
Exploit Articles - H 2020 1 2 3 4 5 6 7 Exploit List - H 2021 2020 2019 2018 1 Exploit blog Exploit blog
Expert exploited an unrestricted File Upload flaw in a PayPal Server to remotely execute code
24.7.2017 securityaffairs Exploit
The security researcher Vikas Anil Sharma exploited an unrestricted File Upload vulnerability in a PayPal Server to remotely execute code.
The security researcher Vikas Anil Sharma has found a remote code execution vulnerability in a PayPal server.
The expert was visiting the PayPal Bug Bounty page using the Burp software, below the response obtained opening the page http://paypal.com/bugbounty/.
PayPal server hack
The expert focused his analysis on the list of PayPal’s domains mentioned in “Content Security Policy:” Response Header, in particular, the “https://*.paypalcorp.com.”
In this first phase, the hacker was interested in finding as much possible valid sub domains to exploit in the attack, tools like Subbrute , Knockpy , enumall, are useful when performing such kind of analysis.
“these are the tools which i normally use , but being lazy on the weekend i made use of VirusTotal this time to enumerate the sub domains you can get the list here :
https://www.virustotal.com/en/domain/paypalcorp.com/information/
Copied the subdomain’s list locally & ran “dig -f paypal +noall +answer” to checkout where all the subdomains are actually pointing to in a neat way” wrote the researcher.
The expert noticed that the domain “brandpermission.paypalcorp.com” was pointing to “https://www.paypal-brandcentral.com/” that is a site hosting an Online Support Ticket System for PayPal Vendors, Suppliers, and Partners where they request for PayPal Brand Permissions.
The website allows users to upload the mockups of the logos and any graphics related to the brand along. The expert decided to create a ticket by uploading a simple image and analyze the folder destination of the picture.
“So, I first created a ticket by uploading a simple image file named “finished.jpg” which got stored as ” finished__thumb.jpg ” in directory :
“/content/helpdesk/368/867/finishedthumb.jpg” “finished _thumb.jpg” was the new file created in the directory “/867/” i quickly checked whether the actual file which we uploaded exists in the directory or not, luckily (You’ll know why later in the post ) “finished.jpg” also existed in the same directory. Cool stuff ;)” continue the bug hunter’s post.
Vikas discovered that the above link includes the ticket number, in the specific case the number of the ticket he has created is “368,” meanwhile “867” is the folder’s id where all the files related to the tickets are stored, including the Mockup files.
The researcher created a new ticket and discovered that ticket id and file id numbers are generated in serial manner. The expert uploaded a “.php” extension file instead of an image and discovered that the application did not validate file type, content, etc.
“As soon as i saw 302 Response , i ran towards opening the ticket & doing a simple right click copy link shit like i was able to do when uploading a image file . But,here in this case if you upload a php file as mock up you can’t see the path of the php file uploaded only thing which is visible is the ticket number.” wrote the expert.
Differently, from the uploading of image files, the expert noticed that it was not possible to discover the folder used to store mockup files.
The expert uploaded a file named success.php,” so for a similarity with the image uploading, he assumed that the file was stored as the success_thumb.php.
At this point, he decided to brute force the folder id for files.

Once discovered the folder id for files, the researcher tried to execute the code:
https://www.paypal-brandcentral.com/content/_helpdesk/366/865/success.php?cmd=uname-a;whoami
“Some cat+/etc/passwd magic to make myself beleive that i have actually found a RCE ;)” he wrote.

Below the timeline for the vulnerability:
Jul 08, 2017 18:03 – Submitted
Jul 11, 2017 18:03 – Fixed
A bug in Gnome pic parser can be exploited to run malicious VBScripts
20.7.2017 securityaffairs Exploit Virus
A bug in your image thumbnailer could represent a new attack vector for hackers that can exploit it for script injection.
Another day, another bug in a popular application. A bug in your image thumbnailer could represent a new attack vector for hackers that can exploit it for script injection.
To create image thumbnails, Gnome Files allows users providing filenames as an executable input.
The flaw was detailed by the researchers Nils Dagsson Moskopp who provided useful suggestions to avoid being hacked.
“Thumbnail generation for MSI files in GNOME Files executes arbitrary VBScript.” states Moskopp.
“Delete all files in /usr/share/thumbnailers. Do not use GNOME Files. Uninstall any other software that facilitates automatically executing parts of filenames as code”.
Dagsson Moskopp published a PoC code leveraging Wine to execute VBScript. He tricks Gnome Files into creating an MSI file called badtaste.txt.

Create MSI Files
Create a file named poc.xml with the following content:
<?xml version="1.0" encoding="utf-8"?>
<Wix xmlns="http://schemas.microsoft.com/wix/2006/wi">
<Product Version="1.0"/>
</Wix>
Execute the following Bourne Shell code:
wixl -o poc.msi poc.xml
cp poc.msi "poc.msi\",0):Set fso=CreateObject(\"Scripting.FileSystemObject\"):Set poc=fso.CreateTextFile(\"badtaste.txt\")'.msi"
Trigger Execution
Start GNOME Files and navigate to the folder with the MSI files. An empty file with the name badtaste.txt should appear.
“Whenever an icon for a Microsoft Windows executable (EXE), installer (MSI), library (DLL), or shortcut (LNK) should be shown, Gnome Files calls /usr/bin/gnome-exe–thumbnailer to either extract an embedded icon from the file in question or deliver a fallback image for the appropriate filetype.” explained the expert.
The expert highlighted that the problem is triggered due to the presence of just one line of code in /usr/bin/gnome-exe-thumbnailer:
DISPLAY=NONE wine cscript.exe //E:vbs //NoLogo Z:\\tmp\\${TEMPFILE1##*/}.vbs 2>/dev/null \
“Instead of parsing an MSI file to get its version number, this code creates a script containing the filename for which a thumbnail should be shown and executes that using Wine. The script is constructed using a template, which makes it possible to embed VBScript in a filename and trigger its execution.” Dagsson Moskopp added.
In order to avoid problems, Dagsson Moskopp suggests developers should not use “ad-hoc parsers” to parse files, should “fully recognise inputs before processing them”, and should use unparsers.
Below the remedy suggestions for both users and developers:
Remedy (for users)
“Delete all files in /usr/share/thumbnailers. Do not use GNOME Files. Uninstall any other software that facilitates automatically executing parts of filenames as code.”
Remedy (for developers)“Do not parse files with bug-ridden ad-hoc parsers. Fully recognize inputs before processing them. Do not use templates, use unparsers instead. Read about LANGSEC.”
EternalSynergy-Based Exploit Targets Recent Windows Versions
19.7.2017 securityweek Exploit
A security researcher has devised an EternalSynergy-based exploit that can compromise versions of Windows newer than Windows 8.
EternalSynergy is one of several exploits allegedly stolen by the hacker group calling themselves the Shadow Brokers from the National Security Agency (NSA)-linked Equation Group. The exploit was made public in April along with several other hacking tools, one month after Microsoft released patches for them.
