Exploit Articles - H 2020 1 2 3 4 5 6 7 Exploit List - H 2021 2020 2019 2018 1 Exploit blog Exploit blog
Election Systems Under Attack via Microsoft Zerologon Exploits
14.10.20 Exploit Threatpost
Cybercriminals are chaining Microsoft’s Zerologon flaw with other exploits in order to infiltrate government systems, putting election systems at risk, a new CISA and FBI advisory warns.
U.S. government officials have warned that advanced persistent threat actors (APTs) are now leveraging Microsoft’s severe privilege-escalation flaw, dubbed “Zerologon,” to target elections support systems.
Days after Microsoft sounded the alarm that an Iranian nation-state actor was actively exploiting the flaw (CVE-2020-1472), the Cybersecurity Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) published a joint advisory warning of further attacks.
The advisory details how attackers are chaining together various vulnerabilities and exploits – including using VPN vulnerabilities to gain initial access and then Zerologon as a post-exploitation method – to compromise government networks.
Threatpost Webinar Promo Retail Security
Click to Register!
“This recent malicious activity has often, but not exclusively, been directed at federal and state, local, tribal and territorial (SLTT) government networks,” according to the security advisory. “Although it does not appear these targets are being selected because of their proximity to elections information, there may be some risk to elections information housed on government networks.”
With the U.S. November presidential elections around the corner – and cybercriminal activity subsequently ramping up to target election infrastructure and presidential campaigns – election security is top of mind. While the CISA and FBI’s advisory did not detail what type of elections systems were targeted, it did note that there is no evidence to support that the “integrity of elections data has been compromised.”
Microsoft released a patch for the Zerologon vulnerability as part of its August 11, 2020 Patch Tuesday security updates. Exploiting the bug allows an unauthenticated attacker, with network access to a domain controller, to completely compromise all Active Directory identity services, according to Microsoft.
Despite a patch being issued, many companies have not yet applied the patches to their systems – and cybercriminals are taking advantage of that in a recent slew of government-targeted attacks.
The CISA and FBI warned that various APT actors are commonly using a Fortinet vulnerability to gain initial access to companies. That flaw (CVE-2018-13379) is a path-traversal glitch in Fortinet’s FortiOS Secure Socket Layer (SSL) virtual private network (VPN) solution. While the flaw was patched in April 2019, exploitation details were publicized in August 2019, opening the door for attackers to exploit the error.
Other initial vulnerabilities being targeted in the attacks include ones in Citrix NetScaler (CVE-2019-19781), MobileIron (CVE-2020-15505), Pulse Secure (CVE-2019-11510), Palo Alto Networks (CVE-2020-2021) and F5 BIG-IP (CVE-2020-5902).
After exploiting an initial flaw, attackers are then leveraging the Zerologon flaw to escalate privileges, researchers said. They then use legitimate credentials to log in via VPN or remote-access services, in order to maintain persistence.
“The actors are leveraging CVE-2020-1472 in Windows Netlogon to escalate privileges and obtain access to Windows AD servers,” they said. “Actors are also leveraging the opensource tools such as Mimikatz and the CrackMapExec tool to obtain valid account credentials from AD servers.”
The advisory comes as exploitation attempts against Zerologon spike, with Microsoft recently warned of exploits by an advanced persistent threat (APT) actor, which the company calls MERCURY (also known as MuddyWater, Static Kitten and Seedworm). Cisco Talos researchers also recently warned of a spike in exploitation attempts against Zerologon.
Earlier in September, the stakes got higher for risks tied to the bug when four public proof-of-concept exploits for the flaw were released on Github. This spurred the Secretary of Homeland Security to issue a rare emergency directive, ordering federal agencies to patch their Windows Servers against the flaw by Sept. 2.
CISA and the FBI stressed that organizations should ensure their systems are patched, and adopt an “assume breach” mentality. Satnam Narang, staff research engineer with Tenable, agreed, saying that “it seems clear that Zerologon is becoming one of the most critical vulnerabilities of 2020.”
“Patches are available for all of the vulnerabilities referenced in the joint cybersecurity advisory from CISA and the FBI,” said Narang in a Monday analysis. “Most of the vulnerabilities had patches available for them following their disclosure, with the exception of CVE-2019-19781, which received patches a month after it was originally disclosed.”
Microsoft Says Iranian Hackers Exploiting Zerologon Vulnerability
6.10.20 Exploit Securityweek
The Iran-linked threat actor known as MuddyWater is actively targeting the Zerologon vulnerability in Windows Server, Microsoft warns.
Also known as Seedworm, MERCURY, and Static Kitten, and initially analyzed in 2017, MuddyWater is mainly focused on organizations in the Middle East and regions nearby. Highly active, the group was observed expanding its target list and leveraging a broad and varied toolset.
Although further details on the threat actor’s operations emerged last year (after an unknown entity published documents on multiple Iranian groups), and despite security researchers’ scrutiny, MuddyWater continues to evolve its strategies.
According to Microsoft, one of the latest changes in the group’s tactics is the adoption of exploits for Zerologon, a Netlogon remote protocol (MS-NRPC) vulnerability that was addressed in August 2020.
By exploiting the bug, an unauthenticated attacker could gain domain administrator access, resulting in full takeover.
“MSTIC has observed activity by the nation-state actor MERCURY using the CVE-2020-1472 exploit (ZeroLogon) in active campaigns over the last 2 weeks. We strongly recommend patching,” Microsoft said on Twitter.
Both Microsoft and CISA previously issued alerts on attackers targeting the vulnerability, urging administrators to apply the available patches as soon as possible, to all domain controllers in their environments.
In fact, CISA even issued an Emergency Directive requiring all federal agencies to apply the patches immediately. Samba too released fixes for the bug.
The patching of this vulnerability will be done in two stages, Microsoft has revealed. The initial one involves applying the August 2020 fixes, while the second one is an enforcement phase that will start on February 9, 2021.
Last week, Microsoft also announced that the exploitation of Zerologon is now being detected by Microsoft Defender for Identity (previously Azure Advanced Threat Protection) and Microsoft 365 Defender (previously Microsoft Threat Protection).
Researchers Fingerprint Exploit Developers Who Help Several Malware Authors
2.10.20 Exploit Virus Thehackernews
Writing advanced malware for a threat actor requires different groups of people with diverse technical expertise to put them all together. But can the code leave enough clues to reveal the person behind it?
To this effect, cybersecurity researchers on Friday detailed a new methodology to identify exploit authors that use their unique characteristics as a fingerprint to track down other exploits developed by them.
By deploying this technique, the researchers were able to link 16 Windows local privilege escalation (LPE) exploits to two zero-day sellers "Volodya" (previously called "BuggiCorp") and "PlayBit" (or "luxor2008").
"Instead of focusing on an entire malware and hunting for new samples of the malware family or actor, we wanted to offer another perspective and decided to concentrate on these few functions that were written by an exploit developer," Check Point Research's Itay Cohen and Eyal Itkin noted.
Fingerprinting an Exploit Writer's Characteristics
The idea, in a nutshell, is to fingerprint an exploit for specific artifacts that can uniquely tie it to a developer. It could be in using hard-coded values, string names, or even how the code is organized and certain functions are implemented.
Check Point said their analysis began in response to a "complicated attack" against one of its customers when they encountered a 64-bit malware executable that exploited CVE-2019-0859 to gain elevated privileges.
Noticing the fact that the exploit and the malware were written by two different sets of people, the researchers used the binary's properties as a unique hunting signature to find at least 11 other exploits developed by the same developer named "Volodya" (or "Volodimir").
"Finding a vulnerability, and reliably exploiting it, will most probably be done by specific teams or individuals who specialize in a particular role. The malware developers for their part don't really care how it works behind the scenes, they just want to integrate this [exploits] module and be done with it," the researchers said.
Interestingly, Volodya — likely of Ukrainian origin — has been previously linked to selling Windows zero-days to cyberespionage groups and crimeware gangs for anywhere between $85,000 to $200,000.
Chief among them was an LPE exploit that leveraged a memory corruption in "NtUserSetWindowLongPtr" (CVE-2016-7255), which has been widely used by ransomware operators like GandCrab, Cerber, and Magniber. It's now believed that Volodya advertised this LPE zero-day on the Exploit.in cybercrime forum in May 2016.
