BigBrothers 2024 2023 2022 2021 2020
U.S. Charges Three Iranian Nationals for Election Interference and Cybercrimes
28.9.24 BigBrothers The Hacker News

U.S. federal prosecutors on Friday unsealed criminal charges against three Iranian nationals who are allegedly employed with the Islamic Revolutionary Guard Corps (IRGC) for their targeting of current and former officials to steal sensitive data.
The Department of Justice (DoJ) accused Masoud Jalili, 36, Seyyed Ali Aghamiri, 34, and Yasar (Yaser) Balaghi, 37, of participating in a conspiracy with other known and unknown actors to undermine the U.S. electoral process.
They are alleged to have hacked into accounts of current and former U.S. officials, members of the media, nongovernmental organizations, and individuals associated with U.S. political campaigns. None of the three operatives, said to be members of the Basij Resistance Force, have been arrested.
"The activity was part of Iran's continuing efforts to stoke discord, erode confidence in the U.S. electoral process, and unlawfully acquire information relating to current and former U.S. officials that could be used to advance the malign activities of the IRGC, including ongoing efforts to avenge the death of Qasem Soleimani, the former commander of the IRGC – Qods Force (IRGC-QF)," the DoJ said.
The activity, per the DoJ, entailed obtaining access to non-public campaign documents and emails related to the election campaign sometime around May 2024. Then the next month, the conspirators engaged in hack-and-leak operations by sharing the stolen campaign material with media publications and individuals associated with the other presidential campaign.
The development comes nearly two weeks after the U.S. Federal Bureau of Investigation (FBI) blamed Iranian threat actors for plundering non-public material from former President Trump's campaign and passing it on to President Biden's campaign and U.S. media organizations.
"These hack-and-leak efforts by Iran are a direct assault on the integrity of our democratic processes," said Assistant Attorney General Matthew G. Olsen of the Justice Department's National Security Division.
"Iranian government actors have long sought to use cyber-enabled means to harm U.S. interests. This case demonstrates our commitment to expose attempts by the Iranian regime or any other foreign actor to interfere with our free and open society."
Jalili, Aghamiri, and Balaghi have also been accused of undertaking a wide-ranging hacking campaign starting back in January 2020 to infiltrate victims' computers and online accounts using a combination of spear-phishing and social engineering techniques.
This involved the use of fake personas to trick users into clicking on malicious links and spoofing login pages to harvest account credentials and using the compromised victim accounts to send phishing messages to other targets. The DoJ said some of these efforts were successful.
The trio have been charged with 18 counts that include conspiracy to commit identity theft, aggravated identity theft, access device fraud, unauthorized access to computers to obtain information from a protected computer, unauthorized access to computers to defraud and obtain a thing of value, and wire fraud.
In coordination with the indictment, the Department of State has issued a reward of up to $10 million for information on Jalili, Aghamiri, and Balaghi, the IRGC's interference in U.S. elections, or associated individuals and entities.
The U.S. Department of the Treasury's Office of Foreign Asset Control (OFAC) has imposed sanctions against seven individuals for their malicious cyber activities, including spear-phishing, hack-and-leak operations, and their alleged interference with political campaigns -
Masoud Jalili
Ali Mahdavian, Fatemeh Sadeghi, Elaheh Yazdi, Sayyed Mehdi Rahimi Hajjiabadi, Mohammad Hosein Abdolrahimi, and Rahmatollah Askarizadeh (employees and executives of Emennet Pasargad)
It's worth noting that the U.S. government previously sanctioned six other employees of the same company in November 2021 for their attempts to interfere in the 2020 U.S. presidential election.
"The Iranian regime is increasingly attempting to influence the outcome of the forthcoming U.S. election because it perceives the outcome will impact U.S. foreign policy towards Iran," the State Department said.
"Iranian state-sponsored actors have undertaken a variety of malicious cyber activities, such as hack-and-leak operations and spear-phishing, in an attempt to undermine confidence in the United States' election processes and institutions while also seeking to influence the political campaigns."
In August, Iran denied accusations that it played any role in the hack, calling them baseless and that Iran's "cyber power is defensive and in proportionate to the threats it faces," Iran's state-controlled news agency IRNA reported.
The indictment is the latest effort by the U.S. government to counter foreign efforts to interfere in the upcoming election. Recently, it also brought criminal charges and sanctions against employees of Russian state media outlet RT for allegedly funding pro-Trump social-media influencers in the U.S.
U.S. Proposes Ban on Connected Vehicles Using Chinese and Russian Tech
24.9.24 BigBrothers The Hacker News
The U.S. Department of Commerce (DoC) said it's proposing a ban on the import or sale of connected vehicles that integrate software and hardware made by foreign adversaries, particularly that of the People's Republic of China (PRC) and Russia.
"The proposed rule focuses on hardware and software integrated into the Vehicle Connectivity System (VCS) and software integrated into the Automated Driving System (ADS)," the Bureau of Industry and Security (BIS) said in a press statement.
"These are the critical systems that, through specific hardware and software, allow for external connectivity and autonomous driving capabilities in connected vehicles."
The agency said nefarious access to such systems could enable adversaries to harvest sensitive data and remotely manipulate cars on American roads.
The proposal extends to all wheeled on-road vehicles such as cars, trucks, and buses. Agricultural and mining vehicles are not included.
The BIS said "certain technologies" from China and Russia pose "undue risk" to U.S. critical infrastructure, as well as those who rely on connected vehicles, leading to a potential scenario that could undermine the national security and privacy of U.S. citizens.
"This rule marks a critical step forward in protecting America's technology supply chains from foreign threats and ensures that connected vehicle technologies are secure from the potential exploitation of entities linked to the PRC and Russia," said Under Secretary of Commerce for Industry and Security Alan F. Estevez.
Pursuant to the ban, the import and sale of vehicles with certain VCS or ADS hardware or software with a nexus to China or Russia will be prohibited.
It also aims to block manufacturers with ties to the PRC or Russia from selling connected vehicles that incorporate VCS hardware or software or ADS software in the U.S., even if the vehicle was made in the country.
"The prohibitions on software would take effect for Model Year 2027 and the prohibitions on hardware would take effect for Model Year 2030, or January 1, 2029 for units without a model year," the BIS said.
In a coordinated statement, the White House said the step is a move to ensure that U.S. automotive supply chains are resilient and secure from foreign threats. It added the increasing connectivity of vehicles to U.S. digital networks creates an environment to gather and exploit sensitive information.
"Certain hardware and software in connected vehicles enable the capture of information about geographic areas or critical infrastructure, and present opportunities for malicious actors to disrupt the operations of infrastructure or the vehicles themselves," the White House also pointed out.
Europol Shuts Down Major Phishing Scheme Targeting Mobile Phone Credentials
20.9.24 BigBrothers The Hacker News

Law enforcement authorities have announced the takedown of an international criminal network that leveraged a phishing platform to unlock stolen or lost mobile phones.
The phishing-as-a-service (PhaaS) platform, called iServer, is estimated to have claimed more than 483,000 victims globally, led by Chile (77,000), Colombia (70,000), Ecuador (42,000), Peru (41,500), Spain (30,000), and Argentina (29,000).
"The victims are mainly Spanish-speaking nationals from European, North American and South American countries," Europol said in a press statement.
The action, dubbed Operation Kaerb, involved the participation of law enforcement and judicial agencies from Spain, Argentina, Chile, Colombia, Ecuador, and Peru.
Pursuant to the joint exercise that took place between September 10 and 17, an Argentinian national responsible for developing and running the PhaaS service since 2018 has been arrested.
In total, the operation led to 17 arrests, 28 searches, and the seizure of 921 items, including mobile phones, electronic devices, vehicles, and weapons. As many as 1.2 million mobile phones are believed to have been unlocked to date.
"While iServer was essentially an automated phishing platform, its specific focus on harvesting credentials to unlock stolen phones set it apart from typical phishing-as-a-service offerings," Group-IB said.
iServer, per the Singapore-based company, offered a web interface that enabled low-skilled criminals, known as "unlockers," to siphon device passwords, user credentials from cloud-based mobile platforms, essentially permitting them to bypass Lost Mode and unlock the devices.
Cybersecurity
The criminal syndicate's administrator advertised the access to these unlockers, who, in turn, used iServer to not only perform phishing unlocks, but also to sell their offerings to other third-parties, such as phone thieves.
The unlockers are also responsible for sending bogus messages to phone theft victims that aim to gather data allowing access to those devices. This is accomplished by sending SMS texts that urge the recipients to locate their lost phone by clicking on a link.
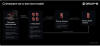
This triggers a redirection chain that ultimately takes the victim to a landing page prompting them to enter their credentials, device passcode, and two-factor authentication (2FA) codes, which are then abused to gain illicit access to the device, turn off Lost Mode, and unlink the device from the owner's account.
"iServer automates the creation and delivery of phishing pages that imitate popular cloud-based mobile platforms, featuring several unique implementations that enhance its effectiveness as a cybercrime tool," Group-IB said.
Ghost Platform Goes Down in Global Action#
The development comes as Europol and the Australian Federal Police (AFP) revealed the dismantling of an encrypted communications network called Ghost ("www.ghostchat[.]net") that facilitated serious and organized crime across the world.
The platform, which came included in a custom Android smartphone for about $1,590 for a six-month subscription, was used to conduct a wide range of illegal activities, such as trafficking, money laundering, and even acts of extreme violence. It's just the latest addition to a list of similar services like Phantom Secure, EncroChat, Sky ECC, and Exclu that have been shut down on similar grounds.
"The solution used three encryption standards and offered the option to send a message followed by a specific code which would result in the self-destruction of all messages on the target phone," Europol said. "This allowed criminal networks to communicate securely, evade detection, counter forensic measures, and coordinate their illegal operations across borders."
Several thousand people are thought to have used the platform, with around 1,000 messages exchanged over the service every day prior to its disruption.

Over the course of the investigation that commenced in March 2022, 51 suspects have been arrested: 38 in Australia, 11 in Ireland, one in Canada, and one in Italy belonging to the Italian Sacra Corona Unita mafia group.
Topping the list is a 32-year-old man from Sydney, New South Wales, who has been charged with creating and administering Ghost as part of Operation Kraken, along with several others who have been accused of using the platform for trafficking cocaine and cannabis, conducting drug distribution, and manufacturing a false terrorism plot.
It's believed that the administrator, Jay Je Yoon Jung, launched the criminal enterprise nine years ago, netting him millions of dollars in illegitimate profits. He was apprehended at his home in Narwee. The operation has also resulted in the takedown of a drug lab in Australia, as well as the confiscation of weapons, drugs, and €1 million in cash.
The AFP said it infiltrated the platform's infrastructure to stage a software supply chain attack by modifying the software update process to gain access to the content stored on 376 active handsets located in Australia.
"The encrypted communication landscape has become increasingly fragmented as a result of recent law enforcement actions targeting platforms used by criminal networks," Europol noted.
"Criminal actors, in response, are now turning to a variety of less-established or custom-built communication tools that offer varying degrees of security and anonymity. By doing so, they seek new technical solutions and also utilize popular communication applications to diversify their methods."
The law enforcement agency, besides stressing the need for access to communications among suspects to tackle serious crimes, called on private companies to ensure that their platforms don't become safe havens for bad actors and provide ways for lawful data access "under judicial oversight and in full respect of fundamental rights."
Germany Takes Down 47 Cryptocurrency Exchanges #
The actions also coincide with Germany's seizure of 47 cryptocurrency exchange services hosted in the country that enabled illegal money laundering activities for cybercriminals, including ransomware groups, darknet dealers, and botnet operators. The operation has been codenamed Final Exchange.
The services have been accused of failing to implement Know Your Customer (KYC) or anti-money laundering programs and intentionally obscuring the source of criminally obtained funds, thereby allowing cybercrime to flourish. No arrests were publicly announced.
"The Exchange services enabled barter transactions without going through a registration process and without checking proof of identity," the Federal Criminal Police Office (aka Bundeskriminalamt) said. "The offer was aimed at quickly, easily and anonymously exchanging cryptocurrencies into other crypto or digital currencies in order to conceal their origin."
U.S. DoJ Charges Two for $230 Million Cryptocurrency Scam#
Capping off the law enforcement efforts to combat cybercrime, the U.S. Department of Justice (DoJ) said two suspects have been arrested and charged with conspiracy to steal and launder over $230 million in cryptocurrency from an unnamed victim in Washington D.C.
Malone Lam, 20, and Jeandiel Serrano, 21, and other co-conspirators are alleged to have carried out cryptocurrency thefts at least since August 2024 by gaining access to victims' accounts, which were then laundered through various exchanges and mixing services.
The ill-gotten proceeds were then used to fund an extravagant lifestyle, such as international travel, nightclubs, luxury automobiles, watches, jewelry, designer handbags, and rental homes in Los Angeles and Miami.
"They laundered the proceeds, including by moving the funds through various mixers and exchanges using 'peel chains,' pass-through wallets, and virtual private networks (VPNs) to mask their true identities," the DoJ said.
U.S. Treasury Sanctions Executives Linked to Intellexa Predator Spyware Operation
17.9.24 BigBrothers The Hacker News
The U.S. Department of Treasury has imposed fresh sanctions against five executives and one entity with ties to the Intellexa Consortium for their role in the development, operation, and distribution of a commercial spyware called Predator.
"The United States will not tolerate the reckless propagation of disruptive technologies that threatens our national security and undermines the privacy and civil liberties of our citizens," said Acting Under Secretary of the Treasury for Terrorism and Financial Intelligence, Bradley T. Smith.
"We will continue to hold accountable those that seek to enable the proliferation of exploitative technologies, while also encouraging the responsible development of technologies that align with international standards."
The sanctioned individuals and entities are listed below -
Felix Bitzios, the beneficial owner of an Intellexa Consortium company that's believed to have supplied Predator to a foreign government client and the manager of Intellexa S.A.
Andrea Nicola Constantino Hermes Gambazzi, the beneficial owner of Thalestris Limited and Intellexa Limited, which are both members of the Intellexa Consortium
Merom Harpaz, a top executive of the Intellexa Consortium and the manager of Intellexa S.A.
Panagiota Karaoli, director of multiple Intellexa Consortium entities that are controlled by or are a subsidiary of Thalestris Limited
Artemis Artemiou, an employee of Intellexa S.A., as well as the general manager and member of the board of Cytrox Holdings, another member of the Intellexa Consortium
Aliada GroupInc., a British Virgin Islands-based company and member of the Intellexa Consortium has facilitated tens of millions of dollars of transactions
Thalestris Limited has been involved in processing transactions on behalf of other entities within the Intellexa Consortium, the Treasury said, adding that Aliada Group is directed by Tal Jonathan Dilian, the founder of the Intellexa Consortium.
The department described the consortium as a "complex international web of decentralized companies that built and commercialized a comprehensive suite of highly invasive spyware products."
The development comes a little over six months after the Treasury sanctioned Dilian, Sara Aleksandra Fayssal Hamou, and five other entities, including Intellexa S.A., on similar grounds.
It also follows a resurgence of Predator spyware activity after a period of relative silence by likely customers in Angola, the Democratic Republic of the Congo (DRC), and Saudi Arabia using new infrastructure that's designed to evade detection.
"The latest evolution of Predator infrastructure includes an additional tier in its delivery infrastructure to improve customer anonymization and enhanced operational security in its server configurations and associated domains," Recorded Future said.
"Although Predator spyware operators have changed significant aspects of their infrastructure setup, including changes that make country-specific attribution more challenging, they have largely retained their mode of operation."
It also follows Apple's decision to file a motion to dismiss its lawsuit against NSO Group for reasons that court disclosures could endanger its efforts to combat spyware, that there are steps being taken to avoid sharing information related to the Pegasus spyware, and that the impact could be diluted as a result of an expanding spyware market with new emerging players.
TIDRONE Espionage Group Targets Taiwan Drone Makers in Cyber Campaign
9.9.24 BigBrothers The Hacker News
A previously undocumented threat actor with likely ties to Chinese-speaking groups has predominantly singled out drone manufacturers in Taiwan as part of a cyber attack campaign that commenced in 2024.
Trend Micro is tracking the adversary under the moniker TIDRONE, stating the activity is espionage-driven given the focus on military-related industry chains.
The exact initial access vector used to breach targets is presently unknown, with Trend Micro's analysis uncovering the deployment of custom malware such as CXCLNT and CLNTEND using remote desktop tools like UltraVNC.
An interesting commonality observed across different victims is the presence of the same enterprise resource planning (ERP) software, raising the possibility of a supply chain attack.
The attack chains subsequently go through three different stages that are designed to facilitate privilege escalation by means of a User Access Control (UAC) bypass, credential dumping, and defense evasion by disabling antivirus products installed on the hosts.
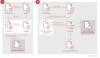
Both the backdoors are initiated by sideloading a rogue DLL via the Microsoft Word application, allowing the threat actors to harvest a wide range of sensitive information,
CXCLNT comes equipped with basic upload and download file capabilities, as well as features for clearing traces, collecting victim information such as file listings and computer names, and downloading next-stage portable executable (PE) and DLL files for execution.
CLNTEND, first detected in April 2024, is a discovered remote access tool (RAT) that supports a wider range of network protocols for communication, including TCP, HTTP, HTTPS, TLS, and SMB (port 445).
"The consistency in file compilation times and the threat actor's operation time with other Chinese espionage-related activities supports the assessment that this campaign is likely being carried out by an as-yet unidentified Chinese-speaking threat group," security researchers Pierre Lee and Vickie Su said.
U.S. Offers $10 Million for Info on Russian Cadet Blizzard Hackers Behind Major Attacks
9.9.24 BigBrothers The Hacker News
The U.S. government and a coalition of international partners have officially attributed a Russian hacking group tracked as Cadet Blizzard to the General Staff Main Intelligence Directorate (GRU) 161st Specialist Training Center (Unit 29155).
"These cyber actors are responsible for computer network operations against global targets for the purposes of espionage, sabotage, and reputational harm since at least 2020," the agencies said.
"Since early 2022, the primary focus of the cyber actors appears to be targeting and disrupting efforts to provide aid to Ukraine."
Targets of the attacks have focused on critical infrastructure and key resource sectors, including the government services, financial services, transportation systems, energy, and healthcare sectors of North Atlantic Treaty Organization (NATO) members, the European Union, Central American, and Asian countries.
The joint advisory, released last week as part of a coordinated exercise dubbed Operation Toy Soldier, comes from cybersecurity and intelligence authorities in the U.S., the Netherlands, the Czech Republic, Germany, Estonia, Latvia, Ukraine, Canada, Australia, and the U.K.
Cadet Blizzard, also known as Ember Bear, FROZENVISTA, Nodaria, Ruinous Ursa, UAC-0056, and UNC2589, gained attention in January 2022 for deploying the destructive WhisperGate (aka PAYWIPE) malware against multiple Ukrainian victim organizations in advance of Russia's full-blown military invasion of the country.
Back in June 2024, a 22-year-old Russian national named Amin Timovich Stigal was indicted in the U.S. for his alleged role in staging destructive cyber attacks against Ukraine using the wiper malware. That said, the use of WhisperGate is said to be not unique to the group.
The U.S. Department of Justice (DoJ) has since charged five officers associated with Unit 29155 for conspiracy to commit computer intrusion and wire fraud conspiracy against targets in Ukraine, the U.S. and 25 other NATO countries.
The names of the five officers are listed below -
Yuriy Denisov (Юрий Денисов), a colonel in the Russian military and a commanding officer of Cyber Operations for Unit 29155
Vladislav Borovkov (Владислав Боровков), Denis Denisenko (Денис Денисенко), Dmitriy Goloshubov (Дима Голошубов), and Nikolay Korchagin (Николай Корчагин), lieutenants in the Russian military assigned to Unit 29155 who worked on cyber operations
"The defendants did so in order to sow concern among Ukrainian citizens regarding the safety of their government systems and personal data," the DoJ said. "The defendants' targets included Ukrainian Government systems and data with no military or defense-related roles. Later targets included computer systems in countries around the world that were providing support to Ukraine."

Concurrent with the indictment, the U.S. Department of State's Rewards for Justice program has announced a reward of up to $10 million for information on any of the defendants' locations or their malicious cyber activity.
Indications are that Unit 29155 is responsible for attempted coups, sabotage, and influence operations, and assassination attempts throughout Europe, with the adversary broadening their horizons to include offensive cyber operations since at least 2020.
The end goal of these cyber intrusions is to collect sensitive information for espionage purposes, inflict reputational harm by leaking said data, and orchestrate destructive operations that aim to sabotage systems containing valuable data.
Unit 29155, per the advisory, is believed to comprise junior, active-duty GRU officers, who also rely on known cybercriminals and other civilian enablers such as Stigal to facilitate their missions.
These comprise website defacements, infrastructure scanning, data exfiltration, and data leak operations that involve releasing the information on public website domains or selling it to other actors.
Attack chains commence with scanning activity that leverages known security flaws in Atlassian Confluence Server and Data Center, Dahua Security, and Sophos' firewall to breach victim environments, followed by using Impacket for post-exploitation and lateral movement, and ultimately exfiltrating data to dedicated infrastructure.
"Cyber actors may have used Raspberry Robin malware in the role of an access broker," the agencies noted. "Cyber actors targeted victims' Microsoft Outlook Web Access (OWA) infrastructure with password spraying to obtain valid usernames and passwords."
Organizations are recommended to prioritize routine system updates and remediate known exploited vulnerabilities, segment networks to prevent the spread of malicious activity, and enforce phishing-resistant multi-factor authentication (MFA) for all externally facing account services.
FBI Cracks Down on Dark Web Marketplace Managed by Russian and Kazakh Nationals
8.9.24 BigBrothers The Hacker News
Two men have been indicted in the U.S. for their alleged involvement in managing a dark web marketplace called WWH Club that specializes in the sale of sensitive personal and financial information.
Alex Khodyrev, a 35-year-old Kazakhstan national, and Pavel Kublitskii, a 37-year-old Russian national, have been charged with conspiracy to commit access device fraud and conspiracy to commit wire fraud.
Khodyrev and Kublitskii, between 2014 and 2024, acted as the main administrators of WWH Club (wwh-club[.]ws) and various other sister sites – wwh-club[.]net, center-club[.]pw, opencard[.]pw, skynetzone[.]org – that functioned as dark web marketplaces, forums, and training centers to enable cybercrime.
The indictment follows an investigation launched by the U.S. Federal Bureau of Investigation (FBI) in July 2020 after determining that WWH Club's primary domain (www-club[.]ws]) resolved to an IP address belonging to DigitalOcean, allowing them to issue a federal search warrant to the infrastructure company.
"WWH Club and sister site members used the marketplaces to buy and sell stolen personal identifying information (PII), credit card and bank account information, and computer passwords, among other sensitive information," the U.S. Department of Justice (DoJ) said.
The forums, on the other hand, acted as a hotspot for discussions on best practices for committing fraud, launching cyber attacks, and evading law enforcement.
Furthermore, the darknet marketplace offered online courses for aspiring and active cyber criminals on how to conduct frauds. The advertised cost of the course ranged from 10,000 rubles to 60,000 rubles (about $110 to $664 as of September 7, 2024) and an additional $200 for training materials.
Court documents show that undercover FBI agents signed up for the site and paid approximately $1,000 in bitcoin to attend a training course offered by the platform that included topics such as the sale of sensitive information, DDoS and hacking services, credit card skimmers, and brute-force programs.
"The training was conducted through a chat function on the forum to a class of approximately 50 students; the various instructors provided training in text format rather than audible instruction," the criminal complaint reads. "It was apparent the purpose of the training was to educate individuals on how to obtain and use stolen credit card data and PII to generate fraudulent proceeds."
WWH Club is estimated to have had 353,000 users worldwide as of March 2023, up from 170,000 registered users in July 2020. Both Khodyrev and Kublitskii are believed to have profited from the membership fees, tuition fees, and advertising revenue.
Flashpoint, in a report published last month, said WWH Club remains operational despite the law enforcement effort, and that "its other administrators are attempting to distance themselves from Kublitskii and Khodyrev."
Khodyrev and Kublitskii "had been living in Miami for the past two years, while secretly continuing to administer WWH Club and its sister dark web marketplaces, forums, and schools," the DoJ said.
If convicted on all counts, they could each face up to 20 years in federal prison. The indictment also requires the forfeiture of Khodyrev's 2023 Mercedes-Benz G63 AMG sport utility vehicle and Kublitskii's 2020 Cadillac CT5 Sport sedan, which are said to have been purchased using proceeds from their criminal enterprise.
Pavel Durov Criticizes Outdated Laws After Arrest Over Telegram Criminal Activity
6.9.24 BigBrothers The Hacker News
Telegram CEO Pavel Durov has broken his silence nearly two weeks after his arrest in France, stating the charges are misguided.
"If a country is unhappy with an internet service, the established practice is to start a legal action against the service itself," Durov said in a 600-word statement on his Telegram account.
"Using laws from the pre-smartphone era to charge a CEO with crimes committed by third-parties on the platform he manages is a misguided approach."
Durov was charged late last month for enabling various forms of criminal activity on Telegram, including drug trafficking and money laundering, following a probe into an unnamed person's distribution of child sexual abuse material.
He also highlighted the struggles to balance both privacy and security, noting that Telegram is ready to exit markets that aren't compatible with its mission to "protect our users in authoritarian regimes."
Durov also blamed "growing pains that made it easier for criminals to abuse our platform." The popular messaging app recently crossed 950 million monthly active users.
"That's why I made it my personal goal to ensure we significantly improve things in this regard," he said. "We've already started that process internally, and I will share more details on our progress with you very soon."
The company has since updated its FAQ to allow users to report illegal content within private and group chats by flagging it for review using a dedicated "Report" button, a major policy shift and a feature that was previously off-limits.
Durov's statement, however, doesn't delve into the lack of end-to-end encryption (E2EE) protections by default, which users have to explicitly enable in one-to-one chats.
"It is also a 'cloud messenger,' meaning that all messages live on Telegram's servers rather than the user's device," Moxie Marlinspike, creator of the E2EE messaging app Signal, pointed out.
"With one query, the Russian Telegram team can get every message the French president has ever sent or received to his contacts, every message those contacts have ever sent or received to their contacts, every message those contacts' contacts have ever sent or received, etc."
Matthew Green, a security researcher and an associate professor of computer science at Johns Hopkins University, further called out the platform for making it an onerous process that requires at least four clicks on Telegram's iOS app.
"The feature is explicitly not turned on for the vast majority of conversations, and is only available for one-on-one conversations, and never for group chats with more than two people in them," Green said.
"As a kind of a weird bonus, activating end-to-end encryption in Telegram is oddly difficult for non-expert users to actually do. Secret Chats only works if your conversation partner happens to be online when you do this."
U.S. Seizes 32 Pro-Russian Propaganda Domains in Major Disinformation Crackdown
5.9.24 BigBrothers The Hacker News
The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 32 internet domains used by a pro-Russian propaganda operation called Doppelganger as part of a sweeping set of actions.
Accusing the Russian government-directed foreign malign influence campaign of violating U.S. money laundering and criminal trademark laws, the agency called out companies Social Design Agency (SDA), Structura National Technology (Structura), and ANO Dialog for working at the behest of the Russian Presidential Administration.
The goal, it said, is to "covertly spread Russian government propaganda with the aim of reducing international support for Ukraine, bolstering pro-Russian policies and interests, and influencing voters in U.S. and foreign elections, including the U.S. 2024 Presidential Election."
Among the methods Doppelganger used to drive viewership to the cybersquatted media domains encompassed the deployment of "influencers" worldwide, paid social media ads, and the creation of social media profiles posing as U.S. (or other non-Russian) citizens to post comments on social media platforms with links to the domains in an attempt to redirect unsuspecting viewers.
The sites dismantled by the U.S. government were filled with Russian government propaganda created by the Kremlin to reduce international support for Ukraine, bolster pro-Russian policies and interests, and influence voters in the U.S. and other countries.
The complete list of domains, which mimic legitimate news outlets like Der Spiegel, Fox News, Le Monde, and The Washington Post, is as follows -
tribunalukraine.info
rrn.media
ukrlm.info
faz.ltd
spiegel.agency
lemonde.ltd
leparisien.ltd
rbk.media
50statesoflie.media
meisterurian.io
artichoc.io
vip-news.org
acrosstheline.press
mypride.press
truthgate.us
warfareinsider.us
shadowwatch.us
pravda-ua.com
waronfakes.com
holylandherald.com
levinaigre.net
grenzezank.com
lexomnium.com
uschina.online
honeymoney.press
sueddeutsche.co
tagesspiegel.co
bild.work
fox-news.top
fox-news.in
forward.pw, and
washingtonpost.pm
Concurrent with the domain seizures, the Treasury Department sanctioned 10 individuals and two entities for engaging in efforts to influence and undermine confidence in the electoral process.
Specifically, it alleged that executives at RT, Russia's state-funded news media publication, covertly recruited unwitting American influencers into its campaign efforts. It's also said to have used a front company to conceal its own involvement or that of the government.
"At Putin's direction, Russian companies SDA, Structura, and ANO Dialog used cybersquatting, fabricated influencers, and fake profiles to covertly promote AI-generated false narratives on social media," said Deputy Attorney General Lisa Monaco. "Those narratives targeted specific American demographics and regions in a calculated effort to subvert our election."
In conjunction, the DoJ also announced the indictment of two RT employees for funneling $9.7 million to further "hidden" Russian government messaging and disinformation by disseminating thousands of videos via a Tennessee-based content creation firm with an ultimate aim to sow discord among Americans.
Court documents allege that Kostiantyn Kalashnikov, 31, and Elena Afanasyeva, 27, along with other RT employees financed the company's operations to publish English-language videos across TikTok, Instagram, X, and YouTube, racking up millions of views. Kalashnikov and Afanasyeva masqueraded as an outside editing team.
The company is estimated to have posted nearly 2,000 videos since its launch in November 2023, sharing commentary related to immigration, inflation, and other topics related to domestic and foreign policy. The videos have been watched over 16 million times on YouTube alone.
"While the views expressed in the videos are not uniform, most are directed to the publicly stated goals of the Government of Russia and RT — to amplify domestic divisions in the United States," the DoJ said, adding the company "never disclosed to its viewers that it was funded and directed by RT."
The two Russian nationals have been charged with conspiracy to violate the Foreign Agents Registration Act (FARA), which carries a maximum sentence of five years in prison, and conspiracy to commit money laundering, which carries a maximum sentence of 20 years in prison.
Furthermore, the State Department has instituted a new policy to restrict visa issuance to individuals acting on behalf of Kremlin-supported media organizations and using them as cover to engage in clandestine influence activities.
It has also designated Rossiya Segodnya, and subsidiaries RIA Novosti, RT, TV-Novosti, Ruptly, and Sputnik, as foreign missions, requiring them to notify the Department of all personnel working in the country, as well as disclose all real property they hold within U.S. borders.
Taken together, the actions signal a broader push by the U.S. government to clamp down on Russian-backed disinformation operations ahead of November's general election.
The development comes amid revelations that a Chinese influence operation dubbed Spamouflage has ramped up its efforts to influence online discourse around the U.S. elections, creating fake personas across social media platforms to push divisive narratives about sensitive social issues by capitalizing on a polarized information environment.
"These accounts have seeded and amplified content denigrating Democratic and Republican candidates, sowing doubt in the legitimacy of the U.S. electoral process, and spreading divisive narratives about sensitive social issues including gun control, homelessness, drug abuse, racial inequality, and the Israel-Hamas conflict," Graphika said.
French Authorities Charge Telegram CEO with Facilitating Criminal Activities on Platform
29.8.24 BigBrothers The Hacker News

