
Exploit Articles - H 2020 1 2 3 4 5 6 7 Exploit List - H 2021 2020 2019 2018 1 Exploit blog Exploit blog
Google publishes PoC Exploit code for iPhone Wi-Fi Chip hack
28.9.2017 securityaffairs Vulnerebility Exploit
Google disclosed details and a proof-of-concept exploit for iPhone Wi-Fi firmware vulnerability affecting Broadcom chipsets in iOS 10 and earlier.
This week Google disclosed details and a proof-of-concept exploit for a Wi-Fi firmware vulnerability affecting Broadcom chipsets in iOS 10 and earlier. The flaw that was patched this week could be exploited by attackers to execute code and establish a backdoor on a targeted device. The attackers just need the iPhone’s MAC address or network-port ID.
The vulnerability, tracked as CVE-2017-11120, is a memory corruption vulnerability, Apple addressed it in the security update for the release of iOS 11.
“Attaching exploit for this issue. The exploit gains code execution on the Wi-Fi firmware on the iPhone 7. The password for the archive is “rrm_exploit”.” states the bug report published by Google Project Zero researcher Gal Beniamini.
“The exploit has been tested against the Wi-Fi firmware as present on iOS 10.2 (14C92), but should work on all versions of iOS up to 10.3.3 (included). However, some symbols might need to be adjusted for different versions of iOS, see “exploit/symbols.py” for more information.

The Beniamini’s exploit code allowed the expert to establish a backdoor into Broadcom chip’s firmware, which allowed him to remotely read and write commands to the firmware.
Upon successful execution of the exploit, a backdoor is inserted into the firmware, allowing remote read/write commands to be issued to the firmware via crafted action frames (thus allowing easy remote control over the Wi-Fi chip).” continues the report.
The exploit code works against the firmware packaged with iOS 10.2 and that it should work on versions up to and including 10.3.3. The experts also verified that BCM4355C0 System on Chip with firmware version 9.44.78.27.0.1.56 is vulnerable.
The vulnerability resides the Broadcom chips that are used in the iPhone and other Apple products, including Apple TV and in the Apple Watch.
This vulnerability is similar to the one Gal Beniamini discovered in the Broadcom WiFi SoC (Software-on-Chip) back in April, and the BroadPwn critical remote code execution vulnerability (CVE-2017-3544), that affects the Broadcom BCM43xx family of WiFi chipsets.
Since there is no way to find out if your device
Users urge to update iPhones to iOS 11 because it is not possible to discover if their device is running the firmware version BCM4355C0.
Hackers exploit an undocumented Word feature for user fingerprinting
19.9.2017 securityaffairs Exploit
Kaspersky researchers discovered a new attack technique leveraging an undocumented Word feature to gather information on users.
Kaspersky researchers discovered a new attack technique leveraging Microsoft Word documents to gather information on users. The technique is innovative because it doesn’t use active content such as macros or exploits, it exploits an undocumented Word feature to fingerprint users.
The attackers sent phishing emails using Word documents in OLE2 format and contained links to PHP scripts hosted on third-party web resources. Once the user opened the files in Microsoft Office, the application accesses one of the links, resulting in the attackers receiving information about the software installed on the target machine.
“They were in OLE2 format and contained no macros, exploits or any other active content. However, a close inspection revealed that they contained several links to PHP scripts located on third-party web resources.” reads the analysis published by Kaspersky Lab. “When we attempted to open these files in Microsoft Word, we found that the application addressed one of the links. As a result, the attackers received information about the software installed on the computer.”
One of the documents analyzed by the researchers contained tips on how to use Google search more effectively, it doesn’t contain active content, no VBA macros, embedded Flash objects or PE files. Once opened Word sends a GET request to an internal link.
“This code effectively sent information about the software installed on the victim machine to the attackers, including info about which version of Microsoft Office was installed,” continues the analysis.
The researchers discovered that the document used an undocumented Word feature, they noticed the presence of an INCLUDEPICTURE field that indicates that an image is attached to certain characters in the text.
The experts highlighted that there is no description for Microsoft Office documentation provides basically no description of the INCLUDEPICTURE field.
The attackers used the INCLUDEPICTURE field to include a suspicious link there, although not the URL addressed by Word.
The text in Word documents is stored in the WordDocument stream in a ‘raw state that doesn’t contain formatting except for so-called fields. The fields are used to instruct Word that a certain segment of the text must be presented in a specific way. The field INCLUDEPICTURE indicates that an image is attached to certain characters in the text.
