
Exploit Articles - H 2020 1 2 3 4 5 6 7 Exploit List - H 2021 2020 2019 2018 1 Exploit blog Exploit blog
Oracle WebLogic Server Flaw Exploited to Deliver Crypto-Miners
16.2.2018 securityweek Vulnerebility Exploit CoinMine
Threat actors are exploiting a recently patched vulnerability in Oracle WebLogic Server to infect systems with crypto-currency mining malware, FireEye reports.
Identified as CVE-2017-10271, the vulnerability resides in the WebLogic Server Security Service (WLS Security) in Oracle WebLogic Server versions 12.2.1.2.0 and older, and was addressed by Oracle it its October 2017 Critical Patch Update (CPU).
After proof-of-concept code exploiting the bug was made public in December, activity associated with the exploitation of this vulnerability increased in volume, FireEye's researchers say. Successful exploitation of the flaw on unpatched systems allows attackers to remotely execute arbitrary code.
“We saw evidence of organizations located in various countries – including the United States, Australia, Hong Kong, United Kingdom, India, Malaysia, and Spain, as well as those from nearly every industry vertical – being impacted by this activity,” FireEye reported.
The crypto-currency market boomed recently, and cybercriminals have not been shy in their attempts to take advantage of the market. However, actors involved in crypto-currency mining operations don’t normally target specific organizations, but rather launch attacks that are opportunistic in nature.
Attackers abusing CVE-2017-10271 to infect targeted systems with crypto-miners used various tactics to achieve their purpose, the researchers discovered. Some of the incidents, for example, used PowerShell to drop the miner directly onto the victim’s system and leveraged ShellExecute() for execution.
In other attacks, PowerShell scripts were used to deliver the miner, instead of downloading the executable directly. In addition to downloading the miner, the script would also attempt to achieve persistence through scheduled tasks.
The script would delete the tasks created by other crypto-miners and would kill processes associated with those programs, in addition to being able to connect to mining pools with wallet key. It would also limit CPU usage to avoid suspicion.
Tactics employed in other attacks also involved the use of tools such as Mimikatz and EternalBlue for lateral movement across Windows environments.
The malware would first determine whether the system is 32-bit or 64-bit, to fetch a specific PowerShell script from the command and control (C&C) server. Next, it checks all network adapters and attempts to connect to every system in the network using extracted credentials, to run a PowerShell to drop and run the malware on the targeted system.
The malware uses WMI (Windows Management Instrumentation) for persistence and can perform a Pass-the-Hash attack using NTLM information derived from Mimikatz, to download and execute the malware on remote machines. It sends the stolen credentials to a remote server using an HTTP GET request.
If it fails moving laterally, the malware uses the PingCastle MS17-010 scanner to determine whether the target is vulnerable to EternalBlue.
In scenarios targeting Linux machines, the vulnerability would be exploited to deliver shell scripts that include functionality similar to that of PowerShell scripts. They would attempt to kill already running crypto-miners and then download and execute the malware, in addition to creating a cron job to maintain persistence.
“Use of cryptocurrency mining malware is a popular tactic leveraged by financially-motivated cyber criminals to make money from victims. We’ve observed one threat actor mining around 1 XMR/day, demonstrating the potential profitability and reason behind the recent rise in such attacks,” FireEye says.
Although they might be seen as less risky when compared to ransomware operations, crypto-currency mining malware does pose a variety of risks. Systems infected with crypto-miners might experience slowed performance, but such operations could also be hiding additional malware.
Intel Offers $250,000 for Side-Channel Exploits
15.2.2018 securityweek Exploit
Intel Opens Bug Bounty Program to All Researchers, Offers up to $250,000 for Flaws Similar to Meltdown and Spectre
Intel on Wednesday announced major changes to its bug bounty program, including that it’s now open to all researchers, and significant rewards for exploits similar to Meltdown and Spectre.
Researchers who find critical hardware vulnerabilities that allow software-based side-channel attacks – just like Meltdown and Spectre – can earn up to $250,000. Flaws classified as high severity are worth up to $100,000, while medium- and low-risk issues are worth up to $20,000 and $5,000, respectively. The severity of a flaw is determined based on its CVSS base score, adjusted depending on the security objectives and threat model of the targeted product.
The part of Intel’s bug bounty program covering side-channel exploits will run until December 31, 2018.
Intel also announced that its bug bounty program is now open to all researchers – it was invitation-only until now. When the company launched this initiative back in March 2017, the maximum reward for hardware vulnerabilities was $30,000, but it has now been increased to $100,000 for critical flaws.
The maximum amount the company is prepared to pay for firmware vulnerabilities has increased from $10,000 to $30,000, and for software flaws from $7,500 to $10,000.
The list of hardware products covered by Intel’s bug bounty program includes processors, chipsets, field-programmable gate array (FPGA) integrated circuits, networking and communications equipment, motherboards, and solid-state drives.
“We believe these changes will enable us to more broadly engage the security research community, and provide better incentives for coordinated response and disclosure that help protect our customers and their data,” said Rick Echevarria, vice president and general manager of Platform Security at Intel.
Intel was made aware of the Spectre and Meltdown attack methods several months before researchers disclosed them, but many are unhappy with the way the company handled the situation.
While Spectre and Meltdown also affect processors from AMD, ARM and IBM, Intel was hit the hardest. The company started releasing microcode updates shortly after the existence of the vulnerabilities was brought to light, but the first round of patches introduced stability problems. Intel started releasing a second round of updates, which should address these issues, only last week.
The company says its future CPUs will include protections against attacks like Meltdown and Spectre.
Hackers have exploited a zero-day in Bitmessage client to steal Electrum wallet keys
15.2.2018 securityaffairs Exploit
Bitmessage developers have issued an emergency update for the PyBitmessage client that patches a critical remote code execution vulnerability that has been exploited in attacks.
Bitmessage development team has rolled out an emergency patch to address a zero-day vulnerability in the PyBitmessage client for Bitmessage, which a Peer-to-Peer (P2P) communications protocol used to send encrypted messages to users.
The flaw is critical remote code execution vulnerability that according to the experts was being exploited in the wild to steal Bitcoin wallet keys.

According to the security advisory published by the development team developers, hackers exploited the flaw in attacks against users running PyBitmessage 0.6.2.
“A remote code execution vulnerability has been spotted in use against some users running PyBitmessage v0.6.2. The cause was identified and a fix has been added and released as 0.6.3.2. If you run PyBitmessage via code, we highly recommend that you upgrade to 0.6.3.2. Alternatively you may downgrade to 0.6.1 which is unaffected.” reads the advisory.
The message encoding vulnerability has been patched with the release of version 0.6.3.2. The developers highlighted that PyBitmessage 0.6.1 is not affected by the vulnerability, this means that users can also downgrade their version to mitigate the attacks.
According to the security advisor, hackers targeted also the Bitmessage core developer Peter Šurda, his keys were most likely compromised for this reason he has created a new support address.
“Bitmessage developer Peter Šurda’s addresses are to be considered compromised.” continues the advisory.
Users are recommended to change their passwords and create new bitmessage keys.
Šurda speculates the attacker exploited the zero-day to create a remote shell and steal bitcoins from Electrum wallets.
“The exploit is triggered by a malicious message if you’re the recipient (including joined chans),”Šurda wrote on Reddit thread. “The attacker ran an automated script but also opened, or tried to open, a remote reverse shell. The automated script looked in ~/.electrum/wallets, but when using the reverse shell he had access to other files as well.”
Bitmessage developers are still investigating the attacks.