In May, a security researcher included EternalSynergy and six other NSA-linked hacking tools (EternalBlue, EternalChampion, EternalRomance, DoublePulsar, Architouch, and Smbtouch) in a network worm called EternalRocks. The tool was pulled weeks later to prevent abuse.
Security researcher Worawit Wang has now made public an EternalSynergy-derived exploit that also leverages EternalRomance and can be used on a wider range of Windows versions.
Available on both GitHub and ExploitDB, the tool targets 64-bit versions of Windows 2016, Windows 2012 R2, Windows 8.1, Windows 2008 R2 SP1, and Windows 7 SP1, as well as the 32-bit versions of Windows 8.1 and Windows 7 SP1.
Security researcher Sheila A. Berta, who is part of Telefonica's Eleven Paths security unit, has published a paper (PDF) on how to exploit Wang’s tool to get a Meterpreter session on Windows Server 2016.
EternalSynergy is based on the CVE-2017-0143 vulnerability, which “stems from not taking the command type of an SMB message into account when determining if the message is part of a transaction,” Microsoft reveals. “In other words, as long as the SMB header UID, PID, TID and OtherInfo fields match the corresponding transaction fields, the message would be considered to be part of that transaction.”
According to Microsoft, EternalSynergy should not work on Windows iterations newer than Windows 8, due to kernel security improvements such as Hypervisor-enforced Code Integrity (HVCI), which prevents unsigned kernel pages from being executed, and Control Flow Guard (CFG), designed to prevent invalid indirect function calls.
The exploit is expected to crash on unsupported operating system releases, but Wang managed to create a stable tool that targets Windows XP and newer versions, except Windows 10. Given a patch is already available from Microsoft, impacted users should consider applying it as soon as possible.
EternalSynergy is only one of the NSA-linked exploits to have caught researchers’ attention over the past several months. EternalBlue might be the most discussed such tool, after it has been abused in global attacks by ransomware such as WannaCry, the UIWIX ransomware, Adylkuzz botnet, and a stealth Remote Access Trojan.
Last month’s destructive NotPetya wiper also used EternalBlue to spread within compromised networks, along with the EternalRomance exploit and various other tools.
Drupal Patches Flaw Exploited in Spam Campaigns
22.6.2017 securityweek Exploit Spam
Drupal security updates released on Wednesday address several vulnerabilities, including one that has been exploited in spam campaigns.
The flaw exploited in the wild, patched with the release of Drupal versions 7.56 and 8.3.4, is a moderately critical access bypass vulnerability tracked as CVE-2017-6922.
The problem is that files uploaded by anonymous users to a private file system can be accessed by all anonymous users, not just the user who uploaded them, as it should be. The security hole only affects websites that allow anonymous users to upload files to a private file system.
Drupal has known about attacks exploiting this flaw since October 2016. At the time, it warned that misconfigured websites had been abused by malicious actors to host files and point users and search engines to them. The latest updates for Drupal 7 and 8 introduce a protection that should prevent exploitation.
“For example, if a webform configured to allow anonymous visitors to upload an image into the public file system, that image would then be accessible by anyone on the internet. The site could be used by an attacker to host images and other files that the legitimate site maintainers would not want made publicly available through their site,” the Drupal Security Team said in its October 2016 advisory.
Drupal 8.3.4 also patches a critical issue related to how the PECL YAML parser handles unsafe objects. An attacker can exploit the flaw, tracked as CVE-2017-6920, for remote code execution.
Another vulnerability fixed in Drupal 8 is a less critical improper field validation bug (CVE-2017-6921).
“A site is only affected by this if the site has the RESTful Web Services (rest) module enabled, the file REST resource is enabled and allows PATCH requests, and an attacker can get or register a user account on the site with permissions to upload files and to modify the file resource,” Drupal said in its advisory.
The Drupal Security Team warned users in mid-April that a serious vulnerability affected a third-party module named References, which had been used by more than 121,000 websites. The module had no longer been supported and Drupal initially advised users to migrate to a different product. However, a new maintainer took over the project shortly after and the flaw was addressed.
Attackers can exploit electronic cigarettes to hack computers
22.6.2017 securityaffairs Exploit
Hackers can exploit electronic cigarettes and any other electronic device to deliver a malware in a poorly protected network.
In November 2014, in a discussion started on the Reddit news media website it has been debated the case of a malware implanted by using electronic cigarettes connected over USB.
Hackers are able to exploit any electronic device to deliver a malware in a poorly protected network. Electronic cigarettes could be an attack vector, the idea may appear hilarious, many electronic cigarettes can be charged over USB, using a special cable or by inserting one end of the cigarette directly into a USB port.
The report posted on the social news Reddit website reported a strange case happened to an executive that discovered a malware in his system without immediately identify its source.
“One particular executive had a malware infection on his computer from which the source could not be determined,” reported a Reddit user “After all traditional means of infection were covered, IT started looking into other possibilities.
Investigating on the case, the man discovered that the electronic cigarettes were infected by a malware hardcoded into the charger, once the victim will connect it to the computer the malicious code will contact the C&C server to drop other malicious code and infect the system
Electronic cigarettes or vape pens properly modified could be an effective hacking tool to infect a targeted computer.
The security researcher Ross Bevington presented at BSides London how to use electronic cigarettes to compromise a computer by tricking it to believe that it was a keyboard.The researchers also explained that it is BSides London how to use electronic cigarettes to compromise a computer by tricking it to believe that it was a keyboard.
It is important to note that Bevington’s attack required the victim’s machine to be unlocked.
“PoisonTap is a very similar style of attack that will even work on locked machines,” Mr Bevington told Sky News.
The researchers also explained that it is possible to use the electronic cigarettes to interfere with its network traffic.
E-cigarettes are powered by a rechargeable lithium-ion battery that can be plugged into a cable or directly connects to the USB port of a computer.
“Security researchers have demonstrated how e-cigarettes can easily be modified into tools to hack computers.” reported SkyNews.
“With only minor modifications, the vape pen can be used by attackers to compromise the computers they are connected to – even if it seems just like they are charging.”
The researcher @FourOctets published a proof-of-concept video which showed arbitrary commands being sent to an unlocked laptop just by charging a vape pen.
Wll buy derby ticket @FourOctets
Sorry if I get vape pens banned at your work place......
5:29 PM - 25 May 2017
801 801 Retweets 1,076 1,076 likes
Twitter Ads info and privacy
Fouroctets modified the vape pen by simply adding a hardware chip which allowed the device to communicate with the laptop as if it were a keyboard or mouse.
“A pre-written script that was saved on the vape made Windows open up the Notepad application and typed “Do you even vape bro!!!!“” reported SkyNews.
SambaCry Flaw Exploited to Deliver Cryptocurrency Miner
12.6.2017 securityweek Exploit
A recently patched Samba flaw known as EternalRed and SambaCry has been exploited in the wild to deliver a cryptocurrency miner to vulnerable machines, researchers warned.