In all, five zero-day and six one-day exploits were identified as developed by Volodya over a period of 2015-2019. Subsequently, the same technique was employed to identify five more LPE exploits from another exploit writer known as PlayBit.
An Extensive Clientele
Stating the exploit samples shared code level similarities to grant SYSTEM privileges to the desired process, the researchers said, "both of our actors were very consistent in their respective exploitation routines, each sticking to their favorite way."
What's more, Volodya also appears to have switched up his tactics during the intervening years, with the developer shifting from selling the exploits as embeddable source code in the malware to an external utility that accepts a specific API.
Besides ransomware groups, Volodya has been found to cater to an extensive clientele, including the Ursnif banking trojan, and APT groups such as Turla, APT28, and Buhtrap.
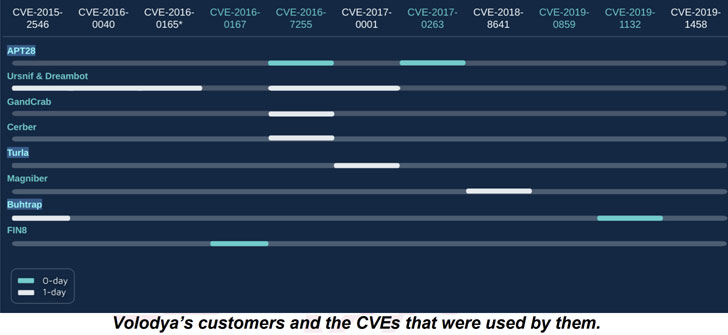
"The APT customers, Turla, APT28, and Buhtrap, are all commonly attributed to Russia and it is interesting to find that even these advanced groups purchase exploits instead of developing them in-house," Check Point observed in its analysis. "This is another point which further strengthens our hypothesis that the written exploits can be treated as a separate and distinct part of the malware."
With cyberattacks expanding in scope, frequency, and magnitude, using an exploit developer's code signature as a means to track down bad actors could provide valuable insight into the black exploit market.
"When Check Point finds a vulnerability, we demonstrate its severity, report it to the appropriate vendor, and make sure it's patched, so it doesn't pose a threat," Cohen said. "However, for individuals trading these exploits, it's a completely different story. For them, finding the vulnerability is just the beginning. They need to reliably exploit it on as many versions as possible, in order to monetize it to a customer's satisfaction."
"This research provides insight into how that is achieved, and the buyers in this market, which often include nation-state actors. We believe that this research methodology can be used to identify additional exploit writers."
Microsoft Exchange Servers Still Open to Actively Exploited Flaw
1.10.20 Exploit Threatpost
Despite Microsoft issuing patches almost eight months ago, 61 percent of Exchange servers are still vulnerable.
Over half of exposed Exchange servers are still vulnerable to a severe bug that allows authenticated attackers to execute code remotely with system privileges – even eight months after Microsoft issued a fix.
The vulnerability in question (CVE-2020-0688) exists in the control panel of Exchange, Microsoft’s mail server and calendaring server. The flaw, which stems from the server failing to properly create unique keys at install time, was fixed as part of Microsoft’s February Patch Tuesday updates – and admins in March were warned that unpatched servers are being exploited in the wild by unnamed advanced persistent threat (APT) actors.
However, new telemetry found that out of 433,464 internet-facing Exchange servers observed, at least 61 percent of Exchange 2010, 2013, 2016 and 2019 servers are still vulnerable to the flaw.
“There are two important efforts that Exchange administrators and infosec teams need to undertake: verifying deployment of the update and checking for signs of compromise,” said Tom Sellers with Rapid7 in a Tuesday analysis.
Researchers warned in a March advisory that unpatched servers are being exploited in the wild by unnamed APT actors. Attacks first started in late February and targeted “numerous affected organizations,” researchers said. They observed attackers leverage the flaw to run system commands to conduct reconnaissance, deploy webshell backdoors and execute in-memory frameworks, post-exploitation.
Previously, in April, Rapid7 researchers found that more than 80 percent of servers were vulnerable; out of 433,464 internet-facing Exchange servers observed, at least 357,629 were open to the flaw (as of March 24). Researchers used Project Sonar, a scanning tool, to analyze internet-facing Exchange servers and sniff out which were vulnerable to the flaw.

Exchange build number distribution status for flaw. Credit: Rapid7
Sellers urged admins to verify that an update has been deployed. The most reliable method to do so is by checking patch-management software, vulnerability-management tools or the hosts themselves to determine whether the appropriate update has been installed, he said.
“The update for CVE-2020-0688 needs to be installed on any server with the Exchange Control Panel (ECP) enabled,” he said. “This will typically be servers with the Client Access Server (CAS) role, which is where your users would access the Outlook Web App (OWA).”
With the ongoing activity, admins should also determine whether anyone has attempted to exploit the vulnerability in their environment. The exploit code that Sellers tested left log artifacts in the Windows Event Log and the IIS logs (which contain HTTP server API kernel-mode cache hits) on both patched and unpatched servers: “This log entry will include the compromised user account, as well as a very long error message that includes the text invalid viewstate,” he said.
Admins can also review their IIS logs for requests to a path under /ecp (usually /ecp/default.aspx), Sellers said, These should contain the string __VIEWSTATE and __VIEWSTATEGENERATOR – and will have a long string in the middle of the request that is a portion of the exploit payload.
“You will see the username of the compromised account name at the end of the log entry,” he said. “A quick review of the log entries just prior to the exploit attempt should show successful requests (HTTP code 200) to web pages under /owa and then under /ecp.”
Cisco Patches Actively Exploited Flaws in Carrier-Grade Routers
30.9.20 Exploit Securityweek
Cisco this week released patches for two high-severity vulnerabilities in IOS XR software that have been actively exploited in attacks for over a month.
Tracked as CVE-2020-3566 and CVE-2020-3569 and featuring a CVSS score of 8.6, the two flaws were made public in late August, when Cisco revealed that hackers were already targeting them in attacks.
The two issues were identified in the Distance Vector Multicast Routing Protocol (DVMRP) feature of IOS XR and could be exploited without authentication to cause the Internet Group Management Protocol (IGMP) process to exhaust process memory and crash.
The bugs, Cisco explains, exist because IGMP packets are not handled correctly, meaning that crafted IGMP traffic can be sent to the affected devices to trigger them. A successful exploit would immediately crash the IGMP process or cause memory exhaustion, thus impacting the stability of other processes, including those of routing protocols.
“In the case of an immediate IGMP process crash, it is not necessary to manually restart the IGMP process because the system has already performed that action. This automated restart will recover the consumed memory,” the company notes in an advisory.
All Cisco devices running IOS XR are affected, “if an active interface is configured under multicast routing,” and if DVMRP traffic is being received, Cisco explains.
Administrators can use the show igmp interface and show igmp traffic commands to determine whether multicast routing is enabled and whether the device is receiving DVMRP traffic. Furthermore, they can employ rate limiter and access control methods to mitigate the memory exhaustion.
This week, Cisco announced that software updates designed to address these vulnerabilities are available for ASR9K-PX, ASR9K-X64, CRS, and NCS5500 platforms.
CISA Warns of Hackers Exploiting Zerologon Vulnerability
29.9.20 Exploit Securityweek
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert to warn of attackers actively targeting a recently addressed vulnerability in the Microsoft Windows Netlogon Remote Protocol (MS-NRPC).
Dubbed Zerologon, the security flaw is tracked as CVE-2020-1472 and was patched in August 2020. Earlier this month, CISA issued an Emergency Directive that required all federal agencies to install the patches within three days.
The vulnerability allows an unauthenticated attacker connected to a domain controller using Netlogon to gain domain administrator access. The attacker would need to leverage a specially crafted application running on a device on the network to successfully exploit the bug.
Samba issued patches for the bug too, and last week Microsoft revealed that it was seeing the first attempts to target the Zerologon flaw, and CISA was quick to issue an alert on such attacks as well.
“The Cybersecurity and Infrastructure Security Agency (CISA) is aware of active exploitation of CVE-2020-1472, an elevation of privilege vulnerability in Microsoft’s Netlogon. A remote attacker can exploit this vulnerability to breach unpatched Active Directory domain controllers and obtain domain administrator access,” the agency said.
CISA again underlined the need to apply the available patches, as that would prevent successful exploitation, and announced the release of a patch validation script that can help organizations identify unpatched Microsoft domain controllers.