DoubleDoor, a new IoT Botnet bypasses firewall using two backdoor exploits
14.2.2018 securityaffairs Exploit IoT
Security researchers spotted a new IoT botnet dubbed DoubleDoor that is able to bypass firewall as well as modem security using two backdoor exploits.
IoT devices continue to be a privileged target of cyber criminals, cyber attackers against so-called smart objects has seen a rapid evolution. Security researchers at NewSky Security (NewSky Security) have detected a new IoT botnet dubbed DoubleDoor that is able to bypass firewall as well as modem security using two backdoor exploits.
The analysis of the honeypot logs allowed the researchers to detect the new threat, it leverages two known backdoor exploits to manage two levels of authentications.
The first malicious code is the Juniper Networks SmartScreen OS exploit, it triggers the flaw CVE-2015–7755 to bypass the firewall authentication.
CVE-2015–7755 hardcoded backdoor affects the Juniper Networks’ ScreenOS software that powers their Netscreen firewalls.
“Essentially the telnet and SSH daemons of Netscreen firewalls can be accessed by using the hardcoded password <<< %s(un=’%s’) = %u with any username, regardless of it being valid or not.We saw its implementation in the initial attack cycle of DoubleDoor as it attacked our honeypots with username “netscreen” and the backdoor password.” wrote Ankit Anubhav, Principal Researcher, NewSky Security.
Once succeeded, the malicious code uses the CVE-2016–10401 Zyxel modem backdoor exploit to take full control over the IoT device.
The code is a privilege escalation exploit, “which is why the DoubleDoor attackers also performed a password based attack to get a basic privilege account like admin:CenturyL1nk before going for the superuser.”
“This time it was CVE-2016–10401 , a backdoor for ZyXEL PK5001Z devices. This backdoor is straight forward too, with a hardcoded su password as zyad5001.” continues the expert.

The experts highlighted that differently from other IoT botnets like Satori or Masuta, the DoubleDoor botnet doesn’t use a unique string in the reconnaissance phase.
“after the threat actors have performed the attack, they want a confirmation whether they were successful of getting control of the IoT device. For this, they try to invoke the shell with invalid commands. If the attacker has succeeded, it will show “{string}: applet not found” where {string} is the invalid command.” observed the research.
“DoubleDoor botnet takes care of this, by using a randomized string in every attack”
The DoubleDoor botnet seems to be in an early stage, most of the attacks are originated from South Korean IPs.
The botnet includes the code to target a limited number of devices, it will succeed only if the victim has a specific unpatched version of Juniper ScreenOS firewall which protects unpatched Zyxel modems.
“Double layer of IoT protection is more common in corporate environments, which don’t rely on built-in IoT authentication and like to protect it with another layer of firewall. Although such corporate devices can be lesser in number, getting control of corporate environment routers can be more valuable for an attacker as it can lead to targeted IoT attacks.” concluded the experts.
Zero-Day in Telegram's Windows Client Exploited for Months
14.2.2018 securityweek Exploit
A zero-day vulnerability impacting Telegram Messenger’s Windows client had been exploited in malicious attacks for months before being discovered and addressed.
Exploitation of the bug involves the use of a classic right-to-left override attack when a file is sent using the messenger service. The special nonprinting right-to-left override (RLO) character represented as ‘U+202E’ is used to reverse the order of the characters following it in the string.
Cybercriminals have discovered that they could leverage the character to mislead victims by hiding the name and extension of an executable file. Thus, if an application is vulnerable to the attack, the filename and extension would be displayed either incompletely or in reverse.
According to Kaspersky, which observed the attacks abusing the flaw, the attack chain involves sending malware in a message, but using the special character to hide it. A JS file could be renamed as photo_high_re*U+202E*gnp.js, which would make Telegram display the string gnp.js in reverse, thus appearing to the unsuspecting user as a PNG image file instead.
The actual file, however, isn’t modified, but remains the same JS file that it always was. If the user clicks on it, a standard Windows security notification would appear – as long as it hasn’t been previously disabled in the system’s settings –, informing the user that it is a JavaScript file.
Kaspersky learned of the issue in October 2017 and, after an investigation into the matter, discovered that cybercriminals had been abusing it since at least March 2017, in a multitude of attack scenarios.
Some of the incidents, the researchers say, resulted in the attackers taking control of the victim’s system. For that, however, analysis of the target system’s environment and the installation of additional modules was necessary.
Such an attack starts with an initial downloader being sent to the target. It would achieve persistence and then begin checking for commands arriving from the control bot. The loader could silently deploy malicious tools such as backdoors, loggers, and other malware on the target system.
The vulnerability was also abused in attacks involving miners, Kaspersky says. The infection would start with an SFX archive with a script designed to launch a BAT file posing as an executable. The program would first open a decoy file, when it would launch two miners as services, using the nssm.exe utility for this operation.
One of the programs was nheq.exe, an Equihash miner for NiceHash (it mined Zcash in the observed attack), while the other was taskmgn.exe, a popular miner implementing the CryptoNight algorithm and used to mine Fantomcoin and Monero.
In some attacks, the batch script had extra capabilities, being able to disable Windows security features and to download an additional payload from a malicious FTP server. The payload contained more miners and a Remote Manipulator System (RMS) client for subsequent remote access.
On the malicious FTP server, the researchers discovered archives containing Telegram directories stolen from the victims, some of which were created in March 2017. Inside the archives, Kaspersky found “an encrypted local cache containing different files used in personal communications: documents, videos and audio records and photos.”
In another attack scenario, an SFX archive launching a VBScript was observed. It too would open a decoy image to distract the user, then fetch and run the payload, another SFX archive containing a script designed to control the launch of the miner CryptoNight (csrs.exe). The script monitors the task list and terminates the miner if a task manager (taskmgr.exe, processhacker.exe) is on that list.
“It appears that only Russian cybercriminals were aware of this vulnerability, with all the exploitation cases that we detected occurring in Russia. Also, while conducting a detailed research of these attacks we discovered a lot of artifacts that pointed to involvement by Russian cybercriminals,” Kaspersky says.
The researchers couldn’t determine which versions of Telegram were affected by the vulnerability, but they believe that the exploitation of flawed Windows clients started in March 2017. Telegram was informed on the bug and has since addressed it in its products.
Hackers in the Russian underground exploited a Telegram Zero-Day vulnerability to deliver malware
14.2.2018 securityaffairs Exploit Virus
Security researcher Alexey Firsh at Kaspersky Lab last discovered a Telegram zero-day in the desktop Windows version that was exploited in attacks in the wild.
Security researcher Alexey Firsh at Kaspersky Lab last discovered a zero-day vulnerability in the desktop Windows version of the popular Telegram instant messaging app.
The bad news is that the Telegram zero-day flaw was being exploited by threat actors in the wild to deliver cryptocurrency miners for Monero and ZCash.
According to the expert, hackers have actively exploited the vulnerability since at least March 2017. Attackers tricked victims into downloading cryptocurrency miners or to establish a backdoor.
“In October 2017, we learned of a vulnerability in Telegram Messenger’s Windows client that was being exploited in the wild. It involves the use of a classic right-to-left override attack when a user sends files over the messenger service.” reads the analysis of the expert.
The flaw is related to the way Telegram Windows client handles the RLO (right-to-left override) Unicode character (U+202E), which is used for any language that uses a right to left writing mode, like Arabic or Hebrew.
The attackers used a hidden RLO Unicode character in the file name that reversed the order of the characters, in this way the file name could be renamed. In a real attack scenario, then the attackers sent the file to the target recipient.
The crooks craft a malicious code to be sent in a message, let assume it is a JS file that is renamed as follows:
evil.js -> photo_high_re*U+202E*gnp.js (— *U+202E* is the RLO character)
The RLO character included in the file name is used by an attacker to display the string gnp.js in reverse masquerading the fact that the file is a js and tricking the victims into believing that it is a harmless .png image.

