Credit: Bitdefender
APT Articles 1- H 2020 1 2 APT List H 2021 2020 2019 2018 2017 2016 APT blog APT blog
Chafer APT Hits Middle East Govs With Latest Cyber-Espionage Attacks
22.5.2020 Threatpost APT
Government and air transportation companies in Kuwait and Saudi Arabia were targeted in a recent attack tracked back to the Chafer APT.
Researchers have uncovered new cybercrime campaigns from the known Chafer advanced persistent threat (APT) group. The attacks have hit several air transportation and government victims in hopes of data exfiltration.
The Chafer APT has been active since 2014 and has previously launched cyber espionage campaigns targeting critical infrastructure in the Middle East. This most recent wave of cyberattacks started in 2018 and have lasted until at least the end of 2019, targeting several unnamed organizations based in Kuwait and Saudi Arabia. The campaigns used a bevy of custom-built tools, as well as “living off the land” tactics. Living off the land tools are features already existing in the target environment, which are abused by attackers to help them achieve persistence.
“Researchers have found attacks conducted by this actor in the Middle East region, dating back to 2018,” according to a Thursday Bitdefender analysis. “The campaigns were based on several tools, including ‘living off the land’ tools, which makes attribution difficult, as well as different hacking tools and a custom built backdoor. Victims of the analyzed campaigns fit into the pattern preferred by this actor, such as air transport and government sectors in the Middle East.”
Liviu Arsene, global cybersecurity analyst with Bitdefender, told Threatpost that researchers can’t specify how many companies have been targeted in each country. However, “it is safe to estimate that the cybercriminal group likely went after more than those we investigated,” he said.
The Campaigns
While the modus operandi behind the attacks against firms in Kuwait and Saudi Arabia shared “some common stages,” researchers noted that the attacks on victims from Kuwait were more sophisticated as attackers were able to move laterally on the network. Researchers believe the threat actors initially infected victims using tainted documents with shellcodes, potentially sent via spear-phishing emails.
“During our investigation, on some of the compromised stations we observed some unusual behavior performed under a certain user account, leading us to believe the attackers managed to create a user account on the victims’ machine and performed several malicious actions inside the network, using that account,” said researchers.
Once they gained a foothold inside the company, attackers then installed a backdoor (imjpuexa.exe), that was executed as a service on some machines. Attackers also deployed several network-scanning and credential-gathering tools used for reconnaissance and to help them move laterally inside the network. For instance, attackers deployed CrackMapExec, a multi-purpose tool used for network scanning, credential dumping, accounts discovery and code injection.
Another custom tool of note that attackers utilized is a modified PLINK tool (called wehsvc.exe). PLINK is a command-line connection tool mostly used for automated operations. The PLINK tool used in the campaign preserves the original functionality, with some new key features such as the possibility to run as a Windows service or to uninstall the service.
“We believe this tool may have been used either to communicate with the [command and control server] C2 or to gain access to some internal machines, but found no conclusive evidence to support these scenarios,” said researchers.
While the attack on the victim in Kuwait achieved further lateral movement, researchers said the attack on the victim in Saudi Arabia was not as elaborate, “either because the attackers did not manage to further exploit the victim, or because the reconnaissance revealed no information of interest.”
For these attacks, researchers said they believe “initial compromise was achieved through social engineering.” After initial compromise, a RAT was loaded and executed twice, with different names (“drivers.exe” and “drivers_x64.exe”). The two executions were three minutes apart, leading researchers to believe that the user was tricked into running them.
The RAT was written in Python and converted into a standalone executable: “Some RATs are very similar to tools that have been previously documented by security researchers, but have been customized for this particular attack,” Arsene told Threatpost. “It’s not uncommon for cybercriminal groups to tweak their tools based on either victim profile or immediate needs. For example, they might change the way the RAT communicates with the C2 server, or they can add other features that were not necessary in the past but currently prove useful.”
Researchers also found three different RAT components that were used at different times. One of these components (“snmp.exe”) was the same as the backdoor (“imjpuexa.exe”) used on the targeted attacks in Kuwait – leading researchers to link the two campaigns.
“While this attack was not as extensive as the one in Kuwait, some forensic evidence suggests that the same attackers might have orchestrated it,” they said. “Despite the evidence for network discovery, we were not able to find any traces for lateral movement, most probably because threat actors were not able to find any vulnerable machines.”
Of note, the threat actor also used “living off the land” tools extensively in both campaigns. This included the heavy use of the Non-Sucking Service Manager (NSSM), which is a legitimate service manager for Microsoft Windows. The NSSM utility manages background and foreground services and processes. Researchers believe the APT used NSSM for ensuring that its critical components, such as the RAT, are up and running.
“We estimate that attackers relied on NSSM to make sure that the services they were monitoring were actually running and not terminated or stopped,” Arsene explained. “It’s a way of ensuring persistence for malicious services and restarting them if they are inadvertently killed or stopped by various other applications.”
