
Cryptocurrency 2024 2023 2022 2021 2020
Beware: Scam-as-a-Service Aiding Cybercriminals in Crypto Wallet-Draining Attacks
31.12.23 Cryptocurrency The Hacker News
Cybersecurity researchers are warning about an increase in phishing attacks that are capable of draining cryptocurrency wallets.
"These threats are unique in their approach, targeting a wide range of blockchain networks, from Ethereum and Binance Smart Chain to Polygon, Avalanche, and almost 20 other networks by using a crypto wallet-draining technique," Check Point researchers Oded Vanunu, Dikla Barda, and Roman Zaikin said.
A prominent contributor to this troubling trend is a notorious phishing group called Angel Drainer, which advertises a "scam-as-a-service" offering by charging a percentage of the stolen amount, typically 20% or 30%, from its collaborators in return for providing wallet-draining scripts and other services.
In late November 2023, a similar wallet-draining service known as Inferno Drainer announced that it was shutting down its operations for good after helping scammers plunder over $70 million worth of crypto from 103,676 victims since its launch in late 2022.
Web3 anti-scam solution provider Scam Sniffer, in May 2023, described the vendor as specializing in multi-chain scams and charging 20% of the stolen assets.
"It has been a long ride with all of you and we'd like to thank you from heart [sic]," the actor said in a message posted on its Telegram channel.
"A big thanks to everyone who has worked with us such as Drakan and every other customer, we hope you can remember us as the best drainer that has ever existed and that we succeeded in helping you in the quest of making money."
At the crux of these services is a crypto-draining kit that's crafted to facilitate cyber theft by illegally transferring cryptocurrency from victims' wallets without their consent.
This is typically accomplished via airdrop or phishing scams, tricking targets into connecting their wallets on counterfeit websites that are propagated via malvertising schemes or unsolicited emails and messages on social media.
Earlier this month, Scam Sniffer detailed a phishing scam in which bogus ads for cryptocurrency platforms on Google and X (formerly Twitter) redirected users to sketchy sites that drained funds from users' digital wallets.
"The user is induced to interact with a malicious smart contract under the guise of claiming the airdrop, which stealthily increases the attacker's allowance through functions like approve or permit," Check Point noted.
"Unknowingly, the user grants the attacker access to their funds, enabling token theft without further user interaction. Attackers then use methods like mixers or multiple transfers to obscure their tracks and liquidate the stolen assets."
To mitigate the risks posed by such scams, users are recommended to employ hardware wallets for enhanced security, verify the legitimacy of smart contracts, and periodically review wallet allowances for signs of any suspicious activity.
Warning: Poorly Secured Linux SSH Servers Under Attack for Cryptocurrency Mining
27.12.23 Cryptocurrency The Hacker News
Poorly secured Linux SSH servers are being targeted by bad actors to install port scanners and dictionary attack tools with the goal of targeting other vulnerable servers and co-opting them into a network to carry out cryptocurrency mining and distributed denial-of-service (DDoS) attacks.
"Threat actors can also choose to install only scanners and sell the breached IP and account credentials on the dark web," the AhnLab Security Emergency Response Center (ASEC) said in a report on Tuesday.
In these attacks, adversaries try to guess a server's SSH credentials by running through a list of commonly used combinations of usernames and passwords, a technique called dictionary attack.
Should the brute-force attempt be successful, it's followed by the threat actor deploying other malware, including scanners, to scan for other susceptible systems on the internet.
Specifically, the scanner is designed to look for systems where port 22 -- which is associated with the SSH service -- is active and then repeats the process of staging a dictionary attack in order to install malware, effectively propagating the infection.
Another notable aspect of the attack is the execution of commands such as "grep -c ^processor /proc/cpuinfo" to determine the number of CPU cores.
"These tools are believed to have been created by PRG old Team, and each threat actor modifies them slightly before using them in attacks," ASEC said, adding there is evidence of such malicious software being used as early as 2021.
To mitigate the risks associated with these attacks, it's recommended that users rely on passwords that are hard to guess, periodically rotate them, and keep their systems up-to-date.
The findings come as Kaspersky revealed that a novel multi-platform threat called NKAbuse is leveraging a decentralized, peer-to-peer network connectivity protocol known as NKN (short for New Kind of Network) as a communications channel for DDoS attacks.
Four U.S. Nationals Charged in $80 Million Pig Butchering Crypto Scam
19.12.23 Cryptocurrency The Hacker News
Four U.S. nationals have been charged for participating in an illicit scheme that earned them more than $80 million via cryptocurrency investment scams.
The defendants – Lu Zhang, 36, of Alhambra, California; Justin Walker, 31, of Cypress, California; Joseph Wong, 32, Rosemead, California; and Hailong Zhu, 40, Naperville, Illinois – have been charged with conspiracy to commit money laundering, concealment money laundering, and international money laundering.
The U.S. Department of Justice (DoJ), which announced the arrests of both Zhang and Walker in connection with the fraudulent operation, said the quartet opened shell companies and bank accounts to carry out pig butchering scams, transferring the ill-gotten funds to domestic and international financial entities.
If convicted, Zhang and Walker face a maximum penalty of 20 years in prison. Their alleged co-conspirators remain at large.
"The overall fraud scheme in the related pig-butchering syndicate involved at least 284 transactions and resulted in more than $80 million in victim losses," the DoJ said. "More than $20 million in victim funds were directly deposited into bank accounts associated with the defendants."
The enforcement action comes as a Nigerian national named Eze Harrison Arinze was sentenced to three years in prison for his role in conducting pig butchering scams and defrauding 34 victims in 13 countries, leading to $592,000 in losses.
Late last month, the U.S. DoJ also announced the seizure of nearly $9 million worth of Tether that were traced to cryptocurrency addresses allegedly associated with a Southeast Asia based organization that exploited over 70 victims through pig butchering scams.
Pig butchering falls under the category of so-called romance-investment scams, wherein people are targeted via dating apps under fictitious identities to gain their trust and dupe them into investing their money in seemingly legitimate and profitable ventures, typically promising high investment returns within a short span of time.

"After persuading the victim to invest, the scammers collect the funds, often using digital payment platforms or cryptocurrencies to make tracking more difficult," Trend Micro said in a report detailing the scam.
"Once they have received a substantial sum from their victims, or once the victims try to withdraw funds from the account, the scammers will suddenly become unreachable, or the brokerage platform will have trouble transferring funds. Scammers could also delete their online presence or create new identities, making it difficult for victims to recover their lost funds."
One of the emerging trends in the space involves the use of group chats, indicating that the cyber criminals are adapting and refining their strategies to make them more effective.
In these cases, prospective victims are added to a fake investment chat group under their control. Should the target express interest in investing in cryptocurrencies, the conversation is moved to a one-to-one chat, where they are introduced to a bogus brokerage platform and persuaded to transfer their funds to the service.
According to the Federal Bureau of Investigation's (FBI) Internet Crime Complaint Center (IC3) report, cryptocurrency investment scams have led to unprecedented losses totaling $2.57 billion in 2022, registering a 183% increase from 2021.
"A significant portion of these phone numbers can be traced back to leaked databases containing personal information," the cybersecurity firm said. "More than half of the numbers added to the fake group chats have been found in such databases, indicating that scammers could be using leaked information to find their next victims."
Crypto Hardware Wallet Ledger's Supply Chain Breach Results in $600,000 Theft
15.12.23 Cryptocurrency The Hacker News
Crypto hardware wallet maker Ledger published a new version of its "@ledgerhq/connect-kit" npm module after unidentified threat actors pushed malicious code that led to the theft of more than $600,000 in virtual assets.
The compromise was the result of a former employee falling victim to a phishing attack, the company said in a statement.
This allowed the attackers to gain access to Ledger's npm account and upload three malicious versions of the module – 1.1.5, 1.1.6, and 1.1.7 — and propagate crypto drainer malware to other applications that are dependent on the module, resulting in a software supply chain breach.
"The malicious code used a rogue WalletConnect project to reroute funds to a hacker wallet," Ledger said.
Connect Kit, as the name implies, makes it possible to connect DApps (short decentralized applications) to Ledger's hardware wallets.
According to security firm Sonatype, version 1.1.7 directly embedded a wallet-draining payload to execute unauthorized transactions in order to transfer digital assets to an actor-controlled wallet.
Versions 1.1.5 and 1.1.6, while lacking an embedded drainer, were modified to download a secondary npm package, identified as 2e6d5f64604be31, which acts as a crypto drainer. The module is still available for download as of writing.

"Once installed into your software, the malware presents the users with a fake modal prompt that invites them to connect wallets," Sonatype researcher Ilkka Turunen said. "Once the users click through this modal, the malware begins draining funds from the connected wallets."
The malicious file is estimated to have been live for around five hours, although the active exploitation window during which the funds were drained was limited to a period of less than two hours.
Ledger has since removed all three malicious versions of Connect Kit from npm and published 1.1.8 to mitigate the issue. It has also reported the threat actor's wallet addresses and noted that stablecoin issuer Tether has frozen the stolen funds.
If anything, the development underscores the continued targeting of open-source ecosystems, with software registries such as PyPI and npm increasingly used as vectors for installing malware through supply chain attacks.