When the user clicks on the file, Windows displays a security notification if it hasn’t been disabled in the system’s settings.

If the user ignores the notification and clicks on ‘Run’, the malicious code executed.
The expert reported the Telegram zero-day to the company that promptly patched the flaw.
“Kaspersky Lab reported the vulnerability to Telegram and, at the time of publication, the zero-day flaw has not since been observed in messenger’s products.” states the analysis published by Kaspersky.
“During their analysis, Kaspersky Lab experts identified several scenarios of zero-day exploitation in the wild by threat actors.”
The analysis of the servers used by the attackers revealed the presence of archives containing a Telegram’s local cache, this means that threat actors exploited the flaw to steal data from the victims.
In another attack scenario, crooks triggered the flaw to install a malware that leverages the Telegram API as a command and control mechanism.
“Secondly, upon successful exploitation of the vulnerability, a backdoor that used the Telegram API as a command and control protocol was installed, resulting in the hackers gaining remote access to the victim’s computer. After installation, it started to operate in a silent mode, which allowed the threat actor to remain unnoticed in the network and execute different commands including the further installation of spyware tools.” continues the analysis.
According to the researcher, the flaw was known only in the Russia crime community, it was not triggered by other crooks.
To mitigate the attack, download and open files only from trusted senders.
The security firm also recommended users to avoid sharing any sensitive personal information in messaging apps and make sure to have a good antivirus software from reliable company installed on your systems.
Cisco Aware of Attacks Exploiting Critical Firewall Flaw
8.2.2018 securityweek Exploit
Cisco informed customers on Wednesday that it has become aware of malicious attacks attempting to exploit a recently patched vulnerability affecting the company’s Adaptive Security Appliance (ASA) software.
No other information has been provided by the networking giant, but it’s worth noting that a proof-of-concept (PoC) exploit designed to cause a denial-of-service (DoS) condition on devices running ASA software was made public this week.
Cato Networks reported finding roughly 120,000 potentially vulnerable Cisco devices connected to the Internet, with a vast majority located in the United States and Europe.
The ASA software vulnerability, tracked as CVE-2018-0101, allows a remote and unauthenticated attacker to execute arbitrary code or cause a DoS condition.
The flaw affects several products running ASA software, including Firepower firewalls, 3000 series industrial security appliances, ASA 5000 and 5500 series appliances, 1000V cloud firewalls, ASA service modules for routers and switches, and Firepower Threat Defense (FTD) software. Cisco first notified customers about the availability of fixes on January 29.
Cisco initially said the security hole was related to the webvpn feature, but it later discovered that more than a dozen other features were impacted as well. The company released new patches this week after identifying new attack vectors and determining that the original fix had been incomplete.
The details of the vulnerability were disclosed on February 2 by Cedric Halbronn, the NCC Group researcher who reported the issue to Cisco.
“When exploited, this vulnerability known as CVE-2018-0101 allows the attacker to see all of the data passing through the system and provides them with administrative privileges, enabling them to remotely gain access to the network behind it,” NCC Group said. “Targeting the vulnerability without a specially-crafted exploit would cause the firewall to crash and would potentially disrupt the connectivity to the network.”
SecurityWeek has reached out to Cisco to see if the company can provide additional details regarding the malicious attacks and will update this article if the company responds.
Cisco on Wednesday also released new advisories describing several critical and high severity vulnerabilities, including a remote code execution flaw in RV132W ADSL2+ and RV134W VDSL2 routers, a DoS flaw in Cisco Virtualized Packet Core-Distributed Instance (VPC-DI) software, a command execution flaw in UCS Central, and an authentication bypass bug in Cisco Policy Suite.
Automated Hacking Tool Autosploit Cause Concerns Over Mass Exploitation
7.2.2018 securityaffairs Exploit
The Autosploit hacking tool was developed aiming to automate the compromising of remote hosts both by collecting automatically targets as well as by using Shodan.io API.
Users can define its platform search queries like Apache, IIS and so forth to gather targets to be attacked. After gathering the targets, the tool uses Metasploit modules of its exploit component to compromise the hosts.
The Metasploit modules to be used will depend on the comparison of the name of the module and the query search. The developer also added a type of attack where all modules can be used at once. As the author noticed, Metasploit modules were added with the intent of enabling Remote Code Execution as well as gaining Reverse TCP Shell or Meterpreter Sessions.

There are different opinions about the release of the tool by experts. As noticed by Bob Noel, Director of Strategic Relationships and Marketing at Plixer:
“AutoSploit doesn’t introduce anything new in terms of malicious code or attack vectors. What it does present is an opportunity for those who are less technically adept to use this tool to cause substantial damage. Once initiated by a person, the script automates and couples the process of finding vulnerable devices and attacking them. The compromised devices can be used to hack Internet entities, mine cryptocurrencies, or be recruited into a botnet for DDoS attacks. The release of tools like these exponentially expands the threat landscape by allowing a wider group of hackers to launch global attacks at will”.
On the other hand, Chris Roberts, chief security architect at Acalvio states:
” The kids are not more dangerous. They already were dangerous. We’ve simply given them a newer, simpler, shinier way to exploit everything that’s broken. Maybe we should fix the ROOT problem”.
The recent revelation that adult sex toys can be accessed remotely by hackers using Shodan is a scenario where the tool can represent a great and grave danger.
The risks and dangers looming around always existed. The release of the tool is not a new attack vector itself according to Gavin Millard, Technical Director at Tenable:
“Most organizations should have a process in place for measuring their cyber risk and identifying issues that could be easily leveraged by automated tools. For those that don’t, this would be an ideal time to understand where those exposures are and address them before a curious kid pops a web server and causes havoc with a couple of commands”.
A recommendation is given by Jason Garbis, VP at Cyxtera: ” In order to protect themselves, organizations need to get a clear, accurate, and up-to-date picture of every service they expose to the Internet. Security teams must combine internal tools with external systems like Shodan to ensure they’re aware of all their points of exposure”.
Sources:
https://www.scmagazine.com/autosploit-marries-shodan-metasploit-puts-iot-devices-at-risk/article/740912/
https://motherboard.vice.com/en_us/article/xw4emj/autosploit-automated-hacking-tool
https://arstechnica.com/information-technology/2018/02/threat-or-menace-autosploit-tool-sparks-fears-of-empowered-script-kiddies/
https://www.wired.com/story/autosploit-tool-makes-unskilled-hacking-easier-than-ever/
https://n0where.net/automated-mass-exploiter-autosploit
http://www.informationsecuritybuzz.com/expert-comments/autosploit/
https://securityledger.com/2018/02/episode-82-skinny-autosploit-iot-hacking-tool-get-ready-gdpr
https://www.kitploit.com/2018/02/autosploit-automated-mass-exploiter.html
https://www.darkreading.com/threat-intelligence/autosploit-mass-exploitation-just-got-a-lot-easier-/a/d-id/1330982
http://www.securityweek.com/autosploit-automated-hacking-tool-set-wreak-havoc-or-tempest-teapot
WannaMine Malware Spreads via NSA-Linked Exploit
1.2.2018 securityweek Virus Exploit
A piece of crypto-mining malware is using sophisticated tools for its operations, including a Windows exploit linked to the National Security Agency, security researchers warn.
Dubbed WannaMine, the crypto-mining worm spreads using EternalBlue, the NSA-linked tool that became public in April 2017, just one month after Microsoft released a patch for it.
Leveraging a vulnerability in Windows’ Server Message Block (SMB) on port 445, the exploit became famous after the WannaCry ransomware was found exploiting it for distribution. Other malware families abused it as well, including botnets, backdoors, NotPetya, and banking Trojans.
