"Only after the target responds to the threat actor's initial email does the threat actor send a followup message linking to what they claim is details about their request or complaint."
Exploit 2024 2023 2022 2021 2020
Chinese Hackers Exploited New Zero-Day in Barracuda's ESG Appliances
27.12.23 Exploit The Hacker News
Barracuda has revealed that Chinese threat actors exploited a new zero-day in its Email Security Gateway (ESG) appliances to deploy backdoor on a "limited number" of devices.
Tracked as CVE-2023-7102, the issue relates to a case of arbitrary code execution that resides within a third-party and open-source library Spreadsheet::ParseExcel that's used by the Amavis scanner within the gateway.
The company attributed the activity to a threat actor tracked by Google-owned Mandiant as UNC4841, which was previously linked to the active exploitation of another zero-day in Barracuda devices (CVE-2023-2868, CVSS score: 9.8) earlier this year.
Successful exploitation of the new flaw is accomplished by means of a specially crafted Microsoft Excel email attachment. This is followed by the deployment of new variants of known implants called SEASPY and SALTWATER that are equipped to offer persistence and command execution capabilities.
Barracuda said it released a security update that has been "automatically applied" on December 21, 2023, and that no further customer action is required.
It further pointed out that it "deployed a patch to remediate compromised ESG appliances which exhibited indicators of compromise related to the newly identified malware variants" a day later. It did not disclose the scale of the compromise.
That said, the original flaw in the Spreadsheet::ParseExcel Perl module (version 0.65) remains unpatched and has been assigned the CVE identifier CVE-2023-7101, necessitating that downstream users take appropriate remedial action.
According to Mandiant, which has been investigating the campaign, a number of private and public sector organizations located in at least 16 countries are estimated to have been impacted since October 2022.
The latest development once again speaks to UNC4841's adaptability, leveraging new tactics and techniques to retain access to high priority targets as existing loopholes get closed.
Hackers Exploiting MS Excel Vulnerability to Spread Agent Tesla Malware
23.12.23 Exploit The Hacker News
Attackers are weaponizing an old Microsoft Office vulnerability as part of phishing campaigns to distribute a strain of malware called Agent Tesla.
The infection chains leverage decoy Excel documents attached in invoice-themed messages to trick potential targets into opening them and activate the exploitation of CVE-2017-11882 (CVSS score: 7.8), a memory corruption vulnerability in Office's Equation Editor that could result in code execution with the privileges of the user.
The findings, which come from Zscaler ThreatLabz, build on prior reports from Fortinet FortiGuard Labs, which detailed a similar phishing campaign that exploited the security flaw to deliver the malware.
"Once a user downloads a malicious attachment and opens it, if their version of Microsoft Excel is vulnerable, the Excel file initiates communication with a malicious destination and proceeds to download additional files without requiring any further user interaction," security researcher Kaivalya Khursale said.
The first payload is an obfuscated Visual Basic Script, which initiates the download of a malicious JPG file that comes embedded with a Base64-encoded DLL file. This steganographic evasion tactic was previously also detailed by McAfee Labs in September 2023.
The concealed DLL is subsequently injected into RegAsm.exe, the Windows Assembly Registration Tool, to launch the final payload. It's worth noting that the executable has also been abused to load Quasar RAT in the past.
Agent Tesla is a .NET-based advanced keylogger and remote access trojan (RAT) that's equipped to harvest sensitive information from compromised hosts. The malware then communicates with a remote server to extract the collected data.
"Threat actors constantly adapt infection methods, making it imperative for organizations to stay updated on evolving cyber threats to safeguard their digital landscape," Khursale said.
The development comes as old security flaws become new attack targets for threat actors. Earlier this week, Imperva revealed that a three-year-old flaw in Oracle WebLogic Server (CVE-2020-14883, CVSS score: 7.2) is being utilized by the 8220 Gang to deliver cryptocurrency miners.
It also coincides with an uptick in DarkGate malware activity after it began to be advertised earlier this year as a malware-as-a-service (MaaS) offering and as a replacement for QakBot following its takedown back in August 2023.
"The technology sector is the most impacted by DarkGate attack campaigns," Zscaler said, citing customer telemetry data.
"Most DarkGate domains are 50 to 60 days old, which may indicate a deliberate approach where threat actors create and rotate domains at specific intervals."
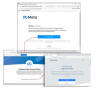
Phishing campaigns have also been discovered targeting the hospitality sector with booking-related email messages to distribute information stealer malware such as RedLine Stealer or Vidar Stealer, according to Sophos.
"They initially contact the target over email that contains nothing but text, but with subject matter a service-oriented business (like a hotel) would want to respond to quickly," researchers Andrew Brandt and Sean Gallagher said.

"Only after the target responds to the threat actor's initial email does the threat actor send a followup message linking to what they claim is details about their request or complaint."
Stealers and trojans notwithstanding, phishing attacks have further taken the form of bogus Instagram "Copyright Infringement" emails to steal users' two-factor authentication (2FA) backup codes via fraudulent web pages with an aim to bypass account protections, a scheme called Insta-Phish-A-Gram.
"The data attackers retrieve from this kind of phishing attack can be sold underground or used to take over the account," the cybersecurity firm said.
Beware: Experts Reveal New Details on Zero-Click Outlook RCE Exploits
19.12.23 Exploit The Hacker News
Technical details have emerged about two now-patched security flaws in Microsoft Windows that could be chained by threat actors to achieve remote code execution on the Outlook email service sans any user interaction.
"An attacker on the internet can chain the vulnerabilities together to create a full, zero-click remote code execution (RCE) exploit against Outlook clients," Akamai security researcher Ben Barnea, who discovered the vulnerabilities, said in a two-part report shared with The Hacker News.
The security issues, which were addressed by Microsoft in August and October 2023, respectively, are listed below -
CVE-2023-35384 (CVSS score: 5.4) - Windows HTML Platforms Security Feature Bypass Vulnerability
CVE-2023-36710 (CVSS score: 7.8) - Windows Media Foundation Core Remote Code Execution Vulnerability
CVE-2023-35384 has been described by Akamai as a bypass for a critical security flaw that Microsoft patched in March 2023. Tracked as CVE-2023-23397 (CVSS score: 9.8), the flaw relates to a case of privilege escalation that could result in the theft of NTLM credentials and enable an attacker to conduct a relay attack.
Earlier this month, Microsoft, Proofpoint, and Palo Alto Networks Unit 42 revealed that a Russian threat actor known as APT28 (aka Forest Blizzard) has been actively weaponizing the bug to gain unauthorized access to victims' accounts within Exchange servers.
It's worth noting that CVE-2023-35384 is also the second patch bypass after CVE-2023-29324, which was also discovered by Barnea and subsequently remediated by Redmond as part of May 2023 security updates.
"We found another bypass to the original Outlook vulnerability — a bypass that once again allowed us to coerce the client to connect to an attacker-controlled server and download a malicious sound file," Barnea said.
CVE-2023-35384, like CVE-2023-29324, is rooted in the parsing of a path by the MapUrlToZone function that could be exploited by sending an email containing a malicious file or a URL to an Outlook client.
"A security feature bypass vulnerability exists when the MSHTML platform fails to validate the correct Security Zone of requests for specific URLs. This could allow an attacker to cause a user to access a URL in a less restricted Internet Security Zone than intended," Microsoft noted in its advisory.
In doing so, the vulnerability can not only be used to leak NTLM credentials, but can also be chained with the sound parsing flaw (CVE-2023-36710) to download a custom sound file that, when autoplayed using Outlook's reminder sound feature, can lead to a zero-click code execution on the victim machine.
CVE-2023-36710 impacts the Audio Compression Manager (ACM) component, a legacy Windows multimedia framework that's used to manage audio codecs, and is the result of an integer overflow vulnerability that occurs when playing a WAV file.
"Finally, we managed to trigger the vulnerability using the IMA ADP codec," Barnea explained. "The file size is approximately 1.8 GB. By performing the math limit operation on the calculation we can conclude that the smallest possible file size with IMA ADP codec is 1 GB."
To mitigate the risks, it's recommended that organizations use microsegmentation to block outgoing SMB connections to remote public IP addresses. Additionally, it also advised to either disable NTLM, or add users to the Protected Users security group, which prevents the use of NTLM as an authentication mechanism.
Microsoft Warns of Hackers Exploiting OAuth for Cryptocurrency Mining and Phishing
13.12.23 Exploit The Hacker News
Microsoft has warned that adversaries are using OAuth applications as an automation tool to deploy virtual machines (VMs) for cryptocurrency mining and launch phishing attacks.
"Threat actors compromise user accounts to create, modify, and grant high privileges to OAuth applications that they can misuse to hide malicious activity," the Microsoft Threat Intelligence team said in an analysis.
"The misuse of OAuth also enables threat actors to maintain access to applications even if they lose access to the initially compromised account."
OAuth, short for Open Authorization, is an authorization and delegation framework (as opposed to authentication) that provides applications the ability to securely access information from other websites without handing over passwords.
In the attacks detailed by Microsoft, threat actors have been observed launching phishing or password-spraying attacks against poorly secured accounts with permissions to create or modify OAuth applications.
One such adversary is Storm-1283, which has leveraged a compromised user account to create an OAuth application and deploy VMs for cryptomining. Furthermore, the attackers modified existing OAuth applications to the account had access to by adding an extra set of credentials to facilitate the same goals.
In another instance, an unidentified actor compromised user accounts and created OAuth applications to maintain persistence and to launch email phishing attacks that employ an adversary-in-the-middle (AiTM) phishing kit to plunder session cookies from their targets and bypass authentication measures.
"In some cases, following the stolen session cookie replay activity, the actor leveraged the compromised user account to perform BEC financial fraud reconnaissance by opening email attachments in Microsoft Outlook Web Application (OWA) that contain specific keywords such as 'payment' and 'invoice," Microsoft said.
