APT 2024 2023 2022 2021 2020
North Korea-linked Lazarus APT targets the COVID-19 research
26.12.2020 APT Securityaffairs
The North Korea-linked Lazarus APT group has recently launched cyberattacks against at least two organizations involved in COVID-19 research.
The North Korea-linked APT group Lazarus has recently launched cyberattacks against two entities involved in COVID-19 research.
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
According to a report published by Kaspersky Lab in January 2020, in the two years the North Korea-linked APT group has continued to target cryptocurrency exchanges evolving its TTPs.
Now Kaspersky researchers revealed to have spotted new attacks that were carried out by the APT group in September and October 2020. The attacks aimed at a Ministry of Health and a pharmaceutical company involved in the development of the COVID-19 vaccine.
The systems at the pharmaceutical company were targeted with the BookCode malware, while in the attack against a Ministry of Health the APT group used the wAgent malware. Lazarus APT used the wAgent malware in attacks against cryptocurrency exchanges and businesses.
“While tracking the Lazarus group’s continuous campaigns targeting various industries, we discovered that they recently went after COVID-19-related entities. They attacked a pharmaceutical company at the end of September, and during our investigation we discovered that they had also attacked a government ministry related to the COVID-19 response.” reads the analysis published by Kaspersky. “Each attack used different tactics, techniques and procedures (TTPs), but we found connections between the two cases and evidence linking those attacks to the notorious Lazarus group.”
The Lazarus APT used different techniques in each attack, but Kaspersky experts believe they were both conducted by Lazarus.

Both backdoors allow the operators to take full control over the infected systems. The experts were not able to determine the initial infection vector in both attacks, they speculate the attackers launched spear-phishing attacks against their victims or used watering hole attacks.
The wAgent backdoor allows the attackers to executed various shell commands to gather information from the infected device. Experts noticed that Lazarus is using the wAgent backdoor to deliver an additional payload that has a persistence mechanism.
The BookCode backdoor was used by Lazarus hackers to gather system and network information from the targeted system, The malware extract infected host information, including password hashes, from the registry SAM dump.
“We assess with high confidence that the activity analyzed in this post is attributable to the Lazarus group.” continues Kaspersky. “In our previous research, we already attributed the malware clusters used in both incidents described here to the Lazarus group. First of all, we observe that the wAgent malware used against the health ministry has the same infection scheme as the malware that the Lazarus group used previously in attacks on cryptocurrency businesses.”
The attacks discovered by Kaspersky confirm the interest of the APT group in gathering intelligence on COVID-19-related activities.
“While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well.” concludes Kaspersky. “We believe that all entities currently involved in activities such as vaccine research or crisis handling should be on high alert for cyberattacks.”
Lazarus Group Hits COVID-19 Vaccine-Maker in Espionage Attack
23.12.2020 APT Threatpost
The nation-state actor is looking to speed up vaccine development efforts in North Korea.
The advanced persistent threat (APT) known as Lazarus Group and other sophisticated nation-state actors are actively trying to steal COVID-19 research to speed up their countries’ vaccine-development efforts.
That’s the finding from Kaspersky researchers, who found that Lazarus Group — widely believed to be linked to North Korea — recently attacked a pharmaceutical company, as well as a government health ministry related to the COVID-19 response. The goal was intellectual-property theft, researchers said.
“On Oct. 27, 2020, two Windows servers were compromised at the ministry,” according to a blog posting issued Wednesday. Researchers added, “According to our telemetry, [the pharmaceutical] company was breached on Sept. 25, 2020….[it] is developing a COVID-19 vaccine and is authorized to produce and distribute COVID-19 vaccines.”
They added, “These two incidents reveal the Lazarus Group’s interest in intelligence related to COVID-19. While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well.”
In the first instance, the cyberattackers installed a sophisticated malware called “wAgent” on the ministry’s servers, which is fileless (it only works in memory) and it fetches additional payloads from a remote server. For the pharma company, Lazarus Group deployed the Bookcode malware in a likely supply-chain attack through a South Korean software company, according to Kaspersky.
“Both attacks leveraged different malware clusters that do not overlap much,” researchers said. “However, we can confirm that both of them are connected to the Lazarus group, and we also found overlaps in the post-exploitation process.”
wAgent
It’s unknown what the initial infection vector was, but the wAgent malware cluster contained fake metadata in order to make it look like the legitimate compression utility XZ Utils. Kaspersky’s analysis showed that the malware was directly executed on the victim machine from a command line shell. A 16-byte string parameter is used as an AES key to decrypt an embedded payload – a Windows DLL – which is loaded in memory.
From there, it decrypts configuration information using a given decryption key, including command-and-control server (C2) addresses. Then it generates identifiers to distinguish each victim using the hash of a random value. POST parameter names are decrypted at runtime and chosen randomly at each C2 connection, researchers explained.
In the final step, wAgent fetches an in-memory Windows DLL containing backdoor functionalities, which the attackers used to gather and exfiltrate victim information through shell commands.
“We’ve previously seen and reported to our Threat Intelligence Report customers that a very similar technique was used when the Lazarus group attacked cryptocurrency businesses with an evolved downloader malware,” they said, adding that “[The malware’s] debugging messages have the same structure as previous malware used in attacks against cryptocurrency businesses involving the Lazarus group.”
Bookcode
As for the Bookcode malware cluster, here too the researchers weren’t able to uncover the initial access vector for certain, but it could be a supply-chain gambit, they said.
“We previously saw Lazarus attack a software company in South Korea with Bookcode malware, possibly targeting the source code or supply chain of that company,” according to Kaspersky. “We have also witnessed the Lazarus group carry out spearphishing or strategic website compromise in order to deliver Bookcode malware in the past.”
Upon execution, the Bookcode malware reads a configuration file and connects with its C2 – after which it provides standard backdoor functionalities, researchers said, and sends information about the victim to the attacker’s infrastructure, including password hashes.
“In the lateral movement phase, the malware operator used well-known methodologies,” they added. “After acquiring account information, they connected to another host with the ‘net’ command and executed a copied payload with the ‘wmic’ command. Moreover, Lazarus used ADfind in order to collect additional information from the Active Directory. Using this utility, the threat actor extracted a list of the victim’s users and computers.”
Kaspersky also discovered an additional configuration file containing four C2 servers, all of which are compromised web servers located in South Korea.
“We discovered several log files and a script from [one of the] compromised servers, which is a first-stage C2 server,” researchers noted. “It receives connections from the backdoor, but only serves as a proxy to a second-stage server where the operators actually store orders.”
Besides implant control features, the C2 script has additional capabilities such as updating the next-stage C2 server address, sending the identifier of the implant to the next-stage server or removing a log file.
Lazarus Rising
“We assess with high confidence that the activity analyzed in this post is attributable to the Lazarus Group,” Kaspersky noted, explaining that both malware suites have been previously attributed to the APT, with Bookcode being exclusive to it. Additionally, the overlaps in the post-exploitation phase are notable.
These include “the usage of ADFind in the attack against the health ministry to collect further information on the victim’s environment,” researchers explained. “The same tool was deployed during the pharmaceutical company case in order to extract the list of employees and computers from the Active Directory. Although ADfind is a common tool for the post-exploitation process, it is an additional data point that indicates that the attackers use shared tools and methodologies.”
Going forward, attacks on COVID-19 vaccine and drug developers and attempts to steal sensitive data from them will continue, Kaspersky recently predicted. As the development race between pharmaceutical firms continues, these cyberattacks will have ramifications for geopolitics, with the “attribution of attacks entailing serious consequences or aimed at the latest medical developments is sure to be cited as an argument in diplomatic disputes.”
There have already been reported espionage attacks on vaccine-makers AstraZeneca and Moderna.
Lazarus covets COVID-19-related intelligence
23.12.2020 APT Securelist
SEONGSU PARK
As the COVID-19 crisis grinds on, some threat actors are trying to speed up vaccine development by any means available. We have found evidence that actors, such as the Lazarus group, are going after intelligence that could help these efforts by attacking entities related to COVID-19 research.
While tracking the Lazarus group’s continuous campaigns targeting various industries, we discovered that they recently went after COVID-19-related entities. They attacked a pharmaceutical company at the end of September, and during our investigation we discovered that they had also attacked a government ministry related to the COVID-19 response. Each attack used different tactics, techniques and procedures (TTPs), but we found connections between the two cases and evidence linking those attacks to the notorious Lazarus group.
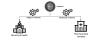
Relationship of recent Lazarus group attack
In this blog, we describe two separate incidents. The first one is an attack against a government health ministry: on October 27, 2020, two Windows servers were compromised at the ministry. We were unable to identify the infection vector, but the threat actor was able to install a sophisticated malware cluster on these servers. We already knew this malware as ‘wAgent’. It’s main component only works in memory and it fetches additional payloads from a remote server.
The second incident involves a pharmaceutical company. According to our telemetry, this company was breached on September 25, 2020. This time, the Lazarus group deployed the Bookcode malware, previously reported by ESET, in a supply chain attack through a South Korean software company. We were also able to observe post-exploitation commands run by Lazarus on this target.
Both attacks leveraged different malware clusters that do not overlap much. However, we can confirm that both of them are connected to the Lazarus group, and we also found overlaps in the post-exploitation process.
wAgent malware cluster
The malware cluster has a complex infection scheme:
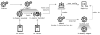
Infection scheme of the wAgent malware cluster
Unfortunately, we were unable to obtain the starter module used in this attack. The module seems to have a trivial role: executing wAgent with specific parameters. One of the wAgent samples we collected has fake metadata in order to make it look like the legitimate compression utility XZ Utils.
According to our telemetry, this malware was directly executed on the victim machine from the command line shell by calling the Thumbs export function with the parameter:
c:\windows\system32\rundll32.exe C:\Programdata\Oracle\javac.dat, Thumbs 8IZ-VU7-109-S2MY
1
c:\windows\system32\rundll32.exe C:\Programdata\Oracle\javac.dat, Thumbs 8IZ-VU7-109-S2MY
The 16-byte string parameter is used as an AES key to decrypt an embedded payload – a Windows DLL. When the embedded payload is loaded in memory, it decrypts configuration information using the given decryption key. The configuration contains various information including C2 server addresses, as well as a file path used later on. Although the configuration specifies two C2 servers, it contains the same C2 server twice. Interestingly, the configuration has several URL paths separated with an ‘@’ symbol. The malware attempts to connect to each URL path randomly.
C2 address in the configuration
When the malware is executed for the first time, it generates identifiers to distinguish each victim using the hash of a random value. It also generates a 16-byte random value and reverses its order. Next, the malware concatenates this random 16-byte value and the hash using ‘@’ as a delimiter. i.e.: 82UKx3vnjQ791PL2@29312663988969
POST parameter names (shown below) are decrypted at runtime and chosen randomly at each C2 connection. We’ve previously seen and reported to our Threat Intelligence Report customers that a very similar technique was used when the Lazarus group attacked cryptocurrency businesses with an evolved downloader malware. It is worth noting that Tistory is a South Korean blog posting service, which means the malware author is familiar with the South Korean internet environment:
plugin course property tistory tag vacon slide parent manual themes product notice portal articles category doc entry isbn tb idx tab maincode level bbs method thesis content blogdata tname
The malware encodes the generated identifier as base64 and POSTs it to the C2. Finally, the agent fetches the next payload from the C2 server and loads it in memory directly. Unfortunately, we couldn’t obtain a copy of it, but according to our telemetry, the fetched payload is a Windows DLL containing backdoor functionalities. Using this in-memory backdoor, the malware operator executed numerous shell commands to gather victim information:
cmd.exe /c ping -n 1 -a 192.[redacted]
cmd.exe /c ping -n 1 -a 192.[redacted]
cmd.exe /c dir \\192.[redacted]\c$
cmd.exe /c query user
cmd.exe /c net user [redacted] /domain
cmd.exe /c whoami
cmd.exe /c ping -n 1 -a 192.[redacted]
cmd.exe /c ping -n 1 -a 192.[redacted]
cmd.exe /c dir \\192.[redacted]\c$
cmd.exe /c query user
cmd.exe /c net user [redacted] /domain
cmd.exe /c whoami
Persistent wAgent deployed
Using the wAgent backdoor, the operator installed an additional wAgent payload that has a persistence mechanism. After fetching this DLL, an export called SagePlug was executed with the following command line parameters:
rundll32.exe c:\programdata\oracle\javac.io, SagePlug 4GO-R19-0TQ-HL2A c:\programdata\oracle\~TMP739.TMP
1
rundll32.exe c:\programdata\oracle\javac.io, SagePlug 4GO-R19-0TQ-HL2A c:\programdata\oracle\~TMP739.TMP
4GO-R19-0TQ-HL2A is used as a key and the file path indicates where debugging messages are saved. This wAgent installer works similarly to the wAgent loader malware described above. It is responsible for loading an embedded payload after decrypting it with the 16-byte key from the command line. In the decrypted payload, the malware generates a file path to proceed with the infection:
C:\Windows\system32\[random 2 characters]svc.drv
This file is disguised as a legitimate tool named SageThumbs Shell Extension. This tool shows image files directly in Windows Explorer. However, inside it contains an additional malicious routine.
While creating this file, the installer module fills it with random data to increase its size. The malware also copies cmd.exe’s creation time to the new file in order to make it less easy to spot.
For logging and debugging purposes, the malware stores information in the file provided as the second argument (c:\programdata\oracle\~TMP739.TMP in this case). This log file contains timestamps and information about the infection process. We observed that the malware operators were checking this file manually using Windows commands. These debugging messages have the same structure as previous malware used in attacks against cryptocurrency businesses involving the Lazarus group. More details are provided in the Attribution section.
After that, the malware decrypts its embedded configuration. This configuration data has a similar structure as the aforementioned wAgent malware. It also contains C2 addresses in the same format:
hxxps://iski.silogica[.]net/events/serial.jsp@WFRForms.jsp@import.jsp@view.jsp@cookie.jsp
hxxp://sistema.celllab[.]com.br/webrun/Navbar/auth.jsp@cache.jsp@legacy.jsp@chooseIcon.jsp@customZoom.jsp
hxxp://www.bytecortex.com[.]br/eletronicos/digital.jsp@exit.jsp@helpform.jsp@masks.jsp@Functions.jsp
hxxps://sac.najatelecom.com[.]br/sac/Dados/ntlm.jsp@loading.jsp@access.jsp@local.jsp@default.jsp
The malware encrypts configuration data and stores it as a predefined registry key with its file name:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\eventlog\Application\Emulate – [random 2 characters]svc
It also takes advantage of the Custom Security Support Provider by registering the created file path to the end of the existing registry value. Thanks to this registry key, this DLL will be loaded by lsass.exe during the next startup.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa – Security Packages : kerberos msv1_0 schannel wdigest tspkg pku2u [random 2 characters]svc.drv
Finally, the starter module starts the [random 2 characters]svc.drv file in a remote process. It searches for the first svchost.exe process and performs DLL injection. The injected [random 2 characters]svc.drv malware contains a malicious routine for decrypting and loading its embedded payload. The final payload is wAgent, which is responsible for fetching additional payloads from the C2, possibly a fully featured backdoor, and loading it in the memory.
Bookcode malware cluster
The pharmaceutical company targeted by Lazarus group’s Bookcode malware is developing a COVID-19 vaccine and is authorized to produce and distribute COVID-19 vaccines. We previously saw Lazarus attack a software company in South Korea with Bookcode malware, possibly targeting the source code or supply chain of that company. We have also witnessed the Lazarus group carry out spear phishing or strategic website compromise in order to deliver Bookcode malware in the past. However, we weren’t able to identify the exact initial infection vector for this incident. The whole infection procedure confirmed by our telemetry is very similar to the one described in ESET’s latest publication on the subject.
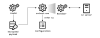
Bookcode infection procedure
Although we didn’t find the piece of malware tasked with deploying the loader and its encrypted Bookcode payload, we were able to identify a loader sample. This file is responsible for loading an encrypted payload named gmslogmgr.dat located in the system folder. After decrypting the payload, the loader finds the Service Host Process (svchost.exe) with winmgmt, ProfSvc or Appinfo parameters and injects the payload into it. Unfortunately, we couldn’t acquire the encrypted payload file, but we were able to reconstruct the malware actions on the victim machine and identify it as the Bookcode malware we reported to our Threat Intelligence Report customers.
Upon execution, the Bookcode malware reads a configuration file. While previous Bookcode samples used the file perf91nc.inf as a configuration file, this version reads its configuration from a file called C_28705.NLS. This Bookcode sample has almost identical functionality as the malware described in the comprehensive report recently published by Korea Internet & Security Agency (KISA). As described on page 57 of that report, once the malware is started it sends information about the victim to the attacker’s infrastructure. After communicating with the C2 server, the malware provides standard backdoor functionalities.
Post-exploitation phase
The Lazarus group’s campaign using the Bookcode cluster has its own unique TTPs, and the same modus operandi was used in this attack.
Extracting infected host information, including password hashes, from the registry sam dump.
Using Windows commands in order to check network connectivity.
Using the WakeMeOnLan tool to scan hosts in the same network.
After installing Bookcode on September 25, 2020, the malware operator started gathering system and network information from the victim. The malware operator also collected a registry sam dump containing password hashes:
exe /c “reg.exe save hklm\sam %temp%\~reg_sam.save > “%temp%\BD54EA8118AF46.TMP~” 2>&1″
exe /c “reg.exe save hklm\system %temp%\~reg_system.save > “%temp%\405A758FA9C3DD.TMP~” 2>&1″
In the lateral movement phase, the malware operator used well-known methodologies. After acquiring account information, they connected to another host with the “net” command and executed a copied payload with the “wmic” command.
exe /c “netstat -aon | find “ESTA” > %temp%\~431F.tmp
exe /c “net use \\172.[redacted] “[redacted]” /u:[redacted] > %temp%\~D94.tmp” 2>&1″
wmic /node:172.[redacted] /user:[redacted] /password:”[redacted]” process call create “%temp%\engtask.exe” > %temp%\~9DC9.tmp” 2>&1″
Moreover, Lazarus used ADfind in order to collect additional information from the Active Directory. Using this utility, the threat actor extracted a list of the victim’s users and computers.
Infrastructure of Bookcode
As a result of closely working with the victim to help remediate this attack, we discovered an additional configuration file. It contains four C2 servers, all of which are compromised web servers located in South Korea.
hxxps://www.kne.co[.]kr/upload/Customer/BBS.asp
hxxp://www.k-kiosk[.]com/bbs/notice_write.asp
hxxps://www.gongim[.]com/board/ajax_Write.asp
hxxp://www.cometnet[.]biz/framework/common/common.asp
One of those C2 servers had directory listing enabled, so we were able to gain insights as to how the attackers manage their C2 server:

Attacker files listed on a compromised website
We discovered several log files and a script from the compromised server, which is a “first-stage” C2 server. It receives connections from the backdoor, but only serves as a proxy to a “second-stage” server where the operators actually store orders.
File name Description
_ICEBIRD007.dat A log file containing the identifier of victims and timestamps.
~F05990302ERA.jpg Second-stage C2 server address:
hxxps://www.locknlockmall[.]com/common/popup_left.asp
Customer_Session.asp Malware control script.
Customer_Session.asp is a first-stage C2 script responsible for delivering commands from the next-stage C2 server and command execution results from the implant. In order to deliver proper commands to each victim, the bbs_code parameter from the implants is used as an identifier. The script uses this identifier to assign commands to the correct victims. Here is how the process of sending an order for a particular victim works:
The malware operator sets the corresponding flag([id]_208) of a specific implant and saves the command to the variable([id]_210).
The implant checks the corresponding flag([id]_208) and retrieves the command from the variable([id]_210) if it is set.
After executing the command, the implant sends the result to the C2 server and sets the corresponding flag.
The malware operator checks the flag and retrieves the result if the flag is set.

Logic of the C2 script
Besides implant control features, the C2 script has additional capabilities such as updating the next-stage C2 server address, sending the identifier of the implant to the next-stage server or removing a log file.
table_nm value Function name Description
table_qna qnaview Set [id]_209 variable to TRUE and save the “content” parameter value to [id]_211.
table_recruit recuritview If [id]_209 is SET, send contents of [id]_211 and reset it, and set [ID]_209 to FALSE.
table_notice notcieview Set [id]_208 and save the “content” parameter value to [id]_210.
table_bVoice voiceview If [id]_208 is SET, send contents of [id]_210 and reset it, and set [id]_208 to FALSE.
table_bProduct productview Update the ~F05990302ERA.jpg file with the URL passed as the “target_url” parameter.
table_community communityview Save the identifier of the implant to the log file. Read the second-stage URL from ~F05990302ERA.jpg and send the current server URL and identifier to the next hop server using the following format:
bbs_type=qnaboard&table_id=[base64ed identifier] &accept_identity=[base64 encoded current server IP]&redirect_info=[base64ed current server URL]
table_free freeview Read _ICEBIRD007.dat and send its contents, and delete it.
Attribution
We assess with high confidence that the activity analyzed in this post is attributable to the Lazarus group. In our previous research, we already attributed the malware clusters used in both incidents described here to the Lazarus group. First of all, we observe that the wAgent malware used against the health ministry has the same infection scheme as the malware that the Lazarus group used previously in attacks on cryptocurrency businesses.
Both cases used a similar malware naming scheme, generating two characters randomly and appending “svc” to it to generate the path where the payload is dropped.
Both malicious programs use a Security Support Provider as a persistence mechanism.
Both malicious programs have almost identical debugging messages.
Here is a side-by-side comparison of the malware used in the ministry of health incident, and the malware (4088946632e75498d9c478da782aa880) used in the cryptocurrency business attack:
Debugging log from ministry of health case Debugging log of cryptocurrency business case
15:18:20 Extracted Dll : [random 2bytes]svc.drv
15:59:32 Reg Config Success !
16:08:45 Register Svc Success !
16:24:53 Injection Success, Process ID : 544
Extracted Dll : [random 2bytes]svc.dll
Extracted Injecter : [random 2bytes]proc.exe
Reg Config Success !
Register Svc Success !
Start Injecter Success !
Regarding the pharmaceutical company incident, we previously concluded that Bookcode is exclusively used by the Lazarus group. According to our Kaspersky Threat Attribution Engine (KTAE), one of the Bookcode malware samples (MD5 0e44fcafab066abe99fe64ec6c46c84e) contains lots of code overlaps with old Manuscrypt variants.
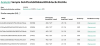
Kaspersky Threat Attribution Engine results for Bookcode
Moreover, the same strategy was used in the post-exploitation phase, for example, the usage of ADFind in the attack against the health ministry to collect further information on the victim’s environment. The same tool was deployed during the pharmaceutical company case in order to extract the list of employees and computers from the Active Directory. Although ADfind is a common tool for the post-exploitation process, it is an additional data point that indicates that the attackers use shared tools and methodologies.
Conclusions
These two incidents reveal the Lazarus group’s interest in intelligence related to COVID-19. While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well. We believe that all entities currently involved in activities such as vaccine research or crisis handling should be on high alert for cyberattacks.
Indicators of compromise
wAgent
dc3c2663bd9a991e0fbec791c20cbf92 %programdata%\oracle\javac.dat
26545f5abb70fc32ac62fdab6d0ea5b2 %programdata%\oracle\javac.dat
9c6ba9678ff986bcf858de18a3114ef3 %programdata%\grouppolicy\Policy.DAT
wAgent Installer
4814b06d056950749d07be2c799e8dc2 %programdata%\oracle\javac.io, %appdata%\ntuser.dat
wAgent compromised C2 servers
http://client.livesistemas[.]com/Live/posto/system.jsp@public.jsp@jenkins.jsp@tomas.jsp@story.jsp
hxxps://iski.silogica[.]net/events/serial.jsp@WFRForms.jsp@import.jsp@view.jsp@cookie.jsp
hxxp://sistema.celllab[.]com.br/webrun/Navbar/auth.jsp@cache.jsp@legacy.jsp@chooseIcon.jsp@customZoom.jsp
hxxp://www.bytecortex.com[.]br/eletronicos/digital.jsp@exit.jsp@helpform.jsp@masks.jsp@Functions.jsp
hxxps://sac.najatelecom.com[.]br/sac/Dados/ntlm.jsp@loading.jsp@access.jsp@local.jsp@default.jsp
http://client.livesistemas[.]com/Live/posto/system.jsp@public.jsp@jenkins.jsp@tomas.jsp@story.jsp
hxxps://iski.silogica[.]net/events/serial.jsp@WFRForms.jsp@import.jsp@view.jsp@cookie.jsp
hxxp://sistema.celllab[.]com.br/webrun/Navbar/auth.jsp@cache.jsp@legacy.jsp@chooseIcon.jsp@customZoom.jsp
hxxp://www.bytecortex.com[.]br/eletronicos/digital.jsp@exit.jsp@helpform.jsp@masks.jsp@Functions.jsp
hxxps://sac.najatelecom.com[.]br/sac/Dados/ntlm.jsp@loading.jsp@access.jsp@local.jsp@default.jsp
wAgent file path
%SystemRoot%\system32\[random 2 characters]svc.drv
%SystemRoot%\system32\[random 2 characters]svc.drv
wAgent registry path
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\eventlog\Application\Emulate - [random 2 characters]svc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\eventlog\Application\Emulate - [random 2 characters]svc
Bookcode injector
5983db89609d0d94c3bcc88c6342b354 %SystemRoot%\system32\scaccessservice.exe, rasprocservice.exe
5983db89609d0d94c3bcc88c6342b354 %SystemRoot%\system32\scaccessservice.exe, rasprocservice.exe
Bookcode file path
%SystemRoot%\system32\C_28705.NLS
%SystemRoot%\system32\gmslogmgr.dat
%SystemRoot%\system32\C_28705.NLS
%SystemRoot%\system32\gmslogmgr.dat
Bookcode compromised C2 servers
hxxps://www.kne.co[.]kr/upload/Customer/BBS.asp
hxxp://www.k-kiosk[.]com/bbs/notice_write.asp
hxxps://www.gongim[.]com/board/ajax_Write.asp
hxxp://www.cometnet[.]biz/framework/common/common.asp
hxxps://www.locknlockmall[.]com/common/popup_left.asp
hxxps://www.kne.co[.]kr/upload/Customer/BBS.asp
hxxp://www.k-kiosk[.]com/bbs/notice_write.asp
hxxps://www.gongim[.]com/board/ajax_Write.asp
hxxp://www.cometnet[.]biz/framework/common/common.asp
hxxps://www.locknlockmall[.]com/common/popup_left.asp
MITRE ATT&CK Mapping.
Tactic
Technique.
Technique Name.
Execution T1059.003
T1569.002
Command and Scripting Interpreter: Windows Command Shell
System Services: Service Execution
Persistence T1547.005
T1543.003
Boot or Logon Autostart Execution: Security Support Provider
Create or Modify System Process: Windows Service
Privilege Escalation T1547.005
T1543.003
T1055.001
Boot or Logon Autostart Execution: Security Support Provider
Create or Modify System Process: Windows Service
Process Injection: Dynamic-link Library Injection
Defense Evasion T1070.006
T1055.001
T1140
T1027.001
Indicator Removal on Host: Timestomp
Process Injection: Dynamic-link Library Injection
Deobfuscate/Decode Files or Information
Obfuscated Files or Information: Binary Padding
Credential Access T1003.002 OS Credential Dumping: Security Account Manager
Discovery T1082
T1033
T1049
System Information Discovery
System Owner/User Discovery
System Network Connections Discovery
Lateral Movement T1021.002 SMB/Windows Admin Shares
Command and Control T1071.001
T1132.001
Application Layer Protocol: Web Protocols
Data Encoding: Standard Encoding
Exfiltration T1041 Exfiltration Over C2 Channel
Group Behind SolarWinds Hack Bypassed MFA to Access Emails at US Think Tank
16.12.2020 APT Securityweek
Using indicators of compromise (IoCs) made available by FireEye, threat intelligence and incident response firm Volexity determined that the threat group behind the SolarWinds hack targeted a U.S. think tank earlier this year, and it used a clever method to bypass multi-factor authentication (MFA) and access emails.
IT management and monitoring solutions provider SolarWinds has confirmed that a sophisticated threat group compromised the software build system for its Orion monitoring platform, allowing it to deliver trojanized updates to the company’s customers between March and June 2020.
The campaign apparently targeted several U.S. government organizations — including the DHS, the Treasury Department and the Commerce Department — as well as many other organizations in North America, Europe, Asia and the Middle East. FireEye was apparently also targeted by the same group, which managed to steal some Red Team tools from the cybersecurity firm.
SolarWinds said in a SEC filing that 18,000 of its 300,000 customers may have used the compromised products. One of those customers, according to Volexity, was a U.S.-based think tank that failed to detect the attackers’ presence and, once it did detect them, failed to keep them out.
Volexity said the group, which it tracks as Dark Halo (FireEye tracks it as UNC2452), remained undetected for several years. When they breached the think tank’s systems for a second time, the hackers leveraged a vulnerability in the organization’s Microsoft Exchange Control Panel and used a novel technique to bypass MFA from Cisco-owned Duo Security and access emails.
When the attackers struck the third time, in June and July 2020, they exploited the SolarWinds Orion product.
“At the time of the investigation, Volexity deduced that the likely infection was the result of the SolarWinds box on the target network; however, it was not fully understood exactly how the breach occurred (i.e., whether there was some unknown exploit in play, or other means of access), therefore Volexity was not in a position to report the circumstances surrounding the breach to SolarWinds,” Volexity said.
However, the most interesting part of Volexity’s report describes how Dark Halo bypassed MFA during the second breach it observed at the think tank. The method involved bypassing the Duo MFA to access an email account through the victim’s Outlook Web App (OWA) service.
“Logs from the Exchange server showed that the attacker provided username and password authentication like normal but were not challenged for a second factor through Duo. The logs from the Duo authentication server further showed that no attempts had been made to log into the account in question. Volexity was able to confirm that session hijacking was not involved and, through a memory dump of the OWA server, could also confirm that the attacker had presented cookie tied to a Duo MFA session named duo-sid,” Volexity explained.
“Volexity’s investigation into this incident determined the attacker had accessed the Duo integration secret key (akey) from the OWA server. This key then allowed the attacker to derive a pre-computed value to be set in the duo-sid cookie. After successful password authentication, the server evaluated the duo-sid cookie and determined it to be valid. This allowed the attacker with knowledge of a user account and password to then completely bypass the MFA set on the account,” it added.
Volexity has clarified that the method did not involve exploitation of a vulnerability in the Duo product. The attack was possible due to the victim’s failure to change all secrets associated with key integrations after the breach was discovered.
SolarWinds also reported observing an attack targeting its Office 365 email systems, but it has yet to determine if it was related to the Orion hack. In a blog post on the attacks, Microsoft also described interesting methods used by the hackers to access emails.
While some reports say Russia is behind the SolarWinds hack, specifically the group tracked as APT29 and Cozy Bear, Volexity said it had found no links during its investigation to a known threat actor. Russia has denied the allegations.
Facebook Shutters Accounts Used in APT32 Cyberattacks
12.12.2020 APT Threatpost
Facebook shut down accounts and Pages used by two separate threat groups to spread malware and conduct phishing attacks.
Facebook has shut down several accounts and Pages on its platform, which were used to launch phishing and malware attacks by two cybercriminal groups: APT32 in Vietnam and an unnamed threat group based in Bangladesh.
The social-media giant said it has removed both groups’ ability to use their infrastructure to abuse its platform, distribute malware and hack other accounts. A new analysis said the two groups were unconnected and targeted Facebook users leveraging “very different” tactics.
“The operation from Vietnam focused primarily on spreading malware to its targets, whereas the operation from Bangladesh focused on compromising accounts across platforms and coordinating reporting to get targeted accounts and Pages removed from Facebook,” said Nathaniel Gleicher, head of security policy, and Mike Dvilyanski, cyber-threat intelligence manager at Facebook, in a Thursday post.
APT32
APT32, also known as OceanLotus, is a Vietnam-linked advanced persistent threat (APT) that has been in operation since at least 2013. More recently the group has been linked to an espionage effort aimed at Android users in Asia (in a campaign dubbed PhantomLance by Kaspersky in April). Researchers also in November warned of a macOS backdoor variant linked to the APT group, which relies of multi-stage payloads and various updated anti-detection techniques.
Facebook said that APT32 leveraged its platform to target Vietnamese human-rights activists, as well as various foreign governments (including ones in Laos and Cambodia), non-governmental organizations, news agencies and a number of businesses.
The threat group created Facebook Pages and accounts in order to target particular followers with phishing and malware attacks. Here, APT23 used various social-engineering techniques, often using romantic lures or posing as activists or business entities to appear more legitimate.
Under the guise of these pages, APT32 would then convince targets to download Android apps through the legitimate Google Play store, which in turn had various permissions enabling broad surveillance of victim devices. Threatpost has reached out to Facebook for further information on specific apps used here. A Google spokesperson also confirmed to Threatpost that the apps used in these attacks have been removed from Google Play.
In addition to apps, APT32 would use these accounts to convince victims to click on compromised websites – or websites that they had created – to include malicious (obfuscated) JavaScript, in watering hole attacks used to compromise victim devices. As part of this attack, APT32 developed custom malware that would detect the victim’s operating system (Windows or Mac), and then send them a tailored payload that executes the malicious code.
Facebook also observed APT32 leveraging previously-utilized tactics in its attacks – such as using links to file-sharing services where they hosted malicious files (that victims would then click and download), including shortened links.
“Finally, the group relied on dynamic-link library (DLL) side-loading attacks in Microsoft Windows applications,” said Facebook. “They developed malicious files in .exe, .rar, .rtf and .iso formats, and delivered benign Word documents containing malicious links in text.”
According to Facebook, “our investigation linked this activity to CyberOne Group, an IT company in Vietnam (also known as CyberOne Security, CyberOne Technologies, Hành Tinh Company Ltd., Planet and Diacauso).”
Threatpost has reached out to CyberOne Group for comment; and has also reached out to Facebook inquiring about the specific links made that tied this company into the activity.
Bangladesh Group
Meanwhile, the Bangladesh-based threat actors targeted local activists, journalists and religious minorities to compromise their Facebook accounts. Facebook alleged it found links in this activity to two non-profit organizations in Bangladesh: Don’s Team (also known as Defense of Nation) and the Crime Research and Analysis Foundation (CRAF).
The company alleged that the groups collaborated to report Facebook users for fictitious violations of its Community Standards – such as alleged impersonation, intellectual property infringements, nudity and terrorism. In addition, the groups allegedly hacked Facebook user accounts and Pages, and used them for their own operational purposes, including to amplify their content.
“On at least one occasion, after a Page admin’s account was compromised, they removed the remaining admins to take over and disable the Page,” said Facebook.
Threatpost reached out to Don’s Team and CRAF for further comment. A Don’s Team spokesperson told Threatpost, “the recent allegations against Don’s Team is totally misleading.”
“This doesn’t relate to the recent Bangladesh Facebook campaign,” said the spokesperson. “Don’s Team is a social media awareness and consultancy platform. We help people to get rid of various Facebook related problems. As Facebook don’t have any of their affiliation places in Bangladesh, users [suffer] from a lot of problems related with Facebook accounts/pages/groups. So as a social media consultancy team we help those users when their account gets hacked, lost access to the account. Following Facebook community standards we help the victims to recover their account when it got disabled.”
Facebook – which has removed infrastructure in the past used by attackers to abuse its platform — warned that the attackers behind these operations are “persistent adversaries” and they expect them to evolve their tactics.
“We will continue to share our findings whenever possible so people are aware of the threats we are seeing and can take steps to strengthen the security of their accounts,” said Gleicher and Dvilyanski.
Facebook links cyberespionage group APT32 to Vietnamese IT firm
12.12.2020 APT Securityaffairs
Facebook has suspended some accounts linked to APT32 that were involved in cyber espionage campaigns to spread malware.
Facebook has suspended several accounts linked to the APT32 cyberespionage that abused the platform to spread malware.
Vietnam-linked APT group APT32, also known as OceanLotus and APT-C-00, carried out cyber espionage campaigns against Chinese entities to gather intelligence on the COVID-19 crisis.
The APT32 group has been active since at least 2012, it has targeted organizations across multiple industries and foreign governments, dissidents, and journalists.
Since at least 2014, experts at FireEye have observed the APT32 group targeting foreign corporations with an interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. The APT32 also targeted peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.
Now the Facebook security team has revealed the real identity of APT32, linking the group to an IT company in Vietnam named CyberOne Group.
“APT32, an advanced persistent threat actor based in Vietnam, targeted Vietnamese human rights activists locally and abroad, various foreign governments including those in Laos and Cambodia, non-governmental organizations, news agencies and a number of businesses across information technology, hospitality, agriculture and commodities, hospitals, retail, the auto industry, and mobile services with malware.” said Nathaniel Gleicher, Head of Security Policy at Facebook, and Mike Dvilyanski, Cyber Threat Intelligence Manager. “Our investigation linked this activity to CyberOne Group, an IT company in Vietnam (also known as CyberOne Security, CyberOne Technologies, Hành Tinh Company Limited, Planet and Diacauso).
Facebook APT32
APT32 created and operated a network of Facebook accounts and pages associated with fake people posing as activists or business entities.
The campaign orchestrated by the APT32 targeted Vietnamese human rights activists locally and abroad, foreign governments, including those in Laos and Cambodia, non-governmental organizations, news agencies, and, businesses across information technology, hospitality, agriculture and commodities, hospitals, retail, the auto industry, and mobile services.
Threat actors were contacting people of interest with romantic lures, they set up pages that were specifically designed to target followers with malware and phishing attacks.
Hackers also shared links to malicious Android apps that were uploaded to the official Google Play Store.
APT32 also carried out watering hole attacks through compromised websites or their own sites. The cyberespionage group employed custom malware designed to compromise the target machines with tailored payloads.
The social network giant also shared information about the cyber group, including YARA rules and malware signatures, with industry partners to allow them to detect and stop this activity. The company also blocked the domains used by the group.
“The latest activity we investigated and disrupted has the hallmarks of a well-resourced and persistent operation focusing on many targets at once, while obfuscating their origin. We shared our findings including YARA rules and malware signatures with our industry peers so they too can detect and stop this activity.” concludes the report.”To disrupt this operation, we blocked associated domains from being posted on our platform, removed the group’s accounts and notified people who we believe were targeted by APT32.”
Operations of Hacker Groups in Vietnam, Bangladesh Disrupted by Facebook
12.12.2020 APT Securityweek
Social media giant Facebook this week revealed that it has disrupted the activity of two groups of hackers — one operating from Vietnam and the other from Bangladesh.
The groups, Facebook says, were engaging in cyber-espionage activities, attempting to compromise accounts to gain access to information of interest. Not connected to one another, the groups targeted individuals on Facebook and other online platforms, employing a variety of tactics.
The Vietnamese group mainly attempted to infect victims with malware, while the Bangladeshi adversary focused on compromising accounts and engaged in coordinated reporting to have certain accounts and pages removed from Facebook.
“The people behind these operations are persistent adversaries, and we expect them to evolve their tactics,” the social platform notes.
Operating out of Bangladesh, the first group targeted activists and journalists, along with religious minorities, both in the country and abroad. The activity was focused on disabling accounts and pages through compromising them and then using them to engage in actions in violation of the social platform’s community standards.
“Our investigation linked this activity to two non-profit organizations in Bangladesh: Don’s Team (also known as Defense of Nation) and the Crime Research and Analysis Foundation (CRAF). They appeared to be operating across a number of internet services,” Facebook reveals.
These two organizations work together to report accounts for fictitious impersonation, alleged infringement of intellectual property, purported nudity, and terrorism. They also conducted hacking attempts, likely using off-platform tactics, such as email and device compromise, but also through abusing Facebook’s account recovery process.
Tracked as APT32, APT-C-00, and OceanLotus, the second group is a Vietnamese adversary known for the targeting of human rights activists, foreign governments (in Cambodia and Laos), news agencies, non-governmental organizations, and businesses in verticals such as agriculture, automotive, commodities, hospitals, hospitality, information technology, mobile services, and retail.
Facebook said it was able to link the activity to Vietnamese IT company CyberOne Group, which is also known as CyberOne Security, CyberOne Technologies, Hành Tinh Company Limited, Planet, and Diacauso.
Tactics, techniques and procedures (TTPs) employed by APT32 include social engineering, surveillance Android applications distributed through Google Play, and compromised and attacker-created websites for malware distribution.
“The latest activity we investigated and disrupted has the hallmarks of a well-resourced and persistent operation focusing on many targets at once, while obfuscating their origin,” Facebook explains.
Facebook Tracks APT32 OceanLotus Hackers to IT Company in Vietnam
12.12.2020 APT Thehackernews
Cybersecurity researchers from Facebook today formally linked the activities of a Vietnamese threat actor to an IT company in the country after the group was caught abusing its platform to hack into people's accounts and distribute malware.
Tracked as APT32 (or Bismuth, OceanLotus, and Cobalt Kitty), the state-aligned operatives affiliated with the Vietnam government have been known for orchestrating sophisticated espionage campaigns at least since 2012 with the goal of furthering the country's strategic interests.
"Our investigation linked this activity to CyberOne Group, an IT company in Vietnam (also known as CyberOne Security, CyberOne Technologies, Hành Tinh Company Limited, Planet and Diacauso)," Facebook's Head of Security Policy, Nathaniel Gleicher, and Cyber Threat Intelligence Manager, Mike Dvilyanski, said.
Exact evidence trail leading Facebook to attribute the hacking activity to CyberOne Group was not disclosed, but according to a description on ITViec — a Vietnamese online platform to find and post job vacancies for IT professionals and software developers — the company advertises itself as a "multinational company" with a focus on developing "products and services to ensure the security of IT systems of organizations and businesses."
As Reuters reported earlier, its website appears to have been taken offline. However, a snapshot captured by the Internet Archive on December 9 shows that the company had been actively looking to hire penetration testers, cyber threat hunters, and malware analysts with proficiency in Linux, C, C++, and .NET.
CyberOne, in a statement given to Reuters, also denied it was the OceanLotus group.
APT32's Long History of Attacks
Facebook's unmasking of APT32 comes months after Volexity disclosed multiple attack campaigns launched via multiple fake websites and Facebook pages to profile users, redirect visitors to phishing pages, and distribute malware payloads for Windows and macOS.
Additionally, ESET reported a similar operation spreading via the social media platform in December 2019, using posts and direct messages containing links to a malicious archive hosted on Dropbox.
The group is known for its evolving toolsets and decoys, including in its use of lure documents and watering-hole attacks to entice potential victims into executing a fully-featured backdoor capable of stealing sensitive information.
OceanLotus gained notoriety early last year for its aggressive targeting of multinational automotive companies in a bid to support the country's vehicle manufacturing goals.
During the height of the COVID-19 pandemic, APT32 carried out intrusion campaigns against Chinese targets, including the Ministry of Emergency Management, with an intent to collect intelligence on the COVID-19 crisis.
Last month, Trend Micro researchers uncovered a new campaign leveraging a new macOS backdoor that enables the attackers to snoop on and steals confidential information and sensitive business documents from infected machines.
Then two weeks ago, Microsoft detailed a tactic of OceanLotus that involved using coin miner techniques to stay under the radar and establish persistence on victim systems, thus making it harder to distinguish between financially-motivated crime from intelligence-gathering operations.
Social Engineering via Facebook
Now according to Facebook, APT32 created fictitious personas, posing as activists and business entities, and used romantic lures to reach out to their targets, ultimately tricking them into downloading rogue Android apps through Google Play Store that came with a wide range of permissions to allow broad surveillance of peoples' devices.
"The latest activity we investigated and disrupted has the hallmarks of a well-resourced and persistent operation focusing on many targets at once, while obfuscating their origin," the researchers said. "To disrupt this operation, we blocked associated domains from being posted on our platform, removed the group's accounts and notified people who we believe were targeted by APT32."
In a separate development, Facebook said it also disrupted a Bangladesh-based group that targeted local activists, journalists, and religious minorities, to compromise their accounts and amplify their content.
"Our investigation linked this activity to two non-profit organizations in Bangladesh: Don's Team (also known as Defense of Nation) and the Crime Research and Analysis Foundation (CRAF). They appeared to be operating across a number of internet services."
MoleRats APT Returns with Espionage Play Using Facebook, Dropbox
11.12.2020 APT Threatpost
The threat group is increasing its espionage activity in light of the current political climate and recent events in the Middle East, with two new backdoors.
The MoleRats advanced persistent threat (APT) has developed two new backdoors, both of which allow the attackers to execute arbitrary code and exfiltrate sensitive data, researchers said. They were discovered as part of a recent campaign that uses Dropbox, Facebook, Google Docs and Simplenote for command-and-control (C2) communications.
MoleRats is part of the Gaza Cybergang, an Arabic speaking, politically motivated collective of interrelated threat groups actively targeting the Middle East and North Africa, with a particular focus on the Palestinian Territories, according to previous research from Kaspersky. There are at least three groups within the gang, with similar aims and targets – cyberespionage related to Middle Eastern political interests – but very different tools, techniques and levels of sophistication, researchers said. One of those is MoleRats, which falls on the less-complex end of the scale, and which has been around since 2012.
The most recent campaign, uncovered by researchers at Cybereason, targets high-ranking political figures and government officials in Egypt, the Palestinian Territories, Turkey and the UAE, they noted. Emailed phishing documents are the attack vector, with lures that include various themes related to current Middle Eastern events, including Israeli-Saudi relations, Hamas elections, news about Palestinian politicians, and a reported clandestine meeting between the Crown Prince of Saudi Arabia, the U.S. Secretary of State Mike Pompeo and Israeli Prime Minister Benjamin Netanyahu.
“Analysis of the phishing themes and decoy documents used in the social engineering stage of the attacks show that they revolve mainly around Israel’s relations with neighboring Arab countries as well as internal Palestinian current affairs and political controversies,” Cybereason researchers noted.
In analyzing the offensive, they uncovered the SharpStage and DropBook backdoors (as well as a new version of a downloader dubbed MoleNet), which are interesting in that they use legitimate cloud services for C2 and other activities.
For instance, the DropBook backdoor uses fake Facebook accounts or Simplenote for C2, and both SharpStage and DropBook abuse a Dropbox client to exfiltrate stolen data and for storing their espionage tools, according to the analysis, issued Wednesday. Cybereason found that both have been observed being used in conjunction with the known MoleRats backdoor Spark; and both have been seen downloading additional payloads, including the open-source Quasar RAT.
Quasar RAT is billed as a legitimate remote administration tool for Windows, but it can be used for malicious purposes, like keylogging, eavesdropping, uploading data, downloading code and so on. It’s been used by various APTs in the past, including MoleRats and the Chinese-speaking APT 10.
Infection Routine & Malware Breakdown
The phishing emails arrive with a non-boobytrapped PDF attachment that will evade scanners, according to Cybereason. When a victim clicks it open, they receive a message that they will need to download the content from a password-protected archive. Helpfully, the message provides the password and gives targets the option of downloading from either Dropbox or Google Drive. This initiates the malware installation.
The SharpStage backdoor is a .NET malware that appears to be under continuous development. The latest version (a third iteration) performs screen captures and checks for the presence of the Arabic language on the infected machine, thus avoiding execution on non-relevant devices, researchers explained. It also has a Dropbox client API to communicate with Dropbox using a token, to download and exfiltrate data.
It also can execute arbitrary commands from the C2, and as mentioned, can download and execute additional payloads.
Victims receive a decoy document as part of the infection gambit. Cybereason said that the document contains information allegedly created by the media department of the Popular Front for the Liberation of Palestine (PLFP) describing preparations for the commemoration of the PLFP’s 53rd anniversary.
“It is it is unclear whether it is a stolen authentic document or perhaps a document forged by the attackers and made to appear as if it originated from the Front’s high-rank official,” according to the report.
DropBook meanwhile is a Python-based backdoor compiled with PyInstaller. Researchers said it can install programs and file names; execute shell commands received from Facebook/Simplenote; and download and execute additional payloads using Dropbox. Like SharpStage, it checks for the presence of an Arabic keyboard. DropBook also only executes if WinRAR is installed on the infected computer, researchers said, probably because it is needed for a later stage of the attack.
As for its use of social media, and the cloud, “DropBook fetches a Dropbox token from a Facebook post on a fake Facebook account,” according to the report. “The backdoor’s operators are able to edit the post in order to change the token used by the backdoor. In case DropBook fails getting the token from Facebook, it tries to get the token from Simplenote.”
After receiving the token, the backdoor collects the names of all files and folders in the “Program Files” directories and in the desktop, writes the list to a text file, and then uploads the file to Dropbox under the name of the current username logged on to the machine. DropBook then checks the fake Facebook account post, this time in order to receive commands.
“The attackers are able to edit the post in order to provide new instructions and commands to the backdoor,” according to Cybereason. “Aside from posting commands, the fake Facebook profile is empty, showing no connections or any personal information about its user, which further strengthens the assumption that it was created solely for serving as a command-and-control for the backdoor.”
Both SharpStage and DropBook exploit legitimate web services to store their weapons and to deliver them to their victims in a stealthy manner, abusing the trust given to these platforms. While the exploitation of social media for C2 communication is not new, it is not often observed in the wild, the team noted.
“While it’s no surprise to see threat actors take advantage of politically charged events to fuel their phishing campaigns, it is concerning to see an increase in social-media platforms being used for issuing C2 instructions and other legitimate cloud services being used for data exfiltration activities,” said Lior Div, Cybereason co-founder and CEO, in a statement.
The campaign shows that MoleRats could be ramping up its activity, according to the firm.
“The discovery of the new cyber-espionage tools along with the connection to previously identified tools used by the group suggest that MoleRats is increasing their espionage activity in the region in light of the current political climate and recent events in the Middle East,” the report concluded.
Russia-linked APT28 uses COVID-19 lures to deliver Zebrocy malware
11.12.2020 APT Securityaffairs
Russia-link cyberespionage APT28 leverages COVID-19 as phishing lures to deliver the Go version of their Zebrocy (or Zekapab) malware.
Russia-linked APT28 is leveraging COVID-19 as phishing lures in a new wave of attacks aimed at distributing the Go version of their Zebrocy (or Zekapab) malware.
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
Researchers from cybersecurity firm Intezer linked the attacks to a group operating under the APT28.
The Zebrocy backdoor was mainly used in attacks targeting governments and commercial organizations engaged in foreign affairs. The threat actors used lures consisted of documents about Sinopharm International Corporation, a pharmaceutical company involved in the development of a COVID-19 vaccine and that is currently going through phase three clinical trials. The phishing messages impersonated evacuation letter from Directorate General of Civil Aviation and contained decoy Microsoft Office documents with macros as well as executable file attachments.
“In November, we uncovered COVID-19 phishing lures that were used to deliver the Go version of Zebrocy. Zebrocy is mainly used against governments and commercial organizations engaged in foreign affairs. The lures consisted of documents about Sinopharm International Corporation” reads the analysis published by Intezer.
The lure was delivered as part of a Virtual Hard Drive (VHD) file that could be accessed only by Windows 10 users. The malware samples analyzed by the researchers were heavily obfuscated, but the analysis of the code allowed the experts to attribute them to the APT28.
Go versions of the backdoor were used since 2018, they initially start collecting info on the compromised system, and then sends it to the command and control server.
The data collected by the malware includes a list of running processes, information gathered via the ”systeminfo” command, local disk information, and a screenshot of the desktop.
The malware connects to the C2 through HTTP POST requests.
The malware also attempts to download and execute a payload from the C2 it.
Upon mounting the VHD file, it appears as an external drive with two files, a PDF document that purports to contain presentation slides about Sinopharm International Corporation and an executable that masquerades as a Word document. When opened, the executable runs the Zebrocy malware.

