Exploit 2024 2023 2022 2021 2020
A Google Docs Bug Could Have Allowed Hackers See Your Private Documents
30.12.2020 Exploit Thehackernews
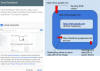
Google has patched a bug in its feedback tool incorporated across its services that could be exploited by an attacker to potentially steal screenshots of sensitive Google Docs documents simply by embedding them in a malicious website.
The flaw was discovered on July 9 by security researcher Sreeram KL, for which he was awarded $3133.70 as part of Google's Vulnerability Reward Program.
Many of Google's products, including Google Docs, come with a "Send feedback" or "Help Docs improve" option that allows users to send feedback along with an option to include a screenshot — something that's automatically loaded to highlight specific issues.
But instead of having to duplicate the same functionality across its services, the feedback feature is deployed in Google's main website ("www.google.com") and integrated to other domains via an iframe element that loads the pop-up's content from "feedback.googleusercontent.com."
This also means that whenever a screenshot of the Google Docs window is included, rendering the image necessitates the transmission of RGB values of every pixel to the parent domain (www.google.com), which then redirects those RGB values to the feedback's domain, which ultimately constructs the image and sends it back in Base64 encoded format.
Sreeram, however, identified a bug in the manner these messages were passed to "feedback.googleusercontent.com," thus allowing an attacker to modify the frame to an arbitrary, external website, and in turn, steal and hijack Google Docs screenshots which were meant to be uploaded to Google's servers.
Notably, the flaw stems from a lack of X-Frame-Options header in the Google Docs domain, which made it possible to change the target origin of the message and exploit the cross-origin communication between the page and the frame contained in it.
While the attack requires some form of user interaction — i.e. clicking the "Send feedback" button — an exploit could easily leverage this weakness to capture the URL of the uploaded screenshot and exfiltrate it to a malicious site.
This can be achieved by embedding a Google Docs file in an iFrame on a rogue website and hijacking the feedback pop-up frame to redirect the contents to a domain of the attacker's choice.
Failing to provide a target origin during cross-origin communication raises security concerns in that it discloses the data that's sent to any website.
"Always specify an exact target origin, not *, when you use postMessage to send data to other windows," Mozilla documentation states. "A malicious site can change the location of the window without your knowledge, and therefore it can intercept the data sent using postMessage."
Google: Microsoft Improperly Patched Exploited Windows Vulnerability
29.12.2020 Exploit Securityweek
Google Project Zero has disclosed a Windows zero-day vulnerability caused by the improper fix for CVE-2020-0986, a security flaw abused in a campaign dubbed Operation PowerFall.
Tracked as CVE-2020-17008, the new vulnerability was reported to Microsoft on September 24. As per Project Zero’s policy, details were made public 90 days later, on December 23, despite the fact that Microsoft missed the patch deadline.
Disclosed in May 2020, CVE-2020-0986 was initially reported to Microsoft in December 2019 and a patch was released in June 2020. Attacks targeting the vulnerability were observed within days after disclosure.
In August 2020, Kaspersky published information on attacks chaining CVE-2020-0986 with a zero-day in Internet Explorer, as part of an attack campaign referred to as Operation PowerFall.
“By using this vulnerability it is possible to manipulate the memory of the splwow64.exe process to achieve execution of arbitrary code in the process and escape the Internet Explorer 11 sandbox because splwow64.exe is running with medium integrity level,” Kaspersky explained in a September post.
Also an elevation of privilege bug in splwow64.exe, CVE-2020-17008 can be abused by simply changing the exploitation method for CVE-2020-0986, an arbitrary pointer dereference flaw affecting the GDI Print/Print Spooler API.
Google Project Zero researcher Maddie Stone explains that CVE-2020-17008 is actually nearly identical to CVE-2020-0986, the only difference being that “for CVE-2020-0986 the attacker sent a pointer and now the attacker sends an offset.”
On Twitter, Stone notes that Microsoft’s fix was faulty because it simply changed the pointers to offsets, failing to prevent an attacker to control “the args to the memcpy.”
The researcher also published proof-of-concept (PoC) code targeting CVE-2020-17008, noting that the exploit is an adaptation of the PoC Kaspersky released for CVE-2020-0986.
“It triggers the memcpy vulnerability twice: first to leak the heap address where the message is stored and what the offset is added to to generate the pointers and then to do the write-what-where,” Stone says.
Microsoft, which acknowledged the issue one day after receiving the vulnerability report, was aiming for the release of a patch in November, but postponed the fix due to issues identified in testing. The company is currently aiming to address the bug in January 2021.
Proportion of Exploited Vulnerabilities Continues to Drop
15.12.2020 Exploit Securityweek
While the number of identified vulnerabilities has increased significantly over the past years, the percentage of flaws that are exploitable or have actually been exploited has been dropping, according to vulnerability management company Kenna Security.
The number of vulnerabilities that received a CVE identifier in 2011 was roughly 4,100, but the number has exceeded 10,000 every year since 2016 — there were 14,000 in 2017, 17,000 in 2018 and 20,000 in 2019. The number of CVEs assigned so far this year has exceeded 17,000.
Kenna Security has conducted an analysis of more than 100,000 vulnerabilities disclosed since 2011 and noticed that the number of exploitable and exploited flaws has been on a downwards trend over the past years.
In 2017, 9.1% of vulnerabilities were exploitable and 0.7% of them were actually exploited. In 2020, only 2.7% of security bugs appear to be exploitable and only roughly 0.4% of them have actually been exploited in attacks.
According to Kenna, in terms of severity, 8.6% of the critical vulnerabilities disclosed this year are exploitable and 2.1% have been exploited in attacks. One percent and 0.002% of the high-severity flaws are exploitable and have been exploited, respectively.
“Although the known universe of vulnerabilities is exploding, an increasingly small number of those vulnerabilities result in actual breaches. Focusing your remediation efforts on high-impact mitigations has never been more important,” Kenna Security told organizations.
While a majority of high- and critical-severity vulnerabilities still impact applications, the company says OS-level flaws account for an increasing proportion of serious flaws.
WordPress Easy WP SMTP zero-day potentially exposes hundreds of thousands of sites to hack
13.12.2020 Exploit Securityaffairs
Threat actors are actively exploiting a zero-day vulnerability in the popular Easy WP SMTP WordPress plugin installed on more than 500,000 sites.
Hackers are actively exploiting a zero-day vulnerability in the popular Easy WP SMTP WordPress plugin to reset passwords for admin accounts.
The SMTP WordPress plugin is installed on more than 500,000 sites, but despite the security patch has been released earlier this week many sites are yet to be patched.
The WP SMTP WordPress plugin allows you to configure and send all outgoing emails via an SMTP server, preventing the emails from going into the junk/spam folder of the recipients.
The zero-day vulnerability affects WP SMTP 1.4.2 and earlier versions, it resides in a feature that creates debug logs for all emails sent by the site and store them in the installation folder.
According to the team at Ninja Technologies Network (NinTechNet), WP SMTP 1.4.2 and older versions of the plugin contain a feature that creates debug logs for all emails (headers and body) sent by the site, which it then stores in its installation folder.
“The Easy WP SMTP plugin has an optional debug log where it writes all email messages (headers and body) sent by the blog. It is located inside the plugin’s installation folder, “/wp-content/plugins/easy-wp-smtp/”. The log is a text file with a random name, e.g., 5fcdb91308506_debug_log.txt.” reads a blog post published by Ninja Technologies Network (NinTechNet).
“The plugin’s folder doesn’t have any index.html file, hence, on servers that have directory listing enabled, hackers can find and view the log,” reads the post published by Ninja Technologies Network (NinTechNet).

Attackers exploit the flaw to identify the admin account in the log and attempt to reset the password for an admin account.
The password reset procedure sends an email with the password reset link to the admin account, and this email is reported in the Easy WP SMTP debug log.
Since a password reset involves sending an email with the password reset link to the admin account, this email is also recorded in the plugin debug log.
The attackers access the debug log after the password reset, scan for the reset link, and take over the site’s admin account.