“CISA urges administrators to patch all domain controllers immediately—until every domain controller is updated, the entire infrastructure remains vulnerable,” the agency said.
Hackers are using Zerologon exploits in attacks in the wild
24.9.20 Exploit Securityaffairs
Microsoft is warning of threat actors that are actively using the Windows Server Zerologon exploits in attacks in the wild.
Microsoft has published a series of Tweets to warn of attackers that are actively exploiting the Windows Server Zerologon in attacks in the wild. The IT giant is urging Windows administrators to install the released security updates as soon as possible.
Microsoft Security Intelligence
✔
@MsftSecIntel
Microsoft is actively tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon. We have observed attacks where public exploits have been incorporated into attacker playbooks.
569
3:29 AM - Sep 24, 2020
Twitter Ads info and privacy
404 people are talking about this
Microsoft Security Intelligence
✔
@MsftSecIntel
· 13h
Replying to @MsftSecIntel
Microsoft 365 customers can refer to the threat analytics report we published in Microsoft Defender Security Center. The threat analytics report contains technical details, mitigations, and detection details designed to empower SecOps to detect and mitigate this threat.
Microsoft Security Intelligence
✔
@MsftSecIntel
We'll continue to monitor developments and update the threat analytics report with latest info. We strongly recommend customers to immediately apply security updates for CVE-2020-1472. Microsoft 365 customers can use threat & vulnerability management data to see patching status.
40
3:29 AM - Sep 24, 2020
Twitter Ads info and privacy
21 people are talking about this
Microsoft also shared sample exploits IoCs [1, 2, 3], which are .NET executables with the filename ‘SharpZeroLogon.exe.’
Microsoft Security Intelligence
✔
@MsftSecIntel
· 13h
Replying to @MsftSecIntel
We'll continue to monitor developments and update the threat analytics report with latest info. We strongly recommend customers to immediately apply security updates for CVE-2020-1472. Microsoft 365 customers can use threat & vulnerability management data to see patching status.

Microsoft Security Intelligence
✔
@MsftSecIntel
Sample exploit IOCs (SHA-256): b9088bea916e1d2137805edeb0b6a549f876746999fbb1b4890fb66288a59f9d, 24d425448e4a09e1e1f8daf56a1d893791347d029a7ba32ed8c43e88a2d06439, c4a97815d2167df4bdf9bfb8a9351f4ca9a175c3ef7c36993407c766b57c805b
65
3:29 AM - Sep 24, 2020
Twitter Ads info and privacy
38 people are talking about this
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
Administrators of enterprise Windows Servers have to install the August 2020 Patch Tuesday to mitigate “unacceptable risk” posed by the flaw to federal networks.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
The only limitation on how to carry out a Zerologon attack is that the attacker must have access to the target network.
The flaw was discovered by researchers from the security firm Secura that also published technical details of the issue along with proof-of-concept exploits.
Researchers from BleepingComputer analyzed one of the samples and discovered that the exploit changes the NTLM hash of the domain controller to “31d6cfe0d16ae931b73c59d7e0c089c0”, which is an empty password.
Secura researchers also released a Python script that uses the Impacket library to test vulnerability for the Zerologon exploit, it could be used by admins to determine if their domain controller is still vulnerable.
Don’t waste time, patch your system now!
Windows Exploit Released For Microsoft ‘Zerologon’ Flaw
16.9.20 Exploit Threatpost
Security researchers and U.S. government authorities alike are urging admins to address Microsoft’s critical privilege escalation flaw.
Proof-of-concept (PoC) exploit code has been released for a Windows flaw, which could allow attackers to infiltrate enterprises by gaining administrative privileges, giving them access to companies’ Active Directory domain controllers (DCs).
The vulnerability, dubbed “Zerologon,” is a privilege-escalation glitch (CVE-2020-1472) with a CVSS score of 10 out of 10, making it critical in severity. The flaw was addressed in Microsoft’s August 2020 security updates. However, this week at least four public PoC exploits for the flaw were released on Github, and on Friday, researchers with Secura (who discovered the flaw) published technical details of the vulnerability.
“This attack has a huge impact: It basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain,” said researchers with Secura, in a Friday whitepaper. “The attack is completely unauthenticated: The attacker does not need any user credentials.”

The flaw stems from the Netlogon Remote Protocol, available on Windows domain controllers, which is used for various tasks related to user and machine authentication.
Specifically, the issue exists in the usage of AES-CFB8 encryption for Netlogon sessions. The AES-CFB8 standard requires that each “byte” of plaintext have a randomized initialization vector (IV), blocking attackers from guessing passwords. However, Netlogon’s ComputeNetlogonCredential function sets the IV to a fixed 16 bits – not randomized – meaning an attacker could control the deciphered text.
In a real-world attack, attackers could send a number of Netlogon messages in which various fields are filled with zeroes, allowing them to bypass these authentication measures, and access and change the computer password of the domain controller that is stored in the Active Directory (AD), researchers said.
“Due to incorrect use of an AES mode of operation it is possible to spoof the identity of any computer account (including that of the [Domain Controller] itself) and set an empty password for that account in the domain,” according to Secura researchers.

The Zerologon attack. Credit: Secura
Of note, in order to exploit this vulnerability, the attacker would need to launch the attack from a machine on the same local-area network (LAN) as their target – meaning they would already need a foothold inside the targeted network.
“A vulnerable client or DC exposed to the internet is not exploitable by itself,” according to researchers with Tenable in an analysis of the flaw. “The attack requires that the spoofed login works like a normal domain login attempt. Active Directory (AD) would need to recognize the connecting client as being within its logical topology, which external addresses wouldn’t have.”
However, if attackers are able to exploit the flaw, they can impersonate the identity of any machine on a network when attempting to authenticate to the Domain Controller – enabling further attacks, including the complete takeover of a Windows domain, researchers said.
“In a hypothetical attack, one could use this vulnerability to deploy ransomware throughout an organization and maintain a persistent presence if cleanup and restoration efforts miss any additional malicious scripts,” said Tenable researchers. “Organizations with network-accessible backups could end up with a perfect storm if a ransomware group destroys backups to increase their likelihood of payout from the victim organization.”
With at least four PoC exploits now available on GitHub, security researchers and U.S. government authorities alike are urging admins to ensure they apply Microsoft’s August patches. These patch address this problem by enforcing Secure Netlogon Remote Protocol (i.e. Netlogon signing and sealing) for all Windows servers and clients in the domain.
Microsoft for its part is addressing the vulnerability in a phased rollout. The initial deployment phase started with Windows updates being released on August 11, 2020, while the second phase, planned for the first quarter of 2021, will be an “enforcement phase.”
“The DCs will be placed in enforcement mode, which requires all Windows and non-Windows devices to use secure Remote Procedure Call (RPC) with Netlogon secure channel or to explicitly allow the account by adding an exception for any non-compliant device,” said Microsoft.
Feds Warn Nation-State Hackers are Actively Exploiting Unpatched Microsoft Exchange, F5, VPN Bugs
15.9.20 Exploit Threatpost
Monday’s CISA advisory is a staunch reminder for federal government and private sector entities to apply patches for flaws in F5 BIG-IP devices, Citrix VPNs, Pulse Secure VPNs and Microsoft Exchange servers.
The U.S. government is warning that Chinese threat actors have successfully compromised several government and private sector entities in recent months, by exploiting vulnerabilities in F5 BIG-IP devices, Citrix and Pulse Secure VPNs and Microsoft Exchange servers.
Patches are currently available for all these flaws – and in some cases, have been available for over a year – however, the targeted organizations had not yet updated their systems, leaving them vulnerable to compromise, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said in a Monday advisory. CISA claims the attacks were launched by threat actors affiliated with the Chinese Ministry of State Security.
Threatpost Webinar Promo Bug Bounty
Click to Register
“CISA and the FBI also recommend that organizations routinely audit their configuration and patch management programs to ensure they can track and mitigate emerging threats,” according to a Monday CISA advisory. “Implementing a rigorous configuration and patch management program will hamper sophisticated cyber threat actors’ operations and protect organizations’ resources and information systems.”
No further details on the specific hacked entities were made public. The threat actors have been spotted successfully exploiting two common vulnerabilities – allowing them to compromise federal government and commercial entities, according to CISA.