The experts identified the following characters inside the document:
Begin = 0x13
Sep = 0x14
End = 0x15
Field = <Begin> *<Field> [Sep] *<Field> <End>

A byte between the separator (SEP) and the end (END) tells words that an image should be inserted at that point. The experts first located the byte sequence with the picture placeholder, then they discovered at which offset the image should be located in the Data stream.
“So, we go to offset 0 in the Data stream and see that the so-called SHAPEFILE form is located there:

Forms are described in a different Microsoft document: [MS-ODRAW]: Office Drawing Binary File Format. This form has a name and, in this case, it is another suspicious link:” continues the analysis.
Experts noticed that a combination of flags was used to indicate that additional data should be attached to the form. According to Kaspersky, this data constitutes a URL that leads to the actual content of the form.
“This indicates that additional data should be attached to the form (it is highlighted in yellow in the screenshot), and that this data constitutes a URL that leads to the actual content of the form. Also, there is a ‘do not save’ flag, which prevents this content from being saved to the actual document when it is opened.” continues the analysis.
The attackers devised this complex technique to fingerprint users opening the Word documents.
“This is a complex mechanism that the bad guys have created to carry out profiling of potential victims for targeted attacks. In other words, they perform serious in-depth investigations in order to stay undetected while they carry out targeted attacks,” Kaspersky says.
According to Kaspersky, the Office feature exists in Word and Windows, Microsoft Office for iOS, and Microsoft Office for Android. LibreOffice and OpenOffice do not implement this feature
Hackers Exploit Recently Patched Apache Struts Flaw
8.9.2017 securityweek Exploit
A critical remote code execution vulnerability patched earlier this week in the Apache Struts 2 open-source development framework is already being exploited in the wild.
The flaw, tracked as CVE-2017-9805, affects applications that use the REST plugin with the XStream handler for XML payloads, and it exists due to the way Struts deserializes untrusted data. An exploit and a Metasploit module for the vulnerability were created within hours after the patch was released.
lgtm, the company that discovered the flaw, warned that at least 65 percent of Fortune 100 companies use Struts and they could all be exposed to remote attacks due to this vulnerability.
However, Contrast Security, which provides protection against these types of exploits, said only less than one percent of its customers’ Java applications use the problematic REST plugin. Furthermore, data from the Maven repository shows that less than a dozen applications use this plugin.
Nevertheless, security firms have already started seeing exploitation attempts. Cisco Talos and Belgium-based NVISO Labs both spotted attacks whose apparent goal was to find vulnerable servers. The attacks spotted by these companies involved a Russian website sending the requests and receiving the results of the exploitation attempt.
Cisco has also observed attacks whose goal was to deliver a potentially malicious file. Researchers were unable to determine what payload had been served, but based on previous Apache Struts attacks, they believe it was likely DDoS bots, spam bots or other malware.
“Within 48 hours of disclosure we were seeing systems activity exploiting the vulnerability. To their credit the researchers disclosed the vulnerability responsibly and a patch was available before disclosure occurred,” explained Cisco’s Nick Biasini. “However, with money at stake bad guys worked quickly to reverse engineer the issue and successfully develop exploit code to take advantage of it. In today's reality you no longer have weeks or months to respond to these type of vulnerabilities, it's now down to days or hours and every minute counts.”
CVE-2017-9805 was patched by Apache Struts developers with the release of version 2.5.13, which also addresses a couple of less severe denial-of-service (DoS) vulnerabilities tracked as CVE-2017-9804 and CVE-2017-9793.
Cisco informed customers on Thursday that it’s working to determine which of its products are affected by these flaws. At the time of publication, only Cisco Emergency Responder is impacted, but not by the critical remote code execution weakness. The previously exploited Apache Struts 2 vulnerability, tracked as CVE-2017-5638, affected more than 20 Cisco products.
In the meantime, Struts developers released another update, version 2.3.34, which addresses an additional remote code execution vulnerability tracked as CVE-2017-12611. However, this vulnerability, related to Freemarker tags, has been classified as having moderate severity.
Exploit Available for Critical Apache Struts Vulnerability
6.9.2017 securityweek Exploit
The latest version of Apache Struts 2 addresses several vulnerabilities, including a critical remote code execution flaw for which an exploit was created within hours after the release of a patch.
Apache Struts is a free and open-source framework designed for creating modern Java web applications. The framework is reportedly used by at least 65 percent of Fortune 100 companies, and they could all be exposed to attacks due to a recently discovered security hole.
Researchers at lgtm, a company that provides code analysis solutions, discovered that all versions of Apache Struts released since 2008 are affected by a severe vulnerability related to the REST communication plugin.
The Apache Struts group has described the flaw, tracked as CVE-2017-9805, as a potential remote code execution issue when the REST plugin is used with the XStream handler for XML payloads.