Other scenarios detected by the tech giant following the theft of session cookies involve the creation of OAuth applications to distribute phishing emails and conduct large-scale spamming activity. Microsoft is tracking the latter as Storm-1286.
To mitigate the risks associated with such attacks, it's recommended that organizations enforce multi-factor authentication (MFA), enable conditional access policies, and routinely audit apps and consented permissions.
Iranian Hackers Exploit PLCs in Attack on Water Authority in U.S.
29.11.23 Exploit The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) revealed that it's responding to a cyber attack that involved the active exploitation of Unitronics programmable logic controllers (PLCs) to target the Municipal Water Authority of Aliquippa in western Pennsylvania.
The attack has been attributed to an Iranian-backed hacktivist collective known as Cyber Av3ngers.
"Cyber threat actors are targeting PLCs associated with [Water and Wastewater Systems] facilities, including an identified Unitronics PLC, at a U.S. water facility," the agency said.
"In response, the affected municipality's water authority immediately took the system offline and switched to manual operations—there is no known risk to the municipality's drinking water or water supply."
According to news reports quoted by the Water Information Sharing & Analysis Center (WaterISAC), CyberAv3ngers is alleged to have seized control of the booster station that monitors and regulates pressure for Raccoon and Potter Townships.
With PLCs being used in the WWS sector to monitor various stages and processes of water and wastewater treatment, disruptive attacks attempting to compromise the integrity of such critical processes can have adverse impacts, preventing WWS facilities from providing access to clean, potable water.
To mitigate such attacks, CISA is recommending that organizations change the Unitronics PLC default password, enforce multi-factor authentication (MFA), disconnect the PLC from the internet, back up the logic and configurations on any Unitronics PLCs to enable fast recovery, and apply latest updates.
Cyber Av3ngers has a history of targeting the critical infrastructure sector, claiming to have infiltrated as many as 10 water treatment stations in Israel. Last month, the group also claimed responsibility for a major cyber assault on Orpak Systems, a prominent provider of gas station solutions in the country.
"Every Equipment 'Made In Israel' Is Cyber Av3ngers Legal Target," the group claimed in a message posted on its Telegram channel on November 26, 2023.
Hackers Can Exploit 'Forced Authentication' to Steal Windows NTLM Tokens
28.11.23 Exploit The Hacker News
Cybersecurity researchers have discovered a case of "forced authentication" that could be exploited to leak a Windows user's NT LAN Manager (NTLM) tokens by tricking a victim into opening a specially crafted Microsoft Access file.
The attack takes advantage of a legitimate feature in the database management system solution that allows users to link to external data sources, such as a remote SQL Server table.
"This feature can be abused by attackers to automatically leak the Windows user's NTLM tokens to any attacker-controlled server, via any TCP port, such as port 80," Check Point security researcher Haifei Li said. "The attack can be launched as long as the victim opens an .accdb or .mdb file. In fact, any more-common Office file type (such as a .rtf ) can work as well."
NTLM, an authentication protocol introduced by Microsoft in 1993, is a challenge-response protocol that's used to authenticate users during sign-in. Over the years, it has been found to be vulnerable to brute-force, pass-the-hash, and relay attacks.
The latest attack, in a nutshell, abuses the linked table feature in Access to leak the NTLM hashes to an actor-controlled server by embedding an .accdb file with a remote SQL Server database link inside of an MS Word document using a mechanism called Object Linking and Embedding (OLE).
"An attacker can set up a server that they control, listening on port 80, and put its IP address in the above 'server alias' field," Li explained. "Then they can send the database file, including the linked table, to the victim."
Should the victim open the file and click the linked table, the victim client contacts the attacker-controlled server for authentication, enabling the latter to pull off a relay attack by launching an authentication process with a targeted NTLM server in the same organization.
The rogue server then receives the challenge, passes it on to the victim, and gets a valid response, which is ultimately transmitted to the sender that challenges the CV as part of the attacker-controlled CV↔ SA authentication process receives valid response and then passes that response to the NTLM server.
While Microsoft has since released mitigations for the problem in the Office/Access version (Current Channel, version 2306, build 16529.20182) following responsible disclosure in January 2023, 0patch has released unofficial fixes for Office 2010, Office 2013, Office 2016, Office 2019, and Office 365.
The development also comes as Microsoft announced plans to discontinue NTLM in Windows 11 in favor of Kerberos for improved security.
Randstorm Exploit: Bitcoin Wallets Created b/w 2011-2015 Vulnerable to Hacking
20.11.23 Exploit The Hacker News
Bitcoin wallets created between 2011 and 2015 are susceptible to a new kind of exploit called Randstorm that makes it possible to recover passwords and gain unauthorized access to a multitude of wallets spanning several blockchain platforms.
"Randstorm() is a term we coined to describe a collection of bugs, design decisions, and API changes that, when brought in contact with each other, combine to dramatically reduce the quality of random numbers produced by web browsers of a certain era (2011-2015)," Unciphered disclosed in a report published last week.
It's estimated that approximately 1.4 million bitcoins are parked in wallets that were generated with potentially weak cryptographic keys. Customers can check whether their wallets are vulnerable at www.keybleed[.]com.
The cryptocurrency recovery company said it re-discovered the problem in January 2022 while it was working for an unnamed customer who had been locked out of its Blockchain.com wallet. The issue was first highlighted way back in 2018 by a security researcher who goes by the alias "ketamine."
The crux of the vulnerability stems from the use of BitcoinJS, an open-source JavaScript package used for developing browser-based cryptocurrency wallet applications.
Especially, Randstorm is rooted in the package's reliance on the SecureRandom() function in the JSBN javascript library coupled with cryptographic weaknesses that existed at that time in the web browsers' implementation of the Math.random() function, which allowed for weak pseudorandom number generation. BitcoinJS maintainers discontinued the use of JSBN in March 2014.
As a result, the lack of enough entropy could be exploited to stage brute-force attacks and recover the wallet private keys generated with the BitcoinJS library (or its dependent projects). The easiest wallets to crack open were those that had been generated before March 2012.
The findings once again cast fresh light on the open-source dependencies powering software infrastructure and how vulnerabilities in such foundational libraries can have cascading supply chain risks, as previously laid bare in the case of Apache Log4j in late 2021.
"The flaw was already built into wallets created with the software, and it would stay there forever unless the funds were moved to a new wallet created with new software," Unciphered noted.
New PoC Exploit for Apache ActiveMQ Flaw Could Let Attackers Fly Under the Radar
16.11.23 Exploit The Hacker News
Cybersecurity researchers have demonstrated a new technique that exploits a critical security flaw in Apache ActiveMQ to achieve arbitrary code execution in memory.
Tracked as CVE-2023-46604 (CVSS score: 10.0), the vulnerability is a remote code execution bug that could permit a threat actor to run arbitrary shell commands.
It was patched by Apache in ActiveMQ versions 5.15.16, 5.16.7, 5.17.6, or 5.18.3 released late last month.
The vulnerability has since come under active exploitation by ransomware outfits to deploy ransomware such as HelloKitty and a strain that shares similarities with TellYouThePass as well as a remote access trojan called SparkRAT.
According to new findings from VulnCheck, threat actors weaponizing the flaw are relying on a public proof-of-concept (PoC) exploit originally disclosed on October 25, 2023.
The attacks have been found to use ClassPathXmlApplicationContext, a class that's part of the Spring framework and available within ActiveMQ, to load a malicious XML bean configuration file over HTTP and achieve unauthenticated remote code execution on the server.
VulnCheck, which characterized the method as noisy, said it was able to engineer a better exploit that relies on the FileSystemXmlApplicationContext class and embeds a specially crafted SpEL expression in place of the "init-method" attribute to achieve the same results and even obtain a reverse shell.
"That means the threat actors could have avoided dropping their tools to disk," VulnCheck said. "They could have just written their encryptor in Nashorn (or loaded a class/JAR into memory) and remained memory resident."
However, it's worth noting that doing so triggers an exception message in the activemq.log file, necessitating that the attackers also take steps to clean up the forensic trail.
"Now that we know attackers can execute stealthy attacks using CVE-2023-46604, it's become even more important to patch your ActiveMQ servers and, ideally, remove them from the internet entirely," Jacob Baines, chief technology officer at VulnCheck, said.
Zero-Day Attacks Exploited Critical Vulnerability in Citrix ADC and Gateway
19.7.23 Exploit The Hacker News
Citrix is alerting users of a critical security flaw in NetScaler Application Delivery Controller (ADC) and Gateway that it said is being actively exploited in the wild.
Tracked as CVE-2023-3519 (CVSS score: 9.8), the issue relates to a case of code injection that could result in unauthenticated remote code execution. It impacts the following versions -
NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.13
NetScaler ADC and NetScaler Gateway 13.0 before 13.0-91.13
NetScaler ADC and NetScaler Gateway version 12.1 (currently end-of-life)
NetScaler ADC 13.1-FIPS before 13.1-37.159
NetScaler ADC 12.1-FIPS before 12.1-55.297, and
NetScaler ADC 12.1-NDcPP before 12.1-55.297
The company did not give further details on the flaw tied to CVE-2023-3519 other than to say that exploits for the flaw have been observed on "unmitigated appliances." However, successful exploitation requires the device to be configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or authorization and accounting (AAA) virtual server.