The development team behind the plugin has addressed the flaw with the release of Easy WP SMTP 1.4.4.
At the time of this writing, it is unclear how many WordPress sites are still running vulnerable versions of the plugin that have the logging feature enabled.
PoC Released for Unpatched Windows Vulnerability Present Since 2006
12.12.2020 Exploit Securityweek
Details and a proof-of-concept (PoC) exploit have been released for an unpatched privilege escalation vulnerability in Windows related to the PsExec administration tool.
The vulnerability was discovered by Tenable researcher David Wells and it was disclosed this week after Microsoft failed to release a patch within 90 days.
Microsoft has not said when or if it will patch the vulnerability, but the tech giant pointed out that “this technique requires an attacker to have already compromised the target machine to run malicious code.”
“We encourage customers to practice good computing habits online, including exercising caution when clicking on links to web pages, opening unknown files, or accepting file transfers,” Microsoft told SecurityWeek in an emailed statement.
According to Wells, the vulnerability is a local privilege escalation issue that can be exploited by a non-admin process to elevate privileges to SYSTEM when PsExec is executed remotely or locally on the targeted computer.
The security hole has been found to impact Windows versions between Windows XP and Windows 10, and PsExec versions between 2.2 (the latest) and 1.7.2 (released in 2006).
PsExec, which is part of the Windows Sysinternals utilities suite, allows users to execute processes on remote Windows systems without the need to install third-party software.
Wells noted that PsExec contains an embedded resource named PSEXESVC that is executed on a remote machine with SYSTEM privileges when the PsExec client is used.
“Communication between the PsExec client and the remote PSEXESVC service takes place over named pipes. Specifically, the pipe named ‘\PSEXESVC,’ is responsible for parsing and executing the PsExec client’s commands, such as ‘which application to execute,’ ‘relevant command line data,’ etc,” the researcher explained.
While normally low-privileged users are not granted read/write access to this \PSEXESVC pipe, Wells discovered that an attacker can use a technique known as “pipe squatting” to achieve this goal. This involves the attacker creating the \PSEXESVC named pipe before the PSEXESVC process is executed, which results in the attacker gaining read/write access to the pipe, allowing their low-privileged app to communicate with PSEXESVC over this pipe and get executed with SYSTEM privileges.
If an attacker were to exploit the vulnerability, they would need to gain low-privileged access to the targeted system, deploy their malicious app, create a \PSEXESVC pipe, and wait for the targeted user to execute PsExec, either locally or remotely. This last requirement can make the security flaw less likely to be exploited in real world attacks.
Wells has published a blog post containing technical details and a PoC exploit has been made available on GitHub.
Cisco fixes exploitable RCEs in Cisco Security Manager
8.12.2020 Exploit Securityaffairs
Cisco released security updates to fix multiple pre-authentication RCE flaws with public exploits affecting Cisco Security Manager.
Cisco has released security updates to address multiple pre-authentication remote code execution vulnerabilities with public exploits affecting Cisco Security Manager (CSM). CSM provides a comprehensive management solution for CISCO devices, including intrusion prevention systems and firewalls (i.e. Cisco ASA appliances, Cisco Catalyst 6000 Series Switches).
The Cisco Product Security Incident Response Team confirmed that it is aware of the public availability of Proof-of-concept exploits since November. The good news is that the company is not aware of any ongoing attacks exploiting these flaws.
“The Cisco Product Security Incident Response Team (PSIRT) is aware of public announcements about these vulnerabilities,” reads the advisory.
“Cisco PSIRT is not aware of malicious use of the vulnerabilities that are described in this advisory.”
The vulnerabilities reported by Code White security researcher Florian Hauser in August and the IT giant disclosed them on November 16.
The researcher also published proof-of-concept exploits for all 12 the vulnerabilities in the Cisco Security Manager because Cisco PSIRT stopped replying his requests.
120 days ago, I disclosed 12 vulnerabilities to @Cisco affecting the web interface of Cisco Security Manager. All unauthenticated, almost all directly giving RCE. #cisco #RCE #unauth
— frycos (@frycos) November 11, 2020
These flaws impact CSM releases 4.22 and earlier.
The IT firm addressed two of the 12 vulnerabilities, tracked as CVE-2020-27125 and CVE-2020-27130.
“A vulnerability in Cisco Security Manager could allow an unauthenticated, remote attacker to access sensitive information on an affected system.” reads the description for CVE-2020-27125.
“The vulnerability is due to insufficient protection of static credentials in the affected software. An attacker could exploit this vulnerability by viewing source code. A successful exploit could allow the attacker to view static credentials, which the attacker could use to carry out further attacks.”
The company has yet to fix the remaining security flaws, collectively tracked as CVE-2020-27131.
“Multiple vulnerabilities in the Java deserialization function that is used by Cisco Security Manager could allow an unauthenticated, remote attacker to execute arbitrary commands on an affected device.” reads the advisory published by Cisco.
“These vulnerabilities are due to insecure deserialization of user-supplied content by the affected software. An attacker could exploit these vulnerabilities by sending a malicious serialized Java object to a specific listener on an affected system. A successful exploit could allow the attacker to execute arbitrary commands on the device with the privileges of NT AUTHORITY\SYSTEM on the Windows target host.”
A remote, unauthenticated attacker could exploit the flaws to execute arbitrary commands on impacted devices.
Cisco has addressed the flaws with the release of CSM Release 4.22 Service Pack 1.
In mid-November, Cisco published multiple security advisories related to critical vulnerabilities affecting the Cisco Security Manager (CSM), including the recently released version 4.22.
Recent Oracle WebLogic Vulnerability Exploited to Deliver DarkIRC Malware
2.12.2020 Exploit Virus Securityweek
Threat actors are targeting an Oracle WebLogic flaw patched last month in an attempt to install a piece of malware named DarkIRC on vulnerable systems.
Tracked as CVE-2020-14882 and leading to code execution, the vulnerability was addressed in the October 2020 Critical Patch Update (CPU). The first attacks targeting it were observed roughly one week after and, in early November, Oracle issued an out-of-band update to address an easy bypass for the initial patch.
According to Juniper Threat Labs’ security researchers, there are approximately 3,100 Oracle WebLogic servers that are accessible from the Internet.
The DarkIRC bot, the researchers say, is only one of the several payloads (including Cobalt Strike, Perlbot, Meterpreter, and Mirai) that adversaries are attempting to drop onto the vulnerable servers they discover.
Currently available on hacking forums for $75, the DarkIRC bot generates command and control (C&C) domains using a unique algorithm, relying on the sent value of a crypto wallet.
As part of the observed attacks, HTTP GET requests are issued to the vulnerable WebLogic servers, to execute a PowerShell script that in turn downloads and executes a binary file from a remote server. The payload is a 6MB .NET file.
A packer is used to conceal the malware’s true intentions and to help avoid detection. The packer also features anti-analysis and anti-sandbox functions, attempting to detect whether it is running in virtualized environments such as VMware, VirtualBox, VBox, QEMU, and Xen.
The bot, which installs itself in the %APPDATA% folder as Chrome.exe and creates an autorun entry for persistency, can act as a browser stealer, keylogger, Bitcoin clipper, and file downloader.
Furthermore, it is capable of launching distributed denial of service (DDoS) attacks, of command execution, and of spreading itself on the network, as a worm.
Commands supported by the bot allow it to steal browser passwords, spread via mssql or RDP (brute force), start/cease flood attacks, update the bot, retrieve version information or username of the infected system, fetch and execute (and remove), get IP address, spread via USB or SMB, steal Discord tokens, and uninstall itself.
In August, the bot was being advertised by a threat actor going by the name of “Freak_OG,” who also posted a FUD (fully undetected) crypter on November 1, priced at $25. However, the researchers are unsure whether the same person is behind the attacks as well.
“This vulnerability was fixed by Oracle in October and a subsequent out of cycle patch was also released in November to fix a hole in the previous patch. We recommend affected systems to patch immediately,” Juniper Threat Labs notes.