French prosecutors on Wednesday formally charged Telegram CEO Pavel Durov with facilitating a litany of criminal activity on the popular messaging platform and placed him under formal investigation following his arrest Saturday.
Russian-born Durov, who is also a French citizen, has been charged with being complicit in the spread of child sexual abuse material (CSAM) as well as enabling organized crime, illicit transactions, drug trafficking, and fraud.
Durov has also been charged with a "refusal to communicate, at the request of competent authorities, information or documents necessary for carrying out and operating interceptions allowed by law," according to an English translation of the press release.
The 39-year-old was detained at Le Bourget airport north of Paris at 8 p.m. local time on Saturday after disembarking from a private jet. To avoid pretrial detention, Durov has been ordered to pay a €5 million bail, but he is barred from leaving the country and must report to the authorities twice a week.
The arrest is in connection with a judicial investigation into an unnamed person that was opened in France on July 8, 2024, primarily driven by Telegram's lax moderation policies that have allowed extremist and malicious activity to thrive on the platform. A preliminary probe is said to have commenced in February 2024.
"The almost total lack of response from Telegram to judicial requisitions was brought to the attention of the cybercrime fighting section (J3) of JUNALCO (National Jurisdiction for the Fight against Organized Crime, within the Paris prosecutor's office), in particular by OFMIN (National Office for Minors)," Paris prosecutor Laure Beccuau said.
"When consulted, other French investigative services and public prosecutors as well as various partners within Eurojust, particularly Belgian ones, shared the same observation. This is what led JUNALCO to open an investigation into the possible criminal liability of the managers of this messaging service in the commission of these offenses."
Other charges against Durov include -
Supply of cryptographic services designed to ensure confidentiality without a declaration of conformity
Supply and import of a cryptographic means that does not exclusively ensure authentication or integrity control functions without prior declaration
The development marks one of the rare instances where a company's top executive has been held liable for what users' post on a major platform that has more than 950 million monthly active users. Durove was previously the CEO of the Russian social media platform Vkontakte which he had founded in 2006. Telegram was subsequently launched in 2013.
Following Durov's arrest, Telegram said in a statement on X that he has "nothing to hide," adding "it is absurd to claim that a platform or its owner are responsible for abuse of that platform." The company also claims it regularly publishes reports of thousands of groups and channels related to child abuse being banned on the messaging service.
It's also worth noting that the site's terms of service specifically state that it does not process any requests related to illegal content shared on Telegram chats and group chats.
Politico has since reported that French authorities issued arrest warrants for Telegram CEO Pavel Durov and his co-founder brother Nikolai in March 2024. French President Emmanuel Macron said Monday that Durov's arrest wasn't a political decision but part of an independent investigation.
The Wall Street Journal further revealed Wednesday that Durov's iPhone was hacked by French spies in a joint exercise with the United Arab Emirates in 2017 as part of a previously unknown operation codenamed Purple Music, citing people familiar with the matter.
"French security officials were acutely concerned about Islamic State's use of Telegram to recruit operatives and plan attacks," the report said.
Dutch Regulator Fines Uber €290 Million for GDPR Violations in Data Transfers to U.S.
26.8.24 BigBrothers The Hacker News
The Dutch Data Protection Authority (DPA) has fined Uber a record €290 million ($324 million) for allegedly failing to comply with European Union (E.U.) data protection standards when sending sensitive driver data to the U.S.
"The Dutch DPA found that Uber transferred personal data of European taxi drivers to the United States (U.S.) and failed to appropriately safeguard the data with regard to these transfers," the agency said.
The data protection watchdog said the move constitutes a "serious" violation of the General Data Protection Regulation (GDPR). In response, the ride-hailing, courier, and food delivery service has ended the practice.
Uber is believed to have collected drivers' sensitive information and retained it on U.S.-based servers for over two years. This included account details and taxi licenses, location data, photos, payment details, and identity documents. In some cases, it also contained criminal and medical data of drivers.
The DPA accused Uber of carrying out the data transfers without making use of appropriate mechanisms, especially considering the E.U. invalidated the E.U.-U.S. Privacy Shield in 2020. A replacement, known as the E.U.-U.S. Data Privacy Framework, was announced in July 2023.
"Because Uber no longer used Standard Contractual Clauses from August 2021, the data of drivers from the E.U. were insufficiently protected, according to the Dutch DPA," the agency said. "Since the end of last year, Uber uses the successor to the Privacy Shield."
In a statement shared with Bloomberg, Uber said the fine is "completely unjustified" and that it intends to contest the decision. It further said the cross-border data transfer process was compliant with GDPR.
Earlier this year, the DPA fined Uber a €10 million penalty for its failure to disclose the full details of its data retention periods concerning European drivers, and the non-European countries to which it shares the data.
"Uber had made it unnecessarily complicated for drivers to submit requests to view or receive copies of their personal data," the DPA noted in January 2024.
"In addition, they did not specify in their privacy terms and conditions how long Uber retains its drivers' personal data or which specific security measures it takes when sending this information to entities in countries outside the [European Economic Area]."
This is not the first time U.S. companies have landed in the crosshairs of E.U. data protection authorities over the lack of equivalent privacy protections in the U.S. with regard to E.U. data transfers, raising concerns that European user data could be subject to U.S. surveillance programs.
Back in 2022, Austrian and French regulators ruled that the transatlantic movement of Google Analytics data was a breach of GDPR laws.
"Think of governments that can tap data on a large scale," DPA chairman Aleid Wolfsen said. "That is why businesses are usually obliged to take additional measures if they store personal data of Europeans outside the European Union."
CISA Urges Federal Agencies to Patch Versa Director Vulnerability by September
24.8.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has placed a security flaw impacting Versa Director to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation.
The medium-severity vulnerability, tracked as CVE-2024-39717 (CVSS score: 6.6), is case of file upload bug impacting the "Change Favicon" feature that could allow a threat actor to upload a malicious file by masquerading it as a seemingly harmless PNG image file.
"The Versa Director GUI contains an unrestricted upload of file with dangerous type vulnerability that allows administrators with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin privileges to customize the user interface," CISA said in an advisory.
"The 'Change Favicon' (Favorite Icon) enables the upload of a .png file, which can be exploited to upload a malicious file with a .PNG extension disguised as an image."
However, a successful exploitation is possible only after a user with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin privileges has successfully authenticated and logged in.
While the exact circumstances surrounding the exploitation of CVE-2024-39717 is unclear, a description of the vulnerability in the NIST National Vulnerability Database (NVD) states that Versa Networks is aware of one confirmed instance in which a customer was targeted.
"The Firewall guidelines which were published in 2015 and 2017 were not implemented by that customer," the description states. "This non-implementation resulted in the bad actor being able to exploit this vulnerability without using the GUI."
Federal Civilian Executive Branch (FCEB) agencies are required to take steps to protect against the flaw by applying vendor-provided fixes by September 13, 2024.
The development comes days after CISA added four security shortcomings from 2021 and 2022 to its KEV catalog -
CVE-2021-33044 (CVSS score: 9.8) - Dahua IP Camera Authentication Bypass Vulnerability
CVE-2021-33045 (CVSS score: 9.8) - Dahua IP Camera Authentication Bypass Vulnerability
CVE-2021-31196 (CVSS score: 7.2) - Microsoft Exchange Server Information Disclosure Vulnerability
CVE-2022-0185 (CVSS score: 8.4) - Linux Kernel Heap-Based Buffer Overflow Vulnerability
It's worth noting that a China-linked threat actor codenamed UNC5174 (aka Uteus or Uetus) was attributed to the exploitation of CVE-2022-0185 by Google-owned Mandiant earlier this March.
CVE-2021-31196 was originally disclosed as part of a huge set of Microsoft Exchange Server vulnerabilities, collectively tracked as ProxyLogon, ProxyShell, ProxyToken, and ProxyOracle.
"CVE-2021-31196 has been observed in active exploitation campaigns, where threat actors target unpatched Microsoft Exchange Server instances," OP Innovate said. "These attacks typically aim to gain unauthorized access to sensitive information, escalate privileges, or deploy further payloads such as ransomware or malware."
New Cyber Threat Targets Azerbaijan and Israel Diplomats, Stealing Sensitive Data
15.8.24 BigBrothers The Hacker News
A previously unknown threat actor has been attributed to a spate of attacks targeting Azerbaijan and Israel with an aim to steal sensitive data.
The attack campaign, detected by NSFOCUS on July 1, 2024, leveraged spear-phishing emails to single out Azerbaijani and Israeli diplomats. The activity is being tracked under the moniker Actor240524.
"Actor240524 possesses the ability to steal secrets and modify file data, using a variety of countermeasures to avoid overexposure of attack tactics and techniques," the cybersecurity company said in an analysis published last week.
The attack chains commence with the use of phishing emails bearing Microsoft Word documents that, upon opening, urge the recipients to "Enable Content" and run a malicious macro responsible for executing an intermediate loader payload codenamed ABCloader ("MicrosoftWordUpdater.log").
In the next step, ABCloader acts as a conduit to decrypt and load a DLL malware called ABCsync ("synchronize.dll"), which then establishes contact with a remote server ("185.23.253[.]143") to receive and run commands.

"Its main function is to determine the running environment, decrypt the program, and load the subsequent DLL (ABCsync)," NSFOCUS said. "It then performs various anti-sandbox and anti-analysis techniques for environmental detection."
Some of the prominent functions of ABCsync are to execute remote shells, run commands using cmd.exe, and exfiltrate system information and other data.
Both ABCloader and ABCsync have been observed employing techniques like string encryption to cloak important file paths, file names, keys, error messages, and command-and-control (C2) addresses. They also carry out several checks to determine if the processes are being debugged or executed in a virtual machine or sandbox by validating the display resolution.
Another crucial step taken by Actor240524 is that it inspects if the number of processes running in the compromised system is less than 200, and if so, it exits the malicious process.
ABCloader is also designed to launch a similar loader called "synchronize.exe" and a DLL file named "vcruntime190.dll" or "vcruntime220.dll," which are capable of setting up persistence on the host.
"Azerbaijan and Israel are allied countries with close economic and political exchanges," NSFOCUS said. "Actor240524's operation this time is likely aimed at the cooperative relationship between the two countries, targeting phishing attacks on diplomatic personnel of both countries."
Belarusian-Ukrainian Hacker Extradited to U.S. for Ransomware and Cybercrime Charges
15.8.24 BigBrothers The Hacker News
A coalition of law enforcement agencies coordinated by the U.K. National Crime Agency (NCA) has led to the arrest and extradition of a Belarussian and Ukrainian dual-national believed to be associated with Russian-speaking cybercrime groups.
Maksim Silnikau (aka Maksym Silnikov), 38, went by the online monikers J.P. Morgan, xxx, and lansky. He was extradited to the U.S. from Poland on August 9, 2024, to face charges related to international computer hacking and wire fraud schemes.
"J.P. Morgan and his associates are elite cyber criminals who practiced extreme operational and online security in an effort to avoid law enforcement detection," the NCA said in a statement.
These individuals, the agency said, were responsible for the development and distribution of ransomware strains such as Reveton and Ransom Cartel, as well as exploit kits like Angler. Reveton, introduced in 2011, has been described as the "first ever ransomware-as-a-service business model."
Victims of Reveton have been found to have received messages purporting to be from law enforcement, accusing them of downloading child abuse material and copyrighted programs and threatening them with large fines to avoid imprisonment and gain access to their locked devices.
The scam resulted in about $400,000 being extorted from victims every month from 2012 to 2014, with Angler infections accounting for an estimated annual turnover of around $34 million at its peak. As many as 100,000 devices are believed to have been targeted by the exploit kit.
Silnikau, alongside Volodymyr Kadariya and Andrei Tarasov, are said to have been involved in the distribution of Angler and for leveraging malvertising techniques from October 2013 through March 2022 to deliver malicious and scam content designed to trick users into providing their sensitive personal information.
The stolen information, such as banking information and login credentials, and access to the compromised devices were then offered for sale in Russian cybercrime forums on the dark web.
"Silnikau and his co-conspirators allegedly used malware and various online scams to target millions of unsuspecting internet users in the United States and around the world," FBI Deputy Director Paul Abbate said. "They hid behind online aliases and engaged in complex, far-reaching cyber fraud schemes to compromise victim devices and steal sensitive personal information."
The criminal scheme not only caused unsuspecting internet users to be forcibly redirected to malicious content on millions of occasions, but also defrauded and attempted to defraud various U.S.-based companies involved in the sale and distribution of legitimate online ads, the U.S. Justice Department (DoJ) said.
Prominent among the methods used to disseminate malware was the Angler Exploit Kit, which leveraged web-based vulnerabilities in web browsers and plugins to serve "scareware" ads that displayed warning messages claiming to have found a computer virus on victims' devices and then deceived them into downloading remote access trojans or disclosing personal identifying or financial information.
"For years, the conspirators tricked advertising companies into delivering their malvertising campaigns by using dozens of online personas and fictitious entities to pose as legitimate advertising companies," the DoJ said.
"They also developed and used sophisticated technologies and computer code to refine their malvertisements, malware, and computer infrastructure so as to conceal the malicious nature of their advertising."
A separate indictment from the Eastern District of Virginia also accused Silnikau of being the creator and administrator of the Ransom Cartel ransomware strain beginning in May 2021.
"On various occasions, Silnikau allegedly distributed information and tools to Ransom Cartel participants, including information about compromised computers, such as stolen credentials, and tools such as those designed to encrypt or 'lock' compromised computers," the DoJ noted.
"Silnikau also allegedly established and maintained a hidden website where he and his co-conspirators could monitor and control ransomware attacks; communicate with each other; communicate with victims, including sending and negotiating payment demands; and manage distribution of funds between co-conspirators."
Silnikau, Kadariya, and Tarasov have been charged with conspiracy to commit wire fraud, conspiracy to commit computer fraud, and two counts of substantive wire fraud. Silnikau has further been charged with conspiracy to commit computer fraud and abuse, conspiracy to commit wire fraud, conspiracy to commit access device fraud, and two counts each of wire fraud and aggravated identity theft.
If convicted on all counts, Silnikau faces more than 50 years in prison. Prior to his extradition, he was arrested from an apartment in Estepona, Spain in July 2023 as part of a coordinated effort between Spain, the U.K., and the U.S.
"Their impact goes far beyond the attacks they launched themselves," NCA Deputy Director Paul Foster said. "They essentially pioneered both the exploit kit and ransomware-as-a-service models, which have made it easier for people to become involved in cybercrime and continue to assist offenders."
"These are highly sophisticated cyber criminals who, for a number of years, were adept at masking their activity and identities."
FBI Shuts Down Dispossessor Ransomware Group's Servers Across U.S., U.K., and Germany
13.8.24 BigBrothers The Hacker News
The U.S. Federal Bureau of Investigation (FBI) on Monday announced the disruption of online infrastructure associated with a nascent ransomware group called Dispossessor (aka Radar).
The effort saw the dismantling of three U.S. servers, three United Kingdom servers, 18 German servers, eight U.S.-based criminal domains, and one German-based criminal domain. Dispossessor is said to be led by individual(s) who go by the online moniker "Brain."
"Since its inception in August 2023, Radar/Dispossessor has quickly developed into an internationally impactful ransomware group, targeting and attacking small-to-mid-sized businesses and organizations from the production, development, education, healthcare, financial services, and transportation sectors," the FBI said in a statement.
As many as 43 companies have been identified as victims of Dispossessor attacks, including those located in Argentina, Australia, Belgium, Brazil, Canada, Croatia, Germany, Honduras, India, Peru, Poland, the U.A.E., the U.K., and the U.S.
Dispossessor, notable for its similarities to LockBit, surfaced as a ransomware-as-a-service (RaaS) group following the same dual-extortion model pioneered by other e-crime gangs. Such attacks work by exfiltrating victim data to hold for ransom in addition to encrypting their systems. Users who refuse to settle are threatened with data exposure.
Attack chains mounted by the threat actors have been observed to leverage systems with security flaws or weak passwords as an entry point to breach targets and gain elevated access to lock their data behind encryption barriers.
"Once the company was attacked, if they did not contact the criminal actor, the group would then proactively contact others in the victim company, either through email or phone call," the FBI said.
"The emails also included links to video platforms on which the previously stolen files had been presented. This was always with the aim of increasing the blackmail pressure and increasing the willingness to pay."
Previous reporting from cybersecurity company SentinelOne found the Dispossessor group to be advertising already leaked data for download and sale, adding it "appears to be reposting data previously associated with other operations with examples ranging from Cl0p, Hunters International, and 8Base."

The frequency of such takedowns is yet another indication that law enforcement agencies across the world are ramping up efforts to combat the persistent ransomware menace, even as the threat actors are finding ways to innovate and thrive in the ever-shifting landscape.
This includes an uptick in attacks carried out via contractors and service providers, highlighting how threat actors are weaponizing trusted relationships to their advantage, as "this approach facilitates large-scale attacks with less effort, often going undetected until data leaks or encrypted data are discovered."
Data gathered by Palo Alto Networks Unit 42 from leak sites shows that industries most impacted by ransomware during the first half of 2024 were manufacturing (16.4%), healthcare (9.6%) and construction (9.4%).

