
Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks
29.12.23 APT The Hacker News
Nation-state actors affiliated to North Korea have been observed using spear-phishing attacks to deliver an assortment of backdoors and tools such as AppleSeed, Meterpreter, and TinyNuke to seize control of compromised machines.
South Korea-based cybersecurity company AhnLab attributed the activity to an advanced persistent threat group known as Kimsuky.
"A notable point about attacks that use AppleSeed is that similar methods of attack have been used for many years with no significant changes to the malware that are used together," the AhnLab Security Emergency Response Center (ASEC) said in an analysis published Thursday.
Kimsuky, active for over a decade, is known for its targeting of a wide range of entities in South Korea, before expanding its focus to include other geographies in 2017. It was sanctioned by the U.S. government late last month for amassing intelligence to support North Korea's strategic objectives.
The threat actor's espionage campaigns are realized through spear-phishing attacks containing malicious lure documents that, upon opening, culminate in the deployment of various malware families.
One such prominent Windows-based backdoor used by Kimsuky is AppleSeed (aka JamBog), a DLL malware which has been put to use as early as May 2019 and has been updated with an Android version as well as a new variant written in Golang called AlphaSeed.
AppleSeed is designed to receive instructions from an actor-controlled server, drop additional payloads, and exfiltrate sensitive data such as files, keystrokes, and screenshots. AlphaSeed, like AppleSeed, incorporates similar features but has some crucial differences as well.
"AlphaSeed was developed in Golang and uses chromedp for communications with the [command-and-control] server," ASEC said, in contrast to AppleSeed, which relies on HTTP or SMTP protocols. Chromedp is a popular Golang library for interacting with the Google Chrome browser in headless mode through the DevTools Protocol.
There is evidence to suggest the Kimsuky has used AlphaSeed in attacks since October 2022, with some intrusions delivering both AppleSeed and AlphaSeed on the same target system by means of a JavaScript dropper.
Also deployed by the adversary are Meterpreter and VNC malware such as TightVNC and TinyNuke (aka Nuclear Bot), which can be leveraged to take control of the affected system.
The development comes as Nisos said it discovered a number of online personas on LinkedIn and GitHub likely used by North Korea's information technology (IT) workers to fraudulently obtain remote employment from companies in the U.S. and act as a revenue-generating stream for the regime and help fund its economic and security priorities.
"The personas often claimed to be proficient in developing several different types of applications and have experience working with crypto and blockchain transactions," the threat intelligence firm said in a report released earlier this month.
"Further, all of the personas sought remote-only positions in the technology sector and were singularly focused on obtaining new employment. Many of the accounts are only active for a short period of time before they are disabled."
North Korean actors, in recent years, have launched a series of multi-pronged assaults, blending novel tactics and supply chain weaknesses to target blockchain and cryptocurrency firms to facilitate the theft of intellectual property and virtual assets.
The prolific and aggressive nature of the attacks points to the different ways the country has resorted in order to evade international sanctions and illegally profit from the schemes.
"People tend to think, … how could the quote-unquote 'Hermit Kingdom' possibly be a serious player from a cyber perspective?," CrowdStrike's Adam Meyers was quoted as saying to Politico. "But the reality couldn't be further from the truth."
Russian SVR-Linked APT29 Targets JetBrains TeamCity Servers in Ongoing Attacks
14.12.23 APT The Hacker News
Threat actors affiliated with the Russian Foreign Intelligence Service (SVR) have targeted unpatched JetBrains TeamCity servers in widespread attacks since September 2023.
The activity has been tied to a nation-state group known as APT29, which is also tracked as BlueBravo, Cloaked Ursa, Cozy Bear, Midnight Blizzard (formerly Nobelium), and The Dukes. It's notable for the supply chain attack targeting SolarWinds and its customers in 2020.
"The SVR has, however, been observed using the initial access gleaned by exploiting the TeamCity CVE to escalate its privileges, move laterally, deploy additional backdoors, and take other steps to ensure persistent and long-term access to the compromised network environments," cybersecurity agencies from Poland, the U.K., and the U.S. said.
The vulnerability in question is CVE-2023-42793 (CVSS score: 9.8), a critical security flaw that could be weaponized by unauthenticated attackers to achieve remote code execution on affected systems. It has since come under active exploitation by hacking crews, including those associated with North Korea, for malware delivery.
"The TeamCity exploitation usually resulted in code execution with high privileges granting the SVR an advantageous foothold in the network environment," the agencies noted.
"If compromised, access to a TeamCity server would provide malicious actors with access to that software developer's source code, signing certificates, and the ability to subvert software compilation and deployment processes — access a malicious actor could further use to conduct supply chain operations."
A successful initial access is typically followed by reconnaissance, privilege escalation, lateral movement, and data exfiltration, while simultaneously taking steps to evade detection using an open-source tool called EDRSandBlast. The end goal of the attacks is to deploy a backdoor codenamed GraphicalProton that functions as a loader to deliver additional payloads.
GraphicalProton, which is also known as VaporRage, leverages OneDrive as a primary command-and-control (C2) communication channel, with Dropbox treated as a fallback mechanism. It has been put to use by the threat actor as part of an ongoing campaign dubbed Diplomatic Orbiter that singles out diplomatic agencies across the world.
As many as 100 devices located across the U.S., Europe, Asia, and Australia are said to have been compromised as a result of what's suspected to be opportunistic attacks.
Targets of the campaign include an energy trade association; firms that provide software for billing, medical devices, customer care, employee monitoring, financial management, marketing, sales, and video games; as well as hosting companies, tools manufacturers, and small and large IT enterprises.
The disclosure comes as Microsoft revealed Russia's multi-pronged assault on Ukraine's agriculture sector between June through September 2023 to penetrate networks, exfiltrate data, and deploy destructive malware such as SharpWipe (aka WalnutWipe).
The intrusions have been tied back to two nation-state groups codenamed Aqua Blizzard (formerly Actinium) and Seashell Blizzard (formerly Iridium), respectively.
Seashell Blizzard has also been observed taking advantage of pirated Microsoft Office software harboring the DarkCrystalRAT (aka DCRat) backdoor to gain initial access, subsequently using it to download a second-stage payload named Shadowlink that masquerades as Microsoft Defender but, in reality, installs a TOR service for surreptitious remote access.
"Midnight Blizzard took a kitchen sink approach, using password spray, credentials acquired from third-parties, believable social engineering campaigns via Teams, and abuse of cloud services to infiltrate cloud environments," the tech giant said.
Microsoft further highlighted a Russia-affiliated influence actor it calls Storm-1099 (aka Doppelganger) for carrying out sophisticated pro-Russia influence operations targeting international supporters of Ukraine since the spring of 2022.
Other influence efforts comprise spoofing mainstream media and deceptively editing celebrity videos shared on Cameo to propagate anti-Ukraine video content and malign President Volodymyr Zelensky by falsely claiming he suffered from substance abuse issues, underscoring continued efforts to warp global perceptions of the war.
"This campaign marks a novel approach by pro-Russia actors seeking to further the narrative in the online information space," Microsoft said. "Russian cyber and influence operators have demonstrated adaptability throughout the war on Ukraine."
Update#
Following the publication of the story, Yaroslav Russkih, head of security at JetBrains, shared the following statement with The Hacker News -
"We were informed about this vulnerability earlier this year and immediately fixed it in TeamCity 2023.05.4 update, which was released on September 18, 2023. Since then, we have been contacting our customers directly or via public posts motivating them to update their software. We also released a dedicated security patch for organizations using older versions of TeamCity that they couldn't upgrade in time. In addition, we have been sharing the best security practices to help our customers strengthen the security of their build pipelines. As of right now, according to the statistics we have, fewer than 2% of TeamCity instances still operate unpatched software, and we hope their owners patch them immediately. This vulnerability only affects the on-premises instances of TeamCity, while our cloud version was not impacted."
Russian APT28 Hackers Targeting 13 Nations in Ongoing Cyber Espionage Campaign
13.12.23 APT The Hacker News
The Russian nation-state threat actor known as APT28 has been observed making use of lures related to the ongoing Israel-Hamas war to facilitate the delivery of a custom backdoor called HeadLace.
IBM X-Force is tracking the adversary under the name ITG05, which is also known as BlueDelta, Fancy Bear, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, Sednit, Sofacy, and TA422.
"The newly discovered campaign is directed against targets based in at least 13 nations worldwide and leverages authentic documents created by academic, finance and diplomatic centers," security researchers Golo Mühr, Claire Zaboeva, and Joe Fasulo said.
"ITG05's infrastructure ensures only targets from a single specific country can receive the malware, indicating the highly targeted nature of the campaign."
Targets of the campaign include Hungary, Türkiye, Australia, Poland, Belgium, Ukraine, Germany, Azerbaijan, Saudi Arabia, Kazakhstan, Italy, Latvia, and Romania.
The campaign involves the use of decoys that are designed to primarily single out European entities with a "direct influence on the allocation of humanitarian aid," leveraging documents associated with the United Nations, the Bank of Israel, the U.S. Congressional Research Service, the European Parliament, a Ukrainian think tank, and an Azerbaijan-Belarus Intergovernmental Commission.
Some of the attacks have been found to employ RAR archives exploiting the WinRAR flaw called CVE-2023-38831 to propagate HeadLace, a backdoor that was first disclosed by the computer Emergency Response Team of Ukraine (CERT-UA) in attacks aimed at critical infrastructure in the country.
It's worth noting that Zscaler revealed a similar campaign named Steal-It in late September 2023 that enticed targets with adult-themed content to trick them into parting with sensitive information.
The disclosure comes a week after Microsoft, Palo Alto Networks Unit 42, and Proofpoint detailed the threat actor's exploitation of a critical security flaw of Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) to gain unauthorized access to victims' accounts within Exchange servers.
The reliance on official documents as lures, therefore, marks a deviation from previously observed activity, "indicative of ITG05's increased emphasis on a unique target audience whose interests would prompt interaction with material impacting emerging policy creation."
"It is highly likely the compromise of any echelon of global foreign policy centers may aid officials' interests with advanced insight into critical dynamics surrounding the International Community's (IC) approach to competing priorities for security and humanitarian assistance," the researchers said.
The development also follows a new advisory in which CERT-UA linked the threat actor known as UAC-0050 to a massive email-based phishing attack against Ukraine and Poland using Remcos RAT and Meduza Stealer.
Researchers Unmask Sandman APT's Hidden Link to China-Based KEYPLUG Backdoor
11.12.23 APT The Hacker News
Tactical and targeting overlaps have been discovered between the enigmatic advanced persistent threat (APT) called Sandman and a China-based threat cluster that's known to use a backdoor known as KEYPLUG.
The assessment comes jointly from SentinelOne, PwC, and the Microsoft Threat Intelligence team based on the fact that the adversary's Lua-based malware LuaDream and KEYPLUG have been determined to cohabit "in the same victim networks.
Microsoft and PwC are tracking the activity under the names Storm-0866 and Red Dev 40, respectively.
"Sandman and Storm-0866/Red Dev 40 share infrastructure control and management practices, including hosting provider selections, and domain naming conventions, the companies said in a report shared with The Hacker News.
"The implementation of LuaDream and KEYPLUG reveals indicators of shared development practices and overlaps in functionalities and design, suggesting shared functional requirements by their operators."
Sandman was first exposed by SentinelOne in September 2023, detailing its attacks on telecommunication providers in the Middle East, Western Europe, and South Asia using a novel implant codenamed LuaDream. The intrusions were recorded in August 2023.
Storm-0866/Red Dev 40, on the other hand, refers to an emerging APT cluster primarily singling out entities in the Middle East and the South Asian subcontinent, including telecommunication providers and government entities.