Now, the same exploit is being used to spread WannaMine, a piece of malware focused on mining for the Monero crypto-currency, but which uses sophisticated capabilities, such as persistence and distribution mechanisms similar to those used by nation-state actors, CrowdStrike says.
WannaMine, the security researchers explain, employs “living off the land” techniques for persistence, such as Windows Management Instrumentation (WMI) permanent event subscriptions. The malware has a fileless nature, leveraging PowerShell for infection, which makes it difficult to block without the appropriate security tools.
The malware uses credential harvester Mimikatz to acquire legitimate credentials that would allow it to propagate and move laterally. If that fails, however, the worm attempts to exploit the remote system via EternalBlue.
To achieve persistence, WannaMine sets a permanent event subscription that would execute a PowerShell command located in the Event Consumer every 90 minutes.
The malware targets all Windows versions starting with Windows 2000, including 64-bit versions and Windows Server 2003. However, it uses different files and commands for Windows Vista and newer platform iterations.
“While the tactics, techniques, and procedures (TTPs) displayed in WannaMine did not require a high degree of sophistication, the attack clearly stands on the shoulders of more innovative and enterprising nation-state and eCrime threat actors. CrowdStrike anticipates that these threat actors will continue to evolve their capabilities to go undetected,” the security company notes.
As Sophos points out, organizations that find the WannaMine malware in their network are also at risk of other malware, including ransomware. It is not uncommon to find multiple malware families on machines that have been compromised once.
Designed to mine for Monero, not to steal user information or crypto-coins, WannaMine would still slow down the infected machines. Laptops could even be damaged, if the malware runs on them continuously for several hours, as the device gets hotter. Also, the battery is drained faster than usual, Sophos points out.
An antivirus application should keep users protected from this malware family. Keeping systems up to date at all times and using strong passwords should also help avoiding a WannaMine infection.
New AMD Processors to Include Protections for Spectre-like Exploits
31.1.2018 securityweek Exploit
AMD’s new Zen 2 and future processors will include protections against Spectre and other similar exploits, the tech giant revealed on Tuesday as it announced its earnings for 2017.
AMD CEO Lisa Su reiterated that the company’s CPUs are not vulnerable to Meltdown attacks and one variant of the Spectre attack is difficult to carry out against its products.AMD processors will include Spectre protections
“For Spectre Variant 1, we continue actively working with our ecosystem partners on mitigations, including operating system patches that have begun to roll out. We continue to believe that Variant 2 of Spectre is difficult to exploit on AMD processors, however we are deploying CPU microcode patches – in combination with OS updates – to provide additional mitigation steps,” Su explained.
The CEO highlighted that in the long-term the company plans on including protections for Specter-like exploits into all future processor cores. These protections have already been implemented into the design of recently unveiled Zen 2 CPUs, which are expected to become available next year.
AMD reported revenue of $5.33 billion for 2017, which it says represents a 25 percent increase compared to the previous year. However, the company warned that the Spectre and Meltdown exploits could have a negative impact on the company’s revenue, including as a result of lawsuits, which have already been filed against the organization.
“Actual or perceived security vulnerabilities of AMD products may subject AMD to adverse publicity, damage to its brand and reputation, and could materially harm AMD’s business or financial results,” the company stated.
Intel also informed customers that it’s working on CPUs that will include built-in protections against Meltdown and Spectre attacks.
In the meantime, existing software and microcode patches have caused problems for many users, which has led to vendors halting updates and disabling mitigations until issues are resolved.
Threat Actors Quickly Adopt Effective Exploits
18.1.2018 securityweek Exploit
Cybercriminals and nation state groups were quick to adopt the most effective exploits last year, a new AlienVault report reveals.
Not only do the most effective exploits proliferate quickly between cybercriminals, but some of them remain popular for years after their initial discovery.
The top 10 list of exploits – by number of occurrences in vendor reports – is dominated by Microsoft Office and Microsoft Windows, data from AlienVault’s Open Threat Exchange (OTX) platform reveals. Adobe Flash, Microsoft .NET, and Android/Linux were also present on the list, with one exploit each.
The exploit to appear most often in vendor reports last year was CVE-2017-0199, a code execution bug affecting Microsoft Office. Detailed in April 2017, when it was already being abused in attacks, the vulnerability started being adopted almost immediately, and the trend continued toward the end of the year as well.
The popularity of this exploit continued to grow even after Microsoft released a patch. Originally abused with malicious Rich Text File (RTF) documents, the flaw was leveraged with PowerPoint Slide Show files by August, and threat actors continued to use it in this manner in the following months as well.
Some attackers combined multiple exploits to avoid detection, using CVE-2017-0199 together with CVE-2012-0158, an old Office flaw that is still exploited in many campaigns and which made it to the third position on AlienVault’s top 10 exploits for last year.
The second place went to CVE-2015-1641, an exploit that was already highly popular one year after it became public. Actors exploiting the vulnerability include the Patchwork cyberespionage group and cybercriminals located in Nigeria.
In addition to CVE-2017-0199, three other exploits discovered in 2017 were among the most reported by vendors, namely CVE-2017-0144, CVE-2017-0262, and CVE-2017-8759. A .NET zero-day, CVE-2017-8759 was patched in September, after it was abused to deliver the FinFisher malware to Russian-speaking individuals.
The only exploit targeting operating systems other than Windows that made it to AlienVault’s top 10 list is CVE-2013-6282, targeting a bug leveraged by Android malware to escalate privileges once installed on a victim’s phone.
A Windows 2000 flaw reported in 2001 was encountered the most by AlienVault’s customers, the company reports. Two vulnerabilities from 2017 made it to the top 10 list of exploits seen the most, namely CVE-2017-0144 and CVE-2017-5638 (an Apache Struts bug).
“This data-set is very large, and consists of many billions of security events. However the data is heavily biased towards “noisy” network based exploit attempts from worms and exploit scanners. This explains why we’re still recording ancient vulnerabilities from 2001 in this table,” AlienVault points out.
Intel Patches CPUs Against Meltdown, Spectre Exploits
5.1.2018 securityweek Exploit
Intel has been working with its partners to release software and firmware updates that should protect systems against the recently disclosed CPU attacks. The company expects patches to become available for a majority of its newer products by the end of next week.
Researchers this week disclosed the details of Spectre and Meltdown, two new side-channel attacks targeting CPUs from Intel, AMD and ARM. The attacks, which leverage three different flaws, can be used to bypass memory isolation mechanisms and gain access to sensitive data, including passwords, photos, documents, and emails. Experts have warned that malicious actors may soon start to remotely exploit the Spectre vulnerabilities in targeted or mass attacks.
AMD has insisted that there is a “near zero risk” to its customers and ARM says only a few of its Cortex processors are impacted.
Intel informed customers on Thursday that system manufacturers have been provided firmware and software updates that address Spectre and Meltdown for processors launched in the last five years – experts believe nearly every Intel processor made since 1995 is impacted. It will now be up to system manufacturers to distribute the patches.
“By the end of next week, Intel expects to have issued updates for more than 90 percent of processor products introduced within the past five years,” Intel said.
In response to concerns that mitigations for the Spectre and Meltdown vulnerabilities can introduce performance penalties of as much as 30 percent, Intel pointed out that average users will not notice any difference.
“While on some discrete workloads the performance impact from the software updates may initially be higher, additional post-deployment identification, testing and improvement of the software updates should mitigate that impact,” Intel said.
The company cited Apple, Microsoft, Amazon and Google, all of which said the mitigations did not create any noticeable performance issues.
