APT 2024 2023 2022 2021 2020
Hackers Abusing BRc4 Red Team Penetration Tool in Attacks to Evade Detection
6.7.22 APT Thehackernews
Malicious actors have been observed abusing legitimate adversary simulation software in their attacks in an attempt to stay under the radar and evade detection.
Palo Alto Networks Unit 42 said a malware sample uploaded to the VirusTotal database on May 19, 2022, contained a payload associated with Brute Ratel C4, a relatively new sophisticated toolkit "designed to avoid detection by endpoint detection and response (EDR) and antivirus (AV) capabilities."
Authored by an Indian security researcher named Chetan Nayak, Brute Ratel (BRc4) is analogous to Cobalt Strike and is described as a "customized command-and-control center for red team and adversary simulation."
The commercial software was first released in late 2020 and has since gained over 480 licenses across 350 customers. Each license is offered at $2,500 per user for a year, after which it can be renewed for the same duration at the cost of $2,250.
BRc4 is equipped with a wide variety of features, such as process injection, automating adversary TTPs, capturing screenshots, uploading and downloading files, support for multiple command-and-control channels, and the ability to keep memory artifacts concealed from anti-malware engines, among others.
The artifact, which was uploaded from Sri Lanka, masquerades as a curriculum vitae of an individual named Roshan Bandara ("Roshan_CV.iso") but in reality is an optical disc image file that, when double-clicked, mounts it as a Windows drive containing a seemingly harmless Word document that, upon launching, installs BRc4 on the user's machine and establishes communications with a remote server.
The delivery of packaged ISO files is typically sent via spear-phishing email campaigns, although it's not clear if the same method was used to deliver the payload to the target environment.

"The composition of the ISO file, Roshan_CV.ISO, closely resembles that of other nation-state APT tradecraft," Unit 42 researchers Mike Harbison and Peter Renals said, calling out similarities to that of a packaged ISO file previously attributed to Russian nation-state actor APT29 (aka Cozy Bear, The Dukes, or Iron Hemlock).
APT29 rose to notoriety last year after the state-sponsored group was blamed for orchestrating the large-scale SolarWinds supply chain attack.
The cybersecurity firm noted it also spotted a second sample that was uploaded to VirusTotal from Ukraine a day later and which exhibited code overlaps to that of a module responsible for loading BRc4 in memory. The investigation has since unearthed seven more BRc4 samples dating back to February 2021.
That's not all. By examining the C2 server that was used as a covert channel, a number of potential victims have been identified. This includes an Argentinian organization, an IP television provider providing North and South American content, and a major textile manufacturer in Mexico.
"The emergence of a new penetration testing and adversary emulation capability is significant," the researchers said. "Yet more alarming is the effectiveness of BRc4 at defeating modern defensive EDR and AV detection capabilities."
Shortly after the findings became public, Nayak tweeted that "proper actions have been taken against the found licenses which were sold in the black market," adding BRc4 v1.1 "will change every aspect of IoC found in the previous releases."
Bitter APT Hackers Continue to Target Bangladesh Military Entities
6.7.22 APT Thehackernews

Military entities located in Bangladesh continue to be at the receiving end of sustained cyberattacks by an advanced persistent threat tracked as Bitter.
"Through malicious document files and intermediate malware stages the threat actors conduct espionage by deploying Remote Access Trojans," cybersecurity firm SECUINFRA said in a new write-up published on July 5.
The findings from the Berlin-headquartered company build on a previous report from Cisco Talos in May, which disclosed the group's expansion in targeting to strike Bangladeshi government organizations with a backdoor called ZxxZ.
Bitter, also tracked under the codenames APT-C-08 and T-APT-17, is said to be active since at least late 2013 and has a track record of targeting China, Pakistan, and Saudi Arabia using different tools such as BitterRAT and ArtraDownloader.
The latest attack chain detailed by SECUINFRA is believed to have been conducted in mid-May 2022, originating with a weaponized Excel document likely distributed by means of a spear-phishing email that, when opened, exploits the Microsoft Equation Editor exploit (CVE-2018-0798) to drop the next-stage binary from a remote server.
ZxxZ (or MuuyDownloader by the Qi-Anxin Threat Intelligence Center), as the downloaded payload is called, is implemented in Visual C++ and functions as a second-stage implant that allows the adversary to deploy additional malware.
The most notable change in the malware involves abandoning the "ZxxZ" separator used when sending information back to the command-and-control (C2) server in favor of an underscore, suggesting that the group is actively making modifications to its source code to stay under the radar.
Also put to use by the threat actor in its campaigns is a backdoor dubbed Almond RAT, a .NET-based RAT that first came to light in May 2022 and offers basic data gathering functionality and the ability to execute arbitrary commands. Additionally, the implant employs obfuscation and string encryption techniques to evade detection and to hinder analysis.
"Almond RATs main purposes seem to be file system discovery, data exfiltration and a way to load more tools/establish persistence," the researchers said. "The design of the tools seems to be laid out in a way that it can be quickly modified and adapted to the current attack scenario."
APT Hackers Targeting Industrial Control Systems with ShadowPad Backdoor
28.6.22 APT Thehackernews
Entities located in Afghanistan, Malaysia, and Pakistan are in the crosshairs of an attack campaign that targets unpatched Microsoft Exchange Servers as an initial access vector to deploy the ShadowPad malware.
Russian cybersecurity firm Kaspersky, which first detected the activity in mid-October 2021, attributed it to a previously unknown Chinese-speaking threat actor. Targets include organizations in the telecommunications, manufacturing, and transport sectors.
"During the initial attacks, the group exploited an MS Exchange vulnerability to deploy ShadowPad malware and infiltrated building automation systems of one of the victims," the company said. "By taking control over those systems, the attacker can reach other, even more sensitive systems of the attacked organization."
ShadowPad, which emerged in 2015 as the successor to PlugX, is a privately sold modular malware platform that has been put to use by many Chinese espionage actors over the years.
While its design allows users to remotely deploy additional plugins that can extend its functionality beyond covert data collection, what makes ShadowPad dangerous is the anti-forensic and anti-analysis technique incorporated into the malware.
"During the attacks of the observed actor, the ShadowPad backdoor was downloaded onto the attacked computers under the guise of legitimate software," Kaspersky said. "In many cases, the attacking group exploited a known vulnerability in MS Exchange, and entered the commands manually, indicating the highly targeted nature of their campaigns."
Evidence suggests that intrusions mounted by the adversary began in March 2021, right around the time the ProxyLogon vulnerabilities in Exchange Servers became public knowledge. Some of the targets are said to have been breached by exploiting CVE-2021-26855, a server-side request forgery (SSRF) vulnerability in the mail server.
Besides deploying ShadowPad as "mscoree.dll," an authentic Microsoft .NET Framework component, the attacks also involved the use of Cobalt Strike, a PlugX variant called THOR, and web shells for remote access.
Although the final goals of the campaign remain unknown, the attackers are believed to be interested in long-term intelligence gathering.
"Building automation systems are rare targets for advanced threat actors," Kaspersky ICS CERT researcher Kirill Kruglov said. "However, those systems can be a valuable source of highly confidential information and may provide the attackers with a backdoor to other, more secured, areas of infrastructures."
New ToddyCat Hacker Group on Experts' Radar After Targeting MS Exchange Servers
21.6.22 APT Thehackernews
An advanced persistent threat (APT) actor codenamed ToddyCat has been linked to a string of attacks aimed at high-profile entities in Europe and Asia since at least December 2020.
The relatively new adversarial collective is said to have commenced its operations by targeting Microsoft Exchange servers in Taiwan and Vietnam using an unknown exploit to deploy the China Chopper web shell and activate a multi-stage infection chain.
Other prominent countries targeted include Afghanistan, India, Indonesia, Iran, Kyrgyzstan, Malaysia, Pakistan, Russia, Slovakia, Thailand, the U.K., and Uzbekistan, just as the threat actor evolved its toolset over the course of different campaigns.
"The first wave of attacks exclusively targeted Microsoft Exchange Servers, which were compromised with Samurai, a sophisticated passive backdoor that usually works on ports 80 and 443," Russian cybersecurity company Kaspersky said in a report published today.
"The malware allows arbitrary C# code execution and is used with multiple modules that allow the attacker to administrate the remote system and move laterally inside the targeted network."
ToddyCat, also tracked under the moniker Websiic by Slovak cybersecurity firm ESET, first came to light in March 2021 for its exploitation of ProxyLogon Exchange flaws to target email servers belonging to private companies in Asia and a governmental body in Europe.
The attack sequence post the deployment of the China Chopper web shell leads to the execution of a dropper that, in turn, is used to make Windows Registry modifications to launch a second-stage loader, which, for its part, is designed to trigger a third-stage .NET loader that's responsible for running Samurai.
The backdoor, besides using techniques like obfuscation and control flow flattening to make it resistant to reverse engineering, is modular in that it the components make it possible to execute arbitrary commands and exfiltrate files of interest from the compromised host.
Also observed in specific incidents is a sophisticated tool named Ninja that's spawned by the Samurai implant and likely functions as a collaborative tool allowing multiple operators to work on the same machine simultaneously.
Its feature similarities to other post-exploitation toolkits like Cobalt Strike notwithstanding, the malware enables the attacker to "control remote systems, avoid detection, and penetrate deep inside a targeted network."
Despite the fact that ToddyCat victims are related to countries and sectors traditionally targeted by Chinese-speaking groups, there is no evidence tying the modus operandi to a known threat actor.
"ToddyCat is a sophisticated APT group that uses multiple techniques to avoid detection and thereby keeps a low profile," Kaspersky security researcher Giampaolo Dedola said.
"The affected organizations, both governmental and military, show that this group is focused on very high-profile targets and is probably used to achieve critical goals, likely related to geopolitical interests."
A Decade-Long Chinese Espionage Campaign Targets Southeast Asia and Australia
9.6.22 APT Thehackernews
A previously undocumented Chinese-speaking advanced persistent threat (APT) actor dubbed Aoqin Dragon has been linked to a string of espionage-oriented attacks aimed at government, education, and telecom entities chiefly in Southeast Asia and Australia dating as far back as 2013.
"Aoqin Dragon seeks initial access primarily through document exploits and the use of fake removable devices," SentinelOne researcher Joey Chen said in a report shared with The Hacker News. "Other techniques the attacker has been observed using include DLL hijacking, Themida-packed files, and DNS tunneling to evade post-compromise detection."
The group is said to have some level of association with another threat actor known as Naikon (aka Override Panda), with campaigns primarily directed against targets in Australia, Cambodia, Hong Kong, Singapore, and Vietnam.
Infections chains mounted by Aoqin Dragon have banked on Asia-Pacific political affairs and pornographic-themed document lures as well as USB shortcut techniques to trigger the deployment of one of two backdoors: Mongall and a modified version of the open-source Heyoka project.
This involved leveraging old and unpatched security vulnerabilities (CVE-2012-0158 and CVE-2010-3333), with the decoy documents enticing targets into opening the files. Over the years, the threat actor also employed executable droppers masquerading as antivirus software to deploy the implant and connect to a remote server.
"Although executable files with fake file icons have been in use by a variety of actors, it remains an effective tool especially for APT targets," Chen explained. "Combined with 'interesting' email content and a catchy file name, users can be socially engineered into clicking on the file."
That said, Aoqin Dragon's newest initial access vector of choice since 2018 has been its use of a fake removable device shortcut file (.LNK), which , when clicked, runs an executable ("RemovableDisc.exe") that sports the icon for the popular note-taking app Evernote but is engineered to function as a loader for two different payloads.
One of the components in the infection chain is a spreader that copies all malicious files to other removable devices and the second module is an encrypted backdoor that injects itself into rundll32's memory, a native Windows process used to load and run DLL files.
Known to be used since at least 2013, Mongall ("HJ-client.dll") is described as a not-so "particularly feature rich" implant but one that packs enough features to create a remote shell and upload and download arbitrary files to and from the attacker-control server.
Also used by the adversary is a reworked variant of Heyoka ("srvdll.dll"), a proof-of-concept (PoC) exfiltration tool "which uses spoofed DNS requests to create a bidirectional tunnel." The modified Heyoka backdoor is more powerful, equipped with capabilities to create, delete, and search for files, create and terminate processes, and gather process information on a compromised host.
"Aoqin Dragon is an active cyber espionage group that has been operating for nearly a decade," Chen said, adding, "it is likely they will also continue to advance their tradecraft, finding new methods of evading detection and stay longer in their target network."
WinDealer dealing on the side
6.6.22 APT Securelist
LuoYu is a lesser-known threat actor that has been active since 2008. It primarily goes after targets located in China, such as foreign diplomatic organizations established in the country, members of the academic community, or companies from the defense, logistics and telecommunications sectors. In their initial disclosures on this threat actor, TeamT5 identified three malware families: SpyDealer, Demsty and WinDealer. The actor behind these families is capable of targeting Windows, Linux and macOS machines, as well as Android devices.
In previous years, Kaspersky investigated LuoYu’s activities and was able to confirm the connection between Demsty and WinDealer. On January 27, we delivered a joint presentation with TeamT5 and ITOCHU Corporation at Japan Security Analyst Conference (JSAC) to provide an update on the actor’s latest activities. In this article, we will focus on one of the most groundbreaking developments: the fact that LuoYu has the ability to perform man-on-the-side attacks.
Delivery method
In the past, LuoYu used watering-hole attacks (for instance, on local news websites) to infect their targets. Seeing that some variants of their Android malware impersonate a popular messaging app in Asia, it is also likely that malicious APKs are distributed in a variety of ways, including social engineering to convince users to install fake updates for their applications.
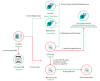
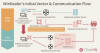
In 2020, we discovered a whole new distribution method for the WinDealer malware that leverages the automatic update mechanism of select legitimate applications. In one case we investigated, we noticed that a signed executable qgametool.exe (MD5 f756083b62ba45dcc6a4d2d2727780e4), compiled in 2012, deployed WinDealer on a target machine. This program contains a hardcoded URL that it uses to check for updates, as shown in the following screenshot:

Update URL hardcoded in qgametool.exe
The executable located at this URL (hxxp://download.pplive[.]com/PPTV(pplive)_forap_1084_9993.exe, MD5 270902c6bb6844dc25ffaec801393245) is benign, but our telemetry shows that on rare occasions, a WinDealer sample (MD5 ce65092fe9959cc0ee5a8408987e3cd4) is delivered instead.

Observed WinDealer infection flow
We also identified online message board posts where Chinese-speaking users reported the discovery of malware under the same name – PPTV(pplive)_forap_1084_9993.exe – on their machine. The posted information was complete enough for us to confirm that they had indeed received a sample of WinDealer.
Leaving the mystery of the delivery method aside for now, let’s look at the capabilities of the malware itself.
WinDealer’s technical description
WinDealer is a modular malware platform. It starts execution by locating an embedded DLL file placed in its resources by looking for a hardcoded pattern, and proceeds to decode it using a 10-byte XOR key.
Layout of the encrypted data
WinDealer’s logic is spread over the initial EXE and its companion DLL: the former contains the setup of the program as well as network communications, while the orders sent by the C2 are implemented in the latter. The malware possesses the following capabilities:
File and file system manipulation: reading, writing and deleting files, listing directories, obtaining disk information;
Information gathering: collecting hardware details, network configuration and/or keyboard layout, listing running processes, installed applications and configuration files of popular messaging applications (Skype, QQ, WeChat and Wangwang);
Download and upload of arbitrary files;
Arbitrary command execution;
System-wide search across text files and Microsoft Word documents;
Screenshot capture;
Network discovery via ping scan;
Backdoor maintenance: set up or remove persistence (via the registry’s RUN key), configuration updates.
A variant we discovered (MD5 26064e65a7e6ce620b0ff7b4951cf340) also featured the ability to list available Wi-Fi networks. Overall, WinDealer is able to collect an impressive amount of information, even when compared to other malware families. And yet, the most extraordinary aspect of WinDealer lies elsewhere.
The impossible infrastructure
The latest WinDealer sample we discovered in 2020 doesn’t contain a hardcoded C2 server but instead relies on a complex IP generation algorithm to determine which machine to contact. The details of this algorithm are left as an exercise to the reader, but the end result is that the IP address is selected at random from one of these two ranges:
113.62.0.0/15 (AS4134, CHINANET XIZANG PROVINCE NETWORK)
111.120.0.0/14 (AS4134, CHINANET GUIZHOU PROVINCE NETWORK)
Once the IP address has been selected, communications take place either over UDP port 6999 or TCP port 55556. In an even weirder twist, a research partner shared with us an additional WinDealer sample (MD5 d9a6725b6a2b38f96974518ec9e361ab) that communicates with the hardcoded URL “http://www[.]microsoftcom/status/getsign.asp”. This domain is obviously invalid and cannot resolve to anything in normal circumstances – yet the malware expects a response in a predetermined format (“\x11\x22\x??\x33\x44”).
Packets exchanged with the C2 server contain a header (described in the next table) followed by AES-encrypted data. They leverage a homemade binary protocol containing magic numbers and flags, making it easy to recognize and filter packets on a large scale.
Offset
Description
Sample value (in hex)
0x00 Magic number 06 81 DA 91 CE C7 9F 43
0x08 Target identifier 57 5B 73 B2
0x0C Flag set by the attacker. Its exact meaning remains unclear 00 or 0B or 16
0x0D Connection type or backdoor command identifier
0 = initial connection
1 = subsequent connection
Others = backdoor command identifiers 00
0x0E Unknown static value 14
0x0F Unknown value 00
0x10 Payload
Initial connection: the generated AES key and its CRC32, encrypted using RSA-2048 with a hardcoded public key.
All other packets: payload size followed by encrypted payload using AES-128 in ECB mode with the generated AES key. 03 4D 5D 44 C3 1E 0A DA
A3 4A 86 A3 CC ED 67 38
…
The man-on-the-side attack
Putting all the pieces together, WinDealer’s infrastructure is nothing short of extraordinary:
It appears to be distributed via plain HTTP requests that normally return legitimate executables.
It communicates with IP addresses selected randomly inside a specific AS.
It can interact with non-existent domain names.
It is very hard to believe that an attacker would be able to control the 48,000 IP addresses of the aforementioned IP ranges, or even a significant portion of them. The only way to explain these seemingly impossible network behaviors is by assuming the existence of a man-on-the-side attacker who is able to intercept all network traffic and even modify it if needed.
Such capabilities are not unheard of: the QUANTUM program revealed in 2014 was the first known instance. The general idea is that when the attacker sees a request for a specific resource on the network, it tries to reply to the target faster than the legitimate server. If the attacker wins the “race”, the target machine will use the attacker-supplied data instead of the normal data. This is consistent with the scenario described earlier in this article, where the target receives an infected executable instead of the normal one. Automatic updaters are prime targets for such attacks as they perform frequent requests – it doesn’t matter if the attackers don’t win most races, as they can try again until they succeed, guaranteeing that they will infect their targets eventually. This class of attack is particularly devastating because there is nothing users can do to protect themselves, apart from routing traffic through another network. This can be done with the use of a VPN, but these may be illegal depending on the jurisdiction and would typically not be available to Chinese-speaking targets.
Confirming our assessment, we later discovered a downloader utility (MD5 4e07a477039b37790f7a8e976024eb66) that uses the same unique user-agent as WinDealer samples we analyzed (“BBB”), tying it weakly to LuoYu.