So far, all of the incidents that researchers uncovered have been stopped: “the investigation in both countries was stopped before concluding when or if the cyberattack had stopped,” Arsene said. “It’s likely that… local authorities were notified and decided to continue the investigation locally.”
Cyber-Espionage
Researchers linked these campaigns with Chafer because some of the tools used bear similarities to the tools used in previously-documented Chafer APT attacks. The C2 domains in these attacks have been previously associated with the same cybercriminal group, Arsene told Threatpost.
It’s only the latest campaign for the Chafer APT. Last year, the Iran-linked APT was spotted targeting various entities based in Iran with an enhanced version of a custom malware that takes a very unique approach to communication by using the Microsoft Background Intelligent Transfer Service (BITS) mechanism over HTTP. Another campaign in February, launched by two Iran-backed APTs who were possibly working together to compromise high-value organizations from the IT, telecom, oil and gas, aviation, government and security sectors in Israel, was loosely linked to the Chafin APT after researchers noted an overlap in approaches.
That said, cyber-espionage campaigns have spiraled downwards overall over the past year, according to the recent 2020 Verizon Data Breach Investigations Report (DBIR), dropping from making up 13.5 percent of breaches in 2018 to a mere 3.2 percent of data breaches in 2019.
Winnti uses a new PipeMon backdoor in attacks aimed at the gaming industry
22.5.2020 Securityaffairs APT
The Winnti hacking group continues to target gaming industry, recently it used a new malware named PipeMon and a new method to achieve persistence.
Winnti hacking group is using a new malware dubbed PipeMon and a novel method to achieve persistence in attacks aimed at video game companies.
The Winnti group was first spotted by Kaspersky in 2013, but according to the researchers the gang has been active since 2007.
The experts believe that under the Winnti umbrella there are several APT groups, including Winnti, Gref, PlayfullDragon, APT17, DeputyDog, Axiom, BARIUM, LEAD, PassCV, Wicked Panda, Group 72, Blackfly, and APT41, and ShadowPad.
The APT group targeted organizations in various industries, including the aviation, gaming, pharmaceuticals, technology, telecoms, and software development industries.
PipeMon is a modular backdoor that was spotted by ESET researchers earlier this year on servers belonging to several developers of massively multiplayer online (MMO) games from South Korea and Taiwan. Each component of the backdoor is implemented by a DLL.
“In February 2020, we discovered a new, modular backdoor, which we named PipeMon. Persisting as a Print Processor, it was used by the Winnti Group against several video gaming companies that are based in South Korea and Taiwan and develop MMO (Massively Multiplayer Online) games.” reads the report published by the company. “Video games developed by these companies are available on popular gaming platforms and have thousands of simultaneous players.”
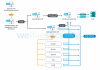
In one case analyzed by the researchers, the hackers compromised a victim’s build system, then they have planted malware inside the video game executable. In another case, the Winnti group compromised the game servers were compromised, which could have allowed the attackers to conduct several malicious actions, including the manipulation of in-game currencies for financial gain.
Experts noticed that the PipeMon backdoor was signed with a certificate belonging to a video game company that was already hacked by Winnti in 2018.
Researchers also reported that the threat actors reused some C2 domains involved in other campaigns and used a custom login stealer that was previously associated with Winnti operations.
The experts discovered two PipeMon variants, but they were able to describe the infection process and how it has achieved persistence only for one of them.
The first stage of the PipeMon backdoor consists of a password-protected RARSFX executable embedded in the .rsrc section of its launcher.
The hackers achieved persistence by using the Windows print processors (DLLs). A malicious DLL loader drops where the print processors reside and registered as an alternative print processor by modifying one of the two registry values:
HKLM\SYSTEM\ControlSet001\Control\Print\Environments\Windows x64\Print Processors\PrintFiiterPipelineSvc\Driver = “DEment.dll”
HKLM\SYSTEM\CurrentControlSet\Control\Print\Environments\Windows x64\Print Processors\lltdsvc1\Driver = “EntAppsvc.dll”
After having registered the Print Processor, PipeMon restarts the print spooler service (spoolsv.exe) to load the malware.
Since the service starts every time the computer reboot, the attackers have achieved persistence.
“After having registered the Print Processor, PipeMon restarts the print spooler service (spoolsv.exe). As a result, the malicious print process is loaded when the spooler service starts. Note that the Print Spooler service starts at each PC startup, which ensures persistence across system resets.” continues the report.
“This technique is really similar to the Print Monitor persistence technique (being used by DePriMon, for example) and, to our knowledge, has not been documented previously.”
PipeMon modules are DLLs exporting a function called IntelLoader and are loaded using a reflective loading technique.
The loader, responsible for loading the main modules (ManagerMain and GuardClient) is Win32CmdDll.dll and is stored in the Print Processors directory. Experts noticed that modules are stored encrypted on disk at the same location with inoffensive-looking names.