The security hole exists due to the way Struts deserializes untrusted data. Serialization is the process where an object is converted to a stream of bytes in order to store or transmit that object to memory or a file. The process in which serialized data is extracted is called deserialization.
Deserialization can introduce serious security problems if not handled properly, as demonstrated by the significant number of vulnerabilities discovered in the past years, including in Android, Java application servers, the Java implementation of Adobe’s Action Message Format (AMF3), and PayPal.
The CVE-2017-9805 vulnerability was reported to the Apache Struts team on July 17 and it was patched on Tuesday with the release of Struts 2.5.13. Users have been advised to update their installations as soon as possible.
While lgtm has not published its exploit in order to give organizations time to update their Apache Struts 2 components, an exploit and a module for the Metasploit pentesting tool have already been made available. Given the popularity of Apache Struts, attacks in the wild leveraging the vulnerability will likely be seen in the next days.
“The Struts framework is used by an incredibly large number and variety of organizations. This vulnerability poses a huge risk, because the framework is typically used for designing publicly-accessible web applications,” explained Man Yue Mo, one of the lgtm researchers who discovered the flaw. “Struts is used in several airline booking systems as well as a number of financial institutions who use it in internet banking applications. On top of that, it is incredibly easy for an attacker to exploit this weakness: all you need is a web browser. Organizations who use Struts should upgrade their components immediately.”
This is the second critical vulnerability found in Apache Struts 2 this year. The first flaw, CVE-2017-5638, has been exploited in the wild since March.
Hackers exploited an Instagram flaw access celebrity profile data
1.9.2017 securityaffairs Exploit
An Instagram flaw allowed hackers to access profile information for high-profile users, the incident was confirmed by the company.
Instagram has recently suffered a possibly serious data breach with hackers gaining access to the phone numbers and email addresses for many “high-profile” users.
Hackers recently accessed personal information of “high-profile” users, including phone numbers and email addresses.
The stolen data could be used by hackers to target victims with social engineering attack aimed to access their accounts and leak their video and photos.
The data breach affected a number of Instagram service, Facebook-owned company has notified all of its verified users the hack.
An unknown hacker has exploited a bug in the application and accessed some of their profile data.
The vulnerability affects the Instagram application programming interface (API) that is used to interact with other apps.

The company did not provide details about the flaw exploited by the hacker, the company has promptly patched it and started an investigation into the incident.
“We recently discovered that one or more individuals obtained unlawful access to a number of high-profile Instagram users’ contact information—specifically email address and phone number—by exploiting a bug in an Instagram API,” reads a statement issued by Instagram.
“No account passwords were exposed. We fixed the bug swiftly and are running a thorough investigation.”
The company did not reveal the name of the high-profile users that have been affected by the data breach. Experts speculate that the recent hack of Selena Gomez’s Instagram account was linked to the flaw exploited by the hacker, the company did comment the hack.
The company notified all verified users of the hack via an email and also warned of possible phishing and social engineering attacks via email, phone calls, and text messages.
Let me suggest to enable two-factor verification on your accounts, start adopting strong passwords, don’t share same credentials on different accounts, be vigilant on suspicious and unsolicited emails.
Simple Exploit Allows Attackers to Modify Email Content — Even After It's Sent!
24.8.2017 thehackernews Exploit
Modify Email Content — Even After It's Sent
Security researchers are warning of a new, easy-to-exploit email trick that could allow an attacker to turn a seemingly benign email into a malicious one after it has already been delivered to your email inbox.
Dubbed Ropemaker (stands for Remotely Originated Post-delivery Email Manipulation Attacks Keeping Email Risky), the trick was uncovered by Francisco Ribeiro, the researcher at email and cloud security firm Mimecast.
A successful exploitation of the Ropemaker attack could allow an attacker to remotely modify the content of an email sent by the attacker itself, for example swapping a URL with the malicious one.
This can be done even after the email has already been delivered to the recipient and made it through all the necessary spam and security filters, without requiring direct access to the recipient’s computer or email application, exposing hundreds of millions of desktop email client users to malicious attacks.
Ropemaker abuses Cascading Style Sheets (CSS) and Hypertext Markup Language (HTML) that are fundamental parts of the way information is presented on the Internet.
"The origin of Ropemaker lies at the intersection of email and Web technologies, more specifically Cascading Style Sheets (CSS) used with HTML," Mimecast's Senior Product Marketing Manager Matthew Gardiner writes in a blog post.
"While the use of these web technologies has made email more visually attractive and dynamic relative to its purely text-based predecessor, this has also introduced an exploitable attack vector for email."