In an attack carried out in November and aimed at Kazakhstan, the threat actors used phishing lures that impersonating an evacuation letter from India’s Directorate General of Civil Aviation.
“Zebrocy is a malware toolset used by the Sofacy threat group. While the group keeps changing obfuscation and delivery techniques, code reuse allowed Intezer to detect and correctly classify this malware.” concludes the report. “With these recent phishing lures, it’s clear that COVID-19 themed attacks are still a threat and we might see more as vaccines become available to the general public.”
New Backdoors Used by Hamas-Linked Hackers Abuse Facebook, Dropbox
11.12.2020 APT Social Virus Securityweek
Two new backdoors have been attributed to the Molerats advanced persistent threat (APT) group, which is believed to be associated with the Palestinian terrorist organization Hamas.
Likely active since at least 2012 and also referred to as Gaza Hackers Team, Gaza Cybergang, DustySky, Extreme Jackal, and Moonlight, the group mainly hit targets in the Middle East (including Israel, Egypt, Saudi Arabia, the UAE and Iraq), but also launched attacks on entities in Europe and the United States.
In early 2020, security researchers at Cybereason's Nocturnus group published information on two new malware families used by the APT, namely Spark and Pierogi. Roughly a month later, Palo Alto Networks revealed that the group had expanded its target list to include insurance and retail industries, in addition to the previously targeted government and telecommunications verticals.
Now, Cybereason reveals that Molerats has expanded its toolset with the addition of two backdoors named SharpStage and DropBook, along with a downloader called MoleNet. All three malware families allow attackers to run arbitrary code and collect data from the infected machines and have been used in an espionage campaign actively targeting Arab-speaking individuals in the Middle East.
What makes the backdoors stand out is the use of legitimate online services for nefarious purposes. For example, both use a Dropbox client for data exfiltration and for storing espionage tools, while DropBook is controlled through fake Facebook accounts. Google Drive is also abused for payload storage.
The security researchers also identified new activity targeting Turkish-speaking entities with the Spark backdoor, as well as a separate campaign in which a new Pierogi variant is used against targets also infected with DropBook, SharpStage, and Spark. The overlap suggests a close connection between Molerats and APT-C-23 (Arid Viper), both considered sub-groups of Gaza Cybergang.
“The newly discovered backdoors were delivered together with the previously reported Spark backdoor, which along with other similarities to previous campaigns, further strengthens the attribution to Molerats,” Cybereason notes.
The malware families were used to target political figures and government officials in the Palestinian Territories, Egypt, Turkey, and UAE, among other Middle East regions. Phishing lures used in these attacks include Hamas elections, Israeli-Saudi relations, Palestinian politicians, and other political events.
Observed samples of SharpStage, a .NET backdoor, show compilation timestamps between October 4 and November 29, 2020. The malware can capture screenshots, download and execute files, execute arbitrary commands, and unarchive data fetched from the C&C.
Built by the developer behind JhoneRAT, DropBook is a Python-based backdoor capable of performing reconnaissance, executing shell commands, and downloading and executing additional malware. The threat only executes if WinRAR and an Arabic keyboard are present on the infected system.
The malware can fetch and run a broad range of payloads, including an updated version of itself, the MoleNet downloader, Quasar RAT, SharpStage, and ProcessExplorer (legitimate tool used for reconnaissance and credential dump).
Previously undocumented, the MoleNet downloader appears to have been in use since 2019, while its infrastructure might have been active since 2017. The heavily obfuscated .NET malware can perform WMI commands for reconnaissance, check the system for debuggers, restart the system, send OS info to the C&C, download additional payloads, and achieve persistence.
“The discovery of the new cyber espionage tools along with the connection to previously identified tools used by the group suggest that Molerats is increasing their espionage activity in the region in light of the current political climate and recent events in the Middle East,” Cybereason concludes.
COVID-19 Vaccine Cyberattacks Steal Credentials, Spread Zebrocy Malware
10.12.2020 APT Threatpost
Cybercriminals are leveraging the recent rollout of the COVID-19 vaccines globally in various cyberattacks – from stealing email passwords to distributing the Zebrocy malware.
Cybercriminals are tapping into the impending rollout of COVID-19 vaccines with everything from simple phishing scams all the way up to sophisticated Zebrocy malware campaigns.
Security researchers with KnowBe4 said that the recent slew of vaccine-related cyberattacks leverage the widespread media attention around the development and distribution of COVID-19 vaccines – as well as recent reports that manufacturers like Pfizer may not be able to supply additional doses of its vaccine to the U.S. large volumes until sometime in Q2.
These lures continue to play into the high emotions of victims during a pandemic – something seen in various phishing and malware campaigns throughout the last year.
Threatpost Webinar Promo Bug Bounty
Click to register.
“Malicious actors had a field day back in March in April as the Coronavirus washed over countries around the world,” said Eric Howes, with KnowBe4, in a Wednesday post. “It was and still is the perfect tool for social engineering scared, confused, and even downright paranoid end users into opening the door to your organization’s network.”
Zebrocy Malware Lures
Researchers with Intezer recently discovered a new Zebrocy malware sample in a campaign that has the hallmarks of a COVID-19 vaccine lure. In November, researchers uncovered a Virtual Hard Drive (VHD) file (VHD is the native file format for virtual hard drives used by Microsoft’s hypervisor, Hyper-V) uploaded to Virus Bulletin.
This VHD file included a file that suggests cybercriminals behind the attack using a COVID-19 vaccine-related spear-phishing lure. This PDF file consisted of presentation slideshows about Sinopharm International Corporation, which is a China-based pharmaceutical company currently working on a COVID-19 vaccine. Sinopharm International Corporation’s vaccine is currently undergoing phase three clinical trials but it has already been distributed to nearly one million people.
The second VHD file, masquerading as a Microsoft file, was a sample of Zebrocy written in Go. Zebrocy (also known as Sednit, APT28, Fancy Bear, and STRONTIUM), a malware used by the threat group Sofacy, operates as a downloaders and collects data about the infected host that is then uploaded to the command-and-control (C2) server before downloading and executing the next stage. Researchers noted that the C2 infrastructure linked to this campaign appears to be new.
Researchers warn that the attackers behind Zebrocy will likely continue to utilize COVID-19 vaccines as a lure: “Given that many COVID-19 vaccines are about to be approved for clinical use, it’s likely that APTs (Advanced Persistent Threat) and financially motivated threat actors will use this malware in their attacks,” they said in a Wednesday post.
‘Fill Out This Form’ To Get Vaccine
A recent phishing scam spotted by researchers lures victims into “fill out a form” to get their vaccine. In reality, they are targeting email credentials. Eric Howes, principal lab researcher at KnowBe4, told Threatpost that researchers “saw a very small number of emails” connected to the campaign, which all went to .EDU email addresses.
“I doubt this particular email was very targeted, so it’s entirely possible – even likely – that plenty of other organizations received copies of that email,” said Howes. “Just how many, we do not know.”
The emails say, “due to less stock covid-19 vaccine and high increase demand of the covid-19 vaccine distribution within the USA,” they need to fill out a form in order to get on the vaccine distribution list.
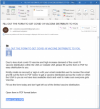
Phishing email sample. Credit: KnowBe4
The email, titled “FILL OUT THE FORM TO GET COVID-19 VACCINE DISTRIBUTE TO YOU,” has plenty of red flags – including grammatical errors and a lack of branding that could make it appear legitimate.
However, Howes said that “desperation, fear, curiosity and anxiety” could cause recipients to ignore these red flags and move forward in clicking the link.
“Given that we’re now nine months into the pandemic in the United States, people are weary and looking for a way out,” he told Threatpost. “Even though this email was not as polished as it could have been, when recipients are highly motivated to learn more about the announced subject of an email, those kinds of obvious red flags can be ignored or not even noticed.”
Should a recipient click on the link provided to what’s purported to be the “PDF form,” they are redirected to a phishing landing page that pretends to be a PDS online cloud document manager. The site (pdf-cloud.square[.]site), which is still active as of article publication, asks users for their email address and password in order to sign in.
This attack piggybacks off recent related COVID-19 vaccine phishing emails from earlier this month, including on that tells recipients to click a link in order to reserve their dose of the COVID-19 vaccine through their “healthcare portal.”
COVID-19 Campaigns
Researchers warn that cybercriminals will continue to leverage the rollout of the COVID-19 vaccine in various novel ways.
For instance, just this week Europol, the European Union’s law-enforcement agency, issued a warning about the rise of vaccine-related Dark Web activity.
Meanwhile, this month a sophisticated, global phishing campaign has been targeting the credentials of organizations associated with the COVID-19 “cold-chain” – companies that ensure the safe preservation of vaccines by making sure they are stored and transported in temperature-controlled environments.
COVID vaccine manufacturer Dr. Reddy’s Laboratories was forced to shut down factories in Brazil, India, the U.K. and U.S. in late October, which were contracted to make the Russian vaccine “Sputnik V.” And the APT group DarkHotel targeted the World Health Organization last March, in an attempt to steal any information they could find related to tests, vaccines or trial cures.
“With these recent phishing lures, it’s clear that COVID-19 themed attacks are still a threat and we might see more as vaccines become available to the general public,” said Intezer researchers. “It’s important that companies use defense-in-depth strategies to protect against threats. Employers should also ensure employees are trained on detecting and reacting to phishing attempts.”
SideWinder APT Targets Nepal, Afghanistan in Wide-Ranging Spy Campaign
10.12.2020 APT Threatpost
Convincing email-credentials phishing, emailed backdoors and mobile apps are all part of the groups latest effort against military and government targets.
The SideWinder advanced persistent threat (APT) group has mounted a fresh phishing and malware initiative, using recent territory disputes between China, India, Nepal and Pakistan as lures. The goal is to gather sensitive information from its targets, mainly located in Nepal and Afghanistan.
According to an analysis, SideWinder typically targets victims in South Asia and surroundings – and this latest campaign is no exception. The targets here include multiple government and military units for countries in the region researchers said, including the Nepali Ministries of Defense and Foreign Affairs, the Nepali Army, the Afghanistan National Security Council, the Sri Lankan Ministry of Defense, the Presidential Palace in Afghanistan and more.
Threatpost Webinar Promo Bug Bounty
Click to register.
The effort mainly makes use of legitimate-looking webmail login pages, aimed at harvesting credentials. Researchers from Trend Micro said that these pages were copied from their victims’ actual webmail login pages and subsequently modified for phishing. For example, “mail-nepalgovnp[.]duckdns[.]org” was created to pretend to be the actual Nepal government’s domain, “mail[.]nepal[.]gov[.]np”.
Convincing-looking phishing page. Source: Trend Micro.
Interestingly, after credentials are siphoned off and the users “log in,” they are either sent to the legitimate login pages; or, they are redirected to different documents or news pages, related either to COVID-19 or political fodder.
Researchers said some of the pages include a May article entitled “India Should Realise China Has Nothing to Do With Nepal’s Stand on Lipulekh” and a document called “Ambassador Yanchi Conversation with Nepali_Media.pdf,” which provides an interview with China’s ambassador to Nepal regarding Covid-19, the Belt and Road Initiative, and territorial issues in the Humla district.
Espionage Effort
The campaign also includes a malware element, with malicious documents delivered via email that are bent on installing a cyberespionage-aimed backdoor. And, there was evidence that the group is planning a mobile launch to compromise wireless devices.
“We identified a server used to deliver a malicious .lnk file and host multiple credential-phishing pages,” wrote researchers, in a Wednesday posting. “We also found multiple Android APK files on their phishing server. While some of them are benign, we also discovered malicious files created with Metasploit.”
Email Infection Routine
On the email front, researchers found that many malicious initial files are being used in the campaign, including a .lnk file that in turn downloads an .rtf file and drops a JavaScript file on the target’s computer; and a .zip file containing a .lnk file that in turn downloads an .hta file (with JavaScript).
“All of these cases end up with either the downloading or dropping of files and then the execution of JavaScript code, which is a dropper used to install the main backdoor plus stealer,” researchers explained.
The downloaded .rtf files in the chain meanwhile exploit the CVE-2017-11882 vulnerability; the exploit allows attackers to automatically run malicious code without requiring user interaction.
The flaw affects all unpatched versions of Microsoft Office, Microsoft Windows and architecture types dating back to 2000. While it was patched in November 2017, Microsoft warned as late as last year that email campaigns were spreading malicious .rtf files boobytrapped with an exploit for it.
“The CVE-2017-11882 vulnerability was fixed in 2017, but to this day, we still observe the exploit in attacks,” Microsoft Security Intelligence tweeted in 2019. “Notably, we saw increased activity in the past few weeks. We strongly recommend applying security updates.”
In this case, the boobytrapped .rtf drops a file named 1.a, which is a JavaScript code snippet. This places the backdoor and stealer into a folder in ProgramData and directly executes it, or creates a scheduled task to execute the dropped files at a later time, Trend Micro found.
“The content of the newly created folder contains a few files, including Rekeywiz, which is a legitimate Windows application,” analysts explained. “This application loads various system DLL libraries, including…a fake DUser.dll [that] decrypts the main backdoor + stealer from the .tmp file in the same directory.”
After decryption, the payload collects system information and uploads it to the command-and-control server (C2), before setting about stealing targeted file types.
“[This] includes information such as privileges, user accounts, computer system information, antivirus programs, running processes, processor information, operating system information, time zone, installed Windows updates, network information, list of directories in Users\%USERNAME%\Desktop, Users\%USERNAME%\Downloads, Users\%USERNAME%\Documents, Users\%USERNAME%\Contacts, as well as information on all drives and installed apps,” Trend Micro said.
Mobile Campaign Pending?
The researchers saw several mobile apps that were under development. Some contained no malicious code (yet); for instance, a mobile app called “OpinionPoll” was lurking on the server, purporting to be a survey app for gathering opinions regarding the Nepal-India political map dispute.
Others contained malicious capabilities but seemed unfinished.
Several mobile apps appear to be under development. Source: Trend Micro.
“While we were unable to retrieve the payload, according to the Manifest that requests numerous privacy-related permissions like location, contacts, call logs, etc., we can infer that it goes after the user’s private data,” researchers wrote.
SideWinder has used malicious apps as part of its operation before, disguised as photography and file manager tools to lure users into downloading them. Once downloaded into the user’s mobile device, they exploited the CVE-2019-2215 and MediaTek-SU vulnerabilities for root privileges.
In this case, “we believe these applications are still under development and will likely be used to compromise mobile devices in the future,” researchers noted.
SideWinder has active throughout late 2019 and in 2020, according to the firm, having been spotted using the Binder exploit to attack mobile devices. Trend Micro said the group also launched attacks earlier this year against Bangladesh, China and Pakistan, using lure files related to COVID-19.
“As seen with their phishing attacks and their mobile device tools’ continuous development, SideWinder is very proactive in using trending topics like COVID-19 or various political issues as a social-engineering technique to compromise their targets,” the firm concluded. “Therefore, we recommend that users and organizations be vigilant.”
Russian APT28 Hackers Using COVID-19 as Bait to Deliver Zebrocy Malware
10.12.2020 APT Thehackernews
A Russian threat actor known for its malware campaigns has reappeared in the threat landscape with yet another attack leveraging COVID-19 as phishing lures, once again indicating how adversaries are adept at repurposing the current world events to their advantage.
Linking the operation to a sub-group of APT28 (aka Sofacy, Sednit, Fancy Bear, or STRONTIUM), cybersecurity firm Intezer said the pandemic-themed phishing emails were employed to deliver the Go version of Zebrocy (or Zekapab) malware.
The cybersecurity firm told The Hacker News that the campaigns were observed late last month.
Zebrocy is delivered primarily via phishing attacks that contain decoy Microsoft Office documents with macros as well as executable file attachments.
First spotted in the wild in 2015, the operators behind the malware have been found to overlap with GreyEnergy, a threat group believed to be the successor of BlackEnergy aka Sandworm, suggesting its role as a sub-group with links to Sofacy and GreyEnergy.
It operates as a backdoor and downloader capable of collecting system information, file manipulation, capturing screenshots, and executing malicious commands that are then exfiltrated to an attacker-controlled server.
While Zebrocy was originally written in Delphi (called Delphocy), it has since been implemented in half a dozen languages, including AutoIT, C++, C#, Go, Python, and VB.NET.
This specific campaign spotted by Intezer uses the Go version of the malware, first documented by Palo Alto Networks in October 2018 and later by Kaspersky in early 2019, with the lure delivered as part of a Virtual Hard Drive (VHD) file that requires victims to use Windows 10 to access the files.
Once mounted, the VHD file appears as an external drive with two files, one a PDF document that purports to contain presentation slides about Sinopharm International Corporation, a China-based pharmaceutical company whose COVID-19 vaccine has been found to be 86% effective against the virus in late-stage clinical trials.
The second file is an executable that masquerades as a Word document that, when opened, runs the Zebrocy malware.
Intezer said it also observed a separate attack likely targeting Kazakhstan with phishing lures impersonating an evacuation letter from India's Directorate General of Civil Aviation.
Phishing campaigns delivering Zebrocy have been spotted several times in the wild in recent months.
In September last year, ESET detailed Sofacy's intrusive activities targeting the Ministries of Foreign Affairs in Eastern European and Central Asian countries.
Then earlier this August, QuoIntelligence uncovered a separate campaign aimed at a government body in Azerbaijan under the pretense of sharing NATO training courses to distribute the Zebrocy Delphi variant.
The Golang version of the Zebrocy backdoor also caught the attention of the US Cybersecurity and Infrastructure Security Agency (CISA), which released an advisory in late October, cautioning that the malware is "designed to allow a remote operator to perform various functions on the compromised system."
To thwart such attacks, CISA recommends exercising caution when using removable media and opening emails and attachments from unknown senders, and scanning for suspicious email attachments, and ensuring the extension of the scanned attachment matches the file header.
Russia-linked hackers actively exploit CVE-2020-4006 VMware flaw, NSA warns
7.12.2020 APT Securityaffairs
The National Security Agency (NSA) warns that Russia-linked hackers are exploiting a recently patched VMware flaw in a cyberespionage campaign.
The US National Security Agency has published a security alert warning that Russian state-sponsored hackers are exploiting the recently patched CVE-2020-4006 VMware flaw to steal sensitive information from their targets.
The US intelligence agency is urging companies to update VMWare products to address the above.
Last week, the company finally released security updates to fix the CVE-2020-4006 zero-day flaw in Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector.
At the end of November, VMware only has released a workaround to address the critical zero-day vulnerability that affects multiple VMware Workspace One components. VMware Workspace ONE allows to simply and securely deliver and manage any app on any device. The flaw is a command injection bug that could be exploited by attackers to execute commands on the host Linux and Windows operating systems using escalated privileges.
Affected versions are:
VMware Workspace One Access 20.10 (Linux)
VMware Workspace One Access 20.01 (Linux)
VMware Identity Manager 3.3.1 up to 3.3.3 (Linux)
VMware Identity Manager Connector 3.3.2, 3.3.1 (Linux)
VMware Identity Manager Connector 3.3.3, 3.3.2, 3.3.1 (Windows)
The Cybersecurity and Infrastructure Security Agency (CISA) also published a security advisory on the CVE-2020-4006 zero-day flaw.
“VMware has released workarounds to address a vulnerability—CVE-2020-4006—in VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector. An attacker could exploit this vulnerability to take control of an affected system.” reads the CISA’s advisory.
At the time of the public disclosure of the flaw, the virtualization giant did not reveal the identity of the organization or researcher who reported the vulnerability. Now the virtualization giant confirmed that the zero-day vulnerability was reported by the US intelligence agency NSA.
“The National Security Agency (NSA) released a Cybersecurity Advisory today detailing how Russian state-sponsored actors have been exploiting a vulnerability in VMware® products to access protected data on affected systems.” reads the advisory published by NSA. “This advisory emphasizes the importance for National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB) system administrators to apply vendor-provided patches to affected VMware® identity management products and provides further details on how to detect and mitigate compromised networks.”
According to the NSA, the threat actors installed a web shell on the VMWare Workspace ONE system and then forged SAML credentials for themselves.
The security advisory published by the NSA did not link the attacks to a specific Russia-linked APT group.
“NSA strongly recommends that NSS, DoD, and DIB system administrators apply the vendor-issued patch as soon as possible. If a compromise is suspected, check server logs and authentication server configurations as well as applying the product update.” concludes the advisory. “In the event that an immediate patch is not possible, system administrators should apply mitigations detailed in the advisory to help reduce risk of exploitation/compromise/attack.”
Cyber mercenaries group DeathStalker uses a new backdoor
6.12.2020 APT Securityaffairs
The group of cyber mercenaries tracked as DeathStalker has been using a new PowerShell backdoor in recent attacks.
The cyber mercenaries group known as DeathStalker has been using a new PowerShell backdoor in recent attacks.
DeathStalker is a hack-for-hire group discovered by Kaspersky, it has been targeting organizations worldwide, mainly law firms and financial entities, since 2012. Victim organizations are small and medium-sized businesses located in Argentina, China, Cyprus, India, Israel, Lebanon, Switzerland, Russia, Taiwan, Turkey, the United Kingdom and the United Arab Emirates.
Kaspersky experts identified a previously unknown backdoor, dubbed PowerPepper, that the group has been using in attacks since mid-July.
“PowerPepper is a Windows in-memory PowerShell backdoor that can execute remotely sent shell commands.” reads the analysis published by Kaspersky. “In strict accordance with DeathStalker’s traditions, the implant will try to evade detection or sandboxes execution with various tricks such as detecting mouse movements, filtering the client’s MAC addresses, and adapting its execution flow depending on detected antivirus products.”

The fileless Windows implant is being constantly improved by the mercenaries, it allows operators to execute shell commands. The backdoor uses multiple tricks to evade detection and leverages DNS over HTTPS (DoH) to communicate with its C2 server, using Cloudflare responders.
PowerPepper has mainly been used against law and consultancy firms in the United States, Europe, and Asia.
The C&C communication is encrypted, experts noticed that the implant uses the same implementation of AES encryption as the Powersing backdoor, with a unique difference in the AES padding mode and a function input format.
PowerPepper regularly polls a C2 server for new commands to execute, the mechanism is implemented by regularly sending TXT-type DNS requests to the name servers (NS) associated with its C&C domain name, that in turn sends the commands. Once executed the command, the malware the malicious code sends back command execution results.
“On top of the DNS C2 communication logic, PowerPepper also signals successful implant startup and execution flow errors to a Python backend, through HTTPS. Such signaling enables target validation and implant execution logging, while preventing researchers from interacting further with the PowerPepper malicious C2 name servers,” Kaspersky reports.
Kaspersky discovered that the Python backends were being hosted on the public, legitimate hosting service PythonAnywhere, the security firm worked with the service provider to take them down.
The PowerPepper attack chain is being delivered through weaponized Word documents distributed through spear-phishing messages.
The malicious item is either embedded as a spear-phishing email body, or downloaded from a malicious link the spear-phishing email. Experts pointed out that the infection chain varied slightly between July and November 2020.
In some attacks, threat actors used a Windows shortcut file to deliver the implant.
Additional technical details about the new backdoor used by DeathStalker are provided in the report published by Kaspersky, including Indicators of Compromise.
“The DeathStalker threat is definitely a cause for concern, with the victimology for its various malware strains showing that any corporation or individual in the world can be targeted by their malicious activities, provided someone has decided they are of interest and passed on the word to the threat actor,” Kaspersky concludes.
Hack-for-Hire Group 'DeathStalker' Uses New Backdoor in Recent Attacks
5.12.2020 APT Securityweek
Over the past several months, the “mercenary” advanced persistent threat (APT) group known as DeathStalker has been using a new PowerShell backdoor in its attacks, Kaspersky reports.
Active since at least 2012 but exposed only in August 2020, DeathStalker is believed to be a cyber-mercenary organization targeting small to medium-sized businesses in a dozen countries, based on customer requests or perceived value.
Kaspersky’s security researchers, who have been tracking the group since 2018, identified a previously unknown implant the group has been using in attacks since mid-July. Dubbed PowerPepper, the malware has been continuously used in attacks and is being constantly improved.
Targeting Windows systems, the in-memory implant can execute shell commands sent by the remote attacker and attempts to evade detection and execution in sandbox environments. It uses DNS over HTTPS (DoH) to communicate with its command and control (C&C) server, and leverages Cloudflare responders for that.
The C&C communication is encrypted and the malware uses the same implementation of AES encryption as the previously detailed Powersing backdoor. However, the AES padding mode is different and a function input format has been changed.
The malware was observed regularly sending TXT-type DNS requests to the name servers (NS) associated with its C&C domain name in order to receive commands. It then sends back command execution results.
“On top of the DNS C2 communication logic, PowerPepper also signals successful implant startup and execution flow errors to a Python backend, through HTTPS. Such signaling enables target validation and implant execution logging, while preventing researchers from interacting further with the PowerPepper malicious C2 name servers,” Kaspersky reports.
The security researchers also discovered that the Python backends were being hosted on the public, legitimate hosting service PythonAnywhere and worked with the service provider to take them down.
This prompted the operators to remove the feature from most PowerPepper delivery documents and to add a compromised WordPress domain that would serve as a reverse-proxy between implants and backends.
PowerPepper is being delivered through malicious Word documents that embed all of the items necessary for malware execution and setting up persistence. In some instances, a Windows shortcut file is used for delivery, with the chain leveraging malicious PowerShell scripts and employing a Word document that acts strictly as a decoy.
PowerPepper has mainly been used against law and consultancy firms in the United States, Europe, and Asia.
“The DeathStalker threat is definitely a cause for concern, with the victimology for its various malware strains showing that any corporation or individual in the world can be targeted by their malicious activities, provided someone has decided they are of interest and passed on the word to the threat actor,” Kaspersky concludes.
DeathStalker APT Spices Things Up with PowerPepper Malware
4.12.2020 APT Threatpost
A raft of obfuscation techniques turn the heat up for the hacking-for-hire operation.
The DeathStalker advanced persistent threat (APT) group has a hot new weapon: A highly stealthy backdoor that researchers have dubbed PowerPepper, used to spy on targeted systems.
DeathStalker offers mercenary, espionage-for-hire services targeting the financial and legal sectors, according to researchers at Kaspersky. They noted that the group has been around since at least 2012 (first spotted in 2018), using the same set of relatively basic techniques, tactics and procedures (TTPs) and selling its services to the highest bidder. In November, though, the group was found using a new malware implant, with different hideout tactics.
“DeathStalker has leveraged several malware strains and delivery chains across the years, from the Python and VisualBasic-based Janicab, to the PowerShell-based Powersing, passing by the JavaScript-based Evilnum,” researchers said in a Thursday posting. “DeathStalker also consistently leveraged anti-detection and antivirus evasion techniques, as well as intricate delivery chains, that would drop lots of files on target’s file systems.”
This particular malware stands out, though, for upping the heat level on its evasion tactics.
Advanced Evasion Tactics
The freshly discovered backdoor spices things up on the obfuscation front by using DNS over HTTPS as a communication channel, in order to hide communications with command-and-control (C2) behind legitimate-looking traffic.
“PowerPepper regularly polls the C2 server for commands to execute,” according to researchers. “In order to do so, the implant sends TXT-type DNS requests (with DoH or plain DNS requests if the later fails) to the name servers (NS) that are associated with a malicious C2 domain name…the server replies with a DNS response, embedding an encrypted command.”

PowerPepper’s main features. Source: Kaspersky.
PowerPepper also adds steganography to the list of evasion techniques, which is the practice of hiding data inside images. In this case, the malicious code is embedded in what appears to be regular pictures of ferns or peppers (hence the name), and it is then extracted by a loader script. The loader is disguised as a verification tool from identity services provider GlobalSign.
And, it uses custom obfuscation, with parts of its malicious delivery scripts hidden in Word-embedded objects, researchers said: “Communications with the implant and servers are encrypted and, thanks to the use of trusted, signed scripts, antivirus software won’t necessarily recognize the implant as malicious at startup.”
Other tactics for evasion, like mouse movement detection, client MAC address filtering, Excel application handling and antivirus products inventory round out its bag of tricks.
Peppering Companies with Espionage
PowerPepper was cultivated to execute remote shell commands sent by DeathStalker operators, which are aimed at stealing sensitive business information.

Targeted geographies in 2020. Source: Kaspersky.
The commands cover the spycraft gamut, including those for gathering the computer’s user and file information, browsing network file shares, downloading additional binaries or copying content to remote locations.
PowerPepper is typically spread via spearphishing emails with the malicious files delivered via the email body or within a malicious link, as is typical for DeathStalker. Kaspersky has observed lures related to international events, carbon-emission regulations and the pandemic, with emails hitting Europe primarily, but also in the Americas and Asia. The primary targets for PowerPepper so far are small and medium-sized organizations – organizations that tend to have less robust security programs.
“PowerPepper once again proves that DeathStalker is a creative threat actor: one capable of consistently developing new implants and toolchains in a short period of time,” said Pierre Delcher, security expert at Kaspersky, in a statement. “PowerPepper is already the fourth malware strain affiliated with the actor, and we have discovered a potential fifth strain. Even though they are not particularly sophisticated, DeathStalker’s malware has proven to be quite effective.”
Pandemic, A Driving Force in 2021 Financial Crime
4.12.2020 APT Threatpost
Ransomware gangs with zero-days and more players overall will characterize financially motivated cyberattacks next year.
Financial cybercrime in 2021 is set to evolve, researchers say, with extortion practices becoming more widespread, ransomware gangs consolidating and advanced exploits being used more effectively to target victims.
That’s according to key predictions from Kaspersky. Researchers said the drastic COVID-19-related changes to the way people live and work has changed the way financial attackers operate. The implications of these shifts for 2021 are significant. Over the past year, companies became less secure due to hastily deployed remote work solutions, researchers said. That has translated into a lack of employee training, default laptop configurations left unchanged and vulnerable remote access connections. Together these trends have opened up a myriad of new attack vectors, including targeted ransomware campaigns.
According to Kasperky, ransomware – above all – will continue to be a main scourge in the year ahead.
“Due to their successful operations and extensive media coverage this year, the threat actors behind targeted ransomware systematically increased the amounts victims were expected to pay in exchange for not publishing stolen information,” researchers said in a Monday posting. “This point is important because it is not about data encryption anymore, but about disclosing confidential information exfiltrated from the victim’s network. Due to payment card industry security and other regulations, leaks like this may result in significant financial losses.”
Kaspersky researchers anticipate an even higher growth in extortion attempts for next year, with more cybercriminals targeting organizations with ransomware or distributed denial of service (DDoS) attacks or both. This could include advanced persistent threat (APT) groups going forward.
“The Lazarus group has tried its hand at the big game with the VHD ransomware family. This received attention, and other APT threat actors followed suit, MuddyWater among them,” researchers said. “Advanced threat actors from countries placed under economic sanctions may rely more on ransomware imitating cybercriminals’ work. They may reuse already-available code or create their own campaigns from scratch.”
Meanwhile, zero-day exploits could become more common among ransomware gangs according to the firm, as they purchase these to expand even further the scale of attacks and boost their success, resulting in more profit.
“Ransomware groups who managed to accumulate funds as a result of a number of successful attacks in 2020 will start using zero-day exploits – vulnerabilities that have not yet been found by developers – as well as N-day exploits to scale and increase the effectiveness of their attacks,” according to Kaspersky. “While purchasing exploits is an expensive endeavor, based on the money some of the ransomware operators were able to obtain from their victims, they now have sufficient funds to invest in them.”
Researchers also noted that financial cybercriminals will likely switch to “transit cryptocurrencies” when demanding payment from victims, for enhanced privacy.
“Special technical capabilities for monitoring, deanonymizing and seizing Bitcoin accounts will prompt a shift in the methods used by many cybercriminals to demand payment,” according to the report. “Other privacy-enhanced currencies such as Monero are likely to be used as a first transition currency, with the funds being later converted to other cryptocurrency, including Bitcoin, to cover criminals’ tracks.”
Aside from ransomware landscape changes, Kaspersky researchers predicted that Magecart payment-skimming attacks will move to the server side, as fewer threat actors rely on client-side attacks that use JavaScript.
And, Bitcoin theft will become more attractive, as many nations are hit hard financially as a result of the pandemic.
“The COVID-19 pandemic is likely to cause a massive wave of poverty, and that invariably translates into more people resorting to crime including cybercrime,” researchers said. “We might see certain economies crashing and local currencies plummeting, which would make Bitcoin theft a lot more attractive. We should expect more fraud, targeting mostly BTC, due to this cryptocurrency being the most popular one.”
Dmitry Bestuzhev, a security researcher at Kaspersky, noted that while this year was substantially different from any other, many trends that were anticipated to come to life last year came true regardless.
“These include new strategies in financial cybercrime – from reselling bank access to targeting investment applications — and the further development of already existing trends, for instance, even greater expansion of card-skimming and ransomware being used to target banks,” he said. “Forecasting upcoming threats is important, as it enables us to better prepare to defend ourselves against them, and we are confident our forecast will help many cybersecurity professionals to work on their threat models.”
What did DeathStalker hide between two ferns?
3.12.2020 APT Securelist
DeathStalker is a threat actor who has been active starting 2012 at least, and we exposed most of his past activities in a previous article, as well as during a GREAT Ideas conference in August 2020. The actor draught our attention in 2018, because of distinctive attacks characteristics that did not fit the usual cybercrime or state-sponsored activities, making us believe that DeathStalker is a “hack-for-hire” company.
DeathStalker leveraged several malware strains and delivery chains across years, from the Python and VisualBasic-based Janicab, to the PowerShell-based Powersing, passing by the JavaScript-based Evilnum. The actor consistently used what we call “dead-drop resolvers” (DDRs), which are some obfuscated content hosted on major public Web services like YouTube, Twitter or Reddit; and which once decoded by a malware would reveal a command-and-control (C2) server address. DeathStalker also consistently leveraged anti-detection and antivirus evasion techniques, as well as intricated delivery chains, that would drop lots of files on target’s filesystems. To kick-start an infection, DeathStalker usually relies on spear-phishing emails with attachments, or links to public file-sharing services, as well as Windows shortcuts-based script execution. We have identified DeathStalker’s malware compromises within clusters or varied targets in all parts of the world, with a possible focus on law and consultancy offices, as well as FINTECH companies, but without any clear or stable visible interest. The targeting does not seem to be politically or strategically defined and does not fit in usual financially motived crime. As so, we concluded that DeathStalker is a cyber-mercenaries organization.
While tracking DeathStalker’s Powersing-based activities in May 2020, we detected a previously unknown implant that leveraged DNS over HTTPS as a C2 channel, as well as parts of its delivery chain. We named this new malware “PowerPepper”. We first spotted a variant of PowerPepper in the wild in mid-July 2020, as dropped from a Word Document that had been submitted on a public multiscanner service. PowerPepper implant and associated delivery chain has been continuously developed and operated since.
Meet PowerPepper: the spicy implant that your bland scripts setup needed
PowerPepper implant
PowerPepper is a Windows in-memory PowerShell backdoor that can execute remotely sent shell commands. In strict accordance with DeathStalker’s traditions, the implant will try to evade detection with various tricks like mouse movements detection, client’s MAC addresses filtering, Excel application handling and antivirus products inventory.

The implant’s C2 logic stands out, as it is based on communications via DNS over HTTPS (DoH), using CloudFlare responders. PowerPepper first try to leverage Microsoft’s Excel as a Web client to send DoH requests to a C2 server, but will fall back to PowerShell’s standard Web client, and ultimately to regular DNS communications, if messages cannot go through.
C2 communications content between the implant and servers is encrypted. We noticed that PowerPepper and the previously described Powersing use an almost identical PowerShell implementation of AES encryption, with only the AES padding mode and a function input format being changed.
PowerPepper DNS command and control
PowerPepper regularly polls a C2 server for commands to execute. In order to do so, the implant sends TXT-type DNS requests (with DoH or plain DNS requests if the later fails) to the name servers (NS) that are associated with a malicious C2 domain name. If the target which runs the implant is validated (we cover that later), the server replies with a DNS response, embedding an encrypted command. Both requests and responses contain patterns that can be easily detected with network intrusion detection systems, but that has been changed across implants variants.

The commands execution results are sent back to the server through a batch of variable-length A-type DNS requests, where queried hostnames contain an identifier, data length, and encrypted data.
During the course of our investigations, we noticed that the PowerPepper C2 name servers were actually open DNS resolvers, that always resolved arbitrary hostnames with the same IP addresses: 128.49.4.4 (a US Navy owned server), 91.214.6.100 and 91.214.6.101 (HSBK UK owned servers). Using this fact and reverse DNS resolutions historical data, we have been able to preemptively identify PowerPepper C2 domains.
PowerPepper signaling and targets validation
On top of the DNS C2 communication logic, PowerPepper is also signaling successful implant startup and execution flow errors to a Python backend, through HTTPS. Such signaling enables targets validation and implant execution logging, while preventing researchers to further interact with PowerPepper malicious C2 name servers. It has also been used directly from some of the malicious documents that were involved in PowerPepper delivery, thought the remote-sources links feature in Office documents.

The signaling Python backends were hosted on a public and legitimate content hosting Web service which is named “PythonAnywhere“, and which allows users to build websites. Discovered Python backend endpoints were shut down by PythonAnywhere in coordination with us. As a result, DeathStalker tried to adapt the signaling feature by removing it from most PowerPepper delivery documents (but keeping it in the implant itself), and by adding a legitimate but compromised WordPress website as a reverse-proxy between implants and backends.
PowerPepper delivery chains: a surprising journey into mercenaries’ tricks, from Russian dolls to plant-covered steganography
The macro-based delivery chain: when you are way too much into this whole “Russian dolls” idea
The first type of PowerPepper delivery (or infection) chain we encountered, back in July 2020, is based on a malicious Word document. Although we could not confirm how such document had been distributed to targets, infection trails and documents we analyzed would show that such item is either embedded as a spear-phishing mail body, or downloaded from a malicious link in a spear-phishing email. This infection chain varied slightly between July and November 2020: some dropped file names, integrated code or remote links changed, but the logic stayed the same.

We will not dive deep in the details of the delivery workflow, as main tricks are approached later. It should however be noted that the delivery chain is based on a monolithic document that embeds all required malicious items. This document notably contains a decoy content, and the malicious logic is handled by Visual Basic for Application (VBA) macros, which ultimately run PowerPepper and setup its persistence.
The LNK-based delivery chain: your direct shortcut to spiciness
This infection chain is based on a Windows shortcut file, with a misleading “.docx.lnk” double extension, and constitutes a more modular approach to PowerPepper delivery.

The delivery chain is very similar to the macro-based one, but implements two major changes:
the malicious macros logic is moved to malicious PowerShell scripts, and the first one is directly embedded in the shortcut file, so there are no more VBA macros;
the Word document from this chain is just a decoy and malicious files storage pack, and is downloaded from a remote location (a public file sharing service) instead of directly embedded somewhere.
The malicious LNK files were most likely distributed as ZIP-ed attachments within spear-phishing mails, and files that are dropped from this delivery chain of course change across varians as well.
A quick look at the decoy contents
Some malicious documents that we could retrieve contained a social-engineering banner, asking users to enable macros execution, and thus explaining how the malicious logic from the macro-based delivery chain could actually be triggered, while macros are disabled by default on most modern Office settings.
Decoy contents we could retrieve are varied: the first we found in the wild was about carbon emissions regulations, but we also identified a fake travel booking form for a very specific event which is planned next year in Turkey, and of course some are about the coronavirus.



We could link most of the decoy contents back to original contents that are published on the Internet by their initial authors, which means that DeathStalker did not craft such contents, but picked appropriate ones that are available on the Internet as is. One of the decoy contents contained sender details that impersonated a legitimate travel agent identity but included changed contact details.
A PowerPepper tricks compilation
PowerPepper delivery chains leverage a lot of obfuscation, execution and masquerading tricks to hinder detection, or deceive targets that are possibly keen on knowing what is happening on their computers, so we thought we should describe some.
Trick #1: hide things in Word embedded shapes properties (and make macro comments fun again)
DeathStalker hides strings in Word embedded shapes and objects (OLE packages) properties, like the “hyperlink” property, to obfuscate the malicious execution workflow, as well as reconstruct and execute commands or scripts.
These properties are notably leveraged as a second stage PowerShell script in the LNK-based delivery chain: the first stage PowerShell script which is embedded in a malicious LNK file will parse a downloaded Word document contents to extract and run a second PowerShell script. These properties artifacts can also contain parts of URLs, dropped files paths, or commands that are directly leveraged by macros in the macro-based delivery chain.
We can also notice from the code extract above that DeathStalker uses macros to further open another subdocument, which is embedded in the first malicious document from the macro-based delivery chain. Last but not least, comments are very helpful.
Trick #2: use Windows Compiled HTML Help (CHM) files as archives for malicious files
In the course of their PowerPepper delivery workflows, DeathStalker leverages CHM files as containers to better evade detection, and uses a Windows built-in tool called “hh” to unpack content, from VBA macros or LNK-embedded PowerShell script.
All the files that are dropped on targeted computers fro delivery chains and that are necessary to run PowerPepper are contained in such archives. The CHM files are embedded in the malicious Word (sub)document of the delivery chains.
Trick #3: masquerade and obfuscate persistent files
DeathStalker uses a Visual Basic Script (VBS) loader to start PowerPepper execution. The loader is launched immediately after delivery, and at each computer startup then, thanks to a companion launcher shortcut which is placed in a Windows startup folder.
This VBS loader is masqueraded as a GlobalSign verification tool with comments as well as deceptive variables or help strings. Furthermore, the script malicious content is obfuscated thanks to a custom encryption function.
Trick #4: hide your implant between two ferns…
And here come our plants… The previously described VBS loader will basically do one thing: deobfuscate and run a PowerShell script against a picture file, that had been previously dropped from the delivery chain.

But the picture is actually a steganography image (representing… ferns), that will be decoded by the VBS loader-embedded script, and contains the PowerPepper implant. In the first discovered delivery chains, the steganography image actually represented peppers, hence the “PowerPepper” name.

Trick #5: get lost in Windows shell commands translation
The Windows shortcut (LNK) file from the LNK-based delivery chain is actually starting a Windows shell with an obfuscated command argument. This command is a specific form of a “FOR” Windows shell loop, that will generate the “PowerShell” string from an “assoc” shell built-in result.

The malicious LNK file will fire a PowerShell script as a result, which in turn will recompose a second stage script from a downloaded Word document, as seen in Trick #1.
Trick #6: kick start it all with a signed binary proxy execution
Be it in the end of the macros execution (for the macro-based delivery chain) or as a last step of the shortcut-embedded scripts (for the LNK-based delivery chain), DeathStalker leveraged a signed binary proxy execution to startup PowerPepper for the first time.
While the first (macro-based) delivery chain we retrieved fired the malicious VBS loader with “rundll32.exe ieadvpack.dll, RegisterOCX wscript.exe <script file> <script argument> pexe”, the recent ones use a “rundll32.exe ieframe.dll, OpenURL <Internet shortcut>” alternative combo. The latest rely on a dropped Internet shortcut file (.url), which will simply open a LNK launcher with a “file://” URL. The LNK launcher in turn runs the VBS loader (take a look at Trick #3).
PowerPepper’s targets geography
We of course cannot get a comprehensive view of all PowerPepper’s targets, but having tracked this implant starting May 2020, we managed to get a partial view of targeted countries before August 2020, as well as in November 2020.