"The specific targeting of cryptocurrency assets demonstrates the evolving tactics of cybercriminals to achieve significant financial gains within the space of hours, directly monetising their malware," Turunen noted.
North Korea's Lazarus Group Rakes in $3 Billion from Cryptocurrency Hacks
30.11.23 Cryptocurrency The Hacker News
Threat actors from the Democratic People's Republic of Korea (DPRK) are increasingly targeting the cryptocurrency sector as a major revenue generation mechanism since at least 2017 to get around sanctions imposed against the country.
"Even though movement in and out of and within the country is heavily restricted, and its general population is isolated from the rest of the world, the regime's ruling elite and its highly trained cadre of computer science professionals have privileged access to new technologies and information," cybersecurity firm Recorded Future said in a report shared with The Hacker News.
"The privileged access to resources, technologies, information, and sometimes international travel for a small set of selected individuals with promise in mathematics and computer science equips them with the necessary skills for conducting cyber attacks against the cryptocurrency industry."
The disclosure comes as the U.S. Treasury Department imposed sanctions against Sinbad, a virtual currency mixer that has been put to use by the North Korea-linked Lazarus Group to launder ill-gotten proceeds.
The threat actors from the country are estimated to have stolen $3 billion worth of crypto assets over the past six years, with about $1.7 billion plundered in 2022 alone. A majority of these stolen assets are used to directly fund the hermit kingdom's weapons of mass destruction (WMD) and ballistic missile programs.
"$1.1 billion of that total was stolen in hacks of DeFi protocols, making North Korea one of the driving forces behind the DeFi hacking trend that intensified in 2022," Chainalysis noted earlier this February.
A report published by the U.S. Department of Homeland Security (DHS) as part of its Analytic Exchange Program (AEP) earlier this September also highlighted the Lazarus Group's exploitation of DeFi protocols.

"DeFi exchange platforms allow users to transition between cryptocurrencies without the platform ever taking custody of the customer's funds in order to facilitate the transition," the report said. "This allows DPRK cyber actors to determine exactly when to transition stolen cryptocurrency from one type of cryptocurrency to another, enabling attribution to be more difficult to determine or even trace."
The cryptocurrency sector is among the top targets for state-sponsored North Korean cyber threat actors, as repeatedly evidenced by the myriad campaigns carried out in recent months.
DPRK hackers are known for adeptly pulling off social engineering tricks to target employees of online cryptocurrency exchanges and then lure their victims with the promise of lucrative jobs to distribute malware that grants remote access to the company's network, ultimately allowing them to drain all available assets and move them to various DPRK controlled wallets.
Other campaigns have employed similar phishing tactics to entice users into downloading trojanized cryptocurrency apps to steal their assets as well as watering hole attacks (aka strategic web compromises) as an initial access vector, alongside engaging in airdrop scams and rug pulls.
Another notable tactic adopted by the group is use of mixing services to conceal the financial trail and cloud attribution efforts. Such services are typically offered on cryptocurrency exchange platforms that do not employ know your customer (KYC) policies or anti-money laundering (AML) regulations.
"Absent stronger regulations, cybersecurity requirements, and investments in cybersecurity for cryptocurrency firms, we assess that in the near term, North Korea will almost certainly continue to target the cryptocurrency industry due to its past success in mining it as a source of additional revenue to support the regime," Recorded Future concluded.
U.S. Treasury Sanctions Sinbad Cryptocurrency Mixer Used by North Korean Hackers
30.11.23 Cryptocurrency The Hacker News

The U.S. Treasury Department on Wednesday imposed sanctions against Sinbad, a virtual currency mixer that has been put to use by the North Korea-linked Lazarus Group to launder ill-gotten proceeds.
"Sinbad has processed millions of dollars' worth of virtual currency from Lazarus Group heists, including the Horizon Bridge and Axie Infinity heists," the department said.
"Sinbad is also used by cybercriminals to obfuscate transactions linked to malign activities such as sanctions evasion, drug trafficking, the purchase of child sexual abuse materials, and additional illicit sales on darknet marketplaces."
The development builds on prior actions undertaken by governments in Europe and the U.S. to blockade mixers such as Blender, Tornado Cash, and ChipMixer, all of which have been accused of providing "material support" to the hacking crew by laundering the stolen assets through their services.
Sinbad, created by an individual who goes by the alias "Mehdi" in September 2022, told WIRED earlier this February that it was a legitimate privacy-preserving initiative and that it was launched as a response to the "growing centralization of cryptocurrency and the erosion of the privacy promises it once appeared to offer."
It also emerged as a replacement for Blender, with the Lazarus Group using it to launder virtual currency plundered following the hacks of Atomic Wallet and Harmony Horizon Bridge.
"Overall, more than one third of funds sent to Sinbad during its lifetime have come from crypto hacks," Chainalysis said. "Following the takedown of Tornado Cash and Blender.io last year, Sinbad emerged as the mixer of choice for DPRK-based hacking activities."
Sinbad has also been used by ransomware actors, darknet markets, and scammers, leveraging it to facilitate illicit transactions by obfuscating their origin, destination, and counterparties.
Blockchain analytics firm Elliptic said there is evidence to suggest that the same individual or group is highly likely behind both Sinbad and Blender based on an examination of on-chain patterns, the way in which the two mixers operate, similarities in their websites, and their connections to Russia.
"Analysis of blockchain transactions shows that, before it was publicly launched, a 'service' address on the Sinbad website received Bitcoin from a wallet believed to be controlled by the operator of Blender – presumably in order to test the service," the company noted.
"A Bitcoin wallet used to pay individuals who promoted Sinbad, itself received Bitcoin from the suspected Blender operator wallet. Almost all of the early incoming transactions to Sinbad originated from the suspected Blender operator wallet."
The development comes as Vitalii Chychasov, a 37-year-old administrator of the now-dismantled online marketplace named SSNDOB, was sentenced to eight years in federal prison in the U.S. for selling personal information, including the names, dates of birth, and Social Security numbers.
Chychasov, an Ukrainian national, was arrested in March 2022 while attempting to enter Hungary. He was subsequently extradited to the U.S. in July 2022. SSNDOB was taken down in a joint operation led by the U.S., Cyprus, and Latvia in June 2022.
Hackers Target Apache Tomcat Servers for Mirai Botnet and Crypto Mining
27.7.23 Cryptocurrency The Hacker News
Misconfigured and poorly secured Apache Tomcat servers are being targeted as part of a new campaign designed to deliver the Mirai botnet malware and cryptocurrency miners.
The findings come courtesy of Aqua, which detected more than 800 attacks against its Tomcat server honeypots over a two-year time period, with 96% of the attacks linked to the Mirai botnet.
Of these attack attempts, 20% (or 152) entailed the use of a web shell script dubbed "neww" that originated from 24 unique IP addresses, with 68% of them originating from a single IP address (104.248.157[.]218).
"The threat actor scanned for Tomcat servers and launched a brute force attack against it, attempting to gain access to the Tomcat web application manager by trying different combinations of credentials associated with it," Aqua security researcher Nitzan Yaakov said.
Upon gaining a successful foothold, the threat actors have been observed deploying a WAR file that contains a malicious web shell class named 'cmd.jsp' that, in turn, is designed to listen to remote requests and execute arbitrary commands on the Tomcat server.
This includes downloading and running a shell script called "neww" after which the file is deleted using the "rm -rf" Linux command.
"The script contains links to download 12 binary files, and each file is suitable for a specific architecture according to the system that has been attacked by the threat actor," Yaakov pointed out.
The final stage malware is a variant of the infamous Mirai botnet that makes use of the infected hosts to orchestrate distributed denial-of-service (DDoS) attacks.
"Once the threat actor gained access to the web application manager using valid credentials, they leveraged the platform to upload a web shell disguised in a WAR file," Yaakov said. "Next, the threat actor executed commands remotely and launched the attack."
To mitigate against the ongoing campaign, it's recommended that organizations secure their environments and follow credential hygiene to prevent brute-force attacks.
The development comes as the AhnLab Security Emergency Response Center (ASEC) reported that poorly managed MS-SQL servers are being breached to deploy a rootkit malware called Purple Fox, which acts as a loader to fetch additional malware such as coin miners.
These findings also demonstrate the lucrative nature of cryptocurrency mining, which has witnessed a 399% increase over last year, with 332 million cryptojacking attacks recorded in the first half of 2023 globally, according to SonicWall.
Python-Based PyLoose Fileless Attack Targets Cloud Workloads for Cryptocurrency Mining
12.7.23 Cryptocurrency The Hacker News
A new fileless attack dubbed PyLoose has been observed striking cloud workloads with the goal of delivering a cryptocurrency miner, new findings from Wiz reveal.
"The attack consists of Python code that loads an XMRig Miner directly into memory using memfd, a known Linux fileless technique," security researchers Avigayil Mechtinger, Oren Ofer, and Itamar Gilad said. "This is the first publicly documented Python-based fileless attack targeting cloud workloads in the wild."
The cloud security firm said it found nearly 200 instances where the attack method was employed for cryptocurrency mining. No other details about the threat actor are currently known other than the fact that they possess sophisticated capabilities.