Also addressed alongside CVE-2023-3519 are two other bugs -
CVE-2023-3466 (CVSS score: 8.3) - An improper input validation vulnerability resulting in a reflected cross-site scripting (XSS) attack
CVE-2023-3467 (CVSS score: 8.0) - An improper privilege management vulnerability resulting in privilege escalation to the root administrator (nsroot)
Wouter Rijkbost and Jorren Geurts of Resillion have been credited with reporting the bugs. Patches have been made available to address the three flaws in the below versions -
NetScaler ADC and NetScaler Gateway 13.1-49.13 and later releases
NetScaler ADC and NetScaler Gateway 13.0-91.13 and later releases of 13.0
NetScaler ADC 13.1-FIPS 13.1-37.159 and later releases of 13.1-FIPS
NetScaler ADC 12.1-FIPS 12.1-55.297 and later releases of 12.1-FIPS, and
NetScaler ADC 12.1-NDcPP 12.1-55.297 and later releases of 12.1-NDcPP
Customers of NetScaler ADC and NetScaler Gateway version 12.1 are recommended to upgrade their appliances to a supported version to mitigate potential threats.
The development comes amid active exploitation of security flaws discovered in Adobe ColdFusion (CVE-2023-29298 and CVE-2023-38203) and the WooCommerce Payments WordPress plugin (CVE-2023-28121).
Leaving security flaws in WordPress plugins could open the door to complete compromise, enabling threat actors to repurpose the compromised WordPress sites for other malicious activities.
Last month, eSentire disclosed an attack campaign dubbed Nitrogen wherein infected WordPress sites have been used to host malicious ISO image files that, when launched, culminate in the deployment of rogue DLL files capable of contacting a remote server to fetch additional payloads, including Python scripts and Cobalt Strike.
Cybercriminals Exploiting WooCommerce Payments Plugin Flaw to Hijack Websites
18.7.23 Exploit The Hacker News
Threat actors are actively exploiting a recently disclosed critical security flaw in the WooCommerce Payments WordPress plugin as part of a massive targeted campaign.
The flaw, tracked as CVE-2023-28121 (CVSS score: 9.8), is a case of authentication bypass that enables unauthenticated attackers to impersonate arbitrary users and perform some actions as the impersonated user, including an administrator, potentially leading to site takeover.
"Large-scale attacks against the vulnerability, assigned CVE-2023-28121, began on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million attacks against 157,000 sites on Saturday, July 16, 2023," Wordfence security researcher Ram Gall said in a Monday post.
Versions 4.8.0 through 5.6.1 of WooCommerce Payments are vulnerable. The plugin is installed on over 600,000 sites. Patches for the bug were released by WooCommerce back in March 2023, with WordPress issuing auto-updates to sites using affected versions of the software.
A common denominator observed in the attacks entails the use of the HTTP request header "X-Wcpay-Platform-Checkout-User: 1" that causes susceptible sites to treat any additional payloads as coming from an administrative user.
Wordfence said the aforementioned loophole is being weaponized to deploy the WP Console plugin, which can be used by an administrator to execute malicious code and install a file uploader to set up persistence and backdoor the compromised site.
Adobe ColdFusion Flaws Exploited in the Wild#
The disclosure comes as Rapid7 reported that it observed active exploitation of Adobe ColdFusion flaws in multiple customer environments starting July 13, 2023, to deploy web shells on infected endpoints.
"Threat actors appear to be exploiting CVE-2023-29298 in conjunction with a secondary vulnerability," Rapid7 security researcher Caitlin Condon said. The additional flaw appears to be CVE-2023-38203 (CVSS score: 9.8), a deserialization flaw that was addressed in an out-of-band update released on July 14.
CVE-2023-29298 (CVSS score: 7.5) concerns an access control bypass vulnerability impacting ColdFusion 2023, ColdFusion 2021 Update 6 and below, and ColdFusion 2018 Update 16 and below.
"The vulnerability allows an attacker to access the administration endpoints by inserting an unexpected additional forward slash character in the requested URL," Rapid7 disclosed last week.
Rapid7, however, warned that the fix for CVE-2023-29298 is incomplete and that it could be trivially modified to bypass the patches released by Adobe.
Users are recommended to update to the latest version of Adobe ColdFusion to secure against potential threats, since the fixes put in place to resolve CVE-2023-38203 breaks the exploit chain.
Hackers Exploit WebAPK to Deceive Android Users into Installing Malicious Apps
18.7.23 Exploit The Hacker News
Threat actors are taking advantage of Android's WebAPK technology to trick unsuspecting users into installing malicious web apps on Android phones that are designed to capture sensitive personal information.
"The attack began with victims receiving SMS messages suggesting the need to update a mobile banking application," researchers from CSIRT KNF said in an analysis released last week. "The link contained in the message led to a site that used WebAPK technology to install a malicious application on the victim's device."
The application impersonates PKO Bank Polski, a multinational banking and financial services company headquartered in Warsaw. Details of the campaign were first shared by Polish cybersecurity firm RIFFSEC.
WebAPK allows users to install progressive web apps (PWAs) to their home screen on Android devices without having to use the Google Play Store.
"When a user installs a PWA from Google Chrome and a WebAPK is used, the minting server "mints" (packages) and signs an APK for the PWA," Google explains in its documentation.
"That process takes time, but when the APK is ready, the browser installs that app silently on the user's device. Because trusted providers (Play Services or Samsung) signed the APK, the phone installs it without disabling security, as with any app coming from the store. There is no need for sideloading the app."
Once installed, the fake banking app ("org.chromium.webapk.a798467883c056fed_v2") urges users to enter their credentials and two-factor authentication (2FA) tokens, effectively resulting in their theft.
"One of the challenges in countering such attacks is the fact that WebAPK applications generate different package names and checksums on each device," CSIRT KNF said. "They are dynamically built by the Chrome engine, which makes the use of this data as Indicators of Compromise (IoC) difficult."
To counter such threats, it's recommended to block websites that use the WebAPK mechanism to carry out phishing attacks.
The development comes as Resecurity revealed that cybercriminals are increasingly leveraging specialized device spoofing tools for Android that are marketed on the dark web in a bid to impersonate compromised account holders and bypass anti-fraud controls.
The antidetect tools, including Enclave Service and MacFly, are capable of spoofing mobile device fingerprints and other software and network parameters that are analyzed by anti-fraud systems, with threat actors also leveraging weak fraud controls to conduct unauthorized transactions via smartphones using banking malware such as TimpDoor and Clientor.
"Cybercriminals use these tools to access compromised accounts and impersonate legitimate customers by exploiting stolen cookie files, impersonating hyper-granular device identifiers, and utilizing fraud victims' unique network settings," the cybersecurity company said.
Cybercriminals Exploit Microsoft Word Vulnerabilities to Deploy LokiBot Malware
17.7.23 Exploit The Hacker News
Microsoft Word documents exploiting known remote code execution flaws are being used as phishing lures to drop malware called LokiBot on compromised systems.
"LokiBot, also known as Loki PWS, has been a well-known information-stealing Trojan active since 2015," Fortinet FortiGuard Labs researcher Cara Lin said. "It primarily targets Windows systems and aims to gather sensitive information from infected machines."
The cybersecurity company, which spotted the campaign in May 2023, said the attacks take advantage of CVE-2021-40444 and CVE-2022-30190 (aka Follina) to achieve code execution.
The Word file that weaponizes CVE-2021-40444 contains an external GoFile link embedded within an XML file that leads to the download of an HTML file, which exploits Follina to download a next-stage payload, an injector module written in Visual Basic that decrypts and launches LokiBot.
The injector also features evasion techniques to check for the presence of debuggers and determine if it's running in a virtualized environment.

An alternative chain discovered towards the end of May starts with a Word document incorporating a VBA script that executes a macro immediately upon opening the document using the "Auto_Open" and "Document_Open" functions.
The macro script subsequently acts as a conduit to deliver an interim payload from a remote server, which also functions as an injector to load LokiBot and connect to a command-and-control (C2) server.
LokiBot, not to be confused with an Android banking trojan of the same name, comes with capabilities to log keystrokes, capture screenshots, gather login credential information from web browsers, and siphon data from a variety of cryptocurrency wallets.
"LokiBot is a long-standing and widespread malware active for many years," Lin said. "Its functionalities have matured over time, making it easy for cybercriminals to use it to steal sensitive data from victims. The attackers behind LokiBot continually update their initial access methods, allowing their malware campaign to find more efficient ways to spread and infect systems."
Hackers Exploit Windows Policy Loophole to Forge Kernel-Mode Driver Signatures
12.7.23 Exploit The Hacker News
A Microsoft Windows policy loophole has been observed being exploited primarily by native Chinese-speaking threat actors to forge signatures on kernel-mode drivers.
"Actors are leveraging multiple open-source tools that alter the signing date of kernel mode drivers to load malicious and unverified drivers signed with expired certificates," Cisco Talos said in an exhaustive two-part report shared with The Hacker News. "This is a major threat, as access to the kernel provides complete access to a system, and therefore total compromise."
Following responsible disclosure, Microsoft said it has taken steps to block all certificates to mitigate the threat. It further stated that its investigation found "the activity was limited to the abuse of several developer program accounts and that no Microsoft account compromise has been identified."
The tech giant, besides suspending developer program accounts involved in the incident, emphasized that the threat actors had already gained administrative privileges on compromised systems prior to use of the drivers.
It's worth pointing out that the Windows maker had rolled out similar blocking protections in December 2022 to prevent ransomware attackers from using Microsoft-signed drivers for post-exploitation activity.
Driver signature enforcement, which requires kernel-mode drivers to be digitally signed with a certificate from Microsoft's Dev Portal, is a crucial line of defense against malicious drivers, which could be potentially weaponized to evade security solutions, tamper with system processes, and maintain persistence. The policy change was introduced with the debut of Windows Vista.
The new weakness discovered by Cisco Talos makes it possible to forge signatures on kernel-mode drivers, thereby allowing Windows certificate policies to be bypassed.