Due to the very partial information we sometimes get for such research, and despite our efforts to filter as much as we can, we cannot rule out that some identified targets could actually be fellow researchers investigating the threat, or DeathStalker’s own testing infrastructure.
We could not precisely identify PowerPepper targets, but law and consultancy firms have been frequent actor’s targets.
Prevention and protection leads
In order to prevent successful PowerPepper execution or delivery, or to protect against associated infection chains, we could not but underline these usual and elementary defense measures:
Content hosters could regularly scan hosted files for malicious content, where regulations allows. They could protect their hosting infrastructure with endpoint protection software and traffic monitoring. They could also stack protections on privileged and remote accesses, with client network addresses filtering, multi-factors authentication (MFA), and authentication logs auditing.
Website owners and editors should frequently and responsively update their CMS backends as well as associated plugins. They could also stack protections on privileged and remote accesses, with client network addresses filtering, MFA and accesses logging on all backend endpoints.
Enterprise IT services should restrict scripts engines (i.e. PowerShell) use on end-users computers with enforced execution policies. They should setup endpoint protection software on end-users’ computers and content servers. They could allow DNS requests to corporate-managed resolvers and relays only, while filtering HTTP and DNS traffic at perimeter. Last but not least, they should train employees not to open attachments and links from unknown mail senders.
Individuals should never open Windows shortcuts that were downloaded from a remote location or attached to a mail, open attachments or click links in mails from unknown senders, or enable macros in documents from unverified source.
Conclusion
It only seems fair to write that DeathStalker tried hard to develop evasive, creative and intricate tools with this PowerPepper implant and associated delivery chains. Nothing is specifically sophisticated in techniques and tricks that are leveraged, yet the whole toolset proven itself to be effective, is pretty well put together, and shows determined efforts to compromise various targets around the world.
This is perfectly consistent with previous knowledge on DeathStalker actor, who demonstrated continuous capabilities to compromise targets since 2012, and to develop new implants and toolchains at fast pace. We discovered the PowerPepper implant in May 2020, and it has been regularly improved or adapted since then. At the same time, we also uncovered another previously unknown malware strain that we strongly believe is from the same actor, but however did not identify any Powersing-related activity since our previous article on DeathStalker in August 2020.
DeathStalker definitely is a threat to feel concerned about, as victimology for its various malware strains shows that any corporation or individual in the world could be targeted by their malicious activities, provided someone decided there is interest to, and passed them the word. Luckily for defenders, DeathStalker relied on a quite limited set of techniques to design its delivery chains until now, and implementing associated counter-measures is an attainable goal for most organizations.
Indicators of compromise
File hashes
IOC Description
A4DD981606EA0497BF9995F3BC672951 Malicious Word document (macro-based delivery chain)
871D64D8330D956593545DFFF069194E Malicious Word document (macro-based delivery chain)
81147EDFFAF63AE4068008C8235B34AF Malicious Windows shortcut (LNK-based delivery chain)
DFC2486DE9E0339A1B38BB4B9144EA83 Malicious Word document (downloaded by LNK-based delivery chain)
74D7DF2505471EADEB1CCFC48A238AEC Malicious CHM container
5019E29619469C74F2B826535C5A8BD8 Malicious CHM container
B4790E70B1297215E0875CFC2A56648E Malicious CHM container
3A6099214F474C1501C110CE66033F3C Malicious VBS Loader
07308FBC3D10FD476F1898ECF6762437 Malicious VBS Loader
1F77FBE4702F787A713D394B62D27B42 Malicious VBS Loader
6E99F6DA77B0620E89F6E88D91198C32 Malicious VBS Loader
5D04D246F3E5DA6A9347EC72494D5610 Malicious startup launcher LNK
BA7AE1C73A78D8DC4B3779BD6A151791 Malicious startup launcher LNK
1DC2B849A858BC479B1EF428491E0353 Malicious startup launcher LNK
9D4066C57C6E1602CE33F15DC7F3841B PowerPepper steganography image (peppers)
6FF8A3D18A6EA930E87AC364379ECEC2 PowerPepper steganography image (peppers)
871D64D8330D956593545DFFF069194E PowerPepper steganography image (peppers)
9CE299BBDD7FDBF9F30F8935C89D2877 PowerPepper steganography image (ferns)
34F086AE78C5319FB64BF1CAE8204D1B PowerPepper steganography image (ferns)
File paths
IOC Description
%PROGRAMDATA%\Support\licenseverification.vbs Malicious VBS Loader
%PROGRAMDATA%\Support\licenseverify.vbs Malicious VBS Loader
%PROGRAMDATA%\MyPrinter\NewFile.vbs Malicious VBS Loader
%PROGRAMDATA%\Printers\NewFile.vbs Malicious VBS Loader
%APPDATA %\Microsoft\Windows\Start Menu\Programs\Startup\System.lnk Malicious startup launcher LNK
%PROGRAMDATA%\MyPrinter\Web.lnk Malicious startup launcher LNK
%PROGRAMDATA%\Printers\Web.lnk Malicious startup launcher LNK
%APPDATA%\Roaming\Microsoft\Windows\Start Menu\Programs\StartUp\StartPrinter.url Malicious startup launcher URL
Domain and IPs
IOC Description
allmedicalpro[.]com PowerPepper C2 domain name
mediqhealthcare[.]com PowerPepper C2 domain name
gofinancesolutions[.]com PowerPepper C2 domain name
mailsigning.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
mailsignature.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
mailservice.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
mailservices.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
footersig.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
globalsignature.pythonanywhere[.]com PowerPepper Signaling hostname (legitimate hoster and root domain)
URLs
IOC Description
hxxps://www.gsn-nettoyage[.]com/wp-snapshots/btoken.php
PowerPepper Signaling hostname (legitimate but compromised Website)
hxxps://www.gsn-nettoyage[.]com/wp-snapshots/etoken.php
hxxps://www.gsn-nettoyage[.]com/wp-snapshots/1.docx
hxxps://www.gsn-nettoyage[.]com/wp-snapshots/Quote 16 db room.docx
Malicious documents download location (legitimate but compromised Website)
hxxps://outlookusers.page[.]link/ Malicious documents download location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYdifkocKujNavvjY?e=hhuBV8 Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYdcbz1YwTJRkOxP4?e=u5wtbX Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYd1921tVEMKWaCUs?e=MyoVNF Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws /w/s!AvXRHBXCKmvYeFdjVtZN0Quljs4?e=dnA6GG Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYeePNerfsAWK0qVY?e=e4SsYM Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYejBpdekg1WUCM9M?e=UkhU10 Malicious document remote location (legitimate hoster and root domain)
hxxps://1drv[.]ws/w/s!AvXRHBXCKmvYe1ulhtazjNVvCqY?e=WptVTC Malicious document remote location (legitimate hoster and root domain)
Mail addresses
IOC Description
a.christy_inbox@outlook[.]com Suspected malicious spear-phishing mails sender (legitimate root domain)
APT annual review: What the world’s threat actors got up to in 2020
3.12.2020 APT Securelist
We track the ongoing activities of more than 900 advanced threat actors; you can find our quarterly overviews here, here and here. Here we try to focus on what we consider to be the most interesting trends and developments of the last 12 months. This is based on our visibility in the threat landscape; and it’s important to note that no single vendor has complete visibility into the activities of all threat actors.
Beyond Windows
While Windows continues to be the main focus for APT threat actors, we have observed a number of non-Windows developments this year. Last year we reported a malware framework called MATA that we attribute to Lazarus. This framework included several components such as a loader, orchestrator and plug-ins. In April, we learned that MATA extended beyond Windows and Linux to include macOS. The malware developers Trojanized an open-source two-factor authentication application and utilized another open-source application template. The MATA framework was not the only way that Lazarus targeted macOS. We found a cluster of activity linked to Operation AppleJeus. We also discovered malware similar to the macOS malware used in a campaign that we call TangDaiwbo – a multi-platform cryptocurrency exchange campaign. Lazarus utilizes macro-embedded Office documents and spreads PowerShell or macOS malware, depending on the victim’s system.
Kaspersky has publicly documented the Penquin family, tracing it back to its Unix ancestors in the Moonlight Maze operation of the 1990s. When researchers at Leonardo published a report in May about Penquin_x64, a previously undocumented variant of Turla’s Penquin GNU/Linux backdoor, we followed up on this latest research by generating network probes that detect Penquin_x64-infected hosts at scale, allowing us to discover that tens of internet hosting servers in Europe and the US are still compromised today. We think it’s possible that, following public disclosure of Turla’s GNU/Linux tools, the Turla threat actor may have been repurposing Penquin to conduct operations other than traditional intelligence.
In our 2020 Q3 APT trends report we described a campaign we dubbed TunnelSnake. By analyzing the activity in this campaign, we were able to uncover the network discovery and lateral movement toolset used by the threat actor after deploying the Moriya rootkit. We saw that the actor also made use of the open-source tools Earthworm and Termite, capable of spawning a remote shell and tunneling traffic between hosts. These tools are capable of operating on multiple architectures widely used by IoT devices, demonstrating a readiness to pivot to such devices.
Infecting UEFI firmware
During an investigation of a targeted campaign, we found a UEFI firmware image containing rogue components that drop previously unknown malware to disk. Our analysis showed that the revealed firmware modules were based on a known bootkit named Vector-EDK, and the dropped malware was a downloader for further components. By pivoting on unique traits of the malware, we uncovered a range of similar samples from our telemetry that have been used against diplomatic targets since 2017 and that have different infection vectors. While the business logic of most of them is identical, we saw that some had additional features or differed in their implementation. Because of this, we infer that the bulk of samples originate from a bigger framework, which we dubbed MosaicRegressor. The targets, diplomatic entities and NGOs in Asia, Europe and Africa, all appear to be connected in some way to North Korea.
Mobile implants
The use of mobile implants by APT threat actors is no longer a novelty: this year we have observed various groups targeting mobile platforms.
In January, we discovered a watering hole utilizing a full remote iOS exploit chain. The site appears to have been designed to target users in Hong Kong, based on the content of the landing page. While the exploits currently being used are known, the actor responsible is actively modifying the exploit kit to target more iOS versions and devices. We observed the latest modifications on February 7. The project is broader than we initially thought, supporting an Android implant, and probably implants for Windows, Linux and macOS. We have named this APT group TwoSail Junk. We believe this is a Chinese-speaking group; it maintains infrastructure mostly within Hong Kong, along with a couple of hosts located in Singapore and Shanghai. TwoSail Junk directs visitors to its exploit site by posting links within the threads of forum discussions, or creating new topic threads of their own. To date, dozens of visits were recorded from within Hong Kong, with a couple from Macau. The technical details around the functionality of the iOS implant, called LightSpy, and related infrastructure, reveal a low-to-mid capable actor. However, the iOS implant is a modular and exhaustively functional iOS surveillance framework.
In August, we published the second of our reports on the recent activities of the Transparent Tribe threat actor. This included an Android implant used by the group to spy on mobile devices. One of the methods used to distribute the app was by disguising it as the Aarogya Setu COVID-19 tracking app developed by the government of India. The fake app was used to target military personnel in India; and, based on public information, may have been distributed by sending a malicious link via WhatsApp, SMS, email or social media.
In June, we observed a new set of malicious Android downloaders which, according to our telemetry, have been actively used in the wild since at least December 2019, and have been used in a campaign targeting victims almost exclusively in Pakistan. The authors spread the malware by mimicking Chat Lite, Kashmir News Service and other legitimate regional Android applications. A report by the National Telecom & Information Technology Security Board (NTISB) from January describes malware sharing the same C2s and spoofing the same legitimate apps. According to the publication, the targets were Pakistani military bodies, and the attackers used WhatsApp messages, SMS, emails and social media as the initial infection vectors. Our own telemetry shows that this malware also spreads through Telegram messenger. The analysis of the initial set of downloaders allowed us to find an additional set of Trojans that we believe are strongly related, as they use the package name mentioned in the downloaders and focus on the same targets. These new samples have strong code similarity with artefacts previously attributed to Origami Elephant.
Big game hunting
In April, we released an early warning about the VHD ransomware, which was first spotted in late March. This ransomware stood out because of its self-replication method. The use of a spreading utility compiled with victim-specific credentials was reminiscent of APT campaigns, but at the time we were unable to link the attack to an existing group. However, we were able to identify an incident in which the VHD ransomware was deployed, in close conjunction with known Lazarus tools, against businesses in France and Asia. This indicates that Lazarus is behind the VHD ransomware campaigns that have been documented so far. As far as we know, this is the first time it has been established that the Lazarus group has resorted to targeted ransomware attacks (known as “big game hunting”) for financial gain.
Continued use of ‘naming and shaming’
Some years ago, we predicted that governments would resort to the “court of public opinion” as a strategy to draw attention to the activities of hostile APT groups; and this trend has developed further in the last year or so.
In February, the US Department of Justice (DoJ) charged four Chinese military officers with computer fraud, economic espionage and wire fraud for hacking into the credit reporting agency Equifax in 2017. The following month, the DoJ charged two Chinese nationals with laundering more than $100 million in cryptocurrency on behalf of North Korea. The indictment alleged that the two men laundered cryptocurrency stolen by North Korean hackers between December 2017 and April 2019, helping to hide the stolen currency from police.
In May, the UK National Cyber Security Centre (NCSC) and the US Department of Homeland Security (DHS) issued a joint advisory warning that both countries are investigating a number of incidents in which other nation states are targeting pharmaceutical companies, medical research organizations and universities, looking for intelligence and sensitive data, including research on COVID-19. The FBI and CISA (Cybersecurity and Infrastructure Security Agency) also issued a warning that threat actors related to the People’s Republic of China have been targeting US organizations engaged in COVID-19-related research.
On July 30, the European Council announced that it was imposing sanctions against six individuals and three entities that it believes are responsible for, or involved in, various cyberattacks, including the attempted attack on the Organisation for the Prohibition of Chemical Weapons (OPCW) and the WannaCry, NotPetya and Operation Cloud Hopper attacks. The sanctions include a travel ban and asset freeze. In addition, EU persons and entities are forbidden from making funds available to those listed.
In September, the US DoJ released three indictments associated with hackers allegedly connected with APT41 and other intrusions tracked as Barium, Winnti, Wicked Panda and Wicked Spider. In addition, two Malaysian nationals were also arrested on September 14, in Sitiawan (Malaysia), for “conspiring to profit from computer intrusions targeting the video game industry”, following cooperation between the US DoJ and Government of Malaysia, including the Attorney General’s Chambers of Malaysia and the Royal Malaysia Police. The indictments contain several indirect IoCs, which allowed us to connect these intrusions to Operation ShadowPad and Operation ShadowHammer, two massive supply-chain attacks that we discovered and investigated.
In October, the US DoJ indicted six Russian military intelligence officers for a number of cyberattacks, including NotPetya, the Olympic Destroyer attacks on the 2018 Winter Olympics and attacks affecting France, Georgia, the Netherlands, Ukraine and the investigation into the 2018 Novichok poisonings in the UK. The UK NCSC also accused Russia’s GRU military intelligence service of attacks on officials and organizations involved in the 2020 Tokyo games, prior to their postponement.
‘Good enough’ is enough
The malware developed by APT threat actors doesn’t always need to be technically sophisticated in order to be effective. The activities of DeathStalker illustrates this. This is a unique threat actor that seems to focus mainly on law firms and companies operating in the financial sector. The group’s interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as an information broker in financial circles. The activities of this threat actor first came to our attention through a PowerShell-based implant called Powersing. This quarter, we unraveled the threads of DeathStalker’s LNK-based Powersing intrusion workflow. The group continues to develop and use this implant, employing tactics that have mostly been identical since 2018, while making greater efforts to evade detection. In August, our public report of DeathStalker’s activities summarized the three scripting language-based toolchains used by the group – Powersing, Janicab and Evilnum.
Following our initial private report on Evilnum, we detected a new batch of implants in late June 2020, showing interesting changes in the (so far) quite static modus operandi of DeathStalker. For instance, the malware directly connects to a C2 server using an embedded IP address or domain name, as opposed to previous variants where it made use of at least two dead drop resolvers (DDRs) or web services, such as forums and code sharing platforms, to fetch the real C2 IP address or domain. Interestingly, for this campaign the attackers didn’t limit themselves merely to sending spear-phishing emails, but actively engaged victims through multiple emails, persuading them to open the decoy to increase the chances of compromise. Furthermore, aside from using Python-based implants throughout the intrusion cycle, in both new and old variants, this was the first time that we had seen the actor dropping PE binaries as intermediate stages to load Evilnum, while using advanced techniques to evade and bypass security products.
We also found another intricate, low-tech implant used since Q2 2020 that we attribute with high confidence to DeathStalker. The delivery workflow uses a Microsoft Word document and drops a previously unknown PowerShell implant that relies on DNS over HTTPS (DoH) as a C2 channel. We dubbed this implant PowerPepper. In October 2020, we identified new samples of DeathStalker’s PowerPepper toolset, containing improvements that included improved sandbox detection techniques. The group also leveraged a new infection chain to deliver PowerPepper.
DeathStalker offers a good example of what small groups or even skilled individuals can achieve, without the need for innovative tricks or sophisticated methods. DeathStalker should serve as a baseline of what organizations in the private sector should be able to defend against, since groups of this sort represent the type of cyberthreat that companies today are most likely to face. We advise defenders to pay close attention to any process creation related to native Windows interpreters for scripting languages, such as powershell.exe and cscript.exe: wherever possible, these utilities should be made unavailable. Security awareness training and security product assessments should also include infection chains based on LNK files.
Exploiting COVID-19
In the wake of the COVID-19 pandemic, and the lockdowns imposed by many countries in response, attackers of all kinds sought to capitalize on people’s fears about the disease. Most of the phishing scams related to COVID-19 have been launched by cybercriminals using the disease as a springboard to make money. However, the list of attackers also includes APT threat actors such as Lazarus, Sidewinder, Transparent Tribe, GroupA21, which we observed using COVID-19-themed lures to target their victims, as well as Kimsuky, APT27, IronHusky and ViciousPanda who did the same, according to OSINT (open source intelligence). In March, we discovered a suspicious infrastructure that could have been used to target health and humanitarian organizations, including the WHO. We weren’t able to firmly attribute this to any specific actor, and it was registered before the COVID-19 crisis. Some private sources suggested it might be related to DarkHotel.
A few months later, there were a series of attacks on supercomputing centers around Europe, including the UK-based ARCHER, the German-based bwHPC and the Swiss National Supercomputing Centre. The EGI Computer Security and Incident Response Team (EGI-CSIRT) also published an alert in May covering two incidents that, according to its report, may or may not be related. Although we weren’t able to establish with a high degree of certainty that the ARCHER hack and the incidents described by EGI-CSIRT are related, we suspect they might be. Some media speculated that all these attacks might be related to COVID-19 research being carried out at the supercomputing centers.
Following publication of our initial report on WellMess (see our APT trends report Q2 2020), the UK National Cyber Security Centre (NCSC) released a joint advisory, along with the Canadian and US governments, on the most recent activity involving WellMess. Specifically, all three governments attribute the use of this malware targeting COVID-19 vaccine research to The Dukes (aka APT29 and Cozy Bear). While the publication of the NCSC advisory increased general public awareness on the malware used in these recent attacks, the attribution statements made by all three governments provided no clear evidence for other researchers to pivot on for confirmation. For this reason, we still assess that the WellMess activity has been conducted by a previously unknown threat actor.
We do not believe that the interest of APT threat actors in COVID-19 represents a meaningful change in terms of TTPs (Tactics Techniques and Procedures): they’re simply using it as a newsworthy topic to lure their victims.
Turla’s ‘Crutch’ Backdoor Leverages Dropbox in Espionage Attacks
3.12.2020 APT Threatpost
In a recent cyberattack against an E.U. country’s Ministry of Foreign Affairs, the Crutch backdoor leveraged Dropbox to exfiltrate sensitive documents.
Researchers have discovered a previously undocumented backdoor and document stealer, which they have linked to the Russian-speaking Turla advanced persistent threat (APT) espionage group.
The malware, which researchers call “Crutch,” is able to bypass security measures by abusing legitimate tools – including the file-sharing service Dropbox – in order to hide behind normal network traffic. Researchers said that the Crutch toolset has been designed to exfiltrate sensitive documents and other files to Dropbox accounts, which Turla operators control.
“[Crutch] was used from 2015 to, at least, early 2020,” said researchers with ESET in a Wednesday analysis. “We have seen Crutch on the network of a Ministry of Foreign Affairs in a country of the European Union, suggesting that this malware family is only used against very specific targets, as is common for many Turla tools.”
Upon further investigation of the cyberattack on the Ministry of Foreign Affairs, researchers found uploaded .zip files to the operator-controlled Dropbox accounts. These .zip files contained commands for the backdoor, which were uploaded to Dropbox by the operators. The backdoor then would read and execute these commands. These commands set the stage for the staging, compression and exfiltration of documents and various files – including the execution of one tongue-in-cheek command: “mkdir %temp%\Illbeback.”
“We were able to capture some of the commands sent by the operators to several Crutch v3 instances, which is helpful to understand the goal of the operation,” they said. “The operators were mainly doing reconnaissance, lateral movement and espionage.”
Updated Variants
Researchers don’t think Crutch is a first-stage backdoor; instead, it is deployed after the attackers already had initially compromised a victim network. They have previously observed first-stage attack vectors (before the deployment of Crutch) that include a first-stage implant, such as the Skipper implant or the PowerShell Empire post-exploitation agent.
In its earliest iterations (used from 2015 up to mid-2019), the Crutch architecture included a backdoor that communicated with Dropbox, as well as a second main binary that targeted files on any removable drives that may be on the system. This binary searched for files with specific extensions (including .pdf, .rtf, .doc, .docx) on removable drives and then staged the files in an encrypted archive.
Then, in a more recent version of Crutch discovered in July 2019, attackers updated the second main binary, so it could now automatically monitor local drives (as well as removable drives).
“The main difference is that it no longer supports backdoor commands. On the other hand, it can automatically upload the files found on local and removable drives to Dropbox storage by using the Windows version of the Wget utility,” said researchers.
Turla Attribution
ESET connected Crutch to the Turla APT due to what researchers called “strong links” between a Crutch dropper from 2016 and a second-stage backdoor used by Turla from 2016 to 2017 (called Gazer, also known as WhiteBear).
Researchers said that both samples were dropped on the same machine with a five-day interval in September 2017, and they both drop CAB files containing the various malware components. The loaders that were installed by the samples also share clearly related PDB paths, and both decrypt their payloads using the same RC4 key.
“Given these elements and that Turla malware families are not known to be shared among different groups, we believe that Crutch is a malware family that is part of the Turla arsenal,” said researchers.
Turla, an infamous cyberespionage group, has been active for more than 10 years. The APT group has targeted many governments worldwide, especially diplomatic entities, and has constantly developed new malware families. This has included an updated version of the ComRAT remote-access trojan (RAT) and a recently updated trio of implants.
“Crutch shows that the group is not short of new or currently undocumented backdoors,” said researchers. “This discovery further strengthens the perception that the Turla group has considerable resources to operate such a large and diverse arsenal.”
Russia-linked APT Turla used a new malware toolset named Crutch
3.12.2020 APT Securityaffairs
Russian-linked cyberespionage group Turla employed a new malware toolset, named Crutch, in targeted attacks aimed at high-profile targets.
Russian-linked APT group Turla has used a previously undocumented malware toolset, named Crutch, in cyberespionage campaigns aimed at high-profile targets, including the Ministry of Foreign Affairs of a European Union country.
The Turla APT group (aka Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON) has been active since at least 2007 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations.
The list of previously known victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The Crutch framework was employed in attacks since 2015 to siphon sensitive data and transfer them to Dropbox accounts controlled by the Russian hacking group. ESET researchers speculate Crutch is not a first-stage backdoor and operators deployed it only after they have gained access to the target’s network.
“During our research, we were able to identify strong links between a Crutch dropper from 2016 and Gazer. The latter, also known as WhiteBear, was a second-stage backdoor used by Turla in 2016-2017.” reads the report published by ESET.
ESET researchers linked Crutch to the Russia-linked APT Turla based on similarities (both samples dropped on the same machine with a five-day interval in September 2017, they drop CAB files containing malware components and a loader that share the same PDP paths, and use the same RC4 key tp decrypt the payloads.
Experts also observed the presence of FatDuke and Crutch at the same time on one machine. FatDuke is a third-stage backdoor that was attributed to the Dukes/APT29, experts believe that both Russia-linked APT groups independently compromised the same machine.
The analysis of the timestamps of 506 ZIP archives uploaded to the Dropbox accounts and containing data stolen between October 2018 and July 2019, revealed the working hours of the attackers, which is UTC+3 time zone (Russia).
Experts believe that Turla attackers used Crutch as a second stage backdoor, while first-stage implants used by the APT group includes Skipper (2017) and the open-source PowerShell Empire post-exploitation framework (from 2017)
Crutch versions employed between 2015 to mid-2019 used backdoor channels to communicate with hardcoded Dropbox account via the official HTTP API and drive monitoring tools that are able to search for certain documents of interest.
In July 2019, experts spotted a new version of Crutch (tracked as ‘version 4’) that no longer supports backdoor commands and added a removable-drive monitor with networking capabilities.
“The main difference is that it no longer supports backdoor commands. On the other hand, it can automatically upload the files found on local and removable drives to Dropbox storage by using the Windows version of the Wget utility.” continues the analysis.
Version 4, like the previous one, uses DLL hijacking to gain persistence on compromised devices on Chrome, Firefox, or OneDrive.
“Crutch shows that the group is not short of new or currently undocumented backdoors. This discovery further strengthens the perception that the Turla group has considerable resources to operate such a large and diverse arsenal.” concludes the report that also provides IoCs for the attacks.
“Crutch is able to bypass some security layers by abusing legitimate infrastructure – here Dropbox – in order to blend into normal network traffic while exfiltrating stolen documents and receiving commands from its operators.”
APT groups targets US Think Tanks, CISA, FBI warn
3.12.2020 APT Securityaffairs
Cybersecurity and Infrastructure Security Agency (CISA) and FBI are warning of attacks carried out by threat actors against United States think tanks.
APT groups continue to target United States think tanks, the Cyber Security and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) warn. The work of US think tanks has a great relevance for nation-state attackers that focus on the U.S. policy.
Threat actors are targeting individuals and organizations that are involved in international affairs or which focus on national security policy with spear-phishing attacks.
The attackers also use third-party messaging services to target both corporate and personal accounts of intended victims.
According to the alert, the APT groups also attempted to compromise devices that are exposed to the Internet.
“These have included low-effort capabilities such as spearphishing emails and third-party message services directed at both corporate and personal accounts, as well as exploiting vulnerable web-facing devices and remote connection capabilities.” reads the alert. “Increased telework during the COVID-19 pandemic has expanded workforce reliance on remote connectivity, affording malicious actors more opportunities to exploit those connections and to blend in with increased traffic.”
Attackers leverage virtual private networks (VPNs) and other remote work tools to gain initial access on a target’s network and achieve persistence. Once gained a persistent access to a network, the attackers used the tools to steal sensitive information, gather user credentials.
“Given the importance that think tanks can have in shaping U.S. policy, CISA and FBI urge individuals and organizations in the international affairs and national security sectors to immediately adopt a heightened state of awareness,” the advisory reads.
The advisory provides technical details about the attacks aimed at the US think tanks and also includes mitigations for leaders, users/staff, IT staff/cybersecurity personnel.
Newly Discovered Turla Backdoor Used in Government Attacks
3.12.2020 APT Threatpost
ESET’s security researchers have discovered yet another piece of malware that Russian cyber-espionage group Turla has been using in its attacks.
Active since at least 2006 and also referred to as Belugasturgeon, KRYPTON, Snake, Venomous Bear, and Waterbug, Turla was recently observed targeting a European government with a cocktail of backdoors.
Dubbed Crutch, the recently identified backdoor too was found on the network of a Ministry of Foreign Affairs, in a European Union country. According to ESET, the malware might be used only against very specific targets, a common feature for many Turla tools.
The Crutch backdoor appears to have been in use since 2015, until at least early 2020. ESET was able to find a link between a 2016 dropper for this malware and Gazer (WhiteBear), a second-stage backdoor that the cyber-espionage group was using in 2016-2017.
In September 2017, both samples were dropped in the same location on the same machine, only five days apart, both dropped malware components packed within CAB files, and the loaders dropped by them shared clearly related PDB paths and used the same RC4 key to decrypt their payloads.
“Given these elements and that Turla malware families are not known to be shared among different groups, we believe that Crutch is a malware family that is part of the Turla arsenal,” ESET says.
The security researchers also discovered that both Crutch and FatDuke (a third-stage payload associated with Dukes/APT29) were present on the same machine at the same time, but did not find evidence of interaction between the two malware families.
Designed to exfiltrate documents and other data of interest to attacker-controlled Dropbox accounts, the Crutch toolset was found on multiple machines within the aforementioned network of a Ministry of Foreign Affairs.
The operators appear to have been focused on performing reconnaissance, some of the commands they sent to the malware suggest. The researchers observed staging, compression, and exfiltration of data, with all operations performed based on manually executed commands.
ESET also notes that Crutch does not appear to be a first-stage backdoor: in one case, the malware was deployed months after the victim network was compromised. The researchers also identified several versions of the malware, showing its operators’ focus on investing in the threat’s evolution.
“In the past few years, we have publicly documented multiple malware families operated by Turla. Crutch shows that the group is not short of new or currently undocumented backdoors. This discovery further strengthens the perception that the Turla group has considerable resources to operate such a large and diverse arsenal,” ESET concludes.
Experts Uncover 'Crutch' Russian Malware Used in APT Attacks for 5 Years
2.12.2020 APT Thehackernews
Cybersecurity researchers today took the wraps off a previously undocumented backdoor and document stealer that has been deployed against specific targets from 2015 to early 2020.
Codenamed "Crutch" by ESET researchers, the malware has been attributed to Turla (aka Venomous Bear or Snake), a Russia-based advanced hacker group known for its extensive attacks against governments, embassies, and military organizations through various watering hole and spear-phishing campaigns.
"These tools were designed to exfiltrate sensitive documents and other files to Dropbox accounts controlled by Turla operators," the cybersecurity firm said in an analysis shared with The Hacker News.
The backdoor implants were secretly installed on several machines belonging to the Ministry of Foreign Affairs in an unnamed country of the European Union.
Besides identifying strong links between a Crutch sample from 2016 and Turla's yet another second-stage backdoor called Gazer, the latest malware in their diverse toolset points to the group's continued focus on espionage and reconnaissance against high-profile targets.
Crutch is delivered either via the Skipper suite, a first-stage implant previously attributed to Turla, or a post-exploitation agent called PowerShell Empire, with two different versions of the malware spotted before and after mid-2019.
While the former included a backdoor that communicates with a hardcoded Dropbox account using the official HTTP API to receive commands and upload the results, the newer variant ("Crutch v4") eschews the setup for a new feature that can automatically upload the files found on local and removable drives to Dropbox by using the Windows Wget utility.
"The sophistication of the attacks and technical details of the discovery further strengthen the perception that the Turla group has considerable resources to operate such a large and diverse arsenal," said ESET researcher Matthieu Faou.
"Furthermore, Crutch is able to bypass some security layers by abusing legitimate infrastructure — here, Dropbox – in order to blend into normal network traffic while exfiltrating stolen documents and receiving commands from its operators."
TA416 APT Rebounds With New PlugX Malware Variant
24.11.20 APT Threatpost
The TA416 APT has returned in spear phishing attacks against a range of victims – from the Vatican to diplomats in Africa – with a new Golang version of its PlugX malware loader.
The TA416 advanced persistent threat (APT) actor is back with a vengeance: After a month of inactivity, the group was spotted launching spear-phishing attacks with a never-before-seen Golang variant of its PlugX malware loader.
TA416, which is also known as “Mustang Panda” and “RedDelta,” was spotted in recent campaigns targeting entities associated with diplomatic relations between the Vatican and the Chinese Communist Party, as well as entities in Myanmar (all of these are previously reported campaigns). The group was also spotted recently targeting organizations conducting diplomacy in Africa.
In further analysis of these attacks, researchers found the group had updated its toolset — specifically, giving its PlugX malware variant a facelift. The PlugX remote access tool (RAT) has been previously used in attacks aimed at government institutions and allows remote users to perform data theft or take control of the affected systems without permission or authorization. It can copy, move, rename, execute and delete files; log keystrokes; fingerprint the infected system; and more.
“As this group continues to be publicly reported on by security researchers, they exemplify a persistence in the modification of their toolset to frustrate analysis and evade detection,” said researchers with Proofpoint, in a Monday analysis. “While baseline changes to their payloads do not greatly increase the difficulty of attributing TA416 campaigns, they do make automated detection and execution of malware components independent from the infection chain more challenging for researchers.”
Renewed Attacks
After nearly a month of inactivity (following previous threat research) by TA416, researchers observed “limited signs” of renewed spear-phishing activity from Sept. 16 to Oct. 10. Of note, this time period included the Chinese national holiday (National Day), and a following unofficial vacation period (“Golden Week”), said researchers.
These more recent spear-phishing attempts included a (continued) utilization of social-engineering lures that allude to the provisional agreement recently renewed between the Vatican Holy See and the Chinese Communist Party (CCP). Researchers with Recorded Future previously uncovered this campaign and said that it came during the September 2020 renewal of the landmark 2018 China-Vatican provisional agreement, called the China-Holy See deal. Proofpoint researchers said they also observed the threat group leveraging a spoofed email header in spear-phishing messages during this time, which appear to imitate journalists from the Union of Catholic Asia News.
“This confluence of themed social-engineering content suggests a continued focus on matters pertaining to the evolving relationship between the Catholic Church and the CCP,” said researchers.
While some of these campaigns were previously reported on, further investigation into the attacks revealed a brand new variant of TA416’s PlugX malware loader.
PlugX Malware
Upon closer investigation, researchers identified two RAR archives which serve as PlugX malware droppers.
Researchers said, the initial delivery vector for these RAR archives could not be identified, “however, historically TA416 has been observed including Google Drive and Dropbox URLs within phishing emails that deliver archives containing PlugX malware and related components,” they said.
PlugX malware attack vector. Credit: Proofpoint
One of these files was found to be a self-extracting RAR archive. Once the RAR archive is extracted four files are installed on the host and the portable executable (PE) Adobelm.exe is executed.
Adobelm.exe is a legitimate Adobe executable that is used for the dynamic link library (DLL) side-loading of hex.dll. It calls an export function of hex.dll, called CEFProcessForkHandlerEx.
“Historically, TA416 campaigns have used the file name hex.dll and the same PE export name to achieve DLL side-loading for a Microsoft Windows PE DLL,” said researchers. “These files served as loaders and decryptors of encrypted PlugX malware payloads.”
This malware loader was identified as a Golang binary; Researchers said they have not previously observed this file type in use by TA416. Go is an open source programming language.
“Both identified RAR archives were found to drop the same encrypted PlugX malware file and Golang loader samples,” they said.
Despite the file type of the PlugX loader changing, the functionality remains largely the same, said researchers.
The file reads, loads, decrypts and executes the PlugX malware payload. The PlugX malware then ultimately calls out to the command and control (C2) server IP, 45.248.87[.]162. Researchers said that continued activity by TA416 demonstrates a persistent adversary making continual changes to documented toolsets.
“The introduction of a Golang PlugX loader alongside continued encryption efforts for PlugX payloads suggest that the group may be conscious of increased detection for their tools and it demonstrates adaptation in response to publications regarding their campaigns,” according to Proofpoint. “These tool adjustments combined with recurrent command and control infrastructure revision suggests that TA416 will persist in their targeting of diplomatic and religious organizations.”
APT Exploits Microsoft Zerologon Bug: Targets Japanese Companies
20.11.20 APT Threatpost
Threat actors mount year-long campaign of espionage, exfiltrating data, stealing credentials and installing backdoors on victims’ networks.
China-backed APT Cicada joins the list of threat actors leveraging the Microsoft Zerologon bug to stage attacks against their targets. In this case, victims are large and well-known Japanese organizations and their subsidiaries, including locations in the United States.
Researchers observed a “large-scale attack campaign targeting multiple Japanese companies” across 17 regions and various industry sectors that engaged in a range of malicious activity, such as credential theft, data exfiltration and network reconnaissance. Attackers also installed the QuasarRAT open-source backdoor and novel Backdoor.Hartip tool to continue surveillance on victims’ systems, according a recent report.
Due to some notable hallmark activity, the attacks appear to be the work of Cicada (aka APT10, Stone Panda, Cloud Hopper), a state-sponsored threat group which has links to the Chinese government, researchers at Broadcom’s Symantec said.
“This campaign has been ongoing since at least mid-October 2019, right up to the beginning of October 2020, with the attack group active on the networks of some of its victims for close to a year,” researchers wrote in a report posted online. “The campaign is very wide-ranging, with victims in a large number of regions worldwide.”
A number of threat patterns and techniques observed in the campaign that link the activity to Cicada, including a third-stage DLL with an export named “F**kYouAnti;” a third-stage DLL using CppHostCLR technique to inject and execute the .NET loader assembly; .NET Loader obfuscation using ConfuserEx v1.0.0; and the delivery of QuasarRAT as the final payload.
Researchers observed attackers leveraging Zerologon, or CVE-2020-1472, a Microsoft zero-day elevation-of-privilege vulnerability first disclosed and patched on Aug. 11. The flaw—which stems from the Netlogon Remote Protocol available on Windows domain controllers–allows attackers to spoof a domain controller account and then use it to steal domain credentials, take over the domain and completely compromise all Active Directory identity services.
“Among machines compromised during this attack campaign were domain controllers and file servers, and there was evidence of files being exfiltrated from some of the compromised machines,” researchers observed.
Zerologon has been a thorn in the side of Microsoft for some time, with multiple APTs and other attackers taking advantage of unpatched systems. Last month Microsoft warned that the Iranian group MERCURY APT has been actively exploiting the flaw, while the Ryuk ransomware gang used it to deliver a lightning-fast attack that moved from initial phish to full domain-wide encryption in just five hours.
Given the length of the campaign discovered, Cicada may well be one of the earliest APT groups to take advantage of Zerologon. The group is known for attacking targets in Japan as well as MSPs with living-off-the-land tools and custom malware. In the latter category, the latest campaign uses Backdoor.Hartip, which researchers said is a brand new tool for the group.
In addition to Zerologon, attackers also extensively used DLL side-loading in the campaign, a common tactic of APT groups that “occurs when attackers are able to replace a legitimate library with a malicious one, allowing them to load malware into legitimate processes,” researchers said. In fact, suspicious activity surrounding DLL side-loading is what tipped Symantec researchers off to campaign when it triggered an alert in Symantec’s Cloud Analytics tool, they said.
“Attackers use DLL side-loading to try and hide their activity by making it look legitimate, and it also helps them avoid detection by security software,” according to the report.
Other tools attackers leveraged in the campaign included: RAR archiving, which can transfer files to staging servers before exfiltration; WMIExec, used for lateral movement and to execute commands remotely; Certutil, a command-line utility that can be exploited to decode information, download files and install browser root certificates; and PowerShell, an environment in the Windows OS that’s often abused by threat actors. The campaign also used legitimate cloud file-hosting service for exfiltration, researchers said
Chinese Hackers Target Japanese Organizations in Large-Scale Campaign
20.11.20 APT Securityweek
China-linked threat actor APT10 was observed launching a large-scale campaign against Japanese organizations and their subsidiaries.
Also referred to as Cicada, Stone Panda, and Cloud Hopper, APT10 is known for launching espionage campaigns for over a decade, including attacks aimed at managed service providers (MSPs) and Japan-linked organizations.
As part of the newly observed campaign, the hacking group has been using a combination of living-off-the-land tools and custom malware, including Backdoor.Hartip, which appears to be a new addition to its arsenal.
During the attacks, the adversary managed to compromise domain controllers and file servers, and the security researchers discovered evidence that data was exfiltrated from some of the infected systems, Symantec, a division of Broadcom, reports.
One of the main characteristics of this attack was the extensive use of DLL side-loading, with recent incidents showing the adoption of an exploit for the Zerologon vulnerability that Microsoft patched in August.
The attacks likely started in mid-October 2019 and continued at least up to the beginning of October 2020. In some cases, the attackers managed to maintain a foothold in the compromised networks for nearly one year.
Victims were mainly large, well-known organizations, many of them headquartered in Japan or with links to Japan. The attacks mainly focused on South and East Asia, with one victim being a Chinese subsidiary of a Japanese organization, an atypical target for a state-sponsored Chinese group.
Targeted sectors include automotive (including suppliers of parts for the motor industry), clothing, conglomerates, engineering, electronics, government, general trading, industrial products, manufacturing, MSPs, pharmaceutical, and professional services.
Although the attackers spent a significant amount of time in the networks of some victims, they left after days from other networks. In some cases, the attackers ceased the activity on a network after a short period of time, but returned months later.
As part of the attacks, the hackers used living-off-the-land, dual-use, and publicly available tools and techniques for network reconnaissance, credential theft, file archiving, and more, including Certutil, Adfind, Csvde, Ntdsutil, WMIExec, and PowerShell.
“The scale and sophistication of this attack campaign indicate that it is the work of a large and well-resourced group, such as a nation-state actor, with Symantec discovering enough evidence to attribute it with medium confidence to Cicada,” Symantec notes.
In a separate report published this week, KELA threat intelligence analyst Victoria Kivilevich explained that data belonging to Japanese corporations (government and educational entities included), is being traded on the Dark Web. Such data includes stolen credentials that provide adversaries with initial access to internal networks. Over 100 million exposed Japanese emails were identified.
Between June and October 2020, KELA observed 11 attacks on Japanese organizations, all carrying ransomware, with manufacturing, construction, and government sectors being affected. While the compromise vector is not certain in all cases, the CVE-2019-11510 Pulse Secure flaw was targeted in at least one incident.
“Among the most prominent threats on the darknet, KELA observed leaks and sales of Japanese entities’ data. While many offers are related to regular users, some actors are specifically looking for corporate data of Japanese organizations,” KELA notes.
Advanced Threat predictions for 2021
19.11.20 APT Securityaffairs
Trying to make predictions about the future is a tricky business. However, while we don’t have a crystal ball that can reveal the future, we can try to make educated guesses using the trends that we have observed over the last 12 months to identify areas that attackers are likely to seek to exploit in the near future.
Let’s start by reflecting on our predictions for 2020.
The next level of false flag attacks
This year, we haven’t seen anything as dramatic as the forging of a malicious module to make it look like the work of another threat actor, as was the case with Olympic Destroyer. However, the use of false flags has undoubtedly become an established method used by APT groups to try to deflect attention away from their activities. Notable examples this year include the campaigns of MontysThree and DeathStalker. Interestingly, in the DeathStalker case, the actor incorporated certificate metadata from the infamous Sofacy in their infrastructure, trading covertness for the chance of having their operation falsely attributed.
From ransomware to targeted ransomware
Last year, we highlighted the shift towards targeted ransomware and predicted that attackers would use more aggressive methods to extort money from their victims. This year, hardly a week has gone by without news of an attempt to extort money from large organizations, including recent attacks on a number of US hospitals. We’ve also seen the emergence of ‘brokers’ who offer to negotiate with the attackers, to try to reduce the cost of the ransom fee. Some attackers seem to apply greater pressure by stealing data before encrypting it and threatening to publish it; and in a recent incident, affecting a large psychotherapy practice, the attackers posted sensitive data of patients.
New online banking and payments attack vectors
We haven’t seen any dramatic attacks on payment systems this year. Nevertheless, financial institutions continue to be targeted by specialist cybercrime groups such as FIN7, CobaltGroup, Silence and Magecart, as well as APT threat actors such as Lazarus.
More infrastructure attacks and attacks against non-PC targets
APT threat actors have not confined their activities to Windows, as illustrated by the extension of Lazarus’s MATA framework, the development of Turla’s Penquin_x64 backdoor and the targeting of European supercomputing centers in May. We also saw the use of multiplatform, multi-architecture tools such as Termite and Earthworm in operation TunnelSnake. These tools are capable of creating tunnels, transferring data and spawning remote shells on the targeted machines, supporting x86, x64, MIPS(ES), SH-4, PowerPC, SPARC and M68k. On top of this, we also discovered the framework we dubbed MosaicRegressor, which includes a compromised UEFI firmware image designed to drop malware onto infected computers.
Increased attacks in regions that lie along the trade routes between Asia and Europe
In 2020, we observed several APT threat actors target countries that had previously drawn less attention. We saw various malware used by Chinese-speaking actors used against government targets in Kuwait, Ethiopia, Algeria, Myanmar and the Middle East. We also observed StrongPity deploying a new, improved version of their main implant called StrongPity4. In 2020 we found victims infected with StrongPity4 outside Turkey, located in the Middle East.
Increasing sophistication of attack methods
In addition to the UEFI malware mentioned above, we have also seen the use of legitimate cloud services (YouTube, Google Docs, Dropbox, Firebase) as part of the attack infrastructure (either geo-fencing attacks or hosting malware and used for C2 communications).
A further change of focus towards mobile attacks
This is apparent from the reports we have published this year. From year to year we have seen more and more APT actors develop tools to target mobile devices. Threat actors this year included OceanLotus, the threat actor behind TwoSail Junk, as well as Transparent Tribe, OrigamiElephant and many others.
The abuse of personal information: from deep fakes to DNA leaks
Leaked/stolen personal information is being used more than ever before in up-close and personal attacks. Threat actors are less afraid than ever to engage in active ongoing communications with their victims, as part of their spear-phishing operations, in their efforts to compromise target systems. We have seen this, for example, in Lazarus’s ThreatNeedle activities and in DeathStalker’s efforts to pressure victims into enabling macros. Criminals have used AI software to mimic the voice of a senior executive, tricking a manager into transferring more than £240,000 into a bank account controlled by fraudsters; and governments and law enforcement agencies have used facial recognition software for surveillance.
Turning our attention to the future, these are some of the developments that we think will take center stage in the year ahead, based on the trends we have observed this year.
APT threat actors will buy initial network access from cybercriminals
In the last year, we have observed many targeted ransomware attacks using generic malware, such as Trickbot, to gain a foothold in target networks. We have also observed connections between targeted ransomware attacks and well-established underground networks like Genesis that typically trade in stolen credentials. We believe APT actors will start using the same method to compromise their targets. Organizations should pay increased attention to generic malware and perform basic incident response activities on each compromised computer to ensure generic malware has not been used deploy sophisticated threats.
More countries using legal indictments as part of their cyberstrategy
Some years ago we predicted that governments would resort to “naming and shaming”, to draw attention to the activities of hostile APT groups. We have seen several cases of this over the last 12 months. We think that US Cyber Command’s “persistent engagement” strategy will begin to bear fruit in the coming year and lead other states to follow suit, not least as “tit for tat” retaliation to US indictments. Persistent engagement involves publicly releasing reports about adversary tools and activities. US Cyber Command has argued that warfare in cyberspace is of a fundamentally different nature, and requires full-time engagement with adversaries to disrupt their operations. One of the ways they do so is by providing indicators that the threat intelligence community can use to bootstrap new investigations – in a sense, it is a way of orienting private research through intelligence declassification.
Tools “burned” in this way become harder to use for the attackers, and can undermine past campaigns that might otherwise have stayed under the radar. Faced with this new threat, adversaries planning attacks must factor in additional costs (the heightened possibility of losing tools or these tools being exposed) in their risk/gain calculus.
Exposing toolsets of APT groups is nothing new: successive leaks by Shadow Brokers provide a striking example. However, it is the first time it has been done in an official capacity through state agencies. While quantifying the effects of deterrence is impossible, especially without access to diplomatic channels where such matters are discussed, we believe that more countries will follow this strategy in 2021. First, states traditionally aligned with the US may start replicating the process, and then, later on, the targets of such disclosures could follow suit as a form of retaliation.
More Silicon Valley companies will take action against zero-day brokers
Until recently, zero-day brokers have traded exploits for well-known commercial products; and big companies such as Microsoft, Google, Facebook and others have seemingly paid little attention to the trade. However, in the last year or so, there have been high-profile cases where accounts were allegedly compromised using WhatsApp vulnerabilities – including Jeff Bezos and Jamal Khashoggi. In October 2019, WhatsApp filed a lawsuit accusing Israel-based NSO Group of having exploited a vulnerability in its software; and that the technology sold by NSO was used to target more than 1,400 of its customers in 20 different countries, including human rights activists, journalists and others. A US judge subsequently ruled that the lawsuit could proceed. The outcome of the case could have far-reaching consequences, not least of which could be to lead other firms to take legal action against companies that deal in zero-day exploits. We think that mounting public pressure, and the risk of reputation damage, may lead other companies to follow WhatsApp’s lead and take action against zero-day brokers, to demonstrate to their customers that they are seeking to protect them.
Increased targeting of network appliances
With the trend towards overall improvement of organizational security, we think that actors will focus more on exploiting vulnerabilities in network appliances such as VPN gateways. We’re already starting to see this happen – see here, here and here for further details. This goes hand-in-hand with the shift towards working from home, requiring more companies to rely on a VPN setup in their business. The increased focus on remote working, and reliance on VPNs, opens up another potential attack vector: the harvesting of user credentials through real-world social engineering approaches such as “vishing” to obtain access to corporate VPNs. In some cases, this might allow the attacker to even accomplish their espionage goals without deploying malware in the victim’s environment.
The emergence of 5G vulnerabilities
5G has attracted a lot of attention this year, with the US exerting a lot of pressure on friendly states to discourage them from buying Huawei products. In many countries, there were also numerous scare stories about possible health risks, etc. This focus on 5G security means that researchers, both public and private, are definitely looking at the products of Huawei and others, for signs of implementation problems, crypto flaws and even backdoors. Any such flaws will certainly receive massive media attention. As usage of 5G increases, and more devices become dependent on the connectivity it provides, attackers will have a greater incentive to look for vulnerabilities that they can exploit.
Demanding money “with menaces”
We have seen several changes and refinements in the tactics used by ransomware gangs over the years. Most notably, attacks have evolved from random, speculative attacks distributed to a large number of potential victims, to highly targeted attacks that demand a considerably greater payout from a single victim at a time. The victims are carefully selected, based on their ability to pay, their reliance on the data encrypted and the wider impact an attack will have. And no sector is considered off limits, notwithstanding the promises ransomware gangs made not to target hospitals. The delivery method is also customized to fit the targeted organization, as we have seen with attacks on medical centers and hospitals throughout the year.
We have also seen ransomware gangs seeking to obtain greater leverage by threatening to publish stolen data if a company fails to pay the ransom demanded by the attackers. This trend is likely to develop further as ransomware gangs seek to maximize their return on investment.
The ransomware problem has become so prevalent that the OFAC (Office of Foreign Assets Control) released instructions for victims and clarified that paying ransoms could constitute a breach of international sanctions. We interpret this announcement as the beginning of a wider crackdown on the cybercrime world by US authorities.
This year, the Maze and Sodinokibi gangs both pioneered an “affiliate” model involving collaboration between groups. Nevertheless, the ransomware eco-system remains very diverse. It’s possible that in the future we will see a concentration of major ransomware players who will start to focus their activities and obtain APT-like capabilities. However, for some time to come, smaller gangs will continue to adopt the established approach that relies on piggybacking botnets and sourcing third-party ransomware.
More disruptive attacks
More and more aspects of our lives are becoming dependent on technology and connectivity to the internet. As a result, we present a much wider attack surface than ever before. It’s likely, therefore, that we will see more disruptive attacks in the future. On the one hand, this disruption could be the result of a directed, orchestrated attack, designed to affect critical infrastructure. On the other hand, it could be collateral damage that occurs as a side-effect of a large-volume ransomware attack targeting organizations that we use in our day-to-day lives, such as educational institutions, supermarkets, postal services and public transportation.
Attackers will continue to exploit the COVID-19 pandemic
The world has been turned upside down by COVID-19, which has impacted nearly every aspect of our lives this year. Attackers of all kinds were quick to seize the opportunity to exploit the keen interest in this topic, including APT threat actors. As we have noted before, this did not mark a change in TTPs, but simply a persistent topic of interest that they could use as a social engineering lure. The pandemic will continue to affect our lives for some time to come; and threat actors will continue to exploit this to gain a foothold in target systems. During the last six months, there have been reports of APT groups targeting COVID-19 research centers. The UK National Cyber Security Centre (NCSC) stated that APT29 (aka the Dukes and Cozy Bear) targeted COVID-19 vaccine development. This will remain a target of strategic interest to them for as long as the pandemic lasts.