Experts also spotted an updated version of PipeMon for which they were able to retrieve the first stage. Its architecture is highly similar to the original variant, but its code was rewritten from scratch.
“Once again, the Winnti Group has targeted video game developers in Asia with a new modular backdoor signed with a code-signing certificate likely stolen during a previous campaign and sharing some similarities with the PortReuse backdoor. This new implant shows that the Winnti Group is still actively developing new tools using multiple open source projects; they don’t rely solely on their flagship backdoors, ShadowPad and the Winnti malware.” concludes ESET.
Iran-linked Chafer APT group targets governments in Kuwait and Saudi Arabia
21.5.2020 Securityaffairs APT
Cybersecurity researchers uncovered an Iranian cyber espionage campaign conducted by Chafer APT and aimed at critical infrastructures in Kuwait and Saudi Arabia.
Cybersecurity researchers from Bitdefender published a detailed report on an Iranian cyber espionage campaign directed against critical infrastructures in Kuwait and Saudi Arabia.
The cyber espionage campaigns were carried out by Iran-linked Chafer APT (also known as APT39 or Remix Kitten).
The Chafer APT group has distributed data stealer malware since at least mid-2014, it was focused on surveillance operations and the tracking of individuals.
The APT group targets telecommunication and travel industries in the Middle East to gather intelligence on Iran’s geopolitical interests.
“Victims of the analyzed campaigns fit into the pattern preferred by this actor, such as air transport and government sectors in the Middle East,” reads the researcher paper published by the experts.
“Some traces indicate that the goal of the attack was data exploration and exfiltration (on some of the victim’s tools such as Navicat, Winscp, found in an unusual location, namely “%WINDOWS%\ime\en-us-ime”, or
SmartFtpPasswordDecryptor were present on their systems).”
The attackers used several tools, including ‘living off the land’ tools, making it hard to attribute the attack to specific threat actors, as well as a custom-built backdoor.
The attacks against entities in Kuwait and Saudi Arabia have multiple similarities and shares some common stages, but experts noticed that the attacks seem more focused and sophisticated on victims from Kuwait.
Chafer APT launched spear-phishing attacks, the messages were used to deliver multiple backdoors that allowed them to gain a foothold, elevate their privileges, conduct internal reconnaissance, and establish persistence in the victim environment.
“Once the victims were compromised, attackers started to bring reconnaissance tools for network scanning (“xnet.exe”, “shareo.exe”) and credential gathering (as “mnl.exe” or “mimi32.exe”) or tools with multiple functionalities, such as CrackMapExec (for users’ enumeration, share listing, credentials harvesting and so on).” continues the report.
“During our investigation, on some of the compromised stations we observed some unusual behavior performed under a certain user account, leading us to believe the attackers managed to create a user account on the victims’ machine and performed several malicious actions inside the network, using that account.”
The attacks against entities in Kuwait appeared more sophisticated, attackers were creating a user account on the compromised machines and performed malicious actions inside the network, including credential harvesting with Mimikatz and lateral movements using multiple hacking tools from their arsenal.
Most of the hacking activity occurs on Friday and Saturday, coinciding with the weekend in the Middle East.
The campaign against a Saudi Arabian entity was characterized by the large use of social engineering attacks to trick the victim into executing a remote administration tool (RAT), The RAT employed in the attacks shares similarities with those used against Kuwait and Turkey.
“The case investigated in Saudi Arabia was not as elaborate, either because the attackers did not manage to further exploit the victim, or because the reconnaissance revealed no information of interest.” continues the report.
“While this attack was not as extensive as the one in Kuwait, some forensic evidence suggests that the same attackers might have orchestrated it. Despite the evidence for network discovery, we were not able to find any traces for lateral movement, most probably because threat actors were not able to find any vulnerable machines.”
The campaigns against Kuwait and Saudi Arabia demonstrate the intense cyberespionage activity carried out by Iran-linked APT groups in the Middle East. Anyway we cannot underestimate that these hacking groups are extending their range of action targeting government and organizations worldwide.
Iranian APT Group Targets Governments in Kuwait and Saudi Arabia
21.5.2020 Thehackernews APT
Today, cybersecurity researchers shed light on an Iranian cyber espionage campaign directed against critical infrastructures in Kuwait and Saudi Arabia.
Bitdefender said the intelligence-gathering operations were conducted by Chafer APT (also known as APT39 or Remix Kitten), a threat actor known for its attacks on telecommunication and travel industries in the Middle East to collect personal information that serves the country's geopolitical interests.
"Victims of the analyzed campaigns fit into the pattern preferred by this actor, such as air transport and government sectors in the Middle East," the researchers said in a report (PDF) shared with The Hacker News, adding at least one of the attacks went undiscovered for more than a year and a half since 2018.
"The campaigns were based on several tools, including 'living off the land' tools, which makes attribution difficult, as well as different hacking tools and a custom-built backdoor."