This is made possible due to an exception carved out by Microsoft to maintain compatibility, which permits cross-signed drivers if the computer was upgraded from an earlier release of Windows to Windows 10, version 1607; Secure Boot is off in the BIOS; and the drivers were "signed with an end-entity certificate issued prior to July 29th 2015 that chains to a supported cross-signed [certificate authority]."
"The third exception creates a loophole that allows a newly compiled driver to be signed with non-revoked certificates issued prior to or expired before July 29, 2015, provided that the certificate chains to a supported cross-signed certificate authority," the cybersecurity company said.
As a result, a driver signed in this manner will not be prevented from being loaded on a Windows device, thereby enabling threat actors to take advantage of the escape clause to deploy thousands of malicious, signed drivers without submitting them to Microsoft for verification.
These rogue drivers are deployed using signature timestamp forging software such as HookSignTool and FuckCertVerifyTimeValidity, which have been publicly available since 2019 and 2018, respectively.
HookSignTool has been accessible via GitHub since January 7, 2020, while FuckCertVerifyTimeValidity was first committed to the code hosting service on December 14, 2018.
"HookSignTool is a driver signature forging tool that alters the signing date of a driver during the signing process through a combination of hooking into the Windows API and manually altering the import table of a legitimate code signing tool," Cisco Talos explained.
Specifically, it involves hooking to the CertVerifyTimeValidity function, which verifies the time validity of a certificate, to change the signing timestamp during execution.
"This tiny project prevents the signtool from verifing [sic] cert time validity and let you sign your bin with outdated cert without changing system time manually," the GitHub page for FuckCertVerifyTimeValidity reads.
"It install hook into crypt32!CertVerifyTimeValidity and make it always return 0 and make kernel32!GetLocalTime return what you want as you can add "-fuckyear 2011" to signtool's command line to sign a cert from year 2011."
That said, pulling off a successful forgery requires a non-revoked code signing certificate that was issued before July 29, 2015, along with the certificate's private key and passphrase.
Cisco Talos said it discovered over a dozen code signing certificates with keys and passwords contained in a PFX file hosted on GitHub in a forked repository of FuckCertVerifyTimeValidity. It's not immediately clear how these certificates were obtained.
What's more, it has been observed that HookSignTool has been used to re-sign cracked drivers in order to bypass digital rights management (DRM) integrity checks, with an actor named "Juno_Jr" releasing a cracked version of PrimoCache, a legitimate software caching solution, in a Chinese software cracking forum on November 9, 2022.
"In the cracked version [...], the patched driver was re-signed with a certificate originally issued to 'Shenzhen Luyoudashi Technology Co., Ltd.,' which is contained in the PFX file on GitHub," Talos researchers said. "This ability to resign a cracked driver removes a significant roadblock when attempting to bypass DRM checks in a signed driver."
That's not all. HookSignTool is also being utilized by a previously undocumented driver identified as RedDriver to forge its signature timestamp. Active since at least 2021, it functions as a driver-based browser hijacker that leverages the Windows Filtering Platform (WFP) to intercept browser traffic and reroute it to localhost (127.0.0.1).
The target browser is chosen at random from a hard-coded list containing the process names of many popular Chinese language browsers like Liebao, QQ Browser, Sogou, and UC Browser, as well as Google Chrome, Microsoft Edge, and Mozilla Firefox.
"I initially found RedDriver while researching certificate timestamp forging on Windows drivers," Chris Neal, outreach researcher for Cisco Talos told The Hacker News. "It was one of the first samples I ran into that was immediately suspicious. What caught my attention was the list of web browsers stored inside the RedDriver file."
The ultimate objective of this browser traffic redirection is not clear, although it goes without saying that such a capability could be abused to tamper with browser traffic at the packet level.
RedDriver infection chains commence with the execution of a binary named "DnfClientShell32.exe," which, in turn, initiates encrypted communications with a command-and-control (C2) server to download the malicious driver.
"We didn't observe the delivery of the initial file, but it's very likely that the file was packaged to masquerade as a game file, and was hosted on a malicious download link," Neal said. "The victim probably thought they were downloading a file from a legitimate source and ran the executable. 'DNFClient' is the name of a file belonging to 'Dungeon Fighter Online' which is an extremely popular game in China and commonly referred to as 'DNF.'"
"RedDriver was likely developed by highly skilled threat actors as the learning curve for developing malicious drivers is steep," Cisco Talos said. "While the threat appears to target native Chinese speakers, the authors are likely Chinese speakers as well."
"The authors also demonstrated a familiarity or experience with software development lifecycles, another skill set that requires previous development experience."
The development comes as Sophos said it found over 100 malicious kernel drivers that had been signed by Microsoft and other companies, some dating as far back as April, and used to either sabotage security software from running as designed or function as a stealthy rootkit capable of monitoring network traffic using WFP.
"It appears the creator of the malicious driver built out one 'parent' version of the driver, then ran the parent version through one or more packer utilities one or more times, creating in some cases dozens of 'child' variants, all of which the creators could submit to Microsoft for signing," Sophos researcher Andrew Brandt said.
"There are a lot of benefits for threat actors to deploy drivers in their infection chain, however they are a lot more difficult to develop than user-mode malware," Neal said. "Drivers are harder to detect for EDR and are hard to analyze, especially if there is any obfuscation employed."
(The story has been updated after publication to include additional information from Sophos about the discovery of malicious drivers.)
Chinese UNC4841 Group Exploits Zero-Day Flaw in Barracuda Email Security Gateway
16.6.23 Exploit The Hacker News
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway (ESG) appliances since October 2022.
"UNC4841 is an espionage actor behind this wide-ranging campaign in support of the People's Republic of China," Google-owned Mandiant said in a new report published today, describing the group as "aggressive and skilled."
The flaw in question is CVE-2023-2868 (CVSS score: 9.8), which relates to a remote code injection affecting versions 5.1.3.001 through 9.2.0.006 that arises as a result of an incomplete validation of attachments contained within incoming emails.
Barracuda addressed the problem on May 20 and 21, 2023, but the company has since urged affected customers to immediately replace the devices "regardless of patch version level."
Now according to the incident response and threat intelligence firm, which was appointed to probe the hack, UNC4841 is said to have sent emails to victim organizations containing malicious TAR file attachments that were designed to exploit the bug as early as October 10, 2022.
These email messages contained generic lures with poor grammar and, in some cases, placeholder values, a tactic deliberately chosen to disguise the communications as spam.
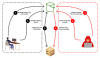
The goal, it noted, was to execute a reverse shell payload on the targeted ESG devices and deliver three different malware strains – SALTWATER, SEASIDE, and SEASPY – in order to establish persistence and execute arbitrary commands, while masquerading them as legitimate Barracuda ESG modules or services.
Also deployed by the adversary is a kernel rootkit named SANDBAR that's configured to conceal processes that begin with a specified name as well as trojanized versions of two different valid Barracuda Lua modules -
SEASPRAY - A launcher for screening incoming email attachments with a particular filename and runs an external C-based utility dubbed WHIRLPOOL to create a TLS reverse shell
SKIPJACK - A passive implant that listens for incoming email headers and subjects and executes the content present in "Content-ID" header field
Source code overlaps have been identified between SEASPY and a publicly available backdoor referred to as cd00r and also between SANDBAR and an open-source rootkit, suggesting that the actor repurposed existing tools to orchestrate the intrusions.
UNC4841 has all the hallmarks of a persistent actor, given its ability to swiftly alter its malware and employ additional persistence mechanisms as Barracuda initiated containment efforts after discovering the activity on May 19, 2023.
In some instances, the threat actor was observed leveraging access to a compromised ESG appliance to conduct lateral movement into the victim network, or to send mail to other victim appliances. Data exfiltration entailed the capture of email related data in a subset of cases.
The high frequency attacks, Mandiant said, targeted an unspecified number of private and public sector organizations located in at least 16 countries, with almost a third being government entities. 55% of the impacted organizations are located in the Americas, followed by 24% in EMEA and 22% in the Asia-Pacific region.
"As of June 10, 2023, approximately 5% of active ESG appliances worldwide have shown evidence of known indicators of compromise," Barracuda told The Hacker News in a statement, adding it's "providing the replacement product to impacted customers at no cost."
"UNC4841 has shown to be highly responsive to defensive efforts and actively modifies TTPs to maintain their operations," Mandiant said, adding it expects the actors to "alter their TTPs and modify their toolkit."
New Supply Chain Attack Exploits Abandoned S3 Buckets to Distribute Malicious Binaries
15.6.23 Exploit The Hacker News
In what's a new kind of software supply chain attack aimed at open source projects, it has emerged that threat actors could seize control of expired Amazon S3 buckets to serve rogue binaries without altering the modules themselves.
"Malicious binaries steal the user IDs, passwords, local machine environment variables, and local host name, and then exfiltrates the stolen data to the hijacked bucket," Checkmarx researcher Guy Nachshon said.
The attack was first observed in the case of an npm package called bignum, which, until version 0.13.0, relied on an Amazon S3 bucket to download pre-built binary versions of an addon named node-pre-gyp during installation.
"These binaries were published on a now-expired S3 bucket which has since been claimed by a malicious third party which is now serving binaries containing malware that exfiltrates data from the user's computer," according to a GitHub advisory published on May 24, 2023.
An unknown threat actor is said to have seized on the opportunity that the S3 bucket was once active to deliver malware when unsuspecting users downloaded the package in question.
"If a package pointed to a bucket as its source, the pointer would continue to exist even after the bucket's deletion," Nachshon explained. "This abnormality allowed the attacker to reroute the pointer toward the taken-over bucket."
A reverse engineering of the malware sample has revealed that it's capable of plundering user credentials and environment details, and transmitting the information to the same hijacked bucket.
Checkmarx said it found numerous packages using abandoned S3 buckets, making them susceptible to the novel attack vector. If anything, the development is a sign that threat actors are constantly on the lookout for different ways to poison the software supply chain.