Since CSS is stored remotely, researchers say an attacker can change the content of an email through remotely initiated changes made to the desired 'style' of the email that is then retrieved remotely and presented to the user, without the recipient, even tech savvy users, knowing about it.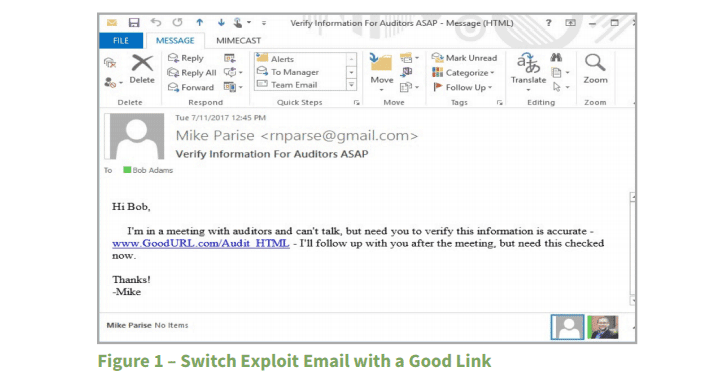
According to the researchers, the Ropemaker attack could be leveraged depending upon the creativity of the threat actors.
For instance, attackers could replace a URL that originally directed the user to a legitimate website by a malicious one that sends the user to a compromised site designed to infect users with malware or steal sensitive info, such as their credentials and banking details.
While some systems are designed to detect the URL switch preventing users from opening up the malicious link, other users could be left at a security risk.
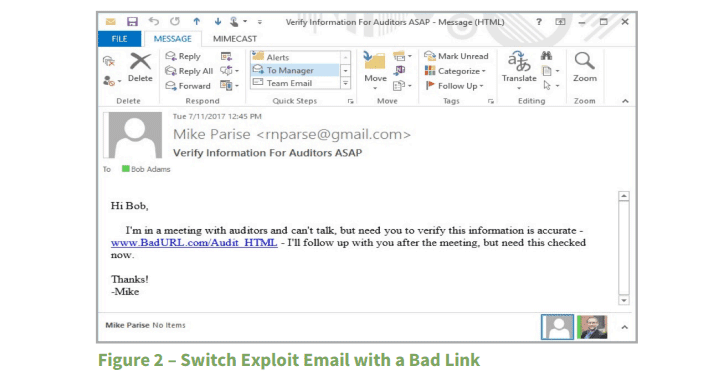
Another attack scenario, called "Matrix Exploit" by the Mimecast, is more sophisticated than the "Switch Exploit", and therefore much harder to detect and defend against.
In a Matrix Exploit attack, attackers would write a matrix of text in an email and then use the remote CSS to selectively control what is displayed, allowing the attacker to display whatever they want—including adding malicious URLs into the body of the email.
This attack is harder to defend against because the initial email received by the user does not display any URL, most software systems will not flag the message as malicious.
"Since the URL is rendered post-delivery, an email gateway solution such as Mimecast cannot find, rewrite, or inspect the destination site on-click, because at the time of delivery there would be no URL to detect," the report reads. "To do so would require the interpretation of CSS files, which is beyond the scope of current email security systems."
Although the security firm has not detected the Ropemaker attack in the wild, it believes that this doesn't mean for sure the attack is "not being used somewhere outside the view of Mimecast."
According to the security firm, Ropemaker could be used by hackers to bypass most common security systems and trick even the tech savvy users into interacting with a malicious URL.
To protect themselves from such attacks, users are recommended to rely on web-based email clients like Gmail, iCloud and Outlook, which aren't affected by Ropemaker-style CSS exploits, according to Mimecast.
However, email clients like the desktop and mobile version of Apple Mail, Microsoft Outlook, and Mozilla Thunderbird are all vulnerable to the Ropemaker attack.
A Company Offers $500,000 For Secure Messaging Apps Zero-Day Exploits
24.8.2017 thehackernews Exploit
Secure Messaging Apps Zero-Day Exploits
How much does your privacy cost?
It will soon be sold for half a Million US dollars.
A controversial company specialises in acquiring and reselling zero-day exploits is ready to pay up to US$500,000 for working zero-day vulnerabilities targeting popular secure messenger applications, such as Signal, Telegram and WhatsApp.
Zerodium announced a new pricing structure on Wednesday, paying out $500,000 for fully functional remote code execution (RCE) and local privilege escalation (LPE) vulnerabilities in Signal, WhatsApp, iMessage, Viber, Facebook Messenger, WeChat, and Telegram.
The payouts for all these secure messengers have been increased after tech companies introduced end-to-end encryption in their apps, making it more difficult for anyone to compromise their messaging platforms.
The same payout is offered for remote code execution and local privilege escalation security flaws in default mobile email applications.