Known to be active since 2014, the Chafer APT has previously taken aim at Turkish government organizations and foreign diplomatic entities based in Iran with the goal of exfiltrating sensitive data.
A FireEye report last year added to growing evidence of Chafer's focus on telecommunications and travel industries. "Telecommunications firms are attractive targets given that they store large amounts of personal and customer information, provide access to critical infrastructure used for communications, and enable access to a wide range of potential targets across multiple verticals," the company said.
APT39 compromises its targets via spear-phishing emails with malicious attachments and using a variety of backdoor tools to gain a foothold, elevate their privileges, conduct internal reconnaissance, and establish persistence in the victim environment.
What makes the Kuwait attack more elaborate, according to Bitdefender, is their ability to create a user account on the victims' machine and perform malicious actions inside the network, including network scanning (CrackMapExec), credential harvesting (Mimikatz), and move laterally inside the networks using a wide arsenal of tools at their disposal.
Most activity occurs on Friday and Saturday, coinciding with the weekend in the Middle East, the researchers said.
The attack against a Saudi Arabian entity, on the other hand, involved the use of social engineering to trick the victim into running a remote administration tool (RAT), with some of its components sharing similarities with those used against Kuwait and Turkey.
"While this attack was not as extensive as the one in Kuwait, some forensic evidence suggests that the same attackers might have orchestrated it," the researchers said. "Despite the evidence for network discovery, we were not able to find any traces for lateral movement, most probably because threat actors were not able to find any vulnerable machines."
The attacks against Kuwait and Saudi Arabia are a reminder that Iran's cyber espionage efforts have shown no sign of slowing down. Given the crucial nature of the industries involved, Chafer's actions continue the trend of striking countries that act against its national ambitions.
"While these two are the most recent attack examples happening in the Middle East, it is important to understand that this type of attack can happen anywhere in the world, and critical infrastructures like government and air transportation remain very sensitive targets," Bitdefender said.
APT group targets high profile networks in Central Asia
17.5.2020 Securityaffairs APT
Security firms have foiled an advanced cyber espionage campaign carried out by Chinese APT and aimed at infiltrating a governmental institution and two companies.
Antivirus firms have uncovered and foiled an advanced cyber espionage campaign aimed at a governmental institution and two companies in the telecommunications and gas sector.
The level of sophistication of the attack and the nature of targets suggests the involvement of an advanced persisten threat, likely from China, focused on cyber espionage activity in Central Asia.
Attackers used multiple commodity malware and previously unknown backdoors in the attacks, the analysis of their code suggests a possible link with multiple campaigns uncovered over several years.
Most of the C2 used by the attackers are hosted by the provider Choopa, LLC, and threat actors made large use of Gh0st RAT, a malware attributed to China-linked cyber espionage groups.
The security firm ESET and Avast first detected the attacks since September and January respectively. The researchers identified a host used as a repository containing hacking tools and backdoors, whose code has many similarities with malware previously associated with China-linked APT groups.
“The samples we analyzed contain links to malware samples and campaigns, such as Microcin, BYEBY, and Vicious Panda, previously described by Kaspersky, Palo Alto Networks, and Check Point, respectively. The backdoors we found are custom tools that have not previously been analyzed, as far as we know.” reads a report published by Avast. “The majority of the C&C servers are registered to Choopa, LLC, a hosting platform that has been used by cybercriminals in the past.”
Below a timeline of the attacks that appeared to be associated with the same threat actor.

“An APT group, which we believe could possibly be from China, planted backdoors to gain long-term access to corporate networks. Based on our analysis, we suspect the group was also behind attacks active in Mongolia, Russia, and Belarus.” continues Avast.
Researchers from ESET that investigared into the attacks discovered three backdoors that collectively tracked as Mikroceen. The backdoors allowed the threat actors to manage the target file system, establish a remote shell, take screenshots, manage services and processes, and run console commands.
Below the list of backdoors published by ESET:
sqllauncher.dll (VMProtected backdoor)
logon.dll (VMProtected backdoor)
logsupport.dll (VMProtected backdoor)
Both “sqllauncher.dll” and “logon.dll” run as services and use the same C2 infrastructure, experts noticed that all of them feature protection against reverse engineering. Two of them, “sqllauncher.dll” and “logon.dll,” run as services and use the same C2 server.
Attackers use a version of the Mimikatz post-exploitation tool and rely on Windows Management Instrumentation (WMI) for lateral movement.
“Avast reported its findings to the local CERT team and reached out to the telecommunications company. We have not heard back from either organization.” concluded Avast.
“Avast has recently protected users in Central Asia from further attacks using the samples we analyzed.”
Both Avast and ESET have published a list of indicators of compromise (IoC) for the above threats.
Chinese APT Tropic Trooper target air-gapped military Networks in Asia
16.5.2020 Securityaffairs APT
Chinese threat actors, tracked as Tropic Trooper and KeyBoy, has been targeting air-gapped military networks in Taiwan and the Philippines.
