The malware comes equipped with capabilities to collect and exfiltrate information about the applications currently running on the compromised workstation, keystrokes typed, and mouse clicks.
APT APT 2024 2023 2022 2021 2020
Microsoft Identifies Storm-0501 as Major Threat in Hybrid Cloud Ransomware Attacks
27.9.24 APT The Hacker News
The threat actor known as Storm-0501 has targeted government, manufacturing, transportation, and law enforcement sectors in the U.S. to stage ransomware attacks.
The multi-stage attack campaign is designed to compromise hybrid cloud environments and perform lateral movement from on-premises to cloud environment, ultimately resulting in data exfiltration, credential theft, tampering, persistent backdoor access, and ransomware deployment, Microsoft said.
"Storm-0501 is a financially motivated cybercriminal group that uses commodity and open-source tools to conduct ransomware operations," according to the tech giant's threat intelligence team.
Active since 2021, the threat actor has a history of targeting education entities with Sabbath (54bb47h) ransomware before evolving into a ransomware-as-a-service (RaaS) affiliate delivering various ransomware payloads over the years, including Hive, BlackCat (ALPHV), Hunters International, LockBit, and Embargo ransomware.
A notable aspect of Storm-0501's attacks is the use of weak credentials and over-privileged accounts to move from organizations on-premises to cloud infrastructure.
Other initial access methods include using a foothold already established by access brokers like Storm-0249 and Storm-0900, or exploiting various known remote code execution vulnerabilities in unpatched internet-facing servers such as Zoho ManageEngine, Citrix NetScaler, and Adobe ColdFusion 2016.
The access afforded by any of the aforementioned approaches paves the way for extensive discovery operations to determine high-value assets, gather domain information, and perform Active Directory reconnaissance. This is followed by the deployment of remote monitoring and management tools (RMMs) like AnyDesk to maintain persistence.
"The threat actor took advantage of admin privileges on the local devices it compromised during initial access and attempted to gain access to more accounts within the network through several methods," Microsoft said.
"The threat actor primarily utilized Impacket's SecretsDump module, which extracts credentials over the network, and leveraged it across an extensive number of devices to obtain credentials."
The compromised credentials are then used to access even more devices and extract additional credentials, with the threat actor simultaneously accessing sensitive files to extract KeePass secrets and conducting brute-force attacks to obtain credentials for specific accounts.
Microsoft said it detected Storm-0501 employing Cobalt Strike to move laterally across the network using the compromised credentials and send follow-on commands. Data exfiltration from the on-premises environment is accomplished by using Rclone to transfer the data to the MegaSync public cloud storage service.
The threat actor has also been observed creating persistent backdoor access to the cloud environment and deploying ransomware to the on-premises, making it the latest threat actor to target hybrid cloud setups after Octo Tempest and Manatee Tempest.
"The threat actor used the credentials, specifically Microsoft Entra ID (formerly Azure AD), that were stolen from earlier in the attack to move laterally from the on-premises to the cloud environment and establish persistent access to the target network through a backdoor," Redmond said.
The pivot to the cloud is said to be accomplished either through a compromised Microsoft Entra Connect Sync user account or via cloud session hijacking of an on-premises user account that has a respective admin account in the cloud with multi-factor authentication (MFA) disabled.
The attack culminates with the deployment of Embargo ransomware across the victim organization upon obtaining sufficient control over the network, exfiltrating files of interest, and lateral movement to the cloud. Embargo is a Rust-based ransomware first discovered in May 2024.
"Operating under the RaaS model, the ransomware group behind Embargo allows affiliates like Storm-0501 to use its platform to launch attacks in exchange for a share of the ransom," Microsoft said.
"Embargo affiliates employ double extortion tactics, where they first encrypt a victim's files and threaten to leak stolen sensitive data unless a ransom is paid."
The disclosure comes as the DragonForce ransomware group has been targeting companies in manufacturing, real estate, and transportation sectors using a variant of the leaked LockBit3.0 builder and a modified version of Conti.
The attacks are characterized by the use of the SystemBC backdoor for persistence, Mimikatz and Cobalt Strike for credential harvesting, and Cobalt Strike for lateral movement. The U.S. accounts for more than 50% of the total victims, followed by the U.K. and Australia.
"The group employs double extortion tactics, encrypting data, and threatening leaks unless a ransom is paid," Singapore-headquartered Group-IB said. "The affiliate program, launched on 26 June 2024, offers 80% of the ransom to affiliates, along with tools for attack management and automation."
N. Korean Hackers Deploy New KLogEXE and FPSpy Malware in Targeted Attacks
26.9.24 APT The Hacker News
Threat actors with ties to North Korea have been observed leveraging two new malware strains dubbed KLogEXE and FPSpy.
The activity has been attributed to an adversary tracked as Kimsuky, which is also known as APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (formerly Thallium), Sparkling Pisces, Springtail, and Velvet Chollima.
"These samples enhance Sparkling Pisces' already extensive arsenal and demonstrate the group's continuous evolution and increasing capabilities," Palo Alto Networks Unit 42 researchers Daniel Frank and Lior Rochberger said.
Active since at least 2012, the threat actor has been called the "king of spear phishing" for its ability to trick victims into downloading malware by sending emails that make it seem like they are from trusted parties.
Unit 42's analysis of Sparkling Pisces' infrastructure has uncovered two new portable executables referred to as KLogEXE and FPSpy.
KLogExe is a C++ version of the PowerShell-based keylogger named InfoKey that was highlighted by JPCERT/CC in connection with a Kimsuky campaign targeting Japanese organizations.

The malware comes equipped with capabilities to collect and exfiltrate information about the applications currently running on the compromised workstation, keystrokes typed, and mouse clicks.
On the other hand, FPSpy is said to be a variant of the backdoor that AhnLab disclosed in 2022, with overlaps identified to a malware that Cyberseason documented under the name KGH_SPY in late 2020.
FPSpy, in addition to keylogging, is also engineered to gather system information, download and execute more payloads, run arbitrary commands, and enumerate drives, folders, and files on the infected device.
Unit 42 said it was also able to identify points of similarities in the source code of both KLogExe and FPSpy, suggesting that they are likely the work of the same author.
"Most of the targets we observed during our research originated from South Korea and Japan, which is congruent with previous Kimsuky targeting," the researchers said.
Cloudflare Warns of India-Linked Hackers Targeting South and East Asian Entities
26.9.24 APT The Hacker News
An advanced threat actor with an India nexus has been observed using multiple cloud service providers to facilitate credential harvesting, malware delivery, and command-and-control (C2).
Web infrastructure and security company Cloudflare is tracking the activity under the name SloppyLemming, which is also called Outrider Tiger and Fishing Elephant.
"Between late 2022 to present, SloppyLemming has routinely used Cloudflare Workers, likely as part of a broad espionage campaign targeting South and East Asian countries," Cloudflare said in an analysis.
SloppyLemming is assessed to be active since at least July 2021, with prior campaigns leveraging malware such as Ares RAT and WarHawk, the latter of which is also linked to a known hacking crew called SideWinder. The use of Ares RAT, on the other hand, has been linked to SideCopy, a threat actor likely of Pakistani origin.
Targets of the SloppyLemming's activity span government, law enforcement, energy, education, telecommunications, and technology entities located in Pakistan, Sri Lanka, Bangladesh, China, Nepal, and Indonesia.
The attack chains involve sending spear-phishing emails to targets that aim to trick recipients into clicking on a malicious link by inducing a false sense of urgency, claiming that they need to complete a mandatory process within the next 24 hours.
Clicking on the URL takes the victim to a credential harvesting page, which then serves as a mechanism for the threat actor to gain unauthorized access to targeted email accounts within organizations that are of interest.
"The actor uses a custom-built tool named CloudPhish to create a malicious Cloudflare Worker to handle the credential logging logic and exfiltration of victim credentials to the threat actor," the company said.
Some of the attacks undertaken by SloppyLemming have leveraged similar techniques to capture Google OAuth tokens, as well as employ booby-trapped RAR archives ("CamScanner 06-10-2024 15.29.rar") that likely exploit a WinRAR flaw (CVE-2023-38831) to achieve remote code execution.
Present within the RAR file is an executable that, besides displaying the decoy document, stealthily loads "CRYPTSP.dll," which serves as a downloader to retrieve a remote access trojan hosted on Dropbox.
It's worth mentioning here that cybersecurity company SEQRITE detailed an analogous campaign undertaken by the SideCopy actors last year targeting Indian government and defense sectors to distribute the Ares RAT using ZIP archives named "DocScanner_AUG_2023.zip" and "DocScanner-Oct.zip" that are engineered to trigger the same vulnerability.
A third infection sequence employed by SloppyLemming entails using spear-phishing lures to lead prospective targets to a phony website that impersonates the Punjab Information Technology Board (PITB) in Pakistan, after which they are redirected to another site that contains an internet shortcut (URL) file.
The URL file comes embedded with code to download another file, an executable named PITB-JR5124.exe, from the same server. The binary is a legitimate file that's used to sideload a rogue DLL named profapi.dll that subsequently communicates with a Cloudflare Worker.
These Cloudflare Worker URLs, the company noted, act as an intermediary, relaying requests to the actual C2 domain used by the adversary ("aljazeerak[.]online").
Cloudflare said it "observed concerted efforts by SloppyLemming to target Pakistani police departments and other law enforcement organizations," adding "there are indications that the actor has targeted entities involved in the operation and maintenance of Pakistan's sole nuclear power facility."
Some of the other targets of credential harvesting activity encompass Sri Lankan and Bangladeshi government and military organizations, and to a lesser extent, Chinese energy and academic sector entities.
Chinese Hackers Infiltrate U.S. Internet Providers in Cyber Espionage Campaign
26.9.24 APT The Hacker News
Nation-state threat actors backed by Beijing broke into a "handful" of U.S. internet service providers (ISPs) as part of a cyber espionage campaign orchestrated to glean sensitive information, The Wall Street Journal reported Wednesday.
The activity has been attributed to a threat actor that Microsoft tracks as Salt Typhoon, which is also known as FamousSparrow and GhostEmperor.
"Investigators are exploring whether the intruders gained access to Cisco Systems routers, core network components that route much of the traffic on the internet," the publication was quoted as saying, citing people familiar with the matter.
The end goal of the attacks is to gain a persistent foothold within target networks, allowing the threat actors to harvest sensitive data or launch a damaging cyber attack.
GhostEmperor first came to light in October 2021, when Russian cybersecurity company Kasperksy detailed a long-standing evasive operation targeting Southeast Asian targets in order to deploy a rootkit named Demodex.
Targets of the campaign included high-profile entities in Malaysia, Thailand, Vietnam, and Indonesia, in addition to outliers located in Egypt, Ethiopia, and Afghanistan.
As recently as July 2024, Sygnia revealed that an unnamed client was compromised by the threat actor in 2023 to infiltrate one of its business partner's networks.
"During the investigation, several servers, workstations, and users were found to be compromised by a threat actor who deployed various tools to communicate with a set of [command-and-control] servers," the company said. "One of these tools was identified as a variant of Demodex."
The development comes days after the U.S. government said it disrupted a 260,000-device botnet dubbed Raptor Train controlled by a different Beijing-linked hacking crew called Flax Typhoon.
It also represents the latest in a string of Chinese state-sponsored efforts to target telecom, ISPs, and other critical infrastructure sectors.
Hacktivist Group Twelve Targets Russian Entities with Destructive Cyber Attacks
20.9.24 APT The Hacker News
A hacktivist group known as Twelve has been observed using an arsenal of publicly available tools to conduct destructive cyber attacks against Russian targets.
"Rather than demand a ransom for decrypting data, Twelve prefers to encrypt victims' data and then destroy their infrastructure with a wiper to prevent recovery," Kaspersky said in a Friday analysis.
"The approach is indicative of a desire to cause maximum damage to target organizations without deriving direct financial benefit."
The hacking group, believed to have been formed in April 2023 following the onset of the Russo-Ukrainian war, has a track record of mounting cyber attacks that aim to cripple victim networks and disrupt business operations.
It has also been observed conducting hack-and-leak operations that exfiltrate sensitive information, which is then shared on its Telegram channel.
Kaspersky said Twelve shares infrastructural and tactical overlaps with a ransomware group called DARKSTAR (aka COMET or Shadow), raising the possibility that the two intrusion sets are likely related to one another or part of the same activity cluster.
"At the same time, whereas Twelve's actions are clearly hacktivist in nature, DARKSTAR sticks to the classic double extortion pattern," the Russian cybersecurity vendor said. "This variation of objectives within the syndicate underscores the complexity and diversity of modern cyberthreats."
The attack chains start with gaining initial access by abusing valid local or domain accounts, after which the Remote Desktop Protocol (RDP) is used to facilitate lateral movement. Some of these attacks are also carried out via the victim's contractors.
"To do this, they gained access to the contractor's infrastructure and then used its certificate to connect to its customer's VPN," Kaspersky noted. "Having obtained access to that, the adversary can connect to the customer's systems via the Remote Desktop Protocol (RDP) and then penetrate the customer's infrastructure."
Prominent among the other tools used by Twelve are Cobalt Strike, Mimikatz, Chisel, BloodHound, PowerView, adPEAS, CrackMapExec, Advanced IP Scanner, and PsExec for credential theft, discovery, network mapping, and privilege escalation. The malicious RDP connections to the system are tunneled through ngrok.
Also deployed are PHP web shells with capabilities to execute arbitrary commands, move files, or send emails. These programs, such as the WSO web shell, are readily available on GitHub.
In one incident investigated by Kaspersky, the threat actors are said to have exploited known security vulnerabilities (e.g., CVE-2021-21972 and CVE-2021-22005) in VMware vCenter to deliver a web shell that then was used to drop a backdoor dubbed FaceFish.
"To gain a foothold in the domain infrastructure, the adversary used PowerShell to add domain users and groups, and to modify ACLs (Access Control Lists) for Active Directory objects," it said. "To avoid detection, the attackers disguised their malware and tasks under the names of existing products or services."
Some of the names used include "Update Microsoft," "Yandex," "YandexUpdate," and "intel.exe."
The attacks are also characterized by the use of a PowerShell script ("Sophos_kill_local.ps1") to terminate processes related to Sophos security software on the compromised host.
The concluding stages entail using the Windows Task Scheduler to launch ransomware and wiper payloads, but not before gathering and exfiltrating sensitive information about their victims via a file-sharing service called DropMeFiles in the form of ZIP archives.
"The attackers used a version of the popular LockBit 3.0 ransomware, compiled from publicly available source code, to encrypt the data," Kaspersky researchers said. "Before starting work, the ransomware terminates processes that may interfere with the encryption of individual files."
The wiper, identical to the Shamoon malware, rewrites the master boot record (MBR) on connected drives and overwrites all file contents with randomly generated bytes, effectively preventing system recovery.
"The group sticks to a publicly available and familiar arsenal of malware tools, which suggests it makes none of its own," Kaspersky noted. "This makes it possible to detect and prevent Twelve's attacks in due time."
Iranian APT UNC1860 Linked to MOIS Facilitates Cyber Intrusions in Middle East
20.9.24 APT The Hacker News
An Iranian advanced persistent threat (APT) threat actor likely affiliated with the Ministry of Intelligence and Security (MOIS) is now acting as an initial access facilitator that provides remote access to target networks.
Google-owned Mandiant is tracking the activity cluster under the moniker UNC1860, which it said shares similarities with intrusion sets tracked by Microsoft, Cisco Talos, and Check Point as Storm-0861 (formerly DEV-0861), ShroudedSnooper, and Scarred Manticore, respectively.
"A key feature of UNC1860 is its collection of specialized tooling and passive backdoors that [...] supports several objectives, including its role as a probable initial access provider and its ability to gain persistent access to high-priority networks, such as those in the government and telecommunications space throughout the Middle East," the company said.
The group first came to light in July 2022 in connection with destructive cyber attacks targeting Albania with a ransomware strain called ROADSWEEP, the CHIMNEYSWEEP backdoor, and a ZEROCLEAR wiper variant (aka Cl Wiper), with subsequent intrusions in Albania and Israel leveraging new wipers dubbed No-Justice and BiBi (aka BABYWIPER).
Mandiant described UNC1860 as a "formidable threat actor" that maintains an arsenal of passive backdoors that are designed to obtain footholds into victim networks and set up long-term access without attracting attention.
Among these tools includes two GUI-operated malware controllers tracked as TEMPLEPLAY and VIROGREEN, which are said to provide other MOIS-associated threat actors with remote access to victim environments using remote desktop protocol (RDP).
Specifically, these controllers are designed to provide third-party operators an interface that offers instructions on the ways custom payloads could be deployed and post-exploitation activities such as internal scanning could be carried out within the target network.
Mandiant said it identified overlaps between UNC1860 and APT34 (aka Hazel Sandstorm, Helix Kitten, and OilRig) in that organizations compromised by the latter in 2019 and 2020 were previously infiltrated by UNC1860, and vice versa. Furthermore, both the clusters have been observed pivoting to Iraq-based targets, as recently highlighted by Check Point.
The attack chains involve leveraging initial access gained by opportunistic exploitation of vulnerable internet-facing servers to drop web shells and droppers like STAYSHANTE and SASHEYAWAY, with the latter leading to the execution of implants, such as TEMPLEDOOR, FACEFACE, and SPARKLOAD, that are embedded within it.
"VIROGREEN is a custom framework used to exploit vulnerable SharePoint servers with CVE-2019-0604," the researchers said, adding that it controls STAYSHANTE, along with a backdoor referred to as BASEWALK.
"The framework provides post-exploitation capabilities including [...] controlling post-exploitation payloads, backdoors (including the STAYSHANTE web shell and the BASEWALK backdoor) and tasking; controlling a compatible agent regardless of how the agent has been implanted; and executing commands and uploading/downloading files.
TEMPLEPLAY (internally named Client Http), for its part, serves as the .NET-based controller for TEMPLEDOOR. It supports backdoor instructions for executing commands via cmd.exe, upload/download files from and to the infected host, and proxy connection to a target server.
It's believed that the adversary has in its possession a diverse collection of passive tools and main-stage backdoors that align with its initial access, lateral movement, and information gathering goals.
Some of the other tools of note documented by Mandiant are listed below -
OATBOAT, a loader that loads and executes shellcode payloads
TOFUDRV, a malicious Windows driver that overlaps with WINTAPIX
TOFULOAD, a passive implant that employs undocumented Input/Output Control (IOCTL) commands for communication
TEMPLEDROP, a repurposed version of an Iranian antivirus software Windows file system filter driver named Sheed AV that's used to protect the files it deploys from modification
TEMPLELOCK, a .NET defense evasion utility that's capable of killing the Windows Event Log service
TUNNELBOI, a network controller capable of establishing a connection with a remote host and managing RDP connections
"As tensions continue to ebb and flow in the Middle East, we believe this actor's adeptness in gaining initial access to target environments represents a valuable asset for the Iranian cyber ecosystem that can be exploited to answer evolving objectives as needs shift," researchers Stav Shulman, Matan Mimran, Sarah Bock, and Mark Lechtik said.

The development comes as the U.S. government revealed Iranian threat actors' ongoing attempts to influence and undermine the upcoming U.S. elections by stealing non-public material from former President Donald Trump's campaign.
"Iranian malicious cyber actors in late June and early July sent unsolicited emails to individuals then associated with President Biden's campaign that contained an excerpt taken from stolen, non-public material from former President Trump's campaign as text in the emails," the government said.
"There is currently no information indicating those recipients replied. Furthermore, Iranian malicious cyber actors have continued their efforts since June to send stolen, non-public material associated with former President Trump's campaign to U.S. media organizations."
Iran's ramping up of its cyber operations against its perceived rivals also comes at a time when the country has become increasingly active in the Middle East region.
Late last month, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that the Iranian APT Lemon Sandstorm (aka Fox Kitten) has carried out ransomware attacks by clandestinely partnering with NoEscape, RansomHouse, and BlackCat (aka ALPHV) crews.
Censys' analysis of the hacking group's attack infrastructure has since uncovered other, currently active hosts that are likely part of it based on commonalities based on geolocation, Autonomous System Numbers (ASNs), and identical patterns of ports and digital certificates.
"Despite attempts at obfuscation, diversion, and randomness, humans still must instantiate, operate, and decommission digital infrastructure," Censys' Matt Lembright said.
"Those humans, even if they rely upon technology to create randomization, almost always will follow some sort of pattern whether it be similar Autonomous Systems, geolocations, hosting providers, software, port distributions or certificate characteristics."
Chinese Engineer Charged in U.S. for Years-Long Cyber Espionage Targeting NASA and Military
19.9.24 APT The Hacker News
A Chinese national has been indicted in the U.S. on charges of conducting a "multi-year" spear-phishing campaign to obtain unauthorized access to computer software and source code created by the National Aeronautics and Space Administration (NASA), research universities, and private companies.
Song Wu, 39, has been charged with 14 counts of wire fraud and 14 counts of aggravated identity theft. If convicted, he faces a maximum sentence of a jail term of 20 years for each count of wire fraud and a two-year consecutive sentence in prison for aggravated identity theft.
He was employed as an engineer at the Aviation Industry Corporation of China (AVIC), a Chinese state-owned aerospace and defense conglomerate founded in 2008 and headquartered in Beijing.
According to information listed on AVIC's website, it has "over 100 subsidiaries, nearly 24 listed companies, and more than 400,000 employees." In November 2020 and June 2021, the company and some of its subsidiaries became the subject of U.S. sanctions, barring Americans from investing in the company.
Song is said to have carried out a spear-phishing campaign that involved creating email accounts to mimic U.S.-based researchers and engineers, which were then utilized to obtain specialized restricted or proprietary software for aerospace engineering and computational fluid dynamics.
The software could also be used for industrial and military applications, including the development of advanced tactical missiles and aerodynamic design and assessment of weapons.
These emails, the U.S. Department of Justice (DoJ) alleged, were sent to employees at NASA, the U.S. Air Force, Navy, and Army, and the Federal Aviation Administration, as well as individuals employed in major research universities in Georgia, Michigan, Massachusetts, Pennsylvania, Indiana, and Ohio.
The social engineering attempts, which started around January 2017 and continued through December 2021, also targeted private sector companies that work in the aerospace field.
The fraudulent messages purported to be sent by a colleague, associate, friend, or other people in the research or engineering community, requesting prospective targets to send or make available source code or software that they had access to. The DoJ did not disclose the name of the software or the defendant's current whereabouts.
"Once again, the FBI and our partners have demonstrated that cyber criminals around the world who are seeking to steal our companies' most sensitive and valuable information can and will be exposed and held accountable," said Keri Farley, Special Agent in Charge of FBI Atlanta.
"As this indictment shows, the FBI is committed to pursuing the arrest and prosecution of anyone who engages in illegal and deceptive practices to steal protected information."
Coinciding with the indictment, the DoJ also unsealed a separate indictment against Chinese national Jia Wei, a member of the People's Liberation Army (PLA), for infiltrating an unnamed U.S.-based communications company in March 2017 to steal proprietary information relating to civilian and military communication devices, product development, and testing plans.
"During his unauthorized access, Wei and his co-conspirators attempted to install malicious software designed to provide persistent unauthorized access to the U.S. company's network," the DoJ said. "Wei's unauthorized access continued until approximately late May 2017."
The development comes weeks after the U.K. National Crime Agency (NCA) announced that three men, Callum Picari, 22; Vijayasidhurshan Vijayanathan, 21; and Aza Siddeeque, 19, pleaded guilty to running a website that enabled cybercriminals to bypass banks' anti-fraud checks and take control of bank accounts.
The service, named OTP.agency, allowed monthly subscribers to socially engineer bank account holders into disclosing genuine one-time-passcodes, or reveal their personal information.
The underground service is said to have targeted over 12,500 members of the public between September 2019 and March 2021, when it was taken offline after the trio were arrested. It's currently not known how much illegal revenue the operation generated during its lifespan.
"A basic package costing £30 a week allowed multi-factor authentication to be bypassed on platforms such as HSBC, Monzo, and Lloyds so that criminals could complete fraudulent online transactions," the NCA said. "An elite plan cost £380 a week and granted access to Visa and Mastercard verification sites."
North Korean Hackers Target Energy and Aerospace Industries with New MISTPEN Malware
18.9.24 APT The Hacker News
A North Korea-linked cyber-espionage group has been observed leveraging job-themed phishing lures to target prospective victims in energy and aerospace verticals and infect them with a previously undocumented backdoor dubbed MISTPEN.
The activity cluster is being tracked by Google-owned Mandiant under the moniker UNC2970, which it said overlaps with a threat group known as TEMP.Hermit, which is also broadly called Lazarus Group or Diamond Sleet (formerly Zinc).
The threat actor has a history of targeting government, defense, telecommunications, and financial institutions worldwide since at least 2013 to collect strategic intelligence that furthers North Korean interests. It's affiliated with the Reconnaissance General Bureau (RGB).
The threat intelligence firm said it has observed UNC2970 singling out various entities located in the U.S., the U.K., the Netherlands, Cyprus, Sweden, Germany, Singapore, Hong Kong, and Australia.
"UNC2970 targets victims under the guise of job openings, masquerading as a recruiter for prominent companies," it said in a new analysis, adding it copies and modifies job descriptions according to their target profiles.
"Moreover, the chosen job descriptions target senior-/manager-level employees. This suggests the threat actor aims to gain access to sensitive and confidential information that is typically restricted to higher-level employees."
The attack chains, also known as Operation Dream Job, entail the use of spear-phishing lures to engage with victims over email and WhatsApp in an attempt to build trust, before sending across a malicious ZIP archive file that's dressed up as a job description.
In an interesting twist, the PDF file of the description can only be opened with a trojanized version of a legitimate PDF reader application called Sumatra PDF included within the archive to deliver MISTPEN by means of a launcher referred to as BURNBOOK.