These attacks, observed by both Kaspersky and Cyphort, were launched shortly after the existence of the security hole was brought to light and proof-of-concept (PoC) exploits were made available.
The vulnerability, tracked as CVE-2017-7494, affects all versions of Samba since 3.5.0 and it has been addressed with the release of versions 4.6.4, 4.5.10 and 4.4.14. The flaw allows a malicious client to upload a shared library to a writable share, and cause the server to execute the file.
In the attacks spotted by researchers, cybercriminals attempted to deliver files with a random name and a .so extension (e.g. GJZjrflB.so, INAebsGB.so, cblRWuoCc.so).
The attackers first identified writable shares to which they could deliver their payload. In earlier attacks, the cybercriminals attempted to guess the local path needed to exploit the vulnerability, but Cyphort noticed that they later turned to using the NetShareGetInfo method, which provides information about a particular shared resource on a server.
The first file delivered is a backdoor that provides the attackers a reverse shell they can leverage to remotely execute commands. Experts pointed out that this part of the attack is based on the Metasploit module released shortly after CVE-2017-7494 was disclosed.
The backdoor is used to download and execute a popular open-source cryptocurrency miner named cpuminer (miderd). The miner is configured to abuse compromised systems to mine Monero (XMR) and send it to a wallet whose address is hardcoded.
Kaspersky analyzed the wallet and found that, as of June 8, the attackers had obtained nearly 100 Monero, which is currently worth roughly $5,500. The domain from which the mining utility is downloaded was registered on April 29 and the attackers’ wallet started receiving Monero the next day.
During the first two weeks the wallet received only one Monero per day, but the amount increased following the disclosure of CVE-2017-7494, and recently the attackers have been earning roughly 5 Monero each day.
“The attacked machine turns into a workhorse on a large farm, mining crypto-currency for the attackers,” Kaspersky researchers said in a blog post. “In addition, through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware.”
The Samba vulnerability has been found to affect many networking devices, including Cisco, Netgear, QNAP, Synology, Varitas and NetApp products.
RIG Exploit Kit Infrastructure Disrupted
6.6.2017 securityweek Exploit
A group of researchers and security firms led by RSA delivered a significant blow to the infrastructure used by the notorious RIG exploit kit and the operation has allowed experts to learn more about the threat.
RSA announced the results of the operation, which it has dubbed “Shadowfall,” on Monday. Several independent researchers and employees of Malwarebytes, Palo Alto Networks and Broad Analysis have contributed to the project.
Following the disappearance of Angler, RIG managed to secure the top position in the exploit kit market, being used to deliver various pieces of malware, including Cerber and CryptoMix ransomware, and the SmokeLoader backdoor. RIG has leveraged several Flash Player, Silverlight, Internet Explorer and Microsoft Edge exploits, which it mainly delivers by injecting malicious iframes into compromised websites.
One important component of RIG attacks is domain shadowing, a technique where attackers steal credentials from domain owners and use them to create subdomains that point to malicious servers. In the case of RIG, researchers identified tens of thousands of shadow domains. An analysis of whois data for these shadow domains showed that many of them had been registered with Internet giant GoDaddy.
With the aid of GoDaddy, tens of thousands of malicious domains were removed in mid-May, striking a significant blow to RIG, particularly a couple of recent campaigns dubbed “Seamless” and “Decimal IP.” However, RSA pointed out that assessing the impact of takedown operations is not an easy task, especially in this case due to the numerous malware campaigns and limited visibility into the threat actor’s activity.
The researchers involved in the operation reported that the exploit kit continued to be active, but noted that it had stopped using Flash Player exploits for a few days. Experts noticed on Monday that RIG had resumed the use of Flash exploits.
As for how attackers managed to hijack the accounts used to create shadow domains, RSA has determined that the compromised credentials don’t appear to come from Pony dumps – the Pony trojan has been used in the past years to steal millions of account credentials.
“In terms of the shadow domains themselves, it is believed that the threat actors waging these campaigns rely upon sophisticated phishing operations to acquire legitimate customer credentials,” RSA said in a blog post. “In terms of the compromised sites, the cross section of affected domain registrars implies a more opportunistic approach. While it remains unclear what methods may have been employed as a means for harvesting these credentials, community research exists on the usage of IoT botnets to brute force WordPress sites.”
Experts shut down tens of thousands of subdomains set up with a domain shadowing campaign
6.6.2017 securityaffairs Exploit
Experts killed tens of thousands of subdomains used by crooks to host the RIG Exploit Kit that were set up with a domain shadowing campaign.
GoDaddy and RSA Security, with the support of other security companies and researchers, have shut down tens of thousands of illegally established subdomains used by crooks to host the RIG Exploit Kit.
The RIG exploit kit is very popular in the criminal ecosystem, early this year security experts at Heimdal Security warned of a spike in cyber attacks leveraging the popular Neutrino and RIG EKs.

The cyber criminals set up the subdomains, most of them used GoDaddy as the primary domain registrar, by obtaining domain account credentials with phishing attacks (so-called domain shadowing).
“Domain shadowing is “a technique in which attackers steal domain account credentials from their owners for the purpose of creating subdomains directed at malicious servers”.” states RSA. “As a direct result of these efforts, tens of thousands of active shadow domain resources were removed from RIG, malvertising, and malspam operations.”
In March experts shut down the subdomains along with hundreds of IP addresses used by crooks to spread malware.
RSA Security published a detailed report titled Shadowfall on the RIG operation.
According to RSA hackers used a data-stealing malware as part of a phishing campaign to steal GoDaddy domain account credentials. Crooks used the account credentials to create new subdomains to use as gates in attacks to redirect visitors to IP addresses hosting the exploit kit.
The RSA researchers mapped domains to registrars and discovered that a most of them were registered with GoDaddy.
The RIG operation allowed the identification of 40,000 network subdomains and 2,000 IP addresses. According to RSA, the Shadow domains were kept alive 24 hours on average and DNS records were cleaned up before new shadow domains were created.
The researchers investigated four campaigns between February and March, two of them were spreading malware, including the Cerber ransomware and Dreambot banking malware.
RSA also helped GoDaddy in building some automation to monitor and detect shadowing attacks.
“The focus moving forward is to continue developing processes for at-scale detection and removal of malicious DNS records, as well as to integrate preventative measures into the domain modification data flow. As these efforts mature in their ability to prevent and disrupt shadowing, the direction will shift away from reliance of submitted indicators for ad-hoc remediation. Instead, they will depend on the analysis of internal datasets to identify and remove malicious records in an automated fashion.” concludes RSA.
“Success in these areas will minimize Time to Detection and Time to Remediation while significantly reducing the shadow domains’ lifespan. Architectural mitigations are also being evaluated for integration into accounts at high risk for domain shadowing. This path of action will keep GoDaddy accounts more secure and reduce the effectiveness of domain shadowing as a technique for malware distribution.”