The first is a vulnerability (CVE-2020-5902) in F5’s Big-IP Traffic Management User Interface, which allows cyber threat actors to execute arbitrary system commands, create or delete files, disable services, and/or execute Java code. As of July, about 8,000 users of F5 Networks’ BIG-IP family of networking devices were still vulnerable to the critical flaw.
Feds also observed the attackers exploiting an arbitrary file reading vulnerability affecting Pulse Secure VPN appliances (CVE-2019-11510). This flaw – speculated to be the cause of the Travelex breach earlier this year – allows bad actors to gain access to victim networks.
“Although Pulse Secure released patches for CVE-2019-11510 in April 2019, CISA observed incidents where compromised Active Directory credentials were used months after the victim organization patched their VPN appliance,” according to the advisory.
Threat actors were also observed hunting for Citrix VPN Appliances vulnerable to CVE-2019-19781, which is a flaw that enables attackers to execute directory traversal attacks. And, they have also been observed attempting to exploit a Microsoft Exchange server remote code execution flaw (CVE-2020-0688) that allows attackers to collect emails of targeted networks.
As part of its advisory, CISA also identified common TTPs utilized by the threat actors. For instance, threat actors have been spotted using the Cobalt Strike commercial penetration testing tool to target commercial and federal government networks; they have also seen the actors successfully deploying the open-source China Chopper tool against organization networks and using open-source tool Mimikatz.
The initial access vector for these cyberattacks vary. CISA said it has observed threat actors utilize malicious links in spearphishing emails, as well as exploit public facing applications. In one case, CISA observed the threat actors scanning a federal government agency for vulnerable web servers, as well as scanning for known vulnerabilities in network appliances (CVE-2019-11510). CISA also observed threat actors scanning and performing reconnaissance of federal government internet-facing systems shortly after the disclosure of “significant CVEs.”
CISA said, maintaining a rigorous patching cycle continues to be the best defense against these attacks.
“If critical vulnerabilities remain unpatched, cyber threat actors can carry out attacks without the need to develop custom malware and exploits or use previously unknown vulnerabilities to target a network,” according to the advisory.
Terence Jackson, CISO at Thycotic, echoed this recommendation, saying the advisory sheds light on the fact that organizations need to keep up with patch management. In fact, he said, according to a recent Check Point report, 80 percent of observed ransomware attacks in the first half of 2020 used vulnerabilities reported and registered in 2017 and earlier – and more than 20 percent of the attacks used vulnerabilities that are at least seven years old.
“Patch management is one of the fundamentals of security, however, it is difficult and we are still receiving a failing grade. Patch management, enforcing MFA and least privilege are key to preventing cyber-attacks in both the public and private sectors,” he told Threatpost.
Cisco Warns of Active Exploitation of Flaw in Carrier-Grade Routers
3.9.20 Exploit Threatpost
Multiple flaws in system software that causes errors in packet handling could allow an attacker to consume memory and crash devices.
Cisco Systems says hackers are actively exploiting previously unpatched vulnerabilities in its carrier-grade routers that could allow adversaries to crash or severely disrupt devices.
The vulnerabilities exist in the Distance Vector Multicast Routing Protocol (DVMRP) feature of Cisco IOS XR Software and could allow an unauthenticated, remote attacker to immediately crash the Internet Group Management Protocol (IGMP) process, the company warned in an advisory over the weekend.
The flaw, tracked as CVE-2020-3566, also allows attackers to make devices consume available memory and eventually crash, something that can “negatively impact other processes that are running on the device,” the company warned.
IOS XR Software runs many of Cisco’s carrier-grade network routers, including the CRS series, 12000 series, and ASR9000 series. The vulnerabilities affect “any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing and it is receiving DVMRP traffic,” the company said.
The cause of the flaws is the incorrect management of how IGMP packets, which help maintain the efficiency of network traffic, are queued, the company said.
“An attacker could exploit these vulnerabilities by sending crafted IGMP traffic to an affected device,” according to the advisory. “A successful exploit could allow the attacker to immediately crash the IGMP process or cause memory exhaustion, resulting in other processes becoming unstable. These processes may include, but are not limited to, interior and exterior routing protocols.”
Cisco is currently working on software updates to address the vulnerabilities, which have no workaround, the company said. However, companies using the affected routers can mitigate attacks depending on their needs and network configuration, according to Cisco.
In the case of a memory exhaustion, Cisco recommends that customers implement a rate limiter, which will require that customers understand their current rate of IGMP traffic and set a rate lower than the current average rate.
“This command will not remove the exploit vector,” the company acknowledged. “However, the command will reduce the traffic rate and increase the time necessary for successful exploitation. The customer can use this time to perform recovery actions.”
It is possible to recover the memory consumed by the IGMP process by restarting the IGMP process, according to Cisco, which provided details for how to do so.
To mitigate both memory exhaustion and the immediate IGMP process crash, Cisco advised that customers implement an access control entry (ACE) to an existing interface access control list (ACL). Alternatively, the customer can create a new ACL for a specific interface that denies DVMRP traffic inbound on that interface, the company said.
If an attacker does successfully crash a router’s IGMP process, operators do not need to manually restart the IGMP process because the system will perform that action, which will recover the consumed memory, according to Cisco.
In addition to mitigations, the company also provided details in the advisory for how network operators will know if a router has been compromised and other details for dealing with any attack on the vulnerabilities until a fix can be found.
Cisco Issues Warning Over IOS XR Zero-Day Flaw Being Targeted in the Wild
1.9.20 Exploit Thehackernews
Cisco has warned of an active zero-day vulnerability in its router software that's being exploited in the wild and could allow a remote, authenticated attacker to carry out memory exhaustion attacks on an affected device.
"An attacker could exploit these vulnerabilities by sending crafted IGMP traffic to an affected device," Cisco said in an advisory posted over the weekend.
"A successful exploit could allow the attacker to cause memory exhaustion, resulting in instability of other processes. These processes may include, but are not limited to, interior and exterior routing protocols."
Although the company said it will release software fixes to address the flaw, it did not share a timeline for when it plans to make it available. The networking equipment maker said it became aware of attempts to exploit the flaw on August 28.
Tracked as CVE-2020-3566, the severity of the vulnerability has been rated "high" with a Common Vulnerability Scoring System score of 8.6 out of a maximum 10.
The bug affects all Cisco gear running its Internetwork Operating System (IOS) XR Software and stems from an issue in the Distance Vector Multicast Routing Protocol (DVMRP) feature that makes it possible for an adversary to send specially crafted Internet Group Management Protocol (IGMP) packets to the susceptible device in question and exhaust process memory.
IGMP is typically used to efficiently use resources for multicasting applications when supporting streaming content such as online video streaming and gaming. The flaw lies in the manner IOS XR Software queues these packets, potentially causing memory exhaustion and disruption of other processes.
While there are no workarounds to resolve the issue, Cisco recommends administrators to run the "show igmp interface" command to determine if multicast routing is enabled.
"If the output of 'show igmp interface' is empty, multicast routing is not enabled and the device is not affected by these vulnerabilities," the company said.
Additionally, admins can also check the system logs for signs of memory exhaustion and implement rate-limiting to reduce IGMP traffic rates to mitigate the risk.
Cisco didn't elaborate on how the attackers were exploiting this vulnerability and with what goal in mind.
But given that resource exhaustion attacks are also a form of denial-of-service attacks, it wouldn't be surprising if bad actors are leveraging the flaw to interfere with the regular functioning of the system.
Hackers are trying to exploit DoS flaw in Cisco IOS XR software running in carrier-grade routers
1.9.20 Exploit Securityaffairs
Cisco warns that threat actors are attempting to exploit a high severity DoS flaw in its Cisco IOS XR software that runs on carrier-grade routers.
Cisco warned over the weekend that attackers are trying to exploit a high severity memory exhaustion denial-of-service (DoS) vulnerability (CVE-2020-3566) affecting the Cisco IOS XR Network OS that runs on carrier-grade routers.
Cisco IOS XR Network OS currently run on multiple router families, including NCS 540 & 560, NCS 5500, 8000, and ASR 9000 series routers.
This flaw affects any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing.
The bad news is that the vulnerability has yet to be addressed by Cisco, at the time of writing the company issued a security advisory that includes mitigation.