Some of the most targeted countries during the time period were the U.S., Canada, the U.K., Germany, Italy, France, Spain, Brazil, Australia and Belgium.
"Newly disclosed vulnerabilities primarily drove ransomware activity as attackers moved to quickly exploit these opportunities," the company said. "Threat actors regularly target vulnerabilities to access victim networks, elevate privileges and move laterally across breached environments."
A noticeable trend is the emergence of new (or revamped) ransomware groups, which accounted for 21 out of the total 68 unique groups posting extortion attempts, and the increased targeting of smaller organizations, per Rapid7.
"This could be for a lot of reasons, not the least of which is that these smaller organizations contain many of the same data threat actors are after, but they often have less mature security precautions in place," it said.
Another important aspect is the professionalization of the RaaS business models. Ransomware groups are not only more sophisticated, they are also increasingly scaling their operations that resemble legitimate corporate enterprises.
"They have their own marketplaces, sell their own products, and in some cases have 24/7 support," Rapid7 pointed out. "They also seem to be creating an ecosystem of collaboration and consolidation in the kinds of ransomware they deploy."
Ukraine Warns of New Phishing Campaign Targeting Government Computers
13.8.24 BigBrothers The Hacker News
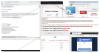
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign that masquerades as the Security Service of Ukraine to distribute malware capable of remote desktop access.
The agency is tracking the activity under the name UAC-0198. More than 100 computers are estimated to have been infected since July 2024, including those related to government bodies in the country.
The attack chains involve the mass distribution of emails to deliver a ZIP archive file containing an MSI installer file, the opening of which leads to the deployment of malware called ANONVNC.
ANONVNC, which is based on an open-source remote management tool called MeshAgent, allows for stealthy unauthorized access to the infected hosts.
The development comes as CERT-UA attributed the hacking group UAC-0102 to phishing attacks propagating HTML attachments that mimic the login page of UKR.NET to steal users' credentials.
Over the past few weeks, the agency has also warned of a surge in campaigns distributing the PicassoLoader malware with the end goal of deploying Cobalt Strike Beacon on compromised systems. The attacks have been linked to a threat actor tracked as UAC-0057.
"It is reasonable to assume that the objects of interest of UAC-0057 could be both specialists of project offices and their 'contractors' from among the employees of the relevant local governments of Ukraine," CERT-UA said.
EastWind Attack Deploys PlugY and GrewApacha Backdoors Using Booby-Trapped LNK Files
13.8.24 BigBrothers The Hacker News
The Russian government and IT organizations are the target of a new campaign that delivers a number of backdoors and trojans as part of a spear-phishing campaign codenamed EastWind.
The attack chains are characterized by the use of RAR archive attachments containing a Windows shortcut (LNK) file that, upon opening, activates the infection sequence, culminating in the deployment of malware such as GrewApacha, an updated version of the CloudSorcerer backdoor, and a previously undocumented implant dubbed PlugY.
PlugY is "downloaded through the CloudSorcerer backdoor, has an extensive set of commands and supports three different protocols for communicating with the command-and-control server," Russian cybersecurity company Kaspersky said.
The initial infection vector relies on a booby-trapped LNK file, which employs DLL side-loading techniques to launch a malicious DLL file that uses Dropbox as a communications mechanism to execute reconnaissance commands and download additional payloads.
Among the malware deployed using the DLL is GrewApacha, a known backdoor previously linked to the China-linked APT31 group. Also launched using DLL side-loading, it uses an attacker-controlled GitHub profile as a dead drop resolver to store a Base64-encoded string of the actual C2 server.
CloudSorcerer, on the other hand, is a sophisticated cyber espionage tool used for stealth monitoring, data collection, and exfiltration via Microsoft Graph, Yandex Cloud, and Dropbox cloud infrastructure. Like in the case of GrewApacha, the updated variant leverages legitimate platforms like LiveJournal and Quora as an initial C2 server.
"As with previous versions of CloudSorcerer, profile biographies contain an encrypted authentication token to interact with the cloud service," Kaspersky said.
Furthermore, it utilizes an encryption-based protection mechanism that ensures the malware is detonated only on the victim's computer by using a unique key that's derived from the Windows GetTickCount() function at runtime.
The third malware family observed in the attacks in PlugY, a fully-featured backdoor that connects to a management server using TCP, UDP, or named pipes, and comes with capabilities to execute shell commands, monitor device screen, log keystrokes, and capture clipboard content.
Kaspersky said a source code analysis of PlugX uncovered similarities with a known backdoor called DRBControl (aka Clambling), which has been attributed to China-nexus threat clusters tracked as APT27 and APT41.
"The attackers behind the EastWind campaign used popular network services as command servers - GitHub, Dropbox, Quora, as well as Russian LiveJournal and Yandex Disk," the company said.
The disclosure comes Kaspersky also detailed a watering hole attack that involves compromising a legitimate site related to gas supply in Russia to distribute a worm named CMoon that can harvest confidential and payment data, take screenshots, download additional malware, and launch distributed denial-of-service (DDoS) attacks against targets of interest.
The malware also collects files and data from various web browsers, cryptocurrency wallets, instant messaging apps, SSH clients, FTP software, video recording and streaming apps, authenticators, remote desktop tools, and VPNs.
"CMoon is a worm written in .NET, with wide functionality for data theft and remote control," it said. "Immediately after installation, the executable file begins to monitor the connected USB drives. This allows you to steal files of potential interest to attackers from removable media, as well as copy a worm to them and infect other computers where the drive will be used."
DOJ Charges Nashville Man for Helping North Koreans Get U.S. Tech Jobs
9.8.24 BigBrothers The Hacker News
The U.S. Department of Justice (DoJ) on Thursday charged a 38-year-old individual from Nashville, Tennessee, for allegedly running a "laptop farm" to help get North Koreans remote jobs with American and British companies.
Matthew Isaac Knoot is charged with conspiracy to cause damage to protected computers, conspiracy to launder monetary instruments, conspiracy to commit wire fraud, intentional damage to protected computers, aggravated identity theft and conspiracy to cause the unlawful employment of aliens.
If convicted, Knoot faces a maximum penalty of 20 years in prison, counting a mandatory minimum of two years in prison on the aggravated identity theft count.
Court documents allege that Knoot participated in a worker fraud scheme by letting North Korean actors get employment at information technology (IT) companies in the U.K. and the U.S. It's believed that the revenue generation efforts are a way to fund North Korea's illicit weapons program.
"Knoot assisted them in using a stolen identity to pose as a U.S. citizen, hosted company laptops at his residences, downloaded and installed software without authorization on such laptops to facilitate access and perpetuate the deception, and conspired to launder payments for the remote IT work, including to accounts tied to North Korean and Chinese actors," the DoJ said.
The unsealed indictment said the IT workers used the stolen identity of a U.S. citizen named "Andrew M." to obtain the remote work, defrauding media, technology, and financial companies of hundreds of thousands of dollars in damages.
Recent advisories from the U.S. government have revealed that these IT workers, part of the Workers' Party of Korea's Munitions Industry Department, are routinely dispatched to live abroad in countries like China and Russia, from where they are hired as freelance IT workers to generate revenue for the hermit kingdom.
Knoot is believed to have run a laptop farm at his Nashville residences between approximately July 2022 and August 2023, with the victim companies shipping the laptops to his home addressed as "Andrew M." Knoot then logged into these computers, downloaded and installed unauthorized remote desktop applications, and accessed the internal networks.
"The remote desktop applications enabled the North Korean IT workers to work from locations in China, while appearing to the victim companies that 'Andrew M.' was working from Knoot's residences in Nashville," the DoJ said.
"For his participation in the scheme, Knoot was paid a monthly fee for his services by a foreign-based facilitator who went by the name Yang Di. A court-authorized search of Knoot's laptop farm was executed in early August 2023."
The overseas IT workers are said to have been paid over $250,000 for their work during the same time period, causing companies more than $500,000 in costs associated with auditing and remediating their devices, systems, and networks. Knoot, the DoJ noted, also falsely reported the earnings to the Internal Revenue Service (IRS) under the stolen identity.
Knoot is the second person to be charged in the U.S. in connection with the remote IT worker fraud scheme after Christina Marie Chapman, 49, who was previously accused of running a laptop farm by hosting multiple laptops at her residence in Arizona.
Last month, security awareness training firm KnowBe4 revealed it was tricked into hiring an IT worker from North Korea as a software engineer, who used the stolen identity of a U.S. citizen and enhanced their picture using artificial intelligence (AI).
The development comes as the U.S. State Department's Rewards for Justice program announced a reward of up to $10 million for information leading to the identification or location of six individuals linked to the Iranian Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC) who were sanctioned in connection with striking critical infrastructure entities in the U.S. and other countries.
DOJ and FTC Sue TikTok for Violating Children's Privacy Laws
4.8.24 BigBrothers The Hacker News
The U.S. Department of Justice (DoJ), along with the Federal Trade Commission (FTC), filed a lawsuit against popular video-sharing platform TikTok for "flagrantly violating" children's privacy laws in the country.
The agencies claimed the company knowingly permitted children to create TikTok accounts and to view and share short-form videos and messages with adults and others on the service.
They also accused it of illegally collecting and retaining a wide variety of personal information from these children without notifying or obtaining consent from their parents, in contravention of the Children's Online Privacy Protection Act (COPPA).
TikTok's practices also infringed a 2019 consent order between the company and the government in which it pledged to notify parents before collecting children's data and remove videos from users under 13 years old, they added.
Cybersecurity
COPPA requires online platforms to gather, use, or disclose personal information from children under the age of 13, unless they have obtained consent from their parents. It also mandates companies to delete all the collected information at the parents' request.
"Even for accounts that were created in 'Kids Mode' (a pared-back version of TikTok intended for children under 13), the defendants unlawfully collected and retained children's email addresses and other types of personal information," the DoJ said.
"Further, when parents discovered their children's accounts and asked the defendants to delete the accounts and information in them, the defendants frequently failed to honor those requests."
The complaint further alleged the ByteDance-owned company subjected millions of children under 13 to extensive data collection that enabled targeted advertising and allowed them to interact with adults and access adult content.
It also faulted TikTok for not exercising adequate due diligence during the account creation process by building backdoors that made it possible for children to bypass the age gate aimed at screening those under 13 by letting them sign in using third-party services like Google and Instagram and classifying such accounts as "age unknown" accounts.
"TikTok human reviewers allegedly spent an average of only five to seven seconds reviewing each account to make their determination of whether the account belonged to a child," the FTC said, adding it will take steps to protect children's privacy from firms that deploy "sophisticated digital tools to surveil kids and profit from their data."
TikTok has more than 170 million active users in the U.S. While the company has disputed the allegations, it's the latest setback for the video platform, which is already the subject of a law that would force a sale or a ban of the app by early 2025 because of national security concerns. It has filed a petition in federal court seeking to overturn the ban.
"We disagree with these allegations, many of which relate to past events and practices that are factually inaccurate or have been addressed," TikTok said. "We offer age-appropriate experiences with stringent safeguards, proactively remove suspected underage users, and have voluntarily launched features such as default screen time limits, Family Pairing, and additional privacy protections for minors."
The social media platform has also faced scrutiny globally over child protection. European Union regulators handed TikTok a €345 million fine in September 2023 for violating data protection laws in relation to its handling of children's data. In April 2023, it was fined £12.7 million by the ICO for illegally processing the data of 1.4 million children under 13 who were using its platform without parental consent.
The lawsuit comes as the U.K. Information Commissioner's Office (ICO) revealed it asked 11 media and video-sharing platforms to improve their children's privacy practices or risk facing enforcement action. The names of the offending services were not disclosed.
"Eleven out of the 34 platforms are being asked about issues relating to default privacy settings, geolocation or age assurance, and to explain how their approach conforms with the [Children's Code]," it said. "We are also speaking to some of the platforms about targeted advertising to set out expectations for changes to ensure practices are in line with both the law and the code."
U.S. Releases High-Profile Russian Hackers in Diplomatic Prisoner Exchange
2.8.24 BigBrothers The Hacker News
In a historic prisoner exchange between Belarus, Germany, Norway, Russia, Slovenia, and the U.S., two Russian nationals serving time for cybercrime activities have been freed and repatriated to their country.
This includes Roman Valerevich Seleznev and Vladislav Klyushin, who are part of a group of eight people who have been swapped back to Russia in exchange for the release of 16 people who were held in detention, counting four Americans, five Germans and seven Russians citizens who were held as political prisoners.
U.S. President Joe Biden called the deal a "feat of diplomacy," adding "some of these women and men have been unjustly held for years." Other nations that played a role in the swap include Poland and Turkey.
Among those released from Russia are former U.S. Marine Paul Whelan, Wall Street Journal reporter Evan Gershkovich, Vladimir Kara-Murza, a green-card holder and a prominent critic of Russian president Vladimir Putin, and Russian-American journalist Alsu Kurmasheva.
Seleznev, also known by the aliases Track2, Bulba, and nCux, was sentenced in 2017 to 27 years in prison for payment card fraud, causing nearly $170 million in damages to small businesses and financial institutions in the U.S. He was subsequently handed another 14-year jail term for his role in a $50 million cyber fraud ring and for defrauding banks of $9 million through a hacking scheme.
The other Russian national going home is Klyushin, the owner of security penetration testing firm M-13 who was sentenced in the U.S. last September for stealing confidential financial information from U.S. companies in a $93 million insider-trading scheme.
"Not since the Cold War has there been a similar number of individuals exchanged in this way and there has never, so far as we know, been an exchange involving so many countries, so many close U.S. partners and allies working together," National Security Adviser Jake Sullivan was quoted as saying.
The development comes as the U.K. National Crime Agency (NCA) announced the shutdown of a fraud platform called Russian Coms ("russiancoms[.]cm") that allowed its customers to make over 1.3 million anonymous calls between 2021 and 2024 by masquerading as banks and law enforcement agencies.
Three individuals allegedly linked to the creation and development of the platform have been arrested and subsequently released on conditional bail. The caller ID spoofing solution, marketed through Snapchat, Instagram and Telegram, cost anywhere from £350 to £1,000 and was available as a bespoke handset and, later, as a web app.
"The platform allowed criminals to hide their identity by appearing to call from pre-selected numbers, most commonly of financial institutions, telecommunications companies, and law enforcement agencies," the NCA said. "This enabled them to gain the trust of victims before stealing their money and personal details."
Cyber Espionage Group XDSpy Targets Companies in Russia and Moldova
1.8.24 BigBrothers The Hacker News
Companies in Russia and Moldova have been the target of a phishing campaign orchestrated by a little-known cyber espionage group known as XDSpy.
The findings come from cybersecurity firm F.A.C.C.T., which said the infection chains lead to the deployment of a malware called DSDownloader. The activity was observed this month, it added.
XDSpy is a threat actor of indeterminate origin that was first uncovered by the Belarusian Computer Emergency Response Team, CERT.BY, in February 2020. A subsequent analysis by ESET attributed the group to information-stealing attacks aimed at government agencies in Eastern Europe and the Balkans since 2011.
Attack chains mounted by the adversary are known to leverage spear-phishing emails in order to infiltrate their targets with a main malware module known as XDDown that, in turn, drops additional plugins for gathering system information, enumerating C: drive, monitoring external drives, exfiltrating local files, and gathering passwords.
Over the past year, XDSpy has been observed targeting Russian organizations with a C#-base dropper named UTask that's responsible for downloading a core module in the form of an executable that can fetch more payloads from a command-and-control (C2) server.
The latest set of attacks entails the use of phishing emails with agreement-related lures to propagate a RAR archive file that contains a legitimate executable and a malicious DLL file. The DLL is then executed by means of the former using DLL side-loading techniques.
In the next phase, the library takes care of fetching and running DSDownloader, which, in turn, opens a decoy file as a distraction while surreptitiously downloading the next-stage malware from a remote server. F.A.C.C.T. said the payload was no longer available for download at the time of analysis.
The onset of the Russo-Ukrainian war in February 2022 has witnessed a significant escalation in cyber attacks on both sides, with Russian companies compromised by DarkWatchman RAT as well as by activity clusters tracked as Core Werewolf, Hellhounds, PhantomCore, Rare Wolf, ReaverBits, and Sticky Werewolf, among others in recent months.
What's more, pro-Ukrainian hacktivist groups such as Cyber.Anarchy.Squad have also set their sights on Russian entities, conducting hack-and-leak operations and disruptive attacks against Infotel and Avanpost.
The development comes as the Computer Emergency Response Team of Ukraine (CERT-UA) warned of a spike in phishing attacks carried out by a Belarusian threat actor called UAC-0057 (aka GhostWriter and UNC1151) that distribute a malware family referred to as PicassoLoader with an aim to drop a Cobalt Strike Beacon on infected hosts.
It also follows the discovery of a new campaign from the Russia-linked Turla group that utilizes a malicious Windows shortcut (LNK) file as a conduit to serve a fileless backdoor that can execute PowerShell scripts received from a legitimate-but-compromised server and disable security features.
"It also employs memory patching, bypass AMSI and disable system's event logging features to impair system's defense to enhance its evasion capability," G DATA researchers said. "It leverages Microsoft's msbuild.exe to implement AWL (Application Whitelist) Bypass to avoid detection."
French Authorities Launch Operation to Remove PlugX Malware from Infected Systems
28.7.24 BigBrothers The Hacker News
French judicial authorities, in collaboration with Europol, have launched a so-called "disinfection operation" to rid compromised hosts of a known malware called PlugX.
The Paris Prosecutor's Office, Parquet de Paris, said the initiative was launched on July 18 and that it's expected to continue for "several months."
It further said around a hundred victims located in France, Malta, Portugal, Croatia, Slovakia, and Austria have already benefited from the cleanup efforts.
The development comes nearly three months after French cybersecurity firm Sekoia disclosed it sinkhole a command-and-control (C2) server linked to the PlugX trojan in September 2023 by spending $7 to acquire the IP address. It also noted that nearly 100,000 unique public IP addresses have been sending PlugX requests daily to the seized domain.
PlugX (aka Korplug) is a remote access trojan (RAT) widely used by China-nexus threat actors since at least 2008, alongside other malware families like Gh0st RAT and ShadowPad.
The malware is typically launched within compromised hosts using DLL side-loading techniques, allowing threat actors to execute arbitrary commands, upload/download files, enumerate files, and harvest sensitive data.
"This backdoor, initially developed by Zhao Jibin (aka. WHG), evolved throughout the time in different variants," Sekoia said earlier this April. "The PlugX builder was shared between several intrusion sets, most of them attributed to front companies linked to the Chinese Ministry of State Security."

Over the years, it has also incorporated a wormable component that enables it to be propagated via infected USB drives, effectively bypassing air-gapped networks.
Sekoia, which devised a solution to delete PlugX, said variants of the malware with the USB distribution mechanism come with a self-deletion command ("0x1005") to remove itself from the compromised workstations, although there is currently no way to remove it from the USB devices itself.
"Firstly, the worm has the capability to exist on air-gapped networks, which makes these infections beyond our reach," it said. "Secondly, and perhaps more noteworthy, the PlugX worm can reside on infected USB devices for an extended period without being connected to a workstation."
Given the legal complications involved in remotely wiping the malware off the systems, the company further noted that it's deferring the decision to national Computer Emergency Response Teams (CERTs), law enforcement agencies (LEAs), and cybersecurity authorities.
"Following a report from Sekoia.io, a disinfection operation was launched by the French judicial authorities to dismantle the botnet controlled by the PlugX worm. PlugX affected several million victims worldwide," Sekoia told The Hacker News. "A disinfection solution developed by the Sekoia.io TDR team was proposed via Europol to partner countries and is being deployed at this time."
"We are pleased with the fruitful cooperation with the actors involved in France (section J3 of the Paris Public Prosecutor's Office, Police, Gendarmerie and ANSSI) and internationally (Europol and police forces of third countries) to take action against long-lasting malicious cyber activities."
U.S. DoJ Indicts North Korean Hacker for Ransomware Attacks on Hospitals
27.7.24 BigBrothers The Hacker News

The U.S. Department of Justice (DoJ) on Thursday unsealed an indictment against a North Korean military intelligence operative for allegedly carrying out ransomware attacks against healthcare facilities in the country and funneling the payments to orchestrate additional intrusions into defense, technology, and government entities across the world.
"Rim Jong Hyok and his co-conspirators deployed ransomware to extort U.S. hospitals and health care companies, then laundered the proceeds to help fund North Korea's illicit activities," said Paul Abbate, deputy director of the Federal Bureau of Investigation (FBI). "These unacceptable and unlawful actions placed innocent lives at risk."
Concurrent with the indictment, the U.S. Department of State announced a reward of up to $10 million for information that could lead to his whereabouts, or the identification of other individuals in connection with the malicious activity.
Hyok, part of a hacking crew dubbed Andariel (aka APT45, Nickel Hyatt, Onyx Sleet, Silent Chollima, Stonefly, and TDrop2), is said to be behind extortion-related cyber attacks involving a ransomware strain called Maui, which was first disclosed in 2022 as targeting organizations in Japan and the U.S.
The ransom payments were laundered through Hong Kong-based facilitators, converting the illicit proceeds into Chinese yuan, following which they were withdrawn from an ATM and used to procure virtual private servers (VPSes) that, in turn, were employed to exfiltrate sensitive defense and technology information.
Targets of the campaign include two U.S. Air Force bases, NASA-OIG, as well as South Korean and Taiwanese defense contractors and a Chinese energy company.
In one instance highlighted by the State Department, a cyber attack that began in November 2022 led to the threat actors exfiltrating more than 30 gigabytes of data from an unnamed U.S.-based defense contractor. This comprised unclassified technical information regarding material used in military aircraft and satellites.
The agencies have also announced the "interdiction of approximately $114,000 in virtual currency proceeds of ransomware attacks and related money laundering transactions, as well as the seizure of online accounts used by co-conspirators to carry out their malicious cyber activity."
Andariel, affiliated with the Reconnaissance General Bureau (RGB) 3rd Bureau, has a track record of striking foreign businesses, governments, aerospace, nuclear, and defense industries with the goal of obtaining sensitive and classified technical information and intellectual property to further the regime's military and nuclear aspirations.
Other recent targets of interest encompass South Korean educational institutions, construction companies, and manufacturing organizations.
"This group poses an ongoing threat to various industry sectors worldwide, including, but not limited to, entities in the United States, South Korea, Japan, and India," the National Security Agency (NSA) said. "The group funds their espionage activity through ransomware operations against U.S. healthcare entities."
Initial access to target networks is accomplished by means of exploiting known N-day security flaws in internet-facing applications, enabling the hacking group to conduct follow-on reconnaissance, filesystem enumeration, persistence, privilege escalation, lateral movement, and data exfiltration steps using a combination of custom backdoors, remote access trojans, off-the-shelf tools, and open-source utilities at their disposal.
Other documented malware distribution vectors entail the use of phishing emails containing malicious attachments, such as Microsoft Windows Shortcut (LNK) files or HTML Application (HTA) script files inside ZIP archives.
"The actors are well-versed in using native tools and processes on systems, known as living-off-the-land (LotL)," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said. "They use Windows command line, PowerShell, Windows Management Instrumentation command line (WMIC), and Linux bash, for system, network, and account enumeration."
Microsoft, in its own advisory on Andariel, described it as constantly evolving its toolset to add new functionality and implement novel ways to bypass detection, while exhibiting a "fairly uniform attack pattern."
"Onyx Sleet's ability to develop a spectrum of tools to launch its tried-and-true attack chain makes it a persistent threat, particularly to targets of interest to North Korean intelligence, like organizations in the defense, engineering, and energy sectors," the Windows maker noted.
Some of the noteworthy tools highlighted by Microsoft are listed below -
TigerRAT - A malware that can steal confidential information and carry out commands, like keylogging and screen recording, from a command-and-control (C2) server
SmallTiger - A C++ backdoor
LightHand - A lightweight backdoor for remote access to infected devices
ValidAlpha (aka Black RAT) - A Go-based backdoor that can run an arbitrary file, list contents of a directory, download a file, take screenshots, and launch a shell to execute arbitrary commands
Dora RAT - A "simple malware strain" with support for reverse shell and file download/upload capabilities
"They have evolved from targeting South Korean financial institutions with disruptive attacks to targeting U.S. healthcare with ransomware, known as Maui, although not at the same scale as other Russian speaking cybercrime groups," Alex Rose, director of threat research and government partnerships at Secureworks Counter Threat Unit, said.
"This is in addition to their primary mission of gathering intelligence on foreign military operations and strategic technology acquisition."
Andariel is just one of the myriad state-sponsored hacking crews operating under the direction of the North Korean government and military, alongside other clusters tracked as the Lazarus Group, BlueNoroff, Kimsuky, and ScarCruft.
"For decades, North Korea has been involved in illicit revenue generation through criminal enterprises, to compensate for the lack of domestic industry and their global diplomatic and economic isolation," Rose added.
"Cyber was rapidly adopted as a strategic capability that could be used for both intelligence gathering and money making. Where historically these objectives would have been covered by different groups, in the last few years there has been a blurring of the lines and many of the cyber threat groups operating on behalf of North Korea have also dabbled in money making activities."
CISA Adds Twilio Authy and IE Flaws to Exploited Vulnerabilities List
25.7.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The vulnerabilities are listed below -
CVE-2012-4792 (CVSS score: 9.3) - Microsoft Internet Explorer Use-After-Free Vulnerability
CVE-2024-39891 (CVSS score: 5.3) - Twilio Authy Information Disclosure Vulnerability
CVE-2012-4792 is a decade-old use-after-free vulnerability in Internet Explorer that could allow a remote attacker to execute arbitrary code via a specially crafted site.
It's currently not clear if the flaw has been subjected to renewed exploitation attempts, although it was abused as part of watering hole attacks targeting the Council on Foreign Relations (CFR) and Capstone Turbine Corporation websites back in December 2012.
On the other hand, CVE-2024-39891 refers to an information disclosure bug in an unauthenticated endpoint that could be exploited to "accept a request containing a phone number and respond with information about whether the phone number was registered with Authy."
Earlier this month, Twilio said it resolved the issue in versions 25.1.0 (Android) and 26.1.0 (iOS) after unidentified threat actors took advantage of the shortcoming to identify data associated with Authy accounts.
"These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise," CISA said in an advisory.
Federal Civilian Executive Branch (FCEB) agencies are required to remediate the identified vulnerabilities by August 13, 2024, to protect their networks against active threats.
Ukrainian Institutions Targeted Using HATVIBE and CHERRYSPY Malware
24.7.24 BigBrothers The Hacker News