The best protection against these attacks is the use of kernel page table isolation (KPTI), a hardening technique designed by a team of researchers at the Graz University of Technology in Austria to isolate kernel space from user space memory. Google, whose researchers independently found the flaws, also developed a novel mitigation named Retpoline.
Microsoft, Apple, Google, Red Hat, VMware and other major tech firms have already started releasing software updates and workarounds to resolve the vulnerabilities.
Intel was hit the hardest by Spectre and Meltdown and the company’s stock lost 6 percent in value shortly after the disclosure. The company’s CEO, Brian Krzanich, sold all the stock he was legally allowed to, worth roughly $24 million, just before the news broke, which has raised insider trading concerns. Intel claims Krzanich had been planning on selling stock for months, but Intel has reportedly known about the vulnerabilities since April 2017.
Botnet's Huawei Router Exploit Code Now Public
2.1.2017 securityweek Exploit
Exploit code used by the Satori botnet to compromise Huawei routers via a zero-day vulnerability became public last week, researchers have discovered.
The exploit has been used in attacks involving the Mirai variant Satori to target Huawei vulnerability CVE-2017–17215, which was unpatched at the time the first assaults started. The vulnerability was found in Huawei HG532 devices in November. Shortly after, Huawei published an advisory on how users can circumvent or prevent the exploit.
Discovered on Pastebin this Christmas, the code could fuel a spike in attempts to exploit the vulnerability. In fact, it has been already used by the destructive BrickerBot malware to target Internet of Things (IoT) devices, NewSky Security says.
In early December, the actor behind BrickerBot dumped some of the code online and announced plans to retire his project. The released code included some of the malware’s attack modules, including one that targeted said Huawei flaw, researchers have discovered.
“While analyzing this code, we also uncovered the usage of CVE-2017–17215, implying that this code has been in blackhats’ hands for a while,” NewSky reveals.
While analyzing the Satori and BrickerBot code, the security researchers noticed that the same attack vector (code injection) is present in both, which led to the conclusion that both malware developers “had copied the exploit source code from the same source.”
The security researchers also point out that the SOAP protocol (Simple Object Access Protocol) has been abused before in attacks involving IoT devices. Several Mirai variants observed last year were using two other SOAP bugs (CVE-2014–8361 and TR-64). One iteration was using them together, to increase the chances of a successful attack.
“IoT attacks are becoming modular day by day. When an IoT exploit becomes freely available, it hardly takes much time for threat actors to up their arsenal and implement the exploit as one of the attack vectors in their botnet code,” NewSky concludes.
A Kernel Exploit for Sony PS4 Firmware 4.05 is available online
30.12.2017 securityaffairs Exploit
The developer SpecterDev finally released a fully-functional kernel exploit for PlayStation 4 (firmware 4.05) dubbed ‘namedobj’.
Good news for PlayStation gamers, the developer SpecterDev finally released a fully-functional kernel exploit for PlayStation 4 (firmware 4.05) dubbed ‘namedobj’.
PS4 gamers who are running firmware version lower than 4.05 need to update their gaming console to trigger the exploit.
The Kernel exploit was released two months after Team Fail0verflow revealed the technical details about the first PS4 Kernel Exploit.
The kernel exploit ‘namedobj’ is now available on Github, it works for the PlayStation 4 on 4.05FW and allows users to run arbitrary code on the device.
“In this project you will find a full implementation of the “namedobj” kernel exploit for the PlayStation 4 on 4.05. It will allow you to run arbitrary code as kernel, to allow jailbreaking and kernel-level modifications to the system. This release however, does not contain any code related to defeating anti-piracy mechanisms or running homebrew. This exploit does include a loader that listens for payloads on port 9020 and will execute them upon receival.” reads the description published on GitHub.

The availability of the kernel exploit could allow developers to write a working jailbreak and kernel-level modifications to the system.
Jailbreaking allows removing hardware restrictions implemented by the operating system, it allows users to run custom code on the console and install mods, games, and third-party applications bypassing the anti-piracy mechanisms implemented by Sony.
“This release, however, does not contain any code related to defeating anti-piracy mechanisms or running homebrew,” SpecterDev said.
“This exploit does include a loader that listens for payloads on port 9020 and will execute them upon receival.”
Reading the “Notes” we can notice that the developer warns that the exploit should not work for some users.
“This exploit is actually incredibly stable at around 95% in my tests. WebKit very rarely crashes and the same is true with kernel. I’ve built in a patch so the kernel exploit will only run once on the system. You can still make additional patches via payloads,” SpecterDev warned.
At this point, experts at Sony will work to identify the flaws triggered by the kernel exploit and fix them.
Huawei router exploit (CVE-2017-17215) involved in Satori and Brickerbot was leaked online
30.12.2017 securityaffairs Exploit
The exploit code used to trigger the CVE-2017-17215 vulnerability in Huawei routers over the past several weeks is now publicly available.
Before Christmas, the Mirai botnet made the headlines once again, a new variant dubbed Satori was responsible for hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers.
The activity of the Satori botnet has been observed over the past month by researchers from Check Point security.
Satori is an updated variant of the notorious Mirai botnet that was first spotted by the malware researchers MalwareMustDie in August 2016. The malicious code was developed to target IoT devices, the Satori version targets port 37215 on Huawei HG532 devices.
The attacks against Huawei HG532 devices were observed in several countries, including the USA, Italy, Germany, and Egypt.

Experts observed that attacks attempt to exploit the CVE-2017-17215 zero-day vulnerability in the Huawei home router residing in the fact that the TR-064 technical report standard, which was designed for local network configuration, was exposed to WAN through port 37215 (UPnP – Universal Plug and Play).
News of the day is that the code used to target the Huawei routers over the past several weeks is now publicly available.
The discovery was made by Ankit Anubhav, a researcher at security firm NewSky.
Anubhav first discovered the code on Pastebin.com early this week.
“NewSky Security observed that a known threat actor released working code for Huawei vulnerability CVE-2017–17215 free of charge on Pastebin this Christmas. This exploit has already been weaponized in two distinct IoT botnet attacks, namely Satori and Brickerbot.” states a blog post published by Anubhav.
The exploit code for the CVE- 2017-17215 was used by a hacker identified as “Nexus Zeta” to spread the Satori bot (aka Okiku).
The availability of the code online represents a serious risk, it could become a commodity in the criminal underground, vxers could use it to build their botnet.
Satori isn’t the only botnet leveraging the CVE-2017-17215 exploit code, earlier in December, the author of the Brickerbot botnet that goes online with the moniker “Janitor” released a dump which contained snippets of Brickerbot source code.
NewSky Security analyzing the code discovered the usage of the exploit code CVE-2017–17215, this means that the code was available in the underground for a long.
“Let us compare this with a binary of Satori botnet (in the image below). Not only we see the same attack vector i.e. code injection in <NewStatusURL>, but also, we witness the other indicator “echo HUAWEIUPNP“ string, implying that both Satori and Brickerbot had copied the exploit source code from the same source.” continues NewSky.

This is not the first time that IoT botnets leverage issues related to the SOAP protocol. Earlier this year, security experts observed several Mirai-based botnets using two other SOAP bugs (CVE-2014–8361 and TR-64) which are code injections in <NewInternalClient> and <NewNTPServer> respectively.
Back to the present, Huawei provided a list of mitigation actions for this last wave of attacks that includes configuring a router’s built-in firewall, changing the default password or using a firewall at the carrier side.
I avoided to provide the link to the code published on Pastebin, but it is very easy to find it with the proper query.
Kernel Exploit for Sony PS4 Firmware 4.05 Released, Jailbreak Coming Soon
27.12.2017 thehackernews Exploit
Wishing you all a very 'belated' Merry Christmas. This holiday season Santa has a very special gift for all PlayStation gamers.