Google Offers $200,000 for TrustZone, Verified Boot Exploits
2.6.2017 securityweek Exploit
Google this week announced increased rewards for security researchers reporting TrustZone or Verified Boot exploit chains. The company is now willing to pay up to $200,000 for such compromises, and will pay up to $150,000 for remote kernel exploits.
The awards are offered as part of the company’s Android Security Rewards program, which turned two this week. The Internet giant paid over $1.5 million in bounties to security researchers reporting Android vulnerabilities over the course of two years, and is looking to pay even more in the future.
During its two-year run, Android Security Rewards has attracted a large number of security researchers, and Google received over 450 qualifying vulnerability reports from the participating researchers over the past 12 months alone.
Google Offers $200,000 bounty for TrustZone, Verified Boot ExploitsThe total program payout doubled to $1.1 million dollars, and the average pay per researcher jumped by 52.3% compared to the first year, Google says.
During the program’s second year, the Internet giant paid $10,000 or more to 31 researchers, and also paid the top research team, C0RE Team, over $300,000 for 118 vulnerability reports. Over the course of a year, the company paid 115 individuals with an average of $2,150 per reward and $10,209 per researcher.
Unfortunately, none of the reports received over the two-year period included a complete remote exploit chain leading to TrustZone or Verified Boot compromise, which would have received the highest award amount available through the program.
Because no researcher claimed the top rewards in two years, the company decided to make changes to all vulnerability reports filed after June 1, 2017 and stir researchers’ interest by significantly increasing the top-line payouts for exploit chains that could claim them.
Thus, the rewards for a remote exploit chain or exploit leading to TrustZone or Verified Boot compromise were increased from $50,000 to $200,000, while those for a remote kernel exploit went from $30,000 to $150,000.
“In addition to rewarding for vulnerabilities, we continue to work with the broad and diverse Android ecosystem to protect users from issues reported through our program. We collaborate with manufacturers to ensure that these issues are fixed on their devices through monthly security updates,” Mayank Jain and Scott Roberts, Android Security team, say.
According to Jain and Roberts, there are over 100 device models with a majority of devices running a security update released within the past 90 days. Furthermore, numerous models run a security update from the last two months, including Google Pixel XL, Pixel, Nexus 6P, Nexus 6, Nexus 5X, Nexus 9.
Various smartphone models from manufacturers such as BlackBerry, Fujitsu, General Mobile, Gionee, LGE, Motorola, Oppo, Samsung, Sharp, Sony, and Vivo also run security patches released over the past two months.
Crowdfunding for Acquiring Shadow Brokers Exploits Canceled
1.6.2017 securityweek Exploit
Researchers announced this week the launch of a crowdfunding initiative whose goal was to raise money to subscribe to the Shadow Brokers’ monthly exploit leaks. However, the funding campaign has been canceled due to legal reasons.
The hacker group called Shadow Brokers announced on Tuesday that interested parties can obtain exploits and information by paying a monthly fee of 100 Zcash (roughly $20,000). The hackers claim they possess a lot of data allegedly stolen from the NSA-linked Equation Group, including exploits, SWIFT network data, and information on nuclear and missile programs in Russia, China, Iran and North Korea.
A group led by Hacker House co-founder Matthew Hickey and the researcher known online as “x0rz” launched a Patreon-based crowdfunding campaign to raise the 100 Zcash needed to subscribe to the Shadow Brokers’ monthly dumps.
The plan was to immediately notify affected vendors of any zero-day exploits in hopes of avoiding another attack similar to the WannaCry ransomware, which leveraged a Windows SMB exploit leaked by Shadow Brokers. While Microsoft patched the flaw in March, weeks before the WannaCry attacks, many companies were not aware of the risks and neglected to patch it.
Hickey conducted a survey to get the infosec community’s view on the crowdfunding idea, and just over half of the roughly 1,800 votes supported the initiative. Some industry professionals pointed to the legal and ethical implications, while others noted that the Shadow Brokers have likely already leaked all the valuable exploits, or that they will leak the data anyway as they are simply doing it for the attention.
The project raised nearly $4,000 in just 36 hours, but the initiators of the campaign decided to pull the plug after seeking legal advice. The pledged bitcoins will be refunded or donated to the Electronic Frontier Foundation (EFF).
“If you ever want to hear a lawyer shout expletives at volume down a phone you need to call him and tell him that you have created the first open source crowd-funded cyber arms acquisition attempt,” Hickey said. “It transpires that should funds change hands from ours to the Shadow Brokers we would be certainly risking some form of legal complications. It was just too risky and the advice was under no circumstances to proceed further with this.”
While it’s still not clear who is behind the Shadow Brokers – some point to Russia, while others to an NSA insider – Hickey said he learned that the group is linked to Russia’s Federal Security Service (FSB), which complicated the situation even further.
The Shadow Brokers have denied having anything to do with Russia and they claim their main goal is to make money. However, all their attempts, including auctions and crowdfunding initiatives, have so far failed. It remains to be seen if anyone signs up for their monthly dump service.
In the meantime, The Washington Post reported – and confirmed speculation – that it was the NSA who informed Microsoft about the Windows vulnerability exploited by WannaCry. The infosec community has been urging the intelligence agency to disclose the Equation Group exploits to affected vendors given that they could be made public at any time.
Experts discovered that the Terror Exploit Kit now includes fingerprinting capabilities
22.5.2017 securityaffairs Exploit
Experts from Talos Team discovered changes made to the Terror exploit kit (EK) that allow it to fingerprint victims and target specific vulnerabilities.
Recent changes made to the Terror exploit kit (EK) allow it to fingerprint victims and target specific vulnerabilities instead of carpet bombing the victims with many exploits at the same time, Talos researchers discovered.
Last week I reported the news of the improvements of the Stegano Exploit kit, today we will speak about the Terror exploit kit that now includes fingerprinting capabilities.
The Terror Exploit Kit first appeared in the threat landscape in January 2017, in April experts observed a significant increase of hacking campaigns leveraging the EK.
Because of similarities with Sundown EK, experts at MalwareBytes initially thought that the Terror EK was simply a new variant of Sundown, but further investigation revealed that it was actually from a different actor (so-called Terror EK by Trustwave).
The Terror EK was advertised on various underground forums by a hacker with the online moniker @666_KingCobra that is offering it for sale under different names (i.e. Blaze, Neptune, and Eris).
Experts at Malwarebytes Labs said that the Terror EK was used in a malvertising campaign distributing the Smoke Loader by exploiting Internet Explorer, Flash, and Silverlight exploits.
The Terror EK was also involved in a campaign using a different landing page that distributes the Andromeda malware.
The compromised websites were used to redirect to the exploit kit landing page via server 302 redirect call and done via script injection.
The powerful exploit kit was observed carpet bombing victims using many exploits at the same time, but now experts from Talos group observed a significant change in their tactic. News of the day is that the Terror Exploit Kit was improved with new exploits and implemented fingerprinting abilities. These latter features allow the EK to determine what exploit would be used in order to compromise the target system.