VMware addresses flaws exploited at recent Tianfu Cup
21.11.20 Exploit Securityaffairs
VMware has addressed two serious ESXi vulnerabilities that were demonstrated at the Tianfu Cup International PWN Contest.
VMware has released patches for two serious ESXi vulnerabilities that were disclosed during the 2020 Tianfu Cup International PWN Contest.
The Tianfu Cup is the most important hacking contest held in China, the total bonus of the contest this year was up to 1 million US dollars.
The participants successfully tested their exploits against the following software:
iOS 14 running on an iPhone 11 Pro
Samsung Galaxy S20
Windows 10 v2004 (April 2020 edition)
Ubuntu
Chrome
Safari
Firefox
Adobe PDF Reader
Docker (Community Edition)
VMWare EXSi (hypervisor)
QEMU (emulator & virtualizer)
TP-Link and ASUS router firmware
The team named “360 Enterprise Security and Government and (ESG) Vulnerability Research Institute,” which is part of the Chinese tech giant Qihoo 360, won the competition. The winning team earned $744,500 of the total $1,210,000 jackpot.
The 360 ESG Vulnerability Research Institute team warned $180,000 for an ESXi guest to host escape exploit.
Experts from VMware who were viewing the hacking contest immediately started working on patches to address the flaws. The company released the first set of patches on Thursday that fixed two vulnerabilities that were exploited by the bug hunters at the hacking competition.
The first vulnerability, tracked as CVE-2020-4004, is a use-after-free vulnerability in XHCI USB controller.
“VMware ESXi, Workstation, and Fusion contain a use-after-free vulnerability in the XHCI USB controller. VMware has evaluated the severity of this issue to be in the Critical severity range with a maximum CVSSv3 base score of 9.3.” reads the advisory.
“A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine’s VMX process running on the host.”
The second flaw, tracked as CVE-2020-4005, is a VMX elevation-of-privilege vulnerability that was caused by the way certain system calls are managed.
“VMware ESXi contains a privilege-escalation vulnerability that exists in the way certain system calls are being managed. VMware has evaluated the severity of this issue to be in the Important severity range with a maximum CVSSv3 base score of 8.8.” continues the advisory.
“A malicious actor with privileges within the VMX process only, may escalate their privileges on the affected system. Successful exploitation of this issue is only possible when chained with another vulnerability (e.g. CVE-2020-4004).”
The white-hat hackers at the Tianfu contest chained the two vulnerabilities to execute code as the virtual machine’s VMX process running on the host.
The Impacted products are:
VMware ESXi
VMware Workstation Pro / Player (Workstation)
VMware Fusion Pro / Fusion (Fusion)
VMware Cloud Foundation
VMware Patches Vulnerabilities Exploited at Chinese Hacking Contest
20.11.20 Exploit Securityweek
VMware on Thursday announced releasing patches for a couple of serious ESXi vulnerabilities that were demonstrated at a recent hacking contest in China.
At the 2020 Tianfu Cup International PWN Contest, which took place earlier this month in China, participants earned a total of more than $1.2 million for exploits targeting Chrome, Safari, Firefox, Adobe Reader, Docker, VMware ESXi, CentOS, the iPhone, the Samsung Galaxy S20 phone, Windows, and routers from TP-Link and Asus.
The 360 ESG Vulnerability Research Institute from Chinese cybersecurity company Qihoo 360 earned more than $740,000 of the total, including $180,000 for a VMware ESXi guest to host escape exploit.
VMware was monitoring the event and it immediately started working on patches. The virtualization giant announced the first patches on Thursday, less than two weeks after Tianfu Cup ended.
An advisory published by VMware describes two vulnerabilities that were chained at the hacking competition — it’s unclear if there are other flaws involved as well.
One of the security holes, CVE-2020-4005, is a privilege escalation issue caused by the way certain system calls are managed. This high-severity flaw allows an attacker who has privileges within the VMX process only to elevate permissions on the targeted system.
This vulnerability can be chained with CVE-2020-4004, an issue rated critical that the Qihoo 360 researchers exploited to execute code as the virtual machine’s VMX process running on the host. The flaw is a use-after-free affecting the XHCI USB controller and exploitation requires local admin privileges on the VM.
CVE-2020-4004 affects ESXi, Fusion, Workstation and VMware Cloud Foundation. Patches and updates have been released, except for Cloud Foundation, for which fixes are pending.
In the case of CVE-2020-4005, it impacts ESXi and Cloud Foundation. Fixes are available for ESXi and they are pending for Cloud Foundation.
Google and Mozilla have also patched the Chrome and Firefox vulnerabilities disclosed at the competition.
At last year’s Tianfu Cup, researchers from Qihoo 360 earned $200,000 for a VMware ESXi exploit. The vulnerabilities leveraged for that exploit were also patched by the virtualization giant after roughly two weeks.
VMware this week also patched a series of vulnerabilities in its SD-WAN Orchestrator product that could have allowed an unauthenticated attacker to remotely execute arbitrary code, which researchers say could lead to the shutdown of an enterprise network or traffic steering.
2 More Google Chrome Zero-Days Under Active Exploitation
13.11.20 Exploit Threatpost
Browser users are once again being asked to patch severe vulnerabilities that can lead to remote code execution.
Google is asking Chrome desktop users to prepare to update their browsers once again as two more zero-day vulnerabilities have been identified in the software. Both allow an unauthenticated, remote attacker to compromise an affected system via the web. And both are being actively exploited in the wild, according to Google.
The disclosure brings to five the total number of actively exploited flaws found in Chrome within the last three weeks.
A stable channel update, 86.0.4240.198 for Windows, Mac and Linux, was released this week and will be rolled out “over the next days and weeks,” Google Chrome’s Prudhvikumar Bommana said in a blog post on Wednesday. The update will patch the two zero-day flaws, being tracked as CVE-2020-16013 and CVE-2020-16017.
Both have a severity rating of “high,” ranking 8.4 out of 10 on the CVSS bug-severity scale, and were reported by an anonymous source.
CVE-2020-16017 is described by Google as a “use-after-free in site isolation,” which is the Chrome component that isolates the data of different sites from each other.
To exploit it, a remote attacker can create a specially crafted web page, trick the victim into visiting it, trigger use-after-free error and execute arbitrary code on the target system, according to researchers at Czech firm Cybersecurity Help.
CVE-2020-16013 meanwhile is an “improperly implemented security check for standard” bug, which is a type of flaw where the software does not implement or incorrectly implements one or more security-relevant checks. In this particular case, Google described the bug as an “inappropriate implementation in V8,” which is an open-source component of Chrome that handles JavaScript and WebAssembly.
To exploit it, a remote attacker can also create a specially crafted web page, trick the victim into visiting it and then be able to compromise the system, Cybersecurity Help noted.
Another zero-day that Google patched earlier this month, CVE-2020-16009, also was due to an inappropriate implementation of V8, but it’s unknown whether the two flaws are related. Google typically refrains from providing specific details about vulnerabilities until well after they are patched.
The latest spate of Chrome zero-day discoveries and patches started on Oct. 19, when security researcher Sergei Glazunov of Google Project Zero discovered a type of memory-corruption flaw called a heap-buffer overflow in FreeType that was being actively exploited. Google patched the vulnerability two days later.
Then last week, Google patched two separate zero-day flaws in Google’s Chrome desktop and Android-based browsers. The desktop bug is the aforementioned V8 vulnerability, which could be used for remote code-execution discovered by researchers at Google’s Threat Analysis Group and Google Project Zero. The Android bug, also with an active exploit, is a sandbox-escape bug that opened up a possible attack based on a heap-buffer overflow in the user interface for Android, the company said.
The Google issues join several other recently patched zero-days, in Apple and Windows.
Indeed, threat actors have been on the offensive lately to target unpatched flaws in the ubiquitous software created by the three tech giants, keeping security researchers on their toes and the companies releasing updates on the fly to stay current with patches.
Muhstik botnet adds Oracle WebLogic and Drupal exploits
12.11.20 BotNet Exploit Securityaffairs
Muhstik botnet leverages known web application exploits to compromise IoT devices, now it targeting Oracle WebLogic, Drupal.
