% of these bugs can be exploited remotely without authentication.
One of the most important vulnerabilities in E-Business Suite (CVE-2017-10244) is an Information Disclosure issue that could allow an attacker “to exfiltrate sensitive business data without requiring a valid user account in the system,” Onapsis, the company that discovered the issue, reveals. The flaw affects all supported Oracle E-Business Suite versions: 12.1.3, 12.2.3, 12.2.4, 12.2.5 and 12.2.6.
“This vulnerability is especially critical as an attacker would only need a web browser and network access to the EBS system to perform it. Any number of critical documents could be stored in the system including invoices, purchase orders, HR information and design documents to start. Even systems in DMZ mode do not ensure these systems are not vulnerable,” Juan Perez-Etchegoyen, Onapsis CTO, said.
Other Oracle E-Business Suite flaws addressed this month include a path traversal vulnerability (CVE-2017-10192), multiple vulnerabilities that allow path traversal attacks (grouped in CVSs CVE-2017-10184 and CVE-2017-10186), two Denial of Service vulnerabilities (CVE-2017-10108 and CVE-2017-10109), a Multiple Cross Site Scripting vulnerability (CVE-2017-10180), two Cross Site Scripting vulnerabilities (CVE-2017-10185 and CVE-2017-10191) and an Information disclosure vulnerability (CVE-2017-10245).
“There are different vulnerabilities which could be used by an attacker to compromise the system and get business critical information. It is crucial to update Oracle E-Business Suite with the last patch to fix all of these vulnerabilities and have the system up to date,” Onapsis says.
The most critical issues resolved in the Oracle July 2017 CPU affect Oracle WebLogic Server component of Oracle Fusion Middleware (CVE-2017-10137 – CVSS score 10.0), the OJVM component of Oracle Database Server (CVE-2017-10202 – CVSS score 9.9), the Oracle Communications BRM component of Oracle Communications Applications (CVE-2015-3253 – CVSS score 9.8), the MICROS PC Workstation 2015 component of Oracle Hospitality Applications (CVE-2017-5689 – CVSS score 9.8), and the MySQL Enterprise Monitor component of Oracle MySQL (CVE-2016-4436 – CVSS score 9.8).
Each quarter starting last year, Oracle has been patching an increasing number of vulnerabilities in its products. After the January 2016 CPU broke the 200 security patches barrier, the April 2017 one hit the 300 mark, and this month’s set of patches sets a new record.
As more and more security researchers focus on finding vulnerabilities in business software, the number of addressed issues is expected to increase. This should result in improved overall security for Oracle software, but only as long as patches are installed in a timely manner, which is a difficult and monotonous task, as ERPScan points out.
Over 70,000 Memcached Servers Still Vulnerable to Remote Hacking
19.7.2017 thehackernews Vulnerebility
Nothing in this world is fully secure, from our borders to cyberspace. I know vulnerabilities are bad, but the worst part comes in when people just don't care to apply patches on time.
Late last year, Cisco's Talos intelligence and research group discovered three critical remote code execution (RCE) vulnerabilities in Memcached that exposed major websites including Facebook, Twitter, YouTube, Reddit, to hackers.
Memcached is a popular open-source and easily deployable distributed caching system that allows objects to be stored in memory.
The Memcached application has been designed to speed up dynamic web applications (for example php-based websites) by reducing stress on the database that helps administrators to increase performance and scale web applications.
It's been almost eight months since the Memcached developers have released patches for three critical RCE vulnerabilities (CVE-2016-8704, CVE-2016-8705 and CVE-2016-8706) but tens of thousands of servers running Memcached application are still vulnerable, allowing attackers to steal sensitive data remotely.
Researchers at Talos conducted Internet scans on two different occasions, one in late February and another in July, to find out how many servers are still running the vulnerable version of the Memcached application.
And the results are surprising...
Results from February Scan:
Total servers exposed on the Internet — 107,786
Servers still vulnerable — 85,121
Servers still vulnerable but require authentication — 23,707
And the top 5 countries with most vulnerable servers are the United States, followed by China, United Kingdom, France and Germany.
Results from July Scan:
Total servers exposed on the Internet — 106,001
servers still vulnerable — 73,403
Servers still vulnerable but require authentication — 18,012
After comparing results from both the Internet scans, researchers learned that only 2,958 servers found vulnerable in February scan had been patched before July scan, while the remaining are still left vulnerable to the remote hack.
Data Breach & Ransom Threats
This ignorance by organisations to apply patches on time is concerning, as Talos researchers warned that these vulnerable Memcached installations could be an easy target of ransomware attacks similar to the one that hit MongoDB databases in late December.
Although unlike MongoDB, Memcached is not a database, it "can still contain sensitive information and disruption in the service availability would certainly lead to further disruptions on dependent services."
The flaws in Memcached could allow hackers to replace cached content with their malicious one to deface the website, serve phishing pages, ransom threats, and malicious links to hijack victim's machine, placing hundreds of millions of online users at risk.
"With the recent spate of worm attacks leveraging vulnerabilities this should be a red flag for administrators around the world," the researchers concluded.
"If left unaddressed the vulnerabilities could be leveraged to impact organisations globally and affect business severely. It is highly recommended that these systems be patched immediately to help mitigate the risk to organisations."
Customers and organisations are advised to apply the patch as soon as possible even to Memcached deployments in "trusted" environments, as attackers with existing access could target vulnerable servers to move laterally within those networks.
Remotely Exploitable Flaw Puts Millions of Internet-Connected Devices at Risk
19.7.2017 thehackernews Vulnerebility
Security researchers have discovered a critical remotely exploitable vulnerability in an open-source software development library used by major manufacturers of the Internet-of-Thing devices that eventually left millions of devices vulnerable to hacking.
The vulnerability (CVE-2017-9765), discovered by researchers at the IoT-focused security firm Senrio, resides in the software development library called gSOAP toolkit (Simple Object Access Protocol) — an advanced C/C++ auto-coding tool for developing XML Web services and XML application.
Dubbed "Devil's Ivy," the stack buffer overflow vulnerability allows a remote attacker to crash the SOAP WebServices daemon and could be exploited to execute arbitrary code on the vulnerable devices.
The Devil's Ivy vulnerability was discovered by researchers while analysing an Internet-connected security camera manufactured by Axis Communications.
"When exploited, it allows an attacker to remotely access a video feed or deny the owner access to the feed," researchers say.
"Since these cameras are meant to secure something, like a bank lobby, this could lead to collection of sensitive information or prevent a crime from being observed or recorded."
Axis confirmed the vulnerability that exists in almost all of its 250 camera models (you can find the complete list of affected camera models here) and has quickly released patched firmware updates on July 6th to address the vulnerability, prompting partners and customers to upgrade as soon as possible.
However, researchers believe that their exploit would work on internet-connected devices from other vendors as well, as the affected software is used by Canon, Siemens, Cisco, Hitachi, and many others.
Axis immediately informed Genivia, the company that maintains gSOAP, about the vulnerability and Genivia released a patch on June 21, 2017.
The company also reached out to electronics industry consortium ONVIF to ensure all of its members, including Canon, Cisco, and Siemens, those who make use of gSOAP become aware of the issue and can develop patches to fix the security hole.
Internet of Things (IoT) devices has always been the weakest link and, therefore, an easy entry for hackers to get into secured networks. So it is always advisable to keep your Internet-connected devices updated and away from the public Internet.
New Linux Malware Exploits SambaCry Flaw to Silently Backdoor NAS Devices
19.7.2017 thehackernews Vulnerebility
Remember SambaCry?
Almost two months ago, we reported about a 7-year-old critical remote code execution vulnerability in Samba networking software, allowing a hacker to remotely take full control of a vulnerable Linux and Unix machines.
We dubbed the vulnerability as SambaCry, because of its similarities to the Windows SMB vulnerability exploited by the WannaCry ransomware that wreaked havoc across the world over two months ago.
Despite being patched in late May, the vulnerability is currently being leveraged by a new piece of malware to target the Internet of Things (IoT) devices, particularly Network Attached Storage (NAS) appliances, researchers at Trend Micro warned.
For those unfamiliar: Samba is open-source software (re-implementation of SMB/CIFS networking protocol), which offers Linux/Unix servers with Windows-based file and print services and runs on the majority of operating systems, including Linux, UNIX, IBM System 390, and OpenVMS.
Shortly after the public revelation of its existence, the SambaCry vulnerability (CVE-2017-7494) was exploited mostly to install cryptocurrency mining software—"CPUminer" that mines "Monero" digital currency—on Linux systems.
However, the latest malware campaign involving SambaCry spotted by researchers at Trend Micro in July mostly targets NAS devices used by small and medium-size businesses.
SHELLBIND Malware Exploits SambaCry to Targets NAS Devices
Dubbed SHELLBIND, the malware works on various architectures, including MIPS, ARM and PowerPC, and is delivered as a shared object (.SO) file to Samba public folders and loaded via the SambaCry vulnerability.
Once deployed on the targeted machine, the malware establishes communication with the attackers' command and control (C&C) server located in East Africa, and modifies firewall rules to ensure that it can communicate with its server.
After successfully establishing a connection, the malware grants the attackers access to the infected device and provides them with an open command shell in the device, so that they can issue any number and type of system commands and eventually take control of the device.
In order to find the affected devices that use Samba, attackers can leverage the Shodan search engine and write the original malware files to their public folders.
"It is quite easy to find devices that use Samba in Shodan: searching for port 445 with a 'samba' string will turn up a viable IP list," researchers said while explaining the flaw.
"An attacker would then simply need to create a tool that can automatically write malicious files to every IP address on the list. Once they write the files into the public folders, the devices with the SambaCry vulnerability could become ELF_SHELLBIND.A victims."
However, it is not clear what the attackers do with the compromised devices and what's their actual motive behind compromising the devices.
The SambaCry vulnerability is hell easy to exploit and could be used by remote attackers to upload a shared library to a writable share and then cause the server to load and execute the malicious code.
The maintainers of Samba already patched the issue in Samba versions 4.6.4/4.5.10/4.4.14, so you are advised to patch your systems against the vulnerability as soon as possible.
Just make sure that your system is running updated Samba version.
Also, attackers need to have writable access to a shared location on the target system to deliver the payload, which is another mitigating factor that might lower the rate of infection.
SHELLBIND IoT malware targets NAS devices exploiting SambaCry flaw
19.7.2017 securityaffairs Vulnerebility
The seven-year-old remote code execution vulnerability SambaCry was exploited by the SHELLBIND IoT malware to target NAS devices.
A new strain of malware dubbed SHELLBIND exploits the recently patched CVE-2017-7494 Samba vulnerability in attacks against Internet of Things devices.
SHELLBIND has infected most network-attached storage (NAS) appliances, it exploits the Samba vulnerability (also known as SambaCry and EternalRed) to upload a shared library to a writable share, and then cause the server to load that library.
This trick allows a remote attacker to execute arbitrary code on the targeted system.
CVE-2017-7494 is a seven-year-old remote code execution vulnerability that affects all versions of the Samba software since 3.5.0. The flaw has been patched by the development team of the project.
The CVE-2017-7494 flaw can be easily exploited, just a line of code could be used for the hack under specific conditions:
make file- and printer-sharing port 445 reachable on the Internet,
configure shared files to have write privileges.
use known or guessable server paths for those files
The Samba vulnerability affects the products of several major vendors, including NAS appliances.
The Samba bug appears to be a network wormable issue that could be exploited by a malicious code to self-replicate from vulnerable machine to vulnerable machine without requiring user interaction.
When SambaCry was discovered, nearly 485,000 Samba-enabled computers were found to be exposed on the Internet.
In June, researchers at Kaspersky Lab set up honeypots to detect SambaCry attacks in the wild. The experts spotted a malware campaign that was exploiting the SambaCry vulnerability to infect Linux systems and install a cryptocurrency miner.
“On May 30th our honeypots captured the first attack to make use of this particular vulnerability, but the payload in this exploit had nothing in common with the Trojan-Crypt that was EternalBlue and WannaCry. Surprisingly, it was a cryptocurrency mining utility!” reported Kaspersky.
The independent security researcher Omri Ben Bassat also observed the same campaign that he dubbed “EternalMiner.” The expert confirmed threat actors started exploiting the SambaCry flaw just a week after its discovery to hijack Linux PCs and to install an upgraded version of “CPUminer,” a Monero miner.
In early July, experts at Trend Micro uncovered a new type of attack involving SambaCry. Crooks have been exploiting the flaw in attacks targeting NAS devices used by small and medium-size businesses. The malicious code was designed to compromise almost any IoT architecture, including MIPS, ARM, and PowerPC.
The attackers can easily find vulnerable devices using the Shodan Internet search engine then and write the malicious code to their public folders.
Experts at Trend Micro discovered that the ELF_SHELLBIND.A is delivered as a SO file to Samba public folders, then the attacker load and execute it by exploiting the SambaCry vulnerability.
“This more recent malware is detected as ELF_SHELLBIND.A and was found on July 3. Similar to the previous reports of SambaCry being used in the wild, it also opens a command shell on the target system. But ELF_SHELLBIND.A has marked differences that separate it from the earlier malware leveraging SambaCry. For one, it targets internet of things (IoT) devices—particularly the Network Attached Storage (NAS) devices favored by small to medium businesses.” reads the analysis published by Trend Micro. “ELF_SHELLBIND also targets different architectures, such as MIPS, ARM, and PowerPC. This is the first time we’ve seen SambaCry being exploited without the cryptocurrency miner as a payload.”

Once the malware is executed, it connects a C&C server located in East Africa “169[.]239[.]128[.]123” over TCP, port 80. , To establish a connection, the malicious code modifies firewall rules, then the attacker will open a command shell on the target system.
“Once the connection is successfully established and authentication is confirmed, then the attacker will have an open command shell in the infected systems where he can issue any number of system commands and essentially take control of the device,” continues Trend Micro.
Sysadmins can protect their systems by updating their installs, if it is not possible for any reason a workaround can be implemented by the adding the line
nt pipe support = no
to the Samba configuration file and restarting the network’s SMB daemon.
The change will limit clients from accessing some network computers.
Organizations Slow to Patch Critical Memcached Flaws
18.7.2017 securityweek Vulnerebility
Tens of Thousands of Internet-Exposed Memcached Servers Are Vulnerable to Attacks
Tens of thousands of servers running Memcached are exposed to the Internet and affected by several critical vulnerabilities disclosed last year by Cisco’s Talos intelligence and research group.
In late October 2016, Talos published an advisory describing three serious flaws affecting Memcached, an open source, high performance distributed memory caching system used to speed up dynamic web apps by reducing the database load.
The vulnerabilities, tracked as CVE-2016-8704, CVE-2016-8705 and CVE-2016-8706, allow a remote attacker to execute arbitrary code on vulnerable systems by sending specially crafted Memcached commands. The flaws can also be leveraged to obtain sensitive data that could allow an attacker to bypass exploit mitigations.
The security holes were patched by Memcached developers before Talos disclosed its findings. A few months later, in late February and early March 2017, researchers conducted Internet scans to find out how many organizations had patched their installations.
The scans uncovered a total of more than 107,000 servers accessible over the Internet and nearly 80 percent of them, or roughly 85,000 servers, were still vulnerable. Furthermore, only approximately 22 percent of the servers, or roughly 24,000, required authentication.
Nearly 30,000 of the vulnerable servers were located in the United States, followed by China (17,000), the United Kingdom (4,700), France (3,200), Germany (3,000), Japan (3,000), the Netherlands (2,600), India (2,500) and Russia (2,300).
After completing the scans, Cisco obtained contact email addresses for all the IP addresses associated with the vulnerable servers and attempted to notify affected organizations.
Six months later, researchers conducted another scan, but the situation improved only slightly, with roughly 10 percent of systems patched since the previous analysis. However, the number of servers requiring authentication dropped to 18,000, or 17 percent of the total.
Interestingly, researchers noticed that more than 28,000 of the previously discovered servers were no longer online. However, since the total number of Internet-facing installations remained the same, experts determined that some servers either changed their IPs or organizations had been deploying new systems with vulnerable versions of Memcached.
Talos warned that these vulnerable Memcached installations could be targeted in ransom attacks similar to the ones that hit MongoDB databases in early 2017. While Memcached is not a database, it can still contain sensitive information and disrupting it could have a negative impact on other dependent services.
“The severity of these types of vulnerabilities cannot be understated,” experts warned. “These vulnerabilities potentially affect a platform that is deployed across the internet by small and large enterprises alike. With the recent spate of worm attacks leveraging vulnerabilities this should be a red flag for administrators around the world. If left unaddressed the vulnerabilities could be leveraged to impact organizations globally and impact business severely.”
The number of Memcached instances accessible from the Internet has remained fairly constant over the past years. An analysis conducted in August 2015 uncovered 118,000 Memcached instances exposing 11 terabytes of data.
Code Execution, DoS Vulnerabilities Found in FreeRADIUS
18.7.2017 securityweek Vulnerebility
Security testing of FreeRADIUS using a technique known as fuzzing revealed more than a dozen issues, including vulnerabilities that can be exploited for denial-of-service (DoS) attacks and remote code execution.
Researcher Guido Vranken recently discovered several flaws in OpenVPN through fuzzing, a technique that involves automatically injecting malformed or semi-malformed data into software to find implementation bugs. One of the flaws also turned out to impact FreeRADIUS, an open source implementation of RADIUS (Remote Authentication Dial-In User Service), a networking protocol for user authentication, authorization and accounting.
After patching the vulnerability, the developers of FreeRADIUS, said to be the world’s most popular RADIUS server, asked Vranken to conduct fuzzing on their software.
Testing conducted by the researcher led to the discovery of 11 security issues and FreeRADIUS developers identified an additional four problems. Of the 15 weaknesses affecting versions 2 and/or 3 of the software, five cannot be exploited and six affect DHCP packet parsers. The security holes were addressed on Monday with the release of versions 2.2.10 and 3.0.15.
The list of vulnerabilities includes memory leak, out-of-bounds read, memory exhaustion, buffer overflow and other issues that can be exploited to remotely execute arbitrary code or cause a DoS condition. The flaws can be exploited by sending specially crafted packets to the targeted server.
The vulnerabilities that can be leveraged for remote code execution are CVE-2017-10984, which affects versions 3.0.0 through 3.0.14, and CVE-2017-10979, which affects versions 2.0.0 through 2.2.9. They can be exploited by sending packets with malformed WiMAX attributes.
“The short summary is that if your RADIUS server is on a private network, accessible only by managed devices, you are likely safe. If your RADIUS server is part of a roaming consortium, then anyone within that consortium can attack it. If your RADIUS server is on the public internet, then you are not following best practices, and anyone on the net can attack your systems,” FreeRADIUS maintainers explained.
They pointed out that writing secure code in C is a big challenge, which is why they have been using several static analysis tools to identify vulnerabilities. However, the fuzzing tests uncovered many flaws that were previously missed by these tools, which is why FreeRADIUS developers plan on integrating the fuzzer into all future releases of their software.
Critical WebEx Flaws Allow Remote Code Execution
18.7.2017 securityweek Vulnerebility
Cisco has updated the WebEx extensions for Chrome and Firefox to address critical remote code execution vulnerabilities identified by researchers working for Google and Divergent Security.
Google Project Zero’s Tavis Ormandy and Cris Neckar of Divergent Security, a former member of the Chrome Security Team, discovered earlier this month that the WebEx extension allows a remote attacker to execute arbitrary code with the privileges of the web browser due to some changes made recently by Cisco.
The security holes, tracked as CVE-2017-6753, were reported to the networking giant on July 6 and they were addressed roughly one week later with the release of version 1.0.12. On Monday, both Cisco and Google Project Zero published advisories detailing the flaws.
According to Cisco, the vulnerabilities are caused by a “design defect” and they can be exploited by an attacker by getting the targeted user to visit a specially crafted webpage. The browser extensions for WebEx Meetings Server, WebEx Centers and WebEx Meetings running on Windows are impacted.
Updates have also been released for the Internet Explorer version of the WebEx plugin, which shares components with the Chrome and Firefox versions, and the WebEx desktop application. Cisco has informed customers that workarounds are not available.
Cisco said it was not aware of any attacks exploiting the vulnerabilities. However, the advisory published by Google Project Zero includes technical details and a working exploit. It also includes details on how Cisco addressed the issues.
This is not the first time Ormandy has found a critical vulnerability in the WebEx plugins. The researcher discovered a remote code execution flaw in January, which led to Google and Mozilla temporarily removing the WebEx extension from their stores.
Cisco’s initial fix turned out to be incomplete and it took the company several days to release proper patches after Ormandy’s disclosure.
For the second time in the year, experts found a flaw in Cisco WebEx Extension
18.7.2017 securityaffairs Vulnerebility
For the second time in a year, a highly critical remote code execution vulnerability was found in the Cisco WebEx Extension.
For the second time in a year, a highly critical remote code execution vulnerability, tracked as CVE-2017-6753, was discovered in the Cisco Systems WebEx browser extension for Chrome and Firefox. The vulnerability could be exploited by attackers to remotely execute malicious code on a target machine with the privileges of the affected browser.
“A vulnerability in Cisco WebEx browser extensions for Google Chrome and Mozilla Firefox could allow an unauthenticated, remote attacker to execute arbitrary code with the privileges of the affected browser on an affected system.” reads the security advisory published by CISCO. “This vulnerability affects the browser extensions for Cisco WebEx Meetings Server, Cisco WebEx Centers (Meeting Center, Event Center, Training Center, and Support Center), and Cisco WebEx Meetings when they are running on Microsoft Windows.”
Cisco WebEx is one of the most popular communication tools used by businesses and internet users for online meetings, webinars, and video conferences. The extension has roughly 20 million active users.
The impact of the flaw is severe if we consider that the extension has roughly more than 20 million installs.
The vulnerability was discovered by the popular Google Project Zero hacked Tavis Ormandy and Cris Neckar of Divergent Security. The CVE-2017-6753 RCE vulnerability is due to a designing bug in the WebEx browser extension, it could allow attackers to gain control of the affected system.
The exploitation of the vulnerability is quite simple, attackers just need to trick victims into visiting a web page containing specially crafted malicious code through the browser with affected WebEx browser extension installed.
“Earlier this week a former colleague from Chrome Security, Cris Neckar from Divergent Security, pointed out that there had been some changes to the way atgpcext worked, and it looked like there may be some new problems. I see several problems with the way sanitization works, and have produced a remote code execution exploit to demonstrate them,” Ormandy said. “This extension has over 20M [million] active Chrome users alone, FireFox and other browsers are likely to be affected as well.”
Cisco acknowledged the RCE flaw and has already patched it in the “Cisco WebEx Extension 1.0.12” update for Chrome and Firefox browsers.
It is important to highlight the absence of “workarounds that address this vulnerability.”
“Cisco has released software updates for Google Chrome and Mozilla Firefox that address this vulnerability. There are no workarounds that address this vulnerability.” continues the CISCO advisory.
According to the advisory, Apple’s Safari, Microsoft Internet Explorer, and Microsoft Edge are not affected by this RCE flaw. Cisco WebEx Productivity Tools, Cisco WebEx browser extensions for Mac or Linux, and Cisco WebEx on Microsoft Edge or Internet Explorer are not affected by the vulnerability.
Critical RCE Vulnerability Found in Cisco WebEx Extensions, Again — Patch Now!
17.7.2017 thehackernews Vulnerebility
A highly critical vulnerability has been discovered in the Cisco Systems’ WebEx browser extension for Chrome and Firefox, for the second time in this year, which could allow attackers to remotely execute malicious code on a victim's computer.
Cisco WebEx is a popular communication tool for online events, including meetings, webinars and video conferences that help users connect and collaborate with colleagues around the world. The extension has roughly 20 million active users.
Discovered by Tavis Ormandy of Google Project Zero and Cris Neckar of Divergent Security, the remote code execution flaw (CVE-2017-6753) is due to a designing defect in the WebEx browser extension.
To exploit the vulnerability, all an attacker need to do is trick victims into visiting a web page containing specially crafted malicious code through the browser with affected extension installed.
Successful exploitation of this vulnerability could result in the attacker executing arbitrary code with the privileges of the affected browser and gaining control of the affected system.
"I see several problems with the way sanitization works, and have produced a remote code execution exploit to demonstrate them," Ormandy said. "This extension has over 20M [million] active Chrome users alone, FireFox and other browsers are likely to be affected as well."
Cisco has already patched the vulnerability and released “Cisco WebEx Extension 1.0.12” update for Chrome and Firefox browsers that address this issue, though "there are no workarounds that address this vulnerability."
"This vulnerability affects the browser extensions for Cisco WebEx Meetings Server, Cisco WebEx Centers (Meeting Center, Event Center, Training Center, and Support Center), and Cisco WebEx Meetings when they are running on Microsoft Windows," Cisco confirmed in an advisory released today.
Download Cisco WebEx Extension 1.0.12
Chrome Extensions
Firefox Extension
In general, users are always recommended to run all software as a non-privileged user in an effort to diminish the effects of a successful attack.
Fortunately, Apple's Safari, Microsoft's Internet Explorer and Microsoft's Edge are not affected by this vulnerability.
Cisco WebEx Productivity Tools, Cisco WebEx browser extensions for Mac or Linux, and Cisco WebEx on Microsoft Edge or Internet Explorer are not affected by the vulnerability, the company confirmed.
The remote code execution vulnerability in Cisco WebEx extension has been discovered second time in this year.
Ormandy alerted the networking giant to an RCE flaw in the WebEx browser extension earlier this year as well, which even led to Google and Mozilla temporarily removing the add-on from their stores.
CISCO issues security patches for nine serious RCEs in SNMP subsystem in IOS and IOS XE
15.7.2017 securityaffairs Vulnerebility
Cisco has fixed nine serious remote code execution flaws in the SNMP subsystem running in all the releases of IOS and IOS XE software.
The tech giant publicly disclosed the vulnerability on June 29 and provided workarounds, not it is notifying customers about the availability of security patches.
The nine issues, that have been tracked with codes from CVE-2017-6736 to CVE-2017-6744, were all patched by the company. All the flaws could be exploited by a remote unauthenticated attacker by sending specially crafted SNMP packets, resulting in arbitrary code execution or causing the system to reload.
“The Simple Network Management Protocol (SNMP) subsystem of Cisco IOS and IOS XE Software contains multiple vulnerabilities that could allow an authenticated, remote attacker to remotely execute code on an affected system or cause an affected system to reload. An attacker could exploit these vulnerabilities by sending a crafted SNMP packet to an affected system via IPv4 or IPv6. Only traffic directed to an affected system can be used to exploit these vulnerabilities.” states the advisory published by CISCO in June.
The experts warned of nine flaws affecting the Simple Network Management Protocol (SNMP) component of IOS and IOS XE software.
The flaws are due to a buffer overflow condition in the SNMP subsystem, all versions of SNMP – Versions 1, 2c, and 3 are affected.
Cisco SNMP
As reported by the advisory, an authenticated attacker who knows the SNMP read-only community string of a target system could remotely execute code or cause the device to reload by sending a specially crafted SNMP packet via IPv4 or IPv6.
The attack is very dangerous because hackers could obtain full control of vulnerable devices and the worst news is that CISCO warned customers that attackers in the wild know about the vulnerabilities and can exploit them in any moment.
“A successful exploit could allow the attacker to execute arbitrary code and obtain full control of the affected system or cause the affected system to reload,” Cisco said in its advisory.
Cisco confirmed that any device configured with a list of particular management information base (MIBs) is also vulnerable. MIBs are databases associated with SNMP implementations and are used to manage devices in a communication network.
CISCO when disclosed the issued The company’s original workaround recommendation was to disable the affected MIBs.
Devices configured with any of the following MIBs are vulnerable:
ADSL-LINE-MIB
ALPS-MIB
CISCO-ADSL-DMT-LINE-MIB
CISCO-BSTUN-MIB
CISCO-MAC-AUTH-BYPASS-MIB
CISCO-SLB-EXT-MIB
CISCO-VOICE-DNIS-MIB
CISCO-VOICE-NUMBER-EXPANSION-MIB
TN3270E-RT-MIB
“Some of the MIBs may not be present on all systems or versions but are enabled when present,” continued the Cisco advisory.
“Administrators may be accustomed to utilizing the show snmp mib command in privileged EXEC mode to display a list of enabled MIBs on a device,” Cisco said. “Not all of the MIBs will be displayed in the output of the show snmp mib command but may still be enabled.” Customers were advised to implement the entire exclude list.
CISCO customers need to apply the patches, the company also recommends network managers to regularly change community strings, which are used to restrict read/write access to SNMP data on a device running IOS or IOS XE.
“These community strings, as with all passwords, should be chosen carefully to ensure they are not trivial,” Cisco said. “They should also be changed at regular intervals and in accordance with network security policies.”
Old Kerberos Bypass Flaw Patched in Windows, Linux
14.7.2017 securityweek Vulnerebility
A 20-year-old authentication bypass vulnerability affecting some implementations of the Kerberos protocol has been patched in Windows, Linux and BSD operating systems.
Kerberos, whose name stems from the mythological three-headed hound Cerberus, is an authentication protocol that uses “tickets” to allow nodes to communicate securely over a non-secure network.
The flaw has been dubbed Orpheus' Lyre because similar to how the bard Orpheus managed to get past Cerberus by putting it to sleep with his lyre, the vulnerability can be used to bypass Kerberos.
Researchers Jeffrey Altman, Viktor Duchovni and Nico Williams first discovered the security hole in the Heimdal implementation of Kerberos, which had been vulnerable since late 1996. Microsoft’s implementation also turned out to be affected, but the MIT Kerberos was never impacted. Orpheus' Lyre vulnerability
The experts have not provided too many technical details in order to give users time to apply the patches. However, they did reveal that the flaw affects the Kerberos v5 specification and it’s related to the use of unauthenticated plaintext.
A man-in-the-middle (MitM) attacker can exploit the vulnerability to steal credentials, escalate privileges, and bypass authentication.
“In _krb5_extract_ticket() the KDC-REP service name must be obtained from encrypted version stored in 'enc_part' instead of the unencrypted version stored in 'ticket'. Use of the unecrypted version provides an opportunity for successful server impersonation and other attacks,” said the developers of Heimdal, who track the flaw as CVE-2017-11103.
Heimdal is used by several Linux distributions, which have already started releasing patches. Red Hat is not affected as it uses the MIT implementation of Kerberos.
The vulnerability has also been addressed in Samba, which includes the Heimdal Kerberos since version 4.0.0. FreeBSD has also published an advisory.
Microsoft, which tracks the flaw as CVE-2017-8495, addressed it in Windows with its latest Patch Tuesday updates.
“A security feature bypass vulnerability exists in Microsoft Windows when Kerberos fails to prevent tampering with the SNAME field during ticket exchange. An attacker who successfully exploited this vulnerability could use it to bypass Extended Protection for Authentication.
To exploit this vulnerability, an attacker would have to be able to launch a man-in-the-middle attack against the traffic passing between a client and the server,” Microsoft said in its advisory.
The experts who discovered Orpheus' Lyre pointed out that this is a client-side bug that cannot be mitigated on the server side.
While the researchers, Samba and Heimdal have classified this as a critical vulnerability, Microsoft and some of the affected Linux distributions assigned it an “important” or “medium” severity rating, likely due to the fact that the attacker requires network access for exploitation.
20 years-old Orpheus’ Lyre vulnerability in Kerberos fixed this week
14.7.2017 securityaffairs Vulnerebility
A 20 years-old vulnerability in Kerberos, dubbed Orpheus’ Lyre, was parched this week for both Microsoft and Linux distros.
A 20 years-old vulnerability in Kerberos was parched this week for both Microsoft and Linux distros.
The vulnerability dubbed Orpheus’ Lyre has been found three months ago by Jeffrey Altman, founder of AuriStor, and Viktor Dukhovni and Nicolas Williams from Two Sigma Investments. The issue
The flaw, tracked as CVE-2017-11103, was found in Heimdal, an open-source implementation of Kerberos, like the mythological character Orpheus played his lyre with such grace that it lulled Cerberus to sleep, this issue can bypass Kerberos.
The issue could result in remote privilege escalation and credential theft, an attacker can trigger it to access the target network.
“The original cryptographic sin of Kerberos is an abundance of unauthenticated plaintext in the protocol. That is, portions of Kerberos messages are neither encrypted nor integrity-protected in some direct cryptographic manner. In some cases that sin is likely born of premature optimization — the mother of many bugs. Kerberos can be secure despite this surfeit of unauthenticated plaintext, but it requires extreme care by implementors to get every detail right so as to authenticate said plaintext.” reads the description for the Orpheus’ Lyre .”Orpheus’ Lyre happened because of one instance of unauthenticated plaintext, and the ease with which the specific plaintext could accidentally be used instead of an authenticated copy of the same text. The unauthenticated plaintext issue at hand is this: the Ticket issued in KDC responses. “
The flaw is related the way Kerberos handles authentication messages, the expert discovered that flawed implementations of Kerberos fetched metadata from unprotected key distribution center (KDC) tickets rather than encrypted KDC responses.
“The attacker needs to be on the network and to have control over a service principle that the client could communicate with,” Altman told The Register. “As far as we know there are no exploits in the wild. But it certainly is exploitable and we consider it to be very serious.”
“Given how broadly Kerberos has been deployed over the last almost 30 years, it clearly is in a wide ecosystem with a lot of different vendors,”
The Orpheus’ Lyre bug affects multiple different Kerberos 5 implementations, including one by Microsoft and by the KTH Royal Institute of Technology in Sweden (Heimdal).

Altman recommends to review every Kerberos implementation, not every vendor can be expected to have fixed the vulnerability and in some cases, the vendors went out of the market.
Altman explained that the flaw could have been prevented by removing the unencrypted fields in order to force the use of the encrypted ones when the authentication request is composed.
“In _krb5_extract_ticket() the KDC-REP service name must be obtained from encrypted version stored in ‘enc_part’ instead of the unencrypted version stored in ‘ticket’. Use of the unecrypted version provides an opportunity for successful server impersonation and other attacks.” wrote Altman.
“The fact that this has been around for as long as it has been in open source, I think, is just one more case that should debunk the theory that open source programming is in some way more secure than closed source programming.”
The expert pointed out that if IT giants like Microsoft failed in identifying the problem other companies missed it, the same story for the entire open source community.
Altman has no doubt, this kind of issues will continue to plague the open-source community because developers are often not compensated for their contributions.
“We will never be reimbursed for the cost to our lives and the lost time to our companies for having done this favor to the world,” Altman concluded. “As a society, we need to understand what the costs of this work are.”
Samsung Tizen Accused of Being Home to at Least 27,000 Findable Bugs
14.7.2017 securityweek Vulnerebility
A purveyor of static code analysis wished to pitch his product to Samsung. What better way, he thought, than to run his product against the Samsung Tizen operating system, and demonstrate the results. The demonstration fell through, and the purveyor decided instead to publish his findings.
The purveyor is Andrey Karpov, CTO at "Program Verification Systems" Co Ltd and one of the developers of PVS-Studio. In a report published Wednesday, he claims that PVS-Studio would find 27,000 coding errors in Tizen. He actually checked only 3.3% of the code; but finding about 900 errors, he believes that would extrapolate to 27,000.
If his figures are correct, it could be a lot worse. He suggests that one use of PVS-Studio will detect "more than 10% of errors that are present in the code." Regular use would push that up to about 20% of the errors -- but either way, if his figures are correct, the implication is that Tizen potentially houses more than 250,000 bugs.
Tizen is a Linux-based open-source operating system designed for wide use in Samsung products: smartphones, tablets, smart TVs, smart watches, cameras and PCs. The project started in 2013, and by 2015 it had reached smartphones. Today it can be found on millions of devices and especially smart TVs.
Tizen is not new to controversy. Earlier this year security researcher Amihai Neiderman, then at Israeli firm Equus Technologies, reported the presence of 40 zero-day vulnerabilities in Tizen. "Right now, Tizen isn't mature enough, isn't ready enough to be sent to the public like this," he commented. "If those vulnerabilities I found in a few hours of research, then somebody who's really going to dedicate himself to be a Tizen researcher will find way more vulnerabilities."
27,000 bugs do not translate to 27,000 vulnerabilities -- but some of them could. For example, Karpov claims to have found 52 errors in which private data is not cleared. Only one is in the direct Samsung code -- the rest are in third-party libraries used in Tizen. "I think this is a serious omission," he writes, "since is does not matter which part of the program will be erroneous, when private data will remain somewhere in memory and then someone will use it."
Karpov wrote an open letter to Samsung in May 2017. He described a number of the errors he had found, and said "Our team is willing to work on improving the quality of Tizen project. The text contains remarks to the code fragments, but this is not criticism. All projects have bugs. The aim was to show by real examples that we aren't talking about abstract recommendations concerning the code improvement, but about real defects that we can find and fix."
Samsung's Youil Kim rejected the approach. Stating that "We currently have our own static analysis tool and run it regularly for Tizen," Kim added, "However, we don't agree with that Tizen has 27,000 defects that should be fixed."
Karpov begs to differ.
SecurityWeek has reached out to Samsung for a statement on this issue, but has had no response at the time of writing. If one is received, it will be appended to the post.
Researcher Claims Samsung's Tizen OS is Poorly Programmed; Contains 27,000 Bugs!
13.7.2017 thehackernews Vulnerebility
A researcher has claimed that Samsung's Tizen operating system that runs on millions of Samsung products is so poorly programmed that it could contain nearly 27,000 programming errors, which could also lead to thousands of vulnerabilities.
Tizen is a Linux-based open-source operating system backed by Intel and Samsung Electronics, which has been in development since early 2012 and designed for smartphones, tablets, smart TVs, smart watches, cameras and PCs.
According to Andrey Karpov — founder of Russia-based company Program Verification Systems that made PVS-Studio, a static code analyzer tool that helps programmers to find and fix bugs in their source codes — his team has discovered hundreds of errors in Tizen project using PVS-Studio.
Samsung's Tizen operating system, written in C/C++ programming language, currently has 72.5 million lines of source code, out of which Karpov's team has analysed some randomly chosen modules i.e. 3.3% of the entire Project and found nearly 900 errors.
"If we extrapolate the results, we will see that our team is able to detect and fix about 27000 errors in Tizen," Karpov says.
In April this year, Israeli researcher Amihai Neiderman called Tizen "the worst code I've ever seen" after he examined the operating system and discovered as many as 40 zero-day vulnerabilities in Tizen code.
After finding almost a thousand bugs in Tizen code, Karpov contacted Samsung to pitch for the sale of static analyser PVS-Studio software, but Youil Kim from Samsung declined the offer.
According to a mail exchanged between Karpov and Kim, Samsung is already using the SVACE technology (Security Vulnerabilities and Critical Errors Detector) to detect potential vulnerabilities and errors in source code of applications created for Tizen.
"We are already aware that another tool can find additional defects. However, we don't agree with that Tizen has 27,000 defects that should be fixed. As you know, many of static analysis warnings are often considered as insignificant issues," Kim added.
Tizen operating system already runs on nearly 30 million Smart TVs, Galaxy Gear-branded watches Smart TVs, cameras, home appliances and some of its smartphones sold in countries like Russia, India and Bangladesh.
Samsung has even plans to have some 10 Million Tizen smartphones in the market at the end of this year.
So, if claims made by the researcher are true — which was also acknowledged by a Samsung representative to some extent — the company should shift their focus mainly towards the security of the operating system in Tizen 4.0, which is due for release in September.
Trend Micro Patches Flaws in Deep Discovery Product
13.7.2017 securityweek Vulnerebility
Trend Micro has released a critical patch for its Deep Discovery Director product to address several vulnerabilities that can be combined to achieve arbitrary command execution.
Deep Discovery Director is a Linux-based on-premises management platform that allows organizations to centralize the deployment of product updates and upgrades, Virtual Analyzer images, and configurations to Deep Discovery products.
Researchers at Core Security discovered in late May that version 1.1 of the product is affected by three potentially serious vulnerabilities, including command injection, hardcoded password and improper backup validation issues. Trend Micro addressed the bugs this week and published a security bulletin to notify customers.
According to Core Security, configuration and database backup archives are not signed or validated. They are encrypted, but the same cryptographic key is used across all virtual appliances.
An attacker with access to the Deep Discovery Director web console can exploit these weaknesses to create specially crafted backup archives that will be loaded by the application. The backup restoration process for accounts used to access the pre-configuration console is affected by a command injection vulnerability, allowing the attacker to leverage the malicious backup archive to execute arbitrary commands and spawn a root shell.
Core Security has published an advisory that contains technical details for each of the vulnerabilities and how they can be combined to achieve arbitrary command execution.
Trend Micro has classified the vulnerabilities as medium severity and pointed out that an attacker requires physical or remote access to the affected machine in order to exploit the flaws.
This is not the only critical patch released in recent months by Trend Micro for a Deep Discovery product. In March, the company informed customers of Deep Discovery Email Inspector (DDEI) 2.5.1 of critical vulnerabilities that can be exploited for remote code execution.
The security holes were reported to Trend Micro via the Zero Day Initiative (ZDI), which published separate advisories for each of the issues.
MS Patch Tuesday fixes 19 critical issues, including two NTLM zero-day flaws
13.7.2017 securityaffairs Vulnerebility
As part of the Microsoft Patch Tuesday, the tech giant fixed two critical flaws in Windows NTLM Security Protocol. Users must apply the patch asap.
As part of the July Patch Tuesday, Microsoft has released security patches for a serious privilege escalation flaw affecting all Windows operating system versions for enterprises released since 2007.
Experts at Security firm Preempt, discovered two zero-day flaws that affect Windows NTLM security protocols. The vulnerabilities could be exploited by attackers to create a new domain administrator account and take over the target domain.
The NT LAN Manager (NTLM) is an ancient authentication protocol, despite it was replaced by Kerberos in Windows 2000, it is still supported by Microsoft and it is used by many organizations.