The Computer Emergency Response Team of Ukraine (CERT-UA) has alerted of a spear-phishing campaign targeting a scientific research institution in the country with malware known as HATVIBE and CHERRYSPY.
The agency attributed the attack to a threat actor it tracks under the name UAC-0063, which was previously observed targeting various government entities to gather sensitive information using keyloggers and backdoors.
The attack is characterized by the use of a compromised email account belonging to an employee of the organization to send phishing messages to "dozens" of recipients containing a macro-laced Microsoft Word (DOCX) attachment.
Opening the document and enabling macros results in the execution of an encoded HTML Application (HTA) named HATVIBE, which sets up persistence on the host using a scheduled task and paves the way for a Python backdoor codenamed CHERRYSPY, which is capable of running commands issued by a remote server.
CERT-UA said it detected "numerous cases" of HATVIBE infections that exploit a known security flaw in HTTP File Server (CVE-2024-23692, CVSS score: 9.8) for initial access.
UAC-0063 has been associated with a Russia-linked nation-state group dubbed APT28 with moderate confidence. APT28, which is also referred to as BlueDelta, Fancy Bear, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422, is affiliated with Russia's strategic military intelligence unit, the GRU.
The development comes as CERT-UA detailed another phishing campaign targeting Ukrainian defense enterprises with booby-trapped PDF files embedding a link that, when clicked, downloads an executable (aka GLUEEGG), which is responsible for decrypting and running a Lua-based loader called DROPCLUE.
DROPCLUE is designed to open a decoy document to the victim, while covertly downloading a legitimate Remote Desktop program called Atera Agent using the curl utility. The attack has been linked to a cluster tracked as UAC-0180.
Kaspersky Exits U.S. Market Following Commerce Department Ban
16.7.24 BigBrothers The Hacker News
Russian security vendor Kaspersky has said it's exiting the U.S. market nearly a month after the Commerce Department announced a ban on the sale of its software in the country citing a national security risk.
News of the closure was first reported by journalist Kim Zetter.
The company is expected to wind down its U.S. operations on July 20, 2024, the same day the ban comes into effect. It's also expected to lay off less than 50 employees in the U.S.
"The company has carefully examined and evaluated the impact of the U.S. legal requirements and made this sad and difficult decision as business opportunities in the country are no longer viable," the company said in a statement.
In late June 2024, the Commerce Department said it was enforcing a ban after what it said was an "extremely thorough investigation." The company was also added to the Entity List, preventing U.S. enterprises from conducting business with it.
It's currently not known what was uncovered as a result of the probe, but the agency said the company's continued operations in the U.S. could serve as a conduit for the Kremlin's offensive cyber capabilities.
"The manipulation of Kaspersky software, including in U.S. critical infrastructure, can cause significant risks of data theft, espionage, and system malfunction," the Bureau of Industry and Security (BIS) noted. "It can also risk the country's economic security and public health, resulting in injuries or loss of life."
Existing U.S. customers have been urged to find alternative tech solutions ahead of September 29, by which the company is expected to stop providing software and antivirus signature updates.
Kaspersky has refuted the allegations, stating it does not engage in activities that could threaten U.S. national security and that the decision was made based on the "present geopolitical climate and theoretical concerns," rather than a comprehensive evaluation of its products and services.
Australian Defence Force Private and Husband Charged with Espionage for Russia
12.7.24 BigBrothers The Hacker News
Two Russian-born Australian citizens have been arrested and charged in the country for spying on behalf of Russia as part of a "complex" law enforcement operation codenamed BURGAZADA.
This includes a 40-year-old woman, an Australian Defence Force (ADF) Army Private, and her husband, a 62-year-old self-employed laborer. Media reports have identified them as Kira Korolev and Igor Korolev, respectively, noting that they had been in Australia for over a decade.
The married couple were arrested at their home in the Brisbane suburb of Everton Park on July 11, 2024, the Australian Federal Police (AFP) said in a statement. They have been charged with one count each of preparing for an espionage offense, which carries a maximum penalty of 15 years' imprisonment.
"It is the first time an espionage offense has been laid in Australia since new laws were introduced by the Commonwealth in 2018," the AFP said.
The federal law enforcement agency has alleged the pair colluded together to obtain sensitive information after the woman traveled to Russia while on a long-term leave from the ADF since 2023.
She is said to have instructed her husband, who remained in Australia, to log into her official work account and instructed him to access specific information and send it directly to her private email account while she was overseas.
"The woman's ADF account credentials were used on a number of occasions to access sensitive ADF information, with the intent to provide it to Russian authorities," the AFP said.
Although the exact documents that were accessed were not disclosed, the AFP said they related to Australian national security interests. An investigation into whether the information was handed over to Russia remains ongoing.
"Espionage is an insidious crime, and at a time of global instability, state actors have ramped-up their efforts to obtain information held by Western democracies, including Australia," AFP Commissioner Reece Kershaw said.
"Espionage is not a victimless crime. It has the potential to impact on Australia's sovereignty, safety and way of life."
The arrests mark the third time individuals have been charged with espionage or foreign interference related offenses since their incorporation into the Criminal Code Act 1995.
Last April, a New South Wales man, 55, was charged with providing information about "Australian defense, economic and national security arrangements" to two individuals associated with a foreign intelligence service who are suspected to be undertaking intelligence gathering activities.
Then in late February 2024, a 68-year-old man from Melbourne was sentenced to two years and nine months in prison for attempting to influence a Federal Parliamentarian on behalf of a foreign government.
Mike Burgess, Director-General of Security in charge of the Australian Security Intelligence Organization (ASIO), said the ongoing threat of espionage is "real," and that "multiple countries are seeking to steal Australia's secrets."
Wikileaks' Julian Assange Released from U.K. Prison, Heads to Australia
25.6.24 BigBrothers The Hacker News
WikiLeaks founder Julian Assange has been freed in the U.K. and has departed the country after serving more than five years in a maximum security prison at Belmarsh for what was described by the U.S. government as the "largest compromises of classified information" in its history.
Capping off a 14-year legal saga, Assange, 52, pleaded guilty to one criminal count of conspiring to obtain and disclose classified U.S. national defense documents. He is due to be sentenced to 62 months of time already served in the Pacific island of Saipan later this week.
According to the Associated Press, the hearing is taking place there because of Assange's "opposition to traveling to the continental U.S. and the court's proximity to Australia."
"This is the result of a global campaign that spanned grass-roots organizers, press freedom campaigners, legislators and leaders from across the political spectrum, all the way to the United Nations," WikiLeaks said in a statement.
"This created the space for a long period of negotiations with the U.S. Department of Justice, leading to a deal that has not yet been formally finalized."
Assange, who was granted bail by the High Court in London on Monday, and has since boarded a flight to Australia. He also faced separate charges of rape and sexual assault in Sweden, claims he has denied.
The U.S. Department of Justice (DoJ) in 2019 said Assange's actions "risked serious harm to United States national security to the benefit of our adversaries and put the unredacted named human sources at a grave and imminent risk of serious physical harm and/or arbitrary detention."
It's believed that the DoJ accepted the plea agreement with no additional prison time because of the fact that Assange had already served longer than most people charged with a similar offense.
Founded in 2006, WikiLeaks is estimated to have published more than 10 million documents related to war, spying, and corruption, including military field logs from the wars in Afghanistan and Iraq, as well as diplomatic cables from the U.S. (dubbed Cablegate) and information about detainees at the Guantanamo Bay detention camp.
Notably, it also released a tranche of cyber warfare and surveillance tools allegedly created by the U.S. Central Intelligence Agency (CIA), a collection cumulatively known as Vault 7 and Vault 8, and documents detailing the National Security Agency's spying of France, Germany, Brazil, and Japan.
Joshua Schulte, a former CIA engineer who was accused of passing on the confidential trove of cyber weapons, has since been sentenced to 40 years in prison.
Another of Assange's collaborators, Chelsea Elizabeth Manning (born Bradley Edward Manning), was sentenced to 35 years in prison for disclosing to WikiLeaks hundreds of thousands of documents that came to be known as the Iraq War Logs and Afghan War Diary before then-president Barack Obama commuted her sentence in January 2017.
U.S. Treasury Sanctions 12 Kaspersky Executives Amid Software Ban
23.6.24 BigBrothers The Hacker News
The U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) imposed sanctions against a dozen individuals serving executive and senior leadership roles at Kaspersky Lab, a day after the Russian company was banned by the Commerce Department.
The move "underscores our commitment to ensure the integrity of our cyber domain and to protect our citizens against malicious cyber threats," Under Secretary of the Treasury for Terrorism and Financial Intelligence, Brian E. Nelson, said.
"The United States will take action where necessary to hold accountable those who would seek to facilitate or otherwise enable these activities."
The sanctions, however, do not extend to Kaspersky Lab, its parent or subsidiary companies, nor the company's founder and chief executive officer (CEO), Eugene Kaspersky, OFAC noted. The 12 C-suite and senior-level executives sanctioned are listed below -
Andrei Gennadyevich Tikhonov, Chief Operating Officer (COO) and board member
Daniil Sergeyevich Borshchev, Deputy CEO and board member
Andrei Anatolyevich Efremov, Chief Business Development Officer (CBDO) and board member
Igor Gennadyevich Chekunov, Chief Legal Officer (CLO) and board member
Andrey Petrovich Dukhvalov, Vice President and Director of Future Technologies
Andrei Anatolyevich Suvorov, Head of Kaspersky Operating System Business Unit
Denis Vladimirovich Zenkin, Head of Corporate Communications
Marina Mikhaylovna Alekseeva, Chief Human Resources (HR) Officer
Mikhail Yuryevich Gerber, Executive Vice President of Consumer Business
Anton Mikhaylovich Ivanov, Chief Technology Officer (CTO)
Kirill Aleksandrovich Astrakhan, Executive Vice President for Corporate Business
Anna Vladimirovna Kulashova, Managing Director for Russia and the Commonwealth of Independent States (CIS)
The development follows actions by the Commerce Department prohibiting Kaspersky from providing its software and other security services in America starting July 20, 2024, citing national security concerns. The company has also been placed on the Entity List.
Russia has said the sales ban on Kaspersky software was a typical move by the U.S. to stifle foreign competition with American products. Kaspersky has maintained that it has no links to the Russian government.
Military-themed Email Scam Spreads Malware to Infect Pakistani Users
23.6.24 BigBrothers The Hacker News
researchers have shed light on a new phishing campaign that has been identified as targeting people in Pakistan using a custom backdoor.
Dubbed PHANTOM#SPIKE by Securonix, the unknown threat actors behind the activity have leveraged military-related phishing documents to activate the infection sequence.
"While there are many methods used today to deploy malware, the threat actors made use of ZIP files with a password-protected payload archive contained within," researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.
The campaign is notable for its lack of sophistication and the use of simple payloads to achieve remote access to target machines.
The email messages come bearing a ZIP archive that purports to be meeting minutes related to the International Military-Technical Forum Army 2024, a legitimate event organized by the Ministry of Defense of the Russian Federation. It's set to be held in Moscow in mid-August 2024.
Present within the ZIP file is a Microsoft Compiled HTML Help (CHM) file and a hidden executable ("RuntimeIndexer.exe"), the former of which, when opened, displays the meeting minutes as well as a couple of images, but stealthily runs the bundled binary as soon as the user clicks anywhere on the document.
The executable is designed to function as a backdoor that establishes connections with a remote server over TCP in order to retrieve commands that are subsequently run on the compromised host.
In addition to passing along system information, it executes the commands via cmd.exe, gathers the output of the operation, and exfiltrates it back to the server. This includes running commands like systeminfo, tasklist, curl to extract the public IP address using ip-api[.]com, and schtasks to set up persistence.
"This backdoor essentially functions as a command line-based remote access trojan (RAT) that provides the attacker with persistent, covert, and secure access to the infected system," the researchers said.
"The ability to execute commands remotely and relay the results back to the C2 server allows the attacker to control the infected system, steal sensitive information or execute additional malware payloads."
U.S. Bans Kaspersky Software, Citing National Security Risks
23.6.24 BigBrothers The Hacker News
The U.S. Department of Commerce's Bureau of Industry and Security (BIS) on Thursday announced a "first of its kind" ban that prohibits Kaspersky Lab's U.S. subsidiary from directly or indirectly offering its security software in the country.
The blockade also extends to the company's affiliates, subsidiaries and parent companies, the department said, adding the action is based on the fact that its operations in the U.S. posed a national security risk. News of the ban was first reported by Reuters.
"The company's continued operations in the United States presented a national security risk — due to the Russian Government's offensive cyber capabilities and capacity to influence or direct Kaspersky's operations — that could not be addressed through mitigation measures short of a total prohibition," the BIS said.
It further said Kaspersky is subject to the jurisdiction and control of the Russian government and that its software provides Kremlin access to sensitive U.S. customer information as well as allows for installing malicious software or withholding critical updates.
"The manipulation of Kaspersky software, including in U.S. critical infrastructure, can cause significant risks of data theft, espionage, and system malfunction," it noted. "It can also risk the country's economic security and public health, resulting in injuries or loss of life."
As part of the ban, Kaspersky will be barred from selling its software to American consumers and businesses starting on July 20. However, the company can still provide software and antivirus signature updates to existing customers until September 29.
It's also urging current individual and business customers to find suitable replacements within the 100-day time period so as to ensure that there are no gaps in security protections. That said, it's worth noting that they can continue to use the products should they choose to do so.
"Russia has shown time and again they have the capability and intent to exploit Russian companies, like Kaspersky Lab, to collect and weaponize sensitive U.S. information, and we will continue to use every tool at our disposal to safeguard U.S. national security and the American people," Secretary of Commerce Gina Raimondo said.
That's not all. Kaspersky has also been added to the Entity List for their "cooperation with Russian military and intelligence authorities in support of the Russian Government's cyber intelligence objectives."
The Moscow-headquartered firm, which serves over 400 million customers and 240,000 corporate clients across 200 countries including Piaggio, Volkswagen Group Retail Spain, and the Qatar Olympic Committee, has long been in the crosshairs of the U.S. government over its ties to Russia.
In September 2017, its products were banned from being used in federal networks, citing national security concerns. Weeks after that announcement, a Wall Street Journal report alleged Russian government hackers had stolen U.S. classified hacking tools stored on a National Security Agency (NSA) contractor's home computer because it was running Kaspersky software.
The New York Times reported days later that Israeli officials notified the U.S. of the espionage operation after they hacked into Kaspersky's network in 2015. The company responded saying it came across the code in 2014 when its antivirus software flagged a 7-Zip file as malicious on a U.S.-based computer.
The tool, later attributed to the Equation Group, was deleted and no third-parties saw the code, the company said at the time following an internal investigation. Equation Group is the name assigned by Kaspersky to a hacking crew with suspected ties to the NSA's Tailored Access Operations (TAO) cyberwarfare unit.
Nearly five years later, Kaspersky was added to the Federal Communications Commission's (FCC) "Covered List" of companies that pose an "unacceptable risk to the national security" of the country. Germany and Canada have enacted similar restrictions in recent years.
Responding to the latest move from the U.S. government, Kaspersky said the Commerce Department made its decision based on the current geopolitical climate and theoretical concerns, adding it "unfairly ignores" evidence of the transparency measures implemented by the company to demonstrate integrity and trustworthiness.
"The primary impact of these measures will be the benefit they provide to cybercrime," it said. "International cooperation between experts is crucial in the fight against malware, and yet this will restrict those efforts."
French Diplomatic Entities Targeted in Russian-Linked Cyber Attacks
20.6.24 BigBrothers The Hacker News
State-sponsored actors with ties to Russia have been linked to targeted cyber attacks aimed at French diplomatic entities, the country's information security agency ANSSI said in an advisory.
The attacks have been attributed to a cluster tracked by Microsoft under the name Midnight Blizzard (formerly Nobelium), which overlaps with activity tracked as APT29, BlueBravo, Cloaked Ursa, Cozy Bear, and The Dukes.
While the monikers APT29 and Midnight Blizzard have been interchangeably used to refer to intrusion sets associated with the Russian Foreign Intelligence Service (SVR), ANSSI said it prefers to treat them as disparate threat clusters alongside a third one dubbed Dark Halo, which has been held responsible for the 2020 supply chain attack via SolarWinds software.
"Nobelium is characterized by the use of specific codes, tactics, techniques, and procedures. Most of Nobelium campaigns against diplomatic entities use compromised legitimate email accounts belonging to diplomatic staff, and conduct phishing campaigns against diplomatic institutions, embassies, and consulates," the agency said.
It's worth noting that the targeting of diplomatic entities is also monitored under the name Diplomatic Orbiter.
The attacks entail sending phishing emails to French public organizations from foreign institutions and individuals previously compromised by the threat actor to initiate a series of malicious actions.
"In May 2023, several European embassies in Kyiv were targeted by a phishing campaign conducted by Nobelium's operators," it said. "The French embassy in Kyiv was one of the targets of this campaign, which was conducted through an email that was themed about a 'Diplomatic car for sale.'"
Another attack observed in the same month targeting the French Embassy in Romania was ultimately unsuccessful, ANSSI noted.
Other intrusions mounted by the threat actor have leveraged security flaws in JetBrains TeamCity servers as part of an opportunistic campaign. In recent months, it has also been linked to breaches of Microsoft and Hewlett Packard Enterprise (HPE).
"The targeting of IT and cybersecurity entities for espionage purposes by Nobelium operators potentially strengthens their offensive capabilities and the threat they represent," the agency said. "The intelligence gathered during recent attacks against IT sector entities could also facilitate Nobelium's future operations."
The disclosure comes as Poland revealed that Russian hackers could be behind the DDoS attack on Telewizja Polska (TVP) that led to the disruption of an online broadcast of the Euro 2024 soccer tournament on June 16, 2024.
Chinese Cyber Espionage Targets Telecom Operators in Asia Since 2021
20.6.24 BigBrothers The Hacker News
Chinese Cyber Espionage
Cyber espionage groups associated with China have been linked to a long-running campaign that has infiltrated several telecom operators located in a single Asian country at least since 2021.
"The attackers placed backdoors on the networks of targeted companies and also attempted to steal credentials," the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with The Hacker News.
The cybersecurity firm did not reveal the country that was targeted, but said it found evidence to suggest that the malicious cyber activity may have started as far back as 2020.
The attacks also targeted an unnamed services company that catered to the telecoms sector and a university in another Asian country, it added.
The choice of tools used in this campaign overlaps with other missions conducted by Chinese espionage groups like Mustang Panda (aka Earth Preta and Fireant), RedFoxtrot (aka Neeedleminer and Nomad Panda), and Naikon (aka Firefly) in recent years.
This includes custom backdoors tracked as COOLCLIENT, QuickHeal, and RainyDay that come equipped with capabilities to capture sensitive data and establish communication with a command-and-control (C2) server.
While the exact initial access pathway used to breach the targets is presently unknown, the campaign is also notable for deploying port scanning tools and conducting credential theft through the dumping of Windows Registry hives.
The fact that the tooling has connections to three different adversarial collectives has raised several possibilities: The attacks are being conducted independently of each other, a single threat actor is using tools acquired from other groups, or diverse actors are collaborating on a single campaign.
Also unclear at this stage is the primary motive behind the intrusions, although Chinese threat actors have a history of targeting the telecoms sector across the world.
In November 2023, Kaspersky revealed a ShadowPad malware campaign targeting one of the national telecom companies of Pakistan by exploiting known security flaws in Microsoft Exchange Server (CVE-2021-26855 aka ProxyLogon).
"The attackers may have been gathering intelligence on the telecoms sector in that country," Symantec postulated. "Eavesdropping is another possibility. Alternatively, the attackers may have been attempting to build a disruptive capability against critical infrastructure in that country."
Ex-NSA Employee Sentenced to 22 Years for Trying to Sell U.S. Secrets to Russia
1.5.24 BigBrothers The Hacker News
A former employee of the U.S. National Security Agency (NSA) has been sentenced to nearly 22 years (262 months) in prison for attempting to transfer classified documents to Russia.
"This sentence should serve as a stark warning to all those entrusted with protecting national defense information that there are consequences to betraying that trust," said FBI Director Christopher Wray.
Jareh Sebastian Dalke, 32, of Colorado Springs was employed as an Information Systems Security Designer between June 6 to July 1, 2022, during which time he had access to sensitive information.
Despite his short tenure at the intelligence agency, Dalke is said to have made contact with a person he thought was a Russian agent sometime between August and September of that year. In reality, the person was an undercover agent working for the Federal Bureau of Investigation (FBI).
To demonstrate his "legitimate access and willingness to share," he then emailed the purported Russian agent snippets of three top-secret National Defense Information (NDI) documents that were obtained during his employment using an encrypted email account.
Dalke, who demanded $85,000 in return for sharing all the files in his possession, claimed the information would be of value to Russia and told his contact that he would share more documents upon his return to Washington, D.C.
He was subsequently arrested on September 28, 2022, shortly after he transferred five files to the supposed Russian spy at Union Station in downtown Denver via a laptop computer. The defendant pleaded guilty to the crime in October 2023.
"As part of his plea agreement, Dalke admitted that he willfully transmitted files to the FBI online covert employee with the intent and reason to believe the information would be used to injure the United States and to benefit Russia," the U.S. Justice Department said.
New U.K. Law Bans Default Passwords on Smart Devices Starting April 2024
30.4.24 BigBrothers The Hacker News
The U.K. National Cyber Security Centre (NCSC) is calling on manufacturers of smart devices to comply with new legislation that prohibits them from using default passwords, effective April 29, 2024.
"The law, known as the Product Security and Telecommunications Infrastructure act (or PSTI act), will help consumers to choose smart devices that have been designed to provide ongoing protection against cyber attacks," the NCSC said.
To that end, manufacturers are required to not supply devices that use guessable default passwords, provide a point of contact to report security issues, and state the duration for which their devices are expected to receive important security updates.
Default passwords can not only be easily found online, they also act as a vector for threat actors to log in to devices for follow-on exploitation. That said, a unique default password is permissible under the law.
The law, which aims to enforce a set of minimum security standards across the board and prevent vulnerable devices from being corralled into a DDoS botnet like Mirai, applies to the following products that can be connected to the internet -
Smart speakers, smart TVs, and streaming devices
Smart doorbells, baby monitors, and security cameras
Cellular tablets, smartphones, and game consoles
Wearable fitness trackers (including smart watches)
Smart domestic appliances (such as light bulbs, plugs, kettles, thermostats, ovens, fridges, cleaners, and washing machines)
Companies that fail to adhere to the provisions of the PSTI act are liable to face recalls and monetary penalties, attracting fines of up to £10 million ($12.5 million) or 4% of their global annual revenues, depending on whichever is higher.
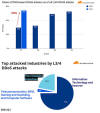
The development makes the U.K. the first country in the world to outlaw default usernames and passwords from IoT devices. According to Cloudflare's DDoS threat report for Q1 2024, Mirai-based attacks continue to be prevalent despite the original botnet being taken down in 2016.
"Four out of every 100 HTTP DDoS attacks, and two out of every 100 L3/4 DDoS attacks are launched by a Mirai-variant botnet," Omer Yoachimik and Jorge Pacheco said. "The Mirai source code was made public, and over the years there have been many permutations of the original."
It also follows a $196 million fine issued by the U.S. Federal Communications Commission (FCC) against telecom carriers AT&T ($57 million), Sprint ($12 million), T-Mobile ($80 million), and Verizon ($47 million) for illegally sharing customers' real-time location data without their consent to aggregators like LocationSmart and Zumigo, who then sold the information to third-party location-based service providers.
"No one who signed up for a cell plan thought they were giving permission for their phone company to sell a detailed record of their movements to anyone with a credit card," U.S. Senator Ron Wyden, who revealed the practice in 2018, said in a statement.
U.S. Treasury Sanctions Iranian Firms and Individuals Tied to Cyber Attacks
25.4.24 BigBrothers The Hacker News