One of the key tools in Storm-0866's arsenal is KEYPLUG, a backdoor that was first disclosed by Google-owned Mandiant as part of attacks mounted by the China-based APT41 (aka Brass Typhoon or Barium) actor to infiltrate six U.S. state government networks between May 2021 and February 2022.
In a report published earlier this March, Recorded Future attributed the use of KEYPLUG to a Chinese state-sponsored threat activity group it's tracking as RedGolf, which it said "closely overlaps with threat activity reported under the aliases of APT41/BARIUM."
"A close examination of the implementation and C2 infrastructure of these distinct malware strains revealed indicators of shared development as well as infrastructure control and management practices, and some overlaps in functionalities and design, suggesting shared functional requirements by their operators," the companies pointed out.
One of the notable overlaps is are two LuaDream C2 domains named "dan.det-ploshadka[.]com" and "ssl.e-novauto[.]com," which has also been put to use as a KEYPLUG C2 server and which has been tied to Storm-0866.
Another interesting commonality between LuaDream and KEYPLUG is that both the implants support QUIC and WebSocket protocols for C2 communications, indicating common requirements and the likely presence of a digital quartermaster behind the coordination.
"The order in which LuaDream and KEYPLUG evaluate the configured protocol among HTTP, TCP, WebSocket, and QUIC is the same: HTTP, TCP, WebSocket, and QUIC in that order," the researchers said. "The high-level execution flows of LuaDream and KEYPLUG are very similar."
The adoption of Lua is another sign that threat actors, both nation-state aligned and cybercrime-focused, are increasingly setting their sights on uncommon programming languages like DLang and Nim to evade detection and persist in victim environments for extended periods of time.
Lua-based malware, in particular, have been spotted only a handful of times in the wild over the past decade. This includes Flame, Animal Farm (aka SNOWGLOBE), and Project Sauron.
"There are strong overlaps in operational infrastructure, targeting, and TTPs associating the Sandman APT with China-based adversaries using the KEYPLUG backdoor, STORM-0866/Red Dev 40 in particular," the researchers said. "This highlights the complex nature of the Chinese threat landscape."
Lazarus Group Using Log4j Exploits to Deploy Remote Access Trojans
11.12.23 APT The Hacker News
The notorious North Korea-linked threat actor known as the Lazarus Group has been attributed to a new global campaign that involves the opportunistic exploitation of security flaws in Log4j to deploy previously undocumented remote access trojans (RATs) on compromised hosts.
Cisco Talos is tracking the activity under the name Operation Blacksmith, noting the use of three DLang-based malware families, including a RAT called NineRAT that leverages Telegram for command-and-control (C2), DLRAT, and a downloader dubbed BottomLoader.
The cybersecurity firm described the latest tactics of the adversary as a definitive shift and that they overlap with the cluster widely tracked as Andariel (aka Onyx Sleet or Silent Chollima), a sub-group within the Lazarus umbrella.
"Andariel is typically tasked with initial access, reconnaissance and establishing long term access for espionage in support of the North Korean government's national interests," Talos researchers Jung soo An, Asheer Malhotra, and Vitor Ventura said in a technical report shared with The Hacker News.
Attack chains involve the exploitation of CVE-2021-44228 (aka Log4Shell) against publicly-accessible VMWare Horizon servers to deliver NineRAT. Some of the prominent sectors targeted include manufacturing, agriculture, and physical security.
The abuse of Log4Shell is not surprising given the fact that 2.8 percent of applications are still using vulnerable versions of the library (from 2.0-beta9 through 2.15.0) after two years of public disclosure, according to Veracode, with another 3.8% using Log4j 2.17.0, which, while not vulnerable to CVE-2021-44228, is susceptible to CVE-2021-44832.
NineRAT, first developed around May 2022, is said to have been put to use as early as March 2023 in an attack aimed at a South American agricultural organization and then again in September 2023 on a European manufacturing entity. By using a legitimate messaging service for C2 communications, the goal is to evade detection.
The malware acts as the primary means of interaction with the infected endpoint, enabling the attackers to send commands to gather system information, upload files of interest, download additional files, and even uninstall and upgrade itself.
"Once NineRAT is activated it accepts preliminary commands from the telegram based C2 channel, to again fingerprint the infected systems," the researchers noted.
"Re-fingerprinting of infected systems indicates that the data collected by Lazarus via NineRAT may be shared by other APT groups and essentially resides in a different repository from the fingerprint data collected initially by Lazarus during their initial access and implant deployment phase."
Also used in the attacks after initial reconnaissance is a custom proxy tool called HazyLoad that was previously identified by Microsoft as used by the threat actor as part of intrusions weaponizing critical security flaws in JetBrains TeamCity (CVE-2023-42793, CVSS score: 9.8). HazyLoad is downloaded and executed by means of another malware called BottomLoader.
Furthermore, Operation Blacksmith has been observed delivering DLRAT, which is both a downloader and a RAT equipped to perform system reconnaissance, deploy additional malware, and retrieve commands from the C2 and execute them in the compromised systems.
"The multiple tools giving overlapping backdoor entry present Lazarus Group with redundancies in the event a tool is discovered, enabling highly persistent access," the researchers said.
The disclosure comes as the AhnLab Security Emergency Response Center (ASEC) detailed Kimsuky's use of AutoIt versions of malware such as Amadey and RftRAT and distributing them via spear-phishing attacks bearing booby-trapped attachments and links in an attempt to bypass security products.
Kimusky, also known by the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (previously Thallium), Nickel Kimball, and Velvet Chollima, is an element operating under North Korea's Reconnaissance General Bureau (RGB), which also houses the Lazarus Group.
It was sanctioned by the U.S. Treasury Department on November 30, 2023, for gathering intelligence to support the regime's strategic objectives.
"After taking control of the infected system, to exfiltrate information, the Kimsuky group installs various malware such as keyloggers and tools for extracting accounts and cookies from web browsers," ASEC said in an analysis published last week.
Microsoft Warns of Kremlin-Backed APT28 Exploiting Critical Outlook Vulnerability
5.12.23 APT The Hacker News
Microsoft on Monday said it detected Kremlin-backed nation-state activity exploiting a critical security flaw in its Outlook email service to gain unauthorized access to victims' accounts within Exchange servers.
The tech giant attributed the intrusions to a threat actor it called Forest Blizzard (formerly Strontium), which is also widely tracked under the monikers APT28, BlueDelta, Fancy Bear, FROZENLAKE, Iron Twilight, Sednit, and Sofacy.
The security vulnerability in question is CVE-2023-23397 (CVSS score: 9.8), a critical privilege escalation bug that could allow an adversary to access a user's Net-NTLMv2 hash that could then be used to conduct a relay attack against another service to authenticate as the user. It was patched by Microsoft in March 2023.
The goal, according to the Polish Cyber Command (DKWOC), was to obtain unauthorized access to mailboxes belonging to public and private entities in the country.
"In the next stage of malicious activity, the adversary modifies folder permissions within the victim's mailbox," DKWOC said. "In most cases, the modifications are to change the default permissions of the 'Default' group (all authenticated users in the Exchange organization) from 'None' to 'Owner.'"
In doing so, the contents of mailbox folders that have been granted this permission can be read by any authenticated person within the organization, enabling the threat actor to extract valuable information from high-value targets.
"It should be emphasized that the introduction of such modifications allows for the maintenance of unauthorized access to the contents of the mailbox even after losing direct access to it," DKWOC added.
Microsoft previously disclosed that the security shortcoming had been weaponized by Russia-based threat actors as a zero-day in attacks targeting government, transportation, energy, and military sectors in Europe since April 2022.

Subsequently, in June 2023, cybersecurity firm Recorded Future revealed details of a spear-phishing campaign orchestrated by APT28 exploiting multiple vulnerabilities in the open-source Roundcube webmail software, while simultaneously noting that the campaign overlaps with activity employing the Microsoft Outlook vulnerability.
The National Cybersecurity Agency of France (ANSSI), in late October, also blamed the hacking outfit for targeting government entities, businesses, universities, research institutes, and think tanks since the second half of 2021 by taking advantage of various flaws, counting CVE-2023-23397, to deploy implants such as CredoMap.
The state-sponsored group is assessed to be linked to Unit 26165 of the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU), the foreign intelligence arm of the Ministry of Defense.
Cybersecurity
In recent months, it has also been connected to attacks on various organizations in France and Ukraine as well as the abuse of the WinRAR flaw (CVE-2023-38831) to steal browser login data using a PowerShell script named IRONJAW.
"Forest Blizzard continually refines its footprint by employing new custom techniques and malware, suggesting that it is a well-resourced and well-trained group posing long-term challenges to attribution and tracking its activities," Microsoft said.
The popularity of Microsoft Outlook in enterprise environments makes it a lucrative attack vector, making it "one of the critical 'gateways' responsible for introducing various cyber threats into organizations," according to Check Point, which laid out the various means by which the service could be abused by bad actors to deliver their exploits.
The development comes as The Guardian reported that the Sellafield nuclear waste site in the U.K. had been breached by hacking crews associated with Russia and China to deploy "sleeper malware" as far back as 2015. However, the U.K. government said it found no evidence to suggest that its networks had been "successfully attacked by state actors."
New 'HrServ.dll' Web Shell Detected in APT Attack Targeting Afghan Government
25.11.23 APT The Hacker News
An unspecified government entity in Afghanistan was targeted by a previously undocumented web shell called HrServ in what's suspected to be an advanced persistent threat (APT) attack.
The web shell, a dynamic-link library (DLL) named "hrserv.dll," exhibits "sophisticated features such as custom encoding methods for client communication and in-memory execution," Kaspersky security researcher Mert Degirmenci said in an analysis published this week.
The Russian cybersecurity firm said it identified variants of the malware dating all the way back to early 2021 based on the compilation timestamps of these artifacts.
Web shells are typically malicious tools that provide remote control over a compromised server. Once uploaded, it allows threat actors to carry out a range of post-exploitation activities, including data theft, server monitoring, and lateral advancement within the network.
The attack chain involves the PAExec remote administration tool, an alternative to PsExec that's used as a launchpad to create a scheduled task that masquerades as a Microsoft update ("MicrosoftsUpdate"), which subsequently is configured to execute a Windows batch script ("JKNLA.bat").
The Batch script accepts as an argument the absolute path to a DLL file ("hrserv.dll") that's then executed as a service to initiate an HTTP server that's capable of parsing incoming HTTP requests for follow-on actions.
"Based on the type and information within an HTTP request, specific functions are activated," Degirmenci said, adding "the GET parameters used in the hrserv.dll file, which is used to mimic Google services, include 'hl.'"

This is likely an attempt by the threat actor to blend these rogue requests in network traffic and make it a lot more challenging to distinguish malicious activity from benign events.
Embedded within those HTTP GET and POST requests is a parameter called cp, whose value – ranging from 0 to 7 – determines the next course of action. This includes spawning new threads, creating files with arbitrary data written to them, reading files, and accessing Outlook Web App HTML data.
If the value of cp in the POST request equals "6," it triggers code execution by parsing the encoded data and copying it into the memory, following which a new thread is created and the process enters a sleep state.
The web shell is also capable of activating the execution of a stealthy "multifunctional implant" in memory that's responsible for erasing the forensic trail by deleting the "MicrosoftsUpdate" job as well as the initial DLL and batch files.
The threat actor behind the web shell is currently not known, but the presence of several typos in the source code indicates that the malware author is not a native English speaker.
"Notably, the web shell and memory implant use different strings for specific conditions," Degirmenci concluded. "In addition, the memory implant features a meticulously crafted help message."
"Considering these factors, the malware's characteristics are more consistent with financially motivated malicious activity. However, its operational methodology exhibits similarities with APT behavior."