China-linked APT10 leverages ZeroLogon exploits in recent attacks
18.11.20 APT Securityaffairs
Researchers uncovered a large-scale campaign conducted by China-linked APT10 targeting businesses using the recently-disclosed ZeroLogon vulnerability.
Symantec’s Threat Hunter Team, a Broadcom division, uncovered a global campaign conducted by a China-linked APT10 cyber-espionage group targeting businesses using the recently-disclosed ZeroLogon vulnerability.
The group, also known as Cicada, Stone Panda, and Cloud Hopper, has been active at least since 2009, in April 2017 experts from PwC UK and BAE Systems uncovered a widespread hacking campaign, tracked as Operation Cloud Hopper, targeting managed service providers (MSPs) in multiple countries worldwide.
The group has been observed while attempting to exploit the Windows Zerologon vulnerability in attacks aimed at Japanese organizations from multiple industry sectors in 17 regions around the globe. Targeted sectors include:
Automotive
Clothing
Conglomerates
Electronics
Engineering
General Trading Company
Government
Industrial Products
Managed Service Providers
Manufacturing
Pharmaceutical
Professional Services
APT10
The latest campaign has been active since mid-October in 2019 and appears to be still ongoing.
The APT10 is well-resourced cyberespionage group that employed multiple tools and sophisticated techniques in its attacks. In the recent campaign, the attackers extensively used DLL side-loading and leveraged the ZeroLogon vulnerability.
Experts observed that attackers using a wide variety of living-off-the-land, dual-use, and publicly available tools.
Other attack techniques used by the group are network reconnaissance, credential theft, command-line utilities able to install browser root certificates and decode data, PowerShell scripts, and both RAR archiving and a legitimate cloud hosting service and data exfiltration.
The APT10 group also employed custom malware, tracked the Backdoor.Hartip, that was never detected before.
“Intelligence gathering and stealing information has generally been the motivation behind Cicada’s attacks in the past, and that would appear to be the case in this attack campaign too.” reads the report published by Symantec. “We observed the attackers archiving some folders of interest in these attacks, including in one organization folders relating to human resources (HR), audit and expense data, and meeting memos.”
The attribution to APT10 is based on multiple pieces of evidence, including clues in how code is obfuscated; the use of a Third-stage DLL with an export named “FuckYouAnti,” the use of QuasarRAT as the final payload.
“Cicada clearly still has access to a lot of resources and skills to allow it to carry out a sophisticated and wide-ranging campaign like this, so the group remains highly dangerous,” Symantec concludes. “Its use of a tool to exploit the recently disclosed ZeroLogon vulnerability and a custom backdoor […] show that it continues to evolve its tools and tactics to actively target its victims.”
Chinese APT FunnyDream targets a South East Asian government
18.11.20 APT Securityaffairs
Researchers spotted a new China-linked APT, tracked as FunnyDream that already infected more than 200 systems across Southeast Asia.
Security experts at BitDefender have uncovered a new China-linked cyber espionage group, tracked as FunnyDream that has already infected more than 200 systems across Southeast Asia over the past two years.
According to Kaspersky Lab, FunnyDream has been active at least since 2018 and targeted high-profile entities in Malaysia, Taiwan and the Philippines. Most of the victims were in Vietnam, the group focuses on foreign government organizations of countries in Southeast Asia.
The group is still active and aims at ensure persistence in the victims’ network for as long as possible, to spy on victims’ activities and to exfiltrate sensitive documents, with a special interest in national security and industrial espionage.
“The attack has a complex and complete arsenal of droppers, backdoors and other tools involving Chinoxy backdoor, PCShare RAT and FunnyDream backdoor binaries, with forensic artefacts pointing towards a sophisticated Chineseactor.” reads the report published by BitDefender. “Some of these open source Remote Access Trojans (RATs) are known to be of Chinese origin, along with some other resources set to Chinese.”
The name of the group comes from a powerful backdoor employed in the attacks of the APT group.
The attacks analyzed by Bitdefender researchers employed three malware payloads tracked as Chinoxy, PCShare, and FunnyDream,
The attackers followed the same killchain in the attack that begins with the execution of the Chinoxy backdoor to gain persistence in the victim’s system after initial access.
The Chinoxy dropper uses a digitally signed binary (Logitech Blutooth Wizard Host Process) to evade detection and exploit a Side Loading attack to load the backdoor dll into the memory.
Then the backdoor deploys the open source Chinese RAT called PcShare, it was used for gathering intelligence from the infected hosts.
FunnyDream is a custom-made backdoor that supports advanced persistence and communication capabilities, it was used by the APT group to gathering intelligence and data exfiltration.
“The attackers used the backdoor prevalently as DLL files, but we observed an executable to be used as well.” continues the report. “The files we found implement many persistence mechanisms, their droppers and loaders use many different file names for the payload, all of that suggesting that the backdoor is custom made.”
The analysis of the tool usage timeline revealed that threat actors initially started by deploying a series of tools meant for quick and covert data exploration and exfiltration, and later developed its own killchain that employed the three malware.

The researchers were able to identify the C2 architecture because the domains or IP addresses of command and control servers are hardcoded in binary files. Most of the servers are located in Hong Kong, except for three ones that were in in Vietnam, China and South Korea respoectively.
“It’s likely that relying on a locally deployed C&C infrastructure would bring several advantages to the APT group. For instance, it could be easier to manage and control, while at the same time the C&C IPs wouldn’t be flagged as suspicious, as they would be part of the same regional internet infrastructure. Opting for a command and control infrastructure deployed anywhere else in the world would have potentially raised some security alarms.” concludes the report. “During this analysis, some forensic artefacts seem to suggest a Chinese-speaking APT group, as some of the resources found in several binaries had a language set to Chinese, and the Chinoxy backdoor used during the campaign is a Trojan known to have been used by Chinese-speaking threat actors. While we’re constantly monitoring for APT-like activity around the world, not all APT-style attacks can be attributed to a known APT group, mostly because some of the used the tools are sometimes share between multiple groups.”
Sophisticated Chinese APT Group Targets Southeast Asian Governments
18.11.20 APT Securityweek
A sophisticated advanced persistent threat (APT) group believed to be operating out of China has been stealthily targeting Southeast Asian governments over the past three years, Bitdefender reports.
The attacker’s infrastructure appears to be active even today, despite many of the command and control (C&C) servers being inactive.
Believed to be state-sponsored, the group was observed using numerous malware families, including the Chinoxy backdoor, PCShare RAT, and the FunnyDream backdoor.
The fact that some of these open-source tools are known to be of Chinese origin and the use of other resources in Chinese led the researchers to the conclusion that the group behind these attacks consists of Chinese speakers.
The attacks appear to have started in 2018, with the activity increasing significantly in early 2019, when more than 200 systems were infected within five months. The attackers strived to maintain persistence within the victim networks for as long as possible.
“Some evidence suggests threat actors may have managed to compromise domain controllers from the victim’s network, allowing them to move laterally and potentially gain control over a large number of machines from that infrastructure,” Bitdefender explains in a report.
For persistence, the adversary employed digitally signed binaries that are leveraged to side-load one of the backdoors into memory. Data of interest is identified and exfiltrated using custom tools.
In 2018, the group was using the Chinoxy backdoor to establish persistence, with the open-source Chinese RAT PcShare being deployed afterwards. A tool called ccf32 was being used for file collection and, starting in 2019, the same tool (along with additional utilities) was being employed in FunnyDream infections.
A command line tool used for data collection, ccf32 can be used to list all files on a hard drive or target specified folders only. It also allows attackers to filter files based on extension, collects files of interest in a hidden folder at the current location, and then adds these files to an archive that is sent to the attackers.
The FunnyDream backdoor is the most complex piece of malware used by the threat actor, delivered to compromised machines mainly as a DLL, but also as an executable in some instances. Some of its capabilities include information gathering and exfiltration, cleaning after itself, evasion detection, and command execution.
The malware contains different components for performing actions such as file collection (Filepak and FilePakMonitor), taking screenshots (ScreenCap), logging keystrokes (Keyrecord), accessing internal networks (TcpBridge), and bypassing network restrictions (TcpTransfer).
A more complex, custom-made backdoor component is Md_client, which is capable of collecting system information, creating a remote shell, listing directories, uploading and downloading files, executing commands, and deleting directories.
During their investigation, Bitdefender’s security researchers discovered that the C&C addresses are hardcoded in the malware binaries and that most of the attackers’ infrastructure is located in Hong Kong, with only three servers elsewhere (in Vietnam, China, and South Korea, respectively).
Chinese APT Hackers Target Southeast Asian Government Institutions
17.11.20 APT Thehackernews
Cybersecurity researchers today unveiled a complex and targeted espionage attack on potential government sector victims in South East Asia that they believe was carried out by a sophisticated Chinese APT group at least since 2018.
"The attack has a complex and complete arsenal of droppers, backdoors and other tools involving Chinoxy backdoor, PcShare RAT and FunnyDream backdoor binaries, with forensic artefacts pointing towards a sophisticated Chinese actor," Bitdefender said in a new analysis shared with The Hacker News.
It's worth noting that the FunnyDream campaign has been previously linked to high-profile government entities in Malaysia, Taiwan, and the Philippines, with a majority of victims located in Vietnam.
According to the researchers, not only around 200 machines exhibited attack indicators associated with the campaign, evidence points to the fact the threat actor may have compromised domain controllers on the victim's network, allowing them to move laterally and potentially gain control of other systems.
The research has yielded little to no clues as to how the infection happened, although it's suspected that the attackers employed social engineering lures to trick unwitting users into opening malicious files.

Upon gaining an initial foothold, multiple tools were found to be deployed on the infected system, including the Chinoxy backdoor to gain persistence as well as a Chinese remote access Trojan (RAT) called PcShare, a modified variant of the same tool available on GitHub.
Besides using command-line utilities such as tasklist.exe, ipconfig.exe, systeminfo.exe, and netstat to gather system information, a number of others — ccf32, FilePak, FilePakMonitor, ScreenCap, Keyrecord, and TcpBridge — were installed to collect files, capture screenshots, logging keystrokes, and exfiltrate the collected information to an attacker-controlled server.
The investigation also uncovered the use of the aforementioned FunnyDream backdoor starting in May 2019, which comes with multiple capabilities to amass user data, clean traces of malware deployment, thwart detection and execute malicious commands, the results of which were transmitted back to command-and-control (C&C) servers situated in Hong Kong, China, South Korea, and Vietnam.
"Attributing APT style attacks to a particular group or country can be extremely difficult, mostly because forensic artefacts can sometimes be planted intentionally, C&C infrastructure can reside anywhere in the world, and the tools used can be repurposed from other APT groups," the researchers concluded.
"During this analysis, some forensic artifacts seem to suggest a Chinese-speaking APT group, as some of the resources found in several binaries had a language set to Chinese, and the Chinoxy backdoor used during the campaign is a Trojan known to have been used by Chinese-speaking threat actors."
Lazarus Group Targets South Korea via Supply Chain Attack
17.11.20 APT Securityweek
The North Korea-linked threat actor known as Lazarus has been targeting users in South Korea through a supply chain attack that involves software typically required by government and financial organizations, ESET reported on Monday.
Lazarus is the most well known hacker group that is believed to be operating on behalf of the North Korean government, with attacks ranging from espionage to profit-driven operations. Unsurprisingly, many of the group’s operations are aimed at South Korea, including an interesting attack that was observed in recent months by ESET.
The campaign, believed to be part of an operation dubbed BookCodes by the Korea Internet & Security Agency, has been linked to Lazarus based on various aspects, including the malware used in the attacks, victimology, and the infrastructure leveraged by the attackers.
According to ESET, the hackers have targeted WIZVERA VeraPort, a piece of software that users need in order to be able to access services provided by some government and banking websites in South Korea.
The cybersecurity firm’s researchers believe the hackers haven’t actually compromised WIZVERA systems, and instead they have targeted the websites that use the software.
The attackers compromise web servers with VeraPort support and configure them to serve a malicious file instead of legitimate software. The malicious file is served when a user who has the VeraPort software installed visits the website associated with the compromised server.
For the attack to work, the hackers needed to sign their malware and in some cases they achieved this by abusing code-signing certificates issued to companies that provide physical and cyber security solutions.
The attackers initially push a signed downloader, followed by a dropper, a loader, another downloader, and then the final payload. The final payload is a RAT that allows the attackers to perform various activities on the compromised device, including to download and execute other malware.
ESET noted that for the attack to succeed, the targeted web server needs to be configured in a certain way, which is why its experts say this malware delivery method has only been used in limited Lazarus operations.
“Attackers are particularly interested in supply-chain attacks, because they allow them to covertly deploy malware on many computers at the same time,” ESET researchers explained. “We can safely predict that the number of supply-chain attacks will increase in the future, especially against companies whose services are popular in specific regions or in specific industry verticals.”
ESET has published a blog post detailing the attacks and it has also shared some indicators of compromise (IoCs) to help organizations detect attacks.
Three APT groups have targeted at least seven COVID-19 vaccine makers
14.11.20 APT Securityaffairs
At least the three nation-state actors have targeted seven COVID-19 vaccine makers, they are Strontium, Lazarus Group, and Cerium, Microsoft warns.
Microsoft revealed that at least three APT groups have targeted seven companies involved in COVID-19 vaccines research and treatments.
“In recent months, we’ve detected cyberattacks from three nation-state actors targeting seven prominent companies directly involved in researching vaccines and treatments for Covid-19.” reads the post published by Microsoft. “The targets include leading pharmaceutical companies and vaccine researchers in Canada, France, India, South Korea and the United States. The attacks came from Strontium, an actor originating from Russia, and two actors originating from North Korea that we call Zinc and Cerium.”
Microsoft linked the attacks to the Russia-linked Strontium APT group (aka APT28, Fancy Bear, Pawn Storm, Sofacy Group, and Sednit) and two North Korea-linked groups tracked as Zinc (aka Lazarus Group) and Cerium.
The group mainly targeted vaccine makers that are testing Covid-19 vaccines, one of them is a clinical research organization involved in trials, while another one has developed a Covid-19 test. Several organizations targeted by the APT groups that have contracts with or investments from government agencies for Covid-19 related work.
Strontium hackers launched password spraying and brute-force attacks to break into victim accounts and steal sensitive information.
Zinc APT targeted the centers with spear-phishing campaigns aimed at employees working at the targeted companies using messages pretending to be sent by recruiters.
Cerium APT also launched Covid-19 themed spear-phishing campaigns using messages that pretend to be sent by representatives from the World Health Organization.
The targets were located in Canada, France, India, South Korea, and the United States, according to Microsoft.
Microsoft revealed that the majority of the attacks were blocked by protections implemented in its solutions, the IT giant already notified all organizations that were breached by the hackers.
Unfortunately, these attacks are just the tip of the iceberg, the healthcare industry is a privileged target for hackers that are also attempting to take advantage of the ongoing pandemic.
Threat actors recently targeted several hospitals and healthcare organizations in the United States. In the last months, hackers hit several hospitals and organizations involved in the response to the pandemic, including the Brno University Hospital in the Czech Republic, Paris’s hospital system, hospitals in Spain and Thailand.
“Today, Microsoft’s president Brad Smith is participating in the Paris Peace Forum where he will urge governments to do more. Microsoft is calling on the world’s leaders to affirm that international law protects health care facilities and to take action to enforce the law.” concludes the post. “We believe the law should be enforced not just when attacks originate from government agencies but also when they originate from criminal groups that governments enable to operate – or even facilitate – within their borders. This is criminal activity that cannot be tolerated.”
Costaricto APT: Cyber mercenaries use previously undocumented malware
13.11.20 APT Securityaffairs
CostaRicto APT is targeting South Asian financial institutions and global entertainment companies with undocumented malware.
Blackberry researchers have documented the activity of a hackers-for-hire group, dubbed CostaRicto, that has been spotted using a previously undocumented piece of malware to target South Asian financial institutions and global entertainment companies.
“During the past six months, the BlackBerry Research and Intelligence team have been monitoring a cyber-espionage campaign that is targeting disparate victims around the globe.” reads the analysis published by BlackBerry. “The campaign, dubbed CostaRicto by BlackBerry, appears to be operated by “hackers-for-hire”, a group of APT mercenaries who possess bespoke malware tooling and complex VPN proxy and SSH tunnelling capabilities.”
CostaRicto targeted entities worldwide, most of them are in India, Bangladesh, Singapore, and China, suggesting that the threat actor could be based in South Asia.
Upon gaining access to the target’s infrastructure using stolen credentials, the cyber mercenaries set up an SSH tunnel to download a backdoor and a payload loader called CostaBricks. CostaBricks is a custom VM-based payload loader that executes an embedded bytecode to decode and inject the payload directly into the memory of the target system.
CostaRicto was observed using the CostaBricks loader to deliver a C++ compiled executable called SombRAT (the name comes from the Overwatch game character Sombra).
The backdoor implements a modular structure, it implements RAT functionalities and is able to execute other malicious payloads, in the form of plugins or standalone binaries. The malware support 50 different commands and is able to perform multiple actions, such as gathering system information, injecting malicious DLLs into memory, enumerating files in storage, exfiltrating data, listing and killing processes, and uploading files to the C2.
The researchers have analyzed six versions of the SombRAT, the first version dates back to October 2019, while the latest variant was spotted in August. Experts believe that the malware is under active development.
Blackberry analysts noticed that one of the IP addresses employed in the attacks of the group has been linked to an earlier phishing campaign initially attributed to the Russia-linked APT28 group. This circumstance suggests that the Costaricto APT carried out attacks on behalf of other threat actors.
“Finally, the diversity and geography of the victims doesn’t fit a picture of a campaign sponsored by a particular state; rather, it’s a mix of targets that could be explained by different assignments commissioned by disparate entities.” concluded the report. “With the undeniable success of Ransomware-as-a-Service (RaaS), it’s not surprising that the cybercriminal market has expanded its portfolio to add dedicated phishing and espionage campaigns to the list of services on offer. Outsourcing attacks or certain parts of the attack chain to unaffiliated mercenary groups has several advantages for the adversary – it saves their time and resources and simplifies the procedures, but most importantly it provides an additional layer of indirection, which helps to protect the real identity of the threat actor.”
Uncovered: APT 'Hackers For Hire' Target Financial, Entertainment Firms
13.11.20 APT Thehackernews
A hackers-for-hire operation has been discovered using a strain of previously undocumented malware to target South Asian financial institutions and global entertainment companies.
Dubbed "CostaRicto" by Blackberry researchers, the campaign appears to be the handiwork of APT mercenaries who possess bespoke malware tooling and complex VPN proxy and SSH tunneling capabilities.
"CostaRicto targets are scattered across different countries in Europe, Americas, Asia, Australia and Africa, but the biggest concentration appears to be in South Asia (especially India, Bangladesh and Singapore and China), suggesting that the threat actor could be based in that region, but working on a wide range of commissions from diverse clients," the researchers said.
The modus operandi in itself is quite straight-forward. Upon gaining an initial foothold in the target's environment via stolen credentials, the attacker proceeds to set up an SSH tunnel to download a backdoor and a payload loader called CostaBricks that implements a C++ virtual machine mechanism to decode and inject the bytecode payload into memory.
In addition to managing command-and-control (C2) servers via DNS tunneling, the backdoor delivered by the above-mentioned loaders is a C++ compiled executable called SombRAT — so named after Sombra, a Mexican hacker, and infiltrator from the popular multiplayer game Overwatch.
The backdoor comes equipped with 50 different commands to carry out specific tasks (can be categorized in core, taskman, config, storage, debug, network functions) that range from injecting malicious DLLs into memory to enumerating files in storage to exfiltrating the captured data to an attacker-controlled server.

In all, six versions of SombRAT have been identified, with the first version dating all the way back to October 2019 and the latest variant observed earlier this August, implying that the backdoor is under active development.
While the identities of the crooks behind the operation are still unknown, one of the IP addresses to which the backdoor domains were registered has been linked to an earlier phishing campaign attributed to Russia-linked APT28 hacking group, hinting at the possibility that the phishing campaigns could have been outsourced to the mercenary on behalf of the actual threat actor.
This is the second hackers-for-hire operation uncovered by Blackberry, the first being a series of campaigns by a group called Bahamut that was found to exploit zero-day flaws, malicious software, and disinformation operations to track targets located in the Middle East and South Asia.
"With the undeniable success of Ransomware-as-a-Service (RaaS), it's not surprising that the cybercriminal market has expanded its portfolio to add dedicated phishing and espionage campaigns to the list of services on offer," Blackberry researchers said.
"Outsourcing attacks or certain parts of the attack chain to unaffiliated mercenary groups has several advantages for the adversary — it saves their time and resources and simplifies the procedures, but most importantly it provides an additional layer of indirection, which helps to protect the real identity of the threat actor."
Chinese APT Uses DLL Side-Loading in Attacks on Myanmar
6.11.20 APT Securityweek
A Chinese threat actor is leveraging DLL side-loading for the execution of malicious code in attacks targeting organizations in Myanmar, Sophos security researchers reveal.
DLL side-loading is a technique that uses malicious DLLs that spoof legitimate ones, and which relies on legitimate Windows applications to load and execute the code.
The method has been abused by many advanced persistent threat (APT) groups, mostly operating out of China, with the earliest attacks observed in 2013. Cybercrime groups have since adopted the technique as well.
As part of the recent attacks, DLL side-loading was used to load code that included poorly written English plaintext strings featuring politically inspired messages. Common to all of the observed samples was the use of the same program database (PDB) path, some of them containing the folder name “KilllSomeOne.”
The attacks, Sophos says, targeted organizations in Myanmar, both non-governmental entities and other organizations.
The targets and the characteristics of the employed malware led the security researchers to the conclusion that the attacks were launched by a Chinese threat actor.
The researchers identified four different side-loading scenarios that the adversary used. In two of them, a simple shell payload was delivered, with more complex malware delivered in the other two. In some attacks, combinations of the two scenarios were used.
Analysis of the attacks also revealed an effort to conceal execution, as well as apparent attempts to remove previous infections with the PlugX malware.
The hackers behind these attacks, Sophos notes, are neither highly skilled, nor below average. They used simple implementations in coding and messages hidden in the code that resemble the activities of script kiddies, while their targeting and deployment resemble those of established APT groups.
“Based on our analysis, it’s not clear whether this group will go back to more traditional implants like PlugX or keep going with their own code,” Sophos notes.
New KilllSomeOne APT group leverages DLL side-loading
5.11.20 APT Securityaffairs
A new Chinese APT group, tracked as KilllSomeOne, appeared in the threat landscape targeting corporate organizations in Myanmar.
A new Chinese APT group, tracked as KilllSomeOne, was spotted by researchers at Sophos. The advanced cyber-espionage group is targeting corporate organizations in Myanmar with DLL side-loading attacks.
The name KilllSomeOne comes from the phrase ‘KilllSomeOne’ used in the DLL side-loading attacks, the group is using poorly-written English messages relating to political subjects.
Dynamic-link library (DLL) side-loading takes advantage of how Microsoft Windows applications handle DLL files. In such attacks, malware places a spoofed malicious DLL file in a Windows’ WinSxS directory so that the operating system loads it instead of the legitimate file.
The technique was already employed by other Chinese APT groups since 2013, later it was also adopted by other cybercrime gangs in attacks in the wild.
According to Sophos researchers, the KilllSomeOne APT group combines four separate types of side-loading attack in its campaigns.
“We have identified four different side-loading scenarios that were used by the same threat actor. Two of these delivered a payload carrying a simple shell, while the other two carried a more complex set of malware. Combinations from both of these sets were used in the same attacks.” reads the analysis published by Sophos.
Each attack type is connected by the same program database (PDB) path, and some of the samples recorded and connected to the cybercriminals contain the folder name ‘KilllSomeOne.’
In a first attack scenario, hackers leverage a Microsoft antivirus component to load mpsvc.dll that acts as a loader for Groza_1.dat. The attackers use a simple XOR encryption algorithm with the string “Hapenexx is very bad” as a key.
In the second attack scenario, hackers employ a sample that leverages AUG.exe, a loader called dismcore.dll. The APT group uses the same payload and key of the previous scenario, the only difference is that both the file name and decryption key are encrypted with a one-byte XOR algorithm.
“In both of these cases, the payload is stored in the file named Groza_1.dat. The content of that file is a PE loader shellcode, which decrypts the final payload, loads into memory and executes it. The first layer of the loader code contains unused string: AmericanUSA.” continues the analysis.
The other two observed types of KillSomeOne DLL side-loading deliver an installer for the simple shell, they use two different payload files called adobe.dat and x32bridge.dat. The executables derived from these two files are essentially the same and both have the same PDB path:
C:\Users\guss\Desktop\Recent Work\U\U_P\KilllSomeOne\0.1\Function_hex\hex\Release\hex.pdb
In these attacks, the encryption key used is the string “HELLO_USA_PRISIDENT.”
The payloads are used to deploy an installer and additional components for other DDL side-loading attacks in a number of directories and set “hidden” and “system” attributes for the files.
“The installer then closes the executable used in the initial stage of the attack, and starts a new instance of explorer.exe to side-load the dropped DLL component,” states Sophos. “This is an effort to conceal the execution.”
The malware also kills running processes with a name starting with “AAM,” and deletes the file associated with it in C:\ProgramData and C:\Users\All Users. This behavior aims at removing mechanism used to prevent such kind of infections.
Before starting the data exfiltration, the malware perform multiple actions to ensure persistence, including the creation of a task that executes the side-loading executable that began the deployment:
schtasks /create /sc minute /mo 5 /tn LKUFORYOU_1 /tr
Sophos researchers believe that the TTPs adopted by the attackers is compatible with sophisticated APTs.
“Based on our analysis, it’s not clear whether this group will go back to more traditional implants like PlugX or keep going with their own code,” Sophos concludes. “We will continue to monitor their activity to track their further evolution.”
Mysterious APT Leaves Curious ‘KilllSomeOne’ Clue
5.11.20 APT Threatpost
APT cloaks identity using script-kiddie messages and advanced deployment and targeting techniques.
Researchers are scratching their heads when it comes to unmasking a new advanced persistent threat (APT) group targeting non-governmental organizations in the Southeast Asian nation Myanmar (formerly Burma).
Based on crude messages, such as “KilllSomeOne”, used in attack code strings, coupled with advanced deployment and targeting techniques, they say the APT has a split personality.
“The messages hidden in their samples [malware] are on the level of script kiddies. On the other hand, the targeting and deployment is that of a serious APT group,” wrote Gabor Szappanos, author of a Sophos technical brief, posted Wednesday, outlining what is known about the APT.
Szappanos wrote that the gang relies primarily on a cyberattack technique known as DLL side-loading. This preferred method of attack gained popularity in China in 2013. That fact, coupled with ongoing border-tensions between ethnic Chinese rebels and Myanmar military, suggest that the gang is a Chinese APT, researchers believe.
“While the [DLL side-loading] is far from new—we first saw it used by (mostly Chinese) APT groups as early as 2013, before cybercrime groups started to add it to their arsenal—this particular payload was not one we’ve seen before,” Szappanos wrote.
Four distinct DLL side-loading scenarios deliver either a shell payload (allowing an adversary to run commands on targeted systems) or plant a “complex set of malware” on systems, researchers said.
DLL side-loading, simply put, is a type of application that appears to be legitimate and can often bypass weak security mechanisms such as application whitelisting. Once trusted, the application gains additional permissions by Windows during its execution.
“Side-loading is the use of a malicious DLL spoofing a legitimate one, relying on legitimate Windows executables to load and execute the malicious code,” describes Sophos.
All four DLL side-loading scenarios execute malicious code and install backdoors in the networks of targeted organizations. Each also share the same program database path and plaintext strings written in poor English with politically inspired messages in their samples, Sophos said.
“The cases are connected by a common artifact: the program database (PDB) path. All samples share a similar PDB path, with several of them containing the folder name ‘KilllSomeOne,'” researchers wrote.
Sample strings of plain text in the KilllSomeOne malware code include “Happiness is a way station between too much and too little” and “HELLO_USA_PRISIDENT”.
“The types of perpetrators behind targeted attacks in general are not a homogeneous pool. They come with very different skill sets and capabilities. Some of them are highly skilled, while others don’t have skills that exceed the level of average cybercriminals,” researchers said. “The group responsible for the attacks we investigated in this report don’t clearly fall on either end of the spectrum. They moved to more simple implementations in coding—especially in encrypting the payload,” they said.
APT Groups Finding Success with Mix of Old and New Tools
4.11.20 APT Threatpost
The APT threat landscape is a mixed bag of tried-and-true tactics and cutting-edge techniques, largely supercharged by geo-politics, a report finds.
Advanced persistent threat (APT) groups continue to use the fog of intense geopolitics to supercharge their campaigns, but beyond these themes, actors are developing individual signature tactics for success.
That’s according to Kaspersky’s most recent APT trends report for Q3 2020, which found that some groups are innovating and pushing technical boundaries, while others take a more low-tech approach, honing messaging around COVID, the elections and other headlines.
“While some threat actors remain consistent over time and simply look to use hot topics such as COVID-19 to entice victims to download malicious attachments, other groups reinvent themselves and their toolsets,” said Ariel Jungheit, senior security researcher at the Global Research and Analysis Team at Kaspersky. “The widening scope of platforms attacked, continuous work on new infection chains and the use of legitimate services as part of their attack infrastructure, is something we have witnessed over the past quarter.”
These divergent approaches were best represented by two groups in particular, according to the report; DeathStalker and MosaicRegressor.
DeathStalker
DeathStalker, the report said, has been successful using the same tactics since 2018 to target law firms and companies in the financial sector.
“The group’s interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services or acting as an information broker in financial circles,” according to the report. “The activities of this threat actor first came to our attention through a PowerShell-based implant called Powersing.”
But while this approach is focused more on messaging around headlines for phishing emails, the report added that a couple of technical developments to DeathStalker’s campaigns are worth nothing.
“For instance, the malware directly connects to a command-and-control (C2) server using an embedded IP address or domain name, as opposed to previous variants where it made use of at least two dead-drop resolvers (DDRs) or web services, such as forums and code-sharing platforms, to fetch the real C2 IP address or domain,” the report explained. “Interestingly, for this campaign the attackers didn’t limit themselves merely to sending spear-phishing emails but actively engaged victims through multiple emails, persuading them to open the decoy, to increase the chance of compromise.”
Researchers added this was the first time they observed a malicious actor both using advanced techniques to bypass security, as well as “dropping PE binaries to load EvilNum.”
The Kaspersky team also noted they suspect DeathStalker is using a novel PowerShell implant they named “PowerPepper.”
“The delivery workflow uses a Microsoft Word document and drops a previously unknown PowerShell implant that relies on DNS over HTTPS (DoH) as a C2 channel,” the report said.
DeathStalker represents a relatively basic, low-tech set of techniques, tactics and procedures (TTPs) — while MosaicRegressor’s UEFI implant occupies the higher-tech end of the APT spectrum.
MosaicRegressor
In early October Kasperky researchers reported the discovery of “rogue UEFI firmware images,” modified to deliver malware, which the team dubbed “MosaicRegressor” as part of a wider framework. Components of the MosaicRegressor framework was part of attacks launched against diplomats and African, Asian and European Non-Government Organizations and traced back to North Korea.
UEFI is a specification that constitutes the structure and operation of low-level platform firmware, including the loading of the operating system itself. It can also be used when the OS is already up and running, for example in order to update the firmware. The UEFI firmware bootkit that’s part of MosaicRegressor loads the operating system itself, meaning a threat actor can modify the system to load malware that will run after the OS is loaded. Thus, it will be resistant to reinstalling the operating system or even replacing the hard drive, researchers said.
The report added that APT attacks have spiked in recent weeks in Southeast Asia, the Middle East and “various regions affected by the activities of Chinese-speaking APT groups.”
“Overall, what this means for cybersecurity specialists is this: defenders need to invest resources in hunting malicious activity in new, possibly legitimate environments that were scrutinized less in the past,” Jungheit concluded. “That includes malware that is written in lesser-known programming languages, as well as through legitimate cloud services. Tracking actors’ activities and TTPs allows us to follow as they adapt new techniques and tools, and thereby prepare ourselves to react to new attacks in time.”
APT trends report Q3 2020
3.11.20 APT Securelist
For more than three years, the Global Research and Analysis Team (GReAT) at Kaspersky has been publishing quarterly summaries of advanced persistent threat (APT) activity. The summaries are based on our threat intelligence research and provide a representative snapshot of what we have published and discussed in greater detail in our private APT reports. They are designed to highlight the significant events and findings that we feel people should be aware of.
This is our latest installment, focusing on activities that we observed during Q3 2020.
Readers who would like to learn more about our intelligence reports or request more information on a specific report are encouraged to contact intelreports@kaspersky.com.
The most remarkable findings
We have already partly documented the activities of DeathStalker, a unique threat group that seems to focus mainly on law firms and companies operating in the financial sector. The group’s interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as an information broker in financial circles. The activities of this threat actor first came to our attention through a PowerShell-based implant called Powersing. This quarter, we unraveled the threads of DeathStalker’s LNK-based Powersing intrusion workflow. While there is nothing groundbreaking in the whole toolset, we believe defenders can gain a lot of value by understanding the underpinnings of a modern, albeit low-tech, infection chain used by a successful threat actor. DeathStalker continues to develop and use this implant, using tactics that have mostly been identical since 2018, while making greater efforts to evade detection. In August, our public report of DeathStalker’s activities summarized the three scripting language-based toolchains used by the group – Powersing, Janicab and Evilnum.
Following our initial private report on Evilnum, we detected a new batch of implants in late June 2020, showing interesting changes in the (so far) quite static modus operandi of DeathStalker. For instance, the malware directly connects to a C2 server using an embedded IP address or domain name, as opposed to previous variants where it made use of at least two dead drop resolvers (DDRs) or web services, such as forums and code sharing platforms, to fetch the real C2 IP address or domain. Interestingly, for this campaign the attackers didn’t limit themselves merely to sending spear-phishing emails but actively engaged victims through multiple emails, persuading them to open the decoy, to increase the chance of compromise. Furthermore, aside from using Python-based implants throughout the intrusion cycle, in both new and old variants, this was the first time that we had seen the actor dropping PE binaries as intermediate stages to load Evilnum, while using advanced techniques to evade and bypass security products.
We also found another intricate, low-tech implant that we attribute to DeathStalker with medium confidence. The delivery workflow uses a Microsoft Word document and drops a previously unknown PowerShell implant that relies on DNS over HTTPS (DoH) as a C2 channel. We dubbed this implant PowerPepper.
During a recent investigation of a targeted campaign, we found a UEFI firmware image containing rogue components that drop previously unknown malware to disk. Our analysis showed that the revealed firmware modules were based on a known bootkit named Vector-EDK, and the dropped malware is a downloader for further components. By pivoting on unique traits of the malware, we uncovered a range of similar samples from our telemetry that have been used against diplomatic targets since 2017 and have different infection vectors. While the business logic of most is identical, we could see that some had additional features or differed in implementation. Due to this, we infer that the bulk of samples originate from a bigger framework that we have dubbed MosaicRegressor. Code artefacts in some of the framework’s components, and overlaps in C2 infrastructure used during the campaign, suggest that a Chinese-speaking actor is behind these attacks, possibly one that has connections to groups using the Winnti backdoor. The targets, diplomatic institutions and NGOs in Asia, Europe and Africa, all appear to be connected in some way to North Korea.
Europe
Since publishing our initial report on WellMess (see our APT trends report Q2 2020), the UK National Cyber Security Centre (NCSC) has released a joint technical advisory, along with Canadian and US governments, on the most recent activity involving WellMess. Specifically, all three governments attribute the use of this malware targeting COVID-19 vaccine research to The Dukes (aka APT29 and Cozy Bear). The advisory also details two other pieces of malware, SOREFANG and WellMail, that were used during this activity. Given the direct public statement on attribution, new details provided in the advisory, as well as new information discovered since our initial investigation, we published our report to serve as a supplement to our previous reporting on this threat actor. While the publication of the NCSC advisory has increased general public awareness on the malware used in these recent attacks, the attribution statements made by all three governments provided no clear evidence for other researchers to pivot on for confirmation. For this reason, we are currently unable to modify our original statement; and we still assess that the WellMess activity has been conducted by a previously unknown threat actor. We will continue to monitor for new activity and adjust this statement in the future if new evidence is uncovered.
Russian-speaking activity
In summer, we uncovered a previously unknown multimodule C++ toolset used in highly targeted industrial espionage attacks dating back to 2018. So far, we have seen no similarities with known malicious activity regarding code, infrastructure or TTPs. To date, we consider this toolset and the actor behind it to be new. The malware authors named the toolset MT3, and based on this abbreviation we have named the toolset MontysThree. The malware is configured to search for specific document types, including those stored on removable media. It contains natural language artefacts of correct Russian and a configuration that seek directories that exist only in Cyrilic version of Windows, while presenting some false flag artefacts suggesting a Chinese-speaking origin. The malware uses legitimate cloud services such as Google, Microsoft and Dropbox for C2 communications.
Chinese-speaking activity
Earlier this year, we discovered an active and previously unknown stealthy implant dubbed Moriya in the networks of regional inter-governmental organizations in Asia and Africa. This tool was used to control public facing servers in those organizations by establishing a covert channel with a C2 server and passing shell commands and their outputs to the C2. This capability is facilitated using a Windows kernel mode driver. Use of the tool is part of an ongoing campaign that we have named TunnelSnake. The rootkit was detected on the targeted machines in May, with activity dating back as early as November 2019, persisting in networks for several months following the initial infection. We found another tool showing significant code overlaps with this rootkit, suggesting that the developers have been active since at least 2018. Since neither rootkit nor other lateral movement tools that accompanied it during the campaign relied on hard-coded C2 servers, we could gain only partial visibility into the attacker’s infrastructure. That said, the bulk of detected tools, apart from Moriya, consisted of both proprietary and well-known pieces of malware that were previously used by Chinese-speaking threat actors, giving a clue to the attacker’s origin.
PlugX continues to be effectively and heavily used across Southeast and East Asia, and also Africa, with some minimal use in Europe. The PlugX codebase has been in use by multiple Chinese-speaking APT groups, including HoneyMyte, Cycldek and LuckyMouse. Government agencies, NGOs and IT service organizations seem to be consistent targets. While the new USB spreading capability is opportunistically pushing the malware throughout networks, compromised MSSPs/IT service organizations appear to be a potential vector of targeted delivery, with CobaltStrike installer packages pushed to multiple systems for initial PlugX installation. Based on our visibility, the majority of activity in the last quarter appears to be in Mongolia, Vietnam and Myanmar. The number of systems in these countries dealing with PlugX in 2020 is at the very least in the thousands.
We discovered an ongoing campaign, dating back to May, utilizing a new version of the Okrum backdoor, attributed to Ke3chang. This updated version of Okrum uses an Authenticode-signed Windows Defender binary using a unique side-loading technique. The attackers used steganography to conceal the main payload in the Defender executable while keeping its digital signature valid, reducing the chance of detection. We haven’t previously seen this method being used in the wild for malicious purposes. We have observed one affected victim, a telecoms company located in Europe.
On September 16, the US Department of Justice released three indictments associated with hackers allegedly connected with APT41 and other intrusion sets tracked as Barium, Winnti, Wicked Panda and Wicked Spider. In addition, two Malaysian nationals were also arrested on September 14, in Sitiawan (Malaysia), for “conspiring to profit from computer intrusions targeting the video game industry”, following cooperation between the US DoJ and the Malaysian government, including the Attorney General’s Chambers of Malaysia and the Royal Malaysia Police. The first indictment alleges that the defendants set up an elite “white hat” network security company, called Chengdu 404 Network Technology Co, Ltd. (aka Chengdu Si Lingsi Network Technology Co., Ltd.), and under its guise, engaged in computer intrusions targeting hundreds of companies around the world. According to the indictment, they “carried out their hacking using specialized malware, such as malware that cyber-security experts named ‘PlugX/Fast’, ‘Winnti/Pasteboy’, ‘Shadowpad’, ‘Barlaiy/Poison Plug’ and ‘Crosswalk/ProxIP'”. The indictments contain several indirect IoCs, which allowed us to connect these intrusions to Operation ShadowPad and Operation ShadowHammer, two massive supply-chain attacks discovered and investigated by Kaspersky in recent years.
Middle East
In June, we observed new activity by the MuddyWater APT group, involving use of a new set of tools that constitute a multistage framework for loading malware modules. Some components of the framework leverage code to communicate with C2s identical to code we observed in the MoriAgent malware earlier this year. For this reason, we decided to dub the new framework MementoMori. The purpose of the new framework is to facilitate execution of further in-memory PowerShell or DLL modules. We detected high-profile victims based in Turkey, Egypt and Azerbaijan.
Southeast Asia and Korean Peninsula
In May, we found new samples belonging to the Dtrack family. The first sample, named Valefor, is an updated version of the Dtrack RAT containing a new feature enabling the attacker to execute more types of payload. The second sample is a keylogger called Camio which is an updated version of its keylogger. This new version updates the logged information and its storage mechanism. We observed signs indicating that these malware programs were tailored for specific victims. At the time of our research our telemetry revealed victims located in Japan.
We have been tracking LODEINFO, fileless malware used in targeted attacks since last December. During this time, we observed several versions as the authors were developing the malware. In May, we detected version v0.3.6 targeting diplomatic organizations located in Japan. Shortly after that, we detected v0.3.8 as well. Our investigation revealed how the attackers operate during the lateral movement stage: after obtaining the desired data, the attackers wipe their traces. Our private report included a technical analysis of the LODEINFO malware and the attack sequence in the victim’s network, to disclose the actor’s tactics and methods.
While tracking Transparent Tribe activity, we discovered an interesting tool used by this APT threat actor: the server component used to manage CrimsonRAT bots. We found different versions of this software, allowing us to look at the malware from the perspective of the attackers. It shows that the main purpose of this tool is file stealing, given its functionalities for exploring the remote file system and collecting files using specific filters. Transparent Tribe (aka PROJECTM and MYTHIC LEOPARD) is a very prolific APT group that has increased its activities in recent months. We reported the launch of a new wide-ranging campaign that uses the CrimsonRAT tool where we were able to set up and analyze the server component and saw the use of the USBWorm component for the first time; we also found an Android implant used to target military personnel in India. This discovery also confirms much of the information already discovered during previous investigations; and it also confirms that CrimsonRAT is still under active development.
In April, we discovered a new malware strain that we named CRAT, based on the build path and internal file name. The malware was spread using a weaponized Hangul document as well as a Trojanized application and strategic web compromise. Since its discovery the full-featured backdoor has quickly evolved, diversifying into several components. A downloader delivers CRAT to profile victims, followed by next-stage orchestrator malware named SecondCrat: this orchestrator loads various plugins for espionage, including keylogging, screen capturing and clipboard stealing. During our investigation, we found several weak connections with ScarCruft and Lazarus: we discovered that several debugging messages inside the malware have similar patterns to ScarCruft malware, as well as some code patterns and the naming of the Lazarus C2 infrastructure.
In June, we observed a new set of malicious Android downloaders which, according to our telemetry, have been actively used in the wild since at least December 2019; and have been used in a campaign targeting victims almost exclusively in Pakistan. Its authors used the Kotlin programming language and Firebase messaging system for the downloader, which mimics Chat Lite, Kashmir News Service and other legitimate regional Android applications. A report by the National Telecom & Information Technology Security Board (NTISB) from January describes malware sharing the same C2s and spoofing the same legitimate apps. According to this publication, targets were Pakistani military bodies, and the attackers used WhatsApp messages, SMS, emails and social media as the initial infection vectors. Our own telemetry shows that this malware also spreads through Telegram messenger. The analysis of the initial set of downloaders allowed us to find an additional set of Trojans that we believe are strongly related, as they use the package name mentioned in the downloaders and focus on the same targets. These new samples have strong code similarity with artefacts previously attributed to Origami Elephant.
In mid-July, we observed a Southeast Asian government organization targeted by an unknown threat actor with a malicious ZIP package containing a multilayered malicious RAR executable package. In one of the incidents, the package was themed around COVID-19 containment. We believe that the same organization was probably the same target of a government web server watering-hole, compromised in early July and serving a highly similar malicious LNK. Much like other campaigns against particular countries that we have seen in the past, these adversaries are taking a long-term, multipronged approach to compromising target systems without utilizing zero-day exploits. Notably, another group (probably OceanLotus) used a similar Telegram delivery technique with its malware implants against the same government targets within a month or so of the COVID-19-themed malicious LNK, in addition to its use of Cobalt Strike.
In May 2020, Kaspersky technologies prevented an attack using a malicious script for Internet Explorer against a South Korean company. Closer analysis revealed that the attack used a previously unknown full chain that consisted of two zero-day exploits: a Remote Code Execution exploit for Internet Explorer and an Elevation of Privilege exploit for Windows. Unlike a previous full chain that we discovered, used in Operation WizardOpium (you can read more here and here), the new full chain targeted the latest builds of Windows 10, and our tests demonstrated reliable exploitation of Internet Explorer 11 and Windows 10 build 18363 x64. On June 8, we reported our discoveries to Microsoft, who confirmed the vulnerabilities. At the time of our report, the security team at Microsoft had already prepared a patch for vulnerability CVE-2020-0986 that was used in the zero-day Elevation of Privilege exploit; but before our discovery, the exploitability of this vulnerability had been considered less likely. The patch for CVE-2020-0986 was released on June 9. Microsoft assigned CVE-2020-1380 to a use-after-free vulnerability in JScript and the patch for this was released on August 11. We are calling this and related attacks Operation PowerFall. Currently, we are unable to establish a definitive link with any known threat actor, but due to similarities with previously discovered exploits we believe that DarkHotel may be behind this attack.
On July 22, we came across a suspicious archive file that was uploaded to VirusTotal from an Italian source. The file seemed to be a triage consisting of malicious scripts, access logs, malicious document files and several screenshots related to suspicious file detections from security solutions. After looking into these malicious document files, we identified that they are related to a Lazarus group campaign that we reported in June. This campaign, dubbed DeathNote, targeted the automobile industry and individuals in the academic field using lure documents containing aerospace and defense-related job descriptions. We are confident that these documents are related to a recently reported attack on an Israeli defense company. We have uncovered webshell scripts, C2 server scripts and malicious documents, identified several victims connected to the compromised C2 server, as well as uncovering the method used to access the C2 server.
We have observed an ongoing Sidewinder campaign that started in February, using five different malware types. The group made changes to its final payloads and continues to target government, diplomatic and military entities using current themes, such as COVID-19, in its spear-phishing efforts. While the infection mechanism remains the same as before, including the group’s exploit of choice (CVE-2017-1182) and use of the DotNetToJScript tool to deploy the final payloads, we found that the actor also used ZIP archives containing a Microsoft compiled HTML Help file to download the last-stage payload. In addition to the existing .NET-based implant, which we call SystemApp, the threat actor added JS Orchestrator, the Rover/Scout backdoor and modified versions of AsyncRAT, warzoneRAT to its arsenal.
Other interesting discoveries
Attribution is difficult at the best of times, and sometimes it’s not possible at all. While investigating an ongoing campaign, we discovered a new Android implant undergoing development, with no clear link to any previously known Android malware. The malware is able to monitor and steal call logs, SMS, audio, video and non-media files, as well as identifying information about the infected device. It also implements an interesting feature to collect information on network routes and topology obtained using the “traceroute” command as well as using local ARP caches. During this investigation we uncovered a cluster of similar Android infostealer implants, with one example being obfuscated. We also found older Android malware that more closely resembles a backdoor, with traces of it in the wild dating back to August 2019.
In April, Cisco Talos described the activities of an unknown actor targeting Azerbaijan’s government and energy sector using new malware called PoetRAT. In collaboration with Kaspersky ICS CERT, we identified supplementary samples of associated malware and documents with broader targeting of multiple universities, government and industrial organizations as well as entities in the energy sector in Azerbaijan. The campaign started in early November 2019; and the attackers switched off the infrastructure immediately following publication of the Cisco Talos report. Since then, no new related documents or PoetRAT samples have been discovered. We observed a small overlap in victimology with Turla, but since there is no technically sound proof of relation between them, and we haven’t been able to attribute this new set of activity to any other previously known actor, we named it Obsidian Gargoyle.
Final thoughts
The TTPs of some threat actors remain fairly consistent over time (such as using hot topics such (COVID-19) to entice users to download and execute malicious attachments sent in spear-phishing emails), while other groups reinvent themselves, developing new toolsets and widening their scope of activities, for example, to include new platforms. And while some threat actors develop very sophisticated tools, for example, MosiacRegressor UEFI implant, others have great success with basic TTPs. Our regular quarterly reviews are intended to highlight the key developments of APT groups.
Here are the main trends that we’ve seen in Q3 2020:
Geo-politics continues to drive the development of many APT campaigns, as seen in recent months in the activities of Transparent Tribe, Sidewinder, Origami Elephant and MosaicRegressor, and in the ‘naming and shaming’ of various threat actors by the NCSC and the US Department of Justice.
Organizations in the financial sector also continue to attract attention: the activities of the mercenary group DeathStalker is a recent example.
We continue to observe the use of mobile implants in APT attacks with recent examples including Transparent Tribe and Origami Elephant.
While APT threat actors remain active across the globe, recent hotspots of activity have been Southeast Asia, the Middle East and various regions affected by the activities of Chinese-speaking APT groups.
Unsurprisingly, we continue to see COVID-19-themed attacks – this quarter they included WellMess and Sidewinder.
Among the most interesting APT campaigns this quarter were DeathStalker and MosaicRegressor: the former underlining the fact that APT groups can achieve their aims without developing highly sophisticated tools; the latter representing the leading-edge in malware development.
As always, we would note that our reports are the product of our visibility into the threat landscape. However, it should be borne in mind that, while we strive to continually improve, there is always the possibility that other sophisticated attacks may fly under our radar.
North Korea-Linked APT Group Kimsuky spotted using new malware
3.11.20 APT Securityaffairs
North Korea-linked APT group Kimsuky was recently spotted using a new piece of malware in attacks on government agencies and human rights activists.
North Korea-linked cyber espionage group Kimsuky (aka Black Banshee, Thallium, Velvet Chollima) was recently observed using a new malware in attacks aimed at government agencies and human rights activists.
The Kimsuky APT group has been analyzed by several security teams, it was first spotted by Kaspersky researcher in 2013, recently its activity was detailed by ESTsecurity and by the team of researchers at my former company Cybaze ZLab.
At the end of October, the US-CERT published a report on Kimusky’s recent activities that provided information of their TTPs and infrastructure.
The APT group mainly targeting think tanks and organizations in South Korea, other victims were in the United States, Europe, and Russia.
Researchers at Cybereason’s Nocturnus team published a new report that includes details on two new pieces of malware associated with the North-Korea linked APT, modular spyware called KGH_SPY and a downloader called CSPY Downloader. Experts also identified a new server infrastructure used by the cyberspies that overlaps with previously identified Kimsuky infrastructure.
“Kimsuky is known for their complex infrastructure that uses free-registered domains, compromised domains, as well as private domains registered by the group.” reads the report published by Cybereason. “Tracking down the infrastructure, the Nocturnus team was able to detect overlaps with BabyShark malware and other connections to different malware such as AppleSeed backdoor”
KGH_SPY is a modular suite of tools that allows attackers to perform reconnaissance, keylogging, information stealing and implements backdoor capabilities
CSPY Downloader is a tool designed to evade analysis and acts as a downloader to deliver additional payloads.
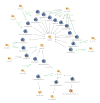
The new malware appears to have been developed recently, but threat actors might have used Backdating, or timestomping to thwart analysis attempts (anti-forensics). The researchers believe that attackers have tampered with the creation date of most of the files employed in the attacks and backdated them to 2016.
The Kimsuky APT group delivered the malware via weaponized documents, the final goal was cyber espionage, the KGH-Browser Stealer was able to exfiltrate stored data from Chrome, Edge, Firefox, Thunderbird, Opera, Winscp.
The CSPY Downloader implements anti-analysis techniques, it is able to determine whether it is running in a virtual environment or a debugger is used.
“The threat actors invested efforts in order to remain under the radar, by employing various anti-forensics and anti-analysis techniques which included backdating the creation/compilation time of the malware samples to 2016, code obfuscation, anti-VM and anti-debugging techniques. At the time of writing this report, some of the samples mentioned in the report are still not detected by any AV vendor,” the Nocturnus team concludes. “While the identity of the victims of this campaign remains unclear, there are clues that can suggest that the infrastructure targeted organizations dealing with human rights violations.”
Iran-linked Phosphorous APT hacked emails of security conference attendees
29.10.20 APT Securityaffairs
Iran-linked APT group Phosphorus successfully hacked into the email accounts of multiple high-profile individuals and security conference attendees.
Microsoft revealed that Iran-linked APT Phosphorus (aka APT35, Charming Kitten, Newscaster, and Ajax Security Team) successfully hacked into the email accounts of multiple high-profile individuals and attendees at this year’s Munich Security Conference and the Think 20 (T20) summit.
“Today, we’re sharing that we have detected and worked to stop a series of cyberattacks from the threat actor Phosphorous masquerading as conference organizers to target more than 100 high-profile individuals.” reads the post published by Microsoft. “Phosphorus, an Iranian actor, has targeted with this scheme potential attendees of the upcoming Munich Security Conference and the Think 20 (T20) Summit in Saudi Arabia.”