Chinese APT group Tropic Trooper, aka KeyBoy, has been targeting air-gapped military networks in Taiwan and the Philippines, Trend Micro researchers reported.
The Tropic Trooper APT that has been active at least since 2011, it was first spotted in 2015 by security experts at Trend Micro when it targeted government ministries and heavy industries in Taiwan and the military in the Philippines.
The threat actor targeted government offices, military, healthcare, transportation, and high-tech industries in Taiwan, the Philippines, and Hong Kong.
Since December 2014, the threat actors are using a malware dubbed USBferry in attacks against military/navy agencies, government institutions, military hospitals, and also a national bank.
“Recently, we discovered the Tropic Trooper group targeting Taiwanese and the Philippine military’s physically isolated environment using a USBferry attack (the name derived from a sample found in a related research).” reads the analysis published by Trend Micro. “USBferry has variants that perform different commands depending on specific targets; it can also combine capabilities, improve its stealth in infected environments, and steal critical information through USB storage”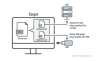
The USBferry USB malware could execute various commands on specific the infected system and allow to exfiltrate sensitive data through USB storage.
According to Trend Micro’s telemetry, attacks that employ USBferry attack are ongoing since December 2014 and has been targeting military or government users located in Asia.
The malware was first mentioned in a PwC report that attributes it to Tropic Trooper APT, but that did not include a detailed analysis.
The attackers would first target organizations related to military or government that implements fewer security measures compared with the real targets, then they attempt to use them as a proxy to the final target. In one case, the hackers compromised a military hospital and used it to move to the military’s physically isolated network.
Trend Micro researchers identified at least three versions of the malware with different variants and components.”
“Tropic Trooper uses the old way of achieving infection: by ferrying the installer into an air-gapped host machine via USB.” continues the report. “They employ the USB worm infection strategy using the USB device to carry the malware into the target’s computer and facilitate a breach into the secure network environment.”
The group used “tracert” and “ping” commands to map the target’s network
architecture (i.e. “tracert -h 8 8.8.8.8” collects the route (path) and measures transit delays of packets across an Internet Protocol (IP) network, while pings allow testing the target network’s connectivity).
The attackers attempted to determine if the infected machine has access to the internal network and the target mail portal.
In the absence of network connectivity, the malware collects information from the machine and copy the data to the USB drive.
The experts also discovered that the hackers use different backdoors in a recent attack, including WelCome To Svchost, Welcome To IDShell, and Hey! Welcome Server.
The arsenal of the APT group includes scanning tools, a command-line remote control listener/port relay tool, and backdoor payload/steganography payload execution loaders.
“This targeted attack operation can be broken down into four important points.” concludes the report. “First, putting critical data in physically isolated networks is not an overarching solution for preventing cyberespionage activities. Second, their preferred technique of steganography isn’t just used to deliver payloads, but also for sending information back to the C&C server. Third, several hacking tools and components can be used to fulfill attacks in different target networks and environments. These tools and components also have a selfdelete command to make it tricky to trace the attack chain and all the related factors. Lastly, using an invisible web shell hides their C&C server location and makes detecting malicious traffic more difficult for network protection products“
Mysterious Chinese APT Linked to Multiple Central Asian Campaigns
16.5.2020 Securityweek APT
An unknown threat actor, possibly Chinese, has been targeting high-profile organizations in Central Asia with a mix of commodity malware and previously unknown backdoors. Coding similarities suggest a possible link with multiple campaigns over several years.
Researchers from Avast started monitoring and analyzing central Asian APT activity back in September 2019. By January 2020, they were joined by researchers from ESET.
In January 2020, Avast detected a new campaign targeting a Central Asian telecommunications company. Analyzing the samples found in this and other campaigns has led the researchers to believe they all use variants of the same malware family -- which the ESET researchers have named 'Mikroceen'. This is partly in deference to Kaspersky's discovery of Microcin malware targeting the Russian military in September 2017, but also to allow inclusion of Palo Alto Network's discovery of BYEBY malware targeting the Belorussian government also in September 2017, and Check Point's discovery of the Vicious Panda campaign targeting the Mongolian public sector in March 2020.
What isn't clear is whether all these campaigns have been waged by the same group, or whether multiple groups have access to the same Mikroceen malware family. (In July 2019, Anomali research concluded that there is a strong sharing culture among Chinese groups.) Avast researcher Luigino Camastra blogged, "An APT group, which we believe could possibly be from China, planted backdoors to gain long-term access to corporate networks. Based on our analysis, we suspect the group was also behind attacks active in Mongolia, Russia, and Belarus."
However, in conversation he was a bit more circumspect. "There are similarities with other known Chinese actors (i.e., Gh0st RAT) and the tools described in Check Point's 'Vicious Panda' research (i.e., RoyalRoad, which exploits vulnerabilities in Microsoft Word)," he told SecurityWeek. "But we cannot with certainty attribute all of these campaigns to the same group. It is possible that there are multiple APT groups sharing resources, but I don't want to speculate."