Developer SpecterDev finally released a fully-functional much-awaited kernel exploit for PlayStation 4 (firmware 4.05) today—almost two months after Team Fail0verflow revealed the technical details of it.
Now available on Github, dubbed "namedobj," the kernel exploit for the PlayStation 4 on 4.05FW allows users to run arbitrary code on the gaming console, enabling jailbreaking and kernel-level modifications to the system.
Although PS4 kernel exploit does not include Jailbreak code, others can develop a full jailbreak exploit using it.
Jailbreaking allows users to run custom code on the console and install mods, cheats, third-party applications, and games that are typically not possible because of the anti-piracy mechanisms implicated on the Sony PlayStation.
"This release, however, does not contain any code related to defeating anti-piracy mechanisms or running homebrew," SpecterDev said.
"This exploit does include a loader that listens for payloads on port 9020 and will execute them upon receival."
It should be noted that for some users it may not work as smooth as it sounds.
"This exploit is actually incredibly stable at around 95% in my tests. WebKit very rarely crashes and the same is true with kernel. I've built in a patch so the kernel exploit will only run once on the system. You can still make additional patches via payloads," SpecterDev warned.
PS4 gamers who are running firmware version lower than 4.05 can simply update their console to take advantage of this exploit.
Of course, Sony would not be happy with the launch of PlayStation 4 kernel exploit and would be trying hard to eliminate any vulnerability for the most recent version of PS4 firmware.
Hackers Exploit Recently Disclosed Microsoft Office Bug to Backdoor PCs
30.11.2017 thehackernews Exploit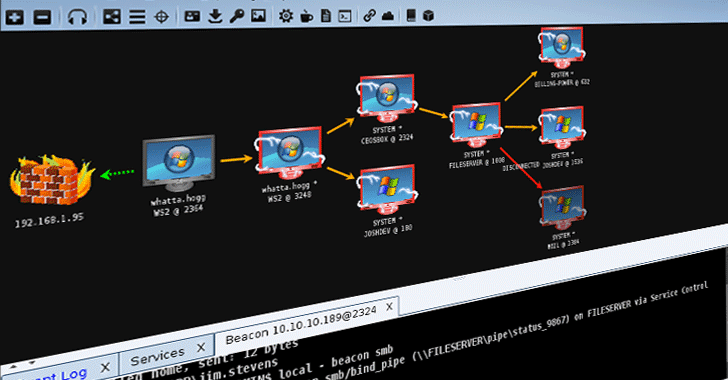
A recently disclosed severe 17-year-old vulnerability in Microsoft Office that lets hackers install malware on targeted computers without user interaction is now being exploited in the wild to distribute a backdoor malware.
First spotted by researchers at security firm Fortinet, the malware has been dubbed Cobalt because it uses a component from a powerful and legitimate penetration testing tool, called Cobalt Strike.
Cobalt Strike is a form of software developed for Red Team Operations and Adversary Simulations for accessing covert channels of a system.
The vulnerability (CVE-2017-11882) that Cobalt malware utilizes to deliver the backdoor is a memory-corruption issue that allows unauthenticated, remote attackers to execute malicious code on the targeted system when opened a malicious file and potentially take full control over it.
This vulnerability impacts all versions of Microsoft Office and Windows operating system, though Microsoft has already released a patch update to address the issue. You can read more details and impact of the vulnerability in our previous article.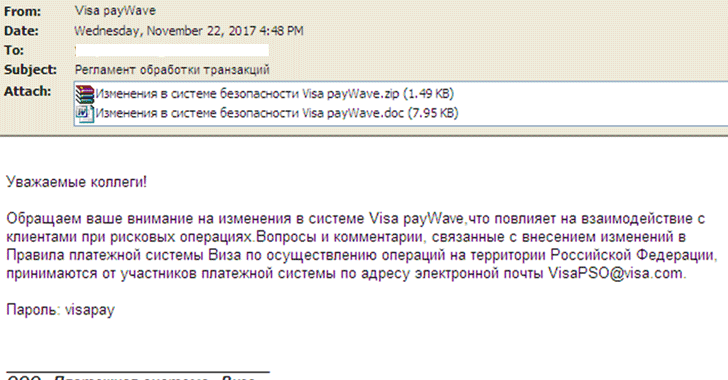
Since cybercriminals are quite quick in taking advantage of newly disclosed vulnerabilities, the threat actors started delivering Cobalt malware using the CVE-2017-11882 exploit via spam just a few days after its disclosure.
According to Fortinet researchers, the Cobalt malware is delivered through spam emails, which disguised as a notification from Visa regarding rule changes in Russia, with an attachment that includes a malicious RTF document, as shown.
The email also contains a password-protected archive with login credentials provided in the email to unlock it in order to trick victims into believing that the email came from the legitimate financial service.
"This is [also] to prevent auto-analysis systems from extracting the malicious files for sandboxing and detection," Fortinet researchers Jasper Manual and Joie Salvio wrote.
"Since a copy of the malicious document is out in the open... so it's possible that this is only to trick the user into thinking that securities are in place, which is something one would expect in an email from a widely used financial service."
Once the document is opened, the user has displayed a plain document with the words "Enable Editing." However, a PowerShell script silently executes in the background, which eventually downloads a Cobalt Strike client to take control of the victim's machine.
With control of the victim's system, hackers can "initiate lateral movement procedures in the network by executing a wide array of commands," the researchers said.
According to the researchers, cybercriminals are always in look for such vulnerabilities to exploit them for their malware campaigns, and due to ignoring software updates, a significant number of users out there left their systems unpatched, making them vulnerable to such attacks.
The best way to protect your computer against the Cobalt malware attack is to download the patch for the CVE-2017-11882 vulnerability and update your systems immediately.
Disdain exploit kit and a side of social engineering deliver Neutrino Bot
13.11.2017 Malwarebytes Exploit
Today we picked up new activity from an exploit kit that was first discovered back in August of this year. The Disdain exploit kit, simply identified by a string of the same name found in its source code, is being distributed again after a short interruption via malvertising chains.
Disdain EK relies on older vulnerabilities that have long been patched and some that do not appear to be working properly. From a traffic to infection point of view, this means that the conversion rates are going to be lower than, say, RIG EK, the other most common exploit kit at the moment.
This may explain why we are seeing Disdain being used as a drive-by download alongside a social engineering attack to increase the likelihood of infections. Case in point, the following site was compromised to serve Disdain EK while also distributing a fake Flash Player update:
What’s interesting is that both payloads (Disdain’s malware drop and the so-called Flash update) are actually the same malicious binary, just delivered by different methods. The former is loaded via an iframe injected into the page which triggers the exploit kit and delivers the payload automatically, while the latter is a regular download that requires user interaction to download and run it.
Disdain’s landing page exploits older Internet Explorer vulnerabilities and attempts to load Flash exploits as well, although in our tests these did not work.
That payload is Neutrino Bot, which we have documented on this blog before when it was served in malicious spam campaigns as well as via the now defunct Neutrino exploit kit. Neutrino Bot, AKA Kasidet , is a multi-purpose piece of malware famous for its information stealing abilities.
In the past few weeks, there have been a few developments in the exploit kit scene beyond the long running RIG exploit kit, where threat actors are attempting new tricks both from an evasion and distribution point of view. Despite this, there remains a lack of innovation in what really matters at the end of the day: the exploits being used to deliver drive-by infections.
While some groups have switched to pure social engineering-based attacks, others are attempting either or both methods at once. In the current threat landscape, the campaigns that have the most success are those that can draw a lot of traffic and use clever techniques to fool users.