It's worth noting that this does not imply a supply chain attack nor is there a vulnerability in the software. Rather the attack has been found to employ an older Sumatra PDF version that has been repurposed to activate the infection chain.
This is a tried-and-tested method adopted by the hacking group as far back as 2022, with both Mandiant and Microsoft highlighting the use of a wide range of open-source software, including PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and muPDF/Subliminal Recording software installer for these attacks.
It's believed that the threat actors likely instruct the victims to open the PDF file using the enclosed weaponized PDF viewer program to trigger the execution of a malicious DLL file, a C/C++ launcher called BURNBOOK.
"This file is a dropper for an embedded DLL, 'wtsapi32.dll,' which is tracked as TEARPAGE and used to execute the MISTPEN backdoor after the system is rebooted," Mandiant researchers said. "MISTPEN is a trojanized version of a legitimate Notepad++ plugin, binhex.dll, which contains a backdoor."
TEARPAGE, a loader embedded within BURNBOOK, is responsible for decrypting and launching MISTPEN. A lightweight implant written in C, MISTPEN is equipped to download and execute Portable Executable (PE) files retrieved from a command-and-control (C2) server. It communicates over HTTP with the following Microsoft Graph URLs.
Mandiant also said it uncovered older BURNBOOK and MISTPEN artifacts, suggesting that they are being iteratively improved to add more capabilities and allow them to fly under the radar. The early MISTPEN samples have also been discovered using compromised WordPress websites as C2 domains.
"The threat actor has improved their malware over time by implementing new features and adding a network connectivity check to hinder the analysis of the samples," the researchers said.
North Korean Hackers Target Cryptocurrency Users on LinkedIn with RustDoor Malware
16.9.24 APT The Hacker News
Cybersecurity researchers are continuing to warn about North Korean threat actors' attempts to target prospective victims on LinkedIn to deliver malware called RustDoor.
The latest advisory comes from Jamf Threat Labs, which said it spotted an attack attempt in which a user was contacted on the professional social network by claiming to be a recruiter for a legitimate decentralized cryptocurrency exchange (DEX) called STON.fi.
The malicious cyber activity is part of a multi-pronged campaign unleashed by cyber threat actors backed by the Democratic People's Republic of Korea (DPRK) to infiltrate networks of interest under the pretext of conducting interviews or coding assignments.
The financial and cryptocurrency sectors are among the top targets for the state-sponsored adversaries seeking to generate illicit revenues and meet an ever-evolving set of objectives based on the regime's interests.
These attacks manifest in the form of "highly tailored, difficult-to-detect social engineering campaigns" aimed at employees of decentralized finance ("DeFi"), cryptocurrency, and similar businesses, as recently highlighted by the U.S. Federal Bureau of Investigation (FBI) in an advisory.
One of the notable indicators of North Korean social engineering activity relates to requests to execute code or download applications on company-owned devices, or devices that have access to a company's internal network.
Another aspect worth mentioning is that such attacks also involve "requests to conduct a 'pre-employment test' or debugging exercise that involves executing non-standard or unknown Node.js packages, PyPI packages, scripts, or GitHub repositories."
Instances featuring such tactics have been extensively documented in recent weeks, underscoring a persistent evolution of the tools used in these campaigns against targets.
The latest attack chain detected by Jamf entails tricking the victim into downloading a booby-trapped Visual Studio project as part of a purported coding challenge that embeds within it bash commands to download two different second-stage payloads ("VisualStudioHelper" and "zsh_env") with identical functionality.
This stage two malware is RustDoor, which the company is tracking as Thiefbucket. As of writing, none of the anti-malware engines have flagged the zipped coding test file as malicious. It was uploaded to the VirusTotal platform on August 7, 2024.
"The config files embedded within the two separate malware samples shows that the VisualStudioHelper will persist via cron while zsh_env will persist via the zshrc file," researchers Jaron Bradley and Ferdous Saljooki said.
RustDoor, a macOS backdoor, was first documented by Bitdefender in February 2024 in connection with a malware campaign targeting cryptocurrency firms. A subsequent analysis by S2W uncovered a Golang variant dubbed GateDoor that's meant for infecting Windows machines.
The findings from Jamf are significant, not only because they mark the first time the malware has been formally attributed to North Korean threat actors, but also for the fact that the malware is written in Objective-C.
VisualStudioHelper is also designed to act as an information stealer by harvesting files specified in the configuration, but only after prompting the user to enter their system password by masquerading it as though it's originating from the Visual Studio app to avoid raising suspicion.
Both the payloads, however, operate as a backdoor and use two different servers for command-and-control (C2) communications.
"Threat actors continue to remain vigilant in finding new ways to pursue those in the crypto industry," the researchers said. "It's important to train your employees, including your developers, to be hesitant to trust those who connect on social media and ask users to run software of any type.
"These social engineering schemes performed by the DPRK come from those who are well-versed in English and enter the conversation having well researched their target."
Iranian Cyber Group OilRig Targets Iraqi Government in Sophisticated Malware Attack
13.9.24 APT The Hacker News
Iraqi government networks have emerged as the target of an "elaborate" cyber attack campaign orchestrated by an Iran state-sponsored threat actor called OilRig.
The attacks singled out Iraqi organizations such as the Prime Minister's Office and the Ministry of Foreign Affairs, cybersecurity company Check Point said in a new analysis.
OilRig, also called APT34, Crambus, Cobalt Gypsy, GreenBug, Hazel Sandstorm (formerly EUROPIUM), and Helix Kitten, is an Iranian cyber group associated with the Iranian Ministry of Intelligence and Security (MOIS).
Active since at least 2014, the group has a track record of conducting phishing attacks in the Middle East to deliver a variety of custom backdoors such as Karkoff, Shark, Marlin, Saitama, MrPerfectionManager, PowerExchange, Solar, Mango, and Menorah for information theft.
The latest campaign is no exception in that it involves the use of a new set of malware families dubbed Veaty and Spearal, which come with capabilities to execute PowerShell commands and harvest files of interest.
"The toolset used in this targeted campaign employs unique command-and-control (C2) mechanisms, including a custom DNS tunneling protocol, and a tailor-made email based C2 channel," Check Point said.
"The C2 channel uses compromised email accounts within the targeted organization, indicating that the threat actor successfully infiltrated the victim's networks."
Some of the actions that the threat actor took in executing the attack, and following it, were consistent with tactics, techniques, and procedures (TTPs) that OilRig has employed when carrying out similar operations in the past.
This includes the use of email-based C2 channels, specifically leveraging previously compromised email mailboxes to issue commands and exfiltrate data. This modus operandi has been common to several backdoors such as Karkoff, MrPerfectionManager, and PowerExchange.
The attack chain is kicked off via deceptive files masquerading as benign documents ("Avamer.pdf.exe" or "IraqiDoc.docx.rar") that, when launched, pave the way for the deployment of Veaty and Spearal. The infection pathway is likely said to have involved an element of social engineering.
The files initiate the execution of intermediate PowerShell or Pyinstaller scripts that, in turn, drop the malware executables and their XML-based configuration files, which include information about the C2 server.
"The Spearal malware is a .NET backdoor that utilizes DNS tunneling for [C2] communication," Check Point said. "The data transferred between the malware and the C2 server is encoded in the subdomains of DNS queries using a custom Base32 scheme."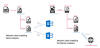
Spearal is designed to execute PowerShell commands, read file contents and send it in the form of Base32-encoded data, and retrieve data from the C2 server and write it to a file on the system.
Also written .NET, Veaty leverages emails for C2 communications with the end goal of downloading files and executing commands via specific mailboxes belonging to the gov-iq.net domain. The commands allow it to upload/download files and run PowerShell scripts.
Check Point said its analysis of the threat actor infrastructure led to the discovery of a different XML configuration file that's likely associated with a third SSH tunneling backdoor.
It further identified an HTTP-based backdoor, CacheHttp.dll, that targets Microsoft's Internet Information Services (IIS) servers and examines incoming web requests for "OnGlobalPreBeginRequest" events and executes commands when they occur.
"The execution process begins by checking if the Cookie header is present in incoming HTTP requests and reads until the; sign," Check Point said. "The main parameter is F=0/1 which indicates whether the backdoor initializes its command configuration (F=1) or runs the commands based on this configuration (F=0)."
The malicious IIS module, which represents an evolution of a malware classified as Group 2 by ESET in August 2021 and another APT34 IIS backdoor codenamed RGDoor, supports command execution and file read/write operations.
"This campaign against Iraqi government infrastructure highlights the sustained and focused efforts of Iranian threat actors operating in the region," the company said.
"The deployment of a custom DNS tunneling protocol and an email-based C2 channel leveraging compromised accounts highlights the deliberate effort by Iranian actors to develop and maintain specialized command-and-control mechanisms."
DragonRank Black Hat SEO Campaign Targeting IIS Servers Across Asia and Europe
13.9.24 APT The Hacker News
A "simplified Chinese-speaking actor" has been linked to a new campaign that has targeted multiple countries in Asia and Europe with the end goal of performing search engine optimization (SEO) rank manipulation.
The black hat SEO cluster has been codenamed DragonRank by Cisco Talos, with victimology footprint scattered across Thailand, India, Korea, Belgium, the Netherlands, and China.
"DragonRank exploits targets' web application services to deploy a web shell and utilizes it to collect system information and launch malware such as PlugX and BadIIS, running various credential-harvesting utilities," security researcher Joey Chen said.
The attacks have led to compromises of 35 Internet Information Services (IIS) servers with the end goal of deploying the BadIIS malware, which was first documented by ESET in August 2021.
It's specifically designed to facilitate proxy ware and SEO fraud by turning the compromised IIS server into a relay point for malicious communications between its customers (i.e., other threat actors) and their victims.
On top of that, it can modify the content served to search engines to manipulate search engine algorithms and boost the ranking of other websites of interest to the attackers.
"One of the most surprising aspects of the investigation is how versatile IIS malware is, and the [detection of] SEO fraud criminal scheme, where malware is misused to manipulate search engine algorithms and help boost the reputation of third-party websites," security researcher Zuzana Hromcova told The Hacker News at the time.
The latest set of attacks highlighted by Talos spans a broad spectrum of industry verticals, including jewelry, media, research services, healthcare, video and television production, manufacturing, transportation, religious and spiritual organizations, IT services, international affairs, agriculture, sports, and feng shui.
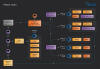
The attack chains commence with taking advantage of known security flaws in web applications like phpMyAdmin and WordPress to drop the open-source ASPXspy web shell, which then acts as a conduit to introduce supplemental tools into the targets' environment.
The primary objective of the campaign is to compromise the IIS servers hosting corporate websites, abusing them to implant the BadIIS malware and effectively repurposing them as a launchpad for scam operations by utilizing keywords related to porn and sex.
Another significant aspect of the malware is its ability to masquerade as the Google search engine crawler in its User-Agent string when it relays the connection to the command-and-control (C2) server, thereby allowing it to bypass some website security measures.
"The threat actor engages in SEO manipulation by altering or exploiting search engine algorithms to improve a website's ranking in search results," Chen explained. "They conduct these attacks to drive traffic to malicious sites, increase the visibility of fraudulent content, or disrupt competitors by artificially inflating or deflating rankings."
One important way DragonRank distinguishes itself from other black hat SEO cybercrime groups is in the manner it attempts to breach additional servers within the target's network and maintain control over them using PlugX, a backdoor widely shared by Chinese threat actors, and various credential-harvesting programs such as Mimikatz, PrintNotifyPotato, BadPotato, and GodPotato.
Although the PlugX malware used in the attacks relies on DLL side-loading techniques, the loader DLL responsible for launching the encrypted payload uses the Windows Structured Exception Handling (SEH) mechanism in an attempt to ensure that the legitimate file (i.e., the binary susceptible to DLL side-loading) can load the PlugX without tripping any alarms.
Evidence unearthed by Talos points to the threat actor maintaining a presence on Telegram under the handle "tttseo" and the QQ instant message application to facilitate illegal business transactions with paying clients.
"These adversaries also offer seemingly quality customer service, tailoring promotional plans to best fit their clients' needs," Chen added.
"Customers can submit the keywords and websites they wish to promote, and DragonRank develops a strategy suited to these specifications. The group also specializes in targeting promotions to specific countries and languages, ensuring a customized and comprehensive approach to online marketing."
Developers Beware: Lazarus Group Uses Fake Coding Tests to Spread Malware
11.9.24 APT The Hacker News
Cybersecurity researchers have uncovered a new set of malicious Python packages that target software developers under the guise of coding assessments.
"The new samples were tracked to GitHub projects that have been linked to previous, targeted attacks in which developers are lured using fake job interviews," ReversingLabs researcher Karlo Zanki said.
The activity has been assessed to be part of an ongoing campaign dubbed VMConnect that first came to light in August 2023. There are indications that it is the handiwork of the North Korea-backed Lazarus Group.
The use of job interviews as an infection vector has been adopted widely by North Korean threat actors, either approaching unsuspecting developers on sites such as LinkedIn or tricking them into downloading rogue packages as part of a purported skills test.
These packages, for their part, have been published directly on public repositories like npm and PyPI, or hosted on GitHub repositories under their control.
ReversingLabs said it identified malicious code embedded within modified versions of legitimate PyPI libraries such as pyperclip and pyrebase.
"The malicious code is present in both the __init__.py file and its corresponding compiled Python file (PYC) inside the __pycache__ directory of respective modules," Zanki said.
It's implemented in the form of a Base64-encoded string that obscures a downloader function that establishes contact with a command-and-control (C2) server in order to execute commands received as a response.
In one instance of the coding assignment identified by the software supply chain firm, the threat actors sought to create a false sense of urgency by requiring job seekers to build a Python project shared in the form of a ZIP file within five minutes and find and fix a coding flaw in the next 15 minutes.

This makes it "more likely that he or she would execute the package without performing any type of security or even source code review first," Zanki said, adding "that ensures the malicious actors behind this campaign that the embedded malware would be executed on the developer's system."
Some of the aforementioned tests claimed to be a technical interview for financial institutions like Capital One and Rookery Capital Limited, underscoring how the threat actors are impersonating legitimate companies in the sector to pull off the operation.
It's currently not clear how widespread these campaigns are, although prospective targets are scouted and contacted using LinkedIn, as recently also highlighted by Google-owned Mandiant.
"After an initial chat conversation, the attacker sent a ZIP file that contained COVERTCATCH malware disguised as a Python coding challenge, which compromised the user's macOS system by downloading a second-stage malware that persisted via Launch Agents and Launch Daemons," the company said.
The development comes as cybersecurity company Genians revealed that the North Korean threat actor codenamed Konni is intensifying its attacks against Russia and South Korea by employing spear-phishing lures that lead to the deployment of AsyncRAT, with overlaps identified with a campaign codenamed CLOUD#REVERSER (aka puNK-002).
Some of these attacks also entail the propagation of a new malware called CURKON, a Windows shortcut (LNK) file that serves as a downloader for an AutoIt version of Lilith RAT. The activity has been linked to a sub-cluster tracked as puNK-003, per S2W.
Experts Identify 3 Chinese-Linked Clusters Behind Cyberattacks in Southeast Asia
11.9.24 APT The Hacker News
A trio of threat activity clusters linked to China has been observed compromising more government organizations in Southeast Asia as part of a renewed state-sponsored operation codenamed Crimson Palace, indicating an expansion in the scope of the espionage effort.
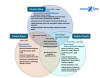
Cybersecurity firm Sophos, which has been monitoring the cyber offensive, said it comprises three intrusion sets tracked as Cluster Alpha (STAC1248), Cluster Bravo (STAC1870), and Cluster Charlie (STAC1305). STAC is an abbreviation for "security threat activity cluster."
"The attackers consistently used other compromised organizational and public service networks in that region to deliver malware and tools under the guise of a trusted access point," security researchers Mark Parsons, Morgan Demboski, and Sean Gallagher said in a technical report shared with The Hacker News.
A noteworthy aspect of the attacks is that it entails the use of an unnamed organization's systems as a command-and-control (C2) relay point and a staging ground for tools. A second organization's compromised Microsoft Exchange Server is said to have been utilized to host malware.
Crimson Palace was first documented by the cybersecurity company in early June 2024, with the attacks taking place between March 2023 and April 2024.
While initial activity associated with Cluster Bravo, which overlaps with a threat group called Unfading Sea Haze, was confined to March 2023, a new attack wave detected between January and June 2024 has been observed targeting 11 other organizations and agencies in the same region.
A set of new attacks orchestrated by Cluster Charlie, a cluster that's referred to as Earth Longzhi, has also been identified between September 2023 and June 2024, some of which also involve the deployment of different C2 frameworks like Cobalt Strike, Havoc, and XieBroC2 in order to facilitate post-exploitation and deliver additional payloads like SharpHound for Active Directory infrastructure mapping.
"Exfiltration of data of intelligence value was still an objective after the resumption of activity," the researchers said. "However, much of their effort appeared to be focused on re-establishing and extending their foothold on the target network by bypassing EDR software and rapidly re-establishing access when their C2 implants had been blocked."
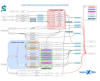
Another significant aspect is Cluster Charlie's heavy reliance on DLL hijacking to execute malware, an approach previously adopted by threat actors behind Cluster Alpha, indicating a "cross-pollination" of tactics.
Some of the other open-source programs used by the threat actor include RealBlindingEDR and Alcatraz, which allow for terminating antivirus processes and obfuscating portable executable files (e.g., .exe, .dll, and .sys) with an aim to fly under the radar.
Rounding off the cluster's malware arsenal is a previously unknown keylogger codenamed TattleTale that was originally identified in August 2023 and is capable of collecting Google Chrome and Microsoft Edge browser data.
"The malware can fingerprint the compromised system and check for mounted physical and network drives by impersonating a logged-on user," the researchers explained.
"TattleTale also collects the domain controller name and steals the LSA (Local Security Authority) Query Information Policy, which is known to contain sensitive information related to password policies, security settings, and sometimes cached passwords."
In a nutshell, the three clusters work hand in hand, while simultaneously focusing on specific tasks in the attack chain: Infiltrating target environments and conducting reconnaissance (Alpha), burrowing deep into the networks using various C2 mechanisms (Bravo), and exfiltrating valuable data (Charlie).
"Throughout the engagement, the adversary appeared to continually test and refine their techniques, tools, and practices," the researchers concluded. "As we deployed countermeasures for their bespoke malware, they combined the use of their custom-developed tools with generic, open-source tools often used by legitimate penetration testers, testing different combinations."
Mustang Panda Deploys Advanced Malware to Spy on Asia-Pacific Governments
11.9.24 APT The Hacker News
The threat actor tracked as Mustang Panda has refined its malware arsenal to include new tools in order to facilitate data exfiltration and the deployment of next-stage payloads, according to new findings from Trend Micro.
The cybersecurity firm, which is monitoring the activity cluster under the name Earth Preta, said it observed "the propagation of PUBLOAD via a variant of the worm HIUPAN."
PUBLOAD is a known downloader malware linked to Mustang Panda since early 2022, deployed as part of cyber attacks targeting government entities in the Asia-Pacific (APAC) region to deliver the PlugX malware.
"PUBLOAD was also used to introduce supplemental tools into the targets' environment, such as FDMTP to serve as a secondary control tool, which was observed to perform similar tasks as that of PUBLOAD; and PTSOCKET, a tool used as an alternative exfiltration option," security researchers Lenart Bermejo, Sunny Lu, and Ted Lee said.
Mustang Panda's use of removable drives as a propagation vector for HIUPAN was previously documented by Trend Micro in March 2023. It's tracked by Google-owned Mandiant as MISTCLOAK, which it observed in connection with a cyber espionage campaign targeting the Philippines that may have commenced as far back as September 2021.
PUBLOAD is equipped with features to conduct reconnaissance of the infected network and harvest files of interest (.doc, .docx, .xls, .xlsx, .pdf, .ppt, and .pptx), while also serving as a conduit for a new hacking tool dubbed FDMTP, which is a "simple malware downloader" implemented based on TouchSocket over Duplex Message Transport Protocol (DMTP).
The captured information is compressed into an RAR archive and exfiltrated to an attacker-controlled FTP site via cURL. Alternatively, Mustang Panda has also been observed deploying a custom program named PTSOCKET that can transfer files in multi-thread mode.
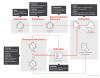
Furthermore, Trend Micro has attributed the adversary to a "fast-paced" spear-phishing campaign that it detected in June 2024 as distributing email messages containing a .url attachment, which, when launched, is used to deliver a signed downloader dubbed DOWNBAIT.
The campaign is believed to have targeted Myanmar, the Philippines, Vietnam, Singapore, Cambodia, and Taiwan based on the filenames and content of the decoy documents used.
DOWNBAIT is a first-stage loader tool that's used to retrieve and execute the PULLBAIT shellcode in memory, which subsequently downloads and runs the first-stage backdoor referred to as CBROVER.
The implant, for its part, supports file download and remote shell execution capabilities, alongside acting as a delivery vehicle for the PlugX remote access trojan (RAT). PlugX then takes care of deploying another bespoke file collector called FILESAC that can collect the victim's files.
The disclosure comes as Palo Alto Networks Unit 42 detailed Mustang Panda's abuse of Visual Studio Code's embedded reverse shell feature to gain a foothold in target networks, indicating that the threat actor is actively tweaking its modus operandi.
"Earth Preta has shown significant advancements in their malware deployment and strategies, particularly in their campaigns targeting government entities," the researchers said. "The group has evolved their tactics, [...] leveraging multi-stage downloaders (from DOWNBAIT to PlugX) and possibly exploiting Microsoft's cloud services for data exfiltration."
Chinese Hackers Exploit Visual Studio Code in Southeast Asian Cyberattacks
9.9.24 APT The Hacker News
The China-linked advanced persistent threat (APT) group known as Mustang Panda has been observed weaponizing Visual Studio Code software as part of espionage operations targeting government entities in Southeast Asia.
"This threat actor used Visual Studio Code's embedded reverse shell feature to gain a foothold in target networks," Palo Alto Networks Unit 42 researcher Tom Fakterman said in a report, describing it as a "relatively new technique" that was first demonstrated in September 2023 by Truvis Thornton.
The campaign is assessed to be a continuation of a previously documented attack activity aimed at an unnamed Southeast Asian government entity in late September 2023.
Mustang Panda, also known by the names BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, and Red Lich, has been operational since 2012, routinely conducting cyber espionage campaigns targeting government and religious entities across Europe and Asia, particularly those located in South China Sea countries.
The latest observed attack sequence is notable for its abuse of Visual Studio Code's reverse shell to execute arbitrary code and deliver additional payloads.
"To abuse Visual Studio Code for malicious purposes, an attacker can use the portable version of code.exe (the executable file for Visual Studio Code), or an already installed version of the software," Fakterman noted. "By running the command code.exe tunnel, an attacker receives a link that requires them to log into GitHub with their own account."
Once this step is complete, the attacker is redirected to a Visual Studio Code web environment that's connected to the infected machine, allowing them to run commands or create new files.
It's worth pointing out that the malicious use of this technique was previously highlighted by a Dutch cybersecurity firm mnemonic in connection with zero-day exploitation of a vulnerability in Check Point's Network Security gateway products (CVE-2024-24919, CVSS score: 8.6) earlier this year.
Unit 42 said the Mustang Panda actor leveraged the mechanism to deliver malware, perform reconnaissance, and exfiltrate sensitive data. Furthermore, the attacker is said to have used OpenSSH to execute commands, transfer files, and spread across the network.
That's not all. A closer analysis of the infected environment has revealed a second cluster of activity "occurring simultaneously and at times even on the same endpoints" that utilized the ShadowPad malware, a modular backdoor widely shared by Chinese espionage groups.
It's currently unclear if these two intrusion sets are related to one another, or if two different groups are "piggybacking on each other's access."
"Based on the forensic evidence and timeline, one could conclude that these two clusters originated from the same threat actor (Stately Taurus)," Fakterman said. "However, there could be other possible explanations that can account for this connection, such as a collaborative effort between two Chinese APT threat actors."
Chinese-Speaking Hacker Group Targets Human Rights Studies in Middle East
6.9.24 APT The Hacker News
Unnamed government entities in the Middle East and Malaysia are the target of a persistent cyber campaign orchestrated by a threat actor known as Tropic Trooper since June 2023.
"Sighting this group's [Tactics, Techniques, and Procedures] in critical governmental entities in the Middle East, particularly those related to human rights studies, marks a new strategic move for them," Kaspersky security researcher Sherif Magdy said.
The Russian cybersecurity vendor said it detected the activity in June 2024 upon discovering a new version of the China Chopper web Shell, a tool shared by many Chinese-speaking threat actors for remote access to compromised servers, on a public web server hosting an open-source content management system (CMS) called Umbraco.
The attack chain is designed to deliver a malware implant named Crowdoor, a variant of the SparrowDoor backdoor documented by ESET back in September 2021. The efforts were ultimately unsuccessful.
Tropic Trooper, also known by the names APT23, Earth Centaur, KeyBoy, and Pirate Panda, is known for its targeting of government, healthcare, transportation, and high-tech industries in Taiwan, Hong Kong, and the Philippines. The Chinese-speaking collective has been assessed to be active since 2011, sharing close ties with another intrusion set tracked as FamousSparrow.
The latest intrusion highlighted by Kaspersky is significant for compiling the China Chopper web shell as a .NET module of Umbraco CMS, with follow-on exploitation leading to the deployment of tools for network scanning, lateral movement, and defense evasion, before launching Crowdoor using DLL side-loading techniques.