The new variant of the Terror Exploit Kit was able to determine the specific OS running on the victim’s PC, the browser version, installed security patches and plugins.
The researchers were served different files when accessing the site via different browsers, such as Internet Explorer 11 or Internet Explorer 8.
Talos malware researchers identified a potentially compromised legitimate website that operates as a malware gate. The website was initially used to redirect visitors to a RIG landing page, after a single day of analysis the gate switched to Terror exploit kit.
“Terror seems to constantly evolving. In this campaign it has added further exploits and no longer carpet bombs the victim. Instead it evaluates data regarding the victim’s environment and then picks potentially successful exploits depending on the victim’s operating system, patch level, browser version and installed plugins. This makes it harder for an investigator to fully uncover which exploits they have.” reads the analysis published by Talos.
“It is interesting to note that the adversaries are using an URL parameter in cleartext for the vulnerability they are going to exploit, e.g. cve2013-2551 = cve20132551 in the URL.”
The compromised website discovered by Talos experts redirects users to the EK landing page by using an HTTP 302 Moved Temporarily response, like previous campaigns.

The page uses obfuscated Javascript code to determine the victim’s browser environment, then uses the return value of this function to submit a hidden form called ‘frm’.
“As mentioned in the executive overview, it uses some obfuscated Javascript code to evaluate the victim’s browser environment, for example it tries to get version information about the following plugins: ActiveX, Flash, PDF reader, Java, Silverlight, QuickTime, etc. Then it uses the return value of this function to submit the hidden form called ‘frm’.” continues the analysis.
The EK also uses cookie-based authentication for downloading the exploits, which prevents third-parties from accessing them, the security researchers discovered. This approach prevents not only investigators from learning where from or how the victims were infected, but also stops competitors from stealing the exploits.
“We have seen that the exploit kit market is experiencing an ongoing change. Big players in this market disappear while new ones show up. The new players are fighting for customers by constantly improving their quality and techniques. They modify these techniques on an ongoing basis to improve their capability to bypass security tools. This clearly shows how important it is to make sure that all your systems are up to date,” concluded Talos.
Terror Exploit Kit Gets Fingerprinting Capabilities
22.5.2017 securityweek Exploit
Recent changes made to the Terror exploit kit (EK) allow it to fingerprint victims and target specific vulnerabilities instead of carpet bombing the victims with many exploits at the same time, Talos researchers discovered.
Terror was initially detailed in January this year, when security researchers observed that it was targeting vulnerabilities with exploits taken from Metasploit or from either Sundown or Hunter EKs. Terror activity increased last month, after the Sundown EK inexplicably disappeared from the threat landscape.
Previously, the EK was observed carpet bombing victims with many exploits at the same time, even if those exploits didn’t match the targeted browser environment. Now, the threat has added more exploits and is fingerprinting victim’s system to determine what exploit would be successful based on operating system, patch level, browser version, and installed plugins.
The use of more targeted exploits makes it more difficult for investigators to determine which exploits the toolkit has. However, “it is interesting to note that the adversaries are using an URL parameter in cleartext for the vulnerability they are going to exploit,” Talos says.
Additionally, Talos researchers identified a potentially compromised legitimate web site that appears to be operating as a malware gate. Initially redirecting visitors to a RIG landing page, the gate switched to Terror after a single day.
The compromised website redirects users to the EK landing page by using a HTTP 302 Moved Temporarily response. The page uses obfuscated Javascript code to evaluate the victim's browser environment, then uses the return value of this function to submit a hidden form called ‘frm’.
More proof that the EK has moved away from its carpet bombing approach is the manner in which it selects exploits when attempting to infect the victim. The researchers were served different files when accessing the site via Internet Explorer 11 than when using Internet Explorer 8.
The EK also uses cookie-based authentication for downloading the exploits, which prevents third-parties from accessing them, the security researchers discovered. This approach prevents not only investigators from learning where from or how the victims were infected, but also stops competitors from stealing the exploits.
“We have seen that the exploit kit market is experiencing an ongoing change. Big players in this market disappear while new ones show up. The new players are fighting for customers by constantly improving their quality and techniques. They modify these techniques on an ongoing basis to improve their capability to bypass security tools. This clearly shows how important it is to make sure that all your systems are up to date,” Talos concludes.
Stegano Exploit Kit now uses the Diffie-Hellman Algorithm
21.5.2017 securityaffairs Exploit
The Stegano exploit kit, also known as Astrum, continues to evolve, recently its authors adopted the Diffie-Hellman algorithm to hinder analysis.
The Stegano exploit kit made was associated in the past with a massive AdGholas malvertising campaign that delivered malware, mostly Gozi and RAMNIT trojans. Experts at TrendMicro also observed the exploit kit in the Seamless malvertising campaign.
“Astrum’s recent activities feature several upgrades and show how it’s starting to move away from the more established malware mentioned above. It appears these changes were done to lay the groundwork for future campaigns, and possibly to broaden its use. With a modus operandi that deters analysis and forensics by abusing the Diffie-Hellman key exchange, it appears Astrum is throwing down the gauntlet.” reads the analysis published by Trend Micro.

In March, the French research Kafeine reported the Stegano EK exploiting the information disclosure vulnerability tracked as CVE-2017-0022. Hackers exploited the flaw to evade antivirus detection and analysis.
A month later, the Stegano exploit kit was updated to prevent security researchers from replaying the malicious network traffic.
“We found that this anti-replay feature was designed to abuse the Diffie-Hellman key exchange—a widely used algorithm for encrypting and securing network protocols. Angler was first observed doing this back in 2015.” continues the analysis.
“Implementing the Diffie-Hellman key exchange prevents malware analysts and security researchers from getting a hold of the secret key Astrum uses to encrypt and decrypt their payloads. Consequently, obtaining the original payload by solely capturing its network traffic can be very difficult.”
According to the experts, the Astrum/ Stegano exploit kit includes exploit codes for a number of vulnerabilities in Adobe Flash, including the CVE-2015-8651 RCE, the CVE-2016-1019 RCE, and the out-of-bound read bug flaw tracked as CVE-2016-4117.
Experts highlighted that currently the Stegano Exploit Kit isn’t used to deliver malware and associated traffic is very low, both circumstances suggest we can soon observe a spike in its activity.
“It wouldn’t be a surprise if [Astrum/Stegano’s] operators turn it into an exclusive tool of the trade—like Magnitude and Neutrino did—or go beyond leveraging security flaws in Adobe Flash. Emulating capabilities from its predecessors such as fileless infections that can fingerprint its targets and deliver encrypted payloads shouldn’t be far off,” concluded Trend Micro.
Stegano Exploit Kit Adopts the Diffie-Hellman Algorithm
19.5.2017 securityweek Exploit
After receiving multiple updates, the Stegano exploit kit (EK) recently adopted the Diffie-Hellman algorithm to hinder analysis, Trend Micro security researchers warn.
Also known as Astrum, Stegano was previously associated with a massive AdGholas malvertising campaign that delivered Trojans such as Gozi and RAMNIT. The EK was also seen being used in the Seamless malvertising campaign, which normally employs RIG instead.