Systems that have been patched regularly would not be affected by this exploit kit, but at the same time users should beware of non-legitimate software updates. Many of the so-called “Flash Player” or “Video Player” updates typically push adware and, as we saw recently with the BadRabbit outbreak, even ransomware.
Malwarebytes users are protected from the Disdain exploit kit and Neutrino Bot malware.
Hack the hackers. Watcha out the NEW IPCAM EXPLOIT, it is a scam!
10.11.2017 securityaffairs Exploit
Security experts have discovered a new hacking tool dubbed NEW IPCAM EXPLOIT containing a backdoor that is offered on several underground hacking forums.
Wannabe hackers, be careful out of free hacking tools, many of them are scams. Recently security experts reported several cases of fake hacking tools hiding backdoors, for example, a fake Facebook hacking tool or the Cobian RAT.
Now, the security researcher Ankit Anubhav has discovered a new tool containing a backdoor that is offered on several underground hacking forums. The hacking tool is a free PHP script that allows users to scan the Internet for vulnerable IP Cameras running a vulnerable version of GoAhead embedded web-server.
“The market is particularly hot for IoT devices using a vulnerable version of an embedded GoAhead server. This arises due to the fact that there are a large number of IP camera vendors that can be hacked using exploits like CVE-2017–8225, and it is already employed successfully by the IoTroop/Reaper botnet.” wrote the researcher in a blog post.
“On 22nd October 2017, we observed a shady yet popular site that often hosts IoT botnet scripts had a new piece of code to offer. Labeled as “NEW IPCAM EXPLOIT”, this script promised to make the work of script kiddies easy by helping them locate IoT devices that use the potentially vulnerable embedded GoAhead server.”

The expert analyzed the NEW IPCAM EXPLOIT and discovered that it includes the code to hack the wannabe criminals using it, this implies that is the script kiddie owns a botnet, scammers can use the tool to take over it.
After going through all levels of decoding, the expert discovered that the NEW IPCAM EXPLOIT scan the web for devices using the GoAhead embedded server by checking for the banner “GoAhead-Webs”. At the bottom of the script, there is a backdoor which uses shellscript to connect to contact a malicious server, download a second-stage script, and execute it.
The NEW IPCAM EXPLOIT IoT scanning script works in four steps:
The script scans a set of IP addresses looking for GoAhead servers vulnerable to the authentication bypass flaw tracked as CVE-2017-8225. The vulnerability affects Wireless IP Camera (P2P) WIFI CAM devices.
The script establishes a secret backdoor by creating the user account (username: VM | password: Meme123) on the wannabe cybercriminal’s system. The scammer gains the same toot privileges as of the victim.
The Script determine the IP address of the wannabe hacker in order to access the compromised systems remotely.
The script runs a second payload on the victim’s system, in some cases, it installs the Kaiten bot.

Experts from Bleeping computers that made further investigations reported that the author of the script already put online backdoored hacking tools.
“Digging deeper into some of the IDs used by the backdoor creator, we also discovered that this wasn’t the first time when he published backdoored malware or had online fights with other hackers. This may explain why Anubhav found a dox file in the hacker’s name. ” reported Bleepingcomputer.
German users exploit a Twitter bug to post 30,000-character tweet
7.11.2017 securityaffairs Exploit
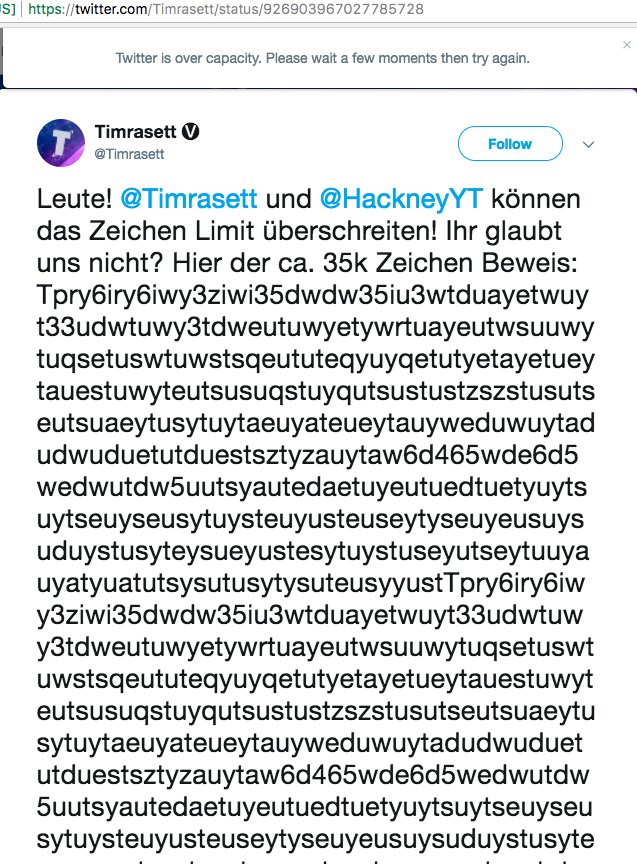
Over the weekend, two German Twitter users successfully bypassed the existing character limit by exploiting a Twitter bug and sending a 30,396-character tweet.
Two German Twitter users, Timrasett and HackneyYT, were able to bypass the 280-character limit by posting a 30,000-character Tweet.
Unfortunately, the side effect was that the long tweet caused problems, with some users complaining of crashes.
The social media giant banned the accounts of the two users for a brief period of time but are now back online after they apologized. Twitter removed the original oversize-Tweet composed of 30,396 that can be viewed here.

According to the The Daily Dot, the German duo exploited a rule Twitter made in 2016 that links would no longer count in the 140-character limit.
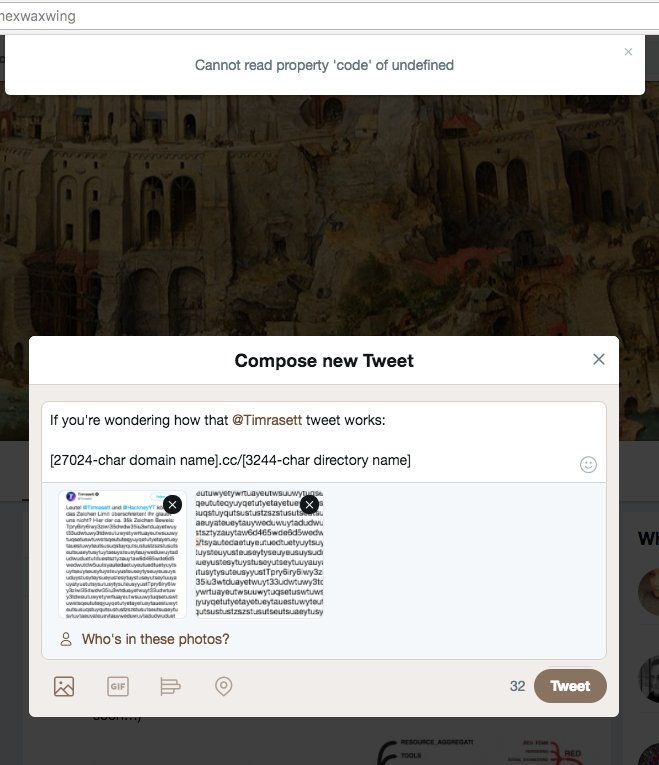
“So how did they do it? By exploiting a rule Twitter made in 2016 that links would no longer count in the 140-character limit. Yes, this is just one big web address with a URL code hidden deep in the large block of text. You can find it by opening up the tweet and searching for “.cc/” reports The Daily Dot.
