A Mirai botnet variant called Pandora has been observed infiltrating inexpensive Android-based TV sets and TV boxes and using them as part of a botnet to perform distributed denial-of-service (DDoS) attacks.
Mirai Botnet Variant 'Pandora' Hijacks Android TVs for Cyberattacks
7.9.23 BotNet The Hacker News

A Mirai botnet variant called Pandora has been observed infiltrating inexpensive Android-based TV sets and TV boxes and using them as part of a botnet to perform distributed denial-of-service (DDoS) attacks.
Doctor Web said the compromises are likely to occur either during malicious firmware updates or when applications for viewing pirated video content are installed.
"It is likely that this update has been made available for download from a number of websites, as it is signed with publicly available Android Open Source Project test keys," the Russian company said in an analysis published Wednesday.
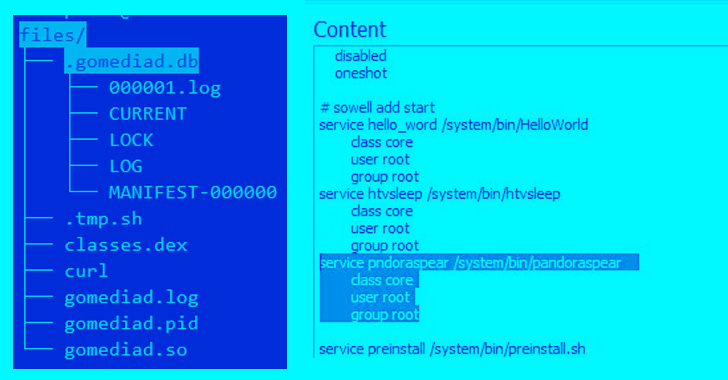
"The service that runs the backdoor is included in boot.img," enabling it to persist between system restarts.
In the alternative distribution methods, it's suspected that users are tricked into installing applications for streaming pirated movies and TV shows through websites that mainly single out Spanish-speaking users.
The list of apps is as follows -
Latino VOD (com.global.latinotvod)
Tele Latino (com.spanish.latinomobile)
UniTV APK (com.global.unitviptv), and
YouCine TV (com.world.youcinetv)
Once an app is installed, it launches a "GoMediaService" service in the background that's then used to unpack a number of files, including an interpreter that runs with elevated privileges and an installer for Pandora.
Pandora, for its part, is designed to contact a remote server, replace the hosts file on the system with a rogue variant, and receive additional commands to mount DDoS attacks via TCP and UDP protocols and open a reverse shell.
The primary targets of the campaign are cheap Android TV boxes such as Tanix TX6 TV Box, MX10 Pro 6K, and H96 MAX X3, which come with quad-core processors from Allwinner and Amlogic, making them an ideal candidate for launching DDoS attacks.
To mitigate such infections, it's recommended that users keep their devices up-to-date and stick to downloading software only from trusted sources.