In late March, Proofpoint security researcher Kafeine discovered the EK abusing CVE-2017-0022, an information disclosure vulnerability in Windows that was patched on March 14. The exploit was used to look for antivirus apps on the system to evade detection and analysis.
In April, the threat received an update that prevented security researchers from replaying the malicious network traffic. The feature abuses the Diffie-Hellman algorithm, which is widely used for encrypting and securing network protocols.
“Implementing the Diffie-Hellman key exchange prevents malware analysts and security researchers from getting a hold of the secret key Astrum uses to encrypt and decrypt their payloads. Consequently, obtaining the original payload by solely capturing its network traffic can be very difficult,” Trend Micro notes.
In addition to the CVE-2017-0022 flaw, Astrum/Stegano is using exploits for a series of vulnerabilities in Adobe Flash, including CVE-2015-8651 (a code execution vulnerability patched December 28, 2015), CVE-2016-1019 (a remote code execution flaw patched April 7, 2016), and CVE-2016-4117 (an out-of-bound read bug in Flash patched May 10, 2016).
At the moment, the EK isn’t distributing established malware, and the threat is maintaining very low traffic, which Trend Micro believes can be seen as dry runs for their future attacks.
“It wouldn’t be a surprise if [Astrum/Stegano’s] operators turn it into an exclusive tool of the trade—like Magnitude and Neutrino did—or go beyond leveraging security flaws in Adobe Flash. Emulating capabilities from its predecessors such as fileless infections that can fingerprint its targets and deliver encrypted payloads shouldn’t be far off,” the researchers note.
Microsoft Warns Governments Against Exploit Stockpiling
15.5.2017 securityweek Exploit
Microsoft Says WannaCry Ransomware Outbreak Should be a Wake Up Call for Governments
Microsoft president and chief legal officer Brad Smith has renewed his call for an international 'Digital Geneva Convention' following the global WannaCrypt ransomware attack that started on Friday.
In 'The need for urgent collective action to keep people safe online: Lessons from last week’s cyberattack', Smith wrote Sunday, "The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world."
Some estimates now suggest that WannaCrypt has affected more than 200,000 users in 200 different countries. But if Smith's proposals were already standard practice, it need never have happened. Earlier this year he called for a digital Geneva Convention that "should mandate that governments report vulnerabilities to vendors rather than stockpile, sell or exploit them."
"This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem," he wrote yesterday. "This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage."
The current worldwide 'incident', which could be described as 'a perfect storm', happened (and is continuing) through the convergence of three primary threats: the continued use of unsupported operating systems (more specifically, Windows XP); the continuing success of phishing; and the availability of 0-day exploits.
The exploits were available because the NSA stockpiled cyber weapons, and Shadow Brokers stole and released them. Smith's digital Geneva convention would have mandated that the NSA report them to Microsoft, and Microsoft could have worked with its users to protect against them. "This is one reason," Smith wrote yesterday, "we called in February for a new 'Digital Geneva Convention' to govern these issues, including a new requirement for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them."
In reality, while a digital Cyber Convention may have prevented this particular outbreak, it would not prevent a similar outbreak combining unsupported operating systems, phishing and 0-day exploits. The one part that would help prevent or minimize similar future incidents would be for customers to upgrade their computers to newer and supported versions -- and this simply is not happening fast enough.
In the UK, the National Health Service was badly affected by WannaCrypt because of its reliance on older systems. This has led to a political row (obviously stoked by the run-up to a general election) over NHS funding. The government claims it has provided funds; the opposition parties claim that funding has been insufficient. A hospital will always be tempted to spend its money on saving lives rather than improving its IT infrastructure. Upgrades need to be mandated rather than recommended.
In the US, President Trump has recognized this. The newly signed CyberSecurity Executive Order states "The President will hold heads of executive departments and agencies (agency heads) accountable for managing cybersecurity risk to their enterprises." It then specifically calls out old systems as a risk to be managed: "The executive branch has for too long accepted antiquated and difficult–to-defend IT." The implication is clear -- executive heads will need to upgrade all unsupported old operating systems to new and supported versions; or be held responsible.
Smith's digital Geneva Convention would have prevented these exploits getting into the public domain; but it cannot mandate operating system upgrades. That doesn't mean it's not a good idea nor that it is not necessary, only that it is not a silver bullet. The convention is part of Microsoft's wider call for an international agreement on Norms -- acceptable international norms of cyber behavior.
It is an uphill struggle. Last week's report from America's Intelligence Community -- delivered just two days before the start of the WannaCrypt incident -- states, "Although efforts are ongoing to gain adherence to certain voluntary, non-binding norms of responsible state behavior in cyberspace, they have not gained universal acceptance, and efforts to promote them are increasingly polarized... Moreover, although some countries might be willing to explore limits on cyber operations against certain targets, few would likely support a ban on offensive capabilities."
The implication is that the NSA is unlikely to heed Smith's call for a Digital Geneva Convention. It will seek to maintain its ability to maintain offensive capabilities, and that will require continued exploit stockpiling.
Ilia Kolochenko, CEO of High-Tech Bridge, says it would be unreasonable and inappropriate to blame the NSA for any significant contribution to the WannaCry attacks.
"Similar 0days are bought and sold almost every day, and many other organizations participate in these auctions - virtually anyone can (un)intentionally leak an exploit and cause similar damage," Kolochenko told SecurityWeek. "The real problem is that in 2017, the largest companies and governments still fail to patch publicly disclosed flaws for months. Practically speaking, the NSA doesn't really need a 0day to get their data - their negligence 'invite' attackers to get in."
Google Researcher Details Linux Kernel Exploit
12.5.2017 securityweek Exploit
Google researcher Andrey Konovalov has revealed details of a Linux kernel vulnerability that can be exploited via packet sockets to escalate privileges.
The issue, he explains, is a signedness issue that leads to an exploitable heap-out-of-bounds write. To trigger the bug, one would need to provide “specific parameters to the PACKET_RX_RING option on an AF_PACKET socket with a TPACKET_V3 ring buffer version enabled.”
Tracked as CVE-2017-7308, the vulnerability is created by the fact that the packet_set_ring function in net/packet/af_packet.c in the Linux kernel up to 4.10.6 does not properly validate certain block-size data. Because of that, a local user can cause a denial of service or gain privileges via crafted system calls.
According to Konovalov, the issue was introduced in August 2011, together with the TPACKET_V3 implementation. In August 2014, an attempt was made to resolve the vulnerability by adding more checks, but a proper fix wasn’t released until March 2017.
“The bug affects a kernel if it has AF_PACKET sockets enabled (CONFIG_PACKET=y), which is the case for many Linux kernel distributions. Exploitation requires the CAP_NET_RAW privilege to be able to create such sockets. However it's possible to do that from a user namespace if they are enabled (CONFIG_USER_NS=y) and accessible to unprivileged users,” the researcher explains.