It's suspected that the web shells are delivered by exploiting known security vulnerabilities in publicly accessible web applications, such as Adobe ColdFusion (CVE-2023-26360) and Microsoft Exchange Server (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207).
Crowdoor, first observed in June 2023, also functions as a loader to drop Cobalt Strike and maintain persistence on the infected hosts, while also acting as a backdoor to harvest sensitive information, launch a reverse shell, erase other malware files, and terminate itself.
"When the actor became aware that their backdoors were detected, they tried to upload newer samples to evade detection, thereby increasing the risk of their new set of samples being detected in the near future," Magdy noted.
"The significance of this intrusion lies in the sighting of a Chinese-speaking actor targeting a content management platform that published studies on human rights in the Middle East, specifically focusing on the situation around the Israel-Hamas conflict."
"Our analysis of this intrusion revealed that this entire system was the sole target during the attack, indicating a deliberate focus on this specific content."
North Korean Hackers Targets Job Seekers with Fake FreeConference App
5.9.24 APT The Hacker News
North Korean threat actors have leveraged a fake Windows video conferencing application impersonating FreeConference.com to backdoor developer systems as part of an ongoing financially-driven campaign dubbed Contagious Interview.
The new attack wave, spotted by Singaporean company Group-IB in mid-August 2024, is yet another indication that the activity is also leveraging native installers for Windows and Apple macOS to deliver malware.
Contagious Interview, also tracked as DEV#POPPER, is a malicious campaign orchestrated by a North Korean threat actor tracked by CrowdStrike under the moniker Famous Chollima.
The attack chains begin with a fictitious job interview, tricking job seekers into downloading and running a Node.js project that contains the BeaverTail downloader malware, which in turn delivers InvisibleFerret, a cross-platform Python backdoor that's equipped with remote control, keylogging, and browser stealing capabilities.
Some iterations of BeaverTail, which also functions as an information stealer, have manifested in the form of JavaScript malware, typically distributed via bogus npm packages as part of a purported technical assessment during the interview process.
But that changed in July 2024 when Windows MSI installer and Apple macOS disk image (DMG) files masquerading as the legitimate MiroTalk video conferencing software were discovered in the wild, acting as a conduit to deploy an updated version of BeaverTail.
The latest findings from Group-IB, which has attributed the campaign to the infamous Lazarus Group, suggest that the threat actor is continuing to lean on this specific distribution mechanism, the only difference being that the installer ("FCCCall.msi") mimics FreeConference.com instead of MiroTalk.
It's believed that the phony installer is downloaded from a website named freeconference[.]io, which uses the same registrar as the fictitious mirotalk[.]net website.
"In addition to Linkedin, Lazarus is also actively searching for potential victims on other job search platforms such as WWR, Moonlight, Upwork, and others," security researcher Sharmine Low said.
"After making initial contact, they would often attempt to move the conversation onto Telegram, where they would then ask the potential interviewees to download a video conferencing application, or a Node.js project, to perform a technical task as part of the interview process."
In a sign that the campaign is undergoing active refinement, the threat actors have been observed injecting the malicious JavaScript into both cryptocurrency- and gaming-related repositories. The JavaScript code, for its part, is designed to retrieve the BeaverTail Javascript code from the domain ipcheck[.]cloud or regioncheck[.]net.
It's worth mentioning here that this behavior was also recently highlighted by software supply chain security firm Phylum in connection with an npm package named helmet-validate, suggesting that the threat actors are simultaneously making use of different propagation vectors.
Another notable change is that BeaverTail is now configured to extract data from more cryptocurrency wallet extensions such as Kaikas, Rabby, Argent X, and Exodus Web3, in addition to implementing functionality to establish persistence using AnyDesk.
That's not all. BeaverTail's information-stealing features are now realized through a set of Python scripts, collectively called CivetQ, which is capable of harvesting cookies, web browser data, keystrokes, and clipboard content, and delivering more scripts. A total of 74 browser extensions are targeted by the malware.
"The malware is able to steal data from Microsoft Sticky Notes by targeting the application's SQLite database files located at `%LocalAppData%\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState\plum.sqlite,` where user notes are stored in an unencrypted format," Low said.
"By querying and extracting data from this database, the malware can retrieve and exfiltrate sensitive information from the victim's Sticky Notes application."
The emergence of CivetQ points to a modularized approach, while also underscoring that the tools are under active development and have been constantly evolving in little increments over the past few months.
"Lazarus has updated their tactics, upgraded their tools, and found better ways to conceal their activities," Low said. "They show no signs of easing their efforts, with their campaign targeting job seekers extending into 2024 and to the present day. Their attacks have become increasingly creative, and they are now expanding their reach across more platforms."
The disclosure comes as the U.S. Federal Bureau of Investigation (FBI) warned of North Korean cyber actors' aggressive targeting of the cryptocurrency industry using "well-disguised" social engineering attacks to facilitate cryptocurrency theft.
"North Korean social engineering schemes are complex and elaborate, often compromising victims with sophisticated technical acumen," the FBI said in an advisory released Tuesday, stating the threat actors scout prospective victims by reviewing their social media activity on professional networking or employment-related platforms.
"Teams of North Korean malicious cyber actors identify specific DeFi or cryptocurrency-related businesses to target and attempt to socially engineer dozens of these companies' employees to gain unauthorized access to the company's network."
Cyberattackers Exploit Google Sheets for Malware Control in Likely Espionage Campaign
30.8.24 APT The Hacker News
Cybersecurity researchers have uncovered a novel malware campaign that leverages Google Sheets as a command-and-control (C2) mechanism.
The activity, detected by Proofpoint starting August 5, 2024, impersonates tax authorities from governments in Europe, Asia, and the U.S., with the goal of targeting over 70 organizations worldwide by means of a bespoke tool called Voldemort that's equipped to gather information and deliver additional payloads.
Targeted sectors include insurance, aerospace, transportation, academia, finance, technology, industrial, healthcare, automotive, hospitality, energy, government, media, manufacturing, telecom, and social benefit organizations.
The suspected cyber espionage campaign has not been attributed to a specific named threat actor. As many as 20,000 email messages have been sent as part of the attacks.
These emails claim to be from tax authorities in the U.S., the U.K., France, Germany, Italy, India, and Japan, alerting recipients about changes to their tax filings and urging them to click on Google AMP Cache URLs that redirect users to an intermediate landing page.
What the page does is inspect the User-Agent string to determine if the operating system is Windows, and if so, leverage the search-ms: URI protocol handler to display a Windows shortcut (LNK) file that uses an Adobe Acrobat Reader to masquerade as a PDF file in an attempt to trick the victim into launching it.
"If the LNK is executed, it will invoke PowerShell to run Python.exe from a third WebDAV share on the same tunnel (\library\), passing a Python script on a fourth share (\resource\) on the same host as an argument," Proofpoint researchers Tommy Madjar, Pim Trouerbach, and Selena Larson said.
"This causes Python to run the script without downloading any files to the computer, with dependencies being loaded directly from the WebDAV share."
The Python script is designed to gather system information and send the data in the form of a Base64-encoded string to an actor-controlled domain, after which it shows a decoy PDF to the user and downloads a password-protected ZIP file from OpenDrive.
The ZIP archive, for its part, contains two files, a legitimate executable "CiscoCollabHost.exe" that's susceptible to DLL side-loading and a malicious DLL "CiscoSparkLauncher.dll" (i.e., Voldemort) file that's sideloaded.
Voldemort is a custom backdoor written in C that comes with capabilities for information gathering and loading next-stage payloads, with the malware utilizing Google Sheets for C2, data exfiltration, and executing commands from the operators.
Proofpoint described the activity as aligned to advanced persistent threats (APT) but carrying "cybercrime vibes" owing to the use of techniques popular in the e-crime landscape.
"Threat actors abuse file schema URIs to access external file sharing resources for malware staging, specifically WebDAV and Server Message Block (SMB). This is done by using the schema 'file://' and pointing to a remote server hosting the malicious content," the researchers said.
This approach has been increasingly prevalent among malware families that act as initial access brokers (IABs), such as Latrodectus, DarkGate, and XWorm.
Furthermore, Proofpoint said it was able to read the contents of the Google Sheet, identifying a total of six victims, including one that's believed to be either a sandbox or a "known researcher."
The campaign has been branded unusual, raising the possibility that the threat actors cast a wide net before zeroing in on a small pool of targets. It's also possible that the attackers, likely with varying levels of technical expertise, planned to infect several organizations.
"While many of the campaign characteristics align with cybercriminal threat activity, we assess this is likely espionage activity conducted to support as yet unknown final objectives," the researchers said.
"The Frankensteinian amalgamation of clever and sophisticated capabilities, paired with very basic techniques and functionality, makes it difficult to assess the level of the threat actor's capability and determine with high confidence the ultimate goals of the campaign."
The development comes as Netskope Threat Labs uncovered an updated version of the Latrodectus (version 1.4) that comes with a new C2 endpoint and adds two new backdoor commands that allow it to download shellcode from a specified server and retrieve arbitrary files from a remote location.
"Latrodectus has been evolving pretty fast, adding new features to its payload," security researcher Leandro Fróes said. "The understanding of the updates applied to its payload allows defenders to keep automated pipelines properly set as well as use the information for further hunting for new variants."
Iranian Hackers Set Up New Network to Target U.S. Political Campaigns
30.8.24 APT The Hacker News
Cybersecurity researchers have unearthed new network infrastructure set up by Iranian threat actors to support activities linked to the recent targeting of U.S. political campaigns.
Recorded Future's Insikt Group has linked the infrastructure to a threat it tracks as GreenCharlie, an Iran-nexus cyber threat group that overlaps with APT42, Charming Kitten, Damselfly, Mint Sandstorm (formerly Phosphorus), TA453, and Yellow Garuda.
"The group's infrastructure is meticulously crafted, utilizing dynamic DNS (DDNS) providers like Dynu, DNSEXIT, and Vitalwerks to register domains used in phishing attacks," the cybersecurity company said.
"These domains often employ deceptive themes related to cloud services, file sharing, and document visualization to lure targets into revealing sensitive information or downloading malicious files."
Examples include terms like "cloud," "uptimezone," "doceditor," "joincloud," and "pageviewer," among others. A majority of the domains were registered using the .info top-level domain (TLD), a shift from the previously observed .xyz, .icu, .network, .online, and .site TLDs.
The adversary has a track record of staging highly-targeted phishing attacks that leverage extensive social engineering techniques to infect users with malware like POWERSTAR (aka CharmPower and GorjolEcho) and GORBLE, which was recently identified by Google-owned Mandiant as used in campaigns against Israel and U.S.
GORBLE, TAMECAT, and POWERSTAR are assessed to be variants of the same malware, a series of ever-evolving PowerShell implants deployed by GreenCharlie over the years. It's worth noting that Proofpoint detailed another POWERSTAR successor dubbed BlackSmith that was used in a spear-phishing campaign targeting a prominent Jewish figure in late July 2024.
The infection process is often a multi-stage one, which involves gaining initial access through phishing, followed by establishing communication with command-and-control (C2) servers, and ultimately exfiltrating data or delivering additional payloads.
Recorded Future's findings show that the threat actor registered a large number of DDNS domains since May 2024, with the company also identifying communications between Iran-based IP addresses (38.180.146[.]194 and 38.180.146[.]174) and GreenCharlie infrastructure between July and August 2024.
Furthermore, a direct link has been unearthed between GreenCharlie clusters and C2 servers used by GORBLE. It's believed that the operations are facilitated by means of Proton VPN or Proton Mail to obfuscate their activity.
"GreenCharlie's phishing operations are highly targeted, often employing social engineering techniques that exploit current events and political tensions," Recorded Future said.
"The group has registered numerous domains since May 2024, many of which are likely used for phishing activities. These domains are linked to DDNS providers, which allow for rapid changes in IP addresses, making it difficult to track the group's activities."
The disclosure comes amid a ramping up of Iranian malicious cyber activity against the U.S. and other foreign targets. Earlier this week, Microsoft revealed that multiple sectors in the U.S. and the U.A.E. are the target of an Iranian threat actor codenamed Peach Sandstorm (aka Refined Kitten).
Additionally, U.S. government agencies said yet another Iranian state-backed hacking crew, Pioneer Kitten, has moonlighted as an initial access broker (IAB) for facilitating ransomware attacks against education, finance, healthcare, defense, and government sectors in the U.S. in collaboration with NoEscape, RansomHouse, and BlackCat crews.
North Korean Hackers Target Developers with Malicious npm Packages
30.8.24 APT The Hacker News
Threat actors with ties to North Korea have been observed publishing a set of malicious packages to the npm registry, indicating "coordinated and relentless" efforts to target developers with malware and steal cryptocurrency assets.
The latest wave, which was observed between August 12 and 27, 2024, involved packages named temp-etherscan-api, ethersscan-api, telegram-con, helmet-validate, and qq-console.
"Behaviors in this campaign lead us to believe that qq-console is attributable to the North Korean campaign known as 'Contagious Interview,'" software supply chain security firm Phylum said.
Contagious Interview refers to an ongoing campaign that seeks to compromise software developers with information stealing malware as part of a purported job interview process that involves tricking them into downloading bogus npm packages or fake installers for video conferencing software such as MiroTalk hosted on decoy websites.
The end goal of the attacks is to deploy a Python payload named InvisibleFerret that can exfiltrate sensitive data from cryptocurrency wallet browser extensions and set up persistence on the host using legitimate remote desktop software such as AnyDesk. CrowdStrike is tracking the activity under the moniker Famous Chollima.
The newly observed helmet-validate package adopts a new approach in that it embeds a piece of JavaScript code file called config.js that directly executes JavaScript hosted on a remote domain ("ipcheck[.]cloud") using the eval() function.
"Our investigation revealed that ipcheck[.]cloud resolves to the same IP address (167[.]88[.]36[.]13) that mirotalk[.]net resolved to when it was online," Phylum said, highlighting potential links between the two sets of attacks.
The company said it also observed another package called sass-notification that was uploaded on August 27, 2024, which shared similarities with previously uncovered npm libraries like call-blockflow. These packages have been attributed to another North Korean threat group called Moonstone Sleet.
"These attacks are characterized by using obfuscated JavaScript to write and execute batch and PowerShell scripts," it said. "The scripts download and decrypt a remote payload, execute it as a DLL, and then attempt to clean up all traces of malicious activity, leaving behind a seemingly benign package on the victim's machine."
Famous Chollima Poses as IT Workers in U.S. Firms#
The disclosure comes as CrowdStrike linked Famous Chollima (formerly BadClone) to insider threat operations that entail infiltrating corporate environments under the pretext of legitimate employment.
"Famous Chollima carried out these operations by obtaining contract or full-time equivalent employment, using falsified or stolen identity documents to bypass background checks," the company said. "When applying for a job, these malicious insiders submitted a résumé typically listing previous employment with a prominent company as well as additional lesser-known companies and no employment gaps."
While these attacks are mainly financially motivated, a subset of the incidents are said to have involved the exfiltration of sensitive information. CrowdStrike said it has identified the threat actors applying to or actively working at more than 100 unique companies over the past year, most of which are located in the U.S., Saudi Arabia, France, the Philippines, and Ukraine, among others.
Prominently targeted sectors include technology, fintech, financial services, professional services, retail, transportation, manufacturing, insurance, pharmaceutical, social media, and media companies.
"After obtaining employee-level access to victim networks, the insiders performed minimal tasks related to their job role," the company further said. In some cases, the insiders also attempted to exfiltrate data using Git, SharePoint, and OneDrive."
"Additionally, the insiders installed the following RMM tools: RustDesk, AnyDesk, TinyPilot, VS Code Dev Tunnels, and Google Chrome Remote Desktop. The insiders then leveraged these RMM tools in tandem with company network credentials, which allowed numerous IP addresses to connect to the victim's system."
New Cyberattack Targets Chinese-Speaking Businesses with Cobalt Strike Payloads
30.8.24 APT The Hacker News
Chinese-speaking users are the target of a "highly organized and sophisticated attack" campaign that is likely leveraging phishing emails to infect Windows systems with Cobalt Strike payloads.
"The attackers managed to move laterally, establish persistence and remain undetected within the systems for more than two weeks," Securonix researchers Den Iuzvyk and Tim Peck said in a new report.
The covert campaign, codenamed SLOW#TEMPEST and not attributed to any known threat actor, commences with malicious ZIP files that, when unpacked, activates the infection chain, leading to the deployment of the post-exploitation toolkit on compromised systems.
Present with the ZIP archive is a Windows shortcut (LNK) file that disguises itself as a Microsoft Word file, "违规远程控制软件人员名单.docx.lnk," which roughly translates to "List of people who violated the remote control software regulations."
"Given the language used in the lure files, it's likely that specific Chinese related business or government sectors could be targeted as they would both employ individuals who follow 'remote control software regulations,'" the researchers pointed out.
The LNK file acts as a conduit to launch a legitimate Microsoft binary ("LicensingUI.exe") that employs DLL side-loading to execute a rogue DLL ("dui70.dll"). Both the files are part of the ZIP archive within a directory called "\其他信息\.__MACOS__\._MACOS_\__MACOSX\_MACOS_." The attack marks the first time DLL side-loading via LicensingUI.exe has been reported.
The DLL file is a Cobalt Strike implant that allows for persistent and stealthy access to the infected host, while establishing contact with a remote server ("123.207.74[.]22").
The remote access is said to have allowed the attackers to conduct a series of hands-on activities, including deploying additional payloads for reconnaissance and setting up proxied connections.
The infection chain is also notable for setting up a scheduled task to periodically execute a malicious executable called "lld.exe" that can run arbitrary shellcode directly in memory, thereby leaving minimal footprints on disk.
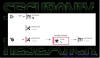
"The attackers further enabled themselves to hide in the weeds in compromised systems by manually elevating the privileges of the built-in Guest user account," the researchers said.
"This account, typically disabled and minimally privileged, was transformed into a powerful access point by adding it to the critical administrative group and assigning it a new password. This backdoor allows them to maintain access to the system with minimal detection, as the Guest account is often not monitored as closely as other user accounts."
The unknown threat actor subsequently proceeded to move laterally across the network using Remote Desktop Protocol (RDP) and credentials obtained via the Mimikatz password extraction tool, followed by setting up remote connections back to their command-and-control (C2) server from each of those machines.
The post-exploitation phase is further characterized by the execution of several enumeration commands and the use of the BloodHound tool for active directory (AD) reconnaissance, the results of which were then exfiltrated in the form of a ZIP archive.
The connections to China are reinforced by the fact that all of the C2 servers are hosted in China by Shenzhen Tencent Computer Systems Company Limited. On top of that, a majority of the artifacts connected with the campaign have originated from China.
"Although there was no solid evidence linking this attack to any known APT groups, it is likely orchestrated by a seasoned threat actor who had experience using advanced exploitation frameworks such as Cobalt Strike and a wide range of other post-exploitation tools," the researchers concluded.
"The campaign's complexity is evident in its methodical approach to initial compromise, persistence, privilege escalation and lateral movement across the network."
Vietnamese Human Rights Group Targeted in Multi-Year Cyberattack by APT32
30.8.24 APT The Hacker News
A non-profit supporting Vietnamese human rights has been the target of a multi-year campaign designed to deliver a variety of malware on compromised hosts.
Cybersecurity company Huntress attributed the activity to a threat cluster tracked as APT32, a Vietnamese-aligned hacking crew that's also known as APT-C-00, Canvas Cyclone (formerly Bismuth), Cobalt Kitty, and OceanLotus. The intrusion is believed to have been ongoing for at least four years.
"This intrusion has a number of overlaps with known techniques used by the threat actor APT32/OceanLotus, and a known target demographic which aligns with APT32/OceanLotus targets," security researchers Jai Minton and Craig Sweeney said.
OceanLotus, active since at least 2012, has a history of targeting company and government networks in East-Asian countries, particularly Vietnam, the Philippines, Laos, and Cambodia with the end goal of cyber espionage and intellectual property theft.
Attack chains typically make use of spear-phishing lures as the initial penetration vector to deliver backdoors capable of running arbitrary shellcode and collecting sensitive information. That said, the group has also been observed orchestrating watering hole campaigns as early as 2018 to infect site visitors with a reconnaissance payload or harvest their credentials.
The latest set of attacks pieced together by Huntress spanned four hosts, each of which was compromised to add various scheduled tasks and Windows Registry keys that are responsible for launching Cobalt Strike Beacons, a backdoor that enables the theft of Google Chrome cookies for all user profiles on the system, and loaders responsible for launching embedded DLL payloads.
The development comes as South Korean users are the target of an ongoing campaign that likely leverages spear-phishing and vulnerable Microsoft Exchange servers to deliver reverse shells, backdoors, and VNC malware to gain control of infected machines and steal credentials stored in web browsers.
APT-C-60 Group Exploit WPS Office Flaw to Deploy SpyGlace Backdoor
28.8.24 APT The Hacker News
A South Korea-aligned cyber espionage has been linked to the zero-day exploitation of a now-patched critical remote code execution flaw in Kingsoft WPS Office to deploy a bespoke backdoor dubbed SpyGlace.
The activity has been attributed to a threat actor dubbed APT-C-60, according to cybersecurity firms ESET and DBAPPSecurity. The attacks have been found to infect Chinese and East Asian users with malware.
The security flaw in question is CVE-2024-7262 (CVSS score: 9.3), which stems from a lack of proper validation of user-provided file paths. This loophole essentially allows an adversary to upload an arbitrary Windows library and achieve remote code execution.
The bug "allows code execution via hijacking the control flow of the WPS Office plugin component promecefpluginhost.exe," ESET said, adding it found another way to achieve the same effect. The second vulnerability is tracked as CVE-2024-7263 (CVSS score: 9.3).
The attack conceived by APT-C-60 weaponizes the flaw into a one-click exploit that takes the form of a booby-trapped spreadsheet document that was uploaded to VirusTotal in February 2024.
Specifically, the file comes embedded with a malicious link that, when clicked, triggers a multi-stage infection sequence to deliver the SpyGlace trojan, a DLL file named TaskControler.dll that comes with file stealing, plugin loading, and command execution capabilities.
"The exploit developers embedded a picture of the spreadsheet's rows and columns inside the spreadsheet in order to deceive and convince the user that the document is a regular spreadsheet," security researcher Romain Dumont said. "The malicious hyperlink was linked to the image so that clicking on a cell in the picture would trigger the exploit."
APT-C-60 is believed to be active since 2021, with SpyGlace detected in the wild as far back as June 2022, according to Beijing-based cybersecurity vendor ThreatBook.
"Whether the group developed or bought the exploit for CVE-2024-7262, it definitely required some research into the internals of the application but also knowledge of how the Windows loading process behaves," Dumont said.
"The exploit is cunning as it is deceptive enough to trick any user into clicking on a legitimate-looking spreadsheet while also being very effective and reliable. The choice of the MHTML file format allowed the attackers to turn a code execution vulnerability into a remote one."
The disclosure comes as the Slovak cybersecurity company noted that a malicious third-party plugin for the Pidgin messaging application named ScreenShareOTR (or ss-otr) has been found to contain code responsible for downloading next-stage binaries from a command-and-control (C&C) server, ultimately leading to the deployment of DarkGate malware.
"The functionality of the plugin, as advertised, includes screen sharing that uses the secure off-the-record messaging (OTR) protocol. However, in addition to that, the plugin contains malicious code," ESET said. "Specifically, some versions of pidgin-screenshare.dll can download and execute a PowerShell script from the C&C server."
The plugin, which also contains keylogger and screenshot capturing features, has since been removed from the third-party plugins list. Users who have installed the plugin are recommended to remove it with immediate effect.
Chinese Volt Typhoon Exploits Versa Director Flaw, Targets U.S. and Global IT Sectors
27.8.24 APT The Hacker News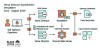
The China-nexus cyber espionage group tracked as Volt Typhoon has been attributed with moderate confidence to the zero-day exploitation of a recently disclosed high-severity security flaw impacting Versa Director.
The attacks targeted four U.S. victims and one non-U.S. victim in the Internet service provider (ISP), managed service provider (MSP) and information technology (IT) sectors as early as June 12, 2024, the Black Lotus Labs team at Lumen Technologies said in a technical report shared with The Hacker News. The campaign is believed to be ongoing against unpatched Versa Director systems.
The security flaw in question is CVE-2024-39717 (CVSS score: 6.6), a file upload bug affecting Versa Director that was added to the Known Exploited Vulnerabilities (KEV) catalog last week by the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
"This vulnerability allowed potentially malicious files to be uploaded by users with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin privileges," Versa said in an advisory released Monday, stating impacted customers failed to implement system hardening and firewall guidelines issued in 2015 and 2017, respectively.
The flaw essentially enables threat actors with administrator privileges to upload malicious files camouflaged as PNG image files by taking advantage of the "Change Favicon" option in the Versa Director GUI. It has been addressed in versions 22.1.4 or later.
Volt Typhoon's targeting of Versa Networks, a secure access service edge (SASE) vendor, is not surprising and is in line with the adversary's historical exploitation of compromised small office and home office (SOHO) network equipment to route network traffic and evade detection for extended periods of time.
The Santa Clara-based company counts Adobe, Axis Bank, Barclays, Capital One, Colt Technology Services, Infosys, Orange, Samsung, T-Mobile, and Verizon among its customers.
"Part of the attribution [to Volt Typhoon] is based on the use of SOHO devices, and the way they were employed," Ryan English, Security researcher at Lumen's Black Lotus Labs, told The Hacker News.
"But there was also a combination of known and observed TTPs including network infrastructure, zero-day exploitation, strategic targeting of specific sectors/victims, web shell analysis, and other confirmed overlaps of malicious activity."
The attack chains are characterized by the exploitation of the flaw to deliver a custom-tailored web shell dubbed VersaMem ("VersaTest.png") that's mainly designed to intercept and harvest credentials that would enable access to downstream customers' networks as an authenticated user, resulting in a large-scale supply chain attack.
Another noteworthy trait of the sophisticated JAR web shell is that it's modular in nature and enables the operators to load additional Java code to run exclusively in-memory.
The earliest sample of VersaMem was uploaded to VirusTotal from Singapore on June 7, 2024. As of August 27, 2024, none of the anti-malware engines have flagged the web shell as malicious. It's believed that the threat actors may have been testing the web shell in the wild on non-U.S. victims before deploying it to U.S. targets.
The web shell "leverages Java instrumentation and Javassist to inject malicious code into the Tomcat web server process memory space on exploited Versa Director servers," the researchers explained.
"Once injected, the web shell code hooks Versa's authentication functionality, allowing the attacker to passively intercept credentials in plaintext, potentially enabling downstream compromises of client infrastructure through legitimate credential use."
"In addition, the web shell hooks Tomcat's request filtering functionality, allowing the threat actor to execute arbitrary Java code in-memory on the compromised server while avoiding file-based detection methods and protecting their web shell, its modules and the zero-day itself."
To counter the threat posed by the attack cluster, it's advised to apply the necessary mitigations, block external access to ports 4566 and 4570, recursively search for PNG image files, and scan for possible network traffic originating from SOHO devices to port 4566 on Versa Director servers.
Volt Typhoon, which is also tracked as Bronze Silhouette, Insidious Taurus, UNC3236, Vanguard Panda, and Voltzite, is an advanced persistent threat that's known to be active for at least five years, targeting critical infrastructure facilities in the U.S. and Guam with the goal of maintaining stealthy access and exfiltrating sensitive data.
"This is a case that shows how Volt Typhoon continues to try to gain access to their ultimate victims patiently and indirectly," English said. "Here they have targeted the Versa Director system as a means of attacking a strategic crossroads of information where they could gather credentials and access, then move down the chain to their ultimate victim."
"Volt Typhoon's evolution over time shows us that while an enterprise may not feel they would draw the attention of a highly skilled nation state actor, the customers that a product is meant to serve may be the real target and that makes us all concerned."
Iranian Cyber Group TA453 Targets Jewish Leader with New AnvilEcho Malware
21.8.24 APT The Hacker News
Iranian state-sponsored threat actors have been observed orchestrating spear-phishing campaigns targeting a prominent Jewish figure starting in late July 2024 with the goal of delivering a new intelligence-gathering tool called AnvilEcho.
Enterprise security company Proofpoint is tracking the activity under the name TA453, which overlaps with activity tracked by the broader cybersecurity community under the monikers APT42 (Mandiant), Charming Kitten (CrowdStrike), Damselfly (Symantec), Mint Sandstorm (Microsoft), and Yellow Garuda (PwC).
"The initial interaction attempted to lure the target to engage with a benign email to build conversation and trust to then subsequently click on a follow-up malicious link," security researchers Joshua Miller, Georgi Mladenov, Andrew Northern, and Greg Lesnewich said in a report shared with The Hacker News.
"The attack chain attempted to deliver a new malware toolkit called BlackSmith, which delivered a PowerShell trojan dubbed AnvilEcho."
TA453 is assessed to be affiliated with Iran's Islamic Revolutionary Guard Corps (IRGC), carrying out targeted phishing campaigns that are designed to support the country's political and military priorities.
Data shared by Google-owned Mandiant last week shows that the U.S. and Israel accounted for roughly 60% of APT42's known geographic targeting, followed by Iran and the U.K.
The social engineering efforts are both persistent and persuasive, masquerading as legitimate entities and journalists to initiate conversations with prospective victims and build rapport over time, before ensnaring them in their phishing traps via malware-laced documents or bogus credential harvesting pages.
"APT42 would engage their target with a social engineering lure to set-up a video meeting and then link to a landing page where the target was prompted to login and sent to a phishing page," Google said.
"Another APT42 campaign template is sending legitimate PDF attachments as part of a social engineering lure to build trust and encourage the target to engage on other platforms like Signal, Telegram, or WhatsApp."
The latest set of attacks, observed by Proofpoint starting July 22, 2024, involved the threat actor contacting multiple email addresses for an unnamed Jewish figure, inviting them to be a guest for a podcast while impersonating the Research Director for the Institute for the Study of War (ISW).
In response to a message from the target, TA453 is said to have sent a password-protected DocSend URL that, in turn, led to a text file containing a URL to the legitimate ISW-hosted podcast. The phony messages were sent from the domain understandingthewar[.]org, a clear attempt to mimic ISW's website ("understandingwar[.]org").
"It is likely that TA453 was attempting to normalize the target clicking a link and entering a password so the target would do the same when they delivered malware," Proofpoint said.
In follow-up messages, the threat actor was found replying with a Google Drive URL hosting a ZIP archive ("Podcast Plan-2024.zip") that, in turn, contained a Windows shortcut (LNK) file responsible for delivering the BlackSmith toolset.
AnvilEcho, which is delivered by means of BlackSmith, has been described as a likely successor to the PowerShell implants known as CharmPower, GorjolEcho, POWERSTAR, and PowerLess. BlackSmith is also designed to display a lure document as a distraction mechanism.
It's worth noting that the name "BlackSmith" also overlaps with a browser stealer component detailed by Volexity earlier this year in connection with a campaign that distributed BASICSTAR in attacks aimed at high-profile individuals working on Middle Eastern affairs.
"AnvilEcho is a PowerShell trojan that contains extensive functionality," Proofpoint said. "AnvilEcho capabilities indicate a clear focus on intelligence collection and exfiltration."
Some of its important functions include conducting system reconnaissance, taking screenshots, downloading remote files, and uploading sensitive data over FTP and Dropbox.
"TA453 phishing campaigns [...] have consistently reflected IRGC intelligence priorities," Proofpoint researcher Joshua Miller said in a statement shared with The Hacker News.
"This malware deployment attempting to target a prominent Jewish figure likely supports ongoing Iranian cyber efforts against Israeli interests. TA453 is doggedly consistent as a persistent threat against politicians, human rights defenders, dissidents, and academics."
The findings come days after HarfangLab disclosed a new Go-based malware strain referred to as Cyclops that has been possibly developed as a follow-up to another Charming Kitten backdoor codenamed BellaCiao, indicating that the adversary is actively retooling its arsenal in response to public disclosures. Early samples of the malware date back to December 2023.
"It aims at reverse-tunneling a REST API to its command-and-control (C2) server for the purposes of controlling targeted machines," the French cybersecurity company said. "It allows operators to run arbitrary commands, manipulate the target's filesystem, and use the infected machine to pivot into the network."
It's believed that the threat actors used Cyclops to single out a non-profit organization that supports innovation and entrepreneurship in Lebanon, as well as a telecommunication company in Afghanistan. The exact ingress route used for the attacks is presently unknown.
"The choice of Go for the Cyclops malware has a few implications," HarfangLab said. "Firstly, it confirms the popularity of this language among malware developers. Secondly, the initially low number of detections for this sample indicates that Go programs may still represent a challenge for security solutions."
"And finally, it is possible that macOS and Linux variants of Cyclops were also created from the same codebase and that we have yet to find them."
Microsoft Patches Zero-Day Flaw Exploited by North Korea's Lazarus Group
20.8.24 APT The Hacker News
A newly patched security flaw in Microsoft Windows was exploited as a zero-day by Lazarus Group, a prolific state-sponsored actor affiliated with North Korea.
The security vulnerability, tracked as CVE-2024-38193 (CVSS score: 7.8), has been described as a privilege escalation bug in the Windows Ancillary Function Driver (AFD.sys) for WinSock.
"An attacker who successfully exploited this vulnerability could gain SYSTEM privileges," Microsoft said in an advisory for the flaw last week. It was addressed by the tech giant as part of its monthly Patch Tuesday update.
Credited with discovering and reporting the flaw are Gen Digital researchers Luigino Camastra and Milánek. Gen Digital owns a number of security and utility software brands like Norton, Avast, Avira, AVG, ReputationDefender, and CCleaner.
"This flaw allowed them to gain unauthorized access to sensitive system areas," the company disclosed last wee, adding it discovered the exploitation in early June 2024. "The vulnerability allowed attackers to bypass normal security restrictions and access sensitive system areas that most users and administrators can't reach."
The cybersecurity vendor further noted that the attacks were characterized by the use of a rootkit called FudModule in an attempt to evade detection.
While the exact technical details associated with the intrusions are presently unknown, the vulnerability is reminiscent of another privilege escalation flaw that Microsoft fixed in February 2024 and was also weaponized by the Lazarus Group to drop FudModule.
Specifically, it entailed the exploitation of CVE-2024-21338 (CVSS score: 7.8), a Windows kernel privilege escalation flaw rooted in the AppLocker driver (appid.sys) that makes it possible to execute arbitrary code such that it sidesteps all security checks and runs the FudModule rootkit.
Both these attacks are notable because they go beyond a traditional Bring Your Own Vulnerable Driver (BYOVD) attack by taking advantage of a security flaw in a driver that's already installed on a Windows host as opposed to "bringing" a susceptible driver and using it to bypass security measures.
Previous attacks detailed by cybersecurity firm Avast revealed that the rootkit is delivered by means of a remote access trojan known as Kaolin RAT.
"FudModule is only loosely integrated into the rest of Lazarus' malware ecosystem," the Czech company said at the time, stating "Lazarus is very careful about using the rootkit, only deploying it on demand under the right circumstances."
Researchers Uncover New Infrastructure Tied to FIN7 Cybercrime Group
20.8.24 APT The Hacker News
Cybersecurity researchers have discovered new infrastructure linked to a financially motivated threat actor known as FIN7.
The two clusters of potential FIN7 activity "indicate communications inbound to FIN7 infrastructure from IP addresses assigned to Post Ltd (Russia) and SmartApe (Estonia), respectively," Team Cymru said in a report published this week as part of a joint investigation with Silent Push and Stark Industries Solutions.
The findings build on a recent report from Silent Push, which found several Stark Industries IP addresses that are solely dedicated to hosting FIN7 infrastructure.
The latest analysis indicates that the hosts linked to the e-crime group were likely procured from one of Stark's resellers.
"Reseller programs are common in the hosting industry; many of the largest VPS (virtual private server) providers offer such services," the cybersecurity company said. "Customers procuring infrastructure via resellers generally must follow the terms of service outlined by the 'parent' entity."

What's more, Team Cymru said it was able to identify additional infrastructure linked to FIN7 activity, including four IP addresses assigned to Post Ltd, a broadband provider operating in Southern Russia and three IP addresses assigned to SmartApe, a cloud hosting provider operating from Estonia.
The first cluster has been observed conducting outbound communications with at least 15 Stark-assigned hosts previously discovered by Silent Push (e.g., 86.104.72[.]16) over the past 30 days. Likewise, the second cluster from Estonia has been identified as communicating with no less than 16 Stark-assigned hosts.
"In addition, 12 of the hosts identified in the Post Ltd cluster were also observed in the SmartApe cluster," Team Cymru noted. The services have since been suspended by Stark following responsible disclosure.
"Reviewing metadata for these communications confirmed them to be established connections. This assessment is based on an evaluation of observed TCP flags and sampled data transfer volumes."
Russian Hackers Using Fake Brand Sites to Spread DanaBot and StealC Malware
16.8.24 APT The Hacker News
Cybersecurity researchers have shed light on a sophisticated information stealer campaign that impersonates legitimate brands to distribute malware like DanaBot and StealC.
The activity cluster, orchestrated by Russian-speaking cybercriminals and collectively codenamed Tusk, is said to encompass several sub-campaigns, leveraging the reputation of the platforms to trick users into downloading the malware using bogus sites and social media accounts.
"All the active sub-campaigns host the initial downloader on Dropbox," Kaspersky researchers Elsayed Elrefaei and AbdulRhman Alfaifi said. "This downloader is responsible for delivering additional malware samples to the victim's machine, which are mostly info-stealers (DanaBot and StealC) and clippers."
Of the 19 sub-campaigns identified to date, three are said to be currently active. The name "Tusk" is a reference to the word "Mammoth" used by the threat actors in log messages associated with the initial downloader. It's worth noting that mammoth is a slang term often used by Russian e-crime groups to refer to victims.
The campaigns are also notable for employing phishing tactics to deceive victims into parting with their personal and financial information, which is then sold on the dark web or used to gain unauthorized access to their gaming accounts and cryptocurrency wallets.
The first of the three sub-campaigns, known as TidyMe, mimics peerme[.]io with a lookalike site hosted on tidyme[.]io (as well as tidymeapp[.]io and tidyme[.]app) that solicits a click to download a malicious program for both Windows and macOS systems that's served from Dropbox.
The downloader is an Electron application that, when launched, prompts the victim to enter the CAPTCHA displayed, after which the main application interface is displayed, while two additional malicious files are covertly fetched and executed in the background.
Both the payloads observed in the campaign are Hijack Loader artifacts, which ultimately launch a variant of the StealC stealer malware with capabilities to harvest a wide range of information.
RuneOnlineWorld ("runeonlineworld[.]io"), the second sub-campaign, involves the use of a bogus website simulating a massively multiplayer online (MMO) game named Rise Online World to distribute a similar downloader that paves the way for DanaBot and StealC on compromised hosts.
Also distributed via Hijack Loader in this campaign is a Go-based clipper malware that's designed to monitor clipboard content and substitute wallet addresses copied by the victim with an attacker-controlled Bitcoin wallet to perform fraudulent transactions.
Rounding off the active campaigns is Voico, which impersonates an AI translator project called YOUS (yous[.]ai) with a malicious counterpart dubbed voico[.]io in order to disseminate an initial downloader that, upon installation, asks the victim to fill out a registration form containing their credentials and then logs the information on the console.
The final payloads exhibit similar behavior as that of the second sub-campaign, the only distinction being the StealC malware used in this case communicates with a different command-and-control (C2) server.
"The campaigns [...] demonstrate the persistent and evolving threat posed by cybercriminals who are adept at mimicking legitimate projects to deceive victims," the researchers said. "The reliance on social engineering techniques such as phishing, coupled with multistage malware delivery mechanisms, highlights the advanced capabilities of the threat actors involved."
"By exploiting the trust users place in well-known platforms, these attackers effectively deploy a range of malware designed to steal sensitive information, compromise systems, and ultimately achieve financial gain."
Russian-Linked Hackers Target Eastern European NGOs and Media
15.8.24 APT The Hacker News
Russian and Belarusian non-profit organizations, Russian independent media, and international non-governmental organizations active in Eastern Europe have become the target of two separate spear-phishing campaigns orchestrated by threat actors whose interests align with that of the Russian government.
While one of the campaigns – dubbed River of Phish – has been attributed to COLDRIVER, an adversarial collective with ties to Russia's Federal Security Service (FSB), the second set of attacks have been deemed the work of a previously undocumented threat cluster codenamed COLDWASTREL.
Targets of the campaigns also included prominent Russian opposition figures-in-exile, officials and academics in the US think tank and policy space, and a former U.S. ambassador to Ukraine, according to a joint investigation from Access Now and the Citizen Lab.
"Both kinds of attacks were highly tailored to better deceive members of the target organizations," Access Now said. "The most common attack pattern we observed was an email sent either from a compromised account or from an account appearing similar to the real account of someone the victim may have known."
River of Phish involves the use of personalized and highly-plausible social engineering tactics to trick victims into clicking on an embedded link in a PDF lure document, which redirects them to a credential harvesting page, but not before fingerprinting the infected hosts in a likely attempt to prevent automated tools from accessing the second-stage infrastructure.