"This new twist in the realm of subdomain takeovers serves as a wake-up call to developers and organizations," Nachshon said. "An abandoned hosting bucket or an obsolete subdomain is not just a forgotten artifact; in the wrong hands, it can become a potent weapon for data theft and intrusion."
The development also comes nearly a week after Cyble unearthed 160 malicious python packages that are estimated to have been downloaded over 45,000 times and featured capabilities to extract login credentials and credit card details.
Microsoft: Lace Tempest Hackers Behind Active Exploitation of MOVEit Transfer App
5.6.23 Exploit The Hacker News
Microsoft has officially linked the ongoing active exploitation of a critical flaw in the Progress Software MOVEit Transfer application to a threat actor it tracks as Lace Tempest.
"Exploitation is often followed by deployment of a web shell with data exfiltration capabilities," the Microsoft Threat Intelligence team said in a series of tweets today. "CVE-2023-34362 allows attackers to authenticate as any user."
Lace Tempest, also called Storm-0950, is a ransomware affiliate that overlaps with other groups such as FIN11, TA505, and Evil Corp. It's also known to operate the Cl0p extortion site.
The threat actor also has a track record of exploiting different zero-day flaws to siphon data and extort victims, with the group recently observed weaponizing a severe bug in PaperCut servers.
CVE-2023-34362 relates to an SQL injection vulnerability in MOVEit Transfer that enables unauthenticated, remote attackers to gain access to the database and execute arbitrary code.
There are believed to be at least over 3,000 exposed hosts utilizing the MOVEit Transfer service, according to data from attack surface management company Censys.
Google-owned Mandiant, which is tracking the activity under the moniker UNC4857 and has labeled the web shell LEMURLOOT, said it identified broad tactical connections with FIN11.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), last week, added the flaw to its Known Exploited Vulnerabilities (KEV) catalog, recommending federal agencies to apply vendor-provided patches by June 23, 2023.
The development follows the similar zero-day mass exploitation of Accellion FTA servers in December 2020 and GoAnywhere MFT in January 2023, making it imperative that users apply the patches as soon as possible to secure against potential risks.
Alert: Hackers Exploit Barracuda Email Security Gateway 0-Day Flaw for 7 Months
31.5.23 Exploit The Hacker News
Enterprise security firm Barracuda on Tuesday disclosed that a recently patched zero-day flaw in its Email Security Gateway (ESG) appliances had been abused by threat actors since October 2022 to backdoor the devices.
The latest findings show that the critical vulnerability, tracked as CVE-2023-2868 (CVSS score: N/A), has been actively exploited for at least seven months prior to its discovery.
The flaw, which Barracuda identified on May 19, 2023, affects versions 5.1.3.001 through 9.2.0.006 and could allow a remote attacker to achieve code execution on susceptible installations. Patches were released by Barracuda on May 20 and May 21.
"CVE-2023-2868 was utilized to obtain unauthorized access to a subset of ESG appliances," the network and email security company said in an updated advisory.
"Malware was identified on a subset of appliances allowing for persistent backdoor access. Evidence of data exfiltration was identified on a subset of impacted appliances."
Three different malware strains have been discovered to date -
SALTWATER - A trojanized module for the Barracuda SMTP daemon (bsmtpd) that's equipped to upload or download arbitrary files, execute commands, as well as proxy and tunnel malicious traffic to fly under the radar.
SEASPY - An x64 ELF backdoor that offers persistence capabilities and is activated by means of a magic packet.
SEASIDE - A Lua based module for bsmtpd establish reverse shells via SMTP HELO/EHLO commands sent via the malware's command-and-control (C2) server.
Source code overlaps have been identified between SEASPY and an open source backdoor called cd00r, according to Google-owned Mandiant, which is investigating the incident. The attacks have not been attributed to a known threat actor or group.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), last week, also added the bug to its Known Exploited Vulnerabilities (KEV) catalog, urging federal agencies to apply the fixes by June 16, 2023.
Barracuda did not disclose how many organizations were breached, but noted they were directly contacted with mitigation guidance. It also warned that the ongoing probe may unearth additional users who may have been affected.
Barracuda Warns of Zero-Day Exploited to Breach Email Security Gateway Appliances
28.5.23 Exploit The Hacker News
Email protection and network security services provider Barracuda is warning users about a zero-day flaw that it said has been exploited to breach the company's Email Security Gateway (ESG) appliances.
The zero-day is being tracked as CVE-2023-2868 and has been described as a remote code injection vulnerability affecting versions 5.1.3.001 through 9.2.0.006.
The California-headquartered firm said the issue is rooted in a component that screens the attachments of incoming emails.
"The vulnerability arises out of a failure to comprehensively sanitize the processing of .tar file (tape archives)," according to an advisory from the NIST's national vulnerability database.
"The vulnerability stems from incomplete input validation of a user-supplied .tar file as it pertains to the names of the files contained within the archive. As a consequence, a remote attacker can specifically format these file names in a particular manner that will result in remotely executing a system command through Perl's qx operator with the privileges of the Email Security Gateway product."
The shortcoming, Barracuda noted, was identified on May 19, 2023, prompting the company to deploy a patch across all ESG devices worldwide a day later. A second fix was released on May 21 as part of its "containment strategy."
Additionally, the company's investigation uncovered evidence of active exploitation of CVE-2023-2868, resulting in unauthorized access to a "subset of email gateway appliances."
The company, which has over 200,000 global customers, did not disclose the scale of the attack. It said affected users have been directly contacted with a list of remedial actions to take.
Barracuda has also urged its customers to review their environments, adding it's still actively monitoring the situation.
The identity of the threat actors behind the attack is currently not known, but Chinese and Russian hacking groups have been observed deploying bespoke malware on vulnerable Cisco, Fortinet, and SonicWall devices in recent months.
The development comes as Defiant alerted of large-scale exploitation of a now-fixed cross-site scripting (XSS) flaw in a plugin called Beautiful Cookie Consent Banner (CVSS score: 7.2) that's installed on over 40,000 sites.
The vulnerability offers unauthenticated attackers the ability to inject malicious JavaScript to a website, potentially allowing redirects to malvertising sites as well as the creation of rogue admin users, resulting in site takeovers.
The WordPress security company said it "blocked nearly 3 million attacks against more than 1.5 million sites, from nearly 14,000 IP addresses since May 23, 2023, and attacks are ongoing."
Update#
The U.S. Cybersecurity and Infrastructure Security Agency on Friday added the remote code injection vulnerability impacting Barracuda ESG appliances to its Known Exploited Vulnerabilities (KEV) catalog, urging federal agencies to apply the fixes by June 16, 2023.
KeePass Exploit Allows Attackers to Recover Master Passwords from Memory
24.5.23 Exploit The Hacker News
A proof-of-concept (PoC) has been made available for a security flaw impacting the KeePass password manager that could be exploited to recover a victim's master password in cleartext under specific circumstances.
The issue, tracked as CVE-2023-32784, impacts KeePass versions 2.x for Windows, Linux, and macOS, and is expected to be patched in version 2.54, which is likely to be released early next month.
"Apart from the first password character, it is mostly able to recover the password in plaintext," security researcher "vdohney," who discovered the flaw and devised a PoC, said. "No code execution on the target system is required, just a memory dump."
"It doesn't matter where the memory comes from," the researcher added, stating, "it doesn't matter whether or not the workspace is locked. It is also possible to dump the password from RAM after KeePass is no longer running, although the chance of that working goes down with the time it's been since then."
It's worth noting that successful exploitation of the flaw banks on the condition that an attacker has already compromised a potential target's computer. It also requires that the password is typed on a keyboard, and not copied from the device's clipboard.

vdohney said the vulnerability has to do with how a custom text box field used for entering the master password handles user input. Specifically, it has been found to leave traces of every character the user types in the program memory.
This leads to a scenario whereby an attacker could dump the program's memory and reassemble the password in plaintext with the exception of the first character. Users are advised to update to KeePass 2.54 once it becomes available.
The disclosure comes a few months after another medium-severity flaw (CVE-2023-24055) was uncovered in the open source password manager that could be potentially exploited to retrieve cleartext passwords from the password database by leveraging write access to the software's XML configuration file.
KeePass has maintained that the "password database is not intended to be secure against an attacker who has that level of access to the local PC."
It also follows findings from Google security research that detailed a flaw in password managers such as Bitwarden, Dashlane, and Safari, which can be abused to auto-fill saved credentials into untrusted web pages, leading to possible account takeovers.
8220 Gang Exploiting Oracle WebLogic Flaw to Hijack Servers and Mine Cryptocurrency
18.5.23 Exploit The Hacker News
The notorious cryptojacking group tracked as 8220 Gang has been spotted weaponizing a six-year-old security flaw in Oracle WebLogic servers to ensnare vulnerable instances into a botnet and distribute cryptocurrency mining malware.
The flaw in question is CVE-2017-3506 (CVSS score: 7.4), which, when successfully exploited, could allow an unauthenticated attacker to execute arbitrary commands remotely.
"This allows attackers to gain unauthorized access to sensitive data or compromise the entire system," Trend Micro researcher Sunil Bharti said in a report published this week.
8220 Gang, first documented by Cisco Talos in late 2018, is so named for its original use of port 8220 for command-and-control (C2) network communications.
"8220 Gang identifies targets via scanning for misconfigured or vulnerable hosts on the public internet," SentinelOne noted last year. "8220 Gang is known to make use of SSH brute force attacks post-infection for the purposes of lateral movement inside a compromised network."
Earlier this year, Sydig detailed attacks mounted by the "low-skill" crimeware group between November 2022 and January 2023 that aim to breach vulnerable Oracle WebLogic and Apache web servers and deploy a cryptocurrency miner.