In fairness, neither Avast nor ESET is the first to link these separate campaigns. In its Vicious Panda research, Check Point noted the similarities to earlier campaigns, and said, "A closer look at this campaign allowed us to tie it to other operations which were carried out by the same anonymous group, dating back to at least 2016. Over the years, these operations targeted different sectors in multiple countries, such as Ukraine, Russia, and Belarus."
Both Avast and ESET now give examples of the coding similarities that link the different campaigns. Avast points to similarities in the decryption loop used to decrypt the main configuration data in one of the backdoors -- it is almost identical. ESET notes that across the different campaigns, "The grammar of commands is quite specific, because each command is truncated to 6 letters and then base64 encoded. That results an 8-letter incomprehensible word in the code."
While there is no certainty, the general feeling is that these multiple campaigns have been operated by a single group. It is likely to be an APT and based in China, based on the quality of the coding and the primary targets (military, telecommunications, government entities). ESET comments, "The malware developers put great effort into the security and robustness of the connection with their victims and the operators managed to penetrate high-profile corporate networks. Moreover, they have a larger toolset of attack tools at their disposal and their projects are under constant development, mostly visible as variations in obfuscation."
If it is a single group, very little is known about it -- although Avast assumes the group is still active. So far, it hasn't been given a name. Going forward, as more is learned and more campaigns are discovered, this will need to be remedied; There are two obvious candidates for this unnamed APT group: Vicious Panda (via Check Point), or the Mikroceen Gang (via ESET).
Russian APT Turla’s COMpfun malware uses HTTP status codes to receive commands
15.5.20 Securityaffairs APT
Russia-linked cyberespionage group Turla targets diplomatic entities in Europe with a new piece of malware tracked as COMpfun.
Security experts from Kaspersky Lab have uncovered a new cyberespionage campaign carried out by Russia-linked APT Turla that employs a new version of the COMpfun malware. The new malware allows attackers to control infected hosts using a technique that relies on HTTP status codes.
COMpfun was first spotted in the wild in 2014 by G DATA researchers, Kaspersky first observed the threat in autumn 2019 when it was employed in attacks against diplomatic entities across Europe.
“You may remember that in autumn 2019 we published a story about how a COMpfun successor known as Reductor infected files on the fly to compromise TLS traffic.” reads the analysis published by Kaspersky. “The campaign operators retained their focus on diplomatic entities, this time in Europe, and spread the initial dropper as a spoofed visa application.”
The Turla APT group (aka Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON) has been active since at least 2007 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations.
The list of previously known victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
In March the APT group employed two new pieces of malware in watering hole attacks targeting several high-profile Armenian websites.
The COMpfun malware analyzed by Kaspersky implements a new technique to receive commands from the C2 as HTTP status codes.
COMpfun is a remote access trojan (RAT) that could collect system data, logs keystrokes, and takes screenshots.
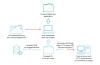
The new variant of the COMpfun malware includes two new features, the ability to monitor when USB removable devices plugged into or unplugged from the host, and the mentioned C2 communication technique.
The first feature was implemented to allow the malware propagating itself to the connected device.
The second feature was implemented to avoid detection, Turla vxers implemented new C2 protocol that relies on HTTP status codes.
HTTP status codes provide a state of the server and instruct clients on action to do (i.e. drop the connection), COMpfun exploited this mechanism to control the bot running on the compromised systems.
“We observed an interesting C2 communication protocol utilizing rare HTTP/HTTPS status codes (check IETF RFC 7231, 6585, 4918). Several HTTP status codes (422-429) from the Client Error class let the Trojan know what the operators want to do. After the control server sends the status “Payment Required” (402), all these previously received commands are executed.” continues the analysis.
For example, if the COMpfun server would respond with a 402 status code, followed by a 200 status code, the malicious code sends collected target data to C2 with the current tickcount.
Below the list of commands associated with common HTTP status codes:
HTTP status RFC status meaning Corresponding command functionality
200 OK Send collected target data to C2 with current tickcount
402 Payment Required This status is the signal to process received (and stored in binary flag) HTTP statuses as commands
422 Unprocessable Entity (WebDAV) Uninstall. Delete COM-hijacking persistence and corresponding files on disk
423 Locked (WebDAV) Install. Create COM-hijacking persistence and drop corresponding files to disk
424 Failed Dependency (WebDAV) Fingerprint target. Send host, network and geolocation data
427 Undefined HTTP status Get new command into IEA94E3.tmp file in %TEMP%, decrypt and execute appended command
428 Precondition Required Propagate self to USB devices on target
429 Too Many Requests Enumerate network resources on target
“The malware operators retained their focus on diplomatic entities and the choice of a visa-related application – stored on a directory shared within the local network – as the initial infection vector worked in their favor. The combination of a tailored approach to their targets and the ability to generate and execute their ideas certainly makes the developers behind COMPFun a strong offensive team.” concludes Kaspersky.