The email messages are sent from Proton Mail email accounts impersonating organizations or individuals that were familiar or known to the victims.
"We often observed the attacker omitting to attach a PDF file to the initial message requesting a review of the 'attached' file," the Citizen Lab said. "We believe this was intentional, and intended to increase the credibility of the communication, reduce the risk of detection, and select only for targets that replied to the initial approach (e.g. pointing out the lack of an attachment)."
The links to COLDRIVER are bolstered by the fact that the attacks use PDF documents that appear encrypted and urge the victims to open it in Proton Drive by clicking on the link, a ruse the threat actor has employed in the past.
Some of the social engineering elements also extend to COLDWASTREL, particularly in the use of Proton Mail and Proton Drive to trick targets into clicking on a link and taken them to a fake login page ("protondrive[.]online" or "protondrive[.]services") for Proton. The attacks were first recorded in March 2023.
However, COLDWASTREL deviates from COLDRIVER when it comes to the use of lookalike domains for credential harvesting and differences in PDF content and metadata. The activity has not been attributed to a particular actor at this stage.
"When the cost of discovery remains low, phishing remains not only an effective technique, but a way to continue global targeting while avoiding exposing more sophisticated (and expensive) capabilities to discovery," the Citizen Lab said.
China-Backed Earth Baku Expands Cyber Attacks to Europe, Middle East, and Africa
15.8.24 APT The Hacker News
The China-backed threat actor known as Earth Baku has diversified its targeting footprint beyond the Indo-Pacific region to include Europe, the Middle East, and Africa starting in late 2022.
Newly targeted countries as part of the activity include Italy, Germany, the U.A.E., and Qatar, with suspected attacks also detected in Georgia and Romania. Governments, media and communications, telecoms, technology, healthcare, and education are some of the sectors singled out as part of the intrusion set.
"The group has updated its tools, tactics, and procedures (TTPs) in more recent campaigns, making use of public-facing applications such as IIS servers as entry points for attacks, after which they deploy sophisticated malware toolsets on the victim's environment," Trend Micro researchers Ted Lee and Theo Chen said in an analysis published last week.
The findings build upon recent reports from Zscaler and Google-owned Mandiant, which also detailed the threat actor's use of malware families like DodgeBox (aka DUSTPAN) and MoonWalk (aka DUSTTRAP). Trend Micro has given them the monikers StealthReacher and SneakCross.
Earth Baku, a threat actor associated with APT41, is known for its use of StealthVector as far back as October 2020. Attack chains involve the exploitation of public-facing applications to drop the Godzilla web shell, which is then used to deliver follow-on payloads.

StealthReacher has been classified as an enhanced version of the StealthVector backdoor loader that's responsible for launching SneakCross, a modular implant and a likely successor to ScrambleCross that leverages Google services for its command-and-control (C2) communication.
The attacks are also characterized by the use of other post-exploitation tools such as iox, Rakshasa, and a Virtual Private Network (VPN) service known as Tailscale. Exfiltration of sensitive data to the MEGA cloud storage service is accomplished by means of a command-line utility dubbed MEGAcmd.
"The group has employed new loaders such as StealthVector and StealthReacher, to stealthily launch backdoor components, and added SneakCross as their latest modular backdoor," the researchers said.
"Earth Baku also used several tools during its post-exploitation including a customized iox tool, Rakshasa, TailScale for persistence, and MEGAcmd for efficient data exfiltration."
University Professors Targeted by North Korean Cyber Espionage Group
8.8.24 APT The Hacker News
The North Korea-linked threat actor known as Kimsuky has been linked to a new set of attacks targeting university staff, researchers, and professors for intelligence gathering purposes.
Cybersecurity firm Resilience said it identified the activity in late July 2024 after it observed an operation security (OPSEC) error made by the hackers.
Kimsuky, also known by the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet, Springtail, and Velvet Chollima, is just one of the myriad offensive cyber teams operating under the direction of the North Korean government and military.
It's also very active, often leveraging spear-phishing campaigns as a starting point to deliver an ever-expanding set of custom tools to conduct reconnaissance, pilfer data, and establish persistent remote access to infected hosts.
The attacks are also characterized by the use of compromised hosts as staging infrastructure to deploy an obfuscated version of the Green Dinosaur web shell, which is then used to perform file operations. Kimuksy's use of the web shell was previously highlighted by security researcher blackorbird in May 2024.
The access afforded by Green Dinosaur is then abused to upload pre-built phishing pages that are designed to mimic legitimate login portals for Naver and various universities like Dongduk University, Korea University, and Yonsei University with the goal of capturing their credentials.
Next, the victims are redirected to another site that points to a PDF document hosted on Google Drive that purports to be an invitation to the Asan Institute for Policy Studies August Forum.
"Additionally on Kimsuky's phishing sites, there is a non-target specific phishing toolkit to gather Naver accounts," Resilience researchers said.
"This toolkit is a rudimentary proxy akin to Evilginx for stealing cookies and credentials from visitors and shows pop-ups telling users they need to login again because communication with the server was disrupted."
The analysis has also shed light on a custom PHPMailer tool used by Kimsuky called SendMail, which is employed to send phishing emails to the targets using Gmail and Daum Mail accounts.
To combat the threat, it's recommended that users enable phishing-resistant multi-factor authentication (MFA) and scrutinize the URLs before logging in.
North Korean Hackers Moonstone Sleet Push Malicious JS Packages to npm Registry
6.8.24 APT The Hacker News
The North Korea-linked threat actor known as Moonstone Sleet has continued to push malicious npm packages to the JavaScript package registry with the aim of infecting Windows systems, underscoring the persistent nature of their campaigns.
The packages in question, harthat-api and harthat-hash, were published on July 7, 2024, according to Datadog Security Labs. Both the libraries did not attract any downloads and were shortly pulled after a brief period of time.
The security arm of the cloud monitoring firm is tracking the threat actor under the name Stressed Pungsan, which exhibits overlaps with a newly discovered North Korean malicious activity cluster dubbed Moonstone Sleet.
"While the name resembles the Hardhat npm package (an Ethereum development utility), its content does not indicate any intention to typosquat it," Datadog researchers Sebastian Obregoso and Zack Allen said. "The malicious package reuses code from a well-known GitHub repository called node-config with over 6,000 stars and 500 forks, known in npm as config."
Attack chains orchestrated by the adversarial collective are known to disseminate bogus ZIP archive files via LinkedIn under a fake company name or freelancing websites, enticing prospective targets into executing next-stage payloads that invoke an npm package as part of a supposed technical skills assessment.
"When loaded, the malicious package used curl to connect to an actor-controlled IP and drop additional malicious payloads like SplitLoader," Microsoft noted in May 2024. "In another incident, Moonstone Sleet delivered a malicious npm loader which led to credential theft from LSASS."
Subsequent findings from Checkmarx uncovered that Moonstone Sleet has also been attempting to spread their packages through the npm registry.
The newly discovered packages are designed to run a pre-install script specified in the package.json file, which, in turn, checks if it's running on a Windows system ("Windows_NT"), after which it contacts an external server ("142.111.77[.]196") to download a DLL file that's sideloaded using the rundll32.exe binary.
The rogue DLL, for its part, does not perform any malicious actions, suggesting either a trial run of its payload delivery infrastructure or that it was inadvertently pushed to the registry before embedding malicious code into it.
The development comes as South Korea's National Cyber Security Center (NCSC) warned of cyber attacks mounted by North Korean threat groups tracked as Andariel and Kimsuky to deliver malware families such as Dora RAT and TrollAgent (aka Troll Stealer) as part of intrusion campaigns aimed at construction and machinery sectors in the country.
The Dora RAT attack sequence is noteworthy for the fact that the Andariel hackers exploited vulnerabilities in a domestic VPN software's software update mechanism to propagate the malware.
Kazakh Organizations Targeted by 'Bloody Wolf' Cyber Attacks
5.8.24 APT The Hacker News
Organizations in Kazakhstan are the target of a threat activity cluster dubbed Bloody Wolf that delivers a commodity malware called STRRAT (aka Strigoi Master).
"The program selling for as little as $80 on underground resources allows the adversaries to take control of corporate computers and hijack restricted data," cybersecurity vendor BI.ZONE said in a new analysis.
The cyber attacks employ phishing emails as an initial access vector, impersonating the Ministry of Finance of the Republic of Kazakhstan and other agencies to trick recipients into opening PDF attachments.
The file purports to be a non-compliance notice and contains links to a malicious Java archive (JAR) file as well as an installation guide for the Java interpreter necessary for the malware to function.
In an attempt to lend legitimacy to the attack, the second link points to a web page associated with the country's government website that urges visitors to install Java in order to ensure that the portal is operational.
Cybersecurity
The STRRAT malware, hosted on a website that mimics the website of the Kazakhstan government ("egov-kz[.]online"), sets up persistence on the Windows host by means of a Registry modification and runs the JAR file every 30 minutes.
What's more, a copy of the JAR file is copied to the Windows startup folder to ensure that it automatically launches after a system reboot.
Subsequently, it establishes connections with a Pastebin server to exfiltrate sensitive information from the compromised machine, including details about operating system version and antivirus software installed, and account data from Google Chrome, Mozilla Firefox, Internet Explorer, Foxmail, Outlook, and Thunderbird.
It's also designed to receive additional commands from the server to download and execute more payloads, log keystrokes, run commands using cmd.exe or PowerShell, restart or shut down the system, install a proxy, and remove itself.
"Using less common file types such as JAR enables the attackers to bypass defenses," BI.ZONE said. "Employing legitimate web services such as Pastebin to communicate with the compromised system makes it possible to evade network security solutions."
China-Linked Hackers Compromise ISP to Deploy Malicious Software Updates
5.8.24 APT The Hacker News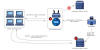
The China-linked threat actor known as Evasive Panda compromised an unnamed internet service provider (ISP) to push malicious software updates to target companies in mid-2023, highlighting a new level of sophistication associated with the group.
Evasive Panda, also known by the names Bronze Highland, Daggerfly, and StormBamboo, is a cyber espionage group that's been active since at least 2012, leveraging backdoors such as MgBot (aka POCOSTICK) and Nightdoor (aka NetMM and Suzafk) to harvest sensitive information.
More recently, the threat actor was formally attributed to the use of a macOS malware strain called MACMA, which has been observed in the wild as far back as 2021.
Cybersecurity
"StormBamboo is a highly skilled and aggressive threat actor who compromises third-parties (in this case, an ISP) to breach intended targets," Volexity said in a report published last week.
"The variety of malware employed in various campaigns by this threat actor indicates significant effort is invested, with actively supported payloads for not only macOS and Windows, but also network appliances."
Public reporting from ESET and Symantec over the past two years have documented Evasive Panda's use of MgBot and its track record of orchestrating watering hole and supply chain attacks targeting Tibetan users.
It was also found to have targeted an international non-governmental organization (NGO) in Mainland China with MgBot delivered via update channels of legitimate applications like Tencent QQ.
While it was speculated that the trojanized updates were either the result of a supply chain compromise of Tencent QQ's update servers or a case of an adversary-in-the-middle (AitM) attack, Volexity's analysis confirms it's the latter stemming from a DNS poisoning attack at the ISP level.
Specifically, the threat actor is said to be altering DNS query responses for specific domains tied to automatic software update mechanisms, going after software that used insecure update mechanisms, such as HTTP, or did not enforce adequate integrity checks of the installers.
"It was discovered that StormBamboo poisoned DNS requests to deploy malware via an HTTP automatic update mechanism and poison responses for legitimate hostnames that were used as second-stage, command-and-control (C2) servers," researchers Ankur Saini, Paul Rascagneres, Steven Adair, and Thomas Lancaster said.
Cybersecurity
The attack chains are fairly straightforward in that the insecure update mechanisms are abused to deliver either MgBot or MACMA depending on the operating system used. Volexity said it notified the concerned ISP to remediate the DNS poisoning attack.
One instance also entailed the deployment of a Google Chrome extension on the victim's macOS device by modifying the Secure Preferences file. The browser add-on purports to be a tool that loads a page in compatibility mode with Internet Explorer, but its main objective is to exfiltrate browser cookies to a Google Drive account controlled by the adversary.
"The attacker can intercept DNS requests and poison them with malicious IP addresses, and then use this technique to abuse automatic update mechanisms that use HTTP rather than HTTPS," the researchers said.
APT41 Hackers Use ShadowPad, Cobalt Strike in Taiwanese Institute Cyber Attack
2.8.24 APT The Hacker News
A Taiwanese government-affiliated research institute that specializes in computing and associated technologies was breached by nation-state threat actors with ties to China, according to new findings from Cisco Talos.
The unnamed organization was targeted as early as mid-July 2023 to deliver a variety of backdoors and post-compromise tools like ShadowPad and Cobalt Strike. It has been attributed with medium confidence to a prolific hacking group tracked as APT41.
"The ShadowPad malware used in the current campaign exploited an outdated vulnerable version of Microsoft Office IME binary as a loader to load the customized second-stage loader for launching the payload," security researchers Joey Chen, Ashley Shen, and Vitor Ventura said.
"The threat actor compromised three hosts in the targeted environment and was able to exfiltrate some documents from the network."
Cisco Talos said it discovered the activity in August 2023 after detecting what it described were "abnormal PowerShell commands" that connected to an IP address to download and execute PowerShell scripts within the compromised environment.
The exact initial access vector used in the attack is not known, although it involved the use of a web shell to maintain persistent access and drop additional payloads like ShadowPad and Cobalt Strike, with the latter delivered by means a Go-based Cobalt Strike loader named CS-Avoid-Killing.
"The Cobalt Strike malware had been developed using an anti-AV loader to bypass AV detection and avoid the security product quarantine," the researchers said.
Alternately, the threat actor was observed running PowerShell commands to launch scripts responsible for running ShadowPad in memory and fetch Cobalt Strike malware from a compromised command-and-control (C2) server. The DLL-based ShadowPad loader, also called ScatterBee, is executed via DLL side-loading.
Some of the other steps carried out as part of the intrusion comprised the use of Mimikatz to extract passwords and the execution of several commands to gather information on user accounts, directory structure, and network configurations.
"APT41 created a tailored loader to inject a proof-of-concept for CVE-2018-0824 directly into memory, utilizing a remote code execution vulnerability to achieve local privilege escalation," Talos said, noting the final payload, UnmarshalPwn, is unleashed after passing through three different stages.
The cybersecurity outfit also pointed out the adversary's attempts to avoid detection by halting its own activity upon detecting other users on the system. "Once the backdoors are deployed the malicious actor will delete the web shell and guest account that allowed the initial access," the researchers said.
The disclosure comes as Germany revealed earlier this week that Chinese state actors were behind a 2021 cyber attack on the country's national mapping agency, the Federal Office of Cartography and Geodesy (BKG), for espionage purposes.
Responding to the allegations, China's embassy in Berlin said the accusation is unfounded and called on Germany "to stop the practice of using cybersecurity issues to smear China politically and in the media."
APT28 Targets Diplomats with HeadLace Malware via Car Sale Phishing Lure
2.8.24 APT The Hacker News
A Russia-linked threat actor has been linked to a new campaign that employed a car for sale as a phishing lure to deliver a modular Windows backdoor called HeadLace.
"The campaign likely targeted diplomats and began as early as March 2024," Palo Alto Networks Unit 42 said in a report published today, attributing it with medium to high level of confidence to APT28, which is also referred to as BlueDelta, Fancy Bear, Fighting Ursa, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422.
It's worth noting that car-for-sale phishing lure themes have been previously put to use by a different Russian nation-state group called APT29 since July 2023, indicating that APT28 is repurposing successful tactics for its own campaigns.
Earlier this May, the threat actor was implicated in a series of campaigns targeting networks across Europe with the HeadLace malware and credential-harvesting web pages.
The attacks are characterized by the use of a legitimate service known as webhook[.]site – a hallmark of APT28's cyber operations along with Mocky – to host a malicious HTML page, which first checks whether the target machine is running on Windows and if so, offers a ZIP archive for download ("IMG-387470302099.zip").
If the system is not Windows-based, it redirects to a decoy image hosted on ImgBB, specifically an Audi Q7 Quattro SUV.
Present within the archive are three files: The legitimate Windows calculator executable that masquerades as an image file ("IMG-387470302099.jpg.exe"), a DLL ("WindowsCodecs.dll"), and a batch script ("zqtxmo.bat").
The calculator binary is used to sideload the malicious DLL, a component of the HeadLace backdoor that's designed to run the batch script, which, in turn, executes a Base64-encoded command to retrieve a file from another webhook[.]site URL.
This file is then saved as "IMG387470302099.jpg" in the users' downloads folder and renamed to "IMG387470302099.cmd" prior to execution, after which it's deleted to erase traces of any malicious activity.
"While the infrastructure used by Fighting Ursa varies for different attack campaigns, the group frequently relies on these freely available services," Unit 42 said. "Furthermore, the tactics from this campaign fit with previously documented Fighting Ursa campaigns, and the HeadLace backdoor is exclusive to this threat actor."
North Korea-Linked Malware Targets Developers on Windows, Linux, and macOS
1.8.24 APT The Hacker News
The threat actors behind an ongoing malware campaign targeting software developers have demonstrated new malware and tactics, expanding their focus to include Windows, Linux, and macOS systems.
The activity cluster, dubbed DEV#POPPER and linked to North Korea, has been found to have singled out victims across South Korea, North America, Europe, and the Middle East.
"This form of attack is an advanced form of social engineering, designed to manipulate individuals into divulging confidential information or performing actions that they might normally not," Securonix researchers Den Iuzvyk and Tim Peck said in a new report shared with The Hacker News.
DEV#POPPER is the moniker assigned to an active malware campaign that tricks software developers into downloading booby-trapped software hosted on GitHub under the guise of a job interview. It shares overlaps with a campaign tracked by Palo Alto Networks Unit 42 under the name Contagious Interview.
Signs that the campaign was broader and cross-platform in scope emerged earlier this month when researchers uncovered artifacts targeting both Windows and macOS that delivered an updated version of a malware called BeaverTail.

Image Source: Palo Alto Networks Unit 42
The attack chain document by Securonix is more or less consistent in that the threat actors pose as interviewers for a developer position and urge the candidates to download a ZIP archive file for a coding assignment.
Present with the archive is an npm module that, once installed, triggers the execution of an obfuscated JavaScript (i.e., BeaverTail) that determines the operating system on which it's running and establishes contact with a remote server to exfiltrate data of interest.
It's also capable of downloading next-stage payloads, including a Python backdoor referred to as InvisibleFerret, which is designed to gather detailed system metadata, access cookies stored in web browsers, execute commands, upload/download files, as well as log keystrokes and clipboard content.
New features added to the recent samples include the use of enhanced obfuscation, AnyDesk remote monitoring and management (RMM) software for persistence, and improvements to the FTP mechanism employed for data exfiltration.
Furthermore, the Python script acts as a conduit to run an ancillary script that's responsible for stealing sensitive information from various web browsers – Google Chrome, Opera, and Brave – across different operating systems.
"This sophisticated extension to the original DEV#POPPER campaign continues to leverage Python scripts to execute a multi-stage attack focused on exfiltrating sensitive information from victims, though now with much more robust capabilities," the researchers said.
The findings come as Recorded Future revealed that North Koreans have continued to use foreign technology – such as Apple, Samsung, Huawei, and Xiaomi devices, as well as various social media platforms like Facebook, X, Instagram, WeChat, LINE, and QQ – to access the internet notwithstanding heavy sanctions.
Another significant change in internet user behavior concerns the use of virtual private networks (VPNs) and proxies to circumvent censorship and surveillance, along with utilizing antivirus software from McAfee, indicating that the country is not as isolated as it's made out to be.
"Despite the sanctions, North Korea continues to import foreign technology, often through its trade relationships with China and Russia," the company said. "This marks a shift towards greater operational security awareness among users who seek to avoid detection by the regime."
APT41 Infiltrates Networks in Italy, Spain, Taiwan, Turkey, and the U.K.
19.7.24 APT The Hacker News
Several organizations operating within global shipping and logistics, media and entertainment, technology, and automotive sectors in Italy, Spain, Taiwan, Thailand, Turkey, and the U.K. have become the target of a "sustained campaign" by the prolific China-based APT41 hacking group.
"APT41 successfully infiltrated and maintained prolonged, unauthorized access to numerous victims' networks since 2023, enabling them to extract sensitive data over an extended period," Google-owned Mandiant said in a new report published Thursday.
The threat intelligence firm described the adversarial collective as unique among China-nexus actors owing to its use of "non-public malware typically reserved for espionage operations in activities that appear to fall outside the scope of state-sponsored missions."
Attack chains involve the use of web shells (ANTSWORD and BLUEBEAM), custom droppers (DUSTPAN and DUSTTRAP), and publicly available tools (SQLULDR2 and PINEGROVE) to achieve persistence, deliver additional payloads, and exfiltrate data of interest.
The web shells act as a conduit to download the DUSTPAN (aka StealthVector) dropper that's responsible for loading Cobalt Strike Beacon for command-and-control (C2) communication, followed by the deployment of the DUSTTRAP dropper post lateral movement.
DUSTTRAP, for its part, is configured to decrypt a malicious payload and execute it in memory, which, in turn, establishes contact with an attacker-controlled server or a compromised Google Workspace account in an attempt to conceal its malicious activities.
Google said the identified Workspace accounts have been remediated to prevent unauthorized access. It, however, did not reveal how many accounts were affected.
The intrusions are also characterized by the use of SQLULDR2 to export data from Oracle Databases to a local text-based file and PINEGROVE to transmit large volumes of sensitive data from compromised networks by abusing Microsoft OneDrive as an exfiltration vector.
It's worth noting here that the malware families that Mandiant tracks as DUSTPAN and DUSTTRAP share overlaps with those that have been codenamed DodgeBox and MoonWalk, respectively, by Zscaler ThreatLabz.
"DUSTTRAP is a multi-stage plugin framework with multiple components," Mandiant researchers said, adding it identified at least 15 plugins that are capable of executing shell commands, carrying out file system operations, enumerating and terminating processes, capturing keystrokes and screenshots, gathering system information, and modifying Windows Registry.
It's also engineered to probe remote hosts, perform domain name system (DNS) lookups, list remote desktop sessions, upload files, and conduct various manipulations to Microsoft Active Directory.
"The DUSTTRAP malware and its associated components that were observed during the intrusion were code signed with presumably stolen code signing certificates," the company said. "One of the code signing certificates seemed to be related to a South Korean company operating in the gaming industry sector."
GhostEmperor Comes Back to Haunt#
The disclosure comes as Israeli cybersecurity company Sygnia revealed details of a cyber attack campaign mounted by a sophisticated China-nexus threat group called GhostEmperor to deliver a variant of the Demodex rootkit.
The exact method used to breach targets is currently not clear, although the group has been previously observed exploiting known flaws in internet-facing applications. The initial access facilitates the execution of a Windows batch script, which drops a Cabinet archive (CAB) file to ultimately launch a core implant module.
The implant is equipped to manage C2 communications and install the Demodex kernel rootkit by using an open-source project named Cheat Engine to get around the Windows Driver Signature Enforcement (DSE) mechanism.
"GhostEmperor employs a multi-stage malware to achieve stealth execution and persistence and utilizes several methods to impede analysis process," Security researcher Dor Nizar said.
TAG-100: New Threat Actor Uses Open-Source Tools for Widespread Attacks
18.7.24 APT The Hacker News
Unknown threat actors have been observed leveraging open-source tools as part of a suspected cyber espionage campaign targeting global government and private sector organizations.
Recorded Future's Insikt Group is tracking the activity under the temporary moniker TAG-100, noting that the adversary likely compromised organizations in at least ten countries across Africa, Asia, North America, South America, and Oceania, including two unnamed Asia-Pacific intergovernmental organizations.
Also singled out since February 2024 are diplomatic, government, semiconductor supply-chain, non-profit, and religious entities located in Cambodia, Djibouti, the Dominican Republic, Fiji, Indonesia, Netherlands, Taiwan, the U.K., the U.S., and Vietnam.
Cybersecurity
"TAG-100 employs open-source remote access capabilities and exploits various internet-facing devices to gain initial access," the cybersecurity company said. "The group used open-source Go backdoors Pantegana and Spark RAT post-exploitation."
Attack chains involve the exploitation of known security flaws impacting various internet-facing products, including Citrix NetScaler, F5 BIG-IP, Zimbra, Microsoft Exchange Server, SonicWall, Cisco Adaptive Security Appliances (ASA), Palo Alto Networks GlobalProtect, and Fortinet FortiGate.
The group has also been observed conducting wide-ranging reconnaissance activity aimed at internet-facing appliances belonging to organizations in at least fifteen countries, including Cuba, France, Italy, Japan, and Malaysia. This also comprised several Cuban embassies located in Bolivia, France, and the U.S.