Muhstik is a botnet that is known to use web application exploits to compromise IoT devices, it has been around for at least 2018.
Botnet operators monetize their efforts via XMRig, cgmining and with DDoS-for-hire services.
The botnet leverages IRC servers for command-and-control (C2) communications, experts noticed that it has consistently used the same infrastructure since it first appeared in the threat landscape.
The bot propagates by compromising home routers, but experts observed multiple attempted exploits for Linux server propagation. The list of targeted routers include GPON home router, DD-WRT router, and the Tomato router.
According to researchers from cloud security firm Lacework, Muhstik operators added Web application exploits for Drupal and Weblogic to their bot.
The bot includes exploits for Oracle WebLogic Server vulnerabilities CVE-2019-2725 and CVE-2017-10271, and the Drupal RCE flaw tracked as CVE-2018-7600.
Researchers from Lacework have analyzed the attack chain implemented by the Muhstik bot.
In the first stage of the attack, a payload downloads the other components. The payload is named “pty” followed by a number used to map the architecture. Below some download URL examples:
hxxp://159.89.156.190/.y/pty2
hxxp://167.99.39.134/.x/pty3
“Upon successful installation Mushtik will contact the IRC channel to receive commands. (For more details on the Muhstik protocol, refer to the write up by Subexsecure). Usually Muhstik will be instructed to download an XMRmrig miner and a scanning module.” reads the analysis published by the researchers. “The scanning module is used for growing the botnet through targeting other Linux servers and home routers.”
The main payload and the scanning module of the Muhstik botnet encrypt their configurations using the Mirai source code which employs a single byte XOR of 0x22.
The decoded configuration for the Muhstik scanning module has common settings that are common to multiple Mirai-based botnets.
The analysis of the botnet’s attack infrastructure exposed some interesting correlations. IRC C2 irc.de-zahlung.eu shared an SSL cert with site jaygame.net, which is an amateur site about a game involving an Anime character named ‘Jay’. The site is currently leveraging Google Analytics ID UA-120919167-1, a reverse Google Analytics search exposed the following 3 domains using the same ID:
fflyy.su
kei.su
“The two other domains linked to the analytics ID (ffly.su and kei.su) were also configured as C2s for various other Linux Tsunami malware linked to the same infrastructure. If the infrastructure is administered by a single attacker then we can presume it’s related.” states the analysis. “This related infrastructure has allowed possible attribution to what Lacework has dubbed “Wasp 8220”. This set of activity has been tied to other cryptomining variants and Linux backdoors . These all have links to the same malware upload path belonging to Chinese forensics firm Shen Zhou Wang Yun Information Technology Co., Ltd. “

Lacework researchers linked the Muhstik botnet to the Chinese forensics firm Shen Zhou Wang Yun Information Technology Co., Ltd.
Experts also observed that original malware samples were uploaded to VirusTotal all at once before Muhstik was spreading in the wild.
The samples contained multiple strings mentioning “shenzhouwangyun,” such as in /home/wys/shenzhouwangyun/shell/downloadFile/tomato.deutschland-zahlung.eu_nvr a circumstance that suggests that the malware was developed by Shen Zhou Wang Yun.
Lacework also shared up to date Indicators of Compromise (IOCs) for the recent attacks.
Google Patches Two More Chrome Zero-Days Exploited in Attacks
12.11.20 Exploit Securityweek
Google has released another update for Chrome 86 to patch two more zero-day vulnerabilities that have been exploited in the wild.
Google has credited “anonymous” for reporting the flaws — it’s unclear if it’s the same or two different anonymous individuals — and it has not shared any information about the attacks in which they have been exploited. It’s also unclear if the vulnerabilities were exploited in the same attack or in different, unrelated attacks.
Both security holes have been rated high severity. One of them, CVE-2020-16013, has been described as an inappropriate implementation issue affecting the V8 JavaScript engine, while the other, CVE-2020-16017, is a use-after-free bug related to site isolation.
These are not the only actively exploited Chrome zero-days that Google has patched in recent weeks. Recent Chrome updates also fixed CVE-2020-15999, which is related to the FreeType font rendering library and which has been exploited alongside a Windows zero-day, CVE-2020-16009, which also impacts he V8 engine, and CVE-2020-16010, which affects Chrome for Android.
Earlier this week, Google released an update for Chrome 86 to address a vulnerability disclosed over the past weekend at the 2020 Tianfu Cup hacking competition that took place in China. The flaw was demonstrated at the event by a team that earned a total of over $740,000, including $100,000 for the Chrome exploit.
BEC Scammers Exploit Flaw to Spoof Domains of Rackspace Customers
5.11.20 Exploit Securityweek
A threat actor specializing in business email compromise (BEC) attacks has been observed exploiting a vulnerability to spoof the domains of Rackspace customers as part of its operations.
UK-based cybersecurity company 7 Elements identified the vulnerability while conducting incident response activities for a customer. An analysis of the attack revealed that the hackers had sent out phishing emails by leveraging a flaw related to how Rackspace SMTP servers hosted at emailsrvr.com authorize users.
The cybersecurity firm has shared few details about the threat group exploiting the vulnerability, but it told SecurityWeek that the cybercriminals focus on BEC attacks aimed at Office 365 users.
According to 7 Elements, the vulnerability allows an attacker who can authenticate to one Rackspace customer’s account to send out emails on behalf of any other customer that uses Rackspace’s hosted email services.
7 Elements researchers determined that an attacker could have sent out emails on behalf of government organizations (including in the US and UK), IT companies, news outlets, and high-profile individuals. They noted that the attack, which they dubbed “SMTP Multipass,” allows cybercriminals to bypass email filters and pass SPF email authentication controls.
SPF allows a mail server to check if an email coming from a specific domain is submitted by an IP authorized by that domain’s admins. The authorized hosts and IP addresses for a domain are published in its DNS records. In the case of SMTP Multipass attacks, there are two major issues.
“The first is the vulnerability within the Rackspace hosted email service that allows an authenticated user of the platform to send emails as any domain (including those that also use the service),” 7 Elements explained. “The second is in how DNS entries configured by legitimate customers of Rackspace specifically authorised the affected Rackspace SMTP servers (emailsrvr.com) for the purpose of sending emails on behalf of that domain. So, any email coming from that IP on behalf of that domain is de facto authorised.”
7 Elements said it reported its findings to Rackspace in August. The vendor notified customers in late October and a fix is expected to be rolled out starting Thursday, November 5. The cloud solutions giant has not responded to an email from SecurityWeek requesting additional information on the vulnerability and the patch.
According to 7 Elements, Rackspace already knew about the vulnerability back in August after being notified by a third party. The UK-based cybersecurity firm says it doesn’t know who else reported the issue to Rackspace, but believes it to be an individual.
“Our investigation showed that this vulnerability was being actively exploited by at least one malicious actor to spoof emails, there’s obviously some serious questions to be answered by Rackspace if it was aware of this vulnerability and its exploitation resulted in reputational or financial loss for a business,” said John Moss, senior security consultant at 7 Elements.
Chrome Browser Updates Plugs Holes Actively Targeted by Exploits
4.11.20 Exploit Threatpost
Patches for both the Chrome desktop and Android browser address high-severity flaws with known exploits available in the wild.
Flaws in Google’s Chrome desktop and Android-based browsers were patched Monday in an effort to prevent known exploits from being used by attackers. Two separate security bulletins issued by Google warned that it is aware of reports that exploits for both exist in the wild. Google’s Project Zero went one step further and asserted that both bugs are actively being exploited.
In its Chrome browser update for Windows, Mac and Linux, Google said that version 86.0.4240.183 fixes 10 vulnerabilities. Tracked as CVE-2020-16009, this bug is the most troubling, rated high-severity and is one of the two with active exploits. The vulnerability is tied to Google’s open source JavaScript and WebAssembly engine called V8. In its disclosure, the flaw is described as an “inappropriate implementation in V8”.