The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) on Monday sanctioned two firms and four individuals for their involvement in malicious cyber activities on behalf of the Iranian Islamic Revolutionary Guard Corps Cyber Electronic Command (IRGC-CEC) from at least 2016 to April 2021.
This includes the front companies Mehrsam Andisheh Saz Nik (MASN) and Dadeh Afzar Arman (DAA), as well as the Iranian nationals Alireza Shafie Nasab, Reza Kazemifar Rahman, Hossein Mohammad Harooni, and Komeil Baradaran Salmani.
"These actors targeted more than a dozen U.S. companies and government entities through cyber operations, including spear-phishing and malware attacks," the Treasury Department said.
Concurrent with the sanctions, the U.S. Department of Justice (DoJ) unsealed an indictment against the four individuals for orchestrating cyber attacks targeting the U.S. government and private entities.
Furthermore, a reward of up to $10 million has been announced as part of the U.S. Department of State's Rewards for Justice program for information leading to the identification or location of the group and the defendants.
It's worth noting that Nasab, who worked for MASN, was charged in a previous indictment that was unsealed on February 29, 2024. The defendants remain at large.
Rahman, also employed by MASN, is alleged to have worked on testing malware intended to target job seekers with a focus on military veterans. He also purportedly worked for the Iranian Organization for Electronic Warfare and Cyber Defense (EWCD), a component of IRGC, from about 2014 through 2020.
MASN (formerly Mahak Rayan Afraz and Dehkadeh Telecommunication and Security Company) is tracked by the cybersecurity community under the name Tortoiseshell and is one of the many contracting companies that act as a cover for malicious campaigns orchestrated by IRGC. It was liquidated in June 2023.
The U.S. Treasury Department said the second sanctioned company also "engaged in malicious cyber campaigns on behalf of the IRGC-CEC," noting that Harooni was employed by DAA and has carried out spear-phishing and social engineering attacks against U.S. organizations.
Salmani is said to be associated with multiple IRGC-CEC front companies, including MASN, and involved in spear-phishing campaigns targeting U.S. entities. Nasab, Harooni, and Salmani have also been responsible for procuring and maintaining the online network infrastructure used to facilitate the intrusions, the DoJ said.
In all, in the coordinated multi-year hacking spree, the defendants primarily singled out private sector defense contractors and other government entities, ultimately compromising more than 200,000 employee accounts.
Each of the defendants has been charged with conspiracy to commit computer fraud, conspiracy to commit wire fraud, and wire fraud. If convicted, they face up to five years in prison for the computer fraud conspiracy, and up to 20 years in prison for each count of wire fraud and conspiracy to commit wire fraud.
Furthermore, Harooni has been charged with knowingly damaging a protected computer, which carries a maximum penalty of 10 years in prison. Nasab, Harooni, and Salmani have also been charged with aggravated identity theft, which carries a mandatory consecutive term of two years in prison.
"Criminal activity originating from Iran poses a grave threat to America's national security and economic stability," said Attorney General Merrick B. Garland in a statement.
"These defendants are alleged to have engaged in a coordinated, multi-year hacking campaign from Iran targeting more than a dozen American companies and the U.S. Treasury and State Departments."
The development comes amid geopolitical tensions in the Middle East after an Israeli air strike bombed Iran's embassy in Syria, prompting the latter to launch a drone-and-missile attack on Israel, which, in turn, led to an Israeli missile strike hitting an air defense radar system near Isfahan.
German Authorities Issue Arrest Warrants for Three Suspected Chinese Spies
24.4.24 BigBrothers The Hacker News
German authorities said they have issued arrest warrants against three citizens on suspicion of spying for China.
The full names of the defendants were not disclosed by the Office of the Federal Prosecutor (aka Generalbundesanwalt), but it includes Herwig F., Ina F., and Thomas R.
"The suspects are strongly suspected of working for a Chinese secret service since an unspecified date before June 2022," the Generalbundesanwalt said.
Thomas R. is believed to have acted as an agent for China's Ministry of State Security (MSS), gathering information about innovative technologies in Germany that could be used for military purposes.
The defendant also sought the help of a married couple, Herwig F. and Ina F., who run a Düsseldorf-based business that established connections with the scientific and research community in Germany.
This materialized in the form of an agreement with an unnamed German university to conduct a study for an unnamed Chinese contractor regarding the operation of high-performance marine engines for use on combat ships.
"At the time of their arrest, the defendants were in further negotiations on research projects that could be useful for expanding China's maritime combat power," the agency said.
"In addition, the defendants purchased a special laser from Germany on behalf of and with payment from the MSS and exported it to China without permission, even though the instrument is subject to the E.U. dual-use regulation."
The development comes as the Generalbundesanwalt announced the arrest of another citizen named Jian G. for acting as an agent for the Chinese Secret Service while working for a German Member of the European Parliament since 2019.
"In January 2024, the accused repeatedly passed on information about negotiations and decisions in the European Parliament to his intelligence client," it said. "In addition, he spied on Chinese opposition members in Germany for the intelligence service."
Last week, the Office of the Federal Prosecutor also executed an arrest warrant against a German-Russian citizen Alexander J. for purported secret service agent activity.
The arrests also follow the charging of Christopher Berry, 32, and Christopher Cash, 29, in the U.K. for passing on sensitive information to China in violation of the Official Secrets Act, according to the Metropolitan Police and the Crown Prosecution Service (CPS).
The two individuals, previously arrested on March 13, 2023, from Oxfordshire and Edinburgh, respectively, and later released on bail, have been accused of sharing "articles, notes, documents, or information" which may have been directly or indirectly useful to an enemy nation.
A spokesperson for the Chinese Embassy told BBC News that the allegations amount to "malicious slander" and urged the U.K. to "stop anti-China political manipulation."
U.S. Imposes Visa Restrictions on 13 Linked to Commercial Spyware Misuse
23.4.24 BigBrothers The Hacker News
The U.S. Department of State on Monday said it's taking steps to impose visa restrictions on 13 individuals who are allegedly involved in the development and sale of commercial spyware or who are immediately family members of those involved in such businesses.
"These individuals have facilitated or derived financial benefit from the misuse of this technology, which has targeted journalists, academics, human rights defenders, dissidents and other perceived critics, and U.S. Government personnel," the department said.
The names of those subjected to visa restrictions were not disclosed, but the move comes more than two months after the U.S. government said it's enacting a new policy that enforces visa constraints on people engaging in practices that could threaten privacy and freedom of expression.
It also aims to counter the misuse and proliferation of commercial spyware that has been put to use by authoritarian governments to spy on civil society members, in addition to promoting accountability.
The development comes as Israeli publication Haaretz reported that Intellexa presented a proof-of-concept (PoC) system in 2022 called Aladdin that enabled the planting of phone spyware through online ads.
The Intellexa Consortium was sanctioned by the U.S. Department of Treasury's Office of Foreign Assets Control (OFAC) last month for developing, operating, and distributing" commercial spyware designed to target government officials, journalists, and policy experts in the country.
It's not just spyware, as Kaspersky recently reported that 31,031 unique users were affected by stalkerware in 2023, up from 29,312 a year prior, with most of them located in Russia, Brazil, and India – a dubious distinction held by the three countries since 2019.
"Stalkerware products are typically marketed as legitimate anti-theft or parental control apps for smartphones, tablets and computers, but in reality, they are something very different. Installed without the knowledge or consent of the person being tracked, these apps operate stealthily and provide a perpetrator with the means to gain control over a victim's life," the company said.
FTC Fines Mental Health Startup Cerebral $7 Million for Major Privacy Violations
16.4.24 BigBrothers The Hacker News
The U.S. Federal Trade Commission (FTC) has ordered the mental telehealth company Cerebral from using or disclosing personal data for advertising purposes.
It has also been fined more than $7 million over charges that it revealed users' sensitive personal health information and other data to third parties for advertising purposes and failed to honor its easy cancellation policies.
"Cerebral and its former CEO, Kyle Robertson, repeatedly broke their privacy promises to consumers and misled them about the company's cancellation policies," the FTC said in a press statement.
While claiming to offer "safe, secure, and discreet" services in order to get consumers to sign up and provide their data, the company, FTC alleged, did not clearly disclose that the information would be shared with third-parties for advertising.
The agency also accused the company of burying its data sharing practices in dense privacy policies, with the company engaging in deceptive practices by claiming that it would not share users' data without their consent.
The company is said to have provided the sensitive information of nearly 3.2 million consumers to third parties such as LinkedIn, Snapchat, and TikTok by integrating tracking tools within its websites and apps that are designed to provide advertising and data analytics functions.
The information included names; medical and prescription histories; home and email addresses; phone numbers; birthdates; demographic information; IP addresses; pharmacy and health insurance information; and other health information.
The FTC complaint further accused Cerebral of failing to enforce adequate security guardrails by allowing former employees to access users' medical records from May to December 2021, using insecure access methods that exposed patient information, and not restricting access to consumer data to only those employees who needed it.
"Cerebral sent out promotional postcards, which were not in envelopes, to over 6,000 patients that included their names and language that appeared to reveal their diagnosis and treatment to anyone who saw the postcards," the FTC said.
Pursuant to the proposed order, which is pending approval from a federal court, the company has been barred from using or disclosing consumers' personal and health information to third-parties for marketing, and has been ordered to implement a comprehensive privacy and data security program.
Cerebral has also been asked to post a notice on its website alerting users of the FTC order, as well as adopt a data retention schedule and delete most consumer data not used for treatment, payment, or health care operations unless they have consented to it. It's also required to provide a mechanism for users to get their data deleted.
The development comes days after alcohol addiction treatment firm Monument was prohibited by the FTC from disclosing health information to third-party platforms such as Google and Meta for advertising without users' permission between 2020 and 2022 despite claiming such data would be "100% confidential."
The New York-based company has been ordered to notify users about the disclosure of their health information to third parties and ensure that all the shared data has been deleted.
"Monument failed to ensure it was complying with its promises and in fact disclosed users' health information to third-party advertising platforms, including highly sensitive data that revealed that its customers were receiving help to recover from their addiction to alcohol," FTC said.
Over the past year, FTC has announced similar enforcement actions against healthcare service providers like BetterHelp, GoodRx, and Premom for sharing users' data with third-party analytics and social media firms without their consent.
It also warned [PDF] Amazon against using patient data for marketing purposes after it finalized a $3.9 billion acquisition of membership-based primary care practice One Medical.
U.S. Treasury Hamas Spokesperson for Cyber Influence Operations
13.4.24 BigBrothers The Hacker News
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) on Friday announced sanctions against an official associated with Hamas for his involvement in cyber influence operations.
Hudhayfa Samir 'Abdallah al-Kahlut, 39, also known as Abu Ubaida, has served as the public spokesperson of Izz al-Din al-Qassam Brigades, the military wing of Hamas, since at least 2007.
"He publicly threatened to execute civilian hostages held by Hamas following the terrorist group's October 7, 2023, attacks on Israel," the Treasury Department said.
"Al-Kahlut leads the cyber influence department of al-Qassam Brigades. He was involved in procuring servers and domains in Iran to host the official al-Qassam Brigades website in cooperation with Iranian institutions."
Alongside Al-Kahlut, two other individuals named William Abu Shanab, 56, and Bara'a Hasan Farhat, 35, for their role in the manufacturing of unmanned aerial vehicles (UAVs) used by Hamas to conduct terrorist operations, including urban warfare and intelligence gathering.
Both Abu Shanab and his assistant Farhat are said to be part of the Lebanon-based al-Shimali unit, where the former is a commander.
Coinciding with the actions taken by the U.S., the European Union imposed sanctions of its own against Al-Qassam Brigades, Al-Quds Brigades, and Nukhba Force for their "brutal and indiscriminate terrorist attacks" targeting Israel last year.
While Al-Quds Brigades is the armed wing of Palestinian Islamic Jihad, Nukhba Force is a special forces unit of Hamas.
The joint action, said Under Secretary of the Treasury for Terrorism and Financial Intelligence Brian E. Nelson, is aimed at "disrupting Hamas's ability to conduct further attacks, including through cyber warfare and the production of UAVs."
The development arrived a little over two months after the U.S. government sanctioned six Iranian officials associated with the Iranian intelligence agency for attacking critical infrastructure entities in the U.S. and other countries.
U.S. Federal Agencies Ordered to Hunt for Signs of Microsoft Breach and Mitigate Risks
12.4.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday issued an emergency directive (ED 24-02) urging federal agencies to hunt for signs of compromise and enact preventive measures following the recent compromise of Microsoft's systems that led to the theft of email correspondence with the company.
The attack, which came to light earlier this year, has been attributed to a Russian nation-state group tracked as Midnight Blizzard (aka APT29 or Cozy Bear). Last month, Microsoft revealed that the adversary managed to access some of its source code repositories but noted that there is no evidence of a breach of customer-facing systems.
The emergency directive, which was originally issued privately to federal agencies on April 2, was first reported on by CyberScoop two days later.
"The threat actor is using information initially exfiltrated from the corporate email systems, including authentication details shared between Microsoft customers and Microsoft by email, to gain, or attempt to gain, additional access to Microsoft customer systems," CISA said.
The agency said the theft of email correspondence between government entities and Microsoft poses severe risks, urging concerned parties to analyze the content of exfiltrated emails, reset compromised credentials, and take additional steps to ensure authentication tools for privileged Microsoft Azure accounts are secure.
It's currently not clear how many federal agencies have had their email exchanges exfiltrated in the wake of the incident, although CISA said all of them have been notified.
The agency is also urging affected entities to perform a cybersecurity impact analysis by April 30, 2024, and provide a status update by May 1, 2024, 11:59 p.m. Other organizations that are impacted by the breach are advised to contact their respective Microsoft account team for any additional questions or follow up.
"Regardless of direct impact, all organizations are strongly encouraged to apply stringent security measures, including strong passwords, multi-factor authentication (MFA) and prohibited sharing of unprotected sensitive information via unsecure channels," CISA said.
The development comes as CISA released a new version of its malware analysis system, called Malware Next-Gen, that allows organizations to submit malware samples (anonymously or otherwise) and other suspicious artifacts for analysis.
Indian Government Rescues 250 Citizens Forced into Cybercrime in Cambodia
1.4.24 BigBrothers The Hacker News
The Indian government said it has rescued and repatriated about 250 citizens in Cambodia who were held captive and coerced into running cyber scams.
The Indian nationals "were lured with employment opportunities to that country but were forced to undertake illegal cyber work," the Ministry of External Affairs (MEA) said in a statement, adding it had rescued 75 people in the past three months.
It also said it's working with "with Cambodian authorities and with agencies in India to crack down on those responsible for these fraudulent schemes."
The development comes in the wake of a report from the Indian Express that said more than 5,000 Indians stuck in Cambodia were forced into "cyber slavery" by organized crime rackets to scam people in India and extort money by masquerading as law enforcement authorities in some cases.
The report also tracks with an earlier disclosure from INTERPOL, which characterized the situation as human trafficking-fuelled fraud on an industrial scale.
This included an accountant from the state of Telangana, who was "lured to Southeast Asia where he was forced to participate in online fraud schemes in inhuman conditions." He was subsequently let go after paying a ransom.
In another instance highlighted by the Indian Express, one of the rescued men was recruited by an agent from the south Indian city of Mangaluru for a data entry job, only to be asked to create fake social media accounts with photographs of women and use them to contact people.
"We had targets and if we didn't meet those, they would not give us food or allow us into our rooms," the individual, identified only as Stephen, was quoted as saying.
China and the Philippines have undertaken similar efforts to free hundreds of Filipinos, Chinese, and other foreign nationals who were entrapped and forced into criminal activity, running what's called pig butchering scams.
These schemes typically start with the scammer adopting a bogus identity to lure prospective victims into investing in non-existing crypto businesses that are designed to steal their funds. The fraudsters are known to gain their target's trust under the illusion of a romantic relationship.
In a report published in February 2024, Chainalysis said the cryptocurrency wallets associated with one of the pig butchering gangs operating out of Myanmar has recorded close to $100 million in crypto inflows, some of which is also estimated to include the ransom payments made by the families of trafficked workers.
"The brutal conditions trafficking victims face on the compounds also lend additional urgency to solving the problem of romance scamming — not only are consumers being bilked out of hundreds of millions of dollars each year, but the gangs behind those scams are also perpetuating a humanitarian crisis," the blockchain analytics firm said.
News of the rescue efforts also follow research from Check Point that threat actors are exploiting a function in Ethereum called CREATE2 to bypass security measures and gain unauthorized access to funds. Details of the scam were previously disclosed by Scam Sniffer in November 2023.
The crux of the technique is the use of CREATE2 to generate a new "temporary" wallet address that has no history of being reported for criminal activity, thus allowing threat actors to make the illicit transactions to the address once the victim approves the contract and circumvent protections that flag such addresses.
"The attack method involves tricking users into approving transactions for smart contracts that haven't been deployed yet, allowing cyber criminals to later deploy malicious contracts and steal cryptocurrencies," the Israeli company said.
Hackers Hit Indian Defense, Energy Sectors with Malware Posing as Air Force Invite
28.3.24 BigBrothers The Hacker News
Indian government entities and energy companies have been targeted by unknown threat actors with an aim to deliver a modified version of an open-source information stealer malware called HackBrowserData and exfiltrate sensitive information in some cases by using Slack as command-and-control (C2).
"The information stealer was delivered via a phishing email, masquerading as an invitation letter from the Indian Air Force," EclecticIQ researcher Arda Büyükkaya said in a report published today.
"The attacker utilized Slack channels as exfiltration points to upload confidential internal documents, private email messages, and cached web browser data after the malware's execution."
The campaign, observed by the Dutch cybersecurity firm beginning March 7, 2024, has been codenamed Operation FlightNight in reference to the Slack channels operated by the adversary.
Targets of the malicious activity span multiple government entities in India, counting those related to electronic communications, IT governance, and national defense.
The threat actor is said to have successfully compromised private energy companies, harvesting financial documents, personal details of employees, details about drilling activities in oil and gas. In all, about 8.81 GB of data has been exfiltrated over the course of the campaign.