Launched in 2015, Zerodium is a Washington, DC-based premium exploit acquisition platform by the infamous French-based company Vupen that buys and sells zero-day exploits to government agencies around the world.
The maximum bounty offered by the company remains for Apple's iOS devices with $1.5 million offered to anyone who can pull off a remote jailbreak of iOS devices without any user interaction, and $1 million for those that require user interaction.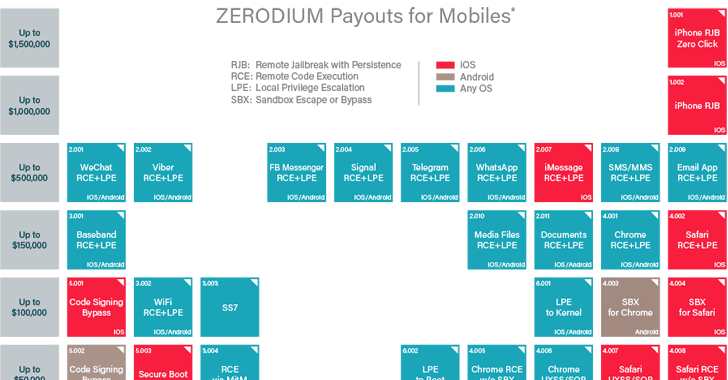
This payout was set last year when Zerodium raised the price for a remote iOS 10 jailbreaks from $1 Million to $1.5 Million, which is more than seven times what Apple is offering (up to $200,000) for iOS zero-days via its bug bounty program.
Zerodium Zero-Day Hit-list:
Zerodium's payout for other new exploit categories for servers and desktop computers include:
Up to $300,000 for a Windows 10 exploit that requires no user interaction
Up to $150,000 for Apache Web Server
Up to $100,000 for Microsoft Outlook
Up to $80,000 for Mozilla Thunderbird
Up to $80,000 for VMware escapes
Up to $30,000 for USB code execution
Zerodium has also raised the prices the company will pay for a range of other exploits, which include:
Chrome RCE and LPE for Windows—from $80,000 to $150,000
PHP Web programming language RCE—from $50,000 to $100,000
RCE in OpenSSL crypto library used to implement TLS—from $50,000 to $100,000
Microsoft Exchange Server RCE—from $40,000 to $100,000
RCE and LPE in the TOR version of Firefox for Linux—from $30,000 to $100,000
RCE and LPE in the TOR version of Firefox for Windows—from $30,000 to $80,000
The zero-day market has long been a lucrative business for private firms that regularly offer more payouts for undisclosed security vulnerabilities than big technology companies.
Companies like Zerodium and Exodus Intelligence who deal in zero-days are the primary cause of incidents like WannaCry and NotPetya, wherein unpatched vulnerabilities held by NSA for years were used after a notorious hacking group, called Shadow Brokers leaked them in public.
Hackers will get the payout within a week of submitting the zero-day vulnerabilities along with a working proof-of-concept, though we recommend you to submit them to the affected vendors because it's a matter of time when some black hat finds and uses them against you and wide audience.
Zerodium Offers $500,000 For Messaging, Email App Exploits
24.8.2017 securityweek Exploit
Zerodium has made some changes to its exploit acquisition program and the company is now offering up to $500,000 for remote code execution and privilege escalation vulnerabilities affecting popular instant messaging and email applications.
The firm has decided to publish separate payout lists for mobile device exploits and desktop/server exploits. A remote jailbreak with no user interaction for iPhone is still worth up to $1.5 million, and up to $1 million can be earned for a similar exploit that involves some user interaction (e.g. clicking on a link or opening a file).
One of the most important changes to Zerodium’s program is the addition of email and instant messaging exploits. The company is prepared to offer up to half a million dollars for WeChat, Viber, Facebook Messenger, Signal, Telegram, WhatsApp and iMessage remote code execution and local privilege escalation exploits on Android and iOS.
The same amount is being offered for SMS/MMS flaws and exploits targeting default email apps on Android and iOS.
New entries in the mobile category also include baseband, and media file and document vulnerabilities that can be leveraged for remote code execution and privilege escalation. These exploits can earn up to $150,000.
Sandbox escapes, code signing bypass, kernel privilege escalation, SS7, and Wi-Fi exploits can earn up to $100,000. Zerodium is also prepared to pay a five-figure sum for other mobile-related exploits.
In the desktop and server systems category, the list of new entries includes a payout of up to $300,000 for Windows 10 remote code execution exploits that require no user interaction. Apache Web Server and Microsoft IIS code execution exploits are worth up to $150,000.