The first flaw involves unprotected Lightweight Directory Access Protocol (LDAP) from NTLM relay, and the second is related to the Remote Desktop Protocol (RDP) Restricted-Admin mode.
Even if LDAP signing protects from both Man-in-the-Middle (MitM) and credential forwarding, the protocol is not able to fully protect against NTLM relay attacks,
The vulnerability could be exploited by an attacker with SYSTEM privileges to use incoming NT LAN Manager sessions and perform the LDAP operations, including the updating of domain objects.
“This allows an attacker with SYSTEM privileges on a machine to use any incoming NTLM session and perform the LDAP operations on behalf of the NTLM user.” reads a blog post published by Preempt.
“To realize how severe this issue is, we need to realize all Windows protocols use the Windows Authentication API (SSPI) which allows downgrade of an authentication session to NTLM.As a result, every connection to an infected machine (SMB, WMI, SQL, HTTP) with a domain admin would result in the attacker creating a domain admin account and getting full control over the attacked network.”
The second NTLM vulnerability affects the RDP Restricted-Admin mode that allows users to access to a remote machine without providing their password.
According to Preempt researchers, the RDP Restricted-Admin allows authentication systems to downgrade to NTLM.
This means that it is possible to perform NTLM relay attacks and password cracking against the RDP Restricted-Admin.
“Preempt discovered that RDP Restricted-Admin, which is sometimes referred to (mistakenly) as Kerberosed RDP, allows downgrade to NT LAN Manager in the authentication negotiation. This means that every attack you can perform with NTLM such as credential relaying and password cracking could be carried out against RDP Restricted-Admin.” continues the analysis.
Chaining the two zero-days, an attacker could create a bogus domain admin account whenever an admin connects with RDP Restricted-Admin and get control of the entire domain.
The NTLM flaws have been reported to Microsoft in April, but the company only acknowledged a month later the NTLM LDAP vulnerability (tracked as CVE-2017-8563). Microsoft did not recognize RDP bug, the tech giant classified it as a “known issue” that could be solved with a proper configuration of the network.
Microsoft recommends companies running vulnerable servers with NT LAN Manager enabled to patch them as soon as possible.
Other mitigation actions are:
turning NT LAN Manager off.
requiring that incoming LDAP and SMB packets are digitally signed in order to prevent credential relay attacks.
Microsoft has released patches for 55 security vulnerabilities, including 19 critical issues, in its products, including Edge, Internet Explorer, Windows, Office and Office Services and Web Apps, .NET Framework, and Exchange Server.
Microsoft Patches LDAP Relay Vulnerability in NTLM
12.7.2017 securityweek Vulnerebility
Microsoft resolved over 50 bugs with its July 2017 set of security patches, one being a vulnerability where the Lightweight Directory Access Protocol (LDAP) wasn’t protected from Microsoft NT LAN Manager (NTLM) relay.
Discovered by the Preempt research team, the LDAP relay attack could be exploited by a hacker to create new domain administrator accounts even when best-practice controls are enabled. A similar attack can be performed by exploiting a RDP relay flaw in NTLM, the security researchers said.
Consisting of a series of security protocols aimed at offering authentication, integrity, and confidentiality, NTLM relay is one of the main attack vectors for hackers and pen-testers, Preempt argues.
The basic manner in which NTLM works is that the user encrypts a server-issued challenge with their password hash to establish a connection. An attacker able to use the challenge in a parallel session with the server needs to forward “the same encrypted hash to create a successful NTLM authentication” and use this to open a session (such as SMB) and infect the target system with malware.
Countermeasures preventing NTLM credential relay include SMB signing – where a derived session key is used to digitally sign all incoming packets, thus preventing server exploitation even if the NTLM session was relayed; and Enhanced Protection for Authentication (EPA) – where the client signs an element of the TLS session with the derived session key, thus protecting the server from credential relaying.
“LDAP protocol is used in Active Directory to query and update all domain objects. There is a special configuration in the Group Policy Object (GPO) - Domain Controller: LDAP server signing requirements. When this GPO is set to Require Signing the domain controller rejects LDAP sessions that are not either digitally signed with a derived session key or the entire session is encrypted over TLS (LDAPS),” Preempt’s Yaron Zinar explains.
Tracked as CVE-2017-8563, the vulnerability resides in LDAPS not having protection for credential forwarding, although it does protect from Man-in-the-Middle (MitM) attacks, the same as LDAP signing.
“This allows an attacker with SYSTEM privileges on a machine to use any incoming NTLM session and perform the LDAP operations on behalf of the NTLM user,” Zinar notes.
Because all Windows protocols use the Windows Authentication API (SSPI), which allows for authentication sessions to be downgraded to NTLM, “every connection to an infected machine (SMB, WMI, SQL, HTTP) with a domain admin would result in the attacker creating a domain admin account and getting full control over the attacked network,” the researcher notes.
The second vulnerability Preempt discovered resides in RDP Restricted-Admin, a protocol that allows users to connect to remote machines revealing their password to the machine. RDP Restricted-Admin, the researchers say, allows downgrade to NTLM in the authentication negotiation, meaning that attacks that can be performed with NTLM can be carried out against RDP Restricted-Admin.
“As RDP Restricted-Mode is often used by support technicians with elevated privileges to access remote machines, this puts their credentials at risk of being compromised. Furthermore, when combined with the first LDAP relay issue, this means that each time an admin connected with RDP Restricted-Admin an attacker was able to create a rogue domain admin,” Zinar says.
Although RDP Restricted-Mode was previously found to allow attackers to connect to remote machines using pass-the-hash, Microsoft told Preempt that the vulnerability was a known issue, and “recommended configuring network to be safe from any sort of NTLM relay.”
HPE Addresses Vulnerabilities in Several Products
12.7.2017 securityweek Vulnerebility
Hewlett Packard Enterprise (HPE) has informed customers of security bypass, information disclosure, remote code execution, cross-site scripting (XSS) and URL redirection vulnerabilities in several of its products. Advisories for each of the affected products were published this week on the Full Disclosure mailing list.
According to the company, the Samba component of HPE NonStop Server is affected by access restriction bypass (CVE-2017-2619) and remote code execution flaws (CVE-2017-7494). The latter is also known as EternalRed and SambaCry, and it has already been exploited in the wild to deliver malware. The vulnerability affects the products of several major software vendors.
HPE has not released patches for the Samba bugs, but it has provided some workarounds that can be used to prevent potential attacks. The security holes affect Samba on NonStop T1201L01 through T1201L01^AAL, and T1201H01 through T1201H01^AAM. Fixes will be included in the upcoming T1201L01^AAO and T1201H01^AAN versions.
The company also informed customers that it has rolled out patches for security bypass, XSS and URL redirection vulnerabilities affecting the HPE Network Node Manager i (NNMi) software.
The flaws, collectively tracked as CVE-2017-8948 with a severity rating of “critical,” can be exploited remotely. The security holes affect versions 10.0x, 10.1x and 10.2x, and patches have been made available for each of them.
The HPE SiteScope application monitoring software is affected by four vulnerabilities, including remote code execution and security restrictions bypass flaws rated “high severity.” The other two weaknesses affecting SiteScope are encryption-related issues that can lead to the disclosure of sensitive information.
The security holes affect versions 11.2x and 11.3x, and they have been addressed with the release of security updates and mitigations.
The SiteScope vulnerabilities were disclosed last month by CERT/CC and researcher Richard Kelley after the discovery of hundreds of potentially vulnerable installations on the Internet. At the time, HPE promised to release patches for the more serious flaws in the third quarter and pointed out that the encryption bugs are covered in the product’s deployment guide.
An updated advisory – initially released in mid-May – has also been published by HPE on the Full Disclosure mailing list this week. The advisory informs users of five critical and high severity remote code execution vulnerabilities affecting the HPE Intelligent Management Center (iMC) network management platform.
Critical Flaws Found in Windows NTLM Security Protocol – Patch Now
12.7.2017 thehackernews Vulnerebility
As part of this month's Patch Tuesday, Microsoft has released security patches for a serious privilege escalation vulnerability which affect all versions of its Windows operating system for enterprises released since 2007.
Researchers at behavioral firewall specialist Preempt discovered two zero-day vulnerabilities in Windows NTLM security protocols, both of which allow attackers to create a new domain administrator account and get control of the entire domain.
NT LAN Manager (NTLM) is an old authentication protocol used on networks that include systems running the Windows operating system and stand-alone systems.
Although NTLM was replaced by Kerberos in Windows 2000 that adds greater security to systems on a network, NTLM is still supported by Microsoft and continues to be used widely.
The first vulnerability involves unprotected Lightweight Directory Access Protocol (LDAP) from NTLM relay, and the second impact Remote Desktop Protocol (RDP) Restricted-Admin mode.
LDAP fails to adequately protect against NTLM relay attacks, even when it has built-in LDAP signing the defensive measure, which only protects from man-in-the-middle (MitM) attacks and not from credential forwarding at all.
The vulnerability could allow an attacker with SYSTEM privileges on a target system to use incoming NTLM sessions and perform the LDAP operations, like updating domain objects, on behalf of the NTLM user.
"To realize how severe this issue is, we need to realize all Windows protocols use the Windows Authentication API (SSPI) which allows downgrade of an authentication session to NTLM," Yaron Zinar from Preempt said in a blog post, detailing the vulnerability.
"As a result, every connection to an infected machine (SMB, WMI, SQL, HTTP) with a domain admin would result in the attacker creating a domain admin account and getting full control over the attacked network."
Video Demonstration of Relay Attack
Preempt researchers also provided a video to demonstrate credential relay attacks.
The second NTLM vulnerability affects Remote Desktop Protocol Restricted-Admin mode – this RDP Restricted-Admin mode allows users to connect to a remote computer without giving their password.
According to Preempt researchers, RDP Restricted-Admin allows authentication systems to downgrade to NTLM. This means the attacks performed with NTLM, such as credential relaying and password cracking, could also be carried out against RDP Restricted-Admin.
When combined with the LDAP relay vulnerability, an attacker could create a fake domain admin account whenever an admin connects with RDP Restricted-Admin and get control of the entire domain.
The researchers discovered and privately reported LDAP and RDP Relay vulnerabilities in NTLM to Microsoft in April.
However, Microsoft acknowledged the NTLM LDAP vulnerability in May, assigning it CVE-2017-8563, but dismissed the RDP bug, claiming it is a "known issue" and recommending configuring a network to be safe from any NTLM relay.
"In a remote attack scenario, an attacker could exploit this vulnerability by running a specially crafted application to send malicious traffic to a domain controller. An attacker who successfully exploited this vulnerability could run processes in an elevated context," Microsoft explained in its advisory.
"The update addresses this vulnerability by incorporating enhancements to authentication protocols designed to mitigate authentication attacks. It revolves around the concept of channel binding information."
So, sysadmins are recommended to patch their vulnerable servers with NT LAN Manager enabled as soon as possible.
You can either consider turning NT LAN Manager off or require that incoming LDAP and SMB packets are digitally signed in order to prevent credential relay attacks.
Besides this NTLM relay flaw, Microsoft has released patches for 55 security vulnerabilities, which includes 19 critical, in several of its products, including Edge, Internet Explorer, Windows, Office and Office Services and Web Apps, .NET Framework, and Exchange Server.
Windows users are strongly advised to install the latest updates as soon as possible in order to protect themselves against the active attacks in the wild.
Microsoft Patches Over 50 Vulnerabilities
12.7.2017 securityweek Vulnerebility
Microsoft has patched more than 50 vulnerabilities in its products, including Windows, Internet Explorer, Edge, Office, SharePoint, .NET, Exchange and HoloLens. While some of them have already been disclosed, the tech giant is not aware of any malicious attacks exploiting these flaws.
One of the weaknesses whose details have already been publicly disclosed is CVE-2017-8584, a critical remote code execution vulnerability affecting HoloLens, Microsoft’s mixed reality headset.
The security hole, caused due to how HoloLens handles objects in memory, can be exploited by sending specially crafted Wi-Fi packets to a device. Successful exploitation can allow the attacker to take control of the targeted system.
This is just one of the 19 vulnerabilities rated critical. The list also includes remote code execution vulnerabilities in Windows Search, Windows Explorer, Internet Explorer and the scripting engines used by Microsoft’s web browsers.
The Windows Search flaw (CVE-2017-8589) can be exploited by sending a specially crafted message to this service, which can allow a hacker to elevate privileges and take control of the device. Microsoft pointed out that in an enterprise environment, a remote attacker can exploit the flaw without authentication using an SMB connection.
Other flaws that have already been disclosed are CVE-2017-8587, a Windows denial-of-service (DoS) issue, and CVE-2017-8611 and CVE-2017-8602, both of which are spoofing vulnerabilities affecting web browsers.
Renato Marinho, director of research at Morphus Labs, believes there are also some “important” vulnerabilities worth mentioning. This includes privilege escalation bugs related to the Windows Common Log File System (CLFS) driver and the NT LAN Manager (NTLM) Authentication Protocol, a PowerShell remote code execution flaw, a Kerberos SNAME security feature bypass, and a remote code execution weakness affecting WordPad.
Trend Micro’s Zero Day Initiative (ZDI) pointed out that with the July 2017 Patch Tuesday fixes, Microsoft has addressed all the vulnerabilities disclosed at this year’s Pwn2Own hacking competition.
Microsoft has also updated the Flash Player libraries used by its products – Adobe patched three vulnerabilities on Tuesday with the release of version 26.0.0.137.
SAP Addresses High Severity Vulnerabilities With July 2017 Patches
12.7.2017 securityweek Vulnerebility
SAP today announced that a total of 12 Security Notes were included in its July 2017 Security Patch Day, including four notes that address high severity vulnerabilities.
Of the 12 Security Notes, 2 were updates to previously released Patch Day Security Notes, the German software maker reveals. Cross-Site Scripting and Information Disclosure bugs were the most common types of isses addressed.
Additionally, SAP released 11 Support Package Notes, for a total of 23 Security Notes. Overall, 11 of the Notes were released after June 13, but before July 11. Of the 23 Notes, 5 were updates to previously released Security Notes, ERPScan reveals.
The most severe of the addressed vulnerabilities involved Missing authorization checks in SAP Point of Sale (POS) Retail Xpress Server. With a CVSS score of 8.1, the bug could be exploited to read, write, or delete files stored on SAP POS server; shutdown the Xpress Server application; and monitor all content displayed on a receipt window of a POS.
“An attacker can use a Missing authorization check vulnerability to access a service without any authorization procedure and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation, and other attacks,” ERPScan explains.
Another High severity bug was a Missing authorization check vulnerability in SAP Host Agent. With a CVSS score of 7.5, the issue “could allow an attacker to remotely restart SAP Host Agent without authentication, through a specific crafted SOAP request,” security firm Onapsis reveals.
The company explains that all SAP Host Agent versions up to 7.21 PL24 are affected, including all Netweaver-based applications and HANA 1 and HANA 2. The issue was resolved in SAP Host Agent version 7.21 PL25. SAP HANA users should upgrade to Revision 122.10 (for SAP HANA1.00 SPS12), Revision 2.02 (for SAP HANA2.0 SPS00), or Revision 12 (for SAP HANA2.0 SPS01).
The remaining High priority security notes include: Improved security for outgoing HTTPS connections in SAP NetWeaver, with a CVSS score of 7.4; and Missing authorization-check in BC-SRV-ALV, with a CVSS score of 6.0. Both are updates to previously released security notes.
Other dangerous vulnerabilities addressed this month in SAP products include a Code injection vulnerability (CVSS Base Score: 6.5) in SAP Governance, Risk and Compliance Access Controls (GRC); Cross-site scripting and Cross-site request forgery (CVSS Base Score: 6.1) in SAP CRM Internet Sales Administration Console; an XML external entity vulnerability (CVSS Base Score: 6.1) in SAP BI Promotion Management Application; and an XML external entity vulnerability (CVSS Base Score: 5.4) in SAP Business Objects Titan.
“This month only 43% of notes require no manual steps besides note installation. Installing these notes is easier than the other ones and patching them has direct impact on information security. This percentage is lower than the average (usually between 60% and 75%) so this means this month’s users should perform more manual steps to have better coverage of patches in their environments,” Onapsis explains.
Adobe Fixes Vulnerabilities in Flash Player, Connect
11.7.2017 securityweek Vulnerebility
Adobe today released updates for its Flash Player and Connect products to address several vulnerabilities that can be exploited for remote code execution, information disclosure, cross-site scripting (XSS) attacks, and clickjacking.
An advisory published by Adobe for Flash Player shows that version 26.0.0.137 patches three critical vulnerabilities, including ones that can be exploited to take control of affected systems.
The list includes a critical memory corruption flaw that can lead to remote code execution (CVE-2017-3099) and two important information disclosure weaknesses caused by memory corruption and security bypass issues (CVE-2017-3100 and CVE-2017-3080). Jihui Lu of Tencent KeenLab and a researcher who uses the online moniker “bo13oy” have been credited for finding CVE-2017-3099, respectively CVE-2017-3100.
In the case of the Connect web conferencing software, Adobe patched three less severe vulnerabilities. The security holes have been described as a user interface bug that can be exploited for clickjacking attacks (CVE-2017-3101) and input validation problems that can allow reflected and stored XSS attacks (CVE-2017-3102, CVE-2017-3103).
The flaws, discovered by Anas Roubi, Adam Willard of Raytheon Foreground Security, and Alexis Laborier, affect Connect for Windows and they have been patched with the release of version 9.6.2.
Adobe said it was not aware of any attacks exploiting these vulnerabilities, but pointed out that some details of the Flash Player flaw tracked as CVE-2017-3080 were made public on July 3.
Experts found an unpatched flaw in Humax WiFi Router model HG-100R
10.7.2017 securityaffairs Vulnerebility
Experts found a flaw in Humax WiFi Router model HG-100R that could be triggered to fully compromise the devices.
A zero-day vulnerability in Humax WiFi Router model HG-100R could be exploited by attackers to compromise the WiFi credentials and obtain the router console administrative password. Trustwave SpiderLabs researchers discovered.
The issue was found by researchers at Trustwave SpiderLabs in May 2017, the company tried to report it to the manufacturer that did reply. the researchers say. The Humax WiFi Router model HG-100R is a default brand/version distributed by a major Internet provider in Brazil, it is also used in many other countries worldwide.
“More recently, in May 2017, Felipe Cerqueira and Thiago Musa, both from Trustwave SpiderLabs, have found a remote vulnerability in the HUMAX WiFi Router model HG-100R*. This vulnerability can allow attackers to compromise the WiFi Credentials and, even more dangerous, to retrieve the router console administrative password.” states the blog post published by Trustwave SpiderLabs.”The equipment is a default brand/version distributed by a major Internet provider in Brazil (where the vulnerability was discovered) but is also used in many other parts of the world.”
The issue is simple to exploit, the attackers just need to send specially crafted requests to the management console to bypass authentication. The experts discovered the router fails to validate the session token while returning answers for some methods in “url/api”.
The exploitation of the flaw could allow an attacker to retrieve sensitive information, such as the private/public IP addresses, SSID names, and passwords.
“The cookie login is basically json data containing uid and pwd encoded in base64: login={“uid”:”admin”,”pwd”:”4cd08a961f5c”};,” states the post. “In the example below you can see a request to the router without providing any authentication as well as the response containing sensitive data such as SSID name, IP addresses and WiFi password.”

A second vulnerability that affects the Humax WiFi Router model HG-100R allows attackers to bypass authentication to access the backup functionality. The feature allows router administrators to save and restore configuration, unfortunately, in both cases, the code fails to check cookies “login” and “login_token.” This implies that attacker can send requests to download and upload the full router configuration.
An attacker can change for example the DNS setting in order to hijack the user’s traffic.
“By using the backup generation/restore functionality provided by the URLs “/view/basic/GatewaySettings.bin” and “/view/basic/ConfigUpload.html” we were able to retrieve, change and finally restore a specially crafted configuration. As an example of the danger of this type of vulnerability, an attacker could use it to change your DNS configuration and redirect your traffic to servers controlled by them in order to steal private information such as passwords or banking account information.” continues the analysis.
The experts also discovered that the GatewaySettings.bin file stores the administrative password in clear text. From byte 96, the file is encoded in base64, decoding it is possible to view the password for “admin” (AAAAAAAA) and “root” (humax) users.
“If your router allows remote configuration management via the Internet, attackers can easily gain access to it and change configurations that will impact your Internet traffic. However, even if configuration management is not available on the Internet facing interface, attackers can still exploit the vulnerability in locations where WiFi routers are public, for instance in a café or airport,” continues the blog post.
To protect your router, disable the option “Remote Configuration Management.”
“Access your HUMAX WiFi Router via the following URL: http://192.168.0.1 and you should be able to find the credentials on the bottom of the router itself. By default, this configuration is not enabled, but you should double check it to make sure. If you don’t have access to your router, try to contact your Internet Service Provider and ask for support or, perhaps, a new router,” Trustwave concludes.
Flaws Found in Dell EMC Data Protection, ESRS Products
7.7.2017 securityweek Vulnerebility
Dell EMC informed customers this week that its Data Protection Advisor and ESRS Policy Manager products are affected by high and medium severity vulnerabilities, and provided patches and workarounds for addressing the issues.
According to an advisory published by the company on the Full Disclosure mailing list, versions prior to 6.8 of the EMC Secure Remote Support (ESRS) Policy Manager are affected by a high severity flaw.
The security hole, discovered by Travis Emmert from Salesforce and tracked as CVE-2017-4976, is caused by the existence of an undocumented account that can be used by a remote attacker to gain unauthorized access to a targeted system.
“EMC ESRS Policy Manager contains an undocumented account (OpenDS admin) with a default password. A remote attacker with the knowledge of the default password may login to the system and gain administrator privileges to the local LDAP directory server,” the company said in its advisory.
Starting with ESRS Policy Manager 6.8, users are prompted to change this default password during the installation process. Customers have also been provided instructions on how to change the password on their existing installations.
A separate advisory published by Dell EMC this week describes medium severity vulnerabilities affecting the EMC Data Protection Advisor data protection management software.
The product is affected by several blind SQL injection flaws (CVE-2017-8002) that can be exploited by a remote, authenticated attacker to gain access to data by executing arbitrary SQL commands, and a path traversal weakness (CVE-2017-8003) that can be exploited by a high privileged user to access information from the underlying OS server.
Users have been advised to update EMC Data Protection Advisor to version 6.4 as soon as possible.
Earlier this month, Beyond Security’s SecuriTeam Secure Disclosure (SSD) project published the details and proof-of-concept (PoC) code for a command injection vulnerability affecting EMC’s IsilonSD Edge software-defined storage solution.
The flaw allows a remote, authenticated attacker to execute arbitrary OS commands, including with root privileges. Researchers reported their findings to EMC on April 24, but it’s unclear if the vulnerability has been patched by the vendor.
Perl devs fix an important flaw in DBD—MySQL that affects encryption between client and server
6.7.2017 securityaffais Vulnerebility
Perl development team solved a flaw in DBD—MySQL in some configurations that wasn’t enforcing encryption allowing an attacker to power MiTM attacks.
The security researcher Pali Rohár reported an important flaw in DBD—MySQL, tracked as CVE-2017-10789, that affects only encryption between client and server.
According to the expert, the issue in some configurations wasn’t enforcing encryption allowing an attacker to power MiTM attacks.
“The DBD::mysql module through 4.043 for Perl uses the mysql_ssl=1 setting to mean that SSL is optional (even though this setting’s documentation has a “your communication with the server will be encrypted” statement), which allows man-in-the-middle attackers to spoof servers via a cleartext-downgrade attack, a related issue to CVE-2015-3152.” reads the description provided by the Mitre.
Rohár discovered that the Perl DBD::mysql driver does not enforce SSL/TLS encryption when option
mysql_ssl=1 is enabled.
“Enabling encryption depends on an announcement from MySQL server what it supports which can man-in-the-middle attack spoof. DBD::mysql does not enforce SSL/TSL encryption even when certificate is specified via connection parameter mysql_ssl_ca_file.” states the advisory published by the expert. “Therefore usage of SSL/TLS encryption in DBD::mysql is insecure.”
The Perl 5 database interface maintainers have issued an important security patch for DBD—MySQL, a note on the GitHub account confirms that the issue leaves systems vulnerable to BACKRONYM and Riddle attacks.
“The important change is that DBD::mysql reject connection to MySQL server (also SSL enabled) if mysql_ssl=1 is set and libmysqlclient.so library cannot enforce SSL encryption (because is vulnerable to BACKRONYM or Riddle).” reads the note on GitHub.
The Riddle has been uncovered in the popular DBMS Oracle MySQL in 2015, the issue can be potentially exploited by attacker powering a man-in-the-middle attack to steal usernames and passwords.
“The Riddle is a critical security vulnerability found in Oracle’s MySQL 5.5 and 5.6 client database libraries. The vulnerability allows an attacker to use riddle in the middle for breaking SSL configured connection between MySQL client and server.” states the description of the flaw.“This vulnerability is a very critical security hole because it affects MySQL — a very popular SQL database — and SSL connection which is by its definition secure.”
The flaw, tracked as CVE-2017-3305, potentially exposes login credentials to eavesdropping, an attacker can capture them when a MySQL clients 5.5 and 5.6 send them to servers.
A security update released for the versions 5.5.49 and 5.6.30 failed to completely fix the bug. The experts noticed that the Versions 5.7 and later, as well as MariaDB systems, are not affected by this issue.
According to security researcher Pali Rohár, the Riddle vulnerability results from the failed attempt to patch the BACKRONYM vulnerability affecting the MySQL database. The Backronym vulnerability exposes passwords to attackers who are in a position to run a man-in-the-middle attack, even if the traffic is encrypted.
The developers fixed the issue forcing the MySQL server to reject a connection if the client can’t enforce the SSL encryption.
Google Patches Critical Vulnerabilities in Android
6.7.2017 securityweek Vulnerebility
Google on Wednesday announced that a total of 138 vulnerabilities were addressed in the Android platform with the release of this month’s set of security patches.
The July 2017 Android Security Bulletin was split in two partial security patch level strings: the 2017-07-01 security patch level that addresses issues in the platform itself, and the 2017-07-05 security patch level, which resolves device-specific vulnerabilities in various components supplied by manufacturers.
While in the security bulletins prior to June 2017 Google focused on detailing the resolved vulnerabilities, starting last month the company moved to underline the vulnerable components and the number of issues affecting them.
The 2017-07-01 security patch level addresses a total of 43 bugs in Android, including 10 vulnerabilities rated Critical, 28 assessed with a High severity ranking, and 5 Moderate.
Media Framework was the most impacted component, with 27 vulnerabilities addressed in it: 10 Critical, 15 High, and 2 Moderate. Google resolved 12 Remote Code Execution (RCE) issues in the component (10 Critical), 1 Elevation of Privilege (EoP), 12 Denial of Service (DoS) bugs, and 2 Information Disclosure (ID) flaws.
“The most severe of these issues is a critical security vulnerability in media framework that could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” Google notes in its advisory.
Other affected components include Runtime (a Moderate RCE), Framework (7 flaws: EoP, ID and DoS), Libraries (3 issues: RCE and DoS), and System UI (5 bugs: RCE and EoP). Affected platform versions include Android 4.4.4, 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, and 7.1.2.
The 2017-07-05 security patch level addresses a total of 95 vulnerabilities: 1 assessed Critical severity, 66 considered High risk, 27 Moderate severity, and 1 Low. Qualcomm closed-source components were affected the most, with 55 High severity vulnerabilities addressed.
Of the remaining 40 vulnerabilities, 25 impact Qualcomm components: 7 High severity and 18 Moderate issues. 22 of the flaws were Elevation of Privilege vulnerabilities, while the remaining three were Information Disclosure issues.
Other impacted components include Broadcom components (a Critical RCE and 2 Moderate EoP bugs), HTC components (Moderate EoP and ID and Low severity ID), Kernel components (4 EoP, 1 DoS and 1 ID issue), MediaTek components (a High severity EoP), and NVIDIA components (High severity EoP and Medium risk ID).
According to Google, all devices running a security patch level of 2017-07-05 will be safe from these vulnerabilities and all of the bugs addressed in previous security patch levels. Nexus and Pixel devices will receive the security patch level of July 05, 2017, the company also announced.
CISCO fixed 3 critical issued in Elastic Services Controller and Ultra Services Framework
6.7.2017 securityaffairs Vulnerebility
CISCO fixed three critical issued in Elastic Services Controller and Ultra Services Framework, admins have to manual patch them.
The last weekly security update list published by CISCO includes three critical vulnerabilities affecting the Elastic Services Controller and Ultra Services Framework.
The flaw, tracked as CVE-2017-6713, in the network function virtualisation management environment Elastic Services Controller is related to the use of static default credentials that would let a remote attacker access to all the instances of the controller’s UI.
“A vulnerability in the Play Framework of Cisco Elastic Services Controller (ESC) could allow an unauthenticated, remote attacker to gain full access to the affected system.” reads the security advisory published by CISCO.
“The vulnerability is due to static, default credentials for the Cisco ESC UI that are shared between installations. An attacker who can extract the static credentials from an existing installation of Cisco ESC could generate an admin session token that allows access to all instances of the ESC web UI.”
As reported in the security advisory the same credentials are shared between multiple installations, allowing an attacker to generate an admin session token to access any instances of the Elastic Services Controller web UI.
A second issue, tracked as CVE-2017-6712, is a privilege escalation bug caused by the presence of the user ‘tomcat‘ having access to shell commands that lets that user overwrite any file on the system, and elevate their privilege to root.
“A vulnerability in certain commands of Cisco Elastic Services Controller could allow an authenticated, remote attacker to elevate privileges to root and run dangerous commands on the server.” states the advisory issued by CISCO.
“The vulnerability occurs because a “tomcat” user on the system can run certain shell commands, allowing the user to overwrite any file on the filesystem and elevate privileges to root. An exploit could allow an authenticated, remote attacker to elevate privileges and run dangerous commands on the server.”
Other issues affect the Ultra Services Framework’s (USF) automation service.
A first bug in the Ultra Services Framework’s (USF) automation service (CVE-2017-6711) is related to an insecure configuration of the Apache ZooKeeper service, which could be exploited by a remote attacker to get access to the orchestrator network.
“A vulnerability in the Ultra Automation Service (UAS) of the Cisco Ultra Services Framework could allow an unauthenticated, remote attacker to gain unauthorized access to a targeted device.” states the advisory.
“The vulnerability is due to an insecure default configuration of the Apache ZooKeeper service used by the affected software. An attacker could exploit this vulnerability by accessing the affected device through the orchestrator network. An exploit could allow the attacker to gain access to ZooKeeper data nodes (znodes) and influence the behavior of the system’s high-availability feature.”
A second bug in the Ultra Services Framework’s (USF) automation service, tracked as CVE-2017-6714, resides in the staging server and could lead Arbitrary Command Execution.
“A vulnerability in the AutoIT service of Cisco Ultra Services Framework Staging Server could allow an unauthenticated, remote attacker to execute arbitrary shell commands as the Linux root user.” states the advisory.
“The vulnerability is due to improper shell invocations. An attacker could exploit this vulnerability by crafting CLI command inputs to execute Linux shell commands as the root user. An exploit could allow the attacker to execute arbitrary shell commands as the Linux root user.”
The last issue in the Ultra Services Framework AutoVNF is a Log File User Credential Information Disclosure Vulnerability (CVE-2017-6709) in the USF’s AutoVNF.
The use of Admin credentials is logged in clear text, an attacker can retrieve them accessing the logfile’s URL.
A vulnerability in the AutoVNF tool for the Cisco Ultra Services Framework could allow an unauthenticated, remote attacker to access administrative credentials for Cisco Elastic Services Controller (ESC) and Cisco OpenStack deployments in an affected system.
“The vulnerability exists because the affected software logs administrative credentials in clear text for Cisco ESC and Cisco OpenStack deployment purposes. An attacker could exploit this vulnerability by accessing the AutoVNF URL for the location where the log files are stored and subsequently accessing the administrative credentials that are stored in clear text in those log files. A successful exploit could allow the attacker to access the administrative credentials for Cisco ESC and Cisco OpenStack deployments in the affected system, which the attacker could use to conduct additional attacks.” states the advisory.
“The same product also has a symbolic link error that exposes the system to arbitrary file read and malicious code execution.”
Zero-Day Found in Humax WiFi Router
5.7.2017 securityweek Vulnerebility
An unpatched vulnerability affecting Humax WiFi Router model HG-100R allows attackers to compromise the WiFi credentials and even retrieve the router console administrative password, Trustwave SpiderLabs researchers discovered.
The vulnerability was found in May 2017, but repeated attempts to alert the manufacturer on it remained unanswered, the researchers say. According to Trustwave, the device is a default brand/version distributed by a major Internet provider in Brazil, while also being used in various other parts of the world.
The issue, Trustwave explains, starts with specially crafted requests sent to the management console, which allow the attacker to bypass authentication. This attack is possible because the router fails to validate the session token while returning answers for some methods in "url/api".
By exploiting the vulnerability, an attacker could retrieve sensitive information, including the private/public IP addresses, SSID names and passwords.
“The cookie login is basically json data containing uid and pwd encoded in base64: login={"uid":"admin","pwd":"4cd08a961f5c"};,” the researchers say.
A second issue with the router enables attackers to bypass authentication to access the backup functionality for saving and restoring configuration. This is possible because both ignore the absence of the cookies "login" and "login_token." Thus, they accept requests to download and upload the full router configuration.
With the help of the backup generation/restore functionality provided by the URLs ‘/view/basic/GatewaySettings.bin’ and ‘/view/basic/ConfigUpload.html’, the security researchers were able to retrieve, change and eventually restore a specially crafted configuration.
By using this vulnerability, an attacker could change the DNS configuration and redirect user’s traffic to servers controlled by the attacker. Thus, they could steal private information, including passwords and banking account information.
While looking at the GatewaySettings.bin file, the security researchers also discovered that it stores the administrative password without any encryption. From byte 96, the file is encoded in base64, and decoding it reveals the password for “admin” (AAAAAAAA) and “root” (humax) users, both saved in clear text.
“If your router allows remote configuration management via the Internet, attackers can easily gain access to it and change configurations that will impact your Internet traffic. However, even if configuration management is not available on the Internet facing interface, attackers can still exploit the vulnerability in locations where WiFi routers are public, for instance in a café or airport,” the researchers say.
To stay protected, and prevent remote exploitation, users should make sure their routers aren’t exposed to the Internet. For that, they should disable the option "Remote Configuration Management."
“Access your HUMAX WiFi Router via the following URL: http://192.168.0.1 and you should be able to find the credentials on the bottom of the router itself. By default, this configuration is not enabled, but you should double check it to make sure. If you don't have access to your router, try to contact your Internet Service Provider and ask for support or, perhaps, a new router,” Trustwave concludes.
Vulnerabilities in Pre-Installed Software expose Dell Systems to hack
4.7.2017 securityaffairs Vulnerebility
According to experts from Talos, security vulnerabilities in pre-installed software expose Dell systems to code execution attacks.
Security vulnerabilities in pre-installed software expose Dell systems to code execution attacks.
Hackers can exploit the flaws to disable security mechanisms, escalate privileges and execute arbitrary code within the context of the application user.
According to the experts from CISCO Talos, the vulnerable pre-installed software is the Dell Precision Optimizer application service and the Invincea-X and Invincea Dell Protected Workspace.
“Talos are releasing advisories for vulnerabilities in the Dell Precision Optimizer application service software, Invincea-X and Invincea Dell Protected Workspace. These packages are pre-installed on certain Dell systems. Vulnerabilities present in these applications could allow attackers to disable security mechanisms, escalate privileges and execute arbitrary code within the context of the application user.” states the advisory published by Cisco Talos.
The first vulnerability in Invincea-X, Dell Protected Workspace 6.1.3-24058, tracked as CVE-2016-9038, is a double fetch in the SboxDrv.sys driver.
An attacker can exploit the flaw by sending crafted data to the \Device\SandboxDriverApi device driver which is read/write accessible to everyone. A
The attacker can exploit the issue to write an arbitrary value to kernel memory space in order to gain local privilege escalation.
The second flaw tracked as CVE-2016-8732 affected the Invincea Dell Protected Workspace version 5.1.1-22303, that is a security solution for endpoints.
According to Talos, the flaws exist within one of the driver components, ‘InvProtectDrv.sys’ that is included in version 5.1.1-22303 of this security software. Weak restrictions on the driver communications channel and insufficient validation could allow an attacker controlled application that is executed on an affected system to leverage the driver to disable protection mechanisms.

Weak restrictions on the driver communications channel and insufficient validation allow an attacker-controlled application executed on the vulnerable machine to leverage the driver and disable some of the protection mechanisms in the software. The bug was fixed in the 6.3.0 release of the application.
A third flaw, tracked as CVE-2017-2802, affects the Dell Precision Optimizer application and could lead to the execution of arbitrary code. The vulnerabilities affects the Dell Precision Tower 5810 with nVidia graphic cards, PPO Policy Processing Engine 3.5.5.0, and ati.dll (PPR Monitoring Plugin) 3.5.5.0.
“During the start of ‘Dell PPO Service’, supplied by Dell Precision Optimizer application, the program “c:\Program Files\Dell\PPO\poaService.exe” loads the dll, “c:\Program Files\Dell\PPO\ati.dll”. This in turn attempts to load “atiadlxx.dll”, which is not present by default in the application directory. The program searches for an appropriately named dll in the directories specified by the PATH environment variable. If it finds a dll with the same name, it will load the dll into poaService.exe without checking the signature of the dll. This can lead to execution of arbitrary code if an attacker supplies a malicious dll of the correct name. ” continues the advisory.
An attacker could supply a malicious DLL having the same name of the “atiadlxx.dll” in one of the directories specified by the PATH environment variable to achieve arbitrary code execution.
The security implications for the flaws are serious because the Invincea Dell Protected Workspace is an application is commonly deployed to secure workstations within high-security environments.
Talos users’ organizations using affected versions of this software to update them to the latest version as soon as possible. It is important anyway to carefully assess any pre-installed software to avoid that flaws affecting them can be exploited by attackers.
“Given that the Invincea Dell Protected Workspace is an application that is commonly deployed to secure workstations within high security environments, it is recommended that organizations using affected versions of this solution update to the latest version as quickly as possible to ensure that the protections provided by this software cannot be bypassed by an attacker. ” concluded Talos.
Pre-Installed Software Flaws Expose Dell Systems to Code Execution
4.7.2017 securityweek Vulnerebility
Flaws in pre-installed software expose Dell systems to attacks that could result in the disabling of security mechanisms, privilege escalation, and arbitrary code execution within the context of the application user.
The vulnerable applications include the Dell Precision Optimizer application service software and Invincea-X and Invincea Dell Protected Workspace, Cisco Talos reveals in an advisory.
Tracked as CVE-2016-9038, the first vulnerability impacting Invincea-X, Dell Protected Workspace 6.1.3-24058, as a result of a device driver being read/write accessible to everyone, which can be triggered by sending specially crafted data to it.
“A successful exploitation results in an arbitrary value written to kernel memory space, which can lead to local privilege escalation,” Cisco explains.
Cisco also warns of CVE-2016-8732, an issue that involves multiple security flaws in the driver component of Invincea Dell Protected Workspace version 5.1.1-22303, a security solution for endpoints.
Weak restrictions on the driver communications channel and insufficient validation allow an attacker-controlled application executed on the vulnerable machine to leverage the driver and disable some of the protection mechanisms in the software. The bug was addressed in the 6.3.0 release of the application.
Tracked as CVE-2017-2802, a third bug impacts the Dell Precision Optimizer application and could lead to execution of arbitrary code. The issue impacts Dell Precision Tower 5810 with nVidia graphic cards, PPO Policy Processing Engine 3.5.5.0, and ati.dll (PPR Monitoring Plugin) 3.5.5.0.
When the Dell PPO Service supplied by Dell Precision Optimizer starts, poaService.exe (located in “c:\Program Files\Dell\PPO\” loads the ati.dll from the same folder. The DLL, in turn, attempts to load atiadlxx.dll, which is not present by default in the directory, and the application searches “for an appropriately named DLL in the directories specified by the PATH environment variable.”
As soon as it finds a DLL with the same name, the app loads it into poaService.exe without checking its signature. Thus, an attacker could supply a malicious DLL of the correct name and achieve arbitrary code execution, Cisco explains.
“Given that the Invincea Dell Protected Workspace is an application that is commonly deployed to secure workstations within high security environments, it is recommended that organizations using affected versions of this solution update to the latest version as quickly as possible to ensure that the protections provided by this software cannot be bypassed by an attacker,” Cisco notes.
Severe flaws found in German e-Government OSCI 1.2 Communication Library
3.7.2017 thehackernews Vulnerebility
Security researchers at SEC-Consult found severe vulnerabilities in the German e-government Communication Library OSCI (Online Services Computer Interface).
According to the experts at SEC-Consult, the German e-government system OSCI (Online Services Computer Interface) is open to padding oracle attacks and other vulnerabilities due to the use of an insecure communications protocol.
The researchers at SEC Consult found severe vulnerabilities in the OSCI 1.2 Transport library that provides a secure message exchange channel over an untrusted network (i.e. Internet) for German government agencies for eGovernment.
An attacker can exploit the vulnerabilities to decrypt messages, modify signed messages and read arbitrary files from the host that implements the vulnerable OSCI protocol.
“However, SEC Consult found that multiple vulnerabilities allow attackers to decrypt encrypted messages as well as modify signed messages. Moreover, a vulnerability can be used to read arbitrary files from any host that implements the OSCI 1.2 transport protocol using this library.” reads the security advisory.
An External Entity Injection (XXE), tracked as CVE-2017-10670, could be exploited by an attacker to read arbitrary files from the target system, or to trigger a denial-of-service condition on it.
“By sending manipulated XML data to any communication partner, an attacker is able to conduct an XXE attack on the receiving system. This attack allows an attacker to read arbitrary files from the file system of the victim host or to conduct a denial of service attack.” reads the Advisory.
The CVE-2017-10668 vulnerability is linked to the implementation of a number of deprecated encryption algorithms (Triple DES, AES 129, AES 192, and AES 256, all in CBC mode) that open the door to padding oracle attacks.
“Since the supported cipher algorithms do not provide protection against modification (malleability) and the library reveals in an error message whether decryption failed (error code 9202), SEC Consult was able to conduct a padding oracle attack. This attack allows an attacker to bypass transport encryption.” states the advisory.
“In our test setup we were able to decrypt an OSCI processDelivery message on a local machine within half an hour.” states a blog post published by SEC Consult.

A Signature Wrapping attack, tracked as CVE-2017-10669, allows the miscreant to change the contents of a message without invalidating the signature.
“Signature Wrapping attack [CVE-2017-10669] By moving XML elements within the document tree, a signature wrapping attack can be conducted. This allows an attacker to modify the contents of a signed message arbitrarily without invalidating the signature.” states the advisory.