It has also been observed making use of an off-the-shelf malware downloader known as PureCrypter as well as a crypter codenamed ScrubCrypt to conceal the miner payload and evade detection by security software.
In the latest attack chain documented by Trend Micro, the Oracle WebLogic Server vulnerability is leveraged to deliver a PowerShell payload, which is then used to create another obfuscated PowerShell script in memory.
This newly created PowerShell script disables Windows Antimalware Scan Interface (AMSI) detection and launches a Windows binary that subsequently reaches out to a remote server to retrieve a "meticulously obfuscated" payload.
The intermediate DLL file, for its part, is configured to download a cryptocurrency miner from one of the three C2 servers – 179.43.155[.]202, work.letmaker[.]top, and su-94.letmaker[.]top – using TCP ports 9090, 9091, or 9092.
Trend Micro said recent attacks have also entailed the misuse of a legitimate Linux tool called lwp-download to save arbitrary files on the compromised host.
"lwp-download is a Linux utility present in a number of platforms by default, and 8220 Gang making this a part of any malware routine can affect a number of services even if it were reused more than once," Bharti said.
"Considering the threat actor's tendency to reuse tools for different campaigns and abuse legitimate tools as part of the arsenal, organizations' security teams might be challenged to find other detection and blocking solutions to fend off attacks that abuse this utility."
China's Mustang Panda Hackers Exploit TP-Link Routers for Persistent Attacks
16.5.23 Exploit The Hacker News

The Chinese nation-state actor known as Mustang Panda has been linked to a new set of sophisticated and targeted attacks aimed at European foreign affairs entities since January 2023.
An analysis of these intrusions, per Check Point researchers Itay Cohen and Radoslaw Madej, has revealed a custom firmware implant designed explicitly for TP-Link routers.
"The implant features several malicious components, including a custom backdoor named 'Horse Shell' that enables the attackers to maintain persistent access, build anonymous infrastructure, and enable lateral movement into compromised networks," the company said.
"Due to its firmware-agnostic design, the implant's components can be integrated into various firmware by different vendors."
The Israeli cybersecurity firm is tracking the threat group under the name Camaro Dragon, which is also known as BASIN, Bronze President, Earth Preta, HoneyMyte, RedDelta, and Red Lich.
The exact method used to deploy the tampered firmware images on the infected routers is currently unknown, as is its usage and involvement in actual attacks. It's suspected that initial access may have been acquired by exploiting known security flaws or brute-forcing devices with default or easily guessable passwords.
What is known is that the C++-based Horse Shell implant provides attackers the ability to execute arbitrary shell commands, upload and download files to and from the router, and relay communication between two different clients.
But in an interesting twist, the router backdoor is believed to target arbitrary devices on residential and home networks, suggesting that the compromised routers are being co-opted into a mesh network with the goal of creating a "chain of nodes between main infections and real command-and-control."
In relaying communications between infected routers by using a SOCKS tunnel, the idea is to introduce an additional layer of anonymity and conceal the final server, as each node in the chain contains information only about the nodes preceding and succeeding it.
Put differently, the methods obscure the origin and destination of the traffic in a manner analogous to TOR, making it a lot more challenging to detect the scope of the attack and disrupt it.
"If one node in the chain is compromised or taken down, the attacker can still maintain communication with the C2 by routing traffic through a different node in the chain," the researchers explained.
That said, this is not the first time China-affiliated threat actors have relied on a network of compromised routers to meet their strategic objectives.
In 2021, the National Cybersecurity Agency of France (ANSSI) detailed an intrusion set orchestrated by APT31 (aka Judgement Panda or Violet Typhoon) that leveraged a piece of advanced malware known as Pakdoor (or SoWat) to allow the infected routers to communicate with each other.
"The discovery is yet another example of a long-standing trend of Chinese threat actors to exploit internet-facing network devices and modify their underlying software or firmware," the researchers said.
Microsoft Warns of State-Sponsored Attacks Exploiting Critical PaperCut Vulnerability
10.5.23 Exploit The Hacker News
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management software, Microsoft disclosed over the weekend.
The tech giant's threat intelligence team said it observed both Mango Sandstorm (Mercury) and Mint Sandstorm (Phosphorus) weaponizing CVE-2023-27350 in their operations to achieve initial access.
"This activity shows Mint Sandstorm's continued ability to rapidly incorporate [proof-of-concept] exploits into their operations," Microsoft said in a series of tweets.
On the other hand, CVE-2023-27350 exploitation activity associated with Mango Sandstorm is said to be on the lower end of the spectrum, with the state-sponsored group "using tools from prior intrusions to connect to their C2 infrastructure."
It's worth noting that Mango Sandstorm is linked to Iran's Ministry of Intelligence and Security (MOIS) and Mint Sandstorm is associated with the Islamic Revolutionary Guard Corps (IRGC).
The ongoing assault comes weeks after Microsoft confirmed the involvement of Lace Tempest, a cybercrime gang that overlaps with other hacking groups like FIN11, TA505, and Evil Corp, in abusing the flaw to deliver Cl0p and LockBit ransomware.
CVE-2023-27350 (CVSS score: 9.8) relates to a critical flaw in PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.
A patch was made available by PaperCut on March 8, 2023. Trend Micro's Zero Day Initiative (ZDI), which discovered and reported the issue, is expected to release more technical information about it on May 10, 2023.
What's more, cybersecurity firm VulnCheck, last week, published details on a new line of attack that can circumvent existing detections, enabling adversaries to leverage the flaw unimpeded.
With more attackers jumping in on the PaperCut exploitation bandwagon to breach vulnerable servers, it's imperative that organizations move quickly to apply the necessary updates (versions 20.1.7, 21.2.11, and 22.0.9 and later).
The development also follows a report from Microsoft which revealed that Iranian threat actors are increasingly relying on a new tactic that combines offensive cyber operations with multi-pronged influence operations to "fuel geopolitical change in alignment with the regime's objectives."
The shift coincides with an increased tempo in adopting newly reported vulnerabilities, the use of compromised websites for command-and-control to better conceal the source of attacks, and harnessing custom tooling and tradecraft for maximum impact.
Researchers Uncover New Exploit for PaperCut Vulnerability That Can Bypass Detection
5.5.23 Exploit The Hacker News
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections.
Tracked as CVE-2023-27350 (CVSS score: 9.8), the issue affects PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.
While the flaw was patched by the Australian company on March 8, 2023, the first signs of active exploitation emerged on April 13, 2023.
Since then, the vulnerability has been weaponized by multiple threat groups, including ransomware actors, with post-exploitation activity resulting in the execution of PowerShell commands designed to drop additional payloads.
Now, VulnCheck has published a proof-of-concept (PoC) exploit that sidesteps existing detection signatures by leveraging the fact that "PaperCut NG and MF offer multiple paths to code execution."
It's worth noting that public exploits for the flaw use the PaperCut printer scripting interface to either execute Windows commands or drop a malicious Java archive (JAR) file.
Both these approaches, per VulnCheck, leave distinct footprints in the Windows System Monitor (aka Sysmon) service and the server's log file, not to mention trigger network signatures that can detect the authentication bypass.
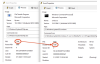
But the Massachusetts-based threat Intelligence firm said it discovered a new method that abuses the print management software's "User/Group Sync" feature, which makes it possible to synchronize user and group information from Active Directory, LDAP, or a custom source.
When opting for a custom directory source, users can also specify a custom authentication program to validate a user's username and password. Interestingly, the user and auth programs can be any executable, although the auth program has to be interactive in nature.
The PoC exploit devised by VulnCheck banks on the auth program set as "/usr/sbin/python3" for Linux and "C:\Windows\System32\ftp.exe" for Windows. All an attacker then needs to execute arbitrary code is to provide a malicious username and password during a login attempt, the company said.
The attack method could be exploited to launch a Python reverse shell on Linux or download a custom reverse shell hosted on a remote server in Windows without activating any of the known detections.
"An administrative user attacking PaperCut NG and MF can follow multiple paths to arbitrary code execution," VulnCheck security researcher Jacob Baines pointed out.
"Detections that focus on one particular code execution method, or that focus on a small subset of techniques used by one threat actor are doomed to be useless in the next round of attacks. Attackers learn from defenders' public detections, so it's the defenders' responsibility to produce robust detections that aren't easily bypassed."
Alert: Active Exploitation of TP-Link, Apache, and Oracle Vulnerabilities Detected
3.5.23 Exploit The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added three flaws to the Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The security vulnerabilities are as follows -
CVE-2023-1389 (CVSS score: 8.8) - TP-Link Archer AX-21 Command Injection Vulnerability
CVE-2021-45046 (CVSS score: 9.0) - Apache Log4j2 Deserialization of Untrusted Data Vulnerability
CVE-2023-21839 (CVSS score: 7.5) - Oracle WebLogic Server Unspecified Vulnerability
CVE-2023-1389 concerns a case of command injection affecting TP-Link Archer AX-21 routers that could be exploited to achieve remote code execution. According to Trend Micro's Zero Day Initiative, the flaw has been put to use by threat actors associated with the Mirai botnet since April 11, 2023.
The second flaw to be added to the KEV catalog is CVE-2021-45046, a remote code execution affecting the Apache Log4j2 logging library that came to light in December 2021.
It's currently not clear how this specific vulnerability is being abused in the wild, although data gathered by GreyNoise shows evidence of exploitation attempts from as many as 74 unique IP addresses over the past 30 days. This, however, also includes CVE-2021-44228 (aka Log4Shell).
Completing the list is a high-severity bug in Oracle WebLogic Server versions 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0 that could allow unauthorized access to sensitive data. It was patched by the company as part of updates released in January 2023.
"Oracle WebLogic Server contains an unspecified vulnerability that allows an unauthenticated attacker with network access via T3, IIOP, to compromise Oracle WebLogic Server," CISA said.