North Korean hackers infect real 2FA app to compromise Macs
10.5.2020 Bleepingcomputer Apple APT
Hackers have hidden malware in a legitimate two-factor authentication (2FA) app for macOS to distribute Dacls, a remote access trojan associated with the North Korean Lazarus group.
Dacls has been used to target Windows and Linux platforms and the recently discovered RAT variant for macOS borrows from them much of the functionality and code.
Setting persistence
The threat actor planted the malware in the freely available MinaOTP application that is prevalent among Chinese users. A sample of its weaponized version with the name TinkaOTP was uploaded from Hong Kong last month to the VirusTotal scanning service.
At that time, on April 8, it passed undetected, say malware analysts from Malwarebytes in a report this week. Currently, the malicious file is spotted by 23 out of 59 antivirus engines.
The malware executes after rebooting the system as it is added to the property list (plist) file used by LaunchDaemons and LaunchAgents to run applications at startup.
“The difference between LaunchAgents and LaunchDaemons is that LaunchAgents run code on behalf of the logged-in user while LaunchDaemon run code as root user” - Malwarebytes
Same RAT, different OS
Connections with the Dacls for Windows and Linux are evident. The researchers discovered in the macOS variant that the names for the certificate and private file - “c_2910.cls” and “k_3872.Cls” - are the same across all three operating systems.
Further evidence to the common root is given by the configuration file of the malware, which is encrypted with the same AES key and initialization vector seen in Dacls RAT for Linux.
Going deeper, the researchers found that six of the seven plugins in the macOS sample are also present in the Linux variant. The novelty is the Socks module that starts a proxy between the malware and the C2 infrastructure.
Researchers at Qihoo 360’s Netlab detailed the functions of the six plugins in analysis published in mid-December 2019. These are used for the following purposes:
CMD/Bash plugin - receiving and executing C2 commands
File plugin - file management (read, write, delete, download from specific server, search); write function is not supported in the Dacls for macOS
Process plugin - process management (kill, run, get process ID, enumerate)
Test plugin - same code in both macOS and Linux versions, tests connection to an IP address and port specified by C2
RP2P (reverse peer-to-peer) plugin - proxy server between C2 and the infected system
LogSend plugin - checks connection to Log server, scans network on ports 8291 or 8292, executes system commands that take a long time
The connection to the C2 server relies on the open-source WolfSSL library for secure communication, which is used by multiple threat actors.
Slipping malware into legitimate applications for macOS is not a first for the Lazarus group. A report in 2018 from Kaspersky revealed that the hackers had trojanized an installer for a cryptocurrency trading platform.
In September 2019, malware researchers analyzed a trading app for macOS that packed malware for stealing user information. Fast forward to December, a new macOS malware from Lazarus and using the same tactic emerged on the public radar.
Nation-Backed Hackers Spread Crimson RAT via Coronavirus Phishing
21.3.2020 Bleepingcomputer APT Phishing Virus
A state-sponsored threat actor is attempting to deploy the Crimson Remote Administration Tool (RAT) onto the systems of targets via a spear-phishing campaign using Coronavirus-themed document baits disguised as health advisories.
This nation-backed cyber-espionage is suspected to be Pakistan-based and it is currently tracked under multiple names including APT36, Transparent Tribe, ProjectM, Mythic Leopard, and TEMP.Lapis.
The group, active since at least 2016, is known for targeting Indian defense and government entities and for stealing sensitive info designed to bolster Pakistan's diplomatic and military efforts.
Coronavirus-themed spear-phishing campaign
APT36's ongoing spear-phishing attacks were first spotted by researchers with QiAnXin's RedDrip Team who discovered malicious documents camouflaged as health advisories and impersonating Indian government officials.
The spear-phishing emails, attributed by the Chinese researchers to the Transparent Tribe hacking group and also analyzed by Malwarebytes Labs' Threat Intelligence Team, are trying to trick the targets into enabling macros so that the Crimson RAT payload can be deployed.
APT36 uses two lure formats in this campaign: Excel documents with embedded malicious macros and RTF documents files designed to exploit the CVE-2017-0199 Microsoft Office/WordPad remote code execution vulnerability.
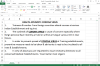
Fake Coronavirus health advisory (Malwarebytes Labs)
Once the malicious documents used as baits are opened and the malicious macros are executed, a 32-bit or a 64-bit version of the Crimson RAT payload will be dropped based on the victim's OS type.
After the device is compromised, the attackers can perform a wide range of data theft tasks including but not limited to:
• Stealing credentials from the victim’s browser
• Listing running processes, drives, and directories on the victim’s machine
• Retrieving files from its C&C server
• Using custom TCP protocol for its C&C communications
• Collecting information about antivirus software
• Capturing screenshots
After being executed, the Crimson RAT will automatically connect to the hardcoded command-and-control addresses and send all the collected info on the victim, including the list of running processes, the machine's hostname, and the currently logged in username.