Russian Hackers Sandworm Cause Power Outage in Ukraine Amidst Missile Strikes
11.11.23 APT The Hacker News
The notorious Russian hackers known as Sandworm targeted an electrical substation in Ukraine last year, causing a brief power outage in October 2022.
The findings come from Google's Mandiant, which described the hack as a "multi-event cyber attack" leveraging a novel technique for impacting industrial control systems (ICS).
"The actor first used OT-level living-off-the-land (LotL) techniques to likely trip the victim's substation circuit breakers, causing an unplanned power outage that coincided with mass missile strikes on critical infrastructure across Ukraine," the company said.
"Sandworm later conducted a second disruptive event by deploying a new variant of CaddyWiper in the victim's IT environment."
The threat intelligence firm did not reveal the location of the targeted energy facility, the duration of the blackout, and the number of people who were impacted by the incident.
The development marks Sandworm's continuous efforts to stage disruptive attacks and compromise the power grid in Ukraine since at least 2015 using malware such as Industroyer.
The exact initial vector used for the cyber-physical attack is presently unclear, and it's believed that the threat actor's use of LotL techniques decreased the time and resources required to pull it off.
The intrusion is thought to have happened around June 2022, with the Sandworm actors gaining access to the operational technology (OT) environment through a hypervisor that hosted a supervisory control and data acquisition (SCADA) management instance for the victim's substation environment.
On October 10, 2022, an optical disc (ISO) image file was used to launch malware capable of switching off substations, resulting in an unscheduled power outage.
"Two days after the OT event, Sandworm deployed a new variant of CaddyWiper in the victim's IT environment to cause further disruption and potentially to remove forensic artifacts," Mandiant said.
CaddyWiper refers to a piece of data-wiping malware that first came to light in March 2022 in connection with the Russo-Ukrainian war.
The eventual execution of the attack, Mandiant noted, coincided with the start of a multi-day set of coordinated missile strikes on critical infrastructure across a number of Ukrainian cities, including the city in which the unnamed victim was situated.
"This attack represents an immediate threat to Ukrainian critical infrastructure environments leveraging the MicroSCADA supervisory control system," the company said.
"Given Sandworm's global threat activity and the worldwide deployment of MicroSCADA products, asset owners globally should take action to mitigate their tactics, techniques, and procedures against IT and OT systems."
Iran-Linked Imperial Kitten Cyber Group Targeting Middle East's Tech Sectors
11.11.23 APT The Hacker News
A group with links to Iran targeted transportation, logistics, and technology sectors in the Middle East, including Israel, in October 2023 amid a surge in Iranian cyber activity since the onset of the Israel-Hamas war.
The attacks have been attributed by CrowdStrike to a threat actor it tracks under the name Imperial Kitten, and which is also known as Crimson Sandstorm (previously Curium), TA456, Tortoiseshell, and Yellow Liderc.
The latest findings from the company build on prior reports from Mandiant, ClearSky, and PwC, the latter of which also detailed instances of strategic web compromises (aka watering hole attacks) leading to the deployment of IMAPLoader on infected systems.
"The adversary, active since at least 2017, likely fulfills Iranian strategic intelligence requirements associated with IRGC operations," CrowdStrike said in a technical report. "Its activity is characterized by its use of social engineering, particularly job recruitment-themed content, to deliver custom .NET-based implants."
Attack chains leverage compromised websites, primarily those related to Israel, to profile visitors using bespoke JavaScript and exfiltrate the information to attacker-controlled domains.
Besides watering hole attacks, there's evidence to suggest that Imperial Kitten resorts to exploitation of one-day exploits, stolen credentials, phishing, and even targeting upstream IT service providers for initial access.
Phishing campaigns involve the use of macro-laced Microsoft Excel documents to activate the infection chain and drop a Python-based reverse shell that connects to a hard-coded IP address for receiving further commands.
Among some of the notable post-exploitation activities entail achieving lateral movement through the use of PAExec, the open-source variant of PsExec, and NetScan, followed by the delivery of the implants IMAPLoader and StandardKeyboard.
Also deployed is a remote access trojan (RAT) that uses Discord for command-and-control, while both IMAPLoader and StandardKeyboard employ email messages (i.e., attachments and email body) to receive tasking and send results of the execution.
"StandardKeyboard's main purpose is to execute Base64-encoded commands received in the email body," the cybersecurity company pointed out. "Unlike IMAPLoader, this malware persists on the infected machine as a Windows Service named Keyboard Service."
The development comes as Microsoft noted that malicious cyber activity attributed to Iranian groups after the start of the war on October 7, 2023, is more reactive and opportunistic.
"Iranian operators [are] continuing to employ their tried-and-true tactics, notably exaggerating the success of their computer network attacks and amplifying those claims and activities via a well-integrated deployment of information operations," Microsoft said.
"This is essentially creating online propaganda seeking to inflate the notoriety and impact of opportunistic attacks, in an effort to increase their effects."
The disclosure also follows revelations that a Hamas-affiliated threat actor named Arid Viper has targeted Arabic speakers with an Android spyware known as SpyC23 through weaponized apps masquerading as Skipped and Telegram, according to Cisco Talos and SentinelOne.
Chinese APT41 Hackers Target Mobile Devices with New WyrmSpy and DragonEgg Spyware
19.7.23 APT The Hacker News
The prolific China-linked nation-state actor known as APT41 has been linked to two previously undocumented strains of Android spyware called WyrmSpy and DragonEgg.
"Known for its exploitation of web-facing applications and infiltration of traditional endpoint devices, an established threat actor like APT 41 including mobile in its arsenal of malware shows how mobile endpoints are high-value targets with coveted corporate and personal data," Lookout said in a report shared with The Hacker News.
APT41, also tracked under the names Axiom, Blackfly, Brass Typhoon (formerly Barium), Bronze Atlas, HOODOO, Wicked Panda, and Winnti, is known to be operational since at least 2007, targeting a wide range of industries to conduct intellectual property theft.
Recent attacks mounted by the adversarial collective have leveraged an open-source red teaming tool known as Google Command and Control (GC2) as part of attacks aimed at media and job platforms in Taiwan and Italy.
The initial intrusion vector for the mobile surveillanceware campaign is not known, although it's suspected to have involved the use of social engineering. Lookout said it first detected WyrmSpy as early as 2017 and DragonEgg at the start of 2021, with new samples of the latter spotted as recently as April 2023.
WyrmSpy primarily masquerades as a default system app used for displaying notifications to the user. Later variants, however, have packaged the malware into apps impersonating as adult video content, Baidu Waimai, and Adobe Flash. On the other hand, DragonEgg has been distributed in the form of third-party Android keyboards and messaging apps like Telegram.
There is no evidence that these rogue apps were propagated through the Google Play Store.
WyrmSpy and DragonEgg's connections to APT41 arise from the use of a command-and-server (C2) with the IP address 121.42.149[.]52, which resolves to a domain ("vpn2.umisen[.]com") previously identified as associated with the group's infrastructure.
Once installed, both strains of malware request intrusive permissions and come fitted with sophisticated data collection and exfiltration capabilities, harvesting users' photos, locations, SMS messages and audio recordings.
The malware has also been observed relying on modules that are downloaded from a now-offline C2 server after the installation of the app to facilitate the data collection, while simultaneously avoiding detection.
WyrmSpy, for its part, is capable of disabling Security-Enhanced Linux (SELinux), a security feature in Android, and making use of rooting tools such as KingRoot11 to obtain elevated privileges on the compromised handsets. A notable feature of DragonEgg is that it establishes contact with the C2 server to fetch an unknown tertiary module that poses as a forensics program.
"The discovery of WyrmSpy and DragonEgg is a reminder of the growing threat posed by advanced Android malware," Kristina Balaam, a senior threat researcher at Lookout, said. "These spyware packages are highly sophisticated and can be used to collect a wide range of data from infected devices."
The findings come as Mandiant disclosed the evolving tactics adopted by Chinese espionage crews to fly under the radar, including weaponizing networking devices and virtualization software, employing botnets to obfuscate traffic between C2 infrastructure and victim environments, and tunneling malicious traffic inside of victim networks through compromised systems.
"Use of botnets, proxying traffic in a compromised network, and targeting edge devices are not new tactics, nor are they unique to Chinese cyber espionage actors," the Google-owned threat intelligence firm said. "However, during the last decade, we have tracked Chinese cyber espionage actors' use of these and other tactics as part of a broader evolution toward more purposeful, stealthy, and effective operations."
Kimsuky Targets Think Tanks and News Media with Social Engineering Attacks
8.6.23 APT The Hacker News
The North Korean nation-state threat actor known as Kimsuky has been linked to a social engineering campaign targeting experts in North Korean affairs with the goal of stealing Google credentials and delivering reconnaissance malware.
"Further, Kimsuky's objective extends to the theft of subscription credentials from NK News," cybersecurity firm SentinelOne said in a report shared with The Hacker News.
"To achieve this, the group distributes emails that lure targeted individuals to log in on the malicious website nknews[.]pro, which masquerades as the authentic NK News site. The login form that is presented to the target is designed to capture entered credentials."
NK News, established in 2011, is an American subscription-based news website that provides stories and analysis about North Korea.
The disclosure comes days after U.S. and South Korean intelligence agencies issued an alert warning of Kimsuky's use of social engineering tactics to strike think tanks, academia, and news media sectors. Last week, the threat group was sanctioned by South Korea's Ministry of Foreign Affairs.
Active since at least 2012, Kimsuky is known for its spear-phishing tactics and its attempts to establish trust and rapport with intended targets prior to delivering malware, a reconnaissance tool called ReconShark.
The ultimate goal of the campaigns is to gather strategic intelligence, geopolitical insights, and access sensitive information that are of value to North Korea.
"Their approach highlights the group's commitment to creating a sense of rapport with the individuals they target, potentially increasing the success rate of their subsequent malicious activities," security researcher Aleksandar Milenkoski said.
The findings also follow new revelations from the South Korean government that more than 130 North Korean watchers have been singled out as part of a phishing campaign orchestrated by the government-backed hacking group.
What's more, with North Korea earning a significant chunk of its foreign-currency income from cyber attacks and cryptocurrency heists, threat actors operating on behalf of the regime's interests have been observed spoofing financial institutions and venture capital firms in Japan, the U.S., and Vietnam.
Cybersecurity company Recorded Future connected the activity to a group tracked as TAG-71, a subgroup of Lazarus which is also known as APT38, BlueNoroff, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.
The adversarial collective has an established track record of mounting financially motivated intrusion campaigns targeting cryptocurrency exchanges, commercial banks, and e-commerce payment systems across the world to illegally extract funds for the sanctions-hit country.
"The compromise of financial and investment firms and their customers may expose sensitive or confidential information, which may result in legal or regulatory action, jeopardize pending business negotiations or agreements, or expose information damaging to a company's strategic investment portfolio," the company noted.
The chain of evidence so far suggests that Lazarus Group's motives are both espionage and financially driven, what with the threat actor blamed for the recent Atomic Wallet hack that led to the theft of crypto assets worth $35 million, making it the latest in a long list of crypto companies to be stung by hacks over the past few years.
"The laundering of the stolen crypto assets follows a series of steps that exactly match those employed to launder the proceeds of past hacks perpetrated by Lazarus Group," the blockchain analytics company said.
"The stolen assets are being laundered using specific services, including the Sinbad mixer, which have also been used to launder the proceeds of past hacks perpetrated by the Lazarus Group."
North Korea's Kimsuky Group Mimics Key Figures in Targeted Cyber Attacks
2.6.23 APT The Hacker News
U.S. and South Korean intelligence agencies have issued a new alert warning of North Korean cyber actors' use of social engineering tactics to strike think tanks, academia, and news media sectors.