The attack chain starts with a phishing message containing an ISO file ("invite.iso"), which, in turn, contains a Windows shortcut (LNK) that triggers the execution of a hidden binary ("scholar.exe") present within the mounted optical disk image.
Simultaneously, a lure PDF file that purports to be an invitation letter from the Indian Air Force is displayed to the victim while the malware clandestinely harvests documents and cached web browser data and transmits them to an actor-controlled Slack channel named FlightNight.
The malware is an altered version of HackBrowserData that goes beyond its browser data theft features to incorporate capabilities to siphon documents (Microsoft Office, PDFs, and SQL database files), communicate over Slack, and better evade detection using obfuscation techniques.
It's suspected that the threat actor stole the decoy PDF during a previous intrusion, with behavioral similarities traced back to a phishing campaign targeting the Indian Air Force with a Go-based stealer called GoStealer.
Details of the activity were disclosed by an Indian security researcher who goes by the alias xelemental (@ElementalX2) in mid-January 2024.
The GoStealer infection sequence is virtually identical to that FlightNight, employing procurement-themed lures ("SU-30 Aircraft Procurement.iso") to display a decoy file while the stealer payload is deployed to exfiltrate information of interest over Slack.
By adapting freely available offensive tools and repurposing legitimate infrastructure such as Slack that's prevalent in enterprise environments, it allows threat actors to reduce time and development costs, as well as easily fly under the radar.
Image source: ElementalX2
The efficiency benefits also mean that it's that much easier to launch a targeted attack, even allowing less-skilled and aspiring cybercriminals to spring into action and inflict significant damage to organizations.
"Operation FlightNight and the GoStealer campaign highlight a simple yet effective approach by threat actors to use open-source tools for cyber espionage," Büyükkaya said.
"This underscores the evolving landscape of cyber threats, wherein actors abuse widely used open-source offensive tools and platforms to achieve their objectives with minimal risk of detection and investment."
Sketchy NuGet Package Likely Linked to Industrial Espionage Targets Developers
27.3.24 BigBrothers The Hacker News
Threat hunters have identified a suspicious package in the NuGet package manager that's likely designed to target developers working with tools made by a Chinese firm that specializes in industrial- and digital equipment manufacturing.
The package in question is SqzrFramework480, which ReversingLabs said was first published on January 24, 2024. It has been downloaded 2,999 times as of writing.
The software supply chain security firm said it did not find any other package that exhibited similar behavior.
It, however, theorized the campaign could likely be used for orchestrating industrial espionage on systems equipped with cameras, machine vision, and robotic arms.
The indication that SqzrFramework480 is seemingly tied to a Chinese firm named Bozhon Precision Industry Technology Co., Ltd. comes from the use of a version of the company's logo for the package's icon. It was uploaded by a Nuget user account called "zhaoyushun1999."
Present within the library is a DLL file "SqzrFramework480.dll" that comes with features to take screenshots, ping a remote IP address after every 30 seconds until the operation is successful, and transmit the screenshots over a socket created and connected to said IP address.
"None of those behaviors are resolutely malicious. However, when taken together, they raise alarms," security researcher Petar Kirhmajer said. "The ping serves as a heartbeat check to see if the exfiltration server is alive."
The malicious use of sockets for data communication and exfiltration has been observed in the wild previously, as in the case of the npm package nodejs_net_server.
The exact motive behind the package is unclear as yet, although it's a known fact that adversaries are steadily resorting to concealing nefarious code in seemingly benign software to compromise victims.
An alternate, innocuous explanation could be that the package was leaked by a developer or a third party that works with the company.
"They may also explain seemingly malicious continuous screen capture behavior: it could simply be a way for a developer to stream images from the camera on the main monitor to a worker station," Kirhmajer said.
The ambiguity surrounding the package aside, the findings underscore the complicated nature of supply chain threats, making it imperative that users scrutinize libraries prior to downloading them.
"Open-source repositories like NuGet are increasingly hosting suspicious and malicious packages designed to attract developers and trick them into downloading and incorporating malicious libraries and other modules into their development pipelines," Kirhmajer said.
U.S. Charges 7 Chinese Nationals in Major 14-Year Cyber Espionage Operation
27.3.24 BigBrothers The Hacker News
The U.S. Department of Justice (DoJ) on Monday unsealed indictments against seven Chinese nationals for their involvement in a hacking group that targeted U.S. and foreign critics, journalists, businesses, and political officials for about 14 years.
The defendants include Ni Gaobin (倪高彬), Weng Ming (翁明), Cheng Feng (程锋), Peng Yaowen (彭耀文), Sun Xiaohui (孙小辉), Xiong Wang (熊旺), and Zhao Guangzong (赵光宗).
The suspected cyber spies have been charged with conspiracy to commit computer intrusions and conspiracy to commit wire fraud in connection with a state-sponsored threat group tracked as APT31, which is also known as Altaire, Bronze Vinewood, Judgement Panda, and Violet Typhoon (formerly Zirconium). The hacking collective has been active since at least 2010.
Specifically, their responsibilities entail testing and exploiting the malware used to conduct the intrusions, managing the attack infrastructure, and conducting surveillance of specific U.S. entities, federal prosecutors noted, adding the campaigns are designed to advance China's economic espionage and foreign intelligence objectives.
Both Gaobin and Guangzong are alleged to be linked to Wuhan Xiaoruizhi Science and Technology Company, Limited (Wuhan XRZ), a front company that's believed to have conducted several malicious cyber operations for the Ministry of State Security (MSS).
Intrusion Truth, in a report published in May 2023, characterized Wuhan XRZ as a "sketchy-looking company in Wuhan looking for vulnerability-miners and foreign language experts."
As well as announcing a reward of up to $10 million for information that could lead to identification or whereabouts of people associated with APT31, the U.K. and the U.S. have also levied sanctions against Gaobin, Guangzong, and Wuhan XRZ for endangering national security and for targeting parliamentarians across the world.
"These allegations pull back the curtain on China's vast illegal hacking operation that targeted sensitive data from U.S. elected and government officials, journalists and academics; valuable information from American companies; and political dissidents in America and abroad," stated U.S. Attorney Breon Peace.
"Their sinister scheme victimized thousands of people and entities across the world, and lasted for well over a decade."
The sprawling hacking operation – which took place between at least 2010 and November 2023 – involved the defendants and other members of APT31 sending more than 10,000 emails to targets of interest that purported to be from prominent journalists and seemingly contained legitimate news articles.
But, in reality, they came with hidden tracking links that would allow information about the victims' location, internet protocol (IP) addresses, network schematics, and the devices used to access the email accounts to be exfiltrated simply upon opening the messages.
This information subsequently enabled the threat actors to conduct more targeted attacks tailored to specific individuals, including by compromising the recipients' home routers and other electronic devices.
The threat actors are also said to have leveraged zero-day exploits to maintain persistent access to victim computer networks, resulting in the confirmed and potential theft of telephone call records, cloud storage accounts, personal emails, economic plans, intellectual property, and trade secrets associated with U.S. businesses.
Other spear-phishing campaigns orchestrated by APT31 have further been found to target U.S. government officials working in the White House, at the Departments of Justice, Commerce, Treasury and State, and U.S. Senators, Representatives, and election campaign staff of both political parties.
The attacks were facilitated by means of custom malware such as RAWDOOR, Trochilus RAT, EvilOSX, DropDoor/DropCat, and others that established secure connections with adversary-controlled servers to receive and execute commands on the victim machines. Also put to use was a cracked version of Cobalt Strike Beacon to conduct post-exploitation activities.
Some of the prominent sectors targeted by the group are defense, information technology, telecommunications, manufacturing and trade, finance, consulting, and legal and research industries. APT31 also singled out dissidents around the world and others who were perceived to be supporting them.
"APT31 is a collection of Chinese state-sponsored intelligence officers, contract hackers, and support staff that conduct malicious cyber operations on behalf of the Hubei State Security Department (HSSD)," the Treasury said.
"In 2010, the HSSD established Wuhan XRZ as a front company to carry out cyber operations. This malicious cyber activity resulted in the surveillance of U.S. and foreign politicians, foreign policy experts, academics, journalists, and pro-democracy activists, as well as persons and companies operating in areas of national importance."
"Chinese state-sponsored cyber espionage is not a new threat and the DoJ's unsealed indictment today showcases the full gambit of their cyber operations in order to advance the People's Republic of China (PRC) agenda. While this is not a new threat, the scope of the espionage and the tactics deployed are concerning," Alex Rose, director of government partnerships at Secureworks Counter Threat Unit, said.
"The Chinese have evolved their typical MO in the last couple of years to evade detection and make it harder to attribute specific cyber-attacks to them. This is part of a broader strategic effort that China is able to execute on. The skills, resources and tactics at the disposal of the PRC make them an ongoing high and persistent threat to governments, businesses, and organizations around the world."
The charges come after the U.K. government pointed fingers at APT31 for targeting parliamentarians' emails in 2021 and an unnamed China state-affiliated threat actor for "malicious cyber campaigns" aimed at the Electoral Commission. The breach of the Electoral Commission led to the unauthorized access of voter data belonging to 40 million people.
The incident was disclosed by the regulator in August 2023, although there is evidence that the threat actors accessed the systems two years prior to it.
Coinciding with the revelations from the U.K. and the U.S., New Zealand said it uncovered links between the Chinese state-sponsored apparatus and cyber attacks against parliamentary entities in the country in 2021. The activity has been attributed to another MSS-backed group tracked as APT40 (aka Bronze Mohawk, Gingham Typhoon, ISLANDDREAMS, and Kryptonite Panda).
Australia, in its own statement, expressed "serious concerns" about the malicious cyber activities conducted by China state-sponsored actors targeting the U.K., and called on "all states to act responsibly in cyberspace." However, it claimed that its own electoral systems "were not compromised by the cyber campaigns targeting the U.K."
China, however, has rejected the accusations, describing them as "completely fabricated" and amounting to "malicious slanders." A spokesperson for the Chinese embassy in Washington D.C. told the BBC News the countries have "made groundless accusations."
"The origin-tracing of cyberattacks is highly complex and sensitive. When investigating and determining the nature of cyber cases, one needs to have adequate and objective evidence, instead of smearing other countries when facts do not exist, still less politicize cybersecurity issues," Foreign Ministry Spokesperson Lin Jian said.
"We hope relevant parties will stop spreading disinformation, take a responsible attitude and jointly safeguard peace and security in the cyberspace. China opposes illegal and unilateral sanctions and will firmly safeguard its lawful rights and interests."
CISA Alerts on Active Exploitation of Flaws in Fortinet, Ivanti, and Nice Products
26.3.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday placed three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
The vulnerabilities added are as follows -
CVE-2023-48788 (CVSS score: 9.3) - Fortinet FortiClient EMS SQL Injection Vulnerability
CVE-2021-44529 (CVSS score: 9.8) - Ivanti Endpoint Manager Cloud Service Appliance (EPM CSA) Code Injection Vulnerability
CVE-2019-7256 (CVSS score: 10.0) - Nice Linear eMerge E3-Series OS Command Injection Vulnerability
The shortcoming impacting Fortinet FortiClient EMS came to light earlier this month, with the company describing it as a flaw that could allow an unauthenticated attacker to execute unauthorized code or commands via specifically crafted requests.
Fortinet has since revised its advisory to confirm that it has been exploited in the wild, although no other details regarding the nature of the attacks are currently available.
CVE-2021-44529, on the other hand, concerns a code injection vulnerability in Ivanti Endpoint Manager Cloud Service Appliance (EPM CSA) that allows an unauthenticated user to execute malicious code with limited permissions.
Recent research published by security researcher Ron Bowes indicates that the flaw may have been introduced as an intentional backdoor in a now-discontinued open-source project called csrf-magic that existed at least since 2014.
CVE-2019-7256, which permits an attacker to conduct remote code execution on Nice Linear eMerge E3-Series access controllers, has been exploited by threat actors as early as February 2020.
The flaw, alongside 11 other bugs, were addressed by Nice (formerly Nortek) earlier this month. That said, these vulnerabilities were originally disclosed by security researcher Gjoko Krstic in May 2019.
In light of the active exploitation of the three flaws, federal agencies are required to apply the vendor-provided mitigations by April 15, 2024.
The development comes as CISA and the Federal Bureau of Investigation (FBI) released a joint alert, urging software manufacturers to take steps to mitigate SQL injection flaws.
The advisory specifically highlighted the exploitation of CVE-2023-34362, a critical SQL injection vulnerability in Progress Software's MOVEit Transfer, by the Cl0p ransomware gang (aka Lace Tempest) to breach thousands of organizations.
"Despite widespread knowledge and documentation of SQLi vulnerabilities over the past two decades, along with the availability of effective mitigations, software manufacturers continue to develop products with this defect, which puts many customers at risk," the agencies said.
German Police Seize 'Nemesis Market' in Major International Darknet Raid
24.3.24 BigBrothers The Hacker News
German authorities have announced the takedown of an illicit underground marketplace called Nemesis Market that peddled narcotics, stolen data, and various cybercrime services.
The Federal Criminal Police Office (aka Bundeskriminalamt or BKA) said it seized the digital infrastructure associated with the darknet service located in Germany and Lithuania and confiscated €94,000 ($102,107) in cryptocurrency assets.
The operation, conducted in collaboration with law enforcement agencies from Germany, Lithuania, and the U.S., took place on March 20, 2024, following an extensive investigation that commenced in October 2022.
Founded in 2021, Nemesis Market is estimated to have had more than 150,000 user accounts and 1,100 seller accounts from all over the world prior to its shutdown. Almost 20$ of the seller accounts were from Germany.
"The range of goods available on the marketplace included narcotics, fraudulently obtained data and goods, as well as a selection of cybercrime services such as ransomware, phishing, or DDoS attacks," the BKA said.
The agency said further investigations against criminal sellers and users of the platform are presently ongoing. That said, no arrests have been made.
The development comes a month after another coordinated law enforcement operation took down the LockBit ransomware group, taking control of the outfit's servers and arresting three affiliates from Poland and Ukraine. The disruption prompted the gang to relaunch its cyber extortion operation.
In recent months, German authorities have also taken down Kingdom Market and Crimemarket, both of which boasted of thousands of users and offered a wide array of money laundering and cybercrime services.
U.S. Justice Department Sues Apple Over Monopoly and Messaging Security
22.3.24 BigBrothers The Hacker News
The U.S. Department of Justice (DoJ), along with 16 other state and district attorneys general, on Thursday accused Apple of illegally maintaining a monopoly over smartphones, thereby undermining, among other things, the security and privacy of users when messaging non-iPhone users.
"Apple wraps itself in a cloak of privacy, security, and consumer preferences to justify its anticompetitive conduct," the landmark antitrust lawsuit said. "Apple deploys privacy and security justifications as an elastic shield that can stretch or contract to serve Apple's financial and business interests."
"Apple selectively compromises privacy and security interests when doing so is in Apple's own financial interest – such as degrading the security of text messages, offering governments and certain companies the chance to access more private and secure versions of app stores, or accepting billions of dollars each year for choosing Google as its default search engine when more private options are available."
The sprawling complaint also alleged that iPhone users who message a non-iPhone user via the Messages app are defaulted to the less secure SMS format (as opposed to iMessage) that lacks support for encryption and offers limited functionality. On the other hand, iMessage is end-to-end encrypted (E2EE) and is even quantum-resistant.
It's worth noting at this stage that iMessage is only available on the iPhone and other Apple devices. Apple has repeatedly said it has no plans of making iMessage interoperable with Android, even stating that doing so "will hurt us more than help us."
Furthermore, the 88-page lawsuit called out the iPhone maker for blocking attempts by third-parties to bring secure cross-platform messaging experience between iOS and Android platform.
In December 2023, Beeper managed to reverse engineer the iMessage protocol and port the service to Android through a dedicated client called Beeper Mini. Apple, however, has shut down those efforts, arguing that Beeper "posed significant risks to user security and privacy, including the potential for metadata exposure and enabling unwanted messages, spam, and phishing attacks."
These limitations have a powerful network effect, driving consumers to continue buying iPhones and less likely to switch to a competing device, the DoJ said, adding, "by rejecting solutions that would allow for cross-platform encryption, Apple continues to make iPhone users' less secure than they could otherwise be."
The development comes as Apple is facing more scrutiny than ever to open up its tightly-controlled software ecosystem -- the so-called "walled garden" -- which regulators say locks in customers and developers. Other major tech giants like Microsoft, Google, Amazon, and Meta have all dealt with similar lawsuits in recent years.
Apple, in a surprise move late last year, announced that it intends to add support for Rich Communication Services (RCS) – an upgraded version of the SMS standard with modern instant messaging features – to its Messages app. It also said it will work with the GSMA members to integrate encryption.
In response to the lawsuit, Cupertino said it will "vigorously defend" itself and that the lawsuit "threatens who we are and the principles that set Apple products apart in fiercely competitive markets." It also said that DoJ winning the lawsuit would "set a dangerous precedent, empowering the government to take a heavy hand in designing people's technology."
U.S. Sanctions Russians Behind 'Doppelganger' Cyber Influence Campaign
21.3.24 BigBrothers The Hacker News
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) on Wednesday announced sanctions against two 46-year-old Russian nationals and the respective companies they own for engaging in cyber influence operations.
Ilya Andreevich Gambashidze (Gambashidze), the founder of the Moscow-based company Social Design Agency (SDA), and Nikolai Aleksandrovich Tupikin (Tupikin), the CEO and current owner of Russia-based Company Group Structura LLC (Structura), have been accused of providing services to the Russian government in connection to a "foreign malign influence campaign."
The disinformation campaign is tracked by the broader cybersecurity community under the name Doppelganger, which is known to target audiences in Europe and the U.S. using inauthentic news sites and social media accounts.
"SDA and Structura have been identified as key actors of the campaign, responsible for providing [the Government of the Russian Federation] with a variety of services, including the creation of websites designed to impersonate government organizations and legitimate media outlets in Europe," the Treasury said.
Both Gambashidze and Tupikin have been accused of orchestrating a campaign in the Fall of 2022 that created a network of over 60 sites designed to masquerade as legitimate news websites and fake social media accounts to disseminate the content originating from those spoofed sites.
The department said the fake websites were built with an intent to mimic the appearance of their actual counterparts, with the portals including embedded images and working links to the legitimate sites and even impersonated the cookie consent pages as part of efforts to trick visitors.
Furthermore, a closer examination of the two cryptocurrency wallets listed by OFAC as associated with Gambashidze reveals that they have received more than $200,000 worth of USDT on the TRON network, with a significant chunk originating from the now-sanctioned exchange Garantex, Chainalysis said.
"He then cashed out most of his funds to a single deposit address at a mainstream exchange," blockchain analytics firm noted. "These transactions highlight Garantex's continued involvement in the Russian government's illicit activities."
Doppelganger, active since at least February 2022, has been described by Meta as the "largest and the most aggressively-persistent Russian-origin operation."
In December 2023, Recorded Future revealed attempts by the malign network to leverage generative artificial intelligence (AI) to create inauthentic news articles and produce scalable influence content.
SDA and Structura, along with Gambashidze, have also been the subject of sanctions imposed by the Council of the European Union as of July 2023 for conducting a digital information manipulation campaign called Recent Reliable News (RRN) aimed at amplifying propaganda declaring support for Russia's war against Ukraine.
"This campaign [...] relies on fake web pages usurping the identity of national media outlets and government websites, as well as fake accounts on social media," the Council said at the time. "This coordinated and targeted information manipulation is part of a broader hybrid campaign by Russia against the E.U. and the member states."
The development comes as the U.S. House of Representatives unanimously passed a bill (Protecting Americans' Data from Foreign Adversaries Act, or H.R.7520) that would bar data brokers from selling Americans' sensitive data to foreign adversaries, counting China, Russia, North Korea, and Iran.
It also arrives a week after Congress passed another bill (Protecting Americans from Foreign Adversary Controlled Applications Act, or H.R.7521) that seeks to force Chinese company ByteDance to divest popular video sharing platform TikTok within six months, or risk facing a ban, due to national security concerns.
U.S. EPA Forms Task Force to Protect Water Systems from Cyberattacks
20.3.24 BigBrothers The Hacker News
The U.S. Environmental Protection Agency (EPA) said it's forming a new "Water Sector Cybersecurity Task Force" to devise methods to counter the threats faced by the water sector in the country.
"In addition to considering the prevalent vulnerabilities of water systems to cyberattacks and the challenges experienced by some systems in adopting best practices, this Task Force in its deliberations would seek to build upon existing collaborative products," the EPA said.
In a letter sent to all U.S. Governors, EPA Administrator Michael Regan and National Security Advisor Jake Sullivan highlighted the need to secure water and wastewater systems (WWS) from cyber attacks that could disrupt access to clean and safe drinking water.
At least two threat actors have been linked to intrusions targeting the nation's water systems, including those by an Iranian hacktivist group named Cyber Av3ngers as well as the China-linked Volt Typhoon, which has targeted communications, energy, transportation, and water and wastewater systems sectors in the U.S. and Guam for at least five years.
"Drinking water and wastewater systems are an attractive target for cyberattacks because they are a lifeline critical infrastructure sector but often lack the resources and technical capacity to adopt rigorous cybersecurity practices," Regan and Sullivan said.
The development coincides with the release of a new fact sheet from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), urging critical infrastructure entities to defend against the "urgent risk posed by Volt Typhoon" by implementing secure by-design principles, robust logging, safeguarding the supply chain, and increasing awareness of social engineering tactics.
"Volt Typhoon have been pre-positioning themselves on U.S. critical infrastructure organizations' networks to enable disruption or destruction of critical services in the event of increased geopolitical tensions and/or military conflict with the United States and its allies," the agency cautioned.
Cybersecurity firm SentinelOne, in a report published last month, revealed how China has launched an offensive media strategy to propagate "unsubstantiated" narratives around U.S. hacking operations for over two years.
"Repeating China's allegations helps the [People's Republic of China] shape global public opinion of the U.S. China wants to see the world recognize the U.S. as the 'empire of hacking,'" Sentinel One's China-focused consultant Dakota Cary said.
"The fact that China is lodging allegations of US espionage operations is still notable, providing insight into the relationship between the US and China, even if China does not support its claims."
RedCurl Cybercrime Group Abuses Windows PCA Tool for Corporate Espionage
14.3.24 BigBrothers The Hacker News
The Russian-speaking cybercrime group called RedCurl is leveraging a legitimate Microsoft Windows component called the Program Compatibility Assistant (PCA) to execute malicious commands.
"The Program Compatibility Assistant Service (pcalua.exe) is a Windows service designed to identify and address compatibility issues with older programs," Trend Micro said in an analysis published this month.
"Adversaries can exploit this utility to enable command execution and bypass security restrictions by using it as an alternative command-line interpreter. In this investigation, the threat actor uses this tool to obscure their activities."
RedCurl, which is also called Earth Kapre and Red Wolf, is known to be active since at least 2018, orchestrating corporate cyber espionage attacks against entities located in Australia, Canada, Germany, Russia, Slovenia, the U.K., Ukraine, and the U.S.
In July 2023, F.A.C.C.T. revealed that a major Russian bank and an Australian company were targeted by the threat actor in November 2022 and May 2023 to pilfer confidential corporate secrets and employee information.
The attack chain examined by Trend Micro entails the use of phishing emails containing malicious attachments (.ISO and .IMG files) to activate a multi-stage process that starts with the use of cmd.exe to download a legitimate utility called curl from a remote server, which then acts as a channel to deliver a loader (ms.dll or ps.dll).
The malicious DLL file, in turn, leverages PCA to spawn a downloader process that takes care of establishing a connection with the same domain used by curl to fetch the loader.
Also used in the attack is the use of the Impacket open-source software for unauthorized command execution.
The connections to Earth Kapre stem from overlaps in the command-and-control (C2) infrastructure as well as similarities with known downloader artifacts used by the group.
"This case underscores the ongoing and active threat posed by Earth Kapre, a threat actor that targets a diverse range of industries across multiple countries," Trend Micro said.
"The actor employs sophisticated tactics, such as abusing PowerShell, curl, and Program Compatibility Assistant (pcalua.exe) to execute malicious commands, showcasing its dedication to evading detection within targeted networks."
The development comes as the Russian nation-state group known as Turla (aka Iron Hunter, Pensive Ursa, Secret Blizzard, Snake, Uroburos, Venomous Bear, and Waterbug) has begun employing a new wrapper DLL codenamed Pelmeni to deploy the .NET-based Kazuar backdoor.
Pelmeni – which masquerades as libraries related to SkyTel, NVIDIA GeForce Experience, vncutil, or ASUS – is loaded by means of DLL side-loading. Once this spoofed DLL is called by the legitimate software installed on the machine, it decrypts and launches Kazuar, Lab52 said.
South Korean Citizen Detained in Russia on Cyber Espionage Charges
12.3.24 BigBrothers The Hacker News
Russia has detained a South Korean national for the first time on cyber espionage charges and transferred from Vladivostok to Moscow for further investigation.
The development was first reported by Russian news agency TASS.
"During the investigation of an espionage case, a South Korean citizen Baek Won-soon was identified and detained in Vladivostok, and put into custody under a court order," an unnamed source was quoted as saying.
Won-soon has been accused of handing over classified "top secret" information to unnamed foreign intelligence agencies.
According to the agency, Won-soon was detained in Vladivostok earlier this year and shifted to Moscow late last month. He is said to be currently at the Lefortovo pretrial detention center. His arrest has been extended for another three months, until June 15, 2024.
The detention center is currently also the place where American journalist Evan Gershkovich is being held, awaiting trial on suspicion of espionage. Gershkovich has denied the charges.
The development comes amid burgeoning geopolitical ties between Russia and North Korea, even as state-sponsored hacking groups associated with the latter have targeted the Kremlin to pursue their strategic intelligence-gathering missions.
It also comes days after the U.S. arrested a former Google engineer for allegedly stealing proprietary information from the tech giant while covertly working for two China-based companies, including one founded by him last year prior to his resignation.
Chinese State Hackers Target Tibetans with Supply Chain, Watering Hole Attacks
7.3.24 BigBrothers The Hacker News
The China-linked threat actor known as Evasive Panda orchestrated both watering hole and supply chain attacks targeting Tibetan users at least since September 2023.
The end of the attacks is to deliver malicious downloaders for Windows and macOS that deploy a known backdoor called MgBot and a previously undocumented Windows implant known as Nightdoor.
The findings come from ESET, which said the attackers compromised at least three websites to carry out watering-hole attacks as well as a supply-chain compromise of a Tibetan software company. The operation was discovered in January 2024.
Evasive Panda, active since 2012 and also known as Bronze Highland and Daggerfly, was previously disclosed by the Slovak cybersecurity firm in April 2023 as having targeted an international non-governmental organization (NGO) in Mainland China with MgBot.
Another report from Broadcom-owned Symantec around the same time implicated the adversary to a cyber espionage campaign aimed at infiltrating telecom services providers in Africa at least since November 2022.
The latest set of cyber assaults entails the strategic web compromise of the Kagyu International Monlam Trust's website ("www.kagyumonlam[.]org").
"The attackers placed a script in the website that verifies the IP address of the potential victim and if it is within one of the targeted ranges of addresses, shows a fake error page to entice the user to download a 'fix' named certificate," ESET researchers said.
"This file is a malicious downloader that deploys the next stage in the compromise chain." The IP address checks show that the attack is specifically designed to target users in India, Taiwan, Hong Kong, Australia, and the U.S.
It's suspected that Evasive Panda capitalized on the annual Kagyu Monlam Festival that took place in India in late January and February 2024 to target the Tibetan community in several countries and territories.
The executable – named "certificate.exe" on Windows and "certificate.pkg" for macOS – serves as a launchpad for loading the Nightdoor implant, which, subsequently, abuses the Google Drive API for command-and-control (C2).
In addition, the campaign is notable for infiltrating an Indian software company's website ("monlamit[.]com") and supply chain in order to distribute trojanized Windows and macOS installers of the Tibetan language translation software. The compromise occurred in September 2023.
"The attackers also abused the same website and a Tibetan news website called Tibetpost – tibetpost[.]net – to host the payloads obtained by the malicious downloads, including two full-featured backdoors for Windows and an unknown number of payloads for macOS," the researchers noted.
The trojanized Windows installer, for its part, triggers a sophisticated multi-stage attack sequence to either drop MgBot or Nightdoor, signs of which have been detected as early as 2020.
The backdoor comes equipped with features to gather system information, list of installed apps, and running processes; spawn a reverse shell, perform file operations, and uninstall itself from the infected system.
"The attackers fielded several downloaders, droppers, and backdoors, including MgBot – which is used exclusively by Evasive Panda – and Nightdoor: the latest major addition to the group's toolkit and which has been used to target several networks in East Asia," ESET said.
U.S. Court Orders NSO Group to Hand Over Pegasus Spyware Code to WhatsApp
2.3.24 BigBrothers The Hacker News
A U.S. judge has ordered NSO Group to hand over its source code for Pegasus and other products to Meta as part of the social media giant's ongoing litigation against the Israeli spyware vendor.
The decision, which marks a major legal victory for Meta, which filed the lawsuit in October 2019 for using its infrastructure to distribute the spyware to approximately 1,400 mobile devices between April and May. This also included two dozen Indian activists and journalists.
These attacks leveraged a then zero-day flaw in the instant messaging app (CVE-2019-3568, CVSS score: 9.8), a critical buffer overflow bug in the voice call functionality, to deliver Pegasus by merely placing a call, even in scenarios where the calls were left unanswered.
In addition, the attack chain included steps to erase the incoming call information from the logs in an attempt to sidestep detection.
Court documents released late last month show that NSO Group has been asked to "produce information concerning the full functionality of the relevant spyware," specifically for a period of one year before the alleged attack to one year after the alleged attack (i.e., from April 29, 2018, to May 10, 2020).
That said, the company doesn't have to "provide specific information regarding the server architecture at this time" because WhatsApp "would be able to glean the same information from the full functionality of the alleged spyware." Perhaps more significantly, it has been spared from sharing the identities of its clientele.
"While the court's decision is a positive development, it is disappointing that NSO Group will be allowed to continue keeping the identity of its clients, who are responsible for this unlawful targeting, secret," said Donncha Ó Cearbhaill, head of the Security Lab at Amnesty International.
NSO Group was sanctioned by the U.S. in 2021 for developing and supplying cyber weapons to foreign governments that "used these tools to maliciously target government officials, journalists, businesspeople, activists, academics, and embassy workers."
The development comes as Recorded Future revealed a new multi-tiered delivery infrastructure associated with Predator, a mercenary mobile spyware managed by the Intellexa Alliance.
The infrastructure network is highly likely associated with Predator customers, including in countries like Angola, Armenia, Botswana, Egypt, Indonesia, Kazakhstan, Mongolia, Oman, the Philippines, Saudi Arabia, and Trinidad and Tobago. It's worth noting that no Predator customers within Botswana and the Philippines had been identified until now.
"Although Predator operators respond to public reporting by altering certain aspects of their infrastructure, they seem to persist with minimal alterations to their modes of operation; these include consistent spoofing themes and focus on types of organizations, such as news outlets, while adhering to established infrastructure setups," the company said.
President Biden Blocks Mass Transfer of Personal Data to High-Risk Nations
29.2.24 BigBrothers The Hacker News
U.S. President Joe Biden has issued an Executive Order that prohibits the mass transfer of citizens' personal data to countries of concern.
The Executive Order also "provides safeguards around other activities that can give those countries access to Americans' sensitive data," the White House said in a statement.
This includes sensitive information such as genomic data, biometric data, personal health data, geolocation data, financial data, and certain kinds of personally identifiable information (PII).
The U.S. government said threat actors could weaponize this information to track their citizens and pass that information to data brokers and foreign intelligence services, which can then be used for intrusive surveillance, scams, blackmail, and other violations of privacy.
"Commercial data brokers and other companies can sell this data to countries of concern, or entities controlled by those countries, and it can land in the hands of foreign intelligence services, militaries, or companies controlled by foreign governments," the government said.
In November 2023, researchers at Duke University revealed that it's trivial to "obtain sensitive data about active-duty members of the military, their families, and veterans, including non-public, individually identified, and sensitive data, such as health data, financial data, and information about religious practices" from data brokers for as low as $0.12 per record.
Stating that the sale of such data poses privacy, counterintelligence, blackmail, and national security risks, it added hostile nations could collect personal information on activists, journalists, dissidents, and marginalized communities with the goal of restricting freedom of expression and curbing dissent.
The government said the countries of concern have a "track record of collecting and misusing data on Americans." According to the U.S. Justice Department, the countries that fall under this category include China, Russia, Iran, North Korea, Cuba, and Venezuela.
The Executive Order directs the federal agencies to issue regulations that establish clear protections for sensitive personal and government-related data from access and exploitation, as well as set high-security standards to limit data access via commercial agreements.
Additionally, the order requires the Departments of Health and Human Services, Defense, and Veterans Affairs to ensure that Federal grants, contracts, and awards are not misused to facilitate access to sensitive data.
"The Administration's decision to limit personal data flows only to a handful of countries of concern, like China, is a mistake," Senator Ron Wyden said in a statement, and that the argument that the U.S. government cannot be banned from buying Americans' data is no longer valid.
"Authoritarian dictatorships like Saudi Arabia and U.A.E. cannot be trusted with Americans' personal data, both because they will likely use it to undermine U.S. national security and target U.S. based dissidents, but also because these countries lack effective privacy laws necessary to stop the data from being sold onwards to China."
The latest attempt to regulate the data broker industry comes as the U.S. added China's Chengdu Beizhan Electronics and Canadian network intelligence firm Sandvine to its Entity List after the latter's middleboxes were found to be used to deliver spyware targeting a former Egyptian member of parliament last year.
A report from Bloomberg in September 2023 also found that Sandvine's equipment had been used by governments in Egypt and Belarus to censor content on the internet.
Access Now said Sandvine's internet-blocking technologies facilitated human rights violations by repressive governments around the world, including in Azerbaijan, Jordan, Russia, Turkey, and the U.A.E., noting it played a "direct role" in shutting down the internet in Belarus in 2020.
"Sandvine supplies deep packet inspection tools, which have been used in mass web-monitoring and censorship to block news as well as in targeting political actors and human rights activists," the U.S. Department of State said, explaining its rationale behind adding the company to the trade restriction list. "This technology has been misused to inject commercial spyware into the devices of perceived critics and dissidents."
Iran and Hezbollah Hackers Launch Attacks to Influence Israel-Hamas Narrative
21.2.24 BigBrothers The Hacker News
Hackers backed by Iran and Hezbollah staged cyber attacks designed to undercut public support for the Israel-Hamas war after October 2023.
This includes destructive attacks against key Israeli organizations, hack-and-leak operations targeting entities in Israel and the U.S., phishing campaigns designed to steal intelligence, and information operations to turn public opinion against Israel.
Iran accounted for nearly 80% of all government-backed phishing activity targeting Israel in the six months leading up to the October 7 attacks, Google said in a new report.
"Hack-and-leak and information operations remain a key component in these and related threat actors' efforts to telegraph intent and capability throughout the war, both to their adversaries and to other audiences that they seek to influence," the tech giant said.
But what's also notable about the Israel-Hamas conflict is that the cyber operations appear to be executed independently of the kinetic and battlefield actions, unlike observed in the case of the Russo-Ukrainian war.
Such cyber capabilities can be quickly deployed at a lower cost to engage with regional rivals without direct military confrontation, the company added.
One of the Iran-affiliated groups, dubbed GREATRIFT (aka UNC4453 or Plaid Rain), is said to have propagated malware via fake "missing persons" site targeting visitors seeking updates on abducted Israelis. The threat actor also utilized blood donation-themed lure documents as a distribution vector.
At least two hacktivist personas named Karma and Handala Hack have leveraged wiper malware strains such as BiBi-Windows Wiper, BiBi-Linux Wiper, ChiLLWIPE, and COOLWIPE to stage destructive attacks against Israel and delete files from Windows and Linux systems, respectively.
Another Iranian nation-state hacking group called Charming Kitten (aka APT42 or CALANQUE) targeted media and non-governmental organizations (NGOs) with a PowerShell backdoor known as POWERPUG as part of a phishing campaign observed in late October and November 2023.
POWERPUG is also the latest addition to the adversary's long list of backdoors, which comprises PowerLess, BellaCiao, POWERSTAR (aka GorjolEcho), NokNok, and BASICSTAR.

Hamas-linked groups, on the other hand, targeted Israeli software engineers with coding assignment decoys in an attempt to dupe them into downloading SysJoker malware weeks before the October 7 attacks. The campaign has been attributed to a threat actor referred to as BLACKATOM.
"The attackers [...] posed as employees of legitimate companies and reached out via LinkedIn to invite targets to apply for software development freelance opportunities," Google said. "Targets included software engineers in the Israeli military, as well as Israel's aerospace and defense industry."
The California-headquartered company described the tactics adopted by Hamas cyber actors as simple but effective, noting their use of social engineering to deliver remote access trojans and backdoors like MAGNIFI to target users in both Palestine and Israel, which has been linked to BLACKSTEM (aka Molerats).
Adding another dimension to these campaigns is the use of spyware targeting Android phones that are capable of harvesting sensitive information and exfiltrating the data to attacker-controlled infrastructure.
The malware strains, called MOAAZDROID and LOVELYDROID, are the handiwork of the Hamas-affiliated actor DESERTVARNISH, which is also tracked as Arid Viper, Desert Falcons, Renegade Jackal, and UNC718. Details about the spyware were previously documented by Cisco Talos in October 2023.

State-sponsored groups from Iran, such as MYSTICDOME (aka UNC1530), have also been observed targeting mobile devices in Israel with the MYTHDROID (aka AhMyth) Android remote access trojan as well as a bespoke spyware called SOLODROID for intelligence collection.
"MYSTICDOME distributed SOLODROID using Firebase projects that 302-redirected users to the Play store, where they were prompted to install the spyware," said Google, which has since taken down the apps from the digital marketplace.
Google further highlighted an Android malware called REDRUSE – a trojanized version of the legitimate Red Alert app used in Israel to warn of incoming rocket attacks – that exfiltrates contacts, messaging data, and location. It was propagated via SMS phishing messages that impersonated the police.
The ongoing war has also had an impact on Iran, with its critical infrastructure disrupted by an actor named Gonjeshke Darande (meaning Predatory Sparrow in Persian) in December 2023. The persona is believed to be linked to the Israeli Military Intelligence Directorate.

The findings come as Microsoft revealed that Iranian government-aligned actors have "launched a series of cyberattacks and influence operations (IO) intended to help the Hamas cause and weaken Israel and its political allies and business partners."
Redmond described their early-stage cyber and influence operations as reactive and opportunistic, while also corroborating with Google's assessment that the attacks became "increasingly targeted and destructive and IO campaigns grew increasingly sophisticated and inauthentic" following the outbreak of the war.
Beside ramping up and expanding their attack focus beyond Israel to encompass countries that Iran perceives as aiding Israel, including Albania, Bahrain, and the U.S., Microsoft said it observed collaboration among Iran-affiliated groups such as Pink Sandstorm (aka Agrius) and Hezbollah cyber units.