While there exists proof-of-concept (PoC) exploits for the flaw, there do not appear to be any public reports of malicious exploitation.
Federal Civilian Executive Branch (FCEB) agencies are required to apply vendor-provided fixes by May 22, 2023, to secure their networks against these active threats.
The advisory also comes a little over a month after VulnCheck revealed that nearly four dozen security flaws that have likely been weaponized in the wild in 2022 are missing from the KEV catalog.
Of the 42 vulnerabilities, an overwhelming majority are related to exploitation by Mirai-like botnets (27), followed by ransomware gangs (6) and other threat actors (9).
Hackers Exploit Outdated WordPress Plugin to Backdoor Thousands of WordPress Sites
24.4.23 Exploit The Hacker News
Threat actors have been observed leveraging a legitimate but outdated WordPress plugin to surreptitiously backdoor websites as part of an ongoing campaign, Sucuri revealed in a report published last week.
The plugin in question is Eval PHP, released by a developer named flashpixx. It allows users to insert PHP code pages and posts of WordPress sites that's then executed every time the posts are opened in a web browser.
While Eval PHP has never received an update in 11 years, statistics gathered by WordPress show that it's installed on over 8,000 websites, with the number of downloads skyrocketing from one or two on average since September 2022 to 6,988 on March 30, 2023.
On April 23, 2023, alone, it was downloaded 2,140 times. The plugin has racked up 23,110 downloads over the past seven days.
GoDaddy-owned Sucuri said it observed some infected websites' databases injected with malicious code into the "wp_posts" table, which stores a site's posts, pages, and navigation menu information. The requests originate from these three IP addresses based in Russia.
"This code is quite simple: It uses the file_put_contents function to create a PHP script into the docroot of the website with the specified remote code execution backdoor," security researcher Ben Martin said.
"Although the injection in question does drop a conventional backdoor into the file structure, the combination of a legitimate plugin and a backdoor dropper in a WordPress post allows them to easily reinfect the website and stay hidden. All the attacker needs to do is to visit one of the infected posts or pages and the backdoor will be injected into the file structure."
Sucuri said it detected over 6,000 instances of this backdoor in the last 6 months alone, describing the pattern of inserting the malware directly into the database as a "new and interesting development."
The attack chain entails installing the Eval PHP plugin on compromised sites and misusing it to establish persistent backdoors across multiple posts that are sometimes also saved as drafts.
"The way the Eval PHP plugin works it's enough to save a page as a draft in order to execute the PHP code inside the [evalphp] shortcodes," Martin explained, adding the rogue pages are created with a real site administrator as their author, suggesting the attackers were able to successfully sign in as a privileged user.
The development once again points to how malicious actors are experimenting with different methods to maintain their foothold in compromised environments and evade server-side scans and file integrity monitoring.
Site owners are advised to secure the WP Admin dashboard as well as watch out for any suspicious logins to prevent threat actors from gaining admin access and install the plugin.
Fortra Sheds Light on GoAnywhere MFT Zero-Day Exploit Used in Ransomware Attacks
20.4.23 Exploit The Hacker News
Fortra, the company behind Cobalt Strike, shed light on a zero-day remote code execution (RCE) vulnerability in its GoAnywhere MFT tool that has come under active exploitation by ransomware actors to steal sensitive data.
The high-severity flaw, tracked as CVE-2023-0669 (CVSS score: 7.2), concerns a case of pre-authenticated command injection that could be abused to achieve code execution. The issue was patched by the company in version 7.1.2 of the software in February 2023, but not before it was weaponized as a zero-day since January 18.
Fortra, which worked with Palo Alto Networks Unit 42, said it was made aware of suspicious activity associated with some of the file transfer instances on January 30, 2023.
"The unauthorized party used CVE-2023-0669 to create unauthorized user accounts in some MFTaaS customer environments," the company said. "For a subset of these customers, the unauthorized party leveraged these user accounts to download files from their hosted MFTaaS environments."
The threat actor further abused the flaw to deploy two additional tools, dubbed "Netcat" and "Errors.jsp," between January 28, 2023 and January 31, 2023, although not every installation attempt is said to have been successful.
Fortra said it directly reached out to affected customers, and that it has not found any sign of unauthorized access to customer systems that have been reprovisioned a "clean and secure MFTaaS environment."
While Netcat is a legitimate program for managing reading and writing data over a network, it's currently not known how the JSP file was used in the attacks.
The investigation also found that CVE-2023-0669 was exploited against a small number of on-premise implementations running a specific configuration of the GoAnywhere MFT solution.
As recommendations, the company is recommending that users rotate the Master Encryption Key, reset all credentials, review audit logs, and delete any suspicious admin or user accounts.
The development comes as Malwarebytes and NCC Group reported a spike in ransomware attacks during the month of March, largely driven by active exploitation of the GoAnywhere MFT vulnerability.
A total of 459 attacks were recorded last month alone, a 91% increase from February 2023 and a 62% jump when compared to March 2022.
"The ransomware-as-a-service (RaaS) provider, Cl0p, successfully exploited the GoAnywhere vulnerability and was the most active threat actor observed, with 129 victims in total," NCC Group said.
Cl0p's exploitation spree marks the second time LockBit has been knocked off the top spot since September 2021. Other prevalent ransomware strains included Royal, BlackCat, Play, Black Basta, and BianLian.
It's worth noting that the Cl0p actors previously exploited zero-day flaws in Accellion File Transfer Appliance (FTA) to breach several targets in 2021.
Google Releases Urgent Chrome Update to Fix Actively Exploited Zero-Day Vulnerability
15.4.23 Exploit The Hacker News
Google on Friday released out-of-band updates to resolve an actively exploited zero-day flaw in its Chrome web browser, making it the first such bug to be addressed since the start of the year.
Tracked as CVE-2023-2033, the high-severity vulnerability has been described as a type confusion issue in the V8 JavaScript engine. Clement Lecigne of Google's Threat Analysis Group (TAG) has been credited with reporting the issue on April 11, 2023.
"Type confusion in V8 in Google Chrome prior to 112.0.5615.121 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page," according to the NIST's National Vulnerability Database (NVD).
The tech giant acknowledged that "an exploit for CVE-2023-2033 exists in the wild," but stopped short of sharing additional technical specifics or indicators of compromise (IoCs) to prevent further exploitation by threat actors.
CVE-2023-2033 also appears to share similarities with CVE-2022-1096, CVE-2022-1364, CVE-2022-3723, and CVE-2022-4262 – four other actively abused type confusion flaws in V8 that were remediated by Google in 2022.
Google closed out a total of nine zero days in Chrome last year. The development comes days after Citizen Lab and Microsoft disclosed the exploitation of a now-patched flaw in Apple iOS by customers of a shadowy spyware vendor named QuaDream to target journalists, political opposition figures, and an NGO worker in 2021.
Users are recommended to upgrade to version 112.0.5615.121 for Windows, macOS, and Linux to mitigate potential threats. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available.
Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk!
1.4.23 Exploit The Hacker News
Unknown threat actors are actively exploiting a recently patched security vulnerability in the Elementor Pro website builder plugin for WordPress.
The flaw, described as a case of broken access control, impacts versions 3.11.6 and earlier. It was addressed by the plugin maintainers in version 3.11.7 released on March 22.
"Improved code security enforcement in WooCommerce components," the Tel Aviv-based company said in its release notes. The premium plugin is estimated to be used on over 12 million sites.
Successful exploitation of the high-severity flaw allows an authenticated attacker to complete a takeover of a WordPress site that has WooCommerce enabled.
"This makes it possible for a malicious user to turn on the registration page (if disabled) and set the default user role to administrator so they can create an account that instantly has the administrator privileges," Patchstack said in an alert of March 30, 2023.
"After this, they are likely to either redirect the site to another malicious domain or upload a malicious plugin or backdoor to further exploit the site."
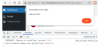
Credited with discovering and reporting the vulnerability on March 18, 2023, is NinTechNet security researcher Jerome Bruandet.
Patchstack further noted that the flaw is currently being abused in the wild from several IP addresses intending to upload arbitrary PHP and ZIP archive files.
Users of the Elementor Pro plugin are recommended to update to 3.11.7 or 3.12.0, which is the latest version, as soon as possible to mitigate potential threats.
The advisory comes over a year after the Essential Addons for Elementor plugin was found to contain a critical vulnerability that could result in the execution of arbitrary code on compromised websites.
Last week, WordPress issued auto-updates to remediate another critical bug in the WooCommerce Payments plugin that allowed unauthenticated attackers to gain administrator access to vulnerable sites.
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
21.3.23 Exploit The Hacker News
The zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group.
American cybersecurity company Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim environments.
The Google-owned threat intelligence and incident response firm is tracking the malicious operation under its uncategorized moniker UNC3886, describing it as a China-nexus threat actor.
"UNC3886 is an advanced cyber espionage group with unique capabilities in how they operate on-network as well as the tools they utilize in their campaigns," Mandiant researchers said in a technical analysis.
"UNC3886 has been observed targeting firewall and virtualization technologies which lack EDR support. Their ability to manipulate firewall firmware and exploit a zero-day indicates they have curated a deeper-level of understanding of such technologies."
It's worth noting that the adversary was previously tied to another intrusion set targeting VMware ESXi and Linux vCenter servers as part of a hyperjacking campaign designed to drop backdoors such as VIRTUALPITA and VIRTUALPIE.
The latest disclosure from Mandiant comes as Fortinet revealed that government entities and large organizations were victimized by an unidentified threat actor by leveraging a zero-day bug in Fortinet FortiOS software to result in data loss and OS and file corruption.
The vulnerability, tracked as CVE-2022-41328 (CVSS score: 6.5), concerns a path traversal bug in FortiOS that could lead to arbitrary code execution. It was patched by Fortinet on March 7, 2023.