The "sustained information gathering efforts" have been attributed to a state-sponsored cluster dubbed Kimsuky, which is also known by the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (previously Thallium), Nickel Kimball, and Velvet Chollima.
"North Korea relies heavily on intelligence gained from these spear-phishing campaigns," the agencies said. "Successful compromises of the targeted individuals enable Kimsuky actors to craft more credible and effective spear-phishing emails that can be leveraged against sensitive, high-value targets."
Acting in tandem, South Korea's Ministry of Foreign Affairs (MOFA) imposed sanctions on the North Korean hacking group and identified two cryptocurrency addresses used by the entity that have received a steady stream of small virtual funds. The government also accused it of being involved in the failed spy satellite launch this week.
Kimsuky refers to an ancillary element within North Korea's Reconnaissance General Bureau (RGB) and is known to collect tactical intelligence on geopolitical events and negotiations affecting the regime's interests. It's known to be active since at least 2012.
"These cyber actors are strategically impersonating legitimate sources to collect intelligence on geopolitical events, foreign policy strategies, and security developments of interest to the DPRK on the Korean Peninsula," Rob Joyce, NSA director of Cybersecurity, said.
This includes journalists, academic scholars, think tank researchers, and government officials, with the ruse primarily designed to single out individuals working on North Korean matters like foreign policy and politics.
The goal of the Kimsuky's cyber programs, the officials said, is to gain illicit access as well as provide stolen data and valuable geopolitical insight to the North Korean government.
Kimsuky has been observed leveraging open source information to identify potential targets of interest and subsequently craft their online personas to appear more legitimate by creating email addresses that resemble email addresses of real individuals they seek to impersonate.
The adoption of spoofed identities is a tactic embraced by other state-sponsored groups and is seen as a ploy to gain trust and build rapport with the victims. The adversary is also known to compromise the email accounts of the impersonated individuals to concoct convincing email messages.
"DPRK [Democratic People's Republic of Korea] actors often use domains that resemble common internet services and media sites to deceive a target," according to the advisory.
"Kimsuky actors tailor their themes to their target's interests and will update their content to reflect current events discussed among the community of North Korea watchers."
Besides using multiple personas to communicate with a target, the electronic missives come with bearing with password-protected malicious documents, either attached directly or hosted on Google Drive or Microsoft OneDrive.
The lure files, when opened, urge the recipients to enable macros, resulting in the provision of backdoor access to the devices through malware such as BabyShark. Additionally, the persistent access is weaponized to stealthily auto-forward all emails landing in a victim's inbox to an actor-controlled email account.
Another tell-tale sign is the use of "fake but realistic versions of actual websites, portals, or mobile applications" to harvest login credentials from victims.
The development comes weeks after cybersecurity firm SentinelOne detailed Kimsuky's use of custom tools like ReconShark (an upgraded version of BabyShark) and RandomQuery for reconnaissance and information exfiltration.
Earlier this March, German and South Korean government authorities sounded the alarm about cyber attacks mounted by Kimsuky that entail the use of rogue browser extensions to steal users' Gmail inboxes.
The alert also follows sanctions imposed by the U.S. Treasury Department against four entities and one individual who are involved in malicious cyber activities and fundraising schemes that aim to support North Korea's strategic priorities.
Dark Pink APT Group Leverages TelePowerBot and KamiKakaBot in Sophisticated Attacks
31.5.23 APT The Hacker News
The threat actor known as Dark Pink has been linked to five new attacks aimed at various entities in Belgium, Brunei, Indonesia, Thailand, and Vietnam between February 2022 and April 2023.
This includes educational institutions, government agencies, military bodies, and non-profit organizations, indicating the adversarial crew's continued focus on high-value targets.
Dark Pink, also called Saaiwc Group, is an advanced persistent threat (APT) actor believed to be of Asia-Pacific origin, with attacks targeting entities primarily located in East Asia and, to a lesser extent, in Europe.
The group employs a set of custom malware tools such as TelePowerBot and KamiKakaBot that provide various functions to exfiltrate sensitive data from compromised hosts.
"The group uses a range of sophisticated custom tools, deploys multiple kill chains relying on spear-phishing emails," Group-IB security researcher Andrey Polovinkin said in a technical report shared with The Hacker News.
"Once the attackers gain access to a target's network, they use advanced persistence mechanisms to stay undetected and maintain control over the compromised system."
The findings also illustrate some key modifications to the Dark Pink attack sequence to impede analysis as well as accommodate improvements to KamiKakaBot, which executes commands from a threat actor-controlled Telegram channel via a Telegram bot.
The latest version, notably, splits its functionality into two distinct parts: One for controlling devices and the other for harvesting valuable information.
The Singapore-headquartered company said it also identified a new GitHub account associated with the threat actor that hosts PowerShell scripts, ZIP archives, and custom malware for subsequent installation onto victim machines. These modules were uploaded between January 9, 2023, and April 11, 2023.
Besides using Telegram for command-and-control, Dark Pink has been observed exfiltrating stolen data over HTTP using a service called webhook[.]site. Another notable aspect is the use of an Microsoft Excel add-in to ensure the persistence of TelePowerBot within the infected host.
"With webhook[.]site, it is possible to set up temporary endpoints in order to capture and view incoming HTTP requests," Polovinkin noted. "The threat actor created temporary endpoints and sent sensitive data stolen from victims."
Dark Pink, its espionage motives notwithstanding, remains shrouded in mystery. That said, it's suspected the hacking crew's victimology footprint could be broader than previously assumed.
While the latest discovery brings the attack tally to 13 (counting the five new victims) since mid-2021, they also indicate the adversary's attempts to maintain a low profile for stealthiness. They are also a sign of the threat actors carefully selecting their targets and keeping the number of attacks at a minimum to reduce the likelihood of exposure.
"The fact that two attacks were executed in 2023 indicates that Dark Pink remains active and poses an ongoing risk to organizations," Polovinkin said. "Evidence shows that the cybercriminals behind these attacks keep updating their existing tools in order to remain undetected."
N. Korean Lazarus Group Targets Microsoft IIS Servers to Deploy Espionage Malware
24.5.23 APT The Hacker News
The infamous Lazarus Group actor has been targeting vulnerable versions of Microsoft Internet Information Services (IIS) servers as an initial breach route to deploy malware on targeted systems.
The findings come from the AhnLab Security Emergency response Center (ASEC), which detailed the advanced persistent threat's (APT) continued abuse of DLL side-loading techniques to run arbitrary payloads.
"The threat actor places a malicious DLL (msvcr100.dll) in the same folder path as a normal application (Wordconv.exe) via the Windows IIS web server process, w3wp.exe," ASEC explained. "They then execute the normal application to initiate the execution of the malicious DLL."
DLL side-loading, similar to DLL search-order hijacking, refers to the proxy execution of a rogue DLL via a benign binary planted in the same directory.
Lazarus, a highly-capable and relentless nation-state group linked to North Korea, was most recently spotted leveraging the same technique in connection with the cascading supply chain attack on enterprise communications service provider 3CX.
The malicious msvcr100.dll library, for its part, is designed to decrypt an encoded payload that's then executed in memory. The malware is said to be a variant of a similar artifact that was discovered by ASEC last year and which acted as a backdoor to communicate with an actor-controlled server.
The attack chain further entailed the exploitation of a discontinued open source Notepad++ plugin called Quick Color Picker to deliver additional malware in order to facilitate credential theft and lateral movement.
The latest development demonstrates the diversity of Lazarus attacks and its ability to employ an extensive set of tools against victims to carry out long-term espionage operations.
"In particular, since the threat group primarily utilizes the DLL side-loading technique during their initial infiltrations, companies should proactively monitor abnormal process execution relationships and take preemptive measures to prevent the threat group from carrying out activities such as information exfiltration and lateral movement," ASEC said.
U.S. Treasury Sanctions North Korean Entities#
The findings also come as the U.S. Treasury Department sanctioned four entities and one individual involved in malicious cyber activities and fundraising schemes that aim to support North Korea's strategic priorities.
This includes the Pyongyang University of Automation, the Technical Reconnaissance Bureau and its subordinate cyber unit, the 110th Research Center, Chinyong Information Technology Cooperation Company, and a North Korean national named Kim Sang Man.
The Lazarus Group and its various clusters are believed to be operated by the Technical Reconnaissance Bureau, which oversees North Korea's development of offensive cyber tactics and tools.
The sanctions-hit nation, besides engaging in crypto currency theft and espionage operations, is known to generate illicit revenue from a workforce of skilled IT workers who pose under fictitious identities to obtain jobs in the technology and virtual currency sectors across the world.
"The DPRK conducts malicious cyber activities and deploys information technology (IT) workers who fraudulently obtain employment to generate revenue, including in virtual currency, to support the Kim regime and its priorities, such as its unlawful weapons of mass destruction and ballistic missile programs," the department said.
"These workers deliberately obfuscate their identities, locations, and nationalities, typically using fake personas, proxy accounts, stolen identities, and falsified or forged documentation to apply for jobs at these companies."
"They earn hundreds of millions of dollars a year by engaging in a wide range of IT development work, including freelance work platforms (websites/applications) and cryptocurrency development, after obtaining freelance employment contracts from companies around the world," the South Korean government warned in December 2022.
New APT Group Red Stinger Targets Military and Critical Infrastructure in Eastern Europe
12.5.23 APT The Hacker News
A previously undetected advanced persistent threat (APT) actor dubbed Red Stinger has been linked to attacks targeting Eastern Europe since 2020.
"Military, transportation, and critical infrastructure were some of the entities being targeted, as well as some involved in the September East Ukraine referendums," Malwarebytes disclosed in a report published today.
"Depending on the campaign, attackers managed to exfiltrate snapshots, USB drives, keyboard strokes, and microphone recordings."
Red Stinger overlaps with a threat cluster Kaspersky revealed under the name Bad Magic last month as having targeted government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea last year.
While there were indications that the APT group may have been active since at least September 2021, the latest findings from Malwarebytes push the group's origins back by nearly a year, with the first operation taking place in December 2020.
The attack chain, over the years, have leveraged malicious installer files to drop the DBoxShell (aka PowerMagic) implant on compromised systems. The MSI file, for its part, is downloaded by means of a Windows shortcut file contained within a ZIP archive.
Subsequent waves detected in April and September 2021 have been observed to leverage similar attack sequences, albeit with minor variations in the MSI file names.
A fourth set of attacks coincided with the onset of Russia's military invasion of Ukraine in February 2022. The last known activity associated with Red Stinger took place in September 2022, as documented by Kaspersky.
"DBoxShell is malware that utilizes cloud storage services as a command-and-control (C&C) mechanism," security researchers Roberto Santos and Hossein Jazi said.
"This stage serves as an entry point for the attackers, enabling them to assess whether the targets are interesting or not, meaning that in this phase they will use different tools."
The fifth operation is also notable for delivering an alternative to DBoxShell called GraphShell, which is so named for its use of the Microsoft Graph API for C&C purposes.
The initial infection phase is followed by the threat actor deploying additional artifacts like ngrok, rsockstun (a reverse tunneling utility), and a binary to exfiltrate victim data to an actor-controlled Dropbox account.
The exact scale of the infections are unclear, although evidence points to two victims located in central Ukraine – a military target and an officer working in critical infrastructure – who were compromised as part of the February 2022 attacks.
In both instances, the threat actors exfiltrated screenshots, microphone recordings, and office documents after a period of reconnaissance. One of the victims also had their keystrokes logged and uploaded.
The September 2022 intrusion set, on the other hand, is significant for the fact that it chiefly singled out Russia-aligned regions, including officers and individuals involved in elections. One of the surveillance targets had data from their USB drives exfiltrated.
