8.3.24 Social The Hacker News
Meta Details WhatsApp and Messenger Interoperability to Comply with EU's DMA Regulations
8.3.24 Social The Hacker News
Meta has offered details on how it intends to implement interoperability in WhatsApp and Messenger with third-party messaging services as the Digital Markets Act (DMA) went into effect in the European Union.
"This allows users of third-party providers who choose to enable interoperability (interop) to send and receive messages with opted-in users of either Messenger or WhatsApp – both designated by the European Commission (EC) as being required to independently provide interoperability to third-party messaging services," Meta's Dick Brouwer said.
DMA, which officially became enforceable on March 7, 2024, requires companies in gatekeeper positions – Apple, Alphabet, Meta, Amazon, Microsoft, and ByteDance – to clamp down on anti-competitive practices from tech players, level the playing field, as well as compel them to open some of their services to competitors.
As part of its efforts to comply with the landmark regulations, the social media giant said it expects third-party providers to use the Signal Protocol, which is used in both WhatsApp and Messenger for end-to-end encryption (E2EE).
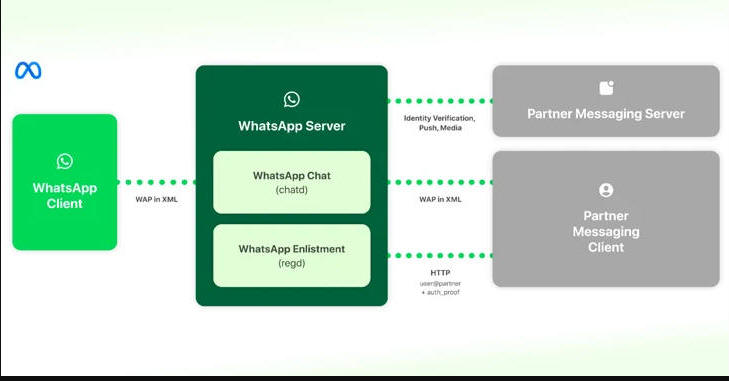
The third-parties are also required to package the encrypted communications into message stanzas in eXtensible Markup Language (XML). Should the message contain media content, an encrypted version is downloaded by Meta clients from the third-party messaging servers using a Meta proxy service.
The company is also proposing what's called a "plug-and-play" model that allows third-party providers to connect to its infrastructure for achieving interoperability.
"Taking the example of WhatsApp, third-party clients will connect to WhatsApp servers using our protocol (based on the Extensible Messaging and Presence Protocol – XMPP)," Brouwer said.
"The WhatsApp server will interface with a third-party server over HTTP in order to facilitate a variety of things including authenticating third-party users and push notifications."
Furthermore, third-party clients are mandated to execute a WhatsApp Enlistment API when opting into its network, alongside providing cryptographic proof of their ownership of the third-party user-visible identifier when connecting or a third-party user registers on WhatsApp or Messenger.
The technical architecture also has provisions for a third-party provider to add a proxy or an intermediary between their client and the WhatsApp server to provide more information about the kinds of content their client can receive from the WhatsApp server.
"The challenge here is that WhatsApp would no longer have direct connection to both clients and, as a result, would lose connection level signals that are important for keeping users safe from spam and scams such as TCP fingerprints," Brouwer noted.
"This approach also exposes all the chat metadata to the proxy server, which increases the likelihood that this data could be accidentally or intentionally leaked."