Clement Lecigne of Google’s Threat Analysis Group and Samuel Gross of Google Project Zero discovered the Chrome desktop bug on Oct. 29, according to a blog post announcing the fixes by Prudhvikumar Bommana of the Google Chrome team. If exploited, the V8 bug can be used for remote code execution, according to a separate analysis by Project Zero’s team.
As for the Android OS-based Chrome browser, also with an active exploit in the wild, Google warned on Monday of a sandbox escape bug (CVE-2020-16010). This vulnerability is rated high-severity and opened up a possible attack based on “heap buffer overflow in UI on Android” conditions. Credited for discovering the bug on Oct. 31 is Maddie Stone, Mark Brand and Sergei Glazunov of Google Project Zero.
‘Actively Exploited in the Wild’
Google said it was withholding the technical details of both bugs, pending the distribution of patches to effected endpoints. While Google said publicly known exploits existed for both bugs, it did not indicate that either one was under active attack. Google’s own Project Zero technical lead Ben Hawkes tweeted on Monday that both were under active attack.
“Today Chrome fixed two more vulnerabilities that were being actively exploited in the wild (discovered by Project Zero/Google TAG last week). CVE-2020-16009 is a v8 bug used for remote code execution, CVE-2020-16010 is a Chrome sandbox escape for Android,” he wrote.
As a precaution, Google said in its security update that it would “also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed,” according to the post.
The Other Android Bugs
The new Chrome Android release also includes stability and performance improvements, according to the Google Chrome team.
Vulnerabilities patched in the Chrome desktop update included a “use after free” bug (CVE-2020-16004); an “insufficient policy enforcement in ANGLE” flaw (CVE-2020-16005); an “insufficient data validation in installer” issue (CVE-2020-16007) and a “stack buffer overflow in WebRTC” bug (CVE-2020-16008). Lastly there Google reported a “heap buffer overflow in UI on Windows” tracked as (CVE-2020-16011).
This week’s Chrome updates come on the heels of zero-day bug reported and patched last week by Google effecting Chrome on Windows, Mac and Linux. The flaw (CVE-2020-15999), rated high-risk, is a vulnerability in Chrome’s FreeType font rendering library.
The latest vulnerabilities mean that in that just over 12 months Google has patched a string of serious vulnerabilities in its Chrome browser. In addition to the three most recently reported flaws, the first was a critical remote code execution vulnerability patched last Halloween night and tracked as CVE-2019-13720, and the second was a type of memory confusion bug tracked as CVE-2020-6418 that was fixed in February.
UNC1945, a sophisticated threat actor used Oracle Solaris Zero-Day exploit
4.11.20 Exploit Securityaffairs
A sophisticated threat actor, tracked as UNC1945, has been observed exploiting vulnerabilities in the Oracle Solaris operating systems for over two years.
Researchers from FireEye reported that a sophisticated threat actor, tracked as UNC1945, has been observed targeting Oracle Solaris operating systems for over two years.
The codename “UNC” used to track the group is used by FireEye for uncategorized groups
According to the experts, the attackers also used an exploit for a recently addressed zero-day vulnerability(CVE-2020-14871) in Oracle Solaris.
The UNC1945 group carried out attacks aimed at telecommunications companies and leveraged third-party networks to target specific financial and professional consulting industries.
“UNC1945 targeted Oracle Solaris operating systems, utilized several tools and utilities against Windows and Linux operating systems, loaded and operated custom virtual machines, and employed techniques to evade detection.” reads the report published by FireEye. “UNC1945 demonstrated access to exploits, tools and malware for multiple operating systems, a disciplined interest in covering or manipulating their activity, and displayed advanced technical abilities during interactive operations.”
In late 2018, the UNC1945 group was spotted compromising a Solaris server that had the SSH service exposed to the Internet to install a backdoor dubbed SLAPSTICK and steal credentials to use in later attacks.
519 later, in mid-2020, researchers observed another Solaris server that was connecting to the infrastructure previously associated with the attackers. In this case, the attackers deployed a remote exploitation tool dubbed EVILSUN designed to exploit the zero-day vulnerability CVE-2020-14871 in Solaris 9 server.
FireEye/Mandiant reported as the CVE-2020-14871 to Oracle, the IT giant addressed it with the release of the October 2020 Critical Patch Update. The CVE-2020-14871 flaw affects the Solaris Pluggable Authentication Module (PAM) and can allow an unauthentication attacker with network access to compromise the operating system.
In April 2020, researchers from Mandiant also discovered the availability of an ‘Oracle Solaris SSHD Remote Root Exploit’ on an underground marketplace. The exploit identified with EVILSUN is available for approximately $3,000 USD.
“According to an April 2020 post on a black-market website, an “Oracle Solaris SSHD Remote Root Exploit” was available for approximately $3,000 USD, which may be identifiable with EVILSUN.” reads the analysis published by Mandiant.
“Additionally, we confirmed a Solaris server exposed to the internet had critical vulnerabilities, which included the possibility of remote exploitation without authentication.”
The threat actor established a foothold on a Solaris 9 server by using the Solaris Pluggable Authentication Module SLAPSTICK backdoor.
Once established the backdoor, the threat actor dropped a custom Linux backdoor called LEMONSTICK on the workstation to achieve command execution, connection tunneling, and file transfer and execution.
UNC1945 obtained and maintained access to their external infrastructure using an SSH Port Forwarding mechanism,
UNC1945 maintained access using an SSH Port Forwarding mechanism, experts observed the group dropping a custom QEMU VM on multiple hosts, using a ‘start.sh’ script to have it executed inside of any Linux system.
The script contained TCP forwarding settings while the VM had preloaded multiple hacking tools, including post-exploitation applications, network scanners, exploits and reconnaissance tools. The list of preloaded tools included Mimikatz, Powersploit, Responder, Procdump, CrackMapExec, PoshC2, Medusa, and JBoss Vulnerability Scanner.
To evade detection, the threat actor placed tool and output files within temporary file system mount points that were stored in volatile memory. UNC1945 also used built-in utilities and public tools to modify timestamps and selectively manipulate Unix log files.
The attackers also collected credentials, escalated privileges, and moved laterally through multiple networks.
“UNC1945 used ProxyChains to download PUPYRAT, an open source, cross-platform multi-functional remote administration and post-exploitation tool mainly written in Python.” continues the report.
“At one target, the threat actor used a virtual machine to initiate a brute-force of SSH targeting Linux and HP-UX endpoints. Beginning with seemingly random usernames and shifting to legitimate Linux and Windows accounts, the threat actor successfully established SSH connections on a Linux endpoint. After successfully escalating privileges on an HP-UX endpoint and a Linux endpoint, UNC1945 installed three backdoors: SLAPSTICK, TINYSHELL, and OKSOLO.”
The attackers also used BlueKeep scanning tool to target Windows systems.
Experts noticed that the hackers did not exfiltrate any data from the victims in the observed attacks, in one case, they deployed the ROLLCOAST ransomware.
“The ease and breadth of exploitation in which UNC1945 conducted this campaign suggests a sophisticated, persistent actor comfortable exploiting various operating systems, and access to resources and numerous toolsets.” the researchers conclude. “Given the aforementioned factors, use of zero-day exploits and virtual machines, and ability to traverse multiple third-party networks, Mandiant expects this motivated threat actor to continue targeted operations against key industries,”
Sophisticated Threat Actor Exploited Oracle Solaris Zero-Day
4.11.20 Exploit Securityweek
A threat actor has been observed targeting Oracle Solaris operating systems for over two years, including with an exploit for a recently addressed zero-day vulnerability, FireEye reported on Monday.
Tracked as UNC1945 — UNC is assigned by FireEye to uncategorized groups — the threat actor was observed compromising telecommunications companies and leveraging third-party networks to target specific financial and professional consulting industries.
Throughout the observed activity, the group used various tools to compromise Windows, Linux, and Solaris operating systems and used custom virtual machines, all while focusing on evading detection.
“UNC1945 demonstrated access to exploits, tools and malware for multiple operating systems, a disciplined interest in covering or manipulating their activity, and displayed advanced technical abilities during interactive operations,” FireEye’s Mandiant security researchers reveal.