"Beginning on April 16, 2024, TAG-100 conducted probable reconnaissance and exploitation activity targeting Palo Alto Networks GlobalProtect appliances of organizations, mostly based in the U.S., within the education, finance, legal, local government, and utilities sectors," the company said.
This effort is said to have coincided with the public release of a proof-of-concept (PoC) exploit for CVE-2024-3400 (CVSS score: 10.0), a critical remote code execution vulnerability affecting Palo Alto Networks GlobalProtect firewalls.
Successful initial access is followed by the deployment of Pantegana, Spark RAT, and Cobalt Strike Beacon on compromised hosts.
The findings illustrate how PoC exploits can be combined with open-source programs to orchestrate attacks, effectively lowering the barrier to entry for less sophisticated threat actors. Furthermore, such tradecraft enables adversaries to complicate attribution efforts and evade detection.
"The widespread targeting of internet-facing appliances is particularly attractive because it offers a foothold within the targeted network via products that often have limited visibility, logging capabilities, and support for traditional security solutions, reducing the risk of detection post-exploitation," Recorded Future said.
North Korean Hackers Update BeaverTail Malware to Target MacOS Users
18.7.24 APT The Hacker News
Cybersecurity researchers have discovered an updated variant of a known stealer malware that attackers affiliated with the Democratic People's Republic of Korea (DPRK) have delivered as part of prior cyber espionage campaigns targeting job seekers.
The artifact in question is an Apple macOS disk image (DMG) file named "MiroTalk.dmg" that mimics the legitimate video call service of the same name, but, in reality, serves as a conduit to deliver a native version of BeaverTail, security researcher Patrick Wardle said.
BeaverTail refers to a JavaScript stealer malware that was first documented by Palo Alto Networks Unit 42 in November 2023 as part of a campaign dubbed Contagious Interview that aims to infect software developers with malware through a supposed job interview process. Securonix is tracking the same activity under the moniker DEV#POPPER.
Besides siphoning sensitive information from web browsers and crypto wallets, the malware is capable of delivering additional payloads like InvisibleFerret, a Python backdoor that's responsible for downloading AnyDesk for persistent remote access.
While BeaverTail has been distributed via bogus npm packages hosted on GitHub and the npm package registry, the latest findings mark a shift in the distribution vector.
"If I had to guess, the DPRK hackers likely approached their potential victims, requesting that they join a hiring meeting, by downloading and executing the (infected version of) MiroTalk hosted on mirotalk[.]net," Wardle said.
An analysis of the unsigned DMG file reveals that it facilitates the theft of data from cryptocurrency wallets, iCloud Keychain, and web browsers like Google Chrome, Brave, and Opera. Furthermore, it's designed to download and execute additional Python scripts from a remote server (i.e., InvisibleFerret).
"The North Korean hackers are a wily bunch and are quite adept at hacking macOS targets, even though their technique often rely on social engineering (and thus from a technical point of view are rather unimpressive)," Wardle said.
The disclosure comes as Phylum uncovered a new malicious npm package named call-blockflow that's virtually identical to the legitimate call-bind library but incorporates complex functionality to download a remote binary file while taking painstaking efforts to fly under the radar.
"In this attack, while the call-bind package has not been compromised, the weaponized call-blockflow package copies all the trust and legitimacy of the original to bolster the attack's success," it said in a statement shared with The Hacker News.
The package, suspected to be the work of the North Korea-linked Lazarus Group and unpublished about an hour and a half later after it was uploaded to npm, attracted a total of 18 downloads. Evidence suggests that the activity, comprising over three dozen malicious packages, has been underway in waves since September 2023.
"These packages, once installed, would download a remote file, decrypt it, execute an exported function from it, and then meticulously cover their tracks by deleting and renaming files," the software supply chain security company said. "This left the package directory in a seemingly benign state after installation."
It also follows an advisory from JPCERT/CC, warning of cyber attacks orchestrated by the North Korean Kimsuky actor targeting Japanese organizations.
The infection process starts with phishing messages impersonating security and diplomatic organizations, and contain a malicious executable that, upon opening, leads to the download of a Visual Basic Script (VBS), which, in turn, retrieves a PowerShell script to harvest user account, system and network information as well as enumerate files and processes.
The collected information is then exfiltrated to a command-and-control (C2) server, which responds back with a second VBS file that's then executed to fetch and run a PowerShell-based keylogger named InfoKey.
"Although there have been few reports of attack activities by Kimsuky targeting organizations in Japan, there is a possibility that Japan is also being actively targeted," JPCERT/CC said.
FIN7 Group Advertises Security-Bypassing Tool on Dark Web Forums
17.7.24 APT The Hacker News
The financially motivated threat actor known as FIN7 has been observed using multiple pseudonyms across several underground forums to likely advertise a tool known to be used by ransomware groups like Black Basta.
"AvNeutralizer (aka AuKill), a highly specialized tool developed by FIN7 to tamper with security solutions, has been marketed in the criminal underground and used by multiple ransomware groups," cybersecurity company SentinelOne said in a report shared with The Hacker News.
FIN7, an e-crime group of Russian and Ukrainian origin, has been a persistent threat since at least 2012, shifting gears from its initial targeting of point-of-sale (PoS) terminals to acting as a ransomware affiliate for now-defunct gangs such as REvil and Conti, before launching its own ransomware-as-a-service (RaaS) programs DarkSide and BlackMatter.
The threat actor, which is also tracked under the names Carbanak, Carbon Spider, Gold Niagara, and Sangria Tempest (formerly Elbrus), has a track record of setting up front companies like Combi Security and Bastion Secure to recruit unwitting software engineers into ransomware schemes under the pretext of penetration testing.
Over the years, FIN7 has demonstrated a high level of adaptability, sophistication, and technical expertise by retooling its malware arsenal – POWERTRASH, DICELOADER (aka IceBot, Lizar, or Tirion), and a penetration testing tool called Core Impact that's delivered via the POWERTRASH loader – notwithstanding the arrests and sentencing of some of its members.
This is evidenced in the large-scale phishing campaigns undertaken by the group to deliver ransomware and other malware families by deploying thousands of "shell" domains that mimic legitimate media and technology businesses, according to a recent report from Silent Push.
Alternately, these shell domains have been occasionally used in a conventional redirect chain to send users to spoofed login pages that masquerade as property management portals.
These typosquat versions are advertised on search engines like Google, tricking users searching for popular software into downloading a malware-laced variant instead. Some of the tools targeted include 7-Zip, PuTTY, AIMP, Notepad++, Advanced IP Scanner, AnyDesk, pgAdmin, AutoDesk, Bitwarden, Rest Proxy, Python, Sublime Text, and Node.js.
It's worth noting that FIN7's use of malvertising tactics was previously highlighted by both eSentire and Malwarebytes in May 2024, with the attack chains leading to the deployment of NetSupport RAT.
"FIN7 rents a large amount of dedicated IPs on a number of hosts, but primarily on Stark Industries, a popular bulletproof hosting provider that has been linked to DDoS attacks in Ukraine and across Europe," Silent Push noted.
The latest findings from SentinelOne show that FIN7 has not only used several personas on cybercrime forums to promote the sale of AvNeutralizer, but has also improvised the tool with new capabilities.
This is based on the fact that multiple ransomware groups began to use updated versions of the EDR impairment program as of January 2023, which was exclusively put to use by the Black Basta group until then.
SentinelLabs researcher Antonio Cocomazzi told The Hacker News that the advertisement of AvNeutralizer on underground forums shouldn't be treated as a new malware-as-a-service (MaaS) tactic adopted by FIN7 without additional evidence.
"FIN7 has a history of developing and using sophisticated tools for their own operations," Cocomazzi said. "However, selling tools to other cybercriminals could be seen as a natural evolution of their methods to diversify and generate additional revenue."
"Historically, FIN7 has used underground marketplaces to generate revenue. For example, the DoJ reported that since 2015, FIN7 successfully stole data for more than 16 million payment cards, many of which were sold on underground marketplaces. While this was more common in the pre-ransomware era, the current advertisement of AvNeutralizer could signal a shift or expansion in their strategy."
"This could be motivated by the increasing protections provided by nowadays EDR solutions compared to previous AV systems. As these defenses have improved, the demand for impairment tools like AvNeutralizer has grown significantly especially among ransomware operators. Attackers now face tougher challenges in bypassing these protections, making such tools highly valuable and expensive."
For its part, the updated version of AvNeutralizer employs anti-analysis techniques and, most importantly, leverages a Windows built-in driver called "ProcLaunchMon.sys" in conjunction with the Process Explorer driver to tamper with the functioning of security solutions and evade detection. The tool is believed to have been in active development since April 2022.
A similar version of this approach has also been put to use by the Lazarus Group, making it even more dangerous as it goes beyond a traditional Bring Your Own Vulnerable Driver (BYOVD) attack by weaponizing a susceptible driver already present by default in Windows machines.
Another noteworthy update concerns FIN7's Checkmarks platform, which has been modified to include an automated SQL injection attack module for exploiting public-facing applications.
"In its campaigns, FIN7 has adopted automated attack methods, targeting public-facing servers through automated SQL injection attacks," SentinelOne said. "Additionally, its development and commercialization of specialized tools like AvNeutralizer within criminal underground forums significantly enhance the group's impact."
China-linked APT17 Targets Italian Companies with 9002 RAT Malware
17.7.24 APT The Hacker News
A China-linked threat actor called APT17 has been observed targeting Italian companies and government entities using a variant of a known malware referred to as 9002 RAT.
The two targeted attacks took place on June 24 and July 2, 2024, Italian cybersecurity company TG Soft said in an analysis published last week.
"The first campaign on June 24, 2024 used an Office document, while the second campaign contained a link," the company noted. "Both campaigns invited the victim to install a Skype for Business package from a link of an Italian government-like domain to convey a variant of 9002 RAT."
APT17 was first documented by Google-owned Mandiant (then FireEye) in 2013 as part of cyber espionage operations called DeputyDog and Ephemeral Hydra that leveraged zero-day flaws in Microsoft's Internet Explorer to breach targets of interest.
It's also known by the monikers Aurora Panda, Bronze Keystone, Dogfish, Elderwood, Helium, Hidden Lynx, and TEMP.Avengers, with the adversary sharing some level of tooling overlap with another threat actor dubbed Webworm.
9002 RAT, aka Hydraq and McRAT, achieved notoriety as the cyber weapon of choice in Operation Aurora that singled out Google and other large companies in 2009. It was also subsequently put to use in another 2013 campaign named Sunshop in which the attackers injected malicious redirects into several websites.
The latest attack chains entail the use of spear-phishing lures to trick recipients into clicking on a link that urges them to download an MSI installer for Skype for Business ("SkypeMeeting.msi").
Launching the MSI package triggers the execution of a Java archive (JAR) file via a Visual Basic Script (VBS), while also installing the legitimate chat software on the Windows system. The Java application, in turn, decrypts and executes the shellcode responsible for launching 9002 RAT.
A modular trojan, 9002 RAT comes with features to monitor network traffic, capture screenshots, enumerate files, manage processes, and run additional commands received from a remote server to facilitate network discovery, among others.
"The malware appears to be constantly updated with diskless variants as well," TG Soft said. "It is composed of various modules that are activated as needed by the cyber actor so as to reduce the possibility of interception."
Iranian Hackers Deploy New BugSleep Backdoor in Middle East Cyber Attacks
16.7.24 APT The Hacker News
The Iranian nation-state actor known as MuddyWater has been observed using a never-before-seen backdoor as part of a recent attack campaign, shifting away from its well-known tactic of deploying legitimate remote monitoring and management (RMM) software for maintaining persistent access.
That's according to independent findings from cybersecurity firms Check Point and Sekoia, which have codenamed the malware strain BugSleep and MuddyRot, respectively.
"Compared to previous campaigns, this time MuddyWater changed their infection chain and did not rely on the legitimate Atera remote monitoring and management tool (RRM) as a validator," Sekoia said in a report shared with The Hacker News. "Instead, we observed that they used a new and undocumented implant."
Some elements of the campaign were first shared by Israeli cybersecurity company ClearSky on June 9, 2024. Targets include countries like Turkey, Azerbaijan, Jordan, Saudi Arabia, Israel, and Portugal.
MuddyWater (aka Boggy Serpens, Mango Sandstorm, and TA450) is a state-sponsored threat actor that's assessed to be affiliated with Iran's Ministry of Intelligence and Security (MOIS).
Cyber attacks mounted by the group have been fairly consistent, leveraging spear-phishing lures in email messages to deliver various RMM tools like Atera Agent, RemoteUtilities, ScreenConnect, SimpleHelp, and Syncro.
Earlier this April, HarfangLab said it noticed an uptick in MuddyWater campaigns delivering Atera Agent since late October 2023 to businesses across Israel, India, Algeria, Turkey, Italy, and Egypt. The sectors targeted include airlines, IT companies, telecoms, pharma, automotive manufacturing, logistics, travel, and tourism.
"MuddyWater places a high priority on gaining access to business email accounts as part of their ongoing attack campaigns," the French cybersecurity firm noted at the time.
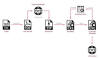
"These compromised accounts serve as valuable resources, enabling the group to enhance the credibility and effectiveness of their spear-phishing efforts, establish persistence within targeted organizations, and evade detection by blending in with legitimate network traffic."
The latest attack chains are no different in that compromised email accounts belonging to legitimate companies are used to send spear-phishing messages that either contain a direct link or a PDF attachment pointing to an Egnyte subdomain, which has been previously abused by the threat actor to propagate Atera Agent.
BugSleep, aka MuddyRot, is an x64 implant developed in C that comes equipped with capabilities to download/upload arbitrary files to/from the compromised host, launch a reverse shell, and set up persistence. Communications with a command-and-control (C2) server take place over a raw TCP socket on port 443.
"The first message to be sent to the C2 is the victim host fingerprint, which is the combination of the hostname and the username joined by a slash," Sekoia said. "If the victim received '-1,' the program stops, otherwise the malware enters in an infinite loop to await new order from the C2."
It's currently not clear why MuddyWater has switched to using a bespoke implant, although it's suspected that the increased monitoring of RMM tools by security vendors may have played a part.
"The increased activity of MuddyWater in the Middle East, particularly in Israel, highlights the persistent nature of these threat actors, who continue to operate against a wide variety of targets in the region," Check Point said.
"Their consistent use of phishing campaigns, now incorporating a custom backdoor, BugSleep, marks a notable development in their techniques, tactics, and procedures (TTPs)."
Void Banshee APT Exploits Microsoft MHTML Flaw to Spread Atlantida Stealer
16.7.24 APT The Hacker News
An advanced persistent threat (APT) group called Void Banshee has been observed exploiting a recently disclosed security flaw in the Microsoft MHTML browser engine as a zero-day to deliver an information stealer called Atlantida.
Cybersecurity firm Trend Micro, which observed the activity in mid-May 2024, the vulnerability – tracked as CVE-2024-38112 – was used as part of a multi-stage attack chain using specially crafted internet shortcut (URL) files.
"Variations of the Atlantida campaign have been highly active throughout 2024 and have evolved to use CVE-2024-38112 as part of Void Banshee infection chains," security researchers Peter Girnus and Aliakbar Zahravi said. "The ability of APT groups like Void Banshee to exploit disabled services such as [Internet Explorer] poses a significant threat to organizations worldwide."
The findings dovetail with prior disclosures from Check Point, which told The Hacker News of a campaign leveraging the same shortcoming to distribute the stealer. It's worth noting that CVE-2024-38112 was addressed by Microsoft as part of Patch Tuesday updates last week.
CVE-2024-38112 has been described by the Windows maker as a spoofing vulnerability in the MSHTML (aka Trident) browser engine used in the now-discontinued Internet Explorer browser. However, the Zero Day Initiative (ZDI) has asserted that it's a remote code execution flaw.
"What happens when the vendor states the fix should be a defense-in-depth update rather than a full CVE?," ZDI's Dustin Childs pointed out. "What happens when the vendor states the impact is spoofing but the bug results in remote code execution?"
Attack chains involve the use of spear-phishing emails embedding links to ZIP archive files hosted on file-sharing sites, which contain URL files that exploit CVE-2024-38112 to redirect the victim to a compromised site hosting a malicious HTML Application (HTA).
Opening the HTA file results in the execution of a Visual Basic Script (VBS) that, in turn, downloads and runs a PowerShell script responsible for retrieving a .NET trojan loader, which ultimately uses the Donut shellcode project to decrypt and execute the Atlantida stealer inside RegAsm.exe process memory.

Atlantida, modeled on open-source stealers like NecroStealer and PredatorTheStealer, is designed to extract files, screenshots, geolocation, and sensitive data from web browsers and other applications, including Telegram, Steam, FileZilla, and various cryptocurrency wallets.
"By using specially crafted URL files that contained the MHTML protocol handler and the x-usc! directive, Void Banshee was able to access and run HTML Application (HTA) files directly through the disabled IE process," the researchers said.
"This method of exploitation is similar to CVE-2021-40444, another MSHTML vulnerability that was used in zero-day attacks."
Not much is known about Void Banshee other than the fact that it has a history of targeting North American, European, and Southeast Asian regions for information theft and financial gain.
The development comes as Cloudflare revealed that threat actors are swiftly incorporating proof-of-concept (PoC) exploits into their arsenal, sometimes as quickly as 22 minutes after their public release, as observed in the case of CVE-2024-27198.
"The speed of exploitation of disclosed CVEs is often quicker than the speed at which humans can create WAF rules or create and deploy patches to mitigate attacks," the web infrastructure company said.
It also follows the discovery of a new campaign that leverages Facebook ads promoting fake Windows themes to distribute another stealer known as SYS01stealer that aims to hijack Facebook business accounts and further propagate the malware.
"Being an infostealer, SYS01 focuses on exfiltrating browser data such as credentials, history, and cookies," Trustwave said. "A big chunk of its payload is focused on obtaining access tokens for Facebook accounts, specifically those with Facebook business accounts, which can aid the threat actors in spreading the malware."
Chinese APT41 Upgrades Malware Arsenal with DodgeBox and MoonWalk
11.7.24 APT The Hacker News
The China-linked advanced persistent threat (APT) group codenamed APT41 is suspected to be using an "advanced and upgraded version" of a known malware called StealthVector to deliver a previously undocumented backdoor dubbed MoonWalk.
The new variant of StealthVector – which is also referred to as DUSTPAN – has been codenamed DodgeBox by Zscaler ThreatLabz, which discovered the loader strain in April 2024.
"DodgeBox is a loader that proceeds to load a new backdoor named MoonWalk," security researchers Yin Hong Chang and Sudeep Singh said. "MoonWalk shares many evasion techniques implemented in DodgeBox and utilizes Google Drive for command-and-control (C2) communication."
APT41 is the moniker assigned to a prolific state-sponsored threat actor affiliated with China that's known to be active since at least 2007. It's also tracked by the broader cybersecurity community under the names Axiom, Blackfly, Brass Typhoon (formerly Barium), Bronze Atlas, Earth Baku, HOODOO, Red Kelpie, TA415, Wicked Panda, and Winnti.
In September 2020, the U.S. Department of Justice (DoJ) announced the indictment of several threat actors associated with the hacking crew for orchestrating intrusion campaigns targeting more than 100 companies across the world.
"The intrusions [...] facilitated the theft of source code, software code signing certificates, customer account data, and valuable business information," the DoJ said at the time, adding they also enabled "other criminal schemes, including ransomware and 'crypto-jacking' schemes."
Over the past few years, the threat group has been linked to breaches of U.S. state government networks between May 2021 and February 2022, in addition to attacks targeting Taiwanese media organizations using an open-source red teaming tool known as Google Command and Control (GC2).
The use of StealthVector by APT41 was first documented by Trend Micro in August 2021, describing it as a shellcode loader written in C/C++ that's used to deliver Cobalt Strike Beacon and a shellcode implant named ScrambleCross (aka SideWalk).
DodgeBox is assessed to be an improved version of StealthVector, while also incorporating various techniques like call stack spoofing, DLL side-loading, and DLL hollowing to evade detection. The exact method by which the malware is distributed is presently unknown.
"APT41 employs DLL side-loading as a means of executing DodgeBox," the researchers said. "They utilize a legitimate executable (taskhost.exe), signed by Sandboxie, to sideload a malicious DLL (sbiedll.dll)."
The rogue DLL (i.e., DodgeBox) is a DLL loader written in C that acts as a conduit to decrypt and launch a second-stage payload, the MoonWalk backdoor.
The attribution of DodgeBox to APT41 stems from the similarities between DodgeBox and StealthVector; the use of DLL side-loading, a technique widely used by China-nexus groups to deliver malware such as PlugX; and the fact that DodgeBox samples have been submitted to VirusTotal from Thailand and Taiwan.
"DodgeBox is a newly identified malware loader that employs multiple techniques to evade both static and behavioral detection," the researchers said.
"It offers various capabilities, including decrypting and loading embedded DLLs, conducting environment checks and bindings, and executing cleanup procedures."
Cybersecurity Agencies Warn of China-linked APT40's Rapid Exploit Adaptation
9.7.24 APT The Hacker News
Cybersecurity agencies from Australia, Canada, Germany, Japan, New Zealand, South Korea, the U.K., and the U.S. have released a joint advisory about a China-linked cyber espionage group called APT40, warning about its ability to co-opt exploits for newly disclosed security flaws within hours or days of public release.
"APT40 has previously targeted organizations in various countries, including Australia and the United States," the agencies said. "Notably, APT40 possesses the ability to quickly transform and adapt vulnerability proofs-of-concept (PoCs) for targeting, reconnaissance, and exploitation operations."
The adversarial collective, also known as Bronze Mohawk, Gingham Typhoon (formerly Gadolinium), ISLANDDREAMS, Kryptonite Panda, Leviathan, Red Ladon, TA423, and TEMP.Periscope, is known to be active since at least 2013, carrying out cyber attacks targeting entities in the Asia-Pacific region. It's assessed to be based in Haikou.
In July 2021, the U.S. and its allies officially attributed the group as affiliated with China's Ministry of State Security (MSS), indicting several members of the hacking crew for orchestrating a multiyear campaign aimed at different sectors to facilitate the theft of trade secrets, intellectual property, and high-value information.
Over the past few years, APT40 has been linked to intrusion waves delivering the ScanBox reconnaissance framework as well as the exploitation of a security flaw in WinRAR (CVE-2023-38831, CVSS score: 7.8) as part of a phishing campaign targeting Papua New Guinea to deliver a backdoor dubbed BOXRAT.
Then earlier this March, the New Zealand government implicated the threat actor to the compromise of the Parliamentary Counsel Office and the Parliamentary Service in 2021.
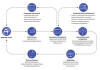
"APT40 identifies new exploits within widely used public software such as Log4j, Atlassian Confluence, and Microsoft Exchange to target the infrastructure of the associated vulnerability," the authoring agencies said.
"APT40 regularly conducts reconnaissance against networks of interest, including networks in the authoring agencies' countries, looking for opportunities to compromise its targets. This regular reconnaissance postures the group to identify vulnerable, end-of-life or no longer maintained devices on networks of interest, and to rapidly deploy exploits."
Notable among the tradecraft employed by the state-sponsored hacking crew is the deployment of web shells to establish persistence and maintain access to the victim's environment, as well as its use of Australian websites for command-and-control (C2) purposes.
It has also been observed incorporating out-of-date or unpatched devices, including small-office/home-office (SOHO) routers, as part of its attack infrastructure in an attempt to reroute malicious traffic and evade detection, an operational style that is akin to that used by other China-based groups like Volt Typhoon.
According to Google-owned Mandiant, this is part of a broader transition in cyber espionage activity originating from China that aims to put stealth front and center by increasingly weaponizing network edge devices, operational relay box (ORB) networks, and living-off-the-land (LotL) techniques to fly under the radar.
Attack chains further involve carrying out reconnaissance, privilege escalation, and lateral movement activities using the remote desktop protocol (RDP) to steal credentials and exfiltrate information of interest.
To mitigate the risks posed by such threats, organizations are recommended to maintain adequate logging mechanisms, enforce multi-factor authentication (MFA), implement a robust patch management system, replace end-of-life equipment, disable unused services, ports, and protocols, and segment networks to prevent access to sensitive data.
New APT Group "CloudSorcerer" Targets Russian Government Entities
8.7.24 APT The Hacker News
A previously undocumented advanced persistent threat (APT) group dubbed CloudSorcerer has been observed targeting Russian government entities by leveraging cloud services for command-and-control (C2) and data exfiltration.
Cybersecurity firm Kaspersky, which discovered the activity in May 2024, the tradecraft adopted by the threat actor bears similarities with that of CloudWizard, but pointed out the differences in the malware source code. The attacks wield an innovative data-gathering program and a slew of evasion tactics for covering its tracks.
"It's a sophisticated cyber espionage tool used for stealth monitoring, data collection, and exfiltration via Microsoft Graph, Yandex Cloud, and Dropbox cloud infrastructure," the Russian security vendor said.
"The malware leverages cloud resources as its command and control (C2) servers, accessing them through APIs using authentication tokens. Additionally, CloudSorcerer uses GitHub as its initial C2 server."
The exact method used to infiltrate targets is currently unknown, but the initial access is exploited to drop a C-based portable executable binary that's used as a backdoor, initiate C2 communications, or inject shellcode into other legitimate processes based on the process in which it is executed – namely mspaint.exe, msiexec.exe, or contains the string "browser."
"The malware's ability to dynamically adapt its behavior based on the process it is running in, coupled with its use of complex inter-process communication through Windows pipes, further highlights its sophistication," Kaspersky noted.
The backdoor component is designed to collect information about the victim machine and retrieve instructions to enumerate files and folders, execute shell commands, perform file operations, and run additional payloads.
The C2 module, for its part, connects to a GitHub page that acts as a dead drop resolver to fetch an encoded hex string pointing to the actual server hosted on Microsoft Graph or Yandex Cloud.
"Alternatively, instead of connecting to GitHub, CloudSorcerer also tries to get the same data from hxxps://my.mail[.]ru/, which is a Russian cloud-based photo hosting server," Kaspersky said. "The name of the photo album contains the same hex string."
"The CloudSorcerer malware represents a sophisticated toolset targeting Russian government entities. Its use of cloud services such as Microsoft Graph, Yandex Cloud, and Dropbox for C2 infrastructure, along with GitHub for initial C2 communications, demonstrates a well-planned approach to cyber espionage."
Kimsuky Using TRANSLATEXT Chrome Extension to Steal Sensitive Data
29.6.24 APT The Hacker News
The North Korea-linked threat actor known as Kimsuky has been linked to the use of a new malicious Google Chrome extension that's designed to steal sensitive information as part of an ongoing intelligence collection effort.
Zscaler ThreatLabz, which observed the activity in early March 2024, has codenamed the extension TRANSLATEXT, highlighting its ability to gather email addresses, usernames, passwords, cookies, and browser screenshots.
The targeted campaign is said to have been directed against South Korean academia, specifically those focused on North Korean political affairs.
Kimsuky is a notorious hacking crew from North Korea that's known to be active since at least 2012, orchestrating cyber espionage and financially motivated attacks targeting South Korean entities.
A sister group of the Lazarus cluster and part of the Reconnaissance General Bureau (RGB), it's also tracked under the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet, Springtail, and Velvet Chollima.
In recent weeks, the group has weaponized a known security flaw in Microsoft Office (CVE-2017-11882) to distribute a keylogger and has used job-themed lures in attacks aimed at aerospace and defense sectors with an aim to drop an espionage tool with data gathering and secondary payload execution functionalities.
"The backdoor, which does not appear to have been publicly documented before, allows the attacker to perform basic reconnaissance and drop additional payloads to take over or remotely control the machine," company CyberArmor said. It has given the campaign the name Niki.

The exact mode of initial access associated with the newly discovered activity is currently unclear, although the group is known to leverage spear-phishing and social engineering attacks to activate the infection chain.
The starting point of the attack is a ZIP archive that purports to be about Korean military history and which contains two files: A Hangul Word Processor document and an executable.
Launching the executable results in the retrieval of a PowerShell script from an attacker-controlled server, which, in turn, exports information about the compromised victim to a GitHub repository and downloads additional PowerShell code by means of a Windows shortcut (LNK) file.
Zscaler said it found the GitHub account, created on February 13, 2024, briefly hosting the TRANSLATEXT extension under the name "GoogleTranslate.crx," although its delivery method is presently unknown.
"These files were present in the repository on March 7, 2024, and deleted the next day, implying that Kimsuky intended to minimize exposure and use the malware for a short period to target specific individuals," security researcher Seongsu Park said.
TRANSLATEXT, which masquerades as Google Translate, incorporates JavaScript code to bypass security measures for services like Google, Kakao, and Naver; siphon email addresses, credentials, and cookies; capture browser screenshots; and exfiltrate stolen data.
It's also designed to fetch commands from a Blogger Blogspot URL in order to take screenshots of newly opened tabs and delete all cookies from the browser, among others.
"One of the primary objectives of the Kimsuky group is to conduct surveillance on academic and government personnel in order to gather valuable intelligence," Park said.
Chinese and N. Korean Hackers Target Global Infrastructure with Ransomware
27.6.24 APT The Hacker News
Threat actors with suspected ties to China and North Korea have been linked to ransomware and data encryption attacks targeting government and critical infrastructure sectors across the world between 2021 and 2023.
While one cluster of activity has been associated with the ChamelGang (aka CamoFei), the second cluster overlaps with activity previously attributed to Chinese and North Korean state-sponsored groups, firms SentinelOne and Recorded Future said in a joint report shared with The Hacker News.
This includes ChamelGang's attacks aimed at the All India Institute of Medical Sciences (AIIMS) and the Presidency of Brazil in 2022 using CatB ransomware, as well as those targeting a government entity in East Asia and an aviation organization in the Indian subcontinent in 2023.
"Threat actors in the cyber espionage ecosystem are engaging in an increasingly disturbing trend of using ransomware as a final stage in their operations for the purposes of financial gain, disruption, distraction, misattribution, or removal of evidence," security researchers Aleksandar Milenkoski and Julian-Ferdinand Vögele said.
Ransomware attacks in this context not only serve as an outlet for sabotage but also allow threat actors to cover up their tracks by destroying artifacts that could otherwise alert defenders to their presence.
ChamelGang, first documented by Positive Technologies in 2021, is assessed to be a China-nexus group that operates with motivations as varied as intelligence gathering, data theft, financial gain, denial-of-service (DoS) attacks, and information operations, according to Taiwanese firm TeamT5.
It's known to possess a wide range of tools in its arsenal, including BeaconLoader, Cobalt Strike, backdoors like AukDoor and DoorMe, and a ransomware strain known as CatB, which has been identified as used in attacks targeting Brazil and India based on commonalities in the ransom note, the format of the contact email address, the cryptocurrency wallet address, and the filename extension of encrypted files.
Attacks observed in 2023 have also leveraged an updated version of BeaconLoader to deliver Cobalt Strike for reconnaissance and post-exploitation activities such as dropping additional tooling and exfiltrating NTDS.dit database file.
Furthermore, it's worth pointing out that custom malware put to use by ChamelGang such as DoorMe and MGDrive (whose macOS variant is called Gimmick) have also been linked to other Chinese threat groups like REF2924 and Storm Cloud, once again alluding to the possibility of a "digital quartermaster supplying distinct operational groups with malware."
The other set of intrusions involves the use of Jetico BestCrypt and Microsoft BitLocker in cyber attacks affecting various industry verticals in North America, South America, and Europe. As many as 37 organizations, predominantly the U.S. manufacturing sector, are estimated to have been targeted.
The tactics observed, per the two companies, are consistent with those attributed to a Chinese hacking crew dubbed APT41 and a North Korean actor known as Andariel, owing to the presence of tools like the China Chopper web shell and a backdoor known as DTrack.
"The activities we observed overlap with past intrusions involving artifacts associated with suspected Chinese and North Korean APT clusters," Milenkoski told The Hacker News, stating visibility limitations have likely prevented detecting the malicious artifacts themselves.
"Our investigations and our review of previous research did not reveal evidence of tooling or other intrusion artifacts associated with suspected Chinese or North Korean APT groups being present concurrently in the same targeted environments."
SentinelOne further said it cannot exclude the possibility that these activities are part of a broader cybercriminal scheme, particularly given that nation-state actors have also taken part in financially motivated attacks from time to time.
"Cyber espionage operations disguised as ransomware activities provide an opportunity for adversarial countries to claim plausible deniability by attributing the actions to independent cybercriminal actors rather than state-sponsored entities," the researchers said.
"The use of ransomware by cyber espionage threat groups blurs the lines between cybercrime and cyber espionage, providing adversaries with advantages from both strategic and operational perspectives."
(The story was updated after publication to include a response from SentinelOne.)
4 FIN9-linked Vietnamese Hackers Indicted in $71M U.S. Cybercrime Spree
25.6.24 APT The Hacker News
Four Vietnamese nationals with ties to the FIN9 cybercrime group have been indicted in the U.S. for their involvement in a series of computer intrusions that caused over $71 million in losses to companies.
The defendants, Ta Van Tai (aka Quynh Hoa and Bich Thuy), Nguyen Viet Quoc (aka Tien Nguyen), Nguyen Trang Xuyen, and Nguyen Van Truong (aka Chung Nguyen), have been accused of conducting phishing campaigns and supply chain compromises to orchestrate cyber attacks and steal millions of dollars.
"From at least May 2018 through October 2021, the defendants hacked the computer networks of victim companies throughout the United States and used their access to steal or attempt to steal non-public information, employee benefits, and funds," the U.S. Department of Justice said in an unsealed indictment last week.
According to court documents, the individuals – after successfully gaining initial access to target networks – stole gift card data, personally identifiable information, and credit card details associated with employees and customers.
They further used the stolen information to further their criminal activities to evade detection, including opening online accounts at cryptocurrency exchanges and setting up hosting servers.
"Tai, Xuyen, and Truong sold stolen gift cards to third parties, including through an account registered with a fake name on a peer-to-peer cryptocurrency marketplace, in order to conceal and disguise the source of the stolen money," the DoJ said.
All the four defendants have been charged with one count of conspiracy to commit fraud, extortion, and related activity in connection with computers; one count of conspiracy to commit wire fraud; and two counts of intentional damage to a protected computer. If convicted on all counts, they face up to 45 years in prison.
Additionally, Tai, Xuyen, and Truong have been charged with one count of conspiracy to commit money laundering, which carries a jail term of up to 20 years. Tai and Quoc have also been saddled with one count of aggravated identity theft and one count of conspiracy to commit identity fraud, charges that can have a maximum penalty of up to 17 years in prison.
The development comes days after the DoJ said that two U.S. members of the ViLE hacking group, Sagar Steven Singh (aka Weep) and Nicholas Ceraolo (aka Convict, Anon, and Ominous), pleaded guilty for their involvement in the compromise of a federal law enforcement database by using stolen credentials and engaging in an extortion scheme.
"The defendants called themselves 'ViLe,' and their actions were exactly that," U.S. Attorney Breon Peace said. "They hacked into a law enforcement database and had access to sensitive personal information, then threatened to harm a victim's family and publicly release that information unless the defendants were ultimately paid money."
The two men, who were originally charged in March 2023, pled guilty to conspiring to commit computer intrusion and aggravated identity theft. They face a minimum sentence of two years in prison, and a maximum of seven years.
It also follows a new wave of sanctions imposed by the European Council against six persons for conducting cyber attacks against critical infrastructure and government systems in the European Union and Ukraine.
This includes Aleksandrovich Peretyatko and Andrey Stanislavovich Korinets, two hackers associated with the COLDRIVER (aka BlueCharlie, Calisto, Gossamer Bear, and Star Blizzard) hacking crew who were previously sanctioned by the U.K. and U.S. governments for carrying out spear-phishing campaigns.
The remaining four encompass Sklianko Oleksandr Mykolaiovych and Chernykh Mykola Serhiiovych of the Gamaredon (aka Armageddon) group and Mikhail Tsarev and Maksim Galochkin of the Wizard Spider gang, the latter two of which are assessed to be key players in the deployment of Conti and TrickBot malware.
"The E.U. remains committed to a global, open, and secure cyberspace and, reiterates the need to strengthen international cooperation to promote the rules-based order in this area," the Council said.
RedJuliett Cyber Espionage Campaign Hits 75 Taiwanese Organizations
25.6.24 APT The Hacker News
A likely China-linked state-sponsored threat actor has been linked to a cyber espionage campaign targeting government, academic, technology, and diplomatic organizations in Taiwan between November 2023 and April 2024.
Recorded Future's Insikt Group is tracking the activity under the name RedJuliett, describing it as a cluster that operates from Fuzhou, China, to support Beijing's intelligence collection goals related to the East Asian country. It's also tracked under the names Flax Typhoon and Ethereal Panda.
Among other countries targeted by the adversarial collective include Djibouti, Hong Kong, Kenya, Laos, Malaysia, the Philippines, Rwanda, South Korea, and the U.S.
In all, as many as 24 victim organizations have been observed communicating with the threat actor infrastructure, including government agencies in Taiwan, Laos, Kenya, and Rwanda. It's also estimated to have targeted at least 75 Taiwanese entities for broader reconnaissance and follow-on exploitation.
"The group targets internet-facing appliances such as firewalls, load balancers, and enterprise virtual private network VPN products for initial access, as well as attempting structured query language SQL injection and directory traversal exploits against web and SQL applications," the company said in a new report published today.
As previously documented by CrowdStrike and Microsoft, RedJuliett is known to employ the open-source software SoftEther to tunnel malicious traffic out of victim networks and leverage living-off-the-land (LotL) techniques to fly under the radar. The group is believed to be active since at least mid-2021.
"Additionally, RedJuliett used SoftEther to administer operational infrastructure consisting of both threat actor-controlled servers leased from virtual private server VPS providers and compromised infrastructure belonging to three Taiwanese universities," Recorded Future noted.
A successful initial access is followed by the deployment of the China Chopper web shell to maintain persistence, alongside other open-source web shells like devilzShell, AntSword, and Godzilla. A few instances have also entailed the exploitation of a Linux privilege escalation vulnerability known as Dirty Cow (CVE-2016-5195).
"RedJuliett is likely interested in collecting intelligence on Taiwan's economic policy and trade and diplomatic relations with other countries," it said.
"RedJuliett, like many other Chinese threat actors, is likely targeting vulnerabilities in internet-facing devices because these devices have limited visibility and security solutions available, and targeting them has proven to be an effective way to scale initial access."
Update#
In a statement released by China's Ministry of Foreign Affairs, spokesperson Mao Ning dismissed the allegations, describing them as "fabricated disinformation on so-called Chinese hacking operations."
ExCobalt Cyber Gang Targets Russian Sectors with New GoRed Backdoor
23.6.24 APT The Hacker News
Russian organizations have been targeted by a cybercrime gang called ExCobalt using a previously unknown Golang-based backdoor known as GoRed.
"ExCobalt focuses on cyber espionage and includes several members active since at least 2016 and presumably once part of the notorious Cobalt Gang," Positive Technologies researchers Vladislav Lunin and Alexander Badayev said in a technical report published this week.
"Cobalt attacked financial institutions to steal funds. One of Cobalt's hallmarks was the use of the CobInt tool, something ExCobalt began to use in 2022."
Attacks mounted by the threat actor have singled out various sectors in Russia over the past year, including government, information technology, metallurgy, mining, software development, and telecommunications.
Initial access to environments is facilitated by taking advantage of a previously compromised contractor and a supply chain attack, wherein the adversary infected a component used to build the target company's legitimate software, suggesting a high degree of sophistication.
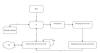
The modus operandi entails the use of various tools like Metasploit, Mimikatz, ProcDump, SMBExec, Spark RAT for executing commands on the infected hosts, and Linux privilege escalation exploits (CVE-2019-13272, CVE-2021-3156, CVE-2021-4034, and CVE-2022-2586).
GoRed, which has undergone numerous iterations since its inception, is a comprehensive backdoor that allows the operators to execute commands, obtain credentials, and harvest details of active processes, network interfaces, and file systems. It utilizes the Remote Procedure Call (RPC) protocol to communicate with its command-and-control (C2) server.
What's more, it supports a number of background commands to watch for files of interest and passwords as well as enable reverse shell. The collected data is then exported to the attacker-controlled infrastructure.
"ExCobalt continues to demonstrate a high level of activity and determination in attacking Russian companies, constantly adding new tools to its arsenal and improving its techniques," the researchers said.
"In addition, ExCobalt demonstrates flexibility and versatility by supplementing its toolset with modified standard utilities, which help the group to easily bypass security controls and adapt to changes in protection methods."
China-Linked 'Muddling Meerkat' Hijacks DNS to Map Internet on Global Scale
30.4.24 APT The Hacker News
A previously undocumented cyber threat dubbed Muddling Meerkat has been observed undertaking sophisticated domain name system (DNS) activities in a likely effort to evade security measures and conduct reconnaissance of networks across the world since October 2019.
Cloud security firm Infoblox described the threat actor as likely affiliated with the People's Republic of China (PRC) with the ability to control the Great Firewall (GFW), which censors access to foreign websites and manipulates internet traffic to and from the country.
The moniker is reference to the "bewildering" nature of their operations and the actor's abuse of DNS open resolvers – which are DNS servers that accept recursive queries from all IP addresses – to send queries from the Chinese IP space.
"Muddling Meerkat demonstrates a sophisticated understanding of DNS that is uncommon among threat actors today – clearly pointing out that DNS is a powerful weapon leveraged by adversaries," the company said in a report shared with The Hacker News.
More specifically, it entails triggering DNS queries for mail exchange (MX) and other record types to domains not owned by the actor but which reside under well-known top-level domains such as .com and .org.
Infoblox, which discovered the threat actor from anomalous DNS MX record requests that were sent to its recursive resolvers by customer devices, said it detected over 20 such domains -
4u[.]com, kb[.]com, oao[.]com, od[.]com, boxi[.]com, zc[.]com, s8[.]com, f4[.]com, b6[.]com, p3z[.]com, ob[.]com, eg[.]com, kok[.]com, gogo[.]com, aoa[.]com, gogo[.]com, zbo6[.]com, id[.]com, mv[.]com, nef[.]com, ntl[.]com, tv[.]com, 7ee[.]com, gb[.]com, tunk[.]org, q29[.]org, ni[.]com, tt[.]com, pr[.]com, dec[.]com
"Muddling Meerkat elicits a special kind of fake DNS MX record from the Great Firewall which has never been seen before," Dr. Renée Burton, vice president of threat intelligence for Infoblox, told The Hacker News. "For this to happen, Muddling Meerkat must have a relationship with the GFW operators."
"The target domains are the domain used in the queries, so it is not necessarily the target of an attack. It is the domain used to carry out the probe attack. These domains are not owned by Muddling Meerkat."
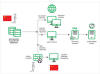
It's known that the GFW relies on what's called DNS spoofing and tampering to inject fake DNS responses containing random real IP addresses when a request matches a banned keyword or a blocked domain.
In other words, when a user attempts to search for a blocked keyword or phrase, the GFW blocks or redirects the website query in a manner that will prevent the user from accessing the requested information. This is achieved via techniques like DNS cache poisoning or IP address blocking.
This also means that if the GFW detects a query to a blocked website, the sophisticated tool injects a bogus DNS reply with an invalid IP address, or an IP address to a different domain, effectively corrupting the cache of recursive DNS servers located within its borders.
"The most remarkable feature of Muddling Meerkat is the presence of false MX record responses from Chinese IP addresses," Burton said. "This behavior [...] differs from the standard behavior of the GFW."
"These resolutions are sourced from Chinese IP addresses that do not host DNS services and contain false answers, consistent with the GFW. However, unlike the known behavior of the GFW, Muddling Meerkat MX responses include not IPv4 addresses but properly formatted MX resource records instead."
The exact motivation behind the multi-year activity is unclear, although it raised the possibility that it may be undertaken as part of an internet mapping effort or research of some kind.
"Muddling Meerkat is a Chinese nation-state actor performing deliberate and highly skilled DNS operations against global networks on an almost daily basis – and the full scope of their operation can not be seen in any one location," Burton said.
"Malware is easier than DNS in this sense – once you locate the malware, it is straightforward to understand it. Here, we know something is happening, but don't understand it fully. CISA, the FBI, and other agencies continue to warn of Chinese prepositioning operations that are undetected. We should be worried about anything we can't fully see or understand."
State-Sponsored Hackers Exploit Two Cisco Zero-Day Vulnerabilities for Espionage
25.4.24 APT The Hacker News
A new malware campaign leveraged two zero-day flaws in Cisco networking gear to deliver custom malware and facilitate covert data collection on target environments.
Cisco Talos, which dubbed the activity ArcaneDoor, attributing it as the handiwork of a previously undocumented sophisticated state-sponsored actor it tracks under the name UAT4356 (aka Storm-1849 by Microsoft).
"UAT4356 deployed two backdoors as components of this campaign, 'Line Runner' and 'Line Dancer,' which were used collectively to conduct malicious actions on-target, which included configuration modification, reconnaissance, network traffic capture/exfiltration and potentially lateral movement," Talos said.
The intrusions, which were first detected and confirmed in early January 2024, entail the exploitation of two vulnerabilities -
CVE-2024-20353 (CVSS score: 8.6) - Cisco Adaptive Security Appliance and Firepower Threat Defense Software Web Services Denial-of-Service Vulnerability
CVE-2024-20359 (CVSS score: 6.0) - Cisco Adaptive Security Appliance and Firepower Threat Defense Software Persistent Local Code Execution Vulnerability
It's worth noting that a zero-day exploit is the technique or attack a malicious actor deploys to leverage an unknown security vulnerability to gain access into a system.
While the second flaw allows a local attacker to execute arbitrary code with root-level privileges, administrator-level privileges are required to exploit it. Addressed alongside CVE-2024-20353 and CVE-2024-20359 is a command injection flaw in the same appliance (CVE-2024-20358, CVSS score: 6.0) that was uncovered during internal security testing.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the shortcomings to its Known Exploited Vulnerabilities (KEV) catalog, requiring federal agencies to apply the vendor-provided fixes by May 1, 2024.