“A vulnerability in the Distance Vector Multicast Routing Protocol (DVMRP) feature of Cisco IOS XR Software could allow an unauthenticated, remote attacker to exhaust process memory of an affected device.” reads the advisory.
“On August 28, 2020, the Cisco Product Security Incident Response Team (PSIRT) became aware of attempted exploitation of this vulnerability in the wild.”
The vulnerability is caused by insufficient queue management for Internet Group Management Protocol (IGMP) packets, it could be exploited by an attacker by sending crafted IGMP traffic to a vulnerable device.
A successful attack could cause memory exhaustion, resulting in instability of other processes, including interior and exterior routing protocols.
The advisory recommends users to run the show igmp interface command to determine if multicast routing is enabled on their device.
Running the command on IOS XR routers were multicast routing is not enabled will produce an empty output.
The following output shows a device with multicast routing enabled:
RP/0/0/CPU0:router# show igmp interface
Loopback0 is up, line protocol is up
Internet address is 10.144.144.144/32
IGMP is enabled on interface
Current IGMP version is 3
IGMP query interval is 60 seconds
IGMP querier timeout is 125 seconds
IGMP max query response time is 10 seconds
Last member query response interval is 1 seconds
IGMP activity: 3 joins, 0 leaves
IGMP querying router is 10.144.144.144 (this system)
TenGigE0/4/0/0 is up, line protocol is up
Internet address is 10.114.8.44/24
IGMP is enabled on interface
Current IGMP version is 3
IGMP query interval is 60 seconds
IGMP querier timeout is 125 seconds
IGMP max query response time is 10 seconds
Last member query response interval is 1 seconds
IGMP activity: 9 joins, 4 leaves
IGMP querying router is 10.114.8.11
The advisory states that there are multiple mitigations available to customers depending on their needs, for example, implementing a rate limiter to reduce the traffic rate and increase the time necessary for successful exploitation.
“This will require that customers understand their current rate of IGMP traffic and set a rate lower than the current average rate.” continues the advisory. “In configuration mode, the customer can enter the lpts pifib hardware police flow igmp rate command as follows:
RP/0/0/CPU0:router(config)# lpts pifib hardware police flow igmp rate <value>
This command will not remove the exploit vector.”
Users can also implement an access control entry (ACE) to an existing interface access control list (ACL) or a new ACL to deny inbound DVRMP traffic to interfaces with multicast routing enabled.
Cisco also recommends disabling IGMP routing for an interface where processing IGMP traffic is not necessary by entering IGMP router configuration mode.
Hackers for hire group target organizations via 3ds Max exploit
27.8.20 Exploit Securityweek
Experts discovered a new hacker hacker-for-hire group that is targeting organizations worldwide with malware hidden inside malicious 3Ds Max plugins.
Security researchers from Bitdefender discovered a new hacker group that is currently targeting companies across the world with malware hidden inside malicious 3Ds Max plugins.
Autodesk 3ds Max, formerly 3D Studio and 3D Studio Max, is a professional 3D computer graphics program for making 3D animations, models, games and images. It is developed and produced by Autodesk Media and Entertainment.[2] It has modeling capabilities and a flexible plugin architecture and must be used on the Microsoft Windows platform. I
3Ds Max is used by engineering, architecture, gaming, or software organizations.
In early August, Autodesk published a security alert warning about a malicious plugin named “PhysXPluginMfx,” it is a variant of the MAXScript exploit.
“A variant of a MAXScript exploit “PhysXPluginMfx” has been identified and a free plugin is now available in the Autodesk App Store to detect and remove the malicious code.” reads the security alert.
Upon loading the malicious plugin inside 3Ds Max, PhysXPluginMfx would execute malicious MAXScript operations to corrupt 3Ds Max settings, run malicious code, and even propagate to other MAX files.
According to Bitdefender, the plugin was designed to deploy a backdoor trojan that could be used to steal sensitive files from the infected systems.
Bitdefender researchers investigated at least one attack against an international architectural and video production company that has been collaborating in billion-dollar real estate projects in New York, London, Australia, and Oman.
“During the investigation, Bitdefender researchers found that threat actors had an entire toolset featuring powerful spying capabilities and made use of a previously unknown vulnerability in a popular software widely used in 3D computer graphics (Autodesk 3ds Max) to compromise the target.” reads the post published by BitDefender.
“Industrial espionage is nothing new, and, since the real estate industry is highly competitive, with contracts valued at billions of dollars, the stakes are high for winning contracts for luxury projects. This could justify turning to mercenary APT groups for gaining a negotiation advantage.”

The threat actor used a malware command and control (C&C) server that was located in South Korea.
“Looking through the telemetry of the C&C, we noticed that there are reports, which include some of the discovered .net assembly internal names found initially on the victims’ machine or downloaded from the C&C.” continues the report. “After analysis, we have managed to gather more tools, based on direct usage or based on common portions of code. Beside this, we have also noticed that all of them share the C&C address from the victim (address + port).”
Some of the samples analyzed by Bitdefender connected to the C&C server from countries South Korea, United States, Japan, and South Africa, a circumstance that suggests the hackers might have also targeted businesses in these countries.
The attackers also use malware to collect details about the compromised host and steal files with specific extensions.
According to the researchers, the attackers compile file-stealing component for each victim to include the list of files they want to steal.
To avoid detection, the malicious binary remains dormant if Task Manager or Performance Monitor were running.
The report includes a lot of technical details about the operation of the group. This year, security firm spotted other hacker-for-hire groups, including Dark Basin and DeathStalker.
Mercenary Cyberspies Used Autodesk 3ds Max Exploits in Attacks
27.8.20 Attack Exploit Securityweek
A sophisticated hack-for-hire group specializing in industrial espionage exploited the Autodesk 3ds Max modeling and animation software in an attack aimed at a company involved in luxury real estate projects, cybersecurity firm Bitdefender reported on Wednesday.
Bitdefender has analyzed what it describes as an “APT-style cyberespionage attack” targeting an international architecture and video production company. The target has not been named, but it’s said to have worked on billion-dollar real estate projects in London, New York, Australia and Oman.
According to Bitdefender researchers, the attackers collected data on the security systems and software used by the target before attempting to exfiltrate valuable information.
The company believes the attack may have started with a malicious 3ds Max plugin being sent to the victim.
The hackers leveraged MAXScript exploits — MaxScript is the scripting language in 3ds Max — to download and execute other files, collect information about the compromised systems, and deliver malware capable of capturing screenshots and stealing passwords and history data from a Chrome database.
Bitdefender believes that other organizations were also targeted with MAXScript exploits before this attack was detected.
“Based on Bitdefender’s telemetry, we also found other similar malware samples communicating with the same command and control server, dating back to just under a month ago. Located in South Korea, United States, Japan, and South Africa, it’s likely the cybercriminal group might have also been targeting select victims in these regions as well,” Bitdefender said in its report.
A security advisory published earlier this month by Autodesk warns 3ds Max users of a MAXScript exploit named PhysXPluginMfx that can “corrupt 3ds Max software’s settings, run malicious code, and propagate to other MAX files (*.max) on a Windows system if scene files containing the script are loaded into 3ds Max.”
The vendor has released a free plugin that can help users detect and remove the malicious code.
The command and control (C&C) infrastructure used in the attack detailed by Bitdefender is located in South Korea, but the company has not shared other information regarding attribution.
Mozilla Offering Rewards for Bypassing Firefox Exploit Mitigations
20.8.20 Exploit Securityweek
Mozilla announced on Thursday that it has expanded its bug bounty program with a new category that focuses on bypass methods for the exploit mitigations, security features and defense-in-depth measures in Firefox.
Mozilla says mitigation bypasses have until now been classified as low- or moderate-severity issues, but they are now eligible for a reward associated with a high-severity flaw as part of the new Exploit Mitigation Bug Bounty.
This means a bypass mitigation with privileged access can earn researchers up to $5,000 if they submit a high-quality report. However, if the mitigation is bypassed without privileged access — this typically involves chaining more than one weakness — researchers can receive a reward for the vulnerability itself and a 50 percent bonus for the mitigation bypass.
Mozilla says it still encourages researchers to test Firefox Nightly, the testing and development version of the browser, but vulnerabilities found in Nightly will only be eligible for a bounty if they’re not found internally by Mozilla within four days of the code change that introduces the flaw being posted to the primary repository.
