26.4.23 Vulnerebility The Hacker News

The maintainers of the Apache Superset open source data visualization software have released fixes to plug an insecure default configuration that could lead to remote code execution.
Apache Superset Vulnerability: Insecure Default Configuration Exposes Servers to RCE Attacks
26.4.23 Vulnerebility The Hacker News
The maintainers of the Apache Superset open source data visualization software have released fixes to plug an insecure default configuration that could lead to remote code execution.
The vulnerability, tracked as CVE-2023-27524 (CVSS score: 8.9), impacts versions up to and including 2.0.1 and relates to the use of a default SECRET_KEY that could be abused by attackers to authenticate and access unauthorized resources on internet-exposed installations.
Naveen Sunkavally, the chief architect at Horizon3.ai, described the issue as "a dangerous default configuration in Apache Superset that allows an unauth attacker to gain remote code execution, harvest credentials, and compromise data."
It's worth noting that the flaw does not affect Superset instances that have changed the default value for the SECRET_KEY config to a more cryptographically secure random string.
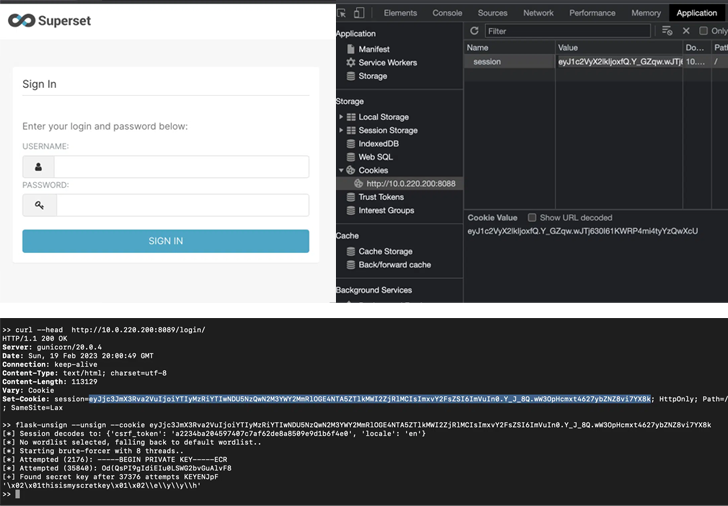
The cybersecurity firm, which found that the SECRET_KEY is defaulted to the value "\x02\x01thisismyscretkey\x01\x02\\e\\y\\y\\h" at install time, said that 918 out of 1,288 publicly-accessible servers were using the default configuration in October 2021.
An attacker who had knowledge of the secret key could then sign in to these servers as an administrator by forging a session cookie and seize control of the systems.
On January 11, 2022, the project maintainers attempted to rectify the problem by rotating the SECRET_KEY value to "CHANGE_ME_TO_A_COMPLEX_RANDOM_SECRET" in the Python code along with user instructions to override it.
Horizon3.ai said it further found two additional SECRET_KEY configurations that were assigned the default values "USE_YOUR_OWN_SECURE_RANDOM_KEY" and "thisISaSECRET_1234."
An expanded search conducted in February 2023 with these four keys unearthed 3,176 instances, out of which 2,124 were using one of the default keys. Some of those affected include large corporations, small companies, government agencies, and universities.
Following responsible disclosure to the Apache security team a second time, a new update (version 2.1) was released on April 5, 2023, to plug the security hole by preventing the server from starting up altogether if it's configured with the default SECRET_KEY.
"This fix is not foolproof though as it's still possible to run Superset with a default SECRET_KEY if it's installed through a docker-compose file or a helm template," Sunkavally said.
"The docker-compose file contains a new default SECRET_KEY of TEST_NON_DEV_SECRET that we suspect some users will unwittingly run Superset with. Some configurations also set admin/admin as the default credential for the admin user."
Horizon3.ai has also made available a Python script that can be used to determine if Superset instances are susceptible to the flaw.
"It's commonly accepted that users don't read documentation and applications should be designed to force users along a path where they have no choice but to be secure by default," Sunkavally concluded. "The best approach is to take the choice away from users and require them to take deliberate actions to be purposefully