Feds Warn of AndroxGh0st Botnet Targeting AWS, Azure, and Office 365 Credentials
18.1.24 BigBrothers The Hacker News

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) warned that threat actors deploying the AndroxGh0st malware are creating a botnet for "victim identification and exploitation in target networks."
A Python-based malware, AndroxGh0st was first documented by Lacework in December 2022, with the malware inspiring several similar tools like AlienFox, GreenBot (aka Maintance), Legion, and Predator.
The cloud attack tool is capable of infiltrating servers vulnerable to known security flaws to access Laravel environment files and steal credentials for high-profile applications such as Amazon Web Services (AWS), Microsoft Office 365, SendGrid, and Twilio.
Some of the notable flaws weaponized by the attackers include CVE-2017-9841 (PHPUnit), CVE-2021-41773 (Apache HTTP Server), and CVE-2018-15133 (Laravel Framework).
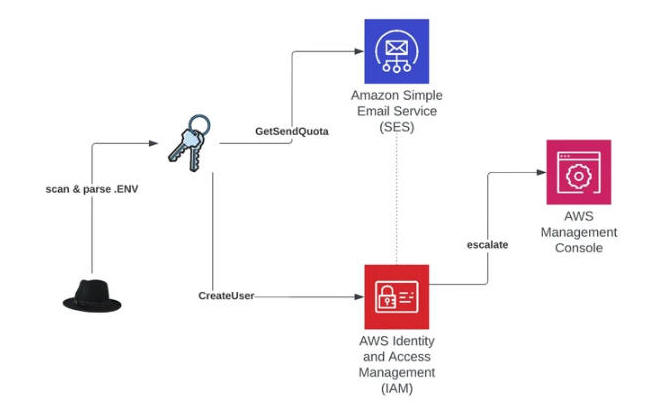
"AndroxGh0st has multiple features to enable SMTP abuse including scanning, exploitation of exposed creds and APIs, and even deployment of web shells," Lacework said. "For AWS specifically, the malware scans for and parses AWS keys but also has the ability to generate keys for brute-force attacks."
The compromised AWS credentials are subsequently used to create new users and user policies, and in several instances, set up new AWS instances for additional, malicious scanning activity.
These features make AndroxGh0st a potent threat that can be used to download additional payloads and retain persistent access to compromised systems.
"Androxgh0st is a consistent nuisance: we regularly see related user-agent strings in network connections scanning our honeypots," Alex Delamotte, senior threat researcher at SentinelLabs, told The Hacker News. "It's excellent to see CISA issuing an advisory against this type of threat, as cloud-focused malware advisories are uncommon."
The development arrives less than a week after SentinelOne revealed a related-but-distinct tool called FBot that is being employed by attackers to breach web servers, cloud services, content management systems (CMS), and SaaS platforms.
"The cloud threat landscape will continue to borrow code from other tools and integrate them into a holistic ecosystem, which is what we see with AlienFox and Legion doing with Androxgh0st and FBot respectively," Delamotte said.
"As actors find new ways to monetize cloud services, we can expect to see tailored tools emerge for those services, much like how these tools focus on exploiting mail services to conduct spamming attacks."
It also follows an alert from NETSCOUT about a significant spike in botnet scanning activity since mid-November 2023, touching a peak of nearly 1.3 million distinct devices on January 5, 2024. A majority of the source IP addresses are associated with the U.S., China, Vietnam, Taiwan, and Russia.
"Analysis of the activity has uncovered a rise in the use of cheap or free cloud and hosting servers that attackers are using to create botnet launch pads," the company said. "These servers are used via trials, free accounts, or low-cost accounts, which provide anonymity and minimal overhead to maintain."