Some have criticized Mozilla for expanding its bug bounty program shortly after it laid off some of its cybersecurity staff. However, the company told SecurityWeek that the recent layoffs did not impact the teams responsible for the security of the Firefox browser and Firefox services.
Mozilla has posted a list of the mitigations covered by the Exploit Mitigation Bug Bounty:

IBM AI-Powered Data Management Software Subject to Simple Exploit
20.8.20 Exploit Threatpost
A low-privileged process on a vulnerable machine could allow data harvesting and DoS.
The IBM’s next-gen data-management software suffers from a shared-memory vulnerability that researchers said could lead to other threats — as demonstrated by a new proof-of-concept exploit for the bug.
The IBM Db2 is a family of hybrid data-management products containing artificial intelligence, which can be used to analyze and manage both structured and unstructured data within enterprises.
According to researchers at Trustwave, the recently disclosed bug (CVE-2020-4414) arises because the platform’s developers forgot to put explicit memory protections around the shared memory used by the Db2 trace facility. If exploited, it could lead to denial-of-service (DoS) or information disclosure.
The trace facility is a function that allows users to isolate certain data points by monitoring selected parameters. This gives users what is essentially a log of control flow information (functions and associated parameter values), which can be helpful in slicing, dicing and separating out data for analysis. As such, the data at risk from an exploit could be literally anything generated within a targeted organization. For a healthcare provider for instance, cybercriminals could make off with HIPAA-protected patient information; a financial company meanwhile could be at risk for a breach of credit-card data.
On the DoS front, Karl Sigler, senior security research manager for SpiderLabs at Trustwave, told Threatpost that “databases are often deployed as critical system. An attacker with a foothold on the system could consistently bring down the database and interrupt whatever system that depends on it and it’s data.”
The crux of the issue is that it allows local privilege-escalation and crashing of the device. The lack of explicit memory protections “allows any local users read-and-write access to that memory area,” Trustwave researchers said, in their PoC exploit writeup for the bug, issued on Thursday. “In turn, this allows them to access critically sensitive data as well as the ability to change how the trace subsystem functions, resulting in a denial-of-service condition in the database.”
They added, “Needless to say, both shouldn’t be possible for regular users.”
While technically an attacker would need to be local, it’s possible to remotely execute such a low-privileged process (i.e., malware) on a vulnerable machine to trigger an exploit: “Low-privileged processes, running on the same computer as Db2 database, can alter Db2 traces and capture sensitive data – and use that later for subsequent attacks,” the researchers explained.
PoC Launched
To exploit the bug, attackers can send a specially crafted request to the trace facility.
Trustwave’s PoC starts with launching Process Explorer or other any similar tool in Windows to check open handles of the Db2 main process. Then, the researchers created a simple console application that tries to open a given memory section by name. Once that’s running, an attacker can enable Db2 tracing, which opens the door to an attack.
“And now we can see what’s been written to those memory sections,” according to Trustwave’s analysis. “In the end, this means that an unprivileged local user can abuse this to cause a denial-of-service condition simply by writing incorrect data over that memory section…there are absolutely no permissions assigned to the shared memory so that anyone can read from and write to it.”
Martin Rakhmanov, security research manager for SpiderLabs at Trustwave, elaborated on the PoC for Threatpost. “I show Process Explorer just to illustrate that shared memory is not protected. It is not required to conduct the attack at all,” he said. “The console application just reads the shared memory and thus can access Db2 trace information. It can be modified (the app) to change the Db2 trace as well. Finally, the attacker needs a low-privileged access to the computer where Db2 server is running.”
He added, “This is not the same as having control of the machine. So anyone who can connect to the computer where Db2 server is running can read/change the Db2 trace which is not good: On the contrary, the tracing facility requires special privileges inside the Db2 but the vulnerability allows to bypass that.”
This shared-memory vulnerability is very similar to one found in the Cisco WebEx Meetings Client on Windows in March (CVE-2020-3347), where any user could read memory dedicated to trace data, Trustwave researchers explained. In that case, any malicious local user or malicious process running on a PC where WebEx is installed can monitor the memory mapped file for a login token. Once found, the token, like any leaked credentials, can be transmitted somewhere so that it can be used to login to the WebEx account in question, download recordings, view/edit meetings and so on.
All fix pack levels of IBM Db2 V9.7, V10.1, V10.5, V11.1, and V11.5 editions on all platforms are affected by this latest shared-memory flaw, and users should update to the latest version to fix the issue, the firm said.
“This attack could have been widespread, as all Db2 instances of up-to-current version (11.5) on Windows were affected,” Trustwave researchers noted.
Actively exploited CVE-2020-1464 Windows Spoofing flaw was known since 2018
19.8.20 Exploit Securityaffairs
The actively exploited Windows spoofing vulnerability (CVE-2020-1464) recently patched by Microsoft has been known for more than two years.
The actively exploited Windows spoofing flaw, tracked as CVE-2020-1464 and patched last week by Microsoft, has been known for more than two years, researchers revealed.
Microsoft’s August 2020 Patch Tuesday security updates addressed 120 vulnerabilities, including two zero-days that have been exploited in attacks in the wild.
The two issues are a Windows spoofing bug and a remote code execution flaw in Internet Explorer.
The Windows spoofing flaw, tracked as CVE-2020-1464 can be exploited by an attacker to bypass security features and load improperly signed files. The flaw is related to Windows incorrectly validating file signatures.
“A spoofing vulnerability exists when Windows incorrectly validates file signatures. An attacker who successfully exploited this vulnerability could bypass security features and load improperly signed files.” reads the advisory published by Microsoft.
“In an attack scenario, an attacker could bypass security features intended to prevent improperly signed files from being loaded.”
The flaw affects many Windows OSs, including Windows 7 and Windows Server 2008, for which the IT giant will not provide security updates because the reached the end-of-life.
Microsoft confirmed that threat actors are actively exploiting the issues in attacks against Windows systems but it did not provide technical details about the attacks.
Experts analyzed the code to address the CVE-2020-1464 flaw and discovered that the vulnerability has been known for years and the most serious aspect is that Microsoft was aware of the bug but did not fix it.
According to the security expert Tal Be’ery, the vulnerability, dubbed GlueBall, has been known since August 2018, because a malware sample exploiting it was uploaded to VirusTotal.
Microsoft was informed about the vulnerability after the submission and a blog post published on VirusTotal in January 2019 included technical details about the GlueBall attack.
“Microsoft Windows keeps the Authenticode signature valid after appending any content to the end of Windows Installer (.MSI) files signed by any software developer. This behaviour can be exploited by attackers to bypass some security solutions that rely on Microsoft Windows code signing to decide if files are trusted.” reads the blog post published by Virus Total. “The scenario is especially dangerous when the appended code is a malicious JAR because the resulting file has a valid signature according to Microsoft Windows and the malware can be directly executed by Java.”
In June 2020, experts discovered that the GlueBall issue was exploited in attacks in the wild to deliver malware.
This means that Microsoft did not fix the flaw for some reasons that are still unclear.
“While the technical details are pretty obvious, the way Microsoft had handled the vulnerability report seems rather strange. It was very clear to everyone involved, Microsoft included, that GlueBall is indeed a valid vulnerability exploited in the wild. Therefore, it is not clear why it was only patched now and not two years ago.” wrote Tal Be’ery
‘EmoCrash’ Exploit Stoppered Emotet For 6 Months
18.8.20 Exploit Threatpost
A researcher developed a killswitch exploiting a buffer overflow in Emotet – preventing the malware from infecting systems for six months.
A researcher was able to exploit a vulnerability in Emotet – effectively causing the infamous malware to crash and preventing it from infecting systems for six months.
Emotet, which first emerged in 2014 and has since then evolved into a full fledged botnet that’s designed to steal account credentials and download further malware, mysteriously disappeared from February until its recent re-emergence in early August.
On Friday, James Quinn with Binary Defense revealed why: He he had developed a killswitch earlier this year, dubbed “EmoCrash,” that exploited a buffer overflow vulnerability found in Emotet’s installation process.
He’s not the only one looking to thwart Emotet: The news comes shortly after researchers discovered that a mysterious vigilante was fighting the threat actors behind the malware’s comeback by replacing malicious Emotet payloads with whimsical GIFs and memes.