Nation-state actors successfully targeted over 100 individuals, including former ambassadors and other senior policy experts.
According to the experts at Microsoft Security Intelligence Center, the attacks are part of a cyber-espionage campaign aims at gathering intelligence on the victims by exfiltrating data from their mailboxs and contact list.
Data was exfiltrated to the de-ma[.]online domain, and the g20saudi.000webhostapp[.]com, and ksat20.000webhostapp[.]com subdomains.
The attackers have been sending spoofed email invitations to to former government officials, policy experts, academics, and leaders from non-governmental organizations. Attackers attempted to exploit the fears of travel during the Covid-19 pandemic by offering remote sessions.

The emails were written in almost perfect English.
Experts believe that this campaign is not tied to the upcoming U.S. Presidential elections.
Microsoft experts have worked with conference organizers who are warning their attendees about the ongoing attacks and suggesting them to remain vigilant to this approach being used in connection with other conferences or events.
“We recommend people evaluate the authenticity of emails they receive about major conferences by ensuring that the sender address looks legitimate and that any embedded links redirect to the official conference domain. As always, enabling multi-factor authentication across both business and personal email accounts will successfully thwart most credential harvesting attacks like these.” suggest Microsoft. “For anyone who suspects they may have been a victim of this campaign, we also encourage a close review of email-forwarding rules in accounts to identify and remove any suspicious rules that may have been set during a successful compromise.”
The Phosphorus group made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media.
Microsoft has been tracking the threat actors at least since 2013, but experts believe that the cyberespionage group has been active since at least 2011. In past campaigns, the APT group launched spear-phishing attacks against activists and journalists focusing on the Middle East, US organizations, and entities located in Israel, the U.K., Saudi Arabia, and Iraq.
Recently Microsoft published a post and a series of tweets to warn of cyber attacks exploiting the Zerologon vulnerability carried out by the Iran-linked APT group known as MuddyWater, aka Mercury.
The IT giant also warned of cyber espionage campaigns carried out by other nation state-sponsored hacking groups operating from Russia and China targeting organizations and individuals involved in this year’s U.S. presidential election.
Russia-linked Turla APT hacked European government organization
29.10.20 APT Securityaffairs
Russia-linked APT Turla has hacked into the systems of an undisclosed European government organization according to Accenture.
According to a report published by Accenture Cyber Threat Intelligence (ACTI), Russia-linked cyber-espionage group Turla has hacked into the systems of an undisclosed European government organization.
The Turla APT group (aka Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON) has been active since at least 2007 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations.
The list of previously known victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The attack against the undisclosed European government organization is in line with the APT’s espionage motivation, the attacker utilized a combination of remote procedure call (RPC)-based backdoors, such as HyperStack and remote administration trojans (RATs), such as Kazuar and Carbon. ACTI researchers observed the attacks between June and October 2020.
“Notably, Accenture researchers recently identified novel command and control (C&C) configurations for Turla’s Carbon and Kazuar backdoors on the same victim network.” reads the report published by Accenture. “The Kazuar instances varied in configuration between using external C&C nodes off the victim network and internal nodes on the affected network, and the Carbon instance had been updated to include a Pastebin project to receive encrypted tasks alongside its traditional HTTP C&C infrastructure.”
HyperStack is one of several RPC backdoors in the Turla’s arsenal that was first observed in 2018, it is a custom implant developed by the ATP group.
HyperStack leverages named pipes to execute remote procedure calls (RPC) from the command end control to the device running the HyperStack client. Lateral movements are implemented attempting to connect to another remote device’s IPC$ share, either using a null session or default credentials.
“IPC$ is a share that facilitates inter-process communication (IPC) by exposing named pipes to write to or read from. If the implant’s connection to the IPC$ is successful, the implant can forward RPC commands from the controller to the remote device, and likely has the capability to copy itself onto the remote device.” continues the report.
Turla uses a variety of command and control (C&C) implementations for each compromise in an attempt to be resilient to countermeasures implemented by the defenders. The Russia-linked APT group has relied on bot compromised web servers as C&C and legitimate web services like Pastebin as C2. One of the Kazuar sample analyzed by the experts was configured to receive commands sent through likely internal nodes in the government’s network.
Turla continues to extensively use the modular Carbon backdoor framework with advanced peer-to-peer capability. One of the Carbon backdoor analyzed by the researchers used the traditional threat actor-owned C&C infrastructure with tasks served from Pastebin. ACTI analysts discovered a Carbon installer that dropped a Carbon Orchestrator, two communication modules, and an encrypted configuration file.
ACTI also shared Indicators of Compromise (IoCs) for this attack to allow Government entities to check for evidence of compromise within their networks.
“Turla will likely continue to use its legacy tools, albeit with upgrades, to compromise and maintain long-term access to its victims because these tools have proven successful against Windows-based networks,” concludes Accenture.
Iran-linked APT Targets T20 Summit, Munich Security Conference Attendees
29.10.20 APT Threatpost
The Phosphorous APT has launched successful attacks against world leaders who are attending the Munich Security Conference and the Think 20 (T20) Summit in Saudi Arabia, Microsoft warns.
Microsoft said that an Iranian threat actor has successfully compromised attendees of two global conferences – including ambassadors and senior policy experts – in an effort to steal their email credentials.
The two conferences targeted include the Munich Security Conference, slated for Feb. 19 to 21, 2021 and the Think 20 (T20) Summit in Saudi Arabia, taking place Oct. 31 to Nov. 1 2020. Both conferences are majority virtual this year and are both longstanding and well respected venues to discuss global and regional security policies, among other things.
Microsoft linked the attack, which targeted more than 100 conference attendees, to Phosphorus, which it said is operating from Iran. The group – also known as APT 35, Charming Kitten and Ajax Security Team – has been known to use phishing as an attack vector.
“We believe Phosphorus is engaging in these attacks for intelligence collection purposes,” wrote to Tom Burt, corporate vice president, Customer Security and Trust at Microsoft, in post outlining the plots on Wednesday. “The attacks were successful in compromising several victims, including former ambassadors and other senior policy experts who help shape global agendas and foreign policies in their respective countries.”
Burt said the attackers have been sending possible attendees spoofed invitations by email. These emails use near-perfect English and were sent to former government officials, policy experts, academics and leaders from non-governmental organizations, he said. They purport to help assuage fears of travel during the Covid-19 pandemic by offering remote sessions.
The emails come from fake conference organizers using the email addresses t20saudiarabia[@]outlook.sa, t20saudiarabia[@]gmail.com and munichconference[@]outlook.com.

The attack vector: Credit: Microsoft
If the target accepts the invitation, the attacker is then asked to send a picture of themselves and bio. The attacker’s request is embedded in an attached password-protected PDF and comes in the form of a short link (inside the PDF). Naturally, the link links to one of several known credential harvesting pages meant to trick targets into handing over their email account credentials via a fake account login page. Malicious domains include de-ma[.]online, g20saudi.000webhostapp[.]com and ksat20.000webhostapp[.]com.
The attackers uses those credentials to log into the victims’ mailbox, where they can then gather further sensitive information and launch more malicious attacks.
“The attacks were successful in compromising several victims, including former ambassadors and other senior policy experts who help shape global agendas and foreign policies in their respective countries,” Burt wrote.
Microsoft said it’s working with conference organizers who have warned their attendees.
Threatpost has reached out to both conference organizers for further information.
Meanwhile, Microsoft recommends that conference-goers evaluate the authenticity of emails they receive about major conferences by ensuring that the sender address looks legitimate and that any embedded links redirect to the official conference domain.
“As always, enabling multi-factor authentication across both business and personal email accounts will successfully thwart most credential harvesting attacks like these,” Burt said. “For anyone who suspects they may have been a victim of this campaign, we also encourage a close review of email-forwarding rules in accounts to identify and remove any suspicious rules that may have been set during a successful compromise.”
The Iran-linked Phosphorus hacking group has made waves this year targeting campaign staffers of both Trump and Biden with phishing attacks. In February the group discovered targeting public figures in phishing attacks that stole victims’ email-account information. Earlier this year, Microsoft also took control of 99 websites utilized by the threat group in attacks. Last year, Phosphorus was also discovered attempting to break into accounts associated with the 2020 reelection campaign of President Trump. And most recently, it was seen using WhatsApp and LinkedIn messages to impersonate journalists.
Iran-Linked Seedworm APT target orgs in the Middle East
24.10.20 APT Securityaffairs
The Iran-linked cyber espionage group tracked as Seedworm started using a new downloader and is conducting destructive attacks.
The Iran-linked cyber-espionage group Seedworm (aka MuddyWater MERCURY, and Static Kitten) was observed using a new downloader in a new wave of attacks. Security experts pointed out that the threat actor started conducting destructive attacks.
Also referred to as MuddyWater, MERCURY, and Static Kitten, the cyber-espionage group was initially analyzed in 2017.
The first MuddyWater campaign was observed in late 2017, then researchers from Palo Alto Networks were investigating a mysterious wave of attacks in the Middle East.
The experts called the campaign ‘MuddyWater’ due to the confusion in attributing these attacks that took place between February and October 2017 targeting entities in Saudi Arabia, Iraq, Israel, United Arab Emirates, Georgia, India, Pakistan, Turkey, and the United States to date.
In September 2018, experts from Symantec found evidence of Seedworm and the espionage group APT28 on a computer in the Brazil-based embassy of an oil-producing nation.
Earlier this month, the Iranian APT group was observed actively targeting the Zerologon flaw.
According to security firm ClearSky and Symantec, Seedworm recently started using a new downloader dubbed PowGoop. Experts noticed that the threat actors used the downloader to deliver the Thanos ransomware in an attack aimed at an organization in the Middle East.
“PowGoop is a loader that was exposed in a PaloAlto report and later used in Operation Quicksand. PowGoop is comprised of a DLL Loader and a PowerShell-based downloader.” reads the report published by ClearSky. “The malicious file impersonates a legitimate goopdate.dll file that is signed as a Google Update executable”
The experts observed the attacks between July 6 and July 9, 2020, the hackers employed a strain of ransomware that was able to evade security tools and that implemented a destructive feature by overwriting the MBR.
Experts pointed out that the primary objectives of previous MuddyWater campaigns were espionage and cyber espionage, but in the latest campaign, tracked as ‘Operation Quicksand’ threat actors used for the first time the destructive malware in attacks on prominent organizations in Israel and in other countries around the world.
“We assess that the group is attempting to employ destructive attacks (the likes of the NotPetya attack from 2017), via a disguised as ransomware attacks” continnues the report.
“Although we didn’t see execution of the destruction in the wild, due to the presence of the destructive capabilities, the attribution to nation-state sponsored threat actor, and the realization of this vector in the past, a destructive purpose is more likely than a ransomware that is being deployed for financial goals.”
Another report published by Symantec connected the dots between MuddyWater and the PowGoopdownlaoder.
“In several recent Seedworm attacks, PowGoop was used on computers that were also infected with known Seedworm malware (Backdoor.Mori). In addition to this, activity involving Seedworm’s Powerstats (aka Powermud) backdoor appears to have been superseded by DLL side-loading of PowGoop.” reads the report published by Symantec.
“Additionally, during PowGoop activity, we also observed the attackers downloading tools and some unknown content from GitHub repos, similar to what has been reported on Seedworm‘s Powerstats in the past.”
Symantec researchers noticed that on the same machine where Seedworm was active, the attackers deployed the PowGoop downloader which is known to be a malware that is part of Seedworm’s arsenal.
PowGoop appears to have been employed in attacks aimed at governments, education, oil and gas, real estate, technology, and telecoms organizations in Afghanistan, Azerbaijan, Cambodia, Iraq, Israel, Georgia, Turkey, and Vietnam.
Symantec’s analysis revealed that the PowGoop was masquerading as a Google tool and noticed the use of SSF and Chisel.
Experts speculate the PowGoop downloader might be an evolution of Powerstats tool employed by MuddyWater in previous attacks.
“Symantec has not found any evidence of a wiper or ransomware on computers infected with PowGoop.”Symantec concludes. “This suggests that either the simultaneous presence of PowGoop and Thanos in one attack was a coincidence or, if the two are linked, that PowGoop is not used exclusively to deliver Thanos,”
Microsoft Exchange, Outlook Under Siege By APTs
20.10.20 APT Threatpost
A new threat report shows that APTs are switching up their tactics when exploiting Microsoft services like Exchange and OWA, in order to avoid detection.
New, sophisticated adversaries are switching up their tactics in exploiting enterprise-friendly platforms — most notably Microsoft Exchange, Outlook Web Access (OWA) and Outlook on the Web – in order to steal business credentials and other sensitive data.
Both Microsoft’s Exchange mail server and calendaring server and its Outlook personal information manager web app provide authentication services – and integration with other platforms – that researchers say are prime for attackers to leverage for launching attacks.
Accenture’s 2020 Cyber Threatscape report, released Monday, shed light on how actors are leveraging Exchange and OWA – and evolving their tactics to develop new malware families that target these services, or using new detection evasion techniques.
“Web-facing, data-intense systems and services that typically communicate externally can make it easier for adversaries to hide their traffic in the background noise, while authentication services could open up a credential-harvesting opportunity for cybercriminals,” according to Accenture researchers on Monday.
APTs Flock Exchange, OWA
One threat group that has been targeting Exchange and OWA is what researchers dub “BELUGASTURGEON” (aka Turla or Whitebear). Researchers say that this group operates from Russia, has been active for more than 10 years and is associated with numerous cyberattacks aimed at government agencies, foreign-policy research firms and think tanks across the globe.
The group is targeting these Microsoft services and using them as beachheads to hide traffic, relay commands, compromise e-mail, exfiltrate data and gather credentials for future espionage attacks, said researchers. For instance, they are manipulating legitimate traffic that’s traversing Exchange in order to relay commands or exfiltrate sensitive data.
“Hosts supporting Exchange and associated services frequently relay large volumes of data to external locations— representing a prime opportunity for malicious actors to hide their traffic within this background noise,” said researchers.
Another group, which researchers call SOURFACE (aka APT39 or Chafer), appears to have developed similar techniques to conceal malicious traffic, manipulating local firewalls and proxying traffic over non-standard ports using native commands, tools and functions, researchers said. Researchers said this group has been active since at least 2014 and is known for its cyberattacks on the oil and gas, communications, transportation and other industries in the Australia, Europe, Israel, Saudi Arabia, the U.S. and other regions.
In addition, threat groups are also creating new malware designed to specifically target Exchange and OWA. Researchers said they discovered several malicious files in the wild in 2019 that they assessed “with moderate confidence” were associated to a group called BLACKSTURGEON, used in targeting government and public sector orgs.
That includes a file that seemed like a version of the group’s customized version of the “RULER” tool, which is designed to abuse Microsoft Exchange services. This file exploits the CVE- 2017-11774 Outlook vulnerability, a security-feature bypass vulnerability that affects Microsoft Outlook and enables attackers to execute arbitrary commands, researchers said.
Other Services Under Attack
Cybercriminals are also targeting services that support Exchange and OWA. For instance, client-access servers (CAS), which handle all client connections to Exchange Server 2010 and Exchange 2013, typically operate in web-login portals for services including OWA. Attackers with access to CAS may be able to deploy capabilities to steal user login credentials, researchers said.
“Notably, an advanced persistent threat actor reportedly deployed web shells to harvest credentials from OWA users as they logged in,” they said.
The Windows Internet Information Services (IIS) platform, which supports OWA, is another increasing target. IIS is a web server software created by Microsoft for use with the Windows family. Researchers said they have observed SOURFACE, for instance, deploying custom Active Server Page Extended (ASPX) Web shells to IIS directories within the victim’s OWA environment. These web shells would include discrete file names, to resemble legitimate files on the victim’s system (for instance “login2.aspx” instead of “login.aspx”). And, to evade static detection, they typically contained limited functionality, often only file upload and download or command execution.
“SOURFACE operators altered their approach as the intrusion progressed. Instead of placing additional files to accomplish malicious functionality, the adversary appended web shell code to legitimate files within IIS,” said researchers. “It is likely they did this to reduce the identification by network defenders and ensure persistent access, even if other web shell files were identified and removed.”
Researchers said moving forward, attackers will continue to innovate their techniques in attacking Microsoft services, like Exchange, in ways that will naturally challenge network defenders. Beyond malware, Microsoft is top of the heap when it comes to hacker impersonations – with Microsoft products and services featuring in nearly a fifth of all global brand phishing attacks in the third quarter of this year, according to Check Point researchers.
“State-aligned operators could continue — in most cases — to need to emphasize stealth and persistence to meet their intelligence- gathering goals,” according to Accenture. “Such capabilities and detection evasion approaches underline the importance of identifying and tracking priority adversaries and then threat hunting against the specific behaviors employed by the priority adversaries.”
Iran-linked Silent Librarian APT targets universities again
19.10.20 APT Securityaffairs
Iran-linked cyberespionage group Silent Librarian has launched a new phishing campaign aimed at universities around the world.
Iran-linked APT group Silent Librarian has launched another phishing campaign targeting universities around the world.
The Silent Librarian, also tracked as Cobalt Dickens and TA407, targeted tens of universities in four continents in the last couple of years.
In August 2018, the security firm SecureWorks uncovered a phishing campaign carried out by the APT group targeting universities worldwide. The operation involved sixteen domains hosting more than 300 spoofed websites for 76 universities in 14 countries, including Australia, Canada, China, Israel, Japan, Switzerland, Turkey, the United Kingdom, and the United States.
Since mid-September, researchers from Malwarebytes observed a new spear-phishing campaign carried out by the group that is expanding its target list to include more countries.
Silent Librarian hackers targeted both employees and students at the universities, experts noticed that the threat actor set up a new infrastructure to avoid a takeover.
“Considering that Iran is dealing with constant sanctions, it strives to keep up with world developments in various fields, including that of technology. As such, these attacks represent a national interest and are well funded,” states Malwarebytes. “The new domain names follow the same pattern as previously reported, except that they swap the top level domain name for another.”
The threat actor used domain names following a pattern observed in past campaigns, although they use a different top-level domain name (the “.me” TLD instead of “.tk” and “.cf”).

The hackers use Cloudflare for phishing hostnames in an attempt to hide the real hosting origin. Anyway, Malwarebytes was able to identify some of the infrastructure which was located in Iran, likely because it is considered a bulletproof hosting option due to the lack of cooperation between US and European law enforcement and local police in Iran.
“Clearly we only uncovered a small portion of this phishing operation. Although for the most part the sites are taken down quickly, the attacker has the advantage of being one step ahead and is going for many possible targets at once,” Malwarebytes concludes.
The security firm also published Indicators of Compromise (IoCs) for this campaign.
IAmTheKing and the SlothfulMedia malware family
15.10.20 APT Securelist
On October 1, 2020, the DHS CISA agency released information about a malware family called SlothfulMedia, which they attribute to a sophisticated threat actor. We have been tracking this set of activity through our private reporting service, and we would like to provide the community with additional context.
In June 2018, we published the first report on a new cluster of activities that we named IAmTheKing, based on malware strings discovered in a malware sample from an unknown family. Amusingly, other strings present inside of it invited “kapasiky antivirus” to “leave [them] alone”.

Over time, we identified three different malware families used by this threat actor, one of which was SlothfulMedia. The aim of this blog post is to introduce all of them and to provide data we have been able to gather about the attackers’ interests.
IAmTheKing’s toolset
KingOfHearts
This C++ backdoor, which contains the character strings discussed above, is the first element of this toolset we encountered. It comes in EXE or DLL variants, and we have been able to find traces of this family dating back to 2014. We believe it was distributed through spear-phishing e-mails containing malicious Word documents, but have been unable to obtain samples of these. The infection process relies on a PowerShell script that downloads from a remote server a base64-encoded payload hidden in an image file.
In terms of capabilities, KingOfHearts offers nothing more than the basic features you would expect from a backdoor:
Arbitrary command execution
File system manipulation: listing drives and files, deleting, uploading and downloading data, etc.
Listing of running processes with the option to terminate any of them
Capturing screenshots using a custom standalone utility, described below
Rather than developing sophisticated features, the malware developers instead opted to include anti-debugging and virtualization detection routines. Communications with the C2 server take place over HTTP(S), implemented with the wsdlpull open source library. The backdoor looks for new orders every second by sending a heartbeat to the C2 (the “HEART” command, hence the name).
We identified two main development branches: one of them sends url-encoded POST data, and the other one sends JSON objects. Both have been used concurrently and otherwise display the same capabilities: we cannot say what motivates attackers to choose the one or the other.
QueenOfHearts
Following our initial discovery, we identified another, more widespread malware family linked to the same threat actor. While it does not contain the anti-analysis countermeasures of its cousin, the rest of its features and overall design decisions map to King of Hearts almost one to one. QueenOfHearts seems to have appeared somewhere in 2017. It is the family designated as PowerPool by our esteemed colleagues from ESET.
QueenOfHearts also interacts with its C2 server over HTTP. It sends simple GET requests containing a backdoor identifier and optional victim machine information, then reads orders located in the cookie header of the reply. Orders come in the form of two-letter codes (e.g.: “xe” to list drives) which tend to vary between samples. As of today, this family is still in active development, and we have observed code refactoring as well as incremental upgrades over 2020. For instance, earlier backdoor responses were sent as base64-encoded payloads in POST requests. They are now compressed beforehand, and additionally supplied through the cookie header.
QueenOfClubs
In the course of our investigations, we discovered another malware strain that appeared to fill the same role as QueenOfHearts. This C++ backdoor also offers similar features as KingOfHearts, as well as the ability to execute arbitrary Powershell scripts. One minute difference is that in this one, screenshot capture capabilities are embedded directly into the program instead of being handled by a separate utility.
It contains a number of links to QueenOfHearts, namely:
Identical hardcoded file names can be found in both malware strains.
We observed a number of command and control servers concurrently handling traffic originating from both families.
QueenOfHearts and QueenOfClubs were on occasion deployed simultaneously on infected machines.
However, it is also our belief that they originate from two separate codebases, although their authors shared common development practices.
The malware designated as SlothfulMedia by US-CERT is an older variant of this family.
JackOfHearts
Astute readers will notice that we did not discuss persistence mechanisms for any of the two aforementioned families. In fact, both of them expect to run in an environment that has already been prepared for them. JackOfHearts is the dropper associated with QueenOfHearts: its role is to write the malware somewhere on the disk (for instance: %AppData%\mediaplayer.exe) and create a Windows service pointing to it as well as a shortcut in the startup folder that is also used to immediately launch QueenOfHearts. This shortcut is the one that contains references to a “david” user highlighted by the DHS CISA report.
Finally, the dropper creates a self-deletion utility in the %TEMP% folder to remove itself from the filesystem.
As of 2020, JackOfHearts is still used to deploy QueenOfHearts.
Screenshot capture utility
A simple program that captures screenshots and saves them as “MyScreen.jpg”. It is sometimes embedded directly inside QueenOfHearts but has also been seen in conjunction with KingOfHearts.
Powershell backdoor
In addition to these malware families, IAmTheKing also leverages an extensive arsenal of Powershell scripts. Recent infection vectors have involved archives sent over e-mail which contain LNK files masquerading as Word documents. Clicking on these links results in the execution of a Powershell backdoor that hides inside custom Windows event logs and retrieves additional scripts over HTTPS, DNS or even POP3S.
The C2 server provides PNG files, which contain additional Powershell scripts hidden through steganography. The code performing this operation comes from the open-source project Invoke-PSImage. This allows operators to stage components on the victim machine, such as:
An information-stealing utility written in Powershell that collects all documents found on the victim’s machine and sends them in password-protected RAR archives. These archives are sent back to the attackers over e-mail.
A command execution utility which obtains orders from DNS TXT records. The code to accomplish this is derived from another open-source project, Nishang.
An information-gathering utility tasked with collecting running processes, disk drives and installed programs with WMI queries. It may also steal passwords saved by the Chrome browser.
A spreader script that lists computers connected to the domain, and tries to open a share on each of them to copy a binary and create a remote scheduled task.
A home-made keylogger.
QueenOfHearts, one of the malware families described above.
Lateral movement
Once the attackers have gained access to a machine through any of the tools described above, they leverage well-known security testing programs to compromise additional machines on the network. In particular, we found evidence of the following actions on the target:
Microsoft’s SysInternals suite: ProcDump to dump the exe process and PsExec to run commands on remote hosts.
LaZagne and Mimikatz to collect credentials on infected machines.
Built-in networking utilities such as ipconfig.exe, net.exe and ping.exe, etc. for network discovery.
Victimology
Until very recently, IAmTheKing has focused exclusively on collecting intelligence from high-profile Russian entities. Victims include government bodies and defense contractors, public agencies for development, universities and companies in the energy sector. This threat actor’s geographic area of interest is so specific that KingOfHearts, QueenOfHearts and even recent versions of JackOfHearts include code referring specifically to the Russian language character set:
In 2020, we discovered rare incidents involving IAmTheKing in central Asian and Eastern European countries. The DHS CISA also reports activity in Ukraine and Malaysia. Our data however indicates that Russia overwhelmingly remains IAmTheKing’s primary area of operation.
There is currently debate within our team on whether this constitutes a slight shift in this threat actor’s targeting, or if its toolset is now shared with other groups. We are unable to provide a definitive answer to this question at this juncture.
Conclusion
While the public has only recently discovered this set of activity, IAmTheKing has been very active for a few years. Considering the type of organizations that cybercriminals have been targeting, we felt that there was little public interest in raising awareness about this group beyond our trusted circle of industry partners. However, now that researchers have started investigating this threat actor, we want to assist the community as much as possible by providing this brief summary of our knowledge of IAmTheKing.
Based on the type of information IAmTheKing is after, we believe that it is state-sponsored. Its toolset is rapidly evolving, and it is not afraid to experiment with non-standard communications channels. The group is characterized by a mastery of traditional pentesting methodologies and a solid command of Powershell. Data available to us indicates that it has achieved operational success on numerous occasions.
Kaspersky will keep investigating incidents related to this group in the foreseeable future and has gathered a detailed view of their 2020 activity so far. We invite individuals or companies who think they might be – or have been – targeted by IAmTheKing to get in touch with us for additional information, or otherwise request access to our Threat Intelligence Portal for regular updates on this threat actor.
YARA rules
In virtually all our investigations, we write YARA rules to hunt for additional malware samples and get a better idea of each family’s prevalence. In the spirit of sharing knowledge with the community and assisting research efforts on this threat actor, we are happy to release a few of these rules, which will allow defenders to identify recent samples from the families described above. If you are unfamiliar with YARA or would like to learn more about the art of writing rules, please check out the online training written by members of GReAT.
Indicators of Compromise
00E415E72A4FC4C8634D4D3815683CE8 KingOfHearts (urlencode variant)
4E2C2E82F076AD0B5D1F257706A5D579 KingOfHearts (JSON variant)
AB956623B3A6C2AC5B192E07B79CBB5B QueenOfHearts
4BBD5869AA39F144FADDAD85B5EECA12 QueenOfHearts
4076DDAF9555031B336B09EBAB402B95 QueenOfHearts
096F7084D274166462D445A7686D1E5C QueenOfHearts
29AA501447E6E20762893A24BFCE05E9 QueenOfClubs
97c6cfa181c849eb87759518e200872f JackOfHearts
7DB4F1547D0E897EF6E6F01ECC484314 Screenshot capture utility
60D78B3E0D7FFE14A50485A19439209B Malicious LNK
90EF53D025E04335F1A71CB9AA6D6592 Keylogger
APT groups chain VPN and Windows Zerologon bugs to attack US government networks
12.10.20 APT Securityaffairs
US government networks are under attack, threat actors chained VPN and Windows Zerologon flaws to gain unauthorized access to elections support systems.
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) published a joint security alert to warn of attackers combining VPN and Windows Zerologon flaws to target government networks.
According to government experts, the attacks aimed at federal and state, local, tribal, and territorial (SLTT) government networks, the agencies also reported attacks against non-government networks.
The alert didn’t provide details about the attackers, it only classify them as “advanced persistent threat (APT) actors, a circumstance that suggests the involvement of state-sponsored hackers.
“CISA is aware of some instances where this activity resulted in unauthorized access to elections support systems; however, CISA has no evidence to date that integrity of elections data has been compromised,” the security alert published by the two agencies reads.
The joint alert includes information on the vulnerabilities exploited by the hackers and recommended mitigation actions for affected organizations.
The agencies warn of risk to elections information housed on government networks.
According to the Alert (AA20-283A), advanced persistent threat (APT) actors are exploiting multiple legacy vulnerabilities in combination with a the recently discovered Zerologon vulnerability (CVE-2020-1472).
The CVE-2020-1472 flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
“CISA has recently observed advanced persistent threat (APT) actors exploiting multiple legacy vulnerabilities in combination with a newer privilege escalation vulnerability—CVE-2020-1472—in Windows Netlogon.” reads the report. “The commonly used tactic, known as vulnerability chaining, exploits multiple vulnerabilities in the course of a single intrusion to compromise a network or application.”
Experts believe that the targets are not being selected because of their proximity to elections information, anyway, the agencies warn of the risk to elections systems operated by the government.
“CISA is aware of some instances where this activity resulted in unauthorized access to elections support systems; however, CISA has no evidence to date that integrity of elections data has been compromised.” continues the alert.
CISA and FBI have observed attacks carried out by APT actors that combined two the CVE-2018-13379 and CVE-2020-1472 flaws.
The CVE-2018-13379 is a path traversal vulnerability in the FortiOS SSL VPN web portal that could be exploited by an unauthenticated attacker to download FortiOS system files, to upload malicious files on unpatched systems and take over Fortinet VPN servers.
Government experts explained that attackers are combining these two flaws to hijack Fortinet servers and use them as an entry point in government networks, then take over internal networks using the Zerologon flaw to compromise all Active Directory (AD) identity services.
Threat actors have then been observed using legitimate remote access tools, including Remote Desktop Protocol (RDP) and VPN, to access the targeted environment with the compromised credentials.
Recently Microsoft observed Iran-linked APT Mercury and the Russian cybercrime gang TA505 exploiting the Zerologon flaw in attacks in the wild.
Microsoft publicly shared some file indicators for the attacks along with variations of the ZeroLogon exploits its experts have detected. Many of these exploits were recompiled versions of well-known, publicly available proof-of-concept code.
Both CISA and the FBI recommend private organizations and public agencies to patch systems and equipment promptly and diligently.
The alert also warns of other vulnerabilities that could be exploited by threat actors and urge to patch vulnerable systems immediately.
“CISA recommends network staff and administrators review internet-facing infrastructure for these and similar vulnerabilities that have or could be exploited to a similar effect, including Juniper CVE-2020-1631, Pulse Secure CVE-2019-11510, Citrix NetScaler CVE-2019-19781, and Palo Alto Networks CVE-2020-2021 (this list is not considered exhaustive).” concludes the alert.
Russian Cybercrime group is exploiting Zerologon flaw, Microsoft warns
11.10.20 APT Securityaffairs
Microsoft has uncovered Zerologon attacks that were allegedly conducted by the infamous TA505 Russia-linked cybercrime group.
Microsoft spotted a series of Zerologon attacks allegedly launched by the Russian cybercrime group tracked as TA505, CHIMBORAZO and Evil Corp.
Microsoft experts spotted the Zerologon attacks involving fake software updates, the researchers noticed that the malicious code connected to command and control (C&C) infrastructure known to be associated with TA505.
TA505 hacking group has been active since 2014 focusing on Retail and banking sectors. The group is also known for some evasive techniques they put in place over time to avoid the security controls and penetrate corporate perimeters with several kinds of malware, for instance abusing the so-called LOLBins (Living Off The Land Binaries), legit programs regularly used by victim, or also the abuse of valid cryptographically signed payloads.
The TA505 group was involved in campaigns aimed at distributing the Dridex banking Trojan, along with Locky, BitPaymer, Philadelphia, GlobeImposter, and Jaff ransomware families.
Security experts from cyber-security firm Prevailion reported that TA505 has compromised more than 1,000 organizations.
The malicious updates employed in the Zerologon attacks are able to bypass the user account control (UAC) security feature in Windows and abuse the Windows Script Host tool (wscript.exe) to execute malicious scripts.
The experts explained that the threat actors abuse MSBuild.exe to compile Mimikatz updated with built-in ZeroLogon functionality.
“Attacks showing up in commodity malware like those used by the threat actor CHIMBORAZO indicate broader exploitation in the near term.” states Microsoft.
This is the second alert published by Microsoft related to Zerologon attack in the wild. Early this week the IT giant published a post and a series of tweets warning of cyber attacks exploiting the Zerologon vulnerability carried out by the Iran-linked APT group known as MuddyWater, aka Mercury.

The CVE-2020-1472 Zerologon flaw is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
At the end of September, DHS CISA issued an emergency directive to tells government agencies to address the Zerologon vulnerability (CVE-2020-1472) by Monday.
Microsoft Warns of Russian Cybercriminals Exploiting Zerologon Vulnerability
11.10.20 APT Securityweek
Microsoft reported this week that it has spotted Zerologon attacks apparently conducted by TA505, a notorious Russia-linked cybercrime group.
According to Microsoft, the Zerologon attacks it has observed involve fake software updates that connect to command and control (C&C) infrastructure known to be associated with TA505, which the company tracks as CHIMBORAZO.
The fake updates are designed to bypass the user account control (UAC) security feature in Windows and they abuse the Windows Script Host tool (wscript.exe) to execute malicious scripts.