The last issue is a deserialization bug that could be exploited to an external entity injection.
“A class in the library defines the method readObject() that is used by Java to deserialize a stream into an object. This method uses an XML parser to achieve this. However, the XML parser used is configured to resolve external entities. Therefore, an attacker who can influence data that deserialized by an application can conduct an XXE attack 1).”
Experts highlighted that the deserialization bug could be exploited even is the vulnerable application is not using the OSCI-Transport library, it is enough the presence of the OSCI-Transport library in the classpath of an application.
German public agencies should use the latest version of the OSCI-Transport library.
Linux Systemd Gives Root Privileges to Invalid Usernames
3.7.2017 securityweek Vulnerebility
A bug in Linux’s systemd init system causes root permissions to be given to services associated with invalid usernames, and while this could pose a security risk, exploitation is not an easy task.
A developer who uses the online moniker “mapleray” last week discovered a problem related to systemd unit files, the configuration files used to describe resources and their behavior. Mapleray noticed that a systemd unit file containing an invalid username – one that starts with a digit (e.g. “0day”) – will initiate the targeted process with root privileges instead of regular user privileges.
Systemd is designed not to allow usernames that start with a numeric character, but Red Hat, CentOS and other Linux distributions do allow such usernames.
“It's systemd's parsing of the User= parameter that determines the naming doesn't follow a set of conventions, and decides to fall back to its default value, root,” explained developer Mattias Geniar.
While this sounds like it could be leveraged to obtain root privileges on any Linux installation using systemd, exploiting the bug in an attack is not an easy task. Geniar pointed out that the attacker needs root privileges in the first place to edit the systemd unit file and use it.
The attack scenarios described by the developer include tricking an administrator into creating a malicious unit file, or exploiting a different vulnerability to obtain write access and using unit files to escalate privileges. Others noted that an administrator can deliberately create a username that starts with a digit and wrongly assume that the program will run with user-level privileges instead of as root. Some scenarios described on Hacker News don’t even require the involvement of the system administrator.
Systemd developers have classified this issue as “not-a-bug” and they apparently don’t plan on fixing it. Linux users are divided on the matter – some believe this is a vulnerability that could pose a serious security risk, while others agree that a fix is not necessary.
“It's an obvious bug (at least on RHEL/CentOS 7), since a valid username does not get accepted by systemd so it triggers unexpected behaviour by launching services as root.
However, it isn't as bad as it sounds and does not grant any username with a digit immediate root access,” Geniar explained.
This is not the only systemd flaw disclosed recently. Chris Coulson, an engineer with Canonical, the developer of the Ubuntu Linux distribution, revealed last week that systemd is affected by an out-of-bounds write vulnerability (CVE-2017-9445) that can be triggered using a specially crafted TCP payload to crash the systemd-resolved daemon or execute arbitrary code in the context of the daemon process.
WordPress Plugin Used by 300,000+ Sites Found Vulnerable to SQL Injection Attack
1.7.2017 thehackernews Vulnerebility
A SQL Injection vulnerability has been discovered in one of the most popular Wordpress plugins, installed on over 300,000 websites, which could be exploited by hackers to steal databases and possibly hijack the affected sites remotely.
The flaw has been discovered in the highly popular WP Statistics plugin, which allows site administrators to get detailed information related to the number of users online on their sites, the number of visits and visitors, and page statistics.
Discovered by Sucuri team, WordPress plugin WP Statistics is vulnerable to SQL Injection flaw that allows a remote attacker, with at least a subscriber account, to steal sensitive information from the website's database and possibly gain unauthorized access to websites.
SQL Injection is a web application bug that allows hackers to inject malicious Structured Query Language (SQL) code to web inputs in order to determine the structure and location of key databases, which eventually allows stealing of the database.
The SQL injection vulnerability in WP Statistics plugin resides in multiple functions, including wp_statistics_searchengine_query().
"This vulnerability is caused by the lack of sanitization in user-provided data," researchers said. "Some attributes of the shortcode wpstatistics are being passed as parameters for important functions and this should not be a problem if those parameters were sanitized."
"One of the vulnerable functions wp_statistics_searchengine_query() in the file 'includes/functions/functions.php' is accessible through WordPress' AJAX functionality thanks to the core function wp_ajax_parse_media_shortcode()."
This function does not check for additional privileges, which allows website subscribers to execute this shortcode and inject malicious code to its attributes.
The researchers at Sucuri privately disclosed the flaw to the WP Statistics team and the team had patched the vulnerability in its latest version WP Statistics version 12.0.8.
So, if you have a vulnerable version of the plugin installed and your website allowing user registration, you are definitely at risk, and you should install the latest version as soon as possible.
Cisco Warns of Serious Flaws in IOS Software
30.6.2017 securityweek Vulnerebility
Cisco has warned users that devices running the company’s IOS or IOS XE software are affected by several high severity vulnerabilities that can be exploited for remote code execution and denial-of-service (DoS) attacks.
There are a total of nine flaws affecting the Simple Network Management Protocol (SNMP) component of IOS and IOS XE software. Patches have yet to be made available by Cisco, but the networking giant has shared some workarounds.
An authenticated attacker who knows the SNMP read-only community string of the targeted system could execute code or cause the device to reload by sending a specially crafted SNMP packet via IPv4 or IPv6. If the attacker can execute code, they may be able to take full control of the affected system.
The vulnerabilities affect IOS devices running any version of SNMP if they are configured with one of nine management information bases (MIBs), which allow organizations to manage devices such as routers and switches in a network.
Cisco said it found these security holes during internal testing, but the company warned customers that individuals outside the company know about the vulnerabilities, which increases the chances of exploitation.
Vulnerabilities in Cisco Prime Infrastructure
Last week, Cisco informed customers of several high and medium severity vulnerabilities found by researchers at SEC Consult in its Prime Infrastructure and Evolved Programmable Network Manager products.
The flaws include SQL injection, XML external entity (XXE), local file disclosure and cross-site scripting (XSS) weaknesses that can be exploited remotely by authenticated or unauthenticated attackers. An advisory published by SEC Consult includes proof-of-concept (PoC) code for each of the vulnerabilities.
While Cisco was informed about these issues in November 2016, the company postponed the release of patches several times. Fixes were finally made available last week.
Cisco IOS Software is affected by RCE flaws that could allow full hack of the devices
30.6.2017 securityaffairs Vulnerebility
Experts at CISCO discovered severe remote code execution vulnerabilities in Cisco IOS Software while conducting internal testing.
Cisco warned users of serious vulnerabilities in IOS software that can be exploited by authenticated, remote attackers for code execution and denial-of-service (DoS) attacks. Experts at CISCO discovered the vulnerabilities while conducting internal testing.
“The Simple Network Management Protocol (SNMP) subsystem of Cisco IOS and IOS XE Software contains multiple vulnerabilities that could allow an authenticated, remote attacker to remotely execute code on an affected system or cause an affected system to reload. An attacker could exploit these vulnerabilities by sending a crafted SNMP packet to an affected system via IPv4 or IPv6. Only traffic directed to an affected system can be used to exploit these vulnerabilities.” states the advisory published by CISCO.
The experts warned of nine flaws affecting the Simple Network Management Protocol (SNMP) component of IOS and IOS XE software.
The flaws are due to a buffer overflow condition in the SNMP subsystem, all versions of SNMP – Versions 1, 2c, and 3 are affected.
As reported by the advisory, an authenticated attacker who knows the SNMP read-only community string of a target system could remotely execute code or cause the device to reload by sending a specially crafted SNMP packet via IPv4 or IPv6.
“To exploit these vulnerabilities via SNMP Version 2c or earlier, the attacker must know the SNMP read-only community string for the affected system. To exploit these vulnerabilities via SNMP Version 3, the attacker must have user credentials for the affected system. A successful exploit could allow the attacker to execute arbitrary code and obtain full control of the affected system or cause the affected system to reload.” continues the advisory.
The attack is very dangerous because hackers could obtain full control of vulnerable devices and the worst news is that CISCO warned customers that attackers in the wild know about the vulnerabilities and can exploit them in any moment.
Devices configured with any of the following MIBs are vulnerable:
ADSL-LINE-MIB
ALPS-MIB
CISCO-ADSL-DMT-LINE-MIB
CISCO-BSTUN-MIB
CISCO-MAC-AUTH-BYPASS-MIB
CISCO-SLB-EXT-MIB
CISCO-VOICE-DNIS-MIB
CISCO-VOICE-NUMBER-EXPANSION-MIB
TN3270E-RT-MIB
Waiting for a fix, users can apply workarounds suggested by the company.
Authentication Bypass Flaw Patched in BIND, Knot DNS
30.6.2017 securityweek Vulnerebility
The developers of the BIND and Knot DNS software have released updates to patch a potentially serious vulnerability that can be exploited to bypass authentication mechanisms.
The flaw, discovered by Clément Berthaux of Synacktiv, is related to Transaction SIGnature (TSIG), an authentication protocol used by the Domain Name System (DNS). The protocol is mainly used to authenticate dynamic DNS updates and zone operations.
An attacker who is able to communicate with an authoritative DNS server and has knowledge of a valid key name can exploit the security hole to bypass TSIG authentication and carry out unauthorized zone transfers or updates.
“This issue is due to the fact that when the server receives a request which TSIG timestamp is out of the time window, it still signs its answer, using the provided digest as prefix even though this digest is invalid and has an incorrect size. This allow an attacker to forge the signature of a valid request, hence bypassing the TSIG authentication,” Berthaux wrote in an advisory.
DNS zone transfer is the process in which a DNS server passes a copy of its database (i.e. zone) to another DNS server. Obtaining a copy of zone records can be useful for an attacker as they may contain information that can be leveraged for DNS spoofing attacks.
The Internet Systems Consortium (ISC) tracks this issue as two separate vulnerabilities – one medium severity flaw that allows unauthorized zone transfers (CVE-2017-3142), and a high severity flaw that can be exploited for unauthorized dynamic updates (CVE-2017-3143).
ISC addressed the problem this week with the release of BIND 9.9.10-P2, 9.10.5-P2 and 9.11.1-P2. Knot DNS patched the vulnerability with the release of versions 2.5.2 and 2.4.5 last week.
TSIG is also supported by, among others, PowerDNS and NSD, but the developers of these DNS servers have not published any advisories to indicate whether or not their products are affected.
Microsoft issued Security fix for important flaw in Azure Active Directory Connect
30.6.2017 securityaffairs Vulnerebility
Microsoft is warning sysadmins to check their Azure Active Directory Connect installs and patch them against an important Privilege Escalation flaw.
Microsoft fixed an important privilege escalation vulnerability in Azure Active Directory (AD) Connect, tracked as CVE-2017-8613, that can be exploited by attackers to hijack the accounts of privileged users.
Azure Active Directory Connect allows organizations to integrate their on-premises identity infrastructure with Azure AD. The flaw resides in the Azure AD Connect feature “password writeback,” which allows users to easily reset their on-premises passwords by configuring Azure AD to write passwords back to the on-premises AD.
Microsoft warned of possible misconfiguration in the password writeback feature in the setup phase that could be abused by a malicious Azure AD administrator. A malicious Azure Active Directive administrator can set the password of an on-premises AD account belonging to a privileged user to a specific value in order to take over the account.
“Password writeback is a component of Azure AD Connect. It allows users to configure Azure AD to write passwords back to their on-premises Active Directory. It provides a convenient cloud-based way for users to reset their on-premises passwords wherever they are.” states the Microsoft security advisory.
“To enable Password writeback, Azure AD Connect must be granted Reset Password permission over the on-premises AD user accounts. When setting up the permission, an on-premises AD Administrator may have inadvertently granted Azure AD Connect with Reset Password permission over on-premises AD privileged accounts (including Enterprise and Domain Administrator accounts),” Microsoft explained in its advisory. “This configuration is not recommended because it allows a malicious Azure AD Administrator to reset the password of an arbitrary on-premises AD user privileged account to a known password value using Password writeback. This in turn allows the malicious Azure AD Administrator to gain privileged access to the customer’s on-premises AD.”

Microsoft solved the privilege escalation flaw by preventing password resets to privileged on-premises accounts.
Microsoft users can update their version to Azure Active Directory Connect 1.1.553.0 version. Users can also mitigate the issue by following the instructions provided by Microsoft.
Microsoft Fixes Privilege Escalation Flaw in Azure AD Connect
29.6.2017 securityweek Vulnerebility
Microsoft has released an update for Azure Active Directory (AD) Connect to address an “important” vulnerability that can be exploited to hijack the accounts of privileged users.
Azure AD Connect is a tool that allows organizations to integrate their on-premises identity infrastructure with Azure AD. One feature of Azure AD Connect is “password writeback,” which allows users to easily reset their on-premises passwords by configuring Azure AD to write passwords back to the on-premises AD.
The problem, according to Microsoft, is that the password writeback feature may not be configured properly during enablement. A malicious Azure AD administrator can set the password of an on-premises AD account belonging to a privileged user to a known value and gain access to that account.
“To enable Password writeback, Azure AD Connect must be granted Reset Password permission over the on-premises AD user accounts. When setting up the permission, an on-premises AD Administrator may have inadvertently granted Azure AD Connect with Reset Password permission over on-premises AD privileged accounts (including Enterprise and Domain Administrator accounts),” Microsoft explained in its advisory.
This privilege escalation vulnerability is tracked as CVE-2017-8613 and it has been resolved by preventing password resets to privileged on-premises accounts.
Microsoft has provided detailed instructions on how organizations can check if they are affected. Users have been advised to update to version 1.1.553.0 of Azure AD Connect or apply mitigations suggested by the vendor.
Last week, Microsoft informed users that it patched yet another remote code execution vulnerability in its Malware Protection Engine. The flaw, discovered by Tavis Ormandy of Google Project Zero, could have been exploited to take control of a targeted system.
Ormandy and other Project Zero researchers identified several vulnerabilities in the Malware Protection Engine in the past weeks, including remote code execution and denial-of-service (DoS) flaws.
A critical flaw allows hacking Linux machines with just a malicious DNS Response
29.6.2017 securityaffairs Vulnerebility
A remote attacker can trigger the buffer overflow vulnerability to execute malicious code on affected Linux systems with just a malicious DNS response.
Chris Coulson, Ubuntu developer at Canonical, has found a critical vulnerability Linux that can be exploited to remotely hack machines running the popular OS. The flaw, tracked as CVE-2017-9445, resides in the Systemd init system and service manager for Linux operating systems.
A remote attacker can trigger the buffer overflow vulnerability to execute malicious code with just a malicious DNS response.
The expert has found the vulnerability in the ‘dns_packet_new‘ function of ‘systemd-resolved,’ that handles a DNS response and provides network name resolution to local applications.
A specially crafted malicious DNS response can crash ‘systemd-resolved’ program remotely every time the system tries to lookup for a hostname on an attacker-controlled DNS service.
The attacker can trigger the flaw by sending a large DNS response that triggers a buffer overflow that leads to remote code execution.
“Certain sizes passed to dns_packet_new can cause it to allocate a buffer that’s too small. A page-aligned number – sizeof(DnsPacket) + sizeof(iphdr) + sizeof(udphdr) will do this – so, on x86 this will be a page-aligned number – 80. Eg, calling dns_packet_new with a size of 4016 on x86 will result in an allocation of 4096 bytes, but 108 bytes of this are for the DnsPacket struct.” explains Coulson.
“A malicious DNS server can exploit this by responding with a specially crafted TCP payload to trick systemd-resolved in to allocating a buffer that’s too small, and subsequently write arbitrary data beyond the end of it.”
The flaw affects the
The flaw affects the Systemd version 223, which is dated back June 2015, and later, including Systemd version 233 launched in March 2017.
The vulnerability affects the Ubuntu versions 17.04 and version 16.10; Debian versions Stretch (aka Debian 9), Buster (aka 10) and Sid (aka Unstable); and various other Linux distributions that use Systemd.
Linux users and system administrators must update their installs as soon as possible.
Kaspersky Patches Flaws in Anti-Virus for Linux File Server
29.6.2017 securityweek Vulnerebility
An update released earlier this month by Kaspersky Lab for its Anti-Virus for Linux File Server product addresses several potentially serious vulnerabilities discovered by researchers at Core Security.
Kaspersky Anti-Virus for Linux File Server is designed to protect workstations and file servers on large corporate networks. Core Security employees determined that the product’s web-based management interface is affected by vulnerabilities that can be exploited for arbitrary code execution and other malicious activities.
One of the security holes is caused by the lack of anti-CSRF tokens in the web interface, which allows a remote attacker to execute shell commands by tricking an authenticated user into accessing a specially crafted webpage.
Researchers also found vulnerabilities that can be exploited to escalate privileges to root, execute arbitrary code via a reflected cross-site scripting (XSS) flaw, and read arbitrary files due to a path traversal bug. Core Security has made available proof-of-concept (PoC) code for each of the vulnerabilities.
The vulnerabilities affect version 8 of Kaspersky Anti-Virus for Linux File Server and they are tracked as CVE-2017-9813, CVE-2017-9810, CVE-2017-9811 and CVE-2017-9812. The flaws were reported to Kaspersky in April and patches were released on June 14. Core Security has confirmed that the update released by the vendor fixes all the security holes.
“Kaspersky Lab would like to thank researchers from Core Security Technologies for pointing out vulnerabilities in Web Console of Kaspersky Anti-Virus for Linux File Server 8, which allowed, under specific conditions, unauthorized access to some product functionality,” Kaspersky Lab told SecurityWeek in an emailed statement. “These vulnerabilities are now fixed. Kaspersky Lab recommends to all customers, using Web Console, to upgrade the Kaspersky Anti-Virus for Linux File Server 8 to new CF4 version.”
Kaspersky has been running a HackerOne-powered bug bounty program that covers its Password Manager 8, Internet Security 2017 and Endpoint Security 10 products. The security firm is offering between $300 and $5,000 for each vulnerability.
Experts found a critical remote buffer overflow vulnerability in Skype
29.6.2017 securityaffairs Vulnerebility
The security expert Benjamin Kunz-Mejri from security firm Vulnerability Lab discovered a remote zero-day stack buffer overflow vulnerability in Skype.
The security expert Benjamin Kunz-Mejri from security firm Vulnerability Lab discovered a Skype zero-day stack buffer overflow vulnerability, tracked as CVE-2017-9948, that could be exploited by a remote attacker to execute malicious code.
Vulnerability Lab reported the flaw to Microsoft on 16th May, Microsoft released a patch on 8 June in Skype version 7.37.178.
The flaw resides in Skype Web messaging and call service and could be exploited during a team conference call.
“The buffer overflow vulnerability can be exploited by local and remote attackers without user interaction and with low privileged Skype user account.” states the security advisory published by Vulnerability Lab.
The flaw was ranked as a high-security risk and received a 7.2 CVSS score and affects Skype versions 7.2, 7.35, and 7.36 on Windows XP, Windows 7 and Windows 8.
“The problem is located in the print clipboard format & cache transmit via remote session on Windows XP, Windows 7, Windows 8 and Windows 10. In Skype v7.37 the vulnerability is patched,” continues the advisory.
A remote attacker can crash the application triggering an unexpected exception error, to overwrite the active process registers, or even execute malicious code on a vulnerable Sky instance.
The problem is caused by the way Skype uses the ‘MSFTEDIT.DLL’ file in case of a copy request on local systems.
“The security vulnerability allows to crash the software application with an unexpected exception error, to overwrite the active process registers to execute own malicious codes.” continues the advisory.
“The security vulnerability is located in the `clipboard format` function of the Skype software. Attackers are able to use a remote computer system with a shared clipboard, to provoke a stack buffer overflow on transmission to Skype. The issue affects the `MSFTEDIT.DLL` dynamic link library of the windows8 (x86) operating system”
The advisory details how to exploit the flaw, an attacker can craft a malicious image file and then copy and paste it from a clipboard of a computer system into a conversation window in the Skype software.
When the image is hosted on a clipboard on both the remote and the local systems, Skype triggers a stack buffer overflow.
“The limitation of the transmitted size and count for images via print of the remote session clipboard has no secure limitations or restrictions. Attackers [can] crash the software with one request to overwrite the EIP register of the active software process,” said researchers from Vulnerability Lab.
“Thus allows local or remote attackers to execute own codes on the affected and connected computer systems via the Skype software,” they added.
Critical Skype Bug Lets Hackers Remotely Execute Malicious Code
28.6.2017 thehackernews Vulnerebility
A critical vulnerability has been discovered in Microsoft-owned most popular free web messaging and voice calling service Skype that could allow hackers to remotely execute malicious code and crash systems.
Skype is a free online service that allows users to communicate with peers by voice, video, and instant messaging over the Internet. The service was acquired by Microsoft Corporation in May 2011 for US$8.5 Billion due to its worldwide popularity.
Security researcher Benjamin Kunz-Mejri from Germany-based security firm Vulnerability Lab discovered the previously unknown stack buffer overflow vulnerability, which is documented in CVE-2017-9948, in Skype Web's messaging and call service during a team conference call.
The vulnerability is considered a high-security risk with a 7.2 CVSS score and affects Skype versions 7.2, 7.35, and 7.36 on Windows XP, Windows 7 and Windows 8, Mejri said in a public security disclosure published on Monday.
"The issue can be exploited remotely via session or by local interaction. The problem is located in the print clipboard format & cache transmit via remote session on Windows XP, Windows 7, Windows 8 and Windows 10. In Skype v7.37 the vulnerability is patched," the security firm wrote.
No User Interaction Needed
What's worst? The stack buffer overflow vulnerability doesn't require any user interaction, and only require a low privilege Skype user account.
So, an attacker can remotely crash the application "with an unexpected exception error, to overwrite the active process registers," or even execute malicious code on a target system running the vulnerable Skype version.
The issue resides in the way Skype uses the 'MSFTEDIT.DLL' file in case of a copy request on local systems.
Here's How Attackers can Exploit this Flaw
According to the vulnerability report, attackers can craft a malicious image file and then copy and paste it from a clipboard of a computer system into a conversation window in the Skype application.
Once this image is hosted on a clipboard on both the remote and the local systems, Skype experiences a stack buffer overflow, causing errors and crashing the application, which left the door open for more exploits.
"The limitation of the transmitted size and count for images via print of the remote session clipboard has no secure limitations or restrictions. Attackers [can] crash the software with one request to overwrite the EIP register of the active software process," researchers from Vulnerability Lab says.
"Thus allows local or remote attackers to execute own codes on the affected and connected computer systems via the Skype software," they added.
Proof-of-Concept Code Released
The security firm has also provided proof-of-concept (PoC) exploit code that you can use to test the flaw.
Vulnerability Lab reported the flaw to Microsoft on 16th May, and Microsoft fixed the issue and rolled out a patch on 8 June in Skype version 7.37.178.
If you are Skype user, make sure that you run the latest version of the application on your system in order to protect themselves from cyber attacks based on this vulnerability.
Google Hacker found a new way to bypass Microsoft Windows Defender
26.6.2017 securityaffairs Vulnerebility
The Google Project Zero expert Tavis Ormandy has found a flaw in Windows Defender that allow attackers to bypass the Microsoft anti-virus tool.
The popular Google Project Zero hacker Tavis Ormandy has discovered a new bug in Windows Defender that allow attackers to circumvent the Microsoft anti-virus tool.
Ormandy publicly disclosed the news of the vulnerability in Windows Defender on Friday after Microsoft released a for its software. Ormandy reported the vulnerability to Microsoft on June 9th.
The vulnerability resides is in the non-sandboxed x86 emulator Windows Defender uses.
The expert explained that “apicall” instruction can invoke internal emulator APIs running them with system privilege, unfortunately, it is exposed to remote attacks by default.
The hacker discovered a heap corruption issue in the KERNEL32.DLL!VFS_Write API.
“I discussed Microsoft’s “apicall” instruction that can invoke a large number of internal emulator apis and is exposed to remote attackers by default in all recent versions of Windows. I asked Microsoft if this was intentionally exposed, and they replied “The apicall instruction is exposed for multiple reasons”, so this is intentional.” wrote Ormandy.
“This full system x86 emulator runs as SYSTEM, is unsandboxed, is enabled by default and remotely accessible to attackers. I took a quick stab at writing a fuzzer and immediately found heap corruption in the KERNEL32.DLL!VFS_Write API, I suspect this has never been fuzzed before.”
Follow
Tavis Ormandy ✔ @taviso
I wrote a fuzzer for the unsandboxed x86 emulator in Windows Defender and found arbitrary read/write. https://bugs.chromium.org/p/project-zero/issues/detail?id=1282 …
8:11 PM - 23 Jun 2017
449 449 Retweets 736 736 likes
Twitter Ads info and privacy
After the disclosure of the bug, Ormandy published a minimal testcase to exploit the bug:
MpApiCall(“NTDLL.DLL”, “VFS_Write”, 1, Buf, 0, 0xffffffff, 0);
MpApiCall(“NTDLL.DLL”, “VFS_Write”, 1, Buf, 0x7ff, 0x41414141, 0);
“The first call extends the length of the file to nOffset, but because the numberOfBytes parameter is 0 no space is allocated. Then you can read and write arbitrary data to an arbitrary offset to the MutableByteStream object buffer. This is a very powerful exploit primitive, and exploitation does not seem difficult.” he added.
Microsoft released a fixed version of the Malware Protection Engine, version 1.1.13903.0.
Siemens Patches Flaws in SIMATIC, XHQ Products
23.6.2017 securityweek Vulnerebility
Siemens and ICS-CERT published advisories this week to alert users of improper authentication and privilege escalation vulnerabilities affecting some SIMATIC and XHQ products.
The SIMATIC communication processor (CP) of the Redundant Network Access (RNA) series, which is designed for connecting S7-400 CPUs to industrial ethernet, is affected by a critical vulnerability that allows a remote, unauthenticated attacker to perform administrative actions on a device.
The security hole, tracked as CVE-2017-6868, affects the SIMATIC CP 44x-1 RNA modules running versions prior to 1.4.1. The flaw can only be exploited if the attacker has network access to TCP port 102 and the processor’s configuration is stored on the corresponding CPU.
In a separate advisory, ICS-CERT and Siemens described a medium severity privilege escalation flaw (CVE-2017-6866) affecting the XHQ automation software, which helps organizations improve enterprise performance by providing and aggregating operational and business data.
The vulnerability affects XHQ 4 versions prior to 4.7.1.3 and XHQ 5 versions prior to 5.0.0.2, and it can be exploited by an authenticated attacker with low privileges to read data they should not be allowed to access.
In the past weeks, Siemens released security updates for several of its products, including SINUMERIK automation products, RUGGEDCOM appliances, and SIMATIC and SCALANCE industrial products.
The company also alerted customers last month that many of its medical devices had been exposed to attacks due to the use of the SMB1 protocol, which the WannaCry ransomware exploited in recent attacks. Siemens updated many of its advisories this month to inform users about the availability of patches.
OpenVPN fixed several remotely exploitable flaws that were not detected by recent audits
23.6.2017 securityaffairs Vulnerebility
OpenVPN fixed several vulnerabilities that could be exploited by remote attackers, the flaws were not detected in a recent audit.
Recently two distinct audits were conducted to discover security issues in the OpenVPN, many flaws were found but some vulnerabilities were not spotted by the experts.
Four of the vulnerabilities in OpenVPN 2.4.2, were found by the researcher Guido Vranken, they were fixed in the OpenVPN 2.4.3 and OpenVPN 2.3.17 releases.
The CVE-2017-7508 vulnerability is the most severe issue, it is a Remotely-triggerable ASSERT() on malformed IPv6 packet bug that can be exploited to remotely shut down an OpenVPN server or client. The vulnerability is exploitable when the triggered if IPv6 and –mssfix are enabled and only if the IPv6 networks used inside the VPN are known.
The second flaw found by the expert, tracked as CVE-2017-7521, is caused by the code that doesn’t free all allocated memory when using the –x509-alt-username option on OpenSSL builds with an extension (argument prefixed with “ext:”).
“Several of our OpenSSL-specific certificate-parsing code paths did not always clear all allocated memory. Since a client can cause a few bytes of memory to be leaked for each connection attempt, a client can cause a server to run out of memory and thereby kill the server. That makes this a (quite inefficient) DoS attack.” states the advisory.
“In particular when using the –x509-alt-username option on openssl builds with an extension (argument prefixed with “ext:”, e.g. “ext:subjectAltName”), the code would not free all allocated memory.”