Packet sockets as a kernel feature are widely used, which results in a large number of popular Linux kernel distributions being impacted, including Ubuntu and Android. A complete list of vulnerable Linux kernel versions is available at SecurityFocus.
While updated Ubuntu kernels are already available, an update for Android won’t arrive until July, the researcher explains. However, he also notes that only some privileged components in the mobile platform have access to AF_PACKET sockets, while untrusted code is blocked from accessing it.
In addition to providing all of the necessary technical details pertaining to the vulnerability and exploit, Konovalov reveals that a way “to fix the overflow is to cast tp_sizeof_priv to uint64 before passing it to BLK_PLUS_PRIV.” He also notes that this is the approach he took in the fix sent upstream.
Creating packet socket requires the CAP_NET_RAW privilege, which can be acquired by unprivileged users inside user namespaces (which create a huge kernel attack surface, resulting in vulnerabilities such as CVE-2017-7184, which was disclosed at Pwn2Own 2017). Completely disabling user namespaces or disallowing using them to unprivileged users can mitigate the issue.
“To disable user namespaces completely you can rebuild your kernel with CONFIG_USER_NS disabled. Restricting user namespaces usage only to privileged users can be done by writing 0 to /proc/sys/kernel/unprivileged_userns_clone in Debian-based kernel. Since version 4.9 the upstream kernel has a similar /proc/sys/user/max_user_namespaces setting,” the researcher says.
Konovalov, who found the bug using the open-source Linux system call fuzzer called syzkaller and dynamic memory error detector KASAN, also published a proof-of-concept local root exploit for the flaw.
Exploitable Details of Intel's 'Apocalyptic' AMT Firmware Vulnerability Disclosed
8.5.2017 securityweek Exploit
Details of the Intel AMT firmware vulnerability announced on May 1, 2017 are now public knowledge; and the suggestion that 'this is somewhere between nightmarish and apocalyptic' has been proven correct.
One day after Intel's alert, Embedi (the firm that discovered the vulnerability back in February this year) published a brief note. One particular sentence stood out to researchers at Tenable: "With 100 percent certainty it is not an RCE but rather a logical vulnerability."
This persuaded Tenable to look at 'authentication' as the possible basis for a logical flaw that allows remote access. Within one day it discovered the flaw by trial and error -- and experience.
"Drawing on past experience," explains Carlos Perez, Tenable's director of reverse engineering in a blog post last Friday, "when we reported an authentication-related vulnerability in which the length of credential comparison is controlled by the attacker (memcmp(attacker_passwd, correct_passwd, attacker_pwd_len)), we tested out a case in which only a portion of the correct response hash is sent to the AMT web server. To our surprise, authentication succeeded!"
Further tests showed that a NULL/empty response hash (response="" in the HTTP Authorization header) still worked. "We had discovered a complete bypass of the authentication scheme."
Tenable asked Intel if this was the flaw in question. Intel said it was, and asked Tenable to delay publication until the end of the day on Thursday Pacific time (effectively Friday). This gave Embedi (the original finder of the flaw) time to simultaneously publish its own findings on Friday.
If Tenable could find the flaw within a single day, blackhats could do the same. The time for obfuscation had passed. While Tenable had found the flaw, Embedi's whitepaper (PDF), also published Friday, explains it.
Embedi had been looking into AMT and its admin account that is present by default and always uses digest authentication. By reverse engineering the firmware it discovered, "The value of the computed response, which is the first argument, is being tested against the one that is provided by user, which is the second argument, while the third argument is the length of the response. It seems quite obvious that the third argument of strncmp() should be the length of computed_response, but the address of the stack variable response_length, from where the length is to be loaded, actually points to the length of the user_response!"
In short, it explains, "Given an empty string the strncmp() evaluates to zero thus accepting an invalid response as a valid one."
Armed with this knowledge, any attacker could get admin control over AMT. It is the power of AMT that makes the vulnerability so severe. "First of all," explains Embedi, "you should remember that Intel AMT provides the ability to remotely control the computer system even if it's powered off (but connected to the electricity mains and network)." Furthermore, it is completely independent of the installed operating system. No traditional security defense could even see, let own prevent, anything done through AMT.
Embedi describes some of the possible attack scenarios. These include, remote load and install of any file onto the target system; read any file; remotely change the boot device to some other virtual image; remotely power on/power off/reboot/reset and do other actions; and even edit the BIOS setup.
The situation now is that any business PC that uses AMT, ISM or SBT that has not received the Intel firmware patch, is vulnerable to a silent, unpreventable, major attack -- and details of how to perform the attack are public knowledge. Several PC vendors have started rolling out the new Intel firmware (Dell, HP, Lenovo, Fujitsu) -- but some older and boutique PCs may never receive the patch.
On Friday, May 5, 2017, Intel issued an update to its original alert. It reiterates its original recommendations. Intel users should first determine whether they are vulnerable (that is, if the devices incorporate AMT, ISM or SBT), and then take the mitigation steps already published. But note, it adds, "capabilities and features provided by AMT, ISM and SBT will be made unavailable by these mitigations."
Intel has also released a discovery tool, which will analyze systems to see if the vulnerability is present.
What is clear, however, is that this flaw (which has existed for more than 9 years) truly is somewhere between nightmarish and apocalyptic. Taking no action is not an option.
Corporate Users Increasingly Targeted With Exploits: Kaspersky
21.4.2017 securityweek Exploit
A report published by Kaspersky Lab on Thursday shows that the number of attacks involving exploits increased significantly in 2016 compared to the previous year, but the number of attacked users actually dropped.
The security firm observed more than 700 million attempts to execute an exploit in 2016, which represents a 25% increase compared to 2015. However, the number of users attacked was only 4.3 million, compared to nearly 5.5 million in the previous year.
This indicates that while fewer users encountered exploits, the likelihood of coming across an exploit increased as the number of websites and spam messages delivering such threats has continued to grow.
Of all the exploit attacks observed by Kaspersky in 2016, more than 15% were aimed at corporate machines. The number of targeted corporate users increased from 538,000 in 2015 to 690,000 in 2016.
While Windows and web browsers were the most targeted applications in both 2015 and 2016, their share decreased significantly last year, making more room for Android and Microsoft Office exploits.
“Exploits for vulnerabilities in Office software became the absolute champions in terms of the number of attacked users. They increased by almost 103% to reach 367,167 attacked users,” Kaspersky said in its report.
The security firm said more than 297,000 users were hit by zero-day or heavily obfuscated known exploits in 2016, and the most common exploit, same as in the previous year, was CVE-2010-2568, a vulnerability leveraged by the notorious Stuxnet malware.
Between 2010 and 2016, malicious actors used more than 80 vulnerabilities in targeted attacks. The Russia-linked threat group known as APT28 and Fancy Bear leveraged 25 flaws, including at least six zero-days, followed by the NSA-linked Equation Group, which used roughly 17 vulnerabilities, including at least eight zero-days.