"Collaboration lowers the barrier to entry, allowing each group to contribute existing capabilities and removes the need for a single group to develop a full spectrum of tooling or tradecraft," Clint Watts, general manager at the Microsoft Threat Analysis Center (MTAC), said.
Last week, NBC News reported that the U.S. recently launched a cyber attack against an Iranian military ship named MV Behshad that had been collecting intelligence on cargo vessels in the Red Sea and the Gulf of Aden.
An analysis from Recorded Future last month also detailed how hacking personas and front groups in Iran are managed and operated through a variety of contracting firms in Iran, which carry out intelligence gathering and information operations to "foment instability in target countries."
"While Iranian groups rushed to conduct, or simply fabricate, operations in the early days of the war, Iranian groups have slowed their recent operations allowing them more time to gain desired access or develop more elaborate influence operations," Microsoft concluded.
U.S. State Government Network Breached via Former Employee's Account
17.2.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has revealed that an unnamed state government organization's network environment was compromised via an administrator account belonging to a former employee.
"This allowed the threat actor to successfully authenticate to an internal virtual private network (VPN) access point," the agency said in a joint advisory published Thursday alongside the Multi-State Information Sharing and Analysis Center (MS-ISAC).
"The threat actor connected to the [virtual machine] through the victim's VPN with the intent to blend in with legitimate traffic to evade detection."
It's suspected that the threat actor obtained the credentials following a separate data breach owing to the fact that the credentials appeared in publicly available channels containing leaked account information.
The admin account, which had access to a virtualized SharePoint server, also enabled the attackers to access another set of credentials stored in the server, which had administrative privileges to both the on-premises network and the Azure Active Directory (now called Microsoft Entra ID).
This further made it possible to explore the victim's on-premises environment, and execute various lightweight directory access protocol (LDAP) queries against a domain controller. The attackers behind the malicious activity are presently unknown.
A deeper investigation into the incident has revealed no evidence that the adversary moved laterally from the on-premises environment to the Azure cloud infrastructure.
The attackers ultimately accessed host and user information and posted the information on the dark web for likely financial gain, the bulletin noted, prompting the organization to reset passwords for all users, disable the administrator account as well as remove the elevated privileges for the second account.
It's worth pointing out that neither of the two accounts had multi-factor authentication (MFA) enabled, underscoring the need for securing privileged accounts that grant access to critical systems. It's also recommended to implement the principle of least privilege and create separate administrator accounts to segment access to on-premises and cloud environments.
The development is a sign that threat actors leverage valid accounts, including those belonging to former employees that have not been properly removed from the Active Directory (AD), to gain unauthorized access to organizations.
"Unnecessary accounts, software, and services in the network create additional vectors for a threat actor to compromise," the agencies said.
"By default, in Azure AD all users can register and manage all aspects of applications they create. These default settings can enable a threat actor to access sensitive information and move laterally in the network. In addition, users who create an Azure AD automatically become the Global Administrator for that tenant. This could allow a threat actor to escalate privileges to execute malicious actions."
U.S. Government Disrupts Russia-Linked Botnet Engaged in Cyber Espionage
17.2.24 BigBrothers The Hacker News
The U.S. government on Thursday said it disrupted a botnet comprising hundreds of small office and home office (SOHO) routers in the country that was put to use by the Russia-linked APT28 actor to conceal its malicious activities.
"These crimes included vast spear-phishing and similar credential harvesting campaigns against targets of intelligence interest to the Russian government, such as U.S. and foreign governments and military, security, and corporate organizations," the U.S. Department of Justice (DoJ) said in a statement.
APT28, also tracked under the monikers BlueDelta, Fancy Bear, Fighting Ursa, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, Pawn Storm, Sednit, Sofacy, and TA422, is assessed to be linked to Unit 26165 of Russia's Main Directorate of the General Staff (GRU). It's known to be active since at least 2007.
Court documents allege that the attackers pulled off their cyber espionage campaigns by relying on MooBot, a Mirai-based botnet that has singled out routers made by Ubiquiti to co-opt them into a mesh of devices that can be modified to act as a proxy, relaying malicious traffic while shielding their actual IP addresses.
The botnet, the DoJ said, allowed the threat actors to mask their true location and harvest credentials and NT LAN Manager (NTLM) v2 hashes via bespoke scripts, as well as host spear-phishing landing pages and other custom tooling for brute-forcing passwords, stealing router user passwords, and propagating the MooBot malware to other appliances.
In a redacted affidavit filed by the U.S. Federal Bureau of Investigation (FBI), the agency said MooBot exploits vulnerable and publicly accessible Ubiquiti routers by using default credentials and implants an SSH malware that permits persistent remote access to the device.
"Non-GRU cybercriminals installed the MooBot malware on Ubiquiti Edge OS routers that still used publicly known default administrator passwords," the DoJ explained. "GRU hackers then used the MooBot malware to install their own bespoke scripts and files that repurposed the botnet, turning it into a global cyber espionage platform."
The APT28 actors are suspected to have found and illegally accessed compromised Ubiquiti routers by conducting public scans of the internet using a specific OpenSSH version number as a search parameter, and then using MooBot to access those routers.
Spear-phishing campaigns undertaken by the hacking group have also leveraged a then-zero-day in Outlook (CVE-2023-23397) to siphon login credentials and transmit them to the routers.
"In another identified campaign, APT28 actors designed a fake Yahoo! landing page to send credentials entered on the false page to a compromised Ubiquiti router to be collected by APT28 actors at their convenience," the FBI said.
As part of its efforts to disrupt the botnet in the U.S. and prevent further crime, a series of unspecified commands have been issued to copy the stolen data and malicious files prior to deleting them and modify firewall rules to block APT28's remote access to the routers.
The precise number of devices that were compromised in the U.S. has been censored, although the FBI noted that it could change. Infected Ubiquiti devices have been detected in "almost every state," it added.
The court-authorized operation – referred to as Dying Ember – comes merely weeks after the U.S. dismantled another state-sponsored hacking campaign originating from China that leveraged a different botnet codenamed KV-botnet to target critical infrastructure facilities.
Last May, the U.S. also announced the takedown of a global network compromised by an advanced malware strain dubbed Snake wielded by hackers associated with Russia's Federal Security Service (FSB), otherwise known as Turla.
Alert: CISA Warns of Active 'Roundcube' Email Attacks - Patch Now
17.2.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a medium-severity security flaw impacting Roundcube email software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The issue, tracked as CVE-2023-43770 (CVSS score: 6.1), relates to a cross-site scripting (XSS) flaw that stems from the handling of linkrefs in plain text messages.
"Roundcube Webmail contains a persistent cross-site scripting (XSS) vulnerability that can lead to information disclosure via malicious link references in plain/text messages," CISA said.
According to a description of the bug on NIST's National Vulnerability Database (NVD), the vulnerability impacts Roundcube versions before 1.4.14, 1.5.x before 1.5.4, and 1.6.x before 1.6.3.
The flaw was addressed by Roundcube maintainers with version 1.6.3, which was released on September 15, 2023. Zscaler security researcher Niraj Shivtarkar has been credited with discovering and reporting the vulnerability.
It's currently not known how the vulnerability is being exploited in the wild, but flaws in the web-based email client have been weaponized by Russia-linked threat actors like APT28 and Winter Vivern over the past year.
U.S. Federal Civilian Executive Branch (FCEB) agencies have been mandated to apply vendor-provided fixes by March 4, 2024, to secure their networks against potential threats.
CISA and OpenSSF Release Framework for Package Repository Security
12.2.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced that it's partnering with the Open Source Security Foundation (OpenSSF) Securing Software Repositories Working Group to publish a new framework to secure package repositories.
Called the Principles for Package Repository Security, the framework aims to establish a set of foundational rules for package managers and further harden open-source software ecosystems.
"Package repositories are at a critical point in the open-source ecosystem to help prevent or mitigate such attacks," OpenSSF said.
"Even simple actions like having a documented account recovery policy can lead to robust security improvements. At the same time, capabilities must be balanced with resource constraints of package repositories, many of which are operated by non-profit organizations."
Notably, the principles lay out four security maturity levels for package repositories across four categories of authentication, authorization, general capabilities, and command-line interface (CLI) tooling -
Level 0 - Having very little security maturity.
Level 1 - Having basic security maturity, such as multi-factor authentication (MFA) and allowing security researchers to report vulnerabilities
Level 2 - Having moderate security, which includes actions like requiring MFA for critical packages and warning users of known security vulnerabilities
Level 3 - Having advanced security, which requires MFA for all maintainers and supports build provenance for packages
All package management ecosystems should be working towards at least Level 1, the framework authors Jack Cable and Zach Steindler note.
The ultimate objective is to allow package repositories to self-assess their security maturity and formulate a plan to bolster their guardrails over time in the form of security improvements.
"Security threats change over time, as do the security capabilities that address those threats," OpenSSF said. "Our goal is to help package repositories more quickly deliver the security capabilities that best help strengthen the security of their ecosystems."
The development comes as the U.S. Department of Health and Human Services' Health Sector Cybersecurity Coordination Center (HC3) warned of security risks arising as a result of using open-source software for maintaining patient records, inventory management, prescriptions, and billing.
"While open-source software is the bedrock of modern software development, it is also often the weakest link in the software supply chain," it said in a threat brief published in December 2023.
U.S. Offers $10 Million Bounty for Info Leading to Arrest of Hive Ransomware Leaders
12.2.24 BigBrothers The Hacker News
The U.S. Department of State has announced monetary rewards of up to $10 million for information about individuals holding key positions within the Hive ransomware operation.
It is also giving away an additional $5 million for specifics that could lead to the arrest and/or conviction of any person "conspiring to participate in or attempting to participate in Hive ransomware activity."
The multi-million-dollar rewards come a little over a year after a coordinated law enforcement effort covertly infiltrated and dismantled the darknet infrastructure associated with the Hive ransomware-as-a-service (RaaS) gang. One person with suspected ties to the group was arrested in Paris in December 2023.
Hive, which emerged in mid-2021, targeted more than 1,500 victims in over 80 countries, netting about $100 million in illegal revenues. In November 2023, Bitdefender revealed that a new ransomware group called Hunters International had acquired the source code and infrastructure from Hive to kick-start its own efforts.
There is some evidence to suggest that the threat actors associated with Hunters International are likely based in Nigeria, specifically an individual named Olowo Kehinde, per information gathered by Netenrich security researcher Rakesh Krishnan, although it could also be a fake persona adopted by the actors to cover up their true origins.
Blockchain analytics firm Chainalysis, in its 2023 review published last week, estimated that ransomware crews raked in $1.1 billion in extorted cryptocurrency payments from victims last year, compared to $567 million in 2022, all but confirming that ransomware rebounded in 2023 following a relative drop off in 2022.
"2023 marks a major comeback for ransomware, with record-breaking payments and a substantial increase in the scope and complexity of attacks — a significant reversal from the decline observed in 2022," it said.
The decline in ransomware activity in 2022 has been deemed a statistical aberration, with the downturn attributed to the Russo-Ukrainian war and the disruption of Hive. What's more, the total number of victims posted on data leak sites in 2023 was 4,496, up from 3,048 in 2021 and 2,670 in 2022.
Palo Alto Networks Unit 42, in its own analysis of ransomware gangs' public listings of victims on dark web sites, called out manufacturing as the most impacted industry vertical in 2023, followed by profession and legal services, high technology, retail, construction, and healthcare sectors.
While the law enforcement action prevented approximately $130 million in ransom payments to Hive, it's said that the takedown also "likely affected the broader activities of Hive affiliates, potentially lessening the number of additional attacks they could carry out." In total, the effort may have averted at least $210.4 million in payments.
Adding to the escalation in the regularity, scope, and volume of attacks, last year also witnessed a surge in new entrants and offshoots, a sign that the ransomware ecosystem is attracting a steady stream of new players who are attracted by the prospect of high profits and lower barriers to entry.
Cyber insurance provider Corvus said the number of active ransomware gangs registered a "significant" 34% increase between Q1 and Q4 2023, growing from 35 to 47 either due to fracturing and rebranding or other actors getting hold of leaked encryptors. Twenty-five new ransomware groups emerged in 2023.
"The frequency of rebranding, especially among actors behind the biggest and most notorious strains, is an important reminder that the ransomware ecosystem is smaller than the large number of strains would make it appear," Chainalysis said.
Besides a notable shift to big game hunting – which refers to the tactic of targeting very large companies to extract hefty ransoms – ransom payments are being steadily routed through cross-chain bridges, instant exchangers, and gambling services, indicating that e-crime groups are slowly moving away from centralized exchanges and mixers in pursuit of new avenues for money laundering.
In November 2023, the U.S. Treasury Department imposed sanctions against Sinbad, a virtual currency mixer that has been put to use by the North Korea-linked Lazarus Group to launder ill-gotten proceeds. Some of the other sanctioned mixers include Blender, Tornado Cash, and ChipMixer.
The pivot to big game hunting is also a consequence of companies increasingly refusing to settle, as the number of victims who chose to pay dropped to a new low of 29% in the last quarter of 2023, according to data from Coveware.
"Another factor contributing to higher ransomware numbers in 2023 was a major shift in threat actors' use of vulnerabilities," Corvus said, highlighting Cl0p's exploitation of flaws in Fortra GoAnywhere and Progress MOVEit Transfer.
"If malware, like infostealers, provide a steady drip of new ransomware victims, then a major vulnerability is like turning on a faucet. With some vulnerabilities, relatively easy access to thousands of victims can materialize seemingly overnight."
Cybersecurity company Recorded Future revealed that ransomware groups' weaponization of security vulnerabilities falls into two clear categories: vulnerabilities that have only been exploited by one or two groups and those that have been widely exploited by multiple threat actors.
"Magniber has uniquely focused on Microsoft vulnerabilities, with half of its unique exploits focusing on Windows Smart Screen," it noted. "Cl0p has uniquely and infamously focused on file transfer software from Accellion, SolarWinds, and MOVEit. ALPHV has uniquely focused on data backup software from Veritas and Veeam. REvil has uniquely focused on server software from Oracle, Atlassian, and Kaseya."

The continuous adaptation observed among cybercrime crews is also evidenced in the uptick in DarkGate and PikaBot infections following the takedown of the QakBot malware network, which had been the preferred initial entry pathway into target networks for ransomware deployment.
Chainalysis further said it found a "correlation" between inflows to initial access broker (IAB) wallets and a spike in ransomware payments, suggesting that keeping tabs on IABs blockchain trails could provide early warning signs for potential intervention and mitigation of attacks.
"Ransomware groups such as Cl0p have used zero-day exploits against newly discovered critical vulnerabilities, which represent a complex challenge for potential victims," Unit 42 said.
"While ransomware leak site data can provide valuable insight on the threat landscape, this data might not accurately reflect the full impact of a vulnerability. Organizations must not only be vigilant about known vulnerabilities, but they must also develop strategies to quickly respond to and mitigate the impact of zero-day exploits."
Chinese Hackers Operate Undetected in U.S. Critical Infrastructure for Half a Decade
8.2.24 BigBrothers The Hacker News

The U.S. government on Wednesday said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some critical infrastructure networks in the country for at least five years.
Targets of the threat actor include communications, energy, transportation, and water and wastewater systems sectors in the U.S. and Guam.
"Volt Typhoon's choice of targets and pattern of behavior is not consistent with traditional cyber espionage or intelligence gathering operations, and the U.S. authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT assets to disrupt functions," the U.S. government said.
The joint advisory, which was released by the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and the Federal Bureau of Investigation (FBI), was also backed by other nations that are part of the Five Eyes (FVEY) intelligence alliance comprising Australia, Canada, New Zealand, the U.K.
Volt Typhoon – which is also called Bronze Silhouette, Insidious Taurus, UNC3236, Vanguard Panda, or Voltzite – a stealthy China-based cyber espionage group that's believed to be active since June 2021.
It first came to light in May 2023 when Microsoft revealed that the hacking crew managed to establish a persistent foothold into critical infrastructure organizations in the U.S. and Guam for extended periods of time sans getting detected by principally leveraging living-off-the-land (LotL) techniques.
"This kind of tradecraft, known as 'living off the land,' allows attackers to operate discreetly, with malicious activity blending in with legitimate system and network behavior making it difficult to differentiate – even by organizations with more mature security postures," the U.K. National Cyber Security Centre (NCSC) said.
Another hallmark tactic adopted by Volt Typhoon is the use of multi-hop proxies like KV-botnet to route malicious traffic through a network of compromised routers and firewalls in the U.S. to mask its true origins.
Cybersecurity firm CrowdStrike, in a report published in June 2023, called out its reliance on an extensive arsenal of open-source tooling against a narrow set of victims to achieve its strategic goals.
"Volt Typhoon actors conduct extensive pre-exploitation reconnaissance to learn about the target organization and its environment; tailor their tactics, techniques, and procedures (TTPs) to the victim's environment; and dedicate ongoing resources to maintaining persistence and understanding the target environment over time, even after initial compromise," the agencies noted.
U.S. Infrastructure
"The group also relies on valid accounts and leverages strong operational security, which combined, allows for long-term undiscovered persistence."
Furthermore, the nation-state has been observed attempting to obtain administrator credentials within the network by exploiting privilege escalation flaws, subsequently leveraging the elevated access to facilitate lateral movement, reconnaissance, and full domain compromise.
The ultimate goal of the campaign is to retain access to the compromised environments, "methodically" re-targeting them over years to validate and expand their unauthorized accesses. This meticulous approach, per the agencies, is evidenced in cases where they have repeatedly exfiltrated domain credentials to ensure access to current and valid accounts.
"In addition to leveraging stolen account credentials, the actors use LOTL techniques and avoid leaving malware artifacts on systems that would cause alerts," CISA, FBI, and NSA said.
"Their strong focus on stealth and operational security allows them to maintain long-term, undiscovered persistence. Further, Volt Typhoon's operational security is enhanced by targeted log deletion to conceal their actions within the compromised environment."
The development comes as the Citizen Lab revealed a network of at least 123 websites impersonating local news outlets spanning 30 countries in Europe, Asia, and Latin America that's pushing pro-China content in a widespread influence campaign linked to a Beijing public relations firm named Shenzhen Haimaiyunxiang Media Co., Ltd.
The Toronto-based digital watchdog, which dubbed the influence operation PAPERWALL, said it shares similarities with HaiEnergy, albeit with different operators and unique TTPs.
"A central feature of PAPERWALL, observed across the network of websites, is the ephemeral nature of its most aggressive components, whereby articles attacking Beijing's critics are routinely removed from these websites some time after they are published," the Citizen Lab said.
In a statement shared with Reuters, a spokesperson for China's embassy in Washington said "it is a typical bias and double standard to allege that the pro-China contents and reports are 'disinformation,' and to call the anti-China ones' true information.'"
Global Coalition and Tech Giants Unite Against Commercial Spyware Abuse
7.2.24 BigBrothers The Hacker News
A coalition of dozens of countries, including France, the U.K., and the U.S., along with tech companies such as Google, MDSec, Meta, and Microsoft, have signed a joint agreement to curb the abuse of commercial spyware to commit human rights abuses.
The initiative, dubbed the Pall Mall Process, aims to tackle the proliferation and irresponsible use of commercial cyber intrusion tools by establishing guiding principles and policy options for States, industry, and civil society in relation to the development, facilitation, purchase, and use of such tools.
The declaration stated that "uncontrolled dissemination" of spyware offerings contributes to "unintentional escalation in cyberspace," noting it poses risks to cyber stability, human rights, national security, and digital security.
"Where these tools are used maliciously, attacks can access victims' devices, listen to calls, obtain photos and remotely operate a camera and microphone via 'zero-click' spyware, meaning no user interaction is needed," the U.K. government said in a press release.
According to the National Cyber Security Centre (NCSC), thousands of individuals are estimated to have been globally targeted by spyware campaigns every year.
"And as the commercial market for these tools grows, so too will the number and severity of cyber attacks compromising our devices and our digital systems, causing increasingly expensive damage and making it more challenging than ever for our cyber defenses to protect public institutions and services," Deputy Prime Minister Oliver Dowden said at the U.K.-France Cyber Proliferation conference.
Notably missing from the list of countries that participated in the event is Israel, which is home to a number of private sector offensive actors (PSOAs) or commercial surveillance vendors (CSVs) such as Candiru, Intellexa (Cytrox), NSO Group, and QuaDream.
Recorded Future News reported that Hungary, Mexico, Spain, and Thailand – which have been linked to spyware abuses in the past – did not sign the pledge.
The multi-stakeholder action coincides with an announcement by the U.S. Department of State to deny visas for individuals that it deems to be involved with the misuse of dangerous spyware technology.
"Until recently, a lack of accountability has enabled the spyware industry to proliferate dangerous surveillance tools around the world," Google said in a statement shared with The Hacker News. "Limiting spyware vendors' ability to operate in the U.S. helps to change the incentive structure which has allowed their continued growth."
One hand, spyware such as Chrysaor and Pegasus are licensed to government customers for use in law enforcement and counterterrorism. On the other hand, they have also been routinely abused by oppressive regimes to target journalists, activists, lawyers, human rights defenders, dissidents, political opponents, and other civil society members.
Such intrusions typically leverage zero-click (or one-click) exploits to surreptitiously deliver the surveillanceware onto the targets' Google Android and Apple iOS devices with the goal of harvesting sensitive information.
That having said, ongoing efforts to combat and contain the spyware ecosystem have been something of a whack-a-mole, underscoring the challenge of fending off recurring and lesser-known players who provide or come up with similar cyber weapons.
This also extends to the fact that CSVs continue to expend effort developing new exploit chains as companies like Apple, Google, and others discover and plug the zero-day vulnerabilities.
Source: Google's Threat Analysis Group (TAG)
"As long as there is a demand for surveillance capabilities, there will be incentives for CSVs to continue developing and selling tools, perpetrating an industry that harms high risk users and society at large," Google's Threat Analysis Group (TAG) said.
An extensive report published by TAG this week revealed that the company is tracking roughly 40 commercial spyware companies that sell their products to government agencies, with 11 of them linked to the exploitation of 74 zero-days in Google Chrome (24), Android (20), iOS (16), Windows (6), Adobe (2), Mozilla Firefox (1) over the past decade.
Unknown state-sponsored actors, for example, exploited three flaws in iOS (CVE-2023-28205, CVE-2023-28206, and CVE-2023-32409) as a zero-day last year to infect victims with spyware developed by Barcelona-based Variston. The flaws were patched by Apple in April and May 2023.
The campaign, discovered in March 2023, delivered a link via SMS and targeted iPhones located in Indonesia running iOS versions 16.3.0 and 16.3.1 with an aim to deploy the BridgeHead spyware implant via the Heliconia exploitation framework. Also weaponized by Variston is a high-severity security shortcoming in Qualcomm chips (CVE-2023-33063) that first came to light in October 2023.
The complete list of zero-day vulnerabilities in Apple iOS and Google Chrome that were discovered in 2023 and have been tied to specific spyware vendors is as follows:
Zero-day Exploit Associated Spyware Vendor
CVE-2023-28205 and CVE-2023-28206 (Apple iOS) Variston (BridgeHead)
CVE-2023-2033 (Google Chrome) Intellexa/Cytrox (Predator)
CVE-2023-2136 (Google Chrome) Intellexa/Cytrox (Predator)
CVE-2023-32409 (Apple iOS) Variston (BridgeHead)
CVE-2023-3079 (Google Chrome) Intellexa/Cytrox (Predator)
CVE-2023-41061 and CVE-2023-41064 (Apple iOS) NSO Group (Pegasus)
CVE-2023-41991, CVE-2023-41992, and CVE-2023-41993 (Apple iOS) Intellexa/Cytrox (Predator)
CVE-2023-5217 (Google Chrome) Candiru (DevilsTongue)
CVE-2023-4211 (Arm Mali GPU) Cy4Gate (Epeius)
CVE-2023-33063 (Qualcomm Adreno GPU) Variston (BridgeHead)
CVE-2023-33106 and CVE-2023-33107 (Qualcomm Adreno GPU) Cy4Gate (Epeius)
CVE-2023-42916 and CVE-2023-42917 (Apple iOS) PARS Defense
CVE-2023-7024 (Google Chrome) NSO Group (Pegasus)
"Private sector firms have been involved in discovering and selling exploits for many years, but the rise of turnkey espionage solutions is a newer phenomena," the tech giant said.
"CSVs operate with deep technical expertise to offer 'pay-to-play' tools that bundle an exploit chain designed to get past the defenses of a selected device, the spyware, and the necessary infrastructure, all to collect the desired data from an individual's device."
U.S. Imposes Visa Restrictions on those Involved in Illegal Spyware Surveillance
6.2.24 BigBrothers The Hacker News
The U.S. State Department said it's implementing a new policy that imposes visa restrictions on individuals who are linked to the illegal use of commercial spyware to surveil civil society members.
"The misuse of commercial spyware threatens privacy and freedoms of expression, peaceful assembly, and association," Secretary of State Antony Blinken said. "Such targeting has been linked to arbitrary detentions, forced disappearances, and extrajudicial killings in the most egregious of cases."
The latest measures, underscoring continued efforts on part of the U.S. government to curtail the proliferation of surveillance tools, are designed to "promote accountability" for individuals involved in commercial spyware misuse.
The new policy covers people who have used such tools to "unlawfully surveil, harass, suppress, or intimidate individuals," as well as those who stand to financially benefit from the misuse.
It also includes the companies (aka private sector offensive actors or PSOAs) that develop and sell the spyware to governments and other entities. It's currently not clear how the new restrictions will be enforced for individuals who possess passports that don't require a visa to enter the U.S.
However, CyberScoop notes that executives potentially affected by the ban would no longer be eligible to participate in the visa waiver program, and that they would need to apply for a visa to travel to the U.S.
The development comes days after Access Now and the Citizen Lab revealed that 35 journalists, lawyers, and human-rights activists in the Middle Eastern nation of Jordan were targeted with NSO Group's Pegasus spyware.
In November 2021, the U.S. government sanctioned NSO Group and Candiru, another spyware vendor, for developing and supplying cyber weapons to foreign governments that "used these tools to maliciously target government officials, journalists, businesspeople, activists, academics, and embassy workers."
Then early last year, U.S. President Joe Biden signed an executive order barring federal government agencies from using commercial spyware that could pose national security risks. In July 2023, the U.S. also placed Intellexa and Cytrox on a trade blocklist.
According to an intelligence assessment released by the U.K. Government Communications Headquarters (GCHQ) in April 2023, at least 80 countries have purchased commercial cyber intrusion software over the past decade.
Google's Threat Analysis Group (TAG), in a comprehensive report about the commercial spyware landscape shared with The Hacker News, said there are dozens of smaller vendors such as Cy4Gate, Negg Group, and Variston who "enable the proliferation of dangerous tools and capabilities used by governments against individuals."
For example, Italian company Cy4Gate, which acquired RCS Lab in March 2022, is the maker of Android and iOS spyware known as Epeius. Negg Group, which is also from Italy, develops a strain of mobile spyware codenamed VBiss that's delivered via one-click exploit chains. It has also been linked to another Android malware known as Skygofree.
"If governments ever had a monopoly on the most sophisticated capabilities, that era is certainly over," TAG said, adding it's tracking nearly 40 companies with varying levels of sophistication. "The private sector is now responsible for a significant portion of the most sophisticated tools we detect."
This is exemplified by the fact that of the 25 zero-days that were exploited in the wild in 2023, 20 were weaponized by PSOAs. Furthermore, 35 out of 72 zero-days found in Google products since 2014 have been actively exploited by commercial vendors.
"The development of surveillance technology often begins with the discovery of a vulnerability and ends with a government customer collecting data from spyware installed on a high risk user's device," TAG further noted, calling out the roles played by exploit developers, exploit brokers, and the vendors themselves, who sell the spyware as a product along with the initial delivery mechanisms and the exploits.
(The story was updated after publication to include additional insights shared by Google's Threat Analysis Group.)
U.S. Sanctions 6 Iranian Officials for Critical Infrastructure Cyber Attacks
3.2.24 BigBrothers The Hacker News
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) announced sanctions against six officials associated with the Iranian intelligence agency for attacking critical infrastructure entities in the U.S. and other countries.
The officials include Hamid Reza Lashgarian, Mahdi Lashgarian, Hamid Homayunfal, Milad Mansuri, Mohammad Bagher Shirinkar, and Reza Mohammad Amin Saberian, who are part of the Iranian Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC).
Reza Lashgarian is also the head of the IRGC-CEC and a commander in the IRGC-Qods Force. He is alleged to have been involved in various IRGC cyber and intelligence operations.
The Treasury Department said it's holding these individuals responsible for carrying out "cyber operations in which they hacked and posted images on the screens of programmable logic controllers manufactured by Unitronics, an Israeli company."
In late November 2023, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) revealed that the Municipal Water Authority of Aliquippa in western Pennsylvania was targeted by Iranian threat actors by exploiting Unitronics PLCs.
The attack was attributed to an Iranian hacktivist persona dubbed Cyber Av3ngers, which came to the forefront in the aftermath of the Israel-Hamas conflict, staging destructive attacks against entities in Israel and the U.S.
The group, which has been active since 2020, is also said to be behind several other cyber attacks, including one targeting Boston Children's Hospital in 2021 and others in Europe and Israel.
"Industrial control devices, such as programmable logic controllers, used in water and other critical infrastructure systems, are sensitive targets," the Treasury Department noted.
"Although this particular operation did not disrupt any critical services, unauthorized access to critical infrastructure systems can enable actions that harm the public and cause devastating humanitarian consequences."
The development comes as another pro-Iranian "psychological operation group" known as Homeland Justice said it attacked Albania's Institute of Statistics (INSTAT) and claimed to have stolen terabytes of data.
Homeland Justice has a track record of targeting Albania since mid-July 2022, with the threat actor most recently observed delivering a wiper malware codenamed No-Justice.
CISA Warns of Active Exploitation of Flaw in Apple iOS and macOS
2.2.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a high-severity flaw impacting iOS, iPadOS, macOS, tvOS, and watchOS to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.
The vulnerability, tracked as CVE-2022-48618 (CVSS score: 7.8), concerns a bug in the kernel component.
"An attacker with arbitrary read and write capability may be able to bypass Pointer Authentication," Apple said in an advisory, adding the issue "may have been exploited against versions of iOS released before iOS 15.7.1."
The iPhone maker said the problem was addressed with improved checks. It's currently not known how the vulnerability is being weaponized in real-world attacks.
Interestingly, patches for the flaw were released on December 13, 2022, with the release of iOS 16.2, iPadOS 16.2, macOS Ventura 13.1, tvOS 16.2, and watchOS 9.2, although it was only publicly disclosed more than a year later on January 9, 2024.
It's worth noting that Apple did resolve a similar flaw in the kernel (CVE-2022-32844, CVSS score: 6.3) in iOS 15.6 and iPadOS 15.6, which was shipped on July 20, 2022.
"An app with arbitrary kernel read and write capability may be able to bypass Pointer Authentication," the company said at the time. "A logic issue was addressed with improved state management."
In light of the active exploitation of CVE-2022-48618, CISA is recommending that Federal Civilian Executive Branch (FCEB) agencies apply the fixes by February 21, 2024.
The development also comes as Apple expanded patches for an actively exploited security flaw in the WebKit browser engine (CVE-2024-23222, CVSS score: 8.8) to include its Apple Vision Pro headset. The fix is available in visionOS 1.0.2.
NSA Admits Secretly Buying Your Internet Browsing Data without Warrants
29.1.24 BigBrothers The Hacker News
The U.S. National Security Agency (NSA) has admitted to buying internet browsing records from data brokers to identify the websites and apps Americans use that would otherwise require a court order, U.S. Senator Ron Wyden said last week.
"The U.S. government should not be funding and legitimizing a shady industry whose flagrant violations of Americans' privacy are not just unethical, but illegal," Wyden said in a letter to the Director of National Intelligence (DNI), Avril Haines, in addition to taking steps to "ensure that U.S. intelligence agencies only purchase data on Americans that has been obtained in a lawful manner."
Metadata about users' browsing habits can pose a serious privacy risk, as the information could be used to glean personal details about an individual based on the websites they frequent.
This could include websites that offer resources related to mental health, assistance for survivors of sexual assault or domestic abuse, and telehealth providers who focus on birth control or abortion medication.
In response to Wyden's queries, the NSA said it has developed compliance regimes and that it "takes steps to minimize the collection of U.S. person information" and "continues to acquire only the most useful data relevant to mission requirements."
The agency, however, said it does not buy and use location data collected from phones used in the U.S. without a court order. It also said it does not use location information obtained from automobile telematics systems from vehicles located in the country.
Ronald S. Moultrie, under secretary of defense for intelligence and security (USDI&S), said Departments of Defense (DoD) components acquire and use commercially available information (CAI) in a manner that "adheres to high standards of privacy and civil liberties protections" in support of lawful intelligence or cybersecurity missions.
The revelation is yet another indication that intelligence and law enforcement agencies are purchasing potentially sensitive data from companies that would necessitate a court order to acquire directly from communication companies. In early 2021, it was revealed the Defense Intelligence Agency (DIA) was buying and using domestic location data collected from smartphones via commercial data brokers.
The disclosure about warrantless purchase of personal data arrives in the aftermath of the Federal Trade Commission (FTC) prohibiting Outlogic (formerly X-Mode Social) and InMarket Media from selling precise location information to its customers without users' informed consent.
Outlogic, as part of its settlement with the FTC, has also been barred from collecting location data that could be used to track people's visits to sensitive locations such as medical and reproductive health clinics, domestic abuse shelters, and places of religious worship.
The purchase of sensitive data from these "shady companies" has existed in a legal gray area, Wyden noted, adding the data brokers that buy and resell this data are not known to consumers, who are often kept in the dark about who their data is being shared with or where it is being used.
Another notable aspect of these shadowy data practices is that third-party apps incorporating software development kits (SDKs) from these data brokers and ad-tech vendors do not notify users of the sale and sharing of location data, whether it be for advertising or national security.
"According to the FTC, it is not enough for a consumer to consent to an app or website collecting such data, the consumer must be told and agree to their data being sold to 'government contractors for national security purposes,'" the Oregon Democrat said.
"I am unaware of any company that provides such warnings to consumers before their data is collected. As such, the lawbreaking is likely industry-wide, and not limited to this particular data broker."
U.S. Cybersecurity Agency Warns of Actively Exploited Ivanti EPMM Vulnerability
19.1.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched critical flaw impacting Ivanti Endpoint Manager Mobile (EPMM) and MobileIron Core to its Known Exploited Vulnerabilities (KEV) catalog, stating it's being actively exploited in the wild.
The vulnerability in question is CVE-2023-35082 (CVSS score: 9.8), an authentication bypass that's a patch bypass for another flaw in the same solution tracked as CVE-2023-35078 (CVSS score: 10.0).
"If exploited, this vulnerability enables an unauthorized, remote (internet-facing) actor to potentially access users' personally identifiable information and make limited changes to the server," Ivanti noted in August 2023.
All versions of Ivanti Endpoint Manager Mobile (EPMM) 11.10, 11.9 and 11.8, and MobileIron Core 11.7 and below are impacted by the vulnerability.
Cybersecurity firm Rapid7, which discovered and reported the flaw, said it can be chained with CVE-2023-35081 to permit an attacker to write malicious web shell files to the appliance.
There are currently no details on how the vulnerability is being weaponized in real-world attacks. Federal agencies are recommended to apply vendor-provided fixes by February 8, 2024.
The disclosure comes as two other zero-day flaws in Ivanti Connect Secure (ICS) virtual private network (VPN) devices (CVE-2023-46805 and CVE-2024-21887) have also come under mass exploitation to drop web shells and passive backdoors, with the company expected to release updates next week.
"We have observed the threat actor target the configuration and running cache of the system, which contains secrets important to the operation of the VPN," Ivanti said in an advisory.
"While we haven't observed this in every instance, out of an abundance of caution, Ivanti is recommending you rotate these secrets after rebuild."
Volexity, earlier this week, revealed that it has been able to find evidence of compromise of over 1,700 devices worldwide. While initial exploitation was linked to a suspected Chinese threat actor named UTA0178, additional threat actors have since joined the exploitation bandwagon.
Further reverse engineering of the twin flaws by Assetnote has uncovered an additional endpoint ("/api/v1/totp/user-backup-code") by which the authentication bypass flaw (CVE-2023-46805) could be abused on older versions of ICS and obtain a reverse shell.
Security researchers Shubham Shah and Dylan Pindur described it as "another example of a secure VPN device exposing itself to wide scale exploitation as the result of relatively simple security mistakes."
Russian COLDRIVER Hackers Expand Beyond Phishing with Custom Malware
19.1.24 BigBrothers The Hacker News
The Russia-linked threat actor known as COLDRIVER has been observed evolving its tradecraft to go beyond credential harvesting to deliver its first-ever custom malware written in the Rust programming language.
Google's Threat Analysis Group (TAG), which shared details of the latest activity, said the attack chains leverage PDFs as decoy documents to trigger the infection sequence. The lures are sent from impersonation accounts.
COLDRIVER, also known by the names Blue Callisto, BlueCharlie (or TAG-53), Calisto (alternately spelled Callisto), Dancing Salome, Gossamer Bear, Star Blizzard (formerly SEABORGIUM), TA446, and UNC4057, is known to be active since 2019, targeting a wide range of sectors.
This includes academia, defense, governmental organizations, NGOs, think tanks, political outfits, and, recently, defense-industrial targets and energy facilities.
"Targets in the U.K. and U.S. appear to have been most affected by Star Blizzard activity, however activity has also been observed against targets in other NATO countries, and countries neighboring Russia," the U.S. government disclosed last month.
Spear-phishing campaigns mounted by the group are designed to engage and build trust with the prospective victims with the ultimate goal of sharing bogus sign-in pages in order to harvest their credentials and gain access to the accounts.
Microsoft, in an analysis of the COLDRIVER's tactics, called out its use of server-side scripts to prevent automated scanning of the actor-controlled infrastructure and determine targets of interest, before redirecting them to the phishing landing pages.
The latest findings from Google TAG show that the threat actor has been using benign PDF documents as a starting point as far back as November 2022 to entice the targets into opening the files.
"COLDRIVER presents these documents as a new op-ed or other type of article that the impersonation account is looking to publish, asking for feedback from the target," the tech giant said. "When the user opens the benign PDF, the text appears encrypted."
In the event the recipient responds to the message stating they cannot read the document, the threat actor responds with a link to a purported decryption tool ("Proton-decrypter.exe") hosted on a cloud storage service.