A downloader utility and WinDealer of 2021 use the unique user-agent “BBB”
The downloader periodically retrieves and runs an executable from hxxp://www.baidu[.]com/status/windowsupdatedmq.exe. This URL normally returns a 404 error and we consider it extremely unlikely that the attackers have control over this domain.
Based on all the evidence laid out above, we speculate that the attackers may have the following capabilities over AS4134:
Intercepting all network traffic, which allows them to receive backdoor responses to random IP addresses without having to deploy actual C2 servers.
Injecting arbitrary TCP and UDP packets on the network, a capability through which they can send orders to WinDealer.
Full control over the DNS, meaning they can provide responses for non-existent domains.
Either QUANTUMINSERT capabilities or the ability to modify the contents of HTTP packets on the fly, thanks to which they can achieve remote, zero-click malware installation by abusing auto-update mechanisms. One noteworthy observation is that the attackers specifically target plain HTTP sessions, indicating that they may not have the ability to break or downgrade HTTPS.
WinDealer’s targets
Our analysis of WinDealer reveals that it specifically looks for popular applications in Asia, such as QQ, WeChat and WangWang. It also contains references to registry keys created by Sogou programs. This indicates to us that the LuoYu APT is predominantly focused on Chinese-speaking targets and organizations related to China. Our telemetry confirms that the vast majority of LuoYu targets are located in China, with occasional infections in other countries such as Germany, Austria, the United States, Czech Republic, Russia and India.
In recent months, LuoYu has started to widen its scope to companies and users in East Asia and their branches located in China.
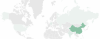
Geographic distribution of WinDealer targets
Conclusion
With this report, we recognize LuoYu as an extremely sophisticated threat actor able to leverage capabilities available only to the most mature attackers. We can only speculate as to how they were able to obtain such capabilities. They could have compromised routers on the route to (or inside) AS4134. Alternatively, they may use signals intelligence methods unknown to the general public. They may even have access (legitimate or fraudulent) to law enforcement tools set up at the ISP level and are abusing them to perform offensive operations. Overall, a threat actor is leveraging capabilities that could be compared (but are distinct) from the QUANTUMINSERT program in order to infect targets located in China.
Man-on-the-side attacks are devastating because they do not require any interaction with the target to lead to a successful infection: simply having a machine connected to the internet is enough. They can only be detected through careful network monitoring, which is outside of the realm of everyday users, or if an endpoint security program catches the payload when it is deployed on the attacked computer.
Whatever the case, the only way for potential targets to defend against such intrusions is to remain extremely vigilant and have robust security procedures involving regular antivirus scans, analysis of outbound network traffic and extensive logging to detect anomalies.
Indicators of Compromise
WinDealer samples
MD5: ce65092fe9959cc0ee5a8408987e3cd4
SHA-1: 87635d7632568c98c0091d4a53680fd920096327
SHA-256: 27c51026b89c124a002589c24cd99a0c116afd73c4dc37f013791f757ced7b7e
MD5: 0c8663bf912ef4d69a1473597925feeb
SHA-1: 78294dfc4874b54c870b8daf7c43cfb5d8c211d0
SHA-256: db034aeb3c72b75d955c02458ba2991c99033ada444ebed4e2a1ed4c9326c400
MD5: 1bd4911ea9eba86f7745f2c1a45bc01b
SHA-1: f64c63f6e17f082ea254f0e56a69b389e35857fd
SHA-256: 25cbfb26265889754ccc5598bf5f21885e50792ca0686e3ff3029b7dc4452f4d
MD5: 5a7a90ceb6e7137c753d8de226fc7947
SHA-1: 204a603c409e559b65c35208200a169a232da94c
SHA-256: 1e9fc7f32bd5522dd0222932eb9f1d8bd0a2e132c7b46cfcc622ad97831e6128
MD5: 73695fc3868f541995b3d1cc4dfc1350
SHA-1: 158c7382c88e10ab0208c9a3c72d5f579b614947
SHA-256: ea4561607c00687ea82b3365de26959f1adb98b6a9ba64fa6d47a6c19f22daa4
MD5: 76ba5272a17fdab7521ea21a57d23591
SHA-1: 6b831413932a394bd9fb25e2bbdc06533821378c
SHA-256: ecd001aeb6bcbafb3e2fda74d76eea3c0ddad4e6e7ff1f43cd7709d4b4580261
MD5: 8410893f1f88c5d9ab327bc139ff295d
SHA-1: 64a1785683858d8b6f4e7e2b2fac213fb752bae0
SHA-256: 318c431c56252f9421c755c281db7bd99dc1efa28c44a8d6db4708289725c318
MD5: cc7207f09a6fe41c71626ad4d3f127ce
SHA-1: 84e749c37978f9387e16fab29c7b1b291be93a63
SHA-256: 28df5c75a2f78120ff96d4a72a3c23cee97c9b46c96410cf591af38cb4aed0fa
MD5: e01b393e8897ed116ba9e0e87a4b1da1
SHA-1: 313b231491408bd107cecf0207868336f26d79ba
SHA-256: 4a9b37ca2f90bfa90b0b8db8cc80fe01d154ba88e3bc25b00a7f8ff6c509a76f
MD5: ef25d934d12684b371a17c76daf3662c
SHA-1: b062773bdd9f8433cbd6e7642226221972ecd4e1
SHA-256: 08530e8280a93b8a1d51c20647e6be73795ef161e3b16e22e5e23d88ead4e226
MD5: faa8eaed63c4e9f212ef81e2365dd9e8
SHA-1: 0d3a5725b6f740929b51f9a8611b4f843e2e07b1
SHA-256: b9f526eea625eec1ddab25a0fc9bd847f37c9189750499c446471b7a52204d5a
Chinese LuoYu Hackers Using Man-on-the-Side Attacks to Deploy WinDealer Backdoor
4.6.22 APT Thehackernews

An "extremely sophisticated" Chinese-speaking advanced persistent threat (APT) actor dubbed LuoYu has been observed using a malicious Windows tool called WinDealer that's delivered by means of man-on-the-side attacks.
"This groundbreaking development allows the actor to modify network traffic in-transit to insert malicious payloads," Russian cybersecurity company Kaspersky said in a new report. "Such attacks are especially dangerous and devastating because they do not require any interaction with the target to lead to a successful infection."
Known to be active since 2008, organizations targeted by LuoYu are predominantly foreign diplomatic organizations established in China and members of the academic community as well as financial, defense, logistics, and telecommunications companies.
LuoYu's use of WinDealer was first documented by Taiwanese cybersecurity firm TeamT5 at the Japan Security Analyst Conference (JSAC) in January 2021. Subsequent attack campaigns have used the malware to target Japanese entities, with isolated infections reported in Austria, Germany, India, Russia, and the U.S.
Other tools that are part of the adversary's malware arsenal include PlugX and its successor ShadowPad, both of which have been used by a variety of Chinese threat actors to enable their strategic objectives. Additionally, the actor is known to target Linux, macOS, and Android devices.
WinDealer, for its part, has been delivered in the past via websites that act as watering holes and in the form of trojanized applications masquerading as instant messaging and video hosting services like Tencent QQ and Youku.
But the infection vector has since been traded for another distribution method that makes use of the automatic update mechanism of select legitimate applications to serve a compromised version of the executable on "rare occasions."
WinDealer, a modular malware platform at its core, comes with all the usual bells and whistles associated with a traditional backdoor, allowing it to hoover sensitive information, capture screenshots, and execute arbitrary commands.
But where it also stands apart is its use of a complex IP generation algorithm to select a command-and-control (C2) server to connect to at random from a pool of 48,000 IP addresses.
"The only way to explain these seemingly impossible network behaviors is by assuming the existence of a man-on-the-side attacker who is able to intercept all network traffic and even modify it if needed," the company said.
A man-on-the-side attack, similar to a man-in-the-middle attack, enables a rogue interloper to read and inject arbitrary messages into a communications channel, but not modify or delete messages sent by other parties.
Such intrusions typically bank on strategically timing their messages such that the malicious reply containing the attacker-supplied data is sent in response to a victim's request for a web resource before the actual response from the server.
The fact that the threat actor is able to control such a massive range of IP addresses could also explain the hijacking of the update mechanism associated with genuine apps to deliver the WinDealer payload, Kaspersky pointed out.
"Man-on-the-side-attacks are extremely destructive as the only condition needed to attack a device is for it to be connected to the internet," security researcher Suguru Ishimaru said.
"No matter how the attack has been carried out, the only way for potential victims to defend themselves is to remain extremely vigilant and have robust security procedures, such as regular antivirus scans, analysis of outbound network traffic, and extensive logging to detect anomalies."
SideWinder Hackers Use Fake Android VPN Apps to Target Pakistani Entities
3.6.22 APT Thehackernews
The threat actor known as SideWinder has added a new custom tool to its arsenal of malware that's being used in phishing attacks against Pakistani public and private sector entities.
"Phishing links in emails or posts that mimic legitimate notifications and services of government agencies and organizations in Pakistan are primary attack vectors of the gang," Singapore-headquartered cybersecurity company Group-IB said in a Wednesday report.
SideWinder, also tracked under the monikers Hardcore Nationalist, Rattlesnake, Razor Tiger, and T-APT-04, has been active since at least 2012 with a primary focus on Pakistan and other Central Asian countries like Afghanistan, Bangladesh, Nepal, Singapore, and Sri Lanka.
Last month, Kaspersky attributed to this group over 1,000 cyber attacks that took place in the past two years, while calling out its persistence and sophisticated obfuscation techniques.
The threat actor's modus operandi involves the use of spear-phishing emails to distribute malicious ZIP archives containing RTF or LNK files, which download an HTML Application (HTA) payload from a remote server.
This is achieved by embedding fraudulent links that are designed to mimic legitimate notifications and services of government agencies and organizations in Pakistan, with the group also setting up lookalike websites posing as government portals to harvest user credentials.
The custom tool identified by Group-IB, dubbed SideWinder.AntiBot.Script, acts as a traffic direction system diverting Pakistani users clicking on the phishing links to rogue domains.
Should a user, whose client's IP address differs from Pakistan's, click on the link, the AntiBot script redirects to an authentic document located on a legitimate server, indicating an attempt to geofence its targets.
"The script checks the client browser environment and, based on several parameters, decides whether to issue a malicious file or redirect to a legitimate resource," the researchers said.
Of special mention is a phishing link that downloads a VPN application called Secure VPN ("com.securedata.vpn") from the official Google Play store in an attempt to impersonate the legitimate Secure VPN app ("com.securevpn.securevpn").
While the exact purpose of the fake VPN app remains unclear, this is not the first time SideWinder has sneaked past Google Play Store protections to publish rogue apps under the pretext of utility software.
In January 2020, Trend Micro detailed three malicious apps that were disguised as photography and file manager tools that leveraged a security flaw in Android (CVE-2019-2215) to gain root privileges as well as abuse accessibility service permissions to harvest sensitive information.
SideWinder Hackers Launched Over a 1,000 Cyber Attacks Over the Past 2 Years
1.6.22 APT Thehackernews
An "aggressive" advanced persistent threat (APT) group known as SideWinder has been linked to over 1,000 new attacks since April 2020.
"Some of the main characteristics of this threat actor that make it stand out among the others, are the sheer number, high frequency and persistence of their attacks and the large collection of encrypted and obfuscated malicious components used in their operations," cybersecurity firm Kaspersky said in a report that was presented at Black Hat Asia this month.
SideWinder, also called Rattlesnake or T-APT-04, is said to have been active since at least 2012 with a track record of targeting military, defense, aviation, IT companies, and legal firms in Central Asian countries such as Afghanistan, Bangladesh, Nepal, and Pakistan.
Kaspersky's APT trends report for Q1 2022 published late last month revealed that the threat actor is actively expanding the geography of its targets beyond its traditional victim profile to other countries and regions, including Singapore.
SideWinder has also been observed capitalizing on the ongoing Russo-Ukrainian war as a lure in its phishing campaigns to distribute malware and steal sensitive information.
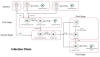
The adversarial collective's infection chains are notable for incorporating malware-rigged documents that take advantage of a remote code vulnerability in the Equation Editor component of Microsoft Office (CVE-2017-11882) to deploy malicious payloads on compromised systems.
Furthermore, SideWinder's toolset employs several sophisticated obfuscation routines, encryption with unique keys for each malicious file, multi-layer malware, and splitting command-and-control (C2) infrastructure strings into different malware components.
The three-stage infection sequence commences with the rogue documents dropping a HTML Application (HTA) payload, which subsequently loads a .NET-based module to install a second-stage HTA component that's designed to deploy a .NET-based installer.
This installer, in the next phase, is both responsible for establishing persistence on the host and loading the final backdoor in memory. The implant, for its part, is capable of harvesting files of interest as well as system information, among others.
No fewer than 400 domains and subdomains have been put to use by the threat actor over the past two years. To add an additional layer of stealth, the URLs used for C2 domains are sliced into two parts, the first portion of which is included in the .NET installer and the latter half is encrypted inside the second stage HTA module.
"This threat actor has a relatively high level of sophistication using various infection vectors and advanced attack techniques," Noushin Shabab of Kaspersky said, urging that organizations use up-to-date versions of Microsoft Office to mitigate such attacks.
Chinese "Twisted Panda" Hackers Caught Spying on Russian Defense Institutes
23.5.22 APT Thehackernews
At least two research institutes located in Russia and a third likely target in Belarus have been at the receiving end of an espionage attack by a Chinese nation-state advanced persistent threat (APT).
The attacks, codenamed "Twisted Panda," come in the backdrop of Russia's military invasion of Ukraine, prompting a wide range of threat actors to swiftly adapt their campaigns on the ongoing conflict to distribute malware and stage opportunistic attacks.
They have materialized in the form of social engineering schemes with topical war and sanctions-themed baits orchestrated to trick potential victims into clicking malicious links or opening weaponized documents.
Israeli cybersecurity firm Check Point, which disclosed details of the latest intelligence-gathering operation, attributed it a Chinese threat actor, with connections to that of Stone Panda (aka APT 10, Cicada, or Potassium) and Mustang Panda (aka Bronze President, HoneyMyte, or RedDelta).
Calling it a continuation of "a long-running espionage operation against Russian-related entities that has been in operation since at least June 2021," most recent traces of the activity is said to have been observed as recently as April 2022.
Targets included two defense research institutions belonging to the Russian state-owned defense conglomerate Rostec Corporation and an unknown entity situated in the Belarusian city of Minsk.
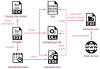
The phishing attacks commenced with emails that contain a link masquerading as the Health Ministry of Russia, but in reality is an attacker-controlled domain, as well as a decoy Microsoft Word document designed to trigger the infection and drop a loader.
The 32-bit DLL ("cmpbk32.dll"), besides establishing persistence by means of a scheduled task, is also responsible for executing a second-stage multi-layered loader, which is subsequently unpacked to run the final payload in memory.
The injected payload, a previously undocumented backdoor named Spinner, makes use of sophisticated techniques such as control flow flattening to conceal the program flow, previously identified as put to use by both Stone Panda and Mustang Panda in their attacks.
"These tools are in development since at least March 2021 and use advanced evasion and anti-analysis techniques such as multi-layer in-memory loaders and compiler-level obfuscations," Check Point said.
Despite its complex code structure, Spinner is a barebones implant that's only equipped to enumerate compromised hosts and run additional payloads retrieved from a remote server.
Check Point noted that its investigation also revealed an earlier variant of the backdoor that's distributed in a similar fashion, indicating that the campaign has been active since June 2021 based on the compilation timestamps of the executables.
But in an interesting twist, while the older version doesn't incorporate the anti-reverse engineering methods, it makes up for it by sporting extra features missing from Spinner, including the ability to list and manipulate files, exfiltrate valuable data, and run operating system commands and arbitrary downloaded payloads.
"In less than a year, the actors significantly improved the infection chain and made it more complex," the researchers said. "All the functionality from the old campaign was preserved, but it was split between multiple components making it harder to analyze or detect each stage."
"The evolution of the tools and techniques throughout this time period indicates that the actors behind the campaign are persistent in achieving their goals in a stealthy manner."
Bitter APT Hackers Add Bangladesh to Their List of Targets in South Asia
12.5.22 APT Thehackernews