Groups that launched targeted attacks have mainly relied on Windows flaws, followed by Flash Player, Office, Java and Internet Explorer. The most popular vulnerability is CVE-2012-0158, which is still being used by APT actors.
Exploits: how great is the threat?
20.4.2017 Kaspersky Exploit
How serious, really, is the danger presented by exploits? The recent leak of an exploit toolset allegedly used by the infamous Equation Group suggests it’s time to revisit that question. Several zero-days, as well as a bunch of merely ‘severe’ exploits apparently used in-the-wild were disclosed, and it is not yet clear whether this represents the full toolset or whether there’s more to come, related to either Equation or another targeted threat actor.
Of course, Equation Group is not the first, and is certainly not the only sophisticated targeted attacker to use stealthy, often zero-day exploits in its activity.
Today we are publishing an overview of the exploit threat landscape. Using our own telemetry data and intelligence reports as well as publically available information, we’ve looked at the top vulnerabilities and applications exploited by attackers.
We have examined them from two equally important perspectives. The first part of the report summarises the top exploits targeting all users in 2015-2016, and the most vulnerable applications. The second part considers the vulnerabilities exploited between 2010 and 2016 by significant targeted threat actors reported on by Kaspersky Lab: that’s 35 actors and campaigns in total.
Key findings on exploits targeting all users in 2015-2016:
In 2016 the number of attacks with exploits increased 24.54%, to 702,026,084 attempts to launch an exploit.
4,347,966 users were attacked with exploits in 2016 which is 20.85% less than in the previous year.
The number of corporate users who encountered an exploit at least once increased 28.35% to reach 690,557, or 15.76% of the total amount of users attacked with exploits.
Browsers, Windows, Android and Microsoft Office were the applications exploited most often – 69.8% of users encountered an exploit for one of these applications at least once in 2016.
In 2016, more than 297,000 users worldwide were attacked by unknown exploits (zero-day and heavily obfuscated known exploits).
2015-2016 witnessed a number of positive developments in the exploit threat landscape. For example, two very dangerous and effective exploit kits – Angler (XXX) and Neutrino, left the underground market, depriving cybercriminals community of a very comprehensive set of tools created to hack computers remotely.
A number of bug bounty initiatives aimed at highlighting dangerous security issues were launched or extended. Together with the ever-increasing efforts of software vendors to fix new vulnerabilities, this significantly increased the cost to cybercriminals of developing new exploits. A clear victory for the infosec community that has resulted in a drop of just over 20% in the number of private users attacked with exploits: from 5.4 million in 2015 to 4.3 million in 2016.
However, alongside this welcome decline, we’ve registered an increase in the number of corporate users targeted by attacks involving exploits. In 2016, the number of attacks rose by 28.35% to reach more than 690,000, or 15.76% of the total amount of users attacked with exploits. In the same year, more than 297,000 users worldwide were attacked by unknown exploits. These attacks were blocked by our Automatic Exploit Prevention technology, created to detect this type of exploits.
Key findings on exploits used by targeted attackers 2010 -2016:
Overall, targeted attackers and campaigns reported on by Kaspersky Lab in the years 2010 to 2016 appear to have held, used and re-used more than 80 vulnerabilities. Around two-thirds of the vulnerabilities tracked were used by more than one threat actor.
Sofacy, also known as APT28 and Fancy Bear seems to have made use of a staggering 25 vulnerabilities, including at least six, if not more zero-days. The Equation Group is not far behind, with approximately 17 vulnerabilities in its arsenal, of which at least eight were zero-days, according to public data and Kaspersky Lab’s own intelligence.
Russian-speaking targeted attack actors take three of the top four places in terms of vulnerability use (the exception being Equation Group in second place), with other English- and Chinese-speaking threat actors further down the list.
Once made public, a vulnerability can become even more dangerous: grabbed and repurposed by big threat actors within hours.
Targeted attackers often exploit the same vulnerabilities as general attackers – there are notable similarities between the list of top vulnerabilities used by targeted threat actors in 2010-2016, and those used in all attacks in 2015-2016.
When looking more closely at the applications used by targeted threat actors to mount exploit-based attacks, we weren’t surprised to discover that Windows, Flash and Office top the list.
Applications and Operation Systems most often exploited by targeted attack groups.
Moreover, the recent leak of multiple exploits allegedly belonging to the Equation cyberespionage group highlighted another known but often overlooked truth: the life of an exploit doesn’t end with the release of a security patch designed to fix the vulnerability being exploited.
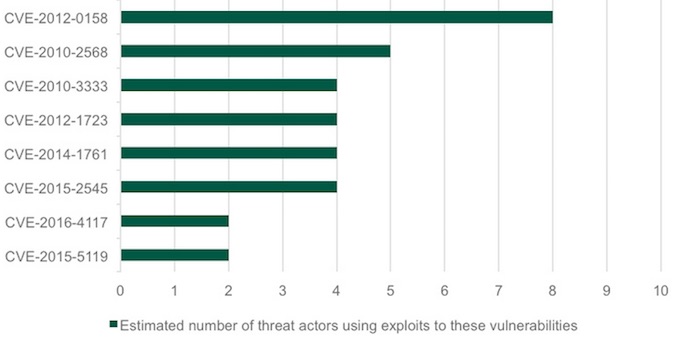
Our research suggests that threat actors are still actively and successfully exploiting vulnerabilities patched almost a decade ago – as can be seen in the chart below:
Everyone loves an exploit
Exploits are an effective delivery tool for malicious payloads and this means they are in high demand among malicious users, whether they are cybercriminal groups, or targeted cyberespionage and cybersabotage actors.
To take just one example, when we looked at our most recent threat statistics we found that exploits to CVE-2010-2568 (used in the notorious Stuxnet campaign) still rank first in terms of the number of users attacked. Almost a quarter of all users who encountered any exploit threat in 2016 were attacked with exploits to this vulnerability.
Conclusion and Advice
The conclusion is a simple one: even if a malicious user doesn’t have access to expensive zero-days, the chances are high that they’d succeed with exploits to old vulnerabilities because there are many systems and devices out there that have not yet been updated.
Even though developers of popular software invest huge resources into finding and eliminating bugs in their products and exploit mitigation techniques, for at least the foreseeable future the challenge of vulnerabilities will remain.
In order to protect your personal or business data from attacks via software exploits, Kaspersky Lab experts advise the following:
Keep the software installed on your PC up to date, and enable the auto-update feature if it is available.
Wherever possible, choose a software vendor which demonstrates a responsible approach to a vulnerability problem. Check if the software vendor has its own bug bounty program.
If you are managing a network of PCs, use patch management solutions that allow for the centralized updating of software on all endpoints under your control.
Conduct regular security assessments of the organization’s IT infrastructure.
Educate your personnel on social engineering as this method is often used to make a victim open a document or a link infected with an exploit.
Use security solutions equipped with specific exploit prevention mechanisms or at least behavior-based detection technologies
Give preference to vendors which implement a multilayered approach to protection against cyberthreats, including exploits.