Chinese Hackers Exploited New Zero-Day in Barracuda's ESG Appliances

CATEGORIE : Exploit |
DATE: 27.12.23 |
| WEB : The Hacker News |
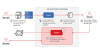
Barracuda has revealed that Chinese threat actors exploited a new zero-day in its Email Security Gateway (ESG) appliances to deploy backdoor on a "limited number" of devices.
Tracked as CVE-2023-7102, the issue relates to a case of arbitrary code execution that resides within a third-party and open-source library Spreadsheet::ParseExcel that's used by the Amavis scanner within the gateway.