The experts broke the limitation by formatting a message as a URL with extensive gibberish. Twitter promptly removed it the message and suspended the accounts of the users.
waxwing:(){ :|: &};: @hexwaxwing
If you're wondering how twitter[.]com/Timrasett/status/926903967027785728 works:
[27024-char domain name].cc/[3244-char directory name]
10:11 PM - Nov 4, 2017
20 20 Replies 464 464 Retweets 585 585 likes
Twitter Ads info and privacy
The accounts of the two users are back online after apologizing for crashing the site.
Both users will continue to look for other bugs on the social platform.
Below the comment of a Twitter spokesperson who confirmed that the flaw exploited by the German duo has been fixed and pointed to its rules, specifically:
To promote a stable and secure environment on Twitter, you may not do, or attempt to do, any of the following while accessing or using Twitter:
Access, tamper with, or use non-public areas of Twitter, Twitter’s computer systems, or the technical delivery systems of Twitter’s providers (except as expressly permitted by the Twitter Bug Bounty program).
Probe, scan, or test the vulnerability of any system or network, or breach or circumvent any security or authentication measures (except as expressly permitted by the Twitter Bug Bounty program).
Interfere with or disrupt the access of any user, host or network, including, without limitation, sending a virus, overloading, flooding, spamming, mail-bombing Twitter’s services, or by scripting the creation of content in such a manner as to interfere with or create an undue burden on Twitter
Russian Hackers Exploit Recently Patched Flash Vulnerability
20.10.2017 securityweek Exploit
The Russia-linked cyber espionage group known as APT28 has been using a recently patched Adobe Flash Player vulnerability in attacks aimed at government organizations and aerospace companies, security firm Proofpoint reported on Thursday.
The Flash Player flaw in question, CVE-2017-11292, was patched by Adobe on October 16. At the time when the patch was released, the vulnerability had a zero-day status, as it had been exploited in targeted attacks by a Middle Eastern threat actor named BlackOasis to deliver FinFisher spyware.
APT28, which is also known as Fancy Bear, Pawn Storm, Strontium, Sofacy, Sednit and Tsar Team, started launching attacks using CVE-2017-11292 on October 18, Proofpoint said. It’s unclear if APT28 discovered the exploit on its own, purchased it, or reverse engineered the one used in the BlackOasis attack.
Nevertheless, Proofpoint pointed out that the cyberspies are likely trying to take advantage of the recently fixed vulnerability before Adobe’s patch is widely deployed by users.
The attacks observed by the security firm were aimed at organizations in the United States, Europe and other countries. The targets included foreign government organizations with responsibilities similar to the U.S. State Department, and private-sector aerospace companies.
The messages delivering the exploits were highly targeted and they were sent out using free email services, Proofpoint said. The attackers leveraged malicious documents and their previously known Flash Player exploit platform named DealersChoice to deliver the first-stage implant, specifically a reconnaissance tool.
While CVE-2017-11292 affects Windows, Mac and Linux systems, APT28 apparently only launched attacks against Windows users. Tests conducted by researchers showed that the exploit works on systems with Windows 7 or Windows 10 with Microsoft Office 2013. The exploit, however, fails to execute on 64-bit systems running Windows 10 Fall Creators Update (RS3) and Office 2016.
“APT28 is a sophisticated state-sponsored group that is using the vulnerability to attack potentially high-value targets but it is likely that other threat actors will follow suit and attempt to exploit this vulnerability more widely, whether in exploit kits or via other attack vectors,” Proofpoint researchers explained.
The security firm has been working on taking down the command and control (C&C) domains used in these attacks.
Recently Patched .NET Flaw Exploited by China-Linked Cyberspies
19.10.2017 securityweek Exploit
A cyber espionage group previously linked to China has been using a recently patched .NET vulnerability in attacks aimed at organizations in the United States, including a shipbuilding company and a university research center with ties to the military.
The threat actor, known for its use of a remote access trojan (RAT) named NanHaiShu, has been active since at least 2014. In the past years, it has targeted various U.S. and Western European organizations with ties to the maritime sector, including naval defense contractors and research institutions.
A report published last year by F-Secure detailed attacks launched by the group against the participants of a Permanent Court of Arbitration case focusing on a dispute between China and the Philippines over the South China Sea.
F-Secure did not directly attribute the attacks to the Chinese government, but researchers found several pieces of evidence suggesting that the NanHaiShu malware had Chinese origins.
The latest round of attacks attributed to this group were observed by researchers at Proofpoint in mid-September. Experts noticed that the attacker sent spear-phishing emails to a U.S. shipbuilding company and a U.S. university research center with ties to the military.
The emails carried documents designed to exploit CVE-2017-8759, a .NET vulnerability patched by Microsoft just days before the attacks were launched. At the time when Microsoft released fixes, the flaw had already been exploited by a Middle Eastern threat actor to deliver spyware.
Proofpoint has also seen attacks launched by the cyber espionage group in early August. These attacks exploited CVE-2017-0199, an Office vulnerability that had also been exploited in attacks when Microsoft released a patch for it back in April.
The attacks targeted several defense contractors and they involved malicious Microsoft Publisher files, PowerPoint presentations, and domains set up to mimic ones belonging to an important provider of military ships and submarines. Researchers from other companies also analyzed these attacks and some pointed out that many of the targets were in South Korea.
In addition to NanHaiShu, the attackers have used a backdoor dubbed “Orz,” which has been spotted in both old attacks and ones launched in August 2017, loaders such as SeDLL and MockDLL, and the Cobalt Strike penetration testing tool.
In some cases, researchers noticed that the attackers used one organization’s compromised email accounts to send malicious attachments to others in the same industry. The hackers also used hijacked servers for command and control (C&C).
“The tools, techniques, and targets consistently connect their work, particular given their attention to naval and maritime defense interests and use of custom backdoors,” Proofpoint researchers said in a blog post. “While defense contractors and academic research centers with military ties should always be cognizant of the potential for cyberattacks, organizations fitting their targeting profiles should be especially wary of legitimate-looking but unsolicited emails from outside entities.”
A man who goes by the nickname LiquidWorm released a FLIR Thermal Camera Exploit
10.10.2017 securityaffairs Exploit
On September 25, 2017, a man which goes by the nickname ‘LiquidWorm’ has released the exploit code for FLIR Thermal Cameras.
On 2017-09-25 another CCTV exploit got release by a man which goes by the nickname ‘LiquidWorm’. He found out that FLIR CCTV ’s by the vendor “FLIR Systems” had a hard-coded ssh login credentials within its Linux distribution image, Those credentials are never exposed to the end user and CANNOT be changed through any normal operation of the camera.

What kind of exploit is this?
This exploit is what we know as a “Backdoor” because it grants Randoms access to the camera’s, and even allows them to download code, or do worse.
What are the Affected version?
So far camera models of F/FC/PT/D Software version 10.0.2.43 and Firmware version: 8.0.0.64 release: 1.4.1, 1.4, 1.3.4 GA, 1.3.3 GA and 1.3.2 are affected by the exploit.
What kind of cameras are those? The FLIR cameras are high-performance, multi-sensor pan/tilt cameras which bring thermal and visible-light imaging together in a system that gives you video and control over both IP and analog networks.
Is this exploit fixable by the end user itself?
No, after testing around with a test model, there isn’t any way of removing the hard-coded ssh login credentials, the vendor itself would have to remove the SSH login credentials from the code.
Is this exploit critical?
Yes, these kinds of exploits are unnecessary and not needed, Since Random people can now scan for affected versions and most likely infect them, the rate of IoT botnets will rise again, which is a bad thing.
What to do?
The only thing the affected camera owners can do is wait until the Vendor releases a patch which removes the hard-coded ssh login of the Linux distribution image.