“To exploit the vulnerability, attackers abuse MSBuild.exe to compile Mimikatz updated with built-in ZeroLogon functionality,” Microsoft said.
The tech giant added, “Attacks showing up in commodity malware like those used by the threat actor CHIMBORAZO indicate broader exploitation in the near term.”
TA505, also known as Evil Corp, has been active for nearly a decade and it’s mainly known for operations involving banking trojans and ransomware. This is not the first time the group has exploited Windows vulnerabilities in its attacks, and researchers recently found some links between campaigns conducted by TA505 and North Korean hackers.
Microsoft first warned users about malicious actors exploiting the Zerologon vulnerability on September 24. Earlier this week, it issued another warning after seeing that the flaw had also been exploited by an Iranian state-sponsored threat actor.
The Zerologon vulnerability, officially tracked as CVE-2020-1472 and described as a privilege escalation issue, affects Windows Server and it has been rated critical. It was patched by Microsoft in August with its monthly security updates.
The flaw allows an attacker who has access to the targeted organization’s network to compromise domain controllers without the need for credentials.
Microsoft has informed customers that applying the patches released in August is only the first phase of addressing the Zerologon vulnerability. The second phase, which will involve placing domain controllers in enforcement mode, will start in February 2021.
A few weeks after the vulnerability was fixed by Microsoft, the DHS issued an emergency directive requiring federal agencies to immediately install the available patches.
MontysThree APT Takes Unusual Aim at Industrial Targets
9.10.20 APT Threatpost
The newly discovered APT specializes in espionage campaigns against industrial holdings — a rare target for spyware.
SAS@Home 2020 – A series of highly targeted attacks by an APT group called MontysThree against industrial targets has been uncovered, with evidence that the campaign dates back to 2018.
That’s according to researchers from Kaspersky, who noted that the group uses a variety of techniques to evade detection, including using public cloud services for command-and-control (C2) communications, and hiding its main malicious espionage module using steganography.
Spy attacks on industrial holdings are far more unusual than campaigns against diplomats and other nation-state targets, according to the firm.
Threatpost Webinar Promo Retail Security
Click to Register!
“Government entities, diplomats and telecom operators tend to be the preferred target for APTs, since these individuals and institutions naturally possess a wealth of highly confidential and politically sensitive information,” according to a Kaspersky analysis, issued on Thursday in tandem with its virtual Security Analyst Summit conference, SAS@Home. “Far more rare are targeted espionage campaigns against industrial entities—but, like any other attacks against industries, they can have devastating consequences for the business.”
The APT uses a toolset that it calls MT3, which consists of separate modules. The first—the loader—is initially spread using RAR self-extracted (SFX) archives. These, delivered via email, contain savvy lures related to employees’ contact lists, technical documentation and medical analysis, to trick industrial employees into downloading the files.
The loader obfuscates itself using steganography, which is the practice of hiding electronic information inside images.
“Steganography is used by actors to hide the fact that data is being exchanged,” according to Kaspersky. “In the case of MontysThree, the main malicious payload is disguised as a bitmap file. If the right command is inputted, the loader will use a custom-made algorithm to decrypt the content from the pixel array and run the malicious payload.”
The main malicious payload uses several encryption techniques of its own to evade detection, namely the use of an RSA algorithm to encrypt communications with the control server and to decrypt the main “tasks” assigned from the malware.
Once installed, it sets about searching for documents with specific extensions (MontysThree is designed to specifically target Microsoft and Adobe Acrobat documents) and in specific company directories. It also takes screenshots and fingerprints compromised devices by gathering information about their network settings, host name and so on, to determine if the target is of interest to the attackers.
Meanwhile, C2 communications are hosted on public cloud services like Google, Microsoft and Dropbox, which, as Kaspersky pointed out, makes the communications traffic difficult to detect as malicious.
“Because no antivirus blocks these services, it ensures the control server can execute commands uninterrupted,” according to the firm.
MontysThree also uses a simple method for gaining persistence on the infected system—a modifier for Windows Quick Launch. Users inadvertently run the initial module of the malware by themselves every time they run legitimate applications, such as browsers, when using the Quick Launch toolbar, researchers explained.
“MontysThree is interesting not just because of the fact that it’s targeting industrial holdings, but because of the combination of sophisticated and somewhat amateurish TTPs,” said Denis Legezo, senior security researcher with Kaspersky’s Global Research and Analysis Team, in a posting on Thursday. “In general, the sophistication varies from module to module, but it can’t compare to the level used by the most advanced APTs.”
Despite the less-complex aspects of the campaign, “they use strong cryptographic standards and there are indeed some tech-savvy decisions made, including the custom steganography,” Legezo said. “Perhaps most importantly, it’s clear that the attackers have put significant effort into developing the MontysThree toolset, suggesting they are determined in their aims—and that this is not meant to be a short-lived campaign.”
As far as attribution, that remains a mystery; Kaspersky has not been able to find any similarities in the malicious code or the infrastructure with any known APTs.
Kaspersky researchers will be presenting technical details on the MontysThree toolset as well as more information on targeting and other aspects of the campaign during SAS@Home on Thursday; Threatpost will update this posting with more information as it surfaces.
Iran-linked APT is exploiting the Zerologon flaw in attacks
6.10.20 APT Securityaffairs
Microsoft researchers reported that Iranian cyber espionage group MuddyWater is exploiting the Zerologon vulnerability in attacks in the wild.
Microsoft published a post and a series of tweets to warn of cyber attacks exploiting the Zerologon vulnerability carried out by the Iran-linked APT group known as MuddyWater, aka Mercury.
The Zerologon vulnerability, tracked as CVE-2020-1472, is an elevation of privilege that resides in the Netlogon. The Netlogon service is an Authentication Mechanism used in the Windows Client Authentication Architecture which verifies logon requests, and it registers, authenticates, and locates Domain Controllers.
An attacker could exploit the vulnerability to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
An attacker could also exploit the flaw to disable security features in the Netlogon authentication process and change a computer’s password on the domain controller’s Active Directory.
The only limitation on how to carry out a Zerologon attack is that the attacker must have access to the target network.
Administrators of enterprise Windows Servers have to install the August 2020 Patch Tuesday to mitigate “unacceptable risk” posed by the flaw to federal networks.
According to Microsoft’s Threat Intelligence Center (MSTIC) the attacks exploiting this vulnerability surged since September 13.
“One of the adversaries noticed by our analysts was interesting because the attacker leveraged an older vulnerability for SharePoint (CVE-2019-0604) to exploit remotely unpatched servers (typically Windows Server 2008 and Windows Server 2012) and then implant a web shell to gain persistent access and code execution.” reads the analysis published by Microsoft. “Following the web shell installation, this attacker quickly deployed a Cobalt Strike-based payload and immediately started exploring the network perimeter and targeting domain controllers found with the ZeroLogon exploit.”
Microsoft linked the attacks to the Iranian cyberespionge group MERCURY, also known as MuddyWater, SeedWorm and TEMP.Zagros.
The first MuddyWater campaign was observed in late 2017 when targeted entities in the Middle East.
The experts called the campaign ‘MuddyWater’ due to the confusion in attributing a wave of attacks that took place between February and October 2017 targeting entities in Saudi Arabia, Iraq, Israel, United Arab Emirates, Georgia, India, Pakistan, Turkey, and the United States to date.
The group evolved over the years by adding new attack techniques to its arsenal.
Microsoft publicly shared some file indicators for the attacks along with variations of the ZeroLogon exploits its experts have detected. Many of these exploits were recompiled versions of well-known, publicly available proof-of-concept code. Microsoft pointed out that MS Defender for Endpoint can also detect certain file-based versions of the CVE-2020-1472 exploit when executed on devices protected by Microsoft Defender for Endpoints.
The MuddyWater attackers have begun around one week after the first proof-of-concept code was published, and Microsoft began detecting the first Zerologon exploitation attempts.
At the time, the Department of Homeland Security’s CISA issued an emergency directive to order government agencies to address the Zerologon vulnerability (CVE-2020-1472) by Monday, September 21.
MosaicRegressor: Lurking in the Shadows of UEFI
6.10.20 APT Securelist
UEFI (or Unified Extensible Firmware Interface) has become a prominent technology that is embedded within designated chips on modern day computer systems. Replacing the legacy BIOS, it is typically used to facilitate the machine’s boot sequence and load the operating system, while using a feature-rich environment to do so. At the same time, it has become the target of threat actors to carry out exceptionally persistent attacks.
One such attack has become the subject of our research, where we found a compromised UEFI firmware image that contained a malicious implant. This implant served as means to deploy additional malware on the victim computers, one that we haven’t come across thus far. To the best of our knowledge, this is the second known public case where malicious UEFI firmware in use by a threat actor was found in the wild.
Throughout this blog we will elaborate on the following key findings:
We discovered rogue UEFI firmware images that were modified from their benign counterpart to incorporate several malicious modules;
The modules were used to drop malware on the victim machines. This malware was part of a wider malicious framework that we dubbed MosaicRegressor;
Components from that framework were discovered in a series of targeted attacks pointed towards diplomats and members of an NGO from Africa, Asia and Europe, all showing ties in their activity to North Korea;
Code artefacts in some of the framework’s components and overlaps in C&C infrastructure used during the campaign suggest that a Chinese-speaking actor is behind these attacks, possibly having connections to groups using the Winnti backdoor;
The attack was found with the help of Firmware Scanner, which has been integrated into Kaspersky products since the beginning of 2019. This technology was developed to specifically detect threats hiding in the ROM BIOS, including UEFI firmware images.
Current State of the Art
Before we dive deep into our findings, let us have a quick recap of what UEFI is and how it was leveraged for attacks thus far. In a nutshell, UEFI is a specification that constitutes the structure and operation of low-level platform firmware, so as to allow the operating system to interact with it at various stages of its activity.
This interaction happens most notably during the boot phase, where UEFI firmware facilitates the loading of the operating system itself. That said, it can also occur when the OS is already up and running, for example in order to update the firmware through a well-defined software interface.
Considering the above, UEFI firmware makes for a perfect mechanism of persistent malware storage. A sophisticated attacker can modify the firmware in order to have it deploy malicious code that will be run after the operating system is loaded. Moreover, since it is typically shipped within SPI flash storage that is soldered to the computer’s motherboard, such implanted malware will be resistant to OS reinstallation or replacement of the hard drive.
This type of attack has occurred in several instances in the past few years. A prominent example is the LowJax implant discovered by our friends at ESET in 2018, in which patched UEFI modules of the LoJack anti-theft software (also known as Computrace) were used to deploy a malicious user mode agent in a number of Sofacy \ Fancy Bear victim machines. The dangers of Computrace itself were described by our colleagues from the Global Research and Analysis Team (GReAT) back in 2014.
Another example is source code of a UEFI bootkit named VectorEDK which was discovered in the Hacking Team leaks from 2015. This code consisted of a set of UEFI modules that could be incorporated into the platform firmware in order to have it deploy a backdoor to the system which will be run when the OS loads, or redeploy it if it was wiped. Despite the fact that VectorEDK’s code was made public and can be found in Github nowadays, we hadn’t witnessed actual evidence of it in the wild, before our latest finding.
Our Discovery
During an investigation, we came across several suspicious UEFI firmware images. A deeper inspection revealed that they contained four components that had an unusual proximity in their assigned GUID values, those were two DXE drivers and two UEFI applications. After further analysis we were able to determine that they were based on the leaked source code of HackingTeam’s VectorEDK bootkit, with minor customizations.
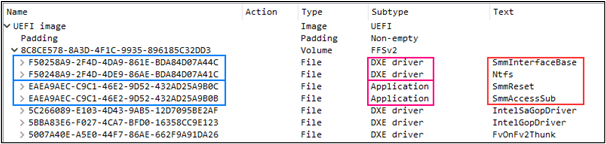
Rogue components found within the compromised UEFI firmware
The goal of these added modules is to invoke a chain of events that would result in writing a malicious executable named ‘IntelUpdate.exe’ to the victim’s Startup folder. Thus, when Windows is started the written malware would be invoked as well. Apart from that, the modules would ensure that if the malware file is removed from the disk, it will be rewritten. Since this logic is executed from the SPI flash, there is no way to avoid this process other than eliminating the malicious firmware.
Following is an outline of the components that we revealed:
SmmInterfaceBase: a DXE driver that is based on Hacking Team’s ‘rkloader’ component and intended to deploy further components of the bootkit for later execution. This is done by registering a callback that will be invoked upon an event of type EFI_EVENT_GROUP_READY_TO_BOOT. The event occurs at a point when control can be passed to the operating system’s bootloader, effectively allowing the callback to take effect before it. The callback will in turn load and invoke the ‘SmmAccessSub’ component.
Ntfs: a driver written by Hacking Team that is used to detect and parse the NTFS file system in order to allow conducting file and directory operations on the disk.
SmmReset: a UEFI application intended to mark the firmware image as infected. This is done by setting the value of a variable named ‘fTA’ to a hard-coded GUID. The application is based on a component from the original Vector-EDK code base that is named ‘ReSetfTA’.
Setting of the fTA variable with a predefined GUID to mark the execution of the bootkit
SmmAccessSub: the main bootkit component that serves as a persistent dropper for a user-mode malware. It is executed by the callback registered during the execution of ‘SmmInterfaceBase’, and takes care of writing a binary embedded within it as a file named ‘IntelUpdate.exe’ to the startup directory on disk. This allows the binary to execute when Windows is up and running.
This is the only proprietary component amongst the ones we inspected, which was mostly written from scratch and makes only slight use of code from a Vector-EDK application named ‘fsbg’. It conducts the following actions to drop the intended file to disk:
Bootstraps pointers for the SystemTable, BootServices and RuntimeServices global structures.
Tries to get a handle to the currently loaded image by invoking the HandleProtocol method with the EFI_LOADED_IMAGE_PROTOCOL_GUID argument.
If the handle to the current image is obtained, the module attempts to find the root drive in which Windows is installed by enumerating all drives and checking that the ‘\Windows\System32’ directory exists on them. A global EFI_FILE_PROTOCOL object that corresponds to the drive will be created at this point and referenced to open any further directories or files in this drive.
If the root drive is found in the previous stage, the module looks for a marker file named ‘setupinf.log’ under the Windows directory and proceeds only if it doesn’t exist. In the absence of this file, it is created.
If the creation of ‘setupinf.log’ succeeds, the module goes on to check if the ‘Users’ directory exists under the same drive.
If the ‘Users’ directory exists, it writes the ‘IntelUpdate.exe’ file (embedded in the UEFI application’s binary) under the ‘ProgramData\Microsoft\Windows\Start Menu\Programs\Startup’ directory in the root drive.
Code from ‘SmmAccessSub’ used to write the embedded ‘IntelUpdate.exe’ binary to the Windows Startup directory
Unfortunately, we were not able to determine the exact infection vector that allowed the attackers to overwrite the original UEFI firmware. Our detection logs show that the firmware itself was found to be malicious, but no suspicious events preceded it. Due to this, we can only speculate how the infection could have happened.
One option is through physical access to the victim’s machine. This could be partially based on Hacking Team’s leaked material, according to which the installation of firmware infected with VectorEDK requires booting the target machine from a USB key. Such a USB would contain a special update utility that can be generated with a designated builder provided by the company. We found a Q-flash update utility in our inspected firmware, which could have been used for such a purpose as well.
Furthermore, the leaks reveal that the UEFI infection capability (which is referred to by Hacking Team as ‘persistent installation’) was tested on ASUS X550C laptops. These make use of UEFI firmware by AMI which is very similar to the one we inspected. For this reason we can assume that Hacking Team’s method of patching the firmware would work in our case as well.
Excerpt from a Hacking Team manual for deployment of infected UEFI firmware, also known as ‘persistent installation’
Of course, we cannot exclude other possibilities whereby rogue firmware was pushed remotely, perhaps through a compromised update mechanism. Such a scenario would typically require exploiting vulnerabilities in the BIOS update authentication process. While this could be the case, we don’t have any evidence to support it.
The Bigger Picture: Enter MosaicRegressor Framework
While Hacking Team’s original bootkit was used to write one of the company’s backdoors to disk, known as ‘Soldier’, ‘Scout’ or ‘Elite’, the UEFI implant we investigated deployed a new piece of malware that we haven’t seen thus far. We decided to look for similar samples that share strings and implementation traits with the dropped binary. Consequently, the samples that we found suggested that the dropped malware was only one variant derived from a wider framework that we named MosaicRegressor.
MosaicRegressor is a multi-stage and modular framework aimed at espionage and data gathering. It consists of downloaders, and occasionally multiple intermediate loaders, that are intended to fetch and execute payload on victim machines. The fact that the framework consists of multiple modules assists the attackers to conceal the wider framework from analysis, and deploy components to target machines only on demand. Indeed, we were able to obtain only a handful of payload components during our investigation.
The downloader components of MosaicRegressor are composed of common business logic, whereby the implants contact a C&C, download further DLLs from it and then load and invoke specific export functions from them. The execution of the downloaded modules usually results in output that can be in turn issued back to the C&C.
Having said that, the various downloaders we observed made use of different communication mechanisms when contacting their C&Cs:
CURL library (HTTP/HTTPS)
BITS transfer interface
WinHTTP API
POP3S/SMTPS/IMAPS, payloads transferred in e-mail messages
The last variant in the list is distinct for its use of e-mail boxes to host the requested payload. The payload intended to run by this implant can also generate an output upon invocation, which can be later forwarded to a ‘feedback’ mail address, where it will likely be collected by the attackers.
The mail boxes used for this purpose reside on the ‘mail.ru’ domain, and are accessed using credentials that are hard-coded in the malware’s binary. To fetch the requested file from the target inbox, MailReg enters an infinite loop where it tries to connect to the “pop.mail.ru” server every 20 minutes, and makes use of the first pair of credentials that allow a successful connection. The e-mails used for login (without their passwords) and corresponding feedback mail are specified in the table below:
Login mail Feedback mail
thtgoolnc@mail.ru thgetmmun@mail.ru
thbububugyhb85@mail.ru thyhujubnmtt67@mail.ru
The downloaders can also be split in two distinct types, the “plain” one just fetching the payload, and the “extended” version that also collects system information:

Structure of the log file written by BitsRegEx, strings marked in red are the original fields that appear in that file
We were able to obtain only one variant of the subsequent stage, that installs in the autorun registry values and acts as another loader for the components that are supposed to be fetched by the initial downloader. These components are also just intermediate loaders for the next stage DLLs. Ultimately, there is no concrete business logic in the persistent components, as it is provided by the C&C server in a form of DLL files, most of them temporary.
We have observed one such library, “load.rem“, that is a basic document stealer, fetching files from the “Recent Documents” directory and archiving them with a password, likely as a preliminary step before exfiltrating the result to the C&C by another component.
The following figure describes the full flow and connection between the components that we know about. The colored elements are the components that we obtained and gray ones are the ones we didn’t:
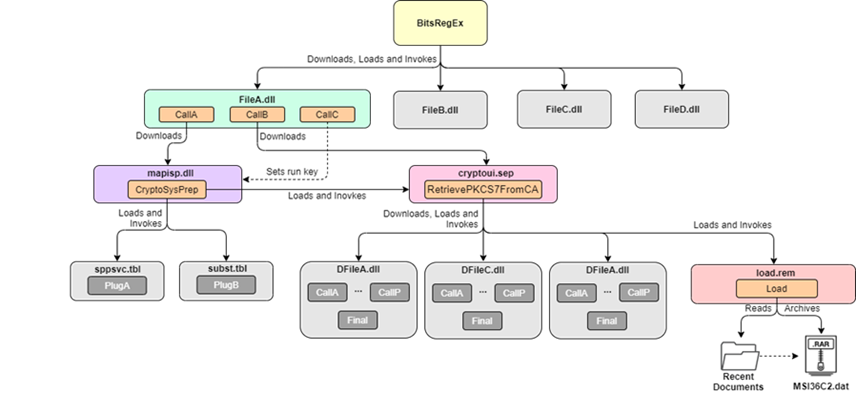
Flow from BitsRegEx to execution of intermediate loaders and final payload
Who were the Targets?
According to our telemetry, there were several dozen victims who received components from the MosaicRegressor framework between 2017 and 2019. These victims included diplomatic entities and NGOs in Africa, Asia and Europe. Only two of them were also infected with the UEFI bootkit in 2019, predating the deployment of the BitsReg component.
Based on the affiliation of the discovered victims, we could determine that all had some connection to the DPRK, be it non-profit activity related to the country or actual presence within it. This common theme can be reinforced through one of the infection vectors used to deliver the malware to some of the victims, which was SFX archives pretending to be documents discussing various subjects related to North Korea. Those were bundled with both an actual document and MosaicRegressor variants, having both executed when the archive is opened. Examples for the lure documents can be seen below.

Examples of lure documents bundled to malicious SFX archives sent to MosaicRegressor victims, discussing DPRK related topics
Who is behind the attack?
When analyzing MosaicRegressor’s variants, we noticed several interesting artefacts that provided us with clues on the identity of the actor behind the framework. As far as we can tell, the attacks were conducted by a Chinese-speaking actor, who may have previously used the Winnti backdoor. We found the following evidence to support this:
We spotted many strings used in the system information log generated by the BitsRegEx variant that contain the character sequence ‘0xA3, 0xBA’. This is an invalid sequence for a UTF8 string and the LATIN1 encoding translates these symbols to a pound sign followed by a “masculine ordinal indicator” (“£º”). An attempt to iterate over all available iconv symbol tables, trying to convert the sequence to UTF-8, produces possible candidates that give a more meaningful interpretation. Given the context of the string preceding the symbol and line feed symbols following it, the best match is the “FULL-WIDTH COLON” Unicode character translated from either the Chinese or Korean code pages (i.e. CP936 and CP949).
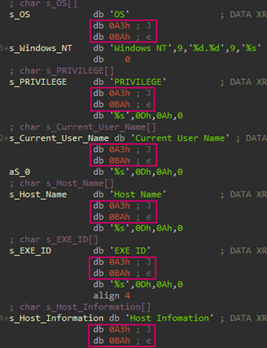
Figure: The BitsRegEx system information log making use of the character sequence 0xA3, 0xBA, likely used to represent a full-width colon, according to code pages CP936 and CP949.
Another artefact that we found was a file resource found in CurlReg samples that contained a language identifier set to 2052 (“zh-CN”)
Chinese language artefact in the resource section of a CurlReg sample
We detected an OLE2 object taken out of a document armed with the CVE-2018-0802 vulnerability, which was produced by the so-called ‘Royal Road’ / ‘8.t’ document builder and used to drop a CurlReg variant. To the best of our knowledge, this builder is commonly used by Chinese-speaking threat actors.
Excerpt from the OLE2 object found within a ‘Royal Road’ weaponized document, delivering the CurlReg variant
A C&C address (103.82.52[.]18) which was found in one of MosaicRegressor’s variants (MD5:3B58E122D9E17121416B146DAAB4DB9D) was observed in use by the ‘Winnti umbrella and linked groups’, according to a publicly available report. Since this is the only link between our findings and any of the groups using the Winnti backdoor, we estimate with low confidence that it is indeed responsible for the attacks.
Conclusion
The attacks described in this blog post demonstrate the length an actor can go in order to gain the highest level of persistence on a victim machine. It is highly uncommon to see compromised UEFI firmware in the wild, usually due to the low visibility into attacks on firmware, the advanced measures required to deploy it on a target’s SPI flash chip, and the high stakes of burning sensitive toolset or assets when doing so.
With this in mind, we see that UEFI continues to be a point of interest to APT actors, while at large being overlooked by security vendors. The combination of our technology and understanding of the current and past campaigns leveraging infected firmware, helps us monitor and report on future attacks against such targets.
The full details of this research, as well as future updates on the underlying threat actor, are available to customers of the APT reporting service through our Threat Intelligence Portal.
IoCs
The followings IoC list is not complete. If you want more information about the APT discussed here, a full IoC list and YARA rules are available to customers of Kaspersky Threat Intelligence Reports. Contact: intelreports@kaspersky.com
UEFI Modules
F5B320F7E87CC6F9D02E28350BB87DE6 (SmmInterfaceBase)
B53880397D331C6FE3493A9EF81CD76E (SmmAccessSub)
91A473D3711C28C3C563284DFAFE926B (SmmReset)
DD8D3718197A10097CD72A94ED223238 (Ntfs)
RAR SFX droppers
0EFB785C75C3030C438698C77F6E960E
12B5FED367DB92475B071B6D622E44CD
3B3BC0A2772641D2FC2E7CBC6DDA33EC
3B58E122D9E17121416B146DAAB4DB9D
70DEF87D180616406E010051ED773749
7908B9935479081A6E0F681CCEF2FDD9
AE66ED2276336668E793B167B6950040
B23E1FE87AE049F46180091D643C0201
CFB072D1B50425FF162F02846ED263F9
Decoy documents
0D386EBBA1CCF1758A19FB0B25451AFE
233B300A58D5236C355AFD373DABC48B
449BE89F939F5F909734C0E74A0B9751
67CF741E627986E97293A8F38DE492A7
6E949601EBDD5D50707C0AF7D3F3C7A5
92F6C00DA977110200B5A3359F5E1462
A69205984849744C39CFB421D8E97B1F
D197648A3FB0D8FF6318DB922552E49E
BitsReg
B53880397D331C6FE3493A9EF81CD76E
AFC09DEB7B205EADAE4268F954444984 (64-bit)
BitsRegEx
DC14EE862DDA3BCC0D2445FDCB3EE5AE
88750B4A3C5E80FD82CF0DD534903FC0
C63D3C25ABD49EE131004E6401AF856C
D273CD2B96E78DEF437D9C1E37155E00
72C514C0B96E3A31F6F1A85D8F28403C
CurlReg
9E182D30B070BB14A8922CFF4837B94D
61B4E0B1F14D93D7B176981964388291
3D2835C35BA789BD86620F98CBFBF08B
CurlRegEx
328AD6468F6EDB80B3ABF97AC39A0721
7B213A6CE7AB30A62E84D81D455B4DEA
MailReg
E2F4914E38BB632E975CFF14C39D8DCD
WinHTTP Based Downloaders
08ECD8068617C86D7E3A3E810B106DCE
1732357D3A0081A87D56EE1AE8B4D205
74DB88B890054259D2F16FF22C79144D
7C3C4C4E7273C10DBBAB628F6B2336D8
BitsReg Payload (FileA.z)
89527F932188BD73572E2974F4344D46
2nd Stage Loaders
36B51D2C0D8F48A7DC834F4B9E477238 (mapisp.dll)
1C5377A54CBAA1B86279F63EE226B1DF (cryptui.sep)
9F13636D5861066835ED5A79819AAC28 (cryptui.sep)
3rd Stage Payload
FA0A874926453E452E3B6CED045D2206 (load.rem)
File paths
%APPDATA%\Microsoft\Credentials\MSI36C2.dat
%APPDATA%\Microsoft\Internet Explorer\%Computername%.dat
%APPDATA%\Microsoft\Internet Explorer\FileA.dll
%APPDATA%\Microsoft\Internet Explorer\FileB.dll
%APPDATA%\Microsoft\Internet Explorer\FileC.dll
%APPDATA%\Microsoft\Internet Explorer\FileD.dll
%APPDATA%\Microsoft\Internet Explorer\FileOutA.dat
%APPDATA%\Microsoft\Network\DFileA.dll
%APPDATA%\Microsoft\Network\DFileC.dll
%APPDATA%\Microsoft\Network\DFileD.dll
%APPDATA%\Microsoft\Network\subst.sep
%APPDATA%\Microsoft\WebA.dll
%APPDATA%\Microsoft\WebB.dll
%APPDATA%\Microsoft\WebC.dll
%APPDATA%\Microsoft\Windows\LnkClass.dat
%APPDATA%\Microsoft\Windows\SendTo\cryptui.sep
%APPDATA%\Microsoft\Windows\SendTo\load.dll %APPDATA%\Microsoft\Windows\load.rem
%APPDATA%\Microsoft\Windows\mapisp.dll
%APPDATA%\Microsoft\exitUI.rs
%APPDATA%\Microsoft\sppsvc.tbl
%APPDATA%\Microsoft\subst.tbl
%APPDATA%\newplgs.dll
%APPDATA%\rfvtgb.dll
%APPDATA%\sdfcvb.dll
%APPDATA%\msreg.dll
%APPDATA\Microsoft\dfsadu.dll
%COMMON_APPDATA%\Microsoft\Windows\user.rem
%TEMP%\BeFileA.dll
%TEMP%\BeFileC.dll
%TEMP%\RepairA.dll
%TEMP%\RepairB.dll
%TEMP%\RepairC.dll
%TEMP%\RepairD.dll
%TEMP%\wrtreg_32.dll
%TEMP%\wrtreg_64.dll
%appdata%\dwhost.exe
%appdata%\msreg.exe
%appdata%\return.exe
%appdata%\winword.exe
Domains and IPs
103.195.150[.]106
103.229.1[.]26
103.243.24[.]171
103.243.26[.]211
103.30.40[.]116
103.30.40[.]39
103.39.109[.]239
103.39.109[.]252
103.39.110[.]193
103.56.115[.]69
103.82.52[.]18
117.18.4[.]6
144.48.241[.]167
144.48.241[.]32
150.129.81[.]21
43.252.228[.]179
43.252.228[.]252
43.252.228[.]75
43.252.228[.]84
43.252.230[.]180
menjitghyukl.myfirewall[.]org
Additional Suspected C&Cs
43.252.230[.]173
185.216.117[.]91
103.215.82[.]161
103.96.72[.]148
122.10.82[.]30
Mutexes
FindFirstFile Message Bi
set instance state
foregrounduu state
single UI
Office Module
process attach Module
XDSpy APT remained undetected since at least 2011
2.10.20 APT Securityaffairs
Researchers from ESET uncovered the activity of a new APT group, tracked as XDSpy, that has been active since at least 2011.
XDSpy is the name used by ESET researchers to track a nation-state actor that has been active since at least 2011. The APT group, recently discovered by ESET, targeted government and private companies in Belarus, Moldova, Russia, Serbia, and Ukraine, including militaries and Ministries of Foreign Affairs.
The activity of the cyber espionage group was first documented by ESET experts Matthieu Faou and Francis Labelle in a talk at the Virus Bulletin 2020 security conference.
“Early in 2020, ESET researchers discovered a previously undisclosed cyber espionage operation targeting several governments in Eastern Europe, the Balkans and Russia. Unusually, our research shows that this campaign has been active since at least 2011 with next to no changes in TTPs.” reads the abstract from the talk. “It is very uncommon to find a cyber espionage operation without any public reporting after almost 10 years of activity.”
Experts believe that the hacker group could have targeted many other countries and a good portion of its operations has yet to be discovered.
In February 2020 Belarussian CERT published a security advisory about an ongoing spear-phishing campaign, linked by ESET to XDSpy, targeting several Belarussian ministries and agencies. At the time, the threat actors were interested into collecting documents from government staff such as diplomats or military personnel, private companies and academic institutions. The nature of the targets suggests that the threat actor is also responsible for economic espionage operations.
Since the publishing of the advisory, the group’s operations have now gone dark.
The tools in the arsenal of the XDSpy APT are quite basic, although efficient, their primary tool is a downloader dubbed named XDDown.
The malware samples analyzed by the researchers are slightly obfuscated using string obfuscation and dynamic Windows API library loading. The malware supports multiple features, including the monitoring of removable drives, taking screenshots, exfiltrating documents, and collecting nearby Wi-Fi access point identifiers.
Experts also noticed that hackers also used NirSoft utilities to recover passwords from web browsers and email clients.
Experts observed the threat actor exploiting a remote code issue in Internet Explorer tracked as CVE-2020-0968 that was addressed by Microsoft with the release of Patch Tuesday security updates for April 2020.
“At the time it was exploited by XDSpy, no proof-of-concept and very little information about this specific vulnerability was available online,” explained ESET. “We think that XDSpy either bought this exploit from a broker or developed a 1-day exploit themselves by looking at previous exploits for inspiration.”
ESET described XDDown as a “downloader” used to infect a victim and then download secondary modules that would perform various specialized tasks.
The XDDown malware has a modular structure, some of the plugins analyzed by ESET are:
XDRecon: Gathers basic information about the victim machine (the computer name, the current username and the Volume Serial Number of the main drive).
XDList: Crawls the C: drive for interesting files (.accdb, .doc, .docm, .docx, .mdb, .xls, .xlm, .xlsx, .xlsm, .odt, .ost, .ppt, .pptm, .ppsm, .pptx, .sldm, .pst, .msg, .pdf, .eml, .wab) and exfiltrates the paths of these files. It can also take screenshots.
XDMonitor: Similar to XDList. It also monitors removable drives to exfiltrate the files matching an interesting extension.
XDUpload: Exfiltrates a hardcoded list of files from the filesystem to the C&C server, as shown in Figure 5. The paths were sent to the C&C servers by XDList and XDMonitor.
XDLoc: Gathers nearby SSIDs (such as Wi-Fi access points), probably in order to geo-locate the victim machines.
XDPass: Grabs saved passwords from various applications such as web browsers and email programs.
XDSpy
The analysis of the spear-phishing campaigns linked to the APT group revealed that the hackers used email subject lines with lures related to lost and found objects and the COVID-19 pandemic. These messages came with malicious attachments such as Powerpoint, JavaScript, ZIP, or shortcut (LNK) files.
ESET researchers noted that many XDSpy malware samples were compiled in the UTC+2 or UTC+3 time zone from Monday to Friday, a circumstance that suggests the involvement of professionals.
“XDSpy is a cyberespionage group mostly undetected for more than nine years while being very busy over the past few months.” concludes the report. “The group’s technical proficiency tends to vary a bit. It has used the same basic malware architecture for nine years, but it also recently exploited a vulnerability patched by the vendor but for which no public proof-of-concept exists, a so-called 1-day exploit.”
The report includes additional technical details, such as Indicators of Compromise (IoCs).
Twitter Removes Iran-Linked Accounts Aimed at Disrupting U.S. Presidential Debate
1.10.20 APT Social Securityweek
Twitter on Wednesday announced that it removed 130 accounts originating from Iran that were aimed at disrupting the first 2020 U.S. presidential debate.
The accounts, the social media platform reveals, were removed after the Federal Bureau of Investigation (FBI) alerted it on the suspicious activity.
“Based on intel provided by the @FBI, last night we removed approximately 130 accounts that appeared to originate in Iran. They were attempting to disrupt the public conversation during the first 2020 US Presidential Debate,” Twitter announced.
The social platform also explains that it was able to quickly identify the accounts and remove them. The accounts had low engagement and weren’t able to impact the public conversation.
The company says that, once its investigation into these accounts has been completed, it will publish all of the necessary details on its Transparency portal.
“As standard, the accounts and their content will be published in full once our investigation is complete. We’re providing this notice to keep people updated in real time about our actions. We wish to thank the @FBI for their assistance,” Twitter said.
The removal of these accounts comes roughly one month after Microsoft warned of attempts from state-sponsored threat actors, including Iranian ones, to disrupt the 2020 U.S. presidential elections. Iran responded swiftly, claiming the allegations were absurd.
Last week, Facebook announced that it shut down a network of fake accounts out of China that were aiming at the US presidential race.
In June, Twitter announced the removal of a total of 30,000 state-linked accounts originating from China, Turkey, and Russia that engaged in manipulation.
Over the past couple of weeks, the FBI and CISA issued several alerts to warn of disinformation campaigns aimed hurting the population’s trust in the election results and the security of voting systems.
North Korea APT group targeted tens of UN Security Council officials
1.10.20 APT Securityaffairs
North Korea-linked APT group targeted UN Security Council officials over the past year, states a report from the United Nations organ.
A North-Korea-linked cyber espionage group has launched spear-phishing attacks aimed at compromising tens of officials from the United Nations Security Council.
The campaign targeted at least 28 UN officials, including at least 11 individuals representing six countries of the UN Security Council.
The campaign was disclosed in a UN report published at the end of August, the attacks took place this year and were spotted by an unnamed UN member state that reported it to the UN Security Council.
“According to information from another Member State, at least 28 individuals, including at least 11 officials from six members of the Security Council, became the targets of a spear-phishing campaign in 2020 which appeared to have been conducted by a Kimsuky advanced persistent threat group.” reads the report. “According to the information, these Democratic People’s Republic of Korea cyberactors launched a “security alert” – themed spear-phishing campaign in mid-March against Gmail accounts of the targeted individuals by placing malicious links in the email, utilizing a link to bypass spam blockers of the potential victims.”
The UN Security Council attributes the attack to the KimSuky APT group.
The Kimsuky APT group has been analyzed by several security teams, it was first spotted by Kaspersky researcher in 2013, recently its activity was detailed by ESTsecurity and by the malware researchers from Cybaze ZLab.
The campaign took place between March and April, threat actors attempted to compromise the Gmail accounts of UN officials by carrying out spear-phishing messages.
The spear-phishing messages were posing as UN security alerts or requests for interviews from journalists, a UN member also reported that the attacks were also launched through WhatsApp.
The emails were designed to look like UN security alerts or requests for interviews from reporters, both designed to convince officials to access phishing pages or run malware files on their systems.
The country which reported the Kimsuky attacks to the UN Security Council also said that similar campaigns were also carried out against members of its own government, with some of the attacks taking place via WhatsApp, and not just email.
The UN Security Council also published another report in March that detailed two other Kimsuky campaigns against its officials.
The first campaign targeted 38 email addresses belonging to members of the Security Council, while the second campaign targeted officials from China, France, Belgium, Peru, and South Africa in August.
“Cyberattacks against the Panel continued. An expert received a phishing email with a fake security alert from the United Nations, and multiple experts received an email in which the attacker spoofed as a member of the editing staff of a journal soliciting an article from experts. The Panel notes the similar cyberattacks against the expert community on the Democratic People’s Republic of Korea in 2020.” concludes the report. “The Panel reiterates its view that cyberattacks, both past and ongoing, against such United Nations bodies as the Committee and the Panel, which are mandated to monitor the implementation of United Nations sanctions, amount to sanctions evasion, considering the persistent and highly disruptive nature of the attacks.”
Chinese APT Group Targets Media, Finance, and Electronics Sectors
30.9.20 APT Securityweek
Cybersecurity researchers on Tuesday uncovered a new espionage campaign targeting media, construction, engineering, electronics, and finance sectors in Japan, Taiwan, the U.S., and China.
Linking the attacks to Palmerworm (aka BlackTech) — likely a China-based advanced persistent threat (APT) — Symantec's Threat Hunter Team said the first wave of activity associated with this campaign began last year in August 2019, although their ultimate motivations still remain unclear.
"While we cannot see what Palmerworm is exfiltrating from these victims, the group is considered an espionage group and its likely motivation is considered to be stealing information from targeted companies," the cybersecurity firm said.
Among the multiple victims infected by Palmerworm, the media, electronics, and finance companies were all based in Taiwan, while an engineering company in Japan and a construction firm in China were also targeted.
In addition to using custom malware to compromise organizations, the group is said to have remained active on the Taiwanese media company's network for a year, with signs of activity observed as recently as August 2020, potentially implying China's continued interest in Taiwan.

This is not the first time the BlackTech gang has gone after business in East Asia. A 2017 analysis by Trend Micro found the group to have orchestrated three campaigns — PLEAD, Shrouded Crossbow, and Waterbear — with an intent to steal confidential documents and the target's intellectual property.
Stating that some of the identified malware samples matched with PLEAD, the researchers said they identified four previously undocumented backdoors (Backdoor.Consock, Backdoor.Waship, Backdoor.Dalwit, and Backdoor.Nomri), indicating "they may be newly developed tools, or the evolution of older Palmerworm tools."
The brand new custom malware toolset alone would have made the attribution difficult if it were not for the use of dual-use tools (such as Putty, PSExec, SNScan, and WinRAR) and stolen code-signing certificates to digitally sign its malicious payloads and thwart detection, a tactic that it has been found to employ before.
Another detail that's noticeably not too clear is the infection vector itself, the method Palmerworm has used to gain initial access to the victim networks. The group, however, has leveraged spear-phishing emails in the past to deliver and install their backdoor, either in the form of an attachment or through links to cloud storage services.
"APT groups continue to be highly active in 2020, with their use of dual-use tools and living-off-the-land tactics making their activity ever harder to detect, and underlining the need for customers to have a comprehensive security solution in place that can detect this kind of activity," Symantec said.
China-Linked 'BlackTech' Hackers Start Targeting U.S.
29.9.20 APT Securityweek
The China-linked BlackTech cyber-spies have adopted new malicious tools in recent attacks, and they have started targeting the United States, Symantec security researchers revealed on Tuesday.
Also referred to as Palmerworm, the hacking group is believed to have been active since at least 2013. The campaign analyzed by Symantec ran from August 2019 until as recently as August 2020, and it targeted organizations in construction, electronics, engineering, media, and finance in Japan, Taiwan, the U.S., and China. The threat actor was previously known to target East Asia.
The recent attacks revealed the use of dual-use tools and a new suite of custom malware, including backdoors such as Consock, Waship, Dalwit, and Nomri. Previously, the threat actor was observed employing the backdoors known as Kivars and Plead (which Symantec refers to as Palmerworm).
“We have not observed the group using these malware families in previous attacks – they may be newly developed tools, or the evolution of older Palmerworm tools,” the security firm notes in a new report.
Despite the use of undocumented malware, other artefacts observed in these attacks, including the use of previously employed infrastructure, suggest that the BlackTech threat actor is behind them.
In addition to the new backdoors, the hackers leveraged a custom loader and a network reconnaissance tool, along with dual-use tools, such as Putty, PSExec, SNScan, and WinRAR.
Furthermore, the threat actor signed the payloads in these attacks with stolen code-signing certificates, a tactic it was observed employing before. While Symantec hasn’t identified the initial attack vector, the actor is known for the use of spear-phishing to access victim networks.
A total of five victims were identified in these attacks, including organizations in media, electronics, and finance based in Taiwan, an engineering company in Japan, and a construction company in China. Some U.S.-based companies were targeted as well, but they haven’t been identified.
The targeting of Taiwanese companies isn’t something new for BlackTech, which previously infiltrated government agencies in the country. Taipei said at the time that the group is operating out of China.
Although the first activity associated with the recent campaign started in August 2019, the attackers were able to maintain presence in the compromised networks for a long time: activity associated with the attack was observed on compromised machines within the media company’s network in August 2020.
“Palmerworm also maintained a presence on the networks of a construction and a finance company for several months. However, it spent only a couple of days on the network of a Japanese engineering company in September 2019, and a couple of weeks on the network of an electronics company in March 2020,” Symantec explains.
The security researchers are unsure what type of data the attackers might have exfiltrated from the compromised organizations, but believe that cyber-espionage might have been the purpose of the attacks.
Microsoft took down 18 Azure AD apps used by Chinese Gadolinium APT
28.9.20 APT Securityaffairs
Microsoft removed 18 Azure Active Directory applications from its Azure portal that were created by a Chinese-linked APT group Gadolinium.
Microsoft announced this week to have removed 18 Azure Active Directory applications from its Azure portal that were created by a China-linked cyber espionage group tracked as APT group Gadolinium (aka APT40, or Leviathan).
The 18 Azure AD apps were taken down by the IT giant in April, Microsoft also published a report that includes technical details about the Gadolinium’s operation.
“Microsoft took proactive steps to prevent attackers from using our cloud infrastructure to execute their attacks and suspended 18 Azure Active Directory applications that we determined to be part of their malicious command & control infrastructure.” states Microsoft’s report.
GADOLINIUM abuses Microsoft cloud services as command and control infrastructure, the experts uncovered a spear-phishing campaign using messages with weaponized attachments.
The threat actor uses a multi-stage infection process and heavily leverages PowerShell payloads. In mid-April 2020, the GADOLINIUM actors launched a COVID-19 themed campaign, upon opening the messages, the target’s system would be infected with PowerShell-based malware payloads.
Once infected computers, the threat actors used the PowerShell malware to install one of the 18 Azure AD apps.
The hackers used an Azure Active Directory application to configure the victim endpoint with the permissions needed to exfiltrate data a Microsoft OneDrive storage under their control.
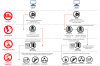
“The use of this PowerShell Empire module is particularly challenging for traditional SOC monitoring to identify. The attacker uses an Azure Active Directory application to configure a victim endpoint with the permissions needed to exfiltrate data to the attacker’s own Microsoft OneDrive storage.” continues the analysis. “From an endpoint or network monitoring perspective the activity initially appears to be related to trusted applications using trusted cloud service APIs and, in this scenario,, no OAuth permissions consent prompts occur. “
Microsoft also took down a GitHub account that was used by the Gadolinium group as part of a 2018 campaign.
Microsoft’s report also includes Indicators of Compromise (IoCs) for the Gadolinium campaign.
U.S. Imposes Sanctions on 'APT39' Iranian Hackers
18.9.20 APT Securityweek
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) on Thursday announced sanctions against Iran-based cyber threat actor APT39, associated individuals, and a front company named Rana Intelligence Computing Company.
Active since at least 2014, APT39 is also known as Chafer, Cadelspy, ITG07, and Remexi, and some of its operations also align with the activity of the OilRig group.
Last year, a series of documents supposedly leaked from the Iranian Ministry of Intelligence and Security (MOIS) revealed information on the activities of Rana, which was tracking individuals both in Iran and outside the country, and on its members.
Rana, the Department of the Treasury says, has been operating for years on behalf of the government of Iran to target Iranian dissidents, journalists, and global firms from the travel sector. Both APT39 and Rana are owned and controlled by Iran’s Ministry of Intelligence and Security.
“Rana advances Iranian national security objectives and the strategic goals of [MOIS] by conducting computer intrusions and malware campaigns against perceived adversaries, including foreign governments and other individuals the MOIS considers a threat,” the Treasury Department says.
In addition to Rana, the U.S. sanctioned 45 individuals “for having materially assisted, sponsored, or providing financial, material, or technological support for, or goods or services to or in support of the MOIS.”
These individuals, the U.S. says, were employed at Rana as managers, programmers, and experts in hacking, offering support for attacks on businesses, institutions, air carriers, and other targets of interest.
Hidden behind Rana, the MOIS helped the Iranian government run abuse and surveillance operations against its own citizen. APT39, operating through Rana, leveraged malware for the hacking and monitoring of Iranian citizens, including dissidents, environmentalists, former government employees, journalists, refugees, university students and faculty, and the employees of international organizations.
APT39 is also said to have targeted Iranian private sector companies and academic institutions, and at least 15 countries in the MENA region. Overall, Rana is said to have targeted hundreds of individuals and organizations in over 30 different countries in Asia, Africa, Europe, and North America, including 15 U.S. companies, primarily from the travel sector.
In an advisory issued on Thursday, the FBI provides information on eight malware families that Iran’s MOIS has been using through Rana to run cyber-intrusion operations, including VBS and AutoIt scripts, the BITS 1.0 and BITS 2.0 malware variants, a malicious program posing as Firefox, a Python-based tool, Android malware, and the Depot.dat malware. The FBI also uploaded samples of these threats to VirusTotal.
This week, the United States announced three separate sets of charges against Iranian threat actors, including three individuals involved in the targeting of satellite and aerospace companies; two hackers who have been targeting aerospace, think tanks, government, non-governmental and non-profit organizations, among others; and two individuals who defaced websites in retaliation to the killing of Qasem Soleimani.
More Details Emerge on Operations, Members of Chinese Group APT41
18.9.20 APT Securityweek
More details have emerged on the operations of the Chinese state-sponsored threat actor known as APT41 and the links between its members, following the indictment of several alleged members of the group earlier this week.
Also tracked as Barium, Wicked Panda, Winnti, and Wicked Spider, the cyber-espionage group is said to have hacked over 100 organizations worldwide, including software and video gaming companies, governments, universities, think tanks, non-profit entities, and pro-democracy politicians and activists in Hong Kong.
APT41’s activity spans over more than a decade, with victims located in the United States, Australia, Brazil, Chile, Hong Kong, India, Indonesia, Japan, Malaysia, Pakistan, Singapore, South Korea, Taiwan, Thailand, and Vietnam.
This week, the United States made public two separate indictments returned by a federal grand jury in August 2019 and August 2020, charging Zhang Haoran and Tan Dailin, and Jiang Lizhi, Qian Chuan, and Fu Qiang, respectively.
In a report published on Thursday, cybersecurity firm Symantec revealed that it has tracked the activity of these hackers as belonging to two different groups, called Grayfly and Blackfly.
Grayfly activity, which has been observed in recent years, is associated with the indictment against Jiang, Qian, and Fu, who hold senior positions in a Chinese company named Chengdu 404, Symantec reports. The hackers launched numerous attacks on food, financial, government, healthcare, hospitality, manufacturing, and telecoms organizations in Asia, Europe, and North America.
Malware used by the threat actor includes Barlaiy/POISONPLUG and Crosswalk/ProxIP (Backdoor.Motnug), with many victims compromised through public facing web servers. Backdoor.Motnug, Symantec explains, offers remote access to the breached environment and also provides proxy access to hard-to-reach segments of the network.
Blackfly, Symantec says, has been active since at least 2010 and is mainly known for the targeting of video gaming companies. However, the hackers also attacked fintech, food, hospitality, materials manufacturing, media and advertising, pharmaceutical, semiconductor, and telecoms industries.
Malware used by the threat actor includes PlugX/Fast (Backdoor.Korplug), Winnti/Pasteboy (Backdoor.Winnti), and Shadowpad (Backdoor.Shadowpad). One specific artifact observed in the group’s attacks was the use of the names of security vendors when naming their malicious binaries.
Attacks associated with the Blackfly tools and tactics, Symantec reveals, can be attributed to two Malaysian nationals, Wong Ong Hua and Ling Yang Ching, who were arrested this month and who were also charged by U.S. authorities, for conspiring with the Chinese nationals. The two are also said to have worked with other hackers in campaigns against computer game companies.
The link between Grayfly and Blackfly, the security firm says, is drawn by two other Chinese nationals that the U.S. indicted as part of the APT41 group, namely Zhang Haoran and Tan Dailin. They allegedly worked at Chengdu 404 for a while, but also collaborated with the Blackfly actors for extra cash.
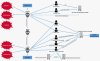
“Grayfly and Blackfly have been prolific attackers in recent years and, while it remains to be seen what impact the charges will have on their operations, the publicity surrounding the indictments will certainly be unwelcome among attackers who wish to maintain a low profile,” Symantec concludes.
In a report shared with SecurityWeek on Thursday, researchers with Secureworks note that APT41, which the security firm tracks as BRONZE ATLAS, is likely reusing old infrastructure in its operations. Two of the analyzed domains, they said, were associated with the group’s activity back in 2013, but continue to be in use.
APT41 Operatives Indicted as Sophisticated Hacking Activity Continues
18.9.20 APT Threatpost
Five alleged members of the China-linked advanced threat group and two associates have been indicted by a Federal grand jury, on dozens of charges.
UPDATE
Five alleged members of the APT41 threat group have been indicted by a federal grand jury, in two separate actions that were unsealed this week.
Meanwhile, the Department of Treasury also imposed sanctions on individuals and organizations associated with Iran-linked APT39.
APT41 (a.k.a. Barium, Winnti, Wicked Panda or Wicked Spider) is known for nation-state-backed cyber-espionage activity as well as financial cybercrime. The Department of Justice alleges that the group “facilitated the theft of source code, software code-signing certificates, customer-account data and valuable business information,” which in turn “facilitated other criminal schemes, including ransomware and cryptojacking.”
The five suspected perpetrators, all of whom are residents and nationals of the People’s Republic of China (PRC), are charged with hacking more than 100 victim companies in the United States and abroad, including software-development companies, computer-hardware manufacturers, telecom providers, social-media companies, video-game companies, nonprofit organizations, universities, think tanks and foreign governments, as well as pro-democracy politicians and activists in Hong Kong.
According to John Hultquist, senior director of analysis at Mandiant Threat Intelligence, APT41 has been the most prolific Chinese threat actor tracked by the firm in the last year.
“This is a unique actor, who carries out global cyber-espionage while simultaneously pursuing a criminal venture,” he said via email. “Their activity traces back to 2012, when individual members of APT41 conducted primarily financially motivated operations focused on the video-game industry, before expanding into traditional espionage, most likely directed by the state. APT41’s ability to successfully blend their criminal and espionage operations is remarkable.”
Lately, APT41 has been involved in several high-profile supply chain incidents according to Mandiant, which often blended its criminal interest in video games with the espionage activity.
“For instance, they compromised video-game distributors to proliferate malware, which could then be used for follow-up operations,” he said. “They have also been connected to well-known incidents involving Netsarang and ASUS updates.”
In terms of targeted sectors, APT41 has been focused on telecom, travel and hospitality – likely because it has been looking to “identify, monitor and track individuals of interest, operations which could have serious, even physical consequences for some victims,” he added. “They have also participated in efforts to monitor Hong Kong during recent democracy protests.”
Intellectual property theft is on the menu too, Hultquist said, when it comes to medical institutions and medical technology, likely related to the COVID-19 pandemic.
“The scope and sophistication of the crimes in these unsealed indictments is unprecedented. The alleged criminal scheme used actors in China and Malaysia to illegally hack, intrude and steal information from victims worldwide,” said Michael Sherwin, acting U.S. attorney for the District of Columbia, in a DoJ statement this week. “As set forth in the charging documents, some of these criminal actors believed their association with the PRC provided them free license to hack and steal across the globe. This scheme also contained a new and troubling cybercriminal component – the targeting and utilization of gaming platforms to both defraud video game companies and launder illicit proceeds.”
Specific Charges
In terms of the specifics, an August 2019 indictment charged Zhang Haoran and Tan Dailin with 25 counts of conspiracy, wire fraud, aggravated identity theft, money laundering and violations of the Computer Fraud and Abuse Act (CFAA). The second indictment, from August of this year, charged Jiang Lizhi, Qian Chuan and Fu Qiang with nine counts of racketeering conspiracy, conspiracy to violate the CFAA, substantive violations of the CFAA, access device fraud, identity theft, aggravated identity theft and money laundering.
The second August 2020 indictment charged Wong Ong Hua and Ling Yang Ching. They were charged with 23 counts of racketeering, conspiracy, identity theft, aggravated identity theft, access device fraud, money laundering, violations of the CFAA and falsely registering domain names. The indictment alleged that Wong and Ling worked with various hackers, including Zhang and Tan, to profit from the hackers’ criminal computer intrusions at video game companies.
All of them are still at large.
The same federal grand jury also returned a third indictment charging two APT41 associates: Both are Malaysian businessmen, who are accused of targeting the video-game industry and aiding APT41 in its efforts to monetize its activities. The duo was arrested on Monday in by Malaysian authorities in Sitiawan; they are now awaiting extradition.
The charges against all of the defendants carry maximum sentences that range between two and 20 years in prison.
Infrastructure Sinkholing
In tandem with the indictments, the U.S. District Court for the District of Columbia this month also paved the way for the seizure hundreds of accounts, servers, domain names and command-and-control (C2) servers used by the defendants to conduct their computer intrusion offenses. The FBI executed a series of warrants in coordination with the private sector, including Microsoft, to deny APT41 access to its hacking infrastructure, various accounts for services that it abuses, and C2 domains.
“The Department of Justice has used every tool available to disrupt the illegal computer intrusions and cyberattacks by these Chinese citizens,” said Deputy Attorney General Jeffrey Rosen. “Regrettably, the Chinese communist party has chosen a different path of making China safe for cybercriminals so long as they attack computers outside China and steal intellectual property helpful to China.”
APT39 Sanctions
As for APT39, the Treasury Department said on Thursday that masked behind its front company, Rana Intelligence Computing Co., the government of Iran used the advanced persistent threat group to carry out a years-long malware campaign that targeted Iranian dissidents, journalists and international companies in the travel sector.
Victims of APT39’s activity have been “subjected to arrest and physical and psychological intimidation” by Iran’s Ministry of Intelligence, according to a press release.
The department named 45 individuals in addition to Rana and APT39, and prohibits U.S. citizens or businesses to interact with them for any financial or commercial purpose.
“We believe the actor, who we have tracked for over five years, is enabling Iranian surveillance,” Mandiant’s Hultquist said. “The actor has focused heavily on the telecommunications and travel industries as part of an effort to collect customer data and personal information on targets of interest. These efforts could threaten the customers of victim organizations who may then be physically endangered by the Iranian security services.”
Lessons in Defense
APT41 and APT39 are just two of many advanced threat groups that target businesses and civil society on behalf of foreign governments – something that organizations need to be aware of, researchers told Threatpost.
“As highlighted in the recent report from the Atlantic Council, the techniques alleged to have been used by the defendants (supply-chain attacks and use of publicly known exploits in commercial and open-source software),continue to be popular and powerful attack vectors for threat actors, both large and small,” Zach Jones, senior director of detection research at WhiteHat Security, told Threatpost. “This case, one of hundreds known publicly over the past two decades, highlights the continued need for increased focus on securing the software that our digital lives depend on.”
To protect themselves, organizations first and foremost should patch vulnerabilities, in both commercial and proprietary software that may have been built on open code bases, he added.
Meanwhile, Hank Schless, senior manager of security solutions at Lookout, told Threatpost the indictments indicate how malicious actors are diversifying their tactics to achieve a broader range of outcomes – something that organizations should take note of.
“In particular, breaching gaming companies to steal in-game items and currency for real-world profit rather than stealing corporate data means security teams need to be sure their efforts are well-distributed across both internal and external systems,” he said – especially as more people are working from home. “The attackers were able to gain access to internal networks and likely moved laterally across the infrastructure to identify the most profitable items.”
Unauthorized access to the infrastructure often starts with a phishing attack, he warned.
“Threat actors will target particular employees and phish their credentials in order to get access to particular parts of the infrastructure,” he said. “These days, phishing attacks primarily start outside of the traditional email channels. The primary channels are now SMS, social media platforms, third-party chat platforms, direct messages in gaming apps, and others that are primarily accessed on mobile devices.”
The onslaught of sophisticated, high-end cyber-activity is unlikely to wane, even with high-profile indictments like this one, Mandiant’s Hultquist concluded.
“Intelligence services leverage criminals such as APT41 for their own ends because they are an expedient, cost-effective and deniable capability,” he said. “APT41’s criminal operations appear to predate the work they do on behalf of the state and they may have been co-opted by a security service who would have significant leverage over them. In situations such as this, a bargain can be reached between the security service and the operators wherein the operators enjoy protection in return for offering high-end talent to the service. Furthermore, the service enjoys a measure in deniability when the operators are identified. Arguably, that is the case right now.”
FBI adds 5 Chinese APT41 hackers to its Cyber's Most Wanted List
17.9.20 APT Thehackernews