The third issue, tracked as CVE-2017-7521, was a potential double-free in –x509-alt-username. The vulnerability is exploitable on configurations that use the –x509-alt-username option with an x509 extension.
“OpenVPN did not check the return value of ASN1_STRING_to_UTF8() in extract_x509_extension(). Ignoring such a failure could result in buf being free’d twice. An error in ASN1_STRING_to_UTF8() can be caused remotely if the peer can make the local process run out of memory.” reads the advisory.
“The problem can only be triggered for configurations that use the –x509-alt-username option with an x509 extension (i.e. the option parameter starts with “ext:”).”
A fourth vulnerability, tracked as CVE-2017-7522, was a post-authentication remote DoS when using the –x509-track option.
“asn1_buf_to_c_string() returned a literal string if the input ASN.1 string contained a NUL character, while the caller expects a mutable string. The caller will attempt to change this string, which allows a client to crash a server by sending a certificate with an embedded NUL character.” continues the advisory. “The other way around is not interesting, as servers are allowed to stop a client by design.”
OpenVPN also fixed other bugs, such as the a pre-authentication remote crash/information disclosure for clients tracked as CVE-2017-7520.
Drupal fixes the CVE-2017-6922 flaw exploited in spam campaigns in the wild
23.6.2017 securityaffairs Vulnerebility
Drupal team released security updates to fix several vulnerabilities, including the critical access bypass flaw CVE-2017-6922 exploited in spam campaigns.
The Drupal development team has released security updates to fix several vulnerabilities, including the critical access bypass flaw tracked as CVE-2017-6922 that has been exploited in spam campaigns.
The CVE-2017-6922 flaw was fixed with the release of Drupal versions 7.56 and 8.3.4.
Drupal Security Team was observing a trend of attacks utilizing a site misconfiguration affecting all websites that allow file uploads by non-trusted or anonymous visitors, and stores the uploaded files in a public file system.
The files uploaded by the users are publicly accessible allowing anyone on the internet to access them. The site could be used by an attacker to host content that the legitimate site maintainers would not want made publicly available through their site.
“The majority of the reports are based around the webform module, however, other modules are vulnerable to this misconfiguration as well.” states the security advisory.
“For example, if a webform configured to allow anonymous visitors to upload an image into the public file system, that image would then be accessible by anyone on the internet. The site could be used by an attacker to host images and other files that the legitimate site maintainers would not want made publicly available through their site.”
Drupal is aware of attacks in the wild exploiting the flaw since October 2016, the new releases will not prevent such kind of abuses.
CVE-2017-6922 drupal
Drupal 8.3.4 also fixed a critical flaw, tracked as CVE-2017-6920, related to how the PECL YAML parser handles unsafe objects, the flaw could be exploited by an attacker for remote code execution.
Drupal also fixed in Drupal 8 is the improper field validation vulnerability tracked as CVE-2017-6921.
“A site is only affected by this if the site has the RESTful Web Services (rest) module enabled, the file REST resource is enabled and allows PATCH requests, and an attacker can get or register a user account on the site with permissions to upload files and to modify the file resource,” reads the advisory.
In April 2017, security experts discovered a critical vulnerability that affects the Drupal References module that is used by hundreds of thousands of websites using the popular CMS.
The Drupal team published a Security advisory on April 12 informing its users of the critical flaw.
The flaw has a huge impact on the Drupal community because the affected module is currently used by more than 121,000 websites.
“The module is currently used by over 120 000 individual Drupal installations, but is no longer maintained. The last update was done in February 2013. Unfortunately, a critical security vulnerability in this references module has been reported by the Drupal core security team as SA-CONTRIB-2017-38:
The module had no longer been supported, fortunately, a new maintainer addressed the flaw.
OpenVPN Patches Remotely Exploitable Vulnerabilities
22.6.2017 securityweek Vulnerebility
OpenVPN this week patched several vulnerabilities impacting various branches, including flaws that could be exploited remotely.
Four of the bugs were found by researcher Guido Vranken through fuzzing, after recent audits found a single severe bug in OpenVPN. While analyzing OpenVPN 2.4.2, the researcher found and reported four security issues that were addressed in the OpenVPN 2.4.3 and OpenVPN 2.3.17 releases this week.
The most important of the four issues is a Remotely-triggerable ASSERT() on malformed IPv6 packet bug that can be exploited to remotely shutdown an OpenVPN server or client. Tracked as CVE-2017-7508, the bug can be triggered if IPv6 and --mssfix are enabled and only if the IPv6 networks used inside the VPN are known.
Tracked as CVE-2017-7521, a second vulnerability involves remote-triggerable memory leaks. The issue is that the code doesn’t free all allocated memory when using the --x509-alt-username option on OpenSSL builds with an extension (argument prefixed with "ext:").
“Several of our OpenSSL-specific certificate-parsing code paths did not always clear all allocated memory. Since a client can cause a few bytes of memory to be leaked for each connection attempt, a client can cause a server to run out of memory and thereby kill the server. That makes this a (quite inefficient) DoS attack,” OpenVPN explains in an advisory.
The third vulnerability Guido Vranken discovered was a potential double-free in --x509-alt-username, tracked as CVE-2017-7521. The bug can be triggered only on configurations that use the --x509-alt-username option with an x509 extension, and this function is very unlikely to fail in real-world usage for other reasons than memory exhaustion, the researcher discovered.
The fourth issue found by Vranken was a post-authentication remote DoS when using the --x509-track option. Tracked as CVE-2017-7522, the vulnerability resides in asn1_buf_to_c_string() returning a literal string not a mutable one, when the input ASN.1 string contains a NUL character. When the caller attempts to change this string, the client can crash a server by sending a certificate with an embedded NUL character.
Another security bug resolved in OpenVPN this week was a pre-authentication remote crash/information disclosure for clients. Tracked as CVE-2017-7520, the issue could allow a man-in-the-middle attacker between the client and the proxy to crash or disclose at most 96 bytes of stack memory (likely containing the proxy password).
The vulnerability can be triggered only on clients that use a HTTP proxy with NTLM authentication and is unlikely to compromise the security of the OpenVPN tunnel itself if the password isn’t reused. Clients that don’t use the --http-proxy option with ntlm2 authentication are not affected.
OpenVPN also resolved a null-pointer dereference in establish_http_proxy_passthru(), where the client could crash “if the peer did not specify the 'realm' and/or 'nonce' values. These pointers are dereferenced in DigestCalcHA1() and DigestCalcResponse?(); hence, if not set, a null-pointer dereference would occur.”
Critical RCE Flaw Found in OpenVPN that Escaped Two Recent Security Audits
22.6.2017 thehackernews Vulnerebility
A security researcher has found four vulnerabilities, including a critical remote code execution bug, in OpenVPN, those were not even caught in the two big security audits of the open source VPN software this year.
OpenVPN is one of the most popular and widely used open source VPN software solutions mostly used for various connectivity needs, but it is especially popular for anonymous and private access to the Internet.
This year, two independent security audits of OpenVPN were carried out to look for flaws, backdoors, and other defects in the open source software – one conducted by a team led by Johns Hopkins University crypto-boffin Dr. Matthew D. Green.
The audits resulted in a patch of a few vulnerabilities in the widely used open source software, giving OpenVPN a clean chit.
Researcher Used Fuzzer to find Bugs in OpenVPN
Researcher Guido Vranken of Netherlands exclusively used a fuzzer and recently discovered four security holes in OpenVPN that escaped both the security audits.
Three of the four flaws the researcher discovered are server-side, two of which cause servers to crash, while the remaining is a client-side bug that could allow an attacker to steal a password to gain access to the proxy.
The most critical vulnerability of all is CVE-2017-7521, which affects OpenVPN server-side and resides in extract_x509_extension() function which deals with SSL certificates.
The vulnerability could allow a remote authenticated attacker to craft and send a certificate that either crashes the OpenVPN service or triggers a double free that potentially lead to remote code execution within the server.
Vranken was not able to demonstrate the RCE bug but argued that the remote code execution could be achieved in theory. In a report published Wednesday, he had explained how one could achieve a remote memory leak because of the service's failure to check a particular return value.
"If you look in the OpenSSL source code, one way through which ASN1_STRING_to_UTF8 can fail is if it cannot allocate sufficient memory," Vranken said in his report. "So the fact that an attacker can trigger a double-free IF the server has insufficient memory, combined with the fact that the attacker can arbitrarily drain the server of memory, makes it plausible that a remote double-free can be achieved."
"But if a double-free is inadequate to achieve remote code execution, there are probably other functions, whose behavior is wildly different under memory duress, that you can exploit."
The second vulnerability, CVE-2017-7520, resides in the way OpenVPN connects to a Windows NTLM version 2 proxy.
A man-in-the-middle attacker between the OpenVPN client and the proxy server can either remotely crash the client or steal the user's password to the proxy from a memory leak.
The vulnerability could be triggered only under certain circumstances, like when the client connects to a proxy through NTLM version 2 authentication, or when the client specifies a username ending with a backslash.
"If clients use a HTTP proxy with NTLM authentication (--http-proxy [|'auto'|'auto-nct'] ntlm2), a man-in-the-middle [MITM] attacker between the client and the proxy can cause the client to crash or disclose at most 96 bytes of stack memory," the OpenVPN team explains.
"The disclosed stack memory is likely to contain the proxy password. If the proxy password is not reused, this is unlikely to compromise the security of the OpenVPN tunnel itself. Clients who do not use the --http-proxy option with ntlm2 authentication are not affected."
Other two vulnerabilities (CVE-2017-7508 and CVE-2017-7522) are remote server crashes which could trigger by sending maliciously-crafted IPv6 packets or malicious data post-authentication.
Patches for Servers and Clients Already Available
Vranken responsibly disclosed all the vulnerabilities he discovered to the OpenVPN team in May and June and the team has already patched the issues in its latest version of the VPN software.
While there is no proof of any of the vulnerabilities had been publicly exploited, users are strongly advised to update their installations to OpenVPN versions 2.4.3 or 2.3.17 as soon as possible in order to be on the safer side.
For more in-depth technical details of all the vulnerabilities, you can head on to the report titled, "The OpenVPN Post-Audit Bug Bonanza," published by Vranken on Wednesday.
Botnets Can Exploit More Vulnerabilities in DVRs
20.6.2017 securityweek Vulnerebility BotNet
Newly discovered vulnerabilities affecting DVR systems could open the door to new, more potent Internet of Things (IoT) botnets, Pen Test Partners security researchers warn.
Following months of investigation into the hardware and software security of more than 30 DVR brands, the researchers discovered a series of flaws that Mirai and other IoT botnets didn’t use, but which could have made these threats far more destructive. These include new telnet credentials and interfaces, as well as an exploitable buffer overflow over port 80 that impacts over 1 million devices.
The researchers also discovered new DVR brands that are vulnerable to Mirai, but which researchers didn’t know about before, and say that DVRs can be used to disable house alarms. They also note that Mirai could have used more default telnet credentials (qazxsw), along with new telnet interfaces that run on port other than 23.
The researchers found the non-standard telnet port 12323 that is used by some DVRs and which uses the same default credentials targeted by Mirai, along with an interface on TCP/9527, with credentials such as admin/blank or admin/123456, or similar, which led to a shell. Via directory traversal, an attacker could abuse the interface to recover the hashed passwords and crack them offline.
The source of the Mirai issue, the researchers suggest, is represented by the manner in which DVR vendors customized the products received from a single original design manufacturer (ODM) called XiongMai. Although vendors could change default credentials, they apparently had only a limited number of credentials to shuffle, and Mirai covers all of them.
However, botnets such as Mirai and Hajime aren’t the biggest threats to DVRs, the Pen Test Partners team argues. Because on some devices the web server running on port 80 is vulnerable to a buffer overflow via the GET request, code execution is possible, and remote access is possible. A botnet exploiting the issue could be larger than Mirai, the researchers say.
A debug interface running on port 9527 and which is present on most XM-based DVRs allows shell access as root with the credentials used for DVR login. Because the interface is port-forwarded by default, it’s likely discoverable on the public Internet in a home user & SME environment. It also packs a directory traversal vulnerability (CVE-2017-7577) and easily guessable default credentials.
The researchers also suggest that BrickerBot, a piece of IoT malware targeting the same devices as Mirai but completely disabling them, was actually meant to be a healing worm, but didn’t work as intended. The issue, they say, is that DVRs run a cut-down version of busybox, which lacks commands for the functionality BrickerBot wants to use. The malware, however, was set to brick the device if it couldn’t fix its vulnerabilities.
The Pen Test Partners researchers also say they found a way to remotely fix Mirai vulnerable devices. However, they decided against publishing the underlying details because the very same method can be used to make Mirai even more potent than it already is, by providing it with persistence over reboots.
'Stack Clash' Flaws Allow Privilege Escalation on Unix Systems
20.6.2017 securityweek Vulnerebility
Linux and other Unix-like operating systems are affected by a type of vulnerability that can be exploited by an attacker for root privilege escalation, Qualys warned on Monday.
The flaw, dubbed Stack Clash, is a memory management issue in Linux, OpenBSD, NetBSD, FreeBSD and Solaris on i386 and amd64 architectures. Affected Linux distributions include Red Hat, Debian, Ubuntu, SUSE, CentOS and Gentoo. Other operating systems and architectures could also be vulnerable.
The vulnerability is related to the memory region known as the stack, which grows automatically if an application requires more memory. The problem is that if the stack memory region grows too much, it can get too close to another region, which can result in the application confusing these regions.
This type of flaw, which attackers can exploit to overwrite the stack with another memory region by triggering a clash, has been known since 2005. After it was exploited again in 2010 (CVE-2010-2240), a protection called “stack guard page” was added to the Linux kernel to prevent stack overflow attacks. The stack guard page serves as a divider between a stack memory region and other regions.
However, researchers at Qualys discovered that the stack guard page protection can be bypassed and they developed several proof-of-concept (PoC) exploits to demonstrate it. The main Stack Clash vulnerability is tracked as CVE-2017-1000364, but there are several other flaws that are either directly related to it or independently exploitable.
The PoC code developed by Qualys shows how a local attacker can exploit the vulnerability to escalate privileges to root. However, the company believes remote attacks may also be possible against certain applications.
The PoC exploits will only be made public after users have had a chance to patch their systems. Technical details on Stack Clash have been made available by both Qualys and Grsecurity.
The developers of the affected operating systems have started releasing fixes and users have been advised to patch their installations. As a workaround, the hard RLIMIT_STACK and RLIMIT_AS resources of local users and remote services can be set to low values, but experts warned that it may be possible to bypass this mitigation.
Qualys recently reported finding a vulnerability that can be exploited by Sudo users on SELinux-enabled systems for root privilege escalation. The company pointed out that a combination of the Sudo flaw with the Stack Clash allows any local user (not just Sudo users) to escalate privileges on any affected Linux system (not just systems with SELinux enabled).
Stack Clash vulnerability allows an attacker to execute code as root
20.6.2017 securityaffairs Vulnerebility
Stack Clash is a local privilege escalation flaw in Linux, BSD, Solaris and other open source systems that allows an attacker to execute code as root.
Linux, BSD, Solaris and other open source systems are vulnerable to a local privilege escalation vulnerability known as Stack Clash that allows an attacker to execute code as root.
Stack Clash is a local privilege escalation vulnerability tracked as CVE-2017-1000364 that affects some open source systems, including Linux, BSD, and Solaris.
The Stack Clash affects the memory management of several OSs, it can be exploited by attackers to corrupt memory and execute arbitrary code.
Security patches have been released today for many Linux and open source distros, and systems running Linux, OpenBSD, NetBSD, FreeBSD or Solaris on i386 or amd64 hardware should be updated soon.
Experts warn of the possibility to chain this flaw with other vulnerabilities to run arbitrary code with the highest privileges.
Researchers at Qualys who discovered this vulnerability have developed seven exploits and seven proofs of concept for this weakness.
“The exploits and proofs of concept that we developed in the course of our research are all Local Privilege Escalations: an attacker who has any kind of access to an affected system can exploit the Stack Clash vulnerability and obtain full root privileges.” states Qualys .
The stack is the memory region used by a program during its execution, it grows automatically when the program needs more stack memory. It this region grows too much it can interfere with the stack of another process, an attacker can force the growth to overwrite another memory region.
“Why is it called the Stack Clash? The first step in exploiting this vulnerability is to collide, or clash, the stack with another memory region. Hence the name: the Stack Clash.” continues the analysis.
The attack bypasses the stack guard-page protection against stack-clashes implemented in Linux in 2010.
The proof of concept exploits is composed of the following steps:
“Clashing” the stack with another memory region: we allocate memory until the stack reaches another memory region, or until another memory region reaches the stack;” states the security advisory published by Qualys.
“Jumping” over the stack guard-page: we move the stack-pointer from the stack and into the other memory region, without accessing the stack guard-page;”
“Smashing” the stack, or the other memory region: we overwrite the stack with the other memory region, or the other memory region with the stack.”
Stack Clash linux
Is it exploitable remotely?
The researchers do not know of any remotely exploitable application, however thay don’t exclude remote exploitation of the Stack Clash.
“The one remote application that we did investigate (the Exim mail server) turned out to be unexploitable by sheer luck.” states the advisory.
In order to temporarily mitigate the attack, Qualys recommends increasing the size of the stack guard-page to 1MB at a minimum.
The advisory also recommends recompiling all userland code with the –fstack-check option in order to prevent the stack pointer from moving into other memory regions.
A Decade Old Unix/Linux/BSD Root Privilege-Escalation Bug Discovered
20.6.2017 thehackernews Vulnerebility
Stack-Clash-Privilege-Escalation-Vulnerability
Security researchers have discovered more than a decade-old vulnerability in several Unix-based operating systems — including Linux, OpenBSD, NetBSD, FreeBSD and Solaris — which can be exploited by attackers to escalate their privileges to root, potentially leading to a full system takeover.
Dubbed Stack Clash, the vulnerability (CVE-2017-1000364) has been discovered in the way memory was being allocated on the stack for user space binaries.
Exploiting Stack Clash Bug to Gain Root Access
The explanation is simple: Each program uses a special memory region called the stack, which is used to store short-term data. It expands and contracts automatically during the execution of any program, depending upon the needs of that program.
According to researchers at Qualys, who discovered and reported this bug, a malicious program can attempt to use more memory space than available on the stack, which could overflow the memory, causing it to collide or clash with nearby memory regions and overwrite their content.
Moreover, the Stack Clash exploit can also bypass the stack guard-page, a memory management protection introduced in 2010, after this issue was exploited in 2005 and 2010.
"Unfortunately, a stack guard-page of a few kilobytes is insufficient: if the stack-pointer 'jumps' over the guard-page—if it moves from the stack into another memory region without accessing the guard-page—then no page-fault exception is raised and the stack extends into the other memory region," an advisory published by Qualys read.
The Stack Clash vulnerability requires local access to the vulnerable system for exploitation, but researchers said it could be exploited remotely depending upon the applications.
For example, a malicious customer with low privilege account with a web hosting company, running vulnerable system, could exploit this vulnerability to gain control over other websites running on the same server, as well as remotely gain root access and execute malicious code directly.
Just yesterday, we reported that how a web hosting company fell victim to a similar attack used to infect Linux servers with a ransomware malware, causing the company to pay more than $1 Million in ransom to get back their files.
Attackers can also combine the Stack Clash bug with other critical vulnerabilities, like the Sudo vulnerability recently patched, and then run arbitrary code with the highest privileges, said Qualys researchers.
7 Proof-of-Concept Exploits
The researchers said they were able to develop seven exploits and seven proofs of concept (PoCs) for the Stack Clash vulnerability, which works on Linux, OpenBSD, NetBSD, FreeBSD and Solaris on 32-bit and 64-bit x86 processors.
However, the researchers have not yet published the exploits and proofs of concept, giving users and admins enough time to patch their systems before they go into the Stack Clash exploits public.
The PoCs follow four steps, which include 'Clashing' the stack with another memory region, running the stack pointer to the stack’s start, 'Jumping' over the stack guard-page and 'Smashing' the stack or the other memory regions.
Among distros and systems affected by Stack Clash include:
Sudo on Debian, Ubuntu, and CentOS
ld.so and most SUID-root binaries on Debian, Ubuntu, Fedora, and CentOS
Exim on Debian
rsh on Solaris 11 and so on
Red Hat Enterprise
The company also believes that other operating systems, including Microsoft's Windows, Apple's OS X/macOS and Google's Linux-based Android OS could also be vulnerable to Stack Clash, though it is yet to be confirmed.
Patch Available; Update Now
Many affected vendors have already issued security patches for the bug, so users and administrators are advised to install patches a soon as possible.
If security patches from your vendor are yet to be released, you can reboot your systems or can manually apply stack limits to local users' applications. Simply, set the hard RLIMIT STACK and RLIMIT_AS of local users and remote services to a low value.
It is also recommended to recompile all userland code (ld.so, libraries, binaries) with the –fstack-check feature. This would prevent the stack pointer from moving into another memory region without accessing the stack guard-page and would kill Stack Clash dead.
Workarounds Provided for HPE SiteScope Vulnerabilities
19.6.2017 securityweek Vulnerebility
Several potentially serious vulnerabilities have been found in HPE SiteScope, and while patches are not available, users can apply workarounds to prevent attacks.
HPE SiteScope is an agentless performance and availability monitoring software for distributed IT infrastructures, including servers, network services, applications, and operating systems.
While conducting a security assessment, expert Richard Kelley identified several vulnerabilities in version 11.31.461 of the product.
Kelley noticed that a critical remote code execution vulnerability disclosed in 2012 and for which a Metasploit module is available still hasn’t been patched by HPE. The vendor noted that users can prevent attacks by setting a specific flag in the “groups/master.config” file to disable old APIs.
A Shodan search conducted by Kelley showed that there are at least 230 SiteScope servers accessible on the Internet.
“I wonder how many admins know about this setting, and why wouldn’t HPE just remove the old APIs from new versions if they are no longer needed?” the researcher said in a blog post.
The expert also discovered that credentials stored in configuration files are encrypted, but the encryption key is hardcoded, allowing an attacker to obtain the password needed to log in to the SiteScope interface with administrator privileges.
Once the attacker has access to the administration interface, they can obtain credentials for Linux and Windows servers monitored via SiteScope. While the admin interface only displays passwords as dots, the actual password is transmitted in clear text over an unsecure connection to the client, allowing a man-in-the-middle (MitM) attacker to easily obtain the information.
Kelley also discovered the existence of a proprietary encryption scheme that uses a hardcoded private key. He determined that this function had still been used to encrypt some configuration data.
HPE said it plans on addressing the insecure transmission of credentials sometime in the third quarter. As for the encryption-related issues, the company pointed out that the problems are covered in chapter 20 of the SiteScope deployment guide.
While HPE has asked the researcher to delay disclosure until the third quarter, Kelley and CERT/CC have decided to make the flaws public to “encourage HPE to provide defender mitigations as soon as possible.”
CERT/CC has published an advisory containing mitigation advice for the unpatched vulnerability.
It’s not uncommon for HPE to provide workarounds for SiteScope vulnerabilities instead of releasing patches. In October 2015, Rapid7 disclosed the details of a command injection flaw that had also been addressed in the product documentation.
Workarounds Provided for HPE SiteScope Vulnerabilities
19.6.2017 securityweek Vulnerebility
Several potentially serious vulnerabilities have been found in HPE SiteScope, and while patches are not available, users can apply workarounds to prevent attacks.
HPE SiteScope is an agentless performance and availability monitoring software for distributed IT infrastructures, including servers, network services, applications, and operating systems.
While conducting a security assessment, expert Richard Kelley identified several vulnerabilities in version 11.31.461 of the product.
Kelley noticed that a critical remote code execution vulnerability disclosed in 2012 and for which a Metasploit module is available still hasn’t been patched by HPE. The vendor noted that users can prevent attacks by setting a specific flag in the “groups/master.config” file to disable old APIs.
A Shodan search conducted by Kelley showed that there are at least 230 SiteScope servers accessible on the Internet.
“I wonder how many admins know about this setting, and why wouldn’t HPE just remove the old APIs from new versions if they are no longer needed?” the researcher said in a blog post.
The expert also discovered that credentials stored in configuration files are encrypted, but the encryption key is hardcoded, allowing an attacker to obtain the password needed to log in to the SiteScope interface with administrator privileges.
Once the attacker has access to the administration interface, they can obtain credentials for Linux and Windows servers monitored via SiteScope. While the admin interface only displays passwords as dots, the actual password is transmitted in clear text over an unsecure connection to the client, allowing a man-in-the-middle (MitM) attacker to easily obtain the information.
Kelley also discovered the existence of a proprietary encryption scheme that uses a hardcoded private key. He determined that this function had still been used to encrypt some configuration data.
HPE said it plans on addressing the insecure transmission of credentials sometime in the third quarter. As for the encryption-related issues, the company pointed out that the problems are covered in chapter 20 of the SiteScope deployment guide.
While HPE has asked the researcher to delay disclosure until the third quarter, Kelley and CERT/CC have decided to make the flaws public to “encourage HPE to provide defender mitigations as soon as possible.”
CERT/CC has published an advisory containing mitigation advice for the unpatched vulnerability.
It’s not uncommon for HPE to provide workarounds for SiteScope vulnerabilities instead of releasing patches. In October 2015, Rapid7 disclosed the details of a command injection flaw that had also been addressed in the product documentation.
High Severity Flaws Patched in Trihedral SCADA Software
15.6.2017 securityweek Vulnerebility
An update released by Trihedral for its VTScada product patches several vulnerabilities, including high severity weaknesses that can be exploited even by less skilled hackers.
VTScada, Trihedral’s flagship product, is a software suite designed for creating human-machine interfaces (HMI) for supervisory control and data acquisition (SCADA) systems. The product is used in various industries, mainly in North America and Europe.
Security researcher Karn Ganeshen discovered several vulnerabilities affecting VTScada versions prior to 11.2.26. The expert told SecurityWeek that a Shodan search showed a few systems running VTScada accessible from the Internet, but he believes there are more vulnerable instances that are exposed to attacks.
One of the flaws, tracked as CVE-2017-6043 and assigned a CVSS score of 7.5, is a denial-of-service (DoS) issue that exists due to the VTScada client’s failure to limit resource usage.
In an advisory published on his website, Ganeshen said an attacker with a non-privileged account can cause excessive CPU and RAM usage by submitting a large payload (up to roughly 80,000 characters) in the username field of the login window.
“Where a full-blown application (or multiple applications in production scenario) is deployed, i.e. with an operational/functional configuration, memory/CPU usage is notably higher than that of a test, blank application,” the expert said. “Repeatedly submitting such a large username input rapidly consumes available server memory resources leading to resource exhaustion. This forces a system reboot eventually.”
Another high severity flaw found by the researcher in VTScada is CVE-2017-6045, an information disclosure issue that exposes potentially sensitive configuration data to unauthenticated attackers.
Ganeshen also informed Trihedral of several cross-site scripting (XSS) vulnerabilities that can be exploited to execute arbitrary JavaScript code in the targeted user’s browser. These security holes are considered medium severity and they are tracked as CVE-2017-6053.
The flaws have been addressed by Trihedral with the release of VTScada 11.2.26. The researcher has confirmed that the resource exhaustion vulnerability has been properly patched.
In a brief statement published on Wednesday on its website, Trihedral pointed out that the vulnerabilities only affect “systems with unsecured internet connections with VTScada internet access enabled.” The company has advised customers to secure their connection and update the product to the latest version.
Ganeshen told SecurityWeek that he submitted two other VTScada vulnerability reports, which should soon be published by ICS-CERT.
OSIsoft Patches Flaws in PI Server, Web API Products
15.6.2017 securityweek Vulnerebility
California-based operational intelligence firm OSIsoft has released updates for its PI Web API and PI Server products to address several vulnerabilities, including ones rated high severity.
ICS-CERT has published two advisories this week to inform organizations about three remotely exploitable flaws affecting the OSIsoft products.
One advisory describes two improper authentication vulnerabilities affecting PI Server, a real-time data storage and distribution engine that powers the company’s PI System data management product.
The most serious of the flaws, rated high severity and tracked as CVE-2017-7930, is a protocol weakness in the PI Data Archive component that can be exploited to access clear text data and spoof a server.
The second flaw, rated medium severity and identified as CVE-2017-7934, affects the PI Network Manager and it allows a malicious user to authenticate on the server and cause the vulnerable component to behave unexpectedly.
These weaknesses affect systems with PI Data Archive versions prior to 2017, and they were patched roughly one month ago with the release of security updates.
Another advisory published by ICS-CERT describes a high severity cross-site request forgery (CSRF) vulnerability affecting PI Web API, a suite of REST services and APIs designed to provide web and mobile programmatic access to PI System data.
“The vulnerability allowed for Cross-Site Request Forgery (CSRF) attacks to occur when an otherwise-unauthorized cross-site request was sent from a browser the server had previously authenticated,” ICS-CERT and OSIsoft wrote in their advisories.
The flaw (CVE-2017-7926) impacts all websites using versions of PI Web API prior to 2017 (1.9.0) as the data access layer. A patch was released in May.
All flaws were discovered by OSIsoft itself and there is no evidence of exploits in the wild. The vendor has also provided a series of recommendations for preventing potential attacks exploiting these flaws.
OSIsoft products are used around the world in several industries, including oil and gas, power and utilities, chemicals and petrochemicals, pulp and paper, pharmaceutical, critical facilities, IT, and federal sectors.
Microsoft Issues Updates for 96 Vulnerabilities You Need to Patch this Month
14.6.017 thehackernews Vulnerebility
As part of June's Patch Tuesday, Microsoft has released security patches for a total of 96 security vulnerabilities across its products, including fixes for two vulnerabilities being actively exploited in the wild.
This month's patch release also includes emergency patches for unsupported versions of Windows platform the company no longer officially supports to fix three Windows hacking exploits leaked by the Shadow Brokers in the April's data dump of NSA hacking arsenal.
The June 2017 Patch Tuesday brings patches for several remote code execution flaws in Windows, Office, and Edge, which could be exploited remotely by hackers to take complete control over vulnerable machines with little or no interaction from the user.
While two of the vulnerabilities have been exploited in live attacks, another three flaws have publicly available proof-of-concept (POC) exploits that anyone could use to target Windows users.
Vulnerabilities Under Active Attack
The two vulnerabilities currently under active attack include a Windows Search Remote Code Execution flaw (CVE-2017-8543) and an LNK Remote Code Execution bug (CVE-2017-8464).
The more critical of the two is the Windows Search RCE vulnerability which is present in most versions of Windows and resides in the Windows Search Services (WSS) — a feature that allows users to search across multiple Windows services and clients.
The vulnerability, which already has publicly disclosed POC exploit code since early February, could allow a remote code execution in the Windows operating system, enabling an attacker to take over the target machine remotely via a network connection.
"To exploit the vulnerability, the attacker could send specially crafted SMB messages to the Windows Search service. An attacker with access to a target computer could exploit this vulnerability to elevate privileges and take control of the computer," Microsoft explains in its advisory.
"Additionally, in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer."
The SMB vulnerabilities can be extremely dangerous, and the best example of it is the WannaCry ransomware that exploited an SMB flaw within a network to replicate itself to all unpatched machines very quickly.
Windows Server 2016, 2012, 2008 along with desktop systems such as Windows 10, 7 and 8.1 are all affected by this vulnerability.
Shares Striking Resemblance with Stuxnet Malware
Another critical flaw under active exploitation is LNK RCE vulnerability resides in the way Windows handles LNK desktop shortcuts, which could allow remote code execution if the icon of a specially crafted shortcut is displayed to a user.
"The attacker could present to the user a removable drive, or remote share, that contains a malicious .LNK file and an associated malicious binary," Microsoft explains.
"When the user opens this drive(or remote share) in Windows Explorer, or any other application that parses the .LNK file, the malicious binary will execute code of the attacker’s choice, on the target system."
According to the Zero Day Initiative (ZDI), the active attack exploiting the LNK vulnerability carries some resemblance to the way the dangerous Stuxnet malware infiltrated and sabotaged critical industrial control systems while carrying out its attacks.
"If you're experiencing déjà vu reading the bug title, it is certainly understandable," ZDI says in its blog post. "This type of vulnerability was used by the Stuxnet malware, then found again several years later through a ZDI program submission."
Another three vulnerabilities that have publicly available proof-of-concept exploits include three flaws in the Edge browser, two of which (CVE-2017-8530 and CVE-2017-8523) could allow security feature bypass, while the third (CVE-2017-8498) allows for information disclosure.
Besides this, the Edge browser also receives patches for three more flaws (CVE-2017-8496, CVE-2017-8497, and CVE-2017-8499) that would enable attackers to carry out remote code execution on vulnerable users.
Other patches include fixes for nine of its own remote code execution flaws in Office that could be targeted via DLL files, email messages, a website, and a PowerPoint file.
Adobe June 2017 Patch Updates
Meanwhile, Adobe has also issued security fixes for its most vulnerable software offerings, Flash Player and Shockwave Player.
The company addresses nine critical bugs in its Flash Player that could allow remote code execution, five of which are due to memory corruption and four are use-after-free conditions in the software.
Users running Chrome, Edge, and Internet Explorer 11 and later will get the update automatically from Google and Microsoft's security teams, while other users should download the patches directly from Adobe.
Shockwave Player received a patch for a single remote code execution vulnerability in the Windows version of its software. Users should download version Shockwave Player 12.2.9.199 in order to protect themselves.
Microsoft Releases Patches for 3 Remaining NSA Windows Exploits
14.6.017 thehackernews Vulnerebility
Did you know… last month's widespread WannaCry ransomware attack forced Microsoft to release security updates against EternalBlue SMB exploit for unsupported versions of Windows, but the company left other three Windows zero-day exploits unpatched?
For those unaware, EternalBlue is a Windows SMB flaw that was leaked by the Shadow Brokers in April and then abused by the WannaCry ransomware to infect nearly 300,000 computers in more than 150 countries within just 72 hours on 12th of May.
Shortly after WannaCry outbreak, we reported that three unpatched Windows exploits, codenamed "EsteemAudit," "ExplodingCan," and "EnglishmanDentist," were also being exploited by individuals and state-sponsored hackers in the wild.
Specially EsteemAudit, one of the dangerous Windows hacking tool that targets remote desktop protocol (RDP) service on Microsoft Windows Server 2003 and Windows XP machines, while ExplodingCan exploits bugs in IIS 6.0 and EnglishmanDentist exploits Microsoft Exchange servers.
But now Microsoft has released free security updates for unsupported versions of its products, including Windows XP and Server 2003, to patch all the three cyber-weapons and block next wave of "destructive cyberattacks" similar to WannaCry.
According to the recent Microsoft blog post, the critical down-level patches for three Windows exploits were prompted by an "elevated risk of destructive cyberattacks" by government organizations, referred to as "nation-state actors or other copycat organizations."
The security patches for Windows XP, Vista, and Server 2003 contain fixes or mitigations for three alleged NSA-developed exploits — EsteemAudit, ExplodingCan, and EnglishmanDentist — though none of these exploits works on supported Windows platform.
Unlike regular Patch Tuesday releases that delivered automatically through the Windows Update mechanism to your devices, these down-level patches must be downloaded and installed manually.
These updates are available in the Microsoft Download Center or, in the Update Catalog, or you can find download links at the bottom of Security Advisory 4025685.
No doubt, this move by Microsoft to protect its customers by releasing security updates for end-of-support products is commendable, but this could also motivate users to stick to 14-years-old unsupported and risky versions of Windows OS that are exposed to all manner of potential threats.
And since Microsoft is fixing known vulnerabilities in Windows XP and Server 2003 that weren't fixed before, the job of migrating away from unsupported versions just got a whole lot harder than before.
However, Eric Doerr, general manager of the company's Security Response Center, said in a separate blog post that the move was only meant to fix flaws that are at "heightened risk of exploitation due to past nation-state activity and disclosures."
"Our decision today to release these security updates for platforms not in extended support should not be viewed as a departure from our standard servicing policies," Doerr said. "Based on an assessment of the current threat landscape by our security engineers, we made the decision to make updates available more broadly."
However, Doerr urged users to adopt new, supported versions of Microsoft products, which are significantly more secured and resistant to exploits, and warned them not to expect regular security updates for out-of-date platforms in the future.
Meanwhile as part of its regular Patch Tuesday, Microsoft has released security updates to patch nearly a hundred flaws in its various Windows operating systems and software, two of which have actively been exploited in the wild.
All the regular releases are delivered automatically through the Windows Update mechanism to users running supported versions of Windows OS, including Windows 10, 8.1, 7, and post-2008 Windows Server releases, on their devices.
The notorious hacking group, Shadow Brokers, who claimed to have stolen a bunch of hacking tools from the NSA's elite hacking team Equation Group, had also promised to leak more zero-days and exploits starting this month.
Microsoft patches two critical remote code execution (RCE) flaws that have been exploited in attacks
14.6.2017 Securityaffairs Vulnerebility
Microsoft released the June 2017 Patch Tuesday to address more than 90 security flaws, including two critical RCE that have been exploited in attacks.
Microsoft released June Patch Tuesday updates that address more than 90 vulnerabilities, including two critical remote code execution (RCE) vulnerabilities that have been exploited in attacks.
The first vulnerability, tracked as CVE-2017-8464, is a LNK remote code execution flaw in Windows that could be triggered by tricking victims into displaying the icon of a specially crafted shortcut file.
“A remote code execution exists in Microsoft Windows that could allow remote code execution if the icon of a specially crafted shortcut is displayed. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.” states the advisory published by Microsoft. “The attacker could present to the user a removable drive that contains a malicious shortcut file and an associated malicious binary. When the user opens this drive in Windows Explorer or any other application that parses the icon of the shortcut, the malicious binary will execute code of the attacker’s choice on the target system,”
Windows RCE vulnerability
According to the experts at the Zero Day Initiative (ZDI), the flaw is similar to one exploited by the Stuxnet worm. The exploit code for the CVE-2017-8464 may affect different components of the code.
In the case of Stuxnet, the remote code execution occurs if a specially crafted shortcut is displayed with a USB thumb drive, but the LNK could also be hosted on a remote drive viewable by the target.
“This type of vulnerability was used by the Stuxnet malware, then found again several years later through a ZDI program submission. While this latest patch may touch different parts of code, the exploit vector remains the same – remote code execution can occur if a specially crafted shortcut is displayed.” states the ZeroDay report. “In the case of Stuxnet, this was done with a USB thumb drive, but the LNK could also be hosted on a remote drive viewable by the target. If there is a positive note here, the exploit only allows for code execution at the logged-on user level – another reminder not to use administrative privileges for daily tasks. Interestingly, there have been reports that the Stuxnet LNK attacks were still prevalent as recently as April 2017, however these appear to be unrelated to this bug.
The good news is that flaw could be exploited to execute code only at the logged-on user level, so for users that don’t have administrator rights in low.
The second RCE vulnerability tracked as CVE-2017-8543, is a remote code execution vulnerability affecting Windows Search.
“A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” states the advisory published by Microsoft.
“To exploit the vulnerability, the attacker could send specially crafted SMB messages to the Windows Search service. An attacker with access to a target computer could exploit this vulnerability to elevate privileges and take control of the computer. Additionally, in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer.”
Microsoft addressed three security feature bypass and information disclosure issues in the Edge web browser.
Microsoft also fixed 18 critical flaws, the last security updates also patch some of the vulnerabilities disclosed at Pwn2Own hacking competition.
Adobe patches tens of vulnerabilities in Flash Player, Shockwave Player, Captivate and Digital Editions
14.6.2017 Securityaffairs Vulnerebility
On Tuesday, Adobe released updates for Flash Player, Shockwave Player, Captivate and Digital Editions addressing a total of 20 vulnerabilities.
Some vulnerabilities fixed by Adobe are critical remote code execution issue, the last release, version 26.0.0.126, addressed nine flaws in Flash Player.
The vulnerabilities were tracked as CVE-2017-3075, CVE-2017-3081, CVE-2017-3083, CVE-2017-3084, CVE-2017-3076, CVE-2017-3077, CVE-2017-3078, CVE-2017-3079, and CVE-2017-3082.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system. ” states the security advisory.
The vulnerabilities in Adobe are classified as critical use-after-free and memory corruption flaws that can be exploited by attackers to remote code execution.
adobe flaws
The flaws have been reported by the researchers bee13oy of CloverSec Labs, Jihui Lu of Tencent KeenLab, and researchers from Google Project Zero reported the issues to Adobe.
Adobe also fixed nine vulnerabilities in the Digital Editions ebook reader, four of which are critical memory corruptions that can be exploited for remote code execution. The remaining vulnerabilities, classified as important, that can lead to privilege escalation and memory address disclosure.
These flaws were reported to Adobe by experts from Tencent, Fortinet, CTU Security and Japan-based researcher Yuji Tounai.
“Adobe has released a security update for Adobe Digital Editions for Windows, Macintosh, iOS and Android. This update resolves critical memory corruption vulnerabilities that could lead to code execution, three vulnerabilities rated important that could lead to escalation of privilege and two memory corruption vulnerabilities rated important that could lead to disclosure of memory addresses.” states the advisory.
Adobe fixed an important information disclosure flaw in the Windows and Macintosh versions of Adobe Captivate, a smart authoring platform to create responsive eLearning content.
“Adobe has released security updates for Adobe Captivate for Windows and Macintosh. These updates resolve an important information disclosure vulnerability (CVE-2017-3087) resulting from abuse of the quiz reporting feature in Captivate. ” states the advisory.
The last issue was reported by Fortinet, it is a remote code execution vulnerability in Shockwave Player for Windows.
“Adobe has released a security update for Adobe Shockwave Player for Windows. This update addresses a critical memory corruption vulnerability that could lead to code execution. ” states the advisory.
Windows XP Receives Patches for More 'Shadow Brokers' Exploits
14.6.2017 securityweek Vulnerebility
Microsoft has released patches for Windows XP and other outdated versions of the operating system to fix several critical vulnerabilities that are at heightened risk of being exploited by state-sponsored actors and other threat groups.
The tech giant informed customers in mid-April that a series of exploits leaked by the group known as Shadow Brokers, which allegedly obtained the files from the NSA-linked Equation Group, had been patched in supported versions of Windows with the March security updates. According to some reports, the NSA itself disclosed these flaws to Microsoft following the Shadow Brokers leaks.
Roughly one month later, following the WannaCry ransomware attacks that hit hundreds of thousands of systems across the world, Microsoft decided to fix the SMB vulnerability leveraged by WannaCry in Windows platforms under custom support agreements.
The company has now decided to release more patches for these versions, including Windows XP, Windows Vista, Windows 8 and Windows Server 2003, to address other vulnerabilities that are at elevated risk of exploitation “due to past nation-state activity and disclosures.”
The list of patched flaws includes ones leveraged by three other exploits leaked by Shadow Brokers, namely EnglishmanDentist (CVE-2017-8487), EsteemAudit (CVE-2017-0176) and ExplodingCan (CVE-2017-7269).
Both supported and unsupported versions of Windows also received patches on Tuesday for two vulnerabilities, CVE-2017-8464 and CVE-2017-8543, that have been exploited in attacks by unnamed threat actors.
The list of older vulnerabilities that have now been fixed in outdated versions of Windows also includes remote code executions described in the MS17-013 bulletin, an Internet Explorer memory corruption (CVE-2017-0222), several Windows SMB flaws (CVE-2017-0267 - CVE-2017-0280), an actively exploited IIS buffer overflow (CVE-2017-7269), a Windows privilege escalation issue (CVE-2017-8552), and an actively exploited Windows olecnv32.dll RCE (CVE-2017-8487).
“Our decision today to release these security updates for platforms not in extended support should not be viewed as a departure from our standard servicing policies. Based on an assessment of the current threat landscape by our security engineers, we made the decision to make updates available more broadly,” said Eric Doerr, General Manager of the Microsoft Security Response Center.
“As always, we recommend customers upgrade to the latest platforms. The best protection is to be on a modern, up-to-date system that incorporates the latest defense-in-depth innovations. Older systems, even if fully up-to-date, lack the latest security features and advancements,” Doerr added.
Microsoft Patches Windows Flaws Exploited in Attacks
14.6.2017 securityweek Vulnerebility
Microsoft released patches for more than 90 vulnerabilities on Tuesday, including two critical remote code execution flaws that have been exploited in attacks and several weaknesses whose details have already been disclosed.
One of the actively exploited vulnerabilities is CVE-2017-8464, a LNK remote code execution flaw in Windows that is triggered when the icon of a specially crafted shortcut file is displayed.
“The attacker could present to the user a removable drive that contains a malicious shortcut file and an associated malicious binary. When the user opens this drive in Windows Explorer, or any other application that parses the icon of the shortcut, the malicious binary will execute code of the attacker’s choice on the target system,” Microsoft said in an advisory.
Researchers at the Zero Day Initiative (ZDI) pointed out that this vulnerability is similar to one exploited by the notorious Stuxnet worm, although they pointed out that CVE-2017-8464 may affect different parts of the code. In addition to the removable drive scenario described by Microsoft, ZDI said an attacker could also plant the malicious file in a remote location that is accessible to the targeted user.
Microsoft noted that the impact of this flaw is less severe if the targeted user does not have administrator rights.
Another vulnerability that has been actively exploited is CVE-2017-8543, a remote code execution bug affecting Windows Search.
“To exploit the vulnerability, the attacker could send specially crafted SMB messages to the Windows Search service. An attacker with access to a target computer could exploit this vulnerability to elevate privileges and take control of the computer,” Microsoft warned. “Additionally, in an enterprise scenario, a remote unauthenticated attacker could remotely trigger the vulnerability through an SMB connection and then take control of a target computer.”
Three of the vulnerabilities patched today by Microsoft – all of them affecting the Edge web browser – have already been publicly disclosed. They have been described as security feature bypass and information disclosure issues, but none of them has been rated critical.
A total of 18 flaws have been rated critical, while the rest are considered important. ZDI pointed out that the latest updates also patch vulnerabilities disclosed at Pwn2Own, but some bugs reported at the hacking competition still haven’t been addressed.
Adobe has also released updates on Tuesday to patch 20 vulnerabilities in Flash Player, Shockwave Player, Captivate and Digital Editions. Microsoft has included the Flash Player patches in its security updates.
SAP Releases 18 Security Notes in June 2017 Patch Day
14.6.2017 securityweek Vulnerebility
SAP this week released its June 2017 set of security patches to address various bugs across its products, including a denial of service vulnerability that potentially impacts over 3,400 services exposed to the Internet.
SAP included 18 security notes in its latest SAP Security Patch Day. Updates to previously released notes and 11 security notes being released after the second Tuesday of the previous month and before the second Tuesday of this month make for a total of 29 security notes being part of the June Patch Day (21 SAP Security Patch Day Notes and 8 Support Package Notes).
Five of the release notes had a High priority rating with two of the vulnerabilities featuring a CVSS score of 7.5. 23 of the issues had a Medium risk rating, and one was considered Low severity, ERPScan, a company that specializes in securing SAP and Oracle products, points out.
The most common vulnerability type addressed this month is Cross-Site Scripting (XSS), at 8 bugs, followed by denial of service (DoS) and information disclosure at 4, XML external entity at 3, missing authorization checks at 2, and cross-site request forgery, SQL injection, authentication bypass, and open redirect at 1 each.
The most important of the addressed issues were DoS bugs in SAP NetWeaver Instance Agent Service, and in BILaunchPad and Central Management Console, featuring a CVSS base score of 7.5 each. By terminating the process of the vulnerable component, an attacker could prevent access to the service.
“One of two Notes assessed at High priority is a DoS vulnerability in SAP Host Agent Service identified by our researchers. The vulnerability is remotely exploitable without authentication. We have also conducted a custom scanning that revealed that there are about 3,400 potentially vulnerable such services available online,” ERPScan’s Darya Maenkova told SecurityWeek in an email.
The issue, ERPScan says, was reported to SAP in November 2016, and could cause response delays and service interruptions, with direct impact on availability. Most of the vulnerable services exposed to the Internet are located in the United States (780), India (691), China (216), Korea (126), and Mexico (114).
Other High priority flaws that SAP addressed this month include a Cross-Site Scripting vulnerability (CVSS Base Score: 7.1) in SAP BusinessObjects Web Intelligence HTML interface and a Missing certificate verification vulnerability (CVSS Base Score: 7) in SAP CommonCryptoLib (a bug related to HTTPS certificates validation).
Another High risk security note is an update to a note released in March 2017: Improved security for outgoing HTTPS connections in SAP NetWeaver (CVSS Base Score: 7.4). As Onapsis explains, this note “includes more information on how to properly configure HTTPS connections securely.”
Adobe Patches 20 Flaws in Flash Player, Other Products
13.6.2017 securityweek Vulnerebility
Updates released by Adobe on Tuesday for Flash Player, Shockwave Player, Captivate and Digital Editions address a total of 20 vulnerabilities, including critical weaknesses that can be exploited for remote code execution.
Nine vulnerabilities have been patched in Flash Player with the release of version 26.0.0.126. The security holes have been described as critical use-after-free and memory corruption flaws that can lead to remote code execution.
bee13oy of CloverSec Labs, Jihui Lu of Tencent KeenLab, and researchers from Google Project Zero reported the issues to Adobe. The flaws have been assigned the following CVE identifiers: CVE-2017-3075, CVE-2017-3081, CVE-2017-3083, CVE-2017-3084, CVE-2017-3076, CVE-2017-3077, CVE-2017-3078, CVE-2017-3079 and CVE-2017-3082.
Nine flaws have also been fixed by Adobe in the Digital Editions ebook reader. However, these bugs have a lower priority rating and only four memory corruptions that can be exploited for remote code execution are considered critical.
The other vulnerabilities, classified as important, can lead to privilege escalation and memory address disclosure. These flaws were reported to Adobe by experts from Tencent, Fortinet, CTU Security and Japan-based researcher Yuji Tounai.
Fortinet employees also informed Adobe of a remote code execution vulnerability in Shockwave Player for Windows. The problem is considered critical, but it has been assigned a priority rating of “2,” which means it’s less likely to be exploited.
One important information disclosure flaw has been fixed in the Windows and Macintosh versions of Adobe Captivate, an authoring tool that is used for creating e-learning content.
SambaCry is reality, crooks are abusing CVE-2017-7494 to spread miners
11.6.2017 securityaffairs Vulnerebility
Security experts from Kaspersky confirmed that threat actors in the wild are exploiting the SambaCry vulnerability CVE-2017-7494 to spread a miner.
At the end of May, a seven-year-old remote code execution vulnerability affecting all versions of the Samba software since 3.5.0 was patched by the development team of the project. An attacker can exploit the CVE-2017-7494 RCE to upload a shared library to a writable share, and then cause the server to load and execute it.
SambaCry allows a remote hacker to take full control of a vulnerable Linux and Unix system.
The flaw, dubbed SambaCry, can be easily exploited, just a line of could be used for the hack under specific conditions:
make file- and printer-sharing port 445 reachable on the Internet,
configure shared files to have write privileges.
use known or guessable server paths for those files.
When the above conditions are satisfied, remote attackers can upload any code of their choosing and cause the server to execute it, possibly with unfettered root privileges, depending on the vulnerable platform.
“All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it.” reads the security advisory issued by Samba.
The announcement published by Samba informed users that a patch addressing this remote code execution vulnerability tracked as CVE-2017-7494 was available at the following URL:
http://www.samba.org/samba/security/
Sysadmins have to patch their versions as soon as possible, if it is not possible for any reason a workaround can be implemented by the adding the line
nt pipe support = no
to their Samba configuration file and restarting the network’s SMB daemon.
The change will limit clients from accessing some network computers.
“Additionally, Samba 4.6.4, 4.5.10 and 4.4.14 have been issued as security releases to correct the defect. Patches against older Samba versions are available at http://samba.org/samba/patches/. Samba vendors and administrators running affected versions are advised to upgrade or apply the patch as soon as possible.”
The Samba bug appears to be a network wormable issue that could be exploited by a malicious code to self-replicate from vulnerable machine to vulnerable machine without requiring user interaction.
When SambaCry was discovered, nearly 485,000 Samba-enabled computers were found to be exposed on the Internet.
Security researcher speculated that a rapid increase in the number of cyber attacks leveraging the SambaCry issue, just like WannaCry attacks.

Researchers at Kaspersky Lab set up honeypots to detect SambaCry attacks in the wild. The experts have spotted a malware campaign that is exploiting SambaCry vulnerability to infect Linux systems and install a cryptocurrency miner.
“On May 30th our honeypots captured the first attack to make use of this particular vulnerability, but the payload in this exploit had nothing in common with the Trojan-Crypt that was EternalBlue and WannaCry. Surprisingly, it was a cryptocurrency mining utility!” reported Kaspersky.
The independent security researcher Omri Ben Bassat also observed the same campaign that he dubbed “EternalMiner.” The expert confirmed threat actors started exploiting the SambaCry flaw just a week after its discovery to hijack Linux PCs and to install an upgraded version of “CPUminer,” a Monero miner.

Omri Ben Bassat @omri9741
Cryptocurrency miner #EternalMiner using #SambaCry #CVE_2017_7494 to infect Linux servers. brand new sample @malwrhunterteam.
10:25 AM - 8 Jun 2017
52 52 Retweets 34 34 likes
Twitter Ads info and privacy
Once compromised a Linux Machine exploiting the SambaCry vulnerability, attackers execute two different payloads on the targeted systems:
INAebsGB.so — A simple reverse shell that allows a remote attacker to access the target system.
cblRWuoCc.so — A backdoor that includes cryptocurrency mining utilities – CPUminer.
“the attacked machine turns into a workhorse on a large farm, mining crypto-currency for the attackers. In addition, through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware” Kaspersky researchers say.
According to Kaspersky, threat actors behind this campaign have already earned 98 XMR, which worth USD 5,380 today. The experts believe that crooks could earn much more with the increase in the number of compromised Linux systems.
“The mining utility is downloaded from the domain registered on April 29th 2017. According to the log of the transactions, the attackers received their first crypto-coins on the very next day, on April 30th. During the first day they gained about 1 XMR (about $55 according to the currency exchange rate for 08.06.2017), but during the last week they gained about 5 XMR per day. This means that the botnet of devices working for the profit of the attackers is growing.,” the researchers say.
First-Ever Data Stealing Malware Found Using Intel AMT Tool to Bypass Firewall
9.6.2017 thehackernews Vulnerebility
It's not hard for a well-funded state-sponsored hacking group to break into corporate networks and compromise systems with malware, but what's challenging for them is to keep that backdoor and its communication undetectable from a firewall and other network monitoring applications.
However, a cyber-espionage group known as "Platinum," that is actively targeting governmental organisations, defense institutes, and telecommunication providers since at least 2009, has found a way to hide its malicious activities from host-based protection mechanisms.
Microsoft has recently discovered that the cyber-espionage group is now leveraging Intel's Active Management Technology (AMT) Serial-over-LAN (SOL) channel as a file-transfer tool to steal data from the targeted computers without detection.
Intel-based chip sets come with an embedded technology, called AMT, which is designed to allow IT administrators to remotely manage and repair PCs, workstations, and servers of their organisations.
The Intel AMT technology operates independently of the operating system and works even when the system is turned off, as long as the platform is connected to a line power and a network cable.
That means, when AMT is enabled, any packet sent to the PC's wired network port will be redirected to the Management Engine and passed on to AMT – the operating system, as well as network monitoring applications installed on a system, never knows what's going around.
Moreover, Linux systems with Intel's chips and AMT enabled may also be exposed to Platinum's malware.
"As this embedded processor is separate from the primary Intel processor, it can execute even when the main processor is powered off and is, therefore, able to provide out-of-band (OOB) remote administration capabilities such as remote power-cycling and keyboard, video, and mouse control (KVM)," Microsoft said.
"Furthermore, as the SOL traffic bypasses the host networking stack, it cannot be blocked by firewall applications running on the host device. To enable SOL functionality, the device AMT must be provisioned."
Unlike the remote authentication flaw discovered last month that enabled hackers to take over full control of a system by using AMT features without the need of any password, Platinum does not exploit any flaw in AMT, instead, requires AMT to be enabled on infected systems.
Microsoft notes that SOL session requires a username and password, so either the hacking group is using stolen credentials to make its malware remotely communicate with the C&C servers, or "during the provisioning process, PLATINUM could select whichever username and password they wish."
The Platinum hacking group has been using zero-day exploits, hot patching technique and other advanced tactics to penetrate in their target systems and networks in South Asian countries, but this is the first time someone is abusing legitimate management tools to evade detection.
Microsoft said it has already updated its own Windows Defender Advanced Threat Protection software that will alert network administrators of any malicious attempts at using AMT SOL, but only for systems running Windows operating system.
CISCO Prime Data Center Network Manager affected by two critical flaws
9.6.2017 securityaffairs Vulnerebility
Cisco èiblished two security advisories to warn customers of the presence of two critical vulnerabilities in the CISCO Prime Data Center Network Manager,
Cisco warns its customers of the presence of two critical vulnerabilities in the CISCO Prime Data Center Network Manager (DCNM) that can be exploited by remote attackers for code execution and to access the administrative console.
The first flaw tracked as CVE-2017-6639, is related to the lack of authentication and authorization for a debugging tool that was left enabled in the product.
A remote, unauthenticated attacker can exploit the flaw by connecting to the debugging tool via TCP.
“A vulnerability in the role-based access control (RBAC) functionality of Cisco Prime Data Center Network Manager (DCNM) could allow an unauthenticated, remote attacker to access sensitive information or execute arbitrary code with root privileges on an affected system.” states the advisory published by CISCO.
“The vulnerability is due to the lack of authentication and authorization mechanisms for a debugging tool that was inadvertently enabled in the affected software. An attacker could exploit this vulnerability by remotely connecting to the debugging tool via TCP. A successful exploit could allow the attacker to access sensitive information about the affected software or execute arbitrary code with root privileges on the affected system.”
Affected versions are the Cisco Prime DCNM releases 10.1(1) and 10.1(2) for Windows, Linux and virtual appliances.