In the infection chain documented by Wiz, initial access is achieved through the exploitation of a publicly accessible Jupyter Notebook service that allowed for the execution of system commands using Python modules.
PyLoose, first detected on June 22, 2023, is a Python script with just nine lines of code that embeds a compressed and encoded precompiled XMRig miner. The payload is retrieved from paste.c-net[.]org into the Python runtime's memory by means of an HTTPS GET request without having to write the file to disk.
The Python code is designed to decode and decompress the XMRig miner and then load it directly into memory via the memfd memory file descriptor, which is used to access memory-resident files.
"The attacker went to great lengths to be untraceable by using an open data-sharing service to host the Python payload, adapting the fileless execution technique to Python, and compiling an XMRig miner to embed its config to avoid touching the disk or using a revealing command line," the researchers said.
The development comes as Sysdig detailed a new attack campaign mounted by a threat actor known as SCARLETEEL that entails the abuse of AWS infrastructure to steal proprietary data and conduct illicit crypto mining.
SCARLETEEL Cryptojacking Campaign Exploiting AWS Fargate in Ongoing Campaign
11.7.23 Cryptocurrency The Hacker News
Cloud environments continue to be at the receiving end of an ongoing advanced attack campaign dubbed SCARLETEEL, with the threat actors now setting their sights on Amazon Web Services (AWS) Fargate.
"Cloud environments are still their primary target, but the tools and techniques used have adapted to bypass new security measures, along with a more resilient and stealthy command and control architecture," Sysdig security researcher Alessandro Brucato said in a new report shared with The Hacker News.
SCARLETEEL was first exposed by the cybersecurity company in February 2023, detailing a sophisticated attack chain that culminated in the theft of proprietary data from AWS infrastructure and the deployment of cryptocurrency miners to profit off the compromised systems' resources illegally.
A follow-up analysis by Cado Security uncovered potential links to a prolific cryptojacking group known as TeamTNT, although Sysdig told The Hacker News that it "could be someone copying their methodology and attack patterns."
The latest activity continues the threat actor's penchant for going after AWS accounts by exploiting vulnerable public-facing web applications with an ultimate aim to gain persistence, steal intellectual property, and potentially generate revenue to the tune of $4,000 per day using crypto miners.
"The actor discovered and exploited a mistake in an AWS policy which allowed them to escalate privileges to AdministratorAccess and gain control over the account, enabling them to then do with it what they wanted," Brucato explained.

It all begins with the adversary exploiting JupyterLab notebook containers deployed in a Kubernetes cluster, leveraging the initial foothold to conduct reconnaissance of the target network and gather AWS credentials to obtain deeper access into the victim's environment.
This is followed by the installation of the AWS command line tool and an exploitation framework called Pacu for subsequent exploitation. The attack also stands out for its use of various shell scripts to retrieve AWS credentials, some of which target AWS Fargate compute engine instances.
"The attacker was observed using the AWS client to connect to Russian systems which are compatible with the S3 protocol," Brucato said, adding the SCARLETEEL actors used stealthy techniques to ensure that data exfiltration events are not captured in CloudTrail logs.
Some of the other steps taken by the attacker include the use of a Kubernetes Penetration Testing tool known as Peirates to exploit the container orchestration system and a DDoS botnet malware called Pandora, indicating further attempts on the part of the actor to monetize the host.
"The SCARLETEEL actors continue to operate against targets in the cloud, including AWS and Kubernetes," Brucato said. "Their preferred method of entry is exploitation of open compute services and vulnerable applications. There is a continued focus on monetary gain via crypto mining, but [...] intellectual property is still a priority."
Japanese Cryptocurrency Exchange Falls Victim to JokerSpy macOS Backdoor Attack
26.6.23 Cryptocurrency The Hacker News
An unknown cryptocurrency exchange located in Japan was the target of a new attack earlier this month to deploy an Apple macOS backdoor called JokerSpy.
Elastic Security Labs, which is monitoring the intrusion set under the name REF9134, said the attack led to the installation of Swiftbelt, a Swift-based enumeration tool inspired by an open-source utility called SeatBelt.
JokerSky was first documented by Bitdefender last week, describing it as a sophisticated toolkit designed to breach macOS machines.
Very little is known about the threat actor behind the attacks other than the fact that the attacks leverage a set of programs written in Python and Swift that come with capabilities to gather data and execute arbitrary commands on compromised hosts.
A primary component of the toolkit is a self-signed multi-architecture binary known as xcc that's engineered to check for FullDiskAccess and ScreenRecording permissions.
The file is signed as XProtectCheck, indicating an attempt to masquerade as XProtect, a built-in antivirus technology within macOS that makes use of signature-based detection rules to remove malware from already infected hosts.
In the incident analyzed by Elastic, the creation of xcc is followed by the threat actor "attempting to bypass TCC permissions by creating their own TCC database and trying to replace the existing one."
"On June 1, a new Python-based tool was seen executing from the same directory as xcc and was utilized to execute an open-source macOS post-exploitation enumeration tool known as Swiftbelt," security researchers Colson Wilhoit, Salim Bitam, Seth Goodwin, Andrew Pease, and Ricardo Ungureanu said.
The attack targeted a large Japan-based cryptocurrency service provider focusing on asset exchange for trading Bitcoin, Ethereum, and other common cryptocurrencies. The name of the company was not disclosed.
The xcc binary, for its part, is launched by means of Bash via three different apps that are named IntelliJ IDEA, iTerm (a terminal emulator for macOS), and Visual Studio Code, indicating that backdoored versions of software development software are likely used to gain initial access.
Another notable module installed as part of the attack is sh.py, a Python implant that's used as a conduit to deliver other post-exploitation tools like Swiftbelt.
"Unlike other enumeration methods, Swiftbelt invokes Swift code to avoid creating command line artifacts," the researchers said. "Notably, xcc variants are also written using Swift."
New Cryptocurrency Mining Campaign Targets Linux Systems and IoT Devices
24.6.23 Cryptocurrency The Hacker News
Internet-facing Linux systems and Internet of Things (IoT) devices are being targeted as part of a new campaign designed to illicitly mine cryptocurrency.
"The threat actors behind the attack use a backdoor that deploys a wide array of tools and components such as rootkits and an IRC bot to steal device resources for mining operations," Microsoft threat intelligence researcher Rotem Sde-Or said.
"The backdoor also installs a patched version of OpenSSH on affected devices, allowing threat actors to hijack SSH credentials, move laterally within the network, and conceal malicious SSH connections."
To pull off the scheme, misconfigured Linux hosts are brute-forced to gain initial access, following which the threat actors move to disable shell history and fetch a trojanized version of OpenSSH from a remote server.
The rogue OpenSSH package is configured to install and launch the backdoor, a shell script that allows the attackers to distribute additional payloads and conduct other post-exploitation activities.
This includes exfiltrating information about the device, installing open-source rootkits called Diamorphine and Reptile from GitHub, and taking steps to obscure its activity by clearing logs that could alert its presence.
"To ensure persistent SSH access to the device, the backdoor appends two public keys to the authorized_keys configuration files of all users on the system," the Windows maker said.
The implant also seeks to monopolize the infected system's resources by eliminating competing crypto mining processes that may be already running on it prior to launching its miner.
Furthermore, it runs a modified version of ZiggyStarTux, an IRC-based distributed denial-of-service (DDoS) client that's capable of executing bash commands issued from the command-and-control (C2) server. It's based on another botnet malware called Kaiten (aka Tsunami).
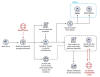
The attacks, the tech giant noted, leverage an unnamed Southeast Asian financial institution's subdomain for C2 communications in an attempt to disguise the malicious traffic.
It's worth pointing out that the modus operandi detailed by Microsoft overlaps with a recent report from the AhnLab Security Emergency Response Center (ASEC), which detailed attacks targeting exposed Linux servers with crypto mining malware and a Tsunami botnet variant dubbed Ziggy.
The operation has been traced back to an actor named asterzeu, who has offered the toolkit for sale on the malware-as-a-service market. "The complexity and scope of this attack are indicative of the efforts attackers make to evade detection," Sde-Or said.
The development comes as multiple known security flaws in routers, digital video recorders, and other network software are being actively exploited by threat actors to deploy the Mirai botnet malware, according to Akamai and Palo Alto Networks Unit 42.
"The Mirai botnet, discovered back in 2016, is still active today," Uni 42 researchers said. "A significant part of the reason for its popularity among threat actors lies in the security flaws of IoT devices."
"These remote code execution vulnerabilities targeting IoT devices exhibit a combination of low complexity and high impact, making them an irresistible target for threat actors."
From Cryptojacking to DDoS Attacks: Diicot Expands Tactics with Cayosin Botnet
17.6.23 Cryptocurrency The Hacker News
Cybersecurity researchers have discovered previously undocumented payloads associated with a Romanian threat actor named Diicot, revealing its potential for launching distributed denial-of-service (DDoS) attacks.
"The Diicot name is significant, as it's also the name of the Romanian organized crime and anti-terrorism policing unit," Cado Security said in a technical report. "In addition, artifacts from the group's campaigns contain messaging and imagery related to this organization."