The amount of money Zerodium is prepared to pay for Chrome, PHP, OpenSSL, Microsoft Exchange Server, Firefox, Tor, Office, WordPress and antivirus exploits has increased considerably. However, the company has decided to reduce its reward for antivirus privilege escalation flaws from $40,000 to only $10,000.
While Adobe and other tech giants plan to kill Flash Player in the next couple of years, Zerodium is still prepared to offer up to $100,000 for exploits targeting the application.
Neptune Exploit Kit Used to Deliver Monero Miner
22.8.2017 securityweek Exploit
Cybercriminals have been using the Neptune exploit kit to deliver cryptocurrency miners via malvertising campaigns, FireEye reported on Tuesday.
Neptune, whose arrival was detailed by researchers in January, is also known as Terror, Blaze and Eris. It was initially considered a variant of the Sundown exploit kit due to many code similarities.
Exploit kit activity has been declining since the disappearance of Angler and Neutrino. Sundown also went silent and the infosec community managed to delivered a significant blow to the infrastructure used by RIG.
Neptune has gained popularity and it continues to be used in malvertising campaigns, particularly ones that aim to deliver cryptocurrency miners. Several changes have been spotted recently by FireEye in Neptune attacks, including URI patterns, landing pages, malvertising campaigns and payloads.
The new URI patterns were first observed by FireEye in mid-July. The attackers have been abusing a legitimate pop-up ad service (present in Alexa’s Top 100) to deliver malware via fake advertisements for hiking clubs. The malicious websites imitate real domains, often using the same domain name with a .club suffix instead of .com (e.g. highspirittreks.com vs highspirittreks.club). One of the domains used to redirect users to the exploit kit landing pages also mimics a YouTube to MP3 online converter.
The ads linked to this Neptune exploit kit campaign have been typically served on popular torrent and hosting websites.
Once victims are taken to the landing page, the EK exploits three Internet Explorer and two Adobe Flash Player vulnerabilities to deliver malware. None of the exploits used by Neptune are new – they target vulnerabilities disclosed between 2014 and 2016.
The payload delivered in the campaign is a piece of malware that mines for Monero (XMR), a cryptocurrency currently worth roughly $86 per unit.
The regions most affected by the campaign are South Korea (29%), Europe (19%), Thailand (13%), Middle East (13%) and the United States (10%).
“Despite an observable decline in exploit kit activity, users are still at risk, especially if they have outdated or unpatched software,” FireEye warned. “This threat is especially dangerous considering drive-by exploit kits (such as Neptune EK) can use malvertisements to seamlessly download payloads without ever alerting the user.”
Leaked Exploits Fueled Millions of Attacks in Q2: Kaspersky
18.8.2017 securityweek Exploit
The public availability of new exploit packages has fueled millions of new attacks on popular applications during the second quarter of 2017, a recent report from Kaspersky Lab reveals.
The Moscow-based security company said that it blocked more than five million attacks involving in-the-wild exploits during the three-month period, but the actual number of incidents should be significantly higher. Highly effective as they don’t usually require user interaction, attacks leveraging exploits can result in malicious code being delivered to the targeted machines without the user suspecting anything.
According to Kaspersky’s IT threat evolution Q2 2017 report, the publication by the Shadow Brokers hacker group of several tools and exploits supposedly associated with the National Security Agency had grave consequences during the quarter. Included in the leak were exploits such as EternalBlue and EternalRomance, which fueled a large wave of malicious attacks.
Despite the fact that Microsoft had patched the vulnerabilities exploited by these tools one month before they were made public, “in the second quarter of 2017 only Kaspersky Lab blocked more over five million attempted attacks involving network exploits from the archive. And the average number of attacks per day was constantly growing: 82% of all attacks were detected in the last 30 days,” the security company says.
The figure is not surprising, considering that EternalBlue was used in a massive, global WannaCry ransomware attack in May. In June, the same exploit was used for lateral movement in an attack involving the NotPetya wiper, which resulted in hundreds of millions in losses. The exploit was employed in various other malware attacks as well.
One other exploit that fueled a large number of attacks was leveraging the CVE-2017-0199 vulnerability in Microsoft Office. Initially a zero-day abused by threat actors, Microsoft addressed the bug in early April, but cybercriminals discovered new ways to leverage it: through the use of PowerPoint Slide Shows. Despite the fix, the number of attacked users peaked at 1.5 million in April, Kaspersky says.
The security company says it detected and repelled 342,566,061 malicious attacks from online resources located in 191 countries during Q2, and that it also identified 33,006,783 unique malicious URLs. In Q1, the company detected 479,528,279 malicious attacks.