Malwarebytes said it also identified a library in the Ukrainian city of Vinnytsia that was infected as part of the same campaign, making it the only Ukraine-related entity to be targeted. The motivations are presently unknown.
While the origins of the threat group are a mystery, it has emerged that the threat actors managed to infect their own Windows 10 machines at some point in December 2022, either accidentally or for testing purposes (given the name TstUser), offering an insight into their modus operandi.
Two things stand out: The choice of English as the default language and the use of Fahrenheit temperature scale to display the weather, likely suggesting the involvement of native English speakers.
"In this case, attributing the attack to a specific country is not an easy task," the researchers said. "Any of the involved countries or aligned groups could be responsible, as some victims were aligned with Russia, and others were aligned with Ukraine."
"What is clear is that the principal motive of the attack was surveillance and data gathering. The attackers used different layers of protection, had an extensive toolset for their victims, and the attack was clearly targeted at specific entities."
Researchers Uncover SideWinder's Latest Server-Based Polymorphism Technique
10.5.23 APT The Hacker News
The advanced persistent threat (APT) actor known as SideWinder has been accused of deploying a backdoor in attacks directed against Pakistan government organizations as part of a campaign that commenced in late November 2022.
"In this campaign, the SideWinder advanced persistent threat (APT) group used a server-based polymorphism technique to deliver the next stage payload," the BlackBerry Research and Intelligence Team said in a technical report published Monday.
Another campaign discovered by the Canadian cybersecurity company in early March 2023 shows that Turkey has also landed in the crosshairs of the threat actor's collection priorities.
SideWinder has been on the radar since at least 2012 and it's primarily known to target various Southeast Asian entities located across Pakistan, Afghanistan, Bhutan, China, Myanmar, Nepal, and Sri Lanka.
Suspected to be an Indian state-sponsored group, SideWinder is also tracked under the monikers APT-C-17, APT-Q-39, Hardcore Nationalist (HN2), Rattlesnake, Razor Tiger, and T-APT4.
Typical attack sequences mounted by the actor entail using carefully crafted email lures and DLL side-loading techniques to fly under the radar and deploy malware capable of granting the actors remote access to the targeted systems.
Over the past year, SideWinder has been linked to a cyber attack aimed at Pakistan Navy War College (PNWC) as well as an Android malware campaign that leveraged rogue phone cleaner and VPN apps uploaded to the Google Play Store to harvest sensitive information.
The latest infection chain documented by BlackBerry mirrors findings from Chinese cybersecurity firm QiAnXin in December 2022 detailing the use of PNWC lure documents to drop a lightweight .NET-based backdoor (App.dll) that's capable of retrieving and executing next-stage malware from a remote server.
What makes the campaign also stand out is the threat actor's use of server-based polymorphism as a way to potentially sidestep traditional signature-based antivirus (AV) detection and distribute additional payloads by responding with two different versions of an intermediate RTF file.
Specifically, the PNWC document employs a method known as remote template injection to fetch the RTF file such that it harbors the malicious code only if the request originates from a user in the Pakistan IP address range.
"It is important to note that in both instances, only the name of the file 'file.rtf' and the file type are the same; however, the contents, file size and the file hash are different," BlackBerry explained.
"If the user is not in the Pakistani IP range, the server returns an 8-byte RTF file (file.rtf) that contains a single string: {\rtf1 }. However, if the user is within the Pakistani IP range, the server then returns the RTF payload, which varies between 406 KB – 414 KB in size."
The disclosure arrives shortly after Fortinet and Team Cymru revealed a new set of attacks perpetrated by a Pakistan-based threat actor known as SideCopy against Indian defense and military targets.
"The latest SideWinder campaign targeting Turkey overlaps with the most recent developments in geopolitics; specifically, in Turkey's support of Pakistan and the ensuing reaction from India," BlackBerry said.
Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
7.5.23 APT The Hacker News
An advanced persistent threat (APT) actor known as Dragon Breath has been observed adding new layers of complexity to its attacks by adopting a novel DLL side-loading mechanism.
"The attack is based on a classic side-loading attack, consisting of a clean application, a malicious loader, and an encrypted payload, with various modifications made to these components over time," Sophos researcher Gabor Szappanos said.
"The latest campaigns add a twist in which a first-stage clean application 'side'-loads a second clean application and auto-executes it. The second clean application side-loads the malicious loader DLL. After that, the malicious loader DLL executes the final payload."
Operation Dragon Breath, also tracked under the names APT-Q-27 and Golden Eye, was first documented by QiAnXin in 2020, detailing a watering hole campaign designed to trick users into downloading a trojanized Windows installer for Telegram.
A subsequent campaign detailed by the Chinese cybersecurity company in May 2022 highlighted the continued use of Telegram installers as a lure to deploy additional payloads such as gh0st RAT.
Dragon Breath is also said to be part of a larger entity called Miuuti Group, with the adversary characterized as a "Chinese-speaking" entity targeting the online gaming and gambling industries, joining the likes of other Chinese activity clusters like Dragon Castling, Dragon Dance, and Earth Berberoka.
Double-Clean-App Technique
The double-dip DLL side-loading strategy, per Sophos, has been leveraged in attacks targeting users in the Philippines, Japan, Taiwan, Singapore, Hong Kong, and China. These attempted intrusions were ultimately unsuccessful.
The initial vector is a fake website hosting an installer for Telegram that, when opened, creates a desktop shortcut that's designed to load malicious components behind the scenes upon launch, while also displaying to the victim the Telegram app user interface.
What's more, the adversary is believed to have created multiple variations of the scheme in which tampered installers for other apps, such as LetsVPN and WhatsApp, are used to initiate the attack chain.
The next stage involves the use of a second clean application as an intermediate to avoid detection and load the final payload via a malicious DLL.
The payload functions as a backdoor capable of downloading and executing files, clearing event logs, extracting and setting clipboard content, running arbitrary commands, and stealing cryptocurrency from the MetaMask wallet extension for Google Chrome.
"DLL sideloading, first identified in Windows products in 2010 but prevalent across multiple platforms, continues to be an effective and appealing tactic for threat actors," Szappanos said.
"This double-clean-app technique employed by the Dragon Breath group, targeting a user sector (online gambling) that has traditionally been less scrutinized by security researchers, represents the continued vitality of this approach."
APT28 Targets Ukrainian Government Entities with Fake "Windows Update" Emails
1.5.23 APT The Hacker News
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks perpetrated by Russian nation-state hackers targeting various government bodies in the country.
The agency attributed the phishing campaign to APT28, which is also known by the names Fancy Bear, Forest Blizzard, FROZENLAKE, Iron Twilight, Sednit, and Sofacy.
The email messages come with the subject line "Windows Update" and purportedly contain instructions in the Ukrainian language to run a PowerShell command under the pretext of security updates.
Running the script loads and executes a next-stage PowerShell script that's designed to collect basic system information through commands like tasklist and systeminfo, and exfiltrate the details via an HTTP request to a Mocky API.
To trick the targets into running the command, the emails impersonated system administrators of the targeted government entities using fake Microsoft Outlook email accounts created with the employees' real names and initials.
CERT-UA is recommending that organizations restrict users' ability to run PowerShell scripts and monitor network connections to the Mocky API.
The disclosure comes weeks after the APT28 was tied to attacks exploiting now-patched security flaws in networking equipment to conduct reconnaissance and deploy malware against select targets.
Google's Threat Analysis Group (TAG), in an advisory published last month, detailed a credential harvesting operation carried out by the threat actor to redirect visitors of Ukrainian government websites to phishing domains.
Russian-based hacking crews have also been linked to the exploitation of a critical privilege escalation flaw in Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) in intrusions directed against the government, transportation, energy, and military sectors in Europe.
The development also comes as Fortinet FortiGuard Labs uncovered a multi-stage phishing attack that leverages a macro-laced Word document supposedly from Ukraine's Energoatom as a lure to deliver the open source Havoc post-exploitation framework.
"It remains highly likely that Russian intelligence, military, and law enforcement services have a longstanding, tacit understanding with cybercriminal threat actors," cybersecurity firm Recorded Future said in a report earlier this year.
"In some cases, it is almost certain that these agencies maintain an established and systematic relationship with cybercriminal threat actors, either by indirect collaboration or via recruitment."
Lazarus Subgroup Targeting Apple Devices with New RustBucket macOS Malware
25.4.23 APT The Hacker News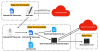
A financially-motivated North Korean threat actor is suspected to be behind a new Apple macOS malware strain called RustBucket.
"[RustBucket] communicates with command and control (C2) servers to download and execute various payloads," Jamf Threat Labs researchers Ferdous Saljooki and Jaron Bradley said in a technical report published last week.
The Apple device management company attributed it to a threat actor known as BlueNoroff, a subgroup within the infamous Lazarus cluster that's also tracked under the monikers APT28, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.
The connections stem from tactical and infrastructure overlaps with a prior campaign exposed by Russian cybersecurity company Kaspersky in late December 2022 likely aimed at Japanese financial entities using fake domains impersonating venture capital firms.
BlueNoroff, unlike other constituent entities of the Lazarus Group, is known for its sophisticated cyber-enabled heists targeting the SWIFT system as well as cryptocurrency exchanges as part of an intrusion set tracked as CryptoCore.
Earlier this year, the U.S. Federal Bureau of Investigation (FBI) implicated the threat actor for the theft of $100 million in cryptocurrency assets from Harmony Horizon Bridge in June 2022.
BlueNoroff's attack repertoire is also said to have witnessed a major shift over the past few months, what with the group making use of job-themed lures to trick email recipients into entering their credentials on fake landing pages.
The macOS malware identified by Jamf masquerades as an "Internal PDF Viewer" application to activate the infection, although it bears noting that the success of the attack banks on the victim manually overriding Gatekeeper protections.
In reality, it's an AppleScript file that's engineered to retrieve a second-stage payload from a remote server, which also carries the same name as its predecessor. Both the malicious apps are signed with an ad-hoc signature.
The second-stage payload, written in Objective-C, is a basic application that offers the ability to view PDF files and only initiates the next phase of the attack chain when a booby-trapped PDF file is opened through the app.
One such nine-page PDF document identified by Jamf purports to offer an "investment strategy," that when launched, reaches out to the command-and-control (C2) server to download and execute a third-stage trojan, a Mach-O executable written in Rust that comes with capabilities to run system reconnaissance commands.
"This PDF viewer technique used by the attacker is a clever one," the researchers explained. "At this point, in order to perform analysis, not only do we need the stage-two malware but we also require the correct PDF file that operates as a key in order to execute the malicious code within the application."
It's not currently not clear how initial access is obtained and if the attacks were successful, but the development is a sign that threat actors are adapting their toolsets to accommodate cross-platform malware by using programming languages like Go and Rust.
The findings also come off a busy period of attacks orchestrated by the Lazarus Group aimed at organizations across countries and industry verticals for collecting strategic intelligence and performing cryptocurrency theft.
Lazarus Group (aka Hidden Cobra and Diamond Sleet) is less a distinct outfit and more of an umbrella term for a mixture of state-sponsored and criminal hacking groups that sit within the Reconnaissance General Bureau (RGB), North Korea's primary foreign intelligence apparatus.
Recent activity undertaken by the threat actor has offered fresh evidence of the threat actor's growing interest in exploiting trust relationships in the software supply chain as entry points to corporate networks.
Last week, the adversarial collective was linked to a cascading supply chain attack that weaponized trojanized installers versions of a legitimate app known as X_TRADER to breach enterprise communications software maker 3CX and poison its Windows and macOS apps.
Around the same time, ESET detailed Lazarus Group's use of a Linux malware dubbed SimplexTea against the backdrop of a recurring social engineering campaign referred to as Operation Dream Job.