The second vulnerability in CISCO Prime Data Center Network Manager (DCNM) tracked as CVE-2017-6640, exists due to a presence of a default user account protected by a static password. A remote attacker can connect to the affected system and use this account to gain privileged access to the server’s administration interface.
Affected versions are the Prime DCNM running software version 10.2(1) for Windows, Linux and virtual appliances.
“A vulnerability in Cisco Prime Data Center Network Manager (DCNM) Software could allow an unauthenticated, remote attacker to log in to the administrative console of a DCNM server by using an account that has a default, static password. The account could be granted root- or system-level privileges.” states the advisory.
“The vulnerability exists because the affected software has a default user account that has a default, static password. The user account is created automatically when the software is installed.”
Both flaws were reported to Cisco by Antonius Mulder of Commonwealth Bank of Australia, the good news is that there is no evidence that they have been exploited in attacks the wild.
Cisco patched the flaws with the release of version 10.2(1), the company informs that no workarounds are not available.
Default Account, Debug Tool Expose Cisco Prime Users to Attacks
9.6.2017 securityweek Vulnerebility
Cisco informed customers this week that its Prime Data Center Network Manager (DCNM) is affected by two critical vulnerabilities that can be exploited for remote code execution and to access the product’s administrative console.
One of the flaws, tracked as CVE-2017-6639, is related to the lack of authentication and authorization for a debugging tool that was inadvertently left enabled.
A remote, unauthenticated attacker can exploit the vulnerability to access sensitive information or execute arbitrary code with root privileges by connecting to the debugging tool via TCP.
The security hole affects Cisco Prime DCNM releases 10.1(1) and 10.1(2) for Windows, Linux and virtual appliances.
The second Prime DCNM vulnerability, identified as CVE-2017-6640, exists due to a default user account protected by a static password. An attacker who can remotely connect to the affected system can use this account to gain privileged access to the server’s administration interface.
The networking giant said this flaw only affects Prime DCNM running software version 10.2(1) for Windows, Linux and virtual appliances.
Both DCNM vulnerabilities were disclosed to Cisco by Antonius Mulder of Commonwealth Bank of Australia and there is no evidence that they have been exploited in the wild. The flaws have been patched with the release of version 10.2(1), but workarounds are not available.
Cisco has also published an advisory for a high severity local privilege escalation vulnerability affecting AnyConnect Secure Mobility Client for Windows versions prior to 4.4.02034. The security hole, reported by Felix Wilhelm of ERNW, allows a local attacker to install and execute a file with SYSTEM privileges.
Another advisory describes a high severity denial-of-service (DoS) vulnerability in the Session Initiation Protocol (SIP) of the Cisco TelePresence Codec (TC) and Collaboration Endpoint (CE) software. A remote, unauthenticated attacker can exploit this flaw to cause a DoS condition by sending a flood of SIP INVITE packets to the vulnerable device.
The weakness, reported to Cisco by Knud Hojgaard of F-Secure, affects several TelePresence MX, Profile, SX, System Profile MXP, System EX, and Integrator C series products. Two Collaboration Desk Endpoint DX series devices are also impacted.
Thousands of Firms Fail to Update Software on Most Computers: Study
9.6.2017 securityweek Vulnerebility
An analysis of 35,000 companies from more than 20 industries across the world showed that many of them are at risk of suffering a data breach due to their failure to ensure that the software running on their computers is up to date.
The study conducted by cybersecurity ratings company BitSight focused on Apple and Microsoft operating systems, and the Firefox, Chrome, Safari and Internet Explorer web browsers.
The research showed that more than 50 percent of computers in over 2,000 organizations run an outdated version of the operating system, and over 8,500 companies have failed to update Web browsers on more than half of their machines.
Looking at each of the analyzed industries, BitSight found that the education and government sectors had the highest usage rate of outdated operating systems and browsers. Nearly 40 percent of computers used in the education sector and more than 25 percent of devices in the government sector had been running outdated operating systems, particularly outdated versions of Mac OS.
The fact that public sector organizations have done a poor job at protecting their systems is not surprising, and even U.S. President Donald Trump called for government agencies to take measures in his recent cybersecurity executive order.
At the other end of the chart we have the legal and energy sectors, which had the fewest devices running outdated software.
“Given that the Energy sector provides critical infrastructure services, organizations in this sector should maintain their proactive approach to security,” BitSight said in its report. “Despite its top performance, researchers found that more than 120 companies in this sector were running out-of-date or unsupported operating systems and more than 400 companies were observed to have greater than 33 percent of Internet browsers out-of-date. This represents a gap in security and presents an opportunity for hackers to exploit weaknesses in this critical sector.”
As for how long it takes organizations to apply patches, BitSight determined that it takes most companies, on average, more than a month to update to the latest version of macOS Sierra. Researchers found that in late March, over two months after version 10.12.3 was released, roughly 40 percent of firms had still been using an older version.
In the case of Windows, more than 60 percent of analyzed PCs were running Windows 7 or earlier, including XP and Vista, which no longer receive updates from Microsoft.
VMware Patches Flaws in Horizon, vSphere Products
9.6.2017 securityweek Vulnerebility
Updates released by VMware this week for its Horizon View Client and vSphere Data Protection (VDP) products address a total of three critical and important vulnerabilities.
One of the advisories published by the company informs users that VDP versions 5.5.x, 5.8.x, 6.0.x and 6.1.x are affected by two critical Java deserialization and credentials management flaws.
The deserialization issue, tracked as CVE-2017-4914, was reported to VMware by Tim Roberts, Arthur Chilipweli and Kelly Correll of NTT Security. According to the vendor, the flaw can be exploited remotely to execute arbitrary commands on vulnerable appliances.
The second vulnerability affecting VDP is CVE-2017-4917 and it was reported to VMware by Marc Ströbel (aka phroxvs) from HvS-Consulting. Ströbel discovered that the locally stored vCenter Server credentials are poorly encrypted, allowing an attacker to obtain the information in plaintext.
Users of the affected product have been advised to update their installations to versions 6.0.5 or 6.1.4. It’s also worth noting that VMware recently announced its intention to discontinue the VDP product.
A second advisory published by VMware this week describes an important command injection vulnerability affecting the VMware Horizon View Client for Mac.
Florian Bogner of Kapsch BusinessCom AG discovered that the application has a command injection flaw in the service status script. An unprivileged user can exploit the vulnerability to escalate privileges to root on the vulnerable Mac OS X system, VMware said.
The flaw, tracked as CVE-2017-4918, affects View Client versions 2.x, 3.x and 4.x and it has been patched with the release of version 4.5.
According to VMware, workarounds or mitigations are not available for any of the vulnerabilities fixed this week. US-CERT has also published an alert advising users to review the advisories and apply necessary updates.
While some vulnerabilities in VMware products are less likely to be exploited, there are cases where the risk of exploitation is higher. For example, VMware determined recently that several of its products were affected by an Apache Struts 2 flaw that had been exploited in the wild. The company also released patches recently for Workstation vulnerabilities exploited at the 2017 Pwn2Own hacking competition.
F-Secure experts found multiple flaws in popular Chinese Internet-connected cameras
9.6.2017 securityaffairs Vulnerebility
Experts at F-Secure discovered tens of vulnerabilities in tens of thousands of Internet-connected cameras from China-based manufacturer Foscam.
Security experts at security firm F-Secure discovered tens of vulnerabilities in tens of thousands of Internet-connected cameras from China-based manufacturer Foscam.
The flaws could be exploited by attackers to take over the Internet-connected cameras, upload and download files from the built-in FTP server, and view video feeds. The devices could be used as an entry point into the target network.
The experts discovered 18 vulnerabilities in two differed camera models available on the market under the brands Foscam C2 and Opticam i5 HD. In both cases, the vulnerabilities are still unpatched despite F-Secure reported the issues to the manufacture several months ago.
“F-Secure’s discovery of multiple flaws in two models of Foscam-made IP cameras is another example of a poorly engineered device that offers attackers an easy target. Should an attacker infiltrate the company network and find such a device, they could infect it with malware that would not only fully compromise the device, but also grant free reign inside the network, including access to network systems and resources.” states the report published by F-Secure.
“Foscam-made IP cameras have multiple vulnerabilities that can lead to full device compromise,” continues the report.“An unauthenticated attacker can persistently compromise these cameras by employing a number of different methods leading to full loss of confidentiality, integrity and availability, depending on the actions of the attacker.”
The experts believe that the same issues may affect 14 other brands that use Foscam internals, including Chacon, 7links, Netis, Turbox, Thomson, Novodio, Nexxt, Ambientcam, Technaxx, Qcam, Ivue, Ebode and Sab.

The vulnerabilities discovered by the experts in the two models of Internet-connected cameras includes:
Insecure default credentials
Hard-coded credentials
Hidden and undocumented Telnet functionality
Remote Command Injections
Incorrect permissions assigned to programming scripts
Firewall leaking details about the validity of credentials
Persistent cross-site scripting
Stack-based Buffer overflow attack
Experts highlighted that even if the users change the default credentials of the IP cameras they will remain vulnerable to cyber attacks because Foscan is using hard-coded credentials.
“Credentials that have been hard-coded by the manufacturer cannot be changed by the user. If the password is discovered and published on the internet (which often happens) attackers can gain access to the device. And as all devices have the same password, malware attacks such as worms can easily spread between devices.” reads the report published by F-Secure.
The list of flaws includes a Hidden and undocumented Telnet functionality could help attackers use Telnet to discover “additional vulnerabilities in the device and within the surrounding network.”
The experts reported three flaws that cannot be fixed, including built-in file transfer protocol server that contains an empty password, a hidden telnet function and incorrect permissions assigned to programming scripts, could be exploited by remote hackers to gain persistent access to the Internet-connected cameras.
“The empty password on the FTP user account can be used to log in. The hidden Telnet functionality can then be activated. After this, the attacker can access the world-writable (non-restricted) file that controls which programs run on boot, and the attacker may add his own to the list,” F-Secure researchers says.
“This allows the attacker persistent access, even if the device is rebooted. In fact, the attack requires the device to be rebooted, but there is a way to force a reboot as well.”
F-Secure experts suggest users who are running one of these IP cameras to avoid exposing them on the Internet and of course to change default credentials.
Critical Flaw Exposes Many WiMAX Routers to Attacks
8.6.2017 securityweek Vulnerebility
Researchers have discovered a critical authentication bypass vulnerability that exposes many WiMAX routers to remote attacks, and there is no indication that affected vendors will release patches any time soon.
WiMAX (Worldwide Interoperability for Microwave Access) is a wireless communications standard that is similar to LTE. The technology is present in many networking devices, including ones that are directly accessible from the Internet.
Researchers at SEC Consult noticed that several WiMAX gateways are affected by a serious flaw that can be exploited by a remote, unauthenticated attacker to change the device’s administrator password by sending it a specially crafted request. The weakness is tracked as CVE-2017-3216.
Once they change the device’s admin password, attackers can access its web interface and conduct various actions, including change the router’s DNS servers for banking and ad fraud, upload malicious firmware, or launch further attacks on the local network or the Internet.Vulnerable ZyXEL gateway
SEC Consult believes the vulnerability is present in several gateways from GreenPacket, Huawei, MADA, ZTE and ZyXEL. It appears the firmware of all affected devices has been developed with a software development kit (SDK) from MediaTek, a Taiwan-based company that provides system-on-a-chip (SoC) solutions for wireless communications.
Experts believe ZyXEL and its sister company MitraStar used the MediaTek SDK to develop firmware for routers that it has sold to ISPs and companies such as GreenPacket, Huawei and ZTE. However, MediaTek claims the vulnerability found by SEC Consult does not affect its SDK, which suggests that the flaw may have been introduced with code added by ZyXEL.
ZyXEL has been notified by CERT/CC, which has also published an advisory, but the company has not provided any information.
Huawei has confirmed that some of its products are affected by the vulnerability, but they will not receive any patches as they reached end-of-service in 2014. The company has published a security notice advising customers to replace their old routers.
An analysis by SEC Consult showed that there are between 50,000 and 100,000 vulnerable devices accessible directly from the Internet. The company has published an advisory that contains the exact device models impacted by the security hole.
Since patches are unlikely to become available any time soon, users have been advised to either replace the devices or take measures to prevent remote access, such as restricting access to only trusted clients and disabling remote device management features.
Multiple Vulnerabilities Found in Popular IP Cameras
8.6.2017 securityweek Vulnerebility
Multiple vulnerabilities have been found in China's Foscam-made IP cameras. The vulnerabilities were reported to the manufacturer several months ago, but no fixes have been made available. Foscam cameras are sold under different brand names, such as OptiCam. Users are advised to check on the manufacture of any IP cameras, and if necessary, take their own mitigation steps.
The vulnerabilities, 18 in all, were discovered by F-Secure, who specifically found them in the Opticam i5 and Foscam C2 cameras. F-Secure warns, however, that these vulnerabilities will likely exist throughout the Foscam range and potentially in all 14 separate brand names that it knows to sell Foscam cameras.
The flaws include insecure default credentials, hard-coded credentials, hidden and undocumented Telnet functionality, command injection flaws, missing authorization, improper access control, cross-site scripting, and a buffer overflow. All are detailed in a report (PDF) published today.
"Security has been ignored in the design of these products," said Janne Kauhanen, cyber security expert at F-Secure. "The developers' main concern is to get them working and ship them. This lack of attention to security puts users and their networks at risk. The irony is that this device is marketed as a way of making the physical environment more secure -- however, it makes the virtual environment less so."
While attention on IoT device security -- especially cameras -- has been focused by the Mirai botnet and the largest DDoS attack against the internet infrastructure in history, the quantity and severity of the Foscam vulnerabilities is particularly concerning. "These vulnerabilities are as bad as it gets," commented Harry Sintonen, the F-Secure senior security consultant who found the vulnerabilities. "They allow an attacker to pretty much do whatever he wants. An attacker can exploit them one by one, or mix and match to get greater degrees of privilege inside the device and the network."
F-Secure gives several example attacks against the products. For example, unauthenticated users able to access a specific port can use a command injection to add a new root user for the device and to enable a standard remote login service (Telnet). Then, when logging in through this remote login service, they have admin privileges on the device.
A second attack could take advantage of three of the individual vulnerabilities. "The empty password on the FTP user account can be used to log in," explains the F-Secure report. "The hidden Telnet functionality can then be activated. After this, the attacker can access the world-writable (non-restricted) file that controls which programs run on boot, and the attacker may add his own to the list. This allows the attacker persistent access, even if the device is rebooted. In fact, the attack requires the device to be rebooted, but there is a way to force a reboot as well."
Since there are no fixes yet available from Foscam, F-Secure recommends that users only install the cameras within a dedicated network or VLAN. In this case, it notes, changing the default password will not increase security since, "because of the Foscam IP cameras' use of hard-coded credentials, in this case an attacker can bypass unique credentials."
Remediation responsibility, however, remains with the manufacturer. F-Secure lists 12 recommendations for Foscam, ranging from the installation of "a truly random default administrative password" with a password sticker attached to the underside of the device, to the removal of built-in credentials and the implementation of a proper iptables firewall.
In general, F-Secure advises vendors to design security within their products from the beginning. "Having product security processes in place," says the report, "and investing even modest resources into security is a differentiator from competitors. This can also work to vendors' advantage when regulation enforces secure design practices."
Organizations Failing to Upgrade Systems, Enforce Patches
7.6.2017 securityweek Vulnerebility
Organizations Are Still Failing to Upgrade Systems and Enforce Patches, Study Finds
Duo Security provides multi-factor authentication to business. Part of its service includes behavioral aspects of the device, which means that Duo analyzes the state of the devices seeking access to its corporate customers' resources. This week the company published its latest analysis of business device security health: The 2017 Duo Trusted Access Report.
The report (PDF) presents an analysis of 4.6 million business endpoints, including 3.5 million mobile phones across multiple industry verticals and geographic regions. In particular, it analyzes the operating system and browser used on computers, and the enabled security features on mobile devices.
"The big takeaway from this report," its researcher Kyle Lady told SecurityWeek, "is that we are still not doing a good enough job at upgrading systems and enforcing patches."
For example, although the uptake of Microsoft's latest Windows 10 (Win10) operating system has doubled from 15% last year to 31% this year, that still means that the vast majority of Windows usage in business is using old and sometimes unsupported versions of Windows. More than half (59%) of business Windows systems are still using Windows 7; and 1% are still using XP.
The importance of upgrading to W10 is illustrated by the recent WannaCry ransomware outbreak -- which rapidly infected more than 200,000 computers in 150 countries. W10 with automatic patching was protected; unpatched W7 (and unsupported W7 on Intel 7th Generation Core processors and AMD Ryzen systems); and all XT systems were vulnerable.
It is noticeable that healthcare continues to run a higher percentage of W7 than business overall (76% compared to 59%), and a higher percentage of XP (3% compared to 1%) -- and healthcare (especially the UK's National Health Service) was especially affected by WannaCry.
It seems that many firms are relying on the standard business hardware refresh cycle to effect their upgrade to Windows 10. "This will eventually get us to full Windows 10 adoption; but how long will that take?" asks Lady. "As we get better at making computers they are lasting longer and refresh cycles are lengthening." Meanwhile, these older systems will become increasingly vulnerable -- something that President Trump's recent cybersecurity executive order recognized in its instruction that government agencies must upgrade any 'antiquated' systems.
But it's not just aging operating systems that are a cause for concern. Duo also analyzed the results from its free simulated phishing solution, Duo Insight. This analysis looked at 3,575 simulated phishing campaigns with more than 80,000 recipients run over the last 12 months; and found that 62% of campaigns captured at least one credential and 68% had at least one out-of-date device.
The combination of successful phishing and out-of-date browsers is important. Just visiting a phishing site without entering credentials would probably not be dangerous (o-days aside) provided the browser being used is fully up-to-date. However, merely visiting the site, having second thoughts and immediately leaving can still compromise the user of unpatched browsers and operating systems.
The browser situation is little better than operating systems, with only 9% of business users browsing with Microsoft's Internet Explorer successor, Edge 14. By far the majority of users browse with IE 11 (76%) on Windows 7, but fully 13% of business users are still using the unsupported IE 8,9 and 10. This makes them particularly vulnerable to phishing and exploit kits.
"As underlined from many of the latest headline breaches," comments Mike Hanley, Sr. director of security for Duo Security, "unpatched, out-of-date software, systems and servers are prime targets for attackers armed with known vulnerabilities and malware. The 2017 Trusted Access Report shows that while we’re making progress in some areas like Windows 10 adoption, there is still much room for improvement across the board."
Chrome 59 Patches 30 Vulnerabilities
6.6.2017 securityweek Vulnerebility
Google announced on Monday the availability of Chrome 59, a version that brings several design and functionality improvements, and fixes for tens of vulnerabilities.
According to Google, a total of 30 flaws have been fixed in the latest version of the popular web browser, including many reported by external researchers. The experts who contributed to making Chrome more secure earned a total of more than $23,000.
The most serious of the vulnerabilities was reported to Google in mid-May by Zhao Qixun, aka S0rryMybad, of the Qihoo 360 Vulcan Team. The hacker discovered a high severity type confusion flaw in the V8 JavaScript engine (CVE-2017-5070) that earned him $7,500.
In April, Choongwoo Han and Rayyan Bijoora informed Chrome developers of high severity out-of-bounds read (CVE-2017-5071) and omnibox address spoofing (CVE-2017-5072) flaws that earned them each $3,000.
High severity use-after-free bugs were uncovered by Khalil Zhani and an anonymous researcher, but these earned them only $2,000 and $1,000, respectively. Emmanuel Gil Peyrot also received $2,000 for disclosing a medium severity information disclosure issue in CSP reporting.
The list of medium and low severity vulnerabilities patched with the release of Chrome 59 have been described as omnibox address spoofing, Skia buffer overflow, command injection in mailto handling, Blink user interface spoofing, extension verification bypass, and inappropriate JavaScript execution on WebUI pages.
Researchers also found a use-after-free vulnerability in the credit card autofill feature, and discovered that the credit card editor had been insufficiently hardened.
Google has paid out more than $9 million since the launch of its bug bounty program in 2010, including more than $3 million last year. As vulnerabilities become more difficult to find, the tech giant recently decided to offer more money for critical flaws.
Yahoo Pays Out Thousands of Dollars for Serious Flaws
5.6.2017 securityweek Vulnerebility
Yahoo has awarded thousands of dollars to a couple of researchers who managed to find serious vulnerabilities in the company’s systems. The bug bounty hunters published blog posts over the weekend describing their findings.
An expert who uses the online moniker “Th3G3nt3lman” said he received $5,500 from Yahoo for a remote code execution vulnerability in Apache Struts 2. The white hat hacker discovered the flaw on a Yahoo subdomain hosting a login page for a Selligent marketing product.
The security hole is CVE-2017–5638, a Struts 2 vulnerability that malicious actors started exploiting in March, shortly after a patch was released. The weakness has been found to affect the products and systems of many companies, including Cisco, VMware and AT&T.
According to Th3G3nt3lman, the initial exploit published for CVE-2017–5638 did not work on the Yahoo website, but he found a different exploit on Twitter – one that can bypass web application firewalls (WAFs) – that could have been used to achieve remote code execution.
Cryptography and information security enthusiast Sam Curry also published a blog post over the weekend describing a critical vulnerability in a Yahoo-owned system. Unlike Th3G3nt3lman, who found the RCE flaw on a Yahoo domain, Curry and a bounty hunter known online as “dawgyg” discovered a bug in the video streaming website SnackTV, which Yahoo took over in late 2014 with the acquisition of Media Group One.
In addition to some low severity issues, Curry and dawgyg noticed that the SnackTV website had been affected by the ImageMagick vulnerability known as ImageTragick. The flaw in the popular image processing suite was disclosed in May 2016, when it had already been exploited in the wild.
The hackers noticed that the server in question was not vulnerable to the generic ImageTragick attack, but after some tweaking they managed to get an exploit to work and achieved command injection. Yahoo patched the flaw within two days after learning of its existence and awarded the experts $3,000.
Yahoo has been informed of several ImageMagick vulnerabilities, and several months ago the company decided to stop using the library after a researcher discovered a critical flaw that could have been exploited to obtain sensitive data belonging to Yahoo Mail users.
Curry reported his findings to Yahoo last month, which suggests that while Yahoo removed ImageMagick from some services, the software is still present on some of its websites.
This was not the only vulnerability disclosed by Curry to Yahoo in recent weeks. In May, he published two other blog posts describing cross-site scripting (XSS) and other weaknesses that earned him a total of more than $2,000.
Over 8,600 Vulnerabilities Found in Pacemakers
5.6.2017 thehackernews Vulnerebility

"If you want to keep living, Pay a ransom, or die." This could happen, as researchers have found thousands of vulnerabilities in Pacemakers that hackers could exploit.
Millions of people that rely on pacemakers to keep their hearts beating are at risk of software glitches and hackers, which could eventually take their lives.
A pacemaker is a small electrical battery-operated device that's surgically implanted in the chest to help control the heartbeats. This device uses low-energy electrical pulses to stimulate the heart to beat at a normal rate.
While cyber security firms are continually improving software and security systems to protect systems from hackers, medical devices such as insulin pumps or pacemakers are also vulnerable to life-threatening hacks.
In a recent study, researchers from security firm White Scope analysed seven pacemaker products from four different vendors and discovered that they use more than 300 third-party libraries, 174 of which are known to have over 8,600 vulnerabilities that hackers could exploit in pacemaker programmers.
"Despite efforts from the FDA to streamline routine cyber security updates, all programmers we examined had outdated software with known vulnerabilities," the researchers wrote in a blog post about the study.
"We believe that this statistic shows that the pacemaker ecosystem has some serious challenges when it comes to keeping systems up-to-date. No one vendor really stood out as having a better/worse update story when compared to their competitors."
The White Scope analysis covered implantable cardiac devices, home monitoring equipment, pacemaker programmers, and cloud-based systems to send patient's vital data over the Internet to doctors for examining.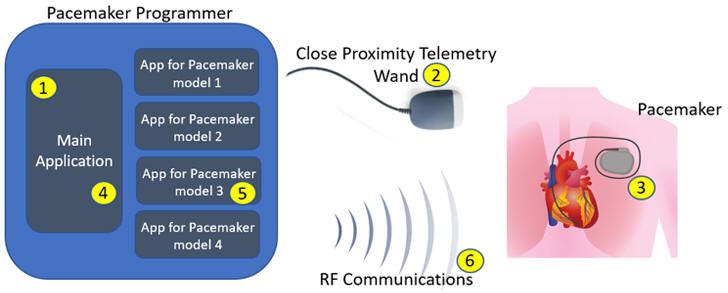
All of the programmers examined by the security firm had outdated software with known vulnerabilities, many of which run Windows XP.
What's even more frightening? Researchers discovered that the Pacemaker devices do not authenticate these programmers, which means anyone who gets their hands on an external monitoring device could potentially harm heart patients with an implanted pacemaker that could harm or kill them.
Another troubling discovery by researchers is with the distribution of pacemaker programmers.
Although the distribution of pacemaker programmers is supposed to be carefully controlled by the manufacturers of pacemaker devices, the researchers bought all of the equipment they tested on eBay.
So, any working tool sold on eBay has the potential to harm patients with the implant. Yikes!
"All manufacturers have devices that are available on auction websites," the researchers said. "Programmers can cost anywhere from $500-$3000, home monitoring equipment from $15-$300, and pacemaker devices $200-$3000."
What's more? In some cases, researchers discovered unencrypted patients' data stored on the pacemaker programmers, including names, phone numbers, medical information and Social Security numbers (SSNs), leaving them wide open for hackers to steal.
Another issue discovered in the pacemaker systems is the lack of the most basic authentication process: login name and password, allowing the physicians to authenticate a programmer or cardiac implant devices without even have to enter a password.
This means anyone within range of the devices or systems can change the pacemaker's settings of a patient using a programmer from the same manufacturer.
Matthew Green, a computer science assistant professor at Johns Hopkins, pointed out on Twitter that doctors are not willing to let security systems block patient care. In other words, the medical staff shouldn't be forced to log in with credentials during an emergency situation.
"If you require doctors to log into a device with a password, you will end up with a post-it note on the device listing the password," Green said.
The list of security vulnerabilities the researchers discovered in devices made by four vendors includes hardcoded credentials, unsecured external USB connections, the failure to map the firmware to protected memory, lack of encrypted pacemaker firmware updates, and using universal authentication tokens for pairing with the implanted device.
White Scope has already contacted the Department of Homeland Security's Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), so the manufacturers of the tested devices can address the flaws.
High-Severity Linux Sudo Flaw Allows Users to Gain Root Privileges
1.6.2017 thehackernews Vulnerebility
A high-severity vulnerability has been reported in Linux that could be exploited by a low privilege attacker to gain full root access on an affected system.
The vulnerability, identified as CVE-2017-1000367, was discovered by researchers at Qualys Security in Sudo's "get_process_ttyname()" function for Linux that could allow a user with Sudo privileges to run commands as root or elevate privileges to root.
Sudo, stands for "superuser do!," is a program for Linux and UNIX operating systems that lets standard users run specific commands as a superuser (aka root user), such as adding users or performing system updates.
The flaw actually resides in the way Sudo parsed "tty" information from the process status file in the proc filesystem.
On Linux machines, sudo parses the /proc/[pid]/stat file in order to determine the device number of the process's tty from field 7 (tty_nr), Qualys Security explains in its advisory.
Although the fields in the file are space-delimited, it is possible for field 2 (the command name) to include whitespace (including newline), which sudo doesn't account for.
Therefore, a local user with sudo privileges (Sudoer) on SELinux-enabled systems can cause sudo to use a device number of his choice "by creating a symbolic link from the sudo binary to a name that contains a space, followed by a number," escalating their privileges to overwrite any file on the filesystem, including root-owned files.
"To exploit the bug, the user can choose a device number that does not currently exist under /dev. If sudo does not find the terminal under the /dev/pts directory, it performs a breadth-first search of /dev...The attacker may then create a symbolic link to the newly-created device in a world-writable directory under /dev, such as /dev/shm," an alert on the sudo project website reads.
"This file will be used as the command's standard input, output and error when an SELinux role is specified on the sudo command line. If the symbolic link under /dev/shm is replaced with a link to another file before [sudo opens it], it is possible to overwrite an arbitrary file by writing to the standard output or standard error. This can be escalated to full root access by rewriting a trusted file such as /etc/shadow or even /etc/sudoers."
The vulnerability, which affects Sudo 1.8.6p7 through 1.8.20 and marked as high severity, has already been patched in Sudo 1.8.20p1, and users are recommended to update their systems to the latest release.
Red Hat yesterday pushed out patches for Red Hat Enterprise Linux 6, Red Hat Enterprise Linux 7, and Red Hat Enterprise Linux Server. Debian has also released fixes for its Wheezy, Jessie and Sid releases and SUSE Linux has rolled out fixes for a number of its products.
Qualys Security said it would publish its Sudoer-to-root exploit once a maximum number of users have had time to patch their systems against the flaw.
Linux Flaw Allows Sudo Users to Gain Root Privileges
1.6.2017 securityweek Vulnerebility
A vulnerability affecting the manner in which Sudo parsed tty information could have resulted in the user gaining root privileges and being able to overwrite any file on the filesystem on SELinux-enabled systems.
Tracked as CVE-2017-1000367, the vulnerability was discovered by Qualys Security in Sudo's get_process_ttyname() for Linux. The issue resides in how Sudo parses tty information from the process status file in the proc filesystem.
The vulnerability could be exploited by a local user with privileges to execute commands via Sudo and could result in the user being able to escalate their privileges to root. Featuring a CVSS3 Base Score of 7.8, the issue is considered High severity.
In their advisory, Qualys Security explains that Sudo's get_process_ttyname() function opens "/proc/[pid]/stat" (man proc) and reads the device number of the tty from field 7 (tty_nr). Although these fields are space-separated, it is possible for field 2 (comm, the filename of the command) to contain spaces, the security researchers explain.
Thus, Sudoer users on SELinux-enabled systems could escalate their privileges to overwrite any file on the filesystem with their command's output, including root-owned files.
To successfully exploit the issue, a Sudo user would have to choose a device number that doesn’t exist under "/dev". Because Sudo performs a breadth-first search of /dev if the terminal isn’t found under the /dev/pts directory, the user could allocate a pseudo-terminal between the two searchers and create a “symbolic link to the newly-created device in a world-writable directory under /dev, such as /dev/shm,” an alert on Sudo reads.
The attacker then uses the file as the command's standard input, output and error when a SELinux role is specified on the sudo command line. If the symbolic link is replaced with another file before Sudo opens it, it allows the overwriting of arbitrary files by writing to the standard output or standard error.
“If SELinux is enabled on the system and Sudo was built with SELinux support, a user with sudo privileges may be able to overwrite an arbitrary file. This can be escalated to full root access by rewriting a trusted file such as /etc/shadow or even /etc/sudoers,” the alert on Sudo reveals.
The issue was found to affect all Sudo versions from 1.8.6p7 through 1.8.20 and was resolved in Sudo 1.8.20p1.
A recently discovered Linux flaw could be exploited by Sudo Users to gain Root Privileges
1.6.2017 securityaffairs Vulnerebility
Security researchers at Qualys Security have discovered a Linux Flaw that could be exploited to escalate privileges and overwrite any file on the filesystem.
Security researchers at Qualys Security have discovered a Linux flaw that could be exploited to gain root privileges and overwrite any file on the filesystem on SELinux-enabled systems.
The high severity flaw, tracked as CVE-2017-1000367, resides in the Sudo’s get_process_ttyname() for Linux and is related to the way Sudo parses tty information from the process status file in the proc filesystem.
The Linux flaw could be exploited by a local user with privileges to execute commands via Sudo and could allow attackers to escalate their privileges to root.
The Sudo’s get_process_ttyname() function opens “/proc/[pid]/stat” (man proc) and reads the device number of the tty from field 7 (tty_nr). These fields are space-separated, the field 2 (comm, the filename of the command) can contain spaces.
Sudoer users on SELinux-enabled systems could escalate their privileges to overwrite any file on the filesystem with their command’s output, including root-owned files.
“We discovered a vulnerability in Sudo’s get_process_ttyname() for Linux: this function opens “/proc/[pid]/stat” (man proc) and reads the device number of the tty from field 7 (tty_nr). Unfortunately, these fields are space-separated and field 2 (comm, the filename of the command) can contain spaces (CVE-2017-1000367).” reads the security advisory. “On an SELinux-enabled system, if a user is Sudoer for a command that does not grant him full root privileges, he can overwrite any file on
the filesystem (including root-owned files) with his command’s output,
because relabel_tty() (in src/selinux.c) calls open(O_RDWR|O_NONBLOCK)
on his tty and dup2()s it to the command’s stdin, stdout, and stderr.
This allows any Sudoer user to obtain full root privileges.”
To exploit the issue, a Sudo user would have to choose a device number that doesn’t exist under “/dev”. If the terminal isn’t present under the /dev/pts directory when the Sudo performs a breadth-first search of /dev, the user could allocate a pseudo-terminal between the two searchers and create a “symbolic link to the newly-created device in a world-writable directory under /dev, such as /dev/shm,”
“Exploiting the bug requires that the user already have sudo privileges. SELinux must also be enabled on the system and sudo must have been built with SELinux support.
To exploit the bug, the user can choose a device number that does not currently exist under /dev. If sudo does not find the terminal under the /dev/pts directory, it performs a breadth-first search of /dev. It is possible to allocate a pseudo-terminal after sudo has checked /dev/pts but before sudo performs its breadth-first search of /dev. The attacker may then create a symbolic link to the newly-created device in a world-writable directory under /dev, such as /dev/shm.” read a Sudo alert.
linux flaw
“This file will be used as the command’s standard input, output and error when an SELinux role is specified on the sudo command line. If the symbolic link under /dev/shm is replaced with a link to an another file before it is opened by sudo, it is possible to overwrite an arbitrary file by writing to the standard output or standard error. This can be escalated to full root access by rewriting a trusted file such as /etc/shadow or even /etc/sudoers.”
The Linus flaw affects all Sudo versions from 1.8.6p7 through 1.8.20, the Sudo 1.8.20p1 fixes it, the issue was rated with a CVSS3 Base Score of 7.8.
Chrome design flaw allows sites to record Audio/Video without indication
1.6.2017 securityaffairs Vulnerebility
A developer has discovered a flaw in the Chrome browser that could be exploited to secretly Record Audio/Video without indication.
The AOL developer Ran Bar-Zik discovered a disconcerting vulnerability in Google’s Chrome browser could be exploited by attackers to record audio or video without giving any visual notification or alert.
“After getting the audio\video usage permissions for WebRTC. JS code can record video\audio without showing the graphical red dot in the tab when the record process is running. i.e. – after the permission is given the site can listen to the user whenever he want to. It is done because JS `window.open` method does not give visual indication on record init. ” reads the security advisory.
Web browser based audio-video communications use WebRTC (Web Real-Time Communications) protocol to enable real-time communication over peer-to-peer connections without the use of plugins.
However, to protect unauthorised streaming of audio and video without user’s permission, the web browser first request users to explicitly allow websites to use WebRTC and access device the camera and the microphone installed on the host. Once granted, a website will have the access to both camera and microphone until the user will explicitly revoke WebRTC permissions.
Modern browsers notify users when audio or video is being recorded in order to prevent abuses even by previously ‘authorised’ websites.
In Google Chrome, users are notified with a red dot icon that appears on the tab.
“Activating this API will alert the user that the audio or video from one of the devices is being captured. Chrome and Firefox implemented this alert (Recording media is not available in Edge yet).” Bar-Zik wrote on a Medium blog post. “This record indication is the last and the most important line of defense. The general video\audio device permission is required one time only and user can err and grant it by mistake. Once you granted it, that’s it. The record alert is given on ANY stream record usage and will prevent any record without the user knowledge. “
The researcher discovered that new HTML5 video\audio API has privacy issues on desktop Chrome allowing to hackers to use the PC as a surveillance device.
The expert demonstrated that after granting the general access from the user it is possible to activate the MediaRecorder from a headless window opened.
chrome hacking
“Developers can exploit small UX manipulation to activate the MediaRecorder API without alerting the users. The process is quite simple.” reads the analsysis shared by the expert. “After granting the general access from the user — Open a headless window and activate the MediaRecorder from that window. In Chrome there will be no visual record indication.”
The issue is related to a design flaw in Chrome that doesn’t display a red-dot indication on headless windows, allowing site developers to “exploit small UX manipulation to activate the MediaRecorder API without alerting the users.”
Bar-Zik also published a proof-of-concept (PoC) code and a demo website that asks the user for permission to use WebRTC, opens a pop-up, and then records 20 seconds of audio without giving any indication to the user.
The demo website has two buttons on a page, the first one is used to ask the device permission like many websites on the web. The second button launches the attack, after 30 seconds users can download MP3.
In a real attack, hackers can use very small pop-under and submit the data anywhere and close it when the user is focusing on it.
“It can use very small pop-under and submit the data anywhere and close it when the user is focusing on it. It can use the camera for millisecond to get your picture. It can (In theory) use XSS to ride on legitimate sites and their permissions.” Bar-Zik concluded.
The reported design issue affects Google Chrome, we cannot exclude its presence also in the implementation of other web browsers. The researcher reported the bug to Google on April 10, 2017, but the company doesn’t classify the issue as a security vulnerability.
it plans to fix the issue in the future, but not immediately.
“This isn’t really a security vulnerability – for example, WebRTC on a mobile device shows no indicator at all in the browser,” a Chromium member replied to the report. “The dot is a best-first effort that only works on the desktop when we have chrome UI space available. That being said, we are looking at ways to improve this situation.”
To protect your PC disable the WebRTC.
Vendors Investigating Impact of Samba Vulnerability
31.5.2017 securityweek Vulnerebility
Companies that provide network-attached storage (NAS) appliances, routers and other types of networking devices have started investigating the impact of a recently disclosed Samba vulnerability on their products.
Updates released last week for Samba, the software suite that provides file and print sharing capabilities between Windows and Unix computers, address a remote code execution flaw (CVE-2017-7494) that affects all versions of the product since 3.5.0, released in March 2010. The fix is included in Samba versions 4.6.4, 4.5.10 and 4.4.14, and a workaround has been made available for unsupported versions.
The security hole can be exploited by a malicious client to upload a shared library to a writable share, and then cause the server to load and execute that library.
While some have compared the vulnerability to the SMB weakness exploited in the recent WannaCry ransomware attacks – due to the fact that one of the protocols implemented by Samba is SMB – others believe CVE-2017-7494 is not as dangerous and there have been no reports of attacks in the wild.
On the other hand, proof-of-concept (PoC) exploits have been released and Rapid7 has identified roughly 110,000 Internet-connected devices running vulnerable versions of Samba.
Samba is used in many products, including routers, NAS systems, servers and IoT devices, and several vendors have already started releasing patches and workarounds.
Cisco has so far only identified two vulnerable products: the Cisco Network Analysis Module and the Cisco Video Surveillance Media Server. The list of products still under investigation includes routers, network and content security, unified computing, communications, and video and telepresence solutions.
NETGEAR informed customers that CVE-2017-7494 affects all its ReadyNAS, all ReadyDATA, and several C, R and N series routers. The company has already released firmware fixes for ReadyNAS 6.x. Until patches become available for other devices, users have been advised to disable write access to shared drives, and remove any USB storage devices connected to their routers or gateways.
QNAP and Synology have also started releasing patches for their affected products, but WD does not appear to have published any security advisories, despite several forum posts on this topic.
Veritas has informed customers that it’s working on patches for its NetBackup Appliances. NetApp has determined that the Samba vulnerability only affects its StorageGRID products, for which the company has released workarounds.
Sophos and F5 Networks told users that their products are not vulnerable to attacks exploiting this flaw.
Chrome Flaw Allows Sites to Secretly Record Audio/Video Without Indication
30.5.2017 thehackernews Vulnerebility
Websites On Chrome Can Secretly Record Audio/Video Without Indication
What if your laptop is listening to everything that is being said during your phone calls or other people near your laptop and even recording video of your surrounding without your knowledge?
Sounds really scary! Isn't it? But this scenario is not only possible but is hell easy to accomplish.
A UX design flaw in the Google's Chrome browser could allow malicious websites to record audio or video without alerting the user or giving any visual indication that the user is being spied on.
AOL developer Ran Bar-Zik reported the vulnerability to Google on April 10, 2017, but the tech giant declined to consider this vulnerability a valid security issue, which means that there is no official patch on the way.
How Browsers Works With Camera & Microphone
Before jumping onto vulnerability details, you first need to know that web browser based audio-video communication relies on WebRTC (Web Real-Time Communications) protocol – a collection of communications protocols that is being supported by most modern web browsers to enable real-time communication over peer-to-peer connections without the use of plugins.
However, to protect unauthorised streaming of audio and video without user's permission, the web browser first request users to explicitly allow websites to use WebRTC and access device camera/microphone.
Once granted, the website will have access to your camera and microphone forever until you manually revoke WebRTC permissions.
In order to prevent 'authorised' websites from secretly recording your audio or video stream, web browsers indicate their users when any audio or video is being recorded.
"Activating this API will alert the user that the audio or video from one of the devices is being captured," Bar-Zik wrote on a Medium blog post. "This record indication is the last and the most important line of defense."
In the case of Google Chrome, a red dot icon appears on the tab, alerting users that the audio or video streaming is live.
How Websites Can Secretly Spy On You
The researcher discovered that if any authorised website pop-ups a headless window using a JavaScript code, it can start recording audio and video secretly, without the red dot icon, giving no indications in the browser that the streaming is happening.
"Open a headless window and activate the MediaRecorder from that window. In Chrome there will be no visual record indication," Bar-Zik said.
This happens because Chrome has not been designed to display a red-dot indication on headless windows, allowing site developers to "exploit small UX manipulation to activate the MediaRecorder API without alerting the users."
Bar-Zik also provided a proof-of-concept (PoC) code for anyone to download, along with a demo website that asks the user for permission to use WebRTC, launches a pop-up, and then records 20 seconds of audio without giving any visual indication.
All you need to do is click on two buttons to allow the website to use WebRTC in the browser. The demo records your audio for 20 seconds and then provides you a download link for the recorded file.
"Real attack will not be very obvious of course. It can use very small pop-under and submit the data anywhere and close it when the user is focusing on it. It can use the camera for millisecond to get your picture," Bar-Zik said. "In Mobile, there is not such visual indication."
The reported flaw affects Google Chrome, but it may affect other web browsers as well.
It's Not A Flaw, Says Google; So No Quick Patch!
Bar-Zik reported the security issue to Google on April 10, 2017, but the company doesn't consider this as a valid security vulnerability. However, it agrees to find ways to "improve the situation" in the future.
"This isn't really a security vulnerability – for example, WebRTC on a mobile device shows no indicator at all in the browser," a Chromium member replied to the researcher's report.
"The dot is a best-first effort that only works on the desktop when we have chrome UI space available. That being said, we are looking at ways to improve this situation."
Google consider this a security vulnerability or not, but the bug is surely a privacy issue, which could be exploited by hackers to potentially launch more sophisticated attacks.
In order to stay on the safer side, simply disable WebRTC which can be done easily if you don't need it. But if you require the feature, allow only trusted websites to use WebRTC and look for any other windows that it may spawn afterward on top of that.
Edward Snowden leaks also revealed Optic Nerve – the NSA's project to capture webcam images every 5 minutes from random Yahoo users. In just six months, 1.8 Million users' images were captured and stored on the government servers in 2008.
Following such privacy concerns, even Facebook CEO Mark Zuckerberg and former FBI director James Comey admitted that they put tape on their laptops just to be on the safer side.
Although putting a tape over your webcam would not stop hackers or government spying agencies from recording your voice, at least, it would prevent them from watching or capturing your live visual feeds.
Vulnerabilities Patched in Aruba Access Policy Platform
30.5.2017 securityweek Vulnerebility
HPE-owned network access solutions provider Aruba informed customers last week that the company’s ClearPass Policy Manager access policy platform is affected by several vulnerabilities.
The most serious of the flaws, based on its CVSS score, is a high severity unauthenticated remote code execution vulnerability tracked as CVE-2017-5824. Another high severity issue is an information disclosure bug (CVE-2017-5647) affecting Apache Tomcat.
The other security holes, classified as medium and low severity, include authenticated remote code execution (CVE-2017-5826), reflected XSS (CVE-2017-5827), privilege escalation (CVE-2017-5825), arbitrary command execution via XXE (CVE-2017-5828), and access restriction bypass issues (CVE-2017-5829).
The vulnerabilities affect all ClearPass Policy Manager versions prior to 6.6.5. Users have been advised to update the product to version 6.6.5 and apply an additional hotfix made available on May 24.
A majority of these vulnerabilities were reported by Luke Young and V. Harishkumar through the company’s Bugcrowd-powered private bug bounty program. The XSS flaw was reported by Phil Purviance of Bishop Fox.
Aruba has been running a private bug bounty program since October 2014 and by the end of 2016 it had already received more than 500 vulnerability reports from 67 researchers. The company has offered up to $1,500 per bug.
In addition to the advisory describing ClearPass Policy Manager flaws, Aruba informed customers last week of a high severity remote code execution vulnerability affecting Airwave Software Glass versions 1.0.0 and 1.0.1. The weakness, tracked as CVE-2017-8946, has been addressed in version 1.0.1-1.
Microsoft Patches Several Malware Protection Engine Flaws
30.5.2017 securityweek Vulnerebility
Microsoft Fixes Several Antimalware Engine Vulnerabilities Found by Google Researchers
Microsoft has released an out-of-band update for its Malware Protection Engine to patch several remote code execution and denial-of-service (DoS) vulnerabilities discovered by Google Project Zero researchers.
Version 1.1.13804.0 of the Microsoft Malware Protection Engine, released on Thursday, addresses a total of eight vulnerabilities identified by various members of Google Project Zero, including Mateusz Jurczyk, Tavis Ormandy, Lokihart and Ian Beer.
Jurczyk has been credited for finding four of the security holes, namely CVE-2017-8536, CVE-2017-8538, CVE-2017-8537 and CVE-2017-8535. The researcher used fuzzing to find heap-based buffer overflow, NULL pointer dereference and other memory corruption vulnerabilities that can lead to arbitrary code execution or a crash of the Malware Protection Engine (MsMpEng) service.
On Friday, after learning of Microsoft’s update for the antimalware engine, Jurczyk published an advisory containing some technical information and proof-of-concept (PoC) code. Ormandy and Beer also made public advisories, including PoC code, for vulnerabilities patched in the latest version of the Malware Protection Engine.
According to Microsoft, the vulnerabilities exist due to the fact that the antimalware engine does not properly scan specially crafted files. An attacker can exploit them for remote code execution and DoS attacks by getting the engine to scan a malicious file, which can be accomplished via several methods.
“For example, an attacker could use a website to deliver a specially crafted file to the victim's system that is scanned when the website is viewed by the user,” Microsoft said. “An attacker could also deliver a specially crafted file via an email message or in an Instant Messenger message that is scanned when the file is opened. In addition, an attacker could take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server.”
The vulnerabilities affect several Microsoft products that use the antimalware engine, including Windows Defender, Exchange Server, Windows Intune Endpoint Protection, Security Essentials, Endpoint Protection and Forefront Endpoint Protection. Users of these products do not have to take any action as the update has been applied automatically.
While Microsoft and Google have had some problems when it comes to vulnerability disclosures – Google Project Zero disclosed the details of several flaws in the past before patches were made available – Microsoft has been moving quickly to resolve Malware Protection Engine issues.
Earlier this month, it took the company less than three days to patch a critical remote code execution vulnerability found by Ormandy and Google Project Zero researcher Natalie Silvanovich. The flaws disclosed by Google last week were reported to Microsoft on May 12 and May 16.
Ormandy recently made available a tool for porting Windows dynamic link library (DLL) files to Linux in an effort to improve fuzzing. He demonstrated the tool’s capabilities by porting the Malware Protection Engine to Linux.
Porting the antimalware engine to Linux has made it easier for Google Project Zero researchers to conduct fuzzing and find vulnerabilities.
FreeRADIUS allows hackers to log in without credentials
30.5.2017 securityaffairs Vulnerebility
The security researcher Stefan Winter has discovered a TLS resumption authentication bypass in FreeRADIUS, the world’s most popular RADIUS Server.
The security researcher Stefan Winter from the Luxembourg’s high-speed academic network RESTENA has discovered a FreeRADIUS TLS resumption authentication bypass.
FreeRADIUS is the world’s most popular RADIUS Server, “it is the basis for multiple commercial offerings. It supplies the AAA needs of many Fortune-500 companies and Tier 1 ISPs. It is also widely used for Enterprise Wi-Fi and IEEE 802.1X network security, particularly in the academic community, including eduroam.”
FreeRADIUS
The flaw, tracked as CVE-2017-9148, resides in the TTLS and PEAP implementations that skip inner authentication when handles a resumed TLS connection.
“The implementation of TTLS and PEAP in FreeRADIUS skips inner authentication when it handles a resumed TLS connection. This is a feature but there is a critical catch: the server must never allow resumption of a TLS session until its initial connection gets to the point where inner authentication has been finished successfully. Unfortunately, affected versions of FreeRADIUS fail to reliably prevent resumption of unauthenticated sessions unless the TLS session cache is” reads the description published in the advisory states. “disabled completely and allow an attacker (e.g. a malicious supplicant) to elicit EAP Success without sending any valid credentials.”
Communications interruptions are very frequent, for example when a user on a TLS connection moves from one cell tower to another, and in due to the flaw it isn’t asked for a new login.
The versions affected by the CVE-2017-9148 flaw are:
2.2.x (EOL but still found in some Linux distros): All versions.
3.0.x (stable): All versions before 3.0.14.
3.1.x and 4.0.x (development): All versions before 2017-02-04.
Sysadmins that works with FreeRADIUS installs need to upgrade to the version 3.0.14 that fixed the issue, temporary mitigation could be obtained by disabling the TLS session caching.
The advisory suggested the following mitigation actions
(a) Disable TLS session caching. Set enabled = no in the cache subsection of eap module settings (raddb/mods-enabled/eap in the standard v3.0.x-style layout).
(b) Upgrade to version 3.0.14.
Giving a look at the timeline of the flaw we can notice that is was also independently reported April 24, 2017, by the researchers Luboš Pavlíèek from the University of Economics, Prague.
Microsoft silently patched a second critical Malware Protection Engine flaw
29.5.2017 securityaffairs Vulnerebility
Microsoft silently patched a second critical vulnerability in its Malware Protection Engine that was discovered on May 12.
Microsoft has patched the critical vulnerability in its Malware Protection Engine that was discovered on May 12 by the researchers at the Google’s Project Zero team.
The vulnerability could be exploited by an attacker that has crafted an executable that when processed by the Malware Protection Engine’s emulator could trigger the RCE flaw.
On May 9, Google’s Project Zero discovered another flaw, tracked as CVE-2017-0290, that was fixed with an emergency patch released just three days after its disclosure.
According to the Project Zero researcher Tavis Ormandy, unlike the CVE-2017-0290 vulnerability, this bug was a silent fix. Ormandy privately disclosed the vulnerability to Microsoft.
Follow
Tavis Ormandy ✔ @taviso
There is an undocumented opcode in the MsMpEng x86 emulator that can access internal emulator commands ¯\_(ツ)_/¯ https://bugs.chromium.org/p/project-zero/issues/detail?id=1260 …
7:12 PM - 25 May 2017
475 475 Retweets 641 641 likes
Twitter Ads info & Privacy
“MsMpEng includes a full system x86 emulator that is used to execute any untrusted files that look like PE executables. The emulator runs as NT AUTHORITY\SYSTEM and isn’t sandboxed,” Ormandy wrote. “Browsing the list of win32 APIs that the emulator supports, I noticed ntdll!NtControlChannel, an ioctl-like routine that allows emulated code to control the emulator.” reads the security advisory.
Malware Protection Engine flaw
The vulnerability recently patched is tied to the way the emulator processes files, meanwhile, the previous one was affecting the MsMpEng’s JavaScript interpreter.
The attacker can exploit the vulnerability to execute a number of control commands.
“Command 0x0C allows allows you to parse arbitrary-attacker controlled RegularExpressions to Microsoft GRETA (a library abandoned since the early 2000s). This library is not safe to process untrusted Regex, a testcase that crashes MsMpEng attached. Note that only packed executables can use RegEx, the attached sample was packed with UPX. ¯\_(ツ)_/¯
Command 0x12 allows you to load additional “microcode” that can replace opcodes. At the very least, there is an integer overflow calculating number of opcodes provided (testcase attached). You can also redirect execution to any address on a “trusted” page, but I’m not sure I understand the full implications of that.
Various commands allow you to change execution parameters, set and read scan attributes and UFS metadata (example attached). This seems like a privacy leak at least, as an attacker can query the research attributes you set and then retrieve it via scan result.” reads the advisory.
The vulnerability is difficult to exploit, even if MsMpEng isn’t sandboxed, many applications are sandboxed, this implies that the attacker needs to evade the sandbox to trigger the issue.
According to Ormandy, the emulator component emulates the client’s CPU, but Microsoft has given it an extra instruction that allows API calls. The hackers highlighted he was surprised finding a special set of instructions for the emulator.
Microsoft did not publish any security advisory for this vulnerability.
FileSystem NTFS Bug Crashes Windows 7 and Windows 8.1
29.5.2017 securityaffairs Vulnerebility
A FileSystem NTFS Bug could be exploited to crash Windows 7 and Windows 8.1, using Chrome browser you can avoid problems.
Until Microsoft patches this problem, use Chrome: a slip in file-path handling allows an attacker to crash Windows 7 and Windows 8.1 with a file call.
A bug in the way Microsoft handle file-path could be exploited by attackers to crash Windows 7 and Windows 8.1 with a simple file call.
The vulnerability is triggered everytime a file call includes the Windows’ Master File Table, for example, if the attackers include $MFT as a link to an image in a website.
The Russian expert “Anatolymik” of Alladin Information Security first reported the issue. he discovered it debugging and reverse engineering the NTFS driver.