An espionage-focused threat actor known for targeting China, Pakistan, and Saudi Arabia has expanded to set its sights on Bangladeshi government organizations as part of an ongoing campaign that commenced in August 2021.
Cybersecurity firm Cisco Talos attributed the activity with moderate confidence to a hacking group dubbed the Bitter APT based on overlaps in the command-and-control (C2) infrastructure with that of prior campaigns mounted by the same actor.
"Bangladesh fits the profile we have defined for this threat actor, previously targeting Southeast Asian countries including China, Pakistan, and Saudi Arabia," Vitor Ventura, lead security researcher at Cisco Talos for EMEA and Asia, told The Hacker News.
"And now, in this latest campaign, they have widened their reach to Bangladesh. Any new country in southeast Asia being targeted by Bitter APT shouldn't be of surprise."
Bitter (aka APT-C-08 or T-APT-17) is suspected to be a South Asian hacking group motivated primarily by intelligence gathering, an operation that's facilitated by means of malware such as BitterRAT, ArtraDownloader, and AndroRAT. Prominent targets include the energy, engineering, and government sectors.
The earliest attacks distributing the mobile version of BitterRAT date back to September 2014, with the actor having a history of leveraging zero-day flaws — CVE-2021-1732 and CVE-2021-28310 — to its advantage and accomplishing its adversarial objectives.

The latest campaign, targeting an elite entity of the Bangladesh government, involves sending spear-phishing emails to high-ranking officers of the Rapid Action Battalion Unit of the Bangladesh police (RAB).
As is typically observed in other social engineering attacks of this kind, the missives are designed to lure the recipients into opening a weaponized RTF document or a Microsoft Excel spreadsheet that exploits previously known flaws in the software to deploy a new trojan dubbed "ZxxZ."
ZxxZ, named so after a separator used by the malware when sending information back to the C2 server, is a 32-bit Windows executable compiled in Visual C++.
"The trojan masquerades as a Windows Security update service and allows the malicious actor to perform remote code execution, allowing the attacker to perform any other activities by installing other tools," the researchers explained.
While the malicious RTF document exploits a memory corruption vulnerability in Microsoft Office's Equation Editor (CVE-2017-11882), the Excel file abuses two remote code execution flaws, CVE-2018-0798 and CVE-2018-0802, to activate the infection sequence.
"Actors often change their tools to avoid detection or attribution, this is part of the lifecycle of a threat actor showing its capability and determination," Ventura said.
Chinese "Override Panda" Hackers Resurface With New Espionage Attacks
3.5.22 APT Thehackernews
A Chinese state-sponsored espionage group known as Override Panda has resurfaced in recent weeks with a new phishing attack with the goal of stealing sensitive information.
"The Chinese APT used a spear-phishing email to deliver a beacon of a Red Team framework known as 'Viper,'" Cluster25 said in a report published last week.
"The target of this attack is currently unknown but with high probability, given the previous history of the attack perpetrated by the group, it might be a government institution from a South Asian country."
Override Panda, also called Naikon, Hellsing, and Bronze Geneva, is known to operate on behalf of Chinese interests since at least 2005 to conduct intelligence-gathering operations targeting ASEAN countries.
Attack chains unleashed by the threat actor have involved the use of decoy documents attached to spear-phishing emails that are designed to entice the intended victims to open and compromise themselves with malware.