"It is also interesting to note that Lazarus can produce and use native malware for all major desktop operating systems: Windows, macOS, and Linux," ESET malware researcher Marc-Etienne M.Léveillé pointed out last week.
Lazarus is far from the only RGB-affiliated state-sponsored hacking group known to conduct operations on behalf of the sanctions-hit country. Another equally prolific threat actor is Kimsuky (aka APT43 or Emerald Sleet), a subgroup of which is monitored by Google's Threat Analysis Group (TAG) as ARCHIPELAGO.
"The actor primarily targets organizations in the U.S. and South Korea, including individuals working within the government, military, manufacturing, academic, and think tank organizations that possess subject matter expertise in defense and security, particularly nuclear security and nonproliferation policy," Google-owned Mandiant noted last year.
Other lesser known targets of Kimsuky include Indian and Japanese government and educational institutions, a set of attacks tracked by Taiwnese cybersecurity company TeamT5 under the name KimDragon.
The group has a history of deploying a raft of cyber weapons to exfiltrate sensitive information through a wide range of tactics such as spear-phishing, fraudulent browser extensions, and remote access trojans.
Latest findings released by VirusTotal highlight Kimsuky's heavy reliance on malicious Microsoft Word documents to deliver its payloads. A majority of the files have been submitted to the malware-scanning platform from South Korea, the U.S., Italy, and Israel, and the U.K.
"The group uses a variety of techniques and tools to conduct espionage, sabotage, and theft operations, including spear-phishing and credential harvesting," the Google Chronicle subsidiary said.
Lazarus Group Adds Linux Malware to Arsenal in Operation Dream Job
20.4.23 APT The Hacker News
The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed at Linux users.
The attacks are part of a persistent and long-running activity tracked under the name Operation Dream Job, ESET said in a new report published today.
The findings are crucial, not least because it marks the first publicly documented example of the adversary using Linux malware as part of this social engineering scheme.
Operation Dream Job, also known as DeathNote or NukeSped, refers to multiple attack waves wherein the group leverages fraudulent job offers as a lure to trick unsuspecting targets into downloading malware. It also exhibits overlaps with two other Lazarus clusters known as Operation In(ter)ception and Operation North Star.
The attack chain discovered by ESET is no different in that it delivers a fake HSBC job offer as a decoy within a ZIP archive file that's then used to launch a Linux backdoor named SimplexTea distributed via an OpenDrive cloud storage account.

While the exact method used to distribute the ZIP file is not known, it's suspected to be either spear-phishing or direct messages on LinkedIn. The backdoor, written in C++, bears similarities to BADCALL, a Windows trojan previously attributed to the group.
Furthermore, ESET said it identified commonalities between artifacts used in the Dream Job campaign and those unearthed as part of the supply chain attack on VoIP software developer 3CX that came to light last month.
This also includes the command-and-control (C2) domain "journalide[.]org," which was listed as one of the four C2 servers used by malware families detected within the 3CX environment.
Indications are that preparations for the supply chain attack had been underway since December 2022, when some of the components were committed to the GitHub code-hosting platform.
The findings not only strengthen the existing link between Lazarus Group and the 3CX compromise, but also demonstrates the threat actor's continued success with staging supply chain attacks since 2020.
Blind Eagle Cyber Espionage Group Strikes Again: New Attack Chain Uncovered
20.4.23 APT The Hacker News
The cyber espionage actor tracked as Blind Eagle has been linked to a new multi-stage attack chain that leads to the deployment of the NjRAT remote access trojan on compromised systems.
"The group is known for using a variety of sophisticated attack techniques, including custom malware, social engineering tactics, and spear-phishing attacks," ThreatMon said in a Tuesday report.
Blind Eagle, also referred to as APT-C-36, is a suspected Spanish-speaking group that chiefly strikes private and public sector entities in Colombia. Attacks orchestrated by the group have also targeted Ecuador, Chile, and Spain.
Infection chains documented by Check Point and BlackBerry this year have revealed the use of spear-phishing lures to deliver commodity malware families like BitRAT and AsyncRAT, as well as in-memory Python loaders capable of launching a Meterpreter payload.
The latest discovery from ThreatMon entails the use of a JavaScript downloader to execute a PowerShell script hosted in Discord CDN. The script, in turn, drops another PowerShell script and a Windows batch file, and saves a VBScript file in the Windows startup folder to achieve persistence.
New Attack Chain
The VBScript code is then run to launch the batch file, which is subsequently deobfuscated to run the PowerShell script that was previously delivered along with it. In the final stage, the PowerShell script is used to execute njRAT.
"njRAT, also known as Bladabindi is a remote access tool (RAT) with user interface or trojan which allows the holder of the program to control the end-user's computer," the cybersecurity firm said.
Google Uncovers APT41's Use of Open Source GC2 Tool to Target Media and Job Sites
17.4.23 APT The Hacker News

A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming tool known as Google Command and Control (GC2) amid broader abuse of Google's infrastructure for malicious ends.
The tech giant's Threat Analysis Group (TAG) attributed the campaign to a threat actor it tracks under the geological and geographical-themed moniker HOODOO, which is also known by the names APT41, Barium, Bronze Atlas, Wicked Panda, and Winnti.
The starting point of the attack is a phishing email that contains links to a password-protected file hosted on Google Drive, which, in turn, incorporates the GC2 tool to read commands from Google Sheets and exfiltrate data using the cloud storage service.
"After installation on the victim machine, the malware queries Google Sheets to obtain attacker commands," Google's cloud division said in its sixth Threat Horizons Report. "In addition to exfiltration via Drive, GC2 enables the attacker to download additional files from Drive onto the victim system."
Google said the threat actor previously utilized the same malware in July 2022 to target an Italian job search website.
The development is notable for two reasons: First, it suggests that Chinese threat groups are increasingly relying on publicly available tooling like Cobalt Strike and GC2 to confuse attribution efforts.
Secondly, it also points to the growing adoption of malware and tools written in the Go programming language, owing to its cross-platform compatibility and its modular nature.
Google further cautioned that the "undeniable value of cloud services" have made them a lucrative target for cybercriminals and government-backed actors alike, "either as hosts for malware or providing the infrastructure for command-and-control (C2)."
A case in point is the use of Google Drive for storing malware such as Ursnif (aka Gozi) and DICELOADER (aka Lizar or Tirion) in the form of ZIP archive files as part of disparate phishing campaigns.
"The most common vector used to compromise any network, including cloud instances is to take over an account's credentials directly: either because there is no password, as with some default configurations, or because a credential has been leaked or recycled or is generally so weak as to be guessable," Google Cloud's Christopher Porter said.
The findings come three months after Google Cloud detailed APT10's (aka Bronze Riverside, Cicada, Potassium, or Stone Panda) targeting of cloud infrastructure and VPN technologies to breach enterprise environments and exfiltrate data of interest.
Russia-Linked Hackers Launches Espionage Attacks on Foreign Diplomatic Entities
15.4.23 APT The Hacker News
The Russia-linked APT29 (aka Cozy Bear) threat actor has been attributed to an ongoing cyber espionage campaign targeting foreign ministries and diplomatic entities located in NATO member states, the European Union, and Africa.
According to Poland's Military Counterintelligence Service and the CERT Polska team, the observed activity shares tactical overlaps with a cluster tracked by Microsoft as Nobelium, which is known for its high-profile attack on SolarWinds in 2020.
Nobelium's operations have been attributed to Russia's Foreign Intelligence Service (SVR), an organization that's tasked with protecting "individuals, society, and the state from foreign threats."
That said, the campaign represents an evolution of the Kremlin-backed hacking group's tactics, indicating persistent attempts at improving its cyber weaponry to infiltrate victim systems for intelligence gathering.
"New tools were used at the same time and independently of each other, or replacing those whose effectiveness had declined, allowing the actor to maintain a continuous, high operational tempo," the agencies said.

The attacks commence with spear-phishing emails impersonating European embassies that aim to entice targeted diplomats into opening malware-laced attachments under the guise of an invitation or a meeting.
Embedded within the PDF attachment is a booby-trapped URL that leads to the deployment of an HTML dropper called EnvyScout (aka ROOTSAW), which is then used as a conduit to deliver three previously unknown strains SNOWYAMBER, HALFRIG, and QUARTERRIG.
SNOWYAMBER, also referred to as GraphicalNeutrino by Recorded Future, leverages the Notion note-taking service for command-and-control (C2) and downloading additional payloads such as Brute Ratel.
QUARTERRIG also functions as a downloader capable of retrieving an executable from an actor-controlled server. HALFRIG, on the other hand, acts as a loader to launch the Cobalt Strike post-exploitation toolkit contained within it.
It's worth noting that the disclosure dovetails with recent findings from BlackBerry, which detailed a Nobelium campaign targeting European Union countries, with a specific emphasis on agencies that are "aiding Ukrainian citizens fleeing the country, and providing help to the government of Ukraine."
Winter Vivern APT Targets European Government Entities with Zimbra Vulnerability
1.4.23 APT The Hacker News
The advanced persistent threat (APT) actor known as Winter Vivern is now targeting officials in Europe and the U.S. as part of an ongoing cyber espionage campaign.
"TA473 since at least February 2023 has continuously leveraged an unpatched Zimbra vulnerability in publicly facing webmail portals that allows them to gain access to the email mailboxes of government entities in Europe," Proofpoint said in a new report.
The enterprise security firm is tracking the activity under its own moniker TA473 (aka UAC-0114), describing it as an adversarial crew whose operations align with that of Russian and Belarussian geopolitical objectives.
What it lacks in sophistication, it makes up for in persistence. In recent months, the group has been linked to attacks targeting state authorities of Ukraine and Poland as well as government officials in India, Lithuania, Slovakia, and the Vatican.
The NATO-related intrusion wave entails the exploitation of CVE-2022-27926 (CVSS score: 6.1), a now-patched medium-severity security flaw in Zimbra Collaboration that could enable unauthenticated attackers to execute arbitrary JavaScript or HTML code.
This also involves employing scanning tools like Acunetix to identify unpatched webmail portals belonging to targeted organizations with the goal of sending phishing email under the guise of benign government agencies.
The messages come with booby-trapped URLs that exploit the cross-site scripting (XSS) flaw in Zimbra to execute custom Base64-encoded JavaScript payloads within the victims' webmail portals to exfiltrate usernames, passwords, and access tokens.
It's worth noting that each JavaScript payload is tailored to the targeted webmail portal, indicating that the threat actor is willing to invest time and resources to reduce the likelihood of detection.
"TA473's persistent approach to vulnerability scanning and exploitation of unpatched vulnerabilities impacting publicly facing webmail portals is a key factor in this actor's success," Proofpoint said.
"The group's focus on sustained reconnaissance and painstaking study of publicly exposed webmail portals to reverse engineer JavaScript capable of stealing usernames, passwords, and CSRF tokens demonstrates its investment in compromising specific targets."
The findings come amid revelations that at least three Russian intelligence agencies, including FSB, GRU (linked to Sandworm), and SVR (linked to APT29), likely use software and hacking tools developed by a Moscow-based IT contractor named NTC Vulkan.
This includes frameworks like Scan (to facilitate large-scale data collection), Amesit (to conduct information operations and manipulate public opinion), and Krystal-2B (to simulate coordinated IO/OT attacks against rail and pipeline control systems).
"Krystal-2B is a training platform that simulates OT attacks against different types of OT environments in coordination with some IO components by leveraging Amesit 'for the purpose of disruption,'" Google-owned Mandiant said.
"The contracted projects from NTC Vulkan provide insight into the investment of Russian intelligence services into developing capabilities to deploy more efficient operations within the beginning of the attack lifecycle, a piece of operations often hidden from our view," the threat intelligence firm added.