A killswitch is often utilized by defenders to disconnect networks from the internet during cyberattacks – but can also be used against malware families as a way to remove them from systems and stop any processes that are running.
“Just as attackers can exploit flaws in legitimate software to cause harm, defenders can also reverse-engineer malware to discover its vulnerabilities and then exploit those to defeat the malware,” said Quinn in a recent post.
In early February, Emotet released a codebase overhaul, which made headlines for allowing the Emotet malware sample to spread to insecure Wi-Fi networks that are located nearby to an infected device.
Part of this overhaul was the modification of Emotet’s various installation and persistence methods. The malware developers removed a word list and file-generation algorithm previously utilized by Emotet, and replaced it with a new algorithm with a new persistence twist.
This new algorithm generated a randomly chosen .exe or .dll system filename, and then encrypted the filename with an exclusive OR (XOR) key and saved it as a registry key.
Quinn discovered a simple buffer overflow within this installation routine, and created a killswitch for this issue with a PowerShell script. The script contained a buffer of 0x340 (832) bytes, which Emotet would attempt to save as the registry key – ultimately causing it to crash during its installation process (before it was fully installed) and completely preventing the malware from installing on systems.
“This tiny data buffer was all that was needed to crash Emotet, and could even be deployed prior to infection (like a vaccine) or mid-infection (like a killswitch),” said Quinn.
Quinn then shared the killswitch discreetly with members of the infosec community, avoiding public channels to ensure maximum uptime of the exploit before the threat actors behind Emotet patched their malware to close the vulnerability.
“With an incredible amount of coordinating between the infosec and CERT communities, especially those at Team Cymru who helped immensely with this, Binary Defense began distributing the EmoCrash exploit script to defenders around the world on Feb. 12, 2020, with strict instructions not to post it publicly,” he said.
The killswitch was active between Feb. 6 until Aug. 5 – at which point Emotet’s developers sent out a core loader update to remove the vulnerable registry value code, killing the killswitch. It was then that Emotet resurfaced after a five-month disappearance, with more than 250,000 malspam messages being sent to email recipients worldwide.
Actively Exploited Windows Spoofing Flaw Patched Two Years After Disclosure
18.8.20 Exploit Vulnerebility Securityaffairs
The actively exploited Windows spoofing vulnerability patched last week by Microsoft has been known for more than two years, researchers pointed out.
Microsoft’s August 2020 Patch Tuesday updates addressed 120 vulnerabilities, including an Internet Explorer zero-day that has been chained with a Windows flaw in attacks linked to the threat actor named DarkHotel, and a Windows spoofing issue tracked as CVE-2020-1464.
The tech giant describes CVE-2020-1464 as a spoofing flaw related to Windows incorrectly validating file signatures. An attacker can exploit the vulnerability to bypass security features and load improperly signed files, Microsoft says in its advisory.
Researchers analyzed CVE-2020-1464 after Microsoft released its patch and noticed that it’s likely a vulnerability that has been known for years and which Microsoft has been refusing to fix.
In a blog post published over the weekend, researcher Tal Be'ery explained that the vulnerability, which has been named GlueBall, has been known since August 2018, when a file sample exploiting it was uploaded to VirusTotal.
Microsoft was informed about the issue at the time and details were disclosed on the VirusTotal blog in January 2019, but the vendor decided not to fix it.
“Microsoft Windows keeps the Authenticode signature valid after appending any content to the end of Windows Installer (.MSI) files signed by any software developer. This behaviour can be exploited by attackers to bypass some security solutions that rely on Microsoft Windows code signing to decide if files are trusted. The scenario is especially dangerous when the appended code is a malicious JAR because the resulting file has a valid signature according to Microsoft Windows and the malware can be directly executed by Java,” Bernardo Quintero, founder of VirusTotal, explained in the January 2019 blog post.
Shortly after the blog post was published, several others analyzed the issue and made their findings public. In June 2020, researchers noticed that someone had been exploiting GlueBall to deliver malware, and in August it was finally patched by Microsoft.
“[The] way Microsoft had handled the vulnerability report seems rather strange,” Be’ery noted. “It was very clear to everyone involved, Microsoft included, that GlueBall is indeed a valid vulnerability exploited in the wild. Therefore, it is not clear why it was only patched now and not two years ago.”
SecurityWeek has reached out to Microsoft, but the company has not provided any clarifications regarding its decision not to patch CVE-2020-1464 sooner.
“A security update was released in August. Customers who apply the update, or have automatic updates enabled, will be protected. We continue to encourage customers to turn on automatic updates to help ensure they are protected,” said a Microsoft spokesperson.
PoC exploit code for two Apache Struts 2 flaws available online
16.8.20 Exploit Securityaffairs
Security researchers have discovered a PoC exploit code available online that can be used to trigger unpatched security flaws in Apache Struts 2.
Security researchers have discovered a PoC code and exploit available on GitHub that that can be used to trigger the security vulnerabilities in Apache Struts 2.
The Proof-of-concept exploit code was released last week, it allows to trigger the CVE-2019-0230 and CVE-2019-0233 vulnerabilities in Apache Struts 2 that are classified as remote code-execution and denial-of-service issues respectively. Both vulnerabilities were addressed by the Apache team in November 2019.
According to an advisory published by the Cybersecurity and Infrastructure Security Agency (CISA) the two flaws impact Apache Struts versions 2.0.0 through 2.5.20. The Apache Struts Security Team urges administrators to upgrade their installs to Struts 2.5.22.
Apache Struts 2 is an open-source, extensible framework for creating enterprise-ready Java web applications.
Unpatched installs could allow attackers to carry out malicious activities. In 2017, the credit reporting agency Equifax suffered a massive data breach, attackers exploited the CVE-2017-5638 Apache Struts vulnerability.
The CVE-2019-0230, for which a PoC exploit code is available only, could be triggered when a threat actor sends a malicious Object-Graph Navigation Language (OGNL) expression that can result in a remote code-execution in the context of the affected application.
Depending on the privileges associated with the affected application, an attacker could perform multiple malicious activities, such as install applications; modify or delete data, or create new admin accounts.
The DoS flaw, tracked as CVE-2019-0233, affects the write permissions of file directories that could lead to conditions ripe for a DoS attack.
According to the Apache Struts Wiki description of the bug, this flaw can be triggered with a file upload to a Strut’s Action that exposes the file.
“When a file upload is performed to an Action that exposes the file with a getter, an attacker may manipulate the request such that the working copy of the uploaded file is set to read-only. As a result, subsequent actions on the file will fail with an error.” reads the advisory. “It might also be possible to set the Servlet container’s temp directory to read only, such that subsequent upload actions will fail,”
The Apache security bulletin recommends to upgrade outdated installs and verify no unauthorized system modifications have occurred on the system.
Internet Explorer and Windows zero-day exploits used in Operation PowerFall
12.8.20 Exploit Securelist
Executive summary
In May 2020, Kaspersky technologies prevented an attack on a South Korean company by a malicious script for Internet Explorer. Closer analysis revealed that the attack used a previously unknown full chain that consisted of two zero-day exploits: a remote code execution exploit for Internet Explorer and an elevation of privilege exploit for Windows. Unlike a previous full chain that we discovered, used in Operation WizardOpium, the new full chain targeted the latest builds of Windows 10, and our tests demonstrated reliable exploitation of Internet Explorer 11 and Windows 10 build 18363 x64.
On June 8, 2020, we reported our discoveries to Microsoft, and the company confirmed the vulnerabilities. At the time of our report, the security team at Microsoft had already prepared a patch for vulnerability CVE-2020-0986 that was used in the zero-day elevation of privilege exploit, but before our discovery, the exploitability of this vulnerability was considered less likely. The patch for CVE-2020-0986 was released on June 9, 2020.
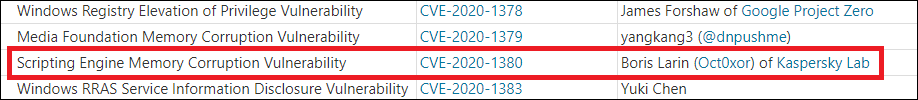
Microsoft assigned CVE-2020-1380 to a use-after-free vulnerability in JScript and the patch was released on August 11, 2020.
We are calling this and related attacks ‘Operation PowerFall’. Currently, we are unable to establish a definitive link with any known threat actors, but due to similarities with previously discovered exploits, we believe that DarkHotel may be behind this attack. Kaspersky products detect Operation PowerFall attacks with verdict PDM:Exploit.Win32.Generic.