The exact initial access pathway used to breach the devices is presently unknown, although UAT4356 is said to have started preparations for it as early as July 2023.
A successful foothold is followed by the deployment of two implants named Line Dancer and Line Runner, the former of which is an in-memory backdoor that enables attackers to upload and execute arbitrary shellcode payloads, including disabling system logs and exfiltrating packet captures.
Line Runner, on the other hand, is a persistent HTTP-based Lua implant installed on the Cisco Adaptive Security Appliance (ASA) by leveraging the aforementioned zero-days such that it can survive across reboots and upgrades. It has been observed being used to fetch information staged by Line Dancer.
"It is suspected that Line Runner may be present on a compromised device even if Line Dancer is not (e.g., as a persistent backdoor, or where an impacted ASA has not yet received full operational attention from the malicious actors)," according to a joint advisory published by cybersecurity agencies from Australia, Canada, and the U.K.
At every phase of the attack, UAT4356 is said to have demonstrated meticulous attention to hiding digital footprints and the ability to employ intricate methods to evade memory forensics and lower the chances of detection, contributing to its sophistication and elusive nature.
This also suggests that the threat actors have a complete understanding of the inner workings of the ASA itself and of the "forensic actions commonly performed by Cisco for network device integrity validation."
Exactly which country is behind ArcaneDoor is unclear, however both Chinese and Russian state-backed hackers have targeted Cisco routers for cyber espionage purposes in the past. Cisco Talos also did not specify how many customers were compromised in these attacks.
The development once again highlights the increased targeting of edge devices and platforms such as email servers, firewalls, and VPNs that traditionally lack endpoint detection and response (EDR) solutions, as evidenced by the recent string of attacks targeting Barracuda Networks, Fortinet, Ivanti, Palo Alto Networks, and VMware.
"Perimeter network devices are the perfect intrusion point for espionage-focused campaigns," Talos said.
"As a critical path for data into and out of the network, these devices need to be routinely and promptly patched; using up-to-date hardware and software versions and configurations; and be closely monitored from a security perspective. Gaining a foothold on these devices allows an actor to directly pivot into an organization, reroute or modify traffic and monitor network communications."
Researchers Detail Multistage Attack Hijacking Systems with SSLoad, Cobalt Strike
25.4.24 APT The Hacker News
Cybersecurity researchers have discovered an ongoing attack campaign that's leveraging phishing emails to deliver malware called SSLoad.
The campaign, codenamed FROZEN#SHADOW by Securonix, also involves the deployment of Cobalt Strike and the ConnectWise ScreenConnect remote desktop software.
"SSLoad is designed to stealthily infiltrate systems, gather sensitive information and transmit its findings back to its operators," security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.
"Once inside the system, SSLoad deploys multiple backdoors and payloads to maintain persistence and avoid detection."
Attack chains involve the use of phishing messages to randomly target organizations in Asia, Europe, and the Americas, with emails containing links that lead to the retrieval of a JavaScript file that kicks off the infection flow.
Earlier this month, Palo Alto Networks uncovered at least two different methods by which SSLoad is distributed, one which entails the use of website contact forms to embed booby-trapped URLs and another involving macro-enabled Microsoft Word documents.
The latter is also notable for the fact that malware acts as a conduit for delivering Cobalt Strike, while the former has been used to deliver a different malware called Latrodectus, a likely successor to IcedID.
The obfuscated JavaScript file ("out_czlrh.js"), when launched and run using wscript.exe, retrieves an MSI installer file ("slack.msi") by connecting to a network share located at "\\wireoneinternet[.]info@80\share\" and runs it using msiexec.exe.
The MSI installer, for its part, contacts an attacker-controlled domain to fetch and execute the SSLoad malware payload using rundll32.exe, following which it beacons to a command-and-control (C2) server along with information about the compromised system.
The initial reconnaissance phase paves the way for Cobalt Strike, a legitimate adversary simulation software, which is then used to download and install ScreenConnect, thereby allowing the threat actors to remotely commandeer the host.
"With full access to the system the threat actors began attempting to acquire credentials and gather other critical system details," the researchers said. "At this stage they started scanning the victim host for credentials stored in files as well as other potentially sensitive documents."
The attackers have also been observed pivoting to other systems in the network, including the domain controller, ultimately infiltrating the victim's Windows domain by creating their own domain administrator account.
"With this level of access, they could get into any connected machine within the domain," the researchers said. "In the end, this is the worst case scenario for any organization as this level of persistence achieved by the attackers would be incredibly time consuming and costly to remediate."
The disclosure comes as the AhnLab Security Intelligence Center (ASEC) revealed that Linux systems are being infected with an open-source remote access trojan called Pupy RAT.
ToddyCat Hacker Group Uses Advanced Tools for Industrial-Scale Data Theft
23.4.24 APT The Hacker News
The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and steal valuable data.
Russian cybersecurity firm Kaspersky characterized the adversary as relying on various programs to harvest data on an "industrial scale" from primarily governmental organizations, some of them defense related, located in the Asia-Pacific region.
"To collect large volumes of data from many hosts, attackers need to automate the data harvesting process as much as possible, and provide several alternative means to continuously access and monitor systems they attack," security researchers Andrey Gunkin, Alexander Fedotov, and Natalya Shornikova said.
ToddyCat was first documented by the company in June 2022 in connection with a series of cyber attacks aimed at government and military entities in Europe and Asia since at least December 2020. These intrusions leveraged a passive backdoor dubbed Samurai that allows for remote access to the compromised host.
A closer examination of the threat actor's tradecraft has since uncovered additional data exfiltration tools like LoFiSe and Pcexter to gather data and upload archive files to Microsoft OneDrive.
The latest set of programs entail a mix of tunneling data gathering software, which are put to use after the attacker has already obtained access to privileged user accounts in the infected system. This includes -
Reverse SSH tunnel using OpenSSH
SoftEther VPN, which is renamed to seemingly innocuous files like "boot.exe," "mstime.exe," "netscan.exe," and "kaspersky.exe"
Ngrok and Krong to encrypt and redirect command-and-control (C2) traffic to a certain port on the target system
FRP client, an open-source Golang-based fast reverse proxy
Cuthead, a .NET compiled executable to search for documents matching a specific extension or a filename, or the date when they are modified
WAExp, a .NET program to capture data associated with the WhatsApp web app and save it as an archive, and
TomBerBil to extract cookies and credentials from web browsers like Google Chrome and Microsoft Edge
Maintaining multiple simultaneous connections from the infected endpoints to actor-controlled infrastructure using different tools is seen as a fallback mechanism and a way to retain access in cases where one of the tunnels is discovered and taken down.

"The attackers are actively using techniques to bypass defenses in an attempt to mask their presence in the system," Kaspersky said.
"To protect the organization's infrastructure, we recommend adding to the firewall denylist the resources and IP addresses of cloud services that provide traffic tunneling. In addition, users must be required to avoid storing passwords in their browsers, as it helps attackers to access sensitive information."
Russia's APT28 Exploited Windows Print Spooler Flaw to Deploy 'GooseEgg' Malware
23.4.24 APT The Hacker News
The Russia-linked nation-state threat actor tracked as APT28 weaponized a security flaw in the Microsoft Windows Print Spooler component to deliver a previously unknown custom malware called GooseEgg.
The post-compromise tool, which is said to have been used since at least June 2020 and possibly as early as April 2019, leveraged a now-patched flaw that allowed for privilege escalation (CVE-2022-38028, CVSS score: 7.8).
It was addressed by Microsoft as part of updates released in October 2022, with the U.S. National Security Agency (NSA) credited for reporting the flaw at the time.
According to new findings from the tech giant's threat intelligence team, APT28 – also called Fancy Bear and Forest Blizzard (formerly Strontium) – weaponized the bug in attacks targeting Ukrainian, Western European, and North American government, non-governmental, education, and transportation sector organizations.
"Forest Blizzard has used the tool [...] to exploit the CVE-2022-38028 vulnerability in Windows Print Spooler service by modifying a JavaScript constraints file and executing it with SYSTEM-level permissions," the company said.
"While a simple launcher application, GooseEgg is capable of spawning other applications specified at the command line with elevated permissions, allowing threat actors to support any follow-on objectives such as remote code execution, installing a backdoor, and moving laterally through compromised networks."
Forest Blizzard is assessed to be affiliated with Unit 26165 of the Russian Federation's military intelligence agency, the Main Intelligence Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU).
Active for nearly 15 years, the Kremlin-backed hacking group's activities are predominantly geared towards intelligence collection in support of Russian government foreign policy initiatives.
In recent months, APT28 hackers have also abused a privilege escalation flaw in Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) and a code execution bug in WinRAR (CVE-2023-38831, CVSS score: 7.8), indicating their ability to swiftly adopt public exploits into their tradecraft.
"Forest Blizzard's objective in deploying GooseEgg is to gain elevated access to target systems and steal credentials and information," Microsoft said. "GooseEgg is typically deployed with a batch script."
The GooseEgg binary supports commands to trigger the exploit and launch either a provided dynamic-link library (DLL) or an executable with elevated permissions. It also verifies if the exploit has been successfully activated using the whoami command.
The disclosure comes as IBM X-Force revealed new phishing attacks orchestrated by the Gamaredon actor (aka Aqua Blizzard, Hive0051, and UAC-0010) that deliver new iterations of the GammaLoad malware -
GammaLoad.VBS, which is a VBS-based backdoor initiating the infection chain
GammaStager, which is used to download and execute a series of Base64-encoded VBS payloads
GammaLoadPlus, which is used to run .EXE payloads
GammaInstall, which serves as the loader for a known PowerShell backdoor referred to as GammaSteel
GammaLoad.PS, a PowerShell implementation of GammaLoad
GammaLoadLight.PS, a PowerShell variant that contains code to spread the spread itself to connected USB devices
GammaInfo, a PowerShell-based enumeration script collecting various information from the host
GammaSteel, a PowerShell-based malware to exfiltrate files from a victim based on an extension allowlist
"Hive0051 rotates infrastructure through synchronized DNS fluxing across multiple channels including Telegram, Telegraph and Filetransfer.io," IBM X-Force researchers said earlier this month, stating it "points to a potential elevation in actor resources and capability devoted to ongoing operations."
"It is highly likely Hive0051's consistent fielding of new tools, capabilities and methods for delivery facilitate an accelerated operations tempo."
FIN7 Cybercrime Group Targeting U.S. Auto Industry with Carbanak Backdoor
19.4.24 APT The Hacker News
The infamous cybercrime syndicate known as FIN7 has been linked to a spear-phishing campaign targeting the U.S. automotive industry to deliver a known backdoor called Carbanak (aka Anunak).
"FIN7 identified employees at the company who worked in the IT department and had higher levels of administrative rights," the BlackBerry research and intelligence team said in a new write-up.
"They used the lure of a free IP scanning tool to run their well-known Anunak backdoor and gain an initial foothold utilizing living off the land binaries, scripts, and libraries (LOLBAS)."
FIN7, also known as Carbon Spider, Elbrus, Gold Niagara, ITG14, and Sangria Tempest, is a well-known financially motivated e-crime group that has a track record of striking a wide range of industry verticals to deliver malware capable of stealing information from point-of-sale (PoS) systems since 2012.
In recent years, the threat actor has transitioned to conducting ransomware operations, delivering various strains like Black Basta, Cl0p, DarkSide, and REvil. Two Ukrainian members of the group, Fedir Hladyr and Andrii Kolpakov, have been sentenced to prison in the U.S. to date.
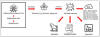
The latest campaign discovered by BlackBerry in late 2023 starts with a spear-phishing email that embeds a booby-trapped link pointing to a bogus site ("advanced-ip-sccanner[.]com") that masquerades as Advanced IP Scanner.
"This fake site redirected to 'myipscanner[.]com,' which in turn redirected to an attacker-owned Dropbox that downloaded the malicious executable WsTaskLoad.exe onto the victim's machine," the Canadian cybersecurity company said.
The binary, for its part, initiates a multi-stage process that ultimately leads to the execution of Carbanak. It's also designed to deliver additional payloads such as POWERTRASH and establish persistence by installing OpenSSH for remote access.
It's currently not known if the threat actors were planning on deploying ransomware, as the infected system was detected early on and removed from the network before it could reach the lateral movement stage.
While the target of the attack was a "large multinational automotive manufacturer" based in the U.S., BlackBerry said it found several similar malicious domains on the same provider, indicating that it may be part of a wider campaign by FIN7.
To mitigate the risks posed by such threats, it's recommended that organizations be on the lookout for phishing attempts, enable multi-factor authentication (MFA), keep all software and systems up-to-date, and monitor for unusual login attempts.
Russian APT Deploys New 'Kapeka' Backdoor in Eastern European Attacks
18.4.24 APT The Hacker News
A previously undocumented "flexible" backdoor called Kapeka has been "sporadically" observed in cyber attacks targeting Eastern Europe, including Estonia and Ukraine, since at least mid-2022.
The findings come from Finnish cybersecurity firm WithSecure, which attributed the malware to the Russia-linked advanced persistent threat (APT) group tracked as Sandworm (aka APT44 or Seashell Blizzard). Microsoft is tracking the same malware under the name KnuckleTouch.
"The malware [...] is a flexible backdoor with all the necessary functionalities to serve as an early-stage toolkit for its operators, and also to provide long-term access to the victim estate," security researcher Mohammad Kazem Hassan Nejad said.
Kapeka comes fitted with a dropper that's designed to launch and execute a backdoor component on the infected host, after which it removes itself. The dropper is also responsible for setting up persistence for the backdoor either as a scheduled task or autorun registry, depending on whether the process has SYSTEM privileges.
Microsoft, in its own advisory released in February 2024, described Kapeka as involved in multiple campaigns distributing ransomware and that it can be used to carry out a variety of functions, such as stealing credentials and other data, conducting destructive attacks, and granting threat actors remote access to the device.
The backdoor is a Windows DLL written in C++ and features an embedded command-and-control (C2) configuration that's used to establish contact with an actor-controlled server and holds information about the frequency at which the server needs to be polled in order to retrieve commands.
Besides masquerading as a Microsoft Word add-in to make it appear genuine, the backdoor DLL gathers information about the compromised host and implements multi-threading to fetch incoming instructions, process them, and exfiltrate the results of the execution to the C2 server.
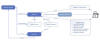
"The backdoor uses WinHttp 5.1 COM interface (winhttpcom.dll) to implement its network communication component," Nejad explained. "The backdoor communicates with its C2 to poll for tasks and to send back fingerprinted information and task results. The backdoor utilizes JSON to send and receive information from its C2."
The implant is also capable of updating its C2 configuration on-the-fly by receiving a new version from the C2 server during polling. Some of the main features of the backdoor allow it to read and write files from and to disk, launch payloads, execute shell commands, and even upgrade and uninstall itself.
The exact method through which the malware is propagated is currently unknown. However, Microsoft noted that the dropper is retrieved from compromised websites using the certutil utility, underscoring the use of a legitimate living-off-the-land binary (LOLBin) to orchestrate the attack.
Kapeka's connections to Sandworm come conceptual and configuration overlaps with previously disclosed families like GreyEnergy, a likely successor to the BlackEnergy toolkit, and Prestige.
"It is likely that Kapeka was used in intrusions that led to the deployment of Prestige ransomware in late 2022," WithSecure said. "It is probable that Kapeka is a successor to GreyEnergy, which itself was likely a replacement for BlackEnergy in Sandworm's arsenal."
"The backdoor's victimology, infrequent sightings, and level of stealth and sophistication indicate APT-level activity, highly likely of Russian origin."
Muddled Libra Shifts Focus to SaaS and Cloud for Extortion and Data Theft Attacks
16.4.24 APT The Hacker News
The threat actor known as Muddled Libra has been observed actively targeting software-as-a-service (SaaS) applications and cloud service provider (CSP) environments in a bid to exfiltrate sensitive data.
"Organizations often store a variety of data in SaaS applications and use services from CSPs," Palo Alto Networks Unit 42 said in a report published last week.
"The threat actors have begun attempting to leverage some of this data to assist with their attack progression, and to use for extortion when trying to monetize their work."
Muddled Libra, also called Starfraud, UNC3944, Scatter Swine, and Scattered Spider, is a notorious cybercriminal group that has leveraged sophisticated social engineering techniques to gain initial access to target networks.
"Scattered Spider threat actors have historically evaded detection on target networks by using living off the land techniques and allowlisted applications to navigate victim networks, as well as frequently modifying their TTPs," the U.S. government said in an advisory late last year.
The attackers also have a history of monetizing access to victim networks in numerous ways, including extortion enabled by ransomware and data theft.
Unit 42 previously told The Hacker News that the moniker "Muddled Libra" comes from the "confusing muddled landscape" associated with the 0ktapus phishing kit, which has been put to use by other threat actors to stage credential harvesting attacks.
A key aspect of the threat actor's tactical evolution is the use of reconnaissance techniques to identify administrative users to target when posing as helpdesk staff using phone calls to obtain their passwords.
The recon phase also extends to Muddled Libra carrying out extensive research to find information about the applications and the cloud service providers used by the target organizations.
"The Okta cross-tenant impersonation attacks that occurred from late July to early August 2023, where Muddled Libra bypassed IAM restrictions, display how the group exploits Okta to access SaaS applications and an organization's various CSP environments," security researcher Margaret Zimmermann explained.
The information obtained at this stage serves as a stepping stone for conducting lateral movement, abusing the admin credentials to access single sign-on (SSO) portals to gain quick access to SaaS applications and cloud infrastructure.
In the event SSO is not integrated into a target's CSP, Muddled Libra undertakes broad discovery activities to uncover the CSP credentials, likely stored in unsecured locations, to meet their objectives.
The data stored with SaaS applications are also used to glean specifics about the infected environment, capturing as many credentials as possible to widen the scope of the breach via privilege escalation and lateral movement.
"A large portion of Muddled Libra's campaigns involve gathering intelligence and data," Zimmermann said.
"Attackers then use this to generate new vectors for lateral movement within an environment. Organizations store a variety of data within their unique CSP environments, thus making these centralized locations a prime target for Muddled Libra."
The discovery actions specifically single out Amazon Web Services (AWS) and Microsoft Azure, targeting services like AWS IAM, Amazon Simple Storage Service (S3), AWS Secrets Manager, Azure storage account access keys, Azure Blob Storage, and Azure Files to extract relevant data.
Data exfiltration is achieved by abusing legitimate CSP services and features. This encompasses tools like AWS DataSync, AWS Transfer, and a technique called snapshot, the latter of which makes it possible to move data out of an Azure environment by staging the stolen data in a virtual machine.
Muddled Libra's tactical shift requires organizations to secure their identity portals with robust secondary authentication protections like hardware tokens or biometrics.
"By expanding their tactics to include SaaS applications and cloud environments, the evolution of Muddled Libra's methodology shows the multidimensionality of cyberattacks in the modern threat landscape," Zimmermann concluded. "The use of cloud environments to gather large amounts of information and quickly exfiltrate it poses new challenges to defenders."
Iranian MuddyWater Hackers Adopt New C2 Tool 'DarkBeatC2' in Latest Campaign
12.4.24 APT The Hacker News
The Iranian threat actor known as MuddyWater has been attributed to a new command-and-control (C2) infrastructure called DarkBeatC2, becoming the latest such tool in its arsenal after SimpleHarm, MuddyC3, PhonyC2, and MuddyC2Go.
"While occasionally switching to a new remote administration tool or changing their C2 framework, MuddyWater's methods remain constant," Deep Instinct security researcher Simon Kenin said in a technical report published last week.
MuddyWater, also called Boggy Serpens, Mango Sandstorm, and TA450, is assessed to be affiliated with Iran's Ministry of Intelligence and Security (MOIS). It's known to be active since at least 2017, orchestrating spear-phishing attacks that lead to the deployment of various legitimate Remote Monitoring and Management (RMM) solutions on compromised systems.
Prior findings from Microsoft show that the group has ties with another Iranian threat activity cluster tracked as Storm-1084 (aka DarkBit), with the latter leveraging the access to orchestrate destructive wiper attacks against Israeli entities.
The latest attack campaign, details of which were also previously revealed by Proofpoint last month, commences with spear-phishing emails sent from compromised accounts that contain links or attachments hosted on services like Egnyte to deliver the Atera Agent software.
One of the URLs in question is "kinneretacil.egnyte[.]com," where the subdomain "kinneretacil" refers to "kinneret.ac.il," an educational institution in Israel and a customer of Rashim, which, in turn, was breached by Lord Nemesis (aka Nemesis Kitten or TunnelVision) as part of a supply chain attack targeting the academic sector in the country.
Lord Nemesis is suspected of being a "faketivist" operation directed against Israel. It's also worth noting that Nemesis Kitten is a private contracting company called Najee Technology, a subgroup within Mint Sandstorm that's backed by Iran's Islamic Revolutionary Guard Corps (IRGC). The company was sanctioned by the U.S. Treasury in September 2022.
"This is important because if 'Lord Nemesis' were able to breach Rashim's email system, they might have breached the email systems of Rashim's customers using the admin accounts that now we know they obtained from 'Rashim,'" Kenin explained.