Every file on an NTFS volume has a reference in the MFT, for this reason, the OS must protect $MFT from user-access. The Russian researcher discovered that if you try to access a file like
c:\$MFT\foo
the NT file system (NTFS) locks $MFT and simply doesn’t release it.
“When the attempt is made to open the file with respect to $ mft file, NtfsFindStartingNode function does not find it, because This function searches a little differently, unlike NtfsOpenSubdirectory function that finds the file at all times.” reads the desciption of the problem published by the expert.
“Consequently, the work cycle begins, starting with the root filesystem. Next NtfsOpenSubdirectory function opens the file and take him ERESOURCE monopoly. On the next iteration of the loop detects that the file is not a directory, and thus interrupt his job with an error. And at the conclusion of its work function by NtfsCommonCreate NtfsTeardownStructures function tries to close it. Function NtfsTeardownStructures, in turn, face the fact that she will not be able to close the file because it opens the file system itself when mounting. At the same time, contrary to expectations NtfsCommonCreate function, NtfsTeardownStructures function frees ERESOURCE $ mft file. Thus, it will be captured forever.”
According to Bleeping Computer, users who have tested the issue have noticed that the bug cannot be triggered in Chrome because the Google browser will not allow loading images with malformed paths, such as the $MFT exploit.
“According to users that have tested the bug and commented on Anatolymik’s blog post, Chrome will refuse to load images with malformed paths, such as the $MFT exploit.” states the blog post published on Bleeping Computer.
“Nonetheless, Bleeping Computer confirmed that the $MFT bug causes a Windows 7 installation to hang via Internet Explorer and Firefox.”
This NTFS bug is very similar to another file path vulnerability discovered in 1990s when you could trigger system crash with the “C:/con/con” bug. The bug affecting Windows 95 and Windows 98 systems.
Thousands of Third-Party Library Flaws Put Pacemakers at Risk
26.5.2017 securityweek Vulnerebility
Researchers have conducted a detailed analysis of pacemaker systems from four major vendors and discovered many potentially serious vulnerabilities.
The fact that implantable cardiac devices such as pacemakers and defibrillators are vulnerable to hacker attacks has been known for years, and while steps have been taken to address issues, security experts still report finding flaws in these products.
WhiteScope, a company founded by Billy Rios, one of the first security researchers to analyze medical devices, recently conducted an analysis of the implantable cardiac device ecosystem architecture and implementation interdependencies, with a focus on pacemakers.
Pacemaker vulnerabilities
The analysis covered home monitoring systems, implantable devices, pacemaker programmers, and the patient support networks of four vendors. Researchers investigated each type of device and the communications between them.
Tests conducted on devices acquired from eBay showed that reverse engineering their firmware is made easy by the fact that many of them use commercial, off-the-shelf microprocessors.
In the case of home monitoring devices, researchers discovered data sheets publicly available on the Internet, allowing attackers to determine how they work and how they can be manipulated. Firmware reverse engineering is also made easy by the lack of packing, obfuscation and encryption.
Debugging functionality present in implanted devices also exposes firmware. Malicious actors could leverage these features to gain privileged access to home monitoring devices and the pacemaker programmers used by physicians to diagnose and program the actual cardiac devices.
WhiteScope has analyzed four pacemaker programmers and found that they use more than 300 third-party libraries. Of these components, 174 are known to have a total of more than 8,000 vulnerabilities.
“Despite efforts from the FDA to streamline routine cybersecurity updates, all programmers we examined had outdated software with known vulnerabilities,” Rios said in a blog post. “We believe that this statistic shows that the pacemaker ecosystem has some serious challenges when it comes to keeping systems up-to-date. No one vendor really stood out as having a better/worse update story when compared to their competitors.”
In some cases, researchers found unencrypted patient data stored on the programmers, including SSNs, names, phone numbers and medical information. Since these programmers typically use removable storage drives, it’s easy for a local attacker to mount the drive and extract the entire file system.
Another potential problem is the fact that programmers do not require any type of authentication for programming implantable cardiac devices.
The list of security holes found by experts in home monitoring devices includes the failure to map the firmware to protected memory, firmware updates not digitally signed or protected against man-in-the-middle (MitM) attacks, hardcoded credentials, unsecured external USB connections, and the usage of universal authentication tokens for pairing with the implanted device.
The vendors have not been named and the details of the vulnerabilities found by WhiteScope have not been disclosed to the public, but they have been reported to ICS-CERT, which will likely alert affected companies.
Samba Patches Code Execution Flaw Introduced in 2010
25.5.2017 securityweek Vulnerebility
The developers of the Samba interoperability software suite announced on Wednesday the availability of security updates that patch a serious remote code execution vulnerability. Researchers have warned that there are many vulnerable systems accessible directly from the Internet.
The flaw, tracked as CVE-2017-7494, affects all versions of Samba since 3.5.0, released in March 2010. The security hole has been addressed in versions 4.6.4, 4.5.10 and 4.4.14, and a workaround has been made available for unsupported versions.
According to Samba maintainers, the vulnerability allows a malicious client to upload a shared library to a writable share, and cause the server to load and execute that file.
The vulnerability exposes various types of systems to attacks, including Linux and network-attached storage (NAS) devices. Rapid7 has warned that many users may not even realize that their systems are running Samba.
Samba provides file and print sharing capabilities between Windows and Unix computers, and it implements many protocols, including SMB, which malicious actors leveraged in the recent WannaCry ransomware attacks. This has led some experts to believe that CVE-2017-7494 could also be exploited for similar worm attacks.
“Unlike SMB, Samba exists on a wide variety of systems from different makers - servers, laptops, home routers, network storage systems, media servers, and many IoT devices. And unlike Windows, those devices may not automatically install an update - even if the manufacturer provides one,” researcher David Longenecker said in a blog post.
Exploiting the vulnerability is easy and proof-of-concept (PoC) code has already been made public, which could lead to in-the-wild attacks. HD Moore, VP of research and development at Atredis, has created a Metasploit module for CVE-2017-7494 and showed how the flaw can be exploited on Ubuntu and a Synology NAS product.
Follow
HD Moore @hdmoore
Re: Samba bug, the metasploit one-liner to trigger is just: simple.create_pipe("/path/to/target.so")
8:23 PM - 24 May 2017
231 231 Retweets 243 243 likes
Twitter Ads info & Privacy
A scan conducted by Rapid7 with its Project Sonar showed more than 104,000 Internet-exposed endpoints running a vulnerable version of Samba, and nearly 90 percent of these systems had been running outdated versions of the software.
Individuals and organizations that still use older versions of Samba can prevent attacks by adding the parameter “nt pipe support = no” to the global section of their smb.conf file. RedHat also pointed out that the SELinux security module blocks potential exploits.
CVE-2017-7494 Samba vulnerability, patch your installation now!
25.5.2017 securityaffairs Vulnerebility
A seven-year-old remote code execution vulnerability, tracked as CVE-2017-7494, affects all versions of the Samba software since 3.5.0.
A seven-year-old remote code execution vulnerability affects all versions of the Samba software since 3.5.0. The flaw has been patched by the development team of the project. An attacker can exploit the CVE-2017-7494 RCE to upload a shared library to a writable share, and then cause the server to load and execute it.
The popular CVE-2017-7494 flaw can be easily exploited, just a line of could be used for the hack under specific conditions:
make file- and printer-sharing port 445 reachable on the Internet,
configure shared files to have write privileges.
use known or guessable server paths for those files.
Follow
HD Moore @hdmoore
Re: Samba bug, the metasploit one-liner to trigger is just: simple.create_pipe("/path/to/target.so")
8:23 PM - 24 May 2017
231 231 Retweets 243 243 likes
Twitter Ads info & Privacy
Those requirements include vulnerable computers that (a) make file- and printer-sharing port 445 reachable on the Internet, (b) configure shared files to have write privileges, and (c) use known or guessable server paths for those files. When those conditions are satisfied, remote attackers can upload any code of their choosing and cause the server to execute it, possibly with unfettered root privileges, depending on the vulnerable platform.
“All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it.” reads the security advisory issued by Samba.
The announcement published by Samba informed users that a patch addressing this remote code execution vulnerability tracked as CVE-2017-7494 was available at the following URL:
http://www.samba.org/samba/security/
Sysadmins have to patch their versions as soon as possible, if it is not possible for any reason a workaround can be implemented by the adding the line
nt pipe support = no
to their Samba configuration file and restarting the network’s SMB daemon.
The change will limit clients from accessing some network computers.
“Additionally, Samba 4.6.4, 4.5.10 and 4.4.14 have been issued as security releases to correct the defect. Patches against older Samba versions are available at http://samba.org/samba/patches/. Samba vendors and administrators running affected versions are advised to upgrade or apply the patch as soon as possible.”
The Samba bug appears to be a network wormable issue that could be exploited by a malicious code to self-replicate from vulnerable machine to vulnerable machine without requiring user interaction.
Hurry up, the exploit for the Samba bug is expected to be available in the days for the Metasploit framework.
HD Moore, who is vice president of research and development at Atredis Partners, posted the following images showing successful exploits against Samba on a computer running Ubuntu and NAS device made by Synology.

HD Moore @hdmoore
Examples of exploiting Samba CVE-2017-7494 on Ubuntu 16.04 and a Synology NAS. Metasploit module should be PRd sometime in the next 24 hours
11:20 PM - 24 May 2017
469 469 Retweets 387 387 likes
Twitter Ads info & Privacy
ubuntu samba exploit
The first crack at a Metasploit PR for Samba CVE-2017-7494 already appeared on GitHub.
Follow
HD Moore @hdmoore
First crack at a Metasploit PR for Samba CVE-2017-7494: https://github.com/rapid7/metasploit-framework/pull/8450 …
2:50 AM - 25 May 2017
Photo published for First crack at Samba CVE-2017-7494 by hdm · Pull Request #8450 · rapid7/metasploit-framework
First crack at Samba CVE-2017-7494 by hdm · Pull Request #8450 · rapid7/metasploit-framework
This PR contains a module for the Samba arbitrary module loading vulnerability. It also includes support for x86 and ARMLE elf-so template formats. This has been extensively tested against an updat...
github.com
171 171 Retweets 161 161 likes
7-Year-Old Samba Flaw Lets Hackers Access Thousands of Linux PCs Remotely
25.5.2017 thehackernews Vulnerebility
A 7-year-old critical remote code execution vulnerability has been discovered in Samba networking software that could allow a remote attacker to take control of an affected Linux and Unix machines.
Samba is an open-source software (re-implementation of SMB networking protocol) that runs on the majority of operating systems available today, including Windows, Linux, UNIX, IBM System 390, and OpenVMS.
Samba allows non-Windows operating systems, like GNU/Linux or Mac OS X, to share network shared folders, files, and printers with Windows operating system.
The newly discovered remote code execution vulnerability (CVE-2017-7494) affects all versions newer than Samba 3.5.0 that was released on March 1, 2010.
"All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it," Samba wrote in an advisory published Wednesday.
Linux version of EternalBlue Exploit?
According to the Shodan computer search engine, more than 485,000 Samba-enabled computers exposed port 445 on the Internet, and according to researchers at Rapid7, more than 104,000 internet-exposed endpoints appeared to be running vulnerable versions of Samba, out of which 92,000 are running unsupported versions of Samba.
Since Samba is the SMB protocol implemented on Linux and UNIX systems, so some experts are saying it is "Linux version of EternalBlue," used by the WannaCry ransomware.
...or should I say SambaCry?
Keeping in mind the number of vulnerable systems and ease of exploiting this vulnerability, the Samba flaw could be exploited at large scale with wormable capabilities.
Home networks with network-attached storage (NAS) devices could also be vulnerable to this flaw.
Exploit Code Released! (Bonus: Metasploit Module)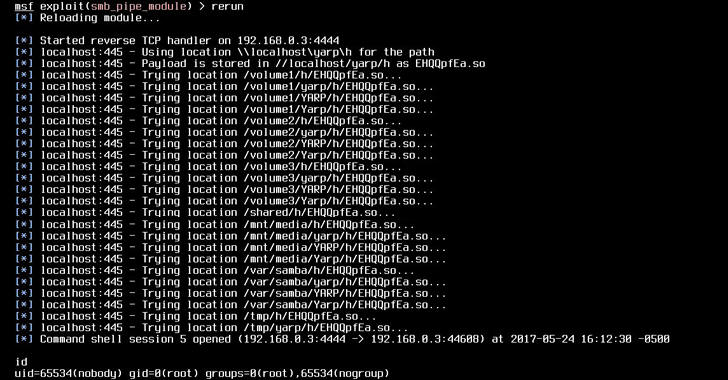
The flaw actually resided in the way Samba handled shared libraries. A remote attacker could use this Samba arbitrary module loading vulnerability to upload a shared library to a writable share and then cause the server to load and execute malicious code.
The vulnerability is hell easy to exploit. Just one line of code is required to execute malicious code on the affected system.
simple.create_pipe("/path/to/target.so")
However, the Samba exploit has already been ported to Metasploit, a penetration testing framework, enabling researchers as well as hackers to exploit this flaw easily.
Patch and Mitigations
The maintainers of Samba has already patched the issue in their new versions Samba versions 4.6.4/4.5.10/4.4.14, and are urging those using a vulnerable version of Samba to install the patch as soon as possible.
But if you can not upgrade to the latest versions of Samba immediately, you can work around the vulnerability by adding the following line to your Samba configuration file smb.conf:
nt pipe support = no
Once added, restart the network's SMB daemon (smbd) and you are done. This change will prevent clients from fully accessing some network machines, as well as disable some expected functions for connected Windows systems.
While Linux distribution vendors, including Red Hat and Ubuntu, have already released patched versions for its users, the larger risk is that from NAS device consumers that might not be updated as quickly.
Craig Williams of Cisco said that given the fact that most NAS devices run Samba and have very valuable data, the vulnerability "has potential to be the first large-scale Linux ransomware worm."
Update: Samba maintainers have also provided patches for older and unsupported versions of Samba.
Meanwhile, Netgear released a security advisory for CVE-2017-7494, saying a large number of its routers and NAS product models are affected by the flaw because they use Samba version 3.5.0 or later.
However, the company currently released firmware fixes for only ReadyNAS products running OS 6.x.
The NAND Busters Data Storage Chips Vulnerable to Attack
25.5.2017 securityaffairs Vulnerebility
Experts found that NAND Data Storage Chips are vulnerable to malicious programs which can corrupt data and even destroy them over time.
Researchers at Carnegie Mellon University, Seagate Technology and Swiss Federal Institute of Technology in Zürich have uncovered a potential flaw in the storage devices that power most cell phones, computers and big data centers around the world. The researchers found that the special chip arrays used to store information are vulnerable to malicious programs which can corrupt data and even destroy the chips over time.
NAND flash memory chips installed on a board array are called solid-state drives (SSDs). The SSDs have all but replaced the venerable magnetic disk hard drives, allowing manufacturers to reduce the size and weight of electronic devices. NAND flash memory chips are found inside most of the current state of the art electronics and often occupy space in our pockets from portable phones, cameras, and USB drives. They are also the heart of massive data centers that power the cloud, holding vast amounts of data for individuals, major corporations, and government.
A key feature of the NAND flash chip is its ability to store a charge without power. The NAND chip contains billions of cells each with different electrical charges which represent the binary ones and zeros that make up data. They are also controlled by an internal architecture which is designed to keep all that data in order. The researchers, working with the assistance of Intel and Seagate, found that the cells inside each chip can be corrupted by programs which abuse the sub-scale electronics and can eventually render them useless.
NAND attacks
Once such exploit discovered by the researchers is a program that rapidly writes, reads and resets data inside a NAND storage chip. The attacker repeatedly performs this series of attacks against individual chip cells holding the binary ones and zeros, causing them to overload and generate interference against other nearby “victim” cells inside the chip. The result is a phenomenon called “Parasitic Capacitance Coupling” which changes the voltage in adjacent memory cells and thereby changes the value of the data stored inside them. The attacker can alter the data stored in targeted victim cells thus data stored by other programs is now corrupted.
As chips become smaller and more powerful, the space between the electronic connections and memory cells has been reduced as well. The fact that these electronic connections are in some cases only a few molecules apart is like having bare copper wires carrying voltage lying next to each other. They often do not have to touch to create disturbance in other nearby components.
This type of interference attack has been described to be similar to a “Row hammer” attack used against the more familiar RAM (Random Access Memory) chips inside computers, where an attacker bombards a row of memory cells in repeated read-write operations, causing electrical interference that changes the values of nearby cells.
“Row hammer” attacks are deliberately introduced interference using software programs. However, Nature can also cause similar errors inside storage memory chips operating under harsh conditions. For example, solar flares and intense radiation have been known to induce the cells inside computer chips – both RAM and Flash – to change values.
Special programming techniques and manufacturing processes called “RAD” hardening had to be introduced for chips installed inside satellites, military equipment, space craft and nuclear reactors to prevent “bit flipping”, changing cell values induced by the Electro-Magnetic Pulse (EMP) of solar flares, and radiation.
According to the researchers, a malicious program can re-create the same kind of EMP electronic interference on a sub-scale. They discovered that such software can take advantage of the NAND chip design and structure to work around safeguards to target specific cells.
While The NAND memory chip can compensate for damaged cells, as more and more cells are attacked, the chip eventually becomes useless and is unable to reliably store information. The attack can dramatically reduce the useable lifetime of the chip, forcing it to be replaced. This replacement process usually would require and entire board or bank of chips to be replaced in high-end applications such as cloud memory, an expensive and time-consuming process.
However, unlike massive cloud and computer storage arrays, the NAND flash memory chips inside consumer devices are usually not replaceable. The malicious software attack could force an entire device to be replaced such as a cell phone, notepad computer or Internet of Things device.
Researchers also discovered a second method of attack called “Read Disturb”. The attack is characterized by a malicious application to quickly perform a large number of reads in a very short amount of time, to induce “Read Disturb” errors that corrupt both data already written to the chip and data that have yet to be written. The basic concept is to corrupt unwritten blocks or cells which are not managed by the chip structure programming. The result is the un-used data cells are corrupted and cannot be repaired because they are outside of the chip management and control.
While the second level of attack does not disrupt already written data by other programs it does eventually destroy the chip and reduce its lifetime of use.
The researchers also suggested their own form of “RAD” hardening in order to reduce the chance of attacks and increase the lifetime of the NAND flash chips. The best solution was to internally buffer data being read and written to the NAND flash drive itself. The concept is that the buffer will absorb all the read and write activity and then place the data correctly into each NAND memory cell. While this method would consume additional overhead in time, up to 15%, and an additional 2 MB of storage, it would also eliminate the chip vulnerability to being corrupted by either the “Capacitance Coupling” or the “Read Disturbance” attacks.
The research paper – titled “Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques” is available at:
https://pdfs.semanticscholar.org/b9bc/a3c9f531002854af48de121cdcc8e0520c7f.pdf
Charles R. Smith is CEO of Softwar Inc. a US based information warfare company and a former national security journalist. You can find Softwar at https://www.softwar.net
Critical DoS Flaws Patched in Asterisk Framework
23.5.2017 securityweek Vulnerebility
Updates released on Friday for the Asterisk communications framework address three critical denial-of-service (DoS) vulnerabilities discovered by Sandro Gauci, a penetration tester and researcher who specializes in VoIP and communications systems.
Asterisk, considered the world’s most popular open source communications framework, is used by government agencies, carriers and other businesses, including most Fortune 1000 companies. According to its developers, more than one million IP PBX systems, VoIP gateways, conference servers and other solutions rely on Asterisk.
Gauci discovered in April that the project is affected by three potentially serious vulnerabilities that can be exploited to cause the system to crash. Separate advisories have been published by Asterisk developers for each of the flaws.
The vulnerabilities affect all versions of Asterisk 13, 14 and Certified Asterisk 13.13. The issues have been addressed with the release of versions 13.15.1, 14.4.1 and 13.13-cert4.
One of the security holes can be exploited by a remote attacker to cause Asterisk to exhaust all available memory by sending a specially crafted Signalling Connection Control Part (SCCP) packet. Removing or disabling support for the SCCP protocol prevents potential attacks.
“A remote memory exhaustion can be triggered by sending an SCCP packet to Asterisk system with ‘chan_skinny’ enabled that is larger than the length of the SCCP header but smaller than the packet length specified in the header. The loop that reads the rest of the packet doesn’t detect that the call to read() returned end-of-file before the expected number of bytes and continues infinitely. The ‘partial data’ message logging in that tight loop causes Asterisk to exhaust all available memory,” Asterisk developers wrote in their advisory.
The other two vulnerabilities found by Gauci affect PJSIP, an open source multimedia communication library that implements SIP (Session Initiation Protocol) and other protocols. The flaws can be exploited remotely to cause a crash by sending specially crafted SIP packets.
The latest Asterisk releases include a version of PJSIP that addresses these vulnerabilities. However, other projects using the PJSIP library are vulnerable as well, and they will need to obtain upstream patches to protect their users against attacks.
VMware Patches Workstation Vulnerabilities
23.5.2017 securityweek Vulnerebility
VMware informed customers last week that updates released for the Linux and Windows versions of Workstation patch privilege escalation and denial-of-service (DoS) vulnerabilities.
One of the flaws, discovered by Jann Horn of Google Project Zero and tracked as CVE-2017-4915, affects VMware Workstation Pro and Player 12.x on Linux. The weakness has been classified as “important” severity.
The security hole, described as an insecure library loading vulnerability, allows an unprivileged host user to escalate their privileges to root on the host via ALSA sound driver configuration files.
The second vulnerability, identified by Borja Merino and tracked as CVE-2017-4916, affects VMware Workstation Pro and Player 12.x on Windows.
This “moderate” severity flaw is a NULL pointer dereference issue that exists in the vstor2 driver. An attacker with regular host user privileges can exploit the vulnerability to cause a DoS condition on the host machine.
The vulnerabilities have been patched with the release of VMware Workstation 12.5.6. There are no workarounds for either of the flaws.
VMware has released eight other security advisories this year, including for an Apache Struts 2 vulnerability that had been exploited in the wild, and security bugs disclosed by white hat hackers at this year’s Pwn2Own competition.
Exploits involving VMware virtual machine escapes earned participants more than $200,000 at Pwn2Own 2017. Researchers at Qihoo 360 received $105,000 for an Edge exploit that achieved a VM escape, while Tencent Security’s Team Sniper earned $100,000 for a Workstation exploit.
WordPress 4.7.5 release addresses six security vulnerabilities
19.5.2017 securityaffairs Vulnerebility
The new WordPress 4.7.5 release fixes six security vulnerabilities affecting version 4.7.4 and earlier, including XSS, CSRF, SSRF flaws.
The WordPress 4.7.5 release patches six vulnerabilities affecting version 4.7.4 and earlier. The latest version addresses cross-site scripting (XSS), cross-site request forgery (CSRF), and server-side request forgery (SSRF) flaws.
Below the list of the security issues fixed with the last update:
Insufficient redirect validation in the HTTP class. Reported by Ronni Skansing.
Improper handling of post meta data values in the XML-RPC API. Reported by Sam Thomas.
Lack of capability checks for post meta data in the XML-RPC API. Reported by Ben Bidner of the WordPress Security Team.
A Cross Site Request Forgery (CSRF) vulnerability was discovered in the filesystem credentials dialog. Reported by Yorick Koster.
A cross-site scripting (XSS) vulnerability was discovered when attempting to upload very large files. Reported by Ronni Skansing.
A cross-site scripting (XSS) vulnerability was discovered related to the Customizer. Reported by Weston Ruter of the WordPress Security Team.
Let’s go into the details of the flaw fixed by the in the details of the flaw fixed by the WordPress 4.7.5 release:
The CSRF flaw patched was reported by the Securify researcher Yorick Koster in the summer of 2016 during the WordPress hacking competition.
It affects the WordPress version 4.5.3 up till and including version 4.7.4.
“The FTP/SSH form functionality of WordPress was found to be vulnerable to Cross-Site Request Forgery.” ” states the advisory published by the company. “This vulnerability can be used to overwrite the FTP or SSH connection settings of the affected WordPress site. An attacker can use this issue to trick an Administrator into logging into the attacker’s FTP or SSH server, disclosing his/her login credentials to the attacker. In order to exploit this vulnerability, the attacker has to lure/force a logged on WordPress Administrator into opening a malicious website.”
The SSRF vulnerability, tracked as CVE-2017-9066, was discovered by the researcher Ronni Skansing, who plans to release a PoC code soon.
12h
Ryan St. Germain @r_stgermain
@skansing Any POC availability?
Follow
Ronni Skansing @skansing
@r_stgermain It will be available at https://hackerone.com/reports/187520 when the report has been fully processed by wp staff, I can request disclosure on the report
2:53 AM - 19 May 2017
Retweets likes
Twitter Ads info & Privacy
Skansing was reported another vulnerability in WordPress, XSS flaw related to uploading very large files.
This isn’t the unique XSS vulnerability fixed, another cross-site-scripting has been reported by Weston Ruter of the WordPress security team in the Customizer feature.
The WordPress 4.7.5 release also patches different vulnerabilities in the same API, such as the Lack of capability checks for post meta data in the XML-RPC API.
WordPress also announced the launch of a public bug bounty program that aims to involve hacking community on the WordPress CMS, BuddyPress, bbPress and GlotPress.
The program will also cover the WordPress.org, WordCamp.org, BuddyPress.org, WordPress.tv, bbPress.org and Jobs.WordPress.net websites.
Cisco Fixes Severe Flaws in Prime Collaboration Product
19.5.2017 securityweek Vulnerebility
Cisco has released updates for its Prime Collaboration Provisioning software to address critical and high severity vulnerabilities that can be exploited remotely without authentication.
The flaws were reported to Cisco by Andrea Micalizzi (aka rgod) through Trend Micro’s Zero Day Initiative (ZDI). Micalizzi, one of ZDI’s top contributors, was credited on Wednesday by the networking giant for finding a total of five vulnerabilities in its Prime Collaboration Provisioning product, which provides a web-based interface for managing Cisco communication services.
The most serious of the flaws, rated critical and tracked as CVE-2017-6622, allows a remote, unauthenticated attacker to bypass authentication and execute arbitrary commands with root privileges.
“The vulnerability is due to missing security constraints in certain HTTP request methods, which could allow access to files via the web interface. An attacker could exploit this vulnerability by sending a crafted HTTP request to the targeted application,” Cisco said in its advisory.
Micalizzi also discovered a high severity information disclosure vulnerability (CVE-2017-6621) in the Prime Collaboration Provisioning software. The weakness can be exploited by a remote attacker, via specially crafted HTTP requests, to obtain information that can be useful in the reconnaissance phase of an attack.
Users have been advised to update the software to versions 11.6 and 12.1 or later to address these vulnerabilities.
Cisco has also published advisories describing medium severity directory traversal vulnerabilities found by the researcher in the Prime Collaboration Provisioning software. These bugs can be leveraged to view and delete files from the system, but they are considered less severe as they can only be exploited by an authenticated attacker.
Cisco said there was no evidence that any of these flaws had been exploited in the wild.
Cisco published nearly two dozen advisories on Wednesday, but most of them cover medium severity issues. There are only two other advisories describing high severity flaws, including a directory traversal that allows a remote attacker to read files from the Cisco TelePresence IX5000 Series filesystem.
A privilege escalation vulnerability in the Cisco Policy Suite (CPS) software has also been rated high severity, but it can only be exploited by an authenticated, local attacker.
Researchers Disclose Unpatched WD TV Media Player Flaws
19.5.2017 securityweek Vulnerebility
Researchers have disclosed several potentially serious vulnerabilities affecting the WD TV Media Player from Western Digital. The vendor has been aware of the flaws since January, but patches have yet to be released.
In March, researchers from Securify, SEC Consult and Exploitee.rs disclosed multiple vulnerabilities identified in WD’s My Cloud storage devices. However, the My Cloud devices were not the only WD products analyzed by SEC Consult.
The company published an advisory on Thursday describing a total of eight security holes affecting the WD TV Media Player, a device that allows users to access media content from a computer, USB drive, network storage device or the Internet directly on their TV.WD TV Media Player vulnerabilities
“By combining the vulnerabilities documented in this advisory an attacker can fully compromise a network which has the WDTV Media Player appliance installed by using it as a jump-host to aid in further attacks,” SEC Consult warned in its advisory.
One flaw discovered by experts is an arbitrary file upload issue that can be exploited to upload files to the web server without authentication. They also found a local file inclusion vulnerability that can be leveraged to execute the previously uploaded file. This can lead to remote code execution if the attacker uploads a malicious PHP script.
Researchers also determined that all devices are shipped with the same private key in the firmware, the web server is unnecessarily running with root privileges, the login page (which requires only a password) is not protected against brute-force attacks, and the full path of the web directory is exposed. The product is also affected by a SQL injection flaw which, in the worst case scenario, can be exploited to create a backdoor on the web server.
Some of the vulnerabilities can be exploited directly from the Internet if the device’s interface is configured for Web access. However, since cross-site request forgery (CSRF) protection is missing, an attacker can also exploit the flaws remotely by getting the targeted user to click on a malicious link.
SEC Consult found these flaws in version 1.03.07 of the firmware, but believes earlier versions are likely affected as well. The weaknesses were reported to the vendor in mid-January at the same time as the issues affecting My Cloud storage devices, but they remain unpatched. The security firm said the last firmware update for the WD TV Media Player was released in April 2016.
SEC Consult has made public some technical details, but the company will not release any proof-of-concept (PoC) code until patches become available.
SecurityWeek has reached out to WD for comment, but the company had not responded by time of publication.
Google Chrome Bug Leads to Windows Credential Theft
19.5.2017 securityweek Vulnerebility
An issue with the manner in which Google Chrome and Windows handle specific file types can lead to credential theft even on up-to-date systems, a DefenseCode researcher has discovered.
While previous research on the leak of authentication credentials using Windows’ Server Message Block (SMB) file sharing protocol focused only on attacks involving Internet Explorer and Edge, DefenseCode’s Bosko Stankovic discovered that even the most popular browser out there can be used as an attack vector.
In a paper titled Stealing Windows Credentials Using Google Chrome (PDF), Stankovic explains that the attack abuses Chrome’s default configuration, where the browser automatically downloads files that it deems safe. What’s more, it doesn’t even prompt the user for a download location, but uses the present one instead.
What this means is that the browser could download malicious files that it deems safe and save them to disk without user’s knowledge. While most files would require some sort of user interaction to perform malicious operations on the systems, there are file types that don’t and an attacker could exploit these to compromise even systems with the latest patches installed.
One of these file types, the security researcher says, is Windows Explorer Shell Command File or SCF (.scf). Although not well-known, this file type goes back as far as Windows 98, and was primarily used as a Show Desktop shortcut in Windows 98/ME/NT/2000/XP.
“It is essentially a text file with sections that determine a command to be run (limited to running Explorer and toggling Desktop) and an icon file location,” the researcher explains.
The same as with shortcut LNK files, the icon location is automatically resolved when the SCF file is shown in Explorer, and attackers are known to have abused this feature by setting an icon location to a remote SMB server in order to abuse the Windows automatic authentication feature when accessing services like remote file shares.
Ever since Stuxnet, Chrome sanitizes LNK files by forcing a .download extension, but doesn’t do the same when SCF files are involved. Because of that, SCF files can be used to trick Windows into an authentication attempt to a remote SMB server. Only two lines of code are needed to conduct such an attack.
“Once downloaded, the request is triggered the very moment the download directory is opened in Windows File Explorer to view the file, delete it or work with other files (which is pretty much inevitable). There is no need to click or open the downloaded file – Windows File Explorer will automatically try to retrieve the ‘icon’,” Stankovic notes.
The remote SMB server can be set to capture the victim's username and NTLMv2 password hash for offline cracking, or can relay the connection to an external service that accepts the same kind of authentication in an attempt to impersonate the victim without ever knowing the password.
“It is worth mentioning that SCF files will appear extensionless in Windows Explorer regardless of file and folder settings. Therefore, file named picture.jpg.scf will appear in Windows Explorer as picture.jpg. This adds to inconspicuous nature of attacks using SCF files,” the researcher explains.
To successfully exploit this attack vector, an actor would simply need to entice users into accessing a website (the attack works even on fully updated Google Chrome and Windows).
The impact of password theft could be dire on enterprise environments (especially if the attack victim is a privileged user) or for Active Directory domains (corporate, government and other networks), where the password theft could lead to escalating internal network breaches.
On Windows 8/10 machines using a Microsoft Account (MSA) instead of a local account, the attack would result in the compromise of all Microsoft services that are integrated with the MSA Single sign-on (SSO). Password reuse could lead to the compromise of accounts unrelated to MSA as well.
“In order to disable automatic downloads in Google Chrome, the following changes should be made: Settings -> Show advanced settings -> check the Ask where to save each file before downloading option. Manually approving each download attempt significantly decreases the risk of NTLMv2 credential theft attacks using SCF files,” the researcher says.
Expert Earns $5,000 for Google Intranet Vulnerability
19.5.2017 securityweek Vulnerebility
A researcher has earned a $5,000 bounty from Google after finding an information disclosure vulnerability in the login page for the tech giant’s intranet system.
Austria-based researcher David Wind was looking for a vulnerable Google service that could earn him a bug bounty when he came across login.corp.google.com, the login page for Google’s intranet, which is dubbed “MOMA.”
The login page is simple, but it does load a random image from static.corp.google.com every time it’s accessed. After unsuccessful attempts to obtain something from this domain, Wind generated a 404 error page by adding a random string to the URL.
Unlike other error pages displayed by Google to users, this one contained a link named “Re-run query with SFFE debug trace,” which pointed to the same URL with the string “?deb=trace” at the end.
The debugging page included various pieces of information, including server name and internal IP, X-FrontEnd (XFE) HTTP requests, service policies, and information related to Cloud Bigtable, Google's NoSQL big data database service.
“The page did not allow any user interaction and I haven’t found anything to ‘go deeper’ into the system so I reported it right away,” Wind said on his blog.
Google awarded the researcher $5,000 for his findings, which is the maximum amount for information leaks affecting highly sensitive applications.
The vulnerability was reported to Google on January 19 and a short-term fix was implemented some days later. The company told Wind that a permanent fix was rolled out on March 16.
The $5,000 reward earned by the researcher is significant compared to what other bug bounty programs pay, but it’s small at Google’s standards, which offers more than $30,000 for remote code execution vulnerabilities.
The company has so far paid out more than $9 million since the launch of its bug bounty program in 2010, including over $3 million last year. The biggest single reward in 2016 was $100,000.
Critical SQL Injection CVE-2017-8917 vulnerability patched in Joomla, update it now!
19.5.2017 securityaffairs Vulnerebility
Joomla maintainers released a fix for a critical SQL injection flaw, tracked as CVE-2017-8917, that can be exploited by a remote attacker to hijack websites
On Wednesday Joomla maintainers released a fix for a critical SQL injection vulnerability, tracked as CVE-2017-8917, that can be easily exploited by a remote attacker to obtain sensitive data and hijack websites.
The vulnerability was reported by the Sucuri researcher Marc-Alexandre Montpas, it only affects Joomla 3.7.0 because it’s related to a new component introduced in this version.
“The vulnerability is caused by a new component, com_fields, which was introduced in version 3.7. If you use this version, you are affected and should update as soon as possible. This vulnerable component is publicly accessible, which means this issue can be exploited by any malicious individual visiting your site.” reads the analysis published by Sucuri.
“Given the nature of SQL Injection attacks, there are many ways an attacker could cause harm – examples include leaking password hashes and hijacking a logged-in user’s session (the latter results in a full site compromise if an administrator session is stolen).”
According to Montpas, the vulnerability only affects Joomla 3.7 because it’s related to the new com_fields component introduced in this version. The component borrows views from an admin-side component that has the same name, unfortunately, it is a publicly accessible component, this means that anyone can exploit the CVE-2017-8917 vulnerability without needing a privileged account on the vulnerable website. An attacker can leverage the flaw to inject nested SQL queries via a specially crafted URL.
Joomla users have been advised to update their installations to the version 3.7.1.
Sucuri has published the technical details for the CVE-2017-8917 vulnerability, it is likely that threat actors in the wild will start exploiting it in the next weeks.
“The only administrator view that can be accessed is fields – and this will grab its data from an admin-side model (due to the $config[‘base_path’] trick we discussed earlier). In this case, the vulnerability we discovered was located in the FieldsModelFields model, in ./administrator/components/com_fields/models/fields.php.” reads the analysis. “So in order to exploit this vulnerability, all an attacker has to do is add the proper parameters to the URL in order to inject nested SQL queries.”