Internet Explorer 11 remote code execution exploit
The most recent zero-day exploits for Internet Explorer discovered in the wild relied on the vulnerabilities CVE-2020-0674, CVE-2019-1429, CVE-2019-0676 and CVE-2018-8653 in the legacy JavaScript engine jscript.dll. In contrast, CVE-2020-1380 is a vulnerability in jscript9.dll, which has been used by default starting with Internet Explorer 9, and because of this, the mitigation steps recommended by Microsoft (restricting the usage of jscript.dll) cannot protect against this particular vulnerability.
CVE-2020-1380 is a Use-After-Free vulnerability that is caused by JIT optimization and the lack of necessary checks in just-in-time compiled code. A proof-of-concept (PoC) that triggers vulnerability is demonstrated below:
To understand this vulnerability, let us take a look at how func() is executed. It is important to understand what value is set to A[5]. According to the code, it should be an O argument. At function start, the O argument is re-assigned to 1, but then the function arguments length is set to 0. This operation does not clear function arguments (as it would normally do with regular array) but allows to put argument O2 into the arguments list at index zero using Array.prototype.push, meaning O = O2 now. Besides that, if the argument F is equal to 1, then O will be re-assigned once again, but to the integer number 2. It means that depending on the value of the F argument, the O argument is equal to either the value of the O2 argument or the integer number 2. The argument A is a typed array of 32-bit floating point numbers, and before assigning a value to index 5 of the array, this value should be converted to a float. Converting an integer to a float is a relatively simple task, but it become less straightforward when an object is converted to a float number. The exploit uses the object abp with an overridden valueOf() method. This method is executed when the object is converted to a float, but inside the method there is code that frees ArrayBuffer, which is viewed by Float32Array and where the returned value will be set. To prevent the value from being stored in the memory of the freed object, the JavaScript engine needs to check the status of the object before storing the value in it. To convert and store the float value safely, JScript9.dll uses the function Js::TypedArray<float,0>::BaseTypedDirectSetItem(). You can see decompiled code of this function below:
As you can see, unlike in interpretation mode, in just-in-time compiled code, the life cycle of ArrayBuffer is not checked, and its memory can be freed and then reclaimed during a call to the valueOf() function. Additionally, the attacker can control at what index the returned value is written. However, in the case when “arguments.length = 0;”and “arguments.push(O2);” are replaced in PoC with “arguments[0] = O2;” then Js::JavascriptConversion::ToFloat_Helper() will not trigger the bug because implicit calls will be disabled and it will not perform a call to the valueOf() function.
To ensure that the function func() is compiled just in time, the exploit executes this function 0x10000 times, performing a harmless conversion of the integer, and only after that func() is executed once more, triggering the bug. To free ArrayBuffer, the exploit uses a common technique abusing the Web Workers API. The function postMessage() can be used to serialize objects to messages and send them to the worker. As a side effect, transferred objects are freed and become unusable in the current script context. When ArrayBuffer is freed, the exploit triggers garbage collection via code that simulates the use of the Sleep() function: it is a while loop that checks for the time lapse between Date.now() and the previously stored value. After that, the exploit reclaims the memory with integer arrays.
When a large number of arrays is created, Internet Explorer allocates new LargeHeapBlock objects, which are used by IE’s custom heap implementation. The LargeHeapBlock objects will store the addresses of buffers allocated for the arrays. If the expected memory layout is achieved successfully, the vulnerability will overwrite the value at the offset 0x14 of LargeHeapBlock with 0, which happens to be the allocated block count.

LargeHeapBlock structure for jscript9.dll x86
After that, the exploit allocates a huge number of arrays and sets them to another array that was prepared at the initial stage of the exploitation. Then this array is set to null, and the exploit makes a call to the CollectGarbage() function. This results in defragmentation of the heap, and the modified LargeHeapBlock will be freed along with its associated array buffers. At this stage, the exploit creates a large amount of integer arrays in hopes of reclaiming the previously freed array buffers. The newly created arrays have a magic value set at index zero, and this value is checked through a dangling pointer to the previously freed array to detect if the exploitation was successful.
As a result, the exploit creates two different JavascriptNativeIntArray objects with buffers pointing to the same location. This makes it possible to retrieve the addresses of the objects and even create new malformed objects. The exploit takes advantage of these primitives to create a malformed DataView object and get read/write access to the whole address space of the process.
After the building of the arbitrary read/write primitives, it is time to bypass Control Flow Guard (CFG) and get code execution. The exploit uses the Array’s vftable pointer to get the module base address of jscript9.dll. From there, it parses the PE header of jscript9.dll to get the address of the Import Directory Table and resolves the base addresses of the other modules. The goal here is to find the address of the function VirtualProtect(), which will be used to make the shellcode executable. After that, the exploit searches for two signatures in jscript9.dll. Those signatures correspond to the address of the Unicode string “split” and the address of the function: JsUtil::DoublyLinkedListElement<ThreadContext>::LinkToBeginning<ThreadContext>(). The address of the Unicode string “split” is used to get a code reference to the string and with its help, to resolve the address of the function Js::JavascriptString::EntrySplit(), which implements the string method split(). The address of the function LinkToBeginning<ThreadContext>() is used to obtain the address of the first ThreadContext object in the global linked list. The exploit locates the last entry in the linked list and uses it to get the location of the stack for the thread responsible for the execution of the script. After that comes the final stage. The exploit executes the split() method and an object with an overridden valueOf() method is provided as a limit argument. When the overridden valueOf() method is executed during the execution of the function Js::JavascriptString::EntrySplit(), the exploit will search the thread’s stack to find the return address, place the shellcode in a prepared buffer, obtain its address, and finally build a return-oriented programming (ROP) chain to execute the shellcode by overwriting the return address of the function.
Next stage
The shellcode is a reflective DLL loader for the portable executable (PE) module that is appended to the shellcode. The module is very small in size, and the whole functionality is located inside a single function. It creates a file within a temporary folder with the name ok.exe and writes to it the contents of another executable that is present in the remote code execution exploit. After that, ok.exe is executed.
The ok.exe executable contains is an elevation of privilege exploit for the arbitrary pointer dereference vulnerability CVE-2020-0986 in the GDI Print / Print Spooler API. Initially, this vulnerability was reported to Microsoft by an anonymous user working with Trend Micro’s Zero Day Initiative back in December 2019. Due to the patch not being released for six months since the original report, ZDI posted a public advisory for this vulnerability as a zero-day on May 19, 2020. The next day, the vulnerability was exploited in the previously mentioned attack.
The vulnerability makes it possible to read and write the arbitrary memory of the splwow64.exe process using interprocess communication, and use it to achieve code execution in the splwow64.exe process, bypassing the CFG and EncodePointer protection. The exploit comes with two executables embedded in its resources. The first executable is written to disk as CreateDC.exe and is used to create a device context (DC), which is required for exploitation. The second executable has the name PoPc.dll and if the exploitation is successful, it is executed by splwow64.exe with a medium integrity level. We will provide further details on CVE-2020-0986 and its exploitation in a follow-up post.

Execution of a malicious PowerShell command from splwow64.exe
The main functionality of PoPc.dll is also located inside a single function. It executes an encoded PowerShell command that proceeds to download a file from www[.]static-cdn1[.]com/update.zip, saves it to the temporary folder as upgrader.exe and executes it. We were unable to analyze upgrader.exe because Kaspersky technologies prevented the attack before the executable was downloaded.
IoCs
www[.]static-cdn1[.]com/update.zip
B06F1F2D3C016D13307BC7CE47C90594
D02632CFFC18194107CC5BF76AECA7E87E9082FED64A535722AD4502A4D51199
5877EAECA1FE8A3A15D6C8C5D7FA240B
7577E42177ED7FC811DE4BC854EC226EB037F797C3B114E163940A86FD8B078B
B72731B699922608FF3844CCC8FC36B4
7765F836D2D049127A25376165B1AC43CD109D8B9D8C5396B8DA91ADC61ECCB1
E01254D7AF1D044E555032E1F78FF38F
81D07CAE45CAF27CBB9A1717B08B3AB358B647397F08A6F9C7652D00DBF2AE24