Diicot (née Mexals) was first documented by Bitdefender in July 2021, uncovering the actor's use of a Go-based SSH brute-forcer tool called Diicot Brute to breach Linux hosts as part of a cryptojacking campaign.
Then earlier this April, Akamai disclosed what it described as a "resurgence" of the 2021 activity that's believed to have started around October 2022, netting the actor about $10,000 in illicit profits.
"The attackers use a long chain of payloads before eventually dropping a Monero cryptominer," Akamai researcher Stiv Kupchik said at the time. "New capabilities include usage of a Secure Shell Protocol (SSH) worm module, increased reporting, better payload obfuscation, and a new LAN spreader module."
The latest analysis from Cado Security shows that the group is also deploying an off-the-shelf botnet referred to as Cayosin, a malware family that shares characteristics with Qbot and Mirai.
The development is a sign that the threat actor now possesses the ability to mount DDoS attacks. Other activities carried out by the group include doxxing of rival hacking groups and its reliance on Discord for command-and-control and data exfiltration.

"Deployment of this agent was targeted at routers running the Linux-based embedded devices operating system, OpenWrt," the cybersecurity company said. "The use of Cayosin demonstrates Diicot's willingness to conduct a variety of attacks (not just cryptojacking) depending on the type of targets they encounter."
Diicot's compromise chains have remained largely consistent, leveraging the custom SSH brute-forcing utility to gain a foothold and drop additional malware such as the Mirai variant and the crypto miner.
Some of the other tools used by the actor are as follows -
Chrome - An internet scanner based on Zmap that can write the results of the operation to a text file ("bios.txt").
Update - An executable that fetches and executes the SSH brute-forcer and Chrome if they don't exist in the system.
History - A shell script that's designed to run Update
The SSH brute-forcer tool (aka aliases), for its part, parses the text file output of Chrome to break into each of the identified IP addresses, and if successful, establishes remote connection to the IP address.
This is then followed by running a series of commands to profile the infected host and using it to either deploy a cryptominer or make it act as a spreader if the machine's CPU has less than four cores.
To mitigate such attacks, organizations are recommended to implement SSH hardening and firewall rules to limit SSH access to specific IP addresses.
"This campaign specifically targets SSH servers exposed to the internet with password authentication enabled," Cado Security said. "The username/password list they use is relatively limited and includes default and easily-guessed credential pairs."
Ransomware Hackers and Scammers Utilizing Cloud Mining to Launder Cryptocurrency
16.6.23 Cryptocurrency The Hacker News
Ransomware actors and cryptocurrency scammers have joined nation-state actors in abusing cloud mining services to launder digital assets, new findings reveal.
"Cryptocurrency mining is a crucial part of our industry, but it also holds special appeal to bad actors, as it provides a means to acquire money with a totally clean on-chain original source," blockchain analytics firm Chainalysis said in a report shared with The Hacker News.
Earlier this March, Google Mandiant disclosed North Korea-based APT43's use of the hash rental and cloud mining services to obscure the forensic trail and wash the stolen cryptocurrency "clean."
Cloud mining services allow users to rent a computer system and use that computer's hash power to mine cryptocurrencies without having to manage the mining hardware themselves.
But according to Chainalysis, it's not just nation-state hacking crews who are leveraging such services in the wild.
In one example highlighted by the company, mining pools and wallets associated with ransomware actors have been used to send funds to a "highly active deposit address" at an unnamed mainstream crypto exchange.
This includes $19.1 million from four ransomware wallet addresses and $14.1 million from three mining pools, with a significant chunk of the funds routed via a network of intermediary wallets and pools.
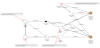
"In this scenario, the mining pool acts similarly to a mixer in that it obfuscates the origin of funds and creates the illusion that the funds are proceeds from mining rather than from ransomware," Chainalysis noted.
In a sign that the trend is gaining traction, the cumulative value of assets sent from ransomware wallets to exchanges through mining pools has surged from less than $10,000 in Q1 2018 to almost $50 million in Q1 2023. any as 372 exchange deposit addresses have been found to receive at least $1 million worth of cryptocurrency from mining pools and any amount from ransomware addresses since January 2018.
"Overall, the data suggests that mining pools may play a key role in many ransomware actors' money laundering strategy," Chainalysis said.
Mining pools have also earned a place in the playbooks of scam operators like the BitClub Network, who have been found commingling their illicit Bitcoin proceeds with assets received from a Russia-based Bitcoin mining operation and BTC-e, a crypto exchange that was set up to facilitate the laundering of money stolen in the infamous Mt. Gox hack.
"Crypto scammers and money launderers working on their behalf are also using mining pools as part of their money laundering process," the company said. "Deposit addresses [with receipts of at least $1 million worth of crypto from mining pools] have received just under $1.1 billion worth of cryptocurrency from scam-related addresses since 2018."
Beware: New DoubleFinger Loader Targets Cryptocurrency Wallets with Stealer
14.6.23 Cryptocurrency The Hacker News
A novel multi-stage loader called DoubleFinger has been observed delivering a cryptocurrency stealer dubbed GreetingGhoul in what's an advanced attack targeting users in Europe, the U.S., and Latin America.
"DoubleFinger is deployed on the target machine, when the victim opens a malicious PIF attachment in an email message, ultimately executing the first of DoubleFinger's loader stages," Kaspersky researcher Sergey Lozhkin said in a Monday report.
The starting point of the attacks is a modified version of espexe.exe – which refers to Microsoft Windows Economical Service Provider application – that's engineered to execute shellcode responsible for retrieving a PNG image file from the image hosting service Imgur.
The image employs steganographic trickery to conceal an encrypted payload that triggers a four-stage compromise chain which eventually culminates in the execution of the GreetingGhoul stealer on the infected host.
A notable aspect of GreetingGhoul is its use of Microsoft Edge WebView2 to create counterfeit overlays on top of legitimate cryptocurrency wallets to withdraw funds from unsuspecting users. Another component residing within the malware captures private keys and seed phrases.
DoubleFinger, in addition to dropping GreetingGhoul, has also been spotted delivering Remcos RAT, a commercial trojan that has been widely used by threat actors to strike European and Ukrainian entities in recent months.
The analysis "reveals a high level of sophistication and skill in crimeware development, akin to advanced persistent threats (APTs)," Lozhkin noted.
"The multi-staged, shellcode-style loader with steganographic capabilities, the use of Windows COM interfaces for stealthy execution, and the implementation of process doppelgänging for injection into remote processes all point to well-crafted and complex crimeware."
Two Russian Nationals Charged for Masterminding Mt. Gox Crypto Exchange Hack
13.6.23 Cryptocurrency The Hacker News
The U.S. Department of Justice (DoJ) has charged two Russian nationals in connection with masterminding the 2014 digital heist of the now-defunct cryptocurrency exchange Mt. Gox.
According to unsealed indictments released last week, Alexey Bilyuchenko, 43, and Aleksandr Verner, 29, have been accused of conspiring to launder approximately 647,000 bitcoins stolen from September 2011 through at least May 2014 as a result of unauthorized access to a server holding crypto wallets used by Mt. Gox customers.
"Starting in 2011, Bilyuchenko and Verner stole a massive amount of cryptocurrency from Mt. Gox, contributing to the exchange's ultimate insolvency," Assistant Attorney General Kenneth A. Polite, Jr. said in a statement.
"Armed with the ill-gotten gains from Mt. Gox, Bilyuchenko allegedly went on to help set up the notorious BTC-e virtual currency exchange, which laundered funds for cyber criminals worldwide."
Bilyuchenko and Verner are also alleged to have made large wire transfers into various offshore bank accounts between March 2012 and in or about April 2013, laundering more than 300,000 of the stolen digital assets using an unnamed New York-based Bitcoin brokerage service.
The BTC-e exchange, opened by Bilyuchenko in 2011 in collaboration with Alexander Vinnik and others using the plundered crypto from Mt. Gox, was shut down by law enforcement in 2017, prior to which it was one of the main conduits through which cyber criminals cashed out the proceeds of their illegal activities.
Vinnik was extradited from Greece to the U.S. last August but has since lobbied to be part of a potential prisoner swap between the U.S. and Russia, the Wall Street Journal reported late last month.
"BTC-e served over one million users worldwide, moving millions of bitcoin worth of deposits and withdrawals and processing billions of dollars' worth of transactions," the DoJ said.
"BTC-e received criminal proceeds of numerous computer intrusions and hacking incidents, ransomware events, identity theft schemes, corrupt public officials, and narcotics distribution rings."
The money laundering charges leveled against the pair could lead to a maximum penalty of 20 years in prison for each of them, if convicted. Bilyuchenko also potentially faces an extra 25-year jail term for operating an unlicensed money services business.
Mt. Gox, which was the largest cryptocurrency exchange at the time, officially collapsed soon after the theft and filed for bankruptcy in February 2014. Mark Karpelès, the exchange's CEO, was considered a prime suspect and was arrested in Japan in August 2015 and charged with fraud and embezzlement.
Karpelès was subsequently convicted in Japan in 2019 and received a 2.5-year suspended prison sentence after he was found guilty of data manipulation by the Tokyo District Court. However, he was cleared of embezzlement charges.