In late 2018, the threat actor was observed compromising a Solaris server that had the SSH service exposed to the Internet, to install the SLAPSTICK backdoor on it, in order to steal credentials. The adversary employed SSH to connect to the server.
In mid-2020, after a 519-day dwell time, a different Solaris server was observed connecting to the attacker’s infrastructure. The threat actor deployed a remote exploitation tool called EVILSUN to exploit a zero-day impacting a Solaris 9 server.
Tracked as CVE-2020-14871, the vulnerability was reported to Oracle, which addressed it as part of the October 2020 Critical Patch Update. The bug affected the Solaris Pluggable Authentication Module (PAM) and allowed an attacker with network access to compromise the operating system without authentication.
Madiant also discovered that, in April 2020, an ‘Oracle Solaris SSHD Remote Root Exploit’ was being offered on an underground marketplace for roughly $3,000, noting that this exploit “may be identifiable with EVILSUN.”
“Additionally, we confirmed a Solaris server exposed to the internet had critical vulnerabilities, which included the possibility of remote exploitation without authentication,” the researchers say.
Using the SLAPSTICK Solaris PAM backdoor, the threat actor maintained a foothold on the compromised Solaris 9 server. After placing the malware onto the compromised system, the adversary dropped a custom Linux backdoor called LEMONSTICK on the workstation, to facilitate command execution, connection tunneling, and file transfer and execution.
UNC1945 maintained access using an SSH Port Forwarding mechanism and dropped a custom QEMU VM on multiple hosts, using a ‘start.sh’ script to have it executed inside of any Linux system. The script contained TCP forwarding settings while the VM had preloaded tools such as Mimikatz, Powersploit, Responder, Procdump, CrackMapExec, PoshC2, Medusa, JBoss Vulnerability Scanner and more.
The adversary leveraged volatile memory to decrease operational visibility, manipulated timestamps and log files using built-in utilities and public tools, and employed anti-forensics techniques. Furthermore, the hackers collected credentials, escalated privileges, and moved laterally through the compromised environment.
The open-source remote access tool PUPYRAT was also employed. At one target, following initial compromise, the adversary deployed three different backdoors: SLAPSTICK, TINYSHELL, and OKSOLO. On a Windows environment, IMPACKET with SMBEXEC was used for remote command execution. A BlueKeep scanning tool was also used.
According to Mandiant, no data exfiltration appears to have happened, despite the multi-staged operation. In one case, however, the ROLLCOAST ransomware was deployed as the final stage of activity, but it’s unclear whether UNC1945 was responsible for this deployment or not, as access to the compromised environment might have been sold to a different actor.
“The ease and breadth of exploitation in which UNC1945 conducted this campaign suggests a sophisticated, persistent actor comfortable exploiting various operating systems, and access to resources and numerous toolsets. Given the aforementioned factors, use of zero-day exploits and virtual machines, and ability to traverse multiple third-party networks, Mandiant expects this motivated threat actor to continue targeted operations against key industries,” the researchers conclude.
Unpatched Windows Zero-Day Exploited in the Wild for Sandbox Escape
3.11.20 Exploit Threatpost
Google Project Zero disclosed the bug before a patch becomes available from Microsoft.
A high-severity Windows driver bug is being exploited in the wild as a zero-day. It allows local privilege escalation and sandbox escape.
The security vulnerability was disclosed by Google Project Zero just seven days after it was reported, since cybercriminals are already exploiting it, according to researchers.
The flaw (CVE-2020-17087) has to do with the way the Windows Kernel Cryptography Driver (cng.sys) processes input/output control (IOCTL), which is a system call for device-specific input/output operations and other operations that cannot be expressed by regular system calls.
“[Cng.sys] exposes a \Device\CNG device to user-mode programs and supports a variety of IOCTLs with non-trivial input structures,” according to the bug report, published on Friday. “We have identified a vulnerability in the processing of IOCTL 0x390400, reachable through [a] series of calls.”
With specially crafted requests, an attacker can trigger a pool-based buffer overflow, which leads to a system crash and opens the door for exploitation.
“The bug resides in the cng!CfgAdtpFormatPropertyBlock function and is caused by a 16-bit integer truncation issue,” the Project Zero team explained. “The integer overflow occurs in line 2, and if SourceLength is equal to or greater than 0x2AAB, an inadequately small buffer is allocated from the NonPagedPool in line 3. It is subsequently overflown by the binary-to-hex conversion loop in lines 5-10 by a multiple of 65536 bytes.”
The team put together a proof-of-concept exploit that shows the ease of triggering an attack. It worked on an up-to-date build of Windows 10 1903 (64-bit), but researchers said that the bug appears to affect Windows versions going back to Windows 7.
“A crash is easiest to reproduce with Special Pools enabled for cng.sys, but even in the default configuration the corruption of 64kB of kernel data will almost surely crash the system shortly after running the exploit,” according to Project Zero.
The director of Google’s Threat Analysis Group, Shane Huntley, said in the disclosure that the attacks are targeted and unrelated to any U.S. election-related targeting. Another Project Zero team member noted that Microsoft is expected to fix the bug on its next Patch Tuesday update, on Nov. 10.
Some quibbled with the short disclosure timeline, but Project Zero researchers Ben Hawkes and Tavis Ormandy defended the move on Twitter:
Ormandy noted, “Your attack is more likely to be detected if you attempt to use documented vulnerabilities, because people know what to look for. The other details of your attack will then be analyzed.”
Mateusz Jurczyk and Sergei Glazunov of Google Project Zero were credited with finding the bug.
Google fixes the second zero-day in Chrome in 2 weeks actively exploited
3.11.20 Exploit Securityaffairs
Google released Chrome 86.0.4240.183 for Windows, Mac, and Linux to fix 10 security vulnerabilities, including an RCE zero-day exploited in the wild.
Google has released Chrome 86.0.4240.183 for Windows, Mac, and Linux that address ten security vulnerabilities including a remote code execution (RCE) zero-day (CVE-2020-16009) exploited by threat actors in the wild.
The RCE is an inappropriate implementation in V8, which is Google’s open-source and C++ based high-performance WebAssembly and JavaScript engine.
The zero-day flaw was discovered on October 29, 2020 by Google white-hat hacker Samuel Groß of Google Project Zero and Clement Lecigne of Google’s Threat Analysis Group.
Google revealed that it is aware of the availability of an exploit for CVE-2020-16009 in the wild, anyway the tech giant did provide any details about the attackers that are exploiting it in the wild.
“Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed.“ reads the advisory published by Google. “Google is aware of reports that an exploit for CVE-2020-16009 exists in the wild.”
Google addressed another zero-day sandbox escape flaw, tracked as CVE-2020-16010, that affects Chrome for Android which is also exploited in attacks in the wild.
Below the remaining high severity security vulnerabilities addressed with the release of Chrome 86.0.4240.183:
[$15000][1138911] High CVE-2020-16004: Use after free in user interface. Reported by Leecraso and Guang Gong of 360 Alpha Lab working with 360 BugCloud on 2020-10-15
[$15000][1139398] High CVE-2020-16005: Insufficient policy enforcement in ANGLE. Reported by Jaehun Jeong(@n3sk) of Theori on 2020-10-16
[$5000][1133527] High CVE-2020-16006: Inappropriate implementation in V8. Reported by Bill Parks on 2020-09-29
[$1000][1125018] High CVE-2020-16007: Insufficient data validation in installer. Reported by Abdelhamid Naceri (halov) on 2020-09-04
[$TBD][1134107] High CVE-2020-16008: Stack buffer overflow in WebRTC. Reported by Tolya Korniltsev on 2020-10-01
[$NA][1143772] High CVE-2020-16009: Inappropriate implementation in V8. Reported by Clement Lecigne of Google’s Threat Analysis Group and Samuel Groß of Google Project Zero on 2020-10-29
[$NA][1144489] High CVE-2020-16011: Heap buffer overflow in UI on Windows. Reported by Sergei Glazunov of Google Project Zero on 2020-11-01
CVE-2020-16009 is the second zero-day discovered in Chrome that was actively exploited in the wild in the past two weeks.