Mélofée: Researchers Uncover New Linux Malware Linked to Chinese APT Groups
29.3.23 APT The Hacker News
An unknown Chinese state-sponsored hacking group has been linked to a novel piece of malware aimed at Linux servers.
French cybersecurity firm ExaTrack, which found three samples of the previously documented malicious software that date back to early 2022, dubbed it Mélofée.
One of the artifacts is designed to drop a kernel-mode rootkit that's based on an open source project referred to as Reptile.
"According to the vermagic metadata, it is compiled for a kernel version 5.10.112-108.499.amzn2.x86_64," the company said in a report. "The rootkit has a limited set of features, mainly installing a hook designed for hiding itself."
Both the implant and the rootkit are said to be deployed using shell commands that download an installer and a custom binary package from a remote server.
The installer takes the binary package as an argument and then extracts the rootkit as well as a server implant module that's currently under active development.
Mélofée's features are no different from other backdoors of its kind, enabling it to contact a remote server and receive instructions that allow it to carry out file operations, create sockets, launch a shell, and execute arbitrary commands.
The malware's ties to China come from infrastructure overlaps with groups such as APT41 (aka Winnti) and Earth Berberoka (aka GamblingPuppet).
Earth Berberoka is the name given to a state-sponsored actor chiefly targeting gambling websites in China since at least 2020 using multi-platform malware like HelloBot and Pupy RAT.
According to Trend Micro, some samples of the Python-based Pupy RAT have been concealed using the Reptile rootkit.
Also discovered by ExaTrack is another implant codenamed AlienReverse, which shares code similarities with Mélofée and makes use of publicly-available tools like EarthWorm and socks_proxy.
"The Mélofée implant family is another tool in the arsenal of Chinese state sponsored attackers, which show constant innovation and development," the company said.
"The capabilities offered by Mélofée are relatively simple, but may enable adversaries to conduct their attacks under the radar. These implants were not widely seen, showing that the attackers are likely limiting its usage to high value targets."
North Korean APT43 Group Uses Cybercrime to Fund Espionage Operations
29.3.23 APT The Hacker News
A new North Korean nation-state cyber operator has been attributed to a series of campaigns orchestrated to gather strategic intelligence that aligns with Pyongyang's geopolitical interests since 2018.
Google-owned Mandiant, which is tracking the activity cluster under the moniker APT43, said the group's motives are both espionage- and financially-motivated, leveraging techniques like credential harvesting and social engineering to further its objectives.
The monetary angle to its attack campaigns is an attempt on the part of the threat actor to generate funds to meet its "primary mission of collecting strategic intelligence."
Victimology patterns suggest that targeting is focused on South Korea, the U.S., Japan, and Europe, spanning government, education, research, policy institutes, business services, and manufacturing sectors.
The threat actor was also observed straying off course by striking health-related verticals and pharma companies from October 2020 through October 2021, underscoring its ability to swiftly change priorities.
"APT43 is a prolific cyber operator that supports the interests of the North Korean regime," Mandiant researchers said in a detailed technical report published Tuesday.
"The group combines moderately-sophisticated technical capabilities with aggressive social engineering tactics, especially against South Korean and U.S.-based government organizations, academics, and think tanks focused on Korean peninsula geopolitical issues."
APT43's activities are said to align with the Reconnaissance General Bureau (RGB), North Korea's foreign intelligence agency, indicating tactical overlaps with another hacking group dubbed Kimsuky (aka Black Banshee, Thallium, or Velvet Chollima).
What's more, it has been observed using tools previously associated with other subordinate adversarial syndicates within RGB, such as the Lazarus Group (aka TEMP.Hermit).
Attack chains mounted by APT43 involve spear-phishing emails containing tailored lures to entice victims. These messages are sent using spoofed and fraudulent personas that masquerade as key individuals within the target's area of expertise to gain their trust.
It's also known to take advantage of contact lists stolen from compromised individuals to identify more targets and steal cryptocurrency to fund its attack infrastructure. The stolen digital assets are then laundered using hash rental and cloud mining services to obscure the forensic trail and convert them into clean cryptocurrency.
The ultimate goal of the attacks is to facilitate credential collection campaigns through domains that mimic a wide range of legitimate services and use the gathered data to create online personas.
"The prevalence of financially-motivated activity among North Korean groups, even among those which have historically focused on cyber espionage, suggests a widespread mandate to self-fund and an expectation to sustain themselves without additional resourcing," Mandiant said.
APT43's operations are actualized through a large arsenal of custom and publicly available malware such as LATEOP (aka BabyShark), FastFire, gh0st RAT, Quasar RAT, Amadey, and an Android version of a Windows-based downloader called PENCILDOWN.
The findings come less than a week after German and South Korean government agencies warned about cyber attacks mounted by Kimsuky using rogue browser extensions to steal users' Gmail inboxes.
"APT43 is highly responsive to the demands of Pyongyang's leadership," the threat intelligence firm said, noting the group "maintains a high tempo of activity."
"Although spear-phishing and credential collection against government, military, and diplomatic organizations have been core taskings for the group, APT43 ultimately modifies its targeting and tactics, techniques and procedures to suit its sponsors, including carrying out financially-motivated cybercrime as needed to support the regime."
Operation Soft Cell: Chinese Hackers Breach Middle East Telecom Providers
23.3.23 APT The Hacker News
Telecommunication providers in the Middle East are the subject of new cyber attacks that commenced in the first quarter of 2023.
The intrusion set has been attributed to a Chinese cyber espionage actor associated with a long-running campaign dubbed Operation Soft Cell based on tooling overlaps.
"The initial attack phase involves infiltrating Internet-facing Microsoft Exchange servers to deploy web shells used for command execution," researchers from SentinelOne and QGroup said in a new technical report shared with The Hacker News.
"Once a foothold is established, the attackers conduct a variety of reconnaissance, credential theft, lateral movement, and data exfiltration activities."
Operation Soft Cell, according to Cybereason, refers to malicious activities undertaken by China-affiliated actors targeting telecommunications providers since at least 2012.
The Soft Cell threat actor, also tracked by Microsoft as Gallium, is known to target unpatched internet-facing services and use tools like Mimikatz to obtain credentials that allows for lateral movement across the targeted networks.
Also put to use by the adversarial collective is a "difficult-to-detect" backdoor codenamed PingPull in its espionage attacks directed against companies operating in Southeast Asia, Europe, Africa, and the Middle East.
Central to the latest campaign is the deployment of a custom variant of Mimikatz referred to as mim221, which packs in new anti-detection features.
"The use of special-purpose modules that implement a range of advanced techniques shows the threat actors' dedication to advancing its toolset towards maximum stealth," the researchers said, adding it "highlights the continuous maintenance and further development of the Chinese espionage malware arsenal."
The attacks ultimately proved to be unsuccessful, with the breaches detected and blocked before any implants could be deployed on the target networks.
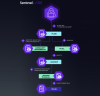
Prior research into Gallium suggests tactical similarities [PDF] with multiple Chinese nation-state groups such as APT10 (aka Bronze Riverside, Potassium, or Stone Panda), APT27 (aka Bronze Union, Emissary Panda, or Lucky Mouse), and APT41 (aka Barium, Bronze Atlas, or Wicked Panda).
This once again points to signs of closed-source tool-sharing between Chinese state-sponsored threat actors, not to mention the possibility of a "digital quartermaster" responsible for maintaining and distributing the toolset.
The findings come amid revelations that various other hacking groups, including BackdoorDiplomacy and WIP26, have set their sights on telecom service providers in the Middle East region.
"Chinese cyber espionage threat actors are known to have a strategic interest in the Middle East," the researchers concluded.
"These threat actors will almost certainly continue exploring and upgrading their tools with new techniques for evading detection, including integrating and modifying publicly available code."
German and South Korean Agencies Warn of Kimsuky's Expanding Cyber Attack Tactics
23.3.23 APT The Hacker News
German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes.
The joint advisory comes from Germany's domestic intelligence apparatus, the Federal Office for the Protection of the Constitution (BfV), and South Korea's National Intelligence Service of the Republic of Korea (NIS).
The intrusions are designed to strike "experts on the Korean Peninsula and North Korea issues" through spear-phishing campaigns, the agencies noted.
Kimsuky, also known Black Banshee, Thallium, and Velvet Chollima, refers to a subordinate element within North Korea's Reconnaissance General Bureau and is known to "collect strategic intelligence on geopolitical events and negotiations affecting the DPRK's interests."
Primary targets of interest include entities in the U.S. and South Korea, particularly singling out individuals working within the government, military, manufacturing, academic, and think tank organizations.
"This threat actor's activities include collecting financial, personal, and client data specifically from academic, manufacturing, and national security industries in South Korea," Google-owned threat intelligence firm Mandiant disclosed last year.
Recent attacks orchestrated by the group suggest an expansion of its cyber activity to encompass Android malware strains such as FastFire, FastSpy, FastViewer, and RambleOn.
The use of Chromium-based browser extensions for cyber espionage purposes is not new for Kimsuky, which has previously used similar techniques as part of campaigns tracked as Stolen Pencil and SharpTongue.

The SharpTongue operation also overlaps with the latest effort in that the latter is also capable of stealing a victim's email content using the rogue add-on, which, in turn, leverages the browser's DevTools API to perform the function.
But in an escalation of Kimsuky's mobile attacks, the threat actor has been observed logging into victims' Google accounts using credentials already obtained in advance through phishing tactics and then installing a malicious app on the devices linked to the accounts.
"The attacker logs in with the victim's Google account on the PC, accesses the Google Play Store, and requests the installation of a malicious app," the agencies explained. "At this time, the target's smartphone linked with the Google account is selected as the device to install the malicious app on."
It's suspected that the apps, which embed FastFire and FastViewer, are distributed using a Google Play feature known as "internal testing" that allows third-party developers to distribute their apps to a "small set of trusted testers."
A point worth mentioning here is that these internal app tests, which are carried out prior to releasing the app to production, cannot exceed 100 users per app, indicating that the campaign is extremely targeted in nature.
Both the malware-laced apps come with capabilities to harvest a wide range of sensitive information by abusing Android's accessibility services. The apps' APK package names are listed below -
com.viewer.fastsecure (FastFire)
com.tf.thinkdroid.secviewer (FastViewer)
The disclosure comes as the North Korean advanced persistent threat (APT) actor dubbed ScarCruft has been linked to different attack vectors that are employed to deliver PowerShell-based backdoors onto compromised hosts.
Winter Vivern APT Group Targeting Indian, Lithuanian, Slovakian, and Vatican Officials
17.3.23 APT The Hacker News
The advanced persistent threat known as Winter Vivern has been linked to campaigns targeting government officials in India, Lithuania, Slovakia, and the Vatican since 2021.
The activity targeted Polish government agencies, the Ukraine Ministry of Foreign Affairs, the Italy Ministry of Foreign Affairs, and individuals within the Indian government, SentinelOne said in a report shared with The Hacker News.
"Of particular interest is the APT's targeting of private businesses, including telecommunications organizations that support Ukraine in the ongoing war," senior threat researcher Tom Hegel said.
Winter Vivern, also tracked as UAC-0114, drew attention last month after the Computer Emergency Response Team of Ukraine (CERT-UA) detailed a new malware campaign aimed at state authorities of Ukraine and Poland to deliver a piece of malware dubbed Aperetif.
Previous public reports chronicling the group show that it has leveraged weaponized Microsoft Excel documents containing XLM macros to deploy PowerShell implants on compromised hosts.
While the origins of the threat actor are unknown, the attack patterns suggest that the cluster is aligned with objectives that support the interests of Belarus and Russia's governments.