Last April, the group was linked to a wide-ranging cyberespionage campaign directed against military organizations in Southeast Asia. Then in August 2021, Naikon was implicated in cyberattacks targeting the telecom sector in the region in late 2020.
The latest campaign spotted by Cluster25 is no different in that it leverages a weaponized Microsoft Office document to kick-start the infection killchain that includes a loader designed to launch a shellcode, which, in turn, injects a beacon for the Viper red team tool.
Available for download from GitHub, Viper is described as a "graphical intranet penetration tool, which modularizes and weaponizes the tactics and technologies commonly used in the process of Intranet penetration."
The framework, similar to Cobalt Strike, is said to feature over 80 modules to facilitate initial access, persistence, privilege escalation, credential Access, lateral movement, and arbitrary command execution.
"By observing Naikon APT's hacking arsenal, it was concluded that this group tends to conduct long-term intelligence and espionage operations, typical for a group that aims to conduct attacks on foreign governments and officials," the researchers pointed out.
"To avoid detection and maximize the result, it changed different [tactics, techniques, and procedures] and tools over time."
APT trends report Q1 2022
29.4.22 APT Securelist
For five years, the Global Research and Analysis Team (GReAT) at Kaspersky has been publishing quarterly summaries of advanced persistent threat (APT) activity. These summaries are based on our threat intelligence research; and they provide a representative snapshot of what we have published and discussed in greater detail in our private APT reports. They are designed to highlight the significant events and findings that we feel people should be aware of.
This is our latest installment, focusing on activities that we observed during Q1 2022.
Readers who would like to learn more about our intelligence reports or request more information on a specific report, are encouraged to contact intelreports@kaspersky.com.
Disclaimer: when referring to APT groups as Russian-speaking, Chinese-speaking or other-“speaking” languages, we refer to various artefacts used by the groups (such as malware debugging strings, comments found in scripts, etc.) containing words in these languages, based on the information we obtained directly or which is otherwise publicly known and reported widely. The use of certain languages does not necessarily indicate a specific geographic relation but rather points to the languages that the developers behind these APT artefacts use.
The most remarkable findings
On January 14, 70 Ukrainian websites were defaced: the attackers posted the message “be afraid and expect the worst”. The defacement message on the Ministry of Foreign Affairs website, written in Ukrainian, Russian and Polish, suggested that personal data uploaded to the site had been destroyed. Subsequently, DDoS attacks hit several government websites. The following day, Microsoft reported that it had found destructive malware, dubbed WhisperGate, on the systems of government bodies and agencies that work closely with the Ukrainian government. We analyzed the associated samples and concluded that the deployed malware was not comparable in complexity or code similarity to malware leveraged in previous destruction campaigns such as NotPetya or BadRabbit; but was much more reminiscent of that typically used by cybercriminals. We also identified two samples developed in December 2021 containing test strings and preceding revisions of the ransom note observed in Microsoft’s shared samples. It remains unclear who is behind the attack, although Serhiy Demedyuk, deputy secretary of Ukraine’s National Security and Defense Council, stated that it was the work of UNC1151, a threat actor believed to be linked to Belarus. Throughout our investigation, we identified two samples developed in December 2021 containing test strings and earlier revisions of the ransom note observed in Microsoft’s shared samples. We concluded with high confidence that these samples were earlier iterations of the wiper reportedly used in Ukraine. Additionally, we suspect that the MBR wiper was initially developed at that time and repurposed more recently for the above campaign. This could have been done either by an advanced actor with the intention of conveying the false notion that the operation was being conducted by criminals; or in cooperation with lower-tier threat actors who contributed their own resources.
On January 26, CERT-UA published a report showing code similarity between WhisperKill (the file wiper used during the WhisperGate campaign) and WhiteBlackCrypt, a wiper used in the first quarter of 2021. While we were unable to obtain the same results by analyzing the CERT-UA samples, we subsequently identified a different WhiteBlackCrypt sample matching the WhisperKill architecture and sharing similar code. We also investigated the Bitcoin wallets used by both WhisperGate and WhiteBlackCrypt, but were unable to uncover any link between the two.
On February 23, ESET published a tweet announcing new wiper malware targeting Ukraine. The malware was more advanced than the samples identified earlier in the year that we documented in two of our private reports. This wiper, named HermeticWiper by the research community, abuses legitimate drivers from EaseUS Partition Master to corrupt the drivers of the compromised system. One of the identified samples was compiled on December 28, 2021, suggesting that this destructive campaign had been planned for months. At the time of publication, we had not identified any similarities between HermeticWiper and other known malware.
The following day, Avast Threat Research announced the discovery of new Golang ransomware in Ukraine, which they dubbed HermeticRansom. This malware was found around the same time as HermeticWiper; and publicly available information from the security community indicated that it was used in recent cyberattacks in Ukraine. Due to its unsophisticated style and poor implementation, this new ransomware was probably only a smokescreen for the HermeticWiper attack, due to its non-sophisticated style and poor implementation. We named this malware Elections GoRansom.
In late February 2022, we identified two archives submitted from network addresses in Ukraine to an online multi-scanner service. Both archives leveraged the name of the Security Service of Ukraine (SBU or СБУ) to trick targets into executing a Remote Access Tool (RAT). We were unable to determine the ultimate goal of deploying such RATs, or associate the campaigns with any known threat actor, but the two archives appear linked together and may have been deployed by the same operators. Such threats pose a risk to Ukrainian organizations and their partners, as well as foreign organizations with premises in Ukraine. The RAT deployment campaigns look like they are targeted at developing access at scale in Ukraine, which could match activities from criminal groups that pledged allegiance to Russia, and may enable further destructive activities.
On March 1, ESET published a blog post related to wipers used in Ukraine and to the ongoing conflict: in addition to HermeticWiper, this post introduced IsaacWiper, used to target specific machines previously compromised with another remote administration tool named RemCom, commonly used by attackers for lateral movement within compromised networks. Contrary to reporting from other vendors, this wiper does not leverage the Isaac PRNG.
On March 10, researchers from the Global Research and Analysis Team shared their insights into past and present cyberattacks in Ukraine. You can find the recording of the webinar here and a summary/Q&A here.
On March 22, the Ukraine CERT published a new alert about the DoubleZero wiper targeting the country. This is a new wiper, written in .NET, with no similarities to previously discovered wipers targeting Ukrainian entities. According to the CERT public statement, the campaign took place on March 17, when several targets in Ukraine received a ZIP archive with the filename “Вирус… крайне опасно!!!.zip” (translation: “Virus… extremely dangerous!!!.zip”).
Russian-speaking activity
In December 2021, as a result of our continued monitoring of the activities of the DustSquad threat actor, we observed new infrastructure and tools being used alongside the already known Octopus Trojan. We had initially analyzed this Delphi malware in April 2018. Since then, the actor has continued to target diplomatic entities of several Central Asian countries; and, according to our telemetry, their consulates in APAC and the Middle East are also affected by recent campaigns. Octopus is only one of DustSquad’s tools, along with other Windows and Android malware such as Zaka, Akinak and Harpoon. For Windows development, Delphi has been the group’s traditional programming language of choice. The actor maintains a two-layered communication scheme, with relays and real C2s, utilizing a JSON-formatted base64-encoded network communication protocol, via the use of a third-party IndyProject library. We have previously seen DustSquad use third-party post-exploitation tools, such as the password dumping utility fgdump; but we have now observed new custom C modules, a first for DustSquad, and Delphi downloaders acting as post-exploitation facilitators, able to gather documents of interest for the actor. Malicious Windows executables have also been compiled with GCC under the MinGW environment.
Chinese-speaking activity
While hunting for malicious IIS modules, following our earlier reports about the mass exploitation of ProxyLogon and the Owowa module, we identified another backdoor module that has been widely deployed since at least June 2021. We named it BlackMoule, as we believe it is an update of BlackMould, a malicious tool that was briefly mentioned by Microsoft in late 2019 as part of GALLIUM activities against telecoms companies (aka Operation SoftCell).
In May 2021, we reported on Websiic, a cluster of activities that formed a set of attacks against high-profile targets in Europe and Asia. The attackers used the infamous ProxyLogon exploit to compromise Exchange servers and deploy a China Chopper web shell, which was in turn used to start a sophisticated infection scheme leading to the execution of a new backdoor that we dubbed Samurai. The toolset includes several unique loaders and installers that had not previously been observed and can be used to load malicious payloads directly into memory, usually in the context of a legitimate process such as svchost.exe. We discovered continued activity involving multiple new loaders and installers, which were supposedly used to deploy different malicious payloads. We also observed that the malware was exclusively used against servers until August 2021; but starting from September, similar samples were also observed targeting desktop environments via messaging applications such as Telegram. Despite the discovery of weak ties to the FunnyDream cluster, we were unable to confidently attribute this new campaign to an existing group, so we dubbed the threat actor behind these attack clusters ToddyCat. Our private report on the matter takes a closer look at the available evidence: we concluded that the overlaps are weak but unlikely to be coincidental, leading us to believe that the actor behind Websiic might be part of the Chinese-speaking nebulae.
At the end of January, the BfV (Federal Office for the Protection of the Constitution of Germany) issued a report detailing activity by the APT27 group (aka LuckyMouse) targeting German commercial companies. Their analysis outlines the usage of a common infection triad leveraged by the group, whereby a legitimate executable (mempeng.exe or vfhost.exe) side-loads a malicious DLL (vftrace.dll), which in turn invokes the execution of the HyperBro malware from position-independent code found within a third file (thumb.dat). By investigating this threat through the lens of Kaspersky’s telemetry, we found an identical intrusion set targeting an enterprise in Taiwan that deals with the manufacture of smart city technology, which may suggest an intent to steal intellectual property, possibly as a means of leveraging the same technology as an instrument of surveillance. Another victim in which the same chain was exhibited is a computer game manufacturer in Cambodia, where the attack could have been used for a different purpose, possibly to infiltrate the company’s supply chain. We determined that the attackers were able to spread across the network and remain active within it for months, while making use of various tools. In addition to the infection chain outlined above, we found post-exploitation tools that were not mentioned by the BfV, including a custom-written keylogger and a publicly available SSH and SFTP credential stealer. Interestingly, we were able to observe the presence of a second malware loader on several hosts in the network that coincided with the deployment of the HyperBro implant. This loader leverages a fake Flash installer implanted with shellcode that is used to fetch a Cobalt Strike payload from a remote C2 server. At the time of writing, we can only assess with medium confidence that this tool is indeed associated with the group’s activity, indicating a possible sharing of initial access to the network with an external entity, or usage of Cobalt Strike as an alternative to HyperBro in the case of unsuccessful deployment.
Middle East
While hunting for malicious modules for Microsoft IIS servers, we identified a poorly detected and widely deployed module that we call XTest. XTest is based on the publicly available IIS-Raid open source, and was identified on hundreds of servers in late February, with 95 percent of them still being compromised at the time of our report. We were not able to determine the exact purpose XTest serves the threat actors, but we believe, with low confidence, that the module may have been deployed as part of malicious activities from the APT35 actor (aka Charming Kitten and Phosphorus).
Southeast Asia and Korean Peninsula
We reported recent, ongoing malicious activity that we attribute to the threat actor Sidecopy, targeting government staff in India. In addition to the known malware types deployed in past campaigns by this actor, such as MargulasRAT, we identified a cluster of activity targeting Linux and macOS platforms, including an unknown Golang-based Linux RAT that we attribute exclusively to this group. The supporting infrastructure for this operation overlaps with an operation described in a report published by Cisco Talos in September 2021, which discusses a campaign targeting government personnel in India using Netwire and Warzone (aka AveMaria RAT) dating back to the end of 2020. According to the authors, the decoys, used in malicious documents and spread in the early stages of these operations, resemble the one used by TransparentTribe (aka APT36 and Mythic Leopard) and Sidecopy. Our private report provides additional and updated indicators of compromise (IoCs) in the context of the same campaign and a description of some Linux and macOS malware that the group behind it has recently adopted.
We identified three campaigns linked to the Konni threat actor, active since mid-2021, targeting Russian diplomatic entities. While the attackers used the same Konni RAT implant throughout the different campaigns, the infection vectors were different in each campaign: documents containing embedded macros, an installer masquerading as a COVID-19 registration application and, finally, a downloader with a new year screensaver decoy. We also identified post-exploitation tools exclusively used by Konni following a successful infection. These are capable of taking screenshots of the active window, deploying a keylogger or listing the connected USB devices and their content. The tools align with the threat actor’s goal of stealing sensitive information from infected systems. We found overlaps in the infrastructure used by a tunneling tool used by the actor and several possible phishing websites set up within the above time frame. One of the registered domains shared similarities with another domain attributed to TA406 that, according to ProofPoint, incorporates the Konni APT.
Monitoring APT10 activities, we discovered new variants of its tools being used against the same targets as in previous campaigns – Japanese government agencies and diplomatic entities. We have seen versions of the LODEINFO backdoor through v0.4.7, v0.4.8, v0.4.9, v0.5.6, and v0.5.8 from January to December 2021, while Lilim RAT received an update to v1.4.1 in June 2021. In 2020, we published private reports featuring LODEINFO, a sophisticated fileless malware first mentioned in a blogpost from JPCERT/CC3. In these reports, we mentioned new families of fileless malware known as DOWNJPIT and Lilim RAT, which replaced the existing tools of the trade. Further, we disclosed, with high confidence, that LODEINFO and its related activities were attributed to APT10, the infamous Chinese-speaking actor. Our latest report on this subject includes technical analysis of the new versions of LODEINFO and Lilim RAT and reviews updates to the malware. In particular, LODEINFO v0.5.6 and v0.5.8 introduced obfuscated backdoor command identifiers to slow down the reversing process. They also implemented the Vigenere cipher to evade detection by certain security products.