Security researchers from Google have disclosed a zero-day vulnerability in the Windows operating system, tracked as CVE-2020-17087, that is currently under active exploitation.
Ben Hawkes, team lead for Google Project Zero team, revealed on Twitter that the vulnerability was chained with another Chrome zero-day flaw, tracked as CVE-2020-15999, that Google recently disclosed.
Google researchers expect a patch for this zero-day flaw to be available on November 10. The Director of Google’s Threat Analysis Group, Shane Huntley (@ShaneHuntley), confirmed that the vulnerability was exploited in targeted attacks that are not related to the forthcoming US election.
Google did not provide info on the attackers that have already exploited the flaw, but experts speculate that they were nation-state actors.
The Chrome zero-day is a sandbox escape issue, it allows attackers to escape Chrome’s secure container and run code on the underlying operating system.
WARNING: Google Discloses Windows Zero-Day Bug Exploited in the Wild
2.11.20 Exploit Thehackernews
Google has disclosed details of a new zero-day privilege escalation flaw in the Windows operating system that's being actively exploited in the wild.
The elevation of privileges (EoP) vulnerability, tracked as CVE-2020-17087, concerns a buffer overflow present since at least Windows 7 in the Windows Kernel Cryptography Driver ("cng.sys") that can be exploited for a sandbox escape.
"The bug resides in the cng!CfgAdtpFormatPropertyBlock function and is caused by a 16-bit integer truncation issue," Google's Project Zero researchers Mateusz Jurczyk and Sergei Glazunov noted in their technical write-up.
The security team made the details public following a seven-day disclosure deadline because of evidence that it's under active exploit.
Project Zero has shared a proof-of-concept exploit (PoC) that can be used to corrupt kernel data and crash vulnerable Windows devices even under default system configurations.
What's notable is that the exploit chain requires linking CVE-2020-17087 with another Chrome browser zero-day (CVE-2020-15999) that was fixed by Google last week.
The Chrome zero-day involves a heap buffer overflow in the Freetype font library to run malicious code in the browser, but the newly revealed Windows zero-day makes it possible for an attacker to break out of Chrome's sandbox protections and run the code on Windows — also called a sandbox escape.
Stating that the exploitation is "not related to any US election-related targeting," Project Zero's Ben Hawkes said a patch for the flaw is expected to be released by Microsoft on November 10.
Hawkes also defended the practice of disclosing zero-days within a week of them being actively exploited.
"We think there's defensive utility to sharing these details, and that opportunistic attacks using these details between now and the patch being released is reasonably unlikely (so far it's been used as part of an exploit chain, and the entry-point attack is fixed)," he said.
"The short deadline for in-the-wild exploit also tries to incentivize out-of-band patches or other mitigations being developed/shared with urgency. Those improvements you might expect to see over a longer term period," Hawkes added.
Microsoft Warns Threat Actors Continue to Exploit Zerologon Bug
31.10.20 Exploit Threatpost
Tech giant and feds this week renewed their urge to organizations to update Active Directory domain controllers.
Threat attackers continue to exploit the Microsoft Zerologon vulnerability, a situation that’s been a persistent worry to both the company and the U.S. government over the last few months. Both on Thursday renewed their pleas to businesses and end users to update Windows systems with a patch Microsoft released in August to mitigate attacks.
Despite patching awareness efforts, Microsoft said it is still receiving “a small number of reports from customers and others” about active exploits of the bug tracked as CVE-2020-1472, or Zerologon, according to a blog post by Aanchal Gupta, vice president of engineering for MSRC, on Thursday.
The zero-day elevation-of-privilege vulnerability—rated as critical and first disclosed and patched on Aug. 11–could allow an attacker to spoof a domain controller account and then use it to steal domain credentials, take over the domain and completely compromise all Active Directory identity services.
The bug is located in a core authentication component of Active Directory within the Windows Server OS and the Microsoft Windows Netlogon Remote Protocol (MS-NRPC). The flaw stems from the Netlogon Remote Protocol, available on Windows domain controllers, which is used for various tasks related to user and machine authentication.
Gupta urged organizations to deploy the Aug.11 patch or later release to every domain controller as the first in a four-step process to fix the vulnerability. Then administrators should monitor event logs to find which devices are making vulnerable connections; address identified non-compliant devices; and enable enforcement to address the bug in the overall environment, he said.
“Once fully deployed, Active Directory domain controller and trust accounts will be protected alongside Windows domain-joined machine accounts,” he said.
In addition to Microsoft’s patches, last month both Samba and 0patch also issued fixes for CVE-2020-1472 to fill in the some of the gaps that the official patch doesn’t address, such as end-of-life versions of Windows.
Microsoft’s latest advisory was enough for the Department of Homeland Security’s (DHS’s) Cybersecurity and Infrastructure Security Agency (CISA) to step in and issue a statement of its own Thursday warning organizations about continued exploit of the bug.
Given the severity of the vulnerability, the government has been nearly as active as Microsoft in urging people to update their systems. Interest from the feds likely has intensified since Microsoft’s warning earlier this month that an Iranian nation-state advanced persistent threat (APT) actor that Microsoft calls MERCURY (also known as MuddyWater, Static Kitten and Seedworm) is now actively exploiting Zerologon.
“CISA urges administrators to patch all domain controllers immediately—until every domain controller is updated, the entire infrastructure remains vulnerable, as threat actors can identify and exploit a vulnerable system in minutes,” according to the CISA alert.
The agency even has released a patch validation script to detect unpatched Microsoft domain controllers to help administers install the update. “If there is an observation of CVE-2020-1472 Netlogon activity or other indications of valid credential abuse detected, it should be assumed that malicious cyber actors have compromised all identity services,” the CISA warned.
Zerologon has been a consistent thorn in Microsoft’s side since its discovery, a scenario that has escalated since early September thanks largely to the publication of four proof-of-concept exploits for the flaw on Github. Soon after the exploits were published, Cisco Talos researchers warned of a spike in exploitation attempts against Zerologon.
The U.S. government first stepped in to rally organizations to update after the publication of the exploits, with the DHS issuing a rare emergency directive that ordered federal agencies to patch their Windows Servers against the flaw by Sept. 21.
Google discloses unpatched Windows zero-day exploited in the wild
31.10.20 Exploit Securityaffairs
Google researchers disclosed today a zero-day vulnerability in the Windows operating system that is currently under active exploitation.
Security researchers from Google have disclosed a zero-day vulnerability in the Windows operating system, tracked as CVE-2020-17087, that is currently under active exploitation.
Ben Hawkes, team lead for Google Project Zero team, revealed on Twitter that the vulnerability was chained with another Chrome zero-day flaw, tracked as CVE-2020-15999, that Google recently disclosed.
Google researchers expect a patch for this zero-day flaw to be available on November 10. The Director of Google’s Threat Analysis Group, Shane Huntley (@ShaneHuntley), confirmed that the vulnerability was exploited in targeted attacks that are not related to the forthcoming US election.
Google did not provide info on the attackers that have already exploited the flaw, but experts speculate that they were nation-state actors.
The Chrome zero-day is a sandbox escape issue, it allows attackers to escape Chrome’s secure container and run code on the underlying operating system.
“We have evidence that the following bug is being used in the wild. Therefore, this bug is subject to a 7 day disclosure deadline.” reads Google’s advisory.
“The Windows Kernel Cryptography Driver (cng.sys) exposes a \Device\CNG device to user-mode programs and supports a variety of IOCTLs with non-trivial input structures. It constitutes a locally accessible attack surface that can be exploited for privilege escalation (such as sandbox escape).”
The Google Project Zero team notified Microsoft last week and gave the company seven days to address the vulnerability, but unfortunately, Microsoft has yet to fix it.
The vulnerability affects all Windows versions between Windows 7 and the most recent Windows 10 release.
Google researchers also published a proof of concept code to exploit this vulnerability.