The United States government today announced charges against 5 alleged members of a Chinese state-sponsored hacking group and 2 Malaysian hackers that are responsible for hacking than 100 companies throughout the world.
Named as APT41 and also known as 'Barium,' 'Winnti, 'Wicked Panda,' and 'Wicked Spider,' the cyber-espionage group has been operating since at least 2012 and is not just involved in strategic intelligence collection from valuable targets in many sectors, but also behind financially motivated attacks against online gaming industry.
According to a press release published by the U.S. Justice Department, two of the five Chinese hackers—Zhang Haoran (张浩然) and Tan Dailin (谭戴林)—were charged back in August 2019, and the other three of them—Jiang Lizhi (蒋立志), Qian Chuan (钱川) and Fu Qiang (付强)—and two Malaysian co-conspirators were in separate indictments in August 2020.
The later indicted three Chinese hackers are associated with a network security company Chengdu 404 Network Technology, operated as a front by the People's Republic of China.
"FU has been working closely with JIANG since at least 2008, and worked with JIANG at multiple internet and video game related companies. FU has been working with QIAN and JIANG together since at least 2013. Before joining CHENGDU 404, FU described himself as a skilled programmer and developer," the court documents say.
As uncovered previously in multiple reports, the APT41 group specializes in software supply-chain attacks, where hackers steal proprietary "source code, software code signing certificates, customer account data, and valuable business information," and distribute digitally signed malicious versions of the software to infect systems at targeted organizations.
According to the court documents, in some cases where the targeted systems didn't have any valuable information, defendants also used ransomware and crypto-jacking malware to monetize their efforts.
The targeted industries include "software development companies, computer hardware manufacturers, telecommunications providers, social media companies, video game companies, non-profit organizations, universities, think tanks, and foreign governments, as well as pro-democracy politicians and activists in Hong Kong."
"The defendants also compromised foreign government computer networks in India and Vietnam, and targeted, but did not compromise, government computer networks in the United Kingdom," the press release says.
The 2 Malaysian hackers—Wong Ong Hua and Ling Yang Ching—were arrested by Malaysian authorities in Sitiawan on September 14, 2020, and are being extradited to the United States. The FBI confirmed that all 5 Chinese nationals remain at large.
"In addition to arresting warrants for all of the charged defendants, in September 2020, the U.S. District Court for the District of Columbia issued seizure warrants that resulted in the recent seizure of hundreds of accounts, servers, domain names, and command-and-control (C2) 'dead drop' web pages used by the defendants to conduct their computer intrusion offenses," the DoJ said.
"The actions by Microsoft [other than Google, Facebook, and Verizon Media] were a significant part of the overall effort to deny the defendants continued access to hacking infrastructure, tools, accounts, and command and control domain names."
The targeted companies were located in the United States and worldwide, including in Australia, Brazil, Chile, Hong Kong, India, Indonesia, Japan, Malaysia, Pakistan, Singapore, South Korea, Taiwan, Thailand, and Vietnam.
Zhang and Tan have been charged with 25 counts of computer fraud and money laundering, which carry a maximum sentence of 20 years in prison.
Jiang, Qian, and Fu are also facing similar charges with nine counts that carry a maximum sentence of 20 years in prison.
The indictment against Wong and Ling charges the defendants with 23 counts of similar charges, but since they are also involved in false registration of domain names, it would increase the maximum sentence of imprisonment for money laundering to 27 years.
APT28 Mounts Rapid, Large-Scale Theft of Office 365 Logins
12.9.20 APT Threatpost
The Russia-linked threat group is harvesting credentials for Microsoft’s cloud offering, and targeting mainly election-related organizations.
The Russia-linked threat group known as APT28 has changed up its tactics to include Office 365 password-cracking and credential-harvesting.
Microsoft researchers have tied APT28 (a.k.a. Strontium, Sofacy or Fancy Bear) to this newly uncovered pattern of O365 activity, which began in April and is ongoing. The attacks have been aimed mainly at U.S. and U.K. organizations directly involved in political elections.
The APT often works to obtain valid credentials in order to mount espionage campaigns or move laterally through networks – in fact, Microsoft telemetry shows that the group launched credential-harvesting attacks against tens of thousands of accounts at more than 200 organizations between last September and June. Between August 18 and September 3, the group (unsuccessfully) targeted 6,912 O365 accounts belonging to 28 organizations.
Threatpost Webinar Promo Bug Bounty
Click to Register
“Not all the targeted organizations were election-related,” the firm explained, in a blog posted on Friday. “However, we felt it important to highlight a potential emerging threat to the 2020 U.S. Presidential Election and future electoral contests in the U.K.”
The activity dovetails with other recent Microsoft findings that, just months before the U.S. presidential election, hackers from Russia, China and Iran are ramping up phishing and malware attacks against campaign staffers. It should be noted that APT28 is widely seen as responsible for election-meddling in 2016 and the attack on the Democratic National Committee (including by the U.S. government).
Raking in a Fall “Harvest”
While APT28 relied heavily upon spear-phishing in its credential harvesting efforts going into the 2016 Presidential Election, this time around it’s turning to brute-forcing and password-spraying.
“This shift in tactics, also made by several other nation-state actors, allows them to execute large-scale credential-harvesting operations in a more anonymized manner,” according to Microsoft. “The tooling Strontium is using routes its authentication attempts through a pool of approximately 1,100 IPs, the majority associated with the Tor anonymizing service.”
This pool of infrastructure — the “tooling” — is quite fluid and dynamic, according to the research, with an average of approximately 20 IPs added and removed from it per day. The attacks utilized a daily average of 1,294 IPs associated with 536 netblocks and 273 ASNs; and, organizations typically see more than 300 authentication attempts per hour per targeted account over the course of several hours or days.
“Strontium’s tooling alternates its authentication attempts amongst this pool of IPs approximately once per second,” Microsoft researchers said. “Considering the breadth and speed of this technique, it seems likely that Strontium has adapted its tooling to use an anonymizer service to obfuscate its activity, evade tracking and avoid attribution.”
APT28 has also been observed using password-spraying – a slight twist on the high-volume brute-forcing efforts described above.
“The tooling attempts username/password combinations in a ‘low-‘n-slow’ manner,” explained Microsoft researchers. “Organizations targeted by the tooling running in this mode typically see approximately four authentication attempts per hour per targeted account over the course of several days or weeks, with nearly every attempt originating from a different IP address.”

Activity overview. Source: Microsoft
Overall, organizations targeted by these attacks saw widespread authentication attempts throughout their footprints, with an average of 20 percent of total accounts suffering an attack.
“In some instances…the tooling may have discovered these accounts simply by attempting authentications against a large number of possible account names until it found ones that were valid,” according to the computing giant.
APT28 — believed to be tied to Russian military intelligence — has attacked more than 200 organizations this year, including political campaigns, advocacy groups, parties and political consultants, Microsoft noted. These include think-tanks such as The German Marshall Fund of the United States, The European People’s Party, and various U.S.-based consultants serving Republicans and Democrats. Organizations and individuals can protect themselves by applying multifactor authentication (MFA) and actively monitoring for failed authentications for the cloud service.
“There are some very simple steps businesses and targeted individuals can take to significantly improve the security of their accounts and make these types of attacks much more difficult,” Microsoft noted.
Chinese, Iranian, and Russian APT groups target 2020 US election
11.9.20 APT Securityaffairs
Microsoft reveals that state-sponsored hackers had tried to breach email accounts belonging to people involved in the US election.
Microsoft announced to have detected a new wave of attacks carried out by Chinese, Iranian, and Russian state-sponsored hackers against the US election. Threat actors had tried to compromise email accounts belonging to people associated with the Biden and Trump election campaigns.
The company attributed the attacks against the APT groups tracked as Strontium (Russia), Zirconium (China), and Phosphorus (Iran).
Microsoft added that the “majority of these attacks” were detected and blocked.
“In recent weeks, Microsoft has detected cyberattacks targeting people and organizations involved in the upcoming presidential election, including unsuccessful attacks on people associated with both the Trump and Biden campaigns.” reads the post published by Tom Burt – Corporate Vice President, Customer Security & Trust at Microsoft.
The post published by Microsoft confirms the information shared this summer by the U.S. National Counterintelligence and Security Center.
In August, the Director of the U.S. National Counterintelligence and Security Center (NCSC) William Evanina shared information on ongoing operations aimed at influencing the 2020 US election.
“Many foreign actors have a preference for who wins the election, which they express through a range of overt and private statements; covert influence efforts are rarer. We are primarily concerned about the ongoing and potential activity by China, Russia, and Iran” reads the press release published by the Office of the Director of the National Intelligence.
Evanina linked the efforts to Russia, China, and Iran, he explained, for example, that Russian actors are supporting President Trump’s candidacy with a coordinated effort on both Russian television and media.
According to Microsoft, Strontium APT has targeted more than 200 organizations including political campaigns, advocacy groups, parties and political consultants. The list of targets includes:
U.S.-based consultants serving Republicans and Democrats;
Think tanks such as The German Marshall Fund of the United States and advocacy organizations;
National and state party organizations in the U.S.; and
The European People’s Party and political parties in the UK.
In recent months, the group carried out brute force attacks and password spray, instead of spear-phishing, likely to automate their operations.
“Strontium also disguised these credential harvesting attacks in new ways, running them through more than 1,000 constantly rotating IP addresses, many associated with the Tor anonymizing service. Strontium even evolved its infrastructure over time, adding and removing about 20 IPs per day to further mask its activity.” states the post.
Zirconium hackers were involved in attacks against high-profile individuals associated with the US election. The threat actors targeted people associated with the Joe Biden for President campaign and prominent leaders in the international affairs community.
Microsoft detected thousands of attacks attributed to this group between March 2020 and September 2020, in this period the Chinese hackers gained access to almost 150 accounts. The attacks aimed at:
People closely associated with US presidential campaigns and candidates.
Prominent individuals in the international affairs community, academics in international affairs.
Phosphorus targeted the personal accounts of people associated with the Donald J. Trump for President campaign.
The attacks of the group are part of a hacking campaign that started in 2019. In October, Microsoft’s Threat Intelligence Center (MSTIC) revealed that an Iran-linked APT group tracked as Phosphorus (aka APT35, Charming Kitten, Newscaster, and Ajax Security Team) attempted to access to email accounts belonging to current and former US government officials, journalists, Iranians living abroad, and individuals involved in a 2020 US presidential campaign.
Now Microsoft confirms that the Iran-linked hackers targeted the Trump campaign and shared details on new activity related to the group.
“Between May and June 2020, Phosphorus unsuccessfully attempted to log into the accounts of administration officials and Donald J. Trump for President campaign staff,” Burt says.
In March 2019, Microsoft announced that it had taken control of 99 domains used by an Iran-linked APT group tracked by the company as Phosphorus.
“We disclose attacks like these because we believe it’s important the world knows about threats to democratic processes. It is critical that everyone involved in democratic processes around the world, both directly or indirectly, be aware of these threats and take steps to protect themselves in both their personal and professional capacities.” concludes the post.”We report on nation-state activity to our customers and more broadly when material to the public, regardless of the actor’s nation-state affiliation. We are taking extra steps to protect customers involved in elections, government and policymaking. We’ll continue to disclose additional significant activity in our efforts to defend democracy.”
Evilnum Cyberspies Update Arsenal in Recent Attacks
8.9.20 APT Securityweek
The threat group tracked as Evilnum was observed using updated tactics and tools in recent attacks, Cybereason’s Nocturnus research team reported last week.
Initially detailed in 2018, Evilnum appears to have been active for nearly a decade, offering ‘mercenary’ hack-for-hire services, a recent report from Kaspersky revealed.
Focused on espionage, Evilnum recently switched from delivering ZIP archives containing multiple LNK files (via spear-phishing) to including a single LNK in the archive, which masquerades as a PDF, Cybereason reveals. Once executed, the shortcut writes to disk a JavaScript that replaces the LNK with the actual PDF.
Furthermore, the hackers have adopted a scheduled task to ensure persistence, moving away from the previously used Run registry key. The scheduled task retrieves and executes the next stage payload, a modified version of “Java Web Start Launcher.”
This payload, however, was designed as a downloader for the next stage, another downloader that instead fetches the final payload and runs it directly in memory, with a scheduled task named “Adobe Update Task.”
Dubbed PyVil RAT and written in Python, the delivered malware was designed to log keystrokes, run cmd commands, take screenshots, download additional Python scripts to expand functionality, drop and upload executables, open an SSH shell, and collect system information (running antivirus program, connected USB devices, Chrome version).
The malware communicates with its command and control (C&C) server via HTTP POST requests that are RC4-encrypted.
Cybereason’s security researchers also observed PyVil RAT receiving from the C&C a custom version of the LaZagne Project, which was employed by the group before. The script was meant to dump passwords and collect cookie information.
The researchers also noticed a change in the attackers’ infrastructure: while in previous attacks the hackers only used IP addresses in C&C communications, over the past several weeks they switched to employing domains for the same operations, and appear to be changing domains at a rapid pace.
Evilnum has remained constant in the targeting of European fintech companies over the past couple of years, but evolved tactics, techniques and procedures (TTPs) to ensure the success of its attacks, and the recent changes are not surprising.
“In recent weeks we observed a significant change in the infection procedure of the group, moving away from the JavaScript backdoor capabilities, instead utilizing it as a first stage dropper for new tools down the line. During the infection stage, Evilnum utilized modified versions of legitimate executables in an attempt to stay stealthy and remain undetected by security tools. […] This innovation in tactics and tools is what allowed the group to stay under the radar, and we expect to see more in the future as the Evilnum group’s arsenal continues to grow,” the Nocturnus researchers conclude.
China-based APT Debuts Sepulcher Malware in Spear-Phishing Attacks
3.9.20 APT Threatpost
The RAT has been distributed in various campaigns over the past six months, targeting both European officials and Tibetan dissidents.
A China-based APT has been sending organizations spear-phishing emails that distribute a never-before-seen intelligence-collecting RAT dubbed Sepulcher.
Researchers discovered the new malware being distributed over the past six months through two separate campaigns. The first, in March, targeted European diplomatic and legislative bodies, non-profit policy research organizations and global organizations dealing with economic affairs. The second, in July, targeted Tibetan dissidents. They tied the campaigns to APT group TA413, which researchers say has been associated with Chinese state interests and is known for targeting the Tibetan community.
“Based on the use of publicly known sender addresses associated with Tibetan dissident targeting and the delivery of Sepulcher malware payloads, [we] have attributed both campaigns to the APT actor TA413,” said Proofpoint researchers in a Wednesday analysis. “The usage of publicly known Tibetan-themed sender accounts to deliver Sepulcher malware demonstrates a short-term realignment of TA413’s targets of interest.”
Two Campaigns
In March, researchers observed a phishing campaign that impersonated the World Health Organization’s guidance on COVID-19 critical preparedness. The emails contained a weaponized RTF attachment that impersonated the WHO’s “Critical preparedness, readiness and response actions for COVID-19, Interim guidance” document. The guidance was initially published on March 7, while the weaponized attachment was delivered by threat actors on March 16, researchers said.
When a target clicks the weaponized RTF attachment (named “Covdi.rtf”), it exploits a Microsoft Equation Editor flaw in order to install an embedded malicious RTF object, in the form of a Windows meta-file (WMF), to a file directory (%\AppData\Local\Temp\wd4sx.wmf). The WMF file’s execution then results in the delivery and installation of the Sepulcher malware.
Sepulcher malware The second phishing campaign, starting at the end of July, targeted Tibetan dissidents with the same strain of Sepulcher malware.
The emails, which purported to come from the “Women’s Association Tibetan,” included a malicious PowerPoint attachment (titled “TIBETANS BEING HIT BY DEADLY VIRUS THAT CARRIES A GUN AND SPEAKS CHINESE.ppsx”). The email was targeting dissidents, with the attachment, once opened, referencing “Tibet, Activism and Information.”
When the PowerPoint attachment is executed, it calls out to the IP 118.99.13[.]4 to download a Sepulcher malware payload named “file.dll.”
“The attachment title, decoy content, impersonated sender, and “Dalai Lama Trust in India”-themed C2 affirms this campaign’s focus on individuals associated with the Tibetan leadership in exile,” said researchers.

Sepulcher Malware
Sepulcher is a basic RAT payload that has the abilities to carry out reconnaissance functionality within the infected host, including obtaining information about the drives, file information, directory statistics, directory paths, directory content, running processes and services.
Sepulcher malware Additionally, it is capable of more active functionalities, like deleting directories and files, creating directories, moving file source to destination, spawning a shell to execute commands, terminating a process, restarting a service, changing a service start type and deleting a service.
Researchers said that the Sepulcher malware “is far from groundbreaking,” but noted its combination with timely social-engineering lures around the pandemic.
They also pointed out that the campaign is reminiscent of a July 2019 campaign that was used to distribute ExileRAT; the TA413 APT group has also previously been documented in association with this RAT. ExileRAT is a simple RAT platform capable of getting system data (computer name, username, listing drives, network adapter, process name), getting/pushing files and executing/terminating processes.
Shifting Focus: COVID-19
Chinese APT TA413 is previously known for targeting Tibetan dissidents, as it did in its July campaign, so the March attack shows the skyrocketing trend of Chinese APTs branching out and adopting COVID-19 lures in espionage campaigns during the first half of 2020.
Researchers said, following an initial interest from Chinese APTs in targeting intelligence on the response of western global economies during the pandemic, this campaign shows a “return to normalcy” in more recent months.
“The usage of publicly known Tibetan-themed sender accounts to deliver Sepulcher malware demonstrates a short-term realignment of TA413’s targets of interest,” said researchers. “While best known for their campaigns against the Tibetan diaspora, this APT group associated with the Chinese state interest prioritized intelligence collection around Western economies reeling from COVID-19 in March 2020, before resuming more conventional targeting later this year.”
Pioneer Kitten APT Sells Corporate Network Access
2.9.20 APT Threatpost
Some underground forum users said they’re monetizing the information through the State Department’s anti-influence-campaign effort.
Personal information for several million American voters has turned up on a Russian underground cybercrime forum, according to reports – and users are purportedly looking to monetize it using a recently launched State Department program meant to prevent election-meddling.
The personal information includes names, dates of birth, gender, physical addresses and email addresses, and election-specific data – such as when an individual registered to vote, voter registration numbers and polling stations – according to Kommersant, a Moscow-based newspaper.
The outlet reported Tuesday that several databases of voter data (including one encompassing 7.6 million voters in Michigan, and others covering between 2 million and 6 million voters each for Arkansas, Connecticut, Florida and North Carolina) turned up in an unnamed marketplace in late 2019. Now, that information is being offered for free in discussion forums by someone going by the handle Gorka9, according to Kommersant. The publication added that the hacker said the data was still valid as of this past March.
Security firm Infowatch confirmed that the databases seem authentic. A spokesperson for Infowatch said that the information could be used to mount influence campaigns bent on swaying U.S. voters towards one candidate or another — but more likely, it could be used to mount convincing phishing efforts.
“As is usual in cases like these, victims (registered voters) will need to be on the lookout for bad actors attempting to use the information gleaned from these databases to obtain even more information about their targets,” Chris Hauk, consumer privacy champion at Pixel Privacy, told Threatpost via email. “It is sad to believe that in this day and age that simply registering to exercise your right to vote can make you the target of hackers.”
Meanwhile, forum users told Kommersant that they have also been able to monetize the data through the U.S. State Department’s $10 million anti-influence program. The Rewards for Justice (RFJ) program, which is administered by the Diplomatic Security Service, is offering millions in rewards for “information leading to the identification or location of any person who works with or for a foreign government for the purpose of interfering with U.S. elections through certain illegal cyber-activities.”
One person told Kommersant that he was paid $4,000 through the program for alerting the Feds about a leaked Connecticut voter database – a claim that has not been confirmed. The State Department did not immediately respond to a request for comment.
As for how the data was obtained, one hacker told the outlet that most of the theft is carried out using server vulnerabilities that can be exploited via SQL injection, which is a method for inserting malicious code into a vulnerable, targeted database. Security researchers said that the claim is entirely plausible.
“New vulnerabilities are reported every hour and database systems are especially prone to attack due to their highly configurable and powerful interactive features,” Mark Kedgley, CTO at New Net Technologies (NNT), told Threatpost. “SQL injection is still a difficult vulnerability to test for as automated tests usually lack the knowledge of the application’s setup and operation. Encryption of data is always an unpopular route due to the heavy impact on system resources and performance. Ideally, security needs to be built in as the application is developed and then a hardened configuration applied to the database system, derived from either the CIS Benchmark or DISA STIG.”
In some cases, hacking may not even be required in order to garner the information, according to Paul Bischoff, privacy advocate with Comparitech. “It’s remarkably easy to get one’s hands on voter databases in most states,” Bischoff said via email. “Many of them are available to the public, including Michigan. Even though there are rules about how the data can be used, rules can be broken. Those who legitimately request receive voter data are responsible for securing it, and not everyone has the same standards of security. I wouldn’t be surprised if we see more voter databases in the hands of foreign threat actors before the 2020 general election.”
As a backdrop, election-meddling continues to be a security concern as the U.S. presidential election looms on the horizon. While direct hacking activity remains a concern, experts say that the bigger issue is influence campaigns bent on spreading divisiveness and disinformation — mainly through online social-media bots and troll farms. In fact, a recent Black Hat attendee survey, more than 70 percent said influence campaigns will have the greatest impact on the elections.
The Iran-based APT has infiltrated multiple VPNs using open-source tools and known exploits.
An APT group known as Pioneer Kitten, linked to Iran, has been spotted selling corporate-network credentials on hacker forums. The credentials would let other cybercriminal groups and APTs perform cyberespionage and other nefarious cyber-activity.
Pioneer Kitten is a hacker group that specializes in infiltrating corporate networks using open-source tools to compromise remote external services. Researchers observed an actor associated with the group advertising access to compromised networks on an underground forum in July, according to a blog post Monday from Alex Orleans, a senior intelligence analyst at CrowdStrike Intelligence.
Pioneer Kitten’s work is related to other groups either sponsored or run by the Iranian government, which were previously seen hacking VPNs and planting backdoors in companies around the world.
Indeed, the credential sales on hacker forums seem to suggest “a potential attempt at revenue stream diversification” to complement “its targeted intrusions in support of the Iranian government,” Orleans wrote. However, Pioneer Kitten, which has been around since 2017, does not appear to be directly operated by the Iranian government but is rather sympathetic to the regime and likely a private contractor, Orleans noted.
Pioneer Kitten’s chief mode of operations is its reliance on SSH tunneling, using open-source tools such as Ngrok and a custom tool called SSHMinion, he wrote. The group uses these tools to communicate “with implants and hands-on-keyboard activity via Remote Desktop Protocol (RDP)” to exploit vulnerabilities in VPNs and network appliances to do its dirty work, Orleans explained.
CrowdStrike observed the group leveraging several critical exploits in particular — CVE-2019-11510, CVE-2019-19781, and most recently, CVE-2020-5902. All three are exploits affect VPNs and networking equipment, including Pulse Secure “Connect” enterprise VPNs, Citrix servers and network gateways, and F5 Networks BIG-IP load balancers, respectively.
Pioneer Kitten’s targets are North American and Israeli organizations in various sectors that represent some type of intelligence interest to the Iranian government, according to CrowdStrike. Target sectors run the gamut and include technology, government, defense, healthcare, aviation, media, academic, engineering, consulting and professional services, chemical, manufacturing, financial services, insurance and retail.
While not as well-known or widespread in its activity as other nation-state threats such as China and Russia, Iran has emerged in recent years as a formidable cyber-enemy, amassing a number of APTs to mount attacks on its political adversaries.
Of these, Charming Kitten—which also goes by the names APT35, Ajax or Phosphorus—appears to be the most active and dangerous, while others bearing similar names seem to be spin-offs or support groups. Iran overall appears to be ramping up its cyber-activity lately. CrowdStrike’s report actually comes on the heels of news that Charming Kitten also has resurfaced recently. A new campaign is using LinkedIn and WhatsApp to convince targets — including Israeli university scholars and U.S. government employees — to click on a malicious link that can steal credentials.
Operating since 2014, Charming Kitten is known for politically motivated and socially engineered attacks, and often uses phishing as its attack of choice. Targets of the APT, which uses clever social engineering to snare victims, have been email accounts tied to the Trump 2020 re-election campaign and public figures and human-rights activists, among others.
Iran-linked APT group Pioneer Kitten sells access to hacked networks
1.9.20 APT Securityaffairs
Iran-linked APT group Pioneer Kitten is now trying to monetize its efforts by selling access to some of the networks it has hacked to other hackers.
Iran-linked APT group Pioneer Kitten, also known as Fox Kitten or Parisite, is now trying to monetize its efforts by selling access to some of the networks it has hacked to other hackers.
The Iranian hacker group has been attacking corporate VPNs over the past months, they have been hacking VPN servers to plant backdoors in companies around the world targeting Pulse Secure, Fortinet, Palo Alto Networks, and Citrix VPNs.
According to a report published by Crowdstrike, the group is now trying to sell access to some to compromised companies on a cybercrime forum.
“PIONEER KITTEN tradecraft is characterized by a pronounced reliance on exploits of remote external services on internet-facing assets to achieve initial access to victims, as well as an almost total reliance on open-source tooling during operations.” reads the report published by Crowdstrike.
“The adversary is particularly interested in exploits related to VPNs and network appliances, including CVE-2019-11510, CVE-2019-19781, and most recently CVE-2020-5902; reliance on exploits such as these lends to an opportunistic operational model.”
PIONEER KITTEN operations leverage on SSH tunneling, through open-source tools such as Ngrok, they also used the custom tool SSHMinion to communication with malware deployed in the target networks.
In the last couple of years, the group attempted to breach corporate networks by exploiting multiple vulnerabilities in VPNs and networking equipment, including:
CVE-2018-13379 – Fortinet VPN servers running FortiOS
CVE-2019-1579 – Palo Alto Networks “Global Protect” VPN servers
CVE-2019-11510 – Pulse Secure “Connect” enterprise VPNs
CVE-2019-19781 – Citrix “ADC” servers and Citrix network gateways
CVE-2020-5902 – F5 Networks BIG-IP load balancers
In late July 2020, Crowdstrike spotted a threat actor associated with PIONEER KITTEN that was attempting to sell access to compromised networks on an underground forum. According to the experts, the threat actors are merely trying to monetize their efforts selling information that have no intelligence value for the Iranian Government.
“In late July 2020, an actor assessed to be associated with PIONEER KITTEN was identified as advertising to sell access to compromised networks on an underground forum.” continues the report. “That activity is suggestive of a potential attempt at revenue stream diversification on the part of PIONEER KITTEN, alongside its targeted intrusions in support of the Iranian government.”
PIONEER KITTEN hackers to date have focused their attacks against entities in North American and Israeli, while targeted sectors include technology, government, defense, healthcare, aviation, media, academic, engineering, consulting and professional services, chemical, manufacturing, financial services, insurance, and retail.
North Korea-linked APT group BeagleBoyz targets banks
30.8.20 APT Securityaffairs
North Korea-linked APT group BeagleBoyz intensified its operations since February, US CISA, Department of the Treasury, FBI, and USCYBERCOM warn.
According to a joint advisory issued by the Cybersecurity and Infrastructure Security Agency (CISA), the Department of the Treasury, the Federal Bureau of Investigation (FBI), and U.S. Cyber Command (USCYBERCOM) North Korea-linked APT group BeagleBoyz was very active since February 2020 targeting banks across the world.
BeagleBoyz (aka Lazarus, APT38, Bluenoroff, and Stardust Chollima) represents a subset of the HIDDEN COBRA threat actors.
The BeagleBoyz APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFT attacks in 2016, the Sony Pictures hack, the FASTCash ATM attacks against banks, and attacks on multiple cryptocurrency exchanges.
“North Korea’s intelligence apparatus controls a hacking team dedicated to robbing banks through remote internet access. To differentiate methods from other North Korean malicious cyber activity, the U.S. Government refers to this team as BeagleBoyz, who represent a subset of HIDDEN COBRA activity.” reads the alert. “The BeagleBoyz’s bank robberies pose severe operational risk for individual firms beyond reputational harm and financial loss from theft and recovery costs. The BeagleBoyz have attempted to steal nearly $2 billion since at least 2015, according to public estimates. Equally concerning, these malicious actors have manipulated and, at times, rendered inoperable, critical computer systems at banks and other financial institutions.”
Government experts reported that the BeagleBoyz often leave destructive anti-forensic tools onto computer networks of victim institutions. In 2018, the group employed a wiper in the attack against the Banco de Chile bank in Chile in 2018.
According to the joint alert, BeagleBoyz performed fraudulent ATM cash outs from banks of 30 countries in a single incident. The conspirators have withdrawn cash from ATM machines operated by various unwitting banks in multiple countries worldwide, including in the United States.
In the arsenal of the group, there is custom malware specifically developed the targeting of switch applications on Windows servers, they also developed malware to target interbank payment processors.
Once compromised a target network, the threat actors selectively exploit systems within the environment and leverage multiple techniques to elevate privileges, execute malicious code, achieve persistence, and evade detection.
“Once inside a financial institution’s network, the BeagleBoyz appear to seek two specific systems—the SWIFT terminal and the server hosting the institution’s payment switch application. As they progress through a network, they learn about the systems they have accessed in order to map the network and gain access to the two goal systems.” continues the alert.
The BeagleBoyz employed multiple malware in their operations, including the CROWDEDFLOUNDER, HOPLIGHT, and COPPERHEDGE RATs, the ECCENTRICBANDWAGON keylogger, the VIVACIOUSGIFT and ELECTRICFISH proxy tunneling tools.
The alert includes technical details on the threats and recommendations to prevent BeagleBoyz attacks.
Iran-linked Charming Kitten APT contacts targets via WhatsApp, LinkedIn
29.8.20 APT Securityaffairs
The Iran-linked Charming Kitten APT group leveraged on WhatsApp and LinkedIn to carry out phishing attacks, researchers warn.
Clearsky security researchers revealed that Iran-linked Charming Kitten APT group is using WhatsApp and LinkedIn to conduct spear-phishing attacks.
Iran-linked Charming Kitten group, (aka APT35, Phosphorus, Newscaster, and Ajax Security Team) made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media.
Microsoft has been tracking the threat actors at least since 2013, but experts believe that the cyberespionage group has been active since at least 2011 targeting journalists and activists in the Middle East, as well as organizations in the United States, and entities in the U.K., Israel, Iraq, and Saudi Arabia.
Now, security researchers from Clearsky reported details about a new phishing campaign in which the threat actors impersonate journalists from ‘DeutscheWelle’ and the ‘Jewish Journal.’ The state-sponsored hackers are employing both email and WhatsApp to trick victims into clicking on a malicious link.
Experts also observed the attackers using fake LinkedIn profiles to establish a first contact with the victims.
In the past few months, the Charming Kitten cyberespionage group has expanded its target’s list, adding the Baha’i community2 , high-ranking American civil servants and officials (including ambassadors and former employees of the US State Department), and COVID-19 related organizations (such as Gilead3 and WHO4 ). In a recent attack, the hackers targeted Israeli scholars and US government employees.
The hackers used a personalized link for each victim and also attempted to send them a ZIP file.
Below the timeline of the attackers that involved fake profiles from “Deutsche Welle” and “Jewish Journal” in the past three years:

“Clearsky alerted “Deutsche Welle” about the impersonation and the watering hole in their website. A “Deutsche Welle” representative confirmed that the reporter which Charming Kitten impersonated, did not send any emails to the victim nor any other academic researcher in Israel in the past few weeks.” reads the analysis published by the experts. “Note that part of “Deutsche Welle”reporters are originally from Iran – a fact that helps Charming Kitten to hide the accent of their operators during a phone call. It should be noted that this attack vector is unique to Charming Kitten, but it has not the only attack vector that has been used in recent months by this threat actor.”
Experts pointed out that the attackers used a well-developed LinkedIn account in this campaign while they showed willingness to speak to the victim on the phone, over WhatsApp, using a legitimate German phone number.
“This TTP is uncommon and jeopardizes the fake identity of the attackers (unlike emails for example). However, if the attackers have successfully passed the phone call obstacle, they can gain more trust from the victim, compared to an email message.” continues the report.
The Charming Kitten attackers targeted Israeli researchers from Haifa and Tel Aviv Universities asking them to participate in an online webinar/meeting about Iran and other subjects of interest for the target (e.g. recent discourse between Iran and the US).
The Charming Kitten attackers implore the victim to respond repeatedly for ten days, and they are prepared to engage in a direct phone call with them to cajole the victim into “activating their account” with the site “Akademie DW”(used as their phishing page). D
The hackers sent messages to the targets repeatedly for ten days, asking them to availability for a direct phone call, and attempting to lure them into activating their account on the site “Akademie DW” (their phishing page).
“If the victim is not willing to share their personal phone number, the attacker will send him a message from the fake LinkedIn account. This message will contain a promise that the webinar is secured by Google, as they sent to the victim on the tenth day,” Clearsky concludes.
Transparent Tribe: Evolution analysis, part 2
26.8.20 APT Securelist
Background + Key findings
Transparent Tribe, also known as PROJECTM or MYTHIC LEOPARD, is a highly prolific group whose activities can be traced as far back as 2013. In the last four years, this APT group has never taken time off. They continue to hit their targets, which typically are Indian military and government personnel.
This is the second of two articles written to share the results of our recent investigations into Transparent Tribe. In the previous article, we described the various Crimson RAT components and provided an overview of impacted users. Here are some of the key insights that will be described in this part:
We found a new Android implant used by Transparent Tribe for spying on mobile devices. It was distributed in India disguised as a porn-related app and a fake national COVID-19 tracking app.
New evidence confirms a link between ObliqueRAT and Transparent Tribe.
Android implant
During our analysis, we found an interesting sample, which follows a variant of the previously described attack scheme. Specifically, the attack starts with a simple document, which is not malicious by itself, does not contain any macro and does not try to download other malicious components, but it uses social engineering tricks to lure the victim into downloading other documents from the following external URLs:
hxxp://sharingmymedia[.]com/files/Criteria-of-Army-Officers.doc
hxxp://sharingmymedia[.]com/files/7All-Selected-list.xls

15DA10765B7BECFCCA3325A91D90DB37 – Special Benefits.docx
The remote files are two Microsoft Office documents with an embedded malicious VBA, which behaves similarly to those described in the previous article and drops the Crimson “Thin Client”. The domain sharingmymedia[.]com was even more interesting: it was resolved with the IP 89.45.67[.]160 and was registered on 2020-01-10 using Namesilo and the following information:
Registrant Name: bluff hunnter
Registrant Organization:
Registrant Street: India Dehli
Registrant City: Dehli
Registrant State/Province: Delhi
Registrant Postal Code: 110001
Registrant Country: IN
Registrant Phone: +91.4214521212
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: hunterbluff007@gmail.com
The same information was used to register another domain, sharemydrives[.]com, which was registered seven days before, on 2020-01-03, using Namesilo. DNS resolution points to the same IP address: 89.45.67[.]160.
Using our Kaspersky Threat Intelligence Portal, we found the following related URL:

Information in Kaspersky Threat Intelligence Portal
The file is a modified version of MxVideoPlayer, a simple open-source video player for Android, downloadable from GitHub and used by Transparent Tribe to drop and execute their Android RAT.

Desi-porn.apk screenshot
The dropper tries to find a list of legitimate packages on the system:
imo.android.imoim
snapchat.android
viber.voip
facebook.lite
If the device was produced by Xiaomi, it also checks if the com.truecaller package is present.

The code used to check if legitimate packages are installed
The first application on the list that is not installed on the system will be selected as the target application. The malware embeds multiple APK files, which are stored in a directory named “assets”. The analyzed sample includes the following packages:
apk a20fc273a49c3b882845ac8d6cc5beac
apk 53cd72147b0ef6bf6e64d266bf3ccafe
apk bae69f2ce9f002a11238dcf29101c14f
apk b8006e986453a6f25fd94db6b7114ac2
apk 4556ccecbf24b2e3e07d3856f42c7072
apk 6c3308cd8a060327d841626a677a0549
The selected APK is copied to /.System/APK/. By default, the application tries to save the file to external storage, otherwise it saves it to the data directory.
Finally, the application tries to install the copied APK. The final malware is a modified version of the AhMyth Android RAT, open-source malware downloadable from GitHub, which is built by binding the malicious payload inside other legitimate applications.
The original AhMyth RAT includes support for the following commands:
Commands Additional fields Value Description
x0000ca extra camlist get a camera list
extra 1 get a photo from the camera with the id 1
extra 0 get a photo from the camera with the id 0
x0000fm extra
path
ls
%dirpath%
get a list of files in the directory specified in the “path” variable.
extra
path
dl
%filepath%
upload the specified file to the C2
x0000sm extra ls get a list of text messages
extra
to
sms
sendSMS
%number%
%message%
send a new text to another number
x0000cl get the call log
x0000cn get contacts
x0000mc sec %seconds% record audio from the microphone for the specified number of seconds and upload the resulting file to the C2.
x0000lm get the device location
Basically, it provides the following features:
camera manager (list devices and steal screenshots)
file manager (enumerate files and upload these to the C2)
SMS manager (get a list of text messages or send a text)
get the call log
get the contact list
microphone manager
location manager (track the device location)
The RAT that we analyzed is slightly different from the original. It includes new features added by the attackers to improve data exfiltration, whereas some of the core features, such as the ability to steal pictures from the camera, are missing.
The operators added the following commands:
x000upd – download a new APK from the URL specified in the “path” field.
x000adm – autodownloader: not implemented in the version we analyzed, but available in other samples.
Moreover, the creators of the RAT also improved its audio surveillance capabilities and included a command to delete text messages with specific contents.
Commands Additional fields Value Description
x000upd path %url% download a new APK from the URL specified in the “path” field
x000adm not implemented in the analyzed version. Other samples use this to start a class named “autodownloader”.
x0000mc extra
sec
au
%seconds%
record audio for x seconds and upload the resulting file to the C2. Duration is specified in the “sec” value.
extra mu stop recording and upload the resulting file to the C2
extra muS
start recording continuously. This generates MP3 files stored in the “/.System/Records/” directory.
x0000fm extra
path
ls
%dirpath%
get a list of files in the directory specified in the “path” variable
extra
path
dl
%filepath%
upload the specified file to hxxp://212.8.240[.]221:80/server/upload.php
sms extra ls get a list of text messages
extra
to
sms
sendSMS
%number%
%message%
Send a new text to another number.
extra
to
sms
deleteSMS
%message%
Delete a text that contains the string specified in the “sms” value. The “to” value is ignored.
x0000cl get the call log
x0000cn get contacts
x0000lm get the device location
The “autodownloader” is a method used for performing the following actions:
upload a contact list
upload a text message list
upload files stored in the following directories:
/.System/Records/
/Download/
/DCIM/Camera/
/Documents/
/WhatsApp/Media/WhatsApp Images/
/WhatsApp/Media/WhatsApp Documents/
The attacker uses the method to collect contacts and text messages automatically. In addition, the method collects the following: audio files created with the “x0000mc” command and stored in /.System/Records/, downloaded files, photos, images and documents shared via WhatsApp and other documents stored on the device.
Another interesting difference between the original AhMyth and the one modified by Transparent Tribe is the technique used for getting the C2 address. The original version stores the C2 server as a string directly embedded in the code, whereas the modified version uses a different approach. It embeds another URL encoded with Base64 and used for getting a configuration file, which contains the real C2 address.
In our sample, the URL was as follows:
hxxp://tryanotherhorse[.]com/config.txt
It provided the following content:
212.8.240.221:5987
http://www.tryanotherhorse.com
The first value is the real C2, which seems to be a server hosted in the Netherlands.
The modified version communicates via a different URL scheme, which includes more information:
Original URL scheme: http://%server%:%port?model=%val%&manf=%val%&release=%val%&id=%val%
Modified URL scheme http://%server%:%port?mac=%val%&battery=%val%&model=%val%&manf=%val%&release=%val%&id=%val%
Covid-19 tracking app
We found evidence of Transparent Tribe taking advantage of pandemic-tracking applications to distribute trojanized code. Specifically, we found an APK file imitating Aarogya Setu, a COVID-19 tracking mobile application developed by the National Informatics Centre under the Ministry of Electronics and Information Technology, Government of India. It allows users to connect to essential health services in India.
The discovered application tries to connect to the same malicious URL to get the C2 IP address:
hxxp://tryanotherhorse[.]com/config.txt
It uses the same URL scheme described earlier and it embeds the following APK packages:
apk CF71BA878434605A3506203829C63B9D
apk 627AA2F8A8FC2787B783E64C8C57B0ED
apk 62FAD3AC69DB0E8E541EFA2F479618CE
apk A912E5967261656457FD076986BB327C
apk 3EB36A9853C9C68524DBE8C44734EC35
apk 931435CB8A5B2542F8E5F29FD369E010
Interestingly enough, at the end of April, the Indian Army issued a warning to its personnel against Pakistani agencies’ nefarious designs to hack the phones of Indian military personnel through a malicious application similar to Aarogya Setu.
According to some Indian online news sites, these applications were found to be sent by Pakistani Intelligence Operatives to WhatsApp groups of Indian Army personnel. It also mentioned that these applications later deployed additional packages:
According to some Indian online news sites, these applications were found to be sent by Pakistani Intelligence Operatives to WhatsApp groups of Indian Army personnel. It also mentioned that these applications later deployed additional packages:
face.apk
imo.apk
normal.apk
trueC.apk
snap.apk
viber.apk
Based on public information, the application may have been distributed by sending a malicious link via WhatsApp, SMS, phishing email or social media.
ObliqueRAT connection
ObliqueRAT is another malicious program, described by Cisco Talos in an interesting article published in February. It was attributed to Transparent Tribe because some samples were distributed through malicious documents forged with macros that resembled those used for distributing Crimson RAT.
The report described two ObliqueRAT variants, one distributed via a malicious document as the infection vector and another one, named “Variant #0” and distributed with a dropper.
4a25e48b8cf515f4cdd6711a69ccc875429dcc32007adb133fb25d63e53e2ac6
Unfortunately, as reported by Talos, “The initial distribution vector of this dropper is currently unknown”.
At this time, we do not have the full infection chain, but we can add another piece to the puzzle, because sharemydrives[.]com also hosted another file:

Information in Kaspersky Threat Intelligence Portal
The wifeexchange.exe sample is another dropper, which disguises itself as a porn clip.
Specifically, the executable file uses the same icon used by Windows for multimedia files.