UAC-0114 has employed a variety of methods, ranging from phishing websites to malicious documents, that are tailored to the targeted organization to distribute its custom payloads and gain unauthorized access to sensitive systems.
In one batch of attacks observed in mid-2022, Winter Vivern set up credential phishing web pages to lure users of the Indian government's legitimate email service email.gov[.]in.
Typical attack chains involve using batch scripts masquerading as virus scanners to trigger the deployment of the Aperetif trojan from actor-controlled infrastructure such as compromised WordPress sites.
Aperetif, a Visual C++-based malware, comes with features to collect victim data, maintain backdoor access, and retrieve additional payloads from the command-and-control (C2) server.
"The Winter Vivern APT is a resource-limited but highly creative group that shows restraint in the scope of their attacks," Hegel said.
"Their ability to lure targets into the attacks, and their targeting of governments and high-value private businesses demonstrate the level of sophistication and strategic intent in their operations."
While Winter Vivern may have managed to evade the public eye for extended periods of time, one group that's not too concerned about staying under the radar is Nobelium, which shares overlaps with APT29 (aka BlueBravo, Cozy Bear, or The Dukes).
The Kremlin-backed nation-state group, notorious for the SolarWinds supply chain compromise in December 2020, has continued to evolve its toolset, developing new custom malware like MagicWeb and GraphicalNeutrino.
It has also been attributed to yet another phishing campaign directed against diplomatic entities in the European Union, with specific emphasis on agencies that are "aiding Ukrainian citizens fleeing the country, and providing help to the government of Ukraine."
"Nobelium actively collects intelligence information about the countries supporting Ukraine in the Russia-Ukraine war," BlackBerry said. "The threat actors carefully follow geopolitical events and use them to increase their possibility of a successful infection."
The phishing emails, spotted by the company's research and intelligence team, contain a weaponized document that includes a link pointing to an HTML file.
The weaponized URLs, hosted on a legitimate online library website based in El Salvador, features lures related to LegisWrite and eTrustEx, both of which are used by E.U. nations for secure document exchange.
The HTML dropper (dubbed ROOTSAW or EnvyScout) delivered in the campaign embeds an ISO image, which, in turn, is designed to launch a malicious dynamic link library (DLL) that facilitates the delivery of a next-stage malware via Notion's APIs.
The use of Notion, a popular note-taking application, for C2 communications was previously revealed by Recorded Future in January 2023. It's worth noting that APT29 has employed various online services like Dropbox, Google Drive, Firebase, and Trello in an attempt to evade detection.
"Nobelium remains highly active, executing multiple campaigns in parallel targeting government organizations, non-governmental organizations (NGOs), intergovernmental organizations (IGOs), and think tanks across the U.S., Europe, and Central Asia," Microsoft stated last month.
The findings also come as enterprise security firm Proofpoint disclosed aggressive email campaigns orchestrated by a Russia-aligned threat actor called TA499 (aka Lexus and Vovan) since early 2021 to trick targets into participating in recorded phone calls or video chats and extract valuable information.
"The threat actor has engaged in steady activity and expanded its targeting to include prominent businesspeople and high-profile individuals that have either made large donations to Ukrainian humanitarian efforts or those making public statements about Russian disinformation and propaganda," the company said.
Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection
17.3.23 APT The Hacker News
Threat activity clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware that's designed to load Cobalt Strike onto infected machines.
Dubbed SILKLOADER by Finnish cybersecurity company WithSecure, the malware leverages DLL side-loading techniques to deliver commercial adversary simulation software.
The development comes as improved detection capabilities against Cobalt Strike, a legitimate post-exploitation tool used for red team operations, is forcing threat actors to seek alternative options or concoct new ways to propagate the framework to evade detection.
"The most common of these include adding complexity to the auto-generated beacon or stager payloads via the utilization of packers, crypters, loaders, or similar techniques," WithSecure researchers said.
SILKLOADER joins other loaders such as KoboldLoader, MagnetLoader, and LithiumLoader that have been recently discovered incorporating Cobalt Strike components.
It also shares overlaps with LithiumLoader in that both employ the DLL side-loading method to hijack a legitimate application with the goal of running a separate, malicious dynamic link library (DLL).
SILKLOADER achieves this via specially crafted libvlc.dll files that are dropped alongside a legitimate but renamed VLC media player binary (Charmap.exe).
"Cobalt Strike beacons are very well known and detections against them on a well-protected machine are all but guaranteed," WithSecure researcher Hassan Nejad said.
"However, by adding additional layers of complexity to the file content and launching it through a known application such as VLC Media Player via side-loading, the attackers hope to evade these defense mechanisms."
WithSecure said it identified the shellcode loader following an analysis of "several human-operated intrusions" targeting various entities spanning a wide range of organizations located in Brazil, France, and Taiwan in Q4 2022.
Although these attacks were unsuccessful, the activity is suspected to be a lead-up to ransomware deployments, with the tactics and tooling "heavily overlapping" with those attributed to the operators of the Play ransomware.
In one attack aimed at an unnamed French social welfare organization, the threat actor gained a foothold into the network by exploiting a compromised Fortinet SSL VPN appliance to stage Cobalt Strike beacons.
"The threat actor maintained a foothold in this organization for several months," WithSecure said. "During this time, they performed discovery and credential stealing activities, followed by deployment of multiple Cobalt Strike beacons."
But when this attempt failed, the adversary switched to using SILKLOADER to bypass detection and deliver the beacon payload.
That's not all. Another loader known as BAILLOADER, which is also used to distribute Cobalt Strike beacons, has been linked to attacks involving Quantum ransomware, GootLoader, and the IcedID trojan in recent months.
BAILLOADER, for its part, is said to exhibit similarities with a crypter codenamed Tron that has been put to use by different adversaries to distribute Emotet, TrickBot, BazarLoader, IcedID, Conti ransomware, and Cobalt Strike.
This has given rise to the possibility that disparate threat actors are sharing Cobalt Strike beacons, crypters, and infrastructure provided by third-party affiliates to service multiple intrusions utilizing different tactics.
In other words, SILKLOADER is likely being offered as an off-the-shelf loader through a Packer-as-a-Service program to Russian-based threat actors.
"This loader is being provided either directly to ransomware groups or possibly via groups offering Cobalt Strike/Infrastructure-as-a-Service to trusted affiliates," WithSecure said.
"Most of these affiliates appear to have been part of or have had close working relationships with the Conti group, its members, and offspring after its alleged shutdown."
SILKLOADER samples analyzed by the company show that early versions of the malware date back to the start of 2022, with the loader exclusively put to use in different attacks targeting victims in China and Hong Kong.
The shift from East Asian targets to other countries such as Brazil and France is believed to have occurred around July 2022, after which all SILKLOADER-related incidents have been attributed to Russian cybercriminal actors.
This has further given way to a hypothesis that "SILKLOADER was originally written by threat actors acting within the Chinese cybercriminal ecosystem" and that the "loader was used by the threat actors within this nexus at least as early as May 2022 till July 2022."
"The builder or source code was later acquired by a threat actor within the Russian cybercriminal ecosystem between July 2022 and September 2022," WithSecure said, adding, "the original Chinese author sold the loader to a Russian threat actor once they no longer had any use for it."
Both SILKLOADER and BAILLOADER are just the latest examples of threat actors refining and retooling their approaches to stay ahead of the detection curve.
"As the cybercriminal ecosystem becomes more and more modularized via service offerings, it is no longer possible to attribute attacks to threat groups simply by linking them to specific components within their attacks," WithSecure researchers concluded.
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company
15.3.23 APT The Hacker News
A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention (DLP) company that caters to government and military entities.
"The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, and trojanized installers of legitimate tools used by the company, which eventually resulted in the execution of malware on the computers of the company's customers," ESET researcher Facundo Muñoz said.
Tick, also known as Bronze Butler, REDBALDKNIGHT, Stalker Panda, and Stalker Taurus, is a suspected China-aligned collective that has primarily gone after government, manufacturing, and biotechnology firms in Japan. It's said to be active since at least 2006.
Other lesser-known targets include Russian, Singaporean, and Chinese enterprises. Attack chains orchestrated by the group have typically leveraged spear-phishing emails and strategic web compromises as an entry point.
In late February 2021, Tick emerged as one of the threat actors to capitalize on the ProxyLogon flaws in Microsoft Exchange Server as a zero-day to drop a Delphi-based backdoor in a web server belonging to a South Korean IT company.
Around the same time, the adversarial collective is believed to have gained access to the network of an East Asian software developer company through unknown means. The name of the company was not disclosed.
This was followed by the deployment of a tampered version of a legitimate application called Q-Dir to drop an open source VBScript backdoor named ReVBShell, in addition to a previously undocumented downloader named ShadowPy.
ShadowPy, as the name indicates, is a Python downloader that's responsible for executing a Python script retrieved from a remote server.
Also delivered during the intrusion were variants of a Delphi backdoor called Netboy (aka Invader or Kickesgo) that comes with information gathering and reverse shell capabilities as well as another downloader codenamed Ghostdown.
"To maintain persistent access, the attackers deployed malicious loader DLLs along with legitimate signed applications vulnerable to DLL search-order hijacking," Muñoz said. "The purpose of these DLLs is to decode and inject a payload into a designated process."
Subsequently, in February and June 2022, the trojanized Q-Dir installers were transferred via remote support tools like helpU and ANYSUPPORT to two of the company's customers, an engineering and a manufacturing firm located in East Asia.
The Slovak cybersecurity company said the goal here was not to perform a supply chain attack against its downstream customers, but rather that the rogue installer was "unknowingly" used as part of technical support activities.
The incident is also likely related to another unattributed cluster detailed by AhnLab in May 2022 that involved the use of Microsoft Compiled HTML Help (.CHM) files to drop the ReVBShell implant.
KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets
13.3.23 APT The Hacker News

The Dark Pink advanced persistent threat (APT) actor has been linked to a fresh set of attacks targeting government and military entities in Southeast Asian countries with a malware called KamiKakaBot.
Dark Pink, also called Saaiwc, was extensively profiled by Group-IB earlier this year, describing its use of custom tools such as TelePowerBot and KamiKakaBot to run arbitrary commands and exfiltrate sensitive information.
The threat actor is suspected to be of Asia-Pacific origin and has been active since at least mid-2021, with an increased tempo observed in 2022.
"The latest attacks, which took place in February 2023, were almost identical to previous attacks," Dutch cybersecurity company EclecticIQ disclosed in a new report published last week.
"The main difference in the February campaign is that the malware's obfuscation routine has improved to better evade anti-malware measures."
The attacks play out in the form of social engineering lures that contain ISO image file attachments in email messages to deliver the malware.
The ISO image includes an executable (Winword.exe), a loader (MSVCR100.dll), and a decoy Microsoft Word document, the latter of which comes embedded with the KamiKakaBot payload.

The loader, for its part, is designed to load the KamiKakaBot malware by leveraging the DLL side-loading method to evade security protections and load it into the memory of the Winword.exe binary.
KamiKakaBot is primarily engineered to steal data stored in web browsers and execute remote code using Command Prompt (cmd.exe), while also embracing evasion techniques to blend in with victim environments and hinder detection.
Persistence on the compromised host is achieved by abusing the Winlogon Helper library to make malicious Windows Registry key modifications. The gathered data is subsequently exfiltrated to a Telegram bot as a ZIP archive.
"The use of legitimate web services as a command-and-control (C2) server, such as Telegram, remains the number one choice for different threat actors, ranging from regular cyber criminals to advanced persistent threat actors," the Amsterdam-based company said.
"The Dark Pink APT group is very likely a cyber espionage-motivated threat actor that specifically exploits relations between ASEAN and European nations to create phishing lures during the February 2023 campaign."