Kaspersky also detected attempted infections with financial malware on 224,675 user computers (down from 288,000 during the previous three months), and blocked crypto-ransomware attacks on 246,675 unique computers (up from 240,799 in Q1). The security firm detected 185,801,835 unique malicious and potentially unwanted objects in Q2 (up from 174,989,956 the previous quarter).
In terms of banking malware attacks, Germany emerged as the most affected country in Q2 (these incidents include banking Trojans and ATM and POS-malware). Zbot, Nymaim, and Emotet were the top 3 banking malware families in the timeframe. WannaCry, Locky, and Cerber were the most spread cryptor families.
Mobile malware was also active in the timeframe. The security firm discovered a Trojan called Dvmap being distributed via Google Play, and also observed attackers attempting to upload new apps containing the malicious Ztorg module to the storefront. The Svpeng banking Trojan remained the most popular mobile threat.
Overall, Kaspersky detected 1,319,148 malicious installation packages during Q2, and reveals that adware registered the biggest growth during the timeframe. Trojan-SMS malware experienced the second-highest growth rate, while spyware registered the biggest decline. Iran was the top country attacked by mobile malware, followed by China, while the United States emerged as the most attacked by mobile ransomware.
“The threat landscape of Q2 provides yet another reminder that a lack of vigilance is one of the most significant cyber dangers. While vendors patch vulnerabilities on a regular basis, many users don’t pay attention to this, which results in massive-scale attacks once the vulnerabilities are exposed to the broad cybercriminal community,” Alexander Liskin, security expert at Kaspersky Lab, said.
New "Disdain" Exploit Kit Spotted on Underground Forums
15.8.2017 securityweek Exploit
A new exploit kit (EK) has emerged recently on underground forums, where a malware developer is advertising it starting at just $80.
Called Disdain and discovered by malware analyst David Montenegro, the toolkit is available for rent on a daily, weekly, or monthly basis, priced at $80, $500, and $1,400, respectively. Security researchers have already managed to track the advert for the EK and learn more about its alleged capabilities.
According to Disdain’s author, the main features of the toolkit include domain rotator, RSA key exchange for exploits, panel server untraceable from payload server, geolocation, browser & IP tracking, and domain scanning capabilities.
The malware developer claims the toolkit can exploit over a dozen vulnerabilities in Firefox (CVE-2017-5375, CVE-2016-9078, CVE-2014-8636, CVE-2014-1510, CVE-2013-1710), Internet Explorer (CVE-2017-0037, CVE-2016-7200 (Edge as well), CVE-2016-0189, CVE-2015-2419, CVE-2014-6332, CVE-2013-2551), Flash (CVE-2016-4117, CVE-2016-1019, CVE-2015-5119), and Cisco Web Ex (CVE-2017-3823).
There has not been a malware distribution campaign fueled by this exploit kit found to date, likely because Disdain hasn’t been around long enough to prove it is a viable tool. Furthermore, its author, who goes by the name of Cehceny, doesn’t have a good reputation among cybercriminals and is considered a scammer on at least one underground hacking forum, BleepingComputer notes.
Although no botnet or malvertising campaign is redirecting traffic to Disdain’s landing pages at the moment, the toolkit could turn into a major threat if miscreants start employing it. As soon as users are redirected to one of the exploit kit’s pages, the toolkit can scan the potential victim’s browser and attempt to exploit one of the discovered vulnerabilities to install malware.
Disdain includes a large number of new exploits, which could help it gain traction, especially since the exploit kit landscape has been greatly shaken over the past year, starting with Angler and Nuclear, both of which went down in the first half of last year.
Exploit kit activity this year has been only a fraction of what it was in early 2016, and continues to diminish as more toolkits are taken down and very few new players observed. Cybercriminals, however, are turning to other methods of distributing malware, including spam emails and other types of attacks.
The Disdain exploit kit appears in the threat landscape
15.8.2017 securityaffairs Exploitvvvvvvvv
The Disdain exploit kit is available for rent on a daily, weekly, or monthly basis for prices of $80, $500, and $1,400 respectively.
The security researcher David Montenegro discovered a new exploit kit dubbed Disdain that is offered for rent on underground hacking forums by a malware developer using the pseudonym of Cehceny.
View image on TwitterView image on TwitterView image on Twitter
Follow
David Montenegro @CryptoInsane
Disdain Exploit Kit - New Exploit Kit up for sale in Underground Forum - Copy && Paste .. 🤔.. Beps Exploit Kit .. 🤔.. $./I_love_weekends.py
7:16 AM - Aug 9, 2017
1 1 Reply 18 18 Retweets 27 27 likes
Twitter Ads info and privacy
The Disdain exploit kit is available for rent on a daily, weekly, or monthly basis for prices of $80, $500, and $1,400 respectively.