The choice of the name "Proton-decrypter.exe" is notable because Microsoft had previously revealed that the adversary predominantly uses Proton Drive to send the PDF lures through the phishing messages.
Google TAG researchers told The Hacker News that the PDF document employed in the attack was hosted on Proton Drive and that the attackers say the tool is used to decrypt the file hosted on the cloud platform.
In reality, the decryptor is a backdoor named SPICA that grants COLDRIVER covert access to the machine, while simultaneously displaying a decoy document to keep up the ruse.
Prior findings from WithSecure (formerly F-Secure) have revealed the threat actor's use of a lightweight backdoor called Scout, a malware tool from the HackingTeam Remote Control System (RCS) Galileo hacking platform, as part of phishing campaigns observed in early 2016.
Scout is "intended to be used as an initial reconnaissance tool to gather basic system information and screenshots from a compromised computer, as well as enable the installation of additional malware," the Finnish cybersecurity company noted at the time.
SPICA, which is the first custom malware developed and used by COLDRIVER, uses JSON over WebSockets for command-and-control (C2), facilitating the execution of arbitrary shell commands, theft of cookies from web browsers, uploading and downloading files, and enumerating and exfiltrating files. Persistence is achieved by means of a scheduled task.
"Once executed, SPICA decodes an embedded PDF, writes it to disk, and opens it as a decoy for the user," Google TAG said. "In the background, it establishes persistence and starts the main C2 loop, waiting for commands to execute."
There is evidence to suggest that the nation-state actor's use of the implant goes back to November 2022, with the cybersecurity arm multiple variants of the "encrypted" PDF lure, indicating that there could be different versions of SPICA to to match the lure document sent to targets.
As part of its efforts to disrupt the campaign and prevent further exploitation, Google TAG said it added all known websites, domains, and files associated with the hacking crew to Safe Browsing blocklists.
Google said it does not have visibility into the number of victims who were successfully compromised with SPICA, but suspects it was only used in "very limited, targeted attacks," adding there has been a focus on "high profile individuals in NGOs, former intelligence and military officials, defense, and NATO governments."
The development comes over a month after the U.K. and the U.S. governments sanctioned two Russian members of COLDRIVER, Ruslan Aleksandrovich Peretyatko and Andrey Stanislavovich Korinets, for their involvement in conducting the spear-phishing operations.
French cybersecurity firm Sekoia has since publicized links between Korinets and known infrastructure used by the group, which comprises dozens of phishing domains and multiple servers.
"Calisto contributes to Russian intelligence efforts to support Moscow's strategic interests," the company said. "It seems that domain registration was one of [Korinets'] main skills, plausibly used by Russian intelligence, either directly or through a contractor relationship."
Iranian Hackers Masquerade as Journalists to Spy on Israel-Hamas War Experts
18.1.24 BigBrothers The Hacker News

High-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the U.K., and the U.S. have been targeted by an Iranian cyber espionage group called Mind Sandstorm since November 2023.
The threat actor "used bespoke phishing lures in an attempt to socially engineer targets into downloading malicious files," the Microsoft Threat Intelligence team said in a Wednesday analysis, describing it as a "technically and operationally mature subgroup of Mind Sandstorm."
The attacks, in select cases, involve the use of a previously undocumented backdoor dubbed MediaPl, indicating ongoing endeavors by Iranian threat actors to refine their post-intrusion tradecraft.
Mint Sandstorm, also known as APT35, Charming Kitten, TA453, and Yellow Garuda, is known for its adept social engineering campaigns, even resorting to legitimate but compromised accounts to send bespoke phishing emails to prospective targets. It's assessed to be affiliated with Iran's Islamic Revolutionary Guard Corps (IRGC).
The sub-cluster, per Redmond, engages in resource-intensive social engineering to single out journalists, researchers, professors, and other individuals with insights on security and policy issues of interest to Tehran.
The latest intrusion set is characterized by the use of lures pertaining to the Israel-Hamas war, sending innocuous emails under the guise of journalists and other high-profile individuals to build rapport with targets and establish a level of trust before attempting to deliver malware to targets.
Microsoft said it's likely the campaign is an effort undertaken by the nation-state threat actor to collect perspectives on events related to the war.
The use of breached accounts belonging to the people they sought to impersonate in order to send the email messages is a new Mind Sandstorm tactic not seen before, as is its use of the curl command to connect to the command-and-control (C2) infrastructure.
Should the targets engage with the threat actor, they are sent a follow-up email containing a malicious link that points to a RAR archive file, which, when opened, leads to the retrieval of Visual Basic scripts from the C2 server to persist within the targets' environments.
The attack chains further pave the way for custom implants like MischiefTut or MediaPl, the former of which was first disclosed by Microsoft in October 2023.
Implemented in PowerShell, MischiefTut is a basic backdoor that can run reconnaissance commands, write outputs to a text file, and download additional tools on a compromised system. The first recorded use of the malware dates back to late 2022.
MediaPl, on the other hand, masquerades as Windows Media Player and is designed to transmit encrypted communications to its C2 server and launch command(s) it has received from the server.
"Mint Sandstorm continues to improve and modify the tooling used in targets' environments, activity that might help the group persist in a compromised environment and better evade detection," Microsoft said.
"The ability to obtain and maintain remote access to a target's system can enable Mint Sandstorm to conduct a range of activities that can adversely impact the confidentiality of a system."
The disclosure comes as Dutch newspaper De Volkskrant revealed earlier this month that Erik van Sabben, a Dutch engineer recruited by Israel and U.S. intelligence services, may have used a water pump to deploy an early variant of the now-infamous Stuxnet malware in an Iranian nuclear facility sometime in 2007.
Feds Warn of AndroxGh0st Botnet Targeting AWS, Azure, and Office 365 Credentials
18.1.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) warned that threat actors deploying the AndroxGh0st malware are creating a botnet for "victim identification and exploitation in target networks."
A Python-based malware, AndroxGh0st was first documented by Lacework in December 2022, with the malware inspiring several similar tools like AlienFox, GreenBot (aka Maintance), Legion, and Predator.
The cloud attack tool is capable of infiltrating servers vulnerable to known security flaws to access Laravel environment files and steal credentials for high-profile applications such as Amazon Web Services (AWS), Microsoft Office 365, SendGrid, and Twilio.
Some of the notable flaws weaponized by the attackers include CVE-2017-9841 (PHPUnit), CVE-2021-41773 (Apache HTTP Server), and CVE-2018-15133 (Laravel Framework).
"AndroxGh0st has multiple features to enable SMTP abuse including scanning, exploitation of exposed creds and APIs, and even deployment of web shells," Lacework said. "For AWS specifically, the malware scans for and parses AWS keys but also has the ability to generate keys for brute-force attacks."
The compromised AWS credentials are subsequently used to create new users and user policies, and in several instances, set up new AWS instances for additional, malicious scanning activity.
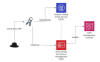
These features make AndroxGh0st a potent threat that can be used to download additional payloads and retain persistent access to compromised systems.
"Androxgh0st is a consistent nuisance: we regularly see related user-agent strings in network connections scanning our honeypots," Alex Delamotte, senior threat researcher at SentinelLabs, told The Hacker News. "It's excellent to see CISA issuing an advisory against this type of threat, as cloud-focused malware advisories are uncommon."
The development arrives less than a week after SentinelOne revealed a related-but-distinct tool called FBot that is being employed by attackers to breach web servers, cloud services, content management systems (CMS), and SaaS platforms.
"The cloud threat landscape will continue to borrow code from other tools and integrate them into a holistic ecosystem, which is what we see with AlienFox and Legion doing with Androxgh0st and FBot respectively," Delamotte said.
"As actors find new ways to monetize cloud services, we can expect to see tailored tools emerge for those services, much like how these tools focus on exploiting mail services to conduct spamming attacks."
It also follows an alert from NETSCOUT about a significant spike in botnet scanning activity since mid-November 2023, touching a peak of nearly 1.3 million distinct devices on January 5, 2024. A majority of the source IP addresses are associated with the U.S., China, Vietnam, Taiwan, and Russia.
"Analysis of the activity has uncovered a rise in the use of cheap or free cloud and hosting servers that attackers are using to create botnet launch pads," the company said. "These servers are used via trials, free accounts, or low-cost accounts, which provide anonymity and minimal overhead to maintain."
FTC Bans Outlogic (X-Mode) From Selling Sensitive Location Data
10.1.24 BigBrothers The Hacker News
The U.S. Federal Trade Commission (FTC) on Tuesday prohibited data broker Outlogic, which was previously known as X-Mode Social, from sharing or selling any sensitive location data with third-parties.
The ban is part of a settlement over allegations that the company "sold precise location data that could be used to track people's visits to sensitive locations such as medical and reproductive health clinics, places of religious worship and domestic abuse shelters."
The proposed order also requires it to destroy all the location data it previously gathered unless it obtains consumer consent or ensures the data has been de-identified or rendered non-sensitive as well as maintain a comprehensive list of sensitive locations and develop a comprehensive privacy program with a data retention schedule to prevent abuse.
The FTC accused X-Mode Social and Outlogic of failing to establish adequate safeguards to prevent the misuse of such data by downstream customers. The development marks the first-ever ban on the use and sale of sensitive location data.
X-Mode, which first attracted attention in 2020 for selling location data to the U.S. military, works by offering precise location data that it collects from proprietary apps and third-party apps that incorporate its software development kit (SDK) into its apps. It's also said to have procured location data from other data brokers and aggregators.
Following the revelations in 2020, both Apple and Google urged app developers to remove the SDK from their apps or face a ban from their respective app stores.
"The raw location data that X-Mode/Outlogic has sold is associated with mobile advertising IDs, which are unique identifiers associated with each mobile device," the FTC said. "This raw location data is not anonymized, and is capable of matching an individual consumer's mobile device with the locations they visited."
The agency further said that the company, until May 2023, did not have any policies in place to remove sensitive locations from the location data it sold, not only putting users' privacy at risk, but also exposing them to potential discrimination, physical violence, emotional distress, and other harms.
The FTC also called out X-Mode for not being transparent about which entities would receive the data when a customer used a third-party app with its SDK and that it failed to ensure that these apps sought informed consumer consent to grant it permission to access their location information in the first place.
Lastly, X-Mode was alleged to have been negligent in honoring requests made by some Android users to opt out of tracking and personalized ads.
In a statement provided to news agency Reuters, Outlogic said it disagreed with the "implications" of the FTC announcement, and there was no finding it misused location data.
"I commend the FTC for taking tough action to hold this shady location data broker responsible for its sale of Americans' location data," U.S. Senator Ron Wyden said in a statement shared with The Hacker News.
"In 2020, I discovered that the company had sold Americans' location data to U.S. military customers through defense contractors. While the FTC's action is encouraging, the agency should not have to play data broker whack-a-mole. Congress needs to pass tough privacy legislation to protect Americans' personal information and prevent government agencies from going around the courts by buying our data from data brokers."
CISA Flags 6 Vulnerabilities - Apple, Apache, Adobe , D-Link, Joomla Under Attack
10.1.24 BigBrothers The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added six security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
This includes CVE-2023-27524 (CVSS score: 8.9), a high-severity vulnerability impacting the Apache Superset open-source data visualization software that could enable remote code execution. It was fixed in version 2.1.
Details of the issue first came to light in April 2023, with Horizon3.ai's Naveen Sunkavally describing it as a "dangerous default configuration in Apache Superset that allows an unauthenticated attacker to gain remote code execution, harvest credentials, and compromise data."
It's currently not known how the vulnerability is being exploited in the wild. Also added by CISA are five other flaws -
CVE-2023-38203 (CVSS score: 9.8) - Adobe ColdFusion Deserialization of Untrusted Data Vulnerability
CVE-2023-29300 (CVSS score: 9.8) - Adobe ColdFusion Deserialization of Untrusted Data Vulnerability
CVE-2023-41990 (CVSS score: 7.8) - Apple Multiple Products Code Execution Vulnerability
CVE-2016-20017 (CVSS score: 9.8) - D-Link DSL-2750B Devices Command Injection Vulnerability
CVE-2023-23752 (CVSS score: 5.3) - Joomla! Improper Access Control Vulnerability
It's worth noting that CVE-2023-41990, patched by Apple in iOS 15.7.8 and iOS 16.3, was used by unknown actors as part of Operation Triangulation spyware attacks to achieve remote code execution when processing a specially crafted iMessage PDF attachment.
Federal Civilian Executive Branch (FCEB) agencies have been recommended to apply fixes for the aforementioned bugs by January 29, 2024, to secure their networks against active threats.
Sea Turtle Cyber Espionage Campaign Targets Dutch IT and Telecom Companies
7.1.24 BigBrothers The Hacker News
Telecommunication, media, internet service providers (ISPs), information technology (IT)-service providers, and Kurdish websites in the Netherlands have been targeted as part of a new cyber espionage campaign undertaken by a Türkiye-nexus threat actor known as Sea Turtle.
"The infrastructure of the targets was susceptible to supply chain and island-hopping attacks, which the attack group used to collect politically motivated information such as personal information on minority groups and potential political dissents," Dutch security firm Hunt & Hackett said in a Friday analysis.
"The stolen information is likely to be exploited for surveillance or intelligence gathering on specific groups and or individuals."
Sea Turtle, also known by the names Cosmic Wolf, Marbled Dust (formerly Silicon), Teal Kurma, and UNC1326, was first documented by Cisco Talos in April 2019, detailing state-sponsored attacks targeting public and private entities in the Middle East and North Africa.
Activities associated with the group are believed to have been ongoing since January 2017, primarily leveraging DNS hijacking to redirect prospective targets attempting to query a specific domain to an actor-controlled server capable of harvesting their credentials.
"The Sea Turtle campaign almost certainly poses a more severe threat than DNSpionage given the actor's methodology in targeting various DNS registrars and registries," Talos said at the time.
In late 2021, Microsoft noted that the adversary carries out intelligence collection to meet strategic Turkish interests from countries like Armenia, Cyprus, Greece, Iraq, and Syria, striking telecom and IT companies with an aim to "establish a foothold upstream of their desired target" via exploitation of known vulnerabilities.
Then last month, the adversary was revealed to be using a simple reverse TCP shell for Linux (and Unix) systems called SnappyTCP in attacks carried out between 2021 and 2023, according to the PricewaterhouseCoopers (PwC) Threat Intelligence team.
"The web shell is a simple reverse TCP shell for Linux/Unix that has basic [command-and-control] capabilities, and is also likely used for establishing persistence," the company said. "There are at least two main variants; one which uses OpenSSL to create a secure connection over TLS, while the other omits this capability and sends requests in cleartext."
The latest findings from Hunt & Hackett show that Sea Turtle continues to be a stealthy espionage-focused group, performing defense evasion techniques to fly under the radar and harvest email archives.
In one of the attacks observed in 2023, a compromised-but-legitimate cPanel account was used as an initial access vector to deploy SnappyTCP on the system. It's currently not known how the attackers obtained the credentials.
"Using SnappyTCP, the threat actor sent commands to the system to create a copy of an email archive created with the tool tar, in the public web directory of the website that was accessible from the internet," the firm noted.
"It is highly likely that the threat actor exfiltrated the email archive by downloading the file directly from the web directory."
To mitigate the risks posed by such attacks, it's advised that organizations enforce strong password policies, implement two-factor authentication (2FA), rate limit login attempts to reduce the chances of brute-force attempts, monitor SSH traffic, and keep all systems and software up-to-date.
Russian Hackers Had Covert Access to Ukraine's Telecom Giant for Months
5.1.24 BigBrothers The Hacker News
Ukrainian cybersecurity authorities have disclosed that the Russian state-sponsored threat actor known as Sandworm was inside telecom operator Kyivstar's systems at least since May 2023.
The development was first reported by Reuters.
The incident, described as a "powerful hacker attack," first came to light last month, knocking out access to mobile and internet services for millions of customers. Soon after the incident, a Russia-linked hacking group called Solntsepyok took responsibility for the breach.
Solntsepyok has been assessed to be a Russian threat group with affiliations to the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU), which also operates Sandworm.
The advanced persistent threat (APT) actor has a track record of orchestrating disruptive cyber attacks, with Denmark accusing the hacking outfit of targeting 22 energy sector companies last year.
Illia Vitiuk, head of the Security Service of Ukraine's (SBU) cybersecurity department, said the attack against Kyivstar wiped out nearly everything from thousands of virtual servers and computers.
The incident, he said, "completely destroyed the core of a telecoms operator," noting the attackers had full access likely at least since November, months after obtaining an initial foothold into the company's infrastructure.
"The attack had been carefully prepared during many months," Vitiuk said in a statement shared on the SBU's website.
Kyivstar, which has since restored its operations, said there is no evidence that the personal data of subscribers has been compromised. It's currently not known how the threat actor penetrated its network.
It's worth noting that the company had previously dismissed speculations about the attackers destroying its computers and servers as "fake."
The development comes as the SBU revealed earlier this week that it took down two online surveillance cameras that were allegedly hacked by Russian intelligence agencies to spy on the defense forces and critical infrastructure in the capital city of Kyiv.
The agency said the compromise allowed the adversary to gain remote control of the cameras, adjust their viewing angles, and connect them to YouTube to capture "all visual information in the range of the camera."






