The development comes as a 39-year-old Romanian national named Mihai Ionut Paunescu was sentenced to three years in prison for running a bulletproof hosting service that "enabled cybercriminals to distribute malware strains like Gozi, Zeus, SpyEye Trojan, BlackEnergy.
Paunescu, who was arrested in Colombia in July 2021 prior to his extradition to the U.S., has also been ordered to forfeit $3.51 million and pay restitution in the amount of $18,945.
The law enforcement action also coincides with the U.S. State Department announcing a reward offer of up to $5 million for information leading to the arrest and conviction of Maximilian Rivkin, a Swedish-based criminal of Serbian origin who was identified as an "administrator and influencer" on the encrypted messaging app AN0M (aka ANoM).
AN0M was a trojan horse set up by the U.S. Federal Bureau of Investigation (FBI) and Australian Federal Police (AFP) in 2018 to surreptitiously monitor the activity of criminal actors on the platform. About 12,000 AN0M-fitted devices were sold to 300 criminal syndicates operating in 100 nations.
The three-year sting operation, dubbed Trojan Shield, led to more than 800 arrests across 18 countries following an analysis of over 27 million messages that involved discussions on narcotics concealment methods, shipments of narcotics, money laundering, and even violent threats.
Beware: 1,000+ Fake Cryptocurrency Sites Trap Users in Bogus Rewards Scheme
12.6.23 Cryptocurrency The Hacker News
A previously undetected cryptocurrency scam has leveraged a constellation of over 1,000 fraudulent websites to ensnare users into a bogus rewards scheme since at least January 2021.
"This massive campaign has likely resulted in thousands of people being scammed worldwide," Trend Micro researchers said in a report published last week, linking it to a Russian-speaking threat actor named "Impulse Team."
"The scam works via an advanced fee fraud that involves tricking victims into believing that they've won a certain amount of cryptocurrency. However, to get their rewards, the victims would need to pay a small amount to open an account on their website."
The compromise chain starts with a direct message propagated via Twitter to lure potential targets into visiting the decoy site. The account responsible for sending the messages has since been closed.
The message urges recipients to sign up for an account on the website and apply a promo code specified in the message to win a cryptocurrency reward amounting to 0.78632 bitcoin (about $20,300).
But once an account is set up on the fake platform, users are requested to activate the account by making a minimal deposit worth 0.01 bitcoin (about $258) to confirm their identity and complete the withdrawal.
"While relatively sizable, the amount necessary to activate the account pales in comparison to what users would get in return," the researchers noted. "However, as expected, recipients never get anything in return when they pay the activation amount."
A public Telegram channel that records every payment made by the victims shows that the illicit transactions have yielded the actors a little over $5 million between December 24, 2022, and March 8, 2023.
Trend Micro said it unearthed hundreds of domains related to this fraud, with some of them being active as far back as 2016. All the fake websites belong to an affiliate "scam crypto project" codenamed Impulse that's been advertised on Russian cybercrime forums since February 2021.
Like ransomware-as-a-service (RaaS) operations, the venture requires affiliate actors to pay a fee to join the program and share a percentage of the earnings with the original authors.
To lend the operation a veneer of legitimacy, the threat actors are believed to have create a lookalike version of a known anti-scam tool known as ScamDoc, which assigns a trust score for different websites, in a plausible attempt to pass off the sketchy crypto services as trustworthy.
Trend Micro said it also stumbled upon private messages, online videos, and ads on other social networks such as TikTok and Mastodon, indicating that the affiliates are using a wide range of methods to advertise the fraudulent activity.
"The threat actor streamlines operations for its affiliates by providing hosting and infrastructure so they can run these scam websites on their own," the researchers said. "Affiliates are then able to concentrate on other aspects of the operation, such as running their own advertising campaigns."
The findings come weeks after Akamai took the wraps off a renewed Romanian cryptojacking campaign named Diicot (previously Mexals) that employs a Golang-based Secure Shell (SSH) worm module and a new LAN spreader for propagation.
Then last month, Elastic Security Labs detailed the use of an open-source rootkit called r77 to deploy the XMRig cryptocurrency miner in several Asian countries.
"r77's primary purpose is to hide the presence of other software on a system by hooking important Windows APIs, making it an ideal tool for cybercriminals looking to carry out stealthy attacks," the researchers said.
"By leveraging the r77 rootkit, the authors of the malicious crypto miner were able to evade detection and continue their campaign undetected."
It's worth pointing out that the r77 rootkit is also incorporated in SeroXen, a nascent variant of the Quasar remote administration tool that's being sold for only $30 for a monthly license or $60 for a lifetime bundle.
New Malware Campaign Leveraging Satacom Downloader to Steal Cryptocurrency
7.6.23 Cryptocurrency The Hacker News
A recent malware campaign has been found to leverage Satacom downloader as a conduit to deploy stealthy malware capable of siphoning cryptocurrency using a rogue extension for Chromium-based browsers.
"The main purpose of the malware that is dropped by the Satacom downloader is to steal BTC from the victim's account by performing web injections into targeted cryptocurrency websites," Kaspersky researchers Haim Zigel and Oleg Kupreev said.
Targets of the campaign include Coinbase, Bybit, KuCoin, Huobi, and Binance users primarily located in Brazil, Algeria, Turkey, Vietnam, Indonesia, India, Egypt, and Mexico.
Satacom downloader, also called Legion Loader, first emerged in 2019 as a dropper for next-stage payloads, including information stealers and cryptocurrency miners.
Infection chains involving the malware begin when users searching for cracked software are redirected to bogus websites that host ZIP archive files containing the malware.
"Various types of websites are used to spread the malware," the researchers explained. "Some of them are malicious websites with a hardcoded download link, while others have the 'Download' button injected through a legitimate ad plugin."
Present within the archive file is an executable called "Setup.exe" that's about 5 MB in size but inflated to roughly 450 MB with null bytes in an attempt to evade analysis and detection.
Launching the binary initiates the malware routine, culminating in the execution of the Satacom downloader that, in turn, uses DNS requests as a command-and-control (C2) method to fetch the URL that hosts the actual malware.
The campaign documented by Kaspersky leads to a PowerShell script, which downloads the browser add-on from a remote third-party server. It also searches for browser shortcut (.LNK) files in the compromised host and modifies the "Target" parameter with the "--load-extension" flag to launch the browser with the downloaded extension.

What's more, the add-on masquerades as a Google Drive extension and employs web injections sent by the C2 server when the victim is visiting one of the targeted cryptocurrency websites to manipulate the content and steal crypto.
The C2 address is concealed within the script and addr fields of the most recent bitcoin transaction associated with an actor-controlled wallet address, employing the same technique as the Glupteba botnet malware to get around domain blockades or takedowns.
"The extension performs various actions on the account in order to remotely control it using the web inject scripts, and eventually the extension tries to withdraw the BTC currency to the threat actors' wallet," the researchers said.
In an additional attempt to conceal its activity, the malicious extension contains scripts to conceal the email confirmation of the fraudulent transaction across Gmail, Hotmail and Yahoo! services by means of an HTML code injection.
A consequence of this injection is that the victim is unaware that an illicit transfer to the threat actors' wallet was made. Another notable aspect of the add-on is its ability to extract system metadata, cookies, browser history, screenshots of opened tabs, and even receive commands from the C2 server.
"The extension can update its functionality due to the technique used to retrieve the C2 server via the last transaction of a specific BTC wallet, which can be modified at any time by making another transaction to this wallet," the researchers said.
"This allows the threat actors to change the domain URL to a different one in case it's banned or blocked by antivirus vendors."
The development comes as several booby-trapped extensions posing as legitimate utilities have been unearthed on the Chrome Web Store with capabilities to spread adware and hijack search results to display sponsored links, paid search results, and potentially malicious links.
The extensions, while offering the promised features, contained obfuscated code that allowed a third-party website to inject arbitrary JavaScript code into all websites that a user visited without their knowledge.
Cybercriminals Targeting Apache NiFi Instances for Cryptocurrency Mining
31.5.23 Cryptocurrency The Hacker News
A financially motivated threat actor is actively scouring the internet for unprotected Apache NiFi instances to covertly install a cryptocurrency miner and facilitate lateral movement.
The findings come from the SANS Internet Storm Center (ISC), which detected a spike in HTTP requests for "/nifi" on May 19, 2023.
"Persistence is achieved via timed processors or entries to cron," said Dr. Johannes Ullrich, dean of research for SANS Technology Institute. "The attack script is not saved to the system. The attack scripts are kept in memory only."
A honeypot setup allowed the ISC to determine that the initial foothold is weaponized to drop a shell script that removes the "/var/log/syslog" file, disables the firewall, and terminates competing crypto-mining tools, before downloading and launching the Kinsing malware from a remote server.
It's worth pointing out that Kinsing has a track record of leveraging publicly disclosed vulnerabilities in publicly accessible web applications to carry out its attacks.
In September 2022, Trend Micro detailed an identical attack chain that utilized old Oracle WebLogic Server flaws (CVE-2020-14882 and CVE-2020-14883) to deliver the cryptocurrency mining malware.
Select attacks mounted by the same threat actor against exposed NiFi servers also entail the execution of a second shell script that's designed to collect SSH keys from the infected host to connect to other systems within the victim's organization.