After the Angler EK and Nuclear EK disappeared from the threat landscape, the Sundown EK conquered the criminal underground.
With the Sundown EK has been inactive since early this year, the Terror EK is being very popular in the cybercriminal ecosystem. The Disdain exploit kit appears very cheap compared to other exploit kits such as Nebula EK, that goes for rent on a daily, weekly, or monthly basis for prices of $100, $600, and $2,000 respectively.
According to security experts at Intsights that found an ad of the Disdain exploit kit on a Russian-speaking forum, its main features are:
Domain Rotator
RSA Key exchange for Exploits
Panel server is untraceable from Payload server
Geolocation available
Browser & IP tracking
Scan domain
When users visit a website hosting the Disdain exploit kit, it gathers info on the specific browser used by the visitor and attempts to use one of the exploits to deliver a malware on the victim’s machine.
Even is the Disdain exploit kit includes a limited number of exploits because it is very young, most of them are newer exploits. Below is the full list of exploits advertise by the author Cehceny:
CVE-2017-5375 – FF
CVE-2017-3823 – Extension (Cisco Web Ex)
CVE-2017-0037 – IE a
CVE-2016-9078 – FF
CVE-2016-7200 – EDGE + IE a
CVE-2016-4117 – FLASH
CVE-2016-1019 – FLASH
CVE-2016-0189 – IE
CVE-2015-5119 – FLASH
CVE-2015-2419 – IE
CVE-2014-8636 – FF
CVE-2014-6332 – IE
CVE-2014-1510 – FF
CVE-2013-2551 – IE
CVE-2013-1710 – FF
According to the experts at Bleepingcomputer, currently, there is no malvertising campaign or botnet leveraging the Disdain exploit kit because Cehceny is considered a scammer on at least one major underground hacking forum.
“The Disdain ad was first spotted last week. Currently, there is no malvertising campaign or botnet redirecting traffic to any Disdain “landing page,” according to a security researcher who spoke with Bleeping Computer about Disdain but did not want to reveal his name.” wrote Catalin Cimpanu.
“One reason why we haven’t seen any active campaign might be that Disdain’s author — Cehceny — is currently banned and marked as a “ripper” (scammer) on at least one major underground hacking forum.”
Looking at exploit kit market we are assisting to a rapid decline due to the difficulty of finding exploitable flaws in modern browsers.
Currently, most popular exploit kits are RIG, Rig-V, Terror, Magnitude, Kaixin, and Nebula.
Stay tuned!
Exploited Windows Flaws Affect Siemens Medical Imaging Products
4.8.2017 securityweek Exploit
Siemens has informed customers that some of its molecular imaging products are exposed to remote attacks due to vulnerabilities affecting Windows and other third-party components.
One advisory, published by both Siemens and ICS-CERT, warns of two critical Windows vulnerabilities that allow a remote, unauthenticated attacker to execute arbitrary code. The security holes impact Siemens Healthineers’ PET/CT and SPECT/CT medical imaging products running on Windows XP.
One of the flaws, CVE-2008-4250, is a critical Server service issue that had been exploited in targeted attacks when Microsoft patched it back in 2008. According to one researcher, it has also been leveraged in the past years to deliver the Conficker malware.Siemens medical imaging device
The second vulnerability is the more recent CVE-2017-7269, a buffer overflow vulnerability in Internet Information Services (IIS) 6.0 that has been exploited in attacks since at least July 2016. Microsoft has released a patch for this vulnerability on all its operating systems, including Windows XP due to the leak by Shadow Brokers of an NSA-linked exploit dubbed ExplodingCan.
Siemens says it’s working on releasing updates for the affected products and, in the meantime, it has advised customers to disconnect the devices from the network or deploy them in secure network segments.

While support for Windows XP ended in April 2014, the fact that Siemens has warned customers using this old version of Microsoft’s operating system is not surprising. Windows XP is still widely used, including in the healthcare sector.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
A second advisory released by Siemens and ICS-CERT warns of other vulnerabilities affecting the molecular imaging products when running on Windows 7.
Siemens discovered that products running on Windows 7 are exposed to attacks due to four critical remote code execution vulnerabilities that can be exploited by an unauthenticated hacker. Three of them, discovered in 2015, affect Persistent Systems Accelerite Radia Client Automation (formerly HP Client Automation).
The fourth vulnerability, CVE-2015-1635, affects Windows and it was patched by Microsoft in April 2015. While the flaw can be exploited for remote code execution, researchers spotted denial-of-service (DoS) attacks leveraging the weakness shortly after it was fixed.
Siemens is also preparing patches for these security holes. Until the fixes become available, customers have been advised to take measures to prevent potential attacks.