In March 2019, Google disclosed that that threat actors were chaining a Chrome zero-day (CVE-2019-5786) with a Windows zero-day (CVE-2019-0808) in attacks in the wild.
Threat actors are actively exploiting Zerologon flaw, Microsoft warns
30.10.20 Exploit Securityweek
Microsoft researchers are warning that threat actors are continuing to actively exploit the ZeroLogon vulnerability in attacks in the wild.
Microsoft is warning that threat actors are actively exploiting the ZeroLogon vulnerability in the Netlogon Remote Protocol.
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
“Microsoft has received a small number of reports from customers and others about continued activity exploiting a vulnerability affecting the Netlogon protocol (CVE-2020-1472) which was previously addressed in security updates starting on August 11, 2020.” reads a post published by MSRC VP of Engineering Aanchal Gupta. “If the original guidance is not applied, the vulnerability could allow an attacker to spoof a domain controller account that could be used to steal domain credentials and take over the domain.”
Microsoft strongly encourages administrators of enterprise Windows Servers to install the August 2020 Patch Tuesday as soon as possible to protect their systems from Zerologon attack that exploits the CVE-2020-1472.
Because the initial documentation regarding Zerologon patching process was not clear enough, Microsoft provided the following updates:
UPDATE your Domain Controllers with an update released August 11, 2020 or later.
FIND which devices are making vulnerable connections by monitoring event logs.
ADDRESS non-compliant devices making vulnerable connections.
ENABLE enforcement mode to address CVE-2020-1472 in your environment.
At the end of September, Microsoft issued a similar warning. The IT giant published a series of Tweets to warn of attackers that are actively exploiting the Windows Server Zerologon in attacks in the wild. The IT giant urged Windows administrators to install the released security updates as soon as possible.
In early October, Microsoft spotted a series of Zerologon attacks allegedly launched by the Russian cybercrime group tracked as TA505, CHIMBORAZO and Evil Corp.
Microsoft experts spotted the Zerologon attacks involving fake software updates, the researchers noticed that the malicious code connected to command and control (C&C) infrastructure known to be associated with TA505.
In the same period, Microsoft published a post and a series of tweets to warn of cyber attacks exploiting the Zerologon vulnerability carried out by the Iran-linked APT group known as MuddyWater, aka Mercury.
On September 18, The Department of Homeland Security’s CISA issued an emergency directive to order government agencies to address the Zerologon vulnerability (CVE-2020-1472) by September 21.
Hackers Can Open Doors by Exploiting Vulnerabilities in Hörmann Device
28.10.20 Exploit Securityweek
Hackers could remotely open garage doors and gates by exploiting vulnerabilities found in a gateway device made by Hörmann, researchers warned on Wednesday.
Hörmann is a Germany-based company that specializes in home and industrial doors. The company’s products are sold in more than 50 countries across North America, Europe and Asia, and according to Wikipedia, it’s the fourth largest door manufacturer in the world.
Customers who want to control garage doors, entrance gates and other smart systems from a smartphone are provided the BiSecur gateway device, a wireless access control system that includes a Hörmann key fob and comes with Wi-Fi and Ethernet interfaces.Hörmann gateway vulnerabilities
Researchers at Austria-based cybersecurity company SEC Consult have discovered a total of 15 vulnerabilities in the gateway device, including issues related to encryption, poorly protected communications, and the associated mobile application.
The flaws can be exploited for both attacks that require access to the local network and attacks that can be launched remotely from the internet. Based on its research, SEC Consult has created an open source Python-based communication library for BiSecur devices.
In one attack scenario described by SEC Consult for SecurityWeek, an attacker who is able to connect to the local network can open doors connected to the Hörmann gateway by executing a small script. The attack does not require authentication and it can be conducted from a mobile phone.
Another scenario involves an attacker on the local network rendering the door-opening hardware unresponsive. In order to restore the system, a manual reset of the device is required, but the device is typically behind the door, which in case of an attack cannot be opened by the victim.
As for attacks that can be launched remotely over the internet, the vulnerabilities found by SEC Consult only allow unauthenticated hackers to impersonate a device and send false status information to the owner. For instance, they can notify the victim via the app that their garage door is opening or that it’s open, when in fact it’s not.
A remote attacker can also impersonate a device over the internet and cause Hörmann’s servers to send the victim’s device username and password to the attacker instead of the door opener.
These remote attacks require the attacker to extract the client certificate and private key from any Hörmann door opener hardware, and then use the extracted key to connect to the vendor’s server. The attacker can then run a script to switch the identity of their device to the targeted user’s device, which is possible due to Hörmann’s failure to ensure that certificates matched the device.
SEC Consult says it has not checked how many potentially vulnerable systems are exposed to the internet due to legal reasons — doing so required accessing the vendor’s servers — but the vulnerable product has been on the market for years and is highly popular.
SEC Consult says Hoermann has taken steps to address the vulnerabilities after being notified. SecurityWeek has reached out to the vendor for comment and will update this article if it responds.
This is not the first time researchers have found vulnerabilities in the Hoermann BiSecur device. Back in 2017, experts showed how hackers could have cloned a legitimate transmitter to take control of gates and doors.
Chrome 86.0.4240.111 fixes actively exploited CVE-2020-15999 zero-day
21.10.20 Exploit Securityaffairs
Google has released Chrome version 86.0.4240.111 that also addresses the CVE-2020-15999 flaw which is an actively exploited zero-day.
Google has released Chrome version 86.0.4240.111 that includes security fixes for several issues, including a patch for an actively exploited zero-day vulnerability tracked as CVE-2020-15999.
The CVE-2020-15999 flaw is a memory corruption bug that resides in the FreeType font rendering library, which is included in standard Chrome releases.
White hat hackers from the Google Project Zero team spotted attacks exploiting the vulnerability in the wild.
The researchers did not disclose technical details about the attacks exploiting the CVE-2020-15999 in the wild to avoid mass exploitation from threat actors.
Google Project Zero is recommending other app development teams who use the same FreeType library to update their software as well.
The FreeType version 2.10.4 address this issue.
Chrome users can update their install to v86.0.4240.111 via the browser’s built-in update function.
Experts pointed out that since the patch for this zero-day is visible in the source code of the FreeType open-source library, threat actors will be able to make a reverse-engineering of the code and develop working exploits for the issue.
In the recent twelve months, Google addressed another two zero-day vulnerabilities tracked as CVE-2019-13720 (Oct. 2019) and CVE-2020-6418 (Feb. 2020) respectively
Chrome Update Patches Actively Exploited FreeType Vulnerability
21.10.20 Exploit Securityweek
A Chrome 86 update released by Google on Tuesday patches several high-severity vulnerabilities, including a zero-day that has been exploited in the wild.
The actively exploited vulnerability is tracked as CVE-2020-15999 and it has been described as a heap buffer overflow bug affecting FreeType, a popular software library for rendering fonts.
In addition to Chrome and Chrome OS, FreeType is used in Linux and UNIX distributions, Android, iOS, ReactOS, and Ghostscript, which means the font engine is present on over a billion devices, according to its developers.
CVE-2020-15999 was discovered by Google Project Zero researcher Sergei Glazunov on October 19. It was immediately also reported to FreeType developers, who created an emergency fix on October 20, which has been included in FreeType 2.10.4.
Glazunov, who shared details about the vulnerability on the FreeType bug tracked, noted that while the emergency fix appears to be working, a long-term patch will require a thorough code review.
The issue is related to Load_SBit_Png, a function that processes PNG images embedded into fonts. Buffer overflow vulnerabilities often allow an attacker to execute arbitrary code. In this case, exploitation apparently involves specially crafted font files.
No information has been shared by Project Zero on the attacks involving this security bug.
Google Project Zero’s Ben Hawkes noted on Twitter that while they have only spotted an exploit aimed at Chrome, other projects that use FreeType should also adopt the fix that was included in version 2.10.4.
Hawkes also clarified that the vulnerability may impact Chrome on Android as well, but Project Zero has yet to confirm this.
This is the second zero-day flaw patched this year in Chrome. The first was addressed in February with a Chrome 80 update.