A notable indicator of the ongoing campaign is that the actual attack and scanning activities are carried out via the IP address 109.207.200[.]43 against port 8080 and port 8443/TCP.
"Due to its use as a data processing platform, NiFi servers often have access to business-critical data," SANS ISC said. "NiFi servers are likely attractive targets as they are configured with larger CPUs to support data transformation tasks. The attack is trivial if the NiFi server is not secured."
New Stealthy Bandit Stealer Targeting Web Browsers and Cryptocurrency Wallets
28.5.23 Cryptocurrency The Hacker News
A new stealthy information stealer malware called Bandit Stealer has caught the attention of cybersecurity researchers for its ability to target numerous web browsers and cryptocurrency wallets.
"It has the potential to expand to other platforms as Bandit Stealer was developed using the Go programming language, possibly allowing cross-platform compatibility," Trend Micro said in a Friday report.
The malware is currently focused on targeting Windows by using a legitimate command-line tool called runas.exe that allows users to run programs as another user with different permissions.
The goal is to escalate privileges and execute itself with administrative access, thereby effectively bypassing security measures to harvest wide swathes of data.
That said, Microsoft's access control mitigations to prevent unauthorized execution of the tool means an attempt to run the malware binary as an administrator requires providing the necessary credentials.
"By using the runas.exe command, users can run programs as an administrator or any other user account with appropriate privileges, provide a more secure environment for running critical applications, or perform system-level tasks," Trend Micro said.
"This utility is particularly useful in situations where the current user account does not have sufficient privileges to execute a specific command or program."
Bandit Stealer incorporates checks to determine if it's running in a sandbox or virtual environment and terminates a list of blocklisted processes to conceal its presence on the infected system.
It also establishes persistence by means of Windows Registry modifications before commencing its data collection activities that include harvesting personal and financial data stored in web browsers and crypto wallets.
Bandit Stealer is said to be distributed via phishing emails containing a dropper file that opens a seemingly innocuous Microsoft Word attachment as a distraction maneuver while triggering the infection in the background.
Trend Micro said it also detected a fake installer of Heart Sender, a service that automates the process of sending spam emails and SMS messages to numerous recipients, that's used to trick users into launching the embedded malware.
The development comes as the cybersecurity firm uncovered a Rust-based info stealer targeting Windows that leverages a GitHub Codespaces webhook controlled by the attacker as an exfiltration channel to obtain a victim's web browser credentials, credit cards, cryptocurrency wallets, and Steam and Discord tokens.
The malware, in what's a relatively uncommon tactic, achieves persistence on the system by modifying the installed Discord client to inject JavaScript code designed to capture information from the application.
The findings also follow the emergence of several strains of commodity stealer malware like Luca, StrelaStealer, DarkCloud, WhiteSnake, and Invicta Stealer, some of which have been observed propagating via spam emails and fraudulent versions of popular software.
Another notable trend has been the use of YouTube videos to advertise cracked software via compromised channels with millions of subscribers.
Data amassed from stealers can benefit the operators in many ways, allowing them to exploit purposes such as identity theft, financial gain, data breaches, credential stuffing attacks, and account takeovers.
The stolen information can also be sold to other actors, serving as a foundation for follow-on attacks that could range from targeted campaigns to ransomware or extortion attacks.
These developments highlight the continued evolution of stealer malware into a more lethal threat, just as the malware-as-a-service (MaaS) market makes them readily available and lowers the barriers to entry for aspiring cybercriminals.
Indeed, data gathered by Secureworks Counter Threat Unit (CTU) has revealed a "thriving infostealer market," with the volume of stolen logs on underground forums like Russian Market registering a 670% jump between June 2021 and May 2023.
"Russian Market offers five million logs for sale which is around ten times more than its nearest forum rival 2easy," the company said.
"Russian Market is well-established among Russian cybercriminals and used extensively by threat actors worldwide. Russian Market recently added logs from three new stealers, which suggests that the site is actively adapting to the ever-changing e-crime landscape."
The MaaS ecosystem, the increasing sophistication notwithstanding, has also been in a state of flux, with law enforcement actions prompting threat actors to peddle their warez on Telegram.
"What we are seeing is an entire underground economy and supporting infrastructure built around infostealers, making it not only possible but also potentially lucrative for relatively low skilled threat actors to get involved," Don Smith, vice president of Secureworks CTU, said.
"Coordinated global action by law enforcement is having some impact, but cybercriminals are adept at reshaping their routes to market."
Kubernetes RBAC Exploited in Large-Scale Campaign for Cryptocurrency Mining
22.4.23 Cryptocurrency The Hacker News
A large-scale attack campaign discovered in the wild has been exploiting Kubernetes (K8s) Role-Based Access Control (RBAC) to create backdoors and run cryptocurrency miners.
"The attackers also deployed DaemonSets to take over and hijack resources of the K8s clusters they attack," cloud security firm Aqua said in a report shared with The Hacker News. The Israeli company, which dubbed the attack RBAC Buster, said it found 60 exposed K8s clusters that have been exploited by the threat actor behind this campaign.
The attack chain commenced with the attacker gaining initial access via a misconfigured API server, followed by checking for evidence of competing miner malware on the compromised server and then using RBAC to set up persistence.
"The attacker created a new ClusterRole with near admin-level privileges," the company said. "Next, the attacker created a 'ServiceAccount', 'kube-controller' in the 'kube-system' namespace. Lastly, the attacker created a 'ClusterRoleBinding', binding the ClusterRole with the ServiceAccount to create a strong and inconspicuous persistence."
In the intrusion observed against its K8s honeypots, the attacker attempted to weaponize the exposed AWS access keys to obtain an entrenched foothold into the environment, steal data, and escape the confines of the cluster.

The final step of the attack entailed the threat actor creating a DaemonSet to deploy a container image hosted on Docker ("kuberntesio/kube-controller:1.0.1") on all nodes. The container, which has been pulled 14,399 times since its upload five months ago, harbors a cryptocurrency miner.
"The container image named 'kuberntesio/kube-controller' is a case of typosquatting that impersonates the legitimate 'kubernetesio' account," Aqua said. "The image also mimics the popular 'kube-controller-manager' container image, which is a critical component of the control plane, running within a Pod on every master node, responsible for detecting and responding to node failures."
Interestingly, some of the tactics described in the campaign bear similarities to another illicit cryptocurrency mining operation that also took advantage of DaemonSets to mint Dero and Monero. It's currently not clear whether the two sets of attacks are related.
Cryptocurrency Stealer Malware Distributed via 13 NuGet Packages
11.4.23 Cryptocurrency The Hacker News
Cybersecurity researchers have detailed the inner workings of the cryptocurrency stealer malware that was distributed via 13 malicious NuGet packages as part of a supply chain attack targeting .NET developers.
The sophisticated typosquatting campaign, which was detailed by JFrog late last month, impersonated legitimate packages to execute PowerShell code designed to retrieve a follow-on binary from a hard-coded server.
The two-stage attack culminates in the deployment of a .NET-based persistent backdoor, called Impala Stealer, which is capable of gaining unauthorized access to users' cryptocurrency accounts.
"The payload used a very rare obfuscation technique, called '.NET AoT compilation,' which is a lot more stealthy than using 'off the shelf' obfuscators while still making the binary hard to reverse engineer," JFrog told The Hacker News in a statement.
.NET AoT compilation is an optimization technique that allows apps to be ahead-of-time compiled to native code. Native AOT apps also have faster startup time and smaller memory footprints, and can run on a machine without .NET runtime installed.
The second-stage payload comes with an auto-update mechanism that enables it to retrieve new versions of the executable from a remote location. It further achieves persistence by injecting JavaScript code into Discord or Microsoft Visual Studio Code apps, thereby activating the launch of the stealer binary.

The binary then proceeds to search for the installation of the Exodus Wallet desktop application and inserts JavaScript code into various HTML files in order to harvest and exfiltrate sensitive data to a hard-coded Discord webhook.
The JavaScript snippet, for its part, is fetched from an online paste website from where it's already been deleted. That said, it's suspected that the code may have been used to steal user credentials and access other information of interest.
"The bad actors used typosquatting techniques to deploy a custom malicious payload [...] which targets the Exodus crypto wallet and leaks the victim's credentials to cryptocurrency exchanges, by using code injection," Shachar Menashe, senior director at JFrog Security Research, said.
"Our investigation proves no open source software repository is completely trust-worthy, so safety measures should be taken at every step of the software development lifecycle to ensure the software supply chain remains secure."
The findings come as Phylum unearthed a malicious npm package named mathjs-min that was uploaded to the repository on March 26, 2023, and found to harbor a credential stealer that grabs Discord passwords from the official app as well as web browsers like Google Chrome, Brave, and Opera.
"This package is actually a modified version of the widely used Javascript math library mathjs, and was injected with malicious code after being forked," the software supply chain security firm said. "The modified version was then published to NPM with the intention of passing it off as a minified version of the genuine mathjs library."
New Rilide Malware Targeting Chromium-Based Browsers to Steal Cryptocurrency
5.4.23 Cryptocurrency The Hacker News
Chromium-based web browsers are the target of a new malware called Rilide that masquerades itself as a seemingly legitimate extension to harvest sensitive data and siphon cryptocurrency.