We recently discovered a Trojanized DeFi application, compiled in November 2021. This application contains a legitimate program called DeFi Wallet, that saves and manages a cryptocurrency wallet, but also implants a malicious file when executed. This malware is a fully featured backdoor containing sufficient capabilities to control the compromised victim. After looking into the functionalities of this backdoor, we discovered numerous overlaps with other tools used by the Lazarus group. The malware operator exclusively used compromised web servers located in South Korea for this attack. To take over the servers, we worked closely with a local CERT and, as a result of this effort, we had the opportunity to investigate a Lazarus group C2 server. The threat actor configured this infrastructure with servers set up as multiple stages. The first stage is the source for the backdoor, while the purpose of the second stage server is to communicate with the implants. This represents a common scheme for Lazarus infrastructure. From the log files originating from the C2 servers, a number of infected hosts are visible. By only using IP addresses we weren’t able to confirm the exact victims of this campaign, given that some may belong to researchers, but they did reveal that this attack targeted entities and/or individuals at a global level.
Since October 2021, the Sidewinder threat actor has been using new malicious JS code with recently created C2 server domains. The attack targets victims with spear-phishing emails containing malicious OOXML files. The OOXML files have an external reference to the attacker’s server and download an RTF document exploiting the CVE-2017-11882 vulnerability. The RTF documents have an embedded JS script in an OLE object that is dropped onto the victim’s machine. Sidewinder has been using this infection chain for over a year; we provided details of these modules and described further payloads in our previous report. Our last report, in November, showed that Sidewinder’s use of the obfuscated JS script has decreased in recent months. Closer investigation of the attacks performed in that period revealed dozens of detections of a new obfuscation technique used in their JS script, while the rest of the infection chain remained fairly consistent. The new attacks use the same infection chain, targeting other victims from their traditional victim profile as well as a number of victims in countries that were not traditionally of interest to SideWinder, such as Singapore. The timestamp of the detections and the registration of the servers used by Sidewinder in these attacks suggest that they started preparing the infrastructure and registering domains for their new wave of attacks in late September. In early October they updated their toolset with new JS obfuscation techniques, and while they continued the use of their old obfuscation routine for a while, they have slowly switched completely to the new one. We described the attacks using the new obfuscated JS scripts in our most recent private report. The attackers also used a new technique to reduce the suspicion raised by some of their spear-phishing documents that had no text content. They followed their first attempt to attack the victim – a spear-phishing email containing a malicious RTF exploit file – with another similar email, but in this case the title of the malicious document was “_Apology Letter.docx”, and it contained some text explaining that the previous email was sent in error and that they are reaching out to apologize for that mistake.
In January, a trusted source forwarded a suspicious email to us. This email is disguised as an invitation from the renowned PyeongChang Peace forum and contains a DropBox link in the email body. The fetched file from the DropBox link contains a malicious Windows shortcut file capable of downloading the next stage payload from the attacker’s server. Fortunately, we were able to acquire the samples from the remote server. We dubbed this malware Phontena; and our analysis revealed the entire infection chain of this attack, made up of multiple stages. From our telemetry, we discovered a full-featured backdoor that is probably the final payload of this infection. After analyzing the samples from the remote server, we recognized that the actor behind this attack was associated with information published by another vendor about a threat actor named APT-C-601 or APT-Q-122. Based on the malware sample we discovered, we assess that this group has many overlaps with the DarkHotel group. Malware used in previous DarkHotel activity, as well as the samples discovered as part of this research, has very similar C2 communication and internal mechanisms. Moreover, the malware author left Korean comments in one of the stager payloads.
Two years after we first reported the activities of a threat actor we named FishingElephant, the group continues to target victims in Bangladesh and Pakistan. While we identified the use of a new keylogger by FishingElephant, it appears that the group still mainly relies on the same TTPs (such as payload and communication patterns) that were covered in our initial reports.
ToddyCat, a relatively new APT actor, is responsible for multiple attacks detected since December 2020. In the first wave of attacks, dubbed Websiic, the attackers exploited a ProxyLogon vulnerability to compromise Exchange Servers of high-profile organizations in Europe and Asia. More recently, we detected a new set of attacks against desktop machines starting in September 2021, named Ninja by the attacker. This Trojan provides a large set of commands allowing the attackers to control target computers. Some capabilities we analyzed are similar to those provided in other notorious post-exploitation toolkits.
Other interesting discoveries
In December we were made aware of a UEFI firmware-level compromise through logs from our firmware scanning technology. Further analysis showed that the attackers modified a single component within the firmware to append a payload to one of its sections and incorporate inline hooks within particular functions. These changes allowed the attackers to intercept the original flow of the firmware code and have it executed alongside a sophisticated infection chain. The introduced malicious flow, in turn, is in charge of persistently executing a malware stager from a Windows service once the operating system is running. By examining other IoCs from the same network, we gathered a trove of evidence that led us to assess, with medium-to-high confidence, that the threat actor involved is closely tied to the APT41 group. More specifically, we inspected communication of other nodes in the same network to infrastructure related to the server from which the payload is retrieved by the malicious stager. This traffic originated from an in-memory modular implant dubbed ScrambleCross, known to be in use by APT41 or a closely affiliated actor. Although we have covered several UEFI-based infections in APT reports in the last few months, those were cases operating through modifications introduced to the Windows boot loader image, which resides on the ESP partition on disk and can be remediated through a reinstallation of the operating system. In this case, however, the malware was found in an image typically based in the SPI flash, which is outside the hard disk and therefore withstands formatting or disk replacement. To the best of our knowledge, this is only the third known case found in the wild of a comparable UEFI implant, following LowJax and MosaicRegressor.
While hunting for recent Deathstalker intrusions, we identified a new Janicab variant used in targeting legal entities in the Middle East during 2020, possibly active into early 2021 and potentially extending an extensive campaign that can be traced back to early 2015 targeting legal, financial and travel organizations in the Middle East and Europe. Janicab was first introduced in 2013 as malware able to run on macOS and Windows operating systems. The Windows version has a VBS script-based implant as the final stage, instead of the C#/PowerShell combination observed previously in Powersing samples. The VBS-based implant samples we have identified to date have a range of version numbers, meaning it was, and still is, in development. Overall, Janicab shows the same functionalities as its counterpart malware families, but instead of downloading several tools later in the intrusion lifecycle, as the group used to do with EVILNUM and Powersing intrusions, the analyzed samples have most of the tools embedded and obfuscated within the dropper. Interestingly, the threat actor continues to use YouTube, Google+, and WordPress web services as Dead Drop Resolvers (DDRs). However, some of the YouTube links observed are unlisted and go back to 2015, indicating possible re-use of infrastructure. Law firms and financial institutions remain the sectors most affected by DeathStalker. However, in the intrusions we analyzed recently, we suspect that travel agencies are a new vertical that we haven’t previously seen this threat actor targeting.
We recently identified additional malicious activities, conducted by Tomiris operators since at least October 2021, against government, telecoms and engineering organizations in Kyrgyzstan, Afghanistan and Russia. In July 2021, we reported the previously unknown Tomiris Golang backdoor, deployed against government organizations within a CIS country through DNS hijacking. We exposed similarities between DarkHalo’s SunShuttle backdoor and the Tomiris implant. Later in 2021, we uncovered associated malicious activities that also used the open-source RATel implant to target several government organizations within Russia and Central Asia, while drawing an additional possible link between Tomiris operators and UNC1514.
Final thoughts
While the TTPs of some threat actors remain consistent over time, relying heavily on social engineering as a means of gaining a foothold in a target organization or compromising an individual’s device, others refresh their toolsets and extend the scope of their activities. Our regular quarterly reviews are intended to highlight the key developments of APT groups.
Here are the main trends that we’ve seen in Q1 2022:
Geopolitics has always been a key driver of APT developments; never more so than during a period of open warfare, as illustrated by the various cyberattacks related to the conflict in Ukraine. We have, of course, seen other activity centered around geopolitics, including the Konni and APT10 campaigns.
One of the trends we discussed in our 2021 APT review and predictions for 2022 was the further development of low-level implants. Moonbounce provides a striking example of this trend.
As always, we would note that our reports are the product of our visibility into the threat landscape. However, it should be borne in mind that, while we strive to continually improve, there is always the possibility that other sophisticated attacks may fly under our radar.
Lazarus Group Behind $540 Million Axie Infinity Crypto Hack and Attacks on Chemical Sector
17.4.22 APT Thehackernews
The U.S. Treasury Department has implicated the North Korea-backed Lazarus Group (aka Hidden Cobra) in the theft of $540 million from video game Axie Infinity's Ronin Network last month.
On Thursday, the Treasury tied the Ethereum wallet address that received the stolen funds to the threat actor and sanctioned the funds by adding the address to the Office of Foreign Assets Control's (OFAC) Specially Designated Nationals (SDN) List.
"The FBI, in coordination with Treasury and other U.S. government partners, will continue to expose and combat the DPRK's use of illicit activities – including cybercrime and cryptocurrency theft – to generate revenue for the regime," the intelligence and law enforcement agency said in a statement.
The cryptocurrency heist, the second-largest cyber-enabled theft to date, involved the siphoning of 173,600 Ether (ETH) and 25.5 million USD Coins from the Ronin cross-chain bridge, which allows users to transfer their digital assets from one crypto network to another, on March 23, 2022.
"The attacker used hacked private keys in order to forge fake withdrawals," the Ronin Network explained in its disclosure report a week later after the incident came to light.
The sanctions prohibit U.S. individuals and entities from transacting with the address in question to ensure that the state-sponsored group can't cash out any further funds. An analysis by Elliptic has found that the actor has managed to launder 18% of the siphoned digital funds (about $97 million) as of April 14.
"First, the stolen USDC was swapped for ETH through decentralized exchanges (DEXs) to prevent it from being seized," Elliptic noted. "By converting the tokens at DEXs, the hacker avoided the anti-money laundering (AML) and 'know your customer' (KYC) checks performed at centralized exchanges."
Nearly $80.3 million of the laundered funds have involved the use of Tornado Cash, a mixing service on the Ethereum blockchain designed to obscure the trail of funds, with another $9.7 million worth of ETH likely to be laundered in the same manner.
Lazarus Group, an umbrella name assigned to prolific state-sponsored actors operating on behalf of North Korean strategic interests, has a track record of conducting cryptocurrency thefts since at least 2017 to bypass sanctions and fund the country's nuclear and ballistic missile programs.
"The country's espionage operations are believed to be reflective of the regime's immediate concerns and priorities, which is likely currently focused on acquiring financial resources through crypto heists, targeting of media, news, and political entities, [and] information on foreign relations and nuclear information," Mandiant pointed out in a recent deep dive.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has painted the cyber actors as an increasingly sophisticated group that has developed and deployed a wide range of malware tools around the world to facilitate these activities.
The group is known to have plundered an estimated $400 million worth of digital assets from crypto platforms in 2021, marking a 40% jump from 2020, according to Chainalysis, which found "only 20% of the stolen funds were Bitcoin, [and that] Ether accounted for a majority of the funds stolen at 58%."
Despite sanctions imposed by the U.S. government on the hacking collective, recent campaigns undertaken by the group have capitalized on trojanized decentralized finance (DeFi) wallet apps to backdoor Windows systems and misappropriate funds from unsuspecting users.
That's not all. In another cyber offensive disclosed by Broadcom Symantec this week, the actor has been observed targeting South Korean organizations operating within the chemical sector in what appears to be a continuation of a malware campaign dubbed "Operation Dream Job," corroborating findings from Google's Threat Analysis Group in March 2022.
The intrusions, detected earlier this January, commenced with a suspicious HTM file received either as a link in a phishing email or downloaded from the internet that, when opened, triggers an infection sequence, ultimately leading to the retrieval of a second-stage payload from a remote server to facilitate further incursions.
The goal of the attacks, Symantec assessed, is to "obtain intellectual property to further North Korea's own pursuits in this area."
The continuous onslaught of illicit activities perpetrated by the Lazarus Group has also led the U.S. State Department to announce a $5 million reward for "information that leads to the disruption of financial mechanisms of persons engaged in certain activities that support North Korea."
The development comes days after a U.S. court in New York sentenced Virgil Griffith, a 39-year-old former Ethereum developer, to five years and three months in prison for helping North Korea use virtual currencies to evade sanctions.
To make matters worse, malicious actors have pilfered $1.3 billion worth of cryptocurrency in the first three months of 2022 alone, in comparison to $3.2 billion that was looted for the entirety of 2021, indicating a "meteoric rise" in thefts from crypto platforms.
"Almost 97% of all cryptocurrency stolen in the first three months of 2022 has been taken from DeFi protocols, up from 72% in 2021 and just 30% in 2020," Chainalysis said in a report published this week.
"For DeFi protocols in particular, however, the largest thefts are usually thanks to faulty code. Code exploits and flash loan attacks — a type of code exploit involving the manipulation of cryptocurrency prices — has accounted for much of the value stolen outside of the Ronin attack," the researchers said.
Lazarus Trojanized DeFi app for delivering malware
3.4.22 APT Securelist
GREAT
For the Lazarus threat actor, financial gain is one of the prime motivations, with a particular emphasis on the cryptocurrency business. As the price of cryptocurrency surges, and the popularity of non-fungible token (NFT) and decentralized finance (DeFi) businesses continues to swell, the Lazarus group’s targeting of the financial industry keeps evolving.
We recently discovered a Trojanized DeFi application that was compiled in November 2021. This application contains a legitimate program called DeFi Wallet that saves and manages a cryptocurrency wallet, but also implants a malicious file when executed. This malware is a full-featured backdoor containing sufficient capabilities to control the compromised victim. After looking into the functionalities of this backdoor, we discovered numerous overlaps with other tools used by the Lazarus group.
The malware operator exclusively used compromised web servers located in South Korea for this attack. To take over the servers, we worked closely with the KrCERT and, as a result of this effort, we had an opportunity to investigate a Lazarus group C2 server. The threat actor configured this infrastructure with servers set up as multiple stages. The first stage is the source for the backdoor while the goal of the second stage servers is to communicate with the implants. This is a common scheme used in Lazarus infrastructure.
Background
In the middle of December 2021, we noticed a suspicious file uploaded to VirusTotal. At first glance, it looked like a legitimate application related to decentralized finance (DeFi); however, looking closer we found it initiating an infection scheme. When executed, the app drops both a malicious file and an installer for a legitimate application, launching the malware with the created Trojanized installer path. Then, the spawned malware overwrites the legitimate application with the Trojanized application. Through this process, the Trojanized application gets removed from the disk, allowing it to cover its tracks.