Dropper icon
Once executed, the process tries to find a specific marker (“*#@”) inside its file image, then drops and opens the following files:
frame.exe – 4a25e48b8cf515f4cdd6711a69ccc875429dcc32007adb133fb25d63e53e2ac6
movie.mp4
Frame.exe is the dropper described by Talos, while movie.mp4 is a small porn clip.
Conclusions
Transparent Tribe members are trying to add new tools to extend their operations and infect mobile devices. They are also developing new custom .NET tools like ObliqueRAT, and as observed in the first report, we do not expect this group to slow down any time soon. We will keep monitoring their activities.
IoC
The followings IoC list is not complete. If you want more information about the APT discussed here, a full IoC list and YARA rules are available to customers of Kaspersky Threat Intelligence Reports. Contact: intelreports@kaspersky.com
15DA10765B7BECFCCA3325A91D90DB37 – Special Benefits.docx
48476DA4403243B342A166D8A6BE7A3F – 7All_Selected_list.xls
B3F8EEE133AE385D9C7655AAE033CA3E – Criteria of Army Officers.doc
D7D6889BFA96724F7B3F951BC06E8C02 – wifeexchange.exe
0294F46D0E8CB5377F97B49EA3593C25 – Android Dropper – Desi-porn.apk
5F563A38E3B98A7BC6C65555D0AD5CFD – Android Dropper – Aarogya Setu.apk
A20FC273A49C3B882845AC8D6CC5BEAC – Android RAT – face.apk
53CD72147B0EF6BF6E64D266BF3CCAFE – Android RAT – imo.apk
BAE69F2CE9F002A11238DCF29101C14F – Android RAT – normal.apk
B8006E986453A6F25FD94DB6B7114AC2 – Android RAT – snap.apk
4556CCECBF24B2E3E07D3856F42C7072 – Android RAT – trueC.apk
6C3308CD8A060327D841626A677A0549 – Android RAT – viber.apk
CF71BA878434605A3506203829C63B9D – Android RAT – face.apk
627AA2F8A8FC2787B783E64C8C57B0ED – Android RAT – imo.apk
62FAD3AC69DB0E8E541EFA2F479618CE – Android RAT – normal.apk
A912E5967261656457FD076986BB327C – Android RAT – snap.apk
3EB36A9853C9C68524DBE8C44734EC35 – Android RAT – trueC.apk
931435CB8A5B2542F8E5F29FD369E010 – Android RAT – viber.apk
hxxp://sharingmymedia[.]com/files/Criteria-of-Army-Officers.doc
hxxp://sharingmymedia[.]com/files/7All-Selected-list.xls
hxxp://sharemydrives[.]com/files/Laptop/wifeexchange.exe
hxxp://sharemydrives[.]com/files/Mobile/Desi-Porn.apk
hxxp://tryanotherhorse[.]com/config.txt – APK URL
212.8.240[.]221:5987 – Android RAT C2
hxxp://212.8.240[.]221:80/server/upload.php – URL used by Android RAT to upload files
Lazarus APT targets cryptocurrency organizations with using LinkedIn lures
26.8.20 APT Securityaffairs
North Korea-linked Lazarus APT group targets cryptocurrency organizations with fake job offers in an ongoing spear-phishing campaign.
North Korea-linked Lazarus APT group (aka HIDDEN COBRA) has been observed while using LinkedIn lures in a spear-phishing campaign targeting the cryptocurrency organizations worldwide, including in the United States, the United Kingdom, Germany, Singapore, the Netherlands, Japan.
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
According to a report published by Kaspersky Lab in January 2020, in the two years the North Korea-linked APT group has continued to target cryptocurrency exchanges evolving its TTPs.
Now F-Secure Labs experts observed an ongoing spear-phishing campaign targeting an organization in the cryptocurrency industry.
Despite the effort of the group in making hard the attribution of the attack, F-Secure researchers found evidence that linked the attack to North Korea.
“In 2019, F-Secure uncovered technical details on Lazarus Group’s1 modus operandi during an investigation of an attack on an organisation in the cryptocurrency vertical, hereafter referred to as “the target”. The attack
was linked to a wider, ongoing global phishing campaign.” reads the report published by F-Secure.
“The attack was linked to this wider set of activity through several common indicators found in samples from the investigation, open source repositories, and proprietary intelligence sources”
F-Secure researchers believe the attack was advanced in nature and is part of a global phishing campaign running since at least January 2018.
Lazarus Group was able to delete traces of its activity, including malware employed in the attack as well as forensic evidence.
“Based on phishing artifacts recovered from Lazarus Group’s attack, F-Secure’s researchers were able to link the incident to a wider, ongoing campaign that’s been running since at least January 2018. According to the report, similar artifacts have been used in campaigns in at least 14 countries: the United States, China, the United Kingdom, Canada, Germany, Russia, South Korea, Argentina, Singapore, Hong Kong, Netherlands, Estonia, Japan, and the Philippines.” states F-Secure’s press release.
“Lazarus Group invested significant effort to evade the target organization’s defenses during the attack, such as by disabling anti-virus software on the compromised hosts, and removing the evidence of their malicious implants.”
The attack chain used in this attack employed a maliciously crafted Word document that claimed to be protected by a General Data Protection Regulation (GDPR) which requires the target to enable content to read it.
Upon enabling the content of the document, it executes malicious embedded macro that connected to a bit.ly link and delivers the final payloads. The malware collects info and sends them back to the attackers’ C2 servers.

The analysis of the bit.ly link revealed it was accessed 73 times since early May 2019 from multiple countries.
“The main implants both contain the capability to download additional files, decompress data in memory, initiate C2 communication, execute arbitrary commands, and steal credentials from a number of sources.” continues the report. “The implants were also observed being used to connect to the network backdoor implants on other target hosts.”
Experts noticed that the Lazarus Group was using a custom version of Mimikatz to capture credentials and was disabling Credential Guard on infected systems to collect them directly from the memory.
“Lazarus Group’s activities are a continued threat: the phishing campaign associated with this attack has been observed continuing into 2020, raising the need for awareness and ongoing vigilance amongst organizations operating in the targeted verticals,” concludes the report.
“It is F-Secure’s assessment that the group will continue to target organizations within the cryptocurrency vertical while it remains such a profitable pursuit, but may also expand to target supply chain elements of the vertical to increase returns and longevity of the campaign.”
DeathStalker cyber-mercenary group targets the financial sector
26.8.20 APT Securityaffairs
A hack-for-hire group, tracked as DeathStalker, has been targeting organizations in the financial sector since 2012 Kaspersky researchers say.
DeathStalker is a hack-for-hire group discovered by Kaspersky, it has been targeting organizations worldwide, mainly law firms and financial entities, since 2012. Victim organizations are small and medium-sized businesses located in Argentina, China, Cyprus, India, Israel, Lebanon, Switzerland, Russia, Taiwan, Turkey, the United Kingdom and the United Arab Emirates.
The APT group rapidly evolved its tactics to compromise the target organization.
“DeathStalker: a unique threat group that appears to target law firms and companies in the financial sector. As far as we can tell, this actor isn’t motivated by financial gain. They don’t deploy ransomware, steal payment information to resell it, or engage in any type of activity commonly associated with the cybercrime underworld.” reads the post published by Kaspersky. “Their interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as some sort of information broker in financial circles.”
The experts are monitoring the group’s activities since 2018, the group employed numerous strains of malware, including linked them to Powersing, Evilnum, and Janicab malware families. Kaspersky speculates the adversary group might have been active since at least 2012.
In recent attacks, DeathStalker mercenaries employed the PowerShell-based implant Powersing, the attackers used spear-phishing messages with an archive containing a malicious LNK file.
Upon clicking on the shortcuts, the execution of a convoluted sequence resulted in the execution of arbitrary code on the victim’s machine.
Powersing allows the attacker to periodically sends screenshot captures to the C2, and to execute arbitrary PowerShell scripts received from the C&C. The malicious code also allows threat actors to install additional tools.
DeathStalker leveraged multiple public services (including Google+, Imgur, Reddit, ShockChan, Tumblr, Twitter, YouTube, and WordPress) as dead drop resolvers, using them to store data via comments, descriptions, public posts, user profiles, and the like.
“The DeathStalkers toolchain leverages a number of public services as dead drop resolvers. These services provide a way for attackers to store data at a fixed URL through public posts, comments, user profiles, content descriptions, etc. Messages left by the attackers follow the following patterns: “My keyboard doesn’t work… [string].” and “Yo bro I sing [Base64 encoded string] yeah”.” continues the report.
Powersing connects the drop resolvers to retrieve the stored information, decode it, and ultimately convert into an IP address that the malware uses to connect to the real C&C server. The analysis of the messages on dead drop resolvers revealed that the implant has been in use since at least August 2017.

The use of trusted public services allows threat actors to hide backdoor communications into legitimate network traffic. Experts also linked the Powersing implant to the Janicab malware family, which was first spotted in 2012.
The two families of malware share the infection stages and the list of the list blacklisted VM MAC addresses.
Janicab uses YouTube as a dead drop resolver and includes features discovered in Powersing.
Evilnum is another malware family first spotted by ESET researchers in 2018, it uses a LNK-based infection chain and GitHub as a dead drop resolver. While Evilnum provides more capabilities than Powersing, it is also able to capture screenshots.
The researchers also discovered that Evilnum samples and Janicab also share portions of the code, the above findings suggest that the three malware families are related.
DeathStalker attackers recently exploited COVID-19 as lure to spread both Janicab and Powersing implants.
Researchers believe that the group is still developing new tools for its arsenal.
The hackers took advantage of the COVID-19 pandemic in recent attacks to deliver both Janicab and Powersing.
“Due to its ongoing operations (DeathStalker notably leveraged COVID-19 for both Janicab and Powersing implant deployment since March 2020) and continuous activity since 2018, we believe that DeathStalker is still developing its toolset, and that we’ll have more to report on in the near future.” concludes the report.
APT Hackers Exploit Autodesk 3D Max Software for Industrial Espionage
26.8.20 APT Thehackernews
It's one thing for APT groups to conduct cyber espionage to meet their own financial objectives. But it's an entirely different matter when they are used as "hackers for hire" by competing private companies to make away with confidential information.
Bitdefender's Cyber Threat Intelligence Lab discovered yet another instance of an espionage attack targeting an unnamed international architectural and video production company that had all the hallmarks of a carefully orchestrated campaign.
"The cybercriminal group infiltrated the company using a tainted and specially crafted plugin for Autodesk 3ds Max," Bitdefender researchers said in a report released today.
"The investigation also found that the Command and Control infrastructure used by the cybercriminal group to test their malicious payload against the organization's security solution, is located in South Korea."
Although there have been previous instances of APT mercenary groups such as Dark Basin and Deceptikons (aka DeathStalker) targeting the financial and legal sector, this is the first time a threat actor has employed the same modus operandi to the real-estate industry.
Last month, a similar campaign — called StrongPity — was found using tainted software installers as a dropper to introduce a backdoor for document exfiltration.
"This is likely to become the new normal in terms of the commoditization of APT groups -- not just state-sponsored actors, but by anyone seeking their services for personal gain, across all industries," the cybersecurity firm said.
Using a Tainted Autodesk 3ds Max Plugin
In an advisory published earlier this month, Autodesk warned users about a variant of "PhysXPluginMfx" MAXScript exploit that can corrupt 3ds Max's settings, run malicious code, and propagate to other MAX files on a Windows system upon loading the infected files into the software.
But according to Bitdefender's forensic analysis, this sketchy MAXScript Encrypted sample ("PhysXPluginStl.mse") contained an embedded DLL file, which subsequently went on to download additional .NET binaries from the C&C server with the ultimate goal of stealing important documents.
The binaries, in turn, are responsible for downloading other malicious MAXScripts capable of collecting information about the compromised machine and exfiltrating the details to the remote server, which transmits a final payload that can capture screenshots and gather passwords from web browsers such as Firefox, Google Chrome, and Internet Explorer.
Aside from employing a sleep mechanism to lie under the radar and evade detection, Bitdefender researchers also found that the malware authors had an entire toolset for spying upon its victims, including a "HdCrawler" binary, whose job is to enumerate and upload files with specific extensions (.webp, .jpg, .png, .zip, .obb, .uasset, etc.) to the server, and an info-stealer with extensive features.
The information amassed by the stealer ranges from the username, computer name, the IP addresses of network adapters, Windows ProductName, version of the .NET Framework, processors (number of cores, the speed, and other information), total and free RAM available, storage details to the names of processes running on the system, the files set to start automatically following a boot, and the list of recent files accessed.
Bitdefender's telemetry data also found other similar malware samples communicating with the same C&C server, dating back to just under a month ago, suggesting that the group targets other victims.
It's recommended that 3ds Max users download the latest version of Security Tools for Autodesk 3ds Max 2021-2015SP1 to identify and remove the PhysXPluginMfx MAXScript malware.
"The sophistication of the attack reveals an APT-style group that had prior knowledge of the company's security systems and used software applications, carefully planning their attack to infiltrate the company and exfiltrate data undetected," the researchers said.
"Industrial espionage is nothing new and, since the real-estate industry is highly competitive, with contracts valued at billions of dollars, the stakes are high for winning contracts for luxury projects and could justify turning to mercenary APT groups for gaining a negotiation advantage."
Lifting the veil on DeathStalker, a mercenary triumvirate
24.8.20 APT Securelist
State-sponsored threat actors and sophisticated attacks are often in the spotlight. Indeed, their innovative techniques, advanced malware platforms and 0-day exploit chains capture our collective imagination. Yet these groups still aren’t likely to be a part of the risk model at most companies, nor should they be. Businesses today are faced with an array of much more immediate threats, from ransomware and customer information leaks, to competitors engaging in unethical business practices. In this blog post, we’ll be focusing on DeathStalker: a unique threat group that appears to target law firms and companies in the financial sector (although we’ve occasionally seen them in other verticals as well). As far as we can tell, this actor isn’t motivated by financial gain. They don’t deploy ransomware, steal payment information to resell it, or engage in any type of activity commonly associated with the cybercrime underworld. Their interest in gathering sensitive business information leads us to believe that DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as some sort of information broker in financial circles.
DeathStalker first came to our attention through a PowerShell-based implant called Powersing. By unraveling this thread, we were able to identify activities dating back to 2018, and possibly even 2012. But before we dive into a history of DeathStalker and possible links to known groups, we’ll start with a bit of background, beginning with this actor’s current arsenal.
The Powersing toolchain
Overview
Recent operations we attribute to this threat actor rely on the same intrusion vector: spear-phishing emails with attached archives containing a malicious LNK file.

Despite looking like documents from the Explorer or popular archive-extraction products, the shortcuts lead to cmd.exe. These shortcut files have the following structure:

Clicking them initiates a convoluted sequence resulting in the execution of arbitrary code on the victim’s machine. A short PowerShell script, passed through cmd.exe’s arguments, bootstraps the following chain:

Stage 0’s role is to extract and execute the next element of the chain, as well as a decoy document embedded inside the LNK file to display to the user. This creates the illusion of having clicked on a real document and ensures the victim doesn’t get suspicious.
Stage 1 is a PowerShell script containing C# assembly designed to connect to a dead drop resolver (more on this in the next paragraph) and obtain cryptographic material used to decode the last stage of the chain by extracting a “DLL” file from the shortcut and locating a Base64-encoded list of URLs at a fixed offset. This establishes persistence by creating a shortcut (using the dropped icon) in the Windows startup folder pointing to the VBE startup script.
Finally, on stage 2, the actual malware implant used to take control of the victim’s machine. It connects to one of the dead drop resolvers to get the address of the real C&C server and enters a loop that looks for orders every few seconds.
Upon system restart, the VBE startup script – which closely resembles stage 0 – is automatically executed, once again leading all the way to Powersing stage 2.
Communications with the C&C server involve the exchange of JSON-encoded objects. Powersing only has two tasks:
Capture periodic screenshots from the victim’s machine, which are immediately sent to the C&C server (two built-in commands allow operators to change screenshot quality and periodicity)
Execute arbitrary Powershell scripts provided by the C&C
On stages 1 and 2, security software evasion is carried out with a high degree of variation across the different samples we’ve analyzed. Depending on the AV detected on the machine, Powersing may opt for alternative persistence methods, or even stop running entirely. We suspect that the group behind this toolset performs detection tests before each of their campaigns and updates their scripts based on the results. This indicates an iterative and fast-paced approach to software design. It’s worth pointing out that stage 2 actively looks for traces of virtualization (for example, vendor specific MAC addresses) and malware analysis tools on the machine, and reports this information to the C&C server.
To wrap up this section, we’d like to mention that Powersing isn’t a monolithic malware platform. Instead, it’s a stealthy foothold inside the victim’s network with its key role to enable the projection of further tools.
Dead drop resolvers
The DeathStalkers toolchain leverages a number of public services as dead drop resolvers. These services provide a way for attackers to store data at a fixed URL through public posts, comments, user profiles, content descriptions, etc. Messages left by the attackers follow the following patterns: “My keyboard doesn’t work… [string].” and “Yo bro I sing [Base64 encoded string] yeah”.

During our investigation of this threat actor, we discovered such messages on:
Google+
Imgur
Reddit
ShockChan
Tumblr
Twitter
YouTube
WordPress
In all likelihood, this list isn’t exhaustive. A number of these messages can be discovered through simple Google queries. Powersing’s first order of business is to connect to any dead drop resolver it knows to retrieve this information. Stage 1 consumes the first string of these messages, which contains the AES key used to decode stage 2. Then stage 2 connects to the dead drop resolver to obtain the integer encoded in the second string. As the code excerpt below shows, this integer is divided by an arbitrary constant (which varies depending on the sample) before being converted to an IP address:
This IP address is then stored on the user’s hard drive and used to establish a connection to the real C&C server used by the operators to control Powersing. Relying on well-known public services allows cybercriminals to blend initial backdoor communications into legitimate network traffic. It also limits what defenders can do to hinder their operations, as these platforms can’t generally be blocklisted at the company level, and getting content taken down from them can be a difficult and lengthy process. However, this comes at a price: the internet never forgets, and it’s also difficult for cybercriminals to remove traces of their operations. Thanks to the data indexed or archived by search engines, we estimate that Powersing was first used around August 2017.
A final detail we’d like to mention is that a number of Powersing C&Cs we discovered had SSL certificates reminiscent of Sofacy’s infamous Chopstick C&C “IT Department” certificates. We’re confident this infrastructure isn’t linked with Sofacy and believe this is an attempt by the threat actor to lead defenders to erroneous conclusions.
DeathStalker links to known groups
Janicab
Sec0wn’s original blog post introducing Powersing hinted at possible links with a malware family called Janicab, whose older samples date back to 2012. However, to the best of our knowledge, this connection was never explored publicly. Ultimately, we obtained one of the malware samples listed by F-Secure in a 2015 blog post (1fe4c500c9f0f7630a6037e2de6580e9) on Janicab to look for similarities.
This file is another LNK pointing to cmd.exe that drops a VBE script on the system when clicked, as well as a decoy document. The script establishes a connection to an unlisted YouTube video to obtain C&C information embedded in the description:
The integer obtained on this page is then divided by a constant before being converted to an IP address:
While the use of YouTube as a dead drop resolver alone wouldn’t be sufficient to establish a link between the two groups, we feel that the process of obtaining an integer somewhere online and dividing it before interpreting it as an IP address is unique enough to draw a first connection.
Janicab’s features also remind us of Powersing’s: the sample contains VM detection based on the MAC address of the machine, looks for malware analysis programs and has familiar antivirus software evasion routines. Janicab also periodically sends screenshot captures of the victim’s desktop to the C&C and appears to enable the execution of arbitrary Python scripts.
More recent versions of Janicab (85ed6ab8f60087e80ab3ff87c15b1174) also involve network traffic reminiscent of Powersing, especially when the malware registers with its C&C server:
Powersing registration request (POST data) Janicab registration request
Evilnum
Another possible connection worth investigating concerns the more recent Evilnum malware family, which was the subject of an in-depth blog post from ESET last July, as well as a couple of our own private reports. ESET’s post details another LNK-based infection chain leading to the execution of Javascript-based malware. Again, we obtained an old Evilnum sample (219dedb53da6b1dce0d6c071af59b45c) and observed that it also obtained C&C information from a dead drop resolver (GitHub) to obtain an IP address converted with the following code:
We can’t help but notice the pattern of looking for a specific string using a regular expression to obtain an integer, then dividing this integer by a constant resulting in the IP address of the C&C server. While Evilnum provides more capabilities than Powersing, it can also capture screenshots and send them to the C&C server.
In terms of victimology, Evilnum focuses on companies in the Fintech sector. It appears to be more interested in business intelligence than financial gain. This is consistent with the DeathStalker activity we’ve observed thus far.
One final connection we want to mention is that recent Evilnum (835d94b0490831da27d9bf4e9f4b429c) and Janicab samples have some slight code overlaps, despite being written in different languages:
Variables with similar names (“ieWatchdogFilename” for Janicab, “ieWatchdogPath” for Evilnum) used in functions performing equivalent tasks
Two functions used for cleanup have identical names: “deleteLeftOvers”
We feel that these names are unique enough to create an additional link between the two malware families. Less conclusively, this Evilnum sample also contains a function called “long2ip” to convert integers to IP addresses, while Powersing contains a similar implementation under the “LongToIP” name.
Summary
Powersing, Janicab and Evilnum are three scripting language-based toolchains exhibiting the following similarities:
All three are distributed through LNK files contained in archives delivered through spear-phishing
They obtain C&C information from dead drop resolvers using regular expressions and hardcoded sentences
IP addresses are obtained in the form of integers that are then divided by a hardcoded constant before being converted
Minor code overlaps between the three malware families could indicate that they’ve been developed by the same team, or inside a group that shares software development practices
The three malware families all have screenshot capture capabilities. While not original in itself, this isn’t usually part of the development priorities of such groups and could be indicative of a shared design specification
Finally, while we don’t have a lot of information about Janicab’s victimology, Powersing and Evilnum both go after business intelligence, albeit in different industry verticals. Both sets of activities are consistent with the hypothesis that they’re run by a mercenary outfit
While none of these points on their own are sufficient in our eyes to draw a conclusion, we feel that together they allow us to assess with medium confidence that Powersing, Evilnum and Janicab are operated by the same group. Additional data shared with us by industry partners that we can’t disclose at the moment also supports this conclusion.
Victimology
DeathStalker primarily targets private entities in the financial sector, including law offices, wealth consultancy firms, financial technology companies, and so on. In one unique instance, we also observed DeathStalker attacking a diplomatic entity.
We’ve been able to identify Powersing-related activities in Argentina, China, Cyprus, Israel, Lebanon, Switzerland, Taiwan, Turkey, the United Kingdom and the United Arab Emirates. We also located Evilnum victims in Cyprus, India, Lebanon, Russia and the United Arab Emirates.
However, we believe that DeathStalkers chooses its targets purely based on their perceived value, or perhaps following customer requests. In this context, we assess that any company in the financial sector could catch DeathStalker’s attention, no matter its geographic location.
Conclusion
In this blog post, we described a modern infection chain that’s still actively used and developed by a threat actor today. It doesn’t contain any innovative tricks or sophisticated methods, and certain components of the chain may actually appear needlessly convoluted. Yet if the hypothesis is correct that the same group operates Janicab and Powersing, it indicates that they’ve been leveraging the same methodologies since 2012. In the infosec world, it doesn’t get more “tried and true” than this.
Based on the limited technological means either of these toolchains display, we believe they’re good examples of what small groups or even skilled individuals can create. The value we see in publicly releasing information about DeathStalker is to have this threat actor serve as a baseline of what the private sector should be able to defend against. Groups like DeathStalker represent the type of cyberthreat most companies today are likely to face more than state-sponsored APTs. Due to its ongoing operations (DeathStalker notably leveraged COVID-19 for both Janicab and Powersing implant deployment since March 2020) and continuous activity since 2018, we believe that DeathStalker is still developing its toolset, and that we’ll have more to report on in the near future.
We advise defenders to pay close attention to any process creation related to native Windows interpreters for scripting languages, such as powershell.exe and cscript.exe. Wherever possible, these utilities should be made unavailable. We also recommend that future awareness trainings and security product assessments include infection chains based on LNK files.
For more information about both DeathStalker and Evilnum activity, subscribe to our private reporting services: intelreports@kaspersky.com
Indicators of Compromise
File hashes
D330F1945A39CEB78B716C21B6BE5D82 Malicious LNK
D83F933B2A6C307E17438749EDA29F02 Malicious LNK
540BC05130424301A8F0543E0240DF1D Malicious LNK
3B359A0E279C4E8C5B781E0518320B46 Malicious LNK
6F965640BC609F9C5B7FEA181A2A83CA Malicious LNK
E1718289718792651FA401C945C17079 Malicious LNK
F558E216CD3FB6C23696240A8C6306AC Malicious LNK
B38D1C18CBCCDDDBF56FDD28E5E6ECBB Loader Script
E132C596857892AC41249B90EA6934C1 PowerSing Stage 1
9A0F56CDACCE40D7039923551EAB241B PowerSing Stage 1
0CEBEB05362C0A5665E7320431CD115A PowerSing Stage 1
C5416D454C4A2926CA6128E895224981 PowerSing Stage 1
DBD966532772DC518D818A3AB6830DA9 PowerSing Stage 1
B7BBA5E70DC7362AA00910443FB6CD58 PowerSing Stage 1
2BE3E8024D5DD4EB9F7ED45E4393992D PowerSing Stage 1
83D5A68BE66A66A5AB27E309D6D6ECD1 PowerSing Stage 1
50D763EFC1BE165B7DB3AB5D00FFACD8 PowerSing Stage 1
C&C servers
54.38.192.174 Powersing C&C
91.229.76.17 Powersing C&C
91.229.76.153 Powersing C&C
91.229.77.240 Powersing C&C
91.229.77.120 Powersing C&C
91.229.79.120 Powersing C&C
54.38.192.174 Powersing C&C
105.104.10.115 Powersing C&C
Transparent Tribe APT hit 1000+ victims in 27 countries in the last 12 months
24.8.20 APT Securityaffairs
The Transparent Tribe cyber-espionage group continues to improve its arsenal while targets Military and Government entities.
The Transparent Tribe APT group is carrying out an ongoing cyberespionage campaign aimed at military and diplomatic targets worldwide.
The group upgraded its Crimson RAT by adding a management console and implementing a USB worming capability that allows it to propagate from machines within an infected network.
The Operation Transparent Tribe was first spotted by Proofpoint Researchers in Feb 2016, in a series of cyber espionage operations against Indian diplomats and military personnel in some embassies in Saudi Arabia and Kazakhstan. At that time, the researchers tracked the sources IP in Pakistan, the attacks were part of a wider operation that relies on multi vector such as watering hole websites and phishing email campaigns delivering custom RATs dubbed Crimson and Peppy. These RATs are capable of exfiltrate information, take screenshot, and record webcam streams.
Transparent Tribe has been active since at least 2013, it targeted entities across 27 countries, most of them in Afghanistan, Germany, India, Iran and Pakistan.
The threat actor remained under the radar for a long period, in January Cybaze ZLab researchers gathered evidence on the return of Operation Transparent Tribe after 4 years of silence.
Crimson is a modular malware that supports multiple features, including:
manage remote filesystems
upload or download files
capture screenshots
perform audio surveillance using microphones
record video streams from webcam devices
capture screenshots
steal files from removable media
execute arbitrary commands
record keystrokes
steal passwords saved in browsers
spread across systems by infecting removable media
Transparent Tribe has also implemented Crimson RAT a new USBWorm component used to steal files from removable drives, spreading across systems by infecting removable media, and downloading and executing a thin-client version of Crimson from a remote server.
“We found two different server versions, the one being a version that we named “A”, compiled in 2017, 2018 and 2019, and including a feature for installing the USBWorm component and executing commands on remote machines.” reads the analysis published by Kaspersky. “The version that we named “B” was compiled in 2018 and again at the end of 2019. The existence of two versions confirms that this software is still under development and the APT group is working to enhance it.”
By analyzing the .NET binary, the researchers were able to set up a working environment that allowed them to communicate with the detected samples.
Researchers discovered a .NET file that initially appeared as a variant of the Crimson RAT, but its analysis revealed that it was a server-side implant used to manage the client components.
The server includes a control panel, which displays the list of infected machines and shows basic information about them.
On top of the control panel, there is a toolbar that allows managing the server or one of the infected systems. At the bottom, there is an output console with displays a list of actions performed by the server in the background.
The interface includes a bot panel with 12 tabs, which allows managing a remote system and collect information. The tabs are associated with various features implemented by the Crimson components, such as exploring the remote file system; downloading, uploading and deleting files; keylogging; and monitoring the remote screen and checking what the user is doing on their system.
The analysis of the new USBWorm component in Crimson RAT revealed that it works as a downloader, infector and USB stealer.
“When started, it checks if its execution path is the one specified in the embedded configuration and if the system is already infected with a Crimson client component,” continues the analysis. “If these conditions are met, it will start to monitor removable media, and for each of these, the malware will try to infect the device and steal files of interest.”
The infection process for USBWorm begins with cataloging all directories of the victim device, then the malware creates a copy of itself in the drive root directory for each one, using the same directory name. The legitimate directories’ attribute is set to “hidden” while the actual directories are being replaced with a copy of the malware using the same directory name. USBWorm uses an icon that mimics a Windows directory to trick the user into launching the malware when trying to access one of the directories.
“This simple trick works very well on default Microsoft Windows installations, where file extensions are hidden and hidden files are not visible,” according to Kaspersky. “The victim will execute the worm every time he tries to access a directory. Moreover, the malware does not delete the real directories and executes ‘explorer.exe’ when started, providing the hidden directory path as argument. The command will open the Explorer window as expected by the user.”
The malware lists all files stored on the device and copies all the files with an extension of interest (i.e. .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pps, .ppsx and .txt.)
“Transparent Tribe continues to show high activity against multiple targets. In the last twelve months, we observed a broad campaign against military and diplomatic targets, using extensive infrastructure to support their operations and continuous improvements in their arsenal.” concludes Kaspersky. “The group continue to invest in their main RAT, Crimson, to perform intelligence activities and spy on sensitive targets. We do not expect any slowdown from this group in the near future and we will continue to monitor their activities.”
Transparent Tribe: Evolution analysis,part 1
20.8.20 APT Securelist
Background and key findings
Transparent Tribe, also known as PROJECTM and MYTHIC LEOPARD, is a highly prolific group whose activities can be traced as far back as 2013. Proofpoint published a very good article about them in 2016, and since that day, we have kept an eye on the group. We have periodically reported their activities through our APT threat intelligence reports, and subscribers of that service already know that in the last four years, this APT group has never taken time off. They continue to hit their targets, which typically are Indian military and government personnel.
The TTPs have remained consistent over the years, and the group has constantly used certain tools and created new programs for specific campaigns. Their favorite infection vector is malicious documents with an embedded macro, which seem to be generated with a custom builder.
Their main malware is a custom .NET RAT publicly known as Crimson RAT, but over the years, we also have observed the use of other custom .NET malware and a Python-based RAT known as Peppy.
Over the past year, we have seen this group undergo an evolution, stepping up its activities, starting massive infection campaigns, developing new tools and strengthening their focus on Afghanistan.
The summary of our recent investigations will be described in two blogposts. This first publication will cover the following key points:
We discovered the Crimson Server component, the C2 used by Transparent Tribe for managing infected machines and conducting espionage. This tool confirmed most of our observations on Crimson RAT and helped us to understand the attackers’ perspective.
Transparent Tribe continues to spread Crimson RAT, infecting a large number of victims in multiple countries, mainly India and Afghanistan.
The USBWorm component is real, and it has been detected on hundreds of systems. This is malware whose existence was already speculated about years ago, but as far as we know, it has never been publicly described.
I will be talking more about the TransparentTribe and its tools on GReAT Ideas. Powered by SAS webinar on August 26, you can register for it here: https://kas.pr/1gk9
Crimson Server
Crimson is the main tool used by Transparent Tribe for their espionage activities. The tool is composed of various components, which are used by the attacker for performing multiple activities on infected machines:
manage remote filesystems
upload or download files
capture screenshots
perform audio surveillance using microphones
record video streams from webcam devices
capture screenshots
steal files from removable media
execute arbitrary commands
record keystrokes
steal passwords saved in browsers
spread across systems by infecting removable media
In the course of our analysis, we spotted a .NET file, identified by our products as Crimson RAT, but a closer look revealed that it was something different: a server-side implant used by the attackers to manage the client components.
We found two different server versions, the one being a version that we named “A”, compiled in 2017, 2018 and 2019, and including a feature for installing the USBWorm component and executing commands on remote machines. The version that we named “B” was compiled in 2018 and again at the end of 2019. The existence of two versions confirms that this software is still under development and the APT group is working to enhance it.
By analysing the .NET binary, we were able to set up a working environment and communicate with samples previously detected on victims’ machines.
Crimson Server version “A”
Main panel
The first window is the main panel, which provides a list of infected machines and shows basic information about the victims’ systems.

Server main panel
Geolocation information is retrieved from a legitimate website using a remote IP address as the input. The URL used by the server is:
http://ip-api.com/xml/<ip>
At the top, there is a toolbar that can be used for managing the server or starting some actions on the selected bot. At the bottom, there is an output console with a list of actions performed by the server in the background. It will display, for example, information about received and sent commands.
The server uses an embedded configuration specified inside a class named “settings”.
Example of embedded configuration
The class contains TCP port values, default file names and installation paths used by each malware component. The server does not include any features to build the other components; they need to be manually placed in specific predefined folders. For example, based on the configuration displayed in the picture above, the “msclient” must be placed in “.\tmps\rfaiwaus.exe”.
This leads us to conclude that the resulting server file was generated by another builder, which created the executable files, directories and the other files used by the application.
Bot panel
The main features are accessible from the “bot panel”, an interface with twelve tabs, which can be used to manage a remote system and collect information.
Update module
The first tab is used for checking the client configuration, uploading Crimson components and executing these on remote system.
Update modules tab
The Crimson framework is composed of seven client components:
Thin Client -> a tiny version of the RAT used for recognizing the victim. The “thin” client is the most common one; it is usually dropped during the infection process by which Transparent Tribe is distributed and is most commonly found on OSINT resources. It contains a limited number of features and can typically be used to:
collect information about infected system
collect screenshots
manage the remote filesystem
download and upload files
get a process list
kill a process
execute a file
Main Client -> the full-featured RAT. It can handle all “Thin Client” features, but it can also be used to:
install the other malware components
capture webcam images
eavesdrop using a computer microphone
send messages to the victim
execute commands with COMSPEC and receive the output.
USB Driver -> a USB module component designed for stealing files from removable drives attached to infected systems.
USB Worm -> this is the USBWorm component developed for stealing files from removable drives, spread across systems by infecting removable media, and download and execute the “Thin Client” component from a remote Crimson server.
Pass Logger -> a credential stealer, used for stealing credentials stored in the Chrome, Firefox and Opera browsers.
KeyLogger -> this is simple malware used for recording keystrokes.
Remover -> this cannot be pushed using the “Update module tab”, but it can be uploaded to an infected machine automatically using the “Delete User” button. Unfortunately, we did not acquire that component and we cannot provide a description of it.
Interestingly, Transparent Tribe tries to circumvent certain vendors’ security tools by configuring the Server to prevent installation of some of the malware components, specifically the “USB Driver” and the “Pass Logger”, on systems protected with Kaspersky products. They also prevent installation of the “Pass Logger” on systems protected by ESET.

Snippet of code that prevents installation of certain components on systems protected by Kaspersky products
File Manager & Auto Download tabs
The file manager allows the attacker to explore the remote file system, execute programs, download, upload and delete files.
File manager tab
Most of the buttons are self-explanatory. The most interesting ones are “USB Drive” and “Delete USB”, used for accessing data stolen by the USB Driver and USB Worm components and the “Auto File Download” feature. This feature opens another window, which can also be accessed via the second last tab. It allows the attacker to configure the bot to search files, filter results and upload multiple files.
Auto download tab
Screen and Webcam monitoring tabs
Screen monitoring tab
Webcam monitoring tab
These tabs are used for managing two simple and powerful features. The first one is designed for monitoring the remote screen and checking what the user is doing on their system. The second one can be used for spying on a remote webcam and performing video surveillance. The attacker can retrieve a single screenshot or start a loop that forces the bot to continuously send screenshots to the server, generating a live stream of sorts. The attacker can also configure the RAT component to record the images on the remote system.
Other tabs
The other tabs are used for managing the following features:
Audio surveillance: The malware uses the NAudio library to interact with the microphone and manage the audio stream. The library is stored server-side and pushed to the victim’s machine using a special command.
Send message: The attacker can send messages to victims. The bot will display the messages using a standard message box.
Keylogger: Collects keyboard data. The log includes the process name used by the victim, and keystrokes. The attacker can save the data or clear the remote cache.
Password Logger: The malware includes a feature to steal browser credentials. The theft is performed by a specific component that enumerates credentials saved in various browsers. For each entry, it saves the website URL, the username and the password.
Process manager: The attacker can obtain a list of running processes and terminate these by using a specific button.
Command execution: This tab allows the attacker to execute arbitrary commands on the remote machine.
Crimson Server version “B”
The other version is quite similar to the previous one. Most noticeably, in this “B” version, the graphical user interface is different.

Main toolbar version B
“Update USB Worm” is missing from the Update Bot tab, which means that the USB Worm feature is not available in these versions.
Update modules tab, version B
This version does not include the check that prevents installation of certain components on systems protected with Kaspersky products, and the Command execution tab is missing. At the same position, we find a different tab, used for saving comments about the infected machine.
Notes
USBWorm
Last January, we started investigating an ongoing campaign launched by Transparent Tribe to distribute the Crimson malware. The attacks started with malicious Microsoft Office documents, which were sent to victims using spear-phishing emails.

Decoy document used in an attack against Indian entities
The documents typically have malicious VBA code embedded, and sometimes protected with a password, configured to drop an encoded ZIP file which contains a malicious payload.
User form with encoded payloads
The macro drops the ZIP file into a new directory created under %ALLUSERPROFILE% and extracts the archive contents at the same location. The directory name can be different, depending on the sample:
%ALLUSERSPROFILE%\Media-List\tbvrarthsa.zip
%ALLUSERSPROFILE%\Media-List\tbvrarthsa.exe

Snippet of VBA code
The executable file is the Crimson “Thin Client”, which allows the attacker to gain basic information about the infected machine, collect screenshots, manipulate the file system and download or upload arbitrary files.
During our analysis, we noticed an interesting sample connected to a Crimson C2 server. This sample was related to multiple detections, all of these having different file names and most of them generated from removable devices.
One of the file path name combinations observed was ‘C:\ProgramData\Dacr\macrse.exe’, also configured in a Crimson “Main Client” sample and used for saving the payload received from the C2 when invoking the usbwrm command.
USBWorm file construction function
We concluded that this sample was the USBWorm component mentioned by Proofpoint in its analysis of the malware.
Based on previous research, we knew that this RAT was able to deploy a module to infect USB devices, but as far as we know, it had never been publicly described.
USB Worm description
Our analysis has revealed that USBWorm is much more than a USB infector. In fact, it can be used by the attacker to:
download and execute the Crimson “Thin Client”
infect removable devices with a copy of USBWorm itself
steal files of interest from removable devices (i.e. USB Stealer)
By default, the program behaves as a downloader, infector and USB stealer. Usually, the component is installed by the Crimson “Main Client”, and when started, it checks if its execution path is the one specified in the embedded configuration and if the system is already infected with a Crimson client component. If these conditions are met, it will start to monitor removable media, and for each of these, the malware will try to infect the device and steal files of interest.
The infection procedure lists all directories. Then, for each directory, it creates a copy of itself in the drive root directory using the same directory name and changing the directory attribute to “hidden”. This results in all the actual directories being hidden and replaced with a copy of the malware using the same directory name.
Moreover, USBWorm uses an icon that mimics a Windows directory, tricking the user into executing the malware when trying to access a directory.

USBWorm icon
This simple trick works very well on default Microsoft Windows installations, where file extensions are hidden and hidden files are not visible. The victim will execute the worm every time he tries to access a directory. Moreover, the malware does not delete the real directories and executes “explorer.exe” when started, providing the hidden directory path as argument. The command will open the Explorer window as expected by the user.
View of infected removable media with default Windows settings
View of infected removable media with visible hidden files and file extensions
The data theft procedure lists all files stored on the device and copies those with an extension matching a predefined list:
File extensions of interest: .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pps, .ppsx, .txt
If the file is of interest, i.e. if the file extension is on the predefined list, the procedure checks if a file with the same name already has been stolen. The malware has a text file with a list of stolen files, which is stored in the malware directory under a name specified in the embedded configuration.
Of course, this approach is a little buggy, because if the worm finds two different files with the same name, it will steal only the first one. Anyway, if the file is of interest and is not on the list of stolen files, it will be copied from the USB to a local directory usually named “data” or “udata”, although the name could be different.
If the worm is executed from removable media, the behavior is different. In this case, it will check if the “Thin Client” or the “Main Client” is running on the system. If the system is not infected, it will connect to a remote Crimson Server and try to use a specific “USBW” command to download and execute the “Thin Client” component.
Snippet of code used to build USBW request
The persistence is guaranteed by a method that is called when the program is closing. It checks if the malware directory exists as specified in an embedded configuration and then copies the malware executable inside it. It also creates a registry key under “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” to execute the worm automatically.
USB Worm distribution
During our investigation, we found around two hundred distinct samples related to Transparent Tribe Crimson components. We used the Kaspersky Security Network (KSN) to collect some statistics about the victims.
Considering all components detected between June 2019 and June 2020, we found more than one thousand distinct victims distributed across twenty-seven countries.
Crimson distribution map
Most of the detections were related to the USB Worm components; and in most of the countries, the number of events was very low.
Crimson detections – USBWorm vs other components
If we check victims compromised with the other client components, we can find the real targets.

Top five infected countries from June 2019 to June 2020 – USBWorm excluded
The graph includes the highest number of distinct victims, and it shows that Transparent Tribe maintained a strong focus on Afghanistan during the final part of 2019 and then started to focus again on Indian users during 2020.
We may speculate that detections in other countries may be related to entities related to main targets, such as personnel of embassies.
Conclusions
Transparent Tribe continues to show high activity against multiple targets. In the last twelve months, we observed a broad campaign against military and diplomatic targets, using extensive infrastructure to support their operations and continuous improvements in their arsenal. The group continue to invest in their main RAT, Crimson, to perform intelligence activities and spy on sensitive targets. We do not expect any slowdown from this group in the near future and we will continue to monitor their activities.
IoC
The followings IOC list is not complete. If you want more information about the APT discussed here, as well as a full IOC list, and YARA rules are available to customers of Kaspersky Threat Intelligence Reports. Contact: intelreports@kaspersky.com
5158C5C17862225A86C8A4F36F054AE2 – Excel document – NHQ_Notice_File.xls
D2C407C07CB5DC103CD112804455C0DE – Zip archive – tbvrarthsa.zip
76CA942050A9AA7E676A8D553AEB1F37 – Zip archive – ulhtagnias.zip
08745568FE3BC42564A9FABD2A9D189F – Crimson Server Version “A”
03DCD4A7B5FC1BAEE75F9421DC8D876F – Crimson Server Version “B”
075A74BA1D3A5A693EE5E3DD931E1B56 – Crimson Keylogger
1CD5C260ED50F402646F88C1414ADB16 – Crimson Keylogger
CAC1FFC1A967CD428859BB8BE2E73C22 – Crimson Thin Client
E7B32B1145EC9E2D55FDB1113F7EEE87 – Crimson Thin Client
F5375CBC0E6E8BF10E1B8012E943FED5 – Crimson Main Client
4B733E7A78EBD2F7E5306F39704A86FD – Crimson Main Client
140D0169E302F5B5FB4BB3633D09B48F – Crimson USB Driver
9DD4A62FE9513E925EF6B6D795B85806 – Crimson USB Driver
1ED98F70F618097B06E6714269E2A76F – Crimson USB Worm
F219B1CDE498F0A02315F69587960A18 – Crimson USB Worm
64.188.25.206 – Crimson C2
173.212.192.229 – Crimson C2
45.77.246.69 – Crimson C2
newsbizupdates.net – Crimson C2
173.249.22.30 – Crimson C2
uronlinestores.net – Crimson C2