"Rilide malware is disguised as a legitimate Google Drive extension and enables threat actors to carry out a broad spectrum of malicious activities, including monitoring browsing history, taking screenshots, and injecting malicious scripts to withdraw funds from various cryptocurrency exchanges," Trustwave SpiderLabs Research said in a report shared with The Hacker News.
What's more, the stealer malware can display forged dialogs to deceive users into entering a two-factor authentication code to withdraw digital assets.
Trustwave said it identified two different campaigns involving Ekipa RAT and Aurora Stealer that led to the installation of the malicious browser extension.
While Ekipa RAT is distributed via booby-trapped Microsoft Publisher files, rogue Google Ads act as the delivery vector for Aurora Stealer – a technique that's become increasingly common in recent months.
Both the attack chains facilitate the execution of a Rust-based loader that, in turn, modifies the browser's LNK shortcut file and makes use of the "--load-extension" command line switch to launch the add-on.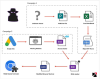
The exact origins of Rilide is unknown, but Trustwave said it was able to find an underground forum post made in March 2022 by a threat actor advertising the sale of a botnet with similar functionalities.
A portion of the malware's source code has since found its way to the forums following what appears to be an unresolved payment dispute.
One notable feature implemented in the leaked source code is the ability to swap cryptocurrency wallet addresses in the clipboard with an actor-controlled address hard-coded in the sample.
Furthermore, a command-and-control (C2) address specified in the Rilide code has made it possible to identify various GitHub repositories belonging to a user named gulantin that contain loaders for the extension. GitHub has taken down the account in question.
"The Rilide stealer is a prime example of the increasing sophistication of malicious browser extensions and the dangers they pose," Trustwave concluded.
"While the upcoming enforcement of manifest v3 may make it more challenging for threat actors to operate, it is unlikely to solve the issue entirely as most of the functionalities leveraged by Rilide will still be available."
Cryptocurrency Companies Targeted in Sophisticated 3CX Supply Chain Attack
4.4.23 Cryptocurrency The Hacker News
The adversary behind the supply chain attack targeting 3CX deployed a second-stage implant specifically singling out a small number of cryptocurrency companies.
Russian cybersecurity firm Kaspersky, which has been internally tracking the versatile backdoor under the name Gopuram since 2020, said it observed an increase in the number of infections in March 2023 coinciding with the 3CX breach.
Gopuram's primary function is to connect to a command-and-control (C2) server and await further instructions that allow the attackers to interact with the victim's file system, create processes, and launch as many as eight in-memory modules.
The backdoor's links to North Korea stem from the fact that it "co-existed on victim machines with AppleJeus, a backdoor attributed to the Korean-speaking threat actor Lazarus," detailing an attack on an unnamed crypto firm located in Southeast Asia in 2020.
The targeting of cryptocurrency companies is another telltale sign of the Lazarus Group's involvement, given the threat actor's recurring focus on the financial industry to generate illicit profits for the sanctions-hit nation.
Kaspersky further said it identified a C2 overlap with a server ("wirexpro[.]com") that was previously identified as employed in an AppleJeus campaign documented by Malwarebytes in December 2022.
"As the Gopuram backdoor has been deployed to less than ten infected machines, it indicates that attackers used Gopuram with surgical precision," the company pointed out, adding the highest infection rates have been detected in Brazil, Germany, Italy, and France.
While the attack chain discovered so far entails the use of rogue installers to distribute an information stealer (known as ICONIC Stealer), the latest findings suggest that the ultimate goal of the campaign may have been to infect targets with the full-fledged modular backdoor.
That said, it's not known how successful the campaign has been, and if it has led to the actual theft of sensitive data or cryptocurrency. It, however, raises the possibility that ICONIC Stealer was used as a reconnaissance utility to cast a wide net and identify targets of interest for follow-on exploitation.
The development comes as BlackBerry revealed that "the initial phase of this operation took place somewhere between the end of summer and the beginning of fall 2022."
A majority of the attack attempts, per the Canadian company, have been registered in Australia, the U.S., and the U.K., with healthcare, pharma, IT, and finance emerging as the top targeted sectors.
It's currently unclear how the threat actor obtained initial access to the 3CX network, and if it entailed the exploitation of a known or unknown vulnerability. The compromise is being tracked under the identifier CVE-2023-29059.
Evidence collected to date indicates that the attackers poisoned 3CX's development environment and delivered trojanized versions of the legitimate app to the company's downstream customers in a SolarWinds or Kaseya-like supply chain attack.
One of the malicious components responsible for retrieving the info-stealer, a library named "d3dcompiler_47.dll," has also been spotted weaponizing a 10-year-old Windows flaw (CVE-2013-3900) to incorporate encrypted shellcode without invalidating its Microsoft-issued signature.
A point worth noting here is that the same technique was adopted by a ZLoader malware campaign unearthed by Israeli cybersecurity firm Check Point Research in January 2022.
Multiple versions of the desktop app – 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS – have been impacted. 3CX has since pinned the attack on a "highly experienced and knowledgeable hacker."
CrowdStrike has tied the incident to a North Korea-aligned nation-state group it tracks under the moniker Labyrinth Chollima, a sub-cluster within the Lazarus Group.
Hackers Steal Over $1.6 Million in Crypto from General Bytes Bitcoin ATMs Using Zero-Day Flaw
22.3.23 Cryptocurrency The Hacker News
Bitcoin ATM maker General Bytes disclosed that unidentified threat actors stole cryptocurrency from hot wallets by exploiting a zero-day security flaw in its software.
"The attacker was able to upload his own java application remotely via the master service interface used by terminals to upload videos and run it using 'batm' user privileges," the company said in an advisory published over the weekend.
"The attacker scanned the Digital Ocean cloud hosting IP address space and identified running CAS services on ports 7741, including the General Bytes Cloud service and other GB ATM operators running their servers on Digital Ocean," it further added.
The company said that the server to which the malicious Java application was uploaded was by default configured to start applications present in the deployment folder ("/batm/app/admin/standalone/deployments/").
In doing so, the attack allowed the threat actor to access the database; read and decrypt API keys used to access funds in hot wallets and exchanges; send funds from the wallets; download usernames, password hashes, and turn off two-factor authentication (2FA); and even access terminal event logs.
It also warned that its own cloud service as well as other operators' standalone servers were infiltrated as a result of the incident, prompting the company to shutter the service.
In addition to urging customers to keep their crypto application servers (CASs) behind a firewall and a VPN, it's also recommending to rotate all users' passwords and API keys to exchanges and hot wallets.
"The CAS security fix is provided in two server patch releases, 20221118.48 and 20230120.44," General Bytes said in the advisory.
The company further emphasized that it had conducted multiple security audits since 2021 and that none of them flagged this vulnerability. It appears to have been unpatched since version 20210401.
General Bytes did not disclose the exact amount of funds stolen by the hackers, but an analysis of the cryptocurrency wallets used in the attack reveals the receipt of 56.283 BTC ($1.5 million), 21.823 ETH ($36,500), and 1,219.183 LTC ($96,500).
The ATM hack is the second breach targeting General Bytes in less than a year, with another zero-day flaw in its ATM servers exploited to steal crypto from its customers in August 2022.
Lookalike Telegram and WhatsApp Websites Distributing Cryptocurrency Stealing Malware
17.3.23 Cryptocurrency The Hacker News
Copycat websites for instant messaging apps like Telegram and WhatApp are being used to distribute trojanized versions and infect Android and Windows users with cryptocurrency clipper malware.
"All of them are after victims' cryptocurrency funds, with several targeting cryptocurrency wallets," ESET researchers Lukáš Štefanko and Peter Strýèek said in a new analysis.
While the first instance of clipper malware on the Google Play Store dates back to 2019, the development marks the first time Android-based clipper malware has been built into instant messaging apps.
"Moreover, some of these apps use optical character recognition (OCR) to recognize text from screenshots stored on the compromised devices, which is another first for Android malware."
The attack chain begins with unsuspecting users clicking on fraudulent ads on Google search results that lead to hundreds of sketchy YouTube channels, which then direct them to lookalike Telegram and WhatsApp websites.
What's novel about the latest batch of clipper malware is that it's capable of intercepting a victim's chats and replacing any sent and received cryptocurrency wallet addresses with addresses controlled by the threat actors.
Another cluster of clipper malware makes use of OCR to find and steal seed phrases by leveraging a legitimate machine learning plugin called ML Kit on Android, thereby making it possible to empty the wallets.
A third cluster is designed to keep tabs on Telegram conversations for certain Chinese keywords, both hard-coded and received from a server, related to cryptocurrencies, and if so, exfiltrate the complete message, along with the username, group or channel name, to a remote server.
Lastly, a fourth set of Android clippers come with capabilities to switch the wallet address as well as harvest device information and Telegram data such as messages and contacts.
The rogue Android APK package names are listed below -
org.telegram.messenger
org.telegram.messenger.web2
org.tgplus.messenger
io.busniess.va.whatsapp
com.whatsapp
ESET said it also found two Windows clusters, one which is engineered to swap wallet addresses and a second group that distributes remote access trojans (RATs) in place of clippers to gain control of infected hosts and perpetrate crypto theft.