Massive attacks on Joomla installations are dangerous events, in October 2016 Joomla released the version 3.6.4 to fix two high severity vulnerabilities, CVE-2016-8870, and CVE-2016-8869. A combination of these flaws can be exploited to upload a backdoor and gain complete control of vulnerable Joomla websites.
Experts from the firm Sucuri observed a spike in the number of attacks in less than 24 hours after Joomla released patches the above critical flaws.
Critical SQL Injection Flaw Patched in Joomla
18.5.2017 securityweek Vulnerebility
A Joomla update released on Wednesday patches a critical SQL injection vulnerability that can be easily exploited by a remote attacker to obtain sensitive data and hijack websites.
The flaw, discovered by Sucuri researcher Marc-Alexandre Montpas and tracked as CVE-2017-8917, affects Joomla 3.7.0 and it has been addressed with the release of version 3.7.1. This is the only security issue fixed in the latest version.
According to Montpas, the vulnerability only affects Joomla 3.7 because it’s related to a new component introduced in this version. The component in question is com_fields, which borrows views from an admin-side component that has the same name.
Since com_fields is a public-facing component, anyone can exploit the vulnerability without needing a privileged account on the targeted website. An attacker can leverage the flaw to inject nested SQL queries via a specially crafted URL.
“Given the nature of SQL Injection attacks, there are many ways an attacker could cause harm – examples include leaking password hashes and hijacking a logged-in user’s session (the latter results in a full site compromise if an administrator session is stolen),” Montpas warned in a blog post published on Wednesday.
Joomla users have been advised to update their installations as soon as possible. Joomla developers even issued a pre-release security announcement last week to inform users of the “very important security fix.”
While Sucuri has not released a proof-of-concept (PoC) exploit, it has made public the flaw’s technical details. Given that it’s easy to exploit, it would not be surprising to see attacks leveraging this vulnerability in the next days.
In October 2016, cybercriminals started exploiting a couple of Joomla vulnerabilities in less than 24 hours after they were patched, despite the fact that only limited technical details had been made public. At the time, attackers leveraged the flaws to create rogue user accounts on popular websites.
One year prior, attackers started hacking Joomla websites within hours after the details of a SQL injection vulnerability were disclosed by researchers. A few months later, Joomla developers rushed to patch a zero-day that had been exploited in the wild for at least two days before fixes were released.
Schneider Patches Flaws in VAMPSET, SoMachine Products
18.5.2017 securityweek Vulnerebility
Updates released by Schneider Electric for its VAMPSET and SoMachine HVAC products patch several medium and high severity vulnerabilities that can be exploited for denial-of-service (DoS) attacks and arbitrary code execution.
Advisories describing the flaws were published recently by both ICS-CERT and Schneider Electric.
One of the advisories focuses on a medium severity memory corruption vulnerability affecting VAMPSET, a piece of software used to configure and maintain protection relays and arc flash protection units. The bug, tracked as CVE-2017-7967, can be triggered using a specially crafted settings file (.vf2).
“This vulnerability causes the software to halt or not start when trying to open the corrupted file,” Schneider wrote in its advisory. “As Windows operating system remains operational and VAMPSET responds, it is able to be shut down through its normal closing protocol.”
According to Fortinet’s Kushal Arvind Shah, the researcher who reported the flaw to the vendor, an attacker may also be able to exploit the weakness for arbitrary code execution.
The flaw has been addressed with the release of VAMPSET 2.2.189. All previous versions are affected.
Separate advisories describe two high severity vulnerabilities found by independent researchers in Schneider’s SoMachine HVAC product, a programming software for Modicon logic controllers. Both security holes have been patched with the release of SoMachine HVAC 2.2.
One of the flaws, CVE-2017-7966, has been described as a DLL hijacking issue that can be exploited by a remote, unauthenticated attacker to execute arbitrary code by planting a malicious library that would get executed instead of the legitimate file.
The second vulnerability, classified as a stack-based buffer overflow and tracked as CVE-2017-7966, is related to a component named AlTracePrint.exe. Schneider and ICS-CERT have not shared any details, but mentioned that the component can be called in a way that leads to a buffer overflow and a crash.
Last month, researchers from Germany-based OpenSource Security disclosed a couple of critical vulnerabilities in Schneider’s Modicon and SoMachine products before the vendor released patches.
The experts reported the flaws to the company in December and decided to make their findings public after not receiving any feedback. Schneider admitted making a mistake and promised to release fixes in mid-June.
0-Day Flaws in Vanilla Forums Let Remote Attackers Hack Websites
13.5.2017 thehackernews Vulnerebility
hacking-vanilla-forum-vulnerability
A security researcher has publicly disclosed two critical zero-day vulnerabilities in Vanilla Forums, an open source software that powers discussion on over 500,000 websites, which could allow unauthenticated, remote attackers to fully compromise targeted websites easily.
Discovered by Polish security researcher Dawid Golunski of Legal Hackers, two separate unpatched vulnerabilities, a remote code execution (CVE-2016-10033) and host header injection (CVE-2016-10073), affect the latest version of Vanilla Forums 2.3, leaving hundreds of thousands of websites and their visitors vulnerable to various hacking attacks.
Vanilla Forums: Remote Code Execution Flaw
According to Golunski, both vulnerabilities technically exist because Vanilla Forum is still using a vulnerable version of PHPMailer, one of the most popular open source PHP libraries used to send emails.
Last year Golunski reported a critical remote code execution flaw (CVE-2016-10033) in PHPMailer library that allows an attacker to remotely execute arbitrary code in the context of the web server and compromise the target web application.
In a proof-of-concept video, Golunski demonstrated that the same PHPMailer exploit also makes the Vanilla Forums vulnerable, and if used in combination with host header injection, it allows attackers to inject arbitrary commands and payloads passed within the HOST header.
"It should be noted that this vulnerability can still be exploited even if Vanilla software is hosted on Apache web server with several name-based vhosts enabled, and despite not being the default vhost," the researcher explained.
Vanilla Forums: Host Header Injection Flaw
The Host Header Injection vulnerability in Vanilla forum can also be independently used to hijack user accounts, let's say admin, by sending a spoofed HTTP request with a custom HOST header (for example attacker-mxserver.com), while initiating a password reset process for a targeted admin user.
This technique also works in a similar manner as the Wordpress flaw, Golunski disclosed just last week, allowing attackers to gain access to user accounts, "carrying Web-cache poisoning attacks, and in some instances, execute arbitrary code."
Golunski reported the vulnerabilities to the Vanilla Forums in January this year. The company acknowledged his reports but went mum for around five months, which made him go public with his findings.
The researcher confirmed both the flaws still exist in the most recent, stable version 2.3 of Vanilla Forums, and believes that older versions of the forum software are also vulnerable.
Until the company fixes the issue, as a temporary mitigation, Golunski advises website administrator to set the sender's email address to a predefined static value in order to block the Vanilla Forums from using the HOST header.
Update: Vanilla Forums fixed the reported vulnerabilities last night, and said the issues only affect its free and open source product, adding "neither of these vulnerabilities affect our cloud customers" at vanillaforums.com, "nor were they at the time of their publication."
Users of its free and open source software are strongly recommended to update their Vanilla Forums software to the latest open source version, Vanilla 2.3.1.
Vanilla Forums software is still affected by a critical remote code execution zero-day first reported in December 2016.
12.5.2017 securityaffairs Vulnerebility
The popular Vanilla Forums software is still affected by a critical remote code execution zero-day first reported to the development team in December 2016.
The exploit code was published by ExploitBox, a remote attacker can chain the flaw with the Host Header injection vulnerability CVE-2016-10073 to execute arbitrary code and take the control of the affected software.

Vanilla Forums is the software mentioned by the popular security researcher Dawid Golunski in the following critical PHPMailer advisories a few months ago:
https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html
https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10045-Vuln-Patch-Bypass.html
“The researcher also developed an Unauthenticated RCE exploit for a popular
open-source application (deployed on the Internet on more than a
million servers) as a PoC for real-world exploitation. It might be published after the vendor has fixed the vulnerabilities. ” wrote Golunski.

Dawid Golunski @dawid_golunski
Another day another #RCE #0day - #Vanilla Forums 2.3 -Patch it up #infosec
Advisory&PoC #exploit at #Exploit_Box https://exploitbox.io/vuln/Vanilla-Forums-Exploit-RCE-0day-Remote-Code-Exec-CVE-2016-10033.html …
4:51 PM - 11 May 2017
50 50 Retweets 57 57 likes
He has been waiting for a few months before publishing the Vanilla Forums RCE exploit together with the WordPress 4.6 RCE exploit.
The Vanilla Forums software leverages PHPMailer that uses PHP’s mail() function as its default transport, as explained by the expert.
The mail() function can then be used to call Sendmail and an attacker can inject extra parameters into Sendmail by chaining the flaw with the CVE-2016-10073 vulnerability.
For example:
“Attacker \” -Param2 -Param3″@test.com
when processed by the PHPMailer (and eventually sent to mail()) function would cause sendmail to execute with:
Arg no. 0 == [/usr/sbin/sendmail]
Arg no. 1 == [-t]
Arg no. 2 == [-i]
Arg no. 3 == [-fAttacker\]
Arg no. 4 == [-Param2]
Arg no. 5 == [-Param3″@test.com]
Dawid Golunski in the ExploitBox post demonstrates how an HTTP 1.0 Web request to the forum will allow code injection down to PHPMailer.
“It should be noted that this vulnerability can still be exploited even if Vanilla software is hosted on Apache web server with several name-based vhosts enabled, and despite not being the default vhost.” wrote Golunski.
“This is possible as the attacker can take advantage of HTTP/1.0 protocol and specify the exact vhost within the URL. This will allow the HOST header to be set to arbitrary value as the Apache server will obtain the SERVER_NAME from the provided URL. This will ensure that the malicious request will reach the affected code despite invalid vhost within the HOST header.”
Below a video PoC of the exploit:
“The exploits and techniques prove that these type of vulnerabilities could be exploited by unauthenticated attackers via server headers such as HOST header that may be used internally by a vulnerable application to dynamically create a sender address.” Golunski told me. “This adds to the originally presented attack surface of contact forms that take user input including From/Sender address.”
These vulnerabilities affect the latest Vanilla Forums stable version 2.3 which unfortunately remains unpatched.
The 0day Vanilla Forums advisories are at:
https://exploitbox.io/vuln/Vanilla-Forums-Exploit-Host-Header-Injection-CVE-2016-10073-0day.html
https://exploitbox.io/vuln/Vanilla-Forums-Exploit-RCE-0day-Remote-Code-Exec-CVE-2016-10033.html
ExploitBox suggests setting the sender’s address to a static value, in this way it is possible to do not use the HOST header.
Audit Finds Only One Severe Vulnerability in OpenVPN
12.5.2017 securityweek Vulnerebility
Two teams of experts have conducted audits of the open-source virtual private network (VPN) application OpenVPN, including its use of cryptography, and they identified only one high severity vulnerability.
One audit, conducted between December 2016 and February 2017, was carried out by cryptography expert Dr. Matthew Green and funded by Private Internet Access (PIA). Green and his team looked for both memory-related vulnerabilities (e.g. buffer overflows and use-after-free) and cryptographic weaknesses.
A security review of OpenVPN was also conducted by Quarkslab over a 50-day period between February and April, with funding from the Open Source Technology Improvement Fund (OSTIF). This audit focused on OpenVPN for Windows and Linux, the OpenVPN GUI, and the TAP driver for Windows. Both audits targeted OpenVPN 2.4.
Quarkslab discovered one vulnerability that has been rated high severity. The flaw, tracked as CVE-2017-7478, is a denial-of-service (DoS) issue that allows an unauthenticated attacker to crash OpenVPN clients and servers. Researchers pointed out that the weakness can be easily exploited.
Quarkslab also identified a medium severity DoS vulnerability (CVE-2017-7479) that can only be exploited by an authenticated attacker. The other security bugs found by the company have been classified as low severity or informational issues.
The audit conducted by Dr. Green’s Cryptography Engineering did not uncover any major flaws.
Experts did find a couple of medium severity vulnerabilities – one of them is related to the fact that sensitive authentication tokens are not wiped from memory in case of certain TLS errors, and the second issue involves potentially flawed TLS control channel encryption. Cryptography Engineering also reported discovering six low severity problems.
The more serious issues have already been addressed by OpenVPN developers, and the less severe problems will be patched in the next official release.
“Given the numerous options and features provided by OpenVPN, vulnerabilities may crop up from certain feature combinations. This will be an ongoing challenge for OpenVPN developers to catch these problems early as the code base continues to evolve and expand,” Cryptography Engineering said in its report. “While the overall cryptographic design of OpenVPN is solid, some of the options available may undermine a user’s ability to deploy a secure VPN solution. As such, we recommend that the OpenVPN developers continue to document the risks of using certain advanced features to users.”
“OpenVPN is much safer after these audits, and the fixes applied to the OpenVPN mean that the world is safer when using this software,” OSTIF said in a blog post. “We have verified that the OpenVPN software is generally well-written with strong adherence to security practices.”
OSTIF pointed out that its next target is OpenSSL 1.1.1, which is the first version to implement TLS 1.3 and which contains numerous code changes.
Vanilla Forums Rushes to Patch Disclosed Vulnerabilities
12.5.2017 securityweek Vulnerebility
The developers of Vanilla, a forum software with nearly one million downloads, rushed to release a security update on Thursday after a researcher made public details and exploits for two unpatched vulnerabilities.
Security researcher Dawid Golunski reported in late December 2016 that he had discovered a critical remote code execution vulnerability in PHPMailer, the world’s most popular email creation and transfer class for PHP. Given the widespread use of the library, many applications were exposed to attacks due to the flaw, including the Vanilla Forums software.
In the case of Vanilla Forums 2.3, the PHPMailer vulnerability can be combined with a host header injection weakness (CVE-2016-10073), allowing a remote, unauthenticated attacker to execute arbitrary code and hijack the targeted website, the expert said.
According to the researcher, the host header injection vulnerability can be exploited by an unauthenticated attacker to intercept Vanilla password reset hashes and gain unauthorized access to the victim’s account.
The flaw exists due to the fact that the value of the user-supplied HTTP HOST header in a request is used to generate the sender’s email address. This security hole is similar to one found recently by Golunski in WordPress.
An attacker can exploit this vulnerability by sending a specially crafted password reset request with the HOST header set to a domain they control. The email received by the victim will appear to come from an address on the attacker’s domain, and the password reset link will also point to the attacker’s server, allowing them to intercept the password reset hash if the victim clicks on the link.
Golunski said he reported the vulnerabilities to Vanilla Forums developers in December 2016, and decided to make his findings public now after receiving no updates from the vendor. The researcher has also published a video showing the exploit in action:
A few hours after the expert published an advisory, Vanilla Forums announced the release of version 2.3.1, which patches these vulnerabilities and fixes some other minor issues. The company pointed out that the flaws only affected the free and open source version of the forum software. Its cloud service at vanillaforums.com was not affected by either of the vulnerabilities.
According to Vanilla Forums, fixing the host header injection vulnerability was a complex matter that needed time. Now that Golunski made his findings public, developers have decided to address the issue by “stripping its use,” which could cause problems for some configurations. The security hole has been classified as “medium” severity.
The company admitted making a mistake in not updating the PHPMailer library sooner, but also blamed Golunski for not following up to remind them of the vulnerability.
Cisco patched CVE-2017-3881 IOS XE Vulnerability leaked in CIA Vault 7 Dump
11.5.2017 securityaffairs Vulnerebility
Cisco patched the critical CVE-2017-3881 flaw that affects CISCO Catalyst switches and that can be potentially exploited by attackers to hijack networks.
Cisco patched a critical security flaw, tracked as CVE-2017-3881, affecting its CISCO Catalyst switches that can be potentially exploited by attackers to hijack networks.
The vulnerability was disclosed in the CIA Vault 7 data leak, according to Switchzilla a remote attacker can exploit it by simply establishing a Telnet connection and sending a cluster management protocol (CMP) command to the affected network device.
“The Cluster Management Protocol utilizes Telnet internally as a signaling and command protocol between cluster members. The vulnerability is due to the combination of two factors:
The failure to restrict the use of CMP-specific Telnet options only to internal, local communications between cluster members and instead accept and process such options over any Telnet connection to an affected device, and
The incorrect processing of malformed CMP-specific Telnet options.
” reads the Cisco security advisory published on Monday.
CVE-2017-3881 flaw CISCO Catalyst switches
The vulnerability affects the default configuration of the flawed devices even when the user doesn’t have switch clusters configured, and can be exploited over either IPv4 or IPv6.
“An attacker could exploit this vulnerability by sending malformed CMP-specific Telnet options while establishing a Telnet session with an affected Cisco device configured to accept Telnet connections,”
Artem Kondratenko published the CVE-2017-3881 Cisco Catalyst RCE Proof-Of-Concept exploit code.
“Do you still have telnet enabled on your Catalyst switches? Think twice, here’s a proof-of-concept remote code execution exploit for Catalyst 2960 switch with latest suggested firmware. Check out the exploit code here.” wrote Kondratenko.”What follows is a detailed write-up of the exploit development process for the vulnerability leaked from CIA’s archive on March 7th 2017 and publicly disclosed by Cisco Systems on March 17th 2017. At the time of writing this post there is no patch available. Nonetheless there is a remediation – disable telnet and use SSH instead.”
Just after the disclosure of the CVE-2017-3881 flaw, CISCO confirmed that the IOS / IOS XE bug affects more than 300 of its switch models, including Cisco Catalyst, Embedded Services, and Industrial Ethernet switch models.
As mitigation measures, experts from CISCO suggested to disabled Telnet connections, SSH remains the best option to remotely access the devices.
Patch your Asus RT wireless routers now to avoid ugly surprises
11.5.2017 securityaffairs Vulnerebility
Security experts at Nightwatch Cybersecurity have found serious flaws in the Asus RT wireless routers that could allow hackers to take over them.
Security experts at Nightwatch Cybersecurity serious flaws in the Asus RT wireless routers. Dozens of models don’t implement an adequate protection against cross-site request forgery attacks.
The vulnerability, tracked as CVE-2017-5891, affects the Asus RT wireless RT-AC and RT-N models running firmware older than version 3.0.0.4.380.7378.

Poorly configured devices left with default credentials could be easily accessed by an attacker that can take the control of the devices.
According to the experts at Nightwatch Cybersecurity, which discovered the security vulnerability, CSRF on the login page could be exploited by attackers to submit a login request to the router without the user’s knowledge
“The login page for the router doesn’t have any kind of CSRF protection, thus allowing a malicious website to submit a login request to the router without the user’s knowledge. Obviously, this only works if the site either knows the username and password of the router OR the user hasn’t changed the default credentials (“admin / admin”). To exploit, submit the base-64 encoded username and password as “login_authorization” form post, to the “/login.cgi” URL of the browser.” reads the blog post published by Nightwatch Cybersecurity.
Below an example of the form that be exploited by an attacker to trigger the issue:

Once the attacker has accessed the admin interface of the router he can change the settings, and hijack the DNS, and perform other malicious activity.
Experts at Nightwatch also discovered two JSONP vulnerabilities that can expose sensitive information, including network map and details about the router.
Asus has solved the CSRF vulnerability with the release of a firmware update in March, anyway, it hasn’t addressed one of the vulnerabilities discovered by Nightwatch, the CVE 2017-5892 flaw.
Below the other bugs fixed with this last firmware release:
CVE-2017-6547, a cross-site scripting bug in the routers’ HTTP daemon.
CVE-2017-6549, a session hijack vulnerability in the HTTP daemon.
CVE-2017-6548, a remote code execution buffer overflow in the routers’
networkmap
command.
Don’t wast time, update your Router.
Microsoft Patches Edge Flaws Disclosed at Pwn2Own
11.5.2017 securityweek Vulnerebility
Microsoft this week patched several memory corruption vulnerabilities in the Edge web browser that were disclosed at the 2017 Pwn2Own hacking competition.
The white hat hackers who signed up for this year’s Pwn2Own earned a total of more than $800,000 for vulnerabilities in Windows, macOS, Ubuntu, Safari, Firefox, Edge, Flash Player, Adobe Reader, and VMware Workstation.
VMware, Mozilla, Adobe, Apple and Linux kernel developers addressed the flaws affecting their products in March and April, and Microsoft has now also started releasing patches. The Zero Day Initiative (ZDI), which organizes Pwn2Own, published six advisories on Wednesday for each of the security holes fixed by Microsoft.
The vulnerabilities affect the scripting engines used by Edge, including the Chakra JavaScript engine, and they can lead to privilege escalation, information disclosure and remote code execution. The following CVE identifiers have been assigned: CVE-2017-0233, CVE-2017-0234, CVE-2017-0240, CVE-2017-0238 and CVE-2017-0228.
According to ZDI, the use-after-free and heap-based buffer overflow vulnerabilities are related to the handling of Array, AudioBuffer, Array.unshift and ArrayBuffer objects. An attacker can exploit the flaws by getting the targeted user to visit a malicious website or open a specially crafted file.
Each of the vulnerabilities patched this week by Microsoft has a severity rating of “medium” in the ZDI advisories, with CVSS scores ranging from 4.3 to 6.9. Microsoft has assigned “critical” severity ratings to only two of the flaws: CVE-2017-0228 and CVE-2017-0240.
While not particularly dangerous on their own, some of the weaknesses can be highly valuable for attackers when combined with other bugs, as researchers demonstrated at the Pwn2Own competition.
There is no evidence that any of these flaws have been exploited in the wild, and exploits have not been released by the experts who found them.
Pwn2Own participants also disclosed several Windows vulnerabilities, including ones leveraged in exploit chains targeting Adobe products and web browsers, but it’s unclear if the Windows flaws have been patched as well.
Microsoft released patches for more than 50 vulnerabilities this week, including four zero-days that have been exploited in attacks by profit-driven cybercriminals and cyber espionage groups linked to Russia.
Rockwell Updates Stratix Routers to Patch Cisco IOS Flaws
11.5.2017 securityweek Vulnerebility
Rockwell Automation has released a firmware update for its Allen-Bradley Stratix 5900 services router to address tens of vulnerabilities patched over the past few years in Cisco’s IOS software.
The Stratix 5900 is a hardened security router that runs Cisco’s IOS software. According to ICS-CERT, the product is used worldwide in the critical manufacturing, energy, and water and wastewater sectors.
Firmware version 15.6.3 released recently by Rockwell Automation for its Stratix 5900 routers patches more than 60 vulnerabilities discovered in Cisco IOS since March 2014. This means that, for more than three years, organizations using these devices were left exposed to potential attacks exploiting these flaws.Rockwell Automation Stratix router
The list of security holes includes improper input validation, authentication, information exposure, path traversal, and resource management vulnerabilities that can be exploited for man-in-the-middle (MitM) attacks, denial-of-service (DoS) attacks, and remote code execution.
A majority of the flaws have been classified as high severity, and they can be exploited remotely without authentication. Cisco has not seen any evidence of exploitation in the wild, but for one vulnerability, tracked as CVE-2016-6415, the hacker group calling itself Shadow Brokers did release an exploit targeting Cisco PIX firewalls. The exploit in question may have been used in attacks by the NSA-linked Equation Group.
Some of the vulnerabilities patched with the latest Stratix 5900 firmware update affect third-party components, such as NTP and OpenSSL.
“Rockwell Automation encourages users of the affected versions to update to the latest available software versions addressing the associated risk, and including improvements to further harden the software and enhance its resilience against similar malicious attacks,” ICS-CERT said in its advisory.
This is the sixth advisory published by ICS-CERT this year for vulnerabilities in Rockwell Automation products. The organization previously disclosed critical, high and medium severity flaws affecting Logix5000, GuardLogix, FlexLogix and CompactLogix controllers, several Stratix switches, the Connected Components Workbench (CCW) software configuration platform, and the FactoryTalk Services Platform.
SAP Patches 17 security flaws, the lowest number of monthly update over the past 6 months
11.5.2017 securityaffairs Vulnerebility
SAP issued the May 2017 Security Update that addresses 17 security Vulnerabilities.
On Tuesday SAP released the May 2017 security update that addresses 17 vulnerabilities in its products, 9 of them were released on this Security Patch Day.
“On 9th of May 2017, SAP Security Patch Day saw the release of 9 security notes. Additionally, there were 2 updates to previously released security notes.” reads the advisory published by the company.
A close look at the list of the security flaws addressed by the company shows the company fixed 5 Missing Authorization Checks and 5 Cross-Site Scripting. Additionally, SAP fixed two Implementation flaws, one XML external entity, one denial of service, one buffer overflow issue, one clickjacking, and an SQL injection vulnerability.
Below the Key takeaways published by the security firm ERPScan:
This set of SAP Security Notes is smaller than usual (the average number of SAP Security Notes closed every month this year equals 25, while May’s bunch of Notes contains 17 fixes).
4 of the closed security loopholes affect SAP Defense Forces & Public Security. The lack of authorization vulnerabilities in this module could allow an attacker (including hacktivists and cyberterrorists) to read read, modify or delete sensitive data.
In the wake of proof-of-concept ransom attack via SAP GUI, the vendor released a fix addressing client-side security issues. SAP GUI for Java allowed opening of new connections from an ABAP program that can be used in multi-stage cyberattacks.
The issue with the greatest CVSS score is a Missing Authorization check in EA-DFPS utilities (2376743) rated with a Medium priority and a CVSS=6.5.
An attacker can exploit a Missing authorization check vulnerability to access a service bypassing authorization causing information disclosure, privilege escalation, and other attacks.
“Missing authorization check vulnerability usually allows a perpetrator to read, modify or delete data, which has restricted access. When it comes to the defense industry and armed forces, the information can be critical in terms of International security and the effect of even such low-impact vulnerabilities could be devastating,” ERPScan notes.
Just for statistics, 17 is the lowest number of monthly issues over the past six months.
Siemens Patches DoS Flaws in Industrial Products
11.5.2017 securityweek Vulnerebility
Siemens has released software updates for some of its industrial products, including SIMATIC and SCALANCE, to patch several medium severity denial-of-service (DoS) vulnerabilities.
Siemens and ICS-CERT have each published three advisories covering a total of four security holes. Two of the advisories describe vulnerabilities affecting products that use the PROFINET Discovery and Configuration Protocol (DCP).
The flaws, caused by improper input validation, can be exploited by attackers with network access to cause a DoS condition on devices by sending specially crafted PROFINET DCP broadcast packets. Manual intervention is required to restore the system after an attack.
The list of affected products includes SIMATIC communication processors, modules, PLCs, identification systems, HMI panels, and remote servicing products; SCALANCE routers, switches and firewalls; SITOP power supply units; and SIRIUS relays. Some SIMOCODE, SINAMICS, SIMOTION, SINEMA, SINAUT, and SINUMERIK products are also impacted.
Duan JinTong, Ma ShaoShuai and Cheng Lei from the NSFOCUS Security Team reported these flaws to Siemens. The vendor has released patches for some of the affected products, and provided mitigation recommendations for products that have yet to receive fixes.
Siemens’ recommendations include using VPNs to protect network communications, and applying cell protection and defense-in-depth concepts as described in the company’s operational guidelines for industrial security.
The third advisory published by Siemens and ICS-CERT describes a DoS vulnerability affecting SIMATIC WinCC SCADA systems, the WinCC Runtime Professional visualization platform, and the WinCC (TIA Portal) Professional engineering software.
The weakness, reported by researchers at Kaspersky Lab, allows an attacker to crash services by sending specially crafted messages to the DCOM interface. This flaw is less severe as the attack requires not only network access, but also administrative credentials.
SAP Patches 17 Vulnerabilities With May 2017 Security Update
11.5.2017 securityweek Vulnerebility
SAP on Tuesday released its May 2017 set of security fixes to address 17 issues in its products, the lowest number of monthly vulnerabilities over the past six months.
Only 9 of the security notes were released on this SAP Security Patch Day, SAP reveals. 4 others were released after the second Tuesday of the previous month and before the second Tuesday of this month, while 4 more are updates to previously released notes.
Missing Authorization Checks (5 vulnerabilities) and Cross-Site Scripting (5 flaws) represented the most common vulnerability types addressed this month. Additionally, SAP resolved two Implementation flaws, along with an XML external entity, one denial of service, a buffer overflow, one clickjacking, and an SQL injection.
The highest CVSS score of the vulnerabilities resolved this month is 6.5. One of the flaws, however, was assessed a Hot News rating, while another was considered High priority, ERPScan notes. The remaining 15 issues included 14 Medium risk vulnerabilities and one Low severity bug.
As security firm Onapsis explains, the High priority vulnerability wasn’t an issue directly in the SAP platform, but a bug in a third-party library that SAP uses. Resolved via note #2380277 (titled “Memory Corruption Vulnerability in IGS”), the bug allows an attacker to update a library component that is being used by Internet Graphics Server (IGS).
The library has been vulnerable for the past year, but it is easy to resolve and there are no reports of it being widely exploited, Onapsis notes. The issue affects products from companies such as Oracle and RedHat too, but they updated it last year.
The most important of the issues SAP Security Patch Day addressed include two missing authorization checks in SAP Defense Forces & Public Security DFPS module (CVSS Base Score of 6.5 and 6.3, respectively), a missing authorization check in SAP NetWeaver ADBC Demo Programs (6.3), and a Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Authentication and SSO (6.1).
A total of 4 vulnerabilities in DFPS module were addressed this month, namely 3 missing authorization checks affecting DFPS and one update to a patch for SQL Injection in the same module. Overall, SAP addressed 18 vulnerabilities in this module (3 High priority and 15 Medium risk). 11 of the bugs were resolved over the past six months.
“Missing authorization check vulnerability usually allows a perpetrator to read, modify or delete data, which has restricted access. When it comes to the defense industry and armed forces, the information can be critical in terms of International security and the effect of even such low-impact vulnerabilities could be devastating,” ERPScan notes.
All but one of the May 2017 SAP Security Patch Day notes are automatic ones, meaning that they have an automatic effect and customers won’t have to take additional steps to secure their deployments, Onapsis says. The only note that has manual steps is #2142551 (“Whitelist Service for Clickjacking Framing Protection in AS ABAP”).
Asus Patches Vulnerabilities in RT Routers
11.5.2017 securityweek Vulnerebility
Asus Patches CSRF, JSONP and XSS Flaws in RT Routers
Asus RT-AC and RT-N devices that are not running the latest firmware version are vulnerable to a series of CSRF, JSONP and XSS vulnerabilities that allow malicious actors to disclose information, change device settings, or inject code.
Asus addressed the flaws in its March 2017 firmware update (which arrived on devices as version 3.0.0.4.380.7378), but some details have been published only this week. According to Nightwatch Cybersecurity researchers, multiple issues affect the web interface RT routers arrive with, although it is normally accessible only from LAN and not from the Internet.
The vulnerabilities, the researchers say, “can facilitate attacks on the router either via a malicious site visited by a user on the same network, or a malicious mobile or desktop application running on the same network.”
The release notes published by Asus on its support website show that a total of five vulnerabilities were addressed in firmware version 3.0.0.4.380.7378. Additionally, the update added log message for brute force attack and fixed various non-security bugs.
Tracked as CVE-2017-5891, the first of the bugs includes a Login Page Cross-Site Request Forgery (CSRF) and Save Settings CSRF, which allow malicious sites to login and change settings in the router. The issue is that the login page for the web interface, the same as the various pages that can save Settings, has no form of CSRF protection.
Because of that, malicious sites could submit login requests without user’s knowledge, but only as long as the site knows the username and password of the router. Devices where the default credentials (admin / admin) haven’t been replaced yet are certainly at risk. Once logged in, the site could change any settings in the router without the user’s knowledge.
Tracked as CVE-2017-5892, the second vulnerability resides in the presence of two JSONP (JSON with Padding) endpoints within the router, which allow “detection of which ASUS router is running and some information disclosure,” coupled with the existence of “multiple JSONP endpoints within the router interface that reveal various data from the router,” Nightwatch Cybersecurity says.
The exposed data includes network information, surrounding access points on both 2.4 GHz and 5GHz bands, network map of devices on the network, origin data, external IP address, and WebDAV information.
Another related issue is the presence of an XML endpoint in the router, which reveals the Wi-Fi password to the router. For exploitation, however, a mobile or desktop application running on the local network is required, because XML cannot be loaded cross origin in the browser.
The third bug is a session hijack vulnerability in HTTPD affecting RT-N and RT-AC running firmware before 3.0.0.4.380.7378, RT-AC68W routers with firmware before 3.0.0.4.380.7266; RT-N routers with firmware before 3.0.0.4.380.9488; and Asuswrt-Merlin firmware before 380.65_2. Tracked as CVE-2017-6549, the bug allows remote attackers to steal any active admin session by sending cgi_logout and asusrouter-Windows-IFTTT-1.0 in certain HTTP headers.
A fourth bug was a cross-site scripting (XSS) vulnerability in HTTPD in the aforementioned firmware versions. Tracked as CVE-2017-6547, the flaw allows remote attackers to inject arbitrary JavaScript by requesting filenames longer than 50 characters.
Finally, Asus also resolved buffer overflows (CVE-2017-6548) in networkmap on said firmware releases, which could “allow remote attackers to execute arbitrary code on the router via a long host or port in crafted multicast messages.”
Owners of affected routers should install the latest firmware release on their devices as soon as possible. They should also consider changing the default credentials, if they haven’t already.
Microsoft Issues Patches for Another Four Zero-Day Vulnerabilities
10.5.2017 thehackernews Vulnerebility
As part of this month's Patch Tuesday, Microsoft has released security patches for a total of 55 vulnerabilities across its products, including fixes for four zero-day vulnerabilities being exploited in the wild.
Just yesterday, Microsoft released an emergency out-of-band update separately to patch a remote execution bug (CVE-2017-0290) in Microsoft's Antivirus Engine that comes enabled by default on Windows 7, 8.1, RT, 10 and Server 2016 operating systems.
The vulnerability, reported by Google Project Zero researchers, could allow an attacker to take over your Windows PC with just an email, which you haven't even opened yet.
May 2017 Patch Tuesday — Out of 55 vulnerabilities, 17 have been rated as critical and affect the company's main operating systems, along with other products like Office, Edge, Internet Explorer, and the malware protection engine used in most of the Microsoft's anti-malware products.
Sysadmins all over the world should prioritize the May's Patch Tuesday as it addresses four critical zero-day vulnerabilities, three of which being actively exploited by cyber-espionage groups in targeted attacks over the past few months.
3 Zero-Days Were Exploited in the Wild by Russian Cyber-Espionage Group
First Zero-Day Vulnerability (CVE-2017-0261) — It affects the 32- and 64-bit versions of Microsoft Office 2010, 2013 and 2016, and resides in how Office handles Encapsulated PostScript (EPS) image files, leading to remote code execution (RCE) on the system.
This Office vulnerability could be exploited by tricking victims into opening a file containing a malformed graphics image in an email. The attack also exploits a Windows privilege escalation bug (CVE-2017-0001) that the company patched on March 14 to gain full control over the system – essentially allowing attackers to install spyware and other malware.
According to the FireEye researchers, the CVE-2017-0261 flaw has been exploited since late March by an unknown group of financially motivated hackers and by a Russian cyber espionage group called Turla, also known as Snake or Uroburos.
Second Zero-Day Vulnerability (CVE-2017-0262) — FireEye and ESET researchers believe that the APT28 hacking group, also known as Fancy Bear, or Pawn Storm, was actively using this EPS-related Microsoft Office zero-day vulnerability which leads to remote code execution on opening a malformed file.
Third Zero-Day Vulnerability (CVE-2017-0263) — The third zero-day bug is an elevation of privilege (EoP) vulnerability in all supported versions of Microsoft's Windows operating system.
This vulnerability exists in the way Windows kernel-mode driver handles objects in memory, allowing attackers to run arbitrary code in kernel mode and then install malware, view, change, or delete data, and even create new accounts with full user rights.
Researchers believe that the Russian cyber-espionage group was also actively exploiting this flaw (CVE-2017-0263) along with the second zero-day vulnerability (CVE-2017-0262).
Fourth Zero-Day Vulnerability (CVE-2017-0222) — Another zero-day vulnerability affects Internet Explorer 10 and 11 and resides in how Internet Explorer handles objects in memory.
Opening a malicious web page can corrupt memory to trigger remote code execution, allowing attackers to take control of an affected system. According to the tech giant, this issue was also exploited in the wild.
Patches for Other Critical Vulnerabilities — This month's security updates also fix critical vulnerabilities in both Edge and Internet Explorer (IE) that could lead to remote code execution by tricking victims into visiting malicious websites or viewing specially crafted advertisements inside the browsers.
Besides this, Microsoft also addresses four critical remote code execution bugs (CVE-2017-0272, CVE-2017-0277, CVE-2017-0278, and CVE-2017-0279) in Windows SMB network file-sharing protocol, which affects Windows 7 through 10 and Windows Server 2008 through 2016.
These vulnerabilities put Windows PCs and server installations at risk of hacking if they use SMBv1, though there have been no reports of any of these flaws exploited in the wild.
As usual, Adobe Flash Players patches are also included in the security update to address 7 CVE-listed flaws in the Windows, macOS, and Linux.
Windows users are strongly advised to install the latest updates as soon as possible in order to protect themselves against the active attacks in the wild.
Cisco Patches CIA Zero-Day Affecting Hundreds of Switches
10.5.2017 securityweek Vulnerebility
Cisco has finally released an update for its IOS and IOS XE software to address a critical vulnerability believed to have been used by the U.S. Central Intelligence Agency (CIA) to target the company’s switches.
Cisco learned of the flaw in mid-March after conducting an analysis of the Vault 7 files made available by WikiLeaks. These files describe exploits allegedly used by the CIA to hack mobile devices, desktop systems, networking equipment and IoT devices.
The vulnerability, tracked as CVE-2017-3881, affects the cluster management protocol (CMP) processing code used by Cisco’s IOS and IOS XE software. An unauthenticated attacker can exploit the flaw remotely to cause devices to reload or for arbitrary code execution with elevated privileges.
“An attacker could exploit this vulnerability by sending malformed CMP-specific Telnet options while establishing a Telnet session with an affected Cisco device configured to accept Telnet connections,” Cisco said in its advisory.
The security hole exists due to the fact that malformed CMP-specific Telnet options are not processed correctly, and due to the failure to restrict the use of these options to internal communications between cluster members.
According to the vendor, more than 300 switches are affected, including Catalyst, Embedded Service, IE (industrial), RF and ME devices. The issue also impacts several service modules.
Cisco warned users on April 10 that an exploit targeting the vulnerability had been made public, but the weakness was only patched this week. The company did, however, share some mitigation advice when it first disclosed the problem.
The networking giant said there was no evidence of malicious exploitation, but if the exploit does belong to the CIA, the agency may have used it in targeted attacks. WikiLeaks claimed that the CIA had “secretly exploited” the vulnerability.
Cisco’s IOS software was also apparently targeted by the Equation Group, an NSA-linked threat actor whose tools were leaked online by a hacker group calling itself Shadow Brokers. Researchers determined last year that the flaw had exposed hundreds of thousands of Cisco devices to attacks.
Cisco is the only major vendor that has admitted finding a critical vulnerability in the Vault 7 files. Security firms and tech giants claim that the latest versions of their products patch a majority of the flaws. On the other hand, WikiLeaks says most companies have not made any effort to obtain the actual exploits possessed by the organization.
Vulnerability Allowed Hackers to Steal iCloud Keychain Secrets
10.5.2017 securityweek Vulnerebility
Apple has recently patched a Keychain vulnerability that could have been exploited by man-in-the-middle (MitM) attackers to obtain sensitive user information. The details of the flaw were disclosed on Monday by the researcher who reported it to the vendor.
One of the many security holes patched by Apple in late March in iOS, macOS and other products is CVE-2017-2448, a Keychain weakness discovered by Alex Radocea of Longterm Security.
According to Radocea, the flaw affects the iCloud Keychain, which stores account names, passwords, credit card data, and Wi-Fi network information. The iCloud Keychain sync feature allows users to synchronize their keychain so that passwords and other data are accessible from all their Apple devices.
Apple designed the iCloud Keychain to be highly secure and it told customers that not even the NSA can access their secrets. The sync feature uses end-to-end encryption to exchange data — the encryption relies on a syncing identity key unique to each device, and the encryption keys are never exposed to iCloud.
Data is transmitted via the iCloud Key-Value Store (KVS), which applications use to synchronize the data of iCloud users. Communications between apps and the KVS are arbitrated by “syncdefaultsd” and other iCloud system services. The KVS is tied to each user’s account and accessing it requires the targeted account’s credentials or intercepted iCloud authentication tokens.
The vulnerability found by Radocea is related to Apple’s open source implementation of the Off-The-Record (OTR) messaging protocol. Devices can only transmit OTR data if they are part of a group of trust called “signed syncing circle,” which is signed with a syncing identity key associated with each device and a key derived from the user’s iCloud password. Joining the circle requires permission from an existing device and user interaction.
The researcher discovered that, due to improper error handling, the signature verification routine for OTR could have been bypassed, allowing an MitM attacker to negotiate an OTR session without needing the syncing identity key.
While an attacker cannot exploit this vulnerability to join a signing circle, it does allow them to impersonate other devices in the circle when keychain data is being synced, and intercept passwords and other secrets, the expert said.
“For an adversary to gain access to user Keychain secrets, an adversary could leverage this flaw with one of several capabilities to receive keychain secrets. First, assuming that two-factor authentication is not enabled for the user, an attacker with the victim’s iCloud password would be able to directly access and modify entries in the user’s iCloud KVS data,” Radocea said in a blog post this week.
“Second, a sophisticated adversary with backend access to iCloud KVS would also be able to modify entries to perform the attack,” the researcher added. “Third, the ‘syncdefaultsd’ service does not perform certificate pinning for TLS communications. Without key-pinning, a maliciously issued TLS certificate from any trusted system Certificate Authority could intercept TLS sessions to the iCloud KVS web servers and also perform the attack.”
Radocea has pointed out that it’s often easy for attackers to obtain iCloud passwords, especially since many people set weak passwords or use the same one across multiple online services.
Apple said it addressed the vulnerability through improved validation for the authenticity of OTR packets.
Microsoft Patch Tuesday updates for May 2017 fix Zero Days exploited by Russian APT groups
10.5.2017 securityaffairs Vulnerebility
Microsoft Patch Tuesday for May 2017 address tens security vulnerabilities, including a number of zero-day flaws exploited by Russian APT groups.
Microsoft Patch Tuesday updates for May 2017 fix more than 50 security flaws, including a number of zero-day vulnerabilities exploited by Russian APT groups.
Microsoft released security updates for Windows, Internet Explorer, Edge, Office, the .NET framework, and Flash Player on Tuesday.
Security experts at Microsoft worked with peers at ESET and FireEye to address the vulnerabilities affecting Encapsulated PostScript (EPS) filter in Office.
Russian APT groups
Researchers at FireEye investigated some attacks attributed to the Russian APT groups and also an unknown financially-motivated threat actor.
“At the end of March 2017, we detected another malicious document leveraging an unknown vulnerability in EPS and a recently patched vulnerability in Windows Graphics Device Interface (GDI) to drop malware. Following the April 2017 Patch Tuesday, in which Microsoft disabled EPS, FireEye detected a second unknown vulnerability in EPS.” reads the analysis shared by FireEye.
“FireEye believes that two actors – Turla and an unknown financially motivated actor – were using the first EPS zero-day (CVE-2017-0261), and APT28 was using the second EPS zero-day (CVE-2017-0262) along with a new Escalation of Privilege (EOP) zero-day (CVE-2017-0263). Turla and APT28 are Russian cyber espionage groups that have used these zero-days against European diplomatic and military entities. The unidentified financial group targeted regional and global banks with offices in the Middle East.”
The Turla group (aka Waterbug, KRYPTON, and Venomous Bear) has been exploiting an Office remote code execution (RCE) vulnerability (CVE-2017-0261) to spread the SHIRIME custom JavaScript malware.
A second group of financially motivated threat actors has been exploiting the same vulnerability to deliver a new variant of the NETWIRE malware.
The experts observed that The Turla APT also leveraged CVE-2017-0001 for privilege escalation, while the cyber crime gang the CVE-216-7255 for privilege escalation.
The experts from the two firms confirmed that the notorious APT28 group exploited a number of zero-day vulnerabilities in targeted attacks, including the CVE-2017-0262 Office RCE vulnerabilities and a Windows privilege escalation tracked as CVE-2017-0263.
The hackers leveraged the above exploits to deliver the GAMEFISH malware (Seduploader).
Microsoft announced that the security updates released this month have fixed vulnerabilities in Office (CVE-2017-0261 and CVE-2017-0262) exploited the Russian APT groups.
The list of flaws fixed by Microsoft on Tuesday includes also a memory corruption issue in Internet Explorer tracked as CVE-2017-0222, this memory corruption zero-day can be exploited by a remote attacker for code execution.
Adobe fixes critical and important flaws in Flash Player and Experience Manager
10.5.2017 securityaffairs Vulnerebility
Adobe has issued security updates to address critical and important security vulnerabilities in Flash Player and Experience Manager.
The last Flash Player release 25.0.0.171 addresses seven vulnerabilities that can be exploited to take over vulnerable systems.
According to the security advisory published by Adobe, the vulnerabilities include a use-after-free and other memory corruption flaws that can be exploited by attackers to execute arbitrary code.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system. ” reads the security advisory.
“These updates resolve a use-after-free vulnerability that could lead to code execution (CVE-2017-3071).
These updates resolve memory corruption vulnerabilities that could lead to code execution (CVE-2017-3068, CVE-2017-3069, CVE-2017-3070, CVE-2017-3072, CVE-2017-3073, CVE-2017-3074).”
The company acknowledged Jihui Lu of Tencent KeenLab and Mateusz Jurczyk and Natalie Silvanovich of Google Project Zero for reporting the vulnerabilities.
Lu reported the following flaws:
CVE-2017-3069, CVE-2017-3070, CVE-2017-3071, CVE-2017-3072, CVE-2017-3073, CVE-2017-3074;
Jurczyk and Silvanovich reported the CVE-2017-3068 vulnerability.
According to Adobe, the vulnerabilities have not been exploited by threat actors in the wild.
Adobe Flash Player
A separate security advisory published by Adobe addresses an important information disclosure vulnerability in the Adobe Experience Manager Forms tracked as CVE-2017-3067.
“Adobe has released security updates for Adobe Experience Manager (AEM) Forms on Windows, Linux, Solaris and AIX. These updates resolve an important information disclosure vulnerability (CVE-2017-3067) resulting from abuse of the pre-population service in AEM Forms.” reads the advisory.”This issue was resolved by providing administrators with additional controls in the configuration manager to restrict the file paths and protocols used to pre-fill a form. Adobe recommends users apply the available updates using the instructions provided in the “Solution” section below.”
The vulnerability was discovered by Ruben Reusser and affects the Versions 6.0 through 6.2 are.
The flaw is related to the abuse of the pre-population service in Experience Manager Forms, also in this case, Adobe confirmed that there is no evidence of exploitation in the wild.
Microsoft Patches Zero-Days Exploited by Russia-Linked Hackers
10.5.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for May 2017 address tens of vulnerabilities, including several zero-day flaws exploited by profit-driven cybercriminals and two notorious Russia-linked cyber espionage groups.
The company has resolved more than 50 security holes affecting Windows, Internet Explorer, Edge, Office, the .NET framework, and Flash Player, for which Adobe released an update on Tuesday.
A blog post published by Microsoft revealed that the company had worked with ESET and FireEye to protect customers against attacks leveraging vulnerabilities in the Encapsulated PostScript (EPS) filter in Office. Both ESET and FireEye have released reports on the attacks they have observed.
FireEye has spotted attacks launched by a couple of cyber espionage groups believed to be connected to the Russian government and an unknown financially-motivated threat actor.
According to the security firm, the group known as Turla, Waterbug, KRYPTON and Venomous Bear has been exploiting an Office remote code execution (RCE) vulnerability tracked as CVE-2017-0261 to deliver a custom JavaScript implant dubbed by FireEye “SHIRIME.” The same vulnerability has also been exploited by profit-driven cybercriminals to deliver a new variant of the NETWIRE malware, a threat used by multiple actors over the past years.
The Turla group’s attacks also leveraged CVE-2017-0001 for privilege escalation, while the cybercriminals used CVE-2016-7255 for privilege escalation.
Both FireEye and ESET have observed attacks involving zero-day vulnerabilities launched by the group known as APT28, Pawn Storm, Fancy Bear, Sofacy, Sednit and Strontium. This Russia-linked group, which some believe could be behind the recent election cyberattacks in France, has leveraged an Office RCE flaw (CVE-2017-0262) and a Windows privilege escalation (CVE-2017-0263). The malware delivered in these attacks is tracked by the security firms as Seduploader and GAMEFISH.
Microsoft pointed out that the Turla attacks were first spotted in March, and customers who had up-to-date systems had already been protected as CVE-2017-0001 was patched earlier that month. In April, the company also rolled out a defense-in-depth protection designed to prevent EPS attacks by disabling the EPS filter by default.
The updates released by the company this month patch the EPS-related vulnerabilities in Office (CVE-2017-0261 and CVE-2017-0262) to ensure that customers who need to use EPS filters are still protected.
Another zero-day patched by Microsoft on Tuesday is CVE-2017-0222, a memory corruption in Internet Explorer that can be exploited for remote code execution. No information has been shared on the attacks leveraging this security hole.
The tech giant has also addressed four vulnerabilities that have been publicly disclosed. The list includes an RCE flaw in the JavaScript engines used by web browsers (CVE-2017-0229), a SmartScreen filter-related browser spoofing vulnerability (CVE-2017-0231), a privilege escalation in Edge (CVE-2017-0241), and a Mixed Content warnings bypass in Internet Explorer (CVE-2017-0064).
Adobe Patches Flaws in Flash Player, Experience Manager
9.5.2017 securityweek Vulnerebility
Updates released by Adobe on Tuesday for Flash Player and Experience Manager patch several vulnerabilities classified as critical and important.
Flash Player 25.0.0.171 addresses a total of seven flaws which, according to the software giant, can be exploited to take control of vulnerable systems.
The security holes have been described as use-after-free and other memory corruption vulnerabilities that can lead to arbitrary code execution. A majority of the weaknesses were reported to Adobe by Jihui Lu of Tencent KeenLab, and one was discovered by Google Project Zero researchers.
The Flash Player vulnerabilities are tracked as CVE-2017-3068, CVE-2017-3069, CVE-2017-3070, CVE-2017-3071, CVE-2017-3072, CVE-2017-3073 and CVE-2017-3074. There is no evidence that they have been exploited in the wild.
Adobe has published a separate advisory for a flaw in the Forms feature of the Experience Manager enterprise content management solution. Versions 6.0 through 6.2 of the product are affected by an information disclosure vulnerability discovered by Ruben Reusser of headwire.com and tracked as CVE-2017-3067.
The flaw is related to the abuse of the pre-population service in Experience Manager Forms.
“This issue was resolved by providing administrators with additional controls in the configuration manager to restrict the file paths and protocols used to pre-fill a form,” Adobe said in its advisory.
Adobe has released hotfixes and cumulative fix packs for each affected version. The company has found no evidence of exploitation in the wild.
The number of vulnerabilities resolved this Patch Tuesday is small compared to last month, when Adobe addressed nearly 60 vulnerabilities, including ones disclosed at this year’s Pwn2Own hacking competition.
Jenkins patched a critical RCE flaw in its open source automation server
9.5.2017 securityaffairs Vulnerebility
Jenkins developers fixed a critical RCE vulnerability in the popular open source automation server along with many other issues.
Jenkins is the most popular open source automation server, it is maintained by CloudBees and the Jenkins community.
The automation server supports developers build, test and deploy their applications, it has more than 133,000 active installations worldwide with more than 1 million users.
The developers of the automation server recently patched several vulnerabilities, including a critical flaw that can be exploited by a remote attacker for arbitrary code execution.
A security researcher recently reported to the Beyond Security’s SecuriTeam Secure Disclosure program that the popular automation server is affected by a critical issue related to Java deserialization.