"APT36 has used many different malware families in the past, but has mostly deployed RATs, such as BreachRAT, DarkComet, Luminosity RAT, and njRAT," Malwarebytes says.
"In past campaigns, they were able to compromise Indian military and government databases to steal sensitive data, including army strategy and training documents, tactical documents, and other official letters.
"They also were able to steal personal data, such as passport scans and personal identification documents, text messages, and contact details."
State-backed groups behind other Coronavirus-themed attacks
APT36 is not the only nation-sponsored threat actor known for using COVID-19-themed malware and phishing emails to attack and infect potential targets.
Chinese APTs (Mustang Panda and Vicious Panda), North Korean APTs (Kimsuky), Russian APTs (Hades and TA542), as well as some without known affiliations such as SWEED have also been recently adopting Coronavirus baits as part of their attacks as recently reported by ZDNet.
Cybercriminals with no nation-state ties have also been playing the Coronavirus card heavily trying to monetize on their targets' COVID-19 fears.
Phishing campaigns using Coronavirus baits have targeted US and UK targets since the start of February, impersonating U.S. Centers for Disease Control and Prevention (CDC) officials and virologists.
New malware strains have also been spotted since the Coronavirus started, such as new ransomware called CoronaVirus used as a cover for the Kpot Infostealer, a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and even a wiper.
The World Health Organization (WHO) also warned of active Coronavirus-themed phishing attacks impersonating WHO officials with the end goal of delivering malware and stealing the targets' sensitive information.
Last but not least, Ancient Tortoise BEC fraudsters have also been seen sending scam emails attempting to use the Coronavirus outbreak as cover for them updating payment information on invoices to bank accounts under their control.
Advanced Russian Hackers Use New Malware in Watering Hole Operation
15.3.2020 Bleepingcomputer APT
Two previously undocumented pieces of malware, a downloader and a backdoor, were used in a watering hole operation attributed to the Russian-based threat group Turla.
To reach targets of interest, the hackers compromised at least four websites, two of them belonging to the Armenian government. This indicates that the threat actor was after government officials and politicians.
Simple, yet effective trick
The new tools are a .NET malware dropper called NetFlash and a Python-based backdoor named PyFlash. They would be delivered following a fake Adobe Flash update notification received by victims.
At least four Armenian websites were infected by yet unknown means in this campaign, which started since at least the beginning of 2019.
armconsul[.]ru: The consular Section of the Embassy of Armenia in Russia
mnp.nkr[.]am: Ministry of Nature Protection and Natural Resources of the Republic of Artsakh
aiisa[.]am: The Armenian Institute of International and Security Affairs
adgf[.]am: The Armenian Deposit Guarantee Fund
After gaining access to the website, the hackers added a piece of malicious JavaScript code that loaded from the external source ‘skategirlchina[.]com’ a script designed to fingerprint the visitor’s web browsers.
Visitors landing on the compromised website for the first time would get a persistent cookie whose code is publicly available. This is used for tracking future visits to sites compromised for this operation.
Security researchers from ESET believe that Turla (a.k.a. Waterbug, WhiteBear, Venomous Bear, Snake) hackers were very selective about their targets, moving to the next stage of the attack only for a small number of visitors.
In the first stage of the attack, victims would see a fake warning for updating Adobe Flash Player, shown in an iFrame. If the visitor acted on it, they would get a malicious executable that installed both a legitimate copy of Flash and a Turla malware variant, ESET says in a report today.
Starting September 2019, the first stage payload from a backdoor named Skipper to the new NetFlash malware downloader, which appears to have been compiled at the end of August and early September of last year.
It is NetFlash’s job to retrieve the second-stage PyFlash backdoor from a hard-coded URL and to make it persistent on the system via a Windows scheduled task.
ESET created the image below to show how Turla used this watering hole operation to target and compromise systems deemed of interest: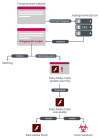
The attackers used the ‘py2exe’ extension to convert their PyFlash script into an executable that runs on Windows without the need of Python.
PyFlash was mainly used to send to the command and control (C2) server information about the victim host. Supported commands are relate to the OS and the network (systeminfo, tasklist, ipconfig, getmac, arp).
The C2 can send additional commands such as for downloading files from a given link, running a Windows command, change the delay time for launching the malware, or removing infection traces by uninstalling the backdoor.
For the last one, confirms the instruction via POST request to the C2 with the following string:
I'm dying :(
Tell my wife that i love her...
Watering hole attacks are a known tactic for Turla but researchers are somewhat surprised that the group used a common trick to deliver their malware. This shows that even sophisticated threat actors can choose a simple solution to achieve their goal.
However, ESET points out that the actor did make an effort to evade detection by using a different payload than Skipper, which was essentially burned from long-time use.