All the analyzed RAT samples are based on the publicly available Gh0st RAT, barring one, which employs more anti-analysis runtime checks during its execution and uses the HP-socket library to communicate with its server.
It's also worth pointing out that these clusters, despite following a similar modus operandi, represent disparate sets of activity likely developed by different threat actors.
The campaign, like a similar malicious cyber operation that came to light last year, is geared towards Chinese-speaking users, primarily motivated by the fact that both Telegram and WhatsApp are blocked in the country.
"People who wish to use these services have to resort to indirect means of obtaining them," the researchers said. "Unsurprisingly, this constitutes a ripe opportunity for cybercriminals to abuse the situation."
Cryptojacking Group TeamTNT Suspected of Using Decoy Miner to Conceal Data Exfiltration
17.3.23 Cryptocurrency The Hacker News
The cryptojacking group known as TeamTNT is suspected to be behind a previously undiscovered strain of malware used to mine Monero cryptocurrency on compromised systems.
That's according to Cado Security, which found the sample after Sysdig detailed a sophisticated attack known as SCARLETEEL aimed at containerized environments to ultimately steal proprietary data and software.
Specifically, the early phase of the attack chain involved the use of a cryptocurrency miner, which the cloud security firm suspected was deployed as a decoy to conceal the detection of data exfiltration.
The artifact – uploaded to VirusTotal late last month – "bear[s] several syntactic and semantic similarities to prior TeamTNT payloads, and includes a wallet ID that has previously been attributed to them," a new analysis from Cado Security has revealed.
TeamTNT, active since at least 2019, has been documented to repeatedly strike cloud and container environments to deploy cryptocurrency miners. It's also known to unleash a crypto mining worm capable of stealing AWS credentials.
While the threat actor willingly shut down their operations in November 2021, cloud security firm Aqua disclosed in September 2022 a fresh set of attacks mounted by the group targeting misconfigured Docker and Redis instances.
That said, there are also indications that rival crews such as WatchDog might be mimicking TeamTNT's tactics, techniques, and procedures (TTPs) to foil attribution efforts.
Another activity cluster of note is Kiss-a-dog, which also relies on tools and command-and-control (C2) infrastructure previously associated with TeamTNT to mine cryptocurrency.
There is no concrete evidence to tie the new malware to the SCARLETEEL attack. But Cado Security pointed out that the sample surfaced around the same time the latter was reported, raising the possibility that this could be the "decoy" miner that was installed.
The shell script, for its part, takes preparatory steps to reconfigure resource hard limits, prevent command history logging, accept all ingress or egress traffic, enumerate hardware resources, and even clean up prior compromises before commencing the activity.
Like other TeamTNT-linked attacks, the malicious payload also leverages a technique referred to as dynamic linker hijacking to cloak the miner process via a shared object executable called libprocesshider that uses the LD_PRELOAD environment variable.
Persistence is achieved by three different means, one of which modifies the .profile file, to ensure that the miner continues to run across system reboots.
The findings come as another crypto miner group dubbed the 8220 Gang has been observed using a crypter called ScrubCrypt to carry out illicit cryptojacking operations.
What's more, unknown threat actors have been found targeting vulnerable Kubernetes container orchestrator infrastructure with exposed APIs to mine the Dero cryptocurrency, marking a shift from Monero.
Cybersecurity company Morphisec, last month, also shed light on an evasive malware campaign that leverages the ProxyShell vulnerabilities in Microsoft Exchange servers to drop a crypto miner strain codenamed ProxyShellMiner.
"Mining cryptocurrency on an organization's network can lead to system performance degradation, increased power consumption, equipment overheating, and can stop services," the researchers said. "It allows threat actors access for even more nefarious ends."
Authorities Shut Down ChipMixer Platform Tied to Crypto Laundering Scheme
16.3.23 Cryptocurrency The Hacker News
A coalition of law enforcement agencies across Europe and the U.S. announced the takedown of ChipMixer, an unlicensed cryptocurrency mixer that began its operations in August 2017.
"The ChipMixer software blocked the blockchain trail of the funds, making it attractive for cybercriminals looking to launder illegal proceeds from criminal activities such as drug trafficking, weapons trafficking, ransomware attacks, and payment card fraud," Europol said in a statement.
The coordinated exercise, besides dismantling the clearnet and dark web websites associated with ChipMixer, also resulted in the seizure of $47.5 million in Bitcoin and 7 TB of data.
Mixers, also called tumblers, offer full anonymity for a fee by commingling cryptocurrency from different users – both legitimate and criminally-derived funds – in a manner that makes it hard to trace the origins.
This is achieved by funneling different payments into a single pool before splitting up each amount and transmitting them to designated recipients, thereby turning it into an attractive option for criminals looking to cash out and exchange the tainted money for fiat currency.
According to a report from Chainalysis in January 2023, "mixers processed a total of $7.8 billion in 2022, 24% of which came from illicit addresses," and "the vast majority of illicit value processed by mixers is made up of stolen funds, the majority of which were stolen by North Korea-linked hackers."
ChipMixer, the world's largest centralized crypto mixer service, is estimated to have laundered no less than $3.75 billion worth of digital assets (152,000 BTC) to further a wide range of criminal schemes.
Blockchain analytics firm Elliptic said ChipMixer has been used to launder over $844 million in Bitcoin that can be linked directly to criminal activity.
"ChipMixer was one of a variety of mixers used to launder the proceeds of hacks perpetrated by North Korea's Lazarus Group," Elliptic's co-founder and chief scientist, Tom Robinson, said.
This comprises the KuCoin theft in September 2020 as well as the Axie Infinity Ronin Bridge and Harmony Horizon Bridge hacks that took place last year.

The Lazarus Group is far from the only infamous client to have used the service to obfuscate the financial tracks. The other prominent actors consist of ransomware crews like LockBit, Sodinokibi (aka REvil), Zeppelin, Mamba, Dharma, and SunCrypt.
Additionally, ChipMixer is said to have attracted more than $200 million in Bitcoin linked to purchases originating from darknet markets, including $60 million from customers of the now-defunct Hydra.
The mixer platform, per the U.S. Department of Justice (DoJ), also processed cryptocurrency used by the Russia-linked APT28 hacking group (aka Fancy Bear or Strontium) to procure infrastructure employed in connection with a malware called Drovorub.
Coinciding with the crackdown, the DoJ further charged a 49-year-old Vietnamese national, Minh Quốc Nguyễn, for his role in creating and running ChipMixer's online infrastructure and advertising its services.
"ChipMixer facilitated the laundering of cryptocurrency, specifically Bitcoin, on a vast international scale, abetting nefarious actors and criminals of all kinds in evading detection," U.S. Attorney Jacqueline C. Romero said.
"Platforms like ChipMixer, which are designed to conceal the sources and destinations of staggering amounts of criminal proceeds, undermine the public's confidence in cryptocurrencies and blockchain technology."
The development is the latest in a string of law enforcement actions undertaken by governments across the world to tackle cybercrime, and comes weeks after "penal procedures" were initiated against suspected core members of the DoppelPaymer ransomware gang.
ChipMixer is also the fourth mixer service to be outlawed over the past few years following the disruption of Bestmixer, Blender, and Tornado Cash, the latter two of which were sanctioned by the U.S. Treasury Department last year for abetting Lazarus Group and other threat actors in laundering ill-gotten proceeds.
New Cryptojacking Operation Targeting Kubernetes Clusters for Dero Mining
15.3.23 Cryptocurrency The Hacker News
Cybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint Dero since the start of February 2023.
"The novel Dero cryptojacking operation concentrates on locating Kubernetes clusters with anonymous access enabled on a Kubernetes API and listening on non-standard ports accessible from the internet," CrowdStrike said in a new report shared with The Hacker News.
The development marks a notable shift from Monero, which is a prevalent cryptocurrency used in such campaigns. It's suspected it may have to do with the fact that Dero "offers larger rewards and provides the same or better anonymizing features."
he attacks, attributed to an unknown financially motivated actor, commence with scanning for Kubernetes clusters with authentication set as --anonymous-auth=true, which allows anonymous requests to the server, to drop initial payloads from three different U.S.-based IP addresses.
This includes deploying a Kubernetes DaemonSet named "proxy-api," which, in turn, is used to drop a malicious pod on each node of the Kubernetes cluster to kick-start the mining activity.

To that end, the DaemonSet's YAML file is orchestrated to run a Docker image that contains a "pause" binary, which is actually the Dero coin miner.
"In a legitimate Kubernetes deployment, 'pause' containers are used by Kubernetes to bootstrap a pod," the company noted. "Attackers may have used this name to blend in to avoid obvious detection."
The cybersecurity company said it identified a parallel Monero-mining campaign also targeting exposed Kubernetes clusters by attempting to delete the existing "proxy-api" DaemonSet associated with the Dero campaign.
This is an indication of the ongoing tussle between cryptojacking groups that are vying for cloud resources to take and retain control of the machines and consume all of its resources.
"Both campaigns are trying to find undiscovered Kubernetes attack surfaces and are battling it out," CrowdStrike threat researchers Benjamin Grap and Manoj Ahuje said.