The web of connections has raised the possibility that MuddyWater may have used the email account associated with Kinneret to distribute the links, thereby giving the messages an illusion of trust and tricking the recipients into clicking them.
"While not conclusive, the timeframe and context of the events indicate a potential hand-off or collaboration between IRGC and MOIS to inflict as much harm as possible on Israeli organizations and individuals," Kenin further added.
The attacks are also notable for relying on a set of domains and IP addresses collectively dubbed DarkBeatC2 that are responsible for managing the infected endpoints. This is accomplished by means of PowerShell code designed to establish contact with the C2 server upon gaining initial access through other means.
According to independent findings from Palo Alto Networks Unit 42, the threat actor has been observed abusing the Windows Registry's AutodialDLL function to side-load a malicious DLL and ultimately set up connections with a DarkBeatC2 domain.
The mechanism, in particular, involves establishing persistence through a scheduled task that runs PowerShell to leverage the AutodialDLL registry key and load the DLL for C2 framework. The cybersecurity firm said the technique was put to use in a cyber attack aimed at an unnamed Middle East target.
Other methods adopted by MuddyWater to establish a C2 connection include the use of a first-stage payload delivered via the spear-phishing email and leveraging DLL side-loading to execute a malicious library.
A successful contact allows the infected host to receive PowerShell responses that, for its part, fetches two more PowerShell scripts from the same server.
While one of the scripts is designed to read the contents of a file named "C:\ProgramData\SysInt.log" and transmit them to the C2 server via an HTTP POST request, the second script periodically polls the server to obtain additional payloads and writes the results of the execution to "SysInt.log." The exact nature of the next-stage payload is currently unknown.
"This framework is similar to the previous C2 frameworks used by MuddyWater," Kenin said. "PowerShell remains their 'bread and butter.'"
Curious Serpens Targets Defense Sector with FalseFont Backdoor#
The disclosure comes as Unit 42 unpacked the inner workings of a backdoor called FalseFont that's used by an Iranian threat actor known as Peach Sandstorm (aka APT33, Curious Serpens, Elfin, and Refined Kitten) in attacks targeting the aerospace and defense sectors.
"The threat actors mimic legitimate human resources software, using a fake job recruitment process to trick victims into installing the backdoor," security researchers Tom Fakterman, Daniel Frank, and Jerome Tujague said, describing FalseFont as "highly targeted."
Once installed, it presents a login interface impersonating an aerospace company and captures the credentials as well as the educational and employment history entered by the victim to a threat-actor controlled C2 server in JSON format.
The implant, besides its graphical user interface (GUI) component for user inputs, also stealthily activates a second component in the background that establishes persistence on the system, gathers system metadata, and executes commands and processes sent from the C2 server.
Other features of FalseFont include the ability to download and upload files, steal credentials, capture screenshots, terminate specific processes, run PowerShell commands, and self-update the malware.
U.S. Cyber Safety Board Slams Microsoft Over Breach by China-Based Hackers
4.4.24 APT The Hacker News
The U.S. Cyber Safety Review Board (CSRB) has criticized Microsoft for a series of security lapses that led to the breach of nearly two dozen companies across Europe and the U.S. by a China-based nation-state group called Storm-0558 last year.
The findings, released by the Department of Homeland Security (DHS) on Tuesday, found that the intrusion was preventable, and that it became successful due to a "cascade of Microsoft's avoidable errors."
"It identified a series of Microsoft operational and strategic decisions that collectively pointed to a corporate culture that deprioritized enterprise security investments and rigorous risk management, at odds with the company's centrality in the technology ecosystem and the level of trust customers place in the company to protect their data and operations," the DHS said in a statement.
The CSRB also lambasted the tech titan for failing to detect the compromise on its own, instead relying on a customer to reach out to flag the breach. It further faulted Microsoft for not prioritizing the development of an automated key rotation solution and rearchitecting its legacy infrastructure to meet the needs of the current threat landscape.
The incident first came to light in July 2023 when Microsoft revealed that Storm-0558 gained unauthorized access to 22 organizations as well as more than more than 500 related individual consumer accounts.
Microsoft subsequently said a validation error in its source code made it possible for Azure Active Directory (Azure AD) tokens to be forged by Storm-0558 using a Microsoft account (MSA) consumer signing key, thus allowing the adversary to infiltrate the mailboxes.
In September 2023, the company divulged that Storm-0558 acquired the consumer signing key to forge the tokens by compromising an engineer's corporate account that had access to a debugging environment hosting a crash dump of its consumer signing system that also inadvertently contained the signing key.
Microsoft has since acknowledged in a March 2024 update that it was inaccurate and that it has not still been able to locate a "crash dump containing the impacted key material." It also said its investigation into the hack remains ongoing.
"Our leading hypothesis remains that operational errors resulted in key material leaving the secure token signing environment that was subsequently accessed in a debugging environment via a compromised engineering account," it noted.
"Recent events have demonstrated a need to adopt a new culture of engineering security in our own networks," a Microsoft spokesperson was quoted as saying to The Washington Post.
As many as 60,000 unclassified emails from Outlook accounts are believed to have been exfiltrated over the course of the campaign that began in May 2023. China has rejected accusations that it was behind the attack.
Earlier this February, Redmond expanded free logging capabilities to all U.S. federal agencies using Microsoft Purview Audit, irrespective of the license tier, to help them detect, respond, and prevent sophisticated cyber attacks.
"The threat actor responsible for this brazen intrusion has been tracked by industry for over two decades and has been linked to 2009 Operation Aurora and 2011 RSA SecureID compromises," said CSRB Acting Deputy Chair Dmitri Alperovitch.
"This People's Republic of China affiliated group of hackers has the capability and intent to compromise identity systems to access sensitive data, including emails of individuals of interest to the Chinese government."
To safeguard against threats from state-sponsored actors, cloud service providers have been recommended to -
Implement modern control mechanisms and baseline practices
Adopt a minimum standard for default audit logging in cloud services
Incorporate emerging digital identity standards to secure cloud services
Adopt incident and vulnerability disclosure practices to maximize transparency
Develop more effective victim notification and support mechanisms to drive information-sharing efforts
"The United States government should update the Federal Risk Authorization Management Program and supporting frameworks and establish a process for conducting discretionary special reviews of the program's authorized Cloud Service Offerings following especially high-impact situations," the CSRB said.
China-linked Hackers Deploy New 'UNAPIMON' Malware for Stealthy Operations
2.4.24 APT The Hacker News
A threat activity cluster tracked as Earth Freybug has been observed using a new malware called UNAPIMON to fly under the radar.
"Earth Freybug is a cyberthreat group that has been active since at least 2012 that focuses on espionage and financially motivated activities," Trend Micro security researcher Christopher So said in a report published today.
"It has been observed to target organizations from various sectors across different countries."
The cybersecurity firm has described Earth Freybug as a subset within APT41, a China-linked cyber espionage group that's also tracked as Axiom, Brass Typhoon (formerly Barium), Bronze Atlas, HOODOO, Wicked Panda, and Winnti.
The adversarial collective is known to rely on a combination of living-off-the-land binaries (LOLBins) and custom malware to realize its goals. Also adopted are techniques like dynamic-link library (DLL) hijacking and application programming interface (API) unhooking.
Trend Micro said the activity shares tactical overlaps with a cluster previously disclosed by cybersecurity company Cybereason under the name Operation CuckooBees, which refers to an intellectual property theft campaign targeting technology and manufacturing companies located in East Asia, Western Europe, and North America.
The starting point of the attack chain is the use of a legitimate executable associated with VMware Tools ("vmtoolsd.exe") to create a scheduled task using "schtasks.exe" and deploy a file named "cc.bat" in the remote machine.
It's currently not known how the malicious code came to be injected in vmtoolsd.exe, although it's suspected that it may have involved the exploitation of external-facing servers.
The batch script is designed to amass system information and launch a second scheduled task on the infected host, which, in turn, executes another batch file with the same name ("cc.bat") to ultimately run the UNAPIMON malware.
"The second cc.bat is notable for leveraging a service that loads a non-existent library to side-load a malicious DLL," So explained. "In this case, the service is SessionEnv."
This paves the way for the execution of TSMSISrv.DLL that's responsible for dropping another DLL file (i.e., UNAPIMON) and injecting that same DLL into cmd.exe. Simultaneously, the DLL file is also injected into SessionEnv for defense evasion.
On top of that, the Windows command interpreter is designed to execute commands coming from another machine, essentially turning it into a backdoor.
A simple C++-based malware, UNAPIMON is equipped to prevent child processes from being monitored by leveraging an open-source Microsoft library called Detours to unhook critical API functions, thereby evading detection in sandbox environments that implement API monitoring through hooking.
The cybersecurity company characterized the malware as original, calling out the author's "coding prowess and creativity" as well as their use of an off-the-shelf library to carry out malicious actions.
"Earth Freybug has been around for quite some time, and their methods have been seen to evolve through time," Trend Micro said.
"This attack also demonstrates that even simple techniques can be used effectively when applied correctly. Implementing these techniques to an existing attack pattern makes the attack more difficult to discover."
Finland Blames Chinese Hacking Group APT31 for Parliament Cyber Attack
29.3.24 APT The Hacker News
The Police of Finland (aka Poliisi) has formally accused a Chinese nation-state actor tracked as APT31 for orchestrating a cyber attack targeting the country's Parliament in 2020.
The intrusion, per the authorities, is said to have occurred between fall 2020 and early 2021. The agency described the ongoing criminal probe as both demanding and time-consuming, involving extensive analysis of a "complex criminal infrastructure."
The breach was first disclosed in December 2020, with the Finnish Security and Intelligence Service (Supo) describing it as a state-backed cyber espionage operation designed to penetrate the Parliament's information systems.
"The police have previously informed that they are investigating the hacking group APT31's connections with the incident," Poliisi said. "These connections have now been confirmed by the investigation, and the police have also identified one suspect."
APT31, also called Altaire, Bronze Vinewood, Judgement Panda, and Violet Typhoon (formerly Zirconium), is a Chinese state-backed group that has been active since at least 2010.
Earlier this week, the U.K. and the U.S. blamed the adversarial collective for engaging in a widespread cyber espionage campaign targeting businesses, government officials, dissidents, and politicians.
Seven operatives associated with the group have been charged in the U.S. for their involvement in the hacking spree. Two of them – Ni Gaobin and Zhao Guangzong – have been sanctioned by the two nations, alongside a company named Wuhan XRZ, which allegedly served as a cover for orchestrating cyber attacks against critical infrastructure.
"Guangzong is a Chinese national who has conducted numerous malicious cyber operations against U.S. victims as a contractor for Wuhan XRZ," the U.S. Treasury said. "Ni Gaobin assisted Zhao Guangzong in many of his most high profile malicious cyber activities while Zhao Guangzong was a contractor at Wuhan XRZ."
In July 2021, the U.S. and its allies implicated APT31 in a widespread campaign exploiting zero-day security flaws in Microsoft Exchange servers with the goal of likely "acquiring personally identifiable information and intellectual property."
China, however, has hit back against the accusations that it's behind the hacking campaign targeting the West. It has accused the Five Eyes (FVEY) alliance of spreading "disinformation about the threats posed by the so-called 'Chinese hackers.'"
"We urge the U.S. and the U.K. to stop politicizing cybersecurity issues, stop smearing China and imposing unilateral sanctions on China, and stop cyberattacks against China," China's Foreign Ministry Spokesperson Lin Jian said. "China will take necessary measures to firmly safeguard its lawful rights and interests."
Two Chinese APT Groups Ramp Up Cyber Espionage Against ASEAN Countries
27.3.24 APT The Hacker News
Two China-linked advanced persistent threat (APT) groups have been observed targeting entities and member countries affiliated with the Association of Southeast Asian Nations (ASEAN) as part of a cyber espionage campaign over the past three months.
This includes the threat actor known as Mustang Panda, which has been recently linked to cyber attacks against Myanmar as well as other Asian countries with a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS.
Mustang Panda, also called Camaro Dragon, Earth Preta, and Stately Taurus, is believed to have targeted entities in Myanmar, the Philippines, Japan and Singapore, targeting them with phishing emails designed to deliver two malware packages.
"Threat actors created malware for these packages on March 4-5, 2024, coinciding with the ASEAN-Australia Special Summit (March 4-6, 2024)," Palo Alto Networks Unit 42 said in a report shared with The Hacker News.
One of the malware package is a ZIP file that contains within it an executable ("Talking_Points_for_China.exe"), that when launched, loads a DLL file ("KeyScramblerIE.dll") and ultimately deploys a known Mustang Panda malware called PUBLOAD, a downloader previously employed to drop PlugX.
It's worth pointing out here that the binary is a renamed copy of a legitimate software called KeyScrambler.exe that's susceptible to DLL side-loading.
The second package, on the other hand, is a screensaver executable ("Note PSO.scr") that's used to retrieve next-stage malicious code from a remote IP address, including a benign program signed by a video game company renamed as WindowsUpdate.exe and a rogue DLL that's launched using the same technique as before.
"This malware then attempts to establish a connection to www[.]openservername[.]com at 146.70.149[.]36 for command-and-control (C2)," the researchers said.
Unit 42 said it also detected network traffic between an ASEAN-affiliated entity and the C2 infrastructure of a second Chinese APT group, suggesting a breach of the victim's environment. This unnamed threat activity cluster has been attributed to similar attacks targeting Cambodia.
"These types of campaigns continue to demonstrate how organizations are targeted for cyber espionage purposes, where nation-state affiliated threat groups collect intelligence of geopolitical interests within the region," the researchers said.
Earth Krahang Emerges in Wild#
The findings arrive a week after Trend Micro shed light on a new Chinese threat actor known as Earth Krahang that has targeted 116 entities spanning 35 countries by leveraging spear-phishing and flaws in public-facing Openfire and Oracle servers to deliver bespoke malware such as PlugX, ShadowPad, ReShell, and DinodasRAT (aka XDealer).
The earliest attacks date back to early 2022, with the adversary leveraging a combination of methods to scan for sensitive data.
Earth Krahang, which has a strong focus in Southeast Asia, also exhibits some level of overlap with another China-nexus threat actor tracked as Earth Lusca (aka RedHotel). Both the intrusion sets are likely managed by the same threat actor and connected to a Chinese government contractor called I-Soon.
"One of the threat actor's favorite tactics involves using its malicious access to government infrastructure to attack other government entities, abusing the infrastructure to host malicious payloads, proxy attack traffic, and send spear-phishing emails to government-related targets using compromised government email accounts," the company said.
"Earth Krahang also uses other tactics, such as building VPN servers on compromised public-facing servers to establish access into the private network of victims and performing brute-force attacks to obtain email credentials. These credentials are then used to exfiltrate victim emails."
The I-Soon Leaks and the Shadowy Hack-for-hire Scene#
Last month, a set of leaked documents from I-Soon (aka Anxun) on GitHub revealed how the company sells a wide array of stealers and remote access trojans like ShadowPad and Winnti (aka TreadStone) to multiple Chinese government entities. This also encompasses an integrated operations platform that's designed to carry out offensive cyber campaigns and an undocumented Linux implant codenamed Hector.
"The integrated operations platform encompasses both internal and external applications and networks," Bishop Fox said. "The internal application is mainly for mission and resource management. The external application is designed to carry out cyber operations."
The obscure hack-for-hire entity has also been implicated in the 2019 POISON CARP campaign aimed at Tibetan groups and the 2022 hack of Comm100, in addition to attacks targeting foreign governments and domestic ethnic minorities to gain valuable information, some of which are carried out independently on their own in hopes of landing a government customer.
"The data leak has provided rare insight into how the Chinese government outsources parts of its cyber operations to private third-party companies, and how these companies work with one another to fulfill these demands," ReliaQuest noted.
Cybersecurity firm Recorded Future, in its own analysis, said the leak unravels the "operational and organizational ties" between the company and three different Chinese state-sponsored cyber groups such as RedAlpha (aka Deepcliff), RedHotel, and POISON CARP.
"It provides supporting evidence regarding the long-suspected presence of 'digital quartermasters' that provide capabilities to multiple Chinese state-sponsored groups."
It also said the overlaps suggest the presence of multiple sub-teams focused on particular missions within the same company. I-Soon's victimology footprint spreads to at least 22 countries, with government, telecommunications, and education representing the most targeted sectors.
Furthermore, the publicized documents confirm that Tianfu Cup – China's own take on the Pwn2Own hacking contest – acts as a "vulnerability feeder system" for the government, allowing it to stockpile zero-day exploits and devise exploit code.
"When the Tianfu Cup submissions aren't already full exploit chains, the Ministry of Public Security disseminates the proof of concept vulnerabilities to private firms to further exploit these proof-of-concept capabilities," Margin Research said.
"China's vulnerability disclosure requirement is one part of the puzzle of how China stockpiles and weaponizes vulnerabilities, setting in stone the surreptitious collection offered by Tianfu Cup in previous years."
The source of the leak is currently not known, although two employees of I-Soon told The Associated Press that an investigation is ongoing in collaboration with law enforcement. The company's website has since gone offline.
"The leak provides some of the most concrete details seen publicly to date, revealing the maturing nature of China's cyber espionage ecosystem," SentinelOne's Dakota Cary and Aleksandar Milenkoski said. "It shows explicitly how government targeting requirements drive a competitive marketplace of independent contractor hackers-for-hire."
Iran-Linked MuddyWater Deploys Atera for Surveillance in Phishing Attacks
26.3.24 APT The Hacker News
The Iran-affiliated threat actor tracked as MuddyWater (aka Mango Sandstorm or TA450) has been linked to a new phishing campaign in March 2024 that aims to deliver a legitimate Remote Monitoring and Management (RMM) solution called Atera.
The activity, which took place from March 7 through the week of March 11, targeted Israeli entities spanning global manufacturing, technology, and information security sectors, Proofpoint said.
"TA450 sent emails with PDF attachments that contained malicious links," the enterprise security firm said. "While this method is not foreign to TA450, the threat actor has more recently relied on including malicious links directly in email message bodies instead of adding in this extra step."
MuddyWater has been attributed to attacks directed against Israeli organizations since late October 2023, with prior findings from Deep Instinct uncovering the threat actor's use of another remote administration tool from N-able.
This is not the first time the adversary – assessed to be affiliated with Iran's Ministry of Intelligence and Security (MOIS) – has come under the spotlight for its reliance on legitimate remote desktop software to meet its strategic goals. Similar phishing campaigns have led to the deployment of ScreenConnect, RemoteUtilities, Syncro, and SimpleHelp in the past.
The latest attack chains involve MuddyWater embedding links to files hosted on file-sharing sites such as Egnyte, Onehub, Sync, and TeraBox. Some of the pay-themed phishing messages are said to have been sent from a likely compromised email account associated with the "co.il" (Israel) domain.
In the next stage, clicking on the link present within the PDF lure document leads to the retrieval of a ZIP archive containing an MSI installer file that ultimately installs the Atera Agent on the compromised system. MuddyWater's use of Atera Agent dates back to July 2022.
The shift in MuddyWater's tactics comes as an Iranian hacktivist group dubbed Lord Nemesis has targeted the Israeli academic sector by breaching a software services provider named Rashim Software in what's case of a software supply chain attack.
"Lord Nemesis allegedly used the credentials obtained from the Rashim breach to infiltrate several of the company's clients, including numerous academic institutes," Op Innovate said. "The group claims to have obtained sensitive information during the breach, which they may use for further attacks or to exert pressure on the affected organizations."
Lord Nemesis is believed to have used the unauthorized access it gained to Rashim's infrastructure by hijacking the admin account and leveraging the company's inadequate multi-factor authentication (MFA) protections to harvest personal data of interest.
It also sent email messages to over 200 of its customers on March 4, 2024, four months after the initial breach took place, detailing the extent of the incident. The exact method by which the threat actor gained access to Rashim's systems was not disclosed.
"The incident highlights the significant risks posed by third-party vendors and partners (supply chain attack)," security researcher Roy Golombick said. "This attack highlights the growing threat of nation-state actors targeting smaller, resource-limited companies as a means to further their geo-political agendas."
"By successfully compromising Rashim's admin account, the Lord Nemesis group effectively circumvented the security measures put in place by numerous organizations, granting themselves elevated privileges and unrestricted access to sensitive systems and data."
N. Korea-linked Kimsuky Shifts to Compiled HTML Help Files in Ongoing Cyberattacks
24.3.24 APT The Hacker News
The North Korea-linked threat actor known as Kimsuky (aka Black Banshee, Emerald Sleet, or Springtail) has been observed shifting its tactics, leveraging Compiled HTML Help (CHM) files as vectors to deliver malware for harvesting sensitive data.
Kimsuky, active since at least 2012, is known to target entities located in South Korea as well as North America, Asia, and Europe.
According to Rapid7, attack chains have leveraged weaponized Microsoft Office documents, ISO files, and Windows shortcut (LNK) files, with the group also employing CHM files to deploy malware on compromised hosts.
The cybersecurity firm has attributed the activity to Kimsuky with moderate confidence, citing similar tradecraft observed in the past.
"While originally designed for help documentation, CHM files have also been exploited for malicious purposes, such as distributing malware, because they can execute JavaScript when opened," the company said.
The CHM file is propagated within an ISO, VHD, ZIP, or RAR file, opening which executes a Visual Basic Script (VBScript) to set up persistence and reach out to a remote server to fetch a next-stage payload responsible for gathering and exfiltrating sensitive data.
Rapid7 described the attacks as ongoing and evolving, targeting organizations based in South Korea. It also identified an alternate infection sequence that employs a CHM file as a starting point to drop batch files tasked with harvesting the information and a PowerShell script to connect to the C2 server and transfer the data.
"The modus operandi and reusing of code and tools are showing that the threat actor is actively using and refining/reshaping its techniques and tactics to gather intelligence from victims," it said.
The development comes as Broadcom-owned Symantec revealed that the Kimsuky actors are distributing malware impersonating an application from a legitimate Korean public entity.
"Once compromised, the dropper installs an Endoor backdoor malware," Symantec said. "This threat enables attackers to collect sensitive information from the victim or install additional malware."
It's worth noting that the Golang-based Endoor, alongside Troll Stealer (aka TrollAgent), has been recently deployed in connection with cyber attacks that target users downloading security programs from a Korean construction-related association's website.
The findings also arrive amid a probe initiated by the United Nations into 58 suspected cyber attacks carried out by North Korean nation-state actors between 2017 and 2023 that netted $3 billion in illegal revenues to help it further develop its nuclear weapons program.
"The high volume of cyber attacks by hacking groups subordinate to the Reconnaissance General Bureau reportedly continued," the report said. "Trends include targeting defense companies and supply chains and, increasingly, sharing infrastructure and tools."
The Reconnaissance General Bureau (RGB) is North Korea's primary foreign intelligence service, comprising the threat clusters widely tracked as the Lazarus Group – and its subordinate elements, Andariel and BlueNoroff – and Kimsuky.
"Kimsuky has shown interest in using generative artificial intelligence, including large language models, potentially for coding or writing phishing emails," the report further added. "Kimsuky has been observed using ChatGPT."
China-Linked Group Breaches Networks via Connectwise, F5 Software Flaws
22.3.24 APT The Hacker News
A China-linked threat cluster leveraged security flaws in Connectwise ScreenConnect and F5 BIG-IP software to deliver custom malware capable of delivering additional backdoors on compromised Linux hosts as part of an "aggressive" campaign.
Google-owned Mandiant is tracking the activity under its uncategorized moniker UNC5174 (aka Uteus or Uetus), describing it as a "former member of Chinese hacktivist collectives that has since shown indications of acting as a contractor for China's Ministry of State Security (MSS) focused on executing access operations."
The threat actor is believed to have orchestrated widespread attacks against Southeast Asian and U.S. research and education institutions, Hong Kong businesses, charities and non-governmental organizations (NGOs), and U.S. and U.K. government organizations between October and November 2023, and again in February 2024 using the ScreenConnect bug.
Initial access to target environments is facilitated by the exploitation of known security flaws in Atlassian Confluence (CVE-2023-22518), ConnectWise ScreenConnect (CVE-2024-1709), F5 BIG-IP (CVE-2023-46747), Linux Kernel (CVE-2022-0185), and Zyxel (CVE-2022-3052).
A successful foothold is followed by extensive reconnaissance and scanning of internet-facing systems for security vulnerabilities, with UNC5174 also creating administrative user accounts to execute malicious actions with elevated privileges, including dropping a C-based ELF downloader dubbed SNOWLIGHT.
SNOWLIGHT is designed to download the next-stage payload, an obfuscated Golang backdoor named GOREVERSE, from a remote URL that's related to SUPERSHELL, an open-source command-and-control (C2) framework that allows attackers to establish a reverse SSH tunnel and launch interactive shell sessions to execute arbitrary code.
Also put to use by the threat actor is a Golang-based tunneling tool known as GOHEAVY, which is likely employed to facilitate lateral movement within compromised networks, as well as other programs like afrog, DirBuster, Metasploit, Sliver, and sqlmap.
In one unusual instance spotted by the threat intelligence firm, the threat actors have been found to apply mitigations for CVE-2023-46747 in a likely attempt to prevent other unrelated adversaries from weaponizing the same loophole to obtain access.
"UNC5174 (aka Uteus) was previously a member of Chinese hacktivist collectives 'Dawn Calvary' and has collaborated with 'Genesis Day' / 'Xiaoqiying' and 'Teng Snake,'" Mandiant assessed. "This individual appears to have departed these groups in mid-2023 and has since focused on executing access operations with the intention of brokering access to compromised environments."
There is evidence to suggest that the threat actor may be an initial access broker and has the backing of the MSS, given their alleged claims in dark web forums. This is bolstered by the fact some of the U.S. defense and U.K. government entities were simultaneously targeted by another access broker referred to as UNC302.
The findings once again underscore Chinese nation-state groups' continued efforts to breach edge appliances by swiftly co-opting recently disclosed vulnerabilities into their arsenal in order to conduct cyber espionage operations at scale.
"UNC5174 has been observed attempting to sell access to U.S. defense contractor appliances, U.K. government entities, and institutions in Asia in late 2023 following CVE-2023-46747 exploitation," Mandiant researchers said.
"There are similarities between UNC5174 and UNC302, which suggests they operate within an MSS initial access broker landscape. These similarities suggest possible shared exploits and operational priorities between these threat actors, although further investigation is required for definitive attribution."
The disclosure comes as the MSS warned that an unnamed foreign hacking group had infiltrated "hundreds" of Chinese business and government organizations by leveraging phishing emails and known security bugs to breach networks. It did not reveal the threat actor's name or origin.
Russia Hackers Using TinyTurla-NG to Breach European NGO's Systems
22.3.24 APT The Hacker News
The Russia-linked threat actor known as Turla infected several systems belonging to an unnamed European non-governmental organization (NGO) in order to deploy a backdoor called TinyTurla-NG (TTNG).
"The attackers compromised the first system, established persistence and added exclusions to antivirus products running on these endpoints as part of their preliminary post-compromise actions," Cisco Talos said in a new report published today.
"Turla then opened additional channels of communication via Chisel for data exfiltration and to pivot to additional accessible systems in the network."
There is evidence indicating that the infected systems were breached as early as October 2023, with Chisel deployed in December 2023 and data exfiltration taking place via the tool a month later, around January 12, 2024.
TinyTurla-NG was first documented by the cybersecurity company last month after it was found to be used in connection with a cyber attack targeting a Polish NGO working on improving Polish democracy and supporting Ukraine during the Russian invasion.
Cisco Talos told The Hacker News at the time that the campaign appears to be highly targeted and focused on a small number of organizations, most of which are located in Poland.
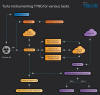
The attack chain involves Turla exploiting their initial access to configure Microsoft Defender antivirus exclusions to evade detection and drop TinyTurla-NG, which is then persisted by creating a malicious "sdm" service that masquerades as a "System Device Manager" service.
TinyTurla-NG acts as a backdoor to conduct follow-on reconnaissance, exfiltrate files of interest to a command-and-control (C2) server, and deploy a custom-built version of the Chisel tunneling software. The exact intrusion pathway is still being investigated.
"Once the attackers have gained access to a new box, they will repeat their activities to create Microsoft Defender exclusions, drop the malware components, and create persistence," Talos researchers said.
APT28 Hacker Group Targeting Europe, Americas, Asia in Widespread Phishing Scheme
18.3.24 APT The Hacker News
The Russia-linked threat actor known as APT28 has been linked to multiple ongoing phishing campaigns that employ lure documents imitating government and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, and North and South America.
"The uncovered lures include a mixture of internal and publicly available documents, as well as possible actor-generated documents associated with finance, critical infrastructure, executive engagements, cyber security, maritime security, healthcare, business, and defense industrial production," IBM X-Force said in a report published last week.
The tech company is tracking the activity under the moniker ITG05, which is also known as Blue Athena, BlueDelta, Fancy Bear, Fighting Ursa, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, Pawn Storm, Sednit, Sofacy, TA422, and UAC-028.
The disclosure comes more than three months after the adversary was spotted using decoys related to the ongoing Israel-Hamas war to deliver a custom backdoor dubbed HeadLace.
APT28 has since also targeted Ukrainian government entities and Polish organizations with phishing messages designed to deploy bespoke implants and information stealers like MASEPIE, OCEANMAP, and STEELHOOK.
Other campaigns have entailed the exploitation of security flaws in Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) to plunder NT LAN Manager (NTLM) v2 hashes, raising the possibility that the threat actor may leverage other weaknesses to exfiltrate NTLMv2 hashes for use in relay attacks.
The latest campaigns observed by IBM X-Force between late November 2023 and February 2024 leverage the "search-ms:" URI protocol handler in Microsoft Windows to trick victims into downloading malware hosted on actor-controlled WebDAV servers.
There is evidence to suggest that both the WebDAV servers, as well as the MASEPIE C2 servers, may be hosted on compromised Ubiquiti routers, a botnet comprising which was taken down by the U.S. government last month.
The phishing attacks impersonate entities from several countries such as Argentina, Ukraine, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the U.S., putting to use a mix of authentic publicly available government and non-government lure documents to activate the infection chains.
"In an update to their methodologies, ITG05 is utilizing the freely available hosting provider, firstcloudit[.]com to stage payloads to enable ongoing operations," security researchers Joe Fasulo, Claire Zaboeva, and Golo Mühr said.
The climax of APT28's elaborate scheme ends with the execution of MASEPIE, OCEANMAP, and STEELHOOK, which are designed to exfiltrate files, run arbitrary commands, and steal browser data. OCEANMAP has been characterized as a more capable version of CredoMap, another backdoor previously identified as used by the group.
"ITG05 remains adaptable to changes in opportunity by delivering new infection methodologies and leveraging commercially available infrastructure, while consistently evolving malware capabilities," the researchers concluded.
Microsoft Confirms Russian Hackers Stole Source Code, Some Customer Secrets
9.3.24 APT The Hacker News
Microsoft on Friday revealed that the Kremlin-backed threat actor known as Midnight Blizzard (aka APT29 or Cozy Bear) managed to gain access to some of its source code repositories and internal systems following a hack that came to light in January 2024.
"In recent weeks, we have seen evidence that Midnight Blizzard is using information initially exfiltrated from our corporate email systems to gain, or attempt to gain, unauthorized access," the tech giant said.
"This has included access to some of the company's source code repositories and internal systems. To date we have found no evidence that Microsoft-hosted customer-facing systems have been compromised."
Redmond, which is continuing to investigate the extent of the breach, said the Russian state-sponsored threat actor is attempting to leverage the different types of secrets it found, including those that were shared between customers and Microsoft in email.
It, however, did not disclose what these secrets were or the scale of the compromise, although it said it has directly reached out to impacted customers. It's not clear what source code was accessed.
Stating that it has increased in its security investments, Microsoft further noted that the adversary ramped up its password spray attacks by as much as 10-fold in February, compared to the "already large volume" observed in January.