Infection timeline
Initial infection
While it’s still unclear how the threat actor tricked the victim into executing the Trojanized application (0b9f4612cdfe763b3d8c8a956157474a), we suspect they sent a spear-phishing email or contacted the victim through social media. The hitherto unknown infection procedure starts with the Trojanized application. This installation package is disguised as a DeFi Wallet program containing a legitimate binary repackaged with the installer.
Upon execution, it acquires the next stage malware path (C:\ProgramData\Microsoft\GoogleChrome.exe) and decrypts it with a one-byte XOR (Key: 0x5D). In the process of creating this next malware stage, the installer writes the first eight bytes including the ‘MZ’ header to the file GoogleChrome.exe and pushes the remaining 71,164 bytes from the data section of the Trojanized application. Next, the malware loads the resource CITRIX_MEETINGS from its body and saves it to the path C:\ProgramData\Microsoft\CM202025.exe. The resulting file is a legitimate DeFi Wallet application. Eventually, it executes the previously created malware with its file name as a parameter:
C:\ProgramData\Microsoft\GoogleChrome.exe “[current file name]”

Malware creation diagram
Backdoor creation
The malware (d65509f10b432f9bbeacfc39a3506e23) generated by the above Trojanized application is disguised as a benign instance of the Google Chrome browser. Upon launch, the malware checks if it was provided with one argument before attempting to copy the legitimate application “C:\ProgramData\Microsoft\CM202025.exe” to the path given as the command line parameter, which means overwriting the original Trojanized installer, almost certainly in an attempt to conceal its prior existence. Next, the malware executes the legitimate file to deceive the victim by showing its benign installation process. When the user executes the newly installed program, it shows the DeFi Wallet software built with the public source code[1].
Screenshot of the manipulated application
Next, the malware starts initializing the configuration information. The configuration shows the structure shown in the table below, consisting of flags, C2 server addresses, victim identification value, and time value. As the structure suggests, this malware can hold up to five C2 addresses, but only three C2 servers are included in this case.
Offset Length(bytes) Description
0x00 4 Flag for starting C2 operation
0x04 4 Random value to select C2 server
0x08 4 Random value for victim identifier
0x0C 0x208 C2 server address
0x214 0x208 C2 server address
0x41C 0x208 C2 server address
0x624 0x208 C2 server address
0x82C 0x208 C2 server address
0xA34 0x464 Buffer for system information
0xE98 0x400 Full cmd.exe path
0x1298 0x400 Temporary folder path
0x1698 8 Time to start backdoor operation
0x16A0 4 Time interval
0x16A4 4 Flag for gathering logical drives
0x16A8 8 Flag for enumerating session information
0x16B0 8 The time value for gathering logical drive and session information
The malware randomly chooses a C2 server address and sends a beacon signal to it. This signal is a hard-coded ‘0x60D49D94’ DWORD without encryption; the response data returned from the C2 carries the same value. If the expected value from the C2 server is received, the malware starts its backdoor operation.
Following further communication with the C2, the malware encrypts data by a predefined method. The encryption is done via RC4 and the hard-coded key 0xD5A3 before additionally being encoded with base64.
The malware generates POST parameters with hard-coded names. The request type (msgID), victim identification value, and a randomly generated value are merged into the ‘jsessid’ parameter. It also uses the ‘cookie’ parameter to store four randomly generated four-byte values. These values are again encrypted with RC4 and additionally base64 encoded. Based on our investigation of the C2 script, we observed this malware not only uses a parameter named ‘jsessid’, but also ‘jcookie’ as well.

Structure of ‘jsessid’ parameter
The following HTTP request shows the malware attempting to connect to the C2 with the request type ’60d49d98′ and a randomly generated cookie value.
jsessid=60d49d980163be8f00019f91&cookie=29f23f917ab01aa8lJ3UYA==2517757b7dfb47f1
Depending on the response from the C2, the malware performs its instructed backdoor task. It carries various functionalities to gather system information and control the victim machine.
Command Description
0x60D49D97 Set time configuration with the current time interval (default is 10) value
0x60D49D9F Set time configuration with delivered data from C2 server
0x60D49DA0 Gather system information, such as IP address, computer name, OS version, CPU architecture
0x60D49DA1 Collect drive information including type and free size
0x60D49DA2 Enumerate files (with file name, size, time)
0x60D49DA3 Enumerate processes
0x60D49DA4 Terminate process
0x60D49DA5 Change working directory
0x60D49DA6 Connect to a given IP address
0x60D49DA7 File timestamping
0x60D49DA8 Execute Windows command
0x60D49DA9 Securely delete a file
0x60D49DAA Spawn process with CreateProcessW API
0x60D49DAB Spawn process with CreateProcessAsUserW API
0x60D49DAC Spawn process with high integrity level
0x60D49DAD Download file from C2 server and save to given file path
0x60D49DAE Send file creation time and contents
0x60D49DAF Add files to .cab file and send it to the C2 server
0x60D49DB0 Collect a list of files at the given path
0x60D49DB1 Send the configuration to the C2 server
0x60D49DB2 Receive new configuration from the C2 server
0x60D49DB3 Set config to the current time
0x60D49DB4 Sleep 0.1 seconds and continue
Infrastructure
Lazarus only used compromised web servers located in South Korea in this campaign. As a result of working closely with the KrCERT in taking down some of them, we had a chance to look into the corresponding C2 script from one of the compromised servers. The script described in this section was discovered in the following path:
http://bn-cosmo[.]com/customer/board_replay[.]asp
1
http://bn-cosmo[.]com/customer/board_replay[.]asp
The script is a VBScript.Encode ASP file, commonly used by the Lazarus group in their C2 scripts. After decoding, it shows the string ’60d49d95′ as an error response code, whereas the string ’60d49d94′ is used as a success message. In addition, the connection history is saved to the file ‘stlogo.jpg‘ and the C2 address for the next stage is stored in the file ‘globals.jpg‘ located in the same folder.

Configuration of C2 script
This script checks what value is delivered in the ‘jcookie’ parameter and, if it’s longer than 24 characters, it extracts the first eight characters as msgID. Depending on the msgID value, it calls different functions. The backdoor command and command execution result delivered by the backdoor get stored to global variables. We have seen this scheme in operation before with the Bookcode[2] cluster. This script uses the following variables as flags and buffers to deliver data and commands between the backdoor and a second stage C2 server:
lFlag: flag to signal that there is data to deliver to the backdoor
lBuffer: buffer to store data to be later sent to the backdoor
tFlag: flag to signal that there is a response from the backdoor
tBuffer: buffer to store incoming data from the backdoor
msgID Function name Description
60d49d98 TFConnect Save the ‘TID’ value (victim identifier) to the log file, send ‘jcookie’ value with the client’s IP address after acquiring the next stage C2 address from the config file (globals.jpg). Forward the response from the next stage server to the client.
60d49d99 TConnect Deliver the command to the backdoor:
If the lFlag is ‘true’, send lBuffer to the client. Reset ‘lBuffer’ and set lFlag to ‘false’. Otherwise, reset ‘tBuffer’ and set tFlag to ‘false’.
60d49d9a LConnect Send the command and return the command execution result:
Set ‘lBuffer’ value to ‘jcookie’ parameter, delivering ‘tBuffer’ to the client.
60d49d9c Check Retrieve host information (computer name, OS version). Delete the configuration file, which saves the C2’s next stage address, if it exists. Then save the new configuration with delivered data through the ‘jcookie’ parameter.
60d49d9d LogDown Deliver log file after base64 encoding and then delete it.
the others N/A Write connections with unknown/unexpected msgID (request type) data to a log file, entries are tagged with ‘xxxxxxxx’.
Attribution
We believe with high confidence that the Lazarus group is linked to this malware as we identified similar malware in the CookieTime cluster. The CookieTime cluster, called LCPDot by JPCERT, was a malware cluster that was heavily used by the Lazarus group until recently. We’ve seen Lazarus group target the defence industry using the CookieTime cluster with a job opportunity decoy. We have already published several reports about this cluster to our Threat Intelligence Service customers, and we identified a Trojanized Citrix application (5b831eaed711d5c4bc19d7e75fcaf46e) with the same code signature as the CookieTime malware. The backdoor discovered in the latest investigation, and the previously discovered Trojanized application, are almost identical. They share, among other things, the same C2 communication method, backdoor functionalities, random number generation routine and the same method to encrypt communication data. Also, this malware was mentioned in an article by Ahnlab discussing connections with the CookieTime (aka LCPDot) malware.
Same backdoor switch of old CookieTime malware
Same backdoor switch of old CookieTime malware
In turn, we identified that the CookieTime cluster has ties with the Manuscrypt and ThreatNeedle clusters, which are also attributed to the Lazarus group. This doesn’t only apply to the backdoor itself, but also to the C2 scripts, which show several overlaps with the ThreatNeedle cluster. We discovered almost all function and variable names, which means the operators recycled the code base and generated corresponding C2 scripts for the malware.
Conclusions
In a previous investigation we discovered that the BlueNoroff group, which is also linked to Lazarus, compromised another DeFi wallet program called MetaMask. As we can see in the latest case, the Lazarus and BlueNoroff groups attempt to deliver their malware without drawing attention to it and have evolved sophisticated methods to lure their victims. The cryptocurrency and blockchain-based industry continues to grow and attract high levels of investment. For this reason, we strongly believe Lazarus’s interest in this industry as a major source of financial gain will not diminish any time soon.
Indicators of Compromise
Trojanized DeFi application
0b9f4612cdfe763b3d8c8a956157474a DeFi-App.exe
Dropped backdoor
d65509f10b432f9bbeacfc39a3506e23 %ProgramData%\Microsoft\GoogleChrome.exe
Similar backdoor
a4873ef95e6d76856aa9a43d56f639a4
d35a9babbd9589694deb4e87db222606
70bcafbb1939e45b841e68576a320603
3f4cf1a8a16e48a866aebd5697ec107b
b7092df99ece1cdb458259e0408983c7
8e302b5747ff1dcad301c136e9acb4b0
d90d267f81f108a89ad728b7ece38e70
47b73a47e26ba18f0dba217cb47c1e16
77ff51bfce3f018821e343c04c698c0e
First stage C2 servers (Legitimate, compromised)
hxxp://emsystec[.]com/include/inc[.]asp
hxxp://www[.]gyro3d[.]com/common/faq[.]asp
hxxp://www[.]newbusantour[.]co[.]kr/gallery/left[.]asp
hxxp://ilovesvc[.]com/HomePage1/Inquiry/privacy[.]asp
hxxp://www[.]syadplus[.]com/search/search_00[.]asp
hxxp://bn-cosmo[.]com/customer/board_replay[.]asp
Second stage C2 servers (Legitimate, compromised)
hxxp://softapp[.]co[.]kr/sub/cscenter/privacy[.]asp
hxxp://gyro3d[.]com/mypage/faq[.]asp
MITRE ATT&CK Mapping
This table contains all the TTPs identified in the analysis of the activity described in this report.
Tactic Technique Technique Name
Execution T1204.002 User Execution: Malicious File
Use Trojanized application to drop malicious backdoor
Persistence T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
Register dropped backdoor to the Run registry key
Defense Evasion T1070.004 Indicator Removal on Host: File Deletion
The Trojanized application overwrites itself after creating a legitimate application to remove its trace
T1070.006 Indicator Removal on Host: Timestomp
Backdoor capable of timestomping specific files
Discovery T1057 Process Discovery
List running processes with backdoor
T1082 System Information Discovery
Gather IP address, computer name, OS version, and CPU architecture with backdoor
T1083 File and Directory Discovery
List files in some directories with backdoor
T1124 System Time Discovery
Gather system information with backdoor
Command and Control T1071.001 Application Layer Protocol: Web Protocols
Use HTTP as C2 channel with backdoor
T1573.001 Encrypted Channel: Symmetric Cryptography
Use RC4 encryption and base64 with backdoor
Exfiltration T1041 Exfiltration Over C2 Channel
Exfiltrates gathered data over C2 channels with backdoor
[1] https://github.com/DeFiCh/app
[2] APT Intel report: Lazarus Covet Covid19 Related Intelligence
Molerats Hackers Hiding New Espionage Attacks Behind Public Cloud Infrastructure
24.1.2022 APT Thehackernews
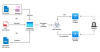
An active espionage campaign has been attributed to the threat actor known as Molerats that abuses legitimate cloud services like Google Drive and Dropbox to host malware payloads and for command-and-control and the exfiltration of data from targets across the Middle East.
The cyber offensive is believed to have been underway since at least July 2021, according to cloud-based information security company Zscaler, continuing previous efforts by the hacking group to conduct reconnaissance on the target hosts and plunder sensitive information.
Molerats, also tracked as TA402, Gaza Hackers Team, and Extreme Jackal, is an advanced persistent threat (APT) group that's largely focused on entities operating in the Middle East. Attack activity associated with the actor has leveraged geopolitical and military themes to entice users to open Microsoft Office attachments and click on malicious links.