According to Mandiant, the attacks mounted by UNC3886 targeted Fortinet's FortiGate, FortiManager, and FortiAnalyzer appliances to deploy two different implants such as THINCRUST and CASTLETAP. This, in turn, was made possible owing to the fact that the FortiManager device was exposed to the internet.
THINCRUST is a Python backdoor capable of executing arbitrary commands as well as reading and writing from and to files on disk.
The persistence afforded by THINCRUST is subsequently leveraged to deliver FortiManager scripts that weaponize the FortiOS path traversal flaw to overwrite legitimate files and modify firmware images.
This includes a newly added payload called "/bin/fgfm" (referred to as CASTLETAP) that beacons out to an actor-controlled server so as to accept incoming instructions that allow it to run commands, fetch payloads, and exfiltrate data from the compromised host.
"Once CASTLETAP was deployed to the FortiGate firewalls, the threat actor connected to ESXi and vCenter machines," the researchers explained. "The threat actor deployed VIRTUALPITA and VIRTUALPIE to establish persistence, allowing for continued access to the hypervisors and the guest machines."
Alternatively, on FortiManager devices that implement internet access restrictions, the threat actor is said to have pivoted from a FortiGate firewall compromised with CASTLETAP to drop a reverse shell backdoor named REPTILE ("/bin/klogd") on the network management system to regain access.
Also employed by UNC3886 at this stage is a utility dubbed TABLEFLIP, a network traffic redirection software to connect directly to the FortiManager device regardless of the access-control list (ACL) rules put in place.
This is far from the first time Chinese adversarial collectives have targeted networking equipment to distribute bespoke malware, with recent attacks taking advantage of other vulnerabilities in Fortinet and SonicWall devices.
The revelation also comes as threat actors are developing and deploying exploits faster than ever before, with as many as 28 vulnerabilities exploited within seven days of public disclosure — a 12% rise over 2021 and an 87% rise over 2020, according to Rapid7.
This is also significant, not least because China-aligned hacking crews have become "particularly proficient" at exploiting zero-day vulnerabilities and deploying custom malware to steal user credentials and maintain long-term access to target networks.
"The activity [...] is further evidence that advanced cyber espionage threat actors are taking advantage of any technology available to persist and traverse a target environment, especially those technologies that do not support EDR solutions," Mandiant said.
New GoLang-Based HinataBot Exploiting Router and Server Flaws for DDoS Attacks
17.3.23 Exploit The Hacker News
A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and use them to stage distributed denial-of-service (DDoS) attacks.
"The malware binaries appear to have been named by the malware author after a character from the popular anime series, Naruto, with file name structures such as 'Hinata-<OS>-<Architecture>,'" Akamai said in a technical report.
Among the methods used to distribute the malware are the exploitation of exposed Hadoop YARN servers and security flaws in Realtek SDK devices (CVE-2014-8361), Huawei HG532 routers (CVE-2017-17215, CVSS score: 8.8).
Unpatched vulnerabilities and weak credentials have been a low-hanging fruit for attackers, representing an easy, well-documented entry point that does not require sophisticated social engineering tactics or other methods.
The threat actors behind HinataBot are said to have been active since at least December 2022, with the attacks first attempting to use a generic Go-based Mirai variant before switching to their own custom malware starting from January 11, 2023.
Since then, newer artifacts have been detected in Akamai's HTTP and SSH honeypots as recently as this month, packing in more modular functionality and added security measures to resist analysis. This indicates that HinataBot is still in active development and evolving.
The malware, like other DDoS botnets of its kind, is capable of contacting a command-and-control (C2) server to listen for incoming instructions and initiate attacks against a target IP address for a specified duration.
While early versions of the botnet utilized protocols such as HTTP, UDP, TCP, and ICMP to carry out DDoS attacks, the latest iteration is limited to just HTTP and UDP. It's not immediately known why the other two protocols were axed.
Akamai, which conducted 10-second attack tests using HTTP and UDP, revealed that the HTTP flood generated 3.4 MB of packet capture data and pushed 20,430 HTTP requests. The UDP flood, on the other hand, created 6,733 packets for a total of 421 MB of packet capture data.
In a hypothetical real-world attack with 10,000 bots, a UDP flood would peak at more than 3.3 terabit per second (Tbps), resulting in a potent volumetric attack. An HTTP flood would generate a traffic of roughly 27 gigabit per second (Gbps)
The development makes it the latest to join the ever-growing list of emerging Go-based threats such as GoBruteforcer and KmsdBot.
"Go has been leveraged by attackers to reap the benefits of its high performance, ease of multi-threading, its multiple architecture and operating system cross-compilation support, but also likely because it adds complexity when compiled, increasing the difficulty of reverse engineering the resulting binaries," Akamai said.
The findings also come as Microsoft revealed that TCP attacks emerged as the most frequent form of DDoS attack encountered in 2022, accounting for 63% of all attack traffic, followed by UDP floods and amplification attacks (22%), and packet anomaly attacks (15%).
Besides being used as distractions to conceal extortion and data theft, DDoS attacks are also expected to rise due to the arrival of new malware strains that are capable of targeting IoT devices and taking over accounts to gain unauthorized access to resources.
"With DDoS attacks becoming more frequent, sophisticated, and inexpensive to launch, it's important for organizations of all sizes to be proactive, stay protected all year round, and develop a DDoS response strategy," the tech giant's Azure Network Security Team said.
Multiple Hacker Groups Exploit 3-Year-Old Vulnerability to Breach U.S. Federal Agency
16.3.23 Exploit The Hacker News
Multiple threat actors, including a nation-state group, exploited a critical three-year-old security flaw in Progress Telerik to break into an unnamed federal entity in the U.S.
The disclosure comes from a joint advisory issued by the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC).
"Exploitation of this vulnerability allowed malicious actors to successfully execute remote code on a federal civilian executive branch (FCEB) agency's Microsoft Internet Information Services (IIS) web server," the agencies said.
The indicators of compromise (IoCs) associated with the digital break-in were identified from November 2022 through early January 2023.
Tracked as CVE-2019-18935 (CVSS score: 9.8), the issue relates to a .NET deserialization vulnerability affecting Progress Telerik UI for ASP.NET AJAX that, if left unpatched, could lead to remote code execution.
It's worth noting here that CVE-2019-18935 has previously found a place among some of the most commonly exploited vulnerabilities abused by various threat actors in 2020 and 2021.
CVE-2019-18935, in conjunction with CVE-2017-11317, has also been weaponized by a threat actor tracked as Praying Mantis (aka TG2021) to infiltrate the networks of public and private organizations in the U.S.
Last month, CISA also added CVE-2017-11357 – another remote code execution bug affecting Telerik UI – to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
Threat actors are said to have leveraged the flaw to upload and execute malicious dynamic-link library (DLL) files masquerading as PNG images via the w3wp.exe process.
The DLL artifacts are designed to gather system information, load additional libraries, enumerate files and processes, and exfiltrate the data back to a remote server.
Another set of attacks, observed as early as August 2021 and likely mounted by a cybercriminal actor dubbed XE Group, entailed the use of aforementioned evasion techniques to sidestep detection.
These DLL files dropped and executed reverse (remote) shell utilities for unencrypted communications with a command-and-control domain to drop additional payloads, including an ASPX web shell for persistent backdoor access.
The web shell is equipped to "enumerate drives; to send, receive, and delete files; and to execute incoming commands" and "contains an interface for easily browsing files, directories, or drives on the system, and allows the user to upload or download files to any directory."
To counter such attacks, it's recommended that organizations upgrade their instances of Telerik UI ASP.NET AJAX to the latest version, implement network segmentation, and enforce phishing-resistant multi-factor authentication for accounts that have privileged access.
CISA warns of actively exploited Plex bug after LastPass breach
12.3.23 Exploit Bleepingcomputer
CISA has added an almost three-year-old high-severity remote code execution (RCE) vulnerability in the Plex Media Server to its catalog of security flaws exploited in attacks.
Tracked as CVE-2020-5741, this security flaw allows threat actors with admin privileges to execute arbitrary Python code remotely in low-complexity attacks that don't require user interaction.
Attackers with "admin access to a Plex Media Server could abuse the Camera Upload feature to make the server execute malicious code," according to an advisory published by the Plex Security Team in May 2020 when it patched the bug with the release of Plex Media Server 1.19.3.
"This could be done by setting the server data directory to overlap with the content location for a library on which Camera Upload was enabled. This issue could not be exploited without first gaining access to the server's Plex account."
While CISA didn't provide any info on the attacks where the CVE-2020-5741 was exploited, this is likely linked to LastPass recently disclosing that a senior DevOps engineer's computer was hacked last year to install a keylogger by abusing a third-party media software RCE bug.
The attackers eventually gained access to the engineer's credentials and LastPass corporate vault. This led to a massive August 2022 data breach after the threat actors exfiltrated LastPass production backups and critical database backups.
Plex RCE reportedly used to hack LastPass engineer
Even though LastPass didn't disclose what software flaw was exploited to hack into the engineer's computer, Ars Technica reported that the software package exploited on the employee's home computer was Plex.
Coincidentally, in August, Plex also notified customers of a data breach and asked them to reset their passwords after LastPass disclosed a second breach of its own.
On Friday, CISA also added a critical severity vulnerability in VMware's Cloud Foundation (tracked as CVE-2021-39144), exploited in the wild since early December, to its Known Exploited Vulnerabilities (KEV) catalog.
According to a November 2021 binding operational directive (BOD 22-01), the U.S. federal agencies are now also required to secure their systems against attacks until March 31st to block attack attempts that might target their networks by exploiting the two flaws.
Although the BOD 22-01 only applies to federal agencies, CISA strongly urged all organizations to patch these bugs to defend against ongoing attacks.