"Midnight Blizzard's ongoing attack is characterized by a sustained, significant commitment of the threat actor's resources, coordination, and focus," it said.
"It may be using the information it has obtained to accumulate a picture of areas to attack and enhance its ability to do so. This reflects what has become more broadly an unprecedented global threat landscape, especially in terms of sophisticated nation-state attacks."
The Microsoft breach is said to have taken place in November 2023, with Midnight Blizzard employing a password spray attack to successfully infiltrate a legacy, non-production test tenant account that did not have multi-factor authentication (MFA) enabled.
The tech giant, in late January, revealed that APT29 had targeted other organizations by taking advantage of a diverse set of initial access methods ranging from stolen credentials to supply chain attacks.
Midnight Blizzard is considered part of Russia's Foreign Intelligence Service (SVR). Active since at least 2008, the threat actor is one of the most prolific and sophisticated hacking groups, compromising high-profile targets such as SolarWinds.
New APT Group 'Lotus Bane' Behind Recent Attacks on Vietnam's Financial Entities
6.3.24 APT The Hacker News
A financial entity in Vietnam was the target of a previously undocumented threat actor called Lotus Bane that was first detected in March 2023.
Singapore-headquartered Group-IB described the hacking outfit as an advanced persistent threat group that's believed to have been active since at least 2022.
The exact specifics of the infection chain remain unknown as yet, but it involves the use of various malicious artifacts that serve as the stepping stone for the next-stage.
"The cybercriminals used methods such as DLL side-loading and data exchange via named pipes to run malicious executables and create remote scheduled tasks for lateral movement," the company said.
Group-IB told The Hacker News that the techniques used by Lotus Bane overlap with that of OceanLotus, a Vietnam-aligned threat actor also known as APT32, Canvas Cyclone (formerly Bismuth), and Cobalt Kitty. This stems from the use of malware like PIPEDANCE for named pipes communication.
It's worth noting that PIPEDANCE was first documented by Elastic Security Labs in February 2023 in connection with a cyber attack targeting an unnamed Vietnamese organization in late December 2022.
"This similarity suggests possible connections with or inspirations from OceanLotus, however, the different target industries make it likely that they are different," Anastasia Tikhonova, head of Threat Intelligence for APAC at Group-IB, said.
"Lotus Bane is actively engaging in attacks primarily targeting the banking sector in the APAC region. Although the known attack was in Vietnam, the sophistication of their methods indicates the potential for broader geographical operations within APAC. The exact duration of their activity prior to this discovery is currently unclear, but ongoing investigations may shed more light on their history."
The development comes as financial organizations across Asia-Pacific (APAC), Europe, Latin America (LATAM), and North America have been the target of several advanced persistent threat groups such as Blind Eagle and the Lazarus Group over the past year.
Another notable financially motivated threat group is UNC1945, which has been observed targeting ATM switch servers with the goal of infecting them with a custom malware called CAKETAP.
"This malware intercepts data transmitted from the ATM server to the [Hardware Security Module] server and checks it against a set of predefined conditions," Group-IB said. "If these conditions are met, the data is altered before being sent out from the ATM server."
UNC2891 and UNC1945 were previously detailed by Google-owned Mandiant in March 2022 as having deployed the CAKETAP rootkit on Oracle Solaris systems to intercept messages from an ATM switching network and perform unauthorized cash withdrawals at different banks using fraudulent cards.
"The presence and activities of both Lotus Bane and UNC1945 in the APAC region highlight the need for continued vigilance and robust cybersecurity measures," Tikhonova said. "These groups, with their distinct tactics and targets, underline the complexity of protecting against financial cyber threats in today's digital landscape."
Iran-Linked UNC1549 Hackers Target Middle East Aerospace & Defense Sectors
29.2.24 APT The Hacker News
An Iran-nexus threat actor known as UNC1549 has been attributed with medium confidence to a new set of attacks targeting aerospace, aviation, and defense industries in the Middle East, including Israel and the U.A.E.
Other targets of the cyber espionage activity likely include Turkey, India, and Albania, Google-owned Mandiant said in a new analysis.
UNC1549 is said to overlap with Smoke Sandstorm (previously Bohrium) and Crimson Sandstorm (previously Curium), the latter of which is an Islamic Revolutionary Guard Corps (IRGC) affiliated group also known as Imperial Kitten, TA456, Tortoiseshell, and Yellow Liderc.
"This suspected UNC1549 activity has been active since at least June 2022 and is still ongoing as of February 2024," the company said. "While regional in nature and focused mostly in the Middle East, the targeting includes entities operating worldwide."
The attacks entail the use of Microsoft Azure cloud infrastructure for command-and-control (C2) and social engineering involving job-related lures to deliver two backdoors dubbed MINIBIKE and MINIBUS.
The spear-phishing emails are designed to disseminate links to fake websites containing Israel-Hamas related content or phony job offers, resulting in the deployment of a malicious payload. Also observed are bogus login pages mimicking major companies to harvest credentials.
The custom backdoors, upon establishing C2 access, act as a conduit for intelligence collection and for further access into the targeted network. Another tool deployed at this stage is a tunneling software called LIGHTRAIL that communicates using Azure cloud.
While MINIBIKE is based in C++ and capable of file exfiltration and upload, and command execution, MINIBUS serves as a more "robust successor" with enhanced reconnaissance features.
"The intelligence collected on these entities is of relevance to strategic Iranian interests and may be leveraged for espionage as well as kinetic operations," Mandiant said.
"The evasion methods deployed in this campaign, namely the tailored job-themed lures combined with the use of cloud infrastructure for C2, may make it challenging for network defenders to prevent, detect, and mitigate this activity."
CrowdStrike, in its Global Threat Report for 2024, described how "faketivists associated with Iranian state-nexus adversaries and hacktivists branding themselves as 'pro-Palestinian' focused on targeting critical infrastructure, Israeli aerial projectile warning systems, and activity intended for information operation purposes in 2023."
This includes Banished Kitten, which unleashed the BiBi wiper malware, and Vengeful Kitten, an alias for Moses Staff that has claimed data-wiping activity against more than 20 companies' industrial control systems (ICS) in Israel.
That said, Hamas-linked adversaries have been noticeably absent from conflict-related activity, something the cybersecurity firm has attributed to likely power and internet disruptions in the region.
Cybersecurity Agencies Warn Ubiquiti EdgeRouter Users of APT28's MooBot Threat
28.2.24 APT The Hacker News
In a new joint advisory, cybersecurity and intelligence agencies from the U.S. and other countries are urging users of Ubiquiti EdgeRouter to take protective measures, weeks after a botnet comprising infected routers was felled by law enforcement as part of an operation codenamed Dying Ember.
The botnet, named MooBot, is said to have been used by a Russia-linked threat actor known as APT28 to facilitate covert cyber operations and drop custom malware for follow-on exploitation. APT28, affiliated with Russia's Main Directorate of the General Staff (GRU), is known to be active since at least 2007.
APT28 actors have "used compromised EdgeRouters globally to harvest credentials, collect NTLMv2 digests, proxy network traffic, and host spear-phishing landing pages and custom tools," the authorities said [PDF].
The adversary's use of EdgeRouters dates back to 2022, with the attacks targeting aerospace and defense, education, energy and utilities, governments, hospitality, manufacturing, oil and gas, retail, technology, and transportation sectors in the Czech Republic, Italy, Lithuania, Jordan, Montenegro, Poland, Slovakia, Turkey, Ukraine, the U.A.E., and the U.S.
MooBot attacks entail targeting routers with default or weak credentials to deploy OpenSSH trojans, with APT28 acquiring this access to deliver bash script and other ELF binaries to collect credentials, proxy network traffic, host phishing pages, and other tooling.
This includes Python scripts to upload account credentials belonging to specifically targeted webmail users, which are collected via cross-site scripting and browser-in-the-browser (BitB) spear-phishing campaigns.
APT28 has also been linked to the exploitation of CVE-2023-23397 (CVSS score: 9.8), a now-patched critical privilege escalation flaw in Microsoft Outlook that could enable the theft of NT LAN Manager (NTLM) hashes and mount a relay attack without requiring any user interaction.
Another tool in its malware arsenal is MASEPIE, a Python backdoor capable of executing arbitrary commands on victim machines utilizing compromised Ubiquiti EdgeRouters as command-and-control (C2) infrastructure.
"With root access to compromised Ubiquiti EdgeRouters, APT28 actors have unfettered access to Linux-based operating systems to install tooling and to obfuscate their identity while conducting malicious campaigns," the agencies noted.
Organizations are recommended to perform a hardware factory reset of the routers to flush file systems of malicious files, upgrade to the latest firmware version, change default credentials, and implement firewall rules to prevent exposure of remote management services.
The revelations are a sign that nation-state hackers are increasingly relying on routers as a launchpad for attacks, using them to create botnets such as VPNFilter, Cyclops Blink, and KV-botnet and conduct their malicious activities.
The bulletin arrives a day after the Five Eyes nations called out APT29 – the threat group affiliated with Russia's Foreign Intelligence Service (SVR) and the entity behind the attacks on SolarWinds, Microsoft, and HPE – for employing service accounts and dormant accounts to access cloud environments at target organizations.
Five Eyes Agencies Expose APT29's Evolving Cloud Attack Tactics
28.2.24 APT The Hacker News
Cybersecurity and intelligence agencies from the Five Eyes nations have released a joint advisory detailing the evolving tactics of the Russian state-sponsored threat actor known as APT29.
The hacking outfit, also known as BlueBravo, Cloaked Ursa, Cozy Bear, Midnight Blizzard (formerly Nobelium), and The Dukes, is assessed to be affiliated with the Foreign Intelligence Service (SVR) of the Russian Federation.
Previously attributed to the supply chain compromise of SolarWinds software, the cyber espionage group attracted attention in recent months for targeting Microsoft, Hewlett Packard Enterprise (HPE), and other organizations with an aim to further their strategic objectives.
"As organizations continue to modernize their systems and move to cloud-based infrastructure, the SVR has adapted to these changes in the operating environment," according to the security bulletin.
These include -
Obtaining access to cloud infrastructure via service and dormant accounts by means of brute-force and password spraying attacks, pivoting away from exploiting software vulnerabilities in on-premise networks
Using tokens to access victims' accounts without the need for a password
Leveraging password spraying and credential reuse techniques to seize control of personal accounts, using prompt bombing to bypass multi-factor authentication (MFA) requirements, and then registering their own device to gain access to the network
Making it harder to distinguish malicious connections from typical users by utilizing residential proxies to make the malicious traffic appear as if it's originating from IP addresses within internet service provider (ISP) ranges used for residential broadband customers and conceal their true origins
"For organizations that have moved to cloud infrastructure, the first line of defense against an actor such as SVR should be to protect against SVR' TTPs for initial access," the agencies said. "Once the SVR gains initial access, the actor is capable of deploying highly sophisticated post compromise capabilities such as MagicWeb."
Mustang Panda Targets Asia with Advanced PlugX Variant DOPLUGS
21.2.24 APT The Hacker News
The China-linked threat actor known as Mustang Panda has targeted various Asian countries using a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS.
"The piece of customized PlugX malware is dissimilar to the general type of the PlugX malware that contains a completed backdoor command module, and that the former is only used for downloading the latter," Trend Micro researchers Sunny Lu and Pierre Lee said in a new technical write-up.
Targets of DOPLUGS have been primarily located in Taiwan, and Vietnam, and to a lesser extent in Hong Kong, India, Japan, Malaysia, Mongolia, and even China.
PlugX is a staple tool of Mustang Panda, which is also tracked as BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Red Lich, Stately Taurus, TA416, and TEMP.Hex. It's known to be active since at least 2012, although it first came to light in 2017.
The threat actor's tradecraft entails carrying out well-forged spear-phishing campaigns that are designed to deploy custom malware. It also has a track record of deploying its own customized PlugX variants such as RedDelta, Thor, Hodur, and DOPLUGS (distributed via a campaign named SmugX) since 2018.
Compromise chains leverage a set of distinct tactics, using phishing messages as a conduit to deliver a first-stage payload that, while displaying a decoy document to the recipient, covertly unpacks a legitimate, signed executable that's vulnerable to DLL side-loading in order to side-load a dynamic-link library (DLL), which, in turn, decrypts and executes PlugX.
The PlugX malware subsequently retrieves Poison Ivy remote access trojan (RAT) or Cobalt Strike Beacon to establish a connection with a Mustang Panda-controlled server.
In December 2023, Lab52 uncovered a Mustang Panda campaign targeting Taiwanese political, diplomatic, and governmental entities with DOPLUGS, but with a notable difference.
"The malicious DLL is written in the Nim programming language," Lab52 said. "This new variant uses its own implementation of the RC4 algorithm to decrypt PlugX, unlike previous versions that use the Windows Cryptsp.dll library."
DOPLUGS, first documented by Secureworks in September 2022, is a downloader with four backdoor commands, one of which is orchestrated to download the general type of the PlugX malware.
Trend Micro said it also identified DOPLUGS samples integrated with a module known as KillSomeOne, a plugin that's responsible for malware distribution, information collection, and document theft via USB drives.
This variant comes fitted with an extra launcher component that executes the legitimate executable to perform DLL-sideloading, in addition to supporting functionality to run commands and download the next-stage malware from an actor-controlled server.
It's worth noting that a customized PlugX variant, including the KillSomeOne module designed for spreading via USB, was uncovered as early as January 2020 by Avira as part of attacks directed against Hong Kong and Vietnam.
"This shows that Earth Preta has been refining its tools for some time now, constantly adding new functionalities and features," the researchers said. "The group remains highly active, particularly in Europe and Asia."
Russian Hackers Target Ukraine with Disinformation and Credential-Harvesting Attacks
21.2.24 APT The Hacker News
Cybersecurity researchers have unearthed a new influence operation targeting Ukraine that leverages spam emails to propagate war-related disinformation.
The activity has been linked to Russia-aligned threat actors by Slovak cybersecurity company ESET, which also identified a spear-phishing campaign aimed at a Ukrainian defense company in October 2023 and a European Union agency in November 2023 with an aim to harvest Microsoft login credentials using fake landing pages.
Operation Texonto, as the entire campaign has been codenamed, has not been attributed to a specific threat actor, although some elements of it, particularly the spear-phishing attacks, overlap with COLDRIVER, which has a history of harvesting credentials via bogus sign-in pages.
The disinformation operation took place over two waves in November and December 2023, with the email messages bearing PDF attachments and content related to heating interruptions, drug shortages, and food shortages.
The November wave targeted no less than a few hundred recipients in Ukraine, including the government, energy companies, and individuals. It's currently not known how the target list was created.
"What's interesting to note is that the email was sent from a domain masquerading as the Ministry of Agrarian Policy and Food of Ukraine, while the content is about drug shortages and the PDF is misusing the logo of the Ministry of Health of Ukraine," ESET said in a report shared with The Hacker News.
"It is possibly a mistake from the attackers or, at least, shows they did not care about all details."
The second disinformation email campaign that commenced on December 25, 2023, is notable for expanding its targeting beyond Ukraine to include Ukrainian speakers in other European nations. All the messages were written in Ukrainian and sent to a diverse set of targets ranging from the Ukrainian government to an Italian shoe
These messages, while wishing recipients a happy holiday season, also adopted a darker tone, going as far as to suggest that they ampute one of their arms or legs to avoid military deployment. "A couple of minutes of pain, but then a happy life!," the email goes.
ESET said one of the domains used to propagate the phishing emails in December 2023, infonotification[.]com, also engaged in sending hundreds of spam messages beginning January 7, 2024, redirecting potential victims to a fake Canadian pharmacy website.
It's exactly unclear why this email server was repurposed to propagate a pharmacy scam, but it's suspected that the threat actors decided to monetize their infrastructure for financial gain after realizing that their domains have been detected by defenders.
"Operation Texonto shows yet another use of technologies to try to influence the war," the company said.
The development comes as Meta, in its quarterly Adversarial Threat Report, said it took down three networks originating from China, Myanmar, and Ukraine across its platforms that engaged in coordinated inauthentic behavior (CIB).
While none of the networks were from Russia, social media analytics firm Graphika said posting volumes by Russian state-controlled media has declined 55% from pre-war levels and engagement has plummeted 94% compared to two years ago.
"Russian state media outlets have increased their focus on non-political infotainment content and self-promotional narratives about Russia since the start of the war," it said. "This could reflect a wider off-platform effort to cater to domestic Russian audiences after multiple Western countries blocked the outlets in 2022."
New Report Reveals North Korean Hackers Targeting Defense Firms Worldwide
21.2.24 APT The Hacker News
North Korean state-sponsored threat actors have been attributed to a cyber espionage campaign targeting the defense sector across the world.
In a joint advisory published by Germany's Federal Office for the Protection of the Constitution (BfV) and South Korea's National Intelligence Service (NIS), the agencies said the goal of the attacks is to plunder advanced defense technologies in a "cost-effective" manner.
"The regime is using the military technologies to modernize and improve the performance of conventional weapons and to develop new strategic weapon systems including ballistic missiles, reconnaissance satellites and submarines," they noted.
The infamous Lazarus Group has been blamed for one of the two hacking incidents, which involved the use of social engineering to infiltrate the defense sector as part of a long-standing operation called Dream Job. The campaign has been ongoing since August 2020 over several waves.
In these attacks, the threat actors either create a fake profile or leverage legitimate-but-compromised profiles on platforms like LinkedIn to approach prospective targets and build trust with them, before offering lucrative job opportunities and shifting the conversation to a different messaging service like WhatsApp to initiate the recruitment process.
Victims are then sent coding assignments and job offer documents laden with malware that, when launched, activate the infection procedure to compromise their computers.
"Universally, the circumstance that employees usually do not talk to their colleagues or employer about job offers plays into the hands of the attacker," the agencies said.
"The Lazarus Group changed its tools throughout the campaign and demonstrated more than once that it is capable of developing whatever is necessary to suit the situation."
The second case concerns an intrusion into a defense research center towards the end of 2022 by executing a software supply chain attack against an unnamed company responsible for maintaining one of the research center's web servers.
"The cyber actor further infiltrated the research facility by deploying remote-control malware through a patch management system (PMS) of the research center, and stole various account information of business portals and email contents," the BfV and NIS said.
The breach, which was carried by another North Korea-based threat actor, unfolded over five stages -
Hack into the web server maintenance company, steal SSH credentials, and gain remote access to the research center's server
Download additional malicious tooling using curl commands, including a tunneling software and a Python-based downloader
Conduct lateral movement and plunder employee account credentials
Leverage the stolen security manager's account information to unsuccessfully distribute a trojanized update that comes with capabilities to upload and download files, execute code, and to collect system information
Persist within target environment by weaponizing a file upload vulnerability in the website to deploy a web shell for remote access and send spear-phishing emails
"The actor avoided carrying out a direct attack against its target, which maintained a high level of security, but rather made an initial attack against its vendor, the maintenance and repair company," the agencies explained. "This indicates that the actor took advantage of the trustful relationship between the two entities."
The security bulletin is the second to be published by BfV and NIS in as many years. In March 2023, the agencies warned of Kimsuky actors using rogue browser extensions to steal users' Gmail inboxes. Kimsuky was sanctioned by the U.S. government in November 2023.
The development comes as blockchain analytics firm Chainalysis revealed that the Lazarus Group has switched to using YoMix bitcoin mixer to launder stolen proceeds following the shutdown of Sinbad late last year, indicating their ability to adapt their modus operandi in response to law enforcement actions.
"Sinbad became a preferred mixer for North Korea-affiliated hackers in 2022, soon after the sanctioning of Tornado Cash, which had previously been the go-to for these sophisticated cybercriminals," the company said. "With Sinbad out of the picture, Bitcoin-based mixer YoMix has acted as a replacement."
The malicious activities are the work of a plethora of North Korean hacking units operating under the broad Lazarus umbrella, which are known to engage in an array of hacking operations ranging from cyber espionage to cryptocurrency thefts, ransomware, and supply chain attacks to achieve their strategic goals.
Russian-Linked Hackers Target 80+ Organizations via Roundcube Flaws
19.2.24 APT The Hacker News
Threat actors operating with interests aligned to Belarus and Russia have been linked to a new cyber espionage campaign that likely exploited cross-site scripting (XSS) vulnerabilities in Roundcube webmail servers to target over 80 organizations.
These entities are primarily located in Georgia, Poland, and Ukraine, according to Recorded Future, which attributed the intrusion set to a threat actor known as Winter Vivern, which is also known as TA473 and UAC0114. The cybersecurity firm is tracking the hacking outfit under the moniker Threat Activity Group 70 (TAG-70).
Winter Vivern's exploitation of security flaws in Roundcube and software was previously highlighted by ESET in October 2023, joining other Russia-linked threat actor groups such as APT28, APT29, and Sandworm that are known to target email software.
The adversary, which has been active since at least December 2020, has also been linked to the abuse of a now-patched vulnerability in Zimbra Collaboration email software last year to infiltrate organizations in Moldova and Tunisia in July 2023.
The campaign discovered by Recorded Future took place from the start of October 2023 and continued until the middle of the month with the goal of collecting intelligence on European political and military activities. The attacks overlap with additional TAG-70 activity against Uzbekistan government mail servers that were detected in March 2023.
"TAG70 has demonstrated a high level of sophistication in its attack methods," the company said. "The threat actors leveraged social engineering techniques and exploited cross-site scripting vulnerabilities in Roundcube webmail servers to gain unauthorized access to targeted mail servers, bypassing the defenses of government and military organizations."
The attack chains involve exploiting Roundcube flaws to deliver JavaScript payloads that are designed to exfiltrate user credentials to a command-and-control (C2) server.
Recorded Future said it also found evidence of TAG-70 targeting the Iranian embassies in Russia and the Netherlands, as well as the Georgian Embassy in Sweden.
"The targeting of Iranian embassies in Russia and the Netherlands suggests a broader geopolitical interest in assessing Iran's diplomatic activities, especially regarding its support for Russia in Ukraine," it said.
"Similarly, espionage against Georgian government entities reflects interests in monitoring Georgia's aspirations for European Union (EU) and NATO accession."
Iranian Hackers Target Middle East Policy Experts with New BASICSTAR Backdoor
19.2.24 APT The Hacker News
The Iranian-origin threat actor known as Charming Kitten has been linked to a new set of attacks aimed at Middle East policy experts with a new backdoor called BASICSTAR by creating a fake webinar portal.
Charming Kitten, also called APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has a history of orchestrating a wide range of social engineering campaigns that cast a wide net in their targeting, often singling out think tanks, NGOs, and journalists.
"CharmingCypress often employs unusual social-engineering tactics, such as engaging targets in prolonged conversations over email before sending links to malicious content," Volexity researchers Ankur Saini, Callum Roxan, Charlie Gardner, and Damien Cash said.
Last month, Microsoft revealed that high-profile individuals working on Middle Eastern affairs have been targeted by the adversary to deploy malware such as MischiefTut and MediaPl (aka EYEGLASS) that are capable of harvesting sensitive information from a compromised host.
The group, assessed to be affiliated with Iran's Islamic Revolutionary Guard Corps (IRGC), has also distributed several other backdoors such as PowerLess, BellaCiao, POWERSTAR (aka GorjolEcho), and NokNok over the past year, emphasizing its determination to continue its cyber onslaught, adapting its tactics and methods despite public exposure.
The phishing attacks observed between September and October 2023 involved the Charming Kitten operators posing as the Rasanah International Institute for Iranian Studies (IIIS) to initiate and build trust with targets.
The phishing attempts are also characterized by the use of compromised email accounts belonging to legitimate contacts and multiple threat-actor-controlled email accounts, the latter of which is called Multi-Persona Impersonation (MPI).
The attack chains typically employ RAR archives containing LNK files as a starting point to distribute malware, with the messages urging prospective targets to join a fake webinar about topics that are of interest to them. One such multi-stage infection sequence has been observed to deploy BASICSTAR and KORKULOADER, a PowerShell downloader script.
BASICSTAR, a Visual Basic Script (VBS) malware, is capable of gathering basic system information, remotely executing commands relayed from a command-and-control (C2) server, and downloading and displaying a decoy PDF file.
What's more, some of these phishing attacks are engineered to serve different backdoors depending on the machine's operating system. While Windows victims are compromised with POWERLESS, Apple macOS victims are targeted with an infection chain culminating in NokNok via a functional VPN application that's laced with malware.
"This threat actor is highly committed to conducting surveillance on their targets in order to determine how best to manipulate them and deploy malware," the researchers said. "Additionally, few other threat actors have consistently churned out as many campaigns as CharmingCypress, dedicating human operators to support their ongoing efforts."
The disclosure comes as Recorded Future uncovered IRGC's targeting of Western countries using a network of contracting companies that also specialize in exporting technologies for surveillance and offensive purposes to countries like Iraq, Syria, and Lebanon.
The relationship between intelligence and military organizations and Iran-based contractors takes the form of various cyber centers that act as "firewalls" to conceal the sponsoring entity.
They include Ayandeh Sazan Sepher Aria (suspected to be associated with Emennet Pasargad), DSP Research Institute, Sabrin Kish, Soroush Saman, Mahak Rayan Afraz, and the Parnian Telecommunication and Electronic Company.
"Iranian contracting companies are established and run by a tight-knit network of personas, who, in some cases, represent the contractors as board members," the company said. "The individuals are closely associated with the IRGC, and in some cases, are even representatives of sanctioned entities (such as the IRGC Cooperative Foundation)."
Kimsuky's New Golang Stealer 'Troll' and 'GoBear' Backdoor Target South Korea
8.2.24 APT The Hacker News
The North Korea-linked nation-state actor known as Kimsuky is suspected of using a previously undocumented Golang-based information stealer called Troll Stealer.
The malware steals "SSH, FileZilla, C drive files/directories, browsers, system information, [and] screen captures" from infected systems, South Korean cybersecurity company S2W said in a new technical report.
Troll Stealer's links to Kimsuky stem from its similarities to known malware families, such as AppleSeed and AlphaSeed malware that have been attributed to the group.
Kimsuky, also tracked under the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (previously Thallium), Nickel Kimball, and Velvet Chollima, is well known for its propensity to steal sensitive, confidential information in offensive cyber operations.
In late November 2023, the threat actors were sanctioned by the U.S. Treasury Department's Office of Foreign Assets Control (OFAC) for gathering intelligence to further North Korea's strategic objectives.
The adversarial collective, in recent months, has been attributed to spear-phishing attacks targeting South Korean entities to deliver a variety of backdoors, including AppleSeed and AlphaSeed.
S2W's latest analysis reveals the use of a dropper that masquerades as a security program installation file from a South Korean company named SGA Solutions to launch the stealer, which gets its name from the path "D:/~/repo/golang/src/root.go/s/troll/agent" that's embedded in it.
"The dropper runs as a legitimate installer alongside the malware, and both the dropper and malware are signed with a valid, legitimate D2Innovation Co.,LTD' certificate, suggesting that the company's certificate was actually stolen," the company said.
A stand-out feature of Troll Stealer is its ability to pilfer the GPKI folder on infected systems, raising the possibility that the malware has been put to use in attacks targeting administrative and public organizations in the country.
Given the absence of Kimsuky campaigns documenting the theft of GPKI folders, it has raised the possibility that the new behavior is either a shift in tactics or the work of another threat actor closely associated with the group that also has access to the source code of AppleSeed and AlphaSeed.
There are also signs that the threat actor may be involved with a Go-based backdoor codenamed GoBear that's also signed with a legitimate certificate associated with D2Innovation Co., LTD and executes instructions received from a command-and-control (C2) server.
"The strings contained in the names of the functions it calls have been found to overlap with the commands used by BetaSeed, a C++-based backdoor malware used by the Kimsuky group," S2W said. "It is noteworthy that GoBear adds SOCKS5 proxy functionality, which was not previously supported by the Kimsuky group's backdoor malware."
China-Linked Hackers Target Myanmar's Top Ministries with Backdoor Blitz
31.1.24 APT The Hacker News
The China-based threat actor known as Mustang Panda is suspected to have targeted Myanmar's Ministry of Defence and Foreign Affairs as part of twin campaigns designed to deploy backdoors and remote access trojans.
The findings come from CSIRT-CTI, which said the activities took place in November 2023 and January 2024 after artifacts in connection with the attacks were uploaded to the VirusTotal platform.
"The most prominent of these TTPs are the use of legitimate software including a binary developed by engineering firm Bernecker & Rainer (B&R) and a component of the Windows 10 upgrade assistant to sideload malicious dynamic-link libraries (DLLs)," CSIRT-CTI said.
Mustang Panda, active since at least 2012, is also recognized by the cybersecurity community under the names BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Red Lich, Stately Taurus, and TEMP.Hex.
In recent months, the adversary has been attributed to attacks targeting an unnamed Southeast Asian government as well as the Philippines to deliver backdoors capable of harvesting sensitive information.
The November 2023 infection sequence starts with a phishing email bearing a booby-trapped ZIP archive attachment containing a legitimate executable ("Analysis of the third meeting of NDSC.exe") that's originally signed by B&R Industrial Automation GmbH and a DLL file ("BrMod104.dll").
The attack takes advantage of the fact that the binary is susceptible to DLL search order hijacking to side-load the rogue DLL and subsequently establish persistence and contact with a command-and-control (C2) server and retrieve a known backdoor called PUBLOAD, which, in turn, acts as a custom loader to drop the PlugX implant.
"The threat actors attempt to disguise the [C2] traffic as Microsoft update traffic by adding the 'Host: www.asia.microsoft.com' and 'User-Agent: Windows-Update-Agent' headers," CSIRT-CTI noted, mirror a May 2023 campaign disclosed by Lab52.
On the other hand, the second campaign observed earlier this month employs an optical disc image ("ASEAN Notes.iso") containing LNK shortcuts to trigger a multi-stage process that uses another bespoke loader called TONESHELL to likely deploy PlugX from a now-inaccessible C2 server.
It's worth noting that a similar attack chain attributed to Mustang Panda was previously unearthed by EclecticIQ in February 2023 in intrusions aimed at government and public sector organizations across Asia and Europe.
"Following the rebel attacks in northern Myanmar [in October 2023], China has expressed concern regarding its effect on trade routes and security around the Myanmar-China border," CSIRT-CTI said.
"Stately Taurus operations are known to align with geopolitical interests of the Chinese government, including multiple cyberespionage operations against Myanmar in the past."
Microsoft's Top Execs' Emails Breached in Sophisticated Russia-Linked APT Attack
20.1.24 APT The Hacker News
Microsoft on Friday revealed that it was the target of a nation-state attack on its corporate systems that resulted in the theft of emails and attachments from senior executives and other individuals in the company's cybersecurity and legal departments.
The Windows maker attributed the attack to a Russian advanced persistent threat (APT) group it tracks as Midnight Blizzard (formerly Nobelium), which is also known as APT29, BlueBravo, Cloaked Ursa, Cozy Bear, and The Dukes.
It further said that it immediately took steps to investigate, disrupt, and mitigate the malicious activity upon discovery on January 12, 2024. The campaign is estimated to have commenced in late November 2023.
"The threat actor used a password spray attack to compromise a legacy non-production test tenant account and gain a foothold, and then used the account's permissions to access a very small percentage of Microsoft corporate email accounts, including members of our senior leadership team and employees in our cybersecurity, legal, and other functions, and exfiltrated some emails and attached documents," Microsoft said.
Redmond said the nature of the targeting indicates the threat actors were looking to access information related to themselves. It also emphasized that the attack was not the result of any security vulnerability in its products and that there is no evidence that the adversary accessed customer environments, production systems, source code, or AI systems.
The computing giant, however, did not disclose how many email accounts were infiltrated, and what information was accessed, but said it was the process of notifying employees who were impacted as a result of the incident.
The hacking outfit, which was previously responsible for the high-profile SolarWinds supply chain compromise, has singled out Microsoft twice, once in December 2020 to siphon source code related to Azure, Intune, and Exchange components, and a second time breaching three of its customers in June 2021 via password spraying and brute-force attacks.
"This attack does highlight the continued risk posed to all organizations from well-resourced nation-state threat actors like Midnight Blizzard," the Microsoft Security Response Center (MSRC) said.