The latest campaign detailed by Zscaler is no different in that it makes use of decoy themes related to ongoing conflicts between Israel and Palestine to deliver a .NET backdoor on infected systems that, in turn, takes advantage of the Dropbox API to establish communications with an adversary-controlled server and transmit data.
The implant, which uses specific command codes to commandeer the compromised machine, supports capabilities to take snapshots, list and upload files in relevant directories, and run arbitrary commands. Investigating the attack infrastructure, the researchers said they found at least five Dropbox accounts used for this purpose.
"The targets in this campaign were chosen specifically by the threat actor and they included critical members of banking sector in Palestine, people related to Palestinian political parties, as well as human rights activists and journalists in Turkey," Zscaler ThreatLabz researchers Sahil Antil and Sudeep Singh said.
Chinese Hackers Spotted Using New UEFI Firmware Implant in Targeted Attacks
24.1.2022 APT Thehackernews
A previously undocumented firmware implant deployed to maintain stealthy persistence as part of a targeted espionage campaign has been linked to the Chinese-speaking Winnti advanced persistent threat group (APT41).
Kaspersky, which codenamed the rootkit MoonBounce, characterized the malware as the "most advanced UEFI firmware implant discovered in the wild to date," adding "the purpose of the implant is to facilitate the deployment of user-mode malware that stages execution of further payloads downloaded from the internet."
Firmware-based rootkits, once a rarity in the threat landscape, are fast becoming lucrative tools among sophisticated actors to help achieve long standing foothold in a manner that's not only hard to detect, but also difficult to remove.
The first firmware-level rootkit — dubbed LoJax — was discovered in the wild in 2018. Since then, three different instances of UEFI malware have been unearthed so far, including MosaicRegressor, FinFisher, and ESPecter.

MoonBounce is concerning for a number of reasons. Unlike FinFisher and ESPecter, which take aim at the EFI System Partition (ESP), the newly discovered rootkit — along the likes of LoJax and MosaicRegressor — targets the SPI flash, a non-volatile storage external to the hard drive.
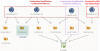
By emplacing such highly persistent bootkit malware within the flash storage that's soldered to a computer's motherboard, the mechanism makes it impossible to get rid of via hard drive replacement and even resistant to re-installation of the operating system.
The Russian cybersecurity company said it identified the presence of the firmware rootkit in a single incident last year, indicative of the highly targeted nature of the attack. That said, the exact mechanism by which the UEFI firmware was infected remains unclear.
Adding to its stealthiness is the fact that an existing firmware component was tampered to alter its behaviour — rather than adding a new driver to the image — with the goal of diverting the execution flow of the boot sequence to a malicious attack sequence that injects the user-mode malware during system startup, which then reaches out to a hardcoded remote server to retrieve the next-stage payload.
"The infection chain itself does not leave any traces on the hard drive, as its components operate in memory only, thus facilitating a fileless attack with a small footprint," the researchers noted, adding that it uncovered other non-UEFI implants in the targeted network communicating with the same infrastructure that hosted the staging payload.

Chief among those components deployed across multiple nodes in the network include a backdoor tracked as ScrambleCross (aka Crosswalk) and a number of post-exploitation malware implants like Microcin and Mimikat_ssp, suggesting that the attackers performed lateral movement after gaining an initial access in order to exfiltrate data from specific machines.
Cybersecurity firm Binarly, in an independent analysis, noted that the MoonBounce UEFI component was built for a target hardware related to a MSI system from 2014, and that the malware could have been delivered to the compromised machine either via physical access or through software modifications resulting from a lack of adequate SPI protections.
To counter such firmware-level modifications, it's recommended to regularly update the UEFI firmware as well as enable protections such as Boot Guard, Secure boot, and Trust Platform Modules (TPM).
"MoonBounce marks a particular evolution in this group of threats by presenting a more complicated attack flow in comparison to its predecessors and a higher level of technical competence by its authors, who demonstrate a thorough understanding of the finer details involved in the UEFI boot process," the researchers said.
BADNEWS! Patchwork APT Hackers Score Own Goal in Recent Malware Attacks
19.1.2022 APT Thehackernews

Threat hunters have shed light on the tactics, techniques, and procedures embraced by an Indian-origin hacking group called Patchwork as part of a renewed campaign that commenced in late November 2021, targeting Pakistani government entities and individuals with a research focus on molecular medicine and biological science.
"Ironically, all the information we gathered was possible thanks to the threat actor infecting themselves with their own [remote access trojan], resulting in captured keystrokes and screenshots of their own computer and virtual machines," Malwarebytes Threat Intelligence Team said in a report published on Friday.
Prominent victims that were successfully infiltrated include Pakistan's Ministry of Defense, National Defence University of Islamabad, Faculty of Bio-Sciences at UVAS Lahore, International Center for Chemical and Biological Sciences (ICCBS), H.E.J. Research Institute of Chemistry, and the Salim Habib University (SBU).
Believed to have been active since 2015, Patchwork APT is also tracked by the wider cybersecurity community under the monikers Dropping Elephant, Chinastrats (Kaspersky), Quilted Tiger (CrowdStrike), Monsoon (Forcepoint), Zinc Emerson, TG-4410 (SecureWorks), and APT-C-09 (Qihoo 360).
The espionage group, primarily known for striking diplomatic and government agencies in Pakistan, China, U.S. think tanks, and other targets located in the Indian subcontinent via spear-phishing campaigns, gets its name from the fact that most of the code used for its malware tooling was copied and pasted from various sources publicly available on the web.
"The code used by this threat actor is copy-pasted from various online forums, in a way that reminds us of a patchwork quilt," researchers from the now-defunct Israeli cybersecurity startup Cymmetria noted in its findings published in July 2016.
Over the years, successive covert operations staged by the actor have attempted to drop and execute QuasarRAT as well as an implant named BADNEWS that acts as a backdoor for the attackers, providing them with full control over the victim machine. In January 2021, the threat group was also observed exploiting a remote code execution vulnerability in Microsoft Office (CVE-2017-0261) to deliver payloads on victim machines.
The latest campaign is no different in that the adversary lures potential targets with RTF documents impersonating Pakistani authorities that ultimately act as a conduit for deploying a new variant of the BADNEWS trojan called Ragnatela — meaning "spider web" in Italian — enabling the operators to execute arbitrary commands, capture keystrokes and screenshots, list and upload files, and download additional malware.
The new lures, which purport to be from the Pakistan Defence Officers Housing Authority (DHA) in Karachi, contains an exploit for Microsoft Equation Editor that's triggered to compromise the victim's computer and execute the Ragnatela payload.
But in what's a case of OpSec failure, the threat actor also ended up infecting their own development machine with the RAT, as Malwarebytes was able to unmask a number of its tactics, including the use of dual keyboard layouts (English and Indian) as well as the adoption of virtual machines and VPNs such as VPN Secure and CyberGhost to conceal their IP address.
"While they continue to use the same lures and RAT, the group has shown interest in a new kind of target," the researchers concluded. "Indeed, this is the first time we have observed Patchwork targeting molecular medicine and biological science researchers."
Chinese APT Hackers Used Log4Shell Exploit to Target Academic Institution
1.1.2022 APT Thehackernews
A never-before-seen China-based targeted intrusion adversary dubbed Aquatic Panda has been observed leveraging critical flaws in the Apache Log4j logging library as an access vector to perform various post-exploitation operations, including reconnaissance and credential harvesting on targeted systems.
Cybersecurity firm CrowdStrike said the infiltration, which was ultimately foiled, was aimed at an unnamed "large academic institution." The state-sponsored group is believed to have been operating since mid-2020 in pursuit of intelligence collection and industrial espionage, with its attacks primarily directed against companies in the telecommunications, technology, and government sectors.
The attempted intrusion exploited the newly discovered Log4Shell flaw (CVE-2021-44228, CVSS score: 10.0) to gain access to a vulnerable instance of the VMware Horizon desktop and app virtualization product, followed by running a series of malicious commands orchestrated to fetch threat actor payloads hosted on a remote server.
"A modified version of the Log4j exploit was likely used during the course of the threat actor's operations," the researchers noted, adding it involved the use of an exploit that was published in GitHub on December 13, 2021.
Aquatic Panda's malicious behavior went beyond conducting reconnaissance of the compromised host, starting with making an effort to stop a third-party endpoint detection and response (EDR) service, before proceeding to retrieve next-stage payloads designed to obtain a reverse shell and harvest credentials.
But after the victim organization was alerted to the incident, the entity "was able to quickly implement their incident response protocol, eventually patching the vulnerable application and preventing further threat actor activity on the host." In light of the attack's successful disruption, the exact intent remains unknown.


