The vulnerability could be exploited by a remote unauthenticated attacker to execute arbitrary code on the target system, a hacker just needs to send two specially crafted requests to the affected server.
“CLI: Unauthenticated remote code execution
SECURITY-429 / CVE-2017-1000353
An unauthenticated remote code execution vulnerability allowed attackers to transfer a serialized Java SignedObject object to the remoting-based Jenkins CLI, that would be deserialized using a new ObjectInputStream, bypassing the existing blacklist-based protection mechanism.
SignedObject has been added to the remoting blacklist.” reads the security advisory published by Jenkins.
Jenkins developers admitted that the flaw “allowed attackers to transfer a serialized Java SignedObject object to the remoting-based Jenkins CLI, that would be deserialized using a new ObjectInputStream, bypassing the existing blacklist-based protection mechanism.”
The development team released the versions 2.57 and 2.46.2 (LTS) to address the issue. The security updates also fixed other problems, such as multiple high severity cross-site request forgery (CSRF) vulnerabilities and high severity cross-site request forgery (CSRF) vulnerabilities.
According to the development team, the CSRF flaws can be exploited by attackers to conduct several malicious activities such as restarting the server and installing plugins.
The security updates also fixed a Login command that allowed to impersonate any Jenkins user (SECURITY-466 / CVE-2017-1000354) and an XStream issue that could cause Java crash when trying to instantiate void/Void (SECURITY-503 / CVE-2017-1000355).
Microsoft Issues Emergency Patch For Critical RCE in Windows Malware Scanner
9.5.2017 thehackernews Vulnerebility
Microsoft's own antivirus software made Windows 7, 8.1, RT and 10 computers, as well as Windows Server 2016 more vulnerable.
Microsoft has just released an out-of-band security update to patch the crazy bad bug discovered by a pair of Google Project Zero researchers over the weekend.
Security researchers Tavis Ormandy announced on Twitter during the weekend that he and another Project Zero researcher Natalie Silvanovich discovered "the worst Windows remote code [execution vulnerability] in recent memory."
Natalie Silvanovich also published a proof-of-concept (PoC) exploit code that fits in a single tweet.
The reported RCE vulnerability, according to the duo, could work against default installations with "wormable" ability – capability to replicate itself on an infected computer and then spread to other PCs automatically.
According to an advisory released by Microsoft, the remotely exploitable security flaw (CVE-2017-0290) exists in Microsoft Malware Protection Engine (MMPE) – the company's own antivirus engine that could be used to fully compromise Windows PCs without any user interaction.
List of Affected Anti-Malware Software
Eventually, every anti-malware software that ship with the Microsoft's Malware Protection Engine are vulnerable to this flaw. The affected software includes:
Windows Defender
Windows Intune Endpoint Protection
Microsoft Security Essentials
Microsoft System Center Endpoint Protection
Microsoft Forefront Security for SharePoint
Microsoft Endpoint Protection
Microsoft Forefront Endpoint Protection
Microsoft's Defender security software comes enabled by default on Windows 7, 8.1, RT 8.1, and Windows 10, as well as Windows Server 2016. All are at risk of full remote system compromise.
Remote Code Execution Flaw in Microsoft's Malware Protection Engine
The flaw resides in the way the Microsoft Malware Protection Engine scan files. It is possible for an attacker to craft a malicious file that could lead to memory corruption on targeted systems.
Researchers have labeled the flaw as a "type confusion" vulnerability that exists in NScript, a "component of mpengine that evaluates any filesystem or network activity that looks like JavaScript," which fails to validate JavaScript inputs.
"To be clear, this is an unsandboxed and highly privileged JavaScript interpreter that is used to evaluate untrusted code, by default on all modern Windows systems. This is as surprising as it sounds," Google security researchers explained in a bug report posted on the Chromium forum.
Since antivirus programs have real-time scanning functionality enabled by default that automatically scans files when they are created, opened, copied or downloaded, the exploit gets triggered as soon as the malicious file is downloaded, infecting the target computer.
The vulnerability could be exploited by hackers in several ways, like sending emails, luring victims to sites that deliver malicious files, and instant messaging.
"On workstations, attackers can access mpengine by sending emails to users (reading the email or opening attachments is not necessary), visiting links in a web browser, instant messaging and so on," researchers explained.
"This level of accessibility is possible because MsMpEng uses a filesystem minifilter to intercept and inspect all system filesystem activity, so writing controlled contents to anywhere on disk (e.g. caches, temporary internet files, downloads (even unconfirmed downloads), attachments, etc.) is enough to access functionality in mpengine."
The injected malicious payload runs with elevated LocalSystem level privileges that would allow hackers to gain full control of the target system, and perform malicious tasks like installing spyware, stealing sensitive files, and login credentials, and much more.
Microsoft responded to the issue very quickly and comes up with a patch within just 3 days, which is very impressive. The patch is now available via Windows Update for Windows 7, 8.1, RT and 10.
The vulnerable version of Microsoft Malware Protection Engine (MMPE) is 1.1.13701.0, and the patched version is 1.1.13704.0.
By default, Windows PCs automatically install the latest definitions and updates for the engine. So, your system will install the emergency update automatically within 1-2 days, but you can also get it installed immediately by pressing 'Check Update' button in your settings.
Microsoft fixes Microsoft Malware Protection Engine RCE vulnerability CVE-2017-0290 found by Google
9.5.2017 securityaffairs Vulnerebility
Microsoft fixes the vulnerability in the Microsoft Malware Protection Engine (CVE-2017-0290) discovered just three days by Google experts.
Last week the researchers at the Google Project Zero team have discovered a new critical Windows RCE vulnerability, tracked as CVE-2017-0290, they defined the bug as the worst Windows RCE in recent memory.
Follow
Tavis Ormandy ✔ @taviso
I think @natashenka and I just discovered the worst Windows remote code exec in recent memory. This is crazy bad. Report on the way. 🔥🔥🔥
4:14 AM - 6 May 2017
2,542 2,542 Retweets 2,793 2,793 likes
The researchers only revealed the following information on the Windows RCE vulnerability:
The PoC exploit the Project Zero team has developed works against default Windows installations.
The Windows RCE vulnerability could be exploited by a remote attacker.
The attack is “wormable,” capability to spread itself.
It took Microsoft less than three days to fix the critical RCE flaw that affects the Microsoft Malware Protection Engine.
Follow
Tavis Ormandy ✔ @taviso
Still blown away at how quickly @msftsecurity responded to protect users, can't give enough kudos. Amazing.
3:14 AM - 9 May 2017
305 305 Retweets 855 855 likes
“Microsoft is releasing this security advisory to inform customers that an update to the Microsoft Malware Protection Engine addresses a security vulnerability that was reported to Microsoft.” reads the advisory published by Microsoft.
“The update addresses a vulnerability that could allow remote code execution if the Microsoft Malware Protection Engine scans a specially crafted file. An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system.
The Microsoft Malware Protection Engine ships with several Microsoft antimalware products.”
CVE-2017-0290 Windows RCE vulnerability
The Flaw affects the “MsMpEng” service, which runs unsandboxed with SYSTEM privileges and is accessible without authentication via Windows services such as Exchange and IIS.
The list of affected software includes Forefront Endpoint Protection, Endpoint Protection, Forefront Security for SharePoint Service Pack 3, System Center Endpoint Protection, Security Essentials, Windows Defender, and Windows Intune Endpoint Protection.
Google Project Zero has published the technical details and the proof-of-concept (PoC) exploit code for the CVE-2017-0290 flaw.
“MsMpEng is the Malware Protection service that is enabled by default on Windows 8, 8.1, 10, Windows Server 2012, and so on. Additionally, Microsoft Security Essentials, System Centre Endpoint Protection and various other Microsoft security products share the same core engine. MsMpEng runs as NT AUTHORITY\SYSTEM without sandboxing, and is remotely accessible without authentication via various Windows services, including Exchange, IIS, and so on.” reads the advisory published by the Google Project Zero Team.”
The Google Project Zero researchers said the vulnerability can be exploited via email – opening the malicious email is not necessary for exploitation – or by getting the targeted user to access a specially crafted link.
“Vulnerabilities in MsMpEng are among the most severe possible in Windows, due to the privilege, accessibility, and ubiquity of the service.” added Google.
“This level of accessibility is possible because MsMpEng uses a file system minifilter to intercept and inspect all system filesystem activity, so writing controlled contents to anywhere on disk (e.g. caches, temporary internet files, downloads (even unconfirmed downloads), attachments, etc) is enough to access functionality in mpengine,” the experts said in their advisory.
The experts highlighted that on workstations, attackers can access mpengine just by sending emails to users (reading the email or opening attachments is not necessary), visiting links in a web browser, instant messaging and so on.
According to Microsoft, the security fix should be sent out automatically to antimalware products that use the Microsoft Malware Protection Engine within 48 hours.
Microsoft Fixes Antimalware Engine Flaw Found by Google Experts
9.5.2017 securityweek Vulnerebility
It took Microsoft less than three days to patch a critical remote code execution vulnerability found by Google Project Zero researchers in the company’s Malware Protection Engine. Most users don’t need to take any action as the affected products should be updated automatically.
The existence of the flaw was disclosed by Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich on Friday. Ormandy described the weakness as “the worst Windows remote code exec [vulnerability] in recent memory.”
The expert said the vulnerability was “wormable,” it affected default Windows installations, and exploitation did not require access to the victim’s network.
Microsoft announced a patch for the vulnerability and published an advisory on Monday. While Ormandy initially described it as a Windows vulnerability, the security hole actually affects the Microsoft Malware Protection Engine, which is shipped with several of the company’s Windows antimalware products.
The list of impacted software includes Forefront Endpoint Protection, Endpoint Protection, Forefront Security for SharePoint Service Pack 3, System Center Endpoint Protection, Security Essentials, Windows Defender, and Windows Intune Endpoint Protection.
Follow
Tavis Ormandy ✔ @taviso
Still blown away at how quickly @msftsecurity responded to protect users, can't give enough kudos. Amazing.
3:14 AM - 9 May 2017
313 313 Retweets 880 880 likes
According to Ormandy and Silvanovich, the vulnerability, tracked as CVE-2017-0290, affects the “MsMpEng” service, which runs unsandboxed with SYSTEM privileges and is accessible without authentication via Windows services such as Exchange and IIS.
The Google Project Zero researchers said the vulnerability can be exploited via email – opening the malicious email is not necessary for exploitation – or by getting the targeted user to access a specially crafted link.
“This level of accessibility is possible because MsMpEng uses a filesystem minifilter to intercept and inspect all system filesystem activity, so writing controlled contents to anywhere on disk (e.g. caches, temporary internet files, downloads (even unconfirmed downloads), attachments, etc) is enough to access functionality in mpengine,” the experts said in their advisory.
The researchers believe that vulnerabilities in the Microsoft Malware Protection Engine “are among the most severe possible in Windows, due to the privilege, accessibility, and ubiquity of the service.”
Google Project Zero has made public technical details and proof-of-concept (PoC) exploit code.
Microsoft pointed out that the patch should be sent out automatically to antimalware products that use the Malware Protection Engine within 48 hours. However, the company has advised users to check their software to ensure that the automatic deployment of updates and malware definitions is working properly.
Google 0-Day Hunters Find 'Crazy Bad' Windows RCE Flaw
8.5.2017 thehackernews Vulnerebility
Google Project Zero's security researchers have discovered another critical remote code execution (RCE) vulnerability in Microsoft’s Windows operating system, claiming that it is something truly bad.
Tavis Ormandy announced during the weekend that he and another Project Zero researcher Natalie Silvanovich discovered "the worst Windows remote code [execution vulnerability] in recent memory. This is crazy bad. Report on the way."
Ormandy did not provide any further details of the Windows RCE bug, as Google gives a 90-day security disclosure deadline to all software vendors to patch their products and disclose it to the public.
This means the details of the new RCE vulnerability in Windows will likely be disclosed in 90 days from now even if Microsoft fails to patch the issue.
However, Ormandy later revealed some details of the Windows RCE flaw, clarifying that:
The vulnerability they claimed to have discovered works against default Windows installations.
The attacker does not need to be on the same local area network (LAN) as the victim, which means vulnerable Windows computers can be hacked remotely.
The attack is "wormable," capability to spread itself.
Despite not even releasing any technical details on the RCE flaw, some IT professionals working for corporates have criticized the Google Project Zero researcher for making the existence of the vulnerability public, while Twitter's infosec community is happy with the work.
"If a tweet is causing panic or confusion in your organization, the problem isn't the tweet, the problem is your organization," Project Zero researcher Natalie Silvanovich tweeted.
This is not the first time when Google's security researchers have discovered flaws in Microsoft’s products. Most recently in February, Google researchers disclosed the details of an unpatched vulnerability impacting Microsoft's Edge and Internet Explorer browsers.
Microsoft released a patch as part of its next Patch Tuesday but criticized Google for making all details public, exposing millions of its Windows users at risk of being hacked.
Microsoft has not yet responded to the latest claims, but the company has its May 2017 Patch Tuesday scheduled tomorrow, May 9, so hopefully, it will include a security patch to resolve this issue.
Critical Flaw Patched in Jenkins Automation Server
8.5.2017 securityweek Vulnerebility
The developers of Jenkins recently patched several vulnerabilities, including a critical weakness that can be exploited by a remote attacker for arbitrary code execution.
Jenkins is the most popular open source automation server, with over 133,000 installations and more than 1 million users worldwide. The product, maintained by CloudBees and the Jenkins community, is designed to help developers build, test and deploy their software.
An independent security researcher recently informed Beyond Security’s SecuriTeam Secure Disclosure program that Jenkins is affected by a serious vulnerability related to Java deserialization.
According to experts, the flaw allows an unauthenticated attacker to execute arbitrary code by sending two specially crafted requests to the vulnerable server. Technical details for the security hole, tracked as CVE-2017-1000353, were published by Beyond Security earlier this month.
In a security advisory published in late April, Jenkins developers said this critical vulnerability “allowed attackers to transfer a serialized Java SignedObject object to the remoting-based Jenkins CLI, that would be deserialized using a new ObjectInputStream, bypassing the existing blacklist-based protection mechanism.”
The flaw has been patched with the release of Jenkins 2.57 and 2.46.2 (LTS), which also address several other types of problems. This includes multiple high severity cross-site request forgery (CSRF) vulnerabilities that can be exploited by an attacker to perform administrative actions by getting targeted users to open a specially crafted webpage.
Jenkins developers said the CSRF flaws can be exploited to restart the server, downgrade Jenkins, install plugins, change users’ API tokens, modify configurations, and create administrator accounts.
Another high severity weakness, tracked as CVE-2017-1000354, allowed an attacker to impersonate Jenkins users. The flaw was related to the “login” command, which stored the encrypted username of successfully authenticated users in a cache file.
The update also fixes a medium severity issue related to the XStream library. This third-party component, which is used by Jenkins for serializing and deserializing XML, is affected by a flaw that can be leveraged to crash the Java process.
Google Researchers Find "Worst" Windows RCE Flaw
8.5.2017 securityweek Vulnerebility
Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich claim to have found a critical vulnerability in Windows. The details of the flaw will likely be disclosed in 90 days from now even if a patch is not available.
Ormandy announced over the weekend on Twitter that he and Silvanovich had discovered “the worst Windows remote code exec [vulnerability] in recent memory.”
The expert has not shared any details, but he has clarified that the exploit they created works against default Windows installations, and the attacker does not need to be on the same local area network as the victim. He also said the attack is “wormable.”
Despite not releasing any technical details on the vulnerability, some members of the industry have criticized the Google Project Zero researchers for making the existence of the flaw public.
Follow
Natalie Silvanovich @natashenka
If a tweet is causing panic or confusion in your organization, the problem isn't the tweet, the problem is your organization
7:58 PM - 6 May 2017
330 330 Retweets 781 781 likes
SecurityWeek has reached out to Microsoft for comment and will update this article if the company responds.
Google typically gives companies 90 days to patch vulnerabilities found by its researchers before making their details public, but the deadline is only 7 days if the weakness has been exploited in attacks.
In November, Project Zero disclosed the details of an actively exploited zero-day affecting the Windows kernel after Microsoft failed to release a fix.
More recently, in February, Google researcher Ivan Fratric made public the details and proof-of-concept (PoC) code for a potentially serious vulnerability affecting the Edge and Internet Explorer browsers. Microsoft patched the vulnerability a few weeks later.
In the past years, Google disclosed the details of several Windows vulnerabilities after 90 days. The search giant made some changes to its disclosure policy in February 2015 due to criticism from Microsoft and members of the industry, but the company continues to strictly apply its 90-day deadline.
Cisco fixes a critical flaw in CISCO CVR100W Wireless-N VPN Small Business Routers
6.5.2017 securityaffairs Vulnerebility
Cisco released a firmware update to fix a critical buffer overflow vulnerability in CISCO CVR100W Wireless-N VPN Small Business Routers.
Cisco has released a firmware update to fix a critical vulnerability in its CVR100W Wireless-N VPN routers.
The flaw, tracked as CVE-2017-3882, can be exploited by attackers to trigger a denial-of-service (DoS) condition and execute arbitrary code with root privileges.
The CVE-2017-3882 vulnerability was discovered by researchers from the Chinese GeekPwn hacker group. The company said there was no evidence of malicious exploitation.

The good news is that CISCO revealed that there was no evidence of exploitation of the flaw in the wild.
“A vulnerability in the Universal Plug-and-Play (UPnP) implementation in the Cisco CVR100W Wireless-N VPN Router could allow an unauthenticated, Layer 2–adjacent attacker to execute arbitrary code or cause a denial of service (DoS) condition. The remote code execution could occur with root privileges.” reads the CISCO security advisory.
The vulnerability resides in the Universal Plug and Play (UPnP) implementation of the CVR100W Wireless-N VPN routers.
The exploitation of the flaw is quite simple, an attacker can trigger the vulnerability by sending a specially crafted request to the UPnP listening port of the router.
“The vulnerability is due to incomplete range checks of the UPnP input data, which could result in a buffer overflow. An attacker could exploit this vulnerability by sending a malicious request to the UPnP listening port of the targeted device. An exploit could allow the attacker to cause the device to reload or potentially execute arbitrary code with root privileges.” continues the analysis.
The flaw affects CVR100W Wireless-N VPN routers running a version of the firmware prior to 1.0.1.22, no other small business routers are affected.
Administrators can determine which firmware release is running on their routers by logging in to the web interface using the http(s)://system-ip access URL.
Below there is an example included in the advisory, in this the router is running Firmware Release 1.0.1.21.
Cisco Small Business
CVR100W Wireless-N VPN Router
Version 1.0.1.21
The CVR100W Wireless-N VPN routers are also affected by a medium severity bug that can be exploited by an unauthenticated attacker to bypass the remote management ACL. This flaw was fixed with the release of version 1.0.1.24.
Unpatched Wordpress Flaw Could Allow Hackers To Reset Admin Password
5.5.2017 thehackernews Vulnerebility
WordPress, the most popular CMS in the world, is vulnerable to a logical vulnerability that could allow a remote attacker to reset targeted users’ password under certain circumstances.
The vulnerability (CVE-2017-8295) becomes even more dangerous after knowing that it affects all versions of WordPress — including the latest 4.7.4 version.
The WordPress flaw was discovered by Polish security researcher Dawid Golunski of Legal Hackers last year in July and reported it to the WordPress security team, who decided to ignore this issue, leaving millions of websites vulnerable.
"This issue has been reported to WordPress security team multiple times with the first report sent back in July 2016. It was reported both directly via security contact email, as well as via HackerOne website," Golunski wrote in an advisory published today. "As there has been no progress, in this case, this advisory is finally released to the public without an official patch."
Golunski is the same researcher who discovered a critical vulnerability in the popular open source PHPMailer libraries that allowed malicious actors to remotely execute arbitrary code in the context of the web server and compromise the target web application.
The vulnerability lies in the way WordPress processes the password reset request, for the user it has been initiated.
In general, when a user requests to reset his/her password through forgot password option, WordPress immediately generates a unique secret code and sends it to user’s email ID already stored in the database.
What's the Vulnerability?
While sending this email, WordPress uses a variable called SERVER_NAME to obtain the hostname of a server to set values of the From/Return-Path fields.
Here, "From" refers to the email address of the sender and "Return-Path" refers to the email address where 'bounce-back' emails should be delivered in the case of failure in the delivery for some reason.
According to Golunski, an attacker can send a spoofed HTTP request with a predefined custom hostname value (for example attacker-mxserver.com), while initiating password reset process for a targeted admin user.
Since the hostname in the malicious HTTP request is an attacker-controlled domain, the From and Return-Path fields in the password reset email will be modified to include an email ID associated with the attacker's domain, i.e. wordpress@attacker-mxserver.com, instead of wordpress@victim-domain.com.
"Because of the modified HOST header, the SERVER_NAME will be set to the hostname of attacker's choice. As a result, Wordpress will pass the following headers and email body to the /usr/bin/sendmail wrapper," Golunski says.
Don't get confused here: You should note that the password reset email will be delivered to victim's email address only, but since the From and Return-Path fields now point to attacker's email ID, the attacker can also receive reset code under following scenarios:
If, in case, the victim replies to that email, it will be delivered to attacker email ID (mentioned in 'From' field), containing a password reset link in the message history.
If, for some reason, victim's email server is down, the password reset email will automatically bounce-back to the email address mentioned in "Return-Path" field, which points to the attacker's inbox.
In another possible scenario, to forcefully retrieve bounce-back email, the attacker can perform a DDoS attack against the victim's email server or send a large number of emails, so that the victim's email account can no longer receive any email.
"The CVE-2017-8295 attack could potentially be carried out both with user interaction (the user hitting the 'reply' button scenario), or without user interaction (spam victim's mailbox to exceed their storage quota)," Golunski told The Hacker News in an email.
For obvious reason, this is not a sure shot method, but in the case of targeted attacks, sophisticated hackers can manage to exploit this flaw successfully.
Another notable fact on which successful exploitation of this flaw depends is that, even if WordPress website is flawed, not all web servers allow an attacker to modify hostname via SERVER_NAME header, including WordPress hosted on any shared servers.
"SERVER_NAME server header can be manipulated on default configurations of Apache Web server (most common WordPress deployment) via HOST header of an HTTP request," Golunski says.
Since the vulnerability has now been publically disclosed with no patch available from the popular CMS company, WordPress admins are advised to update their server configuration to enable UseCanonicalName to enforce static/predefined SERVER_NAME value.
Security researcher disclosed a WordPress Password Reset Vulnerability
5.5.2017 securityaffairs Vulnerebility
A researcher reported a WordPress Password Reset vulnerability, tracked as CVE-2017-8295, and detailed it in a security advisory.
On Wednesday, the popular security experts Dawid Golunski reported a WordPress Password Reset vulnerability, tracked as CVE-2017-8295, and detailed it in a security advisory.
Golunski classified the flaw as a “medium/high severity,” he explained that the issue is caused by the fact that WordPress uses a variable named SERVER_NAME to obtain the hostname of a server when setting the From/Return-Path header in password reset emails sent to users.
The value of the SERVER_NAME variable is often set using the hostname supplied by the client via the HTTP_HOST header, Golunski discovered that an attacker can inject an arbitrary domain by sending a specially crafted request to the targeted WordPress website.
“WordPress is using SERVER_NAME variable to get the hostname of the server in order to create a From/Return-Path header of the outgoing password reset email. However, major web servers such as Apache by default set the SERVER_NAME variable using the hostname supplied by the client (within the HTTP_HOST header): https://httpd.apache.org/docs/2.4/mod/core.html#usecanonicalname” reads the security advisory.
“Because SERVER_NAME can be modified, an attacker could set it to an arbitrary domain of his choice e.g: attackers-mxserver.com which would result in WordPress setting the $from_email to wordpress@attackers-mxserver.com and thus result in an outgoing email with From/Return-Path set to this malicious address.”
Summarizing, an attacker can force a password reset by sending a specially crafted request to the targeted WordPress site, the request will include as the hostname the name of a domain controlled by the attacker, meanwhile the From and Return-Path fields in the password reset email sent to the victim will specify an email address on the attacker’s domain.
Once the targeted user receives the password reset link, there are several methods the attacker can use to obtain it now that the From and Return-Path fields point to their domain.
The attacker can make the victim’s email account unusable, for example via an attack on its DNS server or by sending it large files until to saturate its capacity.
When the victim’s email account stop receiving messages, the password reset email is returned to the sender’s recipient) the attacker’s email account as it is specified in the From and Return-Path fields.
In the case an autoresponder is enabled on the victim’s email account, the attacker will easily obtain a copy of the password reset email includes in the automatic reply.
Another option is to send a large number of password reset emails to the victim, hoping the victim will reply one of them with an email that likely includes the password reset link.
Below the three scenarios described by Golunski:
Attacker can perform a prior DoS attack on the victim’s email account/server (e.g by sending multiple large files to exceed user’s disk quota, attacking the DNS server etc) in order to prevent the password reset email from reaching the victim’s account and bounce back to the malicious sender address that is pointed at the attacker (no user interaction required).
Some autoresponders might attach a copy of the email sent in the body of the auto-replied message (no user interaction required)
Sending multiple password reset emails to force the user to reply to the message to inquiry explanation for endless password reset emails. The reply containing the password link would then be sent to attacker. (user interaction required)
The Password Reset vulnerability affects all versions of WordPress, including the 4.7.4 version released a couple of weeks ago.
Golunski reported the flaw hole to WordPress several times since July 2016, but in an absence of a concrete action, he decided to disclose it.
Golunski has suggested a temporary solution to enable UseCanonicalName to enforce a static SERVER_NAME value https://httpd.apache.org/docs/2.4/mod/core.html#usecanonicalname
On a specific thread on Reddit users discussed possible temporary countermeasures, such as the use of as a utility that notifies users when users reset passwords.
Cisco Patches Critical Flaw in Small Business Router
5.5.207 securityweek Vulnerebility
Cisco has released a firmware update for one of its small business routers to address a critical vulnerability that can be exploited for denial-of-service (DoS) attacks and arbitrary code execution.
The vulnerability, discovered by researchers from GeekPwn, a China-based IoT-focused hacking competition, affects CVR100W Wireless-N VPN routers. The company said there was no evidence of malicious exploitation.
The flaw, tracked as CVE-2017-3882 and described as a buffer overflow, affects the device’s Universal Plug and Play (UPnP) implementation and it can allow an unauthenticated, layer 2-adjacent attacker to execute arbitrary code with root privileges or cause vulnerable routers to reload.Cisco CVR routers vulnerable to hacker attacks

The security hole can be exploited by sending a specially crafted request to the UPnP listening port of the targeted router.
The flaw affects CVR100W Wireless-N VPN routers running a version of the firmware prior to 1.0.1.22. Cisco said no other small business routers are affected. Users can determine which firmware version is running on their device from the product’s web interface.
The same router model is also affected by a medium severity bug that can be exploited by an unauthenticated attacker to bypass the remote management ACL. This security hole has been addressed with the release of version 1.0.1.24.
Cisco on Wednesday also published three other advisories describing high severity vulnerabilities affecting various products.
The networking giant informed customers that several of its Aironet access points are affected by a PnP-related vulnerability that can be exploited for arbitrary code execution with root privileges. While the security hole has been classified “high severity,” Cisco pointed out that there is only a small window for exploitation and the attacker needs to have network access.
The other two flaws, affecting IOS XR and TelePresence Collaboration Endpoint (CE) software, allow a remote, unauthenticated attacker to cause devices to enter a DoS condition.
Patches are available for all vulnerabilities and Cisco says it’s not aware of any in-the-wild attacks where these weaknesses have been exploited.
Unpatched WordPress Password Reset Flaw Disclosed
4.5.2017 securityweek Vulnerebility
A researcher has disclosed the details of a WordPress vulnerability that can be exploited by an unauthenticated attacker to reset a targeted user’s password. The flaw was reported to WordPress months ago, but it still has not been patched.
Security researcher Dawid Golunski, known for finding serious vulnerabilities in MySQL and some popular email-sending PHP libraries, published an advisory on Wednesday detailing a weakness in the WordPress password reset feature.
Successful exploitation of the vulnerability allows an unauthenticated attacker to obtain the password reset link for a targeted WordPress account and change its password. The issue, tracked as CVE-2017-8295, has been classified by Golunski as “medium/high severity.”
The problem, according to the expert, is related to the fact that WordPress uses a variable named SERVER_NAME to obtain the hostname of a server when setting the From/Return-Path header in password reset emails sent to users.
Since the value of this variable is often set using the hostname supplied by the client via the HTTP_HOST header, an attacker can inject an arbitrary domain by sending a specially crafted request to the targeted WordPress website.
In an attack scenario described by Golunski, the attacker sends a specially crafted request to the targeted WordPress site in order to trigger a password reset. Since the hostname in the request is an attacker-controlled domain, the From and Return-Path fields in the password reset email sent to the victim will specify an email address on the attacker’s domain.
Once the targeted user receives the password reset link, there are several methods the attacker can use to obtain it now that the From and Return-Path fields point to their domain.
One possibility, said Golunski, is to get the victim’s email account to stop accepting emails, either via an attack on its DNS server or by sending it large files until the mailbox quota is exceeded. If the email account can no longer receive emails, the password reset email is returned to its sender, which in this case is the attacker’s email account as it is specified in the From and Return-Path fields.
If an autoresponder is enabled on the victim’s email account, the attacker could easily obtain a copy of the password reset email as some autoresponders include a copy of the original message in the automatic reply.
Another option is to send a large number of password reset emails to the victim, which could get them to reply in an effort to find out why they are getting so many messages. The reply, which likely includes the password reset link, goes to the attacker.
According to Golunski, the vulnerability affects all versions of WordPress, including 4.7.4, released two weeks ago. The researcher said he reported the security hole to WordPress’ security team several times since July 2016, and decided to make his findings public after no progress was made.
Until a patch is released, Golunski has proposed a temporary solution. Users have also discussed possible mitigations and workarounds on Reddit.
SecurityWeek has reached out to WordPress for comment and will update this article if they respond. It’s possible that WordPress developers see this as a low risk issue given that an attack would not work against websites hosted on shared servers, and considering that obtaining the password reset link may not be easy.
Industrial Robots Vulnerable to Remote Hacker Attacks
3.5.2017 securityweek Vulnerebility
Researchers have conducted an in-depth analysis of industrial robots in an effort to determine how easy it would be for malicious actors to remotely take control of such machines.
Robots are increasingly present in industrial environments, including in critical sectors, and they are often connected to the outside world, which could make them an easy target for hacker attacks.
On Wednesday, researchers at Trend Micro and the Polytechnic University of Milan released a paper focusing on the cybersecurity risks associated with industrial robots.
During their analysis, experts discovered that a growing number of industrial robots include remote access features designed for monitoring and maintenance. While these features can be useful for operators, they can also introduce serious security risks.
Internet scans conducted using the Shodan, Censys and ZoomEye services showed that some robots are exposed to the Internet via their FTP servers. Experts identified more than two dozen exposed robots in Europe, the United States, East and Southeast Asia, and Australia.
Robots can also be exposed to attacks from the Internet through industrial routers. Researchers discovered more than 80,000 industrial routers, mostly from vendors such as Sierra Wireless (50,000), Moxa (12,000), eWON (6,000) and Westermo (6,000). A majority of these devices are located in the United States, followed by Canada and several European countries.
The problem is that these routers are often misconfigured or affected by vulnerabilities. The security holes identified by experts include outdated software, device information leaks, default credentials or poor authentication, weak transport encryption, and insecure web interfaces.
While the actual robots can cost tens of thousands of dollars and some vendors only provide software and firmware to customers, researchers pointed out that software and firmware is often publicly available, and some manufacturers provide simulators that can be leveraged by hackers to test their attacks.
Researchers described several possible attack scenarios, including ones where the attacker alters the control system or changes calibration to cause the robot to move inaccurately or unexpectedly. An attacker could also tamper with the production logic, manipulate robot status information to trick the operator, and modify the machine’s state.
Robots can be targeted in a wide range of attacks, including to inject faults and microdefects into a product, take control of a machine to cause physical damage or to injure people, cause damage to the production line, and exfiltrate sensitive data. Ransomware attacks are also possible, where the attacker stealthily introduces microdefects in the production chain and then asks for a ransom to reveal which product lots are affected.
Researchers created a setup to demonstrate an actual attack using an IRB140 industrial robot from ABB Robotics:
Trend Micro has notified affected robot and router vendors, but some of them did not seem interested in the company’s findings. The security firm named ABB, eWON and Moxa as the companies that were open to suggestions for making security improvements.
Trend Micro’s research comes shortly after IOActive published a paper describing vulnerabilities in home, business and industrial robots.